New US Bill Aims to Protect Researchers who Disclose Govt Backdoors
14.3.2020 Bleepingcomputer BigBrothers Virus
New legislation has been introduced that amends the Espionage Act of 1917 to protect journalists, whistleblowers, and security researchers who discover and disclose classified government information.
The goal of the new legislation is to amend the Espionage Act of 1917 so it cannot be used to target reporters, whistleblowers, and security researchers who discover and publish classified government secrets.
Concerned that the current laws are being used for partisan prosecution, U.S. Representative Ro Khanna (D - California) introduced the new legislation to Congress on March 5th, 2020 and U.S. Senator Ron Wyden (D - Oregon) will soon introduce it to the Senate.
"My bill with Senator Wyden will protect journalists from being prosecuted under the Espionage Act and make it easier for members of Congress, as well as federal agencies, to conduct proper oversight over any privacy abuses. Our nation’s strength rests on the freedom of the press, transparency, and a functioning system of checks and balances. This bill is a step toward ensuring those same principles apply to intelligence gathering and surveillance operations," said Rep. Ro Khanna.
"This bill ensures only personnel with security clearances can be prosecuted for improperly revealing classified information," Senator Wyden stated.
This new legislation titled 'Espionage Act Reform Act of 2020’ ensures:
Journalists who solicit, obtain, or publish government secrets are safe from prosecution.
Every member of Congress is equally able to receive classified information, specifically from whistleblowers. Current law criminalizes the disclosure of classified information related to signals intelligence to any member of Congress, unless it is in response to a “lawful demand” from a committee. This change puts members in the minority party and those not chairing any committee at a significant disadvantage toward conducting effective oversight.
Federal courts, inspector generals, the FCC, Federal Trade Commission, and Privacy & Civil Liberties Oversight Board can conduct oversight into privacy abuses.
Cybersecurity experts who discover classified government backdoors in encryption algorithms and communications apps used by the public can publish their research without the risk of criminal penalties. The bill correctly places the burden on governments to hide their surveillance backdoors; academic researchers and other experts should not face legal risks for discovering them.
With these new amendments, security researchers are also protected from revealing classified government surveillance backdoors that have been added to encryption algorithms and communications apps that are utilized by the public.
Hacking into government systems or unlawfully obtaining nonpublic government information, though, is still off-limits and would lead to prosecution.
With these changes, researchers would be able to analyze government mobile apps, communication protocols, and algorithms and disclose any vulnerabilities and backdoors without fear of prosecution.
The current legislation can be found in chapter 37 of title 18, United States Code and the proposed amendments can be read here.
Senator Wyden has also released a summary of the bill/FAQ that provides an overview as to why the legislation is being introduced and answers some commonly asked questions.
Emotet Actively Using Upgraded WiFi Spreader to Infect Victims
7.3.2020 Bleepingcomputer Virus
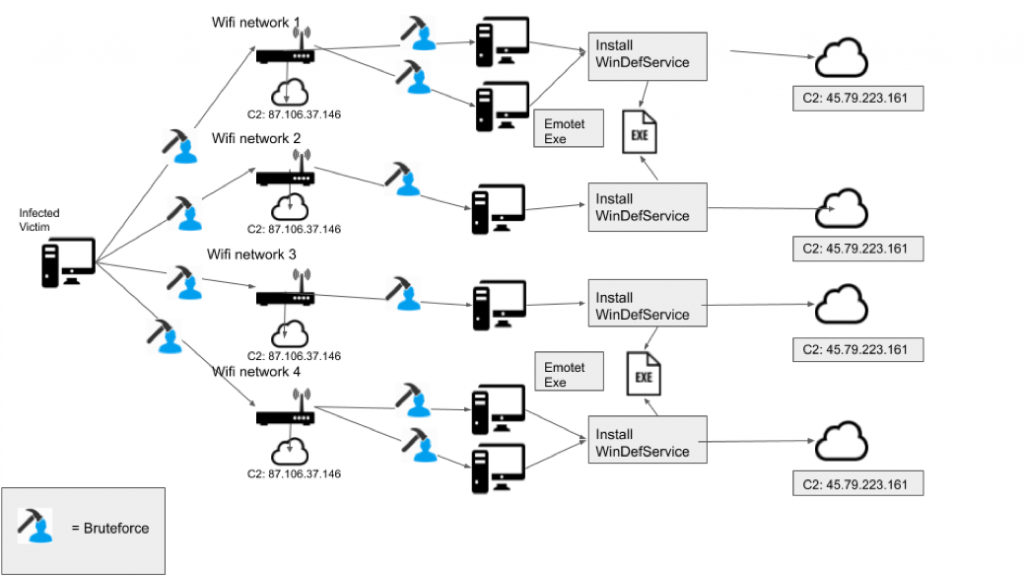
Emotet’s authors have upgraded the malware's Wi-Fi spreader by making it a fully-fledged module and adding new functionality as shown by samples recently spotted in the wild.
We previously reported that Emotet is now capable of spreading to new victims via nearby insecure wireless networks using a Wi-Fi worm module.
The recent updates to the module come after the same stand-alone spreader version was used by the Emotet gang for at least two years without noticeable changes as researchers at Binary Defense show in a report shared with BleepingComputer earlier this week.
This upgraded Wi-Fi worm module is already being used in the wild according to a researcher who found evidence of the Emotet Wi-Fi spreader being used to spread throughout one of his client's networks as Binary Defense threat researcher and Cryptolaemus contributor James Quinn told BleepingComputer.
New Emotet Wi-Fi spreader functionality
Besides its conversion from a stand-alone to a malware module, the Emotet developers also updated it with more verbose debugging and made changes that, in theory, could allow the Wi-Fi spreader to deliver other payloads besides the loader — which was the only known payload deliverer by the previous spreader version.
The spreader is now also capable of brute-forcing ADMIN$ shares on targeted networks when it fails brute-forcing a device's C$ share.
"Additionally, before the spreader attempts to brute-force C$/ADMIN$, it attempts to download, from a hardcoded IP, the service binary that it installs remotely," Binary Defense explains. "If this download fails, it sends the debug string “error downloading file” before quitting."
The malware's authors have also tweaked the service.exe binary used to drop Emotet on infected devices, now downloading the loader from the command-and-control (C&C) server and saving it on the compromised computer as firefox.exe, thus making sure that the latest loader version is being deployed.
This method is also used by Emotet developers "to avoid detections that may flag off the Emotet loader, but not the service executable."
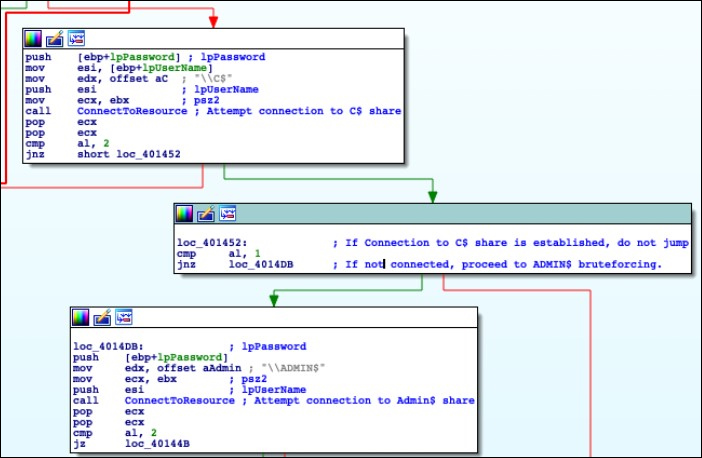
Image: Binary Defense
Binary Defense's research team also observed while analyzing the new Emotet samples that the binary used to deliver the loader and the spreader both featured the loader's hardcoded download URL within their strings, pointing at a previous Emotet version where their functionality was combined within a single binary.
The Emotet authors have also slightly altered the spreader's logging capabilities allowing its operators "to get step-by-step debugging logs from infected victims through the use of a new communication protocol."
This new comms protocol uses two PHP POST arguments delivering info on the bots' MachineGUID and debug strings generated by the malware during runtime.
The Emotet's Wi-Fi spreader module updates are a sign that the malware's authors are now also focusing on adding new infection vectors for their malware loader besides the usual malicious documents delivered to targets via massive spam campaigns.
With the new focus on the spreader, Emotet's authors are on a straight path to developing an even more capable and dangerous Wi-Fi worm module that will most likely be spotted more and more by both researchers and victims while actively in the wild.
Emotet's Wi-Fi spreader in action (Binary Defense)
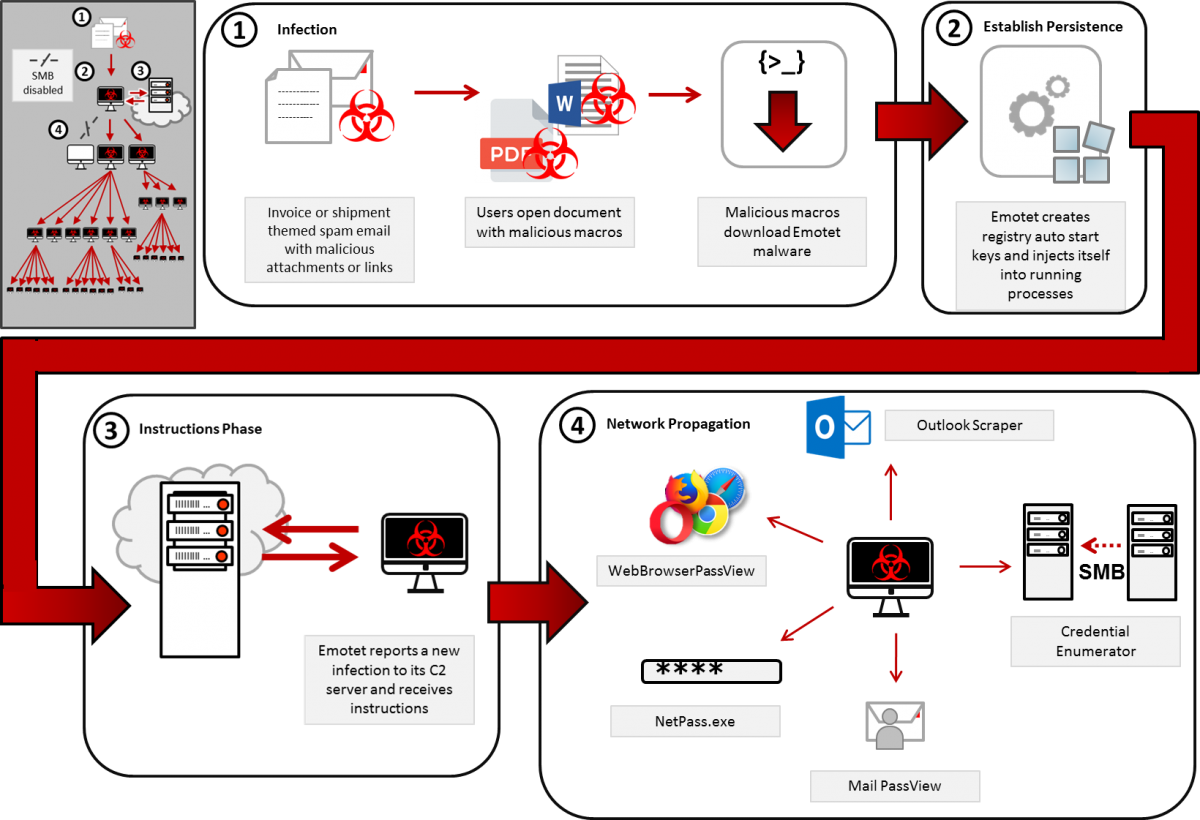
Emotet infections can lead to serious consequences
Emotet was originally a banking trojan first spotted during 2014 and it has evolved into a malware loader used to install various other malware families including the Trickbot banking Trojan (a known vector for delivering Ryuk ransomware payloads).
Recently, the malware was delivered during late January in a malspam campaign that used the recent Coronavirus global health crisis as bait.
Also in January, the Cybersecurity and Infrastructure Security Agency (CISA) warned of increased activity related to targeted Emotet attacks.
The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) also issued a warning on the dangers posed by Emotet attacks, saying that the malware "provides an attacker with a foothold in a network from which additional attacks can be performed, often leading to further compromise through the deployment of ransomware."
Emotet infection chain (CISA)
According to CISA, Emotet infections can lead to very serious outcomes if not immediately addressed including:
• temporary or permanent loss of sensitive or proprietary information,
• disruption to regular operations,
• financial losses incurred to restore systems and files, and
• potential harm to an organization’s reputation.
ACSC provides technical advice on Emotet with best practices to defend against infections, just as CISA does in the Emotet Malware alert issued earlier this year.
Emotet ranked first in a 'Top 10 most prevalent threats' ranking from interactive malware analysis platform Any.Run in December 2019, head and shoulders above the next malware in the top, the Agent Tesla info-stealer, with triple the number of sample uploads submitted for analysis.
More details on Emotet's upgraded Wi-Fi spreader, malware sample hashes, and YARA and SURICATA rules for threat detection are available in the Binary Defense report.
TrickBot Malware Targets Italy in Fake WHO Coronavirus Emails
7.3.2020 Bleepingcomputer Spam Virus
A new spam campaign is underway that is preying on the fears of Coronavirus (COVID-19) to target people in Italy with the TrickBot information-stealing malware.
When sending malicious spam, malware distributors commonly use current events, fears, and politics as themes for the emails to get recipients to open the attached malicious documents.
As there is no bigger news at this time than the spread of Coronavirus and the fears of becoming sick, a new malicious spam campaign has been created that pretends to be from a doctor at the World Health Organization (WHO).
These emails have a subject of "Coronavirus: Informazioni importanti su precauzioni" and pretends to be information about the necessary precautions people in Italy should take to protect themselves from the Coronavirus.
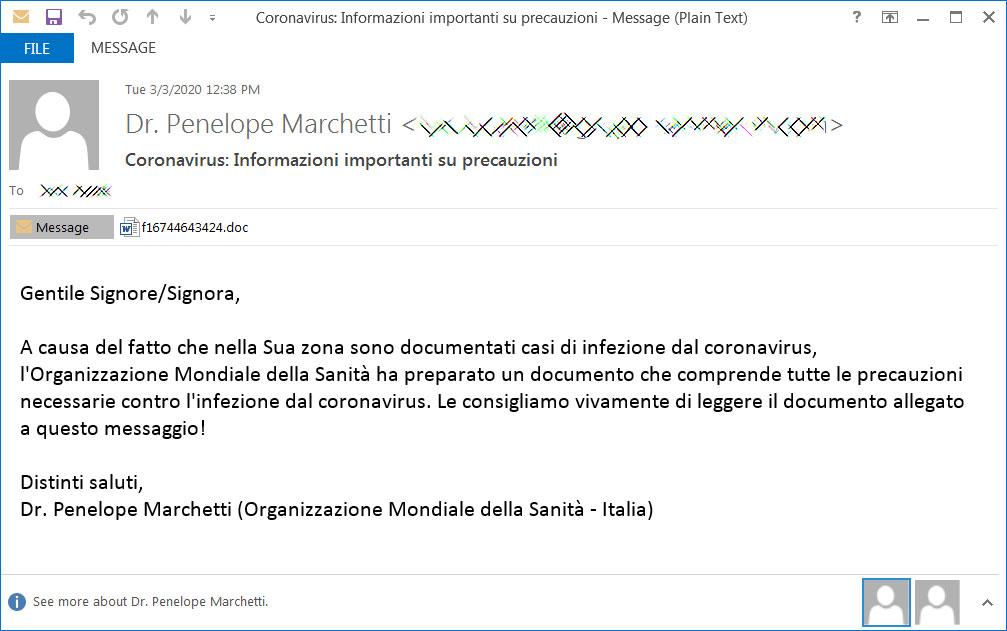
Malicious Spam about Coronavirus
The email in Italian can be read below:
Gentile Signore/Signora,
A causa del fatto che nella Sua zona sono documentati casi di infezione dal coronavirus, l'Organizzazione Mondiale della Sanità ha preparato un documento che comprende tutte le precauzioni necessarie contro l'infezione dal coronavirus. Le consigliamo vivamente di leggere il documento allegato a questo messaggio!
Distinti saluti,
Dr. Penelope Marchetti (Organizzazione Mondiale della Sanità - Italia)
This translates to English as:
Dear Sir / Madam,
Due to the fact that cases of coronavirus infection are documented in your area, the World Health Organization has prepared a document that includes all necessary precautions against coronavirus infection. We strongly recommend that you read the document attached to this message!
With best regards,
Dr. Penelope Marchetti (World Health Organization - Italy)
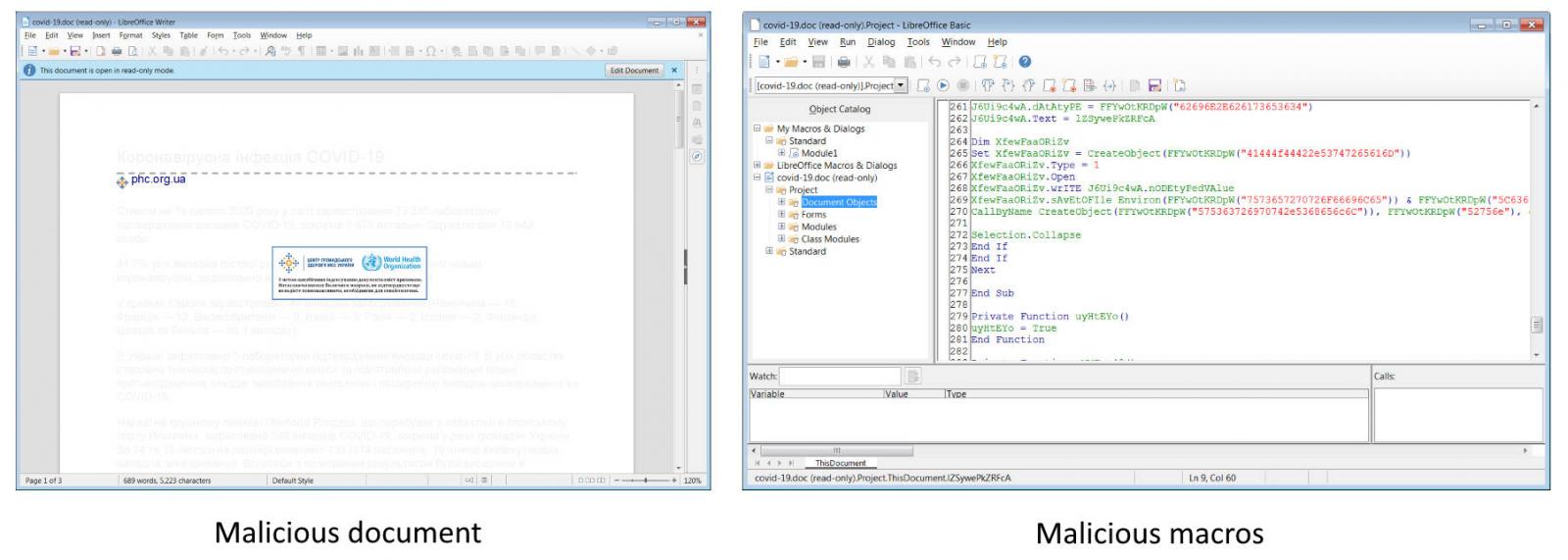
According to new research by Sophos, attached to these emails is a malicious Word document that when opened states that you need to click on the 'Enable Content' button to properly view it.
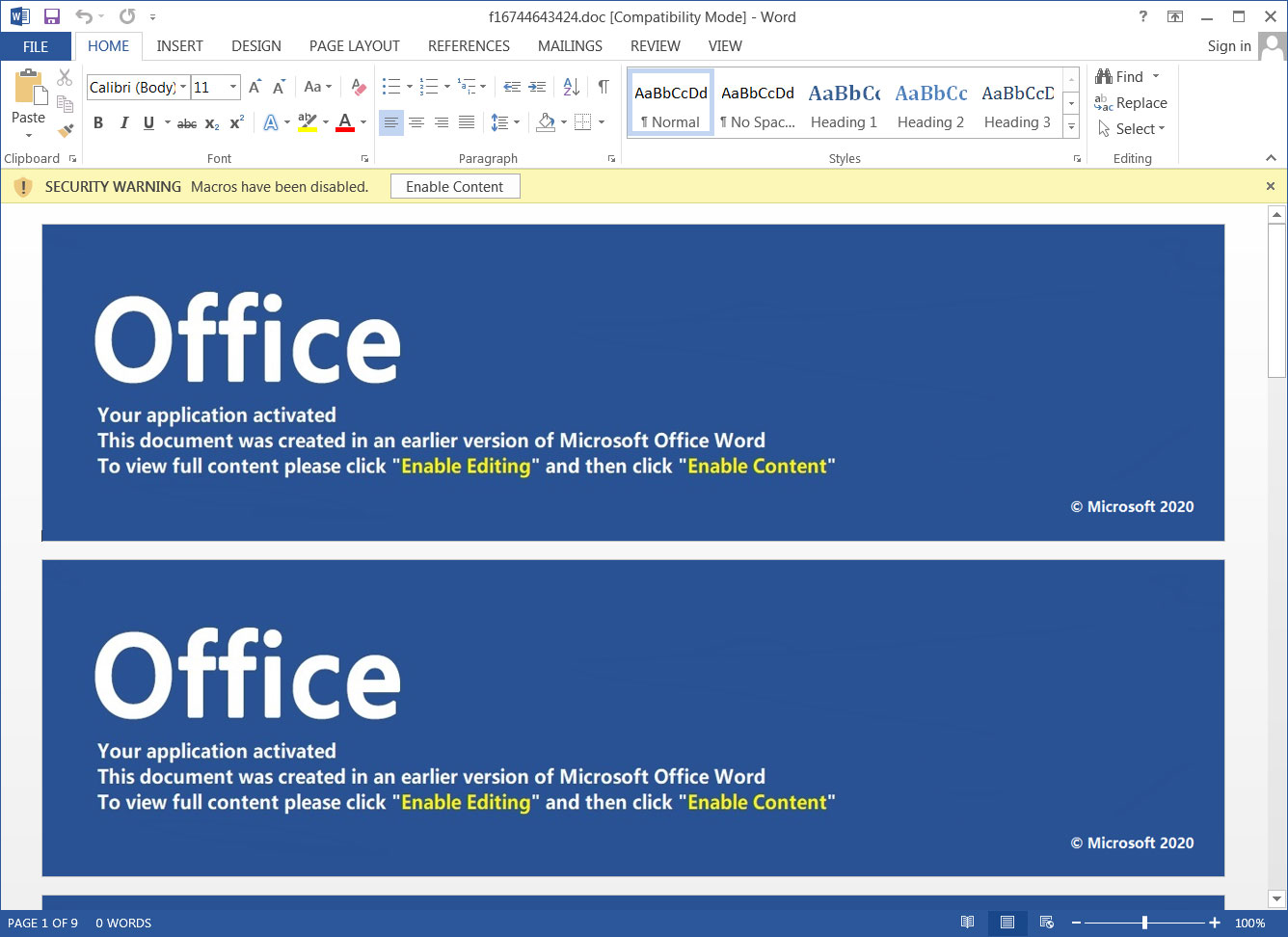
Malicious Word document
Once a recipient clicks on 'Enable Content', though, malicious macros will be executed that extracts various files to install and launch the Trickbot malware as illustrated in the image below by Sophos.
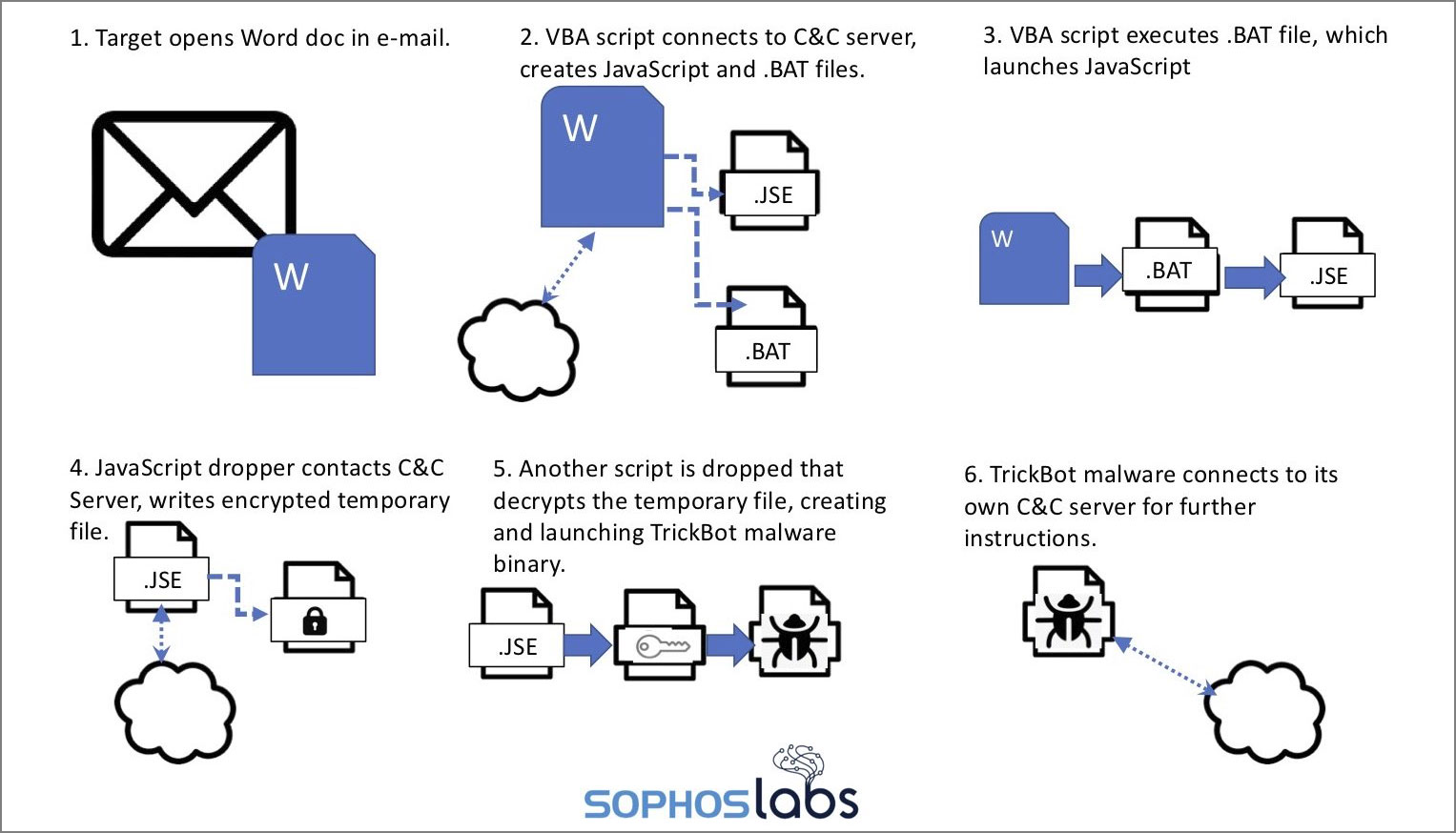
From email to TrickBot infection
(Source: Sophos)
Once TrickBot is installed, it will harvest various information from a compromised computer and then attempt to spread laterally throughout a network to gather more data.
To perform this behavior, TrickBot will download various modules that perform specific behavior such as stealing cookies, browser information, OpenSSH keys, steal the Active Directory Services database, and spreading to other computers.
After harvesting the network of all valuable data, TrickBot will eventually launch PowerShell Empire or Cobalt Strike to give the Ryuk Ransomware actors access to the infected computer.
After these actors perform further reconnaissance of the network, steal data, and gain admin credentials, they will deploy the Ryuk Ransomware and encrypt the files of all the computers on the network.
This is why TrickBot is such a dangerous computer infection as it uses a two-fold attack, with both attacks causing serious damage to your files and personal data.
People need to be suspicious of all emails that they receive and not open any attachment from someone they do not know without first confirming the email is legitimate. This can be done by calling the sender directly and confirming or by scanning the attachment with antivirus software or VirusTotal.
In heightened times of unrest and concern, users need to be even more diligent as there are always people looking to take advantage of a crisis to cause harm to another.
New Evasion Encyclopedia Shows How Malware Detects Virtual Machines
7.3.2020 Bleepingcomputer Virus
A new Malware Evasion Encyclopedia has been launched that offers insight into the various methods malware uses to detect if it is running under a virtual environment.
To evade detection and analysis by security researchers, malware may check if it is running under a virtualized environment such as virtual machine in VirtualBox and VMWare.
If these checks indicate that it is being run in a VM, the malware will simply not run, and in some cases, delete itself to prevent analysis.
The malware Evasion Encyclopedia
Created by Check Point Research, the Malware Evasion Encyclopedia is broken into different categories of information that a malware will use to detect if it is running under a virtual machine.
While sharing this information may allow malware authors to learn some new techniques, Check Point feels that the value to the information security community far outweighs any benefit to malware developers.
"It is our belief the value of sharing with the community is far greater than the risk of malware authors using this," Check Point Research told BleepingComputer.
The current sections in the encyclopedia with listed techniques are:
Filesystem
Registry
Generic OS queries
Global OS objects
UI artifacts
OS features
Processes
Network
CPU
Hardware
Firmware tables
Hooks
macOS
Inside each section are code snippets that illustrate how malware determines if it is running under a virtual environment and suggested countermeasures to defeat these checks.
For example, the 'Processes' section shows how malware checks for certain processes used by VMs, the 'Firmware Tables' section explains how malware looks for certain strings in the BIOS, and the 'Generic OS queries' section lists user names that are commonly looked for.
Example evasion technique by checking for certain user names
Example evasion technique by checking for certain user names
When we asked if Check Point research plans on further updating the encyclopedia, they told us that they will continue to do so and welcome input from the information security community.
"We plan on maintaining this. Actually, this web site is just the “face” for a GitHub account with all the info. Anyone may submit pull requests and add his own technique if he spots one so the encyclopedia can be a valuable tool for everyone. Hopefully, this will help our community keep one step ahead of the bad guys," Check Point responded to us.
If you are building a virtual machine for malware analysis or just want to learn how malware attempts to evade detection, Check Point's encyclopedia is a great place to start.
Hackers Use Windows 10 RDP ActiveX Control to Run TrickBot Dropper
24.2.2020 Bleepingcomputer Spam Virus
A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.
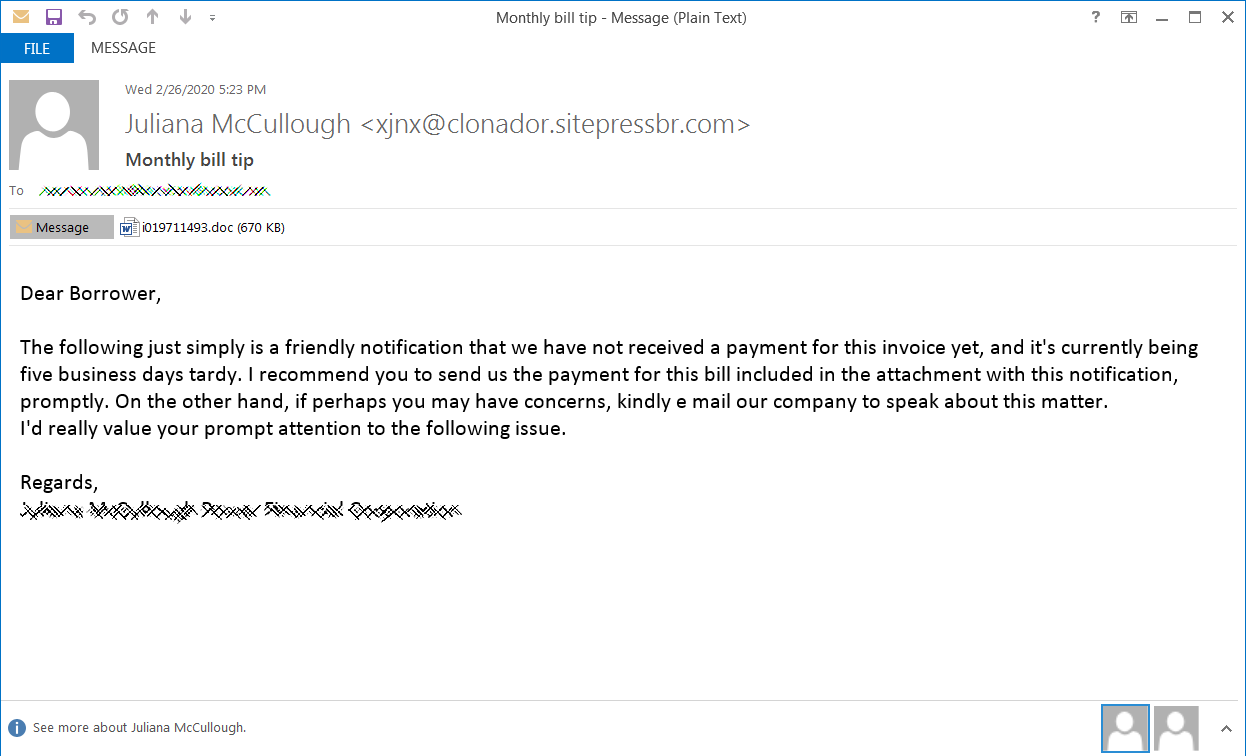
Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.
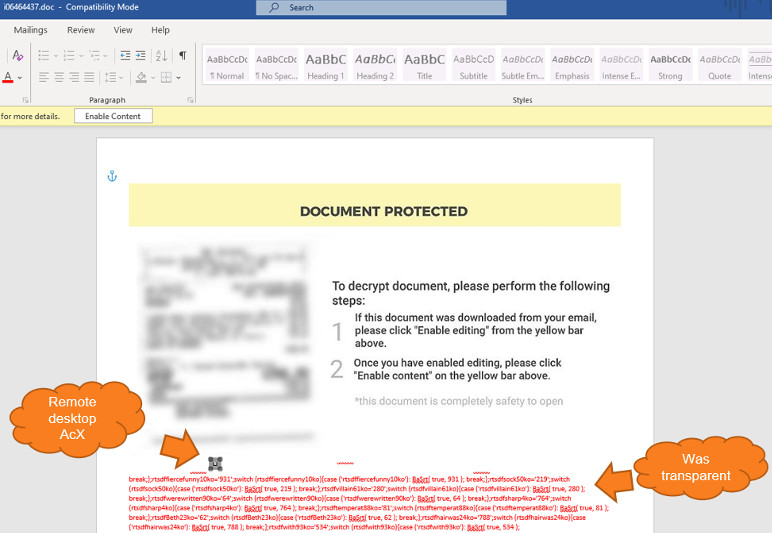
Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.
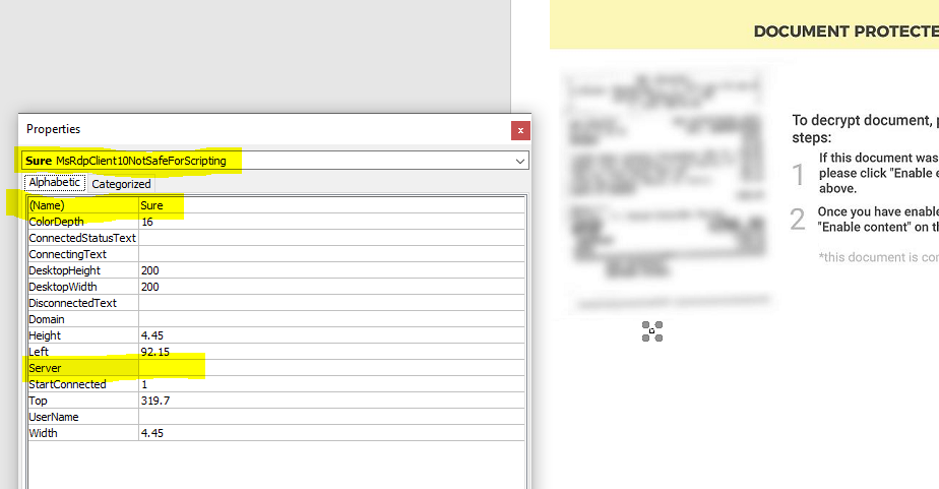
This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.
As Coronavirus Spreads, So Does Covid-19 Themed Malware
24.2.2020 Bleepingcomputer Virus
Threat actors are still taking advantage of the ongoing COVID-19 global outbreak by attempting to drop Remcos RAT and malware payloads on their targets' computers via malicious files that promise to provide Coronavirus safety measures.
Cybaze/Yoroi ZLAb researchers recently spotted a suspicious CoronaVirusSafetyMeasures_pdf.exe executable after it was submitted to their free Yomi Hunter sandbox-based file analysis service.
While the infection vector used by the attackers is not yet known, the most probable method of dissemination is a phishing campaign that would deliver it as an email attachment.
RAT used to steal keystrokes
As the Cybaze/Yoroi ZLAb research team later discovered, the executable is an obfuscated Remcos RAT dropper that would drop a Remcos RAT executable on the compromised computer, together with a VBS file designed to run the RAT.
The malware will also gain persistence on the infected device by adding a Startup Registry key at HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce which allows it to restart itself after the computer is restarted.
After setting up everything it needs for its malicious purposes, the RAT will begin to log the user's keystrokes and store it within a log.dat file in the %AppData%\Local\Temp\onedriv folder.
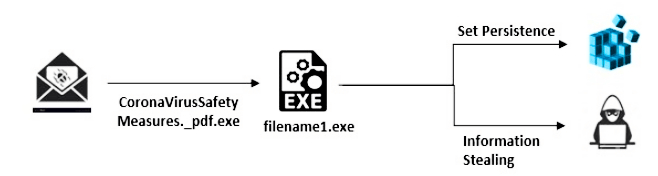
Attack chain (Yoroi)
The stolen information is then exfiltrated to its command and control server hosted at 66[.]154.98.108.
Last year, attackers also took advantage of the United States tax season to install the Remcos RAT via a phishing campaign that targeted accounting firms to steal information from all the taxpayers the tax preparer had as clients.
COVID-19: a popular phishing bait
Earlier this month, IBM X-Force Threat Intelligence researchers discovered another phishing campaign distributing the Lokibot information stealer malware via emails designed to look like they're sent by the Ministry of Health of the People's Republic of China and containing emergency Coronavirus regulations in English.
"Inspired by Emotet and the significant increase of the Coronavirus infection rates, Lokibot operators saw an opportunity to expand its botnet and joins the current trend of scare tactics," the researchers explain.
The Emotet mention is related to a previous campaign from late-January that was also observed distributing Emotet payloads while warning of Coronavirus infection reports in various Japanese prefectures.
Roughly a week ago, security research collective MalwareHunterTeam found a 3-page Coronavirus-themed Microsoft Office document containing malicious macros, pretending to be from the Center for Public Health of the Ministry of Health of Ukraine, and designed to drop a backdoor malware with clipboard stealing, keylogging, and screenshot capabilities.
This malware was spotted right after the media reported about violent protests starting in Kyiv, Ukraine, following a viral fake email from the country's Ministry of Health that spread false info about confirmed COVID-19 infections after the landing of plane carrying Ukrainians evacuated from China’s Hubei province.
MalwareHunterTeam also shared several other malware samples with Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
Other phishing campaigns using Coronavirus lures have targeted U.S. and UK targets while impersonating U.S. Centers for Disease Control and Prevention (CDC) officials and virologists, and alerting their potential victims of infections in their area and providing 'safety measures.'
A report published by Imperva researchers also highlights how "high levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores."
The U.S. Federal Trade Commission (FTC) warned of ongoing scam campaigns using the current Coronavirus global scale health crisis to lure targets from the United States via email and text message phishing campaigns, text messages, as well as on social media.
Last but not least, about a week ago, the World Health Organization (WHO) also warned of active Coronavirus-themed phishing attacks that impersonate the organization with the end goal of delivering malware and stealing sensitive information.
New Mozart Malware Gets Commands, Hides Traffic Using DNS
24.2.2020 Bleepingcomputer Virus
A new backdoor malware called Mozart is using the DNS protocol to communicate with remote attackers to evade detection by security software and intrusion detection systems.
Typically when a malware phones home to receive commands that should be executed, it will do so over the HTTP/S protocols for ease of use and communication.
Using HTTP/S communication to communicate, though, has its drawbacks as security software normally monitors this traffic for malicious activity. If detected, the security software will block the connection and the malware that performed the HTTP/S request.
In the new Mozart backdoor discovered by MalwareHunterTeam, the malware uses DNS to receive instructions from attackers and to evade detection.
Using DNS TXT records to issue commands
DNS is a name resolution protocol that is used to convert a hostname, such as www.example.com, to its IP addresses, 93.184.216.34, so that software can connect to the remote computer.
In addition to converting hostnames to IP address, the DNS protocol also allows you to query TXT records that contain text data.
This feature is commonly used for domain ownership verification for online services and email security policies such as Sender Policy Framework or DMARC.
You can also use these for silly little demonstrations like the TXT record for 'hi.bleepingcomputer.com'.
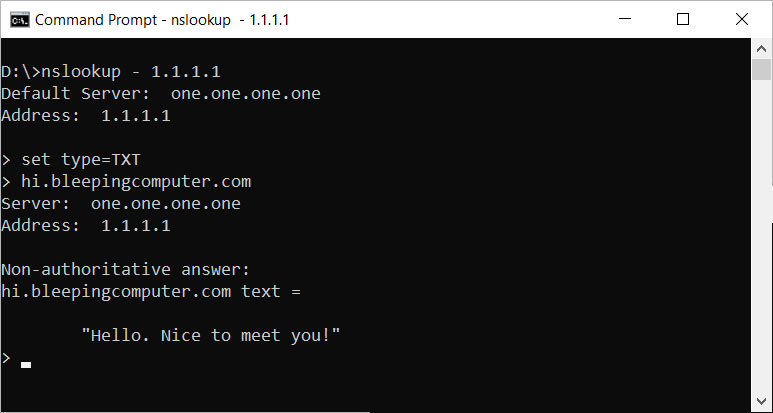
hi.bleepingcomputer.com TXT record
The Mozart attackers are using these DNS TXT records to store commands that are retrieved by the malware and executed on the infected computer.
Mozart makes bad music over DNS
The Mozart malware is believed to be distributed via phishing emails that contain PDFs that link to a ZIP file that was located at https://masikini[.]com/CarlitoRegular[.]zip.
This zip file contains a JScript file that when executed will extract a base64 encoded executable that is saved to the computer as %Temp%\calc.exe and executed.
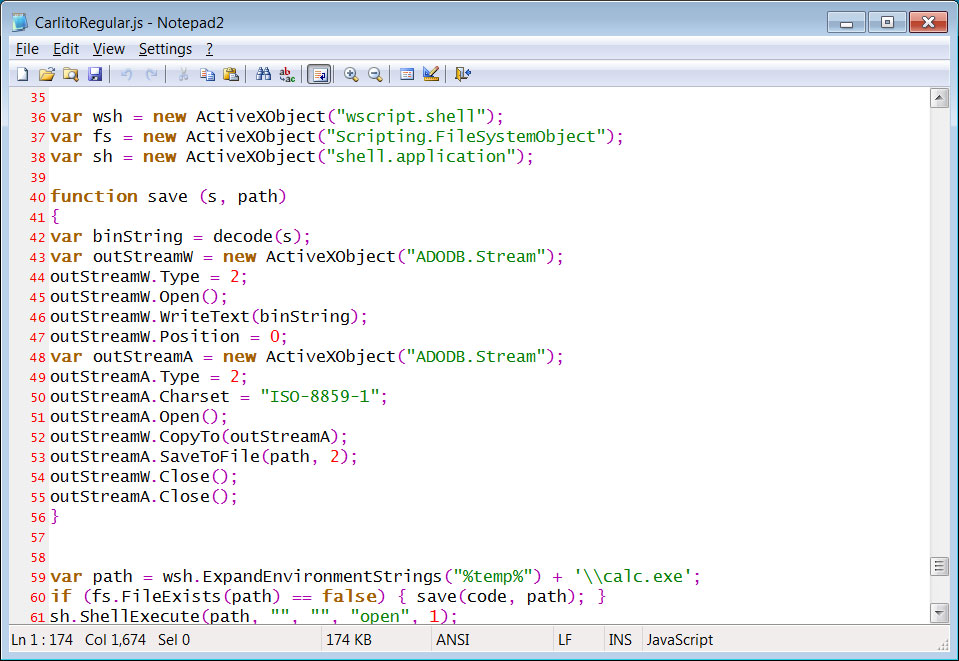
Mozart Jscript installer
According to Head of SentinelLabs Vitali Kremez who analyzed this backdoor and shared his findings with BleepingComputer, the malware will first check for the file %Temp%\mozart.txt.
If it does not exist, it will create the file with the contents of '12345' and perform some preparation work on the computer.
This includes copying the calc.exe file from the %Temp% folder to a random named executable in the %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\ folder to startup every time the victim logs into Windows.
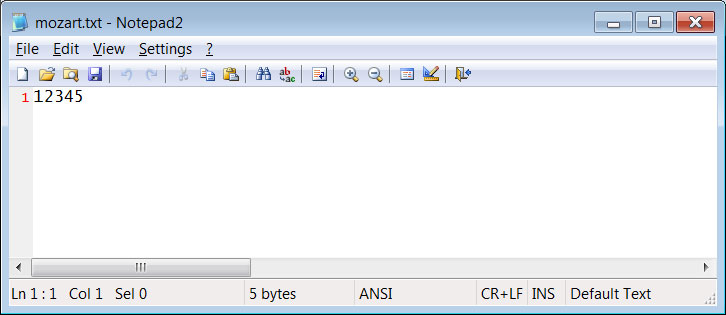
mozart.txt file
According to Kremez, the Mozart malware will communicate with a hardcoded DNS server under the attacker's control at 93[.]188[.]155[.]2 and issue following DNS requests to receive instructions or configuration data:
The loader obtains the bot id and returns Base64-encoded parameters for tasks and further processing:
A. ".getid" (.1)
The bot generation API sequence is as follows:
GetCurrentHwProfileW -> GetUserNameW -> LookupAccountNameW -> ConvertSidToStringSidW
B. ".gettasks" (.1)
Parse tasks with "," delimiter
C.".gettasksize" (.1)
Allocate memory for the task and dnsquery_call
D. ".gettask" (.1)
Parse for the specific task
E. ".reporttask" (.0|.1)
Run the task via CreateProcessW API
F. ".reportupdates" (.0|.1)
Retrieve and check updates via WriteFile and MoveFilW locally for a stored check as ".txt"
H. ".getupdates" (.0|.1)
Check for presence of ".txt" update and write the update with "wb" flag and check for executable extension (".exe") following with ".gettasks" call.
For example, in BleepingComputer's tests, we were assigned the bot of ID '111', which caused Mozart to do DNS TXT lookups for 111.1.getid, 111.1.getupdates, and 111.1.gettasks.
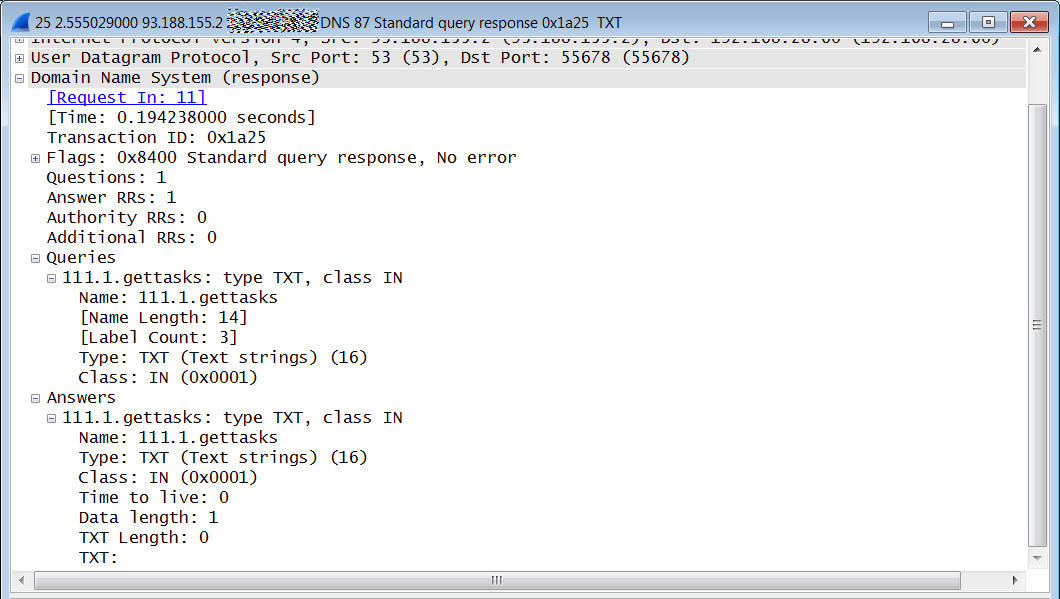
gettasks DNS request
While monitoring Mozart, we noticed that the malware will continually issue 'gettasks' queries to the attacker's DNS server to find commands to execute.
If the TXT record response is empty, as shown above, that means there are no commands to execute and the malware will continue to perform this check over and over until a task is provided.
At this time, it is not known what commands are being executed by Mozart as tests by myself and Kremez did not result in any responses to the DNS queries.
It could be that we did not test for a long enough period or the attackers are currently in the process of building their botnet before transmitting commands.
Blocking this type of threat
It is important to note that malware using DNS to communicate is not unique to the Mozart backdoor.
In 2017, the Cisco Talos group discovered a malware called DNSMessenger that was also using TXT records for malicious communication.
To block Mozart, we could tell you to block DNS requests to 93[.]188[.]155[.]2, but new variants could simply switch to a new DNS server until we get tired of this cat-and-mouse game.
David Maxwell, Software Security Director at BlueCat, offered this suggestion instead:
""At your firewall, block outbound port 53 from everywhere except your official internal DNS server" - this virus goes directly to a fixed external IP, and while you could just block that, the next virus won't use the same IP. Forcing all of your corporate name resolution to go through the resolvers you maintain gives you the ability to monitor traffic and control policy."
It is also important to keep an eye out for novel methods of malicious communication and if your security software and intrusion systems can monitor DNS TXT queries, you should enable it.
Racoon Malware Steals Your Data From Nearly 60 Apps
24.2.2020 Bleepingcomputer Virus
An infostealing malware that is relatively new on cybercriminal forums can extract sensitive data from about 60 applications on a targeted computer.
The malware scene is constantly changing and what used to be top of the line a few years ago is now available for a modest price by comparison and a much richer set of features.
Raccoon infostealer was observed in the wild for the first time almost a year ago and has gained quickly gained in popularity due to its low price and generous features
Unsophisticated yet good enough
Also known as Legion, Mohazo, and Racealer, the malware was initially promoted only on Russian-speaking forums but it soon made its entrance in the English-speaking space. The malware was first seen in the wild April 2019 and it is distributed under the MaaS (malware-as-a-service) model for $75/week or $200/month.
For this money, the attackers get access to an administration panel that lets them customize the malware, access stolen data, and download the builds of the malware.
This model is widely adopted today because it opens the door to a larger number of cybercriminal customers, many lacking the proper technical knowledge but compensating in business experience.
An analysis from CyberArk found that it is written in C++ and is far from being a complex tool. However, it can steal sensitive and confidential information from almost 60 programs (browsers, cryptocurrency wallets, email and FTP clients).
All the popular browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Internet Explorer, Opera, Vivaldi, Waterfox, SeaMonkey, UC Browser) are on the list of targets along with more than 20 other solutions, which are robbed of cookies, history, and autofill information.
Hot cryptocurrency apps like Electrum, Ethereum, Exodus, Jaxx, and Monero, are of interest, searching for their wallet files in the default locations. However, Raccoon also can scan the system to grab wallet.dat files regardless of where they are stored.
From the email client software category, Raccoon looks for data from at least Thunderbird, Outlook, and Foxmail.
In a report today CyberArk researchers say that this infostealer relies on the same procedure to steal the data: locate and copy the file with the sensitive info, apply extraction and decryption routines, and placing the info in a text file ready for exfiltration.
Additional capabilities in the malware include collecting system details (OS version and architecture, language, hardware info, enumerate installed apps).
Attackers can also customize Raccoon's configuration file to snap pictures of the infected systems' screens. Additionally, the malware can act as a dropper for other malicious files, essentially turning it into a stage-one attack tool.
This type of malware is not necessarily used for immediate benefits as it is useful for increasing permissions on the system or for moving to other computers on the network.
"After fulfilling all his stealing capabilities, it gathers all the files that it wrote to temp folder into one zip file named Log.zip. Now all it has to do is send the zip file back to the C&C server and delete its trace" - CyberArk
Like all malware riding the popularity wave, Raccoon is actively improved with fixes for various issues, new functions, and capabilities.
While analyzing one sample, researchers noticed new versions being released, which extended support for targeted apps, adding FileZilla and UC Browser, and adding the option to encrypt malware builds straight from the administration panel and getting them in DLL form.
Raccoon does not use any special techniques to extract information from targeted programs, yet it is one of the most popular infostealers on cybercriminal forums. Recorded Future notes in a report from July 2019 that it was one of the best selling malware in the underground economy.
Three months later, researchers at Cybereason also note that the malware was enjoying positive reviews from the community, many actors praising and endorsing the malware. Established members, though, criticized its simplicity and lacking in features present in tools of the same feather.
However, despite its simplicity, its infection count is at hundreds of thousands of computers across the world.
This shows that technical features are not necessarily what attackers are after when choosing a malicious tool but a good balance between price, accessibility, and capabilities.
"What used to be reserved for more sophisticated attackers, now even novice players can buy stealers like Raccoon with the intention of getting their hands on an organization’s sensitive data" CyberArk
Among the delivery methods used for Raccoon, security researchers observed it being dropped via exploit kits, phishing, and PUA (potentially unwanted applications).
CyberArk's report today comes with indicators of compromise (IoC) and a YARA rule to catch a Raccoon infection.
Over 20,000 WordPress Sites Run Trojanized Premium Themes
23.2.2020 Bleepingcomputer Virus
A threat actor that has infected more than 20,000 WordPress sites by running the same trick for at least three years: distributing trojanized versions of premium WordPress themes and plugins.
The operation counts tens of unofficial marketplaces, likely managed by the same actor, specifically set up to provide nulled (pirated) WordPress components.
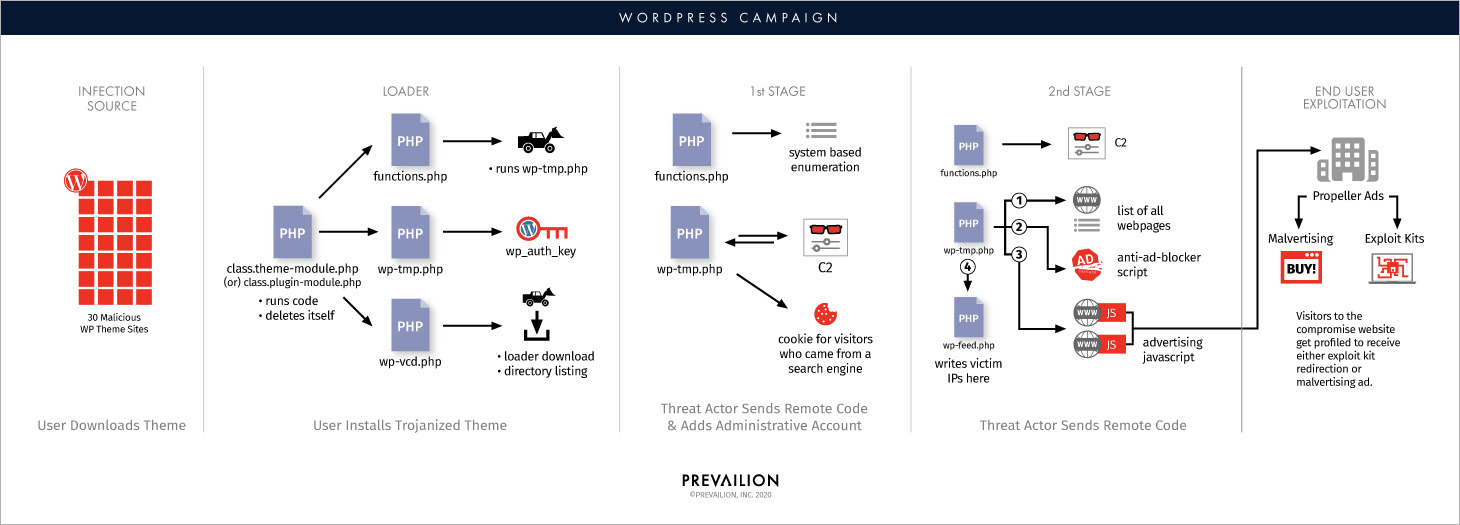
Once the victim uploads a compromised component to the web server, the threat actor can add an administrative account and initiate the attack stages that precede ad-fraud and serving exploit kits to website visitors.
The distribution network has at least 30 websites, listed at the end of the article, that are actively promoted. The network of compromised websites is significant, 20,000 being a conservative estimation since some of tainted plugins and themes have well upwards of 125,000 views. One component ,"Ultimate Support Chat," has about 700,000 views.
As for victims, small and medium-sized businesses in various fields account for a fifth. Some of the more prominent are:
a decentralized crypto-mining website
a U.S. based stock trading firm
a small U.S. based bank
a government run petro/chemical organization
a U.S. based insurance company
a large U.S. based manufacturer
a U.S. payment card solution organization
a U.S. based IT services organization
Behind the takeover is the WP-VCD malware that has been documented in security reports since February 2017 and reported by users on various support forums.
The attackers injected in the WordPress components two malicious PHP files ('class.theme-module.php' and 'class.plugin-modules.php') with functions for command and control (C2) communication and responsible for activating the malware ('wp-vcd.php'). Next, the two files delete themselves.
Researchers at security intelligence company Prevailion found that in the first stage of attack additional code is downloaded to add a persistent cookie to a visitor's browser when they landed on the compromised website from Google, Yahoo, Yandex, MSN, Baidu, Bing, and DoubleClick.
The cookie is set to expire in 1,000 days and includes the referrer website and the compromised domain visited.
"Once the cookie was attached to the end-user, their IP address is added to a list that lives in the file called “wp-feed.php”," Prevailion says in a report today.
To ensure persistence, the attackers added the WP_CD_Code from the initial loading staging to multiple files. This allowed the code to survive and maintain access even when admins deleted a file that included it.
The attackers use 13 domains for command and control, although some of them are just redirects:
vosmas[.]icu
tdreg[.]icu
tdreg[.]top
medsource[.]top
tretas[.]top
piastas[.]gdn
pervas[.]top
vtoras[.]top
dolodos[.]top
piasuna[.]gdn
semasa[.]icu
vosmas[.]icu
devata[.]icu
The objective of the operation, which Prevailion named 'PHP's Labyrinth,' is multi-pronged, search engine optimization (SEO) being one aspect. This side of the campaign aims at increasing visibility of the sites the attacker controls to ensnare more victims.
Ad fraud is another facet of the campaign and the attackers rely on a modified version of a publicly available script (https://chevereto.com/community/threads/how-to-add-anti-adblock-code-php.8457/) that disables ad-blocking software in the browser. This tactic is in use since at least September 2019.
The attacker makes money from showing ads on compromised websites. the network used for this is Propeller advertising service, which has been used in the past for nefarious purposes, malvertising pushing the Fallout Exploit Kit, in particular.
According to Prevailion, the ads displayed by the threat actor were benign and gained them half a cent for each click. Malicious use was also observed, though, for prompting users to download adware that was likely pushing malicious software.
List of websites distributing compromised WordPress themes and plugins:
ull5[.]top
Freedownload[.]network
Downloadfreethemes[.]io
Themesfreedownload[.]net
Downloadfreethemes[.]co
Downloadfreethemes[.]pw
Wpfreedownload[.]press
Freenulled[.]top
Nulledzip[.]download
Download-freethemes[.]download
Wpmania[.]download
Themesdad[.]com
Downloadfreethemes[.]download
Downloadfreethemes[.]space
Download-freethemes[.]download
Themesfreedownload[.]top
Wpmania[.]download
Premiumfreethemes[.]top
Downloadfreethemes[.]space
Downloadfreethemes[.]cc
Freethemes[.]space
Premiumfreethemes[.]top
Downloadfreenulled[.]download
Downloadfreethemes[.]download
Freethemes[.]space
Dlword[.]press
Downloadnulled[.]pw
24x7themes[.]top
null24[.]icu
AZORult Malware Infects Victims via Fake ProtonVPN Installer
22.2.2020 Bleepingcomputer Virus
A fake ProtonVPN website was used since November 2019 to deliver the AZORult information-stealing malware to potential victims in the form of fake ProtonVPN installers as discovered by security researchers at Kaspersky.
ProtonVPN is a security-focused open-source virtual private network (VPN) service provider developed and operated by Proton Technologies AG, the Swiss company behind the end-to-end encrypted email service ProtonMail.
AZORult is an ever-evolving data-stealing Trojan selling for roughly $100 on Russian underground forums, also known to act as a downloader for other malware families when used in multi-stage campaigns.
This Trojan was previously spotted by researchers as part of large scale malicious campaigns spreading ransomware, data and cryptocurrency stealing malware.
AZORult is designed to collect and deliver as much sensitive information as possible to its operators, from files, passwords, cookies, and browser history to cryptocurrency wallets and banking credentials once it infects a targeted machine.
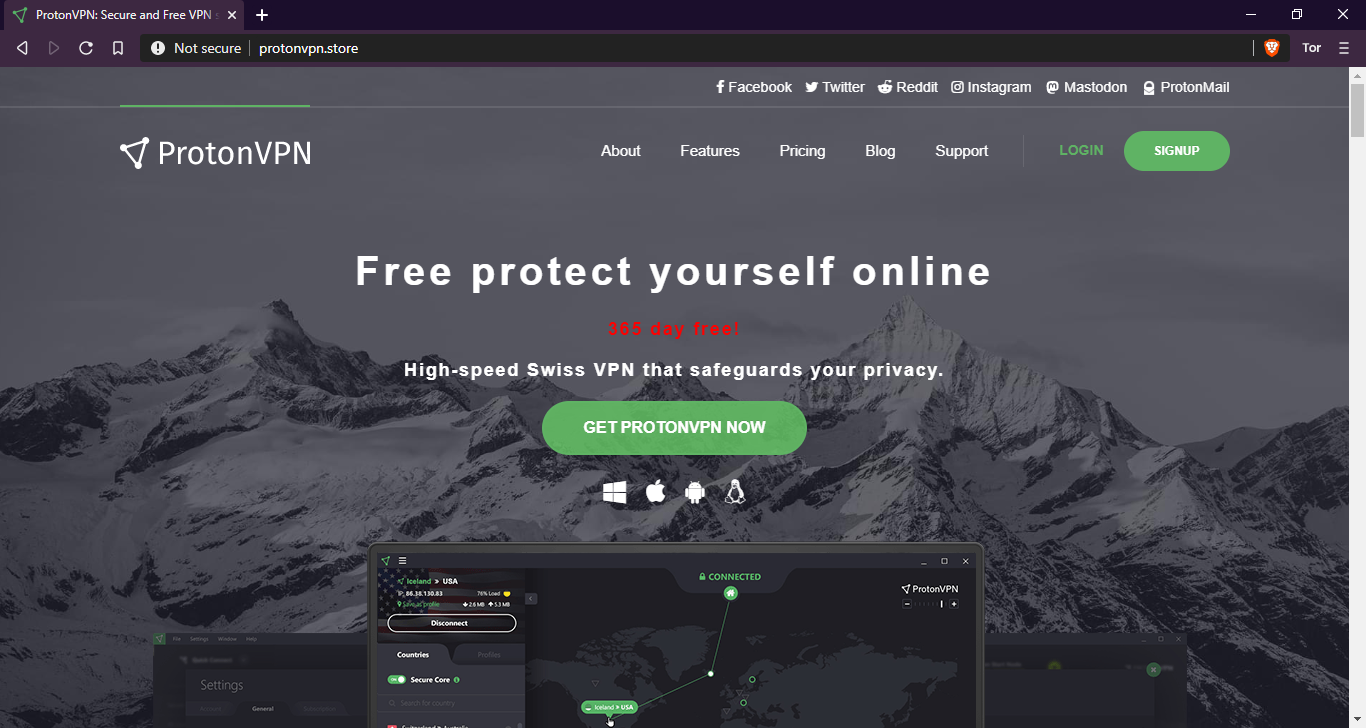
Fake ProtonVPN website (Kaspersky)
Delivery through fake ProtonVPN site
As Kaspersky's researchers discovered, protonvpn[.]store, the website used to deliver the malicious fake ProtonVPN installers (also spotted by DrStache), was registered via a Russian registrar in November 2019.
That is when this campaign also started delivering AZORult malware payloads using affiliation banner network malvertising as one of the initial infection vectors.
"When the victim visits a counterfeit website and downloads a fake ProtonVPN installer for Windows, they receive a copy of the AZORult botnet implant," Kaspersky threat researcher Dmitry Bestuzhev explains.
The campaign's operators made an identical copy of the official ProtonVPN website with the help of the open-source HTTrack web crawler and website downloader utility.
.png)
AZORult malware sample analysis (Kaspersky)
After the fake ProtonVPN installer named ProtonVPN_win_v1.10.0[.]exe is launched and successfully infects a target's computer, the malware starts collecting system information that gets delivered to the command-and-control (C2) server located on the same server as the fake site, at accounts[.]protonvpn[.]store.
The AZORult Trojan then proceeds to "to steal cryptocurrency from locally available wallets (Electrum, Bitcoin, Etherium, etc.), FTP logins and passwords from FileZilla, email credentials, information from locally installed browsers (including cookies), credentials for WinSCP, Pidgin messenger and others."
This information will then be packed and exfiltrated to the threat actors operating this malvertising campaign that abuses the ProtonVPN service.
More details and indicators of compromise (IOCs) including file names and hashes of fake ProtonVPN installers used in this campaign are available within Kaspersky's report.
Previous fake site encounters
This is not the first time attackers have used fake VPN sites to push malware payloads on unsuspecting victims, with an almost perfect clone of the NordVPN VPN service official website being used as a delivery platform for a banking Trojan.
A fake VPN named 'Pirate Chick VPN' was used to infect victims with the AZORult password-stealing Trojan last year after the initial installation.
The AZORult Trojan was also delivered via a fake BleachBit website with the end goal of harvesting and exfiltrating the victims' credentials and files.
Another threat actor created a site that promoted a fake VPN that would install the Vidar and CryptBot password-stealing Trojans and attempt to steal user credentials and other sensitive information from the victims' computers.
Hacker Group Catfishes Israeli Soldiers Into Installing Mobile RAT
22.2.2020 Bleepingcomputer Virus
A hacking group compromised mobile phones belonging to soldiers in the Israel Defense Forces (IDF) using pics of young girls and directing them to download malware disguised as chat apps.
Behind this endeavor is an actor identified as APT-C-23, known for cyberattacks in the Middle East and associated with the Hamas militant group.
Fake profiles, fake apps, fake promises
Baiting Israeli soldiers with pics of attractive women pretending to be fresh immigrants to Israel, the hackers instructed victims to download from a provided link an app that purported to be similar to Snapchat, but not available from an official app store.
IDF believes that the malware made it on the phones of "a few hundred" soldiers, who have been called in for questioning and disinfection routing on their phones.
However, Israeli intelligence was able to track the malware and disrupt the attacker's infrastructure.
Hamas created fake social media profiles, using photos including this one, in an attempt to hack the phones of IDF soldiers.
What Hamas didn’t know was that Israeli intelligence caught onto their plot, tracked the malware & downed Hamas’ hacking system.#CatfishCaught
— Israel Defense Forces (@IDF) February 16, 2020
To maintain appearances, the threat actor set up websites for the apps they used ("GrixyApp”, “ZatuApp”, and “Catch&See"), complete with descriptions and specific imagery.
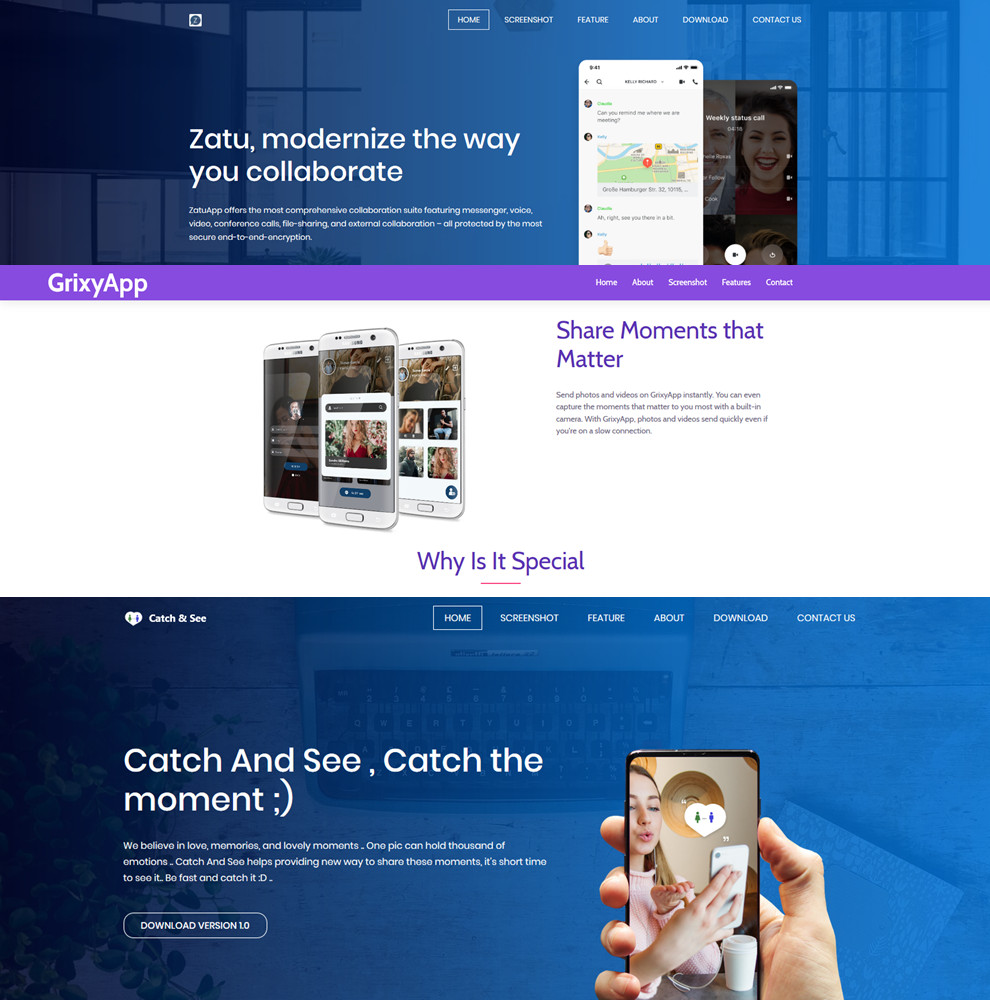
IDF spokesman Brigadier General Hedy Silberman said that the attacker created six female personas to engage soldiers in dialogue via multiple messaging platforms (Facebook, WhatsApp, Telegram, Instagram).
When social engineering proved fruitful, victims were instructed to install one of the fake apps to exchange pictures and for more talk.
The apps were just a disguise for a mobile remote access trojan (MRAT) and showed an error informing that the device is not supported and that the uninstall process would start.
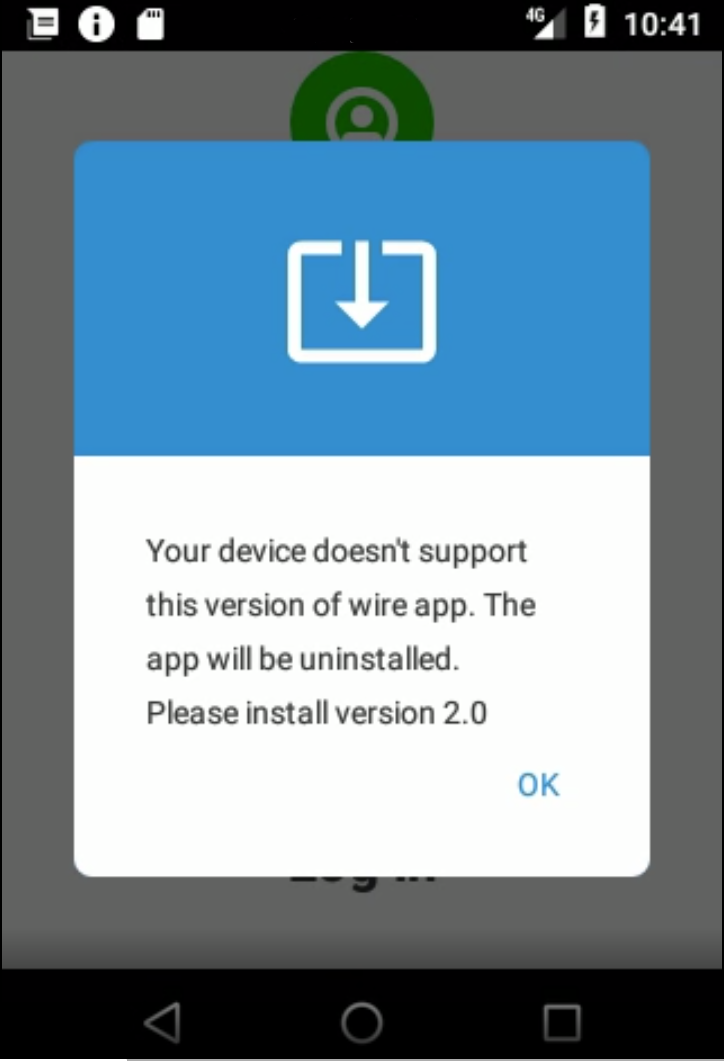
However, the malware would be installed at this stage and would initiate communication with the command and control (C2) server over the MQTT protocol.
The functionality of the MRAT allowed collecting from the device a set of data that includes the phone number, GPS info, storage data, and SMS messages. IDF notes that the malware could also be used to take pictures, steal contact list, downloading and executing files.
Its list of functions could be extended with commands from the C2, note security researchers from Check Point.
A report from IDF explains how APT-C-23 created fake profiles and worked to increase their credibility and popularity. The names used were Sarah Orlova, Maria Jacobova, Eden Ben Ezra, Noa Danon, Yael Azoulay, and Rebecca Aboxis.

The report notes that the threat actor edited the images published on the profiles to make it more difficult to determine the real source. Next, they would contact victims both via text and voice messages.
Although some soldiers fell for the trick, there is no indication of a security impact. Where there was suspicion of an impact, IDF worked with the soldier to eliminate the risk.
In a joint operation dubbed "Rebound", IDF and the Israel Security Agency (ISA, a.k.a. Shin Bet) took down the infrastructure of the threat actor.
U.S. Store Chain Rutter’s Hit by Credit Card Stealing Malware
16.2.2020 Bleepingcomputer Virus
Rutter's, a U.S. convenience store, fast food restaurant, and gas station chain owner, has disclosed today that 71 locations were infected with a point-of-sale (POS) malware that was used by attackers to steal customers' credit card information.
Headquartered in Central Pennsylvania, Rutter’s is a family-owned group of companies with a history dating back to 1747 that operates more than 75 locations throughout Pennsylvania, Maryland, and West Virginia.
Rutter’s disclosed in a Notice of Payment Card Incident published today that it found evidence indicating that some payment card data from cards used on point-of-sale (POS) devices from convenience stores and fuel pumps were accessed by an unauthorized actor using malware installed on the payment processing systems.
While the timeframes of the incident vary for each location, "the general timeframe beginning October 1, 2018 through May 29, 2019."
"There is one location where access to card data may have started August 30, 2018 and nine additional locations where access to card data may have started as early as September 20, 2018," Rutter's said.
Rutter’s recently received a report from a third party suggesting there may have been unauthorized access to data from payment cards that were used at some Rutter’s locations. We launched an investigation, and cybersecurity firms were engaged to assist. We also notified law enforcement.
The attacker used the POS malware to copy card numbers, expiration dates, and internal verification codes from credit cards routed through the compromised payment processing devices (in some cases, cardholder names were also collected).
"However, chip-enabled (EMV) POS terminals are used inside our convenience stores," the notice explains. "EMV cards generate a unique code that is validated for each transaction, and the code cannot be reused."
"As a result, for EMV cards inserted into the chip-reader on the EMV POS devices in our convenience stores, only card number and expiration date (and not the cardholder name or internal verification code) were involved."
Rutter's added that the malware used in the attack didn't copy payment data from all of the cards used at the affected locations and there is no indication that additional customer info was copied by the attacker.
"Payment card transactions at Rutter’s car washes, ATM’s, and lottery machines in Rutter’s stores were not involved," the notice reads.
It is always advisable to review your payment card statements for any unauthorized activity. You should immediately report any unauthorized charges to your card issuer because payment card rules generally provide that cardholders are not responsible for unauthorized charges reported in a timely manner. The phone number to call is usually on the back of your payment card.
Rutter's reminded potentially impacted customers that they can also put a 'security freeze' on their credit file for free to prevent any credit, loans, or other services from being approved in their name without their approval.
In case their info has been misused, Rutter's customers should also file a complaint with the Federal Trade Commission and a police report in case of fraud or identity theft.
Rutter's also set up a dedicated call center at 888-271-9728, available Monday through Friday, from 9:00 am to 9:00 pm for additional questions.
VISA warned in December 2019 that the POS systems of North American fuel dispenser merchants are under an elevated and ongoing threat of being targeted by attacks coordinated by cybercrime groups.
U.S. restaurant and fast-food chains McAlister's Deli, Moe’s Southwest Grill, Schlotzsky’s, Hy-Vee, Krystal, and Landry's also disclosed payment card theft incidents caused by POS malware one after the other starting with October 2019.
A list of all affected Rutter's locations including map locations, addresses, and specific timeframes is available in the table embedded below.
Store Address Timeframe
Rutter’s #58 7680 Lincoln Highway Abbottstown, PA, 17301 Oct 01, 2018 to May 29, 2019
Rutter’s #68 798 West Main Street Annville, PA, 17003 Oct 01, 2018 to May 29, 2019
Rutter’s #56 368 Lewisberry Road New Cumberland, PA, 17070 Oct 01, 2018 to May 29, 2019
Rutter’s #24 2600 Delta Road Brogue, PA, 17309 Oct 01, 2018 to May 29, 2019
Rutter’s #64 1150 Harrisburg Pike Carlisle, PA, 17013 Oct 01, 2018 to May 29, 2019
Rutter’s #66 1455 York Rd Carlisle, PA, 17015 Oct 01, 2018 to May 29, 2019
Rutter’s #65 1391 South Main Street Chambersburg, PA, 17201 Sep 26, 2018 to May 29, 2019
Rutter’s #32 463 West Main Street Dallastown, PA, 17313 Oct 01, 2018 to May 29, 2019
Rutter’s #14 899 North U.S. Route 15 Dillsburg, PA, 17019 Oct 01, 2018 to May 29, 2019
Rutter’s #22 35 East Canal Street Dover, PA, 17315 Oct 01, 2018 to May 29, 2019
Rutter’s #77 77 Benvenue Road Duncannon, PA, 17020 Sep 30, 2018 to May 29, 2019
Rutter’s #71 935 Plank Road Duncansville, PA, 16635 Oct 01, 2018 to May 26, 2019
Rutter’s #79 234 Kuhn Lane Duncansville, PA, 16635 Oct 01, 2018 to May 29, 2019
Rutter’s #17 2115 East Berlin Rd. East Berlin, PA, 17316 Sep 26, 2018 to May 29, 2019
Rutter’s #46 113 Abbottstown Street East Berlin, PA, 17316 Oct 01, 2018 to May 29, 2019
Rutter’s #35 1090 Old Trail Road Etters, PA, 17319 Oct 01, 2018 to May 29, 2019
Rutter’s #53 2215 Old Trail Road Etters, PA, 17319 Oct 01, 2018 to May 29, 2019
Rutter’s #59 69 West Main St. Fawn Grove, PA, 17321 Oct 01, 2018 to May 29, 2019
Rutter’s #5 6837 Lincoln Way East Fayetteville, PA, 17222 Oct 01, 2018 to May 29, 2019
Rutter’s #74 4030 Lincoln Way East Fayetteville, PA, 17222 Oct 01, 2018 to May 29, 2019
Rutter’s #44 6040 Steltz Road Glen Rock, PA, 17327 Oct 01, 2018 to May 29, 2019
Rutter’s #69 100 Grand Street Hamburg, PA, 19526 Oct 01, 2018 to May 29, 2019
Rutter’s #6 1009 York Street Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #33 661 Broadway Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #52 1400 Baltimore Street Hanover, PA, 17331 Oct 01, 2018 to May 29, 2019
Rutter’s #38 700 West Market Street Hellam, PA, 17406 Oct 01, 2018 to May 29, 2019
Rutter’s #27 8210 Derry St Hummelstown, PA, 17036 Oct 01, 2018 to May 29, 2019
Rutter’s #73 5021 Tabler Station Road Inwood, WV, 25428 Oct 01, 2018 to May 29, 2019
Rutter’s #51 35 North Main Street Jacobus, PA, 17407 Oct 01, 2018 to May 29, 2019
Rutter’s #34 370 West Main Street Leola, PA, 17540 Oct 01, 2018 to May 29, 2019
Rutter’s #21 5 South Main Street Manchester, PA, 17345 Oct 01, 2018 to May 29, 2019
Rutter’s #40 1155 River Road Marietta, PA, 17547 Oct 01, 2018 to May 29, 2019
Rutter’s #29 714 West Main Street Mechanicsburg, PA, 17055 Sep 26, 2018 to May 29, 2019
Rutter’s #67 378 North Main Street Mercersburg, PA, 17236 Oct 01, 2018 to May 29, 2019
Rutter’s #20 2800 Vine Street Middletown, PA, 17057 Sep 21, 2018 to Dec 24, 2018
Rutter’s #37 27335 Rt. 75 N Mifflintown, PA, 17059 Oct 01, 2018 to May 29, 2019
Rutter’s #23 3849 Hempland Road Mountville, PA, 17554 Oct 01, 2018 to Apr 05, 2019
Rutter’s #30 2 Broad Street New Freedom, PA, 17349 Oct 01, 2018 to Apr 11, 2019
Rutter’s #9 791 Delta Road Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #28 301 North Main Street Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #48 5 Winterstown Road Red Lion, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #31 1 Airport Road Shippensburg, PA, 17257 Oct 01, 2018 to May 29, 2019
Rutter’s #2 249 N. Main St. Shrewsbury, PA, 17361-1115 Oct 01, 2018 to May 29, 2019
Rutter’s #26 615 South Main Street Shrewsbury, PA, 17361-1713 Oct 01, 2018 to May 29, 2019
Rutter’s #50 420 North Main Street Spring Grove, PA, 17362 Oct 01, 2018 to May 29, 2019
Rutter’s #72 4498 Lincoln Way West St Thomas, PA, 17252 Oct 01, 2018 to May 29, 2019
Rutter’s #42 3 Charles Ave Stewartstown, PA, 17363 Oct 01, 2018 to May 29, 2019
Rutter’s #45 14 West Pennsylvania Avenue Stewartstown, PA, 17363 Oct 01, 2018 to May 29, 2019
Rutter’s #70 405 Historic Drive Strasburg, PA, 17579 Oct 01, 2018 to May 29, 2019
Rutter’s #63 141 South Potomac Street Waynesboro, PA, 17268 Oct 01, 2018 to May 29, 2019
Rutter’s #78 7438 Anthony Highway Waynesboro, PA, 17268 Oct 01, 2018 to May 29, 2019
Rutter’s #39 179 West Main Street Windsor, PA, 17366 Oct 01, 2018 to May 29, 2019
Rutter’s #4 201 Cool Springs Road Wrightsville, PA, 17368 Oct 01, 2018 to May 29, 2019
Rutter’s #1 1099 Haines Rd. York, PA, 17402 Oct 01, 2018 to May 29, 2019
Rutter’s #3 2490 Cape Horn Rd York, PA, 17356 Oct 01, 2018 to May 29, 2019
Rutter’s #7 2251 N George St York, PA, 17402 Sep 26, 2018 to May 29, 2019
Rutter’s #8 129 Leaders Heights Rd. York, PA, 17403 Oct 01, 2018 to May 29, 2019
Rutter’s #10 2115 Bannister Street York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #11 160 North Hills Rd York, PA, 17402 Aug 30, 2018 to May 29, 2019
Rutter’s #12 1425 Seven Valleys Road York, PA, 17408-8871 Sep 20, 2018 to May 29, 2019
Rutter’s #15 2125 Susquehanna Trail York, PA, 17404 Sep 24, 2018 to May 29, 2019
Rutter’s #18 725 Arsenal Road York, PA, 17402 Sep 26, 2018 to May 29, 2019
Rutter’s #25 1520 Pennsylvania Avenue York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #43 1590-B Kenneth Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #47 509 Greenbriar Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #49 2345 Carlisle Road York, PA, 17404 Oct 01, 2018 to May 29, 2019
Rutter’s #54 5305 Susquehanna Trail York, PA, 17406 Oct 01, 2018 to May 29, 2019
Rutter’s #57 1450 Mt. Zion York, PA, 17402 Oct 01, 2018 to May 29, 2019
Rutter’s #60 4425 West Market Street York, PA, 17408 Oct 01, 2018 to May 29, 2019
Rutter’s #16 362 North Main St York (Loganville), PA, 17403 Oct 01, 2018 to May 29, 2019
Rutter’s #36 3050 Heidlersburg Rd York Springs, PA, 17372 Oct 01, 2018 to May 29, 2019
Parallax RAT: Common Malware Payload After Hacker Forums Promotion
16.2.2020 Bleepingcomputer Virus
A remote access Trojan named Parallax is being widely distributed through malicious spam campaigns that when installed allow attackers to gain full control over an infected system.
Since December 2019, security researcher MalwareHunterTeam has been tracking the samples of the Parallax RAT as they have been submitted through VirusTotal and other malware submissions services.
Being offered for as low as $65 a month, attackers have started to heavily use this malware to gain access to a victim's computer to steal their saved login credentials and files or to execute commands on the computer.
The attackers can then use this stolen data to perform identity theft, gain access to online bank accounts, or further spread the RAT to other victims.
Parallax sold on hacker forums
Since early December 2019, the Parallax RAT has been sold on hacker forums where the developers are promoting the software and offering support.
In their pitch to would-be buyers, the "Parallax Team" is promoting their product as having 99% reliability and being suitable for both professionals and beginners.
"Parallax RAT had been developed by a professional team and its fully coded in MASM.
Its created to be best in remote administration. Parallax RAT will provide you all you need.
Suitable for professionals and as well for beginners.
First and most important we offer 99% reliability when it comes to stability.
Parallax was designed to give the user a real multithreaded performance, blazing fast speed and lightweight deployment to your computers with very little resource consumption.
We are a group of developers and we are here to offer quality service.
-Parallax Team, join now!"
Attackers can purchase a one month license to the RAT for as little as $65 or $175 for a three-month license, which provides the following advertised features:
Login credential theft
Remote Desktop capabilities
Upload and download files
Execute remote commands on the infected computer
Encrypted connections
Supports Windows XP through Windows 10.
Standard support
Below you can see an image of the Parallax RAT and the commands that can be executed remotely on victims.
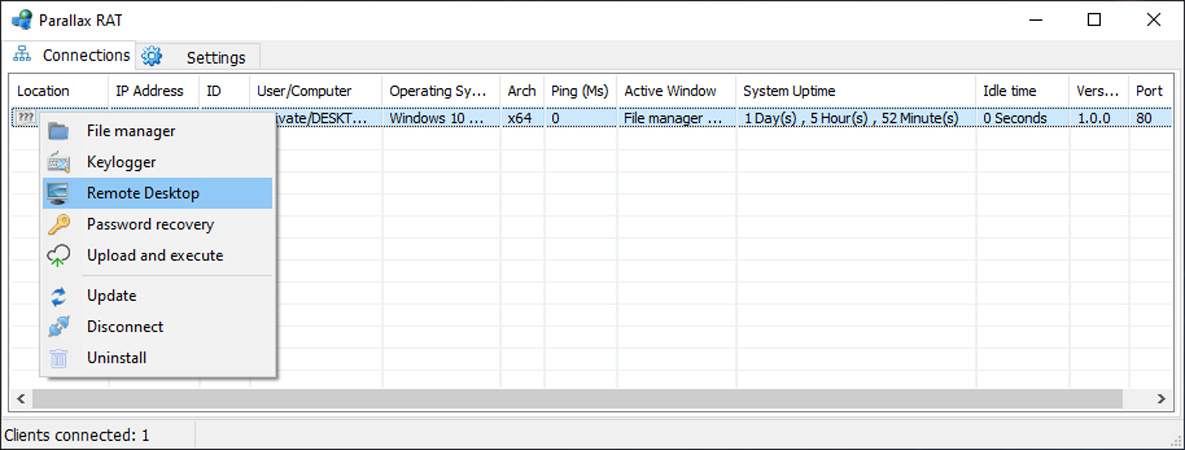
Parallax RAT
The developers also claim that their software can bypass Windows Defender, Avast, AVG, Avira, Eset, and BitDefender, which is not true based on these detections.
Spread via malicious email attachments
While each buyer of the Parallax RAT determines how they will distribute the malware, researchers are commonly seeing it being distributed through spam with malicious attachments.
Security research James has told BleepingComputer that it has become very common to find new spam campaigns with malicious attachments that install Parallax.
For example, the below email pretends to be a company looking to purchase products listed on an attached 'Quote List'.
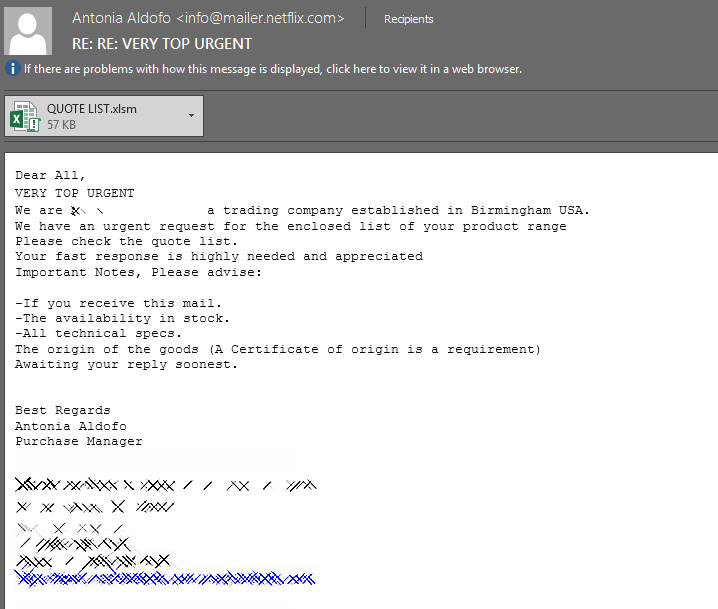
Parallax Spam Campaign
When the attachment is opened, an attempt to exploit the Microsoft Office Equation Editor vulnerability (CVE-2017-11882) will be launched and if the content is enabled, malicious macros will execute to install the RAT.
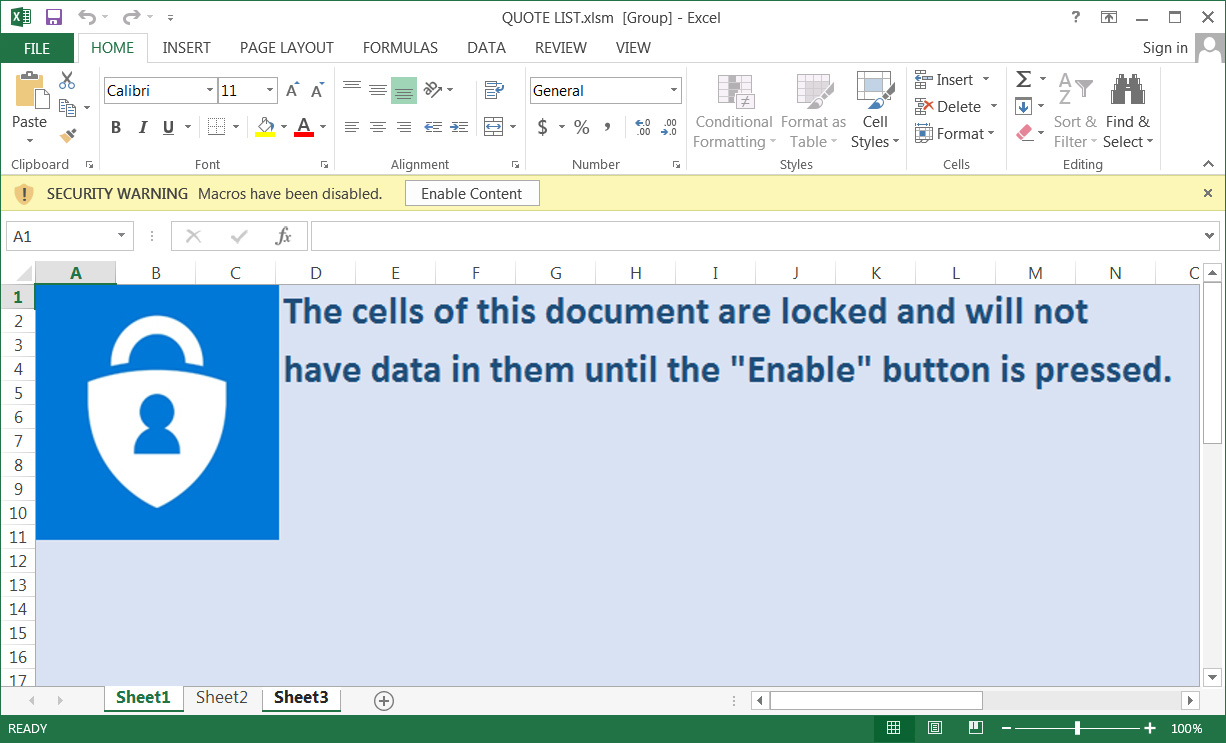
Malicious Parallax attachment
When installing the RAT, attackers are utilizing a variety of methods ranging from intermediary loaders or to directly installing the RAT onto the computer.
For example, both James and Head of SentinelLabs Vitali Kremez have seen a loader downloading an image from the Imgur image sharing site that contains an embedded Parallax executable. This executable is then extracted from the image and launched on the computer.
When executed, the RAT will either be copied to another location and executed or injected into another process.
In a sample analyzed by BleepingComputer, Parallax was injected into the svchost.exe process and in another sample, Kremez saw it injected into cmd.exe.
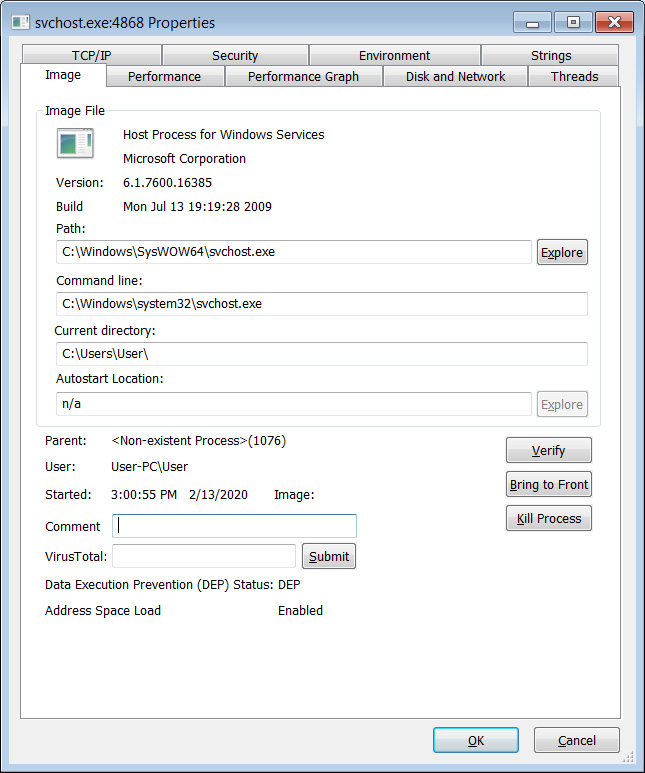
Injected into svchost.exe
Once Parallax is installed, a shortcut to the launcher will be added to the Windows Startup folder so that it is launched automatically when a user logs into the system. In some cases, scheduled tasks will also be created to launch the malware at various intervals.
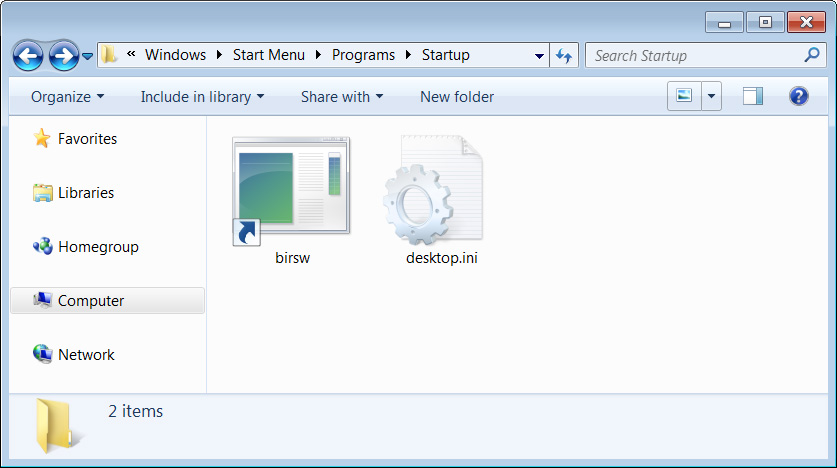
Startup Folder
This allows the attackers to gain persistence on the infected computer and access it whenever they wish.
Now that the attackers have installed the RAT software on the computer, they can use their command and control host to steal the victim's saved passwords, steal files, execute commands, and have full control over the computer.
For many of the Parallax samples, the command & control servers are being hosted on the free dynamic DNS server duckdns.org.
As always, the best defense against this malware is to be wary of any unsolicited emails that you receive that contain attachments. Before opening them, it is best to call the sender to confirm that they sent you the email.
Sextortion Emails Sent by Emotet Earn 10 Times More Than Necurs
16.2.2020 Bleepingcomputer Virus
Sextortion scammers are now targeting potential victims with spam sent to their work emails via the Emotet botnet, a distribution channel 10 times more effective than previous ones according to research published today by IBM X-Force.
Sextortion is a type of email scam first seen in the wild during July 2018 when crooks started emailing potential targets and claiming that they have them recorded on video while browsing adult sites.
To increase their scams messages' credibility, in some cases the scammers also include the victims' passwords leaked with the email addresses as part of a data breach dump.
Attacking victims at work
The new Emotet-powered sextortion campaigns are over 10 times more effective than previous campaigns that were using the Necurs botnet to deliver spam to victims' inboxes.
This drastic increase in effectiveness is due to the way Emotet works and the difference in 'currency' asked by sextortion spam emails delivered via the two botnets.
"First, Emotet infects users at work, versus Necurs, which typically goes to people’s webmail addresses," the researchers explain.
"Getting an extortion email at work might be placing a lot more pressure on recipients; if they fall for the scam, they must pay up before their employers get caught in the crosshairs."
Secondly, Emotet asks for Bitcoin ransoms, a cryptocurrency that carries a higher value than the Dashcoins Necurs spam demands.
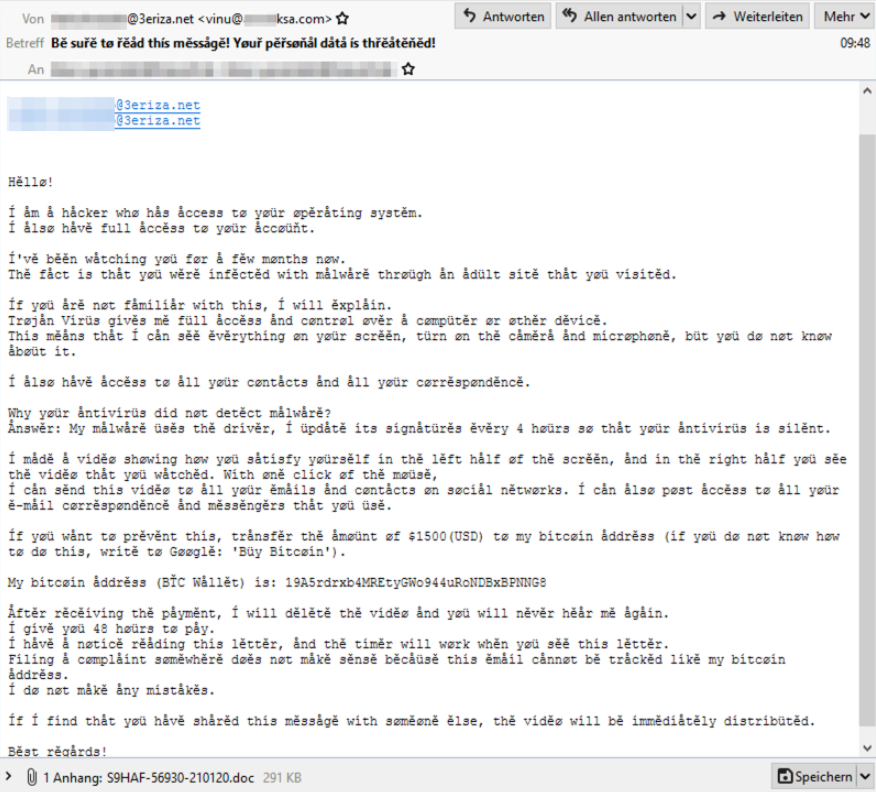
Emotet sextortion email sample (IBM X-Force)
Emotet boosts sextortion conversion rates
In the end, it is all about conversion rate percentages when it comes to choosing scam distribution channels and, in the case of Emotet, scammers to have hit the proverbial jackpot.
"With classic botnet spam, those percentages can be rather low. With targeted spam on already compromised assets, that’s almost a guaranteed infection," the report adds.
The week-long sextortion campaign that used the Emotet botnet for dissemination was able to collect almost $60,000 from victims by targeting people in their workplace and using the fear of putting their careers at risk to trick them into paying the ransom.
This campaign funneled roughly $57,000 into the 24 different Bitcoin wallets used by the threat actors between January 23 and January 28, 2020.
In comparison, a seven-week long sextortion campaign that used the Necurs botnet — distributing sextortion email scams since November 2018 — and ended on December 3, 2019, was only able to collect $4,527 worth of Dashcoin.
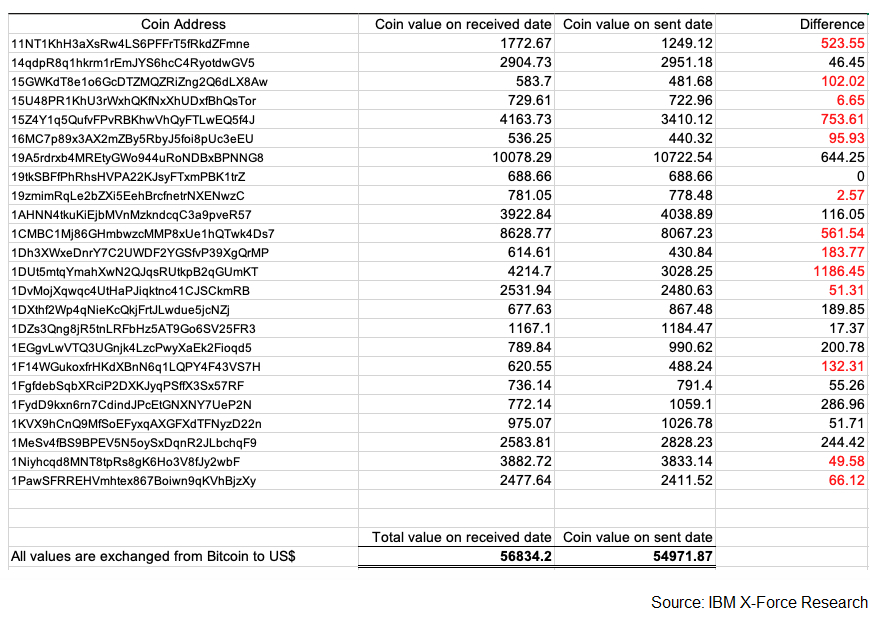
Emotet sextortion campaign wallets (IBM X-Force)
"The new campaigns in which Emotet extorts email recipients do not end with the payment — they continue to infect the victim with the Emotet Trojan," the researchers also found.
"It is likely that this campaign tool is part of what Emotet sells to other gangs, enabling them to use its infrastructure for cybercriminal activities."
The Emotet operators have also started delivering extortion spam since January 2020, claiming that the targets' data was stolen and dropping the Emotet Trojan using a malicious Microsoft Office document that supposedly contains further instructions.
Increased Emotet activity since January
More recently, an Emotet Trojan sample spotted by researchers at Binary Defense has added a Wi-Fi worm module allowing the malware to spread to new victims connected to nearby insecure Wi-Fi networks.
Based on binary timestamps, it's possible that the malware has been infecting victims via wireless networks unnoticed during the last two years.
Emotet has also been observed while using the recent Coronavirus health crisis as a lure as part of a malspam campaign targeting Japan with malware payloads.
The Trojan ranked first in a 'Top 10 most prevalent threats' compiled by interactive malware analysis platform Any.Run in late December, with triple the number of uploads when compared to all other malware included in the top.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert on increased targeted Emotet malware attacks during late-January urging users and admins to review the Emotet Malware alert for detailed guidance.
CISA recommends taking the following measures to mitigate Emotet attacks:
• Block email attachments commonly associated with malware (e.g.,.dll and .exe).
• Block email attachments that cannot be scanned by antivirus software (e.g., .zip files).
• Implement Group Policy Object and firewall rules.
• Implement an antivirus program and a formalized patch management process.
• Implement filters at the email gateway, and block suspicious IP addresses at the firewall.
• Adhere to the principle of least privilege.
• Implement a Domain-Based Message Authentication, Reporting & Conformance (DMARC) validation system.
• Segment and segregate networks and functions.
• Limit unnecessary lateral communications.
Microsoft Urges Exchange Admins to Disable SMBv1 to Block Malware
16.2.2020 Bleepingcomputer Virus
Microsoft is advising administrators to disable the SMBv1 network communication protocol on Exchange servers to provide better protection against malware threats and attacks.
Since 2016, Microsoft has been recommending that administrators remove support for SMBv1 on their network as it does not contain additional security enhancements added to later versions of the SMB protocol.
These enhancements include encryption, pre-authentication integrity checks to prevent man-in-the-middle (MiTM) attacks, insecure guest authentication blocking, and more.
In a new post to the Microsoft Tech Community, the Exchange Team is urging admins to disable SMBv1 to protect their servers from malware threats such as TrickBot and Emotet.
"To make sure that your Exchange organization is better protected against the latest threats (for example Emotet, TrickBot or WannaCry to name a few) we recommend disabling SMBv1 if it’s enabled on your Exchange (2013/2016/2019) server.
There is no need to run the nearly 30-year-old SMBv1 protocol when Exchange 2013/2016/2019 is installed on your system. SMBv1 isn’t safe and you lose key protections offered by later SMB protocol versions. If you want to learn more about SMBv1 and why you should stop using it, I’d recommend reading this blog post published and updated by Ned Pyle."
In 2017, various exploits created by the NSA were released that exploited the SMBv1 protocol to execute commands on vulnerable servers with administrative privileges.
Some of these vulnerabilities, such as EternalBlue and EternalRomance, were soon utilized by malware such as TrickBot, Emotet, WannaCry, Retefe, NotPetya, and the Olympic Destroyer to spread to other machines and either perform destructive acts or steal login credentials.
Due to the inherent security risks exposed by the nearly 30-year old SMBv1 protocol, it is advised that it be disabled on the network and security risks from malware, targeted attacks, and just the
Checking if SMBv1 is enabled
Since Windows 10 version 1709 and Windows Server version 1709, SMBv1 is no longer installed in the operating system by default. Newer versions of the Windows operating systems are using SMBv3.
To check if SMBv1 is enabled on a Windows server, you can execute the following PowerShell commands for your version of Windows Server.
Windows Server 2008 R2: By default, SMBv1 is enabled in Windows Server 2008 R2. Therefore, if the following command does not return an SMB1 value or an SMB1 value of 1, then it is enabled. If it returns an SMB1 value of 0, it is disabled.
Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters | ForEach-Object {Get-ItemProperty $_.pspath}
Windows Server 2012: If the command returns false, SMBv1 is not enabled.
Get-SmbServerConfiguration | Select EnableSMB1Protocol
Windows Server 2012 R2 or higher: If the command returns false, SMBv1 is not enabled.
(Get-WindowsFeature FS-SMB1).Installed
Get-SmbServerConfiguration | Select EnableSMB1Protocol
How to disable SMBv1
If SMBv1 is enabled on your server, you can disable it using the following commands.
Windows Server 2008 R2:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" -Name SMB1 -Type DWORD -Value 0 –Force
Windows Server 2012:
Set-SmbServerConfiguration -EnableSMB1Protocol $false -force
Windows Server 2012 R2 or higher:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Emotet Hacks Nearby Wi-Fi Networks to Spread to New Victims
9.2.2020 Bleepingcomputer Virus
A recently spotted Emotet Trojan sample features a Wi-Fi worm module that allows the malware to spread to new victims connected to nearby insecure wireless networks according to researchers at Binary Defense.
This newly discovered Emotet strain starts the spreading process by using wlanAPI.dll calls to discover wireless networks around an already infected Wi-Fi-enabled computer and attempting to brute-force its way in if they are password protected.
Once it successfully connects the compromised device to another wireless network, the worm will start finding other Windows devices with non-hidden shares.
Next, it scans for all accounts on those devices and tries to brute-force the password for the Administrator account and all the other users it can retrieve.
After successfully breaking into an account, the worm drops a malicious payload in the form of the service.exe binary onto the victim's computer and installs a new service named "Windows Defender System Service" to gain persistence on the system.

Emotet infection over Wi-Fi (Binary Defense)
Wi-Fi spreader flew under the radar
One of the binaries Emotet uses to spread to infect other devices over Wi-Fi is worm.exe, with the sample analyzed by Binary Defense having a 04/16/2018 timestamp.
"The executable with this timestamp contained a hard-coded IP address of a Command and Control (C2) server that was used by Emotet," BinaryDefense explains. "This hints that this Wi-Fi spreading behavior has been running unnoticed for close to two years."
"This may be in part due to how infrequently the binary is dropped. Based on our records, 01/23/2020 was the first time that Binary Defense observed this file being delivered by Emotet, despite having data going back to when Emotet first came back in late August of 2019."
This Emotet worm module not being discovered during the last two years despite researchers dissecting new strains on a daily basis might also be explained by the module not displaying spreading behavior on VMs/automated sandboxes without a Wi-Fi card.
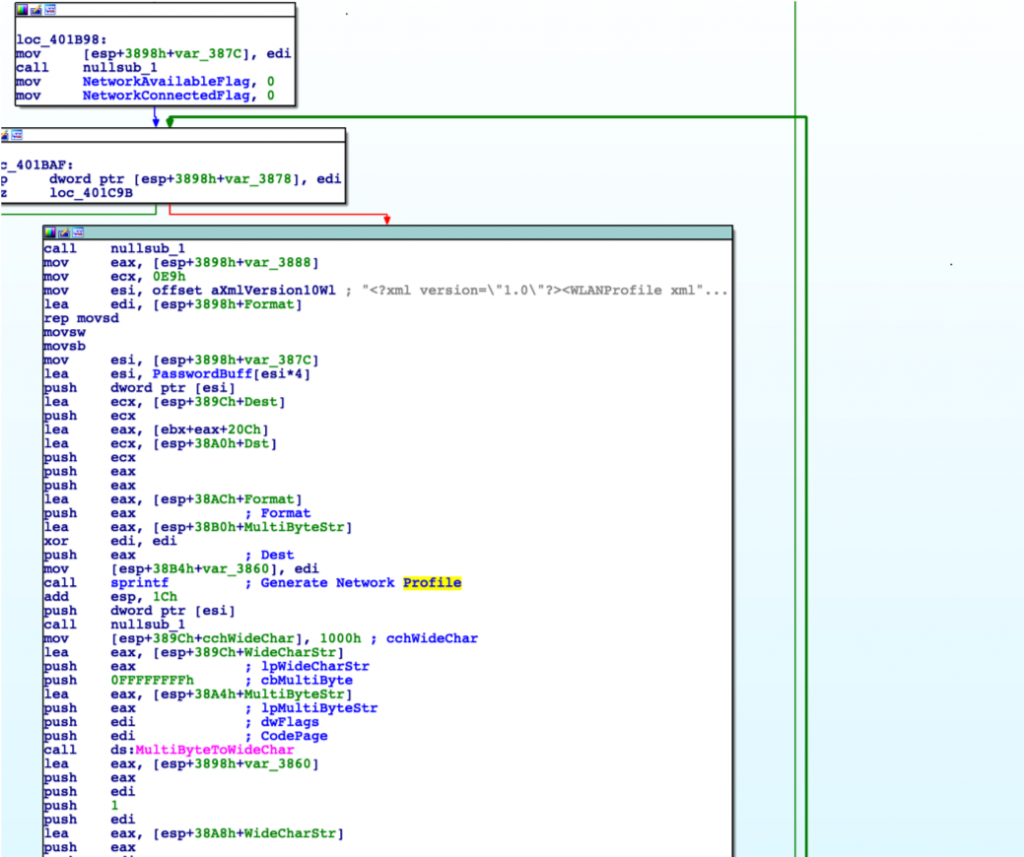
Network profile generation logic (Binary Defense)
The other executable the Trojan uses for Wi-Fi spreading is service.exe, a binary we already mentioned above which also features a peculiarity of its own: while it uses the Transport Layer Security (TLS) port 443 for command and control (C2) server communications, it will actually connect over unencrypted HTTP.
"Previously thought to only spread through malspam and infected networks, Emotet can use this loader-type to spread through nearby wireless networks if the networks use insecure passwords," Binary Defense concludes.
"Binary Defense’s analysts recommend using strong passwords to secure wireless networks so that malware like Emotet cannot gain unauthorized access to the network."
Emotet is a huge threat
Computers infected with Emotet are used by its operators to spread to other victims over Wi-Fi, to deliver malicious spam messages to other targets, and to drop other malware strains including the Trickbot info stealer Trojan known for also delivering ransomware payloads.
The Emotet Trojan ranked first in a 'Top 10 most prevalent threats' drawn up by interactive malware analysis platform Any.Run in late December, with triple the number of uploads for analysis when compared to the next malware family in their top, the Agent Tesla info-stealer.
The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning on increased activity related to targeted Emotet attacks roughly two weeks ago, advising admins and users to review the Emotet Malware alert for guidance.
If you want to find out more about the latest active Emotet campaigns you should follow the Cryptolaemus group, a collective of security researchers who are tracking this malware's activity.
Oscar Nominated Movies Featured in Phishing, Malware Attacks
9.2.2020 Bleepingcomputer Phishing Virus
Attackers are exploiting the hype surrounding this year's Oscar Best Picture nominated movies to infect fans with malware and to bait them to phishing websites designed to steal sensitive info such as credit card details and personal information.
This method is the perfect way to get around movie fans' defenses seeing that many of them are willing to take down their defenses for a chance to get a free preview, especially given that the 92nd Academy Awards ceremonies are just around the corner on February 9th.
High-profile TV shows and films are frequently used as lures in social engineering attacks promising early previews either in the form of fake streaming sites or via malicious files disguised as early released copies.
Over 20 phishing sites use Oscar baits
Kaspersky researchers who discovered these ongoing attacks "found more than 20 phishing websites and 925 malicious files that were presented as free movies, only to attack the user."
"The uncovered phishing websites and Twitter accounts gather users’ data and prompt them to carry out a variety of tasks in order to gain access to the desired film," a press release published today says.
"These can vary from taking a survey and sharing personal details, to installing adware or even giving up credit card details. Needless to say, at the end of the process, the user does not get the content."
To promote their malicious sites, the attackers make use of Twitter accounts that share links to streaming websites that promise access to the movies for free or for a small fee. 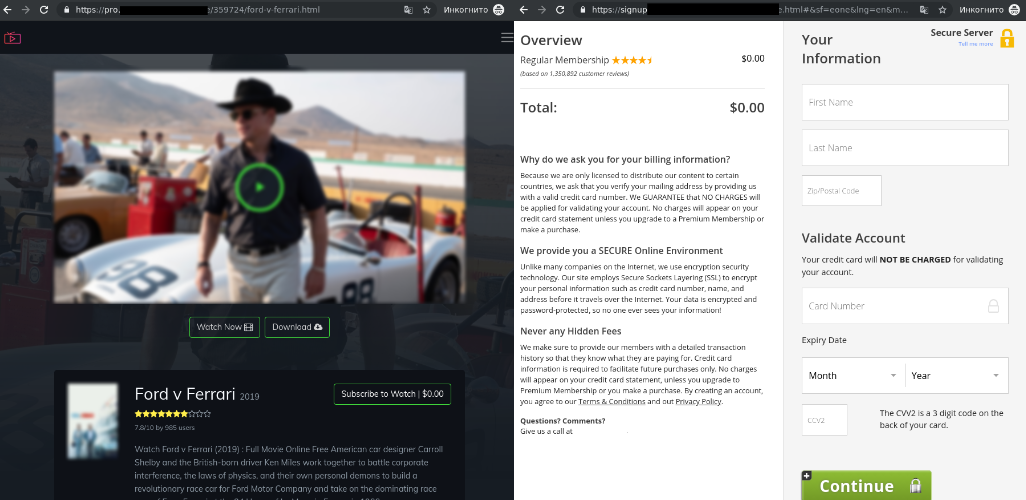
Phishing site asking for credit card info (Kaspersky)
The researchers also discovered that 'Joker' was the most popular movie to use as a malware lure among threat actors with over 300 malicious files being camouflaged as a Joker preview.
"‘1917’ was second in this rating with 215 malicious files, and 'The Irishman' was third with 179 files. Korean film 'Parasite' did not have any malicious activity associated with it," Kaspersky also found.
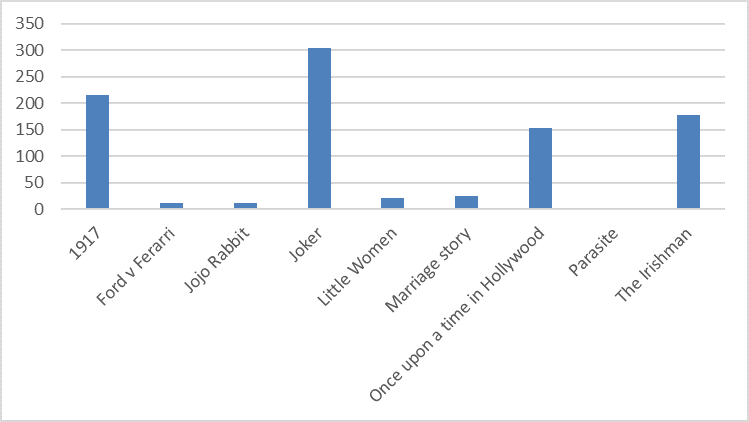
Number of malicious files using nominated films as a lure (Kaspersky)
Movie fans urged to proceed with caution
"Cybercriminals aren’t exactly tied to the dates of film premieres, as they are not really distributing any content except for malicious data," Kaspersky malware analyst Anton Ivanov said.
"However, as they always prey on something when it becomes a hot trend, they depend on users’ demand and actual file availability.
To avoid being tricked by criminals, stick to legal streaming platforms and subscriptions to ensure you can enjoy a nice evening in front of the TV without having to worry about any threats."
To dodge incoming attacks that camouflage malware as Oscar Best Picture Nominees or use them as phishing bait, Kaspersky recommends movie fans to follow these guidelines:
• Pay attention to the official movie release dates in theaters, on streaming services, TV, DVD, or other sources
• Don’t click on suspicious links, such as those promising an early view of a new film; check movie release dates in theaters and keep track of them
• Look at the downloaded file extension. Even if you are going to download a video file from a source you consider trusted and legitimate, the file should have a .avi, .mkv or .mp4 extension, or other video formats; definitely not .exe
• Check the website’s authenticity. Do not visit websites allowing you to watch a movie until you are sure that they are legitimate and start with https. Confirm that the website is genuine, by double-checking the format of the URL or the spelling of the company name, reading reviews about it and checking the domain’s registration data before starting downloads
• Use a reliable security solution, such as Kaspersky Security Cloud, for comprehensive protection from a wide range of threats
More information about the adoption of Oscar best picture nominees as a phishing bait based on their theatrical or Netflix release is available in Kaspersky's press release.
Bitbucket Abused to Infect 500,000+ Hosts with Malware Cocktail
9.2.2020 Bleepingcomputer Virus
Attackers are abusing the Bitbucket code hosting service to store seven types of malware threats used in an ongoing campaign that has already claimed more than 500,000 business computers across the world.
Systems falling victim to this attack would get infected with multiple payloads that steal data, mine for cryptocurrency, and culminate with delivering STOP ransomware.
Commodity malware and easy tricks
Cybercriminals do not shy away from using legitimate online storage platforms like GitHub, Dropbox, or Google Drive since a connection to one of these services looks less suspicious.
For this campaign, the attackers use several Bitbucket accounts to host commodity malware that receives frequent updates, security researchers from cybersecurity Cybereason discovered. The payloads deployed to victim systems are the following:
Predator: information stealer, focuses on credentials from browsers, uses the camera to take pictures, takes screenshots, and steals cryptocurrency wallets
Azorult: information stealer with backdoor capabilities that pilfers passwords, email logins, cookies, browser history, IDs, and cryptocurrencies
Evasive Monero Miner: dropper for a multi-stage XMRig miner for Monero cryptocurrency that integrates evasion techniques
STOP Ransomware: ransomware based on open-source code; it also acts as a malware dropper for other threats
Vidar: information stealer that targets browser cookies and history, digital wallets, and two-factor authentication data; it can take screenshots
Amadey bot: a simple trojan bot mainly used for reconnaissance
IntelRapid: cryptocurrency stealer that targets multiple types of cryptocurrency wallets
Regular updates, the use of Themida as a packer, and the CypherIT Autoit packer help keep all this malware undetected and offer some protection against analysis.
Dropping multiple payloads on a single system allows the attacker to pursue multiple avenues to secure their revenue stream, especially when compromised systems are part of a corporate network.
Payloads downloaded thousands of times
According to research Cybereason published today, the targets are users looking for cracked versions of commercial software, "Adobe Photoshop, Microsoft Office, and others."
The bait programs include Azorult and Predator the Thief infostealers, with the former collecting the data it was built to loot and the latter establishing a connection to Bitbucket to funnel in more malware.
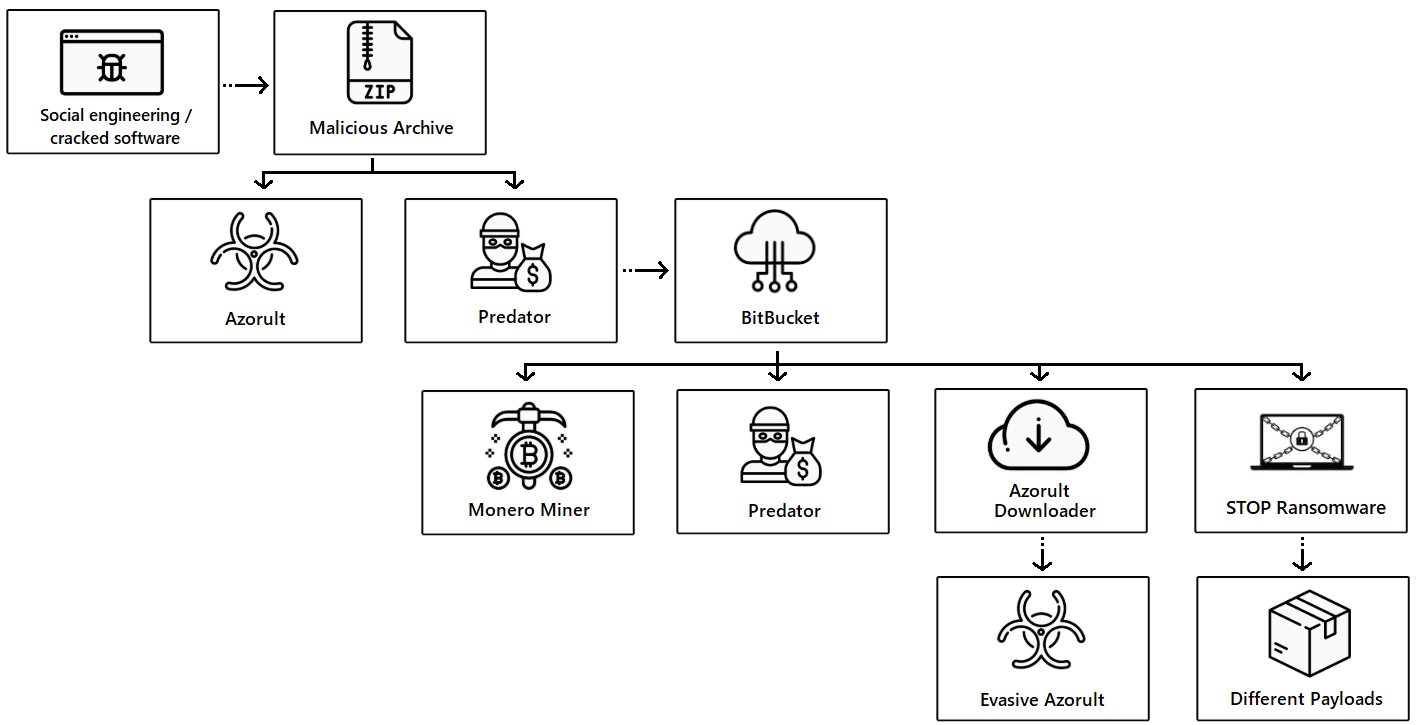
Looking at three Bitbucket repositories linked to each other by the same malware strains with the same names, the researchers noticed that sometimes the threat actor added updates as often as three hours.
In some of the accounts, the download count for some of the malware was in the tens of thousands.
The researchers estimate that more than 500,000 machines have been infected during this campaign, hundreds of them being compromised every hour.
Exhausting all money-making opportunities from a compromised host is a practice cybercriminals have exercised for a long time. Information can be sold on underground forums, cryptocurrency wallets can be depleted, and miners can mint digital coins.
When there is nothing to steal from the infected system, attackers deploy ransomware for one last attempt to make a profit. In this case, however, STOP ransomware can also download other malware, prolonging the compromise.
Emotet Gets Ready for Tax Season With Malicious W-9 Forms
9.2.2020 Bleepingcomputer Virus
The Emotet Trojan is getting ready for the tax season with a fresh spam campaign pretending to be signed W-9 tax forms.
Whether it is holiday party invites, invites to climate change protests, or even information about the Coronavirus, the operators of the Emotet Trojan are known to stay on top of current and upcoming events and tailor their spam emails accordingly.
This is the case with a new campaign discovered by email security company Cofense, where the Emotet operators are sending spam pretending to be a requested signed W-9 tax form.
With 2019 behind us, accounting departments are starting to issue tax forms needed for preparing the 2019 tax returns. As part of this process, companies request a signed W-9 form from their clients, independent contractors, and other people they do business.
With there always being something to do, it is common for a person to sign a W-9 form and quickly shoot it back to the company in a brief email.
This new Emotet spam campaign captures this feeling perfectly by using brief emails with a simple "Please see attached" and a fake W-9.doc attachment.
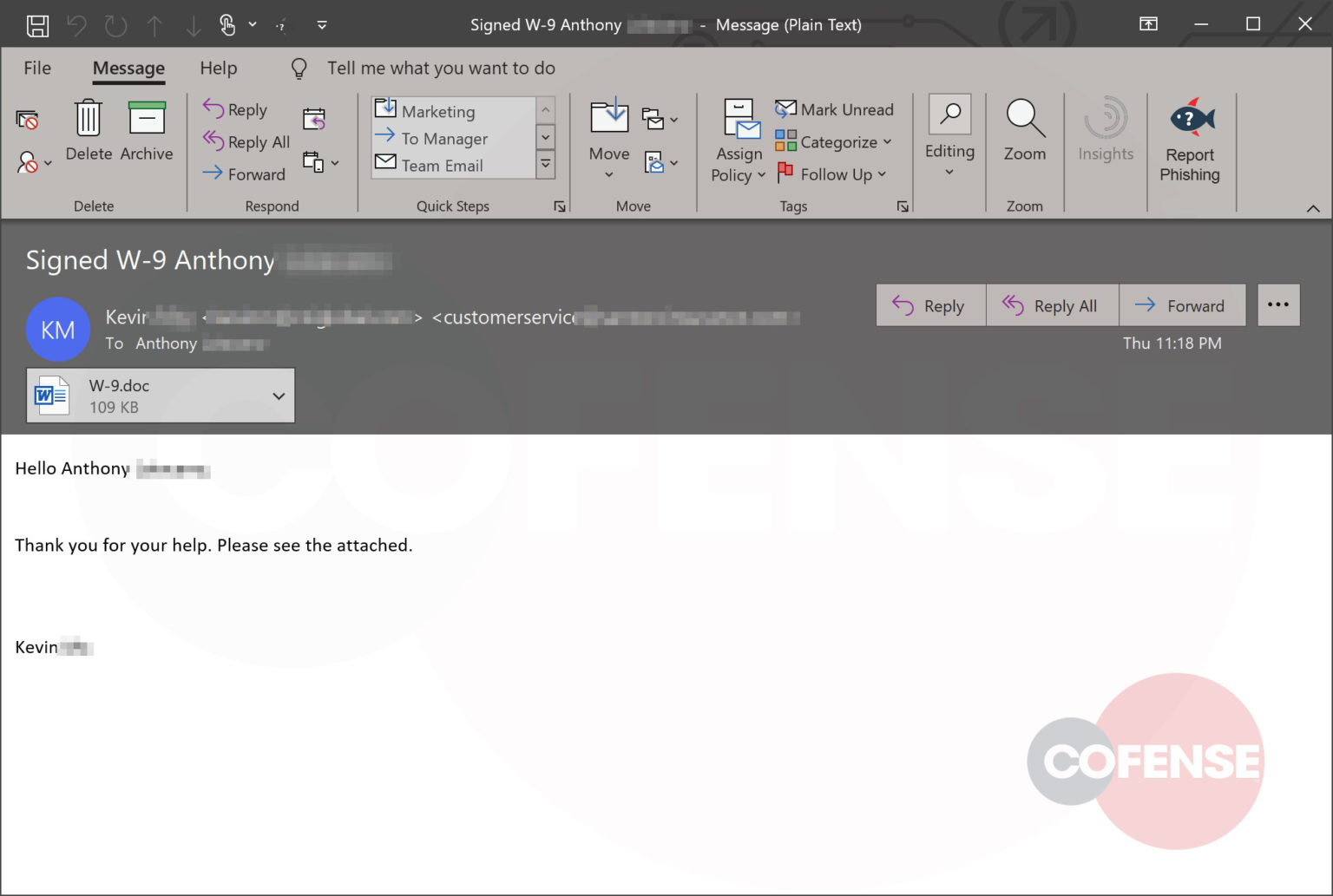
Spam email pretending to be Signed W-9
When a recipient opens the attachment, they will be greeted with the standard Emotet malicious Word document template that states the user needs to 'Enable Content' to properly view it.
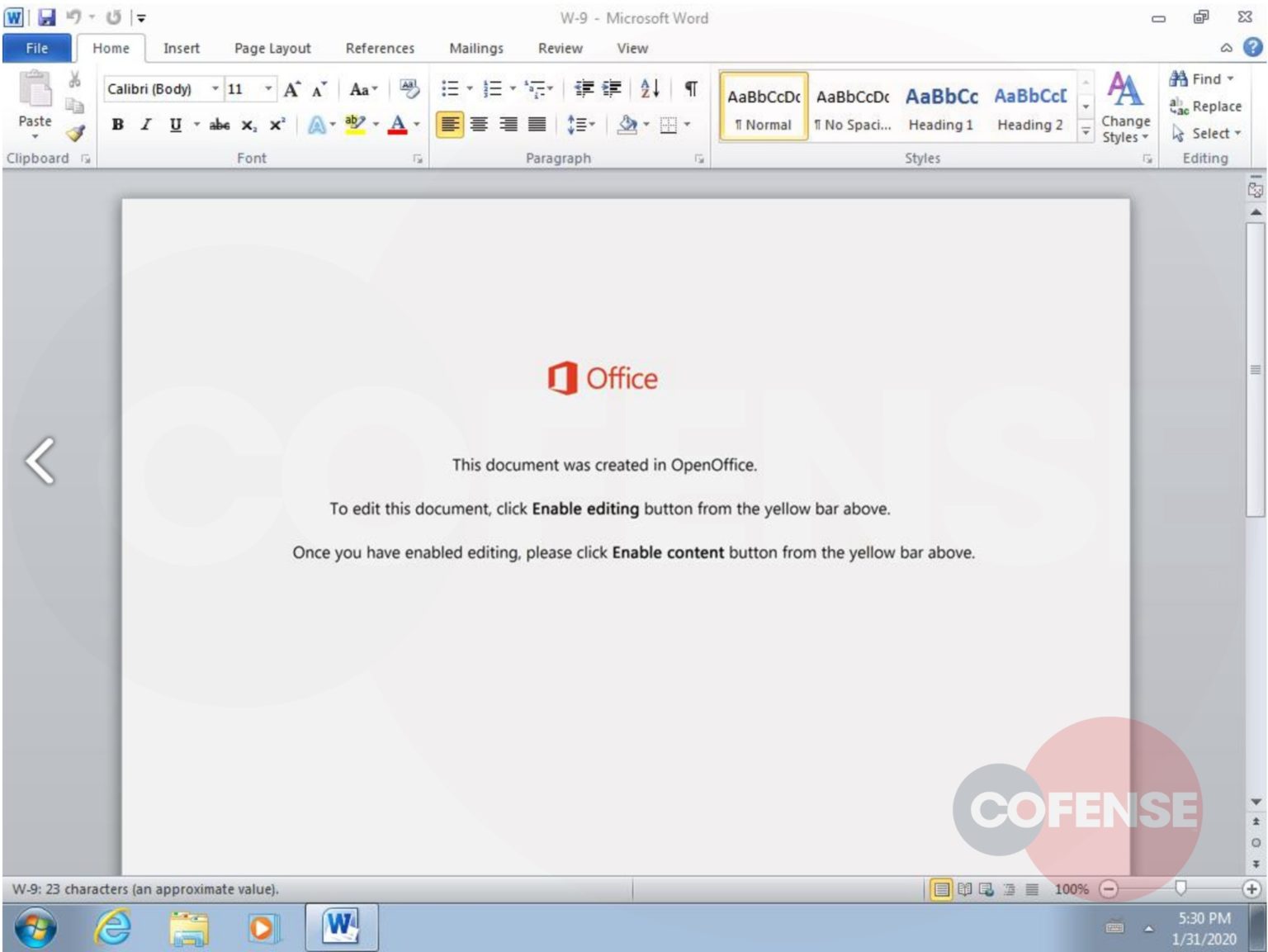
Emotet Word Document
Once enabled, though, malicious macros will fire off that launches a PowerShell command to install and execute the Emotet trojan on the recipient's computer.
This spam campaign is not particularly sophisticated, but Cofense believes that these campaigns will get more sophisticated as we get further into the tax season.
"While this tax season is just getting started, with many tax filing forms due to taxpayers last week, by Jan 31st, we anticipate these campaigns will likely evolve and get better as we move towards the annual filing date of April 15th," Cofense states in their report.
Emotet is a major threat
When installed, Emotet not only uses an infected computer to send out more spam but also downloads other malware onto the computer.
One of the most downloaded payloads is the TrickBot Trojan, which will attempt to steal saved login credentials, cookies, and other data from the network.
For some networks, it will eventually also open a connection back to the actors behind the Ryuk Ransomware who will then attempt to encrypt the entire network.
For this reason, if you become infected with Emotet, it is important to catch it early before it can download any other malware.
This week, the Japan CERT released a new tool called EmoCheck that lets you easily check if a computer is infected with Emotet.
EmoCheck detecting Emotet
If you suspect at all that a user opened an Emotet Word doc and enabled macros, it is strongly suggest that you use EmoCheck to check if the computer is infected.
If it is, you then perform a thorough analysis of the computer to make sure no other malware has been download and whether it has spread to other computers.
New EmoCheck Tool Checks if You're Infected With Emotet
8.2.2020 Bleepingcomputer Virus
A new utility has been released by Japan CERT (computer emergency response team) that allows Windows users to easily check if they are infected with the Emotet Trojan.
The Emotet Trojan is one of the most actively distributed malware that is spread through phishing emails with malicious Word document attachments.
These emails pretend to be invoices, shipping notices, account reports, holiday party invites, and even information about the Coronavirus in the hopes that you will be enticed, or tricked, into opening the attachment.
Emotet Christmas Party Invite
Once installed, Emotet will utilize the infected computer to send further spam to potential victims and also download other malware onto the computer.
Emotet is particularly dangerous as it commonly downloads and installs the Trickbot banking Trojan, which steals saved credentials, cookies, browser history, SSH keys, and more while it attempts to spread to other computers on the network.
If the network is of high-value, TrickBot will also open a reverse shell back to the Ryuk Ransomware operators who will encrypt the network as a final payload.
Due to its severity, it is important that victims quickly find and remove the Emotet Trojan before it can download and install other malware onto an infected computer.
Using EmoCheck to check for the Emotet Trojan
When Emotet is installed by a malicious attachment, it will be stored in a semi-random folder under %LocalAppData%.
It is semi-random because it will not use random characters, but rather a folder name built out of two keywords from the following list:
duck, mfidl, targets, ptr, khmer, purge, metrics, acc, inet, msra, symbol, driver, sidebar, restore, msg, volume, cards, shext, query, roam, etw, mexico, basic, url, createa, blb, pal, cors, send, devices, radio, bid, format, thrd, taskmgr, timeout, vmd, ctl, bta, shlp, avi, exce, dbt, pfx, rtp, edge, mult, clr, wmistr, ellipse, vol, cyan, ses, guid, wce, wmp, dvb, elem, channel, space, digital, pdeft, violet, thunk
As you can see below, Emotet was installed under the 'symbolguid' folder. which is a combination of two of the keywords from the list above.
The Emotet Trojan
To check if you are infected with Emotet, you can download the EmoCheck utility from the Japan CERT GitHub repository.
Once downloaded, extract the zip file and double-click on the emocheck_x64.exe (64-bit version) or emocheck_x86.exe (32-bit version) depending on what you downloaded.
Once running, EmoCheck will scan for the Emotet Trojan and alert you if it is found, what process ID it is running under, and the location of the malicious file.

EmoCheck Output
This information will also be saved to a log file located at [path of emocheck.exe]\yyyymmddhhmmss_emocheck.txt.
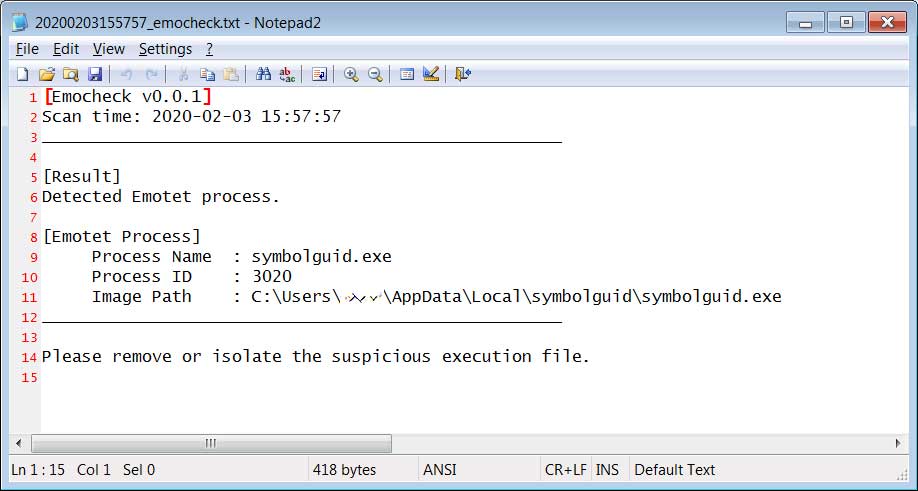
EmoCheck Log File
If you run EmoCheck and discover that you are infected, you should immediately open Task Manager and terminate the listed process.
You should then scan your computer with reputable antivirus software to make sure other malware has not already been downloaded and installed onto the computer.
This tool could also be useful for network administrators to use as part of a login script to quickly find machines that have been infected with Emotet to prevent a full-blown ransomware attack.
Winnti Group Infected Hong Kong Universities With Malware
2.2.2020 Bleepingcomputer CyberCrime Virus
Computer systems at two Hong Kong universities were compromised in a Winnti Group campaign according to ESET researchers, during the Hong Kong protests that started in March 2019.
The attacks were discovered in November 2019 after the security firm's Augur machine-learning engine detected ShadowPad launcher malware samples on multiple devices at the two universities, following previous Winnti malware infections detected two weeks earlier, in October.
These attacks were highly targeted since the Winnti malware and the multimodular Shadowpad backdoor both featured command and control URLs and campaign identifiers related to the names of the impacted universities.
"The campaign identifiers found in the samples we’ve analyzed match the subdomain part of the C&C server, showing that these samples were really targeted against these universities," ESET said.
Winnti Group artifacts and TTPs (ESET)
Three other universities also targeted
Based on the malware used in the attacks — the info stealing focused ShadowPad backdoor — the attackers' end goal was to collect and steal info from the compromised computers.
The ShadowPad variant discovered on the universities' infected devices features keylogging and screen-capture capabilities, provided to the malware by two of the 17 modules it comes with.
The use of a keylogger module enabled by default is a clear indication that the threat actors were interested in stealing info from their victims’ computers according to the researchers. "In contrast, the variants we described in our white paper didn’t even have that module embedded."
During this campaign, ShadowPad's launcher was replaced by the Winnti Group attackers with a simpler one that wasn't obfuscated with VMProtec and it used XOR-encryption rather than the typical RC5 key block encryption algorithm.
ESET research
@ESETresearch
#ESETresearch uncovered a new campaign of the #Winnti Group targeting #HongKong universities with ShadowPad and Winnti. @mathieutartare https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/ … 1/3 pic.twitter.com/d57V1rhBR1
65
11:30 AM - Jan 31, 2020
Twitter Ads info and privacy
54 people are talking about this
ESET thinks that three other Hong Kong universities were targeted in the same series of attacks by the Winnti Group threat actors.
"In addition to the two compromised universities, thanks to the C&C URL format used by the attackers we have reasons to think that at least three additional Hong Kong universities may have been compromised using these same ShadowPad and Winnti variants," ESET researcher Mathieu Tartare explained.
Winnti Group rundown
The Winnti Group is an umbrella term used as the name of a collective of Chinese state-backed hacking groups (tracked as Blackfly and Suckfly by Symantec, Wicked Panda by CrowdStrike, BARIUM by Microsoft, APT41 by FireEye) sharing the same malicious tools that have been in use since around 2011.
That is when Kaspersky researchers found the hackers' Winnti Trojan on a massive number of compromised gaming systems after being deployed via a game's official update server.
Kaspersky also uncovered evidence connecting the methods used by Winnti Group to compromise ASUS' LiveUpdate during Operation ShadowHammer with the ones utilized in other supply-chain attacks including NetSarang and CCleaner from 2017.
Winnti Group updated their arsenal with the new modular PortReuse Windows backdoor they later used to compromise the servers of a high-profile Asian mobile software and hardware manufacturer, as ESET found in 2019.
Microsoft Detects New TA505 Malware Attacks After Short Break
2.2.2020 Bleepingcomputer CyberCrime Virus
Microsoft says that an ongoing TA505 phishing campaign is using attachments featuring HTML redirectors for delivering malicious Excel documents, this being the first time the threat actors have been seen adopting this technique.
The new campaign is detailed in a series of tweets from the Microsoft Security Intelligence account, with the researchers saying that the final payload is being dropped using an Excel document that bundles a malicious macro.
TA505 (also tracked SectorJ04) is a financially motivated cybercrime group active since at least Q3 2014 [1, 2] known for focusing on attacks against retail companies and financial institutions via large-sized malicious spam campaigns driven by the Necurs botnet.
This threat actor distributed remote access Trojans (RATs) and malware downloaders that delivered the Dridex and Trick banking Trojans as secondary payloads, as well as Locky, BitPaymer, Philadelphia, GlobeImposter, Jaff ransomware strains on their targets' computers. [1, 2]
Kafeine from ProofPoint told BleepingComputer that the switch to HTML attachments occurred in the middle of January 2020.
Image: Kafeine at ProofPoint
TA505 back from vacation
"The new campaign uses HTML redirectors attached to emails. When opened, the HTML leads to the download a malicious macro-laden Excel file that drops the payload," Microsoft Security Intelligence's researchers explain. "In contrast, past Dudear email campaigns carried the malware as an attachment or used malicious URLs."
As mentioned in the beginning, this campaign also marks the adoption of HTML redirectors as this is the first time Microsoft observed this technique being used by TA505 as part of their attacks.
Past email campaigns distributing the malware would deliver the payload onto the victim's computer within the attachment or via malicious download URLs.
The phishing messages come with HTML attachments which will automatically start downloading the Excel file used to drop the payload.
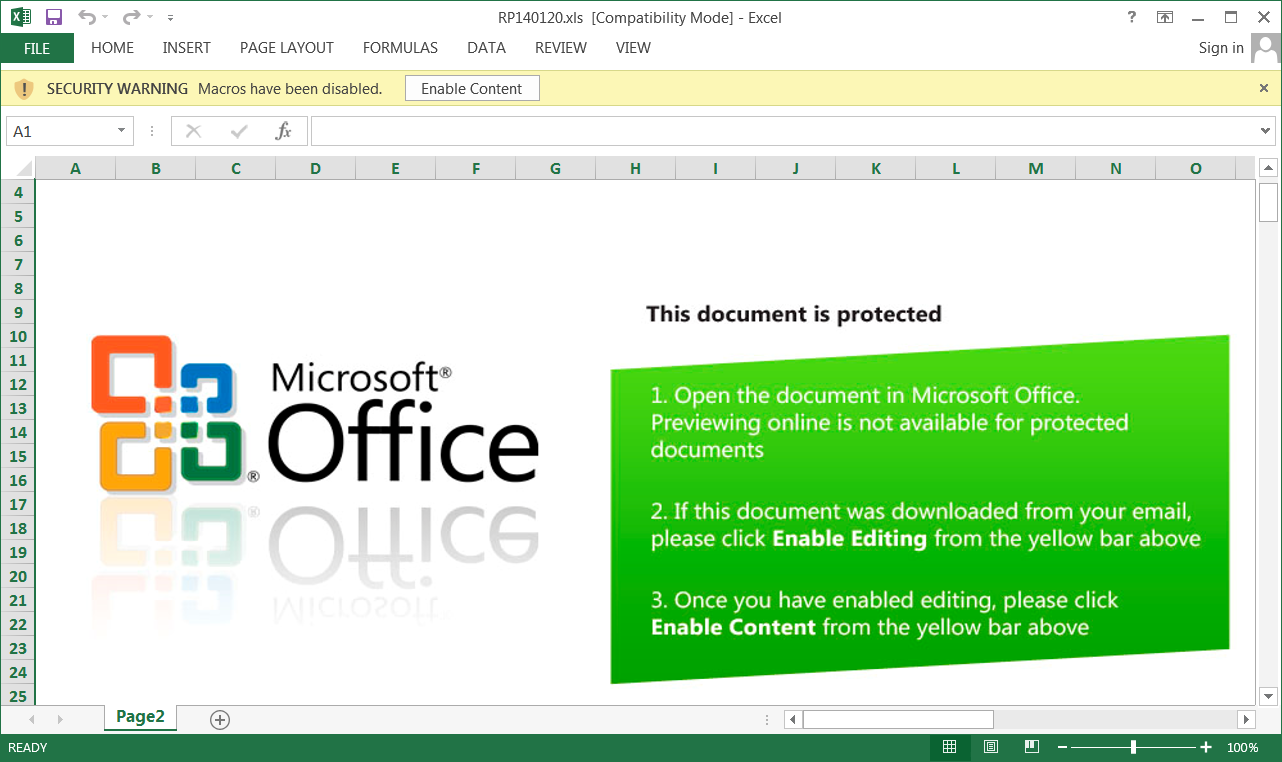
The victims are instructed to open the Excel document on their computer as online previewing is not available and to enable editing to get access to its contents.
"Once you have enabled editing, please click Enable Content from the yellow bar above," the bait Microsoft Office doc adds.
The operators behind this phishing campaign also use localized HTML files in different languages for victims from all around the world.
Also, the attackers make use of an IP traceback service that enables them to "track the IP addresses of machines that download the malicious Excel file."
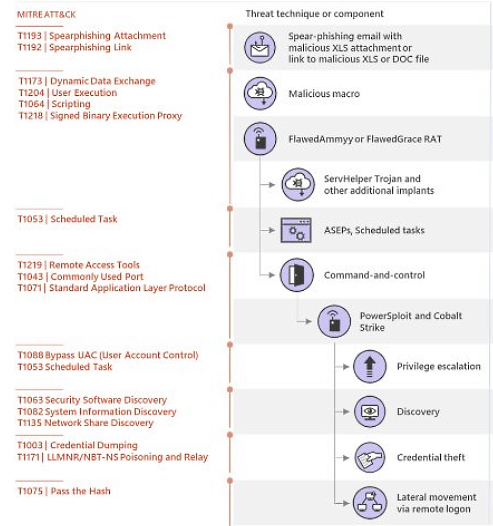
Threat Analytics report (Microsoft)
Once executed on the victim's computer, the malware will also attempt to drop a remote access trojan (RAT) tracked by Microsoft as GraceWire and as FlawedGrace by Proofpoint.
Microsoft Security Intelligence provides a full list of indicators of compromise (IOCs) including SHA-256 hashes of the malware samples used in the campaign here and here.
Update: Cleared up TA505 / Evil Corp confusion.
The Adware Families That Changed the Antivirus Industry
2.2.2020 Bleepingcomputer Virus
This is a guest post by Malwarebytes security researcher Pieter Arntz who takes a look back at the early 2000s when he was not employed in the cybersecurity industry but was part of a group of expert helpers that volunteered their time to help victims remove adware and malware from computers.
This story takes us back to 2003 and for a better understanding, you would need to be aware of the fact that the cybersecurity industry back then was shaped very differently from today.
Antivirus (AV) software dealt with malware such as viruses and worms, dedicated Anti-Trojan software focused entirely on Trojans, and computer infections such as adware, browser hijackers, dialers, spyware, and ad injectors were for the most part not detected by mainstream security software.
Instead, you needed to use dedicated anti-adware programs like Ad-Aware or Spybot to tackle these infections.
Even more problematic is that most adware and hijackers were written by companies who thought what they were doing was legal and would use the courts to prove that. This led to many AV companies just ignoring them to avoid the risk of a lawsuit.
As a consequence, many PC users that were affected by adware, dialers, and other undetected threats flocked to online help-forums to ask for assistance in getting rid of unwanted pop-ups, pop-unders, and browser windows that would spontaneously open to show advertisements.
Those few programs that promised to remove adware usually referred to it as spyware and offered no protection, just removal.
Hijackthis was a savior
I started helping users online in 1999 and removing the adware back then was usually relatively simple.
Most of these adware or hijackers altered the start-page in Internet Explorer or added a Browser Helper Object that was designed to retrieve and show advertisements. You should realize that Firefox and Chrome were not around yet and the alternatives for IE were only used by a few.
Using a simple diagnostic tool called Hijackthis that was created by Merijn Bellekom, we could create a quick fix via a few back and forth messages on a support forum or in a newsgroup and the helper and his client parted ways, both satisfied that the problem was solved.
Hijackthis
Until the user fell victim to another dubious download or bundler, that is.
Since the posts were public, they were indexed by search engines and many other users found the answers provided by the helper and followed the relatively simple instructions to solve their problems.
Many forums at the time had dedicated “HijackThis” sections which were the only subforum where the HijackThis logs were allowed to be posted.
Adware starts to mimic malware
It didn’t take long before adware authors noticed that their hijacks and software were being removed almost as fast as they could publish them.
Due to this, some of them decided to make the removal of their adware more complicated.
First, we have Lop Adware
One of the first families to do this was called Adware.Lop whose goal was to hijack the user's browser so that it sent them to various pay per click search portals run by the now-defunct C2Media. It was named after the main domain the users were hijacked to lop.com.
To hinder removal Adware.Lop started using a random folder and filename and used Scheduled Tasks to trigger the advertising cycles. They were easy enough to recognize for expert helpers, but it made it a lot harder for the people that searched for answers since they couldn’t find any information about the file and folder names they were looking for.
It also raised the required knowledge level of the helper, which limited the number of available helpers.
Soon other adware authors started using random names, such as:
PurityScan (ClickSpring) who added Startup entries in the registry pointing to randomly named files
Wurldmedia who started with randomly named Browser Helper Objects
The Peper Trojan, which manifested itself as a running process that showed porn popups and spawned a new copy of itself under a new name as soon as the process was stopped. Because of that behavior, it was considered a Trojan and the firm that spread Peper was forced to publish an uninstaller.
CoolWebSearch (CWS) arrives
Then came CoolWebSearch; the adware and family that started an active arms-race with the expert helpers as they released new variants each time a fix was learned for the previous one.
When first released, this family started as a hijacker that redirected users to CoolWebSearch (CWS) related sites.
CoolWebSearch Home Page
They then added a new twist with the introduction of a custom CSS stylesheet for Internet Explorer
Custom stylesheet variants
During this increasing aggressiveness in adware programs, helpers had rallied together and had private discussions on IRC and in behind-the-scenes forums to exchange information and to work together on fixes. It took us weeks to find the explanation for the symptoms caused by the custom stylesheet.
These symptoms were extremely slow typing in text boxes and an off-screen popup triggered by a javascript in the stylesheet.
Their next variant was an “improved” version of this hijack that also included a HOSTS file hijack and a startup entry that reloaded the entire hijack every time the system booted. This one was a lot easier to figure out since we had wizened up to the stylesheet hijack.
The stylesheet plot was taken one step further when the CWS gang figured out they could use any filename for the user stylesheet and Internet Explorer would still load it.
On top of that, two domains were added to the Trusted Zone to ensure CWS could do its dirty work and install any updates they saw fit.
Use of Winsock LSPs
CWS then moved to use Winsock Layered Service Providers, which are DLLs that could be used to monitor and modify TCP/IP traffic in Windows. These programs were particularly useful for antivirus software who wanted to monitor network connections for malicious traffic but were also abused by adware to redirect users or inject advertisements.
To my knowledge CWS was the first adware to insert a new Layered Service Provider (LSP) into the TCP/IP stack. Identifying the file responsible was easy, but removing it had to be done properly or it would cause the network connection to break.
Due to this, a special tool called LSP-fix was developed that allowed helpers to remove LSPs without fear of breaking the TCP/IP stack.
LSP-Fix
Creating a webserver on your PC
After a few more variants including a fake driver update that only started in 20% of every system boot, the next deviously clever variant ran a web server on the affected machine that redirected Google, Yahoo, and any mistyped URL to a CWS domain. Users needed to stop the process before they could successfully start the full removal, which took place in the registry and inside the HOSTS file.
Bring in the reinforcements
During this evolution, CWS began to use filenames that looked legitimate at first sight such as svcinit.exe, ctfmon32.exe, msinfo.exe, and svchost32.exe. They also used different startup methods in the variants to come, like win.ini and system.ini entries, URL search hooks, protocol filters, and the Userinit registry key.
By then we had seen 20 different variants in a 6 months!
As these infections became so embedded into the Windows operating system, removing the infection incorrectly could cause Windows to stop operating properly. This also meant that the knowledge required to be a successful helper kept increasing.
To prevent advice that could damage Windows, the help forums started to put restrictions on who was allowed to help with the logs and in 2003 some of the experts started training-facilities for new helpers.
Hijackthis Support Topics on BleepingComputer
They did this on existing forums or started forums for that purpose. Some of the experts started to burn out due to having full-time jobs, but also volunteering many hours of helping, developing fixes, or hunting for and analyzing new malware.
This led some to stop helping and instead started to train new helpers as many who had received help wanted to pay it forward and provide help themselves.
As CWS showed it did not care if a few systems got wrecked during infection or removal, this need for trained helpers was evident.
The LSP hijack was a prime example, but there was also another variant where the Windows Media Player executable was deleted and replaced by the malware. In other variants files were dropped in folders that were hidden by default, and in many cases simply removing the malware files would make either the browser or even the entire system unusable.
If it hadn’t been for some specialized tools like CWShredder and About:Buster undoubtedly a lot more systems would have needed to re-format.
The industry changes
In early 2004, the industry started to change and pay attention to our cries for help.
AV software could no longer look a blind eye at adware that had become malware and started to add more kinds of infections to their definitions. Many of the market leaders of today were among the first to make that transition.
The specialized anti-trojan vendors were bought out or disappeared and a few new companies started to come up. In the same year, we also saw many Anti-Spyware vendors emerge.
Some of them were serious attempts at a solution, but most could be classified as rogues. And for many of these rogues, you could argue that the cure was worse than the problem.
What happened to the tools?
In 2004, the author of About:Buster started working on a program called RogueRemover. This later evolved into Malwarebytes which formally launched in 2008.
In 2007 TrendMicro bought HijackThis and CWShredder and does nothing with them, at least that’s how it looked to the outside world. They certainly stopped further development, much to the chagrin of the helpers that were trained to work with them.
LSP-fix is still available, but their help forums have closed. Also, many of the old helper forums have closed as well.
Only a select few were strong enough to survive the diminished influx of people looking for a solution to their malware problems.
Rearview perspective
My look at the developments during that period may differ from others, but looking back this is how I saw the industry evolving.
While I may be wrong about the underlying reasons, it is my firm belief that the customer's demand for software that could solve their problems was a deciding factor in the way the industry evolved.
The adware families that I described were the most troublesome ones to remove in my experience and could take up to 50 replies with detailed instructions, asking for follow-up logs, and more removal instructions, to help a victim restore his computer to a usable state.
It would almost certainly have been faster to reformat and start from scratch.
But the most important lesson for me was:
Under the right circumstances, a diamond in the rough can become a shining example of how things can and should be done.
This is not only true for some of the software that was developed as a result of this arms-race but very much so for some of the helpers we trained.
.png)
.jpg)
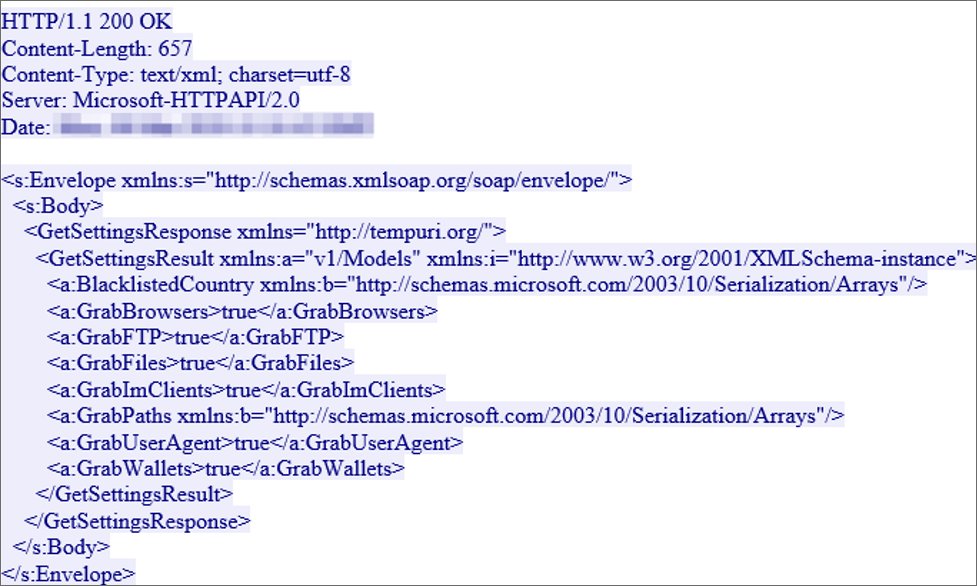
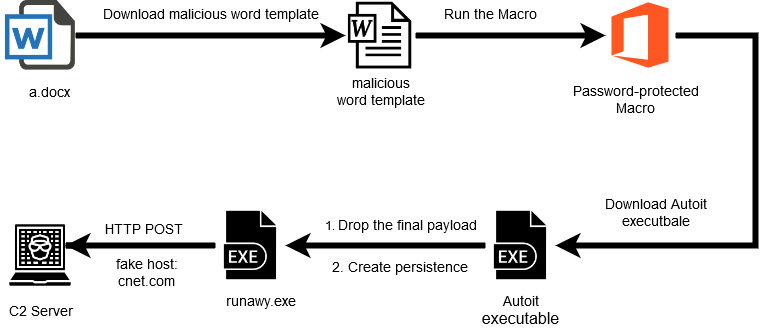
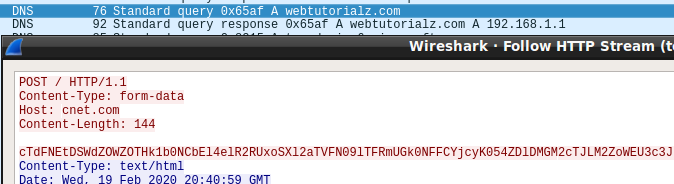
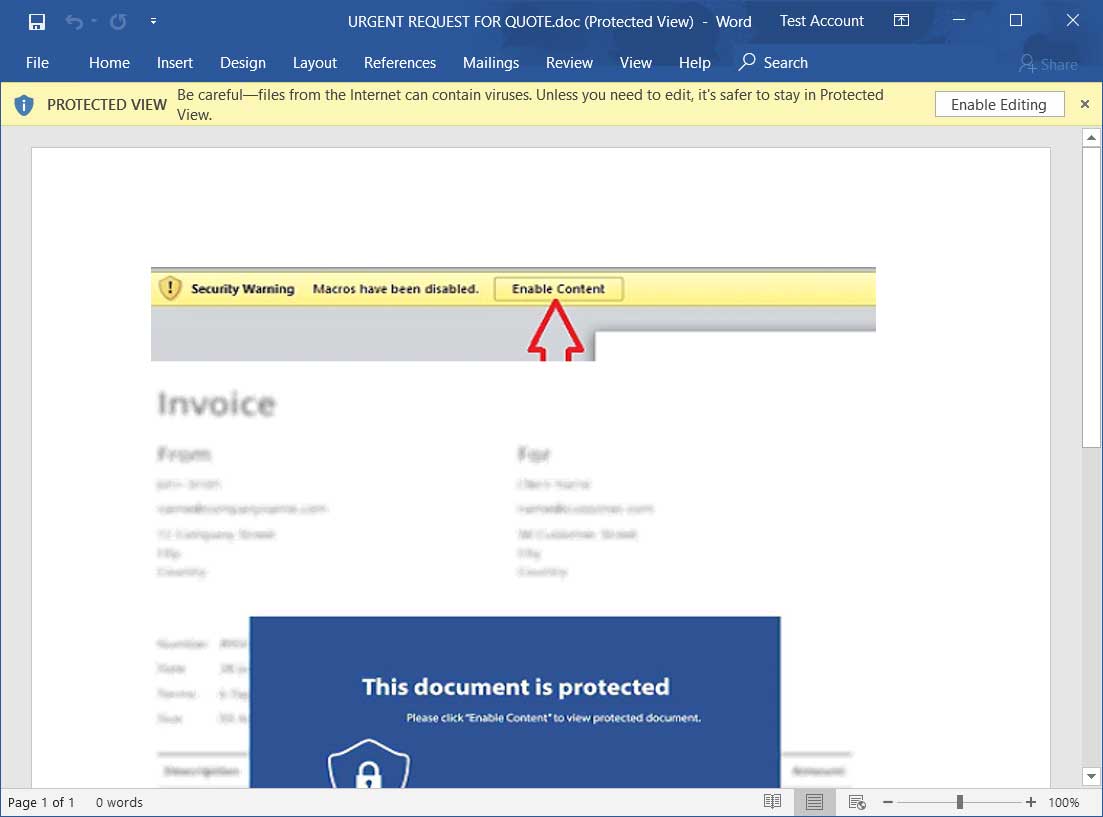
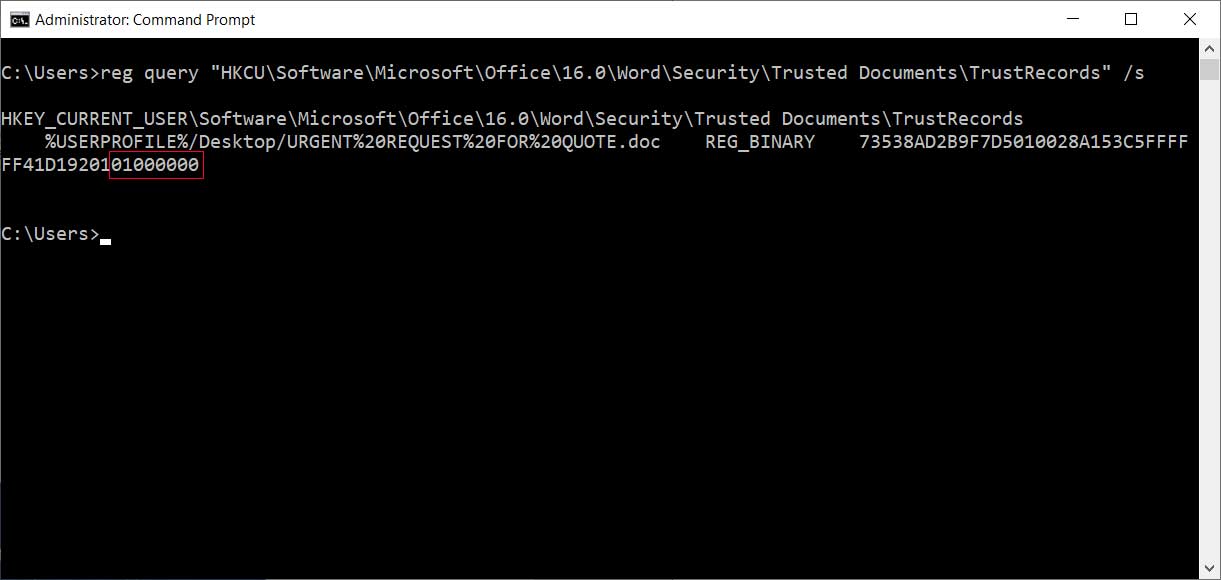
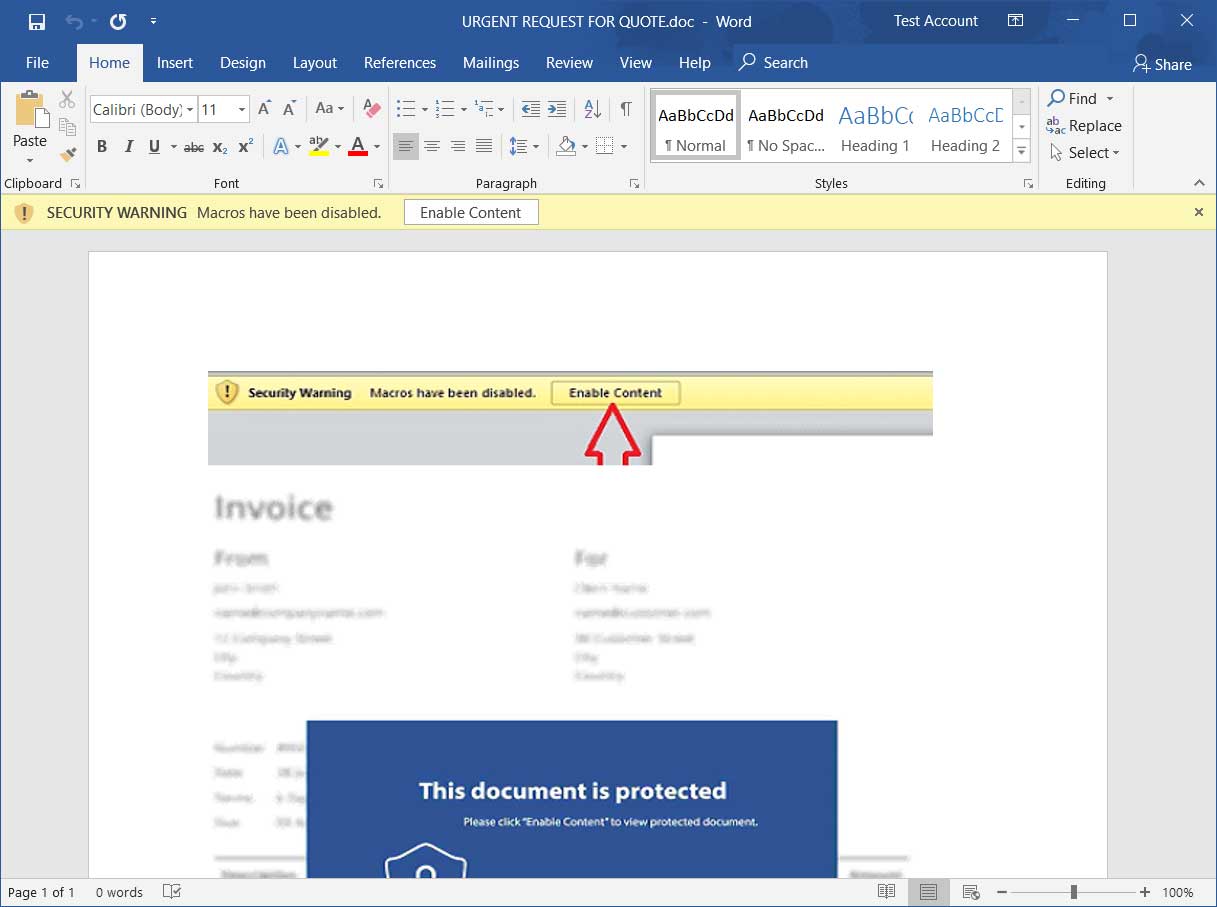
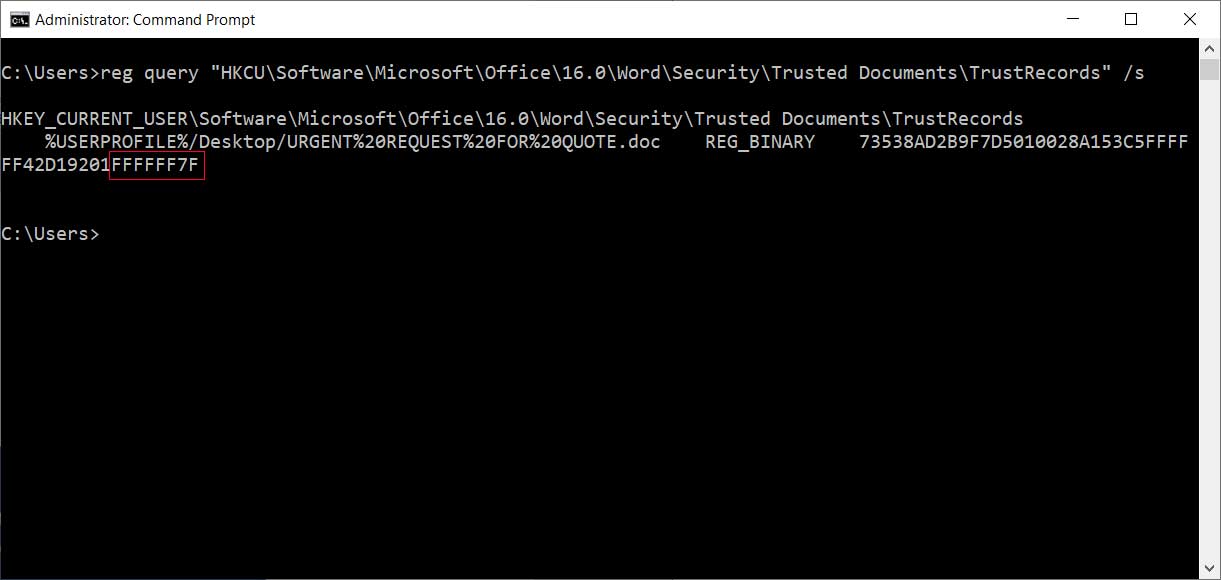
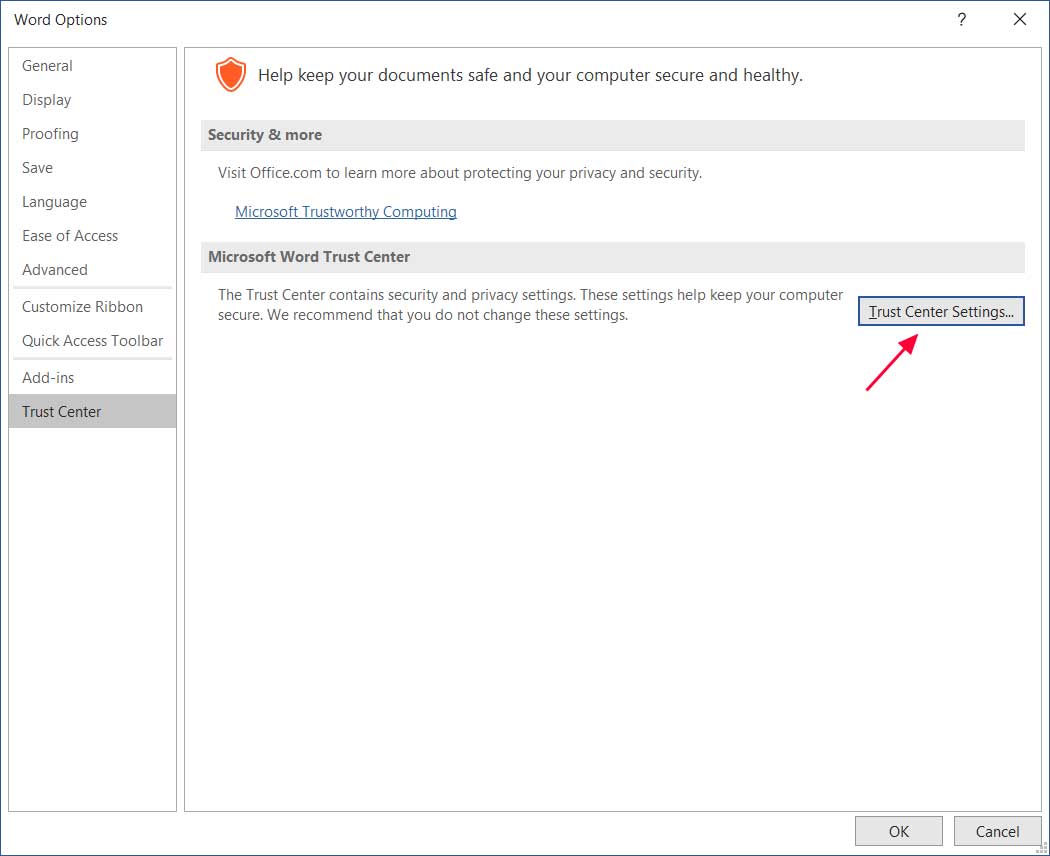
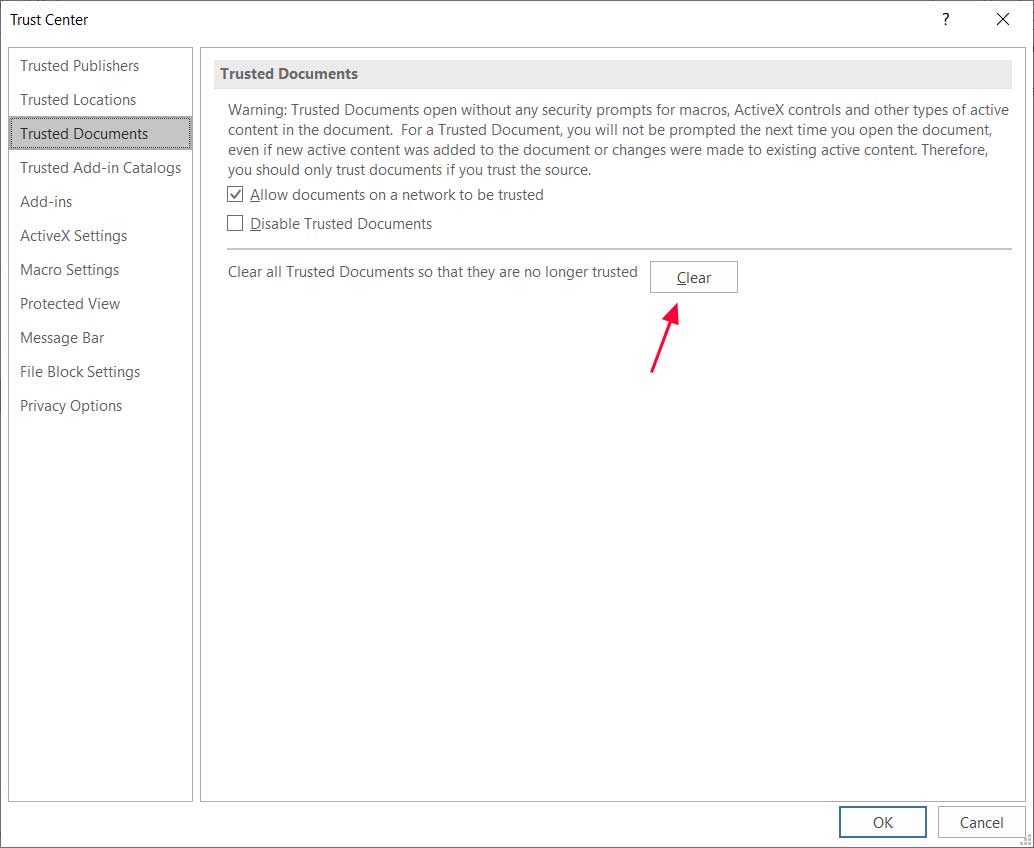
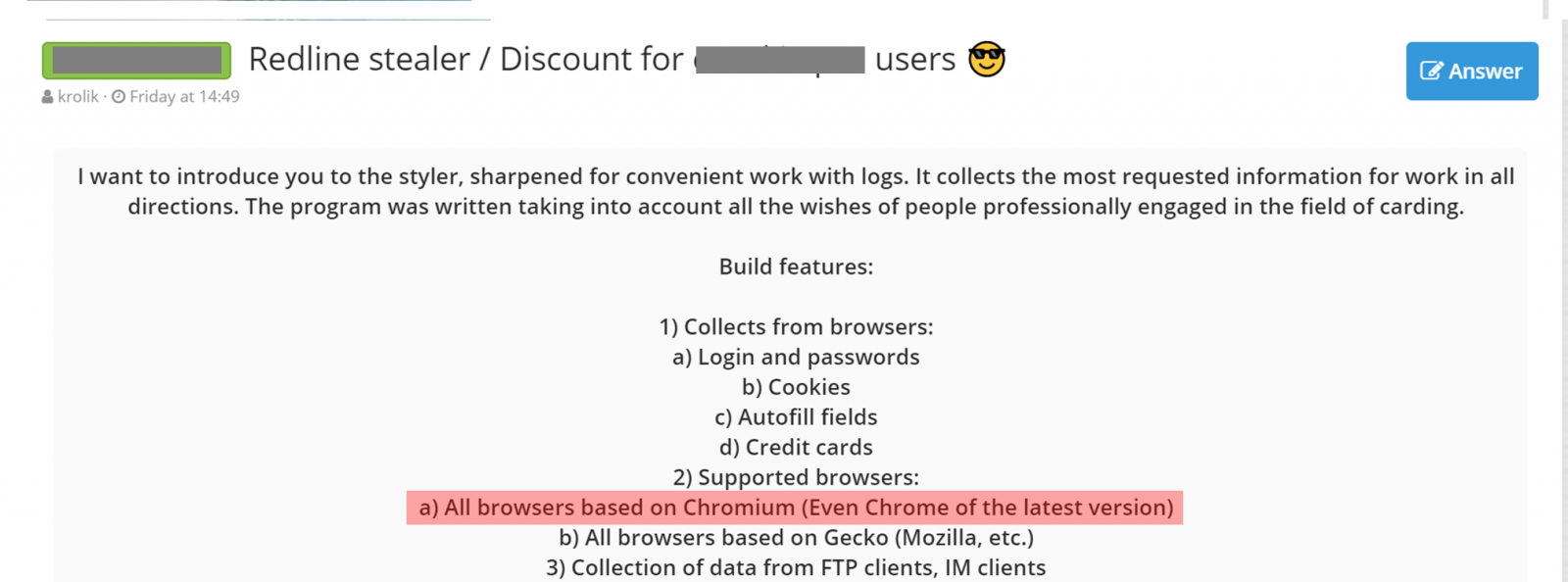
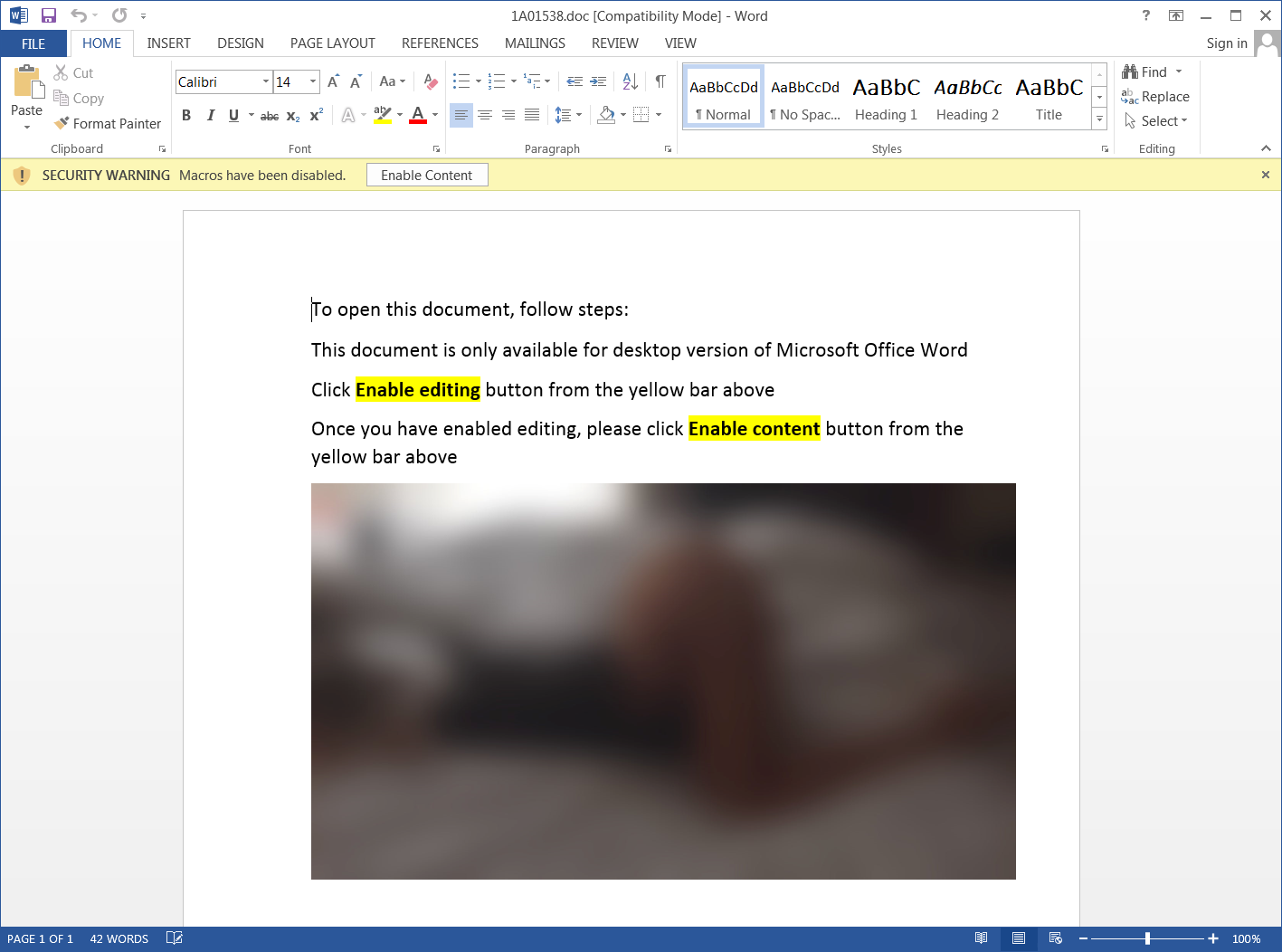




















.png)





























