21.8.24 Phishing The Hacker News
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of new phishing attacks that aim to infect devices with malware.
Phishing 2024 2023 2022 2021 2020
Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks
16.9.24 Phishing The Hacker News
Cybersecurity researchers have warned of ongoing phishing campaigns that abuse refresh entries in HTTP headers to deliver spoofed email login pages that are designed to harvest users' credentials.
"Unlike other phishing webpage distribution behavior through HTML content, these attacks use the response header sent by a server, which occurs before the processing of the HTML content," Palo Alto Networks Unit 42 researchers Yu Zhang, Zeyu You, and Wei Wang said.
"Malicious links direct the browser to automatically refresh or reload a web page immediately, without requiring user interaction."
Targets of the large-scale activity, observed between May and July 2024, include large corporations in South Korea, as well as government agencies and schools in the U.S. As many as 2,000 malicious URLs have been associated with the campaigns.
Over 36% of the attacks have singled out the business-and-economy sector, followed by financial services (12.9%), government (6.9%), health and medicine (5.7%), and computer and internet (5.4%).
The attacks are the latest in a long list of tactics that threat actors have employed to obfuscate their intent and trick email recipients into parting with sensitive information, including taking advantage of trending top-level domains (TLDs) and domain names to propagate phishing and redirection attacks.
The infection chains are characterized by the delivery of malicious links through header refresh URLs containing targeted recipients' email addresses. The link to which to be redirected is embedded in the Refresh response header.
The starting point of the infection chain is an email message containing a link that mimics a legitimate or compromised domain that, when clicked, triggers the redirection to the actor-controlled credential harvesting page.
To lend the phishing attempt a veneer of legitimacy, the malicious webmail login pages have the recipients' email addresses pre-filled. Attackers have also been observed using legitimate domains that offer URL shortening, tracking, and campaign marketing services.
"By carefully mimicking legitimate domains and redirecting victims to official sites, attackers can effectively mask their true objectives and increase the likelihood of successful credential theft," the researchers said.
"These tactics highlight the sophisticated strategies attackers use to avoid detection and exploit unsuspecting targets."
Phishing and business email compromise (BEC) continues to be a prominent pathway for adversaries looking to siphon information and perform financially motivated attacks.
BEC attacks have cost U.S. and international organizations an estimated $55.49 billion between October 2013 and December 2023, with over 305,000 scam incidents reported during the same time period, according to the U.S. Federal Bureau of Investigation (FBI).
The development comes amid "dozens of scam campaigns" that have leveraged deepfake videos featuring public figures, CEOs, news anchors, and top government officials to promote bogus investment schemes such as Quantum AI since at least July 2023.
These campaigns are propagated via posts and ads on various social media platforms, directing users to phony web pages that prompt them to fill out a form in order to sign up, after which a scammer contacts them via a phone call and asks them to pay an initial fee of $250 in order to access the service.
"The scammer instructs the victim to download a special app so that they can 'invest' more of their funds," Unit 42 researchers said. "Within the app, a dashboard appears to show small profits."
"Finally, when the victim tries to withdraw their funds, the scammers either demand withdrawal fees or cite some other reason (e.g., tax issues) for not being able to get their funds back.
"The scammers may then lock the victim out of their account and pocket the remaining funds, causing the victim to have lost the majority of the money that they put into the 'platform.'"
It also follows the discovery of a stealthy threat actor that presents itself as a legitimate enterprise and has been advertising automated CAPTCHA-solving services at scale to other cybercriminals and helping them infiltrate IT networks.
Dubbed Greasy Opal by Arkose Labs, the Czech Republic-based "cyber attack enablement business" is believed to have been operational since 2009, offering to customers a toolkit of sorts for credential stuffing, mass fake account creation, browser automation, and social media spam at a price point of $190 and an additional $10 for a monthly subscription.
The product portfolio runs the cybercrime gamut, allowing them to develop a sophisticated business model by packaging several services together. The entity's revenues for 2023 alone are said to be no less than $1.7 million.
"Greasy Opal employs cutting-edge OCR technology to effectively analyze and interpret text-based CAPTCHAs, even those distorted or obscured by noise, rotation, or occlusion," the fraud prevention company noted in a recent analysis. "The service develops machine-learning algorithms trained on extensive datasets of images."
One of its users is Storm-1152, a Vietnamese cybercrime group that was previously identified by Microsoft as selling 750 million fraudulent Microsoft accounts and tools through a network of bogus websites and social media pages to other criminal actors.
"Greasy Opal has built a thriving conglomerate of multi-faceted businesses, offering not only CAPTCHA-solving services but also SEO-boosting software and social media automation services that are often used for spam, which could be a precursor for malware delivery," Arkose Labs said.
"This threat actor group reflects a growing trend of businesses operating in a gray zone, while its products and services have been used for illegal activities downstream."
New QR Code Phishing Campaign Exploits Microsoft Sway to Steal Credentials
28.8.24 Phishing The Hacker News
Cybersecurity researchers are calling attention to a new QR code phishing (aka quishing) campaign that leverages Microsoft Sway infrastructure to host fake pages, once again highlighting the abuse of legitimate cloud offerings for malicious purposes.
"By using legitimate cloud applications, attackers provide credibility to victims, helping them to trust the content it serves," Netskope Threat Labs researcher Jan Michael Alcantara said.
"Additionally, a victim uses their Microsoft 365 account that they're already logged-into when they open a Sway page, that can help persuade them about its legitimacy as well. Sway can also be shared through either a link (URL link or visual link) or embedded on a website using an iframe."
The attacks have primarily singled out users in Asia and North America, with technology, manufacturing, and finance sectors being the most sought-after sectors.
Microsoft Sway is a cloud-based tool for creating newsletters, presentations, and documentation. It is part of the Microsoft 365 family of products since 2015.
The cybersecurity firm said it observed a 2,000-fold increase in traffic to unique Microsoft Sway phishing pages starting July 2024 with the ultimate goal of stealing users' Microsoft 365 credentials. This is achieved by serving bogus QR codes hosted on Sway that, when scanned, redirect the users to phishing websites.
In a further attempt to evade static analysis efforts, some of these quishing campaigns have been observed to use Cloudflare Turnstile as a way to hide the domains from static URL scanners.
The activity is also notable for leveraging adversary-in-the-middle (AitM) phishing tactics – i.e., transparent phishing – to siphon credentials and two-factor authentication (2FA) codes using lookalike login pages, while simultaneously attempting to log the victim into the service.
"Using QR codes to redirect victims to phishing websites poses some challenges to defenders," Michael Alcantara said. "Since the URL is embedded inside an image, email scanners that can only scan text-based content can get bypassed."
"Additionally, when a user gets sent a QR code, they may use another device, such as their mobile phone, to scan the code. Since the security measures implemented on mobile devices, particularly personal cell phones, are typically not as stringent as laptops and desktops, victims are then often more vulnerable to abuse."
This is not the first time phishing attacks have abused Microsoft Sway. In April 2020, Group-IB detailed a campaign dubbed PerSwaysion that successfully compromised corporate email accounts of at least 156 high-ranking officers at various firms based in Germany, the U.K., the Netherlands, Hong Kong, and Singapore by using Sway as the jumping board to redirect victims to credential harvesting sites.
The development comes as quishing campaigns are getting more sophisticated as security vendors develop countermeasures to detect and block such image-based threats.
"In a clever twist, attackers have now begun crafting QR codes using Unicode text characters instead of images," SlashNext CTO J. Stephen Kowski said. "This new technique, which we're calling 'Unicode QR Code Phishing,' presents a significant challenge to conventional security measures."
What makes the attack particularly dangerous is the fact that it entirely bypasses detections designed to scan for suspicious images, given they are composed entirely of text characters. Furthermore, the Unicode QR codes can be rendered perfectly on screens sans any issue and look markedly different when viewed in plain text, further complicating detection efforts.
CERT-UA Warns of New Vermin-Linked Phishing Attacks with PoW Bait
21.8.24 Phishing The Hacker News
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of new phishing attacks that aim to infect devices with malware.
The activity has been attributed to a threat cluster it tracks as UAC-0020, which is also known as Vermin. The exact scale and scope of the attacks are presently unknown.
The attack chains commence with phishing messages with photos of alleged prisoners of war (PoWs) from the Kursk region, urging recipients to click on a link pointing to a ZIP archive.
The ZIP file contains a Microsoft Compiled HTML Help (CHM) file that embeds JavaScript code responsible for launching an obfuscated PowerShell script.
"Opening the file installs components of known spyware SPECTR, as well as the new malware called FIRMACHAGENT," CERT-UA said. "The purpose of FIRMACHAGENT is to retrive the data stolen by SPECTR and send it to a remote management server."
SPECTR is a known malware linked to Vermin as far back as 2019. The group is assessed to be linked to security agencies of the Luhansk People's Republic (LPR).
Earlier this June, CERT-UA detailed another campaign orchestrated by the Vermin actors called SickSync that targeted defense forces in the country with SPECTR.
SPECTR is a fully-featured tool designed to harvest a wide range of information, including files, screenshots, credentials, and data from various instant messaging apps like Element, Signal, Skype, and Telegram.
New Phishing Scam Uses Google Drawings and WhatsApp Shortened Links
8.8.24 Phishing The Hacker News
Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information.
"The attackers chose a group of the best-known websites in computing to craft the threat, including Google and WhatsApp to host the attack elements, and an Amazon look-alike to harvest the victim's information," Menlo Security researcher Ashwin Vamshi said. "This attack is a great example of a Living Off Trusted Sites (LoTS) threat."
The starting point of the attack is a phishing email that directs the recipients to a graphic that appears to be an Amazon account verification link. This graphic, for its part, is hosted on Google Drawings, in an apparent effort to evade detection.
Abusing legitimate services has obvious benefits for attackers in that they're not only a low-cost solution, but more importantly, they offer a clandestine way of communication inside networks, as they are unlikely to be blocked by security products or firewalls.
"Another thing that makes Google Drawings appealing in the beginning of the attack is that it allows users (in this case, the attacker) to include links in their graphics," Vamshi said. "Such links may easily go unnoticed by users, particularly if they feel a sense of urgency around a potential threat to their Amazon account."
Users who end up clicking on the verification link are taken to a lookalike Amazon login page, with the URL crafted successively using two different URL shorteners -- WhatsApp ("l.wl[.]co") followed by qrco[.]de -- as an added layer of obfuscation and deceive security URL scanners.
The fake page is designed to harvest credentials, personal information, and credit card details, after which the victims are redirected to the original phished Amazon login page. As an extra step, the web page is rendered inaccessible from the same IP address once the credentials have been validated.
The disclosure comes as researchers have identified a loophole in Microsoft 365's anti-phishing mechanisms that could be abused to increase the risk of users opening phishing emails.
Cybersecurity
The method entails the use of CSS trickery to hide the "First Contact Safety Tip," which alerts users when they receive emails from an unknown address. Microsoft, which has acknowledged the issue, has yet to release a fix.
"The First Contact Safety Tip is prepended to the body of an HTML email, which means it is possible to alter the way it is displayed through the use of CSS style tags," Austrian cybersecurity outfit Certitude said. "We can take this a step further, and spoof the icons Microsoft Outlook adds to emails that are encrypted and/or signed."
OneDrive Phishing Scam Tricks Users into Running Malicious PowerShell Script
31.7.24 Phishing The Hacker News
Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive users with the aim of executing a malicious PowerShell script.
"This campaign heavily relies on social engineering tactics to deceive users into executing a PowerShell script, thereby compromising their systems," Trellix security researcher Rafael Pena said in a Monday analysis.
The cybersecurity company is tracking the "crafty" phishing and downloader campaign under the name OneDrive Pastejacking.
The attack unfolds via an email containing an HTML file that, when opened, displays an image simulating an OneDrive page and includes the error message that says: "Failed to connect to the 'OneDrive' cloud service. To fix the error, you need to update the DNS cache manually."
The message also comes with two options, namely "How to fix" and "Details," with the latter directing the email recipient to a legitimate Microsoft Learn page on Troubleshooting DNS.
However, clicking "How to fix" prompts the user to follow a series of steps, which includes pressing "Windows Key + X" to open the Quick Link menu, launching the PowerShell terminal, and pasting a Base64-encoded command to supposedly fix the issue.
Cybersecurity
"The command [...] first runs ipconfig /flushdns, then creates a folder on the C: drive named 'downloads,'" Pena explained. "Subsequently, it downloads an archive file into this location, renames it, extracts its contents ('script.a3x' and 'AutoIt3.exe'), and executes script.a3x using AutoIt3.exe."
The campaign has been observed targeting users in the U.S., South Korea, Germany, India, Ireland, Italy, Norway, and the U.K.
The disclosure builds upon similar findings from ReliaQuest, Proofpoint, and McAfee Labs, indicating that phishing attacks employing this technique – also tracked as ClickFix – are becoming increasingly prevalent.
The development comes amid the discovery of a new email-based social engineering campaign distributing bogus Windows shortcut files that lead to the execution of malicious payloads hosted on Discord's Content Delivery Network (CDN) infrastructure.
Phishing campaigns have also been increasingly observed sending emails containing links to Microsoft Office Forms from previously compromised legitimate email accounts to entice targets into divulging their Microsoft 365 login credentials under the pretext of restoring their Outlook messages.
"Attackers create legitimate-looking forms on Microsoft Office Forms, embedding malicious links within the forms," Perception Point said. "These forms are then sent to targets en-masse via email under the guise of legitimate requests such as changing passwords or accessing important documents, mimicking trusted platforms and brands like Adobe or Microsoft SharePoint document viewer."
What's more, other attack waves have utilized invoice-themed lures to trick victims to sharing their credentials on phishing pages hosted on Cloudflare R2 that are then exfiltrated to the threat actor via a Telegram bot.
It's no surprise that adversaries are constantly on the lookout for different ways to stealthily smuggle malware past Secure Email Gateways (SEGs) so as to increase the likelihood of success of their attacks.
According to a recent report from Cofense, bad actors are abusing how SEGs scan ZIP archive attachments to deliver the Formbook information stealer by means of DBatLoader (aka ModiLoader and NatsoLoader).
Specifically, this involves passing off the HTML payload as an MPEG file to evade detection by taking advantage of the fact that many common archive extractors and SEGs parse the file header information but ignore the file footer that may contain more accurate information about the file format.
"The threat actors utilized a .ZIP archive attachment and when the SEG scanned the file contents, the archive was detected as containing a .MPEG video file and was not blocked or filtered," the company noted.
"When this attachment was opened with common/popular archive extraction tools such as 7-Zip or Power ISO, it also appeared to contain a .MPEG video file, but it would not play. However, when the archive was opened in an Outlook client or via the Windows Explorer archive manager, the .MPEG file is (correctly) detected as being a .HTML [file]."
CrowdStrike Warns of New Phishing Scam Targeting German Customers
27.7.24 Phishing The Hacker News
CrowdStrike is alerting about an unfamiliar threat actor attempting to capitalize on the Falcon Sensor update fiasco to distribute dubious installers targeting German customers as part of a highly targeted campaign.
The cybersecurity company said it identified what it described as an unattributed spear-phishing attempt on July 24, 2024, distributing an inauthentic CrowdStrike Crash Reporter installer via a website impersonating an unnamed German entity.
The imposter website is said to have been created on July 20, a day after the botched update crashed nearly 9 million Windows devices, causing extensive IT disruptions across the world.
"After the user clicks the Download button, the website leverages JavaScript (JS) that masquerades as JQuery v3.7.1 to download and deobfuscate the installer," CrowdStrike's Counter Adversary Operations team said.
"The installer contains CrowdStrike branding, German localization, and a password [is] required to continue installing the malware."
Specifically, the spear-phishing page featured a download link to a ZIP archive file containing a malicious InnoSetup installer, with the malicious code serving the executable injected into a JavaScript file named "jquery-3.7.1.min.js" in an apparent effort to evade detection.
Users who end up launching the bogus installer are then prompted to enter a "Backend-Server" to proceed further. CrowdStrike said it was unable to recover the final payload deployed via the installer.
The campaign is assessed to be highly targeted owing to the fact that the installer is password-protected and requires input that's likely only known to the targeted entities. Furthermore, the presence of the German language suggests that the activity is geared towards German-speaking CrowdStrike customers.
"The threat actor appears to be highly aware of operations security (OPSEC) practices, as they have focused on anti-forensic techniques during this campaign," CrowdStrike said.
"For example, the actor registered a subdomain under the it[.]com domain, preventing historical analysis of the domain-registration details. Additionally, encrypting the installer contents and preventing further activity from occurring without a password precludes further analysis and attribution."

The development comes amid a wave of phishing attacks taking advantage of the CrowdStrike update issue to propagate stealer malware -
A phishing domain crowdstrike-office365[.]com that hosts rogue archive files containing a Microsoft Installer (MSI) loader that ultimately executes a commodity information stealer called Lumma.
A ZIP file ("CrowdStrike Falcon.zip") that contains a Python-based information stealer tracked as Connecio that collects system information, external IP address, and data from various web browsers, and exfiltrates them to SMTP accounts listed on a Pastebin dead-drop URL.
On Thursday, CrowdStrike's CEO George Kurtz said 97% of the Windows devices that went offline during the global IT outage are now operational.
"At CrowdStrike, our mission is to earn your trust by safeguarding your operations. I am deeply sorry for the disruption this outage has caused and personally apologize to everyone impacted," Kurtz said. "While I can't promise perfection, I can promise a response that is focused, effective, and with a sense of urgency."
Previously, the company's chief security officer Shawn Henry apologized for failing to "protect good people from bad things," and that it "let down the very people we committed to protect."
"The confidence we built in drips over the years was lost in buckets within hours, and it was a gut punch," Henry acknowledged. "We are committed to re-earning your trust by delivering the protection you need to disrupt the adversaries targeting you. Despite this setback, the mission endures."
Meanwhile, Bitsight's analysis of traffic patterns exhibited by CrowdStrike machines across organizations globally has revealed two "interesting" data points that it said warrants additional investigation.
"Firstly, on July 16 at around 22:00 there was a huge traffic spike, followed by a clear and significant drop off in egress traffic from organizations to CrowdStrike," security researcher Pedro Umbelino said. "Second, there was a significant drop, between 15% and 20%, in the number of unique IPs and organizations connected to CrowdStrike Falcon servers, after the dawn of the 19th."
"While we can not infer what the root cause of the change in traffic patterns on the 16th can be attributed to, it does warrant the foundational question of 'Is there any correlation between the observations on the 16th and the outage on the 19th?'"
Update#
While the full impact of the IT outage remains to be tallied, cloud insurance services firm Parametrix Solutions estimates that the event impacted nearly a quarter of the Fortune 500 companies, resulting in a direct financial loss of $5.4 billion (excluding Microsoft), including $1.94 billion in losses for healthcare, $1.15 billion for banking, and $0.86 billion for the airlines sector.
John Cable, vice president of program management for Windows servicing and delivery, said the incident "underscores the need for mission-critical resiliency within every organization."
"These improvements must go hand in hand with ongoing improvements in security and be in close cooperation with our many partners, who also care deeply about the security of the Windows ecosystem," Cable said, urging enterprises to have a major incident response plan (MIRP) in place, periodically take data backups, utilize deployment rings, and enable Windows security baselines.
With endpoint detection and response (EDR) software requiring kernel-level access to detect threats in Windows, the disruptive event appears to have also had the desired effect of Microsoft rethinking the entire approach.
Redmond said alternative features like virtualization-based security (VBS) enclaves, which it introduced back in May, could be used by third-party developers to create an "isolated compute environment that does not require kernel mode drivers to be tamper resistant." Azure Attestation, another security solution, enables remote verification of the "trustworthiness of a platform and integrity of the binaries running inside it."
Global Police Operation Disrupts 'LabHost' Phishing Service, Over 30 Arrested Worldwide
18.4.24 Phishing The Hacker News
As many as 37 individuals have been arrested as part of an international crackdown on a cybercrime service called LabHost that has been used by criminal actors to steal personal credentials from victims around the world.
Described as one of the largest Phishing-as-a-Service (PhaaS) providers, LabHost offered phishing pages targeting banks, high-profile organizations, and other service providers located primarily in Canada, the U.S., and the U.K.
As part of the operation, codenamed Nebulae, two LabHost users from Melbourne and Adelaide were arrested on April 17, with three others arrested and charged with drug-related offenses.
"Australian offenders are allegedly among 10,000 cybercriminals globally who have used the platform, known as LabHost, to trick victims into providing their personal information, such as online banking logins, credit card details and passwords, through persistent phishing attacks sent via texts and emails," the Australian Federal Police (AFP) said in a statement.
The Europol-led coordinated effort also witnessed 32 other individuals being apprehended between April 14 and 17, including four in the U.K. who are allegedly responsible for developing and running the service. In total, 70 addresses were searched across the world.
Coinciding with the arrests, LabHost ("lab-host[.]ru") and all its associated cluster of phishing sites have been confiscated and replaced with a message announcing their seizure.
LabHost was documented earlier this year by Fortra, detailing its PhaaS targeting popular brands globally for anywhere between $179 to $300 per month. It first emerged in the fourth quarter of 2021, coinciding with the availability of another PhaaS service called Frappo.
"LabHost divides their available phishing kits between two separate subscription packages: a North American membership covering U.S. and Canadian brands, and an international membership consisting of various global brands (and excluding the NA brands)," the company said.
According to Trend Micro, LabHost also provided phishing pages for Spotify, postal services such as DHL and An Post, car toll services, and insurance providers, besides allowing customers to request the creation of bespoke phishing pages for target brands.
"Since the platform takes care of most of the tedious tasks in developing and managing phishing page infrastructure, all the malicious actor needs is a virtual private server (VPS) to host the files and from which the platform can automatically deploy," Trend Micro said.

The phishing pages – links to which are distributed via phishing and smishing campaigns – are designed to mimic banks, government entities, and other major organizations, deceiving users into entering their credentials and two-factor authentication (2FA) codes.
Customers of the phishing kit, which comprises the infrastructure to host the fraudulent websites as well as email and SMS content generation services, could then use the stolen information to take control of the online accounts and make unauthorized fund transfers from victims' bank accounts.
The captured information encompassed names and addresses, emails, dates of birth, standard security question answers, card numbers, passwords, and PINs.
"Labhost offered a menu of over 170 fake websites providing convincing phishing pages for its users to choose from," Europol said, adding law enforcement agencies from 19 countries participated in the disruption.
"What made LabHost particularly destructive was its integrated campaign management tool named LabRat. This feature allowed cybercriminals deploying the attacks to monitor and control those attacks in real time. LabRat was designed to capture two-factor authentication codes and credentials, allowing the criminals to bypass enhanced security measures."
LabHost's phishing infrastructure is estimated to include more than 40,000 domains. More than 94,000 victims have been identified in Australia and approximately 70,000 U.K. victims have been found to have entered their details in one of the bogus sites.
The U.K. Metropolitan Police said LabHost has received about £1 million ($1,173,000) in payments from criminal users since its launch. The service is estimated to have obtained 480,000 card numbers, 64,000 PIN numbers, as well as no less than one million passwords used for websites and other online services.
PhaaS platforms like LabHost lower the barrier for entry into the world of cybercrime, permitting aspiring and unskilled threat actors to mount phishing attacks at scale. In other words, a PhaaS makes it possible to outsource the need to develop and host phishing pages.
"LabHost is yet another example of the borderless nature of cybercrime and the takedown reinforces the powerful outcomes that can be achieved through a united, global law enforcement front," said AFP Acting Assistant Commissioner Cyber Command Chris Goldsmid.
The development comes as Europol revealed that organized criminal networks are increasingly agile, borderless, controlling, and destructive (ABCD), underscoring the need for a "concerted, sustained, multilateral response and joint cooperation."
TA547 Phishing Attack Hits German Firms with Rhadamanthys Stealer
12.4.24 Phishing The Hacker News
A threat actor tracked as TA547 has targeted dozens of German organizations with an information stealer called Rhadamanthys as part of an invoice-themed phishing campaign.
"This is the first time researchers observed TA547 use Rhadamanthys, an information stealer that is used by multiple cybercriminal threat actors," Proofpoint said. "Additionally, the actor appeared to use a PowerShell script that researchers suspect was generated by a large language model (LLM)."
TA547 is a prolific, financially motivated threat actor that's known to be active since at least November 2017, using email phishing lures to deliver a variety of Android and Windows malware such as ZLoader, Gootkit, DanaBot, Ursnif, and even Adhubllka ransomware.
In recent years, the group has evolved into an initial access broker (IAB) for ransomware attacks. It has also been observed employing geofencing tricks to restrict payloads to specific regions.
The email messages observed as part of the latest campaign impersonate the German company Metro AG and contain a password-protected ZIP file containing a ZIP archive that, when opened, initiates the execution of a remote PowerShell script to launch the Rhadamanthys stealer directly in memory.
Interestingly, the PowerShell script used to load Rhadamanthys includes "grammatically correct and hyper specific comments" for each instruction in the program, raising the possibility that it may have been generated (or rewritten) using an LLM.
The alternate hypothesis is that TA547 copied the script from another source that had used generative AI technology to create it.
"This campaign represents an example of some technique shifts from TA547 including the use of compressed LNKs and previously unobserved Rhadamanthys stealer," Proofpoint said. "It also provides insight into how threat actors are leveraging likely LLM-generated content in malware campaigns."
The development comes as phishing campaigns have also been banking on uncommon tactics to facilitate credential-harvesting attacks. In these emails, recipients are notified of a voice message and are directed to click on a link to access it.
The payload retrieved from the URL is heavily obfuscated HTML content that runs JavaScript code embedded within an SVG image when the page is rendered on the target system.
Present within the SVG data is "encrypted data containing a second stage page prompting the target to enter their credentials to access the voice message," Binary Defense said, adding the page is encrypted using CryptoJS.
Other email-based attacks have paved the way for Agent Tesla, which has emerged as an attractive option for threat actors due to it "being an affordable malware service with multiple capabilities to exfiltrate and steal users' data," according to Cofense.
Social engineering campaigns have also taken the form of malicious ads served on search engines like Google that lure unsuspecting users into downloading bogus installers for popular software like PuTTY, FileZilla, and Room Planner to ultimately deploy Nitrogen and IDAT Loader.
The infection chain associated with IDAT Loader is noteworthy for the fact that the MSIX installer is used to launch a PowerShell script that, in turn, contacts a Telegram bot to fetch a second PowerShell script hosted on the bot.
This PowerShell script then acts as a conduit to deliver another PowerShell script that's used to bypass Windows Antimalware Scan Interface (AMSI) protections as well as trigger the execution of the loader, which subsequently proceeds to load the SectopRAT trojan.
"Endpoints can be protected from malicious ads via group policies that restrict traffic coming from the main and lesser known ad networks," Jérôme Segura, principal threat researcher at Malwarebytes, said.
Hackers Targeting Human Rights Activists in Morocco and Western Sahara
9.4.24 Phishing The Hacker News
Human rights activists in Morocco and the Western Sahara region are the targets of a new threat actor that leverages phishing attacks to trick victims into installing bogus Android apps and serve credential harvesting pages for Windows users.
Cisco Talos is tracking the activity cluster under the name Starry Addax, describing it as primarily singling out activists associated with the Sahrawi Arab Democratic Republic (SADR).
Starry Addax's infrastructure – ondroid[.]site and ondroid[.]store – is designed to target both Android and Windows users, with the latter involving fake websites masquerading as login pages for popular social media websites.
The adversary, believed to be active since January 2024, is known to send spear-phishing emails to targets, urging recipients to install Sahara Press Service's mobile app or a relevant decoy related to the region.
Depending on the operating system from where the request is originating from, the target is either served a malicious APK that impersonates the Sahara Press Service or redirected to a social media login page to harvest their credentials.
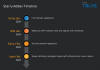
The novel Android malware, dubbed FlexStarling, is versatile and equipped to deliver additional malware components and steal sensitive information from infected devices.
Once installed, it requests the victim to grant it extensive permissions that allow the malware to perform nefarious actions, including fetching commands to be executed from a Firebase-based command-and-control (C2), a sign that the threat actor is looking to fly under the radar.
"Campaigns like this that target high-value individuals usually intend to sit quietly on the device for an extended period," Talos said.
"All components from the malware to the operating infrastructure seem to be bespoke/custom-made for this specific campaign indicating a heavy focus on stealth and conducting activities under the radar."
The development comes amid the emergence of a new commercial Android remote access trojan (RAT) known as Oxycorat that's being offered for sale with diverse information gathering capabilities.
Cybercriminals Targeting Latin America with Sophisticated Phishing Scheme
8.4.24 Phishing The Hacker News
A new phishing campaign has set its eyes on the Latin American region to deliver malicious payloads to Windows systems.
"The phishing email contained a ZIP file attachment that when extracted reveals an HTML file that leads to a malicious file download posing as an invoice," Trustwave SpiderLabs researcher Karla Agregado said.
The email message, the company said, originates from an email address format that uses the domain "temporary[.]link" and has Roundcube Webmail listed as the User-Agent string.
The HTML file points containing a link ("facturasmex[.]cloud") that displays an error message saying "this account has been suspended," but when visited from an IP address geolocated to Mexico, loads a CAPTCHA verification page that uses Cloudflare Turnstile.
This step paves the way for a redirect to another domain from where a malicious RAR file is downloaded. The RAR archive comes with a PowerShell script that gathers system metadata as well as checks for the presence of antivirus software in the compromised machine.
It also incorporates several Base64-encoded strings that are designed to run PHP scripts to determine the user's country and retrieve a ZIP file from Dropbox containing "many highly suspicious files."
Trustwave said the campaign exhibits similarities with that of Horabot malware campaigns that have targeted Spanish-speaking users in Latin America in the past.
"Understandably, from the threat actors' point of view, phishing campaigns always try different [approaches] to hide any malicious activity and avoid immediate detection," Agregado said.
"Using newly created domains and making them accessible only in specific countries is another evasion technique. especially if the domain behaves differently depending on their target country."
The development comes as Malwarebytes revealed a malvertising campaign targeting Microsoft Bing search users with bogus ads for NordVPN that lead to the distribution of a remote access trojan called SectopRAT (aka ArechClient) hosted on Dropbox via a phony website ("besthord-vpn[.]com").
"Malvertising continues to show how easy it is to surreptitiously install malware under the guise of popular software downloads," security researcher Jérôme Segura said. "Threat actors are able to roll out infrastructure quickly and easily to bypass many content filters."
It also follows the discovery of a fake Java Access Bridge installer that serves as a conduit to deploy the open-source XMRig cryptocurrency miner, per SonicWall.
The network security company said it also discovered a Golang malware that "uses multiple geographic checks and publicly available packages to screenshot the system before installing a root certificate to the Windows registry for HTTPS communications to the [command-and-control server]."
Darcula Phishing Network Leveraging RCS and iMessage to Evade Detection
29.3.24 Phishing The Hacker News
A sophisticated phishing-as-a-service (PhaaS) platform called Darcula has set its sights on organizations in over 100 countries by leveraging a massive network of more than 20,000 counterfeit domains to help cyber criminals launch attacks at scale.
"Using iMessage and RCS rather than SMS to send text messages has the side effect of bypassing SMS firewalls, which is being used to great effect to target USPS along with postal services and other established organizations in 100+ countries," Netcraft said.
Darcula has been employed in several high-profile phishing attacks over the last year, wherein the smishing messages are sent to both Android and iOS users in the U.K., in addition to those that leverage package delivery lures by impersonating legitimate services like USPS.
A Chinese-language PhaaS, Darcula is advertised on Telegram and offers support for about 200 templates impersonating legitimate brands that customers can avail for a monthly fee to set up phishing sites and carry out their malicious activities.
A majority of the templates are designed to mimic postal services, but they also include public and private utilities, financial institutions, government bodies (e.g., tax departments), airlines, and telecommunication organizations.
The phishing sites are hosted on purpose-registered domains that spoof the respective brand names to add a veneer of legitimacy. These domains are backed by Cloudflare, Tencent, Quadranet, and Multacom.
In all, more than 20,000 Darcula-related domains across 11,000 IP addresses have been detected, with an average of 120 new domains identified per day since the start of 2024. Some aspects of the PhaaS service were revealed in July 2023 by Israeli security researcher Oshri Kalfon.
One of the interesting additions to Darcula is its capability to update phishing sites with new features and anti-detection measures without having to remove and reinstall the phishing kit.
"On the front page, Darcula sites display a fake domain for sale/holding page, likely as a form of cloaking to disrupt takedown efforts," the U.K.-based company said. "In previous iterations, Darcula's anti-monitoring mechanism would redirect visitors that are believed to be bots (rather than potential victims) to Google searches for various cat breeds."
Darcula's smishing tactics also warrant special attention as they primarily leverage Apple iMessage and the RCS (Rich Communication Services) protocol used in Google Messages instead of SMS, thereby evading some filters put in place by network operators to prevent scammy messages from being delivered to prospective victims.
"While end-to-end encryption in RCS and iMessage delivers valuable privacy for end users, it also allows criminals to evade filtering required by this legislation by making the content of messages impossible for network operators to examine, leaving Google and Apple's on-device spam detection and third-party spam filter apps as the primary line of defense preventing these messages from reaching victims," Netcraft added.
"Additionally, they do not incur any per-message charges, which are typical for SMS, reducing the cost of delivery."
The departure from traditional SMS-based phishing aside, another noteworthy aspect of Darcula's smishing messages is their sneaky attempt to get around a safety measure in iMessage that prevents links from being clickable unless the message is from a known sender.
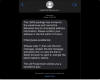
This entails instructing the victim to reply with a "Y" or "1" message and then reopen the conversation to follow the link. One such message posted on r/phishing subreddit shows that users are persuaded to click on the URL by claiming that they have provided an incomplete delivery address for the USPS package.
These iMessages are sent from email addresses such as pl4396@gongmiaq.com and mb6367587@gmail.com, indicating that the threat actors behind the operation are creating bogus email accounts and registering them with Apple to send the messages.
Google, for its part, recently said it's blocking the ability to send messages using RCS on rooted Android devices to cut down on spam and abuse.
The end goal of these attacks is to trick the recipients into visiting bogus sites and handing over their personal and financial information to the fraudsters. There is evidence to suggest that Darcula is geared towards Chinese-speaking e-crime groups.
Phishing kits can have serious consequences as it permits less-skilled criminals to automate many of the steps needed to conduct an attack, thus lowering barriers to entry.
The development comes amid a new wave of phishing attacks that take advantage of Apple's password reset feature, bombarding users with what's called a prompt bombing (aka MFA fatigue) attack in hopes of hijacking their accounts.
Assuming a user manages to deny all the requests, "the scammers will then call the victim while spoofing Apple support in the caller ID, saying the user's account is under attack and that Apple support needs to 'verify' a one-time code," security journalist Brian Krebs said.
The voice phishers have been found to use information about victims obtained from people search websites to increase the likelihood of success, and ultimately "trigger an Apple ID reset code to be sent to the user's device," which, if supplied, allows the attackers to reset the password on the account and lock the user out.
It's being suspected that the perpetrators are abusing a shortcoming in the password reset page at iforgot.apple[.]com to send dozens of requests for a password change in a manner that bypasses rate limiting protections.
The findings also follow research from F.A.C.C.T. that SIM swappers are transferring a target user's phone number to their own device with an embedded SIM (eSIM) in order to gain unauthorized access to the victim's online services. The practice is said to have been employed in the wild for at least a year.
This is accomplished by initiating an application on the operator's website or application to transfer the number from a physical SIM card to an eSIM by masquerading as the victim, causing the legitimate owner to lose access to the number as soon as the eSIM QR Code is generated and activated.
"Having gained access to the victim's mobile phone number, cybercriminals can obtain access codes and two-factor authentication to various services, including banks and messengers, opening up a mass of opportunities for criminals to implement fraudulent schemes," security researcher Dmitry Dudkov said.
Alert: New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
28.3.24 Phishing The Hacker News
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla.
Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user to open an archive file attachment.
The archive ("Bank Handlowy w Warszawie - dowód wpłaty_pdf.tar.gz") conceals a malicious loader that activates the procedure to deploy Agent Tesla on the compromised host.
"This loader then used obfuscation to evade detection and leveraged polymorphic behavior with complex decryption methods," security researcher Bernard Bautista said in a Tuesday analysis.
"The loader also exhibited the capability to bypass antivirus defenses and retrieved its payload using specific URLs and user agents leveraging proxies to further obfuscate traffic."
The tactic of embedding malware within seemingly benign files is a tactic that has been repeatedly employed by threat actors to trick unsuspecting victims into triggering the infection sequence.
The loader used in the attack is written in .NET, with Trustwave discovering two distinct variants that each make use of a different decryption routine to access its configuration and ultimately retrieve the XOR-encoded Agent Tesla payload from a remote server.
In an effort to evade detection, the loader is also designed to bypass the Windows Antimalware Scan Interface (AMSI), which offers the ability for security software to scan files, memory, and other data for threats.
It achieves this by "patching the AmsiScanBuffer function to evade malware scanning of in-memory content," Bautista explained.
The last phase involves decoding and executing Agent Tesla in memory, allowing the threat actors to stealthily exfiltrate sensitive data via SMTP using a compromised email account associated with a legitimate security system supplier in Turkey ("merve@temikan[.]com[.]tr").
The approach, Trustwave said, not only does not raise any red flags, but also affords a layer of anonymity that makes it harder to trace the attack back to the adversary, not to mention save the effort of having to set up dedicated exfiltration channels.
"[The loader] employs methods like patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, ensuring stealthy execution and minimizing traces on disk," Bautista said. "This loader marks a notable evolution in the deployment tactics of Agent Tesla."
The disclosure comes as BlueVoyant uncovered another phishing activity conducted by a cybercrime group called TA544 that leverages PDFs dressed up as legal invoices to propagate WikiLoader (aka WailingCrab) and establish connections with command-and-control (C2) server that almost exclusively encompasses hacked WordPress sites.
It's worth noting that TA544 also weaponized a Windows security bypass flaw tracked as CVE-2023-36025 in November 2023 to distribute Remcos RAT via a different loader family dubbed IDAT Loader, allowing it to seize control of infected systems.
The findings also follow a surge in the use of a phishing kit called Tycoon, which Sekoia said has "become one of the most widespread [adversary-in-the-middle] phishing kits over the last few months, with more than 1,100 domain names detected between late October 2023 and late February 2024."
Tycoon, publicly documented by Trustwave last month, permits cyber criminals to target users of Microsoft 365 with phony login pages to capture their credentials, session cookies, and two-factor authentication (2FA) codes. It's known to be active since at least August 2023, with the service offered via private Telegram channels.
The phishing kit is notable for incorporating extensive traffic filtering methods to thwart bot activity and analysis attempts, requiring site visitors to complete a Cloudflare Turnstile challenge before redirecting users to a credential harvesting page.
Tycoon also shares operational and design-level similarities with the Dadsec OTT phishing kit, raising the possibility that the developers had access to and tweaked the source code of the latter to suit their needs. This is supported by the fact that Dadsec OTT had its source code leaked in October 2023.
"The developer enhanced stealth capabilities in the most recent version of the phishing kit," Sekoia said. "The recent updates could reduce the detection rate by security products of the Tycoon 2FA phishing pages and the infrastructure. Additionally, its ease of use and its relatively low price make it quite popular among threat actors."
New Phishing Attack Uses Clever Microsoft Office Trick to Deploy NetSupport RAT
19.3.24 Phishing The Hacker News
A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan called NetSupport RAT.
Israeli cybersecurity company Perception Point is tracking the activity under the moniker Operation PhantomBlu.
"The PhantomBlu operation introduces a nuanced exploitation method, diverging from NetSupport RAT's typical delivery mechanism by leveraging OLE (Object Linking and Embedding) template manipulation, exploiting Microsoft Office document templates to execute malicious code while evading detection," security researcher Ariel Davidpur said.
NetSupport RAT is a malicious offshoot of a legitimate remote desktop tool known as NetSupport Manager, allowing threat actors to conduct a spectrum of data gathering actions on a compromised endpoint.
The starting point is a salary-themed phishing email that purports to be from the accounting department and urges recipients to open the attached Microsoft Word document to view the "monthly salary report."
A closer analysis of the email message headers – particularly the Return-Path and Message-ID fields – shows that the attackers use a legitimate email marketing platform called Brevo (formerly Sendinblue) to send the emails.
The Word document, upon opening, instructs the victim to enter a password provided in the email body and enable editing, followed by double-clicking a printer icon embedded in the doc to view the salary graph.
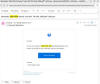
Doing so opens a ZIP archive file ("Chart20072007.zip") containing one Windows shortcut file, which functions as a PowerShell dropper to retrieve and execute a NetSupport RAT binary from a remote server.
"By using encrypted .docs to deliver the NetSupport RAT via OLE template and template injection, PhantomBlu marks a departure from the conventional TTPs commonly associated with NetSupport RAT deployments," Davidpur said, adding the updated technique "showcases PhantomBlu's innovation in blending sophisticated evasion tactics with social engineering."
Growing Abuse of Cloud Platforms and Popular CDNs#
The development comes as Resecurity revealed that threat actors are increasingly abusing public cloud services like Dropbox, GitHub, IBM Cloud, and Oracle Cloud Storage, as well as Web 3.0 data-hosting platforms built on the InterPlanetary File System (IPFS) protocol such as Pinata to generate fully undetectable (FUD) phishing URLs using off-the-shelf kits.
Such FUD links are offered on Telegram by underground vendors like BulletProofLink, FUDLINKSHOP, FUDSENDER, ONNX, and XPLOITRVERIFIER for prices starting at $200 per month as part of a subscription model. These links are further secured behind antibot barriers to filter incoming traffic and evade detection.
Also complementing these services are tools like HeartSender that make it possible to distribute the generated FUD links at scale. The Telegram group associated with HeartSender has nearly 13,000 subscribers.
"FUD Links represent the next step in [phishing-as-a-service] and malware-deployment innovation," the company said, noting attackers are "repurposing high-reputation infrastructure for malicious use cases."
"One recent malicious campaign, which leveraged the Rhadamanthys Stealer to target the oil and gas sector, used an embedded URL that exploited an open redirect on legitimate domains, primarily Google Maps and Google Images. This domain-nesting technique makes malicious URLs less noticeable and more likely to entrap victims."
TimbreStealer Malware Spreading via Tax-themed Phishing Scam Targets IT Users
28.2.24 Phishing The Hacker News
Mexican users have been targeted with tax-themed phishing lures at least since November 2023 to distribute a previously undocumented Windows malware called TimbreStealer.
Cisco Talos, which discovered the activity, described the authors as skilled and that the "threat actor has previously used similar tactics, techniques and procedures (TTPs) to distribute a banking trojan known as Mispadu in September 2023.
Besides employing sophisticated obfuscation techniques to sidestep detection and ensure persistence, the phishing campaign makes use of geofencing to single out users in Mexico, returning an innocuous blank PDF file instead of the malicious one if the payload sites are contacted from other locations.
Some of the notable evasive maneuvers include leveraging custom loaders and direct system calls to bypass conventional API monitoring, in addition to utilizing Heaven's Gate to execute 64-bit code within a 32-bit process, an approach that was also recently adopted by HijackLoader.
The malware comes with several embedded modules for orchestration, decryption, and protection of the main binary, while also running a series of checks to determine if it's running a sandbox environment, the system language is not Russian, and the timezone is within a Latin American region.
The orchestrator module also looks for files and registry keys to double-check that the machine hasn't been previously infected, before launching a payload installer component that displays a benign decoy file to the user, as it ultimately triggers the execution of TimbreStealer's primary payload.
The payload is designed to harvest a wide range of data, including credential information from different folders, system metadata, and the URLs accessed, look for files matching specific extensions, and verify the presence of remote desktop software.
TimbreStealer Malware
Cisco Talos said it identified overlaps with a Mispadu spam campaign observed in September 2023, although the target industries of TimbreStealer are varied and with a focus on manufacturing and transportation sectors.
The disclosure comes amid the emergence of a new version of another information stealer called Atomic (aka AMOS), which is capable of gathering data from Apple macOS systems such as local user account passwords, credentials from Mozilla Firefox and Chromium-based browsers, crypto wallet information, and files of interest, using an unusual combination of Python and Apple Script code.
"The new variant drops and uses a Python script to stay covert," Bitdefender researcher Andrei Lapusneanu said, noting the Apple Script block for collecting sensitive files from the victim's computer exhibits a "significantly high level of similarity" with the RustDoor backdoor.
It also follows the emergence of new stealer malware families such as XSSLite, which was released as part of a malware development competition hosted by the XSS forum, even as existing strains like Agent Tesla and Pony (aka Fareit or Siplog) continued to be used for information theft and subsequent sale on stealer logs marketplaces like Exodus.
Telegram Marketplaces Fuel Phishing Attacks with Easy-to-Use Kits and Malware
1.2.24 Phishing The Hacker News
Cybersecurity researchers are calling attention to the "democratization" of the phishing ecosystem owing to the emergence of Telegram as an epicenter for cybercrime, enabling threat actors to mount a mass attack for as little as $230.
"This messaging app has transformed into a bustling hub where seasoned cybercriminals and newcomers alike exchange illicit tools and insights creating a dark and well-oiled supply chain of tools and victims' data," Guardio Labs researchers Oleg Zaytsev and Nati Tal said in a new report.
"Free samples, tutorials, kits, even hackers-for-hire -- everything needed to construct a complete end-to-end malicious campaign."
This is not the first time the popular messaging platform has come under the radar for facilitating malicious activities, which are in part driven by its lenient moderation efforts.
As a result, what used to be available only on invite-only forums in the dark web is now readily accessible via public channels and groups, thereby opening the doors of cybercrime to aspiring and inexperienced cyber criminals.
In April 2023, Kaspersky revealed how phishers create Telegram channels to educate newbies about phishing as well as advertise bots that can automate the process of creating phishing pages for harvesting sensitive information such as login credentials.
One such malicious Telegram bot is Telekopye (aka Classiscam), which can craft fraudulent web pages, emails, SMS messages to help threat actors pull off large-scale phishing scams.
Guardio said the building blocks to construct a phishing campaign can be readily purchased off Telegram – "some offered at very low prices, and some even for free" – thereby making it possible to set up scam pages via a phishing kit, host the page on a compromised WordPress website via a web shell, and leverage a backdoor mailer to send the email messages.
Backdoor mailers, marketed on various Telegram groups, are PHP scripts injected into already infected-but-legitimate websites to send convincing emails using the legitimate domain of the exploited website to bypass spam filters.
"This situation highlights a dual responsibility for site owners," the researchers said. "They must safeguard not only their business interests but also protect against their platforms being used by scammers for hosting phishing operations, sending deceptive emails, and conducting other illicit activities, all unbeknownst to them."
To further increase the likelihood of success of such campaigns, digital marketplaces on Telegram also provide what's known as "letters," which are "expertly designed, branded templates" that make the email messages appear as authentic as possible to trick the victims into clicking on the bogus link pointing to the scam page.
Telegram is also host to bulk datasets containing valid and relevant email addresses and phone numbers to target. Referred to as "leads," they are sometimes "enriched" with personal information such as names and physical addresses to maximize the impact.
"These leads can be incredibly specific, tailored for any region, niche, demographic, specific company customers, and more," the researchers said. "Every piece of personal information adds to the effectiveness and credibility of these attacks."
The way these lead lists are prepared can vary from seller to seller. They can be procured either from cybercrime forums that sell data stolen from breached companies or through sketchy websites that urge visitors to complete a fake survey in order to win prizes.
Another crucial component of these phishing campaigns is a means to monetize the collected stolen credentials by selling them to other criminal groups in the form of "logs," netting the threat actors a 10-fold return on their investment based on the number of victims who end up providing valid details on the scam page.
"Social media account credentials are sold for as little as a dollar, while banking accounts and credit cards could be sold for hundreds of dollars — depending on their validity and funds," the researchers said.
"Unfortunately, with just a small investment, anyone can start a significant phishing operation, regardless of prior knowledge or connections in the criminal underworld."
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware
20.1.24 Phishing The Hacker News
The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter.
The campaign, observed earlier this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
"The PDFs contained OneDrive URLs that, if clicked, initiated a multi-step infection chain eventually leading to the malware payload, a variant of the WasabiSeed and Screenshotter custom toolset," the enterprise security firm said.
TA866 was first documented by the company in February 2023, attributing it to a campaign named Screentime that distributed WasabiSeed, a Visual Basic script dropper that's used to download Screenshotter, which is capable of taking screenshots of the victim's desktop at regular intervals of time and exfiltrating that data to an actor-controlled domain.
There is evidence to suggest that the organized actor may be financially motivated owing to the fact that Screenshotter acts as a recon tool to identify high-value targets for post-exploitation, and deploy an AutoHotKey (AHK)-based bot to ultimately drop the Rhadamanthys information stealer.
Subsequent findings from Slovak cybersecurity firm ESET in June 2023 unearthed overlaps between Screentime and another intrusion set dubbed Asylum Ambuscade, a crimeware group active since at least 2020 that also engages in cyber espionage operations.
The latest attack chain remains virtually unchanged save for the switch from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive link, with the campaign relying on a spam service provided by TA571 to distribute the booby-trapped PDFs.

"TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install a variety of malware for their cybercriminal customers," Proofpoint researcher Axel F said.
This includes AsyncRAT, NetSupport RAT, IcedID, PikaBot, QakBot (aka Qbot), and DarkGate, the last of which allows attackers to perform various commands such as information theft, cryptocurrency mining, and execution of arbitrary programs.
Splunk, which detected multiple campaigns deploying a loader designed to initiate DarkGate on compromised endpoints, said malicious PDF files act as a carrier for an MSI installer that executes a cabinet (CAB) archive to trigger the execution of DarkGate via AutoIT loader script.
"Darkgate first appeared in 2017 and is sold only to a small number of attack groups in the form of Malware-as-a-Service through underground forums," South Korean cybersecurity company S2W said in an analysis of the malware this week.
"DarkGate continues to update it by adding features and fixing bugs based on analysis results from security researchers and vendors," highlighting continued efforts made by adversaries to implement anti-analysis techniques to bypass detection.
News of TA866's resurgence comes as Cofense revealed that shipping-related phishing emails primarily single out the manufacturing sector to propagate malware like Agent Tesla and Formbook.
"Shipping-themed emails increase during the holiday seasons, albeit only slightly," Cofense security researcher Nathaniel Raymond said.
"For the most part, the yearly trends suggest that these emails follow a particular trend throughout the year with varying degrees of volumes, with the most significant volumes being in June, October, and November."
The development also follows the discovery of a novel evasion tactic that leverages the caching mechanism of security products to get around them by incorporating a Call To Action (CTA) URL that points to a trusted website in the phishing message sent to the targeted individual.
"Their strategy involves caching a seemingly benign version of the attack vector and subsequently altering it to deliver a malicious payload," Trellix said, stating such attacks have disproportionately targeted financial services, manufacturing, retail, and insurance verticals in Italy, the U.S., France, Australia, and India.
When such a URL gets scanned by the security engine, it's marked as safe, and the verdict is stored in its cache for a set time. This also means that if the URL is encountered again within that time period, the URL is not reprocessed, and instead, the cached result is served.
Trellix pointed out that attackers are taking advantage of this quirk by waiting until the security vendors process the CTA URL and cache their verdict, and then altering the link to redirect to the intended phishing page.
"With the verdict being benign, the email smoothly lands in the victim's inbox," security researchers Sushant Kumar Arya, Daksh Kapur, and Rohan Shah said. "Now, should the unsuspecting recipient decide to open the email and click on the link/button within the CTA URL, they would be redirected to the malicious page."