
SAP fixed a flaw in xMII that could open the door to nation-state hackers
10.2.2016 Vulnerebility
SAP fixed a vulnerability affecting SAP MII can be used as a starting point of multi-stage attacks aiming to get control over plant devices and manufacturing systems.
SAP fixed a critical vulnerability in its application that could be exploited by hackers, especially nation-state actors, to compromise industrial manufacturing software. SAP issued a critical software update that patched 23 security vulnerabilities, one of them affecting the SAP Manufacturing Integration and Intelligence (xMII).
The SAP Manufacturing Integration and Intelligence (xMII) solution implements a sort of software hub that connects ERP software (Enterprise Resource Planning) and other enterprise applications with plant floor and Operational Technology devices (OT).
This specific SAP solution is widely adopted in the energy industry that is known to be a privileged target for state-sponsored hackers.
SAP published a SAP Security Notes February 2016 – Review and also a summary docs that contains the information on the Patch Day Security Notes that are released on second Tuesday of every month and fix flaws in SAP solutions.

According to data provided by SAP, most of the fixed holes affects SAP NetWeaver’s J2EE application security, meanwhile Cross Site Scripting represents the principal vulnerability type.

A study conducted by TripWire in January revealed successful cyber attacks on the energy industry increased as never before in 2015.
Data published in the report confirmed that 69% of respondents to the Tripwire study declared they “weren’t confident” their company would be able to detect every cyber attack.

According to US Department of Homeland Security in 2014 the companies in the energy industries suffered 245 incidents.
The flaw fixed by SAP in the in SAP xMII is a directory traversal vulnerability, hackers could exploit it to penetrate into plant floor and OT networks and launch the attack against the connected ICS and SCADA systems.
The flaw could allow attackers to access the file system of the SAP server with unpredictable consequences.
“Any vulnerability affecting SAP MII can be used as a starting point of multi-stage attacks aiming to get control over plant devices and manufacturing systems,” said Polyakov Alexander, CTO at SAP and Oracle security specialists ERPScan, told El Reg. “Similar attack scenarios were presented by us at the BlackHat conference but for the oil and gas [industry] in particular.”
Útočníci se pokouší koupit login do systému Applu přímo od zaměstnanců. Nabízí až 20 000 euro
10.2.2016 Zdroj: Zive.cz Incidenty
Business Insider včera přinesl informace o praktikách útočníků, kteří se pokouší dostat do interních systémů Applu. Místo složitého hackování na to jdou tou nejjednodušší cestou – za přihlašovací údaje nabízí zaměstnancům zajímavé částky – prý to může být až 20 000 euro, tedy přes půl milionu korun. Bussness Insider informace získal od několika zdrojů přímo z Applu.
„Login do interního systému můžu kdykoliv prodat za 20 000 euro.“ - zdroj z Applu
Útočníci se zaměřují především na nové zaměstnance, kteří nastoupí na juniorské manažerské pozice. U těch se dá předpokládat menší vztah k zaměstnavateli a vyzrazení informací je tak pravděpodobnější. Apple prý provozuje interní program Grow Your Own, který má zaměstnance na podobné praktiky připravit a naučit je jim čelit.
Zájem je jak o přihlašovací údaje, tak o citlivé obchodní údaje. Není proto divu, že je Apple i v případě vlastních zaměstnanců velmi obezřetný. V irské centrále tak striktně omezuje fyzický přístup třeba pro zaměstnance z dalších poboček.
Windows 10 Sends Your Data 5500 Times Every Day Even After Tweaking Privacy Settings
10.2.2016 Security
Myth: By disabling all privacy compromising and telemetry features on Windows 10 will stop Microsoft to track your activities.
Fact: Even after all telemetry features disabled, Windows 10 is phoning home more than you could ever think of.1
Ever since the launch of Microsoft's newest operating system, Windows 10 is believed to be spying on its users. I wrote a number of articles to raise concern about Windows 10 privacy issues, including its controversial data mining features and privacy invasion features.
The only solution believed to cope up with these issues is to disable all the telemetry features or use an automated tool to disable all privacy-infringing features in just one click.
But unfortunately, all these efforts got wasted because Microsoft still tracks you, even after you tighten your Windows 10 privacy to an extreme level, claims the recent analysis conducted by a Voat user CheesusCrust.
Traffic Analysis Reveals Extent of Windows 10 Spying
Curious to know the extent of Windows 10 spying, CheesusCrust set up his Linux laptop with a Windows 10 Enterprise virtual machine as well as a DD-WRT router that was being utilized to monitor traffic.
CheesusCrust also disabled every single tracking and telemetry features in the operating system. He then left the machine running Windows 10 overnight in an effort to monitor the connections the OS is attempting to make.
The results are not so surprising:
Eight hours later, he found that the idle Windows 10 box had tried over 5,500 connections to 93 different IP addresses, out of which almost 4,000 were made to 51 different IP addresses belonging to Microsoft.
After leaving the machine for 30 hours, Windows 10 expanded that connection to 113 non-private IP addresses, potentially allowing hackers to intercept this data.
DisableWinTracking
Taking his test to a step further, CheesusCrust again installed Windows 10 Enterprise virtual machine on his laptop, disabled all tracking features and enabled a third-party tool known as DisableWinTracking.
After this, the number was reduced to 2758 connections to 30 different IP addresses in the period of 30 hours.
The interesting fact here is: This analysis was conducted on Windows 10 Enterprise Edition that comes with the most granular level of user control, far more than the standard Windows 10 Home Edition used by a sizable audience.
The Greatest Cost to Owning 'Free' Windows 10
However, based on these logs, it would be inaccurate to say that Windows 10 is sending your personal data to Microsoft's servers. But, thousands of connection attempts in the period of 8 hours just to check for updates or adjust the time, sounds more complicated than thought.
A September 2015 blog from Terry Myerson, head of the Windows team, explained that while Windows 10 does send some of your data to the company, everything is encrypted and doesn't include any of your personal details.1
Here's what Microsoft says about the Windows 10 Spying concerns:
"We collect a limited amount of information to help us provide a secure and reliable experience. This includes data like an anonymous device ID, device type, and application crash data which Microsoft and our developer partners use to continuously improve application reliability. This doesn't include any of your content or files, and we take several steps to avoid collecting any information that directly identifies you, such as your name, email address or account ID."
While this research doesn't provide what details Windows 10 is sending to the company even after disabling the telemetry features, you have to keep this in mind that Nothing comes for FREE. "Free" is just a relative term. May be you are paying the greatest cost to owning Windows 10.
Bye bye, Flash! Google to Ban Flash-based Advertising
10.2.2016 Apple
Google to Ban Adobe Flash-based Advertising
Google had also joined the path of Apple, Facebook, and Youtube to kill the "Adobe Flash Player" by announcing that the company is banning Flash banner support from its Adwords Advertising platform.
"To enhance the browsing experience for more people on more devices, the Google Display Network and DoubleClick Digital Marketing are now going 100% HTML5" Google says.
It's been two decades since Adobe Flash has ruled the Web Space Animation Arena, which was the de facto standard for playing the online videos.
Flash Player had been famous for Zero-day exploits which are a potential threat to online users.
Even Adobe tried to maintain equilibrium by releasing a countless number of patches frequently (that got hiked), for instant reported vulnerabilities, but this had annoyed both customers and companies.
The endless troubleshooting of the Flash Player plugins never resolved the vulnerabilities.
To put a full stop on this issue... many major tech companies like Apple, Facebook, Youtube, Google Chrome, Firefox had been magnetized towards the new substitutor - HTML 5.
Facebook's Security Chief publicly called for Adobe to announce a 'kill-date for Flash.'
Google Chrome has also begun blocking auto-playing Flash ads by default.
In January this year, YouTube moved away from Flash for delivering videos.
Firefox also blocked the Flash plugin entirely.
By ending up Flash, all the above companies found a silver bullet to the security issues that have plagued Adobe Flash for years, as well as eliminated a third party dependency.
Steve Jobs was right about the end of Flash as he quoted as saying in his letter:
“New open standards created in the mobile era, such as HTML5, will win on mobile devices (and PCs too). Perhaps Adobe should focus more on creating great HTML5 tools for the future, and less on criticizing Apple for leaving the past behind.”
HTML 5 has gained a Word of Mouth Popularity by many developers and also have many advantages like to play the video smoothly, in fact, in a better way.
So, Google also officially declared that it would not support Flash ads in Doubleclick Digital Marketing from July 30, 2016.
Moreover, from January 2, 2017, the company will discontinue the support for Google Display Network as a part of complete Flash Wipe Out.
However, as a Result of this awful reputation, Flash Player would be rebranded as “Animate CC” with some additional features like the direct conversion of Flash Files to HTML5 Canvas files.
Adobe Animate CC – mostly looks like an update to the Flash Professional software – supports Adobe Flash (SWF) and AIR formats 'as first-class citizens,' along with other animation and video formats, including HTML5 canvas, 4K and WebGL output.
Crooks are offering Apple employees up to $23,000 for their login credentials
10.2.2016 Apple
According to former Apple employees interviewed by the Business Insider, cyber criminals are offering Apple staffers in Ireland up to $23,000 for their login details.
Insiders are one of the greatest security problems for any organizations, working from the inside they can operate under the radar for a log time stealing information and sabotaging processes and infrastructures.
Modern organizations are often helpless while facing with insiders that are threatening their information assets and intellectual property.
One of the most clamorous cases of insiders was related to the Yandex Search Engine, in December a former employee stole the source code of the Russian Search Engine and tried to sell it and its algorithms for just $29,000 on the black market.
Corrupting an insider is the most easy way to breach an organization, news of the day the attempt to breach with a similar technique the Apple’s European Headquarters in Cork, Ireland.
Apple employees at Operations International in Cork, Ireland
Crooks are offering to the Apple employees 20,000 Euro ($23,000 USD) in exchange of Corporate Login Details of Irish Apple Employees in exchange of 20,000 Euro ($23,000 USD).
Obtaining the Apple employee’s corporate login credentials, attackers could breach the system and move lateraly inside the company network exfiltrating precious information from the company’s archives.
“Hackers are offering Apple employees thousands of euros for their company login details, according to someone that works for the company in Ireland. The employee, who spoke to Business Insider on the condition we kept their anonymity, said there are a lot of people trying to get hold of Apple’s inside information.” reported the Business Insider.
“You’d be surprised how many people get on to us, just random Apple employees,” the Apple employee told to Business Insider. “You get emails offering you thousands [of euros] to get a password to get access to Apple.”
“I could sell my Apple ID login information online for €20,000 ($23,000) tomorrow. That’s how much people are trying” said another employee.
Apple is not underestimating the case, according to the company there are no illicit activities linked to the proposals received by its emaployess, anyway the risk of insiders is high.
As usual, the attackers have a deep knowledge of the victim, another former Apple employee confirmed to Business Insider that crooks contact specific figures inside the organization. Hackers use to apporach Apple staff and offer them money in exchange for login details or company information.
“They look for someone who has jumped diagonally into a junior managerial position, so not a lifer working their way up, and not a lifer who has been there a long time,” said the former Apple employee.
The circumstance suggests the importance of the human factor inside any organization, employees represents the weakest link in the security chain. Disgruntled employees or a staffer not trained to face attacks from outside could become a backdoor even in a armored organization.
Vigilante Hackers Aim to Hijack 200,000 Routers to Make Them More Secure
10.2.2016 Hacking
Vigilante Hackers Aim to Hijack 200,000 Routers to Make Them More Secure
The same "Vigilante-style Hacker," who previously hacked more than 10,000 routers to make them more secure, has once again made headlines by compromising more than 70,000 home routers and apparently forcing their owners to make them secure against flaws and weak passwords.
Just like the infamous hacking group Lizard Squad, the group of white hat hackers, dubbed the White Team, is building up a sizeable botnet consisting of hundreds of thousands of home routers, but for a good purpose.
Lizard Squad, the same group responsible for Sony PlayStation Network and Microsoft Xbox Live outages, uses their botnets to launch DDoS (Distributed Denial of Service) attacks against target websites to flood them with traffic and knock them offline.
Hacking Routers to Make them More Secure
Challenged by Lizard Squad's maliocus work, the White Team of vigilante hackers built their own peer-to-peer botnet that infects routers to close off vulnerabilities, such as:
Weak default passwords
DNS poisoning
Unauthorised access (backdoor)
Disabled firewalls
Their malware, dubbed "Linux.Wifatch" a.k.a "Wifatch" that has been used by the team since last year continues to be updated and has been open-sourced on Github.
The malware, first discovered in November 2014 by an independent malware researcher "Loot Myself" and analysed by Symantec last year, now includes more programs to remove other malicious software and backdoors already on the system.
The White Team has access to around 70,000 devices, according to Symantec, who is continuously watching over the team's botnet.
Good Malware to Fight Bad Malware
Lizard Squad sizable botnet contained somewhere between 120,000 and 150,000 bots, a Lizard spokesperson told Forbes, claiming that their botnet includes not just home routers and PCs, but smart refrigerators, smart TVs and other smart home devices as well.
The White Team aims at hacking and protecting between 150,000 and 200,000 devices from Lizard Squad attacks, thereby removing the rogue gang from people's homes.
However, the team of vigilante hackers face some hurdles, especially when working with the Wifatch malware, which is often too big to install on smaller routers.
"The goal is to use (most) of the 60,000 nodes we have to connect to the hundreds of thousands of boxes that are too small for our normal disinfector and disinfect them remotely," the hacker collective told the publication over encrypted email.
Since there are so many vulnerable devices that can be hacked with little or no effort, these vigilante hackers aren't answer to this widespread problem. They can only help minimize the issue.
The White Team is not the only team of vigilante hackers trying to secure the Internet. Just last week, a hacker replaced a malware with antivirus software. An anonymous hacker was found replacing Dridex, the most active banking malware, with the copies of Avira security software.
Hackers Are Offering Apple Employees $23,000 for Corporate Login Details
10.2.2016 Apple
An unsatisfied Employee may turn into a Nightmare for you and your organization.1
Nowadays, installing an antivirus or any other anti-malware programs would be inadequate to beef up the security to maintain the Corporate Database.
What would you do if your employee itself backstabbed you by breaching the Hypersensitive Corporate Secrets?
Yes! There could be a possibility for an Internal Breach all the time.
Just last year, an ex-employee stole Yandex Search Engine Source Code and tried to sell it for just $29,000 in the underground market.
Over a few years, hackers have adopted various techniques ranging from Stress Attacks to Social Engineering tactics in order to gain the Classified Corporate information.
Hackers Offering $23,000 for Internal Access
Now hackers are rolling their dice for the next Deceptive Step to acquire Corporate Login Details of Irish Apple Employees in exchange of 20,000 Euro ($23,000 USD).
The current situation is being faced by the employees of Apple's European Headquarters in Cork, Ireland.
The offer had been made by the unknown hackers and criminals to the random Apple employees in their mailbox demanding the employee's Apple Login passwords in return of 20,000 Euros.
"You'd be surprised how many people get on to us, just random Apple employees," the anonymous employee said. "You get emails offering you thousands [of euros] to get a password to get access to Apple" stated.
"I could sell my Apple ID login information online for €20,000 ($23,000) tomorrow. That’s how much people are trying" another employee quoted.
This new proposal had been made to the non-lifers of the company who would not spend there. Thus, widening a fluky entry to the database.
By gaining the access to Apple Employee’s Login credentials, hackers could find the jewel in their pocket for their malicious activity from which they could amass the financial profit.
Apple is considering this scam very seriously and till now, no employees had compromised his/her Login Credentials for illicit gain.
Internal Breach
One of the domestic threat to your organization is the INSIDER. According to a survey conducted by SANS last year, it is found that 71% of respondents are feared about the Insider Attack.
The consequence of the threat may even result in the liquidation of your company.
The Department of Homeland Security (DHS) and FBI also had a pressed up the issue by underlining that majority of the threats are the outcomes of an Insider.
Lack of Technical Training to the employees, Lack of Budget and inappropriate policies broaden the chances of a breach.
Hiring a Security Firm, Proper Training to all the Employees about latest threats, Shutting down of an employee Account soon after his/her Termination, Frequent changes applied in the Password, Limited Allowance of employees to sensitive docs, etc. would cover such vulnerabilities.
Now, before purchasing the high-end firewalls or Virus Destructors, just turn around and look…
...Who’s at your back!
February 2016 Patch Tuesday – All Windows are affected by a critical flaw
10.2.2016 Vulnerebility
Microsoft February 2016 Patch Tuesday updates include a total of 13 bulletins that resolve a total of 41 security flaws in Windows, one of them affects all supported versions.
All supported versions of Windows are affected by a critical vulnerability recently fixed by Microsoft. The IT giant has released 13 security bulletins, six issues are rated as critical. The security bulletins resolve a total of 41 security flaws in Microsoft software.
One of the bulletins in the February 2016 Patch Tuesday, the MS16-022, fixes the 22 Flash Player flaws recently resolved by Adobe, including the Flash libraries used in Microsoft Internet Explorer 10 and 11, and Edge browsers.
A vulnerability in the Microsoft Windows 10 operating system, as well as Windows Server 2016 Tech Preview 4, has captured the attention of the security community.
The MS16-013 vulnerability is a memory-corruption flaw and could be exploited by remote attackers to execute arbitrary code as the logged-in user by tricking a user into opening a specially crafted Journal file. Fortunately, according to Microsoft the vulnerability has not been exploited in the wild.
This vulnerability would allow attackers to run malicious programs on a targeted machine and create new accounts with full user rights.
“The vulnerability could allow remote code execution if a user opens a specially crafted Journal file. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.” states the official description published by Microsoft.
The list of February 2016 Patch Tuesday bulletins includes also the MS16-015, which fixes critical vulnerabilities in Microsoft Office security that can be exploited to execute arbitrary code in the context of the targeted user simply tricking victims into opening a specially crafted.
The complete list of fixes is reported below:
MS16-009: A cumulative security update for Internet Explorer 9 through 11. The update patches 13 security issues, including remote-code-execution (RCE) and information disclosure bugs.
MS16-011: Another cumulative update for the Microsoft’s newest Edge browser in Windows 10 patches 6 security issues, 4 of which are remote code execution vulnerabilities.
MS16-012: An update addresses two remote-code-execution flaws in Windows PDF Library and Reader for Windows 8.1, Windows 10 and Server 2012. Flaws could allow attackers to run malicious code on an affected system by tricking users into opening a specially-crafted PDF file.
MS16-015: An update patches 6 memory-corruption vulnerabilities in Microsoft Office, each of which could allow a remote attacker to run arbitrary code by tricking a user intoopening a specially-crafted Office file.
MS16-022: A security update resolves more than two dozen vulnerabilities in Adobe Flash Player on all supported versions of Windows 8.1, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1.
Microsoft also launched a page for public tracking of Windows 10 update (Windows 10 update history) an effort to show users the improvement applied by the company to its OS.
“We’re committed to our customers and strive to incorporate their feedback, both in how we deliver Windows as a service and the info we provide about Windows 10,” states Microsoft .
“In response to this feedback, we are providing more details about the Windows 10 updates we deliver through Windows Update. You’ll see a summary of important product developments included in each update, with links to more details.”
All Versions of Windows affected by Critical Security Vulnerability
10.2.2016 Vulnerebility
Microsoft has released 13 security bulletins, six of which are considered to be critical, resolving a total of 41 security vulnerabilities in its software this month.
Every Windows version Affected:
One of the critical vulnerabilities affects all supported version of Windows, including Microsoft's newest Windows 10 operating system, as well as Windows Server 2016 Tech Preview 4.
The memory-corruption flaw (MS16-013) could allow a remote attacker to execute arbitrary code as the logged-in user by tricking a user into opening a specially crafted Journal file.
This vulnerability would let the attacker run malicious programs on victim's machine, even delete data and create new accounts with full user rights.
Administrator accounts are at the greatest risk than users with a fewer user rights account on the system. However, the good news is the vulnerability has not been spotted in the wild.
List of All Critical Vulnerabilities
Other Critical Security Updates are as listed below:
MS16-009: A cumulative security update for Internet Explorer 9 through 11. The update patches 13 security issues, including remote-code-execution (RCE) and information disclosure bugs.1
MS16-011: Another cumulative update for the Microsoft's newest Edge browser in Windows 10 patches 6 security issues, 4 of which are remote code execution vulnerabilities.
MS16-012: An update addresses two remote-code-execution flaws in Windows PDF Library and Reader for Windows 8.1, Windows 10 and Server 2012. Flaws could allow attackers to run malicious code on an affected system by tricking users into opening a specially-crafted PDF file.
MS16-015: An update patches 6 memory-corruption vulnerabilities in Microsoft Office, each of which could allow a remote attacker to run arbitrary code by tricking a user into opening a specially-crafted Office file.
MS16-022: A security update resolves more than two dozen vulnerabilities in Adobe Flash Player on all supported versions of Windows 8.1, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1.
All of the above critical vulnerabilities were privately reported to the tech giant and were not believed to have been exploited by attackers.
Other security updates rated as "important" issues address Remote Code Execution flaw and Elevation of Privilege bug in Windows, as well as Denial of Service (DoS) vulnerability in Microsoft Windows, .NET Framework and Active Directory Federation Services (ADFS).
Windows 10 Update History Page Goes Live Today
Meanwhile, Microsoft also launched a dedicated page for keeping track of every Windows 10 update in order to improve transparency.
So from today, you can just visit Windows 10 update history to see the latest improvements, features, and changes the company has made to its latest OS.
"We're committed to our customers and strive to incorporate their feedback, both in how we deliver Windows as a service and the info we provide about Windows 10," the company notes.
"In response to this feedback, we are providing more details about the Windows 10 updates we deliver through Windows Update. You'll see a summary of important product developments included in each update, with links to more details."
Windows 10 update history page will regularly be updated, as soon as the company rolls out new updates and security patches to the operating system.
Are you searching for a Facebook Hacking Tool? Be careful!
10.2.2016 Hacking
Security Experts at ESET security firm discovered a new variant of a known trojan disguised as a Facebook Hacking Tool.
Security researchers at ESET have published an interesting post about a new Facebook hacking tool. I receive every week dozen emails requesting me instruction to hack Facebook accounts.
The hacking tool recently discovered is not able to support you in this hard task, instead it could expose users that download it to serious risks.
But Beware of any software that promises you to hack any Facebook account, it could be very dangerous to launch it.
The tool reported by THN is dubbed Remtasu, it is available online as a Facebook hacking tool, but in reality, it is a trojan that could infect Windows systems.
The trojan is a well-known threat that is circulating for a long on the Internet, now crooks have found a differed way to spread it.
Cyber criminals are disguising it as a software to take over any Facebook account and steal Facebook credentials.
The tool contains a Keylogger module that could be used to that can steal users login credentials. Typically a user searching for a Facebook hacking tool finds the malicious application on direct download websites.
Once a user visits one of these websites, the dangerous Win32/Remtasu.Y malware automatically gets downloaded and executed on victim’s machine.”Although these files are from the same family as those witnessed last year, the way they are being spread is different. We are no longer seeing propagation through e-mail. They are instead coming from direct download sites. Once a user downloads and executes the file, their data is compromised.” states a blog post published by ESET.


The Remtasu trojan is able to capture keystrokes and access information from the clipboard, every information collected on the infected system is stored locally in a data file and then sent to an FTP server.
The system gain persistence in the infected system by saving its copy in a folder that it also creates within the system32 folder.
“As is to be expected in this type of threat, the virus always seeks a way to remain on the computer even when the victim reboots their system or attempts to find the threat in the list of active processes.” continues the post.
“In this case, the malware replicates itself, saving the copy in a folder that it also creates within the system32 folder. The new InstallDir folder remains hidden inside the system files, making it difficult for users to access.”
The campaign based on the fake Facebook Hacking Tool mainly infected users from Colombia, Turkey, and Thailand.
Russian Metel group manipulated ruble-dollar exchange rate with malware
10.2.2016 Virus
A Russian group of cyber criminals known as METEL has hacked the systems at the Kazan-based Energobank and manipulate Ruble-Dollar Exchange Rate infecting them with a malware.
A Russian cyber gang has hacked the systems at the Kazan-based Energobank and manipulate Ruble-Dollar Exchange Rate infecting them with a malware.
The event occurred exactly one year ago, in Feb 2015, when the hacking group dubbed METEL breached into the Russian Regional Bank for just 14 minutes resulting in the fluctuation of the exchange between 55 and 66 rubles per dollar.
The Moscow Exchange denied that its systems have been hacked, it also highlighted that its investigation has found no evidence of the currency market manipulation. The Moscow Exchange explained that fluctuations observed by the users could have been caused by traders’ mistakes.
The security firm Group-IB that was involved in the investigation on the case discovered that the Metel Hacking group infected Kazan-based Energobank, the hackers used the Corkow Trojan and placed more than $500 million in orders at non-market rates.
Corkow is a backdoor that breached 250,000 computers worldwide in more than 100 financial institutions.
“This is the first documented attack using this virus and it has potential to do much more damage,” Dmitry Volkov, the head of Group-IB’s cyber intelligence department, told Bloomberg. “Once the malware has penetrated a local network, it is sophisticated enough to infect computers that are even not connected to the Internet.”” Dmitry Volkov, the head of Group-IB’s cyber intelligence department, told Bloomberg.
The threat actors used spear phishing messages containing malicious links to hack the victim’s accounts. The economic impact of the attack has been estimated in 244 Million Rubles, nearly $3.2 million.
The Metel group is the same referred in the report recently published by the Kaspersky Lab on the Carbanak 2.0.
According to Kaspersky, the group targeted a Russian bank with the malware known as Metel (aka Corkow) and compromise banks’ networks via spear-phishing emails.
The financial institution targeted by the group discovered that hackers stole millions of rubles in just one night from the ATMs of other financial institutions. The hackers used ATM balance rollbacks to steal money while balances remained untouched.
“In summer 2015, a bank in Russia discovered it had lost millions of rubles in a single night through a series of strange financial transactions. The bank’s clients were making withdrawals from ATMs belonging to other banks and were able to cash out huge sums of money while their balances remained untouched. The victim bank didn’t realize this until it tried to recoup the money withdrawn from the other banks’ ATMs.” states a blog post published by Kaspersky.
“The malware, used exclusively by the Metel group, infected the bank’s corporate network via e-mail and moved laterally to gain access to the computers within the bank’s IT systems. Having gained access to the bank operator’s money-processing system, the gang pulled off a clever trick by automating the rollback of ATM transactions. This meant that money could be stolen from ATM machines via debit cards while the balance on the cards remained the same, allowing for multiple transactions at different ATM machines.”

According to Kaspersky, the Metel group is still active and targeted at least 30 Russian financial organizations.
Group-IB confirmed it, and added that the group is only known to be active in Russia where affected 73% Russian Banks.
Rent the infamous AlienSpy backdoor is now quite easy
9.2.2016 Virus
Security experts at Kaspersky have spotted in the wild a new variant of AlienSpy RAT Family openly offered with a model of malware-as-a-service.
Today we will speak about a case of malware-as-a-service, in the specific case the threat is a remote access trojan, aka RAT, that could be used to gain control over multiple platforms, including Windows, Linux, Mac OS X, and Android.
The RAT belongs to a family of Java malware that exists since 2013 and that recently is offered for sale as a “commercial” backdoor-as-a-service. It is known as AlienSpy or Adawind, and security experts spotted it in an attack on an employee of a Singapore bank.
In April 2015, experts at Fidelis discovered that variants of the AlienSpy remote access trojan (RAT) were used in global phishing campaigns to deliver the popular Citadel banking Trojan and maintain the persistence inside the targeted architecture with a backdoor mechanism.
AlienSpy implements the typical features of other RATs plus further features, including the ability to capture webcam sessions, to steal browser credentials, to use the victim’s microphone to record environment conversations, to access files and to provide a remote desktop control.
AlienSpy uses plugins to implement the above capabilities and experts have dozens of different plugins.

AlienSpy botnet was destroyed in 2015 when the experts identified the command and control infrastructure and neutralized it.
Security experts at Kaspersky have spotted a new variant of the malware that has been modified and offered as a service in the criminal underground. Researchers at Kaspersky observed more than 150 attack campaigns relying on the new variant of AlienSpy, bad actors in the wild targeted more than 60,000 individuals.
[it] is open for service again to customers ranging from Nigerian scam operators to possible nation-state actors. Ars has confirmed that the service is offered openly through a website on the public Internet.” states Ars.
The analysis of subscribers to the malware-as-a-service revealed that the majority of clients come from the US, Canada, Russia, and Turkey.

The new variant of AlienSpy is dubbed JSocket and jRat and is available for rent on the Internet at prices ranging from $30 for one month to $200 for an unlimited version.
According to the researcher Vitaly Kamluk who analyzed the threat, the operator behind the service‘s author is a native Spanish speaker, likely Mexican.
The new variant of AlienSpy, aka JSocket and jRat, is widely adopted in scam scheme, particularly the Nigerian e-mail-based scam campaigns targeting bank customers.
Máme jména tisíců amerických agentů, chlubí se hackeři. Jde o dvě třetiny FBI
9.2.2016 Hacking
Den poté, co prostřednictvím twitterového účtu zveřejnili jména více než 9000 zaměstnanců amerického ministerstva vnitra, oznámili počítačoví piráti na internetu jména dalších pracovníků americké bezpečnosti. Chlubí se odkrytím totožnosti více než 22 000 zaměstnanců Federálního úřadu pro vyšetřování (FBI). To jsou skoro dvě třetiny personálu FBI. Ministerstvo vnitra ale únik popírá.
„Ať žije Palestina, ať žije Gaza,“ doprovodili hackeři v úterý vydání druhé várky jmen, mezi nimiž figuruje také 1797 zvláštních agentů a zástupce ředitele jednoho specializovaného oddělení.
Britský deník The Daily Telegraph, který záznamy na zašifrovaných stránkách analyzoval, uvedl, že se seznam zdá být pravdivý. Upozornil přitom, že zřejmě jde o všechny zaměstnance FBI s příjmením začínajícím na A a končícím na Je.
FBI na svých webových stránkách tvrdí, že má téměř 35 000 zaměstnanců.
Úřady to popřely
Tisková kancelář amerického ministerstva vnitra k tomu uvedla, že „zprávy prověřuje“.
„Tyto zprávy bereme velmi vážně. Zatím však neexistují náznaky o přístupu k citlivým a osobním informacím,“ dodala.
Piráti však podle britského listu navíc uvádějí, že se jim podařilo z intranetu bezpečnosti ukrást 200 gigabajtů citlivých informací včetně čísel kreditních karet a armádní korespondence.
Údajně zneužili e-mail
Jeden z hackerů se serveru Motherboard pochlubil, že se do systému podařilo proniknout přes e-mailový účet na ministerstvu spravedlnosti. Úřad pak prý bez jakéhokoliv ověřování pirátům poskytl přístupové heslo do interní sítě, kde se dostali na jmenný seznam a k dalšímu terabajtu dat.
Zatím není jasné, kdo za útokem stojí. Objevily se spekulace, že by to mohla být skupina Crackas with attitude (CWA), která se v říjnu loňského roku pochlubila vniknutím do e-mailové schránky ředitele CIA Johna Brennana.
Russian Hackers Manipulate Ruble-Dollar Exchange Rate with Malware
9.2.2016 Virus
Russian Hackers Manipulated Ruble—Dollar Exchange Rate with Malware
Russian Group of Hackers reportedly cracked into the Kazan-based Energobank and messed up with the Ruble-Dollar exchange rates.
In Feb 2015, a hacking group, known by the name METEL, successfully breached into the Russian Regional Bank for just 14 minutes and caused the exchange rate to fluctuate between 55 and 66 rubles per dollar, which finally resulted in the increment of Ruble’s value.
Here's how they did it:
According to Russian security firm, Group-IB, who investigated the incident, the Metel Hacking group infected Kazan-based Energobank with a virus known as the Corkow Trojan and placed more than $500 million in orders at non-market rates.
“This is the first documented attack using this virus, and it has the potential to do much more damage,” Dmitry Volkov, the head of Group-IB’s cyber intelligence department, told Bloomberg.
The hackers had taken the advantage of Spear Phishing Technique, which appears to come from a legit source. A single click on the link in the malicious mail took over the access to the system followed by ultimate exploitation.
After gaining the access to a local system, the trojan was able to cause a havoc deepening the attack to its Intranet. This way, the malware named Corkow found the isolated system which handles the money transaction exclusively to the outer world.
Corkow malware, initially discovered in 2011, regularly updates itself to evade detection by antivirus programs, and has infiltrated more than 250,000 computers worldwide and infected at least 100 financial institutions.
Bank lost 244 Million Rubles ($3.2 million)
The Energobank claimed losses of 244 million rubles ($3.2 million) due to the trades.
But, the Moscow Exchange had denied the allegations of any hacking attempt by the fact that; the changes in the Stock Market would be an output of Trader’s mistakes. They also not found any hint of currency manipulation.
The attack was earlier ported to target ATMs of Russia, affecting Russian bank card system that resulted in hundreds of millions of rubles being stolen via ATMs in August. Another attack with the same malware also facilitated hackers to use credit card limitlessly.
Metel is only known to be active in Russia (affected 73% Russian Banks), although it may present a threat to financial institutions across the globe.
Authority has not yet handcuffed any of its criminals who are raising a global bank threat.
Apple Could Offer iMessage App for Android
9.2.2016 Android
Although Apple has its own operating system for both desktop (Mac OS X) and iPhone (iOS), the com pany has always tried to port its in-house applications to other OS platforms.
Apple debuted on its rival mobile OS platform last year with the launch of Apple Music on Android. However, iTunes and Safari has already been made available for both Windows as well as Mac.
Now, the company will soon move more of its mobile applications to Android if comments made by Chief Executive Tim Cook at the recent company-wide event for Apple employees are to be believed.
iMessage App for Android Platform
Cook reportedly told his staff that sooner Apple may bring other apps and exclusive services to the Android Systems, and added that bringing Apple Music to Android in November was "a way of testing the waters for growing its services division through other platforms," reports 9to5Mac.
So, you could see iMessage, the company's encrypted messaging application, expanded to Android.
iMessage is one of the most famous Apple's apps that allows Apple users to send and receive messages, photos, and videos to their fellow Apple users as long as the device has a data connection.
How Apple Can Read End-to-End Encrypted iMessages
What many of us know is iMessage uses end-to-end encryption that even Apple or anyone else can not access or read your messages, but what we don’t know is backed up messages to Apple's iCloud service are vulnerable to federal warrants.
With iCloud Backup enabled, the copies of all your messages, photographs and every important data stored on your iPhone or iPad are encrypted on iCloud using a key controlled by Apple, and not you.
This would allow Apple and hence, anyone who breaks into your account, to read your messages and see your personal and confidential data.
List of Apple Apps you Might See on Android
Besides iMessages, the list of Apple apps that you could see expanded to Android may include iTunes, Music Memos, Apple Maps, and iCloud.
In September, the company released its first-ever Android application, known as Move to iOS, designed to help Android users transfer their content quickly and safely from an Android device to an iOS device.
Although it is yet unclear when Apple will make the move, if this happens anytime soon, Which one of your favorite Apple apps you want to see on your Android devices?
Let me know in the comments below.
How to Crack GCHQ Crypto Puzzle? — Here's the Solution
9.2.2016 BigBrothers
GCHQ has finally released the solution to their head spinning Xmas Puzzle, after all, the participants failed to reach the final answer.
GCHQ had released a crypto puzzle, dubbed Xmas Puzzle, on 9th December in the form of a Christmas Card that went viral online soon after its release.
Nearly 600,000 people shot a "Go" for the challenge since early December, but only 30,000 had made it reach the final stage.
The puzzle got popped up with a grid-shading Nonogram that resulted in the formation of a QR Code containing a hint to unlock the next level challenges.
Xmas Puzzle prolonged to various topics like Web Link Maze, Word & Numeric Puzzle, Graph Theory and other Cipher Dilemmas. Some of the questions also intrigued on entertaining topics like Lord of the Rings, Ducks, Chess, French, and Semaphores.
Who Created Crypto ‘Xmas Puzzle’?
This brainstorming puzzle was created by a small team of GCHQ Cryptographers under the GCHQ director Robert Hannigan. The given deadline to the puzzle resolvers was January 31st.
Several improvements to resolve this puzzle had created a buzz over various online forums like Reddit, which was a healthy approach to such puzzles to get solved jointly.
Xmas Puzzle helped to broaden the crypto levels of each and bolster to improve their capabilities for the problem-solving methodologies.
David MacBryan, 41, from Edinburgh, Wim Hulpia, 40, from Lovendegem in Belgium and US-born Kelley Kirklin, 54, from London, came closest to the fiendish puzzle game.
These three participants have been considered winners by the GCHQ and will be rewarded with a GCHQ Paperweight and a copy of Bletchley Park codebreaker Alan Turing's biography, signed with a personal message from GCHQ Director.
Unable to Crack? Here’s the Solution
gchq-crypto-quiz
However, GCHQ announced that any of the participants did not completely solve Xmas Puzzle. Hence, it released the full answer to it.
"I thought I had solved it, but a news report came out a few days ago saying nobody had … so I went back and had another look and figured out what I missed, but I was too late at that point. But it seems that everyone else missed it as well, and I was joint closest," David MacBryan told the Guardian.
GCHQ said the Xmas puzzle was not a recruitment ploy, which was initially believed, but the agency said the winners were welcome to apply for jobs.
The solution to the puzzle, including explanations from the puzzle-setters, is now available for you, so you can now check how many you managed to work out.
Here's the Facebook Hacking Tool that Can Really Hack Accounts, But...
9.2.2016 Social Site
Yes, you heard me right.
A newly discovered Facebook hacking tool actually has the capability to hack Facebook account, but YOURS, and not the one you desires to hack.
How to Hack Facebook account? How to Hack my Girlfriends Facebook account? My boyfriend is cheating on me, How do I hack his Facebook Account?
These are the queries that most of the Internet users search on Google.
But Beware! If you come across any Facebook hacking tool that promises you to help you hack your friends Facebook accounts, you may end up downloading a hacking tool that could hack you, instead of them.
Facebook Hacking Tool that Can Really Hack, But Your Accounts
Facebook Hacking Tool
Dubbed Remtasu, the tool is marketing itself as a Facebook hacking tool but actually is a Windows-based Trojan that has accelerated globally over the past year, and has now capability to disguise itself as an app for accessing people's Facebook account credentials.
The tool contains a Keylogger that can capture all your keystrokes and store them in a file that is subsequently sent to the attacker's server.
The malicious Facebook hacking tool is exploiting "the constant desire of a lot of users to take control of accounts from this well-known social network," according to a Monday blog post by IT security company ESET.
How Remtasu Works:
The malicious tool is delivered via direct download websites.
Once a user visits one of these websites, the dangerous Win32/Remtasu.Y malware automatically gets downloaded and executed on victim's machine and hide itself among other files.
Remtasu has capability to:
Open and obtain information from the clipboard.
Capture keystrokes.
Store all the data in a file which is subsequently sent to an FTP server.
The worst part is yet to come:
The malware remains on the infected computer even when the victim reboots their system or attempts to find the malware threat in the list of active processes.
"In this case, the malware replicates itself, saving the copy in a folder that it also creates within the system32 folder," reads the post. "The new InstallDir folder remains hidden inside the system files, making it difficult for users to access."
Most affected parts of the world include Colombia, Turkey, Thailand and elsewhere. In past, Remtasu was distributed through malicious files attached to phishing emails purporting to be from legitimate government or businesses organisations.
eBay se nechystá opravit vážnou chybu ohrožující jeho uživatele
9.2.2016 Zranitelnosti
Poměrně zásadní bezpečnostní chyba zjištěná společností Check Point se prý opravovat nebude. Zvláštní přístup.
V polovině prosince objevili v Check Pointu chybu na eBay. Až natolik závažnou, že je zneužitelná pro vsunutí JavaScriptu do kódu obchodu, který si kdokoliv na eBay může založit. Pomocí vloženého kódu pak může do počítačů uživatelů stahovat další JavaScript z vlastních serverů a dělat, co se mu zlíbí.
Konkrétnější informace o bezpečnostním nedostatku můžete najít například v eBay Platform Exposed to Severe Vulnerability. Jde vlastně o jednu z nejklasičtějších věcí, kterou je nutné ošetřit ve všech systémech, které umožňují uživatelům vkládat data a ta poté zobrazit jiným uživatelům. „Script injection“, tedy vsunutí skriptingu, je základ, který každý informační systém přístupný z internetu řeší (stejně jako mírně související SQL injection).
aBay přitom klasické způsoby vkládaní skriptů ošetřené má (stejně jako vkládání rámců), ale ne moment, kdy je použita speciální cesta, jak kontrolu obejít. Ta funguje tak, že vsouvá kód, aniž by k tomu potřebovala klasické způsoby, ale vystačí si velmi zvláštním způsobem konstruujícím výsledný kód s pomocí pouhých šesti znaků – [], (), + a !. Detailní informace o tom, jak to celé funguje, najdete ve výše uvedeném oznámení od Check Pointu (a příklad na obrázku níže).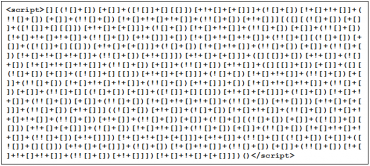
Na celém objevu je nakonec nejpodstatnější to, že z eBay 16. ledna odepsali, že se chybu nechystají řešit. Uvážíme-li, že v tuto chvíli jsou detaily o možném zneužití snadno dostupné a nic nebrání jejich masovému zneužívání, je to dost zvláštní rozhodnutí.
Server The Next Web se pokusil získat z eBay nějaké dodatečné informace a dostal jedno z nejklasičtějších a nejhloupějších vyjádření: eBay nebude nic dělat, protože neobjevili žádné aktivity, které by tuto zranitelnost využívaly.
eBay is committed to providing a safe and secure marketplace for our millions of customers around the world. We take reported security issues very seriously, and work quickly to evaluate them within the context of our entire security infrastructure. We have not found any fraudulent activity stemming from this incident.
A jako zlatý hřeb je tiskové oddělení ujistilo o tom, že škodlivý kód na jejich platformě je vzácný, protože se prý vyskytuje v „méně než dvou výpisech z milionu“, které obsahují aktivní obsah.
Je odkazování na nelegální odkaz trestné? Spor je u soudu
9.2.2016 Zákony
Až dosud je možné odkazovat pomocí hypertextových odkazů na nelegální obsah beztrestně. To se však může brzy změnit.
Představte si, že byste museli kontrolovat, zda jsou všechny vaše odkazy pouze na legální obsah. I to se může přihodit. Nejvyšší instance evropského práva nyní projednává, jestli se bude muset kontrolovat každý hyperlink, zda neporušuje autorská práva. To by mělo za následek značnou proměnu internetu jako takového.
V nedávné GS Media kauze „Svensson“ se Evropský soud rozhodl následovně: Odkazovat na obsah na internetu je legální v případě, že souhlas k tomu již byl dán dříve majitelem autorských práv.
To byla dobrá zpráva pro online svět; otevřela se tím však související otázka. Jak by byla posouzena situace, kdyby obsah, na který se odkazuje, nebyl uveřejněn se souhlasem autora? Bylo by legální pod evropským právem odkazovat na pirátskou kopii? A to se projednává právě nyní – s platností pro všech 28 členských států.
Případný výsledek může být ničivý pro svět internetu. Jestliže by každý uživatel musel kontrolovat obsah odkazované stránky před samotným uveřejněním hyperlinku, mělo by to spousty zatím netušených následků. Např. museli bychom kontrolovat obsah odkazovaných webových stránek, zda-li se na nich náhodou neobjevil nelegální obsah? Musel by odkazující uživatel kontrolovat, jestli mají stránky zaplacené všechny licence? Nebo by musel dokonce kontrolovat i legálnost dalších odkazů na dané stránce?
Když vynecháme už jen to, že běžný uživatel může jen těžko s jistotou říci, že zrovna tento obsah je na webu legálně a licencovaně, nejdůležitější položenou otázkou zůstává ta poslední.
Pokud by odpověď na ni zněla ano, znamenalo by to, že by uživatel musel kontrolovat všechny hyperlinky na dané stránce, hyperlinky na odkazovaných stránkách, hyperlinky na stránkách, na něž odkazovaly tyto stránky až do doby, než by se dostal na konec.
Nemožnost takové kontroly snad přesvědčí Evropský soudní dvůr o tom, že rozhodnutí o nutnosti kontrolovat autorská práva na odkazované stránky, by nevyřešilo vůbec nic. Nahrávat obsah bez svolení autora je jednoznačně trestným činem. Odkazovat na něj by však být nemělo.
Podvodníci zkoušejí přes Facebook nový trik, lákají přihlašovací údaje
9.2.2016 Sociální sítě
S novým trikem, jak vylákat přihlašovací údaje k sociální síti Facebook, přišli v posledních dnech podvodníci v Česku. Rozesílají nevyžádané e-maily, ve kterých se vydávají za bezpečnostní službu Facebooku (Facebook Security).
Ukázka nevyžádaného e-mailu, ve kterém podvodníci loudí přihlašovací údaje k Facebooku.
„Náš systém obdržel zprávy od ostatních uživatelů o zneužití vašeho účtu, kvůli čemuž bude účet deaktivován. Potvrdit svůj účet můžete na adrese support-inc16xat.ua. Pokud nepotvrdíte, váš účet se automaticky vypne natrvalo,“ tvrdí podvodníci ve spamové zprávě.
Problém nastane ve chvíli, kdy uživatelé skutečně na přiložený odkaz kliknou. „Jedná se o snahu vylákat z uživatelů jejich přihlašovací údaje. Odkaz ve zprávě vede na phishingovou stránku požadující zadání přihlašovacích údajů pro přístup do Facebooku,“ varoval před novou hrozbou bezpečnostní analytik týmu CSIRT.CZ Pavel Bašta.

Ukázka nevyžádaného e-mailu, ve kterém podvodníci loudí přihlašovací údaje k Facebooku.
FOTO: repro Facebook Security
Že se jedná o podvodnou zprávu, mohou uživatelé poznat hned na první pohled. Obsahuje totiž řadu chyb a některé věty jsou srozumitelné jen s velkou dávkou důvtipu. Na druhou stranu na zmiňované sociální síti skutečně stránka Facebook Security existuje a je dokonce i ověřená.
S podvodníky ale samozřejmě nemá nic společného. Ti si pouze vypůjčili její jméno.
Stránka Facebook Security informuje uživatele o aktuálních hrozbách a správném nastavení účtu. Právě proto by se mohli někteří uživatelé nechat podvodným e-mailem snadno napálit.
Bezpečnostní experti z týmu CSIRT.CZ už proto začali pracovat na odstranění podvodného phishingového webu, na který podvodníci směřují odkazy v nevyžádaných e-mailech. Není ale vyloučeno, že si podvodníci jednoduše zřídí nějaký nový.
Hacker Leaks Info of 30,000 FBI and DHS Employees
9.2.2016 Hacking
An unknown hacker who promised to release the personal information on government employees has dump online a list of nearly 20,000 Federal Bureau of Investigation (FBI) agents and 9,000 Department of Homeland Security (DHS) officers.
Though the authenticity of the information has not been verified, at least, some of the leaked data appears to be legitimate.
Here's What the Hacker Leaked:
The hacker leaked first round of data belonging to roughly 9,000 DHS employees on Sunday, which was followed by the release of 20,000 FBI agents information on Monday.
The hacker, who goes on Twitter by the username of @DotGovs, published the supposed data on an encrypted text-sharing website, including:
Names
Job titles
Phone numbers
Email addresses
The Reason Behind the Hack
The message at the top of the data dump includes the hashtag "#FreePalestine" and reads "Long Live Palestine, Long Live Gaza: This is for Palestine, Ramallah, West Bank, Gaza, This is for the child that is searching for an answer."
The above message shows the support to Palestine, which could be the motivation behind the hack.
Although it's unclear how much of the hacked data may have been publicly available, the hacker told Motherboard that he had downloaded 200GB of data, out of 1TB total available to him.
If this comes true, the information that has been leaked so far would just be a small percentage of what the hacker has in its box.
How the Hacker did it?
The hacker claimed to have compromised US Department of Justice (DoJ) email account and gained access to the department's Intranet. Then he allegedly downloaded the information of over 20,000 FBI officers, roughly 9,000 DHS employees and an undisclosed number of DoJ staffers.
The hacker also claimed to have some military emails and credit card numbers belonging to federal employees but provided neither proof nor indication that he intended to release them too.
In October, a teenage hacker who goes by "Cracka" carried out a similar hack and targeted several high-profile government employees, including the CIA director John Brennan, the US spy chief James Clapper, the FBI Deputy Director Mark Giuliano, and others.
However, not all hacks are as vast and serious as that of the US Office of Personnel Management (OPM), in which over 21.5 Million government employees were exposed.
DoJ Downplayed the Impact of Hacking
"This unauthorized access is still under investigation; however, there is no indication at this time that there is any breach of sensitive personally identifiable information," a DOJ spokesman said in a statement to the Guardian.
The hacked data posted anonymously on an encrypted Cryptobin website was reviewed by the Guardian, which found that some of the data from the DHS list are outdated, and some listed individuals have not worked for DHS in years.
Others are criticizing the US government for its failure to protect its sensitive data, especially after the embarrassing and damaging OPM hack that exposed personal details on millions of government employees.
Global and Modern Terrorism/Cyber Terrorism
9.2.2016 Hacking
In the following brief I will describe kinetic plot based modern terrorism/Cyber-terrorism and religious affiliations.
Both Jihadist and Non-Jihadist, organized crime associations, data and statistics to show that Radical Muslim Terrorism is the most prominent form in America today.
Modern terrorism and cyberterrorism display the use of violence and threats to intimidate or coerce, normally for political purposes. The state of fear and submission produced by terrorism is known as terrorization. Both are found underlying in espionage, targeted penetrated breaches and kinetic plots. I will outline and compare the plots based on past history.
A brief history according to James Clapper, Director of National Intelligence; in 2011 alone there were over 13,000 reported attacks. This is a 45-year period of data collection, in which 288 plots led to 611 arrests. In 2016, there were a total of 75 people arrested in 43 plots.
From January 2015 to December of 2015 there were 23 plots of Cyber Terrorism reported and 43 people arrested in 189 plots of terrorism with 454 arrests. Out of 44 plots like Boston, where a kinetic plot was tried and successful; Salafist plots totaled 99%, Non-Jihadist- 3% 14 are Jihadist and led to between 900-1,000 active investigations. Out of 35 plots 70% led to arrest. Out of the targets most are Islamic Driven by Terrorist Radicalization noted by James Comey FBI Director.
Here are some results of terrorism related events following 9/11 and the window of opportunity that it created. There were 288 plots following 9/11 and 170 of those were kinetic plots on the homeland. A whopping 59% of these plots led to arrest.
The Islamic extremists plots equaled 90%, 86 were Jihadist and led to 167 investigations. Out of the 167 investigations 8 were successful plots that reached fruition. Out of the 167 investigated, 78 were interdicted, resulting in 37 murders, and 49 injuries. The Islamic state produced 10-11% splinter groups, 5% women, and 7% bad girls.
In regard to Non-Islamic there were 84 plots resulting in 228 investigations. Out of the 228, 25 kinetic plots on the homeland were successful. There were a total of 59 plots interdicted resulting in 77 deaths and 60 injuries caused by crazy white people.
Official ISIS/ISIL terrorism involved 76 plots from 2014-2016. ISIS produced 60% of these and 18 were on US soil. 26 of these attacks produced violence and 26 were kinetic plots. 14% of total attacks were originating from ISIS. One example is Emanuel Luthchman who tried to capture, bomb, and behead Merchants Grill patrons on New Year’s in New York the name of ISIS. In addition, 4 marines were killed in Tennessee by Isis bred Shiite prisoners and 14 were recently slain in the San Bernardino attacks which were insider attacks.
terrorism isis
Global Terrorism is on the rise in greater numbers than US soil, 17 were killed in the Paris attack. 21 Coptic Christians were murdered on the Libyan Coast. In Tunisia, 137 were killed in a Yemen Mosque. In Kuwait, 39 French and Tunisians were killed at a beach resort. Another 27 killed in a Shiite Mosques and many others remain unreported.
On US Soil, 4 marines were killed in Tennessee, In Akron, OH Terrence Joseph McNeil plots to kill100 US service Members, a terrorist stabbed 5 in Mencer, CA.
In the Federal Spectrum, Government contracts and private sector breach is on the rise. Economic espionage has increased at an alarming rate from 1945-2010. There were 200 arrest were made, 90 in Washington DC Metro area, 40% New York State. Much of these attacks resulted in economic loss from the Chinese. There were 4 confirmed plots in California in 2015. Internationally there were 3 major plots, resulting in a total of 9 indictments which were focused on technology transfer in Government Trade Secrets focused on Corporate Espionage.
This is becoming more and more of the normal trend, instead of the old fashioned classic terrorism through traditional bombings. This modern day terrorism is focused on intellectual theft, theft of personally identifiable information that could lead to easy coercing and manipulation of the person in control of the property. It is focused on theft of trade secrets from the inside out; corporate cyber espionage.
Insider attack history includes the terrorist attacks on London in 2005 which came from their own British Citizens. The Boston Marathon attack was carried out by US citizens and the Paris attacks by French Citizens.
US Cyber Command Commander Admiral Mike Rogers noted that the breach of 22 million records from OPM was simply a part of China’s huge data spying ring from Beijing. The records collected were of those with extensive background checks related to (TSSCI) Top Secret Compartmented Information security clearances. This data will likely lead to identification of spies in China and interruption of their activities.
Big Data Analytics made it possible for large bulk data stolen to be scanned for vital information such as Personally Identifiable Information. PII consists of health, medical, dental, birth, marriage, and or death records leading to next of kin or blood relative threat or coercement.
The pertinent PII; Social Security numbers, mother’s maiden name and or health records can be used and tailored for an intelligence perspective and gain pertinent life details about said individuals or for social engineering and manipulation of said data to alter the individual’s original identity and recruited as double agent and or dual spy.
In an attempt to protect the persons identified in the breach, OPM has transferred the personal data on cleared individuals to the Pentagon. They will take over the monitoring and background to create a secure environment for future individual data security. The annual fiscal cost is estimated at $600,000.00.
In contrast, (then and now) with the recent cross over to Cyber Espionage and Global Terrorism manifestation in Going Dark. Some other terms are rogue, and under the radar through hidden applications and data. These new tactics are through apps which can be download through various applications to the cell phone which cannot be traced by government authorities. Espionage related actions totaled 781, over a span of 20 years in which 565 or 21% Russian and 155 cases confirmed China Based Espionage with many diverted cases through proxy hopping.
The Government cannot gain access to the encrypted communications in applications such as WhatsApp, Snap Chat, Confide, and Signal, just to name a few. The latest encryption methods disappear in a matter of seconds after the message is displayed preventing duplication of said message.
Some popular platforms are gaming platforms which can be used to send encrypted messages under false names. These are used to send and receive plots and plans for attacks. Some other targets through Cyber espionage and hacking are to gain access to PII, Personally Identifiable Information through social media, Twitter, LinkedIn, Face Book, and Dark Mafia, to gather intelligence and or compromise personal data.
In comparison, modern terrorism and cyber terrorism has manifest itself primarily through Islamic radical terrorism in various forms. It comes in many names and under various headings. The primary target is to kill the infidel: (anyone not bowing to the name of Allah). Often times the youth and the weak are recruited as targets for ISIS and ISIL because of their desire to fit in and a need to be a part of something. They are targeted to convert to Islam and radicalized via the internet.
In summary, Terrorism and modern Cyber Terrorism will not go away. This is history repeating itself. Just as many years ago Protestants fought against Catholics, now Christianity fights Muslim. In 2014, 2.6% of terrorism victims lived in Western Countries. This is likely to get worse before it gets better. There is not one easy way to combat terrorism as you see it comes in now in your hand-set, head-set, at your finger-tips. Be wise with your choices as it may come knocking at your door.
CVE-2016-0603 – Oracle Issues out-of-box Java emergency patch for Windows
8.2.2016 Vulnerebility
Oracle issued an out-of-box emergency patch for Java platform running on Windows machines that fixes the critical vulnerability coded as CVE-2016-0603.
Oracle issued an out-of-box emergency patch for Java software running on Windows systems that fixes a critical vulnerability coded as CVE-2016-0603. The vulnerability could be exploited by an attacker to trick users into visiting a malicious website and downloading files on the target system before installing Java 6, 7 or 8.
Oracle hasn’t provided much information on the vulnerability, the flaw has received a CVSS Base Score of 7.6.
“Oracle just released Security Alert CVE-2016-0603 to address a vulnerability that can be exploited when installing Java 6, 7 or 8 on the Windows platform. This vulnerability has received a CVSS Base Score of 7.6.” states the security advisory published by Oracle. “To be successfully exploited, this vulnerability requires that an unsuspecting user be tricked into visiting a malicious web site and download files to the user’s system before installing Java 6, 7 or 8. Though considered relatively complex to exploit, this vulnerability may result, if successfully exploited, in a complete compromise of the unsuspecting user’s system.
As explained by Oracle, the successful exploitation of the CVE-2016-0603 flaw could result in “complete compromise” of the target machine.
The user is exposed to the attack only during the Java installation phase, for this reason, they have no need to upgrade existing Java installation, but that take care if are managing old version of Java prior to 6u113, 7u97 or 8u73 and are installing them. In this last scenario, they have to download the latest Java releases 6u113, 7u97 or 8u73 or later.
Below the list of affected product releases:

“Because the exposure exists only during the installation process, users need not upgrade existing Java installations to address the vulnerability. However, Java users who have downloaded any old version of Java prior to 6u113, 7u97 or 8u73, should discard these old downloads and replace them with 6u113, 7u97 or 8u73 or later.” continues the post.
Oracle recommends users to ensure that they are running the most recent version of Java SE and that all older releases of the software have been completely removed. Oracle further advises against downloading Java from sites other than Java.com as these sites may be malicious.
Another suggestion is to download Java software only from the official Java.com website to avoid ugly surprises.
APT-style bank robberies increase with Metel, GCMAN and Carbanak 2.0 attacks
8.2.2016 Zdroj: Kaspersky APT
In late 2014, Kaspersky Lab researchers made a worrying prediction: financially-motivated cyber-criminals would adopt sophisticated tactics and techniques from APT groups for use in bank robberies.
Just a few months later, in February 2015, we announced the discovery of Carbanak, a cyber-criminal gang that used custom malware and APT techniques to steal millions of dollars while infecting hundreds of financial institutions in at least 30 countries.
Since then, we have seen an increase in these covert, APT-style attacks that combine the use of reconnaissance, social engineering, specialized malware, lateral movement tools and long-term persistence to steal money from financial institutions (particularly ATMs and money transfer systems).
In summer 2015, a #bank in #Russia lost millions of rubles in a one night #bankingAPT #TheSAS2016
Tweet
Today at the Security Analyst Summit (SAS 2016), Kaspersky Lab is announcing the discovery of two new gangs engaged in APT-style bank robberies – Metel and GCMAN – and the reemergence of the Carbanak group with new targets in its sights.
In 2015, Kaspersky Lab researchers conducted Incident Response for 29 organizations located in Russia and infected by these three groups.
Due to the active nature of law enforcement investigations and non-disclosure agreements with victim organizations, Kaspersky Lab cannot provide extensive details of the attacks. Kaspersky Lab is releasing crucial Indicators of Compromise (IOC) and other data to help organizations search for traces of these attack groups in their corporate networks (see below).
The story of Metel – ATM balance rollbacks
In summer 2015, a bank in Russia discovered it had lost millions of rubles in a single night through a series of strange financial transactions. The bank’s clients were making withdrawals from ATMs belonging to other banks and were able to cash out huge sums of money while their balances remained untouched. The victim bank didn’t realize this until it tried to recoup the money withdrawn from the other banks’ ATMs.
During our incident response, we discovered the solution to this puzzle: Metel, a modular malware program also known as Corkow.
The malware, used exclusively by the Metel group, infected the bank’s corporate network via e-mail and moved laterally to gain access to the computers within the bank’s IT systems.
Having gained access to the bank operator’s money-processing system, the gang pulled off a clever trick by automating the rollback of ATM transactions. This meant that money could be stolen from ATM machines via debit cards while the balance on the cards remained the same, allowing for multiple transactions at different ATM machines.
Encrypted configuration for Metel malware plugins
Our investigations revealed that the attackers drove around several cities in Russia, stealing money from ATMs belonging to different banks. With the automated rollback in place the money was instantly returned to the account after the cash had been dispensed from the ATM. The group worked exclusively at night, emptying ATM cassettes at several locations.
GCMAN group planted cron script into #bank server, stealing $200/min #bankingAPT #TheSAS2016
Tweet
In all, we discovered Metel in more than 30 financial institutions, but Kaspersky Lab’s incident responders were able to clean the networks before any major damage could be done. It is highly likely that this threat is far more widespread and we urge financial institutions around the world to scan their networks for signs of the Metel malware.
The Metel criminal group is still active. At the moment, we don’t have any information about any victims outside Russia.
GCMAN – penetration testing tools gone bad
A second group, which we call GCMAN because the malware is based on code compiled on the GCC compiler, emerged recently using similar techniques to the Metel Group to infect banking institutions and attempt to transfer money to e-currency services.
The initial infection mechanism is handled by spear-phishing financial institution targets with e-mails carrying a malicious RAR archive to. Upon opening the RAR archive, an executable is started instead of a Microsoft Word document, resulting in infection.
Once inside the network, the GCMAN group uses legitimate and penetration testing tools such as Putty, VNC, and Meterpreter for lateral movement. Our investigation revealed an attack where the group then planted a cron script into bank’s server, sending financial transactions at the rate of $200 per minute. A time-based scheduler was invoking the script every minute to post new transactions directly to upstream payment processing system. This allowed the group to transfer money to multiple e-currency services without these transactions being reported to any system inside the bank.
Decompiled code of GCMAN malware that is responsible for connecting to CnC
In a stroke of luck, the financial institutions discovered the suspicious activity on their network in time to neutralize the threat and cancel the transactions.
One interesting observation is that the real attack happened approximately 18 months before it was discovered. The group used an MS SQL injection in commercial software running on one of bank’s public web services, and about a year and a half later, they came back to cash out. During that time they poked 70 internal hosts, compromised 56 accounts, making their way from 139 attack sources (TOR and compromised home routers).
We discovered that about two months before the incident someone was trying different passwords for an admin account on a banking server. They were really persistent but doing it only three times a week and then only on Saturdays, in an effort to stay under the radar.
Kaspersky Lab’s research team responded to three financial institutions in Russia that were infected with the GCMAN malware. It is likely that this threat is far more widespread and we urge banks to sweep their networks for signs of this cyber-criminal group.
Carbanak 2.0: new targets beyond banks
After our exposure of the Carbanak group exactly a year ago, the group disappeared for about five months, leading us to believe that the operation was disbanded. However, in September last year, our friends at CSIS published a blog detailing a new Carbanak variant affecting one of its customers.
In December 2015, we confirmed that the group was still active. Kaspersky Lab discovered signs of Carbanak in two institutions – a telecommunications company and a financial institution.
Executable files founded in SHIM during Carbanak incident response
One interesting characteristic of Carbanak 2.0 is a different victim profile. The group has moved beyond banks and is now targeting the budgeting and accounting departments in any organization of interest to them, using the same APT-style tools and techniques.
In one remarkable case, the Carbanak 2.0 gang used its access to a financial institution that stores information about shareholders to change the ownership details of a large company. The information was modified to name a money mule as a shareholder of the company, displaying their IDs. It’s unclear how they wanted to make use of this information in future.
#Carbanak gang is now targeting budgeting & accounting departments #bankingAPT #TheSAS2016
Tweet
Kaspersky Lab products successfully detect and block the malware used by the Carbanak 2.0, Metel and GCMAN threat actors with the following detection names:
Trojan-Dropper.Win32.Metel
Backdoor.Win32.Metel
Trojan-Banker.Win32.Metel
Backdoor.Win32.GCMan
Backdoor.Win64.GCMan
Trojan-Downloader.Win32.GCMan
Trojan-Downloader.Win32.Carbanak
Backdoor.Win32.Carbanak
Kaspersky Lab urges all organizations to carefully scan their networks for the presence of Carbanak, Metel and GCMAN and, if detected, to disinfect their systems/computers/networks and report the intrusion to law enforcement.
All this information has been made available to customers of our APT intelligence reporting service and they received the indicators of compromise and context information as soon as they became available.
Oracle Issues Emergency Java Update for Windows
8.2.2016 Vulnerebility
The US-based software maker Oracle delivered an unusual out-of-box emergency patch for Java in an effort to fix a during-installation flaw on the Windows platforms.
The successful exploitation of the critical vulnerability, assigned CVE-2016-0603, could allow an attacker to trick an unsuspecting user into visiting a malicious website and downloading files to the victim's system before installing Java 6, 7 or 8.
Although the vulnerability is considered relatively complex to exploit, a successful attack results in "complete compromise" of the target's machine.
What You Need to Know About the Java Exploit
The successful attack requires an attacker to trick a suitably unskilled user for opening a Java release even though the user is nowhere near the Java Website.
Since the existence of the loophole is only during the installation process, users are not required to upgrade their existing Java installations in order to address the vulnerability.
"However, Java users who have downloaded any old version of Java before 6u113, 7u97 or 8u73, should discard these old downloads and replace them with 6u113, 7u97 or 8u73 or later," says Eric Maurice, Oracle security blogger.
Patch Now! Java Update Released
Not much details about the flaw have been known yet, neither Oracle has provided any public information on the nature of the vulnerability.
However, due to the threat posed by a successful attack, we strongly recommend customers to apply the emergency patch as soon as possible.
Hackers behind Dyre Malware Busted in Police Raid
8.2.2016 Virus
The world's most notorious financial hacking operation disrupted by Russian authorities in November, when they raided the offices associated with a Moscow-based film and production company named 25th Floor.
According to the Russian authorities, 25th Floor was allegedly involved in distributing the notorious password-stealing malware known as Dyre Banking Trojan.
Malware Costs Hundreds of $$$ Millions in Losses
The Dyre banking Trojan was typically distributed via spam campaigns and was responsible for over hundreds of millions of dollars in losses at banking and financial institutions, including Bank of America Corp, PayPal, and JPMorgan Chase & Co.
Dyre, also known as Dyreza, first appeared in July 2014 and updated to target Windows 10 systems and its newest Edge browser.
However, Dyre has not been in use since the November raid, according to cyber security experts, who said the raid represents Russia's biggest effort up to date in cracking down on cyber crime.
It is yet not known whether the Russian authorities anyone has arrested or charged anyone linked to the raid.
However, the sources familiar with the matter told Reuters that the Dyre investigation was aided by security firm Kaspersky Lab that would reveal details about the case at its annual conference for security experts starting Sunday.
The malware authors used a variety of techniques to deliver Dyre malware onto victim's web browser in an effort to alter the communication between customers and over 400 financial institutions.
They Producing Cyber-Crime Thriller Movie — BOTNET
The name came out from the November raid: 25th Floor that distributes movies and Television shows in Russia and other East European and near-east countries.
The company is currently busy in the production of a film called BOTNET – a cyber crime thriller based on a 2010 case in which 37 people from the United States and other countries were charged for a $3 Million scam.
25th Floor hired Moscow-based computer security company Group-IB to advise the Botnet director and writers on the detailed aspects of cybercrime, said Group-IB CEO Ilya Sachkov. He said he was initially approached by Nikolay Volchkov, the CEO of 25th Floor.
Then Sachkov got an urgent call from Volchkov last November, saying he needed to meet.
"He was afraid. His color was totally white," added Sachkov. "He knows there's an ongoing investigation about cybercrime."
To know how the Dyre banking malware works and how you can protect yourself against the malware, you can read this The Hacker News article.
Breaking — India Bans Facebook's Free Basics Service
8.2.2016 Social Site
Facebook's Free Basics Internet service has been Blocked in India.
The Telecom Regulatory Authority of India (TRAI) has banned mobile carriers and broadband providers to charge customers based on what services or content they access over the Internet.
Under Prohibition of Discriminatory Tariffs for Data Services Regulations, 2016, "no service provider shall offer or charge discriminatory tariffs for data services on the basis of content."
With this, Facebook's Free Basics is dead in India.
All Zero-Rated Internet Services are BLOCKED!
It is not just Facebook's Free Basics Internet program that has been blocked inside the country, but also the zero-rated internet services altogether.
Zero-rated internet services means those services that allow people access to some websites and web services without utilizing any of their mobile data allowance. Under the new regulation, no such services are now allowed.
Free Basics (previously known by Internet.org) is a Facebook's service that offers people access to more than three dozen Web services hosted on its platform at free of cost.
Subscribers of Free Basics app must have a Reliance mobile network on their phone and are limited to a range of portals including Wikipedia, BBC News, AccuWeather, Bing, and various health websites, and of course, Facebook and Facebook Messenger.
Free Basics Vs. Net Neutrality
Since its launch, Free Basics has been a controversial subject in the country and violated Net Neutrality principles.
Net Neutrality advocates argued that by offering some websites and services for free, people are discouraged from visiting other sites. Facebook's Free Basics offers a huge advantage to the sites and services it includes.
For example, if the Free Basics includes Facebook Messenger to access for free, any other instant messaging app wouldn't be able to upsurge in this competitive market, and this is nothing but the violation of Net Neutrality.
The Telecom regulator had previously ordered Reliance Communications to temporary suspend Free Basics until the regulatory had come to a decision regarding the implementation of rules on differential data tariffs.
Facebook has been contacted for comment on the new regulation in India, which is the second populous country in the world. We'll update this article when we hear Facebook's response.
Hackers leaked DHS staff records, 200GB of files are in their hands
8.2.2016 Hacking
A hacker accessed an employee’s email account at the Department of Justice and stole 200GB of files including records of 9,000 DHS staffers and 20,000 FBI employees.
Yesterday, the data related a Department of Homeland Security (DHS) staff directory were leaked online, a Twitter account shared the link to an archive containing 9,355 names.
The responsible for the data leakage first contacted Motherboard to share the precious archive.
Each record of the DHS Staff Directory includes name, title, email address, and phone number.
Going deep in the archive it is possible to note that it includes information of DHS security specialists, program analysts, InfoSec and IT and also 100 employees with a title “Intelligence”.
The same Twitter account has announced later the imminent release of an additional data dump containing 20,000 FBI employees.
DHS firewall
Are the records authentic?
Motherboard that obtained the archive reached the operations center of the FBI, and in one case the individual who pick up the phone presented himself with the same name associated with that number in the archive. A similar circumstance occurred with a DHS employee, Motherboard so confirmed that the information is legit.
Which is the source of data?
According to Motherboard, a hacker accessed an employee’s email account at the Department of Justice. As proof, the hacker sent the email message to Motherboard’s contributor Joseph Cox directly from the compromised account.
“A hacker, who wishes to remain anonymous, plans to dump the apparent names, job titles, email addresses and phone numbers of over 20,000 supposed Federal Bureau of Investigation (FBI) employees, as well as over 9,000 alleged Department of Homeland Security (DHS) employees, Motherboard has learned.” wrote Cox in a blog post.
“The hacker also claims to have downloaded hundreds of gigabytes of data from a Department of Justice (DOJ) computer, although that data has not been published.”
The hacker first tried to use the compromised credentials to access a DOJ staff portal, but without success, then he called the department directly and obtained the access through social engineering techniques.
The hacker accessed the DoJ intranet where the database is hosted, then he downloaded around the, out of 1TB that he had access to.
“I HAD access to it, I couldn’t take all of the 1TB,” the hacker told to MotherBoard.
The hackers confirmed his intention to release the rest of the data in the near future.Which is the motivation behind the attack?
It is not clear at the moment why the hacker released the archive, surely it’s not financially motivated. The hacker only left the following message when has leaked the data-
“This is for Palestine, Ramallah, West Bank, Gaza, This is for the child that is searching for an answer…” which are the verses of “Long Live Palestine”
The only certainty right now is that similar incidents are becoming too frequent, apparently the government staff is not properly trained on the main cyber threats or the hacking technique. Similar incidents show the lack of knowledge on the most basic security measures.
Whenever a hacker leaks so sensitive data, I think the number of his peers who had access to the same information with the intent to use them in other attacks or resell them, perhaps to a foreign government.
T9000 backdoor, a sophisticated malware that spies on Skype users
8.2.2016 Virus
The T9000 backdoor discovered by PaloAlto Networks is able to infect victims’ machines to steal files, take screengrabs, and records Skype conversations.
A new threat is targeting Skype users, it is a backdoor trojan dubbed T9000 that is able to infect a victim’s machine to steal files, take screengrabs, and record conversations. The T9000 backdoor was spotted by researchers at Palo Alto Networks, it appears as a hybrid variant of another malware dubbed T5000 that was detected in the wild two years ago.
“In addition to the basic functionality all backdoors provide, T9000 allows the attacker to capture encrypted data, take screenshots of specific applications and specifically target Skype users. The malware goes to great lengths to identify a total of 24 potential security products that may be running on a system and customizes its installation mechanism to specifically evade those that are installed.” states a blog post published by PaloAlto Networks.
The T9000 was used by threat actors to targets organizations worldwide, the researchers observed it used in multiple targeted attacks against US organizations.
The backdoor uses a multistage execution flow, which starts when victims opens an RTF file that contained exploits for specific vulnerabilities (i.e. both CVE-2012-1856 and CVE-2015-1641).
It checks before for the presence of defense solutions and malware analysis tools including Sophos, INCAInternet, DoctorWeb, Baidu, Comodo, TrustPortAntivirus, GData, AVG, BitDefender, VirusChaser, McAfee, Panda, Trend Micro, Kingsoft, Norton, Micropoint, Filseclab, AhnLab, JiangMin, Tencent, Avira, Kaspersky, Rising, and Qihoo 360.
At first stage of the infection the T9000 backdoor collects information on the target system and sends it to the C&C server, then the control infrastructure sends specific command to the bot based on the characteristic of the infected machine.
The researchers at Palo Alto Networks have identified three main plugins in the T9000 backdoor:
tyeu.dat
vnkd.dat
qhnj.dat
tyeu.dat is the component that implemented the features to spy on Skype conversations, when hooking into the Skype API, the victim is presented with the message “explorer.exe wants to use Skype.” Theis Skype module can record both audio and video conversations, spy on text chats and take regular screenshots of video calls.

The vnkd.dat component is loaded to steal files on the infected computer, meanwhile the third module qhnj.dat implements backdoor functionalities to control the local file system (i.e. Create/delete/move, encrypt files and directories, and copy the user’s clipboard).
The experts at Palo Alto sustain that the backdoor was developed by skilled professionals due to the evasion technique implemented by the malicious code.
“The author of this backdoor has gone to great lengths to avoid being detected and to evade the scrutiny of the malware analysis community. We hope that sharing the details of how this tool works as well as the indicators in the section below will help others defend themselves against attacks using this tool.”
Aktualizace Flash Playeru je ve skutečnosti scareware
8.2.2016 Hrozby
Na pozoru by se měli mít v posledních dnech uživatelé počítačů od společnosti Apple. Jako lavina se totiž internetem šíří škodlivý virus, který se vydává za aktualizaci populárního programu Flash Player právě pro operační systém Mac OS X. Ve skutečnosti jde ale o tzv. scareware, varoval Národní bezpečnostní tým CSIRT.
„Uživatelé OS X by se měli mít na pozoru před novou kampaní, při které jsou přesvědčováni, aby provedli update Adobe Flash Playeru,“ varoval konstatoval Pavel Bašta, bezpečnostní analytik týmu CSIRT, který je provozován sdružením CZ.NIC.
Místo updatu si ale podle něj uživatelé stáhnou do svých počítačů s logem nakousnutého jablka scareware. „Ten se pak pokouší přesvědčit uživatele k zavolání na linku podpory pod záminkou vyřešení údajného technického problému,“ doplnil Bašta.
Přesměruje uživatele na podvodný web
O žádné stránky technické podpory ve skutečnosti samozřejmě nejde. Scareware přesměruje uživatele na podvodný web, který obsahuje další hrozby. Tak se do počítače dostanou další nezvaní návštěvníci.
Podobně pracují viry z rodiny scareware prakticky vždy. Snaží se v uživateli vzbudit dojem, že je s jejich počítačem něco špatně a místo skutečné pomoci jej přesměrují na podvodné stránky. U lidí zpravidla v takových situacích sílí negativní emoce, že je s jejich strojem něco špatně, a nejsou tolik pozorní – snadno si pak do PC pustí další škodlivé viry.
Flash Player používají milióny lidí
V současnosti se falešná aktualizace Flash Playeru šíří výhradně na strojích s operačním systémem Mac OS X od Applu. Není ale vyloučeno, že se v dohledné době objeví totožná hrozba cílící také na majitele strojů s Windows nebo Linuxem.
Flash Player si počítačoví piráti nevybrali náhodou. Tento populární přehrávač videí na internetu používají milióny lidí na celém světě, díky čemuž mohou být kyberzločinci během svých útoků velmi úspěšní. S jediným virem totiž mohou napadnout relativně velké množství uživatelů.
Critical Vulnerabilities in 3G/4G Modems or how to build Big Brother
8.2.2016 Vulnerebility
This report is the continuation of "#root via SMS", a research made by the SCADA Strangelove team in 2014. It was devoted to telecommunications equipment vulnerabilities with modem flaws only partially covered. This document describes vulnerabilities found and exploited in eight popular 3G and 4G modems available in Russia and worldwide. The findings include Remote Code Execution (RCE) in web scripts, integrity attacks, Cross-Site Request Forgery (CSRF), and Cross-Site Scripting (XSS).
The research covers a full range of attacks against carrier customers using these types of modems — device identification, code injection, PC infection, SIM card cloning, data interception, determining subscriber location, getting access to user accounts on the operator's website, and APT attacks.
Equipment
We analyzed eight modems of the following vendors:
Huawei (two different modems and a router)
Gemtek (a modem and a router)
Quanta (two modems)
ZTE (one modem)
Not all the modems had vulnerabilities in their factory settings; some of them appeared after the firmware was customized by the service provider.
For convenience, let's call all the network equipment — both modems and routers — collectively, "modems".
Statistics on Vulnerable Modems
The data was gathered passively from SecurityLab.ru between 01/29/2015 and 02/05/2015 (one week). Our statistics lacks information about Huawei modems, but it can be easily found at shodan.io:
Vulnerabilities Detected
All the modem models investigated had critical vulnerabilities leading to complete system compromise. Virtually all the vulnerabilities could be exploited remotely (see the "Modems" table). Description of the detected vulnerabilities ranked by severity:
1. RCE (five devices)
All the modem web servers are based on simple CGI scripts that are not properly filtrated (except for Huawei modems, and even then only after a few security updates since the vulnerabilities have been disclosed).
All the modems work with the file system — they need to send AT commands, read and write SMS messages, configure firewall rules, etc.
Almost no devices had CSRF protection, which allowed remote code execution by power of social engineering and remote requests through a malicious website. Some modems were also vulnerable to XSS attacks.
Combined, these three factors produce a disappointing result — more than 60% of the modems are vulnerable to Remote Code Execution. You could get an updated firmware without all found vulns for only Huawei modems (there's a public description of the vulnerabilities). The other vulnerabilities are still considered to be zero-day.
2. Integrity Attacks (six devices)
Only three modems were protected against arbitrary firmware modifications. Two of them had the same integrity check algorithms (asymmetrically encrypted SHA1 with RSA digital signature), and the third one used the RC4 stream cipher for firmware encryption.
All the cryptographic algorithms proved to be vulnerable to attacks violating integrity and confidentiality. In the former case, we can modify the firmware by injecting an arbitrary code. In the latter case, given the weak implementation of the algorithm, we managed to extract the encryption key and determine the encryption algorithm, which also allows firmware modification.
The other three modems had no protection from integrity attacks, but a local access to COM interfaces was required to update the firmware.
The remaining two modems could be updated only though the carrier's network via Firmware Over-The-Air (FOTA) technology.
3. CSRF (five devices)
CSRF attacks can be used for various purposes, but the primary ones are remote upload of modified firmware and successful arbitrary code injection. Using unique tokens for each request is an efficient protection against this type of attacks.
4. XSS (four devices)
The scope of this attack is quite wide — from host infection to SMS interception. However, our research focuses mainly on its prime target — modified firmware upload bypassing AntiCSRF checks and the Same-Origin Policy.
Attack Vectors
1. Identification
First, you need to identify a modem for a successful attack. You can send all kinds of requests to exploit RCE or try to upload various updates via all the possible addresses, but it seems to be inefficient and too signally for a target user. The time of infection — from user detection to code injection, modification of modem settings, etc. — is also quite important in the real (not simulated) conditions.
For this very reason, you need to identify the target device properly. To do that, you must use a simple set of picture addresses, which can tell you the model of the modem. This method helped us to identify all the investigated modems 100%. An example of the code:


2. Code Injection
This stage is described in the previous section, points 1 and 2. The code can be injected either though RCE in web scripts, or though uploading infected firmware. The first method allowed us to penetrate five modems, it isn't that complicated.
Let's describe the vectors of the second method in detail.
Two modems used the same algorithm to protect firmware integrity: the digital signature of SHA1 hash sum by an asymmetric RSA key was carried out via an OpenSSL library. The verification was incorrect: after uploading the firmware (an archive), the web server extracted two main files from it — the one specifying the size of the verified data and the one with the signed hash sum. Next, the verification script obtained a public key from the file system and sent a request to OpenSSL functions to decrypt signature and compare hashsum. If hashsums were the same, the update was installed. The firmware compression algorithm had a feature — you could add additional files with the same names to the archive, but its first bytes wouldn't change. In addition, when we extracted the firmware, the later files overrode the earlier files. This allows changing the firmware without affecting data integrity checks.
The firmware of the third modem was encrypted by the RC4 algorithm with a constant keystream. As there were three different firmware versions on the Internet, you could get several bytes of plain text where there were bytes 0x00 in a file of the unencrypted firmware.
Then, we extracted the ISO image of the modem's virtual CDROM, which allowed us to decipher the first several kilobytes of the each firmware image. They contained the encryption algorithm and address of the encryption key. By XORing the two pieces of firmware, we obtained the plain text of the key itself.
Dmitry Sklyarov, an experienced cryptanalyst and reverse engineer from Positive Technologies, helped us a lot to conduct attacks against cryptographic protocols.
You can use CSRF for remote upload and HTML5 functions for transferring multipart/form-data, or XSS if an application is protected against CSRF (Huawei modem). Only three Huawei modems had this kind of protection, which could be bypassed via XSS, though. In all other cases, an attacker could use the HTML5 code located on a special web page (you can download an example from http://blog.kotowicz.net/2011/04/how-to-upload-arbitrary-file-contents.html).
Gemtek modems required a special utility for firmware updates installed on PC. In this case, firmware was uploaded though host internet connection via HTTP. After that, the firmware integrity was verified by checksums uploaded from the server. We failed to test this scenario.
However, it’s no use hoping that a vendor that doesn't properly check firmware integrity during upload protects it well enough.
3. Data Interception
Now we can execute an arbitrary code on the modem. You need to do three things: determine the modem’s location (later you will understand why) plus be able to intercept SMS messages and HTTP/HTTPS traffic.
The easiest way to determine location is to find the base station identifier (CellID). Then, with the operator’s MCC and MNC at hand, you can determine the victim’s exact location by means of some public bases, such as opencellid.org. Another method is to use the modem’s Wi-Fi card to scan nearby networks and determine the victim’s location area more accurately, given that one base station may have quite a broad coverage. We managed to obtain the CellID of six modems; Wi-Fi was available in two devices. We had to recompile and upload new network card drivers for one of the modems. Its previous driver allowed only the Ad Hoc mode, which prevents scanning nearby APs.
We studied two types of modems: with and without SMS support. The first type also didn’t allow SMS reading though AT commands. The second type allowed SMS reading via XSS. The messages are usually stored in the file system, and it’s not so difficult to get access to them for reading or sending SMS messages and USSD requests.
Traffic interception is more interesting. There are several ways to do that: by changing the modem’s DNS server settings, or replacing the modem’s gateway with the Wi-Fi interface and connecting to an hacker’s access point (that’s why you should know the victim’s location). The first method is simpler: changing the settings is a piece of cake, as they are also stored in the file system. We managed to do that for all but one modem. We studied the second method only in theory — switching the network card mode from ad hoc to active, connecting to an access point, and changing modem routing.
Not only HTTP traffic can be intercepted. By injecting and executing a VBS code on an HTML page, you can add your certificate to the Trusted Root Certification Authorities and successfully conduct MITM attacks:
4. SIM Card Cloning and 2G Traffic Interception
The attacks against SIM card applications were described in detail by Karsten Nohl and in the “#root via SMS” research. We still have to send binary SMS messages to SIM cards, as we failed to make modems send commands to SIM card applications via APDU.
It’s not that bad, though — by injecting an arbitrary code to a modem, you can extend the attack scope by means of binary SMS messages. Firstly, you can now send these messages “to yourself” from the target SIM card via the AT interface by switching the modem to the test mode and working with the COM port. You can do that in the background —the web interface will be available to the victim, who will hardly notice mode changeover. Secondly, you need to exchange data with the COM port via injecting a VBS code to the modem page and executing it with user rights with the help of social engineering.
Switching the modem to the test mode
The PowerShell script for sending a binary SMS message
Using FakeBTS is the next attack vector, and you also need to know the victim’s location for it. Having the victim’s exact location and IMSI at hand, we can use a fake base station nearby and wait until the subscriber connects to us, or we can force a base station (it is possible for five devices). If the operation is successful, we will be able to send binary SMS messages to the target SIM card without any restrictions from the operator.
5. PC Infection
If we penetrate a modem, we have very few attack vectors. However, infecting a PC connected to the modem provides us with many ways to steal and intercept the PC user's data.
You may have already heard of the main infection vector — bad USB. There are also some other methods involving social engineering:
Virtual CDROM. Almost all the modems have a virtual drive image that is enabled for driver installation. You need to replace the image and force its mounting.
VBS, drive-by-download. Code injection to an HTML page, or forced upload of executable files as updates or “diag utilities”.
Browser 0-days. As an example, we used Adobe Flash 0-day found in the archives of Hacking Team.
Vulnerable client software. One of the operators delivered vulnerable diagnostic software together with its modems, which allowed executing an arbitrary code on Windows and OS X PCs. Reference: we'd like to give a special thanks to Mikhail Firstov from Headlight Security for detecting this vulnerability.
Random Code Execution in the client software of a modem
6. APT Attacks
After infecting the modem and host, you need to stay in the systems somehow — save changes in the modem's even after it is switched off and prevent further firmware updates. It would be useful to detect and infect other vulnerable modems as soon as they will be connected to the PC. Most of the devices can be infected right at the phone store during "checking before buying".
There was another attack we failed to conduct — accessing the modem from the operator's network. Most vulnerable web servers listen at *:80, i.e. there's a chance that the modem's web server will be available from the operator's network. Only a few modems restrict connections incoming from the telecom's network or specify the address for listen 192.168.0.1:80.
7. Additional Information
We also studied getting access to a personal account by sending a USSD request and resetting password via an SMS message.
This vector was demonstrated during the "#root via SMS" presentation. The vulnerability was exploited through an XSS attack that could be conducted by sending an SMS message. However, an attacker can also do that in modems that allow SMS reading via RCE.
XSS exploitation results
Summary
All in all, we have a full infection cycle of devices and related PCs. Using the infected devices, we can determine location, intercept and send SMS messages and USSD requests, read HTTP and HTTPS traffic (by replacing SSL certificates), attack SIM cards via binary SMS messages, and intercept 2G traffic. Further infection can continue through the operator's networks, popular websites or equipment infected by worms (when connecting a new device).
What can we recommend to those clients who constantly work with such devices? Huawei modems with the latest firmware updates are the most protected. It is the only company that delivers firmware (the operators are only allowed to add some visual elements and enable/disable certain functions) and fixes vulnerabilities detected in its software.

Modems
Information Disclosure
Although 90 days had left since the service providers were informed of the vulnerabilities, many flaws remained unfixed. A crucial point: the vulnerabilities found during the research are not always fault of modem vendors. They can be added by telecom operators during software customization.
Masivní DDoS útok vyřadil internetové bankovnictví britské HSBC
8.2.2016 Počítačový útok
Dva dny trvalo největší evropské bance, než znovu zprovoznila osobní internetové bankovnictví. Pachatel dosud nebyl odhalen.
Útok DDoS (Distributed Denial of Service) má vždy stejný scénář. Stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se pak takto napadená webová stránka tváří jako nedostupná.Tisíce zákazníků britské pobočky světové banky HSBC se nemohly během víkendu dostat prostřednictvím internetu ke svým osobním účtům. Internetové bankovnictví HSBC zkolabovalo pod náporem masivního DDoS útoku, při kterém na stránky přicházely tisíce a miliony požadavků z řady počítačů po celém světě, jež zcela vyřadily web z provozu.
Odstávka systému trvala dva dny, po které nebylo možné zadávat platby online. Útok byl načasovaný na dobu, kdy řada Britů podává daňové přiznání za loňský rok. Banka kvůli tomu čelila kritice rozzuřených nespokojených klientů, kteří si často nebrali servítky a zaplavili její profil na Facebooku řadou nadávek.
Jde o druhý velký výpadek v jediném měsíci.
I když se bance podařilo online bankovnictví po víkendovém výpadku zprovoznit, stále ještě nefunguje na sto procent. „Internetové a mobilní služby HSBC jsou částečně funkční, nadále ale pracujeme na obnovení kompletního servisu,“ ujistil zákazníky provozní ředitel britské pobočky HSBC John Hackett. Banka se nechala slyšet, že „úspěšně ochránila“ své systémy před DDoS útokem, ale čelí další vlně útoků, kvůli nimž nemůže zcela obnovit všechny své služby.
Pro britskou HSBC jde o druhý velký výpadek v jediném měsíci: začátkem ledna se tisíce klientů banky nemohly dostat ke svým účtům přes internet kvůli výpadku elektrického proudu.
Opakované kolapsy bankovních systémů nenechávají chladnými britské zákonodárce.
Konzervativní předseda finančního výboru dolní sněmovny britského parlamentu Andrew Tyrie vyzývá k urychlenému řešení situace. „Banky zkrátka nejsou na takovéto případy připraveny. Ohrožuje to nejen je, ale i celé hospodářství a tím se vystavujeme riziku selhání celého systému,“ varoval Tyrie. Mluvčí HSBC ujistil, že víkendový výpadek internetových služeb nevedl k žádným reálným škodám na zákaznických účtech.
Finanční kriminalita přijde britskou státní kasu na 52 miliard liber ročně.
„Známe případy, kdy DDoS útoky proti bankám plnily funkci jakési kouřové clony a kryly další zločinné aktivity, jako jsou kybernetické loupeže, převody velkého objemu peněz nebo krádeže a pozměňování dat klientů,“ upozornil Robert Capps, viceprezident pro rozvoj společnosti NuData Security.
Finanční kriminalita přijde britskou státní kasu na 52 miliard liber ročně (1,85 bilionu korun). Podle inspektora Jamese Phipsona z londýnského policejního ředitelství pro vyšetřování hospodářské kriminality odhalování pachatelů ztěžuje fakt, že nahlášeno bývá jen asi 12 procent případů počítačové kriminality. Případ HSBC policie stále vyšetřuje, viník však uniká.
How to thwart the passcode lock screen on iOS 8 and 9?
8.2.2016 Apple
A security expert discovered an authentication bypass vulnerability in both iOS devices that allows thwarting lock screen passcode.
The security researcher Benjamin Kunz Mejri from Vulnerability Laboratory has discovered an authentication bypass-sized hole in both iPhones and iPads running iOS 8 and iOS 9 that can be exploited by attackers to thwart lock screen passcode.
This threat is real people, there is a video of it and documentation available online. It’s all pretty technical but the upshot is the vulnerability lets an attacker bypass the lockscreen on handsets running iOS 8 and iOS 9.
It is important to highlight that the attacker requires physical access to an unlocked iOS device, for this reason the threat is considered not so critical.
“An application update loop that results in a pass code bypass vulnerability has been discovered in the official Apple iOS (iPhone5&6|iPad2) v8.x, v9.0, v9.1 & v9.2. The security vulnerability allows local attackers to bypass pass code lock protection of the apple iphone via an application update loop issue. The issue affects the device security when processing to request a local update by an installed mobile ios web-application.” states the technical description published by the vulnerability-lab.com.
The attacker can bring the iOS devices into an unlimited loop resulting in a temporarily deactivate of the pass code lock screen.
“Local attacker can trick the iOS device into a mode were a runtime issue with unlimited loop occurs. This finally results in a temporarily deactivate of the pass code lock screen. By loading the loop with remote app interaction we was able to stable bypass the auth of an iphone after the reactivation via shutdown button. The settings of the device was permanently requesting the pass code lock on interaction. Normally the pass code lock is being activated during the shutdown button interaction. In case of the loop the request shuts the display down but does not activate the pass code lock like demonstrated in the attached poc security video.”
The issue could be triggered by powering off the iOS device, upon reboot the passcode authentication feature remains disabled, allowing an attacker to access the device without providing the passcode.
iPhone 6 bypass passcode
The advisory describes the following attack scenario:
First fill up about some % of the free memory in the iOS device with random data.
Now, you open the app-store choose to update all applications (update all push button).
Switch fast via home button to the slide index and perform iOS update at the same time Note: The interaction to switch needs to be performed very fast to successfully exploit. In the first load of the update you can still use the home button. Press it go back to index.
Now, press the home button again to review the open runnings slides.
Switch to the left menu after the last slide which is new and perform to open siri in the same moment. Now the slide hangs and runs all time in a loop.
Turn of via power button the ipad or iphone ….
Reactivate via power button and like you can see the session still runs in the loop and can be requested without any pass code Note: Normally the pass code becomes available after the power off button interaction to stand-by mode.
Successful reproduce of the local security vulnerability!
Kunz reported the vulnerability to the Apple Product Security Team in late 2015, but at the time I was writing the issue is still present.
Are you an iOS user? You should be careful when leaving the mobile device unattended.
Dyre crackdown, the biggest effort to date by Russian authorities against cybercrime
8.2.2016 Crime
Russian authorities raided offices of a Russian film distribution and production company as part of an operation against the Dyre gang.
Russian law enforcement and intelligence agencies in November raided offices of a Russian film distribution and production company as part of an operation against one of the world’s most notorious cybercrime ring.
The authorities were supported by the experts at Kaspersky Lab who confirmed the involvement and announced it would reveal details about the operation at its annual conference.
This is the biggest effort to date of Russian authorities against the cybercrime.
Experts believe that the ring is responsible for the distribution of the infamous Dyre banking trojan that caused overall losses for more than tens of millions of dollars.
The list of victims includes names like Bank of America Corp and JPMorgan Chase & Co.
According to the Reuters that published the news in exclusive, authorities haven’t commented the operations, meanwhile the CEO of the film company refused to provide further information.
“A spokesman for the Russian Interior Ministry’s cybercrime unit said his department was not involved in the case. The FSB, Russia’s main intelligence service, said it had no immediate comment.
Nikolay Volchkov, the chief executive of the film company named 25th Floor, said he could not answer questions about the raid.” wrote the Reuters.
Reuters clarified that it has no evidence that Volchkov or the film company is directly involved the criminal organization.
The unique certainly is that rarely criminal rings operating in from Russian are persecuted by the government if they don’t target Russian organizations.
According to the Heimdal Security, in November 2015 more than 80.000 machines were already infected with Dyre Trojan across the world. The experts at Dell SecureWorks estimated that more than 400 financial institutions have fallen victim of the infamous trojan.
Dyre is usually downloaded by the malicious trojan Upatre, it is a powerful malware capable to perform man-in-the-middle attacks through browser injections and harvest the victim’s credential.

The experts believe that the operation of the Russian authorities has successfully beheaded the organization behind the Dyre Trojan.
“We have seen a disruption over the last few months that is definitely consistent with successful law enforcement action,” explained security expert John Miller from iSight Partners.
There is another mystery in the story, the film company was working on a production called Botnet. a film on cybercrime ring with a story that has many similarities with the Dyre gang.
The company also hired the firm Group-IB to advise the Botnet director and writers on the finer points of cybercrime.
Group-IB CEO, Ilya Sachkov, said he met Volchkov at a security conference.
“He asked if we would be interested in consulting with a scriptwriter they would hire in the United States,” Sachkov said.
In November, Sachkov received a strange and an urgent call from Volchkov, saying he needed to meet.
“He was afraid. His colour was totally white,” said Sachkov. “He knows there is an ongoing investigation about cybercrime.”
Reuse of login credentials put more than 20M Alibaba accounts at risk
8.2.2016 Hacking
The reuse of login credentials on Taobao exposed more than 20 million accounts on Alibaba’s websites to attacks.
According to the state media reports, hackers have targeted over 20 million active accounts on Alibaba Group’s Taobao e-commerce website using Alibaba’s own cloud computing service.
The Chinese Giant detected the attack in “the first instance” and responded requesting users to change their passwords.
According to a report published on a website managed by the Ministry of Public Security, hackers behind the attack obtained a database of 99 million usernames and passwords from a number of websites.
The hackers used the Alibaba’s cloud computing platform in the attempt to use the stolen credentials with the Taobao platform.
The hackers discovered that 20.59 million of the 99 million usernames, were shared among different websites, including the e-commerce platform of the Chinese Giant.
20.59 million represents about five percent of annual active buyers on Chinese retail marketplaces.
Alibaba Taobao 2
‘A spokesman from Alibaba confirmed that hackers rented the cloud computing service to launch the attack, but highlighted that there are no security issues affecting the company’s platform.
“Alibaba’s system was never breached,” the spokesman declared.
The hackers started to test the stolen credentials in mid-October and were discovered in November, when experts at Chinese company discovered the unauthorized accesses reported the case to police.
According to the ministry website, Alibaba discovered and blocked the majority of login attempts.
The experts discovered that the compromised accounts were used in various fraudulent activities. The hackers used them to raise Taobao sellers’ rankings placing fake orders, a mechanism known as ‘brushing’.
The incident once again raises the importance of a proper security posture for Internet users, the bad habit of sharing same login credentials among several web services is one of the main causes of security breaches.
Prohlížeč Avast SafeZone byl nebezpečnější než výchozí Chromium
6.2.2016 Hrozby
Prohlížeč Avast SafeZone byl nebezpečnější než výchozí ChromiumDnes, Milan Šurkala, aktualitaAntivirové společnosti někdy nabízí speciální verze prohlížečů, které mají být ještě bezpečnější než ty běžně používané. Skutečnost je ale často opačná, což platilo i pro Avast SafeZone. Ten trpěl na chybu, která byla ve Chromiu, z něhož vychází, ošetřena.
Už v minulosti se stalo, že speciální "bezpečná" varianta internetového prohlížeče dodávaná v balíčku antivirových programů byla méně bezpečná než prohlížeč, z něhož tato verze vycházela. Jednou z posledních byla např. společnost Comodo, jejíž prohlížeč Chromodo měl některé chyby navíc. Postihlo to také Avast a jeho prohlížeč SafeZone (Avastium). Ten vychází z enginu Chromium. SafeZone bohužel trpí na chybu, kdy je možné vzdáleně spustit prohlížeč a s jeho pomocí procházet celý počítač uživatele.
Stačí k tomu prohlížet útočnou stránku pomocí jakéhokoli prohlížeče, kdy škodlivý kód v JavaScriptu dokáže přes vzdálené volání procedur spustit SafeZone a převzít nad ním kontrolu. Zatímco prohlížeče obvykle dokážou lokálně procházet jen lokální počítač nebo síť, SafeZone tuto ochranu nemá a umožňuje toto procházení i počítačům zvenku. Zajímavé je to zejména proto, že Chromium, z něhož SafeZone vychází, touto ochranou disponuje. Na chybu přišel Tavis Osmandy z Google Project Zero a oznámil ji 18. prosince minulého roku. Problém demonstroval, kdy napsal kód ke vzdálenému přístupu k počítači a pomocí prohlížeče je možné vypsat obsah disku C:. Prohlížeč SafeZone se nyní dočkal opravy (verze 2016.11.1.2253) a už by nemělo být možné vzdáleně přebírat kontrolu nad prohlížečem SafeZone.
Maru OS — Android ROM that Turns into Debian Linux When Connected to a PC
6.2.2016 OS
Good News for Linux Techno Freaks! Do you usually mess with your Android smartphone by trying out the continual ins and outs of various apps and custom ROMs?
Then this news would be a perfect pick for you!
What If, you can effectively carry a Linux computer in your pocket?
Hereby introducing a new Android-based Operating system named "Maru OS" that combine the mobility of a smartphone as well as the power of a desktop on a single device.
Maru OS allows you to turn your smartphone into a desktop when plugging it with an HDMI cable.
Maru custom ROM includes two operating systems:
Android 5.1 Lollipop for mobile phones
Debian-Linux for desktop monitor
When you connect your phone (with Maru OS installed on it) via HDMI to a monitor, it will load Debian Linux automatically on your desktop screen in less than 5 seconds.
"Your phone runs independently of your desktop so you can take a call and work on your big screen at the same time," Maru OS official website explains.
Maru is shipped with Zero Bloatware (no pre-installed apps), which facilitates lots of free space for all your apps and your phone runs fast.
maru-android-os
Advantages of Maru OS
Dual OS in phone
Multi-Tasking
Lightweight Distro Packages
Zero Bloatware, except Google Play
Run a web server from your pocket
You can set up a portable development environment
And the Best One:
If by chance… your phone get disconnected from your screen, Maru OS will preserve your desktop state in the background, helping you pick up right where you left off.
"Your hardware's capabilities are shared across your mobile device and desktop, so you don't have to context-switch around so much," reads the website.
This latest OS is still in beta stage and currently available only in Nexus 5 devices. We hope this limitation might disappear later on.
MIT Develops Hack-Proof RFID Chip — Here's How It Works
6.2.2016 Hacking
MIT Develops Hack-Proof RFID Chip
Do you know about RFID chips and how many you are carrying at this moment?
Today, RFID chips are built-in all sorts of items, including your credit cards, travel swipe cards, library books, grocery store cards, security tags, implanted medical records, passports and even the access cards provided by companies.
But, What actually is an RFID chip?
Radio frequency identification (RFID) is a small electronic device consisting of a chip on which data can be encoded, and an antenna used to transmit that data. It is typically used for short-distance communication of information.
However, there is concern that these RFID chips could easily be hacked, and the information on these chips could easily be stolen by hackers. After all, they don't even require physical access to these chips in order to get data from it.
The good news is:
Researchers at MIT have developed a new way that prevents RFID chips from hacking.
Although the information on RFID chip is protected with a secret cryptographic key that could thwart a casual data thief, skilled RFID hackers have repeatedly used "Side Channel Attacks" to steal information from these chips easily.
Side Channel Attacks:
The 'side-channel attacks' are designed to extract the secret cryptographic key from a system by analyzing the pattern of memory utilization or fluctuations in power usage.
Also Read: This $10 Device Can Clone RFID-equipped Access Cards Easily
However, side-channel attacks only leak a little amount of information for each repetition of a cryptographic algorithm, so a hacker need to run the attack many numbers of times to get a complete secret key.
Power Glitch Attacks:
One way to prevent side channel attacks is to rotate the private key frequently after each transaction with the help of a random-number generator, but a skilled hacker can overcome this with a so-called "Power Glitch Attack."
Repeatedly cutting the RFID chip's power just before it changes the secret cryptographic key is known as power glitch attack.
By using this method, hackers can render the above strategy ineffective and run the same side-channel attack thousands of times, with the same key, in order to get the pattern and fetch the information from the RFID chip.
Here's How MIT Hack-Proof RFID Chip Works:
The new RFID chip developed by MIT researchers and manufactured by Texas Instruments is designed to block power glitch attacks, which is virtually impossible to hack by any current means, researchers claimed.
The new hack-proof RFID chip can resist power-glitch attacks by having:
An on-board power supply that is "virtually impossible to cut."
Non-volatile memory cells that store computations the chip is working on, even if there's a power cut.
This results in resuming of computation once the power gets restored.
"If that computation was an update of the secret key, it would complete the update before responding to a query from the scanner," the researchers wrote in a press release. "Power-glitch attacks won't work."
To achieve this, the new chip takes advantage of a material called Ferroelectric crystals that consist of molecules arranged into a lattice form where positive and negative charges naturally separate.
Also Read: Hacker Implants NFC Chip In His Hand To Hack Android Phones
These ferroelectric crystals can operate as a capacitor for storing power, producing computer memory that retains data even when powered off.
The research team claims that if this high-security RFID chip hits mainstream adoption, it could help prevent contactless card details from being stolen, potentially preventing credit card frauds.
However, nothing is unhackable today, so calling something "hack-proof" or "virtually impossible to hack" doesn't make sense. As hackers nowadays are so skilled that even devices that are designed on the top of security features aren't immune to hacks.
However, new technologies, like this RFID chip, that take the security of users to the next level are always a good idea and importantly required to secure the world.
Researchers spotted a new OS X scareware campaign
6.2.2016 Apple
Experts at the SANS Technology Institute spotted an OS X scareware campaign that leverages fake Adobe Flash Player installers.
Johannes Ullrich, security expert at the SANS Technology Institute, spotted an OS X scareware campaign that leverages fake Adobe Flash Player installers to trick users into downloading malicious software. The expert discovered the malicious campaign while analyzing Facebook clickbait scams.
“They do not rely on a vulnerability in the operating system. Instead, the user is asked to willingly install them, by making them look like genuine Adobe Flash warnings (and we keep telling users to make sure Flash is up to date, so they are likely going to obey the warning and install the update).” states the blog post published by the SANS Technology Institute. “The “Installer” for the fake Flash update will install various scare ware (I observed a couple different varieties when re-running the installer), and it actually installs an up to date genuine version of Flash as well.”
The attackers used a simple and effective trick to deceive victims, the attack starts with a popup window alerting users that their Flash Player software is outdated and providing them the instruction to update it.

Ullrich suspects that the code used to display the popup is injected by an advertisement on the page visited by the victim. If users accept to install the bogus update they will receive a fake Flash Player installer.
The bogus installer is able to bypass the Apple’s Gatekeeper security feature, it appears as a legitimate application and is signed with a valid Apple developer certificate issued to one Maksim Noskov.
“Antivirus coverage was pretty bad yesterday when I came across this (4 out of 51 on Virustotal). On a brand new OS X 10.11 install, the “Installer” appears to install a genuine copy of Adobe Flash in addition to Scareware that asks for money after informing you of various system problems.” continues the post.
The software installs a genuine Flash Player software and attempts to convince users to download applications apparently designed to fix problems on the victim’s machine.
These applications attempt to trick users into calling a “support” line in order to receive instructions for fixing the alleged problems. The security experts published a small video showing what happens when victims install the “update” on a clean OS X 10.11 system:
Critical Flaws Found in NETGEAR Network Management System
5.2.2016 Vulnerebility
Netgear, one of the most popular router manufacturers, has been vulnerable to two different flaws that could allow hackers to compromise your corporate network and connected devices.
Reported critical vulnerabilities reside in the Netgear's ProSafe NMS300 Model (Network Management System) – a centralized and comprehensive management application for network administrators that enables them to discover, monitor, configure, and report on SNMP-based enterprise-class network devices.
SNMP (Simple Network Management Protocol) is a network management protocol which facilitates Netgear's ProSafe NMS300 application to gather data from various network devices such as servers, printers, hubs, switches, and routers.
Remotely collected data includes CPU load, routing tables, and network traffic statistics.
Serious Flaws in Network Management System
Netgear-ProSafe-NMS300-network-managment-system
A joint security dug conducted by Pedro Ribeiro (Security Researcher of UK Based firm Agile Information) along with CERT Committee divulged the vulnerabilities in the web interface of the router that could allow attackers to:
Upload and Execute any malicious file remotely (CVE-2016-1524)
Download any file from Server (CVE-2016-1525)
Unauthorized Arbitrary File Upload Flaw: This flaw comes with the default installation of NMS300, allowing an unauthorized attacker to upload an arbitrary file and execute (Remote Code Execution) malicious code with SYSTEM privileges.
Upload location: http://:8080/fileUpload.do
Upload location: http://:8080/lib-1.0/external/flash/fileUpload.do
Execurition Location: http://:8080/null
Directory Traversal Attack: This vulnerability allows authenticated users to read and download any restricted file by manipulating ‘realName’ parameter of POST request to http://:8080/data/config/image.do?method=add URL.
The security vulnerabilities affect Netgear Management System NMS300, version 1.5.0.11 and earlier.
How to Protect Your Network from Hackers
Since there are no patches yet available from Netgear to fix these vulnerabilities, the only solution that network admins could implement here is strengthening the firewall policy by restricting the untrusted sources.
As threats continue to evolve and increase in volume and frequency, you can no longer rely on static network security monitoring.
Network administrators highly recommended to monitor network-based services or protocols on a continuous basis using any Security monitoring solutions, like (USM), which also includes (IDS) and to help administrators to identify quickly and remediate threats your network.
Netgear had not yet commented to this issue.
United Nations Rules in Favor of WikiLeaks Founder Julian Assange
5.2.2016 BigBrothers
VICTORY!
As a result of the legal action against WikiLeaks founder Julian Assange by both British and Swedish Governments, he has been arbitrarily detained by the United Kingdom and Sweden since his arrest in London over five years ago.
However, Assange filed a complaint against both the governments in September 2014 that has been considered by the United Nations Working Group on Arbitrary Detention.
Last week, Assange gave a statement that if the ruling comes against him, then he will surrender himself to Britain.
But, Victory! The decision is in favor of Assange.
The UN group has ruled that the UK and Swedish authorities had illegally detained Assange in violation of their international human rights obligations.
Julian Assange should be released immediately and allowed to leave the embassy as well as both the UK and Sweden should compensate him for his "deprivation of liberty", the UN Working Group on Arbitrary Detention said in a statement released today.
"Having concluded that there was a continuous deprivation of liberty, the Working Group also found that the detention was arbitrary because he was held in isolation during the first stage of detention and because of the lack of diligence by the Swedish Prosecutor in its investigations, which resulted in the lengthy detention of Mr. Assange," reads the UN report.
But, Will UK and Sweden Let Assange Leave the country?
Despite the decision is in favor of Assange, there could be a possibility that both the countries’ governments will not let Assange leave the country.
The UN group's ruling is not legally binding in the United Kingdom, so the European Arrest Warrant against Assange remains in place, which means the British government continues to have a legal obligation to extradite Assange.
The UK Foreign Office Secretary Philip Hammond said the UN panel's decision was "ridiculous", and Assange was a "fugitive from justice."
Hammond said the report "changes nothing" and Assange can come out "anytime he chooses" but he will still have to face justice in Sweden.
To make this sure, the Met Police, meanwhile, said it will make "every effort" to arrest Assange should he leave the embassy.
Assange has been living in the Ecuadorian embassy in London for over 3 years, after losing a series of appeals in British courts, to avoid extradition to:
Sweden where he is facing sexual assault allegations, which he has always denied.
The United States where he could face cyber espionage charges for publishing classified US military and diplomatic documents via his website Wikileaks.
Assange's Lawyer: Sweden and UK should Respect UN’s Decision
Melinda Taylor, Assange's lawyer, says that if there is a positive ruling for Assange by UN group, Swedish and British government should respect their international obligations and comply with the decision, thereby allowing him to leave freely.
"If WGAD issues a positive determination, Mr. Assange expects the United Kingdom and Sweden to ensure that he can immediately exercise his right to personal liberty, in a manner which is consistent with his right to safety and protection from retaliatory acts associated with his groundbreaking work at WikiLeaks in exposing government violations and abuses," Taylor told Newsweek reporter.
If this is the case, Taylor expects Assange to seek safe passage to Ecuador upon leaving the country's London embassy.
Established in 1991, the UN's Working Group on Arbitrary Detention is made up of 5 legal experts from around the world and has made hundreds of rulings, helping governments to release people.
Similar rulings from the UN panel have resulted in the release of:
Washington Post journalist Jason Rezaian, who was released in Iran last month.
Former pro-democracy President Mohamed Nasheed freed in the Maldives last year.
Burmese stateswoman Aung San Suu Kyi from house arrest in 2010.
Assange was initially arrested in London on 7 December 2010 under a European Arrest Warrant issued by Sweden over rape and sexual molestation charges, however, while on bail in 2012, he claimed asylum in the Ecuadorean embassy in Knightsbridge, where he is currently residing.
Australian NSW Government Department of Resources and Energy under attack. Is it Chinese cyber espionage?
5.2.2016 Safety
According to the NSW Government Department of Resources and Energy Chinese hackers have launched a malware-based attack on its network in December.
The Australian NSW Government Department of Resources and Energy revealed that in December 2015 unknown hackers targeted its systems. In the same period, the organization was launching a number of important projects, including a project of the Shenhua Watermark coal mine.
The project for the Shenhua Watermark coal mine has been estimated in $1.2 billion and indirectly involves the Chinese government, a circumstance that lead the experts in believing that Chinese-nation state hackers may have launched the attack for intelligence purpose.
“In December 2015, NSW Department of Industry IT security systems detected a marked increase in virus/security activity attempting to impact systems at the Division of Resources and Energy (DRE) office in Maitland. The attacks were identified by specialist software we have in place to detect breaches to our firewalls. Given the increased levels of activity we took further steps to ensure that our systems were protected. We do not believe that the attacks penetrated our systems or any data was accessed at this time.
The attack was in the form of an increase in “virus/security activity attempting to impact systems at the Division of Resources and Energy (DRE) office in Maitland”, states the NSW Government Department of Resources and Energy in an official announcement. and steps were taken to increase security after the activity was detected.
The hackers coordinated a malware-based attack to hack into the Department’s network, the organizations already announced that steps were taken to increase security in response to the offensive.
NSW Government Department of Resources and Energy Chinese HACKERS
It is not clear if the hackers successfully breached the network at the NSW Government Department of Resources and Energy, the New South Wales Opposition is calling for further investigation despite the officers believe that no data has been exfiltrated by the hackers.
“These reports are highly disturbing. I have sought a briefing from the minister and his agency as soon as possible. The Opposition will be seeking an assurance from the Baird Government that the integrity of the commercially sensitive data held by the Department of Industry has not been compromised.” declared the Australian politician Adam Searle to the ABC’s The World Today.
The experts speculate the involvement of Chinese hackers, the government of Bejing is considered responsible for a large number of cyber espionage operation worldwide.
“Well you don’t always know if you’ve been compromised in terms of cyber attack, so I think perhaps a more accurate way to put it would be to say they don’t think they’ve been compromised on this occasion. But if it’s like many other areas of government, they will be under constant attack, there will be sort of daily probes, hourly probes on the part of malicious cyber actors looking for vulnerabilities. ” added Peter Jennings, the executive director of the Australia Strategic Policy Institute.
“I think it is possible because we know China has one of the most aggressive cyber intelligence gathering policies around the world and that they are constantly looking to gather information, intellectual property, from the private sector as well as national security information from government departments.” “And in the case of Australia, obviously China has a deep interest in our approach to natural resources.”
In December, Chinese hackers have conducted another major attack on a supercomputer operated by Australia’s Bureau of Meteorology (BoM). The news was disclosed by the Australian Broadcasting Corporation (ABC). The Bureau of Meteorology is Australia’s national weather, climate and water agency, it is the analog of the USA’s National Weather Service.
“China is being blamed for a major cyber attack on the computers at the Bureau of Meteorology, which has compromised sensitive systems across the Federal Government.” states the ABC. “The bureau owns one of Australia’s largest supercomputers and provides critical information to a host of agencies. Its systems straddle the nation, including one link into the Department of Defence at Russell Offices in Canberra.”
The systems at the Bureau of Meteorology elaborate a huge quantity of information and weather data that are provided to various industries, including the military one.
Emergency. Hundreds of compromised WordPress sites serve TeslaCrypt ransomware
5.2.2016 Virus
Operators running websites based on the WordPress must be aware of a spike in the number of compromised platforms used to deliver the TeslaCrypt ransomware.
Administrators running websites based on the popular WordPress CMS must be aware of a spike in hacks that are resulting in the silent delivery of ransomware to the visitors.
According to the experts at the Heimdal Security, threat actors hacked WordPress-based sites to redirect victims to other domains hosting the Nuclear Exploit Kit.
People who visit the compromised WordPress sites using out-of-date versions of popular software, including Flash Player, Adobe Reader and Internet Explorer, can be infected with the Teslacrypt ransomware. The experts at Heimdal discovered that the attackers behind the current WordPress compromises were exploiting an unidentified vulnerability with obfuscated JavaScript. The code redirects victim to the domain chrenovuihren that serves an online ad that forces traffic to the site hosting Nuclear.
“Our team warns that a disproportionate amount of websites that employ the WordPress platform have been compromised by cyber criminals. Hundreds of WordPress websites spreading malware. The attackers fed obfuscated Javascript code to these websites. The users who end up on the hacked websites are redirected on a domain called “chrenovuihren” via multiple servers.” states a blog post published by Heimdal Security.

It isn’t the first time that the Nuclear Exploit Kit is used to drop ransomware, in November it Kit has been used for the first time to serve the ransomware CryptoWall 4.0, meanwhile in the past criminal groups used it to serve instances of the CryptoWall 3.0.
The Heimdal Security researchers identified three IP addresses of Nuclear EK gateways:
159,203.24 [.] 40
164,132.80 [.] 71
162,243.77 [.] 214
The campaign relies on a number of domains to spread the malware, the domains are all subdomains of the chrenovuihren.
“The campaign makes use of several domains to deliver the malicious code, which is why active servers can quickly change depending on which IP as DNS lookup they use,” continues the post.
“We have already blocked more than 85 domains that are being actively used in this campaign, and the list will most likely increase.”
The bad news it the low detection rate for this threat, just 2 of 66 antivirus solutions on VirusTotal are able to detect the malicious agent.
This last campaign based on compromised WordPress-based websites comes a few days later another massive hacking campaign has been identified by experts at Sucuri, the researchers at Heimdal speculate the involvement of the same threat actors for both campaigns.
Website owners based on WordPress must protect their servers and let me share with you, once again, the following key recommendations to get protected against ransomware:
Keep software and your operating system updated at all times
Backup your data, do it often and in multiple locations
Use a security tool that can filter your web traffic and protect you against ransomware, which traditional antivirus cannot detect or block.
Check Point oznámil levné UTM pro malé firmy i systémy pro datová centra
5.2.2016 Zabezpečení
Nová bezpečnostní zařízení řady 700 představil Check Point. Určená jsou pro menší organizace a podle výrobce nabízejí stejnou úroveň ochrany jako specializované systémy pro velké podniky. Stranou ale nezůstala ani ochrana datových center, pro něž Check Point představil sofistikované systémy 15000 a 23000.
Nové produkty nabízejí také vyšší výkon (propustnost firewallového provozu až 4 Gb/s, respektive až 200 Mb/s při aktivování všech funkcí prevence hrozeb) a webovou správní platformu.
Řada 700 zahrnuje výkonnostně rozličné modely 730 a 750, které nabízejí celopu plejádu ochranných prvků - firewall, VPN, prevenci narušení bezpečnosti (IPS), anti-virus, anti-spam, řízení aplikací, filtrování URL a možnost povolit monitorování bezpečnosti sítě.
Cena novinky se pohybuje od 500 dolarů (zhruba 12 tisíc Kč), na přání je k dispozici i modul 802.11ac Wi-Fi, v létě pak i modul pro sítě VDSL.
Zařízení řady 15000 a 23000 (každá obsahuje dva různé modely) chrání náročná síťová firemní prostředí a sítě v datových centrech. Podle dodavatele kombinují pokročilou ochranu před hrozbami se specializovanou platformou, která podporuje bezpečnostní požadavky v oblasti výkonu nebo provozuschopnosti.
Obsahují například plně integrovaný firewall, prevenci narušení systémů (IPS), anti-bot, antivirus, řízení aplikací, filtrování URL a sandboxingovou technologii SandBlast.
K dispozici je i kompletní šifrovaný provoz (SSL), aniž by prý musel být obětovaný výkon, a k dispozici je podpora pro různé prvky, jako jsou komplexní redundance, flexibilní síťová konektivita (měď a optika), obslužnost pomocí vzdálené správy i v případě výpadku primární sítě či rozšiřující 40Gb karty.
Someone Hijacks Botnet Network & Replaces Malware with an Antivirus
5.2.2016 Virus
The Dridex banking trojan that is widely being used by cyber criminals to distribute malware onto users’ machines has now been found distributing a security software.
A portion of the Dridex banking Trojan botnet may have been hacked or compromised by an unknown Whitehat Hacker, who replaced the malicious links with Avira Antivirus installers.
What is Dridex Banking Trojan? How it Works?
Dridex malware – also known as Bugat and Cridex – is believed to have been created by cyber criminals in Eastern Europe in an effort to harvest online banking details. Even after a high-profile takedown operation in late 2015, the Dridex botnet seems to be active again.
The Dridex virus typically distributes itself through spam messages or emails that include malicious attachments, most often a Microsoft Office file or Word document integrated with malicious macros.
Once the malicious file has been clicked, the macros download and install the main payload of the virus – the trojan program itself – from a hijacked server, which installs and runs on the victim's computer.
The Dridex trojan program then creates a keylogger on the infected machine and manipulates banking websites with the help of transparent redirects and web-injects.
This results in stealing victim's personal data like usernames and passwords, with an ultimate aim to break into bank accounts and siphon off cash.
Hacker replaces Trojan with Anti-virus
However, the recent Hack Surprises: Instead of distributing banking trojan, a portion of the Dridex botnet currently seems to be spreading legitimate copies of the free anti-virus software from Avira, as the company has announced itself.
"The content behind the malware download [link] has been replaced, it is now providing [a legitimate], up-to-date Avira web installer instead of the usual Dridex loader," explained Avira malware expert Moritz Kroll, reported Reg.
Avira believes that the white hat hacker or hackers may have hacked into a portion of infected web servers using the same flaws the malware authors used and then replaced the malicious code with the Avira installer.
So, once infected, instead of receiving Dridex malware, the victims get a valid, signed copy of Avira antivirus software.
"We still don't know exactly who is doing this with our installer and why – but we have some theories," said Kroll. "This is certainly not something we are doing ourselves."
Although the motives behind including the Avira software is still unclear, these kinds of actions are considered to be illegal in many countries, said Kroll.
What can be done to protect From Malware Attacks?
The guidance for preventing yourself from being a part of the Dridex Banking Trojan botnet is:
Ensure you have an updated antivirus program running on your PC, which should be able to intercept the malicious attachments before they are opened.
One of the best measures for securing your online environment is to deploy an at the network layer, which is especially useful to quickly detect malware and other threats in your network when integrated with a and SIEM (Security Intelligence and Event Monitoring) solution, such as (USM).
Be careful of opening email attachments sent from an unknown email address, particularly (in this case) Microsoft Word and Excel files.
Disable Macros in MS Office, or at least set the Macros to request permission before they run.
Someone has pwned the Dridex botnet serving the Avira Antivirus
5.2.2016 BotNet
Unknowns have pwned the Dridex botnet and are using it to spread a legitimate copy of the Avira Antivirus software instead the malicious payload.
This story is very intriguing, someone has hacked a portion of the dreaded Dridex botnet and replaced malicious links with references to installers for the Avira Antivirus. The Antivirus company denies any involvement and speculate the involvement of an unknown white hat hacker.
Spam campaigns relying on the Dridex malware are threatening banking users across the world despite the operations conducted by law enforcement on a global scale. We left Dridex malware spreading across the Europe, in particular targeting the customers of the banks in the UK. In October, the NCA has uncovered a series of cyber attacks based on a new strain of the Dridex banking trojan that allowed crooks to steal £20m in the UK alone.

Now Dridex is once again in the headlines, spam emails containing the famous malware are continuing to target netizens despite the arrest of one of its botmasters in August.
In October the experts at Palo Alto Networks confirmed that the overall volume of Dridex emails peaked nearly 100,000 per day, the campaign rapidly reached 20,000 emails, mostly targeting emails accounts in the UK.
Spam messages often include malicious Word documents embedded with macros, when victims open the macros download the Dridex payload from a hijacked server. Dridex is a banking trojan that relies on web injection to manipulate banking websites and use a keylogger component to monitor victim’s activity.
Now someone has pwned the Dridex botnet and is using it to spread a legitimate Antivitus software instead the malicious payload. Despite the noble intent, even the action of this unknown is illegal because he is spreading an installer on the victims’machine without their consensus.
“The content behind the malware download URL has been replaced, it’s now providing an original, up-to-date Avira web installer instead of the usual Dridex loader,” explained Moritz Kroll, a malware researcher at Avira.
“We still don’t know exactly who is doing this with our installer and why – but we have some theories,” said Kroll. “This is certainly not something we are doing ourselves.”
“A whitehat may have hacked into infected web servers using the same vulnerabilities the malware authors used in the first place and has replaced the bad stuff with the Avira installer,” added Kroll.
Avira was involved in a similar case in the past when the installer has been included into the CryptoLocker and Tesla ransomware.
Do you have a Netgear ProSAFE NMS300? Here you are the exploit to hack it
5.2.2016 Vulnerebility
A security researcher has released the exploit code for two serious vulnerabilities in the Netgear ProSAFE NMS300 network management system.
Do you have a Netgear ProSAFE NMS300 Management System? Now you have a reason to worry because the security researcher Pedro Ribeiro has discovered two serious vulnerabilities in the network device.
The Netgear ProSAFE NMS300 Management System allows administrators to monitor and manage their networks by using a user friendly web-based interface.
The device is affected by a vulnerability (Unrestricted Upload of File with Dangerous Type), coded CVE-2016-1524, that could be exploited by a remote, unauthenticated attacker to upload an arbitrary file to the system.
Once uploaded a file, it will be available in the server’s root directory at the following URL:
http://<IP>:8080/null<filename>
and it could be executed with SYSTEM privileges.
The remote code execution vulnerability received a CVSS score of 8.3, it can be exploited by sending a specially crafted POST request to one of two Java servlets present in default NMS300 installations.
“By sending a specially crafted POST request to the servlets, an attacker can upload arbitrary files that will then be accessible from the NMS300 server’s root directory as http://<IP>:8080/null<filename>. The NMS300 server runs with SYSTEM privileges.” states the advisory issued CERT Coordination Center at Carnegie Mellon University .

The second flaw (Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) ), coded CVE-2016-1525, discovered in the Netgear ProSAFE NMS300 is a directory traversal that could be exploited by an authenticated attacker to download any file from the device.
“An authenticated attacker can manipulate the realName parameter of a crafted POST request sent to http://<IP>:8080/data/config/image.do?method=add to load an arbitrary local file from the server host to a predictable location in the web service. The file can then be downloaded from http://<IP>:8080/data/config/image.do?method=export&imageId=<ID>, where <ID> is a count that increments by one every time a file is uploaded in this manner.” continues the advisory.
The security experts Ribeiro reported the flaws to Netgear via CERT/CC in December, but the issues are still present in the systems.
Riberio also published a proof-of-concept-code for the exploitation of the flaws, they are two Metasploit modules available for the download.
Waiting for a fix, let me suggest you to isolate the web management interface of your device from the Internet.
Google vylepšuje bezpečné vyhledávání v Chromu
5.2.2016 Zabezpečení
S rozšířením funkcí bezpečného vyhledávání v Chromu počítejte rovněž s častějším výskytem bezpečnostních varování.
Google dbá na bezpečnost uživatelů prohlížeče Chrome a rozšiřuje technologii Safe Browsing – bezpečného vyhledávání. Cílem je předcházet situacím, kdy neopatrní uživatelé prostřednictvím klamavé reklamy zadají osobní informace někam, kde mohou být zneužity, anebo si do počítače stáhnou škodlivý software tvářící se jako nezbytná aktualizace.
„Rozšiřujeme bezpečné vyhledávání, abychom vás ochránili před škodlivým obsahem,“ uvádí Lucas Ballard, jeden z vývojářů stojících za bezpečným vyhledáváním Googlu.
V praxi se podle něj nové opatření projeví rudou obrazovkou s textem „deceptive site ahead“ - „chystáte se otevřít podvodnou stránku“. Do kategorie „podvodných“ přitom Google řadí všechny ty, které „se tváří, chovají anebo vzbuzují dojem jako důvěryhodné“.
Jako příklad Ballard zmiňuje například sdělení vybízející uživatele ke stažení či aktualizaci softwaru třetích stran údajně nezbytného k zobrazení obsahu webové stránky (často takto bývá zneužíván např. Adobe Flash), což je dlouho užívaná a osvědčená strategie kyberzločinců vedoucí uživatele ke stažení a instalaci např. škodlivého malwaru.
Původně bezpečné vyhledávání od Googlu sloužilo jen k odhalování phishingových útoků (prostřednictvím falešných stránek vybízejících uživatele k zadání osobních údajů, jakož i hesel), společnost jej ale v posledních třech letech vylepšila o indikaci potenciálně závadných downloadů a softwaru pokoušejícího se změnit nastavení prohlížeče.
Loni v listopadu do něj Google přidal také nástroje k identifikaci rovněž různých druhů manipulativních oznamů, klamně uživatele upozorňujících na to, že jejich PC je infikované a pokoušejících se je přesměrovat na škodlivé stránky či call centra, kde jsou od nich požadovány často nemalé finanční částky za domnělou falešnou podporu.
Google na bezpečí svých uživatelů dbá důsledně dlouhodobě, podle svých kritiků tím ale sleduje i vlastní zájmy, kdy si takto „udržuje“ uživatele v mantinelech a na stránkách, které společnosti generují zisk.
Safe Harbor replaced with Privacy Shield
4.2.2016 Security
The alleged Privacy Shield deal swaps the Safe Harbor arrangement that remained for over fifteen years before being smash down by a court in October
United States and European administrators have pounded out a very late arrangement to permit data streams across the Atlantic to proceed without violating the law.
“Surprisingly, the US has given the EU compulsory assurances that the access of public establishments for national safety purposes will be liable to clear protections, limitations and oversight devices,” said Europe’s justice Chief Věra Jourová.
“Additionally, EU nationals will profit by redress mechanisms around there. In the setting of the arrangements for this contract, the United States has guaranteed that it doesn’t lead mass or aimless surveillance of Europeans. We have built up a yearly joint survey with a specific end goal to closely monitor the execution of these assurances.”
Under the terms of the new arrangement, which has yet to be approved by EU individuals, the United States will give a yearly written commitment that it won’t enjoy mass surveillance of EU residents, and this will be reviewed by both sides once per year. .
United States organizations wanting to import EU nationals’ information must give “strong requirements on how private data is handled,” and implement same principles as European data protection laws. In the event that EU natives need to protest how their data is being utilized, organizations must react within time and at no cost to the pursuer.
Chief Jourova and her associate Andrus Ansip, vice president for the Digital Single Market on the European Commission, will now make draft on “adequacy decision” comprising the new standards for states member to approve. The United States will likewise keep on getting its administrative structure altered to lodge the new agreement.
“Our public can make sure that their data is completely secured. Our organizations, particularly the small ones, have the legal guarantee they have to build up their actions across the Atlantic,” said Ansip.
“We have an obligation to check and we will thoroughly monitor the new procedure to ensure it keeps delivering. Today’s choice helps us construct a Digital Single Market in the EU, a dynamic and trusted online environment; additionally it reinforces our close partnership with the United State.
Three months of desperate rewriting
The alleged Privacy Shield deal swaps the Safe Harbor arrangement that remained for over fifteen years before being smash down by a court in October. It’s the aftereffect of 3 months of desperate and sometimes tense consultations between the two trade giants, with tech companies in both regions pushing hard for an arrangement.
The DPAs will now dedicate the following couple of days pounding out the points of interest. There might at present be some individual staying focuses, yet the requirement for activity is moving Europe’s typically massive controllers more rapidly than expected, because of industry pressure.
“We request that Europe’s National data protection authorities DPAs to view this sign from the European Commission as an indication conviction and to hold off with any potential implementation activity until the new arrangement has been completely executed,” said John Higgins, executive general of industry pressure DigitalEurope.
“While they are evaluating the swap for Safe Harbor, we urge Europe’s DPAs to keep on regarding the utilization of other transfer systems, for example, contract clauses (MCCs) and binding corporate rules (BCRs), so information exchanges to the United States can proceed unrestricted.”
But then again there are as of now inquiries being raised about the new arrangement. The language utilized as a part of the official declaration is woolly, best case scenario and there are reasons for alarm that the arrangement struck might be excessively broad for a few, making it impossible to swallow.
safe harbor
“The aftereffects of months of intervention seems weak, and if implemented we are expected to see additional legal trial in the European courts,” stated Ashley Winton, UK head of data protection and privacy at Paul Hastings LLP.
“The European Commission still needs to put forth the case that the United States arrangements of protection laws are basically identical, that data subjects have genuine rights against unbalanced handling in the United States, and that if there is illegal processing then people can have their own information erased and at last change in a appropriate court.”
“With all due appreciation, however a few letters by the Obama organization is in no way, shape or form a legal base to ensure the basic rights of five hundred million European clients over the long run, when there is clear US law permitting mass surveillance,” stated Max Schrems, the Austrian student who bring down the Safe Harbor agreement for a case against Facebook.
“We don’t have the clear idea about the legal structure, yet this could clearly neglect the Court’s verdict. The Court has simply indicated that the United States needs to “guarantee” appropriate security by means of international commitments or domestic law. I question that a European can go to a United States court and claim his basic rights.”
He indicated that the arrangement could likewise come unstuck because of the NSA‘s PRISM plan, which permits the intelligence agencies to take advantage of the data streams for partners such as Microsoft, Google, Apple or Facebook. This would seem to break the contract and the courts are sure to get involved.
There’s additionally the matter of legitimate workarounds. At present Microsoft is battling the United States Department of Justice over the agency’s claims that it can summon data on European servers without a warrant.
Malwarebytes hardly working to fix flaws in its antivirus
4.2.2016 Vulnerebility
The Antivirus firm Malwarebytes is spending a significant effort to fix serious vulnerabilities in its defense solution that was reported by the experts at the Google’s Project Zero team.
The experts at Project Zero discovered that updates for Malwarebytes Antivirus were not digitally signed or downloaded over a secure HTTP connection, opening the user to Man-In-The-Middle attacks. An attacker could manipulate the updates hacking the Antivirus solutions.
Google Project Zero reported the vulnerabilities to Malwarebytes in November, waiting for 90 days before publicly disclosing the vulnerability.
malwarebytes anti-malware
The experts at Malwarebytes were not able to solve the problem in the 90-day period, so the researcher Tavis Ormandy published the details of the security issue.
“Malwarebytes fetches their signature updates over HTTP, permitting a man-in-the-middle attack,” he explained in a blog post.
“Therefore, this scheme is not sufficient to prevent tampering, and the developer should sign them. There are numerous simple ways to turn this into code execution, such as specifying a target file in the network configuration, writing a new TXTREPLACE rule to modify configuration files, or modifying a registry key with a REPLACE rule.”
The Chief executive at MalwareBytes, Marcin Kleczynski, admitted the difficulties in solving the problem, preannouncing many other weeks to fix the problem.
“In early November, a well-known and respected security researcher by the name of Tavis Ormandy alerted us to several security vulnerabilities in the consumer version of Malwarebytes Anti-Malware. Within days, we were able to fix several of the vulnerabilities server-side and are now internally testing a new version (2.2.1) to release in the next 3-4 weeks to patch the additional client-side vulnerabilities. At this time, we are still triaging based on severity.” he said in a blog post. The research seems to indicate that an attacker could use some of the processes described to insert their own code onto a targeted machine. Based on the findings, we believe that this could only be done by targeting one machine at a time.” .
Kleczynski took the opportunity to launch the Malwarebytes Bug Bounty program which will help the company to early discover any flaw in their software and to “encourage other security researchers to responsibly disclose vulnerabilities in Malwarebytes software.”
“I’d also like to take this opportunity to apologise. While these things happen, they shouldn’t happen to our users.”
Microsoft bude lidem podsouvat desítky, nainstalují se jako aktualizace
4.2.2016 OS
Společnost Microsoft nabízí už od loňského roku uživatelům některých starších verzí Windows bezplatný upgrade na nejnovější desítky. Nově se ale Windows 10 mohou lidem nainstalovat jako aktualizace i v případě, že o to nestojí. Je to dáno změnou politiky amerického softwarového gigantu.
Doposud totiž aktualizace na Windows 10 byla uživatelům nabízena jako volitelná, nově ji však Microsoft označuje jako doporučenou. A právě v tom je ten zakopaný pes, který potrápí uživatele, jež o přechod z jakéhokoliv důvodu nestojí.
Dříve totiž mohli lidé pouze odkliknout okénko nestahovat a bylo vyřešeno. Nově se jim však aktualizace může automaticky stáhnout, a dokonce i nainstalovat. V defaultním režimu jsou totiž desítky nastaveny tak, aby se stahovaly a instalovaly i doporučené aktualizace.
Pomůže změna nastavení
Uživatelů, kteří stále na Windows 10 nepřešli, je několik stovek miliónů. Jak upozornil server Extreme Tech, desítky se tak logicky budou nabízet jako aktualizace ještě několik následujících týdnů. Proces distribuce na takové množství strojů je totiž velmi náročný.
Pokud uživatelé nestojí o automatickou aktualizaci na nejnovější verzi operačního systému od Microsoftu, mohou jednoduše změnit nastavení systému. V Ovládacích panelech stačí zvolit nabídku Windows Update a odškrtnout políčko, aby se doporučované aktualizace získávaly stejným způsobem jako doporučené.
Případně je k dispozici také volba „Vyhledávat aktualizace, ale zeptat se, jestli je chci stáhnout a nainstalovat“. Díky této volbě se žádná s aktualizací nebude stahovat ani instalovat, pokud o to uživatel skutečně nebude stát.
Europol, a new move against terrorism and money laundering
4.2.2016 Safety
The Europol is increasing its efforts against terrorism, it has joined forces with EU to fight terrorist financing and money laundering.
Since 1 January 2016, Europol has increased the level of integration among the nodes of the decentralised computer network of the European Union Member States’ Financial Intelligence Units (FIUs), the FIU.net.
“FIU.NET is a decentralised computer network supporting the FIUs in the European Union in their fight against Money Laundering and Terrorist Financing. Decentralised meaning, that there is no central database in one specific Member State where all the exchanged data is stored. When sending the information from one FIU to another, the exchanged data is only and safely stored on the FIU.NET databases at the premises of the FIUs involved in the exchange.” states the description on the website of the FIU network.
The initiative wants to create more synergy between financial and criminal intelligence agencies in the EU, a measure necessary to fight the constant growth of the criminal syndicates and the terrorism in Europe.
“Under the auspices of the EU FIU platform and the renewed provisions set in the IV anti-money laundering Directive, the embedment of FIU.net into Europol aims to create more synergy between financial and criminal intelligence, ultimately boosting efforts to fighting organised crime and terrorism in the EU.” states the official announcement issued by the Europol.
FIU.net was established in 2002 and was co-financed until 2015 by the European Commission, it is an organism created to monitor money laundering activities and terrorist financing. Its pillar is the information sharing between the Financial Intelligence Units. Each FIU has the task to monitor on financial transactions, in particular every transfer of money from entities in different states.
The implementation of a decentralised network implies that only the information shared between two Financial Intelligence Units is securely stored in the FIU.net databases.
europol rob wainwright
The decision to embedment of FIU.net network in the Europol will enhance the exchange of financial intelligence. The information managed by the FIU.net architecture could be integrated with data managed by the Europol.
This is an important step against crime and terrorism, data from financial intelligence could be integrated with information related criminal intelligence activity conducted by the Europol, an important knowledge sustained with data provided by the Law Enforcement agencies of the EU countries.
“Thanks to the analytical capacities of Europol the suspicious money flows and their links to on-going terrorist and criminal activities can be further investigated. The FIU.net exchange platform will join other key Europol’s tools in the field such as the Terrorist Finance Tracking Program (TFTP), the Focal Point Sustrans (support to anti-money laundering investigations) and the network of the EU Asset Recovery Offices (AROs).” continues the Europol.
The decision of joining the efforts against terrorist financing activities is a necessary step to respond threats even more dangerous for every country in the EU and that are assuming a global connotation.
A week ago the director of Europol, Rob Wainwright, announced a new European Counter Terrorism Centre (ECTC) opening this month to fight the terrorism, it is easy to predict that this new structure will benefit also of the new strategic alliance.
Former DoE worker was hacking to steal nuclear secrets and resell them
4.2.2016 Hacking
A former Department of Energy (DoE) employee, Charles Harvey Eccleston [62], has been charged with trying to steal and sell nuclear secrets to foreign governments.
A former employee at the Department of Energy (DoE), Charles Harvey Eccleston [62], has pleaded guilty of cyber espionage. The man attempted to infect al least 80 colleagues at the DOE spreading a malware with the intent to gain control of the victims’ machines.
The man was operating to open the door to foreign hackers, allowing them to exfiltrate sensitive information related to nuclear weapons.
According to the US Department of Justice, Eccleston attempted unauthorized access and intentional damage to a protected computer.
“Charles Harvey Eccleston, 62, a former employee of the U.S. Department of Energy (DOE) and the U.S. Nuclear Regulatory Commission (NRC), pleaded guilty today to a federal offense stemming from an attempted e-mail “spear-phishing” attack in January 2015 that targeted dozens of DOE employee e-mail accounts.” reads the statement issued by officials with the US Department of Justice.
Eccleston worked for both the DOE and the US Nuclear Regulatory Commission, his deep knowledge of the environment allowed him to run surgical attacks against current employees. The employees received a highly targeted spear-phishing e-mails likely containing malicious links.
The man tried to resell information about his colleagues to foreign governments, prosecutors confirmed the case was discovered in 2013, after Eccleston visited an unnamed foreign embassy in Manila, Philippines and offered for sale more than 5,000 e-mail addresses of internal employees (i.e. Officials, engineers, and employees of a US government agency).
The agents from the FBI collected evidence on the man’s intent posing as embassy employees. The man was also offering the access to agency systems to advantage espionage activities.
doe
The man used emails that pretended to be sent by the organizations behind conferences related to nuclear energy.
“Thereafter, Eccleston met and corresponded with FBI undercover employees who were posing as representatives of the foreign country. During a meeting on Nov. 7, 2013, he showed one of the undercover employees a list of approximately 5,000 e-mail addresses that he said belonged to NRC employees. He offered to sell the information for $23,000 and said it could be used to insert a virus onto NRC computers, which could allow the foreign country access to agency information or could be used to otherwise shut down the NRC’s servers.”states the press release.” The undercover employee agreed to purchase a thumb drive containing approximately 1,200 e-mail addresses of NRC employees; an analysis later determined that these e-mail addresses were publicly available. The undercover employee provided Eccleston with $5,000 in exchange for the e-mail addresses and an additional $2,000 for travel expenses.”
“Over the next several months, Eccleston corresponded regularly by e-mail with the undercover employees. A follow-up meeting with a second undercover employee took place on June 24, 2014, in which Eccleston was paid $2,000 to cover travel-related expenses. During this meeting, Eccleston discussed having a list of 30,000 e-mail accounts of DOE employees. He offered to design and send spear-phishing e-mails that could be used in a cyber-attack to damage the computer systems used by his former employer.”
The FBI undercover agents provided a link to Eccleston to include in the malicious email. The man believed the link was pointing to a malicious domain used to serve a malware, instead, it was harmless. Altogether, the defendant sent the e-mail he believed to be infected to approximately 80 DOE employees located at various facilities throughout the country, including offices and laboratories associated with nuclear materials.
Eccleston was fired from the NRC in 2010 for unknown reason, and went to Davos City in the Philippines in 2011.
“Combating cyber-based threats to our national assets is one of our highest priorities,” Assistant Attorney General for National Security John P. Carlin said in a statement.
“We must continue to evolve our efforts and capabilities to confront cyber enabled threats and aggressively detect, disrupt and deter them.”
Eccleston was detained by Philippine law enforcement on March 27, and on Friday he will have the a court appearance on at the U.S. District Court of the District of Columbia.
According to the Justice Department, the man will remain detained until a hearing scheduled for May 20.
This type of crime provides a penalty of up to 10 years and financial penalties, but because the Eccleston age and previous records, according to the advisory federal sentencing guidelines, the former DOE worker likely to receive a prison term of 24 to 30 months and a fine of up to $95,000.
Latest Windows 10 May Have a Linux Subsystem Hidden Inside
3.2.2016 OS
A Few Months Back, Microsoft impressed the world with 'Microsoft loves Linux' announcements, including, development of a custom Linux-based OS for running Azure Cloud Switch and selecting Ubuntu as the operating system for its Cloud-based Big Data services.
Also Read: Microsoft Drops a Cloud Data Center Under the Ocean.
Now, a renowned Windows Hacker and computer expert, who goes by the name ‘WalkingCat’, discovered that the latest version of Windows 10 may have a Linux subsystem secretly installed inside.
According to his tweets, hacker spotted two mysterious files, LXss.sys and LXCore.sys, in the most latest Windows 10 Redstone Build 14251, which are suspected to be part of Microsoft’s Project Astoria.
windows-10-linux-subsystem
Project Astoria, also known as Windows Bridge for Android, is a toolkit that allows running Android apps on Windows 10 Mobile devices.
The naming convention for latest discovered files is very similar to the Android Subsystem files from Project Astoria, i.e. ADss.sys.
So, the "LX" in these name, however, can only be taken for one thing, and that is LINUX, which suggests the Windows 10 will have access to a Linux subsystem also.
Why a Linux Subsystem?
Since Windows 10 has been introduced as a Universal Operating system for all devices, so it might be possible that Microsoft wants to expand Project Astoria from mobile devices to desktop users.
If this comes to be true, adding a Linux subsystem will be beneficial in case Microsoft has plans to offer support for Linux applications, especially servers related technology and software.
Isn't this exciting?
Stay tuned to The Hacker News Facebook page for further developments on this topic.
Podvodníci to zkoušejí na uživatele mBank, lákají z nich přihlašovací údaje
3.2.2016 Phishing
Počítačoví podvodníci zkoušejí tento týden napálit na webu uživatele internetového bankovnictví od mBank. Využívají k tomu podvodné facebookové stránky. Před novým podvodem varoval ve středu Národní bezpečnostní tým CSIRT.CZ, který je provozován sdružením CZ.NIC.
„Na Facebooku se objevila reklamní kampaň směřující na falešný facebookový účet mBank,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
V kampani tvrdí kyberzločinci klientům mBank, že je k dispozici nová verze internetového bankovnictví. Ta má být údajně bezpečnější a zároveň přehlednější než aktuálně dostupná verze.

Ukázka podvodné reklamy na Facebooku, kde se kyberzločinci vydávají za zaměstnance mBanky.
FOTO: repro mBank
Ve skutečnosti jde však o podvodné stránky, jak již potvrdili i zástupci banky. „Velice podobné stránky těm našim připomínají přihlášení do internetového bankovnictví mBank a mají jediný cíl – získat vaše přihlašovací údaje. Stránka je napojena i na facebookové stránky, které se také podobají těm našim,“ stojí v prohlášení mBank.
Banka přitom podobným způsobem s klienty nikdy nekomunikuje. „MBank po vás nikdy nebude chtít sdělovat přístupové údaje, hesla, převody peněz na účty jiných osob apod. Pokud se s podobným požadavkem na internetu setkáte, nereagujte na něj,“ varovali zástupci banky.
„Důrazně žádáme každého, kdo se přihlásil přes podezřelou phishingovou stránku, aby okamžitě volal mLinku na čísle 222 111 999 a vše nám nahlásil. Pro vaši bezpečnost si změňte heslo do internetového bankovnictví,“ uzavřeli zástupci mBank.
Here's Why Microsoft Drops a Cloud Data Center Under the Ocean
3.2.2016 OS
Where tech companies like Facebook and Google prefer to move their data centers to colder countries to reduce their air conditioning bill, Microsoft has come up with an even better home for data centers while cutting high energy costs for cooling them: Under the Sea.
Here's what Microsoft says:
"50% of us live near the coast. Why doesn't our data?"
Building massive data centers underwater might sound crazy, but it is exactly something Microsoft is testing with its first submarine data center, dubbed Leona Philpot.
World's First Underwater Data Center
The testing is part of Microsoft’s plan dubbed Project Natick — an ongoing research project to build and run a data center that is submerged in the ocean, which the company believes, could make data centers faster, cost-effective, environmentally friendly and easier to set up.
Leona Philpot (named after the Halo character from Microsoft's Xbox) was tested last August, when engineers placed an enormous steel capsule a kilometer off the California coast, 30 feet underwater in the Pacific Ocean.
A single datacenter computing rack was placed in an eight-foot-wide steel capsule, which was covered in around 100 sensors to monitor every aspect of the underwater conditions: pressure, humidity, and, most importantly, motion.
The test ran from August to November last year (exactly 105 days) and the engineers said it was more successful than expected.
Why Underwater Data Center?
According to Microsoft, these are the main reasons for experimenting with underwater data centers:
1. Air conditioning cost is one of the biggest pain in running data centers. Traditional data centers are believed to consume up to 3 percent of the world's electricity.
So, placing the data centers in the ocean eliminated the need for cooling and will highly cut energy costs required to cool the heat generated by the racks upon racks of servers that process and store the world's digital lives.
2. Half of the world's population is located within 200 kilometers of the coast, so placing data centers in the sea would reduce latency – the time data takes to travel from its source to customers, which simply means faster delivery of data.
3. Reduce the time to build a data center from 2 Years to 90 Days. Microsoft believes that if it can mass produce the steel capsules, the company could build data centers in just 90 days.
This would make its operations cheaper and much quicker than the time needed to set a data center up on land.
Moreover, the capsules designed by the company would also adopt new, innovative rack designs that do not even need to consider human interaction.
4. Use of Renewable Energy. The project's engineers even believe that in future, underwater data centers might be able to power themselves by renewable energy, as in this case, perhaps underwater turbines or tidal power to generate electricity.
5. Environment-Friendly. Microsoft will also be tackling environmental concerns related to underwater data centers. The company says its current underwater data center prototype emits an "extremely" small amount of heat energy into the surrounding waters.
A Few Limitations:
Data centers on land are open for IT engineers to fix issues and replace servers whenever required, but the company wants its undersea data centers to go without maintenance for years at a time.
Since Microsoft doesn't have a team of Scuba engineers, each Natick data center unit would operate for over 5 years without maintenance and then it would be dragged up to the surface to have its internal parts replaced.
Other obvious risks for submarine data centers could be saltwater that is corrosive and weather that can also be a problem, to name just two potential hurdles.
Future Of The Data Center
The company started working on this idea in 2013, but the development of a physical prototype began in 2014 and August last year with its first ever submarine data server, Leona Philpot.
Since Microsoft's Project Natick has been in its "early days," it is hard to say when underwater data centers can actually adopted. However, Microsoft has plans to design a new version of underwater data centers that's three times larger than Leona Philpot.
It is not just Microsoft; many tech companies are considering new ways of housing data. In 2013, Facebook located one of its latest state-of-the-art data centers in Luleå, the far north of Sweden, to make use of cheap, renewable energy generated by hydroelectric schemes and outside air for cooling.
Comodo's so-called 'Secure Internet Browser' Comes with Disabled Security Features
3.2.2016 Security
Beware Comodo Users!
Have you Safeguarded your PC with a Comodo Antivirus? Then you need to inspect your system for privacy and security concerns.
First of all, make sure whether your default browser had been changed to "Chromodo" -- a free browser offered by Comodo Antivirus.
If your head node is "Yes," then you could be at risk!
Chromodo browser, which is supplied along with the installation of Comodo Anti-Virus Software and marketed as 'Private Internet Browser' for better security and privacy, automatically overrides system settings to set itself as your 'Default Browser.'
And secondly, the main security concern about Comodo Antivirus is that the Chromodo browser has 'Same Origin Policy' (SOP) disabled by default.
Google's security researcher Tavis Ormandy, recently shouted at Comodo for disabling SOP by default in its browser settings that violates one of the strongest browser security policy.
Ormandy notes that "all shortcuts are replaced with Chromodo links and all settings, cookies, etc are imported from Chrome. They also hijack DNS settings, among other shady practices."
Moreover, this is a total unethical movement to change default browser settings without users' knowledge.
Same Origin Policy (SOP) is one of the browser security policies that permits scripts running in a web browser to only make requests to pages on the same domain.
If enabled, Same Origin Policy will prevent malicious scripts on one page from obtaining access to sensitive data on another web page.
What If, Same Origin Policy is Disabled
chromodo-browser
To understand this, assume you are logged into Facebook and somehow visits a malicious website in another tab.
With SOP disabled, various malicious script files on that website could take over the control of your Facebook profile, allowing malicious actors to compromise your account with access to your private messages, post status updates, etc.
The same thing Comodo is doing with its users, by default disabling SOP in Chromodo that could allow attackers to:
Steal session authentication cookies.
Perform malicious actions through script code.
Even Replace trusted websites with attacker-created HTML design.
How to Check, If your Browser has SOP Enabled/Disabled
If you are still unsure whether your browser is SOP disabled, then visit this link.
If you are getting a prompt as "Browser appears to be fine," then you are out of danger.
But, if you are getting a negative approach such as "Your browser is not enforcing the SOP," you are advised to migrate to other browsers such as Chrome or Firefox for your self-defense against any malicious attack.
On Friday, United Nation can decide that Assange is being illegally detained
3.2.2016 BigBrothers
On Friday the United Nation can decide that Assange is being illegally detained, in this case the UK and Sweden must immediately release him.
The United Nations will reveal very soon the results of its investigation on the case of Julian Assange, the Wikileaks founder. WikiLeaks published secret information and classified media from anonymous sources. Wikileaks already published more than 10 million documents, Assange described its platform as “a giant library of the world’s most persecuted documents”
The decision is set to be announced next Friday 4 February, when the US would order the release of Assange.
Julian Paul Assange is an Australian journalist that founded Wikileaks in 2006, he is currently residing in the Ecuador embassy in London, after having been granted political asylum in August 2012.
Many ignore that Assange has a past as a hacker, in 1987 under the pseudonym Mendax he hacked many organizations with two colleagues known as “Trax” and “Prime Suspect.”
The list of victims is long and includes the Pentagon, the U.S. Navy, NASA, and Australia’s Overseas Telecommunications Commission; Citibank, Lockheed Martin, Motorola, Panasonic, and Xerox.
In 1996, he pleaded guilty to twenty-five charges and was ordered to pay reparations of A$2,100 and released on a good behavior bond.
Assange has been residing in the embassy since 2012 to avoid extradition, the popular journalist is facing sexual assault allegations in Sweden, meanwhile, the United States ask him to respond the accusation of cyber espionage for publishing classified US military and diplomat documents.
On September 2014, Julian Assange filed a complaint against Sweden and the United Kingdom, that has been considered by the UN Working Group on Arbitrary Detention.
We have to sit and wait for the decision on the Assanges’ case. If the and if the group will decide that the man is being illegally detained, the UN is expected to call on the UK and Sweden to release him.
“IF THE WGAD FINDS IN FAVOUR OF JULIAN ASSANGE — WHAT HAPPENS NEXT?
If the WGAD finds in Julian Assange’s favour, it will declare that Julian Assange is arbitrarily detained. In this case the UK and Sweden must immediately release and compensate him.”
A severe vulnerability affects eBay, be careful to phishing attacks
3.2.2016 Vulnerebility
Researchers from Check Point have discovered a flaw affecting the eBay platform that could allow attackers to launch phishing attacks against visitors.
A group of researchers from Check Point have discovered a vulnerability affecting the eBay online sales platform that could allow attackers to launch phishing attacks against visitors.
Visitors could be tricked into opening a page on the site that could expose them to phishing attacks, this is possible because the attacker could bypass the site’s code validation and execute malicious JavaScript on users via their browser, or mobile app.
The attack scenario is very simple, hackers can target eBay users by sending them a legitimate page that contains malicious code. By using social engineering the users can be tricked into opening the malicious page triggering the code execution, leading to multiple attack scenarios that range from phishing to binary download.
“Check Point has discovered a severe vulnerability in eBay’s online sales platform. This vulnerability allows attackers to bypass eBay’s code validation and control the vulnerable code remotely to execute malicious Java script code on targeted eBay users. If this flaw is left unpatched, eBay’s customers will continue to be exposed to potential phishing attacks and data theft.” states a blog post published by the company.
ebay flaw
The attacker would have to use JSF**k, a non-standard technique, in their description to pull the code. The researchers discovered that while eBay forbids users from including scripts and iFrames in descriptions by filtering it, the validation mechanism fails in the presence of JSF**k code.
What it the JSF**k?
JSFuck is an esoteric and educational programming style based on the atomic parts of JavaScript that uses only six different characters,– []()!+, to write and execute code, this is the description reported in on the official website.
eBay doesn’t filter it allowing attackers to use it to launch the attack bypassing the validation mechanism in place.
“This allows the attacker to insert a remote controllable JavaScript that he can adjust to, for example, create multiple payloads for a different user agent,” Check Point writes, adding that an attacker could use it to trick a victim into downloading a malicious app or use the vulnerability to carry out phishing attacks.
The bad news it that the researchers reported the issue to eBay on Dec. 15 2015, but just two weeks ago the company replied that it had no plans to solve the problem.
“As we demonstrated to the eBay security team in the proof of concept, we were able to bypass their security policies and insert a malicious code to our seller page without any difficulty or restriction,” continues the post.