
Phishing 2024 2023 2022 2021 2020
Microsoft Warns of a Wide-Scale Phishing-as-a-Service Operation
6.10.21
Phishing
Thehackernews
Microsoft has opened the lid on a large-scale phishing-as-a-service (PHaaS) operation that's involved in selling phishing kits and email templates as well as providing hosting and automated services at a low cost, thus enabling cyber actors to purchase phishing campaigns and deploy them with minimal efforts.
"With over 100 available phishing templates that mimic known brands and services, the BulletProofLink operation is responsible for many of the phishing campaigns that impact enterprises today," Microsoft 365 Defender Threat Intelligence Team said in a Tuesday report.
"BulletProofLink (also referred to as BulletProftLink or Anthrax by its operators in various websites, ads, and other promotional materials) is used by multiple attacker groups in either one-off or monthly subscription-based business models, creating a steady revenue stream for its operators."
The tech giant said it uncovered the operation during its investigation of a
credential phishing campaign that used the BulletProofLink phishing kit on
either on attacker-controlled sites or sites provided by BulletProofLink as part
of their service. The existence of the operation was first made public by OSINT
Fans in October 2020.
Phishing-as-a-service differs from traditional phishing kits in that unlike the latter, which are sold as one-time payments to gain access to packaged files containing ready-to-use email phishing templates, they are subscription-based and follow a software-as-a-service model, while also expanding on the capabilities to include built-in site hosting, email delivery, and credential theft.
Believed to have been active since at least 2018, BulletProofLink is known to operate an online portal to advertise their toolset for as much as $800 a month and allow cybercrime gangs to register and pay for the service. Customers can also avail of a 10% discount should they opt to subscribe to their newsletter, not to mention pay anywhere between $80 to $100 for credential phishing templates that allow them to siphon login information entered by unsuspected victims upon clicking a malicious URL in the email message.
Troublingly, the stolen credentials are not only sent to the attackers but also to the BulletProofLink operators using a technique called "double theft" in a modus operandi that mirrors the double extortion attacks employed by ransomware gangs.
"With phishing kits, it is trivial for operators to include a secondary location for credentials to be sent to and hope that the purchaser of the phish kit does not alter the code to remove it," the researchers said. "This is true for the BulletProofLink phishing kit, and in cases where the attackers using the service received credentials and logs at the end of a week instead of conducting campaigns themselves, the PhaaS operator maintained control of all credentials they resell."
Microsoft Warns of Widespread Phishing Attacks Using Open Redirects
29.8.21
Phishing
Thehackernews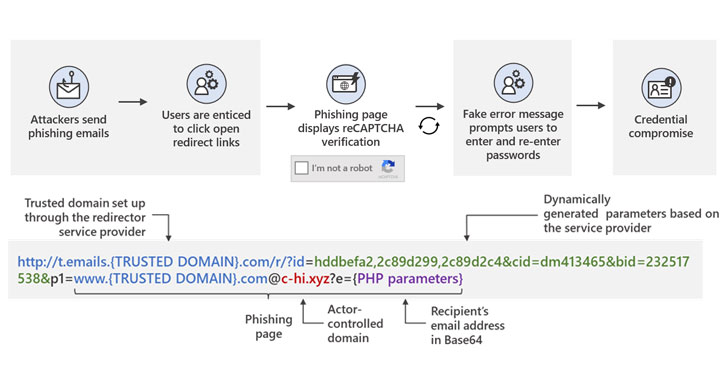
Microsoft is warning of a widespread credential phishing campaign that leverages
open redirector links in email communications as a vector to trick users into
visiting malicious websites while effectively bypassing security software.
"Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking," Microsoft 365 Defender Threat Intelligence Team said in a report published this week.
"Doing so leads to a series of redirections — including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems — before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks."
Although redirect links in email messages serve a vital tool to take recipients to third-party websites or track click rates and measure the success of sales and marketing campaigns, the same technique can be abused by adversaries to redirect such links to their own infrastructure, at the same time keeping the trusted domain in the full URL intact to evade analysis by anti-malware engines, even when users attempt to hover on links to check for any signs of suspicious content.
In order to lead potential victims to phishing sites, the redirect URLs embedded
in the message are set up using a legitimate service, while the final
actor-controlled domains contained in the link leverage top-level domains .xyz,
.club, .shop, and .online (e.g. "c-tl[.]xyz"), but which are passed as
parameters so as to sneak past email gateway solutions.
Microsoft said it observed at least 350 unique phishing domains as part of the campaign — another attempt to obscure detection — underscoring the campaign's effective use of convincing social engineering lures that purport to be notification messages from apps like Office 365 and Zoom, a well-crafted detection evasion technique, and a durable infrastructure to carry out the attacks.
clicking the specially-crafted links redirects the users -> clicking the specially-crafted link redirects the users
"This not only shows the scale with which this attack is being conducted, but it also demonstrates how much the attackers are investing in it, indicating potentially significant payoffs," the researcher said.
To give the attack a veneer of authenticity, clicking the specially-crafted links redirects the users to a malicious landing page that employs Google reCAPTCHA to block any dynamic scanning attempts. Upon completion of the CAPTCHA verification, the victims are displayed a fraudulent login page mimicking a known service like Microsoft Office 365, only to swipe their passwords upon submitting the information.
"This phishing campaign exemplifies the perfect storm of [social engineering, detection evasion, and a large attack infrastructure] in its attempt to steal credentials and ultimately infiltrate a network," the researchers noted. "And given that 91% of all cyberattacks originate with email, organizations must therefore have a security solution that will provide them multi-layered defense against these types of attacks."
Microsoft: Ongoing, Expanding Campaign Bypassing Phishing Protections
25.3.2021
Phishing
Securityweek
A phishing email campaign detailed earlier this month is expanding with the use of additional email services to hide malicious intent, according to a warning from software giant Microsoft.
Dubbed ‘Compact’ Campaign, the operation has been ongoing since December 2020, targeting thousands of users. In early March, researchers with the WMC Global Threat Intelligence Team estimated that more than 400,000 Outlook Web Access and Office 365 credentials had been compromised in multiple, connected campaigns.
At the time, the researchers revealed that the adversary behind the campaign was leveraging trusted domains to ensure that phishing emails successfully bypass email protections.
Compromised accounts at the SendGrid email delivery service were used to send many of the emails. After the researchers and SendGrid started terminating the sending accounts, the threat actor switched to MailGun to send the phishing messages.
Now, Microsoft says that the phishing messages are relying on compromised accounts on email marketing services and leverage configuration settings to bypass phishing protections that organizations might have in place.
In addition to SendGrid, the tech giant reveals, the campaign’s operators abused Amazon SES last year, and started leveraging Mailgun for the same purposes since January.
“Microsoft Defender for Office 365 data shows that this phishing operation is still active today and continues to expand,” the company said on Twitter.
“The attackers abuse another legitimate service to further mask the malicious intent of their phishing emails. To evade domain reputation-based solutions, they use Appspot to create multiple unique phishing URLs per recipient,” the tech giant added.
Microsoft also notes that Appspot has been notified on the abuse, and that the company has already confirmed that the reported URLs are malicious. Appspot already took action against the offending projects and is working with Microsoft on tracking this operation.
Some of the phishing emails used in these attacks masquerade as notifications from video conferencing services, while recent attacks spoof security solutions and productivity tools, Microsoft reveals.
“Because this campaign uses compromised email marketing accounts, we strongly recommend orgs to review mail flow rules for broad exceptions that may be letting phishing emails through,” the company concludes.
Office 365 Phishing Attack Targets Financial Execs
20.3.2021
Phishing
Threatpost
Attackers move on new
CEOs, using transition confusion to harvest Microsoft credentials.
A new phishing scam is on the rise, targeting executives in the insurance and financial services industries to harvest their Microsoft 365 credentials and launch business email compromise (BEC) attacks, according to a new report from Area 1 Security.
These new, sophisticated attacks are aimed at C-suite executives, their assistants and financial departments, and can work around email security and Office 365 defenses. Researchers added, most of the attacks they intercepted attempted to breach financial departments. Researchers said the attacks started last December and continued through February.
“By targeting the financial departments of these companies, the attackers could potentially gain access to sensitive data of third parties through invoices and billing, commonly referred to as a BEC (Business Email Compromise) attack,” researchers said in the Thursday report. “This enables the attackers to send forged invoices from legitimate email addresses to suppliers, resulting in payments being made to attacker-owned accounts.”
These threat actors also specifically look for new CEOs during their transition periods, when they’re likely onboarding for payroll and other internal systems.
“This particular phishing campaign targeted 40 of Area 1 Security’s clients across numerous industries,” Maaz Qureshi, Threat Response Analyst with Area 1 Security, told Threatpost. “The most targeted were within insurance and financial services. Judging from the size of this campaign, there are certainly many more organizations outside of our scope that have been targeted by these malicious actors.”
Anatomy of the Attack
In one version of the campaign, targets get a spoofed
Office 365 security update, sent from domains with Microsoft-themed names to
make them seem even more legitimate, researchers explained. The scammers have
also properly configured SPF records to get by authentication protections, they
added.
“In an effort to further avoid detection, the threat actors leveraged their
Microsoft-imposter domains in the phishing attacks not long after they were
registered,” the report explained. “This quick domain registration turnaround is
a common tactic employed by scammers hoping to bait as many victims as possible
before their newly registered domains are identified as phishing
infrastructure.”
A sample phishing email. Credit: Area 1
Another version of the attack involves taking over other accounts to send the phishing messages. The attackers spoof email addresses of known senders to evade detection.
The goal of the phishing email is to dupe victims into clicking on the “Apply Update” button, disguised as a security update, which takes them to a spoofed Office 365 login page.
“For both the HTML and HTM attachments, the credential harvesting site would automatically load in the victim’s browser once the file was opened,” researchers said.
Once deployed, the threat actors apply HTML “meta” refresh to load the credential harvesting site, which appears to be a Microsoft “Privacy Statement.” If they are duped into clicking on “Accept,” they are taken to a page that looks “identical” to the real thing, according to researchers.
“In some cases, the attackers were even more stealthy by prefetching the localized Office 365 sign-in,” Area 1 said. “If the victim entered their email address, the attacker would verify it was a valid Office 365 address. In instances where the entered email address used Conditional Access, a different single sign-on (SSO), Active Directory Federation Services (ADFS), etc., the phishing kit would essentially break and the victim would simply be redirected to the legitimate sign-in experience.”
After a target submits their password, the threat actors have full control of their email and any other systems where the same password was used, researchers warned.
The attackers have employed a couple of new tactics for this attack, including the use of free front-end web development tools to create the fake Microsoft pages and their use of websockets to take and send the attackers screen shots of the victim’s activity after each click.
“In particular when a victim clicked the “Next” button after entering their email address and password,” the report added.
Microsoft is the Phishing Lure of Choice
What is not new is the use of
Microsoft-related lures, including Office 365 and Teams in BEC attacks. Just
recently, Cofense released a report which found that 45 percent of all the
phishing emails sent in 2020 were Microsoft-themed.
“With the number of organizations migrating to Office 365, targeting these credentials allows the threat actor to gain access to the organization as a legitimate user to go undetected,” researchers with Cofense told Threatpost. They added that they “highly recommend organizations enable [multi-factor authentication] along with their [Office 365] migration/ implementation.”
Office 365 is a treasure trove of exploitable data, because it is so widely used by a remote workforce relying on the service as a central repository for data.
“SaaS platforms like Office 365 are a safe haven for attacker lateral movement, making it paramount to focus on user access to accounts and services,” Chris Morales with Vectra told Threatpost. “When security teams have solid information and expectations about SaaS platforms such as Office 365, malicious behaviors and privilege abuse are much easier to quickly identify and mitigate.”
To avoid such attacks, “when receiving an email that claims to originate from internally and requires clicking on a link or downloading an attachment, it is best practice to confirm the authenticity of the email,” Qureshi told Threatpost. “All employees should be versed in basic cybersecurity, such as refraining from clicking on external, unknown links,” he said.
COVID-19: Examining the threat landscape a year later
15.3.2021
Phishing
Securelist
A year ago — everything changed.
In an effort to stem the tide of a rapidly spreading pandemic, the world shut
down. Shops were forced to shut their doors, and whole countries were placed on
stringent lockdowns. Schools were closed around the world, with more than one
billion children affected, and the vast majority of companies had to switch to
remote work, sometimes with only a week’s notice. As life for large swaths of
the population moved entirely online, the cybercriminals were ready.
In fact, not only did the way people lived and worked changed, but so did the methods and tactics used by criminals on the Internet looking to exploit the massive increase in online traffic.
With the approval of several vaccines against the coronavirus, a post-pandemic future is finally in sight. However, there is still a long way to go before life returns to normal, and some changes, such as remote work, look like they are here to stay — as do the new cyber threats that emerged alongside these shifts.
On the anniversary of the global shutdown, Kaspersky experts decided to take a look back at how the threat landscape has evolved since the beginning of the pandemic — and what that means for users in the years to come.
From targeted attacks to exploiting all things COVID-related, the biggest trends
in spam and phishing
Phishing is still one of the most effective types of
attacks because it exploits users’ emotions, particularly their fear and
anxiety. With both of the former heightened thanks to the pandemic, phishing
attacks proved to be a highly lucrative attack vector for cybercriminals.
In 2020, criminals launched a variety of scams that exploited the pandemic topic
from just about every angle, from advertisements to masks when they were in
short supply to special refunds from the government.
A fake landing page for a mask advertised in a phishing email. Users are prompted to put in their payment details for a mask that will most likely never arrive
Scammers often imitated leading authority figures on the pandemic, like the CDC
and the World Health Organization, to give their emails additional authority —
and increase the chances that users would click a malicious link. Once clicked,
users could end up inadvertently downloading a range of threats on their
computer, from various Trojans (malicious files that allow cybercriminals to do
everything, from deleting and blocking data to interrupting the performance of
the computer) and worms (files that are capable of destroying, blocking,
modifying or copying data). Of course, in other instances, such as those
involving advertisements for masks, the primary goal is stealing money and/or
payment information.
An email supposedly from the CDC claiming that there is an urgent update regarding the pandemic
Surprisingly, one of the most common themes exploited revolved around delivery disruptions. A standard part of business operations is making various business orders, and criminals used the uncertainty surrounding mail services during the pandemic to trick users into downloading malware. They would send emails claiming that, due to COVID, an important delivery had been delayed and that the target must verify the new delivery information (a situation easy to believe in the middle of a pandemic) in order to receive it. However, upon clicking the attachment, the users would download Trojans ranging from spyware to backdoors.
In fact, in 2020, delivery services became one of the top ten organization types targeted by phishers.
Remote work — and the rise of brute-force attacks
With many companies forced
to close their doors with little notice, few had time to put the proper security
measures in place. The result was that many became vulnerable to a host of new
attacks as their employees began logging in to corporate resources from personal
devices and on unsecured networks. Chief among them? Brute-force attacks against
the RDP protocol, Microsoft’s proprietary protocol that enables users to access
Windows workstations or servers. RDP is one of the most popular remote access
protocols used by companies, making it a favorite target for attackers. In a
brute-force attack, attackers attempt to randomly guess a username and password
for the RDP connection by trying different combinations until they guess the
correct one — and gain access to the confidential corporate resources.
In spring of 2020, the number of brute-force attacks against the RDP protocol
skyrocketed across almost the entire planet.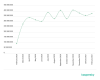
The number of brute-force attacks against the RDP protocol (download)
As shown in the graph, as soon as lockdowns were announced, the number of brute-force RDP attacks radically increased — from 93.1 mln worldwide in February to 277.4 mln in March — a 197 percent increase. While the number of attacks has ebbed and flowed as the pandemic continued, the number of attacks has not returned to pre-pandemic levels. In fact, after new lockdowns were announced in the winter, RDP attacks once again displayed an upward trend. In February 2021, there were 377.5 mln brute-force attacks — a far cry from the 93.1 mln witnessed at the beginning of 2020.
Virtual communication platforms under attack
With the world on lockdown,
Internet demand reached unprecedented levels. Large companies from Facebook to
Netflix to YouTube, were forced to reduce their video quality in order to keep
up with demand. And all those extra users meant a host of new targets for
criminals. By the May of 2020, the average daily number of attacks blocked by
Kaspersky Web Anti-Virus had increased by 25%. In fact, the number of web
attacks, after displaying a decline in the summer of 2020, reached a new peak in
the December as much of the world was facing a second wave of the pandemic.
Number of web-based attacked blocked by Kaspersky Web Anti-Virus from March 2020 through February 2021 (download)
A large portion of users’ time spent online was dedicated to meeting and collaborating virtually. That is why meeting and messenger apps, like Zoom and Teams, became a popular lure for distributing cyberthreats.
Upon examining popular meeting and videoconferencing apps, including Zoom,
Webex, and MS Teams, Kaspersky researchers noticed a growing number of malicious
files spread under the guise of these apps’ names.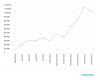
The number of malicious files spread under the guise of popular meeting apps (Webex, Zoom, MS Teams, HighFive, Lifesize, Join.me, Slack, Flock, Gotomeeting) (download)
In the January of this year, there were 1.15 mln such files detected — the highest number since the lockdown began. These files are often bundled as part of seemingly legitimate application installers, which can be encountered in several ways: through phishing emails claiming to have notifications or special offers from their platforms or through phishing web pages.
Lessons learned
Peoples’ lives have become increasingly digital for years,
and this is a trend that is likely to continue. It is still unclear when travel
will get back to normal and with remote work staying in the picture,
videoconferencing and meeting apps will continue to be in high demand. Of
course, the more time users spend online, the more vulnerable they are to
security risks.
While the pandemic may be heading into its final phases, there are still new topics for phishers and scammers to exploit, like health passports for travel or vaccine distribution, and chances are they will exploit them. It is important that users view any email or website referencing the pandemic with a skeptical eye. What is more, recent events have shown how willing criminals are to take advantage of crisis, and, while this pandemic will subside, it certainly will not be the last crisis.
With many organizations already stating that they will continue to make remote work an option and/or adopt a hybrid model, RDP is not going anywhere — and neither are attacks against the protocol. That means businesses need to reevaluate their usage of RDP and learn how to secure remote access.
If there is has ever been a time for companies to reevaluate and bolster their security strategy, that time is now.
Fake Google reCAPTCHA Phishing Attack Swipes Office 365 Passwords
9.3.2021 Phishing Threatpost
microsoft office 365 phishing attack
A phishing attack targeting Microsoft
users leverages a bogus Google reCAPTCHA system.
Microsoft users are being targeted with thousands of phishing emails, in an ongoing attack aiming to steal their Office 365 credentials. The attackers add an air of legitimacy to the campaign by leveraging a fake Google reCAPTCHA system and top-level domain landing pages that include the logos of victims’ companies.
According to researchers, at least 2,500 such emails have been unsuccessfully sent to senior-level employees in the banking and IT sector, over the past three months. The emails first take recipients to a fake Google reCAPTCHA system page. Google reCAPTCHA is a service that helps protect websites from spam and abuse, by using a Turing test to tell humans and bots apart (through asking a user to click on a fire hydrant out of a series of images, for instance).
Once victims “pass” the reCAPTCHA test, they are then redirected to a phishing
landing page, which asks for their Office 365 credentials.
“The attack is notable for its targeted aim at senior business leaders with titles such as Vice President and Managing Director who are likely to have a higher degree of access to sensitive company data,” said researchers with Zscaler’s ThreatLabZ security research team on Friday. “The aim of these campaigns is to steal these victims’ login credentials to allow threat actors access to valuable company assets.”
Fake Phishing Emails: Voicemail Attachments
The phishing emails pretend to be
automated emails from victims’ unified communications tools, which say that they
have a voicemail attachment. For instance, one email tells users that “(503)
***-6719 has left you a message 35 second(s) long on Jan 20” along with a lone
attachment that’s titled “vmail-219.HTM.” Another tells email recipients to
“REVIEW SECURE DOCUMENT.”
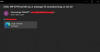
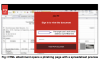
The phishing email sample. Credit: Zscaler
When the victims click on the attachment, they then encounter the fake Google reCAPTCHA screen, which contains a typical reCAPTCHA box – featuring a checkbox that the user must click that says “I’m not a robot,” which then triggers the turing test.
After filling out the fake reCAPTCHA system, victims are then directed to what appears to be a Microsoft login screen. The login pages also contain different logos from the companies which victims work at – such as one containing a logo from software company ScienceLogic and another from office rental company BizSpace. This reveals that attackers have done their homework and are customizing their phishing landing pages to fit their victims’ profile, in order to make the attack appear more legitimate.
Victims are asked to input their credentials into the system; once they do so, a message tells them that the validation was “successful” and that they are being redirected.
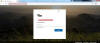
The phishing landing page mimics Microsoft’s login page. Credit: Zscaler
“After giving the login credentials, the phishing campaign will show a fake message that says ‘Validation successful,'” said researchers. “Users are then shown a recording of a voicemail message that they can play, allowing threat actors to avoid suspicion.”
Researchers found a variety of phishing pages associated with the campaign, which were hosted using generic top level domains such as .xyz, .club and .online. These top level domains are typically utilized by cybercriminals in spam and phishing attacks. That’s because they can be purchased for less than $1 each – a low price for adding a level of believability to phishing campaigns.
More Phishing Attacks on Fake Google reCAPTCHA Tactic
Credit: Zscaler
Adversaries have been leveraging bogus reCAPTCHA systems in their attacks for years. For instance, in 2019, a malware campaign targeted a Polish bank and its users with emails containing a link to a malicious PHP file, which eventually downloaded the BankBot malware onto victims’ systems. The attackers used a fake Google reCAPTCHA system to seem more realistic.
Another phishing attack in February purported to be sent from a voicemail service and contained a link to play the voice message “Play Audi Date.wav,” eventually redirecting victims to a malicious site with a reCAPTCHA message.
Both of the above examples show that reCAPTCHA continues to be used in phishing attacks, as the tactic successfully adds legitimacy to the attack: “Similar phishing campaigns utilizing fake Google reCAPTCHAs have been observed for several years, but this specific campaign targeting executives across specific industry verticals started in December 2020,” noted researchers.
Microsoft Office 365 users have faced several sophisticated phishing attacks and scams over the past few months. In October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aimed to steal Office 365 recipients’ login credentials. Also in October, an Office365 credential-phishing attack targeted the hospitality industry, using visual CAPTCHAs to avoid detection and appear legitimate. Phishing attackers have also adopted new tactics like Google Translate or custom fonts to make the scams seem more legitimate.
FINRA Warns of Ongoing Phishing Attacks Targeting Brokerage Firms
9.3.2021
Phishing
Securityweek
The Financial Industry Regulatory Authority (FINRA) has issued an alert to warn brokerage firms of a phishing campaign that is currently ongoing.
A not-for-profit organization, FINRA is U.S. government-authorized and overseen by the Securities and Exchange Commission (SEC). It regulates more than 624,000 brokerage firms and trains and registers broker-dealer personnel.
“FINRA warns member firms of an ongoing phishing campaign that involves fraudulent emails purporting to be from ‘FINRA Membership’ and using the email address ‘supports(at)finra-online.com’,” FINRA says in its alert.
The message, which claims to detail a non-compliance issue that requires immediate attention, attempts to trick the intended victim into clicking on a link or opening a document.
“Please find the following attached report from FINRA on regulatory non-compliance for which your immediate response is required. As part of a disclosure review process, we require this background report be completed. Review the enclosed document in respect to our compliance policy,” a version of the message, which FINRA has shared publicly, reads.
Individuals who received such emails and who might have clicked on a link or image in the email should immediately report the incident to the security team within their organization, FINRA recommends.
The organization also explains that it has no connection to the ‘finra-online.com’ website, urging any firm that receives emails originating from this domain name to immediately delete the messages.
Furthermore, targeted firms are reminded to check any suspicious emails they might receive and be wary of opening unsolicited attachments or clicking on any embedded link.
FINRA also notes that it has already contacted the Internet domain registrar to demand they suspend their services for ‘finra-online.com’.
This is the second warning of this kind that FINRA issues, after a December 2020 alert that revealed details of a phishing attack abusing a lookalike domain to target brokerage firms.
COVID-19 Vaccine Spear-Phishing Attacks Jump 26 Percent
5.3.2021 Phishing Securelist
cybercriminal COVID-19 vaccine cyberattack
Cybercriminals are using the
COVID-19 vaccine to steal Microsoft credentials, infect systems with malware and
bilk victims out of hundreds of dollars.
As Moderna, Pfizer and Johnson & Johnson roll out COVID-19 vaccines cybercriminals are preying on the those hungry to get in line for immunization.
Between October and January the average number of COVID-19 vaccine-related spear-phishing attacks grew 26 percent, said Barracuda Networks researchers. At the same time, researchers with Check Point say they have found at least 294 potentially dangerous vaccine-related domains over the last four months.
The types of cybercriminal activity varies, from sending malicious emails that purport to be from the Centers for Disease Control and Prevention (CDC), to posting advertisements on underground forums touting vaccine doses for sale. But with the vaccines being rolled out on a widespread basis, these new reports show attackers ramping up their activity on all fronts.
The intense emotions spurred by the pandemic – including mass hysteria and anxiety – create a perfect environment for cybercriminals to thrive, said researchers with Barracuda Networks on Thursday: “Capitalizing on fear and uncertainty, the attacks using urgency, social engineering, and other common tactics to lure victims,” they said.
Email-Based Attacks: CDC Scam Hunting Microsoft Credentials
Researchers
pointed to brand impersonation tactics – including many attackers pretending to
be the CDC in an attempt to convince email recipients to either click on a
malicious attachment or hand over their credentials.
Credit: Barracuda Networks
“Vaccine-related phishing emails impersonated a well-known brand or organization and included a link to a phishing website advertising early access to vaccines, offering vaccinations in exchange for a payment, or even impersonating health care professionals requesting personal information to check eligibility for a vaccine,” said Barracuda Networks researchers.
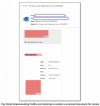
Barracuda Networks researchers, for instance, found malicious emails being distributed as part of an ongoing campaign with the subject “Phase 2 Vaccinations Approved,” using the CDC’s logo. The email tells recipients: “We are happy to announce that phase 2 vaccinations have been approved. Your local health and human services department has determined how and when phase 2 vaccinations are distributed. Click here to learn more about plans for your state/territory.”
The ensuing link then takes victims to an attacker-controlled domain, where they are either asked to enter their credentials, or where malware is downloaded onto their systems, researchers told Threatpost.
Example of a vaccine phishing email. Credit: Barracuda Networks
Separately, Check Point researchers discovered a malicious website impersonating the CDC that asks for victims’ Microsoft credentials. The website pretends to be a Microsoft Office 365 login page, using Microsoft’s logo and asking for the victim’s email, phone or Skype name connected with their account and their password.
The main domain (infection-alerts[.]com) was created in April 2020 – but Check Point researchers said they believe the website’s sub-domains were only created recently.
“Browsing to this malicious website was first spotted in late January 2021, and
a few weeks before, there was another similar subdomain used by hackers –
covid19\.vaccine\.infection-alerts\.com, which is now inactive,” they said.
Credit: Check Point Research
Another email-based attack spotted by Barracuda researchers has a different objective: Business email compromise, with the aim of convincing victims to send over funds to attacker-controlled accounts.
Researchers said they saw attacks from employee accounts who say they need an “urgent favor” while they step out to get a vaccine, or emails from the accounts of human resources specialists who advise that the organizations has secured vaccinations for the company. These lures, typically from compromised email accounts within a victim’s organization, start an initial dialogue between the email recipient and the attacker – which eventually leads to the victim being convinced to transfer money over.
COVID-19 Vaccines For Sale on Underground Forums
Cybercriminals are also
trying to make a quick buck by selling COVID-19 vaccines, purporting to be from
Pfizer/BioNTech, AstraZeneca, and Moderna (as well as unverified vaccines), on
underground forums.
Kaspersky researchers who found advertisements for the vaccines across 15 underground marketplaces on Thursday warned that there’s no indication that these vaccine doses are legitimate. Regardless, the sales appear to be working, with many sellers conducting between 100 to 500 transactions.

Advertisement for a Moderna vaccine dose at $500. Credit: Kaspersky
“Of course, when you go digging for products being sold illegally, you always run the risk of wasting your money on a product that will never materialize, and vaccine doses on the dark web are no exception to the rule,” according to Kaspersky researchers. “However, just how many vaccine sellers are distributing real medicine is unclear.”
The prices per dose range from $250 to $1,200 – and average around $500, said researchers. Typically payments are requested in Bitcoin, allowing the sellers to protect their identity and making payments more difficult to track.
“Further analysis showed that pricing had increased significantly following publication of Moderna’s and Pfizer’s effectiveness, as did the number of advertisements,” said Kaspersky researchers. “Sellers primarily come from France, Germany, the UK, and the USA, and communications use encrypted messaging apps such as Wickr and Telegram.”
In December, European Union law-enforcement agency Europol issued an alert about such Dark Web activity, warning consumers against looking for vaccine alternatives online.
Protecting Against COVID-19 Vaccines
While activity has ramped up since
mass-rollout of the vaccines, cybercriminals have been leveraging the
vaccinations as a lure – for sophisticated Zebrocy malware campaigns, for
instance – since last year.
Phishing attacks and other malicious activity relating to the pandemic in general has been ongoing since COVID-19 took hold across many countries last year – including attacks that take advantages of lifting coronavirus lockdowns as well as financial relief scams.
Researchers offered up various best practice tips to avoid becoming victim to such scams, including:
Staying suspicious of vaccine-related emails: Watch for classic phishing red
flags in these emails, such as misspellings in the email body, or sketchy
domains.
Keeping away from ‘buy vaccines online’ offers: Avoid purchasing
vaccines from online marketplaces.
Deploying account-takeover protection:
Ensure business email compromise type attacks don’t occur by adding protections
to recognize when internal emails have been compromised.
Educating employees:
Keep company employees up to date on the latest types of scams, and how train
them to protect against these types of attacks.
Microsoft Lures Populate Half of Credential-Swiping Phishing Emails
25.2.2021
Phishing
Threatpost
As more organizations migrate to Office 365, cybercriminals are using Outlook, Teams and other Microsoft-themed phishing lures to swipe user credentials.
Almost half of phishing attacks in 2020 aimed to swipe credentials using Microsoft-related lures – from the Office 365 enterprise service lineup to its Teams collaboration platform.
According to a Tuesday report by Cofense, which analyzed millions of emails related to various attacks, 57 percent were phishing emails aiming to steal victim usernames and passwords. The remainder of malicious emails were utilized in business email compromise (BEC) attacks or for malware delivery.
Of those phishing emails, 45 percent were Microsoft-themed, said researchers: Cybercriminals are both relying on Microsoft-themed lures for their emails, as well as using ensuing phishing landing pages that either spoof or leverage legitimate Microsoft domains or services.
“With the number of organizations migrating to Office 365, targeting these credentials allows the threat actor to gain access to the organization as a legitimate user to go undetected,” researchers with Cofense told Threatpost. They added that they “highly recommend organizations enable [multi-factor authentication] along with their [Office 365] migration/ implementation.”
Microsoft Users Under Attack by Phishing Emails
Malicious email lures can
vary; it could be a straightforward “‘Joe wants to share a document with you’
SharePoint alert you would normally see from Microsoft,” researchers explained —
or it could be a simple attached file that includes a link to a website asking
users to login with Microsoft credentials.
One phishing campaign in October pretended to be an automated message from Microsoft Teams telling victims they had a missed Teams chat. In reality, the attack aimed to steal Office 365 recipients’ login credentials.

Examples of Microsoft phishing lures. Credit: Cofense
Another December attack used embedded URLs that redirected to fake, never-seen-before Microsoft Office 365 phishing pages. The attack started with emails impersonating businesses like eFax, which is an internet fax service that allows users to receive faxes via email or online.
“We also see [cybercriminals] giving the user options to choose from the most commonly used email platforms,” said researchers. “The phishing emails often contain URLs hosted on legitimate domains that maintain a broad consumer base to avoid being blocked by content rules and filters.”
According to researchers, beyond the 45 percent of credential-stealing phishing attacks targeting Microsoft, the next-largest category was “generic”– meaning there wasn’t a specific brand associated with the email or the landing page asking the recipient to log in.
However, beyond Microsoft’s trusted collaboration services such as SharePoint, OneDrive or Office 365, researchers said they have seen other cloud provider products being leveraged in attacks. This includes Google (such as Google Forms), Adobe and file-sharing services.
“Other popular brands we observed asking for credentials were other various cloud hosting services such as Adobe, Dropbox, Box, DocuSign or WeTransfer,” researchers told Threatpost. “Threat actors have been able to scour the internet looking for file-sharing websites that are deemed ‘business related’ in order to make it past the secure email gateway controls, as well as the web proxy filters.”
Finance-Related Malicious Email Attacks
Researchers found that almost 17
percent of the emails identified as malicious were related to a financial
transaction.

Various industries hit by different email attacks. Credit: Cofense
Many of these phishing emails may relate to invoices and transactions needed for work. One recent example of such an attack, for instance, involved invoice-themed emails sent to at least 20,000 mailboxes that purport to share information about an electronic funds transfer (EFT) payment. The emails found earlier this month carried a fairly vanilla subject line, “TRANSFER OF PAYMENT NOTICE FOR INVOICE,” and contain a link to download an “invoice” from the cloud.
These types of attacks work because “finance teams are under extreme pressure to process invoices and payments in a timely fashion to keep the business running, especially during month- or quarter-end when financial reporting is critical,” said researchers. “So, if a user hasn’t heard anything back about the email they reported, they will most likely interact with that message.”
The Rise of the GuLoader Malware
Researchers found that in 2020, the GuLoader
dropper rose as one of the top malware delivery mechanisms in email attacks.
The malware, which first appeared in the first quarter and surged during the second quarter of 2020, is used to deliver remote administration tools, keyloggers, credential stealers and other malware phenotypes.

Quick stats. Click to enlarge. Credit: Cofense
For instance, one June email campaign was discovered targeting mid-level employees across Austria, Germany and Switzerland with malicious Excel attachments. Once opened, and with macros enabled, the Microsoft Excel attachments would then download and execute GuLoader, which in turn would download and execute the Hakbit ransomware.
The malware’s advanced techniques make it a lucrative tool for cybercriminals to utilize to sidestep network- and email-security detections. For instance, the malware contains false code instructions designed to thwart analysis tools and a wide array of tricks to avoid executing in virtual or sandbox environments, said researchers. The attackers behind the malware also store their malicious payloads on cloud platforms like Google Drive or Microsoft OneDrive – which because they are legitimate services, are not frequently blocked.
“While GuLoader is an executable, it is normally deployed through weaponized office documents that are built to bypass security controls and download the malware directly from the victim’s computer system,” said researchers. “GuLoader’s continued evolution of sophisticated delivery and execution techniques make it increasingly useful in delivering threats.”
10K Microsoft Email Users Hit in FedEx Phishing Attack
24.2.2021
Phishing
Threatpost
Microsoft users are receiving emails pretending to be from mail couriers FedEx and DHL Express – but that really steal their credentials.
Researchers are warning of recent phishing attacks targeting at least 10,000 Microsoft email users, pretending to be from popular mail couriers – including FedEx and DHL Express.
Both scams have targeted Microsoft email users and aim to swipe their work email account credentials. They also used phishing pages hosted on legitimate domains, including those from Quip and Google Firebase – allowing the emails to slip by security filters built to block known bad links.
“The email titles, sender names and content did enough to mask their true intention and make victims think the emails were really from FedEx and DHL Express respectively,” said researchers with Armorblox on Tuesday. “Emails informing us of FedEx scanned documents or missed DHL deliveries are not out of the ordinary; most users will tend to take quick action on these emails instead of studying them in detail for any inconsistencies.”
FedEx Phishing Emails: Using Quip, Google Firebase
The phishing email
spoofing American multinational delivery services company FedEx was entitled,
“You have a new FedEx sent to you,” with a date that the email was sent.
This email contained some information about the document to make it seem legitimate – such as its ID, number of pages and type of document – along with a link to view the supposed document. If the recipients clicked on the email, they would be taken to a file hosted on Quip. Quip, which comes in a free version, is tool for Salesforce that offers documents, spreadsheets, slides, and chat services.
An example of the FedEx phishing attack. Credit: Armorblox
“We have observed a continuing trend of malicious actors hosting phishing pages on legitimate services like Google Sites, Box and Quip (in this case),” said researchers. “Most of these services have free versions and are easy to use, which make them beneficial for millions of people around the world, but unfortunately also lower the bar for cybercriminals to launch successful phishing attacks.”
This page contained the FedEx logo and was titled “You have received some incoming FedEx files.” It then included a link for victims to review the supposed document. Once the victims clicked on this page, they would finally be taken to a phishing page that resembled the Microsoft login portal, which is hosted on Google Firebase, a platform developed by Google for creating mobile and web applications. Google Firebase has increasingly been utilized by phishing attacks over the past year to sidestep detection.
Of note, if a victim enters their credentials on the page, it re-loaded the login portal with an error message asking the victim to enter correct details.
“This might point to some backend validation mechanism in place that checks the veracity of entered details,” said researchers. “Alternately, attackers might be looking to harvest as many email addresses and passwords as possible and the error message will keep appearing regardless of the details entered.”
DHL Express Phishing Attack: Curious Adobe Login Prompt
A separate campaign
impersonated German international courier DHL Express, with emails telling
recipients that “Your parcel has arrived,” with their email addresseses at the
end of the title.
The email told recipients that a parcel could not be delivered to them due to incorrect delivery details – and that the parcel is instead ready for pickup at the post office.
An example of the phishing landing page. Credit: Armorblox
The email prompted recipients to check out attached “shipping documents” if they want to receive their delivery. The attached document was an HTML file (titled “SHIPPING DOC”) that, when opened, previewed a spreadsheet that looked like shipping documents.
The preview was layered over with a login request box impersonating Adobe’s PDF reader. Researchers noted that it’s possible that attackers were trying to phish for Adobe credentials – but it’s more likely that they were trying to get victims’ work email credentials.
“The email field in the login box was pre-filled with the victim’s work email,” said researchers. “Attackers are banking on victims to think before they act and enter their work email password into this box without paying too much attention to the Adobe branding.”
Similarly to the FedEx phishing attack, when victims entered their details on this page, it returned an error message.
Tapping into COVID-19 Trends
With COVID-19 making more people turn to online
platforms for purchasing goods, groceries and various household accessories –
rather than in-person stores – online shipping is at an all-time high.
Cybercriminals are tapping into this, as seen in these recent phishing emails – but they have also leveraged many other tinely lures, from Covid-19 relief funds, vaccine rollouts and personal protective equipment (PPE) needs.
“During the pandemic, we have all been getting online deliveries, often contactless deliveries and being in mail correspondence with FedEx/DHL is thus a common part of our lives now,” Preet Kumar, director of Customer Success at Armorblox told Threatpost. “Attackers are banking on victims buying into the legitimacy of this email and taking quick action without thinking about it too much.
Malformed URL Prefix Phishing Attacks Spike 6,000%
20.2.2021
Phishing
Threatpost
Sneaky attackers are flipping backslashes in phishing email URLs to evade protections, researchers said.
Researchers from GreatHorn report they have observed a nearly 6,000-percent jump in attacks using “malformed URL prefixes” to evade protections and deliver phishing emails that look legit. They look legit, that is, unless you look closely at the symbols used in the prefix before the URL.
“The URLs are malformed, not utilizing the normal URL protocols, such as http:// or https://,” researchers
said in a blog post about their findings. “Instead, they use http:/\ in their URL prefix.”
The slashes in the address are largely superfluous, the GreatHorn report explained, so browsers and many scanners don’t even look at them.
Typosquatting is a common phishing email tactic where everyday business names are mispelled, like “amozon.com” — to try and trick unobservant users into clicking. But these days, researchers explained, most people know to look for these kinds of email scams, so threat actors have had to evolve too.
Email Protections Ignore Backslashes in URL Prefix
“The URLs don’t fit the
‘known bad’ profiles developed by simple email scanning programs, allowing them
to slip through undetected,” researchers said. “They may also slip past human
eyes that aren’t accustomed to looking in the prefix for signs of suspicious
activity.”
The researchers reported they first noticed this new tactic last October, and said that it has been quickly gaining momentum ever since — with attacks between January and early February spiking by 5,933 percent, they said.
What Does a Malformed URL Attack Look Like?
GreatHorn provided an example of
a malformed URL phishing email with the address:
“http:/\brent.johnson.australiasnationalskincheckday.org.au//exr/brent.johnson@impacteddomain.com”
The phishing email appears to be sent from a voicemail service; the researchers
explained. The email contains a link to play the voice message “Play Audi
Date.wav” which redirects to a malicious site, the team reported.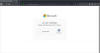
A phishing page with a ReCAPTCHA. Source: GreatHorn.
“The website even includes a reCAPTCHA, a common security feature of legitimate websites, showing the sophistication and subtlety of the attempted attack,” they explained.
The next page looks like an Office login page and asks for a username and password, the report said. Once entered, the attackers have control of the account credentials.
Office 365 users were far more likely to experience this type of breach, the
report added, at a “much higher rate than organizations running Google Workspace
as their cloud email environment.”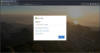
A fake Microsoft sign-in page. Source: GreatHorn.
The attackers using these malformed URLs have engaged in a variety of tactics to deliver their malware, including using a spoofed display name to impersonate the user’s company internal email system; avoiding scanners searching for “known bad” domains by sending from an address with no established relationship with the business; embedding a link in phishing emails which opens a redirector domain; and using language to give the user a sense of “urgency” in the message, the report explained.
The report recommended “that security teams search their organizational email
for messages containing URLs that match the threat pattern (http:/\) and remove
any matches,” to keep their systems protected.
An example of an email with an “audio message” alert. Source: GreatHorn.
Kevin O’Brien, CEO and co-founder of GreatHorn, told Threatpost that these malformed URL attacks could be mitigated through third-party solutions able to perform more nuanced analysis.
“There are a variety of API-native solutions that have come into the market in the last five years,” O’Brien said. “Many of these solutions are designed to specifically address the kinds of threats that both legacy secure email gateways and platforms are incapable of analyzing or identifying, providing robust remediation options, and highlighting to users when they’re about to go somewhere they don’t need to go to, such as what we saw in this attack.”
Email Phishing Scams More Common, More Expensive
The report drops amid a
particularly lucrative period for phishing scams. Proofpoint’s recent 2020 State
of the Phish showed a 14 percent jump in U.S. phishing attacks over the past
year.
“Threat actors worldwide are continuing to target people with agile, relevant and sophisticated communications—most notably through the email channel, which remains the top threat vector,” Alan LeFort, senior vice president and general manager of Security Awareness Training for Proofpoint said. “Ensuring users understand how to spot and report attempted cyberattacks is undeniably business-critical, especially as users continue to work remotely — often in a less secured environment. While many organizations say they are delivering security awareness training to their employees, our data shows most are not doing enough.”
Hackers abusing the Ngrok platform phishing attacks
17.2.2021
Phishing
Securityaffairs
Researchers from threat intelligence Cyble have discovered threat actors abusing
the Ngrok platform in a fresh phishing campaign.
Researchers at the threat
intelligence firm Cyble discovered a new wave of phishing attacks targeting
multiple organizations that are abusing the ngrok platform, a secure and
introspectable tunnel to the localhost.
ngrok is a cross-platform application used to expose a local development server to the Internet, the server appears to be hosted on a subdomain of ngrok (e.g., 4f421deb219c[.]ngrok[.]io) by creating a long-lived TCP tunnel to the localhost. The experts pointed out that ngrok server software runs on a VPS or a dedicated server and can bypass NAT mapping and Firewall restriction.
Threat actors are abusing the protocol for multiple malicious purposes.
“Multiple threat actors have abused the ngrok platform to gain unauthorized access to the target for delivering the additional payload, exfiltrating financial data such as credit/debit card information, and carrying out targeted phishing attacks.” reads the post published by Cyble.
Experts pointed out that attacks abusing the ngrok platform are hard to detect because connections to subdomains of ngrok.com are not filtered by security measures.

Experts provided a list of ngrok-based attacks conducted by cybercrime
organizations and nation-stated actors such as Fox Kitten and Pioneer Kitten APT
groups.
The experts reported multiple malware strains and phishing campaigns abusing ngrok tunnelling, including
Some of the new strains of malware/phishing campaign using ngrok tunneling are:
Njrat
DarkComet
Quasar RAT
asynrat
Nanocore RAT
Cyble focuses on
threat actors abusing ngrok.io to deliver phishing attacks.
“Interestingly, we found multiple ngrok.io links used in darkweb markets/leaks
and cybercrime forums by different threat actors such as BIN CARDERS, Telegram-
carder data, and linlogpass.” continues Cybler.
Cyble also spotted a phishing tool kit, named “KingFish3 (Social master), advertised on a cybercrime forum. The experts discovered that a threat actor shared on the forum a Github link to the tool, which also abuses ngrok tunnels to carry out the attack.
Below the steps identified by the experts to abuse the ngrok tunnels and carry out phishing attacks:
The tool creates a tunnel using ngrok to the chosen phishing URL with the
specified port.
The hacker tracks real-time logs in the first session and
waits for the victims to enter their phone number.
The hacker then logs into
the affected application’s official site with the harvested credentials and
generates an OTP (2FA).
Victims then enter the received OTP in the phishing
site, which the hacker captures.
Finally, the hacker gains access to the
victims’ official account using the OTP(2FA).
The post includes a partial
list of ngrok based phishing Indicators of Compromise (IOCs).
Below, Cyble experts’ recommendations:
Users of ngrok and other tunnelling services are advised to obtain authorization
from their information security teams.
It is advised to password-protect
their tunnel access and enable IP whitelisting to restrict access to only
trusted IP addresses.
Turn on the automatic software update feature on your
computer, mobile, and other connected devices wherever possible and pragmatic.
Regularly monitor your financial transactions, and if you notice any suspicious
activity, contact your bank immediately.
Use a reputed anti-virus and
Internet security software package on your connected devices, including PC,
laptop, and mobile.
People concerned about their exposure to the Dark web
can register at AmiBreached.com to ascertain their exposure.
Refrain from
opening untrusted links and email attachments without verifying their
authenticity.
Spam and phishing in 2020
16.2.2021 Phishing Spam Securelist
The share of spam in email traffic amounted to 50.37%, down by 6.14 p.p. from
2019.
Most spam (21.27%) originated in Russia.
Kaspersky solutions
detected a total of 184,435,643 malicious attachments.
The email antivirus
was triggered most frequently by email messages containing members of the
Trojan.Win32.Agentb malware family.
The Kaspersky Anti-Phishing component
blocked 434,898,635 attempts at accessing scam sites.
The most frequent
targets of phishing attacks were online stores (18.12 per cent).
Trends of
the year
Contact us to lose your money or account!
In their email
campaigns, scammers who imitated major companies, such as Amazon, PayPal,
Microsoft, etc., increasingly tried to get users to contact them. Various
pretexts were given for requesting the user to get in touch with “support”:
order confirmation, resolving technical issues, cancellation of a suspicious
transaction, etc. All of these messages had one thing in common: the user was
requested to call a support number stated in the email. Most legitimate messages
give recipients constant warnings of the dangers of opening links that arrive by
email. An offer to call back was supposed to put the addressees off their guard.
Toll-free numbers were intended to add further credibility, as the support
services of large companies often use these. The scammers likely expected their
targets to use the provided phone number to get help instantly in a critical
situation, rather than to look for a contact number or wait for a written
response from support.
The contact phone trick was heavily used both in email messages and on phishing
pages. The scammers were simply betting on the visitor to turn their attention
to the number and unsettling warning message against the red background, rather
than the address bar of the fake website.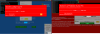
We assume that those who called the numbers were asked to provide the login and password for the service that the scammers were imitating, or to pay for some diagnostics and troubleshooting services.
Reputation, bitcoins or your life?
In 2020, Bitcoin blackmailers stuck to
their old scheme, demanding that their victims transfer money to a certain
account and threatening adversity for failure to meet their demands. Threats
made by extortionists grew in diversity. In most cases, scammers, as before,
claimed to have used spyware to film the blackmail victim watching adult videos.
In a reflection of the current trends for online videoconferencing, some email
campaigns claimed to have spied on their victims with the help of Zoom. This
year, too, blackmailers began to take advantage of news sensations to add
substance to their threats. This is very similar to the techniques of “Nigerian”
scammers, who pose as real political figures or their relatives, offering tons
of money, or otherwise link their messages with concurrent global events. In the
case of bitcoin blackmail, the media component was supposed to be a strong
argument in the eyes of the victim for paying the ransom without delay, so
cybercriminals cited the example of media personalities whose reputation
suffered because of an explicit video being published.
This year, we have seen threats made against companies, too. A company was told
to transfer a certain amount to a Bitcoin wallet to prevent a DDoS attack that
the cybercriminals threatened to unleash upon it. They promised to provide a
demonstration to prove that their threats were real: no one would be able to use
the services, websites or email of the company under attack for thirty minutes.
Interestingly, the cybercriminals did not limit their threats to DDoS. As with
blackmail aimed at individuals, they promised to damage the company’s reputation
even more, should it fail to pay up, by stealing confidential information,
specifically, its business data. The attackers introduced themselves as
well-known APT groups to add weight to their threats. For example, in the
screenshot below, they call themselves Venomous Bear, also known as Waterbug or
Turla.
The senders of an email that talked about a bomb planted in company’s offices
went much further with their threats. The amount demanded by the blackmailers
was much larger than in previous messages: $20,000. To make their threats sound
convincing enough, the cybercriminals provided details of the “attack”: an
intention to blow up the bomb if the police intervened, the substance used, the
explosive yield and plans to threaten other blackmail victims with the
explosion.
Attacks on the corporate sector
Theft of work accounts and infecting of
office computers with malware in targeted attacks are the main risk that
companies have faced this year. Messages that imitated business email or
notifications from major services offered to view a linked document or attached
HTML page. Viewing the file required entering the password to the recipient’s
corporate email account.
Reasons given for asking users to open a link or attachment could be varied: a
need to install an update, unread mail, quarantined mail or unread chat
messages. The cybercriminals created web pages that were designed to look like
they belonged to the company under attack. URL parameters including the
corporate email address were pushed to the fake page with the help of
JavaScript. This resulted in the user seeing a unique page with a pre-entered
email address and a design generated to imitate the company’s corporate style.
The appearance of that page could lull the potential victim into a false sense
of security, as all they needed to do was enter their password.
During this type of attacks scammers began to make broader use of “voice
messaging”. The appearance of the messages imitated business email.
The link could lead directly to a phishing site, but there also was a more
complex scenario, in which the linked page looked like an audio player. When the
recipient tried playing the file, they were asked to enter the credentials for
their corporate mailbox.
Demand for online videoconferencing amid remote work led to a surge in fake
online meeting invitations. A significant distinctive feature, which should have
alarmed the recipients of the fake invitations, were the details that the page
was asking them to enter in order to join the meeting. To access a real Zoom
meeting, you need to know the meeting ID and password. The fake videoconference
links opened fake Microsoft and WeTransfer pages, which contained fields for
entering the login and password for a work account.
Messengers targeted
Scammers who were spreading their chain mail via social
networks and instant messaging applications began to favor the latter. Message
recipients, mostly in WhatsApp, were promised a discount or prize if they opened
a link sent to them. The phishing web page contained a tempting message about a
money prize, award or other, equally desirable, surprises.
The recipient had to fulfill two conditions: answer a few simple questions or
fill out a questionnaire, and forward the message to a certain number of their
contacts. Thus, the victim turned into a link in the spam chain, while
subsequent messages were sent from a trusted address, thus avoiding anti-spam
filters.
Besides that, a message from someone that the recipient knew would have much
more credibility. Thus, the chain continued to grow, and the scammers went on
enriching themselves. After all, even if the victim did fulfill the conditions,
getting that promised prize proved not so simple, as the “lucky” recipient was
urged to pay bank commission.
COVID-19
“Public relief” by spammers
Many governments did their best to
help citizens during the pandemic. That initiative, together with the fact that
people on the whole were willing to get payouts, became a theme for spam
campaigns. Both individuals and companies were exposed to the risk of being
affected by cybercriminals’ schemes.
Messages offering financial aid to businesses hurt by the pandemic or to
underprivileged groups could crop up in social media feeds or arrive through
instant messaging networks. The main requirement for getting the funds was
filling out a detailed personal questionnaire. Those who took the step found
that a small commission was required as well. Real government payouts these days
are made through public portals that also serve other purposes and do not
require additional registration, questionnaires or commissions.
Cybercriminals who offered tax deductions to companies employed a similar
scheme. As in the examples above, the reason provided for the easing of tax
policy was the pandemic, and in particular, anticipation of a second wave of
COVID-19.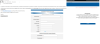
However, offers of tax deductions and compensations were hiding not just the
danger of losing money but losing one’s account to the scammers, too, as many of
the messages contained phishing links.
Malicious links
Email campaigns that promised compensation could also
threaten computer security. Messages in Turkish, just as those mentioned
earlier, offered a payout from Turkey’s Ministry of Health – not always
mentioned by name – but getting the money required downloading and installing an
APK file on the recipient’s smartphone. The attack was targeting Android users,
and the downloadable application contained a copy of the
Trojan-Dropper.AndroidOS.Hqwar.cf.
A fear of being infected with a new virus and a desire to know as much as
possible about it could prompt recipients to review the email and open the links
that it contained, as long as the message had been sent by a well-known
organization. Fake letters from the WHO purporting to contain the latest safety
advice were distributed in a variety of languages. The attachment contained
files with various extensions. When the recipient tried to open these, malware
was loaded onto the computer. In the message written in English, the attackers
spread the Backdoor.Win32.Androm.tvmf, and in the one written in Italian, the
Trojan-Downloader.MSOffice.Agent.gen.
Viral postal services
COVID-19 was also mentioned in fake email messages that
mimicked notifications from delivery services. The sender said that there was a
problem with delivering an order due to the pandemic, so the recipient needed to
print out the attachment and take it to the nearest DHL office. The attached
file contained a copy of the HEUR:Trojan.Java.Agent.gen.
The corporate sector
Spam that targeted companies also exploited the COVID-19
theme, but the cybercriminals occasionally relied on a different kind of tricks.
For example, one of the emails stated that technical support had created a
special alert system to minimize the risk of a new virus infection. All
employees were required to log in to this system using their corporate account
credentials and review their schedules and tasks. The link opened a phishing
page disguised as the Outlook web interface.
In another instance, scammers were sending copies of the
HEUR:Trojan-PSW.MSIL.Agensla.gen in the form of an email attachment. The
scammers explained that the recipient needed to open the attached file, because
the previous employee, who was supposed to send the “documentation”, had quit
over COVID-19, and the papers had to be processed within three days.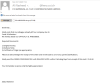
“Nigerian” crooks making money from the pandemic
Email from “Nigerian”
scammers and fake notifications of surprise lottery winnings regularly tapped
the pandemic theme. The message in Korean shown below says that the recipient’s
email address had been selected randomly by some center in Istanbul for a
coronavirus-related emergency payout. Such surprise notices of winnings and
compensations were generally sent out in a variety of languages. Messages from
some lucky individuals who had won a huge sum and wished to support their fellow
creatures in the difficult times of the pandemic were another variation on the
“Nigerian” scam.
Where messages were signed as being from a lawyer trying to find a new owner for
no-man’s capital, the sender emphasized that the late owner of the fortune had
died of COVID-19.
An unusual turn of events
Regular “Nigerian” scam email is easy to recognize:
it talks about millionaires or their relatives trying to inherit a huge fortune
or bequeath it to someone who bears the same last name. The public seems to have
become so accustomed to that type of junk mail that it has ceased to react, so
cybercriminals have come up with a new cover story. To avoid being found out
right away, they refrain from mentioning astronomical sums of money, instead
posing as a mother from Russia who is asking for help with her daughter’s effort
to collect postcards from around the world. The key point of this kind of
messages is to get the potential victim to reply: the “mother’s” request sounds
absolutely innocent and easy to do, so it can resonate with recipients. If the
victim agrees to send a postcard, they are in for a lengthy email exchange with
the scammers, who will offer them to partake in a large amount of money by
paying a small upfront fee.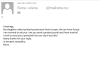
“Nigerian” scammers are not the only ones that have been getting creative.
Spammers who sent out their messages through website feedback forms employed yet
another unusual trick. The messages were signed as being from an outraged
graphic artist or photographer, their names changing with each new message. The
sender insisted that the website contained their works and thus violated their
copyright, and demanded that the content be taken down immediately, threatening
legal action.
The deadline for meeting the demand was quite tight, as the scammers needed the victim to open the link as soon as possible, while pondering on the consequences of that action as little as possible. A law-abiding site owner was likely to do just that. This is confirmed by related discussions in various blogs, with the users reporting that they immediately tried checking what photographs they had “stolen”. The links were not functional at the time the “complaints” were discovered, but in all likelihood, they had previously linked to malicious files or phishing programs.
Statistics: spam
Proportion of spam in email traffic
The share of spam in
global email traffic in 2020 was down by 6.14 p.p. when compared to the previous
reporting period, averaging 50.37%.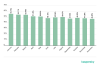
Proportion of spam in global email traffic, 2020 (download)
The percentage of junk mail gradually decreased over the year, with the highest figure (55.76%) recorded in January and the lowest (46.83%), in December. This may be due to the universal transition to remote work and a resulting increase in legitimate email traffic.
Sources of spam by country
The group of ten countries where the largest
volumes of spam originated went through noticeable change in 2020. United States
and China, which had shared first and second places (10.47% and 6.21%,
respectively) in the previous three years, dropped to third and fourth. The
“leader” was Russia, which was the source of 21.27% of all spam email in 2020.
It was followed by Germany (10.97%), which was just 0.5 percentage points ahead
of the United States.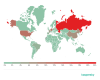
Sources of spam by country in 2020 (download)
France gained 2.97 p.p. as compared to the year 2019, remaining fifth with 5.97%, while Brazil lost 1.76 p.p. and sunk to seventh place with 3.26%. The other countries in last year’s “top ten”, India, Vietnam, Turkey and Singapore, dropped out, giving way to the Netherlands (4.00%), which skipped to sixth place, Spain (2.66%), Japan (2.14%) and Poland (2.05%).
Malicious email attachments
Attacks blocked by the email antivirus in 2020 (download)
In 2020, our solutions detected 184,435,643 dangerous email attachments. The peak in malicious activity, 18,846,878 email attacks blocked, fell on March, while December was the quietest month, with 11,971,944 malicious attachments, as it was in 2019.
Malware families
TOP 10 malware families in 2020 (download)
Members of the Trojan.Win32.Agentb family were the most frequent (7.75%) malware spread by spammers. The family includes backdoors, capable of disrupting the functioning of a computer, and copying, modifying, locking or deleting data. The Trojan-PSW.MSIL.Agensla family was second with 7.70%. It includes malware that steals data stored by the browser, as well as credentials for FTP and email accounts.
Equation Editor vulnerability exploits, Exploit.MSOffice.CVE-2017-11882, dropped to third place with 6.55 percent. This family had topped the ranking of malware spread through spam in the previous two years.
Trojan.MSOffice.SAgent malicious documents dropped from second to fourth place with 3.41%. These contain a VBA script, which runs PowerShell to download other malware secretly.
In fifth place, with 2.66%, were Backdoor.Win32.Androm modular backdoors, which,
too, are frequently utilized for delivering other malware to an infected system.
These were followed by the Trojan.Win32.Badun family, with 2.34%. The
Worm.Win32.WBVB worms, with 2.16%, were seventh. Two families, in eighth and
ninth place, contain malware that carefully evades detection and analysis:
Trojan.Win32.Kryptik trojans, with 2.02%, use obfuscation, anti-emulation and
anti-debugging techniques, while Trojan.MSIL.Crypt trojans, with 1.91%, are
heavily obfuscated or encrypted. The Trojan.Win32.ISO family, with 1.53%, rounds
out the rankings.
TOP 10 malicious email attachments in 2020 (download)
The rankings of malicious attachments largely resemble those of malware families, but there are several subtle differences. Thus, our solutions detected the exploit that targeted the CVE-2017-11882 vulnerability more frequently (6.53%) than the most common member of the Agensla family (6.47%). The WBVB worm, with 1.93%, and the Kryptik trojan, with 1.97%, switched positions, too. Androm-family backdoors missed the “top ten” entirely, but the Trojan-Spy.MSIL.Noon.gen, with 1.36%, which was not represented in the families rankings, was tenth.
Countries targeted by malicious mailshots
Spain was the main target for
malicious email campaigns in 2020, its share increasing by 5.03 p.p. to reach
8.48%. As a result of this, Germany, which had topped the rankings since 2015,
dropped to second place with 7.28% and Russia, with 6.29%, to third.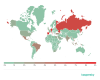
Countries targeted by malicious mailshots in 2020 (download)
Italy’s share (5.45%) fell slightly, but that country remained in fourth place. Vietnam, which had previously rounded out the top three, dropped to fifth place with 5.20%, and the United Arab Emirates, with 4.46%, to sixth. Mexico, with 3.34%, rose from ninth to seventh place, followed by Brazil, with 3.33%. Turkey, with 2.91%, and Malaysia, with 2.46%, rounded out the rankings, while India, 2.34%, landed in eleventh place last year.
Statistics: phishing
In 2020, Anti-Phishing was able to block 434,898,635
attempts at redirecting users to phishing web pages. That is 32,289,484 fewer
attempts than in 2019. A total of 13.21% of Kaspersky users were attacked
worldwide, with 6,700,797 masks describing new phishing websites added to the
system database.
Attack geography
In 2020, Brazil regained its leadership by number of
Anti-Phishing detections, with 19.94% of users trying to open phishing links at
least once.
Geography of phishing attacks in 2020 (download)
TOP 10 countries by number of attacked users
The countries with the largest
numbers of attempts at opening phishing websites in 2018 “topped the rankings”
again in 2020: Brazil, with 19.94%, in first place, and Portugal, with 19.73%,
in second place. Both countries’ indicators dropped remarkably from 2019, Brazil
“losing” 10.32 p.p. and Portugal, 5.9 p.p. France, which had not been seen among
the ten “leaders” since 2015, was in third place with 17.90%.
Venezuela, last year’s “leader”, had the largest numbers in the first two quarters of 2020, but came out eighth overall, the share of attacked users in that country decreasing by 14.32 p.p. to 16.84%.
Country Share of attacked users (%)*
Brazil 19.94
Portugal 19.73
France
17.90
Tunisia 17.62
French Guiana 17.60
Qatar 17.35
Cameroon 17.32
Venezuela 16.84
Nepal 16.72
Australia 16.59
* Share of users on whose
devices Anti-Phishing was triggered out of all Kaspersky users in the country in
2020
Top-level domains
Most scam websites, 24.36% of the total number, had a .com
domain name extension last year. Websites with a .ru extension were 22.24 p.p.
behind with 2.12%. All other top-level domains in the “top ten” are various
country-code TLDs: the Brazilian .com.br with 1.31% in third place, with
Germany’s .de, (1.23%), and Great Britain’s .co.uk (1.20%) in fourth and fifth
places, respectively. In sixth place was the Indian domain extension .in, with
1.10%, followed by France’s .fr with 1.08%, and Italy’s .it with 1.06%. Rounding
out the rankings were the Dutch .nl, with 1.03%, and the Australian .com.au,
with 1.02%.
Most frequent top-level domains for phishing pages in 2020 (download)
Organizations under attack
The rating of attacks by phishers on different
organizations is based on detections by Kaspersky Lab’s Anti-Phishing
deterministic component. The component detects all pages with phishing content
that the user has tried to open by following a link in an email message or on
the web, as long as links to these pages are present in the Kaspersky database.
Last year’s events affected the distribution of phishing attacks across the categories of targeted organizations. The three largest categories had remained unchanged for several years: banks, payment systems and global Internet portals. The year 2020 brought change. Online stores became the largest category with 18.12%, which may be linked to a growth in online orders due to pandemic-related restrictions. Global Internet portals remained the second-largest category at 15.94%, but their share dropped by 5.18 p.p. as compared to 2019, and banks were third with a “modest” 10.72%.
Online games and government and taxes dropped out of the “top ten” in 2020. They
were replaced by delivery companies and financial services.
Distribution of organizations targeted by phishers, by category in 2020 (download)
Conclusion
With its pandemic and mass transition to remote work and online
communication, last year was an unusual one, which was reflected in spam
statistics. Attackers exploited the COVID-19 theme, invited victims to
non-existent video conferences and insisted that their targets register with
“new corporate services”. Given that the fight against the pandemic is not over
yet, we can assume that the main trends of 2020 will stay relevant into the near
future.
The general growing trend of targeted attacks on the corporate sector will continue into next year, all the more so because the remote work mode, increasingly popular, makes employees more vulnerable. Users of instant messaging networks should raise their guard, as the amount of spam and phishing messages received by their mobile devices is likely to grow as well. Besides, the number of email messages and schemes exploiting the COVID-19 theme one way or another has a high likelihood of rising.
Gmail users from US most targeted by email-based phishing and malware
14.2.2021
Phishing
Securityaffairs
Google revealed that Gmail users from the United States are the most targeted by
email-based phishing and malware.
A joint five-month study conducted by
Google with Stanford University researchers analyzed over 1.2 billion
email-based phishing and malware attacks against Gmail users to determine what
are factors influence the risk of attack.
Experts discovered that malicious campaigns are typically short-lived and indiscriminately target users worldwide.
“However, by modeling the distribution of targeted users, we find that a person’s demographics, location, email usage patterns, and security posture all significantly influence the likelihood of attack.” reads the study published by Google. “During our measurement window, we find that attackers targeted, on average, 17.0 million users every week with hundreds of thousands of campaigns that last a median of just one day. These attacks follow a skewed distribution: 10% of phishing campaigns accounted for 76% of phishing attacks, and 10% of malware campaigns accounted for 61% of malicious attachments. Attackers broadly targeted users around the globe as part of their campaigns, with the majority of targets residing in North America and Europe. While 90% of attacks occurred in English, we show evidence that some attackers localize their efforts.”
According to the study, 42% of all targets were from the US, followed by the UK (10% of all attacks) and Japan (5% of attacks).
Both phishing and malware attacks are bursty, experts observed the volume of attacks increasing by 500% at times from week to week. At its peak, the researchers observed 117 million phishing emails targeting 41 million distinct users during the week of May 11, 2020.
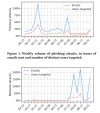
“Over the course of our measurement period, we observed a total of
406,002
distinct phishing campaigns and 1,724,160 malware campaigns. Both classes of
attacks exhibit a highly skewed distribution.
The top 10% of phishing
campaigns account for 76% of phishing
emails, while the top 10% of malware
campaigns account for 61% of
emails with malicious attachments.” continues
the report.
According to the experts, 89% of malware campaigns last just one day, while the
median phishing campaign lasts three days or less. The short duration
a
choice of the attackers to evade detection.
Other factors of high risk of being targeted by phishing attacks reported by the experts are:
The availability of email or other personal details online froom a third-party
data breach.
The country where a user accesses Gmail, the highest risk
countries are in Europe and Africa.
The age, 55- to 64-year-olds are more
exposed to attacks compared to 18- to 24-year-olds.
Type of devices. Compared
to users owning multiple types of devices, users who own only a personal
computer face slightly lower odds of targeting (0.90) and mobile-only users face
even lower risks of attack (0.80).
Email activity. The odds of being targeted
increase with the level of engagement with Gmail. Of course, active users face
higher likelihoods of being targeted, with those most frequently interacting
with Gmail being, on average, 5.18 times more likely to be targeted than an
inactive user.
Vast Majority of Phishing and Malware Campaigns Are Small-Scale and Short-Lived
14.2.2021
Phishing
Securityweek
Researchers from Google and Stanford University have analyzed the patterns of more than 1.2 billion email-based phishing and malware attacks targeting Gmail users, and found that most attack campaigns are short-lived and sent to fewer than 1,000 targets.
Users in North America are targeted the most, they found, with 42% of the observed attacks targeted users in the United States, 10% hitting people in the United Kingdom, and 5% aimed at users in Japan.
Most of the analyzed 406,002 phishing campaigns and 1,724,160 malware campaigns, the researchers say, were short, with fewer than 1000 users targeted by 91% of the phishing emails and 99% of the malware emails.
Furthermore, the majority of attacks were brief, with 89% of malware campaigns lasting just one day, and 80% of the phishing campaigns lasting less than a week.
“This short duration is likely a direct response to attackers attempting to re-configure campaigns to evade detection. Absent cycling to new campaigns, traffic to phishing pages has been found to disappear within a few hours after detection,” the researchers explain in a newly published report.
While 83% of phishing and 97% of malware emails were written in English, attackers to employ localization in some cases: 78% of emails targeting users in Japan were written in Japanese, 66% of attacks aimed at Brazilian users occurred in Portuguese, 4% of the attacks targeting users in France were employed emails written in French.
According to the report, the research has revealed that an individual’s email usage patterns, security posture, demographics, and location have a significant impact on the likelihood of attack. The risk would increase with each subsequent age group, and those who had their personal data exposed in a third-party breach are more likely to be targeted.
Users who haven’t yet enabled additional security protections are more at risk, just as those who are more active on Gmail. The use of multiple devices also increases the odds of an attack, the report reveals.
“We identified several stable factors that have a bearing on an individual’s risk level, including age, locality, device classes, and even prior security incidents. Our results represent a first step towards empirically identifying at-risk user populations and the promise of tailoring protections to those users that need it most,” the researchers conclude.
Ukraine’s police arrested the author of the U-Admin phishing kit
10.2.2021
Phishing
Securityaffairs
An international operation conducted by Ukraine’s police, along with the US and
Australia peers, shut down the world’s largest phishing Service U-Admin.
Last
week, an international operation conducted by Ukraine’s police, along with the
US and Australian authorities, lead to the shut down of the world’s phishing
framework U-Admin.
The National Police and its Main Investigation Department identified a man (39) from the Ternopil region who developed a phishing package and an admin panel that could be used by the customers of the service.
“As a result of an international special operation, the Office of the Attorney General, together with employees of the Cyberpolice Department of the National Police of Ukraine and the Main Investigation Department of the National Police, as well as law enforcement officers of the United States and Australia, closed one of the world’s largest phishing services.” reads the press release published by published by Ukraine police.
The phishing service was involved in attacks aimed at financial institutions in 11 countries (Australia, Spain, the U.S., Italy, Chile, the Netherlands, Mexico, France, Switzerland, Germany, and the U.K.) and caused tens of millions of dollars in losses.
According to the authorities, more than 50% of all phishing attacks in 2019 in Australia were carried using the U-Admin phishing service.
“Cyber cops in Ukraine carried out an arrest and several raids last week in connection with the author of a U-Admin, a software package used to administer what’s being called “one of the world’s largest phishing services.” The operation was carried out in coordination with the FBI and authorities in Australia, which was particularly hard hit by phishing scams perpetrated by U-Admin customers.” wrote the popular investigator Brian Krebs.

Source: krebsonsecurity.com
The police conducted five searches in the
Ternopil region, during which the agents seized computer equipment, mobile
phones, and hard drives. The analysis of the seized equipment allowed the
identification of more than 200 active buyers of the phishing framework.
The cybercriminal created his own online store on DarkNet to sell his products to customers, he is also accused to have provided technical support for phishing attacks to its users.
Accordind to Krebs, one of the biggest selling points for U-Admin is a module that allows attackers to intercept multi-factor authentication codes through web injection. Phishers can dynamically interact with victims in real-time by injecting content into the phishing page that prompts the victim to enter additional information, such as OTP codes.
The Ukrainian hacker has been arrested and faces up to six years of jail if will be found guilty.
Novel phishing technique uses Morse code to compose malicious URLs
9.2.2021
Phishing
Securityaffairs
Cybercriminals devised a new phishing technique that leverages the Morse code to
hide malicious URLs and bypass defense.
Experts spotted a new targeted
phishing campaign that leverages a new obfuscation technique based on the Morse
code to hide malicious URLs in an email attachment and bypass secure mail
gateways and mail filters.
The Morse code encodes each letter and number in a series of dots and dashes.
BleepingComputer that first reported the news, confirmed that this is the first time that threat actors in the wild started using the Morse encoding for the malicious URLs in phishing.
The technique was initially detailed in a post on Reddit, now remouved (copy webcache), but BleepingComputer researchers were able to find multiple samples involved in this phishing campaign that were uploaded to VirusTotal since early February.
The campaign uses with subject ‘Revenue_payment_invoice February_Wednesday 02/03/2021.’ The HTML attachment appears to be an Excel invoice, the naming convention used is ‘[company_name]_invoice_[number]._xlsx.hTML.’
The HTML code includes a JavaScript that implements the Morse coding/decoding operations.
phishing morse coding
The script includes both morseCode() and morseDecode() functions to implement
the novel phishing technique. The hexadecimal string corresponding to the
encoded URL is further decoded into JavaScript tags that are injected into the
HTML page.
“These injected scripts combined with the HTML attachment contain the various resources necessary to render a fake Excel spreadsheet that states their sign-in timed out and prompts them to enter their password again.” reads the post published by BleepingComputer.
Upon providing the password, it will be submitted to a remote site.
The threat actors used the logo.clearbit.comservice to insert logos for the recipient’s companies into the login form. In case the logo is not available, it will use a generic Office 365 logo.
Source BleepingComputer
BleepingComputer reported that at least eleven
companies were targeted with this novel phishing technique. The list of the
company is reported in the analysis published by BleepingComputer.
LogoKit Simplifies Office 365, SharePoint ‘Login’ Phishing Pages
29.1.2021
Phishing
Threatpost
A phishing kit has been found running on at least 700 domains – and mimicking services via false SharePoint, OneDrive and Office 365 login portals.
A newly-uncovered phishing kit, dubbed LogoKit, eliminates headaches for cybercriminals by automatically pulling victims’ company logos onto the phishing login page. This gives attackers the tools needed to easily mimic company login pages, a task that can sometimes be complex.
Cybercriminals have relied on LogoKit to launch phishing attacks on more than 700 unique domains over the past 30 days (including 300 in the past week). These targeted services range from generic login portals to false SharePoint, Adobe Document Cloud, OneDrive, Office 365, and cryptocurrency exchange login portals.
“With LogoKit’s intended functionality to be centered around singular emails per URL and extracting company logos, this dramatically improves ease of carrying out targeted attacks against organizations; and reusing pretexts without changing templates,” said Adam Castleman, security researcher with RiskIQ on Wednesday.
Phishing Kits
Phishing kits, which can be purchased by cybercriminals for
anything between $20 and $880, require little technical knowledge to operate
beyond modest programming skills. These kits are utilized to steal various data
from victims – including usernames, passwords, credit card numbers, social
security numbers and more.
In order to operate a kit, a cybercriminal must first install it on a remote server – either by compromising a legitimate content management system, or by utilizing their own infrastructure. Once installed, an attacker merely spams victims – via email messages, SMS or social media messages – with the URL that will take them to the phishing kit’s landing page. Some phishing kits contain administrator dashboards where cybercriminals can track the number of visits to their malicious website and view the sensitive data disclosed.
Phishing kits are nothing new – however, LogoKit makes the deployment of phishing login pages even easier for cybercriminals. Many times, cybercriminals that use phishing kits on top of compromised, legitimate content management systems deal with complex website layouts and multiple files. This could lead to glitches in the login page that serve as potential red flags for victims.
LogoKit skips over this problem with its simplicity, said researchers, as it executes only a few lines of customizable JavaScript. This allows bad actors to easily integrate the kit into either existing HTML pretext templates or build simple login forms to mimic corporate login portals.
The kit also stands out in that it has the ability to load resources from trusted sources, including legitimate object storage buckets. This is another trick that’s not necessarily brand new – but that makes fake login pages appear less malicious by having users navigate to a known domain name.
In some cases, for instance, attackers have been observed hosting their phishing pages on Google Firebase as part of the LogoKit attack. Google Firebase is a mobile and web application development platform that is backed by Google Cloud Storage and provides secure file uploads and downloads for Firebase apps.
How It Works
While LogoKit has been found using these legitimate hosting
services, researchers have also observed compromised web sites – many running
WordPress — to be hosting LogoKit variants. In both cases, cybercriminals send
victims a specially crafted URL containing their email address. An example of a
crafted URL that contains the email would be:
“phishingpage[.]site/login.html#victim@company.com.”
“The location hash is then broken down into slices,” according to researchers. “The slice’s delimiter is the ‘@’ symbol, allowing the script to extract the user’s/company’s domain to fetch the logo and eventually redirect a victim.”
If victim clicks on the URL, LogoKit then fetches the company logo from a third-party service, such as marketing data engine Clearbit or Google’s database for favicons (the graphic icons associated with particular webpages).
A phishing page running LogoKit. Credit: RiskIQ
The victim’s email is also auto-filled into the email or username input field of the login graphic. Researchers noted, this trick makes victims believe they have previously logged into the site.
Should a victim enter their password, LogoKit performs an AJAX request, sending the target’s email and password to an external source.
In some cases, as an added trick, after performing validation to ensure data is entered and a valid email address is present, the kit will “fake a user out” by telling them that their password is incorrect and prompting them to enter the password again. Then, as a final step, the victim is redirected to their corporate website after entering their password.
Several sectors have been targeted by attackers using LogoKit, including financial, legal, and entertainment, said researchers.
“The LogoKit presents a unique opportunity for attackers, allowing for easy integration into either existing HTML pretext templates or building simple login forms to mimic corporate login portals,” said Castleman. “Also, with the flexibility of either leveraging compromised infrastructure, attacker-hosted infrastructure, or object storage, attackers can quickly change their delivery source.”
LogoKit, a new phishing kit that dynamically creates phishing forms
29.1.2021
Phishing
Securityaffairs
Researchers from RiskIQ have discovered a new phishing kit dubbed LogoKit that
dynamically compose phishing content.
Researchers from RiskIQ discovered a
new phishing kit that outstands for its ability to dynamically create phishing
messages to target specific users.
LogoKit has a modular structure that makes it easy to implement a phishing-as-as-Service model.
This toolkit, unlike other ones, is an embeddable set of JavaScript functions. The kit uses specially crafted URLs containing the email address of the recipient. The crafted URLs contain the email as a location hash as reported in the following example:
phishingpage[.]site/login.html#victim@company.com
Upon navigating the URL, the LogoKit kit fetches the company logo from a
third-party service (i.e. Clearbit or Google’s favicon database) and auto-fills
the landing page with the victim’s username or email address in order to trick
victims into feeling like they have previously logged into the site. Once the
victim entered its password, LogoKit performs an AJAX request, sending the
recipient’s credentials to an external source, and, finally, redirecting it to
their corporate web site.
“RiskIQ has tracked LogoKit being used in simple login forms to trick users and
embedded into more complex HTML documents pretending to be other services. Due
to the simplicity of LogoKit, attackers can easily compromise sites and embed
their script or host their own infrastructure.” reads the report published by
the experts. “In some cases, attackers have been observed using legitimate
object storage buckets, allowing them to appear less malicious by having users
navigate to a known domain name, i.e., Google Firebase.”
RiskIQ spotted more
than seven hundred unique domains running with LogoKit in the last thirty days.
Threat actors targeted multiple services including MS SharePoint, Adobe Document
Cloud, OneDrive, Office 365, and Cryptocurrency exchanges.
In some instances, RiskIQ experts noticed LogoKit kits that were preventing victims from using keyboard shortcuts in order to view/inspect webpage content.
LogoKit is very small and can be hosted on compromised sites, experts added that the collection of JavaScript files, its resources can also be hosted on public trusted services like Firebase, GitHub, and Oracle Cloud.
“The LogoKit presents a unique opportunity for attackers, allowing for easy integration into either existing HTML pretext templates or building simple login forms to mimic corporate login portals. Also, with the flexibility of either leveraging compromised infrastructure, attacker-hosted infrastructure, or object storage, attackers can quickly change their delivery source.” concludes the report. “With LogoKit’s intended functionality to be centered around singular emails per URL and extracting company logos, this dramatically improves ease of carrying out targeted attacks against organizations; and reusing pretexts without changing templates.”
TikTok Flaw Lay Bare Phone Numbers, User IDs For Phishing Attacks
27.1.2021 Phishing Threatpost
A security flaw in TikTok could have allowed attackers to query query the platform’s database – potentially opening up for privacy violations.
A vulnerability in the popular TikTok short-form video-sharing platform could have allowed attackers to easily compile users’ phone numbers, unique user IDs and other data ripe for phishing attacks.
TikTok, owned by ByteDance, has more than 800 million active users worldwide. The vulnerability, which was reported and patched before its disclosure on Tuesday, existed in the “Find Friends” feature of the TikTok mobile app. This feature allows users to find their friends, either via their contacts, via Facebook or by inviting friends.
In order to help users find friends through their contacts, TikTok contained a
sync feature for contacts who had TikTok accounts. That means that it is
possible to connect profile details with phone numbers. Researchers said an
attacker could leverage this feature in order to query TikTok’s entire database
– potentially opening up for privacy violations.
“The vulnerability could have allowed an attacker to build a database of user details and their respective phone numbers,” said Oded Vanunu, head of products vulnerabilities research at Check Point. “An attacker with that degree of sensitive information could perform a range of malicious activities, such as spear phishing or other criminal actions.”
The Attack
To launch an attack, a bad actor would need to first bypass
TikTok’s HTTP message signing mechanism, which aims to protect threat actors
from tampering with HTTP messages or modifying the body of the HTTP request.
Researchers were able to achieve this using TikTok’s own signing service, executed in the background. By using a dynamic analysis framework like Frida, an attacker could hook the function, change the data of the function’s arguments (in this case the contacts the attacker wants to sync) and re-sign the modified request to send to the TikTok application server.
TikTok’s “Find Friends” feature. Credit: Check Point Research
From there, an attacker could automate the process of uploading and syncing contacts at a large scale. This could allow them to build a database of users and their connected phone numbers. Other profile details that would be accessible include the nickname associated with the account, profile and avatar pictures, unique user IDs, as well as certain profile settings, such as whether a user is a follower or if user’s profile is hidden. This type of data can give attackers the tools they need for social-engineering attacks used in phishing and spear-phishing emails. For instance, if an attacker demonstrates to a phishing victim that they have their phone number or unique user ID associated with their TikTok account, the victim is more apt to believe them.
One caveat of note is that this flaw could have only impacted users who had chosen to associate a phone number with their account, or who had logged in with a phone number. Neither of these options is required for users.
Researchers disclosed their findings to ByteDance, which deployed a solution. Now, under the “Find Friends” feature, users can only invite their friends rather than discover contacts that have TikTok accounts.
“The security and privacy of the TikTok community is our highest priority, and we appreciate the work of trusted partners like Check Point in identifying potential issues so that we can resolve them before they affect users,” said a TikTok spokesperson in a statement. “We continue to strengthen our defenses, both by constantly upgrading our internal capabilities such as investing in automation defenses, and also by working with third parties.”
TikTok Flaws
TikTok, which has previously triggered controversy for its
privacy policies, earlier in 2020 faced scrutiny over various vulnerabilities
found in its platform. Researchers said the most serious vulnerability in the
platform could allow attackers to remotely take control over parts of victims’
TikTok account, such as uploading or deleting videos, and changing settings on
videos to make “hidden” videos public.
Vanunu urged TikTok users to “share the bare minimum when it comes to your personal data,” and “update your OS and applications to the latest versions.”
Targeted Phishing Attacks Strike High-Ranking Company Executives
27.1.2021
Phishing
Thehackernews 
An evolving phishing campaign observed at least since May 2020 has been found to
target high-ranking company executives across manufacturing, real estate,
finance, government, and technological sectors with the goal of obtaining
sensitive information.
The campaign hinges on a social engineering trick that involves sending emails to potential victims containing fake Office 365 password expiration notifications as lures. The messages also include an embedded link to retain the same password that, when clicked, redirects users to a phishing page for credential harvesting.
"The attackers target high profile employees who may not be as technically or cybersecurity savvy, and may be more likely to be deceived into clicking on malicious links," Trend Micro researchers said in a Monday analysis.
"By selectively targeting C-level employees, the attacker significantly increases the value of obtained credentials as they could lead to further access to sensitive personal and organizational information, and used in other attacks."

According to the researchers, the targeted email addresses were mostly collected
from LinkedIn, while noting that the attackers could have purchased such target
lists from marketing websites that offer CEO/CFO email and social media profile
data.
The Office 365 phishing kit, currently in its fourth iteration (V4), is said to have been originally released in July 2019, with additional features added to detect bot scanning or crawling attempts and provide alternative content when bots are detected. Interestingly, the alleged developer behind the malware announced V4's availability on their "business" Facebook page in mid-2020.
Aside from selling the phishing kit, the actor has also been found to peddle account credentials of CEOs, chief financial officers (CFOs), finance department members, and other high-profile executives on social media pages.
What's more, Trend Micro's investigation unearthed a possible link to a user handle on underground forums that was spotted selling a credential harvester tool as well as stolen C-Level account passwords anywhere between $250 to $500, echoing previous reports late last year.
The researchers uncovered at least eight compromised phishing sites hosting the
V4 phishing kit, raising the possibility that they were used by different actors
for a wide range of phishing campaigns directed against CEOs, presidents, board
members, and founders of companies located in the U.S., the U.K., Canada,
Hungary, the Netherlands, and Israel.
"While organizations are aware and wary of the information they include in public-facing websites and platforms, their respective employees should be constantly reminded to be mindful of the details they disclose on personal pages," the researchers concluded. "These can be easily used against them for attacks using social engineering techniques."
Phishers Target C-Suite with Fake Office 365 Password Expiration Reports
26.1.2021
Phishing
Securityweek
An ongoing phishing campaign delivering fake Office 365 password expiration reports has managed to compromise tens of C-Suite email accounts to date, according to a warning from anti-malware vendor Trend Micro.
Targeting organizations in finance, government, manufacturing, real estate, and technology sectors, the campaign has claimed victims in Japan, the United States, U.K., Canada, Australia, and several European countries.
To date, more than 300 unique compromised URLs were identified, along with 70 e-mail addresses from eight websites. The phishers were able to compromise 40 legitimate email addresses of CEOs, directors, company founders, and owners, as well as those of other enterprise employees.
As lures, the attackers used fake Office 365 password expiration reports, requesting the victim to click on an embedded link that would allegedly allow them to continue using the same password. However, once the potential victim clicks on the “Keep Password” option, they are taken to the phishing page.
Compromised infrastructure and stolen credentials are abused to host phishing pages and target more victims.
As part of the attack, the hackers used a phishing kit that was first detailed last year, when used in similar attacks leveraging fake Microsoft login pages. Available for purchase, the kit allows cybercriminals to validate stolen credentials.
Trend Micro also discovered that cybercriminals are advertising stolen credentials for Office 365 accounts of CEOs, chief financial officers (CFOs), and employees in the finance department, among others.
“Those posts were seen in multiple English- and Russian-speaking forums, including an underground forum that seemingly matched with another user’s advertisement. Notably, all posts on the Russian-speaking forums were done in English and using recently registered accounts,” Trend Micro explains in a blog post.
Most of the phishing emails in this campaign were sent using a virtual private server (VPS) from FireVPS, a firm that provides customers with various Windows remote desktop protocol (RDP) plans.
Trend Micro says they alerted the company of its service being abused in the phishing campaign, but hasn’t heard back yet.
The phishing kit, which appears to be the evolution of similar toolkits, also includes an extensive list of IP address ranges and domain names, aiming to block access for security companies and large cloud providers, likely in an attempt to evade detection.
The phishing kit’s developer is actively advertising the creation on social media sites and is engaged in the selling of stolen credentials. Trend Micro was eventually able to link the developer’s business Facebook page with the personal one, and has already provided authorities with details on the issue.
Trend Micro also linked sites abused in this campaign to other phishing attacks, including one that exclusively targeted company CEOs, presidents, and founders in the United States. Another campaign targeted directors and managers from Canada, Israel, Hungary, the Netherlands, the UK, and the US.
The email addresses of CEOs in the United States are clearly the main target of this campaign and others using the same phishing kit. Such emails allow attackers to conduct further phishing, compromise sensitive information, and conduct business email compromise (BEC) and other social engineering attacks.
“Phishing attacks and attackers often target employees — usually the weakest link in an organization’s security chain. […] By selectively targeting C-level employees, the attacker significantly increases the value of obtained credentials as they could lead to further access to sensitive personal and organizational information, and used in other attacks,” Trend Micro concludes.
Passwords stolen via phishing campaign available through Google search
22.1.2021
Phishing
Securityaffairs
Bad ops of operators of a phishing campaign exposed credentials stolen in
attacks and made them publicly available through Google queries.
Check Point
Research along with experts from cybersecurity firm Otorio shared details on
their investigation into a large-scale phishing campaign that targeted thousands
of global organizations.
The campaign has been active since August, the attackers used emails that masqueraded as Xerox scan notifications that were urging recipients into opening a malicious HTML attachment. This trick allowed the attackers to bypass Microsoft Office 365 Advanced Threat Protection (ATP) filtering and stole over a thousand corporate employees’ credentials.
The experts noticed that operators behind the phishing campaign focused on
Energy and Construction companies, but they accidentally exposed credentials
stolen in attacks that were publicly viewable with a simple Google search.
Operators of a phishing campaign targeting the construction and energy sectors
exposed credentials stolen in attacks that were publicly viewable with a simple
Google search.
“Interestingly, due to a simple mistake in their attack chain, the attackers behind the phishing campaign exposed the credentials they had stolen to the public Internet, across dozens of drop-zone servers used by the attackers. With a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attacker.” reads the post published by Check Point.
Once the victim double-clicked the HTML file, a blurred image with a preconfigured email within the document is opened in the browser.
Upon launching the HTML file, a JavaScript code will be executed in the background, it gathers the password, sends the data to the attackers’ server, and redirect the user to a legitimate Office 365 login page.
Phishers used both unique infrastructure and compromised WordPress websites used to store the stolen data.
“We discovered dozens of compromised WordPress servers that hosted the malicious PHP page (named “go.php”, “post.php”, “gate.php”, “rent.php” or “rest.php”) and processed all incoming credentials from victims of the phishing attacks.” continues the post.
“Attackers usually prefer to use compromised servers instead of their own infrastructure because of the existing websites’ well-known reputations. The more widely recognized a reputation is, the chances are higher that the email will not be blocked by security vendors”
The emails were sent from a Linux server hosted on Microsoft’s Azure, they were often sent by using PHP Mailer 6.1.5 and delivered using 1&1 email servers.
Attackers also sent out spam messages through compromised email accounts to make messages appear to be from legitimate sources.
Data sent to the drop-zone servers were saved in a publicly visible file that was indexable by Google. This means that they were available to anyone with a simple Google search.
The analysis of a subset of ~500 stolen credentials revealed that victims belong to a wide range of target industries, including IT, healthcare, real estate, and manufacturing.
Check Point shared its findings with Google.
Experts noticed that the JavaScript encoding used in this campaign was the same used in another phishing campaign from May 2020, a circumstance that suggests that the group threat actor is behind the two campaigns.
The report also includes Indicators of Compromise (IoCs).
Passwords stolen via phishing campaign available through Google search
22.1.2021
Phishing
Securityaffairs
Bad ops of operators of a phishing campaign exposed credentials stolen in
attacks and made them publicly available through Google queries.
Check Point
Research along with experts from cybersecurity firm Otorio shared details on
their investigation into a large-scale phishing campaign that targeted thousands
of global organizations.
The campaign has been active since August, the attackers used emails that masqueraded as Xerox scan notifications that were urging recipients into opening a malicious HTML attachment. This trick allowed the attackers to bypass Microsoft Office 365 Advanced Threat Protection (ATP) filtering and stole over a thousand corporate employees’ credentials.

The experts noticed that operators behind the phishing campaign focused on
Energy and Construction companies, but they accidentally exposed credentials
stolen in attacks that were publicly viewable with a simple Google search.
Operators of a phishing campaign targeting the construction and energy sectors
exposed credentials stolen in attacks that were publicly viewable with a simple
Google search.
“Interestingly, due to a simple mistake in their attack chain, the attackers behind the phishing campaign exposed the credentials they had stolen to the public Internet, across dozens of drop-zone servers used by the attackers. With a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attacker.” reads the post published by Check Point.
Once the victim double-clicked the HTML file, a blurred image with a preconfigured email within the document is opened in the browser.
Upon launching the HTML file, a JavaScript code will be executed in the background, it gathers the password, sends the data to the attackers’ server, and redirect the user to a legitimate Office 365 login page.
Phishers used both unique infrastructure and compromised WordPress websites used to store the stolen data.
“We discovered dozens of compromised WordPress servers that hosted the malicious PHP page (named “go.php”, “post.php”, “gate.php”, “rent.php” or “rest.php”) and processed all incoming credentials from victims of the phishing attacks.” continues the post.
“Attackers usually prefer to use compromised servers instead of their own infrastructure because of the existing websites’ well-known reputations. The more widely recognized a reputation is, the chances are higher that the email will not be blocked by security vendors”
The emails were sent from a Linux server hosted on Microsoft’s Azure, they were often sent by using PHP Mailer 6.1.5 and delivered using 1&1 email servers.
Attackers also sent out spam messages through compromised email accounts to make messages appear to be from legitimate sources.
Data sent to the drop-zone servers were saved in a publicly visible file that was indexable by Google. This means that they were available to anyone with a simple Google search.
The analysis of a subset of ~500 stolen credentials revealed that victims belong to a wide range of target industries, including IT, healthcare, real estate, and manufacturing.
Check Point shared its findings with Google.
Experts noticed that the JavaScript encoding used in this campaign was the same used in another phishing campaign from May 2020, a circumstance that suggests that the group threat actor is behind the two campaigns.
The report also includes Indicators of Compromise (IoCs).