
Data in medical records are precious commodities for crooks that can use them for identity theft and medical billing frauds and scams.
Cyber attacks against the healthcare industry are expected to grow
24.12.2016 securityaffairs Cyber
The number of cyber attacks against organizations in the healthcare industry is increasing, this trend is expected to continue in 2017.
The monitoring of the activity in the cyber criminal underground is essential for investigators and security experts. The value of illegal products and services gives us a precious information on cyber criminal trends. Security experts are observing a significant drop in the black market value of stolen medical records, this data suggests criminal organizations are focusing their efforts elsewhere.
Criminal organizations are more focused on stealing data to spread ransomware, according to a report released by the security firm TrapX.
Crooks are offering stolen records for a price ranging between $1.50 and $10 each. Across the months the price is dropped as never before, this summer cyber criminals offered 10 million patient records on TheRealDeal black marketplace for about $820,000, roughly $12 per record. Lots of data containing a smaller number of records were offered with a price per single records ranging from $40 up to $60. In 2012 the World Privacy Forum estimated the value of medical records on the criminal underground at around $50 each.
Data in medical records are precious commodities for crooks that can use them for identity theft and medical billing frauds and scams.
Anthony James, CMO at TrapX explained that the black market has become saturated, in 2015 expert estimated that about 112 million records were stolen, including 80 million records from the Anthem data breach.
“2015 was obviously a year where cybersecurity came to the forefront for the health care industry,” James told to CSOonline.
Another interesting data emerged from the report is the number of organizations breached by cyber criminals that passed from 57 last year to 93 this year, up from 36 in 2015.
The overall number of records lost fell by nearly 90 percent to just 12 million records.
TrapX analyzed all the breaches reported to the Department of Health and Human Services resulting from hacking activities.
According to the experts, 31% of all major HIPAA data breaches were caused by sophisticated attacks, a 300% increase over the past three years.
“Researchers pinpointed two major trends from 2016: the continued discovery and evolution of medical device hijacking, which TrapX calls MEDJACK and MEDJACK.2, and the increase of ransomware across a variety of targets.” reported DarkReading.
The researchers explained that companies that have six months to report the incident, this means that we will have news of some attacks occurred in 2016 during H1 2017 and the estimates made by the experts at TrapX could be pejorative.
The experts highlighted that the falling price for stolen records is pushing scammers to try to monetize their efforts in other ways, like ransomware-based attacks.
“That’s why ransomware has started to increase,” James said. “That’s where they’re getting their money now.”
This trend is expected to continue in 2017 that will be a difficult year for the healthcare.
Signal implements ‘domain fronting’ technique to bypass censorship
23.12.2016 securityaffairs Hacking
The latest update of Signal introduces the ‘domain fronting’ technique that has been implemented to circumvent censorship.
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app.
The latest update of Signal has just been developed to implement mechanisms to circumvent censorship and restrictions applied by governments that want to avoid its use.
Some states are already blocking the application with the support of ISPs. The Government of Egypt and the United Arab Emirates applied measures to block Signal, for this reason, the Open Whisper Systems who develop the app has revised the Android version introducing a technique called domain fronting.
“With today’s release, domain fronting is enabled for Signal users who have a phone number with a country code from Egypt or the UAE,” said company founder Moxie Marlinspike in a blog post. “When those users send a Signal message, it will look like a normal HTTPS request to www.google.com. To block Signal messages, these countries would also have to block all of google.com.”
The domain fronting is a technique that relies on the use of different domain names at different application layers to evade censorship.
The domain fronting techniques “hides the remote endpoint of a communication. Domain fronting works at the application layer, using HTTPS, to communicate with a forbidden host while appearing to communicate with some other host, permitted by the censor,” as described in a paper published by researchers from the University of California, Berkeley, Psiphon, and Brave New Software.
“The key idea is the use of different domain names at different layers of communication. One domain appears on the “outside” of an HTTPS request—in the DNS request and TLS Server Name Indication—while another domain appears on the “inside”—in the HTTP Host header, invisible to the censor under HTTPS encryption.” continues the paper.”A censor, unable to distinguish fronted and nonfronted traffic to a domain, must choose between allowing circumvention traffic and blocking the domain entirely, which results in expensive collateral damage”
The Domain fronting technique is easy to deploy and use and doesn’t require special activities by network intermediaries.
If the front domain is a popular website like ‘google.com, if the censor will block it would have a serious impact on the users.
Domain fronting has a cost.
Domain fronting leverages a CDN that have to receive the request and forward it to the domain in the HTTP host header, or a service that provides similar functionality, like Google’s App Engine.
Such services typically have a cost that according to the paper ranges from $0.10–0.25 per GB using a service like Google App Engine, Amazon CloudFront, Microsoft Azure, Fastly, and CloudFlare. This may explain why Signal isn’t making domain fronting a default everywhere.
Due to this cost, Signal isn’t providing domain fronting by default.
What about domain fronting for the iOS version of Signal?
Marlinspike confirmed that an iOS version of Signal that supports domain fronting is expected soon, meantime it is available a beta version.
A flaw in Cisco CloudCenter Orchestrator exploited by hackers in the wild
23.12.2016 securityaffairs Vulnerebility
Cisco is warning customers about a critical privilege escalation flaw that has been exploited in attacks against the Cisco CloudCenter Orchestrator systems.
Cisco has warned its customers of a critical privilege escalation flaw in Cisco CloudCenter Orchestrator systems, tracked as CVE-2016-9223, that has been exploited in cyber attacks.
The Cisco CloudCenter is a hybrid cloud management platform composed of a CloudCenter Manager and CloudCenter Orchestrator. The CloudCenter Manager is the interface utilized by users and administrators, while the CloudCenter Orchestrator allows to model, deploy and manage new and existing applications.

An unauthenticated attacker can remotely install malicious Docker containers with high privileges by exploiting a vulnerability in the Docker Engine configuration.
“A vulnerability in the Docker Engine configuration of Cisco CloudCenter Orchestrator (CCO; formerly CliQr) could allow an unauthenticated, remote attacker to install Docker containers with high privileges on the affected system.” states the security advisory published by CISCO.
An attacker can exploit this issue to load Docker containers with arbitrary privileges, including root.
“The vulnerability is due to a misconfiguration that causes the Docker Engine management port to be reachable outside of the CloudCenter Orchestrator system. An attacker could exploit this vulnerability by loading Docker containers on the affected system with arbitrary privileges. As a secondary impact this may allow the attacker to gain root privileges on the affected CloudCenter Orchestrator.”
The experts from CISCO discovered the critical flaw while working on a support case. The issue exists due to a misconfiguration that exposed the Docker Engine management port from the outside.
According to CISCO, vulnerable Cisco CloudCenter Orchestrator (CCO) deployments have the Docker Engine TCP port 2375 open and bound to local IP address 0.0.0.0.
The command netstat -ant | grep 2375 command could allow a rapid check of a configuration.
The Cisco Product Security Incident Response Team (PSIRT) confirmed that the flaw had been exploited in attacks in the wild.
CISCO fixed the issue by releasing the CCO version 4.6.2. The company also suggests as a workaround to restrict the Docker Engine port to the localhost IP address 127.0.0.1.
Is Mirai Really as Black as It’s Being Painted?
23.12.2016 Kaspersky Virus
The Mirai botnet, which is made up of IoT devices and which was involved in DDoS attacks whose scale broke all possible records, causing denial of service across an entire region, has been extensively covered by the mass media. Given that the botnet’s source code has been made publicly available and that the Internet of Things trend is on the rise, no decline in IoT botnet activity should be expected in the near future.
To put this in perspective, recall the year 2012, when the source code of the Zeus banker Trojan was made publicly available. A huge number of modifications of the Trojan appeared as a result of this, many of which are still active and rank among the most widespread financial malware. Similarly, the recent leak is likely to result in the emergence of Mirai modifications, created by cybercriminals and based on the source code that was made public.
The botnet remains active. We carried out an analysis of its activity to find out how Mirai operates, what objectives its owners are pursuing and, most importantly, what needs to be done to avoid becoming part of the botnet in the future.
How Mirai Works
Based on the botnet’s source code that was published on a user forum, Mirai consists of the following components:
a command-and-control center (C&C) that contains a MySQL database of all infected IoT devices (bots) and sends commands to intermediate command distribution servers;
a Scan Receiver component that collects the results of each bot’s operation and forwards them to the component that downloads the bot onto vulnerable devices (the Distributor);
a downloader component, which delivers the bot’s binary file to a vulnerable device (using the wget and tftp utilities – but if they are not present in the system, it uses its own proprietary downloader);
a bot, which, after being launched on an infected device, connects to the command-and-control center, scans an IP range (SYN scanning) for vulnerable IoT devices and sends the scan results to the Scan Receiver component in order for further malicious code to be subsequently downloaded to the device.
An important feature of the way the Mirai botnet scans devices is that the bot uses a login and password dictionary when trying to connect to a device. The author of the original Mirai included a relatively small list of logins and passwords for connecting to different devices. However, we have seen a significant expansion of the login and password list since then, achieved by including default logins and passwords for a variety of IoT devices, which means that multiple modifications of the bot now exist.
List of logins and passwords used by the original Mirai in its search for vulnerable IoT devices
However, this is by no means all the Mirai botnet can tell us about itself.
Analysis of the Botnet’s Activity
All you need to do to evaluate the Mirai botnet’s current activity is to deploy a server with an open telnet port somewhere on the Internet and analyze connection attempts made by different bots. For example, we detected the first attempts to connect to our telnet port, by several different hosts, within three minutes of putting our experimental server online.
Two facts indicate that these connections are made by bots of the original Mirai or its modifications (i.e., by infected devices):
the accounts used by the bots in their attempts to establish a connection are found on the original botnet’s brute force word list;
an analysis of connection sources has shown that infected hosts that perform scanning are in most cases IoT devices (cameras and routers of different manufacturers).
Connection attempts by infected Mirai workstations in search of IoT devices using default passwords
Here is a list of login and password pairs most often used by Mirai bots in connection attempts:
“Login:password” combinations
1 admin : admin
2 root : xc3511
3 root : vizxv
4 root : juantech
5 root : default
6 admin : admin1234
7 root : password
8 root : root
9 root : xmhdipc
10 admin : smcadmin
If you ignore trivial combinations like “root:root” or “admin:admin”, you can get a good idea of which equipment the botnet is looking for. For example, the pairs “root:xc3511” and “root:vizxv” are default accounts for IP cameras made by rather large Chinese manufacturers.
Admin panel for managing an IP camera that is part of the botnet
As for the activity of the botnet itself, you can analyze the number of login attempts over 24 hours and see for yourself. On December 13, 2016 we recorded 5,553 attempts by Mirai bots to connect to our server, while 10 days before that, on December 3, 2016, we recorded 8,689 connection attempts. Does this mean that the botnet is losing power? Reduced activity related to searching for new potential bots might certainly be an indication that the rate at which Mirai is infecting new devices is falling, but it is too early to draw any conclusions.
How to Avoid Becoming Part of the Mirai Botnet
We recommend the following measures to prevent your devices from being included in the Mirai botnet:
Change the default account parameters on each of your devices. Account passwords should be at least 8 characters long and include digits, upper-case letters and special characters.
On each device, install the latest updates provided by the manufacturer.
It is a good idea to block all potential entry points to the operating system on your devices (telnet/SSH/web panel, etc.) from being accessed over the Internet.
Kaspersky Security Bulletin 2016. The ransomware revolution
23.12.2016 Kaspersky Analysis
Introduction
In 2016, ransomware continued its rampage across the world, tightening its hold on data and devices, and on individuals and businesses.
The numbers speak for themselves:
62 new ransomware families made their appearance.
There was an 11-fold increase in the number of ransomware modifications: from 2,900 new modifications in January/March, to 32,091 in July/September.
Attacks on business increased three-fold between January and the end of September: the difference between an attack every 2 minutes and one every 40 seconds.
For individuals the rate of increase went from every 20 seconds to every 10 seconds.
One in five small and medium-sized business who paid the ransom never got their data back.
2016 also saw ransomware grow in sophistication and diversity, for example: changing tack if it encountered financial software, written in scripting languages, exploiting new infection paths, becoming more targeted, and offering turn-key ransomware-as-a-service solutions to those with fewer skills, resources or time – all through a growing and increasingly efficient underground ecosystem.
At the same time, 2016 saw the world begin to unite to fight back:
The No More Ransom project was launched in July, bringing togetheal Police, Europol, Intel Security and Kaspersky Lab. A further 13 organizations joined in October. Among other things, the collaboration has resulted in a number of free online decryption tools that have so far helped thousands of ransomware victims to recover their data.
This is just the tip of the iceberg – much remains to be done. Together we can achieve far more than any of us can on our own.
What is ransomware?
Ransomware comes in two forms. The most common form of ransomware is the cryptor. These programs encrypt data on the victim’s device and demand money in return for a promise to restore the data. Blockers, by contrast, don’t affect the data stored on the device. Instead, they prevent the victim from accessing the device. The ransom demand, displayed across the screen, typically masquerades as a notice from a law enforcement agency, reporting that the victim has accessed illegal web content and indicating that they must pay a spot-fine. You can find an overview of both forms of ransomware here.
Ransomware: the main trends & discoveries of 2016
“Most ransomware thrives on an unlikely relationship of trust between the victim and their attacker: that, once payment is received, the ransomed files will be returned. Cybercriminals have exhibited a surprising semblance of professionalism in fulfilling this promise.”
GReAT, Threat Predictions for 2017
Kaspersky Security Bulletin 2016. Story of the year
Arrivals and departures
Arrivals – in 2016, the world said hello to Cerber, Locky and CryptXXX – as well as to 44,287 new ransomware modifications
Cerber and Locky arrived in the early Spring. Both are nasty, virulent strains of ransomware that are propagated widely, mainly through spam attachments and exploit kits. They rapidly established themselves as ‘major players’, targeting individuals and corporates. Not far behind them was CryptXXX. All three families continue to evolve and to hold the world to ransom alongside well-established incumbents such as CTB-Locker, CryptoWall and Shade.
Locky ransomware has so far been spread across 114 countries #KLReport
As of October 2016, the top ransomware families detected by Kaspersky Lab products look like this:
Name Verdicts* percentage of users**
1 CTB-Locker Trojan-Ransom.Win32.Onion /
Trojan-Ransom.NSIS.Onion 25.32
2 Locky Trojan-Ransom.Win32.Locky /
Trojan-Dropper.JS.Locky 7.07
3 TeslaCrypt (active till May 2016) Trojan-Ransom.Win32.Bitman 6.54
4 Scatter Trojan-Ransom.Win32.Scatter /
Trojan-Ransom.BAT.Scatter /
Trojan-Downloader.JS.Scatter /
Trojan-Dropper.JS.Scatter 2.85
5 Cryakl Trojan-Ransom.Win32.Cryakl 2.79
6 CryptoWall Trojan-Ransom.Win32.Cryptodef 2.36
7 Shade Trojan-Ransom.Win32.Shade 1.73
8 (generic verdict) Trojan-Ransom.Win32.Snocry 1.26
9 Crysis Trojan-Ransom.Win32.Crusis 1.15
10 Cryrar/ACCDFISA Trojan-Ransom.Win32.Cryrar 0.90
* These statistics are based on the detection verdicts returned by Kaspersky Lab products, received from usersof Kaspersky Lab products who have consented to provide their statistical data.
** Percentage of users targeted by a certain crypto-ransomware family relative to all users targeted with crypto-ransomware.
Departures – and goodbye to Teslascrypt, Chimera and Wildfire – or so it seemed…
Kaspersky Security Bulletin 2016. Story of the year
Probably the biggest surprise of 2016 was the shutdown of TeslaCrypt and the subsequent release of the master key, apparently by the malware actors themselves.
TeslaCrypt “committed suicide” – while the police shut down Encryptor RaaS and Wildfire #KLReport
Encryptor RaaS, one of the first Trojans to offer a Ransomware-as-a-Service model to other criminals shut up shop after part of its botnet was taken down by the police.
Then, in July, approximately 3,500 keys for the Chimera ransomware were publicly released by someone claiming to be behind the Petya/Mischa ransomware. However, since Petya used some of the Chimera source code for its own ransomware, it could in fact be the same group, simply updating its product suite and causing mischief.
Similarly, Wildfire, whose servers were seized and a decryption key developed following a combined effort by Kaspersky Lab, Intel Security and the Dutch Police, now appears to have re-emerged as Hades.
Abuse of ‘educational’ ransomware
Kaspersky Security Bulletin 2016. Story of the year
Well-intentioned researchers developed ‘educational’ ransomware to give system administrators a tool to simulate a ransomware attack and test their defenses. Criminals were quick to seize upon these tools for their own malicious purposes.
Ransomware developed for ‘education’ gave rise to Ded Cryptor and Fantom, among others #KLReport
The developer of the educational ransomware Hidden Tear & EDA2 helpfully posted the source code on GitHub. Inevitably, 2016 saw the appearance of numerous malicious Trojans based on this code. This included Ded Cryptor, which changed the wallpaper on a victim computer to a picture of an evil-looking Santa Claus, and demanded a massive two Bitcoins (around $1,300) as a ransom. Another such program was Fantom, which simulated a genuine-looking Windows update screen.
Unconventional approaches
Why bother with a file when you can have the disk?
New approaches to ransomware attacks that were seen for the first time in 2016 included disk encryption, where attackers block access to, or encrypt, all the files at once. Petya is an example of this, scrambling the master index of a user’s hard drive and making a reboot impossible. Another Trojan, Dcryptor, also known as Mamba, went one step further, locking down the entire hard drive. This ransomware is particularly unpleasant, scrambling every disk sector including the operating system, apps, shared files and all personal data – using a copy of the open source DiskCryptor software.
Attackers are now targeting back-ups and hard drives – and brute-forcing passwords #KLReport
The ‘manual’ infection technique
Dcrypter’s infection is carried out manually, with the attackers brute-forcing passwords for remote access to a victim machine. Although not new, this approach has become significantly more prominent in 2016, often as a way to target servers and gain entry into a corporate system.
If the attack succeeds, the Trojan installs and encrypts the files on the server and possibly even on all the network shares accessible from it. We discovered TeamXRat taking this approach to spread its ransomware on Brazilian servers.
Two-in-one infection
In August we discovered a sample of Shade that had unexpected functionality: if an infected computer turned out to belong to financial services, it would instead download and install a piece of spyware, possibly with the longer term aim of stealing money.
Shade downloaded spyware if it found financial software #KLReport
Ransomware in scripting languages
Kaspersky Security Bulletin 2016. Story of the year
Another trend that attracted our attention in 2016 was the growing number of cryptors written in scripting languages. In the third quarter alone, we came across several new families written in Python, including HolyCrypt and CryPy, as well as Stampado written in AutoIt, the automation language.
A long line of amateurs and copycats
Many of the new ransomware Trojans detected in 2016 turned out to be of low-quality; unsophisticated, with software flaws and sloppy errors in the ransom notes.
Poor quality ransomware increases likelihood of data being lost forever #KLReport
This was accompanied by a rise in copycat ransomware. Among other things, we spotted that:
Bart copies the ransom note & the style of Locky’s payment page.
An Autoit-based copycat of Locky (dubbed AutoLocky) uses the same extension “.locky”.
Crusis (aka Crysis) copies the extension “.xtbl” originally used by Shade.
Xorist copies the whole naming scheme of the files encrypted by Crusis.
Probably the most prominent copycat we discovered this year was Polyglot (aka MarsJoke). It fully mimics the appearance and file processing approach of CTB-Locker.
These trends are all expected to increase in 2017.
“As the popularity continues to rise and a lesser grade of criminal decides to enter the space, we are likely to encounter more and more ‘ransomware’ that lacks the quality assurance or general coding capability to actually uphold this promise. We expect ‘skiddie’ ransomware to lock away files or system access or simply delete the files, trick the victim into paying the ransom, and provide nothing in return.”
GReAT, Threat Predictions for 2017
The thriving ransomware economy
Kaspersky Security Bulletin 2016. Story of the year
The rise of RaaS
While Ransomware-as-a-Service is not a new trend, in 2016 this propagation model continued to develop, with ever more ransomware creators offering their malicious product ‘on demand’. This approach has proved immensely appealing to criminals who lack the skills, resources or inclination to develop their own.
Ransomware is increasingly for hire on the criminal underground #KLReport
Notable examples of ransomware that appeared in 2016 and use this model are Petya/Mischa and Shark ransomware, which was later rebranded under the name Atom.
This business model is increasingly sophisticated:
The Petya ransomware partner site
The partner often signs up to a traditional commission-based arrangement. For example, the “payment table” for Petya ransomware shows that if a partner makes 125 Bitcoins a week thy will walk away with 106.25 Bitcoins after commission.
Petya payment table
There is also an initial usage fee. Someone looking to use the Stompado ransomware, for example, needs to come up with just $39.
With other criminals offering their services in spam distribution, ransomware notes etc. it’s not difficult for an aspiring attacker to get started.
From commission-based networks to customer support and branding
The most ‘professional’ attackers offered their victims a help desk and technical support, guiding them through the process of buying Bitcoins to pay the ransom, and sometimes even being open to negotiation. Every step further encouraged the victim to pay.
Criminals offer customer support to ensure more victims pay #KLReport
Further, Kaspersky Lab experts studying ransomware in Brazil noticed that for many attacks, branding the ransomware was a matter of some importance. Those looking for media attention and customer fear would opt for a high profile, celebrity theme or gimmick – while those more concerned about staying under the radar would forgo the temptation of fame and leave their victims facing just an e-mail for contacting the bad guys and a Bitcoin address to pay into.
It’s still all about the Bitcoins
Throughout 2016, the most popular ransomware families still favored payment in Bitcoins. Most ransomware demands were not excessive, averaging at around $300, although some were charged – and paid – a great deal more.
Others, particularly regional and hand-crafted operations, often preferred a local payment option – although this also meant that they were no longer able to hide in plain sight and blend in with the rest of the ransomware noise.
Ransomware turned its weapons on business
Kaspersky Security Bulletin 2016. Story of the year
In the first three months of 2016, 17% of ransomware attacks targeted corporates – this equates to an attack hitting a business somewhere in the world every two minutes1. By the end of Q3 this had increased to 23.9% – an attack every 40 seconds.
A business is attacked with ransomware every 40 seconds #KLReport
According to Kaspersky Lab research, in 2016, one in every five businesses worldwide suffered an IT security incident as a result of a ransomware attack.
42% of small and medium-sized businesses were hit by ransomware in the last 12 months.
32% of them paid the ransom.
One in five never got their files back, even after paying.
67% of those affected by ransomware lost part or all of their corporate data – and one- in-four spent several weeks trying to restore access.
One in five SMBs never gets their data back, even after paying #KLReport
Social engineering and human error remain key factors in corporate vulnerability. One in five cases involving significant data loss came about through employee carelessness or lack of awareness.
“We are seeing more targeted ransomware, where criminal groups carefully hand-pick and spear-phish their targets because of the data they possess and/or their reliance on the availability of this valuable data.”
John Fokker, Digital team Coordinator with the Dutch National High Tech Crime unit
port1
Some industry sectors are harder hit than others, but our research shows that all are at risk
There is no such thing as a low-risk sector anymore #KLReport
Industry sector % attacked with ransomware
1 Education 23
2 IT/Telecoms 22
3 Entertainment/Media 21
4 Financial Services 21
5 Construction 19
6 Government/
public sector/defence 18
7 Manufacturing 18
8 Transport 17
9 Healthcare 16
10 Retail/wholesale/leisure 16
Ransomware attacks that made the headlines
Hospitals became a prime target – with potentially devastating impact as operations were cancelled, patients diverted to other hospitals and more.
The most notorious example of a ransomware attack took place in March when criminals locked down the computers of the Hollywood Presbyterian Medical Center in Los Angeles, until the hospital paid $17,000.
Within weeks, a number of hospitals in Germany were also hit.
In the UK, 28 National Health Service trusts admit to being attacked in 2016.
Hosted desktop and cloud provider VESK paid nearly $23,000 dollars in ransom to recover access to one of its systems following an attack in September.
Leading media, including the New York Times, the BBC and AOL were hit by malware carrying ransomware in March 2016.
The University of Calgary in Canada, a major research center, acknowledged it had paid around $16,000 to recover emails that been encrypted for a week.
A small police station in Massachusetts, ended paying a $500 ransom (via Bitcoin) in order to retrieve essential case-related data, after an officer opened a poisonous email attachment.
Even motor racing was hit: a leading NASCAR racing team faced losing data worth millions to a TeslaCrypt attack in April.
Fighting Back
Kaspersky Security Bulletin 2016. Story of the year
Through technology
The latest versions of Kaspersky Lab products for smaller companies have been enhanced with anti-cryptomalware functionality. In addition, a new, free anti-ransomware tool has been made available for all businesses to download and use, regardless of the security solution they use.
A new free, AV-independent anti-ransomware tool is available #KLReport
Kaspersky Lab’s Anti-Ransomware Tool for Business is a ‘light’ solution that can function in parallel with other antivirus software. The tool uses two components needed for the early detection of Trojans: the distributed Kaspersky Security Network and System Watcher, which monitors applications’ activity.
Kaspersky Security Network quickly checks the reputation of files and website URLs through the cloud, and System Watcher monitors the behavior of programs, and provides proactive protection from yet-unknown versions of Trojans. Most importantly, the tool can back up files opened by suspicious applications and roll back the changes if the actions taken by programs prove malicious.
Through collaboration: The No More Ransom Initiative
On 25 July 2016, the Dutch National Police, Europol, Intel Security and Kaspersky Lab announced the launch of the No More Ransom project – a non-commercial initiative that unites public and private organizations and aims to inform people of the dangers of ransomware and help them to recover their data.
The online portal currently carries eight decryption tools, five of which were made by Kaspersky Lab. These can help to restore files encrypted by more than 20 types of cryptomalware. To date, more than 4,400 victims have got their data back – and more than $1.5 million dollars in ransom demands has been saved.
No More Ransom has so far got 4.400 people their data back – and deprived criminals of $1.5 million in ransom #KLReport
In October, law enforcement agencies from a further 13 countries joined the project, including: Bosnia and Herzegovina, Bulgaria, Colombia, France, Hungary, Ireland, Italy, Latvia, Lithuania, Portugal, Spain, Switzerland and the United Kingdom.
Eurojust and the European Commission also support the project’s objectives, and more partners from the private sector and law enforcement are expected to be announced soon.
“Public/Private partnerships are the essence and the strength of the NMR initiative. They are essential to effectively and efficiently tackle the problem, providing us with much greater capability and reach than law enforcement could have alone.”
Steven Wilson, Head of Europol’s EC3
port2
Standing up to ransomware – how to stay safe
Back up data regularly.
Use a reliable security solution, and remember to keep key features – such as System Watcher – switched on.
Always keep software updated on all the devices you use.
Treat email attachments, or messages from people you don’t know, with caution. If in doubt, don’t open it.
If you’re a business, you should also educate your employees and IT teams; keep sensitive data separate; restrict access; and back up everything, always.
If you are unlucky enough to fall victim to an encryptor, don’t panic. Use a clean system to check our No More Ransom site; you may well find a decryption tool that can help you get your files back.
Last, but not least, remember that ransomware is a criminal offence. Report it to your local law enforcement agency.
“We urge people to report an attack. Every victim holds an essential piece of evidence that provides invaluable insight. In return, we can keep them informed and protect them from dodgy third-party ‘offers’ to unencrypt data. But we need to ensure that more law enforcement offices know how to deal with digital crime.”
Ton Maas, Digital team Coordinator with the Dutch National High Tech Crime unit
port3
Why you shouldn’t pay – advice from the Dutch National High Tech Crime Unit
You become a bigger target.
You can’t trust criminals – you may never get your data back, even if you pay.
Your next ransom will be higher.
You encourage the criminals.
Can we ever win the fight against ransomware?
We believe we can – but only by working together. Ransomware is a lucrative criminal business. To make it stop the world needs to unite to disrupt the criminals’ kill-chain and make it increasingly difficult for them to implement and profit from their attacks.
1Estimates based on: 17% of 372,602 unique users with ransomware attacks blocked by Kaspersky Lab products in Q1, 2016 and 23.9% of 821,865 unique users with ransomware attacks blocked by Kaspersky Lab products in Q3,2016.
Kaspersky Security Bulletin 2016. Review of the year. Overall statistics for 2016
23.12.2016 Kaspersky Analysis
Introduction
If they were asked to sum up 2016 in a single word, many people around the world – particularly those in Europe and the US – might choose the word ‘unpredictable’. On the face of it, the same could apply to cyberthreats in 2016: the massive botnets of connected devices that paralysed much of the Internet in October; the relentless hacking of high profile websites and data dumps; the SWIFT-enabled bank heists that stole billions of dollars, and more. However, many of these incidents had been in fact been predicted, sometimes years ago, by the IT security industry, and the best word for them is probably ‘inevitable’.
For cyberthreats, 2016 was the year when “sooner or later” became “now” #KLReport
Most of all, in 2016, ransomware continued its relentless march across the world – with more new malware families, more modifications, more attacks and more victims. However, there are rays of hope, including the new, collaborative No More Ransom initiative. Kaspersky Lab has designated the revolution in ransomware its Story of the Year for 2016 and you can read more about its evolution and impact here.
Elsewhere on the cybersecurity landscape, targeted cyberespionage attacks, financial theft, ‘hacktivism’ and vulnerable networks of connected devices all played their part in what has been a tense and turbulent year.
This Executive Summary provides an overview of the top threats and statistics for 2016. Full details are included in the accompanying Review & Statistics.
It also considers what these threats mean to organisations trying spot a breach or cyberattack. How ready are businesses to proactively prevent and mitigate a cyberthreat? What can be done to help them?
Six things we learned this year that we didn’t know before
1. That the underground economy is more sophisticated and bigger than ever: xDedic – the shady marketplace
In May, we uncovered a large, active cybercriminal trading platform, called xDedic. xDedic listed and facilitated the buying and selling of hacked server credentials. Around 70,000 compromised servers were on offer – although later evidence suggests that there could have been as many as 176,000 – located in organisations around the world. In most cases, the legitimate owners had no idea that one of their servers, humming away in a back room or data center, had been hijacked and was being passed from criminal to criminal.
xDedic is not the first underground marketplace, but it is evidence of the growing complexity and sophistication of the black market economic ecosystem.
“xDedic is a hacker’s dream, simplifying access to victims, making it cheaper and faster, and opening up new possibilities for both cybercriminals and advanced threat actors.”
GReAT
2. That the biggest financial heist did not involve a stock exchange: the SWIFT-enabled transfers
One of the most serious attacks in 2016 was that using the inter-bank network, SWIFT (Society for Worldwide Interbank Financial Telecommunication). In February 2016, hackers used the SWIFT credentials of Bangladesh Central Bank employees to send fraudulent transaction requests to the Federal Reserve Bank of New York, asking it to transfer millions of dollars to various bank accounts in Asia. The hackers were able to get $81 million transferred to the Rizal Commercial Banking Corporation in the Philippines and an additional $20 million to Pan Asia Banking. The campaign was cut short when the bank spotted a typo in one of the transfer requests. You can read the story here. In the following months, further bank attacks using SWIFT credentials came to light.
Following the theft of $100 million many banks were forced to improve their authentication and SWIFT software update procedures #KLReport
3. That critical infrastructure is worryingly vulnerable: the BlackEnergy attacks
BlackEnergy deserves a place in this list even though, strictly speaking, it took place at the end of 2015. However, it was only in early 2016 that the full effect of the BlackEnergy cyber-attack on the Ukrainian energy sector became clear. The attack was unique in terms of the damage it caused. This included disabling the power distribution system in Western Ukraine, wiping software on targeted systems and unleashing a Distributed Denial of Service (DDoS) attack on the technical support services of affected companies. Kaspersky Lab has supported the investigation into BlackEnergy since 2010, with among other things, an analysis of the tool used to penetrate the target systems. You can find our 2016 report here.
The BlackEnergy cyberattack on the Ukrainian energy sector revealed the vulnerability of critical infrastructures worldwide #KLReport
To help organizations working with industrial control systems (ICS) to identify possible points of weakness, Kaspersky Lab experts have conducted an investigation into ICS threats. Their findings are published in the Industrial Control Systems Threat Landscape report.
4. That a targeted attack can have no pattern: the ProjectSauron APT
In 2016 we discovered the ProjectSauron APT: a likely nation-state backed cyberespionage group that has been stealing confidential data from organisations in Russia, Iran and Rwanda – and probably other countries – since June 2011. Our analysis uncovered some remarkable features: for example, the group adopted innovative techniques from other major APTs, improving on their tactics in order to remain undiscovered. Most importantly of all: tools are customized for each given target, reducing their value as Indicators of Compromise (IoCs) for any other victim. An overview of the methods available to deal with such a complex threat can be found here.
ProjectSauron’s pattern-less spying platform has far-reaching implications for some basic principles of threat detection #KLReport
5. That the online release of vast volumes of data can be an influential tactic: ShadowBrokers and other data dumps
2016 saw a number of remarkable online data dumps. The most famous is probably that by a group calling itself the ShadowBrokers. On August 13, they appeared online claiming to possess files belonging to the ultimate APT predator, the Equation Group. Our research suggests there are similarities between the data dumped by ShadowBrokers and that used by the Equation Group. The initial data dump included a number of unreported zero-days, and there have been further dumps in recent months. The long-term impact of all this activity is unknown, but is has already revealed the huge and rather worrying influence such data dumps can potentially have on public opinion and debate.
In 2016 we also witnessed data breaches at beautifulpeople.com, Tumblr, the nulled.io hacker forum, Kiddicare, VK.com, Sage, the official forum of DotA 2, Yahoo, Brazzers, Weebly and Tesco Bank – for motives ranging from financial gain to personal reputation blackmail.
A LinkedIn hack made public in 2016 revealed over a million uses of the password ‘123456’. #KLReport
6. That a camera could be part of a global cyber-army: the insecure Internet of Things
Connected devices and systems, from homes and vehicles to hospitals and smart cities, exist to make our lives safer and easier. However, many were designed and manufactured without much thought for security – and sold to people who underestimated the need to protect them with more than default factory security settings.
The risk of connecting everything without proper safeguards – after 2016, need we say more? #KLReport
As the world now knows, all these millions of insecure connected devices represent a powerful temptation to cybercriminals. In October, attackers used a botnet of over half a million internet-connected home devices to launch a DDoS attack against Dyn – a company that provides DNS services to Twitter, Amazon, PayPal, Netflix and others. The world was shocked, but warnings about unstable IoT security have been around for a long time.
For example, in February, we showed how easy it was to find a hospital, gain access to its internal network and take control of an MRI device – locating personal data about patients and their treatment procedures and obtaining access to the MRI device file system. In April, we published the results of our research into, among other things, the vulnerability of city traffic sensors and smart ticket terminals.
Manufacturers need to work with the security industry to implement ‘security-by-design’ #KLReport
Other top threats
Inventive APTs
At least 33 countries were targeted by APTs reported on by Kaspersky Lab #KLReport
In February, we reported on Operation Blockbuster, a joint investigation by several major IT security companies into the activities of the Lazarus gang, a highly malicious entity responsible for data destruction.
The Lazarus group is believed to have been behind the attack on Sony Pictures Entertainment in 2014 #KLReport
Adwind, is a cross-platform, multi-functional RAT (Remote Access Tool) distributed openly as a paid service, where the customer pays a fee in return for use of the malicious software. It holds the dubious distinction of being one of the biggest malware platforms currently in existence, with around 1,800 customers in the system by the end of 2015.
Adwind’s malware-for-rent had a customer base of 1,800 #KLReport
APTs everywhere continued to make the most of the fact that not everyone promptly installs new software updates – in May we reported that at least six different groups across the Asia-Pacific and Far East regions, including the newly discovered Danti and SVCMONDR groups, were exploiting the CVE-2015-2545 vulnerability. This flaw enables an attacker to execute arbitrary code using a specially-crafted EPS image file. A patch for the vulnerability was issued back in 2015.
Over six APT groups used the same vulnerability – patched back in 2015 #KLReport
New zero-days
Zero-days remained a top prize for many targeted attackers.
In June, we reported on a cyber-espionage campaign launched by a group named ScarCruft and code-named Operation Daybreak, which was using a previously unknown Adobe Flash Player exploit (CVE-2016-1010). Then in September we discovered a Windows zero-day, CVE-2016-3393, being used by a threat actor known as FruityArmor to mount targeted attacks.
In all, new Kaspersky Lab technologies designed to identify and block such vulnerabilities helped us to uncover four zero-days in 2016. The other two are an Adobe Flash vulnerability CVE-2016-4171 and a Windows EoP (Escalation of Privilege) exploit CVE-2016-0165 .
The hunt for financial gain
Tricking people into either disclosing personal information or installing malware that then seizes the details for their online bank account remained a popular and successful option for cyber-thieves in 2016. Kaspersky Lab solutions blocked attempts to launch such malware on 2,871,965 devices. The share of attacks targeting Android devices increased more than four-fold.
A third of banking malware attacks now target Android devices #KLReport
Some APT groups were also more interested in financial gain than cyberespionage. For example, the group behind Metel infiltrated the corporate network of banks in order to automate the roll-back of ATM transactions: gang members could then use debit cards to repeatedly steal money from ATMs without ever affecting the balance on the card. At the end of 2016 this group remains active.
Metel launched targeted attacks on banks – then sent teams to ATMs at night to withdraw the cash #KLReport
In June, Kaspersky Lab supported the Russian police in their investigation into the Lurk gang. The collaboration resulted in the arrest of 50 suspects allegedly involved in creating networks of infected computers and the theft of more than 45 million dollars from local banks, other financial institutions and commercial organizations.
During the investigation, researchers spotted that users attacked by Lurk had the remote administration software Ammyy Admin installed on their computers. This led to the discovery that that the official Ammyy Admin website had most probably been compromised, with the Trojan was downloaded to users’ computers along with the legitimate Ammyy Admin software.
The takedown of the Lurk gang was the largest ever arrest of hackers in Russia #KLReport
The ultimate vulnerability: people
2016 also revealed that targeted attack campaigns don’t always need to be technically advanced in order to be successful. Human beings – from hapless employees to malicious insiders – often remained the easiest access route for attackers and their tools.
In July, we reported on a group called Dropping Elephant (also known as ‘Chinastrats’ and ‘Patchwork’). Using high quality social engineering combined with old exploit code and some PowerShell-based malware, the group was able to successfully steal sensitive data from high-profile diplomatic and economic organisations linked to China’s foreign relations.
Dropping Elephant and Operation Ghoul confirmed the fearsome power of high quality social engineering #KLReport
Further, Operation Ghoul sent spear-phishing e-mails that appeared to come from a bank in the UAE to top and middle level managers of numerous companies. The messages claimed to offer payment advice from the bank and attached a look-like SWIFT document containing malware.
“Cybercriminals are using insiders to gain access to telecommunications networks and subscriber data, recruiting disaffected employees through underground channels or blackmailing staff using compromising information gathered from open sources.” Threat Intelligence Report for the Telecommunications Industry
Mobile advertising
The main mobile threats in 2016 were advertising Trojans able to obtain ‘root’ or superuser rights on an infected Android device – a level of access that allowed them to do pretty much whatever they wanted. This included hiding in the system folder, thereby making themselves almost impossible to delete, and silently installing and launching different apps that aggressively display advertising. They can even buy new apps from Google Play.
22 of the 30 most popular Trojans in 2016 are advertising Trojans – twice as many as in 2015 #KLReport
Many such Trojans were distributed through the Google Play Store: some of them were installed more than 100,000 times, and one – an infected Pokemon GO Guide app was installed more than 500,000 times.
Malware distributed through Google Play was downloaded hundreds of thousands of times #KLReport
One Android Trojan installed and even updated as a ‘clean’ (malware-free) app before hitting targets with an infected version. Others, including Svpeng, used the Google AdSense advertising network for distribution
Further, some Trojans found new ways to bypass Android security features – in particular the screen overlays and the need to request permission before opening a new app – forcing the user to sign over the access rights the Trojan was looking for.
Mobile ransomware also evolved to make use of overlays, blocking rather than encrypting data since this is generally backed-up.
To read more on these stories, please download the full annual Review for 2016 here.
For an in-depth look at the Statistics for 2016, please register to download the Statistics report here.
The impact on business
The 2016 threat landscape indicates a growing need for security intelligence
The Kaspersky Security Bulletin 2016 highlights the rise of complex and damaging cybersecurity threats, many of which have a far-reaching impact on businesses. This impact is also reflected in our Corporate IT Security Risks Reports (1, 2) based on a 2016 survey of more than 4000 businesses worldwide.
Among other things, the survey asked companies about the most crucial metric of incident detection and response: time.
Incident detection time is critical
Previously unreleased findings from the research show that the typical time required to detect an IT Security event is several days – 28.7% of companies said it took them that long to detect a security breach on average.
Time required to detect an IT security event
Only 8.2% of businesses managed to detect security breaches almost instantly, and for 19.1% of businesses it took several weeks to detect a serious security event. When we asked how they eventually detected a long-standing breach, the replies were revealing.
Going beyond prevention
Average time frame required to detect a security event, across all security events
within the last 12 months
In this chart we combine the average time to discover a security event with the responses we received on how businesses detected a breach. Apparently, businesses that struggle to detect a breach quickly, eventually spot them through one or more of the following: an external or internal security audit, or, sadly, notification from a third party.
It turns out that for these businesses a security audit of any kind is the best measure of ‘last resort’ to finally bring it to light. But should it be only a last resort?
This is where our report detects an obvious discrepancy between theory and practice. Although 65% of businesses admit that a security audit is an effective security measure, less than half of the companies surveyed (48%) have conducted such audit in the last 12 months. Further, 52% of companies operate under the assumption that their IT security will inevitably be compromised at some point, although 48% are not ready to accept this. In short: many businesses find a structured detection and response strategy difficult to embrace.
The cost of delay
It is safe to assume that the longer it takes to detect a security breach, the higher the mitigation costs and the greater the potential damage. The results reveal the shocking truth that failure to discover an attack within a few days, results in a doubling, or more of the costs.
Cost of recovery vs. time needed to discover a security breach for enterprises
For enterprises, an attack undiscovered for a week or more costs 2.77 times that of a breach detected almost instantly. SMBs end up paying 3.8 times more to recover from an incident detected too late.
It is clear that better detection significantly reduces business costs. But the implementation of incident detection and response strategies is quite different from ensuring proper prevention. The latter provides a choice of well-established corporate solutions. The former requires security intelligence, a deep knowledge of the threat landscape, and security talent capable of applying that expertise to the unique specifics of a company. According to our special Corporate IT Security Risks report, businesses that struggle to attract security experts end up paying twice as much for their recovery after an incident.
A security expert found a 0-Day flaw in NETGEAR WNR2000 Routers
23.12.2016 securityaffairs Vulnerebility
An expert found flaws in NETGEAR WNR2000 routers that could be remotely exploited by an attacker to take full control of the affected device.
The security expert Pedro Ribeiro discovered vulnerabilities in NETGEAR WNR2000 Routers, including a zero-day flaw, that could be exploited remotely to take full control of the device if remote administration is enabled.
Ribeiro has already discovered around 10,000 vulnerable devices with the remote admin enabled that are affected by an RCE flaw. According to the expert, the overall number of affected devices could be much greater.
The expert decided to publish the advisory and to release the exploit code because NETGEAR did not respond his emails.
The vulnerabilities were found in NETGEAR WNR2000v5, which doesn’t have remote administration enabled by default on the latest firmware. Remote attacks against WNR2000v5 routers would be possible if a user had manually enabled remote administration.
The expert explained that the NETGEAR WNR2000 router allows an administrator to perform sensitive actions by invoking the CGI apply.cgi URL on the web server on the device. The URL is exposed by the embedded web server uhttpd . While reverse engineering
Ribeiro reverse engineering the uhttpd discovered that another function, the apply_noauth.cgi, allows an unauthenticated user to perform sensitive actions on the device. It could be used to reboot the router or to reset factory settings.
Below the code to reboot the router:
====
POST /apply_noauth.cgi?/reboot_waiting.htm HTTP/1.1
Host: 192.168.1.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
submit_flag=reboot&yes=Yes
====
The researcher also discovered that it is possible to invoke other functions (i.e. Changing Internet WLAN settings or retrieving the admin password) by sending a “timestamp” variable attached to the URL.
“Some of the functions, such as rebooting the router, can be exploited straight away by an unauthenticated attacker. Other functions, such as changing Internet, WLAN settings or retrieving the administrative password, require the attacker to send a “timestamp” variable attached to the URL. This timestamp is generated every time the target page is accessed and functions as a sort of anti-CSRF token.” states the advisory published by Ribeiro. “The timestamp generating function was reverse engineered and due to incorrect use of random number generation (details below) it is possible to identify the token in less than 1000 attempts with no other previous knowledge.”
The expert explained that it is easy for an attacker in the same LAN to obtain a root shell on the router by exploiting an information leakage vulnerability to recover the administrator password and then use it to enable telnet functionality in the router.
Finally, the researcher found a stack buffer overflow that could be exploited by an unauthenticated attacker to take full control over the device and execute code remotely. The exploitation of this flaw leverages the apply_noauth.cgi issue and the timestamp identifying attack.
“Finally, a stack buffer overflow was also discovered, which combined with the apply_noauth.cgi vulnerability and the timestamp identifying attack allows an unauthenticated attacker to take full control of the device and execute code remotely. This vulnerability allows the attacker to execute code in the LAN and in the WAN.” added Riberio.
Recently experts found NETGEAR R7000, R6400, and R8000 routers affected by a security flaw that could be exploited by hackers to gain root access on the device and remotely run code.
NIST Calls Development of Quantum-Proof Encryption Algorithms
22.12.2016 thehackernews Krypto
Quantum Computers – Boon or Bane?
Quantum computers can perform operations much more quickly and efficiently even with the use of less energy than conventional computers, but that's bad news for encryption — a process which scrambles data according to a massively complex mathematical code.
In theory, quantum computers can break almost all the existing encryption algorithms used on the Internet today due to their immense computing power.
Quantum computers are not just in theories; they're becoming a reality.
With countries like China that holds the top two position in the world's most powerful supercomputers (Sunway TaihuLight and Tianhe-2), followed by the United States' Titan, the day is not far when Quantum computers will work on an industrial scale.
Although it's hard to move quantum computing to an industrial scale, it has become a matter of concern for the United States' National Institute of Standards and Technology (NIST) over the fact that "if large-scale quantum computers are ever built, they will be able to break many of the public-key cryptosystems currently in use."
Although Quantum computers are not yet in action, we have seen evidence of the NSA's practical ability to crack some cryptography standards available today with its $11 billion-per-year budget dedicated to "groundbreaking cryptanalytic capabilities."
To tackle this situation, NIST has issued a Federal Register notice Tuesday, requesting private sector and academic cryptographers for help in writing new encryption standards that are sophisticated and powerful enough to withstand quantum computers' cracking attempts.
NIST announced that it would be accepting submissions from the candidates until 30th November 2017.
"With the public's participation," NIST's Cryptographic Technology Group says in a blog post, "NIST intends to spend the next few years gathering, testing and ultimately recommending new algorithms that would be less susceptible to a quantum computer's attack."
In the past deploying Quantum Computers on a large scale was just a theoretical possibility, but after some prototypes of quantum computing, many computer scientists now believes that the arrival of the quantum computing era is near.
But before today's very early prototypes grow into something more practical, NIST has to prepare its "information security systems to be able to resist quantum computing."
In a series of documents called the Federal Information Processing Standards (FIPS), NIST has also published the minimum standards for cryptographic technologies used by the United States government.
The list contains recommended NIST-approved algorithms for various encryption standards used to secure data, communications, and identity.
NIST-approved algorithms are widely used and are considered the gold standard for cryptography and would take hundreds of years to brute-force with currently available conventional computers.
But those algorithms are expected to be much more vulnerable to the advanced power of quantum computers, therefore calling NIST to develop quantum-proofed encryption algorithms.
The development of "new public-key cryptography standards will specify one or more additional unclassified, publicly disclosed digital signature, public-key encryption, and key establishment algorithms that are capable of protecting sensitive government information well into the foreseeable future, including after the advent of quantum computers," the agency says.
Submission of encryption algorithms will close on November 30 next year. After that period, NIST will review the proposals, and the selected candidate will be invited to present their quantum-proof public key cryptography algorithms at a workshop in early 2018.
Kapustkiy hacked the website of the Costa Rica Embassy in China
22.12.2016 securityaffairs Hacking
The popular hacker Kapustkiy continues to target websites of embassies across the world, the last victim is the Costa Rica Embassy in China.
The hacker Kapustkiy continues its string of hack, today he announced a news data breach, the victim is the Costa Rica Embassy in China.
Kapustkiy accessed a database containing 280 login credentials, but just published online 50 of them as a proof of the attack. Just after the attack, the Costa Rica Embassy in China, costaricaembassycn.com, was not reachable.

The website has 280 user entries, it was running on a WordPress platform and after a few tests, the hacker discovered that it was affected by several SQL Injection flaws.
“The first thing I did was to start the exploitation of a SQL vulnerability I have discovered.” said Kapustkiy. “Then I tried brute force and I got a huge list of users”
“I have published around 50 users, the rest is private”
The hacker, who discovered 4 databases in the hack, leaked data belonging to Costa Rica Embassy in China at the following URL:
http://pastebin.com/hEWsuaq2
Leaked records include IDs, emails, and encrypted passwords. Kapustkiy confirmed me that he has reported the vulnerability to the CNCERT/CC and to the website administrator.
The young hacker is very active, a few days ago he announced the data breach of the Slovak Chamber of Commerce (www.scci.sk) that affected more than 4,000 user records.
Recently Kapustkiy targeted several organizations, including the Consular Department of the Embassy of the Russian Federation, the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
A curiosity, in the manifesto published on PasteBin the hacker wrote
“A SQL Weapon is the most dangerous weapon on the Internet”
and the facts seem to confirm it.
Ourmine hacked the Netflix’s US Twitter account
22.12.2016 securityaffairs Social
The OurMine crew has hacked the Netflix US Twitter account (@Netflix) to post s promoting its website and hacking services.
On Wednesday, hackers belonging to the OurMine group hijacked the Netflix’s US Twitter account (@Netflix).
OurMine took over the Twitter account to promote its website. The incident is very serious, considering that the Netflix US Twitter account has 2.5 million followers. An attacker could compromise the attack to deliver malicious links and infect a huge number of followers.
OurMine is a very popular hacker group, in has multiple high-profile Twitter accounts in the past. The list of victims is very long and includes Mark Zuckerberg, Twitter co-founder Evan Williams, David Guetta Daniel Ek, former Twitter CEO Dick Costolo, the CEO and founder of Spotify, Google CEO Sundar Pichai, and many others.
Which is the motivation?
It seems that the OurMine group is linked to a Security Firm that is trying to obtain notoriety from the attacks and is offering its services to the targets, that evidently need them to avoid further incidents.

One of the messages posted by the group states:
“We are just testing people security (sic), we never change their passwords, we did it because there is other hackers can hack them and change everything.”
Back to the hack of the Netflix’s US Twitter account, the OurMice crew posted the following message to the hacked account:
“Don’t worry we are just testing your security,” states the post.
I strongly invite you to enable two-factor authentication for any platform that supports it.
At the time I was writing this post, @Netflix was restored to normality.
I’m trying to get in contact with the Ourmine crew for an interview … stay tuned!
Fraudsters are stealing money from several Groupon users
22.12.2016 securityaffairs Social
Many Groupon customers reported massive theft after crooks have placed orders in their name by using victims’ credentials likely retrieved elsewhere.
Fraudsters are targeting Groupon users stolen thousands of pounds from their bank accounts. Many customers reported a massive theft after crooks placed orders in their name by using victims’ credentials likely retrieved elsewhere.
Hackers take over the Groupon users’ accounts and place expensive orders, in one case the theft reached over £2,420.
Cyber criminals targeted customers of the online voucher service paying for holiday, gaming consoles (i.e. PlayStation 4) and iPhone with the hacked accounts. Below some of the messages posted on twitter by the victims:

Source The Telegraph
Of course, Groupon users are blaming the company for failing to detect the fraudulent activities, in many cases customers that have reported the suspicious transactions did not receive a response for several days.
Groupon clarified that its users are not at risk because its systems had been hacked, it confirms that fraudulent transactions were carried with account credentials stolen elsewhere, for example in one of the numerous massive data breaches recently occurred.
“What we are seeing is a very small number of customers who have had their account taken over by fraudsters,” said a spokesman for the company cited by the Telegraph. “As with any major online retailer, we take fraud extremely seriously and have a dedicated team to investigate customer issues as soon as they are reported.
“If someone believes they’ve been a victim of a fraudulent attack, we investigate it and if confirmed – block the account immediately and refund the customer’s money back to them.”
As usual, let me suggest to use strong passwords and never share them among multiple web services. When a service provides a two-factor authentication mechanism you have to enable it.
Fancy Bear APT tracked Ukrainian artillery units with an Android implant
22.12.2016 securityaffairs APT
The Russian APT group Fancy Bear used a malware implant on Android devices to track and target Ukrainian artillery units from late 2014 through 2016.
The popular hacking group, known as Fancy Bear, APT 28, Pawn Storm, Sednit or Sofacy, is once again in the headlines. Experts from the cyber security firm CrowdStrike reported the alleged Russian nation-state actor used malware implant on Android devices to track and target Ukrainian artillery units from late 2014 through 2016.
The malicious code was used by spy on target communication and retrieve locational data of the Ukrainian artillery units, this information would have likely been used by pro-Russian separatists fighting in eastern Ukraine to launch attacks against Ukrainian units. Late in the summer of 2016, researchers from CrowdStrike Intelligence began investigating a curious Android Package (APK) named ‘Попр-Д30.apk’ (MD5: 6f7523d3019fa190499f327211e01fcb). The APK contains a number of Russian language artifacts that were military in nature. Hackers used an implant for a legitimate app, but there is no evidence the application was made available in the Android app store.
“From late 2014 and through 2016, FANCY BEAR X-Agent implant was covertly distributed on Ukrainian military forums within a legitimate Android application developed by Ukrainian artillery officer Yaroslav Sherstuk.” states the report published by Crowdstrike. “The original application enabled artillery forces to more rapidly process targeting data for the Soviet-era D-30 Howitzer employed by Ukrainian artillery forces reducing targeting time from minutes to under 15 seconds. According to Sherstuk’s interviews with the press, over 9000 artillery personnel have been using the application in Ukrainian military.”
![]()
“Initial research identified that the filename suggested a relationship to the D-30 122mm towed howitzer, an artillery weapon first manufactured in the Soviet Union in the 1960s but still in use today.” states the report.
If the analysis published by the experts it correct, it means that the Kremlin military strategy made a large use of hacking campaigns to influence internal affairs of foreign governments and to support military operations.
Experts believe the Fancy Bear hacker group operates on behalf of the Russia’s military intelligence agency, GRU. According to the US intelligence, the group was responsible for hacks during the 2016 Presidential Election, its hacking operations aimed to support Donald Trump.
Russia has repeatedly denied hacking accusations.
The malicious code developed by Fancy Bear to track Ukrainian artillery units has many similarities with the one used in the hack of the Democratic National Committee.
Is the malicious implant effective?
According to open source data cited in the report, Ukrainian artillery forces have lost over 50% of their weapons in the 2 years of conflict and over 80% of D-30 howitzers. This represents the highest percentage of loss of any other Ukrainian artillery units.
One aspect very interesting of the story is the implant, an unseen variant of the X-Agent. The use of a malware with its characteristic demonstrates “FANCY BEAR’s expansion in mobile malware development from iOS-capable implants to Android devices”
Further details are available on the CrowdStrike report.
New Alice ATM Malware, a lightweight and efficient threat
22.12.2016 securityaffairs Virus
Alice ATM malware is a new threat targeting ATMs discovered by researchers at Trend Micro as part of a joint research project with Europol EC3.
Security experts from Trend Micro have discovered a strain of ATM malware, dubbed Alice, that was designed to target the safes of the self-serve machines.
The malware is very essential, it doesn’t implement data stealing capabilities and cannot be controlled via the numeric keypad of the ATM.
Researchers spotted for the first time the Alice ATM malware in November 2016 as part of a joint research project on ATM malware with Europol EC3, but they speculate is has been around since 2014.
When Alice was spotted for the first time, researchers thought if was a new variant of the known ATM malware Padpin .Further investigation led to the discovery of a new a new family called Alice.
“Trend Micro has discovered a new family of ATM malware called Alice, which is the most stripped down ATM malware family we have ever encountered.” states the analysis published by Trend Micro.”Unlike other ATM malware families, Alice cannot be controlled via the numeric pad of ATMs; neither does it have information stealing features. It is meant solely to empty the safe of ATMs.”
Alice ATM malware
According to the researcher, crooks need to physically access the ATM in order to empty its dispenser, a circumstance that suggests Alice has been designed for money mules.
“The existence of a PIN code prior to money dispensing suggests that Alice is used only for in-person attacks. Neither does Alice have an elaborate install or uninstall mechanism – it works by merely running the executable in the appropriate environment,” the researchers say.
The Alice ATM malware can also be used via Remote Desktop Protocol (RDP), but researchers haven’t found evidence of such use.
When Alice is executed, it creates in the root directory an empty 5 MB+ sized file called xfs_supp.sys and an error logfile called TRCERR.LOG. The first file is filled with zeros and doesn’t contain data, the second file (TRCERR.LOG) is an error log file used by the Alice malware. The log file traces any XFS API calls and related messages/errors. This file remains on the machine even when the malware is removed, likely for future troubleshooting or simply because the vxers forgot to remove it.
The researchers noticed that the malware only connects to the CurrencyDispenser1 peripheral and doesn’t include the code to use the PIN pad, likely it was designed to allow crooks with a physical access to the ATM to infect it via USB or CD-ROM.
“It only connects to the CurrencyDispenser1 peripheral and it never attempts to use the machine’s PIN pad. The logical conclusion is that the criminals behind Alice need to physically open the ATM and infect the machine via USB or CD-ROM, then connect a keyboard to the machine’s mainboard and operate the malware through it.” continues the analysis.
The Alice ATM malware was packed with a commercial, off-the-shelf packer/obfuscator called VMProtect. The malware implements a number of features to avoid the analysis of the researchers, it prevents the execution in environments that are not ATM and debuggers.
Alice supports the following three commands each issued via specific PINs:
Drop a file for uninstallation.
Exit the program run the uninstallation/cleanup routine.
Open the “operator panel,” to see the amount of cash available into the ATM.
In the attack scenario, the money mule enter the ID of the cassette ID for the ATM to dispense the money in it. The dispense command is sent to the CurrencyDispenser1 peripheral via the WFSExecute API.
ATMs typically have a 40-banknote dispensing limit, this means that crooks need to repeat the operation multiple times to dispense all the stored cash in the cassette.
Alice has no persistence method, crooks manually replace the Windows Task Manager (taskmgr.exe) with Alice, any command that would invoke the Task Manager would instead invoke Alice.
The report also includes the Indicators of Compromise, below the SHA256 hashes of the malware:
04F25013EB088D5E8A6E55BDB005C464123E6605897BD80AC245CE7CA12A7A70
B8063F1323A4AE8846163CC6E84A3B8A80463B25B9FF35D70A1C497509D48539
Hackers Suspected of Causing Second Power Outage in Ukraine
21.12.2016 thehackernews Hacking
The same group of hackers that caused the power outage across several regions in Ukraine last Christmas holidays might have once again shut down power supply in northern Ukraine during the weekend.
According to Ukrainian energy provider Ukrenergo, a cyber attack on Kyiv's power grid may have caused the power outages in the country on Saturday, December 17, near midnight.
The blackout affected the northern part of Kiev, the country's capital, and surrounding areas, Ukrenergo Director Vsevolod Kovalchuk explained in a post on Facebook.
Shortly after the incident, Ukrenergo engineers switched to manual mode and started restoring power in approximately 30 minutes in an effort to deal with the cyber attack. Power was fully restored after just an hour and fifteen minutes of the blackout.
According to Kovalchuk, the one responsible for the weekend outage could be an "external interference through data network," however, the company's cybersecurity experts are investigating the incident and will provide more information soon.
Although the reason for the outage is not yet confirmed, authorities believe that the unexpected power outage could be the latest in the series of cyber attacks that managed to strike the Ukrainian electric grid and financial infrastructure in December 2015.
The 2015 energy blackouts were caused with the help of a malware attack, known as BlackEnergy, which was distributed through boobytrapped Word documents and tricked recipients into enabling macros to activate the malicious payload.
Last year, the Ukraine's state security service SBU blamed Russia for causing outages by planting malware on the networks of several regional energy companies.
Also, the United States Cyber firm iSight Partners identified the perpetrator as a Russian group of hackers known as "Sandworm."
While security experts have found no hard evidence that links these attacks on Ukrainian energy grid to Russia, they believe that the attackers appear to be a nation state with significant resources.
SCADA system has always been an attractive target for cybercrooks, given the success of Stuxnet malware that was developed by the US and Israeli together to sabotage the Iranian nuclear facilities a few years ago, and "Havex" that previously targeted organizations in the energy sector.
Linux/Rakos, the new Linux malware threatening devices and servers
21.12.2016 securityaffairs Virus
A new Linux malware, dubbed Linux/Rakos is threatening devices and servers. The malware searches for victims via SSH scan.
A new Linux malware, dubbed Linux/Rakos is threatening devices and servers. The malicious code is written in the Go language and the binary is usually compressed with the standard UPX tool.
Apparently, frustrated users complain more often recently on various forums about their embedded devices being overloaded with computing and network tasks.
The attack is carried out via brute force attempts at SSH logins like many other Linux malware, including Linux/Moose. The new Linux/Rakos is able to compromise both embedded devices and servers with an open SSH port which is protected by an easy-to-guess password. The malware once compromised a device is able to recruit is in a botnet that could be abused for several malicious activities. The malware starts scanning the internet from a limited list IP addresses, then it spreads incrementally to more targets.
In some cases, attackers were able to compromise devices protected with a strong password that anyway had online service enabled and it was reverted to a default password after a factory reset.
The attack chain starts with the loading of a configuration file via standard input (stdin) in YAML format, the file contains information like lists of C&Cs, all the list of credentials to use in the brute force attacks against targets devices.
An example of Linux/Rakos configuration is available on ESET’s Github: https://github.com/eset/malware-ioc/tree/master/rakos.

As the second step, the malware starts a local HTTP service available at http://127.0.0.1:61314.
“There are two reasons why this is installed: the first is as a cunning method for the future versions of the bot to kill the running instances regardless of their name by requesting http://127.0.0.1:61314/et; second, it tries to parse a URL query for parameters “ip”, “u”, “p” by requesting http://127.0.0.1:61314/ex. The purpose of this /ex HTTP resource is still unclear at the time of writing and it seems not to be referenced elsewhere in the code.” reads the analysis published by ESET.
Experts from ESET also noticed that Linux malware creates a web server listening on all interfaces.
The bot scans the SSH service on various IP addresses obtained from the C&C server. Malware researchers also noticed that previous versions of the trojan also scanned for the SMTP service, a feature that is disabled in current versions.
When the malware is able to access a device with its credentials it runs two commands (id, uname -m). Then the malicious code checks whether if it is possible to upload to the new victim and goes on.
The backdoor is able to update the configuration file (from https://{C&C}/upgrade/vars.yaml) and also to upgrade itself.
The Linux/Rakos isn’t able to maintain persistence after the system is rebooted. Researchers at ESET provided the following suggestions to clean up infected devices:
connect to your device using SSH/Telnet,
look for a process named .javaxxx,
run commands like netstat or lsof with -n switch to confirm that it is responsible for unwanted connections,
(voluntarily) collect forensic evidence by dumping the memory space of the corresponding process (with gcore for example). One could also recover the deleted sample from /proc with cp /proc/{pid}/exe {output_file}
the process with the -KILL
How to hack Panasonic In-Flight Entertainment IFE Systems
21.12.2016 securityaffairs Hacking
A researcher at IOActive disclosed several vulnerabilities found in Panasonic Avionics in-flight entertainment, aka IFE systems.
The in-flight entertainment (IFE) and communications systems manufactured by Panasonic Avionics are among the most common components in the aviation industry.
According to data provided by the company, it has delivered more than 8,000 in-flight entertainment and communications systems and 1,300 in-flight connectivity solutions to major airlines.
Older models of Panasonic IFE systems (e.g. 3000/3000i) rely on Linux, but the newer ones belonging to the X Series products run on Android OS.
The security of IFE systems is crucial, the Panasonic Avionics recently launched a private bug bounty program offering rewards ranging between $100 and $10,000 to the participants.
Main components of the IFE systems are:
The seat display unit (SDU) that an embedded device that allows passengers to watch movies and connect to the Internet via a touchscreen. Sometimes the SDU is also equipped with a personal control unit (PCU).
The cabin crew panel that controls lights and other features of the aircraft.
The system control unit (SCU) is the server that provides flight information, and other features such as on-board shopping capabilities.
IFE systems
Ruben Santamarta, a security researcher from IOActive decided to participate the bug bounty program. He analyzed the latest firmware updates for the IFE systems used by major airlines, including Emirates, Air France, United, American, KLM, Scandinavian, Aerolineas Argentinas, Virgin, Iberia, Singapore, FinnAir, Qatar, and Etihad.
Santamarta found several flaws in the firmware updates, including a SQL Injection flaw and a bug that allows bypassing credit card checks.
Below the video PoCs published by the researcher that demonstrate how to bypass credit card checks, to trigger arbitrary file access issues and a SQL injection flaw. In the video the hacker interacted with the IFE systems using the touchscreen and PCU.
According to Santamarta, the hack of the IFE system could allow the attacker to interfere with flight operations and to steal sensitive information. It is important to highlight that if the IFE system is physically separated from aircraft control system, such kind of attacks will have no impact on the flight safety.
“On the IT side, compromising the IFE means an attacker can control how passengers are informed aboard the plane. For example, an attacker might spoof flight information values such as altitude or speed, and show a bogus route on the interactive map. An attacker might compromise the CrewApp unit, controlling the PA, lighting, or actuators for upper classes. If all of these attacks are chained, a malicious actor may create a baffling and disconcerting situation for passengers.” reads the analysis published by IOActive.
“The capture of personal information, including credit card details, while not in scope of this research, would also be technically possible if backends that sometimes provide access to specific airlines’ frequent-flyer/VIP membership data were not configured properly.”
Unfortunately, in some cases, the lack of a physical separation between IFE systems and control systems could allow an attacker to threaten the flight safety.
“In some scenarios such an attack would be physically impossible due to the isolation of these systems, while in other an attack remains theoretically feasible. The ability to cross the ‘red line’ between the passenger entertainment and owned devices domain and the aircraft control domain relies heavily on the specific devices, software and configuration deployed on the target aircraft,” Santamarta added.
IOActive reported these findings to Panasonic Avionics in March 2015, but there is no information about their fix.
Victims of the CryptXXX v.3 can now use a free tool to decrypt their files
21.12.2016 securityaffairs Virus
Security researchers have released a decryption tool for unlocking files encrypted by the notorious CryptXXX v.3 ransomware.
CryptXXX v.3 ransomware was defeated, researchers have released a decryption tool for unlocking encrypted files. The decryption tool was included in the RannohDecryptor utility, a free application shared by the No Ransom Project.
The utility was already able to unlock a limited list of files encrypted by the CryptXXX v.3, but not it is able to recover almost any file targeted by the v.3.
The CryptXXX ransomware is one of the ransomware with the highest number of victims in the wild that targeted mostly US users. Russia, Germany and Japan are also in the top-targeted countries.
CryptXXX ransomware was first spotted in April, experts believe it allowed criminal organizations to earn a lot of money.
The experts noted an intense activity involving the malware that was spread in campaigns leveraging on Angler, Neutrino, and Magnitude exploit kits.
Since April, CryptXXX has rapidly evolved, according to the firm SentinelOne, in June a new campaign that fixed the security flaws that allowed decrypting locked files without paying the ransom.
In May, experts at Kaspersky Lab have updated their decryption tool to adapt to the second version of the CryptXXX ransomware in the RannohDecryptor 1.9.1.0.
Every time the author of the CryptXXX released a new version, experts from Kaspersky were able to exploit flaws in the code of the ransomware to unlock the encrypted files.
The researchers from Kaspersky Lab, discovered the malware leverage on a DLL written in Delphi and uses several encryption algorithms to lock the files.
Once CryptXXX v.3 locks files, it appends the extensions .crypt, .cryp1 and .crypz. The latest variant of the malware also includes a module called stiller.dll that is tasked with stealing account credentials from the victim’s machine
“After the files are encrypted and all the valuable data is transferred to the criminals, the Trojan displays a message to the victim demanding a ransom,” Kaspersky Lab researchers said.
If you are one of the victims of ransomware give a look at the list of available decryption utilities that was included in the No Ransom website.
MethBot advertising fraud campaign is making up to $5M Revenue per Day
21.12.2016 securityaffairs Virus
A criminal gang dubbed AFT13 is making between $3 Million to $5 Million per day from US and media companies in biggest advertising fraud ever dubbed Methbot
This is a case study, a criminal gang dubbed AFT13 is making between $3 Million to $5 Million per day from US and media companies in biggest advertising fraud ever.
Experts from the online fraud-prevention firm White Ops who discovered the Ad fraud campaign dubbed it as Methbot. The structure implemented by the criminal organization is able to generate more than 300 Million fraudulent video ad impressions every day.
What is Methbot?
“Controlled by a single group based in Russia and operating out of data centers in the US and Netherlands, this “bot farm” generates $3 to $5 million in fraudulent revenue per day by targeting the premium video advertising ecosystem. We continue to detect and block fraudulent activity generated by Methbot on behalf of all of our customers.” states the report published by White Op.
The AFT13 gang has built an army of automated browsers that spoof fraudulently acquired IP addresses that is able to “watch” as many as 300 million video ads per day on falsified websites designed to look like premium publisher inventory.
“More than 6,000 premium domains were targeted and spoofed, enabling the operation to attract millions in real advertising dollars.” states the report.
According to the researchers, the criminal organization has registered more than 6,000 domains and 250,267 distinct URLs impersonating major brands and high-profile websites like Vogue, CBS Sports, Fox News and the Huffington Post, and selling fake video ad slots.
White Ops spotted the fraudulent activity associated to Methbot last year in September, but in October 2016 they observed a significant increase of their activities.
The gang seems to have Russian origin and used servers hosted in Texas and Amsterdam to power more than 570,000 bots with forged IP addresses.
Below a Snapshot of the Methbot Operation:
The cyber criminals used a sort of inventory of video-ad to display to its fake media websites for money, with this simple mechanism it was fooling the ad marketplace into thinking that ad content it was proposing was being watched by legitimate website visitors.
The video ads were viewed by Methbot bots, the software was developed to mimic a user interaction while watching ads (i.e. social network login information and mouse movements).
“Since both human audiences and premium publisher inventory are in high demand, Methbot focuses on manufacturing both of these as its product. By supplying faked audiences and hijacking the brand power of prestigious publishers through faked domains and falsified inventory, Methbot is able to siphon away millions in real advertising dollars.” continues the report.

The Methbot bots watched as many as 300 Million ads per day, with an average payout of $13.04 per 1000 faked views for each compromised IP address, and they used 570,000 compromised IP addresses.
White Ops generates between $3 Million and $5 Million in revenue every 24 hours.
White Ops reported its findings to the FBI and it is supporting authorities during the investigation.
Google presents the Project Wycheproof to test crypto libraries against known attacks
21.12.2016 securityaffairs Attack
Google released the Project Wycheproof, an open source tool designed to test most popular cryptographic software libraries against known attacks.
Google presented the Project Wycheproof, an open source Crypto Library Testing Tool that was launched to allow development teams to discover security vulnerabilities in popular cryptographic software libraries.
“Project Wycheproof tests crypto libraries against known attacks. It is developed and maintained by members of Google Security Team, but it is not an official Google product.” states the description of the project.
“At Google, we rely on many third party cryptographic software libraries. Unfortunately, in cryptography, subtle mistakes can have catastrophic consequences, and we found that libraries fall into such implementation pitfalls much too often and for much too long.”
The Project Wycheproof is completely developed in Java and implements tests for the most popular cryptographic libraries, including AES-EAX, AES-GCM, DH, DHIES, DSA, ECDH, ECDSA, ECIES and RSA. The more than 80 test cases developed by Google experts have led to the discovery of over 40 bugs in RSA, DSA.
In a single platform, researchers at Google included more than 80 test cases that cover known attacks scenarios against the crypto libraries. Google wants to share its experience to improve the security in development processes.
“Project Wycheproof is named after Mount Wycheproof, the smallest mountain in the world. The main motivation for the project is to have a goal that is achievable. The smaller the mountain the more likely it is to be able to climb it.” states Google.
The researchers who developed the platform explained that Project Wycheproof help them to discover the bugs present in the third party cryptographic software libraries they use for their projects. The testing tool allowed them to uncover more than 40 bugs.
“We have over 80 test cases which have uncovered more than 40 bugs. For example, we found that we could recover the private key of widely-used DSA and ECDHC implementations.” continues Google.

The Project Wycheproof is maintained by members of the Google Security Team, but it is not an official Google product. It is an open project, this means that everyone could share its experience to add another testing cases.
The maintainers will include them only after the development teams behind vulnerable libraries will patch them.
The bug discovered by the security experts that will be submitted to the Google Team qualify for a reward if the maintainers of the affected library cover it with a bug bounty program.
'MethBot' Ad Fraud Operators Making $5 Million Revenue Every Day
21.12.2016 thehackernews Virus
The biggest advertising fraud ever!
A group of hackers is making between $3 Million to $5 Million per day from United States brands and media companies in the biggest digital ad fraud ever discovered.
Online fraud-prevention firm White Ops uncovered this new Ad fraud campaign, dubbed "Methbot," that automatically generates more than 300 Million fraudulent video ad impressions every day.
The cyber criminal gang, dubbed AFT13, has developed Methbot robo-browser that spoofs all the necessary interactions needed to initiate, carry out and complete the ad transactions.
The hackers, allegedly based in Russia, registered more than 6,000 domains and 250,267 distinct URLs impersonating brand and names of high-profile websites like ESPN, Vogue, CBS Sports, Fox News and the Huffington Post, and selling fake video ad slots.
Cyber criminals behind Methbot are using servers hosted in Texas and Amsterdam to power more than 570,000 bots with forged IP addresses, mostly belongs to the United States, which make it appear ads are being viewed by US visitors.

The cyber criminals then obtain video-ad inventory to display to its fake media websites for top dollar and fools the ad marketplace into thinking the ad content is being watched by legitimate website visitors.
But in reality, these video ads are viewed by Methbot's fake viewers, as the fraud also includes an automated software program that mimics a user watching ads.
To make their bots look more real, the gang is using methods like automated faked clicks, social network login information, and mouse movements.
The security firm found that the fraudsters’ bot army watched as many as 300 Million ads per day, with an average payout of $13.04 per 1000 faked views.
If you multiply this number by more than 570,000 compromised IP addresses, the money rolls in.
The company believes that Methbot creates an estimated between 200 Million and 300 Million fraudulent video ad impressions per day, targets roughly 6,000 publishers and generates between $3 Million and $5 Million in revenue every 24 hours.
White Ops initially noticed the activity of Methbot last year in September, but in October 2016, the campaign dramatically risen.
The Methbot operation is headquartered in Russia but uses data centers in Dallas and Amsterdam. Although this information is not enough to prove that the hackers are of Russian origin, White Ops evidently believes that the hacker group is based in Russia.
White Ops has notified the FBI about the scam and has been working with federal law enforcement for weeks now.
Hacker Demonstrates How Easy In-flight Entertainment System Can Be Hacked
21.12.2016 thehackernews Hacking
Next time when you hear an announcement in the flight, “Ladies and gentlemen, this is your captain speaking…," the chances are that the announcement is coming from a hacker controlling your flight.
Dangerous vulnerabilities in an in-flight entertainment system used by the leading airlines, including Emirates, United, American Airlines, Virgin, and Qatar, could let hackers hijack several flight systems and even take control of the plane.
According to security researchers from IOActive, the security vulnerabilities resides in the Panasonic Avionics In-Flight Entertainment (IFE) system used in planes run by 13 major airlines, providing a gateway for hackers which is absolutely terrifying.
The security holes could be exploited by hackers that could allow them to spoof flight information like map routes, speed statistics, and altitude values, and steal credit card information.
IOActive's Ruben Santamarta managed to "hijack" in-flight displays to change information like altitude and location, control the cabin lighting, as well as hack into the announcements system.
"Chained together this could be an unsettling experience for passengers," said Santamarta. "I don't believe these systems can resist solid attacks from skilled malicious actors. This only depends on the attacker's determination and intentions, from a technical perspective it's totally feasible."
Besides these critical issues, the researcher said in some instances; hackers could access credit card details of passengers stored in the automatic payment system and use their frequent flyer membership details to capture personal data.
The vulnerabilities affect 13 different airlines that use Panasonic Avionics system, which include American Airlines, United, Virgin, Emirates, Etihad, Qatar, FinnAir, KLM, Iberia, Scandinavian, Air France, Singapore, and Aerolineas Argentinas.
The vulnerabilities were reported to Panasonic in March last year, and the researcher waited more than a year and a half to go public, so the company had "enough time to produce and deploy patches, at least for the most prominent vulnerabilities."
Emirates is working with Panasonic to resolve these issues and regularly update its systems. "The safety of our passengers and crew on board is a priority and will not be compromised," Emirates said, reported the Telegraph.
Santamarta is the same researcher who warned of security issues in systems used by different aircraft in the past.
Back in 2014, he discovered that it was possible to reverse engineer a bug, which let him connect to the Wi-Fi signal or the in-flight entertainment system to connect to airplanes’ equipment, including the navigation system.
For in-depth technical details about the new vulnerabilities discovered by Santamarta, you can head on to IOActive's official blog post published today.
Chtěli slevu a šeredně se napálili. Podvodníkům naservírovali karty na zlatém podnosu
20.12.2016 Novinky/Bezpečnost Viry
Využít aktuálního shonu se snaží kybernetičtí piráti pouhých pár dní před Vánoci. Jak varovali bezpečnostní experti antivirové společnosti Eset, podvodníci se na síti vydávají za prodejce známých módních značek a z důvěřivců lákají informace o jejich platebních kartách. Snaha ušetřit při nákupu vánočních dárků se tak může krutě vymstít.
Slevové akce se objevují na různých sociálních sítích a klidně i legitimních webech. Doposud piráti lákali například na nákup kabelek Michael Kors, bot Ugg či sandálů Birkenstock s výraznými slevami.
Žádná ze jmenovaných společností ale samozřejmě nemá s falešnými weby nic společného. „Tyto podvodné stránky se šíří e-mailem nebo přes legitimní účty na Facebooku, které útočníci hacknuli buď pomocí technik sociálního inženýrství, nebo pomocí škodlivého kódu,“ uvedl Ondrej Kubovič, specialista na digitální bezpečnost ve společnosti Eset.
Zboží za nereálně nízké ceny
„Bez souhlasu skutečného majitele účtu na Facebooku sdílejí na jeho profilu fotografie propagující toto falešné zboží za nereálně nízké ceny,“ doplnil Kubovič.
Podle něj falešné obchody nepoužívají šifrovanou komunikaci. Počítačoví piráti se kvůli tomu dokážou snadno dostat například k číslu platební karty, ověřovacímu bezpečnostnímu kódu a zároveň i k osobním údajům uživatele.
„Předvánoční období představuje pro podvodníky skvělou příležitost. Jejich falešné stránky si totiž lidé ve shonu při hledání vánočních dárků velmi lehce spletou s legitimními weby. Na stránkách by si proto měli všímat jakýchkoli podezřelých znaků. Těmi jsou například extrémně nízké ceny, vysoké slevy, překlepy, gramatické chyby či absence certifikátu SSL,“ uzavřel bezpečnostní expert.
Není to poprvé
Falešné obchody, které byly pro vylákání informací o platebních kartách doposud využity, naleznete v tabulce níže. Není nicméně vyloučeno, že se kyberzločinci nebudou snažit uživatele napálit i s nějakými úplně jinými smyšlenými e-shopy.
Podobné triky počítačových pirátů nejsou nijak výjimečné. V minulém týdnu se zase tuzemské uživatele snažili napálit slevovými akcemi velkých obchodních řetězců. [celá zpráva]
Podvodné e-shopy zachycené bezpečnostními experty
Uggclassicstyle.com
Ugg-sk.com
Uggs.cz
Bk-sale.com
Uggaustraliabox.com
Michaelkorsbuy.com
Shoesfootus.com
Zdroj: Eset
Nenechte se vydírat. Nový nástroj zatočí s téměř každým ransomwarem
20.12.2016 cnews.cz Viry
Bezpečnostní experti ze společnosti Cybereason vytvořili nový nástroj RansomFree. Už název prozrazuje to hlavní – bojuje s ransomwarem. To je specifický druh malwaru, který se usadí na počítači a zablokuje část jeho funkcí nebo přístup k souborům, přičemž odblokování podmiňuje zaplacením.
Cybereason slibuje lepší ochranu, než jakou poskytují běžné antiviry. Ty většinou pouze porovnávají otisk škodlivého kódu s vlastní databází malwaru. Jenže denně vzniká nová havěť nebo existují takové typy malwaru, které pravidelně mění podobu (tedy i digitální otisk) a jsou těžko stopovatelné.
RansomFree používá behaviorální ochranu. Neporovnává škodlivý kód s databází, ale vytvoří na počítači tzv. honeypot, do kterého se chytí i nový, dosud nepopsaný, ransomware. Nástroj vytvoří náhodně vygenerované soubory a složky na disku a sleduje jejich chování. Pojmenovává je tak, aby v seznamu byly vždy nahoře.
Ochrana sleduje, které aplikace se snaží se soubory pracovat, měnit je nebo dokonce šifrovat (to dělá většina ransomwaru). Protože jsou náhodné soubory první na ráně, RansomFree po detekci zablokuje záškodnický proces v provádění další činnosti. Při podezření pochopitelně upozorní uživatele.

RansomFree generuje náhodné soubory jako vábničku pro ransomware
Nástroj si poradí také s ransomwarem, který nešifruje soubory na disku, ale využívá děr ve Flashi, prohlížečích apod., aby získal hlubší přístup do systému a zablokoval jeho části.
Cybereason sledoval chování tisíců různých ransomwarů, které ale vycházejí ze základů několika desítek různých kódů (Locky, Cryptowall, TeslaCrypt, Jigsaw, Cerber apod.). Žádná ochrana není dokonalá, ale RansomFree slibuje 99% účinnost. Ideálně by měl fungovat i s dobrou antivirovou ochranou. Na pozadí spolkne asi 50 MB RAM a nijak nezatěžuje procesor.

RansomFree zachytil hrozbu
RansomFree je (a bude) zdarma. Zatím podporuje jen Windows 7, 8, 10, 2008 R2 a 2012 R2, ale v budoucnu se možná dostane i na jiné systémy. Stáhnout si jej můžete z této stránky.
Je třeba mít na paměti dvě věci. RansomFree i další podobné nástroje slouží k prevenci. Napadený počítač nevyléčí. Pokud už ransomware zašifroval soubory, je pozdě. Vůbec nejlepší ochranou je navštěvovat jen ověřené weby a nestahovat neověřené soubory z webu ani e-mailových příloh.
Nebezpečný virus vydávají za reklamu. Ochromí celou počítačovou síť
20.12.2016 Novinky/Bezpečnost Viry
Národní bezpečnostní tým CSIRT.CZ varoval před nebezpečným virem, který se v posledních dnech šíří internetem doslova jako lavina. Škodlivý kód zvaný DNSChanger napadá výhradně routery – brány do světa internetu, prostřednictvím kterých se pak počítačoví piráti dostanou do celé počítačové sítě.
Hrozba je závažná především tím, že se lidé mohou nakazit na legitimních webech, nebo dokonce i sociálních sítích. „Útočník nejdříve ukryje škodlivý kód do obrázku, který umístí jako reklamu na populární servery,“ podotkl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
„Kód v obrázku následně přesměruje oběti na server útočníka, kde je připraven samotný exploit kit DNSChanger. Ten se pak postará o napadení špatně zabezpečeného routeru, na kterém nastaví DNS servery útočníka,“ konstatoval Bašta.
Tím má kyberzločinec celou síť pod kontrolou. „Útočníkovi to umožňuje ovládnout síťový provoz na všech zařízeních za tímto routerem, bez ohledu na používaný operační systém,“ podotkl bezpečnostní expert.
DNSChanger může výše popsaným způsobem napadnout více než 150 různých typů routerů. Jde například o modely D-Link DSL-2740R, NetGear WNDR3400v3, Netgear R6200, COMTREND ADSL Router CT-5367 C01_R12 či Pirelli ADSL2/2+ Wireless Router P.DGA4001N.
Zablokují či přesměrují připojení
Že je router zavirovaný, mohou uživatelé poznat například podle toho, že jim přestane z připojených počítačů zcela fungovat internetové připojení, případně se při snaze o připojení na nějakou webovou stránku zobrazí úplně jiný web.
Přesně to se stalo už v minulosti kvůli zranitelnosti známé jako „rom-0“. Místo serverů, jako jsou například Seznam.cz nebo Google.com, se poškozeným zobrazila hláška o nutnosti instalace Flash playeru. Místo té se ale do PC stáhnul další virus. Útočníci tak rázem měli přístup nejen k routeru, ale i k připojenému počítači.
Na brány do světa internetu se zaměřují kyberzločinci stále častěji. Využívají toho, že zabezpečení těchto internetových zařízení uživatelé především v domácnostech velmi podceňují, někdy to ale platí i o firmách. Březnová studie Cisco Annual Security Report totiž ukázala, že devět z deseti internetových zařízení má slabá místa.
Uživatelé nejsou úplně bezbranní
Hlavní problém je podle bezpečnostních expertů v tom, že routery není možné chránit antivirovými programy, jako je tomu u počítačů. I tak ale nejsou uživatelé úplně bezbranní.
„Hlavní způsob, jak této hrozbě předejít, představuje upgrade firmwaru routeru na aktuální verzi a nepoužívat mnohdy triviální přednastavené přihlašovací jméno a heslo. Rovněž je vhodné zvážit přihlašování k routeru pouze z vnitřní sítě, a nikoliv z internetu,“ uvedl již dříve Pavel Matějíček, manažer technické podpory společnosti Eset.
Do konfigurace routerů by se nicméně neměli pouštět méně zkušení uživatelé. Mohou totiž nevhodným nastavením způsobit více škody než užitku. Paradoxně tak mohou klidně otevřít zadní vrátka pro útočníky.
RansomFree Tool Detects Never-Seen-Before Ransomware Before It Encrypts Your Data
20.12.2016 thehackernews Virus
Ransomware has risen dramatically since last few years, so rapidly that it might have already hit you or someone you know.
With hundred of thousands of ransomware variants emerging every day, it is quite difficult for traditional signature-based antivirus tools to keep their signature database up-to-date.
So, if signature-based techniques are not enough to detect ransomware infection, then what else can we do?
The solution is RansomFree.
Boston-based cyber security firm Cybereason has released RansomFree — a real-time ransomware detection and response software that can spot most strains of Ransomware before it starts encrypting files and alert the user to take action.
RansomFree is a free standalone product and is compatible with PCs running Windows 7, 8 and 10, as well as Windows Server 2010 R2 and 2008 R2.
Instead of regularly updated malware signatures to fight the bad programs, RansomFree uses "behavioral and proprietary deception" techniques to detect new ransomware variants in action before the threat has a chance to encrypt your data.
The company analyzed tens of thousands of ransomware variants belonging to more than 40 ransomware strains, including Locky, TeslaCrypt, Cryptowall, and Cerber and "identified the behavioral patterns that distinguish ransomware from legitimate applications."
"The ability to detect and stop never-before-seen ransomware is one of the features that makes RansomFree so unique," the company's spokesperson told The Hacker News. "The tool identifies ransomware behaviors including attempts targeting local disks, as well as detecting and stopping encryption over shared network drives."
If it finds any such behavior on your PC, RansomFree suspends that program and flags it for your review. It’s then up to you to either enable the program or allow RansomFree to stop it permanently.
By default, the anti-ransomware tool suspends any activity it finds suspicious — even if it is a legitimate encryption software that has some behavior in common with ransomware.
With this type of approach, even brand new ransomware infections will be stopped in their tracks without you having to worry about updates to the malicious software.
"Pervasive ransomware variants have outsmarted traditional endpoint defenses, such as antivirus software, leaving individuals exposed to the real dangers of cyber crime," said Uri Sternfield, Cybereason Senior Security Researcher.
"What's worse, a major part of the consumer population threatened by ransomware attacks have little recourse but to either pay the ransom, or risk losing their stolen content."
RansomFree can detect 99 percent of all ransomware strains and will also offer you protection against future ransomware strains, as the company said RansomFree would be updated daily in an attempt to stay ahead in this arms race.
RansomFree is free to download directly from Cybereason's official site.
Earlier this year, we also reported about another behavior-based anti-ransomware tool, dubbed RansomWhere, available for Mac OS X users that can identify ransomware-like behavior by continually monitoring the file-system for the creation of encrypted files by suspicious processes.
RansomWhere also works in a similar way like RansomFree, blocking the suspicious processes and waiting for the user to decide whether to allow or stop the process.
Besides using an anti-ransomware tool, you are also recommended to regularly backup your files, keep your OS and software programs up-to-date, disable Java and Flash when possible, do not download apps from unknown, untrusted websites, and be extra conscious when opening links and downloading attachments in an email.
A new Ukraine power outage may have been caused by hackers
20.12.2016 securityaffairs Hacking
A cyber attack against the Government Ukraine energy company Ukrenergo may be the root cause of power outage that occurred in Ukraine late on Saturday.
A new cyber attack may be the root cause of power outage that occurred in Ukraine late on Saturday.
According to the Ukraine energy company Ukrenergo, the power outage occurred at the midnight between Saturday and Sunday, the problems affected the”North” substation at Petrivtsi.
The incident caused blackouts in the city of Kiev and neighboring regions.
The company published an official statement to announce the power outage, unfortunately at the time I was writing the website of the Government Ukraine energy company Ukrenergo is down.
The head of the NEC “Ukrenergo” Vsevolod Kovalchuk explained in a message posted on Facebook that experts at the company were able to restore power in 30 minutes with a manual procedure. According to Kovalchuk, the operations were fully restored after just over an hour.
“Our experts quickly switched the equipment into the manual mode and already after 30 minutes began restoring power. In one hour and fifteen minutes power was fully restored,” he wrote.
“For the time being, the main version is the external interference through the data network. Our experts in cybersecurity promise to provide a report in the near future,” he added.
Kovalchuk pointed out that an equipment malfunction or a cyber attack can be the cause of the problem. According to Kovalchuk, an “external interference through the data network” could have caused the power outage.
The experts at Ukrenergo are investigating the power outage.
Of course, the incident brought to mind the power outage that occurred in December 2015 in Ukraine. The Ukrainian security service SBU and several security experts accused Russia of causing outages.
According to a report published by Booz Allen Hamilton, the attacks that caused the power outage in Ukraine were part of a huge hacking campaign that targeted across the years the critical infrastructure of the country.
Experts at eiSight Partners speculated that the Russian Sandworm APT group was responsible for the Ukrainian power outage.
Alleged Russian state-sponsored hackers have used the BlackEnergy malware alongside with a DDoS attack to compromise the power plants in Ukraine and delay restore operations.
In 2015 power outage, Ukrainian experts were able to restore service within 3-6 hours with manual operations.
Wordfence warns of a huge increase in brute force attacks on WordPress
20.12.2016 securityaffairs Attack
Security experts from Wordfence observed a huge increase in Brute Force attacks in the last three weeks.
The security firm Wordfence is warning the WordPress community of a spike in the number of brute force attacks against websites running WordPress. has increased significantly in December compared to the previous period.
The researchers observed brute force attacks on WordPress websites soar in December.
Brute force attacks still represent a valid method to guess the admin credentials. According to Wordfence, in the last weeks, such kind of attacks increased in a significant way.
“Three weeks ago, on November 24th, we started seeing a rise in brute force attacks. As a reminder, a brute force attack is one that tries to guess your username and password to sign into your WordPress website.” states a blog post published by Wordfence.
In the period between October 16 and November 24, the experts observed less than 500,000 websites were attacked each day. The number of websites attacked soared starting with November 24, it was greater than 700,000 in some days. Wordfence blocked as many as 23 million brute force attack attempts per day.

The number of unique attack IPs also increased in the same period, passing from an average of roughly 13,000 per day to more than 30,000.
Top 20 countries from which the brute force attacks were launched during the past 24 hours is led by Ukraine (15,7% of total attacks), followed by France (11.1%), Russia (6.8%), the U.S. (6.6%), India (5.8%), China (4.2%), Germany (3.2%), Italy (2.4%) and the U.K. (2.2%).
“Most of the attacks come from 8 IP addresses in Ukraine.” states the analysis. “These IPs all belong to the same organization and are on the same network. Doing a Google search on the top IP brings back many reports of abuse around the Internet. They belong to a hosting company in Ukraine called “Pp Sks–lugan“. The servers are a mix. Some aren’t running any services. Others appear to be running Windows IIS web server. ” “These IPs are using brute force attacks exclusively. They don’t launch any sophisticated attacks. They are hammering away at WordPress sites at a rate of over a quarter million login attempts each, in some cases, during a 24 hour period.”
The researcher also tracked other specific networks used in the attacks, France sources have been tracked back to a company called Iliad-Entreprises. Other organizations involved in the cyber attacks are OVH, GoDaddy and BSNL.
hacker
Recently the firm RIPS Technologies published a report based on the analysis of 44,705 plugins in the official WordPress plugins directory and discovered that more than 8,800 of them are flawed.
When it comes to WordPress attacks involving the exploitation of vulnerabilities, malicious actors usually target unpatched plugins. A study conducted recently by RIPS Technologies has showed that of 44,000 plugins available in the official WordPress plugins directory, 8,800 are affected by at least one vulnerability.
Faketoken, the Android ransomware banker that encrypted files
20.12.2016 securityaffairs Android
The banker Android ransomware Faketoken that steals financial informaton and sensitive data now also implements file-encrypting abilities.
Security experts from Kaspersky Lab have spotted a strain of known Android malware that now implements also ransomware-like abilities.According to the researchers, Vxers are adding file-encrypting capabilities to traditional mobile banking trojans, the result is a malware that is able both to steal sensitive data and lock user files on the phone’s SD card.This malware with hybrid capabilities is also called ransomware banker.The ransomware functionality in mobile banking Trojans is considered an exception, the Svpeng malware discovered in 2014 is one of the first malware with this ability. The modern mobile ransomware doesn’t limit their actions to block the screen, but it also encrypts user files.The trojan discovered by Kaspersky is dubbed Faketoken, the name suggests its primary feature is to steal login credentials by generating fake login screens for more than 2,000 financial applications. Faketoken is also able to steal credit card information by displaying victims displays phishing pages.
Researchers noticed that file-encrypting capabilities were implemented in Faketoken since July and have since released thousands of versions that include new features.
“We have managed to detect several thousand Faketoken installation packages capable of encrypting data, the earliest of which dates back to July 2016.” reads a blog post published by Kaspersky.
Trojan-Banker.AndroidOS.Faketoken is distributed under the guise of various programs and games, often imitating Adobe Flash Player.”
The researchers confirmed the number of the victims exceeds 16,000 users, they observed infections in 27 countries, mostly in Russia, Ukraine, Germany, and Thailand.
Faketoken uses an AES symmetric encryption algorithm to encrypt the files, this is a good news for the victims that have a chance of decrypting them without paying a ransom.
“The Trojan receives the encryption key and the initialization vector from the C&C server. The encrypted files include both media files (pictures, music, videos) and documents. The Trojan changes the extension of the encrypted files to .cat.” continues the analysis.
The researchers highlighted the fact that file encryptions are not popular with the mobile malware developers because most files stored on a mobile device are usually copied to the cloud.
For more in on Faketoken give a look at the technical analysis published by Kaspersky.
NASA na svou síť instalovala VPN, je rychlejší i bezpečnější
20.12.2016 SecurityWorld Zabezpečení
AT&T pomohla americké vesmírné agentuře NASA se zabezpečením mezinárodní sítě antén Deep Space Network (DSN). Propojila je pomocí virtuální privátní sítě.
„Naše technologie pomáhá NASA prozkoumávat nejhlubší kouty známého vesmíru,“ říká Mike Leff, viceprezident AT&T. „Deep Space Network je mocný systém pro řízení, sledování a monitorování stavu sond a dalších kosmických lodí, vysílaných na meziplanetární cesty.“
Nová síť poskytne vysoce zabezpečené a spolehlivé komunikační rozhraní pro přenos telemetrických dat sesbíraných z rádiových signálů kosmických lodí, sond a stanic.
DSN tvoří síť velkých antén a tří komunikačních stanic (rozmístěných v USA, Španělsku a Austrálii), využívaných mimo jiné i pro radarové mapování prolétávajících asteroidů. Síť rovněž umí odesílat informace objektům – mimo jiné ovládala Mars rover nebo New Horizons a Juno sondy, obíhající Jupiter.
DSN je strategicky rozmístěna po celé planetě, díky čemuž umožňuje stabilní komunikaci se sondami a jinými vesmírnými objekty. Využívá ji také evropská agentura ESA a japonská JAXA.
Jak planeta postupně rotuje a sondy ztrácí dosah jedné komunikační sítě, jiná naopak signál pochytí a pokračuje v komunikaci bez přerušení.
Podle Mika Leffa byla VPN instalována ve dvou fázích. První fáze skončila letos v létě, zatímco druhá na začátku prosince.
Nově zřízená VPN umožňuje až trojnásobně rychlejší přenos dat než dříve a podporuje komunikaci v téměř reálném čase, přičemž zároveň informace mnohem lépe zabezpečuje.
„Ochrana integrity dat plynoucích s DSN je klíčová pro vědecký výzkum,“ popsal Leff Computerworldu. „Bohužel žijeme ve světě, kde jednotlivci i celé státy jsou ochotni a připraveni hacknout jakýkoli počítačový systém pro různé vlastní potřeby.“
Ezra Gottheil, analytik u Technology Business Research, říká, že dává smysl pro jakoukoli uzavřenou síť – nehledě na její velikost – používat VPN.
„Tato síť je velká jen vzdáleností, ne počtem uzlů,“ dodává. „Potřebují kompresi a zabezpečení, takže VPN je vhodná volba.“
Patrick Moorhead, analytik u Moor Insights & Strategy, souhlasí.
„Jsem překvapený že nepoužívali VPN už předtím a myslím, že bez ní existuje velká hrozba ztráty duševního vlastnictví i sabotáže,“ popisuje. „Hackeři jsou aktivní již desítky let. Miliardy dolarů se utrácí na průzkum vesmíru a mnoho ze vzniklých technologií lze použít pro obranné účely. Vesmírný program je tedy lákavý cíl pro kriminální živly… je chytré využít VPN k zabezpečení svých investic.“
Více než 8 800 pluginů pro WordPress ze 44 705 je děravých
19.12.2016 Root.cz Zranitelnosti
Společnost RIPS Technologies prověřila bezpečnost pluginů pro známý blogovací systém WordPress. Výsledek není dobrý: každý pátý plugin obsahuje bezpečnostní mezeru.
Bezpečnostní odborníci ze společnosti RIPS Technologies publikovali podrobnou studii, ve které se zabývali bezpečností pluginů pro populární blogovací nástroj WordPress. Stáhli jsme všech 47 959 pluginů a podrobili jsme je analýze našimi nástroji. Překvapivě každý druhý velký plugin obsahuje středně nebezpečnou chybu, píše se v analýze.
Byly testovány jen takové pluginy, které obsahují alespoň jeden soubor s kódem v PHP. Těch je celkem 44 705. Průměrně obsahují rozšíření 8,43 souborů a v každém z nich je průměrně 602 řádek. Většina pluginů je přitom velmi malých, více než 14 000 z nich (32 %) obsahuje jen mezi dvěma a pěti soubory.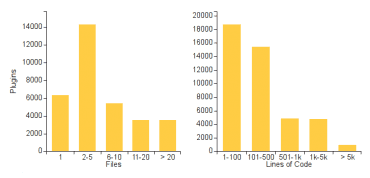
Počet souborů a řádků v pluginech
Existuje celkem 10 523 větších pluginů, tedy takových, které mají více než 500 řádek kódu. Z nich má 4 559 (43 %) alespoň jednu středně závažnou bezpečnostní chybu, jako například cross-site scripting. Důležité ale je, jak je závažnost chyb rozprostřena mezi pluginy. Celkem bylo objeveno 8878 děravých rozšíření.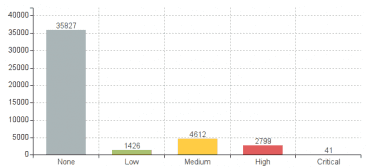
Závažnost bezpečnostních chyb
Celkem bylo objeveno 67 486 problémů bezpečnostního charakteru a z výše uvedeného grafu plyne, že ve většině pluginů nebyl objeven žádný. A obráceně: v poměrně malé skupině pluginů bylo objeveno hodně chyb. Domníváme se, že je to proto, že většina pluginů je velmi malých. Je těžší udělat chybu ve stořádkovém kódu než v 5000 řádcích, říká analýza.
Následující graf ukazuje korelaci mezi velikostí pluginu a počtem chyb. Modré tečky ukazují, že většina pluginů má méně než 1000 řádek a většina z nich neobsahuje žádnou chybu. Jakmile ale začne počet řádků růst, začne chyb výrazně přibývat. To podporuje naši teorii, že většina pluginů neobsahuje chyby, protože jsou příliš malé.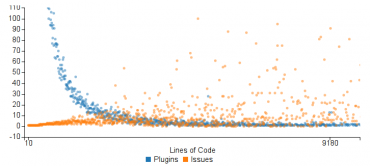
Řádky kódu a chyby
Jaký druh chyb se objevuje nejčastěji? Asi není překvapením, že v 68,4% jde o cross-site scripting, ke kterému dochází, když stránka ukáže uživatelsky vložený výstup bez ošetření HTML vstupu. Tato chyba se objevuje nejčastěji, protože výstup dat je nejčastější operací v PHP, tudíž je zatížena bezpečnostními problémy častěji než jiné. Tyto chyby jsou navíc velmi závažné, protože umožňují například injektovat PHP kód skrz editor šablon. Naštěstí vyžadují interakci se správcem.
Druhým nejčastějším problémem, který zasahuje 20,7 % děravých pluginů, je SQL injection. Jsou výrazně nebezpečnější než cross-site scripting, protože v nejhorším případě umožňují vyčtení citlivých informací z databáze – například hesel. Velmi často jsou proto zneužívány k automatizovaným útokům.
Název chyby Četnost
Cross-Site Scripting 38778
SQL Injection 11746
Resource Injection 1747
Path Traversal 778
File Upload 590
File Delete 441
Session Fixation 414
File Create 399
Weak Cryptography 348
File Write 300
PHP Object Injection 251
Open Redirect 227
Connection String Injection 177
CVE 109
File Inclusion 108
PHP Object Instantiation 101
Command Execution 78
XML/XXE Injection 65
Code Execution 61
XPath Injection 9
LDAP Injection 6
Zajímavá je také statistika o nejčastěji napadaných pluginech. Analytici kvůli ní provozují honeypot, na kterém sledují, kam míří které útoky. Během letošního roku bylo takto zaznamenáno více než 200 útoků a nejčastějšími cíli jsou následující pluginy:
Revolution Slider: 69 útoků
Beauty & Clean Theme: 46 útoků
MiwoFTP: 41 útoků
Simple Backup: 33 útoků
Gravity Forms: 11 útoků
Wordpress Marketplace: 9 útoků
CP Image Store: 8 útoků
Wordpress Download Manager: 6 útoků
Všechny útoky byly provedeny pomocí chyb, které jsou známé a zdokumentované. Většinu z nich je velmi snadné zneužít a umožňují spuštění libovolného kódu. To je činí zajímavými pro vytváření PHP botnetů, píše se v analýze.
Ekosystém okolo WordPressu je veliký a komunitou vytvářené pluginy obsahují často chyby. Analýza ukazuje, že většina je jich v poměrně malé skupině pluginů, ovšem s rostoucí velikostí roste taky šance na chybu. Bylo by tedy zajímavé korelovat chybovost a nebezpečnost s popularitou jednotlivých pluginů.
Zero day zranitelnost Linuxu způsobená emulátorem SNES
19.12.2016 Root.cz Zranitelnosti
Bezpečnostní odborník Chris Evans zveřejnil novou zero day zranitelnost, která ohrožuje linuxové distribuce. Překvapivě za problémem stojí emulátor SNES, který je integrován do systémových knihoven.
S kuriózní chybou přišel Chris Evans, který zároveň předvedl velmi spolehlivý exploit. K jeho spuštění stačí, aby uživatel navštívil upravenou webovou stránku, na které je umístěn zvukový soubor s příponou .flac nebo .mp3. Ve skutečnosti jde ale o audio soubor ve formátu SPC – hudební soubor z herní platformy Nintendo SNES.
Chyba byla předvedena na distribucích Fedora 25 a Ubuntu 16.04 LTS, ale pravděpodobně bude funkční i na dalších distribucích. Evans předvedl, jak pomocí upraveného hudebního souboru stáhne a spustí libovolný kód, který pak poběží s právy uživatele, který se soubor pokusil přehrát.
Názorně je to vidět na dvou krátkých videích, kde je demonstrováno prosté spuštění kalkulačky.
Na exploitu je zajímavé to, že využívá chybu v knihovně GStreamer. Ta dovoluje mimo jiné přehrávat zvukové soubory z herní konzole SNES a dělá to pomocí emulace zvukového procesoru Sony SPC700 založeného na MOS 6502.
Konkrétně je problém v knihovně Game_Music_Emu, která takto dovoluje emulovat různý starý hardware právě pro potřeby přehrávání zvukových souborů. Právě v emulaci SPC se ale nacházejí dvě vážné chyby, které je možné zneužít a uniknout z emulátoru ven. Evans vše velmi podrobně rozepsal na svém blogu.
Pro zneužití chyby je potřeba hudební soubor otevřít tak, aby k jeho zpracování byl použit právě GStreamer. Ten je ale automaticky volán například ve správci souborů Nautilus, video přehrávači Totem nebo prohlížeči Chrome (ten je použit v ukázce).

Autor: Wikimedie, CC BY-SA 3.0
Tak to je on, zvukový čip v SNES
Podstatné je, že takto zneužitá chyba může například uživateli odcizit veškerá data, nainstalovat libovolný malware nebo jinak libovolně zneužít přístupu do systému. Sám Evans uvádí, že chybějící sandboxing (oddělení aplikací) výrazně přispívá ke zneužitelnosti chyby. Žijeme ve světě, kde by sandboxy pro parsování médií měly být povinné, píše na svém blogu a dodává, že je tu jistá naděje na změnu, protože jeho dřívější odhalení už přiměla vývojáře vytvořit sandbox pro Gnome Tracker.
Zároveň vysvětluje, že dopad exploitu závisí na konkrétní distribuci. V Ubuntu je například příslušná knihovna gstreamer1-plugins-bad nainstalována už v základu, pokud uživatel při instalaci vybral podporu formátu mp3. Autoři Fedory se GStreamer rozhodli rozdělit do několika různých balíků a ve výchozí instalaci knihovna Game Music Emu chybí. Fedora ale ochotně nabídne její instalaci, pokud se uživatel pokusí otevřít relevantní zvukový formát.
Christ Evans nedávno zveřejnil podobný problém týkající se emulace NES, kdy byl schopen obejít 64bitový ASLR pomocí přehrávání zvukových souborů NSF. Problém se ale týkal staré verze knihovny GStreamer 0.10.x, takže exploit fungoval jen na velmi starých distribucích. Bylo potřeba mít přesně verzi Ubuntu 12.04.5.
ESET varuje před vánočními slevovými nabídkami na Facebooku, hrozí zcizení údajů o platebních kartách
19.12.2016 cnews.cz Sociální sítě
Praha, 19. prosince 2016 – Bezpečnostní analytici společnosti ESET zaznamenali nové případy útoků na české a slovenské uživatele sociální sítě Facebook. V předvánočním období se útočníci rozhodli zneužít jména známých módních značek, aby vylákali z uživatelů informace o jejich platebních kartách. Lákadlem jsou falešné stránky propagující nákup kabelek Michael Kors, bot Ugg či sandálů Birkenstock s výraznými slevami. Žádná z těchto společností však není tvůrcem falešných stránek.
„Tyto podvodné stránky se šíří e-mailem nebo přes legitimní účty na Facebooku, které útočníci hacknuli buď pomocí technik sociálního inženýrství, nebo pomocí škodlivého kódu. Bez souhlasu skutečného majitele účtu na Facebooku sdílejí na jeho profilu fotografie propagující toto falešné zboží za nereálně nízké ceny,“ vysvětluje Ondrej Kubovič, specialista na digitální bezpečnost ve společnosti ESET.
Tyto online obchody totiž při zpracovávání platby nepoužívají šifrovanou komunikaci a jejich majitel se tak dokáže velmi jednoduše dostat například k číslu platební karty a osobním údajům uživatele.
„Předvánoční období představuje pro podvodníky skvělou příležitost. Jejich falešné stránky si totiž lidé ve shonu při hledání vánočních dárků velmi lehce spletou s legitimními weby. Na stránkách by si proto měli všímat jakýchkoli podezřelých znaků. Těmi jsou například extrémně nízké ceny, vysoké slevy, překlepy, gramatické chyby či absence certifikátu SSL,“ dodává Kubovič.
ESET tyto online obchody označuje u svých zákazníků jako stránky s potenciálně nebezpečným obsahem. Do seznamu patří:
Uggclassicstyle.com
Ugg-sk.com
Uggs.cz
Bk-sale.com
Uggaustraliabox.com
Michaelkorsbuy.com
Shoesfootus.com
Uživatelům, kteří na nich již stihli nakoupit zboží, společnost ESET doporučuje zablokovat platební kartu použitou pro tento nákup a kontaktovat svou banku.
Tato nová vlna útoků nápadně připomíná situaci, o které společnost ESET informovala v dubnu. V té době se prostřednictvím Facebooku šířily českým a slovenským uživatelům nabídky na nákup brýlí značky Ray-Ban se slevou 90 procent. Tyto weby ale ve skutečnosti sbíraly informace o platebních kartách.
Uživatelé produktů ESET jsou na tyto podezřelé weby upozorněni.
Kapustkiy hacked the Slovak Chamber of Commerce
19.12.2016 securityaffairs Hacking
Kapustkiy announced the data breach of the Slovak Chamber of Commerce (www.scci.sk), more than 4,000 users record were accessed.
New Week, new hack! This is Kapustkiy ‘s motto that announced the breach of the Slovak Chamber of Commerce (www.scci.sk). The popular hacker accessed data belonging to more than 4,000 users and published it on Pastebin.
The hacker exploited an SQLInjection vulnerability, the archive contains users’ data including real names, email addresses, phone numbers and encrypted passwords.
Kapustkiy told me that there is no specific reason for the choice of this specific target, he was just searching for a government website while scanning the Internet.
“I breached this target because it is related to the Government its funny to see how bad their security is.” he told me.
He added to have hacked the website to make awareness and push admis to adopt a better security posture to protect their users.
“My motivation is to let admins see the consequence of a data breach.” said Kapustkiy. “And understand the danger.”

The hacker tried to report the issue to the admins two days ago, but he received no response.
Kapustkiy also told me that he joined the New World Hackers team.
“I work as Researcher and Pentester there” he told me.
Recently Kapustkiy targeted several organizations, the last in order of time is the Consular Department of the Embassy of the Russian Federation.
Kapustkiy also has breached the Argentinian Ministry of Industry, the National Assembly of Ecuador, the Venezuela Army, the High Commission of Ghana & Fiji in India, the India Regional Council as well as organizations and embassies across the world.
He also broke into the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Russian hacker Rasputin allegedly stole logins from the US election agency EAC
19.12.2016 securityaffairs Hacking
The Russian-speaking hacker Rasputing was attempting to sell the allegedly stolen login credentials from the US Election Assistance Commission (EAC).
According to the security firm Record Future, a Russian-speaking hacker was offering for sale stolen login credentials for a U.S. agency that tests and certifies voting equipment, the U.S. Election Assistance Commission (EAC).
The EAC Agency was formed in 2002, it is tasked of certifying voting systems and developing best practices for administering elections.
More than 100 allegedly compromised U.S. Election Assistance Commission login credentials were offered for sale by a hacker that uses the Rasputin online moniker.
“On December 1, 2016, Recorded Future threat intelligence technology identified chatter related to a suspected breach of the U.S. Election Assistance Commission (EAC).” Record Future said in a Thursday blog post.
“Further research identified a Russian hacker (Recorded Future refers to this actor as Rasputin) soliciting a buyer for EAC database access credentials.”
Researchers discovered that some of these credentials included the highest administrative privileges that could be used by an attacker to steal sensitive information from the U.S. Election Assistance Commission or deploy an Exploit kit to compromise targeted individuals in a watering hole attack.
Recorded Future shared multiple screenshots that demonstrate the hacker had access to the system at the U.S. Election Assistance Commission.

Election and software systems test reports (image provided by Rasputin).
The Rasputin hacker claimed to have broken in the system via an unpatched SQL injection (SQLi) vulnerability.
The U.S. Election Assistance Commission (EAC) investigated the incident with authorities and has terminated access to the vulnerable application.
“The U.S. Election Assistance Commission (EAC) has become aware of a potential intrusion into an EAC web-facing application. The EAC is currently working with Federal law enforcement agencies to investigate the potential breach and its effects.” reads a statement issued by the Agency.
The Election Assistance Commission clarified that it does not administer elections.
“The EAC does not maintain voter databases. The EAC does not tabulate or store vote totals,” added the commission.
The discovery of this new data breach raises the debate around possible interference with 2016 Presidential. The US Government blamed the Russia for attempted to influence the U.S. election through several high-profile cyber attacks.
Who is the Rasputin hacker?
Record Future has been following Rasputin since 2015, according to the security firm he may also have tried to sell details about the SQL injection to a broker working on behalf of a Middle Eastern government.
Based on Rasputin’s historical criminal forum activity, the experts exclude he is sponsored by a foreign government.
Now the important question is how long the flaw remained unpatched and who exploited it too.
Indian Institute of Technology Kharagpur hacked by Cryptolulz666
19.12.2016 securityaffairs Hacking
Cryptolulz666 announced another data breach, he hacked the database of the Indian Institute of Technology Kharagpur, the second of the country.
Just after 24 hours of the hack of the Indian Institute of Technology – IIT Bombay, Cryptolulz666 notified me another data breach, he hacked the database of the Indian Institute of Technology Kharagpur, the second of the country.
Cryptolulz666 broke into the database of the Indian Institute of Technology Kharagpur and accessed users data, including emails, passwords, phone numbers, and security questions.
The hacker told me to have accessed data belonging to 12000 plus users, but as proof of the hack, he leaked only a small portion of them on Pastebin.

When I asked more details about the data breach he told be that he found a SQL injection flaw in the website.
“In this hack, I triggered an error based SQL injection… and I leaked the data on Pastebin” the hacker told me.
The database contains had around 12555 users but I just leaked even less than a quarter of it as the institution might get sued on this info disclosure.
Once again the hacker highlights the lack of security of the organizations. His intent is creating awareness amongst the authorities.
“If you make a website to you definitely have to protect it on every aspect.” he added.
Cryptolulz666 explained that many hackers would love to get their hands on such kind of data so it is important to address these flaws before them.
Last week Cryptolulz666 broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data. The hacker also launched DDoS attacks against a Russian and Italian Government websites.
LinkedIn Lynda.com online learning platform started notifying users of data breach
19.12.2016 securityaffairs Social
Lynda.com is notifying customers a data breach, according to the company an unauthorized third party accessed a database containing user information.
Lynda.com is an online learning platform that was acquired last year by LinkedIn.
The company started notifying its customers over the weekend, hackers accessed learning data, including attempted courses and contact data. At the time I was writing there is no evidence of password exposure anyway and the company has notified law enforcement. LinkedIn, who owns the company, confirmed the incident and revealed that passwords of 55,000 users have been reset as a precaution, the overall number of impacted users could reach 9.5 million.
“You may have received an email notification from Lynda.com explaining that we recently became aware that an unauthorized third party accessed a database that included some Lynda.com learning data, such as contact information and courses viewed. We are informing users out of an abundance of caution.” reads the official statement from the company.
“We have no evidence that any data has been made publicly available.”

In response to the data breach LinkedIn announced further measures to protect Lynda.com user accounts.
This isn’t the first time LinkedIn suffers a data breach, in 2012 the company was hacked and data belonging to 117 million users were stolen by hackers. It was initially believed that the incident only affected 6.5 million accounts.
In October, the Czech police, working with the FBI, arrested a Russian man at a hotel in Prague that is suspected to be involved in the 2012 LinkedIn hack.
The cascading effects of the 2012 LinkedIn breach are still being felt throughout the business world. In June, CERT-Bund, Germany’s Computer Emergency Response Team for federal agencies, released a warning that corporate executives may be being targeted with malicious emails using information likely gained by hackers as a result of the 2012 breach.
CERT-Bund released a screenshot via its twitter feed, of an email containing a fake invoice targeting a business executive at an undisclosed organization.
In November, researchers from Heimdal Security reported a recent LinkedIn phishing campaign aiming to collect confidential information from unsuspecting users.
The Turkish Government has blocked the Tor access once again
19.12.2016 securityaffairs Privacy
The Turkish Government has applied restrictions on the Tor anonymity network, the discovery was made the Turkey Blocks internet censorship watchdog.
“Our study indicates that service providers have successfully complied with a government order to ban VPN services.” reads a blog post published by the Turkey Blocks.
Users in the country started reporting connectivity issues around the same time, a circumstance that suggests the adoption of new measures to control the access to the Internet.
Tor popularity in Turkey is increasing due to the censorship applied by the local authorities.
The Turkish Government has applied new sophisticated “blocking measures” that will not allow circumventing social media shutdowns in Turkey. The Government is blocking Tor and any other VPN service as part of the Turkey’s internet censorship of the central government.
The Government of Ankara recently ordered ISPs to block access to the Tor and many other VPN services. Earlier in December, the Turk Internet that represents the ISPs in the country reported the high pressure on the Government to complete the ban. The Government ordered ISPs a weekly status update on the applied restrictions.
In the recent years, the Turkish Government as applied several times the block of the social media networks during national emergencies and political unrest and street demonstrations.
In the following graph, it is reported the number of direct connected Tor users (Source Tor Metrics), it is easy to verify the increased popularity of the tool in the country since last year.


The experts from the Turkey Blocks also noticed Tor usage via bridges is being downgraded due to the restrictions applied by the Turkish Government.
“Turkey Blocks finds that the Tor direct access mode is now restricted for most internet users throughout the country; Tor usage via bridges including obfs3 and obfs4 remains viable, although we see indications that obfs3 is being downgraded by some service providers with scope for similar on restrictions obfs4. The restrictions are being implemented in tandem with apparent degradation of commercial VPN service traffic.” continues the analysis published by the Turkey Blocks.
The study conducted by the organizations corroborates user reports that Tor access with the default configuration is now widely restricted. At the time I was writing, the ban isn’t total and the Turkish government is not covering corporate or custom VPN solutions.
Odhalit kybernetické vyděrače je opět těžší. Přicházejí s pokročilejší formou maskování
19.12.2016 SecurityWorld Hacking
Bezpečnostní tým Talos společnosti Cisco varuje před novou kampaní počítačových vyděračů. Kampaň, která začala pravděpodobně 24. listopadu, využívá nevyžádanou poštu k šíření vyděračského softwaru Cerber 5.0.1. CHtějí 1000 dolarů.
Provedení útoku je poměrně jednoduché – v nevyžádané poště obdrží oběť jednoduchý odkaz, který využívá přesměrování Google a anonymizační služby Tor. Klikem na odkaz dojde ke stažení infikovaného dokumentu v MS Word. Po rozkliknutí odkazu v něm jsou data oběti zašifrována. Za jednoduchým postupem se však skrývá pokročilé maskování útočníka. Ransomware kampaně vždy využívaly Tor, avšak vůbec poprvé se setkáváme s tím, že Tor slouží k hostingu nakaženého dokumentu i spouštěného souboru.
Tento postup znamená, že je mnohem obtížnější odstavit servery, na kterých je umístěn škodlivý obsah. Nová verze ransomwaru Cerber po obětech nejčastěji vyžaduje platbu v hodnotě téměř 1,4 bitcoinů, tedy zhruba 1000 dolarů. V případě, že částku uživatel neuhradí do 5 dnů, hrozí útočníci zdvojnásobením požadované částky.
Nejnovější distribuční kampaň ukazuje, že se útoky počítačových vyděračů neustále vyvíjí. Kyberzločinci využívají stále pokročilejší metody k infikování napadených systémů a zároveň skrývání škodlivé aktivity před odhalením a analýzou. V tomto případě se setkáváme s případem, kdy s využitím systému Tor distribuují nakažený dokument (ve Wordu) i spouštěný soubor.
Nový útok se od jiných vyděračských kampaní liší navenek svojí relativní jednoduchostí – nevyužívá profesionálně vytvořené podvodné e-maily a pokročilé skriptovací techniky ke skryté instalaci vyděračského softwaru. Zprávy naopak působí velmi neprofesionálně, jsou stručné a bez příloh. Zdánlivou legitimitu jim dodává jméno adresáta v předmětu, jehož se snaží přimět ke kliknutí na odkaz v těle zprávy.
Z hlediska technického provedení útoku se však jedná o nový přístup založený na anonymizační službě Tor k zamaskování aktivity a znemožnění vysledování serverů, na nichž je škodlivý software uložen. K němu se uživatel dostane právě kliknutím na odkaz, který zneužívá přesměrování Google. Užití domény „onion.to“ v prvotním přesměrování umožňuje útočníkům využít proxy službu Tor2Web k přístupu ke zdrojům v síti Tor bez nutnosti instalace klienta Tor do napadeného systému. Systém oběti pouze stáhne speciálně upravený dokument MS Word, který po otevření (za předpokladu, že má uživatel povolená makra) do počítače stáhne a spustí samotný vyděračský software Cerber.
Security expert disclosed a full zero-day drive-by exploit for Linux leveraging SNES
18.12.2016 securityaffairs Exploit
The security expert Chris Evans has disclosed a zero-day exploit successfully tested on Ubuntu and Fedora distributions that may affect other distros.
The security expert Chris Evans has disclosed a zero-day exploit for Ubuntu and Fedora distributions. The flaw is a full drive-by download exploit that may impact also other Linux distributions.
The researcher successfully the full zero-day drive-by exploit against Fedora 25 + Google Chrome and Ubuntu 16.04 LTS, and relies on breaking out of Super Nintendo Entertainment System (SNES) emulation “via subtle cascading side effects from an emulation error.”
“full reliable 0day drive-by exploit against Fedora 25 + Google Chrome, by breaking out of Super Nintendo Entertainment System emulation via cascading side effects from a subtle and interesting emulation error.” explained Evans in a blog post.
The problem lies within the Sony SPC700 emulated processor and exploits cascading subtle side effects of an emulation hole.
The Linux GStreamer media playback framework supports the playback of SNES music files by emulating the SNES CPU and audio processor due to an agreement with Game Music Emu.

The emulation process supported by the Sony SPC700 processor is affected by at least two flaws, a missing X register value clamp for the MOV (X)+, A instruction, and a missing SP register value clamp for the RET1 instruction.
Evans chained the two issues for his attack, he demonstrated that it possible to compromise the target system by tricking the user into visiting a malicious web page that contains audio files encoded in the SPC music format, but saved with the. flac and. mp3 extensions.
The files work as the vector for the malicious code that loaded and executed by the victims with the same privileges as those of the current user.
The full drive-by download exploit could allow the attacker to steal personal data, including photos, videos, or documents, as well as data stored in the browser.
Evans published the following video PoC videos working on Fedora 25 and Ubuntu 16.04 LTS alongside the files needed to test the exploit.
Evans provided further details on the impact of the hack on both Linux distribution he tested, he highlighted that the general lack of sandboxing contributes to the severity of the issue.
“Impact is mixed. On Ubuntu, the faulty code is installed and on the attack surface by default, if you select the “mp3” option during install — which I certainly always do. On Fedora, there’s a very sensible decision to split gstreamer1-plugins-bad into multiple packages, with only gstreamer1-plugins-bad-free installed by default. This limits the attack surface and does not include Game Music Emu. Of course, the gstreamer framework will happily offer to install gstreamer1-plugins-bad-free-extras, with a very nice UI, if the victim simply tries to open the relevant media file.” added Evans.
“As always, the general lack of sandboxing here contributes to the severity. I think we inhabit a world where media parsing sandboxes should be mandatory these days. There’s hope: some of my other recent disclosures appear to have motivated a sandbox for Gnome’s tracker.”
DNSChanger Exploit kit targets Home routers in malvertising campaign
18.12.2016 securityaffairs Exploit
Security experts observed malvertising campaign leveraging the DNSChanger malware to compromise multiple models of home routers.
The Christmas season can be the busiest time of the year for online shopping in many countries. Researchers at Proofpoint have recently announced the discovery of a new and improved version of the DNSChanger Exploit Kit.
“Since the end of October, we have seen an improved version of the “DNSChanger EK” [1] used in ongoing malvertising campaigns. DNSChanger attacks internet routers via potential victims’ web browsers; the EK does not rely on browser or device vulnerabilities but rather vulnerabilities in the victims’ home or small office (SOHO) routers. ” states the analysis published by ProofPoint.
The malware is used in malvertising campaigns and targets home routers.
When a victim clicks on a malicious link the malware, differently from most exploit kits in the wild, doesn’t attack the operating system or the browser but the home or small office router.
Once the router is compromised the victim’s internet traffic can be routed to any possible phishing sites and the victim could remain under constant malvertising attack that would help criminal to increase the damage they cause.
The similarities this attack campaign has with the “CSRF Soho Pharming” campaign uncovered at the beginning of 2015 suggests the same actors could be behind this new view of the attack. However, researchers note that several improvements were made to the exploit kit, which renders it more dangerous.
“Attack pattern and infection chain similarities led us to conclude that the actor behind these campaigns was also responsible for the “CSRF (Cross-Site Request Forgery) Soho Pharming” operations in the first half of 2015 [1].” continues the analysis.
The new version includes some additional features such as;
External DNS resolution for internal addresses
An AES key to decrypt the list of fingerprints / default credentials and local resolutions
Dozens of recent router exploits
When possible the exploit kit modifies the network rules to make the administration ports available from external addresses, exposing the router to additional attacks like those perpetrated by the Mirai botnets
The malvertising chain is now accepting Android devices as well.
The victim is initially compromised by advertisements on legitimate websites. Once the malware is installed on the victim’s browser (Chrome for Windows and Android), it tries to locate and identify the router. The exploit kit then receives the instructions to exploit that specific make/model. The exploit kit makes extensive use of steganography techniques such as HTML code hidden in the comment field of a PNG file.
DNSChanger seems to target large ad agencies by redirecting their traffic to other third party ad services.
The malware can currently exploit a large number of different router make and models including the following newly added exploits;
D-Link DSL-2740R
COMTREND ADSL Router CT-5367 C01_R12
NetGear WNDR3400v3 (and likely other models in this series)
Pirelli ADSL2/2+ Wireless Router P.DGA4001N
Netgear R6200
There are currently no real effective mitigation techniques for this attack except making sure the router firmware is updated to the latest version.
Any attack compromising the DNS on any network can provide the attacker with a wide range of new attack vectors including man-in-the-middle, frauds, and phishing attacks.
Cryptolulz666 hacked the Indian Institute of Technology – IIT Bombay
18.12.2016 securityaffairs Hacking
Cryptolulz666 is once again in the headlines, this time he hacked the Indian Institute of Technology – IIT Bombay, one of the best Indian colleges.
Cryptolulz666 is back, now he hacked the Indian Institute of Technology – IIT Bombay, one of the best Indian colleges, that has a current world rank of 200.
The hacker broke into the database of the college and leaked on Pastebin its database containing 54 tables.
The hacker told me to have used Blind SQL Injection attack, he sent an email to the admins, but he did not receive any response yet.
The motivation of the hack is the intent of creating awareness of cyber security. It is curious that one of the Top 200 colleges of the world has a so low level of security.

Cryptolulz666 also told me that the site of the IIT Bombay is also affected by a cross-site scripting flaw.
Cryptolulz666 told me that this attack has a special meaning for him.
“I am an Indian guy passionate about cyber security. This hack is very important for me because I spent my entire life in dreaming to be accepted at the IIT Bombay.
I’m so young, but I was enough skilled to broke into one of the most prestigious college in India and all over the world.” Cryptolulz666 told me.
This week Cryptolulz666 broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data. The hacker also launched DDoS attacks against a Russian and Italian Government websites.
Odinaff Trojan behind financial attacks mostly in Turkey
18.12.2016 securityaffairs Virus
Akbank, one of the largest Turkish banks seems to be the latest victim of the Odinaff trojan, a threat similar to the Carbanak malware.
Odinaff; a malware similar to Carbanak, has been targeting financial institutions around the world since the beginning of the year.
“Since January 2016, discreet campaigns involving malware called Trojan.Odinaff have targeted a number of financial organizations worldwide. These attacks appear to be extremely focused on organizations operating in the banking, securities, trading, and payroll sectors. Organizations who provide support services to these industries are also of interest.” states a blog post published by Symantec. “These additional tools bear the hallmarks of a sophisticated attacker which has plagued the financial industry since at least 2013–Carbanak. This new wave of attacks has also used some infrastructure that has previously been used in Carbanak campaigns.”
Financial organizations from the U.S.A to Australia, from Ukraine to Hong Kong were targeted by the malware.
The bank issued a short statement mentioning the fraudulent SWIFT activities. While very little information has been disclosed, current data at hand and information gathered from internal sources suggest the following scenario.
The initial attack vector is spear-phishing. An employee is targeted with a Microsoft Office Document containing a malicious macro that downloads the Odinaff malware. As seen in the sample below, the malicious document prompts the user to allow the macros.

Source: Symantec
Attackers gain persistence and start activities in the bank’s network using Windows components such as Powershell and WMI. Earlier Odinaff attacks involved the use of light and known tools such as Psexec, Netscan, Ammyy and lightweight hacking tools such as Mimikatz.
The use of “legitimate” software allows attackers and malware to remain under the radar of antivirus software which usually looks for unknown or new files.
Attackers collected credit card information and executed money transfer via the SWIFT system. Also seen in previous Odinaff attacks the malware is able to hide logs and SWIFT messages related to the fraudulent transactions made by the attackers.
Two other Turkish banks may also have been compromised using the same attack method, however, no official statements were made at the time of this writing.
The vast majority of Odinaff attacks were against financial targets (34%), experts observed a small number of attacks also against organizations in the securities, legal, healthcare, and government.
“Around 60 percent of attacks were against targets whose business sector was unknown, but in many cases these were against computers running financial software applications, meaning the attack was likely financially motivated.” explained Symantec.
For further details, including the Indicators of compromise, give a look at the analysis published by Symantec.
Ransomware útočí každých 10 sekund. Obrana není snadná
17.12.2016 Novinky/Bezpečnost Viry
Útoky vyděračských virů jsou stále častější. Tito nezvaní návštěvníci, často označováni souhrnným názvem ransomware, se snažili dostat do počítačů v domácnostech každých 10 sekund. V porovnání se situací z první poloviny roku tak jde o dvojnásobný nárůst. Vyplývá to z analýzy antivirové společnosti Kaspersky Lab.
Vyděračské viry samozřejmě útočí také na podniky. U nich k útokům dochází každých 40 sekund, ještě zkraje letošního roku byl přitom tento interval dvě minuty.
V posledních 12 měsících přitom přibylo více než šest desítek ransomwarových rodin. Hrozba vyděračských virů je tak v poslední době daleko větší, než by se mohlo na první pohled zdát. Bezpečností experti společnosti Kaspersky Lab proto varují, že škodlivé kódy požadující výkupné jsou jednou z největších hrozeb současnosti.
Na chlup stejné útoky
Útoky vyděračských virů probíhají prakticky vždy na chlup stejně. Nejprve zašifrují záškodníci všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Poškození nejčastěji pocházejí z Japonska, Chorvatska a Jižní Koreje.
Počet obětí vyděračských virů vzrostl ve třetím kvartálu 2,6krát. To jinými slovy znamená, že za zmiňované tři měsíce se obětí stalo více než 821 tisíc lidí z různých koutů světa.
Poškození nejčastěji pocházejí z Japonska (4,83 %), Chorvatska (3,71 %), Jižní Koreje (3,36 %), Tuniska (3,22 %) a Bulharska (3,2 %). V předchozím kvartále bylo na prvním místě také Japonsko, ale druhé, třetí a čtvrté místo bylo obsazeno Itálií, Džibutskem a Lucemburskem.
Jaké množství z poškozených uživatelů představují Češi, analýza neuvádí.
Nejčastěji se šíří CTB-Locker
Nejvíce počítačoví piráti šíří vyděračský virus zvaný CTB-Locker, který je zodpovědný za téměř třetinu všech uskutečněných útoků (28,34 %). Ten zašifruje data uložená na pevném disku a za jejich odemčení požaduje výkupné v bitcoinech, v přepočtu jde o téměř 50 tisíc korun.
Sluší se připomenout, že výkupné by ale lidé neměli platit, protože nemají žádné záruky, že data budou skutečně zpřístupněna. Z podobných případů, které se objevovaly v minulosti, dokonce vyplývá, že nedochází k odšifrování dat prakticky nikdy. Jediným řešením je počítač odvirovat, což však nemusí být jednoduché.
To platí i pro další dva vyděračské viry, které se umístily v čele žebříčku. Druhý ve třetím čtvrtletí skončil škodlivý kód Locky (9,6 %) a třetí CryptXXX (8,95 %).
Konec zpravodajským hoaxům na Facebooku. Sociální síť oznámila, jak s nimi bude bojovat
16.12.2016 Živě.cz Sociální sítě
Facebook oficiálně oznámil, jak bude na své vlastní síti bojovat proti nesmyslům – ať už nechtěně šířeným fámám, tak cíleným hoaxům, které mají leckoho zdiskreditovat.
Sociální síť bude v USA spolupracovat s weby Politifact a FactCheck.org, které se orientují na ověřování faktů, a s některými mediálními domy – třeba ABC News. Tato média budou fungovat jako kurátoři, kteří pomohou z Facebooku vymýtit cíleně šířené nepravdy.
Facebook ale zapojí do práce i samu komunitu, která bude moci označovat lživé a manipulativní příspěvky stejným způsobem jako ty, které jsou již dnes za hranou pravidel služby.
Boj proti hoaxům podle Facebooku
Jaká Češi používají hesla? Expert analyzoval hacknutou databázi e-shopu Xzone.cz
16.12.2016 cnews.cz Zabezpečení
Dostalo se nám pod ruku přes sto tisíc hesel jednoho českého e-shopu, která hacker odcizil minulý rok a nedávno je umístil na pastebinu. Z nich jsem analyzoval 16 587 kousků obnažených v plaintextu, ostatní hesla byla zveřejněna v nic neříkající číselné reprezentaci; zřejmě se je nepodařilo rozhashovat.
Předkládám vám tuto svou skromnou studii, která původně neměla za cíl nic jiného, než si povšechně zaokounět nad podobou českých hesel, nakonec se však vyvinula v kolůsek, který Národnímu bezpečnostnímu CSIRTu pomohl vyvinout lepší způsob regulární analýzy nad množinou dat.
Soudě dle uživatelských jmen se z dobré poloviny jedná o hesla majitelů e-mailu na Seznamu, z šestiny na Gmailu, z desetiny na Centru.
Počet znaků v hesle
Promítli-li bychom si délky hesel na gaussovu křivku, našli bychom její střed v bodě osm, celá čtvrtina vzorku používá 8znaké heslo (4401). Téměř shodný počet lidí používá kratší heslo (4857), zbylá polovina má heslo delší (7329). Celých 90 % hesel je mezi 6 a 11 znaky. Pouze 6 hesel je delší 18 znaků: jedna snadno zapamatovatelná anglická fráze, frontman Slipknotu s číselnou řadou, vyjádření lásky k hrám Doom a Far Cry. A kraluje 26znakové heslo, které se skládá ze slova „prosím“ a úctyhodných dvaceti číslovek, které musí být med si pamatovat. 3znaké heslo máme jen jedno: „.85′.“.

Délka hesel
Kořeny slov
Stáhl jsem si seznam lemmat českého národního korpusu, odstranil lemmata kratší než 4 znaky a porovnal s textem, abych zjistil, jaké kořeny slov se v heslech nacházejí. Seznam obsahuje všechna používaná slova, tj. nejenom česká, ale narazil jsem i na anglická (player), německá (Wassermann), francouzská (maison), profláklá latinská (deus). Třetina hesel se nepodobá ničemu (‚kekeke78‘, ‚.“y!W‘, ‚IDkfa75jj‘), přes deset tisíc hesel však obsahuje nějaké rozpoznatelné slovo.
Vůbec nejoblíbenější řetězec je „zone“, vyskytuje se v obměnách celkem 184× (‚xzonelogin‘, ‚xzone44‘, ‚psikzone‘). Jistě ne náhodou je to část jména e-shopu – z toho je vidět, jak lidé rádi jméno služby používají v hesle.
Dominují především jména: potkal jsem 103 petrů, 85 janů, na 70 lukášů a martinů, 60 tomášů, 50 davidů, 40 pavlů, na 30 jardů, adamů, míš, jakubů, honzů, pepů a 24 výskytů ojedinělě anglického jména john (další anglické jméno je až george – 8 výskytů). Vzorek není dostatečně reprezentativní, ale zdá se, že převažují jména mužská, ženy se zřejmě volí do zdrobnělin.
Ženám vede 22 lenek, 14 peter a aniček, 13 páj, 13 lucek – a zvlášť 13 lucinek, 12 elišek, 8 velkých terez a 9 malých terezek, které mají za sebou důsledně 2 či 4místné číslo nebo partnera martina. Kromě toho 176 hesel obsahuje ženské příjmení končící „-ova“. U 50 z nich obsahuje příjmení i uživatelské jméno a zde v dobré polovině případů totéž příjmení. Lze spekulovat, že druhá polovina představuje jméno ženy za svobodna. Uživatelských jmen na „ova“ je celkem 1186 (po odečtení n-ová-ků).
V říši zvířat jsem našel 33 psů (z toho 13 i se svým jménem), 22 draků a 7 dragonů, 18 lam, 8 králíků a slonů, 7 orlů a kaprů, 6 klokanů, opic, ryb a veverek, 4 osli, tygři a kuřata, 3 očíslované kočky, 6 kocourů, 6 mourků, 3 myši a 3 potkani, 2 krávy, 1 slepici, žirafu, vlka, vlkodlaka a vlka jakuba, 1 pavouka a 6 spiderů.
Co jsem našel dál? Parentální vztahy (11× mama, 10× maminka, 9× tata, 2× tatinek a 1 tataracek), městskou příslušnost (12x Praha, 11x Brno, 8x Ostrava), vyznání (14× sparta, 8× banik, 4× slavie), výrobky (11× asus, 9× acer, 9× nokia, 8× samsung), hambatosti (4× nas*at, 7 orgánů ženského pohlaví, 15 kokotů, 11 hoven a 13× pr*el (v kombinaci s rokem narození, množstvím v ní obsaženého či prováděnou činností); pr*el je k tomu i 6× v e-mailu a coby bonus nalézáme 9× prd v různých situacích), sex (je spíše v uživatelských jménech – 15×, oproti 10 výskytům v heslech) a návykové látky (4x piva, 1x fernet, 1x becherovka).
Nejfrekventovanější heslo coby podstatné jméno je „heslo“ – 68 výskytů (‚tajneheslo1998‘, ‚heslonetreba‘, ‚Megaheslo‘, ‚heslo‘ a číslo…). Se 43 výskyty se objevuje lemma „kolo“ (43×), v závěsu jsou tři anglicismy „game“ (38×), „star“ (34×), pozitivní „kill“ (24×) a „ahoj“ (19×). Následuje seznam slov s alespoň 3 výskyty. Ovšem slova pod deset výskytů jsou zde většinou, jen pokud patří k delším nebo zajímavějším kouskům. Vypsal-li bych všechna ojedinělá kraťoučká slova, asi by vás to nebavilo.
17× shop
16× moto
15× dark
14× fotbal
13× master
12× nakup
12× poklop, super, tiscali (tito autoři nepoužívají současně schránku na doméně tiscali), veslo (asi že se rýmuje s ‚heslo‘: ‚vESLO‘, ‚hesloveslo5‘, ‚oveslo1′,’prdaveslo‘)
11× rock, craft, kolik, destiny, auto
10× forever, team, mega
9× magor a milacek
8× cert (což asi nebude zkratka pro náš bezpečnostní tým CSIRT.CZ), rambo
7× kofola a matrix
7× sluníčko a motor
6× silver a street
5× policie, jahoda, lopata, okurka, kostra, password, shadow, future, citron, mazlik, trabant
5× vanoce a geniove
4× aragorn, chleb, gothic, storm, milanek
3× slunce, kytara, wanted a meloun
Nutno podotknout, že jsem ignoroval lemmata, u nichž se zdálo, že drtivě nereprezentují konkrétní slovo – například hned druhé nejfrekventovanější lemma vůbec, „inka“ (149×), se vyskytuje jen v koncovkách (‚Dusinka‘, ‚pavlinka90‘, ‚zibrinka‘) – skutečnou slečnu „Inka12“ máme jenom jednu.
Cestou hesly jsem nezachytil snad vůbec žádnou diakritiku. Buď nebyla rozhashována, nebo se ji Češi zdráhají v heslech používat (což je možná škoda). Též všechno jsou jen první pády – pokud si někdo zvykne používat třeba sedmý pád, hned bude odolnější vůči slovníkovému útoku. Lemmat (základních tvarů) existuje na 120 000; pokud použijeme i pády a další tvary slov, hned se topíme v miliónech kombinací.
Skupiny znaků
Žádné heslo o méně než 5 znacích není tvořeno jen malými písmeny; tací autoři se snaží. Vyjma „T601“ a „Pes5“ se jedná o obtížná hesla, co bych asi neuhodl a co by stroji crackujícímu hash mohla trvat i několik vteřin. Na pěti písmenech začíná největší šlendrián – „UTERY“ (alespoň že velkými), „drzek“, 2x „Gabka“ (přičemž jedna z nich se tak jmenuje) apod.
Rozdělil jsem všechna hesla podle kategorií, zda obsahují písmena malá, velká, číslice a všechny ostatní, speciální znaky.

Speciální znaky
Vypadá to, že žádné heslo není tvořeno jen speciálními znaky. Kolik hesel je tvořeno jen číslicemi, nedovedu říct – nerozpoznám je od nerozhashovaných hesel. Celkem máme 720 hesel, která používají speciální znak; 124 mají speciální znaky dva, v 46 případech jsou dva speciální znaky za sebou. Nejoblíbenější je tečka, vyskytuje se 211×, z toho 57× na konci slova.
Přidávám úplný seznam speciálních znaků.

Skupiny složitosti hesel
Znak „větší než“ nemá nikdo. Též nikdo nepoužívá dvojtečku, což mě překvapuje, protože je na klávesnicích běžně k dostání, rozhodně o něco více než „větší než“ > a třeba circumflex ^.
Nejčastější kombinace skupin
Hesel, která jsou tvořeny písmeny s číslicemi na konci je většina – 8037 výskytů (‚pepa1256‘, ‚frank167‘, ‚pidos007‘, ‚obchod1254‘). Z toho dvě tisícovky hesel končí na 2 číslice, další dvě na 4 číslice, tisíc a půl hesel je zakončeno 3 číslicemi, tisícovka jedinou číslicí a půl tisíce má dokonce 6 číslic.
Pokud je v hesle číslice, bude to s největší pravděpodobností jednička (5542 hesel). Pokud jsou v hesle dvě číslice za sebou, bude to jedna dva (1101 hesel); pokud číslice mají být totožné, jsou to dvě nuly (584 hesel).
Korelace s přihlašovacím jménem
Zkoumal jsem zajímavou otázku, zda lidé používají heslo, které se podobá přihlašovacímu jménu. Ano; když jsem vzal každý sled pěti znaků hesla a hledal je v řetězci jména, ukázalo se, že každý třináctý uživatel: 1297 hesel má 5 a více znaků stejných nebo zcela shodných s e-mailem.
ondraluk@email.cz → 2ondraluk
zinule.m@seznam.cz → zinulem
genius1006@gmail.com → netGENIUS11
martin.sn@atlas.cz → martin0117
pmachtik@centrum.cz → machta100
alledain@seznam.cz → Alledain
Závěr
Osobně si myslím, že je lepší heslo delší nežli složitější – deset jednoduchých znaků se vyplatí mnohem více než tři složité. Ovšem jak vidíme, ať je heslo dlouhé či krátké, ať obsahuje obskurní znaky nebo jenom latinku, všechno marné, když poskytovatel příliš nehashuje. Vzpomínám si na vtipy o hackerovi, lamerovi a looserovi. Looser si dá heslo ‚zuzana‘, protože kdo by mohl tušit, že se jeho manželka jmenuje Zuzana? Hacker si dá heslo ‚zuzana‘, protože je mu jedno, jestli ho někdo hackne. Lamer si dá heslo ‚n#FG*[f83‘ a každý týden ho zapomene.
Používejte jiná hesla na různé služby; ach, alespoň na ty kruciální.
Pro psaní článku byl využit Český národní korpus: Srovnávací frekvenční seznamy. Ústav Českého národního korpusu FF UK, Praha 2010. Dostupné z WWW: http:ucnk.ff.cuni.cz/srovnani10.php
Citlivá data použitá v článku jsou pozměněna – všechny e-mailové adresy a některá hesla. Někdo má hezké krátké heslo, tak mu ho tu neprásknu.
Obama pohrozil Rusům odplatou za hackerské útoky
16.12.2016 Novinky/Bezpečnost Kyber
Spojené státy neponechají bez odpovědi vměšování ruských hackerů do amerických voleb, pohrozil odcházející šéf Bílého domu. Moskva tato obvinění popírá, nově zvolený prezident Donald Trump je zpochybňuje.
„Je jasné, že když se cizí vláda, ať je jakákoliv, pokouší zasahovat do našich voleb, tak musíme jednat. A uděláme to - v místě a době, o které sami rozhodneme,” prohlásil prezident Barack Obama v rozhlasovém rozhovoru, jehož výňatky byly zveřejněny ještě před odvysíláním celého interview stanicí NPR.
Obama uvedl, že některé odvetné kroky budou explicitní a veřejné, zatímco jiná opatření taková být nemohou. „Pan Putin si je dobře vědom mých pocitů pocitů, protože jsem s ním o tom přímo mluvil,” řekl.
Povahu odvetných kroků blíže neupřesnil.
Budoucí americký prezident Donald Trump ovšem ve čtvrtek zpochybnil roli Ruska na kybernetickém útoku proti serverům Demokratické strany.
Nesmysl, tvrdí Rusko
Kritika chování Ruska se objevila už před listopadovými volbami. V říjnu například oficiálně obvinila Rusko z hackerských útoků Obamova vláda. Prezident Obama tehdy varoval kremelského šéfa Vladimira Putina před následky.
Americké zpravodajské služby podle zdrojů tamních médií dospěly k závěru, že s postupem kampaně letošních prezidentských voleb věnovali ruští vládní představitelé zvýšenou pozornost snaze pomoci Trumpovi zvítězit. Dokazuje to podle nich fakt, že ruští hackeři se dostali k datům obou politických stran, ale na veřejnost pustili jen informace o demokratické kandidátce Hillary Clintonové.
Rusko jakékoli obvinění z kybernetických útoků či z vměšování do voleb v USA odmítlo.
Televize NBC dříve oznámila, že američtí zpravodajci "s velkou mírou pravděpodobnosti" věří, že kybernetickou kampaň proti americkým volbám řídil osobně Putin. „Je to prostě pitomost. Marnost pokusů kohokoli o tom přesvědčit je zjevná,” zareagoval ruský ministr zahraničí Sergej Lavrov v televizi Rossija 24.
New Kickass Torrents Site is Back Online by Original Staffers
16.12.2016 thehackernews IT
KickassTorrents is back from the dead!
Back in July, the world's largest and most notorious BitTorrent distribution site KickassTorrents (KAT) with millions of unique daily visitors was shut down by the U.S. authorities following the arrest of its alleged owner Artem Vaulin.
Shortly after the shutdown, a group of devoted original KAT staffers launched the Katcr.co forum in hopes of bringing back KickassTorrents to its former glory, in the near future.
Now, Katcr.co has launched a fully operational torrent website, which looks identical to the original Kickass Torrents (KAT) portal, TorrentFreak reports.
Note: In case the new KickassTorrents website does not immediately load, give it a few tries, as the site is experiencing a massive surge in traffic.
Launched today and located at KATcr.co/new, the new Kickass Torrents site starts with a clean user database while many members of the original staff are back on board, including its dedicated uploaders.
Here's what the KATcr team said on the sit’s launch:
"We have all our major uploaders on board, and they continued to share tirelessly even before the torrent engines returned. The torrent community can continue to expect to see uploads from all the names they know and trust."
Meanwhile, in a separate news, the Federal Court of Australia has ordered Internet service providers (ISPs) to block access to 5 Torrent websites, including The Pirate Bay, Torrentz, TorrentHound, IsoHunt, and SolarMovie, within next 15 days.
Following the shutdown of the original KickassTorrents portal earlier this year, several mirror sites came up online, claiming to be the real reincarnation.
However, in reality, many of those mirrors include malicious copycats that target unsuspecting pirates and attempts to steal their personal information and credit card credentials.
The KATcr team behind the new katcr.co/new site promises that the pirates are safe and secure at its new portal.
"In order to keep our members safe we chose to rebuild and keep only safe elements. Despite the fact that a rebuild took longer, the safety of our community comes first," one of the team members told TorrentFreak.
The KATcr crew members also believe that the original operators of the KickassTorrents website will walk free.
How to Hack Apple Mac Encryption Password in Just 30 Seconds
16.12.2016 thehackernews Apple
Macintosh computers are often considered to be safer than those running Windows operating system, but a recently discovered attack technique proves it all wrong.
All an attacker needs is a $300 device to seize full control of your Mac or MacBook.
Swedish hacker and penetration tester Ulf Frisk has developed a new device that can steal the password from virtually any Mac laptop while it is sleeping or even locked in just 30 seconds, allowing hackers to unlock any Mac computer and even decrypt the files on its hard drive.
So, next time when you leave your Apple's laptop unattended, be sure to shut it down completely rather than just putting the system in sleep mode or locked.
Here's How an Attacker can steal your Mac FileVault2 Password
The researcher devised this technique by exploiting two designing flaws he discovered last July in Apple's FileVault2 full-disk encryption software.
The first issue is that the Mac system does not protect itself against Direct Memory Access (DMA) attacks before macOS is started.
It's because the Mac EFI or Extensible Firmware Interface (similar to a PC's BIOS) let devices plugged in over Thunderbolt to access memory without enabling DMA protections, which allows Thunderbolt devices to read and write memory.
Secondly, the password to the FileVault encrypted disk is stored in clear text in memory, even when the computer is in sleep mode or locked. When the computer reboots, the password is put in multiple memory locations within a fixed memory range, making it readable by hacking devices.
Dubbed PCILeech and costs approximately $300, the hacking device exploits these two vulnerabilities to carry out DMA attacks and extract Mac FileVault2 passwords from a device's memory in clear text before macOS boots, and anti-DMA protections come into effect.
To do this, all an attacker needs is access to a target Mac computer for just a few minutes to connect the PCILeech hacking device to the computer via its Thunderbolt port, which would allow the attacker to have full access to its data.
Video Demonstration of the Attack
Frisk also provided a video demonstration, which shows how he just plugged in a card flashed with his open source PCILeech software tool into the Mac's Thunderbolt port, which ran the hacking tool on the target Mac or MackBook, rebooted the system, and read the Mac password on the other laptop.
Yes, the attack only works if an attacker has physical access to a target Mac or MacBook, but all it takes is just 30 seconds to carry out successfully.
"Anyone including, but not limited to, your colleagues, the police, the evil maid and the thief will have full access to your data as long as they can gain physical access - unless the Mac is completely shut down," Frisk explained in a blog post on Thursday.
"If the Mac is sleeping it is still vulnerable. Just stroll up to a locked Mac, plug in the Thunderbolt device, force a reboot (ctrl+cmd+power) and wait for the password to be displayed in less than 30 seconds!"
Frisk reported his findings to Apple in August and the company fixed the issues in macOS 10.12.2 released on 13 December.
So Apple desktop users are required to update their devices to the latest version of its operating system to be safe.
Ubuntu’s Crash Report Tool Allows Remote Code Execution
16.12.2016 thehackernews OS
No software is immune to being Hacked! Not even Linux.
A security researcher has discovered a critical vulnerability in Ubuntu Linux operating system that would allow an attacker to remotely compromise a target computer using a malicious file.
The vulnerability affects all default Ubuntu Linux installations versions 12.10 (Quantal) and later.
Researcher Donncha O'Cearbhaill discovered the security bug which actually resides in the Apport crash reporting tool on Ubuntu.

A successful exploit of this CrashDB code injection issue could allow an attacker to remotely execute arbitrary code on victim's machine. All an attacker needs is to trick the Ubuntu user into opening a maliciously booby-trapped crash file.
This would inject malicious code in Ubuntu OS's crash file handler, which when parsed, executes arbitrary Python code.
"The code first checks if the CrashDB field starts with { indicating the start of a Python dictionary," O'Cearbhaill explains.
"If found, Apport will call Python’s builtin eval() method with the value of the CrashDB field. eval() executes the passed data as a Python expression which leads to straightforward and reliable Python code execution."
The flawed code was introduced on 2012-08-22 in Apport revision 2464 and was initially included in release 2.6.1.
O'Cearbhaill has published the copy of his proof-of-concept (PoC) source code on GitHub.
Video Demonstration of the CrashDB Code Injection Attack
The researcher has also shared a video demonstration, showing that it is possible to gain control over the targeted Ubuntu box system using this flaw with the help of a malicious file.
O'Cearbhaill launched Gnome calculator with a simple Apport crash report file and explained that the code could be saved with the .crash extension or with any other extension that's not registered on Ubuntu.
The researcher reported the crash reporting app bug (listed as CVE-2016-9949 and a related path traversal bug as CVE-2016-9950) to the Ubuntu team, and the good news is that the team has already patched the flaw in Ubuntu on December 14 with O'Cearbhaill receiving $10,000 bounty.
Users and administrators of Ubuntu Linux desktops are strongly advised to patch their systems as soon as possible via the usual update mechanism.
PROMETHIUM and NEODYMIUM APTs used same Zero-Day to Target Turkish citizens
16.12.2016 securityaffairs APT
Microsoft discovered two distinct APT groups, PROMETHIUM and NEODYMIUM, that exploited the same Flash Player zero-day flaw on same targets.
Security researchers have discovered two distinct APT groups, PROMETHIUM and NEODYMIUM, that exploited the same Flash Player zero-day vulnerability (CVE-2016-4117) in cyber espionage campaigns on Turkish citizens living in Turkey and various other European countries. Both groups exploited the flaw before its public disclosure and against the same type of targets.
We have already read about the activities of the PROMETHIUM APT group in a report published by Kaspersky Lab that named it StrongPity. In October, Kaspersky published a report on cyber espionage activities conducted by StrongPity APT that most targeted Italians and Belgians with watering holes attacks.
The experts noticed many similarities in the operation of both groups, a circumstance that suggests a possible link between them. The ATP groups used different infrastructure and malware, but there are some similarities that indicate a possible connection at a higher organizational level.
The flaw was patched by Adobe on May 12, but according to the experts from the firm Recorded Future published a report on the most common vulnerabilities used by threat actors in the exploit kits.
The PROMETHIUM APT has been active since at least 2012, the hackers used instant messaging applications as the attack vector and shared malicious links that pointed to documents to exploit the CVE-2016-4117 vulnerabilities. Microsoft observed that the attacker used a specific strain of malware dubbed Truvasys that was designed to compromise target devices with Turkish locale settings.
“The attack itself began with certain individuals receiving links in instant messenger clients. These links led to malicious documents that invoked exploit code and eventually executed a piece of malware called Truvasys on unsuspecting victims’ computers” states the Microsoft Security Intelligence Report.
The PROMETHIUM APT also used another malware dubbed Myntor in targeted attacks.
The NEODYMIUM also exploited the CVE-2016-4117 flaw in targeted attacks in May via spear-phishing messages. This second APT leveraged a backdoor, dubbed Wingbird, that shows many similarities with surveillance software FinFisher.
“NEODYMIUM used a backdoor detected by Windows Defender as Wingbird, whose characteristics closely match FinFisher, a government-grade commercial surveillance package. Data about Wingbird activity indicates that it is typically used to attack individuals and individual computers instead of networks” continues the Report.

The vast majority of the NEODYMIUM victims was located in Turkey (80%), but several infections were also detected in the U.S., Germany and the U.K.
Let me suggest reading the Microsoft Security Intelligence Report to have more details on PROMETHIUM and NEODYMIUM, including indicators of compromise (IoC).
Cryptolulz666 continues targeting Government websites with DDoS
16.12.2016 securityaffairs Hacking
Cryptolulz666 is back targeting government websites to demonstrate that it is very simple for hackers to bring down them with DDoS attacks.
A few days ago a reported the attack conducted by the black hat hacker Cryptolulz ( @Cryptolulz666), a former member of the Powerful Greek Army, who hacked the website of Russian embassy of Armenia (www.embassyru.am). He hacked the website of Russian embassy of Armenia to create awareness amongst the authorities, the hacker confirmed me that he used a blind SQL Injection vulnerability.
Now Cryptolulz is back, he wanted to demonstrate that it is very simple for hackers, even small groups, to launch a massive DDoS attack against any target.
Yesterday he first launched a DDoS attack against the website http://italiastartupvisa.mise.gov.it/ belonging to the Italian Government.
It was just testing his own botnet, then later he targeted the website of the Russian Federal Drug Control Service liquidation commission.
The Russian website was down for several hours.
When I asked a comment he told me:
“from my perspective…. this is just low security, and for a government, it’s quite bad” said Cryptolulz666
He confirmed me to be a youngster with a great passion for cyber security that aims to spread awareness on the risks.
He launched a DDoS attack leveraging on the NetBIOS amplification technique. NetBIOS is a protocol used in computer software to allow applications to talk to each other via LAN networks.
“A NetBIOS NBSTAT query will obtain the status from a NetBIOS-speaking endpoint, which will include any names that the endpoint is known to respond to as well as the device’s MAC address for that endpoint. A NBSTAT response is roughly 3x the size of the request, and because NetBIOS utilizes UDP, this can be used to conduct traffic amplification attacks against other assets, typically in the form of distributed reflected denial of service (DRDoS) attacks.” states Rapid7.
The hacker scanned roughly 10 % of the Internet searching for potential bots to use in the attack and he found 2 million bots.
“which is pretty perfect for amp vectors..” he told me.
He confirmed me to have shut down the site of the Russian government with a single shot and maintained it down for hours.
In this specific attack he other two spoofing server in order to guarantee a stable malicious traffic against the target, and he made this with python scripts.
“I used another two spoofing servers to launch dos attacks with my self-coded python scripts.” he added.I did it to create awareness among the authorities and users of the website.
I did it to create awareness among the authorities and users of the website.
He confirmed me that he will target other government websites in next attacks, always for the same reason.
“you see the government don’t care about security so we gonna exploit it hard.” added Cryptolulz666
More than 8,800 WordPress Plugins out of 44,705 are flawed
16.12.2016 securityaffairs Vulnerebility
Security firm RIPS Technologies has analyzed 44,705 in the official WordPress plugins directory and discovered that more than 8,800 of them are flawed.
Experts from the security company RIPS Technologies have conducted an interesting analysis of WordPress plugins.
The researchers have analyzed 44,705 of the roughly 48,000 plugins available in the official WordPress plugins.
“To do this we downloaded all 47,959 plugins that are available from the official WordPress repository and analyzed them with our static code analyzer RIPS! Shockingly, about every second larger plugin contains at least one medium severity issue” states the analysis from the company.
The experts conducted a static code analysis of all the plugins searching for those that have at least one PHP file.
Before they analyzed the flaws in the plugins they collected general data on them to provide a better evaluation of the WordPress components.
Roughly 14,000 plugins are composed of 2-5 files and only 10,500 of them have more than 500 lines of code and for this reason, they have been classified as “larger plugins”.

The analysis of “larger plugins” (10,523) revealed that 43% of them (4,559) contain at least one medium severity issue. The experts discovered a total of 67,486 vulnerabilities in the plugins.

Roughly 36,000 plugins are not affected by any vulnerabilities, 1,426 had only low severity vulnerabilities, medium severity bugs affect more than 4,600 plugins, high-severity holes have been found in 2,799 plugins, while 41 plugins are affected by critical issues.
A close look at the types of vulnerabilities revealed the more than 68% of flawed plugins are affected by cross-site scripting (XSS) issues and just over 20% are SQL injections.
This means that XSS vulnerabilities are one of the principal problems for WordPress websites, but experts noticed that their exploitations require administrator interaction. SQL injection vulnerabilities can be exploited without user interaction through automated scanning activities.
Experts at RIPS used a honeypot between January and December 2016 to better analyze the attacks against WordPress plugins. The honeypot allowed the experts to count more than 200 attacks against WordPress plugins.
“We are running a small WordPress honeypot for quite some time know and could extract the information from our logs. Overall, over 200 attacks were recorded from January of 2016 to December of 2016” continues the report.
69 attacks targeted the Revolution Slider plugin, 46 against Beauty & Clean Theme, 41 against MiwoFTP and 33 against Simple Backup.
All the attacks observed by RIPS involved easy-to-exploit and well-known flaws.
The Shadow Brokers are offering the NSA arsenal for direct sale
16.12.2016 securityaffairs BigBrothers
The Shadow Brokers group has changed the model of sale, it has put up the NSA’s hacking arsenal for direct sale on an underground website.
The Shadow Brokers – Summary of the events
We have seen the notorious hacker group at the end of October, when the hackers leaked a fresh dump containing a list of servers that were hacked by the NSA-linked group known as Equation Group.
The Equation group compromised these targets using the hacking tools codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .
The first archive was containing roughly 300MBs of data, including firewall exploits, hacking tools, and scripts with cryptonyms like BANANAUSURPER, BLATSTING, and BUZZDIRECTION.
The security researchers Mustafa Al-Bassam published an interesting post that lists all the exploits, implants, and tools for hacking firewalls (“Firewall Operations”) included in the dump.
The Equation Group ‘s hackers targeted products made by Cisco, Fortigate, Juniper, TOPSEC, and Watchguard.
The majority of files are at least three years old, meanwhile, the newest timestamp dating to October 2013.
Early October, TheShadowBrokers complained that no one seems to be bidding on their precious archive, an alleged member of the hacker group expressed his dissent on the lack of interest in ponying up bitcoins to release the full NSA data dump.
A couple of weeks before the group announced the launch of a crowdfunding campaign for the stolen arsenal because its auction received offers for less than two bitcoins.
The hacker group that’s believed to be behind the high-profile cyber theft of NSA hacking tools and exploits that sparked a larger debate on the Internet concerning abilities of US intelligence agencies and their own security.
Back to the present
Now, once again, the group has changed the model of sale, it has put up the NSA’s hacking arsenal for direct sale on an underground website.
The file offered on the website contains a file signed with the cryptographic key of The Shadow Brokers, confirming the intent of the group in selling the entire NSA arsenal directly to buyers one by one.
Someone using the Boceffus Cleetus online moniker published a post on Medium titled “Are the Shadow Brokers selling NSA tools on ZeroNet?” announcing that the Shadow Brokers hackers are now offering for sale the “NSA tools individually.”
Segui
Boceffus Cleetus @CleetusBocefus
I just published “Are the Shadow Brokers selling NSA tools on ZeroNet?” https://medium.com/p/are-the-shadow-brokers-selling-nsa-tools-on-zeronet-6c335891d62a …
11:35 - 14 Dic 2016
Photo published for Are the Shadow Brokers selling NSA tools on ZeroNet?

Are the Shadow Brokers selling NSA tools on ZeroNet?
“…this is for the people of the sun!”
medium.com
18 18 Re 14 14 Mi piace
ZeroNet is a decentralized network of peer-to-peer users for hosting websites.
“ZeroNet uses bitcoin cryptography and the BitTorrent network.The BitTorrent website Play hosts a magnet link repository on ZeroNet, which links to copyrighted content. There is a Reddit community which offers support for ZeroNet.” states Wikipedia.
“Well howdy partners! I don’t wanna be getting arrested for passing on fake news and all. I rekon [sic] I ain’t no security professional but I am whutcha might call a ZeroNet enthusiast,” Cleetus writes. ZeroNet is a platform for hosting websites using blockchain and BitTorrent technology.
“Those dastardly ole shadow brokers have themselves a zite on ZeroNet. Yep and fars as I can tell they appears to be sellin NSA tools individually now,” added Cleetus.
The website includes a list of the products available for sale as explained by Joseph Cox from Motherboard.
The items are classified type, the list includes “exploits,” “Trojans,” and “implant-”

“The site includes a long list of supposed items for sale, with names like ENVOYTOMATO, EGGBASKET, and YELLOWSPIRIT. Each is sorted into a type, such as “implant,” “trojan,” and “exploit,” and comes with a price tag between 1 and 100 bitcoins ($780—$78,000). Customers can purchase the whole lot for 1000 bitcoins ($780,000).” states the post published on Motherboard.
“The site also lets visitors download a selection of screenshots and files related to each item. Along with those is a file signed with a PGP key with an identical fingerprint to that linked to the original Shadow Brokers dump of exploits from August. This newly uncovered file was apparently signed on 1 September; a different date to any of The Shadow Brokers’ previously signed messages.”
“If you like, you email TheShadowBrokers with name of Warez [the item] you want make purchase,” a message on the site reads. “TheShadowBrokers emailing you back bitcoin address. You make payment. TheShadowBrokers emailing you link + decryption password. Files as always being signed,” states the message on the website.
Během zátahu na DDoS služby zadržela policie desítky lidí, vyslechla mnoho dalších
15.12.2016 SecurityWorld Kriminalita
Pořádkové síly zadržely 34 podezřelých ve 13 státech v rámci zátahu na poskytovatele distribuovaných Denial-of-Service útoků. O všech zadržených se domnívá, že využili služeb serverů, které DDoS na zakázku zařizují.
Tyto DDoS služby dostávají zaplaceno za přehlcení webových stránek nebo jiných internetových systémů požadavky, čímž je shodí a dočasně k nim znemožní přistupovat; objednavatel služby nemusí dělat prakticky nic, nepotřebuje tedy více než základní znalost práce s počítačem a dostatek financí.
Kromě 34 zadržených se jednotlivé bezpečnostní složky zúčastněných států zaměřily na dalších 101 jednotlivců, jež vyslechly a varovaly před nelegální činností. Mnohým z podezřelých nebylo ani 20 let, stojí v prohlášení Europolu.
Většina zákazníků DDoS služeb je využívá k drsnějším vtípkům, často v prostředí online her; například zahltí IP adresu hráče-protivníka a odpojí ho tak ze hry.
DDoS útoky však lze snadno využít k mnohem horším činnostem – hackeři je již využili například ke shození služeb online podniků jako součást vydírání.
V extrémních případech lze pomocí DDoS útoky přerušit internetového spojení napříč státy, jako se to stalo během „bombardování“ DNS poskytovatele Dyn, které zpomalilo nebo úplně znemožnilo přístup k mnoha oblíbeným webovým stránkám ve Spojených státech.
Externí DDoS služby navíc umožňují útočit i naprostým amatérům, což rozhodně celkové situaci nepomáhá. Bezpečnostní firma Imperva odhaduje, že procento DDoS útoků fungujících prostřednictvím těchto služeb vzrostlo na celých 93 %.
Jedna ze služeb, na které se bezpečnostní složky zaměřily, byla Netspoof, vyplývá z vyjádření britské National Crime Agency. Nabízela „předplatné balíčky“ od pouhých 5 dolarů až po 480 dolarů. Někteří zákazníci dle informací agentury zaplatili přes 10 000 dolarů za zprostředkování stovek útoků.
„Oběti zahrnují poskytovatele herních služeb, vládní úřady, internetové hostingové služby, školy a univerzity,“ píše agentura.
V rámci zátahu FBI zadržela šestadvacetiletého muže z Kalifornie jménem Sean Sharma, podezřívají jej ze zakoupení externích DDoS služeb. Je obviněn z útoků proti nejmenované chatovací službě ze San Francisca. Pokud bude usvědčen, hrozí mu až 10 let vězení, píše v prohlášení FBI.
Není jasné, kolik DDoS služeb bylo během zásahu přerušeno, vyšetřování však kromě Velké Británie a Spojených států probíhalo také v Austrálii a dále ve Francii, Španělsku a dalších Evropských zemích. Česká republika zmíněna není, z nejbližších zemí se zátahu účastnily bezpečnostní složky Maďarska.
Nejobávanější viry, které se šíří i na českém internetu
15.12.2016 Novinky/Bezpečnost Viry
Patří mezi největší hrozby. Zároveň se počítačovým pirátům jimi daří pravidelně infikovat velké množství počítačů po celém světě. Na jaké škodlivé kódy by si měli dávat tuzemští uživatelé největší pozor.
Žebříček nezvaných návštěvníků, které obtěžují uživatele v Česku a na Slovensku nejčastěji, sestavila bezpečnostní společnost Check Point.
Conficker
Conficker byl nejrozšířenější hrozbou prakticky po celý rok 2009, pak se po něm slehla na několik měsíců zem. V letošním roce jej ale počítačoví piráti začali opět hojně využívat, díky čemuž se z něj stala nejrozšířenější hrozba, a to v tuzemsku i zahraničí.
Conficker využívá zranitelnost operačního systému Windows. Pro tu už dávno existuje bezpečnostní záplata, ale jak je ze statistik zřejmé, s její instalací si velká část uživatelů hlavu neláme. Na konci dubna se dokonce ukázalo, že se tento nebezpečný červ uhnízdil v počítačích v bavorské jaderné elektrárně Gundremmingen.
Autoři Confickera vybudovali po celém světě velkou síť infikovaných PC, využitelných na libovolnou úlohu, poněvadž počítače mohou díky viru ovládat na dálku. Na jeho řízení použili autoři červa inovativní způsob. Každý den se vygenerují nové náhodné domény, kam se vir hlásí a žádá instrukce.
Cryptowall
Cryptowall je hlavní ransomwarový trojan, který šifruje soubory na infikovaném počítači a pak žádá po uživatelích zaplacení výkupného za dešifrování. Šíří se prostřednictvím škodlivých reklamních a phishingových kampaní. Cryptowall se poprvé objevil již v roce 2014.
HackerDefender
HackerDefender je primárně určen pro operační systémy Windows 2000 a XP. Útočit nicméně může také na novějších platformách od Microsoftu. Jde o nezvaného návštěvníka, který upravuje různé funkce v operačním systému, aby se vyhnul detekci bezpečnostním softwarem. HackerDefender je široce rozšířený, protože je volně k dispozici na internetu a lze snadno nainstalovat. S jeho pomocí mohou útočníci maskovat další škodlivé kódy
Locky
Locky patří aktuálně k nejrozšířenějším vyděračským virům na světě. Kybernetičtí zločinci jej navíc transformovali do nové formy, ta je přitom přinejmenším stejně nebezpečná jako samotný Locky. Nová hrozba je stejně jako předchůdce šířena nejčastěji e-mailovými zprávami s přiloženým infikovaným excelovým dokumentem.
„Locky byl v minulých dnech objeven v nové formě. Nová varianta dostala jméno Osiris podle koncovek zašifrovaných souborů,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Samotný útok tedy probíhá úplně stejně, jako tomu bylo dříve u Lockyho. Sluší se připomenout, že tento vyděračský virus počítačoví piráti začali v minulých týdnech šířit nejen prostřednictvím e-mailů, ale také skrze falešné fotky na sociálních sítích.
Ani u jednoho ze zmiňovaných vyděračských virů se po úspěšném útoku lidé ke svým datům již nedostanou.
Zeus
Zeus je široce rozšířený trojan zaměřený na Windows a nejčastěji je používá ke krádežím bankovních přihlašovacích údajů. Je-li stroj infikován, malware posílá informace, například přihlašovací údaje k účtu. Trojan je také používán k distribuci vyděračských virů.
Zeus byl poprvé identifikován v červenci 2007, kdy byl použit ke krádeži informací z United States Department of Transportation. V průběhu několika dalších let malware infikoval stovky tisíc strojů a stal se jedním z největších světových botnetů. Malware byl distribuován především prostřednictvím e-mailů.
Tinba
Na pozoru by se měli mít uživatelé také před škodlivým kódem zvaným Tinba. Tento bankovní trojský kůň se zaměřuje především na evropské zákazníky bank. Krade přihlašovací údaje oběti – jakmile se uživatel pokusí připojit ke svému účtu na jedné z internetových stránek vytipované banky. Následně zobrazí falešné webové stránky na obrazovce zprávu, která uživatele žádá, aby vyplnil své osobní údaje.
Tinba je známý od roku 2012 a cíle jsou většinou v Evropě, zejména v Polsku a Itálii. Nicméně stroje infikované Tinbou byly detekovány po celém světě.
Cryptoload
Cryptoload je obecný název pro skripty vytvořené ke stahování malwaru (především vyděračských virů) a obvykle jsou poslané jako archívy v příloze spamových kampaní. Skripty byly použity ke stažení například ransomwarů Cryptowall, TeslaCrypt a Locky.
CTB-Locker
Jedním z dalších zástupců vyděračských virů, před kterým by se měli mít uživatelé na pozoru, je CTB-Locker. Ten se zaměřuje na platformu Windows. Zašifruje všechna uživatelská data a za dešifrování požaduje platbu.
Malware se obvykle šíří jako spam s nebezpečnou přílohou ZIP nebo CAB. Malware je s největší pravděpodobností vyvíjen a distribuován ruskými kyberzločinci a je prodáván většinou také ruským subjektům. Jako označení se používají i další názvy, například Critroni nebo Onion.
RookieUA
RookieUA je určen ke krádežím informací. Získává informace o uživatelských účtech, jako jsou přihlašovací jména a hesla, a odesílá je na vzdálený server.
Pozor na divné reklamy. Mohou během několika sekund zavirovat i váš Wi-Fi router
15.12.2016 Živě.cz Viry
Máte antivirus na Windows?
Nestahujete divná APK pro Android?
Fajn, ale co váš router? Je stejně dobře zabezpečený?
Netgear se musel v posledních dnech vypořádat se zranitelností několika svých populárních Wi-Fi routerů a rychle vydal alespoň betaverzi firmwarů pro postižené modely.
Routery Netgear obsahují kritickou chybu. Stáhněte si aktualizaci firmwaru
Bezpečnostní kauza připomněla dvě věci:
Útočníci se stále více zajímají o domácí routery, které jsou neustále připojené k internetu a uživatelé jim nevěnují takovou pozornost jako svému počítači a mobilu. Jsou tedy ideálním cílem.
Firmware routerů by se měl proto pokud možno aktualizovat průběžně a automaticky stejně jak to dnes dělají desktopové operační systémy. Hromada domácností přitom používá routery, které vyžadují ruční instalaci firmwaru, a tak jsou často nehorázně děravé.
Útoky na domácí Wi-Fi routery jsou z těchto důvodů poměrně oblíbené a záškodníci si svůj cíl mnohdy pečlivě vybírají. Nezajímají je spravované podnikové Wi-Fi sítě, ale přesně ta drobná wifinka u pana Nováka, který nejspíše nemá ani páru o tom, co že to ten firmware vlastně je.
Krásným příkladem je tento pečlivě zdokumentovaný útok, který dlouhé týdny studovali specialisté ze společnosti Proofpoint. Pojďme se tedy podívat do hlav záškodníků, kteří jej naplánovali krok za krokem.
Jak může vypadat útok na domácí Wi-Fi
Oběť bychom mohli nakazit třeba pomocí takzvaného malvertisingu, při kterém se snaží záškodník na svůj cíl zaútočit skrze podvodnou reklamu. V tomto případě však neútočí na váš mobil, laptop nebo třeba webový prohlížeč, ale právě na váš domácí router, přes který vše protéká, a tak je jeho ovládnutí mnohem lákavější a perspektivnější.
Jak tedy taková nákaza routeru propukne? Na začátku může být zdánlivě nevinný reklamní banner a to nikoliv na pochybné stránce s warezem nebo třeba pornografií, ale na vcelku běžném webu. Záškodník si totiž zakoupí jako každý jiný standardní reklamní prostor.
Vše začne zjištěním lokální IP adresy oběti
Součástí reklamního banneru je nicméně i docela drobný javascriptový kód, který pomocí technologie WebRTC a STUN získá vaši lokální IP adresu. Jak je to možné, je nad rámec tohoto článku, nicméně takové zjištění lokální IP adresy pomocí prostého Javascriptu si můžete vyzkoušet třeba na této stránce.
Je to domácí Wi-Fi? Tak to pokračujeme!
Pokud skript zjistí, že se jedná o typickou adresu malé domácí Wi-Fi sítě, třeba 192.168.1.154, zpozorní. V opačném případě jej přestaneme zajímat a prostě nám naservíruje nějakou relativně standardní reklamu, aniž by vzbudil podezření.
Když by však můj počítač měl onu pro něj lákavou IP adresu, bude se o mě skript dále zajímat a stáhne již záškodnický PNG obrázek. Na první pohled to bude reklama jako každá jiná, ale uvnitř souboru je v oblasti, kde jsou popisné informace, EXIF aj. uložený také HTML kód, který Javascript vyseparuje a zpracuje.
Vypadá to jako běžný reklamní obrázek, v jeho nitru je však v sekci metadat uložený HTML kód, který otevře neviditelný IFRAME a načte v něm další web
Jedná se o neviditelný IFRAME, ve kterém se ze serveru záškodníka načte další javascriptový kód, který opět stáhne drobný obrázek, v jehož útrobách je tentokrát uložený dešifrovací AES klíč. Skript jej opět vyseparuje a použije pro dešifrování dalších dat, která stáhne ze serveru záškodníka.
Tento kód stáhne další obrázek, ve kterém je schovaný dešifrovací AES klíč, který pomocí knihovny CryptoJS použije k dešifrování následných dat
166 Wi-Fi routerů
Jedná se především o databází 166 fingerprintů nejrůznějších modelů domácích routerů. Fingerprintem je v tomto případě nějaký jednoznačný identifikátor daného modelu – třeba drobný kus kódu jeho webové administrace, která je v tomto rozsahu dostupná zpravidla na adrese 192.168.1.1.
Jakmile si útočný skript stáhne a dešifruje fingerprinty, pokusí se spojit s webovou administrací routeru a zkouší jeden za druhým. Pokud by měl router XYZ ve své administraci třeba atypický obrázek netgear1234.gif o velikosti 154×23 pixelů, mohla by přesně tato informace sloužit jako jeho fingerprint.
Databáze fingerprintů 166 routerů
Dejme tomu, že má oběť opravdu špatný den a záškodníkův skript, který stále běží v neviditelném IFRAMU na stránce s jeho reklamou, opravdu identifikuje model routeru ve své databázi. V tom případě útok pokročí do další fáze a skript konečně stáhne malware, který zneužije některé ze zranitelností daného modelu, který, jak už víme, nemá poměrně často aktualizovaný firmware se záplatami.
A teď už jen naservírovat malware
Takový malware může být sám o sobě docela jednoduchý. Může se jednat podobně jako v případě Netgearu o vstup do jeho nitra prostým zadáním speciální URL adresy, která se správnými parametry otevře některé klíčové TCP porty zvenčí a umožní tak záškodníkovi vstup třeba skrze protokol telnetu.
Příklad HTTP POST příkazu na zranitelný router, který obsahuje příkaz ve formátu SOAP pro zpřístupnění vnitřního portu 23 (telnet) na vnějším portu 8780
V tomto konkrétním případě, který zdokumentoval Proofpoint, se útočníci soustředili především na nastavení vlastního DNS serveru na routeru, čehož zneužívají pro zobrazování vlastních bannerů skrze cizí reklamní systémy.
Dejme tomu, že na webu bude reklamní systém, který načítá bannery z adresy http://nejlepsireklamnisystem.cz. Záškodnický DNS server pak tuto doménu nepřeloží na správnou IP adresu, ale na tu svoji, která oběti naservíruje úplně jinou reklamu, anebo do každé stránky vloží Javascript, který se bude pokoušet otevírat nepopulární pop-upy.
Záškodnický DNS server přesměroval doménu na jinou IP adresu a server, který do kýžené stránky vložil kód, který po jakémkoliv kliku na stránce otevře popup
Hotový zlatý důl
A to je celé. Útočník zkompromitoval router oběti jednoduše proto, aby se vám v prohlížeči zobrazovaly jeho reklamy a on na tom všem vydělal. Pokud nebude jeho zásah do kódu, který k vám skrze hrdlo routeru putuje z internetu, příliš agresivní, možná si toho nebohý surfař ani nevšimne a bude jen nadávat na některý ze zcela běžných webů, že na něm opět přibyla hromada bannerů, ačkoliv realita může být trošku jiná.
Ovládnutí domácího Wi-Fi routeru tedy může být hotový zlatý důl, a jelikož je to brána mezi domácí a internetovou sítí, jeho napadením útočník získává kontrolu nad celým tokem dat, aniž by musel tradičními viry infikovat všechny počítače v síti.
Je ironií doby, že zatímco své počítače chráníme antiviry a tvůrci operačních systémů chrlí jednu záplatu za druhou, leckterá domácnost s podobně chráněnými desktopy, laptopy a mobily je k internetu připojená skrze často letitou krabičku, jejíž vlastní operační systém od výroby nikdo neaktualizoval.
Ostatně tuto praxi potvrzuje i můj projekt Wifileaks, pomocí kterého jsme s několika tisíci dobrovolníků zaměřili od roku 2012 bezmála 400 tisíc Wi-Fi sítí se zabezpečením WEP. To je přitom již velmi zastaralé a prolomitelné během několika málo minut. Lze tedy předpokládat, že se jedná právě o staré síťové krabičky – Wi-Fi routery a AP hotspoty, které dodnes slouží a nikomu to nepřipadne zvláštní, přestože již dávno patří do koše.
Nový level podvodu: útočníci si platí inzerci na Facebooku, která vede na falešné online bankovnictví
15.12.2016 Živě.cz Sociální sítě
Phishing je nejjednodušší a také nejčastější způsob, jak se útočníci dostávají do cizího bankovnictví. Stačí nepozornou oběť nalákat na stránku vydávající se za oficiální bankovní web a předložit jí přihlašovací formulář, z něhož odposlechnou jméno a heslo. Aktuálně se ale šíří především na Facebooku nová phishingová vlna, která tento typ podvodu posunula na novou úroveň. Útočníci se totiž nezdráhají platit za sponzorované příspěvky na sociální síti.
Podvodný facebookový profil od toho oficiálního rozeznáte jen těžko. Kdo by také od podvodníků čekal, že si budou platit inzerci. Uživatele by však měla varovat především podivná adresa, na kterou vede odkaz (foto: mBank)
Na praktiku upozorňuje mBank, zároveň se ale stejný typ útoku může týkat kterékoliv jiné banky. Na facebookové zdi se vám může objevit příspěvek označený jako Sponzorovaný, jenž se tváří jako reklama oficiální facebookové stránky banky. Má stejné jméno i stejnou fotku, takže odhalení podvodu si žádá minimálně rozkliknutí profilu.
V příspěvku se většinou nachází odkaz na web, kde je slíbeno nové internetové bankovnictví s odměnou za jeho používání a vede na podezřelé adresy typu ibnew.esy.es, ibnewmban.com nebo mbanking24.esy.es. Obsahují samozřejmě přihlašovací formulář pro vyplnění vašich údajů, ale v žádném případě je na takovou stránku nezadávejte. Pokud se tak stane, ihned změňte heslo a kontaktuje zákaznickou linku banky, kde se dočkáte další pomoci.
Další ukázky podvodných příspěvků na Facebooku. Na podobné odkazy nikdy neklikejte (foto: mBank)
Při každém přihlašování do internetového bankovnictví kontrolujte adresu stránky a také její certifikát zobrazený v adresním řádku. Rovněž nikdy nezadávejte údaje do bankovnictví, na které se dostanete prostřednictvím odkazu na sociálních sítích, v e-mailu či kdekoliv jinde než na oficiálním webu.
FBI Most Wanted Fugitive JPMorgan Hacker Arrested in New York
15.12.2016 THEHACKERNEWS Crime
One of the FBI's most wanted hackers who was behind the largest theft of financial data has finally been arrested at the JFK airport in New York.
Joshua Samuel Aaron is accused of being part of a hacking group that attacked several major financial institutions, including JPMorgan Chase, and according to the officials, which was "the largest theft of user data from a U.S. financial institution in history."
Aaron was believed to have been living as a fugitive in Moscow, Russia after being charged with hacking crimes in 2015, which exposed the personal information of more than 100 Million people.
On June 2015, a federal arrest warrant was issued for Aaron by the United States District Court, and the FBI and US secret service agents arrested him upon his arrival at the JFK airport in NY, announced the US Department of Justice.
"Aaron allegedly worked to hack into the networks of dozens of American companies, ultimately leading to the largest theft of personal information from US financial institutions ever," said Manhattan US Attorney Preet Bharara.
"For pursuing what we have called ‘hacking as a business model,’ and thanks to the efforts of the FBI and the US Secret Service, Aaron will now join his co-defendants to face justice in a Manhattan federal courtroom."
In 2015, the US Court of the Southern District of New York charged three men -- Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron -- with 23 counts, including hacking, identity theft, securities fraud, and money laundering, among others.
All the three hackers were accused of running an illegal payment processing business that the men used to stole $18 Million (£14.3 Million) from victims.
The three of them also hacked into a credit card company investigating their payment processing business in an effort to avoid detection.
Shalon and Orenstein were arrested in Israel in July 2015 and already extradited to the United States in June 2016.
Aaron is scheduled to appear in a Manhattan court on Thursday, according to the US authorities.
The Shadow Brokers are offering the NSA arsenal for direct sale
15.12.2016 securityaffairs BigBrothers
The Shadow Brokers group has changed the model of sale, it has put up the NSA’s hacking arsenal for direct sale on an underground website.
The Shadow Brokers – Summary of the events
We have seen the notorious hacker group at the end of October, when the hackers leaked a fresh dump containing a list of servers that were hacked by the NSA-linked group known as Equation Group.
The Equation group compromised these targets using the hacking tools codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .codenamed as INTONATION and PITCHIMPAIR. The ShadowBrokers provided the links to two distinct PGP-encrypted archives, the first one offered for free as a proof of the hack (its passphrase was ‘auctioned’), for the second one the group requested 1 million BTC .
The first archive was containing roughly 300MBs of data, including firewall exploits, hacking tools, and scripts with cryptonyms like BANANAUSURPER, BLATSTING, and BUZZDIRECTION.
The security researchers Mustafa Al-Bassam published an interesting post that lists all the exploits, implants, and tools for hacking firewalls (“Firewall Operations”) included in the dump.
The Equation Group ‘s hackers targeted products made by Cisco, Fortigate, Juniper, TOPSEC, and Watchguard.
The majority of files are at least three years old, meanwhile, the newest timestamp dating to October 2013.
Early October, TheShadowBrokers complained that no one seems to be bidding on their precious archive, an alleged member of the hacker group expressed his dissent on the lack of interest in ponying up bitcoins to release the full NSA data dump.
A couple of weeks before the group announced the launch of a crowdfunding campaign for the stolen arsenal because its auction received offers for less than two bitcoins.
The hacker group that’s believed to be behind the high-profile cyber theft of NSA hacking tools and exploits that sparked a larger debate on the Internet concerning abilities of US intelligence agencies and their own security.
Back to the present
Now, once again, the group has changed the model of sale, it has put up the NSA’s hacking arsenal for direct sale on an underground website.
The file offered on the website contains a file signed with the cryptographic key of The Shadow Brokers, confirming the intent of the group in selling the entire NSA arsenal directly to buyers one by one.
Someone using the Boceffus Cleetus online moniker published a post on Medium titled “Are the Shadow Brokers selling NSA tools on ZeroNet?” announcing that the Shadow Brokers hackers are now offering for sale the “NSA tools individually.”
Segui
Boceffus Cleetus @CleetusBocefus
I just published “Are the Shadow Brokers selling NSA tools on ZeroNet?” https://medium.com/p/are-the-shadow-brokers-selling-nsa-tools-on-zeronet-6c335891d62a …
11:35 - 14 Dic 2016

Photo published for Are the Shadow Brokers selling NSA tools on ZeroNet?
Are the Shadow Brokers selling NSA tools on ZeroNet?
“…this is for the people of the sun!”
medium.com
17 17 Re 14 14 Mi piace
ZeroNet is a decentralized network of peer-to-peer users for hosting websites.
“ZeroNet uses bitcoin cryptography and the BitTorrent network.The BitTorrent website Play hosts a magnet link repository on ZeroNet, which links to copyrighted content. There is a Reddit community which offers support for ZeroNet.” states Wikipedia.
“Well howdy partners! I don’t wanna be getting arrested for passing on fake news and all. I rekon [sic] I ain’t no security professional but I am whutcha might call a ZeroNet enthusiast,” Cleetus writes. ZeroNet is a platform for hosting websites using blockchain and BitTorrent technology.
“Those dastardly ole shadow brokers have themselves a zite on ZeroNet. Yep and fars as I can tell they appears to be sellin NSA tools individually now,” added Cleetus.
The website includes a list of the products available for sale as explained by Joseph Cox from Motherboard.
The items are classified type, the list includes “exploits,” “Trojans,” and “implant-”

“The site includes a long list of supposed items for sale, with names like ENVOYTOMATO, EGGBASKET, and YELLOWSPIRIT. Each is sorted into a type, such as “implant,” “trojan,” and “exploit,” and comes with a price tag between 1 and 100 bitcoins ($780—$78,000). Customers can purchase the whole lot for 1000 bitcoins ($780,000).” states the post published on Motherboard.
“The site also lets visitors download a selection of screenshots and files related to each item. Along with those is a file signed with a PGP key with an identical fingerprint to that linked to the original Shadow Brokers dump of exploits from August. This newly uncovered file was apparently signed on 1 September; a different date to any of The Shadow Brokers’ previously signed messages.”
“If you like, you email TheShadowBrokers with name of Warez [the item] you want make purchase,” a message on the site reads. “TheShadowBrokers emailing you back bitcoin address. You make payment. TheShadowBrokers emailing you link + decryption password. Files as always being signed,” states the message on the website.
Routery Netgear obsahují kritickou chybu. Stáhněte si aktualizaci firmwaru
15.12.2016 Živě.cz Zranitelnosti
Majitelé routerů značky Netgear by měli zbystřit. Několik populárních modelů je totiž náchylných na kritickou zranitelnost. Využití chyby je tak jednoduché, že odborníci z organizace CERT doporučili nepoužívat dotyčná zařízení. Informace o hrozbě zveřejnila CERT na svých internetových stránkách. Netgear však rychle zareagoval a již uvolnil betaverze opravných firmwarů.
Do Česka dorazila další vlna útoků na domácí routery. Obrana je přitom triviální
Jako první na chybu upozornil uživatel s přezdívkou Acew0rm, který na Twitteru zveřejnil i jednoduchý koncept útoku. Zranitelnost spočívá v tom, že neautorizovaný uživatel dokáže provést libovolný příkaz v prostředí routeru s nejvyšším root oprávněním.
Příklad útočného skriptu, který otevře službu Telnet na portu 45 - se znalostí IP routeru:
http://192.168.1.1/;telnetd$IFS-p$IFS'45 '
Může jít přitom o spuštění služby Telnet na určitém portu za účelem vytvoření zadních vrátek. Stejně se však dá i manipulovat s firmwarem a vložit do zařízení například škodlivý kód, který připojí router do botnetu. Možností zneužití je neomezené množství.
Chyba se nevyhnula ani vrcholnému modelu R8000
Chybu je možné využít pouze z lokální počítačové sítě. Přesto stačí, když se hackerům podaří přesvědčit oběť, aby například navštívila infikované internetové stránky. Ty budou obsahovat skript, který na pozadí, bez jakékoli interakce uživatele, infikuje zranitelný router.
Netgear se snažil uživatelům zjednodušit konfiguraci svých produktů, přičemž vytvořil speciální portál www.routerlogin.net. Po jeho zadání se otevře webové rozhraní připojeného routeru. Uživatel, naneštěstí ani útočník, tak nemusí znát přesnou IP adresu zařízení a dokáže se na něj připojit.
Netgear se za chybu omluvil a rychle pracuje na nápravě. Postupně uvolňuje nové verze firmwaru pro jednotlivé modely, byť zatím jen v rychle vytvořené betaverzi. Toto jsou modely, u kterých byla chyba zjištěna a opravný firmware je již k dispozici:
R6250
R6400
R6700
R6900
R7000
R7100LG
R7300DST
R7900
R8000
D6220
D6400
Zjistit, zda je váš Netgear router zranitelný, nebo ne, lze podle jednoduchého testu. Stačí kliknout na tento odkaz: www.routerlogin.net/cgi-bin/;uname$IFS-a Pokud je odpovědí chybové hlášení (např. 404 - Not Found), respektive zcela prázdná stránka, router netrpí touto zranitelností. V případě, že se objeví něco jiného, například informace typu: Linux R7000 2.6.36.4brcmarm + # 30 SMP PREEMPT, zařízení obsahuje chybu.
Napadnutelných routerů je daleko více. Záplata ale před hackery zavře dveře
15.12.2016 Živě.cz Zranitelnosti
Kritickou bezpečnostní chybu mohl v minulých dnech využít prakticky jakýkoliv počítačový pirát v routerech společnosti Netgear. Zneužít trhlinu v těchto branách do světa internetu mohli k zachytávání citlivých informací i k přesměrování síťového provozu na všech připojených zařízeních. Čerstvě vydaná oprava však všechny tyto problémy řeší.
O vydání záplaty informoval ve středu Piotr Dudek, regionální ředitel společnosti Netgear pro střední a východní Evropu.
Ten zároveň upozornil, že chyba se týkala daleko více routerů, než bylo původně uváděno. Podle amerického bezpečnostního týmu US-CERT totiž trhlinu obsahovaly pouze prémiové modely R7000 a R6400. Už tehdy se nicméně předpokládalo, že postižených zařízení bude kvůli použití jednotného uživatelského prostředí daleko více. [celá zpráva]
A to nyní potvrdil i samotný výrobce. Chyba se tak tedy týká modelů R6250, R6400, R6700, R6900, R7000, R7100LG, R7300DST, R7900, R8000, D6220, D6400 a D7000. Seznam navíc nemusí být ani v tuto chvíli konečný, další zařízení totiž pracovníci Netgearu stále ještě prověřují.
Nový ovládací software
Chybu v dotčených zařízeních již výrobce opravil v nové verzi ovládacího softwaru (firmwaru). Ten je však v současnosti k dispozici pouze v testovací verzi. I tak lze ale její instalaci s ohledem na možná rizika doporučit, jinak totiž budou moci kyberzločinci trhlinu zneužít.
Finální verze aktualizace by měla být pro všechny uživatele k dispozici v horizontu maximálně několika dní.
S využitím chyby mohou počítačoví piráti v domácí nebo podnikové síti udělat pěknou neplechu. Zranitelnost totiž umožňuje na napadeném zařízení spustit libovolný škodlivý kód na dálku, klidně i z druhého konce planety.
Přístup k připojenému PC
Že je router zavirovaný, mohou uživatelé poznat například podle toho, že jim přestane z připojených počítačů zcela fungovat internetové připojení, případně se při snaze o připojení na nějakou webovou stránku zobrazí úplně jiný web.
Přesně to se stalo už v minulosti kvůli zranitelnosti známé jako „rom-0“. Místo serverů, jako jsou například Seznam.cz nebo Google.com, se poškozeným zobrazila hláška o nutnosti instalace flash playeru. Místo té se ale do PC stáhnul další virus. Útočníci tak rázem měli přístup nejen k routeru, ale i k připojenému počítači.
S instalací aktualizace by tak lidé neměli rozhodně otálet.
Yahoo oznámilo rekordní únik dat - hackeři mají údaje více než miliardy uživatelů
15.12.2016 Živě.cz Hacking
Půlmiliardový únik uživatelský dat, který Yahoo potvrdilo v září letošního roku nebyl zdaleka největší. Včera totiž Yahoo zveřejnilo výsledky vyšetřování, které vedlo v souvislosti s napadením jeho systému v srpnu 2013. A zjištění je značně šokující – útočníci získali údaje k více než miliardě účtů včetně hesel zabezpečených slabý hešovacím algoritmem MD5.
Hesla nejsou zdaleka jediným údajem, který mají útočníci k dispozici. Patří k nim kromě uživatelských jmen také jména reálná, telefonní čísla, data narození i odpovědi na bezpečnostní otázky. Některé z nich mohou být v podobě holého textu. Hackeři se tak naštěstí nedostali k platebním údajům, které jsou uloženy v oddělené databázi.
Část e-mailu s informacemi o úniku dat, který aktuálně Yahoo rozesílá svým uživatelům
Aby toho nebylo málo, Yahoo ve své zprávě píše i o dalším bezpečnostním průšvihu. Útočníci totiž získali přístup ke zdrojovému kódu služeb Yahoo a dokázali podvrhnout uživatelské soubory cookies. Díky tomu se mohli jednoduše přihlásit k cizím uživatelským účtům. Firma takto postiženým uživatelům cookies zneplatnila.
Yahoo samozřejmě nabádá všechny uživatele, kteří měli v roce 2013 registrovaný účet ke změně hesla a firma taktéž resetovala bezpečnostní otázky, jejichž odpovědi nebyly šifrované. Zarážející je však především prohlášení v e-mailu pro uživatele, v němž se píše, že útočníci nezískali hesla v holém textu. To je však pravda pouze z části – na straně Yahoo byl využíván algoritmus MD5, který se za dostatečné zabezpečení dá považovat stěží. Můžeme tedy předpokládat, že potenciální útočníci velkou část hesel již dávno získali. Jak (ne)funguje MD5 si každý může ověřit třeba na webu Hashkiller.co.uk.
Levné Androidy s malware: v Rusku takových našli desítky
15.12.2016 Root.cz Android
Kupujete levný telefon či tablet s Androidem od málo známého výrobce? Tak to si dejte pozor, aby v systému nebyl i nechtěný přídavek v podobě malware. Ruský trh je jím zaplavený.
Bezpečnost operačního systému Android je dlouhodobě problematická, hlavně proto, že výrobci pomalu záplatují svoje verze operačního systému. Zde se alespoň situace pomalu vyvíjí k lepšímu. Koupí zařízení s Androidem se však můžete setkat i s mnohem horšími bezpečnostními problémy. Výzkumníci z antivirové společnosti Dr.Web odhalili, že řada chytrých telefonů a tabletů rovnou z výroby obsahuje trojského koně.
Než se začnete děsit, je třeba dodat, že jde převážně o zařízení určená pro ruský trh. Zároveň jde o značky pomyslné třetí kategorie, o kterých jste možná ani neslyšeli. Jmenovitě např. Irbis, Bravis, Supra, Nomi, Ritmix nebo Marshal. Trojský kůň byl nalezen v celkem 26 modelech. Trochu známější už je značka Prestigio, jejíž tablet MultiPad Wize 3021 se prodával i v České republice. Obraz systému však velmi pravděpodobně mohl být jiný.
Seznam kompromitovaných zařízení na ruském trhu: MegaFon Login 4 LTE, Irbis TZ85, Irbis TX97, Irbis TZ43, Bravis NB85, Bravis NB105, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Pixus Touch 7.85 3G, Itell K3300, General Satellite GS700, Digma Plane 9.7 3G, Nomi C07000, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, Irbis tz56, Jeka JK103.
Trojan se živí hlavně z reklam
Android.DownLoader.473.origin je stahovač, který se spustí vždy se zapnutím zařízení. Malware monitoruje Wi-Fi adaptér a poté se připojí ke command and control serveru, aby získal konfigurační soubor s instrukcemi. Soubor obsahuje informace o dalších aplikacích, které má trojan stáhnout. Po stažení je potají nainstaluje, popisují výzkumníci počáteční aktivitu malwaru. Takto může instalovat jak další škodlivé programy, tak prosté otravné aplikace nebo třeba vkládat reklamu na různá místa v systému. Odinstalace nechtěných programů obvykle nepomůže, protože je základní trojan nainstaluje znovu.
Payload od Android.Sprovider.7 je umístěn v samostatném modulu, který je detekován jako Android.Sprovider.12.origin. Je zašifrován a uložen ve zdrojích hlavního malwaru. Když uživatel odemkne domovskou obrazovku, trojan zkontroluje, zda je modul stále aktivní. Pokud ne, Android.Sprovider.7 znovu získá komponentu ze svého těla a spustí ji, píše se na stránkách Dr.Web. Poté už může dělat mnoho různých věcí. Z toho nejhoršího zmiňme možnost volat na libovolné číslo, zobrazovat reklamy ve stavovém řádku nebo ve všech aplikacích, otevírat odkazy v prohlížeči nebo instalovat balíčky (k tomu však musí dát uživatel svolení).
Původcem je zřejmě dodavatel systému
Ptáte se, jak se trojan vůbec do systému mohl dostat a kdo ho tam dal? Přesnou odpověď neznáme, nicméně výroba noname zařízení je celkem přímočará. Firma objedná hardware, obvykle v Číně, a mnohdy od někoho objedná i hotový obraz systému. Na starost už má potom jen prodej a distribuci. Vzhledem k tomu, že se problém týká širokého spektra značek, je dost možné, že samotní výrobci-značky o malwaru ani neví a nic z něj nemají. Systém o malware zřejmě „obohatil“ dodavatel obrazu systému.
Malou útěchou může být, že malware zřejmě nekrade data nebo se nepokouší uživatele nějak víc špehovat. Jde mu zkrátka o to vydělat svému tvůrci co nejvíc peněz, hlavně z všudypřítomných reklam apod. Jeho funkcionalita se však může rozšiřovat a není vyloučeno, že časem zdivočí. Zatím není znám způsob, jak systém očistit. Dr.Web informoval výrobce a teď je na nich, jak se k situaci postaví a zda vydají čistou aktualizaci systému. Dost možná nikoliv. Jediným řešením tak zůstává zařízení rootnout a o očištění se pokusit svépomocí, případně nahrát důvěryhodnou ROM. Komunitní podpora noname zařízení však často bývá slabá.
Jaké z toho plyne ponaučení? Asi nevěřit velmi levným zařízením od neznámých firem. Modely oficiálně distribuované v ČR sice pravděpodobně budou čisté, ale pokud objednáváte z Číny nebo jiných dalekých končin, už to může být horší a nebudete vědět, co je pro vás v zařízení přichystáno. Zřejmě nejlepším řešením, pokud už chcete koupit levný noname smartphone či tablet, je vybrat rozšířený model s dobrou komunitní podporou a nahrát do něj slušnou ROM.
After Failed Auction, Shadow Brokers Opens NSA Hacking Tools for Direct Sales
15.12.2016 thehackernews BigBrothers
Remember The Shadow Brokers?
The hacker group that's believed to be behind the high-profile cyber theft of NSA hacking tools and exploits that sparked a larger debate on the Internet concerning abilities of US intelligence agencies and their own security
The group put the stolen cyber weapons on auction but received not much response and gone quiet for some time.
However, The Shadow Brokers has now appeared to have put up the NSA's hacking tools and exploits for direct sale on an underground website.
A newly uncovered site reportedly contains a file signed with the cryptographic key of The Shadow Brokers, suggesting the hacker group has now moved to sell NSA hacking tools directly to buyers one by one, Motherboard reports.
On Wednesday, someone going by pseudonym Boceffus Cleetus published a post on Medium, saying that the Shadow Brokers hackers are now selling "NSA tools individually."
"The site also lets visitors download a selection of screenshots and files related to each item," notes Joseph Cox of Motherboard. "Along with those is a file signed with a PGP key with an identical fingerprint to that linked to the original Shadow Brokers dump of exploits from August."
The blog titled "Are the Shadow Brokers selling tools on ZeroNet?," reports a list of items, supposedly for sale on ZeroNet by the Shadow Brokers, with titles like "ENVOYTOMATO, EGGBASKET, and YELLOWSPIRIT."
ZeroNet is a decentralized Internet-like network for hosting websites using blockchain cryptography as DNS servers and BitTorrent technology as file servers.
Each of the items (NSA hacking tools) on the site is categorized into a type — like "exploits," "Trojans," and "implant" — each of which is ranged from 1 to 100 Bitcoins (from $780 to $78,000).
Anyone, including state-sponsored hackers with nation’s funding, could buy all the exploits for around $780,000.
BlackEnergy hackers, now TeleBots, target Ukrainian banks
15.12.2016 securityaffairs Virus
The BlackEnergy hacker group that targeted the Ukrainian grid one year ago, now identified as TeleBots, are targeting Ukrainian banks.
The BlackEnergy hacker group that targeted the Ukrainian grid one year ago causing a power outage in the country are now targeting Ukrainian banks. The Ukrainian government accused Russia of being involved in the attack, but further analysis revealed that the BlackEnergy malware was not directly responsible for the outages.
According to the experts at the ESET firm, the gang is exploiting the TeleBots malware against banks in Ukraine. The malicious code shares a number of similarities with the malware used by the BlackEnergy group. ESET speculates that the BlackEnergy group crew has evolved across the time into the threat actors called TeleBots group.
“In the second half of 2016, ESET researchers identified a unique malicious toolset that was used in targeted cyberattacks against high-value targets in the Ukrainian financial sector. We believe that the main goal of attackers using these tools is cybersabotage. This blog post outlines the details about the campaign that we discovered.” reads a blog post published by ESET.
“We will refer to the gang behind the malware as TeleBots. However it’s important to say that these attackers, and the toolset used, share a number of similarities with the BlackEnergy group, which conducted attacks against the energy industry in Ukraine in December 2015 and January 2016. In fact, we think that the BlackEnergy group has evolved into the TeleBots group.”
The hackers are leveraging on spear phishing message with Microsoft Excel documents containing malicious macros.
Once a victim clicks on the Enable Content button, the macro in TeleBots documents drops a malicious binary using the explorer.exe filename and then to execute it. The malicious code is trojan downloader, that is written in the Rust programming language, that download and executes another strain of malware. This trojan downloader is written in the Rust programming language.
“Once a victim clicks on the Enable Content button, Excel executes the malicious macro. Our analysis shows that the code of the macro used in TeleBots documents matches the macro code that was used by the BlackEnergy group in 2015.” continues ESET.
Below the similarities between BlackEnergy and TeleBots source codes.

“The main purpose of the macro is to drop a malicious binary using the explorer.exe filename and then to execute it. The dropped binary belongs to a trojan downloader family, its main purpose being to download and execute another piece of malware. This trojan downloader is written in the Rust programming language.”
TeleBots hackers are able to fully compromise the machine and spread in the target network, the experts noticed that it is also able to drop the KillDisk malware onto the target machine making it unbootable before displaying a FSociety Mr Robot-themed logo on the computers’ screens as a sign-off.
The experts have no doubts, the TeleBots threat actors aim to conduct cybersabotage attacks, clearly, Russia was the prime suspect.
Phishing campaign on Office 365 Business users leverages Punycode
15.12.2016 securityaffairs Phishing
Security researchers discovered a new phishing campaign leveraging Punycode and a bug in Office 365 defense systems to deceive victims.
Office 365 business email users continue to be the target of phishing campaigns, a new wave of attacks was leveraging Punycode to avoid detection of Microsoft’s default security and desktop email filters.
Punycode is a method added to the Domain Name System (DNS) in order to support non-ASCII characters within a web URL.
Security researchers from Avanan security warn of a new phishing campaign that aims to steal Office 365 credentials and abuses a vulnerability in how Office 365 anti-phishing and URL-reputation security layers deal with Punycode.
Office 365 is even popular as corporate email solution, for this reason, hackers are increasing their interest on it.
“Avanan’s cloud security researchers uncovered a new attack method against Office 365 business email that goes undetected by Microsoft’s Office 365 default security and bypasses desktop email filters.” states a blog post published by Avanan.”The attack includes a phishing scheme to steal Office 365 credentials, and leverages what appears to be a vulnerability in how Office 365 anti-phishing and URL-reputation security layers translate Punycode”
Punycode was already exploited in past attacks in order to trick victims into clicking links that looked legitimate, in this last attack it was designed to bypass the Office 365 anti-phishing filters and email phishing protection systems instead.
The researchers explained that this specific attack is possible due to a gap in the Office 365 phishing filters.
“What makes this attack different is that instead of fooling the user, it was designed to fool the anti-phishing filters found in Office 365 and other email phishing protection systems. Hackers have identified a gap in the Office 365 phishing filters and are starting to leverage it in order to compromise accounts.” continues the analysis.
The phishing campaign detected by Avanan leverages on fake FedEx emails that URLs that appear to be legitimate.
Leveraging on the vulnerability in the phish-detection engine, the URL actually resolves to two different domains, one followed by the malware protection filter and the second one followed by the browser when the user clicks on it.
The legitimate and safe URL is the one followed by protection systems implemented in Office 365, while the malicious one is followed by the browser redirecting the victims to a bogus domain.
“What makes this attack nefarious is that by using Punycode and a flaw in the phish-detection engine, the URL actually goes to TWO different sites, one followed by the malware protection filter and the other followed by the end-user’s browser when he or she clicks on it.” states the analysis.
The experts discovered that Office 365’s default security systems check domain reputation by analyzing it as plain ASCII.
The rapid diffusion of the Office 365 solution in the business environments will continues attract cyber criminal syndicates.
Počet kybernetických útoků roste. Češi se ale příliš bát nemusí
15.12.2016 Novinky/Bezpečnost Kriminalita
Bezpečnostní společnost Check Point zveřejnila aktuální žebříček virových hrozeb. Z něj je patrné, že počet nejrůznějších počítačových útoků ve světě stoupá. Paradoxně ve vodách českého internetu je ale bezpečněji. Virová nákaza hrozí více například i na sousedním Slovensku.
Žebříčku zemí, kde útočí viry nejčastěji, dominuje Indie. Na druhém místě se pak umístily Spojené státy a na třetím Filipíny. První pětku pak uzavírá Brazílie a Turecko.
Přední pozice v žebříčku samozřejmě lichotivé nejsou. Umístění na horních příčkách znamená, že nákaza virem je daleko pravděpodobnější než v zemích, které jsou na spodních pozicích.
Tuzemské uživatele bude ale patrně nejvíce zajímat situace v našich končinách. A ta byla překvapivě podle aktuálních dat Check Pointu v říjnu lepší než v září. „Česká republika zaznamenala v říjnu jeden z největších posunů mezi bezpečnější země a umístila se až na 115. pozici, zatímco v září byla na 72. místě,“ upozornil David Řeháček, bezpečnostní odborník ze společnosti Check Point.
Virů je více
„Podobně se mezi bezpečnější země posunulo i Slovensko, které je na 99. místě, když v září bylo na 61. pozici,“ konstatoval Řeháček. Přesto je ale rizika nákazy počítačovým virem u našich východních sousedů vyšší než v tuzemsku.
Pozitivních posunů bylo v žebříčku více. „Vůbec největší pozitivní posun zaznamenala Argentina, která se z 59. zářijové pozice posunula na 120. příčku. Naopak nejvýrazněji se mezi méně bezpečné země posunulo Bělorusko, které se z bezpečné 117. příčky posunulo až na 33. pozici. Na prvním místě se v Indexu hrozeb umístila stejně jako v září Botswana,“ podotkl bezpečnostní odborník.
Celkový počet virů, které brázdí internetem, však v říjnu rostl. Počet aktivních malwarových rodin se zvýšil ve srovnání s předchozím měsícem o pět procent. Je tedy patrné, že se kyberzločinci připravují na Vánoce – v tomto období totiž tradičně koluje sítí nejvíce hrozeb v celém roce. Obezřetnost je tedy na místě.
Ransomware vede
Experti varují především před hrozbami, které se internetem šíří nejčastěji. „Ransomware Locky, který se poprvé objevil v únoru letošního roku, i nadále roste a posunul se ze třetí příčky mezi nejrozšířenějšími malwarovými rodinami na druhou,“ konstatoval Řeháček.
„Bankovní trojan Zeus se posunul o dvě místa a vrátil se do Top 3. Důvodem dalšího vzestupu Lockyho je konstantní vytváření nových variant a rozšíření distribučního mechanismu, který převážně využívá nevyžádané e-maily. Tvůrci neustále mění typy souborů používané pro stahování ransomwaru, včetně doc, xls a wsf souborů, a také významně mění strukturu rozesílaného spamu,“ doplnil bezpečnostní expert.
Ransomware je souhrnné označení pro vyděračské viry, které nasazují kyberzločinci v poslední době stále častěji. Tento nezvaný návštěvník uzamkne data v počítači a za jejich odemčení požaduje výkupné. Ani po jeho zaplacení však uživatelé nemají jistotu, že jim budou data opět zpřístupněna.
Hackeři se zmocnili údajů miliardy uživatelů portálu Yahoo
15.12.2016 Novinky/Bezpečnost Incidenty
Hackeři ukradli údaje z účtů více než miliardy lidí používajících e-maily a další služby firmy Yahooo. Oznámila to ve středu americká internetová společnost, podle níž k útoku kybernetických zločinců došlo v roce 2013. Podle agentury AP jde o největší známý průnik do systému některé ze společností poskytujících e-mailové účty.
Ukradené informace mohou podle Yahoo zahrnovat jména, e-mailové adresy, telefonní čísla, data narození a takzvané ověřovací otázky a odpovědi na ně. Citlivější údaje jako data o bankovních účtech či čísla platebních karet podle firmy hackeři nezískali.
Mohly se jim však dostat do ruky hesla od uživatelských účtů. To by mohlo přinést potíže lidem, kteří používají stejná hesla pro své další internetové účty a služby.
Experti na internetovou se podle AP domnívají, že akce je nejspíš dílem některé ze zahraničních vlád, která se snažila získat informace o konkrétních lidech. Proto se prý většina klientů firmy nemusí obávat. Pokud by čin spáchali běžní hackeři jednající na vlastní pěst, data by se zřejmě pokusili prodat na webu, což se nestalo.
Druhý velký únik
Společnost oznámila podobný únik už v září; tehdy šlo o kybernetický útok z roku 2014 a ukradena byla data z 500 miliónů účtů. Viník ani tehdy zjištěn nebyl.
Oba případy podle AP vrhají pochybnosti na chystanou koupi digitálních aktivit firmy Yahoo telekomunikačním gigantem Verizon - obě společnosti se předběžně dohodly na částce 4,8 miliardy dolarů (121 miliard korun). Pokud by však oznámení úniků vedlo k odlivu zákazníků Yahoo, mohl by Verizon ztratit o obchod zájem.
Yahoo rovněž uvedla, že informuje všechny dotčené uživatele a poradí jim, jak se chránit. Doporučila také všem uživatelům změnit hesla. Pokud stejné heslo užívají i pro přístup na jiné stránky, měli by tato hesla rovněž změnit.
Jak má vypadat správné heslo?
Bezpečné heslo by mělo mít minimálně šest znaků a mělo by obsahovat číslice a ideálně velká i malá písmena. Heslo by naopak v žádném případě nemělo být tvořeno jménem uživatele, jednoduchými slovy (jako například „heslo”) nebo pouhou posloupností číslic.
Je důležité zdůraznit, že databáze může představovat pro uživatele potenciální riziko i po letech, a to i v případě, že si již změnili přístupové heslo. Celá řada lidí totiž používá stejné přihlašovací údaje k různým webovým službám. Pro počítačové piráty tedy není nic jednoduššího než hesla vyzkoušet i na jiných serverech.
V případě, že lidé používají totožná hesla jako ke službě Yahoo i na jiných webových službách, je vhodné je změnit samozřejmě i tam.
Ashley Madison Dating Site Agrees to Pay $1.6 Million Fine Over Massive Breach
15.12.2016 thehackernews Incindent
Ashley Madison, an American most prominent dating website that helps married people cheat on their spouses has been hacked, has agreed to pay a hefty fine of $1.6 Million for failing to protect account information of 36 Million users, after a massive data breach last year.
Yes, the parent company of Ashley Madison, Ruby Corp. will pay $1.6 Million to settle charges from both Federal Trade Commission (FTC) and 13 states alleging that it misled its consumers about its privacy practices and did not do enough to protect their information.
Not only the company failed to protect the account information of its 36 Million users, but also it failed to delete account information after regretful users paid a $20 fee for "Full Delete" of their accounts.
Moreover, the Ashley Madison site operators were accused of creating fake accounts of "female" users in an effort to attract new members.
Avid Life Media denied the claim at the time, but a year later when the company rebranded as Ruby Corp., it admitted that tens of thousands of female users on AshleyMadison.com had just been lines of code.
Last year, a group of hackers released tons of gigabytes of critical data belonging to the company's internal operation as well as millions of Ashley Madison users that led to blackmails and even suicides.
Ruby Corp. was intended to pay a total of $17.5 Million fine -- $8.75 million fine to the FTC and another $8.75 million to 13 states that also filed complaints -- but the company can afford to pay just $1.6 Million fine.
"Today's settlement closes an important chapter on the company's past and reinforces our commitment to operating with integrity and to building a new future for our members, our team and our company," Rob Segal, Ruby's newly-appointed CEO, wrote in a blog post.
Besides this, Ruby Corp. has agreed to 20 years' worth of the FTC overseeing its network security to ensure that user data is being protected.
Here's the federal court order [PDF] that requires Ashley Madison to:
Perform a risk assessment to protect customer data
Implement new data security protocols
Upgrade systems based on the assessments
Offer periodic security risk assessment (both internal and third-party)
Require "reasonable safeguards" against any potential cyber attacks from their service providers
Ashley Madison was hacked in July 2015, resulting in the disclosure of personal information belonging to 35 Million users, including their usernames, first and last names, passwords, credit card data info, street names, phone numbers, transactions records, and email addresses.
Simple Bug allows Hackers to Read all your Private Facebook Messenger Chats
15.12.2016 thehackernews Vulnerebility
A security researcher has discovered a critical vulnerability in Facebook Messenger that could allow an attacker to read all your private conversation, affecting the privacy of around 1 Billion Messenger users.
Ysrael Gurt, the security researcher at BugSec and Cynet, reported a cross-origin bypass-attack against Facebook Messenger which allows an attacker to access your private messages, photos as well as attachments sent on the Facebook chat.
To exploit this vulnerability, all an attacker need is to trick a victim into visiting a malicious website; that’s all.
Once clicked, all private conversations by the victim, whether from a Facebook's mobile app or a web browser, would be accessible to the attacker, because the flaw affected both the web chat as well as the mobile application.
Dubbed "Originull," the vulnerability actually lies in the fact that Facebook chats are managed from a server located at {number}-edge-chat.facebook.com, which is separate from Facebook's actual domain (www.facebook.com).
"Communication between the JavaScript and the server is done by XML HTTP Request (XHR). In order to access the data that arrives from 5-edge-chat.facebook.com in JavaScript, Facebook must add the "Access-Control-Allow-Origin" header with the caller’s origin, and the "Access-Control-Allow-Credentials" header with "true" value, so that the data is accessible even when the cookies are sent," Gurt explained.
The root of this issue was misconfigured cross-origin header implementation on Facebook's chat server domain, which allowed an attacker to bypass origin checks and access Facebook messages from an external website.
The root of this issue was misconfigured cross-origin header implementation on Facebook's chat server domain, which allowed an attacker to bypass origin checks and access Facebook messages from an external website.
Gurt has also released a proof-of-concept video demonstration of the Originull vulnerability, which shows the cross-origin bypass-attack in action.
Gurt has also released a proof-of-concept video demonstration of the Originull vulnerability, which shows the cross-origin bypass-attack in action.
However, Secret Conversations, Facebook Messenger's end-to-end encrypted chat feature was not affected by this bug, as it can be initiated or launched only using its mobile app.
"This security flaw meant that the messages of 1-billion active monthly Messenger users were vulnerable to attackers," said Stas Volfus, Chief Technology Officer of BugSec.
"This was an extremely serious issue, not only due to the high number of affected users, but also because even if the victim sent their messages using another computer or mobile, they were still completely vulnerable."
The researcher disclosed the severe vulnerability to Facebook through its Bug Bounty program. The Facebook security team acknowledged the issue and patched the vulnerable component.
You can read the full details of the flaw on Cynet’s blog post published on Tuesday.
Yahoo Admits 1 Billion Accounts Compromised in Newly Discovered Data Breach
15.12.2016 thehackernews Incindent
In what believe to be the largest data breach in history, Yahoo is reporting a massive data breach that disclosed personal details associated with more than 1 Billion user accounts in August 2013.
…And it's separate from the one disclosed by Yahoo! in September, in which hackers compromised as many as 500 Million user accounts in late 2014.
What's troubling is that the company has not been able to discovered how "an unauthorized third party" were able to steal the data associated with more than one Billion users.
The data breach officially disclosed on Wednesday actually occurred in 2013 and, just like the one in 2014, allowed the cyber crooks to obtain personal information of its users but not credit card details.
Here's what Yahoo's chief information security officer Bob Lord says the hackers obtained:
"The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5) and, in some cases, encrypted or unencrypted security questions and answers."
The hashed passwords used an aging algorithm called MD5 that can easily be cracked. Moreover, in some incidents, the hack revealed unencrypted security questions and answers that would provide quick access to users accounts.
The public disclosure of this latest data breach came upon "further analysis" of data that law enforcement provided Yahoo in November.
Change your Password and Security Q&A Immediately
Of course, if you are one of those potentially affected users, you are strongly recommended to change your passwords and invalidate affected security questions.
Also, if you are using the same password and answers for security questions somewhere else, change them too.
Yahoo has started notifying the account holders affected by the massive data breach, requiring them to change their passwords immediately.
Both the data breaches at Yahoo! came after the company negotiated a deal to sell its core internet business to Verizon Communication Inc for $4.8 Billion.
The September disclosure of half a billion users' breach prompted Verizon to say in October that it might withdraw from the agreement to buy Yahoo.
Here's the statement from Verizon spokesman Bob Verettoni about the recent largest data breach:
"As we've said all along, we will evaluate the situation as Yahoo continues its investigation. We will review the impact of this new development before reaching any final conclusions."
Previous data breach news had already magnified company's problems, and now when another data breach affecting a Billion users has been disclosed, would Yahoo be able to save its acquisition deal?
Yahoo admits one billion accounts exposed in a newly discovered data breach
15.12.2016 securityaffairs Incindent
The tech giant Yahoo admitted crooks have probably stolen details from more than a billion user accounts, and the incident is not linked to previous ones.
Bad news for Yahoo!, the company admitted crooks have probably stolen details from more than a billion user accounts. In 2013, hackers broke into the systems of Yahoo and accessed one billion user accounts containing names, addresses, phone numbers, and hashed passwords easy to crack. The passwords were protected with MD5 hashing algorithm that is easy to crack, the leaked data also include some encrypted and cleartext security questions and answers have been compromised too.
The company is urging its customers to reset their passwords.
According to the Yahoo CISO, Bob Lord, data is genuine and this discovery is not linked to past data breaches. The company dates the incident back in August 2013 and blames an unauthorised third party that it hasn’t identified.
“We analysed this (stolen) data with the assistance of outside forensic experts and found that it appears to be Yahoo user! data,” Lord says.
“Based on further analysis of this data by the forensic experts, we believe an unauthorised third party, in August 2013, stole data associated with more than one billion user accounts.
“We have not been able to identify the intrusion associated with this theft. “
The incident is alarming if we also consider past breaches alleged suffered by the Tech Giant.
“The number of affected accounts was double the number implicated in a 2014 breach that the internet company disclosed in September and blamed on hackers working on behalf of a government. News of that attack, which affected at least 500 million accounts, prompted Verizon Communication Inc to say in October that it might withdraw from an agreement to buy Yahoo’s core internet business for $4.83 billion.” reported the Reuters.
It seems that no financial data was exposed in the incident, anyway we have to consider that Yahoo users are not exposed to a great potential risk of attacks such as identity theft. Crooks can exploit stolen data to target users with social engineering attacks and launch spear phishing campaigns.
Of course, the news will have a significant impact on the acquisition of the company by Verizon because the hackers have stolen the main asset of the tech giant, the data. Analysts speculate a possible interference with the announced $4.8 billion sale of the company to Verizon.
“we will review the impact of this new development before reaching any final conclusions.” commented Verizon.
A Yahoo spokesman told Reuters that the company has been in communication with Verizon during its investigation, he is confident the data breach will not affect the acquisition.
Cryptolulz hacked the website of the Russian embassy of Armenia
15.12.2016 securityaffairs Hacking
The black hat hacker Cryptolulz broke into the database of the website of Russian embassy of Armenia (www.embassyru.am) and leaked data.
The black hat hacker Cryptolulz, a former member of the Powerful Greek Army, hacked the website of Russian embassy of Armenia (www.embassyru.am).
“I would like to tell you that I have successfully penetrated the site” Cryptolulz told me via Twitter. “I have taken over its database”

He exploited a blind SQL Injection vulnerability, he hacked the website of Russian embassy of Armenia to create awareness amongst the authorities.
“because I don’t think they care much about security … lol”
The hacker tried to contact the admins of the website some time ago, but he hasn’t received any response.
“I left them an email but no reply so I decided to leak a short amount of their database…” he added.
He broke into the database a0014414_embassy that contains 36 tables, but the hacker leaked only the “user” table which contains the credentials for the admin, the editor and other people in the stuff. He avoided disclosing the members’ records because they may include classified information.
Data was published on Pastebin, leaked records include id, name, type, email, login, password, last visit IP address, last visit date, profile creation date.
Cryptolulz was involved in several data leaks of government websites, including the Mexican telecommunication website and several DDoS attacks against government website and banks. He defined its motivation as “politically driven hacking.”
My reason for targeting this website was to create awareness amongst the people and higher authorities… because I don’t think they
Cryptolulz now joined a new hacking team called Fallensec.
Microsoft releases 12 Security Updates; Including 6 Critical Patches
14.12.2016 thehackernews Vulnerebility
For the last Patch Tuesday for this year, Microsoft has released 12 security bulletins, half of which are rated 'critical' as they give attackers remote code execution capabilities on the affected computers.
The security bulletins address vulnerabilities in Microsoft's Windows, Office, Internet Explorer and Edge.
The first critical security bulletin, MS16-144, patches a total of 8 security vulnerabilities in Internet Explorer, 3 of which had publicly been disclosed before Microsoft issued patches for them, though the company said they're not being exploited in the wild.
The 3 publicly disclosed vulnerabilities include a Microsoft browser information disclosure vulnerability (CVE-2016-7282), a Microsoft browser security feature bypass bug (CVE-2016-7281) and a scripting engine memory corruption vulnerability (CVE-2016-7202) that allow remote code execution on the affected computer.
The remaining 5 security flaws include a scripting engine memory corruption bug, two memory corruption vulnerabilities, an information disclosure bug, and a Windows hyperlink object library information disclosure bug.
Next critical bulletin, MS16-145, addresses a total of 11 flaws in the Edge browser, 3 of which have also been publicly disclosed but the company they are not actively being exploited.
Two flaws (CVE-2016-7282 and CVE-2016-7281) are the same as in IE, and the third one is an information disclosure vulnerability (CVE-2016-7206) whose existence has also been made public.
Remaining 8 vulnerabilities allow an attacker to perform remote code execution and information disclosure.
Another critical bulletin, MS16-146, includes the monthly security patch for Microsoft graphics components, addressing two RCE flaws in Windows graphics components, as well as one Windows GDI information disclosure flaw.
The most severe flaws in each of the above bulletins are remote code execution (RCE) bugs, wherein viewing a specially crafted web page or opening a malicious document could remotely execute malicious code on a victim's computer.
Other critical bulletins include MS16-147 that addresses a security issue in Windows Uniscribe and MS16-148 that fixes a total of 16 security flaws in Microsoft Office, Office Services, and Web Apps.
Those 16 vulnerabilities include 4 memory corruption, one Office OLE DLL side-loading flaw, 3 security feature bypass bugs, one GDI information disclosure issue, 6 MS Office information disclosure bug, and one elevation of privilege bug in Microsoft Auto Update (MAU).
Last, but not the least, critical bulletin, MS16-154, addresses a total of 17 flaws in the embedded Adobe Flash Player for Edge and Internet Explorer, one of which includes a zero-day exploited in targeted attacks.
This bulletin contains 7 use-after-free vulnerabilities that could lead to remote code execution, 4 buffer overflow flaws, 5 memory corruption bugs that could also result in remote code execution and one security bypass issue.
Remaining are the important security bulletins that address an elevation of privilege bug in the Windows Secure Kernel Mode, an information disclosure bug in the .NET framework, two elevation of privilege bulletins in Windows and the Windows kernel-mode drivers, and an information disclosure bug in Windows.
Users and IT administrators are strongly recommended to apply these critical security updates as soon as possible, since some of the vulnerabilities had already been publicly disclosed, giving hackers chance to get into your systems.
5-year-old Skype Backdoor Discovered — Mac OS X Users Urged to Update
14.12.2016 thehackernews Vulnerebility
Those innocent-looking apps in your smartphone can secretly spy on your communications or could allow hackers to do so.
Hard to believe, but it's true.
Recently, Trustwave's SpiderLabs analysts discovered a hidden backdoor in Skype for Apple's macOS and Mac OS X operating systems that could be used to spy on users' communications without their knowledge.
The backdoor actually resides in the desktop Application Programming Interface (API) that allows third-party plugins and apps to communicate with Microsoft-owned Skype — the popular video chat and messaging service.
Appeared to have been around since at least 2010, the backdoor could allow any malicious third-party app to bypass authentication procedure and provide nearly complete access to Skype on Mac OS X.
How an Attacker can Take Complete Control of Your Skype
The malicious app could bypass authentication process if they "identified themselves as the program responsible for interfacing with the Desktop API on behalf of the Skype Dashboard widget program."
Accessing this backdoor is incredibly easy. All hackers need to do is change a text string in apps to this value → "Skype Dashbd Wdgt Plugin," and the desktop API would provide access to sensitive features of Skype.
An attacker or any malicious program abusing this hidden backdoor could perform the following actions:
Read notifications of incoming messages (and their contents)
Intercept, read and modify messages
Log and record Skype call audio
Create chat sessions
Retrieve user contact information
The researchers have also provided proof-of-concept Objective-C code that initiates the connection process without asking the user for permission for the process to attach to Skype:
The backdoor believes to have been created by a developer at Skype before Microsoft acquired the company and likely exposed more than 30 Million Mac OS X users.
Update Your Skype Installation Now!
Trustwave notified Microsoft of the vulnerability in October, and the company has patched the issue in Skype 7.37 and later versions.
Here's what a Microsoft spokesperson said about the backdoor:
"We do not build backdoors into our products, but we do continuously improve the product experience [and] product security and encourage customers to always upgrade to the latest version."
Trustwave also speculated that the backdoor believed to have been accidently left in Skype "during the process of implementing the dashboard plugin," as the Skype dashboard widget does not appear to utilize it.
All versions of Skype for macOS and Mac OS X, including 7.35 version, are vulnerable. So users are strongly recommended to update their Skype installation as soon as possible.
Expedia Hacked By Its Own Employee, a case study
14.12.2016 securityaffairs Hacking
The Expedia employee, John Ly, is accused of hacking into executives computers to access corporate confidential information.
Its no secret, cyber criminals are constantly looking towards greener pastures – money green that is. The most sought pastures…. insider trading and market manipulation. It’s a perfect storm scenario with almost everyone losing but the hacker. Luckily regulators are very well aware, dedicating massive resources to detect and deter such fraud. A recent case pursued by the SEC paints a small picture of how these frauds are evolving. It also demonstrates their determination in pursuing these cases.
Last week the SEC published the results of its investigation against one of Expedia IT specialists. The employee, John Ly, is accused of hacking into executives computers to access corporate confidential information.
Over a 3 year span from 2013 to 2016, Ly was able to exploit his managerial role, access privileges and credentials to hack executives’ computers which contained unreleased financial reports that included earnings and market reaction opinions. All cyber criminals wear cloaks, usually multiple cloaks – when those criminals are employees their concealment can be misleading.
In this particular case, the Expedia employee attempted to mask himself by using stolen credentials and passwords belonging to other employees. The earnings reports that were obtained were then used to trade on, prior to their release. In all, Ly was able to execute a total of 9 trades, most under 50k, and the largest at almost 120k, netting him an approximate profit of 350k. A nice pay day for 3 years of work, but pretty minuscule in the grand scheme of things. When the scheme was eventually discovered (by Expedia), they immediately reported it to the FBI. After
All cyber criminals wear cloaks, usually multiple cloaks – when those criminals are employees their concealment can be misleading. In this particular case, Ly attempted to mask himself by using stolen credentials and passwords belonging to other employees. The earnings reports that were obtained were then used to trade on, prior to their release. In all, Ly was able to execute a total of 9 trades, most under 50k, and the largest at almost 120k, netting him an approximate profit of 350k. A nice pay day for 3 years of work, but pretty minuscule in the grand scheme of things. When the scheme was eventually discovered (by Expedia), they immediately reported it to the FBI. After an SEC investigation, Ly was ultimately charged with violating rule 10-b and 17-a of the SEC Act.
This is not the first case of cyber-related insider trading/market manipulation. The largest case of its kind was a large scale breach committed by FIN4 which saw a team of foreign hackers accessed corporate nonpublic information from sites like PRNewswire.
Those reports were then traded on through a systematic network, prior to release, for an estimated profit 100 Mill. In a separate attack, hackers were able to employ a targeted spear phishing campaign to access (and weaponize) information on upcoming mergers. This case does, however, contain some unique characteristics. It is one of the first reported cases of an IT director committing an inside hack with the intent of insider trading, effectively demonstrating that insider trading is not limited to fraud perpetrated by outside actors.
This really applies to cyber crime in general. Organizations can all too easily get overly caught up with implementing digital cyber security controls to shield their networks from outside intrusions while overlooking the human element and cyber/crime risks sitting next to them. Accordingly, companies should be employing training and controls to identify suspicious internal/employee behavior. Lastly, this case also demonstrates that the SEC is paying close attention, aggressively investigating and pursuing even seemingly smaller cases.
Expedia
In reviewing the sequence of events, it is important to note the degree to which internal control failures may have contributed. For one, the IT professional was able to utilize passwords of employees with seemingly, a certain level of ease. Controls that require employees to change their passwords after working with any IT professionals or flag suspicious behavior could have helped minimize or eliminate such unauthorized usage. Secondly, the employee was able to continue this fraud even after being let go, via a secretly kept company laptop. Something such as a kill switch to cut off remote access from the company issued, mobile devices, also could have helped minimize the damage. Sure, this is all easy to say in retrospect and we don’t mean to sound like a Monday morning quarterback, but rather we address these concerns simply to raise awareness for organizations looking to build more robust controls. Lastly, the fact that this scheme was perpetrated over a period of 3 years, with a total of 9 trades, is an important detail in order to highlight just how long intrusions remain undetected. In this particular
Lastly, the fact that this scheme was perpetrated over a period of 3 years, with a total of 9 trades, is an important detail in order to highlight just how long intrusions remain undetected. In this particular case, the damage surmounted to 350k, and in large part, that alone may be a key reason for having gone undetected as long as it did…however, it should go without saying that the damage could have be considerably more severe. The fact the hacker was also an employee in this case, undoubtedly contributed to the long duration-to-discovery.
These types of insider trading security events can inflict significant damage. To start, the costs to comply with a prolonged regulatory investigation can be severe – from e-forensics to document production to defense costs. More frightening however is the potential for following shareholder/investor litigation following a stock drop. These claims will often assert negligence and/or failure to implement adequate security controls to prevent such an event. The fact that this fraud was perpetrated over a 3-year span is troubling. It can often be easy for companies to relate all cyber losses back to a cyber insurance policy, however, there is often a bigger picture that needs to be addressed. We briefly address insurance, because when intrusions such as these occur, the initial reaction (understandably so) is to look to the underlying insurance carrier for indemnification. Companies instinctively looking to their cyber insurance carrier would mostly be looking in the wrong direction. Cyber policies regularly contain broad “securities” exclusions which eliminate any coverage. The fact that the fraud was committed by an employee creates an additional barrier to coverage since most cyber policies are worded to provide coverage for intrusions by “outside” actors. Much of these damages, however, can be insured against through a well-structured Directors and officers insurance policy which extends coverage for CISOs, and CTOs that also might be named in a lawsuit. This is particularly true for public companies for whom D&O insurance is an absolute must to protect against these exact claims. Whole there are many lessons to be learned here, this is just one case, of likely many to come, demonstrating how security failures can result in “securities” fraud.
About the Author Evan bundschuh
Evan bundschuh is vice president and commercial lines head at GB&A, an independent insurance brokerage located in New York focused on insurance programs and risk management solutions for tech companies, financial & professional services, manufacturers and product-based businesses. As an RPLU with 15 years of industry experience, Evan assists clients with insurance program coordination and client-side advising on Directors & Officers (D&O), Professional Liability (E&O) and Cyber Insurance, and is a contributor on the topics of cyber risk.
Infected firmware spotted in well-known low-cost Android devices
14.12.2016 securityaffairs Android
Experts from Doctor Web spotted new Trojans into the firmware of several dozens of low-cost Android smartphones and tablets.
Again problems with low-cost Android smartphones and tablets, once again experts discovered certain mobile devices shipped with malicious firmware.
According to malware researchers from antivirus firm Dr.Web, the firmware of a large number of popular Android devices operating on the MediaTek platform was compromised with at least two types of downloader Trojans.
These low-cost Android smartphones and tablets are mostly marketed in Russia.
“Doctor Web’s security researchers found new Trojans incorporated into firmwares of several dozens of Android mobile devices. Found malware programs are stored in system catalogs and covertly download and install programs.” states the blog post published by Dr.Web.
“One of these Trojans, dubbed Android.DownLoader.473.origin, was found in firmwares of a large number of popular Android devices operating on the MTK platform.”
Both malware found in low-cost Android mobile devices, detected as Android.DownLoader.473.origin and Android.Sprovider.7 are able to collect users’ data, displays advertisements on top of running applications and downloads unwanted apps.
Researchers found the malicious code on the following 26 models of low-cost Android mobile devices:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
Android.DownLoader.473.origin is a downloader Trojan which is executed every time a mobile device is turned on, it can be used by crooks to download both benign apps and also malware and unwanted applications.
“It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software,” the researchers pointed out. “Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users.” continues the report.
The Android.Sprovider.7 Trojan was spotted in the firmware of Lenovo A319 and Lenovo A6000 smartphones. Below the list of abilities observed by the researchers for this specific malware.:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
Unfortunately, the number of similar cases is increasing, last month, security researchers from Kryptowire discovered a backdoor in the firmware installed on low-cost Android phones. The backdoor affects mobile phones from BLU Products that are available for sale on both Amazon and Best Buy.
A few days later, researchers from Anubis Networks discovered that a third-party firmware included in more than 2.8 million low-cost Android devices could be exploited to compromise the smartphones Over-the-Air (OTA) updates and gain root privileges.
The firmware affected by the backdoor is developed by the Chinese company Ragentek Group. The problem resides in the lack of encryption for the OTA mechanisms that expose users to MITM attacks. The analysis revealed that the Ragentek firmware running on the smartphone implements an insecure Over-the-Air update mechanism that establishes an unprotected connection to remote servers via an unencrypted communications channel.
Adobe patches multiple flaws including a Flash Zero-Day exploited in the wild
14.12.2016 securityaffairs Vulnerebility
Adobe issued security patches that address multiple flaws in 9 products, including fixes for zero-day vulnerabilities that has been exploited in the wild.
Adobe has issued security updates to fix vulnerabilities in nine products, including patches for zero-day flaws that has been exploited in targeted attacks.
The version 24.0.0.186 of Flash Player addresses 17 vulnerabilities, some of them can be exploited by attackers for arbitrary code execution. The most severe vulnerability fixed by the updates is a use-after-free issue, tracked as is CVE-2016-7892, that was reported to Adobe by an individual who wanted to remain anonymous.
The remaining flaws in the Adobe Flash Player vulnerabilities were reported to the company by independent researchers and experts from multiple organizations, Pangu LAB, Tencent, Microsoft, CloverSec Labs, Qihoo 360, Trend Micro’s Zero Day Initiative (ZDI) and Palo Alto Networks.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities that could potentially allow an attacker to take control of the affected system.” reads the Adobe Security Bulletin.
“Adobe is aware of a report that an exploit for CVE-2016-7892 exists in the wild, and is being used in limited, targeted attacks against users running Internet Explorer (32-bit) on Windows.”
Adobe confirmed the existence in the wild of an exploit code for the CVE-2016-7892 vulnerability, the company also revealed that it was used in limited, targeted attacks against Windows users running a 32-bit version of Internet Explorer.
Adobe also issued other security updates that patch vulnerabilities in other products, including Animate, Experience Manager Forms, DNG Converter, InDesign, ColdFusion Builder, Digital Editions, and RoboHelp.
None of the above vulnerabilities had been exploited in the wild.
More Firmware Backdoor Found In Cheap Android Phones
13.12.2016 thehackernews Android
Here's some bad news for Android users again.
Certain low-cost Android smartphones and tablets are shipped with malicious firmware, which covertly gathers data about the infected devices, displays advertisements on top of running applications and downloads unwanted APK files on the victim's devices.
Security researchers from Russian antivirus vendor Dr.Web have discovered two types of downloader Trojans that have been incorporated in the firmware of a large number of popular Android devices operating on the MediaTek platform, which are mostly marketed in Russia.
The Trojans, detected as Android.DownLoader.473.origin and Android.Sprovider.7, are capable of collecting data about the infected devices, contacting their command-and-control servers, automatically updating themselves, covertly downloading and installing other apps based on the instructions it receives from their server, and running each time the device is restarted or turned on.
The list of Android device models that are affected by the malicious firmware includes:
Lenovo A319, Lenovo A6000, MegaFon Login 4 LTE, Bravis NB85, Bravis NB105, Irbis TZ85, Irbis TX97, Irbis TZ43, Irbis tz56, Pixus Touch 7.85 3G, SUPRA M72KG, SUPRA M729G, SUPRA V2N10, Itell K3300, Digma Plane 9.7 3G, General Satellite GS700, Nomi C07000, Optima 10.1 3G TT1040MG, Marshal ME-711, 7 MID, Explay Imperium 8, Perfeo 9032_3G, Prestigio MultiPad Wize 3021 3G, Prestigio MultiPad PMT5001 3G, Ritmix RMD-1121, Oysters T72HM 3G, Irbis tz70, and Jeka JK103.
"It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software," the researchers pointed out. "Therefore, [both Trojans] were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users."
More Firmware Backdoor Found In Cheap Android Phones
Android.Sprovider.7 Trojan was discovered in the firmware of Lenovo A319 and Lenovo A6000 smartphones. The Trojan is capable of doing a lot of things including:
Download, install and run APK files.
Open the specified link in a browser.
Make phone calls to certain numbers by using a standard system application.
Run a standard system phone application in which a specified number is already dialed.
Show advertisement on top of all apps.
Also, display advertisements in the status bar.
Create a shortcut on the home screen.
Update a major malicious module.
On the other hand, Android.DownLoader.473.origin found in the remaining devices, which downloads and installs other malware programs and unwanted apps, including an advertising program called H5GameCenter.
H5GameCenter app displays a small box image on top of all running applications, and there is no option to disable it. Even if the infected users remove this app, the firmware Trojan reinstalls the app.
Last month, security researchers from Kryptowire discovered hidden backdoor in the firmware of many budget Android smartphones sold in the US, which also covertly gathers data on phone owners and sends it to a Chinese server without users knowledge.
The backdoored firmware software was developed by China-based company Shanghai AdUps Technology, which claims that its software runs updates for more than 700 Million devices worldwide.
In separate research last month, security rating firm BitSight discovered a flaw in the Ragentek firmware used by certain low-cost Android devices that allowed attackers to remotely execute malicious code with root privileges, turning over full control of the devices to hackers.
Hacking McAfee VirusScan Enterprise for Linux, upgrade it asap
13.12.2016 securityaffairs Vulnerebility
Intel Security McAfee VirusScan Enterprise for Linux is affected by ten vulnerabilities that can be chained for remote code execution with root privileges.
The security expert Andrew Fasano discovered multiple vulnerabilities in the Intel Security’s McAfee VirusScan Enterprise solution for Linux, one of them can be chained by attackers to gain root privileges and remote execute code.
Mr. Fasano reported the issues to Intel Security via CERT/CC in June, but public disclosure of the issues arrived a few days ago once the company issues necessary patches last week. The security researcher has also published proof-of-concept (PoC) code for this attack chain.
The security solution is affected by a wide range of flaws, including information disclosure, cross-site request forgery (CSRF), cross-site scripting (XSS), remote code execution, privilege escalation, special element injection, authentication brute-force, SQL injection, and arbitrary file write issues.
“A system running Intel’s McAfee VirusScan Enterprise for Linux can be compromised by remote attackers due to a number of security vulnerabilities. Some of these vulnerabilities can be chained together to allow remote code execution as root.” wrote Fasano in a blog post.
Four out of ten vulnerabilities are rated as having high severity, while the remaining issued have been rated medium severity.

Fasano explained the entire attack chain to compromise the Intel Security’s McAfee VirusScan Enterprise solution for Linux, the hack starts triggering a flaw that allows the remote use of authentication tokens (CVE-2016-8022) that have been brute-forced (CVE-2016-8023).
The attacker then deploys a malicious update server and triggers the CVE-2016-8022 to configure the product to use that server. The attacker exploits an arbitrary file write vulnerability (CVE-2016-8021) to create a malicious script obtained from the update server. The script can be executed with root privileges by exploiting the privilege escalation CVE-2016-8020.
The last step consists in sending a malformed request with authentication token to start virus scan that instead executes the malicious script with root permissions.
“To execute code as the root user on a remote machine:
Brute force authentication token using Vulnerability 7 and Vulnerability 8.
Start running malicious update server.
Send request with authentication token to update update server using Vulnerability 7.
Force target to create malicious script on their system using Vulnerability 6.
Send malformed request with authentication token to start virus scan but execute malicious script instead by using Vulnerability 5 and Vulnerability 6.
The malicious script is then run by the root user on the victim machine.
Exploiting this vulnerability depends on the existence of a valid login token which is generated whenever a user logs into the web interface. These tokens are valid for approximately an hour after login.” states Fasano.
According to Intel Security, the flaws affect VirusScan Enterprise for Linux (VSEL) 2.0.3 and earlier. The company urges users to upgrade to Endpoint Security for Linux (ENSL) 10.2 or later because the VSEL product will soon reach the end of life
The CERT/CC published a security advisor to inform customers of the flaws in the McAfee Virus Scan Enterprise.
“McAfee has discontinued the Virus Scan Enterprise product in favor of the new McAfee Endpoint Security product, which addresses these vulnerabilities. Affected users are encouraged to upgrade to Endpoint Security version 10.2 or later as soon as possible. The upgrade is available free of charge to existing users.” is the solution provided by the CERT.
Zcash, or the return of malicious miners
13.12.2016 Kaspersky Virus
On 28 October, the cryptocurrency world saw the emergence of a new player, the Zcash (ZEC) cryptocurrency. Its developers have described it rather figuratively: “If Bitcoin is like HTTP for money, Zcash is HTTPS.” They continue by noting that “unlike Bitcoin, Zcash transactions can be shielded to hide the sender, the recipient and value of all transactions.”
The cryptocurrency market has been looking for this level of anonymity for a while now, so ZEC has attracted considerable interest from investors, miners and cybercriminals alike. Several major cryptocurrency exchanges were quick to offer support for the new currency.
Zcash got off to a flying start; within the first few hours, 1 ZEC reached $30,000. It should be pointed out, however, that there were only a few dozen coins in existence at that time, so the actual turnover was very low.
In the following days, ZEC’s value steadily declined against Bitcoin. At the time of writing, it had leveled out temporarily at 0.07 – 0.01 ZEC/BTC (around $70). Despite this dramatic drop from the initial values (which was anticipated), Zcash mining remains among the most profitable compared to other cryptocurrencies.
Ranking of cryptocurrency mining profitability, as reported by the CoinWarz website
This has led to the revival of a particular type of cybercriminal activity – the creation of botnets for mining. A few years ago, botnets were created for bitcoin mining, but the business all but died out after it became only marginally profitable.
In November, we recorded several incidents where Zcash mining software was installed on users’ computers without permission. Because these software programs are not malicious in themselves, most anti-malware programs do not react to them, or detect them as potentially unwanted programs (PUP). Kaspersky Lab products detect them as not-a-virus:RiskTool.Win64.BitCoinMiner.
Cybercriminals use rather conventional ways to distribute mining software – they are installed under the guise of other legitimate programs, such as pirated software distributed via torrents. So far, we have not seen any cases of mass-mailings or vulnerabilities in websites being exploited to distribute mining software; however, provided mining remains as profitable as it is now, this is only a matter of time. The software can also be installed on computers that were infected earlier and became part of a for-rent botnet.
The most popular mining software to date is nheqminer from the mining pool Micemash. It has two known variations: one earns payments in bitcoins, the other in Zcash. Both are detected by Kaspersky Lab products, with the respective verdicts not-a-virus:RiskTool.Win64.BitCoinMiner.bez and not-a-virus:RiskTool.Win64.BitCoinMiner.bfa.
All that cybercriminals need to do to start profiting from a mining program on infected computers is to launch it and provide details of their own bitcoin or Zcash wallets. After that, the “coin mining” profit created by the pool will be credited to the cybercriminals’ addresses, from where it can be withdrawn and exchanged for US dollars or other cryptocurrencies. This is what allows us to ‘snoop’ on some of the wallets used by cybercriminals. Here’s just one example:
Using a wallet’s address, we can find out how much money arrived and from which source (i.e. the mining pool) (https://explorer.zcha.in/accounts/t1eVeeBYfPPLgonvi1zk8e9SnrhZdoCBAeM)
We see that the address was created on 31 October, just a couple of days after Zcash launched, and payments are still being made to it at the current time. You may be wondering what happened to the promised anonymity. Actually, there are two types of wallets in Zcash: completely private purses (z-address) and public wallets like that shown above (t-address). At the current time, the completely private wallets are not very popular (they are not supported by exchanges), and are only used to store around 1% of all existing Zcash coins.
We found approximately 1,000 unique users who have some version of the Zcash miner installed on their computers under a different name, which suggests these computers were infected without their owners’ knowledge. An average computer can mine about 20 hashes per second; a thousand infected computers can mine about 20,000 hashes a second. At current prices, that equals about $6,200 a month, or $75,000 a year in net profits.
Here are just a few real-life examples of the names used by these program and where they are installed on infected computers:
diskmngr.exe
mssys.exe
C:\system\taskmngr.exe
system.exe
nsdiag.exe
taskmngr.exe
svchost.exe
C:\Users\[username]\AppData\Roaming\MetaData\mdls\windlw\mDir_r\rhost.exe
qzwzfx.exe
C:\Users\[username]\AppData\Local\Temp\afolder\mscor.exe
C:\Program Files\Common Files\nheqminer64.exe
C:\Windows\Logs\Logsfiles64\conhost.exe
apupd.exe
As you can see, the names of many mining programs coincide with those of legitimate applications, but the installation location is different. For instance, the legitimate Windows Task Manager app (taskmgr.exe) should be located in the system folder C:\Windows\System32 and not in C:\system.
To ensure that the mining program is launched each time the operating system starts, the necessary records are added either to Task Scheduler or to the registry auto-run keys. Here are some examples of these records:
Task Scheduler\Microsoft\Windows Defender\Mine
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Miner
A couple of detected websites distributing mining programs:
http://execsuccessnow[.]com/wp-includes/m/nheqminer.exe
https://a.pomf[.]cat/qzwzfx.exe
Additional DLLs are required for the mining program to work. These DLLs, shown below, are installed along with the mining program.
cpu_tromp_AVX.dll
cpu_tromp_SSE2.dll
cudart64_80.dll
cuda_tromp.dll
logsetuplib.dll
msvcp120.dll
msvcr120.dll
So, what are the threats facing a user who is unaware that their computer is being used for cryptocurrency mining?
Firstly, these operations are power hungry: the computer uses up a lot more electricity, which, in some countries, could mean the user ends up with a hefty electricity bill.
Secondly, a mining program typically devours up to 90% of the system’s RAM, which dramatically slows down both the operating system and other applications running on the computer. Not exactly what you want from your computer.
To prevent the installation of mining programs, Kaspersky Lab users should check their security products and make sure detection of unwanted software is enabled.
All other users are encouraged, at the very least, to check their folders and registry keys for suspicious files and records.
Kyberzločinci oprášili starý trik, na Facebooku lákají na odměnu 1000 Kč
13.12.2016 Novinky/Bezpečnost Sociální sítě
Krátce před vánočními svátky oprášili kyberzločinci starý trik. Na sociální síti Facebook se vydávají za pracovníky banky a lákají je na odměnu ve výši až 1000 Kč za to, že vyzkouší novou verzi internetového bankovnictví. Ve skutečnosti jim však chtějí vybílit účet.
Ukázka podvodné nabídky na zkoušku nové verze internetového bankovnictví.
FOTO: repro mBank
Stejný trik zkoušeli v průběhu letošního roku počítačoví piráti hned několikrát pod hlavičkou České spořitelny. V aktuální vlně útoků se však vydávají za zaměstnance mBank.
Samotný útok však probíhá zcela identicky. „Přejděte na novou verzi internetového bankovnictví a získejte bonus 1000 Kč! Bezpečnější bankovnictví s přehlednějším rozvržením pro jednoduchou správu vašich financí,“ stojí v lákavě vyhlížející nabídce.
Na Facebooku je možné narazit hned na několik podobných nabídek. Liší se u nich zpravidla jen částky, které podvodníci nabízejí – zpravidla jde však o tisíc nebo 400 Kč.

Ukázka podvodné nabídky na zkoušku nové verze internetového bankovnictví.
FOTO: repro mBank
Reklamu doplňuje odkaz, který samozřejmě nesměřuje na oficiální web banky, ale na podvodné stránky, jejichž prostřednictvím se snaží kyberzločinci vylákat od důvěřivců přihlašovací údaje k internetovému bankovnictví. Vyplněním přihlašovacích údajů na podvodných stránkách se přitom lidé vystavují velkému riziku.
Počítačoví piráti jsou totiž už jen kousek od toho, aby jim mohli vybílit účet – stačí, aby propašovali virus na jejich chytrý telefon. Prostřednictvím něj pak budou schopni odchytávat potvrzovací SMS zprávy pro platby, jako tomu bylo už v minulosti.
Neprodleně kontaktovat banku
Zástupci banky v úterý před podobnými triky důrazně varovali: „Důrazně doporučujeme kontrolovat odkaz, přes který se přihlašujete do svého internetového bankovnictví! Nikdy se nepřihlašujte přes jiné odkazy!“
„Podvodné odkazy byly například ibnew.esy.es, ibnewmban.com, mbanking24.esy.es, apod. Pokud se přihlásíte přes podvodnou stránku, okamžitě kontaktujte naši mLinku na čísle 222 111 999 a změňte si přihlašovací heslo do bankovnictví,“ doporučili zástupci mBank.
Obezřetní by v případě podobných nabídek měli být také uživatelé jiných bankovních institucí. Není totiž vyloučeno, že stejný trik budou počítačoví piráti zkoušet příště pod hlavičkou úplně jiné společnosti.

Stejný trik zkoušeli počítačoví piráti už pod hlavičkou České spořitelny.
FOTO: repro Facebook
McAfee pro Linux má chránit před viry. Samo ale trpí kritickými zranitelnostmi, varují specialisté
13.12.2016 Živě.cz Zranitelnosti
Fanoušci Linuxu se celé roky smáli Windows pro jeho chyby a zranitelnosti. Nadávat na operační systém Redmondu a považovat ten komunitní za nenapadnutelný, bývalo otázkou dobrého bontonu, než se útočníci začali ve velkém orientovat i na tuto platformu.
Záhy se zjistilo, že kritické knihovny linuxového a unixového světa nikdo neaudituje – vzpomeňme třeba na aféru Heartbleed, že jsou mnohé linuxové instance na hostingu nejen od Amazonu zapojené nevědomky v botnetech a že zejména s příchodem IoT jsou mnohé linuxové síťové krabičky počínaje starými Wi-Fi routery a konče chytrými ledničkami hotovou časovanou bombou, protože jejich firmware poměrně často nikdo neaktualizuje, a tak jsou plně bohatě zdokumentovaných a neopravených bezpečnostních děr.
Intel se částečně zbavuje McAfee, prodal 51 % společnosti za 3,1 miliardy dolarů
O linuxové systémy se ve velkém začaly zajímat antivirové společnosti, a tak bylo jen otázkou času, kdy se v tomto světě objeví i všudypřítomné McAfee.
A je to právě McAfee pro Linux, které nyní ironií osudu může otevírat zadní vrátka do linuxového systému. Ach ty životní paradoxy.
McAfee pro Linux trpí zranitelností, která může předat moc nad systémem útočníkovi – třeba zrovna nějakému botnetu, který pak může zneužít toho, že linuxový systém zpravidla běží někde na serveru, anebo ve zmíněné IoT krabici, a je tedy stále spuštěný a stále online.
Bezpečnostní specialisté zdokumentovali několik takových zranitelností už koncem června a v červenci kontaktovali přímo McAfee. Ten však následující měsíce vůbec nereagoval a ozval se až počátkem prosince v okamžiku, kdy jej specialisté informovali o datu zveřejnění zranitelnosti. Krátce poté firma informovala o zranitelnosti i své klienty.
Bezpečnostní specialisté se nakonec zranitelností dle plánu pochlubili včera 12. prosince s tím, že se dotýká všech verzí počínaje 1.9.2 z února 2015 až 2.0.2 z letošního jara.
A v čem je tato zranitelnost vlastně nebezpečná? Hlavně proto, že má antivirový program administrátorská práva, takže útočník, který ovládne linuxové McAfee, může v krajních případech získat práva pro přístup hluboko do systému. Detaily
Radost byla předčasná, vyděračský virus CrySis je opět na scéně
13.12.2016 Novinky/Bezpečnost Viry
Na konci listopadu se bezpečnostní experti antivirové společnosti Kaspersky Lab pochlubili, že vyzráli na vyděračský virus zvaný CrySis. Radost však byla tak trochu předčasná, neboť počítačoví piráti tento škodlivý kód začali během pár týdnů distribuovat v upravené verzi. A na tu jsou zatím všechna bezpečnostní řešení krátká.
CrySis využívali kyberzločinci k uzamykání cizích počítačů několik posledních měsíců. Na konci listopadu však výzkumníci získali dešifrovací klíče, s jejichž pomocí byli schopni zamčená data opět zpřístupnit.
Tento záškodník z rodiny ransomware – jak jsou souhrnně označovány vyděračské viry – se však zakrátko objevil v nové verzi. Ta je prakticky na chlup stejná jako ta předchozí, ale využívá jiný šifrovací algoritmus.
To jinými slovy znamená, že po infiltraci viru CrySis už nemohou lidé bezplatně svá data pomocí nástroje společnosti Kaspersky Lab zpřístupnit. Respektive odšifrovat je možné data pouze na takových počítačích, které byly napadeny ještě starší verzí tohoto ransomwaru.
Scénář útoku jako přes kopírák
Útok nové verze škodlivého kódu CrySis probíhá podle stejného scénáře jako u dalších vyděračských virů. Nejprve tedy tento záškodník zašifruje všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení výkupného. Ani pak se nicméně uživatelé ke svým datům nemusejí dostat.
Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Stovky různých verzí
Sluší se nicméně podotknout, že škodlivé kódy z rodiny ransomware představují pro uživatele stále velké riziko. Různě upravených verzí totiž existují podle nejstřízlivějších odhadů desítky, spíše však stovky. A kyberzločinci se je snaží nasazovat při drtivé většině útoků.
V září například velkou hrozbu představoval vyděračský virus DetoxCrypto, který nebylo na první pohled snadné rozeznat. Maskoval se totiž za antivirové řešení od společnosti Malwarebytes. Uživatelé si tak často mysleli, že instalují program na ochranu svého počítače, ve skutečnosti na pevný disk vypustili nezvaného návštěvníka.
Kapustkiy hacked the Consular Department of the Embassy of the Russian Federation
13.12.2016 securityaffairs Hacking
Kapustkiy breached website for the Consular Department of the Embassy of the Russian Federation in the Netherlands and accessed passport numbers and PPI.
The white hat hacker Kapustkiy breached the website for the Consular Department of the Embassy of the Russian Federation in the Netherlands (ambru.nl). The hacker broke into the database and accessed personal information of approximately 30,000 users, as proof of the attack he leaked only 129 records in order to give the opportunity to administrators to fix the issue. Exposed records include emails, phone numbers, passport numbers, and IP addresses.
Embassy of the Russian Federation
“So this could happend? And we give zero fucks about this? You should be a shame ambru.nl When are you guys going to fucking listen to me. A lot people have emailed you guys. SO TELL ME WHY YOU IGNORE ME FFS?” states the hacker’s manifesto published on PasteBin.
When asked about the hacking vulnerability exploited and the attack technique used, Kapustkiy told me that he has exploited a blind SQL Injection.
He hacked the website to push website administrators to boost the security of their platform and patch vulnerabilities that would expose personal details of the users.
Why the Consular Department of the Embassy of the Russian Federation?
Segui
Kapustkiy @Kapustkiy
Going to breach a database that is related to the Russian Government. Tuesday!
21:50 - 11 Dic 2016
9 9 Re 17 17 Mi piace
There is no political motivation, the hacker was searching for the embassy websites like the Indian ones he breached weeks ago.
IT staff at the Consular Department of the Embassy of the Russian Federation contacted Kapustkiy and told him that they are working to solve the problem.
Kapustkiy reported the data breach to the Russian authorities, but he didn’t receive a response.
Recently Kapustkiy has breached the Argentinian Ministry of Industry and the National Assembly of Ecuador and leaked the data via PasteBin. A few days ago the hacker breached the Venezuela Army and many other websites.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Facebookem se šíří podvodná kampaň lákající na slevy v supermarketech. Nereagujte na ni
13.12.2016 Živě.cz Sociální sítě
Pokud na Facebooku nebo v Messengeru zaregistrujete nabídku na 2 500 Kč do jednoho ze supermarketů, potom ji ignorujte. Lidl, Penny Market, Albert ani jiný řetězec o akci neví a jde o klasický podvod, který má za úkol primárně sběr uživatelů na stránkách Facebooku.
Odpovězte na tři otázky, sdílejte odkaz a my vám dáme 2 500 Kč na nákup v Lidlu. Samozřejmě jde o podvod, řetězce o takové akci nic neví
Odkaz na formulář, který je třeba vyplnit pro „získání“ slevového kuponu se šíří jak běžným sdílením na facebookovou zeď, tak Messengerem. Mezi další podmínky totiž kromě zodpovězení otázek patří právě sdílení na Facebooku a rozeslání odkazu desíti lidem prostřednictvím Messengeru.
Uživatelé si však kromě spamování stěžují také na nabídky aktualizace zařízení v případě, že formulář vyplňují prostřednictvím smartphonu. Ve hře je tak i možné stažení potenciálně nebezpečné aplikace do zařízení s Androidem.
V případě, že na zprávu či příspěvek s tímto bonusem narazíte, určitě jej ignorujte a upozorněte odesílatele, že se jedná o podvod.
Vyděračský ransomware letos vydělá svým tvůrcům miliardu dolarů, odhaduje FBI
13.12.2016 Novinky/Bezpečnost Viry
Nejzákeřnější způsob kybernetického útoku šifruje soubory v napadeném zařízení a poté požaduje po oběti zaplacení výkupného. Ne vždy to ale vede k odšifrování dat, varuje americká FBI.
Škodlivé kampaně takzvaného ransomwaru letos nebývale nabývají na intenzitě. Útočníci se nezaměřují pouze na jednotlivé uživatele internetu, ale stále více i na firmy a veřejné instituce. Ve Spojených státech jsou velmi oblíbeným terčem zdravotnická zařízení, která se neobejdou bez dat o pacientech.
Hollywoodská Presbyteriánská nemocnice takto musela nedávno zaplatit 17 tisíc dolarů (přibližně 420 tisíc korun) ve virtuální měně BitCoin, jinak by přišla o veškerou zdravotnickou dokumentaci. Americký federální úřad pro vyšetřování (FBI) odhaduje, že tvůrci ransomwaru si takto letos celkově přijdou až na miliardu dolarů (25 miliard korun).
„Poté, co si zločinci ověřili ziskovost ransomwarových kampaní u individuálních uživatelů internetu, stále častěji pronikají do firemního segmentu a hledají v něm co nejzranitelnější oběti,“ říká Miroslav Dvořák, technický ředitel antivirové společnosti ESET.
Zaplacení výkupného přitom nemusí vést k odšifrování napadených počítačů. Někteří útočníci poté opakovaně požadují další částky. Americká FBI proto obětem těchto škodlivých kampaní radí výkupné neplatit. „Existuje sice vysoká pravděpodobnost, že takto o data definitivně přijdou, ale pokud je mají správně zálohovaná, škoda by zase nemusela být tak drastická,“ říká Dvořák.
Pozor na škodlivé přílohy e-mailu
Důležité je, aby externí disky, na které firma nebo jednotlivec zálohuje data, nebyly trvale připojeny k počítačové síti. V takovém případě by totiž ransomware zašifroval i zálohy. Někdy však mají napadené společnosti více štěstí než rozumu.
Pokud hackerské skupiny, které využívají k trestné činnosti ransomware, ukončí svoji činnost nebo přestanou využívat některé druhy ransomwaru, poměrně často zveřejní na některém z veřejných internetových fór přístupové klíče, které umožní zašifrované počítače a soubory odblokovat. Tak se to stalo například v případu ransomware Crysis letos v listopadu nebo nechvalně proslulého TeslaCrypt koncem letošního května.
V obou případech připravila společnost ESET jednoduchý nástroj pro dešifrování dat napadených ransomwarem, který bylo možné zdarma stáhnout z jejích internetových stránek. „Ransomware stále zůstává významnou hrozbou na internetu, na kterou nejlépe platí prevence. Kromě pravidelné aktualizace operačního systému a instalovaného softwaru a kvalitního bezpečnostního řešení doporučujeme také pravidelné zálohovat všechna důležitá a cenná data na zabezpečená off-line úložiště,“ zdůrazňuje Miroslav Dvořák.
Uživatelé by měli věnovat zvýšenou pozornost při otevírání nevyžádaných e-mailových zpráv či příloh, kterými se ransomware nejčastěji šíří.
Routery od Netgearu mohou snadno napadnout kyberzločinci. Záplata chybí
13.12.2016 Novinky/Bezpečnost Zranitelnosti
Na pozoru by se měli mít majitelé routerů od společnosti Netgear. Podle amerického bezpečnostního týmu US-CERT, který monitoruje zranitelnosti jednotlivých zařízení a aktuální trendy kyberzločinců na síti, totiž dva prémiové modely tohoto výrobce mají kritickou bezpečnostní chybu, kterou mohou počítačoví piráti snadno zneužít.
Trhlina se týká routerů Netgear R7000 a R6400, které cílí především na náročnější uživatele a menší podniky. Právě kvůli tomu ale objevená chyba představuje ještě větší riziko – především v podnikové síti totiž mohou počítačoví piráti udělat velkou neplechu.
„Zranitelnost umožňuje útočníkovi spustit na zařízení libovolný kód s právy uživatele root, pokud se mu podaří nalákat uživatele na speciálně připravenou webovou stránku,“ varoval Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Podvodné webové stránky
To jinými slovy znamená, že útok začíná ve chvíli, kdy uživatel navštíví podvodnou webovou stránku. Prostřednictvím ní se dostane do routeru záškodník, s pomocí kterého může kyberzločinec například řídit síťový provoz.

Netgear R6400
Že je router zavirovaný, mohou uživatelé poznat například podle toho, že jim přestane z připojených počítačů zcela fungovat internetové připojení, případně se při snaze o připojení na nějakou webovou stránku zobrazí úplně jiný web.
Přesně to se stalo už v minulosti kvůli zranitelnosti známé jako „rom-0“. Místo serverů, jako jsou například Seznam.cz nebo Google.com, se poškozeným zobrazila hláška o nutnosti instalace flash playeru. Místo té se ale do PC stáhnul další virus. Útočníci tak rázem měli přístup nejen k routeru, ale i k připojenému počítači.
Routery nepoužívat
„K dispozici je již i kód (exploit), který umožňuje provedení útoku. Zatím však není k dispozici žádná oprava, uživatelům se proto nedoporučuje routery dále používat,“ konstatoval Bašta.
Prozatím byla chyba prokázána pouze u zmiňovaných routerů Netgear R7000 a R6400. Není nicméně vyloučeno, že totožnou trhlinu v ovládacím softwaru používají i další modely tohoto výrobce.
Společnost NetGear se k objevené zranitelnosti zatím oficiálně nevyjádřila. Lze ale předpokládat, že v průběhu několika dnů či týdnů bude vydána aktualizace, která chybu opraví.
Podvodníci zkoušejí nový trik. Důvěřivce lákají na atraktivní výhry
13.12.2016 Novinky/Bezpečnost Sociální sítě
Chcete vyhrát iPhone 6S nebo iPad Pro? Přesně na takové atraktivní ceny lákají podvodníci v nové vlně phishingových podvodů, které se šíří i ve vodách českého internetu. Při lákání citlivých dat se přitom vydávají za tvůrce webových prohlížečů, kvůli čemuž se skutečně může nechat mnoho lidí napálit.
Ukázka podvodné výherní stránky
FOTO: repro Mozilla.cz
Útok začíná ve chvíli, kdy se na obrazovce zobrazí informace o návštěvnickém průzkumu. Za vyplnění dotazníku nabízejí kyberzločinci hodnotné výhry – zpravidla elektroniku s logem nakousnutého jablka.
„Aby tento dotazník vzbudil důvěru, snaží se vypadat jako dotazník od vašeho prohlížeče – vybere barevně podobné logo, přizpůsobí oslovení, otázky se týkají četnosti a dalšího používání,“ varoval Michal Stanke ze serveru Mozilla.cz.

Ukázka podvodné výherní stránky
FOTO: repro Mozilla.cz
Je přitom jedno, jaký prohlížeč uživatelé používají. Falešný průzkum dokáže aktuální browser detekovat a na základě toho ušít podvodnou nabídku doslova na míru.
Cíl útoku je tedy zřejmý – stejně jako u celé řady dalších phishingových zpráv se snaží od důvěřivců vylákat důvěrné informace, jako jsou jméno e-mail či telefonní číslo. Není nicméně vyloučeno, že podobnou cestou se od důvěřivců budou kyberzločinci snažit vylákat i přihlašovací hesla k různým službám. „V žádném případě takový dotazník nevyplňujte,“ konstatoval Stanke.
Útočníci jsou jako rybáři
Pojem phishing je možné přeložit do češtiny jako rybaření. Útočníci si totiž podobně jako rybáři skutečně počínají. Při této technice trpělivě vyčkávají na své oběti, aby je mohli nalákat na nějakou návnadu – například výhru či finanční hotovost.
Od důvěřivců pak vylákají klidně i hesla, čísla kreditních karet nebo jiné údaje. Uživatelé tak nevědomky pomáhají počítačovým pirátům ovládnout jejich účet nebo klidně i umožní ukrást peníze přes internetové bankovnictví.
Podobné phishingové útoky se nejčastěji síří prostřednictvím nevyžádaných e-mailů. V poslední době ale kyberzločinci velmi rádi používají také nejrůznější reklamy a sociální sítě.
Podvodná soutěž od Seznamu
Podobné podvody nejsou vůbec výjimečné. V minulých měsících se například internetem šířily falešné soutěže pod hlavičkou společnosti Seznam.cz. Podvodníci v nich zneužívají logo a maskota české internetové jedničky.
Soutěžní výzva se zobrazuje nejčastěji jako reklama, a to na počítačích, tabletech i chytrých telefonech. Podvodníci tvrdí, že uživatel vyhrál nějaké atraktivní zařízení, pro jeho získání je však nutné zájem potvrdit prostřednictvím SMS zprávy. Za tu si pak útočníci naúčtují tučný poplatek. Ten je v jednotlivých nabídkách různý, pohybuje se v řádech desetikorun, ale může se vyšplhat až na rovnou stovku.

Ukázka podvodné výherní obrazovky
FOTO: Seznam.cz
V některých podvodných soutěžích, ve kterých se útočníci vydávají za zástupce společnosti Seznam, jde zase o osobní údaje. Když je kyberzločinci od uživatele vylákají, mohou je zneužít k dalším útokům nebo je prodat na černém trhu.
Pozornější uživatelé si přitom mohou všimnout, že jde o podvod. Soutěž totiž nikdy neběží na webu společnosti Seznam, ale na úplně jiných stránkách. Některé nabídky navíc obsahují i celou řadu pravopisných chyb a špatně vyskloňovaná slova. Na podobné soutěže by uživatelé neměli vůbec reagovat.
Zástupci společnosti Seznam.cz se od podvodu distancovali již dříve. „Buďte obezřetní při otvírání neznámých odkazů a všímejte si toho, kam směřují. U zpráv, které vybízejí k transakcím, platí tato rada dvojnásob. Neznámé přílohy neotvírejte a v případě, že je počítač infikován, využijte antivirový program a nezvaného útočníka odstraňte,“ poradil uživatelům Martin Kožíšek, manažer pro internetovou bezpečnost společnosti Seznam.cz.
Informovat o podobných soutěžích mohou lidé zástupce Seznamu na e-mailové adrese seznamsebezpecne@firma.seznam.cz.
Europol arrests 34 Teenagers for using DDoS Attack Tools
13.12.2016 thehackernews Crime
Europol has announced that the law enforcement agencies from 13 countries around the globe have arrested 34 users of Netspoof DDoS attack tool and interviewed and warned 101 suspects in a global crackdown.
According to the report published on the official website of Europol, law enforcement authorities worldwide have made the arrest between 5 December and 9 December 2016.
Europol's European Cybercrime Centre (EC3) supported the law enforcement agencies in their efforts to identify suspects in the European Union and beyond.
Arrested Suspects Are Mainly Teenagers
All those arrested are mainly "young adults under the age of 20," who are suspected of paying for Netspoof stresser as well as booters services to maliciously deploy DDoS-for-hire software and using them to launch cyber attacks.
The ddos attacks flooded target websites and web servers with massive amounts of data, leaving those services inaccessible to users.
Europol's European Cybercrime Centre (EC3) head Steven Wilson hopes that the latest arrests would deliver a message to any wannabe hackers, saying:
"Today's generation is closer to technology than ever before, with the potential of exacerbating the threat of cyber crime. Many IT enthusiasts get involved in seemingly low-level fringe cybercrime activities from a young age, unaware of the consequences that such crimes carry."
"One of the key priorities of law enforcement should be to engage with these young people to prevent them from pursuing a criminal path, helping them understand how they can use their skills for a more constructive purpose."
This international operation involved Europol working alongside law enforcement from Australia, Belgium, France, Hungary, the Netherlands, Norway, Lithuania, Spain, Sweden, Portugal, Romania, the United Kingdom, and the United States.
All the participating countries worked together in the framework set out by the EMPACT (European Multidisciplinary Platform against Criminal Threats) – a project with the aim of targeting cyberattacks that affect critical infrastructure and information systems in the EU.
Dozens of teenagers arrested by the Europol over DDoS attacks
13.12.2016 securityaffairs Attack
The Europol announced a joint international operation targeting teenagers suspected to have used DDOS cyber attack tools.
The Europan law enforcement agency Europol has announced that police from 13 countries across the world have arrested 34 users of DDoS attack tools and interviewed and warned 101 suspects.
“From 5 to 9 December 2016, Europol and law enforcement authorities from Australia, Belgium, France, Hungary, Lithuania, the Netherlands, Norway, Portugal, Romania, Spain, Sweden, the United Kingdom and the United States carried out a coordinated action targeting users of Distributed Denial of Service (DDoS) cyber-attack tools, leading to 34 arrests and 101 suspects interviewed and cautioned.” states the official announcement from the Europol.
Europol ddos arrests
The Europol’s European Cybercrime Centre (EC3) provided its support to law enforcement worldwide to identify suspects in the EU and beyond. The individuals arrested are mainly teenagers under the age of 20.
“The participating countries worked together in the framework of the EMPACT (European Multidisciplinary Platform against Criminal Threats) project targeting cyber-attacks that affect critical infrastructure and information systems in the EU.” continues the Europol.
All the arrested people are suspected of paying for booters services that they used to launch massive DDoS attacks. The tools used to power the cyber attacks are part of the criminal ‘DDoS for hire’ facilities.
“Today’s generation is closer to technology than ever before, with the potential of exacerbating the threat of cybercrime. Many IT enthusiasts get involved in seemingly low-level fringe cybercrime activities from a young age, unaware of the consequences that such crimes carry.” Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3), commented. “One of the key priorities of law enforcement should be to engage with these young people to prevent them from pursuing a criminal path, helping them understand how they can use their skills for a more constructive purpose. “
Ransomware infections suffered by companies tripled in 12 months
13.12.2016 securityaffairs Virus
According to a new report published by Kaspersky Lab, the number of ransomware infections suffered by companies threefold from January to September.
The number of ransomware infections suffered by companies continues to increase and according to a new report published by the security firm Kaspersky Lab, it increased threefold from January to September.
One in every five businesses worldwide has been victims of a ransomware and the rate of ransomware attacks increased from one every two minutes to one every 40 seconds.
This alarming data confirm that the ransomware is one of the most dangerous threats in the current cyber security landscape.
Ransomware could have a dramatic impact on companies, 67 percent of the firm that was affected lost part or all of their corporate data and 25% victims spent several weeks trying to decrypt the data.
Experts from Kaspersky have detected 32,091 new ransomware variations in the third quarter, a significant increase compared to 2,900 variations discovered during the first quarter. According to the experts, 62 new ransomware families were observed in the wild this year.
The situation is even more worrisome when dealing with consumers, in their case the infection data reached one attack every 10 seconds in September.
In the criminal underground, such kind of threat is becoming even more popular, malware authors are developing new ransomware that presents sophisticated features and that are able to evade detection.
Ransomware allows criminal organizations to rapidly cash out their efforts, despite the numerous recommendation to avoid paying the ransom still a large number of victims prefer to pay it to decrypt their documents.
“Ransomware has completely dominated the current threat landscape,” explained Bharat Mistry, cyber-security consultant at Trend Micro.
“During the first part of 2016, we blocked and detected almost 80 million ransomware threats and identified 79 new ransomware families – comparing to 29 in the whole of 2015. That’s a 179 percent increase. Quite a few of those were built with routines that are designed to attack enterprise machine and endpoints. It’s time companies take heed.”
The analysis conducted by Kaspersky confirmed that SMBs are mostly targeted by ransomware, 42 percent of them suffered a ransomware-based attack over the past 12 months. Of those, one in three paid up the ransom, but one in five never got their files back, despite paying.
Giving a close look at the threats, CTB-Locker has represented one of the most dangerous threat. One of four ransomware victims was infected by the CTB-Locker. Other successful ransomware were Locky (7 percent) and TeslaCrypt (6.5 percent).
The researchers observed that ransomware infections are the result of more targeted attacks leveraging on spear-phishing messages and social engineering attacks against specific organizations.
Targeted attacks allow cyber criminals to maximize the likelihood victims will pay up the ransom.
How to defeat the ransomware?
Kaspersky urges companies to increase awareness about the threat by training its employees and to back up sensitive data regularly.
It is important to adopt security solutions and to maintain installed software up to date.
Below key figures of the report:
62 new ransomware families made their appearance.
There was an 11-fold increase in the number of ransomware modifications: from 2,900 new modifications in January/March, to 32,091 in July/September.
Attacks on business increased three-fold between January and the end of September: the difference between an attack every 2 minutes and one every 40 seconds.
For individuals the rate of increase went from every 20 seconds to every 10 seconds.
One in five small and medium-sized business who paid the ransom never got their data back.
I suggest you read the report.
Nejrozšířenějším škodlivým kódem v Česku je virus Danger
12.12.2016 Novinky/Bezpečnost Viry
Již několik měsíců za sebou je nejrozšířenějším virem v Česku Danger. Jinak tomu nebylo ani v listopadu, kdy měl tento škodlivý kód na svědomí každý druhý útok v tuzemských počítačových sítích. Vyplývá to ze statistik antivirové společnosti Eset.
Danger – plným jménem JS/Danger.ScriptAttachment – je jednou z nejrozšířenějších hrozeb prakticky po celý letošní rok. Zarážející je především jeho dramatický nárůst v posledních měsících. Aktuálně je totiž zodpovědný za 54,91 % útoků. Ještě v říjnu to přitom bylo o dvacet procentních bodů méně.
„Nárůst počtu případů JS/Danger.ScriptAttachment je opravdu mimořádný. Tento malware je zákeřný v tom, že nemusí být nebezpečný sám o sobě, ale do napadeného zařízení stahuje další škodlivé kódy,“ uvedl Miroslav Dvořák, technický ředitel společnosti Eset.
Vyděračské viry na scéně
Nejčastěji touto cestou kyberzločinci šíří vyděračské viry z rodiny ransomware. Tyto škodlivé kódy začnou šifrovat obsah počítače a uživateli zobrazí oznámení, že za dešifrování počítače musí zaplatit, jinak se ke svým datům údajně již nikdy nedostane.
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat. V některých případech to ale není možné.
Všechny další hrozby, kterým patřily přední příčky žebříčku nejrozšířenějších virových hrozeb, mají přitom ve srovnání s Dangerem naprosto zanedbatelný podíl. Na druhé příčce se umístil trojský kůň FakejQuerys s podílem 2,56 procenta detekcí.
Šíří se před nevyžádané e-maily
Třetí příčka pak patří viru Nemucod, který byl přitom ještě v říjnu na druhém místě. Tehdy stál za každou osmou detekcí (podíl 12,32 procenta), v listopadu jeho podíl klesl o 10 procentních bodů na 2,04 procenta.
Nemucod se stejně jako Danger nejčastěji šíří prostřednictvím nevyžádaných e-mailů. Také s pomocí tohoto viru mohou počítačoví piráti do napadeného stroje stahovat další škodlivé kódy.
Seznam deseti nejrozšířenějších hrozeb za měsíc listopad naleznete v tabulce níže:
Deset nejrozšířenějších počítačových hrozeb – listopad 2016
1. JS/Danger.ScriptAttachment (54,91 %)
2. JS/TrojanDownloader.FakejQuery (2,56%)
3. Java/Adwind (2,28 %)
4. JS/TrojanDownloader.Nemucod (2,04 %)
5. JS/Kryptik.RE (1,76 %)
6. JS/ProxyChanger (1,38 %)
7. Win32/Exploit.CVE-2014-1761 (1,33 %)
8. Win32/Injector.DHND (1,04 %)
9. JS/TrojanDownloader.Iframe (0,88 %)
10. PDF/Fraud (0,88 %)
Test charakteru: Nový ransomware vám dá na výběr. Buď zaplatíte, nebo musíte nakazit další nešťastníky
12.12.2016 Živě.cz Viry
Představte si tu situaci. Nechtělo se vám platit za vypůjčení filmu skrze některou z webových služeb, a tak jste si stáhli jeden z mnoha klonů pirátského Popcorn Time. Jenže ouha, namísto katalogu posledních trháků se zobrazila hláška, která vás vyzvala k zaplacení 1 BTC, jinak byste přišli o všechna osobní data na počítači. Právě jste totiž nainstalovali jeden z mnoha ransomwarů.
Zobrazit obrázek na TwitteruZobrazit obrázek na TwitteruZobrazit obrázek na TwitteruZobrazit obrázek na Twitteru
Sledovat
MalwareHunterTeam @malwrhunterteam
Next ransomware on the table: Popcorn Time.
Not yet finished.
4th screenshot, "Why we do that?" part. Okay...@BleepinComputer @demonslay335
21:23, 7. pro. 2016
77 77 reů 50 50lajků
Tento se však podle skupiny MalwareHunterTeam přeci jen poněkud liší, svým obětem totiž dává ještě jednu možnost, jak se vyhnout platbě a získat dešifrovací klíč. V zoufalství se mohou pokusit nakazit alespoň dvě další osoby pomocí osobního URL. Pokud tyto dvě osoby pak skutečně zaplatí, získáte i svůj dešifrovací klíč. Jedná se tedy o zvrácenou formu provizního (affiliate) systému přeneseného do světa malwaru.
Pokud nechcete platit 1 BTC, máte ještě jednu možnost, jak získat dešifrovací klíč – nakazit další. Viz označený odstavec.
Autoři ransomwaru se dokonce snaží obhájit, proč vlastně škodí. Údajně se jedná o chudé studenty z válkou postižené Sýrie a tímto způsobem si chtějí vydělat v nelehké době na živobytí.
Německu podle kontrarozvědky hrozí před volbami hackerské útoky
12.12.2016 Novinky/Bezpečnost BigBrother
Množí se indicie, že německé parlamentní volby v příštím roce se někdo pokusí ovlivnit hackerskými útoky, řekl ve čtvrtek v Berlíně šéf německé kontrarozvědky Hans-Georg Maassen. Ohroženi podle něj mohou být poslanci i členové vlády. O vlivu hackerských útoků na demokratické volby se v poslední době mluvilo zejména v souvislosti s hlasováním o prezidentovi Spojených států.
Šéf německé kontrarozvědky Hans-Georg Maassen
„V politické oblasti pozorujeme stále agresivnější kybernetickou špionáž. Vidíme možné ohrožení pro členy vlády, poslance Spolkového sněmu a spolupracovníky demokratických stran," uvedl Maassen, který stojí v čele německé civilní kontrarozvědky - Spolkového úřadu na ochranu ústavy (BfV).
Varoval také, že by se ve volební kampani mohly objevit informace získané hackerskými útoky, jejichž cílem je diskreditace politiků.
„Propaganda a dezinformace, kybernetické útoky, kybernetická špionáž a kybernetické sabotáže jsou součásti hybridních hrozeb pro západní demokracie," konstatoval Maassen, jehož úřad v posledních měsících zaznamenal výrazný nárůst pokusů o útoky zaměřené na politické strany a poslanecké frakce.
Hackerské útoky nejsou výjimečné
Hackerským útokům v minulosti v Německu čelila například Křesťanskodemokratická unie (CDU) kancléřky Angely Merkelové nebo Spolkový sněm. Loni v dubnu se hackerům podařilo proniknout do parlamentní počítačové sítě a k osobním údajům o poslancích a jejich asistentech, ale i k interním materiálům jednotlivých poslaneckých klubů a většiny výborů.
V posledních týdnech letošní americké prezidentské kampaně se na veřejnost po hackerském útoku dostala komunikace vedení Demokratické strany. Spekuluje se o tom, že za útokem stálo Rusko, což Moskva popírá.
Velká Británie se připravuje na Velkého bratra. „Charta fízlů“ bude evidovat každý krok v kyberprostoru
12.12.2016 Živě.cz BigBrother
Velká Británie bude mít silnou monitorovací legislativu
Úřady se dozví, co Britové dělají na webu, i bez soudního příkazu
Bizarních nařízení je ale více
Alžběta II. za svůj dlouhý život signovala nespočet zákonů, o podpisu z 29. listopadu se však bude na britské scéně mluvit asi ještě hodně dlouho. Investigatory Powers Act mnozí považují za ono symbolické překročení hranice mezi soukromím a skutečnou velkobratrskou společností.
Zkraje příštího roku jej zároveň doplní jen o něco méně kontroverzní Digital Economy Bill, který bude v druhém čtení za pár dnů projednávat horní komora tamního parlamentu.A čeho se tedy především technická a lidskoprávní komunita děsí? Co že se to připravuje v jedné z kolébek moderní evropské demokracie?
Charta fízlů
Začněme tím prvním zákonem, který britská média přezdívají Snooper's Charter– charta fízlů. Jedná se o zákon, který mimo jiné upravuje tzv legislativu data retention, která určuje, jaké informace o nás mají archivovat telekomunikační operátoři – ať už telefonní v rámci hlasových služeb, nebo ti internetoví.
Data retention v Česku
Podobná legislativa je v dnešním světě poměrně rozšířená – před lety třeba odstartovala kauzu okolo NSA a Edwarda Snowdena – a máme ji samozřejmě i u nás, upravuje ji totiž zákon č. 127/2005 Sb., o elektronických komunikacích a to v paragrafu 97 a odstavci 3.
První věta 3. odst. § 97 zákona č. 127/2005 Sb.
Právnická nebo fyzická osoba zajišťující veřejnou komunikační síť nebo poskytující veřejně dostupnou službu elektronických komunikací je povinna uchovávat po dobu 6 měsíců provozní a lokalizační údaje, které jsou vytvářeny nebo zpracovávány při zajišťování jejích veřejných komunikačních sítí a při poskytovávání jejích veřejně dostupných služeb elektronických komunikací
V případě České republiky tedy telefonní operátoři po dobu šesti měsíců archivují, kdo, komu, odkud a kam (dle BTS stanice) a jak dlouho volal nebo posílal SMS. Poskytovatelé internetového připojení zase analogicky zaznamenávají IP a MAC adresy, porty, identifikátor klienta a čas.
Suma sumárum, vyšetřovatelé sice neví, co bylo obsahem komunikace, ale podle IP adres a dalších indicií se toho mohou v mnoha případech dovtípit. Je tedy naprosto klíčové, aby k podobným informacím měly úřady přístup opravdu jen v závažných případech a s posvěcením soudní autority.
Se souhlasem soudů tedy mohou do podobné databáze operátora nahlédnout jen Policie ČR, ČNB, BIS a Vojenské zpravodajství.
Britský Velký bratr
Tak a teď zpátky na britské ostrovy. Jejich čerstvý Investigatory Powers Act je vlastně analogií českého zákona o elektronických komunikacích, jde však mnohem dál.
Kontroverzní je především ve dvou rovinách. Jestli české právo vyžaduje alespoň souhlas soudu, v případě Velké Británie se k těmto záznamům dostanou desítky organizací – prakticky celý státní aparát bez potřeby soudního příkazu.
Na seznamu povolených Velkých bratrů jsou vedle pochopitelných policejních úřadů a bezpečnostních služeb kupodivu také ministerstva zdravotnictví, dopravy, sociálních věcí nebo další státem zřízené instituce.
Tím to však nekončí. Nejen že může britský stát bez svolení soudů nahlížet, kdo kde a kdy v posledním roce surfoval, ale z moci úřední může přikázat tamním technologickým společnostem, aby odkryly vaši šifrovanou komunikaci.
A to je už problém, v poslední době se totiž stále více prosazuje end-to-end šifrování, nad kterým samotný operátor nemá žádnou kontrolu a hlavně nemá žádný klíč. Když tedy end-to-end šifrování aktivujete třeba v Messengeru od Facebooku, firma Marka Zuckerberga nemá žádné páky, jak na příkaz policie takovou komunikaci dešifrovat. Nový zákon ji to přitom nařizuje.
Facebook Messenger v režimu end-to-end šifrování, které neumí rozluštit ani provozovatel, dešifrovací klíč má totiž pouze mobil příjemce
Problém má tři možná řešení. Buď by Facebook, Apple, Google a další podobné šifrovací mechanizmy na Ostrovech nepoužívaly, nebo by pokračovaly ve stávající praxi a vyčkávaly na první precedentní případ, anebo je tu ještě třetí možnost a to ta, že by podobné služby nabízely surfařům skrze třetí osobu – účelově vytvořený podnik, který by neměl v Británii právní zastoupení. Tím by ale na druhou stranu riskovaly celoplošnou blokaci, se kterou má Británie také bohaté zkušenosti, poněvadž už roky blokuje třeba stovky warezových webů včetně The Pirate Bay.
Jen vkusná erotika
Aby toho nebylo málo, šmírovací zákon možná brzy doplní další – v úvodu zmíněný Digital Economy Bill, který pro změnu obšírně popisuje samotný kybernetický svět.
Dolní komorou parlamentu už úspěšně prošel a nyní jej projednává Sněmovna lordů. Pokud mu dá zelenou i ona, pak už bude zbývat jen podpis královny.
Britové mají smůlu. Úřady dohlédnou, aby na webu koukali jen na vkusnou erotiku
Ani DEB přitom neunikl posměškům i ostré kritice, skrývá v sobě totiž mnohá bizarní nařízení. O jednom z nich jsme psali už v listopadu, kdy si ostrovní média všimla, že se do zákona dostala zmínka o tom, že veškerý obsah pro dospělé musí být v souladu s archaickými pravidly filmové rady BBFC. Stručně řečeno, britský surfař by měl na internetu objevit jen schválený druh erotiky.
Klepněte pro větší obrázek
Soubor zákonů upravující digitální byznys by v krajním případě rozhodoval i o povoleném vkusu u obsahu pro dospělé
Podle tamních provozovatelů lechtivých webových stránek by z internetu zmizel dnes již zcela běžný obsah, pravidla BBFC totiž v některých ohledech připomínají viktoriánskou dobu. O výčet toho, co přesně by takový průměrný Brit na internetu nesměl vidět, se ve svém článku rozepsal třeba The Guardian. Je to místy detailní sonda do lidské anatomie.
Jen připomenu, že se tu nebavíme o Číně, Íránu, nebo třeba Rusku, ale o Velké Británii.
Deset let za warez
V rámci Digital Economy Bill by mělo zároveň dojít k harmonizaci trestů. Jinými slovy, ať už něco ukradnete v hmotném světě, nebo na webu, je to jedno a totéž.
Možná by to dávalo i smysl, ale jen do chvíle, než si uvědomíte, že onou krádeží může být i nepovolená distribuce digitálního díla, za kterou by mohl Britům hrozit opravdu drakonický trest. Jak vysoký? Teoreticky až deset let.
Jistě, je velmi málo pravděpodobné, že by snad nějaký britský soud odsoudil surfaře k desetiletému nepodmíněnému trestu za to, že nahrál na Ulož.to kinorip, přesto to však bude možné a nelze se divit autorským svazům, že podobné zpřísnění způsobené právní harmonizací pochopitelně kvitují.
České tendence
Britskou sondu bych nyní mohl zakončit obvyklými slovy, že bychom si měli vážit našeho sice malého, ale zatím velmi svobodného internetu, nicméně i u nás rok od roku sílí volání po zpřísnění pravidel ať už z řad české policie, nebo rozvědky. Není se jim čemu divit – chtějí pružnější a rychlejší vyšetřování všemožných kauz, nicméně za jakou cenu?
Vojenská rozvědka se promění v NSA. Bude nás moci všechny sledovat. Přinášíme detailní rozbor novely zákona
Byl to marný boj. Senátoři dali zelenou prvnímu českému státnímu blacklistu
Český „Blacklist“: boj proti nesmyslné a nebezpečné internetové cenzuře pokračuje
Již brzy také pravděpodobně skončí éra formálně neblokovaného internetu, letos totiž prošla oběma komorami českého parlamentu novela, která umožní ministerstvu financi spravovat první český blacklist zakázaných webů. Fakt, že bude evidovat výhradně ilegální webové sázkové hry, je zcela irelevantní. Proč? Protože blacklist velmi snadno objede každý teenager, který umí spustit webový prohlížeč (třeba Operu s integrovaným VPN tunelem), a veškeré náklady pod hrozbou pokut ponesou poskytovatelé připojení.
Nelze než doufat, že těmito aktivitami to zatím končí a český internet si zachová svoji stále exkluzivnější otevřenost.
Vojenská rozvědka se promění v NSA. Bude nás moci všechny sledovat. Přinášíme detailní rozbor novely zákona
12.12.2016 Živě.cz BigBrother
Vláda připravila novelu o Vojenském zpravodajství
Agenti se dostanou do každé sítě
Operátoři o tom budou muset mlčet
Český parlament připravuje novelu zákona č. 289/2005 Sb., o Vojenském zpravodajství, která rozšíří působnost armádní rozvědky i na kyberprostor. S informací přišla jako první Mafra.
Co to znamená v praxi? Vládou navrženou novelu najdete na webu Poslanecké sněmovny jako tisk 931, který prošel prvním čtením a zatím se zastavil ve výborech. Plně znění v PDF a s tučně vyznačenými změnami pak najdete na této adrese.
Pojďme se na ty změny podívat bod po bodu.
Novela mění hned § 1, ve kterém přibyl nový odstavec, který praví, že Vojenské zpravodajství plní úkoly obrany České republiky v kybernetickém prostoru.
§ 1, odst. 3
Vojenské zpravodajství za podmínek stanovených tímto zákonem plní úkoly obrany České republiky v kybernetickém prostoru (dále jen „kybernetická obrana“).
Mohou nás odposlouchávat
No dobrá, ale jak ty úkoly budou vlastně naši vojenští zpravodajci plnit? Tomu se již obšírně věnuje část čtvrtá s podtitulem Kybernetická obrana a § 16. Píše se v něm, že specialisté mohou využívat nejrůznější technické prostředky k předcházení, zastavení nebo odvrácení kybernetického útoku.
Zajímavé je to slovíčko předcházení, které již implikuje, že Vojenské zpravodajství může mít přístup k informacím i v době klidu. Paragraf zároveň dává zpravodajcům právo používat technické prostředky k odposlechu osob, i když to bude v rozporu se zákonem o elektronických komunikacích.
§ 16a, odst. 2 a 3
(2) Vojenské zpravodajství může při zajišťování kybernetické obrany využívat technické prostředky kybernetické obrany, kterými jsou věcné technické prostředky vedoucí k předcházení, zastavení nebo odvrácení kybernetického útoku ohrožujícího zajišťování obrany České republiky; Vojenské zpravodajství při zajišťování kybernetické obrany společně s technickými prostředky kybernetické obrany k dosažení shodného účelu využívá také související postupy a opatření.
(3) Využívat technické prostředky kybernetické obrany na území České republiky, pokud lze očekávat, že naruší důvěrnost zpráv podle zákona o elektronických komunikacích a s nimi spojených provozních a lokalizačních údajů konkrétní osoby, lze výlučně za podmínek stanovených pro použití zpravodajské techniky tímto zákonem.
Takže Vojenské zpravodajství dohlíží na kybernetický mír a má k tomu technické prostředky a právo porušovat důvěrnost elektronické komunikace stejně jako třeba americká NSA, britská GCHQ a další.
Černé krabičky
Jenže aby mohli zpravodajci na cokoliv dohlížet, tak musejí mít nejprve fyzický přístup k samotné digitální dálnici, po které tečou naše pakety – přístup do sítě. No a to už se dostáváme k oněm černým krabičkám, jak se jim slangově říká. Prostě k softwarovým nebo hardwarovým přípojkám do infrastruktur operátorů a dalších telekomunikačních společností.
Umisťování podobných blackboxů upravují paragrafy § 16b a § 16c. Vstup zpravodajců do cizí digitální infrastruktury navrhne ministr obrany a posvětí Vláda ČR a není k tomu tedy potřeba rozhodnutí soudu.
§ 16b a § 16c
(16b) Umístění technických prostředků kybernetické obrany podle § 16a může být provedeno výlučně na základě jeho schválení vládou, která rovněž schválí podmínky jejich používání k zajištění kybernetické obrany. Návrh na umístění technických prostředků kybernetické obrany, jehož součástí je také návrh podmínek jejich používání, předkládá vládě ministr obrany na základě návrhu ředitele Vojenského zpravodajství.
(16c) Vojenské zpravodajství může za podmínek schválených vládou podle § 16b a v rozsahu potřebném pro zajišťování kybernetické obrany požadovat od právnické nebo podnikající fyzické osoby zajišťující síť elektronických komunikací nebo poskytující službu elektronických komunikací zřízení a zabezpečení rozhraní pro připojení technických prostředků kybernetické obrany.
Zaplatí to stát
Samozřejmě se nabízí otázka, kdo to bude všechno hradit. Pro drobného operátora s omezenými prostředky by bylo zhotovení podobných zadních vrátek do jeho systému krajně problematické.
Novela na to pamatuje a na rozdíl od již schváleného hazardního blacklistu, kde veškeré náklady zůstanou na provozovateli sítě, v tomto případě vše zaplatí český stát.
Operátoři i technici budou muset mlčet
Jestli operátor podobný blackbox do své sítě nainstaluje, či nenainstaluje, se však nikdy nedozvíte, bude to totiž tajné a ISP se tím nebude moci chlubit ani zpětně, kdy už se o jeho síť nebude Vojenské zpravodajství jakkoliv zajímat.
Toto vše upravují tři odstavce § 98a.
§ 98a
(1) Právnická nebo podnikající fyzická osoba zajišťující síť elektronických komunikací nebo poskytující službu elektronických komunikací je povinna, je-li o to požádána za účelem plnění úkolů kybernetické obrany Vojenským zpravodajstvím na základě zákona o Vojenském zpravodajství, zřídit a zabezpečit ve vhodných bodech své sítě rozhraní pro připojení technických prostředků kybernetické obrany.
(2) Za plnění povinností podle odstavce 1 náleží právnické nebo podnikající fyzické osobě od Vojenského zpravodajství úhrada efektivně vynaložených nákladů. Způsob určení výše efektivně vynaložených nákladů a způsob jejich úhrady stanoví prováděcí právní předpis.
(3) Osoba uvedená v odstavci 1, jakož i jiné osoby podílející se na plnění povinnosti podle odstavce 1, jsou povinny zachovávat mlčenlivost o připojení technických prostředků kybernetické obrany podle odstavce 1 a s tím souvisejících skutečnostech. Tato povinnost trvá i poté, kdy tato osoba přestane být osobou podle odstavce 1 nebo osobou podílející se na plnění povinnosti podle věty první.
Dvacetimilionová pokuta
Na závěr se nabízí otázka, co se stane, když se operátor postaví na zadní a Vojenskému zpravodajství řekne prostě NE! Nu, nic veselého, bude se totiž jednat o správní delikt, který v odstavci 22 upravuje § 118.
§ 118, odst. 22
Právnická nebo podnikající fyzická osoba se jako osoba zajišťující síť elektronických komunikací nebo poskytující službu elektronických komunikací dopustí správního deliktu tím, že
a) v rozporu s § 98a odst. 1 nezřídí nebo nezabezpečí v určených bodech své sítě rozhraní pro připojení technických prostředků kybernetické obrany na žádost Vojenského zpravodajství, nebo
b) poruší povinnost zachovávat mlčenlivost podle § 98a odst. 3.
Následující odstavec poté stanoví výši pokuty, která je v případě kybernetické obrany státu ta nejvyšší možná – 20 000 000 korun.
§ 118, odst. 23c (zkrácený)
20 000 000 Kč, jde-li o správní delikt podle .... odstavce 16 až 22.
Povinnost mlčenlivosti se samozřejmě týká i zainteresovaných fyzických osob – typicky zaměstnanců operátora, techniků, kteří budou se zpravodajci spolupracovat při instalaci blackboxů.
Pokud se budou chlubit třeba na Facebooku a jinak porušovat povinnost mlčenlivosti, bude se jednat dle § 119, odst. 7 o přestupek, který mohou úřady ocenit pokutou do 100 000 korun.
Tor Project Releases Sandboxed Tor Browser 0.0.2
12.12.2016 thehackernews Safety
The non-profit organization behind TOR – the largest online anonymity network that allows people to hide their real identity online – has launched an early alpha version of Sandboxed Tor Browser 0.0.2.
Yes, the Tor Project is working on a sandboxed version of the Tor Browser that would isolate the Tor Browser from other processes of the operating system and limit its ability to interact or query low-level APIs that can lead to the exposure of real IP addresses, MAC addresses, computer name, and more.
Sandboxing is a security mechanism for separating running programs. When an application is sandboxed, its process runs in a separate environment from the underlying operating system, so that errors or security issues in that application can not be leveraged to affect other parts of the OS.
Sandbox applications are enabled in their own sequestered area and memory, where they can be worked on without posing any threat to other applications or the operating system.
Major modern browsers, including Chrome, Firefox, and Edge, use sandboxed environments to separate themselves from the operating system.
However, the Tor Browser, which itself is based on the open-source Mozilla Firefox browser, did not use the sandboxing environment that left the browser somewhat insecure even after so many privacy protection features.
Just rewind the FBI's 2015 investigation into child pornography site Playpen, in which the agency hacked into some 8,700 computers across 120 different countries.
The FBI used Tor exploits to identify and catch visitors of PlayPen hiding their real identity using Tor. Such exploits targeting the Tor Browser can also be used to unmask the identity of journalists, political dissidents, and others.
Keeping this in mind, the Tor Project started working on a Sandboxed version of the Tor Browser in September this year.
The idea behind the move is that exploits and vulnerabilities targeting Tor Browser are trapped inside the sandbox environment and can not get out and affect the rest of the computer or unmask anyone.
Tor developers have released the first version of its new and improved Tor Browser, though the version is still very much an alpha; so one can expect bugs, some potentially major ones.
One of the developers working on the project describes the browser features as:
A Gtk+3 based UI for downloading/installing/updating Tor Browser, configuring tor, and launching the sandboxed browser. Think `tor-browser-launcher`, that happens to run Tor Browser in a bunch of containers.
Linux seccomp-bpf + namespace based containers for Tor Browser, that attempts to prevent/mitigate exploits and reduce the amount of personally identifiable information to a minimum, centered around bubblewrap (runtime dependency).
This version is yet only available for Linux. Official binaries should be available sometime next week. For now, confident users could compile it themselves from the source code, though I strongly suggest people to wait.
If you are more privacy conscious, you should use a Virtual Private Network (VPN) with Tor.
As I previously recommended, Privatoria VPN provides a number of great features, including VPN, VPN Tor, Proxy, Proxy Tor, and Anonymous Emails, which makes it one of the reliable VPN services available in the market.
You can try Privatoria VPN Free Trial today and secure your web experience.
Beware of New Celebrity Sex Tape (Scam) Leaked on Facebook!
12.12.2016 thehackernews Social
If you came across a celebrity sex video on Facebook featuring Jessica Alba or any other celebrity, just avoid clicking it.
Another Facebook scam is circulating across the social networking website that attempts to trick Facebook users into clicking on a link for a celebrity sex tape that instead downloads malware onto their computers.
Once installed, the malware would force web browsers to display aggressive advertising web pages which include sites with nudity and fake lotteries.
The spam campaign was uncovered by researchers at Cyren, who noted that a malicious Google Chrome extension is spreading nude celebrity PDFs through private messages and posts on various Facebook groups.
If opened, the PDF file takes victims to a web page with an image containing a play button, tricking users that the PDF may contain a video.
Once clicked, the link redirects users of Internet Explorer, Firefox, or Safari to a web page with overly-aggressive popups and advertisements related to nudity and fake lottery.
But on the other hand, this celebrity sex tape scam makes the matter worse for Google Chrome users.
Beware of New Celebrity Sex Tape (Scam) Leaked on Facebook!
Once clicked on the scam link, Chrome desktop users are redirected to a fake YouTube page that leads up a pop-up window inviting victims to install a Google Chrome extension to view the videos.
Once victims get to install the malicious extension, the browser directs users to the Facebook.com login page and prompt them to re-authenticate, allowing attackers to collect Facebook users' credentials and then use their accounts to spread the malicious campaign further.
When analyzed the Chrome extension's source code, the Cyren team discovered that the extension comes with support for monitoring and intercepting web traffic in real-time, to determine what users can access through their browsers.
The malicious Chrome extension contains a long list of Antivirus and AntiSpam domains that it blocks and prevents the user from opening.
Besides this, the malicious Chrome extension also prevents victims from accessing the Chrome Extensions settings page, so that victims can not disable the malicious add-on.
"It also blocks the chrome extensions and chrome devtools tabs from being opened, preventing the user from uninstalling the malicious Chrome extension," the researchers say.
The PDF uploaded to Facebook is generated by selecting the name of a celebrity randomly from the script file and combining the selected name with random characters.
The name of celebrities includes Selena Gomez, Jessica Alba, Jennifer Lawrence, Hilary Duff, Paris Hilton, Rihanna, Kim Kardashian, Scarlett Johansson, Kelly Brook, Doutzen Kroes, Elodie Varlet and Nicki Minaj.
According to Cyren researchers, the cyber criminals behind this malicious spam campaign managed to upload their extension to the Chrome Web Store, though the extension has since been removed by the Google's security team.
How to remove the Malicious Chrome Extension?
To remove this malicious extension, the infected users would first have to delete the Registry key from the Registry Editor.
To do this, Go to Start Button → Type "regedit" in the Search/Run option, which will open the Windows Registry Editor.
Now, use the side menu in the new window to find the folder below, right-click it and select "Remove."
This is the path to the Registry Editor:
HKEY_LOCAL_MACHINE\Software\Google\Chrome\Extension
Now the second step is to remove the extension from the browser. Since the malicious Chrome extension prevents victims from accessing the native Chrome Extensions settings page, one must remove the extension by deleting the following folder from one's PC.
C:\Users\USER\AppData\Local\Google\Chrome\User Data\Default\Extensions
This action will remove all Chrome extensions from your computer. You have no option other than deleting the folder completely to get rid of the malicious threat, as you can not access the Chrome Extensions settings page to get the ID of the malicious extension.
Last but not the least, no celebrity recently have had their sex tape leaked (at least not one that's available online). So if you come across any link claiming to show a leaked sex tape of Jessica Alba, Jennifer Lawrence or any other, remember just to report it.
Become a Linux Expert — Get this Online 5-Course Training Bundle
12.12.2016 thehackernews IT
Linux is considered as one of the most favorite operating systems for hackers and security researchers. The open source operating system is often used for building technologies as it offers developers much room for modifications.
Linux is used on many hardware platforms, servers, gaming platforms, and much more. So it is essential for anyone, who want to become a Linux pro or seeking a career in system administrator, to understand Linux.
But Are you tired of searching multiple resources to fully understand Linux?
This process is not just time-consuming, but also expensive as one has to pay for different courses to know and learn how to setup, maintain and operate a fully backend infrastructure powered by Linux Operating System.
Not now! You don't need to waste your time and money, as today's THN Deals will help you choose an excellent course specifically designed to teach you all thing Linux.
Deal Of the Day — Linux Essentials Bundle (82% Discount)
Linux Essentials Bundle
Linux Essentials Bundle is a complete package that covers everything that is required to become a Linux Pro.
From an introductory course for absolute beginners, Linux Essentials Bundle will work your way through BASH and Shell Programming, administering Linux/UNIX systems, creating apps with Docker, using 'vi' for coding and more.
The original value of this course is $225, but at THN Deals Store, you can get this Linux Essentials Bundle course for $39 after 82% of flat discount.
The classes in Linux Essentials Bundle include:
Fundamentals of Unix & Linux System Administration
Learn Docker from Scratch
Linux Shell Programming for Beginners
Linux for Absolute Beginners
Learn To Code Like a Pro With vi Editor
Over 50 hours of the training course, you will learn how to build on the Linux OS, develop apps with Docker Access, edit code with vi Editor, and build efficient systems.
So, head on to THN Deals Store now and get Linux Essentials Bundle for a super low price of just $39.
Zcash cryptocurrency, a new opportunity for cyber criminals
12.12.2016 securityaffairs Virus
Zcash (ZEC) is a new cryptocurrency that promises a total anonymity, it is already attracting a great interest from miners and of course cybercriminals.
Zcash (ZEC) is the cryptocurrency of the moment, it was presented on October, 2016 and respect the popular Bitcoin it is totally anonymous. With this premise, the Zcash has attracted a great interest from investors, miners and of course cybercriminals.
A few hours, 1 ZEC reached $30,000, and this is normal considering that there was a high request and only a few dozen coins available. Now the situation is normal, the value of a ZEC declined compared to the one of the Bitcoin, at the time of writing, it is 0.07 – 0.01 ZEC/BTC (around $70).
According to the experts from Kaspersky Lab, despite this drop, Zcash mining remains among the most profitable compared to other cryptocurrencies, this means more opportunity for cyber criminals that started creating botnets for mining.
“In November, we recorded several incidents where Zcash mining software was installed on users’ computers without permission. Because these software programs are not malicious in themselves, most anti-malware programs do not react to them, or detect them as potentially unwanted programs (PUP). Kaspersky Lab products detect them as not-a-virus:RiskTool.Win64.BitCoinMiner.” reads a blog post published by Kaspersky.
Crooks are distributing Zcash miners through pirated software via torrents, but the experts still haven’t seen any cases of mass-mailings campaign with this specific purpose.
Kaspersky also discovered a couple of websites distributing mining programs:
http://execsuccessnow[.]com/wp-includes/m/nheqminer.exe
https://a.pomf[.]cat/qzwzfx.exe
Anyway, malware researchers believe that it is only a matter of time, criminal organizations will their botnets to deliver the miner on already infected systems or to spread the threat.
Consider that an average machine is able to mine about 20 hashes per second. A botnet composed of one thousand computers can mine about 20,000 hashes a second, that at current prices correspond to $6,200 a month in net profits.
The researchers explained that the most popular mining software to date is nheqminer from the mining pool Micemash, which allows earning payments in both bitcoins and Zcash.
“Both are detected by Kaspersky Lab products, with the respective verdicts not-a-virus:RiskTool.Win64.BitCoinMiner.bez and not-a-virus:RiskTool.Win64.BitCoinMiner.bfa.” continues Kaspersky.
The researchers explained that also for Zcash is possible to ‘snoop’ on some of the wallets used by criminal organizations and discovery the amount of money they received. (i.e. https://explorer.zcha.in/accounts/t1eVeeBYfPPLgonvi1zk8e9SnrhZdoCBAeM)
Zcash allows two types of wallets, completely private purses (z-address) and public wallets like the one shown above (t-address).
“At the current time, the completely private wallets are not very popular (they are not supported by exchanges), and are only used to store around 1% of all existing Zcash coins.”
Kaspersky has spotted roughly 1,000 unique users who have some version of the Zcash miners installed on their machine under a different name, a circumstance that suggests their computers were infected.
Give a look at the analysis published by Kaspersky for more information.
Critical flaw in PricewaterhouseCoopers SAP security tool, but PwC tries downplay it
12.12.2016 securityaffairs Vulnerebility
A PricewaterhouseCoopers SAP software, the Automated Controls Evaluator (ACE), is affected by a critical security flaw that could be exploited by hackers.
A software developed by PricewaterhouseCoopers for SAP systems, the Automated Controls Evaluator (ACE), is affected by a critical security flaw.
The vulnerability was discovered by the security firm ESNC who analyzed the tool. The Automated Controls Evaluator (ACE) is a diagnostic SAP tool that extracts security and configuration data from SAP systems in order to analyze them in order to discover backdoors (such as configuration, customization and security settings) and misconfiguration that could be exploited by attackers to commit fraud.”
“The purpose of this tool is to analyze SAP security settings and identify privileged access and potential segregation of duties issues accurately and efficiently”; and – “The ABAP files introduce no changes to the production systems and settings”. states the PricewaterhouseCoopers website.
The researchers from ESNC have discovered that the PwC ACE software is affected by a remotely exploitable security flaw that could be exploited to inject and execute malicious ABAP code on the remote SAP system. The potential impact on the companies that uses the tool is critical, the vulnerability may allow an attacker bypass change management control, bypass segregation of duty restrictions, and of course, manipulate accounting documents and financial results exposing the business to fraudulent activities.
“This security vulnerability may allow an attacker to manipulate accounting documents and financial results, bypass change management controls, and bypass segregation of duties restrictions,” states the advisory published by ESNC.
“This activity may result in fraud, theft or manipulation of sensitive data including PII such as customer master data and HR payroll information, unauthorized payment transactions and transfer of money.” “The attacks may be executed from the local network via SAPGui, or from the public Internet via http/https ICF services such as WebGui and Report, if the systems are accessible.”
The vulnerability affects version 8.10.304, and potentially also earlier versions might also be affected.
A PricewaterhouseCoopers spokeswoman tried to downplay the issue by explaining that the company is not aware of any problem with his software.
“The code referenced in this bulletin is not included in the current version of the software which is available to all of our clients,” a PwC spokeswoman told The Reg. “The bulletin describes a hypothetical and unlikely scenario – we are not aware of any situation in which it has materialized.”
The Reg highlighted the difficulties faced by ESNC in reporting the issue to PricewaterhouseCoopers. The flaw was reported in August, but PwC initially didn’t provide a response, then its lawyers sent an email to the security researchers to “desist” their investigation.
Below the Vulnerability Timeline shared by ESNC
19.08.2016 PwC contacted
22.08.2016 Meeting with PwC, informed them about the impact and the details of the vulnerability and responsible disclosure
05.09.2016 Asked PwC about updates and whether a patch is available
13.09.2016 Received a Cease & Desist letter from PwC lawyers
18.11.2016 Informed that 90 days have passed and ESNC is planning to release a security advisory; asked for any details PwC can share about this matter including risk, affected versions, how to obtain a patch
22.11.2016 Received another Cease & Desist letter from PwC lawyers
07.12.2016 Public disclosure
This is a wrong approach to cyber security.
How much cost a StingRay? Surveillance is a profitable business
12.12.2016 securityaffairs Safety
Motherboard published an interesting blog post which includes further details on the cost of StingRay phone surveillance equipment.
A couple of years ago I published a post on Stingray Technology trying to explain how governments track cellular devices.
A StingRay is an IMSI-catcher (International Mobile Subscriber Identity) designed and commercialized by the Harris Corporation. At the time of the article, the cellular surveillance system was costing as much as $400,000 in the basic configuration, and its price varied with add-ons ordered by the agency.
The IMSI-catcher is a surveillance solution used by military and intelligence agencies for telephone eavesdropping. It allows for intercepting mobile phone traffic and tracking movements of mobile phone users. Essentially, an IMSI catcher operates as a bogus mobile cell tower that sits between the target mobile phone and the service provider’s real towers. The IMSI catcher runs a Man In the Middle (MITM) attack that could not be detected by the users without using specific products that secure communication on mobile devices.
The use of the IMSI-catcher is raising a heated debate in the United States because devices like StingRay and other similar cellphone tracking solutions are being widely adopted by law enforcement agencies across the country.
StingRay allows law enforcement to intercept calls and Internet traffic, send fake texts, inject malware on a mobile device, and to locate the targets.
Now Curtis Waltman from Motherboard published an interesting blog post which provided further details on the cost of the StingRay phone surveillance tool.
Waltman published data provided by the Rochester Police Department in New York that responded to the Cell Site Simulator Census, an initiative that census the cellphone surveillance equipment use and policy.
“A mapping of police departments and agencies nationwide that are using IMSI catcher (Stingray) technology. Included in this mapping is a focus on the policies, procedure and contractual agreements that department’s are formulating as they adopt the controversial surveillance device.” states the description for the census.
Data shared by Motherboard are very interesting and provides useful insights about their surveillance systems, their components, and prices. It a “completely unredacted quote list of Harris Corporation products”.
Documents shared by the Rochester Police Department show clearly how Harris sells the Stingray equipment to law enforcement.
According to the documents, devices are often sold in packages, like the StingRay II Vehicular System that is offered for sale with devices (i.e. Three different kinds of Harris’ Harpoon signal amplifiers) that allow its use for a patrol vehicle.
How much cost a StingRay II Vehicular System?
The package includes a laptop, three kinds of software for accessing different types of cellular networks, and an AmberJack cellphone tracker goes for a grand total of $148,000.
“The Amberjack is an important accessory for the surveillance systems like Stingray, Gossamer, and Kingfish. It is a direction-finding system antenna that is used for cellular device tracking. It costs nearly $35,015″ I wrote in a blog post published early this year.
The prices for the AmberJack is quite similar I published early this year.
According to documents published by Motherboard, The KingFish package, Harris Corporations smaller, mobile version of the StingRay, is sold for $157,000.
The single KingFish device is not so expensive as I have reported early this year.
“Kingfish is a surveillance transceiver that is used by law enforcement and intelligence agencies to track cellular devices and exfiltrate information from mobile devices over a targeted area. It could be concealed in a briefcase and allows gathering of unique identity codes and shows connections between phones and numbers being dialed. Its cost is slightly higher than $25,000.” 
The Rochester PD expressed its interest for the entire KingFish, except the laptop.
The company is including in the surveillance packages also training activities that go for $12,000.
“These packages also come with the option of a training package, costing $12,000, and a one year maintenance package that will cost $169,000 if your department decided to splurge for the whole line of Harris’ products (this was 2011 so the 4G network cell site simulator the HailStorm wasn’t released yet.) Training isn’t included interestingly enough, so police departments are more or less forced to pay for training on these complicated and powerful devices.” states the post published by Motherboard.
The note at the end of the document provides also further details of the surveillance technology, including the specifications required to use the equipment in a real scenario.
“The StingRay and Kingfish can be run out of a car’s cigarette lighter, while the StingRay II requires a 2000W power inverter. That is hungrier for power than almost any household appliance, save a dryer or oven.” continues the post.
If you are interested in StingRay surveillance technology, give a look at the article “StingRay Technology: How Government Tracks Cellular Devices”
Odhalte interní hrozby hned v počátku
12.12.2016 SecurityWorld Zabezpečení
Interní hrozby představují velmi časté riziko, před kterým jsou bezpečnostní profesionálové neustále varovaní. Podle expertů potřebujeme software nové generace, integrovanou inteligenci pro odhalování hrozeb a schopnost najít vzájemné souvislosti mezi velkým množstvím událostí z protokolů a kontextem. Jak by tedy mohla vypadat výzbroj proti těmto hrozbám?
Odborníci jsou přesvědčeni, že pokročilé nástroje jsou pro blokování útoků a zotavení z nich, pokud by byly úspěšné, nezbytné. Bohužel když firmy zjistí, že došlo k jejich kompromitaci, velmi často se dozvědí i to, že jejich systémy byly napadené už delší dobu.
„Interní hrozby mohou zahrnovat kombinaci zločinců z řad vlastního personálu, nevědomých kompromitovaných zaměstnanců a nedbalých pracovníků,“ vysvětluje Wade Williamson, ředitel produktového marketingu ve společnosti Vectra Networks.
„K identifikaci všech těchto hrozeb budete potřebovat speciální řešení, které se ale liší v chování i ve způsobech, jak může rizika v zabezpečení odhalit.“
Sesbírali jsme rady od několika bezpečnostních expertů, kteří se zaměřují právě na pomoc firmám odhalit interní útok v co nejranější fázi.
Tip 1: Hledejte ve svých DNS přenosech neobvyklé vzory
„DNS je často opomíjenou vrstvou,“ tvrdí Arno Meulenkamp, systémový inženýr společnosti Infoblox. „Lze ji používat jako cestu pro únik dat. Neobvyklé vzory v DNS provozu, jako jsou například změti dat, mohou signalizovat, že se děje něco nekalého.“
Tip 2: Kontrolujte, zda protokoly neobsahují informace o autentizacích hostitel-hostitel
„Pokud vidíte, že se někdo autentizuje vůči hostiteli z jiného hostitele, zatímco ten cílový se obvykle autentizuje pomocí řadiče domény, můžete mít problém,“ varuje Yonathan Klijnsma, hlavní analytik pro inteligenci zaměřenou na hrozby ve společnosti Fox-IT.
„V této souvislosti je důležité znát nástroje, které útočníci používají – například PSExec (a jeho varianty) nebo Mimikatz –, a hledat provoz odpovídající těmto nástrojům.
Je běžné, že takovéto nástroje jsou používané právě prostřednictvím komunikace mezi hostiteli (host-to-host) pro laterální pohyb – k přechodu mezi počítači se systémem Windows zapojenými v síti.“
Tip 3: Kontrolujte, zda na webu nenajdete vystavené přihlašovací údaje zaměstnanců
„Monitorujte weby, jako je například Pastebin, zda se na nich nevyskytnou přihlašovací údaje vašich zaměstnanců,“ radí Nagraj Seshadri, viceprezident marketingu společnosti Recorded Future.
„Pokud došlo ke zneužití přihlašovacích údajů uniklých na web, možná máte uvnitř firmy záškodníka, a přitom zaměstnanec, kterému dané přihlašovací údaje patří, nemusí o ničem vědět. Zareagujte změnou hesel a zvažte zavedení dvoufaktorové autentizace.“
Tip 4: Sledujte datové toky týkající se klíčových aktiv.
„Záškodník z řad zaměstnanců bude často krást velké objemy dat během krátkého časového období. Shromažďování velkých objemů dat lze snadno zjistit monitorováním interního majetku,“ dodává Williamson ze společnosti Vectra Networks.
„Sledováním interních přenosů mohou týmy rychle zjistit, zda dochází k tunelování dat ze sítě nebo jestli se data přenášejí na více zařízení kvůli jejich následné krádeži.“
Tip 5: Mapujte vícenásobná přihlašování počítačů do cloudových služeb úložišť
„Hledejte uživatele, kteří se přihlašují k různým počítačům ze stejného účtu, přistupují k velkým datovým úložištím a synchronizují svá data s cloudovými službami úložišť, jako je například Dropbox,“ radí Itsik Mantin, ředitel výzkumu zabezpečení ve společnosti Imperva.
„Interní záškodník totiž může využít vyzrazené přihlašovací údaje uživatele pro přístup k uživatelským účtům Dropboxu – takové odesílání dat pak může vypadat jako běžné firemní využití služeb.“
Tip 6: Používejte falešné přihlašovací údaje a soubory jako návnady
„Vnitřní zloduch se bude pohybovat v síti, vyhledávat nové přihlašovací údaje a používat svá nově získaná privilegia pro přístup k datům,“ prohlašuje Haroon Meer, zakladatel a výzkumník společnosti Thinkst.
„Použití falešných přihlašovacích údajů a falešných souborů jako návnad umožňuje vidět, když se tyto přihlašovací údaje začnou používat (a nikdy by k tomu vlastně dojít nemělo).“
Tip 7: Hledejte věci, které již neexistují
„Záškodníci z řad zaměstnanců se často snaží zakrýt své stopy – podobně jako malware, který se pokouší si zajistit dlouhodobě neodhalenou existenci pomocí mazání mnoha kompromitujících věcí,“ prohlašuje Fabien Perigaud, bezpečnostní expert divize Airbus Defence and Space – CyberSecurity.
„Hledejte klíče registru, služby a objekty, ke kterým někdo přistupoval, v minulosti je používal, ale nyní již v počítači neexistují. Mohly by být neklamnou známkou výskytu záškodníka.“
Tip 8: Mapujte protokoly autentizace koncového bodu pomocí protokolů Active Directory
„Pokud uživatel dříve využíval jen tři až čtyři zařízení v síti, ale nyní se za krátký čas tento počet výrazně zvýšil, je možné, že máte problém s vnitřním zloduchem,“ vysvětluje Mark Schloesser, výzkumník zabezpečení ze společnosti Rapid7.
„Je nutné hledat souvislosti mezi protokoly z Active Directory (AD) a protokoly z koncových bodů, protože obsahují události lokální autentizace účtu, které nejsou pro AD viditelné.“
Tip 9: Vyhledejte první instanci události
„Hledejte první výskyt vykonávané aktivity,“ doporučuje Johan den Hartog, technik společnosti Tenable Network Security. „Pokud taková aktivita dříve neexistovala, mohlo by to ukazovat na začátek útoku interního záškodníka a je třeba to vyprofilovat.
Například společnosti HSBC a Sabre zažily případy, kdy došlo k vytvoření stínových zaměstnanců pomocí aliasů a nové aktivity byly vykonávané právě pod těmito aliasy.“
Tip 10: Identifikujte použití nástrojů stínových IT
„V naší nedávné zprávě o používání aplikací a hrozbách jsme uvedli, že více než 4 400 organizací zažilo současné používání pěti a více unikátních aplikací pro vzdálený přístup. Očekávatelné množství je ale jedna nebo dvě, rozhodně ale ne pět,“ popisuje Greg Day, viceprezident a ředitel zabezpečení pro oblast EMEA ve společnosti Palo Alto Networks.
„Přestože může jít o záměrné využívání, může nasazení těchto nástrojů v konečném důsledku vést k nepředvídatelným následkům.“
Tip 11: Před smazáním malwaru jej analyzujte
„Protože je udržení provozu hlavní prioritou, vytvořily si společnosti zvyk okamžitě při identifikaci malwaru obnovit infikované systémy z bitových kopií, aby mohly opět hned fungovat,“ popisuje Ralph Pisani, výkonný viceprezident provozu společnosti Exabeam.
„Malware je příznakem, že se děje něco špatného, takže by firmy neměly tuto důležitou stopu tak rychle eliminovat – mohla by totiž jim pomoci pochopit smrtící kybernetickou posloupnost.
Malware totiž často nepředstavuje konec, ale naopak začátek problému. Je velmi důležité vědět, co uživatelé udělali předtím, než došlo k detekci malwaru, a také co se dělo po infekci.“
UK National Security Strategy, Cyber Security is a top priority
securityaffairs Cyber
The UK Government published the first annual report on the implementation of the 2015 National Security Strategy.
The strategy considers cyber security a top priority alongside the resurgence of state-based threats (Russia’s actions in Syria and Ukraine) and the terrorism (extremism and instability).
When dealing with the impact of technology, especially cyber threats the report states:
“The range of cyber threats and cyber actors threatening the UK has grown significantly – both from state and non-state actors. The UK increasingly relies on networked technology in all areas of society, business and government. This means that we could be vulnerable to attacks on parts of networks that are essential for the day-to-day running of the country and the economy.” reads the “National Security Strategy and Strategic Defence and Security Review 2015 First Annual Report 2016“
The Government is working with private industry in order to prevent and reduce the effects of cyber attacks against its infrastructure. Communications service providers, for example, are crucial partners for threat intelligence activities that is one of the main activities of the National Cyber Security Centre.

According to the updates for the National Cyber Security Strategy in November 2016, the PM Theresa May’s administration will increase focus on investment in automated detection systems and active cyber defence (response).
“We continue to invest in cyber detection and response, as attacks against the UK continue to rise. Over the last year, we have developed new technical capabilities to improve our ability to detect and analyse sophisticated cyber threats.” continues the report. “Law enforcement continues to work with industry partners to increase specialist capability and expertise, as well as providing additional training in digital forensics. We are also continuing to progress our Active Cyber Defence measures against high-level threats, by strengthening UK networks against high volume/ low sophistication malware.”
The UK National Cyber Security Strategy also highlights a skill shortage in cyber security, for this reason, the UK government wants to launch a cyber security education program that will involve also teenagers in schools and university.
“A new Cyber Security Skills Strategy is now under development, which will set out how we will work with industry and academic providers to secure a pipeline of competent cyber security professionals.” states the report. “The first cohort of 14-17 year olds will begin training under this programme in 2017.”
The UK Government is working with industry to establish specific cyber apprenticeships for three critical national infrastructure sectors, the energy, finance and transport.
The National Cyber Security Strategy includes a specific session that addresses the cyber crime. Law enforcement bodies are working with the private industry actors to increase the efficiency of their action against the cyber crime. To tackle
The UK Government intends to tackle abuses in the ‘dark web‘, announcing new Dark Web Intelligence Unit within the NCA.
The UK Government is also investing in regional cyber crime prevention coordinators, who “engage with SMEs and the public to provide bespoke cyber security advice”.
Many other information related to the UK National Security Strategy is included in the report, enjoy it.
Georgia traced an attempted breach of voter registration database to DHS
11.12.2016 securityaffairs Cyber
Georgia’s secretary of state, Brian Kemp, revealed that voter registration database was targeted by hackers with IP address linked to the DHS.
While President Barack Obama has ordered US intelligence agencies to deeper investigate the alleged Russian interference with the 2016 Presidential Election, Georgia announced it’s traced an attempted breach of the state’s voter registration database to the DHS.
The Georgia’s secretary of state, Brian Kemp, revealed that the voter registration database was targeted by hackers with IP address linked to the DHS.
The news is disconcerting as curious. Why IP addresses belonging to the DHS are involved in this cyber attack?
The first hypothesis sees a group of hacked systems at DHS that were used by a threat actor to access voter registration database. This means that hackers breached the systems of the US Government and are using them to move laterally and steal sensitive information.
In November 2014 the State Department has taken the unprecedented step of shutting down its entire unclassified email system in response to a suspected cyber attack.
‘Activity of concern’ was detected in the system concurrently with another cyber attack which hit the network at the White House computer network. A State Department staffer answering a call to the State Department Operations Center revealed that, as a precautionary measure, the e-mail system remained down.
In the same period, other US agencies were targeted by hackers, including the U.S. Postal Service and the National Weather Service, the U.S. Military confirmed that its systems were secured, according to official sources, none of the State Department’s classified systems were affected.
These are just a few examples of attacks that hit the US Government.
A second hypothesis sees someone in the US intelligence that is conducting a covert operation, for example, to build “false flag” for an alleged Russian attack, but sincerely this scenario is implausible. Another possibility is that agents at the DHS were conducting a penetration testing without authorization with the intent to measure the resilience of the Firewall to a cyber attack.
According to Georgia Secretary of State Brian Kemp, hackers were blocked by the firewall that protects Georgia’s voter registration database.
“Recently, I was made aware of a failed attempt to breach the firewall that protects Georgia’s voter registration database by an IP address associated with the Department of Homeland Security. On Thursday morning, , I sent a letter to DHS Secretary Jeh Johnson demanding to know why.” Georgia’s secretary of state, Brian Kemp wrote on his Facebook page.
The Wall Street Journal who visioned a copy of the letter sent by Mr Kemp, revealed the attempted attack occurred on November 15, just after the presidential election.
implausible. Another possibility is that agents at the DHS were conducting a penetration testing without authorization with the intent to measure the resilience of the Firewall to a cyber attack.
According to Georgia Secretary of State Brian Kemp, hackers were blocked by the firewall that protects Georgia’s voter registration database.
“Recently, I was made aware of a failed attempt to breach the firewall that protects Georgia’s voter registration database by an IP address associated with the Department of Homeland Security. On Thursday morning, , I sent a letter to DHS Secretary Jeh Johnson demanding to know why.” Georgia’s secretary of state, Brian Kemp wrote on his Facebook page.
The Wall Street Journal who visioned a copy of the letter sent by Mr Kemp, revealed the attempted attack occurred on November 15, just after the presidential election.
“We are looking into the matter. DHS takes the trust of our public and private sector partners seriously, and we will respond to Secretary Kemp directly,” the DHS said in a statement.
“At no time has my office agreed to or permitted DHS to conduct penetration testing or security scans of our network,” Kemp wrote in his letter. “Moreover, your department has not contacted my office since this unsuccessful incident to alert us of any security event that would require testing or scanning of our network.”
The hacking of election systems represented a major concern during the last 2016 Presidential Election, in many cases experts highlighted that it was possible that foreign hackers attempted to do it. The US intelligence agencies had found evidence that foreign hackers were trying to access state voter registration systems, in April 2016 the FBI issued a “flash” alert to election officials across the country confirming that foreign hackers have compromised state election systems in two states.
In response to the attacks the DHS offered a series of services to assess the security of voting systems, including cyber hygiene scans that were specifically designed to find flaws in the systems used during the election.
Anyway Kemp seems to have refused the DHS support
“But Georgia’s top election official is balking at the offers of assistance — and accusing the Obama administration of using exaggerated warnings of cyberthreats to intrude on states’ authority.” states a post published by Politico. “Georgia Secretary of State Brian Kemp’s objections add to a bumpy start for the Department of Homeland Security’s attempt to shore up safeguards for the election, during a summer when cyberattacks on the Democratic National Committee have called attention to weaknesses across the electoral system.”
President Obama Orders 'Full Review' of Possible Russian hacking in US Election
11.12.2016 thehackernews Cyber
In his final month in office, President Barack Obama has ordered U.S. intelligence agencies to conduct a "full review" of pre-election cyber attacks against Democratic Party organizations that many believe affected the outcome of the 2016 presidential election.
The United States intelligence agencies have attributed those series of cyber-attacks to Russia that shook the US election season.
"The President earlier this week instructed the intelligence community to conduct a full review of the pattern of malicious cyber activity related to our presidential election cycle," White House spokesman Eric Schultz told reporters.
At an event hosted by the Christian Science Monitor, White House's counterterrorism adviser Lisa Monaco announced that the president had "directed the Intelligence Community to conduct a full review of what happened during the 2016 election process."
President is expecting a full report before the end of his term, and President-elect Donald Trump takes office in January of 2017, as Monaco said that the results of the pre-election hacking's investigation would be released to Congress before President Obama left office.
At a Heritage Foundation event on Wednesday, Chairman of House Homeland Security Michael McCaul, also called for "consequences" for Russia's interference in the 2016 election. "If we don’t respond and show them that there are consequences," McCaul said, "the bad behavior will continue… our democracy itself is being targeted."
The announcement comes after Democrats in Congress forced the White House office to reveal details of Russian hacking and disinformation in the presidential election.
"We may be crossed into a new threshold, and it is incumbent upon us to take stock of that, to review, to conduct some after-action, to understand what this means, what has happened and to impart those lessons learned," Obama told reporters.
Monaco said the new administration would inherit a rapidly growing national security threat that comes from the Internet across all dimensions.
Meanwhile, Trump has said he was not convinced Russia was behind the pre-election cyber attacks.
"I don't believe they interfered," Trump told in an interview with Time magazine this week. "That became a laughing point – not a talking point, a laughing point. Anytime I do something, they say, 'Oh, Russia interfered.'"
In October, the DHS and the US intelligence agency officially blamed Russia of hacking the Democratic National Committee (DNC) and other political organizations "intended to interfere with the US election process." Though Russia has denied all accusations.
Russian hackers also allegedly stole private emails from a Clinton associate that were later published by WikiLeaks just weeks before election day.
With that, the full report by Obama administration on pre-election hacking might face serious challenges in the next government.
Waiting for a fix, stop using Netgear R7000 and R6400 routers to avoid hacks
11.12.2016 securityaffairs Vulnerebility
Waiting for security patches, the CERT/CC suggests to stop using Netgear R7000 and R6400 routers to avoid being hacked. Other routers potentially exposed.
IoT devices are privileged targets for threat actors, the Mirai botnet is the demonstration of the effects of a massive attack powered with smart objects, including routers, CCTV and DVRs.
Now the security experts are warning of serious security issues in two Netgear routers. The Netgear R7000 and R6400 routers are affected by a critical vulnerability that could be exploited by remote attackers to run malicious code with root privileges.
Unfortunately, current and latest versions of the Netgear R7000 and R6400 routers running current and latest versions of the firmware are vulnerable to arbitrary command injection attacks.
At the time I was writing we cannot exclude that also other models may be vulnerable.
The Carnegie Mellon University CERT published a security advisory (Vulnerability Note VU#582384) to warn of multiple Netgear routers are vulnerable to arbitrary command injection.
The exploitation of the flaw is quite simple, attackers just need victims info into visiting a website that contains specially crafted malicious code to trigger the vulnerability.
“Netgear R7000, firmware version 1.0.7.2_1.1.93 and possibly earlier, and R6400, firmware version 1.0.1.6_1.0.4 and possibly earlier, contain an arbitrary command injection vulnerability.” reads the advisory issued by the CERT/CC.”By convincing a user to visit a specially crafted web site, a remote attacker may execute arbitrary commands with root privileges on affected routers. A LAN-based attacker may do the same by issuing a direct request.
The advisory states that in order to exploit the flaw, the victim could visit a website like:
http://<router_IP>/cgi-bin/;COMMAND
then the malicious commands would execute automatically with root privileges.

The code exploit for this vulnerability has been publicly released.
At the time I was writing there is no available fix for the issue neither a workaround, for this reason, the CERT strongly recommended Netgear users to “consider discontinuing use” of vulnerable Netgear R7000 and R6400 routers, until a patch is released by the company.
“Exploiting this vulnerability is trivial. Users who have the option of doing so should strongly consider discontinuing use of affected devices until a fix is made available.” states the CERT.
APT 28 group is ramping up information warfare against Germany
11.12.2016 securityaffairs APT
According to the German Intelligence, the APT 28 group, also known as Fancy Bear, is ramping up information warfare against Germany and the rest of West.
US intelligence agencies blame the Russian government for ramping up infowar against the US and the West. According to the US Government, Russian-state hackers hacked the Democratic National Committee (DNC) and other political organizations worldwide.
Hackers conducted campaigns to interfere with the internal affairs of foreign states, last victim in order of time is Germany, this is the opinion of the Germany’s chief of domestic intelligence who warned of this threat last week.
On December 8, the Germany’s Bundesamt für Verfassungsshutz (BfV) has issued a press release warning of a rise in Russian propaganda and hacking campaigns.
“We see aggressive and increased cyber spying and cyber operations that could potentially endanger German government officials, members of parliament and employees of democratic parties,” reads a statement issued by Hans-Georg Maassen, head of the BfV agency
The goal of Russian hackers is to spread uncertainty, strengthen extremist groups and parties, with the intent of “weaken or destabilise the Federal Republic of Germany.”
Both the heads of the German foreign intelligence agency (BND), Bruno Kahl, and the domestic intelligence agency (BfV), Hans-Georg Maassen, have warned about increasing Russian cyber operations in the country.

Foto: Johannes Simon/ ddp
Social media are becoming a new battlefield, the BfV observed a spike in propaganda activities as part of PSYOps and noted an increased number of “spear phishing attacks against German political parties and parliamentary groups.” The German intelligence confirmed that hackers are using the strain of malware that were used to broke in the system of the US Democratic National Committee.
“Spear-phishing against political parties and parliamentary groups have increased dramatically. They are attributed to the APT 28 campaign, which was also responsible for the DNC hack. APT 28 successfully exfiltrated data from the German Bundestag in 2015.”
In March security experts at Trend Micro, who follow a long time the operations of the Russian-linked Pawn Storm cyber spies (aka APT 28, Sednit, Sofacy, Fancy Bear and Tsar Team) discovered that the Russian spies targeted the political party of Chancellor Angela Merkel, the Christian Democratic Union.
Some experts speculate that also the recent attack against the Deutsche Telekom routers was powered is linked to Russia.
The German Parliament, the Bundestag, was targeted by hackers that also hit a number of German politicians, including the Chancellor Angela Merkel.
“Such cyber-attacks, or hybrid conflicts as they are known in Russian doctrine, are now part of daily life and we must learn to cope with them.” commented the Chancellor Angela Merkel.
“There are findings that cyber-attacks take place which have no other meaning than to create political uncertainty. There is a kind of pressure on public discourse and on democracy, which is unacceptable.”Kahl told the Süddeutsche Zeitung, “Attribution to a state actor is technically difficult, but there is some evidence that it is at least tolerated or desired by the state.”
The German intelligence observed a rise in Russian online propaganda in Germani since the start of the Ukraine crisis.
“Since the start of the Ukraine crisis, we have seen a significant increase in Russian propaganda and disinformation campaigns in Germany.” reads a statement issued by the BfV.
The German intelligence has explicitly blamed the APT28 as the threat actors behind the hacking campaign used for disinformation activities, the group appears to be specialized in false flag activities. Something similar occurred when Russian Hackers have broken into the French TV5 pretending to be an ISIS-linked group.
“This approach represents a previously unseen methodology in campaigns that are controlled by Russia.”
According to Maassen, APT 28 activity is responsible for an unprecedented disinformation campaign.
“Propaganda, disinformation, cyber-attacks, cyber espionage and cyber sabotage are part of hybrid threats against western democracies.” said Maassen warning of significant an increase in political cyber espionage.”
“Stolen information could be used in the election campaign to discredit German politicians.”
On the other side, the Kremlin denies involvement and warns the US and asked Washington clarifications for US cyber threats.
NSA a britská GCHQ dokážou odposlouchávat mobily a notebooky v letadlech
10.12.2016 Živě.cz BigBrother
Přinejmenším americká NSA a britská GCHQ už roky monitorují hovory, SMS a webová data z letadel, které tuto službu nabízejí svým zákazníkům. Tvrdí to alespoň The Intercept a Le Monde na základě dat, které získaly od Edwarda Snowdena.
Systém se podle zveřejněné prezentace jmenuje Thieving Magpie (Straka zlodějka) a dokáže monitorovat libovolné letadlo každé dvě minuty.
GSM/GPRS komunikace v letadle a seznam podporovaných arelinek
Jak je to možné? NSA a GCHQ neodposlouchávají letadlo samotné, ale satelitní komunikací provozovatele palubních GSM buněk. Když se tedy letadlo dostane do běžné letové hladiny, personál zapne palubní GSM vysílače a ty se spojí s telekomunikačním satelitem, který pak data přenáší do pozemní stanice. A právě tento signál mezi satelitem a pozemní stanicí agentury odposlouchávají (těžko říci, jestli s vědomím majitele – blackbox, anebo pirátsky).
Podle prezentace dokážou agentury ze zaznamenaného signálu dešifrovat základní údaje o komunikaci a to u libovolného letu každé dvě minuty
Podle prezentace dokážou odhalit jak identifikační údaje jednotlivých telefonů na palubě, tak některé střípky z internetové komunikace včetně zasílaných e-mailových adres, adresátů skypových chatů a v prezentaci se dokonce objevila zmínka, že někteří cestující na palubě letadel spouštějí BitTorrent.
President Obama Orders 'Full Review' of Possible Russian hacking in US Election
10.12.2016 thehackernews Hacking
In his final month in office, President Barack Obama has ordered U.S. intelligence agencies to conduct a "full review" of pre-election cyber attacks against Democratic Party organizations that many believe affected the outcome of the 2016 presidential election.
The United States intelligence agencies have attributed those series of cyber-attacks to Russia that shook the US election season.
"The President earlier this week instructed the intelligence community to conduct a full review of the pattern of malicious cyber activity related to our presidential election cycle," White House spokesman Eric Schultz told reporters.
At an event hosted by the Christian Science Monitor, White House's counterterrorism adviser Lisa Monaco announced that the president had "directed the Intelligence Community to conduct a full review of what happened during the 2016 election process."
President is expecting a full report before the end of his term, and President-elect Donald Trump takes office in January of 2017, as Monaco said that the results of the pre-election hacking's investigation would be released to Congress before President Obama left office.
At a Heritage Foundation event on Wednesday, Chairman of House Homeland Security Michael McCaul, also called for "consequences" for Russia's interference in the 2016 election. "If we don’t respond and show them that there are consequences," McCaul said, "the bad behavior will continue… our democracy itself is being targeted."
The announcement comes after Democrats in Congress forced the White House office to reveal details of Russian hacking and disinformation in the presidential election.
"We may be crossed into a new threshold, and it is incumbent upon us to take stock of that, to review, to conduct some after-action, to understand what this means, what has happened and to impart those lessons learned," Obama told reporters.
Monaco said the new administration would inherit a rapidly growing national security threat that comes from the Internet across all dimensions.
Meanwhile, Trump has said he was not convinced Russia was behind the pre-election cyber attacks.
"I don't believe they interfered," Trump told in an interview with Time magazine this week. "That became a laughing point – not a talking point, a laughing point. Anytime I do something, they say, 'Oh, Russia interfered.'"
In October, the DHS and the US intelligence agency officially blamed Russia of hacking the Democratic National Committee (DNC) and other political organizations "intended to interfere with the US election process." Though Russia has denied all accusations.
Russian hackers also allegedly stole private emails from a Clinton associate that were later published by WikiLeaks just weeks before election day.
With that, the full report by Obama administration on pre-election hacking might face serious challenges in the next government.
Stop Using these 2 Easily Hackable Netgear Router Models — US CERT Warns
10.12.2016 thehackernews Vulnerebility
Bad news for consumers with Netgear routers: Two popular Netgear routers are vulnerable to a critical security bug that could allow attackers to run malicious code with root privileges.
Netgear's R7000 and R6400 routers, running current and latest versions of firmware, are vulnerable to arbitrary command injection attacks, though the number of users affected by the flaw is still unclear.
In an advisory published on Friday in Carnegie Mellon University's public vulnerability database (CERT), security researchers said that all an attacker needs to do is trick a victim into visiting a website that contains specially crafted malicious code to exploit the flaw.
As soon as the victim lands on the page, the malicious commands would execute automatically with root privileges on affected routers.
A working exploit leveraging the vulnerability has also been publicly released so that anyone can carry out attacks against the vulnerable routers.
Researchers warned that other router models might also be affected by the vulnerability, advising Netgear users to stop using the routers until a patch is released.
Your router could be compromised with no fixed release date for a patch. So, CERT strongly recommended Netgear users to "consider discontinuing use" of the affected routers until a patch is made available.
Hackers are increasingly targeting insecure, vulnerable routers with the purpose of making them part of nasty IoT botnets that are used to launch massive distributed denial-of-service (DDoS) attacks to knock online services offline.
Over a month ago, we saw Mirai Botnet taking entire Internet offline for few hours just by launching DDoS attacks (came from insecure IoT devices) against Dyn DNS service that crippled some of the world's biggest and most popular websites.
Just last week, nearly 1 Million users in Germany were also deprived of telephony, television, and Internet service after a supposed cyber-attack hijacked home broadband routers belonging to Deutsche Telekom.
Lax Cybersecurity at Nuclear Facilities is a Recipe For Widespread Disaster
10.12.2016 securityaffairs Cyber
Experts at the Nuclear Industry Summit (NIT) explained how to reduce the risk of damaging cyberattacks at nuclear facilities.
The threat of cyber attacks on nuclear power plants and other nuclear facilities is substantial and on the increase, according to experts at the Nuclear Industry Summit, held earlier in the year. Hackers are becoming more skillful and dangerous in a way that could have a devastating impact on nuclear facilities and grids.
It is imperative that businesses, governments, and regulators make cybersecurity an industry-wide priority. Experts at the Nuclear Industry Summit (NIT) emphasized that hackers have turned their focus on these systems because therein lies the key to causing massive chaos and damage.
The most successful publicly known cyberattack on a nuclear facility utilized malware which caused serious damage to production equipment at an Iranian plant that was enriching nuclear materials. That virus was the infamous Stuxnet, which was able to induce the facility’s centrifuges to spin out of control and break down.
Potential attacks on non-nuclear, major industrial sites is also gravely concerning. For instance, an attack on Ukraine’s electrical grid left thousands of people without power. The attackers used a program called BlackEnergy which targets industrial control systems. According to RegBlog, “cybersecurity threats are an all-too-real risk for many buildings and electric grids connected to the Internet. According to a U.S. Department of Homeland Security report, although ‘the energy sector only represents 5-6 percent of U.S. GDP, the energy industry is subject to roughly 32 percent of all cyberattacks.”
In October, Yukiya Amano, Director-General of the International Atomic Energy Agency (IAEA), United Nations (UN) nuclear watchdog, a nuclear power plant in Germany was hit by a “disruptive” cyber attack two to three years ago.
At that time, Security Affairs noted that it was not the first time that news of a cyber attack on a nuclear plant had been announced. There had already been three publicly known attacks against nuclear plants:
Monju NPP (Japan 2014)
Korea Hydro and Nuclear Power plant (S.Korea 2014)
Gundremmingen NPP (Germany 2016).
To make matters worse, it is also believed that ISIS hackers could target European nuclear power stations. This warning was issued by the UN in October. The organization’s nuclear watchdog group indicated that cyber cyberjihadis will attempt to hack into any vulnerable installations in their quest to commit large-scale acts of terrorism.
According to The Sun, the Brussels bombers had previously researched attacking a Belgian power plant prior to their deadly suicide attack on the capital’s airport and metro.
“International security experts have warned that as their territorial dominance abates, they will focus more of their attention on cyber terror.
Though blowing up a nuclear power station is still thought to be beyond the capabilities of most militant groups at present some vulnerabilities could still be exploited, boffins warned.
Belgium’s nuclear plants are a potential target, according to European Union officials. But, countries are not prepared to handle nuclear facility attacks and the nuclear industry continues to underestimates cyber security risk–the components of a recipe for a nuclear disaster.nuclear disaster.nuclear disaster.nuclear disaster.
A report published this week, by the Nuclear Threat Initiative (NTI), outlines a set of recommendations for improving cyber security at nuclear facilities. The recommendations are based on 12-months of analysis by an international group of technical and operational experts.
One of the most crucial recommendations involves efforts to essentially institutionalize cybersecurity. Nuclear facilities would need to learn from their safety and physical security programs, as well as integrate these methods into their cybersecurity programs.
In addition to institutionalizing cybersecurity, the following was also recommended:
Governments and regulators are encouraged to assist by prioritizing the development and implementation of regulatory frameworks, in addition to attracting skilled people into this field.
Employ active defenses. Experts caution that a determined adversary will likely be capable of breaching the systems of a nuclear facility, so organizations must be prepared and capable of responding to such incidents.
Threat information should be shared, incidence response exercises conducted, more resources obtained from governments and active defense capabilities developed.
Digital systems should be designed with less complexity.
Engage in research which will lead to the development of difficult to hack systems. Ideally, this would include governments “investing in transformative research, the nuclear industry supporting the cybersecurity efforts of relevant organizations, and international organizations encouraging creativity for mitigating cyber threats.”
While these recommendations are being carried out, emphasis should be placed on the human element. The Stuxnet incident demonstrates how a tenacious hacker can overcome cyber protection efforts simply by targeting vulnerable employees.
Ryan Kalember, of Proofpoint, a cybersecurity firm, has remarked that, “the lesson from that is that people are always the weak link in the [cybersecurity] chain.”
Popcorn Time ransomware, pay up the ransom or spread it to decrypt the files
10.12.2016 securityaffairs Virus
Malware researchers from the MalwareHunterTeam have discovered a new strain of ransomware dubbed Popcorn Time on the Dark Web.
Malware researchers from MalwareHunterTeam have spotted a new ransomware, dubbed Popcorn Time, that appears to be still under development.
The researchers at MalwareHunterTeam found the Popcorn Time ransomware code on the Dark Web.
This ransomware comes with a singular feature, it allows victims to either pay up or they can opt to infect two others using a referral link. Then is the two other potential victims pay the ransom the original target receives a free key to unlock his encrypted files.
“Time that intends to give victim‘s a very unusual, and criminal, way of getting a free decryption key for their files. With Popcorn Time, not only can a victim pay a ransom to get their files back, but they can also try to infect two other people and have them pay the ransom in order to get a free key.” wrote Lawrence Abrams from BleepingComputer.com.
The researchers noticed that the ransom note offers two options, pay up the ransom or spread the infections.
“We are sorry to say that your computer and your files have been encrypted, but wait, don’t worry. There is a way you can restore your computer and all of your files… Send the link below to other people, if two or more people will install the file and pay, we will decrypt your files for free.” states the ransom note.

Lawrence explained that it is the first ransomware ever seen with this characteristic.
Abrams, who analyzed the code of the ransomware, said it is incomplete, some of the command and control servers are not working and there are many features that still have to be developed.
The ransom note demands 1 bitcoin, victims have a limited number of attempts to provide a decryption key.
“To make matters worse, there is unfinished code in the ransomware that may indicate that if a user enters the wrong decryption key 4 times, the ransomware will start deleting files.” added Abrams.
The Popcorn Time ransomware is able to encrypt more than 500 file types using AES-256 encryption. The malware appends the .filock extension to the encrypted files.
The ransom note reveals that the authors of the Popcorn Time ransomware developers claim to be “a group of computer science students from Syria.”
Another interesting aspect of this ransomware is the content of the note who promises that ransomware proceeds will go to food, medicine, and shelter for the victims of the civil war in Syria.
“We are extremely sorry that we are forcing you to pay,” states the note.
Zabezpečte se i bez peněz
10.12.2016 SecurityWorld Zabezpečení
Přinášíme ukázku metod a produktů, pomocí kterých mohou malé a středně velké firmy zlepšit své zabezpečení, aniž musejí vydávat nějaké další výdaje.
Problémem je, že řada dobrých rad existuje jen ve znalostech nejzkušenějších bezpečnostních profesionálů a společností, takže se k malým a středně velkým firmám nedostanou, a nemohou jim tedy pomoci.
Mezi menšími firmami stále přetrvává dojem, že zlepšení jejich zabezpečení vyžaduje obrovské organizační změny a značné investice v takovém rozsahu, který se pravděpodobně vymyká jejich aktuálním možnostem.
Náprava největších slabin však vždy nemusí vyžadovat velké finanční náklady. Přinášíme některá z doporučení expertů.
1. Přestaňte ignorovat e-mailové hrozby
E-mail je hlavní branou, kterou se útočníci vždy pokusí využít jako první, když se chtějí zaměřit na firemní systémy. To, jak dobře a snadno tato taktika funguje, ukazují četné případové studie incidentů z reálného světa kybernetického zločinu.
Stačí jen zaslat jeden e-mail s přílohou s nastraženým malwarem jakoby od známého uvedeného kontaktu a útočník snadno získá záchytné místo v systému. Odtud může zasílat e-maily dalším kontaktům a přistupovat do části sítě, takže se útok rychle rozšíří.
Říkat lidem, aby neotevírali přílohy zaslané od neznámých osob, je rada upřímně řečeno téměř k ničemu – pokud lidé nesmějí otevírat přílohy od třetích stran, k čemu jim potom e-mail vůbec je? Nevyhnutelně to budou dělat.
Prvním zlepšením je podívat se na používané e-mailové systémy. Hostované služby Exchange a Gmail lze nakonfigurovat tak, aby používaly whitelisty tvořené z kontaktů přidaných do adresáře, a používají také své vlastní filtrování v první řadě za účelem snížit zátěž podezřelými e-maily.
Všichni nezastaralí e-mailoví klienti včetně webmailových služeb, jako je například Gmail, budou také považovat přílohy od neznámých kontaktů za automaticky podezřelé a podobně přísná pravidla budou používat i pro e-maily obsahující odkazy. To je začátek.
Problém spočívá v tom, že útočníci stejně často používají phishingové útoky formou napodobení komunikace legitimních webů, takže druhá vrstva obrany vyžaduje vyškolení uživatelů, tak aby dokázali rozpoznat jemné příznaky napadení.
To se samozřejmě snáze řekne, než udělá, ale řada firem nabízí antiphishingová školení a systémy testování, které ale obvykle stojí určité peníze.
Předpokládejme zranitelnost webů
Využívání děr na webech e-commerce pomocí injektáže SQL, skriptování mezi weby (XSS) atd. je dalším naprosto standardním způsobem, jak zaútočit na firmu. Dokonce i největší firmy bojují s tím, co by už v současné době mělo být dobře pochopenou záležitostí – jak třeba nedávno ukázaly škody vzniklé z útoku na společnost TalkTalk.
K dispozici je mnoho skenerů webových zranitelností. Např. od firem Qualys, AlienVault a Acunteix (obvykle jsou nabízené také bezplatné zkušební verze) nebo je možné použít četné nástroje open source, které však vyžadují větší odborné znalosti.
Pro začátek mohou být dobré nástroje, jako jsou Vega, W3af a SQLmap.
Zablokujte rizikový software
Většina počítačů obsahuje příliš mnoho softwaru a část z toho může být nainstalovaná zaměstnanci, aniž o tom správci vědí. Je to neuvěřitelně riskantní, ale naštěstí je možná náprava prostým odstraněním softwaru, který je známý jako neustálý zdroj zranitelností nultého dne.
Hlavními pachateli jsou zásuvné moduly Flash prohlížečů, aplikace PDF Reader společnosti Adobe a Java Runtime Environment (JRE včetně starých verzí) a téměř cokoli publikované společností Apple – nic z toho už není nezbytné tak, jako to bylo v minulosti.
Takový software odstraňte a zbavíte se velké části rizika při minimálních nevýhodách. Potřebujete PDF? Nejnovější browsery využívají prohlížeč v izolovaném prostoru bez potřeby spouštět celý program nebo dokonce stahovat soubor.
Přinejmenším rozhraní, jako je například Flash, by se měla zapínat jen v případě potřeby tak, že by je uživatelé spouštěli ručně.
„Pokud software nemůžete zablokovat, je přinejmenším nutné, abyste věděli, co ve vašich prostředích běží. Monitorujte, monitorujte a monitorujte. Kontrolujte, kdo co dělá, k jakým souborům se přistupuje, kdo se přihlašuje atd. Seznamte se zkrátka s tím, jak váš systém vypadá,“ radí Javvad Malik z bezpečnostní společnosti AlienVault.
Šifrování používejte uvážlivě
Žádná technologie není tak často zmiňovaná jako jednoduchý způsob zlepšení, jako je tomu u šifrování, ale jeho nasazení není jednoduchým všelékem. První problém spočívá v tom, že šifrování je často nákladné, proprietární pro konkrétní aplikace a také samozřejmě je nutné někam bezpečně ukládat klíče.
Šifrování může být užitečné pro ochranu uložených dat, zejména těch v mobilních zařízeních na platformách iOS a Android, které v novějších verzích nabízejí bezpečné šifrování standardně.
Firemní notebooky bývají v současné době poskytované s možností plného šifrování disku (FDE, Full Disk Encryption), což by měly malé a středně velké firmy vždy využít. USB disky by se měly šifrovat vždy.
Šifrování desktopů v malém měřítku je vždy trochu složitější. O to více, když svého času slavný a spolehlivý open source program TrueCrypt už nadále není považovaný za důvěryhodný.
Microsoft nabízí vynikající nástroj BitLocker ve verzích Pro svého systému Windows včetně nejnovějšího Windows 10, což by měl být základ konfigurace každého desktopu s tímto operačním systémem, ze kterého se přistupuje k důležitým datům.
Nástroje se liší ve způsobu fungování v případě šifrování jednotlivých souborů či šifrování celých svazků. Mezi zajímavé nástroje pracující se svazky patří DiskCryptor a FreeOTFE. Symantec navíc nabízí nástroj Drive Encryption, ale ačkoli je relativně drahý, neposkytuje některé funkce centrální správy.
This Ransomware Unlocks Your Files For Free If You Infect Others
9.12.2016 thehackernews Virus
Is your PC infected with Ransomware? Either pay the ransom amount to the attacker or spread the infection further to get the decryption keys.
Yes, this new technique has been employed by cyber criminals with the latest round of ransomware threat, dubbed Popcorn Time.
Initially discovered by MalwareHunterTeam, the new Popcorn Time Ransomware has been designed to give the victim's a criminal way of getting a free decryption key for their encrypted files and folders.
Popcorn Time works similar to other popular ransomware threats, such as the Crysis Ransomware and TeslaCrypt, that encrypt various data stored on the infected computer and ask victims to pay a ransom amount to recover their data.
But to get their important files back, Popcorn Time gives victims option to pay a ransom to the cyber criminal or infect two other people and have them pay the ransom to get a free decryption key.
What's even worse? The victims are encouraged to pay the ransom of 1 Bitcoin (~$750) within seven days to receive decryption keys stored on a remote server owned by Popcorn Time's developers.
If the ransom is not paid within this duration, the decryption key will be permanently deleted and retrieve important files will become impossible.
Moreover, the code of the ransomware is incomplete that may indicate that if victims enter the wrong decryption key four times, the Popcorn Time ransomware will start deleting victims' files.
Here's How the Popcorn Time Ransomware Threat Works: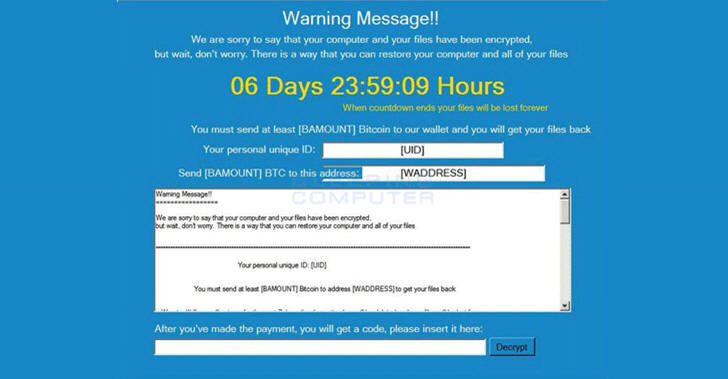
Once infected, the Popcorn Time Ransomware will check to see if the ransomware has been run already on the PC. If yes, the ransomware will terminate itself.
If not, the Popcorn Time Ransomware will either download various images to use as backgrounds or start encrypting the files using AES-256 encryption. The encrypted files will have the ".filock" or ".kok" extension appended to it.
While encrypting the data, the ransomware will display a fake screen that pretends to be the installation of the program.
As soon as the encryption is finished, it will convert two base64 strings, save them as ransom notes known as restore_your_files.html and restore_your_files.txt, and then automatically display the HTML ransom note asking for 1 Bitcoin.
Want a Free Decryption Key? Infect Two More People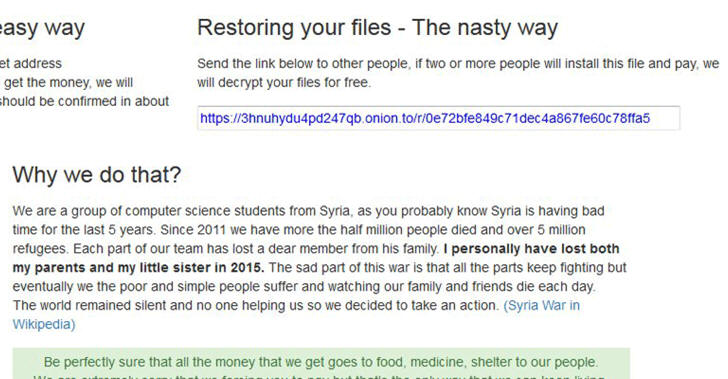
The Popcorn Time author provides a "nasty way" for a victim to get the free decryption key: Spread the Ransomware to two other people via the victim's "referral" link."
If those two infected victims pay the ransom, then the first victim will supposedly get a free decryption key.
To make this possible, the ransom note contains a URL pointing to a file located on the Popcorn Time's TOR server.
Entering Wrong Decryption Key 4 Times and You are Screwed Up!
When executed, the Popcorn Time ransomware will display a lock screen filled in with various information relating to victim's particular installation.
The victim will also find a field where he/she can enter the decryption key given to them by the attacker after paying the ransom.
The source code for Popcorn Time contains a function that suggests the threat to delete files if the victim enters the wrong decryption code four times.
Since the Popcorn Time ransomware is still under development at the time of writing, many things are unclear and may change with time.
Uber Now Tracks Your Location Even After Your Ride
9.12.2016 thehackernews BigBrothers
Uber was in controversies at the mid of this year for monitoring the battery life of its users, as the company believed that its users were more likely to pay a much higher price to hire a cab when their phone's battery is close to dying.
Uber is now tracking you even when your ride is over, and, according to the ride-hailing company, the surveillance will improve its service.
Uber recently updated its app to collect user location data in the background.
So, if you have updated your Uber app recently, your app's location tracking permissions have changed, allowing the app to monitor your location before and five minutes after your trip ends, even if you have closed the app.
A popup on the Uber app will ask you, "Allow 'Uber' to access our location even when you are not using the app?" You can click "Allow" or "Don't Allow" in response to this request. If you don't allow it, Uber won't track you.
According to the company, this information helps not only drivers find riders without making phone calls, but also Uber monitor driver service, making sure riders are picked up and dropped off on the proper side of the street in order to enhance safety.
Here's what Uber said in a statement:
"We're always thinking about ways we can improve the rider experience from sharpening our ETA estimates to identifying the best pick up location on any given street. Location is at the heart of the Uber experience, and we're asking riders to provide us with more information to achieve these goals."
Location data during a trip is collected during the following time periods:
When you're interacting with Uber and the app is foregrounded and visible.
When you are on a trip: from the time you request a trip until the trip is ended or canceled by the driver, even if the app is running in the background, but not visible to you.
Up to 5 minutes after the driver ends a trip, even if the Uber app is close in the background.
Uber announced the move last year which prompted a complaint [PDF] with the Federal Trade Commission. At te time, the Electronic Privacy Information Center said that "this collection of user's information far exceeds what customers expect from the transportation service."
It's unexpected from a big company like Uber "to collect location information when customers are not actively using the app." However, "the FTC failed to act, and Uber is now tracking users non-stop."
How to Stop Uber From Tracking Your Location
If you are worried, there's a way to get around it. The company also explains how to turn this feature off. Here's what to do to shut down this feature:
For Android Users: Settings → Apps → Uber → scroll to "Permission" → toggle "Location."
For users running Android Lollipop (5.1) and earlier: Settings → Location → toggle Off.
For iOS Users: Settings → Privacy → Location Services → Uber → choose "Never."
For more information on the feature, you can head on to the updated data collection agreement made by Uber.
Surface Defense DDoS platform – Gamification of attacks
9.12.2016 securityaffairs Attack
A Turkish hacker is advertising into the hacking underground a new DDoS platform, dubbed Surface Defense (Translation to English).
According to the security firm Forcepoint the hacker started prompting the DDoS platform in Turkey. He was offering a tool known as Balyoz, the Turkish word for Sledgehammer, that can be exploited by hackers to launch powerful DDoS attacks against a select number of websites.
“We were quickly led into a world where hacking crews from around Turkey come together to perform Distributed Denial of Service (DDoS) attacks on a target list of victim organizations. Individuals gain points by participating in these DDoS attacks, which are then exchanged for software that enable them to perform online fraud.” states a report published by Forcepoint.
The hacker rewards with a point its customers for every ten minutes they hit a website. These prizes include a more powerful DDoS attacking tool, access to bots designed to generate revenue from
These hacker is offering interesting prizes for the users of its Sledgehammer platform. they include a more powerful DDoS attacking tool, a malicious code that can be used to scare the victim with sounds and images, and the access to a click fraud botnet that could allow them to earn money.
The researchers discovered that DDoS platform has been advertised on Turkish hacking forums, but Forcepoint has no idea about the number of participants recruited with this gamification of DDoS attacks.
The list of websites targeted by the tool is composed of 24 political websites having a specific position with regards of Turkey.
“Most, if not all, of the targets identified on the target list were chosen because of their political position with regards to Turkey. Kurdistan was prominent, with organizations such as the Kurdistan Workers Party (PKK)2 and its military wing the People’s Defense Force (HPG)3 being targeted. But the German Christian Democratic Party (CDU) was also among the targets, as was the Armenian Genocide archive run by the Armenian National Institute in Washington DC” continues the report.

Users can also suggest new websites to include in the list of targets, the platform displays live scoreboard for participants in the attacks.
The author of the DDoS platform has implemented a series of rules to optimize the use and the access to the Surface Defense, for example, the participants can run the tool only on a single machine, a measure necessary to ensure fairness during the competition.
But Forcepoint noticed that the DDoS attack tool given to the participants also contains a backdoor that will secretly install a Trojan on the computer.
Who is the hacker behind the Surface Defense platform?
Experts believe he is a hacker using the online moniker “Mehmet,” based in the city of Eskisehir (Turkey).
Přílohy v e-mailu – momentálně dominantní bezpečnostní hrozba v Česku
9.12.2016 SecurityWorld Viry
Podíl škodlivého kódu Danger v tuzemsku stoupl oproti říjnu takřka o dvacet procentních bodů – nově tak stojí za každou druhou kybernetickou hrozbou.
Více než polovinu všech počítačových hrozeb v České republice v listopadu představoval podle zjištění Esetu škodlivý kód Danger, který se šíří prostřednictvím příloh e-mailů.
Danger je nejčetnější kybernetickou hrozbou v tuzemsku po většinu letošního roku, v listopadu však dosáhl jeho podíl na celkových IT hrozbách výjimečné hodnoty 54,91 procenta. To je takřka o 20 procentních bodů více než v říjnu.
„Nárůst počtu případů JS/Danger.ScriptAttachment je opravdu mimořádný. Tento malware je zákeřný v tom, že nemusí být nebezpečný sám o sobě, ale do napadeného zařízení stahuje další škodlivé kódy včetně ransomwaru, který dokáže zašifrovat data a požadují po uživateli výkupné,“ říká Miroslav Dvořák, technický ředitel Esetu.
Všechny další hrozby zaznamenané v listopadu vykázaly ve srovnání s Danger zanedbatelných podílů – druhý nejčetnější malware, trojan FakejQuery, představoval jen 2,56 procenta detekcí.
Výrazný pokles četnosti v listopadu zaznamenal downloader Nemucod. Zatímco v říjnu stál za každou osmou detekcí (podíl 12,32 procenta), v listopadu jeho podíl klesl o 10 procentních bodů na 2,04 procenta. Aktuálně jde o čtvrtou nejčetnější kybernetickou hrozbu v Česku po malware Danger, FakejQuery a Java/Adwind.
Top 10 hrozeb v České republice za listopad 2016
1. JS/Danger.ScriptAttachment (54,91 %)
2. JS/TrojanDownloader.FakejQuery (2,56%)
3. Java/Adwind (2,28 %)
4. JS/TrojanDownloader.Nemucod (2,04 %)
5. JS/Kryptik.RE (1,76 %)
6. JS/ProxyChanger (1,38 %)
7. Win32/Exploit.CVE-2014-1761 (1,33 %)
8. Win32/Injector.DHND (1,04 %)
9. JS/TrojanDownloader.Iframe (0,88 %)
10. PDF/Fraud (0,88 %)
Hackers targeted the heavy industry ThyssenKrupp and stole industrial secrets
9.12.2016 securityaffairs Hacking
Alleged Asian hackers have targeted the German heavy industry giant ThyssenKrupp to steal company secrets.
Hackers from Southeast Asia targeted the German heavy industry giant ThyssenKrupp in the attempt of obtaining “technological know-how and research results.”
The news was announced on Thursday by a company spokesman that confirmed a report in the Wirschaftswoche weekly and added that the company as successfully repelled the attack.
The cyber attack was discovered by the IT security office, which spotted the hacking activities while they were ongoing and blocked them.
“The attack is over and had been repelled,” said the company spokesman.
The investigators speculate the attack was carried out by a group of professional hacked from Southeast Asia that is interested in the technological know-how and research activities of the company.
At the time I was writing there are no further details on the cyber attack neither the exact nature of the attackers (i.e. nation-state actors, cybercriminals).
The hackers launched a “massive cyber attack” against the divisions dealing with orders planning of industrial plants, the conglomerate’s Industrial Solutions, and Steel Europe business divisions.
Critical IT systems at the ThyssenKrupp such as the Marine Systems business unit and blast furnaces and power plants in Duisburg, were not affected
The ThyssenKrupp Marine should be a privileged target for hackers because it is the division that builds warships, including submarines for the German and Israeli navies.
The company excluded any sabotage or manipulation of data or applications, but it was unable to estimate if a limited portion of data, “data fragments,” had been stolen by the hackers.
“Experts say that in the complex IT landscapes of large companies, it is currently virtually impossible to provide viable protection against organized, highly professional hacking attacks,” the company added.
Yahoo Flaw Allowed Hackers to Read Anyone's Emails
9.12.2016 thehacknews Vulnerebility
Yahoo has patched a critical security vulnerability in its Mail service that could have allowed an attacker to spy on any Yahoo user's inbox.
Jouko Pynnönen, a Finnish Security researcher from security firm Klikki Oy, reported a DOM based persistent XSS (Cross-Site Scripting) in Yahoo mail, which if exploited, allows an attacker to send emails embedded with malicious code.
In his blog post published today, the researcher demonstrated how a malicious attacker could have sent the victim's inbox to an external site, and created a virus that attached itself to all outgoing emails by secretly adding a malicious script to message signatures.
Since the malicious code is in the message's body, the code will get executed as soon as the victim opens the boobytrapped email and its hidden payload script will covertly submit victim's inbox content to an external website controlled by the attacker.
This issue is because Yahoo Mail failed to properly filter potentially malicious code in HTML emails.
"It would be possible to embed a number of HTML attributes that are passed through Yahoo's HTML filter and treated specially," Pynnönen says in his blog post.
Pynnönen says he found the vulnerability by force-feeding all known HTML tags and attributes in order to the filter that Yahoo uses to weed out malicious HTML, but certain malicious HTML code managed to pass through.
"As a proof of concept I supplied Yahoo Security with an email that, when viewed, would use AJAX to read the user's inbox contents and send it to the attacker's server," Pynnönen says.
Pynnönen privately disclosed the vulnerability to Yahoo through its HackerOne bug bounty program and was awarded a $10,000 bounty.
Pynnönen reported a similar vulnerability in the web version of the Yahoo! Mail service earlier this year for which he earned $10,000. He also reported a stored XSS vulnerability in Flickr to Yahoo in December 2015 for which he earned $500.
Israeli TV broadcast hacked, attackers played Muslim call to prayer
9.12.2016 securityaffairs Hacking
On Tuesday night, a group of unknown hackers took control of the Israeli TV broadcast Channel 2 and played Muslim call to prayer.
On Tuesday night, a group of hackers took control of an Israeli news Channel 2 and played Muslim call to prayer. The hackers want to protest a controversial bill that limits the volume of the call to prayer from mosques.
The hackers broke into the Israeli TV broadcast and disrupted the transmissions after gained access to TV satellites.
According to Israeli media, the hacker appeared to be from Saudi Arabia

Source teztv.com
Segui
חדשות 2 ✔ @Channel2News
האקרים השתלטו על שידורי מהדורת חדשות 2, ובמקום - שידרו קריאת מואזין
20:41 - 29 Nov 2016
24 24 Re 50 50 Mi piace
In November, the representatives of the Knesset have given their approval to the “muezzin bill” that bans religious leaders from using loudspeakers that call the worshippers for prayers.
The Israeli Government’s bill aims to protect its citizens from noise.
“While the bill is primarily targeted at curbing noise pollution, critics have noted the proposed law contains a clause which says that “freedom of religion should not be harmful to quality of life nor used to convey religious or nationalist messages, and sometimes even words of incitement”, which they say is targeted at Muslims.” states the Independent.
The hackers are protesting of a the bill, they spread messages written in the Hebrew language warning of “punishment from God” and said that “the fire burned hearts”.
“The fire burned hearts” and “To for big great God [is] war from God (the fire burns you).” states the other messages.
“Residents in northern Israel viewing Channel 2 via satellite TV reported that during the evening broadcast someone took over central control of the broadcast and played the voice of the muezzin,” reported the Tribune.
The Arab politicians Ahmad Tibi and Taleb Abu Arar staged a Muslim call to prayer, the ‘Azan,’ in the parliament in protest against the bill.
The bill has received the Israeli Prime Minister Benjamin Netanyahu’s support.
“I cannot count the times – they are simply too numerous – that citizens have turned to me from all parts of Israeli society, from all religions, with complaints about the noise and suffering caused them by the excessive noise coming to them from the public address systems of houses of prayer,” Mr Netanyahu told a cabinet meeting.
Thieving Magpie allows NSA spies to snoop on in-flight mobile calls
9.12.2016 securityaffairs BigBrothers
The Thieving Magpie programme allows the NSA and the GCHQ to intercept data from passengers traveling on board commercial aircrafts.
This isn’t a sci-fi movie, the GCHQ and the NSA have spied on air passengers using in-flight GSM mobile services for years.
The news was revealed by new documents obtained by Edward Snowden and recently published by The Intercept.
Today, approximately 100 companies permit the in-flight use of mobile devices.
Passengers of the principal airlines (British Airways, Virgin Atlantic, Lufthansa, and many Arab and Asian companies) can access in-flight GSM mobile services using the system designed by the UK company AeroMobile and SitaOnAir. The passengers connect to the on-board GSM servers that communicate with satellites operated by British firm Inmarsat.
The spy agencies could target in-flight passengers through the “Thieving Magpie” programme. The system allows spying on the victims even when targets are not using the mobile devices for calls or any data transfer. It is sufficient that the phone is switched on and registered with the in-flight GSM service.
Below an excerpt from the presentation
“If a target’s phone is switched on, it Will attempt to register to its home network that it using the OnAir service even if they don’t actually make/receive a call.
Registration requests can be combined with the right number/callsign of the aircraft
Available in near real time (approximately 10 minute delay)”
According to the presentation leaked by Snowden, the GCHQ and the NSA are able to intercept the transmission from the satellites to the ground stations.

Thieving Magpie allowed the intelligence agencies to spy on flights in Europe, the Middle East, and Africa, but according to the presentation, it was designed for a global surveillance.
The surveillance program allows data collection in “near real time,” spies can track aircraft every two minutes while in flight.
Thieving Magpie program allows spying on any data sent via the GSM network, the cyber spies could access gather e-mail addresses, Facebook IDs, and Skype addresses. It also allows monitoring of Twitter, Google Maps, BitTorrent, and VoIP.
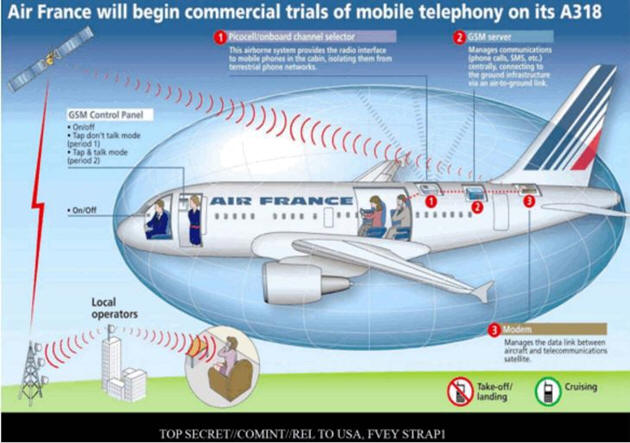
According to Le Monde, the CIA was especially interested in Air France and Air Mexico flights, because they are potential targets for terrorists.
“We can read that, as from the end of 2003, ‘the CIA considered that Air France and Air Mexico flights were potential targets for terrorists’.” states the article published by Le Monde “The legal department of the NSA stated at this point ‘there is absolutely no legal problem in targeting aircraft from these two companies abroad’ and ‘they should be kept under strict surveillance from the point at which they enter American air space’.”
Russia proposes 10 Year in Prison Sentence for Hackers and Malware Authors
8.12.2016 thahackernews Crime
The Russian government has introduced a draft bill that proposes prison sentences as punishment for hackers and cyber criminals creating malicious software used in targeting critical Russian infrastructure, even if they have no part in actual cyber attacks.
The bill, published on the Russian government’s website on Wednesday, proposes amendments to the Russian Criminal Code and Criminal Procedure Code with a new article titled, "Illegal influence upon the critical informational infrastructure of the Russian Federation."
The article introduces punishment for many malicious acts, including the "creation and distribution of programs or information, which can be used for the destruction, blocking or copying data from the Russian systems."
When suspects found as part of any hacking operation, they will face a fine between 500,000 and 1 Million rubles (about $7,700 to $15,400) and up to five years in prison, even if the hacking causes little or no harm.
Also Read: Hacker who exposed Steubenville Rape Faces longer Prison term than Rapists.
However, if the cyber attacks lead to serious consequences or create a threat of such outcome, the bill orders the prison term of up to ten years for those involved in it.
Moreover, hackers obtaining unauthorized access to protected data have to pay a penalty of up to 2 Million rubles (approx. $31,500) and can face up to five years of forced labor and six years in prison.
The proposed bill was drafted in a short period of time after Russian President Vladimir Putin recently signed an updated doctrine on Russia's Information Security.
The doctrine is aimed at "reinforcing the country’s sovereignty, territorial integrity, maintaining political and social stability, protecting human and civil rights and liberties, as well as crucial IT infrastructure."
According to the document, "the opportunities of cross-border circulation of data are increasingly used to achieve geopolitical, military and political (in contravention of international law), terrorist, extremist, and other illegitimate goals to the detriment of international security," the website reads.
The new bill introducing criminal punishment for hackers has been submitted to the State Duma, the lower chamber of the Russian Parliament.
The move is great because Russian hackers are always in the news for cyber attacks, malware, POS exploit, banking Trojans, exploit kits, and many cyber threats.
Nebezpečný Locky se transformoval. Nový virus připraví uživatele o data
8.12.2016 Novinky/Bezpečnost Viry
Locky patří aktuálně k nejrozšířenějším vyděračským virům na světě. Kybernetičtí zločinci jej navíc transformovali do nové formy, ta je přitom přinejmenším stejně nebezpečná jako samotný Locky. Upozornil na to Národní bezpečnostní tým CSIRT.CZ.
K uzamčeným datům se bez hesla uživatelé nedostanou.
Jak útočí vyděračské viry
Na napadeném stroji dokážou vyděračské viry udělat pěkný nepořádek. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Dnes 16:01
„Locky, byl v minulých dnech objeven v nové formě. Nová varianta dostala jméno Osiris podle koncovek zašifrovaných souborů,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Oba škodlivé kódy mají přitom stejný rodokmen – patří do skupiny vyděračských virů, které se souhrnně označují jako ransomware.
Nová hrozba je stejně jako předchůdce šířena nejčastěji e-mailovými zprávami s přiloženým infikovaným Excel dokumentem.
„Po spuštění souboru je uživatel vyzván k povolení maker. Spuštěné makro pak následně spustí systémový proces Rundll32.exe s načtenou infikovanou dll knihovnou obsahující Osiris. Při nákaze dochází k zašifrování dokumentů, fotek a dalších obvyklých typů uživatelských dat,“ vysvětlil technickou stránku věci Bašta.
Dešifrovací algoritmus není znám
Samotný útok tedy probíhá úplně stejně, jako tomu bylo dříve u Lockyho. Sluší se připomenout, že tento vyděračský virus počítačoví piráti začali v minulých týdnech šířit nejen prostřednictvím e-mailů, ale také skrze falešné fotky na sociálních sítích.
Ani u jednoho ze zmiňovaných vyděračských virů se po úspěšném útoku lidé ke svým datům již nedostanou. „K odstranění nákazy již existují doporučené postupy, ale dešifrovací algoritmus zaručující obnovu dat zatím není znám,“ uzavřel Bašta.
Stegano děsí bezpečnostní experty. Zákeřný záškodník číhá v reklamách
8.12.2016 Novinky/Bezpečnost Viry
Před zákeřným záškodníkem zvaným Stegano varovali bezpečnostní experti společnosti Eset. Tento škodlivý kód číhá v reklamních bannerech na internetových stránkách, uživatel si tedy nezvaného návštěvníka pustí do svého stroje už jen tím, že daný web navštíví.
„Stegano je zákeřný v tom, že k nákaze počítače může postačit, aby uživatel navštívil webovou stránku, kde se vyskytuje škodlivá reklama. Nemusí dojít k žádné interakci, kliknutí na banner nebo k aktivnímu stahování obsahu,“ prohlásil Miroslav Dvořák, technický ředitel společnosti Eset.
Podle něj se přitom podobné bannery obsahující nezvaného návštěvníka neobjevovaly pouze na malých webech, ale i na velkých renomovaných serverech. Údajně šlo i o známé zpravodajské stránky. O jaké konkrétní weby šlo, však bezpečnostní experti neprozradili.
Detekční systémy zmiňované antivirové společnosti nicméně odhalily, že škodlivý virus se podle nejstřízlivějších odhadů zobrazil více než miliónu uživatelů.
Chyba Internet Exploreru
Stegano využívá k infiltraci do počítače zranitelnost webového prohlížeče Internet Explorer a zároveň i trhliny, kterou obsahuje oblíbený Flash Player od společnosti Adobe. Tento přehrávač videí na internetu používají po celém světě desítky miliónů lidí.
Nový záškodník jim pak dovoluje do napadeného stroje stahovat další škodlivé kódy. „Jsou mezi nimi bankovní trojany, tzv. backdoory nebo spyware,“ varoval Dvořák.
Kyberzločinci tak mohou na napadený stroj snadno nasadit špionážní software, případně celou sestavu ovládat na dálku.
Důležité jsou aktualizace
„Útočníkům se podařilo obejít opatření, která mají odhalit a blokovat škodlivý obsah v online reklamních systémech, čímž ohrozili milióny čtenářů populárních zpravodajských webů. Škodlivé verze reklamy se navíc zobrazují pouze určité skupině uživatelů se zranitelnou konfigurací systému,“ doplnil Dvořák.
Z řádků výše je patrné, že virus Stegano představoval – a v podstatě stále ještě představuje – hrozbu pouze pro uživatele, kteří nemají staženy nejnovější verze Internet Exploreru a Flash Playeru. Tvůrci obou programů totiž již dříve zmiňované chyby opravili.
Turkish Hackers Are Giving Away Prizes For Participating In DDoS Attacks
8.12.2016 thehackernews Hacking
DDoS has become a game now that could knock any service offline.
A Turkish hacking group is encouraging individuals to join its DDoS-for-Points platform that features points and prizes for carrying out distributed denial-of-service (DDoS) attacks against a list of predetermined targets.
The points earned can later be redeemed for various online click-fraud and hacking tools.
Dubbed Sath-ı Müdafaa, translated as Surface Defense in English, this DDoS-for-Points platform is advertised via local Turkish hacking forums, including Turkhackteam and Root Developer.
Surface Defense prompts other hackers in Turkey to sign up and asks them to attack political websites using a DDoS tool known as Balyoz, translated as Sledgehammer.
According to Forcepoint security researchers, who discovered this program, Balyoz works via Tor and requires a username and password to log in. The tool then uses a DoS technique to flood targets with traffic.
Here's How the Balyoz Tool Works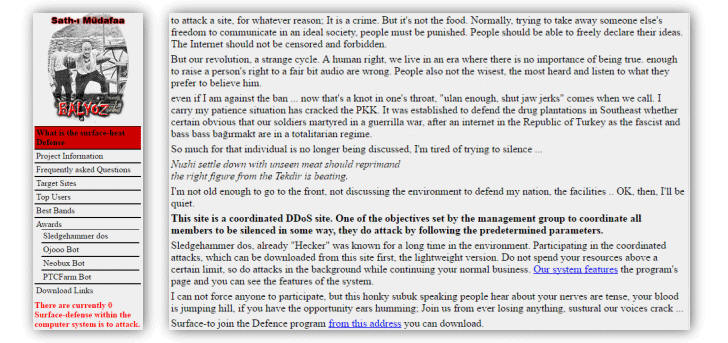
Once a user downloads the Surface Defense collaboration software from hacking forums and registers, the program then runs locally on a computer, prompting the user to download DDoS attack tool in order to assault the limited list of target sites.
The DDoS traffic is then routed through Tor to disrupt online services. For every 10 minutes the tool attack a website with fraudulent traffic, the participant receives a point.
The points can then be used to obtain rewards including a more powerful version of the Balyoz DDoS attacking tool, "click-fraud" bots that automatically clicks on ads for pay-to-click (PTC) services like Ojooo and Neobux PTC to generate revenue, and a program that has ability to infect PCs and scare the victim with images and sounds.
The DDoS Tool Contains Hidden Backdoor
The DDoS platform software also contains a hidden backdoor that allows the Surface Defense operator to "hack the hackers," raising concerns over the operator's actual motives.
"The backdoor is a very small Trojan and its sole purpose is to download, extract and execute another .NET assembly from within a bitmap image," Forcepoint researchers said.
"It also downloads a secondary 'guard' component which it installs as a service. This 'guard' component ensures that if the backdoor is deleted then it will be re-downloaded and also installed as a service."
The list of predefined targets includes Kurdish websites of the Kurdistan Workers Party (PKK), its military wing the People's Defense Force (HPG), an organization by NATO members, Kurdish radio and TV stations, Kurdish hacking crews, and more.
Other politically-motivated targets include the Armenian Genocide website, the German Christian Democratic Party -- which is led by Angela Merkel -- and many Israeli websites.
"Users can also suggest new websites to add to the list of targets," Forcepoint researchers said. "There is a live scoreboard for participants to see how they compare to other participants."
The researchers have managed to track down the IP address of the Surface Defense software, despite running on the Dark Web through Tor.
This development helped researchers gathered some information on the hacker's identity, like the operator might act under the handle "Mehmet," runs two YouTube channels advertising the Balyoz DDoS tool, and the operator is possibly based in the Turkish city of Eskisehir.
For more technical details on the Surface Defense platform, you can head on to the Forcepoint's 30-page research paper [PDF] titled, "Sledgehammer - Gamification of DDoS attacks (for ideology, profit & mischief)."
Floki Bot rapidly evolves and targets also PoS data
8.12.2016 securityaffairs BotNet
Cisco Talos and Flashpoint have teamed up to analyze the Floki Bot, a Zeus-based banking Trojan that is rapidly evolving in the cybercrime underground.
Security researchers from Cisco Talos and Flashpoint have conducted an investigation of the Floki Bot in a joint effort.
The Floki bot is a banking Trojan based on Zeus that has been sold on cybercrime underground since September 2016. The malware was developed starting from the Zeus source code that was leaked in 2011, it is offered for $1,000 worth of bitcoins. However, researchers determined that the malware includes some new capabilities, including anti-detection features.
“Floki Bot is a new malware variant that has recently been offered for sale on various darknet markets. It is based on the same codebase that was used by the infamous Zeus trojan, the source code of which was leaked in 2011.” reads the analysis published by the Talos Team. “Rather than simply copying the features that were present within the Zeus trojan “as-is”, Floki Bot claims to feature several new capabilities making it an attractive tool for criminals.”
The Floki bot is rapidly evolving, the authors implemented new features, including sophisticated anti-detection techniques and the use of the Tor network.
The malware researchers at Talos discovered a new source code that allows the threat to use the Tor network, but the feature seems to be still not active.
“During our analysis of Floki Bot, Talos identified modifications that had been made to the dropper mechanism present in the leaked Zeus source code in an attempt to make Floki Bot more difficult to detect. Talos also observed the introduction of new code that allows Floki Bot to make use of the Tor network.” continues the analysis.
The experts from Flashpoint speculate that the Floki Bot has a Brazilian origin, the threat actor behind the malware is currently using the “flokibot” moniker and communicates in Portuguese. It targets Brazilian IPs and domains and targeted systems have default language set to Portuguese.
The “flokibot” actor act as a sort of “connector,” he is present in several major crime communities across the world, particularly Russian and English-speaking dark web communities.
Even the analysis of its activity in the underground suggests that the actor is located in Brazil, it is most active on underground forums during hours within Brazil’s UTC -3 timezone.
“Beyond the unique intelligence obtained by Flashpoint analysts and the campaign targeting Brazil, flokibot, a Portuguese-speaking member of English and Russian-language communities, was identified by several markers as very likely to be Brazilian” states the analysis published by FlashPoint.
• Use of the Portuguese language within the actor’s communications
• Targeting computers with the default language set to Portuguese
• Targeting Brazilian domains or IP ranges
• Targeting computers with the default timezone set to Brazil UTC -03:00
• Other unique intelligence obtained by Flashpoint analysts
The presence of flokibot in several major underground communities suggests the gang import knowledge and tools into the Brazilian cybercrime underground.
“While Brazilian cybercriminals are not typically as technically sophisticated as their Russian counterparts, they will often solicit new forms of malware (to include point of sale [PoS] ransomware and banking Trojans), or offer their own services,” Vitali Kremez, senior intelligence analyst at Flashpoint, said in a blog post. “It appears that a presence on Russian [Deep and Dark Web] communities may be a likely factor in flokibot’s progression.”
Now it’s Christmas time, the best period for cyber criminals that attempt to steal credit card data, in this period we observe the proliferation of PoS malware used for this purpose.
Researchers discovered that the new strain of Floki Bot also includes the code to scrape payment card data from the memory PoS systems.
“One way in which flokibot’s technical competency has evolved is in the actor’s use of hooking methods to capture track data from PoS devices. While the malware originates from the well-known ZeuS 2.0.8.9 source code, flokibot adds this hooking method to grab track data from memory thereby extending the malware operations beyond regular banking trojan functionality making it more potent and versatile.” states FlashPoint.
A campaign analyzed by Flashpoint revealed that 225 Floki bots have collected a total of 1,375 card dumps.
Researchers have observed a spike in the number of attacks based on Floki Bot against U.S., Canadian and Brazilian banks, and insurance firms.
Both Talos and Flashpoint will continue monitoring the threat.
CVE-2016-8655 – A new 5-Year-Old flaw found in the Linux Kernel
8.12.2016 securityaffairs Vulnerebility
A security expert discovered a serious five-year-old privilege-escalation vulnerability, tracked as CVE-2016-8655, that affects every Linux distro.
In October, the security expert Phil Oester discovered a flaw in the Linux kernel, dubbed ‘Dirty COW‘ that could be exploited by a local attacker to escalate privileges.
The name “Dirty COW” is due to the fact that it’s triggered by a race condition in the way the Linux kernel’s memory subsystem handles copy-on-write (COW) breakage of private read-only memory mappings.
Now a security expert discovered a serious five-year-old privilege-escalation vulnerability, tracked as CVE-2016-8655, that affects every Linux distro, including Ubuntu, Red Hat, and Debian.
“A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer,” reads the security advisory issued Red Hat.
“A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system.”
The flaw was disclosed today by the security researcher Philip Pettersson, it dates back to 2011.
CVE-2016-8655
The vulnerability could be exploited by an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
“This is an announcement about CVE-2016-8655 which is a race-condition I found in Linux (net/packet/af_packet.c). It can be exploited to gain kernel code execution from unprivileged processes.” wrote Pettersson. ” The bug was introduced on Aug 19, 2011: https://github.com/torvalds/linux/commit/f6fb8f100b807378fda19e83e5ac6828b638603a“
The security expert created an exploit to gain a root shell on an Ubuntu 16.04 LTS system (Linux Kernel 4.4) and also defeated SMEP/SMAP (Supervisor Mode Execution Prevention/Supervisor Mode Access Prevention) protection to gain kernel code execution abilities.
An attacker can use the Pettersson’s exploit to run arbitrary malicious code with administrative privileges on the targeted PC or cause a denial of service.
“A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer,” Red Hat security advisory explains.
“A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system.”
“On Android, processes with gid=3004/AID_NET_RAW are able to create AF_PACKET sockets (mediaserver) and can trigger the bug,” added Pettersson.
Below the Timeline for the CVE-2016-8655 bug that was fixed in the mainline kernel last week
2016-11-28: Bug reported to security () kernel org
2016-11-30: Patch submitted to netdev, notification sent to linux-distros
2016-12-02: Patch committed to mainline kernel
2016-12-06: Public announcement
Don’t waste time, update your Linux distro as soon as possible.
Employee’s Provident Fund organisation, India website found INSECURE
8.12.2016 securityaffairs Incindent
Security firm’ Eioneus Systems’ claims to have found a serious security flaw in Universal Account Number(UAN) website (India).
In a recent incident an information security firm’ Eioneus Systems’ claims to have found a serious security flaw in Universal Account Number(UAN) website (India) which could have led to the theft of millions of user’s data. Eioneus Systems is an information Security firm based out of Pune. According to the official at Eioneus Systems Snehil Khare, the issue was reported immediately to CERT-IN, NIC, and other government sources which were felt necessary at the time.

As per reports the issue was critical and gave access to country’s entire Provident Fund database. Moreover, it stated that vulnerability could be exploited to gain complete access to the machine leading to full compromise. Well, the tech firm demonstrated an excellent behavior in doing a responsible vulnerability disclosure.
Due to the sensitive nature of the incident, complete details of the vulnerability was not shared but it came to light that the bug gave access to information such as Provident fund balance, Individual’s KYC details, phone numbers, PAN numbers, bank details ;etc of every provident fund user in the country. The tech firm has shared few screenshots to support their claims of accessing the massive database.


In a chat with Security Affairs, Snehil Khare clarified his intentions further stating “Our motive is to do a responsible vulnerability disclosure and not to abuse the information which was accessed. Our intention was to draw the attention of authorities towards major security concern identified, without ignoring it.”
According to Eioneus systems , the issue came to their knowledge on 3rd Dec 2016 while browsing the website for usual UAN related features that website offers. The issue was reported immediately to CERT-IN (Computer emergency response team) and was acknowledged by CERT-IN in no time.


Chyba v Chromu blokovala certifikáty firmy Symantec
7.12.2016 SecurityWorld Zranitelnosti
Uživatele nejpopulárnějšího prohlížeče světa, Chromu, se mohli v nedávných měsících setkat s chybami při pokusu připojit se na webové stránky zabezpečené protokolem HTTPS; chyby se objevily jak při připojení z mobilu s Androidem, tak z klasických PC.
Chyba postihla potvrzování některých SSL certifikátů vydávaných firmou Symantec, jedné z největších společností vydávající certifikáty, známé také pro svůj antivirový program Norton. Chyba postihla i GeoTrust a Thawte, které také certifikáty vydávají. Vlastní je rovněž Symantec.
Chyba se objevila v Chromu verze 53, postihla i Android WebView komponent, který Androidí aplikace používají pro zobrazení webového obsahu, píše Rick Andrew, technický ředitel Symantecu v příspěvku na blogu.
K opravě problému na mobilním zařízení by si uživatelé měli aktualizovat WebView na nejnovější verzi spolu s pozdější aktualizací Chromu na verzi 55.
„Vývojáři používající Android Open Source Platform (AOSP) si budou sami muset ověřit kompatibilitu vlastních aplikací.“
Ačkoli jde o součást systému, od Androidu 5.0 (Lollipop) je WebView dodáván ve fformě aplikačního balíčku, aktualizovatelného skrze Google Play obchod.
Verze 55 WebView byla vydána 1. prosince, ale Chrome zatím setrvává ve verzi 54 z pozdního října.
Google ve verzi 54 udělal některé změny ve Windows, Macu, Linuxu i iOS, stejně jako v Chromium a Chrome Custom Tabs aplikacích tak, aby certifikáty Symantecu nevyvolávaly varování o nedůvěryhodnosti. V Chromu 55 je již problém zcela opraven na všech platformách, potvrdil Andrews.
V rámci zabezpečení je doporučeno na verzi 55 aktualizovat jakmile to jen bude možné. Na většině platforem to jde od 1. prosince.
Problém začal rozhodnutím Googlu – ten donutil Symantec publikovat veškeré certifikáty vydané po 1. červnu 2016 do veřejného registru – Certificate Transparency (CT).
Rozhodnutí přišlo po interním zkoumání Symantecu. Zajímal se o neautorizované udělování prodloužené platnosti (EV) certifikátům pro google.com, zkoumání však nedopadlo podle plánů a Google hrozil postihy proti Symantecu; svou hrozbu také splnil.
Protože poskytovatelé certifikátů závisí na prohlížečích, které se rozhodnout jimi uděleným certifikátům věřit, mají vůči nim firmy jako Google, Mozilla nebo Microsoft silnou páku. Po incidentu se Symantecem Google do Chromu implementoval mechanismus, který označil jako důvěryhodné pouze certifikáty po 1. červnu 2016.
Google však má ještě další mechanismus, kdy Chrome nastaví desetitýdenní limit pro důvěru certifikátům, aby informace nezastaraly. Když se to zkombinovalo s druhou kontrolou pro Symantec, výsledkem byla nechtěná nedůvěra v certifikáty i pro certifikáty splňující požadavky firmy.
V bezpečnostních IP kamerách Sony byla nalezena „zadní vrátka“, umožnila administrátorský přístup komukoli
7.12.2016 Novinky/Bezpečnost Zranitelnosti
S rozmachem internetu věcí vzniká i rozmach bezpečnostních hrozeb z počtu zařízení, která lze hacknout kvůli chybám v jejich zabezpečení. Ironií je, že tentokrát se ale problém objevil u profesionálních bezpečnostních kamer od Sony řady Ipela Engine.
Jak objevila bezpečnostní společnost SEC Consult, kamery měly ve firmwaru zabudovaný „backdoor“ (zadní vrátka“), která umožňovala tajný administrátorský přístup ke kameře komukoli a odkudkoli. Jednalo se o účet, který se nacházel přímo ve firmwaru (User: primana, Password: primana), nejednalo se tak o nějakou chybu, která může při návrhu hardwaru a softwaru vzniknout. Dle vyjádření šlo pravděpodobně o účet sloužící pro testování a kalibraci. Proč ho tam ale Sony nechalo, není jasné. Nalezen byl i další skrytý účet s názvem „debug“ a heslem „popeyeConnection“.
Dalším problémem, který se podařilo odhalit, byla defaultní hesla, která byla rovněž přímo ve firmwaru a nijak se negenerovala. To už se vymstilo u obrovského počtu zařízení, která hackeři ovládali do velkých botnetů.
Sony dle informací už vydala aktualizaci firmwaru, který by měl bezpečnostní problémy vyřešit.
Zombie routery chystaly útok v Německu a Británii, stejný vir dříve odstavil Twitter
7.12.2016 Novinky/Bezpečnost Kyber
Říjnový masový výpadek sociální sítě Twitter, ale také internetového obchodu Amazon nebo Facebooku ve Spojených státech, k němuž došlo při masovém DDoS útoku přes zařízení napojená na sítě Internetu věcí, se tento týden v menším měřítku zopakoval v Německu a ve Velké Británii.
K útokům vedeným na infrastruktury konkrétních operátorů hackeři opět využili botnet Mirai. Začátkem týdne se útočníkům podařilo odstavit síť pro Internet věcí německé telekomunikační společnosti Deutsche Telekom.
Výpadek se dotkl 900 tisíc zákazníků, kteří nemohli využívat chytrá zařízení ve svých domácnostech a připojit se k internetu. Původní záměr hackerů byl ale mnohem ambicióznější: plánovali využít domácí routery zákazníků Deutsche Telekomu k masivnímu DDoS útoku, který by byl podobně rozsáhlý jako říjnový výpadek internetových služeb ve Spojených státech.
Jeden z hlavních serverů, jehož prostřednictvím byl veden útok, se podle webu Infosecurity-magazine.com nacházel v Kyjevě a byl zapsán pod pseudonymem Peter Parker (skutečné jméno filmového Spidermana). Výpadky sítě Deutsche Telekom ovlivnily nejen internet, ale také hlasové a televizní služby poskytované touto společností.
„Sledujeme nový nebezpečný trend. V září se udál útok na webové stránky Briana Krebse o síle 665 gigabitů za sekundu, v říjnu ve Spojených státech šlo o více než 1 terabit. Pro srovnání – průměrný datový tok českého peeringového uzlu NIX.cz je přibližně 250 gigabitů za sekundu. Je zřejmé, že takovému útoku se lze bránit jen za velmi vysokou cenu,“ upozorňuje Miroslav Dvořák, technický ředitel antivirové společnosti ESET.
Britové museli resetovat routery
Jen několik dní po útoku na infrastrukturu Deutsche Telekom se s podobnými problémy potýkala britská pošta a mobilní operátor TalkTalk. Zákazníci těchto společností byli odříznuti od internetového připojení poté, co někdo na dálku vypnul jejich domácí routery. Po jejich restartování připojení opět bez problémů fungovalo.
Bezpečnostní experti předpokládají, že k tomuto útoku byla použita jedna z nejnovějších verzí botnetu Mirai. Výpadek probíhal podobným způsobem jako u Deutsche Telekomu a dotkl se 100 tisíc zákazníků. Britská BBC informovala, že odstavenými routery byly modely ZyXEL AMG1302, používané britskou poštou, a D-Link DSL-3780, který svým zákazníkům poskytuje operátor TalkTalk.
Bezpečnost musí být vždy komplexní a je nutné zabezpečit každé zařízení, které má přístup na internet.
Miroslav Dvořák, technický ředitel společnosti ESET software spol. s r. o.
„Router je povětšinou vnímán jako v uvozovkách hloupé zařízení, o které není potřeba se starat, ale opak je pravdou. Jednoduchou prevencí jsou v tomto případě pravidelná aktualizace firmwaru routeru, změna výchozího hesla a správná konfigurace, například zákaz dostupnosti administračního rozhraní z internetu,“ vypočítává Miroslav Dvořák ze společnosti ESET.
Základní chybou mnoha internetových uživatelů je používání výchozího hesla routeru, které bylo nastaveno od poskytovatele internetového připojení nebo od jeho výrobce a jež lze velmi jednoduše zjistit. Takový uživatel se pak vydává v milost či nemilost internetového útočníka.
„Rádi bychom ujistili naše zákazníky, že z napadených zařízení neunikla žádná jejich osobní data. Identifikovali jsme zdroj problému a nasadili řešení, které v současné době chrání všechny naše zákazníky,“ citovala BBC mluvčího britské pošty. Podle Miroslava Dvořáka však nestačí chránit pouze routery. „Bezpečnost musí být vždy komplexní a je nutné zabezpečit každé zařízení, které má přístup na internet. Počítač, mobilní zařízení a další. Nejlepším nástrojem ochrany je v tomto případě aktualizovaný a spolehlivý nástroj internetové ochrany,“ radí Dvořák.
Hacker who stole Celebrity Emails, Sex Tapes, Movie Scripts Gets 5 Years in Prison
7.12.2016 thehackernews Hacking
Hacker who stole Celebrity Emails, Sex Tapes, Movie Scripts Gets 5 Years in Prison
A hacker who was arrested last year for hacking into celebrities' email accounts to steal the unreleased movie and television scripts, their private messages, and sex tapes to sell them has finally been sentenced five years in prison.
Alonzo Knowles, a 24-year-old Bahamian man, was convicted by U.S. District Judge Paul A. Engelmayer in Manhattan on Tuesday.
Knowles, who maintained a list of emails and phone numbers of 130 celebrities, pleaded guilty in May to charges of identity theft and criminal copyright infringement.
The sentence is twice longer than the amount of years the federal sentencing guidelines suggested, as the judge felt that Knowles "would be a clear and present danger to commit the very same crime again," the New York Times reports.
The hacker expressed remorse in court and had already handed over unreleased scripts, songs, and $1,900 in cash.
The authorities arrested Knowles late December and seized his laptop that was later destroyed by investigators. The authorities found folders containing stolen data that includes:
Social Security numbers for actors and professional athletes
Private, explicit images
Scripts for unreleased TV shows and movies and even contract documents
Emails and phone numbers of at least 130 celebrities
Sex tapes of celebrities
The hacker was arrested after flying to New York from the Bahamas to sell 15 movie and TV shows scripts and the Social Security Numbers (SSNs) of a movie actress and two athletes to an undercover U.S. Department of Homeland Security agent for $80,000.
According to prosecutors, Knowles appeared anxious to continue exploiting celebrities once released even after pleading guilty.
The judge cited the book the hacker claimed he would someday write to "shake up Hollywood," with plans to sell them at $35 per copy, in which Knowles said: "When I get out, I'm going to shake up Hollywood."
The book, Knowles claimed, will contain information that can "jeopardize their careers, their security, and their personal relationships."
The affected celebrities were not identified, though the judge acknowledged that the court received a statement from 20th Century Fox. However, Knowles apologized for his conduct on Tuesday, saying he regretted "the stupid things I did and said."
5-Year-Old Linux Kernel Local Privilege Escalation Flaw Discovered
7.12.2016 thehackernews Vulnerebility
A 5-year-old serious privilege-escalation vulnerability has been discovered in Linux kernel that affects almost every distro of the Linux operating system, including Redhat, and Ubuntu.
Over a month back, a nine-year-old privilege-escalation vulnerability, dubbed "Dirty COW," was discovered in the Linux kernel that affected every distro of the open-source operating system, including Red Hat, Debian, and Ubuntu.
Now, another Linux kernel vulnerability (CVE-2016-8655) that dates back to 2011 disclosed today could allow an unprivileged local user to gain root privileges by exploiting a race condition in the af_packet implementation in the Linux kernel.
Philip Pettersson, the researcher who discovered the flaw, was able to create an exploit to gain a root shell on an Ubuntu 16.04 LTS system (Linux Kernel 4.4) and also defeated SMEP/SMAP (Supervisor Mode Execution Prevention/Supervisor Mode Access Prevention) protection to gain kernel code execution abilities.
In other words, a local unprivileged attacker can use this exploit to cause a denial of service (crashing server) or run arbitrary malicious code with administrative privileges on the targeted system.
"A race condition issue leading to a use-after-free flaw was found in the way the raw packet sockets implementation in the Linux kernel networking subsystem handled synchronization while creating the TPACKET_V3 ring buffer," Red Hat security advisory explains.
"A local user able to open a raw packet socket (requires the CAP_NET_RAW capability) could use this flaw to elevate their privileges on the system."
This threat creates a potential danger for service providers to have their servers crashed or hacked through this Linux kernel vulnerability.
"On Android, processes with gid=3004/AID_NET_RAW are able to create AF_PACKET sockets (mediaserver) and can trigger the bug," Pettersson explains.
The vulnerability was patched in the mainline kernel last week, so users are advised to update their Linux distro as soon as possible.
An individual hacked back the San Francisco Muni hacker
7.12.2016 securityaffairs Hacking
In November, an unknown attacker hacked the computer systems of the San Francisco’s Municipal, now an individual hacked back the San Francisco Muni hacker.
A couple of weeks ago, an unknown attacker hacked the computer systems of the San Francisco’s Municipal railway giving riders a free ride all day on Saturday. Now the same hacker seems to have been hacked. According to the popular investigator Brian Krebs, an individual took over the email account of one of the San Francisco’s Municipal hackers that was reported in the ransom note provided in the attack.
The ransom demanded in the specific case to the FMTA was 100 BTC, or $73,184 USD with current exchange rates.
The hackers that targeted the San Francisco’s Municipal railway left the following message on the compromised machines in the Muni stations:
“Contact for key (cryptom27@yandex.com)”

Infected machine at the SF Muni station (Source: Brian Krebs)
The individual who hacked backed the Muni hacker broke into the email account by guessing the security question protecting it, then he reset the password and locked down the account and secondary address cryptom2016@yandex.com.
“On Monday, KrebsOnSecurity was contacted by a security researcher who said he hacked this very same cryptom27@yandex.com inbox after reading a news article about the SFMTA incident. The researcher, who has asked to remain anonymous, said he compromised the extortionist’s inbox by guessing the answer to his secret question, which then allowed him to reset the attacker’s email password.” wrote Krebs. “A screen shot of the user profile page for cryptom27@yandex.com shows that it was tied to a backup email address, cryptom2016@yandex.com, which also was protected by the same secret question and answer.”
The analysis of the Bitcoin wallets used by the Muni hacker revealed that he earned $140,000 in the last three months, a circumstance that confirms that he is a cyber criminal. In this period he used to continuously switch Bitcoin wallets randomly every few days or weeks in order to make harder the investigation. Most of the attampts of extortion targeted US-based construction and manufacturing companies, and in many cases, the victims appear to have complied with the demands.
“On Nov. 20, hacked emails show that he successfully extorted 63 bitcoins (~$45,000) from a U.S.-based manufacturing firm.” added Krebs. ““Emails from the attacker’s inbox indicate some victims managed to negotiate a lesser ransom. China Construction of America Inc., for example, paid 24 Bitcoins (~$17,500) on Sunday, Nov. 27 to decrypt some 60 servers infected with the same ransomware — after successfully haggling the attacker down from his original demand of 40 Bitcoins. Other construction firms apparently infected by ransomware attacks from this criminal include King of Prussia, Pa. based Irwin & Leighton; CDM Smith Inc. in Boston; Indianapolis-based Skillman; and the Rudolph Libbe Group, a construction consulting firm based in Walbridge, Ohio.””
The analysis of the account revealed a number of messages sent to the attacker’s cryptom2016@yandex.com account. These messages show a financial relationship with at least two different hosting providers. The hacked inbox also included emails containing credentials needed to manage one of those servers, then Krebs shared them with some experts such as Alex Holden, chief information security officer at Hold Security Inc.
The expets discovered that the server was used to hack into systems worldwide, it was hosting several open-source hacking tools.
“It appears our attacker has been using a number of tools which enabled the scanning of large portions of the Internet and several specific targets for vulnerabilities,” Holden said. “The most common vulnerability used ‘weblogic unserialize exploit’ and especially targeted Oracle Corp. server products, including Primavera project portfolio management software.”
The experts discovered that the Muni hacker used internet addresses based in Iran, they found also some notes which were translated into Farsi.
“That server kept detailed logs about the date, time and Internet address of each login. A review of the more than 300 Internet addresses used to administer the server revealed that it has been controlled almost exclusively from Internet addresses in Iran. Another hosting account tied to this attacker says his contact number is +78234512271, which maps back to a mobile phone provider based in Russia.” continues Krebs. “But other details from the attack server indicate that the Russian phone number may be a red herring.”
It is bad time also for crooks!
Argentinian Ministry of Industry hacked by Kapustkiy
7.12.2016 securityaffairs Hacking
The young hacker Kapustkiy and his colleague Kasimierz have broken into another website, the Argentinian Ministry of Industry (Ministerio de Produccion).
The data breach exposed personal information, contact details (i.e. names, addresses, emails, phone numbers, Facebook and Twitter accounts), and private documents of a large number of individuals.
The hackers breached the Argentinian Ministry of Industry website produccion.gob.ar by gaining access to an administrator account. The hackers confirmed that the login credentials used to protect the website are very weak demonstrating the poor level of security at the Argentinian Ministry.
Kapustkiy shared evidence of the data breach and provided the credentials for the admin panel that allowed the hackers accessing to personal information of employees and documents belonging to the ministry.
“When I was in the admin panel. I managed to download all the files that they got.”Kapustkiy told me.
Argentinian Ministry of Industry hacked by Kapustkiy
According to Kapustkiy, the overall archive includes approximately 18,000 accounts, he confirmed that he will not leak the stolen data to protect the users of the Argentinian Ministry of Industry website.
Kapustkiy reported the data breach to the Argentinian Ministry of Industry that still hasn’t replied.
When asked about the hacking technique used, Kapustkiy told me that they didn’t use a SQL injection, but he avoided to provide me further details.
Recently Kapustkiy has breached the National Assembly of Ecuador and leaked the data via PasteBin. Once again he exploited a SQL injection.
A few days ago the hacker announced to have hacked the Venezuela Army, but the list of victims is long.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento dellaFunzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya.
Hacking Millions with Just an Image — Recipe: Pixels, Ads & Exploit Kit
7.12.2016 THEHACKERNEWS Hacking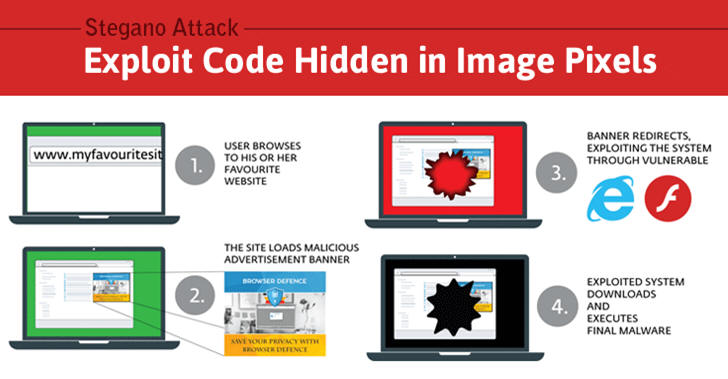
If you have visited any popular mainstream website over the past two months, your computer may have been infected — Thanks to a new exploit kit discovered by security researchers.
Researchers from antivirus provider ESET released a report on Tuesday stating that they have discovered an exploit kit, dubbed Stegano, hiding malicious code in the pixels of banner advertisements that are currently in rotation on several high profile news websites.
Stegano originally dates back to 2014, but since early October this year, cyber crooks had managed to get the malicious ads displayed on a variety of unnamed reputable news websites, each with Millions of daily visitors.
Stegano derived from the word Steganography, which is a technique of hiding messages and content inside a digital graphic image, making the content impossible to spot with the naked eye.
In this particular malvertising campaign, operators hide malicious code inside transparent PNG image's Alpha Channel, which defines the transparency of each pixel, by altering the transparency value of several pixels.
The malvertising campaign operators then packed the altered image as an advertisement and managed to display those malicious ads on several high-profile websites.
According to the researchers, the malicious ads promote applications called "Browser Defense" and "Broxu," and the methodology makes it tough for ad networks to detect.
Here's How the Stegano Attack Works:
Once a user visits a site hosting malicious advertisement, the malicious script embedded in the ad reports information about the victim's computer to the attacker's remote server without any user interaction.
The malicious code then uses the CVE-2016-0162 vulnerability in Microsoft's Internet Explorer (IE) browser in order to scan the target computer to see if it is running on a malware analyst's machine.
After verifying the targeted browser, the malicious script redirects the browser to a website that hosts Flash Player exploits for three now-patched Adobe Flash vulnerabilities: CVE-2015-8651, CVE-2016-1019, and CVE-2016-4117.
"Upon successful exploitation, the executed shell code collects information on installed security products and performs – as paranoid as the cybercriminals behind this attack – yet another check to verify that it is not being monitored," ESET researchers wrote in a blog post. "If results are favorable, it will attempt to download the encrypted payload from the same server again, disguised as a gif image."
When downloaded to the victim's computer, the encrypted payload is then decrypted and launched via regsvr32.exe or rundll32.exe in Microsoft Windows.
Just Visit a Site, and You'll be Hacked in Just 2-3 Sec
Below is an ESET infographic that explains the working of Stegano's exploit attack: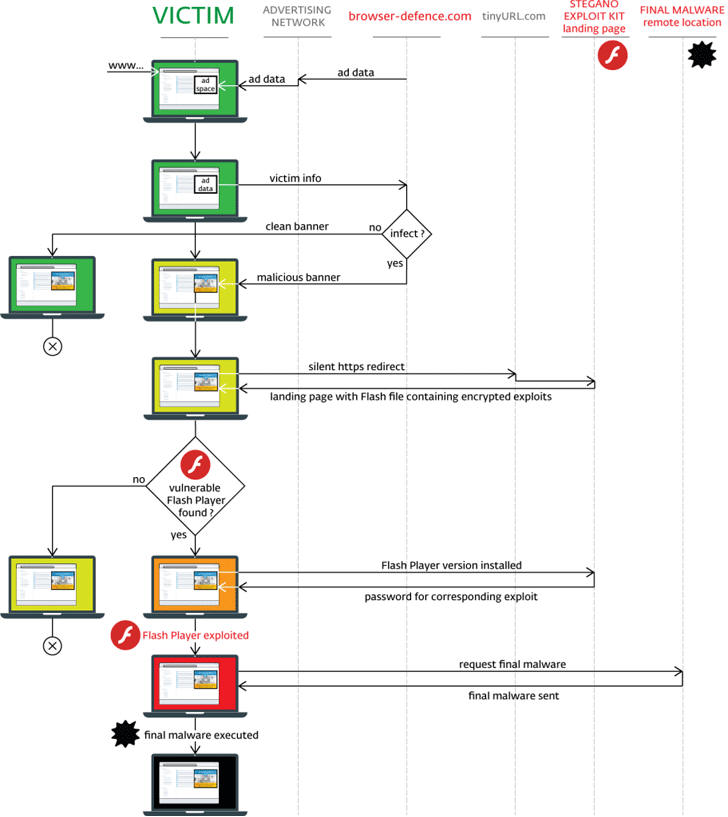
All the above operations execute automatically without any user interactions and takes place in the span of just 2-3 seconds.
So far, the Stegano exploit kit has pushed various trojan downloaders, the Ursnif and Ramnit banking trojans, backdoors, spyware, and file stealers.
The Stegano exploit kit was initially used in 2014 to target people in the Netherlands, and then in 2015, moved on to residents in the Czech Republic. The latest attack campaign is targeting people in Canada, the UK, Australia, Spain, and Italy.
The best way to protect yourself against any malvertising campaign is always to make sure you are running updated software and apps. Also use reputed antivirus software that can detect such threats before they infect your system.
Adobe Flash Player flaws remain the most used by Exploit Kits
7.12.2016 securityaffairs Exploit
Experts from the firm Recorded Future published a report on the most common vulnerabilities used by threat actors in the exploit kits.
Recorded Future published an interesting report on the most common vulnerabilities used by threat actors in the exploit kits.
The experts observed that Adobe Flash Player and Microsoft products (Internet Explorer, Silverlight, Windows) continue to be privileged targets of threat actors. Hacking campaigns conducted by nation-state actors have dominated the threat landscape in 2016, while crooks used exploit kits to deliver several families of malware, including ransomware and banking trojans.
The experts noticed that hackers have used new exploit kits targeting new vulnerabilities.
The researchers highlighted that the Adobe Flash Player comprised six of the top 10 vulnerabilities triggered by the exploit kits in a period from November 16, 2015 to November 15, 2016.

RecordedFuture analyzed 141 exploit kits, experts noticed that the Internet Explorer flaw tracked as CVE-2016-0189 was the most referenced on security blogs, deep web forum postings and dark web sites.
This vulnerability was widely exploited by hackers behind the CNACOM campaign and its had been exploited in targeted attacks against Windows users in South Korea before Microsoft fixed it.
Experts from startup Theori have made a reverse engineering of the MS16-053 that fixed the CVE-2016-0189 flaw and published a PoC exploit for the vulnerability.
The PoC code works on Internet Explorer 11 running on Windows 10, a great gift for fraudsters that included it in the Neutrino EK and Magnitude, and many other exploit kits such as Angler, RIG, Nuclear, Spartan and Hunter.

The above list of vulnerabilities used by exploit kits also includes the Adobe Flash flaw tracked as CVE-2016-1019, CVE-2016-4117, CVE-2016-1010, and CVE-2015-8651.
The list includes also Microsoft Silverlight flaw tracked as CVE-2016-0034 and Microsoft Windows flaw tracked as CVE-2014-4113
According to Recorded Future after the Angler and Nuclear EKs disappeared from the threat landscape RIG became the most used EK, while the popularity of the Sundown EK rapidly increased.
Let me close with the Key Takeaways published by Recorded Future.
Adobe Flash Player provided six of the top 10 vulnerabilities used by exploit kits in 2016. Since our 2015 ranking, Flash Player’s popularity with cyber criminals remains after increased Adobe security issue mitigation efforts.
Vulnerabilities in Microsoft’s Internet Explorer, Windows, and Silverlight rounded out the top 10 vulnerabilities used by exploit kits. None of the vulnerabilities identified in last year’s report carried over to this year’s top 10.
A 2016 Internet Explorer vulnerability (CVE-2016-0189) saw the most linkage to exploit kits, notably Sundown EK which quickly adopted an exploit in July 2016.
Sundown, RIG, and Neutrino exploit kits filled the void created by Angler Exploit Kit’s June 2016 demise. This crimeware can be used for anywhere from $200 a week (RIG) to $1,500 a week (Neutrino).
Adobe Flash Player’s CVE-2015-7645 has been incorporated into seven exploit kits, the highest penetration level of our analyzed vulnerabilities likely because it was the first zero-day discovered after significant Adobe security changes.
Identifying frequently exploited vulnerabilities can drive action by vulnerability assessment teams.
Dozens of Sony cameras affected by a secret backdoor
7.12.2016 securityaffairs Virus
Many Sony cameras could be hijacked by hackers and infected with Mirai-like malware due to the presence of a sort of secret backdoor.
Sony has closed a sort of debug backdoor that was spotted in 80 web-connected surveillance cameras. The hardcoded logins in the firmware of the Sony cameras can be exploited to hijack the devices and open the doors to Mirai like malware.
The flawed devices are branded Sony Professional Ipela Engine IP surveillance cameras.
The backdoor was discovered by Stefan Viehböck from SEC Consult in October, the expert reported the issue to Sony and the company fixed it with firmware updates.
“SEC Consult has found a backdoor in Sony IPELA Engine IP Cameras, mainly used professionally by enterprises and authorities. This backdoor allows an attacker to run arbitrary code on the affected IP cameras.” reads a blog post published by SEC Consult.”An attacker can use cameras to take a foothold in a network and launch further attacks, disrupt camera functionality, send manipulated images/video, add cameras into a Mirai-like botnet or to just simply spy on you. This vulnerability affects 80 different Sony camera models. Sony was informed by SEC Consult about the vulnerability and has since released updated firmware for the affected models.”

Sony thanked the experts for the support they provided.
“We are grateful to SEC Consult for their assistance in enhancing network security for our network cameras,” Sony said.
The expert spotted two hardcoded permanently enabled application-level backdoor accounts in the web-based admin console:
User debug, Password: popeyeConnection
User primana, Password: primana
Both accounts are allowed to access specific, undocumented CGI functionality.
The expert explained that it is possible to remotely enable Telnet/SSH services and a backdoor allows an attacker to gain access to a Linux shell with root privileges.
“The vulnerabilities are exploitable in the default configuration over the network. Exploitation over the Internet is possible, if the web interface of the device is exposed.” continues the analysis.
The following URLs, once sent to a vulnerable web-facing device, will enable telnet access:
http://primana:primana@HOST/command/prima-factory.cgi?foo=bar&Telnet=zKw2hEr9
http://primana:primana@HOST/command/prima-factory.cgi?foo=bar&Telnet=cPoq2fi4cFk
The requests trigger the prima-factory.cgi in Sony’s fifth-generation Ipela Engine cameras to open the backdoor by starting the inetd, which runs a telnet daemon on port 23. Devices belonging to Gen6 generation use the magic string “himitunokagi” (Japanese for “secret key”).
Once the telnet or SSH service is enabled, attacker can login as root and get command-line-level access to the OS. Below are the password hashes for the OS-level backdoor user:
$1$$mhF8LHkOmSgbD88/WrM790 (gen-5 models)
iMaxAEXStYyd6 (gen-6 models)
Ill-intentioned could easily crack the above root passwords, the researchers avoided to do it in order to prevent their exploitation in the wild.
Experts suggest the application of the security updates for the following Sony cameras:
SNC-CX600, SNC-CX600W, SNC-EB600, SNC-EB600B, SNC EB602R, SNC-EB630, SNC-EB630B, SNC-EB632R, SNC-EM600, SNC-EM601, SNC-EM602R, SNC-EM602RC, SNC-EM630, SNC-EM631, SNC-EM632R, SNC-EM632RC, SNC-VB600, SNC-VB600B, SNC-VB600B5, SNC-VB630, SNC-VB6305, SNC-VB6307, SNC-VB632D, SNC-VB635, SNC-VM600, SNC-VM600B, SNC-VM600B5, SNC-VM601, SNC-VM601B, SNC-VM602R, SNC-VM630, SNC-VM6305, SNC-VM6307, SNC-VM631, SNC-VM632R, SNC-WR600, SNC-WR602, SNC-WR602C, SNC-WR630, SNC-WR632, SNC-WR632C, SNC-XM631, SNC-XM632, SNC-XM636, SNC-XM637, SNC-VB600L, SNC-VM600L, SNC-XM631L, SNC-WR602CL, SNC-CH115, SNC-CH120, SNC-CH160, SNC-CH220, SNC-CH260, SNC-DH120, SNC-DH120T, SNC-DH160, SNC-DH220, SNC-DH220T, SNC-DH260, SNC-EB520, SNC-EM520, SNC-EM521, SNC-ZB550, SNC-ZM550, SNC-ZM551, SNC-EP550, SNC-EP580, SNC-ER550, SNC-ER550C, SNC-ER580, SNC-ER585, SNC-ER585H, SNC-ZP550, SNC-ZR550, SNC-EP520, SNC-EP521, SNC-ER520, SNC-ER521, and SNC-ER521C.
North Koreans Red Star OS can be easily hacked remotely
6.12.2016 securityaffairs OS
The North Korean operating system Red Star OS isn’t hacker proof, researchers demonstrated that it can be easily hacked remotely.
Red Star OS is an operating system used by the population in North Korea. According to two German researchers from the IT security company ERNW who analyzed it early this year, it is characterized by a high degree of paranoia and invasive surveilling on users.
Florian Grunow and Niklaus Schiess downloaded the software from a website outside North Korea and explored the code in detail.

North Korea operating system ©Reuters
These are their findings:
Latest version is from around 2013.
Red Star OS is based on the Fedora Linux distro.
It has an Apple OSX look, the country’s leader Kim Jong-un, like his father, has been photographed near Macs.
Own version of encryption files, the North Korea wants to avoid the spread of any code that might compromise OS files.
If you believe that the North Korean operating system is hacker proof you are wrong, in fact, it can be easily hacked remotely.
According to the experts at security firm Hacker House, the Red Star OS is affected by a critical vulnerability that could be exploited by remote hackers to access the PC. The attacker just needs to trick a victim into opening a link.
“Hacker House team have previously disclosed a number of local root vulnerabilities [3] & [4] in Red Star OS to show how insecure programming practices are in use by the RedStar OS developers. We are sharing another amusing example of this in the form of a remote client-side command injection vulnerability to mark RedStar’s anniversary leak.” reads a blog post published by the Hacker House.”This exploit is a client-side remote exploit which can be triggered from the Internet/Intranet and used to install malware or exploit computers running RedStar OS just by having a user click a hyperlink.”
The latest version of the Red Star OS ships with the web browser Naenara which is the landing point for a remote attacker that wants to take over the system.
The experts exploited a certain Red Star application, the ‘nnrurlshow’, that handles Uniform Request Identifiers (URI), in particular the “mailto” URI ordinarily used for email could be used to remotely “execute arbitrary commands.” The Naenara web browser doesn’t sanitize the command line when handling URI argument allowing attackers to remote execute arbitrary code.
“Whilst probing for vulnerabilities it was noticed that registered URL handlers were passed to a command line utility “/usr/bin/nnrurlshow”. This application (aside from having null ptr de-refs and other cute bugs) takes URI arguments for registered URI handlers when handling application requests such as “mailto” and “cal”. Naenara doesn’t sanitize the command line when handling these URI argument requests and as such you can trivially obtain code execution by passing malformed links to the nnrurlshow binary.” continues the analysis of the experts.
“An attacker can get a user of RedStar OS 3.0 to execute arbitrary commands by enticing them to click on a link which points to “mailto:`cmd`”. Commands will then be executed as arguments when passed to evolution mail. An example of exploitation can be seen in the image below with the output of the “id” command visibly shown in the evolution-based mail client output.”

Nintendo announced its bug bounty program for 3DS Consoles. Rewards up to $20,000
6.12.2016 securityaffairs Security
Nintendo presented its bug bounty program for 3DS consoles, the company is willing to pay between $100 and $20,000 for vulnerabilities found in the product.
Good news, Nintendo joins the club of the “bug bounty program,” companies that decide to exploit this mechanism to involve ethical hacking communities.
The company is the last in order of time to adopt a similar strategy, HackerOne already hosts bug bounty program launched by Kaspersky, Qualcomm, Uber, and also the “Hack the Army” promoted by the U.S. Army.
The bug bounty program has been hosted on the HackerOne platform, in this phase is it limited to 3DS consoles as explained by the giant.
“Nintendo’s goal is to provide a secure environment for our customers so that they can enjoy our games and services. In order to achieve this goal, Nintendo is interested in receiving vulnerability information that researchers may discover regarding Nintendo’s platforms.” reads the announcement published on HackerOne. “Currently, in the context of the HackerOne program, Nintendo is only interested in vulnerability information regarding the Nintendo 3DS™ family of systems and is not seeking vulnerability information regarding other Nintendo platforms, network service, or server-related information.”
The company will pay for 3DS vulnerabilities that allow to take over the console or a privilege escalation on ARM11 and ARM 9 processors.

Nintendo aims to prevent illegal activities such as piracy, cheating, and dissemination of inappropriate content to children.
The giant is willing to pay also hardware vulnerabilities regarding the Nintendo 3DS family of systems, including low-cost cloning and security key detection via information leaks.
Nintendo will pay rewards from $100 USD to $20,000 USD, of course, it will determine at its discretion whether a flaw has to be rewarded. The company doesn’t provide details on the process of evaluation for each flaw.
“A report is evaluated to be high quality if you show that the vulnerability is exploitable by providing a proof of concept (functional exploit code is even better),” continues Nintendo. “If you don’t yet have a proof of concept, or functional exploit code, we still encourage you to report to us sooner rather than later such that you do not to lose the opportunity to become the first reporter; you can then submit a proof of concept or functional exploit code later (within three weeks of the initial report) and it will be considered to be a part of the report.”
Nintendo intends to prohibit hackers from disclosing vulnerability information even after a patch becomes available.
North Korea's Linux-based Red Star OS can be Hacked Remotely with just a Link
6.12.2016 thehackernews Hacking
North Korea's own homegrown computer operating system, that's supposed to be fully hacker proof and more secure than foreign OS, like Microsoft's Windows, can easily be hacked remotely.
A group of hackers managed to break into Red Star OS — North Korea's government sanctioned Linux-based OS — using just a link.
Red Star OS is North Korea's own homegrown OS that looks remarkably just like Apple's OS X and gives North Korean authorities more control over the computers, providing not only security but also spying tools that help track files in a way that if the government wants, every bit of user's data can be traced easily.
According to the information security company Hacker House, Red Star OS contains a critical vulnerability that makes it possible for hackers to gain remote access to any PC running North Korea's OS just by tricking victims into opening a hyperlink.
The latest version of Red Star OS ships with a Firefox-based web browser called Naenara, and according to researchers, the "trivial remote exploit attack vectors" contained in the web browser allows attackers to hack into the system.
Here's how the exploit work:
The Hacker House hackers exploited a particular Red Star application that handles Uniform Request Identifiers (URI) – a string of characters used to identify resources in a network.
Hackers noted that the "mailto" URI request used for email could be exploited by hackers to remotely "execute arbitrary commands."
Since this particular URI does not remove requests from the application's command line, hackers could "trivially obtain code execution" just by injecting malicious links into the command line.
"Whilst probing for vulnerabilities it was noticed that registered URL handlers were passed to a command line utility '/usr/bin/nnrurlshow.' This application (aside from having null ptr de-refs and other cute bugs) takes URI arguments for registered URI handlers when handling application requests such as 'mailto' and 'cal,' the Hacker House hackers explains.
"Naenara doesn't sanitize the command line when handling these URI argument requests and as such you can trivially obtain code execution by passing malformed links to the nnrurlshow binary."
In short, this security flaw can be used easily to install malware or exploit PCs running the Red Star operating system.
Rival South Korea has long blamed North Korea for mounting various cyber attacks against its government, military, and other organizations.
Just recently, the South Korean military blamed North Korea for breaching its military cyber command. A spokesman for the military cyber command told BBC that classified information was thought to have been stolen, although it's not clear exactly what data was accessed.
[Video] How to Hack a Credit Card in 6 Seconds, Experts Reveal
6.12.2016 thehackernews Hacking
As India attempts an upgrade to a cashless society, cyber security experts have raised serious concerns and revealed how to find credit card information – including expiration dates and CVV numbers – in just 6 Seconds.
And what's more interesting? The hack uses nothing more than guesswork by querying multiple e-commerce sites.
In a new research paper entitled "Does The Online Card Payment Landscape Unwittingly Facilitate Fraud?" published in the academic journal IEEE Security & Privacy, researchers from the University of Newcastle explains how online payments remain a weak spot in the credit card security which makes it easy for fraudsters to retrieve sensitive card information.
The technique, dubbed Distributed Guessing Attack, can circumvent all the security features put in place to protect online payments from fraud. The similar technique is believed to be responsible for the hack of thousands of Tesco customers in the U.K last month.
The issue relies on the Visa payment system, where an attacker can guess and attempt all possible permutations and combinations of expiration dates and CVV numbers on hundreds of websites.
Researchers discovered two weaknesses in the way online transactions are verified using the Visa payment system. They are as follows:
Online payment systems do not detect multiple incorrect payment requests if they're performed across multiple sites. They also allow a maximum of 20 attempts per card on each site.
Web sites do not run checks regularly, varying the card information requested.
Newcastle University PhD candidate Mohammed Ali says neither weakness is alone too severe, but when used together and exploited properly, a cyber criminal can recover a credit card's security information in just 6 seconds, presenting "a serious risk to the whole payment system."
The attack is nothing but a very clever brute force attack that works against some of the most popular e-commerce sites.
So, instead of brute-forcing just one retailer's website that could trigger a fraud detection system due to incorrect guesses or lock the card, the researchers spread out guesses for the card's CVC number across multiple sites with each attempt narrowing the possible combinations until a valid expiration dates and CVV numbers are determined.
The video demonstration shows that it only takes 6 seconds for a specially designed tool to reveal a card's secure code.
First, an attacker needs a card's 16-digit number, which can be obtained either from black-market websites for less than $1, or from a smartphone equipped with a near-field communication (NFC) reader to skim them.
Once a valid 16-digit number is obtained, the hacker use web bots to brute force three-digit card verification value (or CVV) and expiration date to hundreds of retailers at once. The CVV takes a maximum of 1,000 guesses to crack it and the expiry date takes no more than 60 attempts.
The bots then work to obtain the billing address, if required. The paper suggests the whole attack can be carried out in just 6 seconds.
"These experiments have also shown that it is possible to run multiple bots at the same time on hundreds of payment sites without triggering any alarms in the payment system," researchers explain in the paper.
"Combining that knowledge with the fact that an online payment request typically gets authorized within two seconds makes the attack viable and scalable in real time. As an illustration, with the website bot configured cleverly to run on 30 sites, an attacker can obtain the correct information within four seconds."
The attack works against Visa card customers, as the company does not detect multiple attempts to use a card across its network, while MasterCard detects the brute force attack after fewer than 10 attempts, even when the guesses are spread across multiple websites.
How to Protect yourself?
The team investigated the Alexa top-400 online merchants’ payment websites and found that the current payment platform facilitates the distributed guessing attack.
The researchers contacted the 36 biggest websites against which they ran their distributed card number-guessing attack and notified them of their findings. As a result of the disclosure, eight sites have already changed their security systems to thwart the attacks.
However, the other 28 websites made no changes despite the disclosure.
For Visa, the best way to thwart the distributed card number-guessing attack is to adopt a similar approach to MasterCard and lock a card when someone tries to guess card details multiple times, even tried across multiple websites.
For customers, avoid using Visa credit or debit cards for making online payments, always keep an eye on your statements, and keep spending limit on your Visa card as low as possible.
Nintendo announced its bug bounty program for 3DS Consoles. Rewards up to $20,000
6.12.2016 securityaffairs Security
Nintendo presented its bug bounty program for 3DS consoles, the company is willing to pay between $100 and $20,000 for vulnerabilities found in the product.
Good news, Nintendo joins the club of the “bug bounty program,” companies that decide to exploit this mechanism to involve ethical hacking communities.
The company is the last in order of time to adopt a similar strategy, HackerOne already hosts bug bounty program launched by Kaspersky, Qualcomm, Uber, and also the “Hack the Army” promoted by the U.S. Army.
The bug bounty program has been hosted on the HackerOne platform, in this phase is it limited to 3DS consoles as explained by the giant.
“Nintendo’s goal is to provide a secure environment for our customers so that they can enjoy our games and services. In order to achieve this goal, Nintendo is interested in receiving vulnerability information that researchers may discover regarding Nintendo’s platforms.” reads the announcement published on HackerOne. “Currently, in the context of the HackerOne program, Nintendo is only interested in vulnerability information regarding the Nintendo 3DS™ family of systems and is not seeking vulnerability information regarding other Nintendo platforms, network service, or server-related information.”
The company will pay for 3DS vulnerabilities that allow to take over the console or a privilege escalation on ARM11 and ARM 9 processors.

Nintendo aims to prevent illegal activities such as piracy, cheating, and dissemination of inappropriate content to children.
The giant is willing to pay also hardware vulnerabilities regarding the Nintendo 3DS family of systems, including low-cost cloning and security key detection via information leaks.
Nintendo will pay rewards from $100 USD to $20,000 USD, of course, it will determine at its discretion whether a flaw has to be rewarded. The company doesn’t provide details on the process of evaluation for each flaw.
“A report is evaluated to be high quality if you show that the vulnerability is exploitable by providing a proof of concept (functional exploit code is even better),” continues Nintendo. “If you don’t yet have a proof of concept, or functional exploit code, we still encourage you to report to us sooner rather than later such that you do not to lose the opportunity to become the first reporter; you can then submit a proof of concept or functional exploit code later (within three weeks of the initial report) and it will be considered to be a part of the report.”
Nintendo intends to prohibit hackers from disclosing vulnerability information even after a patch becomes available.
85 Million user accounts stolen from the Video-sharing website Dailymotion
6.12.2016 securityaffairs Incindent
The popular video sharing website Dailymotion has suffered a massive data breach that leads the exposure of 87 million accounts.
According to the data breach notification service LeakedSource, millions of user accounts allegedly stolen from the Video-sharing Website Dailymotion. LeakedSource confirmed to have received a database containing 87.6 million accounts belonging to roughly 85 million users having unique email addresses.
The records include usernames, email addresses and more than 18 million of them includes password hashes.
The passwords were protected with the Bcrypt hashing algorithm, with 10 rounds of rekeying. Fortunately, the website used the Bcrypt hashing algorithm which is considered secure and hard to crack.

Source: Bleepingcomputer.com
According to the data breach notification service LeakedSource, hackers have stolen the Dailymotion archive around October 20.
Risks and countermeasures
Bcrypt hashing algorithm gives a reasonable level of security to the users, anyway, I suggest Dailymotion users change their password after the data breach.
The bad news is that all the email contained in the Dailymotion websites could be used by spammers in their campaign, crooks could also use them to target them with targeted phishing campaigns.
In November the company that owns AdultFriendFinder and other adult websites, FriendFinder Networks, has been hacked, data breach exposes 412 million accounts making this the largest 2016 hack. Also in this case LeakedSource obtained the leaked data.
Android opět pod útokem, na vině je AirDroid
6.12.2016 SecurityWorld Android
Nepříliš zdařilá implementace šifrování v oblíbené aplikaci na vzdálenou správu systému v Androidu umožňuje hackerům útok pomocí vzdáleného spuštění kódu a potenciálně ohrožuje miliony uživatelů.
Podle výzkumníků z firmy Zimperium, která se specializuje na mobilní zabezpečení, posílá aplikace na sdílení obrazovky a vzdálenou kontrolu AirDroid ověřovací informace zašifrované pomocí pevně přiděleného klíče. Tato informace umožňuje man-in-the-middle útočníkům (MITM, také „člověk uprostřed“) vynutit si škodlivou aktualizaci aplikace, díky kterým získají částečná práva na zásahy do systému, stejná, jako má AirDroid.
AirdDroid v základu může přístupovat ke kontaktům uživatele, informacím o poloze, textovým zprávám, fotografiím, záznamům hovorů, foťáku, mikrofonu a obsahu na SD kartě. Může také uskutečňovat platby (alespoň ty v aplikaci), měnit některá systémová nastavení, zrušit zámek displeje, měnit nebo zrušit síťové spojení a ještě mnohem více.
Aplikace, vyvinutá týmem jménem Sand Studio, je v Google Play obchodu již od roku 2011 a od té doby má, podle dat vývojářů, přes 20 milionů stažení.
Ačkoli AirDroid využívá pro většinu svých funkcí zašifrované HTTPS spojení, některá komunikace se vzdálenými servery přesto probíhá skrze základní http, popisují vědci z firmy Zimperium v příspěvku na blogu. Vývojáři se pokusili takto odesílaná data zabezpečit pomocí DES standardu, ale šifrovací klíč je statický a zakódovaný přímo do aplikace, takže si jej může kdokoli zjistit, vysvětlují vědci.
Jednou z takto zranitelných funkcí je sběr statistik, které aplikace posílá na server pomocí DES metodou šifrovaných JSON nákladů. Lze z nich zjistit informace vedoucí k identifikaci účtu a zařízení uživatele a mohou být použitý k vydávání se za daný chytrý telefon, což útočníkům umožní připojit se k jiným serverům, které aplikace využívá.
„S touto informací se může útočník vydávat za mobilní zařízení oběti a vykonávat různé HTTP a HTTPS požadavky jeho jménem přímo na koncových bodech API AirDroidu,“ vysvětlují vědci.
Tak například MITM útočník může tímto způsobem přesměrovávat žádosti na server, využívané pro vyhledání nových aktualizací, a vložit tam svůj infikovaný kód. Uživatel dostane standardní oznámení o dostupné aktualizaci a pravděpodobně ji nainstaluje; tím hacker dostane přístup k pravomocem samotné aplikace.
Vědci ze Zimperium již vývojáře AirDroidu o problému informovali v květnu; ze zářijové odpovědi vyplynulo, že oprava má přijít v listopadových aktualizacích 4.0.0 a 4.0.1, aplikace však přesto zůstává zranitelná. Pracovníci firmy se tak rozhodli zranitelnost veřejně oznámit.
Podle šéfky marketingu Sand Studio, Betty Chenové, má opravná aktualizace vyjít do dvou týdnů. Vývojářský tým potřebuje čas na nalezení řešení a synchronizaci kódu u všech svých klientů na různých platformách a serverech, než nové šifrování vypustí do světa. Není totiž kompatibilní s předchozími verzemi, vysvětlila.
Vznikl zde jistý komunikační šum, neboť datum, které společnost dalo firmě Zimperium, se skutečně týkalo vydání AirDroidu 4.0, který sice učinil nějaké související změny, ne však samotnou opravu.
Není to poprvé kdy se v AirDroidu objevila významná zranitelnost. V dubnu 2015 odhalil výzkumník, že skrze AirDroid může převzít kontrolu nad zařízení s Androidem prostým odesláním infikovaného odkazu uživateli skrze SMS. V únoru zase jiní výzkumníci z firmy Check Point přišli na způsob, jak ukrást data ze zařízení skrze systém kontaktů vCards s použitím právě AirDroidu.
Výzkumníci ze Zimperium doporučují aplikaci deaktivovat nebo odstranit do doby, než vyjde oficiální oprava. Instalovat v mezidobí jiné aktualizace této aplikace může pro uživatele být velmi nebezpečné.
Chrome má desítky bezpečnostních chyb. Některé jsou velmi vážné
6.12.2016 Novinky/Bezpečnost Zranitelnosti
Více než tři desítky chyb byly objeveny v oblíbeném webovém prohlížeči Chrome. Nejnovější verze tohoto browseru je však všechny opravuje. Vzhledem k tomu, že některé z objevených trhlin jsou vážné, neměli by uživatelé s instalací aktualizace otálet.
Nová verze prohlížeče s pořadovým číslem 55 opravuje celkem 36 bezpečnostních trhlin. Z nich 11 je přitom označeno nálepkou „vysoce závažné“.
To jinými slovy znamená, že je počítačoví piráti mohou zneužít k tomu, aby do počítače propašovali prakticky libovolný škodlivý kód. Stejně tak ale mohou přistupovat k nastavení napadeného stroje či uloženým datům na pevném disku.
Teoreticky mohou počítačoví piráti zneužít také některé trhliny, které mají nálepku „důležité“. U nich se nicméně nepředpokládá, že by v praxi došlo k jejich masivnímu zneužívání, jako je tomu u vysoce závažných bezpečnostních nedostatků.
Zlepšení funkčnosti
Zbylé aktualizace pak slouží především ke zlepšení funkčnosti jednotlivých součástí internetového prohlížeče. Tyto důležité záplaty by tedy neměly pro uživatele představovat žádné velké bezpečnostní riziko.
S instalací aktualizace Chromu by s ohledem na možná rizika neměli uživatelé otálet. Stahovat opravy je možné prostřednictvím automatických aktualizací.
Nainstalovat aktualizaci manuálně je možné prostřednictvím nápovědy, konkrétně v části „O aplikaci Chrome“. Po rozkliknutí této nabídky se uživateli automaticky nabídne instalace nejnovější verze.
Druhá největší ruská banka VTB se stala terčem kybernetického útoku
6.12.2016 Novinky/Bezpečnost Počítačový útok
Druhá největší ruská banka VTB se v pondělí stala terčem kybernetického útoku. Informovala o tom agentura AFP. Podle ní byla akce počítačových pirátů zaměřena na internetovou stránku banky, žádného z klientů se ale prý nijak nedotkla.
Co je DDoS
Útok DDoS (Distributed Denial of Service) má vždy stejný scénář. Stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se pak takto napadená webová stránka tváří jako nedostupná.
K útoku došlo v době, kdy se ruské finanční instituce obávají častějších nepřátelských aktivit počítačových pirátů. Ruská kontrarozvědka FSB minulý týden obvinila „zahraniční zpravodajské služby”, že se chystají s pomocí kybernetických útoků destabilizovat ruský finanční systém.
„Stránky skupiny VTB byly vystaveny útoku typu DDoS. IT infrastruktura funguje normálně a klienti banky nebyli nijak postiženi,” uvedla banka.
Centrála, z které jsou útoky na ruské banky údajně řízeny, se podle FSB nachází v Nizozemsku a patří ukrajinské společnosti BlazingFast. Kyjev a Moskva se pravidelně vzájemně obviňují z pokusů o destabilizaci.
Ruská centrální banka v pátek sdělila, že se do jejího systému letos dostali hackeři a s pomocí zfalšovaných hesel se pokusili ukrást přes dvě miliardy rublů (800 miliónů Kč). V prohlášení uvedla, že více než polovinu této částky se podařilo zachránit, kde je zbytek, ale nesdělila.
DailyMotion Hacked — 85 Million User Accounts Stolen
6.12.2016 thehackernews Incindent
This time a popular video sharing platform DailyMotion has allegedly been hacked and tens of millions of users information have been stolen.
Breach notification service LeakedSource announced the data breach on Monday after the company obtained 85.2 Million records from Dailymotion.
According to LeakedSource, the DailyMotion data breach appears to have taken place on October 20, 2016, which means it is possible that hackers have been circulating the data for over a month.
The stolen data consists of 85.2 Million unique email addresses and usernames and around 20 percent of the accounts (more than 18 Million users) had hashed passwords tied to them.
The passwords were protected using the Bcrypt hashing algorithm with ten rounds of rekeying, making it difficult for hackers to obtain user's actual password.
Bcrypt is a cryptographic algorithm that makes the hashing process so slow that it would literally take centuries to actual brute-force password of a user.
ZDNet received a sample of the stolen data and confirmed that the data came from the Dailymotion website, but representatives for Vivendi, the majority owner of Dailymotion did not yet respond to any comments.
If you are one of the 18 million DailyMotion users who had their hashed password leaked, you are advised to change your password on the entertainment website as well as on others where you have reused your password.
LeakedSource has added the DailyMotion stolen data to its search index, so you can check if your account has been affected.
Also use a good password manager to create complex passwords for different sites as well as remember them. We have listed some good password managers that could help you understand the importance of password manager and choose one according to your requirement.
Chinese hackers behind the CNACOM campaign hit Taiwan website
6.12.2016 securityaffairs APT
Security firm Zscaler have been monitoring a cyber espionage campaign dubbed ‘CNACOM’ that was targeting government organization in Taiwan.
Security researchers from the firm Zscaler have been monitoring a cyber espionage campaign dubbed ‘CNACOM‘ that was targeting government organization in Taiwan. According to the researchers, the hackers behind the CNACOM campaign are linked to China and exploited an IE vulnerability, tracked as CVE-2016-0189, patched by Microsoft early 2016.
The CVE-2016-0189 had been exploited in targeted attacks against Windows users in South Korea before Microsoft fixed it.
In order to trigger the vulnerability, victims have to visit a compromised website or open a spear-phishing email containing a malicious link.
The threat actors used watering hole attacks to spread a malware, among the sites compromised by the hackers, there is a major public service organization in Taiwan.
Experts from startup Theori have made a reverse engineering of the MS16-053 that fixed the CVE-2016-0189 flaw and published a PoC exploit for the vulnerability.
The PoC code works on Internet Explorer 11 running on Windows 10, a great gift for fraudsters that included it in the Neutrino EK as confirmed by FireEye.
Since researchers released the full proof of concept for the CVE-2016-0189 flaw, experts at Zscaler ThreatLabZ have been closely tracking its proliferation.
The exploit code for the flaw was first spotted as part of the Sundown exploit kit (EK), later it was included in the Magnitude and the KaiXin EK.
“This blog details CNACOM, a web-based campaign that appears to be related to a well-known nation-state actor more commonly associated with spear-phishing attacks.” reads the analysis published by Zscaler. “On November 7, we spotted a malicious injection on the registration page of a major Taiwanese public service website. An iframe was injected into the footer of the page, which then loaded a unique landing page containing the CVE-2016-0189 exploit code.”

The hackers behind the CNACOM campaign used the same PoC code, but they leveraged on another Internet Explorer privilege escalation flaw, tracked as CVE-2015-0016.
The experts highlighted that that CNACOM campaign specifically targeted Taiwanese government entities. The exploit code collects information from the device, including its IP address. If the victim uses the IE and the IP address belongs to the Taiwanese government, the exploit delivers a strain of the Ixeshe malware.
The Ixeshe malware has been around since at least 2009, in August 2013 security experts at FireEye observed a series of cyber attacks conducted by the Chinese APT group known as APT12 targeting the US media. The experts linked the threat actors to the campaign that targeted the New York Times in 2012.
The variant of Ixeshe malware used in the CNACOM campaign is different from older ones.
“Unlike many historical IXESHE samples, it appears that this variant doesn’t utilize campaign codes embedded in the malware itself. This may be due to a more centralized tracking system that only relies on the malware reporting a machine ID.” continues the analysis.
Government agencies and private firms in Taiwan are often victims of cyber espionage likely launched by Chinese hackers, a few weeks ago the Tropic Trooper APT hit government Taiwanese organizations and companies in the energy sector.
Another Russian Bank, the VTB bank, was hit by a cyber attack
6.12.2016 securityaffairs Cyber
The Russian state-controlled bank VTB confirmed that its websites had been targeted by a cyber attack. It is the last attack in order of time.
The Russian state-controlled bank VTB confirmed that its websites had been targeted by a cyber attack. The VTB is the second largest bank in the country.
Fortunately, the defenses of the bank were able to repel the DDoS attack that hit the systems of the VTB bank.
“A DDoS (distributed denial of service) attack was carried out against VTB Group internet sites,” reads a statement issued by the Russian bank.
“Our IT infrastructure is working as normal and the bank’s clients are not experiencing any difficulties.”

Last week the Russian intelligence service FSB revealed that an unnamed foreign power is planning to undermine Russian Banks with cyber attacks and PSYOPS via social media.
According to the Russian intelligence, a group of servers in the Netherlands and leased to the Ukrainian web hosting firm BlazingFast were ready to launch an assault next Monday.
“Russia’s domestic intelligence agency, the Federal Security Service (FSB), said that the servers to be used in the alleged cyber attack were located in the Netherlands and registered to a Ukrainian web hosting company called BlazingFast.” reported the Reuters.
“The attack, which was to target major national and provincial banks in several Russian cities, was meant to start on Dec. 5, the FSB said in a statement.”
A few hours after the announcement made by the FSB, the Russian Central Bank confirmed that hackers have stolen 2 billion rubles, roughly 31 million US dollars, from accounts at the Russian central bank.
The Russian authorities haven’t disclosed the identity of the alleged threat actor behind the attack.
The Russian bank industry was recently hit by a string of cyber attacks, a few day ago experts from Kaspersky Lab revealed that at least five of Russia’s largest banks were targeted by massive DDoS attacks.
The attacks were powered by devices located in 30 countries across the world, including the United States.
The Russian Government was accused by Washington of interference in the recent US Presidential Election.
The Office of the Director of National Intelligence and the Department of Homeland Security have issued a joint security statement to accuse the Russian government of a series of intrusions into the networks of US organizations and state election boards involved in the Presidential Election.
“The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts. These thefts and disclosures are intended to interfere with the US election process” reads the statement.
“We will take action to protect our interests, including in cyberspace, and we will do so at a time and place of our choosing,” a senior administration official told AFP.
“The public should not assume that they will necessarily know what actions have been taken or what actions we will take.”
Two weeks ago, the US Vice President Joe Biden during an interview with NBC explained that “message” would be sent to Russian President Vladimir Putin over the alleged hacking.
It is a historical declaration, for the first time in a diplomatic context, a member of a government invoke a cyber attack as a deterrent measure.
“Vice President Joe Biden told “Meet the Press” moderator Chuck Todd on Friday that “we’re sending a message” to Putin and that “it will be at the time of our choosing, and under the circumstances that will have the greatest impact.” reported the NBCnews.
“When asked if the American public will know a message was sent, the vice president replied, “Hope not.“”
According to NBC, the CIA was preparing a retaliatory cyber attack “designed to harass and ’embarrass’ the Kremlin leadership.”
Did the US launch a series of cyber attacks against the Russia as retaliation for the alleged interference in its internal affairs?
Nebezpečný malware cílí na klienty bank. Útočí na Android
5.12.2016 Novinky/Bezpečnost Android
Na pozoru by se měli mít v poslední době majitelé přístrojů s operačním systémem Android. Na tuto platformu se totiž podle všeho soustředí počítačoví piráti stále častěji. Jeden z posledních zachycených kyberútoků může udělat pěkné vrásky na čele především klientům bank, nezvaný návštěvník se je totiž snaží obrat o peníze.
Před bankovním malwarem, jejž bezpečnostní výzkumníci pojmenovali SmsSecurity, varoval Národní bezpečnostní tým CSIRT.CZ.
Počet zaznamenaných útoků navíc není podle vyjádření expertů zanedbatelný. „V poslední době bylo zaznamenáno množství útoků nové verze škodlivé aplikace SmsSecurity cílící na zákazníky bank,“ varoval Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Podle něj byly doposud zaznamenány útoky na klienty bank v Rakousku, Německu, Maďarsku, Rumunsku a Švýcarsku. Není nicméně vyloučeno, že tento nebezpečný malware se budou počítačoví piráti snažit nasadit i v Česku.
Převzetí kontroly nad zařízením
Při snaze o infiltraci škodlivého kódu jsou navíc kyberzločinci velmi vynalézaví. „Aplikace pro operační systém Android se maskuje jako součást dvoufaktorové autentizace některé z bankovních aplikací,“ podotkl Bašta.
„Podvodným oznámením o nutnosti aktualizace se škodlivý software stáhne a v dalších krocích získá kontrolu nad zařízením pomocí instalace aplikace TeamViewer QuickSupport, obvykle využívané pro vzdálenou podporu uživatelů. Cílem aplikace je kromě převzetí kontroly nad zařízením také krádež hesel,“ doplnil bezpečnostní expert.
V případě, že se uživatelé setkají s nestandardním fungováním aplikace pro internetové bankovnictví, měli by se neprodleně obrátit na zástupce své banky. A to platí i v případě, kdy ve svém mobilním přístroji objeví program, jehož původ je neznámý.
Oficiální zdroj není zárukou bezpečí
Vhodné je také stahovat veškeré aplikace pouze z oficiálních zdrojů, v případě operačního systému Android tedy přímo z Google Play. Ani tak ale uživatelé nemají 100% záruku, že budou v bezpečí.
Na podzim se totiž například v oficiálním obchodu od této internetové společnosti objevila podvodná aplikace Guide for Pokémon Go (Průvodce hrou Pokémon Go), která dokázala v chytrém telefonu udělat pěknou neplechu. Útočníci se totiž jejím prostřednictvím mohli zmocnit přístupových práv, a tím pádem i celého napadeného zařízení.
Jak je už z názvu podvodné aplikace zřejmé, útočníci se tehdy snažili využít velkého zájmu lidí o hru Pokémon Go.

Podvodná aplikace Guide for Pokémon Go
Soutěží od Seznamu přibývá. Jde ale o podvod
5.12.2016 Novinky/Bezpečnost Podvod
Se soutěžemi, ve kterých se podvodníci vydávají za zástupce společnosti Seznam.cz, se roztrhnul pytel. Lidé pro získání ceny musí zaslat prémiovou SMS, jež je vyjde klidně i na 100 Kč. Ve skutečnosti ale žádnou výhru nezískají, protože jde o podvod. V dalších soutěžích se kyberzločinci zase snaží vylákat od důvěřivců osobní údaje.
Před falešnými soutěžemi, které zneužívají logo a maskota české internetové jedničky, varovaly Novinky.cz již v říjnu.
Přesto se od té doby na stejné podvody nachytaly stovky lidí. Těm se soutěžní výzva zobrazuje nejčastěji jako reklama, a to na počítačích, tabletech i chytrých telefonech. Podvodníci tvrdí, že uživatel vyhrál nějaké atraktivní zařízení, pro jeho získání je však nutné zájem potvrdit prostřednictvím SMS zprávy.
Za tu si pak útočníci naúčtují tučný poplatek. Ten je v jednotlivých nabídkách různý, pohybuje se v řádech desetikorun, ale může se vyšplhat až na rovnou stovku.
Chtějí osobní údaje
V některých podvodných soutěžích, ve kterých se útočníci vydávají za zástupce společnosti Seznam, jde zase o osobní údaje. Když je kyberzločinci od uživatele vylákají, mohou je zneužít k dalším útokům nebo je prodat na černém trhu.

Ukázka podvodné výherní obrazovky
FOTO: Seznam.cz
Pozornější uživatelé si přitom mohou všimnout, že jde o podvod. Soutěž totiž nikdy neběží na webu české internetové jedničky, ale na úplně jiných stránkách. Některé nabídky navíc obsahují i celou řadu pravopisných chyb a špatně vyskloňovaná slova. Na podobné soutěže by uživatelé neměli vůbec reagovat.
Podvod je vhodné nahlásit
Zástupci společnosti Seznam.cz se od podvodu distancovali již dříve. „Buďte obezřetní při otvírání neznámých odkazů a všímejte si toho, kam směřují. U zpráv, které vybízejí k transakcím, platí tato rada dvojnásob. Neznámé přílohy neotvírejte a v případě, že je počítač infikován, využijte antivirový program a nezvaného útočníka odstraňte,“ poradil uživatelům Martin Kožíšek, manažer pro internetovou bezpečnost společnosti Seznam.cz.
Informovat o podobných soutěžích mohou lidé zástupce Seznamu na e-mailové adrese seznamsebezpecne@firma.seznam.cz.
Při hlášení podvodu je vhodné vložit otisk obrazovky falešné nabídky, přesnou internetovou adresu podvodu a informaci o tom, kde se s výherní nabídkou lidé setkali. Díky tomu budou moci zástupci české internetové jedničky usilovat o to, aby byly podobné soutěže na internetu zablokovány a nenapálil se nikdo další.
Uber asks to track your location even when you’re not using the app
5.12.2016 securityaffairs BigBrothers
The last update for the Uber app raises great concerns because it asks to track users’ location even when they’ve been dropped off and exited the program.
The last update of the Uber App allows it to track the passengers’ locations even when they have been dropped off and the application is running in the background of a customer’s smartphone. With this new feature, the application is able to track passenger up to five minutes after a trip has finished.

Before this upgrade, Uber was able to follow its passengers only when they had the app open.
According to Uber, the new feature has been implemented to better allow drivers and passengers in locating each other. A representative from the company explained that the upgrade will improve the user experience reducing the ETA estimates.
“We do this to improve pickups, drop-offs, customer service, and to enhance safety. Trip Related Location Data is collected during the following times:
– When you are interacting with the Uber app and the app is foregrounded and visible.
– When you’re on a trip: from the time you request a trip until when the trip is ended or cancelled by the driver, even if the Uber app is running in the background and not visible to you.
– Up to five minutes after the driver ends a trip, even if the Uber app is in the background.” reads the statement published by Uber on its website.
Anyway, don’t worry, you still have the ability to choose to share or not your data setting information sharing options to “Always” or “Never.”
Watch out, if you chose the “Never” option, every time your will need to take a ride you will be forced to enter the pick-up and drop-off locations manually.
Obviously, the upgrade has raised heated debate by privacy advocates in the US.
The Electronic Privacy Information Centre promptly filed a complaint with the US Federal Trade Commission for what it considers as “unfair and deceptive trade practice.”
Kapustkiy hacked the National Assembly of Ecuador website
5.12.2016 securityaffairs Hacking
Kapustkiy’s has breached the National Assembly of Ecuador and leaked the data via PasteBin. Once again he exploited a SQL injection.
Here we go again with a Kapustkiy’s hack, this time the young hacker has breached the National Assembly of Ecuador and leaked the data via PasteBin.
The hacker broke into the backend of the www.asambleanacional.gob.ec website accessing a total of 930 records. As proof of concept of the hack the hacker leaked roughly 550-600 records.
According to Wikipedia the National Assembly (Spanish: Asamblea Nacional) is the legislative branch of the government of Ecuador that replaced the National Congress in 2009, under the 2008 Constitution.

I reached Kapustkiy to receive more info about the data breach and he confirmed me that once again he exploited an SQLinjection flaw.
“I used an simple SQLi to gain acces and I have reported it. I did not leak real names etc..” Kapustkiy told me.
A few days ago the hacker announced to have hacked the Venezuela Army.
He also hacked the website at the High Commission of Ghana & Fiji in India and the India Regional Council as well as organizations and embassies across the world.
Recently he hacked the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy.
Data breach at the Japanese Shiseido, 420,000 users’ records exposed
5.12.2016 securityaffairs Incindent
The Japanese giant of the cosmetic industry Shiseido Co. announced a data breach. Data leak on 420,000 shoppers, including financial information.
Another week, a new data breach has been announced by the press, this time the victim is the Japanese giant of the cosmetic industry Shiseido Co.
The company Shiseido announced the incident on Friday, the hackers broke into the online store, which sells cosmetics products and that is run by the subsidiary IPSA Co.
The firm IPSA discovered the data leak when it received a report from a payment agency on Nov. 4.
The firm revealed that hackers accessed personal information on about 420,000 customers, and compromised data may have leaked.
“Japanese cosmetics maker Shiseido Co. said Friday that the online store run by subsidiary IPSA Co. has suffered illegal access and that personal information on about 420,000 customers may have leaked as a result.” reported The Mainichi website.
According to the Japanese press agency, the stolen records include customers’ names and addresses. The company confirmed that also financial data of a portion of customers may have been exposed, credit card information on up to around 56,000 of the customers may also have leaked.
The company admitted that credit card data belonging to users who made purchases at the online store between December 14, 2011, and November 4, 2016 may have been exposed.
Shiseido promptly reported the data breach to the Japanese authorities, including the Ministry of Economy, Trade and Industry. The Japanese police started an investigation on the case.
In response to the incident, IPSA company has temporarily suspended the online store.
US Presidential commission presents recommendations on cybersecurtiy
4.12.2016 securityaffairs Cyber
The US Commission on Enhancing National Cybersecurity, tasked by President Barack Obama, issued its final report with recommendations on cybersecurity.
Cyber security is a primary issue in the agenda of many countries, the U.S. Presidential commission has recently issued recommendations to urge a proactive cooperation between private and public sectors. The collaboration aims to improve the security of computer networks and counteract the action of threat actors. The U.S. presidential commission on cyber security recommended issued a “wide-ranging report” on the subject.
The commission was established early this year by an executive order from President Obama. Now the commission has released a final report that includes 16 recommendations for Obama’s administration and that of President-elect Donald Trump.
Obama Executive Order cybersecurity
The commission created by President Barack Obama earlier this year also recommended that the president and Congress accelerate the pace at which technology is updated in the federal sector and that the president appoints an ambassador for cyber security for efforts abroad.
“Technological advancement is outpacing security and will continue to do so unless we change how we approach and implement cybersecurity strategies and practices,” states the report issued by US Government.
The report details the Obama’s vision on cybersecurity that expressed great concerns on the evolution of cyber threats and provides recommendation to secure national infrastructures.
“Obama said in a statement after meeting the commission’s head, his former national security adviser Tom Donilon, on Friday that his administration strongly supported the commission’s “thoughtful and pragmatic” recommendations.” reported the Reuters.
Obama, who will leave office on Jan. 20 said he had asked the commission to brief the transition team of President-elect Donald Trump at the earliest opportunity.
“The Commission’s recommendations affirm the course that this Administration has laid out, but make clear that there is much more to do,” Obama said in a statement. “Deepening public-private cooperation will help us better protect critical infrastructure and respond to cyber incidents when they occur.”
The report identified potential attack vectors like IoT technology and the global supply chain of manufacturers, it focuses on the protection of critical infrastructure.
The commission made a number of recommendations for the incoming administration, including:
Harmonization of international cyber-security policies and global norms of behavior.
The adoption of a cyber-security “nutritional label” for impartial product safety ratings.
Justice Department and other agencies should assess the law on liabilities for harm caused by insecure internet-connected devices.
The appointment of an “ambassador for cybersecurity” who would “lead US engagement with the international community” on relevant strategies, standards and practices.
Work with other states to develop and promote global cybersecurity norms and behavior.
Improve cooperation between the government and private sector to combat cybersecurity threats.
The departments of State and Homeland Security as well as other agencies should support foreign countries in their cybersecurity efforts and promote peacetime cybersecurity norms.
Distributed Guessing Attack to hack VISA cards in just six seconds
4.12.2016 securityaffairs Attack
A group of security researchers discovered a new method dubbed Distributed Guessing Attack to hack VISA credit card in just 6 seconds.
A group of security researchers from the Newcastle University devised a method to hack VISA credit cards is just six seconds.
The technique relies on a Distributed Guessing Attack in which online payment websites are used to discover the data on VISA credit cards. The attackers submit data to online payment websites and analyze the reply to the transaction to discover whether or not the data was correct.
“Research published in the academic journal IEEE Security & Privacy, shows how the so-called Distributed Guessing Attack is able to circumvent all the security features put in place to protect online payments from fraud.” reads the press release. “
“By automatically and systematically generating different variations of the cards security data and firing it at multiple websites, within seconds hackers are able to get a ‘hit’ and verify all the necessary security data.”

Below a video PoC of Distributed Guessing Attack:
How it takes just six seconds to hack a credit card
The investigators speculated the method is likely to have been used in the recent cyber attack against the Tesco bank that resulted in the theft of £2.5m.
The researchers demonstrated that is is possible to launch a Distributed Guessing Attack to guess card numbers, expiry dates and security codes of any Visa credit or debit card. The method is simple as effective, the experts discovered that online payment systems don’t detect multiple invalid payment requests from different websites. An attacker can try an unlimited amount of guesses on each card data field splitting the attempts os several websites. The attackers can make between 10 and 20 guesses on each website.
“This sort of attack exploits two weaknesses that on their own are not too severe but when used together, present a serious risk to the whole payment system,” explains Mohammed Ali, a PhD student in Newcastle University’s School of Computing Science and lead author on the paper.
“Firstly, the current online payment system does not detect multiple invalid payment requests from different websites. This allows unlimited guesses on each card data field, using up to the allowed number of attempts – typically 10 or 20 guesses – on each website.
“Secondly, different websites ask for different variations in the card data fields to validate an online purchase. This means it’s quite easy to build up the information and piece it together like a jigsaw.”
Ali explained that attackers can gather the card information one field at a time making impossible for merchants to detect the fraudulent activity.
“The unlimited guesses, when combined with the variations in the payment data fields make it frighteningly easy for attackers to generate all the card details one field at a time.”
The attacker can use each generated card field in succession to generate the next field and so on.
“So even starting with no details at all other than the first six digits – which tell you the bank and card type and so are the same for every card from a single provider – a hacker can obtain the three essential pieces of information to make an online purchase within as little as six seconds.”
The researchers highlighted that only the VISA network was vulnerable to the Distributed Guessing Attack.
The MasterCard network is centralized and is able to detect a Distributed Guessing Attack after less than 10 attempts, even when those payments were distributed across multiple networks.
Experts from CloudFlare spotted a new dangerous botnet
4.12.2016 securityaffairs BotNet
Security experts from CloudFlare observed a new botnet that emerged in the wild and it could be dangerous as its predecessor Mirai.
Which is the most dreaded botnet in the current threat landscape? The Mirai botnet of course, it was used by threat actors in the wild to power massive DDoS attack, such as the one that hit the Dyn DNS service.
Now, security experts observed a new botnet is emerging in the wild and it could be dangerous as its predecessor Mirai.
The botnet was first spotted on November 23 by researchers at the content delivery network CloudFlare.
The DDoS attacks lasted 8.5 hours, attackers launched the offensive for six days at roughly the same time. The attacks were peaking at 400Gbps and hitting 320Gbps for hours on end.
“On November 23, the day before US Thanksgiving, our systems detected and mitigated an attack that peaked at 172Mpps and 400Gbps.” states the report published CloudFlare. “The attack started at 1830 UTC and lasted non-stop for almost exactly 8.5 hours stopping at 0300 UTC. It felt as if an attacker ‘worked’ a day and then went home.”
The new string of cyber attacks are not powerful such as the ones launched through the Mirai malware, but anyway, they reached a significant volume.
Researchers discovered that the attacks are not powered from the Mirai botnet because they are launched from a differed software and are very large Layer3 and Layer4 DDoS attacks.
The researchers observed that the attacks were concentrated in a small number of locations mostly on the US west coast.
CloudFlare did not disclose further details of the DDoS attacks, it is not clear if the botnet is composed of IoT devices such as Mirai.
The new botnet will likely continue to grow and most experts fear it could be combined with other malicious infrastructure powering unprecedented DDoS attacks.
Russian Central bank loses $31 million in cyber heist
3.12.2016 securityaffairs Hacking
It’s official, hackers have stolen 2 billion rubles, roughly 31 million US dollars, from accounts at the Russian central bank.
While I was reporting the news that the FSB unnamed foreign hackers are planning to undermine Russian Banks, the Russian Central Bank confirmed hackers have stolen 2 billion rubles (roughly $31M) in cyber attacks
Central bank official Artyom Sychyov confirmed the incident and added that the hackers had attempted to steal much more, about 5 billion rubles.
“We were lucky to return some of money,” said a Russian central bank spokesperson.

Sychyov was commenting on a central bank report released yesterday by the FSB. The hackers broke into bank accounts by faking a client’s credentials. The bank provided few other details in its lengthy report.
“Hackers stole more than 2 billion rubles ($31 million) from correspondent accounts at the Russian central bank, the bank said on Friday, the latest example of an escalation of cyber attacks on financial institutions around the globe.” reported the Reuters.
At the time I was writing there are no details about the attack.
The recent string of attacks against the SWIFT system urged financial regulators around the world to force banks to beef up cyber security.
In September the SWIFT disclosed more attacks against banks worldwide, pressures banks on security and urged member banks to implement the new SWIFT software by November 19.
In the last months, a worrisome string of cyber attacks against banks worldwide through the SWIFT system has alarmed the banking industry. The so-called “SWIFT hackers” have conducted multiple cyber attacks against financial institutions. We reported the successful cyber heists on the Bangladesh bank, against a Ukrainian bank, and the Ecuadorian bank, meanwhile, a Vietnam bank reported to have blocked an ongoing cyber heist.
In May, a fourth Bank in the Philippines was a victim of the SWIFT hackers and the experts at Symantec confirmed the malware used by the crooks shares code with tools used by the notorious Lazarus group linked to the North Korean Government.
According to the Reuters agency, the SWIFT issued a new warning urging member banks to implement the new SWIFT software by 19 November.
The latest version of SWIFT’s software implements new security features specifically designed to defeat such kind of attacks. The authentication processes have been improved such as the implementation of mechanisms to early detect fraudulent activities.
FSB accuses foreign hackers of plotting to undermine the Russian banks
3.12.2016 securityaffairs Hacking
According to the FSB unnamed foreign hackers are planning to undermine Russian Banks with cyber attacks and PSYOPS via social media.
The Kremlin is accusing unnamed foreign hackers of plotting to undermine the Russian banks in the country.
The Russian Government believes that foreign powers plan to conduct a PSYOps to destabilize the banks. Hackers could combine the diffusion of fake documents about the status of Russian banks with massive cyber attacks.
The news was spread by the Russia’s intelligence service, the FSB. According to the Russian intelligence, a group of servers in the Netherlands and leased to the Ukrainian web hosting firm BlazingFast were ready to launch an assault next Monday.
“Russia’s domestic intelligence agency, the Federal Security Service (FSB), said that the servers to be used in the alleged cyber attack were located in the Netherlands and registered to a Ukrainian web hosting company called BlazingFast.” reported the Reuters.
“The attack, which was to target major national and provincial banks in several Russian cities, was meant to start on Dec. 5, the FSB said in a statement.”
russian banks
Servers physically located in the Netherlands and leased to BlazingFast, a Ukrainian web-hosting firm, were primed to launch an assault next Monday.
“It was planned that the cyber attack would be accompanied by a mass send-out of SMS messages and publications in social media of a provocative nature regarding a crisis in the Russian banking system, bankruptcies and license withdrawals.” reads a statement issued by the FSB.
“The FSB is carrying out the necessary measures to neutralise threats to Russia’s economic and information security.”
The Russia’s central bank confirmed to the Reuters agency that it was aware of the imminent threat, for this reason, it is working with the security services.
“The situation is under control. Banks have been given necessary guidance,” the central bank said. “Banks have been given necessary guidance.”
Anton Onoprichuk, the director of the firm BlazingFast, told Reuters that he was not aware of the alleged plan of attack, neither the FSB nor any other intelligence agency had been in touch with him.
Recently Russian banks were targeted by a series of massive DDoS attacks powered by the Mirai IoT botnet.
50 Million installations potentially impacted by AirDroid issues
3.12.2016 securityaffairs Android
At least 10 million Android users are exposed to cyber attacks due to multiple vulnerabilities affecting the popular AirDroid app.
According to experts from the firm Zimperium, multiple vulnerabilities in the Android remote management tool AirDroid could expose more than 50 million devices
The flaws could be exploited to abuse built-in features and use them against the application’s users.
Experts highlight that AirDroid uses insecure communication channels allowing attackers to power Man-in-the-Middle (MitM) attacks and other types of attacks.
Researchers from Zimperium discovered that communication channels used to send authentication data to the statistics server are not properly protected because the encryption key is hardcoded inside the application.
An attacker that shares the same network with the victim could run MitM attacks to capture authentication credentials from the first HTTP request the application performs, and use them to act on behalf of the user.
“A malicious party could perform a MITM network attack and grab the device authentication information as shown in the “Details” section from the very first HTTP request the application performs.” reads the blog post published by Zimperium. “This HTTP request can be decrypted at runtime using the 890jklms key hardcoded inside the application and the authentication fields parsed from the resulting JSON.
Having this information, the attacker can now impersonate the victim’s device and perform various HTTP or HTTPS requests on its behalf to the AirDroid API endpoints.
For instance, a payload like the following ( encrypted in DES with the same exact key ) can be sent to the https://id4.airdroid.com/p14//user/getuserinfoviadeviceid.html endpoint :”
Tha attacker could craft a payload encrypted in DES with the same key to trick the server into revealing user information, including the email and password hash.

The attacker could power a MitM attack alto to redirect HTTP traffic to a malicious transparent proxy that allows him to modify the response for the /phone/vncupgraderequest. In this way the attacker could inject a fake update or could execute malicious code remotely.
“Moreover, an attacker performing a MITM attack and redirecting HTTP traffic to a malicious transparent proxy, could modify the response for the /phone/vncupgrade request which is normally used by the application to check for addons updates:
GET /p14/phone/vncupgrade/?q=[DES ENCRYPTED PAYLOAD]&ver=20151 HTTP/1.1
Host: srv3.airdroid.com
Connection: close
User-Agent: Apache-HttpClient/UNAVAILABLE (java 1.4)
Injecting a new update, thus remotely executing custom code on the target device, is just a matter of modifying this response:”
In order to fix these issues, the AirDroid should use only secure communication channels (HTTPS), should implement key pinning to avoid SSL MitM, should use safe key exchange mechanisms, and should leverage and digital verify the update files.
Útočili na nás hackeři, tvrdí ruská Centrální banka
2.12.2016 Novinky/Bezpečnost Hacking
Do systému ruské Centrální banky se letos dostali hackeři a s pomocí zfalšovaných hesel se pokusili ukrást přes dvě miliardy rublů (800 milionů korun). Hlavní ruská banka to v pátek oznámila v Moskvě. Víc než polovinu částky se podařilo zachránit, stojí v prohlášení. Kam se poděl zbytek, banka neuvádí.
Informaci o hackerském útoku obsahovala bankovní výroční zpráva o stabilitě ruského finančního systému.
„Rizika kybernetických útoků mohou ovlivňovat finanční stabilitu, jsou-li terčem strategicky důležité banky a opory finanční infrastruktury,“ uvádí se v prohlášení.
Ruská kontrarozvědka FSB v pátek obvinila „zahraniční zpravodajské služby“, že se chystají s pomocí kybernetických útoků destabilizovat ruský finanční systém.
Centrála, odkud se útoky údajně mají řídit, se nachází v Nizozemsku a patří ukrajinské společnosti BlazingFast. Ta uvedla, že podezření prověří. Sérii útoků prý chystají cizí tajné služby už v pondělí.
Vše pod kontrolou
Rusko varovalo před útoky ze zahraniční nedlouho po informaci amerických bezpečnostních služeb, že ruští hackeři podnikli útoky na servery Demokratické strany s cílem ovlivnit prezidentské volby. Viceprezident Joe Biden tehdy pohrozil, že USA na ruské útoky „náležitě“ odpoví.
Po varování FSB se pátek v ruském tisku objevily zprávy ujišťující veřejnost, že finanční systém je proti kybernetickým útokům zajištěn. Dokonalou ochranu před hackery mají prý hlavní banky, Centrální banka má jejich bezpečnostní zajištění pod kontrolou.
Také hlavní ruští mobilní operátoři a poskytovatelé přístupu do internetu ujistili uživatele, že žádné nebezpečí nehrozí.
Kapustkiy hacked a website belonging to the Venezuela Army
2.12.2016 securityaffairs Hacking
The hacker Kapustkiy has breached the Venezuela Army and leaked 3000 user records containing personal information such as names, emails, and phones.
We left the young hacker Kapustkiy after his hack at the High Commission of Ghana & Fiji in India when he also confirmed to have joined the Powerful Greek Army hacked crew.
The hacker breached the India Regional Council as well as organizations and embassies across the world. Recently he hacked the ‘Dipartimento della Funzione Pubblica’ Office of the Italian Government, the Paraguay Embassy of Taiwan (www.embapartwroc.com.tw), and the Indian Embassies in Switzerland, Mali, Romania, Italy, Malawi, and Libya. Kapustkiy.
Now the hacker is back announcing that he left the Powerful Greek Army and that he hacked the Venezuela Army.
Segui
Kapustkiy @Kapustkiy
Venezuela Army #Leaked http://pastebin.com/8iXAFJj8 3000 Users Exposed CC: @fbajak @jammastergirish @RCTVenlinea @Noticias24
09:59 - 2 Dic 2016
1 1 Re 9 9 Mi piace
Kapustkiy has hacked the Venezuela Army and leaked 3000 user records on Pastebin containing personal information such as names, emails, and phones.

The hacker breached the CATROPAEJ (“Caja de Ahorros de la Tropa Profesional del Ejercito Bolivariano Venezolano”) database, he also discovered some logins for the Army’s webmail system, but he did use them.
I reached Kapustkiy that confirmed me the exploitation of an SQLi vulnerability in the target application.
He triggered an Error-Based SQL Injection, this means that he tried to trigger errors in the database by passing unsanitized input in the URL.
Kapustkiy reported the problem to Venezuela Army more than a week ago, but he received no reply.
He told me that he is focusing on South America Governments and Asian organizations.
The Immaterial Khilafah – Global Intelligence Insight Report
2.12.2016 securityaffairs Cyber
As the coalition forces started to enter the Iraqi city of Mosul, many have seen Al-Baghdadi’s speech as desperate plea, exhorting his fighters to stand and fight for the Caliphate until their dying breath while he was cowardly running away from the fray.
“Turn the disbelievers’ night into day, bring destruction to their homes, make their blood flow like rivers, for therein you will find the richest share of reward and means for achieving great success, attaining the companionship of those upon whom Allah has bestowed favor: the prophets, the truthful, the martyrs, and the righteous.”
Abu Bakr Al-Husayni Al-Baghdadi
Audio release through Al Furqan Media Agency, November 02nd, 2016
As the coalition forces started to enter the Iraqi city of Mosul, many have seen Al-Baghdadi’s speech as desperate plea, exhorting his fighters to stand and fight for the Caliphate until their dying breath while he was cowardly running away from the fray.
But the truth may very well require a more in-depth analysis though. As we monitor hundreds of protected channels, correlate trends and analyze communication patterns at Global Intelligence Insight, for some months the idea of a “new” type of jihad – in terms of methodology – has been gaining significant strength and popularity among online jihadists, who seem increasingly engaged and eager to learn and play an active role in it. And this idea is set on two main pillars:
The what: “Immaterial Caliphate”
The how: Urban Warfare
terrorism-1
Eulogy to Abu Baseer Nasir Al-Wihaishi, Inspire Magazine, vol. 16, Al-Malahem Media
After losing the cities of Fallujah, Manbij and Dabiq, and the eventual fall of Mosul and Raqqah – it’s just a matter of when – the self-proclaimed Islamic State is facing severe difficulties in recruiting, smuggling and funding its operations and resistance. Plus, precise chirurgical drone strikes have been taking down important figures one by one, like the instigators Mohammed Al-Adnani and Al-Furqan, or even the minister of war Mohammed Al-Shishani, among many others of the group’s core. Allegedly, Al-Baghdadi himself escaped from an American reaper’s hellfire as the battle for Mosul begun.
Nonetheless, even when faced with such apparent adversity, it seemed to us that the senior online pro-ISIS subjects under our monitoring grid were accepting these events as if they were already expecting them. A good example is this brief interview/chat that George Washington University’s Fellow and Researcher Amarnath Amarasingam, had with an ISIS fighter following the loss of Dabiq, posted on Twitter in mid-October:

Looking beyond the “play-it-cool & and play-it-down” attitude (and do not be surprised, they use slang terms like ‘LOL’ just as everyone else), the main idea of having a physical caliphate confined to Syria and Iraq is deeply erroneous and short-sighted. As matter of fact, they believe the caliphate lives in each mujaheed’s heart, especially of the ones spread out across the West, living under the anonymity of major European cities. Hence, the “we don’t fight for land” and “there will always be land” speech.
We have been observing this idea of a “new” non-physical caliphate growing stronger online, as the group’s fighters on the ground in both Syria and Iraq – the ones who did not defect, firmly convinced they’re fighting a holy war – know they will lose but are ready and more than willing to die fighting.
The bottom line is: Iraq and Syria can be purged of ISIS’s physical presence. But the idea of an immaterial caliphate, set on a twisted metapolitical conception of violence, spread out and festering through underground cells and lone wolves – many of them seasoned ex-fighters with tactical experience that managed to flee the conflict zones – will be much harder to tackle.
But how do they intend to proceed? Through hundreds of non-centralized online command structures, not necessarily interconnected, aiming to organize persistent but low-level attacks to soft targets in a first stage, that may gradually increase in terms of scope or degree.
Instructions on how to carry attacks with knives and/or other sharp objects in public places, US Army and US Marine Corps manuals “Close Quarter Combat”, “Kill or Get Killed” and “Military Ops in Urbanized Terrain”, kravmaga manuals, CIA manuals on how to live a double life and avoid detection, and detailed manuals on secure online comms clearly written by IT professionals were widely distributed throughout hundreds of encrypted, protected and/or invite-only pro-ISIS communication platforms. All of this aiming to train lone wolves and sleeper cells to be immediately activated upon request.
The following stage of this urban warfare is planned to be focused on the use of homemade bombs (pressure cooker bomb, trapdoor bomb, magnetic car-bomb and parcel bomb), suicide drones rigged with explosives and DIY fire weapons in crowded areas. We have also noticed a growing investment of resources in how these instructions and incitements are being released: firstly, through somewhat dense manuals, then in pro-ISIS media agencies’ magazines like Dabiq, Inspire, Rumiyah or Al-Risalah using easy-to-read flowcharts, and more recently through videos with gore executions.
The dedication spent on how well the message is convened and how effectively it will be assimilated by who reads/sees it, is also a clear sign of their commitment. We can see it also on the languages used by their propaganda machine. Some examples:

Instructions on how to make a pressure cook bomb, Inspire Magazine, Vol 16, Al-Malahem Media

Video released by Ar-Raqqah Media with ISIS fighter Abu Nur ash-Shami showing how to produce explosives with simple, easy-to-get materials, November 25th 2016

Latest Al-Furat Media’s Dabiq Magazine, translated to Finnish language

Al-Hayat Media center claims it can deliver propaganda in more than 30 different languages
As we have been explaining in every report we have been delivering to our clients, one of the most direct and clear indicators of the spread of radicalization in a certain country, is not only the language(s) used in propaganda, or in which language sleeper cells or lone wolves communicate. Instead, it’s the quality of the languages used. The translation of the latest Dabiq to native Finnish is a perfect example of this, besides the common use of native Arabic, French, English, Italian, German and Urdu – these are always a given.
While everyone has their eyes set on the physical caliphate in Syria and Iraq, with western and eastern media clashing every day, each side constantly trying to sell us their story on what is happening in Aleppo, other pieces of this intricate chess table are moving.
The idea of having a new underground spread-out worldwide caliphate of terror – a new model of caliphate – is already being prepared, and it has now become the focus for pro-ISIS online instigators and preachers, and a growing general trend among hundreds of encrypted communication channels under our surveillance.
NOTE: This brief article is part of a full intelligence report developed by Global Intelligence Insight, available under subscription. Contact us to access our database.
A flaw allows to bypass the activation lock on iPhone and iPad
2.12.2016 securityaffairs Apple
Researchers discovered a bug that can be exploited to bypass Apple’s Activation Lock feature and gain access to the homescreen of locked Apple devices.
Security experts have discovered a new bug that could be exploited to bypass Activation Lock feature on Apple devices (iPhone, iPad).
The bug could allow gaining access to the homescreen of a locked device running the latest version of the Apple iOS.
Researchers reported at least two different variations of the issue, a first one working on iOS 10.1 and the second one on the latest iOS 10.1.1.
In case of a theft or loss of an Apple device (iPhone, iPad or iPod), users can activate the Lost Mode through the Find My iPhone service.
This mode automatically enables the Activation Lock to prevent the reactivation of the device without the owner’s permission.
When a user starts a locked device, he is prompted to connect to a Wi-Fi network. In case the “Other Network” option is selected, the user must enter the name of the network and choose a security protocol (e.g. WEP, WPA2, etc.).

Of course, the user has to provide a username and a password, but researchers noticed that there is no limitation on the number of characters that can be entered into the name, username and password fields.
An attacker can trigger a crash that exposes the device’s homescreen by entering a very long string into these fields.
The crash can be caused one of the following methods: Apple’s iPad smart cases, which cause the device to wake or sleep when the case is opened or closed.
Leveraging on the Apple’s iPad smart cases, which cause the mobile device to wake or sleep when the case is opened or closed.
Leveraging the screen rotation feature and Night Shift mode as demonstrated in the video PoC published by Vulnerability Lab.
Apple iOS v10.1.1 - iCloud & Device Lock Bypass via local Buffer Overflow Vulnerability Video
The first method was first analyzed by Hemant Joseph, who tested the Activation Lock feature after purchasing a locked iPad from eBay. The method worked on iOS 10.1 and was fixed by Apple with the iOS 10.1.1 release.
The second method was discovered by researchers at Vulnerability Lab and works also on iOS 10.1.1.
How much money earns cybercriminals? Mostly from $1,000 to $3,000, but …
2.12.2016 securityaffairs Crime
According to a report published by the threat intelligence firm Recorded Future cybercriminals earn between $1,000 and $3,000 a month.
How much money earns a cyber criminal? According to a report published by the threat intelligence firm Recorded Future crooks earn between $1,000 and $3,000 a month, but one of five earns $20,000 a month or more reaching also $200,000.The curious report gives us an idea about the criminal underground and its financial aspects. Researchers from Recorded Future is based on a survey conducted by a closed underground community.
“We actually saw criminals who made way more than that, $50,000 to $200,000 a month,” he said. “This is what they keep, this is not revenues, but pure profit. This is what they can spend on loose women, fast cars and nice clothes.” explained Andrei Barysevich, director of advanced collection at Recorded Future.
Recorded Future was investigating activities in invitation-only cybercriminal forums when discovered the precious information.
“Recorded Future has recently identified a survey, conducted among members of a closed underground community, revealing that the majority of cyber criminals are earning a mere $1,000 to $3,000 a month, while only 20% are earning significantly larger amounts of $20,000 a month or more.” reads the report.
Roughly two hundred cyber criminals anonymously participated in the survey and revealed details about how they worked, including financial aspects of their dirty affairs.
“What we saw actually supported our previous research,” Barysevich said. This is what they keep, this is not revenues, but pure profit. This is what they can spend on loose women, fast cars and nice clothes.“Our job involves engaging with cybercriminals and we talk to them all the time,” he added. “And they share with us quite intimate details, which city they are in, if they actually have a regular job, if they have families. And we see a lot of weird stuff.”
Who are the cyber criminals in these criminal underground communities? Are they part of established criminal groups or lone actors?
The survey revealed that they are mostly lone actors with a clean criminal record that maintain a stable day job and that occasionally is involved in criminal activities. The researchers believe that they are introduced to the criminal underground during their early college years and remain active for a long to follow.
Anyway the significant portion of criminals is aggregated in cyber-criminal syndicates which maintain a strict hierarchy that includes highly skilled members.
“A typical group is controlled by a single mastermind “boss” — a very intelligent and highly educated person — and includes bankers with extensive connections in the financial industry to arrange money laundering and cash out of stolen funds.” continues the report.
cybercriminals
Individuals who run criminal syndicates are considered by law enforcement the most dangerous and prolific actors of these communities.
“They are not dilettantes,” he said. “They are professionals, but in real life, and in cybercrime. They plan their operations very carefully, they have trusted people on the team of different professionals, so they have lawyers and ex-law enforcement officers. They also have professional forgers if they need to establish shell companies and need fake documents. They have people responsible for money laundering. They have real estate developers that help them build a legitimate business empire on the profits they make from illegal activities.”
The monitoring and the analysis of activities in the dark web are crucial for understanding cyber crime trends and to contrast their action.
Rule 41 — FBI Gets Expanded Power to Hack any Computer in the World
1.12.2016 thehackernews BigBrothers
Hacking multiple computers across the world just got easier for the United States intelligence and law enforcement agencies from today onwards.
The changes introduced to the Rule 41 of the Federal Rules of Criminal Procedure by the United States Department of Justice came into effect on Thursday, after an effort to block the changes failed on Wednesday.
The change grants the FBI much greater powers to hack into multiple computers within the country, and perhaps anywhere in the world, with just a single warrant authorized by any US judge (even magistrate judges). Usually, magistrate judges only issue warrants for cases within their jurisdiction.
That's the same the FBI did in its 2015 investigation into child pornography site Playpen, in which the agency hacked into some 8,700 computers across 120 different countries.
The Supreme Court approved the changes to Rule 41 in April, allowing any U.S. judge to issue search warrants that give the FBI and law enforcement agencies authority to remotely hack computers in any jurisdiction, or even outside the United States.
Democratic Senator Ron Wyden attempted three times to block changes to Rule 41 that potentially risks people using Tor, a VPN, or some other anonymizing software to hide their whereabouts, but the efforts were blocked by Republican Senator John Cornyn of Texas.
The rule change should take effect on 1st December, today, barring surprises.
On the one hand, privacy advocates and legal experts have described the rule change as the extensive expansion of extraterritorial surveillance power that will allow agencies like the FBI to carry out international hacking operations with a lot less of a hassle.
On the other hand, the DOJ argued that the changes to the rule will help investigate modern internet criminals, allowing investigators access computers whose locations are "concealed through technological means," like the Tor anonymity network or VPNs (Virtual Private Networks), and devices used in botnets that have become powerful cyber weapons.
Assistant Attorney General Leslie Caldwell highlighted these concerns in a blog post published last week, saying if a criminal suspect is using Tor or VPN to hide its real location, it becomes tough for investigators to know his/her current location.
"So in those cases, the Rules do not clearly identify which court the investigators should bring their warrant application to," Caldwell said.
But what would happen if the FBI hacks the botnet victims, rather than the perpetrators? Or what if the government abuses this power to target nation states?
In a speech, Wyden said that the changes to Rule 41 amounted to "one of the biggest mistakes in surveillance policy in years," giving federal investigators "unprecedented authority to hack into Americans' personal phones, computers, and other devices," Reuters reports.
Other critics worry that the changes to Rule 41 would give the FBI unfettered ability to hack innocent users whose electronic devices have been infected with botnet malware without their knowledge, or anyone who keeps their identities private online.
To this concern, Caldwell argued that investigators accessing the devices of botnet victims "would, typically, be done only to investigate the extent of the botnet," or in order to "obtain information necessary to liberate victims’ computers from the botnet."
Caldwell further argued that the rule change would not allow the FBI to conduct "Mass Hacking;" in fact, failing to implement the rule change "would make it more difficult for law enforcement to combat mass hacking by actual criminals."
The dreaded Shamoon Wiper is back in a new attack
1.12.2016 securityaffairs Virus
Shamoon wiper is back, security experts from Palo Alto Networks and Symantec spotted it in an attack on a single Saudi company.
Do you remember the Shamoon malware?
Shamoon, also known as Disttrack, was first spotted in a wave of attacks that targeted companies in Saudi Arabia in 2012. Among the victims, there was the petrol giant Saudi Aramco. The principal capability of Shamoon is a feature that allows it to wipe data from hard drives of the infected systems.
In the attack against Saudi Aramco Shamoon wipe data on over 30,000 computers and rewrite the hard drive MBR (Master Boot Record) with an image of a burning US flag.
The first team that discovered the malware was Kaspersky Lab that had analyzed some instances of the threat linked to the “wiper agent” due to the presence of a module of a string with a name that includes “wiper” as part of it.
The researcher of Seculert who analyzed Shamoon discovered that it has also the ability to overwrite the machine’s MBR. Before Shamoon makes unusable the infected PC, it gathers data from the victim, it steals information, taking data from the ‘Users’, ‘Documents and Settings’, and ‘System32/Drivers’ and ‘System32/Config’ folders on Windows computers, and send them to another infected PC on the same internal network.
The malware was developed to destroy target systems, making the machine unusable. The malware was able to infect several OSs, including Windows 95, Windows 98, Windows XP, Windows 200, Windows Vista, Windows NT, Windows ME, Windows 7, Windows Server 2003, and Windows Server 2008.
Now the threat is back, security experts detected it in a new wave of attacks. Experts from Palo Alto Networks and Symantec reported an attack a single Saudi company.
“Why Shamoon has suddenly returned again after four years is unknown. However, with its highly destructive payload, it is clear that the attackers want their targets to sit up and take notice,” reported Symantec.
“Last week, Unit 42 came across new Disttrack samples that appear to have been used in an updated attack campaign. The attack targeted at least one organization in Saudi Arabia, which aligns with the targeting of the initial Shamoon attacks. It appears the purpose of the new Disttrack samples were solely focused on destruction, as the samples were configured with a non-operational C2 server to report to and were set to begin wiping data exactly on 2016/11/17 20:45. In another similarity to Shamoon, this is the end of the work week in Saudi Arabia (their work week is from Sunday to Thursdays), so the malware had potentially the entire weekend to spread. The Shamoon attacks took place on Lailat al Qadr, the holiest night of the year for Muslims; another time the attackers could be reasonably certain employees would not be at work.” reads an analysis published by Palo Alto Networks.
The new variant of Shamoon detected by the experts is able to rewrite the MBR on affected computers with an image of a three-year-old Syrian boy named Alan Kurdi that lay dead on a Turkish beach.
According to Symantec, this is a carefully planned operation. The malware was configured with passwords that appear to have been stolen from the targeted organizations. Attackers used these credentials to rapidly spread the threat across the targeted organization’s network. It is still unclear how the attackers obtained the credentials, anyway this .
The malware comes with a default configuration, it launched the disk-wiping component at 8:45pm local time on Thursday, November 17. Considering that in Saudi Arabia the working week runs from Sunday to Thursday, the attacker tried to exploit the pause in order to maximize the effects of the attack.
“The malware had a default configuration that triggered the disk-wiping payload at 8:45pm local time on Thursday, November 17. The Saudi Arabian working week runs from Sunday to Thursday. It would appear that the attack was timed to occur after most staff had gone home for the weekend in the hope of reducing the chance of discovery before maximum damage could be caused.” wrote Symantec.
The attack was planned to start on Laylat al Qadr (Night of Decree) that is a Muslim holiday.
The analysis of the malware revealed that is was almost identical to the one used in the 2012 attacks.
Its infrastructure is composed of three components, a dropper, a wiper, and a module for communications that assured the attackers to remotely control the malware.
In the recent attack, the component for the remote communications was configured with the IP 1.1.1.1, that didn’t host the Shamoon C&C server. This circumstance suggests that attackers plan did not include the possibility of changing the treat.
According to PaloAlto Networks, from a functionality standpoint, the wiper is powered by EldoS RawDisk driver utility that is able to overwrite files on the system without any interaction with the OS.
Experts believe that the group behind this last attack is the responsible for the 2012 hack too, for example, the researchers noticed that the EldoS RawDisk driver altered the infected host’s system time to August 2012, just a day before the expiration date for the driver’s temporary license. The license was the same used in the 2012 attacks.
“The current attack campaign has several TTP overlaps with the original Shamoon campaign, especially from a targeting and timing perspective. Also, Disttrack malware used in the recent attacks is very similar to the variant used in the 2012 attacks, which uses the exact same RawDisk device driver as well (down to the same, temporary license key).. The main purpose of the Disttrack malware is to overwrite files and storage partitions in an attempt to destroy data and render the system unusable. To maximize its destruction, the Disttrack tool attempts to spread to other systems on the network using stolen administrator credentials, which suggests that the threat actors had previous access to the network or carried out successful phishing attacks prior to the attack using Disttrack.”states PaloAlto Networks.
Give a look at the report that includes also IoC for the last Shamoon attack.
Firefox má kritickou chybu. Oprava zatím chybí
1.12.2016 Novinky/Bezpečnost Zranitelnosti
Kritická bezpečnostní chyba byla objevena v internetovém prohlížeči Firefox. Útočníci ji mohou zneužít k tomu, aby do cizího počítače propašovali škodlivý kód. Záplata opravující trhlinu přitom zatím není k dispozici.
Internetový prohlížeč Firefox
Před chybou, kterou mohou zneužít počítačoví piráti, varoval Národní bezpečnostní tým CSIRT.CZ.
„Webový prohlížeč Mozilla Firefox obsahuje chybu, pomocí které může útočník spustit škodlivý kód. Společnost Mozilla potvrdila, že se chyba nachází ve verzích 41 až 50,“ uvedl Pavel Bašta, bezpečnostní analytik týmu CSIRT.CZ, který je provozován sdružením CZ.NIC.
To jinými slovy znamená, že kyberzločinci mohou na cizí stroj propašovat prakticky libovolný virus. A klidně i na dálku celou sestavu ovládnout.
V ohrožení jen uživatelé Windows
V ohrožení jsou však podle Bašty pouze uživatelé na operačním systému Windows. Firefox na jiných platformách totiž tuto chybu neobsahuje.
Vyzrát na tuto trhlinu mohou uživatelé i přesto, že záplata zatím chybí. Stačí nainstalovat vhodný doplněk. „Dočasně je možné se chránit používáním doplňků jako NoScript apod.,“ konstatoval bezpečnostní analytik.
Zástupci společnosti Mozilla již potvrdili, že na opravě pracují. Kdy bude vydána, však doposud neprozradili.
Z pornowebu Xhamster unikly přihlašovací údaje, útočníci jich získali 380 tisíc
1.12.2016 Živě.cz Incidenty
Xhamster, který je po Pornhubu nejpopulárnější web s pornoobsahem, řeší závažný problém – z jeho databáze útočníci získali údaje o 380 tisících uživatelích. Jde především o jména, loginy a také špatně šifrovaná hesla. O incidentu informoval Motherboard s odvoláním na Leakbase.
Data mají pocházet z tohoto roku, kdy útočníci objevili mezeru v zabezpečení databáze. Hesla mají být podle Leakbase zabezpečena pouze pomocí hašovacího algoritmu MD5 bez soli, a tudíž snadno dešifrovatelná.
Xhamster je po Pornhubu druhý nejpopulárnější pornoweb
Mezi e-maily se již tradičně nachází i několik exemplářů patřící členům armády Spojených států nebo 30 e-mailů různých vládních složek. Což samozřejmě nemusí znamenat, že se jejich prostřednictvím registrovali přímo majitelé, Xhamster totiž v minulosti nevyžadoval ověřování adresy.
Po zveřejnění databáze a rozšíření zprávy v médiích zareagoval na incident mluvčí Xhamsteru. Podle něj se jedná o fhack, tedy falešný hack. Jejich databáze je prý zabezpečena mnohem lépe a k úniku dat nedošlo. Na druhou stranu, redaktoři webu Motherboard vzali náhodných 50 e-mailů z úniku a pokusili se je zaregistrovat. Ve všech případech web vracel chybovou zprávu o tom, že e-mail je již registrován.
Ať už je realita jakákoliv, uživatelé webu by neměli otálet se změnou přihlašovacích údajů. A to především v případě, že stejné údaje používají na více službách.
Infikované hlasovací přístroje? Rusko se podle expertů snažilo ovlivnit americké volby
1.12.2016 Novinky/Bezpečnost Viry
Ruská vláda během kampaně před americkými prezidentskými volbami nejen prováděla hackerské útoky, po kterých zveřejňovala citlivé dokumenty s cílem zamíchat s jejich výsledkem, ale využívala také sociální média jako zbraň k ovlivnění pohledu na hlasování. Podle agentury Bloomberg to tvrdí americká společnost FireEye, která se zaměřuje na kybernetickou bezpečnost. Ruští představitelé zásah do amerických voleb opakovaně odmítají.
Analytici FireEye prověřili tisícovky dokumentů, internetových příspěvků a odkazů a dospěli k závěru, že materiál ukradený z amerických sítí ruskými tajnými službami byl na internetu masivně propagován. Využívány k tomu byly i falešné webové účty či odkazování na smyšlené a zavádějící informace. Vše prý navíc neslo podobné stopy dřívějších kybernetických aktivit Ruska proti Gruzii, Ukrajině či Estonsku.
„Vzestup Ruska jako kybernetické mocnosti se dostal na úplně jinou úroveň, než tomu bylo kdy dříve," řekl šéf firmy David DeWalt. „Zažili jsme něco, co je podle mě v dějinách americké demokracie, pokud jde o kampaň Ruska, možná tou největší historickou událostí," dodal. Operaci Moskvy označil za zcela novou a agresivní eskalaci situace v kybernetickém prostředí.
Těsnost listopadových voleb, ve kterých zvítězil republikán Donald Trump, upřela pozornost na šíření falešných zpráv a přiměla kandidátku Strany zelených Jill Steinovou požádat o přepočet hlasů v klíčových státech, kde prohrála demokratka Hillary Clintonová. Trump na takový krok reagoval twitterovým prohlášením, že pro demokratku hlasovaly nelegálně milióny lidí. Žádné důkazy pro své tvrzení ale neposkytl.
Infikované hlasovací přístroje?
Počítačový odborník pracující pro Steinovou Alex Halderman se domnívá, že hackeři mohli ve státě Pensylvánie infikovat hlasovací přístroje škodlivým softwarem. Ten mohl být navržen tak, aby po celé týdny zůstal nečinný, aktivoval se až 8. listopadu v den voleb a poté se bez zanechání stop sám vymazal.
FireEye však Haldermanovu obavu nesdílí.
Podle společnosti se nenašel žádný důkaz, který by ukázal na proniknutí do hlasovacích systémů. Tento názor zastávají i představitelé amerických bezpečnostních úřadů. „Nezjistili jsme nic, co bych charakterizoval jako významné," prohlásil ministr vnitřní bezpečnosti Jeh Johnson. „Tu a tam byly menší incidenty, které se dají očekávat, ale nic vážného," dodal.
Vláda Spojených států před volbami otevřeně obvinila Rusko, že jeho hackeři napadli servery Demokratické strany a že se snaží volby ovlivnit. Moskva se proti nařčením ohradila a vměšování odmítl i ruský prezident Vladimir Putin.
Mozilla podruhé v tomto týdnu záplatovala Firefox. Aktualizujte také Tor
1.12.2016 cnews.cz Zranitelnosti
Mozilla před dvěma týdny vydala Firefox 50 s tím, že další velké vydání přivítáme až v novém roce. Mělo však dojít nejméně k jednomu servisnímu vydání. Nakonec krátce po sobě došlo ke dvěma. První vyšlo 28. listopadu a opravilo kritickou díru spojenou s přesměrováním z připojení přes protokol HTTP na adresu data: s tím, že nové adrese byl přidělen původ předchozí adresy. Toho se dalo zneužít k manipulaci s cookies.
Jestliže v pondělí vyšel Firefox 50.0.1, od středy je oficiálně dostupný Firefox 50.0.2. I on opravuje kritickou díru. Tentokrát umožňovala skrze animace v grafických souborech SVG spustit škodlivý kód v hostitelských počítačích. Bohužel již byla aktivně zneužívána, a to na počítačích s Windows. Na situaci rychle zareagoval Tor, protože uživatelstvo tohoto prohlížeče bylo skrze díru odhalováno, což je přesný opak anonymity, kterou slibuje.

V tomto týdnu byly vydány dvě servisní verze Firefoxu (Ilustrační foto)
Proto pokud používáte Tor, rovněž aktualizujte, a to na verzi 6.0.7. Podle příspěvku na blogu Toru nebyl útok na počítače s Linuxem či macOS zjištěn, v bezpečí byli také ti, kdo měli v prohlížeči nastavenou vysokou hodnotu úroveň zabezpečení. Mozilla opravila Firefox nejen pro Windows, ale také pro další dvě zmíněné počítačové platformy. Podle příspěvku na Bugzille byla chyba v prohlížeči přítomná již pět let.
Díra opravená ve Firefoxu 50.0.2 (a ve Firefoxu ESR 45.5.1 a Thunderbirdu 45.5.1) je podle redaktora webu Ars Technica silně podobná té, kterou v roce 2013 využívala FBI k odhalování překupníků a překupnic materiálů s dětskou pornografií. Bezpečnostní expert pro Ars Technicu řekl, že podobnosti vedou ke spekulacím, zda byla tato díra záměrně vytvořena FBI nebo jinou vládní agenturou. To však zatím nebylo potvrzeno.
Malware Gooligan napadá starší zařízení s Androidem. Ohroženo je více než milion účtů
1.12.2016 cnews.cz Android
Experti z Check Pointu objevili a dlouhodobě sledovali malware nazvaný Gooligan. Na zařízeních s Androidem potichu převezme kontrolu nad systémem. Může získat data ze služeb Googlu, ale primárně má útočníkům vydělávat. Napadeno je minimálně milion účtů.

Malware Gooligan napadl více než milion účtů
Gooligan využívá zranitelností ve starších verzích Androidu (4.x a 5.x), které najdeme na přibližně třech čtvrtinách aktivních zařízení. Ohrožené jsou primárně účty v Asii (57 %), těch evropských je jen 9 %. Do zařízení se malware dostane instalací falešné aplikace ze zdrojů třetích stran. Tedy přímou instalací APK nebo použitím jiného obchodu než Play Storu. (Ty jsou kvůli nedostupnosti Googlu rozšířeny především v Asii.)
Malware získá pomocí exploitů Vroot nebo Towelroot rootovská práva. Pak se dostane k autentizačním tokenům Googlu, takže má přístup k uloženým datům i bez znalosti hesla či potřeby projít dvoufázové ověření. Na napadené telefonu lze přistupovat do Dokumentů, Disku, Gmailu, Fotek a především Google Play.
Skrz již oficiální obchod Googlu stahuje nové aplikace (i vícekrát díky falšování IMEI a IMSI) a hodnotí je, takže v Play Storu stoupá jejich prestiž. Kromě do zařízení instaluje adware, který pak v systému obtěžuje reklamou.
Bezmocný Google
Google již o problému ví a s Check Pointem spolupracuje. Na své straně toho ale moc nevyřeší. Chyby ve starších Androidech již opravil, ale záplaty se kvůli liknavosti výrobců nedostaly do všech zařízení. Android 6.0+ už navíc má i ochranu, která hlídá i aplikace instalované z neověřených zdrojů. Je to pro něj ale signál, na které závadné aplikace v Play Storu si dát pozor.
Gooligan se nachází v necelé stovce falešných aplikací (seznam níže). Jejich smazání nepomůže, řešením není ani obnova do továrního nastavení. Jediným lékem je přeinstalace systému pomocí flashnutím obrazu, který poskytuje výrobce telefonu. Bude také nutné změnit heslo k účtu. Check Point nabízí též nástroj, pomocí něhož si můžete ověřit, zdali jste obětí Gooliganu. Stačí zadat e-mail.
Falešné aplikace s Gooliganem
Assistive Touch
ballSmove_004
Battery Monitor
Beautiful Alarm
Best Wallpapers
Billiards
Blue Point
CakeSweety
Calculator
Clean Master
Clear
com.browser.provider
com.example.ddeo
com.fabullacop.loudcallernameringtone
com.so.itouch
Compass Lite
Daily Racing
Demm
Demo
Demoad
Detecting instrument
Dircet Browser
Fast Cleaner
Fingerprint unlock
Flashlight Free
Fruit Slots
FUNNY DROPS
gla.pev.zvh
Google
GPS
GPS Speed
Hip Good
Hot Photo
HotH5Games
Html5 Games
Chrono Marker
Kiss Browser
KXService
Light Advanced
Light Browser
memory booste
memory booster
Memory Booster
Minibooster
Multifunction Flashlight
Music Cloud
OneKeyLock
Pedometer
Perfect Cleaner
phone booster
PornClub
PronClub
Puzzle Bubble-Pet Paradise
QPlay
SettingService
Sex Cademy
Sex Photo
Sexy hot wallpaper
Shadow Crush
Simple Calculator
Slots Mania
Small Blue Point
Smart Touch
SmartFolder
Snake
So Hot
StopWatch
Swamm Browser
System Booster
Talking Tom 3
TcashDemo
Test
Touch Beauty
tub.ajy.ics
UC Mini
Virtual
Weather
Wifi Accelerate
WiFi Enhancer
Wifi Master
Wifi Speed Pro
YouTube Downloader
youtubeplayer
UPDATE Firefox and Tor to Patch Critical Zero-day Vulnerability
1.12.2016 thehackernews Vulnerebility
The critical Firefox vulnerability being actively exploited in the wild to unmask Tor users has been patched with the release of new browser updates.
Both Mozilla and Tor Project has patched the vulnerability that allows attackers to remotely execute malicious code on Windows operating system via memory corruption vulnerability in Firefox web browser.
Tor Browser Bundle is a repackaged version of the open-source Mozilla Firefox browser that runs connections through the Tor anonymizing network configured to hide its user's public IP address.
However, the exploit code released by an unnamed online user was currently being exploited against Tor Browser users to leak the potentially identifying information of Tor users.
"The security flaw responsible for this urgent release is already actively exploited on Windows systems," an official of the anonymity network wrote in an advisory published on Wednesday.
"Even though there is currently...no similar exploit for OS X or Linux users available, the underlying [Firefox] bug affects those platforms as well. Thus we strongly recommend that all users apply the update to their Tor Browser immediately."
Soon after the Tor Project released the updated version of its browser, Mozilla also posted a blog post that said the company has also released an updated version of Firefox that patched the underlying vulnerability.
The vulnerability, assigned CVE-2016-9079 and rated critical, also affects Mozilla's Thunderbird e-mail application and the Firefox Extended Support Release (ESR) version used by the Tor Browser.
The attack code exploiting the underlying vulnerability initially circulated Tuesday on a Tor discussion list by an admin of the SIGAINT privacy-oriented public email service.
"The exploit took advantage of a bug in Firefox to allow the attacker to execute arbitrary code on the targeted system by having the victim load a web page containing malicious JavaScript and SVG code," said Mozilla security official Daniel Veditz.
"It used this capability to collect the IP and MAC address of the targeted system and report them back to a central server. While the payload of the exploit would only work on Windows, the vulnerability exists on Mac OS and Linux as well."
Firefox and Tor users are strongly recommended to update their web browsers to the latest Firefox version 50.0.2 and Tor Browser 6.0.7, respectively, as soon as possible.
Meanwhile, people using both Tor and mainstream versions of Firefox can set the Firefox security slider to "High" in order to protect themselves from the attack.
Doing so would render the exploit moot, Georg Koppen, Tor Browser Team Lead, told The Hacker News in an email, although the setting will prevent many websites from working as expected.
"Apart from that we are currently working on sandboxing techniques that have [the] potential to mitigate this kind of attack," Koppen added. "They are, alas, not ready for the stable series yet. We plan to ship prototypes with the next planned alpha releases."
For more details about the critical Firefox vulnerability, you can head on to our previous article, Firefox Zero-Day Exploit to Unmask Tor Users Released Online.