
Phishing 2024 2023 2022 2021 2020
Europol Busts Phishing Gang Responsible for Millions in Losses
22.6.22
Phishing Thehackernews
Europol on Tuesday announced the dismantling of an organized crime group that
dabbled in phishing, fraud, scams, and money laundering activities.
The cross-border operation, which involved law enforcement authorities from Belgium and the Netherlands, saw the arrests of nine individuals in the Dutch nation.
The suspects are men between the ages of 25 and 36 from Amsterdam, Almere, Rotterdam, and Spijkenisse and a 25-year-old woman from Deventer, according to a statement from the National Police Force.
Also confiscated as part of 24 house searches were firearms, ammunition, jewelry, designer clothing, expensive watches, electronic devices, tens of thousands of euros in cash, and cryptocurrency, the officials said.
"The criminal group contacted victims by email, text message and through mobile messaging applications," the agency noted. "These messages were sent by the members of the gang and contained a phishing link leading to a bogus banking website."
Unsuspecting who clicked on the link were tricked into entering their credentials that were subsequently stolen by the syndicate to fraudulently cash out several million euros from the victim's accounts with the help of money mules.
Additionally, some members of the group are said to have connections with drugs and possible firearms trafficking.
The bust comes less than a month after Europol, in collaboration with Australia, Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden, Switzerland, the Netherlands, and the U.S., took down the infrastructure associated with FluBot Android malware.
Microsoft Seizes 41 Domains Used in Spear-Phishing Attacks by Bohrium Hackers
6.6.22 Phishing Thehackernews
Microsoft's Digital Crimes Unit (DCU) last week disclosed that it had taken
legal proceedings against an Iranian threat actor dubbed Bohrium in connection
with a spear-phishing operation.
The adversarial collective is said to have targeted entities in tech, transportation, government, and education sectors located in the U.S., Middle East, and India.
"Bohrium actors create fake social media profiles, often posing as recruiters," Amy Hogan-Burney of the DCU said in a tweet. "Once personal information was obtained from the victims, Bohrium sent malicious emails with links that ultimately infected their target's computers with malware."
According to an ex parte order shared by the tech giant, the goal of the intrusions was to steal and exfiltrate sensitive information, take control over the infected machines, and carry out remote reconnaissance.
To halt the malicious activities of Bohrium, Microsoft said it took down 41 ".com," ".info," ".live," ".me," ".net," ".org," and ".xyz" domains that were used as command-and-control infrastructure to facilitate the spear-phishing campaign.
The disclosure comes as Microsoft revealed that it identified and disabled malicious OneDrive activity perpetrated by a previously undocumented threat actor codenamed Polonium since February 2022.
The incidents, which involved the use of OneDrive as command-and-control, were part of a larger wave of attacks the hacking group launched against over 20 organizations based in Israel and Lebanon.
HTML attachments in phishing e-mails
5.6.22
Phishing Securelist
The use of embedded HTML documents in phishing e-mails is a standard technique employed by cybercriminals. It does away with the need to put links in the e-mail body, which antispam engines and e-mail antiviruses usually detect with ease. HTML offers more possibilities than e-mail for camouflaging phishing content.
There are two main types of HTML attachments that cybercriminals use: HTML files with a link to a fake website or a full-fledged phishing page. In the first case, the attackers can not only hide a link in the file, but also automatically redirect the user to the fraudulent site when they open this file. The second type of HTML attachment makes it possible to skip creating the website altogether and save on hosting costs: the phishing form and the script that harvests the data are embedded directly in the attachment. In addition, an HTML file, like an e-mail, can be modified according to the intended victim and attack vector, allowing for more personalized phishing content.
Fig.1. Example e-mail with an HTML attachment
Structure of phishing HTML attachments
Phishing elements in HTML attachments
are usually implemented using JavaScript, which handles redirecting the user to
a phishing site or collecting and sending credentials to scammers.
Fig. 2. Phishing HTML page and its source code
Typically, the HTML page sends data to a malicious URL specified in the script. Some attachments consist entirely (or mostly) of a JS script.
In the e-mail source code, the HTML attachment looks like plain text, usually Base64-encoded.
Fig. 3. HTML attachment in e-mail source code
If a file contains malicious scripts or links in plaintext, the security software can quickly parse and block it. To avoid this, cybercriminals resort to various tricks.
JavaScript obfuscation
JavaScript obfuscation is one of the most common
techniques used to disguise HTML attachments. To prevent the URL in the file
from being quickly spotted and blocked, phishers obfuscate either the phishing
link itself or the entire script, and sometimes the whole HTML file. In some
cases, cybercriminals obfuscate the code manually, but often they use ready-made
tools, of which many are freely available, such as JavaScript Obfuscator.
For example, opening the HTML attachment in the phishing e-mail supposedly from HSBC Bank (see Fig. 1) in a text editor, we see some pretty confusing JS code, which, it would seem, hints neither at opening a link nor at any other meaningful action.
Fig. 4. Example of obfuscation in an HTML attachment
However, it actually is an obfuscated script that redirects the user to a phishing site. To disguise the phishing link, the attackers used a ready-made tool, allowing us to easily deobfuscate the script.
Fig. 5. Deobfuscated script from an attachment in an e-mail seemingly from HSBC Bank: link for redirecting the user
If a script, link, or HTML page is obfuscated manually, it is much harder to restore the original code. To detect phishing content in such a file, dynamic analysis may be required, which involves running and debugging the code.
Encoding
Sometimes attackers use more interesting methods. In one phishing
e-mail, for instance, we found an unusual HTML attachment. As in the example
above, it contained JavaScript. Because the code was so compact, one might think
it was doing the same as the code in the fake HSBC e-mail — that is, redirecting
the user to a phishing site. But upon running it, we found a full-fledged
phishing page encoded in this small script.
Fig. 6. HTML file using the unescape() method — the source code of the file contains only five lines, one of which is empty
Fig. 7. Phishing page in the HTML attachment
The cybercriminals used an interesting trick that involves the deprecated JS method unescape(). This method substitutes the “%xx” character sequences with their ASCII equivalents in the string that is passed to it. Running the script and viewing the source code of the resulting page, we see plain HTML.
Fig. 8. The resulting HTML file
Instead of unescape(), JavaScript now uses the decodeURI() and decodeURIComponent() methods, yet most modern browsers still support unescape(). We cannot say for sure why the attackers chose a deprecated method, but it could be because modern methods are more likely to be interpreted and detected by antispam engines.
Statistics
In the first four months of 2022, Kaspersky security solutions
detected nearly 2 million e-mails containing malicious HTML attachments. Nearly
half of them (851,328) were detected and blocked in March. January was the
calmest month, with our antispam solutions detecting 299,859 e-mails with
phishing HTML attachments.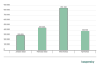
Number of detected e-mails with malicious HTML attachments, January–April 2022 (download)
Conclusion
Phishers deploy a variety of tricks to bypass e-mail blocking and
lure as many users as possible to their fraudulent sites. A common technique is
HTML attachments with partially or fully obfuscated code. HTML files allow
attackers to use scripts, obfuscate malicious content to make it harder to
detect, and send phishing pages as attachments instead of links.
Kaspersky security solutions detect HTML attachments containing scripts regardless of obfuscation.
Phishing-kit market: what’s inside “off-the-shelf” phishing packages
3.4.22 Phishing
Securelist
What are phishing kits?
One of the most common tricks
scammers use in phishing attacks is to create a fake official page of a famous
brand. Attackers tend to copy design elements from the real website, which is
why users can find it hard to distinguish the fake pages from the official ones.
Even phishing page domain name can often look like the real web address of a
certain brand, as cybercriminals include the name of the company or service they
are posing as in the URL. This trick is known as combosquatting.
Combosquatting: registering a fake website with a domain name which contains “facebook.com”
Given phishing websites can be efficiently blocked or added to anti-phishing databases, cybercriminals have to generate these pages quickly and in large numbers. Creating them from scratch over and over again is time-consuming, and not all cybercriminals have the web-development and administration skills it takes. That is why cybercriminals favor phishing kits, which are like model aircraft or vehicle assembly kits. They consist of ready-made templates and scripts which can be used to create phishing pages quickly and on a massive scale. Phishing kits are fairly easy to use, which is why even inexperienced attackers who do not have any technical skills can get their heads around them.
Cybercriminals tend to use hacked official websites to host pages generated using the phishing kits or rely on companies which offer free web-hosting providers. The latter are constantly working to combat phishing and block the fake pages, although phishing websites often manage to serve the intended purpose within their short period of activity, which is to collect and send personal data of victims to criminals.
Contents of phishing kits: basic and complex phishing kits
Phishing kits are
ready-to-deploy packages which require the bare minimum effort to use. Moreover,
their developers usually provide instructions with their products for
inexperienced attackers. Phishing kits usually are designed to generate copies
of websites representing famous brands with large audiences. After all, the more
potential victims there are, the more money there is to be stolen. The phishing
kits we detected in 2021 most frequently created copies of Facebook, the Dutch
banking group ING, the German bank Sparkasse, as well as Adidas and Amazon.
The most basic option phishing kits offer is a ready-made phishing page which is fairly simple to upload on a web-hosting service.
Contents of simple phishing-kit archive
These phishing kits have two essential components for practical reasons:
An HTML page with a phishing data-entry form and related content (style, images,
scripts and other multimedia components). Attackers aim to make the page look
identical to pages on the company’s official website whose users they want to
target in the attack. However, the fake page’s HTML code differs from the
original code.
The phishing script that sends data victims enter on the fake
page to cybercriminals. It is usually a simple script which parses the phishing
data-entry form. In the phishing script’s code, cybercriminals also indicate the
Telegram bot authentication token, e-mail address or other third-party online
resources where stolen data will be sent using the phishing kit. The phishing
kit’s creators often comment the line where an address or token needs to be
entered.
Telegram bot token in a phishing kit’s code
Instead of providing ready-to-load pages, more sophisticated phishing kits contain their elements (images, forms, phishing script, text fragments etc.), along with a separate script which creates new pages from these elements.
Contents of a phishing-kit archive: phishing pages created automatically when index.php file is run
There are also advanced phishing packages which not only come with all the tools and elements needed to assemble the web pages, but also include a control center with a user interface. Attackers can use this control center to tailor how a phishing page functions, e.g., by specifying how they would like to receive stolen data. Some sophisticated phishing kits allow to generate pages which target users from different countries using a built-in dictionary containing the same phrases in different languages.
Dictionary from an advanced phishing kit
In addition to tools for attackers to create phishing pages themselves, some phishing kits can include scripts for sending out messages to potential victims via popular messaging apps or e-mail which contain links to phishing pages. These mailings tend to be the go-to channel cybercriminals use to get their pages out there. The contact details of potential victims can be found on the dark web, where a colossal amount of databases are sold which detail clients of various companies and services.
Many of the scripts for sending out messages included in phishing kits or sold separately can add a URL parameter in the links which contains the recipient’s e-mail address. This parameter is used extensively in corporate phishing attacks. Some known phishing kits which target the corporate sector are able to capture the e-mail domain located in the URL parameter and generate a phishing page tailored to this domain name. There are several common ways to deploy this dynamic content generation:
The text on the page adapts to the domain name, which makes it look more
personalized to increase the victim’s trust.
Icons are loaded from the
Internet which are related to the victim’s domain name, where the domain itself
is essentially the key word used in a search request to load icons.
Code with the URL of a loaded icon corresponding to the victim’s domain
User-Related Dynamic Content: content from phishing website along with text and an icon loaded using the domain name in the URL
Legal iFrame Background: based on the e-mail domain, an iFrame opens with the
legitimate website in the background and a phishing entry form imposed on top of
it.
iFrame with legitimate website as the background
Anti-detection methods
Some sophisticated phishing kits include functional
elements which prevent a page from being accessed by unwelcome agents, such as
bots used by known anti-phishing solution developers or search engines. The
latter are unwelcome, because if a phishing page ends up being a search-result
hit, there’s a high risk it’ll soon get blocked.
Contents of sophisticated phishing-kit archive with bot detection
Apart from that, some of the phishing kits we detected used geoblocking. For example, phishing attacks written in Japanese had pages which could only be opened from Japanese IP addresses. Blocking tended to be triggered by the detection of the User Agent string, which identifies the user’s browser, or based on their IP address, although there are also some technologies which analyze request headers. This was all done in order to reduce the risk of detection by bots from the developers of anti-phishing solutions scanning the phishing page, and to avoid ending up in anti-phishing databases.
Some phishing kits add various obfuscation options for the generated pages and pure “junk” code which aims to make it harder for anti-phishing solutions to detect and block these pages. Some tricks worth highlighting include:
Caesar cipher. Every character in the text is replaced by a character which is a
fixed number of positions further along in the alphabet. This results in the
text in the original code of the phishing page looking like alphabet soup, but
when the page is loaded the shift reverts back and the user sees the page with
normal decoded text. The script for implementing Caesar code is written by the
creators of the phishing kits themselves.
Code of a page with text encrypted in Caesar code
Page source encoding. Text or even the page’s entire HTML code is encoded using
an algorithm such as base64 or AES and decoded on the browser’s end. Unlike
Caesar code, the algorithms for decoding and decrypting data in the phishing
kit’s code are implemented using standard libraries.
Invisible HTML tags. A
large amount of code is added to the page which does not do anything during the
rendering process when code becomes what’s visible on screen — its aim is to
make the page harder to detect. See the example below, where chunks of text are
hidden among junk HTML tags which do not appear on screen according to the
information in the style sheet. Junk
HTML tags
Junk
HTML tags
String slicing. Cutting a string into groups of characters which can be
rearranged, and referring to characters by their number in a code table instead
of explicitly writing them out. A massive puzzle of these substrings is pieced
together when a page is loaded to form the full string.
String slicing:
concealing malicious links in code
Randomized HTML attributes. The randomization of tag attribute values which then
have no further use in the code. This is used to trick anti-phishing
technologies which work by analyzing layout: when a page’s code contains a lot
of variable attributes, the detection rules the technology relies on cannot
count all of them because the probability of making a false detection is too
high.
It is also worth mentioning that similar forms of obfuscation can also
be used by the developers of phishing kits themselves with the aim of getting
hold of data their clients have managed to collect using their product. In this
case, it is not the text of the phishing page that’s obfuscated, but the code
responsible for transferring information back to the creator of the phishing kit
is made obscure to prevent the client using the kit from understanding it.
These methods may aim to prevent anti-phishing solutions from finding clues in the original page which would allow them to classify it as a phishing page. However, we have learned how to detect and successfully block these fake pages using deep automated analysis of content.
Phishing-kit pricing and marketplace
Phishing kits can be purchased on
insider forums on the dark web or through private Telegram channels. Prices vary
and more often than not depend on the level of sophistication and quality a
particular kit has to offer. For instance, phishing kits up for sale on one
Telegram channel are priced from USD 50 to 900. Moreover, some phishing kits are
freely available online.
Phishing kits up for sale on a Telegram channel
Phishing kits are also sold as part of software-as-a-service (SaaS) package. It’s dubbed Phishing-as-a-Service (PHaaS) and lately it’s been growing more popular. The packages consist of a wide range of specialized scamming services: from the creation of fake websites posing as a popular brand to launching a targeted data-theft campaign. This includes studying the target audience, sending out phishing messages, as well as encrypting and sending the stolen data to the client.
For example, one online resource offering Phishing-as-a-Service has a phishing kit for stealing login credentials from a Microsoft account using an invitation to view an Excel document as bait, which can be purchased for a relatively small sum of money. The seller guarantees the product has been tried and tested on all device types. It claims 100% of buyers were satisfied with the quality of the product, and promises to send the victim’s data via e-mail.
Phishing kit for creating a fake website using an Excel document as bait, sold as Phishing-as-a-Service
Statistics
Last year we detected 469 individual phishing kits, which allowed
us to block 1.2 million phishing websites. The graph below shows the dynamics of
the TOP 10 phishing kits we detected over a period from August 2021 to January
2022, along with the number of unique domains where each of these phishing kits
were encountered. Overall, the number of unique domains where we detected
content unboxed from phishing kits exceeded 25,000 in October.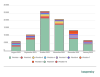
Number of unique domains using the TOP 10 phishing kits, August 2021 — January 2022 (download)
Based on the data presented here, we can conclude that some phishing kits are used fairly extensively and survive for a rather long time, while others are no longer visible after a month or two.
Conclusion and advice
Scammers often rely on phishing kits to orchestrate
phishing campaigns, especially those who are inexperienced and have a poor grasp
of programming. They are relatively simple tools for quickly creating fake
websites and collecting the data cybercriminals steal using them. Some kits can
also include tools for sending out phishing e-mails, a control panel and
dictionaries to localize the phishing attacks.
Cybercriminals usually get their phishing kits from forums on the dark web or closed Telegram channels. Scammers who are poor or on a tight budget can find some basic open-source tools accessible online. Those who are better-off can commission Phishing-as-a-Service, which often includes various phishing kits.
Last year alone, we detected and blocked around 1.2 million phishing pages created using phishing kits. In addition to no-frills phishing kits, we encountered more sophisticated ones which had anti-bot features, geoblocking and anti-detection methods, such as obfuscation and junk code.
Phishing websites are most frequently circulated in spam campaigns via e-mail or messaging app. We recommend users take the following precautions to avoid getting reeled in by the phishers:
Treat links in e-mails and messages sent by people you don not know with
suspicion, as well as “viral” messages which prompt you to forward them to a set
number of your contacts. Avoid clicking on links where possible and manually
type out the URL in the address bar instead or open the app in question.
Before entering your login credentials on a website, make sure the URL in the
address bar is correct.
Use a reliable security solution which blocks
attempts to follow links leading to phishing websites.