A sample phishing email. Credit: Abnormal Security
Phishing 2024 2023 2022 2021 2020
GoDaddy apologized for insensitive phishing email sent to its employees offering
a fake bonus
27.12.2020
Phishing
Securityaffairs
GoDaddy made the headlines for an initiative that is dividing cybersecurity
community, it sent phishing messages offering bonuses to its employees.
GoDaddy sent an email to its employee that promised a Christmas bonus to help
them to face economic problems caused by the ongoing COVID-19 pandemic. The web
provider apologized Thursday for the cyber security test aimed at verifying the
response of its personnel to a phishing campaign.
“GoDaddy takes the security of our platform extremely seriously. We understand some employees were upset by the phishing attempt and felt it was insensitive, for which we have apologized,” a spokesman for GoDaddy told AFP in a statement.
“While the test mimicked real attempts in play today, we need to do better and be more sensitive to our employees,”
The approach was criticized by part of the cyber security community due to the bait used in the test and the period chosen for the simulation. On the other side, the company opted for this test because it mimics a real attack that could happen at any time and that could take advantage of the pandemic.
The test took place in December, the message deceived around 500 employees who clicked on it. The email stated that GoDaddy was offering a Christmas bonus of $650 and asked them to fill out a form with their personal details.
“Though we cannot celebrate together during our annual Holiday Party, we want to
show our appreciation and share a $650 one-time Holiday bonus!” the email reads.
“To ensure that you receive your one-time bonus in time for the Holidays, please
select your location and fill in the details by Friday, December 18th.”
Two
days later, the employees were informed by email of the ongoing security test,
the message received by the ones that opened the email states:
“You’re getting this email because you failed our recent phishing test,” the company’s chief security officer Demetrius Comeswrote. “You will need to retake the Security Awareness Social Engineering training.”
Those who failed the test are invited to retake the Security Awareness Social Engineering training.
Subway Sandwich Loyalty-Card Users Suffer Ham-Handed Phishing Scam
16.12.2020 Phishing Threatpost
Subway loyalty program members in U.K. and Ireland have been sent scam emails to trick them into downloading malware.
Count the Subway sandwich faithful among the latest victims of cybercriminals. Researchers at Sophos discovered a phishing campaign aimed at Subway loyalty-card members in the U.K. and Ireland, in an attempt to trick them into downloading malware.
The campaign wasn’t particularly impressive, according to Sophos researchers.
“As phishes go, this one isn’t terribly sophisticated or believable, and the scam itself requires several clicks, each one more suspicious than the last,” the report said.
Subway Scam
Sophos published a couple of different versions of the emails,
but the message was the same: you have an order on the way, and “click here” if
you would like to know more details.
One email supplied to Sophos appeared to have been sent from a “subwaysubcard” domain. It was personalized with the recipient’s first name. A second email with the same text was delivered to another loyalty cardholder and supplied to Sophos with the same message.
“Thanks for shopping with us!” the scam email read. “You’ll find a summary of your most recent purchase below.”
Both messages also shared an identical misspelling: “anather” in stead of “another.”
A third communication told recipients to click on a link to view “order documents.” That link leads to a scam “FreshBooks” page and then a fake DocuSign page, Sophos reported.
The goal of the phishing campaign is to get victims to change their Excel security settings, allowing the malicious actors to run macros and deliver malware to the victim’s device, Sophos explained. The code creates a URL from a hidden “Files” sheet. The URL then grabs the malware.
“The crooks are hoping you will think that turning macros on will somehow increase security, when in fact you are enabling a feature that makes it possible for the criminals to download and install malware.”
Subway spokesperson Shani Shaker Kekati told Threatpost that the company has “no evidence guest accounts have been hacked,” adding, “however, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit-card details. Crisis protocol was initiated and compromised systems locked down.”
But according to Paul Ducklin, principal research scientist at Sophos, an email address and first name is plenty for criminals to target unsuspecting customers.
“The bad news about this scam is that even if all a cybercriminal knows about you is a first name, an email address and a brand they know you buy from, they can still make plenty of trouble for you,” Ducklin told Threatpost. “Even just saying ‘Dear Paul’ instead of ‘Dear customer’ makes the opening gambit so much more plausible and softens you up for what follows.”
Loyalty Cards a Target
While there’s not much clarity around how the crooks
got the Subway loyalty-card list, Allan Liska, intelligence analyst for Recorded
Future, told Threatpost in a recent webinar that loyalty-card lists are
increasingly easy to find on the dark web.
“Turns out that there’s some value in those; so, if you are a brand that has loyalty cards, monitor for large dumps of your loyalty cards,” Liska said. He explained airline miles and points programs of all sorts can easily be turned into goods, services and even cash.
Criminals have also deployed AI and automation against rewards and loyalty programs, according to Robert Capps, NuData’s vice president of marketplace innovation.
“We had a client that had the ability for you to take your receipt home and sign up for loyalty program, and have that receipt applied to your account, based on random digits at the bottom of the receipt,” Capps told Threatpost. “And those random digits weren’t random.”
He added that automation helped the criminals crack the code and rack up rewards.
“Someone figured out the patterns and started running tens of thousands of these receipt combinations through an automated checker, to add the residual value that was unclaimed on those transactions to a given set of rewards accounts,” Capps said. “And they were buying product, and fulfilling on eBay, Amazon and other online-order systems.”
Luckily for Subway loyalty-card holders, this latest attack phishing attack against Subway wasn’t nearly as difficult to identify.
“The good news is that every step of this particular scam had a telltale sign that someone was up to no good,” Ducklin said. “And that is a great reminder of a very useful general rule: *always* take those extra few seconds to check for things that don’t add up, and make the crooks pay for any operational blunders they make. And if you want to ask for advice, never rely on any contact information in the message itself. Find your own way to ask for help, using contact details you already know.”
Microsoft Office 365 Credentials Under Attack By Fax ‘Alert’ Emails
15.12.2020 Phishing Threatpost
Emails from legitimate, compromised accounts are being sent to numerous enterprise employees with the aim of stealing their O365 credentials.
Researchers are warning of a coordinated phishing attack that targeted “numerous” enterprise organizations last week.
The attackers behind the attack leveraged hundreds of compromised, legitimate email accounts in order to target organizations with emails, which pretended to be document delivery notifications. In reality, the phishing attack stole victims’ Office 365 credentials.
“The widespread use of hundreds of compromised accounts and never-seen-before URLs indicate the campaign is designed to bypass traditional threat intelligence solutions accustomed to permitting known but compromised accounts into the inbox,” said researchers with Abnormal Security, in a Monday analysis.
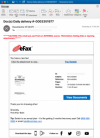
The attack starts with a lure convincing email recipients that they received a document. The email impersonates businesses like eFax, which is an internet fax service making it easy to receive faxes via email or online.
One sample email uses the legitimate eFax branding and has an email title: “Doc(s) Daily delivery #-0003351977.” It tells recipients, “You have a new fax!” and includes a small picture that is a sample image of a fax the recipient apparently received. The email also tells recipients to “click the attachment to view” and contains a link in a button that says “View Documents.”
The email appears to be legitimate and even has a tag at the bottom that markets eFax’s plans, telling recipients: “Tip: Switch to an annual plan – it’s like getting 2 months free every year! Call (800)958-2983 or email help@mail.efax[.]com.”
“The above example is one of many similarly crafted campaigns that originate from multiple compromised accounts,” said researchers. “The reason the bypass works is because the compromised email addresses are known and trusted by the organization based on prior and legitimate communications.”
The embedded URLs redirect to fake, never-seen-before Microsoft Office 365 phishing pages, said researchers. Hundreds of these phishing landing pages have been detected and are hosted on digital publishing sites like Joom, Weebly and Quip, they said.

A sample phishing email. Credit: Abnormal Security
The landing page again includes a sample fax image, Caller ID and reference number, and again tells recipients to “View Document.”
Here, “the attacker attempts to legitimize the campaign with official-looking landing pages similar to those used by eFax,” said researchers.
When the employee clicks this next “View Documents” link, they are taken to the final credential-phishing campaign.
Making detection and prevention of this campaign more difficult, “When one email is detected and caught, the attackers appear to be running a script that changes the attack to a new impersonated sender and phishing link to continue the campaign,” said researchers.
Microsoft Office 365 users have faced several sophisticated phishing attacks and scams over the past few months. In October, researchers warned of a phishing campaign that pretends to be an automated message from Microsoft Teams. In reality, the attack aimed to steal Office 365 recipients’ login credentials. Also in October, an Office365 credential-phishing attack targeted the hospitality industry, using visual CAPTCHAs to avoid detection and appear legitimate.
Finally, earlier this month, a spearphishing attack spoofed Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets, including financial services, healthcare, manufacturing and utility providers.
Hacked Subway UK marketing system used in TrickBot phishing campaign
14.12.2020
BotNet Phishing
Securityaffairs
Subway UK confirmed the hack of a marketing system that was used to send out
phishing messages to deliver malware to the customers.
Hackers have
compromised a marketing system in Subway UK and used it to send out phishing
messages to deliver malware to the customers.
Subway UK customers received emails from ‘Subcard’ about the processing of an alleged Subway order. The malicious emails were including a link to a weaponized Excel document containing confirmation of the order.
The Excel documents would install the latest version of the TrickBot malware that was recently discovered by Advanced Intel’s Vitali Kremez.
Experts from Bleeping Computer reported the suspicious messages to the Subway UK that confirmed a security incident
“We are aware of some disruption to our email systems and understand some of our guests have received an unauthorised email. We are currently investigating the matter and apologise for any inconvenience.” a Subway spokesperson told BleepingComputer. “As soon as we have more information, we will be in touch, until then, as a precautionary measure, we advise guests delete the email.”
The company later disclosed the compromise of a server responsible for their email campaigns.
“Having investigated the matter, we have no evidence that guest accounts have been hacked. However, the system which manages our email campaigns has been compromised, leading to a phishing campaign that involved first name and email. The system does not hold any bank or credit card details.” confirmed the company.
“Crisis protocol was initiated and compromised systems locked down. The safety of our guests and their personal data is our overriding priority and we apologise for any inconvenience this may have caused,”
Subway immediately started the incident response procedure and started sending out data breach notification emails to the impacted customers. The compromised data include customer’s first name and last name.
At the time of this writing it is not clear how many customers were affected.
Spearphishing Attack Spoofs Microsoft.com to Target 200M Office 365 Users
9.12.2020
Phishing
Threatpost
It remains unknown as to
why Microsoft is allowing a spoof of their very own domain against their own
email infrastructure.
A spearphishing attack is spoofing Microsoft.com to target 200 million Microsoft Office 365 users in a number of key vertical markets, including financial services, healthcare, manufacturing and utility providers.
Researchers at Ironscales discovered the campaign targeting several thousand mailboxes at nearly 100 of the email security firm’s customers, Lomy Ovadia, Ironscales vice president of research and development, said in a report posted online Monday. Other industries being targeted including telecom and insurance companies, he said.
The attack is particularly deceiving because it deploys an exact domain spoofing technique, “which occurs when an email is sent from a fraudulent domain that is an exact match to the spoofed brand’s domain,” Ovadia wrote. This means even savvy users who check sender addresses to ensure an email is legitimate might be fooled, he said.
The attack is comprised of a realistic-looking email that attempts to persuade users to take advantage of a relatively new Office 365 capability that allows for them to reclaim emails that have been accidentally marked as spam or phishing messages, according to the report. The messages come from sender “Microsoft Outlook.”
“Specifically, the fraudulent message is composed of urgent and somewhat fear-inducing language intended to convince users to click on what is a malicious link without hesitation,” Ovadia wrote. “As inferred by the message, the link will redirect users to a security portal in which they can review and take action on ‘quarantined messages’ captured by the Exchange Online Protection (EOP) filtering stack, the new feature that has only been available since September.”
Once a user clicks on the link, they are asked to type in legitimate Office 365 login credentials on a fake log-in page controlled by attackers to harvest and likely sell on the dark web, according to Ironscales.
One interesting aspect of the campaign is its success in getting past secure email gateway (SEG) controls. Typically, exact domain spoofs aren’t very hard for them to detect, according to Ironscales; the company found in previous research that this tactic was represented in less than 1 percent of total spoofing attacks that bypass SEGs in a given year.
“Even non cloud-native and legacy email security tools are fairly efficient at stopping these sorts of attacks,” Ovadia noted. “The reason why SEGs can traditionally stop exact domain spoofing is because, when configured correctly, this control is compliant with the domain-based message authentication, reporting & conformance (DMARC), an email authentication protocol built specifically to stop exact domain spoofing (SPF/DKIM).”
However, Ironscales found that Microsoft servers are not currently enforcing the DMARC protocol, which means the exact domain spoofing messages get through controls such as Office 365 EOP and Advanced Threat Protection.
“Any other email service that respects and enforces DMARC would have blocked such emails,” Ovadia wrote. “It remains unknown as to why Microsoft is allowing a spoof of their very own domain against their own email infrastructure.”
The situation is particularly curious as Microsoft is typically one of the top domain names if not the top domain imitated by hackers in phishing campaigns, he observed.
To mitigate attacks, Ironscales advised organizations to configure their email defense and protection systems for DMARC, which should detect and reject emails coming from the latest Office 365 campaign, according to the report.
“Advanced mailbox-level email security that continuously studies every employee’s inbox to detect anomalies based on both email data and metadata extracted from previously trusted communications can help stop email spoofs that slip through the cracks,” Ovadia added.
FINRA Warns Brokerage Firms of Phishing Campaign
3.12.2020
Phishing
Securityweek
Cybercriminals are using a recently registered lookalike domain in a phishing campaign targeting United States organizations, FINRA (the Financial Industry Regulatory Authority) warns.
A government-authorized not-for-profit organization, FINRA regulates over 624,000 brokerage firms in the United States.
Overseen by the Securities and Exchange Commission (SEC), FINRA enforces compliance with its own-issued rules, registers and trains broker-dealer personnel, and offers regulatory services for equities and options markets, among others.
In a recently issued notice, the organization warned brokerage firms of a phishing campaign leveraging the fraudulent domain invest-finra[.]org, which has no connection with FINRA.
“FINRA recommends that anyone who clicked on any link or image in the email immediately notify the appropriate individuals in their firm of the incident. […] firms should delete all emails originating from this domain name,” the organization says.
invest-finra[.]org was registered on November 5 with French registrar Gandi, and FINRA has already contacted the Internet domain registrar to suspend services for the fake domain.
“FINRA reminds firms to verify the legitimacy of any suspicious email prior to responding to it, opening any attachments or clicking on any embedded links,” FINRA underlines.
This is not the first time cybercriminals have leveraged FINRA lookalike domains in phishing campaigns. The tactic is widely employed by scammers, including those launching business email compromise (BEC) attacks.
Chip maker Advantech hit by Conti ransomware gang
29.11.20
Phishing
Securityaffairs
The IIoT chip maker Advantech was hit by the Conti ransomware, the gang is now
demanding over $13 million ransom from the company.
The Conti ransomware gang
hit infected the systems of industrial automation and Industrial IoT (IIoT) chip
maker Advantech and is demanding over $13 million ransom (roughly 750 BTC) to
avoid leaking stolen files and to provide a key to restore the encrypted files.
Advantech has 8,000 employees worldwide and has reported a yearly sales revenue of over $1.7 billion in 2019.
The ransomware gang announced on November 21, 2020 the leak of stolen data if the chipmaker would not have paid the ransom within the next day.
As proof of the capability to restore the data, Conti ransomware operators are willing to decrypt two of the encrypted files.
On November 26, the ransomware operators began leaking the data stolen from Advantech, an archive of 3.03GB that accounts for 2% of the total amount of stolen data.
According to Bleeping Computer, the Conti ransomware gang also promised to remove any backdoors from the company’s network after the payment of the ransom. The operators also announced that the stolen data will be permanently removed from its servers and it will provide security tips on how to secure the network to prevent future infections.
Conti ransomware operators implement a private Ransomware-as-a-Service (RaaS), the malware appeared in the threat landscape at the end of December 2019 and was distributed through TrickBot infections.
Since August 2020, the group launched its leak site to threaten its victim to release the stolen data.
Google Services Weaponized to Bypass Security in Phishing, BEC Campaigns
21.11.20
Phishing
Threatpost
Attackers exploiting an array of Google Services, including Forms, Firebase, Docs and more to boost phishing and BEC campaigns.
A spike in recent phishing and business email compromise (BEC) attacks can be traced back to criminals learning how to exploit Google Services, according to research from Armorblox.
Social distancing has driven entire businesses into the arms of the Google ecosystem looking for a reliable, simple way to digitize the traditional office. Armorblox co-founder and head of engineering Arjun Sambamoorthy just published a report detailing how now-ubiquitous services like Google Forms, Google Docs and others are being used by malicious actors to give their spoofing attempts a false veneer of legitimacy, both to security filters and victims.
“Open APIs, extensible integrations and developer-friendly tools mean that entire virtual offices — complete with virtual workflows — can exist in a Google ecosystem,” Sambamoorthy wrote. “Unfortunately, Google’s open and democratized nature is being exploited by cybercriminals to defraud individuals and organizations of money and sensitive data.”
The report gives several specific examples of how Google Services help attackers with their schemes.
Google Forms
One campaign used a Google Form and an American Express logo to
try and get victims to enter sensitive information.
“Hosting the phishing page on a Google Form helps the initial email evade any
security filters that block known bad links or domains,” according to
Sambamoorthy. “Since Google’s domain is inherently trustworthy, and Google forms
are used for several legitimate reasons, no email security filter would
realistically block this link on ‘day zero.'”
The American Express scam. Source: Armorblox.
Another attack Sambamoorthy found used a fictious letter from a childless widow looking for someone to whom she could bequeath her fortune. The link in the email leads to a Google Form with a blank question field. In this instance, the Google Form helps attackers with the social engineering strategy, the report said.
“Many people will feel the email is suspicious after going through the content and visiting this dummy form,” he continued. “But some people will submit the only option allowed by the form, or they will send a reply to the address provided in the email. This allows attackers to shortlist the most naive and emotionally susceptible email recipients, who will be prime targets for follow-up emails from the childless widow.
Google Firebase, Google Sites & Google Docs
Google’s mobile platform Firebase
was used in another scheme to host a phishing page, which allowed it to sneak
through email filters for the same reason – because Firebase is trusted.
In a Google-services-powered payroll diversion fraud scam that Sambamoorthy highlighted, a scam email link sent recipients to a Google Doc file to “confirm” their payment details.
And in yet another attack, an email was delivered to victims, purportedly from their own IT team, asking them to review a secure message on Microsoft Teams from a colleague. The link led to web page with a bogus Office 365 login portal hosted on Google Sites.
“The malice of the page’s intent was hidden behind the legitimacy of the page’s domain,” Sambamoorthy added. “This page would pass most eye tests during busy mornings (which is when the email was sent out), with people happily assuming it to be a legitimate Microsoft page.”
Hijacking Google Services: A Trend
The ability for malicious actors to
leverage Google Services for their activities is starting to emerge as a
full-fledged trend.
At the beginning of November, researchers found 265 Google Forms impersonating brands like AT&T, Citibank and Capitol One and even government agencies like the Internal Revenue Service and the Mexican Government used in phishing attacks.
The forms were removed by Google after researchers from Zimperium reported them.
The Teams phish. Source: Armorblox.
Just days earlier, scammers were found to be using a legitimate Google Drive collaboration to trick victims into clicking on malicious links.
Even Google Calendar has been abused in the past, in a sophisticated cyberattack that targeted mobile Gmail users through fraudulent, unsolicited meeting notifications.
For its part, Google stresses the company is taking every measure to keep malicious actors off their platforms.
“We are deeply committed to protecting our users from phishing abuse across our services, and are continuously working on additional measures to block these types of attacks as methods evolve,” a Google spokesperson told Threatpost by email.
The statement added that Google’s abuse policy prohibits phishing and emphasized that the company is aggressive in combating abuse.
“We use proactive measures to prevent this abuse and users can report abuse on our platforms,” the statement said. “Google has strong measures in place to detect and block phishing abuse on our services.”
Sambamoorthy told Threatpost that the security responsibility does not rest on Google alone and that organizations should not rely solely on Google’s security protections for their sensitive data.
“Google faces a fundamental dilemma because what makes their services free and easy to use also lowers the bar for cybercriminals to build and launch effective phishing attacks,” he said. “It’s important to remember that Google is not an email security company — their primary responsibility is to deliver a functioning, performant email service.”
Sambamoorthy said two-factor authentication (2FA) and maintaining strong passwords with a password manager are the best ways for users to protect themselves. Besides those best practices, the report recommended “rigorous eye tests” of emails “related to money and data.”
Organizations, he said, should establish basic security policies and set up mechanisms which are able to adapt to new and evolving threats.
“Security has an important ‘process’ component, so organizations should ensure they have the right controls, checks, and balances in place to protect users and data,” Sambamoorthy said. “Since these attack patterns are always evolving, organizations should invest in security technologies that have built-in feedback mechanisms. These mechanisms should learn from new attacks and refine detection algorithms with time ”
Tis’ the Season for Online Holiday Shopping; and Phishing
20.11.20 Phishing Threatpost
Watch out for these top phishing approaches this holiday season.
While online holiday shopping is nothing new, more of us will be avoiding the malls and brick-and-mortar stores this year — which opens up big opportunities for cybercriminals. This, along with COVID-19, is expected to anchor most of the scam and phishing lures in circulation this season.
Since pandemic lockdowns began in early 2020, contactless transactions skyrocketed, and seasonal holiday shopping will likely continue that trend. According to a recent survey from CreditCards.com, more than 70 percent of Americans will make most of their holiday purchases online this year, compared with 51 percent in 2019.
Unfortunately, that also means we have to look forward to more cyberthreats trying to cash in on the spirit of gift-giving and charity donations during the holidays.
Meanwhile, we already know that COVID-19-related phishing scams skyrocketed 600 percent between February and March this year, shortly after the pandemic took hold across Europe and the U.S. This year, along with the usual garden-variety holiday scams, we’re likely to see more phishing attacks both directly and indirectly related to the pandemic.
Although phishing scams are likely to target consumers in volume during the holiday season, there are many versions, such as whale-phishing, that are designed to target high-level executives and other key individuals.
In fact, the majority of your remote employees who use either personal or corporate-owned devices probably encounter at least one of these scams every day. Even one successful breach could put your company’s data at risk, especially if a hacker manages to get a remote employee’s corporate login credentials.
It’s also important to note that while there are all kinds of complex online scams, many hackers go for the easiest targets — usually mobile users who lack robust security awareness and protection on their devices.
Top Phishing Scams to Watch For
Email Phishing: It’s hard to believe that
email phishing scams are still around and just as successful as they’ve always
been. Sure, they’re a tad more sophisticated than the mocked-up bank emails from
20 years ago, but their shtick is still the same: Convince the user there’s a
problem with their bank account, online order, etc., and direct them to a fake
website to enter their login credentials, which, of course, the hacker then
steals for future use.
Spear-Phishing: Unlike most email phishing campaigns that cast a wide net, spear-phishing horns in on specific individuals — using personal details that can make these scams more believable. For example, let’s say a user recently booked a holiday home through a vacation reservations site. The next day, the user receives a message stating that there’s a problem with their recent reservation, with links to a fake website to update credit-card or other personal information.
Vishing: Voice-based phishing or “vishing” attacks can be highly deceiving. In this case, a hacker actually calls the user and tricks the person into giving the attacker their credentials or sharing other useful information. Remember that the Twitter hack from back in July actually started with a hacker calling a Twitter employee and convincing the person that he was a colleague. Little by little, the hacker was able to use employee credentials and company information gathered from the calls to gain access to some of the world’s most high-profile, verified Twitter accounts.
Smishing: Text-based or SMS “smishing” threats are also on the rise. In fact, according to Verizon’s 2020 Mobile Security Index, smishing attacks have increased from 2 percent to 13 percent in just the past year. In the pandemic era, with more people ordering online, smishing attacks frequently target users with fake delivery messages from carriers. They might convince the user that there’s a problem with the delivery, such as an insufficient address, and direct the user to a fake website to enter personal information. Now with the holiday season well underway, we’re likely to see these attacks continue to increase.
Avoid Unwanted Security ‘Presents’
So, how can consumers prevent hackers from
gaining access to their personal and company apps and data? Like most prevention
tips, awareness is key.
Staying alert is especially important nowadays when mobile users are constantly distracted by other things such as work, family, shopping and the millions of other things that demand our attention while we’re on our phones. The key is to know that these types of attacks are out there and avoid clicking on links sent to your email or phone.
If you get an authentic-looking message from a company you normally do business with, simply take the extra step and go directly to the website without clicking on the link in the message you received. If it’s legit, you’ll see the message on your account, and it will save you the potential risk of handing your credentials or personal information over to hackers.
For mobile-security professionals, now is always a great time to review your mobile security practices to better protect users from these scams. While it’s important to educate mobile employees, it’s up to IT to prevent hackers from getting through to them in the first place. At minimum, mobile security should include the ability to access a phishing URL database to immediately prevent known phishing attempts from coming across text and SMS messages, instant messages, social media and other modes of communication.
While phishing scams will probably always exist in some form, more of our daily life is now taking place on mobile devices, apps and social media. As we gear up for contactless holiday shopping and beyond, that’s where our security focus should be as well.
Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade
detection
18.11.20
Phishing
Securityaffairs
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at
enterprises that is able to detect sandbox solutions and evade detection.
Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting
enterprises, the attacks are able to detect sandbox solutions and evade
detection.
“We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message published by Microsoft via Twitter.
“The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc.”
Threat actors behind the campaign leverage redirector URLs with the capability to detect incoming connections from sandbox environments.
Upon detecting connections for sandboxes the redirector will redirect them to legitimate sites to evade detection, while connections from real potential victims are redirected to phishing pages.
The phishing messages are also heavily obfuscated to bypass secure email gateways.
Microsoft experts also noticed that threat actors behind this campaign are also generating custom subdomains to use with redirector sites for each of the targets.
The subdomains always contain the target’s username and org domain name, Microsoft added.
This subdomain is unique in an attempt to evade detection and attackers add it
to a set of base domains, typically compromised sites. The phishing URLs have an
extra dot after the TLD, which is followed by the Base64-encoded email address
of the recipient.
“The use of custom subdomains helps increase the believability of the lure. In addition, the campaign uses patterns in sender display names consistent with the social engineering lure: “Password Update”, “Exchange proteccion”, “Helpdesk-#”, “SharePoint”, “Projects_communications”.” continues Microsoft in a series of tweets published by its official account.
“The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection.”
Attackers used display name patterns like “Password Update”, “Exchange protection”, “Helpdesk-#”, “SharePoint”, and “Projects_communications” to trick the victims into believing that the messages are from legitimate source and clicking the phishing link embedded within each email.
Microsoft pointed out that its Defender for Office 365 product is able to detect phishing and other email threats and correlates threat data across email and data, endpoints, identities, and apps.
Recently, researchers at WMC Global have spotted a new creative Office 365 phishing campaign that has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by security solutions that scans the web for phishing sites.
In July, experts from Check Point reported that cybercriminals are increasingly leveraging public cloud services such as Google Cloud Services in phishing campaigns against Office 365 users.
Office 365 phishing campaign uses redirector URLs and detects sandboxes to evade
detection
18.11.20
Phishing
Securityaffairs
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at
enterprises that is able to detect sandbox solutions and evade detection.
Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting
enterprises, the attacks are able to detect sandbox solutions and evade
detection.
“We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message published by Microsoft via Twitter.
“The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc.”
Threat actors behind the campaign leverage redirector URLs with the capability to detect incoming connections from sandbox environments.
Upon detecting connections for sandboxes the redirector will redirect them to legitimate sites to evade detection, while connections from real potential victims are redirected to phishing pages.
The phishing messages are also heavily obfuscated to bypass secure email gateways.
Microsoft experts also noticed that threat actors behind this campaign are also generating custom subdomains to use with redirector sites for each of the targets.
The subdomains always contain the target’s username and org domain name, Microsoft added.
One of the interesting techniques we observed in this campaign is the use of redirector sites with a unique subdomain for each target. The subdomain follows different formats but generally always contains the recipient’s username and org domain name. pic.twitter.com/YpUVEfmlUH
— Microsoft Security Intelligence (@MsftSecIntel) November 16, 2020
This
subdomain is unique in an attempt to evade detection and attackers add it to a
set of base domains, typically compromised sites. The phishing URLs have an
extra dot after the TLD, which is followed by the Base64-encoded email address
of the recipient.
This unique subdomain is added to a set of base domains, typically compromised sites. Notably, the phishing URLs have an extra dot after the TLD, followed by the Base64-encoded email address of the recipient.
— Microsoft Security Intelligence (@MsftSecIntel) November 16, 2020
“The use
of custom subdomains helps increase the believability of the lure. In addition,
the campaign uses patterns in sender display names consistent with the social
engineering lure: “Password Update”, “Exchange proteccion”, “Helpdesk-#”,
“SharePoint”, “Projects_communications”.” continues Microsoft in a series of
tweets published by its official account.
“The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection.”
Attackers used display name patterns like “Password Update”, “Exchange protection”, “Helpdesk-#”, “SharePoint”, and “Projects_communications” to trick the victims into believing that the messages are from legitimate source and clicking the phishing link embedded within each email.
Microsoft pointed out that its Defender for Office 365 product is able to detect phishing and other email threats and correlates threat data across email and data, endpoints, identities, and apps.
Recently, researchers at WMC Global have spotted a new creative Office 365 phishing campaign that has been inverting images used as backgrounds for landing pages to avoid getting flagged as malicious by security solutions that scans the web for phishing sites.
In July, experts from Check Point reported that cybercriminals are increasingly leveraging public cloud services such as Google Cloud Services in phishing campaigns against Office 365 users.
Phishing campaign targets LATAM e-commerce users with Chaes Malware
18.11.20
Phishing
Securityaffairs
Experts from Cybereason Nocturnus uncovered an active campaign that targets
users of a large e-commerce platform in Latin America with Chaes malware.
Cybereason Nocturnus security researchers have identified an active campaign
focused on the users of a large e-commerce platform in Latin America.
Experts
at Cybereason Nocturnus have uncovered an active campaign targeting the users of
a large e-commerce platform in Latin America with malware tracked as Chaes.
The Chaes malware was first spotted in the middle to late 2020 by Cybereason
researchers, it is a multistage information stealer that focuses
on Brazilian
customers of MercadoLivre, the largest e-commerce company in Latin America. In
2019, over 320 million users were registered with the MercadoLivre e-commerce
platform.
Chaes is written in several programming languages including Javascript,
Vbscript, .NET , Delphi and Node.js. Experts believe that the malicious code is
under development.
“Chaes specifically targets the Brazilian website of e-commerce company MercadoLivre and its payment page MercadoPago to steal its customers’ financial information. The final payload of Chaes is a Node.Js information stealer that exfiltrates data using the node process.” reads the analysis published by Cybereason.
Chaes is also able to take screenshots of the victim’s machine, and
hook and
monitor the Chrome web browser to collect user information from infected hosts.
The kill chain starts with phishing messages that use a .docx file that once is
opened triggers a template injection attack.
Upon connecting to the
command-and-control server, the malware downloads the first malicious payload in
the form of a .msi file, which deploys a .vbs file used to execute other
processes, as well as uninstall.dll and engine.bin. The malware also installs
three other files, hhc.exe, hha.dll and chaes1.bin, researchers also observed
the use of a cryptocurrency mining module.
The attackers use Microsoft Word’s built-in feature to fetch a payload from a
remote server, by changing the template target of the settings.xml file which is
embedded in the document and populating this field with a download URL of the
next payload.
Chaes attack chain is composed of several stages that include
the use
of LoLbins and other legitimate software to avoid detection by AV
products.
Experts observed several variants over the recent months, it authors have improved encryption and implemented new functionality of the final Node.js module.
“Multistage malware that uses such techniques in the LATAM region and specifically in Brazil have already been observed and investigated by Cybereason in the past years. Chaes demonstrates how sophisticated and creative malware authors in the Latin America region can be when attempting to reach their goals.” concludes the report. “The malware not only serves as a warning sign to information security researchers and IT professionals not to take lightly the existence of files that are legitimate in nature, but also raises the concern of a possible future trend in using the Puppeteer library for further attacks in other major financial institutions”
Spam and phishing in Q3 2020
12.11.20
Phishing Spam
Securelist
Quarterly highlights
Worming their way in: cybercriminal tricks of the trade
These days, many
companies distribute marketing newsletters via online platforms. In terms of
capabilities, such platforms are quite diverse: they send out advertising and
informational messages, harvest statistics (for example, about clicked links in
emails), and the like. At the same time, such services attract both spammers,
who use them to send their own mailings, and cybercriminals, who try to gain
access to user accounts, usually through phishing. As a result, attackers also
get their hands on user-created mailing lists, which allows them to disseminate
mass advertising or phishing messages that filtering systems sometimes let
through.
Accordingly, in Q3 we registered an increase in the number of messages sent
using the Sendgrid platform. A significant portion of them were phishing attacks
aimed at stealing login credentials for major resources. The emails were no
different from traditional phishing, save for the legitimate headers and link to
Sendgrid, which redirected the recipient to a phishing site. To the observant
eye, the address bar and From field would reveal the messages to be fake.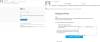
Call me!
In our previous quarterly report, we talked about an increasingly
common scam whereby fraudsters send emails purportedly from large companies with
a request to urgently contact support at the given phone number. Users who
contacted the operator were then asked for information, such as bank card
details, which could then be used to empty their account. The most commonly used
toll-free numbers have specific three-digit prefixes after the country code (for
example: 800, 888, 844).
In Q3 2020, we observed new versions of such schemes warning not only about
unauthorized account access, but about money transactions supposedly made by the
user. The attackers’ calculation is that, on seeing a message about a financial
transaction, the client will grab their phone and dial the support number
highlighted in bold. Such emails do not contain links, and the message itself is
an image, which makes it harder to detect.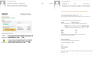
Scammers like such schemes, because sending spam is much cheaper and easier than calling potential victims. To avoid swallowing the bait, either call the support service using the number on the organization’s official website (not the one in the email), or use an app that protects against telephone fraud by checking outgoing call numbers.
COVID-19 and spam topics
Facebook grants
In Q3 2020, many users of social
networks and messengers saw a screenshot with some interesting news: CNBC, it
said (in broken English — always a red flag), had reported that Facebook was
paying out compensation to victims of COVID-19. To get yours, all you had to do
was follow the link and fill out a number of documents.
The link had nothing to do with Facebook and led to a fake page resembling the website of Mercy Corps, an organization dedicated to helping victims of natural disasters and armed conflict. To apply, you had to enter your Facebook username and password, then verify your identity by providing personal information, including SSN (social security number, issued to US citizens). This last detail suggests that the attack was aimed at US residents. Users that entered all the requested data gave the cybercriminals not only access to their social network account, but also personal information that could then be used for identity theft or bank card fraud.
It should be noted that the scheme was based on official news that Facebook was indeed ready to provide support to victims of COVID-19. But it only concerned grants for companies, not individuals.
Tourist phishing
The coronavirus pandemic — which has decimated the tourist
trade — has also had an effect on scammers: this quarter saw fewer emails
offering attractive summer breaks than usual. However, the pandemic did not stop
scammers, only redirected their attention.
In Q3, Airbnb and Expedia Group users were the most frequent targets of phishing attacks. Fake pages hungry for user credentials were very faithful to the design of the official websites, distinguishable only by looking closely at the address bar, where most often the domain was unrelated to the target company or belonged to a free hosting service.
So as not to reveal their cards too soon, scammers use URL-shortening services
and distribute messages in social networks and messengers where shortened links
look organic. In their messages, scammers offer cheap tickets or bargain hotel
deals. And it is impossible to know where such links lead before clicking them,
which is what attackers play upon. Accounts stolen in this way can be used, for
example, for money laundering.
Phishers also forged pages with rental offers: visitors could view photos of apartments and read detailed information about the alleged terms and conditions. Lower down the page were rave reviews from past clients intended to lull the victim into a false sense of security.
The “landlord” in each case agreed to rent out the apartment, but asked for an
advance payment. And then disappeared as soon as the money was deposited,
together with the fake page. In this instance, the cybercriminals also banked on
the fact that the juicy offer (low price, big discount) would distract the
victim from looking at the URL and checking the information on the site.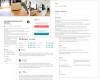
Attacks on the corporate sector
Malicious mail
We already told about the
distribution of malicious files disguised as notifications from delivery
services. They continued this quarter as well: we uncovered a mailing targeting
employees connected to sales in some capacity. The scammers persuaded recipients
to open the attached documents supposedly to pay customs duties for the import
of goods. Instead of documents, the attachment contained
Backdoor.MSIL.Crysan.gen.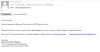
Malicious mailings with “reminders” about online meetups are worth a separate
mention. For example, one of them asked the recipient to join a Zoom conference
by clicking the attached link. Instead of a meeting, the user ended up on a
WeTransfer phishing page. If the user fell for the trap and entered their
WeTransfer credentials, the attackers gained access to the company’s files
stored in this cloud.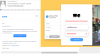
Another mailing informed users that a Microsoft SharePoint document had been
shared with them. After clicking the link, the victim was taken to a fake
Microsoft login page that helped cybercriminals steal account usernames and
passwords.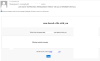
Far more dangerous were meeting notifications containing malicious files. For
example, the at-first-glance harmless message below contained
HEUR:Trojan-Downloader.Script.Generic.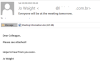
And Trojan-Banker.Win32.ClipBanker, downloaded via the link in the email below,
is used to steal financial (including cryptocurrency-related) information.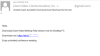
Mail scanner
To gain access to corporate accounts, cybercriminals distributed
messages stating that a virus had been found in the recipient’s mailbox, and
advising an urgent scan, otherwise the account would be disabled. The messages,
disguised as notifications from infosec companies, were sent from a free mail
address and employed neutral names like Email Security Team to avoid unnecessary
specifics.
The cybercriminals reckoned on the combined threat of a computer virus and a deactivated work email account forcing the recipient to ignore some of the oddities of the message. For example, such emails could be from the company’s IT or security department, but not a third party. The page that opened on clicking the link did not resemble a corporate resource by either its address or layout. Plus, for added believability, the cybervillains placed on it the logos of all major infosec companies.
To start a “virus scan”, the user was asked to enter the username and password
for their corporate mailbox. That said, the “scan” started even if arbitrary
credentials were entered in the fields: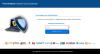
Statistics: spam
Proportion of spam in mail traffic
Proportion of spam in global mail traffic, Q2 2020 – Q3 2020 (download)
In Q3 2020, the largest share of spam was recorded in August (50.07%). The average share of spam in global mail traffic was 48.91%, down 1.27 p.p. against the previous reporting period.
Sources of spam by country
Sources of spam by country, Q3 2020 (download)
The Top 5 countries by amount of outgoing spam remained the same as in the previous quarter. Only their shares changed. The biggest increase came from Russia, which ranked first, jumping by 5 p.p. to 23.52%. The shares of the remaining top-fivers did not fluctuate by more than one percentage point. Second-place Germany gained 11.01%, the US in third picked up 10.85%, France 6.69%, and China in fifth 6.33%.
The bottom half of the Top 10 changed more significantly. For instance, it said goodbye to Turkey, which this time took 11th place (1.73%). Sixth place was taken by the Netherlands (3.89%), seventh by Brazil (3.26%), eighth by Spain (2.52%), ninth by Japan (2.30%), and Poland (1.80%) rounds out the Top 10, up one position on last quarter.
Spam email size
Spam email size, Q2 2020 – Q3 2020 (download)
The downward trend in the number of very small emails continued in Q3 2020; their share decreased significantly — by 13.21 p.p. to 38.09%. The share of emails sized 20–50 KB grew by 12.45 p.p. to 28.20% of the total number of registered spam emails. But the number of emails 10–20 KB in size fell to 8.31% (–2.78 p.p.). Also lower was the share of spam messages sized 100–200 KB; this time their share was 1.57%.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q2 2020 – Q3 2020 (download)
Throughout Q3 2020, our security solutions detected a total of 51,025,889
malicious email attachments, which is almost 8 million more than in the previous
reporting period.
Top 10 malicious attachments in mail traffic, Q3 2020 (download)
The most widespread malware in Q3 mail traffic was assigned the verdict
Trojan-PSW.MSIL.Agensla.gen (8.44%). In second place was
Exploit.MSOffice.CVE-2017-11882.gen (5.67%), while Trojan.MSOffice.SAgent.gen
(4.85%) came third.
Top 10 malware families in mail traffic, Q3 2020 (download)
This quarter’s most widespread malware family was Trojan-PSW.MSIL.Agensla (12.67%), having ranked second in the last reporting period. While last quarter’s leader Trojan.Win32.Agentb finished second (8.78%). Third place, as in the previous quarter, went to Exploit.MSOffice.CVE-2017-11882 (8.03%).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q3 2020 (download)
Since the beginning of the year, Spain has led the way by number of Mail Anti-Virus triggerings. In Q3, users in this country accounted for 7.76% of attacks. In second place this time was Germany (7.05%), knocking Russia (5.87%) into third.
Statistics: phishing
In Q3 2020, the Anti-Phishing system prevented
103,060,725 attempts to redirect users to fake pages, which is almost 3.2
million fewer than in Q2. The share of unique attacked users amounted to 7.67%
of the total number of users of Kaspersky products
Attack geography
This time, the country with the largest proportion of users
attacked by phishers was Mongolia (15.54%).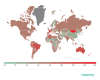
Geography of phishing attacks, Q3 2020 (download)
Israel (15.24%) lies close behind in second place, with France (12.57%) this time in third.
Top-level domains
The most popular top-level domain with phishers this
quarter, as before, was COM (40.09% of the total number of top-level domains
used in attacks). Silver went to XYZ (5.84%), and bronze to NET (3.00%). RU
finished in fourth place (2.93%), and BUZZ in fifth (2.57%).
Top-level domains most popular with phishers, Q3 2020 (download)
Organizations under attack
The rating of attacks by phishers on different
categories of organizations is based on detections by the Kaspersky
Anti-Phishing component. This component detects pages with phishing content that
the user tried to access by following email or web links, regardless of how the
user got to the page: by clicking a link in a phishing email or in a message on
a social network, or after being redirected by a malicious program. When the
component is triggered, a banner is displayed in the browser warning the user
about a potential threat.
As before, the Online Stores category absorbed the most phishing attacks,
despite its share dropping slightly against Q2 2020 (by 0.20 p.p.) to 19.22%.
Global Web Portals (14.48%) in second position and Banks (10.89%) in third were
also non-movers.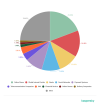
Distribution of organizations subjected to phishing attacks by category, Q3 2020 (download)
Conclusion
The COVID-19 topic, which appeared in Q1 this year, is still in
play for spammers and phishers. In our view, the so-called second wave could
lead to a surge in mailings offering various coronavirus-related treatments.
Moreover, against the backdrop of the worsening economic situation, we could see
a rise in the number of scam mailings promising a big payout in exchange for a
small upfront sum.
The average share of spam in global mail traffic (48.91%) this quarter decreased by 1.27 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 103 million.
First place in the list of spam-source countries in Q3 again went to Russia, with a share of 23.52%. Our security solutions blocked 51,025,889 malicious attachments; the most popular malware family in spam mailings was Trojan-PSW.MSIL.Agensla, with a 12.67% share of mail traffic.
Creative Office 365 phishing inverts images to avoid detection bots
9.11.20
Phishing
Securityaffairs
Experts spotted a creative Office 365 phishing campaign that inverts images used
as backgrounds for landing pages to avoid getting flagged as malicious.
Researchers at WMC Global have spotted a new creative Office 365 phishing
campaign that has been inverting images used as backgrounds for landing pages to
avoid getting flagged as malicious by security solutions that scans the web for
phishing sites.
The bot avoidance mechanism has been deployed on multiple phishing websites designed to steal Office 365 credentials.
WMC Global researchers observed this technique was implemented in a phishing kit developed by a threat actor that is selling it to multiple users.
“Because image recognition software is improving and becoming more accurate,
this new technique aims to deceive scanning engines by inverting the colors of
the image, causing the image hash to differ from the original. This technique
can hinder the software’s ability to flag this image altogether.” reads the
analysis published by WMC Global. 

The phishing kit that use this trick automatically reverts the backgrounds using
Cascading Style Sheets (CSS) to make them look just like the backgrounds of
legitimate Office 365 login pages.
While phishing detection web crawlers are served the inverted image, the
potential victims are redirected to one of these phishing landing pages that
will see the original background instead of the inverted one.
Summarizing,
the phishing kit displays different versions of the same phishing landing page
to victims and scanning engines.
“However, a victim visiting the website would likely recognize that the inverted picture is illegitimate and exit the website. As a result, the threat actor has stored the inverted image and, within the index.php code, has used a CSS method to revert the color of the image to its original state.” continues the analysis. “This approach results in the final website’s appearing legitimate to users who visit, while crawlers and scanning engines are highly unlikely to detect the image as being an inverted copy of the Office 365 background.”
Recently experts observed other phishing campaigns aimed at Office 365 users that were using innovative techniques, such as leveraging public cloud services Google Cloud Services to host the phishing landing pages.