26.12.23 Phishing The Hacker News

The threat actor referred to as Cloud Atlas has been linked to a set of spear-phishing attacks on Russian enterprises.
Phishing 2024 2023 2022 2021 2020
Cloud Atlas' Spear-Phishing Attacks Target Russian Agro and Research Companies
26.12.23
Phishing
The Hacker News
The threat actor referred to as Cloud Atlas has been linked to a set of
spear-phishing attacks on Russian enterprises.
Targets included a Russian agro-industrial enterprise and a state-owned research company, according to a report from F.A.C.C.T., a standalone cybersecurity company formed after Group-IB's formal exit from Russia earlier this year.
Cloud Atlas, active since at least 2014, is a cyber espionage group of unknown origin. Also called Clean Ursa, Inception, Oxygen, and Red October, the threat actor is known for its persistent campaigns targeting Russia, Belarus, Azerbaijan, Turkey, and Slovenia.
In December 2022, Check Point and Positive Technologies detailed multi-stage attack sequences that led to the deployment of a PowerShell-based backdoor referred to as PowerShower as well as DLL payloads capable of communicating with an actor-controlled server.
The starting point is a phishing message bearing a lure document that exploits CVE-2017-11882, a six-year-old memory corruption flaw in Microsoft Office's Equation Editor, to kick-start the execution of malicious payloads, a technique Cloud Atlas has employed as early as October 2018.
"The actor's massive spear-phishing campaigns continue to use its simple but
effective methods in order to compromise its targets," Kaspersky noted in August
2019. "Unlike many other intrusion sets, Cloud Atlas hasn't chosen to use open
source implants during its recent campaigns, in order to be less
discriminating."
F.A.C.C.T. described the latest kill chain as similar to the one described by Positive Technologies, with successful exploitation of CVE-2017-11882 via RTF template injection paving the way for shellcode that's responsible for downloading and running an obfuscated HTA file. The mails originate from popular Russian email services Yandex Mail and VK's Mail.ru.
The malicious HTML application subsequently launches Visual Basic Script (VBS) files that are ultimately responsible for retrieving and executing an unknown VBS code from a remote server.
"The Cloud Atlas group has been active for many years, carefully thinking through every aspect of their attacks," Positive Technologies said of the group last year.
"The group's toolkit has not changed for years—they try to hide their malware from researchers by using one-time payload requests and validating them. The group avoids network and file attack detection tools by using legitimate cloud storage and well-documented software features, in particular in Microsoft Office."
The development comes as the company said that at least 20 organizations located in Russia have been compromised using Decoy Dog, a modified version of Pupy RAT, attributing it to an advanced persistent threat actor it calls Hellhounds.
The actively maintained malware, besides allowing the adversary to remotely control the infected host, comes with a scriptlet designed to transmit telemetry data to an "automated" account on Mastodon with the name "Lamir Hasabat" (@lahat) on the Mindly.Social instance.
"After materials on the first version of Decoy Dog were published, the malware authors went to a lot of effort to hamper its detection and analysis both in traffic and in the file system," security researchers Stanislav Pyzhov and Aleksandr Grigorian said.
BazaCall Phishing Scammers Now Leveraging Google Forms for Deception
14.12.23
Phishing
The Hacker News
The threat actors behind the BazaCall call back phishing attacks have been
observed leveraging Google Forms to lend the scheme a veneer of credibility.
The method is an "attempt to elevate the perceived authenticity of the initial malicious emails," cybersecurity firm Abnormal Security said in a report published today.
BazaCall (aka BazarCall), which was first observed in late 2020, refers to a series of phishing attacks in which email messages impersonating legitimate subscription notices are sent to targets, urging them to contact a support desk to dispute or cancel the plan, or risk getting charged anywhere between $50 to $500.
By inducing a false sense of urgency, the attacker convinces the target over a phone call to grant them remote access capabilities using remote desktop software and ultimately establish persistence on the host under the guise of offering help to cancel the supposed subscription.
Some of the popular services that are impersonated include Netflix, Hulu, Disney+, Masterclass, McAfee, Norton, and GeekSquad.
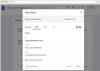
In the latest attack variant detected by Abnormal Security, a form created using Google Forms is used as a conduit to share details of the purported subscription.
It's worth noting that the form has its response receipts enabled, which sends a copy of the response to the form respondent by email, so that the attacker can send an invitation to complete the form themselves and receive the responses.
"Because the attacker enabled the response receipt option, the target will receive a copy of the completed form, which the attacker has designed to look like a payment confirmation for Norton Antivirus software," security researcher Mike Britton said.
The use of Google Forms is also clever in that the responses are sent from the address "forms-receipts-noreply@google[.]com," which is a trusted domain and, therefore, have a higher chance of bypassing secure email gateways, as evidenced by a recent Google Forms phishing campaign uncovered by Cisco Talos last month.
"Additionally, Google Forms often use dynamically generated URLs," Britton
explained. "The constantly changing nature of these URLs can evade traditional
security measures that utilize static analysis and signature-based detection,
which rely on known patterns to identify threats."
Threat Actor Targets Recruiters With More_eggs Backdoor#
The disclosure
arrives as Proofpoint revealed a new phishing campaign that's targeting
recruiters with direct emails that ultimately lead to a JavaScript backdoor
known as More_eggs.
The enterprise security firm attributed the attack wave to a "skilled, financially motivated threat actor" it tracks as TA4557, which has a track record of abusing legitimate messaging services and offering fake jobs via email to ultimately deliver the More_eggs backdoor.
"Specifically in the attack chain that uses the new direct email technique, once the recipient replies to the initial email, the actor was observed responding with a URL linking to an actor-controlled website posing as a candidate resume," Proofpoint said.

"Alternatively, the actor was observed replying with a PDF or Word attachment
containing instructions to visit the fake resume website."
More_eggs is offered as malware-as-a-service, and is used by other prominent cybercriminal groups like Cobalt Group (aka Cobalt Gang), Evilnum, and FIN6. Earlier this year, eSentire linked the malware to two operators from Montreal and Bucharest.
Governments May Spy on You by Requesting Push Notifications from Apple and
Google
8.12.23
Phishing
The Hacker News
Unspecified governments have demanded mobile push notification records from
Apple and Google users to pursue people of interest, according to U.S. Senator
Ron Wyden.
"Push notifications are alerts sent by phone apps to users' smartphones," Wyden said.
"These alerts pass through a digital post office run by the phone operating system provider -- overwhelmingly Apple or Google. Because of that structure, the two companies have visibility into how their customers use apps and could be compelled to provide this information to U.S. or foreign governments."
Wyden, in a letter to U.S. Attorney General Merrick Garland, said both Apple and Google confirmed receiving such requests but noted that information about the practice was restricted from public release by the U.S. government, raising questions about the transparency of legal demands they receive from governments.
When mobile apps for Android and iOS send push notifications to users' devices, they are routed through Apple and Google's own infrastructure known as the Apple Push Notification (APN) service and Firebase Cloud Messaging, respectively. Microsoft and Amazon have similar systems in place called Windows Push Notification Service (WNS) and Amazon Device Messaging (ADM).
As a result, the letter alleges that both companies can be compelled by governments to hand over the information. It's currently not clear which governments have sought notification data from Apple and Google.
That said, the U.S. is one among them, according to the Washington Post, which found more than two dozen search warrant applications related to federal requests for push notification data.
"The data these two companies receive includes metadata, detailing which app received a notification and when, as well as the phone and associated Apple or Google account to which that notification was intended to be delivered," the letter read.
"In certain instances, they also might also receive unencrypted content, which could range from backend directives for the app to the actual text displayed to a user in an app notification."
It also urged that Apple and Google should be permitted to disclose whether they have facilitated this practice, and if so, publish aggregate statistics about the number of demands they receive, and notify specific customers about demands for their data.
In a statement shared with Reuters, which first reported the development, Apple said the letter gave them the "opening" they needed to share more details about how governments monitored push notifications.
"When users allow an application they have installed to receive push notifications, an Apple Push Notification Service (APNs) token is generated and registered to that developer and device," Apple now notes in its updated Legal Process Guidelines document [PDF].
"Some apps may have multiple APNs tokens for one account on one device to differentiate between messages and multi-media. The Apple ID associated with a registered APNs token may be obtained with a subpoena or greater legal process."
Google, meanwhile, noted that it already publishes this information in its transparency reports although it's not specifically broken down by government requests for push notification records.
Cybercriminals Using Telekopye Telegram Bot to Craft Phishing Scams on a Grand
Scale
25.11.23
Phishing
The Hacker News
More details have emerged about a malicious Telegram bot
called Telekopye that's used by threat actors to pull off large-scale phishing
scams.
"Telekopye can craft phishing websites, emails, SMS messages, and more," ESET security researcher Radek Jizba said in a new analysis.
The threat actors behind the operation – codenamed Neanderthals – are known to run the criminal enterprise as a legitimate company, spawning a hierarchical structure that encompasses different members who take on various roles.
Once aspiring Neanderthals are recruited via advertisements on underground forums, they are invited to join designated Telegram channels that are used for communicating with other Neanderthals and keeping track of transaction logs.
The ultimate goal of the operation is to pull off one of the three types of scams: seller, buyer, or refund.
In the case of the former, Neanderthals pose as sellers and try to lure unwary Mammoths into purchasing a non-existent item. Buyer scams entail the Neaderthals masquerading as buyers so as to dupe the Mammoths (i.e., merchants) into entering their financial details to part with their funds.
Other scenarios fall into a category called refund scams wherein Neaderthals trick the Mammoths a second time under the pretext of offering a refund, only to deduct the same amount of money again.
Singapore headquartered cybersecurity firm Group-IB previously told The Hacker News that the activity tracked as Telekopye is the same as Classiscam, which refers to a scam-as-a-service program that has netted the criminal actors $64.5 million in illicit profits since its emergence in 2019.
"For the Seller scam scenario, Neanderthals are advised to prepare additional photos of the item to be ready if Mammoths ask for additional details," Jizba noted. "If Neanderthals are using pictures they downloaded online, they are supposed to edit them to make image search more difficult."
Choosing a Mammoth for a buyer scam is a deliberate process that takes into
account the victim's gender, age, experience in online marketplaces, rating,
reviews, number of completed trades, and the type of items they are selling,
indicating a preparatory stage that involves extensive market research.
Also utilized by Neanderthals are web scrapers to sift through online marketplace listings and pick an ideal Mammoth who is likely to fall for the bogus scheme.
Should a mammoth prefer in-person payment and in-person delivery for sold goods, the Neanderthals claim "they are too far away or that they are leaving the city for a business trip for a few days," while simultaneously demonstrating heightened interest in the item to increase the likelihood of success of the scam.
Neanderthals have also been observed use VPNs, proxies, and TOR to stay anonymous, while also exploring real estate scams wherein they create bogus websites with apartment listings and entice Mammoths into paying for a reservation fee by clicking on a link that points to a phishing website.
"Neanderthals write to a legitimate owner of an apartment, pretending to be interested and ask for various details, such as additional pictures and what kind of neighbors the apartment has," Jizba said.
"The Neanderthals then take all this information and create their own listing on another website, offering the apartment for rent. They cut the expected market price by about 20%. The rest of the scenario is identical to the Seller scam scenario."
The disclosure comes as Check Point detailed a rug pull scam that managed to pilfer nearly $1 million by luring unsuspecting victims into investing in fake tokens and executing simulated trades to create a veneer of legitimacy.
"Once the token had sufficiently lured in investors, the scammer executed the final move – withdrawal of liquidity from the token pool, leaving token purchasers with empty hands and depleted funds," the company said.
How Multi-Stage Phishing Attacks Exploit QRs, CAPTCHAs, and Steganography
22.11.23
Phishing
The Hacker News
Phishing attacks are steadily becoming more sophisticated, with cybercriminals
investing in new ways of deceiving victims into revealing sensitive information
or installing malicious software. One of the latest trends in phishing is the
use of QR codes, CAPTCHAs, and steganography. See how they are carried out and
learn to detect them.
Quishing#
Quishing, a phishing technique resulting from the combination of
"QR" and "phishing," has become a popular weapon for cybercriminals in 2023.
By concealing malicious links within QR codes, attackers can evade traditional spam filters, which are primarily geared towards identifying text-based phishing attempts. The inability of many security tools to decipher the content of QR codes further makes this method a go-to choice for cybercriminals.
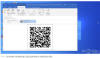
An email containing a QR code with a malicious link
Analyzing a QR code with
an embedded malicious link in a safe environment is easy with ANY.RUN:
Simply open this task in the sandbox (or upload your file with a QR code).
Navigate to the Static Discovering section (By clicking on the name of the file
in the top right corner).
Select the object containing the QR code.
Click
"Submit to Analyze."
The sandbox will then automatically launch a new task
window, allowing you to analyze the URL identified within the QR code.
Black Friday Offer
Take advantage of ANY.RUN's Black Friday Offer
Purchase
an annual Searcher or Hunter plan subscription and get another for your
colleague completely free of charge. Available November 20-26.
Get It Now
CAPTCHA-based attacks#
CAPTCHA is a security solution used on
websites to prevent automated bots from creating fake accounts or submitting
spam. Attackers have managed to exploit this tool to their advantage.
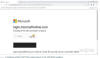
A phishing attack CAPTCHA page shown in the ANY.RUN sandbox
Attackers are
increasingly using CAPTCHAs to mask credential-harvesting forms on fake
websites. By generating hundreds of domain names using a Randomized Domain
Generated Algorithm (RDGA) and implementing CloudFlare's CAPTCHAs, they can
effectively hide these forms from automated security systems, such as web
crawlers, which are unable to bypass the CAPTCHAs.
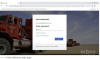
A fake Halliburton login page
The example above shows an attack targeting
Halliburton Corporation employees. It first requires the user to pass a CAPTCHA
check and then uses a realistic Office 365 private login page that is difficult
to distinguish from the real page.
Once the victim enters their login credentials, they are redirected to a legitimate website, while the attackers exfiltrate the credentials to their Command-and-Control server.
Learn more about CAPTCHA attacks in this article.
Steganography malware campaigns#
Steganography is the practice of hiding data
inside different media, such as images, videos, or other files.
A typical phishing attack that employs steganography begins with a carefully crafted email designed to appear legitimate. Embedded within the email is an attachment, often a Word document, accompanied by a link to a file-sharing platform like Dropbox. In the example below, you can see a fake email from a Colombian government organization.
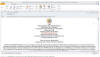
A phishing email is typically the first stage of an attack
The unsuspecting
user that clicks the link inside the document downloads an archive, which
contains a VBS script file. Upon execution, the script retrieves an image file,
seemingly harmless but containing hidden malicious code. Once executed, the
malware infects the victim's system.
To understand how steganography attacks are carried out and detected, check out this article.
Expose phishing attacks with ANY.RUN#
ANY.RUN is a malware analysis sandbox
that is capable of detecting a wide range of phishing tactics and letting users
examine them in detail.
Check out ANY.RUN's Black Friday Offer, available November 20-26.
Fully interactive Windows 7,9,10,11 virtual machines
Comprehensive reports
with IOCs and malware configs
Private analysis of an unlimited number of
files and links
Major Phishing-as-a-Service Syndicate 'BulletProofLink' Dismantled by Malaysian
Authorities
13.11.23
Phishing
The Hacker News
Malaysian law enforcement authorities have announced the
takedown of a phishing-as-a-service (PhaaS) operation called BulletProofLink.
The Royal Malaysia Police said the effort, which was carried out with assistance from the Australian Federal Police (AFP) and the U.S. Federal Bureau of Investigation (FBI) on November 6, 2023, was based on information that the threat actors behind the platform were based out of the country.
To that end, eight individuals aged between 29 and 56, including the syndicate's mastermind, have been arrested across different locations in Sabah, Selangor, Perak, and Kuala Lumpur, New Straits Times reported.
Along with the arrests, authorities confiscated servers, computers, jewelry, vehicles, and cryptocurrency wallets containing approximately $213,000.
BulletProofLink, also called BulletProftLink, is known for offering ready-to-use phishing templates on a subscription basis to other actors for conducting credential harvesting campaigns. These templates mimic the login pages of well-known services like American Express, Bank of America, DHL, Microsoft, and Naver.
According to an analysis from Microsoft in September 2021, BulletProofLink actors also engaged in what's called double theft wherein the stolen credentials are sent to both their customers and the core developers, resulting in additional monetization avenues.
"BulletProftLink is associated with the threat actor AnthraxBP who also went by the online nicknames TheGreenMY and AnthraxLinkers," cybersecurity firm Intel 471 said last week.
"The actor maintained an active website advertising phishing services. The actor
has an extensive underground footprint and operated on a number of clear web
underground forums and Telegram channels using multiple handles."
Believed to be active since at least 2015, BulletProftLink's online storefront is estimated to have no less than 8,138 active clients and 327 phishing pages templates as of April 2023.
Another noteworthy feature is its integration of the Evilginx2 to facilitate adversary-in-the-middle (AiTM) attacks that make it possible for threat actors to steal session cookies and bypass multi-factor authentication protections.
"PhaaS schemes like BulletProftLink provide the fuel for further attacks," Intel 471 said. "Stolen login credentials are one of the primary ways that malicious hackers gain access to organizations."
In a sign that threat actors are constantly updating tactics in response to disruptions and taking more sophisticated approaches, AiTM attacks have also been observed employing intermediary links to documents hosted on file-sharing solutions like DRACOON that contain the URLs to adversary-controlled infrastructure.
"This new method can bypass email security mitigations since the initial link appears to be from a legitimate source and no files are delivered to the victim's endpoint as the hosted document containing the link can be interacted with via the file-sharing server within the browser," Trend Micro said.
The development comes as a 33-year-old Serbian and Croatian national, Milomir Desnica, pleaded guilty in the U.S. to operating a drug trafficking platform called Monopoly Market on the dark web and for conspiring to distribute over 30 kilograms of methamphetamine to U.S. customers.
The illicit marketplace, which was set up by Desnica in 2019, was taken offline in December 2021 as part of a coordinated exercise in partnership with Germany and Finland. Desnica was arrested in Austria in November 2022 and extradited to the U.S. to face drug trafficking charges in June 2023.
Microsoft Uncovers Banking AitM Phishing and BEC Attacks Targeting Financial
Giants
10.6.23
Phishing The Hacker News
Banking and financial services organizations are the targets of a new
multi-stage adversary-in-the-middle (AitM) phishing and business email
compromise (BEC) attack, Microsoft has revealed.
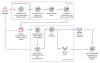
"The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations," the tech giant disclosed in a Thursday report.
Microsoft, which is tracking the cluster under its emerging moniker Storm-1167, called out the group's use of indirect proxy to pull off the attack.
This enabled the attackers to flexibly tailor the phishing pages to their targets and carry out session cookie theft, underscoring the continued sophistication of AitM attacks.
The modus operandi is unlike other AitM campaigns where the decoy pages act as a reverse proxy to harvest credentials and time-based one-time passwords (TOTPs) entered by the victims.
"The attacker presented targets with a website that mimicked the sign-in page of the targeted application, as in traditional phishing attacks, hosted on a cloud service," Microsoft said.
"The said sign-in page contained resources loaded from an attacker-controlled server, which initiated an authentication session with the authentication provider of the target application using the victim's credentials."
The attack chains commence with a phishing email that points to a link, which, when clicked, redirects a victim into visiting a spoofed Microsoft sign-in page and entering their credentials and TOTPs.

The harvested passwords and session cookies are then used to impersonate the
user and gain unauthorized access to the email inbox by means of a replay
attack. The access is then abused to get hold of sensitive emails and
orchestrate a BEC attack.
What's more, a new SMS-based two-factor authentication method is added to the target account in order to sign in using the pilfered credentials sans attracting any attention.
In the incident analyzed by Microsoft, the attacker is said to have initiated a
mass spam campaign, sending more than 16,000 emails to the compromised user's
contacts, both within and outside of the organization, as well as distribution
lists.
The adversary has also been observed taking steps to minimize detection and establish persistence by responding to incoming emails and subsequently taking steps to delete them from the mailbox.
Ultimately, the recipients of the phishing emails are targeted by a second AitM
attack to steal their credentials and trigger yet another phishing campaign from
the email inbox of one of the users whose account was hacked as a result of the
AitM attack.
"This attack shows the complexity of AiTM and BEC threats,
which abuse trusted relationships between vendors, suppliers, and other partner
organizations with the intent of financial fraud," the company added.
The development comes less than a month after Microsoft warned of a surge in BEC attacks and the evolving tactics employed by cybercriminals, including the use of platforms, like BulletProftLink, for creating industrial-scale malicious mail campaigns.
Another tactic entails the use of residential internet protocol (IP) addresses to make attack campaigns appear locally generated, the tech giant said.
"BEC threat actors then purchase IP addresses from residential IP services matching the victim's location creating residential IP proxies which empower cybercriminals to mask their origin," Redmond explained.
"Now, armed with localized address space to support their malicious activities in addition to usernames and passwords, BEC attackers can obscure movements, circumvent 'impossible travel' flags, and open a gateway to conduct further attacks."
Chinese PostalFurious Gang Strikes UAE Users with Sneaky SMS Phishing Scheme
7.6.23 Phishing
The Hacker News
A Chinese-speaking phishing gang dubbed PostalFurious has been linked to a new SMS campaign that's targeting users in the U.A.E. by masquerading as postal services and toll operators, per Group-IB.
The fraudulent scheme entails sending users bogus text messages asking them to pay a vehicle trip fee to avoid additional fines. The messages also contain a shortened URL to conceal the actual phishing link.
Clicking on the link directs the unsuspecting recipients to a fake landing page that's designed to capture payment credentials and personal data. The campaign is estimated to be active as of April 15, 2023.
"The URLs from the texts lead to fake branded payment pages that ask for personal details, such as name, address, and credit card information," Group-IB said. "The phishing pages appropriate the official name and logo of the impersonated postal service provider."
The exact scale of the attacks is currently unknown. What's known is that the text messages were sent from phone numbers registered in Malaysia and Thailand, as well as via email addresses through the Apple iMessage service.
In a bid to stay undetected, the phishing links are geofenced such that the pages can only be accessed from U.A.E.-based IP addresses. The threat actors have also been observed registering new phishing domains every day to expand their reach.
According to the Singapore-based cybersecurity company, a second near-identical
campaign observed on April 29, 2023, mimicked a U.A.E. postal operator.
The
smishing activity marks an expansion of the threat actor's efforts since at
least 2021, when it began targeting users in the Asia-Pacific region. Group-IB
said PostalFurious operations demonstrate the "transnational nature of organized
cybercrime."
To avoid falling prey to such scams, it's recommended to practice careful clicking habits when it comes to links and attachments, keep software up-to-date, and ensure strong digital hygiene routines.
The development comes on the heels of a similar postal-themed phishing campaign dubbed Operation Red Deer that has been discovered targeting various Israeli organizations to distribute a remote access trojan called AsyncRAT. The attacks have been pinned on a threat actor codenamed Aggah.
Don't Click That ZIP File! Phishers Weaponizing .ZIP Domains to Trick Victims
30.5.23 Phishing
The Hacker News
A new phishing technique called "file archiver in the browser" can be leveraged
to "emulate" a file archiver software in a web browser when a victim visits a
.ZIP domain.
"With this phishing attack, you simulate a file archiver software (e.g., WinRAR) in the browser and use a .zip domain to make it appear more legitimate," security researcher mr.d0x disclosed last week.
Threat actors, in a nutshell, could create a realistic-looking phishing landing page using HTML and CSS that mimics legitimate file archive software, and host it on a .zip domain, thus elevating social engineering campaigns.
In a potential attack scenario, a miscreant could resort to such trickery to redirect users to a credential harvesting page when a file "contained" within the fake ZIP archive is clicked.
"Another interesting use case is listing a non-executable file and when the user clicks to initiate a download, it downloads an executable file," mr.d0x noted. "Let's say you have an 'invoice.pdf' file. When a user clicks on this file, it will initiate the download of a .exe or any other file."
On top of that, the search bar in the Windows File Explorer can emerge as a sneaky conduit where searching for a non-existent .ZIP file opens it directly in the web browser should the file name correspond to a legitimate .zip domain.
"This is perfect for this scenario since the user would be expecting to see a ZIP file," the researcher said. "Once the user performs this, it will auto-launch the .zip domain which has the file archive template, appearing pretty legitimate."
The development comes as Google rolled out eight new top-level domains (TLDs), including ".zip" and ".mov," that have raised some concerns that it could invite phishing and other types of online scams.
This is because .ZIP and .MOV are both legitimate file extension names, potentially confusing unsuspecting users into visiting a malicious website rather than opening a file and dupe them into accidentally downloading malware.
"ZIP files are often used as part of the initial stage of an attack chain, typically being downloaded after a user accesses a malicious URL or opens an email attachment," Trend Micro said.
"Beyond ZIP archives being used as a payload, it's also likely that malicious actors will use ZIP-related URLs for downloading malware with the introduction of the .zip TLD."
While reactions are decidedly mixed on the risk posed as a result of confusion between domain names and file names, it's expected to equip actors acting in bad faith with yet another vector for phishing.
The discovery also comes as cybersecurity company Group-IB said it detected a 25% surge in the use of phishing kits in 2022, identifying 3,677 unique kits, when compared to the preceding year.
Of particular interest is the uptick in the trend of using Telegram to collect stolen data, almost doubling from 5.6% in 2021 to 9.4% in 2022.
That's not all. Phishing attacks are also becoming more sophisticated, with cybercriminals increasingly focusing on packing the kits with detection evasion capabilities such as the use of antibots and dynamic directories.
"Phishing operators create random website folders that are only accessible by the recipient of a personalized phishing URL and cannot be accessed without the initial link," the Singapore-headquartered firm said.
"This technique allows phishers to evade detection and blacklisting as the
phishing content will not reveal itself."
According to a new report from
Perception Point, the number of advanced phishing attacks attempted by threat
actors in 2022 rose 356%. The total number of attacks increased by 87% over the
course of the year.
This continued evolution of phishing schemes is exemplified by a fresh wave of attacks that have been observed leveraging compromised Microsoft 365 accounts and restricted-permission message (.rpmsg) encrypted emails to harvest users' credentials.
"The use of encrypted .rpmsg messages means that the phishing content of the message, including the URL links, are hidden from email scanning gateways," Trustwave researchers Phil Hay and Rodel Mendrez explained.
Another instance highlighted by Proofpoint entails the possible abuse of legitimate features in Microsoft Teams to facilitate phishing and malware delivery, including utilizing meeting invites post-compromise by replacing default URLs with malicious links via API calls.
"A different approach that attackers can utilize, given access to a user's Teams token, is using Teams' API or user interface to weaponize existing links in sent messages," the enterprise security firm noted.
"This could be done by simply replacing benign links with links pointing to nefarious websites or malicious resources."
New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing
Phishing Pages
13.5.23
Phishing The Hacker News
A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been
leveraged by cybercriminals to target business users of the Microsoft 365 cloud
service since at least mid-2022, effectively lowering the bar to entry for
phishing attacks.
"Greatness, for now, is only focused on Microsoft 365 phishing pages, providing its affiliates with an attachment and link builder that creates highly convincing decoy and login pages," Cisco Talos researcher Tiago Pereira said.
"It contains features such as having the victim's email address pre-filled and displaying their appropriate company logo and background image, extracted from the target organization's real Microsoft 365 login page."
Campaigns involving Greatness have mainly manufacturing, health care, and technology entities located in the U.S., the U.K., Australia, South Africa, and Canada, with a spike in activity detected in December 2022 and March 2023.
Phishing kits like Greatness offer threat actors, rookies or otherwise, a cost-effective and scalable one-stop shop, making it possible to design convincing login pages associated with various online services and bypass two-factor authentication (2FA) protections.
Specifically, the authentic-looking decoy pages function as a reverse proxy to
harvest credentials and time-based one-time passwords (TOTPs) entered by the
victims.
Attack chains begin with malicious emails containing an HTML
attachment, which, upon opening, executes obfuscated JavaScript code that
redirects the user to a landing page with the recipient's email address already
pre-filled and prompts for their password and MFA code.
The entered credentials and tokens are subsequently forwarded to the affiliate's Telegram channel for obtaining unauthorized access to the accounts in question.
The AiTM phishing kit also comes with an administration panel that enables the affiliate to configure the Telegram bot, keep track of stolen information, and even build booby-trapped attachments or links.
What's more, each affiliate is expected to have a valid API key in order to be
able to load the phishing page. The API key also prevents unwanted IP addresses
from viewing the phishing page and facilitates behind-the-scenes communication
with the actual Microsoft 365 login page by posing as the victim.
"Working
together, the phishing kit and the API perform a 'man-in-the-middle' attack,
requesting information from the victim that the API will then submit to the
legitimate login page in real time," Pereira said.
"This allows the PaaS affiliate to steal usernames and passwords, along with the authenticated session cookies if the victim uses MFA."
The findings come as Microsoft has begun enforcing number matching in Microsoft Authenticator push notifications as of May 8, 2023, to improve 2FA protections and fend off prompt bombing attacks.
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels
7.4.23 Phishing
The Hacker News
In yet another sign that Telegram is increasingly becoming a thriving hub for
cybercrime, researchers have found that threat actors are using the messaging
platform to peddle phishing kits and help set up phishing campaigns.
"To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type of personal data do you prefer?'," Kaspersky web content analyst Olga Svistunova said in a report published this week.
The links to these Telegram channels are distributed via YouTube, GitHub, and the phishing kits that are developed by the crooks themselves. The Russian cybersecurity firm said it detected over 2.5 million malicious URLs generated using phishing kits in the past six months.
One of the prominent services offered is to provide threat actors with Telegram bots that automate the process of generating phishing pages and collecting user data.
Although it's the scammer's responsibility to distribute the fake login pages to targets of interest, the credentials captured in those pages are sent back by means of another Telegram bot.
Other bot services go a step further by advertising options to generate phishing pages that mimic a legitimate service, which are then used to lure potential victims under the pretext of giving away free likes on social media services.
"Scammer-operated Telegram channels sometimes post what appears to be exceptionally generous offers, for example, zipped up sets of ready-to-use phishing kits that target a large number of global and local brands," Svistunova said.
In some cases, phishers have also been observed sharing users' personal data with other subscribers for free in hopes of attracting aspiring criminals, only to sell paid kits to those who wish to pull off more such attacks. The scammers further offer to teach "how to phish for serious cash."
Using free propositions is also a way for scammers to trick cash-strapped and newbie criminals into using their phishing kits, resulting in double theft, where the stolen data is also sent to the creator without their knowledge.
Paid services, on the other hand, include advanced kits that boast of an appealing design and features like anti-bot detection, URL encryption and geoblocking that threat actors could use to commit more advanced social engineering schemes. Such pages cost anywhere between $10 to $280.
Another paid category entails the sale of personal data, with credentials of bank accounts advertised at different rates based on the balance. For example, an account with a balance of $49,000 was put up for $700.
What's more, phishing services are marketed via Telegram on a subscription basis
(i.e., phishing-as-a-service or PhaaS), wherein the developers rent the kits for
a monthly fee in return for providing regular updates.
Also promoted as a
subscription is a one-time password (OTP) bot that calls users and convinces
them to enter the two-factor authentication code on their phones to help bypass
account protections.
Setting up these services are relatively straightforward. What's more difficult is earning the trust and loyalty of the customers. And some vendors go out of their way to assure that all the information is encrypted so that no third-parties, including themselves, can read it.
The findings also follow an advisory from Cofense earlier this January, which revealed an 800% increase year-over-year in the use of Telegram bots as exfiltration destinations for phished information.
"Wannabe phishers used to need to find a way onto the dark web, study the forums there, and do other things to get started," Svistunova said. "The threshold to joining the phisher community lowered once malicious actors migrated to Telegram and now share insights and knowledge, often for free, right there in the popular messaging service."
Microsoft Warns of Large-Scale Use of Phishing Kits to Send Millions of Emails
Daily
14.3.23
Phishing The Hacker News
An open source adversary-in-the-middle (AiTM) phishing kit has found a number of takers in the cybercrime world for its ability to orchestrate attacks at scale.
Microsoft Threat Intelligence is tracking the threat actor behind the development of the kit under its emerging moniker DEV-1101.
An AiTM phishing attack typically involves a threat actor attempting to steal and intercept a target's password and session cookies by deploying a proxy server between the user and the website.
Such attacks are more effective owing to their ability to circumvent multi-factor authentication (MFA) protections.
DEV-1101, per the tech giant, is said to be the party behind several phishing kits that can be purchased or rented by other criminal actors, thereby reducing the effort and resources required to launch a phishing campaign.
"The availability of such phishing kits for purchase by attackers is part of the industrialization of the cybercriminal economy and lowers the barrier of entry for cybercrime," Microsoft said in a technical report.
The service-based economy that fuels such offerings can also result in double theft, wherein the stolen credentials are sent to both the phishing-as-a-service provider as well as their customers.
The open source kit from DEV-1101 comes with features that make it possible to
set up phishing landing pages mimicking Microsoft Office and Outlook, not to
mention manage campaigns from mobile devices and even use CAPTCHA checks to
evade detection.
The service, since its debut in May 2022, has undergone several enhancements, chief among them being the ability to manage servers running the kit through a Telegram bot. It currently has a price tag of $300 for a monthly licensing fee, with VIP licenses costing $1,000.
Microsoft said it has detected numerous high-volume phishing campaigns spanning millions of phishing emails per day from various actors that leverage the tool.
This includes an activity cluster dubbed DEV-0928 that Redmond described as one
of "DEV-1101's more prominent patrons" and which has been linked to a phishing
campaign comprising over one million emails since September 2022.
The attack
sequence commences with document-themed email messages containing a link to a
PDF document, that when clicked, directs the recipient to a login page that
masquerades as Microsoft's sign-in portal, but not before urging the victim to
complete a CAPTCHA step.
"Inserting a CAPTCHA page into the phishing sequence could make it more difficult for automated systems to reach the final phishing page, while a human could easily click through to the next page," Microsoft said.
Although these AiTM attacks are designed to bypass MFA, it's crucial that organizations adopt phishing-resistant authentication methods, such as using FIDO2 security keys, to block suspicious login attempts.