
Ransom 2024 2023 2022 2021 2020
Researchers Detail Techniques LockBit Ransomware Using to Infect its Targets
8.7.22 Ransomware
Thehackernews
LockBit ransomware attacks are constantly evolving by making use of a wide range of techniques to infect targets while also taking steps to disable endpoint security solutions.
"The affiliates that use LockBit's services conduct their attacks according to their preference and use different tools and techniques to achieve their goal," Cybereason security analysts Loïc Castel and Gal Romano said. "As the attack progresses further along the kill chain, the activities from different cases tend to converge to similar activities."
LockBit, which operates on a ransomware-as-a-service (RaaS) model like most groups, was first observed in September 2019 and has since emerged as the most dominant ransomware strain this year, surpassing other well-known groups like Conti, Hive, and BlackCat.
This involves the malware authors licensing access to affiliates, who execute the attacks in exchange for using their tools and infrastructure and earn as much as 80% of each successful ransom payment received from the victims.
LockBit also utilizes the popular technique of double extortion to exfiltrate vast amounts of data prior to encrypting the assets of the target, netting the cybercriminal syndicate no fewer than 850 victims on its data leak site as of May 2022.
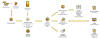
Attack Life Cycle - Case Study 1
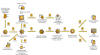
According to a leak site data analysis by Palo Alto Networks Unit 42, LockBit
accounted for 46% of all ransomware-related breach events for the first quarter
of 2022. In June alone, the group has been tied to 44 attacks, making it the
most active ransomware strain.
LockBit ransomware attacks are known to employ several avenues for initial infection: Exploiting publicly-exposed RDP ports, relying on phishing emails to download malicious payloads, or leveraging unpatched server flaws that allow the affiliates to gain remote access to the targeted network.
Following this step are reconnaissance and credential theft activities, which enable the actors to move laterally across the network, establish persistence, escalate privileges, and launch the ransomware. This is also accompanied by running commands to delete backups and subvert detection by firewalls and antivirus software.
In the three years since LockBit appeared on the scene, the RaaS scheme has received two notable upgrades, with the threat actors debuting LockBit 2.0 in June 2021 and launching the third installment of the service, LockBit 3.0, last month with support for Zcash cryptocurrency payment options and a bug bounty program — the first for a ransomware group.
The initiative claims to offer rewards of up to $1 million for finding security blind spots in its website and locker software, submitting brilliant ideas, doxing the head of the gang's affiliate program, or identifying ways that could expose the IP of the server hosting the website on the TOR network.
The bug bounty program is yet another sign that hacker groups are increasingly functioning as legitimate IT enterprises, incorporating HR departments, regular feature releases, and even bonuses for solving challenging problems.
However, indications are that LockBit 3.0, also called LockBit Black, is inspired by another ransomware family known as BlackMatter, a rebranded version of DarkSide that shuttered in November 2021.
"Large portions of the code are ripped straight from BlackMatter/Darkside," Emsisoft researcher Fabian Wosar said in a tweet earlier this week. "Guess it is clear that LockBit got their dirty hands on another group's code."
North Korean Maui Ransomware Actively Targeting U.S. Healthcare Organizations
7.7.22 Ransomware
Thehackernews
In a new joint
cybersecurity advisory, U.S. cybersecurity and intelligence agencies have warned
about the use of Maui ransomware by North Korean government-backed hackers to
target the healthcare sector since at least May 2021.
"North Korean state-sponsored cyber actors used Maui ransomware in these incidents to encrypt servers responsible for healthcare services—including electronic health records services, diagnostics services, imaging services, and intranet services," the authorities noted.
The alert comes courtesy of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of the Treasury.
Cybersecurity firm Stairwell, whose findings formed the basis of the advisory, said the lesser-known ransomware family stands out because of a lack of several key features commonly associated with ransomware-as-a-service (RaaS) groups.
This includes the absence of "embedded ransom note to provide recovery instructions or automated means of transmitting encryption keys to attackers," security researcher Silas Cutler said in a technical overview of the ransomware.
Instead, analysis of Maui samples suggests that the malware is designed for manual execution by a remote actor via a command-line interface, using it to target specific files on the infected machine for encryption.
Besides encrypting target files with AES 128-bit encryption with a unique key, each of these keys is, in turn, encrypted with RSA using a key pair generated the first time when Maui is executed. As a third layer of security, the RSA keys are encrypted using a hard-coded RSA public key that's unique to each campaign.
What sets Maui apart from other traditional ransomware offerings is also the fact that it's not offered as a service to other affiliates for use in return for a share of monetary profits.
In some instances, the ransomware incidents are said to have disrupted health services for extended periods of time. The initial infection vector used to conduct the intrusions is unknown as yet.
It's worth noting that the campaign is predicated on the willingness of healthcare entities to pay ransoms to quickly recover from an attack and ensure uninterrupted access to critical services. It's the latest indication of how North Korean adversaries are adapting their tactics to illegally generate a constant stream of revenue for the cash-strapped nation.
According to the Sophos' State of Ransomware in Healthcare 2022 report, 61% of healthcare organizations surveyed opted to settle compared with the global average of 46%, with only 2% of those that paid the ransom in 2021 getting their complete data back.
That said, the use of a manually operated ransomware family by an APT group also raises the possibility that the operation could be a diversionary tactic designed to act as a cover for other malicious motives, as recently observed in the case of Bronze Starlight.
"Nation state-sponsored ransomware attacks have become typical international acts of aggression," Peter Martini, co-founder of iboss, said in a statement. "Unfortunately, North Korea specifically has shown it is very willing to indiscriminately target various industries, including healthcare, to secure untraceable cryptocurrency that is funding its nuclear weapons program."
Hive Ransomware Upgrades to Rust for More Sophisticated Encryption Method
6.7.22 Ransomware
Thehackernews
The operators of the Hive ransomware-as-a-service (RaaS) scheme have overhauled
their file-encrypting software to fully migrate to Rust and adopt a more
sophisticated encryption method.
"With its latest variant carrying several major upgrades, Hive also proves it's one of the fastest evolving ransomware families, exemplifying the continuously changing ransomware ecosystem," Microsoft Threat Intelligence Center (MSTIC) said in a report on Tuesday.
Hive, which was first observed in June 2021, has emerged as one of the most prolific RaaS groups, accounting for 17 attacks in the month of May 2022 alone, alongside Black Basta and Conti.
The shift from GoLang to Rust makes Hive the second ransomware strain after BlackCat to be written in the programming language, enabling the malware to gain additional benefits such as memory safety and deeper control over low-level resources as well as make use of a wide range of cryptographic libraries.
What it also affords is the ability to render the malware resistant to reverse engineering, making it more evasive. Furthermore, it comes with features to stop services and processes associated with security solutions that may stop it in its tracks.

Hive is no different from other ransomware families in that it deletes backups
to prevent recovery, but what's changed significantly in the new Rust-based
variant is its approach to file encryption.
"Instead of embedding an encrypted key in each file that it encrypts, it generates two sets of keys in memory, uses them to encrypt files, and then encrypts and writes the sets to the root of the drive it encrypts, both with .key extension," MSTIC explained.
To determine which of the two keys is used for locking a specific file, an encrypted file is renamed to include the file name containing the key that's then followed by an underscore and a Base64-encoded string (e.g., "C:\myphoto.jpg.l0Zn68cb _ -B82BhIaGhI8") that points to two different locations in the corresponding .key file.
The findings come as the threat actor behind the lesser-known AstraLocker ransomware ceased operations and released a decryption tool as part of a shift to crytojacking, Bleeping Computer reported this week.
But in an indication that the cybercriminal landscape is in constant flux, cybersecurity researchers have discovered a new ransomware family called RedAlert (aka N13V) that's capable of targeting both Windows and Linux VMWare ESXi servers.
Researchers Share Techniques to Uncover Anonymized Ransomware Sites on Dark Web
5.7.22 Ransomware
Thehackernews
Cybersecurity researchers have detailed the various measures ransomware actors
have taken to obscure their true identity online as well as the hosting location
of their web server infrastructure.
"Most ransomware operators use hosting providers outside their country of origin (such as Sweden, Germany, and Singapore) to host their ransomware operations sites," Cisco Talos researcher Paul Eubanks said. "They use VPS hop-points as a proxy to hide their true location when they connect to their ransomware web infrastructure for remote administration tasks."
Also prominent are the use of the TOR network and DNS proxy registration services to provide an added layer of anonymity for their illegal operations.
But by taking advantage of the threat actors' operational security missteps and other techniques, the cybersecurity firm disclosed last week that it was able to identify TOR hidden services hosted on public IP addresses, some of which are previously unknown infrastructure associated with DarkAngels, Snatch, Quantum, and Nokoyawa ransomware groups.
While ransomware groups are known to rely on the dark web to conceal their illicit activities ranging from leaking stolen data to negotiating payments with victims, Talos disclosed that it was able to identify "public IP addresses hosting the same threat actor infrastructure as those on the dark web."
"The methods we used to identify the public internet IPs involved matching threat actors' [self-signed] TLS certificate serial numbers and page elements with those indexed on the public internet," Eubanks said.
Besides TLS certificate matching, a second method employed to uncover the
adversaries' clear web infrastructures entailed checking the favicons associated
with the darknet websites against the public internet using web crawlers like
Shodan.
In the case of Nokoyawa, a new Windows ransomware strain that appeared earlier this year and shares substantial code similarities with Karma, the site hosted on the TOR hidden service was found to harbor a directory traversal flaw that enabled the researchers to access the "/var/log/auth.log" file used to capture user logins.
The findings demonstrate that not only are the criminal actors' leak sites accessible for any user on the internet, other infrastructure components, including identifying server data, were left exposed, effectively making it possible to obtain the login locations used to administer the ransomware servers.

Further analysis of the successful root user logins showed that they originated
from two IP addresses 5.230.29[.]12 and 176.119.0[.]195, the former of which
belongs to GHOSTnet GmbH, a hosting provider that offers Virtual Private Server
(VPS) services.
"176.119.0[.]195 however belongs to AS58271 which is listed under the name Tyatkova Oksana Valerievna," Eubanks noted. "It's possible the operator forgot to use the German-based VPS for obfuscation and logged into a session with this web server directly from their true location at 176.119.0[.]195."
LockBit adds a bug bounty program to its revamped RaaS operation
The
development comes as the operators of the emerging Black Basta ransomware
expanded its attack arsenal by using QakBot for initial access and lateral
movement, and taking advantage of the PrintNightmare vulnerability
(CVE-2021-34527) to conduct privileged file operations.
What's more, the LockBit ransomware gang last week announced the release of LockBit 3.0 with the message "Make Ransomware Great Again!," in addition to launching their own Bug Bounty program, offering rewards ranging between $1,000 and $1 million for identifying security flaws and "brilliant ideas" to improve its software.

"The release of LockBit 3.0 with the introduction of a bug bounty program is a
formal invitation to cybercriminals to help assist the group in its quest to
remain at the top," Satnam Narang, senior staff research engineer at Tenable,
said in a statement shared with The Hacker News.
"A key focus of the bug bounty program are defensive measures: Preventing security researchers and law enforcement from finding bugs in its leak sites or ransomware, identifying ways that members including the affiliate program boss could be doxed, as well as finding bugs within the messaging software used by the group for internal communications and the Tor network itself."
"The threat of being doxed or identified signals that law enforcement efforts are clearly a great concern for groups like LockBit. Finally, the group is planning to offer Zcash as a payment option, which is significant, as Zcash is harder to trace than Bitcoin, making it harder for researchers to keep tabs on the group's activity."
Ex-Canadian Government Employee Pleads Guilty Over NetWalker Ransomware Attacks
1.7.22 Ransomware Thehackernews
A former Canadian government employee this week agreed to plead guilty in the
U.S. to charges related to his involvement with the NetWalker ransomware
syndicate.
Sebastien Vachon-Desjardins, who was extradited to the U.S. on March 10, 2022, is accused of conspiracy to commit computer fraud and wire fraud, intentional damage to a protected computer, and transmitting a demand in relation to damaging a protected computer.
The 34-year-old IT consultant from Gatineau, Quebec, was initially apprehended in January 2021 following a coordinated law enforcement operation to dismantle the dark web infrastructure used by the NetWalker ransomware cybercrime group to publish data siphoned from its victims. The takedown also brought its activities to a standstill.
A search warrant executed at Vachon-Desjardins's home in Canada resulted in the seizure of 719 bitcoin, valued at approximately $28.1 million at the time, and $790,000 in Canadian currency. In February 2022, the Ontario Court of Justice sentenced him to six years and eight months in prison after he pleaded guilty to five criminal charges before his extradition to the U.S.
Stating that the defendant "excelled at what he did," the court said that the individual "even improved upon the ransom messages used by NetWalker affiliates and eventually convinced the creator of NetWalker to use 'mixing services' to disguise funds paid for ransoms in Bitcoin." The ruling also called him "good-looking, presentable, and instantly likeable."
Attacks mounted by the NetWalker gang are believed to have targeted dozens of
victims all over the world, specifically singling out the healthcare sector
during the COVID-19 pandemic in an attempt to capitalize on the global crisis
opportunistically.
It's known to adopt the lucrative tactic of double extortion to steal sensitive personal information prior to encrypting it and hold that data hostage in return for a cryptocurrency payment or risk getting the information published online.
Vachon-Desjardins, in his capacity as one of the 100 affiliates for the NetWalker gang, is suspected to be linked to at least 91 attacks since April 2020, in addition to working for other RaaS groups like Sodinokibi (REvil), Suncrypt, and Ragnarlocker.
According to court documents filed in a district court in Florida, the NetWalker crew amassed 5,058 bitcoin in illegal payments (about $40 million at the time of the transaction), with Vachon-Desjardins named as "one of the most prolific NetWalker ransomware affiliates" and responsible for the extortion of about 1,864 bitcoin.
His role in the criminal scheme allegedly ranged from researching on victims and controlling the servers hosting tools for reconnaissance, privilege escalation, and data theft to operating accounts that posted the stolen data on the data leak site and receiving payouts after a successful attack.
The defendant, as part of the plea deal, has now agreed to forfeit all the digital assets held in his crypto wallet as well as dozens of equipment that consist of laptops, tablets, phones, gaming consoles, and external hard drives, among others.
Cybersecurity Experts Warn of Emerging Threat of "Black Basta" Ransomware
27.6.22 Ransomware Thehackernews
The Black Basta ransomware-as-a-service (RaaS) syndicate has amassed nearly 50 victims in the U.S., Canada, the U.K., Australia, and New Zealand within two months of its emergence in the wild, making it a prominent threat in a short window.
"Black Basta has been observed targeting a range of industries, including manufacturing, construction, transportation, telcos, pharmaceuticals, cosmetics, plumbing and heating, automobile dealers, undergarments manufacturers, and more," Cybereason said in a report.
Similar to other ransomware operations, Black Basta is known to employ the tried-and-tested tactic of double extortion to plunder sensitive information from the targets and threaten to publish the stolen data unless a digital payment is made.
A new entrant in the already crowded ransomware landscape, intrusions involving the threat have leveraged QBot (aka Qakbot) as a conduit to maintain persistence on the compromised hosts and harvest credentials, before moving laterally across the network and deploying the file-encrypting malware.
Furthermore, the actors behind Black Basta have developed a Linux variant designed to strike VMware ESXi virtual machines (VMs) running on enterprise servers, putting it on par with other groups such as LockBit, Hive, and Cheerscrypt.
The findings come as the cybercriminal syndicate added Elbit Systems of America, a manufacturer of defense, aerospace, and security solutions, to the list of its victims over the weekend, according to security researcher Ido Cohen.
Black Basta is said to be comprised of members belonging to the Conti group
after the latter shuttered its operations in response to increased law
enforcement scrutiny and a major leak that saw its tools and tactics entering
the public domain after siding with Russia in the country's war against Ukraine.
"I cannot shoot anything, but I can fight with a keyboard and mouse," the Ukrainian computer specialist behind the leak, who goes by the pseudonym Danylo and released the treasure trove of data as a form of digital retribution, told CNN in March 2022.
The Conti team has since refuted that it's associated with Black Basta. Last week, it decommissioned the last of its remaining public-facing infrastructure, including two Tor servers used to leak data and negotiate with victims, marking an official end to the criminal enterprise.
In the interim, the group continued to maintain the facade of an active operation by targeting the Costa Rican government, while some members transitioned to other ransomware outfits and the brand underwent a organizational revamp that has seen it devolve into smaller subgroups with different motivations and business models ranging from data theft to working as independent affiliates.
According to a comprehensive report from Group-IB detailing its activities, the Conti group is believed to have victimized more than 850 entities since it was first observed in February 2020, compromising over 40 organizations worldwide as part of a "lightning-fast" hacking spree that lasted from November 17 to December 20, 2021.
Dubbed "ARMattack" by the Singapore-headquartered company, the intrusions were
primarily directed against U.S. organizations (37%), followed by Germany (3%),
Switzerland (2%), the U.A.E. (2%), the Netherlands, Spain, France, the Czech
Republic, Sweden, Denmark, and India (1% each).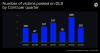
The top five sectors historically targeted by Conti have been manufacturing
(14%), real estate (11.1%), logistics (8.2%), professional services (7.1%), and
trade (5.5%), with the operators specifically singling out companies in the U.S.
(58.4%), Canada (7%), the U.K. (6.6%), Germany (5.8%), France (3.9%), and Italy
(3.1%).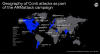
"Conti's increased activity and the data leak suggest that ransomware is no longer a game between average malware developers, but an illicit RaaS industry that gives jobs to hundreds of cybercriminals worldwide with various specializations," Group-IB's Ivan Pisarev said.
"In this industry, Conti is a notorious player that has in fact created an 'IT company' whose goal is to extort large sums. It is clear [...] that the group will continue its operations, either on its own or with the help of its 'subsidiary' projects."
State-Backed Hackers Using Ransomware as a Decoy for Cyber Espionage Attacks
24.6.22 Ransomware Thehackernews
A China-based advanced persistent threat (APT) group is possibly deploying
short-lived ransomware families as a decoy to cover up the true operational and
tactical objectives behind its campaigns.
The activity cluster, attributed to a hacking group dubbed Bronze Starlight by Secureworks, involves the deployment of post-intrusion ransomware such as LockFile, Atom Silo, Rook, Night Sky, Pandora, and LockBit 2.0.
"The ransomware could distract incident responders from identifying the threat actors' true intent and reduce the likelihood of attributing the malicious activity to a government-sponsored Chinese threat group," the researchers said in a new report. "In each case, the ransomware targets a small number of victims over a relatively brief period of time before it ceases operations, apparently permanently."
Bronze Starlight, active since mid-2021, is also tracked by Microsoft under the emerging threat cluster moniker DEV-0401, with the tech giant emphasizing its involvement in all stages of the ransomware attack cycle right from initial access to the payload deployment.
Unlike other RaaS groups that purchase access from initial access brokers (IABs) to enter a network, attacks mounted by the actor are characterized by the use of unpatched vulnerabilities affecting Exchange Server, Zoho ManageEngine ADSelfService Plus, Atlassian Confluence (including the newly disclosed flaw), and Apache Log4j.
Since August 2021, the group is said to have cycled through as many as six different ransomware strains such as LockFile (August), Atom Silo (October), Rook (November), Night Sky (December), Pandora (February 2022), and most recently LockBit 2.0 (April).
What's more, similarities have been uncovered between LockFile and Atom Silo as well as between Rook, Night Sky, and Pandora — the latter three derived from Babuk ransomware, whose source code leaked in September 2021 — indicating the work of a common actor.

"Because DEV-0401 maintains and frequently rebrands their own ransomware
payloads, they can appear as different groups in payload-driven reporting and
evade detections and actions against them," Microsoft noted last month.
Upon gaining a foothold inside a network, Bronze Starlight is known to rely on techniques like using Cobalt Strike and Windows Management Instrumentation (WMI) for lateral movement, although starting this month, the group has begun replacing Cobalt Strike with the Sliver framework in their attacks.

Other observed tradecraft relates to the use of HUI Loader to launch next-stage
encrypted payloads such as PlugX and Cobalt Strike Beacons, the latter of which
is employed to deliver the ransomware, but not before obtaining privileged
Domain Administrator credentials.
"The use of HUI Loader to load Cobalt Strike Beacon, the Cobalt Strike Beacon configuration information, the C2 infrastructure, and the code overlap suggest that the same threat group is associated with these five ransomware families," the researchers explained.
It's worth pointing out that both HUI Loader and PlugX, alongside ShadowPad, are
malware historically put to use by Chinese nation-state adversarial collectives,
lending credence to the possibility that Bronze Starlight is more geared towards
espionage than immediate monetary benefits.
On top of that, the victimology pattern spanning across the different ransomware strains shows that a majority of the targets are likely to be of more interest to Chinese government-sponsored groups focused on long-term intelligence gathering.
The key victims encompass pharmaceutical companies in Brazil and the U.S., a U.S.-based media organization with offices in China and Hong Kong, electronic component designers and manufacturers in Lithuania and Japan, a law firm in the U.S., and an aerospace and defense division of an Indian conglomerate.
To that end, the ransomware operations, besides providing a means to exfiltrate data as part of the double extortion "name-and-shame" scheme, also offer twin advantages in that it allows the threat actor to destroy forensic evidence of their malicious activities and act as a distraction from data theft.
"It is plausible that Bronze Starlight deploys ransomware as a smokescreen rather than for financial gain, with the underlying motivation of stealing intellectual property or conducting espionage," the researchers said.
BlackCat Ransomware Gang Targeting Unpatched Microsoft Exchange Servers
17.6.22 Ransomware Thehackernews
Microsoft is warning that the BlackCat ransomware crew is leveraging exploits
for unpatched Exchange server vulnerabilities to gain access to targeted
networks.
Upon gaining an entry point, the attackers swiftly moved to gather information about the compromised machines, followed by carrying out credential theft and lateral movement activities, before harvesting intellectual property and dropping the ransomware payload.
The entire sequence of events played out over the course of two full weeks, the Microsoft 365 Defender Threat Intelligence Team said in a report published this week.
"In another incident we observed, we found that a ransomware affiliate gained initial access to the environment via an internet-facing Remote Desktop server using compromised credentials to sign in," the researchers said, pointing out how "no two BlackCat 'lives' or deployments might look the same."
BlackCat, also known by the names ALPHV and Noberus, is a relatively new entrant to the hyperactive ransomware space. It's also known to be one of the first cross-platform ransomware written in Rust, exemplifying a trend where threat actors are switching to uncommon programming languages in an attempt to evade detection.
The ransomware-as-a-service (RaaS) scheme, irrespective of the varying initial access vectors employed, culminates in the exfiltration and encryption of target data that's then held ransom as part of what's called double extortion.
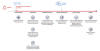
The RaaS model has proven to be a lucrative gig economy-style cybercriminal
ecosystem consisting of three different key players: access brokers (IABs), who
compromise networks and maintain persistence; operators, who develop and
maintain the ransomware operations; and affiliates, who purchase the access from
IABs to deploy the actual payload.
According to an alert released by the U.S. Federal Bureau of Investigation (FBI), BlackCat ransomware attacks have victimized at least 60 entities worldwide as of March 2022 since it was first spotted in November 2021.

Furthermore, Microsoft said that "two of the most prolific" affiliate threat
groups, which have been associated with several ransomware families such as
Hive, Conti, REvil, and LockBit 2.0, are now distributing BlackCat.
This includes DEV-0237 (aka FIN12), a financially motivated threat actor that was last seen targeting the healthcare sector in October 2021, and DEV-0504, which has been active since 2020 and has a pattern of shifting payloads when a RaaS program shuts down.
"DEV-0504 was responsible for deploying BlackCat ransomware in companies in the energy sector in January 2022," Microsoft noted last month. "Around the same time, DEV-0504 also deployed BlackCat in attacks against companies in the fashion, tobacco, IT, and manufacturing industries, among others."
If anything, the findings are an indicator as to how affiliate actors are increasingly jumping on the RaaS bandwagon to monetize their attacks, while embracing markedly different pre-ransom steps to deliver the ransomware payload inside a target organization's network, posing significant challenges to conventional defense approaches.
"Detecting threats like BlackCat, while good, is no longer enough as human-operated ransomware continues to grow, evolve, and adapt to the networks they're deployed or the attackers they work for," the researchers said. "These types of attacks continue to take advantage of an organization's poor credential hygiene and legacy configurations or misconfigurations to succeed."
A Microsoft Office 365 Feature Could Help Ransomware Hackers Hold Cloud Files
Hostage
17.6.22 Ransomware Thehackernews
A "dangerous piece of functionality" has been discovered in Microsoft 365 suite
that could be potentially abused by a malicious actor to ransom files stored on
SharePoint and OneDrive and launch attacks on cloud infrastructure.
The cloud ransomware attack makes it possible to launch file-encrypting malware to "encrypt files stored on SharePoint and OneDrive in a way that makes them unrecoverable without dedicated backups or a decryption key from the attacker," Proofpoint said in a report published today.
The infection sequence can be carried out using a combination of Microsoft APIs, command-line interface (CLI) scripts, and PowerShell scripts, the enterprise security firm added.
The attack, at its core, hinges on a Microsoft 365 feature called AutoSave that creates copies of older file versions as and when users make edits to a file stored on OneDrive or SharePoint Online.
It commences with gaining unauthorized access to a target user's SharePoint Online or OneDrive account, followed by abusing the access to exfiltrate and encrypt files. The three most common avenues to obtain the initial foothold involve directly breaching the account via phishing or brute-force attacks, tricking a user into authorizing a rogue third-party OAuth application, or taking over the web session of a logged-in user.
But where this attack stands apart from traditional endpoint ransomware activity is that the encryption phase requires locking each file on SharePoint Online or OneDrive more than the permitted versioning limit.
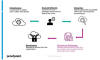
Microsoft elaborates the versioning behavior in its documentation as follows -
Some organizations allow unlimited versions of files and others apply limitations. You might discover, after checking in the latest version of a file, that an old version is missing. If your most recent version is 101.0 and you notice that there is no longer a version 1.0, it means that the administrator configured the library to allow only 100 major versions of a file. The addition of the 101st version causes the first version to be deleted. Only versions 2.0 through 101.0 remain. Similarly, if a 102nd version is added, only versions 3.0 through 102.0 remain.
By leveraging the access to the account, an attacker can either create too many versions of a file or alternatively reduce the version limit of a document library to a low number such as "1" and then proceed to encrypt each file twice.
"Now all original (pre-attacker) versions of the files are lost, leaving only the encrypted versions of each file in the cloud account," the researchers explained. "At this point, the attacker can ask for a ransom from the organization."
Microsoft, in response to the findings, pointed out that older versions of files can be potentially recovered and restored for an additional 14 days with the assistance of Microsoft Support, a process which Proofpoint found to be unsuccessful.
When reached for comment, a Microsoft spokesperson told The Hacker News: "This technique requires a user to have already been fully compromised by an attacker. We encourage our customers to practice safe computing habits, including exercising caution when clicking on links to webpages, opening unknown file attachments, or accepting file transfers."
To mitigate such attacks, it's recommended to enforce a strong password policy, mandate multi-factor authentication (MFA), prevent large-scale data downloads to unmanaged devices, and maintain periodic external backups of cloud files with sensitive data.
The tech giant, for its part, further drew attention to a OneDrive ransomware detection feature that notifies Microsoft 365 users of a potential attack and allows victims to restore their files. Microsoft is also encouraging business users to use conditional access to block or limit access to SharePoint and OneDrive content from unmanaged devices.
"Files stored in a hybrid state on both endpoint and cloud such as through cloud sync folders will reduce the impact of this novel risk as the attacker will not have access to the local/endpoint files," the researchers said. "To perform a full ransom flow, the attacker will have to compromise the endpoint and the cloud account to access the endpoint and cloud-stored files."
HelloXD Ransomware Installing Backdoor on Targeted Windows and Linux Systems
13.6.22 Ransomware Thehackernews
Windows and Linux systems are being targeted by a ransomware variant called
HelloXD, with the infections also involving the deployment of a backdoor to
facilitate persistent remote access to infected hosts.
"Unlike other ransomware groups, this ransomware family doesn't have an active leak site; instead it prefers to direct the impacted victim to negotiations through Tox chat and onion-based messenger instances," Daniel Bunce and Doel Santos, security researchers from Palo Alto Networks Unit 42, said in a new write-up.
HelloXD surfaced in the wild on November 30, 2021, and is based off leaked code from Babuk, which was published on a Russian-language cybercrime forum in September 2021.
The ransomware family is no exception to the norm in that the operators follow the tried-and-tested approach of double extortion to demand cryptocurrency payments by exfiltrating a victim's sensitive data in addition to encrypting it and threatening to publicize the information.
The implant in question, named MicroBackdoor, is an open-source malware that's used for command-and-control (C2) communications, with its developer Dmytro Oleksiuk calling it a "really minimalistic thing with all of the basic features in less than 5,000 lines of code."

Notably, different variants of the implant were adopted by the Belarusian threat
actor dubbed Ghostwriter (aka UNC1151) in its cyber operations against Ukrainian
state organizations in March 2022.
MicroBackdoor's features allow an attacker to browse the file system, upload and download files, execute commands, and erase evidence of its presence from the compromise machines. It's suspected that the deployment of the backdoor is carried out to "monitor the progress of the ransomware."
Unit 42 said it linked the likely Russian developer behind HelloXD — who goes by the online aliases x4k, L4ckyguy, unKn0wn, unk0w, _unkn0wn, and x4kme — to further malicious activities such as selling proof-of-concept (PoC) exploits and custom Kali Linux distributions by piecing together the actor's digital trail.
"x4k has a very solid online presence, which has enabled us to uncover much of his activity in these last two years," the researchers said. "This threat actor has done little to hide malicious activity, and is probably going to continue this behavior."
The findings come as a new study from IBM X-Force revealed that the average duration of an enterprise ransomware attack — i.e., the time between initial access and ransomware deployment — reduced 94.34% between 2019 and 2021 from over two months to a mere 3.85 days.
The increased speed and efficiency trends in the ransomware-as-a-service (RaaS) ecosystem has been attributed to the pivotal role played by initial access brokers (IABs) in obtaining access to victim networks and then selling the access to affiliates, who, in turn, abuse the foothold to deploy ransomware payloads.
"Purchasing access may significantly reduce the amount of time it takes ransomware operators to conduct an attack by enabling reconnaissance of systems and the identification of key data earlier and with greater ease," Intel 471 said in a report highlighting the close working relationships between IABs and ransomware crews.
"Additionally, as relationships strengthen, ransomware groups may identify a victim who they wish to target and the access merchant could provide them the access once it is available."
Evil Corp Cybercrime Group Shifts to LockBit Ransomware to Evade Sanctions
8.6.22 Ransomware Thehackernews
The threat cluster dubbed UNC2165, which shares numerous overlaps with a
Russia-based cybercrime group known as Evil Corp, has been linked to multiple
LockBit ransomware intrusions in an attempt to get around sanctions imposed by
the U.S. Treasury in December 2019.
"These actors have shifted away from using exclusive ransomware variants to LockBit — a well-known ransomware as a service (RaaS) — in their operations, likely to hinder attribution efforts in order to evade sanctions," threat intelligence firm Mandiant noted in an analysis last week.
Active since 2019, UNC2165 is known to obtain initial access to victim networks via stolen credentials and a JavaScript-based downloader malware called FakeUpdates (aka SocGholish), leveraging it to previously deploy Hades ransomware.
Hades is the work of a financially motivated hacking group named Evil Corp, which is also called by the monikers Gold Drake and Indrik Spider and has been attributed to the infamous Dridex (aka Bugat) trojan as well as other ransomware strains such as BitPaymer, DoppelPaymer, WastedLocker, Phoenix, PayloadBIN, Grief, and Macaw over the past five years.
UNC2165's pivot from Hades to LockBit as a sanctions-dodging tactic is said to have occurred in early 2021.
Interestingly, FakeUpdates has also, in the past, served as the initial infection vector for distributing Dridex that then was used as a conduit to drop BitPaymer and DoppelPaymer onto compromised systems.
Mandiant said it noted further similarities between UNC2165 and an Evil Corp-connected cyber espionage activity tracked by Swiss cybersecurity firm PRODAFT under the name SilverFish aimed at government entities and Fortune 500 companies in the E.U and the U.S.
A successful initial compromise is followed by a string of actions as part of the attack lifecycle, including privilege escalation, internal reconnaissance, lateral movement, and maintaining long-term remote access, before delivering the ransomware payloads.
With sanctions increasingly being used as a means to rein in ransomware attacks, in turn barring victims from negotiating with the threat actors, adding a ransomware group to a sanctions list — without naming the individuals behind it — has also been complicated by the fact that cybercriminal syndicates often tend to shutter, regroup, and rebrand under a different name to circumvent law enforcement.
"The adoption of an existing ransomware is a natural evolution for UNC2165 to attempt to obscure their affiliation with Evil Corp," Mandiant said, while also ensuring that sanctions are "not a limiting factor to receiving payments from victims."
"Using this RaaS would allow UNC2165 to blend in with other affiliates, the company added, stating, "it is plausible that the actors behind UNC2165 operations will continue to take additional steps to distance themselves from the Evil Corp name."
The findings from Mandiant, which is in the process of being acquired by Google, are particularly significant as the LockBit ransomware gang has since alleged that it had breached into the company's network and stole sensitive data.
The group, beyond threatening to release "all available data" on its data leak portal, didn't specify the exact nature of the contents in those files. However, Mandiant said there is no evidence to support the claim.
"Mandiant has reviewed the data disclosed in the initial LockBit release," the company told The Hacker News. "Based on the data that has been released, there are no indications that Mandiant data has been disclosed but rather the actor appears to be trying to disprove Mandiant's June 2, 2022 research on UNC2165 and LockBit."
New ransomware trends in 2022
5.6.22
Ransomware Securelist
Ahead of the Anti-Ransomware Day, we summarized the tendencies that characterize
ransomware landscape in 2022. This year, ransomware is no less active than
before: cybercriminals continue to threaten nationwide retailers and
enterprises, old variants of malware return while the new ones develop. Watching
and assessing these tendencies not only provides us with threat intelligence to
fight cybercrime today, but also helps us deduce what trends may see in the
months to come and prepare for them better.
In the report, we analyze what happened in late 2021 and 2022 on both the technological and geopolitical levels and what caused the new ransomware trends to emerge. First, we will review the trend of cross-platform ransomware development that is becoming more and more widespread among threat actors. Next, we will concentrate on how the ransomware gangs continue to industrialize and evolve into real businesses by adopting techniques of benign software companies. Last, we will delve into how ransomware gangs put on a political hat and engaged in the conflict between Russia and Ukraine.
Trend #1: Threat actors are trying to develop cross-platform ransomware to be as
adaptive as possible
As a consequence of the Big Game Hunting (BGH) scheme
that has become increasingly popular over the years, cybercriminals have been
penetrating more and more complex environments where a wide variety of systems
are running. In order to cause as much damage as possible and to make recovery
very difficult (if not impossible), they try to encrypt as many systems as
possible. This means that their ransomware should be able to run on different
combinations of architectures and operation systems.
One way to overcome this is to write the ransomware in a “cross-platform programming language” such as Rust or Golang. There are a few other reasons to use a cross-platform language. For example, even though the ransomware might be aimed at one platform at the moment, writing it in a cross platform makes it easier to port it to other platforms. Another reason is that analysis of cross-platform binaries is a bit harder than that of malware written in plain C.
In our crimeware reporting section on the Threat Intelligence Platform we cover some of these ransomware variants that work on different platforms. The following are the most important highlights from these reports.
Conti cross-platform functionality
Conti is a group conducting BGH, targeting
a wide variety of organizations across the globe. Just like many other BGH
groups, it uses the double extortion technique as well as an affiliate-based
structure.
We noticed that only certain affiliates have access to a Linux variant of the Conti ransomware, targeting ESXi systems. It supports a variety of different command-line arguments that can be used by the affiliate to customize the execution. The version for Linux supports the following parameters:
Parameter Description
–detach The sample is executed in the background and it
is detached from the terminal
–log For debugging purposes, with a filename
specified, Conti will write the actions to a log file
–path Conti needs this
path to encrypt the system. With the selected path, the ransomware will encrypt
the entire folder structure recursively
–prockiller This flag allows the
ransomware to kill those processes that have the selected files for encryption
–size Function not implemented
–vmlist Flag used to skip virtual machines
during the encryption process
–vmkiller It will terminate all the virtual
machines for the ESXi ecosystem
Conti parameters (Linux ESXi)
BlackCat cross-platform functionality
BlackCat started offering their
services in December 2021 on the dark web. Although the malware is written in
Rust from scratch, we found some links to the BlackMatter group as the actor
used the same custom exfiltration tool that had been observed earlier in
BlackMatter activities. Due to Rust cross-compilation capabilities, it did not
take long time for us to find BlackCat samples that work on Linux as well.
The Linux sample of BlackCat is very similar to the Windows one. In terms of functionality, it has slightly more, as it is capable of shutting down the machine and deleting ESXi VMs. Naturally, typical Windows functionality (e.g., executing commands through cmd.exe) was removed and replaced with the Linux equivalent so the ransomware still holds the same functionality on the different platforms it operates on.
Deadbolt cross-platform functionality
Deadbolt is an example of ransomware
written in a cross-platform language, but currently aimed at only one target –
QNAP NAS systems. It is also an interesting combination of Bash, HTML and
Golang. Deadbolt itself is written in Golang, the ransom note is an HTML file
that replaces the standard index file used by the QNAP NAS, and the Bash script
is used to start the decryption process if the provided decryption key is
correct. There is another peculiar thing about the ransomware: it doesn’t need
any interaction with attackers because a decryption key is provided in a Bitcoin
transaction OP_RETURN field. The Bash file is shown below.
Trend #2: The ransomware ecosystem is evolving and becoming even more
“industrialized”
Just like legitimate software companies, cybercriminal
groups are continually developing their tool kit for themselves and their
customers – for example, to make the process of data exfiltration quicker and
easier. Another trick that threat actors sometimes pull off is rebranding their
ransomware, changing bits and pieces in the process. Let’s delve into the new
tools and “business” strategies ransomware gangs are employing these days.
Evolution of Lockbit, one of the most successful RaaS since 2019
Lockbit
started in 2019, and then in 2020, its affiliate program was announced. Over
time, the group has been developing actively, as can be seen in the figure
below:
When the group started with its malicious activities, it did not have any leak portal, was not doing double extortion, and there was no data exfiltration before data encryption.
The infrastructure was also improved over time. Like other ransomware families, Lockbit’s infrastructure suffered several attacks that forced the group to implement some countermeasures to protect its assets. These attacks included hacking of the Lockbit’s administration panels and DDOS-attacks to force the group to shut down its activity.
The latest security addition made by the Lockbit developers is a “waiting page” that redirects users to one of the available mirrors.
StealBIT: custom data exfiltration tool utilized by Lockbit ransomware
Data
exfiltration, which is used when groups apply double extortion, is possible in
many different ways. Initially cybercriminals used publicly available tools such
as Filezilla, and then later replaced them with their own custom tools such as
StealBIT. There are a few reasons for this:
Publicly available tools are not always known for their speed. For ransomware
operators speed is important, because the longer it takes to exfiltrate data,
the greater the chance that ransomware operators will be caught,
Flexibility
is another reason. Standard tools are not designed with the requirements for
ransomware operators in mind. For example, with most tools it is possible to
upload the data only to one host. If that host is down, another host must be
specified manually. There is always the chance that criminal infrastructure will
be taken down or fall into the hands of LEAs. To provide more flexibility and
overcome these limitations, StealBIT has a list of hardcoded hosts the data can
be exfiltrated to. If the first one is down for some reason, the second host is
tried.
Ransomware operators have requirements that are not met with publicly
available tools. One such requirement is to exfiltrate not all the data, but
only the interesting data. In StealBIT this is implemented by having a hardcoded
list of extensions that should be extracted. Another functionality is that the
affiliate ID is sent when data is uploaded.
In the figure below, the data
exfiltration is compared (by the authors) to that of other tools:
SoftShade deploys Fendr exfiltration client
Fendr, also known as Exmatter, is
a malicious data exfiltration tool used by several ransomware groups such as
BlackMatter, Conti and BlackCat. Fendr was not seen in all the BlackMatter and
Conti incidents we observed, but we did see them in all BlackCat-related
incidents. Therefore, we believe that Fendr was used by a crimeware group that
participated in a few affiliate schemes.
Internally, SoftShade developers called it “file_sender” and “sender2”. The malware is written in C# .Net, and was frequently deployed alongside BlackMatter and Conti malware as a packed .Net executable, but most samples deployed alongside Conti and BlackCat ransomware were not packed (except for one Conti incident in November 2021). It is designed to efficiently manage large amounts of selective file collection and upload activity on a victim system and then remove itself from the system. Fendr is built with several open-source libraries, and its design is clearly the result of maturing, professionalised experience in the ransomware space, handling arbitrary large file volumes across various Windows systems and networks.
Also interesting is the deployment and packaging of Fendr and their chosen ransomware. Across each affiliate scheme (except for one Conti incident), the ransomware and Fendr are delivered simultaneously across a network to many systems as “v2.exe” and “v2c.exe”, or as “v2.exe” and “sender2.exe”. This simultaneous push seems to prioritize coordination and efficiency over raising risk of detection. In a Conti-related exception, it appears that a Fendr variant was pushed across the network to many systems as “\\hostname\$temp\sender2.exe”.
Trend #3 Ransomware gangs take sides in geopolitical conflicts
Cybercriminals
use news headlines to achieve their malicious goals. We saw this during the
initial phase of the global Covid-19 pandemic, when there was a surge of
Covid-19-related spam and phishing e-mails. The same happened with the
geopolitical conflict in Ukraine in 2022.
There is, however, one big difference. The usage of the pandemic wasn’t personal because it was just another topic from a long list of holidays, events, incidents, etc. In the case of the conflict, threat actors decided to choose sides, and this makes the topic much more personal.
Typically in a geopolitical conflict such as this one, one would associate the source of the cyberattacks with state-sponsored threat actors. This is not always true, as we have noted a new type of engagement in this conflict: cybercrime forums and ransomware groups reacting to the situation and taking action.
There have been consequences: for example, the disclosure of the Conti-related information. We also see this in malware variants that have been recently deployed. Specific variants that are exclusively found in Ukraine or in Russia often choose sides, either against Ukraine or against Russia. Let’s look at the most notable ransomware gang activity around the conflict.
Ransomware gangs taking sides
The most significant reaction of all is likely
the Conti ransomware group. On February 25, Conti published a message on its
news site with a statement that it would retaliate with full capabilities
against any “enemy’s” critical infrastructure if Russia became a target of
cyberattacks. This is probably a rare example of a cybercriminal group
supporting a nation-state publicly. As a result, an allegedly Ukrainian member
shared chats and other internal Conti-related information online.
Conti ransomware group posting a warning message on its news site
On the other side there are other communities such as Anonymous, IT Army of Ukraine and Belarusian Cyber Partisans openly supporting Ukraine.
The table below highlights the position of several groups and forums during the beginning of the conflict.
Open UA support Open RU support Neutral
RaidForums Conti Lockbit
Anonymous
collective CoomingProject
IT Army of Ukraine Stormous
Belarusian Cyber
Partisans
Freeud: brand-new ransomware with wiper capabilities
Kaspersky
recently discovered Freeud, a brand-new ransomware variant that supports
Ukraine. The Freeud’s ransom note says — not very subtly — that Russian troops
should leave Ukraine. The choice of words and how the note is written suggest
that it is written by a native Russian speaker. Other language artifacts that we
found suggest the authors are non-native English speakers. For example, the word
“lending” was found several times in places where the writers should have used
“landing”.
The political view of the malware authors is expressed not only through the ransom note but also through the malware features. One of them is wiping functionality. If the malware contains a list of files, instead of encrypting, the malware wipes them from the system.
Another property that stands out is the high quality of the malware, highlighted by the encryption methods applied and the way multithreading is used.
Elections GoRansom (HermeticRansom) covering up destructive activity
GoRansom
was found at the end of February in Ukraine at the same time the HermeticWiper
attack was carried out. We covered in a post published in March. There are a few
things that GoRansom does that are different from other ransomware variants:
It creates hundreds of copies of itself and runs them.
The function naming
scheme refers to the US presidential elections.
There is no obfuscation and
it has pretty straightforward functionality.
Self-copies made by HermeticRansom
For these reasons we believe it was created to boost the effectiveness of cyberoperations in Ukraine.
Stormous ransomware joins the Ukraine crisis with a PHP malware
It is not
very often that we come across malware written in PHP. Most of the time when we
analyze PHP code it is either a web shell or some botnet panel code. Stormous is
one of the few exceptions. Aside from being a backdoor, it also contains
ransomware functionality. The threat actor hunts for web servers supporting PHP
technology and weaknesses that are vulnerable to web apps.
An analysis of the malware suggests the threat actor is Arabic speaking from a
North African region. Stormous sides with Russia: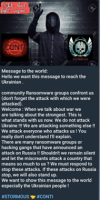
The PHP script provides a web interface for remote interaction over HTTP, where several encryption options are offered: “OpenSSL”, “Mcrypt” and “Xor”. It is quite possible that these three were developed into the script because of external considerations at the target, like the version of PHP running on the server (some extensions are deprecated or unavailable from one version to the next).
DoubleZero wiper targets Ukraine
The DoubleZero wiper was initially published
by the Ukrainian CERT on the March 22. It is a completely new wiper written in
C#; it is not similar to any other known wipers and targets only Ukrainian
entities. The binary itself is heavily obfuscated by an unknown C# obfuscator.
Classes and method names are randomly generated.
Obfuscation
Control flow is organized using a function-flattening mechanism created to slow down analysis of malicious code.
Obfuscated decompiled code
When all the preparations are over, malware starts its wiping operations. First, it checks for user (nonsystem files) by comparing folder names with a hardcoded list and starts wiping them using quite an interesting implementation of NtFsControlFile API.
Hardcoded list of folders
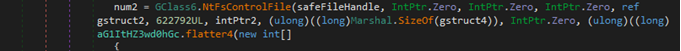
File wiping
The NtFsControlFile routine sends a control code directly to a specified file system or file system filter driver, causing the corresponding driver to perform the specified action. As seen in the screenshot, the control code has the value of 622792 (0x980C8in hex), which corresponds to the FSCTL_SET_ZERO_DATA control code of the FCSTL structure. Data in the file will be overwritten by ZERO values that are pointed by intPtr2 variable. If the function fails, the wiper will execute the standard .Net FileStream.Write function for the same purpose. Then malware wipes the system files found.
Malware then deletes the Windows registry tree subkeys in HKU, HKLM and kills the “lsass” process to reboot the infected machine.
Conclusion
As the saying goes, forewarned is forearmed, and this also applies
to cybersecurity. In recent years, ransomware groups have come a long way from
being scattered gangs to businesses with distinctive traits of full-fledged
industry. As a result, attacks have become more sophisticated and more targeted,
exposing victims to more threats. Monitoring the activity of ransomware groups
and their developments provides us with threat intelligence that enables better
defences.
We witnessed cross-platform ransomware written in Rust and Golang becoming a weapon of the “new-generation” of ransomware groups. Thanks to the software’s flexibility, the attacks can be conducted on a larger scale with no regard to what operating system the victim is using. This flexibility allows ransomware gangs to quickly adapt their strategy when carrying out attacks, diversify their targets and affect more victims.
Second, we witnessed a significant development in how ransomware groups rebuild their inner processes to facilitate their activity increasingly resembling legitimate software developers. While their efforts in branding (and re-branding) aren’t entirely new, the segmentation of their ‘businesses’ as well creation of new exfiltration tools point towards maturing Ransomware-as-a-Service industry, where the ransomware owner simplifies the job for the operators as much as possible.
Finally, ransomware group’s engagement in the conflict between Russia and Ukraine have set a precedent in the way cybercriminals operate in relation to geopolitics. While it is widely seen that advanced persistent threat (APT) actors are usually the ones to take on the mission of carrying out advanced attacks in the interest of the state, we now see that ransomware actors voluntarily engage in such activities as well, often leading to quite destructive consequences.
These tendencies are already affecting the way we need to defend against ransomware today. Ahead of the Anti-Ransomware Day, Kaspersky encourages organization to follow these best practices that help them safeguard against ransomware:
Always keep software updated on all the devices you use, to prevent attackers
from infiltrating your network by exploiting vulnerabilities.
Focus your
defence strategy on detecting lateral movements and data exfiltration to the
internet. Pay special attention to the outgoing traffic to detect
cybercriminals’ connections. Set up offline backups that intruders cannot tamper
with. Make sure you can quickly access them in an emergency when needed.
Enable ransomware protection for all endpoints. There is a free Kaspersky
Anti-Ransomware Tool for Business that shields computers and servers from
ransomware and other types of malware, prevent exploits and is compatible with
already installed security solutions.
Install anti-APT and EDR solutions,
enabling capabilities for advanced threat discovery and detection, investigation
and timely remediation of incidents. Provide your SOC team with access to the
latest threat intelligence and regularly upskill them with professional
training. All of the above is available within Kaspersky Expert Security
framework.
Provide your SOC team with access to the latest threat
intelligence (TI). The Kaspersky Threat Intelligence Portal is a single point of
access for the company’s TI, including crimeware, providing cyberattack data and
insights gathered by Kaspersky spanning over 20 years. To help businesses enable
effective defences in these turbulent times, Kaspersky announced access to
independent, continuously updated and globally-sourced information on ongoing
cyberattacks and threats, at no charge. Request your access to this offer here:
crimewareintel[at]kaspersky.com.
Conti Leaks Reveal Ransomware Gang's Interest in Firmware-based Attacks
3.6.22 Ransomware Thehackernews
An analysis of leaked chats from the notorious Conti ransomware group earlier
this year has revealed that the syndicate has been working on a set of firmware
attack techniques that could offer a path to accessing privileged code on
compromised devices.
"Control over firmware gives attackers virtually unmatched powers both to directly cause damage and to enable other long-term strategic goals," firmware and hardware security firm Eclypsium said in a report shared with The Hacker News.
"Such level of access would allow an adversary to cause irreparable damage to a system or to establish ongoing persistence that is virtually invisible to the operating system."
Specifically, this includes attacks aimed at embedded microcontrollers such as the Intel Management Engine (ME), a privileged component that's part of the company's processor chipsets and which can completely bypass the operating system.
It's worth noting that the reason for this evolving focus is not because there are new security vulnerabilities in Intel chipsets, but rather it banks on the possibility that "organizations do not update their chipset firmware with the same regularity that they do their software or even the UEFI/BIOS system firmware."

The conversations among the Conti members, which leaked after the group pledged
its support to Russia in the latter's invasion of Ukraine, have shed light on
the syndicate's attempts to mine for vulnerabilities related to ME firmware and
BIOS write protection.
This entailed finding undocumented commands and vulnerabilities in the ME interface, achieving code execution in the ME to access and rewrite the SPI flash memory, and dropping System Management Mode (SMM)-level implants, which could be leveraged to even modify the kernel.
The research ultimately manifested in the form of a proof-of-concept (PoC) code
in June 2021 that can gain SMM code execution by gaining control over the ME
after obtaining initial access to the host by means of traditional vectors like
phishing, malware, or a supply chain compromise, the leaked chats show.
"By shifting focus to Intel ME as well as targeting devices in which the BIOS is write protected, attackers could easily find far more available target devices," the researchers said.
That's not all. Control over the firmware could also be exploited to gain long-term persistence, evade security solutions, and cause irreparable system damage, enabling the threat actor to mount destructive attacks as witnessed during the Russo-Ukrainian war.
"The Conti leaks exposed a strategic shift that moves firmware attacks even further away from the prying eyes of traditional security tools," the researchers said.
"The shift to ME firmware gives attackers a far larger pool of potential victims to attack, and a new avenue to reaching the most privileged code and execution modes available on modern systems."
New 'GoodWill' Ransomware Forces Victims to Donate Money and Clothes to the Poor
31.5.22 Ransomware Thehackernews
Cybersecurity researchers have disclosed a new ransomware strain called GoodWill
that compels victims into donating for social causes and provide financial
assistance to people in need.
"The ransomware group propagates very unusual demands in exchange for the decryption key," researchers from CloudSEK said in a report published last week. "The Robin Hood-like group claims to be interested in helping the less fortunate, rather than extorting victims for financial motivations."
Written in .NET, the ransomware was first identified by the India-based cybersecurity firm in March 2022, with the infections rendering sensitive files inaccessible without decrypting them. The malware, which makes use of the AES algorithm for encryption, is also notable for sleeping for 722.45 seconds to interfere with dynamic analysis.
The encryption process is followed by displaying a multiple-paged ransom note
that requires the victims to carry out three socially-driven activities to be
able to obtain the decryption kit.
This includes donating new clothes and blankets to the homeless, taking any five underprivileged children to Domino's Pizza, Pizza Hut, or KFC for a treat, and offering financial support to patients who need urgent medical attention but don't have the financial means to do so.
Additionally, the victims are asked to record the activities in the form of screenshots and selfies and post them as evidence on their social media accounts.
"Once all three activities are completed, the victims should also write a note on social media (Facebook or Instagram) on 'How you transformed yourself into a kind human being by becoming a victim of a ransomware called GoodWill,'" the researchers said.
There are no known victims of GoodWill and their exact tactics, techniques, and procedures (TTPs) used to facilitate the attacks are unclear as yet.
Also unrecognized is the identity of the threat actor, although an analysis of the email address and network artifacts suggests that the operators are from India and that they speak Hindi.
Further investigation into the ransomware sample has also revealed significant overlaps with another Windows-based strain called HiddenTear, the first ransomware to have been open-sourced as a proof-of-concept (PoC) back in 2015 by a Turkish programmer.
"GoodWill operators may have gained access to this allowing them to create a new ransomware with necessary modifications," the researchers said.
New Chaos Ransomware Builder Variant "Yashma" Discovered in the Wild
25.5.22 Ransomware Thehackernews
Cybersecurity researchers have disclosed details of the latest version of the
Chaos ransomware line, dubbed Yashma.
"Though Chaos ransomware builder has only been in the wild for a year, Yashma claims to be the sixth version (v6.0) of this malware," BlackBerry research and intelligence team said in a report shared with The Hacker News.
Chaos is a customizable ransomware builder that emerged in underground forums on June 9, 2021, by falsely marketing itself as the .NET version of Ryuk despite sharing no such overlaps with the notorious counterpart.
The fact that it's offered for sale also means that any malicious actor can purchase the builder and develop their own ransomware strains, turning it into a potent threat.
It has since undergone five successive iterations aimed at improving its functionalities: version 2.0 on June 17, version 3.0 on July 5, version 4.0 on August 5, and version 5.0 in early 2022.
While the first three variants of Chaos functioned more like a destructive trojan than traditional ransomware, Chaos 4.0 added further refinements so as to increase the upper limit of files that can be encrypted to 2.1MB.
Version 4.0 has also been actively weaponized by a ransomware collective known as Onyx as of April 2022 by making use of an updated ransom note and a refined list of file extensions that can be targeted.

"Chaos 5.0 attempted to resolve the largest problem of previous iterations of
the threat, namely that it was unable to encrypt files larger than 2MB without
irretrievably corrupting them," the researchers explained.
Yashma is the latest version to join this list, featuring two new improvements, including the ability to stop execution based on a victim's location and terminate various processes associated with antivirus and backup software.
"Chaos started as a relatively basic attempt at a .NET compiled ransomware that instead functioned as a file-destructor or wiper," the researchers said. "Over time it has evolved to become a full-fledged ransomware, adding additional features and functionality with each iteration."
The development comes as a Chaos ransomware variant has been spotted siding with Russia in its ongoing war against Ukraine, with the post-encryption activity leading to an alert containing a link that directs to a website with pro-Russian messages.
"The attacker has no intention of providing a decryption tool or file recovery instructions for its victims to recover their affected files," Fortinet FortiGuard Labs disclosed last week, adding it "makes the malware a file destroyer."
Conti Ransomware Operation Shut Down After Splitting into Smaller Groups
25.5.22 Ransomware Thehackernews
Even as the operators of Conti threatened to overthrow the Costa Rican
government, the notorious cybercrime gang officially took down its attack
infrastructure in favor of migrating their malicious cyber activities to other
ancillary operations, including Karakurt and BlackByte.
"From the negotiations site, chatrooms, messengers to servers and proxy hosts - the Conti brand, not the organization itself, is shutting down," AdvIntel researchers Yelisey Bogusalvskiy and Vitali Kremez said in a report. "However, this does not mean that the threat actors themselves are retiring."
The voluntary termination, with the exception of its name-and-shame blog, is said to have occurred on May 19, 2022, while an organizational rejig was happening simultaneously to ensure a smooth transition of the ransomware group's members.
AdvIntel said Conti, which is also tracked under the moniker Gold Ulrick, orchestrated its own demise by utilizing information warfare techniques.
The disbanding also follows the group's public allegiance to Russia in the country's invasion of Ukraine, dealing a huge blow to its operations and provoking the leak of thousands of private chat logs as well as its toolset, making it a "toxic brand."
The Conti team is believed to have been actively creating subdivisions over the course of the last two months. But in tandem, the group began taking steps to control the narrative, sending out "smoke signals" in an attempt to simulate the movements of an active group.
"The attack on Costa Rica indeed brought Conti into the spotlight and helped them to maintain the illusion of life for just a bit longer, while the real restructuring was taking place," the researchers said.
"The only goal Conti had wanted to meet with this final attack was to use the platform as a tool of publicity, performing their own death and subsequent rebirth in the most plausible way it could have been conceived."

The diversion tactics aside, Conti's infiltration specialists are also said to
have forged alliances with other well-known ransomware groups such as BlackCat,
AvosLocker, Hive, and HelloKitty (aka FiveHands).
Additionally, the cybersecurity firm said it had seen internal communication alluding to the fact that Russian law enforcement agencies had been putting pressure on Conti to halt its activities in the wake of increased international scrutiny and the high-profile nature of the attacks conducted by the criminal syndicate.
Conti's affiliation with Russia has also had other unintended consequences, chief among them being its inability to extract ransom payments from victims in light of severe economic sanctions imposed by the West on the country.
That said, although the brand may cease to exist, the group has adopted what's called a decentralized hierarchy that involves multiple subgroups with different motivations and business models ranging from data theft (Karakurt, BlackBasta, and BlackByte) to working as independent affiliates.
This is not the first time Gold Ulrick has revamped its inner workings. TrickBot, whose elite Overdose division spawned the creation of Ryuk and its successor Conti, has since been shut down and absorbed into the collective, turning TrickBot into a Conti subsidiary. It has also taken over BazarLoader and Emotet.
"The diversification of Conti's criminal portfolio paired with its shockingly swift dissolution does bring into question whether their business model will be repeated among other groups," AdvIntel noted last week.
"Ransomware Inc. is less like the gangs they are often called and much more like cartels as time goes on," Sam Curry, chief security officer at Cybereason, said in a statement shared with The Hacker News.
"This means partner agreements, specialized roles, business-like R&D and marketing groups and so on. And because Conti is beginning to mirror the sorts of activities we see among legitimate companies, it's no surprise they are changing."
QNAP Urges Users to Update NAS Devices to Prevent Deadbolt Ransomware Attacks
20.5.22 Ransomware Thehackernews
Taiwanese network-attached storage (NAS) devices maker QNAP on Thursday warned
its customers of a fresh wave of DeadBolt ransomware attacks.
The intrusions are said to have targeted TS-x51 series and TS-x53 series appliances running on QTS 4.3.6 and QTS 4.4.1, according to its product security incident response team.
"QNAP urges all NAS users to check and update QTS to the latest version as soon as possible, and avoid exposing their NAS to the internet," QNAP said in an advisory.
This development marks the third time QNAP devices have come under assault from DeadBolt ransomware since the start of the year.

In late January, as many as 4,988 DeadBolt-infected QNAP devices were
identified, prompting the company to release a forced firmware update. A second
uptick in new infections was observed in mid-March.
DeadBolt attacks are also notable for the fact that they allegedly leverage zero-day flaws in the software to gain remote access and encrypt the systems.

According to a new report published by Group-IB, exploitation of security
vulnerabilities in public-facing applications emerged as the third most used
vector to gain initial access, accounting for 21% of all ransomware attacks
investigated by the firm in 2021.
Russian Conti Ransomware Gang Threatens to Overthrow New Costa Rican Government
19.5.22 Ransomware Thehackernews
The notorious Conti ransomware gang, which last month staged an attack on Costa Rican administrative systems, has threatened to "overthrow" the new government of the country.
"We are determined to overthrow the government by means of a cyber attack, we have already shown you all the strength and power," the group said on its official website. "We have our insiders in your government. We are also working on gaining access to your other systems, you have no other options but to pay us."
In a further attempt to increase pressure, the Russian-speaking cybercrime syndicate has raised its ransom demand to $20 million in return for a decryption key to unlock their systems.
Another message posted on its dark web portal over the weekend issued a warning stating it will delete the decryption keys in a week, a move that would make it impossible for Costa Rica to recover access to the files encrypted by the ransomware.
"I appeal to every resident of Costa Rica, go to your government and organize rallies so that they would pay us as soon as possible if your current government cannot stabilize the situation? Maybe it's worth changing it?," the message read.
The devastating attack, which took place on April 19, has caused the new government to declare a state of emergency, while the group has leaked troves of data stolen from the infected systems prior to encryption.
Conti attributed the intrusion to an affiliate actor dubbed "UNC1756," mimicking
the moniker threat intelligence firm Mandiant assigns to uncategorized threat
groups.
Affiliates are hacking groups who rent access to already-developed ransomware tools to orchestrate intrusions into corporate networks as part of what's called a ransomware-as-a-service (RaaS) gig economy, and then split the earnings with the operators.
Linked to a threat actor known as Gold Ulrick (aka Grim Spider or UNC1878), Conti has continued to target entities across the world despite suffering a massive data leak of its own earlier this year in the wake of its public support to Russia in the country's ongoing war against Ukraine.
Microsoft's security division, which tracks the cybercriminal group under the cluster DEV-0193, called Conti the "most prolific ransomware-associated cybercriminal activity group active today."
"DEV-0193's actions and use of the cybercriminal gig economy means they often
add new members and projects and utilize contractors to perform various parts of
their intrusions," Microsoft Threat Intelligence Center (MSTIC) said.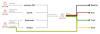
"As other malware operations have shut down for various reasons, including legal actions, DEV-0193 has hired developers from these groups. Most notable are the acquisitions of developers from Emotet, Qakbot, and IcedID, bringing them to the DEV-0193 umbrella."
The interminable attacks have also led the U.S. State Department to announce rewards of up to $10 million for any information leading to the identification of key individuals who are part of the cybercrime cartel.
Iranian Hackers Leveraging BitLocker and DiskCryptor in Ransomware Attacks
14.5.22 Ransomware Thehackernews
A ransomware group with an Iranian operational connection has been linked to a string of file-encrypting malware attacks targeting organizations in Israel, the U.S., Europe, and Australia.
Cybersecurity firm Secureworks attributed the intrusions to a threat actor it tracks under the moniker Cobalt Mirage, which it said is linked to an Iranian hacking crew dubbed Cobalt Illusion (aka APT35, Charming Kitten, Newscaster, or Phosphorus).
"Elements of Cobalt Mirage activity have been reported as Phosphorus and TunnelVision," Secureworks Counter Threat Unit (CTU) said in a report shared with The Hacker News.
The threat actor is said to have conducted two different sets of intrusions, one of which relates to opportunistic ransomware attacks involving the use of legitimate tools like BitLocker and DiskCryptor for financial gain.
The second set of attacks are more targeted, carried out with the primary goal
of securing access and gathering intelligence, while also deploying ransomware
in select cases.
Initial access routes are facilitated by scanning internet-facing servers vulnerable to highly publicized flaws in Fortinet appliances and Microsoft Exchange Servers to drop web shells and using them as a conduit to move laterally and activate the ransomware.
"The threat actors completed the attack with an unusual tactic of sending a ransom note to a local printer," the researchers said. "The note includes a contact email address and Telegram account to discuss decryption and recovery."
However, the exact means by which the full volume encryption feature is triggered remains unknown, Secureworks said, detailing a January 2022 attack against an unnamed U.S. philanthropic organization.
Another intrusion aimed at a U.S. local government network in mid-March 2022 is believed to have leveraged Log4Shell flaws in the target's VMware Horizon infrastructure to conduct reconnaissance and network scanning operations.
"The January and March incidents typify the different styles of attacks conducted by Cobalt Mirage," the researchers concluded.
"While the threat actors appear to have had a reasonable level of success gaining initial access to a wide range of targets, their ability to capitalize on that access for financial gain or intelligence collection appears limited."
New REvil Samples Indicate Ransomware Gang is Back After Months of Inactivity
11.5.22 Ransomware Thehackernews
The notorious ransomware operation known as REvil (aka Sodin or Sodinokibi) has
resumed after six months of inactivity, an analysis of new ransomware samples
has revealed.
"Analysis of these samples indicates that the developer has access to REvil's source code, reinforcing the likelihood that the threat group has reemerged," researchers from Secureworks Counter Threat Unit (CTU) said in a report published Monday.
"The identification of multiple samples with varying modifications in such a short period of time and the lack of an official new version indicates that REvil is under heavy active development once again."
REvil, short for Ransomware Evil, is a ransomware-as-a-service (RaaS) scheme and attributed to a Russia-based/speaking group known as Gold Southfield, arising just as GandCrab activity declined and the latter announced their retirement.
It's also one of the earliest groups to adopt the double extortion scheme in which stolen data from intrusions is used to generate additional leverage and compel victims into paying up.
Operational since 2019, the ransomware group made headlines last year for their high-profile attacks on JBS and Kaseya, prompting the gang to formally shut shop in October 2021 after a law enforcement action hijacked its server infrastructure.
Earlier this January, several members belonging to the cybercrime syndicate were arrested by Russia's Federal Security Service (FSB) in the wake of raids conducted at 25 different locations in the country.
The apparent resurgence comes as REvil's data leak site in the TOR network began redirecting to a new host on April 20, with cybersecurity firm Avast disclosing a week later that it had blocked a ransomware sample in the wild "that looks like a new Sodinokibi / REvil variant."
While the sample in question was found to not encrypt files and only add a random extension, Secureworks has chalked it up to a programming error introduced in the functionality that renames files that are being encrypted.
On top of that, the new samples dissected by the cybersecurity firm — which carry a timestamp of March 11, 2022 — incorporate notable changes to the source code that set it apart from another REvil artifact dated October 2021.
This includes updates to its string decryption logic, the configuration storage location, and the hard-coded public keys. Also revised are the Tor domains displayed in the ransom note, referencing the same sites that went live last month -
REvil leak site:
blogxxu75w63ujqarv476otld7cyjkq4yoswzt4ijadkjwvg3vrvd5yd[.]onion
REvil ransom
payment site: landxxeaf2hoyl2jvcwuazypt6imcsbmhb7kx3x33yhparvtmkatpaad[.]onion
REvil's revival is also likely tied to Russia's ongoing invasion of Ukraine,
following which the U.S. backed out of a proposed joint cooperation between the
two countries to safeguard critical infrastructure.
If anything, the development is yet another sign that ransomware actors disband only to regroup and rebrand under a different name and pick up right from where they left off, underscoring the difficulty in completely rooting out cybercriminal groups.
U.S. Offering $10 Million Reward for Information on Conti Ransomware Hackers
10.5.22 Ransomware Thehackernews
The U.S. State Department has announced rewards of up to $10 million for any
information leading to the identification of key individuals who are part of the
infamous Conti cybercrime gang.
Additionally, it's offering another $5 million for intelligence information that could help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack.
The department called the Conti variant the "costliest strain of ransomware ever documented."
Conti, the work of a Russia-based transnational organized crime group dubbed Gold Ulrick, is one most prolific ransomware cartels that has continued to strike entities globally while simultaneously expanding its empire by absorbing TrickBot and running side hustles that involve data extortion.
After the syndicate expressed public support for Russia's invasion of Ukraine in February, it suffered a major breach of its own after its source code and internal chats were released on the public domain. But the leaks have done precious little to slow it down.
According to the State Department, Conti is said to have victimized more than 1,000 organizations as of January 2022, with victim payouts surpassing $150 million. Last month, the group claimed credit for an attack on Costa Rica's government networks.
This is not the first time the U.S. government has offered bounties as part of its efforts to "disrupt and dismantle transnational organized crime globally, including cybercrime" and protect "potential ransomware victims around the world from exploitation by cyber criminals."
In November 2021, it offered similar monetary rewards for locating criminal parties associated with DarkSide and REvil ransomware, which were used in high-profile attacks on Colonial Pipeline and Kaseya last year.
Experts Analyze Conti and Hive Ransomware Gangs' Chats With Their Victims
3.5.22 Ransomware Thehackernews
An analysis of four months of chat logs spanning more than 40 conversations
between the operators of Conti and Hive ransomware and their victims has offered
an insight into the groups' inner workings and their negotiation techniques.
In one exchange, the Conti Team is said to have significantly reduced the ransom demand from a staggering $50 million to $1 million, a 98% drop, suggesting a willingness to settle for a far lower amount.
"Both Conti and Hive are quick to lower ransom demands, routinely offering substantial reductions multiple times throughout negotiations," Cisco Talos said in a report shared with The Hacker News. "This signals that despite popular belief, victims of a ransomware attack actually have significant negotiating power."
Conti and Hive are among the most prevalent ransomware strains in the threat landscape, cumulatively accounting for 29.1% of attacks detected during the three-month-period between October and December 2021.
A key takeaway from the review of the chat logs is the contrast in communication styles between the two groups. While Conti's conversations with victims are professional and marked by the use of different persuasion tactics to convince victims to pay the ransom, Hive employs a "much shorter, more direct" informal approach.
Besides offering holidays and special discounts, Conti is also known to offer "IT support" to prevent future attacks, sending its victims a so-called security report that lists a series of steps the affected entities can take to secure their networks.
Additionally, the financially motivated group has made use of scare tactics,
cautioning victims of the reputational damage and legal issues stemming as a
consequence of a data leak and threatening to share the stolen information with
competitors and other stakeholders.
"After encrypting victim networks, ransomware threat actors increasingly used 'triple extortion' by threatening to (1) publicly release stolen sensitive information, (2) disrupt the victim's internet access, and/or (3) inform the victim's partners, shareholders, or suppliers about the incident," CISA noted in an advisory earlier this year.
Another point of distinction is Conti's flexibility when it comes to payment deadlines. "These behaviors suggest Conti operators are highly opportunistic cybercriminals who ultimately would prefer some payment as opposed to none," Talos researcher Kendall McKay said.
Hive, on the other hand, has been observed to quickly raise its ransom demands should a victim fail to make the payment by the stipulated date.
What's also notable is Hive's emphasis on speed over accuracy during the encryption process, making it vulnerable to cryptographic blunders that allow for recovering the master key.
"Like many cybercriminals, Conti and Hive are opportunistic actors who likely seek to compromise victims through the easiest and fastest means possible, which often include exploiting known vulnerabilities," McKay said. "This is a reminder to all organizations to implement a strong patch management system and keep all systems up-to-date."
AvosLocker Ransomware Variant Using New Trick to Disable Antivirus Protection
3.5.22 Ransomware Thehackernews
Cybersecurity researchers have disclosed a new variant of the AvosLocker
ransomware that disables antivirus solutions to evade detection after breaching
target networks by taking advantage of unpatched security flaws.
"This is the first sample we observed from the U.S. with the capability to disable a defense solution using a legitimate Avast Anti-Rootkit Driver file (asWarPot.sys)," Trend Micro researchers, Christoper Ordonez and Alvin Nieto, said in a Monday analysis.
"In addition, the ransomware is also capable of scanning multiple endpoints for the Log4j vulnerability (Log4shell) using Nmap NSE script."
AvosLocker, one of the newer ransomware families to fill the vacuum left by REvil, has been linked to a number of attacks that targeted critical infrastructure in the U.S., including financial services and government facilities.
A ransomware-as-a-service (RaaS) affiliate-based group first spotted in July 2021, AvosLocker goes beyond double extortion by auctioning data stolen from victims should the targeted entities refuse to pay the ransom.
Other targeted victims claimed by the ransomware cartel are said to be located in Syria, Saudi Arabia, Germany, Spain, Belgium, Turkey, the U.A.E., the U.K., Canada, China, and Taiwan, according to an advisory released by the U.S. Federal Bureau of Investigation (FBI) in March 2022.
Telemetry data gathered by Trend Micro shows that the food and beverage sector was the most hit industry between July 1, 2021 and February 28, 2022, followed by technology, finance, telecom, and media verticals.
The entry point for the attack is believed to have been facilitated by leveraging an exploit for a remote code execution flaw in Zoho's ManageEngine ADSelfService Plus software (CVE-2021-40539) to run an HTML application (HTA) hosted on a remote server.
"The HTA executed an obfuscated PowerShell script that contains a shellcode, capable of connecting back to the [command-and-control] server to execute arbitrary commands," the researchers explained.
This includes retrieving an ASPX web shell from the server as well as an installer for the AnyDesk remote desktop software, the latter of which is used to deploy additional tools to scan the local network, terminate security software, and drop the ransomware payload.
Some of the components copied to the infected endpoint are a Nmap script to scan the network for the Log4Shell remote code execution flaw (CVE-2021-44228) and a mass deployment tool called PDQ to deliver a malicious batch script to multiple endpoints.
The batch script, for its part, is equipped with a wide range of capabilities that allows it to disable Windows Update, Windows Defender, and Windows Error Recovery, in addition to preventing safe boot execution of security products, creating a new admin account, and launching the ransomware binary.
Also used is aswArPot.sys, a legitimate Avast anti-rootkit driver, to kill processes associated with different security solutions by weaponizing a now-fixed vulnerability in the driver the Czech company resolved in June 2021.
"The decision to choose the specific rootkit driver file is for its capability to execute in kernel mode (therefore operating at a high privilege)," the researchers pointed out. "This variant is also capable of modifying other details of the installed security solutions, such as disabling the legal notice."
Gold Ulrick Hackers Still in Action Despite Massive Conti Ransomware Leak
26.4.22 Ransomware Thehackernews
The infamous ransomware group known as Conti has continued its onslaught against entities despite suffering a massive data leak of its own earlier this year, according to new research.
Conti, attributed to a Russia-based threat actor known as Gold Ulrick, is one of the most prevalent malware strains in the ransomware landscape, accounting for 19% of all attacks during the three-month-period between October and December 2021.
One of the most prolific ransomware groups of the last year along the likes of LockBit 2.0, PYSA, and Hive, Conti has locked the networks of hospitals, businesses, and government agencies, while receiving a ransom payment in exchange for sharing the decryption key as part of its name-and-shame scheme.
But after the cybercriminal cartel came out in support of Russia over its invasion of Ukraine in February, an anonymous Ukrainian security researcher under the Twitter handle ContiLeaks began leaking the source code as well as private conversations between its members, offering an unprecedented insight into the group's workings.
"The chats reveal a mature cybercrime ecosystem across multiple threat groups with frequent collaboration and support," Secureworks said in a report published in March. The groups include Gold Blackburn (TrickBot and Diavol), Gold Crestwood (Emotet), Gold Mystic (LockBit), and Gold Swathmore (IcedID).
Indeed, Intel 471's technical monitoring of Emotet campaigns between December 25, 2021, and March 25, 2022, identified that over a dozen Conti ransomware targets were, in fact, victims of Emotet malspam attacks, highlighting how the two operations are intertwined.
That said, the leaks don't seem to have put a dampener on the syndicate's activities, with the number of Conti victims posted in March surging to the second-highest monthly total since January 2021, per the Atlanta-headquartered cybersecurity firm.
What's more, the group is said to have added 11 victims in the first four days of April, even as the operators continue to "evolve its ransomware, intrusion methods, and approaches" in response to the public disclosure of their arsenal.
The findings have also been corroborated by NCC Group late last month, which said that "Conti operators continue their business as usual by proceeding to compromise networks, exfiltrating data and finally deploying their ransomware."
A web of connections between Conti and Karakurt
The development comes as
financial and tactical overlaps have been uncovered between Conti and the
Karakurt data extortion group based on information published during the
ContiLeaks saga, weeks after TrickBot's operators had been subsumed into the
ransomware cartel.
An analysis of blockchain transactions associated with cryptocurrency addresses
belonging to Karakurt has shown "Karakurt wallets sending substantial sums of
cryptocurrency to Conti wallets," according to a joint investigation by
researchers from Arctic Wolf and Chainalysis.
The shared wallet hosting is also said to involve the now-defunct TrickBot gang's Diavol ransomware, with a "Diavol extortion address hosted by a wallet containing addresses used in Conti ransomware attacks," indicating that Diavol is being deployed by the same set of actors behind Conti and Karakurt.
Further forensic examination of an unnamed client that was hit with a subsequent wave of extortion attacks following a Conti ransomware infection has revealed that the second group used the same Cobalt Strike backdoor left behind by Conti, implying a strong association between seemingly disparate cybercrime actors.
"Whether Karakurt is an elaborate side hustle by Conti and Diavol operatives or whether this is an enterprise sanctioned by the overall organization remains to be seen," Arctic Wolf said.
"This connection perhaps explains why Karakurt is surviving and thriving despite some of its exfiltration-only competitors dying out," the researchers said, adding, "Or, alternatively, perhaps this was the trial run of a strategic diversification authorized by the main group."
FBI Warns of BlackCat Ransomware That Breached Over 60 Organisations Worldwide
26.4.22 Ransomware Thehackernews
The U.S. Federal Bureau of Investigation (FBI) is sounding the alarm on the
BlackCat ransomware-as-a-service (RaaS), which it said victimized at least 60
entities worldwide between as of March 2022 since its emergence last November.
Also called ALPHV and Noberus, the ransomware is notable for being the first-ever malware written in the Rust programming language, which is known to be memory safe and offer improved performance.
"Many of the developers and money launderers for BlackCat/ALPHV are linked to DarkSide/BlackMatter, indicating they have extensive networks and experience with ransomware operations," the FBI said in an advisory published last week.
The disclosure comes weeks after twin reports from Cisco Talos and Kasperksy uncovered links between BlackCat and BlackMatter ransomware families, including the use of a modified version of a data exfiltration tool dubbed Fendr that's been previously only observed in BlackMatter-related activity.
"Aside from the developing advantages Rust offers, the attackers also take advantage of a lower detection ratio from static analysis tools, which aren't usually adapted to all programming languages," AT&T Alien Labs pointed out earlier this year.
Like other RaaS groups, BlackCat's modus operandi involves the theft of victim data prior to the execution of the ransomware, with the malware often leveraging compromised user credentials to gain initial access to the target system.
In a BlackCat ransomware incident analyzed by Forescout's Vedere Labs, an internet-exposed SonicWall firewall was penetrated to gain initial access to the network, before moving to and encrypting a VMware ESXi virtual farm. The ransomware deployment is said to have taken place on March 17, 2022.
The law enforcement agency, besides recommending victims to promptly report ransomware incidents, also said it doesn't encourage paying ransoms as there is no guarantee that this will enable the recovery of encrypted files. But it did acknowledge that victims may be compelled to heed to such demands to protect shareholders, employees, and customers.
As recommendations, the FBI is urging organizations to review domain controllers, servers, workstations, and active directories for new or unrecognized user accounts, take offline backups, implement network segmentation, apply software updates, and secure accounts with multi-factor authentication.
New Incident Report Reveals How Hive Ransomware Targets Organizations
23.4.22 Ransomware Thehackernews
A recent Hive ransomware attack carried out by an affiliate involved the
exploitation of "ProxyShell" vulnerabilities in the Microsoft Exchange Server
that were disclosed last year to encrypt an unnamed customer's network.
"The actor managed to achieve its malicious goals and encrypt the environment in less than 72 hours from the initial compromise," Varonis security researcher, Nadav Ovadia, said in a post-mortem analysis of the incident.
Hive, which was first observed in June 2021, follows the lucrative ransomware-as-a-service (RaaS) scheme adopted by other cybercriminal groups in recent years, enabling affiliates to deploy the file-encrypting malware after gaining a foothold into their victims' networks.
ProxyShell — tracked as CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473 — involves a combination of security feature bypass, privilege escalation, and remote code execution in the Microsoft Exchange Server, effectively granting the attacker the ability to execute arbitrary code on affected servers.
The issues were addressed by Microsoft as part of its Patch Tuesday updates for April and May 2021.
In this case, successful exploitation of the flaws allowed the adversary to deploy web shells on the compromised server, using them to run malicious PowerShell code with SYSTEM privileges to create a new backdoor administrator user, hijack the domain admin account, and perform lateral movement.

The web shells used in the attack are said to have been sourced from a public
git repository and given filenames containing a random mix of characters to
evade detection, Ovadia said. Also executed was an additional obfuscated
PowerShell script that's part of the Cobalt Strike framework.
From there, the threat actor moved to scan the network for valuable files, before proceeding to deploy the Golang ransomware executable (named "Windows.exe") to complete the encryption process and display the ransom note to the victim.
Other operations carried out by the malware include deleting shadow copies, turning off security products, and clearing Windows event logs to avoid detection, prevent recovery, and ensure that the encryption happens without any hiccup.
If anything, the findings are yet another indicator that patching for known vulnerabilities is key to thwarting cyberattacks and other nefarious activities.
"Ransomware attacks have grown significantly over the past years and remain the preferred method of threat actors aiming to maximize profits," Ovadia said. "It may potentially harm an organization's reputation, disrupt regular operations and lead to temporary, and possibly permanent, loss of sensitive data."
Researchers Share In-Depth Analysis of PYSA Ransomware Group
18.4.22
Ransomware Thehackernews
An 18-month-long analysis of the PYSA ransomware operation has revealed that the cybercrime cartel followed a five-stage software development cycle from August 2020, with the malware authors prioritizing features to improve the efficiency of its workflows.
This included a user-friendly tool like a full-text search engine to facilitate the extraction of metadata and enable the threat actors to find and access victim information quickly.
"The group is known to carefully research high-value targets before launching its attacks, compromising enterprise systems and forcing organizations to pay large ransoms to restore their data," Swiss cybersecurity company PRODAFT said in an exhaustive report published last week.
PYSA, short for "Protect Your System, Amigo" and a successor of the Mespinoza ransomware, was first observed in December 2019 and has emerged as the third most prevalent ransomware strain detected during the fourth quarter of 2021.
Since September 2020, the cybercriminal gang is believed to have exfiltrated sensitive information belonging to as many as 747 victims until its servers were taken offline earlier this January.
Most of its victims are located in the U.S. and Europe, with the group primarily striking government, healthcare, and educational sectors. "The U.S. was the most-impacted country, accounting for 59.2% of all PYSA events reported, followed by the U.K. at 13.1%," Intel 471 noted in an analysis of ransomware attacks recorded from October to December 2021.
PYSA, like other ransomware families, is known to follow the "big game hunting"
approach of double extortion, which involves publicizing the stolen information
should a victim refuse to comply with the group's demands.
Every eligible file is encrypted and given a ".pysa" extension, decoding which requires the RSA private key that can only be obtained after paying the ransom. Almost 58% of the PYSA victims are said to have made digital payments.
PRODAFT, which was able to locate a publicly available .git folder managed by PYSA operators, identified one of the project's authors as "dodo@mail.pcc," a threat actor who is believed to be located in a country that observes daylight savings time based on the commit history.
At least 11 accounts, a majority of which were created on January 8, 2021, are
said to be in charge of the overall operation, the investigation has revealed.
That said, four of these accounts — named t1, t3, t4, and t5 — account for over
90% of activity on the group's management panel.
Other operational security mistakes made by the group's members also made it possible to identify a hidden service running on the TOR anonymity network — a hosting provider (Snel.com B.V.) located in the Netherlands — offering a glimpse into the actor's tactics.
PYSA's infrastructure also consists of dockerized containers, including public leak servers, database, and management servers, as well as an Amazon S3 cloud to store the encrypted files, which amount to a massive 31.47TB.
Also put to use is a custom leak management panel to search confidential documents in the files exfiltrated from victims' internal networks prior to encryption. Besides using the Git version control system to manage the development processes, the panel itself is coded in PHP 7.3.12 using the Laravel framework.
What's more, the management panel exposes a variety of API endpoints that enables the system to list files, download files, and analyze the files for full-text search, which is designed to categorize the stolen victim information into broad categories for easy retrieval.
"The group is supported by competent developers who apply modern operational paradigms to the group's development cycle," the researcher said. "It suggests a professional environment with well-organized division of responsibilities, rather than a loose network of semi-autonomous threat actors."
If anything, the findings are yet another indicator that ransomware gangs like PYSA and Conti operate and are organized like legitimate software companies, even including an HR department to recruit new hires and an "employee of the month" award for tackling challenging problems.
The disclosure also comes as a report from cybersecurity company Sophos found that two or more threat actor groups spent at least five months within the network of an unnamed regional U.S. government agency before deploying a LockBit ransomware payload at the start of the year.
Researchers Connect BlackCat Ransomware with Past BlackMatter Malware Activity
9.4.22 Ransomware Thehackernews
Cybersecurity researchers have uncovered further links between BlackCat (aka
AlphaV) and BlackMatter ransomware families, the former of which emerged as a
replacement following international scrutiny last year.
"At least some members of the new BlackCat group have links to the BlackMatter group, because they modified and reused a custom exfiltration tool [...] and which has only been observed in BlackMatter activity," Kaspersky researchers said in a new analysis.
The tool, dubbed Fendr, has not only been upgraded to include more file types but also used by the gang extensively to steal data from corporate networks in December 2021 and January 2022 prior to encryption, in a popular tactic called double extortion.
The findings come less than a month after Cisco Talos researchers identified overlaps in the tactics, techniques, and procedures (TTPs) between BlackCat and BlackMatter, describing the new ransomware variant as a case of "vertical business expansion."

BlackCat stands out for two reasons: it's an affiliate actor that has deployed
BlackMatter in the past and its malware is written in Rust, indicating how
threat actors are increasingly pivoting to programming languages with
cross-compilation capabilities.
The group "provides infrastructure, malware samples, ransom negotiations, and probably cash-out," the researchers noted. "Anyone who already has access to compromised environments can use BlackCat's samples to infect a target."
Once executed, the malware gets the Windows system's MachineGuid from the registry — a unique key generated during the installation of the operating system — as well as its UUID, before proceeding to bypass User Account Control (UAC), delete shadow backups, and start the encryption process.
"This use of a modified Fendr, also known as ExMatter, represents a new data point connecting BlackCat with past BlackMatter activity," the researchers said.
"The modification of this reused tool demonstrates a more sophisticated planning and development regimen for adapting requirements to target environments, characteristic of a maturing criminal enterprise."
Experts Find Strategic Similarities b/w NotPetya and WhisperGate Attacks on
Ukraine
24.1.2022
Ransomware Thehackernews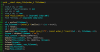
Latest analysis into the wiper malware that targeted dozens of Ukrainian
agencies earlier this month has revealed "strategic similarities" to NotPetya
malware that was unleashed against the country's infrastructure and elsewhere in
2017.
The malware, dubbed WhisperGate, was discovered by Microsoft last week, which
said it observed the destructive cyber campaign targeting government,
non-profit, and information technology entities in the nation, attributing the
intrusions to an emerging threat cluster codenamed "DEV-0586."
"While
WhisperGate has some strategic similarities to the notorious NotPetya wiper that
attacked Ukranian entities in 2017, including masquerading as ransomware and
targeting and destroying the master boot record (MBR) instead of encrypting it,
it notably has more components designed to inflict additional damage," Cisco
Talos said in a report detailing its response efforts.
Stating that stolen credentials were likely used in the attack, the cybersecurity company also pointed out that the threat actor had access to some of the victim networks months in advance before the infiltrations took place, a classic sign of sophisticated APT attacks.
The WhisperGate infection chain is fashioned as a multi-stage process that
downloads a payload that wipes the master boot record (MBR), then downloads a
malicious DLL file hosted on a Discord server, which drops and executes another
wiper payload that irrevocably destroys files by overwriting their content with
fixed data on the infected hosts.
The findings come a week after roughly 80 Ukrainian government agencies'
websites were defaced, with the Ukrainian intelligence agencies confirming that
the twin incidents are part of a wave of malicious activities targeting its
critical infrastructure, while also noting that the attacks leveraged the
recently disclosed Log4j vulnerabilities to gain access to some of the
compromised systems.
"Russia is using the country as a cyberwar testing
ground — a laboratory for perfecting new forms of global online combat," Wired's
Andy Greenberg noted in a 2017 deep-dive about the attacks that took aim at its
power grid in late 2015 and caused unprecedented blackouts.
"Systems in Ukraine face challenges that may not apply to those in other regions of the world, and extra protections and precautionary measures need to be applied," Talos researchers said. "Making sure those systems are both patched and hardened is of the utmost importance to help mitigate the threats the region faces."
FIN8 Hackers Spotted Using New 'White Rabbit' Ransomware in Recent Attacks
21.1.2022
Ransomware Thehackernews
The financially motivated FIN8 actor, in all likelihood, has resurfaced with a
never-before-seen ransomware strain called "White Rabbit" that was recently
deployed against a local bank in the U.S. in December 2021.
That's according to new findings published by Trend Micro, calling out the malware's overlaps with Egregor, which was taken down by Ukrainian law enforcement authorities in February 2021.
"One of the most notable aspects of White Rabbit's attack is how its payload binary requires a specific command-line password to decrypt its internal configuration and proceed with its ransomware routine," the researchers noted. "This method of hiding malicious activity is a trick that the ransomware family Egregor uses to hide malware techniques from analysis."
Egregor, which commenced operations in September 2020 until its operations took a huge hit, is widely believed to be a reincarnation of Maze, which shut down its criminal enterprise later that year.
Besides taking a leaf out of Egregor's playbook, White Rabbit adheres to the double extortion scheme and is believed to have been delivered via Cobalt Strike, a post-exploitation framework that's put to use by threat actors to reconnoiter, infiltrate, and drop malicious payloads into the affected system.

Double extortion, also known as pay-now-or-get-breached, refers to an
increasingly popular ransomware strategy in which valuable data from the targets
is exfiltrated prior to launching the encryption routine, followed by
pressurizing the victims into paying up to prevent the stolen information from
being published online.
Indeed, the ransom note displayed after the completion of the encryption process warns the victim that their data will be published or sold once the four-day deadline to meet their demands elapses. "We will also send the data to all interested supervisory organizations and the media," the note adds.
Although real-world attacks involving White Rabbit have gained attention only recently, digital forensic clues piecing together its trail point to a string of malicious activities commencing as early as July 2021.
What's more, analysis of the ransomware samples dating back to August 2021 shows that the malware is an updated version of the Sardonic backdoor, which Bitdefender described last year as an actively developed malware encountered in the aftermath of an unsuccessful attack targeting a financial institution in the U.S.
"The exact relationship between the White Rabbit group and FIN8 is currently unknown," cybersecurity company Lodestone said, adding it found a "number of TTPs suggesting that White Rabbit, if operating independently of FIN8, has a close relationship with the more established threat group or is mimicking them."
"Given that FIN8 is known mostly for its infiltration and reconnaissance tools, the connection could be an indication of how the group is expanding its arsenal to include ransomware," Trend Micro said. "So far, White Rabbit's targets have been few, which could mean that they are still testing the waters or warming up for a large-scale attack."