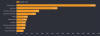
Ransom
2024 2023
2022
2021
2020
FBI Takes Down BlackCat Ransomware, Releases Free Decryption Tool
21.12.23
Ransom
The Hacker News
The U.S. Justice Department (DoJ) has officially announced the disruption of the
BlackCat ransomware operation and released a decryption tool that more than 500
affected victims can use to regain access to files locked by the malware.
Court documents show that the U.S. Federal Bureau of Investigation (FBI)
enlisted the help of a confidential human source (CHS) to act as an affiliate
for the BlackCat group and gain access to a web panel used for managing the
gang's victims, in what's a case of hacking the hackers.
The confiscation effort involved collaboration and assistance from multiple law
enforcement agencies from the U.S., Germany, Denmark, Australia, the U.K.,
Spain, Switzerland, and Austria.
BlackCat, also called ALPHV, GOLD BLAZER, and Noberus, first emerged in December
2021 and has since gone on to be the second most prolific
ransomware-as-a-service variant in the world after LockBit. It's also the first
Rust-language-based ransomware strain spotted in the wild.
The development puts an end to speculations of a rumored law enforcement action
after its dark web leak portal went offline on December 7, only to resurface
five days later with just a single victim.
The FBI said it worked with dozens of victims in the U.S. to implement the
decryptor, saving them from ransom demands totaling about $68 million, and that
it also gained insight into the ransomware's computer network, allowing it to
collect 946 public/private key pairs used to host the TOR sites operated by the
group and dismantle them.
One important thing to note here is that creating a hidden service with the
.onion URL on the TOR anonymization network generates a unique key pair
comprising a private and public key (aka the identifier) that can be used to
access and control the URL.
An actor who is in possession of the key pair can, therefore, broadcast a new
route redirecting traffic for the .onion site to a different server under their
control.
BlackCat, like several other ransomware gangs, uses a ransomware-as-a-service
model involving a mix of core developers and affiliates, who rent out the
payload and are responsible for identifying and attacking high-value victim
institutions.
It also employs the double extortion scheme to put pressure on victims to pay up
by exfiltrating sensitive data prior to encryption.
"BlackCat affiliates have gained initial access to victim networks through a
number of methods, including leveraging compromised user credentials to gain
initial access to the victim system," the DoJ said.
In all, the financially motivated actor is estimated to have compromised the
networks of more than 1,000 victims across the world to earn nearly $300 million
in illegal revenues as of September 2023.

Image Source: Resecurity
If anything, the takedown has proven to be a
blessing in disguise for rival groups like LockBit, which is already
capitalizing on the situation by actively recruiting displaced affiliates,
offering its data leak site to resume victim negotiations.
Speaking to malware research group vx-underground, a BlackCat spokesperson said
"they have moved their servers and blogs," claiming that the law enforcement
agencies only had access to a "stupid old key" for the old blog site which was
deleted by the group a long time ago and has since not been used.
The threat actor's newest leak website remains operational as of writing. "On
December 13, the group published the first victim to its new leak site,"
Secureworks said. "As of December 19, five victims were posted to the new site,
demonstrating the group retained some operational capacity."
However, hours after the takedown, the BlackCat group took steps to "unseize"
the main leak site using the same set of cryptographic keys necessary to host
the hidden service on the TOR network and post its own seizure notice.
It has also given affiliates the green light to infiltrate critical
infrastructure entities such as hospitals and nuclear power plants as well as
other targets with the exception of those inside the Commonwealth of Independent
States (CIS) as a retaliatory measure. The FBI has since re-seized the website.
"The threats seem like 'now you've done it' posturing but, this group has a
documented history of attacking healthcare and energy infrastructure targets
already, so it feels like bluster," Secureworks Counter Threat Unit (CTU) told
The Hacker News.
"Given that such activity appears more likely to bring law enforcement attention
– which is why many groups explicitly avoid it – it seems unlikely that
affiliates will choose to specifically target such organizations, especially as
ransomware is a crime of opportunity for the most part and based on available
access to victim networks."
"That said, some less risk averse affiliates may be more willing to target
energy and healthcare organizations. The flip side is that it is just as likely
that the uncertainty caused by the law enforcement disruption will drive
affiliates away from BlackCat into the arms of other ransomware operators, such
as LockBit. Such interventions breed distrust and paranoia among ransomware
group members and affiliates."
In a conversation with vx-underground, a LockBit administrator described the
situation as "unfortunate" and that security loopholes in their infrastructure
are a primary threat to "my business."
Behind the Scenes of Matveev's Ransomware Empire: Tactics and Team
19.12.23
Ransom
The Hacker News

Cybersecurity researchers have shed light on the inner workings of the
ransomware operation led by Mikhail Pavlovich Matveev, a Russian national who
was indicted by the U.S. government earlier this year for his alleged role in
launching thousands of attacks across the world.
Matveev, who resides in Saint Petersburg and is known by the aliases Wazawaka,
m1x, Boriselcin, Uhodiransomwar, Orange, and waza, is alleged to have played a
crucial part in the development and deployment of LockBit, Babuk, and Hive
ransomware variants since at least June 2020.
"Wazawaka and his team members prominently exhibit an insatiable greed for
ransom payments, demonstrating a significant disregard for ethical values in
their cyber operations," Swiss cybersecurity firm PRODAFT said in a
comprehensive analysis shared with The Hacker News.
"Employing tactics that involve intimidation through threats to leak sensitive
files, engaging in dishonest practices, and persisting in retaining files even
after the victim complies with the ransom payment, they exemplify the ethical
void prevalent in the practices of traditional ransomware groups."
PRODAFT's findings are the result of data compiled between April and December
2023 by intercepting thousands of communication logs between various threat
actors affiliated with various ransomware variants.
Matawveev is said to lead a team of six penetration testers – 777, bobr.kurwa,
krbtgt, shokoladniy_zayac, WhyNot, and dushnila – to execute the attacks. The
group has a flat hierarchy, fostering better collaboration between the members.

"Each individual contributes resources and expertise as needed, showcasing a
remarkable level of flexibility in adapting to new scenarios and situations,"
PRODAFT said.
Matveev, besides working as an affiliate for Conti, LockBit, Hive, Monti,
Trigona, and NoEscape, also had a management-level role with the Babuk
ransomware group up until early 2022, while sharing what's being described as a
"complex relationship" with another actor named Dudka, who is likely the
developer behind Babuk and Monti.

Attacks mounted by Matveev and his team involve the use of Zoominfo and services
like Censys, Shodan, and FOFA to gather information about the victims, relying
on known security flaws and initial access brokers for obtaining a foothold, in
addition to using a mix of custom and off-the-shelf tools to brute-force VPN
accounts, escalate privileges, and streamline their campaigns.
"Following the attainment of initial access, Wazawaka and his team primarily
employ PowerShell commands to execute their preferred Remote Monitoring and
Management (RMM) tool," the company said. "Distinctively, MeshCentral stands out
as the team's unique toolkit, frequently utilized as their preferred open-source
software for various operations."
PRODAFT's analysis further uncovered connections between Matveev and Evgeniy
Mikhailovich Bogachev, a Russian national linked to the development of the
GameOver Zeus botnet, which was dismantled in 2014, and Evil Corp.
It's worth noting that the Babuk ransomware operations rebranded as PayloadBIN
in 2021, with the latter tied to Evil Corp in an apparent effort to get around
sanctions imposed against it by the U.S. in December 2019.
"This technical association, coupled with the known relationship between
Wazawaka and the notorious cybercriminal Bogachev, suggests deeper connections
among Wazawaka, Bogachev, and the operations of Evil Corp," PRODAFT said.
Double-Extortion Play Ransomware Strikes 300 Organizations Worldwide
19.12.23
Ransom
The Hacker News
The threat actors behind the Play ransomware are
estimated to have impacted approximately 300 entities as of October 2023,
according to a new joint cybersecurity advisory from Australia and the U.S.
"Play ransomware actors employ a double-extortion model, encrypting systems
after exfiltrating data and have impacted a wide range of businesses and
critical infrastructure organizations in North America, South America, Europe,
and Australia," authorities said.
Also called Balloonfly and PlayCrypt, Play emerged in 2022, exploiting security
flaws in Microsoft Exchange servers (CVE-2022-41040 and CVE-2022-41082) and
Fortinet appliances (CVE-2018-13379 and CVE-2020-12812) to breach enterprises
and deploy file-encrypting malware.
It's worth pointing out that ransomware attacks are increasingly exploiting
vulnerabilities rather than using phishing emails as initial infection vectors,
jumping from nearly zero in the second half of 2022 to almost a third in the
first half of 2023, per data from Corvus.
Cybersecurity firm Adlumin, in a report published last month, revealed that Play
is being offered to other threat actors "as a service," completing its
transformation into a ransomware-as-a-service (RaaS) operation.
Ransomware attacks orchestrated by the group are characterized by the use of
public and bespoke tools like AdFind to run Active Directory queries, GMER,
IOBit, and PowerTool to disable antivirus software, and Grixba to enumerate
network information and for collecting information about backup software and
remote administration tools installed on a machine.
The threat actors have also been observed to carry out lateral movement and data
exfiltration and encryption steps, banking on Cobalt Strike, SystemBC, and
Mimikatz for post-exploitation.
"The Play ransomware group uses a double-extortion model, encrypting systems
after exfiltrating data," the agencies said. "Ransom notes do not include an
initial ransom demand or payment instructions, rather, victims are instructed to
contact the threat actors via email."
According to statistics compiled by Malwarebytes, Play is said to have claimed
nearly 40 victims in November 2023 alone, but significantly trailing behind its
peers LockBit and BlackCat (aka ALPHV and Noberus).
The alert comes days after U.S. government agencies released an updated bulletin
about the Karakurt group, which is known to eschew encryption-based attacks in
favor of pure extortion after obtaining initial access to networks via
purchasing stolen login credentials, intrusion brokers (aka initial access
brokers), phishing, and known security flaws.
"Karakurt victims have not reported encryption of compromised machines or files;
rather, Karakurt actors have claimed to steal data and threatened to auction it
off or release it to the public unless they receive payment of the demanded
ransom," the government said.
The developments also come amid speculations that the BlackCat ransomware may
have been a target of a law enforcement operation after its dark web leak
portals went offline for five days. However, the e-crime collective pinned the
outage on a hardware failure.
What's more, another nascent ransomware group known as NoEscape is alleged to
have pulled an exit scam, effectively "stealing the ransom payments and closing
down the group's web panels and data leak sites," prompting other gangs like
LockBit to recruit their former affiliates.
That the ransomware landscape is constantly evolving and shifting, whether be it
due to external pressure from law enforcement, is hardly surprising. This is
further evidenced by the collaboration between the BianLian, White Rabbit, and
Mario ransomware gangs in a joint extortion campaign targeting publicly traded
financial services firms.
"These cooperative ransom campaigns are rare, but are possibly becoming more
common due to the involvement of initial access brokers (IABs) collaborating
with multiple groups on the dark web," Resecurity said in a report published
last week.
"Another factor that may be leading to greater collaboration are law enforcement
interventions that create cybercriminal diaspora networks. Displaced
participants of these threat actor networks may be more willing to collaborate
with rivals."
Microsoft Warns of Malvertising Scheme Spreading CACTUS Ransomware
4.12.23
Ransom
The Hacker News
Microsoft has warned of a new wave of CACTUS ransomware attacks that leverage
malvertising lures to deploy DanaBot as an initial access vector.
The DanaBot infections led to "hands-on-keyboard activity by ransomware operator
Storm-0216 (Twisted Spider, UNC2198), culminating in the deployment of CACTUS
ransomware," the Microsoft Threat Intelligence team said in a series of posts on
X (formerly Twitter).
DanaBot, tracked by the tech giant as Storm-1044, is a multi-functional tool
along the lines of Emotet, TrickBot, QakBot, and IcedID that's capable of acting
as a stealer and a point of entry for next-stage payloads.
UNC2198, for its part, has been previously observed infecting endpoints with
IcedID to deploy ransomware families such as Maze and Egregor, as detailed by
Google-owned Mandiant in February 2021.
Per Microsoft, the threat actor has also taken advantage of initial access
provided by QakBot infections. The change to DanaBot is likely the result of a
coordinated law enforcement operation in August 2023 that took down QakBot's
infrastructure.
"The current Danabot campaign, first observed in November, appears to be using a
private version of the info-stealing malware instead of the malware-as-a-service
offering," Redmond further noted.
The credentials harvested by the malware are transmitted to an actor-controlled
server, which is followed by lateral movement via RDP sign-in attempts and
ultimately handing off access to Storm-0216.
The disclosure comes days after Arctic Wolf revealed another set of CACTUS
ransomware attacks that are actively exploiting critical vulnerabilities in a
data analytics platform called Qlik Sense to gain access to corporate networks.
It also follows the discovery of a new macOS ransomware strain dubbed Turtle
that's written in the Go programming language and is signed with an adhoc
signature, thereby preventing it from being executed upon launch due to
Gatekeeper protections.
CACTUS Ransomware Exploits Qlik Sense Vulnerabilities in Targeted Attacks
30.11.23
Ransom
The Hacker News
A CACTUS ransomware campaign has been observed exploiting
recently disclosed security flaws in a cloud analytics and business intelligence
platform called Qlik Sense to obtain a foothold into targeted environments.
"This campaign marks the first documented instance [...] where threat actors
deploying CACTUS ransomware have exploited vulnerabilities in Qlik Sense for
initial access," Arctic Wolf researchers Stefan Hostetler, Markus Neis, and Kyle
Pagelow said.
The cybersecurity company, which said it's responding to "several instances" of
exploitation of the software, noted that the attacks are likely taking advantage
of three flaws that have been disclosed over the past three months -
CVE-2023-41265 (CVSS score: 9.9) - An HTTP Request Tunneling vulnerability that
allows a remote attacker to elevate their privilege and send requests that get
executed by the backend server hosting the repository application.
CVE-2023-41266 (CVSS score: 6.5) - A path traversal vulnerability that allows an
unauthenticated remote attacker to transmit HTTP requests to unauthorized
endpoints.
CVE-2023-48365 (CVSS score: 9.9) - An unauthenticated remote code
execution vulnerability arising due to improper validation of HTTP headers,
allowing a remote attacker to elevate their privilege by tunneling HTTP
requests.
It's worth noting that CVE-2023-48365 is the result of an
incomplete patch for CVE-2023-41265, which along with CVE-2023-41266, was
disclosed by Praetorian in late August 2023. A fix for CVE-2023-48365 was
shipped on November 20, 2023.
In the attacks observed by Arctic Wolf, a successful exploitation of the flaws
is followed by the abuse of the Qlik Sense Scheduler service to spawn processes
that are designed to download additional tools with the goal of establishing
persistence and setting up remote control.
This includes ManageEngine Unified Endpoint Management and Security (UEMS),
AnyDesk, and Plink. The threat actors have also been observed uninstalling
Sophos software, changing the administrator account password, and creating an
RDP tunnel via Plink.
The attack chains culminate in the deployment of CACTUS ransomware, with the
attackers also using rclone for data exfiltration.
The Ever-Evolving Ransomware Landscape#
The disclosure comes as the
ransomware threat landscape has become more sophisticated, and the underground
economy has evolved to facilitate attacks at scale via a network of initial
access brokers and botnet owners who resell access to victim systems to several
affiliate actors.
According to data compiled by industrial cybersecurity firm Dragos, the number
of ransomware attacks impacting industrial organizations declined from 253 in
the second quarter of 2023 to 231 in the third quarter. In contrast, 318
ransomware attacks were reported across all sectors for the month of October
2023 alone.
Despite ongoing efforts by governments across the world to tackle ransomware,
the ransomware-as-a-service (RaaS) business model has continued to be an
enduring and lucrative pathway to extort money from targets.
Black Basta, a prolific ransomware group that came onto the scene in April 2022,
is estimated to have raked in illegal profits to the tune of at least $107
million in Bitcoin ransom payments from more than 90 victims, per new joint
research released by Elliptic and Corvus Insurance.
A majority of these proceeds were laundered through Garantex, a Russian
cryptocurrency exchange that was sanctioned by the U.S. government in April 2022
for facilitating transactions with the Hydra darknet marketplace.
What's more, the analysis uncovered evidence tying Black Basta to the
now-defunct Russian cybercrime group Conti, which discontinued around the same
time the former emerged, as well as QakBot, which was used to deploy the
ransomware.
"Approximately 10% of the ransom amount was forwarded on to Qakbot, in cases
where they were involved in providing access to the victim," Elliptic noted,
adding it "traced Bitcoin worth several million dollars from Conti-linked
wallets to those associated with the Black Basta operator."
DJVU Ransomware's Latest Variant 'Xaro' Disguised as Cracked Software
29.11.23
Ransom
The Hacker News
A variant of a ransomware strain known as DJVU has been
observed to be distributed in the form of cracked software.
"While this attack pattern is not new, incidents involving a DJVU variant that
appends the .xaro extension to affected files and demanding ransom for a
decryptor have been observed infecting systems alongside a host of various
commodity loaders and infostealers," Cybereason security researcher Ralph
Villanueva said.
The new variant has been codenamed Xaro by the American cybersecurity firm.
DJVU, in itself a variant of the STOP ransomware, typically arrives on the scene
masquerading as legitimate services or applications. It's also delivered as a
payload of SmokeLoader.
A significant aspect of DJVU attacks is the deployment of additional malware,
such as information stealers (e.g., RedLine Stealer and Vidar), making them more
damaging in nature.
In the latest attack chain documented by Cybereason, Xaro is propagated as an
archive file from a dubious source that masquerades as a site offering
legitimate freeware.
Opening the archive file leads to the execution of a supposed installer binary
for a PDF writing software called CutePDF that, in reality, is a pay-per-install
malware downloader service known as PrivateLoader.
PrivateLoader, for its part, establishes contact with a command-and-control (C2)
server to fetch a wide range of stealer and loader malware families like RedLine
Stealer, Vidar, Lumma Stealer, Amadey, SmokeLoader, Nymaim, GCleaner, XMRig, and
Fabookie, in addition to dropping Xaro.
"This shotgun-approach to the download and execution of commodity malware is
commonly observed in PrivateLoader infections originating from suspicious
freeware or cracked software sites," Villanueva explained.
The goal appears to be to gather and exfiltrate sensitive information for double
extortion as well as ensure the success of the attack even if one of the
payloads gets blocked by security software.
Xaro, besides spawning an instance of the Vidar infostealer, is capable of
encrypting files in the infected host, before dropping a ransom note, urging the
victim to get in touch with the threat actor to pay $980 for the private key and
the decryptor tool, a price that drops by 50% to $490 if approached within 72
hours.
If anything, the activity illustrates the risks involved with downloading
freeware from untrusted sources. Last month, Sucuri detailed another campaign
called FakeUpdateRU wherein visitors to compromised websites are served bogus
browser update notices to deliver RedLine Stealer.
"Threat actors are known to favor freeware masquerading as a way to covertly
deploy malicious code," Villanueva said. "The speed and breadth of impact on
infected machines should be carefully understood by enterprise networks looking
to defend themselves and their data."
Key Cybercriminals Behind Notorious Ransomware Families Arrested in Ukraine
28.11.23
Ransom
The Hacker News
A coordinated law enforcement operation has led to the arrest of key individuals
in Ukraine who are alleged to be a part of several ransomware schemes.
"On 21 November, 30 properties were searched in the regions of Kyiv, Cherkasy,
Rivne, and Vinnytsia, resulting in the arrest of the 32-year-old ringleader,"
Europol said in a statement today. "Four of the ringleader's most active
accomplices were also detained."
The development comes more than two years after 12 people were apprehended in
connection with the same operation. The individuals are primarily linked to
LockerGoga, MegaCortex, and Dharma ransomware families.
The suspects are estimated to have targeted over 1,800 victims across 71
countries since 2019. They have also been accused of deploying the now-defunct
Hive ransomware against high-profile organizations.
Some of the co-conspirators are believed to be involved in penetrating IT
networks by orchestrating brute-force attacks, SQL injections, and sending
phishing emails bearing malicious attachments in order to steal usernames and
passwords.
Following a successful compromise, the attackers stealthily moved within the
networks, while dropping additional malware and post-exploitation tools such as
TrickBot, Cobalt Strike, and PowerShell Empire to ultimately drop the
file-encrypting malware.
The other members of the cybercrime network are suspected to be in charge of
laundering cryptocurrency payments made by victims to decrypt their files.
"The investigation determined that the perpetrators encrypted over 250 servers
belonging to large corporations, resulting in losses exceeding several hundreds
of millions of euros," Europol said.
The collaborative effort involved authorities from France, Germany, the
Netherlands, Norway, Switzerland, Ukraine, and the U.S.
The disclosure comes less than two weeks after Europol and Eurojust announced
the takedown of a prolific voice phishing gang by Czech and Ukrainian police
that's believed to have netted millions in illegal profits by tricking victims
into transferring funds from their 'compromised' bank accounts to 'safe' bank
accounts under their control.
It also arrives a month after Europol revealed that law enforcement and judicial
authorities from eleven countries dismantled the infrastructure associated with
Ragnar Locker ransomware and arrested a "key target" in France.
LockBit Ransomware Exploiting Critical Citrix Bleed Vulnerability to Break In
22.11.23
Ransom
The Hacker News
Multiple threat actors, including LockBit ransomware
affiliates, are actively exploiting a recently disclosed critical security flaw
in Citrix NetScaler application delivery control (ADC) and Gateway appliances to
obtain initial access to target environments.
The joint advisory comes from the U.S. Cybersecurity and Infrastructure Security
Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information
Sharing and Analysis Center (MS-ISAC), and Australian Signals Directorate's
Australian Cyber Security Center (ASD's ACSC).
"Citrix Bleed, known to be leveraged by LockBit 3.0 affiliates, allows threat
actors to bypass password requirements and multifactor authentication (MFA),
leading to successful session hijacking of legitimate user sessions on Citrix
NetScaler web application delivery control (ADC) and Gateway appliances," the
agencies said.
"Through the takeover of legitimate user sessions, malicious actors acquire
elevated permissions to harvest credentials, move laterally, and access data and
resources."
Tracked as CVE-2023-4966 (CVSS score: 9.4), the vulnerability was addressed by
Citrix last month but not before it was weaponized as a zero-day, at least since
August 2023. It has been codenamed Citrix Bleed.
Shortly after the public disclosure, Google-owned Mandiant revealed it's
tracking four different uncategorized (UNC) groups involved in exploiting
CVE-2023-4966 to target several industry verticals in the Americas, EMEA, and
APJ.
The latest threat actor to join the exploitation bandwagon is LockBit, which has
been observed taking advantage of the flaw to execute PowerShell scripts as well
as drop remote management and monitoring (RMM) tools like AnyDesk and Splashtop
for follow-on activities.
The development once again underscores the fact that vulnerabilities in exposed
services continue to be a primary entry vector for ransomware attacks.
The disclosure comes as Check Point released a comparative study of ransomware
attacks targeting Windows and Linux, noting that a majority of the families that
break into Linux heavily utilize the OpenSSL library along with ChaCha20/RSA and
AES/RSA algorithms.
"Linux ransomware is clearly aimed at medium and large organizations compared to
Windows threats, which are much more general in nature," security researcher
Marc Salinas Fernandez said.
The examination of various Linux-targeting ransomware families "reveals an
interesting trend towards simplification, where their core functionalities are
often reduced to just basic encryption processes, thereby leaving the rest of
the work to scripts and legitimate system tools."
Check Point said the minimalist approach not only renders these ransomware
families heavily reliant on external configurations and scripts but also makes
them more easier to fly under the radar.
Play Ransomware Goes Commercial - Now Offered as a Service to Cybercriminals
22.11.23
Ransom
The Hacker News
The ransomware strain known as Play is now being offered to other threat actors
"as a service," new evidence unearthed by Adlumin has revealed.
"The unusual lack of even small variations between attacks suggests that they
are being carried out by affiliates who have purchased the
ransomware-as-a-service (RaaS) and are following step-by-step instructions from
playbooks delivered with it," the cybersecurity company said in a report shared
with The Hacker News.
The findings are based on various Play ransomware attacks tracked by Adlumin
spanning different sectors that incorporated almost identical tactics and in the
same sequence.
This includes the use of the public music folder (C:\...\public\music) to hide
the malicious file, the same password to create high-privilege accounts, and
both attacks, and the same commands.
Play, also called Balloonfly and PlayCrypt, first came to light in June 2022,
leveraging security flaws in Microsoft Exchange Server – i.e., ProxyNotShell and
OWASSRF – to infiltrate networks and drop remote administration tools like
AnyDesk and ultimately deploy the ransomware.
Besides using custom data gathering tools like Grixba for double extortion, a
notable aspect that set Play apart from other ransomware groups was the fact
that the operators in charge of developing the malware also carried out the
attacks.
The new development, therefore, marks a shift and completes its transformation
into a RaaS operation, making it a lucrative option for cybercriminals.
"When RaaS operators advertise ransomware kits that come with everything a
hacker will need, including documentation, forums, technical support, and ransom
negotiation support, script kiddies will be tempted to try their luck and put
their skills to use," Adlumin said.
"And since there are probably more script kiddies than 'real hackers' today,
businesses and authorities should take note and prepare for a growing wave of
incidents."
CISA and FBI Issue Warning About Rhysida Ransomware Double Extortion Attacks
16.11.23
Ransom
The Hacker News
The threat actors behind the Rhysida ransomware engage in
opportunistic attacks targeting organizations spanning various industry sectors.
The advisory comes courtesy of the U.S. Cybersecurity and Infrastructure
Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the
Multi-State Information Sharing and Analysis Center (MS-ISAC).
"Observed as a ransomware-as-a-service (RaaS) model, Rhysida actors have
compromised organizations in education, manufacturing, information technology,
and government sectors and any ransom paid is split between the group and
affiliates," the agencies said.
"Rhysida actors leverage external-facing remote services, such as virtual
private networks (VPNs), Zerologon vulnerability (CVE-2020-1472), and phishing
campaigns to gain initial access and persistence within a network."
First detected in May 2023, Rhysida makes use of the time-tested tactic of
double extortion, demanding a ransom payment to decrypt victim data and
threatening to publish the exfiltrated data unless the ransom is paid.
It's also said to share overlaps with another ransomware crew known as Vice
Society (aka Storm-0832 or Vanilla Tempest), owing to similar targeting patterns
and the use of NTDSUtil as well as PortStarter, which has been exclusively
employed by the latter.
According to statistics compiled by Malwarebytes, Rhysida has claimed five
victims for the month of October 2023, putting it far behind LockBit (64),
NoEscape (40), PLAY (36), ALPHV/BlackCat (29), and 8BASE (21).
The agencies described the group as engaging in opportunistic attacks to breach
targets and taking advantage of living-off-the-land (LotL) techniques to
facilitate lateral movement and establish VPN access.
In doing so, the idea is to evade detection by blending in with legitimate
Windows systems and network activities.
Vice Society's pivot to Rhysida has been bolstered in the wake of new research
published by Sophos earlier last week, which said it observed the same threat
actor using Vice Society up until June 2023, when it switched to deploying
Rhysida.
The cybersecurity company is tracking the cluster under the name TAC5279.

"Notably, according to the ransomware group's data leak site, Vice Society has
not posted a victim since July 2023, which is around the time Rhysida began
reporting victims on its site," Sophos researchers Colin Cowie and Morgan
Demboski said.
The development comes as the BlackCat ransomware Gang is attacking corporations
and public entities using Google ads laced with Nitrogen malware, per eSentire.
"This affiliate is taking out Google ads promoting popular software, such as
Advanced IP Scanner, Slack, WinSCP and Cisco AnyConnect, to lure business
professionals to attacker-controlled websites," the Canadian cybersecurity
company said.
The rogue installers, which come fitted with Nitrogen, which is an initial
access malware capable of delivering next-stage payloads onto a compromised
environment, including ransomware.
Cybersecurity
"Known examples of ransomware-associated initial access malware
that leverage browser-based attacks include GootLoader, SocGholish, BATLOADER,
and now Nitrogen," eSentire said. "Interestingly, ALPHV has been observed as an
end-game for at least two of these browser-based initial access pieces of
malware: GootLoader and Nitrogen."
The ever-evolving nature of the ransomware landscape is further evidenced by the
fact that 29 of the 60 ransomware groups currently active began operations this
year, per WithSecure, in part driven by the source code leaks of Babuk, Conti,
and LockBit over the years.
"Data leaks aren't the only thing that leads to older groups cross-pollinating
younger ones," WithSecure said in a report shared with The Hacker News.
"Ransomware gangs have staff just like an IT company. And like an IT company,
people change jobs sometimes, and bring their unique skills and knowledge with
them. Unlike legit IT companies, however, there's nothing stopping a cyber
criminal from taking proprietary resources (such as code or tools) from one
ransomware operation and using it at another. There's no honor among thieves."
Hackers Could Exploit Google Workspace and Cloud Platform for Ransomware Attacks
16.11.23
Ransom
The Hacker News
A set of novel attack methods has been demonstrated
against Google Workspace and the Google Cloud Platform that could be potentially
leveraged by threat actors to conduct ransomware, data exfiltration, and
password recovery attacks.
"Starting from a single compromised machine, threat actors could progress in
several ways: they could move to other cloned machines with GCPW installed, gain
access to the cloud platform with custom permissions, or decrypt locally stored
passwords to continue their attack beyond the Google ecosystem," Martin Zugec,
technical solutions director at Bitdefender, said in a new report.
A prerequisite for these attacks is that the bad actor has already gained access
to a local machine through other means, prompting Google to mark the bug as not
eligible for fixing "since it's outside of our threat model and the behavior is
in line with Chrome's practices of storing local data."
However, the Romanian cybersecurity firm has warned that threat actors can
exploit such gaps to extend a single endpoint compromise to a network-wide
breach.
The attacks, in a nutshell, rely on an organization's use of Google Credential
Provider for Windows (GCPW), which offers both mobile device management (MDM)
and single sign-on (SSO) capabilities.
This enables administrators to remotely manage and control Windows devices
within their Google Workspace environments, as well as allows users to access
their Windows devices using the same credentials that are used to login to their
Google accounts.
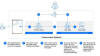
GCPW is designed to use a local privileged service account named Google Accounts
and ID Administration (GAIA) to seamlessly facilitate the process in the
background by connecting to Google APIs for verifying a user's credentials
during the sign-in step and storing a refresh token to obviate the need for
re-authentication.
With this setup in place, an attacker with access to a compromised machine can
extract an account's refresh OAuth tokens, either from the Windows registry or
from the user's Chrome profile directory, and bypass multi-factor authentication
(MFA) protections.
The refresh token is subsequently utilized to construct an HTTP POST request to
the endpoint "https://www.googleapis[.]com/oauth2/v4/token" to obtain an access
token, which, in turn, can be abused to retrieve, manipulate, or delete
sensitive data associated with the Google Account.
A second exploit concerns what's called the Golden Image lateral movement, which
focuses on virtual machine (VM) deployments and takes advantage of the fact that
creating a machine by cloning another machine with pre-installed GCPW causes the
password associated with the GAIA account to be cloned as well.
"If you know the password to a local account, and local accounts on all machines
share the same password, then you know the passwords to all machines," Zugec
explained.
"This shared-password challenge is similar to having the same local
administrator password on all machines that has been addressed by Microsoft's
Local Administrator Password Solution (LAPS)."
The third attack entails access to plaintext credentials by leveraging the
access token acquired using the aforementioned technique to send an HTTP GET
request to an undocumented API endpoint and get hold of the private RSA key that
is required to decrypt the password field.
"Having access to plaintext credentials, such as usernames and passwords,
represents a more severe threat," Zugec said. "This is because it enables
attackers to directly impersonate legitimate users and gain unrestricted access
to their accounts, potentially leading to complete account takeover."
New Ransomware Group Emerges with Hive's Source Code and Infrastructure
14.11.23
Ransom
The Hacker News
The threat actors behind a new ransomware group called
Hunters International have acquired the source code and infrastructure from the
now-dismantled Hive operation to kick-start its own efforts in the threat
landscape.
"It appears that the leadership of the Hive group made the strategic decision to
cease their operations and transfer their remaining assets to another group,
Hunters International," Martin Zugec, technical solutions director at
Bitdefender, said in a report published last week.
Hive, once a prolific ransomware-as-a-service (RaaS) operation, was taken down
as part of a coordinated law enforcement operation in January 2023.
While it's common for ransomware actors to regroup, rebrand, or disband their
activities following such seizures, what can also happen is that the core
developers can pass on the source code and other infrastructure in their
possession to another threat actor.
Reports about Hunters International as a possible Hive rebrand surfaced last
month after several code similarities were identified between the two strains.
It has since claimed five victims to date.
The threat actors behind it, however, have sought to dispel these speculations,
stating that it purchased the Hive source code and website from its developers.
"The group appears to place a greater emphasis on data exfiltration," Zugec
said. "Notably, all reported victims had data exfiltrated, but not all of them
had their data encrypted," making Hunters International more of a data extortion
outfit.
Bitdefender's analysis of the ransomware sample reveals its Rust-based
foundations, a fact borne out by Hive's transition to the programming language
in July 2022 for its increased resistance to reverse engineering.
"In general, as the new group adopts this ransomware code, it appears that they
have aimed for simplification," Zugec said.
"They have reduced the number of command line parameters, streamlined the
encryption key storage process, and made the malware less verbose compared to
earlier versions."
The ransomware, besides incorporating an exclusion list of file extensions, file
names, and directories to be omitted from encryption, runs commands to prevent
data recovery as well as terminate a number of processes that could potentially
interfere with the process.
"While Hive has been one of the most dangerous ransomware groups, it remains to
be seen if Hunters International will prove equally or even more formidable,"
Zugec noted.
"This group emerges as a new threat actor starting with a mature toolkit and
appears eager to show its capabilities, [but] faces the task of demonstrating
its competence before it can attract high-caliber affiliates."
Local Governments Targeted for Ransomware – How to Prevent Falling Victim
21.7.23
Ransom The
Hacker News
Regardless of the country, local government is essential in
most citizens' lives. It provides many day-to-day services and handles various
issues. Therefore, their effects can be far-reaching and deeply felt when
security failures occur.
In early 2023, Oakland, California, fell victim to a ransomware attack. Although
city officials have not disclosed how the attack occurred, experts suspect a
phishing email is the most likely cause. As a result, city officials brought
down their servers to contain the attack.
Governments have been the target to many ransomware attacks and breaches. As
most local governments maintain a small IT staff, there is potential for shared
passwords, reused credentials, and a lack of multi-factor authentication
security, exposing vulnerabilities for a breach.
Oakland is Breached#
It was first noticed on a Wednesday evening in early
February; when Oakland, California city officials quickly took most services'
backend servers offline and posted a message to the city website. Just a few
days later, a local state of emergency was issued. In addition to several
offices closing, many services remained offline for some time, including Oak311,
Parking Citation Assistance Center, Business Tax Licenses, and Permitting.
The Play ransomware group claimed responsibility for breaching city services and
posted about the hack on their group website. In their first release, they made
available 10GB of data containing decades worth of files. In their second,
larger breach, up to 600GB of data was compromised.

The impact of the security breach went beyond the disruption of city services,
affecting both Oakland residents and city employees on a personal level. From
July 2010 to January 2022, city employees were notified that their personal
information may have been compromised. Additionally, certain Oakland residents,
such as those filing a claim against the city or applying for federal programs
through the city, may have also been affected.
As expected, this ongoing situation is a nightmare for both IT services and city
administration, and it is also a public relations nightmare. Many concerned
citizens continue to question how they are impacted and how to protect
themselves against identity theft.
The Ramifications of a Breach#
Any system breach is serious. In this case,
the data was encrypted, rendering services unusable. But, with a compromised
infrastructure, threat actors could have leveraged that access to further infect
city residents and employees. The Oakland breach may have been limited to lost
data, but depending on the group responsible, the consequences could have been
far worse.
The job of city IT services is already difficult due to typically smaller
budgets and overworked IT staff. The myriad of security vulnerabilities to track
in popular software and the difficulty of staying on top of ever-changing
threats makes IT jobs even more challenging. Therefore, it is important to
implement policies and procedures that can go a long way in securing and
protecting your local government.
Underpinning so many services are the passwords and policies that control access
to critical services. Common best practice guidelines such as the NIST 800-63B,
ISO 27001/27002, and SOC 2 ensure that your organization is set up for success.
Implementing these standards is difficult, and tools such asSpecops Password
Policy with Breached Password Protection make strapped IT professionals' lives
far easier.
Protecting Users with Specops Password Policy and Breached Password Protection#
Keeping up with best practices and standards is difficult. Fortunately, there
are tools available like,Specops Password Policy that enforces stronger password
policies in Active Directory, helps meet security compliance standards and
blocks over 3 billion know compromised passwords from use to help keep your
users safe from ransomware attacks from organizations like Play.

Specops Password Policy provides various features to help keep your organization
secure. These include custom dictionaries, unique and customizable password
policies, and powerful protection against cracked passwords.
Keeping Cities Safe from Ransomware#
The ongoing challenges faced by Oakland,
California, are difficult for both residents and city officials. The unknown
threat of how stolen information may be used for further hacks or identity theft
leaves many uneasy and afraid. By implementing ways to proactively protect your
government entity with tools such as Specops Password Policy, you can go a long
way in limiting the scope of attacks and bolster security prevention.
Mallox Ransomware Exploits Weak MS-SQL Servers to
Breach Networks
21.7.23
Ransom The
Hacker News

Mallox ransomware activities in 2023 have witnessed a 174% increase when
compared to the previous year, new findings from Palo Alto Networks Unit 42
reveal.
"Mallox ransomware, like many other ransomware threat actors, follows the double
extortion trend: stealing data before encrypting an organization's files, and
then threatening to publish the stolen data on a leak site as leverage to
convince victims to pay the ransom fee," security researchers Lior Rochberger
and Shimi Cohen said in a new report shared with The Hacker News.
Mallox is linked to a threat actor that's also linked to other ransomware
strains, such as TargetCompany, Tohnichi, Fargo, and, most recently, Xollam. It
first burst onto the scene in June 2021.
Some of the prominent sectors targeted by Mallox are manufacturing, professional
and legal services, and wholesale and retail.
A notable aspect of the group is its pattern of exploiting poorly secured MS-SQL
servers via dictionary attacks as a penetration vector to compromise victims'
networks. Xollam is a deviation from the norm in that it has been observed using
malicious OneNote file attachments for initial access, as detailed by Trend
Micro last month.
Upon gaining a successful foothold on the infected host, a PowerShell command is
executed to retrieve the ransomware payload from a remote server.
The binary, for its part, attempts to stop and remove SQL-related services,
delete volume shadow copies, clear system event logs, terminate security-related
processes, and bypass Raccine, an open-source tool designed to counter
ransomware attacks, prior to commencing its encryption process, after which a
ransom note is dropped in every directory.
TargetCompany remains a small,
closed group, but it has also been observed recruiting affiliates for the Mallox
ransomware-as-a-service (RaaS) affiliate program on the RAMP cybercrime forum.
The development comes as ransomware continues to be a lucrative financial
scheme, netting cybercriminals no less than $449.1 million in the first half of
2023 alone, per Chainalysis.
The sudden surge in Mallox infections is also symptomatic of a broader trend
where ransomware attacks have witnessed a 221% jump year-over-year as of June
2023, with 434 attacks reported in June 2023 alone, largely driven by Cl0p's
exploitation of the MOVEit file transfer software vulnerability.
"The Mallox ransomware group has been more active in the past few months, and
their recent recruiting efforts may enable them to attack more organizations if
the recruitment drive is successful," the researchers said.
Ransomware Extortion Skyrockets in 2023, Reaching $449.1 Million and Counting
12.7.23 Ransom
The Hacker News
Ransomware has emerged as the only cryptocurrency-based
crime to grow in 2023, with cybercriminals extorting nearly $175.8 million more
than they did a year ago, according to findings from Chainalysis.
"Ransomware attackers are on pace for their second-biggest year ever, having
extorted at least $449.1 million through June," the blockchain analytics firm
said in a midyear crypto crime report shared with The Hacker News. "If this pace
continues, ransomware attackers will extort $898.6 million from victims in 2023,
trailing only 2021's $939.9 million."
In contrast, crypto scams have pulled in 77% less revenue than they did through
June of 2022, largely driven by the abrupt exit of VidiLook, which pays users
VDL tokens in return for watching digital ads that then can be exchanged for
large rewards. So have the inflows to illicit addresses associated with malware,
darknet markets, child abuse material, and fraud shops.
The development, following a decline in ransomware revenues in 2022, marks a
reversal of sorts, with Chainalysis attributing it to the return of big game
hunting after a downturn last year and the increasing number of successful small
attacks carried by groups like Dharma and Phobos.
On the other end of the spectrum lie advanced groups like Cl0p (or Clop),
BlackCat, and Black Basta, which tend to be more selective in their targeting,
while also striking bigger organizations to demand higher ransoms. Cl0p's
average payment size for the first half of 2023 stands at $1,730,486, in
contrast to Dharma's $275.

Cl0p, in particular, has been on a rampage in recent months, exploiting security
flaws in MOVEit Transfer application to breach 257 organizations across the
world to date, per Emsisoft researcher Brett Callow. More than 17.7 million
individuals are said to be impacted as a result of the ransomware attacks.
"Clop's preference for targeting larger companies (>$5 million/year revenue) and
capitalizing on newer-but-disclosed vulnerabilities has been the primary driver
of its success in the first half of 2023," Sophos researcher David Wallace said
in a report earlier this week, calling the group a "loud, adaptable, persistent
player."
While law enforcement efforts to actively pursue ransomware groups
and sanction services offering cashout services, coupled with the availability
of decryptors, have emboldened victims to not pay up, it's suspected that the
trend "may be prompting ransomware attackers to increase the size of their
ransom demands" to extract funds from companies who are still willing to settle.
Last but not least, the Russia-Ukraine War is also said to have been a
contributing factor to the decline in ransomware attacks in 2022, causing the
Conti operation to shut shop after declaring support for Russia.
"The conflict likely displaced ransomware operators and diverted them away from
financially inspired cyber intrusions," Chainalysis said. "It stands to reason
that the conflict disrupted ransomware operators' ability to conduct attacks or
perhaps even their mandate for such attacks," especially considering that a
majority of ransomware actors are tied to Russia.
Beware of Big Head Ransomware: Spreading Through
Fake Windows Updates
11.7.23
Ransom The Hacker News
A
developing piece of ransomware called Big Head is being distributed as part of a
malvertising campaign that takes the form of bogus Microsoft Windows updates and
Word installers.
Big Head was first documented by Fortinet FortiGuard Labs last month, when it
discovered multiple variants of the ransomware that are designed to encrypt
files on victims' machines in exchange for a cryptocurrency payment.
"One Big Head ransomware variant displays a fake Windows Update, potentially
indicating that the ransomware was also distributed as a fake Windows Update,"
Fortinet researchers said at the time. "One of the variants has a Microsoft Word
icon and was likely distributed as counterfeit software."
A majority of the Big Head samples have been submitted so far from the U.S.,
Spain, France, and Turkey.
In a new analysis of the .NET-based ransomware, Trend Micro detailed its inner
workings, calling out its ability to deploy three encrypted binaries: 1.exe to
propagate the malware, archive.exe to facilitate communications over Telegram,
and Xarch.exe to encrypt the files and" display a fake Windows update.
"The malware displays a fake Windows Update UI to deceive the victim into
thinking that the malicious activity is a legitimate software update process,
with the percentage of progress in increments of 100 seconds," the cybersecurity
company said.
Big Head is no different from other ransomware families in that it deletes
backups, terminates several processes, and performs checks to determine if it's
running within a virtualized environment before proceeding to encrypt the files.
In addition, the malware disables the Task Manager to prevent users from
terminating or investigating its process and aborts itself if the machine's
language matches that of Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz,
Armenian, Georgian, Tatar, and Uzbek. It also incorporates a self-delete
function to erase its presence.

Trend Micro said it detected a second Big Head artifact with both ransomware and
stealer behaviors, the latter of which leverages the open-source WorldWind
Stealer to harvest web browser history, directory lists, running processes,
product key, and networks.
Also discovered is a third variant of Big Head
that incorporates a file infector called Neshta, which is used to insert
malicious code into executables on the infected host.
"Incorporating Neshta into the ransomware deployment can also serve as a
camouflage technique for the final Big Head ransomware payload," Trend Micro
researchers said.
"This technique can make the piece of malware appear as a different type of
threat, such as a virus, which can divert the prioritization of security
solutions that primarily focus on detecting ransomware."
The identity of the threat actor behind Big Head is currently not known, but
Trend Micro said it identified a YouTube channel with the name "aplikasi premium
cuma cuma," suggesting an adversary likely of Indonesian origin.
"Security teams should remain prepared given the malware's diverse
functionalities," the researchers concluded. "This multifaceted nature gives the
malware the potential to cause significant harm once fully operational, making
it more challenging to defend systems against, as each attack vector requires
separate attention."
BlackByte 2.0 Ransomware: Infiltrate, Encrypt, and
Extort in Just 5 Days
7.7.23
Ransom The Hacker News
Ransomware attacks are a major problem for organizations everywhere, and the
severity of this problem continues to intensify.
Recently, Microsoft's Incident Response team investigated the BlackByte 2.0
ransomware attacks and exposed these cyber strikes' terrifying velocity and
damaging nature.
The findings indicate that hackers can complete the entire attack process, from
gaining initial access to causing significant damage, in just five days. They
waste no time infiltrating systems, encrypting important data, and demanding a
ransom to release it.
This shortened timeline poses a significant challenge for organizations trying
to protect themselves against these harmful operations.
BlackByte ransomware is used in the final stage of the attack, using an 8-digit
number key to encrypt the data.
To carry out these attacks, hackers use a powerful combination of tools and
techniques. The investigation revealed that they take advantage of unpatched
Microsoft Exchange Servers—an approach that has proven highly successful. By
exploiting this vulnerability, they gain initial access to the target networks
and set the stage for their malicious activities.
The ransomware further employs process hollowing and antivirus evasion
strategies to guarantee successful encryption and circumvent detection.

Furthermore, web shells equip them with remote access and control, enabling them
to maintain a presence within the compromised systems.
The report also highlighted the deployment of Cobalt Strike beacons, which
facilitate command and control operations. These sophisticated tools give
attackers a wide range of skills, making it more difficult for organizations to
defend against them.
Alongside these tactics, the investigation uncovered
several other troubling practices cybercriminals use. They utilize
"living-off-the-land" tools to blend in with legitimate processes and escape
detection.
The ransomware modifies volume shadow copies on infected machines to prevent
data recovery through system restore points. The attackers also deploy
specially-crafted backdoors, ensuring continued access for the attackers even
after the initial compromise.
The disturbing upsurge in ransomware attacks requires immediate action from
organizations worldwide. In response to these findings, Microsoft has provided
some practical recommendations.
Organizations are primarily urged to implement robust patch management
procedures, ensuring they timely apply critical security updates. Enabling
tamper protection is another essential step, as it strengthens security
solutions against malicious attempts to disable or bypass them.
BlackCat Operators Distributing Ransomware Disguised as WinSCP via Malvertising
3.7.23 Ransom
The Hacker News
Threat actors associated with the BlackCat ransomware have been observed
employing malvertising tricks to distribute rogue installers of the WinSCP file
transfer application.
"Malicious actors used malvertising to distribute a piece of malware via cloned
webpages of legitimate organizations," Trend Micro researchers said in an
analysis published last week. "In this case, the distribution involved a webpage
of the well-known application WinSCP, an open-source Windows application for
file transfer."
Malvertising refers to the use of SEO poisoning techniques to spread malware via
online advertising. It typically involves hijacking a chosen set of keywords to
display bogus ads on Bing and Google search results pages with the goal of
redirecting unsuspecting users to sketchy pages.
The idea is to trick users searching for applications like WinSCP into
downloading malware, in this instance, a backdoor that contains a Cobalt Strike
Beacon that connects to a remote server for follow-on operations, while also
employing legitimate tools like AdFind to facilitate network discovery.
The access afforded by Cobalt Strike is further abused to download a number of
programs to conduct reconnaissance, enumeration (PowerView), lateral movement
(PsExec), bypass antivirus software (KillAV BAT), and exfiltrate customer data
(PuTTY Secure Copy client). Also observed is the use of the Terminator defense
evasion tool to tamper with security software by means of a Bring Your Own
Vulnerable Driver (BYOVD) attack.
In the attack chain detailed by the cybersecurity company, the threat actors
managed to steal top-level administrator privileges to conduct post-exploitation
activities and attempted to set up persistence using remote monitoring and
management tools like AnyDesk as well as access backup servers.
"It is highly likely that the enterprise would have been substantially affected
by the attack if intervention had been sought later, especially since the threat
actors had already succeeded in gaining initial access to domain administrator
privileges and started establishing backdoors and persistence," Trend Micro
said.

The development is just the latest example of threat actors leveraging the
Google Ads platform to serve malware. In November 2022, Microsoft disclosed an
attack campaign that leverages the advertising service to deploy BATLOADER,
which is then used to drop Royal ransomware.
It also comes as Czech cybersecurity company Avast released a free decryptor for
the fledgling Akira ransomware to help victims recover their data without having
to pay the operators. Akira, which first appeared in March 2023, has since
expanded its target footprint to include Linux systems.
"Akira has a few similarities to the Conti v2 ransomware, which may indicate
that the malware authors were at least inspired by the leaked Conti sources,"
Avast researchers said. The company did not disclose how it cracked the
ransomware's encryption algorithm.
The Conti/TrickBot syndicate, aka Gold Ulrick or ITG23, shut down in May 2022
after suffering a series of disruptive events triggered by the onset of the
Russian invasion of Ukraine. But the e-crime group continues to exist to this
date, albeit as smaller entities and using shared crypters and infrastructure to
distribute their warez.
IBM Security X-Force, in a recent deep dive, said
the gang's crypters, which are applications designed to encrypt and obfuscate
malware to evade detection by antivirus scanners and hinder analysis, are being
used to also disseminate new malware strains such as Aresloader, Canyon,
CargoBay, DICELOADER, Lumma C2, Matanbuchus, Minodo (formerly Domino), Pikabot,
SVCReady, and Vidar.
"Previously, the crypters were used predominantly with the core malware families
associated with ITG23 and their close partners," security researchers Charlotte
Hammond and Ole Villadsen said. "However, the fracturing of ITG23 and emergence
of new factions, relationships, and methods, have affected how the crypters are
used."
Despite the dynamic nature of the cybercrime ecosystem, as nefarious cyber
actors come and go, and some operations partner together, shut down, or rebrand
their financially motivated schemes, ransomware has lingered as a constant
threat.
This includes the emergence of a new ransomware-as-a-service (RaaS) group called
Rhysida, which has primarily singled out education, government, manufacturing,
and technology sectors across Western Europe, North and South America, and
Australia.
"Rhysida is a 64-bit Portable Executable (PE) Windows cryptographic ransomware
application compiled using MINGW/GCC," SentinelOne said in a technical write-up.
"In each sample analyzed, the application's program name is set to Rhysida-0.1,
suggesting the tool is in early stages of development."
8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses
28.6.23 Ransom
The Hacker News

A ransomware threat called 8Base that has been operating under the radar for
over a year has been attributed to a "massive spike in activity" in May and June
2023.
"The group utilizes encryption paired with 'name-and-shame' techniques to compel
their victims to pay their ransoms," VMware Carbon Black researchers Deborah
Snyder and Fae Carlisle said in a report shared with The Hacker News. "8Base has
an opportunistic pattern of compromise with recent victims spanning across
varied industries."
8Base, according to statistics gathered by Malwarebytes and NCC Group, has been
linked to 67 attacks as of May 2023, with about 50% of the victims operating in
the business services, manufacturing, and construction sectors. A majority of
the targeted companies are located in the U.S. and Brazil.
With very little known about the operators of the ransomware, its origins remain
something of a cipher. What's evident is that it has been active since at least
March 2022 and the actors describe themselves as "simple pentesters."
VMware said 8Base is "strikingly" similar to that of another data extortion
group tracked as RansomHouse, citing overlaps in the ransom notes dropped on
compromised machines and the language used in the respective data leak portals.
"The verbiage is copied word for word from RansomHouse's welcome page to 8Base's
welcome page," the researchers said. "This is the case for their Terms of
Service pages and FAQ pages."
A comparison of the two threat groups reveals that while RansomHouse openly
advertises their partnerships, 8Base does not. Another crucial differentiator is
their leak pages.
But in an interesting twist, VMware noted that it was able to identify a Phobos
ransomware that uses the ".8base" file extension for encrypted files, raising
the possibility that 8Base could be a successor to Phobos or that the attackers
are simply making use of already existing ransomware strains without having to
develop their own custom locker.
"The speed and efficiency of 8Base's current operations does not indicate the
start of a new group but rather signifies the continuation of a well-established
mature organization," the researchers said. "Whether 8Base is an offshoot of
Phobos or RansomHouse remains to be seen."
8Base is part of a wave of
ransomware newbies entering the market such as CryptNet, Xollam, and Mallox,
even as known families like BlackCat, LockBit, and Trigona have witnessed
continuous updates to their features and attack chains to broaden their horizons
beyond Windows to infect Linux and macOS systems.
One instance highlighted by Cyble entails the use of BATLOADER to deploy Mallox,
suggesting that the threat actors are actively refining their tactics to
"enhance evasiveness and maintain their malicious activities."
"Groups adopt other groups' code, and affiliates — which can be considered
cybercrime groups in their own right — switch between different types of
malware," Kaspersky said in an analysis last week. "Groups work on upgrades to
their malware, adding features and providing support for multiple, previously
unsupported, platforms, a trend that existed for some time now."
Third Flaw Uncovered in MOVEit Transfer App Amidst Cl0p Ransomware Mass Attack
16.6.23 Ransom
The Hacker News
Progress Software on Thursday disclosed a third
vulnerability impacting its MOVEit Transfer application, as the Cl0p cybercrime
gang deployed extortion tactics against affected companies.
The new flaw, which is yet to be assigned a CVE identifier, also concerns an SQL
injection vulnerability that "could lead to escalated privileges and potential
unauthorized access to the environment."
The company is urging its customers to disable all HTTP and HTTPs traffic to
MOVEit Transfer on ports 80 and 443 to safeguard their environments while a
patch is being prepared to address the weakness.
The revelation comes a week after Progress divulged another set of SQL injection
vulnerabilities (CVE-2023-35036) that it said could be weaponized to access the
application's database content.
The vulnerabilities join CVE-2023-34362, which was exploited as a zero-day by
the Clop ransomware gang in data theft attacks. Kroll said it found evidence
that the group, dubbed Lace Tempest by Microsoft, had been testing the exploit
as far back as July 2021.

The development also coincides with the Cl0p actors listing the names of 27
companies that it claimed were hacked using the MOVEit Transfer flaw on its
darknet leak portal. According to a report from CNN, this also includes multiple
U.S. federal agencies such as the Department of Energy.
"The number of potentially breached organizations so far is significantly
greater than the initial number named as part of Clop's last MFT exploitation:
the Fortra GoAnywhere MFT campaign," ReliaQuest said.
Censys, a web-based
search platform for assessing attack surface for internet-connected devices,
said nearly 31% of over 1,400 exposed hosts running MOVEit are in the financial
services industry, 16% in healthcare, 9% in information technology, and 8% in
government and military sectors. Nearly 80% of the servers are based in the U.S.
Per Kaspersky's analysis of 97 families spread via the malware-as-a-service
(MaaS) business model between 2015 and 2022, ransomware leads with a 58% share,
followed by information stealers (24%) and botnets, loaders, and backdoors
(18%).
"Money is the root of all evil, including cybercrime," the Russian cybersecurity
company said, adding the MaaS schemes allow less technically proficient
attackers to enter the fray, thereby lowering the bar for carrying out such
attacks.
LockBit Ransomware Extorts $91 Million from U.S.
Companies
15.6.23
Ransom The Hacker News
The
threat actors behind the LockBit ransomware-as-a-service (RaaS) scheme have
extorted $91 million following hundreds of attacks against numerous U.S.
organizations since 2020.
That's according to a joint bulletin published by the U.S. Cybersecurity and
Infrastructure Security Agency (CISA), the Federal Bureau of Investigation
(FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and
other partner authorities from Australia, Canada, France, Germany, New Zealand,
and the U.K.
"The LockBit ransomware-as-a-service (RaaS) attracts affiliates to use LockBit
for conducting ransomware attacks, resulting in a large web of unconnected
threat actors conducting wildly varying attacks," the agencies said.
LockBit, which first burst onto the scene in late 2019, has continued to be
disruptive and prolific, targeting as many as 76 victims in May 2023 alone, per
statistics shared by Malwarebytes last week. The Russia-linked cartel has
claimed responsibility for at least 1,653 ransomware attacks to date.
The cybercrime operation has attacked a wide array of critical infrastructure
sectors, including financial services, food and agriculture, education, energy,
government and emergency services, healthcare, manufacturing, and
transportation.
LockBit has received three substantial upgrades so far: LockBit Red (June 2021),
LockBit Black (March 2022), and LockBit Green (January 2023), the last of which
is based on leaked source code from the now-disbanded Conti gang.
The ransomware strain has since been adapted to target Linux, VMware ESXi, and
Apple macOS systems, transforming it into an ever-evolving threat. The RaaS
operation is also notable for paying people to get tattoos of its insignia and
instituting the first-ever bug bounty program.
The business model involves the core developers renting out their warez to
affiliates who perform the actual ransomware deployment and extortion. But in a
twist, the group allows the affiliates to receive ransom payments before sending
a cut to the main crew.
Attack chains involving LockBit have leveraged recently disclosed flaws in
Fortra GoAnywhere Managed File Transfer (MFT) and PaperCut MF/NG servers as well
as other known bugs in Apache Log4j2, F5 BIG-IP and BIG-IQ, and Fortinet devices
to obtain initial access.
Also used by the affiliates are over three dozen freeware and open-source tools
that allow for network reconnaissance, remote access and tunneling, credential
dumping, and file exfiltration. The intrusions have been found to further abuse
legitimate red team software such as Metasploit and Cobalt Strike.
"LockBit has been successful through its innovation and continual development of
the group's administrative panel (i.e., a simplified, point-and-click interface
making ransomware deployment accessible to those with lower degrees of technical
skill), affiliate supporting functions, and constant revision of TTPs," the
agencies said.
The development comes as CISA issued a Binding Operational
Directive 23-02, instructing federal agencies to secure network devices like
firewalls, routers, and switches that are exposed to the public internet within
14 days of discovery and take steps to minimize the attack surface.
"Too often, threat actors are able to use network devices to gain unrestricted
access to organizational networks, in turn leading to full-scale compromise,"
CISA Director, Jen Easterly, said. "Requiring appropriate controls and
mitigations [...] is an important step in reducing risk to the federal civilian
enterprise."
The developments also follow a new advisory highlighting threats to Baseboard
Management Controller (BMC) implementations that could potentially enable threat
actors to establish a "beachhead with pre-boot execution potential."
"Hardened credentials, firmware updates, and network segmentation options are
frequently overlooked, leading to a vulnerable BMC," CISA and the U.S. National
Security Agency (NSA) noted in a joint alert.
"Additionally, a malicious actor could disable security solutions such as the
trusted platform module (TPM) or UEFI secure boot, manipulate data on any
attached storage media, or propagate implants or disruptive instructions across
a network infrastructure."
Clop Ransomware Gang Likely Aware of MOVEit Transfer Vulnerability Since 2021
10.6.23 Ransom
The Hacker News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Federal
Bureau of Investigation (FBI) have published a joint advisory regarding the
active exploitation of a recently disclosed critical flaw in Progress Software's
MOVEit Transfer application to drop ransomware.
"The Cl0p Ransomware Gang, also known as TA505, reportedly began exploiting a
previously unknown SQL injection vulnerability in Progress Software's managed
file transfer (MFT) solution known as MOVEit Transfer," the agencies said.
"Internet-facing MOVEit Transfer web applications were infected with a web shell
named LEMURLOOT, which was then used to steal data from underlying MOVEit
Transfer databases."
The prolific cybercrime gang has since issued an ultimatum to several impacted
businesses, urging them to get in touch by June 14, 2023, or risk getting all
their stolen data published.
Microsoft is tracking the activity under the moniker Lace Tempest (aka
Storm-0950), which has also been implicated in the exploitation of a critical
security vulnerability in PaperCut servers.
Active since at least February 2019, the adversary has been linked to a wide
range of activities in the cybercrime ecosystem, including operating a
ransomware-as-a-service (RaaS) and acting as an affiliate for other RaaS
schemes.
It has also been observed acting as an initial access broker (IAB) to profit off
access to compromised enterprise networks and also as a customer of other IABs,
underscoring the interconnected nature of the threat landscape.

Source: Kroll
The abuse of CVE-2023-34362, an SQL injection flaw in MOVEit
Transfer, is a sign of the adversary continuously seeking zero-day exploits in
internet-facing applications and using them to their advantage in order to
extort victims.
Huntress has since revealed that the vulnerability can further be exploited by
an unauthenticated actor to achieve remote code execution, potentially
culminating in the deployment of ransomware or other payloads.
It's worth noting that Cl0p carried out similar mass exploitation attacks on
other managed file transfer applications such as SolarWinds Serv-U Managed File
Transfer, Accellion FTA, and GoAnywhere MFT since December 2020.

Attack surface management firm Censys said it has observed a drop in the number
of hosts running exposed MOVEit Transfer instances from over 3,000 hosts to
little more than 2,600.
"Several of these hosts are associated with high-profile organizations,
including multiple Fortune 500 companies and both state and federal government
agencies," Censys noted, highlighting finance, technology, and healthcare as the
sectors with the most exposures.
Kroll, in an analysis shared with The
Hacker News, said it identified activity indicating that the Clop threat actors
were likely experimenting with ways to exploit this particular flaw in April
2022 and as far back as July 2021.
The finding is particularly significant as it serves to illustrate the
attacker's technical expertise and the planning that has gone into staging the
intrusions much before the recent wave of exploitations began.
"Commands during the July 2021 time frame appeared to be run over a longer
amount of time, suggesting that testing may have been a manual process at that
point before the group created an automated solution that it began testing in
April 2022," Kroll said.
The July 2021 exploitation is said to have originated from an IP address
(45.129.137[.]232) that was previously attributed to the Cl0p actor in
connection with attempts to exploit flaws in SolarWinds Serv-U product around
the same time.
"This is the third time Cl0p ransomware group have used a zero day in webapps
for extortion in three years," security researcher Kevin Beaumont said. "In all
three cases they were products with security in the branding."
Cyclops Ransomware Gang Offers Go-Based Info Stealer to Cybercriminals
7.6.23 Ransomware
The Hacker News
Threat actors associated with the Cyclops ransomware have
been observed offering an information stealer malware that's designed to capture
sensitive data from infected hosts.
"The threat actor behind this [ransomware-as-a-service] promotes its offering on
forums," Uptycs said in a new report. "There it requests a share of profits from
those engaging in malicious activities using its malware."
Cyclops ransomware is notable for targeting all major desktop operating systems,
including Windows, macOS, and Linux. It's also designed to terminate any
potential processes that could interfere with encryption.
The macOS and Linux versions of Cyclops ransomware are written in Golang. The
ransomware further employs a complex encryption scheme that's a mix of
asymmetric and symmetric encryption.
The Go-based stealer, for its part, is designed to target Windows and Linux
systems, capturing details such as operating system information, computer name,
number of processes, and files of interest matching specific extensions.
The harvested data, which comprises .TXT, .DOC, .XLS, .PDF, .JPEG, .JPG, and
.PNG files, is then uploaded to a remote server. The stealer component can be
accessed by a customer from an admin panel.
The development comes as SonicWall detailed a new strain of information stealer
called Dot Net Stealer to siphon information from web browsers, VPNs, installed
apps, and cryptocurrency wallets, in what's a further evolution of the
cybercrime ecosystem into a more lethal threat.
"These capabilities provide attackers to obtain valuable information from the
victim's systems that can lead to big financial frauds which can make huge
financial losses to victims," SonicWall said.
New Linux Ransomware Strain BlackSuit Shows Striking Similarities to Royal
5.6.23 Ransomware
The Hacker News
An analysis of the Linux variant of a new ransomware
strain called BlackSuit has covered significant similarities with another
ransomware family called Royal.
Trend Micro, which examined an x64 VMware ESXi version targeting Linux machines,
said it identified an "extremely high degree of similarity" between Royal and
BlackSuit.
"In fact, they're nearly identical, with 98% similarities in functions, 99.5%
similarities in blocks, and 98.9% similarities in jumps based on BinDiff, a
comparison tool for binary files," Trend Micro researchers noted.
A comparison of the Windows artifacts has identified 93.2% similarity in
functions, 99.3% in basic blocks, and 98.4% in jumps based on BinDiff.
BlackSuit first came to light in early May 2023 when Palo Alto Networks Unit 42
drew attention to its ability to target both Windows and Linux hosts.
In line with other ransomware groups, it runs a double extortion scheme that
steals and encrypts sensitive data in a compromised network in return for
monetary compensation. Data associated with a single victim has been listed on
its dark web leak site.
The latest findings from Trend Micro show that, both BlackSuit and Royal use
OpenSSL's AES for encryption and utilize similar intermittent encryption
techniques to speed up the encryption process.
The overlaps aside, BlackSuit incorporates additional command-line arguments and
avoids a different list of files with specific extensions during enumeration and
encryption.
"The emergence of BlackSuit ransomware (with its similarities to Royal)
indicates that it is either a new variant developed by the same authors, a
copycat using similar code, or an affiliate of the Royal ransomware gang that
has implemented modifications to the original family," Trend Micro said.
Given that Royal is an offshoot of the erstwhile Conti team, it's also possible
that "BlackSuit emerged from a splinter group within the original Royal
ransomware gang," the cybersecurity company theorized.
The development once again underscores the constant state of flux in the
ransomware ecosystem, even as new threat actors emerge to tweak existing tools
and generate illicit profits.
This includes a new ransomware-as-a-service
(RaaS) initiative codenamed NoEscape that Cyble said allows its operators and
affiliates to take advantage of triple extortion methods to maximize the impact
of a successful attack.
Triple extortion refers to a three-pronged approach wherein data exfiltration
and encryption is coupled with distributed denial-of-service (DDoS) attacks
against the targets in an attempt to disrupt their business and coerce them into
paying the ransom.
The DDoS service, per Cyble, is available for an added $500,000 fee, with the
operators imposing conditions that forbid affiliates from striking entities
located in the Commonwealth of Independent States (CIS) countries.
Improved BlackCat Ransomware Strikes with Lightning Speed and Stealthy Tactics
1.6.23 Ransomware
The Hacker News
The threat actors behind BlackCat ransomware have come up
with an improved variant that prioritizes speed and stealth in an attempt to
bypass security guardrails and achieve their goals.
The new version, dubbed Sphynx and announced in February 2023, packs a "number
of updated capabilities that strengthen the group's efforts to evade detection,"
IBM Security X-Force said in a new analysis.
The "product" update was first highlighted by vx-underground in April 2023.
Trend Micro, last month, detailed a Linux version of Sphynx that's "focused
primarily on its encryption routine."
BlackCat, also called ALPHV and Noberus, is the first Rust-language-based
ransomware strain spotted in the wild. Active since November 2021, it has
emerged as a formidable ransomware actor, victimizing more than 350 targets as
of May 2023.
The group, like other ransomware-as-a-service (RaaS) offerings, is known to
operate a double extortion scheme, deploying custom data exfiltration tools like
ExMatter to siphon sensitive data prior to encryption.
Initial access to targeted networks is typically obtained through a network of
actors called initial access brokers (IABs), who employ off-the-shelf
information stealer malware to harvest legitimate credentials.

BlackCat has also been observed to share overlaps with the now-defunct
BlackMatter ransomware family, according to Cisco Talos and Kaspersky.
The latest findings provide a window into the ever-evolving cybercrime ecosystem
wherein threat actors enhance their tooling and tradecraft to increase the
likelihood of a successful compromise, not to mention thwart detection and evade
analysis.
Specifically, the Sphynx version of BlackCat incorporates junk code and
encrypted strings, while also reworking the command line arguments passed to the
binary.
Sphynx also incorporates a loader to decrypt the ransomware payload that, upon
execution, performs network discovery activities to hunt for additional systems,
deletes volume shadow copies, encrypts files, and finally drops the ransom note.
Despite law enforcement campaigns against cybercrime and ransomware groups, the
continuous shift in tactics is proof that BlackCat remains an active threat to
organizations and has "no signs of winding down."

Source: WithSecure
Finnish cybersecurity firm WithSecure, in a recent
research, described how the illicit financial proceeds associated with
ransomware attacks have led to a "professionalization of cyber crime" and the
advent of new supporting underground services.
"Many major ransomware groups are operating a service provider or RaaS model,
where they supply tooling and expertise to affiliates, and in return take a cut
of the profits," the company said.
"These profits have driven the rapid development of a service industry,
providing all the tools and services that an up and coming threat group could
need, and thanks to cryptocurrency and dark web routing services the many
different groups involved are able to anonymously buy and sell services, and
access their profits."
Buhti Ransomware Gang Switches Tactics, Utilizes Leaked LockBit and Babuk Code
25.5.23 Ransomware
The Hacker News
The threat actors behind the nascent Buhti ransomware
have eschewed their custom payload in favor of leaked LockBit and Babuk
ransomware families to strike Windows and Linux systems.
"While the group doesn't develop its own ransomware, it does utilize what
appears to be one custom-developed tool, an information stealer designed to
search for and archive specified file types," Symantec said in a report shared
with The Hacker News.
The cybersecurity firm is tracking the cybercrime group under the name
Blacktail. Buhti was first highlighted by Palo Alto Networks Unit 42 in February
2023, describing it as a Golang ransomware targeting the Linux platform.
Later that same month, Bitdefender revealed the use of a Windows variant that
was deployed against Zoho ManageEngine products that were vulnerable to critical
remote code execution flaws (CVE-2022-47966).
The operators have since been observed swiftly exploiting other severe bugs
impacting IBM's Aspera Faspex file exchange application (CVE-2022-47986) and
PaperCut (CVE-2023-27350) to drop the ransomware.
The latest findings from Symantec show that Blacktail's modus operandi might be
changing, what with the actor leveraging modified versions of the leaked LockBit
3.0 and Babuk ransomware source code to target Windows and Linux, respectively.
Both Babuk and LockBit have had its ransomware source code published online in
September 2021 and September 2022, spawning multiple imitators.
One notable cybercrime group that's already using the LockBit ransomware builder
is the Bl00dy Ransomware Gang, which was recently spotlighted by U.S. government
agencies as exploiting vulnerable PaperCut servers in attacks against the
education sector in the country.
Despite the rebranding changes, Blacktail has been observed utilizing a custom
data exfiltration utility written in Go that's designed to steal files with
specific extensions in the form of a ZIP archive prior to encryption.
"While the reuse of leaked payloads is often the hallmark of a less-skilled
ransomware operation, Blacktail's general competence in carrying out attacks,
coupled with its ability to recognize the utility of newly discovered
vulnerabilities, suggests that it is not to be underestimated," Symantec said.
Ransomware continues to pose a persistent threat for enterprises. Fortinet
FortiGuard Labs, earlier this month, detailed a Go-based ransomware family
called Maori that's specifically designed to run on Linux systems.
While the
use of Go and Rust signals an interest on part of threat actors to develop
"adaptive" cross-platform ransomware and maximize the attack surface, it's also
a sign of an ever-evolving cybercrime ecosystem where new techniques are adopted
on a continual basis.
"Major ransomware gangs are borrowing capabilities from either leaked code or
code purchased from other cybercriminals, which may improve the functionality of
their own malware," Kaspersky noted in its ransomware trends report for 2023.
Indeed, according to Cyble, a new ransomware family dubbed Obsidian ORB takes a
leaf out of Chaos, which has also been the foundation for other ransomware
strains like BlackSnake and Onyx.
What makes the ransomware stand out is that it employs a rather distinctive
ransom payment method, demanding that victims pay the ransom through gift cards
as opposed to cryptocurrency payments.
"This approach is effective and convenient for threat actors (TAs) as they can
modify and customize the code to their preferences," the cybersecurity firm
said.
Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
20.5.23 Ransomware
The Hacker News
The notorious cybercrime group known as FIN7 has been
observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first
ransomware campaign since late 2021.
Microsoft, which detected the activity in April 2023, is tracking the
financially motivated actor under its new taxonomy Sangria Tempest.
"In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH
to load the Lizar post-exploitation tool and get a foothold into a target
network," the company's threat intelligence team said. "They then use OpenSSH
and Impacket to move laterally and deploy Clop ransomware."
FIN7 (aka Carbanak, ELBRUS, and ITG14) has been linked to other ransomware
families such as Black Basta, DarkSide, REvil, and LockBit, with the threat
actor acting as a precursor for Maze and Ryuk ransomware attacks.
Active since at least 2012, the group has a track record of targeting a broad
spectrum of organizations spanning software, consulting, financial services,
medical equipment, cloud services, media, food and beverage, transportation, and
utilities.
Another notable tactic in its playbook is its pattern of setting up fake
security companies – Combi Security and Bastion Secure – to recruit employees
for conducting ransomware attacks and other operations.
Last month, IBM Security X-Force revealed that members of the now-defunct Conti
ransomware gang are using a new malware called Domino that's developed by the
cybercrime cartel.
FIN7's use of POWERTRASH to deliver Lizar (aka DICELOADER or Tirion) was also
highlighted by WithSecure a few weeks ago in connection with attacks exploiting
a high-severity flaw in Veeam Backup & Replication software (CVE-2023-27532) to
gain initial access.
The latest development signifies FIN7's continued reliance on various ransomware
families to target victims as part of a shift in its monetization strategy by
pivoting away from payment card data theft to extortion.
Inside Qilin Ransomware: Affiliates Take Home 85% of Ransom Payouts
16.5.23 Ransomware
The Hacker News
Ransomware affiliates associated with the Qilin ransomware-as-a-service (RaaS)
scheme earn anywhere between 80% to 85% of the ransom payments, according to new
findings from Group-IB.
The cybersecurity firm said it was able to infiltrate the group in March 2023,
uncovering details about the affiliates' payment structure and the inner
workings of the RaaS program following a private conversation with a Qilin
recruiter who goes by the online alias Haise.
"Many Qilin ransomware attacks are customized for each victim to maximize their
impact," the Singapore-headquartered company said in a new report. "To do this,
the threat actors can leverage such tactics as changing the filename extensions
of encrypted files and terminating specific processes and services."
Qilin, also known as Agenda, was first documented by Trend Micro in August 2022,
starting off a Go-based ransomware before switching to Rust in December 2022.
The adoption of Rust is also significant not only because of evasion detection
capabilities, but also for the fact that it allows the threat actors to target
Windows, Linux, and VMware ESXi servers.
Attacks mounted by the group make use of phishing emails containing malicious
links as a means to obtain initial access and encrypt sensitive data, but not
before exfiltrating it as part of a double extortion model.
Data from as many as 12 different companies have been posted on Qilin's data
leak portal on the dark web between July 2022 and May 2023.
The victims, which mainly span critical infrastructure, education, and
healthcare sectors, are located in Australia, Brazil, Canada, Colombia, France,
Japan, Netherlands, Serbia, the U.K., and the U.S.
Group-IB said the Qilin actors also provide affiliates – who are recruited to
identify targets of interest and stage the attacks – with an administrative
panel to effectively oversee various parts of their operations.
"Qilin ransomware group has an affiliate panel divided into sections such as
Targets, Blogs, Stuffers, News, Payments, and FAQs to manage and coordinate its
network of affiliates," security researcher Nikolay Kichatov said.
Targets - A section to configure ransom notes, files, directories, and
extensions to be skipped, extensions to be encrypted, processes to be
terminated, and the mode of encryption, among others
Blogs - A section for
affiliates to create blog posts with information about attacked companies that
have not paid the ransom
Stuffers - A section for the threat actors to create
accounts for other members of the team and manage their privileges
News - A
section to post updates related to their ransomware partnerships (currently
blank)
Payments - A section that contains transaction details, affiliate
wallet balances, and options to withdraw illicit proceeds
FAQs - A section
featuring support and documentation information that details the steps to use
the ransomware
"Although Qilin ransomware gained notoriety for targeting
critical sector companies, they are a threat to organizations across all
verticals," Kichatov said.
"Moreover, the ransomware operator's affiliate program is not only adding new
members to its network, but it is weaponizing them with upgraded tools,
techniques, and even service delivery."
New Ransomware Gang RA Group Hits U.S. and South Korean Organizations
15.5.23 Ransomware
The Hacker News
A new ransomware group known as RA Group has become the
latest threat actor to leverage the leaked Babuk ransomware source code to spawn
its own locker variant.
The cybercriminal gang, which is said to have been operating since at least
April 22, 2023, is rapidly expanding its operations, according to cybersecurity
firm Cisco Talos.
"To date, the group has compromised three organizations in the U.S. and one in
South Korea across several business verticals, including manufacturing, wealth
management, insurance providers and pharmaceuticals," security researcher Chetan
Raghuprasad said in a report shared with The Hacker News.
RA Group is no different from other ransomware gangs in that it launches double
extortion attacks and runs a date leak site to apply additional pressure on
victims into paying ransoms.
The Windows-based binary employs intermittent encryption to speed up the process
and evade detection, not to mention delete volume shadow copies and contents of
the machine's Recycle Bin.
"RA Group uses customized ransom notes, including the victim's name and a unique
link to download the exfiltration proofs," Raghuprasad explained. "If the victim
fails to contact the actors within three days, the group leaks the victim's
files."
It also takes steps to avoid encrypting system files and folders by means of a
hard-coded list so that it allows the victims to download the qTox chat
application and reach out to the operators using the qTox ID provided on the
ransom note.
What sets RA Group apart from other ransomware operations is that the threat
actor has also been observed selling the victim's exfiltrated data on its leak
portal by hosting the information on a secured TOR site.

The development comes less than a week after SentinelOne disclosed that threat
actors of varying sophistication and expertise are increasingly adopting the
Babuk ransomware code to develop a dozen variants that are capable of targeting
Linux systems.
"There is a noticeable trend that actors increasingly use the Babuk builder to
develop ESXi and Linux ransomware," the cybersecurity firm said. "This is
particularly evident when used by actors with fewer resources, as these actors
are less likely to significantly modify the Babuk source code."
Other
ransomware actors that have adopted the Babuk source code over the past year
include AstraLocker and Nokoyawa. Cheerscrypt, another ransomware strain based
on Babuk, has been linked to a Chinese espionage actor called Emperor Dragonfly
that's known for operating short-lived ransomware schemes such as Rook, Night
Sky, and Pandora.
The findings also follow the discovery of two other new ransomware strains
codenamed Rancoz and BlackSuit, the latter of which is designed to target both
Windows and VMware ESXi servers.
"The constant evolution and release of new ransomware variants highlight the
advanced skills and agility of [threat actors], indicating that they are
responding to cybersecurity measures and checks being implemented and
customizing their ransomware accordingly," Cyble said.
New 'MichaelKors' Ransomware-as-a-Service Targeting Linux and VMware ESXi
Systems
15.5.23
Ransomware The Hacker News
A new ransomware-as-service (RaaS) operation called MichaelKors has become the
latest file-encrypting malware to target Linux and VMware ESXi systems as of
April 2023.
The development points to cybercriminal actors increasingly setting their eyes
on the ESXi, cybersecurity firm CrowdStrike said in a report shared with The
Hacker News.
"This trend is especially noteworthy given the fact that ESXi, by design, does
not support third-party agents or AV software," the company said.
"In fact, VMware goes as far as to claim it's not required. This, combined with
the popularity of ESXi as a widespread and popular virtualization and management
system, makes the hypervisor a highly attractive target for modern adversaries."
The targeting of VMware ESXi hypervisors with ransomware to scale such campaigns
is a technique known as hypervisor jackpotting. Over the years, the approach has
been adopted by several ransomware groups, including Royal.
What's more, an analysis from SentinelOne last week revealed that 10 different
ransomware families, including Conti and REvil, have utilized leaked Babuk
source code in September 2021 to develop lockers for VMware ESXi hypervisors.
Other notable e-crime outfits that have updated their arsenal to target ESXi
consist of ALPHV (BlackCat), Black Basta, Defray, ESXiArgs, LockBit, Nevada,
Play, Rook, and Rorschach.
Part of the reason why VMware ESXi hypervisors are becoming an attractive target
is that the software runs directly on a physical server, granting a potential
attacker the ability to run malicious ELF binaries and gain unfettered access
over the machine's underlying resources.
Attackers looking to breach ESXi hypervisors can do so by using compromised
credentials, followed by gaining elevated privileges and either laterally moving
through the network or escaping the confines of the environment via known flaws
to advance their motives.
VMware, in a knowledge base article last updated in September 2020, notes that
"antivirus software is not required with the vSphere Hypervisor and the use of
such software is not supported."
"More and more threat actors are
recognizing that the lack of security tools, lack of adequate network
segmentation of ESXi interfaces, and [in-the-wild] vulnerabilities for ESXi
creates a target rich environment," CrowdStrike said.
Ransomware actors are from the only outfits to strike virtual infrastructure. In
March 2023, Google-owned Mandiant attributed a Chinese nation-state group to the
use of novel backdoors dubbed VIRTUALPITA and VIRTUALPIE in attacks aimed at
VMware ESXi servers.
To mitigate the impact of hypervisor jackpotting, organizations are recommended
to avoid direct access to ESXi hosts, enable two-factor authentication, take
periodic backups of ESXi datastore volumes, apply security updates, and conduct
security posture reviews.
"Adversaries will likely continue to target VMware-based virtualization
infrastructure," CrowdStrike said. "This poses a major concern as more
organizations continue transferring workloads and infrastructure into cloud
environments – all through VMWare Hypervisor environments."
Bl00dy Ransomware Gang Strikes Education Sector with Critical PaperCut
Vulnerability
13.5.23
Ransomware The Hacker News
U.S. cybersecurity and intelligence agencies have warned of attacks carried out
by a threat actor known as the Bl00dy Ransomware Gang that attempt to exploit
vulnerable PaperCut servers against the education facilities sector in the
country.
The attacks took place in early May 2023, the Federal Bureau of Investigation
(FBI) and Cybersecurity and Infrastructure Security Agency (CISA) said in a
joint cybersecurity advisory issued Thursday.
"The Bl00dy Ransomware Gang gained access to victim networks across the
Education Facilities Subsector where PaperCut servers vulnerable to
CVE-2023-27350 were exposed to the internet," the agencies said.
"Ultimately, some of these operations led to data exfiltration and encryption of
victim systems. The Bl00dy Ransomware Gang left ransom notes on victim systems
demanding payment in exchange for decryption of encrypted files."
Additionally, the Bl00dy actors are said to have used TOR and other proxies from
within victim networks for external communications in an attempt to mask
malicious traffic and avoid detection.
conduct remote code execution on the following affected installations. ->
conduct remote code execution on the following affected installations: 8.0.0 to
19.2.7, 20.0.0 to 20.1.6, 21.0.0 to 21.2.10, and 22.0.0 to 22.0.8.
CVE-2023-27350 is a now-patched critical security flaw affecting some versions
of PaperCut MF and NG that enables a remote actor to bypass authentication and
conduct remote code execution on the following affected installations.
Malicious exploitation of the vulnerability has been observed since mid-April
2023, with attacks primarily weaponizing it to deploy legitimate remote
management and maintenance (RMM) software and use the tool to drop additional
payloads such as Cobalt Strike Beacons, DiceLoader, and TrueBot on compromised
systems.
The disclosure comes as cybersecurity firm eSentire unearthed new activity
targeting an unnamed education sector customer that involved the exploitation of
CVE-2023-27350 to drop an XMRig cryptocurrency miner.
Attacks against PaperCut print management servers have also been deployed by
Iranian state-sponsored threat groups Mango Sandstorm (aka MuddyWater or
Mercury) and Mint Sandstorm (aka Phosphorus), Microsoft revealed last week.
Babuk Source Code Sparks 9 Different Ransomware Strains Targeting VMware ESXi
Systems
12.5.23
Ransomware The Hacker News
Multiple threat actors have capitalized on the leak of Babuk (aka Babak or
Babyk) ransomware code in September 2021 to build as many as nine different
ransomware families capable of targeting VMware ESXi systems.
"These variants emerged through H2 2022 and H1 2023, which shows an increasing
trend of Babuk source code adoption," SentinelOne security researcher Alex
Delamotte said in a report shared with The Hacker News.
"Leaked source code enables actors to target Linux systems when they may
otherwise lack expertise to build a working program."
A number of cybercrime groups, both big and small, have set their sights on ESXi
hypervisors. What's more, at least three different ransomware strains – Cylance,
Rorschach (aka BabLock), and RTM Locker – that have emerged since the start of
the year are based on the leaked Babuk source code.
SentinelOne's latest analysis shows that this phenomenon is more common, with
the cybersecurity company identifying source code overlaps between Babuk and
ESXi lockers attributed to Conti and REvil (aka REvix).
Other ransomware families that have ported various features from Babuk into
their respective code include LOCK4, DATAF, Mario, Play, and Babuk 2023 (aka
XVGV) ransomware.
Despite this noticeable trend, SentinelOne said it observed no parallels between
Babuk and ALPHV, Black Basta, Hive, and LockBit's ESXi lockers, adding it found
"little similarity" between ESXiArgs and Babuk, indicating an erroneous
attribution.
"Based on the popularity of Babuk's ESXi locker code, actors may also turn to
the group' Go-based NAS locker," Delamotte said. "Golang remains a niche choice
for many actors, but it continues to increase in popularity."
The development comes as threat actors associated with Royal ransomware, who are
suspected to be former Conti members, have expanded their attack toolkit with an
ELF variant that's capable of striking Linux and ESXi environments.
"The ELF variant is quite similar to the Windows variant, and the sample does
not contain any obfuscation," Palo Alto Networks Unit 42 said in a write-up
published this week. "All strings, including the RSA public key and ransom note,
are stored as plaintext."
Royal ransomware attacks are facilitated by means of various initial access
vectors such as callback phishing, BATLOADER infections, or compromised
credentials, which are then abused to drop a Cobalt Strike Beacon as a precursor
to ransomware execution.
Since bursting on the scene in September 2022, Royal ransomware has claimed
responsibility for targeting 157 organizations on their leak site, with most of
the attacks targeting manufacturing, retail, legal services, education,
construction, and healthcare services in the U.S., Canada, and Germany.
New Ransomware Strain 'CACTUS' Exploits VPN Flaws to Infiltrate Networks
10.5.23 Ransomware
The Hacker News
Cybersecurity researchers have shed light on a new
ransomware strain called CACTUS that has been found to leverage known flaws in
VPN appliances to obtain initial access to targeted networks.
"Once inside the network, CACTUS actors attempt to enumerate local and network
user accounts in addition to reachable endpoints before creating new user
accounts and leveraging custom scripts to automate the deployment and detonation
of the ransomware encryptor via scheduled tasks," Kroll said in a report shared
with The Hacker News.
The ransomware has been observed targeting large commercial entities since March
2023, with attacks employing double extortion tactics to steal sensitive data
prior to encryption. No data leak site has been identified to date.
Following a successful exploitation of vulnerable VPN devices, an SSH backdoor
is set up to maintain persistent access and a series of PowerShell commands are
executed to conduct network scanning and identify a list of machines for
encryption.
CACTUS attacks also utilize Cobalt Strike and a tunneling tool referred to as
Chisel for command-and-control, alongside remote monitoring and management (RMM)
software like AnyDesk to push files to the infected hosts.
Also taken are steps to disable and uninstall security solutions as well as
extract credentials from web browsers and the Local Security Authority Subsystem
Service (LSASS) for escalating privileges.
Privilege escalation is succeeded by lateral movement, data exfiltration, and
ransomware deployment, the last of which is achieved by means of a PowerShell
script that has also been used by Black Basta.
A novel aspect of CACTUS is the use of a batch script to extract the ransomware
binary with 7-Zip, followed by removing the .7z archive before executing the
payload.
"CACTUS essentially encrypts itself, making it harder to detect and helping it
evade antivirus and network monitoring tools," Laurie Iacono, associate managing
director for cyber risk at Kroll, told The Hacker News.
"This new ransomware variant under the name CACTUS leverages a vulnerability in
a popular VPN appliance, showing threat actors continue to target remote access
services and unpatched vulnerabilities for initial access."
The development comes days after Trend Micro shed light on another type of
ransomware known as Rapture that bears some similarities to other families such
as Paradise.
"The whole infection chain spans three to five days at most," the company said,
with the initial reconnaissance followed by the deployment of Cobalt Strike,
which is then used to drop the .NET-based ransomware.
The intrusion is suspected to be facilitated through vulnerable public-facing
websites and servers, making it imperative that companies take steps to keep
systems up-to-date and enforce the principle of least privilege (PoLP).
"Although its operators use tools and resources that are readily available, they
have managed to use them in a way that enhances Rapture's capabilities by making
it stealthier and more difficult to analyze," Trend Micro said.
CACTUS and Rapture are the latest additions to a long list of new ransomware
families that have come to light in recent weeks, including Gazprom, BlackBit,
UNIZA, Akira, and a NoCry ransomware variant called Kadavro Vector.
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts
28.4.23 Ransomware
The Hacker News
The threat actors behind RTM Locker have developed a
ransomware strain that's capable of targeting Linux machines, marking the
group's first foray into the open source operating system.
"Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be
inspired by Babuk ransomware's leaked source code," Uptycs said in a new report
published Wednesday. "It uses a combination of ECDH on Curve25519 (asymmetric
encryption) and Chacha20 (symmetric encryption) to encrypt files."
RTM Locker was first documented by Trellix earlier this month, describing its
developers as a private ransomware-as-a-service (RaaS) provider. It has its
roots in a cybercrime group called Read The Manual (RTM) that's known to be
active since at least 2015.
The group is notable for deliberately avoiding high-profile targets such as
critical infrastructure, law enforcement, and hospitals so as to draw as little
attention as possible. It also leverages affiliates to ransom victims, in
addition to leaking stolen data should they refuse to pay up.
The Linux flavor is specifically geared to single out ESXi hosts by terminating
all virtual machines running on a compromised host prior to commencing the
encryption process. The exact initial infector employed to deliver the
ransomware is currently unknown.
"It is statically compiled and stripped, making reverse engineering more
difficult and allowing the binary to run on more systems," Uptycs explained.
"The encryption function also uses pthreads (aka POSIX threads) to speed up
execution."
Following successful encryption, victims are urged to contact
the support team within 48 hours via Tox or risk getting their data published.
Decrypting a file locked with RTM Locker requires the public key appended to the
end of the encrypted file and the attacker's private key.
The development comes as Microsoft revealed that vulnerable PaperCut servers are
being actively targeted by threat actors to deploy Cl0p and LockBit ransomware.
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware
28.4.23 Ransomware
The Hacker News
Microsoft has confirmed that the active exploitation of
PaperCut servers is linked to attacks that are designed to deliver Cl0p and
LockBit ransomware families.
The tech giant's threat intelligence team is attributing a subset of the
intrusions to a financially motivated actor it tracks under the name Lace
Tempest (formerly DEV-0950), which overlaps with other hacking groups like
FIN11, TA505, and Evil Corp.
"In observed attacks, Lace Tempest ran multiple PowerShell commands to deliver a
TrueBot DLL, which connected to a C2 server, attempted to steal LSASS
credentials, and injected the TrueBot payload into the conhost.exe service,"
Microsoft said in a series of tweets.
The next phase of the attack entailed the deployment of Cobalt Strike Beacon
implant to conduct reconnaissance, move laterally across the network using WMI,
and exfiltrate files of interest via the file-sharing service MegaSync.
Lace Tempest is a Cl0p ransomware affiliate that's said to have previously
leveraged Fortra GoAnywhere MFT exploits as well as initial access gained via
Raspberry Robin infections (attributed to another actor dubbed DEV-0856).
Raspberry Robin, also called QNAP worm, is believed to be an access-as-a-service
malware that's used as a delivery vehicle for next-stage payloads such as
IcedID, Cl0p, and LockBit. It's known to incorporate various obfuscation,
anti-debugging, and anti-virtual machine measures to evade detection.
Microsoft said the threat actor subsumed PaperCut flaws (2023-27350 and
CVE-2023-27351) into its attack toolkit as early as April 13, corroborating the
Melbourne-based print management software provider's earlier assessment.
Successful exploitation of the separate clustertwo security vulnerabilities
could allow unauthenticated remote attackers to achieve arbitrary code execution
and gain unauthorized access to sensitive information.
A separate cluster of activity has also been detected weaponizing the same
flaws, including those that lead to LockBit ransomware infections, Redmond
further added.
According to an update shared by cybersecurity firm Huntress, the PaperCut flaws
have come under broader exploitation by opportunistic threat actors looking to
deploy Monero cryptocurrency miners on infected systems.
FIN7 Exploits Veeam Flaw CVE-2023-27532#
The development comes as the Russian
cybercrime group monitored as FIN7 has been connected to attacks exploiting
unpatched Veeam backup software instances to distribute POWERTRASH, a staple
PowerShell-based in-memory dropper that executes an embedded payload.

The activity, detected by WithSecure on March 28, 2023, likely involved the
abuse of CVE-2023-27532, a high-severity flaw in Veeam Backup & Replication that
permits an unauthenticated attacker to obtain encrypted credentials stored in
the configuration database and gain access to the infrastructure hosts. It was
patched last month.
"The threat actor used a series of commands as well as custom scripts to gather
host and network information from the compromised machines," the Finnish
cybersecurity company said. "Furthermore, a series of SQL commands were executed
to steal information from the Veeam backup database."
Also utilized in the attacks were custom PowerShell scripts to retrieve stored
credentials from the backup servers, gather system information, and set up an
active foothold in the compromised host by executing DICELOADER (aka Lizar or
Tirion) every time the device boots up.
The hitherto undocumented persistence script has been codenamed POWERHOLD, with
the DICELOADER malware decoded and executed using another unique loader referred
to as DUBLOADER.
"The goal of these attacks were unclear at the time of
writing, as they were mitigated before fully materializing," security
researchers Neeraj Singh and Mohammad Kazem Hassan Nejad said, adding the
findings point to the group's evolving tradecraft and modus operandi.
POWERHOLD and DUBLOADER are far from the only new pieces of malware added by
FIN7 to its attack arsenal. IBM Security X-Force recently shed light on a loader
and backdoor called Domino that's designed to facilitate follow-on exploitation.
Mirai Botnet Adds TP-Link Archer Wi-Fi Router Bug to the Mix#
In a related
development, the Zero Day Initiative (ZDI) disclosed that the Mirai botnet
authors have updated their malware to include CVE-2023-1389, a high-severity
flaw in TP-Link Archer AX21 routers that could allow an unauthenticated
adversary to execute arbitrary code on affected installations.
CVE-2023-1389 (CVSS score: 8.8) was demonstrated at the Pwn2Own hacking contest
held in Toronto in December 2022 by researchers from Team Viettel and Qrious
Security, prompting the vendor to issue fixes in March 2023.
The first signs of in-the-wild exploitation, per ZDI, emerged on April 11, 2023,
with the threat actors leveraging the flaw to make an HTTP request to the Mirai
command-and-control (C2) servers to download and execute payloads responsible
for co-opting the device into the botnet and launch DDoS attacks against game
servers.
"This is nothing new for the maintainers of the Mirai botnet, who are known for
quickly exploiting IoT devices to maintain their foothold in an enterprise," ZDI
threat researcher Peter Girnus said. "Applying this patch is the only
recommended action to address this vulnerability."
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack
25.4.23 Ransomware
The Hacker News

Threat actors are employing a previously undocumented "defense evasion tool"
dubbed AuKill that's designed to disable endpoint detection and response (EDR)
software by means of a Bring Your Own Vulnerable Driver (BYOVD) attack.
"The AuKill tool abuses an outdated version of the driver used by version 16.32
of the Microsoft utility, Process Explorer, to disable EDR processes before
deploying either a backdoor or ransomware on the target system," Sophos
researcher Andreas Klopsch said in a report published last week.
Incidents analyzed by the cybersecurity firm show the use of AuKill since the
start of 2023 to deploy various ransomware strains such as Medusa Locker and
LockBit. Six different versions of the malware have been identified to date. The
oldest AuKill sample features a November 2022 compilation timestamp.
The BYOVD technique relies on threat actors misusing a legitimate, but
out-of-date and exploitable, driver signed by Microsoft (or using a stolen or
leaked certificate) to gain elevated privileges and turn off security
mechanisms.
By using valid, susceptible drivers, the idea is to bypass a key Windows
safeguard known as Driver Signature Enforcement that ensures kernel-mode drivers
have been signed by a valid code signing authority before they are allowed to
run.
"The AuKill tool requires administrative privileges to work, but it cannot give
the attacker those privileges," Klopsch noted. "The threat actors using AuKill
took advantage of existing privileges during the attacks, when they gained them
through other means."
This is not the first time the Microsoft-signed Process Explorer driver has been
weaponized in attacks. In November 2022, Sophos also detailed LockBit
affiliates' use of an open source tool called Backstab that abused outdated
versions of the driver to terminate protected anti-malware processes.
Then earlier this year, a malvertising campaign was spotted utilizing the same
driver as part of an infection chain distributing a .NET loader named MalVirt to
deploy the FormBook information-stealing malware.
The development comes as the AhnLab Security Emergency response Center (ASEC)
revealed that poorly managed MS-SQL servers are being weaponized to install the
Trigona ransomware, which shares overlaps with another strain referred to as
CryLock.
It also follows findings that the Play ransomware (aka PlayCrypt) actors have
been observed using custom data harvesting tools that make it possible to
enumerate all users and computers on a compromised network and copy files from
the Volume Shadow Copy Service (VSS).
Grixba, a .NET-based information stealer, is designed to scan a machine for
security programs, backup software, and remote administration tools, and
exfiltrate the gathered data in the form of CSV files that are then compressed
into ZIP archives.
Also used by the cybercriminal gang, tracked by Symantec as Balloonfly, is a VSS
Copying Tool written in .NET that makes use of the AlphaVSS framework to list
files and folders in a VSS snapshot and copy them to a destination directory
prior to encryption.
Play ransomware is notable for not only utilizing
intermittent encryption to speed up the process, but also for the fact that it's
not operated on a ransomware-as-a-service (RaaS) model. Evidence gathered so far
points to Balloonfly carrying out the ransomware attacks as well as developing
the malware themselves.
Grixba and VSS Copying Tool are the latest in a long list of proprietary tools
such as Exmatter, Exbyte, and PowerShell-based scripts that are used by
ransomware actors to establish more control over their operations, while also
adding extra layers of complexity to persist in compromised environments and
evade detection.
Another technique increasingly adopted by financially-motivated groups is the
use of the Go programming language to develop cross-platform malware and resist
analysis and reverse engineering efforts.
Indeed, a report from Cyble last week documented a new GoLang ransomware called
CrossLock that employs the double-extortion technique to increase the likelihood
of payment from its victims, alongside taking steps to sidestep event tracing
for Windows (ETW).
"This functionality can enable the malware to avoid detection by security
systems that depend on event logs," Cyble said. "CrossLock Ransomware also
performs several actions to reduce the chances of data recovery while
simultaneously increasing the attack's effectiveness."
LockBit Ransomware Now Targeting Apple macOS Devices
18.4.23
Ransomware The Hacker News
Threat actors behind the LockBit ransomware operation have developed new
artifacts that can encrypt files on devices running Apple's macOS operating
system.
The development, which was reported by the MalwareHunterTeam over the weekend,
appears to be the first time a big-game ransomware crew has created a
macOS-based payload.
Additional samples identified by vx-underground show that the macOS variant has
been available since November 11, 2022, and has managed to evade detection by
anti-malware engines until now.
LockBit is a prolific cybercrime crew with ties to Russia that has been active
since late 2019, with the threat actors releasing two major updates to the
locker in 2021 and 2022.
According to statistics released by Malwarebytes last week, LockBit emerged as
the second most used ransomware in March 2023 after Cl0p, accounting for 93
successful attacks.
An analysis of the new macOS version ("locker_Apple_M1_64"_ reveals that it's
still a work in progress, relying on an invalid signature to sign the
executable. This also means that Apple's Gatekeeper protections will prevent it
from being run even if it's downloaded and launched on a device.
The payload, per security researcher Patrick Wardle, packs in files like
autorun.inf and ntuser.dat.log, suggesting that the ransomware sample was
originally designed to target Windows.
"While yes it can indeed run on Apple Silicon, that is basically the extent of
its impact," Wardle said. "Thus macOS users have nothing to worry about ...for
now!"
Wardle also pointed out additional safeguards implemented by Apple,
such as System Integrity Protection (SIP) and Transparency, Consent, and Control
(TCC) that prevent the execution of unauthorized code and require apps to seek
users' permission to access protected files and data.
"This means that without an exploit or explicit user-approval users files will
remain protected," Wardle pointed out. "Still an additional layer or
detection/protection may be warranted."
The findings, despite the artifacts' overall bugginess, are a definite sign that
threat actors are increasingly setting their sights on macOS systems.
A LockBit representative has since confirmed to Bleeping Computer that the macOS
encryptor is "actively being developed," indicating that the malware is likely
to pose a serious threat to the platform.
Vice Society Ransomware Using Stealthy PowerShell Tool for Data Exfiltration
17.4.23 Ransomware
The Hacker News
Threat actors associated with the Vice Society ransomware
gang have been observed using a bespoke PowerShell-based tool to fly under the
radar and automate the process of exfiltrating data from compromised networks.
"Threat actors (TAs) using built-in data exfiltration methods like [living off
the land binaries and scripts] negate the need to bring in external tools that
might be flagged by security software and/or human-based security detection
mechanisms," Palo Alto Networks Unit 42 researcher Ryan Chapman said.
"These methods can also hide within the general operating environment, providing
subversion to the threat actor."
Vice Society, tracked by Microsoft under the name DEV-0832, is an
extortion-focused hacking group that emerged on the scene in May 2021. It's
known to rely on ransomware binaries sold on the criminal underground to meet
its goals.
In December 2022, SentinelOne detailed the group's use of a ransomware variant,
dubbed PolyVice, that implements a hybrid encryption scheme that combines
asymmetric and symmetric encryption to securely encrypt files.
Vice Society Ransomware
The PowerShell script discovered by Unit 42 (w1.ps1)
works by identifying mounted drives on the system, and then recursively
searching through each of the root directories to facilitate data exfiltration
over HTTP.
The tool also makes use of exclusion criteria to filter out system files,
backups, and folders pointing to web browsers as well as security solutions from
Symantec, ESET, and Sophos. The cybersecurity firm said the overall design of
the tool demonstrates a "professional level of coding."
The discovery of the
data exfiltration script illustrates the ongoing threat of double extortion in
the ransomware landscape. It also serves as a reminder for organizations to
prioritize robust security protections and stay vigilant against evolving
threats.
"Vice Society's PowerShell data exfiltration script is a simple tool for data
exfiltration," Chapman said. "Multi-processing and queuing are used to ensure
the script does not consume too many system resources."
"However, the script's focus on files over 10 KB with file extensions and in
directories that meet its include list means that the script will not exfiltrate
data that doesn't fit this description."
RTM Locker: Emerging Cybercrime Group Targeting Businesses with Ransomware
14.4.23 Ransomware
The Hacker News

Cybersecurity researchers have detailed the tactics of a "rising" cybercriminal
gang called "Read The Manual" (RTM) Locker that functions as a private
ransomware-as-a-service (RaaS) provider and carries out opportunistic attacks to
generate illicit profit.
"The 'Read The Manual' Locker gang uses affiliates to ransom victims, all of
whom are forced to abide by the gang's strict rules," cybersecurity firm Trellix
said in a report shared with The Hacker News.
"The business-like set up of the group, where affiliates are required to remain
active or notify the gang of their leave, shows the organizational maturity of
the group, as has also been observed in other groups, such as Conti."
RTM, first documented by ESET in February 2017, started off in 2015 as a banking
malware targeting businesses in Russia via drive-by downloads, spam, and
phishing emails. Attack chains mounted by the group have since evolved to deploy
a ransomware payload on compromised hosts.
In March 2021, the Russian-speaking group was attributed to an extortion and
blackmail campaign that deployed a trifecta of threats, including legitimate
remote access tools, a financial trojan, and a ransomware strain called Quoter.
Trellix told The Hacker News that there is no relationship between Quoter and
the RTM Locker ransomware executable used in the latest attacks.
A key trait of the threat actor is its ability to operate under the shadows by
deliberately avoiding high-profile targets that could draw attention to its
activities. To that end, CIS countries, as well as morgues, hospitals, COVID-19
vaccine-related corporations, critical infrastructure, law enforcement, and
other prominent companies are off-limits for the group.
"The RTM gang's goal is to attract as little attention as possible, which is
where the rules help them to avoid hitting high-value targets," security
researcher Max Kersten said. "Their management of affiliates to accomplish that
goal requires some level of sophistication, though it's not a high level per
se."
RTM Locker malware builds are bound by strict mandates that forbid
affiliates from leaking the samples, or else risk facing a ban. Among the other
rules laid out is a clause that locks out affiliates should they remain inactive
for 10 days sans a notification upfront.
"The effort the gang put into avoiding drawing attention was the most unusual,"
Kersten explained. "The affiliates need to be active as well, making it harder
for researchers to infiltrate the gang. All in all, the gang's specific efforts
in this area are higher than normally observed compared to other ransomware
groups."
It's suspected that the locker is executed on networks that are already under
the adversary's control, indicating that the systems may have been compromised
by other means, such as phishing attacks, malspam, or the exploitation of
internet-exposed vulnerable servers.
The threat actor, like other RaaS groups, uses extortion techniques to compel
victims into paying up. The payload, for its part, is capable of elevating
privileges, terminating antivirus and backup services, and deleting shadow
copies before commencing its encryption procedure.
It's also designed to empty the Recycle Bin to prevent recovery, change the
wallpaper, wipe event logs, and execute a shell command that self-deletes the
locker as a last step.
The findings suggest that cybercrime groups will continue to "adopt new tactics
and methods to avoid the headlines and help them fly under the radar of
researchers and law enforcement alike," Kersten noted.
Taiwanese PC Company MSI Falls Victim to Ransomware Attack
9.4.23
Ransomware The Hacker News
Taiwanese PC company MSI (short for Micro-Star International) officially
confirmed it was the victim of a cyber attack on its systems.
The company said it "promptly" initiated incident response and recovery measures
after detecting "network anomalies." It also said it alerted law enforcement
agencies of the matter.
That said, MSI did not disclose any specifics about when the attack took place
and if it entailed the exfiltration of any proprietary information, including
source code.
"Currently, the affected systems have gradually resumed normal operations, with
no significant impact on financial business," the company said in a brief notice
shared on Friday.
In a regulatory filing with the Taiwan Stock Exchange, it said that it's setting
up enhanced controls of its network and infrastructure to ensure the security of
data.
MSI is further urging users to obtain firmware/BIOS updates only from its
official website, and refrain from downloading files from other sources.
The disclosure comes as a new ransomware gang known as Money Message added the
company to its list of victims. The threat actor was spotlighted by Zscaler late
last month.
"The group utilizes a double extortion technique to target its
victims, which involves exfiltrating the victim's data before encrypting it,"
Cyble noted in an analysis published this week. "The group uploads the data on
their leak site if the ransom is unpaid."
The development comes a month after Acer confirmed a breach of its own that
resulted in the theft of 160 GB of confidential data. It was advertised on March
6, 2023, for sale on the now-defunct BreachForums.
Microsoft Takes Legal Action to Disrupt Cybercriminals' Illegal Use of Cobalt
Strike Tool
7.4.23
Ransomware The Hacker News
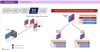
Microsoft said it teamed up with Fortra and Health Information Sharing and
Analysis Center (Health-ISAC) to tackle the abuse of Cobalt Strike by
cybercriminals to distribute malware, including ransomware.
To that end, the tech giant's Digital Crimes Unit (DCU) revealed that it secured
a court order in the U.S. to "remove illegal, legacy copies of Cobalt Strike so
they can no longer be used by cybercriminals."
While Cobalt Strike, developed and maintained by Fortra (formerly HelpSystems),
is a legitimate post-exploitation tool used for adversary simulation, illegal
cracked versions of the software have been weaponized by threat actors over the
years.
Ransomware actors, in particular, have leveraged Cobalt Strike after obtaining
initial access to a target environment to escalate privileges, lateral move
across the network, and deploy file-encrypting malware.

"The ransomware families associated with or deployed by cracked copies of Cobalt
Strike have been linked to more than 68 ransomware attacks impacting healthcare
organizations in more than 19 countries around the world," Amy Hogan-Burney,
general manager of DCU, said.
By disrupting the use of legacy copies of Cobalt Strike and compromised
Microsoft software, the goal is to hinder the attacks and force the adversaries
to rethink their tactics, the company added.
Redmond further noted the
misuse of Cobalt Strike by nation-state groups whose operations align with that
of Russia, China, Vietnam, and Iran, adding it detected malicious infrastructure
hosting Cobalt Strike across the globe, counting China, the U.S., and Russia.
The legal crackdown comes months after Google Cloud identified 34 different
hacked release versions of the Cobalt Strike tool in the wild in an attempt to
"make it harder for bad guys to abuse."
Rorschach Ransomware Emerges: Experts Warn of Advanced Evasion Strategies
5.4.23 Ransomware
The Hacker News
Cybersecurity researchers have taken the wraps off a previously undocumented
ransomware strain called Rorschach that's both sophisticated and fast.
"What makes Rorschach stand out from other ransomware strains is its high level
of customization and its technically unique features that have not been seen
before in ransomware," Check Point Research said in a new report. "In fact,
Rorschach is one of the fastest ransomware strains ever observed, in terms of
the speed of its encryption."
The cybersecurity firm said it observed the ransomware deployed against an
unnamed U.S.-based company, adding it found no branding or overlaps that connect
it to any previously known ransomware actors.
However, further analysis of Rorschach's source code reveals similarities to
Babuk ransomware, which suffered a leak in September 2021, and LockBit 2.0. On
top of that, the ransom notes sent out to the victims appear to be inspired by
that of Yanluowang and DarkSide.
The most significant aspect of the intrusion is the use of a technique called
DLL side-loading to load the ransomware payload, a method rarely observed in
such attacks. The development marks a new sophistication in the approaches
adopted by financially motivated groups to sidestep detection.
Specifically, the ransomware is said to have been deployed by abusing Palo Alto
Network's Cortex XDR Dump Service Tool (cy.exe) to sideload a library named
"winutils.dll."
Another unique characteristic is its highly customizable nature and the use of
direct syscalls to manipulate files and bypass defense mechanisms.
Rorschach ransomware is also tasked with terminating a predefined list of
services, deleting shadow volumes and backups, clearing Windows events logs to
erase forensic trail, disabling the Windows firewall, and even deleting itself
after completing its actions.
Internal propagation is achieved by compromising the domain controller and
creating a group policy, according to Check Point and South Korean cybersecurity
company AhnLab, which erroneously attributed the infection chain to DarkSide
earlier this February.
The ransomware, like other malware strains observed in the wild, skips machines
that are located in the Commonwealth of Independent States (CIS) countries by
checking the system language.
"The Rorschach ransomware employs a highly effective and fast
hybrid-cryptography scheme, which blends the curve25519 and eSTREAM cipher
hc-128 algorithms for encryption purposes," researchers Jiri Vinopal, Dennis
Yarizadeh, and Gil Gekker explained.
This process is designed to only encrypt a specific portion of the original file
content instead of the entire file, and employs additional compiler optimization
methods that make it a "speed demon."
In five separate tests carried out by Check Point in a controlled environment,
220,000 files were encrypted using Rorschach within four minutes and 30 seconds
on average. LockBit 3.0, on the other hand, took approximately seven minutes.
"Its developers implemented new anti-analysis and defense evasion techniques to
avoid detection and make it more difficult for security software and researchers
to analyze and mitigate its effects," the researchers said.
"Additionally, Rorschach appears to have taken some of the 'best' features from
some of the leading ransomwares leaked online, and integrated them all together.
In addition to Rorschach's self-propagating capabilities, this raises the bar
for ransom attacks."
The findings come as the Fortinet FortiGuard Labs detailed two emerging
ransomware families called PayMe100USD, a Python-based file-locking malware, and
Dark Power, which is written in the Nim programming language.
Rorschach (aka BabLock) Attacks Spotted in Asia, Europe, and the Middle East#
Singapore-headquartered Group-IB said it has identified Rorschach attacks
targeting small and medium-sized companies and industrial firms across Asia,
Europe, and the Middle East.
The cybersecurity company has christened the
ransomware strain BabLock, so named for its source code similarities to Babuk
and LockBit. It's said to be active since at least June 2022 and has
capabilities to strike ESXi and Linux systems as well.
"The absence of [a data leak site], along with relatively modest ransom requests
ranging from 50,000 to 1,000,000 USD, allows the group to operate stealthily and
remain under the radar," Group-IB researchers Andrey Zhdanov and Vladislav
Azersky said.

In the incident aimed at an unnamed industrial sector company in Europe, the
threat actors leveraged a remote code execution flaw impacting Zimbra
Collaboration (CVE-2022-41352, CVSS score: 9.8) to gain initial access.
The attack entailed no data exfiltration prior to encryption, instead
pressurizing victims to pay up by threatening to "attack your company again in
the future" and "delete all your data from your networks."
The Linux counterpart, according to Group-IB, is an 32-bit ELF binary written in
Go 1.18.3, whereas the ESXi variant is a 64-bit program for Linux in ELF format
compiled using GNU Compiler (GCC). Both the versions are based on the leaked
Babuk ransomware source code.
"It would make more sense for the threat actors to use a simpler program based
on Babuk to encrypt Windows systems, but they preferred developing their own,
more sophisticated program, which overall is not similar to other families," the
researchers said.
Palo Alto Networks, in an informational bulletin released on April 4, said it's
aware of attacks leveraging its Cortex XDR Dump Service Tool to load the
Rorschach payload, adding they don't affect macOS and Linux platforms. It's also
expected to release a patch to address the issue next week.
"When removed from its installation directory, the Cortex XDR Dump Service Tool
(cydump.exe), which is included with Cortex XDR agent on Windows, can be used to
load untrusted dynamic link libraries (DLLs) with a technique known as DLL
side-loading," the cybersecurity company said.
"Rorschach ransomware uses a copy of this tool and this technique to evade
detection on systems that do not have sufficient endpoint protection. When the
Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool
process is running from the installation path, it is not possible to side-load
DLLs with this technique."
Researchers Shed Light on CatB Ransomware's Evasion Techniques
21.3.23
Ransomware The Hacker News
The threat actors behind the CatB ransomware operation have been observed using
a technique called DLL search order hijacking to evade detection and launch the
payload.
CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said
to be an "evolution or direct rebrand" of another ransomware strain known as
Pandora based on code-level similarities.
It's worth noting that the use of Pandora has been attributed to Bronze
Starlight (aka DEV-0401 or Emperor Dragonfly), a China-based threat actor that's
known to employ short-lived ransomware families as a ruse to likely conceal its
true objectives.
One of the key defining characteristics of CatB is its reliance on DLL hijacking
via a legitimate service called Microsoft Distributed Transaction Coordinator
(MSDTC) to extract and launch the ransomware payload.
"Upon execution, CatB payloads rely on DLL search order hijacking to drop and
load the malicious payload," SentinelOne researcher Jim Walter said in a report
published last week. "The dropper (versions.dll) drops the payload (oci.dll)
into the System32 directory."

The dropper is also responsible for carrying out anti-analysis checks to
determine if the malware is being executed within a virtual environment, and
ultimately abusing the MSDTC service to inject the rogue oci.dll containing the
ransomware into the msdtc.exe executable upon system restart.
"The [MSDTC] configurations changed are the name of the account under which the
service should run, which is changed from Network Service to Local System, and
the service start option, which is changed from Demand start to Auto start for
persistency if a restart occurs," Minerva Labs researcher Natalie Zargarov
explained in a previous analysis.
One striking aspect of the ransomware is its absence of a ransom note. Instead,
each encrypted file is updated with a message urging the victims to make a
Bitcoin payment.
Another trait is the malware's ability to harvest sensitive
data such as passwords, bookmarks, history from web browsers Google Chrome,
Microsoft Edge (and Internet Explorer), and Mozilla Firefox.

"CatB joins a long line of ransomware families that embrace semi-novel
techniques and atypical behaviors such as appending notes to the head of files,"
Walter said. "These behaviors appear to be implemented in the interest of
detection evasion and some level of anti-analysis trickery."
This is not the first time the MSDTC service has been weaponized for malicious
purposes. In May 2021, Trustwave disclosed a novel malware dubbed Pingback that
leveraged the same technique to achieve persistence and bypass security
solutions.
LockBit 3.0 Ransomware: Inside the Cyberthreat That's Costing Millions
18.3.23 Ransomware
The Hacker News
U.S. government agencies have released a joint
cybersecurity advisory detailing the indicators of compromise (IoCs) and
tactics, techniques, and procedures (TTPs) associated with the notorious LockBit
3.0 ransomware.
"The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service
(RaaS) model and is a continuation of previous versions of the ransomware,
LockBit 2.0, and LockBit," the authorities said.
The alert comes courtesy of the U.S. Federal Bureau of Investigation (FBI), the
Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State
Information Sharing & Analysis Center (MS-ISAC).
Since emerging in late 2019, the LockBit actors have invested significant
technical efforts to develop and fine-tune its malware, issuing two major
updates — LockBit 2.0, released in mid-2021, and LockBit 3.0, released in June
2022. The two versions are also known as LockBit Red and LockBit Black,
respectively.
"LockBit 3.0 accepts additional arguments for specific operations in lateral
movement and rebooting into Safe Mode," according to the alert. "If a LockBit
affiliate does not have access to passwordless LockBit 3.0 ransomware, then a
password argument is mandatory during the execution of the ransomware."
The ransomware is also designed to infect only those machines whose language
settings do not overlap with those specified in an exclusion list, which
includes Romanian (Moldova), Arabic (Syria), and Tatar (Russia).
Initial access to victim networks is obtained via remote desktop protocol (RDP)
exploitation, drive-by compromise, phishing campaigns, abuse of valid accounts,
and weaponization of public-facing applications.
Upon finding a successful ingress point, the malware takes steps to establish
persistence, escalate privileges, carry out lateral movement, and purge log
files, files in the Windows Recycle Bin folder, and shadow copies, before
initiating the encryption routine.
"LockBit affiliates have been observed using various freeware and open source
tools during their intrusions," the agencies said. "These tools are used for a
range of activities such as network reconnaissance, remote access and tunneling,
credential dumping, and file exfiltration."
One defining characteristic of the attacks is the use of a custom exfiltration
tool referred to as StealBit, which the LockBit group provides to affiliates for
double extortion purposes.
In November, the U.S. Department of Justice reported that the LockBit ransomware
strain has been used against at least 1,000 victims worldwide, netting the
operation over $100 million in illicit profits.
Industrial cybersecurity firm Dragos, earlier this year, revealed that LockBit
3.0 was responsible for 21% of 189 ransomware attacks detected against critical
infrastructure in Q4 2022, accounting for 40 incidents. A majority of those
attacks impacted food and beverage and manufacturing sectors.
The FBI's Internet Crime Complaint Center (IC3), in its latest Internet Crime
Report, listed LockBit (149), BlackCat (114), and Hive (87) as the top three
ransomware variants victimizing critical infrastructure in 2022.
Despite LockBit's prolific attack spree, the ransomware gang suffered a huge
blow in late September 2022 when a disgruntled LockBit developer released the
builder code for LockBit 3.0, raising concerns that other criminal actors could
take advantage of the situation and spawn their own variants.
The advisory
comes as the BianLian ransomware group has shifted its focus from encrypting its
victims' files to pure data-theft extortion attacks, months after cybersecurity
company Avast released a free decryptor in January 2023.
In a related development, Kaspersky has published a free decryptor to help
victims who have had their data locked down by a version of ransomware based on
the Conti source code that leaked after Russia's invasion of Ukraine last year
led to internal friction among the core members.
"Given the sophistication of the LockBit 3.0 and Conti ransomware variants, it
is easy to forget that people are running these criminal enterprises," Intel 471
noted last year. "And, as with legitimate organizations, it only takes one
malcontent to unravel or disrupt a complex operation."
Clop ransomware gang begins extorting GoAnywhere zero-day victims
12.3.23
Ransomware
Bleepingcomputer
The Clop ransomware gang has begun extorting companies whose data was stolen
using a zero-day vulnerability in the Fortra GoAnywhere MFT secure file-sharing
solution.
In February, the GoAnywhere MFT file transfer solution developers warned
customers that a zero-day remote code execution vulnerability was being
exploited on exposed administrative consoles.
GoAnywhere is a secure web file transfer solution that allows companies to
securely transfer encrypted files with their partners while keeping detailed
audit logs of who accessed the files.
While no details were publicly shared on how the vulnerability was exploited, a
proof-of-concept exploit was soon released, followed by a patch for the flaw.
The day after the release of the GoAnywhere patch, the Clop ransomware gang
contacted BleepingComputer and said they were responsible for the attacks.
The extortion group said they used the flaw over ten days to steal data from 130
companies. At the time, BleepingComputer could not independently confirm these
claims, and Fortra did not respond to our emails.
Since then, two companies, Community Health Systems (CHS) and Hatch Bank,
disclosed that data was stolen in the GoAnywhere MFT attacks.
Clop begins extorting GoAnywhere customers
Last night, the Clop ransomware
gang began publicly exploiting victims of the GoAnywhere attacks by adding seven
new companies to their data leak site.
Only one of the victims, Hatch Bank, is publicly known to have been breached
using the vulnerability. However, BleepingComputer has learned that at least two
other listed companies had their data stolen using this flaw as well.
The entries on the data leak site all state that the release of data is "coming
soon" but include screenshots of allegedly stolen data.
Hatch Bank listed on Clop's data leak site
Source: BleepingComputer
Furthermore, BleepingComputer has been told that victims have begun to receive
ransom demands from the ransomware gang.
While it is unclear how much the threat actors are demanding, they had
previously demanded $10 million in ransoms in similar attacks using an Accellion
FTA zero-day vulnerability in December 2020.
During these attacks, the extortion group stole large amounts of data from
nearly 100 companies worldwide, with the threat actors slowly leaking data from
companies while demanding million-dollar ransoms.
Organizations that had their Accellion servers hacked include, among others,
energy giant Shell, cybersecurity firm Qualys, supermarket giant Kroger, and
multiple universities worldwide such as Stanford Medicine, University of
Colorado, University of Miami, University of California, and the University of
Maryland Baltimore (UMB).