Ransom
2024
2023 2022
2021 2020
New Ransomware Variants Flourish Amid Law Enforcement Actions
27.12.2021
Ransomware Thehackernews
Ransomware groups
continue to evolve their tactics and techniques to deploy file-encrypting
malware on compromised systems, notwithstanding law enforcement's disruptive
actions against the cybercrime gangs to prevent them from victimizing additional
companies.
"Be it due to law enforcement, infighting amongst groups or people abandoning
variants altogether, the RaaS [ransomware-as-a-service] groups dominating the
ecosystem at this point in time are completely different than just a few months
ago," Intel 471 researchers said in a report published this month. "Yet, even
with the shift in the variants, ransomware incidents as a whole are still on the
rise."
Sweeping law enforcement operations undertaken by government agencies in recent
months have brought about rapid shifts in the RaaS landscape and turned the
tables on ransomware syndicates like Avaddon, BlackMatter, Cl0p, DarkSide,
Egregor, and REvil, forcing the actors to slow down or shut down their
businesses altogether.
But just as these variants are fading into obscurity, other up-and-coming groups
have stepped in to fill the vacuum. Intel 471's findings have uncovered a total
of 612 ransomware attacks between July to September 2021 that can be attributed
to 35 different ransomware variants.
Roughly 60% of the observed infections were tied to four variants alone — topped
by LockBit 2.0 (33%), Conti (15.2%), BlackMatter (6.9%), and Hive (6%) — and
primarily impacted manufacturing, consumer and industrial products, professional
services and consulting, and real estate sectors.

Avos Locker is one among the many such cartels that have not only witnessed a
surge in attacks, but have also adopted new tactics to pursue their financially
motivated schemes, chief among them being the ability to disable endpoint
security products on the targeted systems and boot into Windows Safe Mode to
execute the ransomware. Also installed is the AnyDesk remote administration tool
to maintain access to the machine while running in Safe Mode.
"The reason for this is that many, if not most, endpoint security products do
not run in Safe Mode — a special diagnostic configuration in which Windows
disables most third-party drivers and software, and can render otherwise
protected machines unsafe," SophosLabs principal security researcher, Andrew
Brandt, said. "The techniques deployed by Avos Locker are simple yet clever,
with attackers ensuring that the ransomware has the best chance of running in
Safe Mode and allowing the attackers to retain remote access to the machines
throughout the attack."

Hive's RaaS program, for its part, has been dubbed "aggressive" for its use of
pressure tactics to make victim organizations pay ransoms, with Group-IB linking
the strain to attacks on 355 companies as of October 16 since it emerged on the
landscape in late June 2021. Meanwhile, Russian-language ransomware group
Everest is taking its extortion tactics to the next level by threatening to sell
off access to targeted systems if their demands aren't met, NCC Group said.
"While selling ransomware-as-a-service has seen a surge in popularity over the
last year, this is a rare instance of a group forgoing a request for a ransom
and offering access to IT infrastructure — but we may see copycat attacks in
2022 and beyond," the U.K.-based cybersecurity company pointed out.
What's more, a relatively new ransomware family dubbed Pysa (aka Mespinoza) has
unseated Conti as one of the top ransomware threat groups for the month of
November alongside LockBit 2.0. The ransomware witnessed a 50% increase in the
number of targeted companies and a 400% spike in attacks against
government-sector systems when compared to the month of October.
"While law enforcement around the world has gotten more aggressive in their
efforts to arrest those behind attacks, developers are still easily shutting
down popular variants, laying low, and coming back with finely-tuned malware
used by themselves as well as affiliates," Intel 471 researchers said. "As long
as the developers can remain in countries where they are granted safe harbor,
the attacks will continue, albeit with different variants."
Hackers Exploit Log4j Vulnerability to Infect Computers with Khonsari Ransomware
17.12.2021
Ransomware Thehackernews
Romanian cybersecurity
technology company Bitdefender on Monday revealed that attempts are being made
to target Windows machines with a novel ransomware family called Khonsari as
well as a remote access Trojan named Orcus by exploiting the recently disclosed
critical Log4j vulnerability.
The attack leverages the remote code execution (RCE) flaw to download an
additional payload, a .NET binary, from a remote server that encrypts all the
files with the extension ".khonsari" and displays a ransom note that urges the
victims to make a Bitcoin payment in exchange for recovering access to the
files.
Tracked as CVE-2021-44228, the RCE vulnerability is also known by the monikers
"Log4Shell" or "Logjam" and impacts versions 2.0-beta9 to 2.14.1 of the software
library. In simple terms, the bug could force an affected system to download
malicious software, giving the attackers a digital beachhead on servers located
within corporate networks.
Log4j is an open-source Java library maintained by the nonprofit Apache Software
Foundation. Amassing about 475,000 downloads from its GitHub project and adopted
widely for application event logging, the utility is also a part of other
frameworks, such as Elasticsearch, Kafka and Flink, that are used in many
popular websites and services.
The disclosure comes as the U.S. Cybersecurity and Infrastructure Security
Agency (CISA) sounded an alarm warning of active, widespread exploitation of the
flaw that, if left unaddressed, could grant unfettered access and unleash a new
round of cyber attacks, as fallout from the bug has left companies rushing to
find and patch vulnerable machines.
"An adversary can exploit this vulnerability by submitting a specially crafted
request to a vulnerable system that causes that system to execute arbitrary
code," the agency said in guidance issued Monday. "The request allows the
adversary to take full control over the system. The adversary can then steal
information, launch ransomware, or conduct other malicious activity."

Furthermore, CISA has also added the Log4j vulnerability to its Known Exploited
Vulnerabilities Catalog, giving federal agencies a deadline of December 24 to
incorporate patches for the flaw. Similar advisories have been previously issued
by government agencies in Austria, Canada, New Zealand, and the U.K.

So far, active exploitation attempts recorded in the wild have involved the
abuse of the flaw to rope the devices into a botnet, and drop additional
payloads such as Cobalt Strike and cryptocurrency miners. Cybersecurity firm
Sophos said it also observed attempts to exfiltrate Amazon Web Services (AWS)
keys and other private data from compromised systems.
In a sign that the threat is rapidly evolving, Check Point researchers cautioned
of 60 new variations of the original Log4j exploit being introduced in less than
24 hours, adding it blocked more than 1,272,000 intrusion attempts, with 46% of
the attacks staged by known malicious groups. The Israeli security company
dubbed Log4Shell a "true cyber pandemic."
A vast majority of the exploitation attempts against Log4Shell have originated
in Russia (4,275), based on telemetry data from Kaspersky, followed by Brazil
(2,493), the U.S. (1,746), Germany (1,336), Mexico (1,177), Italy (1,094),
France (1,008), and Iran (976). In comparison, only 351 attempts were mounted
from China.
The mutating nature of the exploit notwithstanding, the prevalence of the tool
across a multitude of sectors has also put industrial control systems and
operational technology environments that power critical infrastructure on high
alert.
"Log4j is used heavily in external/internet-facing and internal applications
which manage and control industrial processes leaving many industrial operations
like electric power, water, food and beverage, manufacturing, and others exposed
to potential remote exploitation and access," said Sergio Caltagirone, vice
president of threat intelligence at Dragos. "It's important to prioritize
external and internet-facing applications over internal applications due to
their internet exposure, although both are vulnerable."
The development once again highlights how major security vulnerabilities
identified in open-source software could spark a serious threat to organizations
that include such off-the-shelf dependencies in their IT systems. The broad
reach aside, Log4Shell is all the more concerning for its relative ease of
exploitation, laying the foundation for future ransomware attacks.
"To be clear, this vulnerability poses a severe risk," CISA Director Jen
Easterly said. "This vulnerability, which is being widely exploited by a growing
set of threat actors, presents an urgent challenge to network defenders given
its broad use. Vendors should also be communicating with their customers to
ensure end users know that their product contains this vulnerability and should
prioritize software updates."
Ransomware Affiliate Arrested in Romania; 51 Stolen Data Brokers Arrested in
Ukraine
17.12.2021
Ransomware Thehackernews
Europol, the European Union's premier law enforcement agency, has announced the
arrest of a third Romanian national for his role as a ransomware affiliate
suspected of hacking high-profile organizations and companies and stealing large
volumes of sensitive data.
The 41-year-old unnamed individual was apprehended Monday morning at his home in
Craiova, Romania, by the Romanian Directorate for Investigating Organized Crime
and Terrorism (DIICOT) following a joint investigation in collaboration with the
U.S. Federal Bureau of Investigation (FBI).
It's not currently known which ransomware gang the suspect was working with, but
the development comes a little over a month after Romanian authorities arrested
two affiliates of the REvil ransomware family, who are believed to have
orchestrated no fewer than 5,000 ransomware attacks and extorted close to
$600,000 from victims.
Affiliates play a key role in the subscription-based ransomware-as-a-service
(RaaS) business models, and are chiefly responsible for renting the toolset and
the backend infrastructure from the core developers and launching their own
attacks against a potential list of targets.
These actors are often recruited by the ransomware operators on underground
forums, where their warez are advertised to Russian-speaking users or English
speakers with a Russian-speaking guarantor, but only after vetting their
technical skills. The affiliates also earn a large share of each successful
ransom payment, ranging anywhere between 65% and 90%, making it an increasingly
successful and profitable enterprise for cybercriminals.
According to Europol, the suspect is said to have targeted a large Romanian IT
company delivering services to clients in the retail, energy and utilities
sectors. Subsequently, the affiliate deployed ransomware and siphoned troves of
data from the company's customers located in the country and beyond, before
proceeding to encrypting the files.
"The information stolen included the companies' financial information, personal
information about employees, customers' details and other important documents,"
Europol said in a statement. "The suspect would then ask for a sizeable ransom
payment in cryptocurrency, threatening to leak the stolen data on cybercrime
forums should his demands not be met."
Ukraine Arrests 51 For Selling Stolen Data of 300 Million People
In a
separate law enforcement action, the Cyberpolice Department of the National
Police of Ukraine announced it had arrested 51 people in connection with
illegally possessing about 100 databases containing personal information of more
than 300 million citizens of Ukraine, Europe, and the U.S.
The databases also included "confidential information on financial and economic
activities of individuals and legal entities, information about customers of
banking and commercial institutions, authorization data on emails, social
networks, online stores and more," the department said in a statement.
As part of the operation codenamed "DATA," the officials conducted a total of
117 searchers in various parts of the country and shut down an unnamed website
that offered the stolen data — such as telephone numbers, names, and, in some
cases, vehicle registration information — for sale.
"More than 30 channels of illegal dissemination of information were blocked
during the investigation," the agency noted, with Serhiy Lypka, head of the
Department for Combating Crimes in the Field of Computer Systems, stating "the
cost of databases ranged from 500 to 50,000 hryvnias — depending on its content
and commercial value."
BlackCat: A New Rust-based Ransomware Malware Spotted in the Wild
12.12.2021
Ransomware Thehackernews

Details have emerged about what's the first Rust-language-based ransomware
strain spotted in the wild that has already amassed "some victims from different
countries" since its launch last month.
The ransomware, dubbed BlackCat, was disclosed by MalwareHunterTeam. "Victims
can pay with Bitcoin or Monero," the researchers said in a series of tweets
detailing the file-encrypting malware. "Also looks they are giving credentials
to intermediaries" for negotiations.
BlackCat, akin to many other variants that have sprung before it, operates as a
ransomware-as-a-service (RaaS), wherein the core developers recruit affiliates
to breach corporate environments and encrypt files, but not before stealing the
said documents in a double extortion scheme to pressure the targets into paying
the requested amount or risk exposure of the stolen data should the companies
refuse to pay up.
Security researcher Michael Gillespie called it a "very sophisticated
ransomware."
South Korean cybersecurity company S2W, in a separate analysis of BlackCat, said
that the ransomware conducts its malicious actions by referring to an internal
configuration like other RaaS programs, calling out its similarities with
BlackMatter, another ransomware that emerged from the ashes of DarkSide in July
only to sunset its activities in early November.

While it's typical of ransomware groups to go underground, regroup, and
resurface under a new name, the researchers cautioned against calling BlackCat a
BlackMatter rebrand, citing differences in the programming language used (Rust
vs. C++), the myriad execution options, and the dark web infrastructure
maintained by the actor.
BlackCat, starting December 4, 2021, has been advertised on Russian-language
underground markets like XSS and Exploit under the username "alphv" and as
"ransom" on the RAMP forum in a bid to recruit other participants, including
penetration testers, and join what it called "the next generation of
ransomware."
The ransomware actor is also said to be operating five onion domains, three of
which function as the group's negotiation site, with the rest categorized as an
"Alphv" public leak site and a private leak site. Only two victims have been
identified so far, suggesting that the nascent ransomware is being actively
deployed against companies in real-world attacks.
"After information about the BlackCat ransomware and Alphv leak site was
revealed on Twitter, they deleted all information of both two victims and added
their warning message on Alphv leak site," S2W researchers noted.
The development signals a growing trend where threat actors are adopting
lesser-known programming languages such as Dlang, Go, Nim, and Rust, to bypass
security protections, evade analysis, and hamper reverse engineering efforts.
Rust is also gaining traction for its ability to achieve high-performance
compared to that of languages such as C and C++, while simultaneously offering
memory safety guarantees that could be leveraged to create malware that's less
susceptible to exploitation and render them powerless.
VirusTotal Releases Ransomware Report Based on Analysis of 80 Million Samples
15.10.21
Ransomware
Thehackernews

As many as 130 different ransomware families have been found to be active in
2020 and the first half of 2021, with Israel, South Korea, Vietnam, China,
Singapore, India, Kazakhstan, Philippines, Iran, and the U.K. emerging as the
most affected territories, a comprehensive analysis of 80 million
ransomware-related samples has revealed.
Google's cybersecurity arm VirusTotal attributed a significant chunk of the
activity to the GandCrab ransomware-as-a-service (RaaS) group (78.5%), followed
by Babuk (7.61%), Cerber (3.11%), Matsnu (2.63%), Wannacry (2.41%), Congur
(1.52%), Locky (1.29%), Teslacrypt (1.12%), Rkor (1.11%), and Reveon (0.70%).
"Attackers are using a range of approaches, including well-known botnet malware
and other Remote Access Trojans (RATs) as vehicles to deliver their ransomware,"
VirusTotal Threat Intelligence Strategist Vicente Diaz said. "In most cases,
they are using fresh or new ransomware samples for their campaigns."
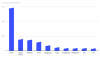
Some of the other key points uncovered in the study are as follows —
GandCrab accounted for most of the ransomware activity in the first two quarters
of 2020, with the Babuk ransomware family driving a surge of infections in July
2021.
95% of ransomware files detected were Windows-based executables or
dynamic link libraries (DLLs), while 2% were Android-based.
Around 5% of the
analyzed samples were associated with exploits related to Windows elevation of
privileges, SMB information disclosures, and remote execution.
Emotet, Zbot,
Dridex, Gozi, and Danabot were the primary malware artifacts used to distribute
ransomware.
The findings come in the wake of a relentless wave of ransomware
attacks aimed at critical infrastructure, with cybercriminal gangs aggressively
pursuing victims in critical sectors, including pipeline operators and
healthcare facilities, even as the landscape has witnessed a continuous shift
wherein ransomware groups evolve, splinter, and reorganize under new names, or
fall off the radar to evade scrutiny.

If anything, the explosion of new malware families has drawn new actors into
participating in these lucrative schemes, turning ransomware into a profitable
criminal business model.
"While big campaigns come and go, there is a constant baseline of ransomware
activity of approximately 100 ransomware families that never stops," the report
said. "In terms of ransomware distribution attackers don't appear to need
exploits other than for privilege escalation and for malware spreading within
internal networks."
Ransomware Group FIN12 Aggressively Going After Healthcare Targets
9.10.21
Ransomware
Thehackernews

An "aggressive" financially motivated threat actor has been identified as linked
to a string of RYUK ransomware attacks since October 2018, while maintaining
close partnerships with TrickBot-affiliated threat actors and using a publicly
available arsenal of tools such as Cobalt Strike Beacon payloads to interact
with victim networks.
Cybersecurity firm Mandiant attributed the intrusions to a Russian-speaking
hacker group codenamed FIN12, and previously tracked as UNC1878, with a
disproportionate focus on healthcare organizations with more than $300 million
in revenue, among others, including education, financial, manufacturing, and
technology sectors, located in North America, Europe, and the Asia Pacific.
"FIN12 relies on partners to obtain initial access to victim environments,"
Mandiant researchers said. "Notably, instead of conducting multifaceted
extortion, a tactic widely adopted by other ransomware threat actors, FIN12
appears to prioritize speed and higher revenue victims."
The use of initial access brokers to facilitate ransomware deployments isn't
new. In June 2021, findings from enterprise security company Proofpoint revealed
that ransomware actors are increasingly shifting from using email messages as an
intrusion route to purchasing access from cybercriminal enterprises that have
already infiltrated major entities, with Ryuk infections mainly leveraging
accesses obtained via malware families like TrickBot and BazaLoader.
FIN12's targeting of the healthcare sector suggests that its initial access
brokers "cast a wider net and allow FIN12 actors to choose from a list of
victims after accesses are already obtained."

Mandiant also noted that it observed, in May 2021, threat actors obtaining a
foothold in the network through phishing email campaigns distributed internally
from compromised user accounts, before leading to the deployment of Cobalt
Strike Beacon and WEIRDLOOP payloads. Attacks mounted between mid-February and
mid-April of 2021 are said to also have taken advantage of remote logins by
getting hold of credentials to victims' Citrix environments.
Although FIN12's tactics in late 2019 involved using TrickBot as a means to
maintain a foothold in the network and carry out latter-stage tasks, including
reconnaissance, delivering malware droppers, and deploying the ransomware, the
group has since consistently banked on Cobalt Strike Beacon payloads for
performing post-exploitation activities.
FIN12 also distinguishes itself from other intrusion threat actors in that it
doesn't engage in data theft extortion — a tactic that's used to leak
exfiltrated data when victims refuse to pay up — which Mandiant says stems from
the threat actor's desire to move quickly and strike targets that are willing to
settle with minimal negotiation.
"The average time to ransom (TTR) across our FIN12 engagements involving data
theft was 12.4 days (12 days, 9 hours, 44 minutes) compared to 2.48 days (2
days, 11 hours, 37 minutes) where data theft was not observed," the researchers
said. "FIN12's apparent success without the need to incorporate additional
extortion methods likely reinforces this notion."
"[FIN12 is the] first FIN actor that we are promoting who specializes in a
specific phase of the attack lifecycle — ransomware deployment — while relying
on other threat actors for gaining initial access to victims," Mandiant noted.
"This specialization reflects the current ransomware ecosystem, which is
comprised of various loosely affiliated actors partnering together, but not
exclusively with one another."
Ransomware Hackers Who Attacked Over 100 Companies Arrested in Ukraine
9.10.21
Ransomware
Thehackernews
Law enforcement
agencies have announced the arrest of two "prolific ransomware operators" in
Ukraine who allegedly conducted a string of targeted attacks against large
industrial entities in Europe and North America since at least April 2020,
marking the latest step in combating ransomware incidents.
The joint exercise was undertaken on September 28 by officials from the French
National Gendarmerie, the Ukrainian National Police, and the U.S. Federal Bureau
of Investigation (FBI), alongside participation from the Europol's European
Cybercrime Centre and the INTERPOL's Cyber Fusion Centre.
"The criminals would deploy malware and steal sensitive data from these
companies, before encrypting their files," Europol said in a press statement on
Monday. "They would then proceed to offer a decryption key in return for a
ransom payment of several millions of euros, threatening to leak the stolen data
on the dark web should their demands not be met."
Besides the two arrests, the international police operation witnessed a total of
seven property raids, leading to the seizure of $375,000 in cash and two luxury
vehicles costing €217,000 ($251,543), as well as the freezing of cryptocurrency
assets worth $1.3 million.
The suspects are believed to have demanded hefty sums ranging anywhere between
€5 to €70 million as part of their extortion spree, and are connected to a gang
that's staged ransomware attacks against more than 100 different companies,
causing damages upwards of $150 million, according to the Ukrainian National
Police. The identity of the syndicate has not been disclosed.
One of the two arrestees, a 25-year-old Ukrainian national, allegedly deployed
"virus software" by breaking into remote working programs, with the intrusions
staged through social engineering campaigns that delivered spam messages
containing malicious content to corporate email inboxes, the agency added.
The development comes over three months after the Ukrainian authorities took
steps to arrest members of the Clop ransomware gang and disrupt the
infrastructure the group employed in attacks targeting victims worldwide dating
all the way back to 2019.
Cring Ransomware Gang Exploits 11-Year-Old ColdFusion Bug
6.10.21
Ransomware
Thehackernews
Unidentified threat
actors breached a server running an unpatched, 11-year-old version of Adobe's
ColdFusion 9 software in minutes to remotely take over control and deploy
file-encrypting Cring ransomware on the target's network 79 hours after the
hack.
The server, which belonged to an unnamed services company, was used to collect
timesheet and accounting data for payroll as well as to host a number of virtual
machines, according to a report published by Sophos and shared with The Hacker
News. The attacks originated from an internet address assigned to the Ukrainian
ISP Green Floid.
"Devices running vulnerable, outdated software are low-hanging-fruit for
cyberattackers looking for an easy way into a target," Sophos principal
researcher Andrew Brandt said. "The surprising thing is that this server was in
active daily use. Often the most vulnerable devices are inactive or ghost
machines, either forgotten about or overlooked when it comes to patching and
upgrades."
The British security software firm said the "rapid break-in" was made possible
by exploiting an 11-year-old installation of Adobe ColdFusion 9 running on
Windows Server 2008, both of which have reached end-of-life.
Cring Ransomware
Upon gaining an initial foothold, the attackers used a wide
range of sophisticated methods to conceal their files, inject code into memory,
and cover their tracks by overwriting files with garbled data, not to mention
disarm security products by capitalizing on the fact that tamper-protection
functionalities were turned off.
Specially, the adversary took advantage of CVE-2010-2861, a set of directory
traversal vulnerabilities in the administrator console in Adobe ColdFusion 9.0.1
and earlier that could be abused by remote attackers to read arbitrary files,
such as those containing administrator password hashes ("password.properties").
In the next stage, the bad actor is believed to have exploited another
vulnerability in ColdFusion, CVE-2009-3960, to upload a malicious Cascading
Stylesheet (CSS) file to the server, consequently using it to load a Cobalt
Strike Beacon executable. This binary, then, acted as a conduit for the remote
attackers to drop additional payloads, create a user account with admin
privileges, and even disable endpoint protection systems and anti-malware
engines like Windows Defender, before commencing the encryption process.
"This is a stark reminder that IT administrators benefit from having an accurate
inventory of all their connected assets and cannot leave out-of-date critical
business systems facing the public internet," Brandt said. "If organizations
have these devices anywhere on their network, they can be sure that
cyberattackers will be attracted to them."
Russian Ransomware Group REvil Back Online After 2-Month Hiatus
10.9.21
Ransomware
Thehackernews

The operators behind the REvil ransomware-as-a-service (RaaS) staged a surprise
return after a two-month hiatus following the widely publicized attack on
technology services provider Kaseya on July 4.
Two of the dark web portals, including the gang's Happy Blog data leak site and
its payment/negotiation site, have resurfaced online, with the most recent
victim added on July 8, five days before the sites mysteriously went off the
grid on July 13. It's not immediately clear if REvil is back in the game or if
they have launched new attacks.
"Unfortunately, the Happy Blog is back online," Emsisoft threat researcher Brett
Callow tweeted on Tuesday.
The development comes a little over two months after a wide-scale supply chain
ransomware attack aimed at Kaseya, which saw the Russia-based cybercrime gang
encrypting approximately 60 managed service providers (MSPs) and over 1,500
downstream businesses using a zero-day vulnerability in the Kaseya VSA remote
management software.
In late May, REvil also spearheaded the attack on the world's largest meat
producer JBS, forcing the company to shell out $11 million in ransom to the
extortionists to recover from the incident.
Following the attacks and increased international scrutiny in the wake of the
global ransomware crisis, the group took its dark web infrastructure down,
leading to speculations that it may have temporarily ceased operations with the
goal of rebranding under a new identity so as to attract less attention.
REvil, also known as Sodinokibi, emerged as the fifth most commonly reported
ransomware strains in Q1 2021, accounting for 4.60% of all submissions in the
quarter, according to statistics compiled by Emsisoft.
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
29.8.21
Ransomware
Thehackernews

A new ransomware family that emerged last month comes with its own bag of tricks
to bypass ransomware protection by leveraging a novel technique called
"intermittent encryption."
Called LockFile, the operators of the ransomware have been found exploiting
recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows
servers and deploy file-encrypting malware that scrambles only every alternate
16 bytes of a file, thereby giving it the ability to evade ransomware defences.
"Partial encryption is generally used by ransomware operators to speed up the
encryption process and we've seen it implemented by BlackMatter, DarkSide and
LockBit 2.0 ransomware," Mark Loman, Sophos director of engineering, said in a
statement. "What sets LockFile apart is that, unlike the others, it doesn't
encrypt the first few blocks. Instead, LockFile encrypts every other 16 bytes of
a document."
"This means that a file such as a text document remains partially readable and
looks statistically like the original. This trick can be successful against
ransomware protection software that relies on inspecting content using
statistical analysis to detect encryption," Loman added.
Sophos' analysis of LockFile comes from an artifact that was uploaded to
VirusTotal on August 22, 2021.
Once deposited, the malware also takes steps to terminate critical processes
associated with virtualization software and databases via the Windows Management
Interface (WMI), before proceeding to encrypt critical files and objects, and
display a ransomware note that bears stylistic similarities with that of LockBit
2.0.
The ransom note also urges the victim to contact a specific email address
"contact@contipauper.com," which Sophos suspects could be a derogatory reference
to a competing ransomware group called Conti.
What's more, the ransomware deletes itself from the system post successful
encryption of all the documents on the machine, meaning that "there is no
ransomware binary for incident responders or antivirus software to find or clean
up."
"The message here for defenders is that the cyberthreat landscape never stands
still, and adversaries will quickly seize every possible opportunity or tool to
launch a successful attack," Loman said.
The disclosure comes as the U.S. Federal Bureau of Investigation (FBI) released
a Flash report detailing the tactics of a new Ransomware-as-a-Service (RaaS)
outfit known as Hive, consisting of a number of actors who are using multiple
mechanisms to compromise business networks, exfiltrate data and encrypt data on
the networks, and attempt to collect a ransom in exchange for access to the
decryption software.
Researchers Warn of 4 Emerging Ransomware Groups That Can Cause Havoc
25.8.21
Ransomware
Thehackernews
Cybersecurity
researchers on Tuesday took the wraps off four up-and-coming ransomware groups
that could pose a serious threat to enterprises and critical infrastructure, as
the ripple effect of a recent spurt in ransomware incidents show that attackers
are growing more sophisticated and more profitable in extracting payouts from
victims.
"While the ransomware crisis appears poised to get worse before it gets better,
the cast of cybercrime groups that cause the most damage is constantly
changing," Palo Alto Networks' Unit 42 threat intelligence team said in a report
shared with The Hacker News.
"Groups sometimes go quiet when they've achieved so much notoriety that they
become a priority for law enforcement. Others reboot their operations to make
them more lucrative by revising their tactics, techniques and procedures,
updating their software and launching marketing campaigns to recruit new
affiliates."
The development comes as ransomware attacks are getting bigger and more
frequent, growing in size and severity, while also evolving beyond financial
extortion to an urgent national security and safety concern that has threatened
schools, hospitals, businesses, and governments across the world, prompting
international authorities to formulate a series of actions against both
operators of ransomware and the broader ecosystem of IT and money laundering
infrastructure that's abused to siphon funds.

Chief among the new entrants is AvosLocker, a ransomware-as-a-service (RaaS)
group that commenced operations in late June via "press releases" that are
branded with a blue beetle logo to recruit new affiliates. The cartel, which
also runs a data leak and extortion site, is said to have breached six
organizations in the U.S., U.K., U.A.E., Belgium, Spain, and Lebanon, with
ransom demands ranging anywhere from $50,000 to $75,000.
In contrast, Hive, despite opening shop in the same month as AvosLocker, has
already hit several healthcare providers and mid-size organizations, including a
European airline company and three U.S.-based entities, among other victims
located in Australia, China, India, Netherlands, Norway, Peru, Portugal,
Switzerland, Thailand, and the U.K.
Also detected in the wild is a Linux variant of the HelloKitty ransomware, which
singles out Linux servers running VMware's ESXi hypervisor. "The observed
variants impacted five organizations in Italy, Australia, Germany, the
Netherlands and the U.S.," Unit 42 researchers Doel Santos and Ruchna Nigam
said. "The highest ransom demand observed from this group was $10 million, but
at the time of writing, the threat actors have only received three transactions
that sum up to about $1.48 million."
Last to join the list is LockBit 2.0, an established ransomware group that
resurfaced in June with 2.0 version of their affiliate program touting its
"unparalleled benefits" of "encryption speed and self-spread function." Not only
do the developers claim it's "the fastest encryption software all over the
world," the group offers a stealer named StealBit that enables the attackers to
download victims' data.

Since its June 2021 debut, LockBit 2.0 has compromised 52 organizations in
accounting, automotive, consulting, engineering, finance, high-tech,
hospitality, insurance, law enforcement, legal services, manufacturing,
non-profit energy, retail, transportation, and logistics industries spanning
across Argentina, Australia, Austria, Belgium, Brazil, Germany, Italy, Malaysia,
Mexico, Romania, Switzerland, the U.K., and the U.S.
If anything, the emergence of new ransomware variants show that cybercriminals
are doubling down on ransomware attacks, underscoring the extremely profitable
nature of the crime.
"With major ransomware groups such as REvil and DarkSide lying low or rebranding
to evade law enforcement heat and media attention, new groups will emerge to
replace the ones that are no longer actively targeting victims," the researchers
said. "While LockBit and HelloKitty have been previously active, their recent
evolution makes them a good example on how old groups can re-emerge and remain
persistent threats."
Cybercrime Group Asking Insiders for Help in Planting Ransomware
20.8.21
Ransomware
Thehackernews
A Nigerian threat
actor has been observed attempting to recruit employees by offering them to pay
$1 million in bitcoins to deploy Black Kingdom ransomware on companies' networks
as part of an insider threat scheme.
"The sender tells the employee that if they're able to deploy ransomware on a
company computer or Windows server, then they would be paid $1 million in
bitcoin, or 40% of the presumed $2.5 million ransom," Abnormal Security said in
a report published Thursday. "The employee is told they can launch the
ransomware physically or remotely. The sender provided two methods to contact
them if the employee is interested—an Outlook email account and a Telegram
username."
Black Kingdom, also known as DemonWare and DEMON, attracted attention earlier
this March when threat actors were found exploiting ProxyLogon flaws impacting
Microsoft Exchange Servers to infect unpatched systems with the ransomware
strain.
Abnormal Security, which detected and blocked the phishing emails on August 12,
responded to the solicitation attempt by creating a fictitious persona and
reached out to the actor on Telegram messenger, only to have the individual
inadvertently spill the attack's modus operandi, which included two links for an
executable ransomware payload that the "employee" could download from WeTransfer
or Mega.nz.
"The actor also instructed us to dispose of the .EXE file and delete it from the
recycle bin. Based on the actor's responses, it seems clear that he 1) expects
an employee to have physical access to a server, and 2) he's not very familiar
with digital forensics or incident response investigations," said Crane Hassold,
director of threat intelligence at Abnormal Security.

Besides taking a flexible approach to their ransom demands, the plan is believed
to have been concocted by the chief executive of a Lagos-based social networking
startup called Sociogram, with the goal of using the siphoned funds to "build my
own company." In one of the conversations that took place over the course of
five days, the individual even took to calling himself "the next Mark
Zuckerberg."
Also of particular note is the method of using LinkedIn to collect corporate
email addresses of senior-level executives, once again highlighting how business
email compromise (BEC) attacks originating from Nigeria continue to evolve and
expose businesses to sophisticated attacks like ransomware.
"There's always been a blurry line between cyberattacks and social engineering,
and this is an example of how the two are intertwined. As people become better
at recognizing and avoiding phishing, it should be no surprise to see attackers
adopt new tactics to accomplish their goals," Tim Erlin, vice president of
product management and strategy at Tripwire, said.
"The idea of a disgruntled insider as a cybersecurity threat isn't new. As long
as organizations require employees, there will always be some insider risk. The
promise of getting a share of the ransom might seem attractive, but there's
almost zero guarantee that this kind of complicity will actually be rewarded,
and it's highly likely that someone taking this attacker up on their offer would
get caught," Erlin added.
Hades Ransomware Gang Exhibits Connections to Hafnium
30.3.2021
Ransomware
Securityaffairs
hades ransomware analysis
There could be more than immediately meets the eye
with this targeted attack group.
The Hades ransomware gang has several unique characteristics that set it apart
from the rest of the pack, according to researchers – including potentially
having more than extortion on the to-do list. The group appears to use multiple
nation-state tools and techniques.
The researchers said that its investigations into the group’s cyberattacks at
the end of 2020 suggest one of two possibilities: There is an advanced
persistent threat (APT) is operating under the guise of Hades, possibly Hafnium;
or, several different groups coincidentally compromised the same environments,
“potentially due to weak security practices in general.”
The Hafnium Connection
In one Hades ransomware attack, the Awake team
identified a Hafnium domain as an indicator of compromise within the timeline of
the Hades attack.
Hafnium is an APT believed to be liked to the Chinese government, which
Microsoft identified as carrying out zero-day attacks on Microsoft Exchange
servers using the group of vulnerabilities now known as ProxyLogon.
“Moreover, this domain was associated with an Exchange server and was being used
for command and control in the days leading up to the encryption event,”
according to the posting. “Based on [another team’s] analysis this domain was
first seen in a Hades attack in December 2020. Clearly at this point the
vulnerability in Exchange had not been publicly disclosed but this attack time
frame aligns more closely with the DevCore vulnerability discovery date. This
clearly provides evidence of the attack prior to January 2021, which has been
the consensus until now.”
Connections to Other Groups
Awake researchers also found evidence of other
threat actors within some Hades victim environments.
For instance, artifacts pointing to the TimosaraHackerTerm (THT) ransomware
group (named after a town in Romania) were seen in multiple cases, likely left a
few weeks before the Hades attack. According to Awake, these included:
VSS Admin was used to clear shadow copies of the local machine
Bitlocker or
BestCrypt (bcfmgr) was used for encryption on the local machines
External IP
connection was made to Romania IP 185[.]225[.]19[.]240
For the THT indicators
of compromise (IoCs), the IP address mentioned from Romania was observed between
October and November with malicious behavior and associated with two new files
tracked on VirusTotal.
Hades Victimology
According to the Awake analysis,
the Hades gang appears to be picky about its targets, and mainly goes after
organizations with a focus in manufacturing, especially those in the automotive
supply chain as well as those with insulation products.
“The locations of the attack were slightly dispersed as each of the companies
were global in their operational footprints,” according to Awake. “While these
organizations were impacted across multiple geographies, we have evidence to
suggest that the ransomware attack was focused on…Canada, Germany, Luxembourg,
Mexico and the United States.”
The group of known victims is small, and Awake analysis found that Hades asked
between $5 to $10 million in ransom. However, victims said that Hades was slow
to respond in negotiations.
“In some cases, they may not have responded at all,” according to the analysis.
“In fact, one Twitter user even claimed [Hades] never responds. If there were
only a few organizations attacked, why would it take so long to respond to
requests for ransom? Was there another potential motive here?”
Advanced Data-Theft Techniques
Hades’ toolset and approaches include several
that are often used by espionage-related threat actors, according to Awake Labs.
For instance, researchers said the group leveraged valid accounts throughout
victim environments, including both service account and privilege admin accounts
that were used by the threat actor.
“We also are aware of at least one environment where Mimikatz was used as a
method to extract credentials,” according to the post. “This was the same
environment with the file winexesvc.exe on the Exchange system where the Hafnium
domain was identified.”
Hades then moved laterally from system to system across domains to access and
prep files for exfiltration.
“The Hades actors searched local file systems and databases to find files of
interest and sensitive data prior to exfiltration,” said Awake researchers.
“They also searched and collected data from network shares on remote systems.
Common targets of this were accessible shared directories on file servers. Awake
identified these activities on multiple systems by analyzing the ShellBags
registry artifact.”
Leak Sites
One of the not-so-advanced tactics used by the gang is its
penchant for “methods for both their leaks and their drop sites that would
likely be taken down within a very short time,” Awake researchers said. “There
was very little sophistication in this setup, something that stands apart from
other ransomware actors.”
Also, the data leaked on the group’s sites seems oddly chosen, researchers said.
“[It was] not the most consequential data the actor could have leaked,” they
noted. “The data chosen for the leak was a very limited set with little
repercussions to the victims. Meanwhile the exfiltrated data was very different,
containing large amounts of data focused on manufacturing processes. The
question that therefore arises, what was the objective of stealing the crown
jewels but disclosing less significant bits of information? Did they hold back
on publicly sharing the most valuable data because they had alternate means to
monetize the proprietary secrets?”
In all, Awake researchers noted that there are several unique aspects to the
Hades modus operandi.
“[Hades] appeared to exhibit a number of characteristics that were at once
unlike other ransomware gangs, almost amateurish in a sense, while at the same
time showing the type of sophistication and obfuscation that is more the forte
of nation-state-based APT,” explained researchers from Awake Labs, in a blog
posting on Monday. “Our ‘spidey sense’ certainly went off.”
London-based academies Harris Federation hit by ransomware attack
30.3.2021
Ransomware
Securityaffairs
Harris Federation, the multi-academy trust of 50 primary and secondary academies
in and around London, was hit by a ransomware attack.
A ransomware attack hit
the IT systems of London-based nonprofit multi-academy trust Harris Federation
on Saturday, March 27.
Harris Federation is a multi-academy trust of 50 primary and secondary academies
in and around London educating more than 36,000 students.
Once discovered the ransomware infection, the IT staff at the nonprofit
organization has taken its systems offline along with the email and landline
phone systems, and students’ devices. All the phone calls were being redirected
to mobile phones.
“A ransomware attack means that cyber-criminals have
accessed our IT systems and encrypted, or hidden, their contents.” reads a
statement published by the organization. “This is a highly sophisticated attack
that will have significant impact on our academies but it will take time to
uncover the exact details of what has or has not happened, and to resolve”
Harris Federation is investigating the incident with the support of the National
Crime Agency, the National Cyber Security Centre, and experts from a
cybersecurity firm.
The nonprofit organization declared that at least another three multi-academy
trust to have been targeted in March.
All Harris Federation’s schools will
finish the current term on Wednesday 31st March except for ten academies that
will finish on April 1st.
During the past months, we have observed a significant increase in targeted
ransomware attacks against education institutions.
Two weeks ago, the FBI has issued an alert to warn about an increase in PYSA
ransomware attacks against education institutions in the United States and the
United Kingdom.
Ziggy ransomware admin announced it will refund victims who paid the ransom
30.3.2021
Ransomware
Securityweek
Administrator of Ziggy ransomware recently announced the end of the operation,
and now is promising that its victims will have back their money.
In an
unusual move, the administrator of Ziggy ransomware after the announcement of
the end of the operation now is promising that they will give back their money.
Ziggy ransomware ceased the operation in early February, when announced the
decision “to publish all decryption keys.”
The news was confirmed by the researcher M. Shahpasandi to BleepingComputer. The
mastermind behind the Ziggy Ransomware operation announced on Telegram the
decision to shut down their activity.
“In an interview with BleepingComputer, the ransomware admin said they created
the ransomware to generate money as they live in a “third-world country.””
reported BleepingComputer.
Ransomware operators are concerned about recent law enforcement activity that
results in the operation against Netwalker ransomware.
Ziggy ransomware admin leaked a SQL file containing 922 decryption keys along
with a decryptor. The ransomware admin also shared the source code for a
different decryptor with BleepingComputer that includes offline decryption keys
that could be used when the infected system is not connected to the Internet.
In order to decrypt the files, the victims have to provide three decryption keys
that are included in the SQL file.
The ransomware gang released offline
decryption tool to decrypt infected files while not being connected to the
Internet or the command and control server was unreachable.
Now, as first reported by BleepingComputer, on March 19, the Ziggy ransomware
administrator announced they will refund the victims.
Victims that paid the ransom should contact the group via email at
ziggyransomware@secmail.pro to be refunded in about two weeks. Victims have to
provide the payment receipt and the computer’s unique ID.
Experts believe that the Ziggy ransomware operators have monetized their efforts
anyway due to the rise in the price of Bitcoin in the past months. Bitcoin price
passed from $29,000 as December 31 up to $56,900 at the time of this writing
allowing the gang to make a huge profit.
Recently another ransomware gang shut down its operations, it was the group
behind the Fonix ransomware likely fearing the operation of law enforcement
agencies.
In January, law enforcement authorities in the U.S. and Europe seized the dark
web sites used by NetWalker ransomware operators. The authorities also charged a
Canadian national involved in the NetWalker ransomware operations.
More Ransomware Gangs Targeting Vulnerable Exchange Servers
30.3.2021
Ransomware
Securityweek
The Black Kingdom/Pydomer ransomware operators have joined the ranks of threat
actors targeting the Exchange Server vulnerabilities that Microsoft disclosed in
early March.
The zero-day bugs, four in total, had been targeted in live attacks well before
patches were released for them on March 2, with exponentially more adversaries
picking them up over the past three weeks, despite the availability of
additional mitigations.
The number of unpatched Exchange installations has dropped significantly, going
from roughly 80,000 on March 14 to fewer than 30,000 on March 22.
“As of today, we have seen a significant decrease in the number of
still-vulnerable servers – more than 92% of known worldwide Exchange IPs are now
patched or mitigated. We continue to work with our customers and partners to
mitigate the vulnerabilities,” Microsoft noted in a March 25 blog post.
The number of attacks targeting the still-vulnerable servers, however, hasn’t
diminished. In fact, the tech company reveals that additional ransomware
families and botnets are now attempting to compromise the vulnerable servers.
DoejoCrypt, also known as DearCry, was the first ransomware family to target the
Exchange vulnerabilities, more than two weeks ago. The Black Kingdom/Pydomer
ransomware has since joined the fray, Microsoft says.
Known to be targeting publicly disclosed vulnerabilities, including Pulse Secure
VPN flaws, Pydomer operators were observed mass scanning for and attempting to
compromise unpatched Exchange servers.
“They started later than some other attackers, with many compromises occurring
between March 18 and March 20, a window when fewer unpatched systems were
available,” the tech giant reveals.
The webshell dropped by the gang was observed on approximately 1,500 servers,
but ransomware wasn’t deployed on all of them. However, it’s likely that the
adversaries would attempt to monetize the obtained unauthorized access in a
different manner, Microsoft says.
On systems where the ransomware was deployed, however, a “non-encryption
extortion strategy” was adopted, with the attackers only dropping a ransom note
to inform victims on their demands.
“The note should be taken seriously if encountered, as the attackers had full
access to systems and were likely able to exfiltrate data,” the tech company
points out.
Within the past few weeks, another adversary to have joined the Exchange party
was the gang behind the Lemon Duck cryptocurrency botnet, which employed “a
fileless/web shell-less option of direct PowerShell commands from w3wp (the IIS
worker process) for some attacks,” but relied on various exploit styles in
others.
“While still maintaining their normal email-based campaigns, the Lemon Duck
operators compromised numerous Exchange servers and moved in the direction of
being more of a malware loader than a simple miner,” Microsoft explains.
The company also underlines that attacks targeting Exchange servers may continue
to impact organizations even after patches have been applied, through the use of
stolen credentials, or persistent access.
“Attackers exploit the on-premises Exchange Server vulnerabilities in
combination to bypass authentication and gain the ability to write files and run
malicious code. The best and most complete remediation for these vulnerabilities
is to update to a supported Cumulative Update and to install all security
updates,” Microsoft concludes.
'Hades' Ransomware Hits Big Firms, but Operators Slow to Respond to Victims
30.3.2021
Ransomware
Securityweek
Researchers from CrowdStrike, Accenture, and Awake Security have dissected some
of the attacks involving the Hades ransomware and published information on both
the malware itself and the tactics, techniques and procedures (TTPs) employed by
its operators.
Initially observed in December 2020, the self-named Hades ransomware (a
different malware family from the Hades Locker ransomware that emerged in 2016)
employs a double-extortion tactic, exfiltrating victim data and threatening to
leak it publicly unless the ransom is paid.
The adversary appears mainly focused on enterprises, with some of the victims
being multi-national organizations with more than $1 billion in annual revenues.
The attacks mainly affected Canada, Germany, Luxembourg, Mexico, and the United
States.
The Hades ransomware operators targeted a few industries only, including
transportation and logistics, consumer products, and manufacturing and
distribution — a logistics provider and organizations in the automotive supply
chain and manufacturing of insulation products are known victims. At least three
of the victims are U.S. companies with more than $1 billion in annual revenue,
Accenture notes.
In the ransom note dropped onto the compromised machines, each victim is
directed to a unique Tor website — six such sites were identified to date,
suggesting that Hades has made at least six victims. On that website, the victim
is instructed to contact the attackers using the Tox peer-to-peer instant
messenger.
The ransomware operators demand payments in the range of $5 to $10 million from
their victims. Interestingly enough, despite a relatively low number of victims
and the large payment demands, the adversaries appear slow to respond to
requests for ransom payment instructions.
In addition to encrypting files on the victim’s machines, the Hades ransomware
operators also exfiltrate data deemed to be of interest, and extort the victim
into paying the ransom by threatening to make the stolen data public.
However, in the few instances where the attackers followed through with their
threat, the leak had a small impact on the victim, despite far more valuable
data being exfiltrated during the attack.
“The question that therefore arises, what was the objective of stealing the
crown jewels but disclosing less significant bits of information? Did they hold
back on publicly sharing the most valuable data because they had alternate means
to monetize the proprietary secrets?” Awake notes.
A typical Hades ransomware attack involves the use of legitimate credentials for
connecting to Internet-facing systems via Remote Desktop Protocol (RDP) or
Virtual Private Network (VPN), followed by the deployment of Cobalt Strike and
Empire implants for persistence.
The attackers also leverage various scripts to perform reconnaissance, harvest
credentials to elevate privileges when necessary, and identify and compromise
additional systems in the network.
In some cases, the adversary would compile the ransomware binary at the same
time as data was being exfiltrated out of the victim’s environment. The
attackers are believed to have been employing a “hands on keyboard” approach in
their attacks.
What is yet unclear, however, is who exactly might be operating Hades. While
Accenture hasn’t made an attribution yet, Awake has drawn some connections with
other threat actors out there, including Hafnium, the Chinese hacking group
involved in the recently disclosed Exchange Server hacks.
CrowdStrike, on the other hand, believes that Hades is the work of the infamous
Evil Corp gang, the Russian threat actor known for the use of Dridex Trojan,
Locky ransomware, and multiple other malware families. Hades, the security firm
says, shows multiple code similarities with WastedLocker, a piece of ransomware
attributed to Evil Corp last year.
“Hades is merely a 64-bit compiled variant of WastedLocker with additional code
obfuscation and minor feature changes. […] Hades ransomware shares the majority
of its functionality with WastedLocker; the ISFB-inspired static configuration,
multi-staged persistence/installation process, file/directory enumeration and
encryption functionality are largely unchanged,” CrowdStrike notes.
Additionally, the security firm says that Hades also marks changes in the TTPs
employed by Evil Corp (also known as TA505, and INDRIK SPIDER), which might be a
reaction to the U.S. Treasury Department’s Office of Foreign Assets Control
(OFAC) announcing sanctions against the gang and the Department of Justice (DOJ)
indicting two members of the group.
“The continued development of WastedLocker ransomware is the latest attempt by
the notorious adversary to distance themselves from known tooling to aid them in
bypassing the sanctions imposed upon them. The sanctions and indictments have
undoubtedly significantly impacted the group and have made it difficult for
INDRIK SPIDER to successfully monetize their criminal endeavors,” CrowdStrike
concludes.
Clop Ransomware gang now contacts victims’ customers to force victims into pay a
ransom
28.3.2021
Ransomware
Securityaffairs
Clop ransomware operators now email victim’s customers and ask them to demand a
ransom payment to protect their privacy to force victims into paying the ransom.
Clop ransomware operators are switching to a new tactic to force victims into
paying the ransom by emailing their customers and asking them to demand a ransom
payment to protect their privacy.
The new technique aims at making the double-extortion tactic more efficient,
crooks sent emails directly to victims’ customers found in documents stolen
during the ransomware attack.
According to BleepingComputer, the first victim threatened with this new tactic
was Flagstar Bank followed by the University of Colorado.
“In an email seen by BleepignComputer, Clop is now using the same tactic to the
customers of an online maternity clothing store, which will not be naming.”
reported BleepingComputer. “In these emails, Clop is sending customers
threatening emails with the subject “Your personal data has been stolen and will
be published.”
Clop ransomware operators invited the victim’s customer to contact the victim
and ask it protect their privacy by paying the ransomware.
Ransomware operators continue to evolve their tactics, recently the REvil
ransomware gang announced that they are using DDoS attacks and voice calls to
the victim’s business partners and journalists to force the victims into pay the
ransom.
Insurance Giant CNA Hit with Novel Ransomware Attack
27.3.2021
Ransomware
Threatpost
The incident, which forced the company to disconnect its systems, caused
significant business disruption.
A novel ransomware attack forced insurance giant CNA to take systems offline and
temporarily shutter its website. The attack occurred earlier this week and
leveraged a new variant of the Phoenix CryptoLocker malware.
The Chicago-based company—the seventh largest commercial insurance provider in
the world—said it “sustained a sophisticated cybersecurity attack” on Sunday,
March 21, according to a statement on the home page of its website. The
statement is the only functionality the company’s site currently maintains.
“The attack caused a network disruption and impacted certain CNA systems,
including corporate email,” according to the statement.
Though the company
did not elaborate on the nature of the attack, a report in BleepingComputer said
CNA was the victim of a new ransomware called Phoenix CryptoLocker.
Cryptolockers are an oft-used type of ransomware that immediately encrypt files
on the machines they attack and demand a ransom from the victims in exchange for
the key to unlocking them.
Moreover, the threat actors behind Phoenix CryptoLocker are likely known
entities–the cybercrime group Evil Corp, which recently resurfaced after taking
a short hiatus from cybercriminal activity, according to the report.
The impact of the group’s latest attack was so serious that CNA disconnected its
systems from its network “out of an abundance of caution” and is currently
providing workarounds for employees where possible so the company can continue
operating to serve its customers, the company said.
Sources familiar with the attack have told BleepingComputer that threat actors
encrypted more than 15,000 devices on CNA’s network—including those of employees
working remotely who were logged onto the company’s VPN at the time—when they
deployed the new ransomware on Sunday, according to the report.
Attackers encrypted devices by appending the .phoenix extension to encrypted
files and creating a ransom note named PHOENIX-HELP.txt, according to
BleepingComputer.
Evil Corp has been in the crosshairs of U.S. authorities since 2019, when they
offered up $5 million for information leading to the arrest of Evil Corp leader
Maksim V. Yakubets, 32, of Russia, who goes under the moniker “aqua” and is
known for leading a lavish lifestyle.
Indeed, the cybercrime group has reaped millions from various nefarious
activities, which previously included capturing banking credentials with the
Dridex banking trojan and then making unauthorized electronic funds transfers
from unknowing victims’ bank accounts.
Sources believe that Phoenix Cryptolocker is a product of Evil Corp based on
similarities in the code to previous ransomware used by the group, according to
the report. In previous ransomware attacks—such as one against GPS technology
provider Garmin last year–Evil Corp used WastedLocker ransomware to encrypt
victims’ files.
CNA aims to restore its systems using backup rather than pay the ransom demanded
by attackers, according to BleepingComputer. The company is currently in the
midst of an ongoing investigation into the incident that started immediately
after its discovery, the company said.
“We have alerted law enforcement and will be cooperating with them as they
conduct their own investigation,” the company said.
CNA is unaware at this time if the incident impacted any customer data, but will
notify parties directly if this is found to be the case, according to the
statement.
CNA also did not give a timeline for when its website and systems will be up and
running in a fully operational way again. In the meantime, the company posted
specific directions on its website for how its customers should contact the
company during the time of disruption based on their various needs.
Hades ransomware gang targets big organizations in the US
27.3.2021
Ransomware
Securityaffairs
Accenture security researchers published an analysis of the latest Hades
campaign, which is ongoing since at least December 2020.
Accenture’s Cyber
Investigation & Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI)
teams published an analysis of the latest campaign conducted by financially
motivated threat group Hades which have been operating since at least December
2020.
Experts discovered that threat actors targeted a large US transportation &
logistics organization, a large US consumer products organization, and a global
manufacturing organization. At the time of this writing, it is unclear if the
Hades gang operates a ransom-as-a-service model.
The profile of the victims suggests the attackers are focusing on Big Game
Hunting, targeted organizations with annual revenues exceeding $1 billion USD.
Experts identified Tor hidden services and clearnet URLs via various open-source
reporting that could be associated with the activity of the Hades ransomware.
The ransom note left by the malware points to Tor pages that are uniquely
generated for each victim.
Accenture researchers also noticed that the Hades ransom notes share portions
with the one used by the REvil ransomware operators, unique differences are the
operators’ contact information and the formatting of the ransom notes. While the
ransom notes are similar, we do not have any evidence to suggest the threat
groups or operations have any overlap at this time.
Researchers from
Crowdstrike speculate that the new variant is a successor to WastedLocker
ransomware and linked the operations to Evil Corp operations.
The attack
chain begins with attacks to internet-facing systems via Remote Desktop Protocol
(RDP) or Virtual Private Network (VPN) using legitimate credentials.
Upon running on the victim’s machine, the malicious code creates a copy of
itself and relaunches itself via the command line. The copy is then deleted and
an executable is unpacked in memory. Then the malware perform a scan in local
directories and network shares for content to encrypt. Experts noticed that each
Hades ransomware sample uses a different extension to files that it encrypts and
drops a ransom note with file name “HOW-TO-DECRYPT-[extension].txt”
“The use of legitimate credentials, service creation, and distribution of
Command and Control (C2) beacons across victim environments through the use of
Cobalt Strike and Empire, so far appear to be the predominant approach used by
the unknown threat group to further their foothold and maintain persistence. In
addition, the threat actors operated out of the root of C:\ProgramData where
several executables tied to the intrusion set were found.” reads the analysis
published by Accenture.

The analysis of the malware revealed the use of code obfuscation to avoid
detection, while privilege escalation is achieved through credential harvesting
and the use of tooling and manual enumeration of credentials.
Like other ransomware, Hades ransomware steal data before starting the
encryption process and send them back to the C2.
“Prior to deploying Hades ransomware, the unknown threat group has employed the
7zip utility to archive data that was then staged and exfiltrated to an
attacker-controlled server hosted in Mega[.]nz cloud infrastructure, leveraging
the MEGAsync utility.” concludes the report. “In addition to data theft, actors
deploy Hades ransomware to encrypt files identified on the victim network. Hades
operators leverage this approach for “double-extortion” tactics.”
CIFR and ACTI also provided Indicators of Compromise (IoC) for the Hades
attacks.
Mamba Ransomware Leverages DiskCryptor for Encryption, FBI Warns
26.3.2021
Ransomware
Securityweek
The Federal Bureau of Investigation (FBI) this week published an alert to warn
of the fact that the Mamba ransomware is abusing the DiskCryptor open source
tool to encrypt entire drives, including the operating system.
Also referred to as HDDCryptor and HDD Cryptor, the ransomware has been around
for roughly half a decade, and has been abusing DiskCryptor for nearly as long.
An open source tool, DiskCryptor was designed to provide users with the option
to encrypt all disk drives, including the system partition. Claiming to provide
a better alternative to Microsoft’s BitLocker, the application was released with
the purpose of helping users keep their data secure.
The Mamba ransomware, however, is abusing the open source application for
malicious purposes, and has been doing so in a multitude of attacks.
Some of these incidents, the FBI warns, targeted local governments, legal and
technology services, public transportation agencies, and industrial, commercial,
manufacturing, and construction entities.
“Mamba ransomware weaponizes DiskCryptor—an open source full disk encryption
software—to restrict victim access by encrypting an entire drive, including the
operating system,” the FBI notes, adding that DiskCryptor is not a malicious
application by nature.
“The ransomware program consists of the open source, off-the-shelf, disk
encryption software DiskCryptor wrapped in a program which installs and starts
disk encryption in the background using a key of the attacker’s choosing,” the
FBI explains.
Upon the installation of DiskCryptor, the system is restarted. After the
encryption process has been completed, the system is restarted a second time,
and a ransom note is displayed to the user.
The ransom note includes information such as host system name, the threat
actor’s email address, the ransomware file name, and indications on where to
enter the decryption key. Furthermore, victims are told to contact the attackers
by email to receive information on how they can pay a ransom to receive the
decryption key.
The FBI notes that the ransomware saves the encryption key, along with the
shutdown time variable, to a configuration file named myConf.txt. The file is
accessible and readable until the second system restart, which concludes the
encryption process.
“If any of the DiskCryptor files are detected, attempts should be made to
determine if the myConf.txt is still accessible. If so, then the password can be
recovered without paying the ransom. This opportunity is limited to the point in
which the system reboots for the second time,” the FBI reveals.
To stay protected from Mamba and other ransomware families out there, users are
advised to always keep their data backed up, to avoid clicking on links or
opening documents received via email, to keep all applications updated,
including an antivirus program, and to apply all of the usual proactive measures
to prevent malware infection.
“The FBI does not encourage paying ransoms. Payment does not guarantee files
will be recovered. It may also embolden adversaries to target additional
organizations, encourage other criminal actors to engage in the distribution of
ransomware, and/or fund illicit activities,” the FBI notes.
Black Kingdom Ransomware Hunting Unpatched Microsoft Exchange Servers
26.3.2021
Ransomware
Thehackernews

More than a week after Microsoft released a one-click mitigation tool to
mitigate cyberattacks targeting on-premises Exchange servers, the company
disclosed that patches have been applied to 92% of all internet-facing servers
affected by the ProxyLogon vulnerabilities.
The development, a 43% improvement from the previous week, caps off a whirlwind
of espionage and malware campaigns that hit thousands of companies worldwide,
with as many as 10 advanced persistent threat (APT) groups opportunistically
moving quickly to exploit the bugs.
According to telemetry data from RiskIQ, there are roughly 29,966 instances of
Microsoft Exchange servers still exposed to attacks, down from 92,072 on March
10.
While Exchange servers were under assault by multiple Chinese-linked
state-sponsored hacking groups prior to Microsoft's patch on March 2, the
release of public proof-of-concept exploits fanned a feeding frenzy of
infections, opening the door for escalating attacks like ransomware and
hijacking web shells planted on unpatched Microsoft Exchange servers to deliver
cryptominers and other malware.
"To make matters worse, proof-of-concept automated attack scripts are being made
publicly available, making it possible for even unskilled attackers to quickly
gain remote control of a vulnerable Microsoft Exchange Server," cybersecurity
firm F-Secure noted in a write-up last week.
In the weeks since Microsoft first released its patches, at least two different
strains of ransomware have been discovered as leveraging the flaws to install
"DearCry" and "Black Kingdom."
Cybersecurity firm Sophos' analysis of Black Kingdom paints the ransomware as
"somewhat rudimentary and amateurish in its composition," with the attackers
abusing the ProxyLogon flaw to deploy a web shell, utilizing it to issue a
PowerShell command that downloads the ransomware payload, which encrypts the
files and demands a bitcoin ransom in exchange for the private key.
"The Black Kingdom ransomware targeting unpatched Exchange servers has all the
hallmarks of being created by a motivated script-kiddie," Mark Loman, director
of engineering at Sophos, said. "The encryption tools and techniques are
imperfect but the ransom of $10,000 in bitcoin is low enough to be successful.
Every threat should be taken seriously, even seemingly low-quality ones."
The volume of attacks even before the public disclosure of ProxyLogon has
prompted experts to investigate if the exploit was shared or sold on the Dark
Web, or a Microsoft partner, with whom the company shared information about the
vulnerabilities through its Microsoft Active Protections Program (MAPP), either
accidentally or purposefully leaked it to other groups.
Ransomware Attack Foils IoT Giant Sierra Wireless
25.3.2021
Ransomware
Threatpost
The ransomware attack
has impacted the IoT manufacturer’s production lines across multiple sites, and
other internal operations.
A ransomware attack on leading internet-of-things (IoT) manufacturer Sierra
Wireless this week ground its production activity to a halt and froze various
other internal operations.
The Canadian multinational manufacturer creates a broad array of communications
equipment – from gateways to routers, cellular modems to modules, and smart
connectivity solutions for IoT devices.
The ransomware attack first hit on March 20, pushing the company’s IT systems
offline and halting production across its manufacturing sites. Sierra Wireless’
website and other internal operations have also been disrupted by the attack, it
said on Tuesday. The company’s website (sierrawireless.com) is currently down,
saying “Site is under maintenance.”
The company said that it’s currently working to bring its internal IT systems
back online, and hopes to restart production at its facilities “soon.”
“Once the company learned of the attack, its IT and operations teams immediately
implemented measures to counter the attack in accordance with established
cybersecurity procedures and policies that were developed in collaboration with
third-party advisors,” according to Sierra Wireless.
Due to the disruptions caused by the cyberattack, the company is also
withdrawing its first-quarter 2021 guidance, which had been provided on Feb. 23
— highlighting the potential financial damages that the attack may have on the
company.
However, the company said, at this time it does not believe its customer-facing
products and services have been impacted by the attack. It’s not clear whether
customer data has been affected.
At this time, Sierra Wireless did not specify how the cyberattack initially
occurred, what type of ransom was demanded and whether it was considering
paying. It’s also not clear how many production centers have been impacted by
the cyberattack. Sierra Wireless operates a global network operation center
(NOC), and research-and-development centers in Asia, Europe and North America.
Sierra Wireless declined to comment further: “Beyond notifying the third-party
advisors, our customers and others impacted by the attack, we do not share our
protocols for dealing with any ransomware attacks as this is considered highly
sensitive and confidential,” a spokesperson told Threatpost.
Matt Sanders, director of security at LogRhythm, said that the incident is an
example of the impact that a ransomware can have on an organization.
“Unfortunately, Sierra Wireless’ entire production has halted thanks to an
attack that has completely debilitated them,” said Sanders. “When an
organization falls victim to ransomware, the pressure to get back to normal
business operations is huge, and the ability to do so in a timely manner may be
pivotal to the company’s ability to continue operating at all.”
Ransomware attacks have continued to plague companies across multiple industries
this year — from a February attack on a major Finnish IT provider that forced it
to turn off some services and infrastructure in a disruption to customers, to
PYSA ransomware attacks in early March disrupting the education sector.
Black Kingdom ransomware is targeting Microsoft Exchange servers
25.3.2021
Ransomware
Securityaffairs
Security experts reported that a second ransomware gang, named Black Kingdom, is
targeting Microsoft Exchange servers.
After the public disclosure of
ProxyLogon vulnerabilities, multiple threat actors started targeting vulnerable
Microsoft Exchange servers exposed online. The first ransomware gang exploiting
the above issues in attacks in the wild was a group tracked as DearCry.
Last crew in order of time exploiting recently disclosed flaws in Microsoft
Exchange servers is a ransomware gang named Black Kingdom.

Black Kingdom ransomware was first spotted in late February 2020 by security
researcher GrujaRS, the ransomware encrypts files and appends the .DEMON
extension to filenames of the encrypted documents. In June 2020, Black Kingdom
ransomware operators started targeting organizations using unpatched Pulse
Secure VPN software to deploy their malware.
Now the group, leveraging the availability online for the ProxyLogon PoC exploit
code, expanded its operations targeting vulnerable Exchange mail servers.
The popular researchers Marcus Hutchins first reported the activity of the Black
Kingdom group.


The expert pointed out that the ransomware gang was dropping a ransom note on
vulnerable installs demanding a payment of $10,000 worth of Bitcoin, but for
unknown reasons, the files were not encrypted. Unfortunately, according to
security experts, the group now fixed its problems and is able to encrypt the
files on compromised Exchange servers.
Sierra Wireless halted production at its manufacturing sites due to ransomware
attack
24.3.2021
Ransomware
Securityaffairs
This week, IoT company Sierra Wireless disclosed a ransomware attack that hit
its internal IT systems on March 20 and disrupted its production.
Sierra
Wireless is a Canadian multinational wireless communications equipment designer
and manufacturer headquartered in Richmond, British Columbia, Canada.
The company sells mobile computing and machine-to-machine (M2M) communications
products that work over cellular networks. Sierra Wireless sells 2G, 3G and 4G
mobile broadband wireless modems, routers and gateways as well as software,
tools, and services. Sierra Wireless products and technologies are used in a
variety of markets and industries, including automotive and transportation,
energy, field service, healthcare, industrial and infrastructure, mobile
computing and consumers, networking, sales and payment, and security. It also
maintains a network of experts in mobile broadband and M2M integration to
support customers worldwide.
Sierra Wireless announced it has halted its production at manufacturing
facilities due to the ransomware attack, it is currently working to restart the
production “soon.”
“Sierra Wireless (NASDAQ: SWIR) (TSX: SW), the world’s leading IoT solutions
provider, today announced that it discovered it was the subject of a ransomware
attack on its internal IT systems on March 20, 2021.” reads the announcement
issued by the company. “Once the company learned of the attack, its IT and
operations teams immediately implemented measures to counter the attack in
accordance with established cybersecurity procedures and policies that were
developed in collaboration with third-party advisors.”
The company is investigating the incident with the help of third-party experts,
it is working to bring its internal IT systems back online.
The attack took
the website offline and impacted internal operations. The vendor believes the
attack did not impact the systems of its customers because are separated by its
internal IT systems.
“These teams, with the assistance of these and additional third-party advisors,
believe they have addressed the attack, and are currently working to bring
Sierra Wireless’ internal IT systems back online.” continues the announcement.
“At this time, Sierra Wireless believes the impact of the attack was limited to
Sierra Wireless systems, as the company maintains a clear separation between its
internal IT systems and customer facing products and services.”
Due to these disruptions caused by the ransomware attack, the company is
withdrawing the First Quarter 2021 guidance it provided on February 23, 2021.
At the time of this writing, the company did not reveal the family of ransomware
that hit its systems.
Sierra Wireless Says Ransomware Disrupted Production at Manufacturing Facilities
24.3.2021
Ransomware
Securityweek
Canada-based IoT company Sierra Wireless revealed on Tuesday that its internal
IT systems were hit by a ransomware attack on March 20.
Sierra Wireless specializes in designing and manufacturing wireless
communications equipment. Their products are used worldwide in industrial and
enterprise settings, including in the commercial facilities, communications,
government, energy, transportation, and water sectors.
Sierra Wireless said the ransomware forced it to halt production at
manufacturing facilities, but it hopes to restart production “soon.” Its website
and other internal operations have also suffered disruptions, but the company
believes the attack has only impacted its own systems, pointing out that it
“maintains a clear separation between its internal IT systems and customer
facing products and services.”
“Once the company learned of the attack, its IT and operations teams immediately
implemented measures to counter the attack in accordance with established
cybersecurity procedures and policies that were developed in collaboration with
third-party advisors,” the company said in a press release. “These teams, with
the assistance of these and additional third-party advisors, believe they have
addressed the attack, and are currently working to bring Sierra Wireless’
internal IT systems back online.”
The U.S. Securities and Exchange Commission (SEC) has also been notified about
the incident. The disruption caused by the ransomware has forced the company to
withdraw its Q1 2021 guidance.
Sierra Wireless’ website is still inaccessible at the time of writing.
SecurityWeek has reached out to the company for more information on the attack.
It’s not uncommon for ransomware attacks on major companies to cause disruption
to production operations. A couple of recent examples are the attacks on
beverage conglomerate Molson Coors and packaging giant WestRock.
REvil ransomware gang hacked Acer and is demanding a $50 million ransom
21.3.2021
Ransomware
Securityaffairs
Taiwanese multinational hardware and electronics corporation Acer was victim of
a REvil ransomware attack, the gang demanded a $50,000,000 ransom.
Taiwanese
computer giant Acer was victim of the REvil ransomware attack, the gang is
demanding the payment of a $50,000,000 ransom, the largest one to date.
Acer is the world’s 6th-largest PC vendor by unit sales as of January 2021, it
has more than 7,000 employees (2019) and in 2019 declared 234.29 billion in
revenue.
The ransomware gang claimed to have stolen data from the systems of the vendor
before encrypting them, then published on their data leak site some images of
allegedly stolen documents (i.e. financial spreadsheets, bank documents and
communications) as proof of the hack.
Acer is currently investigating the security breach.
“Acer routinely monitors its IT systems, and most cyberattacks are well
defensed. Companies like us are constantly under attack, and we have reported
recent abnormal situations observed to the relevant law enforcement and data
protection authorities in multiple countries.” reads a statement issued by the
company. “”We have been continuously enhancing our cybersecurity infrastructure
to protect business continuity and our information integrity. We urge all
companies and organizations to adhere to cyber security disciplines and best
practices, and be vigilant to any network activity abnormalities.”
A REvil ransomware sample on malware analysis site Hatching Triage was
discovered by TechTarget sister publication LeMagIT Friday, which contained a
link to a REvil ransomware demand for $50 million in Monero (213,151 XMR as of
publishing).
Researchers at LegMagIT while investigating the security breach discovered a
REvil ransomware sample employed in the attacks on Acer, it includes a link to a
REvil ransomware demand for $50 million worth of Monero.
“We have since found a sample of the Revil / Sodinokibi ransomware that leads to
an engaged discussion between victim and attacker. The latter start by providing
a link that leads to their blog page… devoted to Acer. Conservation started on
March 14.” reported LegMagIT. “Cyber criminals have offered a 20% discount on
the requested amount, provided the settlement reaches them by March 17.
Currently, they are asking for $ 50 million. Their interlocutor proposed $ 10
million. The attackers are leaving Acer until March 28 to meet their demands or
find an arrangement. After this deadline, they will demand $ 100 million. “
REvil ransomware operators offered a 20% discount if payment was completed by
this week, on Wednesday.
Source LeMagIT
According to BleepingComputer, the popular malware researcher
Vitali Kremez shared evidence with its experts that one of the affiliates to the
Revil RaaS recently targeted an Acer’s Microsoft Exchange server.
Tesla Ransomware Hacker Pleads Guilty; Swiss Hacktivist Charged for Fraud
20.3.2021
Ransomware
Thehackernews
The U.S. Department of Justice yesterday announced updates on two separate cases
involving cyberattacks—a Swiss hacktivist and a Russian hacker who planned to
plant malware in the Tesla company.
A Swiss hacker who was involved in the intrusion of cloud-based surveillance
firm Verkada and exposed camera footage from its customers was charged by the
U.S. Department of Justice (DoJ) on Thursday with conspiracy, wire fraud, and
identity theft.
Till Kottmann (aka "deletescape" and "tillie crimew"), 21, of Lucerne,
Switzerland, and their co-conspirators were accused of hacking dozens of
companies and government agencies since 2019 by targeting their "git" and other
source code repositories and posting the proprietary data of more than 100
entities on a website called git[.]rip, according to the indictment.
Kottmann is alleged to have cloned the source code and other confidential files
containing hard-coded administrative credentials and access keys, using them to
infiltrate the internal infrastructure of victims further and copy additional
records and intellectual property. Additionally, the prosecutors said the U.S.
Federal Bureau of Investigation (FBI) seized the domain that was used to publish
hacked data online.
The defendant's long list of victims includes Nissan, Intel, Mercedes-Benz, and
many others, including the Verkada breach that happened earlier this month,
thereby gaining access to more than 150,000 of the company's cameras installed
in various locations ranging from Tesla warehouses to gyms, psychiatric
hospitals, and health clinics.
Kottmann, who calls the hacktivist collective "Advanced Persistent Threat
69420," told Bloomberg the breach "exposes just how broadly we're being
surveilled, and how little care is put into at least securing the platforms used
to do so, pursuing nothing but profit," while attempting to justify their
actions as part of a "fight for freedom of information and against intellectual
property."
Then last Friday, Swiss authorities raided Kottmann's apartment and seized the
hacker's electronic devices at the behest of U.S. authorities.
"Stealing credentials and data, and publishing source code and proprietary and
sensitive information on the web is not protected speech — it is theft and
fraud," said Acting U.S. Attorney Tessa M. Gorman. "These actions can increase
vulnerabilities for everyone from large corporations to individual consumers.
Wrapping oneself in an allegedly altruistic motive does not remove the criminal
stench from such intrusion, theft, and fraud."
It's not immediately clear if U.S. prosecutors intend to extradite Kottmann, who
still remains at large in Lucerne.
Russian National Pleads Guilty for Tesla Hacking Plot

In other related news, a Russian national pleaded guilty to offering a Tesla
employee $1 million to plant ransomware at the electric carmaker's Gigafactory
plant in Nevada.
According to court documents, the suspect, Egor Igorevich Kriuchkov, 27,
traveled to the U.S. in July on a tourist visa and made contact with a
Russian-speaking employee in an attempt to install malware into the company's
computer network with the goal of exfiltrating data and holding it for ransom.
But the extortion scheme fell apart after the employee in question alerted the
company of the incident, which then involved the FBI into the matter.
"This was a serious attack," CEO Elon Musk said in an August 2020 tweet.
Kriuchkov, who previously denied any wrongdoing in September before a federal
magistrate judge, on Thursday pleaded guilty to one count of conspiracy to cause
damage to a protected computer intentionally. Kriuchkov is scheduled to be
sentenced on May 10.
"This case highlights our office's commitment to protecting trade secrets and
other confidential information belonging to U.S. businesses — which is becoming
even more important each day as Nevada evolves into a center for technological
innovation," said Acting U.S. Attorney Christopher Chiou for the District of
Nevada. "Along with our law enforcement partners, we will continue to prioritize
stopping cybercriminals from harming American companies and consumers."
FBI warns of PYSA Ransomware attacks against Education Institutions in US and UK
18.3.2021
Ransomware
Securityaffairs
The FBI has issued an alert to warn about an increase in PYSA ransomware attacks
on education institutions in the US and UK.
The FBI has issued Tuesday an
alert to warn about an increase in PYSA ransomware attacks against education
institutions in the United States and the United Kingdom.
In March 2020, CERT France cyber-security agency warned about a new wave of
ransomware attack that was targeting the networks of local government
authorities. Operators behind the attacks were spreading a new version of the
Mespinoza ransomware (aka Pysa ransomware).
According to the experts, the first infections were observed in late 2019,
victims reported their files were encrypted by a strain of malware. The
malicious code appended the extension .locked to the filename of the encrypted
files.
The Mespinoza ransomware evolved over time, and in December a new version
appeared in the threat landscape. This new version used the .pysa file extension
that gives the name to this piece ransomware.
The variant was initially used to target big enterprises in the attempt of
maximizing the operators’ efforts, but the alert issued by the French CERT warns
that the Pysa ransomware is targeting French organizations, especially local
government agencies.
CERT-FR’s alert states that the Pysa ransomware code based on public Python
libraries.
According to the report issued by the CERT-FR, operators behind the Pysa
ransomware launched brute-force attacks against management consoles and Active
Directory accounts.
Once compromised the target network, attackers attempt to exfiltrate the
company’s accounts and passwords database.
Operators behind the Pysa ransomware, also employed a version of the PowerShell
Empire penetration-testing tool, they were able to stop antivirus products.
One of the incidents handled by CERT-FR sees the involvement of a new version of
the Pysa ransomware, which used the .newversion file extension instead of .pysa.
According to the FBI Flash alert, unidentified threat actors are targeting
higher education, K-12 schools, and seminaries. The attackers implement a double
extortion model using the PYSA ransomware to exfiltrate data from victims prior
to encrypting their files.
“FBI reporting has indicated a recent increase in PYSA ransomware targeting
education institutions in 12 US states and the United Kingdom. PYSA, also known
as Mespinoza, is a malware capable of exfiltrating data and encrypting users’
critical files and data stored on their systems.” reads the FBI’s alert. “The
unidentified cyber actors have specifically targeted higher education, K-12
schools, and seminaries. These actors use PYSA to exfiltrate data from victims
prior to encrypting victim’s systems to use as leverage in eliciting ransom
payments.”
Since March 2020, the PYSA ransomware was involved in attacks against US and
foreign government entities, educational institutions, private companies, and
the healthcare sector. Threat actors deploy the ransomware by gaining
unauthorized access to victim networks by compromising Remote Desktop Protocol
(RDP) credentials and/or through phishing campaigns. The attackers use Advanced
Port Scanner and Advanced IP Scanner to conduct network reconnaissance, then
they install open-source post-exploitation tools, including PowerShell Empire,
Koadic, and Mimikatz. The attackers are also able to deactivate antivirus on the
victim network before delivering the ransomware.
“The cyber actors then exfiltrate files from the victim’s network, sometimes
using the free open source tool WinSCP5, and proceed to encrypt all connected
Windows and/or Linux devices and data, rendering critical files, databases,
virtual machines, backups, and applications inaccessible to users. In previous
incidents, cyber actors exfiltrated employment records that contained personally
identifiable information (PII), payroll tax information, and other data that
could be used to extort victims to pay a ransom.” continues the alert.
In recent attacks, threat actors uploaded the stolen data to the file sharing
service MEGA.NZ, in some cases they also installed the MEGA client software
directly on the victim’s computer.
The FBI’s alert contains indicators of compromise (IoCs) for these attacks.
Over the past year, the FBI also issued flash alerts and PIN alerts to warn
organizations about attacks involving DoppelPaymer, Egregor, and NetWalker
ransomware.
PYSA Ransomware Pillages Education Sector, Feds Warn
17.3.2021
Ransomware
Threatpost
A major spike of attacks against higher ed, K-12 and seminaries in March has
prompted the FBI to issue a special alert.
The FBI has issued a warning about an uptick in cyberattacks on the education
sector that are delivering the PYSA ransomware.
In a “Flash” alert to the cybersecurity community issued on Tuesday, the Feds
said that PYSA has been seen in attacks on schools in 12 U.S. states and in the
United Kingdom in March alone. The attacks have cast a wide net, hitting higher
education, K-12 schools and seminaries, the alert warned.
In addition, the unknown cyber-adversaries have targeted a handful of government
entities, healthcare and private companies, the FBI said.
PYSA (a.k.a. Mespinoza), like most ransomware, is capable of exfiltrating data
and encrypting users’ critical files and data stored on their systems. The FBI
noted that it sets about gaining initial access in the usual way: Either by
brute-forcing Remote Desktop Protocol (RDP) credentials and/or through phishing
emails.
Attacks Feature Wide Use of Open-Source, Legitimate Tools
The FBI researchers
have also observed the attackers using Advanced Port Scanner and Advanced IP
Scanner to conduct network reconnaissance. These are open-source tools that
allow users to find open network computers and discover the versions of programs
on those ports. From there, the attackers are installing various open-source
tools for lateral movement.
According to the alert, these include Mimikatz, a post-exploitation toolkit that
pulls passwords from memory, as well as hashes and other authentication
credentials; and Koadic, a penetration toolkit that has several options for
staging payloads and creating implants.
Another open-source lateral movement toolkit used in the attacks is PowerShell
Empire, which provides the ability to run PowerShell agents without needing
powershell.exe. It also provides modules ranging from keyloggers to Mimikatz,
and features adaptable communications to avoid network detection.
The cyber-actors then execute commands to deactivate antivirus capabilities on
the victim network and exfiltrate files, the FBI warned, sometimes using the
free open-source tool WinSCP. WinSCP provides secure file transfer between local
and remote computer systems.
The email addresses associated with the campaign are all Tor domains, but the
adversaries have uploaded stolen data to Mega.nz, a cloud-storage and
file-sharing service, by uploading the data through the Mega website or by
installing the Mega client application directly on a victim’s computer,
according to the FBI.
After all of that, PYSA then deploys the actual ransomware, appending encrypted
files with the .pysa suffix.
PYSA Double-Extortion Ransom Technique
It’s capable of encrypting “all
connected Windows and/or Linux devices and data rendering critical files,
databases, virtual machines, backups and applications inaccessible to users,”
according to the Flash warning. “In previous incidents, cyber actors exfiltrated
employment records that contained personally identifiable information (PII),
payroll tax information and other data that could be used to extort victims to
pay a ransom.”
To encourage victims to pay, the ransomware notes warns that stolen information
will be uploaded and monetized on the Dark Web.
“Observed instances of the malware showed a filename of svchost.exe, which is
most likely an effort by the cyber actors to trick victims and disguise the
ransomware as the generic Windows host process name,” according to the warning.
“In some instances, the actors removed the malicious files after deployment,
resulting in victims not finding any malicious files on their systems.”
Ransomware continues to be an escalating scourge. For instance, hackers were
found last week exploiting vulnerable Microsoft Exchange servers and installing
a new family of ransomware called DearCry.
And, the Monero Miner cryptocurrency ransominer, impersonating an ad blocker and
OpenDNS service, has infected more than 20,000 users in less than two months.
FBI Warns of PYSA Ransomware Attacks on Education Institutions in US, UK
17.3.2021
Ransomware
Securityweek
An alert issued on Tuesday by the FBI warns about an increase in PYSA ransomware
attacks on education institutions in the United States and the United Kingdom.
Last year, authorities in the UK and France also issued alerts for the PYSA
ransomware, following attacks on government and other types of organizations.
According to the FBI, PYSA attacks have been launched by “unidentified cyber
actors” against higher education, K-12 schools and seminaries in a dozen U.S.
states, as well as the U.K.
The threat actors behind PYSA attacks are known to encrypt data on compromised
systems, but they also steal information from victims and threaten to leak it in
an effort to increase their chances of getting paid.
PYSA, also known as Mespinoza, has been around since at least October 2019 and
the FBI has been tracking it since March 2020. PYSA ransomware attacks have been
observed against government organizations, educational institutions, the
healthcare sector and private businesses.
The threat actors often use phishing and RDP attacks for initial access to
targeted networks, and then use tools such as Advanced Port/IP Scanner,
PowerShell Empire, Mimikatz and Koadic to gain further access.
After exfiltrating potentially valuable files from the victim’s network — this
often includes employment records and financial information — the cybercriminals
start encrypting files on Windows and Linux devices.
The FBI’s alert contains some technical information on these attacks, as well as
indicators of compromise (IoC). The agency has advised organizations not to pay
up, but noted that it “understands that when victims are faced with an inability
to function, all options are evaluated to protect shareholders, employees and
customers.”
Victims of PYSA ransomware attacks have been advised to file a report with the
FBI.
“Educational institutions are big targets for hackers as thousands of people’s
sensitive information is potentially involved, and the substantial shift towards
e-learning has made them even more appealing to hackers and ransomware,” James
Carder, CSO at LogRhythm, told SecurityWeek. “These attacks on schools can bring
education to a halt while potentially exposing every student and teacher’s
personal data within the organization. Parents are also targets and may be
coerced into paying ransom for personal information or school assignments if
information falls into bad actors’ hands.”
“This FBI warning is an important reminder that educational institutions need to
take a proactive approach and invest in cybersecurity solutions that detect
malicious behavior and enable network infrastructure to block any further access
attempts. Institutions should patch aggressively, create backups, prepare a
response plan, and prioritize educational training to ensure they are equipped
to handle attacks and proceed without disruption,” Carder added.
Over the past year, the FBI issued advisories to warn organizations about
attacks involving DoppelPaymer, NetWalker and Egregor ransomware.
NCSC is not aware of ransomware attacks compromising UK orgs through Microsoft
Exchange bugs
15.3.2021
Ransomware
Securityaffairs
The UK’s National Cyber Security Centre (NCSC) urges UK organizations to install
the patches for the recently disclosed vulnerabilities in Microsoft Exchange.
The UK’s National Cyber Security Centre is urging UK organizations to install
security patches for their Microsoft Exchange installs.
The UK agency revealed to have helped UK organisations to secure their installs,
around 2,100 vulnerable Microsoft Exchange servers.
On March 2nd, Microsoft released emergency out-of-band security updates that
address four zero-day issues (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858,
and CVE-2021-27065) in all supported MS Exchange versions that are actively
exploited in the wild.
The IT giant reported that at least one China linked APT group, tracked as
HAFNIUM, chained these vulnerabilities to access on-premises Exchange servers to
access email accounts, and install backdoors to maintain access to victim
environments.
According to Microsoft, the Hafnium APT exploited these vulnerabilities in
targeted attacks against US organizations. The group historically launched cyber
espionage campaigns aimed at US-based organizations in multiple industries,
including law firms and infectious disease researchers.
“The NCSC strongly advises all organisations using affected versions of
Microsoft Exchange Servers to proactively search systems for evidence of
compromise” reads the advisory published by the GCHQ. “If organisations cannot
install the updates, or apply any of the mitigations, the NCSC recommends
isolating the Exchange server from the internet “
The agency added that it is not aware of successful ransomware attacks against
UK organizations that exploited Microsoft Exchange ProxyLogon flaws.
The NCSC also recommends organizations to run Microsoft Safety Scanner to detect
webshells employed in the attacks spotted by Microsoft and remove them.
“We
are working closely with industry and international partners to understand the
scale and impact of UK exposure, but it is vital that all organisations take
immediate steps to protect their networks.” said NCSC Director for Operations,
Paul Chichester.
“Whilst this work is ongoing, the most important action is to install the latest
Microsoft updates.” “Organisations should also be alive to the threat of
ransomware and familiarise themselves with our guidance. Any incidents affecting
UK organisations should be reported to the NCSC.”
REvil Group Claims Slew of Ransomware Attacks
13.3.2021
Ransomware
Threatpost
The threat group behind the Sodinokibi ransomware claimed to have recently
compromised nine organizations.
The REvil ransomware threat group is on a cyberattack tear, claiming over the
past two weeks to have infected nine organizations across Africa, Europe, Mexico
and the U.S.
The organizations include two law firms, an insurance company, an architectural
firm, a construction company and an agricultural co-op, all located in the U.S.;
as well as two large international banks (one in Mexico and one in Africa); and
a European manufacturer. In an email interview with Threatpost, researchers with
eSentire, who wrote an analysis of the threat group’s claims, said they would
not name the victim companies.
“These new ransomware incidents, which the…gang is claiming, could certainly be
plausible,” said Rob McLeod, senior director of the Threat Response Unit (TRU)
for eSentire. “These attacks come directly on the heels of an extensive and
well-planned drive-by-download campaign, which was launched in late December.
This malicious campaign’s sole purpose is to infect business professionals’
computer systems with the…ransomware, the Gootkit banking trojan or the Cobalt
Strike intrusion tool.”
The threat group is also known as the Sodinokibi ransomware gang, and is called
“Sodin” by eSentire. The malware, which first surfaced in 2019, has since
proliferated to hit an array of victims, including New York-based celebrity law
firm Grubman Shire Meiselas & Sacks, Travelex and Brown-Forman Corp. (the maker
behind Jack Daniels).
Ransomware Attacks
Researchers said that REvil cybercriminals posted
documents on underground forums that purported to be from the victims’ systems –
including company computer file directories, partial customer lists, customer
quotes and copies of contracts. Researchers said they also posted what appears
to be several official IDs, either belonging to an employee or a customer of the
victim companies.
“We do not know the amount of the ransom they have demanded or if a ransom has
been paid,” McLeod told Threatpost. “However, we have seen some victims posted,
and then their information and name have been pulled from the website. We wonder
if this indicates payment.”
Authentic Victims?
While researchers can’t be 100 percent sure the claims are
accurate, “in reviewing several of the documents that the Sodin gang claims are
from their new victims, many of them appear to be authentic,” said McLeod.
For one, the documents appear to relate to the business of each victim, they
said. The documents also include dated timestamps that show that the attacks may
have occurred not too long ago.
For one of the victims – the manufacturing company – researchers found news
reports that the manufacturer had been hit by ransomware and had to stop
production for a day or two. “As evidence, [REvil provided] Excel spreadsheets
of annual budgets, purportedly from the manufacturer,” McLeod told Threatpost.
There is one caveat – a few documents relating to a bank in Africa and an
insurance firm have older date stamps listed. This made researchers question
whether these two firms were actually victims of the REvil gang — or instead if
somehow the threat actors gained access to some old files belonging to the
organizations.
Regardless, “Sodin gang has been very successful in compromising large
organizations, as we have seen, and they have resources and the techniques to
carry these ransomware attacks so it is extremely plausible these are real,”
said McLeod.
REvil on the Move
Researchers said one puzzle piece to REvil’s recent success
with ransomware attacks may be the Gootloader malware loader, which they said is
“designed to seed the ransomware.”
This loader previously used for distributing the REvil ransomware as well as the
Gootkit malware family, and has evolved into an increasingly sophisticated
loader framework. It now also expanded the number of payloads its delivers to
include the Kronos trojan and the Cobalt Strike commodity malware.
“We know this campaign has had some success because not only have we seen
reports from other security groups, but we have also discovered multiple
incidents where business professionals have been duped and have downloaded
Gootloader onto their work computers,” said McLeod. “Luckily, we were able to
disrupt the activity in midstream, preventing numerous related malware
infections within the employee organizations, two of which were law firms and
one which was a professional consulting firm.”
Researchers said they have seen REvil expanding its extortion tricks tactics and
procedures (TTPs) to now contact victims’ business associates and the media, in
order to put on the maximum amount of pressure on the victim to pay.
They noted that in the last couple days, the threat group also appears to be
updating its website to make it easier to browse their victim list.
“The Sodin gang is well equipped with very good set of adversarial capabilities,
and we do not believe they have shown their entire hand of what they can do,”
McLeod warned. “Once they get on a system, they are very good and staying on and
spreading throughout the victim’s environment.”
Ransomware Operators Start Targeting Microsoft Exchange Vulnerabilities
13.3.2021
Ransomware
Securityweek
In addition to state-sponsored threat actors, the recently disclosed
vulnerabilities affecting Microsoft Exchange Server are now being targeted by
ransomware operators.
A total of four critical zero-day vulnerabilities that are collectively referred
to as ProxyLogon were patched in Exchange Server at the beginning of this month,
and activity surrounding the bugs has only intensified since.
This week, ESET revealed that it has identified at least 10 threat actors that
are attempting to exploit these vulnerabilities in their attacks, including
Calypso, LuckyMouse (also tracked as APT27), Mikroceen, ShadowPad, Tick (also
known as Bronze Butler), Tonto Team (CactusPete), Websiic, Winnti Group (BARIUM,
APT41), and DLTMiner.
Some of these threat actors had been targeting the vulnerabilities before
Microsoft released patches for them, while others have been picking up exploits
for them after that.
Now, security researchers say that ransomware operators too are starting to
target these vulnerabilities in their attacks. According to Microsoft security
researcher Phillip Misner, the attacks are hands-on-keyboard and not automated.
“Microsoft observed a new family of human operated ransomware attack customers –
detected as Ransom:Win32/DoejoCrypt.A. Human operated ransomware attacks are
utilizing the Microsoft Exchange vulnerabilities to exploit customers,” Misner
said on Twitter.
The ransomware family used in these attacks is also referred to as DearCry, and
Microsoft’s researchers are not the only ones to notice the activity.
Thousands of Exchange servers are believed to be vulnerable to attacks, and at
least hundreds of them have already been compromised since the attacks started.
This week, the FBI and CISA issued a joint advisory to warn of these attacks.
“Unfortunately, we recently became aware of several hundred organizations in
Switzerland that got compromised by a threat actor that exploited the said
vulnerability,” the Swiss Government Computer Emergency Response Team
(GovCERT.ch) said earlier this week.
“As a result, we have started informing possible compromised organizations based
on information provided to us by trusted third parties,” GovCERT.ch added.
Amid increasingly numerous reports of attacks on Exchange servers, a Vietnamese
independent security researcher, Nguyen Jang, this week published
proof-of-concept code exploiting the vulnerabilities, only to see it removed
from the Microsoft-owned software development platform GitHub several hours
later.
SecurityWeek has contacted Microsoft for a comment on the removal of the PoC and
will update the article as soon as a reply arrives.
Hackers Are Targeting Microsoft Exchange Servers With Ransomware
13.3.2021
Ransomware
Thehackernews

It didn't take long. Intelligence agencies and cybersecurity researchers had
been warning that unpatched Exchange Servers could open the pathway for
ransomware infections in the wake of swift escalation of the attacks since last
week.
Now it appears that threat actors have caught up.
According to the latest reports, cybercriminals are leveraging the heavily
exploited ProxyLogon Exchange Server flaws to install a new strain of ransomware
called "DearCry."
"Microsoft observed a new family of human operated ransomware attack customers –
detected as Ransom:Win32/DoejoCrypt.A," Microsoft researcher Phillip Misner
tweeted. "Human operated ransomware attacks are utilizing the Microsoft Exchange
vulnerabilities to exploit customers."
In a joint advisory published by the U.S. Cybersecurity and Infrastructure
Security Agency (CISA) and the Federal Bureau of Investigation (FBI), the
agencies warned that "adversaries could exploit these vulnerabilities to
compromise networks, steal information, encrypt data for ransom, or even execute
a destructive attack."
Successful weaponization of the flaws allows an attacker to access victims'
Exchange Servers, enabling them to gain persistent system access and control of
an enterprise network. With the new ransomware threat, unpatched Servers are not
only at risk of potential data theft but also get potentially encrypted,
preventing access to an organization's mailboxes.

Meanwhile, as nation-state hackers and cybercriminals pile on to take advantage
of the ProxyLogon flaws, a proof-of-concept (PoC) code shared on Microsoft-owned
GitHub by a security researcher has been taken down by the company, citing that
the exploit is under active attack.
In a statement to Vice, the company said, "In accordance with our Acceptable Use
Policies, we disabled the gist following reports that it contains proof of
concept code for a recently disclosed vulnerability that is being actively
exploited."
The move has also sparked a debate of its own, with researchers arguing that
Microsoft is "silencing security researchers" by removing PoCs shared on GitHub.
"This is huge, removing a security researchers code from GitHub against their
own product and which has already been patched," TrustedSec's Dave Kennedy said.
"It was a PoC, not a working exploit — none of the PoCs have had the RCE. Even
if it did, that's not their call on when the appropriate time to release is.
It's an issue in their own product, and they are silencing security researchers
on that."
This was also echoed by Google Project Zero researcher Tavis Normandy.
"If the policy from the start was no PoC/metasploit/etc — that would suck, but
it's their service," Normandy said in a tweet. "Instead they said OK, and now
that it's become the standard for security pros to share code, they have elected
themselves the arbiters of what is 'responsible.' How convenient."
If anything, the avalanche of attacks should serve as a warning to patch all
versions of the Exchange Server as soon as possible, while also take steps to
identify signs of indicators of compromise associated with the hacks, given that
the attackers were exploiting these zero-day vulnerabilities in the wild for at
least two months before Microsoft released the patches on March 2.
We have reached out to Microsoft for more details, and we will update the story
if we hear back.
Ransomware Attack Strikes Spain’s Employment Agency
12.3.2021
Ransomware
Threatpost
Reports say that the agency in charge of managing Spain’s unemployment benefits
has been hit by the Ryuk ransomware.
The Spanish State Employment Service (SEPE) in Spain has been hit by a
cyberattack, suspending its communications systems across hundreds of offices
and delaying thousands of appointments.
SEPE is an “autonomous body” in Spain that manages and controls unemployment
benefits. The cyberattack hit during an already strenuous time for the agency,
which is dealing with an overflow of requests for unemployment benefits as the
coronavirus pandemic has forced companies globally to make cuts to their
workforces.
According to Spanish trade union Central Sindical Independiente y de
Funcionarios (CSIF), the attack has has affected the organization’s 710 offices.
The labor union claimed that the cyberattack stemmed from ransomware – however,
further details about the attack, including its origin and the ransom demand,
are unknown.
“The SEPE is being subjected to a security incident during which the
availability of its information and communication systems has been affected,”
according to a Google-translated version of a message on the SEPE’s website.
“The first urgent actions carried out have been carried out as quickly as
possible and with the main objective of containing the incident, isolating and,
therefore, mitigating its impact on the SEPE systems.”
According to Business Insider Spain, the cyberattack is the work of the Ryuk
ransomware. The threat group has hit a number of organizations over the past
year, such as Universal Health Services.
CSIF said the incident has delayed the management of “hundreds of thousands” of
appointments in Spain for those trying to file for unemployment benefits. SEPE,
for its part, said that it is still working to manually process unemployment
benefit requests and it is not necessary to renew requests.
“Currently, work is being done with the aim of restoring priority services as
soon as possible, among which is the portal of the State Public Employment
Service and then gradually other services to citizens, companies, benefit and
employment offices,” said SEPE.
However, CSIF alleged that SEPE has been dragging its feet when it comes to
technological investment for months, and relying on applications and computer
systems with an “average age of about 30 years.”
“From CSIF, we regret the disruption that this problem is causing in users who
had their appointment scheduled for today, both in person and online, who are
being duly informed of the incident,” according to CSIF.
To this point, experts like Jigar Shah, vice president at Valtix, said that
organizations need to be “forward-thinking” when it comes to securing their
infrastructure and fending off ransomware threats.
“A lot of people are overly focused on the tactical response after a ransomware
incident happens,” Shah told Threatpost. “Often, paying the ransom does not even
let you recover as the attacker just vanishes and does not help free locked
resources. At this point, the big costs are on how to recover and rebuild.”
Companies already battered by the pandemic continue to be dangerous targets when
it comes to ransomware. A slew of hospitals worldwide have been hit by
ransomware attacks, for instance, while ransomware threat actors also targeted
schools already struggling with taking classes online.
Cyberattack Forces Brewery Shutdown at Molson Coors
12.3.2021
Ransomware
Securityweek
Cyberattack Against Molson Coors Impacts Brewery Operations, Production, and
Shipments
The wave of big-name companies falling victim to disruptive malware attacks is
showing no signs of slowing down with beverage conglomerate Molson Coors
Beverage Company announcing on Thursday that it was recovering from an incident
that severely disrupted its production operations.
The company’s disclosure of the incident, believed to be a ransomware infection,
was contained in an 8K filing with the Securities and Exchange Commission (SEC)
that discusses an “a systems outage that was caused by a cybersecurity
incident.”
Molson Coors, makers of popular beer brands in the U.S., confirmed the malware
attack has caused delays and disruptions to parts of the business handling
brewery operations, production, and shipments.
The company produces several iconic beer brands including Coors Light, Miller
Lite, Molson Canadian, Carling, Coors Banquet, Blue Moon and others.
The company said it was “actively managing” the incident through an engagement
with leading forensic information technology firms.
“[We are] working around the clock to get its systems back up as quickly as
possible,” the company said in the filing.
The company did not provide technical details of the incident.
The Molson Coors Beverage Company’s problems with ransomware mirror similar
attacks that have resulted in production being disrupted for a manufacturing
company. Earlier this month, French boat maker Groupe Beneteau fell victim to a
cyberattack that forced a production shut down for several days. Last month
packaging giant WestRock said a ransomware incident impacted the company’s
information technology (IT) and operational technology (OT) systems.
“High profile attacks are becoming all too common, as attackers have realized
they are immensely more profitable when they target large organizations and
disrupt their critical business operations – in this case, the brewing
operations of the world’s biggest, well known beer brands," Edgard Capdevielle,
CEO at Nozomi Networks, told SecurityWeek.
"While the company hasn’t released details, this scenario could be ransomware
and this type of situation should be factored into an organization’s incident
response and business continuity plan," Capdevielle continued. "Beyond a
technical response, decision makers need to be prepared to weigh the risks and
consequences of alternate actions. Ransomware threat actors typically rely on
spear phishing links or vulnerable public services to gain initial entry into a
network. Afterward, they move laterally to gain access to as many nodes of the
network as possible, allowing them to increase the magnitude of the disruption."
Last summer beverages company Lion, a major supplier of beer and milk in
Australia and New Zealand, was hit by a ransomware attack that caused
disruptions to manufacturing processes and customer service.
Japanese car maker Honda was also hit by ransomware last summer, which impacted
production operations at some plants in the United States.
Tech firms have long issued warnings that industrial control systems that power
manufacturing plants and utilities are prime targets for ransomware attacks. In
a December 2020 report from IBM and industrial cybersecurity firm Dragos,
researchers noted that ransomware attacks against industrial entities jumped
more than 500 percent over the last two years.
Another French hospital hit by a ransomware attack
10.3.2021
Ransomware
Securityaffairs
A ransomware attack hit the Oloron-Sainte-Marie hospital in southwest France, it
is the third such attack in the last month.
A ransomware attack paralyzed the
systems at the Oloron-Sainte-Marie hospital in southwest France. The incident
took place on Monday, the ransomware gang is demanding the payment of a ransom
of $50,000 worth of Bitcoin.
The infection was first discovered by Rémi Rivière, an engineer in charge of all
the installations, on March 8 afternoon. In response to the attack, the IT staff
took offline part of the hospital network to prevent the spread of the malware.
“We reacted as quickly as possible. This virus is of the Ransomware type, the
same one that hit the Dax hospital a month ago. Hackers enter the hospital’s
computer system and encrypt all the data which makes them unreadable for our
services and then sends a ransom demand message in exchange for their original
return.“ said a spokesman for the hospital.
Attacks against hospitals and
health care organizations are very dangerous, especially during the ongoing
pandemic, At the time of the attack, the French hospital was taking part in
vaccination efforts against Covid-19.
The operations were heavily impacted by the ransomware attack, digital patient
records are not available, and forced the personnel to work with pens and paper.
The infection also affected the system used to monitor medicine stocks and other
supplies.
“We might get our systems back in 48 hours or in three months,” hospital
director Frederic Lecenne told local newspaper La Republique des Pyrenees.
In February, two other hospitals in France were hit with ransomware attacks.
Disruptions at Pan-American Life Likely Caused by Ransomware Attack
9.3.2021
Ransomware
Securityweek

Recent service disruptions at the Pan-American Life Insurance Group (PALIG) were
likely caused by a cyberattack conducted by a threat actor known for using the
REvil ransomware.
New Orleans-based PALIG provides life, accident and health insurance services
across the Americas. The group has more than 20 member companies and employs
roughly 2,000 people worldwide.
The official website of PALIG (palig.com) currently only displays some contact
information and the following message: “Pan-American Life Insurance Group is
currently experiencing a disruption to some of our services and we are working
to restore them. To facilitate communication during this time, we have created
temporary email accounts as an official communication channel.”
Cybersecurity researcher Anis Haboubi noticed over the weekend that a Tor-based
website operated by a cybercrime group that uses the ransomware known as REvil
(Sodinokibi) claimed to have stolen 170 GB of files as a result of breaching the
company.

The REvil ransomware is designed to encrypt files on infected systems and
instruct the victim to pay a ransom to recover them. The cybercriminals in many
cases also steal data from victims to increase their chances of getting paid —
victims are told that their files will be made public if they don’t pay up. They
are known to demand tens of millions of dollars from some of their victims.
Haboubi told SecurityWeek that in the case of the Pan-American Life Insurance
Group, the compromised files appeared to include financial reports covering all
PALIG regions, as well as health-related data.
At the time of writing, PALIG is no longer listed on the REvil leak website,
which Haboubi believes could be a sign that the company is in the process of
negotiating with the cybercriminals.
SecurityWeek has reached out to PALIG for more information on the incident and
will update this article if the company responds.
UPDATE: PALIG has provided the following statement:
We recently took our systems offline after we detected suspicious activity. This
has caused a disruption to our regular services and systems. We are taking the
matter very seriously and investigating the activity quickly and thoroughly with
the help of internal and external experts. We take the security of the data we
maintain with the utmost degree of seriousness and our investigation is ongoing.
We will take appropriate steps once we have sufficient and meaningful
information to enable those steps. Despite the systems disruption, we have
continued to service our customers and are focusing on bringing our systems back
online responsibly.
Managed Services provider CompuCom by Darkside ransomware
6.3.2021
Ransomware
Securityaffairs
US managed service provider CompuCom was the victim of a cyberattack that
partially disrupted its operations, experts believe it was a ransomware attack.
US managed service provider CompuCom was the victim of a cyberattack that
partially disrupted its services and some of its operations. Even if the company
initially did not provide technical details about the attack, security experts
speculated the involvement of ransomware due to the observed effects.
The provider is a wholly-owned subsidiary of The ODP Corporation, it provides
Managed Workplace Services including IT solutions and hardware and software
resale, integration, and support services.
According to BleepingComputer,
the company was the victim of a ransomware attack conducted by the Darkside
ransomware gang.
“Certain CompuCom information technology systems have been
affected by a malware incident which is affecting some of the services that we
provide to certain customers. Our investigation is in its early stages and
remains ongoing. We have no indication at this time that our customers’ systems
were directly impacted by the incident.” reads the statement launched by the
company.
“As soon as we became aware of the situation, we immediately took steps to
contain it, and engaged leading cybersecurity experts to begin an investigation.
We are also communicating with customers to provide updates about the situation
and the actions we are taking. We are in the process of restoring customer
services and internal operations as quickly and safely as possible. We regret
the inconvenience caused by the interruption and appreciate the ongoing support
of our customers.“
CompuCom confirmed that its systems were infected with
malware that impacted its services, the provider immediately launched an
investigation into the incident.
At the time of this writing, the ongoing investigation did not provide any
evidence that customers’ systems were directly impacted by the attack.
CompuCom later shared a ‘Customer FAQ Regarding Malware Incident’ that provides
additional technical details about the attack, such as the use of Cobalt Strike
beacons on several systems in their environment.
“Based on our expert’s analysis to date, we understand that the attacker
deployed a persistent Cobalt Strike backdoor to several systems in the
environment and acquired administrative credentials,” the CompuCom FAQ reads,
according to BleepingComputer. “These administrative credentials were then used
to deploy the Darkside Ransomware.”
DarkSide Ransomware gang usually steals data before encrypting the victims’
systems, which means that it is possible that the threat actors have also
exfiltrated company data.
At the time of this writing, the data from CompuCom has yet to be published on
the DarkSide gang’s leak site.
Group-IB: ransomware empire prospers in pandemic-hit world. Attacks grow by 150%
5.3.2021
Ransomware
Securityaffairs
Group-IB published a report titled “Ransomware Uncovered 2020-2021”. analyzes
ransomware landscape in 2020 and TTPs of major threat actors.
Group-IB, a
global threat hunting and adversary-centric cyber intelligence company, has
presented its new report “Ransomware Uncovered 2020-2021”. The research dives
deep into the global ransomware outbreak in 2020 and analyzes major players’
TTPs (tactics, techniques, and procedures).
By the end of 2020, the ransomware market, fuelled by the pandemic turbulence,
had turned into the biggest cybercrime money artery. Based on the analysis of
more than 500 attacks observed during Group-IB’s own incident response
engagements and cyber threat intelligence activity, Group-IB estimates that the
number of ransomware attacks grew by more than 150% in 2020, with many restless
players having joined the Big Game Hunting last year.
In 2020, ransomware attacks on average caused 18 days of downtime for the
affected companies, while the average ransom amount increased almost twofold.
Ransomware operations turned into robust competitive business structures going
after large enterprises, with Maze, Conti, and Egregor gangs having been at the
forefront last year. North America, Europe, Latin America, and the Asia-Pacific
became the most commonly attacked regions respectively.
To keep the cybersecurity professionals up to date with how ransomware gangs
operate and help the defense teams thwart their attacks, Group-IB’s DFIR team
has for the first time mapped the most commonly used TTPs in 2020 in accordance
with MITRE ATT&CK®. If you are a cybersecurity executive, make sure your
technical team receives a copy of this report for comprehensive threat hunting
and detection tips.

The gold rush of 2020
COVID-19 made many organizations, distracted with mitigating the fallout from
the pandemic, vulnerable to cyber threats. Ransomware turned out to be the one
that capitalized on the crisis most. The attacks not only grew in numbers (more
than 150%) but also in scale and sophistication – the average ransom demand
increased by more than twofold and amounted to $170,000 in 2020. The norm seems
to be shifting toward the millions. Group-IB DFIR team found out that Maze,
DoppelPaymer, and RagnarLocker were the greediest groups, with their ransom
demands averaging between $1 million and $2 million.
On a technical level, public-facing RDP servers were the most common target for
many ransomware gangs last year. Against the backdrop of the pandemic that
caused many people to work from home, the number of such servers grew
exponentially. In 52% of all attacks, analyzed by Group-IB DFIR team, publicly
accessible RDP servers were used to gain initial access, followed by phishing
(29%), and exploitation of public-facing applications (17%).
Big Game Hunting – targeted ransomware attacks against wealthy enterprises –
continued to be one of the defining trends in 2020. In hope to secure the
biggest ransom possible, the adversaries were going after large companies. Big
businesses cannot afford downtime, averaging 18 days in 2020. The operators were
less concerned about the industry and more focused on scale. It’s no surprise
that most of the ransomware attacks, that Group-IB analyzed, occurred in North
America and Europe, where most of the Fortune 500 firms are located, followed by
Latin America and the Asia-Pacific respectively.
A chance of easy money prompted many gangs to join the Big Game Hunting.
State-sponsored threat actors who were seen carrying out financially motivated
attacks were not long in coming. Groups such as Lazarus and APT27 started to use
ransomware during their operations.
Conti, Egregor, and DarkSide all joined the ransomware gold rush in 2020. Many
of them were so prolific that they made it to the top of the most active gangs
in their debut year. The top 5 most active ransomware families, according to
Group-IB, were Maze, Conti, Egregor, DoppelPaymer, and REvil. Not all of them
lasted for long for various reasons.

The growing threat of ransomware has put it in the spotlight of law enforcement.
Some gangs operating under the Ransomware-as-a-Service (RaaS) model, such as
Egregor and Netwalker, were impacted by the police efforts. Another notorious
RaaS collective, Maze, called it quits at the end of 2020. Despite these events,
the ransomware business continues prospering, with the Ransomware-as-a-Service
model being of the driving forces behind this phenomenal growth.
Very organized crime
Ransomware-as-a-Service involves the developers selling/leasing malware to the
program affiliates for further network compromise and ransomware deployment. The
profits are shared between the operators and program affiliates. This business
model with everyone focusing on what they do best can generate millions as the
earnings are only limited to the number of affiliates the operators can attract.
Group-IB DFIR team observed that 64% of all ransomware attacks it analyzed in
2020 came from operators using the RaaS model.
The prevalence of affiliate programs in the underground was the underlying trend
of 2020. Group-IB Threat Intelligence & Attribution system recorded the
emergence of 15 new public ransomware affiliate programs last year.

Mortal Combo: most common TTPs
With the rise of ransomware in 2020, cybercrime actors who use commodity malware
such as Trickbot, Qakbot, and Dridex helped many ransomware operators to obtain
initial access to target networks more and more often. Last year, a lot of
botnet operators partnered with ransomware gangs.

It’s important to detect malware like Trickbot at the early stages to prevent
the data from being encrypted before the attackers move laterally. Most of these
commodity malware families are capable to perform their activities silently and
can hide from traditional sandboxing solutions without raising the flag.
Advanced malware detonation platforms allow detecting such threats by performing
behavior analysis of emails, files, and links. It is crucial to extract and
fully detonate discovered payloads in a safe isolated environment, harvesting
indicators of compromise that help in subsequent threat hunting activities.
PowerShell was the most frequently abused interpreter for launching the initial
payload. Its popularity among the attackers is explained by the fact that the
interpreter is part of every Windows-based system, hence it’s easier to disguise
malicious activity. Another theme of 2020, however, was the active exploitation
of Linux with some threat actors adding corresponding versions to their arsenal.
In the credential access stage, threat actors often used brute force withNLBrute
and Hydra being the most popular tools, based on Group-IB’s IR engagements. To
obtain valid privileges, ransomware operators in 2020 often used credential
dumping – retrieving all the passwords from the machine. The attackers’ favorite
tools here were ProcDump, Mimikatz, and LaZagne.
Based on Group-IB’s DFIR team observations, in 2020, ransomware operators spent
13 days on average in the compromised network before encrypting data for impact.
Before deploying ransomware, operators did their best to find and remove any
available backups, so that it would be impossible for the victim to recover
encrypted files. Another factor, which allowed the gangs to ensure a higher
success rate, was the exfiltration of critical data to use it as a leverage to
increase the chances of the ransom being paid – the trend set by the infamous
Maze collective.
“The pandemic has catapulted ransomware into the threat landscape of every
organization and has made it the face of cybercrime in 2020,” says Oleg Skulkin,
senior digital forensics analyst at Group-IB. “From what used to be a rare
practice and an end-user concern, ransomware has evolved last year into an
organized multi-billion industry with competition within, market leaders,
strategic alliances, and various business models. This successful venture is
only going to get bigger from here. Due to their profitability, the number of
RaaS programs will keep growing, more cybercriminals will focus on gaining
access to networks for resale purposes. Data exfiltration effectiveness can make
it another big niche, with some actors abandoning the use of ransomware at all.
Growing ransom demands will be accompanied by increasingly advanced techniques.
Given that most attacks are human-operated it is paramount for organizations to
understand how attackers operate, what tools they use in order to be able to
counter ransomware operators’ attacks and hunt for them proactively. It is
everyone’s concern now.”
The full technical analysis of the adversaries’ TTPs mapped to and organized in
accordance with MITRE ATT&CK® as well as threat hunting and detection tips put
together by Group-IB Digital Forensics and Incident Response (DFIR) team, is
available in the new report “Ransomware Uncovered 2020-2021”.
RTM Cybergang Adds New Quoter Ransomware to Crime Spree
4.3.2021
Ransomware
Threatpost
The Russian-speaking RTM threat group is targeting organizations in an ongoing
campaign that leverages a well-known banking trojan, brand new ransomware strain
and extortion tactics.
The Russian-speaking group behind the infamous RTM banking trojan is now packing
a trifecta of threats as it turns up the heat – part of a massive new money-grab
campaign. Beyond the banking malware it is known for, attackers have enlisted a
recently-discovered ransomware family called Quoter as part of a new
double-extortion cyberattack strategy.
The triple-threat attack, which started its “active phase” in December 2020 and
is ongoing, has hit at least ten Russian organizations in the transport and
finance sectors via malicious email messages, according to Kaspersky in a report
released this week.
Should the money-stealing tactics of RTM group’s hallmark
Trojan-Banker.Win32.RTM payload fail, the attackers have a backup plan. Plan “B”
is deploy a never-before-seen ransomware family, which researchers are calling
Quoter. The name Quoter is derived from the fact the ransomware code embeds
quotes from popular movies. Next, if attackers hit a brick wall, they try to
extort money from victims, threatening that they will release breached data
stolen from the targets if they don’t pay up.
“What’s remarkable about this story is the evolution of the group behind the RTM
ransomware,” according to a translation of Kaspersky’s research report. They
said the group has gone far beyond its tried-and-true methods of “making money”
– via extortion and doxing. They added, it’s unusual for Russian-speaking
cybercriminals to attack organizations in Russia, although, the ransomware is
also used in targeted attacks outside the country.
RTM Email Attack: Downloading RTM Trojan
Kaspersky said that the initial
infection phase of the campaign initially hit corporations back in mid-2019,
when several companies reported receiving various phishing emails with
corporate-themed headings. These included subject lines that included such terms
as “Subpoena,” “Request for refund,” “Closing documents” or “Copies of documents
for the last month.”
The text of the email was brief and asked email recipients to open an attached
file for more detailed information. If the email recipient opened the
attachment, Trojan-Banker.Win32.RTM was installed.
The Trojan-Banker.Win32.RTM (also known as the RTM Trojan) is a popular banking
trojan. According to a Kaspersky report in November, Trojan-Banker.Win32.RTM was
the fifth most popular banking malware family in the third quarter of 2020,
taking 7.4 percent of the share behind Emotet, Zbot and more.
As in this attack, the malware is typically distributed via malicious emails
(using messages disguised as accounting or finance correspondence) and once
installed provides attackers with full control over the infected systems.
After initial infection, attackers used legitimate remote access programs, to
avoid detection, for lateral movement within companies’ local networks. These
programs include LiteManager, remote control and administration software for
Windows, Linux and MacOS.
Once downloaded, the RTM trojan typically substitutes account details, while a
victim attempts to make a payment or transfer funds. According to Kaspersky, the
RTM trojan can also be used by attackers to manually transfer money from
victim’s accounts using remote access tools.
Quoter Ransomware
Should the banking trojan’s methods fail, researchers found
that attackers used their initial foothold on systems in order to deploy a
never-before-seen ransomware, which they called Ransom.Win32.Quoter.
The ransomware encrypted the contents of computers, using the AES-256 CBC
algorithm, and left a message demanding a ransom. The code of these encrypted
file included several quotes from popular movies.
Researchers said, “by this time, several months had passed since the RTM had
been consolidated in the organization’s network.”
Threatpost has reached out to Kaspersky researchers for further information on
the Quoter ransomware and will update this report if possible.
Double-Extortion Tactics
If victims failed to pay the ensuing ransom demand,
attackers have yet another trick up their sleeves. Here, the RTM group relied on
a ransomware tactic called double extortion. They hold compromised data for
ransom and threaten to release or leak it if the victims don’t pay up.
“If the backup plan did not work for one reason or another, then after a couple
of weeks the attackers switched to blackmail,” said researchers.
Victims receive a message that their data has been stolen a would cost a million
dollars (in Bitcoin) to return – or the confidential data would be posted on the
internet for free download.
Double extortion is an increasingly popular tactic amongst ransomware actors.
The tactic, which first emerged in late 2019 by Maze operators, has been rapidly
adopted over the past few months by various cybercriminals behind the Clop,
DoppelPaymer and Sodinokibi ransomware families.
Clop ransomware gang leaks data allegedly stolen from cybersecurity firm Qualys
4.3.2021
Ransomware
Securityaffairs
Cybersecurity firm Qualys seems to have suffered a data breach, threat actors
allegedly exploited zero-day flaw in their Accellion FTA server.
Cybersecurity firm Qualys is the latest victim of a cyber attack, the company
was likely hacked by threat actors that exploited a zero-day vulnerability in
their Accellion FTA server.
A couple of weeks ago, security experts from FireEye linked a series of cyber
attacks against organizations running Accellion File Transfer Appliance (FTA)
servers to the cybercrime group UNC2546, aka FIN11.
“Starting in mid-December 2020, malicious actors that Mandiant tracks as UNC2546
exploited multiple zero-day vulnerabilities in Accellion’s legacy File Transfer
Appliance (FTA) to install a newly discovered web shell named DEWMODE.” reported
FireEye. “The motivation of UNC2546 was not immediately apparent, but starting
in late January 2021, several organizations that had been impacted by UNC2546 in
the prior month began receiving extortion emails from actors threatening to
publish stolen data on the “CL0P^_- LEAKS” .onion website. Some of the published
victim data appears to have been stolen using the DEWMODE web shell.”
The wave of attacks began in mid-December 2020, threat actors exploited multiple
zero-day vulnerabilities in the Accellion File Transfer Appliance (FTA) software
to deploy a shell dubbed DEWMODE on the target networks.
The attackers exfiltrate sensitive data from the target systems and then
published it on the CLOP ransomware gang’s leak site.
It has been estimated that the group has targeted approximately 100 companies
across the world between December and January.
FireEye pointed out that despite FIN11 hackers are publishing data from
Accellion FTA customers on the Clop ransomware leak site, they did not encrypt
systems on the compromised networks.
In response to the wave of attacks, the vendor has released multiple security
patches to address the vulnerabilities exploited by the hackers. The company is
also going to retire legacy FTA server software by April 30, 2021.
Recently other organizations were hit with the same technique, including
Transport for New South Wales, and Bombardier.
Now, Clop ransomware operators claimed to have stolen data from Qualys and
shared screenshots of stolen files on its leak site as proof of the hack.
The leaked data includes invoices, purchase orders, tax documents, and scan
reports.
According to LegMagIT and BleepingComputer, Qualys was using an Accellion FTA
server that was was located at fts-na.qualys.com since February 18th, 2021.
Ryuk Ransomware: Now with Worming Self-Propagation
3.3.2021
Ransomware
Threatpost
The Ryuk scourge has a new trick in its arsenal: Self-replication via SMB shares
and port scanning.
A new version of the Ryuk ransomware is capable of worm-like self-propagation
within a local network, researchers have found.
The variant first emerged in Windows-focused campaigns earlier in 2021,
according to the French National Agency for the Security of Information Systems
(ANSSI). The agency said that it achieves self-replication by scanning for
network shares, and then copying a unique version of the ransomware executable
(with the file name rep.exe or lan.exe) to each of them as they’re found.
“Ryuk looks for network shares on the victim IT infrastructure. To do so, some
private IP ranges are scanned: 10.0.0.0/8; 172.16.0.0/16; and 192.168.0.0/16,”
according to a recent ANSSI report. “Once launched, it will thus spread itself
on every reachable machine on which Windows Remote Procedure Call accesses are
possible.”
The fresh version of Ryuk also reads through infected devices’ Address
Resolution Protocol (ARP) tables, which store the IP addresses and MAC addresses
of any network devices that the machines communicate with. Then, according to
ANSSI, it sends a “Wake-On-LAN” packet to each host, in order to wake up
powered-off computers.
“It generates every possible IP address on local networks and sends an ICMP ping
to each of them,” according to ANSSI. “It lists the IP addresses of the local
ARP cache and sends them a [wake-up] packet.”
For each identified host, Ryuk will then attempt to mount possible network
shares using SMB, or Server Message Block, according to the report. SMB is a
Windows function that allows the sharing, opening or editing files with/on
remote computers and servers.
Once all of the available network shares have been identified or created, the
payload is then installed on the new targets and is self-executed using a
scheduled task, allowing Ryuk to encrypt the targets’ content and delete any
Volume Shadow Copies to prevent file recovery.
“The scheduled task is created through a call to the schtasks.exe system tool, a
native-Windows tool,” ANSSI explained.
The files are encrypted using Microsoft CryptoAPI with the AES256 algorithm,
using a unique AES key which is generated for each file. The AES key is also
wrapped with an RSA public key stored in the binary code, according to the
analysis.
The malware also interrupts multiple programs based on hardcoded lists,
including a list of 41 processes to be killed (task kill) and a list of 64
services to stop, ANSSI found.
How to Contain a Ryuk Worm Infection
As for avoiding infection, Ryuk
ransomware is usually loaded by an initial “dropper” malware that acts as the
tip of the spear in any attack; these include Emotet, TrickBot, Qakbot and
Zloader, among others. From there, the attackers look to escalate privileges in
order to set up for lateral movement.
An effective defense thus should involve developing countermeasures that will
prevent that initial foothold.
Once infected, things become more complicated. In the 2021 campaign observed by
ANSSI researchers, the initial infection point is a privileged domain account.
And the analysis shows that the worm-like spread of this version of Ryuk can’t
be thwarted by choking off this initial infection point.
“A privileged account of the domain is used for malware propagation,” according
to the report. “If this user’s password is changed, the replication will
continue as long as the Kerberos tickets [authentication keys] are not expired.
If the user account is disabled, the issue will remain the same.”
And on top of the self-propagation functions, this version of Ryuk also lacks
any exclusion mechanisms, meaning that there’s nothing preventing infections of
the same machine over and over again, which makes fumigation more difficult.
Previous versions of the malware used Mutual Exclusion Objects (MUTEX) to make
sure that any given host had access to only one Ryuk process at a time.
“As the malware does not check if a machine has already been infected, no simple
system object creation that could prevent infection,” according to the ANSSI
report.
One way to tackle an active infection, ANSSI recommended, would be to change the
password or disable the account for the privileged user, and then proceed to
force a domain password change through KRBTGT. The KRBTGT is a local default
account found in Active Directory that acts as a service account for the Key
Distribution Center (KDC) service for Kerberos authentication.
“This would induce many disturbances on the domain – and most likely require
many reboots – but would also immediately contain the propagation,” according to
ANSSI.
Ryuk: A Many-Headed Beast
The Ryuk ransomware was first observed in August
2018, as a variant of the Hermes 2.1 ransomware. But unlike Hermes, it’s not
peddled on underground markets like the Exploit forum.
“A doubt…remains as to the origins of Ryuk,” according to ANSSI’s report. “The
appearance of Ryuk could…be a result of the acquisition of the Hermes 2.1 source
code by another attacker group, which may have developed Ryuk from this starting
point.”
Deloitte researchers have theorized that Ryuk is sold as a toolkit to attacker
groups, which use it to develop their own “flavors” of the ransomware. There
could therefore be as many variants as there are attacker groups that buy the
code.
In early 2021, it was estimated that Ryuk operators have raked in at least $150
million, according to an examination of the malware’s money-laundering
operations.
Distributor of Asian food JFC International hit by Ransomware
3.3.2021
Ransomware
Securityweek
JFC International, a major wholesaler and distributor of Asian food products in
the United States, was hit by ransomware.
JFC International, a major
distributor and wholesaler of Asian food products, announced it has recently
suffered a ransomware attack.
The ransomware attack only impacted JFC International’s Europe Group, the
malware caused the disruption of some of its IT systems.
“JFC International (Europe) was recently subject to a ransomware attack that
briefly disrupted its IT systems. A full forensic investigation by inhouse
specialists together with external cyber experts was immediately started and is
underway. Normal conduct of business in Europe will be up and running after a
brief interruption for security reasons.” reads a press release published by the
company. “The affected servers were secured. JFC International (Europe) is
cooperating closely with the relevant authorities.”
The company notified relevant authorities and reported the security incident to
employees and business partners.
The company is investigating the intrusion with the help of external cyber
experts, it announced that the affected servers were already secured.
At the time of this writing, it is not clear which is the family of ransomware
involved in the attack and whether any information was stolen by the attackers.
Researchers Unearth Links Between SunCrypt and QNAPCrypt Ransomware
3.3.2021
Ransomware
Thehackernews
SunCrypt, a ransomware strain that went on to infect several targets last year,
may be an updated version of the QNAPCrypt ransomware, which targeted
Linux-based file storage systems, according to new research.
"While the two ransomware [families] are operated by distinct different threat
actors on the dark web, there are strong technical connections in code reuse and
techniques, linking the two ransomware to the same author," Intezer Lab
researcher Joakim Kennedy said in a malware analysis published today revealing
the attackers' tactics on the dark web.
First identified in July 2019, QNAPCrypt (or eCh0raix) is a ransomware family
that was found to target Network Attached Storage (NAS) devices from Taiwanese
companies QNAP Systems and Synology. The devices were compromised by
brute-forcing weak credentials and exploiting known vulnerabilities with the
goal of encrypting files found in the system.
The ransomware has since been tracked to a Russian cybercrime group referred to
as "FullOfDeep," with Intezer shutting down as many as 15 ransomware campaigns
using the QNAPCrypt variant with denial of service attacks targeting a list of
static bitcoin wallets that were created for the express intent of accepting
ransom payments from victims, and prevent future infections.
SunCrypt, on the other hand, emerged as a Windows-based ransomware tool written
originally in Go in October 2019, before it was ported to a C/C++ version in
mid-2020. Besides stealing victims' data prior to encrypting the files and
threatening with public disclosure, the group has leveraged distributed
denial-of-service (DDoS) attacks as a secondary extortion tactic to pressure
victims into paying the demanded ransom.
Most recently, the ransomware was deployed to target a New South Wales-based
medical diagnostics company called PRP Diagnostic Imaging on December 29, which
involved the theft of "a small volume of patient records" from two of its
administrative file servers.

Although the two ransomware families have directed their attacks against
different operating systems, reports of SunCrypt's connections to other
ransomware groups have been previously speculated.
Indeed, blockchain analysis company Chainalysis earlier last month quoted a
"privately circulated report" from threat intelligence firm Intel 471 that
claimed representatives from SunCrypt described their strain as a "rewritten and
rebranded version of a 'well-known' ransomware strain."
Now according to Intezer's analysis of the SunCrypt Go binaries, not only does
the ransomware share similar encryption functions with QNAPCrypt, but also in
the file types encrypted and the methods used to generate the encryption
password as well as perform system locale checks to determine if the machine in
question is located in a disallowed country.
Also of note is the fact that both QNAPCrypt and SunCrypt make use of the
ransomware-as-a-service (RaaS) model to advertise their tools on underground
forums, wherein affiliates carry out the ransomware attacks themselves and pay a
percentage of each victim's payment back to the strain's creators and
administrators.
Taking into account the overlaps and the behavioral differences between the two
groups, Intezer suspects that "the eCh0raix ransomware was transferred to and
upgraded by the SunCrypt operators."
"While the technical based evidence strongly provides a link between QNAPCrypt
and the earlier version of SunCrypt, it is clear that both ransomware are
operated by different individuals," the researchers concluded.
"Based on the available data, it is not possible to connect the activity between
the two actors on the forum. This suggests that when new malware services
derived from older services appear, they may not always be operated by the same
people."
Ryuk Ransomware With Worm-Like Capabilities Spotted in the Wild
2.3.2021
Ransomware
Securityweek
In early 2021, security researchers identified a variant of the infamous Ryuk
ransomware that is capable of lateral movement within the infected networks.
Active since at least 2018 and believed to be operated by Russian
cyber-criminals, the Ryuk ransomware has been involved in numerous high-profile
attacks and researchers estimate the enterprise is worth $150 million.
Ryuk has long been associated with the TrickBot malware, supposedly being
operated by the same gang. However, the ransomware’s operations have continued
even after a TrickBot takedown attempt by Microsoft and other organizations.
Sometimes also distributed through Emotet, Ryuk has been heavily reliant on
BazarLoader for distribution since September 2020, with phishing emails used as
the attack vector.
In a recently published report, the French National Agency for the Security of
Information Systems (ANSSI) said that it identified one Ryuk sample that could
spread automatically within infected networks earlier this year.
The ransomware has long relied on the use of other malware for the initial
deployment and did not show signs of worm-like capabilities before, although it
was able to encrypt data on network shares and removable drives.
Ryuk uses a combination of symmetric (AES) and asymmetric (RSA) algorithms for
encryption, kills specific processes on the infected system, appends the .RYK
extension to the encrypted files, can turn on workstations using the Wake-on-LAN
feature, and destroys all shadow copies to prevent data recovery.
The newly identified version of Ryuk has all of the functions typically found
within the ransomware, with the ability to replicate itself over the local
network added on top.
To propagate to other machines, the ransomware copies the executable on
identified network shares with a rep.exe or lan.exe suffix, after which it
creates a scheduled task on the remote machine.
“Through the use of scheduled tasks, the malware propagates itself - machine to
machine - within the Windows domain. Once launched, it will thus spread itself
on every reachable machine on which Windows RPC accesses are possible,” ANSSI
explains.
The French agency also notes that the identified sample does not appear to
include a mechanism for blocking its execution, meaning that the same device
could be re-infected over and over again.
Asian Food Distribution Giant JFC International Hit by Ransomware
2.3.2021
Ransomware
Securityweek
JFC International, a major distributor and wholesaler of Asian food products,
last week revealed that it was recently targeted in a ransomware attack that
disrupted some of its IT systems.
The attack apparently only impacted JFC International’s Europe Group, which said
it had notified authorities, employees and business partners about the incident.
“A full forensic investigation by in-house specialists together with external
cyber experts was immediately started and is underway. Normal conduct of
business in Europe will be up and running after a brief interruption for
security reasons. The affected servers were secured,” the company said in a
statement posted on its European website.
SecurityWeek has reached out to JFC for more information on the type of
ransomware involved in the attack and to find out whether any information was
compromised. It is possible that the attackers also gained access to some
information given that the company described it as a “data security incident.”
JFC International, a subsidiary of Japanese food manufacturer Kikkoman, has been
around in various forms for more than a century. In addition to importing
branded products from other companies, JFC offers its own products to retailers
and restaurants.
Hotarus Corp gang hacked Ecuador’s Ministry of Finance and Banco Pichincha
28.2.2021
Ransomware
Securityaffairs
‘Hotarus Corp’ Ransomware operators hacked Ecuador’s largest private bank, Banco
Pichincha, and the country’s Ministry of Finance.
A cybercrime group called
‘Hotarus Corp’ has breached the Ecuador’s largest private bank, Banco Pichincha,
and the local Ministry of Finance (the Ministerio de Economía y Finanzas de
Ecuador).
The group claims to have also stolen data from the Banco Pichincha bank and
infected a system at Ministry of Finance using for training purposes with
PHP-based ransomware.
An alleged member of the @HotarusCorp leaked on a hacking forum a link to a file
containing 6500 records (Email, Identity Card numbers, and passwords) that
claims to Ministry of Finance.

The bank published an official statement to confirm the security intrusion.
“We know that there was unauthorized access to the systems of a provider that
provides marketing services for the Pichincha Miles program. In relation to this
information leak, and based on an extensive investigation, we have found no
evidence of damage or access to the Bank’s systems and, therefore, the security
of our clients’ financial resources is not compromised.” reads the statement.
“We know that, through a fraudulent email, the attacker sends communications on
behalf of Banco Pichincha to some clients of said program in order to obtain
information necessary to carry out illegitimate transactions. We remind our
clients that we never request sensitive data such as: users, passwords, card or
account data, via telephone, email, social networks or text messages.”
Security researcher Germán Fernández confirmed the compromise of the Equador’s
Ministry of Finance via Twitter.

Fernandez revealed that the PHP ransomware employed in the attack is
Ronggolawe/AwesomeWare.
The bank has confirmed the attack in an official statement but states that it
was a hacked marketing partner and not their internal systems.
New Ryuk ransomware implements self-spreading capabilities
27.2.2021
Ransomware
Securityaffairs
French experts spotted a new Ryuk ransomware variant that implements
self-spreading capabilities to infect other devices on victims’ local networks.
Experts from French national cyber-security agency ANSSI have spotted a new Ryuk
ransomware variant that implements worm-like capabilities that allow within
local networks.
“On top of its usual functions, this version holds a new attribute allowing it
to self replicate over the local network.” reads the report published by the
ANSSI. “Through the use of scheduled tasks, the malware propagates itself –
machine to machine – within the Windows domain. Once launched, it will thus
spread itself on every reachable machine on which Windows RPC accesses are
possible.”
This Ryuk ransomware variant doesn’t include any mechanism for blocking the
execution of the ransomware (MUTEX like or else), it copies itself with a
rep.exe or lan.exe suffix.
The ransomware generates every possible IP address on local networks and sends
them an ICMP ping. It lists the IP addresses of the local ARP cache and sends
them a packet, then it lists all the sharing resources opened on the found IPs,
mounts each of them, and attempts to encrypt their content. This variant is also
able to remotely create a scheduled task to execute itself on this host.
Scheduled tasks are created using the Windows native tool schtasks.exe.
“The Ryuk variant analyzed in this document does have self-replication
capabilities. The propagation is achieved by copying the executable on
identified network shares. This step is followed by the creation of a scheduled
task on the remote machine.” continues the report. “The content of this
scheduled task is described in the analysis present in this document. Some
filenames were identified for this copy: rep.exe and lan.exe. Finally, Ryuk
deletes the Volume Shadow Copies to prevent file recovery.”
The ransomware achieves persistence by setting the registry key
HKEY_CURRENT_USER\SOFTWARE\Microsoft
\Windows\CurrentVersion\Run\svchost with
its filepath.
ANSSI report revealed that the ransomware does not check if a machine has
already been infected, the malicious code uses a privileged account of the
domain for its propagation. French experts pointed out that even if the user’s
password is changed, the replication will continue as long as the Kerberos
tickets are not expired.
“One way to tackle the problem could be to change the password or disable the
user account (according to the used account) and then proceed to a double KRBTGT
domain password change. This would induce many disturbances on the domain – and
most likely require many reboots but would also immediately contain the
propagation.” continues the report.
ANSSI also provided Indicators of compromise (IOCs) associated with this new
Ryuk ransomware variant.
Dutch Research Council (NWO) confirms DoppelPaymer ransomware attack
27.2.2021
Ransomware
Securityaffairs
Dutch Research Council (NWO) confirmed that the recent cyberattack that forced
it to take its servers offline was caused by the DoppelPaymer ransomware gang.
On February 14, Dutch Research Council (NWO) was hit by a cyber attack that
compromised its network and impacted its operations.
In response to the incident, the Dutch Research Council (NWO) was forced to take
its servers offline.
The attackers stole documents from the NWO and demanded a ransom to avoid
leaking them online, but the research council refused to pay.
“On 8 February,
the DoppelPaymer hacker group gained access to the NWO network. As part of the
Dutch national government, NWO does not address the demands of criminals on
grounds of principle. That is why DoppelPaymer started on 24 February to leak
internal NWO documents from the past years on the dark web.” reads an update
published by the company.
“Although NWO deeply regrets that data of its own employees are now being made
public unauthorized, this does not change this choice. This will mean that
stolen files may be made public again soon.”
Now the Dutch Research Council (NWO) confirmed that the family of ransomware
involved in the attack was DoppelPaymer.
“The Dutch Research Council (NWO
Dutch: Nederlandse Organisatie voor Wetenschappelijk Onderzoek) is the national
research council of the Netherlands. NWO funds thousands of top researchers at
universities and institutes and steers the course of Dutch science by means of
subsidies and research programmes. NWO promotes quality and innovation in
science. NWO is an independent administrative body under the auspices of the
Dutch Ministry of Education, Culture and Science. NWO directs its approximate
budget of 1 billion euros towards Dutch universities and institutes, often on a
project basis.” states Wikipedia about the organization.
This week, the DoppelPaymer ransomware operators started leaking a batch of
files stolen from the NWO network as proof of the hack.

The NWO confirmed that the hackers compromised network disks containing the data
processed by some internal offices and other organizations such as the TKI-HTSM,
TKI Chemie, European Polar Board, and the LNVH.
“The network disks containing the data processed by NWO, the NWO-I office, SIA
and NRO. It also contains the mail servers of NWO, office NWO-I, SIA and NRO.
Furthermore, links with various external applications have gone wrong or have
been closed.” states the organization in FAQ page.
The NWO staff is still working on restoring the operations, the activity is
expected to go on for a few weeks.
The list of victims of the DoppelPaymer ransomware is long and includes Bretagne
Télécom. Compal, the City of Torrance (California), Hall County in Georgia,
Newcastle University, and PEMEX (Petróleos Mexicanos).
Airplane manufacturer Bombardier has disclosed a security breach, data leaked
online
25.2.2021
Ransomware
Securityaffairs
Hackers posted data stolen from manufacturer of business jets Bombardier on Clop
ransomware leak site following alleged FTA hack.
Hackers exploited
vulnerabilities in Accellion FTA file-sharing legacy servers to steal data from
the airplane maker Bombardier and leak data on the site operated by the Clop
ransomware gang.
Bombardier Clop ransomware
The wave of attacks exploiting multiple zero-day
vulnerabilities in the Accellion File Transfer Appliance (FTA) software began in
mid-December 2020, threat actors use to deploy a shell dubbed DEWMODE on the
target networks. Security experts from FireEye linked the cyber attacks to the
cybercrime group UNC2546, aka FIN11. The attackers exfiltrate sensitive data
from the target systems and then published it on the CLOP ransomware gang’s leak
site.
It has been estimated that the group has targeted approximately 100 companies
across the world between December and January.
Bombardier disclosed a security breach after some of its data was published on a
dark web portal operated by the Clop ransomware gang.
“Bombardier announced today that it recently suffered a limited cybersecurity
breach.” reads a statement published by the company. “An initial investigation
revealed that an unauthorized party accessed and extracted data by exploiting a
vulnerability affecting a third-party file-transfer application, which was
running on purpose-built servers isolated from the main Bombardier IT network.”
The company notified appropriate authorities and hired cybersecurity and
forensic professionals to investigate the incident.
The experts determined that personal and other confidential information relating
to employees, customers and suppliers was compromised. The investigation
indicates that the attackers had access only to data stored on the specific
servers.
“Approximately 130 employees located in Costa Rica were impacted. Bombardier has
been proactively contacting customers and other external stakeholders whose data
was potentially compromised. The ongoing investigation indicates that the
unauthorized access was limited solely to data stored on the specific servers.”
continues the statement.
Bombardier pointed out that manufacturing and customer support operations have
not been impacted.
The press release did not mention Accellion FTA servers, but confirmed that the
company was hit as part of a campaign that targeted multiple organizations
exploiting a vulnerability in an unnamed application.
Another circumstance that suggests the exploitation of the flaws in FTA servers
was that the company systems were not encrypted with the Clop ransomware. The
attack scenario is the one recently described by FireEye that linked the attack
to the cybercrime gang FIN11.
Below a press release published by Accellion this week.
“Accellion does not access the information that its customers transmit via FTA.
Following the attack, however, Accellion has worked at many customers’ request
to review their FTA logs to help understand whether and to what extent the
customer might have been affected. As a result, Accellion has identified two
distinct groups of affected FTA customers based on initial forensics. Out of
approximately 300 total FTA clients, fewer than 100 were victims of the attack.
Within this group, fewer than 25 appear to have suffered significant data theft.
Within this group, fewer than 25 appear to have suffered significant data
theft.” reads the press release published by Accellion.
“These exploits apply exclusively to Accellion FTA clients: neither kiteworks
nor Accellion the company were subject to these attacks.”
Finnish IT Giant Hit with Ransomware Cyberattack
24.2.2021
Ransomware
Threatpost
A major Finnish IT provider has been hit with a ransomware attack that has
forced the company to turn off some services and infrastructure in a disruption
to customers, while it takes recovery measures.
Norwegian business journal E24 reported the attack on Espoo, Finland-based
TietoEVRY on Tuesday, claiming to have spoken with Geir Remman, a communications
director at the company. Remman acknowledged technical problems with several
services that TietoEVRY provides to 25 customers, which are “due to a ransom
attack,” according to the report.
Remman told E24 that the company considers the attack “a serious criminal act.”
TietoEVRY turned off the unspecified services and infrastructure affected “as a
preventative measure” until it can recover relevant data, and restart systems
“in a controlled manner,” he said.
However, at this time, it does not seem that any critical or personal data has
been accessed or stolen by the attackers, Remman added.
TietoEVRY is a software and service company providing IT and product engineering
services in 20 countries. The publicly traded company is listed on the NASDAQ
OMX Helsinki and Stockholm exchanges.
The company has informed customers of the incident and is in ongoing
communication with them as the situation unfolds, according to the report.
“TietoEVRY takes this incident very seriously, and apologizes for the
inconvenience this causes to our customers,” Christian Pedersen, managing
partner in Tietoevry Norway, said in a media statement. “We have activated an
extended team with the necessary capacity and competence, and are working with
relevant partners to handle the situation.”
Those partners include the National Security Authority (NSM) and NorCert, the
agencies in Finland who handle cyber attacks, which TietoEVRY immediately
contacted after the attack, Remman said, according to the report.
“We are in dialogue with the police about the case,” he told E24. “At the same
time, we recommend that customers also report the case to the police.”
Finland’s NSM confirmed that TietoEVRY contacted it and that the agency is
supporting the company in mitigating and investigating the incident, to “see if
similar malware has been used elsewhere,” spokeswoman Mona Strøm Arnøy told the
media. The NSM also will help the company restore its infrastructure, she said.
Saryu Nayyar, CEO at Gurucul, noted that most ransomware gangs are out of the
reach of law enforcement.
“While Finnish IT firm TietoEVRY may be able to recover effectively, it is
unlikely they will get justice even after involving the appropriate
law-enforcement organizations,” she told Threatpost. “Many of these cybercrime
gangs are international in scope and operate from locales that turn a blind eye
to crimes against foreign targets, if not tacitly support their activities. That
makes law enforcement’s job harder, and puts a greater burden on organizations
to keep their own defenses fully up to date and effective.”
At this time it’s not known which ransomware group is responsible for the
attack. Several have been active lately, including the Clop ransomware gang,
which has been linked to recent global zero-day attacks on users of the
Accellion legacy File Transfer Appliance product; DoppelPaymer, which hit Kia
Motors with an attack demanding $20 billion in ransom last week; and HelloKitty,
which is suspected to be behind the attack of CD Projekt Red, the
videogame-development company behind Cyberpunk 2077, earlier this month.
“The attacks on TietoEVRY should be a message to every enterprise with a public
facing internet exposure: You are being scanned for available hosts, network
port openings, vulnerabilities and misconfigurations,” Garret Grajek, CEO at
YouAttest, told Threatpost. “The hackers are opportunity-based. The malware that
is implanted is almost immaterial to the first phase of the cyber kill chain
(reconnaissance).”
He added, “Once an open server is deemed open, vulnerability scans are run on
the server/service to see what malware can be implanted. It can be a bot for
further spamming or exploration – or it could be trojans that continue the cyber
kill chain and enumerate your environment, escalate their privileges and move
across your enterprise. The final result may be a ransomware attack or an
exfiltration of data to be sold on the dark web.”
TietroEVRY did not immediately reply to an email by Threatpost Tuesday
requesting confirmation and details of the attack. The company is not publicly
speculating or revealing specifics until it investigates further, Pedersen told
E24.
This is a developing story.
Accellion FTA Zero-Day Attacks Show Ties to Clop Ransomware, FIN11
23.2.2021
Ransomware
Threatpost
The threat actors stole data and used Clop’s leaks site to demand money in an
extortion scheme, though no ransomware was deployed.
Researchers have identified a set of threat actors (dubbed UNC2546 and UNC2582)
with connections to the FIN11 and the Clop ransomware gang as the cybercriminal
group behind the global zero-day attacks on users of the Accellion legacy File
Transfer Appliance product.
Multiple Accellion FTA customers, including the Jones Day Law Firm, Kroger and
Singtel, have all been attacked by the group, receiving extortion emails
threatening to publish stolen data on the “CL0P^_- LEAKS” .onion website,
according to an investigation from Accellion and FireEye Mandiant. Around 100
companies have been victims of the attack, analysts found, with around 25
suffering “significant data theft.” No ransomware was used in the attacks.
“Notably, the number of victims on the “CL0P^_- LEAKS” shaming website has
increased in February 2021 with organizations in the United States, Singapore,
Canada and the Netherlands recently outed by these threat actors,” according to
the Mandiant findings, issued on Monday.
4 Accellion FTA Zero-Days
As noted, the point of entry for the attacks was
Accellion FTA, a 20-year-old legacy product used by large corporations around
the world. Accellion said that it became aware of a zero-day security
vulnerability in FTA in mid-December, which it scrambled to patch quickly. But
that turned out to be just one of a cascade of zero-days in the platform that
the company discovered only after they came under attack from cyber-adversaries.
“This initial incident was the beginning of a concerted cyberattack on the
Accellion FTA product that continued into January 2021,” the company explained.
“Accellion identified additional exploits in the ensuing weeks, and rapidly
developed and released patches to close each vulnerability.”
Four zero-day security holes were exploited in the attacks, according to the
investigation:
CVE-2021-27101 – SQL injection via a crafted Host header
CVE-2021-27102 – OS
command execution via a local web service call
CVE-2021-27103 – SSRF via a
crafted POST request
CVE-2021-27104 – OS command execution via a crafted POST
request
And, the published victim data appears to have been stolen using a
distinct “DEWMODE” web shell, according to Mandiant, which added, “The
exfiltration activity has affected entities in a wide range of sectors and
countries.”
DEWMODE Web Shell for Stealing Information
Mandiant found that a specific web
shell, which it calls DEWMODE, was used to exfiltrate data from Accellion FTA
devices. The adversaries first exploited one of the zero-days, then used that
access to install DEWMODE.
“Across these incidents, Mandiant observed common infrastructure usage and TTPs
[tactics, techniques and procedures], including exploitation of FTA devices to
deploy the DEWMODE web shell,” Mandiant determined. “A common threat actor we
now track as UNC2546 was responsible for this activity. While complete details
of the vulnerabilities leveraged to install DEWMODE are still being analyzed,
evidence from multiple client investigations has shown multiple commonalities in
UNC2546’s activities.”
The firm is still analyzing the zero-day exploitation, but it did say that in
the early attacks in December, UNC2546 leveraged an SQL injection vulnerability
in the Accellion FTA as its primary intrusion vector. SQL injection was then
followed by subsequent requests to additional resources.
“UNC2546 has leveraged this SQL injection vulnerability to retrieve a key which
appears to be used in conjunction with a request to the file
sftp_account_edit.php,” according to the analysis. “Immediately after this
request, the built-in Accellion utility admin.pl was executed, resulting in an
eval web shell being written to oauth.api. Almost immediately following this
sequence, the DEWMODE web shell is written to the system.”
DEWMODE, once embedded, extracts a list of available files from a MySQL database
on the FTA and lists those files and corresponding metadata—file ID, path,
filename, uploader and recipient—on an HTML page. UNC2546 then uses the
presented list to download files through the DEWMODE web shell.
In a subset of incidents, Mandiant observed UNC2546 requesting a file named
cache.js.gz – an archive that likely contained a dump of a database.
Extortion via Clop Leaks Site
Once DEWMODE was installed, victims began to
receive extortion emails from an actor claiming association with the Clop
ransomware team gang.
These are tailored to each victim and sent from a free email account, to a small
number of addresses at the victim organization. If the victim did not respond in
a timely manner, more emails are sent, this time to hundreds or thousands of
different email accounts, using varied SMTP infrastructure.

The initial extortion note sent to victims of the Accellion FTA attacks. Source:
FireEye Mandiant.
“In at least one case, UNC2582 also sent emails to partners of the victim
organization that included links to the stolen data and negotiation chat,”
according to Mandiant.
The firm also found through monitoring the CL0P^_- LEAKS shaming website that
UNC2582 has followed through on threats to publish stolen data.
“Several new victims have appeared on the site in recent weeks, including at
least one organization that has publicly confirmed that their Accellion FTA
device had been recently targeted,” according to Mandiant.
FIN11, Clop and UNC2546
FIN11 is a financially motivated group that has been
around for at least four years, conducting widespread phishing campaigns.
However, it continues to evolve. It added the use of Clop (which emerged in
February 2019) and double extortion in October; and added point-of-sale (POS)
malware to its arsenal in 2018. In 2019, it started conducting run-of-the-mill
ransomware attacks.
Mandiant has previously found that FIN11 threatened to post stolen victim data
on the same .onion site used in the Accellion FTA attacks, usually in a
double-extortion demand following the deployment of Clop ransomware. However,
researchers found that the cybercriminals involved in these latest attacks are
likely distinct from FIN11 itself despite sharing some overlaps.
“We are currently tracking the exploitation of the zero-day Accellion FTA
vulnerabilities and data theft from companies running the legacy FTA product as
UNC2546, and the subsequent extortion activity as UNC2582,” according to
Mandiant. “We have identified overlaps between UNC2582, UNC2546 and prior FIN11
operations, and we will continue to evaluate the relationships between these
clusters of activity.”
Some of the overlaps between UNC2582’s data-theft extortion activity and prior
FIN11 operations include common email senders.
“Some UNC2582 extortion emails observed in January 2021 were sent from IP
addresses and/or email accounts used by FIN11 in multiple phishing campaigns
between August and December 2020, including some of the last campaigns that were
clearly attributable to the group,” according to the analysis.
FIN11 has also used same the CL0P^_- LEAKS shaming site and is known for
deploying Clop ransomware.
“The UNC2582 extortion emails contained a link to the CL0P^_- LEAKS website
and/or a victim specific negotiation page,” according to Mandiant. “The linked
websites were the same ones used to support historical Clop operations, a series
of ransomware and data theft extortion campaigns we suspect can be exclusively
attributed to FIN11.”
When it comes to the zero-day cluster of activity, attributed to UNC2546, there
are also limited overlaps with FIN11. Specifically, many of the organizations
compromised by UNC2546 were previously targeted by FIN11.
And, “an IP address that communicated with a DEWMODE web shell was in the
‘Fortunix Networks L.P.’ netblock, a network frequently used by FIN11 to host
download and FRIENDSPEAK command-and-control (C2) domains.”
There’s also a connection between UNC2546 and UNC2582, the firm found: In at
least one case, the UNC2546 attackers interacted with DEWMODE from a host that
was used to send UNC2582-attributed extortion email.
“The overlaps between FIN11, UNC2546 and UNC2582 are compelling, but we continue
to track these clusters separately while we evaluate the nature of their
relationships,” Mandiant concluded. “One of the specific challenges is that the
scope of the overlaps with FIN11 is limited to the later stages of the attack
life cycle. UNC2546 uses a different infection vector and foothold, and unlike
FIN11, we have not observed the actors expanding their presence across impacted
networks.”
Also, using SQL injection to deploy DEWMODE would represent a significant shift
in FIN11 TTPs, “given the group has traditionally relied on phishing campaigns
as its initial infection vector and we have not previously observed them use
zero-day vulnerabilities,” Mandiant added.
After IT Outage, Carmakers Kia and Hyundai Say No Evidence of Ransomware Attack
20.2.2021
Ransomware
Securityweek
Kia possibly hit by ransomware
Carmakers Kia and Hyundai, both owned by the South Korea-based Hyundai Motor
Group, said they had found no evidence that the outages they suffered in the
past week in the United States were the result of a ransomware attack.
Kia Motors America was the first to notify customers via its website that it had
been experiencing an IT service outage impacting some of its systems, including
internal, customer and dealer systems. Hyundai Motor America later also
confirmed some disruptions, but appeared to be less impacted.
“Kia Motors America, Inc. (Kia) has been experiencing an extended systems outage
since Saturday but can confirm that the UVO app and owner’s portal are now
operational,” Kia told SecurityWeek in a statement on Thursday.
“We anticipate remaining primary customer-facing affected systems will continue
to come back online within the next 24-48 hours, with our most critical systems
first in line. We apologize for the inconvenience to affected customers,
especially those impacted by winter storms, who felt the outage of our remote
start and heating feature most acutely. Kia is wholly focused on fully resolving
this issue and would like to thank our customers for their continued patience,”
it added.
Reports have emerged about the outages being caused by a ransomware attack on
Kia and Hyundai systems. One individual claimed on Twitter that a Kia dealership
in Arizona had told her that computers had been down for three days due to
ransomware.
However, Kia and Hyundai said they were not aware of any ransomware.
“We are aware of online speculation that Kia is subject to a ransomware attack,”
Kia said in its emailed statement. “At this time, and based on the best and most
current information, we can confirm that we have no evidence that Kia or any Kia
data is subject to a ransomware attack.”
BleepingComputer obtained a ransom note from a cybercrime group that uses the
DoppelPaymer ransomware, claiming that they had managed not only to encrypt
files but also to steal “all your private data.” The hackers reportedly want
roughly $20 million in bitcoin to decrypt the data and not leak the stolen files
— the amount goes up to $30 million if the ransom is not paid within a certain
number of days.
SecurityWeek has checked the website where the DoppelPaymer hackers leak data
from victims and post proof that they breached companies, but at the time of
writing there is no mention of Hyundai or Kia.
It remains to be seen if the carmakers end up confirming being hit by ransomware
or if the hackers start leaking data allegedly stolen from them. In some recent
attacks, cybercriminals only stole data from victims, but did not encrypt their
files, which could make the breach more difficult to detect. However, in this
case the ransom note suggests that files have been encrypted, which would make
the breach obvious.
Kia Motors Hit With $20M Ransomware Attack – Report
19.2.2021
Ransomware
Threatpost
DoppelPaymer ransomware gang claims credit for Kia’s outage, demands $20 million
in double-extortion attack.
So far, Kia Motors America has publicly acknowledged an “extended system
outage,” but ransomware gang DoppelPaymer claimed it has locked down the
company’s files in a cyberattack that includes a $20 million ransom demand.
That $20 million will gain Kia a decryptor and a guarantee to not to publish
sensitive data bits on the gang’s leak site.
The ransom note from DoppelPaymer, first published by BleepingComputer, said the
attack was on Hyundai Motor America, the parent company of Kia Motors America,
based in Irvine, Calif. It went on to say that the company has two to three
weeks to pay up 404 Bitcoins, which is around $20 million as of this writing. To
add a sense of urgency, the threat actors warn that a delay in payment could
result in the ransom being raised to $30 million.
The outage affected Kia’s mobile apps like Kia Access with UVO Link, UVO
eServices and Kia Connect, as well as self-help portals and customer support,
the company told the outlet in a statement, adding, “We are also aware of online
speculation that Kia is subject to a ‘ransomware” attack. At this time, we can
confirm that we have no evidence that Kia or any Kia data is subject to a
‘ransomware’ attack.”
Kia told Threatpost that the UVO app and owner’s portal are now operational and
added that there’s still have no evidence of a ransomware attack.
Kia Customers Out in the Cold
While Kia is not disclosing details about the
cause of the interruption, Kia customers have noticed and are taking to social
media to try and find answers.
Over the weekend social-media posts described the fallout of the outage felt by
Kia customers, particularly those in the midst of extreme winter weather
conditions who were unable to access features like remote start on their cars
because the app was down.
“Coldest day of the year and my #kia #uvo app doesn’t work,” Twitter user
@big2mo wrote on Feb. 13. “The server is not responding.”
Another Twitter user, @trustartz, posted this, tagging Kia, “Perfect weather for
my @Kia access not to work,” he wrote. “At the time I actually need it.”
The Kia Motors account responded with this vague apology, without much detail,
on Feb. 15, days after the first reports of outages started to emerge on Feb.
13.
“We apologize we are having server issues that may affect your ability to login
to the UVO app or send commands. We are working to resolve it as quickly as
possible. An update will be provided as soon as possible. Thank you for your
patience.”
Andrea Carcano, co-founder of Nozomi Networks, said ransomware attacks like
these are becoming commonplace and that this looks a lot like other DopplePaymer
attacks he has seen.
“DoppelPaymer and others are immensely more profitable when they target large
organizations and disrupt their critical IT operations – in this case, KIA’s
mobile UVO Link apps, payment systems, owner’s portals and internal dealership
sites,” Carcano said.
Groups like DoppelPaymer are experts at figuring out how to cause their victims
the most pain to get them to pay up, Erich Kron from KnowBe4 explained.
“In this case, the attack has impacted many significant IT systems, including
those needed for customers to take delivery of their newly purchased vehicles.
This could cost the organization a considerable amount of money as well as
reputational damage with current and potential customers,” Kron said.
Double Extortion
Beyond hobbling critical operations, ransomware threat
actors have learned how to add on the pressure to companies, threatening that
their most sensitive stolen data could be exposed on well-known leak sites if
they don’t pay up fast. This tactic is known as double-extortion.
“Like so many modern types of ransomware, DoppelPaymer not only cripples the
organization’s ability to conduct business, but also extracts sensitive data
that is used for leverage against the victim, in an effort to get them to pay
the ransom,” Kron explained. “Unfortunately, with very few exceptions, once the
data has left the organization, a data breach has occurred, and the organization
will be subject to regulatory and other fines as a result. Even if the data is
not published publicly, it will most likely be sold eventually or traded on the
dark web.”
Kron added these breaches most often occur with social-engineered attacks, like
spearphishing.
“DoppelPaymer, like most other ransomware strains, is generally spread through
phishing emails, so organizations should ensure employees are trained to spot
and report the suspicious emails that could potentially be used to attack them,”
he said. “Combining ongoing training and regularly scheduled simulated phishing
tests, is extremely effective in preparing employees to defend against these
types of attacks.”
But besides expanding cybersecurity training for employees, Trevor Morgan,
product manager for comforte AG recommends companies like Kia take steps to
protect their most sensitive data before a breach occurs.
“The ironic thing is that enterprises can avoid the threat of leaked hijacked
data simply by taking a data-centric approach to protecting sensitive
information,” Morgan said. “Using tokenization or format-preserving encryption,
businesses can obfuscate any sensitive data within their data ecosystem,
rendering it incomprehensible no matter who has access to it. These reports
should all be treated as cautionary tales, as an enterprise might find
themselves in the same boat without the proper data-centric approach.”
Information Posted Online After N Carolina Ransomware Attack
18.2.2021
Ransomware
Securityweek
An investigation into a ransomware attack on a North Carolina county’s computer
network showed personal information posted for sale on the “dark web,” the
county said.
The Chatham County network was hit on Oct. 28 with ransomware that originated in
a phishing email with a malicious attachment, The News & Observer of Raleigh
reported Tuesday. It encrypted much of the county’s network infrastructure and
associated business systems, the county announced.
County spokeswoman Kara Dudley said the hacker sent a ransom note asking for 50
bitcoins, or about $2.4 million. The county refused to pay.
County staffers are working with the N.C. Department of Health and Human
Services and the N.C. Attorney General’s Office to identify files affected by
the breach and to notify people whose personally identifiable information or
personal health information may be at risk, County Manager Dan LaMontagne told
the board of commissioners Monday.
The cyberattack shut down most county functions and temporarily cut off public
access to services. Data also was stolen from county systems, but LaMontagne
said it’s not known what specifically was taken.
The Chatham News & Record reported last week that it found sensitive files,
including county employee personnel records, eviction notices and Chatham County
Sheriff’s Office investigation documents, posted to the internet, including to
the dark web.
There were two releases, according to the News & Record. On Nov. 4, “mostly
innocuous” files were uploaded, LaMontagne told the newspaper. In January, a
second upload included more sensitive data. The newspaper was able to take
screenshots of a counter on the site showing the files had been viewed over
30,000 times.
Staff had to wipe and re-image the county’s servers and over 550 staff
computers, LaMontagne said. Staff computers, internet, office phones and
voicemail are almost recovered, and they are adding security measures and
reinforcing employee training, he said.
French and Ukrainian police arrested Egregor ransomware affiliates/partners in
Ukraine
16.2.2021
Ransomware
Securityaffairs
An international operation conducted in Ukraine and France lead to the arrest of
criminals believed to be affiliated with the Egregor RaaS.
Some affiliated
with the Egregor RaaS, not the main ransomware gang, have been arrested as a
result of a joint operation conducted by law enforcement in Ukraine and France.
Authorities did not reveal the name of the suspects, according to France media
the suspects are in contact with Egregor ransomware operators and provided
logistical and financial support to them.
The Egregor ransomware gang has been active since September 2020, it began
operating shortly after the Maze ransomware operators shut down their
operations.
Like other ransomware operators, the gang implements a double
extortion model, which means that it threatens the victims to release stolen
data on its leak site if they do not pay the ransom.
“It is a vast Franco-Ukrainian operation. Since Tuesday morning, the police of
the two countries have been cooperating in an attempt to dismantle a group of
cybercriminals, suspected of being at the origin of several hundred attacks
through ransomware (programs that block the computer and demand a ransom) since
September 2020.” reported France Inter. “According to information from France
Inter, police officers from the Central Office for the Fight against Cybercrime
of the Judicial Police participated in the arrest of several hackers, suspected
of being in contact with Egregor, a cyber criminal group : hackers, logistical
and financial support, etc.”
Early this year, the FBI has issued a Private Industry Notification (PIN) to
warn private organizations of Egregor ransomware attacks.
The Egregor ransomware first appeared on the threat landscape in September 2020,
since then the gang claimed to have compromised over 150 organizations.
The list of known victims includes Barnes and Noble, Cencosud, Crytek, Kmart,
and Metro Vancouver’s transportation agency TransLink. Several major French
organizations were hit by the gang, including gaming firm Ubisoft, the
SIPA-Ouest France group, and logistics firm Gefco.
Egregor is known to target printers of the compromised organizations,
instituting them to print the ransom note.
“The FBI assesses Egregor ransomware is operating as a Ransomware as a Service
Model. In this model, multiple different individuals play a part in conducting a
single intrusion and ransomware event. Because of the large number of actors
involved in deploying Egregor, the tactics, techniques, and procedures (TTPs)
used in its deployment can vary widely, creating significant challenges for
defense and mitigation.” reads the FBI alert. “Egregor ransomware utilizes
multiple mechanisms to compromise business networks, including targeting
business network and employee personal accounts that share access with business
networks or devices.”
Threat actors use phishing emails with malicious attachments as attack vector,
they also exploit insecure Remote Desktop Protocol(RDP) or Virtual Private
Networks to gain access to the networks.
Once gained access to the target network, the threat actors attempt to escalate
privileges and make lateral movements using Cobalt Strike, Qakbot/Qbot, Advanced
IP Scanner, and AdFind.
Feds also added that the ransomware operators leverages tools like Rclone
(sometimes renamed or hidden as svchost) and 7zip for data exfiltration.
FBI discourages victims to pay the ransom and urge them to report incidents to
local FBI offices.
Frence authorities, along with other European police bodies, launched an
investigation into the activity of the group last year and were able to identify
some members of the Egregor gang that operates an infrastructure in Ukraine.
The infrastructure used by the Egregor ransomware gang, including the leak site,
was shut down after the arrests. At the time of this writing, it is not clear if
the servers were seized by the authorities or took offline by the ransomware
operators to evade the detection of law enforcement.
Avaddon ransomware decryptor released, but operators quickly reacted
11.2.2021
Ransomware
Securityaffairs
An expert released a free decryption tool for the Avaddon ransomware, but
operators quickly updated malware code to make it inefficient.
The Spanish
student Javier Yuste has released a free decryption tool for the Avaddon
ransomware that can be used by the victims to recover their encrypted files for
free.
Yuste is a student at the Rey Juan Carlos University in Madrid, he developed the
AvaddonDecrypter utility that could be used by victims of the ransomware when
their computers should not have been powered off after the infection.
The utility developed by the experts dumps the RAM memory of the infected system
and scans it for data that could allow to recover the encryption key.
“If enough information is recovered, the tool can then be used to decrypt files
and help victims recover from Avaddon attacks without needing to pay the gang’s
ransom demand.” reported ZDNet.
Unfortunately, the Avaddon ransomware operators were informed of the
availability of the decrypted and released an update for the code of their
malware that makes the tool inefficient.
Source ZDNet
Multiple security experts pointed out that the decision to
publicly release decryption tools is not a good option when the decryptor
exploit some flaws in the malware code, because it could help ransomware
operators to fix the issues.

The fact that the Avaddon ransomware operators quickly addressed their code
demonstrate the efficiency of their operations.
CD Projekt Red game maker discloses ransomware attack
11.2.2021
Ransomware
Securityaffairs
The gaming firm CD Projekt Red, which developed popular games like Cyberpunk
2077 and The Witcher, has disclosed a ransomware attack.
The gaming firm CD
Projekt Red, which developed popular games like Cyberpunk 2077 and The Witcher
series, has suffered a ransomware attack.
The company confirmed the security breach with a series of messages on its
social media channels (Facebook and Twitter).
The attack took place on February 8, a threat actor breached its corporate
network and encrypted some of its devices.
“Yesterday we discovered that we have become a victim of a targeted cyber
attack, due to which some of our internal systems have been compromised.” reads
a statement published by the company.
“An unidentified actor gained unauthorized access to our internal network,
collected certain data belong to CD PROJEKT capital group and left a ransom note
the content of which we release to the public. Although some devices in our
network have been encrypted, our backups remain intact. We have already secured
our IT infrastructure and begun restoring the data,”
According to BleepingComputer, the attack was conducted by a ransomware group
named HelloKitty, which claimed to have stolen copies of the source code for
popular games like Cyberpunk 2077, Gwent, and The Witcher 3.
Emisoft’s expert Fabian Wosar confirmed that the systems of the game maker were
infected with a ransomware strain dubbed ‘HelloKitty.’

The group also claims to have obtained a copy of an unreleased version of The
Witcher 3 game.
CD PROJEKT RED reported the incident to the police and relevant authorities,
including the President of the Personal Data Protection Office, it also hired IT
forensic specialists to investigate the intrusion.
The gaming firm confirmed
that it wouldn’t be paying any ransom demand.
“We will not give in to the demands nor negotiate with the actor, being aware
that this may eventually lead to the release of the compromised data,” the
company adds.
The company revealed that the compromised systems did not contain players’
personal data.
Recently other prominent gaming firms were victims of a ransomware attack,
including Ubisoft and Crytek (hit by Egregor ransomware gang), and Capcom (hit
by the Ragnar Locker).
Cyberpunk 2077 Publisher Hit with Hack, Threats and Ransomware
10.2.2021
Ransomware
Threatpost
CD Projekt Red was hit with a cyberattack (possibly the work of the “Hello
Kitty” gang), and the attackers are threatening to release source code for
Witcher 3, corporate documents and more.
UPDATE
CD Projekt Red, the videogame-development company behind Cyberpunk 2077 and the
wildly popular Witcher series, has suffered a ransomware attack that could soon
result in troves of company data being dumped online – including game source
code.
The Warsaw-based company tweeted out a notice on Tuesday, warning of “a targeted
cyberattack in which some of our systems have become compromised.”
The news comes on the heels of weeks of controversy over the company’s
blockbuster release of Cyberpunk 2077, which suffered glitches and console
problems that engendered high levels of dissatisfaction among fans, who had
waited more than a year for the much-hyped giant sandbox game.
However, unhappy players are not likely behind the event. Researcher Fabian
Wosar noted that the adversaries, according to his analysis, are likely the same
ransomware group that hacked the Brazilian energy company CEMIG last December.
“The amount of people that are thinking this was done by a disgruntled gamer is
laughable. Judging by the ransom note that was shared, this was done by a
ransomware group we track as ‘HelloKitty,'” he said. “This has nothing to do
with disgruntled gamers and is just your average ransomware.”
What is the Best Ransomware Defense? Backups
An unidentified cyberattack
group “gained access to our internal network, collected certain data belonging
to CD PROJEKT Capital Group and left a ransom note,” the company said.
The ransomware also encrypted the company’s systems. But interestingly, that
seemed to be an afterthought for the threat actors. The company noted, “Our
backups remain intact. We have already secured our IT infrastructure and begun
restoring the data” – and that is exactly what the attackers seemed to have
expected.
In the ransom note (also tweeted out), the cybercriminals said, “we have
encrypted all of your servers, but we understand that you can most likely
recover from backups.”
So, the real game afoot has to do with the information that the attackers claim
to have stolen. Cyber-extortion in this case appears to be evolving to holding
data for hostage rather than preventing access to mission-critical systems.
Which also means that the sophistication level of the attackers in this case is
probably fairly high, researchers said.
“We’ve seen ransomware evolve, not only is it enough for criminals to encrypt
data, but they will spend time within the victim’s organization, stealing
valuable data, working out which data is worth encrypting and how much they
should set the ransom at,” Javvad Malik, security awareness advocate at KnowBe4,
told Threatpost. “In many cases, these criminals go undetected in victim
organizations for many months at a time.”
Wosar noted via Twitter that breadcrumbs point to the attackers being
English-speaking rather than one of the Russian-language gangs most known for
spreading ransomware.
“They certainly have a better command of the English language than your average
ransomware thug,” he tweeted. “The ransomware is also missing the usual check
for CIS countries [the Commonwealth of Independent States, made up of ex-Soviet
Iron Bloc countries]. So I wouldn’t be surprised if the group or the affiliate
who pulled off the hack grew up with western culture.”
Cyber-Extortion Evolves: Data Threats
The cyberattackers told CD Projekt Red
they have “dumped full copies” of the source code for Cyberpunk 2077, Gwent, the
Witcher 3 and an “unreleased version” of the Witcher 3; and, stolen sensitive
corporate information relating to accounting, administration, HR, investor
relations, legal and more.
“Source codes will be sold or leaked online, and your documents will be sent to
our contacts in gaming journalism,” according to the note, which went on to say
that not paying up has an impact to the company’s public image, stock price and
investor confidence. The attackers claimed that the information will expose how
terribly the company is run.

Toss a coin to your Witcher. Source: CD Projekt Red.
Release of the source code would allow fans to develop game hacks and perform
all kinds of “modding” (i.e., development of custom features) and jailbreaks;
and would be a gift to competitors.
And, “if the attackers were able to exfiltrate source code for the popular
Cyberpunk 2077 and Witcher games it could lead to more targeted exploit
development aimed at a widespread player base,” said Chris Clements, vice
president of solutions architecture at Cerberus Sentinel.
To boot, the company does financially have much to lose: CD Projekt Red stock is
traded in the over-the-counter (OTC) market in the U.S. under the ticker symbol
“OTGLY.” As of last year, it had reached a valuation of $8.1 billion, making it
the largest video game company in Europe, even ahead of Ubisoft. At press time
the stock was trading around $77 per share.
“In this case, the ransomware itself isn’t the issue – it’s more of a statement
to signal that they have breached the organization,” Malik said. “The fact that
the ransom note was addressed to them shows it was a targeted attack.”
He added, “The issue with this approach is that even if the victim pays the
money, there is no way to guarantee the criminals will actually delete the
data.”
CD Projekt Red isn’t giving in, though: “We will not give into the demands nor
negotiate with the actor, being aware that this may eventually lead to the
release of the compromised data,” it said, adding that “the compromised systems
did not contain any personal data of our players or users of our services.”


This approach is not unheard of for gaming targets. In October, the Egregor gang
claimed to have lifted both source code and some proprietary files from game
publisher Ubisoft. Specifically, the group threatened Watch Dogs: Legion, which
at the time was still unreleased.
Insult to Injury: Cyberpunk 2077 Woes
CD Projekt Red has had its share of
problems in the last few months. The company’s release of Cyberpunk 2077 in the
fall didn’t go as expected, with glitches getting so bad that Sony even pulled
the game from the PlayStation store, offering those who purchased it already a
full refund. To make matters even worse, some users seeking refunds then
experienced problems with downloading the form to register for that refund.
Meanwhile, last week the company warned about “a vulnerability in external DLL
files the game uses which can be used to execute code on PCs,” which it released
a hotfix for a couple of days later. The bug would allow a malicious desktop
“mod” – players can use third-party modules to customize the game – to take over
machines.
The title has also been a target for malware scams. Before the game was even
released, threat actors were exploiting its popularity with scams offering “free
copies” of the game while stealing personal information.
And in December, the CoderWare ransomware was found masquerading as a download
of Cyberpunk 2077 from a fake version of the Google Play mobile app marketplace.
This post was updated at 11:40 a.m. ET with information about the Hello Kitty
ransomware gang and additional researcher comments.
Cyberpunk 2077 Video Game Developer Hit by Hack Attack
10.2.2021
Ransomware
Securityweek
Polish video game maker CD Projekt RED, the company behind The Witcher and
Cyberpunk 2077, said Tuesday hackers had stolen data in a "targeted cyber
attack".
"An unidentified actor gained unauthorized access to our internal network,
collected certain data belonging to CD PROJEKT capital group, and left a ransom
note," the company said on Twitter.
The game developer said the incident happened on Monday and it had contacted the
police.
CD Projekt published a copy of the ransom note in which the hackers claimed to
have stolen the source codes for Cyberpunk 2077 and The Witcher 3 as well as
internal administrative documents.
"If we will not come to an agreement, then your source codes will be sold or
leaked online," it read, giving the company 48 hours to respond.
"Investors will lose trust in your company and the stock will dive even lower."
CD Projekt's shares were down 5.2 percent on the Warsaw stock exchange at around
0900 GMT.
The company's stock has taken a beating after a series of problems surrounding
the release of the much-hyped Cyberpunk 2077 in December.
The shares rose again last month after tech billionaire Elon Musk praised its
design.
The company said it would not "give in to the demands nor negotiate with the
actor" even though it was aware that data could be released.
"We are taking necessary steps to mitigate the consequences of such a release,"
it said.
"At this time we can confirm that -- to our best knowledge -- the compromised
systems did not contain any personal data of our players or users of our
services."
U.S. Agencies Publish Ransomware Factsheet
10.2.2021
Ransomware
Securityweek
The National Cyber Investigative Joint Task Force (NCIJTF) on Friday released a
joint-sealed ransomware factsheet detailing common attack techniques and means
to ensure prevention and mitigation.
The factsheet has been developed by an interagency group of experts in
ransomware, from more than 15 government agencies, and is meant to help increase
awareness on the threat that ransomware poses to critical infrastructure.
The two-page document explains that, in addition to encrypting the data on
victim systems to make it unusable, ransomware operators might also pressure
victims into paying the ransom by threatening to destroy the data or release it
to the public.
Ransomware attacks affect all sectors, including state, local, tribal, and
territorial governments, but also impact hospitals, police, fire departments,
municipalities, and other critical infrastructure.
Common ransomware infection vectors, the document explains, include email
phishing campaigns (in which victims receive messages with malicious attachments
or links to ransomware), remote desktop protocol (RDP) misconfigurations, and
software vulnerabilities.
Ransomware has already had a great impact on the public sector, yet the total
costs associated with a ransomware infection are often difficult to calculate,
as they involve not only the ransom paid, but also recovery and possibly
additional costs.
While one U.S. county ended up paying $132.000 to Ryuk operators to recover
encrypted systems, another spent $1 million to rebuild its systems using new
equipment instead of paying a $1.2 million ransom.
One U.S. city that refused to pay the 13 Bitcoin (approximately $76,000) ransom
to Robin Hood ransomware operators, however, ended up spending more than $9
million to restore systems and services.
Using multi-factor authentication, ensuring that systems are always updated and
patched, and keeping data, system images, and configurations backed up should
help minimize risks associated with ransomware.
The FBI says that ransomware victims should not pay the ransom, as this does not
guarantee that data is recovered, but instead encourages cybercriminals to
target more individuals and organizations. Victims are encouraged to report
attacks, to help track ransomware operators.
Ransomware Demands Spike 320%, Payments Rise
9.2.2021
Ransomware
Threatpost
Remote work continues to fueling a spike in phishing and cyberattacks,
particularly in the U.S.
When it comes to paying the ransom in a ransomware attack, demands are on the
rise. Yet, many companies that paid the ransom failed to receive a decryption
key, in a survey issued Monday.
In fact, pandemic-themed phishing scams, a sustained onslaught of ransomware
attacks and the rise of a remote global workforce all colluded to make the last
12 months particularly brutal for information-security professionals, according
to the report.
Proofpoint’s State of the Phish report for 2020 surveyed 600 informational
security pros across seven countries: Australia, France, Germany, Japan, Spain,
U.K and the U.S.; incorporated highlights from an additional third-party survey
of 3,500 adult workers across the same countries; and analyzed more than 60
million simulated phishing attacks to reach its conclusions, the company said.
Additional Ransom Demands Spike
Of the 75 percent of companies which
responded to the State of the Phish report saying they were infected by
ransomware, more than half decided to pay the ransom to get their data back,
Proofpoint said. Of that half who paid, only 60 percent were given back access
to their data. The other 40 percent were hit with additional ransom demands,
which is up 320 percent over last year.
Instead of reacting after they’ve lost control of their data, Gretel Egan,
senior security awareness and training strategist for Proofpoint, told
Threatpost that organizations need to make decisions about how to react well
before the breach.
“Reaction to a ransomware infection is a very individual thing,” Egan said. “The
scale of the infection, impact to operations, and amount of ransom are all
likely to factor into the ultimate decision about how to handle an attack. But a
good best practice is to have a thoroughly prepared and tested response in place
before a ransomware attack takes hold, one that considers a number of different
ransomware scenarios. It’s critical to evaluate the risk vs. reward of making a
payment, and alternatives they can pursue.
Companies Net Record Phishing Attempts
The report shows a sharp uptick in
phishing attempts, particularly in the U.S., where attacks are up 14 percent
over last year and run 30 percent higher than the rest of the world.
And while wide-net bulk phishing attacks are being deployed, threat actors are
getting even better at more targeted social engineering scams like spear
phishing, whaling and business email compromise (BEC) attacks.
Email continues to be the channel of choice for phishers because undertrained
employees make it easy, the report explained, but security professionals also
need to consider other social-engineering schemes that organizations are facing,
like those using social media, voicemail “vishing,” SMS/text phishing or
“smishing,” and even malicious USB drops.
“Threat actors worldwide are continuing to target people with agile, relevant,
and sophisticated communications—most notably through the email channel, which
remains the top threat vector,” Alan LeFort, senior vice president and general
manager of Security Awareness Training for Proofpoint said. “Ensuring users
understand how to spot and report attempted cyberattacks is undeniably
business-critical, especially as users continue to work remotely—often in a less
secured environment. While many organizations say they are delivering security
awareness training to their employees, our data shows most are not doing
enough.”
Security-Awareness Training Works
While 90 percent of U.S. survey respondents
indicated their workforce shifted to remote work in 2020, only 29 percent of
those offered any training to employees about safe remote working habits,
Proofpoint said, creating an entirely fresh hunting ground for phishing
attackers practically overnight.
Across the 12-month period Proofpoint measured, there were more than 800,000
active credential phishing attacks and 35,000 phishing emails containing malware
including remote access trojans (RATs), keyloggers and advanced persistent
threats (APTs), the report said.
“The findings related to remote-working situations in the U.S. are eye-opening,”
LeFort added. “Nearly all the American infosec professionals we surveyed said
they supported a new, remote-working model for at least half of their
organization’s workers last year. And yet fewer than a third of these
respondents said workers were trained about security practices related to
working from home.”
At the same time, three-quarters of U.S. workers said they allow their friends
and family to access work-issued devices to do things like shop online and play
games.
“These gaps represent a significant risk and reinforce the need for security
awareness training initiatives that are tailored to the remote workforce,”
LeFort said.
The report stressed that security-awareness training works. Proofpoint found
that 80 percent of the organizations who contributed to their survey found that
training “reduced phishing susceptibility.” When tested, it was purchasing teams
who were the most security conscious, Proofpoint found, while maintenance and
facilities employees scored the worst.
How to Prevent Ransomware, Phishing
Egan also suggested proactive safeguards
like a dedicated advanced email security gateway, robust data back-ups and
consistent patching to keep systems updated.
“As well, most attacks require human interaction to be successful — and they are
overwhelmingly aimed at specific people,” Egan explained. “We recommend
conducting continuous security-awareness training for every employee and
contractor with access to corporate systems. Some ransomware variants will ask
the individual for payment so it’s important that employees know to not make any
payments on their own and to flag them to their supervisors.”
There is good news. The total number of reported ransomware infections remained
about the same, and Proofpoint said the number of malware infections as a result
of phishing was down 17 percent. Better yet, there was a 47 percent drop in the
number of respondents reporting a direct financial loss, which the report added
“could indicate that organizations have implemented stronger preventative
measures against these types of attacks,” and better yet, that those measures
are working.
WestRock Ransomware Attack Hinders Packaging Production
9.2.2021
Ransomware
Threatpost
The ransomware attack, affecting OT systems, resulted in some of WestRock’s
facilities lagging in production levels.
WestRock – the second-largest packaging company in the U.S. – continues to
restore its systems, two weeks after it discovered it was the victim of a
ransomware attack.
WestRock, which has more than 320 manufacturing facilities globally, creates
packaging supplies for a bevy of high-profile clients, including General Motors,
Heinz and Home Depot.
The ransomware attack was discovered on Jan. 23 and affected the company’s
operational technology (OT) systems. These systems are comprised of equipment
used to manage, monitor and control industrial operations. That means that
several of WestRock’s factory processes – including mill system production and
packaging-converting operations – were crippled.
“WestRock is undertaking extensive efforts to identify, contain and recover from
this incident quickly and securely,” said the company, in a new update on the
attack, Friday. “Upon discovering the incident, WestRock immediately began an
investigation, implemented business-continuity processes and initiated response
containment protocols with the support of cybersecurity experts.”
Ransomware Attack: Impact on WestRock
In a presentation on its first-quarter
earnings results for 2021 for its investors, WestRock said that there is
currently no evidence that customer or coworker data has been compromised by
attackers.
As a result of the ransomware attack, shipments for some of the company’s
facilities have lagged in production levels, according to the company. For
instance, the firm’s mill system production, through Feb. 4, was approximately
85,000 tons lower than planned, it said.
For context, according to its 2020 annual report, WestRock’s annual production
capacity for corrugated packaging mills (to create cardboard utilized by various
commercial companies) in 2020 was almost 12 million, while its annual production
capacity for consumer packaging mills was almost 4 million.
Dirk Schrader, global vice president at New Net Technologies (NNT), said that
while WestRock was quick in reporting the incident, this lag points to struggles
around the company’s initial “response and containment protocols.”
“Being affected by a cyberattack at production control and plant level is not
only going to cost you revenue from that loss in production, it affects the
reputation and the supply chain of your up-stream customers,” Schrader said.
The attack also hits a company that has shifted to high gear to keep up with the
increased demand for online shopping — and consequently, more packaging —
triggered by COVID-19. WestRock said it has been working to support critical
infrastructure, supply chains and other manufacturers in delivering their goods
to consumers during the ongoing pandemic.
WestRock Takes Ransomware Remediation Steps
Despite the lag in production,
WestRock said this “gap is closing quickly as systems are restored.” Its
packaging converting operations are also close to returning to full planned
production levels.
“The WestRock team remains in regular communication with its customers to share
information and updates and to meet their business needs,” said WestRock on
Friday. “WestRock is also working with its vendors so they are informed, and
supply chains remain operational.”
What’s still unknown is what kind of ransomware was used in the attack, whether
a ransom was paid and how the attack was launched. Threatpost has reached out to
WestRock for further comment.
Cyberattacks on Industrial Control Systems
The effect of ransomware attacks
on company OT systems – such as production lines – are particularly dire. The
impacts of such attacks extend beyond financial detriment to include
supply-chain issues or even physical danger.
These types of attacks have been ramping up over the past year. For instance,
aluminum giant Norsk Hydro fell victim to a serious ransomware attack in 2020
that forced it to shut down or isolate several plants and send several more into
manual mode. And the Snake ransomware in June 2020 reportedly hit Honda and a
South American energy-distribution company called Enel Argentina.
Flaws in the industrial space are also continuing to crop up: A report released
last week analyzed all publicly disclosed vulnerabilities in ICS (industrial
control system) networks in the second half of 2020 – and found a nearly 33
percent increase in ICS disclosures over 2018.
“Operational technology has for long been seen as ‘this is not IT, why should I
bother about’ from cybersecurity folks, and neither did the ICS folks,” Schrader
said. “The results are a dangerous mixture of differing languages and focus
about what security is.”
Still, he said, “the essential security controls have to be placed regardless of
one’s perspective on IT and OT cybersecurity. Whether you prioritize
availability (OT) or confidentially (IT), you will need to manage your
vulnerabilities and to control unwanted change in order to maintain both.”
Victims of Ziggy ransomware can recover their files for free
9.2.2021
Ransomware
Securityaffairs
The Ziggy ransomware gang has shut down its operations and released the
decryption keys fearing the ongoing investigation of law enforcement.
Good
news for the victims of the Ziggy ransomware, the ransomware operators have shut
down their operations and released the victims’ decryption keys. The victims can
now recover their encrypted files without needing to pay the ransom.
The news was confirmed by the researcher M. Shahpasandi to BleepingComputer. The
mastermind behind the Ziggy Ransomware operation announced on Telegram the
decision to shut down their activity.
“In an interview with BleepingComputer, the ransomware admin said they created
the ransomware to generate money as they live in a “third-world country.””
reported BleepingComputer.
Ransomware operators are concerned about recent law enforcement activity that
results in the operation against Netwalker ransomware.
Ziggy ransomware admin leaked a SQL file containing 922 decryption keys along
with a decryptor. The ransomware admin also shared the source code for a
different decryptor with BleepingComputer that includes offline decryption keys
that could be used when the infected system is not connected to the Internet.
In order to decrypt the files, the victims have to provide three decryption keys
that are included in the SQL file.
Source BleepingComputer
Ransomware infections use offline decryption keys to
decrypt victims infected while not being connected to the Internet or the
command and control server was unreachable.
As usual, it is recommended to the victims to only use decryptor developed by
security firms, because the one released by ransomware operators could hide
malware.
Recently another ransomware gang shut down its operations, it was the group
behind the Fonix ransomware.
Packaging giant WestRock is still working to resume after recent Ransomware
Attack
7.2.2021
Ransomware
Thehackernews
Packaging giant WestRock revealed this week that the recent ransomware attack
impacted the company’s IT and operational technology (OT) systems.
American
corrugated packaging company WestRock announced at the end of January that it
was the victim of a ransomware attack that impacted its information technology
(IT) and operational technology (OT) systems.
WestRock did not share details about the security incident, it only confirmed
that its staff discovered the attack on January 23. The company reported the
ransomware attack to law enforcement and notified its customers. The company is
responding to the incident with the help of leading cyber defense firms.
On Friday the company provided an update on the security incident while it is
working on restoring impacted systems. WestRock hasn’t shared any details about
the attack, such as the family of ransomware that infected its systems. In
response to the security breach, the company proactively shut down certain
systems and is implementing new measures to enhance its cybersecurity posture.
WestRock confirmed that the ransomware attack impacted its production, the good
news is that it has recovered most of the operations. Meantime the staff is
performing some tasks manually until all systems are restored.
WestRock is still assessing the overall operational and financial impact of the
ransomware attack.
“The Company’s mill system production through February 4
was approximately 85,000 tons lower than plan, and the packaging converting
operations are close to returning to full planned production levels.” reads the
press release published by the company.
“As a result of this incident, shipments from some of the Company’s facilities
have lagged production levels. This gap is closing quickly as systems are
restored. The WestRock team remains in regular communication with its customers
to share information and updates and to meet their business needs. WestRock is
also working with its vendors so they are informed, and supply chains remain
operational.”
WestRock confirmed that it has cyber insurance business interruption insurance.
“The Company maintains a variety of insurance policies, including cyber
insurance and business interruption insurance. There may be a time lag between
the initial incurrence of costs and the receipt of any insurance proceeds as the
Company’s operations return to normal,” adds WestRock.
Ransomware attacks, and more in general any cyber attack, could have a
significant impact on the victims, including important financial losses.
Trucking giant Forward Air Corporation, which recently suffered a ransomware
attack, estimated that the security breach would have an impact of $7.5 million.
Ransomware Attacks Hit Major Utilities
6.2.2021
Ransomware
Threatpost
Eletrobras, the largest power company in Latin America, faces a temporary
suspension of some operations.
Two state-owned utility companies in Brazil suffered separate ransomware attacks
in the past week, forcing them to shut down some operations and services
temporarily, In one case, sensitive data was stolen and dumped online, including
network access logins and engineering plans.
Centrais Eletricas Brasileiras (Eletrobras) and Companhia Paranaense de Energia
(Copel) both reported attacks, the latter of which appears to be the work of
Darkside, which flogged data stolen from the attack online, according to a
published report.
Darkside is a technically innovative ransomware group that’s tried to brand
itself as an altruistic, digital Robin Hood by making charitable donations with
the Bitcoin it’s stolen from victims.
In this case, the group said it stole more than 1,000 gigabytes of Copel data in
the attack, including sensitive information allowing for access to key
infrastructure, personally identifiable information (PII) of top management and
customers, and detailed engineering plans of the company’s network, according to
the report, which included a snapshot of an ad for the data from a hacker forum.
Both utilities are state-owned and have a significant presence in the country.
Eletrobras is the largest utility in Latin America and owner of Eletronuclear,
which constructs and operates nuclear power plants. Copel is the largest utility
provider in the Brazilian state of Parana.
Eletrobras Cyberattack Impacts Nuclear Plant Subsidiary
It’s not clear at
this time who is behind the Eletrobras attack, which the company acknowledged in
a press release posted earlier this week. The attack hit the administrative
network of its Eletronuclear subsidiary, which runs two nuclear power
plants—Angra1 and Angra 2.
In the case of the attack on Eletronuclear, the company had to suspend some of
its systems to protect the integrity of data, the company said.
However, the administrative network is not connected to the operational
technology (OT) systems that run the nuclear power plants, which are isolated
from that network for security reasons, according to the release. Because of
this, there was no impact on safety or the operation of the Almirante Álvaro
Alberto Nuclear Power Station (CNAAA), nor damage to the supply of electricity
to the National Interconnected System, according to Electrobras.
The company did not provide details on whether any data was stolen in the
attack, and if there is any indication of who the culprit may be. Eletrobras has
reported the attack to the appropriate authorities and is continuing to
investigate, it said.
Reams of Data Stolen from Copel Utility
The Copel attack was not publicly
disclosed but mentioned in an SEC filing on Monday, according to Bleeping
Computer, which appears to have had contact with Darkside about its hand in the
attack.
Hackers said they gained access to the company’s CyberArk cloud security
solution for privileged access management and exfiltrated plaintext passwords
across Copel’s local and internet infrastructure, according to the report.
Specifically, attackers said the 1,000 GB cache of data they pilfered includes:
Data from CyberArk storage with clear-text passwords from all local and internet
infrastructure; network maps and diagrams; backup schemes and schedules; domain
zones for cope.com and copel.nt domains; a database that stores ActiveDirectory
data; phone numbers, emails and ID and other personal data of employers and
customers, including top management; and NDAs, finances and contract info; and
detailed engineering schemes, plans and network switches.
Ransomware Remains a Top Cyberthreat
Ransomware continues to be one of the
top threats plaguing organizations, spurred by gangs’ success in extorting large
sums of money from victims. 2020 went down as a banner year for this type of
cybercrime, which hit less lucrative organizations such as hospitals
particularly hard due to the COVID-19 pandemic.
Ransomware gangs don’t appear to be letting up in 2021 either, with new variants
of ransomware already detected — such as Babuk Locker, which is targeting
corporations.
That said, there has been some promising news for potential ransomware victims
this year thanks to global efforts to take down the criminal gangs behind major
malware distribution schemes. Last week, an international law-enforcement
consortium disrupted one of the most prolific malware strains, Emotet, by
dismantling servers and infections. The malware is often used as a gateway
infection to distributing ransomware.
And in an unrelated effort, authorities in Canada charged a suspect believed to
be responsible for NetWalker ransomware attacks, and seized $454,500 in
cryptocurrency from ransom payments made by three separate victims.
Forward Air Corporation says that December Ransomware attack caused a loss of
$7.5M
6.2.2021
Ransomware
Securityaffairs
Trucking and freight transportation logistics giant Forward Air Corporation said
a December 2020 ransomware attack had $7.5M Impact.
Trucking and freight
transportation logistics giant Forward Air Corporation announced that the
ransomware attack that hit the company in December will impact its
fourth-quarter financial results.
This week the company filed a FORM 8-K with SEC that revealed that the
ransomware attack that took place in December impacted that infected its systems
caused service delays.
The company spent at least two weeks to recover the operations, it also declared
that the infection was expected to cause loss of revenue.
“The Company is in ongoing communication with its customers to address any
interim service delays. Although the Company is actively managing this incident,
it has caused and may continue to cause a delay in parts of the Company’s
business and may result in a deferral or loss of revenue as well as incremental
costs that may adversely impact the Company’s financial results.” reads the 8-K
form filed with SEC “As of the date of this filing, all the Company’s terminals
and facilities are operational.”
The security breach is expected to cause a loss $7.5 million of LTL revenue.
Forward Air did not reveal details on the attack such as the family of
ransomware that infected its systems.
FreightWaves reported that the company systems were infected with the Hades
ransomware.
Packaging Giant WestRock Says Ransomware Attack Hit Production
6.2.2021
Ransomware
Securityweek
Atlanta-based packaging giant WestRock (NYSE: WRK) on Friday shared an update on
the recent ransomware incident that impacted the company’s information
technology (IT) and operational technology (OT) systems.
The company has been investigating the incident while working on restoring
impacted systems. The response process has involved proactively shutting down
certain systems and enhancing cybersecurity measures.
The incident has impacted production, but WestRock says its operations are
nearly back to normal. Some tasks are being performed manually by staff until
all systems are restored.
“The Company’s mill system production through February 4 was approximately
85,000 tons lower than plan,” the company said in a press release on Friday.
To put that in perspective, WestRock’s annual report for 2020 says its
corrugated packaging mills had an annual production capacity of nearly 12
million tons, while its consumer packaging mills had a production capacity of
nearly 4 million tons.
The company has not shared any information about the attack itself and the
ransomware that was used.
WestRock said it continues to assess the overall operational and financial
impact of the incident, but noted that it does have cyber insurance.
“The Company maintains a variety of insurance policies, including cyber
insurance and business interruption insurance. There may be a time lag between
the initial incurrence of costs and the receipt of any insurance proceeds as the
Company’s operations return to normal,” WestRock said.
The company’s stock fell by roughly 4 percent after news of the breach broke,
and it has yet to recover.
This was not the only recently disclosed ransomware attack that had an impact on
not only IT systems, but also OT systems. Trucking giant Forward Air, which
suffered a ransomware attack that hit OT and IT systems in December 2020,
estimated this week that the incident would have an impact of $7.5 million.
Trucking Giant Says Ransomware Attack Had $7.5M Impact
5.2.2021
Ransomware
Securityweek
In a filing with the Securities and Exchange Commission (SEC) this week, North
American trucking and freight transportation logistics giant Forward Air
Corporation said a December 2020 ransomware attack had an impact on its fourth
quarter financial results.
For three decades, the Greeneville, Tennessee-based company has been providing
ground transportation and related logistics services to the air freight and
expedited less than load (LTL) market in North America.
In a December 2020 filing with SEC, the company revealed that a ransomware
incident affected its operational and information technology systems, causing
service delays.
The company was able to quickly contain the incident, after which it launched an
investigation into it and also informed the appropriate authorities.
Recovery operations lasted for at least a couple of months, and the company said
at the time that the incident was expected to cause loss of revenue, due to
continuous delays in the company’s business.
In an 8-K form filed with SEC this week, the transportation giant revealed that
the ransomware attack indeed had a financial impact.
“While the Company’s systems recovery efforts are completed and the Company’s
operations are fully functional, the incident did result in a loss of revenue as
well as incremental costs for the month of December which will adversely impact
the Company’s fourth quarter 2020 results,” Forward Air said.
Overall, the incident is expected to result in the loss of an estimated $7.5
million of LTL revenue, mainly because it had to suspend “electronic data
interfaces with its customers,” the transportation company says.
While Forward Air did not provide information on the ransomware family
responsible for the attack, FreightWaves reported that the Hades ransomware gang
was behind the incident.
SecurityWeek has contacted Forward Air for additional details on the incident
and the attackers’ demands and will update the article if a response arrives.
Ransomware operators exploit VMWare ESXi flaws to encrypt disks of VMs
3.2.2021
Ransomware
Securityaffairs
Ransomware operators are exploiting two VMWare ESXi vulnerabilities,
CVE-2019-5544 and CVE-2020-3992, to encrypt virtual hard disks.
Security
experts are warning of ransomware attacks exploiting two VMWare ESXi
vulnerabilities, CVE-2019-5544 and CVE-2020-3992, to encrypt virtual hard disks.
According to ZDNet, threat actors are using VMWare ESXi exploits to encrypt the
disks of virtual machines deployed in enterprise environments.
Since October, the RansomExx Ransomware gang (also known as Defray777) expanded
its operations by targeting VMWare virtual machines.
Victims reported that their VMs were abruptly shut down and then all files on
the datastore were encrypted (vmdk, vmx, logs). Threat actors left the ransom
note at the datastore level.
The news of the attack was also confirmed by the popular cybersecurity
researchers Kevin Beaumont that reported that threat actors are using the two
issues to bypass all Windows OS security, by shutting down VMs and encrypting
the VMDK’s directly on hypervisor.
Both CVE-2019-5544 and CVE-2020-3992 vulnerabilities in VMware ESXi impact the
Service Location Protocol (SLP), reside in the OpenSLP open-source
implementation of the Service Location Protocol (SLP), which allows the software
to locate resources on a network.
The CrowdStrike experts, Sergei Frankoff and Eric Loui, also reported that the
Sprite Spider ransomware operators also started targeting ESXi hosts since July
2020.
ZDNet reported that at the time of this writing only RansomExx
ransomware operators are exploiting the above issues, but it is aware that the
operators of the Babuk Locker ransomware will implement a similar attack chain.
System administrators are recommended to update their VMWare ESXi installs or
disable SLP support to secure them.
Fonix Ransomware Operators Close Shop, Release Decryption Keys
2.2.2021
Ransomware
Securityweek
The cybercriminals behind the Fonix ransomware have announced plans to shut down
their activity, and have already released the master decryption key for the
malware.
Also known as FonixCrypter and Xonif, the ransomware has been operating since
June 2020, with several variants observed since. The ransomware would add the
.FONIX, .XINOF, .Fonix, or .repter extensions to the encrypted files.
“You know about Fonix team but we have come to the conclusion. We should use our
abilities in positive ways and help others. […] Anyway now main admin has
decided to put all previous work aside and decrypt all infected systems at no
cost. And the decryption key will be available to the public,” the cyber-group
announced on Twitter.
In the shutdown announcement, the operators also said that the ransomware’s
source code was deleted, but warned that some people involved in the project
might attempt to scam others by selling them fake code.
In a separate message on the social platform, the group published a link to the
master RSA key needed to restore encrypted files, as well as to a sample
decryptor, which victims can use to recover their files without having to pay a
ransom.
They also announced that victims can send emails to XINOF [@] cock.li to have
their files decrypted for free. Furthermore, the Fonix operators offered to help
security researchers create decryption tools for the ransomware.
According to its operators, the Fonix project was launched due to their poor
financial situation, and the shutdown would help the developers stop feeling
guilty.
While the group did not make it clear what influenced the decision to close the
operation, it should be noted that other ransomware operators made similar moves
in the past, including those behind GandCrab, Shade, and TeslaCrypt.
Fonix’ shutdown announcement was made the same week law enforcement revealed the
infrastructure behind the massive Emotet botnet was disrupted and taken over by
authorities, with a cleanup operation set to begin within the next few months.
UK Research and Innovation (UKRI) discloses ransomware attack
31.1.2021
Ransomware
Securityaffairs
A ransomware infected the systems at the UK Research and Innovation (UKRI), at
leat two services were impacted.
The UK Research and Innovation (UKRI)
discloses a ransomware incident that impacted a number of UKRI-related web
assets.
Two services were impacted, a portal for our UK Research Office (UKRO) based in
Brussels and an extranet used by our Councils.
At the time of writing, it is
not clear if threat actors exfiltrated data from the UK agency that reported the
incident to the National Crime Agency, the National Cyber Security Centre and
Information Commissioner’s Office.
Launched in April 2018, UKRI is a non-departmental public body sponsored by the
Department for Business, Energy and Industrial Strategy (BEIS).
Our organisation brings together the seven disciplinary research councils,
Research England, which is responsible for supporting research and knowledge
exchange at higher education institutions in England, and the UK’s innovation
agency, Innovate UK.
The organizations it working to recover from the incident as well as conducting
forensic investigation to determine the extent of the incident.
“We are treating an IT incident that has impacted a number of UKRI-related web
assets as a cyber attack that has resulted in data being encrypted by a third
party.” reads the statement published by UKRI. “The UKRO portal provides an
information service to subscribers. The extranet is used to support the peer
review process for various parts of UKRI.”
One of the impacted services is an extranet that UKRI councils use for their
peer review activity, this means that grant applications and review information
might have been compromised. The same service, for a limited number of UKRI
review panel members, is used to support the processing of expense claims.
The second service, the UKRO subscription service one, has 13,000 users, but the
agency pointed out that it does not contain sensitive personal data.
“We do not yet know whether any financial details have been taken, but we will
endeavor to contact panel members to advise on personal protection against
possible fraud in this situation” continues the statement.
Victims of FonixCrypter ransomware could decrypt their files for free
31.1.2021
Ransomware
Securityaffairs
FonixCrypter ransomware operators shut down their operations, released the
master decryption key for free, and deleted malware’s source code.
Good news
for the victims of the FonixCrypter ransomware, the operators behind the threat
shut down their operations and released the master decryption key. The
FonixCrypter gang also closed its Telegram channel that was used to advertise
the malware in the cybercrime underground. The availability of the master
decryption key allows the victims to recover their encrypted files for free.
The FonixCrypter ransomware operators also deleted the ransomware’s source code
as their claim in a message published on Twitter:

The FonixCrypter operators also released containing a decryption tool and the
master decryption key, along with instructions to recover the files.
Experts who tested the decryption tool confirmed that it works and allows to
recover encrypted files for free. It is expected that some experts could use the
package released by the gang to build an easy to use and effective decryption
tool.
Unfortunately, at the time of writing the RAR archive is not available.
The popular Emsisoft security researcher Michael Gillespie told ZDNet that his
company is working on a decrypted and suggested avoiding use the one provided by
the FonixCrypter gang due to the possibility that its code could hide a
backdoor.
Michael Gillespie also told BleepingComputer that the master keys work but only
on some Fonix ransomware versions, including the ones that append .Fonix,
.FONIX, .repter, .XINOF extensions to filenames of encrypted files.
The FonixCrypter ransomware gang has been active since at least June 2020, it
was available with a ransomware-as-a-service model.
This ransomware encrypts user files using Salsa + RSA, and provides victims an
email address to receive the instructions to pay the ransom. The ransomware
received multiple updates over time.
The security researcher Andrew Ivanov published technical details about this
specific threat in a blog post.
Authorities Seize Dark-Web Site Linked to the Netwalker Ransomware
29.1.2021
Ransomware
Thehackernews

U.S. and Bulgarian authorities this week took control of the dark web site used
by the NetWalker ransomware cybercrime group to publish data stolen from its
victims.
"We are striking back against the growing threat of ransomware by not only
bringing criminal charges against the responsible actors, but also disrupting
criminal online infrastructure and, wherever possible, recovering ransom
payments extorted from victims," said Acting Assistant Attorney General Nicholas
L. McQuaid of the Justice Department's Criminal Division.
"Ransomware victims should know that coming forward to law enforcement as soon
as possible after an attack can lead to significant results like those achieved
in today's multi-faceted operation."
In connection with the takedown, a Canadian national named Sebastien
Vachon-Desjardins from the city of Gatineau was charged in the U.S. state of
Florida for extorting $27.6 million in cryptocurrency from ransom payments.
Separately, the Bulgarian National Investigation Service and General Directorate
Combating Organized Crime seized a dark web hidden resource used by NetWalker
ransomware affiliates — i.e., cybercrime groups responsible for identifying and
attacking high-value victims using the ransomware — to provide payment
instructions and communicate with victims.
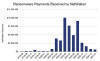
Visitors to the website will now be greeted by a seizure banner notifying them
that it has been taken over by law enforcement authorities.
Chainalysis, which aided in the investigation, said it has "traced more than $46
million worth of funds in NetWalker ransoms since it first came on the scene in
August 2019," adding "it picked up steam in mid-2020, growing the average ransom
to $65,000 last year, up from $18,800 in 2019."
In recent months, Netwalker emerged as a popular choice of ransomware strain
besides Ryuk, Maze, Doppelpaymer, and Sodinokibi, with numerous companies,
municipalities, hospitals, schools, and universities targeted by the
cybercriminals to extort victims.
Before the takedown, the NetWalker administrator, who goes by the moniker
"Bugatti" on darknet forums, is said to have posted an advertisement in May 2020
looking for additional Russian-speaking affiliates as part of a transition to a
ransomware-as-a-service (RaaS) model, using the partners to compromise targets
and steal data before encrypting the files.
The NetWalker operators have also been part of a growing ransomware trend called
double extortion, where the attackers hold the stolen data hostage and threaten
to publish the information should the target refuse to pay the ransom.

"After a victim pays, developers and affiliates split the ransom," the U.S.
Department of Justice (DoJ) said.
Chainalysis researchers suspect that besides involving in at least 91 attacks
using NetWalker since April 2020, Vachon-Desjardins worked as an affiliate for
other RaaS operators such as Sodinokibi, Suncrypt, and Ragnarlocker.
The NetWalker disruption comes on the same day that European authorities
announced a coordinated takedown targeting the Emotet crimeware-as-a-service
network. The botnet has been used by several cybercrime groups to deploy
second-stage malware — most notably Ryuk and TrickBot.
NetWalker Ransomware Suspect Charged: Tor Site Seized
28.1.2021
Ransomware
Threatpost
The suspect allegedly has extorted $27.6 million from ransomware victims, mostly
in the healthcare sector.
Hot on the heels of the Emotet takedown announced Wednesday, the NetWalker
ransomware has also been partially disrupted by an international police action.
The Department of Justice said Wednesday that it has brought charges “against a
Canadian national in relation to NetWalker ransomware attacks,” while also
seizing around $454,500 in cryptocurrency from ransom payments made by three
separate victims.
The Canadian in question, Sebastien Vachon-Desjardins of Gatineau, is alleged to
have raked in more than $27.6 million overall from NetWalker activities. It’s
unclear what specific part he played in the ransomware’s overall operations, nor
if he is in custody. Threatpost has reached out for further information.
“This represents a significant win for the good guys,” Brett Callow, threat
analyst at Emisoft, told Threatpost. “Historically, too few cybercriminals have
been prosecuted. Hopefully, actions such as this will create a real deterrent
and, coupled with other measures, start to have an impact on ransomware and
other forms of cybercrime.”
He pointed out that according to Third Way, the effective enforcement rate for
cybercrime in the U.S. is only 0.05 percent – which the think-tank describes as
a “stunning enforcement gap.”
NetWalk of Shame
The NetWalker ransomware has impacted numerous types of
victims since bursting on the scene in 2020; but it has made healthcare targets
a particular focus, using the COVID-19 pandemic to better extort organizations.
NetWalker’s victims include the University of California – San Francisco (a
leading institution in biological and medical research and home to a medical
school and a medical center); the Crozer-Keystone Health System,
Champaign-Urbana Public Health District and the College of Nurses of Ontario. It
is also the scourge behind one of the Toll Group attacks.
In mid-2020, NetWalker authors notably transitioned to a ransomware-as-a-service
(RaaS) model, where they rent the malware and surrounding services to affiliates
who carry out the actual attacks. Authors and affiliates then split the profits.
Its operators are known for placing a heavy emphasis on targeting and attracting
technically advanced affiliates, according to researchers, with special
expertise in network access.
Dark Web Site Seized
Meanwhile, the Bulgarian national police force has
disabled “a Dark Web hidden resource used to communicate with NetWalker
ransomware victims” to provide payment instructions; researchers said the Tor
node is also the group’s leaks site, where it publishes stolen victim
information if the target refuses to pay a ransom in a form of double extortion.
“We are striking back against the growing threat of ransomware by not only
bringing criminal charges against the responsible actors, but also disrupting
criminal online infrastructure and, wherever possible, recovering ransom
payments extorted from victims,” said Acting Assistant Attorney General Nicholas
L. McQuaid of the Justice Department’s Criminal Division, in a statement.
“Ransomware victims should know that coming forward to law enforcement as soon
as possible after an attack can lead to significant results like those achieved
in today’s multi-faceted operation.”
Earlier on Wednesday researchers reported on Twitter that NetWalker’s Dark Web
site was displaying a purported seizure notice.

The Feds confirmed the action a few hours later.
Law enforcement announced global action against NetWalker Ransomware
28.1.2021
Ransomware
Securityaffairs
A joint operation of U.S. and EU law enforcement authorities allowed the seizure
of the leak sites used by NetWalker ransomware operators.
Law enforcement
authorities in the U.S. and Europe have seized the dark web sites used by
NetWalker ransomware operators. The authorities also charged a Canadian national
involved in the NetWalker ransomware operations.
“The Department of Justice today announced a coordinated international law
enforcement action to disrupt a sophisticated form of ransomware known as
NetWalker.” reads the press release published by DoJ.
“NetWalker ransomware has impacted numerous victims, including companies,
municipalities, hospitals, law enforcement, emergency services, school
districts, colleges, and universities. Attacks have specifically targeted the
healthcare sector during the COVID-19 pandemic, taking advantage of the global
crisis to extort victims.”
The group has been active since 2019, the NetWalker ransomware has been offered
with the Ransomware-as-a-Service (RaaS) model.
The list of victims of the
group is long, it includes Pakistan’s largest private power company K-Electric,
Argentina’s official immigration agency, Dirección Nacional de Migraciones, and
the University of California San Francisco (UCSF), the latter paid a $1.14
million ransom to recover its files.
In August 2020, the FBI has issued a security alert about Netwalker ransomware
attacks targeting U.S. and foreign government organizations.
NetWalker is also believed to have been responsible for compromising the network
of the University of California San Francisco (UCSF), which paid over $1 million
to recover from the incident. In July, the FBI warned of NetWalker attacks
targeting government organizations.
The Department of Justice also charged against the Canadian national Sebastien
Vachon-Desjardins in relation to NetWalker ransomware attacks, he is alleged to
have obtained at least over $27.6 million as a result of the offenses charged in
the indictment. The law enforcement also seized $454,530.19 in cryptocurrency
obtained from ransom payments.
Bulgarian authorities seized a dark website used by NetWalker affiliates to
communicate with victims.

“This case illustrates the FBI’s capabilities and global partnerships in
tracking ransomware attackers, unmasking them, and holding them accountable for
their alleged criminal actions,” said Special Agent in Charge Michael F.
McPherson of the FBI’s Tampa Field Office. “If you are a victim of ransomware,
contact your local FBI field office or submit a tip to tips.fbi.gov. You can
also file a complaint with the FBI’s Internet Crime Complaint Center at
www.ic3.gov.”
NetWalker Ransomware’s Sites Seized by Law Enforcement
28.1.2021
Ransomware
Securityweek
Law enforcement authorities in the U.S. and Europe have seized the dark web
sites associated with the NetWalker ransomware operations and also charged a
Canadian national in relation to the malware.
First spotted in 2019 and also known as Mailto, NetWalker has been available as
Ransomware-as-a-Service (RaaS), and is responsible for multiple high-profile
attacks, including the targeting of a public health organization in the United
States, and a transportation and logistics company in Australia.
NetWalker is also believed to have been responsible for compromising the network
of the University of California San Francisco (UCSF), which paid over $1 million
to recover from the incident. In July, the FBI warned of NetWalker attacks
targeting government organizations.
In an August 2020 report, McAfee’s security researchers estimated the total
revenue generated by NetWalker to have been in excess of $25 million by July
2020.
In an announcement today, the U.S. Department of Justice pointed out that
NetWalker has been used in attacks on emergency services, hospitals, law
enforcement, municipalities, school districts, colleges, universities, and
private companies.
“Attacks have specifically targeted the healthcare sector during the COVID-19
pandemic, taking advantage of the global crisis to extort victims,” the DoJ
noted.
The Department also announced charges against Sebastien Vachon-Desjardins of
Gatineau, a Canadian national, in relation to NetWalker ransomware attacks. He
is believed to have obtained “at least over $27.6 million” in proceeds from the
offenses described in the indictment.
On Jan. 10, authorities seized approximately $454,530.19 in cryptocurrency,
composed from ransom payments received from victims. This week, Bulgarian
authorities managed to dismantle the dark web sites the NetWalker operators were
using to communicate with victims.
Visitors of the Tor websites are now shown a notice informing them of the law
enforcement’s action: “This hidden site has been seized by the Federal Bureau of
Investigation, as part of a coordinated law enforcement action taken against the
NetWalker Ransomware.”
Responding to a SecurityWeek inquiry, Ivan Righi, cyber threat intelligence
analyst at Digital Shadows, revealed that the leaks site (where RaaS affiliates
made data stolen from their victims public) went down around 9-10 AM (CT).
Nefilim Ransomware Gang Hits Jackpot with Ghost Account
27.1.2021
Ransomware
Threatpost
An unmonitored account belonging to a deceased employee allowed Nefilim to
exfiltrate data and infiltrate systems for a month, without being noticed.
A Nefilim ransomware attack that locked up more than 100 systems stemmed from
the compromise of an unmonitored account belonging to an employee who had died
three months previously, researchers said.
Nefilim (a.k.a. Nemty) is a ransomware strain that emerged in 2020, with its
operators adopting the tactic that researchers call double extortion. In other
words, Nefilim threatens to release victims’ data to the public if they fail to
pay the ransom; it has its own leaks site called Corporate Leaks, which resides
on a TOR node. Most famously, it attacked Australian transportation giant Toll
Group early last year.
According to Sophos researcher Michael Heller, this latest victim was
compromised by exploiting vulnerable versions of Citrix software, after which
the gang gained access to an admin account. From there, it stole the credentials
for a domain admin account using Mimikatz.
Nefilim Lurks for a Month, Stealing Data
A Sophos forensic analysis found
that the organization’s installed Citrix Storefront 7.15 CU3 was vulnerable at
time of incident to a known critical security bug (CVE-2019-11634) and four
high-severity issues (CVE-2019-13608, CVE-2020-8269, CVE-2020-8270,
CVE-2020-8283). Storefront is an enterprise app store that employees can use to
download approved applications.
It’s almost certain, the team found, that this was the initial point of entry
into the victim’s network.
After exploiting the Citrix installation and establishing an initial foothold,
the attackers also used Remote Desktop Protocol (RDP) logins to maintain remote
access to the initial admin account used in the attack.
To move laterally, the threat actor used Mimikatz, which allows attackers to
enumerate and view the credentials stored on the system. Armed with that
knowledge, they were then able to compromise a domain administrator account.
Domain admin in Windows is a user account that can edit information in Active
Directory. It can modify the configuration of Active Directory servers and can
modify any content stored in Active Directory. This includes creating new users,
deleting users, and changing their permissions. As such, it gives its controller
a lot of power and visibility into the network.
“The Rapid Response investigation then uncovered PowerShell commands as well as
the use of RDP and Cobalt Strike to move laterally to multiple hosts, conduct
reconnaissance and enumerate the network,” Heller explained in a Tuesday
analysis. “The threat actor installed the file transfer and synchronization
application MEGA in order to exfiltrate data; [and] the Nefilim ransomware
binaries were deployed using Windows Management Instrumentation (WMI) via the
compromised domain admin account.”
In all, the Nefilim operators were inside the victim’s network for about one
month before launching the ransomware itself, Heller said, often carrying out
activities in the middle of the night to avoid detection.
“The attacker gained access to that admin account, then spent one month quietly
moving around to steal credentials for a domain admin account, finding the trove
of data they wanted, exfiltrating hundreds of GB of data, and then finally
announcing their presence with the ransomware attack,” he noted in a Tuesday
posting.
Ghost Account: A Failing of Best Security Practices
The issue is that the
administrative account that handed the cybercriminals the keys to the company’s
data kingdom belonged to someone who is no longer with the company – indeed who
no longer walks the earth. These types of “ghost” accounts present above-average
risk to enterprises, researchers said, because of the lack of oversight in terms
of how and when such accounts are used, given that there’s no daily user to keep
tabs on activity.
Sophos Rapid Response manager Peter Mackenzie told the customer that another
type of attacker, a more stealthy one, could have lurked for months, stealing
all sensitive information in the company’s systems.
“If they hadn’t [deployed ransomware], how long would they have had domain admin
access to the network without the customer knowing?”
Thus, alerts for when domain admin accounts are created or used could
potentially have prevented the attack. In a previous case, Sophos researchers
saw an attacker gaining access to an organization’s network, creating a new
user, and adding that account to the domain admin group in Active Directory –
but, no alerts were set off.
“That new domain admin account went on to delete about 150 virtual servers and
used Microsoft BitLocker to encrypt the server backups,” Mackenzie said.
Best practices would dictate taking such accounts out of commission completely,
but the organization said it was kept active “because there were services that
it was used for.”
“If an organization really needs an account after someone has left the company,
they should implement a service account and deny interactive logins to prevent
any unwanted activity,” Heller noted. “Or, if they don’t need the account for
anything else, disable it and carry out regular audits of Active Directory.
Active Directory Audit Policies can be set to monitor for admin account activity
or if an account is added to the domain admin group.”
Mackenzie said that in general, far fewer accounts need to be designated as
domain admins than most people think.
“People assume because a person is an executive or is in charge of the network
that they need to be using a domain admin account. This isn’t true and it’s
dangerous,” he said. “No account with privileges should be used by default for
work that doesn’t require that level of access. Users should elevate to using
the required accounts when needed and only for that task.”
Best practices to avoid attacks like this include only granting access
permissions that are needed for a specific task or role; disabling accounts that
are no longer needed; implementing a service account and denying interactive
logins for any “ghost” accounts; and carrying out regular audits of Active
Directory to monitor for admin account activity or if an unexpected account is
added to the domain admin group.
“Ransomware will continue to plague organizations for the foreseeable future, so
it’s important that the root causes are looked at. In this case, the criminals
were successful in their attack by being able to take over an orphan or ghost
account which had administrative privileges,” Javvad Malik, security awareness
advocate at KnowBe4, said via email. “Account management, and in particular,
privileged account management is an important security control for which all
organizations should have processes in place.”
Ransomware attack hit WestRock IT and OT systems
26.1.2021
Ransomware
Securityaffairs
Packaging giant WestRock disclosed a ransomware attack that impacted its
information technology (IT) and operational technology (OT) systems.
American
corrugated packaging company WestRock announced it was the victim of a
ransomware attack that impacted its information technology (IT) and operational
technology (OT) systems.
WestRock did not share details about the security incident, it only confirmed
that its staff discovered the attack on January 23. The company reported the
ransomware attack to law enforcement and notified its customers. The company is
responding to the incident with the help of leading cyber defense firms.
“Systems recovery efforts are in process and being implemented as quickly as
possible, and teams are working to maintain the Company’s business operations
and to minimize the impact on its customers and teammates.” reads the
announcement published by WestRock.
“Although WestRock is actively managing this incident and will continue to do
so, it has caused and may continue to cause delays in parts of the Company’s
business and may result in a deferral or loss of revenue and incremental costs
that may adversely impact WestRock’s financial results.”
At the time of this writign, it is not clear the extent of the attack either the
type of OT systems impacted in the incident.
Packaging Giant WestRock Says Ransomware Attack Impacted OT Systems
26.1.2021
Ransomware
Securityweek
American packaging giant WestRock (NYSE: WRK) on Monday revealed that it was
recently targeted in a ransomware attack that impacted both information
technology (IT) and operational technology (OT) systems.
The company has shared few details about the incident, which it discovered on
January 23, when it “promptly” initiated response and containment protocols. Law
enforcement has been notified and customers are being kept in the loop about the
incident, WestRock said in a press release.
“Systems recovery efforts are in process and being implemented as quickly as
possible, and teams are working to maintain the Company’s business operations
and to minimize the impact on its customers and teammates,” WestRock stated.
It added, “Although WestRock is actively managing this incident and will
continue to do so, it has caused and may continue to cause delays in parts of
the Company’s business and may result in a deferral or loss of revenue and
incremental costs that may adversely impact WestRock’s financial results.”
The value of WestRock stock dropped by more than 4 percent on Monday morning
after the breach was disclosed.
While the extent of the impact on OT systems is unclear, industrial
cybersecurity companies and experts have long warned about the threat posed by
ransomware.
There are at least seven ransomware families known to target industrial software
and a report released last year by IBM and industrial cybersecurity firm Dragos
warned that industrial control systems (ICS) powering manufacturing plants and
utilities are a prime target for threat groups specializing in ransomware
attacks.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) reported last
year that a ransomware infection at a natural gas compression facility in the
United States resulted in a two-day operational shutdown of an entire pipeline
asset.
Ransomware Attackers Publish 4K Private Scottish Gov Agency Files
23.1.2021
Ransomware
Threatpost
Up to 4,000 stolen files
have been released by hackers who launched a ransomware attack against the
Scottish Environmental Protection Agency on Christmas Eve.
On the heels of a ransomware attack against the Scottish Environmental
Protection Agency (SEPA), attackers have now reportedly published more than
4,000 files stolen from the agency – including contracts and strategy documents.
After hitting SEPA on Christmas Eve with the attack, cybercriminals encrypted
1.2GB of information. The attack has affected SEPA’s email systems, which remain
offline as of Thursday, according to the agency. However, SEPA, which Scotland’s
environmental regulator, stressed on Thursday that it will not “engage” with the
cybercriminals.
“We’ve been clear that we won’t use public finance to pay serious and organized
criminals intent on disrupting public services and extorting public funds,” said
SEPA chief executive Terry A’Hearn in a statement.
The agency is charged with protecting Scotland’s environment via national flood
forecasting, flood warnings and more. As such, the stolen data included various
information related to environmental businesses – including publicly-available
regulated site permits, authorizations and enforcement notices, as well as data
related to SEPA corporate plans, priorities and change programs. Other
compromised data was related to publicly available procurement awards and
commercial work with SEPA’s international partners. Also stolen was the personal
data of SEPA’s staff.
Despite these broad categories, SEPA said it still does not know – and may never
know – the full details of all files stolen. Some of the compromised information
was already publicly available, while other data was not, it confirmed.
“Working with cyber security experts, a dedicated team has been established to
identify the detail of business or partner information loss and, where
identified, direct contact will be made as quickly as possible with affected
organizations,” according to SEPA.
SEPA’s email and other systems remain down, and “it is now clear is that with
infected systems isolated, recovery may take a significant period,” according to
the agency in its update. “A number of SEPA systems will remain badly affected
for some time, with new systems required.”
What’s still unclear is how the ransomware attack first started and how much
attackers are demanding in terms of a ransom payment. Regardless of the ransom
amount, attackers are now putting more pressure on the agency to pay up: This
data has now been thrown out on underground forums. According to reports,
hackers said on their website that almost 1,000 people so far have viewed the
compromised documents.
Brett Callow, threat analyst with Emsisoft, told Threatpost that the Conti
ransomware gang has taken responsibility for the attack.
“Attacks on governments have become increasingly common over the last couple of
years, and will almost certainly continue at the current level until some
positive action is taken,” said Callow. “That may be investing to bolster
security in the public sector, using policy to close the enforcement gap or
finding other ways to make ransomware less profitable or any combination of
these.”
Ransomware actors are also looking at government and public sector victims for
rooting out personal data. In 2019, up to 22 Texas entities and government
agencies were hit by a ransomware attack that Texas officials say was part of a
targeted attack launched by a single threat actor. And in October 2020, the
National Guard was called in to help stop a series of government-focused
ransomware attacks in Louisiana.
The incident also points to ransomware actors evolving from previously
destroying critical data or bringing companies’ services and operations to a
standstill, to now threatening to disclose sensitive data publicly, Joseph
Carson, chief security scientist and Advisory CISO at Thycotic told Threatpost.
“It’s no longer good enough to have solid backups to protect against
ransomware,” Carson told Threatpost. “Strong access controls and encryption are
now vital to prevent data being easily stolen and released. As ransomware
evolves, we must also evolve our protection to reduce the risk of falling victim
to it.”
Ransomware Took Heavy Toll on US in 2020: Researchers
21.1.2021
Ransomware
Securityweek
Ransomware attacks took a heavy toll on the United States last year with more
than 2,000 victims in government, education and health care, security
researchers say in a new report.
The study released Monday by the security firm Emsisoft said ransomware attacks
-- which encrypt and disable computer systems while demanding a ransom --
affected 113 federal, state and municipal governments, 560 health facilities and
1,681 schools, colleges and universities last year.
"The attacks caused significant, and sometimes life-threatening, disruption:
ambulances carrying emergency patients had to be redirected, cancer treatments
were delayed, lab test results were inaccessible, hospital employees were
furloughed and 911 (emergency) services were interrupted," the report said.
The security firm said it was unable to estimate the losses from the attacks due
to a lack of data but that it was "safe to assume that the total cost runs to
multiple billions."
The numbers of attacks were little changed from 2019 but there were "more
successful attacks on the healthcare sector," including incidents affecting
groups with multiple hospitals, according to Emsisoft spokesman Brett Callow.
Similarly, Callow said, "the education sector saw a similar number of attacks,
but more schools were affected due to bigger districts" hit.
The targets included large regional cities and municipalities, major hospital
systems and large colleges and universities, according to Emsisoft.
The researchers said hackers are stepping up by not only encrypting but stealing
data which may be sold to competing firms or various governments.
"We anticipate there will be more cases of data theft in 2021 than there were in
2020," the report said. "Like legitimate businesses, criminal enterprises adopt
strategies that are proven to work, and data theft has indeed been proven to
work. "
Emsisoft's chief technical officer Fabian Wosar said much of the risk from
ransomware can be eliminated with preventive steps.
"Proper levels of investment in people, processes and IT would result in
significantly fewer ransomware incidents and those incidents which did occur
would be less severe, less disruptive and less costly," he said in a statement.
Researchers Estimate Ryuk Ransomware Operations to Be Worth $150 Million
19.1.2021
Ransomware
Securityweek
The Ryuk ransomware criminal enterprise is estimated to be worth more than
$150,000,000, security researchers say.
Initially detailed in 2018 and believed to be operated by Russian
cybercriminals, Ryuk has become one of the most prevalent malware families,
being used in various high-profile attacks, such as the targeting of
Pennsylvania-based UHS and Alabama hospital chain DCH Health System.
Ryuk’s is believed to be operated by the same cybercriminals as the TrickBot
Trojan, and its distribution has been associated with the TrickBot botnet, which
in October survived a takedown attempt.
In October 2020, the DFIR Report published a comprehensive analysis of a Ryuk
attack, explaining how operators used phishing emails as the initial attack
vector, performed extensive reconnaissance on the local network, and then
proceeded to deploy and run Ryuk.
The attackers deployed Ryuk 29 hours after initial compromise, and demanded a
ransom payment of approximately $6 million to be made. Many of the payments
Ryuk’s operators receive (mainly through a broker) amount to millions of
dollars, but most of them are in the hundreds of thousands range.
Going after high profile victims appears to have allowed Ryuk operators to build
a highly lucrative enterprise, which might have generated more than $150,000,000
in revenue over the past two years and a half.
The estimate was made by Brian Carter, principal researcher at HYAS, and Vitali
Kremez, CEO and chairman of Advanced Intelligence LLC, after they had a look
into transactions for known Bitcoin addresses associated with Ryuk.
Carter and Kremez were able to trace 61 deposit addresses associated with the
ransomware and discovered that the majority of the funds were sent to exchanges
through intermediaries, for cash out.
The cybercriminals appear to be primarily using the Asian crypto-exchanges Huobi
and Binance, although both require documents to exchange crypto-coins to fiat
currency, and both claim to be willing to cooperate with law enforcement.
Additionally, Ryuk operators are sending “significant flows of crypto currency”
to several small addresses that are believed to be “a crime service that
exchanges the cryptocurrency for local currency or another digital currency.”
“Significant volumes of Bitcoin move from the laundering service to Binance,
Huobi, and crime markets that we have identified through traced payments,” the
two researchers say.
CAPCOM: 390,000 people impacted in the recent ransomware Attack
15.1.2021
Ransomware
Securityaffairs
Capcom revealed that the recent ransomware attack has potentially impacted
390,000 people, an increase of approximately 40,000 people from the previous
report.
In November, Japanese game developer Capcom admitted to have suffered
a cyberattack that is impacting business operations.
The company has developed multiple multi-million-selling game franchises,
including Street Fighter, Mega Man, Darkstalkers, Resident Evil, Devil May Cry,
Onimusha, Dino Crisis, Dead Rising, Sengoku Basara, Ghosts ‘n Goblins, Monster
Hunter, Breath of Fire, and Ace Attorney as well as games based on Disney
animated properties.
At the time, the Notice Regarding Network Issues published by the company
revealed that on the morning of November 2nd, 2020 is suffered a cyberattack, In
response to the incident the game developer shut down portions of their
corporate network to prevent the malware from spreading.
The incident has not impacted connections for its players, the company initially
declared that had not found any evidence that customer data was stolen.
In Mid-November, the company confirmed that the attackers accessed the personal
information of its employees, along with financial and business information. The
company believes that other information potentially accessed includes sales
reports, financial information, game development documents, other information
related to business partners.
No credit card information was compromised in the security breach.
After the attack, the Ragnar Locker ransomware operators claimed to have stolen
over 1TB of data from the company.
In an update published by the Ragnar ransomware gang on it leak site the
operators leaked a collection of archives as proof of the hack.
“Unfortunately even such worldwide leading company as CAPCOM doesn’t values much
privacy and security. They was notified about vulnerability and data leak
numerous time.” reads the post published by Ragnar gang on its leak site. They
checked our page with proofs but even this didn’t help them to make a right
decision and save data from leakage. Also we would help them to decrypt and also
provide with recommendations on security measures improvement, to avoid such
issues in future.” reads the post published by the ransomware on its leak site.
“We are sure that everyone should know about CAPCOM’s decision and careless
attitude regarding data privacy. This might seems crazy in 21st century, all
corporates should work harder on their security measures, especially IT and
online based companies.”

This week, Capcom provided an update on its investigation, that revealed the
incident was worse than initially thought because the number of impacted people
is larger than initially believed.
Capcom revealed that the personal information of 16,415 people was stolen by the
ransomware gang. Impacted people includes 3,248 business partners, 9,164 former
employees, and related parties, and 3,994 employees and related parties. Only 9
people were impacted.
“Further, because the overall number of potentially compromised data cannot
specifically be ascertained due to issues including some logs having been lost
as a result of the attack, Capcom has listed the maximum number of items it has
determined to potentially have been affected at the present time.” reads the
update published by the company.
Cumulative maximum number of potentially impacted people is 390,000, an increase
of approximately 40,000 people from the previous report.
1. Information
verified to have been compromised (updated)
I. PERSONAL INFORMATION 16,406 people *cumulative total since investigation
began: 16,415 peopleBusiness partners, etc.: 3,248 people
At least one of the
following: name, address, phone number, email address, etc.Former employees and
related parties: 9,164 people
At least one of the following: name, email
address, HR information, etc.Employees and related parties: 3,994 people
At
least one of the following: name, email address, HR information, etc.
II.
OTHER INFORMATION Sales reports, financial information, game development
documents, other information related to business partners
2. Potentially
compromised data (updated)
I. PERSONAL INFORMATION Applicants: approx. 58,000 people
At least one of the
following: name, address, phone number, email address, etc.*Cumulative maximum
number of potentially compromised data for customers,
business partners and
other external parties: 390,000 people*Regarding the cumulative maximum number
of potentially compromised data above: as part of its ongoing investigation,
Capcom has determined that it currently does not see evidence for the
possibility of data compromise for the approximate 18,000 items of personal
information from North America (Capcom Store member information and esports
operations website members) that the company included in its November 16, 2020
announcement. As such, these have been removed from this cumulative maximum
number of potentially compromised data.
The company pointed out that the
investigation is still ongoing and that new fact may come to light.
“At this point in time, Capcom’s internal systems have in large part recovered,
and business operations have returned to normal.” concludes the update.
Capcom Says Personal Data of Thousands More Stolen in Ransomware Attack
15.1.2021
Ransomware
Securityweek
Video game giant Capcom this week revealed that thousands more people than
initially believed had their personal information stolen in a ransomware attack
in November 2020.
Known for video games such as Devil May Cry, Monster Hunter, Resident Evil,
Street Fighter, Ace Attorney and Mega Man, the Japanese company has operations
in Asia, Europe, and the United States.
On November 4, the game maker announced that it detected unauthorized access to
its network, and two weeks later confirmed that the attackers accessed the
personal information of employees, as well as financial information, sales
reports, and other business data.
The operators of the Ragnar Locker ransomware, who claimed the attack, said in
November they were able to download over 1TB of data from the company.
This week, Capcom announced that its investigation into the incident revealed
that the number of people who had their personal information compromised in the
ransomware attack is larger than initially believed.
Specifically, the company now says that a total of 16,415 people (including
3,248 business partners, 9,164 former employees and related parties, and 3,994
employees and related parties) had their personal information stolen. Initially,
Capcom said only 9 people were impacted.
Affected information includes names, physical and email addresses, phone
numbers, HR information, birthdates, passport information, and the like.
The “potential maximum number of customers, business partners and other external
parties” that might have been affected by the incident is of approximately
390,000 people (up roughly 40,000 people from previous estimates), Capcom says.
The company removed approximately 18,000 items of personal information from the
list, as it has no evidence that the data might have been affected.
Game development documents, sales reports, financial information, and other
information related to business partners was also accessed during the ransomware
attack. The company also expects for new details to emerge as the investigation
progresses.
“Further, because the overall number of potentially compromised data cannot
specifically be ascertained due to issues including some logs having been lost
as a result of the attack, Capcom has listed the maximum number of items it has
determined to potentially have been affected at the present time,” the video
game maker notes.
Just as before, the company underlined that no credit card information was
compromised in the incident, as such information is not stored internally
(online transactions are handled by a third-party service provider).
Capcom says that it was able to recover most of the affected internal systems
and that business operations have returned to normal.
Bitdefender releases free decrypter for Darkside ransomware
13.1.2021
Ransomware
Securityaffairs
Security firm Bitdefender released a tool that allows victims of the Darkside
ransomware to recover their files without paying the ransom.
Good news for
the victims of the Darkside ransomware, they could recover their files for free
using a tool that was released by the security firm Bitdefender. The decrypter
seems to work for all recent versions of the Darkside ransomware.
Darkside ransomware first appeared in the threat landscape in August 2020, its
operators were distributing it using a ransomware-as-a-service business model.

Like other ransomware gangs, Darkside ransomware operators threaten to leak
files stolen from the victims if they don’t pay the ransom.
The group is still active but has yet to publish data of its victims on its leak
site.
What will the gang do in the next weeks?
The ransomware author have to review their operations and improve their file
encryption process to make the free decryption inefficient.
Intel Packs Ransomware Detection Directly Into vPro Platform
13.1.2021
Ransomware
Securityweek
At the virtual Consumer Electronics Show (CES) on Monday, chipmaker Intel
announced CPU-based ransomware detection capabilities have been fitted directly
into the Intel vPro platform.
Increasingly targeting businesses, ransomware has become the most prominent
threat to enterprises, requiring advanced solutions to keep their data and the
data of their users safe.
Most traditional detection solutions, Intel suggests, are reactionary, not to
mention the fact that ransomware operators use various means to evade detection.
Ragnar Locker, for example, deploys virtual machines to perform operations
unhindered by the security solutions running on the system.
CPU threat detection, Intel says, is not dependent on the security solutions
available at OS or application level and can immediately identify encryption
attempts at the lowest level.
Courtesy of Intel Threat Detection Technology (Intel TDT), Intel’s vPro platform
can detect encryption attempts and can also filter ransomware activity from
other encryption behavior. Furthermore, the detection is immune to bypasses,
Intel claims.
“Intel TDT is a key feature of the Intel vPro platform which makes profiling and
detection possible across the entire device stack. Intel TDT uses a combination
of CPU telemetry and ML heuristics to detect attack-behavior. It detects
ransomware and other threats that leave a footprint on Intel CPU performance
monitoring unit (PMU),” Intel said in its CES announcement.
CPU behavior monitoring and threat detection through Intel TDT are supported on
Intel 10th Gen and newer Intel Core processor-based PCs, in conjunction with
security vendors that packed such capabilities into their solutions.
Cybereason is one of the vendors that partnered with Intel to deliver CPU–level
ransomware protection on 11th Gen Intel Core vPro mobile platforms, which come
equipped with Intel Hardware Shield and Intel TDT. Market availability is
expected for the first half of 2021.
Through this partnership, Cybereason says, enterprises get better protection
against attacks courtesy of CPU-based threat detection, full-stack visibility,
machine learning (accelerated through the integrated graphics controller (GPU)
in the CPU), and accelerated endpoint prevention, detection, and response.
The collaboration between the two companies will also result in additional
intelligence for ransomware detection available through the integration of Intel
TDT capabilities into the Cybereason Defense Platform.
According to Intel, systems powered by the vPro platform with Intel Hardware
Shield can also prevent lateral movement, courtesy of capabilities such as
hardware-enforced isolation of virtualized containers, secure boot, firmware
security, and memory protections.
Intel TDT, which is enabled by solutions from top security vendors, including
Microsoft Defender, SentinelOne Singularity, and Blackberry Optics, also
includes EDR remediation workflows, to help recovery, by allowing for the
identification of data affected by ransomware, as well as recovery points.
Decryptor Released for Ransomware That Allegedly Helped Cybercriminals Make
Millions
12.1.2021
Ransomware
Securityweek
Bitdefender on Monday announced the availability of a free tool that
organizations can use to recover files encrypted by DarkSide, a piece of
ransomware that cybercriminals claim helped them make millions.
DarkSide is a ransomware-as-a-service (RaaS) offering that was first announced
on cybercrime forums in August 2020. DarkSide operators have been making money
not only by encrypting important files on compromised systems, but also by
stealing valuable information to pressure victims into paying up.
DarkSide victims have been instructed to pay hundreds of thousands and even
millions of dollars to recover their files and prevent data leaks, and the group
behind the ransomware said it only targeted companies that could afford to pay
up, but claimed that it would not target hospitals, educational institutions,
government organizations or NGOs.
The DarkSide ransomware has made headlines for being introduced through a press
release, for its affiliate program, for donating some of their profit to
charity, and providing customers storage systems for stolen data.
While at this point many DarkSide victims likely restored encrypted files from
backups or recovered them by paying the ransom, some companies may be happy to
hear that Bitdefender has released a free tool that automatically scans the
system for encrypted files and decrypts them.
The tool has to be executed locally on systems where the encrypted files are
stored. Users are advised to create backups — a feature that is also available
in Bitdefender’s free tool — before initiating the decryption process.
“To remove the encrypted files left behind, you should search for files matching
the extension and mass-remove them. We do not encourage you to do this until you
made sure that your files can be opened safely and there is no damage to the
decrypted files,” Bitdefender said in a blog post announcing the tool.
Dassault Falcon Jet hit by Ragnar Locker ransomware gang
10.1.2021
Ransomware
Securityaffairs
Dassault Falcon Jet has disclosed a data breach that exposed personal
information belonging to current and former employees.
In December Dassault,
Dassault Falcon Jet (DFJ) was the victim of a cyber attack that may have exposed
personal information belonging to current and former employees.
The data security incident also exposed information belonging to employees’
spouses and dependents, states the notice of data breach sent by the US
subsidiary of French aerospace company Dassault Aviation to its customers.
“on December 6, 2020, Dassault Falcon Jet Corp. discovered a data security
incident affecting some of our systems and some of our subsidiaries
(collectively, “Dassault Falcon Jet” or “we”).” states the notice. “Upon
discovery of this security incident, we immediately took all affected systems
offline and engaged third-party cybersecurity experts to aid in our
investigation, as we work to safely restore our systems in a manner that
protects the security of your information.”
The company has 2,453 employees and generated more than €7.3 billion in revenues
in 2019.
The exposed for current and former employees includes name, personal and company
email address, personal mailing address, employee ID number, driver’s license
number, passport information, financial account number, Social Security number,
date of birth, work location, compensation and benefit enrollment information,
and date of employment.
The data breach noticed states that information regarding current or former
employees’ spouses and dependents exposed in the incident may include name,
address, date of birth, Social Security number, and benefit enrollment
information.
According to the media, the data breach was the result of Ragnar Locker
ransomware infection that also impacted the systems of several Dassault Falcon
Jet subsidiaries.
I have found on the leak site of the Ragnar group some a specific section
containing the links to the archives containing the alleged stolen files.

The company is investigating the incident with the support of the FBI, it also
announced that it is taking steps to enhance its security program to prevent
similar incidents in the future.
“In a number of cases, we have rebuilt systems anew to maintain our operations
while the investigation continues.” continues the notice.
“As we restore and rebuild systems, we are also strengthening the security
protections in place to protect those systems and the data stored on them,”
In November, the U.S. Federal Bureau of Investigation (FBI) issued a flash alert
(MU-000140-MW) to warn private industry partners of an increase of the Ragnar
Locker ransomware activity following a confirmed attack from April 2020.
Ryuk Rakes in $150M in Ransom Payments
9.1.2021
Ransomware
Threatpost
An examination of the
malware gang’s payments reveals insights into its economic operations.
The Ryuk ransomware has earned its operators an estimated $150 million,
according to an examination of the malware’s money-laundering operations.
Joint research released this week from Brian Carter, principal researcher at
HYAS, and Vitali Kremez, CEO at Advanced Intelligence, took a the look under the
Ryuk hood concerning the business operations of the group. The two were able to
trace payments involving 61 Bitcoin deposit addresses attributed to the Ryuk
ransomware.
“The Ryuk criminals send a majority of their Bitcoin to exchanges through an
intermediary to cash out,” the researchers explained. This “well-known broker”
essentially collects Bitcoin payments from ransomware victims and then exchanges
them for fiat currency – traditional paper money – for the Ryuk gang.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“These payments sometimes amount to millions of dollars and typically run in the
hundreds of thousands range,” the researchers said. “After tracing Bitcoin
transactions for the known addresses attributable to Ryuk, the authors estimate
that the criminal enterprise may be worth more than $150 million.”
In terms of the exchanges used for this process, the researchers traced the
cash-outs to large, legitimate exchanges Huobi and Binance, both of which are
located in Asia. Carter and Kremez said that the exchanges’ business practices
allow users to maintain some level of anonymity.
“Huobi and Binance are interesting choices because they claim to comply with
international financial laws and are willing to participate in legal requests,
but are also structured in a way that probably wouldn’t obligate them to
comply,” the researchers said. They added, “both exchanges require identity
documents in order to exchange cryptocurrencies for fiat currency or to make
transfers to banks, however it isn’t clear if the documents they accept are
scrutinized in any meaningful way.”
Aside from the two legitimate exchanges, Carter and Kremez’ examination also
uncovered large pools of cryptocurrency being cashed out using a collection of
addresses that do not appear to be linked to established exchanges. These
“probably represent a crime service that exchanges the cryptocurrency for local
currency or another digital currency,” researchers noted.
The analysis also found that Ryuk operators typically use two unique Protonmail
addresses for each victim in order to communicate.
“Ryuk doesn’t currently use a web-based chat like many other ransomware
operations do,” the researchers noted, which has allowed them some limited
visibility into how the Ryuk operators interact with their victims.
In analyzing the correspondence, “it’s painfully clear that the criminals behind
Ryuk are very business-like and have zero sympathy for the status, purpose or
ability of the victims to pay,” they noted. “Sometimes the victims will attempt
to negotiate with Ryuk and their significant offers are denied with a one-word
response. Ryuk did not respond or acknowledge one organization that claimed to
be involved in poverty relief and lacked the means to pay.”
Carter and Kremez also found evidence of significant reconnaissance activity
when it came to victim selection, by way of “precursor malware families” that
evaluate how lucrative an organization may prove to be as a target.
These malware families “are used to create a score for the victim,” the
researchers explained. “For example, the number of domain trusts is one
significant indicator that is collected automatically by precursor malware that
is observed prior to a Ryuk incident. This score is then used to identify victim
networks that would be the most likely to pay a large ransom.”
In all, a picture emerges of a crime group that functions with an eye toward
ROI.
“Some of these ransomware families are operated by successful and disciplined
criminal enterprises that function like any technology-focused business with
developers, testers and recruiters,” the researchers said.
As for avoiding infection, most ransomware is loaded by an initial “dropper”
malware that acts as the tip of the spear in any attack; these include Emotet,
Trickbot, Qakbot and Zloader, among others. The researchers said that an
effective defense thus should involve developing countermeasures that will
prevent that initial foothold.
Top ways to do this, according to the post, are to restrict execution of
Microsoft Office macros to prevent malicious macros from running; and making
sure that all remote-access points are up-to-date and require two-factor
authentication (2FA); and limit the use of remote-access tools such as Citrix
and Microsoft RDP should be limited to a specific list of IP addresses and only
when required.
New Year, New Ransomware: Babuk Locker Targets Large Corporations
8.1.2021
Ransomware
Threatpost
Despite being a mostly run-of-the-mill ransomware strain, Babuk Locker’s
encryption mechanisms and abuse of Windows Restart Manager sets it apart.
Only a few days into the new year, one of the first new ransomware strains of
2021 has been discovered. Dubbed Babuk Locker, the ransomware appears to have
successfully compromised five companies thus far, according to new research.
The research author, Chuong Dong, a computer science student at Georgia Tech,
said that he first saw the ransomware mentioned in a tweet by a security
researcher who goes by “Arkbird” on Twitter. He then discovered information
about Babuk on RaidForums, which is a forum for sharing databases of breaches
and leaks.
Dong said, according to the website embedded in Babuk’s ransom note, and based
on information from the RaidForums leaks, the ransomware has successfully
compromised five different companies worldwide. According to a report by
BleepingComputer, these victim companies range from a medical testing products
manufacturer to an air conditioning and heating company in the U.S. — and at
least one of the companies has agreed to pay an $85,000 ransom.
While Babuk has some hallmark characteristics that range from unsophisticated to
run-of-the-mill, it also touts more novel tricks, specifically when it comes to
encryption and the abuse of legitimate Windows features, said Dong.
2020 Reader Survey: Share Your Feedback to Help Us Improve
“Babuk is a new ransomware that started at the beginning of this year,” said
Dong in an analysis this week. “Despite the amateur coding practices used, its
strong encryption scheme that utilizes Elliptic-curve Diffie–Hellman algorithm
has proven effective in attacking a lot of companies so far.”
Babuk’s Features
The ransomware, which comes in the form of a 32-bit .EXE
file, notably lacks obfuscation. It’s also not yet clear how the ransomware is
initially spread to victims.
“So far, we don’t know how the ransomware got into the company, but it’s most
likely phishing similar to other ransomware groups’ approaches,” Dong told
Threatpost.
After infection, Babuk contains a hard-coded list of services and processes to
be closed before encryption. These include various system-monitoring services,
including BackupExecVSSProvider, YooBackup and BackupExecDiveciMediaService. On
the processes side, Babuk looks to snuff out 31 processes – from sql.exe to
oracle.exe and outlook.exe.
“Closing applications is beneficial because those applications might be opening
files when the ransomware is ran,” Dong explained to Threatpost. “In order to
encrypt files, it must be able to open it. If another application already did
that, then encryption will fail.”
Babuk also attempts to delete shadow copies before and after encryption. Shadow
copies exist in Microsoft Windows and are used to create backup copies or
snapshots of various files.
“After deleting the shadow copies, Babuk checks if the system is running under
an 64-bit processor,” according to Dong. “If it is, then
Wow64RevertWow64FsRedirection is called to enable file system redirection
again.”
Encryption Method
Of note is Babuk’s encryption mechanism: It uses its own
implementation of SHA hashing, ChaCha8 encryption and the Elliptic-curve
Diffie–Hellman (ECDH) key generation and exchange algorithm to encrypt files in
the attack – making them near-impossible for victims to recover.
“Because of ECDH’s mechanism, the ransomware author can generate the shared
secret using his own private key and the victim’s public key to decrypt files,”
said Dong. “This makes it impossible for the victim to decrypt on their own
unless they can capture the randomly-generated private key in the malware before
it finishes encrypting.”
Babuk also uses multithreading. Many computers contain one or more multi-core
CPUs, which is used to allow parallel execution of processes and better system
utilization. Ransomware, like Babuk, can be developed to leverage this
multithreading process in order to “parallelize individual tasks to ensure
faster and, subsequently, more harmful impact before victims discover they’re
under attack,” Sophos researchers have said.
However, Dong said the ransomware’s “approach to multithreading is pretty
mediocre.”
For one, its multithreading process uses recursion for traversing files, he
said. This process starts with a thread at the highest directory (for example,
C:// drive), which, in the main encrypting function, will go through each item
in the parent directory. If it finds a file, it encrypts it. If a new directory
is found, the process will call the main encrypting function again with that
directory as the parent directory to traverse that folder. This process
continues for multiple layers until Babuk has crawled through every folder and
file, Dong explained.
“This is the old-school and basic approach for ransomware, and it’s typically
used by people who are new to malware development,” Dong told Threatpost. “The
idea is fine, but this is a crazy amount of work considering how a normal system
has at least 10,000 files.”
The ransomware’s multithreading process also determines the number of threads to
spawn by doubling the number of cores on the victim’s machine and then
allocating an array to store all of the thread handles.
“A huge amount of threads can potentially be created for each process,” said
Dong. “However, in an ideal situation, it’s better to have one thread running
per processor to avoid having threads competing with each other for the
processor’s time and resource during encryption.”
In contrast, Dong added, a correct approach for multithreading has been utilized
by the Conti ransomware, which spawns one thread for each processing core.
“Its encryption is crazy-fast with just under 30 seconds to encrypt the C://
drive,” he said.
Windows Restart Manager
Babuk also leverages Microsoft’s legitimate Windows
Restart Manager feature, which enables users to shut down and restart all
applications and services (minus critical ones). The ransomware uses this
feature to terminate any process that is using files – which Dong said ensures
that nothing will prevent the malware from opening and encrypting the files.
Other popular ransomware families have previously abused Windows Restart
Manager, including the Conti ransomware (as seen in a July 2020 attack) and the
REvil ransomware (seen in a new May 2020 version).
Once all files have been encrypted, Babuk’s ransom note tells victims their
computers and servers are encrypted, and demands the victim contact them using a
Tor browser.
However, “if the victim tries to pay the ransom they must upload files in a chat
so that the ‘hackers’ can make sure they are able decrypt the files,” Lamar
Bailey, senior director of security research at Tripwire, said in an email. “I
expect there is a pretty high failure rate. Will they make money? Absolutely.
But like many fads, this will be a thing of the past in a few months and will
not generate a lot of money long-term. Until then, stay away from 32 bit .exe
files.”
The new ransomware strain comes as ransomware attacks continue to rise – with
the number of ransomware attacks jumping by 350 percent since 2018. Healthcare
systems have been hit particularly hard over the past year by ransomware actors,
with a recent report saying that healthcare organizations have seen a 45 percent
increase in cyberattacks since November.
Ryuk ransomware operations already made over $150M
8.1.2021
Ransomware
Securityaffairs
The Ryuk ransomware had a disruptive impact on multiple industries around the
world, operators already earned more than $150 million.
The Ryuk ransomware
gang is one of the most prolific criminal operations that caused destruction in
multiple industries around the world. According to a joint report published by
security firms Advanced-intel and HYAS, Ryuk operators already earned more than
$150 million worth of Bitcoin from ransom paid by their victims.
The experts traced payments involving 61 wallet addresses associated with Ryuk
ransomware operations. The gang transfers most of its crypto-funds to exchanges
through an intermediary to cash out. Experts noticed that the two primary
(known) exchanges used by the group are the Asian exchange Huobi and Binance.
Both exchanges are structured in a way that probably wouldn’t obligate them to
comply with law enforcement requests and both were founded by Chinese nationals
that moved their business to countries that are more friendly to cryptocurrency
exchanges.
“Both exchanges require identity documents in order to exchange cryptocurrencies
for fiat or to make transfers to banks, however it isn’t clear if the documents
they accept are scrutinized in any meaningful way. A legal authority can request
identity details for the individuals receiving the payments.” reads the report.
“We would not expect successful criminal enterprises like Ryuk to make use of a
US-based exchange although we have observed other ransomware operators taking
this approach.”
Experts reported that Ryuk operators receive a significant amount of their
ransom payments from a well-known broker that makes payments on behalf of the
ransomware victims. The analysis of the transactions allowed the researchers to
estimate that the gang earned $150,000,000.
The researchers also identified
significant flows of crypto currency to a set of addresses that are likely part
of a crime service that exchanges the cryptocurrency for local currency or
another digital currency. The experts also traced significant volumes of bitcoin
moving from the laundering service to Binance, Huobi, and crime markets.
“These payments sometimes amount to millions of dollars and typically run in the
hundreds of thousands range. After tracing bitcoin transactions for the known
addresses attributable to Ryuk, the authors estimate that the criminal
enterprise may be worth more than $150,000,000.” continues the analysis.
In order to limit their exposure, Ryuk operators create a couple of unique
Protonmail addresses for each victim and use them to communicate with them.
“Enterprises that suffer from ransomware aren’t infected because they lack up to
date antivirus software or because they chose the blue vendor instead of the red
vendor.” concludes the report. “They’re encounting ransomware because they
haven’t considered developing countermeasures that will prevent the initial
foothold that is obtained by precursor malware like Emotet, Zloader, and Qakbot
(to name a few).”
Researchers Warn of New Babuk Ransomware Targeting Enterprise Networks
7.1.2021
Ransomware
Securityweek
Security researchers have spotted a brand new ransomware family taking aim at
corporate networks, warning that professional cybercriminals have already hit
multiple organizations with the file-encryption scheme.
The new ransomware family, called Babuk, has claimed at least four corporate
victims facing data recovery extortion attempts.
According to researcher Chuong Dong, the ransomware is pretty standard and lacks
obfuscation but he warned that the cybercriminals have found success with the
use of strong encryption.
"Despite the amateur coding practices used, its strong encryption scheme that
utilizes Elliptic-curve Diffie–Hellman algorithm has proven effective in
attacking a lot of companies so far," Dong explained.
Similar to other ransomware families out there, Dong said Babuk uses techniques
such as multi-threading encryption. It was also observed abusing the Windows
Restart Manager, similar to the Conti and REvil ransomware strains.
Babuk uses a proprietary implementation of ChaCha8 encryption, SHA256 hashing,
and Elliptic-curve Diffie–Hellman (ECDH) algorithm for key generation and
exchange for securing keys and encrypting files. Furthermore, for each malware
sample, the authors use a single private key.
The ransomware only encrypts local machines if no command line parameters are
supplied. With parameters, it can either encrypt locally only or move to
encrypting network shares after encrypting local machines.
Babuk also includes functionality to close specific services and processes
before starting the encryption operation. It targets multiple backup services,
as well as processes for database, office applications, browser, and email
clients.
It uses Windows Restart Manager to terminate processes, to ensure files can be
encrypted, and attempts to delete shadow copies, both before and after the
encryption.
The key generation mechanism used by Babuk is rather complex, meant to ensure
that the victim can’t recover their files, but allowing the attackers to easily
generate the shared secret needed for decryption. The approach to
multithreading, however, can be considered mediocre, Dong said.
Ransomware Gang Collects Data from Blood Testing Lab
5.1.2021
Ransomware
Threatpost
Apex Laboratory patient data was lifted and posted on a leak site.
Apex Laboratory, which provides blood work at home for patients in New York
City, Long Island and South Florida, has been hit with a ransomware attack that
also resulted in patient data being stolen.
Though the company just disclosed the attack, it took place on July 25, when
“certain systems in its environment were encrypted and inaccessible,” according
to a website notice from last week.
Working with a cybersecurity firm, Apex was able to secure its network and
resume operations two days later. But the forensic investigation went on,
eventually determining on Dec. 15 that the attackers had posted information on
their blog about the attack and claimed to have lifted personal and health
information, the company said in a New Year’s Eve notice.
2020 Reader Survey: Share Your Feedback to Help Us Improve
That data includes patient names, dates of birth, test results, and for some
individuals, Social Security numbers and phone numbers, Apex said. It was likely
taken from Apex’s systems between July 21 and July 25 as part of a “double
extortion” attack where criminals not only lock up systems but also exfiltrate
data.
“Apex is unaware of any actual or attempted misuse of any information other than
the extracting of this data as part of the cyberattack,” the company said. “Apex
is in the process of preparing written, mailed notice to impacted individuals
for whom it has addresses.” It added that the investigation is still ongoing.
“While the typical ransomware business model involves encrypting data in place
and then selling the victim decryption capabilities (aka the ransom), business
models always evolve,” Oliver Tavakoli, CTO at Vectra, told Threatpost. “In
order to maximize the likelihood of getting a targeted organization to pay such
ransoms, attackers may choose to impose multiple types of pain – in this case,
the attackers employed both the possible loss of data through encryption as well
as the public release of confidential information, thereby getting two bites at
the apple. While Apex Laboratory had good enough data backups to overcome the
first threat, the second threat was the attacker’s failsafe to still get a
ransom.”
Other details were scant on the attack, but Threatpost reached out to Apex for
more information on the ransomware gang involved and other data.
The news comes as healthcare organizations continue to be a top target for
ransomware gangs,
“I’d say the predominant issue facing healthcare right now is ransomware,” Beau
Woods, a Cyber Safety Innovation Fellow with the Atlantic Council, founder and
CEO of Stratigos Security and a leader with the I Am The Cavalry grassroots
initiative, told Threatpost in a recent video interview. “Ransomware continues
to be a leading thorn in the side of care delivery, being able to deliver care
to patients. ransomware comes in and shuts down clinical operations, it can
cause patient care to go on divert, which is where they basically send
ambulances to other hospitals, or even cause hospitals to move patients to
another facility that’s not impacted by ransomware.”
Medical organizations have a unique set of challenges that make them ripe
targets, researchers said.
“The healthcare industry has a particularly challenging setting — they have to
prioritize fighting healthcare-related fires all the time and have to work with
software (and hardware) that takes years to certify for safety,” Mohit Tiwari,
co-founder and CEO at Symmetry Systems, told Threatpost. “This means the compute
infrastructure lags behind due to both business and technical reasons.
Healthcare executives need a shift in mindset. They must understand compute
infrastructure in hospitals is key to healthcare, and computing failures are
healthcare failures. Further, computing flaws are highly correlated and can
spread quickly — ransomware or breach of large data stores — or compromise of
medical equipment on a network.”
Apex Laboratory disclose data breach after a ransomware attack
5.1.2021
Ransomware
Securityaffairs
At-home laboratory services provider Apex Laboratory discloses a ransomware
attack and consequent data breach.
Apex Laboratory, Inc. is a clinical
laboratory that has been providing home laboratory services to homebound and
Nursing Home patients in the NY Metropolitan Area for over 20 years.
The at-home laboratory services provider Apex Laboratory disclosed a ransomware
attack, the hackers also stole some patient in the incident that took place on
July 25, 2020.
“On July 25, 2020, Apex Laboratory of Farmingdale, NY (“Apex”) discovered that
it was the victim of a cyber-attack and that certain systems in its environment
were encrypted and inaccessible.” reads the data breach notification published
by the company.
The company started the investigation with the help of third-party forensic and
cyber security specialists after it resumed the operations on July 27th.
Apex Laboratory confirmed it was able to secure its network, restore affected
data, and resume operations.
The company initially added that it has not found evidence of unauthorized
access or acquisition of patient information.
“However, on December 15, 2020, Apex learned that the hackers posted information
on their blog about the attack and listed data taken that contained personal and
health information for some patients,” the company revealed.
Further investigation allowed the company to discover that the data might have
been stolen from its systems between July 21 and July 25, 2020.
The provider discovered that threat actors stole info for some of its patients,
including names, dates of birth, phone numbers, Social Security numbers, and
test results.
“Although the investigation is ongoing, at this point, the data believed to be
taken includes, for a subset of patients: patient names, dates of birth, test
results, and for some individuals, Social Security numbers, and phone numbers.
Additionally, Apex is unaware of any actual or attempted misuse of any
information other than the extracting of this data as part of the cyber-attack.”
continues the company. “Apex is in the process of preparing written, mailed
notice to impacted individuals for whom it has addresses, as well as posting
notice on its website.”
Apex is notifying affected individuals via written mail while the investigation
is still ongoing.
According to the DataBreaches website, the company was hit by the DoppelPaymer
ransomware gang.
“DataBreaches.net recently reported that Apex Laboratory Inc. had apparently
been attacked by DoppelPaymer ransomware threat actors. Apex was added to their
leak site on December 15.” reads the post published by DataBreaches.
On December 15, DoppelPaymer operators published thousands of files allegedly
stolen from Apex on its leak site. Leaked data includes patients’ data and
employee information.
Ransomware Attacks Linked to Chinese Cyberspies
5.1.2021
Ransomware
Securityweek
China-linked cyber-espionage group APT27 is believed to have orchestrated recent
ransomware attacks, including one where a legitimate Windows tool was used to
encrypt the victim’s files.
Active since at least 2010 and tracked by different security firms as Emissary
Panda, TG-3390, Iron Tiger, Bronze Union, and Lucky Mouse, APT27 is known for
cyber-espionage campaigns targeting hundreds of organizations around the world.
In addition to government organizations, the group was also observed targeting
U.S. defense contractors, a European drone maker, financial services firms, and
a national data center in Central Asia, among others.
More recently, however, the cyberspies appear to have switched to
financially-motivated attacks. In one such incident, the Windows tool BitLocker
was used to encrypt core servers at a compromised organization.
The attack, boutique cybersecurity services company Profero explains in a
detailed report, had similarities in code and TTPs with the DRBControl campaign
that Trend Micro linked in early 2020 to Chinese APT groups APT27 and Winnti.
Targeting gambling and betting operations in Southeast Asia, DRBControl stood
out for the use of specific backdoors, alongside malware such as PlugX RAT,
Trochilus RAT, HyperBro backdoor, and the Cobalt Strike implant.
During their investigation of the ransomware attack, Security Joes and Profero
researchers identified a backdoor they linked to DRBControl, as well as an
ASPXSpy webshell, a PlugX sample, and Mimikatz.
“With regards to who is behind this specific infection chain, there are
extremely strong links to APT27/Emissary Panda, in terms of code similarities,
and TTPs,” the security researchers say.
The victim was infected through a third-party service provider that too was
compromised through another third-party service provider. Also unusual for a
ransomware attack was the use of BitLocker, a local tool, instead of a
ransomware family.
“Previously, APT27 was not necessarily focused on financial gain, and so
employing ransomware actor tactics is highly unusual, however this incident
occurred at a time where COVID-19 was rampant across China, with lockdowns being
put into place, and therefore a switch to a financial focus would not be
surprising,” Profero notes.
This, however, does not appear to be a singular ransomware incident attributed
to the Chinese hacking group: in late November 2020, Positive Technologies
detailed an APT27 attack in which the Polar ransomware was used.
Apex Laboratory Says Patient Data Stolen in Ransomware Attack
5.1.2021
Ransomware
Securityweek
At-home laboratory services provider Apex Laboratory said hackers stole some
patient data during a ransomware attack that took place several months ago.
Established in 1997 and headquartered in Farmingdale, New York, Apex Laboratory
provides medical testing services in the New York Metropolitan and surrounding
areas. In 2007, Apex opened a South Florida location.
In a data breach notification published last week, the company announced that,
on July 25, 2020, it discovered a cyberattack that resulted in systems being
encrypted and becoming inaccessible.
Apex said it was able to secure its network, restore affected data, and resume
operations on July 27, and claims that its investigation into the incident did
not reveal evidence of unauthorized access or acquisition of patient
information.
“However, on December 15, 2020, Apex learned that the hackers posted information
on their blog about the attack and listed data taken that contained personal and
health information for some patients,” the company revealed.
While looking into the attackers’ claims, Apex discovered that the data might
have been stolen from its systems between July 21 and July 25, 2020.
The medical services provider says that, for some of its patients, stolen data
includes names, dates of birth, phone numbers, Social Security numbers, and test
results.
“Additionally, Apex is unaware of any actual or attempted misuse of any
information other than the extracting of this data as part of the cyber-attack,”
the company said.
While continuing to investigate the security incident, Apex is in the process of
notifying affected individuals via written mail and said it also contacted law
enforcement.
While the company did not reveal information on the threat actor behind the
attack, DataBreaches reports that the DoppelPaymer ransomware was used to
encrypt Apex Laboratory’s systems.
DoppelPaymer operators are known for exfiltrating data from compromised
environments, to pressure victims into paying the ransom.
On December 15, DoppelPaymer operators made public roughly 10,000 files they
claim to have been stolen from Apex. In addition to data on hundreds of
patients, employee information was also stolen in the incident, it appears.
In its data breach notification, Apex Laboratory said it “ensured that the data
was removed from the hacker’s blog,” without providing further details on
whether that involved paying the attackers or whether the hackers continue to be
in the possession of stolen data.
What’s Next for Ransomware in 2021?
1.1.2021
Ransomware
Threatpost
Ransomware response demands a whole-of-business plan before the next attack,
according to our roundtable of experts.
Ransomware works. That’s the simplest way to explain why incidents of ransomware
attacks have sharply increased over the last year — with no end in sight.
The number of ransomware attacks has jumped by 350 percent since 2018, the
average ransom payment increased by more than 100 percent this year, downtime is
up by 200 percent and the average cost per incident is on the rise, according to
a recent report from PurpleSec.
Groups with names such as Ragnar Locker, Ryuk, Egregor, Conti and many others
are ruthless, well-funded and willing to target anyone; from COVID-19 vaccine
manufacturers, retailers, banks, local governments and schools to get their
payday.
Hospitals Hardest Hit by Ransomware
Since the start of the pandemic,
hospitals have been particularly hard hit.
The situation became so dire in the fall that the Cybersecurity Infrastructure
Security Agency (CISA), the Federal Bureau of Investigation (FBI) and U.S.
Department of Health and Human Services were forced to issue a bulletin warning
about “credible information of an increased an imminent cybercrime threat to
U.S. hospitals and healthcare providers.”
Healthcare Security in the COVID-19 Era
Rising ransoms have also helped evolve ransomware from what was historically a
basic scam run by ragtag criminals into a professionalized criminal organization
with deep benches of top cybersecurity talent.
With the threat of ransomware attacks being ratcheted up every day, Threatpost
gathered a panel of ransomware experts together on Dec. 16 to help unpack the
current landscape, but more importantly, get ahead of the next, inevitable
attack.
‘Ransomware Works’
“Cybercriminals do what works,” Austin Merritt,
cyber-threat analyst from Digital Shadows, told the audience during the webinar.
“You know, it works well for them. Pressure tactics are working great.”
Super-fueling the explosion of ransomware crimes is the technical barriers to
pull it off are lower than ever, thanks to established players selling
ransomware-as-a-service options.
“And you don’t just get cybercriminals doing cybercrime, there are really
organized gangs that are added as well and they’re the ones that are causing the
biggest trouble,” Limor Kessem, executive security advisor for IBM security and
Threatpost webinar panelist, said during the event.
While IT departments will undoubtedly lead efforts to shore up defenses against
attacks, including backups, patching, updating and employee-awareness training,
our panel of experts agree that preparing a critical-response plan which
includes the entire organization — from the executives on down the org chart —
is the best way to minimize cost, damage and downtime.
Ransomware Business Intelligence
Critically, organizations can’t discount
whether the stolen data might have value for someone else willing to pay.
“It’s actually about the information that’s potentially stolen as well, which a
lot of times can be much more costly for the company than the ransom itself,”
Mellen said. “What’s interesting about the role of cyber-insurance and
ransomware is that ransomware attacks actually accounted for something like 40
percent of cyber-insurance claims filed in the first half of 2020.”
She advises companies not to rely solely on insurance for protection at the
expense of investing in security infrastructure, but instead try to strike a
careful balance between the two.
“I definitely see the value of cyber-insurance. Absolutely,” Mellen explained.
“I think it’s an important part of a strong security strategy, but at the same
time, now that these attacks are really more targeted, especially when it comes
to these ransomware attacks, my question is, is this the best place to be
investing so much of your money, and where’s the limit there?”
All three panelists agreed that cyber-insurance is not a substitute for
security, but the consensus was best summed up by Merritt who added, “So, there
are a lot of different angles there, but I would not want to be an organization
that regrets not having cyber-insurance at the end of the day.”
Paying ransoms aren’t necessarily the answer. Our experts point out that paying
the ransom doesn’t ensure your data won’t be sold anyway. Worse, Kessem explains
there are rules and regulations prohibiting paying ransoms to operators in
countries on the U.S. sanctions list. Besides running afoul of the feds, paying
money to fund state-sponsored terrorism isn’t a good look for any company.
Ransomware attacks might be simple to pull off, but they create a tangled mess
of complicated questions for organizations. Until we can achieve what Kessen
explained as “breaking the business model” of ransomware, a combined technical
incident-response plus business-recovery plan for response is the best offense.
“So I really think you have to think of it from a multi-faceted way,” Merrit
said. “There’s so many ways they can get in. What can you be doing? How can you
be on top of things to avoid getting to that point where you’re saying, “oh my
god, do I have to pay a ransom?”
For more, watch the entire Threatpost webinar, What’s Next for Ransomware,
recorded on Dec. 16, available free and on-demand here. It features experts
Limor Kessem with IBM Security, Allie Mellen with Cyberreason and Austin Merritt
with Digital Shadows and hosted by Threatpost’s Becky Bracken.
A lightly edited transcript of the webinar follows.
What’s Next for Ransomware
Becky Bracken: Hi, Everybody. Welcome to
Threatpost’s holiday edition of our webinar series. Today we are going to be
talking about important topic: ransomware. So, I want to welcome everybody here
today. I know it’s been a crazy week. So hopefully this will just be an hour for
us to take a breath and look a little bit ahead rather than what’s right in
front of us and what we’re weeding through right now.
Before we get started, I want to introduce myself. I’m Becky Bracken, I’m with
Threatpost, and I’ll be the host of today’s conversation. Let me introduce Allie
Mellen, security strategist with Cyberreason in the office of the CSO. She’s a
computer scientist. She spent the last decade working, both for venture
capitalist, backed startups, non-profits, and on the research side with roles,
with MIT and BU. So, welcome very much to you.
Let me go ahead and introduce Limor Kessem. She’s from IBM Security, she’s a
world-class authority on emerging cybercrime threats. And we are thrilled that
she’s been able to make it and share her insights. Welcome.
We also have Austin Merritt. He is a cyber-threat intelligence analyst with
Digital Shadows. Prior to joining Digital Shadows, Austin served in the U.S.
Army as a Human Intelligence Collector with a concentration in the Russian
language, which no doubt comes in very handy in your work today.
So welcome all of you. Were thrilled to have you.
To get us started, I wanted to go through some of the headlines. We know them.
We’ve seen them there everywhere. But just recently, DHS attack in the attacks
on the U.S. infrastructure is huge. Hospitals are being pummeled by ransomware
attacks and then we’ve got retailers like Kmart. It goes on and on and on. No,
industry is immune. No organization is too large or too small. We know this. And
so the goal today is to try and get ahead of what the next attack.
To get us started, I would love the audience to answer our poll question. Pretty
simple. “Have you dealt with a ransomware attack in the past 12 months?”
Let’s launch this. You should see it on your screen. Just answer yes or no. We
just want to know if this is something you’re currently grappling with or are
trying to get ahead of us.
Our responses are coming in, And it looks like a sizeable portion of you have
not dealt with them yet which is great news so we are right where we need to be.
All right. We’re going to go ahead and close that poll, so if everybody could
get their answers in.
All right. So, like I said, 77 percent of our respondents in the audience said
no, they haven’t and 23 percent said, yes.
So, that’s a pretty interesting metric.
We’re gonna start today with Alie, who’s going to frame for us why because
ransomware isn’t new, ransomware isn’t novel, why is it still such a big deal?
Why is it still having such a huge impact on so many organizations right now?
Maybe you can kick us off with your thoughts on that.
Allie Mellen: Yeah. I’ll start with the defender side, and then maybe we can
jump into the attacker’s as well on the Defender side. Ransomware is still a big
deal because it costs defenders a lot of money. When it happens, and we’re not
just talking about the ransom payments, although that does cost money as well,
but we’re also talking about things like business continuity and just actually
not being able to perform the functions that you need to. The. A great example
of this that you mentioned, Becky, is hospitals.
When hospitals are hit, people die, and that is a huge, huge toll to take for
any type of organization, of course. But hospitals, especially, we also see this
with any type of organization that needs, as close to 100 percent uptime as
possible, also known as the five nines.
And so, if they are impacted by a ransomware attack, it can cause major issues
for them, and for their business, as opposed to just one-time ransomware
payment.
Becky Bracken: Austin, do you have anything you want to add to that?
Austin Merritt: I would like to add that, you know, like a lot of cybercrime
that we’ve been seeing throughout the years, cybercriminals do what works. You
know, it works well for them. Pressure tactics are working great.
And by going after hospitals, like you mentioned, they’re really going after
the, I guess, the sweetest spot of what information security is about. I mean
the first and foremost thing is we want to make sure that there is no loss of
human life, that’s like the top priority before everything else.
So this is where they find themselves, you know, having success and also
threatening the things that matter most you.
Limor Kessem: Yeah, I think Allie hit on it with talking about hospitals and
just the … pandemic in general. We’ve just seen so many different areas for
threat actors to exploit and when they use high pressure tactics. Particularly
in a healthcare environment, when you’re talking about a life, you know, life
and death situation. You’re putting people in a position to where they, they
feel like they have to pay a ransom. And they might not feel like they, they
have another option.
And when someone’s life is on the line, unfortunately people are taking
advantage of that. And it’s causing huge problems, but not just in the
healthcare industry.
We’ve just seen a huge uptick in which we will talk about later just different
pressure tactics that we haven’t seen as much as we have this year.
And I think the remote workforce has really given them a great opportunity to
exploit many different avenues.
Allie Mellen: Yeah, from the attacker perspective, also like ransomware we all
thought ransomware is going to fade away a few years ago or many people did, but
in reality, it surged back into more advanced way than ever the past few years.
And I think that that’s really because traditional ransomware is about that
thing. It’s that immediate initial access and deploying ransomware and then
getting the ransom payment moving on, It’s very spray and pray automated, not
really worried about who it’s targeting, just wanting to target as many people
as possible.
In contrast we’ve seen the average ransomware payments skyrocket over the past
few years, and really a shift towards a different type of ransomware, that is
not about that big thing. It’s about the slow burn, it’s about getting access to
the environment, and then spreading as much as possible moving laterally. And
then ultimately also gathering as much important data as it can, and … trading
it back to the C2 server.
So it does all of this slow and low quietly before it’s actually deploying the
ransomware at the right moment. And once it’s able to do that, it gets a double
pay off, because it can go the extortion route, it’s going the ransom route, and
it can also just sell it some of that data on the internet.
So, it’s interesting to see it evolving, and kind of, even when we thought that
it was going to kind of die out, they just found a different way to make it even
more profitable for themselves.
Becky Bracken: Do you want to talk a little bit about this slide where the, the
evolution? I think this is a really interesting snapshot of how progression has
happened.

The evolution of ransomware. Source: Cybereason
Allie Mellen: Yeah, Great. Thank you. As I was saying before, this is
potentially much more lucrative. And we’ve also seen that over time, there’s
been kind of a specialization between different malware authors.
For example, a great example of this is Ryuk, it’s very good at being
ransomware, But it’s actually acting to combine with other types of malware,
like for example, TrickBot for actual deployment, because that’s one thing that
TrickBot does that very well.
So we’re seeing that different types of malware are being adopted to make one
even stronger malware. Like almost like a transformer It’s this thing that makes
it so that you can actually not have to worry about making those parts yourself
Specialize in what you need to specialize in and then gain the benefits from
that.
Limor Kessem: So, I think that, you know, if we’re talking about the evolution
of it, and, you know, you talked about it in the beginning, about the
spray-and-pray attacks and the automation, everything, we still have that. And
all those ransomed as a service, stuff that you’d find in any underground forum.
We can find ransomware that can be simply grabbed for free,from some sort of a
hacking site. All these automated attacks are just done by would-be criminals,
people who dabble in cybercrime, and find it to be something that they can try
out.
So, this is where the attack begins as O.K., let’s, you know, infect them with
ransomware, but it turns into a targeted attack. You know, it might start as
opportunistic in the beginning.
And it turns into, you know, having all the characteristics of a targeted attack
were now they’re gonna dig through their network and escalate privileges, we
then move laterally until they find you know what they’re looking for. And,
eventually, it’s going to be the day when, you know, they’re gonna wait for a
weekend or a long weekend, holiday, whatever.
And that’s where they’re going to really just start the entire encryption
process at that point.
And you don’t just get cybercriminals doing cybercrime, there are really
organized gangs that are added as well and they’re the ones that are causing the
biggest trouble.
Those are the ones who are asking hospitals to pay $42 million.
I think that we’ve also seen how much more ransomware-as-a-service is being
offered and used. Really just as its own software-as-a-service there. We have
these people who are non-technical or who are just really looking to make some
money. And they’re able to use these tools to get in on this.
Or, you could develop it within no time. I mean, you know, some people have kind
of followed some users in the underground from being zero to hero kind of thing,
and they saw that it took them very little time to get up to speed.
Some of these affiliates, you can subscribe for access to the malware like with
Egregor ransomware. They might even be able to bypass a vetting process, if a
ransomware group just has such a monopoly and can make so much money, the more
affiliates they have going out and spreading the ransomware form, the more
money.
And on top of that, it just makes attribution so much harder if you don’t have
just one organization using it but a variety of different cybercriminals taking
advantage of it back to you.
Allie Mellen: I was intending to use this slide to talk about the evolution of
ransomware. And the way that we’ve seen it grow from just traditional ransom,
payments to this much more lucrative form of data stealing and ransomware
payments.
And this timeline just shows some examples of ransomware and the different types
of ransomware that have cropped up over the past 20, 30 years.
So it’s not something that I anticipate will go away, even though it may have
quiet times. But I’m sure we’ll talk more about this later in the presentation,
the different trends that we’re seeing with ransomware and how it’s going to
evolve again.
Becky Bracken: OK, well, now we’re going to talk about models, double extortion,
dump sites, copycat crimes, DDoS attacks. And what we’re talking about is
business intelligence, intelligence gathering, what Allie called that slow burn,
hanging out in the network and seeing where the pressure points really are.
Austin Merritt: Yeah. So I wanted to talk about some of the pressure tactics
they’re using. and double extortion has been so prevalent this year.
So double extortion involves extracting large quantities of sensitive data
before applying the encryption lock from the ransomware event. So the encryption
lock is, you know what a victim sees on their screen, the skull and crossbones,
saying, hey, you need to pay a ransom. At the same time they’re taking the data
that they’ve stolen and they’re putting it on their, their data leak site. So
why is this important?
Well, the files are taking our sensitive customer information, it could be
proprietary data, personally, identify it, personally identifiable information,
anything they can use. They can repurpose, they can sell it or they can even
auction it.
So I think before 2020, this tactic was not as popular. I think it really became
mainstream late, 2019, early 2020. And, you know, before it was the ransomware
operative research, we’re saying, give us some way to get your files back. Now,
they’re saying the same thing, but they’re also saying, we will expose your
files to the public and they can be used against you.
So, that creates more pressure on a victim organization to give money back.
And it’s not just small-and-medium organizations, even though those are likely
to be targeted just because they might not have the robust security
infrastructure that a bigger organization may have, but you’re also seeing for
example, Garmin was attacked, Carnival was attacked. Garmin ended up paying $10
million. And that’s a big company.
So they’re going after these big companies on the hope that they’ll pay out a
big grants and payments.
Limor Kessem: Yeah, and you know what? There are some cases where I’m located in
Tel Aviv in Israel, so one of the cases they skip the ransomware altogether.
They just said, hey, we’ve got your files, pay up or we’re exposing them on the
internet.
The company didn’t choose to pay and they had been exposing a ton of information
most recently the CEO’s passport.
They encrypt a lot more data than they’re able to exfiltrate, because it’s
probably going to show up somewhere on the network. And tons of information
going out. They take the time to do it, so they take some critical stuff or some
customer information wherever they can find that would be of value and would put
that pressure on companies.
And also, they’re quite aware that pressures can come from regulators from
having to pay fines to regulators, from reputational damage, from customers
leaving and these kind of strains and churn, and the business can actually cost
businesses 30 percent of their income. I mean, this is really a very heavy
amount of money to lose. And criminals know that. They calculated.
They look at how much a company makes, and they’re planning it so they can
pressure them in with an amount that would kind of maximize what they can get
from them, and still make it worse for them to pay, rather than not.
Becky Bracken: So, it’s an extraordinary aspect of their ability to pinpoint the
price that, you know, is just enough, you know, lower than the price, just to
make it just a bit less painful to pay. Can you talk a little bit about that?
The ability of them to set these very pinpointed prices.
Limor Kessem: The ransoms when we’re dealing with organized crime kind of
criminals that are like Austin mentioned, you know, get a big company to pay $10
million. That is, you know, your everyday people. These are people who are just
as intelligent as their counterparts on the better side of the of the screen.
They’re looking at what are companies making? What kind of revenues are they
looking at? What kind of fines will they have? How much data are they able to
get from them that will actually cross the threshold of having them find a
certain amount?
They’re looking at all these things. These are highly intelligent people. We
look at the codes they develop, we look at the work they do, they have so much
operational security and so many other aspects of the attack are so
sophisticated that this just stands to reason. You know, I can see how they’re
just sitting there looking at it.
Becky Bracken: OK, Austin. Let’s talk a little bit about copycats.
Austin Merritt: So when we think when we think of copycats, there’s quite a few
different things that are being copied by other ransomware groups. And we saw a
lot of groups copying Maze, because Maze had such a foothold earlier this year
in the in the ransomware field. But we had a number of groups going to the
double extortion method, and ransomware-as-a-service model.
Yeah, with the ransomware-as-a-service model, we saw so many ransomware groups
just trying to do exactly what a big group might do. Because they’ve been the
most successful. They’ve earned the most money. They’re like, “how can how can I
model that behavior and earn more money?
And so one of the things that that Maze did, which was kind of interesting, was
called data leaking as-a-service at their height, before they went defunct back
in November (or they claimed they were but then Ragnar Locker ransomware group
started posting some of their information on their site). And, the way that this
worked was by hosting their leaked data on Maze news, they gained more notoriety
because their strain, may or may not have been, as well known as Maze. And Maze
was making money off of this. And, because it worked, Ragnar Locker said hey, we
could do this too.
But we’ve also seen the auction platform took place on Maze, which is basically
taking this stolen data and auctioning off to other cybercriminals. And the site
called Happy Blog they were doing the exact same thing. They were actually
auctioning off data on celebrities earlier this year.
So, yeah, it’s, it’s, it’s just pretty amazing to see, how they’ll model their
behavior after one group, just because of the amount of success that they’ve
had, they’re working to publicize these dump sites, right. They want everybody
to know, to troll and to continually chat, right?
Becky Bracken: Because it’s about drawing those consistent eyeballs on this
compromised data, right?
Austin Merritt: Yeah, it is, because depending on what the intention of the
ransomware operator is, the more attention they can attract to either the victim
organization to pay the ransom, or to other cybercriminals out in the field that
may be interested in this data, to repurpose it. That’s good business for them.
So they know that this is just one other way to get people to pay up.
They were posting the majority of organizations data on their sites compared to
other groups. The other ones were relatively similar. Maze decided that they
were going to shut off the site, It’s still up, but they haven’t been posting
other organizations’ data on there.
Becky Bracken: But what do we think has happened in there?
Austin Merritt: So what we’ve seen inQ4 2020, the Egregor ransomware variant
kinda filled that void. As of December, they accounted for 41 to 41 percent of
the incidents that we’ve taken in.
So that’s accounting for a lot of organizations. And a lot of security
researchers think that the Egregor ransomware could just be the same operators,
the Maze operators. One of the reasons being, the obfuscation techniques that
they’re using are similar. The ransom note that Egregor is using is similar to
Maze, and the news and the data leak site follows a similar naming format.
The timing kind of makes sense. Why would Maze just stop posting things and then
Egregor immediately fills that void and post just as many organizations if not
more.
Becky Bracken: Allie do you want to talk about single-stage ransomware?
Allie Mellen: Yeah. These slides are just meant to show what we’ve been talking
about here with the difference between traditional ransomware and current, more
modern and evolved models so to speak.
So you can see here, single-stage ransomware really starts with that initial
access. Sometimes they’ll look to gain persistence. Sometimes they won’t. Before
ultimately, after detonating the ransomware, they immediately look to get the
ransom paid.
And if you go to the next slide, you can see that comparison with multistage
ransomware, which has additional steps, which here are highlighted in yellow,
showing that credential stealing and lateral movement, and then actually selling
that data, or using it for blackmail, so it’s kind of just a way to visualize
what we’ve been talking about.
We have an elite research team at Cybereason called Nocturnus and their whole
job is to do research into the latest and greatest threats that we’re seeing.
And this is one example of that, the goal is really just to share with the
community and also, of course, make our own products better. This one in
particular is called Anchor.
It is a hacking operation that’s targeting financial services industries.
Specifically point of sale systems. And it was able to impact the U.S. and
Europe.
I think we saw this in December of 2019, so just about a year ago today.
If you can go to the next slide, this is a timeline of the attack, so that
people can actually see what’s going on in each stage.
But it starts with initial access, of course, through a phishing e-mail and is
able to download and inject TrickBot into the existing machine.
From there it goes to the discovery stage is performing reconnaissance activity.
It’s looking to connect to the C2, and it’s gaining more information, like, what
operating system version.
This is on, seeing if this is a high value target, or if there are others that
it should target, before really jumping into that interactive hacking. And this
is where we’re saying, it’s really important that this is the type of attack
that you see, when an attacker is really targeting specific organizations or
specific individuals. This is not the type of automated spray-and-pray
ransomware that is really that single-stage version. But what’s interesting here
is the attacker uses this to access the domain controller, really move laterally
implant some other types of malware like CobaltStrike and then just exfiltrate
as much data as it can.
Once it’s done that, it deploys the ransomware.
So this is a real live example of something that we actually saw in environments
that we monitor of a multistage ransomware attack, and of each part of that, and
really that hacking operation that ends with ransomware.
Becky Bracken: OK, well now we’re going to get into something I think is really
interesting and really forward-thinking, and this is something we touched on
before, which is the pricing of ransomware, but also this rising role of
cyber-insurance in discussions about paying ransom and how to deal with these
attacks. So, let’s start another poll, which I think is an important one.
We want to know, do you have cyber-insurance, does your organization carry it
now? And is this something you’re considering right now? So go ahead and take a
minute and answer that.
And it’s interesting that there’s already a huge number of you who are saying,
Yes, we do, or no, but we’re considering it.
So, this is something that most businesses in most organizations are having too,
think about, and we want to help provide you with a little bit of expert advice
on the best way to think about it.
So I’m going to go ahead and close this poll.
What we came up with was 45 percent of you, responded that yes, you have
cyber-insurance. Currently, 16 percent of you say no, not not, but we’re
considering it.
So, that’s a sizable number, 39 percent of you say no. So, I really want our
panelists to unpack this and to talk about what you really need to think about
in terms of cyber-insurance.
Allie Mellen: Yeah, so as I mentioned earlier, the average ransom payment has
skyrocketed and ultimately, this is due to a couple of things. It’s not just as
we’ve mentioned, it’s not just about the ransom. It’s actually about the
information that’s potentially stolen as well, which a lot of times can be much
more costly for the company than the ransom itself. What’s interesting about the
role of cyber-insurance and ransomware is that ransomware attacks actually
accounted for something like 40 percent of cyber-insurance claims filed in the
first half of 2020.
So it really is something that a lot of people are using in the context of
ransomware attacks that they’re being hit with, But my question, like I
definitely see the value of cyber-insurance. Absolutely.
I think it’s an important part of a strong security strategy. But at the same
time, now that these attacks are really more targeted, especially when it comes
to these ransomware attacks, my question is, is this the best place to be
investing so much of your money, and where’s the limit there?

Ransomware payouts over time. Source: Cybereason
Because potentially, if you know one organization has cyber-insurance and you
know that they’re more apt to pay out the ransom, because of that, would you
really make these organizations? Would that make them a more compelling and
appealing target?
Or, is that something that, that may be you, when you think about your security
strategy, you’re considering implementing less controls, and putting more money
towards cyber-insurance? Because that’s the situation where I think it would
really be a negative and a detriment to security teams. But I know Limor and I
were talking earlier, and she had some great thoughts on this, so I’d love to
pass it over to her.
Limor Kessem: Sure, though, I think, First of all, I agree with you, I don’t
think attacker’s know who has cyber-insurance or not, but they probably could
use that in the negotiation. Or, you know, how there are some companies that
negotiate the ransom payment for companies.
They could throw in, hey, if you have cyber-insurance or include that in the mix
of how they want to convince and pressure companies to pay. But, you know, when
we look at cyber-insurance, although it became a very popular and, you know,
seemingly, just like that, everybody has it, know the payouts for it, and maybe
not as evident because, you know, insurance ultimately will look to cover
themselves. They’re not out here to make enormous payments now for every attack,
then that’s just escalating. That’s not good business.
So, they’re looking for, you know, who’s a co-operator, how much you’re gonna
pay out, how much you’re not going to pay out, where can you not pay at all? And
so on insurance, I don’t think it’s something to lean on, per se.
And cyber-insurance is definitely coming to the table as one more layer, or one
more layer in decisions to perhaps pay, or how to pay for costs for recovering.
Let’s say, if the company does not want to pay, it’s still costing them a ton of
money to recover from the attack, they might want to try to cover that from
their insurance company.
And so this is definitely becoming a part of the whole ransomware overall game
plan. What to do. How to recover. Do we pay do we not pay?
And I think it’s an important thing, but like you said, I don’t think it comes
as a replacement for security or for security controls.
I know that insurance, as a rule, you know, has a role within the security
program as a transfer of liability, you know, if I have a certain risk, I don’t
want to accept the risk. How would I transfer that liability and a transfer the
risk to mind? Sure.
So, again, I hope to see companies invest more in their security, then
insurance, although it is an important layer to have there as well.
Allie Mellen: I think it’ll be really interesting to see how big a role it
plays, because one thing I was reading about, of course, SolarWinds and
everything that’s going on there. And one of the key points that an individual
writing about it made was that potentially one of the reasons that SolarWinds
was such an appetizing target is because they advertise all of their customers
or many of their high-profile customers on their website. And so, my question
is, maybe as cyber-insurance gained prominence, we will see the same thing
there. Where ransomware authors will take a look at those customers of
cyber-insurance in particular and see if they maybe would be willing to pay out
more, but I agree, it is potentially too early to see if that actually comes to
fruition.
Austin Merritt: Just gonna say, like Limor said, there’s no substitute for
improving your security, but you don’t also don’t want to be an organization
that wishes you had cyber-insurance after an attack. So, I think putting
emphasis on security should be at the forefront, especially like hardening.
Maybe having outside penetration testers testing that security infrastructure,
those firewalls.
Because if you’re just doing it in an in-house penetration test to test your
security or a vulnerability scanner, you might miss something that an outside
experienced hacker could actually exploit and find on their own. So, there’s a
lot of different angles there, but, uh, yeah, I would not want to be an
organization that regrets not having cyber-insurance at the end of the day.
Becky Bracken: OK, let’s move on to emerging tactics and trends. Limor this is
your bit here, so start walk us through what we’re going to be seeing.
Limor Kessem: Although our poll showed that not a lot of our participants today
have experienced a ransom attack, we do see that it’s becoming the bane of
security nowadays. It started somewhere in 2016 to really pick up speed, and at
this point, we’re just seeing it across networks. And unfortunately, I think
it’s still gonna get worse as long as it works, as long as we don’t break that
business model, and we don’t find ways to do it by pulling in law enforcement,
by pulling in whatever we can.
In order to break that profit model for cybercriminals, are probably going to
see it just getting worse. And more companies getting targeted by these
attackers are probably less experienced. Attackers also going after lower
hanging fruit. And going after small to medium businesses, you know, they don’t
have to ask for $42 million. Maybe they can ask for $1 million from smaller
businesses, which can still be very impactful. So we’re seeing that ransomware
and cyber-extortion have become one and the same, and instead of dying down
getting worse.
On my slide that you’re looking at, you can grab a few words on what we’re
seeing from experts actually, that ransom demands are obviously increasing.
Yeah. It works. They’re going after bigger companies, when they ask for that $42
million. One went after a whole hospital chain.
So it wasn’t just one hospital, there was actually a bunch of them grouped
together, which, you know, total income still makes for more money. We’re seeing
that business is booming for these. Ransomware is like if we’re talking about …,
know, Austin was saying how they have been publishing stuff and selling and
auctioning stuff off.
Their most recent claim is that they got data on President Trump’s spiritual
advisor. They want to go and publish that person’s data. So God only knows
what’s in there and how many confessions. But, you know, it’s going good for
them, they have data to sell, it could be interesting. Now that’s not the first
time that President Trump’s data was being captured by cybercriminals.
And we’re seeing that attackers are finding schools and universities to be a
good target for them. And this is quite obvious, when you have an organization
with so many people in it, you need security awareness. It’s completely
different from a company.