Ransom
2024
2023 2022
2021 2020
Ransomware in 2020: A Banner Year for Extortion
29.12.2020
Ransomware
Threatpost
From attacks on the UVM Health Network that delayed chemotherapy appointments,
to ones on public schools that delayed students going back to the classroom,
ransomware gangs disrupted organizations to inordinate levels in 2020.
Remote learning platforms shut down. Hospital chemotherapy appointments
cancelled. Ransomware attacks in 2020 dominated as a top threat vector this past
year. Couple that with the COVID-19 pandemic, putting strains on the healthcare
sector, and we witnessed ransomware exact a particularly cruel human toll as
well. Attacks had an impact on nearly all sectors of the global economy –
costing business $20 billion collectively and creating major cybersecurity
headaches for others.
Below are the most impactful ransomware stories of 2020.
250K Databases For Sale: MySQL Ransomware Disaster
In December, researchers
warned of an active ransomware campaign that plagued MySQL database servers. The
ransomware, called PLEASE_READ_ME, not only breached at least 85,000 servers
worldwide over the past year – but the attackers behind the malware gave the
campaign a double-extortion twist, posting at least 250,000 stolen databases on
a website for sale.
Garmin Haggles Over Evil Corp Ransom
In August, GPS and aviation tech
specialist Garmin reportedly negotiated with Evil Corp for an decryption key to
unlock its files in the wake of a WastedLocker ransomware attack. The attack,
which occurred on July 23, knocked out Garmin’s fitness-tracker services,
customer-support outlets and commercial aviation offerings such as flight-plan
filing, account-syncing and database-concierge capabilities.
U.S. Gov Mulls Ransomware Sanctions, Restrictions – To Dismay of Some
ransomware Fin11
ransomware alert
Over the past year, U.S. local and federal governments have increasingly looked
at regulatory efforts regarding ransomware payments. In January, New York State
mulled banning municipalities from paying ransomware demands in the event of a
cyberattack. Meanwhile, in October, the U.S. Department of the Treasury said
that companies that facilitate ransomware payments to cyber-actors on behalf of
victims may face sanctions for encouraging crime and future ransomware payment
demands.
These efforts have generated mixed reviews from the security space: While the
feds have always recommended not paying ransoms, in reality, the decision to pay
up or to not is an individual choice that has to be made given the context of
any given situation, researchers argue.
IoT Chipmaker Reels From $14M Conti Ransom Demand
In November, chip
manufacturer Advantech confirmed that it received a ransom note from a Conti
ransomware operation on Nov. 26 demanding 750 Bitcoin, which translates into
about $14 million, to decrypt compromised files and delete the data they stole.
The scammers behind the attack published a list of files from a stolen .zip
archive on their leak site. The ransom note claimed that the 3.03GB of data
posted on the leak site accounted for about 2 percent of the total amount of
data lifted ripped off from Advantech.
Ransomware Election Woes: Georgia Voter Database Hit
With the 2020 November
U.S. presidential elections this year, the security space braced for an
onslaught of cyberattacks targeting election infrastructure. In October, reports
emerged of one of the first breaches of the voting season, on Hall County, Ga.
The county’s database of voter signatures was impacted in the attack along with
other government systems. Although the county said the voting process wasn’t
impacted by the ransomware attack, the incident served as a warning to other
municipalities to lock down their systems, particularly in these last days
leading up to the election.
U.S. Pipeline Downed For Two Days
Operational Technology (OT) continued to
worry security experts from a ransomware attack perspective in 2020. In
February, feds warned that a ransomware attack hit a natural gas compression
facility in the U.S.
The attack resulted in a two-day pipeline shutdown as the unnamed victim worked
to bring systems back online from backups. The attackers were able penetrate the
IT portion of the facility’s network, and then move beyond that to eventually
infiltrate the control and communication assets on the OT side of the house.
Double Extortion: A Growing Ransomware Threat
Cybercriminals this past year
increasingly relied on a ransomware tactic, called “double extortion,” where
they increasingly inflict more pain on ransomware victims by threatening to leak
compromised data or use it in future spam attacks, if ransom demands aren’t met.
Double extortion first emerged in late 2019 by Maze operators – but has been
rapidly adopted over the past year by various cybercriminals behind the Clop,
DoppelPaymer and Sodinokibi ransomware families, who have set up websites as a
way to leak data when their ransom demands were not met.
Ransomware: The New “Snow Day”
ransomware web hosting service attackForget
snow days – ransomware attacks are the new cause of schools being shut down for
days in 2020, with a slew of cyberattacks plaguing back-to-school plans. In
September, attacks in Hartford, Conn. and Clark County, Nev. forced public
schools to postpone the first day of school, while an attack against the Newhall
School District in Valencia closed down remote learning for 6,000 elementary
school students. Also in September, personal data for students in the Clark
County School District (which includes Las Vegas) reportedly turned up on an
underground forum, after a ransomware attack linked to the Maze gang.
Ransomware Shake Up TTPs During Strange Times
Overall, COVID-19 reshaped the
ransomware landscape and how organizations were affected by ransomware.
Cybercriminals, for their part, stepped up their game this past year, with
ransomware attacks more than doubling year-over-year (up 109 percent). Many
ransomware attacks utilized COVID-19 related lures in spear phishing attacks.
Hospitals Face Disruption, Appointment Reschedules
While ransomware gangs
initially pledged not to hit hospitals during the COVID-19 pandemic, these
promises turned out to be empty.
The UVM Health Network, Universal Health Services and University of California,
San Francisco (UCSF) medical school were only a few medical entities to be hit
by ransomware attacks in 2020.
The increase in attacks – and the consequential impact not just on patient data,
but access to healthcare resources during a pandemic – caused U.S. feds to warn
of “credible information of an increased and imminent cybercrime threat to U.S.
hospitals and healthcare providers.”
Nefilim ransomware operators leak data stolen from Whirlpool
29.12.2020
Ransomware
Securityaffairs
The American multinational manufacturer and marketer of home appliances
Whirlpool was hit by the Nefilim ransomware gang.
The American multinational
manufacturer and marketer of home appliances Whirlpool suffered a ransomware
attack, Nefilim ransomware operators claim to have stolen data from the company
and threaten to release the full dump if the company will not pay the ransom.
The leak comes after failed negotiations with the executives of Whirlpool.
The company markets multiple brands, including Whirlpool, Maytag, KitchenAid,
JennAir, Amana, Gladiator GarageWorks, Inglis, Estate, Brastemp, Bauknecht,
Ignis, Indesit, and Consul. Their website also mentions Diqua, Affresh, Acros,
and Yummly brands.
The company has over 77,000 employees at 59 manufacturing
& technology research centers worldwide and generated $20 billion in revenue for
2019.
During the weekend, the Nefilim ransomware operators published the first batch
of data that includes documents related to employee benefits, accommodation
requests, medical information requests, and other info.
“This leak comes after long negotiations and unwillingness of executives of
Whirlpool Corporation to uphold the interests of their stakeholders. Whirpools
cybersecurity is very fragile, which allowed us to breach their network for the
second time after they stopped the negotiations.” states the message published
by the ransomware gang on their leak site.
The Nefilim ransomware gang leaked a text file and a 7zip archive named
Whirlpool_filelist.txt and Whirlpool_part1.7z respectively.
Bleeping Computer reported that the security breach took place in early
December.
In October the Nefilim ransomware operators leaked a long list of files
belonging to Italian eyewear and eyecare giant Luxottica.
Other victims of the ransomware gang are the mobile network operator Orange, the
independent European leader in multi-technical services The SPIE Group, the
German largest private multi-service provider Dussman Group, and the Toll Group.
Vermont Hospital confirmed the ransomware attack
28.12.2020
Ransomware
Securityaffairs
The Burlington-based University of Vermont Health Network has finally admitted
that ransomware was behind the October attack.
In October, threat actors hit
the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont
Health Network. The cyber attack took place on October 28 and disrupted services
at the UVM Medical Center and affiliated facilities.
A month later, the University of Vermont Medical Center was continuing to
recover from the cyber attack that paralyzed the systems at the Burlington
hospital.
In early December, Hospital CEO Dr. Stephen Leffler announced that the attack
that took place in late October on the computer systems of the University of
Vermont Medical Center is costing the hospital about $1.5 million a day in lost
revenue and recovery costs.
Leffler estimated that they are about 70% recovered from the attack and that
they are still working to determine the root cause of the attack.
“Hospital CEO Dr. Stephen Leffler estimated on a call with reporters on Tuesday
that they are about 70% recovered from the attack.” state the post published by
the Associated Press.
“Leffler says they’re still trying to pinpoint the exact root of the
cyberattack, but they hope to provide more details about the investigation next
week, including whether it was a ransomware attack similar to what other
hospitals around the country experienced.”
Leffler revealed that the malware employed in the attack infected all 5,000
computers on the hospital’s network. The IT staff at the hospital will decouple
parts of the network and it is going to enhance security measures.
Now
officials at the Vermont Hospital confirmed that the incident was the result of
a ransomware attack.
“On Tuesday, hospital officials said its information technology workers found a
file directing them to contact the attackers if they wanted their systems
restored, but it did not contain a request for money.” states the post published
by the Associated Press.
“We considered it for about five seconds,” said Doug Gentile, the chief
information officer for the UVM Health Network.
The hospital notified federal police which is still investigating the security
breach, the good news is that patient data was not exposed.
The hospital has been restoring the backups and rebuilding all its 1,300, the
operations are expected to be fully restored by early next month.
The hospital officials pointed out that they had already implemented strong
security measures before the cyber attack, but evidently it was not enough.
“It’s become clear, really this is an arms race. I think you’ve all seen in the
news some of the recent sophistication of cyberattacks that are being launched
and it’s really just going to continue,” Doug Gentile added. “So, we all have to
stay vigilant. We all are going to continually have to update our tools and our
approaches to try to stay ahead of the bad guys in this situation.”
REvil gang threatens to release intimate pictures of celebs who are customers of
The Hospital Group
27.12.2020
Ransomware
Securityaffairs
REvil ransomware gang, aka Sodinokibi, hacked The Hospital Group and threatens
to release before-and-after pictures of celebrity clients.
The Hospital Group
has 11 clinics and has a celebrity clientele, but it made the headlines because
the REvil ransomware gang, aka Sodinokibi, claims to have hacked its systems and
threatens to release before-and-after pictures of celebrity clients.
Its clinics specializing in bariatric weight loss surgery, breast enlargements,
nipple corrections, and nose adjustments.
The Hospital Group has confirmed
the ransomware attack and notified the Information Commissioner about the
security breach. The Hospital Group also notified via email all customers.
“We can confirm that our IT systems have been subject to a data security
breach.” The Hospital Group said in a statement. “None of our patients’ payment
card details have been compromised but at this stage, we understand that some of
our patients’ personal data may have been accessed.”
“The Hospital Group, which has been endorsed by celebs including Kerry Katona
and Joey Essex, confirmed the ransomware attack.” states The Sun.
The REvil ransomware operators have published some pictures of the hacked
systems on their leak site hosted on the Tor Network, they claims to have stolen
about 600 GB of documents. Stolen data includes personal data of customers along
with intimate photos of these customers.


“Unfortunately, time is going on very quickly, but we have not seen any positive
reaction from our friends from TheHospitalGroup.org.
Center for Plastic
Surgery in the UK.” reads the message posted on the leak site.
“It’s time to introduce you to them too. We pumped out about 600 gb of the most
important documents, personal data of customers, as well as intimate photos of
these customers (this is not a completely pleasant sight:))”
The ransomware gang plans to post the first batch of files, named “Pacient
Personal – 20гб TMG OFFICIAL Documents – 50гб” at the beginning of next week.
REvil gang is one of the major ransomware operations, it has been active since
April 2019, its operators claim to earn over $100 million a year through its
RaaS service.
In a recent interview with the public-facing representative of REvil, the
ransomware operation claims to earn over $100 million a year in extortion
payments.
The list of the victims of the group is long and includes Travelex,
Kenneth Cole, SeaChange, Brown-Forman, BancoEstado, Grubman Shire Meiselas &
Sacks (GSMLaw), Valley Health Systems, Telecom Argentina, the Managed.com
hosting provider, and Lion.
Clop ransomware gang paralyzed flavor and fragrance producer Symrise
21.12.2020
Ransomware
Securityaffairs
Flavor and fragrance producer Symrise is the last victim of the Clop ransomware
gang that claims to have stolen 500 GB of unencrypted files.
Symrise AG, a
major producer of flavours and fragrances, was hit by Clop ransomware operators.
The threat actors claim to have stolen 500 GB of unencrypted files.
The attack was reported last week by Handelsblatt, the website databreaches.net
also reported the news after @Chum1ng0 alerted them.
The company shut down its systems to prevent the malware from spreading into its
network.
“In order to be able to assess the consequences and to prevent possible further
effects, the company shut down all essential systems,” said Symrise .
“As far as we know, it is a criminal act with extortion intent,” said a
company’s spokeswoman. Symrise launched an investigation into the incident and
notified the State Criminal Police Office.
At the time of the disclosure the company did not reveal the family of malware
that hit its system either the ransom amount.
BleepingComputer reported that the company was hit by the Clop ransomware that
encrypted 1,000 devices.
“The Clop ransomware gang has claimed responsibility for the attack on Symrise
and have told BleepingComputer that they allegedly encrypted 1,000 devices.”
reported Bleeping Computer.
Clop ransomware operators revealed told BleepingComputer they attack vector were
phishing emails.
The ransomware gang published images of allegedly stolen files on its leak site,
including passport scans, accounting documents, and emails.
In early December, the group claimed to have stolen 2 million credit cards from
E-Land Clop ransomware.
Other victims of the Clop ransomware were the Maastricht University, Software AG
IT, and ExecuPharm.
Ransomware Gangs Use 'SystemBC' Tor Backdoor in Attacks
19.12.2020
Ransomware
Securityweek
Researchers at Sophos noticed recently that the operators of multiple ransomware
families have been using a backdoor named SystemBC, which provides attackers a
connection to compromised devices and which uses the Tor anonymity network to
hide command and control (C&C) communications.
Initially observed in 2019, SystemBC enables persistent access to the system,
providing attackers with means to conceal communications and remotely control
the infected devices.
Designed with support for the execution of commands and to allow adversaries to
download and execute scripts, executables, and DLLs, the backdoor is
continuously evolving, with recent samples having switched from creating a
SOCKS5 proxy to using the Tor network for communication purposes.
Over the past months, Sophos researchers identified hundreds of attacks
employing SystemBC, some of them being recent Ryuk and Egregor ransomware
assaults, in which the backdoor was deployed in combination with other
post-exploitation tools, including Cobalt Strike.
In some instances, the backdoor was deployed after the attackers were able to
compromise administrative accounts and moved deep into the network.
For persistence, the malware copies itself to a folder in the ProgramData
directory and schedules the copy as a task that is launched using the ‘start’
command, as a scheduled service. It searchers for a process associated with
Emsisoft’s anti-malware software and skips the creation of the service if the
process is found.
Most of the communication with the C&C server is performed over a Tor
connection, using an implementation closely resembling the mini-tor open-source
library.
When executed from the scheduled task, the malware collects information such as
the active Windows user name, OS build number, system architecture (32-bit or
64-bit), and volume serial number, and sends it encrypted to the C&C. It also
enables attackers to send and execute files and commands.
“Collectively, these capabilities give attackers a point-and-shoot capability to
perform discovery, exfiltration and lateral movement with packaged scripts and
executables—without having to have hands on keyboard. These capabilities were
originally intended for mass exploitation, but they have now been folded into
the toolkit for targeted attacks—including ransomware,” Sophos notes.
The Ryuk and Egregor attacks employing SystemBC were performed either by
affiliates of ransomware operators or by the ransomware gangs themselves,
through malware-as-a-service (MaaS) service providers. The threat actors
lingered for weeks on the victim networks, for data exfiltration.
“SystemBC is an attractive tool in these types of operations because it allows
for multiple targets to be worked at the same time with automated tasks,
allowing for hands-off deployment of ransomware using Windows built-in tools if
the attackers gain the proper credentials,” Sophos explains.
RubyGems Packages Laced with Bitcoin-Stealing Malware
18.12.2020
Cryptocurrency
Ransomware
Threatpost
Two malicious software building blocks that could be baked into web applications
prey on unsuspecting users.
RubyGems, an open-source package repository and manager for the Ruby web
programming language, has taken two of its software packages offline after they
were found to be laced with malware.
RubyGems provides a standard format for distributing Ruby programs and libraries
in the service of building web applications. These programs and libraries are
collected into software packages called “gems,” which can be used to extend or
modify functionality in Ruby applications.
Two of these gems available in its open-source software repository,
“pretty_color” and “ruby-bitcoin,” were discovered by researchers at Sonatype to
be corrupted to steal Bitcoin from unsuspecting web-application users.
“The gems contained malware that ran itself persistently on infected Windows
machines and replaced any Bitcoin or cryptocurrency wallet address it found on
the user’s clipboard with the attacker’s,” according to Ax Sharma, researcher at
Sonatype, writing in a Wednesday posting. “This means if a user [of a corrupted
web app built using the gems]…[were] to copy-paste a Bitcoin recipient wallet
address somewhere on their system, the address would be replaced with that of
the attacker, who’d now receive the Bitcoins.”
The first gem contained legitimate code from a real package along with the
malware, in order to evade detection by developers using it. The pretty_color
gem contained the legitimate complete code and a fully descriptive README.file
of a trusted open-source component called “colorize.” Colorize is used for
setting text colors, background colors and text effects for web apps, and has
been downloaded 55 million times.
Along with being an exact replica of the colorize package, pretty_color contains
a rogue version.rb file responsible for the malicious functionality. It’s
obfuscated code which, on Windows systems, generates and runs a malicious
VBScript called “the_Score.vbs,” presumably referring to crook lingo for a
heist.
“A casual observer may otherwise overlook [it] by mistaking it for version
metadata,” Sharma explained.
Once decoded, the malicious code carries out various tasks according to the
analyst, the most important of which is creating another malicious VBScript.
“%PROGRAMDATA%\Microsoft Essentials\Software Essentials.vbs” monitors the user’s
clipboard every second for a Bitcoin address and replaces it with the attacker’s
wallet address if detected, Sharma said.
Thus, if a user copies an address to the clipboard, the script may be monitoring
it at just the right second to instantaneously swap it out, with the user being
none the wiser.
Also, Sharma said that to achieve persistence, the_Score.vbs also adds the path
of the newly dropped Software Essentials.vbs to the appropriate Windows registry
key, so the malware runs every time the system boots.
The other malicious gem, called ruby-bitcoin, is much simpler and only contains
the malicious version.rb code mentioned above. While only containing the
malicious code, is a variation of “bitcoin-ruby,” which is a legitimate gem,
Sharma told Threatpost “Bitcoin-ruby” is a Ruby library for interacting with the
bitcoin protocol/network, with half a million downloads.
“Both gems capitalized on typosquatting and brandjacking: a developer making
human error and getting the wrong package than what they had intended to,” he
noted. “You can see why attackers would love to deploy typosquatting and
brandjacking attacks — they offer a higher chance of success due to a developer
making an honest mistake.”
Unfortunately, anyone can upload a gem to the RubyGems repository, including
threat actors.
“With any open-source system, if the honest users and the general public have
access to it, so do the adversaries,” Sharma said.
The good news is that the gems, having been caught early on, didn’t score many
downloads, according to Sonatype. For example, the pretty_color package that
imitated a legitimate colorize package was published December 13th and yanked
the very next day, after being downloaded five dozen times, according to
RubyGems. Likewise, ruby-bitcoin scored under 100 downloads.
“With open-source software supply chain attacks though, we can never be certain
of their actual impact, which might be much larger,” Sharma told Threatpost in
an emailed interview. “We don’t know who downloaded these packages and if they
were included by a developer in their application as a dependency. If that was
the case, we can’t tell who further downloaded those applications shipped with
pretty_color or ruby_bitcoin in them.”
The code was also found outside of the RubyGems repository.
“A variant of the plaintext code for the_Score.vbs generated by the obfuscated
version.rb has also existed on GitHub, under an unrelated third party’s
account,” Sharma said. “Although the identical file on GitHub is called
‘wannacry.vbs,’ Sonatype Security Research team did not find any hard evidence
linking the code to the original WannaCry ransomware operators.”
Supply-Chain Attacks
This is an example of how attackers are starting to turn
more and more to corrupting the software supply chains that developers rely on
to build their applications, Sharma noted, flagging that Sonatype has seen a 430
percent increase in upstream software supply-chain attacks over the past year.
“While these gems stole cryptocurrency, as we have repeatedly seen with
open-source malware striking GitHub, npm and RubyGems, attackers can exploit
trust within the open-source community to deliver pretty much anything
malicious, from sophisticated spying trojans like njRAT, to a whole new family
of Discord info-stealing malware CursedGrabber.”
He added, “A concern I discuss is whether or not open-source ecosystems might
lure adversaries like ransomware ops in. Luckily, that hasn’t happened yet, but
that is not to say it can’t.”
Going forward, attacks on software supply chains are only expected to grow and
be adopted by more advanced threat actors over time.
“Gitpaste-12 returned rather soon with 30 new exploits for vulnerabilities, a
lot of which concern open-source components, as opposed to the previous 12 it
had exploited,” said Sharma. “As more and more adversaries step in, and security
companies catch up, the nature of these attacks is only expected to become more
advanced, complex and harder to detect without at least some form of automation
in place.”
Making malicious code changes that then make their way into open-source projects
used by developers around the world is a hard-to-track tactic, he added. And it
also means that propagation of malware is limited only by the number of
applications that are built using corrupted components.
“It is virtually impossible to manually chase and keep track of such
components,” he said.
To even begin knowing whether you have vulnerable code, developers and
organizations need to keep a software bill of materials (SBOM) for all of their
apps, so they can easily track and trace the location of every single component
embedded within their production software applications, he told Threatpost.
“It’s the only way to immediately assess and remediate exposure every time new
open-source vulnerabilities are publicly disclosed, whether they’re malicious or
not,” he noted. “But to do this manually can be virtually impossible. What if
malware lurks in a dependency of a dependency (a transitive dependency) used in
your software application? What if the malicious code, as we saw in
pretty_color, is hidden via techniques such as obfuscation and minification in
places where you’d least expect it?”
At minimum, developers and organizations should have tooling in place to create
SBOMs. “But, having automated solutions in place capable of performing deep
binary analysis and the ability to spot counterfeit components can be built into
your DevSecOps workflow as a more reliable prevention strategy,” Sharma added.
DoppelPaymer ransomware gang now cold-calling victims, FBI warns
18.12.2020
Ransomware
Securityaffairs
FBI says DoppelPaymer ransomware gang is harassing victims who refuse to pay,
threatening to send individuals to their homes.
FBI is warning of a new
escalation in the extortion activities of the DoppelPaymer ransomware gang, the
operators have been calling victims, threatening to send individuals to their
homes if they don’t pay the ransom.
According to a private industry notification alert (PIN), sent by the FBI to
private organizations, the Bureau is aware of extortion activities that have
been happening since February 2020.
Early this month, Evgueni Erchov, Director of IR & Cyber Threat Intelligence at
Arete Incident Response, told ZDNet that multiple ransomware gangs are
cold-calling victims if they don’t pay the ransom and attempt to restore from
backups. This criminal practice is adopted since August by several gangs,
including Sekhmet, Conti, and Ryuk.
The FBI PIN, Number 20201210-001, was issued on December 10, 2020, and provides
details about Doppelpaymer’s criminal activity and the sectors on which the
group focuses (Healthcare, Emergency Services, and Educational Institutions).
The report also details additional tactics, techniques, and procedures
associated with the threat, including intimidation through phone calls.
“As of February 2020, in multiple instances, DoppelPaymer actors had followed
ransomware infections with calls to the victims to extort payments through
intimidation or threatening to release exfiltrated data. In one case an actor,
using a spoofed US-based telephone number while claiming to be located in North
Korea, threatened to leak or sell data from an identified business if the
business did not pay the ransom.” states the FBI’s PIN. “During subsequent
telephone calls to the same business, the actor threatened to send an individual
to the home of an employee and provided the employee’s home address. The actor
also called several of the employee’s relatives.”
The agency then goes on to detail one particular incident where threats
escalated from the attacked company to its employees and even relatives. From
the PIN alert:
The threat actor threatened to send an individual to the home of an employee and
provided the employee’s home address.
Clearly, threats of violence are not realistic and only aim at making pressure
on the victims.
The alert also includes the following recommended mitigations to prevent
ransomware attacks:
Ensure backups are secure and are disconnected from the network at the
conclusion of each backup session.
Audit user accounts regularly,
particularly Remote Monitoring and Management accounts that are publicly
accessible. Patch operating systems, software, firmware, and endpoints.
Monitor inbound and outbound network traffic; set alerts for data exfiltration.
Apply two-factor authentication to user login credentials, receiving responses
by text rather than email as actors may be in control of victim email accounts.
Implement least privilege for file, directory, and network share permissions.
FBI Warns of DoppelPaymer Ransomware Targeting Critical Infrastructure
18.12.2020
Ransomware
Securityweek
The Federal Bureau of Investigation has released a Private Industry Notification
to warn of DoppelPaymer ransomware attacks on critical infrastructure.
DoppelPaymer emerged as a forked version of BitPaymer (also known as FriedEx),
both believed to be the work of TA505, the threat actor best known for the
infamous Dridex Trojan and Locky ransomware families.
“Since its emergence in June 2019, DoppelPaymer ransomware has infected a
variety of industries and targets, with actors routinely demanding six-and
seven-figure ransoms in Bitcoin (BTC),” the FBI says in its alert.
According to the FBI, the ransomware has been used worldwide, in attacks on
verticals such as healthcare, emergency services, and education.
The Bureau also warns businesses that the threat actor behind DoppelPaymer
engages in double extortion: prior to encrypting targeted systems with
ransomware, they exfiltrate data they later abuse for extortion or to pressure
the victim into paying the ransom.
A September 2020 attack targeting a German hospital prevented emergency service
personnel from communicating with the hospital, forcing the re-routing of an
individual who required emergency services. The individual later died, but
German authorities blamed it on poor health and not the attack.
In July 2019, DoppelPaymer infected 13 servers of a US medical center, demanding
50 Bitcoin (approximately $600,000 at the time) in ransom. The medical center
was able to restore its systems from offsite backups, but the process took
several weeks.
Also in September 2020, the threat actor behind DoppelPaymer compromised a
county’s E911 Center, making changes that prevented access to the county’s
computer-aided dispatch (CAD) system.
“The actors reset passwords, removed accounts from the domain administrators
group, and created an admin account called ‘AD.’ In a separate attack on a
different county, the actors encrypted servers used by the county responsible
for emergency dispatch, patrol, jail, and payroll departments,” the FBI
explains.
In another attack during the summer of 2020, the adversary disrupted police,
emergency services, and other government functions in a US city. As part of the
attack, ransomware was used to encrypt files on Windows 7, 10, Windows Server
2008, Server 2012, and Server 2016 systems.
A DoppelPaymer attack on a community college had an impact on in-person classes,
as it resulted in restricted access to the campus for several days. An attack
targeting a different college resulted in three infected servers and restricted
network access.
“As of February 2020, in multiple instances, DoppelPaymer actors had followed
ransomware infections with calls to the victims to extort payments through
intimidation or threatening to release exfiltrated data,” the FBI explains.
The agency also included a series of mitigation recommendations in its
notification.
Two Malware-Laced Gems Found in RubyGems Repository
18.12.2020
Cryptocurrency
Ransomware
Securityweek
Two Ruby gems that were found to pack malware capable of running persistently on
infected machines were removed recently from the RubyGems hosting service.
The two gems, pretty_color and ruby-bitcoin, contained malware that was
targeting Windows machines and which was meant to replace any cryptocurrency
wallet address in the clipboard with an attacker-supplied one.
By replacing the crypto-wallet addresses, the malware helps the attackers hijack
transactions and steal the victim’s funds.
While analyzing the two gems, software development and security firm Sonatype
discovered that pretty_color contained legitimate files from colorize, a trusted
open source component, which made detection more difficult.
“In fact, pretty_color is an identical replica of the benign colorize package
and has all its code, including a fully descriptive README,” Sonatype says.
The gem included a file named version.rb that poses as version metadata, but
which contains obfuscated code meant to run a malicious script on Windows
computers.
The code also included a reference to ReversingLabs threat analyst Tomislav
Maljic, who previously identified more than 700 typosquatting RubyGems designed
to mine for Bitcoin on infected machines.
The ruby-bitcoin gem, Sonatype’s security researchers explain, only includes the
malicious code present in the version.rb file from pretty_color.
A plain-text variant of the malicious script used in these gems was found on
GitHub under an unrelated account, suggesting a possible connection to WannaCry.
However, there’s no hard evidence linking the code to the WannaCry operation.
“Of all activities a ransomware group may conduct on a compromised system,
replacing Bitcoin wallet address on the clipboard feels more akin to a trivial
mischief by an amateur threat actor than to a sophisticated ransomware
operation,” Sonatype notes.
Ryuk, Egregor Ransomware Attacks Leverage SystemBC Backdoor
17.12.2020
Ransomware
Threatpost
In the past few months
researchers have detected hundreds of attempted SystemBC deployments globally,
as part of recent Ryuk and Egregor ransomware attacks.
Commodity malware backdoor SystemBC has evolved to now automate a number of key
activities, as well as use the anonymizing Tor platform. These overarching
changes make it both easier for cybercriminals to deploy the backdoor, as well
as cloak the destination of the command-and-control (C2) traffic.
SystemBC, a proxy and remote administrative tool, was first discovered in 2019.
Researchers believe it is being used by ransomware-as-a-service affiliates due
to it being associated with multiple types of ransomware that are deployed in
the same way. Once it’s executed, the backdoor is used by ransomware actors to
set up a persistent connection on victim systems.
“While SystemBC has been around for over a year, we’ve seen both its use and its
features continue to evolve,” said Sivagnanam Gn and Sean Gallagher, researchers
with Sophos, in a Wednesday analysis. “The most recent samples of SystemBC carry
code that, instead of acting essentially as a virtual private network via a
SOCKS5 proxy, uses the Tor anonymizing network to encrypt and conceal the
destination of command and control traffic.”
Researchers warn that over the past few months they have detected hundreds of
attempted SystemBC deployments globally. The backdoor has been utilized in
recent Ryuk and Egregor ransomware attacks, and has also often been leveraged in
combination with post-exploitation tools such as Cobalt Strike, they said.
SystemBC Proliferation
Initially, ransomware groups that leverage SystemBC
have been observed first infecting systems using spam or phishing emails. These
emails then trick the victim into downloading the Buer loader, QBot, ZLoader or
other types of malware, which are used for initial exploitation and lateral
movement.
From there, attackers then use SystemBC (along with Cobalt Strike, in some
cases) in order to scoop up passwords from victim systems – although in some
cases, the SystemBC backdoor was only deployed to servers after attackers gained
administrative credentials, and then used it to move deeper into the targeted
network, researchers said.
SystemBC is used primarily to gain further persistence on the victim system. In
what’s now a more automated process, the backdoor can deploy PowerShells; .CMD
scripts (A CMD script file features one or more commands in plain text format
that are executed in order to perform various tasks); Windows commands;
malicious executables and dynamic link libraries (DLLs).
Researchers said, these key activities have been automated now so that operators
can launch multiple attacks without the need for hands-on-keyboard activity.
They are used for further exploitation and the deployment of the final
ransomware (which in recent cases have been Ryuk or Egregor).
SystemBC Updates
The backdoor also acts both as a network proxy for concealed
communications; here a primary change exists in how SystemBC has evolved.
Before, SystemBC primarily set up SOCKS5 proxies on victim computers, which
could then be used by threat actors to tunnel/hide the malicious traffic
associated with other malware. A SOCKS5 proxy server creates a Transmission
Control Protocol (TCP) connection to another server behind the firewall on the
client’s behalf, then exchanges network packets between the client and the
actual server.
“With the proxies initialized, the client now begins to retrieve data requested
from the C2 via HTTPS,” researchers with Proofpoint said in a writeup in 2019,
after the malware was discovered. “The use of SOCKS5 is not a major
differentiator; it’s just another potential technology malware authors can use
for this purpose and the primary proxy protocol,” they noted at the time.
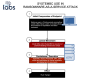
Most of the C2 communications with the more recent versions of SystemBC,
however, are over a Tor connection: “The Tor communications element of SystemBC
appears to be based on mini-Tor, an open-source library for lightweight
connectivity to the Tor anonymized network,” said Sophos reserchers. “The code
of mini-Tor isn’t directly duplicated in SystemBC. But the bot’s implementation
of the Tor client closely resembles the implementation used in the open-source
program, including its extensive use of the Windows Crypto Next Gen (CNG) API’s
Base Crypto (BCrypt) functions.”
These changes to the backdoor “are likely an effort to make it more difficult to
detect the network traffic associated with command and control of SystemBC,”
Sophos’ Gallagher told Threatpost.
“I can’t say if it’s more effective to use Tor instead of a SOCKS5 proxy, but it
gives the attacker a more obfuscated and encrypted way of sending commands,
scripts, and more malware to the bot,” Gallagher explained. “A single SOCKS5
proxy could be quickly blocked, while Tor is more resilient in its routing.”
SystemBC proves to be another useful tool for cybercriminals who have been
launching increased levels of ransomware attacks. This past year, in fact,
ransomware attacks more than doubled year-over-year (up 109 percent).
Ransomware Attackers Using SystemBC Malware With RAT and Tor Proxy
17.12.2020
Ransomware
Thehackernews
Cybercriminals are
increasingly outsourcing the task of deploying ransomware to affiliates using
commodity malware and attack tools, according to new research.
In a new analysis published by Sophos today and shared with The Hacker News,
recent deployments of Ryuk and Egregor ransomware have involved the use of
SystemBC backdoor to laterally move across the network and fetch additional
payloads for further exploitation.
Affiliates are typically threat actors responsible for gaining an initial
foothold in a target network.
"SystemBC is a regular part of recent ransomware attackers' toolkits," said
Sophos senior threat researcher and former Ars Technica national security editor
Sean Gallagher.
"The backdoor can be used in combination with other scripts and malware to
perform discovery, exfiltration and lateral movement in an automated way across
multiple targets. These SystemBC capabilities were originally intended for mass
exploitation, but they have now been folded into the toolkit for targeted
attacks — including ransomware."
First documented by Proofpoint in August 2019, SystemBC is a proxy malware that
leverages SOCKS5 internet protocol to mask traffic to command-and-control (C2)
servers and download the DanaBot banking Trojan.
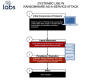
The SystemBC RAT has since expanded the breadth of its toolset with new
characteristics that allow it to use a Tor connection to encrypt and conceal the
destination of C2 communications, thus providing attackers with a persistent
backdoor to launch other attacks.
Researchers note that SystemBC has been used in a number of ransomware attacks —
often in conjunction with other post-exploitation tools like CobaltStrike — to
take advantage of its Tor proxy and remote access features to parse and execute
malicious shell commands, VBS scripts, and other DLL blobs sent by the server
over the anonymous connection.
It also appears that SystemBC is just one of the many commodity tools that are
deployed as a consequence of initial compromise stemming from phishing emails
that deliver malware loaders like Buer Loader, Zloader, and Qbot — leading the
researchers to suspect that the attacks may have been launched by affiliates of
the ransomware operators, or by the ransomware gangs themselves through multiple
malware-as-a-service providers.
"These capabilities give attackers a point-and-shoot capability to perform
discovery, exfiltration and lateral movement with packaged scripts and
executables — without having to have hands on a keyboard," the researchers said.
The rise of commodity malware also points to a new trend where ransomware is
offered as a service to affiliates, like it's in the case of MountLocker, where
the operators provide double extortion capabilities to affiliates so as to
distribute the ransomware with minimal effort.
"The use of multiple tools in ransomware-as-a-service attacks creates an ever
more diverse attack profile that is harder for IT security teams to predict and
deal with," Gallagher said. "Defense-in-depth, employee education and
human-based threat hunting are essential to detecting and blocking such
attacks."
Norwegian cruise company Hurtigruten was hit by a ransomware
16.12.2020
Ransomware
Securityaffairs
Norwegian cruise company Hurtigruten disclosed a cyber attack that impacted its
entire worldwide digital infrastructure.
The Norwegian cruise company
Hurtigruten announced its entire worldwide digital infrastructure was the victim
of a cyber attack.
“It’s a serious attack,” said the Hurtigruten’s chief digital officer Ole-Marius
Moe-Helgesen in a statement. “The entire worldwide digital infrastructure of
Hurtigruten seems to have been hit.” “The attack seems to be a so-called
ransomware.”
The company detected the attack overnight Sunday to Monday, the systems at the
company were infected with a ransomware.
The company’s website is currently displaying a message that says “Sorry, the
website isn’t working right now”

The company notified local authorities immediately after the security breach was
discovered.
It is a terrible period for the company and the entire cruise liner industry
that is facing the stop of the operations imposed due to the COVID-19 pandemic.
The company relaunched its cruisers in June but suspended them again in
September for the second wave of the pandemic that infected dozens of crew
members and passengers.
At the time of this writing, it is not clear which is the family of ransomware
that hit the company either if the hackers have exfiltrated any data from the
company.
Mount Locker Ransomware Offering Double Extortion Scheme to Other Hackers
12.12.2020
Ransomware
Thehackernews
A relatively new ransomware strain behind a series of breaches on corporate
networks has developed new capabilities that allow it to broaden the scope of
its targeting and evade security software—as well as with ability for its
affiliates to launch double extortion attacks.
The MountLocker ransomware, which only began making the rounds in July 2020, has
already gained notoriety for stealing files before encryption and demanding
ransom amounts in the millions to prevent public disclosure of stolen data, a
tactic known as double extortion.
"The MountLocker Operators are clearly just warming up. After a slow start in
July they are rapidly gaining ground, as the high-profile nature of extortion
and data leaks drive ransom demands ever higher," researchers from BlackBerry
Research and Intelligence Team said.
"MountLocker affiliates are typically fast operators, rapidly exfiltrating
sensitive documents and encrypting them across key targets in a matter of
hours."
MountLocker also joins the likes of other ransomware families like Maze (which
shut down its operations last month) that operate a website on the dark web to
name and shame victims and supply links to leaked data.
To date, the ransomware has claimed five victims, although the researchers
suspect the number could be "far greater."
Offered as Ransomware-as-a-Service (RaaS), MountLocker was notably deployed
earlier this August against Swedish security firm Gunnebo.
Although the company said it had successfully thwarted the ransomware attack,
the criminals who orchestrated the intrusion ended up stealing and publishing
online 18 gigabytes of sensitive documents, including schematics of client bank
vaults and surveillance systems, in October.

Now according to BlackBerry's analysis, threat actors behind MountLocker-related
affiliate campaigns leveraged remote desktop (RDP) with compromised credentials
to gain an initial foothold on a victim's environment — something that was
observed in Gunnebo's hack as well — and subsequently deploy tools to carry out
network reconnaissance (AdFind), deploy the ransomware and laterally spread
across the network, and exfiltrate critical data via FTP.
The ransomware in itself is lightweight and efficient. Upon execution, it
proceeds to terminate security software, trigger encryption using ChaCha20
cipher, and create a ransom note, which contains a link to a Tor .onion URL to
contact the criminals via a "dark web" chat service to negotiate a price for
decrypting software.
It also uses an embedded RSA-2048 public key to encrypt the encryption key,
deletes volume shadow copies to thwart restoration of the encrypted files, and
eventually removes itself from the disk to hide its tracks.
The researchers, however, point out that the ransomware uses a cryptographically
insecure method called GetTickCount API for a key generation that may be
susceptible to a brute-force attack.
MountLocker's list of encryption targets is extensive, with support for over
2600 file extensions spanning databases, documents, archives, images, accounting
software, security software, source code, games, and backups. Executable files
such as .exe, .dll, and .sys are left untouched.
That's not all. A new variant of MountLocker spotted in late November (dubbed
"version 2") goes a step further by dropping the list of extensions to be
included for encryption in favor of a lean exclusion list: .exe, .dll, .sys,
.msi, .mui, .inf, .cat, .bat, .cmd, .ps1, .vbs, .ttf, .fon, and .lnk.
"Since its inception, the MountLocker group has been seen to both expand and
improve their services and malware," the researchers concluded. "While their
current capabilities are not particularly advanced, we expect this group to
continue developing and growing in prominence over the short term."
PLEASE_READ_ME Ransomware Attacks 85K MySQL Servers
11.12.2020
Ransomware
Threatpost
Ransomware actors behind the attack have breached at least 85,000 MySQL servers,
and are currently selling at least compromised 250,000 databases.
Researchers are warning on an active ransomware campaign that’s targeting MySQL
database servers. The ransomware, called PLEASE_READ_ME, has thus far breached
at least 85,000 servers worldwide – and has posted at least 250,000 stolen
databases on a website for sale.
MySQL is an open-source relational database management system. The attack
exploits weak credentials on internet-facing MySQL servers, of which there are
close to 5 million worldwide. Since first observing the ransomware campaign in
January, researchers said that attackers have switched up their techniques to
put more pressure on victims and to automate the payment process for the ransom.
“The attack starts with a password brute-force on the MySQL service. Once
successful, the attacker runs a sequence of queries in the database, gathering
data on existing tables and users,” said Ophir Harpaz and Omri Marom,
researchers with Guardicore Labs, in a Thursday post. “By the end of execution,
the victim’s data is gone – it’s archived in a zipped file which is sent to the
attackers’ servers and then deleted from the database.”
From there, the attacker leaves a ransom note in a table, named “WARNING,” which
demands a ransom payment of up to 0.08 BTC. The ransom note tells victims
(verbatim), “Your databases are downloaded and backed up on our servers. If we
dont receive your payment in the next 9 Days, we will sell your database to the
highest bidder or use them otherwise.”
Researchers believe that the attackers behind this campaign have made at least
$25,000 in the first 10 months of the year.
Researchers said that PLEASE_READ_ME (so-called because it’s the name of the
database that the attackers create on a compromised server) is an example of an
untargeted, transient ransomware attack that does not spend time in the network
besides targeting what’s required for the actual attack – meaning there’s
typically no lateral movement involved.
The attack may be simple, but it’s also dangerous, researchers warned, because
it’s almost fileless. “There are no binary payloads involved in the attack
chain, making the attack ‘malwareless,'” they said. “Only a simple script which
breaks in the database, steals information and leaves a message.”
That said, a backdoor user mysqlbackups’@’%’ is added to the database for
persistence, providing the attackers with future access to the compromised
server, researchers said.
Attack Evolution
Researchers first observed PLEASE_READ_ME attacks in
January, in what they called the “first phase” of the attack. In this first
phase, victims were required to transfer BTC directly to the attacker’s wallet.

The attack timeline. Credit: Guardicore Labs
The second phase of the ransomware campaign started in October, which
researchers said marked an evolution in the campaign’s techniques, tactics and
procedures (TTPs). In the second phase, the attack evolved into a
double-extortion attempt, researchers say – meaning attackers are publishing
data while pressuring victims to pay the ransom. Here, attackers put up a
website in the TOR network where payments can be made. Victims paying the ransom
can be identified using tokens (as opposed to their IP/domain), researchers
said.
“The website is a good example of a double-extortion mechanism – it contains all
leaked databases for which ransom was not paid,” said researchers. “The website
lists 250,000 different databases from 83,000 MySQL servers, with 7 TB of stolen
data. Up till now, [we] captured 29 incidents of this variant, originating from
seven different IP addresses.”
Ransomware attacks have continued to hammer hospitals, schools and other
organizations in 2020. The ransomware tactic of “double extortion” first emerged
in late 2019 by Maze operators – but has been rapidly adopted over the past few
months by various cybercriminals behind the Clop, DoppelPaymer and Sodinokibi
ransomware families.
Looking forward, researchers warn that the PLEASE_READ_ME operators are trying
to up their game by using double extortion at scale: “Factoring their operation
will render the campaign more scalable and profitable,” they said.
Misery of Ransomware Hits Hospitals the Hardest
11.12.2020
Ransomware
Threatpost
Ransomware attacks targeting hospitals have exacted a human cost as well as
financial.
Despite hospitals being on the front lines during the pandemic, bad actors have
continued to target them with ransomware. In addition to wreaking havoc on
operational processes in medical facilities at the worst possible time, the
attacks have evolved to threaten patient safety.
Free eBook on Healthcare and CybersecurityIn September, employees at Universal
Health Services (UHS), a Fortune-500 owner of a nationwide network of hospitals,
reported widespread outages that resulted in delayed lab results, a fallback to
pen and paper, and patients being diverted to other hospitals. The culprit
turned out to be the Ryuk ransomware, which locked up hospital systems for days.
“No patients died tonight in our [emergency room] but I can surely see how this
could happen in large centers due to delay in patient care,” a Reddit user
identifying themselves as a nurse, wrote at the time.
The concern isn’t overblown. Earlier that month, a ransomware attack at a
Dusseldorf University hospital in Germany resulted in emergency-room diversions
to other hospitals. According to a report by the Ministry of Justice of the
State North Rhine-Westphalia, a patient died who had to be taken to a more
distant hospital in Wuppertal because of the attack on the clinic’s servers.
[Editor’s Note: This article is part of an exclusive FREE eBook, sponsored by
ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a Covid-Era World”,
examines the pandemic’s current and lasting impact on cybersecurity. Get the
whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
This turn of events comes after several ransomware gangs actually pledged not to
hit hospitals because of the ongoing COVID-19 scourge. The Maze and DoppelPaymer
groups, for instance, said they would not target medical facilities and, if
accidentally hit, would provide the decryption keys at no charge. The Netwalker
operators, meanwhile, said they would not target hospitals, however if
accidentally hit, the hospital would still have to pay the ransom.
Ransomware Attacks on Hospitals: When Malware Gets DeadlyOther groups have less
scruples, and in fact, some (like Netwalker) have reneged on their pledges. In
fact, incidents of ransomware attacks against hospitals skyrocketed in October.
So much so that, the U.S. Cybersecurity
and Infrastructure Security Agency, the Federal Bureau of Investigation, and the
U.S. Department of Health and Human Services issued a security bulletin warning
of “credible information of an increased and imminent cybercrime threat to U.S.
hospitals and healthcare providers.”
Among those hit lately include well-known facilities like University Hospital in
New Jersey, Boston’s Children’s Hospital and Children’s Hospital in Little Rock.
“The promise not to attack hospitals was always an empty one given the number of
players in the ransomware game that would not restrain from it,” said Erich
Kron, security awareness advocate at KnowBe4. “Spanish hospitals were targeted
by Netwalker campaigns using COVID-19 related messaging in the attacks, although
promising not to.”
The poor outcomes around patient diversions are a sign of the cyber-times,
according to Heather Paunet, senior vice president at Untangle.
“We all trust that hospitals have the ability to address any life-threatening
case or create a sense of stability before transferring patients for additional
care,” she said. “It does bring to light the synergy between medical
professionals and technology used to create that patient stability.”
And to that point, patient diversions may not be the most worrying aspect of
ransomware’s impact on physical well-being. “Any time malware infects a hospital
to the point that systems have to be taken offline, or that records are
unavailable, this poses a risk to the patients’ safety,” Kron said. “From
potential drug interactions to allergies, the information is vital to doctors,
nurses and support staff, such as anesthesiologists, to ensure the safety of
patients. The loss of access to patient data is the biggest threat to patients’
safety.”
It’s clear that cybersecurity best practices should also be medical best
practices. But the ransomware epidemic has exposed plenty of unhealthy habits
among hospitals nationwide. For instance, the American Hospital Association has
reported a big uptick in phishing emails laden with malware and malicious links,
often themed with promises of N95 masks for sale or even the availability of
lifesaving ventilators. This is the initial attack vector for many ransomware
attacks, likely including the UHS incident.
Also, many facilities don’t have backups, as was seen in a recent attack on a
vaccine research facility.
“With each ransomware attack on a hospital or medical center, it becomes
increasingly clear that back-up plans are being developed or initiated as an
immediate response while networks are down,” Paunet said.
Fortunately, there are prescriptions for avoiding the worst that ransomware has
to offer, starting with putting the aforementioned plans in place immediately –
including remote or offline patient data backups.
Also, since ransomware is typically spread through email phishing or through
attacks on remote-access methods, Kron noted that organizations can greatly
benefit from focusing on email phishing defenses.
“This includes a serious assessment of current controls in place and the state
of their employee awareness training, and securing and monitoring remote-access
options,” he said.
Paunet also noted that medical instruments, such as ventilators, insulin pumps
and other internet-of-things (IoT) devices that may be unpatched or outdated can
become vulnerable network-access points.
“These devices need to be audited constantly for software updates, patches and
other upgrades to ensure that outdated software isn’t leaving the network open
for criminals,” she said.
And finally, like any organization, hospitals must look to build barriers
against ransomware while understanding that cybercriminals continue to improve
their tactics. The spate of attacks in the medical arena is unlikely to wane
soon, so organizations should assume they’re being targeted – especially since
paying the ransom is not uncommon.
“As healthcare pays ransoms and the large dollar amounts they pay are
highlighted in the news, this becomes an indication that this is a sector that
is willing to pay. Attackers set their targets and evolve their techniques where
they feel they will be most successful,” Paunet said.
Ransomware Gang Hits Exposed MySQL Databases
11.12.2020
Ransomware
Securityweek
Exploiting weak credentials on MySQL servers connected to the Internet, an
ongoing ransomware campaign has compromised more than 250,000 databases to date,
according to a warning from security vendor Guardicore.
Dubbed PLEASE_READ_ME, Guardicore said the campaign started as early as January
2020, with more than 83,000 victims successfully breached to date.
With more than five million Internet-facing MySQL servers on the internet, the
attacks are expected to continue against those with weak authentication
credentials.
Guardicore security researchers say that the attackers are engaging in double
extortion in an attempt to force victims into paying the ransom demand for the
encrypted data.
Originating from 11 IP addresses, most located in Ireland and the UK, the
attacks appear to have resulted in 7TB of data.
Between January and November, the attackers would include a Bitcoin wallet in
the ransom note, instructing the victim to make payments there. This resulted in
roughly $25,000 being paid to the attackers.
Starting in October, the victims were being directed to a TOR website,
hn4wg4o6s5nc7763.onion, where the attackers list all databases for which a
ransom was not paid. A total of 250,000 entries from 83,000 MySQL servers were
identified.
The attackers gain access to the targeted databases by brute-forcing the
passwords for the MySQL servers. Next, they run queries to gather information on
tables and users, and to archive and exfiltrate the victim’s data. Next, the
database is swept clean and a ransom note is left, demanding a ransom of up to
0.08 BTC.
A backdoor is also added to the database, so that the adversary can re-access it
if needed.
On their TOR website, the attackers offer the stolen databases for sale at 0.03
Bitcoin (roughly $520). All entries are listed per token, with approximately
83,000 unique tokens identified, Guardicore said.
The attacks are not targeted, with the adversary lacking interest in the
victim’s identity or size. Researchers surmise that the immediate focus is
compromising as many victims as possible, for financial gain (but they are
making less money per victim, the security researchers note).
“The PLEASE_READ_ME operators are trying to up their game by using double
extortion in scale. Factoring their operation will render the campaign more
scalable and profitable,” Guardicore Labs concludes.
RansomExx Ransomware Gang Dumps Stolen Embraer Data: Report
8.12.2020
Ransomware
Threatpost
The group published
files stolen from the Brazilian aircraft manufacturer in a ransomware attack
last month.
Hackers have dumped sensitive company data that was stolen during a ransomware
attack last month on aircraft manufacturer Embraer. The compromised data
appeared on a new dark web site created to publish leaked information, according
to a published report.
The move appears to be a revenge for the Brazilian-based company’s refusal to
pay a ransom in the attack, choosing instead to restore affected systems from
backup, according to a report in ZDNet published early Monday. The files were
published on a recently-created dark web site managed by the RansomExx
ransomware gang, also known as Defray 777, according to the report.
Embraer is the third-largest producer of airliners behind Boeing and Airbus. The
company acknowledged in a statement on Nov. 30 that a cyberattack that accessed
“only a single environment of the company’s files” occurred on Nov. 25.
“As a result of this occurrence, the Company immediately initiated its
procedures of investigation and resolution of the event, as well as proceeding
with the proactive isolation of some of its systems to protect the systems
environment, thus causing temporary impact on some of its operations,” according
to the statement.
Embraer did not specify what kind of attack the company suffered, or if data was
stolen from the accessed environment. The hundreds of megabytes of data files
found on the RansomExx site include folders pertaining to employee data,
supply-chain subcontracts, and source code, 3D models and photos of Embraer
aircraft, according to the report.
Embraer is not the only company with leaked data appearing on the leak site,
which reportedly launched over the weekend on Saturday. Data stolen from other
companies that were victims of the ransomware group also appeared on the site,
according to ZDNet.
Ransomware gangs have been particularly active lately in numerous high-profile
attacks on large companies. RansomExx/Defray is one of the smaller groups
currently operating, though perhaps the launch of the leak site is an indication
that they will boost their level of activity in the coming months.
Other ransomware groups that also manage leak sites for the data stolen in
ransomware attacks include Conti, Clop, Egregor and REvil, among others. Several
of these groups have pulled off a number of significant attacks in the last few
months, some of which resulted in data being leaked on their respective sites.
Last week Egregor hit both the Vancouver metro system Translink and U.S.
retailer Kmart with ransomware attacks. Prior to that, the group also mounted
major attacks in October against bookseller Barnes & Noble and gaming companies
Ubisof and Crytek.
Clop and Conti also have been responsible for attacks in recent months. Last
week Clop galloped off with 2 million credit cards from an attack on South
Korean retail group E-Land. Conti, meanwhile, made off with data from chip
manufacturer Advantech in November, publishing a list of files on its leak site
to try to pressure the company to pay the hefty ransom of 750 Bitcoin, or about
$14 million.
A ransomware attack hit the Greater Baltimore Medical Center
8.12.2020
Ransomware
Securityaffairs
The Greater Baltimore Medical Center, Maryland, was hit by a ransomware attack
that impacted computer systems and operations.
The Greater Baltimore Medical
Center in Towson, Maryland was a victim of a ransomware attack that impacted its
IT systems.
At the time of this writing, it is not clear the family of ransomware that hit
the healthcare providers, it only confirmed that the security breach forced some
procedures scheduled for Monday to be canceled.
“On the morning of Sunday, December 6, 2020, GBMC HealthCare detected a
ransomware incident that impacted information technology systems. Although many
of our systems are down, GBMC HealthCare has robust processes in place to
maintain safe and effective patient care.” states the Computer Network Incident
Update published by the healthcare provider. “Some procedures scheduled for
Monday, December 7 may be affected. All patient’s whose procedures may be
rescheduled have already been contacted. We regret any inconvenience to our
patients, doctors and healthcare partners.”
GBMC HealthCare operates several facilities, including the Greater Baltimore
Medical Center, Gilchrist, Greater Baltimore Health Alliance, and GBMC Health
Partners. The Greater Baltimore Medical Center (GBMC) has 342 beds and handles
more than 23,000 admissions and over 52,000 emergency room visits annually.
GBMC confirmed that it is responding to the incident in accordance with its
well-planned process and policies.
Unfortunately, ransomware attacks are becoming frequent in the US, in September
the Universal Health Services (UHS), one of the largest hospital and healthcare
services providers, has shut down systems at healthcare facilities in the United
States after they were infected with the Ryuk ransomware.
In late October, the FBI, the DHS’s Cybersecurity and Infrastructure Security
Agency (CISA), and the Department of Health and Human Services (HHS) has issued
a joint alert to warn hospitals and healthcare providers of imminent ransomware
attacks from Russia.
DoppelPaymer ransomware gang hit Foxconn electronics giant
8.12.2020
Ransomware
Securityaffairs
Electronics contract manufacturer Foxconn is the last victim of the DoppelPaymer
ransomware operators that hit a Mexican facility.
DoppelPaymer ransomware
operators infected the systems at a Mexican facility of Foxconn electronics
giant over the Thanksgiving weekend.
The plan is located in Ciudad Juárez, Chihuahua, Mexico.
The hackers also
claim to have stolen unencrypted files before encrypting the targeted systems.
Foxconn manufactures electronic products for major American, Canadian, Chinese,
Finnish, and Japanese companies. The list of products manufactured by the
company includes the BlackBerry, iPad, iPhone, iPod, Kindle, Nintendo 3DS, Nokia
devices, Xiaomi devices, PlayStation 3, PlayStation 4, Wii U, Xbox 360, Xbox
One, and several CPU sockets, including the TR4 CPU socket on some motherboards.
The electronics manufacturing giant has over 800,000 employees worldwide, it
recorded revenue of $172 billion in 2019.
BleepingComputer first reported the news of the attack, now the DoppelPaymer
ransomware published files belonging to Foxconn NA on their leak site.
“The leaked data includes generic business documents and reports but does not
contain any financial information or employee’s personal details.” reported
BleepingComputer. “Sources in the cybersecurity industry have confirmed that
Foxconn suffered an attack around November 29th, 2020, at their Foxconn CTBG MX
facility located in Ciudad Juárez, Mexico.”
BleepingComputer obtained a copy of the ransom note, DoppelPaymer ransomware
operators are demanding a 1804.0955 BTC ransom (approximately $34,686,000). The
hackers claim to have encrypted about 1,200 servers and stole 100 GB from
Foxconn.
After the ransomware attack, the website of the Mexican facility went down, the
attackers claim to have destroyed approximately 20-30TB of data.
The list of victims of the DoppelPaymer ransomware is long and includes Bretagne
Télécom. Compal, the City of Torrance (California), Hall County in Georgia,
Newcastle University, and PEMEX (Petróleos Mexicanos).
Greater Baltimore Medical Center Hit by Ransomware Attack
7.12.2020
Ransomware
Securityweek
The Greater Baltimore Medical Center in Towson, Maryland was hit by a ransomware
attack that impacted computer systems and medical procedures, the healthcare
provider said Sunday.
While few details have been provided, operator GBMC HealthCare says the incident
has impacted information technology systems and forced some procedures scheduled
for Monday to be cancelled.
“Although many of our systems are down, GBMC HealthCare has robust processes in
place to maintain safe and effective patient care. We are collectively
responding in accordance with our well-planned process and policies for this
type of event,” the announcement said.
“Some procedures scheduled for Monday, December 7 may be affected. All patient’s
whose procedures may be rescheduled have already been contacted,” it added.
GBMC HealthCare operates several facilities, including the Greater Baltimore
Medical Center, Gilchrist, Greater Baltimore Health Alliance, and GBMC Health
Partners. It is unclear if other entities in its portfolio have been impacted.
The ransomware attack is the latest of many that have impacted healthcare
providers over recent months. In September, a ransomware attack forced the
shutdown of more than 250 locations operated by Universal Health Services (UHS).
Also in September, an attack shutdown IT systems at a hospital in Duesseldorf,
Germany, resulting in the death of a woman after she had to be taken to another
city for urgent treatment.
In late October, the U.S. government warned hospitals and healthcare providers
of an “increased and imminent” ransomware threat. The alert warned that threat
actors are targeting the healthcare sector with the TrickBot malware in attacks
that often lead to ransomware infections, data theft and disruption of
healthcare services.
TrickBot has been updated with functionality that allows it to scan the
UEFI/BIOS firmware of targeted system for vulnerabilities, security researchers
recently discovered.
HR Giant Randstad Hit by Egregor Ransomware
7.12.2020
Ransomware
Securityweek
Human resources giant Randstad last week revealed that its IT systems were
targeted in a recent cyberattack involving a relatively new piece of ransomware
named Egregor.
Netherlands-based Randstad is one of the world’s largest HR services providers,
with more than 38,000 employees and operations in nearly 40 countries. The
company claims it helped over 2 million people find a job last year and it
reported a revenue of €23.7 billion ($28.7 billion).
Randstad said the incident impacted a limited number of servers and its
operations have not been disrupted. However, it has confirmed that the attackers
have accessed some data.
The cybercriminals behind the Egregor ransomware are known to steal data in
addition to using the malware to encrypt the victim’s files, in an effort to
increase their chances of getting paid. If a victim refuses to pay, the hackers
either leak stolen data on a website that is accessible through the Tor network
or they try to sell it to others.
“To date, our investigation has revealed that the Egregor group obtained
unauthorized and unlawful access to our global IT environment and to certain
data, in particular related to our operations in the US, Poland, Italy and
France,” Randstad said in its statement. “They have now published what is
claimed to be a subset of that data. The investigation is ongoing to identify
what data has been accessed, including personal data, so that we can take
appropriate action with regard to identifying and notifying relevant parties.”
The hackers have so far released roughly 60Mb of information stolen from
Randstad systems. The leaked files are mainly financial documents, mostly PDFs
and Excel spreadsheets, which they claim represents only one percent of the
stolen files.
Randstad hit by Egregor ransomware
The operators of the Egregor ransomware recently also targeted TransLink, the
transportation agency of Metro Vancouver in British Columbia, Canada. TransLink
has reportedly decided not to pay the ransom, but there is no mention of the
company on the Egregor website so far.
Digital Shadows, a provider of digital risk protection solutions, whose
researchers have been monitoring Egregor ransomware attacks, told SecurityWeek
that the cybercriminals named 176 victims on their website between September 25
and December 2. A majority of victims are in the United States (82), followed by
France (19), Italy (15) and Germany (9).
LockBit Ransomware operators hit Swiss helicopter maker Kopter
7.12.2020
Ransomware
Securityaffairs
LockBit ransomware operators have compromised the systems at the helicopter
maker Kopter and published them on their darkweb leak site.
The helicopter
maker Kopter was hit by LockBit ransomware, the attackers compromised its
internal network and encrypted the company’s files.
Kopter Group is Switzerland-based company that was founded in 2007 that was
acquired by Leonardo in April 2020.
The company focuses on the design of small and medium-class civilian helicopters
such as the SH09 helicopter.
After Kopter refused to pay the ransom, LockBit ransomware operators published
the stolen files on their leak site on the dark web
The files published by the ransomware gang on the leak site include internal
projects, business documents, and various aerospace and defense industry
standards.

Source ZDNet
LockBit ransomware operators told ZDNet that they have accessed
the network of the helicopter maker via a VPN appliance that was poorly
protected.
“In an email, the operators of the LockBit ransomware told ZDNet that they
breached Kopter’s network last week by exploiting a VPN appliance that used a
weak password and did not have two-factor authentication (2FA) enabled.”
reported ZDNet.
At the time of this writing, Kopter has yet to publicly disclose the ransomware
infection.
Human resource consulting giant Randstad hit by Egregor ransomware
6.12.2020
Ransomware
Securityaffairs
Multinational human resource consulting firm Randstad NV announced that they
were a victim of the Egregor ransomware.
Egregor ransomware operators have
breached the network of the multinational human resource consulting firm
Randstad NV and have stolen unencrypted files during the attack.
Randstad operates in 39 countries and employs over 38,000 people and generated
€23.7 billion in revenue for 2019.
The Egregor ransomware operators published 1% of the alleged stolen data as
proof of the attack. The archive is 32.7MB in size and contains 184 files.
The leaked files include financial reports, legal documents, and accounting
spreadsheets.

Source Bleeping Computer
Randstad published a data breach notification to
disclose the incident and confirmed that the Egregor ransomware infected its
systems.
“Randstad NV (“Randstad”) recently became aware of malicious activity in its IT
environment and an internal investigation into this incident was launched
immediately with our 24/7 incident response team. Third party cyber security and
forensic experts were engaged to assist with the investigation and remediation
of the incident.” reads the statement published by the company.
The human resource consulting firm revealed that the malware only infected a
limited number of servers and that the operations were not impacted.
The company added that attackers accessed data related to their operations in
the US, Poland, Italy, and France, but the investigation is still ongoing.
“To date, our investigation has revealed that the Egregor group obtained
unauthorized and unlawful access to our global IT environment and to certain
data, in particular related to our operations in the US, Poland, Italy and
France. They have now published what is claimed to be a subset of that data.”
continues the notification. “The investigation is ongoing to identify what data
has been accessed, including personal data, so that we can take appropriate
action with regard to identifying and notifying relevant parties.”
Egregor ransomware operators are very active in this period, this week they hit
Metro Vancouver’s transportation agency TransLink causing the disruption of its
services and payment systems.
The ransomware gang recently targeted several other major companies worldwide,
including Barnes and Noble, Cencosud, Crytek, Kmart, and Ubisoft.
Vancouver Metro Disrupted by Egregor Ransomware
5.12.2020
Ransomware
Threatpost
The attack, which prevented Translink users from using their metro cards or
buying tickets at kiosks, is the second from the prolific threat group just this
week.
The threat actors behind the Egregor ransomware are showing a prolificacy in
their early months of activity. On the heels of targeting struggling U.S.
retailer Kmart, the Egregor gang also disrupted the Vancouver metro system with
a ransomware attack.
Translink, the Canadian city’s public transportation network, confirmed Thursday
via a statement by its CEO Kevin Desmond on Twitter that it was “the target of a
ransomware attack on some of our IT infrastructure” that “included
communications to Translink through a printed message.”
The attack took place on Dec. 1 and left Vancouver residents and other users of
the public transit service unable to use their Compass metro cards or pay for
new tickets via the agency’s Compass ticketing kiosks, according to media
reports. Translink officials avoided acknowledging the attack for two days,
passing it off as a technical issue before being pressed by multiple local news
agencies about what really was going on.
“Working with my colleague @pjimmyradio, we can confirm for @NEWS1130 that
@TransLink has been hacked,” tweeted Martin MacMahon, a senior news reporter at
local radio news station News 1130. “Our information comes from multiple sources
within the transit authority, who have shared the ransom letter with us.”
Though officials did not come out and say Egregor was responsible for the
attack—and the threat actors behind the ransomware have not ‘fessed up to it
either — the ransom note that accompanied the attack points to the group as the
culprit.
Jordan Armstrong, a reporter from another local news outlet, Global BC, tweeted
a photo of the ransom note in the early hours of Friday morning, saying it was
“rolling off the printers at @TransLink.”
“Sources tell me, at this point, @TransLink does NOT intend to pay,” he wrote.
“But a cybersecurity expert we spoke to says this is a sophisticated new type of
ransomware attack… and many victims do pay.”
The ransom note threatens to release data stolen from Translink to the media as
well as its customers and partners so the attack will be widely known, a move
that is a hallmark of Egregor. The malware uses a tactic of siphoning off
corporate information and threatening this “mass-media” release of it before
encrypting all files.
The group also is at this time the only known ransomware to run scripts that
cause printers at the organization to continuously print out the ransom note,
according to a report in BleepingComputer. The same thing happened in an attack
on South American retailer Cencosud in mid-November, an action that was
documented in a video on Twitter.
Translink continues to investigate the attack and mitigate any damage done by
it, Desmond said. Meanwhile, the service has been restored to Compass vending
machines and tap-to-pay gates at transportation stations so travelers can once
again use their cards, he said.
Egregor — the name of which refers to an occult term meant to signify the
collective energy or force of a group of individuals–has been busy since it was
first spotted in the wild in September and October. Earlier this week an attack
on Kmart encrypted devices and servers connected to the company’s networks,
knocking out back-end services.
In October, Egregor also claimed to have hacked gaming giant Ubisoft, lifting
the source code for Watch Dogs: Legion, which was released on Oct. 29. It also
took responsibility for a separate attack on gaming creator Crytek, relating to
gaming titles like Arena of Fate and Warface.
Egregor also recently made headlines after it claimed responsibility for the
Barnes & Noble cyberattack, first disclosed on Oct. 15. The bookseller had
warned that it had been hacked in emailed notices to customers, “which resulted
in unauthorized and unlawful access to certain Barnes & Noble corporate
systems.”
Egregor ransomware attack paralyzed for 3 days payment systems at Metro
Vancouver’s transportation agency TransLink
5.12.2020
Ransomware
Securityaffairs
The Egregor ransomware operators hit Metro Vancouver’s transportation agency
TransLink disrupting services and payment systems.
Egregor ransomware
operators made the headlines again, this time they hit Metro Vancouver’s
transportation agency TransLink causing the disruption of its services and
payment systems.
The news was also confirmed by Global News which has obtained the ransom letter
sent to TransLink after the company announced to have detected “suspicious
network activity” this week that has caused several major problems across the
transit system.
On December 1st, TransLink’s announced that they were having IT issues that
impacted phones, online services. The payments with credit or debit cards were
not possible for three days, according to the company, the transit services were
unaffected by IT problems.

Upon restoring the payment systems, Metro Vancouver’s transportation agency
TransLink issued a statement announcing that a ransomware attack was the root
cause of IT issues.
TransLink CEO Kevin Desmond confirmed the ransomware attack in a media release
late Thursday.
“We are now in a position to confirm that TransLink was the target of a
ransomware attack on some of our IT infrastructure. This attack included
communications to TransLink through a printed message,” said Desmond.

Global BC anchor Jordan Armstrong shared a picture of the ransom note that was
repeatedly printed by TransLink printers after the attack. The image confirmed
that the company was hit by the Egregor operators, a group that intensifies its
operations after the Maze ransomware shutdown its activities.
Egregor is known to target printers of the compromised organizations,
instituting them to print the ransom note.
The Egregor ransomware operators recently targeted several other major companies
worldwide, including Barnes and Noble, Cencosud, Crytek, Kmart, and Ubisoft.
Metro Vancouver Transportation Agency TransLink Hit by Ransomware
5.12.2020
Ransomware
Securityweek
TransLink, the transportation agency of Metro Vancouver in British Columbia,
Canada, has been hit by ransomware, and the ransom note delivered by the
attackers suggests the incident involved a piece of ransomware named Egregor.
TransLink first reported issues related to its IT systems on December 1, when it
informed customers that some online services may be unavailable.
On December 2, the company said it was investigating “suspicious network
activity,” and that it had disabled access to some online services, such as its
trip planner tool. Customers were also told that they could not use their
payment card at Compass vending machines and Tap to Pay fare gates.
TransLink restoried payment services on Thursday and said the incident has not
impacted transit services and transit safety systems.
TransLink CEO Kevin Desmond confirmed in a statement issued late on Thursday
that the company was targeted in a ransomware attack, and said the attack
“included communications to TransLink through a printed message.”
Global BC reporter Jordan Armstrong reported on Twitter that the attack involved
the ransom note being sent to TransLink printers. A screenshot he made available
shows that the attackers used the Egregor ransomware. It’s unclear how much
money the cybercriminals have demanded, but Armstrong learned from sources that
the transportation agency does not intend to pay up.
Desmond said a comprehensive forensic investigation will be conducted in an
effort to determine what type of information may have been accessed by the
attackers. However, he has clarified that TransLink uses a third-party payment
processor for fare transactions and it does not store payment data.
“TransLink employs a number of tools to prevent, identify and mitigate these
types of attacks,” Desmond said. “Upon detection, we took immediate steps to
isolate and shut-down key IT assets and systems in order to contain the threat
and reduce the impact on our operations and infrastructure.”
Egregor is a relatively new piece of ransomware that was first spotted in late
September. Digital Shadows, a provider of digital risk protection solutions,
reported last month that Egregor had a lot of potential to become a significant
threat to organizations, with its operators claiming to have targeted 71
organizations across 19 industry verticals by November 17.
Egregor is a “double extortion” ransomware, which means its operators not only
encrypt files, but also steal valuable data, in an effort to convince the victim
to pay the ransom.
Clop Gang Gallops Off with 2M Credit Cards from E-Land
4.12.2020
Ransomware
Securityaffairs
The ransomware group pilfered payment-card data and credentials for over a year,
before ending with an attack last month that shut down many of the South Korean
retailer’s stores.
The Clop ransomware group is at it again. On Thursday, the gang claimed that it
stole 2 million credit cards from South Korean retailer E-Land over a one-year
period, in a campaign that culminated with a ransomware attack on the company’s
headquarters in November.
Operators of Clop ransomware reportedly said that they were responsible for the
November attack that forced E-Land — a subsidiary of E-Land Global — to shut
down 23 of its New Core and NC Department Store locations.
But the group had infiltrated the organization long before that, and was already
stealing data before the attack using point-of-sale (POS) malware it had
installed on the network, operators said in a Bleeping Computer interview posted
Thursday.
“Over a year ago, we hacked their network, everything is as usual,” the group
told Bleeping Computer. “We thought what to do, installed POS malware and left
it for a year.”
The group claimed that the company did not suspect it was leaking data and
seemed taken by surprise by the Clop ransomware attack on Nov. 22, which forced
E-Land to suspend operations at nearly half of its stores in South Korea,
according to the report.
E-Land acknowledged that a ransomware attack against the company’s headquarters
server not only forced some store closures but also caused some damage to
E-Land’s network and systems, in a statement on its website posted the day of
the attack. E-Land immediately shut down the server to prevent further damage,
the company said.
However, customer information and sensitive data were safe from the attack
because these “are encrypted on a separate server,” the company said at the
time. “It is in a safe state because it is managed.”
E-Land began working with authorities immediately after the attack to recover
damage, according to an investigation and recovery that is ongoing.
The Clop ransomware gang was first discovered in February 2019 by
MalwareHunterTeam and since then has been a persistent threat with a
particularly potent modus operandi. Clop uses a tactic called “double
extortion,” which means it steals the data and then if the victim doesn’t meet
ransom demands, dumps it on underground criminal forums for anyone to access.
The group’s last major known attack happened in October, when it targeted
Software AG, a German conglomerate with operations in more than 70 countries,
and demanded a massive $23 million ransom, threatening to dump stolen data if
the company didn’t pay.
In April, the Clop gang struck biopharmaceutical company ExecuPharm and
reportedly leaked some of the company’s compromised data on cybercriminal forums
after the ransom went unpaid.
Clop and other ransomware groups such as Conti, Ragnar Locker, Maze and others
have been taking major advantage of the move to a remote workforce during the
COVID-19 pandemic.
Security holes plague many organizations that were unprepared for the move, and
threat actors have been attacking vulnerable systems and zero-day flaws with
abandon.
The threat is so great that ransomware and subsequent extortion tactics by
cybercriminals are among the leading threats on the horizon for 2021, largely
due to the fallout from the pandemic, researchers from Kaspersky said in a
predictive report posted last week.
Clop Ransomware gang claims to have stolen 2 million credit cards from E-Land
3.12.2020
Ransomware
Securityaffairs
E-Land Retail suffered a ransomware attack, Clop ransomware operators claim to
have stolen 2 million credit cards from the company.
E-Land Retail is a South
Korean conglomerate headquartered in Changjeon-dong Mapo-gu Seoul, South Korea.
E-Land Group takes part in retail malls, restaurants, theme parks, hotels and
construction businesses as well as its cornerstone, fashion apparel business. It
has operations worldwide through its subsidiary E-Land World.
Clop ransomware is claiming to have stolen 2 million credit cards from E-Land
Retail during the last 12 months.
Last month, the company was forced to shut down 23 NC Department Store and New
Core locations after a CLOP ransomware infection.
The company said that customer was encrypted on a server that was not impacted,
it also added to have notified relevant authorities.
“We are striving to quickly recover damage and normalize business. Most branches
across the country have the first emergency measures Basic sales activities are
possible.” reads the security breach notice.
“Although this ransomware attack caused some damage to the company’s network and
systems, customer information and sensitive data are encrypted on a separate
server. It is in a safe state because it is managed.”
Unfortunately, the situation could be quite different, as CLOP ransomware
operators told Bleeping Computer. The ransomware gang claimed to have initially
compromised E-Land a year ago and to have stolen credit card data using PoS
malware.
The hackers claim to have siphoned and deciphered, for 12 months, the credit
card data (Track 2 data) without being discovered by the company.
CLOP told BleepingComputer that they stole data for 2 million credit cards.

Source Bleeping Computer
CLOP ransomware operators claim to have stolen
credit card Track 2 data, which includes a credit card number, the expiration
date, and other information. Credit cards CVV code is not included in Track 2
data. Track 1 data can only be used to clone credit cards and use them for
in-store purchases.
Online Learning Company K12 Paying Ransom Following Ransomware Attack
1.12.2020
Ransomware
Securityweek
Online learning solutions provider K12 Inc., which recently announced changing
its name to Stride Inc., said on Monday that it had decided to pay a ransom to
cybercriminals who managed to breach its systems and deploy a piece of
ransomware.
The company said it recently detected unauthorized activity on its network. The
attackers deployed a piece of ransomware and accessed information stored on some
corporate back-office systems. This includes student and employee information,
but Stride has yet to determine exactly what type of information has been
compromised.
Stride pointed out that the attack did not disrupt its learning management
system, nor any major corporate systems — it claimed accounting, payroll,
procurement, enrollment and shipping systems remained operational. It also
claimed that data on the learning management system was not accessed during the
breach.
However, due to the fact that the attackers did manage to obtain some
information, the company has decided to pay them.
“We carry insurance, including cyber insurance, which we believe to be
commensurate with our size and the nature of our operations. We have already
worked with our cyber insurance provider to make a payment to the ransomware
attacker, as a proactive and preventive step to ensure that the information
obtained by the attacker from our systems will not be released on the Internet
or otherwise disclosed,” Stride said on Monday.
It added, “While there is always a risk that the threat actor will not adhere to
negotiated terms, based on the specific characteristics of the case, and the
guidance we have received about the attack and the threat actor, we believe the
payment was a reasonable measure to take in order to prevent misuse of any
information the attacker obtained.”
It’s currently unclear what type of ransomware was used in the attack and how
much the company is paying to the cybercriminals. SecurityWeek has reached out
to Stride for more information and will update this article if the company
responds.
The company does not expect the incident to have a material impact on its
operations or financial results. It has also created a team of data security
compliance advisors, which includes former US Attorneys and Attorneys General,
to guide its response to the incident, including in terms of compliance with
federal and state laws.
The U.S. Department of the Treasury recently issued an advisory to warn
companies that facilitate ransomware payments of the potential legal
implications resulting from dealing with sanctioned entities.
A cybersecurity company reported last year that K12 had exposed a database
containing nearly 7 million student records.
Conti Gang Hits IoT Chipmaker Advantech with $14M Ransom Demand
1.12.2020
Ransomware
Threatpost
The ransomware group has leaked stolen data to add pressure on the company to
pay up.
Advantech, the chip manufacturer, has confirmed that it received a ransom note
from a Conti ransomware operation on Nov. 26 demanding 750 Bitcoin, which
translates into about $14 million, to decrypt compromised files and delete the
data they stole.
Just to let Advantech know they weren’t bluffing, the scammers published a list
of files from a stolen .zip archive on their leak site. The ransom note claimed
that the 3.03GB of data posted on the leak site accounted for about 2 percent of
the total amount of data lifted ripped off from Advantech.
Advantech specializes in internet-of-things (IoT) intelligent systems, Industry
4.0, machine automation, embedded computing, embedded systems, transportation
and more.
A statement provided to Bleeping Computer on behalf of Advantech acknowledged
the attack and said “the stolen data was confidential but only contained
low-value documents.” The statement added that the company is recovering and
“functioning normally,” and will not be commenting on whether the ransom was
paid.
Ransomware Leak Sites
Professionalized ransomware groups including Conti,
Ragnar Locker, Maze, Clop and others have been exploiting security holes created
by the emergency shift to remote work due to the pandemic, coupled with
well-publicized leak sites to wreak havoc and wring millions out of unsuspecting
companies like Advantech. And in the case of Advantech, the longer it waits to
decide, the more expensive the ransom gets.
“In August 2020, the Conti ransomware group created a data leak website, called
Conti.News, following the trend of other highly successful ransomware variants,
such as Maze, Sodinokibi and NetWalker,” Digital Shadows threat researcher Kacey
Clark told Threatpost. “The group’s ransom demands require victims to make their
payments in Bitcoin, and for each day a victim does not contact the attackers,
the ransom demand increases by BTC 0.5.”
Clark added that Conti ransomware was likely developed by the same group behind
Ryuk ransomware.
“Ryuk version 2 code and Conti ransomware code maintain notable similarities,
the Conti ransom note uses the same template utilized in early Ryuk ransomware
attacks and Conti ransomware operators appear to leverage the same TrickBot
infrastructure used in Ryuk ransomware attacks,” she said.
Ransomware Rising
Kaspersky researchers released a report Monday that said
ransomware will be one of cybersecurity’s biggest threats in the year ahead, and
pointed specifically to leak sites as the single biggest factor driving up
ransom prices.
“Due to their successful operations and extensive media coverage this year, the
threat actors behind targeted ransomware systematically increased the amounts
victims were expected to pay in exchange for not publishing stolen information,”
Kaspersky researchers said. “This point is important because it is not about
data encryption anymore, but about disclosing confidential information
exfiltrated from the victim’s network. Due to payment card industry security and
other regulations, leaks like this may result in significant financial losses.”
It’s up to organizations to shore up their defenses in preparation for the next
inevitable ransomware attack, researchers noted.
Ransomware Defenses
The first line of defense is a regular, smart backup
strategy, according to Shawn Smith, DevOps engineer at nVisium.
“Attacks like this are why proper backups and disaster recovery plans are so
vital,” Smith said in an email to Threatpost. “In the unfortunate event a breach
manifests, as long as you have proper backups, you can restore files, resume
operations and start to mitigate the fallout. Attackers aren’t trustworthy given
the nature of what they do, and if you put yourself in a situation where you’re
forced to pay them money, your results may vary wildly depending on the group
you have to deal with.”
Besides regular data backups, basics like security awareness training, patching
and antivirus protection are all key, according to Daniel Norman, senior
solutions analyst at the Information Security Forum. He also recommended that
organizations train for ransomware response.
“Organizations should have an incident-response or crisis-management plan for
ransomware events, knowing who to contact and what to do,” Norman advised. “This
should be regularly rehearsed so that if ransomware hits, the organization can
recover swiftly.”
And while those preparations seem wise, what about companies stuck without
either a backup or a strategy? Then it comes down to which costs more, recovery
or the ransom?
“Payment of a ransom is also a contentious discussion – in many cases the ransom
may be cheaper than replacing a suite of locked devices,” Norman said.
“Therefore, it becomes a cost-decision. However, you can never trust that the
attacker will unlock the devices, so it remains a grey area.”
Media Production Giant Banijay Hit by Ransomware
30.11.20
Ransomware
Securityweek
Banijay, one of the world’s largest media production and distribution companies,
last week disclosed a cybersecurity incident that resulted in the theft of
sensitive information.
A global production giant was created earlier this year when France-based
Banijay completed the acquisition of Endemol Shine for $2.2 billion from Disney
and private equity group Apollo. Netherlands-based Endemol Shine is the company
behind popular TV shows such as Big Brother, Survivor, Deal or No Deal, The
Voice and MasterChef, as well as the Black Mirror and Peaky Blinders series.
Banijay says it’s home to more than 120 production companies across over 20
countries.
In a notification posted last week, Banijay said the cyber incident impacted
“pre-existing Endemol Shine Group and Endemol Shine International networks” in
the UK and the Netherlands.
“The business has reason to believe certain personal data of current and
ex-employees may have been compromised, as well as commercially sensitive
information,” the company said.
Banijay has launched an investigation and it has informed local authorities in
the UK and the Netherlands about the incident. It has also promised to contact
impacted individuals.
A cybercrime group that uses a piece of ransomware named DoppelPaymer
(DopplePaymer) has taken credit for the attack. On the DoppelPaymer leak
website, the hackers reference the Endemol Shine UK site and they have posted
four files allegedly stolen from the company, including two Word documents and
two PowerPoint presentations. The leaked files are related to compliance and
they do not appear to include any sensitive information.
The file-encrypting ransomware DoppelPaymer emerged in the summer of 2019 and in
February 2020 its operators launched a leak website where they have been
publishing data stolen from companies that don’t pay the ransom.
The leak website lists over 100 alleged victims, including Mexican state-owned
oil company Petróleos Mexicanos (Pemex). The DoppelPaymer group is also said to
be behind the recent attack on a German hospital that led to a delay in
treatment, resulting in a person’s death.
Sopra Steria estimates financial Impact of ransomware attack could reach €50
Million
30.11.20
Ransomware
Securityaffairs
IT services provider Sopra Steria estimates that a recent ransomware attack will
have a financial impact ranging between €40M and €50M.
At the end of October,
French IT outsourcer Sopra Steria has been hit by a ransomware attack. While the
company did not reveal the family of malware that infected its systems, local
media speculate the involvement of the Ryuk ransomware. The European IT firm has
46,000 employees operating in 25 countries worldwide. It provides a wide range
of IT services, including software development and consulting.
Now the company estimates that a recent ransomware attack will have a financial
impact ranging between €40 million ($48 million) and €50 million ($60 million).
In a new statement issued by Sopra Steria, the company confirmed that it has
detected an attack involving the Ryuk ransomware on 21 October.
The internal cybersecurity staff rapidly blocked the threat and the measures
implemented allowed the company to contain the virus to only a limited part of
the Group’s infrastructure.
“At this stage, Sopra Steria has not identified any leaked data or damage caused
to its customers’ information systems.” states the company.
“The secure remediation plan launched on 26 October is nearly complete. Access
has progressively been restored to workstations, R&D and production servers, and
in-house tools and applications. Customer connections have also been gradually
restored.”
“The remediation and differing levels of unavailability of the various systems
since 21 October is expected to have a gross negative impact on the operating
margin of between €40 million and €50 million. The Group’s insurance coverage
for cyber risks totals €30 million.” the company added.
The IT services provider said that sales activity for the fourth quarter should
not be significantly affected by this event.
Sopra Steria expects to see negative organic revenue growth of between 4.5% and
5.0% (previously ‘between -2% and -4%’) for the financial year 2020. The company
also estimates an operating margin on business activity of around 6.5%
(previously ‘between 6% and 7%’), and free cash flow of between €50 million and
€100 million (previously ‘between €80m and €120m’).”
Delaware County, Pennsylvania, opted to pay 500K ransom to DoppelPaymer gang
30.11.20
Ransomware
Securityaffairs
Delaware County, Pennsylvania opted to pay a $500,000 ransom after it was the
victim of a DoppelPaymer ransomware attack last weekend.
During the last
weekend Delaware County, Pennsylvania, was the victim of a DoppelPaymer
ransomware attack that brought down part of its network.
According to local media, the ransomware operators have compromised systems
containing sensitive information, including police reports and payroll.
“Sources told Action News, the cybercriminals gained control of the network on
Saturday encrypting files, including police reports, payroll, purchasing, and
other databases. Prosecution evidence, however, has not been affected.” reads
the post published by Philadelphia’s 6abc’s Action News.
“Sources said the county is in the process of paying the $500,000 ransom as it’s
insured for such attacks.”
The infection did not impact the Bureau of Elections and the County’s Emergency
Services Department.
The incident was disclosed on Monday and now Delaware County has paid a $500,000
ransom.
“The County of Delaware recently discovered a disruption to portions
of its computer network. We commenced an immediate investigation that included
taking certain systems offline and working with computer forensic specialists to
determine the nature and scope of the event. We are working diligently to
restore the functionality of our systems,” states the incident notice published
by Delaware County. “The investigation is ongoing and we are working with
computer forensic specialists to understand the full nature and scope of the
event and confirm accurate information before sharing the details.”
The notice also confirmed that County employees have been already notified, the
FBI is also investigating the attack.
BleepingComputer was informed that the Delaware County was hit by the
DoppelPaymer ransomware gang.
“BleepingComputer was also told that the ransomware gang advised Delaware County
to change all of their passwords and modify their Windows domain configuration
to include safeguards from the Mimikatz program.” reported BleepingComputer.
A few days ago, the Microsoft Security Response Center (MSRC) warned customers
of the DoppelPaymer ransomware, the tech giant provided useful information on
the threat and how it spreads.
In November, the Mexican state-owned oil company Petróleos Mexicanos (Pemex) was
infected with the DoppelPaymer ransomware.
Early November, the DoppelPaymer ransomware disrupted IT operations in the
territory of Nunavut (Canada), all government services requiring access to
electronic data were impacted.
The TA505 cybercrime group that is known for the distribution of the Dridex
Trojan and the Locky ransomware, in mid-2017 released the BitPaymer ransomware
(aka FriedEx) that was used in attacks against high profile targets and
organizations. The ransomware was being distributed through Remote Desktop
Protocol (RDP) brute force attacks.
In July, CrowdStrike experts found a new variant of the ransomware tracked as
DoppelPaymer. The discovery suggests that some members of TA505 gang left the
group and forked the source code of both Dridex and BitPaymer to develop new
malware. Some of the crooks behind the Dridex Trojan have split from the gang
and released a forked version of the BitPaymer ransomware dubbed DoppelPaymer.
Both BitPaymer and DoppelPaymer continue to operate in parallel since then.
Other victims of the DoppelPaymer are the City of Torrance in California, the
Hall County, Georgia, Newcastle University, Banijay Group SAS, Bretagne Télécom,
Compal, and Visser Precision.
Chip maker Advantech hit by Conti ransomware gang
29.11.20
Phishing
Securityaffairs
The IIoT chip maker Advantech was hit by the Conti ransomware, the gang is now
demanding over $13 million ransom from the company.
The Conti ransomware gang
hit infected the systems of industrial automation and Industrial IoT (IIoT) chip
maker Advantech and is demanding over $13 million ransom (roughly 750 BTC) to
avoid leaking stolen files and to provide a key to restore the encrypted files.
Advantech has 8,000 employees worldwide and has reported a yearly sales revenue
of over $1.7 billion in 2019.
The ransomware gang announced on November 21, 2020 the leak of stolen data if
the chipmaker would not have paid the ransom within the next day.
As proof of the capability to restore the data, Conti ransomware operators are
willing to decrypt two of the encrypted files.
On November 26, the ransomware operators began leaking the data stolen from
Advantech, an archive of 3.03GB that accounts for 2% of the total amount of
stolen data.
According to Bleeping Computer, the Conti ransomware gang also promised to
remove any backdoors from the company’s network after the payment of the ransom.
The operators also announced that the stolen data will be permanently removed
from its servers and it will provide security tips on how to secure the network
to prevent future infections.
Conti ransomware operators implement a private Ransomware-as-a-Service (RaaS),
the malware appeared in the threat landscape at the end of December 2019 and was
distributed through TrickBot infections.
Since August 2020, the group launched its leak site to threaten its victim to
release the stolen data.
Canon publicly confirms August ransomware attack and data breach
27.11.20
Ransomware
Securityaffairs
Canon finally confirmed that it has suffered a ransomware attack in early August
that resulted in the theft of data from its servers.
Canon has finally
confirmed that it was the victim of a ransomware attack in early August and that
the threat actors also stole data from its servers.
In August, BleepingComputer first revealed the ransomware attack after it has
obtained an internal memo that confirmed the outage suffered by Canon a few days
before was caused by a ransomware attack.
The memo also reveals that the company has hired an external security firm to
investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious
outage on Canon’s image.canon cloud photo and video storage service. According
to the media outlet, the incident resulted in the loss of data for users of
their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six
days, until August 4th.
At the time the company only confirmed an internal investigation on a problem
related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files
saved prior to June 16 were “lost,” but it pointed out that they were not
exposed in a data leak.
In mid-August, the Maze ransomware gang took credit for the attack and published
unencrypted files allegedly stolen the Canon during the ransomware attack.
BleepingComputer obtained from its source a portion of the ransom note and an
internal notification that Canon sent to its employees.

Canon internal notice – Source BleepingComputer
Maze ransomware operators
started publishing data stolen from the company on its data leak site. The gang
has published a 2.2 GB archive called “STRATEGICPLANNINGpart62.zip” that
attackers claim contain around 5% of the total amount of documents stolen during
the attack,

The archive contains files related to Canon’s website and marketing materials,
according to BleepingComputer’s source it does not appear to contain any
financial information, employee information, or other sensitive data.
The investigation conducted by Canon found evidence of unauthorized accesses on
its network between July 20 and August 6.
The hackers accessed company file
servers that contained information about current and former employees from 2005
to 2020 and their beneficiaries and dependents.
This week, Canon confirmed the ransomware attack and the data breach, according
to a company’s statement stolen data included employees’ names, Social Security
number, date of birth, the number for the driver’s license number or
government-issued ID, the bank account number for direct deposits from Canon,
and their electronic signature.
“We identified a security incident involving ransomware on August 4, 2020.”
reads the statement. “We determined that there was unauthorized activity on our
network between July 20, 2020 and August 6, 2020. During that time, there was
unauthorized access to files on our file servers. We completed a careful review
of the file servers on November 2, 2020 and determined that there were files
that contained information about current and former employees from 2005 to 2020
and their beneficiaries and dependents.”
On November 1, the Maze gang shut down its operations. The list of victims of
the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, LG
Electronics, Xerox, and City of Pensacola.


















