
Apple Articles 2022- H 2021 2020 1 2 iOS Apple List - H 2021 2020 2019 2018 iOS
Apple's New "Lockdown Mode" Protects iPhone, iPad, and Mac Against Spyware
7.7.22 Apple Thehackernews

Apple on Wednesday announced it plans to introduce an enhanced security setting called Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura to safeguard high-risk users against "highly targeted cyberattacks."
The "extreme, optional protection" feature, now available for preview in beta versions of its upcoming software, is designed to counter a surge in threats posed by private companies developing state-sponsored surveillanceware such as Pegasus, DevilsTongue, Predator, and Hermit.
Lockdown Mode, when enabled, "hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware," Apple said in a statement.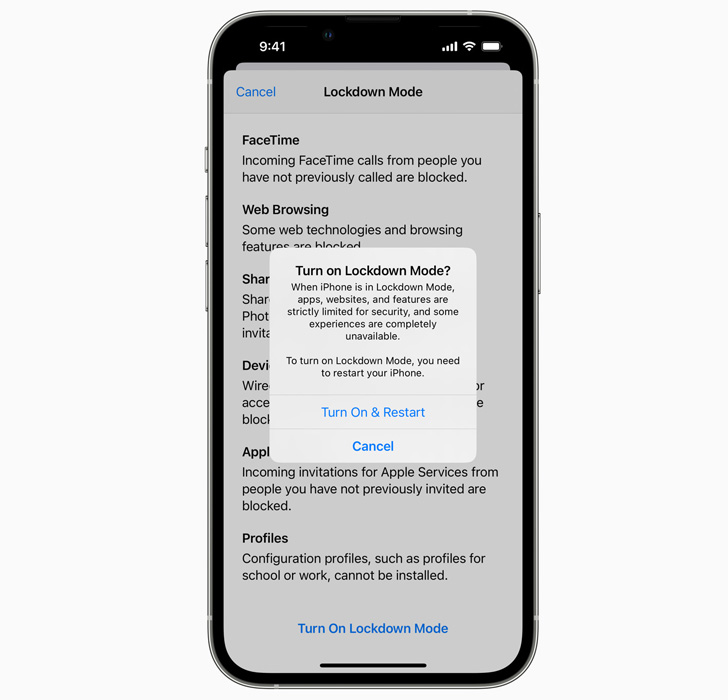
This includes blocking most message attachment types other than images and disabling link previews in Messages; rendering inoperative just-in-time (JIT) JavaScript compilation; removing support for shared albums in Photos; and preventing incoming FaceTime calls from unknown numbers.
Other restrictions cut off wired connections with a computer or accessory when an iPhone is locked and, most importantly, prohibit configuration profiles — a feature that's been abused to sideload apps bypassing the App Store — from being installed.
The tech giant also noted that it plans to incorporate additional countermeasures to Lockdown Mode over time, while simultaneously inviting feedback from the security research community to identify "qualifying findings" that will be eligible for up to $2 million in bug bounties.
It's worth noting that the feature will not be switched on by default, but can be accessed by heading to Settings > Privacy & Security > Lockdown Mode.
The announcement arrives a month after Apple debuted a new Rapid Security Response feature in iOS 16 and macOS Ventura that aims to deploy security fixes without the need for a full operating system version update.
Google and Meta offer analogous software features known as Advanced Account Protection and Facebook Protect that are meant to secure the accounts of individuals who are at an "elevated risk of targeted online attacks" from takeover attempts. But it won't be surprising if Google follows suit with a similar feature on Android.
Google Researchers Detail 5-Year-Old Apple Safari Vulnerability Exploited in the Wild
21.6.22 Apple Thehackernews
A security flaw in Apple Safari that was exploited in the wild earlier this year was originally fixed in 2013 and reintroduced in December 2016, according to a new report from Google Project Zero.
The issue, tracked as CVE-2022-22620 (CVSS score: 8.8), concerns a case of a use-after-free vulnerability in the WebKit component that could be exploited by a piece of specially crafted web content to gain arbitrary code execution.
In early February 2022, Apple shipped patches for the bug across Safari, iOS, iPadOS, and macOS, while acknowledging that it "may have been actively exploited."
"In this case, the variant was completely patched when the vulnerability was initially reported in 2013," Maddie Stone of Google Project Zero said. "However, the variant was reintroduced three years later during large refactoring efforts. The vulnerability then continued to exist for 5 years until it was fixed as an in-the-wild zero-day in January 2022."
While both the 2013 and 2022 bugs in the History API are essentially the same, the paths to trigger the vulnerability are different. Then subsequent code changes undertaken years later revived the zero-day flaw from the dead like a "zombie."
Stating the incident is not unique to Safari, Stone further stressed taking adequate time to audit code and patches to avoid instances of duplicating the fixes and understanding the security impacts of the changes being carried out.
"Both the October 2016 and the December 2016 commits were very large. The commit in October changed 40 files with 900 additions and 1225 deletions. The commit in December changed 95 files with 1336 additions and 1325 deletions," Stone noted.
"It seems untenable for any developers or reviewers to understand the security implications of each change in those commits in detail, especially since they're related to lifetime semantics."
Apple's New Feature Will Install Security Updates Automatically Without Full OS Update
7.6.22 Apple Thehackernews
Apple has introduced a Rapid Security Response feature in iOS 16 and macOS Ventura that's designed to deploy security fixes without the need for a full operating system version update.
"macOS security gets even stronger with new tools that make the Mac more resistant to attack, including Rapid Security Response that works in between normal updates to easily keep security up to date without a reboot," the company said in a statement on Monday.
The feature, which also works on iOS, aims to separate regular software updates from critical security improvements and are applied automatically so that users are protected against in-the-wild attacks. It's worth noting that Apple tested an analogous option in iOS 14.5.
Another key security feature announced by Apple at its annual Worldwide Developers Conference (WWDC) includes support for third-party two-factor authentication apps with the built-in Passwords feature in the Settings app.
What's more, iOS 16 will now permit users to edit strong passwords suggested by Safari to adjust for site‑specific requirements, not to mention requiring apps to request users' permission to access the clipboard to paste content from another app.
In a similar permissions-related update, USB-C and Thunderbolt accessories barring power adapters and standalone displays will be made to explicitly ask for users' consent before they can communicate with macOS devices.
"On portable Mac computers with Apple silicon, new USB and Thunderbolt accessories require user approval before the accessory can communicate with macOS for connections wired directly to the USB-C port," the release notes reads.
Apple, lastly, also confirmed it's bringing support for passkeys in the Safari web browser, a next-generation passwordless sign-in standard that allows users to log in to websites and apps across platforms using Touch ID or Face ID for biometric verification.
The mechanism, established by the FIDO Alliance and already backed by Google and Microsoft, aims to supplant standard passwords by providing unique digital keys that are stored locally on the device.
"Passkeys replace passwords with an easier and safer sign‑in method," the tech behemoth said. "Passkeys never leave your device and are specific to the site you created them for, making it almost impossible for them to be phished."
UpdateAgent Returns with New macOS Malware Dropper Written in Swift
17.5.22 Apple Thehackernews
A new variant of the macOS malware tracked as UpdateAgent has been spotted in the wild, indicating ongoing attempts on the part of its authors to upgrade its functionalities.
"Perhaps one of the most identifiable features of the malware is that it relies on the AWS infrastructure to host its various payloads and perform its infection status updates to the server," researchers from Jamf Threat Labs said in a report.
UpdateAgent, first detected in late 2020, has since evolved into a malware dropper, facilitating the distribution of second-stage payloads such as adware while also bypassing macOS Gatekeeper protections.
The newly discovered Swift-based dropper masquerades as Mach-O binaries named "PDFCreator" and "ActiveDirectory" that, upon execution, establish a connection to a remote server and retrieve a bash script to be executed.
"The primary difference [between the two executables] is that it reaches out to a different URL from which it should load a bash script," the researchers noted.
These bash scripts, named "activedirec.sh" or "bash_qolveevgclr.sh", include a URL pointing to Amazon S3 buckets to download and run a second-stage disk image (DMG) file to the compromised endpoint.
"The continued development of this malware shows that its authors continue to remain active, trying to reach as many users as possible," the researchers said.
Hackers Infect macOS with New DazzleSpy Backdoor in Watering-Hole Attacks
26.1.2022 Apple Thehackernews
A previously undocumented cyber-espionage malware aimed at Apple's macOS operating system leveraged a Safari web browser exploit as part of a watering hole attack targeting politically active, pro-democracy individuals in Hong Kong.
Slovak cybersecurity firm ESET attributed the intrusion to an actor with "strong technical capabilities," calling out the campaign's overlaps to that of a similar digital offensive disclosed by Google Threat Analysis Group (TAG) in November 2021.
The attack chain involved compromising a legitimate website belonging to D100 Radio, a pro-democracy internet radio station in Hong Kong, to inject malicious inline frames (aka iframes) between September 30 and November 4, 2021. Separately, a fraudulent website called "fightforhk[.]com" was also registered for the purpose of luring liberation activists.
In the next phase, the tampered code acted as a conduit to load a Mach-O file by leveraging a remote code execution bug in WebKit that was fixed by Apple in February 2021 (CVE-2021-1789). "The exploit used to gain code execution in the browser is quite complex and had more than 1,000 lines of code once formatted nicely," ESET researchers said.
The success of the WebKit remote code execution subsequently triggers the execution of the intermediate Mach-O binary that, in turn, exploits a now-patched local privilege escalation vulnerability in the kernel component (CVE-2021-30869) to run the next stage malware as a root user.
While the infection sequence detailed by Google TAG culminated in the installation of an implant called MACMA, the malware delivered to visitors of the D100 Radio site was a new macOS backdoor that ESET has codenamed DazzleSpy.
The malware provides attackers "a large set of functionalities to control, and exfiltrate files from, a compromised computer," the researchers explained, in addition to incorporating a number of other features, including —
Harvesting system information
Executing arbitrary shell commands
Dumping iCloud Keychain using a CVE-2019-8526 exploit if the macOS version is lower than 10.14.4
Starting or terminating a remote screen session, and
Deleting itself from the machine
"This campaign has similarities with one from 2020 where LightSpy iOS malware (described by Trend Micro and Kaspersky) was distributed the same way, using iframe injection on websites for Hong Kong citizens leading to a WebKit exploit," the researchers said. That said, it's not immediately clear if both the campaigns were orchestrated by the same group.
New Unpatched Apple Safari Browser Bug Allows Cross-Site User Tracking
19.1.2022 Apple Thehackernews
A software bug introduced in Apple Safari 15's implementation of the IndexedDB API could be abused by a malicious website to track users' online activity in the web browser and worse, even reveal their identity.
The vulnerability, dubbed IndexedDB Leaks, was disclosed by fraud protection software company FingerprintJS, which reported the issue to the iPhone maker on November 28, 2021.
IndexedDB is a low-level JavaScript application programming interface (API) provided by web browsers for managing a NoSQL database of structured data objects such as files and blobs.
"Like most web storage solutions, IndexedDB follows a same-origin policy," Mozilla notes in its documentation of the API. "So while you can access stored data within a domain, you cannot access data across different domains."
Same-origin is a fundamental security mechanism that ensures that resources retrieved from distinct origins — i.e., a combination of the scheme (protocol), host (domain), and port number of a URL — are isolated from each other. This effectively means that "http[:]//example[.]com/" and "https[:]//example[.]com/" are not of the same origin because they use different schemes.
By restricting how a script loaded by one origin can interact with a resource from another origin, the idea is to sequester potentially malicious scripts and reduce potential attack vectors by preventing a rogue website from running arbitrary JavaScript code to read data from another domain, say, an email service.
But that's not the case with how Safari handles the IndexedDB API in Safari across iOS, iPadOS, and macOS.
"In Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, the IndexedDB API is violating the same-origin policy," Martin Bajanik said in a write-up. "Every time a website interacts with a database, a new (empty) database with the same name is created in all other active frames, tabs, and windows within the same browser session."
A consequence of this privacy violation is that it allows websites to learn what other websites a user is visiting in different tabs or windows, not to mention precisely identify users on Google services services like YouTube and Google Calendar as these websites create IndexedDB databases that include the authenticated Google User IDs, which is an internal identifier that uniquely identifies a single Google account.
"Not only does this imply that untrusted or malicious websites can learn a user's identity, but it also allows the linking together of multiple separate accounts used by the same user," Bajanik said.
To make matters worse, the leakage also affects Private Browsing mode in Safari 15 should a user visit multiple different websites from within the same tab in the browser window. We have reached out to Apple for further comment, and we'll update the story if we hear back.
"This is a huge bug," Jake Archibald, developer advocate for Google Chrome, tweeted. "On OSX, Safari users can (temporarily) switch to another browser to avoid their data leaking across origins. iOS users have no such choice, because Apple imposes a ban on other browser engines."
Apple Releases iPhone and iPad Updates to Patch HomeKit DoS Vulnerability
19.1.2022 Apple Thehackernews
Apple on Wednesday rolled out software updates for iOS and iPadOS to remediate a persistent denial-of-service (DoS) issue affecting the HomeKit smart home framework that could be potentially exploited to launch ransomware-like attacks targeting the devices.
The iPhone maker, in its release notes for iOS and iPadOS 15.2.1, termed it as a "resource exhaustion issue" that could be triggered when processing a maliciously crafted HomeKit accessory name, adding it addressed the bug with improved validation.
The so-called "doorLock" vulnerability, tracked as CVE-2022-22588, affects HomeKit, the software API for connecting smart home devices to iOS applications.
Should it be successfully exploited, iPhones and iPads can be sent into a crash spiral simply by changing the name of a HomeKit device to a string larger than 500,000 characters and tricking the target into accepting a malicious Home invitation.
Even worse, since HomeKit device names are backed up to iCloud, signing back into the affected iCloud account linked to the HomeKit device can re-trigger the DoS condition and cause the devices to enter an endless cycle of crash and reboot that can only be ended by restoring them to their factory settings.
Although the company attempted to mitigate the problem by introducing a limit on the length of the name an app or the user can set, it was found that it did nothing to prevent an attacker from running an earlier version that allows excessively long device names and then getting the victim to accept a rogue invitation via a phishing email.
The fix comes weeks after security researcher Trevor Spiniolas, who discovered the vulnerability, called out the company for failing to "take the matter seriously" despite having reported it in August 2021 and leaving its customers exposed to a pretty serious issue.
"Apple's lack of transparency is not only frustrating to security researchers who often work for free, it poses a risk to the millions of people who use Apple products in their day-to-day lives by reducing Apple's accountability on security matters," Spiniolas said.
Microsoft Details macOS Bug That Could Let Attackers Gain Access to User Data
19.1.2022 Apple Thehackernews
Microsoft on Monday disclosed details of a recently patched security vulnerability in Apple's macOS operating system that could be weaponized by a threat actor to expose users' personal information.
Tracked as CVE-2021-30970, the flaw concerns a logic issue in the Transparency, Consent and Control (TCC) security framework, which enables users to configure the privacy settings of their apps and provide access to protected files and app data. The Security & Privacy pane in the macOS System Preferences app serves as the front end of TCC.
Microsoft 365 Defender Research Team, which reported the vulnerability to Apple on July 15, 2021, dubbed the flaw "powerdir." Apple addressed the issue as part of macOS 11.6 and 12.1 updates released in December 2021 with improved state management.
While Apple does enforce a policy that limits access to TCC to only apps with full disk access, it's possible to orchestrate an attack wherein a malicious application could work around its privacy preferences to retrieve sensitive information from the machine, potentially allowing an adversary to access microphone to record private conversations or capture screenshots of sensitive information displayed on the user's screen.
"We discovered that it is possible to programmatically change a target user's home directory and plant a fake TCC database, which stores the consent history of app requests," Jonathan Bar Or of Microsoft 365 Defender Research Team said. "If exploited on unpatched systems, this vulnerability could allow a malicious actor to potentially orchestrate an attack based on the user's protected personal data."
In other words, if a bad actor gains full disk access to the TCC databases, the intruder could edit it to grant arbitrary permissions to any app of their choice, including their own, effectively permitting the app run with configurations previously not consented to.
CVE-2021-30970 is also the third TCC-related bypass vulnerability to be discovered after CVE-2020-9934 and CVE-2020-27937, both of which have since been remediated by Apple. Then in May 2021, the company also patched a then zero-day flaw in the same component (CVE-2021-30713) that could allow an attacker to gain full disk access, screen recording, or other permissions without users' explicit consent.
"This shows that even as macOS or other operating systems and applications become more hardened with each release, software vendors like Apple, security researchers, and the larger security community, need to continuously work together to identify and fix vulnerabilities before attackers can take advantage of them," Bar Or said.
New Trick Could Let Malware Fake iPhone Shutdown to Spy on Users Secretly
14.1.2022 Apple Thehackernews
Researchers have disclosed a novel technique by which malware on iOS can achieve persistence on an infected device by faking its shutdown process, making it impossible to physically determine if an iPhone is off or otherwise.
The discovery — dubbed "NoReboot" — comes courtesy of mobile security firm ZecOps, which found that it's possible to block and then simulate an iOS rebooting operation, deceiving the user into believing that the phone has been powered off when, in reality, it's still running.
The San Francisco-headquartered company called it the "ultimate persistence bug […] that cannot be patched because it's not exploiting any persistence bugs at all — only playing tricks with the human mind."
NoReboot works by interfering with the routines used in iOS to shutdown and restart the device, effectively preventing them from ever happening in the first place and allowing a trojan to achieve persistence without persistence as the device is never actually turned off.
Automatic GitHub Backups
This is accomplished by injecting specially crafted code onto three iOS daemons, namely the InCallService, SpringBoard, and Backboardd, to feign a shut down by disabling all audio-visual cues associated with a powered-on device, including the screen, sounds, vibration, the camera indicator, and touch feedback.
Put differently, the idea is to give the impression that the device has been shut down without really shutting it down by hijacking the event that's activated when the user simultaneously presses and holds the side button and one of the volume buttons, and drags the "slide to power off" slider.
"Despite that we disabled all physical feedback, the phone still remains fully functional and is capable of maintaining an active internet connection," the researchers explained. "The malicious actor could remotely manipulate the phone in a blatant way without worrying about being caught because the user is tricked into thinking that the phone is off, either being turned off by the victim or by malicious actors using 'low battery' as an excuse."
The malware strain then forces the SpingBoard, which refers to iOS's graphical user interface, to exit (as opposed to the entire OS), followed by commanding the BackBoardd, the daemon that handles all touch and physical button click events, to display the Apple logo effect should the user opt to turn the running phone back on, while the malicious code continues to persist.
What's more, this technique could be theoretically extended to manipulate a force restart associated with an iPhone by deliberately causing the Apple logo to appear a few seconds earlier when such an event is recorded via the Backboardd, fooling the victim into releasing the side button without genuinely triggering a force restart.
Although no malware to date has been detected or publicly documented using a method resembling NoReboot, the findings highlight that even the iOS restart process isn't immune to being hijacked once an adversary has gained access to a target device, something that's well within the reach of nation-state groups and cyber mercenaries alike.
"Non-persistent threats achieved 'persistency' without persistence exploits," the researchers concluded. A proof-of-concept (PoC) exploit demonstrating NoReboot can be accessed via GitHub here.
Researchers Detail New HomeKit 'doorLock' Bug Affecting Apple iOS
5.1.2022 Apple Thehackernews
A persistent denial-of-service (DoS) vulnerability has been discovered in Apple's iOS mobile operating system that's capable of sending affected devices into a crash or reboot loop upon connecting to an Apple Home-compatible appliance.
The behavior, dubbed "doorLock," is trivial in that it can be triggered by simply changing the name of a HomeKit device to a string larger than 500,000 characters.
This causes an iPhone or iPad that attempts to connect to the device to become unresponsive and enter an indefinite cycle of system failure and restart that can only be mitigated by restoring the affected device from Recovery or DFU (Device Firmware Update) Mode.
HomeKit is Apple's software framework that allows iOS and iPadOS users to configure, communicate with, and control connected accessories and smart-home appliances using Apple devices.
"Any device with an affected iOS version installed that loads the string will be disrupted, even after rebooting," security researcher Trevor Spiniolas said. "Restoring a device and signing back into the iCloud account linked to the HomeKit device will again trigger the bug."
The flaw impacts the latest version of iOS, 15.2, and goes back at least as far as version 14.7, with the weakness likely present on all versions of iOS 14 from 14.0. Apple, for its part, was made aware of the bug on August 10, 2021, with the company aiming to resolve the flaw in early 2022.
While iPhone maker has attempted to mitigate the issue by introducing a local size limit on the renaming of HomeKit devices, Spiniolas noted that the core issue of how iOS handles HomeKit device names remains unresolved.
In a real-world attack scenario, doorLock could be exploited by an attacker by sending a malicious invite to connect to a HomeKit device with an abnormally large string as its name, effectively locking users out of their local data and preventing them from logging back into iCloud on iOS.
To make matters worse, since HomeKit device names are also stored on iCloud, signing in to the same iCloud account with a restored device will set off the crash once again, unless the device owner opts to switch off the option to sync HomeKit data.
"This bug poses a significant risk to the data of iOS users, but the public can protect themselves from the worst of its effects by disabling Home devices in [the] control center in order to protect local data," Spiniolas said. "I believe this issue makes ransomware viable for iOS, which is incredibly significant."