Ransom 2024 2023 2022 2021 2020
Microsoft Warns of New INC Ransomware Targeting U.S. Healthcare Sector
19.9.24 Ransom The Hacker News
Microsoft has revealed that a financially motivated threat actor has been observed using a ransomware strain called INC for the first time to target the healthcare sector in the U.S.
The tech giant's threat intelligence team is tracking the activity under the name Vanilla Tempest (formerly DEV-0832).
"Vanilla Tempest receives hand-offs from GootLoader infections by the threat actor Storm-0494, before deploying tools like the Supper backdoor, the legitimate AnyDesk remote monitoring and management (RMM) tool, and the MEGA data synchronization tool," it said in a series of posts shared on X.
In the next step, the attackers proceed to carry out lateral movement through Remote Desktop Protocol (RDP) and then use the Windows Management Instrumentation (WMI) Provider Host to deploy the INC ransomware payload.
The Windows maker said Vanilla Tempest has been active since at least July 2022, with previous attacks targeting education, healthcare, IT, and manufacturing sectors using various ransomware families such as BlackCat, Quantum Locker, Zeppelin, and Rhysida.
It's worth noting that the threat actor is also tracked under the name Vice Society, which is known for employing already existing lockers to carry out their attacks, as opposed to building a custom version of their own.
The development comes as ransomware groups like BianLian and Rhysida have been observed increasingly using Azure Storage Explorer and AzCopy to exfiltrate sensitive data from compromised networks in an attempt to evade detection.
"This tool, used for managing Azure storage and objects within it, is being repurposed by threat actors for large-scale data transfers to cloud storage," modePUSH researcher Britton Manahan said.
U.S. Agencies Warn of Iranian Hacking Group's Ongoing Ransomware Attacks
29.8.24 Ransom The Hacker News
U.S. cybersecurity and intelligence agencies have called out an Iranian hacking group for breaching multiple organizations across the country and coordinating with affiliates to deliver ransomware.
The activity has been linked to a threat actor dubbed Pioneer Kitten, which is also known as Fox Kitten, Lemon Sandstorm (formerly Rubidium), Parisite, and UNC757, which it described as connected to the government of Iran and uses an Iranian information technology (IT) company, Danesh Novin Sahand, likely as a cover.
"Their malicious cyber operations are aimed at deploying ransomware attacks to obtain and develop network access," the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and the Department of Defense Cyber Crime Center (DC3) said. "These operations aid malicious cyber actors in further collaborating with affiliate actors to continue deploying ransomware."
Targets of the attacks include education, finance, healthcare, and defense sectors, as well as local government entities in the U.S., with intrusions also reported in Israel, Azerbaijan, and the United Arab Emirates (U.A.E.) to pilfer sensitive data.
The goal, the agencies assessed, is to gain an initial foothold to victim networks and subsequently collaborate with ransomware affiliate actors associated with NoEscape, RansomHouse, and BlackCat (aka ALPHV) to deploy file-encrypting malware in exchange for a cut of the illicit proceeds, while keeping their nationality and origin "intentionally vague."
The attack attempts are believed to have commenced as early as 2017 and are ongoing as recently as this month. The threat actors, who also go by the online monikers Br0k3r and xplfinder, have been found to monetize their access to victim organizations on underground marketplaces, underscoring attempts to diversify their revenue streams.
"A significant percentage of the group's U.S.-focused cyber activity is in furtherance of obtaining and maintaining technical access to victim networks to enable future ransomware attacks," the agencies noted. "The actors offer full domain control privileges, as well as domain admin credentials, to numerous networks worldwide."
"The Iranian cyber actors' involvement in these ransomware attacks goes beyond providing access; they work closely with ransomware affiliates to lock victim networks and strategize on approaches to extort victims."
Initial access is accomplished by taking advantage of remote external services on internet-facing assets that are vulnerable to previously disclosed flaws (CVE-2019-19781, CVE-2022-1388, CVE-2023-3519, CVE-2024-3400, and CVE-2024-24919), followed by a series of steps to persist, escalate privileges, and set up remote access through tools like AnyDesk or the open-source Ligolo tunneling tool.
Iranian state-sponsored ransomware operations are not a new phenomenon. In December 2020, cybersecurity companies Check Point and ClearSky detailed a Pioneer Kitten hack-and-leak campaign called Pay2Key that specifically singled out dozens of Israeli companies by exploiting known security vulnerabilities.

"The ransom itself ranged between seven and nine Bitcoin (with a few cases in which the attacker was negotiated down to three Bitcoin)," the company noted at the time. "To pressure victims into paying, Pay2Key's leak site displays sensitive information stolen from the target organizations and makes threats of further leaks if the victims continue to delay payments."
Some of the ransomware attacks are also said to have been conducted through an Iranian contracting company named Emennet Pasargad, according to documents leaked by Lab Dookhtegan in early 2021.
The disclosure paints the picture of a flexible group that operates with both ransomware and cyber espionage motives, joining other dual-purpose hacking outfits like ChamelGang and Moonstone Sleet.
Peach Sandstorm Delivers Tickler Malware in Long-Running Campaign#
The development comes as Microsoft said it observed Iranian state-sponsored threat actor Peach Sandstorm (aka APT33, Curious Serpens, Elfin, and Refined Kitten) deploying a new custom multi-stage backdoor referred to as Tickler in attacks against targets in the satellite, communications equipment, oil and gas, as well as federal and state government sectors in the U.S. and U.A.E. between April and July 2024.
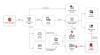
"Peach Sandstorm also continued conducting password spray attacks against the educational sector for infrastructure procurement and against the satellite, government, and defense sectors as primary targets for intelligence collection," the tech giant said, adding it detected intelligence gathering and possible social engineering targeting higher education, satellite, and defense sectors via LinkedIn.
These efforts on the professional networking platform, which date back to at least November 2021 and have continued into mid-2024, materialized in the form of phony profiles masquerading as students, developers, and talent acquisition managers supposedly based in the U.S. and Western Europe.
The password spray attacks serve as a conduit for the Tickler custom multi-stage backdoor, which comes with capabilities to download additional payloads from an adversary-controlled Microsoft Azure infrastructure, perform file operations, and gather system information.
Some of the attacks are notable for leveraging Active Directory (AD) snapshots for malicious administrative actions, Server Message Block (SMB) for lateral movement, and the AnyDesk remote monitoring and management (RMM) software for persistent remote access.
"The convenience and utility of a tool like AnyDesk is amplified by the fact that it might be permitted by application controls in environments where it is used legitimately by IT support personnel or system administrators," Microsoft said.
Peach Sandstorm is assessed to be operating on behalf of the Iranian Islamic Revolutionary Guard Corps (IRGC). It's known to be active for over a decade, carrying out espionage attacks against a diverse array of public and private sector targets globally. Recent intrusions targeting the defense sector have also deployed another backdoor called FalseFont.
Iranian Counterintelligence Operation Uses HR Lures to Harvest Intel#
In what's evidence of ever-expanding Iranian operations in cyberspace, Google-owned Mandiant said it uncovered a suspected Iran-nexus counterintelligence operation that's aimed at collecting data on Iranians and domestic threats who may be collaborating with its perceived adversaries, including Israel.
"The collected data may be leveraged to uncover human intelligence (HUMINT) operations conducted against Iran and to persecute any Iranians suspected to be involved in these operations," Mandiant researchers Ofir Rozmann, Asli Koksal, and Sarah Bock said. "These may include Iranian dissidents, activists, human rights advocates, and Farsi speakers living in and outside Iran."

The activity, the company said, shares "weak overlap" with APT42 and aligns with IRGC's track record of conducting surveillance operations against domestic threats and individuals of interest to the Iranian government. The campaign has been active since 2022.
The attack lifecycle's backbone is a network of over 40 fake recruitment websites that impersonate Israeli human resources firms that are then disseminated via social media channels like X and Virasty to trick prospective victims into sharing their personal information (i.e., name, birth date, email, home address, education, and professional experience).
These decoy websites, posing as Optima HR and Kandovan HR, state their alleged purpose is to "recruit employees and officers of Iran's intelligence and security organizations" and have Telegram handles that reference Israel (IL) in their handles (e.g., PhantomIL13 and getDmIL).
Mandian further said further analysis of the Optima HR websites led to the discovery of a previous cluster of fake recruitment websites that targeted Farsi and Arabic speakers affiliated with Syria and Lebanon (Hezbollah) under a different HR firm named VIP Human Solutions between 2018 and 2022.
"The campaign casts a wide net by operating across multiple social media platforms to disseminate its network of fake HR websites in an attempt to expose Farsi-speaking individuals who may be working with intelligence and security agencies and are thus perceived as a threat to Iran's regime," Mandiant said.
BlackByte Ransomware Exploits VMware ESXi Flaw in Latest Attack Wave
28.8.24 Ransom The Hacker News
The threat actors behind the BlackByte ransomware group have been observed likely exploiting a recently patched security flaw impacting VMware ESXi hypervisors, while also leveraging various vulnerable drivers to disarm security protections.
"The BlackByte ransomware group continues to leverage tactics, techniques, and procedures (TTPs) that have formed the foundation of its tradecraft since its inception, continuously iterating its use of vulnerable drivers to bypass security protections and deploying a self-propagating, wormable ransomware encryptor," Cisco Talos said in a technical report shared with The Hacker News.
The exploitation of CVE-2024-37085, an authentication bypass vulnerability in VMware ESXi that has also been weaponized by other ransomware groups, is a sign that the e-crime group is pivoting from established approaches.
BlackByte made its debut in the second half of 2021 and is purported to be one of the ransomware variants to have emerged in the months leading up to shutdown of the infamous Conti ransomware crew.
The ransomware-as-a-service (RaaS) group has a history of exploiting ProxyShell vulnerabilities in Microsoft Exchange Server to obtain initial access, while avoiding systems that use Russian and a number of Eastern European languages.
Like RaaS groups, it also leverages double extortion as part of attacks, adopting a name-and-shame approach via a data leak site operated on the dark web to pressurize victims into paying up. Multiple variants of the ransomware, written in C, .NET, and Go, have been observed in the wild to date.
While a decryptor for BlackByte was released by Trustwave in October 2021, the group has continued to refine its modus operandi, even going to the extent of employing a custom tool named ExByte for data exfiltration prior to commencing encryption.
An advisory released by the U.S. government in early 2022 attributed the RaaS group to financially motivated attacks targeting critical infrastructure sectors, including financial, food and agriculture, and government facilities.
One of the important aspects of their attacks is the use of vulnerable drivers to terminate security processes and bypass controls, a technique known as bring your own vulnerable driver (BYOVD).
Cisco Talos, which investigated a recent BlackByte ransomware attack, said the intrusion was likely facilitated using valid credentials to access the victim organization's VPN. It's believed that the initial access was obtained through a brute-force attack.
"Given BlackByte's history of exploiting public-facing vulnerabilities for initial access, the use of VPN for remote access may represent a slight shift in technique or could represent opportunism," security researchers James Nutland, Craig Jackson, Terryn Valikodath, and Brennan Evans said. "The use of the victim's VPN for remote access also affords the adversary other advantages, including reduced visibility from the organization's EDR."
The threat actor subsequently managed to escalate their privileges, using the permissions to access the organization's VMware vCenter server to create and add new accounts to an Active Directory group named ESX Admins. This, Talos said, was done by exploiting CVE-2024-37085, which enables an attacker to gain administrator privileges on the hypervisor by creating a group with that name and adding any user to it.
This privilege could then be abused to control virtual machines (VMs), modify host server's configuration, and gain unauthorized access to system logs, diagnostics, and performance monitoring tools.
Talos pointed out that the exploitation of the flaw took place within days of public disclosure, highlighting the speed at which threat actors refine their tactics to incorporate newly disclosed vulnerabilities into their arsenal and advance their attacks.
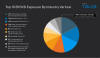
Furthermore, the recent BlackByte attacks culminate with the encrypted files being rewritten with the file extension "blackbytent_h," with the encryptor also dropping four vulnerable drivers as part of the BYOVD attack. All the four drivers follow a similar naming convention: Eight random alphanumeric characters followed by an underscore and an incremental numerical value -
AM35W2PH (RtCore64.sys)
AM35W2PH_1 (DBUtil_2_3.sys)
AM35W2PH_2 (zamguard64.sys aka Terminator)
AM35W2PH_3 (gdrv.sys)
The professional, scientific, and technical services sectors have the greatest exposure to the observed vulnerable drivers, accounting for 15% of the total, followed by manufacturing (13%) and educational services (13%). Talos has also assessed that the threat actor is likely more active than what it appears to be, and that only an estimated 20-30% of victims are publicly posted, although the exact reason for this disparity remains unclear.
"BlackByte's progression in programming languages from C# to Go and subsequently to C/C++ in the latest version of its encryptor – BlackByteNT – represents a deliberate effort to increase the malware's resilience against detection and analysis," the researchers said.
"Complex languages like C/C++ allow for the incorporation of advanced anti-analysis and anti-debugging techniques, which have been observed across the BlackByte tooling during detailed analysis by other security researchers."
The disclosure comes as Group-IB unpacked the tactics associated with two other ransomware strains tracked as Brain Cipher and RansomHub, underscoring the potential connections of the former with ransomware groups such as EstateRansomware, SenSayQ, and RebornRansomware.

"There are similarities in terms of style and content of the Brain Cipher's ransom note to those by SenSayQ ransomware," the Singaporean cybersecurity company said. "The TOR websites of Brain Cipher ransomware group and SenSayQ ransomware group use similar technologies and scripts."
RansomHub, on the other hand, has been observed recruiting former affiliates of Scattered Spider, a detail that first came to light last month. A majority of the attacks have targeted healthcare, finance, and government sectors in the U.S., Brazil, Italy, Spain, and the U.K.
"For initial access the affiliates usually purchase compromised valid domain accounts from Initial Access Brokers (IABs) and external remote services," Group-IB said, adding the "accounts have been acquired via LummaC2 stealer."
"RansomHub's tactics include leveraging compromised domain accounts and public VPNs for initial access, followed by data exfiltration and extensive encryption processes. Their recent introduction of a RaaS affiliate program and use of high-demand ransom payments illustrate their evolving and aggressive approach."
New Qilin Ransomware Attack Uses VPN Credentials, Steals Chrome Data
24.8.24 Ransom The Hacker News
The threat actors behind a recently observed Qilin ransomware attack have stolen credentials stored in Google Chrome browsers on a small set of compromised endpoints.
The use of credential harvesting in connection with a ransomware infection marks an unusual twist, and one that could have cascading consequences, cybersecurity firm Sophos said in a Thursday report.
The attack, detected in July 2024, involved infiltrating the target network via compromised credentials for a VPN portal that lacked multi-factor authentication (MFA), with the threat actors conducting post-exploitation actions 18 days after initial access took place.
"Once the attacker reached the domain controller in question, they edited the default domain policy to introduce a logon-based Group Policy Object (GPO) containing two items," researchers Lee Kirkpatrick, Paul Jacobs, Harshal Gosalia, and Robert Weiland said.
The first of them is a PowerShell script named "IPScanner.ps1" that's designed to harvest credential data stored within the Chrome browser. The second item is a batch script ("logon.bat") contacting commands to execute the first script.
"The attacker left this GPO active on the network for over three days," the researchers added.
"This provided ample opportunity for users to log on to their devices and, unbeknownst to them, trigger the credential-harvesting script on their systems. Again, since this was all done using a logon GPO, each user would experience this credential-scarfing each time they logged in."
The attackers then exfiltrated the stolen credentials and took steps to erase evidence of the activity before encrypting the files and dropping the ransom note in every directory on the system.
The theft of credentials stored in the Chrome browser means that affected users are now required to change their username-password combinations for every third-party site.
"Predictably, ransomware groups continue to change tactics and expand their repertoire of techniques," the researchers said.
"If they, or other attackers, have decided to also mine for endpoint-stored credentials – which could provide a foot in the door at a subsequent target, or troves of information about high-value targets to be exploited by other means – a dark new chapter may have opened in the ongoing story of cybercrime."
Ever-evolving Trends in Ransomware#
The development comes as ransomware groups like Mad Liberator and Mimic have been observed using unsolicited AnyDesk requests for data exfiltration and leveraging internet-exposed Microsoft SQL servers for initial access, respectively.
The Mad Liberator attacks are further characterized by the threat actors abusing the access to transfer and launch a binary called "Microsoft Windows Update" that displays a bogus Windows Update splash screen to the victim to give the impression that software updates are being installed on the machine while the data is being plundered.
The abuse of legitimate remote desktop tools, as opposed to custom-made malware, offers attackers the perfect disguise to camouflage their malicious activities in plain sight, allowing them to blend in with normal network traffic and evade detection.
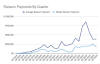
Ransomware continues to be a profitable venture for cybercriminals despite a series of law enforcement actions, with 2024 set to be the highest-grossing year yet. The year also saw the largest ransomware payment ever recorded at approximately $75 million to the Dark Angels ransomware group.
"The median ransom payment to the most severe ransomware strains has spiked from just under $200,000 in early 2023 to $1.5 million in mid-June 2024, suggesting that these strains are prioritizing targeting larger businesses and critical infrastructure providers that may be more likely to pay high ransoms due to their deep pockets and systemic importance," blockchain analytics firm Chainalysis said.
Ransomware victims are estimated to have paid $459.8 million to cybercriminals in the first half of the year, up from $449.1 million year-over-year. However, total ransomware payment events as measured on-chain have declined YoY by 27.29%, indicating a drop in payment rates.
What's more, Russian-speaking threat groups accounted for at least 69% of all cryptocurrency proceeds linked to ransomware throughout the previous year, exceeding $500 million.
According to data shared by NCC Group, the number of ransomware attacks observed in July 2024 jumped month-on-month from 331 to 395, but down from 502 registered last year. The most active ransomware families were RansomHub, LockBit, and Akira. The sectors that were most frequently targeted include industrials, consumer cyclicals, and hotels and entertainment.
Industrial organizations are a lucrative target for ransomware groups due to the mission-critical nature of their operations and the high impact of disruptions, thus increasing the likelihood that victims could pay the ransom amount demanded by attackers.
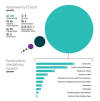
"Criminals focus where they can cause the most pain and disruption so the public will demand quick resolutions, and they hope, ransom payments to restore services more quickly," said Chester Wisniewski, global field chief technology officer at Sophos.
"This makes utilities prime targets for ransomware attacks. Because of the essential functions they provide, modern society demands they recover quickly and with minimal disruption."
Ransomware attacks targeting the sector have nearly doubled in Q2 2024 compared to Q1, from 169 to 312 incidents, per Dragos. A majority of the attacks singled out North America (187), followed by Europe (82), Asia (29), and South America (6).
"Ransomware actors are strategically timing their attacks to coincide with peak holiday periods in some regions to maximize disruption and pressure organizations into payment," NCC Group said.
Malwarebytes, in its own 2024 State of Ransomware report, highlighted three trends in ransomware tactics over the past year, including a spike in attacks during weekends and early morning hours between 1 a.m. and 5 a.m., and a reduction in the time from initial access to encryption.

Another noticeable shift is the increased edge service exploitation and targeting of small and medium-sized businesses, WithSecure said, adding the dismantling of LockBit and ALPHV (aka BlackCat) has led to an erosion of trust within the cybercriminal community, causing affiliates to move away from major brands.
Indeed, Coveware said over 10% of the incidents handled by the company in Q2 2024 were unaffiliated, meaning they were "attributed to attackers that were deliberately operating independently of a specific brand and what we typically term 'lone wolves.'"
"Continued takedowns of cybercriminal forums and marketplaces shortened the lifecycle of criminal sites, as the site administrators try to avoid drawing law enforcement (LE) attention," Europol said in an assessment released last month.
"This uncertainty, combined with a surge in exit scams, have contributed to the continued fragmentation of criminal marketplaces. Recent LE operations and the leak of ransomware source codes (e.g., Conti, LockBit, and HelloKitty) have led to a fragmentation of active ransomware groups and available variants."
CISA Warns of Critical Jenkins Vulnerability Exploited in Ransomware Attacks
20.8.24 Ransom The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw impacting Jenkins to its Known Exploited Vulnerabilities (KEV) catalog, following its exploitation in ransomware attacks.
The vulnerability, tracked as CVE-2024-23897 (CVSS score: 9.8), is a path traversal flaw that could lead to code execution.
"Jenkins Command Line Interface (CLI) contains a path traversal vulnerability that allows attackers limited read access to certain files, which can lead to code execution," CISA said in a statement.
It was first disclosed by Sonar security researchers in January 2024 and addressed in Jenkins versions 2.442 and LTS 2.426.3 by disabling the command parser feature.
Back in March, Trend Micro said it uncovered several attack instances originating from the Netherlands, Singapore, and Germany, and that it found instances where remote code execution exploits for the flaw were actively being traded.

In recent weeks, CloudSEK and Juniper Networks have revealed real-world attacks exploiting CVE-2024-23897 in the wild to infiltrate the companies BORN Group and Brontoo Technology Solutions.
The attacks have been attributed to threat actor known as IntelBroker and the RansomExx ransomware gang, respectively.
"CVE-2024-23897 is an unauthenticated LFI vulnerability that allows attackers to read arbitrary files on the Jenkins server," CloudSEK said. "This vulnerability arises from improper input validation, enabling attackers to manipulate specific parameters and trick the server into accessing and displaying the contents of sensitive files."
In light of the active exploitation of the vulnerability, Federal Civilian Executive Branch (FCEB) agencies have time till September 9, 2024, to apply the fixes and secure their networks against active threats.
RansomHub Group Deploys New EDR-Killing Tool in Latest Cyber Attacks
15.8.24 Ransom The Hacker News
A cybercrime group with links to the RansomHub ransomware has been observed using a new tool designed to terminate endpoint detection and response (EDR) software on compromised hosts, joining the likes of other similar programs like AuKill (aka AvNeutralizer) and Terminator.
The EDR-killing utility has been dubbed EDRKillShifter by cybersecurity company Sophos, which discovered the tool in connection with a failed ransomware attack in May 2024.
"The EDRKillShifter tool is a 'loader' executable – a delivery mechanism for a legitimate driver that is vulnerable to abuse (also known as a 'bring your own vulnerable driver,' or BYOVD, tool)," security researcher Andreas Klopsch said. "Depending on the threat actor's requirements, it can deliver a variety of different driver payloads."
RansomHub, a suspected rebrand of the Knight ransomware, surfaced in February 2024, leveraging known security flaws to obtain initial access and drop legitimate remote desktop software such as Atera and Splashtop for persistent access.
Last month, Microsoft revealed that the notorious e-crime syndicate known as Scattered Spider has incorporated ransomware strains such as RansomHub and Qilin into its arsenal.
Executed via command-line along with a password string input, the executable decrypts an embedded resource named BIN and executes it in memory. The BIN resource unpacks and runs a Go-based final, obfuscated payload, which then takes advantage of different vulnerable, legitimate drivers to gain elevated privileges and disarm EDR software.
"The binary's language property is Russian, indicating that the malware author compiled the executable on a computer with Russian localization settings," Klopsch said. "All of the unpacked EDR killers embed a vulnerable driver in the .data section."
To mitigate the threat, it's recommended to keep systems up-to-date, enable tamper protection in EDR software, and practice strong hygiene for Windows security roles.
"This attack is only possible if the attacker escalates privileges they control, or if they can obtain administrator rights," Klopsch said. "Separation between user and admin privileges can help prevent attackers from easily loading drivers."
Black Basta-Linked Attackers Target Users with SystemBC Malware
15.8.24 Ransom The Hacker News
An ongoing social engineering campaign with alleged links to the Black Basta ransomware group has been linked to "multiple intrusion attempts" with the goal of conducting credential theft and deploying a malware dropper called SystemBC.
"The initial lure being utilized by the threat actors remains the same: an email bomb followed by an attempt to call impacted users and offer a fake solution," Rapid7 said, adding "external calls were typically made to the impacted users via Microsoft Teams."
The attack chain then convinces the user to download and install a legitimate remote access software named AnyDesk, which acts as a channel for deploying follow-on payloads and exfiltrate sensitive data.
This includes the use of an executable called "AntiSpam.exe" that purports to download email spam filters and urges users to enter their Windows credentials to complete the update.
The step is followed by the execution of several binaries, DLL files, and PowerShell scripts, which includes a Golang-based HTTP beacon that establishes contact with a remote server, a SOCKS proxy, and SystemBC.
To mitigate the risk posed by the threat, it's advised to block all unapproved remote desktop solutions and be on the lookout for suspicious phone calls and texts purporting to be from internal IT staff.
The disclosure comes as SocGholish (aka FakeUpdates), GootLoader, and Raspberry Robin have emerged as the most commonly observed loader strains in 2024, which then act as a stepping stone for ransomware, according to data from ReliaQuest.
"GootLoader is new to the top-three list this year, replacing QakBot as its activity declines," the cybersecurity company said.
"Malware loaders are frequently advertised on dark web cybercriminal forums such as XSS and Exploit, where they are marketed to cybercriminals seeking to facilitate network intrusions and payload delivery. These loaders are often offered through subscription models, with monthly fees granting access to regular updates, support, and new features designed to evade detection."
One advantage to this subscription-based approach is that it allows even threat actors with limited technical expertise to mount sophisticated attacks.
Phishing attacks have also been observed delivering an information stealer malware known as 0bj3ctivity Stealer by means of another loader called Ande Loader as part of a multi-layered distribution mechanism.
"The malware's distribution through obfuscated and encrypted scripts, memory injection techniques, and the ongoing enhancement of Ande Loader with features like anti-debugging and string obfuscation underscore the need for advanced detection mechanisms and continuous research," eSentire said.
These campaigns are just the latest in a spate of phishing and social engineering attacks that have been uncovered in recent weeks, even as threat actors are increasingly weaponizing fake QR codes for malicious purposes -
A ClearFake campaign that leverages compromised web pages to spread .NET malware under the pretext of downloading a Google Chrome update
A phishing attack that employs job-themed lures to deliver AsyncRAT, Pure HVNC, XWorm, Venom RAT through a Python shellcode loader
A campaign that uses fake websites masquerading as HSBC, Santander, Virgin Money, and Wise to serve a copy of the AnyDesk Remote Monitoring and Management (RMM) software to Windows and macOS users, which is then used to steal sensitive data
A fake website ("win-rar[.]co") seemingly distributing WinRAR that's used to deploy ransomware, cryptocurrency miner, and information stealer called Kematian Stealer that are hosted on GitHub
Drive-by download campaigns that make use of malicious advertisements or compromised websites that serve as a conduit for NetSupport RAT
A social media malvertising campaign that hijacks Facebook pages to promote a seemingly legitimate artificial intelligence (AI) photo editor website through paid ads that lure victims to download ITarian's RMM tool and use it to deliver Lumma Stealer
"The targeting of social media users for malicious activities highlights the importance of robust security measures to protect account credentials and prevent unauthorized access," Trend Micro researchers said.
FBI and CISA Warn of BlackSuit Ransomware That Demands Up to $500 Million
8.8.24 Ransom The Hacker News
The ransomware strain known as BlackSuit has demanded as much as $500 million in ransoms to date, with one individual ransom demand hitting $60 million.
That's according to an updated advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI).
"BlackSuit actors have exhibited a willingness to negotiate payment amounts," the agencies said. "Ransom amounts are not part of the initial ransom note, but require direct interaction with the threat actor via a .onion URL (reachable through the Tor browser) provided after encryption."
Attacks involving ransomware have targeted several critical infrastructure sectors spanning commercial facilities, healthcare and public health, government facilities, and critical manufacturing.
An evolution of the Royal ransomware, it leverages the initial access obtained via phishing emails to disarm antivirus software and exfiltrate sensitive data before ultimately deploying the ransomware and encrypting the systems.
Other common infection pathways include the use of Remote Desktop Protocol (RDP), exploitation of vulnerable internet-facing applications, and access purchased via initial access brokers (IABs).
BlackSuit actors are known to use legitimate remote monitoring and management (RMM) software and tools like SystemBC and GootLoader malware to maintain persistence in victim networks.
"BlackSuit actors have been observed using SharpShares and SoftPerfect NetWorx to enumerate victim networks," the agencies noted. "The publicly available credential stealing tool Mimikatz and password harvesting tools from Nirsoft have also been found on victim systems. Tools such as PowerTool and GMER are often used to kill system processes."
CISA and FBI have warned of an uptick in cases where victims receive telephonic or email communications from BlackSuit actors regarding the compromise and ransom, a tactic that's increasingly being adopted by ransomware gangs to ramp up pressure.
"In recent years, threat actors appear to be increasingly interested in not merely threatening organizations directly, but also secondary victims," cybersecurity firm Sophos said in a report published this week. "For instance, as reported in January 2024, attackers threatened to 'swat' patients of a cancer hospital, and have sent threatening text messages to a CEO's spouse."
That's not all. Threat actors have also claimed to assess stolen data for evidence of illegal activity, regulatory non-compliance, and financial discrepancies, even going to the extent of stating that an employee at a compromised organization had been searching for child sexual abuse material by posting their web browser history.
Such aggressive methods can not only be used as further leverage to coerce their targets into paying up, they also inflict reputational damage by criticizing them as unethical or negligent.
The development comes amid the emergence of new ransomware families like Lynx, OceanSpy, Radar, Zilla (a Crysis/Dharma ransomware variant), and Zola (a Proton ransomware variant) in the wild, even as existing ransomware groups are constantly evolving their modus operandi by incorporating new tools into their arsenal.
A case example is Hunters International, which has been observed using a new C#-based malware called SharpRhino as an initial infection vector and a remote access trojan (RAT). A variant of the ThunderShell malware family, it's delivered through a typosquatting domain impersonating the popular network administration tool Angry IP Scanner.
It's worth pointing out that malvertising campaigns have been spotted delivering the malware as recently as January 2024, per eSentire. The open-source RAT is also called Parcel RAT and SMOKEDHAM.
"On execution, it establishes persistence and provides the attacker with remote access to the device, which is then utilized to progress the attack," Quorum Cyber researcher Michael Forret said. "Using previously unseen techniques, the malware is able to obtain a high level of permission on the device in order to ensure the attacker is able to further their targeting with minimal disruption."
Hunters International is assessed to be a rebrand of the now-defunct Hive ransomware group. First detected in October 2023, it has claimed responsibility for 134 attacks in the first seven months of 2024.
VMware ESXi Flaw Exploited by Ransomware Groups for Admin Access
31.7.24 Ransom The Hacker News
A recently patched security flaw impacting VMware ESXi hypervisors has been actively exploited by "several" ransomware groups to gain elevated permissions and deploy file-encrypting malware.
The attacks involve the exploitation of CVE-2024-37085 (CVSS score: 6.8), an Active Directory integration authentication bypass that allows an attacker to obtain administrative access to the host.
"A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group ('ESXi Admins' by default) after it was deleted from AD," Broadcom-owned VMware noted in an advisory released in late June 2024.
In other words, escalating privileges on ESXi to the administrator was as simple as creating a new AD group named "ESX Admins" and adding any user to it, or renaming any group in the domain to "ESX Admins" and adding a user to the group or using an existing group member.
Microsoft, in a new analysis published on July 29, said it observed ransomware operators like Storm-0506, Storm-1175 (a China-based threat actor known for deploying Medusa ransomware), Octo Tempest, and Manatee Tempest leveraging the post-compromise technique to deploy Akira and Black Basta.
Cybersecurity
"VMware ESXi hypervisors joined to an Active Directory domain consider any member of a domain group named 'ESX Admins' to have full administrative access by default," researchers Danielle Kuznets Nohi, Edan Zwick, Meitar Pinto, Charles-Edouard Bettan, and Vaibhav Deshmukh said.
"This group is not a built-in group in Active Directory and does not exist by default. ESXi hypervisors do not validate that such a group exists when the server is joined to a domain and still treats any members of a group with this name with full administrative access, even if the group did not originally exist."
In one attack staged by Storm-0506 against an unnamed engineering firm in North America, the threat actor weaponized the vulnerability to gain elevated permissions to the ESXi hypervisors after having obtained an initial foothold using a QakBot infection and exploiting another flaw in the Windows Common Log File System (CLFS) Driver (CVE-2023-28252, CVSS score: 7.8) for privilege escalation.
Subsequently, phases entailed the deployment of Cobalt Strike and Pypykatz, a Python version of Mimikatz, to steal domain administrator credentials and move laterally across the network, followed by dropping the SystemBC implant for persistence and abusing the ESXi admin access to deploy Black Basta.
"The actor was also observed attempting to brute force Remote Desktop Protocol (RDP) connections to multiple devices as another method for lateral movement, and then again installing Cobalt Strike and SystemBC," the researchers said. "The threat actor then tried to tamper with Microsoft Defender Antivirus using various tools to avoid detection."

"It's important to note that exploitation is very dependent on the host having been configured to use AD for user management," Scott Caveza, staff research engineer at Tenable, said in a statement. "In addition, an attacker would also need privileged access to the AD environment in order to successfully exploit this vulnerability."
"Despite this significant barrier to entry, we cannot underestimate ransomware groups' abilities and determination to escalate privileges and advance their attack path once they obtain initial access."
The development comes as Google-owned Mandiant revealed that a financially motivated threat cluster called UNC4393 is using initial access obtained via a C/C++ backdoor codenamed ZLoader (aka DELoader, Terdot, or Silent Night) to deliver Black Basta, moving away from QakBot and DarkGate.
"UNC4393 has demonstrated a willingness to cooperate with multiple distribution clusters to complete its actions on objectives," the threat intelligence firm said. "This most recent surge of Silent Night activity, beginning earlier this year, has been primarily delivered via malvertising. This marked a notable shift away from phishing as UNC4393's only known means of initial access."
The attack sequence involves making use of the initial access to drop Cobalt Strike Beacon and a combination of custom and readily-available tools to conduct reconnaissance, not to mention relying on RDP and Server Message Block (SMB) for lateral movement. Persistence is achieved by means of SystemBC.
ZLoader, which resurfaced after a long gap late last year, has been under active development, with new variants of the malware being propagated via a PowerShell backdoor referred to as PowerDash, per recent findings from Walmart's cyber intelligence team.
Over the past few years, ransomware actors have demonstrated an appetite for latching onto novel techniques to maximize impact and evade detection, increasingly targeting ESXi hypervisors and taking advantage of newly disclosed security flaws in internet-facing servers to breach targets of interest.
Qilin (aka Agenda), for instance, was originally developed in the Go programming language, but has since been redeveloped using Rust, indicating a shift towards constructing malware using memory-safe languages. Recent attacks involving ransomware have been found to leverage known weaknesses in Fortinet and Veeam Backup & Replication software for initial access.
"The Qilin ransomware is capable of self-propagation across a local network," Group-IB said in a recent analysis, adding it's also equipped to "carry out self-distribution using VMware vCenter."
Another notable malware employed in Qilin ransomware attacks is a tool dubbed Killer Ultra that's designed to disable popular endpoint detection and response (EDR) software running on the infected host as well as clear all Windows event logs to remove all indicators of compromise.
Organizations are recommended to install the latest software updates, practice credential hygiene, enforce two-factor authentication, and take steps to safeguard critical assets using appropriate monitoring procedures and backup and recovery plans.
North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks
26.7.24 Ransom The Hacker News
A North Korea-linked threat actor known for its cyber espionage operations has gradually expanded into financially-motivated attacks that involve the deployment of ransomware, setting it apart from other nation-state hacking groups linked to the country.
Google-owned Mandiant is tracking the activity cluster under a new moniker APT45, which overlaps with names such as Andariel, Nickel Hyatt, Onyx Sleet, Stonefly, and Silent Chollima.
"APT45 is a long-running, moderately sophisticated North Korean cyber operator that has carried out espionage campaigns as early as 2009," researchers Taylor Long, Jeff Johnson, Alice Revelli, Fred Plan, and Michael Barnhart said. "APT45 has been the most frequently observed targeting critical infrastructure."
It's worth mentioning that APT45, along with APT38 (aka BlueNoroff), APT43 (aka Kimsuky), and Lazarus Group (aka TEMP.Hermit), are elements within North Korea's Reconnaissance General Bureau (RGB), the nation's premier military intelligence organization.
APT45 is notably linked to the deployment of ransomware families tracked as SHATTEREDGLASS and Maui targeting entities in South Korea, Japan, and the U.S. in 2021 and 2022. Details of SHATTEREDGLASS were documented by Kaspersky in June 2021.

"It is possible that APT45 is carrying out financially-motivated cybercrime not only in support of its own operations but to generate funds for other North Korean state priorities," Mandiant said.
Another prominent malware in its arsenal is a backdoor dubbed Dtrack (aka Valefor and Preft), which was first used in a cyber attack aimed at the Kudankulam Nuclear Power Plant in India in 2019, marking one of the few publicly known instances of North Korean actors striking critical infrastructure.
"APT45 is one of North Korea's longest running cyber operators, and the group's activity mirrors the regime's geopolitical priorities even as operations have shifted from classic cyber espionage against government and defense entities to include healthcare and crop science," Mandiant said.
"As the country has become reliant on its cyber operations as an instrument of national power, the operations carried out by APT45 and other North Korean cyber operators may reflect the changing priorities of the country's leadership."
The findings come as security awareness training firm KnowBe4 said it was tricked into hiring an IT worker from North Korea as a software engineer, who used a stolen identity of a U.S. citizen and enhanced their picture using artificial intelligence (AI).
"This was a skillful North Korean IT worker, supported by a state-backed criminal infrastructure, using the stolen identity of a U.S. citizen participating in several rounds of video interviews and circumvented background check processes commonly used by companies," the company said.
The IT worker army, assessed to be part of the Workers' Party of Korea's Munitions Industry Department, has a history of seeking employment in U.S.-based firms by pretending to be located in the country when they are actually in China and Russia and logging-in remotely through company-issued laptops delivered to a "laptop farm."
KnowBe4 said it detected suspicious activities on the Mac workstation sent to the individual on July 15, 2024, at 9:55 p.m. EST that consisted of manipulating session history files, transferring potentially harmful files, and executing harmful software. The malware was downloaded using a Raspberry Pi.

Twenty-five minutes later, the Florida-based cybersecurity company said it contained the employee's device. There is no evidence that the attacker gained unauthorized access to sensitive data or systems.
"The scam is that they are actually doing the work, getting paid well, and giving a large amount to North Korea to fund their illegal programs," KnowBe4's chief executive Stu Sjouwerman said.
"This case highlights the critical need for more robust vetting processes, continuous security monitoring, and improved coordination between HR, IT, and security teams in protecting against advanced persistent threats."
New Linux Variant of Play Ransomware Targeting VMware ESXi Systems
23.7.24 Ransom The Hacker News
Cybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play (aka Balloonfly and PlayCrypt) that's designed to target VMware ESXi environments.
"This development suggests that the group could be broadening its attacks across the Linux platform, leading to an expanded victim pool and more successful ransom negotiations," Trend Micro researchers said in a report published Friday.
Play, which arrived on the scene in June 2022, is known for its double extortion tactics, encrypting systems after exfiltrating sensitive data and demanding payment in exchange for a decryption key. According to estimates released by Australia and the U.S., as many as 300 organizations have been victimized by the ransomware group as of October 2023.
Statistics shared by Trend Micro for the first seven months of 2024 show that the U.S. is the country with the highest number of victims, followed by Canada, Germany, the U.K., and the Netherlands.
Manufacturing, professional services, construction, IT, retail, financial services, transportation, media, legal services, and real estate are some of the top industries affected by the Play ransomware during the time period.
The cybersecurity firm's analysis of a Linux variant of Play comes from a RAR archive file hosted on an IP address (108.61.142[.]190), which also contains other tools identified as utilized in previous attacks such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
"Though no actual infection has been observed, the command-and-control (C&C) server hosts the common tools that Play ransomware currently uses in its attacks," it said. "This could denote that the Linux variant might employ similar tactics, techniques, and procedures (TTPs)."
The ransomware sample, upon execution, ensures that it's running in an ESXi environment before proceeding to encrypt virtual machine (VM) files, including VM disk, configuration, and metadata files, and appending them with the extension ".PLAY." A ransom note is then dropped in the root directory.
Further analysis has determined that the Play ransomware group is likely using the services and infrastructure peddled by Prolific Puma, which offers an illicit link-shortening service to other cybercriminals to help them evade detection while distributing malware.

Specifically, it employs what's called a registered domain generation algorithm (RDGA) to spin up new domain names, a programmatic mechanism that's increasingly being used by several threat actors, including VexTrio Viper and Revolver Rabbit, for phishing, spam, and malware propagation.
Revolver Rabbit, for instance, is believed to have registered over 500,000 domains on the ".bond" top-level domain (TLD) at an approximate cost of more than $1 million, leveraging them as active and decoy C2 servers for the XLoader (aka FormBook) stealer malware.
"The most common RDGA pattern this actor uses is a series of one or more dictionary words followed by a five-digit number, with each word or number separated by a dash," Infoblox noted in a recent analysis. "Sometimes the actor uses ISO 3166-1 country codes, full country names, or numbers corresponding to years instead of dictionary words."
RDGAs are a lot more challenging to detect and defend against than traditional DGAs owing to the fact that they allow threat actors to generate many domain names to register them for use – either all at once or over time – in their criminal infrastructure.
"In an RDGA, the algorithm is a secret kept by the threat actor, and they register all the domain names," Infoblox said. "In a traditional DGA, the malware contains an algorithm that can be discovered, and most of the domain names will not be registered. While DGAs are used exclusively for connection to a malware controller, RDGAs are used for a wide range of malicious activity."
The latest findings indicate a potential collaboration between two cybercriminal entities, suggesting that the Play ransomware actors are taking steps to bypass security protocols through Prolific Puma's services.
"ESXi environments are high-value targets for ransomware attacks due to their critical role in business operations," Trend Micro concluded. "The efficiency of encrypting numerous VMs simultaneously and the valuable data they hold further elevate their lucrativeness for cybercriminals."
Scattered Spider Adopts RansomHub and Qilin Ransomware for Cyber Attacks
17.7.24 Ransom The Hacker News
The infamous cybercrime group known as Scattered Spider has incorporated ransomware strains such as RansomHub and Qilin into its arsenal, Microsoft has revealed.
Scattered Spider is the designation given to a threat actor that's known for its sophisticated social engineering schemes to breach targets and establish persistence for follow-on exploitation and data theft. It also has a history of targeting VMWare ESXi servers and deploying BlackCat ransomware.
It shares overlaps with activity clusters tracked by the broader cybersecurity community under the monikers 0ktapus, Octo Tempest, and UNC3944. Last month, it was reported that a key member of the group was arrested in Spain.
RansomHub, which arrived on the scene earlier this February, has been assessed to be a rebrand of another ransomware strain called Knight, according to an analysis from Broadcom-owned Symantec last month.
"RansomHub is a ransomware-as-a-service (RaaS) payload used by more and more threat actors, including ones that have historically used other (sometimes defunct) ransomware payloads (like BlackCat), making it one of the most widespread ransomware families today," Microsoft said.
The Windows maker said it also observed RansomHub being deployed as part of post-compromise activity by Manatee Tempest (aka DEV-0243, Evil Corp, or Indrik Spider) following initial access obtained by Mustard Tempest (aka DEV-0206 or Purple Vallhund) through FakeUpdates (aka Socgholish) infections.
It's worth mentioning here that Mustard Tempest is an initial access broker that has, in the past, utilized FakeUpdates in attacks that have led to actions resembling pre-ransomware behavior associated with Evil Corp. These intrusions were also notable for the fact that FakeUpdates was delivered via existing Raspberry Robin infections.
The development comes amid the emergence of fresh ransomware families like FakePenny (attributed to Moonstone Sleet), Fog (distributed by Storm-0844, which has also propagated Akira), and ShadowRoot, the last of which has been observed targeting Turkish businesses using fake PDF invoices.
"As the threat of ransomware continues to increase, expand, and evolve, users and organizations are advised to follow security best practices, especially credential hygiene, principle of least privilege, and Zero Trust," Microsoft said.
New HardBit Ransomware 4.0 Uses Passphrase Protection to Evade Detection
15.7.24 Ransom The Hacker News

Cybersecurity researchers have shed light on a new version of a ransomware strain called HardBit that comes packaged with new obfuscation techniques to deter analysis efforts.
"Unlike previous versions, HardBit Ransomware group enhanced the version 4.0 with passphrase protection," Cybereason researchers Kotaro Ogino and Koshi Oyama said in an analysis.
"The passphrase needs to be provided during the runtime in order for the ransomware to be executed properly. Additional obfuscation hinders security researchers from analyzing the malware."
HardBit, which first emerged in October 2022, is a financially motivated threat actor that, similar to other ransomware groups, operates with an aim to generate illicit revenues via double extortion tactics.
What makes the threat group stand out is that it does not operate a data leak site, and instead pressurizes victims to pay up by threatening to conduct additional attacks in the future. Its primary mode of communication occurs over the Tox instant messaging service.
The exact initial access vector used to breach target environments is currently not clear, although it's suspected to involve brute-forcing RDP and SMB services.
The follow-up steps encompass performing credential theft using tools like Mimikatz and NLBrute, and network discovery via utilities such as Advanced Port Scanner, allowing the attackers to laterally move across the network by means of RDP.
"Having compromised a victim host, the HardBit ransomware payload is executed and performs a number of steps that reduce the security posture of the host before encrypting victim data," Varonis noted in its technical write-up about HardBit 2.0 last year.
Encryption of the victim hosts is carried out by deploying HardBit, which is delivered using a known file infector virus called Neshta. It's worth noting that Neshta has been used by threat actors in the past to also distribute Big Head ransomware.
HardBit is also designed to disable Microsoft Defender Antivirus and terminate processes and services to evade potential detection of its activities and inhibit system recovery. It then encrypts files of interest, updates their icons, changes desktop wallpaper, and alters the system's volume label with string "Locked by HardBit."

Besides being offered to operators in the form of command-line or GUI versions, the ransomware requires an authorization ID in order for it to be successfully executed. The GUI flavor further supports a wiper mode to irrevocably erase files and wipe the disk.
"Once threat actors successfully input the decoded authorization ID, HardBit prompts for an encryption key to encrypt the files on the target machines and it proceeds with ransomware procedure," Cybereason noted.
"Wiper mode feature needs to be enabled by the HardBit Ransomware group and the feature is likely an additional feature that operators need to purchase. If the operators need wiper mode, the operator would need to deploy hard.txt, an optional configuration file of HardBit binary and contains authorization ID to enable wiper mode."
The development comes as cybersecurity firm Trellix detailed a CACTUS ransomware attack that has been observed exploiting security flaws in Ivanti Sentry (CVE-2023-38035) to install the file-encrypting malware using legitimate remote desktop tools like AnyDesk and Splashtop.
Ransomware activity continues to "remain on an upward trend" in 2024, with ransomware actors claiming 962 attacks in the first quarter of 2024, up from 886 attacks reported year-over-year. LockBit, Akira, and BlackSuit have emerged as the most prevalent ransomware families during the time period, Symantec said.
According to Palo Alto Networks' 2024 Unit 42 Incident Response report, the median time it takes to go from compromise to data exfiltration plummeted from nine days in 2021 to two days last year. In almost half (45%) of cases this year, it was just under 24 hours.
"Available evidence suggests that exploitation of known vulnerabilities in public-facing applications continues to be the main vector for ransomware attacks," the Broadcom-owned company said. "Bring Your Own Vulnerable Driver (BYOVD) continues to be a favored tactic among ransomware groups, particularly as a means of disabling security solutions."
New Ransomware Group Exploiting Veeam Backup Software Vulnerability
11.7.24 Ransom The Hacker News

A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware.
Singapore-headquartered Group-IB, which discovered the threat actor in early April 2024, said the modus operandi involved the exploitation of CVE-2023-27532 (CVSS score: 7.5) to carry out the malicious activities.
Initial access to the target environment is said to have been facilitated by means of a Fortinet FortiGate firewall SSL VPN appliance using a dormant account.
"The threat actor pivoted laterally from the FortiGate Firewall through the SSL VPN service to access the failover server," security researcher Yeo Zi Wei said in an analysis published today.
"Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252."
Next, the threat actors proceeded to establish RDP connections from the firewall to the failover server, followed by deploying a persistent backdoor named "svchost.exe" that's executed daily through a scheduled task.
Subsequent access to the network was accomplished using the backdoor to evade detection. The primary responsibility of the backdoor is to connect to a command-and-control (C2) server over HTTP and execute arbitrary commands issued by the attacker.
Group-IB said it observed the actor exploiting Veeam flaw CVE-2023-27532 with an aim to enable xp_cmdshell on the backup server and create a rogue user account named "VeeamBkp," alongside conducting network discovery, enumeration, and credential harvesting activities using tools like NetScan, AdFind, and NitSoft via the newly created account.
"This exploitation potentially involved an attack originating from the VeeamHax folder on the file server against the vulnerable version of Veeam Backup & Replication software installed on the backup server," Zi Wei hypothesized.
"This activity facilitated the activation of the xp_cmdshell stored procedure and subsequent creation of the 'VeeamBkp' account."

The attack culminated in the deployment of the ransomware, but not before taking steps to impair defenses and moving laterally from the AD server to all other servers and workstations using compromised domain accounts.
"Windows Defender was permanently disabled using DC.exe [Defender Control], followed by ransomware deployment and execution with PsExec.exe," Group-IB said.
The disclosure comes as Cisco Talos revealed that most ransomware gangs prioritize establishing initial access using security flaws in public-facing applications, phishing attachments, or breaching valid accounts, and circumventing defenses in their attack chains to increase dwell time in victim networks.
The double extortion model of exfiltrating data prior to encrypting files has further given rise to custom tools developed by the actors (e.g., Exmatter, Exbyte, and StealBit) to send the confidential information to an adversary-controlled infrastructure.
This necessitates that these e-crime groups establish long-term access to explore the environment in order to understand the network's structure, locate resources that can support the attack, elevate their privileges, or allow them to blend in, and identify data of value that can be stolen.
"Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," Talos said.
"The diversification highlights a shift toward more boutique-targeted cybercriminal activities, as groups such as Hunters International, Cactus, and Akira carve out specific niches, focusing on distinct operational goals and stylistic choices to differentiate themselves."
New Ransomware-as-a-Service 'Eldorado' Targets Windows and Linux Systems
8.7.24 Ransom The Hacker News
An emerging ransomware-as-a-service (RaaS) operation called Eldorado comes with locker variants to encrypt files on Windows and Linux systems.
Eldorado first appeared on March 16, 2024, when an advertisement for the affiliate program was posted on the ransomware forum RAMP, Singapore-headquartered Group-IB said.
The cybersecurity firm, which infiltrated the ransomware group, noted that its representative is a Russian speaker and that the malware does not overlap with previously leaked strains such as LockBit or Babuk.
"The Eldorado ransomware uses Golang for cross-platform capabilities, employing Chacha20 for file encryption and Rivest Shamir Adleman-Optimal Asymmetric Encryption Padding (RSA-OAEP) for key encryption," researchers Nikolay Kichatov and Sharmine Low said. "It can encrypt files on shared networks using Server Message Block (SMB) protocol."
The encryptor for Eldorado comes in four formats, namely esxi, esxi_64, win, and win_64, with its data leak site already listing 16 victims of June 2024. Thirteen of the targets are located in the U.S., two in Italy, and one in Croatia.
These companies span various industry verticals such as real estate, education, professional services, healthcare, and manufacturing, among others.
Further analysis of the Windows version of artifacts has revealed the use of a PowerShell command to overwrite the locker with random bytes before deleting the file in an attempt to clean up the traces.
Eldorado is the latest in the list of new double-extortion ransomware players that have sprung up in recent times, including Arcus Media, AzzaSec, dan0n, Limpopo (aka SOCOTRA, FORMOSA, SEXi), LukaLocker, Shinra, and Space Bears once again highlighting the enduring and persistent nature of the threat.

LukaLocker, linked to an operator dubbed Volcano Demon by Halcyon, is notable for the fact that it does not make use of a data leak site and instead calls the victim over the phone to extort and negotiate payment after encrypting Windows workstations and servers.
The development coincides with the discovery of new Linux variants of Mallox (aka Fargo, TargetCompany, Mawahelper) ransomware as well as decryptors associated with seven different builds.

Mallox is known to be propagated by brute-forcing Microsoft SQL servers and phishing emails to target Windows systems, with recent intrusions also making use of a .NET-based loader named PureCrypter.
"The attackers are using custom python scripts for the purpose of payload delivery and victim's information exfiltration," Uptycs researchers Tejaswini Sandapolla and Shilpesh Trivedi said. "The malware encrypts user data and appends .locked extension to the encrypted files."
A decryptor has also been made available for DoNex and its predecessors (Muse, fake LockBit 3.0, and DarkRace) by Avast by taking advantage of a flaw in the cryptographic scheme. The Czech cybersecurity company said it has been "silently providing the decryptor" to victims since March 2024 in partnership with law enforcement organizations.
"Despite law enforcement efforts and increased security measures, ransomware groups continue to adapt and thrive," Group-IB said.
Data shared by Malwarebytes and NCC Group based on victims listed on the leak sites show that 470 ransomware attacks were recorded in May 2024, up from 356 in April. A majority of the attacks were claimed by LockBit, Play, Medusa, Akira, 8Base, Qilin, and RansomHub.
"The ongoing development of new ransomware strains and the emergence of sophisticated affiliate programs demonstrate that the threat is far from being contained," Group-IB noted. "Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate the risks posed by these ever-evolving threats."
Rust-Based P2PInfect Botnet Evolves with Miner and Ransomware Payloads
28.6.24 Ransom The Hacker News
The peer-to-peer malware botnet known as P2PInfect has been found targeting misconfigured Redis servers with ransomware and cryptocurrency miners.
The development marks the threat's transition from what appeared to be a dormant botnet with unclear motives to a financially motivated operation.
"With its latest updates to the crypto miner, ransomware payload, and rootkit elements, it demonstrates the malware author's continued efforts into profiting off their illicit access and spreading the network further, as it continues to worm across the internet," Cado Security said in a report published this week.
P2PInfect came to light nearly a year ago, and has since received updates to target MIPS and ARM architectures. Earlier this January, Nozomi Networks uncovered the use of the malware to deliver miner payloads.
It typically spreads by targeting Redis servers and its replication feature to transform victim systems into a follower node of the attacker-controlled server, subsequently allowing the threat actor to issue arbitrary commands to them.
The Rust-based worm also features the ability to scan the internet for more vulnerable servers, not to mention incorporating an SSH password sprayer module that attempts to log in using common passwords.
Cybersecurity
Besides taking steps to prevent other attackers from targeting the same server, P2PInfect is known to change the passwords of other users, restart the SSH service with root permissions, and even perform privilege escalation.
"As the name suggests, it is a peer-to-peer botnet, where every infected machine acts as a node in the network, and maintains a connection to several other nodes," security researcher Nate Bill said.
"This results in the botnet forming a huge mesh network, which the malware author makes use of to push out updated binaries across the network, via a gossip mechanism. The author simply needs to notify one peer, and it will inform all its peers and so on until the new binary is fully propagated across the network."
Among the new behavioral changes to P2PInfect include the use of the malware to drop miner and ransomware payloads, the latter of which is designed to encrypt files matching certain file extensions and deliver a ransom note urging the victims to pay 1 XMR (~$165).
"As this is an untargeted and opportunistic attack, it is likely the victims are to be low value, so having a low price is to be expected," Bill pointed out.
Also of note is a new usermode rootkit that makes use of the LD_PRELOAD environment variable to hide their malicious processes and files from security tools, a technique also adopted by other cryptojacking groups like TeamTNT.
It's suspected that P2PInfect is advertised as a botnet-for-hire service, acting as a conduit to deploy other attackers' payloads in exchange for payment.
This theory is bolstered by the fact that the wallet addresses for the miner and ransomware are different, and that the miner process is configured to take up as much processing power as possible, causing it to interfere with the functioning of the ransomware.
"The choice of a ransomware payload for malware primarily targeting a server that stores ephemeral in-memory data is an odd one, and P2Pinfect will likely see far more profit from their miner than their ransomware due to the limited amount of low-value files it can access due to its permission level," Bill said.
"The introduction of the usermode rootkit is a 'good on paper' addition to the malware. If the initial access is Redis, the usermode rootkit will also be completely ineffective as it can only add the preload for the Redis service account, which other users will likely not log in as."
Cybersecurity
The disclosure follows AhnLab Security Intelligence Center's (ASEC) revelations that vulnerable web servers that have unpatched flaws or are poorly secured are being targeted by suspected Chinese-speaking threat actors to deploy crypto miners.
"Remote control is facilitated through installed web shells and NetCat, and given the installation of proxy tools aimed at RDP access, data exfiltration by the threat actors is a distinct possibility," ASEC said, highlighting the use of Behinder, China Chopper, Godzilla, BadPotato, cpolar, and RingQ.
It also comes as Fortinet FortiGuard Labs pointed out that botnets such as UNSTABLE, Condi, and Skibidi are abusing legitimate cloud storage and computing services operators to distribute malware payloads and updates to a broad range of devices.
"Using cloud servers for [command-and-control] operations ensures persistent communication with compromised devices, making it harder for defenders to disrupt an attack," security researchers Cara Lin and Vincent Li said.
Akira Ransomware Gang Extorts $42 Million; Now Targets Linux Servers
19.4.24 Ransom The Hacker News
Threat actors behind the Akira ransomware group have extorted approximately $42 million in illicit proceeds after breaching the networks of more than 250 victims as of January 1, 2024.
"Since March 2023, Akira ransomware has impacted a wide range of businesses and critical infrastructure entities in North America, Europe, and Australia," cybersecurity agencies from the Netherlands and the U.S., along with Europol's European Cybercrime Centre (EC3), said in a joint alert.
"In April 2023, following an initial focus on Windows systems, Akira threat actors deployed a Linux variant targeting VMware ESXi virtual machines."
The double-extortion group has been observed using a C++ variant of the locker in the early stages, before shifting to a Rust-based code as of August 2023. It's worth noting that the e-crime actor is completely different from the Akira ransomware family that was active in 2017.
Initial access to target networks is facilitated by means of exploiting known flaws in Cisco appliances (e.g., CVE-2020-3259 and CVE-2023-20269).
Alternate vectors involve the use of Remote Desktop Protocol (RDP), spear-phishing, valid credentials, and virtual private network (VPN) services lacking in multi-factor authentication (MFA) protections.
Akira actors are also known to leverage various ways to set up persistence by creating a new domain account on the compromised system, as well as evade detection by abusing the Zemana AntiMalware driver to terminate antivirus-related processes via what's called a Bring Your Own Vulnerable Driver (BYOVD) attack.
To aid in privilege escalation, the adversary relies on credential scraping tools like Mimikatz and LaZagne, while Windows RDP is utilized to move laterally within the victim's network. Data exfiltration is accomplished through FileZilla, WinRAR, WinSCP, and RClone.
"Akira ransomware encrypts targeted systems using a hybrid encryption algorithm that combines Chacha20 and RSA," Trend Micro said in an analysis of the ransomware published in October 2023.
"Additionally, the Akira ransomware binary, like most modern ransomware binaries, has a feature that allows it to inhibit system recovery by deleting shadow copies from the affected system."
Blockchain and source code data suggests that Akira ransomware group is likely affiliated with the now-defunct Conti ransomware gang. A decryptor for Akira was released by Avast last July, but it's highly likely the shortcomings have since been plugged.

Akira's mutation to target Linux enterprise environments also follows similar moves by other established ransomware families such as LockBit, Cl0p, Royal, Monti, and RTM Locker.
LockBit's Struggles to Come Back#
The disclosure comes as Trend Micro revealed that the sweeping law enforcement takedown of the prolific LockBit gang earlier this February has had a significant operational and reputational impact on the group's ability to bounce back, prompting it to post old and fake victims on its new data leak site.
"LockBit was one of the most prolific and widely used RaaS strains in operation, with potentially hundreds of affiliates, including many associated with other prominent strains," Chainalysis noted in February.
The blockchain analytics firm said it uncovered cryptocurrency trails connecting a LockBit administrator to a journalist based in Sevastopol known as Colonel Cassad, who has a history of soliciting donations for Russian militia group operations in the sanctioned jurisdictions of Donetsk and Luhansk following the onset of the Russo-Ukrainian war in 2022.
It's worth pointing out that Cisco Talos, in January 2022, linked Colonel Cassad (aka Boris Rozhin) to an anti-Ukraine disinformation campaign orchestrated by the Russian state-sponsored group known as APT28.
"Following the operation, LockBitSupp [the alleged leader of LockBit] appears to be attempting to inflate the apparent victim count while also focusing on posting victims from countries whose law enforcement agencies participated in the disruption," Trend Micro said in a recent deep dive.
"This is possibly an attempt to reinforce the narrative that it would come back stronger and target those responsible for its disruption."
In an interview with Recorded Future News last month, LockBitSupp acknowledged the short-term decline in profits, but promised to improve their security measures and "work as long as my heart beats."
"Reputation and trust are key to attracting affiliates, and when these are lost, it's harder to get people to return. Operation Cronos succeeded in striking against one element of its business that was most important: its brand," Trend Micro stated.

Agenda Returns with an Updated Rust Version#
The development also follows the Agenda ransomware group's (aka Qilin and Water Galura) use of an updated Rust variant to infect VMWare vCenter and ESXi servers through Remote Monitoring and Management (RMM) tools and Cobalt Strike.
"The Agenda ransomware's ability to spread to virtual machine infrastructure shows that its operators are also expanding to new targets and systems," the cybersecurity company said.

Even as a fresh crop of ransomware actors continues to energize the threat landscape, it's also becoming clearer that "crude, cheap ransomware" sold on the cybercrime underground is being put to use in real-world attacks, allowing lower-tier individual threat actors to generate significant profit without having to be a part of a well-organized group.
Interestingly, a majority of these varieties are available for a single, one-off price starting from as low as $20 for a single build, while a few others such as HardShield and RansomTuga are offered at no extra cost.
"Away from the complex infrastructure of modern ransomware, junk-gun ransomware allows criminals to get in on the action cheaply, easily, and independently," Sophos said, describing it as a "relatively new phenomenon" that further lowers the cost of entry.
"They can target small companies and individuals, who are unlikely to have the resources to defend themselves or respond effectively to incidents, without giving anyone else a cut."
Critical Atlassian Flaw Exploited to Deploy Linux Variant of Cerber Ransomware
17.4.24 Ransom The Hacker News
Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware.
The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account.
Armed with this access, a threat actor could take over affected systems, leading to a full loss of confidentiality, integrity, and availability.
According to cloud security firm Cado, financially motivated cybercrime groups have been observed abusing the newly created admin account to install the Effluence web shell plugin and allow for the execution of arbitrary commands on the host.
"The attacker uses this web shell to download and run the primary Cerber payload," Nate Bill, threat intelligence engineer at Cado, said in a report shared with The Hacker News.
"In a default install, the Confluence application is executed as the 'confluence' user, a low privilege user. As such, the data the ransomware is able to encrypt is limited to files owned by the confluence user."
It's worth noting that the exploitation of CVE-2023-22518 to deploy Cerber ransomware was previously highlighted by Rapid7 in November 2023.
Written in C++, the primary payload acts as a loader for additional C++-based malware by retrieving them from a command-and-control (C2) server and then erasing its own presence from the infected host.
It includes "agttydck.bat," which is executed to download the encryptor ("agttydcb.bat") that's subsequently launched by the primary payload.
It's suspected that agttydck functions akin to a permission checker for the malware, assessing its ability to write to a /tmp/ck.log file. The exact purpose of this check is unclear.
The encryptor, on the other hand, traverses the root directory and encrypts all contents with a .L0CK3D extension. It also drops a ransom note in each directory. However, no data exfiltration takes place despite claims to the contrary in the note.
The most interesting aspect of the attacks is the use of pure C++ payloads, which are becoming something of a rarity given the shift to cross-platform programming languages like Golang and Rust.
"Cerber is a relatively sophisticated, albeit aging, ransomware payload," Bill said. "While the use of the Confluence vulnerability allows it to compromise a large amount of likely high value systems, often the data it is able to encrypt will be limited to just the confluence data and in well configured systems this will be backed up."
"This greatly limits the efficacy of the ransomware in extracting money from victims, as there is much less incentive to pay up," the researcher added.
The development comes amid the emergence of new ransomware families like Evil Ant, HelloFire, L00KUPRU (an Xorist ransomware variant), Muliaka (based on the leaked Conti ransomware code), Napoli (a Chaos ransomware variant), Red CryptoApp, Risen, and SEXi (based on the leaked Babuk ransomware code) that have been spotted targeting Windows and VMware ESXi servers.
Ransomware actors are also leveraging the leaked LockBit ransomware source code to spawn their own custom variants like Lambda (aka Synapse), Mordor, and Zgut, according to reports from F.A.C.C.T. and Kaspersky.
The latter's analysis of the leaked LockBit 3.0 builder files has revealed the "alarming simplicity" with which attackers can craft bespoke ransomware and augment their capabilities with more potent features.
Kaspersky said it uncovered a tailored version with the ability to spread across the network via PsExec by taking advantage of stolen administrator credentials and performing malicious activities, such as terminating Microsoft Defender Antivirus and erasing Windows Event Logs in order to encrypt the data and cover its tracks.
"This underscores the need for robust security measures capable of mitigating this kind of threat effectively, as well as adoption of a cybersecurity culture among employees," the company said.
TeamCity Flaw Leads to Surge in Ransomware, Cryptomining, and RAT Attacks
20.3.24 Ransom The Hacker News
Multiple threat actors are exploiting the recently disclosed security flaws in JetBrains TeamCity software to deploy ransomware, cryptocurrency miners, Cobalt Strike beacons, and a Golang-based remote access trojan called Spark RAT.
The attacks entail the exploitation of CVE-2024-27198 (CVSS score: 9.8) that enables an adversary to bypass authentication measures and gain administrative control over affected servers.
"The attackers are then able to install malware that can reach out to its command-and-control (C&C) server and perform additional commands such as deploying Cobalt Strike beacons and remote access trojans (RATs)," Trend Micro said in a new report.
"Ransomware can then be installed as a final payload to encrypt files and demand ransom payments from victims."
Following public disclosure of the flaw earlier this month, it has been weaponized by threat actors associated with BianLian and Jasmin ransomware families, as well as to drop the XMRig cryptocurrency miner and Spark RAT.
Organizations relying on TeamCity for their CI/CD processes are recommended to update their software as soon as possible to safeguard against potential threats.
The development comes as ransomware continues to be both formidable and profitable, with new strains like DoNex, Evil Ant, Lighter, RA World, and WinDestroyer emerging in the wild, even as notorious cybercrime crews like LockBit are still accepting affiliates into their program despite law enforcement actions against them.

WinDestroyer, in particular, stands out for its ability to encrypt files and render targeted systems unusable with no means to recover the data, raising the possibility that the threat actors behind it are geopolitically motivated.
"One of the major issues when tackling ransomware crime is the nature of the affiliate program, with actors often working for multiple RaaS outfits at a time," Cisco Talos said. "It's going to take persistent, strategic efforts to significantly damage RaaS operations and weaken the regenerative power of these gangs."
Data shared by the U.S. Federal Bureau of Investigation's (FBI) Internet Crime Complaint Center (IC3) shows that 2,825 ransomware infections were reported in 2023, causing adjusted losses of more than $59.6 million. Of these, 1,193 came from organizations belonging to a critical infrastructure sector.
The top five ransomware variants impacting critical infrastructure in the U.S. include LockBit, BlackCat (aka ALPHV or Noberus), Akira, Royal, and Black Basta.
Besides offering a bigger chunk of the proceeds to court affiliates, the landscape is witnessing increased collaboration between different ransomware groups that share their malicious tooling with each other.
These partnerships also manifest in the form of ghost groups, in which one ransomware operation outsources its skills to another, as seen in the case of Zeon, LockBit, and Akira.

Broadcom-owned Symantec, in a report published last week, revealed that "ransomware activity remains on an upward trend despite the number of attacks claimed by ransomware actors decreasing by slightly more than 20% in the fourth quarter of 2023."
According to statistics published by NCC Group, the total number of ransomware cases in February 2024 increased by 46% from January, up from 285 to 416, led by LockBit (33%), Hunters (10%), BlackCat (9%), Qilin (9%), BianLian (8%), Play (7%), and 8Base (7%).
"Recent law enforcement activity has the potential to polarize the ransomware landscape, creating clusters of smaller RaaS operators that are highly active and harder to detect due to their agility in underground forums and markets," Matt Hull, global head of threat intelligence at NCC Group, said.
"It appears that the attention drawn by the larger 'brand' ransomware, such as LockBit and Cl0p, is leading to new and small generic RaaS affiliate partnerships becoming the norm. As a result, detection and attribution could become harder, and affiliates may easily switch providers due to low entry thresholds and minimal monetary involvement."
This has also been complemented by threat actors finding novel ways to infect victims by mainly exploiting vulnerabilities in public-facing applications and evade detection, as well as refining their tactics by increasingly banking on legitimate software and living-off-the-land (LotL) techniques.
Also popular among ransomware attackers are utilities like TrueSightKiller, GhostDriver, and Terminator, which leverage the Bring Your Own Vulnerable Driver (BYOVD) technique to disable security software.
"BYOVD attacks are attractive to threat actors, as they can provide a means by which to disable AV and EDR solutions at the kernel level," Sophos researchers Andreas Klopsch and Matt Wixey said in a report this month. "The sheer amount of known vulnerable drivers means that attackers have a wealth of options to choose from."
BianLian Threat Actors Exploiting JetBrains TeamCity Flaws in Ransomware Attacks
11.3.24 Ransom The Hacker News
The threat actors behind the BianLian ransomware have been observed exploiting security flaws in JetBrains TeamCity software to conduct their extortion-only attacks.
According to a new report from GuidePoint Security, which responded to a recent intrusion, the incident "began with the exploitation of a TeamCity server which resulted in the deployment of a PowerShell implementation of BianLian's Go backdoor."
BianLian emerged in June 2022, and has since pivoted exclusively to exfiltration-based extortion following the release of a decryptor in January 2023.
The attack chain observed by the cybersecurity firm entails the exploitation of a vulnerable TeamCity instance using CVE-2024-27198 or CVE-2023-42793 to gain initial access to the environment, followed by creating new users in the build server and executing malicious commands for post-exploitation and lateral movement.
It's currently not clear which of the two flaws were weaponized by the threat actor for infiltration.
BianLian actors are known to implant a custom backdoor tailored to each victim written in Go, as well as drop remote desktop tools like AnyDesk, Atera, SplashTop, and TeamViewer. The backdoor is tracked by Microsoft as BianDoor.
"After multiple failed attempts to execute their standard Go backdoor, the threat actor pivoted to living-off-the-land and leveraged a PowerShell implementation of their backdoor, which provides an almost identical functionality to what they would have with their Go backdoor," security researchers Justin Timothy, Gabe Renfro, and Keven Murphy said.
The obfuscated PowerShell backdoor ("web.ps1") is designed to establish a TCP socket for additional network communication to an actor-controlled server, allowing the remote attackers to conduct arbitrary actions on an infected host.
"The now-confirmed backdoor is able to communicate with the [command-and-control] server and asynchronously execute based on the remote attacker's post-exploitation objectives," the researchers said.
The disclosure comes as VulnCheck detailed fresh proof-of-concept (PoC) exploits for a critical security flaw impacting Atlassian Confluence Data Center and Confluence Server (CVE-2023-22527) that could lead to remote code execution in a fileless manner and load the Godzilla web shell directly into memory.
The flaw has since been weaponized to deploy C3RB3R ransomware, cryptocurrency miners and remote access trojans over the past two months, indicating widespread exploitation in the wild.
"There's more than one way to reach Rome," VulnCheck's Jacob Baines noted. "While using freemarker.template.utility.Execute appears to be the popular way of exploiting CVE-2023-22527, other more stealthy paths generate different indicators."
Exit Scam: BlackCat Ransomware Group Vanishes After $22 Million Payout
7.3.24 Ransom The Hacker News
The threat actors behind the BlackCat ransomware have shut down their darknet website and likely pulled an exit scam after uploading a bogus law enforcement seizure banner.
"ALPHV/BlackCat did not get seized. They are exit scamming their affiliates," security researcher Fabian Wosar said. "It is blatantly obvious when you check the source code of the new takedown notice."
"There is absolutely zero reason why law enforcement would just put a saved version of the takedown notice up during a seizure instead of the original takedown notice."
The U.K.'s National Crime Agency (NCA) told Reuters that it had no connection to any disruptions to the BlackCat infrastructure.
Recorded Future security researcher Dmitry Smilyanets posted screenshots on the social media platform X in which the BlackCat actors claimed that the "feds screwed us over" and that they intended to sell the ransomware's source code for $5 million.
The disappearing act comes after it allegedly received a $22 million ransom payment from UnitedHealth's Change Healthcare unit (Optum) and refused to share the proceeds with an affiliate that had carried out the attack.
The company has not commented on the alleged ransom payment, instead stating it's only focused on investigation and recovery aspects of the incident.
According to DataBreaches, the disgruntled affiliate – who had their account suspended by the administrative staff – made the allegations on the RAMP cybercrime forum. "They emptied the wallet and took all the money," they said.
This has raised speculations that BlackCat has staged an exit scam to evade scrutiny and resurface in the future under a new brand. "A re-branding is pending," a now-former admin of the ransomware group was quoted as saying.
Menlo Security, citing HUMINT sources with direct contact to the affiliate, described them as likely associated with Chinese nation-state groups. The affiliate, who goes by the name Notchy, is said to have engaged on ransomware-related topics in the RAMP forum as early as 2021.
BlackCat had its infrastructure seized by law enforcement in December 2023, but the e-crime gang managed to wrest control of their servers and restart its operations without any major consequences. The group previously operated under the monikers DarkSide and BlackMatter.
"Internally, BlackCat may be worried about moles within their group, and closing up shop preemptively could stop a takedown before it occurs," Malachi Walker, a security advisor with DomainTools, said.
"On the other hand, this exit scam might simply be an opportunity for BlackCat to take the cash and run. Since crypto is once again at an all-time high, the gang can get away with selling their product 'high.' In the cybercrime world, reputation is everything, and BlackCat seems to be burning bridges with its affiliates with these actions."
The group's apparent demise and the abandonment of its infrastructure come as malware research group VX-Underground reported that the LockBit ransomware operation no longer supports Lockbit Red (aka Lockbit 2.0) and StealBit, a custom tool used by the threat actor for data exfiltration.
LockBit has also tried to save face by moving some of its activities to a new dark web portal after a coordinated law enforcement operation took down its infrastructure last month following a months-long investigation.
It also comes as Trend Micro revealed that the ransomware family known as RA World (formerly RA Group) has successfully infiltrated healthcare, finance, and insurance companies in the U.S., Germany, India, Taiwan, and other countries since emerging in April 2023.
Attacks mounted by the group "involve multi-stage components designed to ensure maximum impact and success in the group's operations," the cybersecurity firm noted.
Alert: GhostSec and Stormous Launch Joint Ransomware Attacks in Over 15 Countries
6.3.24 Ransom The Hacker News
The cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker.
"TheGhostSec and Stormous ransomware groups are jointly conducting double extortion ransomware attacks on various business verticals in multiple countries," Cisco Talos researcher Chetan Raghuprasad said in a report shared with The Hacker News.
"GhostLocker and Stormous ransomware have started a new ransomware-as-a-service (RaaS) program STMX_GhostLocker, providing various options for their affiliates."
Attacks mounted by the group have targeted victims in Cuba, Argentina, Poland, China, Lebanon, Israel, Uzbekistan, India, South Africa, Brazil, Morocco, Qatar, Turkiye, Egypt, Vietnam, Thailand, and Indonesia.
Some of the most impacted business verticals include technology, education, manufacturing, government, transportation, energy, medicolegal, real estate, and telecom.
GhostSec – not to be confused with Ghost Security Group (which is also called GhostSec) – is part of a coalition called The Five Families, which also includes ThreatSec, Stormous, Blackforums, and SiegedSec.
It was formed in August 2023 to "establish better unity and connections for everyone in the underground world of the internet, to expand and grow our work and operations."
Late last year, the cybercrime group ventured into ransomware-as-a-service (RaaS) with GhostLocker, offering it to other actors for $269.99 per month. Soon after, the Stormous ransomware group announced that it will use Python-based ransomware in its attacks.
The latest findings from Talos show that the two groups have banded together to not only strike a wide range of sectors, but also unleash an updated version of GhostLocker in November 2023 as well as start a new RaaS program in 2024 called STMX_GhostLocker.
"The new program is made up of three categories of services for the affiliates: paid, free, and another for the individuals without a program who only want to sell or publish data on their blog (PYV service)," Raghuprasad explained.
STMX_GhostLocker, which comes with its own leak site on the dark web, lists no less than six victims from India, Uzbekistan, Indonesia, Poland, Thailand, and Argentina.
GhostLocker 2.0 (aka GhostLocker V2) is written in Go and has been advertised as fully effective and offering speedy encryption/decryption capabilities. It also comes with a revamped ransom note that urges victims to get in touch with them within seven days or risk getting their stolen data leaked.
The RaaS scheme also allows affiliates to track their operations, monitor encryption status, and payments through a web panel. They are also provided with a builder that makes it possible to configure the locker payload according to their preferences, including the directories to encrypt and the processes and services to be terminated before commencing the encryption process.
Once deployed, the ransomware establishes connection with a command-and-control (C2) panel and proceeds with encryption routine, but not before killing the defined processes or services and exfiltrating files matching a specific list of extensions.
Talos said it discovered two new tools likely used by GhostSec to compromise legitimate sites. "One of them is the 'GhostSec Deep Scan toolset' to scan legitimate websites recursively, and another is a hack tool to perform cross-site scripting (XSS) attacks called "GhostPresser,'" Raghuprasad said.
GhostPresser is mainly designed to break into WordPress sites, allowing the threat actors to alter site settings, add new plugins and users, and even install new themes, demonstrating GhostSec's commitment to evolving its arsenal.
"The group themselves has claimed they've used it in attacks on victims, but we don't have any way to validate any of those claims. This tooling would likely be used by the ransomware operators for a variety of reasons," Talos told The Hacker News.
"The deep scan tool could be leveraged to look for ways into victim networks and the GhostPresser tool, in addition to compromising victim websites, could be used to stage payloads for distribution, if they didn't want to use actor infrastructure."
FBI Warns U.S. Healthcare Sector of Targeted BlackCat Ransomware Attacks
28.2.24 Ransom The Hacker News

The U.S. government is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the healthcare sector as recently as this month.
"Since mid-December 2023, of the nearly 70 leaked victims, the healthcare sector has been the most commonly victimized," the government said in an updated advisory.
"This is likely in response to the ALPHV/BlackCat administrator's post encouraging its affiliates to target hospitals after operational action against the group and its infrastructure in early December 2023."
The advisory comes from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS).
The BlackCat ransomware operation suffered a major blow late last year after a coordinated law enforcement operation led to the seizure of its dark leak sites. But the takedown turned out to be a failure after the group managed to regain control of the sites and switched to a new TOR data leak portal that continues to remain active to date.
It has also ramped up against critical infrastructure organizations in recent weeks, having claimed responsibility for attacks on Prudential Financial, LoanDepot, Trans-Northern Pipelines, and UnitedHealth Group subsidiary Optum.
The development has prompted the U.S. government to announce financial rewards of up to $15 million for information leading to the identification of key members as well as affiliates of the e-crime group.
BlackCat's ransomware spree coincides with the return of LockBit after similar disruption efforts led by the U.K. National Crime Agency (NCA) last week.
According to a report from SC Magazine, threat actors breached Optum's network by leveraging the recently disclosed critical security flaws in ConnectWise's ScreenConnect remote desktop and access software.
The flaws, which allow for remote code execution on susceptible systems, have also been weaponized by the Black Basta and Bl00dy ransomware gangs as well as by other threat actors to deliver Cobalt Strike Beacons, XWorm, and even other remote management tools like Atera, Syncro, and another ScreenConnect client.
Attack surface management firm Censys said it observed more than 3,400 exposed potentially vulnerable ScreenConnect hosts online, with most of them located in the U.S., Canada, the U.K., Australia, Germany, France, India, the Netherlands, Turkey, and Ireland.

"It's clear that remote access software like ScreenConnect continues to be a prime target for threat actors," Censys security researcher Himaja Motheram said.
The findings come as ransomware groups like RansomHouse, Rhysida, and a Phobos variant called Backmydata have continued to compromise various organizations in the U.S., U.K., Europe, and the Middle East.
In a sign that these cybercrime groups are shifting to more nuanced and sophisticated tactics, RansomHouse has developed a custom tool dubbed MrAgent to deploy the file-encrypting malware at scale.
"MrAgent is a binary designed to run on [VMware ESXi] hypervisors, with the sole purpose of automating and tracking the deployment of ransomware across large environments with a high number of hypervisor systems," Trellix said. Details of MrAgent first came to light in September 2023.
Another significant tactic adopted by some ransomware groups is the sale of direct network access as a new monetization method via their own blogs, on Telegram channels, or data leak websites, KELA said.
It also follows the public release of a Linux-specific, C-based ransomware threat known as Kryptina, which surfaced in December 2023 on underground forums and has since been made available for free on BreachForums by its creator.

"The release of the RaaS source code, complete with extensive documentation, could have significant implications for the spread and impact of ransomware attacks against Linux systems," SentinelOne researcher Jim Walter said.
"It is likely to increase the ransomware builder's attractiveness and usability, drawing in yet more low-skilled participants to the cybercrime ecosystem. There is also significant risk that it will lead to the development of multiple spin-offs and an increase in attacks."
LockBit Ransomware Group Resurfaces After Law Enforcement Takedown
27.2.24 Ransom The Hacker News

The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers.
To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as of writing.
The administrator behind LockBit, in a lengthy follow-up message, said some of their websites were confiscated by most likely exploiting a critical PHP flaw tracked as CVE-2023-3824, acknowledging that they didn't update PHP due to "personal negligence and irresponsibility."
"I realize that it may not have been this CVE, but something else like 0-day for PHP, but I can't be 100% sure, because the version installed on my servers was already known to have a known vulnerability, so this is most likely how the victims' admin and chat panel servers and the blog server were accessed," they noted.
Cybersecurity
They also claimed the U.S. Federal Bureau of Investigation (FBI) "hacked" their infrastructure because of a ransomware attack on Fulton County in January and the "stolen documents contain a lot of interesting things and Donald Trump's court cases that could affect the upcoming U.S. election."
In addition to calling for attacking the ".gov sector" more often, they stated that the server from which the authorities obtained more than 1,000 decryption keys held almost 20,000 decryptors, most of which were protected and accounted for about half of the total number of decryptors generated since 2019.
The group further went on to add that the nicknames of the affiliates have "nothing to do with their real nicknames on forums and even nicknames in messengers."
That's not all. The post also attempted to discredit law enforcement agencies, claiming the real "Bassterlord" has not been identified, and that the FBI actions are "aimed at destroying the reputation of my affiliate program."
"Why did it take 4 days to recover? Because I had to edit the source code for the latest version of PHP, as there was incompatibility," they said.
"I will stop being lazy and make it so that absolutely every build loker will be with maximum protection, now there will be no automatic trial decrypt, all trial decrypts and the issuance of decryptors will be made only in manual mode. Thus in the possible next attack, the FBI will not be able to get a single decryptor for free."
Russia Arrests Three SugarLocker Members#
The development comes as Russian law enforcement officials have arrested three individuals, including Aleksandr Nenadkevichite Ermakov (aka blade_runner, GustaveDore, or JimJones), in connection with the SugarLocker ransomware group.
"The attackers worked under the guise of a legitimate IT firm Shtazi-IT, which offers services for the development of landing pages, mobile applications, scripts, parsers, and online stores," Russian cybersecurity firm F.A.C.C.T. said. "The company openly posted ads for hiring new employees."
The operators have also been accused of developing custom malware, creating phishing sites for online stores, and driving user traffic to fraudulent schemes popular in Russia and the Commonwealth of Independent States (CIS) nations.
SugarLocker first appeared in early 2021 and later began to be offered under the ransomware-as-a-service (RaaS) model, leasing its malware to other partners under an affiliate program to breach targets and deploy the ransomware payload.
Cybersecurity
Nearly three-fourths of the ransom proceeds go to the affiliates, a figure that jumps to 90% if the payment exceeds $5 million. The cybercrime gang's links to Shtazi-IT were previously disclosed by Intel 471 last month.
The arrest of Ermakov is notable, as it comes in the wake of Australia, the U.K., and the U.S. imposing financial sanctions against him for his alleged role in the 2022 ransomware attack against health insurance provider Medibank.
The ransomware attack, which took place in late October 2022 and attributed to the now-defunct REvil ransomware crew, led to the unauthorized access of approximately 9.7 million of its current and former customers.
The stolen information included names, dates of birth, Medicare numbers, and sensitive medical information, including records on mental health, sexual health, and drug use. Some of these records also found their way to the dark web.
It also follows a report from news agency TASS, which revealed that a 49-year-old Russian national is set to face trial on charges of carrying out a cyber attack on technological control systems that left 38 settlements of the Vologda region without power.
LockBit Saga — Timeline of Events#
FEBRUARY 20, 2024
LockBit Busted - Authorities Seize Darknet Domains#
An international law enforcement operation, including 11 countries and Europol, successfully seized darknet domains linked to the ransomware group LockBit, which has extorted over $91 million since 2019. The operation, named Cronos, used a PHP security flaw to disrupt LockBit's websites, marking a significant blow to the group's activities.
FEBRUARY 21, 2024
LockBit Hackers Arrested - Decryption Tool Released#
UK's NCA shuts down LockBit ransomware, arrests 2 in Poland/Ukraine, freezes 200+ crypto accounts, indicts 2 Russians in US. Seized LockBit's code, intelligence, dismantled 34 servers, retrieved 1k decryption keys. LockBit affected 2.5k victims globally, netted $120M. Decryption tool available for victims.
FEBRUARY 22, 2024
$15 Million Bounty on LockBit Ransomware Leaders#
US State Dept offers $15M reward for info on LockBit ransomware leaders, involved in 2k+ global attacks since 2020, causing $144M in damages. Law enforcement disrupted LockBit, arresting affiliates and seizing assets. LockBit, known for ransomware-as-a-service, extensive affiliate network, and innovative tactics like a bug bounty program, remains a significant cyber threat despite setbacks.
FEBRUARY 25, 2024
LockBit Ransomware Kingpin 'Engages' with Police#
The individual(s) behind the LockBit ransomware service, known as LockBitSupp, has reportedly engaged with law enforcement following a significant international crackdown on the ransomware-as-a-service operation named Operation Cronos.
FEBRUARY 26, 2024
LockBit is Back - Calls for Attacks on US Government#
The LockBit ransomware group has re-emerged on the dark web with a new infrastructure shortly after law enforcement seized its servers. The group has listed 12 new victims on its data leak portal and discussed the seizure of its websites, attributing it to a potential exploitation of a PHP vulnerability.
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
22.2.24 Ransom The Hacker News

The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation.
"Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States, and around the world, causing costly disruptions to operations and the destruction or exfiltration of sensitive information," the State Department said.
"More than $144 million in ransom payments have been made to recover from LockBit ransomware events."
The development comes as a sweeping law enforcement operation led by the U.K. National Crime Agency (NCA) disrupted LockBit, a Russia-linked ransomware gang that has been active for more than four years, wreaking havoc on business and critical infrastructure entities around the world.
Ransomware-as-a-service (RaaS) operations like LockBit and others work by extorting companies by stealing their sensitive data and encrypting them, making it a lucrative business model for Russian e-crime groups that act with impunity by taking advantage of the fact that they are outside of the jurisdiction of Western law enforcement.
The core developers tend to tap into a network of affiliates who are recruited to carry out the attacks using LockBit's malicious software and infrastructure. The affiliates, in turn, are known to purchase access to targets of interest using initial access brokers (IABs).
"LockBit rose to be the most prolific ransomware group since Conti departed the scene in mid-2022," Chester Wisniewski, global field CTO at Sophos, said.
"The frequency of their attacks, combined with having no limits to what type of infrastructure they cripple has also made them the most destructive in recent years. Anything that disrupts their operations and sows distrust amongst their affiliates and suppliers is a huge win for law enforcement."
LockBit is also known to be the first ransomware group to announce a bug bounty program in 2022, offering rewards of up to $1 million for finding security issues in website and locker software.
"LockBit's operation grew in scale by consistently delivering new product features, providing good customer support, and at times, marketing stunts that included paying people to tattoo themselves with the group's logo," Intel 471 said.
Image Source: X
"LockBit flipped the script, letting its affiliates collect the ransom and trusting them to pay it a portion. This made affiliates confident that they were not going to lose out on a payment, thus attracting more affiliates."
SecureWorks Counter Threat Unit (CTU), which is tracking the group under the name Gold Mystic, said it investigated 22 compromises featuring LockBit ransomware from July 2020 through January 2024, some of which relied solely on data theft to extort victims.
The cybersecurity company further pointed out that LockBit's practice of ceding control to its affiliates to handle ransom negotiation and payments allowed the syndicate to scale up and draw several affiliates over the years.
LockBit's takedown followed a months-long investigation that commenced in April 2022, leading to the arrest of three affiliates in Poland and Ukraine, the indictment in the U.S. of two other alleged members, as well as the seizure of 34 servers and 1,000 decryption keys that can help victims recover their data without making any payment.
These arrests include a 38-year-old man in Warsaw and a "father and son" duo from Ukraine. LockBit is estimated to have employed about 194 affiliates between January 31, 2022, and February 5, 2024, with the actors using a bespoke data exfiltration tool known as StealBit.
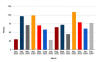
"StealBit is an example of LockBit's attempt to offer a full 'one-stop shop' service to its affiliates," the NCA said, adding the executable is used to export the data through the affiliate's own infrastructure before StealBit's in a likely effort to evade detection.
That said, the fluid structure of these RaaS brands means that shutting them down may not decisively impact the criminal enterprise, allowing them to regroup and resurface under a different name. If the recent history of similar takedowns is any indication, it won't be long before they rebrand and continue from where they left off.
"Comprehensive degradation of LockBit's infrastructure will likely result in a short cessation in activity from LockBit operatives before they resume operations – either under the LockBit name or an alternative banner," ZeroFox said.
"Even if we don't always get a complete victory, like has happened with QakBot, imposing disruption, fueling their fear of getting caught and increasing the friction of operating their criminal syndicate is still a win," Wisniewski added. "We must continue to band together to raise their costs ever higher until we can put all of them where they belong – in jail."
LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys Released
21.2.24 Ransom The Hacker News
The U.K. National Crime Agency (NCA) on Tuesday confirmed that it obtained LockBit's source code as well as a wealth of intelligence pertaining to its activities and their affiliates as part of a dedicated task force called Operation Cronos.
"Some of the data on LockBit's systems belonged to victims who had paid a ransom to the threat actors, evidencing that even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised," the agency said.
It also announced the arrest of two LockBit actors in Poland and Ukraine. Over 200 cryptocurrency accounts linked to the group have been frozen. Indictments and sanctions have also been unsealed in the U.S. against two other Russian nationals who are alleged to have carried out LockBit attacks.
Artur Sungatov and Ivan Gennadievich Kondratiev (aka Bassterlord) have been accused of deploying LockBit against numerous victims throughout the U.S., including businesses nationwide in the manufacturing and other industries, as well as victims around the world in the semiconductor and other industries, per the U.S. Department of Justice (DoJ).
Kondratyev has also been charged with three criminal counts arising from his use of the Sodinokibi, also known as REvil, ransomware variant to encrypt data, exfiltrate victim information, and extort a ransom payment from a corporate victim based in Alameda County, California.
The development comes in the aftermath of an international disruption campaign targeting LockBit, which the NCA described as the "world's most harmful cyber crime group."
As part of the takedown efforts, the agency said it took control of LockBit's services and infiltrated its entire criminal enterprise. This includes the administration environment used by affiliates and the public-facing leak site hosted on the dark web.
In addition, 34 servers belonging to LockBit affiliates have also been dismantled and more than 1,000 decryption keys have been retrieved from the confiscated LockBit servers.
LockBit, since its debut in late 2019, runs a ransomware-as-a-service (RaaS) scheme in which the encryptors are licensed to affiliates, who carry out the attacks in exchange for a cut of the ransom proceeds. It is run by a threat actor known as LockBitSupp.
The attacks follow a tactic called double extortion to steal sensitive data prior to encrypting them, with the threat actors applying pressure on victims to make a payment in order to decrypt their files and prevent their data from being published.
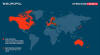
"The ransomware group is also infamous for experimenting with new methods for pressuring their victims into paying ransoms," Europol said.
"Triple extortion is one such method which includes the traditional methods of encrypting the victim's data and threatening to leak it, but also incorporates distributed denial-of-service (DDoS) attacks as an additional layer of pressure."
The data theft is facilitated by means of a custom data exfiltration tool codenamed StealBit. The infrastructure, which was used to organize and transfer victim data, has since been seized by authorities from three countries, counting the U.S.
According to Eurojust and DoJ, LockBit attacks are believed to have affected over 2,500 victims all over the world and netted more than $120 million in illicit profits. A decryption tool has also been made available via No More Ransom to recover files encrypted by the ransomware at no cost.
"Through our close collaboration, we have hacked the hackers; taken control of their infrastructure, seized their source code, and obtained keys that will help victims decrypt their systems," NCA Director General Graeme Biggar said.
"As of today, LockBit are locked out. We have damaged the capability and most notably, the credibility of a group that depended on secrecy and anonymity. LockBit may seek to rebuild their criminal enterprise. However, we know who they are, and how they operate."
LockBit Ransomware's Darknet Domains Seized in Global Law Enforcement Raid
21.2.24 Ransom The Hacker News
Update: The U.K. National Crime Agency (NCA) has confirmed the takedown of LockBit infrastructure. Read here for more details.
An international law enforcement operation has led to the seizure of multiple darknet domains operated by LockBit, one of the most prolific ransomware groups, marking the latest in a long list of digital takedowns.
While the full extent of the effort, codenamed Operation Cronos, is presently unknown, visiting the group's .onion website displays a seizure banner containing the message "The site is now under the control of law enforcement."
Authorities from 11 countries, Australia, Canada, Finland, France, Germany, Japan, the Netherlands, Sweden, Switzerland, the U.K., and the U.S., alongside Europol participated in the joint exercise.
Malware research group VX-Underground, in a message posted on X (formerly Twitter), said the websites were taken down by exploiting a critical security flaw impacting PHP (CVE-2023-3824, CVSS score: 9.8) that could result in remote code execution.
Law enforcement agencies also left on a note on the affiliate panel, stating they are in possession of the "source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much, much more," adding it was made possible due to LockBit's "flawed infrastructure."
LockBit, which emerged on September 3, 2019, has been one of the most active and notorious ransomware gangs in history, claiming more than 2,000 victims to date. It's estimated to have extorted at least $91 million from U.S. organizations alone.
According to data shared by cybersecurity firm ReliaQuest, LockBit listed 275 victims on its data leak portal in the fourth quarter of 2023, dwarfing all its competitors.
There is no word as yet of any arrest or sanctions, but the development is a definite blow to LockBit's near-term operations and arrives two months after the BlackCat ransomware operation was dismantled by the U.S. government.
The coordinated takedown also coincides with the arrest of a 31-year-old Ukrainian national for gaining unauthorized access to Google and online bank accounts of American and Canadian users by deploying malware and selling access to other threat actors on the dark web for financial gain.
CISA Warning: Akira Ransomware Exploiting Cisco ASA/FTD Vulnerability
17.2.24 Ransom The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched security flaw impacting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software to its Known Exploited Vulnerabilities (KEV) catalog, following reports that it's being likely exploited in Akira ransomware attacks.
The vulnerability in question is CVE-2020-3259 (CVSS score: 7.5), a high-severity information disclosure issue that could allow an attacker to retrieve memory contents on an affected device. It was patched by Cisco as part of updates released in May 2020.
Late last month, cybersecurity firm Truesec said it found evidence suggesting that it has been weaponized by Akira ransomware actors to compromise multiple susceptible Cisco Anyconnect SSL VPN appliances over the past year.
"There is no publicly available exploit code for [...] CVE-2020-3259, meaning that a threat actor, such as Akira, exploiting that vulnerability would need to buy or produce exploit code themselves, which requires deep insights into the vulnerability," security researcher Heresh Zaremand said.
According to Palo Alto Networks Unit 42, Akira is one of the 25 groups with newly established data leak sites in 2023, with the ransomware group publicly claiming nearly 200 victims. First observed in March 2023, the group is believed to share connections with the notorious Conti syndicate based on the fact that the ransom proceeds have been routed to Conti-affiliated wallet addresses.
In the fourth quarter of 2023 alone, the e-crime group listed 49 victims on its data leak portal, putting it behind LockBit (275), Play (110), ALPHV/BlackCat (102), NoEscape (76), 8Base (75), and Black Basta (72).
Federal Civilian Executive Branch (FCEB) agencies are required to remediate identified vulnerabilities by March 7, 2024, to secure their networks against potential threats.
CVE-2020-3259 is far from the only flaw to be exploited for delivering ransomware. Earlier this month, Arctic Wolf Labs revealed the abuse of CVE-2023-22527 – a recently uncovered shortcoming in Atlassian Confluence Data Center and Confluence Server – to deploy C3RB3R ransomware, as well as cryptocurrency miners and remote access trojans.
The development comes as the U.S. State Department announced rewards of up to $10 million for information that could lead to the identification or location of BlackCat ransomware gang key members, in addition to offering up to $5 million for information leading to the arrest or conviction of its affiliates.
The ransomware-as-a-service (RaaS) scheme, much like Hive, compromised over 1,000 victims globally, netting at least $300 million in illicit profits since its emergence in late 2021. It was disrupted in December 2023 following an international coordinated operation.
The ransomware landscape has become a lucrative market, attracting the attention of cybercriminals looking for quick financial gain, leading to the rise of new players such as Alpha (not to be confused with ALPHV) and Wing.
There are indications that Alpha could be connected to NetWalker, which shuttered in January 2021 following an international law enforcement operation. The links pertain to overlaps in the source code and the tactics, techniques, and procedures (TTPs) used in attacks.
"Alpha may be an attempt at reviving the old ransomware operation by one or more of the original NetWalker developers," Broadcom-owned Symantec said. "Alternatively, the attackers behind Alpha may have acquired and modified the original NetWalker payload in order to launch their own ransomware operation."
The U.S. Government Accountability Office (GAO), in a report published towards the end of January 2024, called for enhanced oversight into recommended practices for addressing ransomware, specifically for organizations from critical manufacturing, energy, healthcare and public health, and transportation systems sectors.
Rhysida Ransomware Cracked, Free Decryption Tool Released
12.2.24 Ransom The Hacker News

Cybersecurity researchers have uncovered an "implementation vulnerability" that has made it possible to reconstruct encryption keys and decrypt data locked by Rhysida ransomware.
The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA).
"Through a comprehensive analysis of Rhysida Ransomware, we identified an implementation vulnerability, enabling us to regenerate the encryption key used by the malware," the researchers said.
The development marks the first successful decryption of the ransomware strain, which first made its appearance in May 2023. A recovery tool is being distributed through KISA.
The study is also the latest to achieve data decryption by exploiting implementation vulnerabilities in ransomware, after Magniber v2, Ragnar Locker, Avaddon, and Hive.
Rhysida, which is known to share overlaps with another ransomware crew called Vice Society, leverages a tactic known as double extortion to apply pressure on victims into paying up by threatening to release their stolen data.

An advisory published by the U.S. government in November 2023 called out the threat actors for staging opportunistic attacks targeting education, manufacturing, information technology, and government sectors.
A thorough examination of the ransomware's inner workings has revealed its use of LibTomCrypt for encryption as well as parallel processing to speed up the process. It has also been found to implement intermittent encryption (aka partial encryption) to evade detection by security solutions.
"Rhysida ransomware uses a cryptographically secure pseudo-random number generator (CSPRNG) to generate the encryption key," the researchers said. "This generator uses a cryptographically secure algorithm to generate random numbers."
Specifically, the CSPRNG is based on the ChaCha20 algorithm provided by the LibTomCrypt library, with the random number generated also correlated to the time at which Rhysida ransomware is running.
That's not all. The main process of Rhysida ransomware compiles a list of files to be encrypted. This list is subsequently referenced by various threads created to simultaneously encrypt the files in a specific order.
"In the encryption process of the Rhysida ransomware, the encryption thread generates 80 bytes of random numbers when encrypting a single file," the researchers noted. "Of these, the first 48 bytes are used as the encryption key and the [initialization vector]."
Using these observations as reference points, the researchers said they were able to retrieve the initial seed for decrypting the ransomware, determine the "randomized" order in which the files were encrypted, and ultimately recover the data without having to pay a ransom.
"Although these studies have a limited scope, it is important to acknowledge that certain ransomwares [...] can be successfully decrypted," the researchers concluded.
Albabat, Kasseika, Kuiper: New Ransomware Gangs Rise with Rust and Golang
30.1.24 Ransom The Hacker News
Cybersecurity researchers have detected in the wild yet another variant of the Phobos ransomware family known as Faust.
Fortinet FortiGuard Labs, which detailed the latest iteration of the ransomware, said it's being propagated by means of an infection that delivers a Microsoft Excel document (.XLAM) containing a VBA script.
"The attackers utilized the Gitea service to store several files encoded in Base64, each carrying a malicious binary," security researcher Cara Lin said in a technical report published last week. "When these files are injected into a system's memory, they initiate a file encryption attack."
Faust is the latest addition to several ransomware variants from the Phobos family, including Eking, Eight, Elbie, Devos, and 8Base. It's worth noting that Faust was previously documented by Cisco Talos in November 2023.
The cybersecurity firm described the variant as active since 2022 and "does not target specific industries or regions."
The attack chain commences with an XLAM document that, when opened, downloads Base64-encoded data from Gitea in order to save a harmless XLSX file, while also stealthily retrieving an executable that masquerades as an updater for the AVG AntiVirus software ("AVG updater.exe").
The binary, for its part, functions as a downloader to fetch and launch another executable named "SmartScreen Defender Windows.exe" in order to kick-start its encryption process by employing a fileless attack to deploy the malicious shellcode.
"The Faust variant exhibits the ability to maintain persistence in an environment and creates multiple threads for efficient execution," Lin said.
The development comes as new ransomware families such as Albabat (aka White Bat), Kasseika, Kuiper, Mimus, and NONAME have gained traction, with the former a Rust-based malware that's distributed in the form of fraudulent software such as a fake Windows 10 digital activation tool and a cheat program for the Counter-Strike 2 game.
Trellix, which examined the Windows, Linux, and macOS versions of Kuiper earlier this month, attributed the Golang-based ransomware to a threat actor named RobinHood, who first advertised it on underground forums in September 2023.
"The concurrency focused nature of Golang benefits the threat actor here, avoiding race conditions and other common problems when dealing with multiple threads, which would have otherwise been a (near) certainty," security researcher Max Kersten said.

"Another factor that the Kuiper ransomware leverages, which is also a reason for Golang's increased popularity, are the language's cross-platform capabilities to create builds for a variety of platforms. This flexibility allows attackers to adapt their code with little effort, especially since the majority of the code base (i.e., encryption-related activity) is pure Golang and requires no rewriting for a different platform."
NONAME is also noteworthy for the fact that its data leak site imitates that of the LockBit group, raising the possibility that it could either be another LockBit or that it collects leaked databases shared by LockBit on the official leak portal, researcher Rakesh Krishnan pointed out.
The findings follow a report from French cybersecurity company Intrinsec that connected the nascent 3AM (also spelled ThreeAM) ransomware to the Royal/BlackSuit ransomware, which, in turn, emerged following the shutdown of the Conti cybercrime syndicate in May 2022.
The links stem from a "significant overlap" in tactics and communication channels between 3 AM ransomware and the "shared infrastructure of ex-Conti-Ryuk-TrickBot nexus."
That's not all. Ransomware actors have been observed once again using TeamViewer as an initial access vector to breach target environments and attempt to deploy encryptors based on the LockBit ransomware builder, which leaked in September 2022.
"Threat actors look for any available means of access to individual endpoints to wreak havoc and possibly extend their reach further into the infrastructure," cybersecurity firm Huntress said.
In recent weeks, LockBit 3.0 has also been distributed in the form of Microsoft Word files disguised as resumes targeting entities in South Korea, according to the AhnLab Security Intelligence Center (ASEC).
Despite the amorphous and ever-evolving nature of the ransomware ecosystem, there are signs that victims are increasingly refusing to pay up, causing the proportion of ransomware victims that opted to pay to decline to 29% in Q4 2023, down from 41% in Q3 and 34% in Q2. A previous low of 28% was recorded in Q3 2022.
The average ransom payment for the time period dropped 33%, dropping from $850,700 to $568,705, figures shared by ransomware negotiation firm Coveware show. The median ransom payment, on the other hand, remained unchanged at $200,000, up from $190,424 in Q2 2023.
"The industry continues to get smarter on what can and cannot be reasonably obtained with a ransom payment," the company said. "This has led to better guidance to victims and fewer payments for intangible assurances."
Medusa Ransomware on the Rise: From Data Leaks to Physical Threats
12.1.24 Ransom The Hacker News

The threat actors associated with the Medusa ransomware have ramped up their activities following the debut of a dedicated data leak site on the dark web in February 2023 to publish sensitive data of victims who are unwilling to agree to their demands.
"As part of their multi-extortion strategy, this group will provide victims with multiple options when their data is posted on their leak site, such as time extension, data deletion or download of all the data," Palo Alto Networks Unit 42 researchers Anthony Galiette and Doel Santos said in a report shared with The Hacker News.
"All of these options have a price tag depending on the organization impacted by this group."
Medusa (not to be confused with Medusa Locker) refers to a ransomware family that appeared in late 2022 before coming into prominence in 2023. It's known for opportunistically targeting a wide range of industries such as high technology, education, manufacturing, healthcare, and retail.
As many as 74 organizations, mostly in the U.S., the U.K., France, Italy, Spain, and India, are estimated to have been impacted by the ransomware in 2023.
Ransomware attacks orchestrated by the group commence with the exploitation of internet-facing assets or applications with known unpatched vulnerabilities and hijacking of legitimate accounts, often employing initial access brokers to obtain a foothold to target networks.
In one instance observed by the cybersecurity firm, a Microsoft Exchange Server was exploited to upload a web shell, which was then used as a conduit to install and execute the ConnectWise remote monitoring and management (RMM) software.
A notable aspect of the infections is the reliance on living-off-the-land (LotL) techniques to blend in with legitimate activity and sidestep detection. Also observed is the use of a pair of kernel drivers to terminate a hard-coded list of security products.
The initial access phase is followed by discovery and reconnaissance of the compromised network, with the actors ultimately launching the ransomware to enumerate and encrypt all files save for those with the extensions .dll, .exe, .lnk, and .medusa (the extension given to the encrypted files).
For each compromised victim, Medusa's leak site displays information about the organizations, ransom demanded, the amount of time left before the stolen data is released publicly, and the number of views in a bid to exert pressure on the company.
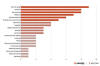
The actors also offer different choices to the victim, all of which involve some form of extortion to delete or download the pilfered data and seek a time extension to prevent the data from being released.
As ransomware continues to be a rampant threat, targeting tech companies, healthcare, critical infrastructure, and everything in between, the threat actors behind it are getting more brazen with their tactics, going beyond publicly naming and shaming organizations by resorting to threats of physical violence and even dedicated public relations channels.
"Ransomware has changed many facets of the threat landscape, but a key recent development is its increasing commoditization and professionalization," Sophos researchers said last month, calling ransomware gangs "increasingly media-savvy."
Medusa, per Unit 42, not only has a media team to likely handle their branding efforts, but also leverages a public Telegram channel named "information support," where files of compromised organizations are shared and can be accessed over the clearnet. The channel was set up in July 2021.
"The emergence of the Medusa ransomware in late 2022 and its notoriety in 2023 marks a significant development in the ransomware landscape," the researchers said. "This operation showcases complex propagation methods, leveraging both system vulnerabilities and initial access brokers, while adeptly avoiding detection through living-off-the-land techniques."
The development comes as Arctic Wolf Labs publicized two cases in which victims of Akira and Royal ransomware gangs were targeted by malicious third-parties posing as security researchers for secondary extortion attempts.
"Threat actors spun a narrative of trying to help victim organizations, offering to hack into the server infrastructure of the original ransomware groups involved to delete exfiltrated data," security researchers Stefan Hostetler and Steven Campbell said, noting the threat actor sought about 5 bitcoin in exchange for the service.
It also follows a new advisory from the Finnish National Cyber Security Centre (NCSC-FI) about a spike in Akira ransomware incidents in the country towards the end of 2023 by exploiting a security flaw in Cisco VPN appliances (CVE-2023-20269, CVSS score: 5.0) to breach domestic entities.
Free Decryptor Released for Black Basta and Babuk's Tortilla Ransomware Victims
10.1.24 Ransom The Hacker News
Free Ransomware Decryptor
A decryptor for the Tortilla variant of the Babuk ransomware has been released by Cisco Talos, allowing victims targeted by the malware to regain access to their files.
The cybersecurity firm said the threat intelligence it shared with Dutch law enforcement authorities made it possible to arrest the threat actor behind the operations.
The encryption key has also been shared with Avast, which had previously released a decryptor for Babuk ransomware after its source code was leaked in September 2021. The updated decryptor can be accessed here [EXE file].
"A single private key is used for all victims of the Tortilla threat actor," Avast noted. "This makes the update to the decryptor especially useful, as all victims of the campaign can use it to decrypt their files."
The Tortilla campaign was first disclosed by Talos in November 2021, with the attacks leveraging ProxyShell flaws in Microsoft Exchange servers to drop the ransomware within victim environments.

Tortilla is one among the many ransomware variants that have based their file-encrypting malware on the leaked Babuk source code. This includes Rook, Night Sky, Pandora, Nokoyawa, Cheerscrypt, AstraLocker 2.0, ESXiArgs, Rorschach, RTM Locker, and RA Group.
The development comes as German cybersecurity firm Security Research Labs (SRLabs) released a decryptor for Black Basta ransomware called Black Basta Buster by taking advantage of a cryptographic weakness to recover a file either partially or fully.
"Files can be recovered if the plaintext of 64 encrypted bytes is known," SRLabs said. "Whether a file is fully or partially recoverable depends on the size of the file."
"Files below the size of 5000 bytes cannot be recovered. For files between 5000 bytes and 1GB in size, full recovery is possible. For files larger than 1GB, the first 5000 bytes will be lost but the remainder can be recovered."
Bleeping Computer reported late last month that the Black Basta developers have since fixed the issue, preventing the tool from working with newer infections.














































