
Shad0wS3C group hacked the Paraguay Secretary of National Emergency
29.8.2016 securityaffeirs Hacking
Shad0wS3C hacker group has hacked the Paraguay’s Secretary of National Emergency (SNE) and leaked online a dump from a PostgreSQL database.
Not so long ago I interviewed Gh0s7, the leader of the Shad0wS3C hacker crew, now he contacted me to announce the hack of the Paraguay’s Secretary of National Emergency (SNE).
“The reason for this data leak. The government of Paraguay has violated so many human rights, and either the UN (Don’t rely on them) or anyone has done anything. just to name a few:
Impunity and justice system
Torture and other ill-treatment
Violation of Women’s and girls’ rights
Violation against Human rights defenders”
this is the Shad0wS3C message.
The group has shared as proof of the hack a data dump from a PostgreSQL database, just after the announced security breach the Government website sen.gov.py was up.
The leaked data dump includes information about material stocks and also PII belonging to Paraguay’s Secretary of National Emergency employees. Users’ records include names, emails, phone numbers, addresses, salary information, and other data related to their activity within the Government organization (i.e Roles in the case of national emergencies).

The leaked data also includes details on hundreds website login credentials, with hashed passwords.
Shad0wS3c is a hacker group recently formed, in July it claimed responsibility for the data breach of the EJBCA that resulted in the exposure of credentials and certificates.
DNC staffers are invited to use ‘Snowden-Approved’ App Signal in response to the hack
29.8.2016 securityaffeirs Hacking
In the aftermath of the DNC hack the staffers were instructed in the use of the popular instant messaging Signal app, also called the “Snowden-approved” app.
The need of privacy is pushing the IT industry in developing secure messaging systems that implement end-to-end encrypted to protect users from prying eyes. Signal is probably the most popular app in this moment.
Signal app comes from Open Whisper Systems and is available for both Androids and iOS devices. If you are looking for the most secure messaging app, you can use Signal and strengthen security in your texts and phone calls. It is free of charge and it encrypts your data.
The app is automatically in sync with your address book and this makes it really easy to encrypt your communication with all your contacts. In this way, you do not need special login credentials for accessing the app and initializing its effectiveness.
If you search for Signal on the Internet you will discover that Edward Snowden is probably his most illustrious users and testimonial.
“Use anything by Open Whisper Systems” Snowden says.
signal app
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app, recently we so the application also in the popular TV series Mr. Robot.
There is no doubt, Signal is the first choice for hackers and security experts … and not only them.
In the aftermath of the Democratic National Committee hack the staffers were instructed in the use of the popular instant messaging app, also called the “Snowden-approved” app.
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
Edward Snowden ✔ @Snowden
2015: Even if he revealed unlawful government surveillance, put him in jail!
2016: wait what apps does he use
22:58 - 27 Ago 2016
6.251 6.251 Retweet 10.505 10.505 Mi piace
“Signal, staffers in the meeting were told, was “Snowden-approved.” A week after the meeting at the campaign headquarters, according to two people who have worked with the D.N.C. and the Clinton campaign, an e-mail was sent out instructing staffers where to download the app and how to use it.” reported Vanity Fair.
“Edward Snowden, who famously requires that people place their cell phones in a freezer before he agrees to meet with them in person (the freezer, or fridge, acts as a faraday cage and blocks any N.S.A.-like snooping of people’s whereabouts), has touted the security of Signal numerous times, saying on Twitter, “I use Signal every day.””
Segui
Edward Snowden ✔ @Snowden
Report: Russia hijacking activist accounts via telcos.
Use Signal, and always do this: (http://support.whispersystems.org/hc/en-us/articles/213134107-How-do-I-verify-the-person-I-m-sending-messages-to-is-who-they-say-they-are- …) https://twitter.com/FredericJacobs/status/726128513695109120 …
12:55 - 30 Apr 2016
854 854 Retweet 833 833 Mi piace
A few days after the DNC security breach was publicly disclosed, the DNC staffers received a memo containing detailed instructions on how to download and use the Signal app.
The use of the popular messaging app among DNC staffer is a clear sign of the need of a proper security posture among top political officials and staffer managing sensitive information.
If you want to give a look to the other Secure Messaging Apps on the market, you can read the post I published here.
The Network of NewSat satellite telco firm was the ‘most corrupted’ of ever
29.8.2016 securityaffeirs Security
The Network of NewSat satellite firm was the ‘most corrupted’ of ever, it was hacked by foreign hackers and it had interception kit in its data centre.
The story demonstrates the high interest of spy agencies in hacking communication systems.
Once upon a time, the Australian satellite company was deeply hacked by cyber spies that completely corrupted its network. The company is not out of the business, its assets were sold off last year after it went into administration.
According to a former staffer that has spoken on condition of anonymity to the Australian Broadcasting Corporation, it was ‘the most corrupted’ network the nation’s intelligence had encountered.
According to the ABC broadcast, the news of the hack was already reported in 2013, when the company reported the security breach to the Australian Signals Directorate. The Chinese nation-state hackers made the organization “the most corrupted network [the Directorate had ever seen”, the ABC reports.
Former Central Intelligence Agency Chief Michael Hayden declared that the China’s efforts against Australia aimed at “the theft of information, and really by and large the theft of information for commercial profit.”
According to the official hackers were interested in sensitive information such as the plans for a Lockheed Martin-designed satellite dubbed Jabiru-1.
“Given we were up against China, state-sponsored, a lot of money behind them and a lot of resources and we were only a very small IT team, it certainly wasn’t a fair fight for us,” Newsat’s former IT manager Daryl Peter said.
The issue had come to the headlines because the Newsat company was planning to install a restricted encryption tool to allows the NSA to spy on satellite communications, so it notified its intent to the ASD.
The Australian Signals Directorate refused to release the encryption tool to Newsat until it was able to eradicate the intruders from its systems. intelligence officials replied to the company telling its networks were “the most corrupted” they had seen.
NewSat satellite communications
Australian satellite company Newsat Ltd was forced to rebuild its entire network in secret. (Four Corners)
Intelligence officials who examined the Newsat infrastructure confirmed it was “the most corrupted” they had seen.
“They actually said to us that we were the worst,” Mr Peter said.
“What came out of that meeting was we had a serious breach on our network and it wasn’t just for a small period of time, they’d been inside our network for a long period, so maybe about two years. And the way it was described to us was they are so deep inside our network it’s like we had someone sitting over our shoulder for anything we did.”
According to the anonymous source that has revealed the story to the ABC, the Newsat network was completely rebuilt.
Anyway the NewSat company installed an Australian Government communications interception system in its data centre, but the Australian Government had refused to deploy the restricted NSA encryption tool due to the security breach it discovered.
“They (NewSat) had a lot of dealings with Middle East organisations,” the source said.
Let me suggest reading a detailed analysis published by the ABC’s Four Corners that confirms Australian Government computer networks were breached by hackers.
IT threat evolution in Q2 2016. Overview
29.8.2016 Safety
Targeted attacks and malware campaigns
Cha-ching! Skimming off the cream
Earlier in the year, as part of an incident response investigation, we uncovered a new version of the Skimer ATM malware. The malware, which first surfaced in 2009, has been re-designed. So too have the tactics of the cybercriminals using it. The new ATM infector has been targeting ATMs around the world, including the UAE, France, the United States, Russia, Macau, China, the Philippines, Spain, Germany, Georgia, Poland, Brazil and the Czech Republic.
Rather than the well-established method of fitting a fake card-reader to the ATM, the attackers take control over the whole ATM. They start by installing the Skimer malware on the ATM – either through physical access or by compromising the bank’s internal network. The malware infects the ATM’s core – the part of the device responsible for interaction with the wider bank infrastructure, card processing and dispensing of cash. In contrast to a traditional card skimmer, there are no physical signs that the ATM is infected, leaving the attackers free to capture data from cards used at the ATM (including a customer’s bank account number and PIN) or steal cash directly.
The cybercriminal ‘wakes up’ the infected ATM by inserting a card that contains specific records on the magnetic stripe. After reading the card, Skimer is able execute a hard-coded command, or receive commands through a special menu activated by the card. The Skimer user interface appears on the display only after the card is ejected and only if the cybercriminal enters the correct session key within 60 seconds. The menu offers 21 different options, including dispensing money, collecting details of cards that have been inserted in the ATM, self-deletion and performing updates. The cybercriminal can save card details on the chip of their card, or print the details it has collected.
The attackers are careful to avoid attracting attention. Rather than take money directly from the ATM – which would be noticed immediately – they wait (sometimes for several months) before taking action. In most cases, they collect data from skimmed cards in order to create cloned cards later. They use the cloned cards in other, non-infected ATMs, casually withdrawing money from the accounts of the victims in a way that can’t be linked back to the compromised ATM.
Kaspersky Lab has several recommendations to help banks protect themselves. They should carry out regular anti-virus scans; employ whitelisting technologies; apply a good device management policy; make use of full disk encryption; password protect the BIOS of ATMs; enforce hard disk booting and isolate the ATM network from the rest of the bank infrastructure. The magnetic strip of the card used by the cybercriminals to activate the malware contains nine hard-coded numbers. Banks may be able to proactively look for these numbers within their processing systems: so we have shared this information, along with other Indicators of Compromise (IoCs).
In April, one of our experts provided an in-depth examination of ATM jackpotting and offered some insights into what should be done to secure these devices.
New attacks, old exploit
In recent months we have been tracking a wave of cyber-espionage attacks conducted by different APT groups across the Asia-Pacific and Far East regions. They all share one common feature: they exploit the CVE-2015-2545 vulnerability. This flaw enables an attacker to execute arbitrary code using a specially crafted EPS image file. It uses PostScript and can evade the Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP) protection methods built into Windows. The Platinum, APT16, EvilPost and SPIVY groups were already known to use this exploit. More recently, it has also been used by the Danti group.
Danti, first identified in February 2016 and still active, is highly focused on diplomatic bodies. The group predominantly targets Indian government organizations, but data from the Kaspersky Security Network (KSN) indicates that it has also infected targets in Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal and the Philippines.
The exploit is delivered using spear-phishing e-mails spoofed to look as though they have been sent by high-ranking Indian government officials. When the victim clicks on the attached DOCX file, the Danti backdoor is installed, allowing the attackers to capture sensitive data.
The origin of the Danti group is unclear, but we suspect that it might be connected to the NetTraveler and DragonOK groups: it’s thought that Chinese-speaking hackers are behind these attacks.
Kaspersky Las has also seen another campaign that makes use of the CVE-2015-2545 vulnerability: we’ve called this SVCMONDR after the Trojan that is downloaded once the attackers get a foothold in the victim’s computer. This Trojan is different to the one used by the Danti group, but it shares some common features with Danti and with APT16 – the latter is a cyber-espionage group believed to be of Chinese origin.
One of the most striking aspects of these attacks is that they are successfully making use of a vulnerability that was patched by Microsoft in September 2015. In November, we predicted that APT campaigns would invest less effort in developing sophisticated tools and make greater use of off-the-shelf malware to achieve their goals. This is a case in point: using a known vulnerability, rather than developing a zero-day exploit. This underlines the need for companies to pay more attention to patch management to secure their IT infrastructure.
New attack, new exploit
Of course, there will always be APT groups that seek to take advantage of zero-day exploits. In June, we reported on a cyber-espionage campaign – code-named ‘Operation Daybreak‘ and launched by a group named ScarCruft – that uses a previously unknown Adobe Flash Player exploit (CVE-2016-1010). This group is relatively new and has so far managed to stay under the radar. We think the group might have previously deployed another zero-day exploit (CVE-2016-0147) that was patched in April.
The group have targeted a range of organizations in Russia, Nepal, South Korea, China, India, Kuwait and Romania. These include an Asian law enforcement agency, one of the world’s largest trading companies, a mobile advertising and app monetization company in the United States, individuals linked to the International Association of Athletics Federations and a restaurant located in one of Dubai’s top shopping centres. The attacks started in March 2016: since some of them are very recent, we believe that the group is still active.
The exact method used to infect victims is unclear, but we think that the attackers use spear-phishing e-mails that point to a hacked website hosting the exploit. The site performs a couple of browser checks before redirecting victims to a server controlled by the hackers in Poland. The exploitation process consists of three Flash objects. The one that triggers the vulnerability in Adobe Flash Player is located in the second SWF file delivered to the victim. At the end of the exploitation chain, the server sends a legitimate PDF file, called ‘china.pdf’, to the victim: this seems to be written in Korean.
In Q2 2016, @kaspersky #mobile security products detected 3.6M malicious installation packages #KLreport
Tweet
The attackers use a number of interesting methods to evade detection, including exploiting a bug in the Windows Dynamic Data Exchange (DDE) component in order to bypass security solutions – a method not seen before. This flaw has been reported to Microsoft.
Flash Player exploits are becoming rare, because in most cases they need to be coupled with a sandbox bypass exploit – this makes them tricky to do. Moreover, although Adobe is planning to drop Flash support soon, it continues to implement new mitigations to make exploitation of Flash Player increasingly difficult. Nevertheless, resourceful groups such as ScarCruft will continue to try and find zero-day exploits to target high-profile victims.
While there’s no such thing as 100 per cent security, the key is to increase security defences to the point that it becomes so expensive for an attacker to breach them that they give up or choose an alternative target. The best defence against targeted attacks is a multi-layered approach that combines traditional anti-virus technologies with patch management, host-based intrusion prevention and a default-deny whitelisting strategy. According to a study by the Australian Signals Directorate, 85 per cent of targeted attacks analysed could have been stopped by employing four simple mitigation strategies: application whitelisting, updating applications, updating operating systems and restricting administrative privileges.
Kaspersky Lab products detect the Flash exploit as ‘HEUR:Exploit.SWF.Agent.gen’. The attack is also blocked proactively by our Automatic Exploit Prevention (AEP) component. The payloads are detected as ‘HEUR:Trojan.Win32.ScarCruft.gen’.
XDedic: APT-as-a-Service
Kaspersky Lab recently investigated an active cybercriminal trading platform called xDedic, an online black market for hacked server credentials around the world – all available through the Remote Desktop Protocol (RDP). We initially thought that this market extended to 70,000 servers, but new data suggests that the XDedic market is much wider – including credentials for 176,000 servers. XDedic includes a search engine, enabling potential buyers to find almost anything – from government and corporate networks – for as little as $8 per server. This low price provides ‘customers’ with access to data on such servers and their use as a bridgehead for further targeted attacks.
The owners of the ‘xdedic[.]biz’ domain claim that they have no relation to those selling access to hacked servers – they are simply selling a secure trading platform for others. The XDedic forum has a separate sub-domain, ‘partner[.]xdedic[.]biz’, for the site’s ‘partners’ – that is, those selling hacked servers. The Xdedic owners have developed a tool that automatically collects information about the system, including websites available, software installed and more. They also provide others tools to its partners, including a patch for RDP servers to support multiple logins for the same user and proxy installers.
The existence of underground markets is not new. But we are seeing a greater level of specialisation. And while the model adopted by the XDedic owners isn’t something that can be replicated easily, we think it’s likely that other specialized markets are likely to appear in the future.
Data from KSN helped us identify several files that were downloaded from the XDedic partner portal: Kaspersky Lab products detect these files as malicious. We have also blacklisted the URLs of control servers used for gathering information about the infected systems. Our detailed report on XDedic contains more information on hosts and network-based IoCs.
Lurking around the Russian Internet
Sometimes our researchers find malware that is particular about where it infects. On the closed message boards used by Russian cybercriminals, for example, you sometimes see the advice ‘Don’t work with RU’ – offered by experienced criminals to the younger generation: i.e. don’t infect Russian computers, don’t steal money from Russians and don’t use them to launder money. There are two good reasons for this. First, online banking is not as common as it is in the west. Second, victims outside Russia are unlikely to lodge a complaint with the Russian police – assuming, of course, that they even know that Russian cybercriminals are behind the malware that has infected them.
But there are exceptions to every rule. One of these is the Lurk banking Trojan that has been used to steal money from victims in Russia for several years. The cybercriminals behind Lurk are interested in telecommunications companies, mass media and news aggregators and financial institutions. The first provide them with the means to transfer traffic to the attackers’ servers. The news sites provide them with a way to infect a large number of victims in their ‘target audience’ – i.e. the financial sector. The Trojan’s targets appear to include Russia’s four largest banks.
The primary method used to spread the Lurk Trojan is drive-by download, using the Angler exploit pack: the attackers place a link on compromised websites that leads to a landing page containing the exploit. Exploits (including zero-days) are typically implemented in Angler before being used in other exploit packs, making it particularly dangerous. The attackers also distribute code through legitimate websites, where infected files are served to visitors from the .RU zone, but others receive clean files. The attackers use one infected computer in a corporate network as a bridgehead to spread across the organization. They use the legitimate PsExec utility to distribute the malware to other computers; and then use a mini-dropper to execute the Trojan’s main module on the additional computers.
In Q2 2016, @kaspersky #mobile security products detected 83,048 mobile #ransomware Trojans #KLreport
Tweet
There are a number of interesting features of the Lurk Trojan. One distinct feature, that we discussed soon after it first appeared, is that it is ‘file-less’ malware, i.e. it exists only in RAM and doesn’t write its code to the hard drive.
The Trojan is also set apart because it is highly targeted. The authors do their best to ensure that they infect victims that are of interest to them without catching the attention of analysts or researchers. The incidents known to us suggest Lurk is successful at what it was designed for: we regularly receive reports of thefts from online banking systems; and forensic investigations after the incidents reveal traces of Lurk on the affected computers.
Malware stories
Cybercriminals get ready for Rio
Fraudsters are always on the lookout for opportunities to make money off the back of major sporting events, so it’s no surprise that we’ve seen an increase in cybercriminal activity related to the forthcoming Olympic Games in Brazil.
We’ve seen an increase in spam e-mails. The spammers try to cash in on people’s desire to watch the games live, sending out messages informing the recipient that they have won a (fake) lottery (supposedly organized by the International Olympic Committee and the Brazilian government): all they need to do to claim their tickets is to reply to the e-mail and provide some personal details.
Some messages point to fake websites, like this one offering direct sale of tickets without the need to make an application to the official lottery:
These fake ticketing sites are very convincing. Some fraudsters go the extra mile by obtaining legitimate SSL certificates to provide a secure connection between the victim’s browser and the site – displaying ‘https’ in the browser address bar to lure victims into a false sense of security. The scammers inform their victims that they will receive their tickets two or three weeks before the event, so the victim doesn’t become suspicious until it’s too late and their card details have been used by the cybercriminals. Kaspersky Lab is constantly detecting and blocking new malicious domains, many of which include ‘rio’ or ‘rio2016’ in the title.
It’s too late to buy tickets through official channels, so the best way to see the games is to watch on TV or online. We advise everyone to beware of malicious streaming websites – probably the last-ditch attempt by cybercriminals to scam people out of their money.
Cybercriminals also take advantage of our desire to stay connected wherever we go – to share our pictures, to update our social network accounts, to find out the latest news or to locate the best places to eat, shop or stay. Unfortunately, mobile roaming charges can be very high, so often people look for the nearest Wi-Fi access point. This is dangerous, because data sent and received over an open Wi-Fi network can be intercepted. So passwords, PINs and other sensitive data can be stolen easily. On top of this, cybercriminals also install fake access points, configured to direct all traffic through a host that can be used to control it – even functioning as a ‘man-in-the-middle’ device that is able to intercept and read encrypted traffic.
To gauge the extent of the problem, we drove by three major Rio 2016 locations and passively monitored the available Wi-Fi networks that visitors are most likely to try and use during their stay – the Brazilian Olympic Committee building, the Olympic Park and the Maracana, Maracanazinho and Engenhao stadiums. We were able to find around 4,500 unique access points. Most are suitable for multimedia streaming. But around a quarter of them are configured with weak encryption protocols: this means that attackers can use them to sniff the data of unsuspecting visitors that connect to them.
To reduce your exposure, we would recommend any traveller (not just those who plan to visit Rio!) to use a VPN connection, so that data from your device travels to the Internet through an encrypted data channel. Be careful though. Some VPNs are vulnerable to DNS leak attacks – meaning that, although your immediate sensitive data is sent via the VPN, your DNS requests are sent in plain text to the DNS servers set by the access point hardware. This would allow an attacker to see what you’re browsing and, if they have access to the compromised Wi-Fi network, define malicious DNS servers – i.e. letting them redirect you from a legitimate site (your bank, for example) to a malicious site. If your VPN provider doesn’t support its own DNS servers, consider an alternative provider or a DNSCrypt service.
There’s one other thing that we need if we want to stay connected – electricity: we need to keep our mobile devices charged. Today you can find charging-points in shopping centres, airports and even taxis. Typically they provide connectors for leading phone models, as well as a USB connector that a visitor can use with their own cable. Some also provide a traditional power supply that can be used with a phone charger.
But remember that you don’t know what’s connected to the other end of the USB connector. If an attacker compromises the charging-point, they can execute commands that allow them to obtain information about your device, including the model, IMEI number, phone number and more: information they can use to run a device-specific attack that would then enable them to infect the device. You can find more information about the data that’s transmitted when you connect a device using USB and how an attacker could use it to compromise a mobile device.
This doesn’t mean that you shouldn’t charge your device when you’re away from home. But you should take steps to protect yourself. It’s always best to use your own charger, rather than using charging cables at a public charging-point or buying one from an unknown source. You should also use a power outlet, instead of a USB socket.
Cybercriminals also continue to exploit established ways to make money. This includes using ATM skimmers to steal credit card data. The most basic skimmers install a card reader and a camera to record the victim’s PIN. The best way to protect yourself from this is to cover the keypad as you enter your PIN. However, sometimes cybercriminals replace the whole ATM, including the keypad and screen, in which case the typed password is stored on the fake ATM system. So it’s also important to check the ATM before you insert your card. Check to see if the green light on the card reader is on: typically, they replace the card reader with a version where there is no light, or it’s switched off. Also check the machine to see if there is anything suspicious, such as missing or broken parts.
Card cloning is another problem facing visitors to Rio 2016. While chip-and-PIN makes life harder for cybercriminals, it’s possible for them to exploit flaws in the EMV transaction implementation. It’s difficult to protect yourself against this type of attack, because usually the point-of-sale is modified in order to save the data – to be collected later by the cybercriminals. Sometimes they don’t need physical access to extract the stolen data, as they collect it via Bluetooth. However, there are some steps you can take to reduce your exposure to this type of attack. Sign up for SMS notifications of card transactions from your bank, if they provide this service. Never give your card to the retailer: if they can’t bring the machine to you, go to the machine. If the device looks suspicious, use a different payment method. Before typing your PIN, make sure you’re on the card payment screen and ensure that your PIN isn’t going to be displayed on the screen.
Ransomware: backup or pay up?
Towards the end of last year, we predicted that ransomware would gain ground on banking Trojans – for the attackers, ransomware is easily monetized and involves a low cost per victim. So it’s no surprise that ransomware attacks are increasing. Kaspersky Lab products blocked 2,315,931 ransomware attacks between April 2015 and April 2016 – that’s an increase of 17.7 per cent on the previous year. The number of cryptors (as distinct from blockers) increased from 131,111 in 2014-15 to 718,536 in 2015-16. Last year, 31.6 per cent of all ransomware attacks were cryptors. You can find further information, including an overview of the development of ransomware, in our KSN Report: PC ransomware in 2014-16.
Most ransomware attacks are directed at consumers – 6.8 per cent of attacks in 2014-15 and 13.13 percent in 2015-16 targeted the corporate sector.
However, the figures are different for cryptors: throughout the 24 months covered by the report, around 20 per cent of cryptor attacks targeted the corporate sector.
Hardly a month goes by without reports of ransomware attacks in the media – including recent reports of a hospital and online casino falling victim to ransomware attacks. Yet while public awareness of the problem is growing, it’s clear that consumers and organizations alike are not doing enough to combat the threat; and cybercriminals are capitalizing on this – this is clearly reflected in the number of attacks we’re seeing.
It’s important to reduce your exposure to ransomware (and we’ve outlined important steps you can take here and here). However, there’s no such thing as 100 per cent security, so it’s also important to mitigate the risk. In particular, it’s vital to ensure that you have a backup, to avoid facing a situation where the only choices are to pay the cybercriminals or lose your data. It’s never advisable to pay the ransom. Not only does this validate the cybercriminals’ business model, but there’s no guarantee that they will decrypt your data once you’ve paid them – as one organization discovered recently to its cost. If you do find yourself in a situation where your files are encrypted and you don’t have a backup, ask if your anti-malware vendor is able to help. Kaspersky Lab, for example, is able to help recover data encrypted by some ransomware.
Mobile malware
Displaying adverts remains one of the main methods of monetization for detected mobile objects. Trojan.AndroidOS.Iop.c became the most popular mobile Trojan in Q2 2016, accounting for more than 10% of all detected mobile malware encountered by our users during the reporting period. It displays adverts and installs, usually secretly, various programs using superuser privileges. Such activity quickly renders the infected device virtually unusable due to the amount of adverts and new applications on it. Because this Trojan can gain superuser privileges, it is very difficult to delete the programs that it installs.
In our report IT threat evolution in Q1 2016 we wrote about the Trojan-Banker.AndroidOS.Asacub family of banking malware. Representatives of this family have an unusual technique for bypassing the security mechanisms used by operating systems – they overlay the regular system window requesting device administrator privileges with their own window containing buttons. The Trojan thereby conceals the fact that it is gaining elevated privileges in the system, and tricks the user into approving these privileges. In Q2 2016, Asacub introduced yet another method for deceiving users: the Trojan acquired SMS messenger functionality and started offering its services in place of the device’s standard SMS app.
Dialog window of Trojan-Banker.AndroidOS.Asacub.i asking for the rights to be the main SMS application
This allows the Trojan to bypass system constraints first introduced in Android 4.4 as well as delete or hide incoming SMSs from the user.
Back in October 2015, we wrote about representatives of the Trojan-PSW.AndroidOS.MyVk family that steal passwords from user accounts on the VK.com social network. This quarter, those responsible for distributing Trojans from this family introduced a new approach for bypassing Google Play security mechanisms that involved first publishing an app containing useful functionality with no malicious code. Then, at least once, they updated it with a new version of the application – still without any malicious code. It was more than a month after the initial publication that the attackers eventually added malicious code to an update. As a result, thousands of users downloaded Trojan-PSW.AndroidOS.MyVk.i.
Data breaches
Personal information is a valuable commodity, so it’s no surprise that cybercriminals target online providers, looking for ways to bulk-steal data in a single attack. We’ve become accustomed to the steady stream of security breaches reported in the media. This quarter has been no exception, with reported attacks on beautifulpeople.com, the nulled.io hacker forum (underlining the fact that it’s not just legitimate systems that are targeted), kiddicare, Tumblr and others.
Some of these attacks resulted in the theft of huge amounts of data, highlighting the fact that many companies are failing to take adequate steps to defend themselves. It’s not simply a matter of defending the corporate perimeter. There’s no such thing as 100 per cent security, so it’s not possible to guarantee that systems can’t be breached. But any organization that holds personal data has a duty of care to secure it effectively. This includes hashing and salting customer passwords and encrypting other sensitive data.
Consumers can limit the damage of a security breach at an online provider by ensuring that they choose passwords that are unique and complex: an ideal password is at least 15 characters long and consists of a mixture of letters, numbers and symbols from the entire keyboard. As an alternative, people can use a password manager application to handle all this for them automatically. Unfortunately, all too often people use easy-to-guess passwords and re-use the same password for multiple online accounts – so that if the password for one is compromised, all the victim’s online IDs are vulnerable. This issue was highlighted publicly in May 2016 when a hacker known as ‘Peace’ attempted to sell 117 million LinkedIn e-mails and passwords that had been stolen some years earlier. More than one million of the stolen passwords were ‘123456’!
Many online providers offer two-factor authentication – i.e. requiring customers to enter a code generated by a hardware token, or one sent to a mobile device, in order to access a site, or at least in order to make changes to account settings. Two-factor authentication certainly enhances security – if people choose to take advantage of it.
Several companies are hoping to replace passwords altogether. Apple allows fingerprint authorization for iTunes purchases and payments using Apple Pay. Samsung has said it will introduce fingerprint, voice and iris recognition for Samsung Pay. Amazon has announced ‘selfie-pay’. MasterCard and HSBC have announced the introduction of facial and voice recognition to authorize transactions. The chief benefit, of course, is that it replaces something that customers have to remember (a password) with something they have – with no opportunity to short-circuit the process (as they do when they choose a weak password).
Biometrics are seen by many as the way forward. However, they are not a security panacea. Biometrics can be spoofed, as we’ve discussed before (here, here and here); and biometric data can be stolen. In the end, multi-factor authentication is essential – combining something you know, something you have and something you are.
A malware was found in Iran petrochemical complexes, but it’s not linked to recent incidents
29.8.2016 Virus
The head of Iran’s civilian defense confirmed that a malware was found in petrochemical complexes, but it hasn’t caused the fires under investigation.
Last week, I reported the news related to a series of fires at Iranian petrochemical plants. The Iran’s Supreme National Cyberspace Council started an investigation to discover if the incidents at oil and petrochemical fires were caused by cyber attacks. Authorities fear that nation state actors may have launched an attack similar to Stuxnet one.
Mr. Abolhassan Firouzabadi, the secretary of Iran’s Supreme National Cyberspace Council, announced that a team of cyber experts will be involved in the investigation to understand if the incidents are linked and if they were caused by cyber attacks.
fires petrochemical complexes Iran
Source The Tehrantimes.com
“Abolhassan Firouzabadi, secretary of Iran’s Supreme National Cyberspace Council, says a team of experts will look at the possibility of cyberattacks as being a cause, Press TV reported on Sunday.
Special teams will be sent to the afflicted sites to study the possibility of cyber systems having a role in the recent fires, he said.” reported the Tehran Times.
Iranian cyber experts have spotted and removed two malware that infected systems at two petrochemical plants. The news was confirmed by a senior military official and reported by Venturebeat.com.
“Iran has detected and removed malicious software from two of its petrochemical complexes, a senior military official said on Saturday, after announcing last week it was investigating whether recent petrochemical fires were caused by cyber attacks.” reported by Venturebeat.com.
The official also added that the malware was not responsible for the incidents occurred at the petrochemical complexes, the experts discovered that it was inactive and not linked to the fires.
“In periodical inspection of petrochemical units, a type of industrial malware was detected and the necessary defensive measures were taken,” Gholamreza Jalali, head of Iran’s civilian defense, said the state news agency IRNA.
“the discovery of this industrial virus is not related to recent fires.”
As declared by the oil minister, the string of fires in petrochemical complexes was caused by the lack of proper safety measures caused by the cut of the budgets operated by the firms in the energy sector.
Opera Browser Sync Service Hacked; Users' Data and Saved Passwords Compromised
28.8.2016 thehackernews Hacking
Opera has reset passwords of all users for one of its services after hackers were able to gain access to one of its Cloud servers this week.
Opera Software reported a security breach last night, which affects all users of the sync feature of its web browser.
So, if you’ve been using Opera’s Cloud Sync service, which allows users to synchronize their browser data and settings across multiple platforms, you may have hacked your passwords, login names, and other sensitive data.
Opera confirmed its server breach on Friday, saying the "attack was quickly blocked" but that it "believe some data, including some of [their] sync users’ passwords and account information, such as login names, may have been compromised."
Opera has around 350 Million users across its range products, but around 1.7 Million users using its Sync service had both their synchronized passwords as well as their authentication passwords leaked in the hack.
Since the company has already reset passwords of all of its registered Opera Sync users and emailed them with details, you need not worry about your account.
"Although we only store encrypted (for synchronized passwords) or hashed and salted (for authentication) passwords in this system, we have reset all the Opera sync account passwords as a precaution," Opera Software explained in a blog post.
Additionally, the company has also informed all Opera Sync users about the security breach and recommended them to change passwords for their Opera Sync accounts as soon as possible. You can obtain a new password for Opera sync using the password resetting page.
The complete details about the intrusion and extent of the breach are yet unknown.
Opera Software encouraged users to reset passwords for any third party websites they may have synced with its service.
However, if you are the one using the same password for multiple sites, you are also advised to change your passwords for those sites manually.
Since we’ve repeatedly seen folks reusing passwords across multiple services with recent high-profile account hacking, you are advised to use a good password manager always to keep a strong, unique password for your online accounts.
We have listed some best password managers that would help you understand the importance of password managers and choose a suitable one according to your requirement.
Megaupload Domains Seized by FBI 'Hijacked' to Host Porn Ads
28.8.2016 thehackernews Hacking
Well, we all know that the FBI has previously hosting porn on the Internet. I still remember the case of PlayPen, the world's largest dark web child pornography site, which was seized by FBI and ran from agency’s own servers to uncover the site's visitors.
Now, one of the most popular sites owned and operated by the FBI has been serving porn as well.
FBI-owned Megaupload.org and several other domains were allegedly serving up ads for "casual sex," "adult cam chat," "adult affair dating," and "live sex cams" and other 18+ entertainment.
Megaupload was once a famous and highly popular site for pirate and copyright contents that agency seized from Kim Dotcom almost five years ago.
Since a criminal case against Dotcom is still pending in the United States, the FBI also retained control over several of the company’s assets, including cash, cars, and over a dozen of Megaupload’s former domain names, including Megastuff.co, Megaworld.mobi, Megaclicks.org, Megaupload.com, and Megavideo.com.
Initially, these Megaupload domains served a banner indicating the federal agents had seized them as part of a criminal investigation, those users who visited the site yesterday were surprised to see soft porn ads, offering links to adult entertainment.
But, How did this Happen?
'Lost control'
Yes, the hijacking of the Megaupload domains was not the result of some sophisticated hack that allowed hackers to serve you soft porn and sex ads, rather the FBI had "lost control" of the domains in the same way it lost control last year.
TorrentFreak suggests the FBI forgot to renew an expired domain, CIRFU.NET, which the feds used for their "name server" to redirect traffic from sites it had seized, and that someone else just purchase it and linked it to the Megaupload domains.
The Federal Bureau of Investigation fell into the same trap last year when the web addresses it seized led people onto to sites peddling porn, fake security software, malware, adware and bogus special offers.
Though the federal authorities reportedly removed the nameservers altogether to fix the issue, the exact identity of who got control of Megaupload.org and its associated sites is not known. However, it is clear that the feds have not learned from their past mistakes.
The FBI has yet to comment on what happened to the domains.
Global cost of cybercrime will grow from $3 trillion in 2015 to $6 trillion annually by 2021
28.8.2016 securityaffairs Crime
The cost of cybercrime could reach $6 trillion by 2021 (global annual cybercrime costs has been estimated $3 trillion in 2015).
The global cost of cybercrime continues to increase, this isn’t a surprise due to the intensification of this kind of illegal practice. According to an analysis conducted by Cybersecurity Ventures, the cost of cybercrime could reach $6 trillion by 2021 (global annual cybercrime costs has been estimated $3 trillion in 2015).
Security experts are questioning about the effective grow of the cost of cybercrime in the next five years, trillion dollars plus is a worrying trend, but anyway possible as explained by Larry Ponemon, founder of the Ponemon Institute.
“a trillion dollars plus is a real possibility,” commented Larry Ponemon. “If you asked me five or six years ago, I’d fall over,”
The growth of the cybercrime activities will force an increase in the global spending on cyber security products and services. Global spending is expected to exceed $1 trillion cumulatively over the next five years, from 2017 to 2021.
Criminal activities will evolve from targeting computers and mobile devices to IoT, transportations, and power grids.

The cybercrime cost evaluated by the researchers takes into account all possible damages associated with cybercrime activities including:
damage and destruction of data, stolen money.
theft of intellectual property.
theft of personal and financial data, embezzlement.
fraud.
lost productivity.
reputational harm.
post-attack disruption to the normal course of business, forensic investigation.
restoration and deletion of hacked data and systems.
We have also to consider that a significant portion of the overall cost of cybercrime is not calculated due to unreported crimes.
The report highlights the lack of an effective law enforcement agency for financial cybercrime today. Despite the recent successes of law enforcement against criminal organizations worldwide, it is necessary a supplementary effort against the growing threats.
The U.S. has declared a national emergency to deal with the cyber threats, more exposed to them are small businesses.
“The world’s cyber attack surface will grow an order of magnitude larger between now and 2021.” states the report.
IT threat evolution in Q2 2016. Statistics
28.8.2016 Kaspersky Security
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components. The data was collected from KSN users who agreed to provide it. Millions of Kaspersky Lab product users from 213 countries and territories worldwide participate in this global exchange of information about malicious activity.
Q2 figures
According to KSN data, Kaspersky Lab solutions detected and repelled 171,895,830 malicious attacks from online resources located in 191 countries all over the world.
54,539,948 unique URLs were recognized as malicious by web antivirus components.
Kaspersky Lab’s web antivirus detected 16,119,489 unique malicious objects: scripts, exploits, executable files, etc.
Attempted infections by malware that aims to steal money via online access to bank accounts were registered on 1,132,031 user computers.
Crypto ransomware attacks were blocked on 311,590 computers of unique users.
Kaspersky Lab’s file antivirus detected a total of 249,619,379 unique malicious and potentially unwanted objects.
Kaspersky Lab mobile security products detected:
3,626,458 malicious installation packages;
27,403 mobile banker Trojans (installation packages);
83,048 mobile ransomware Trojans (installation packages).
Mobile threats
In Q2 2016, Kaspersky Lab detected 3,626,458 malicious installation packages – 1.7 times more than in the previous quarter.
Number of detected malicious installation packages (Q3 2015 – Q2 2016)
Distribution of mobile malware by type
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports.
Distribution of new mobile malware by type (Q1 2016 and Q2 2016)
In Q2 2016, RiskTool software, or legal applications that are potentially dangerous to users, topped the ranking of detected malicious objects for mobile devices. Their share increased from 31.6% in Q1 to 45.1% this quarter.
Adware occupies second place. The share of these programs fell 1.4 p.p. compared to the previous quarter, and accounted for 14.2%.
The share of SMS Trojans fell from 18.5% to 10.8%, pushing this category of malicious programs down from second to third place in the ranking. Trojan-SMS.AndroidOS.Agent.qu and Trojan-SMS.AndroidOS.Agent.f accounted for most of the detected SMS Trojans, with both accounting for approximately 30% of all malicious files in this category.
The Trojan-Dropper share also fell – from 14.5% in Q1 to 9.2%. Trojan-Dropper.AndroidOS.Agent.v led the way: we detected more than 50,000 installation packages related to this Trojan.
TOP 20 mobile malware programs
Please note that this ranking of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
Name % of attacked users*
1 DangerousObject.Multi.Generic 80.87
2 Trojan.AndroidOS.Iop.c 11.38
3 Trojan.AndroidOS.Agent.gm 7.71
4 Trojan-Ransom.AndroidOS.Fusob.h 6.59
5 Backdoor.AndroidOS.Ztorg.a 5.79
6 Backdoor.AndroidOS.Ztorg.c 4.84
7 Trojan-Ransom.AndroidOS.Fusob.pac 4.41
8 Trojan.AndroidOS.Iop.t 4.37
9 Trojan-Dropper.AndroidOS.Gorpo.b 4.3
10 Trojan.AndroidOS.Ztorg.a 4.30
11 Trojan.AndroidOS.Ztorg.i 4.25
12 Trojan.AndroidOS.Iop.ag 4.00
13 Trojan-Dropper.AndroidOS.Triada.d 3.10
14 Trojan-Dropper.AndroidOS.Rootnik.f 3.07
15 Trojan.AndroidOS.Hiddad.v 3.03
16 Trojan-Dropper.AndroidOS.Rootnik.h 2.94
17 Trojan.AndroidOS.Iop.o 2.91
18 Trojan.AndroidOS.Rootnik.ab 2.91
19 Trojan.AndroidOS.Triada.e 2.85
20 Trojan-SMS.AndroidOS.Podec.a 2.83
* Percentage of unique users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
First place is occupied by DangerousObject.Multi.Generic (80.87%), the classification used for malicious programs detected by cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
As in the previous quarter, 16 Trojans that use advertising as their main means of monetization (highlighted in blue in the table) made it into the TOP 20. Their goal is to deliver as many adverts as possible to the user, employing various methods, including the installation of new adware. These Trojans may use superuser privileges to conceal themselves in the system application folder, from which it will be very difficult to delete them.
Trojan.AndroidOS.Iop.c (11.38%) moved from third to second in the TOP 20 and became the single most popular malicious program of the quarter. Over the reporting period we detected this Trojan in 180 countries, but the majority of attacked users were in Russia, India and Algeria. Iop.c can exploit a variety of vulnerabilities in the system to gain superuser privileges. The main method of monetization is displaying advertising and installing (usually secretly) various programs on the user’s device, including other malicious programs.
Q2’16, @kaspersky repelled 172M malicious attacks via online resources located in 191 countries #KLreport #Infosec
Tweet
Representatives of the Trojan-Ransom.AndroidOS.Fusob ransomware family claimed fourth and seventh places. These Trojans demand a ransom of $100-200 from victims to unblock their devices. Attacks using this Trojan were registered in over 120 countries worldwide in Q2, with a substantial number of victims located in Germany and the US.
Trojan-SMS.AndroidOS.Podec.a (2.83%) has now spent over a year in the mobile malware TOP 20, although it is starting to lose ground. It used to be an ever-present in the TOP 5 mobile threats, but for the second quarter in a row it has only made it into the bottom half of the ranking. Its functionality has remained practically unchanged; its main means of monetization is to subscribe users to paid services.
The geography of mobile threats
The geography of attempted mobile malware infections in Q2 2016 (percentage of all users attacked)
TOP 10 counties attacked by mobile malware (ranked by percentage of users attacked)
Country* % of users attacked **
1 China 36.31
2 Bangladesh 32.66
3 Nepal 30.61
4 Uzbekistan 22.43
5 Algeria 22.16
6 Nigeria 21.84
7 India 21.64
8 Indonesia 21.35
9 Pakistan 19.49
10 Iran 19.19
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
China topped the ranking, with more than 36% of users there encountering a mobile threat at least once during the quarter. China also came first in this ranking in Q1 2016.
In all the countries of this ranking, except China, the most popular mobile malware was the same – advertising Trojans that appeared in the TOP 20 mobile malware, and AdWare. The most popular malicious program was Trojan.AndroidOS.Iop.c. In China, a significant proportion of attacks also involved advertising Trojans, but the majority of users there encountered the Backdoor.AndroidOS.GinMaster and Backdoor.AndroidOS.Fakengry families, while Trojan.AndroidOS.Iop.c only occupied sixteenth place.
Russia (10.4%) was 26th in this ranking, Germany (8.5%) 38th, Italy (6.2%) 49th, and France (5.9%) 52th. The US (5.0%) came 59th and the UK (4.6%) 64th.
The safest countries were Austria (3.6%), Sweden (2.9%) and Japan (1.7%).
Mobile banking Trojans
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports. Over the reporting period, we detected 27,403 mobile Trojans, which is 1.2 times less than in Q1.
Number of mobile banking Trojans detected by Kaspersky Lab solutions (Q3 2015 – Q2 2016)
The TOP 5 most popular mobile banking Trojans in Q2 consisted of representatives from just two families – Trojan-Banker.AndroidOS.Asacub and Trojan-Banker.AndroidOS.Svpeng.
Trojan-Banker.AndroidOS.Asacub.i was the most popular mobile banking Trojan of the quarter. It uses different methods to trick users and bypass system constraints. In Q1 we identified a modification of this mobile Trojan that overlaid the regular system window requesting device administrator privileges with its own window containing buttons. The Trojan thereby conceals the fact that it is gaining elevated privileges in the system from the user, and tricks the user into approving these privileges. In Q2, we detected a modification that requested the user’s permission to become the main SMS application.
Dialog window of Trojan-Banker.AndroidOS.Asacub.i asking for the user’s approval to become the main SMS application
This allows the Trojan to bypass the system constraints introduced in Android 4.4, and to hide incoming SMSs from the user (as a rule, it hides messages from banks and payment systems). In order to make users save this malicious program in the settings as the main SMS application, the Trojan authors had to, among other things, implement a messenger interface.
The Trojan-Banker.AndroidOS.Asacub.i interface used to create and send messages
Asacub is actively distributed via SMS spam.
Russia and Germany lead in terms of the number of users attacked by mobile banking Trojans:
Geography of mobile banking threats in Q2 2016 (percentage of all users attacked)
The number of attacked users depends on the overall number of users within each individual country. To assess the risk of a mobile banker Trojan infection in each country, and to compare it across countries, we created a country ranking according to the percentage of users attacked by mobile banker Trojans.
TOP 10 counties attacked by mobile banker Trojans (ranked by percentage of users attacked)
Country* % of users attacked**
1 Russia 1.51
2 Australia 0.73
3 Uzbekistan 0.45
4 Korea 0.35
5 China 0.34
6 Ukraine 0.33
7 Denmark 0.28
8 Germany 0.24
9 Turkey 0.23
10 Kyrgyzstan 0.17
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
In Q2 2016, first place was occupied by Russia (1.51%) where the majority of affected users encountered the Trojan-Banker.AndroidOS.Asacub, Trojan-Banker.AndroidOS.Svpeng and Trojan-Banker.AndroidOS.Faketoken families of mobile banker Trojans.
China, last quarter’s leader, fell to fifth place this quarter.
In second place again was Australia where the Trojan-Banker.AndroidOS.Acecard family was replaced by the Trojan-Banker.AndroidOS.Marcher family as the most popular threat.
Banking Trojans were especially popular with attackers in Russia and Australia. The percentage of users attacked by this malware in the two countries relative to all attacked users accounted for 14%.
Mobile Trojan-Ransomware
As of this quarter, we will calculate the distribution of mobile malware by type based on the number of detected malicious installation packages rather than modifications, as was the case in earlier reports.
In Q2 2016, we detected 83,048 mobile Trojan-Ransomware installation packages, which is about the same number as the previous quarter and seven times more than in Q4 2015.
Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab
(Q3 2015 – Q2 2016)
The sharp rise in the number of mobile Trojan-Ransomware installation packages in 2016 was caused by the active proliferation of the Trojan-Ransom.AndroidOS.Fusob family of Trojans. In the first quarter of 2016, this family accounted for 96% of users attacked by mobile ransomware. In Q2 its share was 85%.
In Q2 2016, 54.5M unique malicious URLs were recognized by @kaspersky web antivirus components #KLreport #IT
Tweet
Trojan-Ransom.AndroidOS.Fusob.h became the most popular mobile Trojan-Ransomware in the second quarter – it accounted for nearly 60% of users attacked by mobile ransomware. Once run, the Trojan requests administrator privileges, collects information about the device, including the GPS coordinates and call history, and downloads the data to a malicious server. After that, it may get a command to block the device. In the second quarter we registered a growth in the number of installation packages related to Trojan-Ransom.AndroidOS.Congur.b: their share grew from 0.8% to 8.8%. This Trojan, targeting Chinese-speaking users, changes the system password (PIN), or installs it if no password was installed earlier, thus making it impossible to use the device. The notification containing the ransom demand is displayed on the screen of the blocked device.
Germany, the US and Russia had the highest number of users attacked by Trojan-Ransomware this quarter:
Geography of mobile Trojan-Ransomware in Q2 2016 (percentage of all users attacked)
To assess the risk of a mobile banker Trojan infection in each country, and to compare it across countries, we created a country ranking according to the percentage of users attacked by mobile Trojan-Ransomware.
TOP 10 counties attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked)
Country* % of users attacked**
1 Canada 2.01
2 Germany 1.89
3 US 1.66
4 Switzerland 1.63
5 Mexico 1.55
6 UK 1.51
7 Denmark 1.35
8 Italy 1.35
9 Kazakhstan 1,35
10 Netherlands 1.15
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
In all the countries of the TOP 10, except for Kazakhstan, the most popular Trojan-Ransom family was Fusob. In the US, the Trojan-Ransom.AndroidOS.Svpeng family was also popular. These Trojans demand a ransom of $100-500 from victims to unblock their devices.
In Kazakhstan and Uzbekistan, the main threat to users originated from representatives of the Small mobile Trojan-Ransom family. This is a fairly simple ransomware program that blocks operation of a device by overlaying all the windows on the device with its own window and demanding $10 to unblock it.
Vulnerable applications exploited by cybercriminals
In Q2 2016, exploits for Adobe Flash Player remained popular. During the reporting period two new vulnerabilities were discovered in this software:
СVE-2016-4117
CVE-2016-4171
An exploit for CVE-2016-4117 was added to the Magnitude and Neutrino exploit kits. The CVE-2016-4171 vulnerability was used by the ScarCruft group to carry out targeted attacks. We wrote a more detailed account of this group’s activities in a blog published in mid-June.
In Q2 2016, @kaspersky web #antivirus detected 16,119,489 unique malicious objects #KLreport #netsec
Tweet
The main event this quarter was the demise of the long-term market leaders – the Angler and Nuclear exploit kits. Angler’s departure resulted in market players shifting to other kits to distribute malware. In particular, we registered a dramatic growth in the popularity of the Neutrino exploit kit.
This is how the overall picture for the use of exploits in the second quarter looks:
Distribution of exploits used in attacks by the type of application attacked, Q2 2016
The chart shows that despite the exit of the market leaders the breakdown of exploits was almost unchanged from the previous quarter: the proportion of exploits for Microsoft Office (14%) and Java (7%) fell by 1 p.p., while the share for Android grew 2 p.p. and reached 24%. This suggests that demand for exploit kits has been spread among the remaining players: RIG, Magnitude and Neutrino. The latter was the undisputed leader this quarter in terms of the number of attempts to download malware.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are created deliberately by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
In the second quarter of 2016, Kaspersky Lab’s web antivirus detected 16,119,489 unique malicious objects: scripts, exploits, executable files, etc. 54,539,948 unique URLs were recognized as malicious by web antivirus components.
Online threats in the banking sector
These statistics are based on the detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
Number of users attacked by malware targeting finances<
Due to the constant emergence of new representatives of banking Trojans and functional changes in existing banking Trojans, in the second quarter of 2016 we have significantly updated the list of verdicts classed as banking risks. This means the number of financial malware victims has changed significantly compared to the data published in previous quarters. As a comparison, we have recalculated the statistics for the previous quarter, taking into account all the malware from the updated list.
Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on 1,132,031 computers in Q2 2016. The quarter saw an increase in financial malware activity: the figure for Q2 is 15.6% higher than that for the previous quarter (979, 607).
Number of users attacked by malware targeting finances, Q2 2016
Geography of attack
To evaluate and compare the risk of being infected by banking Trojans worldwide, we calculate the percentage of Kaspersky Lab product users who encountered this type of threat during the reporting period in the country, relative to all users of our products in the county.
Geography of banking malware attacks in Q2 2016 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
Country* % of attacked users**
1 Turkey 3.45
2 Russia 2.92
3 Brazil 2.63
4 Pakistan 2.60
5 Venezuela 1.66
6 Tunisia 1.62
7 Japan 1.61
8 Singapore 1.58
9 Libya 1.57
10 Argentina 1.48
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by banking Trojan attacks as a percentage of all unique users of Kaspersky Lab products in the country.
The highest percentage of Kaspersky Lab users attacked by banking Trojans was in Turkey. One of the reasons for the growth in financial threats there was a burst of activity by the Gozi banking Trojan whose developers have joined forces with the creators of the Nymaim Trojan.
In Russia, 2.92% of users encountered a banking Trojan at least once in Q2, placing it second in this ranking.
Brazil rounds off the top three. We expect a surge in financial threats in Latin America in the next quarter due to the Olympic Games in Brazil. This event is just too tempting for cybercriminals to ignore – they regularly use the theme of major sporting events in their attacks to lure potential victims.
The top five countries where users were least affected by banking Trojans were Canada (0.33%), the US (0.4%), the UK (0.4%), France (0.43%) and the Netherlands (0.5%).
The percentage of banking Trojan victims in Italy was 0.62%, in Spain it was 0.83%, while in Germany the figure was 1.03%.
The TOP 10 banking malware familie>
The table below shows the top 10 malware families most commonly used in Q2 2016 to attack online banking users (as a percentage of users attacked):
Name* Percentage of users attacked**
1 Trojan-Spy.Win32.Zbot 15.72
2 Trojan-Banker.Win32.Gozi 3.28
3 Trojan.Win32.Qhost 2.35
4 Trojan-Banker.Win32.Shiotob 2.27
5 Trojan-Banker.Win32.BestaFera 2.12
6 Trojan.Win32.Nymaim 1.98
7 Trojan-Banker.Win32.ChePro 1.90
8 Trojan-Banker.Win32.Banbra 1.77
9 Trojan.Win32.Neurevt 0.67
10 Backdoor.Win32.Shiz 0.66
* The detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malware in question as a percentage of all users attacked by financial malware.
Trojan-Spy.Win32.Zbot in first place is a permanent fixture in the leading positions of this ranking, and it is no coincidence: the source codes of this Trojan became publicly available back in 2012. This has resulted in the emergence of new banking Trojans that have adopted fragments of the Zbot code.
The second quarter of 2016 saw a surge in malicious activity by Trojan.Win32.Nymaim. As a result, this Trojan made it into the top 10 for the first time, going straight in at sixth place. Nymaim was initially designed to block access to valuable data and then demand a ransom (ransomware) to unblock it, but the latest version now also includes banking Trojan functionality for stealing financial information. This can be explained by the fact that the creators of Nymaim and Gozi (which also appears in the Q2 TOP 10 financial risks) have joined forces. Nymaim’s source code now includes fragments of Gozi code that provide attackers with remote access to infected computers.
In Q2 2016, Attempted infections by financial #malware were registered on 1.1M user computers #KLreport #banking
Tweet
A permanent resident in this ranking and one of the reasons financial threats are so prominent in Brazil is the Trojan-Banker.Win32.ChePro family. This banking malware lets cybercriminals take screenshots, register keystrokes, and read the contents of the clipboard, i.e., it possess functionality capable of attacking almost any online banking system. Criminals are trying to implement new techniques to avoid detection for as long as possible. Some of the Trojans from this family use geolocation or ask for the time zone and the Windows version from the system in order to infect users in a particular region.
Yet another newcomer to the top 10 most active financial threats in Q2 was the Trojan.Win32.Neurevt family. Representatives of this family were first discovered in 2013 and are used by cybercriminals not only to steal user payment data in online banking systems but also to send out spam (some versions, for example, sent spam messages on Skype) and implement DDoS attacks (with the addition of functionality capable of performing the Slowloris HTTP flooding scenario).
Ransomware Trojans
The overall number of cryptor modifications in our virus collection to date is approximately 26,000. A total of 28 new cryptor families and 9,296 new modifications were detected in Q2.
The following graph shows the rise in the number of newly created cryptor modifications over the last two quarters.
Number of Trojan-Ransom cryptor modifications (Q1 2016 vs Q2 2016)
Some of the more high-profile or unusual Trojans detected in Q2 2016 are listed below:
CryptXXX (Trojan-Ransom.Win32.CryptXXX)
This cryptor has been widely distributed via exploit kits since April 2016. Its earlier versions contained gaps in the file encryption algorithm which allowed Kaspersky Lab to release a utility to decrypt them. Unfortunately, the attackers have made adjustments to subsequent versions, making it impossible to decrypt the files affected by later CryptXXX modifications.
ZCryptor (Trojan-Ransom.MSIL.Zcryptor)
This malware combines cryptor functionality and a worm distribution method. Trojan ransomware does not usually include tools for self-propagation, and ZCryptor just happens to be an exception to this rule. Like a classic worm, while infecting, it creates copies of its body on removable media and generates the autorun.inf file to implement the automatic launch of its executable file once the media is connected to another system (if, of course, autorun is not disabled).
RAA (Trojan-Ransom.JS.RaaCrypt)
Sometimes we come across cryptors that differ from their peers in terms of functionality, and sometimes an unusual implementation will catch the attention of an analyst. In the case of RAA, the choice of programming language was curious: it was written entirely in JavaScript. The whole body of the program was included in a single .js file delivered to the victim as an attachment in a spam message. When run, it displays a fake error message, and in the meantime, encrypts the user’s files.
Bart (Trojan-Ransom.Win32.Bart)
This cryptor puts the victim’s files in password-protected ZIP archives; and it creates passwords using the Diffie-Hellman algorithm on an elliptic curve. The design of the ransom note and the payment site is an exact copy of that used by the notorious Locky.
Satana (Trojan-Ransom.Win32.Satan)
This is a combination of MBR blocker and file cryptor, probably inspired by similar functionality in the notorious Petya + Mischa Trojans. Satana, unlike Petya, does not encrypt MFT; in fact, its MBR module is obviously incomplete because the process of checking the password entered by the victim results in nothing more than a continuous cycle. Below is a fragment of the code demonstrating this.
The number of users attacked by ransomware
Number of users attacked by Trojan-Ransom cryptor malware (Q2 2016)
In Q2 2016, 311,590 unique users were attacked by cryptors, which is 16% less than the previous quarter. Approximately 21% of those attacked were in the corporate sector.
It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models and issue the Generic verdict, which does not distinguish the type of malicious software.
Top 10 countries attacked by cryptors
Country* % of users attacked by cryptors**
1 Japan 2.40
2 Italy 1.50
3 Djibouti 1.46
4 Luxembourg 1.36
5 Bulgaria 1.34
6 Croatia 1.25
7 Maldives 1.22
8 Korea 1.21
9 Netherlands 1.15
10 Taiwan 1.04
* We excluded those countries where the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by ransomware as a percentage of all unique users of Kaspersky Lab products in the country.
In Q2, half of the top 10 were European countries – one less than the previous quarter.
Japan, which came ninth in Q1, topped the ranking of countries attacked by cryptors with 2.40%: the most widespread cryptor families in the country were Teslacrypt, Locky and Cryakl.
Newcomers to this ranking were Djibouti (1.46%), Korea (1.21%) and Taiwan (1.04%).
Top 10 most widespread cryptor families
Name Verdict* Percentage of users**
1 CTB-Locker Trojan-Ransom.Win32.Onion/Trojan-Ransom.NSIS.Onion 14.59
2 Teslacrypt Trojan-Ransom.Win32.Bitman 8.36
3 Locky Trojan-Ransom.Win32.Locky 3.34
4 Shade Trojan-Ransom.Win32.Shade 2.14
5 Cryrar/ ACCDFISA Trojan-Ransom.Win32.Cryrar 2.02
6 Cryptowall Trojan-Ransom.Win32.Cryptodef 1.98
7 Cryakl Trojan-Ransom.Win32.Cryakl 1.93
8 Cerber Trojan-Ransom.Win32. Zerber 1.53
9 Scatter Trojan-Ransom.BAT.Scatter/Trojan-Downloader.JS.Scatter/Trojan-Dropper.JS.Scatter/Trojan-Ransom.Win32.Scatter 1.39
10 Rakhni Trojan-Ransom.Win32.Rakhni/Trojan-Downloader.Win32.Rakhni 1.13
* These statistics are based on detection verdicts received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by a specific Trojan-Ransom family as a percentage of all users of Kaspersky Lab products attacked by Trojan-Ransom malware.
First place in Q2 was occupied by the CTB-Locker (Trojan-Ransom.Win32/NSIS.Onion) family. In second place was the TeslaCrypt family represented by one verdict: Trojan-Ransom.Win32.Bitman. The Trojan-Ransom.JS.Cryptoload verdict, which in the past downloaded malware and was associated with TeslaCrypt, is no longer characteristic of this family only. TeslaCrypt was earlier a major contributor to the statistics, but fortunately ceased to exist in May 2016 – the owners disabled their servers and posted a master key to decrypt files.
In Q2 2016, #crypto #ransomware attacks were blocked on 311,590 computers of unique users #KLreport
Tweet
Cerber and Cryrar are the only changes to this ranking compared to the previous quarter.
The Cerber cryptor spreads via spam and exploit kits. The cryptor’s site on the Tor network is translated into lots of languages. Cerber’s special features include the following:
It explores the infected system meticulously: checks for the presence of an antivirus, if it is running under a virtual machine (Parallels, VmWare, QEMU, VirtualBox) or Wine, checks for utilities from various researchers and analysts (it does this by searching for certain processes and files on the disk drive), it even has a blacklist of system drive serial numbers.
It checks the keyboard layout and the IP address of the infected system. If it detects that the machine is located in a CIS country, it stops infecting it.
It attempts to bypass antivirus protection by terminating their processes, interrupting services, deleting files.
In addition to notifying users about encryption in the form of TXT and HTML files, as is the case with other families, it also runs the VBS script which reproduces the following voice message: “Attention! Attention! Attention! Your documents, photos, databases and other important files have been encrypted!”
The Cryrar cryptor also known as the Anti Cyber Crime Department of Federal Internet Security Agency (ACCDFISA), Anti-Child Porn Spam Protection, etc. first appeared back in 2012. It has the distinctive feature of placing the victim’s files in password-protected self-extracting RAR archives. According to KSN statistics, it shows no signs of conceding its position to newer rivals.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources that were used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q2 2016, Kaspersky Lab solutions blocked 171,895,830 attacks launched from web resources located in 191 countries around the world. 54,539,948 unique URLs were recognized as malicious by web antivirus components.
81% of notifications about blocked web attacks were triggered by attacks coming from web resources located in 10 countries.
Distribution of web attack sources by country, Q2 2016
The US (35.44%) returned to the top of this ranking in the second quarter. Russia (10.28%) moved up one place to second. The previous quarter’s leader, the Netherlands, dropped to fourth place after its share fell by 17.7 percentage points. Germany completed the Top 3 with a share of 8.9%. Bulgaria left the Top 10, while Canada was a newcomer in ninth place with 0.96%.
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
Country* % of unique users attacked**
1 Azerbaijan 32.10
2 Russia 30.80
3 China 29.35
4 Slovenia 27.54
5 Ukraine 27.46
6 Kazakhstan 27.03
7 Vietnam 26.02
8 Algeria 25.63
9 Armenia 25.09
10 Belarus 24.60
11 Brazil 24.05
12 France 22.45
13 Moldova 22.34
14 Kyrgyzstan 22.13
15 Bulgaria 22.06
16 Italy 21.68
17 Chile 21.56
18 Qatar 20.10
19 India 20.00
20 Portugal 19.84
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In Q2, Azerbaijan moved up from fourth to first place and became the new leader of this ranking with 32.1%. Russia (30.8%) dropped from first to second, while Kazakhstan (27.03%) fell from second to sixth place.
Since the previous quarter, Spain, Lithuania, Croatia and Turkey have all left the TOP 20. The newcomers to this ranking were Bulgaria (22.06%), Chile (21.56%), Qatar (20.10%) and Portugal (19.84%).
The countries with the safest online surfing environments included Canada (15%), Romania (14.6%), Belgium (13.7%), Mexico (13.2%), the US (12.8%), Switzerland (12. 4%), New Zealand (12.1%), Czech Republic (12%), Argentina (9.9%), Japan (9.5%), the Netherlands (8.3), Sweden (8.2%) and Germany (8%).
On average, 19.4% of computers connected to the Internet globally were subjected to at least one web attack during the three months. This is a fall of 1.8 p.p. compared to Q1 2016.
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q2 2016, Kaspersky Lab’s file antivirus detected 249,619,379 unique malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each of the countries, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus was triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
Top 20 countries with the highest levels of computer infection
Country* % of unique users**
1 Somalia 65.80
2 Vietnam 63.33
3 Tajikistan 62.00
4 Russia 61.56
5 Kyrgyzstan 60.80
6 Bangladesh 60.19
7 Afghanistan 60.00
8 Armenia 59,74
9 Ukraine 59.67
10 Nepal 59.66
11 Ethiopia 59.63
12 Laos 58.43
13 Kazakhstan 57.72
14 Rwanda 57.33
15 Djibouti 56.07
16 Yemen 55.98
17 Venezuela 55.76
18 Algeria 55.58
19 Cambodia 55.56
20 Iraq 55.55
These statistics are based on the detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
** The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
Somalia remained the leader of this ranking in Q2 2016 with 65.8%. Yemen (55.98%) fell from second to sixteenth place, while Vietnam (63.33%) jumped from eighth to second. Tajikistan (62%) rounded off the TOP 3. Russia moved up one place from fifth to fourth, although the figure for that country declined by 2.62 percentage points to 61.56%.
In Q2 2016, 27,403 #mobile #banking Trojans were detected by @kaspersky mobile security products #KLreport
Tweet
Newcomers to this ranking are Djibouti in fifteenth place (56.07%), Venezuela in seventeenth (55.76%), and Cambodia in nineteenth (55.56%).
The safest countries in terms of local infection risks were Croatia (29%), Singapore (28.4%), Germany (28.1%), Norway (27.6%), the US (27.1%), Switzerland (26.3%), Japan (22.1%), Denmark (21.4%) and Sweden (21.3%).
An average of 43.3% of computers globally faced at least one local threat during Q2 2016, which is 1.2 p.p. less than in the previous quarter.
Hacker reveals How He Could have Hacked Multiple Facebook Accounts
27.8.2016 thehackernews Hacking
How to Hack a Facebook Account?
That's possibly the most frequently asked question on the Internet today. Though the solution is hard to find, a white hat hacker has just proven how easy it is to hack multiple Facebook accounts with some basic computer skills.
Your Facebook account can be hacked, no matter how strong your password is or how much extra security measures you have taken. No joke!
Gurkirat Singh from California recently discovered a loophole in Facebook's password reset mechanism that could have given hackers complete access to the victim's Facebook account, allowing them to view message conversations and payment card details, post anything and do whatever the real account holder can.
The attack vector is simple, though the execution is quite difficult.
The issue, Gurkirat (@GurkiratSpeca) says, actually resides in the way Facebook allows you to reset your password. The social network uses an algorithm that generates a random 6-digit passcode ‒ that's 10⁶ = 1,000,000 possible combinations ‒ which does not change until gets 'used' (if you request it from mbasic.facebook.com).
"That could possibly mean that if 1 million people request a password within a short amount of time such that no one uses their code to reset the password, then 1,000,0001 person to request a code will get a passcode that someone from the batch has already been assigned," Gurkirat explains in a blog post.
How to Hack Multiple Facebook Accounts?
Gurkirat first collected valid Facebook IDs by making queries to Facebook Graph API starting with 100,000,000,000,000, since Facebook IDs are generally 15-digit long and then visited www.facebook.com/[ID] with a valid ID number in place of [ID].
Once entered, the URL automatically redirected and changed the Facebook ID to the user's username. In this way, first, he was able to make a list of 2 Million valid Facebook usernames.
"I first reported this bug on May 3, 2016, but Facebook didn't believe me such large-scale execution could have been possible. They wanted proof," Gurkirat told The Hacker News. "So I spent close to a month learning and building the infrastructure to target a batch of 2 million Facebook users. I then re-submitted this bug, and they agreed that it indeed was an issue."
Then using a script, hundreds of proxies and random user-agents, Gurkirat automatically initiated the password reset requests for those 2 million users, each assigned a 6-digit password reset code, thus consuming the complete 6-digit range.
Gurkirat then randomly picked a 6-digit number, i.e. 338625, and started the password reset process using a brute forcing script against all those usernames in his list, hoping that this number had been assigned by Facebook to someone in his list of 2 million usernames.
Gurkirat practically executed this thing and managed to find a right password reset code and username combination that allowed him to reset the password and hijack a random user's Facebook account.
Also Read: How to Hack Someones Facebook Account Just by Knowing their Phone Numbers.
Although Facebook has patched the bug after been reported by Gurkirat and rewarded him $500 (that's little less), Gurkirat has doubt that the patch is not "strong enough to mitigate this vulnerability."
"I would have never imagined that a company as big as Facebook would be susceptible to sheer computing power. The efficacy of the bug I found relied on just that," Gurkirat told the Hacker News.
"I was informed by Facebook that the patch has been applied and that they have started throttling aggressively per IP address. Given a much larger pool of IP addresses that can simulate a global network flow combined with little social engineering, I still doubt if their patch is strong enough to mitigate this vulnerability."
However, Facebook provides you an extra layer of security to protect your account against such attacks.
Here's How you can Protect Your Facebook account:
Enable Login Approvals: Users are recommended to enable "Login Approvals" as an extra layer of security in order to prevent their Facebook accounts against these kinds of attacks.
With Login Approvals turned ON, Facebook will send you a 6-digit security code via a text message to your registered cell phone if someone tries to log into your Facebook account from a new computer or device or a different web browser.
So, even if your Facebook username and password are entered by an attacker, that 6-digit security code, which has been delivered to your phone, will still be required to log into your account, preventing hackers from accessing your account.
Enable Login Notification Alerts: Facebook also provides a security feature, "Login Alerts," that send you an email or SMS whenever it suspects an unauthorized user is accessing your account.
If your Facebook account is accessed from a remote device, Facebook sends you an email or SMS alert. If that is an unauthorized access, you can quickly follow the steps listed in the email to disable access for that device.
Use Password Manager: It's a general, must-do advice to have a strong, unique password for every online account. We have listed some best password managers that would help you understand the importance of password manager and choose a suitable one, according to your requirement.
Ransomware jako služba
27.8.2016 SecurityWorld Viry
Experti bezpečnostní firmy odhalují, jak funguje Cerber, jeden z ransomwaru, který funguje na bázi služby, a jak snadné je využít jej pro své nekalé účely.
V 60stránkové zprávě zveřejnil Check Point Threat Intelligence and Research Team ve spolupráci s partnerskou výzkumnou organizací IntSights Cyber Intelligence nové podrobnosti a informace o technickém a obchodním pozadí ransomwaru Cerber.
Z reportu vyplývá, že ze všech ransomwarů má Cerber výrazně vyšší míru infekce a je ziskovější. Cerber v současné době využívá více než 160 aktivních kampaní po celém světě a předpokládané celkové roční příjmy jsou ve výši přibližně 2,3 milionů dolarů.
Každý den je v průměru spuštěno osm nových kampaní. Jen v červenci výzkum odhalil přibližně 150 tisíc obětí v 201 zemích a teritoriích. V České republice byla v červenci infikována zařízení více než 700 uživatelů.
Affiliates program Cerber je také úspěšnou pračkou peněz. Cerber používá bitcoinovou měnu, aby se vyhnul sledování a vytváří pro každou ze svých obětí unikátní peněženku pro příjem finančních prostředků.
Po zaplacení výkupného (obvykle jeden bitcoin, který má ale v současné době hodnotu 590 dolarů) obdrží oběť dešifrovací klíč. Bitcoin je přesunutý k vývojáři malwaru přes službu, která zahrnuje desetitisíce bitcoinových peněženek, takže je téměř nemožné je jednotlivě vysledovat. Na konci tohoto procesu získá vývojář peníze a partneři obdrží svůj podíl.
Cerber také otevírá dveře dalším rádoby hackerům. Umožňuje totiž i netechnickým jednotlivcům a skupinám podílet se na vysoce výnosném obchodu a spouštět nezávislé kampaně s využitím speciálních kontrolních a řídících (C&C) serverů a pohodlného ovládacího panelu, který je k dispozici v 12 různých jazycích.
Expert detailně mapovali od června 2016 komplexní systém vytvořený kolem ransomwaru Cerber a celou globální distribuční infrastrukturu. Byli schopní obnovit virtuální peněženky obětí, což týmu umožnilo sledovat platby a transakce a analyzovat pohyb zisků z malwaru a finanční toky.
Navíc tyto informace prý umožňují vytvořit dešifrovací nástroj, který může opravit infikované systémy, aniž by uživatelé nebo organizace museli kyberzločincům platit výkupné.
Počítače terorizuje nový vyděračský virus. Bezpečnostní experti už mají řešení
27.8.2016 Novinky/Bezpečnost Viry
Internetem se bez nadsázky jako lavina začal šířit nový vyděračský virus zvaný Alma. Tento nezvaný návštěvník zamkne data v počítači a požaduje výkupné. Vrásky na čele nicméně uživatelům příliš dělat nemusí, protože bezpečnostním expertům se na něj podařilo již vyzrát.
Na nového člena z rodiny ransomware, jak jsou souhrnně označovány vyděračské viry, upozornili výzkumníci ze společnosti PhishLabs. Ta se zabývá hledáním a analyzováním nových bezpečnostních hrozeb.
Škodlivý kód Alma útočí prakticky úplně stejně jako ostatní vyděračské viry. Nejprve začne šifrovat obsah počítače a uživateli zobrazí oznámení, že za dešifrování dat musí zaplatit, jinak se ke svým datům údajně již nikdy nedostane.
Výkupné neplatit
Ani po zaplacení výkupného ale nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat. V některých případech to ale není možné.
To však naštěstí o škodlivém kódu Alma již neplatí. Bezpečnostní experti dokázali v rekordně krátkém čase tohoto nezvaného návštěvníka analyzovat a vyvinout dekryptovací program.
S touto bezplatnou utilitou se uživatelé dostanou zpět ke všem svým datům, aniž by museli vyděračům zaplatit byť jen jedinou korunu. Samotný program i návod k jeho použití je možné stahovat ze stránek tvůrců, k dispozici je však pouze v anglickém jazyce.
New Locky Ransomware variant uses DLLs for distribution
27.8.2016 thehackernews Virus
A new Locky Ransomware variant has been spotted by researchers at Cyren, it uses DLLs for distribution.
The Locky Ransomware is one of the most popular threats since its first detection in the wild early 2016. The ransomware has evolved over the time, crooks have improved it adding new evasion detection features and changing the distribution methods.
Security experts observe the implementation of sophisticated sandbox evasion techniques, they documented a new strain of the malware that used a new extension (aka Zepto variant) for the encrypted files meanwhile another version was able to use of offline encryption.
When it first appeared in the threat landscape, Locky was leveraging on documents for its distribution, later it used malicious macros, JavaScript attachments and also Windows script (WSF) files.
Recently, experts from the security firm Cyren discovered a new variant that added a supplementary layer of obfuscation to its downloader script. The new strain of Locky is delivered via spam campaigns, each malicious email includes a ZIP-archived JavaScript.
“The email being sent in this latest wave, as often before, uses business finance-related topics to lure users into opening its attachment, which is ZIP-archived JavaScript. Comparing this variant to the earlier variants, it has added another layer of obfuscation which decrypts and executes the real Locky downloader script.” states the analysis published by Cyren.

The downloader script works in a way similar to other strain of the Locky ransomware, the downloaded files are decrypted and saved in the Windows Temp directory, but differently from the past, the malicious payload is DLL file instead a .EXE. The DLL library is loaded using rundll32.exe, it leverages a custom packer to prevent anti-malware scanners from detecting it.
Once it is executed, the new Locky ransomware searches for the affected system and network shares for files to encrypt, it uses the .zepto extension for locked file. When the encryption process has been completed, this variant of Locky ransomware drops and displays a ransom payment instruction page.
Researchers noticed that the .onion address provided in the ransom note directs victims to the same Locky decryptor page that has been used in previous campaigns.
“Clicking on the onion link directs the user to the same Locky Decryptor page we have seen in previous Locky waves.” closes the report.
Secret data on DCNS Scorpene submarines leaked online, it could be a disaster.
27.8.2016 thehackernews Hacking
The Australian newspaper published over 22,000 secret documents on six DCNS Scorpene submarines that are being built in India.
According to The Australian, Indian authorities is investigating a security breach that affected the French Submarine Firm DCNS, which is 35 percent owned by Thales.
The investigation started after more than 22,000 pages related to six DCNS Scorpene submarines being built in India were leaked.
“DCNS has been made aware of articles published in the Australian press related to the leakage of sensitive data about Indian Scorpene.This serious matter is thoroughly investigated by the proper French national authorities for Defense Security. This investigation will determine the exact nature of the leaked documents, the potential damages to DCNS customers as well as the responsibilities for this leakage.” reads the press information published by the company.
The journalists at The Australian had reviewed over 4,450 pages on the Scorpene’s underwater sensors, over 4,300 pages on its combat systems, 4,200 pages of data on above-water sensors.
The DCNS claimed it was the victim of economic cyber espionage, a DCNS spokeswoman told Reuters that the security breach could have a dramatic impact on the company due to the exposure of sensitive information related the collaboration of the company with some governments.
“Asked if the leak could affect other contracts, a company spokeswoman said it had come against a difficult commercial backdrop and that corporate espionage could be to blame.” reported the Reuters. “Competition is getting tougher and tougher, and all means can be used in this context,” she said. “There is India, Australia and other prospects, and other countries could raise legitimate questions over DCNS. It’s part of the tools in economic warfare.”
The Australian newspaper published some 22,400 documents containing technical details of six DCNS Scorpene submarines that are being built at a shipyard in Mumbai, India.
“I understand there has been a case of hacking,” Indian Defence Minister Manohar Parrikar told reporters. “We will find out what has happened.”
The DCNS Scorpene submarines are technological jewels, the documents include highly sensitive details of the submarine including manuals and models of the boat’s antennae.
This new generation of submarines has significant intelligence-gathering capabilities, is it equipped with advanced combat systems and high-tech devices for communication.
As anticipated the leaked documents also include secret information related the activities conducted by the French firm with various governments. The leaked files include secret information on sea trials that the Malaysian Navy is conducting with its fleet of DCNS Scorpene submarines. Some documents are related to business information with Chile and Russia, in the first case the company provided radar systems for some Chilean frigates, meanwhile the Russian government received amphibious assault vessels.
In a brief statement, the DCNS said it is aware of the leak on the Indian Scorpenes and noted that the appropriate French authorities are currently investigating the breach. “This investigation will determine the exact nature of the leaked documents, the potential damages to DCNS customers as well as the responsibilities for this leakage.”
The Australian hasn’t revealed the source of the documents but confirmed that the security breach could have serious repercussions on a $38 billion project that the DCNS is currently negotiating with the Australian government.
Nový virus pro Android je vychytralý, útočníci ho ovládají přes Twitter
27.8.2016 Živě.cz Viry
Populární sociální síť Twitter nemusí sloužit pouze pro sdílení krátkých příspěvků mezi lidmi. Kyberzločinci totiž dokážou přes Twitter ovládat i své viry.
Bezpečnostní experti odhalili nový škodlivý kód, jehož cílem jsou zařízení s operačním systémem Android. Slouží jako vstupní brána pro další viry, přičemž ho útočníci dokážou nenápadně ovládat přes Twitter. Informace o hrozbě zveřejnila společnost Eset na svém webu.
Malware čeká na příkazy z Twitteru
Malware označený názvem Android / Twitoor se šíří prostřednictvím pochybných internetových stránek s aplikacemi. Byly však zaznamenány i případy, kdy byl odkaz na jeho stažení rozesílán prostřednictvím SMS či MMS zpráv.
Po úspěšném nainstalování zůstane ukrytý v operačním systému, přičemž vyčkává na řídicí příkazy. Na rozdíl od běžných virů, které v mnoha případech komunikují přímo se serverem útočníků a jsou tak odhalitelné na základě datového provozu, tato varianta zneužívá sociální síť Twitter.
V pravidelných intervalech probíhá kontrola předem definovaného twitterového účtů. Na něm autoři zanechávají tweety obsahující zašifrované řetězce. Software je dešifruje a provede příkaz. Řídící twitterový kanál lze samozřejmě průběžně měnit a mezi přijímanými příkazy je například možnost stažení a instalace libovolné aplikace.
Může přijít vydírání
Na základě těchto vlastností dokážou kyberzločinci vytvořit rozsáhlou síť složenou z infikovaných chytrých telefonů. Následné využití takového botnetu může být různé. Lze provádět DDoS útoky, těžit virtuální měny či globálně infikovat stovky telefonů a tabletů malwarem či spamem.
Prostřednictvím Android / Twitoor se v současnosti šíří různé verze bankovních virů. Jak však experti zdůrazňují, útočníci mohou přes botnet kdykoli začít distribuovat jakýkoli jiný typ virů, včetně vyděračského ransomwaru.
Uvedená hrozba sice nebyla nalezena v žádném oficiálním obchodě s aplikacemi, přesto jde o zajímavý obrat ve vývoji škodlivých kódů určených pro chytré telefony. Ovládání infikovaných zařízení přes Twitter přitom není žádnou novinkou. Již v roce 2009 se objevily první botnety zneužívající Twitter. V té době však šlo o počítače s operačním systémem Windows.
Opera pod útokem. Raději resetovala hesla všem svým uživatelům
27.8.2016 cnews.cz Počítačový útok
Norská Opera právě oznámila, že resetovala hesla svých uživatelů ke službě Opera Sync. Ta slouží k synchronizaci záložek, nastavení, historie i hesel. Důvodem pro tento krok bylo detekování útoku na některé své servery, při kterých zřejmě unikla některá uživatelská data (hesla prý ale jen v zašifrované podobě). Opera přesto raději resetovala hesla všem uživatelům této služby. Pro obnovení stačí kliknout na obnovení hesla a zadání nového.
Počet uživatelů služby Opera Link činí 1,7 milionu, což je ani ne půl procenta všech uživatelů Opery. Přitom Opera Sync je jednou z nejdůležitějších služeb prohlížeče, stejně jako obdobné služby u ostatních prohlížečů. Nedávno měli o koupi Opery zájem Číňané, které se ale (možná naštěstí) nakonec neuskutečnilo.
Apple releases 'Emergency' Patch after Advanced Spyware Targets Human Rights Activist
26.8.2016 thehackernews Vulnerebility
Apple has released iOS 9.3.5 update for iPhones and iPads to patch three zero-day vulnerabilities after a piece of spyware found targeting the iPhone used by a renowned UAE human rights defender, Ahmed Mansoor.
One of the world's most invasive software weapon distributors, called the NSO Group, has been exploiting three zero-day security vulnerabilities in order to spy on dissidents and journalists.
The NSO Group is an Israeli firm that sells spying and surveillance software that secretly tracks a target's mobile phone.
The zero-day exploits have allowed the company to develop sophisticated spyware tools that can access the device location, contacts, texts, calls logs, emails and even microphone.
Apple fixed these three vulnerabilities within ten days after being informed by two security firms, Citizen Lab and Lookout, who conducted a joint investigation.
Background Story: Malware Discovery
Mansoor, 46, ‘Martin Ennals Award’ winner from the United Arab Emirates, received a text message on his iPhone on August 10, from an unknown number.
Mansoor found the message suspicious and knowing that government hackers had already targeted him in the past, he forwarded that message directly to Citizen Lab researcher Bill Marczak.
Citizen Lab brought in Lookout, a San Francisco mobile security company, to help examine the message.
After analyzing the message content, the researchers found that the link led to a sophisticated piece of malware that exploited three different unknown flaws in Apple’s iOS that would have allowed the attackers to get complete control of Mansoor’s iPhone.
Those links, if clicked, "Mansoor’s iPhone would have been turned into a sophisticated bugging device controlled by UAE security agencies," the Citizen Lab explained in a blog post.
"They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it. They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts."
According to a blog post published by Lookout, the three zero-day flaws, dubbed "Trident" by the firm, involved:
A memory corruption vulnerability in WebKit that could allow hackers to exploit a device when a user clicks on a malicious link.
Two kernel bugs (allowing device jailbreak) that an attacker secretly installs malware on victim’s device to carry out surveillance.
Apple released the patch update, iOS 9.3.5, on Thursday, and labeled it "important," advising its users to install the latest version of iOS as soon as possible to protect their devices against these potential security exploits.
You can install the security update over-the-air (OTA) via your iPhone or iPad's settings.
Germany and France declare War on Encryption to Fight Terrorism
26.8.2016 thehackernews Safety
Yet another war on Encryption!
France and Germany are asking the European Union for new laws that would require mobile messaging services to decrypt secure communications on demand and make them available to law enforcement agencies.
French and German interior ministers this week said their governments should be able to access content on encrypted services in order to fight terrorism, the Wall Street Journal reported.
French interior minister Bernard Cazeneuve went on to say that the encrypted messaging apps like Telegram and WhatsApp "constitute a challenge during investigations," making it difficult for law enforcement to conduct surveillance on suspected terrorists.
Also Read: How to Send and Receive End-to-End Encrypted Emails
The proposal calls on the European Commission to draft a law that would "impose obligations on operators who show themselves to be non-cooperative, in particular when it comes to withdrawing illegal content or decrypting messages as part of an investigation."
The proposed laws would force major technology companies including Apple, WhatsApp, Facebook, Telegram, and many others, to build encryption backdoors into their messaging apps.
The European Union has always been a strong supporter of privacy and encryption, but the recent series of terrorist attacks across both France and Germany this summer, including Normandy church attack carried out by two jihadists who reportedly met on Telegram, which made the countries shout for encryption backdoors loudly.
Although the proposal acknowledges encryption to be a critical part in securing communications and financial transactions, it says that solutions must be found to "enable effective investigation" while protecting users’ privacy.
Privacy advocates have been alarmed by the new proposals, as recent NSA hack just recently proved all of us that no system is hack-proof for hackers with right hacking skills and sufficient resources.
Related Read: Microsoft handed over encrypted messages and Skype calls to NSA
So, what happened to the NSA, which is the highly sophisticated intelligence agency of the world, could happen to encrypted messaging services that would feature an encryption backdoor for law enforcement.
The European Commission is believed to come up with new laws on privacy and security for telecom operators this fall, which would include third-party services such as WhatsApp or Telegram.
WhatsApp to Share Your Data with Facebook — You have 30 Days to Stop It
26.8.2016 thehackernews Safety
WhatsApp to Share Your Data with Facebook
Nothing comes for Free, as "Free" is just a relative term used by companies to develop a strong user base and then use it for their own benefits.
The same has been done by the secure messaging app WhatsApp, which has now made it crystal clear that the popular messaging service will begin sharing its users’ data with its parent company, Facebook.
However, WhatsApp is offering a partial opt-out for Facebook targeted ads and product related purposes, which I will let you know later in this article, but completely opting out of the data-sharing does not seem to be possible.
Let's know what the company has decided to do with your data.
Of course, Facebook is willing to use your data to sell more targeted advertisements.
WhatsApp introduced some significant changes to its privacy policy and T&Cs today which, if accepted once, gives it permission to connect users' Facebook accounts to WhatsApp accounts for the first time, giving Facebook more data about users for delivering more relevant ads on the social network.
The messaging service will also begin pushing users to share some of their account details, including phone numbers, with Facebook, allowing the social network to suggest phone contacts as friends.
When Facebook acquired WhatsApp for $19 Billion in 2014, users were worried about the company's commitment to protecting its users' privacy. But, WhatsApp reassured them that their privacy would not be compromised in any way.
"Respect for your privacy is coded into our DNA, and we built WhatsApp around the goal of knowing as little about you as possible," said WhatsApp co-founder Jan Koum in a blog post published at that time.
Now the WhatsApp users are feeling betrayed by the company's latest move.
However, you need not to worry about the contents of your WhatsApp messages, like words and images, as they are end-to-end encrypted, meaning that even the company cannot read them.
Ultimately, the two companies will be sharing, what they called, a limited amount of user data, which includes phone numbers and other information about users.
No Option to Completely Opt-Out of Data Sharing
If you think WhatsApp is more privacy conscious than Facebook’s Messenger, it is not anymore.
WhatsApp is offering a solution partially to opt out the data sharing, specifically for Facebook ad targeting and product-related purposes.
However, the company notes that data will still be shared "for other purposes such as improving infrastructure and delivery systems, understanding how our services or theirs are used, securing systems, and fighting spam, abuse, or infringement activities."
So, those who are thinking to opt out of the data-sharing entirely: There's no possible way to opt totally out.
Though one short solution is to stop using WhatsApp.
Here's How to opt -out of sharing data for Facebook ad-targeting purpose:
The company has outlined two ways to opt out of the exchange of information with Facebook on its blog.
One way is for those users who have not yet agreed to the new terms of service and privacy policy, so before agreeing to the new terms, follow these simple steps:
When prompted to accept the updated T&Cs, tap Read to expand the full text.
A checkbox option at the bottom of the policy for sharing your data on Facebook will appear.
Untick this option before hitting Agree. This will let you opt out of the data-sharing.
The second option is for those who have already accepted the new T&Cs without unchecking the box to share their information with Facebook.
WhatsApp is also offering a thirty-day window for users to make the same choice via the settings page in the app. To exercise your opt-out in this scenario you need to follow these steps:
Go to Settings → Account → Share my account info in the WhatsApp app
Uncheck the box displayed there within 30 days, as after that this partial opt-out window will expire.
However, WhatsApp states Facebook will still receive your data in some situations.
After introducing end-to-end encryption, WhatsApp has become one of the most popular secure messaging apps, but this sudden shift in its privacy policy may force some users to switch to other secure apps like Telegram and Signal.
vBulletin vulnerabilities exposed more than 27 million users’ records
26.8.2016 securityaffairs Vulnerebility
Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, many of them belonging to gamers on mail.ru.
The Data breach monitoring service LeakedSource has disclosed 11 new data breaches. Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, the majority of which belongs to three games on mail.ru.
At the time of notification, the researchers from LeakedSource had managed to crack 12,463,300 passwords.
Another data breach suffered by expertlaw.com exposed more than 190,000 accounts, meanwhile, a similar incident on gamesforum.com compromised more than 100,000 accounts.
Giving a close look to the compromised mail.ru accounts they belong from CFire, parapa.mail.ru (ParaPa Dance City game), and tanks.mail.ru (Ground War: Tank game).
The Subdomains belonging to mail.ru that were hacked in August of 2016 are:
cfire.mail.ru – 12,881,787 users, 6,226,196 passwords cracked at the time of this post.
parapa.mail.ru (main game) – 5,029,530 users, 3,329,532 passwords cracked at the time of this post.
parapa.mail.ru (forums) – 3,986,234 users, 2,907,572 passwords cracked at the time of this post.
tanks.mail.ru – 3,236,254 users, 0 passwords cracked at the time of this post.
mail.ru records include usernames, email addresses, IP addresses, and phone numbers. The other accounts compromised include usernames, passwords, email addresses, birthdays, and IP address.
“Not a single website used proper password storage, they all used some variation of MD5 with or without unique salts,” LeakedSource said.
What have in common all the compromised websites?
All of the hacked domains were running unpatched versions of the vBulletin CMS. Hackers exploited SQL Injection vulnerabilities in the Forumrunner add-on on vBulletin installations older than 4.2.2 or 4.2.3 to access their database.
Once again the wrong security posture is the root cause of these data breaches, million of users’ records exposed due to security issues fixed by vBulletin months ago.
“A security issue has been reported to us that affects vBulletin 4. We have released security patches for vBulletin 4.2.2 & 4.2.3 to account for this vulnerability. The issue could potentially allow attackers to perform SQL Injection attacks via the included Forumrunner add-on.” states the security advisory issued by vBulletin in June. “It is recommended that all users update as soon as possible. If you’re using a version of vBulletin 4 older than 4.2.2, it is recommended that you upgrade to the latest version as soon as possible. Please note that you need to update regardless of whether you have Forumrunner enabled. You can download the patch for your version here: http://members.vbulletin.com/patches.php“
In August a new security update was issued to fix multiple vulnerabilities exploited by hackers in the wild.
Linux.PNScan Trojan is back to compromise routers and install backdoors
26.8.2016 securityaffairs Virus
The Linux Trojan Linux.PNScan is back and it is actively targeting routers based on x86 Linux in an attempt to install backdoors on them.
Yesterday I wrote about a new Linux Trojan dubbed Linux.Rex.1, a new Linux malware that is capable of self-spreading and creating a peer-to-peer botnet, now experts from Malware Must Die discovered a new strain of malware that emerged more than a year ago.
The Linux Trojan is Linux.PNScan, it was first spotted last year when it was used to infect devices based on ARM, MIPS, or PowerPC architectures.
Now the threat was discovered in the wild actively targeting routers based on x86 Linux in an attempt to install backdoors on them.
“As per shown in title, it’s a known ELF malware threat, could be a latest variant of “Linux/PnScan”, found in platform x86-32 that it seems run around the web within infected nodes before it came to my our hand. This worm is more aiming embed platform and I am a bit surprised to find i86 binary is hitting some Linux boxes.” states the analysis published by Malware Must Die!
“This threat came to MalwareMustDie ELF team task before and I posted analysis in Mon Sep 28, 2015 on kernelmode [link] along with its details and threat, I thought the threat is becoming inactive now and it looks like I’m wrong, as the malware works still in infection now as worm functions and is hardcoded to aim 183.83.0.0 / 16 segment (located in network area of Telangana and Kashmir region of India), where it was just spotted. Since I never write about this threat in this blog (except kernelmode), it will be good to raise awareness to an active working and alive worm.”
The new strain of Linux.PNScan.2, unlike the original variant Linux.PNScan.1, which attempted to brute force router login using a special dictionary, the new threat targets specific IP addresses and attempts to establish an SSH connection by using the following credentials:combinations:
root;root;
admin;admin;
ubnt;ubnt.
The new Linux.PNScan.2 was compiled on compatibility of GCC(GNU) 4.1.x via the compiler tool Toolchains with cross compiler option for i686 using the SSL enabled configuration.
When the threat infects a device, it will fork its process 4 times, creating certain files on the infected system, daemonizing and listening to 2 TCP ports, targeting hardcoded IPs, and sending HTTP/1.1 requests via SSL to twitter.com on port 443 to hide its malicious traffic.
As its predecessor, also this variant can brute forcing logins.
The malware researchers who analyzed the threat suggest it might be of Russian origin.
“I guess this happened from 6 months ago until now, and the hacker is sitting there in Russia network for accessing any accessible infected nodes.” continues the analysis.
The experts from Malware Must Die! also published a list of infection symptoms, routers have specific processes running in the initial stage of the infection, the launched attack can be seen in the network connectivity, each connected target is logged in the “list2” file and the brute list is traced in file “login2.”
Cisco Updates ASA Software to fix the Equation Group’s EXTRABACON exploit
26.8.2016 securityaffairs Vulnerebility
Cisco has started releasing patches for its ASA software to address the Equation Group’s EXTRABACON exploit included in the NSA data dump leaked online.
Security firms and IT giants are analyzing the huge archive leaked by the Shadow Brokers crew after the hack of the NSA-linked Equation Group.
We reported that some of the exploits included in the archive are effective against CISCO, Fortinet, and Juniper network appliance.
For example, the BENIGNCERTAIN tool included in the NSA data dump could be exploited by remote attackers to extract VPN passwords from certain Cisco devices, meanwhile the EXTRABACON was analyzed by the Hungary-based security consultancy SilentSignal to hack into the newer models of Cisco’s Adaptive Security Appliance (ASA).
The EXTRABACON tool exploits the CVE-2016-6366 vulnerability to allow an attacker who has already gained a foothold in a targeted network to take full control of a CISCO ASA firewall.
The CVE-2016-6366 flaw affects Cisco’s ASA appliances, both firewalls and routers, Firepower products, Firewall Services Modules, industrial security appliances, and PIX firewalls.
CISCO ASA Software 2
The EXTRABACON tool leverages on a flaw that resides in the Simple Network Management Protocol (SNMP) implemented by the ASA software.
“A vulnerability in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) Software could allow an authenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” states the advisory published by CISCO.
“The vulnerability is due to a buffer overflow in the affected code area. The vulnerability affects all versions of SNMP. An attacker could exploit this vulnerability by sending crafted SNMP packets to the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system or to cause a reload of the affected system. The attacker must know the SNMP community string to exploit this vulnerability.”
Cisco promptly analyzed the exploits and released the necessary patches. Network administrators that manage CISCO ASA 7.2, 8.0, 8.1, 8.2, 8.3, 8.4, 8.5, 8.6 and 8.7 have to update their installations to version 9.1.7(9) or later. The vulnerability has been fixed in the ASA 9.1, 9.5 and 9.6 with the release of versions 9.1.7(9), 9.5(3) and 9.6.1(11).
The remaining versions will be fixed by the IT giant in the upcoming days, anyway, the company provided a detailed description of the workarounds to implement as a temporary solution.
The company will not issue any patch for no longer supported devices, including firewall modules and PIX firewalls.
Druhý Snowden? Hacker dělá NSA vrásky na čele
26.8.2016 Novinky/Bezpečnnost Hacking
Americká tajná služba NSA, jež si díky odhalením Edwarda Snowdena vysloužila pověst světového slídila, teď zažívá horké chvíle. Na digitální aukci se totiž ocitají její vlastní hackerské nástroje, což potvrzují znalci.
„Určitě to vypadá jako nástroje použité NSA,“ citoval server Yahoo francouzského experta Matta Suicheho. Zásluhu na „vykradení“ obávané NSA si připsala hackerská skupina The Shadow Brokers, a slíbila, že zveřejní ještě víc.
Krátce nato se ozval hacker s twitterovým účtem 1x0123 a oznámil, že hodlá nástroje NSA prodat na digitální aukci za osm tisíc dolarů. Z jeho ne zcela jasného vyjádření vyplývá, že je ukradl skupině The Shadow Brokers.

Twitterový účet hackera, který vystupuje pod přezdívkou 1x0123.
FOTO: repro Twitter
Nebylo by to poprvé, kdy by něco podobného udělal, a jeho šikovnost před několika měsíci na Twitteru ocenil z ruského azylu i Snowden. „Běžná podezření znovu začínají u Ruska, ačkoli se zdá, že je málo důkazů, jež by taková obvinění doložila,“ napsala agentura Reuters.
Pokud by totiž podle ní nástroje NSA skutečně ukradli Rusové, nemělo by smysl to zveřejňovat, natož je nabízet k prodeji. „Logičtější vysvětlení by byla krádež zevnitř,“ domnívá se agentura, čímž nadhodila možnost, že uvnitř NSA může pracovat další Snowden.
Pokud to tak je, je o důvod víc pochybovat o užitečnosti služby, která tajně shromažďuje soukromé informace miliónů Američanů, ale nedokáže zabránit odcizení svých nejcennějších dat.
Ruský hacker Selezňov byl v USA odsouzen za krádeže karetních dat
26.8.2016 Novinky/Bezpečnnost Hacking
Soud v americkém Seattlu ve čtvrtek uznal ruského hackera Romana Selezňova vinným z krádeže čísel téměř dvou miliónů kreditních karet. Muž, jehož předloňské zadržení na Maledivách označilo Rusko za únos, je podle soudu vinen ve 38 bodech obžaloby zahrnujících mimo jiné počítačové pirátství a podvod, informovala agentura AP. Hrozí mu až 34 let vězení.
Selezňov si podle žalobců přišel na bezmála 17 miliónů dolarů (více než 407 miliónů Kč) tím, že na nelegálních webech prodával identifikační čísla kreditních karet. Ta získával z počítačových systémů pizzerií a restaurantů většinou ve státě Washington na severozápadě USA. Prokuratura uvedla, že takto získal citlivé údaje o 1,7 miliónu karet.
Follow
112 News @112NewsFeed
#US court finds #Russian #hacker #Seleznev guilty of #cybercrimehttp://goo.gl/VqGWGV
10:24 PM - 25 Aug 2016
Retweets likes
Roman Selezňov
Jeho obhájci tvrdili, že žaloba přesvědčivě neprokázala spojitost mezi útoky na počítače podniků a Selezňovem. Rovněž napadli věrohodnost důkazů získaných z jeho laptopu, s nímž podle obhajoby nedovoleně manipulovali příslušníci tajné služby.
Soud dal však za pravdu prokuratuře a o výši trestu se bude rozhodovat 2. prosince.
Selezňov tuto činnost provozoval od roku 2010 až do svého zadržení. Americká justice jej obvinila už v roce 2011, ale v Rusku ho zadržet nemohla. Když v roce 2014 Selezňov odjel na dovolenou na Maledivy, požádal Washington tamní úřady o spolupráci. Podle Ruska šlo o organizovaný únos a porušení mezinárodního práva.
Unknown Bidder Buys 2,700 Bitcoins (worth $1.6 million) at US Government Auction
23.8.2016 thehackernews Security
A winning anonymous bidder bought 2,700 Bitcoins (worth roughly $1.6 Million) in an auction held by the United States Marshals Service (USMS) on Monday.
The US government announced at the beginning of this month its plans to auction 2,719 Bitcoins that were seized during several criminal, civil and administrative cases like Silk Road.
The US Marshals confirmed to CoinDesk that four bids were received in the auction that took place between 13:00 and 19:00 UTC on August 22.
The majority of the Bitcoins in the auction were stemmed from investigations of the Silk Road online black marketplace.
Included 2,719 Bitcoins in the auction were:
Around 1,300 Bitcoins seized from a civil case related to Matthew Gillum, a Silk Road drug dealer, who was sentenced to nine years in prison in 2015.
Only 2.8 Bitcoins directly came from Silk Road founder Ross Ulbricht, who was found guilty of operating Silk Road for illegal goods and handed two life sentences.
Some 65 Bitcoins came from Carl Force, a former Drug Enforcement Administration agent, who was sentenced for stealing Bitcoins during the Silk Road investigation.
Around 665 Bitcoins came from the case of Sean Roberson, a Florida man who allegedly created an online shop for selling stolen credit and debit cards.
The last date for registration was 18 August and only five bidders registered to claim the 2,700 BTC block, according to the agency.
However, this is not the first Bitcoin auction conducted by the US Marshals Service. The federal law enforcement agency has been selling off Bitcoins in a series of auctions.
The last USMS auction took place on November 15, when 11 bidders, including bitcoin exchange itBit, over-the-counter trading firm Cumberland Mining, and investor Tim Draper, bought 44,000 Bitcoins, worth $14.6 Million.
Epic Games Forum Hacked, Once Again — Over 800,000 Gamers' Data Stolen
23.8.2016 thehackernews Hacking
If you are a fan of Unreal Tournament from Epic Games or ever have participated in discussions on the online forums run by Epic Games, you possibly need to change your forum password as soon as possible.
It seems the Unreal Engine and its creators, Epic Games' forums have recently been compromised by an unknown hacker or a group of hackers, who have stolen more than 800,000 forum accounts with over half a Million from the Unreal Engine's forums alone.
The hackers get their hands on the forum accounts by exploiting a known vulnerability resided in an outdated version of the vBulletin forum software, which allowed them to get access to the full database.
Epic believes registration information that includes usernames, scrambled passwords, email addresses, dates of birth, IP addresses, and date of joining, may have been obtained in the attack.
"We believe a recent Unreal Engine and Unreal Tournament forum compromise revealed email addresses and other data entered into the forums, but no passwords in any form, neither salted, hashed, nor plaintext," announcement on the Unreal Engine forum website reads.
However, ZDNet reports "their full history of posts and comments including private messages, and other user activity data from both sets of forums" have also been compromised.
Most of the stolen passwords are scrambled that can not be cracked easily, but hackers could exploit other stolen data to send phishing messages to forum members' email addresses in an effort to infect their systems with ransomware or other malicious software.
Epic Game Players at Risk
Moreover, there is bad news for players of Infinity Blade, UDK, Gears of War, and older Unreal Tournament games, as hackers may have compromised their salted hashed passwords, along with their email addresses and other data entered into the forums.
At the time of writing, the Epic Games' forum and Unreal Engine forums both appeared to be down.
So, users are advised to change their passwords for the forum accounts as soon as possible and keep a longer and stronger one this time and change passwords for other online services, especially if you use the same password for multiple sites.
You can use a good password manager that allows you to create complex passwords for different sites and remember them for you.
We have listed some best password managers that could help you understand the importance of password manager and help you choose a suitable one, according to your requirement.
LeakedSource, a search engine site that indexes leaked login credentials from data breaches, has added the breached data from the Epic Games' forums into its database, which includes the password hashes to allow its users to search for their stolen data.
IoT – Shocking : How your home sockets could aid in Cyber attacks
23.8.2016 securityaffairs Security
IoT devices are dramatically enlarging our surface of attack, hackers can exploit smart sockets to shut down Critical Systems.
I love some of the gangster nicknames people come up with. Knuckles, Fat Tony , Stab Happy or even Bambi. Names are characteristic of their personality and attitude. It’s time to add Toaster Socket to the name as in the age of Smart Grid, criminals are getting updated.
The Internet of Things (IoT) ,which soon may become the “Internet of Everything,” is something that has made every security professional reanalyse all his security strategies. Security has been a challenge when it came to handling our basic Information and Communication Technology (ICT) systems. With the disruptive and highly welcomed IoT age upon us we may soon have larger challenges.
A recent research by Bitdefender found that smart electrical sockets can be exploited easily and be made a zombie on a bot network.
“The vulnerable device is a smart electrical switch that plugs into any wall socket and enables users to schedule a connected electronic device on and off from their smartphone. It can power any gadget – thermostats, smart TVs, coffee makers, security cameras, garage doors, and medical devices and so on.” states BitDefender.
IoT hacking critical systems
For those who know the challenges an enterprise can face while fending off attacks from such botnets, would realize we are adding ammunition to the cyber criminal’s arsenal.
Other than exploiting the inbuilt Operating System to execute commands it can affect the user by gaining access to his email, gain login credentials to his other wireless systems, cause overheating and hence create fire “accidents” . The possibilities are endless.
Electrical and electronic appliances have had their recent fair share of negative media when it comes to being actors in cyber attacks. Surveillance cameras could be recruited in powerful botnets, smart LED light bulbs giving away WiFi passwords or refrigerators launching DDoS attacks.
A common issue found in the power outlet by security researchers is the lack of robust password and username combination security strength, the lack of encrypted configuration mechanism when joining your personal network (Eg.: Home WiFi network)and weak encoded information sharing between vendor servers and appliance.
Based on the above discoveries Bitdefender outlined some ways of launching attacks and compromising your system where the attack vector is your smart socket.
First, gain access to your email and hence disable your two factor authentication process (Great security measure by the way) .
Second, use a ill-filtered password checking system to in a way inject codes to pretty much reset your entire system.
Well coming to the meat of the matter, an attacker always wants to gain root access to a system . These few stated methods and a little effort could give them that. Hence your socket may end up being weaponized for cyber attacks, be used to monitor and harm you (the user) , gain access to other systems in your network and a major overlooked issue affect your privacy.
The solution is evident. You the user has to demand security as a basic need while buying such systems or you may have to have bail money for your toaster switch a.k.a. cyber criminal.
It is time to purchase a security solution specifically designed for IoT devices.
New Gozi Campaigns Target Global Brands with sophisticated features
23.8.2016 securityaffairs Virus
Researchers from Buguroo discovered new Gozi campaigns using new techniques that targeted many banks and financial services worldwide.
The Gozi malware was first spotted in 2007, its source code has been leaked twice in the criminal underground allowing the creation of new sophisticated version. Recently security experts from the IBM X-Force Research spotted a new threat dubbed GozNym Trojan that combines the Gozi ISFB and Nymaim malware abilities.
Researchers from Buguroo discovered new Gozi campaigns that targeted mainly banks and financial services in Spain, Poland, and Japan, the experts also noticed some targeted attacks on users in Canada, Italy, and Australia.
Threat actors behind the new Gozi campaigns are using new techniques spreading the malware in the United States and Western Europe.
In Spain, attackers delivered the malware by exploiting compromised WordPress websites. The malware was spread via malicious links leveraging URL shortening services.
The new campaigns are using dynamic web injection and automatically optimize the selection of mules after profiling the victim.
Web injections are very sophisticated and optimized to avoid detection, according to the report the operators refined the mechanism after an attack has been discovered.
The greatest number of infections was observed in Poland and Japan, threat actors behind the campaign also used servers located in Canada, Italy, and Australia in other Gozi campaigns that hit these countries.

The new campaigns impacted popular brands, including BNP Paribas, Bank of Tokyo, CitiDirect BE, ING Bank, PayPal, Société Générale, BNP Paribas.
“A detailed analysis of how the webinjects work revealed that when an infected user at a target financial institution attempts a transaction, the C2 (Command and Control server) is notified in real time and sends the user’s browser the information necessary for carrying out fraudulent transfers. What the user sees: The injected code presents a fraudulent
What the user sees: The injected code presents a fraudulent deposit pending alert requesting the security key to complete the transfer.
What the bank sees: Hidden underneath, however, is the actual real transfer page being presented to the bank. The unsuspecting user is inadvertently entering their key, not to receive money, but to send their money to a “mule” designated by the malware operators”
The victim is inadvertently entering the requested information and sends money to one of the selected “mule.”
The new Gozi campaigns also revealed that, for certain versions of the webinjects, the Trojan would send a kind of biometric information to the control panel. The information includes details on how long the user takes to move from an input field to the next one, this kind of information is precious to bypass protection systems that leverage user behavior.
The experts noticed some similarities between the webinjects used in these new Gozi campaigns and the one implemented by a malware family dubbed Gootkit.
“The webinjects used in these campaigns also revealed key similarities to GOOTKIT, not just related to the code and the techniques used, but also to the dates and times corresponding to its updates in the corresponding ATS panels—prompted by affected companies launching security measures to prevent the malware’s operation.” states the report.”This development points to the professionalization of malware services trend. The services are sold underground by independent businesses and are able to deliver malicious code for use by different organizations, families of malware and campaigns.”
Members call for a Tor General Strike and shut down Tor for a day
23.8.2016 securityaffairs Safety
A few members of the community are calling for a ‘Tor general strike’ to protest against some decisions taken recently by the core members.
Last month, the Tor Project announced that an internal investigation had confirmed the allegations of sexual misconduct against the notorious member Jacob Appelbaum.
The allegations divided the internet privacy community, as a result of events the entire board of directors of the project was replaced.
News of the day is that a few members of the community are calling for a ‘Tor general strike.’ They want to express their dissent on the way the investigation was handled.
A message published on Twitter invites those who run parts of the Tor network infrastructure to shut down their machines, developers to stop working on Tor, and of course, users to stop using the anonymizing network.
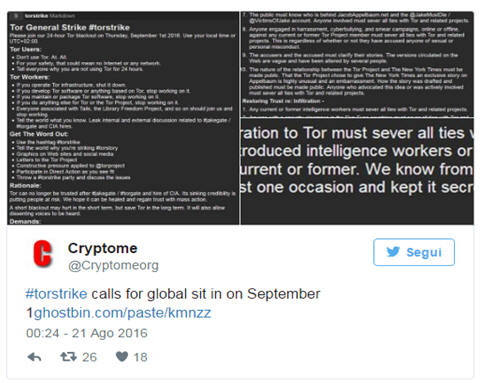
Cryptome @Cryptomeorg
#torstrike calls for global sit in on September 1https://ghostbin.com/paste/kmnzz
00:24 - 21 Ago 2016
26 26 Retweet 18 18 Mi piace
The members who are calling for a Tor General Strike are also opposed to the decision of the Tor Project to hire an ex-CIA official.
“Tor can no longer be trusted after #jakegate / #torgate and hire of CIA,” states the Ghostbin post that calls for the Tor Global Strike. “Its sinking credibility is putting people at risk. We hope it can be healed and regain trust with mass action. A short blackout may hurt in the short term, but save Tor in the long term. It will also allow dissenting voices to be heard.”
Joseph Cox from Motherboard reported a leaked chat log from an internal Tor Project IRC channel that demonstrated that part of the members of the Project did not agree on the move of hiring a supposed ex-CIA agent, “DaveC1”.
Some internal members of the Tor Project were not aware of the past of DaveC1.
Tor Global Strike
A Tor General Strike is probably the worst way to express the dissent, many individuals worldwide rely on the Tor network to avoid censorship and express their ideas without fearing for their life.
“Journalists and activists use Tor in countries where people can be killed for the things they say,” Shari Steele, the Tor Project’s executive director told Motherboard. “Shutting down the Tor network would shut down their speech or, even more dangerous, could force them to use unsafe methods of communication.”
The call to the Tor General Strike includes 16 requests to the Tor Project, one of them invoke the sacking the co-founder Roger Dingledine.
Many demands included in the call for the Tor General Strike are related to the internal investigation on Appelbaum’s conduct. They demand more details on the claims against Appelbaum to be made public.
The news of the strike comes after the Tor relay operator Stephan Seitz shut down its node.
“The situation how the affair about Jake was handled by the Tor project has made me feel very uneasy. After digging through several material (for example https://shiromarieke.github.io/tor) I find that I am no longer believing in this project or trust it. That’s why I’m shutting down my tor relay fsingtor now.“ Seitz wrote to a Tor Project.
BHU Wi-Fi router, it is really too easy to hack these network devices
22.8.2016 securityaffairs Hacking
A security expert analyzed a BHU Wi-Fi router and found that it is easy to hack by an unauthenticated attacker that can access sensitive information.
Tao Sauvage, an expert from IOActive, has analyzed a BHU Wi-Fi router that he purchased during a travel. The BHU Wi-Fi router appears like a surveillance box, but according to the analysis of the experts, it is affected by multiple vulnerabilities.
BHU Wi-Fi router
The network device is completely pwnable by an unauthenticated attacker that can access sensitive information.
The expert also explained that the BHU Wi-Fi router comes with hidden users, SSH enabled by default and a hardcoded root password … not so bad for an attacker, what do you think about?
Last scaring discovery about the Chinese-made router is that it injects a third-party JavaScript file into all users’ HTTP traffic.
“The BHU WiFi uRouter, manufactured and sold in China, looks great – and it contains multiple critical vulnerabilities. An unauthenticated attacker could bypass authentication, access sensitive information stored in its system logs, and in the worst case, execute OS commands on the router with root privileges.” wrote Sauvage.”
Sauvage has exploited the UART debug pins to extract the firmware and analyzed it, it has found multiple security vulnerabilities.
The expert noticed that the CGI script running everything reveals the session ID of the admin cookie, this means that it could easily hijacked by an attacker that obtains admin privileges.
The BHU Wi-Fi router includes a hard-coded SID, 700000000000000, an attacker can get access to “all authenticated features” by presenting it to the router.
Once presented the above SID to the device, it revealed the hidden user dms:3.
“So far, we have three possible ways to gain admin access to the router’s administrative web interface:
Provide any SID cookie value
Read the system logs and use the listed admin SID cookie values
Use the hardcoded hidden 700000000000000 SID cookie value
” explained Sauvage.
It is incredible, the BHU Wi-Fi router is full of security holes, the researchers also discovered that the device fails to perform XML address value sanitization, this allows an attacker to carry out an OS command injection. Sauvage claims that the router could be used to eavesdrop on router traffic using a command-line packet analyzer like
The router could be used by attackers to eavesdrop on the device traffic using a command-line packet analyzer like tcpdump or to hijack it for other malicious purposes.
“At this point, we can do anything:
Eavesdrop the traffic on the router using tcpdump
Modify the configuration to redirect traffic wherever we want
Insert a persistent backdoor
Brick the device by removing critical files on the router “.
I invite you to give a look to the analysis published by IOActive, it is amazing the number of issues affecting this specific device, and probably many others suffer the same problems.
Lets hope the Chinese manufactured that designed the device, the BHU Networks Technology Co., is now aware how insecure is its router.
Don’t forget that the many powerful botnets leverages on compromised SOHO devices.
Threat intelligence report for the telecommunications industry
22.8.2016 Kaspersky Security
The telecommunications industry keeps the world connected. Telecoms providers build, operate and manage the complex network infrastructures used for voice and data transmission – and they communicate and store vast amounts of sensitive data. This makes them a top target for cyber-attack.
According to PwC’s Global State of Information Security, 2016, IT security incidents in the telecoms sector increased 45% in 2015 compared to the year before. Telecoms providers need to arm themselves against this growing risk.
In this intelligence report, we cover the main IT security threats facing the telecommunications industry and illustrate these with recent examples.
Our insight draws on a range of sources. These include:
The latest telecoms security research by Kaspersky Lab experts.
Kaspersky Lab monitoring systems, such as the cloud antivirus platform, Kaspersky Security Network (KSN), our botnet tracking system and multiple other internal systems including those used to detect and track sophisticated targeted (advanced persistent threat, APT) attacks and the corresponding malware.
Underground forums and communities.
Centralized, specialized security monitoring systems (such as Shodan).
Threat bulletins and attack reports.
Newsfeed aggregation and analysis tools.
Threat intelligence is now a vital weapon in the fight against cyber-attack. We hope this report will help telecoms providers to better understand the cyber-risk landscape so that they can develop their security strategies accordingly.
We can provide more detailed sector and company-specific intelligence on these and other threats. For more information on our Threat Intelligence Reporting services please email intelligence@kaspersky.com.
Executive summary
Telecommunications providers are under fire from two sides: they face direct attacks from cybercriminals intent on breaching their organization and network operations, and indirect attacks from those in pursuit of their subscribers. The top threats currently targeting each of these frontlines feature many classic attack vectors, but with a new twist in terms of complexity or scale that place new demands on telecoms companies.
These threats include:
Distributed Denial of Service (DDoS) attacks. DDoS attacks continue to increase in power and scale and, according to the 2016 Data Breach Investigations Report, the telecommunications sector is hit harder than any other. Kaspersky Lab’s research reveals that in Q2, 2016, the longest DDoS attack lasted for 291 hours (or 12.1 days) – significantly longer than the previous quarter’s maximum (8.2 days), with vulnerable IoT devices increasingly used in botnets. Direct DDoS attacks can reduce network capacity, degrade performance, increase traffic exchange costs, disrupt service availability and even bring down Internet access if ISPs are hit. They can be a cover for a deeper, more damaging secondary attack, or a route into a key enterprise subscriber or large-scale ransomeware attack.
The exploitation of vulnerabilities in network and consumer devices. Our intelligence shows that vulnerabilities in network devices, consumer or business femtocells, USBs and routers, as well as root exploits for Android phones, all provide new channels for attacks – involving malware and technologies that individuals, organisations and even basic antivirus solutions cannot always easily remove.
Compromising subscribers with social engineering, phishing or malware. These classic techniques remain popular and can easily be mastered by entry-level cybercriminals, although 2016 sees changes in how more sophisticated attackers conduct their campaigns. Growing numbers of cyber-attackers now combine data sets from different sources, including open sources, to build up detailed pictures of potential targets for blackmail and social engineering purposes.
Insider threat is growing. Detailed profiles of targets are also used to recruit insiders to help perpetrate cybercrime. Some insiders help voluntarily, others are cooerced through blackmail. Insiders from cellular service providers are recruited mainly to provide access to data, while staff working for Internet service providers are chosen to support network mapping and man-in-the-middle attacks.
Other threats facing telecommunications companies include targeted attacks; poorly configured access controls, particularly where interfaces are publicly available to any Internet user; inadequate security for 2G/3G communications; and the risk of telecoms providers being drawn into unrelated attacks that exploit telecoms resources, and suffering collateral damage as a result.
Typical threats targeting telecoms
Overview
We can divide the main threats facing the telecommunications industry into two, interrelated, categories:
Threats targeting telecommunication companies directly. These include DDoS attacks, targeted attacks (APT campaigns), network device vulnerabilities and human-related threats like insider access, social engineering and the risk of allowing third parties to access information.
Threats targeting subscribers of telecoms services – particularly the customers of cellular service providers (CSPs) and Internet service providers (ISPs). These include malware for mobile devices, subscriber data harvesting, end-user device vulnerabilities, and more.
Threats directed at telecoms companies
DDoS
DDoS (distributed denial of service) attacks remain a serious threat to telecoms providers around the world as attackers discover ever more ways of boosting the power and scale of attacks. Kaspersky Lab’s DDoS intelligence report for Q2, 2016 notes that websites in 70 countries were targeted with attacks. By far the most affected country was China, with South Korea and the US also among the leaders. 70.2% of all detected attacks were launched from Linux botnets, with cybercriminals paying close attention to financial institutions working with cryptocurrency. Another trend observed in Q2 was the use of vulnerable IoT devices in botnets to launch DDoS attacks.
The telecommunications sector is particularly vulernable to DDoS attacks. According to the 2016 Data Breach Investigations Report, the telecommunications sector was hit around twice as hard as the second placed sector (financial exchanges), with a median DDoS packet count of 4.61 million packets per second (compared to 2.4 Mpps for exchanges.)
The impact of a DDoS attack should not be underestimated. Direct attacks can reduce network capacity, degrade performance, increase traffic exchange costs, disrupt service availability and even bring down Internet access if ISPs are affected. With a growing number of connected devices and systems supporting mission-critical applications in areas such as healthcare and transport, unexpected downtime could be life threatening.
Further, DDoS attacks can be a cover for a deeper, more damaging secondary attack, or a route into a key enterprise subscriber or large-scale ransomeware attack.
A good example of the first is the 2015 cyber-attack on the UK telecoms company, TalkTalk. The hack, alledgedly perpetrated by a couple of teenagers, resulted in the loss of around 1.2 million customers’ email addresses, names and phone numbers, as well as many thousands of customer dates of birth and financial information – all ideal for use in financially-motivated social engineering campaigns. The forensic investigation revealed that the hackers had used a smokescreen DDoS attack to conceal their main activities.
DDoS attacks are also evolving. 2015 saw attackers amplify the power of DDoS attacks by turning them into DrDoS (Distributed reflection Denial of Service) attacks through the use of standard network protocols like NTP, RIPv1, NetBIOS (Network Basic Input/Output System) and BGP (Border Gateway Patrol). Another approach that is becoming more commonplace is the compromise of end-user routers via network-scanning malware and firmware vulnerabilities. Today’s faster mobile data transfer speeds and the growing adoption of 4G are also making smartphone-based botnets more useful for implementing DDoS attacks.
The worrying thing is that even inexperienced attackers can organize quite an effective DDoS campaign using such techniques.
Targeted attacks
The core infrastructure of a telecommunications company is a highly desirable target for cybercriminals, but gaining access is extremely difficult. Breaking into the core requires a deep knowledge of GSM architecture, rarely seen except among the most skilled and resourced cybercriminals. Such individuals can generally be found working for advanced, international APT groups and nation-state attackers, entities that have a powerful interest in obtaining access to the inner networks of telecommunication companies. This is because compromised network devices are harder to detect by security systems and they offer more ways to control internal operations than can be achieved through simple server/workstation infiltration.
Once inside the core infrastructure, attackers can easily intercept calls and data, and control, track and impersonate subscibers.
Other APTs with telecommunications on their radar
The Regin APT campaign, discovered in 2014, remains of the most sophisticated ever seen and has the ability to infiltrate GSM networks, while the Turla group, has developed the ability to hijack satellite-based Internet links as part of it’s Command & Control process, successfully obscuring its actual location.
Others, such as Dark Hotel and a new cyber-espionage threat actor likely to be of Chinese origin, exploit telecoms networks in their targeted campaigns. In these cases, the telecoms providers often suffer collateral damage even though they are not directly related to the attack. Further details on these can be found on Kaspersky Lab’s expert Securelist blog or through a subscription to the Kaspersky APT Threat Intelligence Reporting service.
Unaddressed software vulnerabilities
Despite all the high profile hacks and embarrassing data leaks of the last 12 months, attackers are still breaching telecoms defenses and making off with vast quantities of valuable, personal data. In many cases, attackers are exploiting new or under-protected vulnerabilities. For example, in 2015, two members of the hacker group, Linker Squad gained access to Orange Spain through a company website vulnerable to a simple SQL injection, and stole 10 million items of customer and employee data.
SQL injection vulnerability on Orange Spain web site
The impact of service misconfiguration
In many cases, the hardware used by by the telecommunications industry carries configuration interfaces that can be accessed openly via HTTP, SSH, FTP or telnet. This means that if the firewall is not configured correctly, the hardware in question becomes an easy target for unauthorized access.
The risk presented by publicly exposed GTP/GRX (GPRS Tunneling Protocol/GPRS Roaming Exchange) ports on devices provides a good example of this.
As CSPs encrypt the GPRS traffic between the devices and the Serving GPRS Support Node (SGSN), it is difficult to intercept and decrypt the transferred data. However, an attacker can bypass this restriction by searching on Shodan.io for devices with open GTP ports, connecting to them and then encapsulating GTP control packets into the created tunnel.
Table 1. Top 10 countries with GTP/GRX ports exposed to Internet access
# Country Number of GTP/GRX
1 China 52.698
2 Turkey 8.591
3 United States of America 6.403
4 Canada 5.807
5 Belgium 5.129
6 Colombia 2.939
7 Poland 2.842
8 Morocco 1.585
9 Jamaica 862
10 United Arab Emirates 808
The Border Gateway Protocol (BGP) is the routing protocol used to make decisions on routing between autonomous systems. Acceptance and propagation of routing information coming from other peers can allow an attacker to implement man-in-the-middle (MITM) attacks or cause denial of service. Any route that is advertised by a neighboring BGP speaker is merged in the routing database and propagated to all the other BGP peers.
Table 2. Top five countries with BGP protocol exposed to Internet access
# Country Number of devices
(end of 2015)
1 Republic of Korea 16.209
2 India 8.693
3 United States of America 8.111
4 Italy 2.909
5 Russian Federation 2.050
An example of such an attack took place in March 2015, when Internet traffic for 167 important British Telecom customers, including a UK defense contractor that helps to deliver the country’s nuclear warhead program, was illegally diverted to servers in Ukraine before being passed along to its final destinations.
To avoid probable attacks against BGP from unauthorized remote malefactors, we recommend that companies provide network filtering, allowing only a limited number of authorized peers to connect to BGP services. To protect against malicious re-routing and hijacking initiated through authorized autonomous systems we recommend that they monitor anomalies in BGP communications (this can be done through specialized software solutions or by subscribing to alerts from vendors providing this kind of monitoring.)
Vulnerabilities in network devices
Routers and other network devices are also primary targets for attacks against telecommunications companies.
In September 2015, FireEye researchers revealed the router malware “SYNful knock”, a combination of leaked privilege (root) credentials and a way of replacing device firmware that targets Cisco 1841, 2811 and 3825 routers (see Cisco advisory here).
Put simply, SYNful knock is a modified device firmware image with backdoor access that can replace the original operating system if the attacker has managed to obtain privileged access to the device or can physically connect to it.
SYNful is not a pure software vulnerability, but a combination of leaked privileged credentials combined with a certain way of replacing device firmware. Still, it is a dangerous way of compromising an organization’s IT infrastructure.
SYNful knock backdoor sign-in credentials request
Worldwide distribution of devices with the SYNful knock backdoor
The latest information on the number of potentially compromised devices is available through the link https://synfulscan.shadowserver.org/stats/.
A second Cisco vulnerability, CVE-2015-6389 enables attackers to access some sensitive data, such as the password file, system logs, and Cisco PCA database information, and to modify data, run internal executables and potentially make the system unstable or inaccessible. Cisco Prime Collaboration Assurance Software releases prior to 11.0 are vulnerable. Follow this Cisco bulletin for remediation actions.
For further information on Cisco fixes for its devices see https://threatpost.com/cisco-warning-of-vulnerabilities-in-routers-data-center-platforms/115609.
Juniper, another network device manufacturer has been found to carry vulnerabilities in its operating system for its NetScreen VPN appliances, enabling third-party access to network traffic. The issue was reported by the vendor in the security advisory JSA10713 on December 18th, 2015, along with the release of the patch.
It appears that the additional code with hardcoded password was planted in the source code in late 2013. The backdoor allows any user to log in with administrator privileges using hard-coded password “<<< %s(un=’%s’) = %u”.This vulnerability has been identified as CVE-2015-7755 and is considered highly critical.
Top countries where ScreenOS devices are used are the Netherlands, the United States, China, Italy and Mexico.
Juniper ScreenOS-powered devices worldwide
Another Juniper backdoor, CVE-2015-7756, affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20 and allows a third party to monitor traffic inside VPN connections due to security flaws in the Dual_EC PRNG algorithm for random number generation.
To protect the organization from misconfiguration and network device vulnerabilitiy, Kaspresky Lab recommendats that companies pay close attention to vulnerabilities in the network services of telecommunication equipment, establish effective vulnerability and configuration management processes, and regularly perform security assessments, including penetration testing for different types of attackers (a remote intruder, a subscriber, a contractor, etc.).
Malicious insiders
Even if you consider your critical systems and devices protected and safe, it is difficult to fully control some attack vectors. People rank at the very top of this list. Their motivations are often hard to predict and anticipate, ranging from a desire for financial gain to disaffection, coercion and simple carelessness.
While insider-assisted attacks are uncommon, the impact of such attacks can be devastating as they provide a direct route to the most valuable information.
Examples of insider attacks in recent years include:
A rogue telecoms employee leaking 70 million prison inmate calls, many breaching client-attorney privilege.
An SMS center support engineer who had intercepted messages containing OTP (One-Time Passwords) for the two-step authentication required to login to customer accounts at a popular fintech company. The engineer was found to be freely offering his services on a popular DarkNet forum.
For attackers, infiltrating the networks of ISPs and CSPs requires a certain level of experience – and it is often cheaper and easier to stroll across the perimeter with the help of a hired or blackmailed insider. Cybercriminals generally recruit insiders through two approaches: enticing or coercing individual employees with relevant skills, or trawling around underground message boards looking for an appropriate employee or former employee.
Employees of cellular service providers are in demand for fast track access to subscriber and company data or SIM card duplication/illegal reissuing, while staff working for Internet service providers are needed for network mapping and man-in-the-middle attacks.
A particularly promising and successful attack vector for recruiting an insider for malicious intrusion is blackmail.
Data breaches, such as the 2015 Ashley Madison leak reveal information that attackers can compare with other publically available information to track down where people work and compromise them accordingly. Very often, these leaked databases contain corporate email addresses, including those of telecommunication companies.
Further information on the emerging attack vectors based on the harvesting of Open Source Intelligence (OSINT) can be obtained using Kaspersky Lab’s customer-specific Intelligence Reporting services.
Threats targeting CSP/ISP subscribers
Overview
Attacks targeting the customers of cloud and Internet service providers remain a key area of interest for cybercriminals. We’ve revealed a number of malware activities and attack techniques based on internal information and incidents that were caught in our scope. As a result of analyzing this data the following main threats were identified:
Obtaining subscribers’ credentials. This is growing in appeal as consumers and businesses undertake ever more activity online and particularly on mobile. Further, security levels are often intentionally lowered on mobile devices in favor of usability, making mobile attacks even more attractive to criminals.
Compromising subscribers’ devices. The number of mobile malware infections is on the rise, as is the sophistication and functionality of the malware. Experienced and skilled programmers are now focusing much of their attention on mobile – looking to exploit payment services as well as low-valued assets like compromised Instagram or Uber accounts, collecting every piece of data from the infected devices.
Compromising small-scale telecoms cells used by consumers and businesses. Vulnerabilities in CSP-provided femtocells allow criminals to compromise the cells and even gain access to the entire cloud provider’s network.
Successful Proof-Of-Concept attacks on USIM cards. Recent research shows that the cryptography of 3G/4G USIM cards is no longer unbreakable. Successful attacks allow SIM card cloning, call spoofing and the interception of SMS.
Social engineering, phishing and other ways in
Social engineering and phishing remain popular activities and they continues to evolve and improve, targeting unaware or poorly aware subscribers and telecoms employees.
The attackers exploit trust and naiivity. In 2015, the TeamHans hacker group penetrated one of Canada’s biggest communications groups, Rogers, simply by repeatedly contacting IT support and impersonating mid-ranking employees, in order to build up enough personal information to gain access to the employee’s desktop. The attack provided hackers with access to contracts with corporate customers, sensitive corporate e-mails, corporate employee IDs, documents, and more.
Both social engineering and phishing approaches are worryingly successful. The Data Breach Investigations Report 2016 found that 30% of phishing emails were opened, and that 12% clicked on the malicious attachment – with the entire process taking, on average, just 1 minute and 40 seconds.
Social engineers and phishers also use multiple ways for increasing the likeness of authenticity in their attacks, enriching their data with leaked profiles, or successfully impersonating employees or contractors. Recently criminals have successfully stolen tens of thousands of euros from dozens of people across Germany after finding a way around systems that text a code to confirm transactions to online banking users. After infecting their victims with banking malware and obtaining their phone numbers, they called the CSP’s support and, impersonating a retail shop, asked for a new SIM card to be activated, thus gaining access to OTP (One Time Passwords) or “mTan’s” used for two-factor authentication in online banking.
Kaspersky Lab recommends that telecommunications providers implement notification services for financial organizations that alert them when a subscriber’s SIM card has been changed or when personal data is modified.
Some CSPs have also implemented a threat exchange service to inform financial industry members when a subscriber’s phone is likely to have been infected with malware.
Vulnerable kit
USBs, modems and portable Wi-Fi routers remain high-risk assets for subscribers, and we continue to discover multiple vulnerabilities in their firmware and user interfaces. These include:
Vulnerabilities in web interfaces designed to help consumers configure their devices. These can be modified to trick a user into visiting a specially crafted page.
Vulnerabilities that result from insufficient authentication. These can allow for the modification of device settings (like DNS server addresses), and the interception, sending and receiving of SMS messages, or USSD requests, by exploiting different XSS and CSRF vulnerabilities.
RCE (Remote Code Execution) vulnerabilities based on different variants of embedded Linux that can enable firmware modification and even a complete remote compromise.
Built-in “service” backdoor allowing no-authentication access to device settings
Examples of these kind of vulnerabilities were demonstrated in research by Timur Yunusov from the SCADAStrangeLove team. The author assessed a number of 3G/4G routers from ZTE, Huawei, Gemtek and Quanta. He has reported a number of serious vulnerabilities:
Remote Code Execution from web scripts.
Arbitrary device firmware modification due to insufficient consistency checks.
Cross Site Request Forgert and Cross Site Scripting attacks.
All these vectors can be used by an external attacker for the following scenarios:
Infecting a subscriber’s computer via PowerShell code or badUSB attack.
Traffic modification and interception.
Subscriber account access and device settings modification.
Revealing subscriber location.
Using device firmware modification for APT attack persistence.
Most of these issues exist due to web interface vulnerabilities (like insufficient input validation or CSRF) or modifications made by the vendor during the process of branding its devices for a specific telecommunications company.
The risk of local cells
Femtocells, which are essentially a personal NodeB with an IP network connection, are growing in popularity as an easy way to improve signal coverage inside buildings. Small business customers often receive them from their CSPs. However, unlike core systems, they are not always submitted to suitably thorough security audits.
ktt_2016_eng_6
Femtocell connection map
Over the last year, our researchers have found a number of serious vulnerabilities in such devices that could allow an attacker to gain complete control over them. Compromising a femtocell can lead to call interception, service abuse and even illegal access to the CSP’s internal network.
At the moment, a successful attack on a femtocell requires a certain level of engineering experience, so risks remain low – but this is likely to change in the future.
USIM card vulnerabilities
Research presented at BlackHat USA in 2015 revealed successful attacks on USIM card security. USIMs had previously been considered unbreakable thanks to the AES-based MILENAGE algorithm used for authentication. The reseachers conducted differential power analysis for the encryption key and secrets extraction that allowed them to clone the new generation of 3G/4G SIM cards from different manufacturers.
Right byte guess peak on differential power analysis graph
Conclusion
Telecommunications is a critical infrastructure and needs to be protected accordingly. The threat landscape shows that vulnerabilities exist on many levels: hardware, software and human, and that attacks can come from many directions. Telecoms providers need to start regarding security as a process – one that encompasses threat prediction, prevention, detection, response and investigation.
A comprehensive, multi-layered security solution is a key component of this, but it is not enough on its own. It needs to be complemented by collaboration, employee education and shared intelligence. Many telecommunications companies already have agreements in place to share network capability and capacity in the case of disruption, and now is the time to start reaping the benefit of shared intelligence.
Our Threat Intelligence Reporting services can provide customer-specific insight into the threats facing your organization. If you’ve ever wondered what your business looks like to an attacker, now’s the time to find out.
Lidé podceňují zabezpečení. Každý dvanáctý Čech čelil v zahraničí útoku hackerů
22.8.2016 Novinky/ Bezpečnost Zabezpečení
Útoky hackerů nejsou ničím výjimečným, a to ani v době dovolených. V zahraničí se s nimi setkal každý 12. Čech. Vyplývá to z průzkumu antivirové společnosti Kaspersky Lab, podle kterého celkem 15 procent Čechů přišlo někdy v zahraničí o peníze, 12 procent se setkalo s on-line podvodem a osmi procentům někdo zneužil jejich platební karty.
Vzhledem k chování Čechů na cestách nejsou tyto údaje podle Kaspersky Lab překvapující. Průzkum ukázal, že tři čtvrtiny dotázaných se připojují k jakýmkoli veřejným Wi-Fi sítím, které mohou být zneužity kybernetickými zločinci. Přes potenciálně nebezpečná připojení pak téměř polovina českých respondentů používá internetové bankovnictví a více než třetina nakupuje on-line.
Bezpečnou VPN při připojení k veřejným sítím používá pouze 26 procent Čechů. Téměř čtvrtina v průzkumu přiznala, že se při připojování k internetu nijak nechrání.
"Připojit se k internetu pomocí nezabezpečené Wi-Fi sítě v zahraničí je jednoduché. Lidé pak automaticky pokračují v rutinních činnostech, jako je použití internetového bankovnictví nebo nakupování. Nepřemýšlí už ale, jaké následky může jejich chování mít," uvedl analytik Kaspersky Lab David Emm.
Uživatelé by se měli při cestování a připojování k internetu v zahraničí dostatečně chránit. Nikdy by neměli spustit z dohledu své platební karty a k internetu by se měli připojovat pouze pomocí zabezpečeného VPN připojení.
Does your WebCam Crash after Windows 10 Anniversary Update? Here’s How to Fix It
21.8.2016 thehackernews IT
If your webcam has stopped working after installing recently-released Microsoft's big Anniversary Update for Windows 10, you are not alone.
With some significant changes to improve Windows experience, Windows 10 Anniversary Update includes the support for webcams that has rendered a number of different webcams inoperable, causing serious issues for not only consumers but also the enterprise.
The problem is that Microsoft added some new ways for applications to access webcams with Microsoft's new Windows Camera Frame Server, preventing webcams from using two particular compression formats—H.264 and MJPEG.
Microsoft decided that the Camera Frame Server should only receive an uncompressed YUY2 encoding stream from the webcam, which is affecting far more devices than Microsoft expected, causing Millions of cameras to crash.
This is the reason why your camera hangs, freezes, or simply not works when you try to do a video calling with your friend over Skype. Brad Sams of Thurrot first discovered this issue.
"Since it will take some extra time for the H.264 work to go through this additional layer of testing, and we would prefer not to delay the MJPEG changes [fix], we will ship these two separately. You can expect the MJPEG media type work to reach you first," reads a post in Microsoft's Support Forum from Windows Camera Team member Mike M.
Although Microsoft has planned to fix the issue and roll out an official fix in September, Windows users who do not want to wait for a month for Microsoft's update can use a workaround suggested by Rafael Rivera to re-enable the old behavior of webcam and fix the issue.
Here's how to Fix Your Webcam:
The workaround is a registry hack, so if you are comfortable tweaking the registry, make the below changes. The hack is pretty simple; you just need to stick to the following instructions.
Go to the Start Menu, type "regedit" and press Enter. This opens 'The Registry Editor'.
Navigate to "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Foundation\Platform" in the left sidebar.
Right-click the "Platform" key and select New → DWORD (32-bit) Value.
Name this value "EnableFrameServerMode" and set the value to "0" by double clicking on it.
These are the steps if you are using a 32-bit version of Windows 10.
If you are using a 64-bit version of Windows 10, you will need to navigate to "HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows Media Foundation\Platform" in the left sidebar and follow step 3 and 4 mentioned above.
Now close the registry editor and just re-launch the application in which your webcam was freezing. They should now work normally – no reboot, no sign out required.
When Microsoft actually fixes the issue after a month, just revisit the same location in the registry editor and delete the "EnableFrameServerMode" value you added to undo this change.
The hack is simple but follow the above steps correctly because a small mistake in The Registry Editor tool can render your system unstable or even inoperable.
Bitcoins move from the seized SilkRoad wallet to the ShadowBrokers
21.8.2016 securityaffairs Security
A security expert noticed strange transactions from the Bitcoin wallet of the SilkRoad (now in the hands of Feds) to the ShadowBrokers ‘ wallet.
I was surfing the Internet searching for interesting data about the ShadowBrokers group that leaked exploits and hacking tools belonging to the NSA Equation Group.
I have found a very intriguing analysis of the popular security researcher krypt3ia that has analyzed the Bitcoin transactions linked to the #ShadowBrokers account. It seems that the account is receiving small amounts of money (at about $990.00 a couple of days ago), but the real surprise is that some of the payments are coming from the seized Silk Road bitcoins and account.

Hey, wait a moment, the Silk Road Bitcoin are under the control of the FBI after the seizure of the popular black market.
krypt3ia decided to investigate the overall transactions and discovered that also the US Marshall service was involved in the transfers.
“So, is this to say that these coins are still in the coffers of the feds and they are being sent to ShadowBrokers to chum the water here? Maybe get a conversation going? Maybe to get the bitcoins flying so others can trace some taint? Of course once you start to look at that address and the coins in and out there you get some other interesting hits. Suddenly you are seeing US Marshall service as well being in that loop. Which makes sense after the whole thing went down with the theft of coins and such by rogue agents of the USSS and DEA.” wrote krypt3ia in a blog post.
Analyzing the transactions the expert noticed transactions of 0,001337 BTC for the for ShadowBrokers.

We are aware that Silk Road coins are in the hands of the US GOV, but someone is sending ShadowBrokers fractions of them.
“What if, and you can see this once you start to dig around with Maltego, the coins being paid to the account so far also come from other accounts that are, shall we call them cutout accounts for the government?” added the experts.
At this point, the researcher invited readers to analyze transactions involving all the accounts that passed money to Bitcoin Wallets used by the Government and that were used to transfer money to the ShadowBrokers.
At the time I’m writing the ShadowBroker wallet was involved in 41 transactions for a total of 1.738 BTC, and the highest bidder is of 1.5 bitcoin, or around $850.
NSA BENIGNCERTAIN tool can obtain VPN Passwords from CISCO PIX
21.8.2016 securityaffairs Safety
Researchers tested the BENIGNCERTAIN tool included in the NSA data dump that allows attackers to extract VPN passwords from certain Cisco devices.
Following the disclosure of the NSA dump, IT vendors Cisco and Fortinet issued security patches to fix the flaws exploited by the Equation Group in their products.

Now, security researchers have uncovered another exploit included in the leaked dump, dubbed BENIGNCERTAIN that allows the extraction of VPN passwords from certain Cisco devices.
The expert Mustafa Al-Bassam who analyzed the data dump has called the attack “PixPocket” after the name of the Cisco products hacked by the tool, the Cisco PIX.
The CISCO PIX product family was declared phase out back in 2009, but it is widely adopted by government entities and enterprises.
According to the expert, the tool works against the CISCO PIX versions 5.2(9) up to 6.3(4).
Al-Bassam discovered that the tool could be used to send a packet to the target machine that makes it dump a portion of the memory that includes the VPN’s authentication password.
The security expert Brian Waters also tested the BENIGNCERTAIN exploits confirming that it works.
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
Brian H₂O's @int10h
I can confirm that BENIGNCERTAIN works against real hardware @XORcat @GossiTheDog @musalbas @marcan42 @msuiche
07:49 - 19 Ago 2016
148 148 Retweet 115 115 Mi piace
“it’s a PIX 501 running 6.3(5)145; and I used v1110 of the exploit” added 501 running 6.3(5)145; and I used v1110 of the exploit” added Waters in a second Tweet, this means that the BENIGNCERTAIN could work also against other versions of the PIX.
This means that NSA could have remotely sent a packet to a target VPN to obtain its preshared key and decrypt the traffic.
Cisco published the blog post titled “The Shadow Brokers EPICBANANAS and EXTRABACON Exploits” to provide further details about its investigation of the tools included in the arsenal of the Equation Group leaked online.
The Cisco security team is still investigating the content of the leaked data dump to verify the if other hacking tools could be exploited against its products.
“On August 19th, articles were release regarding the BENIGNCERTAIN exploit potentially being used to exploit legacy Cisco PIX firewalls. Our investigation so far has not identified any new vulnerabilities in current products related to the exploit. Even though the Cisco PIX is not supported and has not been supported since 2009 (see EOL / EOS notices), out of concern for customers who are still using PIX we have investigated this issue and found PIX versions 6.x and prior are affected. PIX versions 7.0 and later are confirmed to be unaffected by BENIGNCERTAIN. The Cisco ASA is not vulnerable.” wrote CISCO.
Is security enabling or compromising productivity?
20.8.2016 netsecurity Hacking
While most organizations fundamentally believe connecting people to the best technology is vital to business productivity, many struggle to achieve agility due to traditional on-premise security mindsets, according to an Okta survey of 300 IT and security professionals.
Failing to adapt and upgrade security tools is putting organizations at risk. 65% of respondents think that a data breach will happen within the next 12 months if they do not upgrade legacy security solutions in time.
“In order to be more productive, organizations worldwide are investing in cloud and mobile technologies, enabling their staff to work from virtually anywhere. But this isn’t enough to ensure true agility. As organizations become increasingly connected, the traditional idea of the enterprise network boundary is vanishing and businesses need to prioritise strong security,” said David Baker, CSO at Okta. “To successfully navigate the new perimeter and avoid compromising on security and productivity, IT leaders need to adopt tools that span traditional company and network boundaries and enable agility across the organization.”
Organizations are unsure if security is enabling or compromising productivity and agility
When asked if security measures compromised or enabled productivity in their organization, respondents’ opinions were mixed. Just over half (52%) said that their current security solutions compromise productivity, while 48% believe their security measures enable the organization to adopt best of breed solutions that enable productivity and agility.
Visibility into application usage is limited
Okta’s research shows that 85% of IT leaders suffer from a lack of insight over who has access to applications within their organization. Even more worrying, 80% of respondents pointed to weak passwords or weak access controls as a security issue.
Investing in new mobile, automation, and cloud technologies is paying dividends for organizations
92% of respondents believe their organization could do more to integrate and support cloud applications into their infrastructure and systems. This reveals a massive opportunity for IT teams to further drive agility and productivity, and the chance to drive this percentage down.
Warning — Bitcoin Users Could Be Targeted by State-Sponsored Hackers
20.8.2016 thehackernews Hacking
Another day, another bad news for Bitcoin users.
A leading Bitcoin information site is warning users that an upcoming version of the Blockchain consolidation software and Bitcoin wallets could most likely be targeted by "state-sponsored attackers."
Recently, one of the world's most popular cryptocurrency exchanges, Bitfinex, suffered a major hack that resulted in a loss of around $72 Million worth of Bitcoins.
Now, Bitcoin.org, the website that hosts downloads for Bitcoin Core, posted a message on its website on Wednesday warning users that the next version of the Bitcoin Core wallet, one of the most popular bitcoin wallets used to store bitcoins, might be replaced with a malicious version of the software offered by government-backed hackers.
Specifically, Chinese bitcoin users and services are encouraged to be vigilant "due to the origin of the attackers."
Bitcoin.org doesn't believe it has sufficient resources to defend against the attack. However, the website did not reveal the name of the country planning the attack.
The Warning Message from the Bitcoin.org site reads:
"Bitcoin.org has reason to suspect that the binaries for the upcoming Bitcoin Core release will likely be targeted by state-sponsored attackers. As a website, Bitcoin.org does not have the necessary technical resources to guarantee that we can defend ourselves from attackers of this calibre. We ask the Bitcoin community, and in particular the Chinese Bitcoin community to be extra vigilant when downloading binaries from our website."
"In such a situation, not being careful before you download [the software] could cause you to lose all your coins. This malicious software might also cause your computer to participate in attacks against the Bitcoin network."
Also Read: Bitcoin Exchange Offers $3.5 Million Reward for Information of Stolen Bitcoins.
In such cases, it is likely that hackers will try to hijack and replace the official binary files used to run Bitcoin software on mining pools, either:
By compromising the Bitcoin.org official site
By conducting a man-in-the-middle attack to fake a cryptographic certificate that would allow hackers to intercept victim’s encrypted HTTPS connection and replace the legitimate download with a malicious one, tricking users into installing a malicious version of the Bitcoin software.
However, Bitcoin Core developer Eric Lombrozo told The Reg that "there's absolutely nothing in the Bitcoin Core binaries, as built by the Bitcoin Core team, that has been targeted by state-sponsored attackers that we know of at this point."
"Perhaps certain sites where people download the binaries could end up getting compromised, but let's not unnecessarily spread paranoia about the Bitcoin Core binaries themselves."
Verify Signatures and Hashes
As a countermeasure, users are recommended to verify the Signature securely and hashes of Bitcoin Core binaries that are cryptographically signed with a key before running Bitcoin Core binaries to ensure the binaries are legitimate as being created by the Core developers team.
"We strongly recommend that you download that key, which should have a fingerprint of 01EA5486DE18A882D4C2684590C8019E36C2E964. You should securely verify the signature and hashes before running any Bitcoin Core binaries," the advisory states.
Moreover, you are advised to download the binaries from the official Bitcoin site only; otherwise, you may end up getting compromised.
Omegle, the Popular 'Chat with Strangers' Service Leaks Your Dirty Chats and Personal Info
20.8.2016 thehackernews Security
Ever since the creation of online chat rooms and then social networking, people have changed the way they interact with their friends and associates.
However, when it comes to anonymous chatting services, you don't even know what kinds of individuals you are dealing with.
Sharing identifiable information about yourself with them could put you at risk of becoming a victim of stalking, harassment, identity theft, webcam blackmail, and even phishing scams.
Have you heard of Omegle? The popular, free online anonymous chat service that allows you to chat with random strangers, without any registration. The service randomly pairs you in one-on-one chat window where you can chat anonymously over text or webcam.
But, are your chats actually Anonymous?
No, all your chats are recorded and saved by the service. So, if you have shared your personal details such as your name, phone number, or email address, with anyone over the service, you are no more anonymous.
Even the website describes its service as, "When you use Omegle, we pick someone else at random and let you talk one-on-one. To help you stay safe, chats are anonymous unless you tell someone who you are (not suggested!), and you can stop a chat at any time."
And here comes the worst part:
The recorded online conversations are saved in such a way that anyone with a little knowledge of hacking can pilfer them, revealing your personal information along with those dirty chats that could be used to harass or blackmail you.
Indrajeet Bhuyan (@Indrajeet_b), a young Indian bug hunter, has shown The Hacker News that how Omegle is saving screenshots of every 'so-called' anonymous chat session at a specific location on their web server, which could be downloaded by anyone with little knowledge of website structure.
omegle-online-chat-hack
Bhuyan wrote a simple python script, Omegle-Chat-Hack, that automatically downloads the saved screenshots from the website.
As a proof-of-concept, he also published some of those screenshots, showing how easily people, especially teenagers, share their personal details and contact info with strangers on a service, where they are supposed to stay anonymous.
"People on Omegle often think their chats are private and automatically get deleted once they disconnect from the conversation," Bhuyan told me. "Due to this false sense of security, people often share their sensitive information on the service. Omegle-Chat-Hack is a tool that demonstrates how insecure these online chat services are and how one can read your private messages sent over the service."
So, you should be careful with what identifiable information you are sharing over such online service while chatting with strangers. The more personal information you share, the more chances there are for others to misuse your information.
Frankly, you should take your online privacy very seriously.
Brazilian banking Trojans meet PowerShell
20.8.2016 Kaspersky Virus
Crooks are always creating new ways to improve the malware they use to target bank accounts, and now Brazilian bad guys have made an important addition to their arsenal: the use of PowerShell. Brazil is the most infected country worldwide when it comes to banking Trojans, according to our Q1 2016 report, and the quality of the malware is evolving dramatically. We found Trojan-Proxy.PowerShell.Agent.a in the wild a few days ago, marking a new achievement by Brazil’s cybercriminals.
The malware is distributed using a malicious email campaign disguised as a receipt from a mobile operator with a malicious .PIF file. After the file is executed it changes the proxy configuration in Internet Explorer to a malicious proxy server that redirects connections to phishing pages for Brazilian banks. It’s the same technique used by malicious PACs that we described in 2013, but this time no PACs are used; the changes in the system are made using a PowerShell script. As Windows 7 and newer OS versions are now the most popular in Brazil, the malware will not face a problem running on victims’ computers.
The malware has no C&C communication. After execution it spawned the process “powershell.exe” with the command line “-ExecutionPolicy Bypass -File %TEMP%\599D.tmp\599E.ps1” aiming to bypass PowerShell execution policies. The .ps1 file in the temp folder uses random names. It’s a base64 encoded script capable of making changes in the system.
After some deobfuscation we can see the goal of the script: to change the Internet Settings key and enable a proxy server on it:
And this is the result in the browser of the victim – a small change in the proxy settings:
This change will not only affect IE but all other browsers installed in the system as well, as they tend to use the same proxy configuration set on IE. The proxy domains used in the attack are listed below. All of them use dynamic DNS services and their goal is to redirect all traffic to a server located in the Netherlands (89.34.99.45), where there are several phishing pages for Brazilian banks:
gbplugin.[REMOVED].com.br
moduloseguro.[REMOVED].com.br
x0x0.[REMOVED].com.br
X1x1.[REMOVED].com.br
The malware also has other features of interest: it checks for the language of the OS and aborts if it’s not PTBR, a clever trick to avoid infecting Windows versions in languages other than Brazilian Portuguese.
To protect a network against malware that uses PowerShell, it is important to modify its execution, using administrative templates that only allow signed scripts. We are sure this is the first of many that Brazil’s bad guys will code.
Hash of the malware: cancelamento.pif -> MD5: 9419e7cd60487532313a43559b195cb0
Australian Police obtained access to the Love Zone Child Porn Site and Got 30 IPs from US
20.8.2016 securityaffairs Security
The Australian police had targeted the Love Zone child porn site, ran it for a while and managed to gain access at least to 30 US IPs.
Apart from FBI, there are other organizations that have tried to identify the participants of child porn websites, so that they could get their hands on them and make them pay. In fact, recently the Australian police managed to access a website called The Love Zone.
This is where they got to 30 US IPs at least. So, instead of Americans revealing IPs overseas and prosecuting them, it is the other way around here.
The website was in the dark web and used Tor. It was based in the US, which means that the Australian police (Queensland Police Service’s Task Force Argos, to be specific) had to hack them and access their sensitive data. At some point, over 29,000 members had already subscribed to the site, which is shocking news!
In order to lure the members of the site, the police sent a video file. The members wanted to open it, of course; it was relevant to their own preferences, after all!
More analytically:
“When a user clicked on that hyperlink, the user was advised that the user was attempting to open a video file from an external website. If the user chose to open the file, a video file containing images of child pornography began to play, and the [foreign law enforcement agency] captured and recorded the IP address of the user accessing the file. FLA configured the video file to open an Internet connection outside of the Network software, thereby allowing FLA to capture the user’s actual IP address, as well as a session identifier to tie the IP address to the activity of a particular user account.”
The whole investigation is not the same as that of the FBI and its 135 US cases. Yet, the Aussies handed over the evidence they had collected to the FBI. In this way, justice would finally emerge. It is worth pointing out that the owner of the Love Zone, Shannon McCoole, is serving a 35-year sentence for child sexual abuse.
It remains unclear whether or not the investigation of the Australian police was just against US targets.
As for the FBI, the only comments about the operation of the Love Zone were the following: “The FBI, led by its Legal Attaches in numerous countries around the world, seeks to foster strategic partnerships with foreign law enforcement, intelligence, and security services as well as with other US government agencies by sharing knowledge, experience, capabilities and by exploring joint operational opportunities.”
Iran investigates possible cyber attacks behind a string Oil Industry incidents
20.8.2016 securityaffairs Virus
Iran ’s cyberspace security authorities are investigating a string of fires in the country oil and gas facilities. Incidents or cyber sabotage?
Once again, something of strange is happening in Iran, the Government of Teheran is investigating a recent string of incidents occurred in critical infrastructure in the country.
The Iran’s Supreme National Cyberspace Council is investigating whether the oil and petrochemical fires were caused by cyber attacks, authorities fears that nation state actors may have launched an attack similar to Stuxnet.
The first incident occurred on July 6, in the Bouali petrochemical plant on the Persian Gulf coast, a couple of days after the fire was put out, a liquefied gas pipeline exploded in the Marun Oil and Gas Production Company, unfortunately, a worker died. On July 29 another fire occurred at the Bisotoon petrochemical plant.
The incidents were originally blamed on human error but after another explosion of a gas pipeline near Gonaveh the Iranian Petroleum Ministry started an investigation to understand the real cause of the anomalous string of incidents.
“The Iranian Petroleum Ministry, in charge of all of the affected sites denied the plants were sabotaged and the Iranian oil minister Bijan Namdar Zanganeh said the fires and explosions were due to technical faults and human error.” reported the Time.com “However when an explosion in a gas pipeline near Gonaveh, which killed a worker, and another fire in the Imam Khomeini petrochemical plant, occurred within hours of each other on Aug. 6, the ministry refused to comment until after investigations.“
Mr. Abolhassan Firouzabadi, the secretary of Iran’s Supreme National Cyberspace Council, confirmed that a team of investigators will work on the case trying to understand if the incidents are linked and if they were caused by a cyber attack.
fires cyber attacks Iran
Source The Tehrantimes.com
“Abolhassan Firouzabadi, secretary of Iran’s Supreme National Cyberspace Council, says a team of experts will look at the possibility of cyberattacks as being a cause, Press TV reported on Sunday.
Special teams will be sent to the afflicted sites to study the possibility of cyber systems having a role in the recent fires, he said.” reported the Tehran Times.
According to SCMagazine.com, Idan Udi Edry, CEO at Nation-E, speculates that the evidence leads experts into believing that the incidents being caused by a cyberattack.
“One indicator is that some of these attacks took place within hours of each other – some people may chalk this up to coincidence, but the fact that several of these incidences took place within a few weeks gives us reason to believe an attacker learned how to successfully implement a cyberattack on Iran’s oil and gas facilities, then continued to keep doing so on larger scales,” he told SCMagazine.com in an email.
This string of incidents raises the debate on the security of critical infrastructure and the dangers of cyber attack.
We all have in mind what has happened in 2010, when the systems at the Natanz nuclear facility were hit with the Stuxnet malware.
A new LOCKY ransomware campaign targets the healthcare
20.8.2016 securityaffairs Virus
Malware researchers at FireEye security firm have spotted a new Locky ransomware campaign mainly targeting the healthcare sector.
Security experts from FireEye have spotted a Locky ransomware campaign mainly targeting the healthcare sector, Telecom and Transportation industries.

Attackers launched a massive phishing campaign to deliver the threat. The campaign bit organizations worldwide, mostly in the US, Japan, South Korea.
Threat actors behind this Locky campaign leveraged on DOCM FORMAT email attachments to deliver the ransomware, instead Javascript based downloaders.
“From our trend analysis, Locky ransomware started being delivered via DOCM format email attachments more extensively beginning in August. This marks a change from the large campaigns we observed in March, where a JavaScript based downloader was generally being used to infect systems.” reads the report published by FireEye.
“These detection spikes and change in tactics suggest that the cybercriminals are investing more to infect systems and maximize their profits. Additionally, we have observed that the delivery of Dridex via this distribution channel seems to have stopped, or nearly so, which could explain why we are seeing the Locky uptick.”
The researchers believe crooks are investing to compromise systems maximizing their efforts. Another interesting trend reported by FireEye is the pause in the distribution of the Dridex banking Trojan through the same channel.
Experts noticed many similarities in the macro code used by Attackers in three distinct Locky campaigns running on Aug. 9, Aug. 11 and Aug. 15.
The following are the key comparisons:
Each email campaign has a specific “one-off” campaign code that is used to download the Locky ransomware payload from the malicious malware server.
The malicious URL embedded within macro code is encoded using the same encoding function, but with a different key for each campaign. Each character is encoded by multiplying its ASCII code with a specified key (an integer). Hence, its decoder would perform a division using the specified integer.
The downloaded payload is encoded using 32 bytes rolling XOR key. A different key is used for each campaign. Rolling XOR is described as follows:
Plain [i] = Cipher [i] ^ Key [i % length of Key], where Plain is the computed plain text, Cipher is the cipher text, Key is the xor key, and i is the byte offset.
The evidence collected by the researchers suggest the involvement of a single or multiple attackers in a coordinated effort.
Emails among dumps published by Wikileaks includes 300+ malware
20.8.2016 securityaffairs Virus
A malware researcher has analyzed the attachments of in the WikiLeaks email dumps and discovered more than 300 pieces of malware.
WikiLeaks has published more than 300 pieces of malicious code among its caches of dumped emails. Dr Vesselin Bontchev (@bontchev), a top Bulgarian malware researcher, has analyzed documents published by the organization and detected 324 instances of malware in its archive of dumped emails.
A check to the instance of malware allowed the malware expert to discover that the almost any instance appears to be an attachment of the dumped email.
The malicious codes are recognized by the Virus Total malware and URL online scanning service, they were likely sent by attackers to the recipients in the attempt to hack them.
“The following table contains the confirmed malware residing on the Wikileaks site. The list is by no means exhaustive; I am just starting with the analysis. But what is listed below is definitely malware; no doubts about it.” wrote Dr Bontchev on GitHub.
“The first column contains a link to the e-mail on the Wikileaks site that contains the malicious attachment. The e-mail itself is safe to view (although the text is usually spam/scam/phish/whatever).”

The situation may be worse because the piece of malware found by the Bulgarian researchers were identified in an initial search effort.
If you want to test the malware adopt all the necessary countermeasures to avoid infecting your machine.
Fortunately, the piece of malware are well known to the principal antivirus solutions, according to the malware researcher, the majority of the malicious codes have a Virus Total detection rate from 80 to 100 percent.
Anyway … be careful managing email attachments from Wikileaks archives.
Nebezpečné triky počítačových pirátů
19.8.2016 Securityworld Kriminalita
Kyberzločinci se snaží neustále hledat nové cesty, jak se dostat lidem do PC. V posledních měsících jejich snahy stále častěji směřují také k chytrým telefonům. Často jim přitom nejde pouze o získání citlivých dat, důmyslné podvody jim vydělávají velké peníze.
Jednou z hlavních motivací k šíření nebezpečných virů je relativně snadný zisk. Například díky vyděračskému viru zvanému TeslaCrypt si počítačoví piráti jen za první čtvrtletí letošního roku vydělali podle odhadů FBI více než 200 miliónů dolarů, tedy v přepočtu bezmála pět miliard korun.
Na napadeném stroji dokáže tento nezvaný návštěvník udělat pěkný nepořádek. Nejprve zašifruje všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun. Zmiňované miliardy tak útočníkům zaplatili skutečně samotní uživatelé.
Prostřednictvím dalších virů mohou kyberzločinci zase počítač doslova zotročit, získají tedy nad ním absolutní nadvládu.
Mobily jsou zlatý důl
Podobný nezvaný návštěvník se ale nemusí zabydlet pouze v počítači, v dnešní době dokážou kyberzločinci zotročit i chytrý telefon. Takový úlovek je pak pro piráty doslova zlatý důl.
Většina bankovních účtů je totiž jištěna proti neoprávněnému čerpání financí právě prostřednictvím mobilů – pomocí SMS zpráv. Když se dostanou kyberzločinci do chytrého telefonu, mají bankovní účet doslova na dosah ruky.
Útočníci vyzvou například prostřednictvím nevyžádané pošty klienty internetového bankovnictví k instalaci bezpečnostní aplikace do mobilního telefonu.
Ve skutečnosti se však nejedná o bezpečnostní aplikaci, ale hlášku vygenerovanou virem v počítači.
Před podobnými nezvanými hosty dokážou počítače, tablety i chytré telefony ochránit speciální programy. Kromě klasických antivirů jde například o aplikace, které se soustředí pouze na špionážní software a hledání trojských koní.
Škodlivý kód HummingBad se šíří jako lavina
Bezpečnostním expertům dělá v posledních měsících vrásky na čele škodlivý kód HummingBad, který se zaměřuje na telefony a tablety s operačním systémem Android. Tento nezvaný návštěvník totiž nakazil za pouhých pár měsíců na deset miliónů mobilních zařízení. Vyplývá to z analýzy bezpečnostní společnosti Check Point.
Severokorejský chytrý mobil Arirang
Nezvaný návštěvník dovoluje počítačovému pirátovi převzít nad napadeným strojem absolutní kontrolu. „Tento malware se zaměřuje na zařízení se systémem Android. Vytváří trvalý rootkit na zařízení,“ upozornil David Řeháček, bezpečnostní odborník ze společnosti Check Point. Schopnost škodlivého kódu se v zařízení maskovat – tedy zmiňovaný rootkit – značně znesnadňuje možnost jeho odhalení na napadeném zařízení.
Ve chvíli, kdy se HummingBad na mobilním zařízení zahnízdí, začne dál škodit. „Instaluje podvodné aplikace a umožňuje další škodlivé aktivity, jako například instalace keyloggerů, krádeže přihlašovacích údajů a obcházení šifrování e-mailů pro lepší zachycení podnikových dat,“ konstatoval Řeháček.
Jinými slovy počítačoví piráti převezmou nad napadeným přístrojem naprostou kontrolu. Mohou jen vyčkávat a sledovat aktivitu uživatele, stejně tak ale dovedou odchytávat zprávy týkající se internetového bankovnictví. Teoreticky tedy mohou uživatele připravit o peníze.
HummingBad se šíří zatím výhradně v prostředí platformy Android, a to zpravidla jako součást aplikací z neoficiálních zdrojů. Stejně tak se ale do přístroje může dostat prostřednictvím nevyžádaného e-mailu.
Falešná hra Pokémon Go uzamkne displej mobilu
Hra Pokémon Go je celosvětovým fenoménem. Toho se snaží využít také počítačoví piráti, kteří prostřednictvím falešných verzí šíří škodlivé kódy. Jedním z nich je i nový virus – tzv. lockscreen, který uzamkne displej telefonu a tím jej zcela zablokuje. Upozornili na něj experti antivirové společnosti Eset.
Doposud kyberzločinci šířili škodlivé kódy výhradně prostřednictvím neoficiálních verzí aplikace, které se objevovaly na různých webech. Nikoliv tedy prostřednictvím oficiálních internetových obchodů s aplikacemi.
U nového viru, který se maskuje za hru Pokémon Go, je tomu ale jinak. „Pokemon GO Ultimate je první zaznamenanou falešnou aplikací v Google Play s funkčností lockscreen. Ve skutečnosti není příliš škodlivá, jejím cílem je skryté klikání na porno reklamy,“ uvedl Petr Šnajdr, bezpečnostní expert společnosti Eset.
Záměr útočníků je tedy zřejmý. Nesnaží se uživatele nějak poškodit, nebo odcizit jeho data. Pouze se snaží prostřednictvím umělého navýšení kliků na bannery zvýšit příjmy daných webů z reklamy. Zamčený displej nejde žádným způsobem odemknout.
V mnoha případech je jediným řešením tzv. tvrdý restart zařízení, který se dělá jednoduše vyndáním baterie nebo kombinací určitých kláves. I po restartu ale zvládne nezvaný návštěvník klikat na porno stránky na pozadí a tím ukrajovat výkon smarpthonu.
Virus Keydnap krade hesla
Na pozoru by se měli mít uživatelé počítačů od společnosti Apple. V prostředí operačního systému Mac OS X se totiž šíří nebezpečný virus zvaný Keydnap. Ten dokáže na napadeném stroji udělat pěknou neplechu, především krade hesla k různým službám.
Mac Pro
Podle bezpečnostních expertů se škodlivý kód šíří především v souborech s koncovkou .zip, přičemž se pomocí jiné ikony snaží maskovat za textový dokument nebo obrázek. Nezvaný návštěvník se tak logicky nejčastěji šíří prostřednictvím nevyžádaných e-mailů. V počítači s operačním systémem Mac OS X se pak Keydnap snaží získat přístup k části systému, do které se ukládají hesla. Zároveň se snaží napadený stroj zařadit do tzv. botnetu, tedy do sítě zotročených počítačů.
Počítačoví piráti díky tomu pak mohou z napadeného stroje rozesílat další nevyžádané e-maily, případně je mohou zneužít k útokům typu DDoS. Při něm stovky až tisíce počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se takto napadená webová stránka tváří jako nedostupná.
Podle bezpečnostních expertů jsou v bezpečí uživatelé, kteří mají nastavenou funkci Gatekeeper tak, aby umožňovala spouštění pouze aplikací digitálně podepsaných pomocí vývojářského ID přiděleného společností Apple.
Přes Facebook šíří poplašné zprávy
Facebookem se začal šířit nový podvod, prostřednictvím kterého se snaží počítačoví piráti vylákat přihlašovací údaje jednotlivých uživatelů. Kyberzločinci tvrdí, že se Praha stala terčem teroristického útoku. Na poplašnou zprávu se podle bezpečnostních expertů antivirové společnosti Eset nechalo nachytat již několik tisíc Čechů a Slováků.
Útok má poměrně jednoduchý scénář. Na Facebooku některého z přátel se objeví odkaz na falešný zpravodajský článek pojednávající o údajném teroristickém útoku s větším množstvím obětí.
Zpráva má už na první pohled podezřelý titulek „30 minut před: 1 teroristického útoku došlo v Praze, při kterých nejméně 187 lidí bylo zabi”. Je navíc doplněna o fotografii z údajného místa útoku, která však zcela evidentně nepochází z hlavního města České republiky. Pořízena byla při útoku v Bagdádu v roce 2010, další varianta zase používá snímek z nedávného útoku v Nice.
V některých případech navíc kyberzločinci podvodné zprávy ještě více specifikují, aby nalákali co možná nejvíce důvěřivců. Jeden z odkazů, které bezpečnostní experti zachytili, tvrdil, že český prezident Miloš Zeman byl zavražděn ve vlastním domě. K šíření podvodných zpráv útočníci využívají účty na Facebooku, které se jim již podařilo napadnout. Právě proto se mohou podobné zprávy objevovat i pod hlavičkou skutečných přátel.
Smartphone dokážou ovládnout kyberzločinci na dálku
Bezpečnostní experti bijí na poplach. Objevili totiž hned čtyři zranitelnosti, jejichž prostřednictvím mohou počítačoví piráti ovládnout cizí smartphone na dálku. Podle prvních odhadů je v ohrožení více než 900 miliónů chytrých telefonů. Trhliny se týkají výhradně přístrojů postavených na platformě Android.
Celkem čtyři chyby nicméně neobsahuje samotný operační systém, ale ovladače čipsetu od společnosti Qualcomm. Nutno podotknout, že tuto čipovou sadu používá drtivá většina aktuálně nabízených smartphonů. Záplaty pro tři zranitelnosti jsou již k dispozici, na čtvrtou se však stále čeká. Tato chyba je přitom kritická, kyberzločinci ji mohou zneužít k napadení prakticky jakéhokoli přístroje s operačním systém Android 6 a všech dřívějších verzí.
Na přístroj stačí propašovat škodlivou aplikaci, jejímž prostřednictvím počítačoví piráti získají práva administrátora. Pak mohou libovolně přistupovat ke všem datům uloženým v telefonu, případně měnit jeho nastavení. Vše přitom probíhá v tichosti, uživatel si nemusí žádné nekalé aktivity všimnout. Uživatelé by se měli mít na pozoru před instalací programů z neznámých zdrojů. Právě tam se nejčastěji ukrývají nezvaní návštěvníci, které mohou kyberzločinci zneužít.
LOGmanager ve verzi 2.0 nabídne lepší práci s parsery i alerty
19.8.2016 Securityworld Zabezpečení
Novou verze svého řešení LOGmanager, systému pro log management a SIEM, uvedla na náš trh tuzemská firma Sirwisa.
LOGmanager ve verzi 2.0 nabídne lepší práci s parsery i alerty

Hlavní inovací varianty 2.0 jsou podle výrobce uživatelsky definované parsery přes grafické rozhraní, dále klasifikátory parserů podle zdrojů a nová podoba systému varovných hlášení s velmi detailní definicí podmínek.
V nové variantě LOGmanageru se uživatelé mohou setkat rovněž s přepracovaným uživatelským prostředím GUI, který přináší výrazně rychlejší odezvu webového rozhraní.
Doplněná byla podpora pro správu přidání vlastních certifikátů a aktualizovaný je také Windows Event Sender, agent pro sběr logů z prostředí Windows, který v nové verzi podporuje šifrovaný režim přenosu a ověřování validity certifikátů.
Produkt na našem trhu distribuuje firma Veracomp.
Eset vylepšuje NOD32 i Smart Security
19.8.2016 Securityworld Zabezpečení
Nové verze – varianty 10 -- svých bezpečnostních řešení NOD32 a Smart Security představil Eset. Nabízejí mj. ochranu před skriptovými útoky či zabránění zneužití webové kamery.
Eset zahájil prodej nové řady produktů pro SOHO a domácnosti. Nabízejí řadu nových funkcí, mezi které patří například ochrana před skriptovými útoky, která je součástí antivirové ochrany NOD32 Antivirus.
Smart Security navíc nově obsahuje ochranu webové kamery - uživatel může jednoduše povolit nebo zablokovat aplikace (dočasně i trvale), které se snaží webkameru použít.
Nové funkce v bezpečnostních řešeních Esetu podle výrobce
Ochrana před skriptovými útoky detekuje útoky škodlivých skriptů, které se snaží zneužít prostředí Windows PowerShell, a Javascriptové útoky ve všech běžných internetových prohlížečích. Funkce je obsažena ve všech uváděných produktech.
Ochrana domácí sítě umožňuje otestovat domácí router na různé zranitelnosti, jako je slabé heslo nebo neaktuální firmware. Poskytuje seznam aktuálně připojených zařízení a uživatel je může pro lepší přehlednost řadit do různých kategorií. Funkce je obsažena v produktu Smart Security.
Ochrana webkamery monitoruje všechny procesy a aplikace běžící na počítači a upozorní uživatele na nestandardní použití webové kamery. Funkce je obsažena v produktu Smart Security.
Remote code execution in D-Link routers
19.8.2016 Vulnerebility
D-Link has released new firmware for a number of routers to address a highly critical security vulnerability SB2016081203 (CVE-2016-5681). The affected routers are:
DIR-850L B1, DIR-822 A1, DIR-823 A1, DIR-895L A1, DIR-890L A1, DIR-885L A1, DIR-880L A1, DIR-868L B1, DIR-868L C1, DIR-817L(W) and DIR-818L(W).
The vulnerability exists within the cgibin binary, intended to handle session cookie. This binary is called from different parts of D-Link web interface, including the service, exposed through the WAN network interface on port 8181/TCP. A remote attacker can send a specially crafted "uid" cookie via the HTTP POST request to "/dws/api/Login" login page, cause buffer overflow and execute arbitrary code on the target system.
Successful exploitation of this vulnerability may allow an attacker to obtain full access to vulnerable device and use it to gain access to local network.
Public exploit code was also released by D-Link support website. Below is a dump of HTTP POST request, which can be used to trigger a buffer overflow:
----------------- REQUEST:
POST /dws/api/Login HTTP/1.1
Host: IP:8181
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:46.0) Gecko/20100101 Firefox/46.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 21
Cookie: uid="A"*3220 + "AAAA" + "BBBB" +"CCCC" +"DDDD" +"EEEE" +"FFFF" +"GGGG" +"HHHH" +"XXXX" << This causes the stack buffer overflow
Connection: close
id=test&password=test
-----------------
To resolve this vulnerability we recommend to install the latest version of firmware, available from vendor’s website:
DIR-850L Rev. B1 Official FW v2.07 (v2.07WWB05)
DIR-817 Rev. Ax Official FW End Aug. 2016
DIR-818L Rev. Bx Beta FW v2.05b03beta03 End Aug. 2016
DIR-822 Rev. A1 Official FW v3.01 (v3.01WWb02)
DIR-823 Rev. A1 Official FW v1.00 (v1.00WWb05)
DIR-895L Rev. A1 Official FW v1.11 (v1.11WWb04)
DIR-890L Rev A1 Official FW v1.09 (v1.09b14)
DIR-885L Rev. A1 Official FW v1.11 (v1.11WWb07)
DIR-880L Rev. A1 Official FW v1.07 (v1.07WWb08)
DIR-868L Rev. B1 Official FW v2.03 (v2.03WWb01)
DIR-868L Rev. C1 Official FW v3.00 (v3.00WWb01)
We also would suggest to filter all traffic on TCP port 8181 at least on WAN interface.
Compromising Linux virtual machines via FFS Rowhammer attack
19.8.206 helpnetsecurity Attack
A group of Dutch researchers have demonstrated a variant of the Rowhammer attack that can be used to successfully compromise Linux virtual machines on cloud servers.
The Flip Feng Shui (FFS) attack is not performed by triggering a software vulnerability. Instead, it relies on exploiting the widespread Rowhammer DRAM glitch to induce bit flips in controlled physical memory pages, and the Linux’ memory deduplication system.

A short version of the attack sequence goes like this:
“An attacker rents a virtual server on the same host as your virtual server. Next, the attacker ensures that the hypervisor deduplicates a certain part of the memory that both virtual servers share. That means that both systems store certain information that they both process, in the same part of the physical memory. By employing the so-called rowhammer technique, the attacker is able to change the information in this memory without the hypervisor or your virtual server noticing.”
The researchers were able to perform two attacks on servers running Debian and Ubuntu. In the first one they made the server download malware instead of a software update, and in the second one they managed to access the target’s VM by corrupting their OpenSSH public keys.
According to a fact sheet published by the National Cyber Security Centre (NSCS) of the Dutch government, the attack can be leveraged against virtual machines on workstations as well as servers, but the attacker needs to have access to another virtual machine on the same host.
As the researchers didn’t publish attack code, replicating these attacks is out of reach for most low level attackers, but not for a criminal organization or a foreign intelligence service, NSCS noted.
Temporary solutions to this problem include disabling memory deduplication in the configuration of the hypervisor, or switching to (less efficient) zero-page deduplication.
The researchers informed OpenSSH, GnuPG, VM monitor vendors, and Debian and Ubuntu of the results of their researcher, and GnuPG has already strengthened their key signature checks to protect against the attack.
More technical details about the attack and video demonstrations can be found here and here.
Microsoft Open Sources PowerShell; Now Available for Linux and Mac OS X
19.8.2016 thehackernews IT
'Microsoft loves Linux' and this has never been so true than now.
Microsoft today made its PowerShell scripting language and command-line shell available to the open source developer community on GitHub under the permissive MIT license.
The company has also launched alpha versions of PowerShell for Linux (specifically Red Hat, Ubuntu, and CentOS) and Mac OS X, in addition, of course, to Windows.
Now, people can download binaries of the software, as well as access source code of the app from the new PowerShell GitHub page.
"Users across Windows and Linux, current and new PowerShell users, even application developers can experience a rich interactive scripting language as well as a heterogeneous automation and configuration management that works well with your existing tools," Microsoft says in its blog post.
"Your PowerShell skills are now even more marketable, and your Windows and Linux teams, who may have had to work separately, can now work together more easily."
PowerShell is Microsoft’s command line shell for Windows power users, and an extensible scripting language for automating system tasks.
Microsoft is aware that the company now operates in a "multi-platform, multi-cloud, multi-OS world." Since PowerShell is built on Microsoft's .NET platform, the company brought .NET Core, the version of .NET which runs cross-platform, to bring PowerShell to other platforms.
Microsoft has already planned to ship PowerShell "Core" with Nano Server for Windows Server 2016, and the newly announced release will run on .NET Core on Mac as well as Linux.
Although this recent release of PowerShell is Alpha-based and community supported, an official Microsoft version of PowerShell based on open source to anyone running a supported version of Windows will be published in the future, Microsoft notes.
Bitcoin.org warns state-sponsored attacks against the Bitcoin Core
19.8.2016 securityaffairs Hacking
The organization that controls the development of the Bitcoin software warns users that nation-state actors may hit the upcoming Bitcoin Core release.
The organization that controls the development of the Bitcoin system, Bitcoin.org, has warned of possible cyber attacks coordinated by nation-state attackers.
Bitcoin Core is the open source client for Bitcoin, the version Bitcoin Core 0.12.1 was released in April and a new one will be soon available (version 0.13.0).
This week, Bitcoin.org published a security notice to inform users that it is possible that the Bitcoin Core 0.13.0 version will be targeted by state-sponsored hackers.
“Bitcoin.org has reason to suspect that the binaries for the upcoming Bitcoin Core release will likely be targeted by state-sponsored attackers.” states the security notice.
“We ask the Bitcoin community, and in particular the Chinese Bitcoin community to be extra vigilant when downloading binaries from our website,”
The organization is warning is a specific way the Chinese Bitcoin community, inviting it to be vigilant and to adopt all the necessary measured to avoid security breaches.
When dealing with a persistent attacker such as a nation-state actor in is necessary a supplementary effort of the entire community due to the abilities of the adversaries.
“In such a situation, not being careful before you download binaries could cause you to lose all your coins. This malicious software might also cause your computer to participate in attacks against the Bitcoin network. We believe Chinese services such as pools and exchanges are most at risk here due to the origin of the attackers,” Bitcoin.org warned.
The Bitcoin.org suggests checking the hashes of Bitcoin Core binaries that are cryptographically signed with a known tkey.
“We strongly recommend that you download that key, which should have a fingerprint of 01EA5486DE18A882D4C2684590C8019E36C2E964. You should securely verify the signature and hashes before running any Bitcoin Core binaries. This is the safest and most secure way of being confident that the binaries you’re running are the same ones created by the Core Developers.”
In a thread on the news.ycombinator.com, experts discussed about the fact that bbitcoin.org does not implement HTTP Public Key Pinning (HPKP), this means that any government that controls a CA can generate its own cert for bitcoin.org, hijack the site’s IP and replace this page with their own fingerprint.

China controls the root CA China Internet Network Information Center (CNNIC) whom new certificates were banned last year by Mozilla and Google after one of its intermediate certificates was used to issue fake Google certificates.
Unfortunately, many threat actors are interested in launching cyber attacks against the Bitcoin users.
Recently several Bitcoin exchanges have been hacked, clamorous the security breach suffered by the Asian Bitfinex that led the theft of 120,000 Bitcoin.
The Bitcoin value significantly dropped after the discovery of the breach, it was observed a 20 percent decrease.
Crooks abused Google AdSense network to deliver malware on Android Devices
19.8.2016 securityaffairs Virus
Security experts from Kaspersky spotted a malware-based campaign that abused the Google Adsense Advertising network to spread a malicious code.
Mobile malware is becoming an even more insidious threat, security experts are observing a rapid diffusion of spyware that is able to steal sensitive data from victim’s mobile devices.
Very common are also malware that impersonates login pages of most popular applications and websites in the attempt of tricking users to provide their login credentials. Such kind of malware is able to steal private data, including banking credentials and social media account credentials.
Recently malware researchers from Kaspersky have spotted a new hacking campaign that abused Google AdSense to deliver a malware on Android devices. The malware is delivered on the victim’s mobile device when they visit certain Russian websites, even without user’s interaction.
The malicious code asks for admin rights and attempts to steal user credentials via displaying bogus login pages. The malware is able to perform other malicious operations, such as intercepting and deleting text messages.
“By simply viewing their favorite news sites over their morning coffee users can end up downloading last-browser-update.apk, a banking Trojan detected by Kaspersky Lab solutions as Trojan-Banker.AndroidOS.Svpeng.q. There you are, minding your own business, reading the news and BOOM! – no additional clicks or following links required. And be careful – it’s still out there!” reads a blog post published by Kaspersky.
Android malware Google adsense 3
The malware leverages on the Google AdSense advertising network to spread itself and many websites use this ad network.
Google has promptly fixed the problem, according to an email to a Google spokesman there is no indication that other websites are affected by the malware.
“The issue has since been resolved, a Google spokeswoman said in an email, adding that there’s no indication the attack ever affected more than one website. The company has said in the past that it works to block malware attacks from third-party ads distributed through its networks. The effort has become increasingly critical as Google and other advertising networks try to dissuade users from filtering out ads altogether with adblocking tools, which also aim to reduce ad-delivered malware and the web beacons used to track users across websites.” states the fastcompany.com.
In order to protect your mobile device keep your mobile OS up to date, install apps only from legitimate app stores and install security solutions.
Hackeři napadli i počítače amerických republikánů
19.8.2016 Novinky/Bezpečnost Hacking
Hackeři napadli počítače americké Republikánské strany i pracovníků kampaně jejího kandidáta na prezidenta Donalda Trumpa. S odvoláním na zdroje z vyšetřování to ve čtvrtek napsala agentura Reuters. Už dříve americká média oznámila, že hackeři napadli i konkurenční Demokratickou stranu.
Republikánský kandidát Donald Trump
Podle Reuters hackeři umístili škodlivý software do napadených republikánských počítačů v loňském roce. Trumpova kampaň poté najala bezpečnostní firmu CrowdStrike, která pomáhá i Demokratické straně řešit následky hackerského útoku proti ní. Republikáni se k záležitosti nevyjádřili.
Za útoky na Demokratickou stranu podle amerických vyšetřovatelů stáli hackeři z Ruska. E-maily získané hackery od demokratických představitelů ukázaly, že vedení Demokratické strany dávalo v primárkách přednost Clintonové před jejím soupeřem Berniem Sandersem. Kvůli aféře podala demisi předsedkyně demokratů Debbie Wassermanová Schultzová.
Tajné služby jdou po zranitelnostech v hardwaru
19.8.2016 Root.cz Hacking
bulletin Cisco exploit Hack hacker Hacking kyberbezpečnost NSA zranitelnost
Minulý týden, v pátek, jsme psali o zranitelnosti vzdáleného spuštění kódu v D-link routerech, postihující 11 modelů zařízení.
Nedávný hack Equation Group (úzce spojený s NSA) zveřejnil informaci o exploitech proti síťovému zařízení, vyrobeném největšími americkými výrobci: Cisco, Juniper a Fortinet.
Jen dnes jsme zjistili několik bezpečnostních bulletinů popisujících dvě zero-day zranitelnosti v CISCO ASA Appliances (CVE-2016–6366, CVE-2016–6367), vzdálené spuštění kódu ve FortiOS (SB2016081801) a velmi nepříjemný problém s výchozím veřejným ssh-key ve VMWare Photon OS (CVE-2016–5332).
Cisco potvrdilo EXTRABACON a EPICBANANA exploity, avšak nejsou žádné informace od dalších dodavatelů. Fortinet neudělal oficiální prohlášení, jen uvolnil bulletiny popisující zranitelnost vzdáleného spuštění kódu ve FortiOS. Není známo, zda je problém spojený s únikem.
Začátkem letošního roku musel Juniper čelit backdooru v ScreenOS zdrojovém kódu, který byl přítomen v bezpečnostním řešení minimálně od roku 2009.
Je zřejmé, že takový zájem o zranitelnosti v síťových zařízeních je kvůli nedostatku implementovaných ochranných mechanismů. Zatímco pracovní stanice a servery jsou často aktualizovány a jsou vybaveny firewally a antivirovými softwary, zařízení určené k poskytnutí základní ochrany zklamalo. Proces aktualizace firmwaru pro většinu síťových zařízení je komplikovaný a často vyžaduje dodatečné úsilí od pracovníků IT, anebo může způsobit výpadek.
Situace se zranitelnosmi v hardwaru je velmi znepokojujíci. Zařízení, která by měla poskytovat alespoň nejzákladnější stupeň ochrany pro vaše síťové prostředky, můhou být jednoduše zkompromitována, jako každý jiný hostitel. Už není vůbec bezpečené, spoléhat se jen na zařízení od vašeho dodavatele. A i když máte tucet firewallů, neznamená to, že nemají vadnou implementaci některých síťových protokolů.
Každopádně vám doporučujeme omezit přístup ke službám, které čelí internetu přímo. Můžete použít náš Online scanner zranitelností zdarma k prozkoumání otevřených portů a přítomnosti zranitelného softwaru ve vašem systému.
By Cybersecurity Help =)
anchors in page */ $(document).ready(function() { $('div[class*="rs-img-"] a') //only .filter(function(i) { return $(this).children('img').length > 0; }) .addClass('lightbox') .append('') .filter(function(i) { if(this.nodeName == 'A' && this.href.match(/-orig.[a-z]+$/)) { $(this).addClass('orig'); return false; } else { return true; } }) .attr('rel', 'clanek-img') .fancybox({ 'titleShow' : false, 'transitionIn' : 'elastic', 'transitionOut' : 'elastic' }); });
The NSA Hack — What, When, Where, How, Who & Why?
18.8.2016 thehackernews Hacking
You might have heard about the recent ongoing drama of NSA hack that has sparked a larger debate on the Internet concerning abilities of US intelligence agencies as well as their own security.
Saturday morning the news broke that a mysterious group of hackers calling themselves "The Shadow Brokers" claimed it hacked an NSA-linked group and released some NSA hacking tools with a promise to sell more private "cyber weapons" to the highest bidder.
The group dumped a bunch of private hacking tools from "Equation Group" – an elite cyber attack unit linked to the NSA – on GitHub and Tumblr.
The Shadow Brokers hacking group has published the leaked data in two parts; one includes many hacking tools designed to inject malware into various servers and another encrypted file containing the "best files" that they made available for sale for 1 Million Bitcoins.
However, GitHub deleted the files from its page, not due to any government pressure, but because the hackers were demanding cash to release more data and the company's policy don't allow the auction or sale of stolen property on its source code management platform.
NSA Hack Raises a Few Important Question? The leak of advanced hacking tools allegedly stolen from the Equation Group has raised few questions in everyone's mind:
Is Equation Group an elite cyber attack unit linked to the NSA?
Are the Equation Group Hack and leaked exploits legitimate?
If Legit, Do the advanced hacking tools actually belong to Equation Group?
Who is behind the hack? Russia?
Here's all you need to know about the NSA Hack:
Kaspersky Confirmed: Leaked Hacking Tools Belong to NSA-tied Group
According to a technical report published Tuesday by security firm Kaspersky Lab, the leaked advanced hacking tools contains digital signatures that are identical to those in hacking software and malware previously used by the Equation Group.
"While we cannot surmise the attacker's identity or motivation nor where or how this pilfered trove came to be, we can state that several hundred tools from the leak share a strong connection with our previous findings from the Equation group," Kaspersky researchers said in a blog post.
Over 300 computer files found in the Shadow Brokers archive have a common implementation of RC5 and RC6 encryption algorithms – which has been used extensively by the Equation Group.
Also, the implementation of encryption algorithms is identical to the RC5 and RC6 code in the Equation Group malware.
"There are more than 300 files in the Shadow Brokers' archive which implement this specific variation of RC6 in 24 other forms," the researcher wrote. "The chances of all these being fakes or engineered is highly unlikely."
"The code similarity makes us believe with a high degree of confidence that the tools from the Shadow Brokers' leak are related to the malware from the Equation group."
Here's the comparison of the older Equation RC6 code and the code from the new leak, which shows that they have identical functionally and share rare specific traits in their implementation:
Kaspersky Lab previously linked Equation Group to the NSA, describing it as "a threat actor that surpasses anything known in terms of complexity and sophistication of techniques, and that has been active for almost two decades."
The security firm also claimed Equation Group to be behind a variety of malware types, including Stuxnet and Flame, which are associated with cyber attacks launched by the United States.
Former NSA Personnel also Confirms the Authenticity of Leaked Data
Now, adding more proofs to the possibility and making the speculations stronger, some ex-NSA insiders say the leaked hacking tools are legitimate and linked to the NSA.
One former NSA employee who worked in its special hacking division, Tailored Access Operations (TAO), told the Washington Post that "without a doubt, they're the keys to the kingdom."
"The stuff you are talking about would undermine the security of a lot of major government and corporate networks both here and abroad," said the former TAO employee, who asked Post to remain anonymous.
Moreover, another former TAO employee who also saw the leaked file said, "From what I saw, there was no doubt in my mind that it was legitimate."
So, after Kaspersky Labs analysis and former-TAO employees statements, it is clear that the leaked NSA hacking tools are legitimate.
Hack Or An Inside Job?
Moreover, it has also been speculated that the NSA hack could be an insider’s job, as concluded by Matt Suiche, founder of UAE-based security startup after he discussed this incident with a former NSA TAO employee.
"The repository containing the NSA TAO Toolkit is stored on a physically segregated network which does not touch the internet and has no reason to (remember it's a toolkit repository)," Suiche wrote in a blog post.
"There is no reason for those files to have ever been on a staging server in the first place unless someone did it on purpose. The file hierarchy and the unchanged file naming convention tends to say that the files were directly copied from its source."
Experts and Snowden suggest Russia is behind the NSA Hack
nsa-hack-russia-snowden
Most cyber security experts, as well as former NSA contractor and whistleblower Edward Snowden, believes Russia to be behind the NSA hack.
In past few weeks, WikiLeaks and an unknown hacker using an alias Guccifer 2.0 have published a large number of documents came from the breach of the Democratic National Committee (DNC) and another separate hack of the Democratic Congressional Campaign Committee (DCCC).
Several officials from US intelligence agencies and security companies have pointed fingers towards Russia for the recent Democratic hacks, though Russia has denied any involvement.
"The Federal Bureau of Investigation and U.S. intelligence agencies have been studying the Democratic hacks, and several officials have signaled it was almost certainly carried out by Russian-affiliated hackers," the WSJ reports. "Russia has denied any involvement, but several cybersecurity companies have also released reports tying the breach to Russian hackers."
Now, both Snowden and Dave Aitel, a security expert who spent 6 years as an NSA security scientist, are speculating that the latest leak by the Shadow Brokers is in response to growing tensions between the United States and Russia over the Democratic groups' hacks.
In a stream of tweets yesterday, Snowden said the hack is likely of Russian origin, tweeting "No one knows, but I suspect this is more diplomacy than intelligence, related to the escalation around the DNC hack."
Here's the combined statement by Snowden:
"Circumstantial evidence and conventional wisdom indicate Russian responsibility. Here's why that is significant:
This leak is likely a warning that someone can prove US responsibility for any attacks that originated from this malware server. That could have significant foreign policy consequences. Particularly if any of those operations targeted US allies. Particularly if any of those operations targeted elections. Accordingly, this may be an effort to influence the calculus of decision-makers wondering how sharply to respond to the DNC hacks. TL;DR: This leak looks like a somebody sending a message that an escalation in the attribution game could get messy fast."
Following Snowden tweets, Aitel also published a blog post, saying Russia is the most likely suspect behind the Democratic hacks as well as the latest leak of the NSA spying tools.
Apart from speculation, Wikileaks, which previously made it clear to harm Hillary Clinton's chances from becoming US President, also said it already own the "auction" files from the Shadow Brokers and will publish them in "due course," though the tweet has since been deleted.
Still, many questions remain unanswered — who is the Shadow Brokers, how the group broke into Equation Group and stole their private hacking tools and malware, and is the group really willing to bid the auction files for 1 Million Bitcoins or is it just a distraction?
Operation Ghoul: targeted attacks on industrial and engineering organizations
18.8.2016 Kaspersky Attack
Kaspersky Lab has observed new waves of attacks that started on the 8th and the 27th of June 2016. These have been highly active in the Middle East region and unveiled ongoing targeted attacks in multiple regions. The attackers try to lure targets through spear phishing emails that include compressed executables. The malware collects all data such as passwords, keystrokes and screenshots, then sends it to the attackers.
#OpGhoul targeting industrial, manufacturing and engineering organizations in 30+ countries
Tweet
We found that the group behind this campaign targeted mainly industrial, engineering and manufacturing organizations in more than 30 countries. In total, over 130 organizations have been identified as victims of this campaign. Using the Kaspersky Security Network (KSN) and artifacts from malware files and attack sites, we were able to trace the attacks back to March 2015. Noteworthy is that since the beginning of their activities, the attackers’ motivations are apparently financial, whether through the victims’ banking accounts or through selling their intellectual property to interested parties, most infiltrated victim organizations are considered SMBs (Small to Medium size businesses, 30-300 employees), the utilization of commercial off-the-shelf malware makes the attribution of the attacks more difficult.
In total, over 130 organizations have been identified as victims of Operation Ghoul #OpGhoul
Tweet
In ancient Folklore, the Ghoul is an evil spirit associated with consuming human flesh and hunting kids, originally a Mesopotamian demon. Today, the term is sometimes used to describe a greedy or materialistic individual.
Main infection vector: malicious emails
The following picture represents emails that are being used to deliver malware to the victims, in what looks like a payment document. The e-mails sent by attackers appear to be coming from a bank in the UAE, the Emirates NBD, and include a 7z file with malware. In other cases, victims received phishing links. A quick analysis of the email headers reveals fake sources being utilised to deliver the emails to victims.
Malicious attachments
In the case of spear phishing emails with an attachment, the 7z does not contain payment instructions but a malware executable (EmiratesNBD_ADVICE.exe). We have observed executables with the following MD5s:
Malware MD5 hashes
fc8da575077ae3db4f9b5991ae67dab1
b8f6e6a0cb1bcf1f100b8d8ee5cccc4c
08c18d38809910667bbed747b2746201
55358155f96b67879938fe1a14a00dd6
Email file MD5 hashes
5f684750129e83b9b47dc53c96770e09
460e18f5ae3e3eb38f8cae911d447590
The spear phishing emails are mostly sent to senior members and executives of targeted organizations, most likely because the attackers hope to get access to core intelligence, controlling accounts and other interesting information from people who have the following positions or similar:
Chief Executive Officer
Chief Operations Officer
General Manager
General Manager, Sales and Marketing
Deputy General anager
Finance and Admin Manager
Business Development Manager
Manager
Export manager
Finance Manager
Purchase manager
Head of Logistics
Sales Executive
Supervisor
Engineer
Technical details
Malware functionality
The malware is based on the Hawkeye commercial spyware, which provides a variety of tools for the attackers, in addition to malware anonymity from attribution. It initiates by self-deploying and configuring persistence, while using anti-debugging and timeout techniques, then starts collecting interesting data from the victim’s device, including:
Keystrokes
Clipboard data
FileZilla ftp server credentials
Account data from local browsers
Account data from local messaging clients (Paltalk, Google talk, AIM…)
Account data from local email clients (Outlook, Windows Live mail…)
License information of some installed applications
#OpGhoul malware collects all data such as #passwords, keystrokes and screenshots
Tweet
Data exfiltration
Data is collected by the attackers using primarily:
Http GET posts
Sent to hxxp://192.169.82.86
Email messages
mail.ozlercelikkapi[.]com (37.230.110.53), mail to info@ozlercelikkapi[.]com
mail.eminenture[.]com (192.185.140.232), mail to eminfo@eminenture[.]com
Both ozlercelikkapi[.]com and eminenture[.]com seem to belong to compromised organisations operating in manufacturing and technology services.
Malware command center
The malware connects to 192.169.82.86 to deliver collected information from the victim’s PC. This information includes passwords, clipboard data, screenshots…
hxxp://192.169.82.86/~loftyco/skool/login.php
hxxp://192.169.82.86/~loftyco/okilo/login.php
The IP address 192.169.82.86 seems to belong to a compromised device running multiple malware campaigns.
Victim information
Victim organizations are distributed in different countries worldwide with attackers focused on certain countries more than others:
Number of Victim Organisations by Country
Countries marked as “others” have less than three victim organizations each, they are: Switzerland, Gibraltar, USA, Sweden, China, France, Azerbaijan, Iraq, Turkey, Romania, Iran, Iraq and Italy.
Victim industry information
Victim industry types were also indicators of targeted attacks as attackers were looking to infiltrate organizations that belong to the product life cycle of multiple goods, especially industrial equipment.
#Manufacturing #transportation #travel targets of #OpGhoul
Tweet
Number of Victim Organizations by Industry Type
Victim industry description
Industrial Petrochemical, naval, military, aerospace, heavy machinery, solar energy, steel, pumps, plastics
Engineering Construction, architecture, automation, chemical, transport, water
Shipping International freight shipping
Pharmaceutical Production/research of pharmaceutical and beauty products
Manufacturing Furniture, decor, textiles
Trading Industrial, electronics and food trading
Education Training centers, universities, academic publishing
Tourism Travel agencies
Technology/IT Providers of IT technologies and consulting services
Unknown Unidentified victims
The last attack waves
Kaspersky Lab user statistics indicate the new waves of attacks that started in June 2016 are focused on certain countries more than others.
#opghoul highly active in #MiddleEast
Tweet
Hundreds of detections have been reported by Kaspersky Lab users; 70% of the attacked users were found in the United Arab Emirates alone, the other 30% were distributed in Russia, Malaysia, India, Jordan, Lebanon, Turkey, Algeria, Germany, Iran, Egypt, Japan, Switzerland, Bahrain and Tunisia.
Other attack information
Phishing pages have also been spotted through 192.169.82.86, and although they are taken down quickly, more than 150 user accounts were identified as victims of the phishing links sent by the attackers. Victims were connecting from the following devices and inserting their credentials, a reminder that phishing attacks do work on all platforms:
Windows
Mac OS X
Ubuntu
iPhone
Android
The malware files are detected using the following heuristic signatures:
Trojan.MSIL.ShopBot.ww
Trojan.Win32.Fsysna.dfah
Trojan.Win32.Generic
Conclusion
Operation Ghoul is one of the many attacks in the wild targeting industrial, manufacturing and engineering organizations, Kaspersky Lab recommends users to be extra cautious while checking and opening emails and attachments. In addition, privileged users need to be well trained and ready to deal with cyber threats; failure in this is, in most cases, the cause behind private or corporate data leakage, reputation and financial loss.
Indicators of Compromise
The following are common among the different malware infections; the presence of these is an indication of a possible infection.
Filenames and paths related to malware
C:\Users\%UserName%\AppData\Local\Microsoft\Windows\bthserv.exe
C:\Users\%UserName%\AppData\Local\Microsoft\Windows\BsBhvScan.exe
C:\Users\%UserName%\AppData\Local\Client\WinHttpAutoProxySync.exe
C:\Users\%UserName%\AppData\Local\Client\WdiServiceHost.exe
C:\Users\%UserName%\AppData\Local\Temp\AF7B1841C6A70C858E3201422E2D0BEA.dat
C:\Users\%UserName%\AppData\Roaming\Helper\Browser.txt
C:\Users\%UserName%\AppData\Roaming\Helper\Mail.txt
C:\Users\%UserName%\AppData\Roaming\Helper\Mess.txt
C:\Users\%UserName%\AppData\Roaming\Helper\OS.txt
C:\ProgramData\Mails.txt
C:\ProgramData\Browsers.txt
List of malware related MD5 hashes
55358155f96b67879938fe1a14a00dd6
f9ef50c53a10db09fc78c123a95e8eec
b8f6e6a0cb1bcf1f100b8d8ee5cccc4c
07b105f15010b8c99d7d727ff3a9e70f
ae2a78473d4544ed2acd46af2e09633d
21ea64157c84ef6b0451513d0d11d02e
08c18d38809910667bbed747b2746201
fc8da575077ae3db4f9b5991ae67dab1
8d46ee2d141176e9543dea9bf1c079c8
36a9ae8c6d32599f21c9d1725485f1a3
cc6926cde42c6e29e96474f740d12a78
6e959ccb692668e70780ff92757d2335
3664d7150ac98571e7b5652fd7e44085
d87d26309ef01b162882ee5069dc0bde
5a97d62dc84ede64846ea4f3ad4d2f93
5a68f149c193715d13a361732f5adaa1
dabc47df7ae7d921f18faf685c367889
aaee8ba81bee3deb1c95bd3aaa6b13d7
460e18f5ae3e3eb38f8cae911d447590
c3cf7b29426b9749ece1465a4ab4259e
List of malware related domains
Indyproject[.]org
Studiousb[.]com
copylines[.]biz
Glazeautocaree[.]com
Brokelimiteds[.]in
meedlifespeed[.]com
468213579[.]com
468213579[.]com
357912468[.]com
aboranian[.]com
apple-recovery[.]us
security-block[.]com
com-wn[.]in
f444c4f547116bfd052461b0b3ab1bc2b445a[.]com
deluxepharmacy[.]net
katynew[.]pw
Mercadojs[.]com
Observed phishing URLs
hxxp://free.meedlifespeed[.]com/ComCast/
hxxp://emailreferentie.appleid.apple.nl.468213579[.]com/
hxxp://468213579[.]com/emailreferentie.appleid.apple.nl/emailverificatie-40985443/home/login.php
hxxp://verificatie.appleid.apple.nl.referentie.357912468[.]com/emailverificatie-40985443/home/lo…
hxxp://192.169.82.86/~gurgenle/verify/webmail/
hxxp://customer.comcast.com.aboranian[.]com/login
hxxp://apple-recovery[.]us/
hxxp://apple.security-block[.]com/Apple%20-%20My%20Apple%20ID.html
hxxp://cgi.ebay.com-wn[.]in/itm/2000-Jeep-Wrangler-Sport-4×4-/?ViewItem&item=17475607809
hxxp://https.portal.apple.com.idmswebauth.login.html.appidkey.05c7e09b5896b0334b3af1139274f266b2hxxp://2b68.f444c4f547116bfd052461b0b3ab1bc2b445a[.]com/login.html
hxxp://www.deluxepharmacy[.]net
Other malware links
Malware links observed on 192.169.82.86 dating back to March and April 2016:
hxxp://glazeautocaree[.]com/proforma-invoice.exe
hxxp://brokelimiteds[.]in/cdn/images/bro.exe
hxxp://brokelimiteds[.]in/cdn/images/onowu.exe
hxxp://brokelimiteds[.]in/cdn/images/obe.exe
hxxp://brokelimiteds[.]in/wp-admin/css/upload/order.exe
hxxp://brokelimiteds[.]in/wp-admin/css/upload/orders.exe
hxxp://papercuts[.]info/SocialMedia/java.exe
hxxp://studiousb[.]com/mercadolivrestudio/f.zip
hxxp://copylines[.]biz/lasagna/gate.php?request=true
Terčem hackerů se stala nadace Clintonových. Stopy vedou do Ruska
18.8.2016 Hacking
Nadace Billa a Hillary Clintonové si najala bezpečnostní společnost FireEye, aby po známkách hackerského útoku prověřila její datové systémy. S odvoláním na dva nejmenované zdroje o tom v noci na čtvrtek informovala agentura Reuters. Na veřejnost podle nich zatím neunikl žádný dokument, u kterého by bylo jasně patrné, že se tam dostal prostřednictvím hackerů.
Američtí činitelé pod podmínkou zachování anonymity sdělili, že hackeři použili stejnou techniku jako ruské zpravodajské služby nebo jejich zprostředkovatelé během kybernetického útoku proti institucím z americké Demokratické strany, za kterou Clintonová kandiduje na prezidentku Spojených států. To by prý mohlo naznačovat, že Rusové zaútočili také na nadaci Clintonových.
Jeden z těchto zdrojů a dva američtí činitelé uvedli, že hackeři využili takzvaný cílený phishing. Součástí této techniky bylo podle zdrojů vytváření podvodných internetových stránek a e-mailů, kterými se počítačoví piráti chtěli vlomit do e-mailů pracovníků nadace Clintonových a později do nadace samotné.
Terčem nedávného hackerského útoku na instituce Demokratické strany se staly počítače jejího vedení (DNS) a stranický výbor pro získávání finančních prostředků pro kandidáty do Sněmovny reprezentantů. Americké úřady Moskvu s útokem na tyto počítače oficiálně nespojují a Rusko účast na akci odmítá.
Cisco, Fortinet issue fixes against Equation Group exploits
18.8.2016 Vulnerebility
Customers of Cisco and Fortinet security firms need to patch their products to fix the flaws exploited by the Equation Group exploits and hacking tools.
While security experts are analyzing the hacking tools leaked in the data dump by the Shadow Brokers, security firms are working to fix the vulnerabilities exploited by the Equation Group toolsets.
Both Fortinet and Cisco have issued patches to address exploits that were leaked online, the list of affected products includes versions of Cisco’s PIX and ASA firewalls and versions of Fortinet Fortigate firewalls.

Cisco has confirmed that the two exploits EPICBANANA and EXTRABACON can be used to achieve remote code execution on Cisco firewalls.
Cisco confirmed that the code leaked by the “Shadow Brokers” includes exploits for the following flaws:
Cisco ASA SNMP Remote Code Execution Vulnerability
Cisco ASA CLI Remote Code Execution Vulnerability
The Cisco ASA SNMP Remote Code Execution vulnerability is a newly found vulnerability, both TALOS and Cisco IPS have produced signatures to detect them:
Snort Rule ID: 3:39885
Legacy Cisco IPS Signature ID: 7655-0
The Cisco ASA CLI Remote Code Execution Vulnerability was addressed in a defect fixed in 2011.
Fortinet also confirmed the bugs in its systems in a security advisory, the flaw is present in versions prior to 2012 of the FortiGate firmware.
The company informed its customers of the presence of a cookie parser buffer overflow, confirming that Versions 5.x are not affected.
“FortiGate firmware (FOS) released before Aug 2012 has a cookie parser buffer overflow vulnerability. This vulnerability, when exploited by a crafted HTTP request, can result in execution control being taken over.” states the advisory.
“Affected firmware versions are lower versions of 4.x firmware release.
FOS 5.x firmware is NOT affected.”
“This vulnerability, when exploited by a crafted HTTP request, can result in execution control being taken over”, the advisory says. If a product can support 5.x firmware, that should be installed; if not, version 4.3.9 or above also fixes it.”
Customers of the company targeted by the exploits included in the leaked archive are invited to read the security advisory from the security vendors and to adopt the necessary countermeasure.
Let’s remind that despite the vast majority of the files is dated back 2013, in some cases the hacking tools could result still effective.
Hackeři se dostali k heslům desítek miliónů lidí. Jsou mezi nimi i Češi
18.8.2016 Novinky/Bezpečnost Hacking
Na pozoru by se měli mít uživatelé, kteří používali internetovou službu iMesh. Počítačoví piráti se totiž dostali k desítkám miliónů uživatelských účtů z tohoto serveru. Kromě přihlašovacích jmen znají také přístupová hesla. Upozornil na to server Leaked Source.
Služba iMesh v současnosti už nefunguje. Únik hesel přesto představuje pro uživatele riziko.
Hackerům se podařilo získat hesla k více než 53 miliónům účtů na službě iMesh. Nejvíce postižených uživatelů je z USA, kyberzločinci se totiž zmocnili bezmála 14 miliónů přihlašovacích údajů Američanů.
Nezanedbatelné procento z úniku nicméně tvoří také Češi. Podle informací serveru Leaked Source, který uniklá hesla analyzoval, bylo kompromitováno přinejmenším 168 tisíc hesel tuzemských uživatelů.
Jak k úniku došlo, zatím není jasné. Služba iMesh totiž oficiálně ukončila svou činnost už zkraje června, v současnosti je tedy nedostupná. Otazník visí také nad tím, zda se databáze počítačoví piráti zmocnili ještě před koncem fungování serveru, nebo až poté.
Ukradená hesla jsou stále hrozbou
Odcizená hesla nicméně představují velkou hrozbu i poté, co služba přestala oficiálně existovat. Celá řada uživatelů totiž používá stejná hesla na různých serverech – na e-mailu, sociálních sítích či například v internetových obchodech. V případě, že stejné přihlašovací údaje používají uživatelé také na jiných službách, měli by neprodleně změnit hesla i tam.
Přímo server Leaked Source již stihl databázi odcizených hesel analyzovat. Na zmiňovaných webových stránkách si tedy uživatelé mohou ověřit, zda se sami stali obětí útoku. Do příslušného okna na úvodní stránce stačí zadat svou e-mailovou adresu, načež uživatel bude upozorněn, zda si má změnit heslo.
Při hledání přitom server Leaked Source neprochází pouze hesla z útoku na službu iMesh, ale také z dalších úniků. V databázi má bezmála dvě miliardy odcizených hesel.
Za únik informací o 1,5 milionu zákazníků přišla pokuta 3,5 milionu korun. Tak dopadl T-Mobile
18.8.2016 Živě Kriminalita
Úřad pro ochranu osobních údajů (ÚOOÚ) vyčíslil pokutu za červnový únik citlivých dat zákazníků T-Mobilu. Operátor podle úřadu databázi dostatečně nezabezpečil a dopustil se tak správního deliktu, za který má zaplatit pokutu ve výši 3,6 milionu korun. Jde o jednu z nejvyšších pokut, kterou ÚOOÚ kdy udělil. Maximální výše sankce je v tomto případě až 10 milionů korun.
Úřad také odhalil přesnější údaje o zcizených datech. Šlo o osobní údaje zhruba pětiny všech klientů operátora (cca 1,2 milionu zákazníků), přičemž databáze obsahovala jména, příjmení, data narození, adresy, telefonní čísla i čísla účtů zákazníků. Z databáze je ukradl bývalý zaměstnanec operátora.
ÚOOÚ sankci udělil 10. srpna. T-Mobile se proti pokutě může odvolat do 15 dní od rozhodnutí úřadu. Operátor ale této možnosti podle svého vyjádření nevyužije, i když se mu pokuta zdá vysoká:
„Udělený postih akceptujeme, byť se nám pokuta, s ohledem na okolnosti, zdá nepřiměřená. V daném případě šlo o fatální selhání bývalého zaměstnance, který je již trestně stíhán. Ihned po zjištění incidentu jsme zpřísnili bezpečnostní opatření a věříme, že ve spolupráci s ÚOOÚ nastavíme standardy vedoucí k dalšímu zkvalitnění bezpečnosti dat zákazníků.“
Vawtrak banking Trojan improved once again, now with SSL Pinning
17.8.2016 securityaffairs Virus
Security experts from Fidelis firm spotted a new version of the Vawtrak banking Trojan that includes significant improvements such as the SSL pinning.
Malware researchers from security firm Fidelis have spotted a new strain of the infamous Vawtrak banking Trojan that leverages on a DGA mechanism to generates .ru domains with a pseudorandom number generator (PRNG) discovered in the loader.
Vawtrak, aka Neverquest, has been around for several years, it was used by criminal organizations to target online banking customers worldwide.
Vawtrak banking Trojan
The new variant of the Vawtrak banking trojan includes new significant improvements such as the use of the HTTPS protocol to protect communication with the control infrastructure. The threat leverages on certificate pinning which isn’t so common for malware.
The SSL pinning provides an addition level of protection against man-in-the-middle attacks, in the specific case, the certificate pinning is implemented to avoid detection of security solutions that use their own certificates to inspect the traffic.
The new variant of the Vawtrak banking Trojan conducts some checks based on the Common Name, in this way the threat is able to establish connections only to legitimate C2 servers.
“This new Vawtrak DLL contains code for performing an HTTPS connection as well, but it also performs some checks on the certificate it receives from the C2 server. It adds up all the characters in the Common Name and then divides the byte by 0x1a and adds 0x61, which should match the first character (Figure 5). It also uses a public key from the aforementioned initial inject header to verify the signature hash that was passed in the SubjectKeyIdentifier field of the certificate.” states the blog post published by the Fidelis firm.
The threat was delivered via both mass-spam campaigns, threat actors behind it also spread the malware through exploit kits.
“Vawtrak has been a very successful banking trojan, delivered via both mass-spam campaigns as well as through exploit kits. Keeping this in consideration, it’s not surprising that new features and techniques are being introduced.” continues the blog post. “The use of DGAs and TLS is widespread across various crime families, but SSL pinning is still rare,”
Vawtrak is an efficient banking trojan thanks to the continuous improvements, the SSL pinning recently introduced represents a novelty in the banking malware landscape.
Gartner: výdaje na bezpečnost dosáhnou 81,6 miliard USD
17.8.2016 securityworld Bezpečnost
Celosvětové výdaje v oblasti informační bezpečnosti v letošním roce podle analytiků společnosti Gartner porostou o 7,9 %. Největší část peněz půjde do oblasti konzultací a IT outsourcingu, v následujících letech nicméně nejvíce poroste oblast bezpečnostního testování, společně s outsourcingem a prevencí ztráty dat (DLP).
Oblast bezpečnostní prevence bude nadále vykazovat silný růst, neboť řada manažerů bezpečnosti preferuje právě pořizování preventivních opatření. Nicméně řešení jako je správa bezpečnostních informací a událostí (SIEM) či bezpečné webové brány (SWG) nabízejí stále více možností jak bezpečnostní hrozby detekovat a reagovat na ně.
Oblast SWG podle analytiků tak do roku 2020 poroste tempem 5 až 10 procent ročně s tím, jak se organizace budou stále více zaměřovat na detekci a reakci na útoky.
„Rostoucí zájem o řešení pro detekci a odražení útoků je důsledkem neúspěšnosti preventivních opatření při ochraně před agresivními útočníky,“ vysvětluje analytička společnosti Gartner Elizabeth Kimové. „Jednoznačně proto organizacím doporučujeme, aby rovnoměrně investovaly do obou oblastí.“
Podle Kimové budou výdaje na bezpečnost stále více inklinovat směrem ke službám, zejména v důsledku nedostatku vhodných odborníků na pracovním trhu. Objevují se služby jako řízená detekce a odražení útoků (MDR), o něž je zájem zejména mezi organizacemi, které bojují s efektivním nasazením a správou řešení v této oblasti – zejména v případě pokročilých cílených útoků nebo interních hrozeb.
Stále více poskytovatelů MDR se zaměřuje také na středně velké organizace a analytici proto očekávají, že právě tato oblast přispěje k růstu výdajů na bezpečnost jak u velkých, tak u středních a menších podniků.
Naopak růst výdajů v oblastech, jako je bezpečnostní software a řešení pro koncové zákazníky, zabezpečení emailových bran nebo ochrana koncových zařízení, postupně zpomaluje zejména kvůli jejich komoditizaci.
Analytici Gartneru vydali pro oblast informační bezpečnosti také několik předpovědí:
Průměrná prodejní cena firewallů poroste v následujících dvou letech o 2-3 % ročně. Souvisí to zejména s vyšší poptávkou po špičkových modelech ze strany poskytovatelů cloudových i jiných služeb.
Do roku 2018 nasadí 90 procent organizací (tedy o polovinu více než dnes) alespoň jeden typ integrovaného řešení typu DLP. Tato řešení byla doposud nasazována zejména proto, že je vyžadovala legislativa či předpisy, případně pro ochranu duševního vlastnictví, monitoring a zvýšení viditelnosti dat. Nová generace DLP nicméně nabízí analýzu uživatelských entit a chování, analýzu obrazu, strojové učení či techniky pro porovnávání dat.
Rostoucí využívání veřejného cloudu v nejbližších třech letech výrazně neovlivní výdaje na nákup firewallů, následně se ale začne výrazněji projevovat. V minulém roce byly služby SaaS „první“ volbou jen pro 16 % dotazovaných CIO. Přesun do cloudu bude tedy probíhat pozvolna - oblast bezpečnosti SaaS (ale také IaaS a PaaS) budou postupně pokrývat poskytovatelé služeb CASB (zprostředkovatelé zabezpečeného přístupu do cloudu). Výrobci firewallů budou také muset vyřešit otázku „masivního“ dešifrování SSL.
Polovina středních a větších organizací bude do roku 2019 u svých firewallů požadovat pokročilé funkce monitorování provozu. Požadavky na výkon a propustnost už nebudou pro velkou část zákazníků jediným kritériem: mezi stále častěji požadované funkce budou patřit nejen filtrování webových paketů či prevence průniku, ale také izolace (sandboxing) malware.
Someone is Spying on Researchers Behind VeraCrypt Security Audit
17.8.2016 thehackernews Krypto
After TrueCrypt mysteriously discontinued itself, VeraCrypt became the most popular open source disk encryption software used by activists, journalists, and privacy conscious people.
Due to the huge popularity of VeraCrypt, security researchers from the OSTIF (The Open Source Technology Improvement Fund) announced at the beginning of this month that it had agreed to audit VeraCrypt independently.
Using funds donated by DuckDuckGo and VikingVPN, the OSTIC hired vulnerability researchers from QuarksLab to lead the audit, which would look for zero-day vulnerabilities and other security holes in VeraCrypt's code.
Now, the most troubling part comes here:
The OSTIF announced Saturday that its confidential PGP-encrypted communications with QuarkLabs about the security audit of VeraCrypt were mysteriously intercepted.
"We have now had a total of four email messages disappear without a trace, stemming from multiple independent senders." the OSTIF said. "Not only have the emails not arrived, but there is no trace of the emails in our "sent" folders. In the case of OSTIF, this is the Google Apps business version of Gmail where these sent emails have disappeared."
The information linked to the VeraCrypt security audit is so confidential that the OSTIF instructed QuarksLab research team to give "any results of this audit directly to the lead developer of VeraCrypt using heavily encrypted communications."
This strict instruction was suggested at the beginning of this project to prevent the zero-day vulnerabilities from going into wrong hands or snoopers.
The team of researchers behind this security audit hopes to go public with their findings in mid-September after reporting all the detected vulnerabilities, if any, in VeraCrypt to its original authors and get them patched.
Until then, all the participants of the VeraCrypt Audit Project are required to maintain the utmost secrecy.
However, the sudden disappearance of four PGP-encoded email messages, each sent by independent parties involved in the project, has raised concerned about the leakage of confidential data, including weaknesses found in VeraCrypt.
The OSTIF suspects some outsiders are attempting to listen in on and/or interfere with the VeraCrypt security audit process.
"If nation-states are interested in what we are doing we must be doing something right," the OSTIF concludes.
Now, the OSTIF has switched to an alternative (undisclosed) encrypted communications process in order to move forward with the VeraCrypt audit project.
For more information Stay Tuned!
CVE-2016-569 Linux flaw leaves 1.4 billion Android devices vulnerable to hack
17.8.2016 securityaffairs Vulnerebility
Experts from Lookout revealed that all Android versions running the Linux Kernel 3.6 to the latest are affected by the CVE-2016-569 Linux flaw.
Recently I wrote about a severe vulnerability (CVE-2016-5696) affecting the Linux version 3.6, deployed in 2012. The flaw was discovered by researchers from the University of California, Riverside, and the U.S. Army Research Laboratory that presented their findings at the USENIX Security 2016 conference.
The TCP/IP networking flaw allows attackers to spot communications between two entities and can be exploited to hijack the traffic and manipulate it if the exchange is not encrypted.
The attack is not considerable a man-in-the-middle attack, the attackers just need to send spoofed packets to both sides of the connection by simply knowing their IP addresses and destination ports.

According to the experts at Lookout security, the Linux vulnerability affects 80% of Android devices, it appears to have been introduced into Android version 4.4 (also called KitKat) and it is still present in the current versions.
“Lookout recently discovered a serious exploit in TCP reported this week also impacts nearly 80% of Android, or around 1.4 billion devices, based on an install base reported by Statista. The vulnerability lets attackers obtain unencrypted traffic and degrade encrypted traffic to spy on victims.” reported Lookout security in a blog post.
The Linux vulnerability could be exploited by attackers to hijack traffic, inject malware into downloads and web pages, and run a wide range of attacks.
In a classic attack scenario, hackers can inject a malicious JavaScript into unencrypted network traffic and display a message that falsely claims the user has been logged out of his account and request him to provide the login credentials.
A patch for the Linux kernel was available since July 11, 2016, but checking the latest developer preview of Android Nougat, the Google OS is still affected by the flaw.
A Google spokesman confirmed that it is already working on the issue by “taking the appropriate actions.” The Google representative highlighted that the Android security team only rates the risk “moderate.”
Virus nakazil statisíce mobilů. Kyberzločinci zneužívají populární aplikaci Prisma
16.8.2016 Novinky/bezpečnost Viry
Prisma je bezesporu jednou z nejpopulárnějších mobilních aplikací letošního léta. Toho si všimli také počítačoví piráti, kteří začali internetem šířit její podvodné verze. Nachytat se nechaly statisíce lidí, uvedli bezpečnostní experti antivirové společnosti Eset.
Zachycené podvodné aplikace byly určeny výhradně pro operační systém Android. Tak velké množství telefonů – dohromady více než 1,5 miliónu – se kyberzločincům podařilo nakazit především proto, že falešné programy propašovali také na oficiální obchod Google Play.
„Většina falešných aplikací Prisma detekovaných na Google Play neměla žádnou funkci pro úpravu fotografií. Místo toho zobrazovaly pouze reklamy, varování nebo falešné průzkumy a nabádaly uživatele, aby poskytli své osobní údaje, nebo si zaplatili falešné a drahé služby prostřednictvím prémiových SMS,“ uvedl Petr Šnajdr, bezpečnostní expert společnosti Eset.
Některé verze obsahují downloader
Některé verze podvodných aplikací nicméně obsahují downloader, prostřednictvím kterého jsou počítačoví piráti schopni do zařízení dostat další nezvané návštěvníky. „Za nejnebezpečnější falešnou verzi aplikace Prisma, jež se vyskytla na Google Play předtím, než byla uvolněna pravá aplikace, považuje společnost Eset aplikaci, která obsahuje malware detekovaný jako Android/TrojanDownloader.Agent.GY,“ konstatoval Šnajdr.
„Ten po infiltraci odesílá informace o napadeném zařízení svému řídícímu serveru a na základě vzdálených příkazů stahuje další moduly a aktivuje je,“ doplnil bezpečnostní expert s tím, že v současnosti již byla tato nebezpečná aplikace z Google Play stažena.
Podvodné aplikace obsahující downloader se nicméně v současnosti mohou šířit přes neoficiální zdroje.
Se snahou podvodníků o šíření podvodných aplikací se mohou uživatelé setkat také u dalších populárních programů. „V podobných případech je třeba být obezřetnější než obvykle. Nad rámec základních doporučení si důkladně zkontrolujte například název dané aplikace a jméno vývojáře. Vše musí přesně souhlasit, nikoli se jen podobat skutečným názvům,“ uzavřel Šnajdr.
Co umí aplikace Prisma?
Aplikace Prisma dovede proměnit obyčejné fotky doslova v umění. Umělá inteligence prý dovede v chytrém telefonu analyzovat jednotlivé aspekty fotografie a pomocí přednastavených algoritmů je převede do umělecké podoby. Samoučící neuronová síť, která malby vytváří, pracuje v cloudovém prostředí.

Ukázka aplikace Prisma.
FOTO: archív tvůrců
Zní to poměrně složitě, v praxi je to ale naopak jednoduché. Prisma dokáže například obyčejný portrét převést tak, jako kdyby jej nakreslil nějaký slavný světový malíř.
V aplikaci si uživatelé mohou nastavit, do jakého stylu nebo uměleckého žánru chtějí svoji fotografii přemalovat. Vybírat je přitom možné i z konkrétních malířů a grafiků. V některých případech se přitom momentky změní doslova k nepoznání.
NSA's Hacking Group Hacked! Bunch of Private Hacking Tools Leaked Online
15.8.2016 thehackernews Hacking
It seems like the NSA has been HACKED!
An unknown hacker or a group of hackers just claimed to have hacked into "Equation Group" -- a cyber-attack group allegedly associated with the United States intelligence organization NSA -- and dumped a bunch of its hacking tools (malware, private exploits, and hacking tools) online.
Not just this, the hackers, calling themselves "The Shadow Brokers," are also asking for 1 Million Bitcoins (around $568 Million) in an auction to release the 'best' cyber weapons and more files.
I know, it is really hard to believe, but some cybersecurity experts who have been examining the leak data, exploits and hacking tools, believe it to be legitimate.
Widely believed to be part of the NSA, Equation Group was described as "a threat actor that surpasses anything known in terms of complexity and sophistication of techniques, and that has been active for almost two decades," according to a report published by security firm Kaspersky in 2015.
Equation Group was also linked to previous infamous Regin and Stuxnet attacks, allegedly the United States sponsored hacks, though the link was never absolutely proven.
Two days back, The Shadow Brokers released some files, which it claimed came from the Equation Group, on Github (deleted) and Tumblr.
Exploits for American & Chinese Firewalls Leaked:
The files mostly contained installation scripts, configurations for command-and-control (C&C) servers, and exploits allegedly designed to target routers and firewalls from American manufacturers including, Cisco, Juniper, and Fortinet.
According to the leaked files, Chinese company 'Topsec' was also an Equation Group target.
The leak mentioned names of some of the hacking tools that correlate with names used in the documents leaked by whistleblower Edward Snowden, like "BANANAGLEE" and "EPICBANANA."
"We follow Equation Group traffic," says the Shadow Broker. "We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof no? You enjoy!!! You break many things. You find many intrusions. You write many words. But not all, we are auction the best files."
It is yet not confirmed whether the leaked documents are legitimate or not, but some security experts agree that it likely is.
"I haven't tested the exploits, but they definitely look like legitimate exploits," Matt Suiche, founder of UAE-based cyber security firm Comae Technologies, told the Daily Dot.
NSA Planted Stuxnet-Type Malware Deep Within Hard Drive Firmware
While some are saying that the leak could be a very well-researched hoax, and the Bitcoin auction could be nothing but a distraction in an attempt to gain media attention.
"If this is a hoax, the perpetrators put a huge amount of effort in," security researcher The Grugq told Motherboard. "The proof files look pretty legit, and they are exactly the sorts of exploits you would expect a group that targets communications infrastructure to deploy and use."
However, if NSA has successfully been hacked, the hack would be a highly critical cyber security incident.
DDoSCoin — New Crypto-Currency Pays Users for Participating in DDoS Attacks
14.8.2016 thehackernews Attack
It’s 2016, and now, you can earn some dollars by contributing into well-organized DDoS attack scheme.
Do you know while mining Bitcoins you are actually contributing a significant computational power to keep the Bitcoin network running?
In Bitcoins, the miners actually build and maintain massive public ledger containing a record of every Bitcoin transaction in history.
When one user tries to send Bitcoins to another user, the miners validate the transfer by checking the ledger to make sure the sender is not transferring money he/she does not have, adding the transaction to the ledger and then finally sealing it behind layers and layers of computational work to protect that ledger from getting compromised or hacked.
So for this, miners are rewarded with Bitcoins.
So, basically, you are contributing the massive amount of computing power that keeps the Bitcoin transactions running and makes you earn some cryptocurrency in return as an incentive.
However, Bitcoin has long been criticized for not utilizing that huge amount of computational power into something useful as well.
To utilize all those CPU cycles, a few years back researchers came forward with another cryptocurrency, called "PrimeCoin."
In PrimeCoin, the miners’ computational power is not only used to keep the transaction running but also used to find the long chain of the prime number, which plays a great role in encryption and cryptography.
But, this time, a pair of curious researchers recently proposed the weirdest concept:
A malicious digital currency that can be mined only if the miners participate in Distributed Denial of Service (DDoS) attacks against preselected target websites make them temporarily unavailable by flooding them with Millions of simultaneous requests.
Proof-of-DDoS: Participate in DDoS Attack and Earn Reward
DDoSCoin, developed by Eric Wustrow and Benjamin VanderSloot from the University of Colorado Boulder and the University of Michigan, is a theoretical cryptocurrency that rewards a miner for opening a large number of TLS connections to target web servers.
The malicious proof-of-work (which the duo called "Proof-of-DDoS") model used by DDoSCoin miners functions only with websites that support TLS 1.2, and since over half of the top million websites support TLS 1.2 version of the protocol, it will be easy for miners to earn the reward.
"In modern versions of TLS, the server signs a client-provided parameter during the handshake, along with server-provided values used in the key exchange of the connection," the researchers wrote in the paper DDoSCoin: Cryptocurrency with a Malicious Proof-of-Work [PDF], allowing the client to prove that it has participated in the DDoS attack against the target server.
In this way, the new system will reward users who prove they have participated in a DDoS attack.
Miners with DDoSCoin blocks could then trade their cryptocurrencies for other, including Bitcoin and Ethereum, the researchers suggested.
The researchers presented their paper at the Usenix 2016 security conference, noting that Bitcoin's computationally intensive proof-of-DDoS "does not contribute to any useful problems besides securing the currency from attack."
If you want to set up a target for DDoS, you can use the PAY_TO_DDOS transaction that includes two arguments:
Domain of the victim website.
The number of TLS connections that need to be established.
These transactions are recorded as DDoSCoin blocks inside a database (or blockchain). Now, miners only need to select one of the blocks, launch attacks, and thus receive DDoSCoin as a reward for fulfilling the transaction.
What If Everybody wants to DDoS Everybody?
Now, the question here is: How this cryptocurrency will decide, which target should get DDoSed on priority?
According to researchers, multiple miners must participate and decide together which domain to be attacked.
Future Schemas and DDoS Frameworks
Till now, we have seen multiple hire-for-DDoS services in the underground market, where anyone willing to take down a targeted website can just pay hackers and get their job done.
At the current, this paper is only a theoretical concept, and the DDoSCoin crypto-currency currently does not exist.
However, I can predict that soon we would see similar business models by blackhat hackers, where to earn money, people would themselves join botnet networks to contribute their bandwidth for DDoS attacks.
Hitler ransomware just deletes files instead encrypt them
14.8.2016 securityaffairs Virus
Security experts detected and analyzed a new threat, the Hitler ransomware, that doesn’t encrypt files but simply deletes them. Ransomware is one of the most dreaded threats for Internet users and a profitable business for crooks. In the last months, we have seen a number of malware belonging to this category, one of the most recent is a Hitler-themed ransomware that doesn’t encrypt files, but simply deletes them.

In reality, the threat appears to be a work in progress project developed by coders without specific skills.
The Windows ransomware displays a lock screen featuring Hitler, together with a message that warns users that files have been encrypted.
The ransomware requests the payment of only 25 euros, in the form of a Vodafone cash card. It is unusual for such kind of crimes.
The lock screen features a misspelling “Ransonware.”
The website Bleeping Computer published a detailed analysis of the Hitler ransomware that was first spotted by the malware analyst Jakub Kroustek from AVG.
“This ransomware appears to be a test variant based on the comments in the embedded batch file and because it does not encrypt any files at all. Instead this malware will remove the extension for all of the files under various directories, display a lock screen, and then show a one hour countdown as shown in the lock screen below.” reads the post published by Bleeping Computer “After that hour it will crash the victim’s computer, and on reboot, delete all of the files under the %UserProfile% of the victim. I hope this is not the actual code that this ransomware developer plans on using if it goes live.”
Visualizza l'immagine su Twitter
Segui
Jakub Kroustek @JakubKroustek
*sigh* #Hitler #Ransomware. #GrammarNazi. https://www.virustotal.com/en/file/06c8e0f6fa2616f4fa92c610a1faea23887ac31db8fa78cede49b6b8c80ec22f/analysis/1470566199 …
21:09 - 7 Ago 2016
27 27 Retweet 21 21 Mi piace
The experts have found the string “Das ist ein Test” (“This is a test”) in an embedded batch file, a circumstance that suggests the developer are German based.
Vedení amerického Kongresu vědělo o ruských hackerských útocích
13.8.2016 Novinky/Bezpečnost Hacking
Americké tajné služby již před rokem informovaly vedení Kongresu USA o ruských hackerských útocích na počítače Demokratické strany. Podle agentury Reuters to v pátek uvedly nejmenované zdroje z prostředí zpravodajských služeb. Hackeři, kteří i podle vysokých představitelů demokratů pocházeli z Ruska, ukradli straně desetitisíce důvěrných e-mailů. Terčem útoků byla i prezidentská kandidátka Hillary Clintonová.
Američtí zpravodajci podle zdrojů Reuters věděli o ruských aktivitách namířených proti demokratům a dlouhodobě je monitorovali. Před rokem pak o nich podle pravidel informovali vedení zákonodárného sboru.
V osmičlenné skupině politiků, kteří se o tom dozvěděli, byli čtyři republikáni včetně šéfa Sněmovny reprezentantů Johna Boehnera a čtyři demokraté. Mezi nimi figuroval i šéf senátní menšiny Harry Reid nebo kongresmanka Nancy Pelosiová.
Právě ona ve středu přišla s obviněním, že za útokem stála Moskva. Pelosiová prohlásila, že útok byl rozsáhlý a škody jsou stále vyšetřovány. Rusku již dříve akci připsala i Clintonová. [celá zpráva]
Veřejnost se o útoku dozvěděla až v červenci během sjezdu demokratů. Podle listu The New York Times zasáhl více než 100 stranických představitelů a skupin spojených s demokraty. Americký činitel obeznámený s vyšetřováním uvedl, že zatím nejsou důkazy, že by hackeři pronikli do osobního serveru Clintonové nebo do utajovaných systémů.
Administrativa prezidenta Baracka Obamy veřejně Rusko za strůjce útoku neoznačila. Vyšetřovatelé ale podle Reuters došli k závěru, že útočníky řídily ruská vojenská rozvědka GRU a kontrarozvědka FSB. Rusko svou účast na útoku popřelo.
Weby Wedosu jsou pod palbou. Firma hlásí plošný DDoS
13.8.2016 Root.cz Počítačový útok
Tuzemská hostingová firma se ocitla pod palbou útoku. Podle hlášení čtenářů jde o akci, která zlobí servery společnosti celý tento týden.
Firma chce vybudovat v jihočeské Hluboké jedno z nejbezpečnějších datacenter v Česku. Tento týden se jí ale nedařilo a ještě v pátek odpoledne bojovala s masivním DDoS útokem.
Sledovat
Hosting WEDOS.cz @WEDOS_cz
Momentálně je na nás veden velmi silný plošný útok. Na vyřešení situace pracujeme. Omlouváme se za komplikace.
Podle čtenáře Jana Nejmana jde tento týden o několikátý útok. „Útok je zřejmě opravdu plošný, Wedos má kompletní výpadek,“ tvrdí Nejman. To potvrzují i dotazy na Twitteru, které kromě dneška zmiňují výpadek osmého, desátého srpna.
Pro webhostingovou firmu to není nic nového. S útoky se setkává pravidelně. Pokaždé ale připomíná, že se na DDoS připravuje a zesiluje obranu.
Wedos dnes webhosting a virtuální servery živí. Za normálních okolností aktivních hostingů hlásí firma 80 tisíc. Za rok 2014 zaznamenal růst obratu o více než 47 procent. „Za rok 2015 bude růst o něco málo menší, protože nemáme IP adresy verze 4, a tak uměle brzdíme prodej virtuálních serverů. Zároveň jsme část sil věnovali přípravě datacentra a hodně úsilí i ochraně proti DDoS útokům,“ tvrdil loni na podzim šéf firmy Josef Grill s tím, že s novou datovou budovou je zaděláno na další růst.
Microsoftu unikl univerzální zavaděč, obchází UEFI Secure Boot
12.8.2016 Root.cz Incidenty
Objevená mezera ve spolupráci Windows a secure boot (UEFI) sice může ohrozit bezpečnost zařízení, ale také umožní instalaci alternativních systémů na zamčená zařízení od Microsoftu.
Dvojice bezpečnostních výzkumníků, kteří si říkají MY123 a Slipstream, zveřejnila informaci, že operační systém Windows obsahuje mezeru umožňující obejít zabezpečení Secure Boot. V tomto případě hovoříme o pomyslném zlatém klíči, protože podle všeho Microsoft tuto mezeru zřídil záměrně, aby mohl takto chráněná zařízení odemknout. O zlatém klíči by se samozřejmě neměl dozvědět nikdo nepověřený. To se ale nepovedlo.
Než se pustíme do popisu samotného problému, upřesněme, co je vlastně secure boot. Jedná se o vlastnost UEFI (nástupce BIOSu), která umožňuje na daném počítači zavést pouze patřičně podepsaný operační systém. Většina prodávaných počítačů sice má secure boot aktivní, nicméně uživatel ho může bez problémů vypnout. To sice omezí zabezpečení, ale zase si potom můžeme snadno instalovat různé linuxové distribuce atp.
Část zařízení má však secure boot nastavený tak, aby UEFI zavádělo pouze systémy podepsané Microsoftem. Mezi ně nepřekvapivě patří hlavně hardware od Microsoftu – chytré telefony, tablety nebo brýle HoloLens. Není to ale problém pouze těchto zařízení. Přestože domácí uživatelé považují secure boot spíš za otravnou omezující věc, některé firmy ho třeba používají a počítají s ním v bezpečnostní strategii.
Chyba v systému pravidel
Výzkumníci svůj objev popsali na speciální stránce (pozor, je trochu hyperaktivní), zde se to pokusíme jednodušeji shrnout. Pravidla secure boot jsou obsažena v binárním blobu ASN.1, který rovněž musí být podepsán Microsoftem a který je načten v rané fázi bootování. Pravidla také obsahují číslo zařízení DeviceID, které se musí shodovat s DeviceID Windows Boot Manager (bootmgr). V opačném případě použije výchozí pravidla.
Problém je v tom, že v jedné z vývojových verzí výroční aktualizace Windows 10, pracovně označované jako Redstone, byla přidána tzv. dodatková pravidla. Ve stručnosti jde o to, že dodatková pravidla, které v Microsoftu zapomněli dát pryč, lze bez další kontroly aplikovat na výchozí pravidla a změnit nastavení. Včetně aktivace testsigningu – to znamená, že se načte jakýkoliv podepsaný systém, je úplně jedno kým. Čili je to v podstatě totéž jako žádné ověření.
Nejde o nějaký backdoor v negativním slova smyslu jako spíš chybu v návrhu řešení, které mělo usnadnit testování vývojových verzí systému bez nutnosti každé sestavení podepisovat. Také je nutné dodat, že Microsoftu neunikl podpisový klíč, jak by se podle označení zlatý klíč mohlo naznačovat. Ohrožena nejsou ani zašifrovaná data v zařízení. Jde zkrátka o mezeru ve Windows Boot Manager.
Řešení a důsledky
Nálezci chybu nahlásili už v březnu tohoto roku. Zpočátku se s nimi Microsoft moc nechtěl bavit, ale nakonec chybu uznal a nálezce finančně odměnil. Ti však opravy považovali za nedostatečné a proto šli s informacemi o chybě na veřejnost. Chyba v bootmgr byla opravena s výroční aktualizací Windows 10. Znamená to, že jsou počítače s touto verzí Windows v bezpečí a nelze na nich spustit Microsoftem nepodepsaný systém? Nikoliv.
Stačí totiž bootmgr nahradit starší problémovou verzí, což je možné, a opět můžete chybu využít a spustit na zařízení v podstatě jakýkoliv systém. Možným řešením by samozřejmě bylo omezení na konkrétní verze bootmgr, ale to by přineslo další velké problémy. Pro Microsoft je prakticky nemožné zablokovat všechny starší verze bootmgr, protože by to rozbilo instalační média, obnovovací oddíly, zálohy a další, píšou výzkumníci.
Chyba je určitě nepříjemná pro všechny, kdo na secure boot spoléhali, ale pravděpodobně se nejedná o kritický bezpečnostní problém. Pro instalaci pozměněné verze systému s bootkitem či rootkitem by útočník zřejmě potřeboval fyzický přístup k zařízení a ne úplně malé množství času.
Jak to ale často bývá, všechno zlé je pro něco dobré. Pro mobily a tablety s Windows se zřejmě začnou vytvářet různé alternativní systémy, linuxové distribuce, androidí ROM atd. A tak zájemci z řad uživatelů budou mít možnost zařízení, kterým už brzy bude končit podpora, znovu oživit. Určitě bude zajímavé sledovat, jak moc se komunita moderů/hackerů bezpečnostní mezery chytne a co všechno vytvoří.
Zadní vrátka nejsou vhodné řešení
Nálezci chyby v prohlášení věnovali i odstaveček FBI, které by tento případ měl ukázat, že backdoory či jiné cílené omezení bezpečnosti rozhodně nejsou dobrý nápad. O tom se čím dál častěji hovoří v souvislosti s možným omezením šifrování, které navrhují někteří američtí polici a často také zástupci bezpečnostních složek. Velmi medializovaná byla kauza odemčení iPhonu teroristů, které požadovala FBI, ale Apple odmítl.
Každá mezera, vytvořená s dobrým či špatným úmyslem, jednou může být zneužita, a to může způsobit dalekosáhlé problémy. Pro příklad nemusíme chodit daleko. Americká TSA (úřad pro bezpečnost v dopravě) certifikovala kufry, ke kterým měla zlatý klíč (ve skutečnosti jich bylo několik), aby mohla rychle prověřovat zavazadla cestujících. Design klíčů unikl na veřejnost a dnes si takový univerzální klíč, který padne do každého zámku schváleného kufru, může vyrobit každý.
V tomto případu nejde o klasický backdoor, ale jasně vidíme, že chyby dělají i v těch největších společnostech. A také vidíme, že zadní vrátka vždy není možné okamžitě zavřít.
Stali jste se obětí hackerského útoku? Tato stránka vám to řekne
12.8.2016 Živě.cz Hacking
Internetoví útočníci několikrát do roka překonají zabezpečení mnoha velkých internetových služeb a na veřejnost se dostanou obrovské seznamy plné e-mailů, hesel a dalších citlivých údajů o jejich uživatelích. Možná i o vás!
Jenže jak zjistit, jestli nejste mezi obětmi i vy? Podobných útoků se totiž v posledních letech odehrálo takové množství, že se v tom už nikdo nevyzná.
Naštěstí existují speciální vyhledávače, kam stačí zadat váš e-mail, který používáte při registraci na internetu. Tyto vyhledávače evidují všechny podobné krádeže dat a váš e-mail poté zkontrolují ve své databázi až stovek milionů uniklých účtů. K nejlepším patří LeakedSource a Hacked-db.
Na webu LeakedSource stačí ve formuláři vybrat e-mail nebo třeba uživatelské jméno, vyplnit jej a počkat si. Služba se podívá do obří databáze dvou miliard uniklých účtů v minulosti, jestli se tam tyto údaje nacházejí. Služba je placená, základní vyhledání je ale zdarma.
To je špatné, zadaný e-mail figuruje hned v několika únicích na obří služby Adobe, Linkedin a další. Pokud se vám to také stane a neměnili jste hesla, raději to zvažte.
Ačkoliv jsou podobné vyhledávače zpravidla placené, zdarma vám alespoň vypíšou, jestli je e-mailová adresa také na seznamu některého z minulých útoků. A pokud ano, raději zvažte změnu hesla na internetu, pakliže jste tak už tedy v minulosti neučinili. A zvláště to platí pro ty případy, pokud používáte jen jedno heslo napříč Facebookem a dalšími oblíbenými weby.
Tajné služby USA prý rok sledovaly hackerské útoky Rusů
12.8.2016 Novinky/Bezpečnost Hacking
Americké zpravodajské služby věděly už před rokem, že ruští hackeři útočí na servery Demokratické strany. Agentuře Reuters to ve čtvrtek řekly zdroje obeznámené se situací. Informace ale prý byla tak tajná, že se o útoku nemohli dozvědět ani poslanci Kongresu.
Informace o ruských útocích se dostaly na veřejnost minulý měsíc, kdy Federální úřad pro vyšetřování (FBI) oznámil, že se zabývá útokem na servery stranického ústředí demokratů. O ruském podílu na útoku se ale žádná oficiální zpráva nezmiňuje. Moskva podíl na útoku popřela.
Zpráva o sledování údajného ruského útoku byla přísně tajná, protože jejím vyzrazením by vyšlo najevo, že americké tajné služby hackerský útok monitorují a odhalen by mohl být i způsob, jak to dělají a jakých zdrojů využívají. Na útočné akci se prý podílely dvě ruské zpravodajské služby.
Nový poradní sbor pro kybernetickou bezpečnost
Materiál o sledování „ruské stopy“ byl zakódován a přístup k němu měla jen malá skupina expertů, napsal Reuters. Z veřejných činitelů byla informována jen malá skupina osmi čelných poslanců Kongresu, nazývaná v USA „gang osmi“.
Tvoří ji šéfové obou komor Mitch McConnell a Paul Ryan, předsedové demokratů v obou komorách Nancy Pelosiová a Harry Reid a čtyři členové branných a bezpečnostních výborů Kongresu.
Úřadující šéfka Demokratické strany Donna Brazileová ve čtvrtek oznámila, že vytváří poradní sbor pro kybernetickou bezpečnost, který má „zabránit budoucím útokům a zajistit prvotřídní ochranu serverů Demokratické strany“.
Ransomware/RAT combo searches for solvent businesses
12.8.2016 helpnetsecurity Virus
The latest version of the Shade ransomware comes with a stealthy remote access Trojan, likely used to better gauge the amount of money the criminals can demand from the victims.
This variant of the Shade ransomware (also known as Troldesh) was made with specific targets in mind: companies in Russia and the CIS region.

The Trojan searches the list of installed applications and looks for strings associated with bank software
“For the initial check, the updated Trojan searches the list of installed applications and looks for strings associated with bank software. After that the ransomware looks for ‘BUH’, ‘BUGAL’, ‘БУХ’, ‘БУГАЛ’ (accounting) in the names of the computer and its user. If a match is found, the Trojan skips the standard file search and encryption procedure and instead downloads and executes a file from the URL stored in the Trojan’s configuration, and then exits,” Kaspersky Lab researchers have discovered.
The downloaded file is Teamspy, a modified version of the TeamViewer 6 legal remote control utility that doesn’t have a GUI or an icon. It also comes with two plugins: one that covertly installs the TeamViewer VPN driver, and one that installs the RDP Wrapper Library and opens a RDP connection on the computer.
Thus equipped, the infected computer is ready to be spied on.
Among the things Teamspy can do is record audio and video, allow the attackers to remotely access the machine, and to download and execute other malicious files.
That last capability will come in handy if the attackers decide that the target could be forced into paying a considerable ransom.
“The option of remote access to an infected accounting system allows the malefactor to secretly keep an eye on the victim’s activities and collect detailed information on the victim’s solvency in order to use the most efficient way of getting cash,” Kaspersky’s Fedor Sinitsyn noted.
They might ultimately opt for stealing banking credentials and try to syphon as much money as possible from the company account.
Victims of Shade ransomware versions 1 or 2 can try to decrypt encrypted files through the No More Ransom website, set up by the Dutch National Police, Europol, Intel Security and Kaspersky Lab.
Information warfare – The Rise of the Cyber Offense
12.8.2016 securityaffairs Security
Information warfare – The development of cyber capabilities is strategic for any governments, computer systems and Internet of Things even more at risk.
By the mid-1990’s the US intelligence agencies, especially the NSA, were beginning to wake up to a grim reality – the world was quickly becoming connected and the tools to connect that world were no longer confined to the government and universities, but now were in the hands of smart and very capable people outside of academia and government snoops.
In 1998, Richard A. Clarke, then Security Advisor the Clinton administration, took a quick flight from D.C. up to Cambridge, Massachusetts to meet with a team of hackers that would change forever, the way the US government looked at the world.
Clarke’s contact in Cambridge was to be a hacker known as “Mudge.” Mudge was the mouthpiece for a hacker group known as the L0pht. After about an hour of waiting patiently in a local bar, Clarke grew tired thinking Mudge got cold feet. As he started to get up from the table, the gentle next to him introduced himself as Mudge, who had been sitting beside Clarke the whole time. Not only was Mudge observing Clarke from afar, but so was the entire L0pht team: Brain Oblivion, tan, Kingpin, Weld Pond, Space Rogue, and Stefan Von Neuman, who later would drive right on through the gate of the NSA parking lot with nothing more than a salute!
After small talk, Mudge took Clarke to “the L0pht”, the second floor of a Cambridge warehouse where the L0pht team kludged and cobbled together an impressive arsenal of computing power capable of doing some serious damage if the team so desired.
Clarke left that night with more than an uneasy feeling. Though not a cyber security person himself, he knew damn well that if a group of college students and geeks could dumpster dive enough equipment to be a serious threat, so could a nation-state actor! Clarke invited L0pht to testify to Congress. Though Congress was certainly concerned, little changed in the way Congress went about its business but for the Department of Defense, FBI, CIA, and especially the NSA, the situation couldn’t have been bleaker – unfortunately, the prognosis has changed little.
Over the past decade, the offensive capabilities of nation-state actors has grown exponentially. China, Israel, and Russia all of whom have had robust offensive capabilities for years have become efficient and well manage espionage machines likely equal to that of the United States. Other countries are quickly catching up: Syria, Iran, and a rabble of former Soviet States, have formidable offensive expertise. It’s not just governments either, hacking tools and techniques are becoming so ubiquitous it is nearly impossible for anyone to keep up.
Of particular concern is the world’s critical infrastructure. The last couple of years has been earmarked with attacks on power plants, distribution systems, and even water treatment facilities. More recently, a report surfaced that the world’s Global Positioning System (GPS), the space-based navigational system the world’s relies on is now at risk of illegal jamming.
Information Warfare
Information Warfare (Source Akamai)
Experts have warned for years the GPS system is vulnerable to attack not just to jamming but to spoofing as well – though encryption is provided for the military’s use only. Great, but it won’t help the wave of new and next generation devices that will be part of the so-called Internet of Things (IOT).
The everyday devices that power our lives will soon be connected to the Internet – refrigerators, dish washers, in-home camera systems, and even the watering bowl for your dog will be connected to the web where Fido’s water can be refreshed by simply tapping an app on your cellphone. So who cares is a hacker gets my carpet wet? It’s a fair question, but if a hacker can exploit the insecure code on the dog’s watering bowl, it likely will act as a portal to more important areas of our life, like our bank accounts!
The real takeaway from the GPS jamming device and precisely what worried Richard Clarke on that fateful night in Cambridge, was the reality that offensive capabilities were being wrestled out of the realm, and control, of the spooks and the military. Simple jamming techniques have been used to disable key fobs, popular in today’s new automobiles. On a larger scale, jamming devices were used to steal a truck full of pharmaceuticals in Florida. Even the North Koreans are in on the act, recently jamming the GPS of about 280 South Korean vessels.
On a larger scale, jamming devices were used to steal a truck full of pharmaceuticals in Florida. Even the North Koreans are in on the act, recently jamming the GPS of about 280 South Korean vessels.
L0pht’s contributions to the history of the security of the United States shouldn’t be diminished by the fact that we have seemingly seen little progress. In fact, they should be applauded for taking the risk of going to D.C. in the first place, particularly in the late nineties where computer geeks were just that – geeks! Perhaps the team’s biggest contribution is killing the myth that only a well-funded government can wreak havoc; clearly, not true. Mudge knew it, Clarke knew it, and now we’re all waking up to this new reality.
Linux TCP Flaw allows Hackers to Hijack Internet Traffic and Inject Malware Remotely
11.8.2016 thehackernews Attack
If you are using the Internet, there are the possibilities that you are open to attack.
The Transmission Control Protocol (TCP) implementation in all Linux systems deployed since 2012 (version 3.6 and above of the Linux kernel) poses a serious threat to Internet users, whether or not they use Linux directly.
This issue is troubling because Linux is used widely across the Internet, from web servers to Android smartphones, tablets, and smart TVs.
Researchers have uncovered a serious Internet flaw, which if exploited, could allow attackers to terminate or inject malware into unencrypted communication between any two vulnerable machines on the Internet.
The vulnerability could also be used to forcefully terminate HTTPS encrypted connections and downgrade the privacy of secure connections, as well as also threatens anonymity of Tor users by routing them to certain malicious relays.
The flaw actually resides in the design and implementation of the Request for Comments: 5961 (RFC 5961) – a relatively new Internet standard that's designed to make commonly used TCP more robust against hacking attacks.
TCP protocol is the heart of all Internet communications, as all application level protocols, including HTTP, FTP, SSH, Telnet, DNS, and SMTP, stand on TCP.
Web servers and other applications make use of TCP protocol to establish connections between hosts to transfer data between them.
A team of six security researchers from the University of California, Riverside and the U.S. Army Research Laboratory has demonstrated a proof-of-concept exploit at the USENIX Security Symposium that can be used to detect if two hosts are communicating over TCP and ultimately attack that traffic.
Linux TCP Flaw allows Hackers to Hijack Internet Traffic and Inject Malware Remotely
Typically, TCP protocol assembles messages into a series of data packets that are identified by unique sequence numbers and transmitted to the receiver. When received, the data packets are then reassembled by the receiver into the original message.
Researchers found that 'Side channels' attack allows hackers to guess the TCP packet sequence numbers accurately within first 10 seconds of the attack by using no more information than just the IP addresses of both parties.
This means, an attacker with spoofed IP address does not need a man-in-the-middle (MITM) position, apparently intercepting and injecting malicious TCP packets between any two arbitrary machines on the Internet.
The researchers detailed their findings in the paper titled, 'Off-Path TCP Exploits: Global Rate Limit Considered Dangerous' [PDF], which they presented at the conference, showing the audience how they injected a phishing form inside the USA Today website.
You can watch the video demonstration above that shows the attack in work.
The researchers also show how the flaw (CVE-2016-5696) can be exploited to break Secure Shell (SSH) connections and tamper with encrypted communications traveling over Tor anonymity network.
"In general, we believe that a DoS [Denial of Service] attack against Tor connections can have a devastating impact on both the availability of the service as a whole and the privacy guarantees that it can provide," the paper reads.
"The default policy in Tor is that if a connection is down between two relay nodes, say a middle relay and an exit relay, the middle relay will pick a different exit relay to establish the next connection. If an attacker can dictate which connections are down (via reset attacks), then the attacker can potentially force the use of certain exit relays."
The team also provided recommendations on how to mitigate the attack.
Here's How to Mitigate TCP Attack
While patches to fix the vulnerability are developed and distributed for the current Linux kernel, as a workaround you can raise the ACK rate limit on your Linux machine or gadget to large values so that it cannot be reached.
For this, you are required to append the following to /etc/sysctl.conf:
net.ipv4.tcp_challenge_ack_limit = 999999999
Once done, use sysctl -p to activate the new rule. You need to perform root to do this.
The researchers also note that while Linux version 3.6 and above are vulnerable to this attack, Windows, OS X and FreeBSD are not believed to be vulnerable because they have not yet fully implemented RFC 5961.
Chyba ohrožuje stovky miliónů uživatelů Windows. Oprava je v nedohlednu
11.8.2016 Novinky/Bezpečnost Zranitelnosti
Poslední generace Windows zavedly úplně nový způsob spouštění samotného operačního systému. Díky tomu by se měla minimalizovat šance, že se během spouštění uhnízdí na pevném disku nějaké viry. Jak se ale nyní ukázalo, tento standard má kritickou bezpečnostní chybu, kterou mohou zneužít počítačoví piráti. V ohrožení jsou stovky miliónů uživatelů.
Jak funguje UEFI a Secure Boot?
Drtivá většina moderních počítů používá UEFI. To se stalo běžně používaným standardem už v době operačního systému Windows 7, samozřejmostí je tedy pochopitelně i v novější verzích operačního systému od Microsoftu.
Výrobci začali na UEFI houfně přecházet, protože tento standard podporoval funkci zvanou Secure Boot. Jak už samotný název napovídá, jejím hlavním úkolem je chránit pevný disk před nezvanými návštěvníky v době, kdy samotný počítač startuje.
Tedy ve chvíli, kdy uložená data ještě nechrání antivirový program. Ten se totiž spouští až po startu samotného systému. V minulosti se totiž objevilo hned několik škodlivých kódů, které dokázaly útočit ještě před startem počítače, viry se jednoduše uhnízdily v zavaděči systému.
Objevená chyba se týká tzv. jednotného rozšiřitelného firmwarového rozhraní (UEFI), které využívá drtivá většina moderních počítačů a notebooků.
Trhlina dává – zjednodušeně řečeno – útočníkům absolutní kontrolu nad spouštěním operačního systému.
Co to znamená v praxi? Ať má uživatel zabezpečen počítač sebelepším antivirovým programem, útočník do něj může kvůli chybě propašovat škodlivý kód ještě před startem operačního systému.
Může totiž prostřednictvím trhliny ovládnout celý spouštěcí proces a jednoduše mu nařídit, aby bezpečnostní kontrolu ignoroval. Účinná obrana proti případnému útoku tak v podstatě nexistuje.
Je to stejné, jako kdyby měli zloději klíče od bytu a jednoduše si odemkli.
S trochou nadsázky se dá říci, že je to stejné, jako kdyby měli zloději klíče od bytu a jednoduše si odemkli. Úplně stejně totiž tímto „klíčem“ dokážou obejít tzv. Secure Boot a propašovat virus na pevný disk. Pokud se nezvaný návštěvník uhnízdí právě v zavaděči, je jeho odstranění velmi složité.
„Zranitelnost UEFI Secure bootu u zařízení s Windows umožňuje hackerům spuštění bootkitů/rootkitů na zařízeních s tímto operačním systémem,“ vysvětlil technickou stránku věci bezpečnostní analytik Pavel Bašta z Národního bezpečnostního týmu CSIRT.CZ.
Na trhlinu upozornili bezpečnostní experti, kteří vystupují na internetu pod přezdívkami My123 a Slipstrea. Ti zjistili, že celý systém je podobným způsobem napadnutelný přinejmenším několik posledních měsíců.
Microsoft problém řeší
My123 a Slipstream amerického softwarového giganta na toto obří riziko, které se týká stovek miliónů uživatelů po celém světě, upozornili již na jaře. „Microsoft se sice pokouší tuto chybu opravit, avšak doposud ne zcela úspěšně,“ konstatoval Bašta.
Některé hlasy zahraničních expertů navíc naznačují, že 100% oprava prakticky není možná. Po důkladnějším zkoumání to tvrdí dokonce i My123 a Slipstream.
„Bezpečnostní analytici se domnívají, že tento bezpečnostní problém nemůže být zcela eliminován,“ uzavřel Bašta.
Zástupci amerického softwarového gigantu se zatím oficiálně k možnému ohrožení uživatelů nevyjádřili.
Secure Boot má chránit Windows před viry. Kvůli chybě ale otevře zadní vrátka útočníkům
11.8.2016 Živě Zranitelnosti
S příchodem nových verzí Windows a UEFI, které postupně vystřídalo starý BIOS na zánovních počítačích, je start operačního systému mnohem bezpečnější, protože se o něj stará systém Secure Boot, který kontroluje, jestli je vše digitálně podepsané – jak samotný operační systém, tak všechny fáze startu.
Principem Secure Bootu je ochrana před malwarem, který by se chtěl usadit přímo v oblasti zavaděče a načítat viry ve chvíli, kdy je operační systém poměrně bezbranný.
Startování Windows 10
Bezpečnostní specialisté My123 a Slipstream se však nyní pochlubili (via The Register) se zjištěním, podle kterého byl celý systém nejméně posledních několik měsíců kriticky děravý – chyba pravděpodobně vznikla během vývoje čerstvého Anniversary Updatu.
Oč jde? Aby mohli v Redmondu na desítkách a stovkách modelů notebooků testovat Windows co možná nejflexibilněji, mohou systému Secure Boot přikázat, aby kontrolu startu OS jednoduše ignoroval. Slouží k tomu speciální politika, která se aktivuje hned na začátku celého procesu, takže vývojář poté může spustit jakýkoliv kód i operační systém a zavaděč si bude myslet, že je vše v pořádku.
Pokud by se tato politika dostala do nesprávných rukou, případný útočník by ji mohl použít pro svůj malware, který by poté infikoval počítač na úplném startu OS, kdy je prakticky bezbranný. Nový rootkit/bootkit by rázem mohl ovládnout celá Windows.
A přesně toto se během jara opravdu stalo, dvojice specialistů totiž objevila speciální božskou politiku i v sestaveních Windows, která se dostala k běžným smrtelníkům. Poté informovali Microsoft, který však údajně problém zpočátku ignoroval. Teprve poté, co připravili funkční test zneužití, začali v Redmondu problém řešit a postupně připravili několik záplat Windows, které se v posledních týdnech skutečně nainstalovaly a díru částečně řeší.
Proof-of-concept s aktivátorem politiky, která zablokuje kontroly v Secure Bootu
Podle My123 a Slipstreama jsou však opravy zatím nedostatečné a Microsoft bude muset ještě zapracovat.
Případ zároveň ukazuje na principiální bezpečnostní chybu, kdy se může celý bezpečnostní systém zhroutit jako domeček z karet, pokud existuje nějaký master klíč, který vše odemkne – v tomto případě ona politika, která vypne veškeré kontroly během startu Windows.
Přesně po takovém „božském klíči“ přitom touží třeba všemožné státní instituce, americká FBI a další, kteří se dušují, potřebují kvůli odhalování trestných činů a teroristických hrozeb tu odemknout zašifrovaný iPhone, tu nahlédnout do šifrované komunikace na WhatsAppu a tak dále. Pokud by jim nějakým master heslem výrobci skutečně vyšli vstříc, riziko vzniku podobné bezpečnostní díry jako v případě Secure Bootu vzroste doslova exponenciálně.
CRIME, TIME, BREACH and HEIST: A brief history of compression oracle attacks on HTTPS
11.8.2016 netsecurity Hacking
compression oracle attacksThe HEIST vulnerability was presented at Black Hat USA 2016 by Mathy Vanhoef and Tom Van Goethem. In this presentation, new techniques were presented that enhanced previously presented padding oracle attacks on HTTPS, making them more practical.
In a padding oracle attack, the attacker has partial control of part of a message that contains secret information, and is compressed, then encrypted before being sent over the network. An example of this is a web page that contains a CSRF token and echoes an attacker’s message.
This type of attack is not new, it was originally proposed by John Kelsey in 2002, then practically demonstrated by Juliano Rizzo and Thai Duong as CRIME in 2012 at ekoparty. CRIME worked by exploiting TLS compression on messages sent from the client to the server. This technique required a man-in-the-middle position.
In March 2013 at Black Hat EU, Tal Be’ery presented an extension of CRIME called TIME that introduced two new enhancements:
1. Using CRIME for server-to-client messages.
2. Exploiting TCP window sizes to allow the attack to take place without a man-in-the-middle position.
Later in 2013 at Black Hat USA, Angelo Prado, Neal Harris and Yoel Gluck presented BREACH, an attack that reproduced enhancement 1. from the TIME attack.
BREACH got more press than TIME did, and was generally much more well-known in the infosec community (for example, the Wikipedia article on CRIME mentions BREACH but not TIME).
The HEIST presentation in 2016 re-introduced the forgotten enhancement 2. from TIME, but used a slightly different technique (the Fetch API, which did not exist in 2013), and applied the attack in a novel way to HTTP/2 (also did not exist in 2013).
It turns out that each of these presentations introduced something that was previously discovered as if it were new.
1. The original CRIME presentation described the server-to-client attack that was presented as new in both TIME and BREACH. Note: the BREACH team retroactively added references to TIME and the original CRIME slides that introduced the attack in the final version of their paper.
2. TIME described the TCP window timing side-channel that was re-discovered in HEIST.
In conclusion, it’s hard to find truly original ideas in information security. When presenting results that build on previous research, it occasionally happens that other people may have found the same results. The information security community should try to be as thorough as possible when researching prior art and crediting existing research.
Blackhat Firm Offers $500,000 for Zero-day iOS Exploit; Double Than Apple’s Highest Bounty
11.8.2016 thehackernews Vulnerebility
Last week, Apple finally announced a bug bounty program for researchers and white hat hackers to find and get paid for reporting details of zero-day vulnerabilities in its software and devices.
The company offers the biggest payout of $200,000, which is 10 times the maximum reward that Google offers and double the highest bounty paid by Microsoft.
But now Apple is going to face competition from a blackhat company named, Exodus Intelligence.
Exodus Intelligence is offering more than double Apple's maximum payout for zero-day vulnerabilities affecting the newest versions of iOS.
The company is willing to pay more than $500,000 for zero-day vulnerabilities and exploits affecting iOS 9.3 and above.
Although Exodus labeled itself as ‘Research Sponsorship Program,’ the company actually makes money by buying and selling zero-day vulnerabilities and exploits.
On Wednesday, Exodus launched its new bonus structure for the acquisition of details and exploits for zero-day vulnerabilities.
Zero-Day Hit-list:
Exodus Intelligence's hit-list also shows that the firm will pay:
Up to $150,000 for a zero day in Google Chrome (which is 50% more than the Google's highest payout)
Up to $125,000 for a serious flaw in Microsoft's Edge browser (which is $500 and $1,500 currently offered by Microsoft)
Up to $80,000 for a serious flaw in Mozilla's Firefox.
Up to $75,000 reward for a local privilege escalation vulnerability in Windows 10
Also, Smaller payouts of $60,000 for flaws in both Adobe Reader and Flash Player
The zero-day market has long been a lucrative business for private companies that regularly offer more payouts for vulnerabilities than big technology firms.
Last year, security firm Zerodium paid $1 Million to a group of hackers for an iPhone hack, though that figure was later lowered to "up to $500,000" for subsequent iOS exploits.
The market for zero-day and exploits has become strong because governments, law enforcements, criminals, and the private sector shop for zero-days for surveillance or research purposes.
The well-known example is the latest fight between Apple and the FBI, which came to end when the FBI reportedly paid over $1 Million for an iPhone exploit that helped the FBI to break into the iPhone of one of the San Bernardino shooters.
There's one more thing Apple should be worried about: While Apple’s bug bounty program is invitation-only, at least for the time being, anyone can register on Exodus’s website and participate in the program to submit vulnerabilities.
Serious Linux design flaw CVE-2016-569 allows Traffic Hijacking
11.8.2016 securityaffairs Vulnerebility
A severe design flaw in the Linux kernel could be exploited by attackers to hijack traffic, inject malware into connections, and run a wide range of attacks.
A severe flaw in the Linux kernel could be exploited by attackers to hijack traffic, inject malware into downloads and web pages, and run a wide range of attacks, break Tor connections.
“In general, we believe that a DoS attack against Tor connections can have a devastating impact on both the availability of the service as a whole and the privacy guarantees that it can provide,” the team wrote in a white paper .
The flaw is widespread, vulnerable Linux distros are everywhere, in PC, servers, mobile devices and IoT devices.
The serious flaw (CVE-2016-5696) exists since version 3.6, deployed in 2012. It was discovered by researchers from the University of California, Riverside, and the U.S. Army Research Laboratory that present their findings at USENIX Security Symposium. The study is detailed in a paper titled “Off-Path TCP Exploits: Global Rate Limit Considered Dangerous,” that also includes recommendations on how to mitigate the issue.
The TCP/IP networking flaw allows attackers to spot communications between two entities and can be exploited to hijack the traffic and manipulate it if the exchange is not encrypted.
The attack is not considerable a man-in-the-middle attack, the attackers just need to send spoofed packets to both sides of the connection by simply knowing their IP addresses and destination ports.
“The unique aspect of the attack we demonstrated is the very low requirement to be able to carry it out,” explained Zhiyun Qian project leader.
“Essentially, it can be done easily by anyone in the world where an attack machine is in a network that allows IP spoofing. The only piece of information that is needed is the pair of IP addresses (for victim client and server), which is fairly easy to obtain.”
Giving a close look at the RFC 5961 we can note that it addresses spoofed packet injection attacks by introducing challenge ACK packets.
The researchers exploited the feature that Linux rate limits the output of these challenge ACKs.
The attacker can send malicious packets to confuse to the server, that in turn sends challenge ACKs to the client until it reaches its limit and temporarily stops sending them. In this phase, the attacker can turn to the client and send spoofed IP packets to break the connection or to substitute the silenced server in the connection.

“The root cause of the vulnerability is the introduction of the challenge ACK responses and the global rate limit imposed on certain TCP control packets.” explained the researchers.
“Through extensive experimentation, we demonstrate that the attack is extremely effective and reliable. Given any two arbitrary hosts, it takes only 10 seconds to successfully infer whether they are communicating. If there is a connection, subsequently, it takes also only tens of seconds to infer the TCP sequence numbers used on the connection. To demonstrate the impact, we perform case studies on a wide range of applications.
The basic idea is to repeat the following steps: 1) send spoofed packets to the connection under test (with a specific four-tuple), 2) create contention on the global challenge ACK rate limit, ie, by creating a regular connection from the attacker to the server and intentionally triggering the maximum allowed challenge ACKs per second, and 3) count the actual number of challenge ACKs received on that connection. If this number is less than the system limit, some challenge ACKs must have been sent over the connection under test, as responses to the spoofed packets.”
Waiting for a patch, users can raise the rate limit for the challenge ACK packets so that it cannot be reached, it can be done by modifying the rule it in the /etc/sysctl.conf:
net.ipv4.tcp_challenge_ack_limit = 999999999
then execute sysctl -p to activate it and root the machine.
Tha attack could be also effective on encrypted communication, but just to break them. The researchers also added that Windows, OS X and FreeBSD aren’t vulnerable because partially implemented the RFC 5961.
Below a video PoC of the attack:
Exodus announces a bug bounty program. Who will pay more for a zero-day?
11.8.2016 securityaffairs Vulnerebility
The bug hunting company Exodus announced its bug bounty program. Who will pay more for a 0-day exploit? Reflecting on the zero-day market.
Almost every IT giant has launched its bug bounty program, the last in order of time is Apple that last week announced the initiative during the Black Hat Conference.
How much is a vulnerability in Apple product?
The awards are very interesting, bug hunters can earn up to $200,000 for a critical vulnerability affecting the secure boot firmware components, up to $100,000 for a flaw that could be exploit to extract sensitive data protected by the Secure Enclave, up to $50,000 for arbitrary code execution with kernel privileges and unauthorized access to iCloud account data, and up to $25,000 for access from a sandboxed process to user data outside the sandbox.
But we all know that zero-day market is crowded by private firms and nation-state actors that could decide to pay much more for an exploit of unknown flaws in most popular products.
The zero-day broker company Exodus Intelligence has announced its new acquisition programme for both vulnerabilities and exploits.
Today, Exodus Intelligence has unveiled the new Research Sponsorship Program (RSP), focused on acquiring vulnerability research and exploits from the global cybersecurity research community. While continuing to acquire Zero-Day research, the RSP is the first widely available acquisition program to offer bounties for exploits that exercise N-Day vulnerabilities.” reads the official statement released by the firm.
“Exodus is also excited to be rolling out a new bonus structure for the acquisition of research that leads to Zero-Day vulnerabilities.”
Exodus will share details of vulnerabilities and exploits to customers who pay a subscription fee of roughly $200,000 per year.
Let’s compare the awards offered by the company with the Apple ones.
iOS vulnerabilities are paid by Exodus more than double Apple’s maximum payout, the bug-hunting company will pay a maximum of $500,000 for zero-day in iOS 9.3 or above.

Now it is clear that a bug hunter searching for a remuneration for his efforts will contact companies like Exodus, instead IT giants like Apple because their bug bounty programs pay more for 0-day exploits.
There is also another incentive for bug hunters that will contact Exodus, the company will pay an extra cash for every quarter that the zero-day is still effective.
“For each new Zero-Day acquired, Exodus will offer the researcher an initial payment, received after the request is reviewed and accepted. Once accepted, the researcher could receive payments every quarter the Zero-Day exploit is still alive. The specific values of the initial payment and quarterly bonus will be included in an offer presented to the researcher, following the review of their work. Additionally, Exodus also offers payment in the form of Bitcoin for Zero-Day research.” continues the announcement.
Speaking about Apple zero-day exploits, let’s remind that last year the zero-day vendor Zerodium paid a $1 million payout for disclosing a iOS zero-day vulnerability that could allow an attacker to remotely hack any Phone.
The bug bounty program launched by Exodus is open, everyone can submit vulnerabilities to the company, meanwhile, other programs are by invitation-only.
For further information on Exodus’ program give a look at the new RSP website.
Backdoor keys allow attackers to the bypass UEFI Secure Boot
11.8.2016 securityaffairs Vulnerebility
Once again Microsoft failed in fixing a severe Secure Boot vulnerability that can be exploited to install rootkits on Windows devices.
Microsoft has accidentally leaked the Secret keys to Bypass UEFI Secure Boot. The Secure Boot is a UEFI (Unified Extensible Firmware Interface) feature that should prevent the execution of unauthorized code during the boot process. The Secure Boot is implemented in devices running Windows 8 and later, it ensures that every component loaded at boot is trustable because it is signed and validated.
The Secure Book prevents rootkit infections and also prevents the execution of non-Microsoft operating system on the device.
The Secret keys were disclosed by two security researchers, using the monikers MY123 and Slipstream.
The security duo discovered that Microsoft introduced a new policy for the Secure Boot during the development of Windows 10 Anniversary Update (v1607).
The experts discovered that the new policies, called “supplemental” policies, are loaded by the boot manager without implementing the proper checks.
The supplemental policy was implemented to allow developers to install self-signed third-party drivers on a Windows machine, the feature is also known as “test-signing.”
An attacker can exploit this feature to bypass the Secure Boot and load a rootkit at the device boot.
“The “supplemental” policy does NOT contain a DeviceID. And, because they were meant to be merged into a base policy, they don’t contain any BCD rules either, which means that if they are loaded, you can enable testsigning. Not just for windows (to load unsigned driver, ie rootkit), but for the {bootmgr} element as well, which allows bootmgr to run what is effectively an unsigned .efi (ie bootkit)!!! (In practise, the .efi file must be signed, but it can be self-signed) You can see how this is very bad!!” reads a blog post published by Slipstream. “A backdoor, which MS put into secure boot because they decided to not let the user turn it off in certain devices, allows for secure boot to be disabled everywhere!”

The bad news for Microsoft is that it is impossible to fully revoke the leaked keys, this means that any Windows-based device can be potentially unlocked due to the presence of the backdoor.
Microsoft has recently released the August Patch Tuesday that tried to fix the issue in the Secure Boot, but for the second consecutive month, it evidently has failed.
Milióny škodovek a volkswagenů jdou otevřít odposlechnutým kódem
11.8.2016 Zive.cz Hacking
Pokud odemykáte auto dálkovým ovládáním, vždy hrozí, že někdo odposlechne přenášený kód. Proto jsou tato data šifrovaná, aby byl přenos kódů bezpečný.
Nyní se ale ukazuje, že v případě vozů z koncernu Volkswagen není to zabezpečení na tak skvělé úrovni. Jak upozornil Wired, výzkumníci z univerzity v Birminghamu a německé firmy Kasper & Oswald našli chybu v zabezpečení (PDF), kterou otevřou téměř 100 miliónů automobilů. Jedna chyba otevře cokoli od Volkswagenu za posledních dvacet let, druhá chyba se týká dalších výrobců jako Alfa Romeo, Citroen, Fiat, Ford, Mitsubishi, Nissan, Opel a Peugeot.
Tučně označená auta výzkumníci úspěšně otestovali a otevřeli, kvůli sdíleným modulům je ale postižených mnohem více vozů
Vážnější je ten útok proti Volkswagenu, protože se zjistilo, že pouhé čtyři privátní klíče stačí k otevření 100 miliónů aut. Výzkumníkům se totiž podařilo z vnitřního počítače auta získat privátní klíče. Nezměněné zabezpečení z roku 1995 nebylo pro dnešní prostředky výraznou překážkou.
Odposlech kódů zajistí klidně malé zařízení schované v kapse
Potom stačí odposlechnout rádiový signál z klíče při otevírání a při znalosti hlavního klíče získat šifrovací klíč pro konkrétní vůz. Odposlech signálu zajistí klidně krabička z Arduina, antény a pár pomocných obvodů.
Druhá chyba cílí na šifrování HiTag2, které je už 18 let staré a najdete jej v miliónech vozů. Tady není ani potřeba znalost hlavního klíče, je ale potřeba odposlechnout alespoň osm signálů pro otevření nebo zavření. To se dá urychlit tak, že budete rušit signál a majitel vozu bude opakovaně zkoušet auto zamknout nebo odemknout. Se znalostí sekvence kódů je pak prolomení šifry s dnešními prostředky otázkou minuty.
Tyto zranitelnosti pouze otevřou automobil. Neřeší obejití imobilizéru, na který se musí používat jiný útok. Ale i na imobilizér už existují hacky.
Už dříve se se ukázala zranitelnost bezklíčových systémů, kdy pro otevření stačí mít klíč v kapse a přiblížit se k autu. Pomocí zesilovačů a opakovačů signálu může útočník zaměřit klíč daleko v domě a otevřít jeho signálem automobil.
Opět se tedy potvrzuje, že pomalý cyklus vývoje počítačů v automobilech a spoléhání se na staré principy zabezpečení dělá z aut snadnou oběť technologicky zdatných zlodějů. Dříve sice stačil zahnutý drát a dnes potřebujete chytrou krabičku s anténami, pokud si ale zloděj vytipuje nějaké auto, základní zabezpečení od výrobce málokdy poskytne těžko překonatelnou překážku.
Hackeři napadli fórum Doty 2, získali téměř 2 miliony loginů
11.8.2016 Zive.cz Hacking
Dota 2 aktuálně patří k nejhranějším hrám vůbec. Není proto divu, že hack oficiálního vývojářského fóra (dev.dota2.com) znamenal nemalý počet účtů, které byly odcizeny. Podle webu LeakedSource.com jde o 1,92 milionů záznamů obsahující uživatelská jména, e-maily, IP adresy a šifrované heslo.
Útočníci získali do databáze diskuzního fóra přístup 10. července a vystačili si s technikou SQL Injection. Proti té nebylo zabezpečeno fórum, které využívalo starší sytém vBulletin. Hesla jsou šifrována pomocí MD5, které není považováno za bezpečné – podle LeakedSource je možné 80 % získaných záznamů konvertovat do čitelného stavu.
Statistika nejpoužívanějších mailů v odcizené databázi (zdroj: LeakedSource)
Pokud se váš účet nachází v databázi, což lze ověřit na LeakedSource, změňte svoje heslo nejen na fóru, ale také na ostatních stránkách, kde byl využíván stejný login.
Nigerijští weboví podvodníci se nakazili vlastními viry
11.8.2016 Zive.cz Kriminalita
Skupina nigerijských webových podvodníků nedobrovolně odhalila svoji identitu a ilegální práci. Infikovala totiž sama sebe svým malwarem.
Podvodníci byli nalezeni při útoků jménem wire-wire, který jim umožnil získat velké množství peněz od podniků z celého světa. Uvádí to zpráva serveru IEEE Spectrum. Na případ narazili bezpečnostní experti Joe Stewart a James Bettke.
Typickou podvodnou metodou je v Africe technika známá pod názvem Business Email Compromise (BEC). Spočívá v tom, že kriminálníci pomocí interních podnikových emailů vykonávají podvodné transakce. Wire-wire je sofistikovanější BEC a je tězší jí odhalit. Stewart a Bettke na ni narazili v únoru, jelikož pět podvodníků si infikovalo počítače pomocí stejného malwaru, který používali ke krádežím od jiných.
Malware totiž nepřetržitě posílal screenshoty a úhozy klávesnice z infikovaných počítačů do otevřené webové databáze, kterou Stewart a Bettke našli pomocí nástroje na prohlížení emailových příloh. Zjistili dokonce, že podvodníci trénují nové členy, což více odhalilo jak technika funguje. S každou transakcí Nigerijci získali od 30 000 do 60 000 dolarů. Skupina čítala 30 lidí. Ročně měla na svědomí krádeže v hodnotě 3 milionů dolarů.
Bezpečnostní experti okamžitě postižené společnosti kontaktovali a o podvodu jim řekli. Případ již vyšetřují příslušné nigerijské úřady.
Over 300 new cyber threats pop up on underground markets each week
10.8.2016 helpsecuritynet Security
Approximately 305 new cyber threats are added each week on cybercrime markets and forums, mostly located on dark nets and the deep web.
The threats include information on newly developed malware and exploits that have not yet been deployed in a cyber-attack – information that could be very useful for cyber defenders.

The discovery was made by Arizona State University researchers, who have developed and deployed a system for cyber threat intelligence gathering and used it on 27 marketplaces and 21 hacking forums.
The group, some members of which have also recently released the results of an investigation into the supply on 17 underground hacker markets, also noted that, in a period spanning four weeks, 16 exploits for zero-day vulnerabilities had been offered for sale.
Among these was an exploit for a remote code execution flaw in Internet Explorer 11 (priced at a little over 20 BTC), and for a RCE flaw in Android Web View (price: nearly 41 BTC).
“The Android WebView zero-day affects a vulnerability in the rendering of web pages in Android devices. It affects devices running on Android 4.3 Jelly Bean or earlier versions of the operating system. This comprised of more than 60% of the Android devices in 2015,” they explained.
“After the original posting of this zero-day, a patch was released in Android KitKit 4.4 and Lollipop 5.0 which required devices to upgrade their operating system. As not all users have/will update to the new operating system, the exploit continues to be sold for a high price. Detection of these zero-day exploits at an earlier stage can help organizations avoid an attack on their system or minimize the damage. For instance, in this case, an organization may decide to prioritize patching, updating, or replacing certain systems using the Android operating system.”
Not to mention that the vendors whose software is obviously vulnerable could try to come up with a patch or at least temporary mitigations that could minimize the risk of these exploits being leveraged against users.
The researchers’ system has also shown some promise when it comes to mapping the underlying social network of vendors.
The group is currently in the process of transitioning the system to a commercial partner, but the database they created by using it has been made available to security professionals, to help them identify emerging cyber threats and capabilities.
Microsoft Releases 9 Security Updates to Patch 34 Vulnerabilities
10.8.2016 thehackernews Vulnerebility
Microsoft's August Patch Tuesday offers nine security bulletins with five rated critical, resolving 34 security vulnerabilities in Internet Explorer (IE), Edge, and Office, as well as some serious high-profile security issues with Windows.
A security bulletin, MS16-102, patches a single vulnerability (CVE-2016-3319) that could allow an attacker to control your computer just by getting you to view specially-crafted PDF content in your web browser.
Users of Microsoft Edge on Windows 10 systems are at a significant risk for remote code execution (RCE) attacks through a malicious PDF file.
Web Page with PDF Can Hack Your Windows Computer
Since Edge automatically renders PDF content when the browser is set as a default browser, this vulnerability only affects Windows 10 users with Microsoft Edge set as the default browser, as the exploit would execute by simply by viewing a PDF online.
Web browsers for all other affected operating systems do not automatically render PDF content, so an attacker would have to convince users into opening a specially crafted PDF file, typically via an email or instant message, Microsoft said in its advisory.
Once exploited, the flaw corrupts memory, allowing a hacker to run malicious code with the same privileges as the user. All the hacker needs is to either lure victims to a website containing a malicious PDF or add an infected PDF file to a website that accepts user-provided content.
While this vulnerability has not been publicly disclosed nor seen in any attacked, it is expected to be an attractive attack vector for hackers.
Other Critical Bugs can Take Complete Control of Your PC
A separate critical update for Edge listed in MS16-096 patches five remote code execution (RCE) flaws and three information disclosure bugs.
The company also released its monthly cumulative security update, MS16-095, for Internet Explorer (IE), patching nine vulnerabilities that can be exploited by a malicious web page to pull off remote code execution through memory corruption bug or disclose information about the system.
Another critical update includes Microsoft Office Patch MS16-099 that addresses four memory corruption bugs in Office that can be exploited by booby-trapped documents remotely to execute malicious code on a victim's system, taking full control of the victim machines.
The update also includes a patch for an information disclosure hole in Microsoft OneNote, which discloses memory contents and information that could be used to compromise a machine.
In addition to Windows versions of Office going back to Office 2007, Microsoft is also releasing a patch for Office for Mac 2011 and 2016.
The final critical bulletin, MS16-097, patches three Remote Code Execution flaws in the font handling library of Microsoft Graphics Component found in Windows, Office, Skype for Business and Lync that can be exploited by a malicious web page or an Office document.
For the second time, the technology giant also released a security update for Secure Boot. Rated important, MS16-100, the update patches a security feature bypass vulnerability that occurs when Secure Boot loads a vulnerable (install a hidden bootkit or rootkit) boot manager.
This designing flaw has been fixed in all supported versions of Windows and Windows Server.
Other important bulletins address vulnerabilities that lead to man-in-the-middle attacks on Windows and Windows Server, an information disclosure vulnerability in the Universal Outlook component for Windows 10, and four elevation of privilege flaws in kernel-mode drivers for Windows Vista through Windows 10 and Windows Server 2008 and 2012.
The company has also issued Cumulative Updates (KB3176493, KB3176495, KB3176492) for Windows 10 users, so those who have upgraded their systems to the Microsoft's new operating system should install the updates as soon as possible.
Users are advised to patch their system and software as soon as possible.
Oops! Microsoft Accidentally Leaks Backdoor Keys to Bypass UEFI Secure Boot
10.8.2016 thehackernews Vulnerebility
Microsoft has accidentally leaked the Secret keys that allow hackers to unlock devices protected by UEFI (Unified Extensible Firmware Interface) Secure Boot feature.
What's even worse?
It will be impossible for Microsoft to undo its leak.
Secure Boot is a security feature that protects your device from certain types of malware, such as a rootkit, which can hijack your system bootloader, as well as, Secure Boot restricts you from running any non-Microsoft operating system on your device.
In other words, when Secure Boot is enabled, you will only be able to boot Microsoft approved (cryptographically signature checking) operating systems.
However, the Golden Keys disclosed by two security researchers, using alias MY123 and Slipstream, can be used to install non-Windows operating systems, say GNU/Linux or Android, on the devices protected by Secure Boot.
Moreover, according to the blog post published by researchers, it is impossible for Microsoft to fully revoke the leaked keys, potentially giving law enforcement (such as FBI and NSA) special backdoor that can be used to unlock Windows-powered devices in criminal cases.
The issue actually resides in the Secure Boot policy loading system, where a specially signed policy loads early and disables the operating system signature checks, the reg reports.
This specific Secure Boot policy was created and signed by Microsoft for developers, testers, and programmers for debugging purposes.
"During the development of Windows 10 v1607 'Redstone,' MS added a new type of secure boot policy. Namely, "supplemental" policies that are located in the EFIESP partition…" researcher said.
"...a backdoor, which MS put into secure boot because they decided to not let the user turn it off in certain devices, allows for secure boot to be disabled everywhere!"
Yesterday, Microsoft released August Patch Tuesday that includes a security patch for designing flaw in Secure Boot for the second time in two months, but unfortunately, the patch is not complete.
Linux.Lady, a Go-based Linux Trojan that mines cryptocurrency
10.8.2016 securityaffairs Virus
Russian antivirus company Doctor Web discovered a new Linux Trojan dubbed Linux.Lady that is used by crooks to mine cryptocurrency.
According to a new report published by the antivirus company Doctor Web, a Go-Based Linux Trojan, Dubbed Linux.Lady.1, is exploited by cyber criminals for cryptocurrency mining.
“Doctor Web analysts have detected and examined a new Linux Trojan which is able to run a cryptocurrency mining program on an infected computer. Its key feature lies in the fact that it is written in Go, a language developed by Google.” states the report published by Doctor Web.
The Linux.Lady Linux Trojan is written in Google’s Go programming language and it uses various libraries that are available on GitHub. Go was introduced by Google in 2009, the use of the Go programming language to develop a malicious code is not a novelty, it was first used with the intent of creating malware in 2012 despite it isn’t so popular in the vxer community.
When the Linux.Lady infects a system, it gathers information on the system, including the Linux operating system version, the number of CPUs and processes.
Once collected info on the infected host, the malware sent it back to a command and control (C&C) server, which in turn provides a configuration file for downloading a cryptocurrency mining application.
The sample of Linux.Lady analyzed by Doctor Web was mining a cryptocurrency named Monero.

Another interesting feature implemented in the Linux.Lady allows the malware to spread to other Linux computers on the infected network.
“The Trojan receives a configuration file containing information necessary for the Trojan’s operation. Then it downloads and launches a cryptocurrency mining program. The malware determines an external IP address of the infected computer using special websites specified in the configuration file.” states the report on the threat. “The Trojan then calculates the mask of the subnet External_ip\8 (mask is 255.0.0.0) and tries to connect to the remote hosts via port 6379 (redis) without entering a password. If the connection is established, Linux.Lady.1 opens the URL specified in the configuration file, downloads a script detected as Linux.DownLoader.196, and adds it to the cron scheduler of the infected computer:”
In the past other Linux malware were discovered by the experts at Doctor Web, including the Encoder ransomware and the Ekoms malware.
Mining activities are a profitable business for cyber criminals that exploits victims’ computational resources to make money.
Další zranitelnosti v Androidu, Qualcomm přispěchal s opravami
10.8.2016 Zdroj: SecurityWorld Zranitelnosti
Miliony zařízení s čipovými sadami od firmy Qualcomm, na kterých zároveň běží Android, jsou vystaveny minimálně jedné z čtyř kritických zranitelností. Ty umožní aplikacím i bez patřičných oprávnění převzít nad přístrojem kontrolu.
Všechny čtyři chyby odhalil bezpečnostní analytik Adam Donenfeld z Check Point Software Technologies; nález oznámil v neděli na hackerské konferenci DEF CON v Las Vegas. Qualcommu byly oznámeny již během února a dubna, výrobce na to zareagoval patřičnými opravami, poté, co zranitelnosti shledal vysoce rizikovými.
Bohužel to neznamená, že jsou všechna zařízení chráněna. Z důvodu velké roztříštěnosti ekosystému Androidu běží mnoho mobilů a tabletů na starších verzích operačního systému a již nedostávají aktualizace firmwaru, nebo je získávají až s několikaměsíčním zpožděním. Takovým zařízením pak nebezpečí stále hrozí.
Dokonce ani Google, který vydává bezpečnostní záplaty pro svou Nexus řadu chytrých telefonů a tabletů každý měsíc, ještě neopravil všechny chyby.
Zranitelnostem se jako celku říká QuadRooter, protože při zneužití dávají útočníkovi root pravomoce – tedy nejvyšší možné pravomoce na Linuxu založených systémech, mezi které Android patří. Individuálně se zranitelnosti označují jako CVE-2016-2059, CVE-2016-2503, CVE-2016-2504 a CVE-2016-5340. Nachází se v různých ovladačích, jež Qualcomm dodává výrobcům zařízení.
Během dubna a července Qualcomm vydal aktualizace, které tyto chyby opravují, tvrdí v e-mailu Alex Gantman, viceprezident strojírenské sekce Qualcomm Product Security Initiative.
Google zatím pro svá Nexus zařízení opravil jen tři ze čtyř chyb; vlastní opravy předem sdílí s výrobci a také je publikuje na Android Open Source Project (AOSP), dostanou se k nim tedy téměř všichni.
Zařízení běžící na Androidu 6.0 a více (Marshmallow buildy) s aktualizacemi z 5. května by již měli být chráněny proti všem zranitelnostem s výjimkou CVE-2016-5340. Androidy s oblíbenou verzí 4.4.4 (KitKat) či 5.0.2 a 5.1.1 (Lollipop) s aktualizacemi z 5. května jsou prozatím chráněny jen před dvěmi objevenými chybami, a to CVE-2016-2503 a CVE-2016-2504. V jejich případě je CVE-2016-2059 zneužitelný, Google jej však označil jen jako mírně nebezpečný, vzhledem k existující ochraně systému.
Čtvrtá zranitelnost, CVE-2016-5340, zůstává Googlem neopravena úplně. Výrobci by však mohli získat záplatu přímo od Qualcommu, skrze jeho open-source projekt Code Aurora.
„Této chybě se budeme věnovat v našem nadcházejícím bezpečnostním bulletinu. Partneři Androidu však mohou reagovat rychleji a využít možností veřejné opravy, jíž Qualcomm poskytl,“ popsal mluvčí Googlu skrze e-mail. Zneužití kterékoli z těchto čtyř zranitelností by uživatele vystavilo stažení infikovaných aplikací, řekl dále k věci Google.
„Naše Verify App a SafetyNet ochrany pomáhají identifikovat, zablokovat a odstranit aplikace, které takovéto zranitelnosti zneužívají,“ dodal mluvčí.
Je pravda, že ohrozit přístroje těmito chybami je možné jen skrze závadné aplikace. Přímé způsoby útoku jako prohlížení webu, přiložené soubory v e-mailu nebo SMS v tomto případě nelze aplikovat. Aplikace však dle tvrzení Check Pointu nepotřebují žádná zvýšená oprávnění, což jejich nebezpečí výrazně zvyšuje.
Výzkumníci Check Pointu a Google se mezitím neshodli na nebezpečnosti zranitelnosti CVE-2016-2059. Zatímco Qualcomm ji společně se zbytkem chyb označil jako vysoce rizikovou, Google ji posuzuje jen jako mírně nebezpečnou, neboť podle vyjádření firmy lze rizika zmírnit pomocí nástavby SELinux.
SELinux je rozšíření jádra, které činí zneužití některých chyb výrazně složitější pomocí vynucování přístupu. Mechanismus byl využíván k vynucení sandboxových hranic aplikacím již od verze 4.3 (Jelly Bean).
Check Point ovšem s postojem Googlu nesouhlasí. Během Donenfeldova projevu na DEF CONu ukázal, jak CVE-2016-2059 dokáže „přecvaknout“ SELinux z vynucovacího do liberálního módu, čímž efektivně vyřadí jeho ochranu.
Je těžké identifikovat, která konkrétní zařízení jsou zranitelná, neboť někteří výrobci mohou s aktualizacemi čekat na Google, zatímco jiní již mohli opravu převzít přímo od Qualcommu. Aby si uživatelé sami mohli svůj přístroj otestovat, vydal Check Point aplikaci zdarma zvanou QuadRoot Scanner, dostupnou z obchodu Google Play. Ta uživatelům umožní svá zařízení na tyto čtyři zneužití otestovat.
Tisíce Čechů a Slováků naletěly na status o útoku v Praze. Podvodníci jim ukradli hesla
9.8.2016 Zdroj:Novinky/Bezpečnost Sociální sítě
Jako lavina se českým a slovenským internetem začal šířit nový podvod, prostřednictvím kterého se snaží počítačoví piráti vylákat přihlašovací údaje jednotlivých uživatelů. Kyberzločinci tvrdí, že se Praha stala terčem teroristického útoku. Fiktivní zprávou se však z důvěřivců snaží pouze vytáhnout přihlašovací údaje.
Před novou hrozbou varovali v úterý bezpečnostní experti antivirové společnosti Eset. Ti zároveň upozornili, že na tento trik se nechalo nachytat již několik tisíc Čechů a Slováků.
Útok má poměrně jednoduchý scénář. Na Facebooku některého z přátel se objeví odkaz na falešný zpravodajský článek pojednávající o údajném teroristickém útoku s větším množstvím obětí. Zpráva má už na první pohled podezřelý titulek „30 minut před: 1 teroristického útoku došlo v Praze, při kterých nejméně 187 lidí bylo zabi”. Je navíc doplněna o fotografii z údajného místa útoku, která však zcela evidentně nepochází z hlavního města České republiky. Pořízena byla při útoku v Bagdádu v roce 2010, další varianta zase používá snímek z nedávného útoku v Nice.
Využívají napadené účty
K šíření podvodných zpráv tak útočníci využívají účty na Facebooku, které se jim již podařilo napadnout. Právě proto se mohou podobné zprávy objevovat na zmiňované sociální síti i pod hlavičkou skutečných přátel.
„Pokud na tento link klikne další oběť, neotevře se jí zpravodajský článek, ale falešná verze přihlašovací stránky k Facebooku. Zadáním přihlašovacích údajů je oběť nevědomě předá útočníkovi a ztrácí tím kontrolu nad svým facebookovým účtem. Mezitím mohou útočníci podvodné stránky šířit dál skrze profil nové oběti,“ vysvětlil Pavel Matějíček, manažer technické podpory společnosti Eset.
Podvodníci tedy využívají zájmu lidí o aktuální dění. „Oběť vyplní přihlašovací údaje, protože se domnívá, že se tím dostane ke zpravodajskému článku o velké tragédii, která se měla odehrát geograficky blízko. Útočník proto využívá nejen její zvědavosti, ale i strachu,“ doplnil Matějíček.
Český prezident Miloš Zeman byl zavražděn ve vlastním domě.
Podvodná zpráva na Faceboooku
V některých případech navíc kyberzločinci podvodné zprávy ještě více specifikují, aby nalákali co možná nejvíce důvěřivců. Jeden z odkazů, které bezpečnostní experti zachytili, tvrdil, že český prezident Miloš Zeman byl zavražděn ve vlastním domě.
„V jiných případech útočník přes profil napadeného uživatele okomentuje informaci o teroristickém útoku s tím, že ve svém komentáři označí kontakty této oběti, čímž se snaží nalákat více lidí. Útočníkem ovládaný profil sdílí škodlivý link i do facebookových skupin, jejichž členem je podvedená oběť. Útočník přitom ke sběru používá několik desítek falešných stránek, které Eset pro své uživatele z bezpečnostních důvodů blokuje,“ podotkl manažer technické podpory společnosti Eset.
„Lidé by měli zbystřit vždy, když si od nich nějaká stránka vyžádá přihlašovací údaje k účtu na sociální síti a i v případě, že vypadá jako Facebook, Twitter nebo Instagram. V tom případě oběti stačí zkontrolovat adresu samotné stránky, která se názvu Facebooku či jiné sociální sítě vůbec nepodobá,“ uzavřel Matějíček.
Podvodů na Facebooku přibývá
Facebook využívají počítačoví piráti k útokům stále častěji. Loni se například snažili důvěřivce nalákat na výhru chytrého telefonu iPhone od společnosti Apple. Ve skutečnosti je však zaregistrovali k odběru placených SMS zpráv.
Prostřednictvím této sociální sítě se počítačoví piráti snaží často vylákat také přihlašovací údaje k internetovému bankovnictví. Z nich pak následně odčerpají peníze, případně si přímo na uživatele zřídí úvěr. Připravit tak klienty mohou o daleko více peněz, než kolik mají naspořeno na účtu.
Hacknout jde i monitor
9.8.2016 Zdroj: SecurityWorlds Hacking
Nevěřte všemu, co vidíte – jak se přesvědčili účastníci každoroční hackerské konference Def Con, hacknout jde i monitor.
V pátek výzkumníci ukázali cestu, jakou lze manipulovat přímo s pixely na displeji monitoru. Odpovědní za tento objev jsou Ang Cui a Jatin Kataria z Red Balloon Security, které zajímalo, jak fungují monitory od firmy Dell a podařilo se jim pomocí reverzního inženýrství dosáhnout zajímavých výsledků.
Rozebrali Dell U2410 na jednotlivé díly a zjistili, že řadič displeje uvnitř může být použit ke změně či záznamu pixelů, které se na obrazovce objevují.
Během své prezentace na Def Conu ukázali, jak mohl jejich hacknutý monitor zdánlivě měnil detaily na webových stránkách. V jednom příkladu vyměnili zůstatek na PayPal účtu z 0 dolarů na 1 milion dolarů, ačkoli ve skutečnosti šlo pouze o rekonfiguraci pixelů na monitoru.
Nejde o zrovna jednoduchý hack – přesněji řečeno, oběma pánům zabral dva roky jejich volného času. Porozumět technologii, provést výzkum a objevit zranitelnost nebylo snadné.
Nezaměřili se však výhradně na značku Dell – prohlíželi též monitory jiných značek, včetně např. Samsungu, Aceru nebo HP, a zjistili, že podobný postup je teoreticky možný u každého z nich.
Kámen úrazu leží ve firmwaru monitorů, respektive softwaru v nich zabudovaném.
„V aktualizacích firmwaru monitorů neexistuje zabezpečení a jsou velmi otevřené,“ popisoval Cui, který je zároveň generálním ředitelem firmy Red Balloon.
Zneužití chyby vyžaduje přímý přístup do monitoru, ať už skrze HDMI nebo USB. Pokud se povede, otevírá dveře jiným útokům, včetně v poslední době všudypřítomného ransomwaru.
Kybernetičtí zločinci by například mohli z pixelů na monitor vyskládat trvalou zprávu a žádat peníze za její odstranění, popisuje Kataria. Nebo by mohli sledovat činnost uživatelé skrze zaznamenávání pixelů – to je potenciálně ještě nebezpečnější.
Oba výzkumníci svůj výzkum prováděli z osvětových důvodů. Jejich objevy jsou dostupné online.
„Je zabezpečení monitoru důležité? Myslím, že ano,“ uzavírá Cui.
Hackeři napadli bitcoinovou burzu Bitfinex. Klienti přijdou o třetinu vkladů
9.8.2016 Zdroj: Novinky/Bezpečnost Hacking
Bitcoinová burza Bitfinex, která přišla při hackerském útoku o bitcoiny za více než 70 miliónů USD (1,7 miliardy Kč), rozdělí ztrátu mezi všechny své klienty. Burza o víkendu oznámila zákazníkům, že přijdou o 36 procent aktiv na svých účtech u burzy. Tyto ztráty jim však chce burza kompenzovat poukázkami.
Ztráty z krádeže při hackerském útoku burza přenese na všechny své klienty a aktiva, tedy nejen na ty klienty, z jejichž účtů se bitcoiny ztratily. Po přihlášení do platformy všichni klienti burzy uvidí pokles hodnoty svého majetku o 36,067 procenta.
Všichni klienti také obdrží poukázky, které jim mají kompenzovat ztráty. Poukázky bude moci burza odkoupit nebo je bude možné vyměnit za akcie společnosti iFinex, která je mateřskou firmou burzy. Bitfinex uvedl, že svoji metodiku vysvětlí později a že o kompenzaci zákazníkům jednal s investory.
Hackeři při útoku ukradli z burzy Bitfinex celkem 119 756 bitcoinů, což byla druhá největší krádež v historii této měny. Ukradený počet bitcoinů představuje zhruba 0,75 procenta z celkového počtu bitcoinů v oběhu.
Bitfinex patří mezi největší bitcoinové burzy na světě. Obchoduje se zde však i s dalšími kryptoměnami. Podle prohlášení burzy přijdou o své peníze nejen ti, kteří mají bitcoinový účet, ale majitelé všech účtů, tedy i účtů s jinými digitálními měnami, napsala agentura Reuters.
Virtuální měny představují velké riziko
Virtuální měna bitcoin vznikla v roce 2009, větší popularitě se ale těší v posledních letech. Vytvořena byla tak, aby se nedala ovlivňovat žádnou vládou ani centrální bankou.
Kybernetické mince "razí" síť počítačů se specializovaným softwarem naprogramovaným tak, aby uvolňoval nové mince stabilním, ale stále klesajícím tempem. Počet mincí v oběhu má dosáhnout nakonec 21 miliónů, což má být kolem roku 2140.
Bitcoiny se těší velké popularitě především coby prostředek pro investici. Kurzy však často kolísají. Evropský bankovní úřad kvůli tomu dokonce varoval spotřebitele, že neregulované virtuální měny představují velké riziko. Jejich vklady totiž nejsou nijak chráněny.
Bruce Schneier: Internet věcí přinese útoky, které si neumíme představit
9.8.2016 Zdroj: Lupa Hacking
Propojení produktů a zařízení reálného světa s internetem zadělává na katastrofu. Tvrdí to známý bezpečnostní odborník Bruce Schneier.
Divíte se Bruce Schneierovi, že varuje před bezpečnostními problémy přicházejícími s nástupem tzv. Internetu věcí (IoT)? Ono se vlastně nejde nedivit. Stačí se podívat na čerstvý případ závažných bezpečnostních děr v „chytrých“ žárovkách od společnosti Osram. Jsou plné zásadních chyb a některé z nich se Osram ani nechystá opravit. Jsou přitom zneužitelné k útoku na domácí či firemní sítě, získávání hesla k bezdrátovým sítím a děravý je i protokol (ZigBee), který používají žárovky pro komunikaci.
Pokud bude výroba internetově připojených produktů neřízeně ponechána v rukou ignorantů, nelze očekávat nic jiného, než před čím Schneier ve svém článku pro magazín Motherboard varuje. Říká, že útočníci mohou s daty dělat tři zásadní věci – krást je, měnit je nebo zabraňovat vlastníkům v přístupu k nim. Právě poslední dva druhy útoků se s příchodem IoT mohou podle Schneiera stát extrémně účinné.
Je rozdíl mezím tím, jestli někdo použije váš chytrý zámek ke zjištění, jestli je někdo doma, a tím, když útočník může zámek odemknout a dveře otevřít, nebo, ještě hůře, když vám dokáže znemožnit dveře otevřít. „Útočník, který vám může zabránit řídit vaše auto či jej dokáže ovládnout, je nebezpečnější než někdo, kdo odposlouchává vaši konverzaci či sleduje, kde se vaše auto nachází,“ říká Schneier.
Manipulace při volbách
Něco na Schneierově tvrzení, že IOT přinese útoky, „které si ještě ani nedokážeme představit“, bude. Pokud seriózní a velké firmy přistupují k bezpečnosti IoT natolik laxně jako Osram, jak asi bude vypadat trh zaplavený levnými IoT senzory a zařízeními z Číny? Stačí se podívat, jak na tom jsou s bezpečností dětské chůvičky. Coby předzvěst stavu zařízení Internetu věcí je to dostatečně vypovídající.
Nakonec už loni hackeři předvedli, jak mohou na dálku ovládat auto. Stejně jako v případě žárovek se zde ukázalo, že Chrysler a jejich UConnect jsou hackerům pro srandu. Od té doby se ukázalo, že podobně laxní přístup k bezpečnosti je v automobilovém průmyslu běžný. Ukázalo se ale také to, že místo zabezpečení se automobiloví výrobci spíše starají o to, jak právně znemožnit zveřejňování informací o jejich mizerné práci.
Schneier pochopitelně upozorňuje, že nástup IoT může znamenat, že někdo ovládne nejen auto, ale dokonce i letadlo. Ale také může zaútočit na medicínská zařízení či prostým ovládáním termostatu způsobit zásadní zvýšení či snížení teploty.
Postupující elektronizace voleb navíc podle Schneiera znamená, že v budoucnosti budeme muset více a více řešit manipulace s hlasováním. A nejde jen o útoky hackerů, ale také o možné zásahy vlád samotných. Poukazuje přitom na čerstvý případ, kdy ruští hackeři pronikli do systému DNC (Democratic National Commitee) a přes WikiLeaks vypustili tisíce interních e-mailů.
Nedostatek zkušeností, ale také povědomí
Už dříve se řešilo, že IoT si bude muset projít stejnou cestou jako každá jiná kategorie zařízení. Počítače i mobily byly před mnoha lety ve stejné situaci, do které se vzápětí dostaly webové aplikace a informační systémy vůbec. Dodnes je možné narazit na děravé weby, na absurdní začátečnické chyby, nedodržování pravidel a postupů, o kterých víme řadu let.
Počítačový i mobilní hardware i software, stejně jako internet, má dnes vybudované tolik potřebné bezpečné architektury, postupy, pravidla. Internet věcí prozatím nic takového nemá. Miniaturnost zařízení a jejich hardware, ale i rozdílné komunikační metody a protokoly, znamenají, že je vše nevyzkoušené. Stejně jako v dřívějších případech i tady navíc občas platí, že se firky snaží některé produkty uvádět na trh co nejrychleji – bez ohledu na to, zda jsou dokončené a bezpečné.
IoT je podobné BYOD, tedy situaci, kdy se do firem přinášejí vlastní zařízení a správci firemních informačních systémů a sítí si s tím moc neví rady. Stejně jako si s tím v zásadě neví rady tvůrci těchto zařízení, protože s nějakým použitím ve firemním prostředí nepočítají.
Jak asi dopadne svět, když podle Gartnerů máme už tento rok využívat 6,4 miliardy zařízení spadajících do IoT. Za další čtyři roky by to mělo být 20,8 miliardy zařízení. Řada z těchto zařízení navíc bude mít oproti běžnému životnímu cyklu mobilních telefonů, tabletů či laptopů podstatně delší životnost. Jak bude výrobce automobilů schopen chránit bezpečnost modelu z roku 2020 o deset let později? Nebo ledničky, která vám doma může stát i dobrých patnáct let? Jak dlouho trvalo, než se Microsoft naučil, jak aktualizovat vlastní operační systém?
Dokud nezemřou první lidé
„Příští prezident bude pravděpodobně nucen řešit rozsáhlé internetové neštěstí, které usmrtí řadu lidí,“ píše Schneier. Můžete si o něm sice říkat, že maluje čerty na zeď a je zbytečně negativní, ale to, co říká, je logické a odpovídá to tomu, že se dnes kdejaká hloupost stává počítačem.
To samotné by až tak velkou hrozbou nebylo, ale vzájemná propojitelnost a ovladatelnost (i na dálku) znamená, že cokoliv takového se může stát terčem útočníků. Nakonec samořiditelná auta sice určitě budou jednou běžně jezdit po silnicích, ale než k nim dojdeme, bude zde ještě mnoho případů, kdy nebude jasné, zda za smrt člověka může auto nebo člověk v něm. Nemluvě o situacích, kdy se má auto rozhodnout, koho obětovat.
Nezbytné ale bude nakonec i to, aby se do celé téhle patálie vložily vlády. Je více než jisté, že bez jasných zákonů, dohledu a tlaku se nic „samo“ nevyřeší. Výrobci IoT zařízení mají nakonec jenom stále stejnou motivaci: co nejdříve uvést na trh a co nejvíce prodat.
Remote Butler attack: APT groups’ dream come true
8.8.2016 helpnetsecurity APT
Microsoft security researchers have come up with an extension of the “Evil Maid” attack that allows attackers to bypass local Windows authentication to defeat full disk encryption: “Remote Butler”.

Evil Maid and Remote Butler attacks, illustrated (triangles are Domain Controllers)
Demonstrated at Black Hat USA 2016 by researchers Tal Be’ery and Chaim Hoch, the Remote Butler attack has one crucial improvement over Evil Maid: it can be effected by attackers who do not have physical access to the target Windows computer that has, at one time, been part of a domain, i.e. enterprise virtual network, and was authenticated to it via a domain controller.
Evil Maid attacks got the name from the fact that even a hotel maid (or someone posing as one) could execute the attack while the computer is left unattended in a hotel room.
The most recent of those was demonstrated by researcher Ian Haken at Black Hat Europe 2015, when he managed to access the target user’s data even when the disk of its computer was encrypted by BitLocker, Windows’ full disk encryption feature.
The vulnerability that allowed this attack was definitely patched by Microsoft in February 2016, and the good news is that this patch also prevents attackers from effecting a “Remote Butler” attack.
But its unlikely that everybody applied the patch.
“While being a clever attack, the physical access requirement for [Haken’s Evil Maid attack] seems to be prohibitive and would prevent it from being used on most APT campaigns. As a result, defenders might not correctly prioritize the importance of patching it,” Be’ery and Hoch explained, and urged those admins who haven’t already implemented it to do so as soon as possible.
Or, if that’s not possible, to implement some network and system hardening and defense-in-depth policy to minimize the risk of the attack being executed.
More technical details about the attack, as well as mitigation options are detailed in this whitepaper.
Cerber2 ransomware released, no decryption tool available
8.8.2016 helpnetsecurity Virus
The author of the widely distributed Cerber ransomware has released a newer version, and files encrypted with Cerber2, unfortunately, can’t be decrypted without paying the ransom.
Cerber2
Several weeks ago, Trend Micro released a tool that can be used to decrypt files encrypted by a number of popular ransomware families and versions. Among these is the first version of Cerber (with certain limitations), but also CryptXXX, BadBlock, and TeslaCrypt.
But, as a Trend Micro researcher that goes by the online handle PanicAll recently discovered, the Cerber ransomware author must have looked at the Trend Micro tool’s code and found a way to foil it.
Files encrypted by Cerber2 get the .cerber2 extension, and the malware shows a new ransom message.
The encryption method has also changed: Cerber2 now uses the Microsoft API CryptGenRandom to generate the 32-bytes-long encryption key.
Finally, the new variant also uses a packer to make malware analysis more difficult.
The Trend Micro Ransomware File Decryptor tool has been updated on Friday, but unfortunately there is no solution yet for stumping Cerber2.
Users who have been hit can back up all their encrypted files and hope that one will be provided soon.
Nová chyba Qualcommu ukazuje naplno bezpečnostní problém Androidu
8.82016 Zdroj: Živě Zranitelnosti
Proběhla bezpečnostní konference Def Con a na světě je rázem několik nově oznámených bezpečnostních problémů. Pro mobilní telefony s Androidem to jsou čtyři bezpečnostní chyby.
Problém je konkrétně v ovladačích Qualcommu, které do mobilního telefonu instaluje výrobce. Tři ze čtyř chyb již mají dostupné opravy a čtvrtá bude brzy následovat. Chyba umožňuje bez upozornění systémem získat větší práva na Androidu 6 a dřívějším. V lepším případě to pomůže k dobrovolnému rootu telefonu, v tom horším získá podvodná aplikace kompletní přístup k vašim datům a nic se nedozvíte.
Když uvidíte obrázek vlevo, máte problém. Pravý uvidíte s procesory Mediatek, Kirin, Exynos a dalšími
V současnosti jsou opravené akorát telefony Nexus 5X, 6 a 6P. Ostatní stále čekají na opravu od výrobce. Každý telefon s procesorem Snapdragon potřebuje opravu. Zda jste postižení, můžete zkontrolovat nástrojem QuadRooter Scanner od tvůrce antivirů Check Point Software.
Bezpečnostní aktualizace pro telefony ale vydává jen velmi málo výrobců. Google se to snaží sice zjednodušit oddělením záplat od větších aktualizací systému, vždy je ale nutná aktivita ze strany výrobce mobilního telefonu. Pokud pro něj zájem o bezpečnost uživatelů končí v okamžiku prodeje telefonu, hrozí tu milióny telefonů se známými, dobře zdokumentovanými, ale neopravenými chybami.
Pokud bude váš telefon zranitelný, měli byste se vyvarovat instalacím aplikací z neznámých zdrojů. Paradoxně může pomoci root telefonu. Pak bude mít uživatel opravdu kompletní kontrolu nad telefonem. Pro neznalého uživatele je ale pochopitelně případný root telefonu spojený s mnoha dalšími bezpečnostními riziky.
Microsoft má problém, uživatelům zamrzá Windows 10 po instalaci Anniversary update
8.82016 Zdroj: Živě Hrozby
po instalaci výroční aktualizace některým uživatelům zamrzne systém
Závažná chyba znemožní další práci, její odstranění zpravidla obnáší přeinstalování systému nebo návrat na předchozí sestavení
Microsoft má problém, uživatelům zamrzá Windows 10 po instalaci Anniversary update
Microsoft uvolnil výroční aktualizaci Anniversary Update teprve minulý týden a postupně ji distribuuje mezi další uživatele. Podobně jako každý větší update však i tento letní přinesl části uživatelů také velké starosti – systém jim totiž konstantě zamrzá.
Na problém upozornil web Neowin, který čerpá z dlouhého vlákna na Redditu. V tom se sešlo několik stovek komentářů od uživatelů, kterým systém zamrzne ihned po startu či krátce po něm. Aplikace často zobrazí svoje okna, nicméně zůstávají ve stále stejném nečinném stavu. Následně dojde k jejich zčernání a chybové hlášce, že Windows přestal pracovat.
Ačkoliv se ve vláknu objevilo několik možných řešení, ani jedno z nich se nezdá být univerzálním. Někteří z uživatelů vyřešili problém odpojením druhého disku, přeinstalací systému z obrazu ISO, objevil se také krátký návod na úpravu registrů, která může pomoci. U každého řešení však velký počet diskutérů píše, že na situaci nic nezměnilo.
Chyba se objevuje u uživatelů s mnoha různými konfiguracemi – bez ohledu na to, zda se jedná o desktop či notebook a nezáleží ani na konfiguraci samotných komponent. Na fóru Microsoftu pak najdeme popsaný stejný problém, zatím zde však objevíme pouze reakci jednoho ze zaměstnanců podpory v podobě univerzální odpovědi.
Pokud se setkáte s podobným problémem, pak je zatím jediné možné řešení – návrat ke staršímu buildu.
Google: Adware napadá miliony zařízení a poškozuje inzerenty, weby i uživatele
8.8.2016 Mobilní
S pochybnými společnostmi produkujícími podvodné pluginy i aplikace navíc spolupracují i firmy jako Opera, Skype či Yahoo.
Amonetize, InstallMonetizer, OpenCandy a Outbrowse jsou čtyři jména velkých firem, které se specializují na „placení za instalaci“ (PPI, pay per install). Projevují se záplavou aktivit vedoucích k instalaci add-onů či dalšího nechtěného softwaru, který (v tom nejméně škodlivém případě) v tichosti a bez vědomí uživatelů vyměňuje reklamy ve webových stránkách, případně je vkládá tam, kde žádné reklamy na webu nejsou.
V průběhu ročního výzkumu (PDF) Google zjistil, že tyto podvodné aktivity vedly k více než třem miliardám pokusů o stažení a následným desítkám milionů instalací. Nutno dodat, že nechtěných instalací, tedy takových, které uživatel nejen nechtěl, ale ani neschválil. Vedle manipulace s inzercí se adware pokouší i o manipulaci s výsledky vyhledávání nebo sledování chování uživatelů. Ve všech případech jsou tyto aktivity monetizovány.
Ze čtyř výše jmenovaných příkladů už dnes nenajdete InstallMonetizer, který ukončil činnost (ale nepochybně se brzy někde objeví pod jiným jménem), a Outbrowse má momentálně nedostupný web. Další stále fungují. 
Některé z dalších ani nijak neskrývají to, že jejich software zasahuje do prohlížečů uživatelů. A chlubí se až zázračnou mírou konverze 95 % (což je vcelku logické, pokud instalují automaticky bez vědomí uživatele).
Co na tom, že ve Wikipedii i na stovkách dalších míst je najdete jasně zařazené mezi malware (viz například adware od Amonetize, malware od OpenCandy, shrnutí o InstallMonetizer na HackerNews) a Google je zaplaven návody, jak tyhle nechtěné věci dostávat z počítačů. Sám Google také při hledání na OpenCandy přímo zobrazí rámeček s upozorněním na to, že OpenCandy je řazeno mezi malware.
Celý model PPI je postaven na tom, že ti, kdo tyto služby nabízejí, neberou žádné ohledy na to, jestli uživatel něco chce instalovat. Za každou instalaci dostávají až 1,50 USD, je tedy více než jisté, že podvodné a automatické instalace jsou zásadním prvkem jejich „obchodního modelu“.
Velmi často se s adwarem a malwarem tohoto typu setkáte v instalačních programech, kde si buď nevšimnete nenápadného varování, nebo žádné varování nedostanete. A zároveň s instalací softwaru, který chcete, se do počítače dostane něco, co nechcete.
Alarmující na analýze od Googlu je, že zjistili využití těchto způsobů šíření softwaru u firem jako je Opera, Skype a Yahoo. Prvně jmenovaná společnost využívala služeb všech čtyř výše uvedených služeb, Skype aktivně využíval OpenCandy a Yahoo služeb Outbrowse, které používaly k instalaci jejich vyhledávání do prohlížečů uživatelů.
Ve spojitosti s výše uvedenou čtveřicí šiřitelů malwaru a adwaru navíc zjistíte, že řada z nich byla klasickými startupy, které se těšily mimořádné pozornosti a obdivu médií. Bez ohledu na to, že miliony uživatelů se marně snažily jejich software dostat z počítačů a nikdo z nich si nelámal hlavu s tím, co vlastně do počítačů napadených jejich softwarem dodávají.
Warning! Over 900 Million Android Phones Vulnerable to New 'QuadRooter' Attack
8.8.2016 Android
Android has Fallen! Yet another set of Android security vulnerabilities has been discovered in Qualcomm chipsets that affect more than 900 Million Android smartphones and tablets worldwide.
What's even worse: Most of those affected Android devices will probably never be patched.
Dubbed "Quadrooter," the set of four vulnerabilities discovered in devices running Android Marshmallow and earlier that ship with Qualcomm chip could allow an attacker to gain root-level access to any Qualcomm device.
The chip, according to the latest statistics, is found in more than 900 Million Android tablets and smartphones.
That's a very big number.
The vulnerabilities have been disclosed by a team of Check Point researchers at the DEF CON 24 security conference in Las Vegas.
Critical Quadrooter Vulnerabilities:
The four security vulnerabilities are:
CVE-2016-2503 discovered in Qualcomm's GPU driver and fixed in Google's Android Security Bulletin for July 2016.
CVE-2016-2504 found in Qualcomm GPU driver and fixed in Google's Android Security Bulletin for August 2016.
CVE-2016-2059 found in Qualcomm kernel module and fixed in April, though patch status is unknown.
CVE-2016-5340 presented in Qualcomm GPU driver and fixed, but patch status unknown.
Qualcomm is the world's leading designer of LTE (Long Term Evolution) chipsets with a 65% share of the LTE modem baseband market. If any one of the four flaws is exploited, an attacker can trigger privilege escalations for gaining root access to an affected device.
All an attacker needs is to write a piece of malware and send it to the victim. When installed, the malware offers the attacker privilege escalation on the affected devices.
According to the researchers, the attack can also be conducted through a malicious app. An attacker needs to trick a user into installing a malicious app that, unlike other malware, would execute without requiring any special permission checks.
"Such an app would require no special permissions to take advantage of these vulnerabilities, alleviating any suspicion users may have when installing," Check Point researchers write in a blog post.
If any of the four vulnerabilities are successfully exploited, an attacker could gain root access to an affected device, giving the attacker full access to the device, including its data, camera and microphone.
List of Affected Devices (Popular)
More than 900 Million Android devices that ship with Qualcomm chip are vulnerable to the flaws.
Here's the list of some of the popular affected devices, though there are far more devices that are impacted by one or more Quadrooter vulnerabilities.
Samsung Galaxy S7 and Samsung S7 Edge
Sony Xperia Z Ultra
OnePlus One, OnePlus 2 and OnePlus 3
Google Nexus 5X, Nexus 6 and Nexus 6P
Blackphone 1 and Blackphone 2
HTC One, HTC M9 and HTC 10
LG G4, LG G5, and LG V10
New Moto X by Motorola
BlackBerry Priv
How to Check if Your Device is Vulnerable?
You can check if your smartphone or tablet is vulnerable to Quadrooter attack using Check Point's free app.
Since the vulnerable software drivers, which control communication between Qualcomm chipset components, come pre-installed on these devices at the time of manufacturing, they can only be fixed by installing a patch from the devices' distributors or carriers after receiving fixed driver packs from Qualcomm.
"This situation highlights the inherent risks in the Android security model," the researchers say. "Critical security updates must pass through the entire supply chain before they can be made available to end users."
Three of the four vulnerabilities have already been fixed in Google's latest set of monthly security updates, and a patch for the remaining flaw will be rolled out in the upcoming September update.
Since Qualcomm has already released the code, the phone manufacturers could be able to issue patches to the individual devices as soon as possible.
Android Nexus devices are already patched via the over-the-air updates, but other smartphone models will need to wait until their lazy phone manufacturers integrate the fixes into their own custom Android ROMs.
Analyzing CIA Director BRENNAN’s talk at Council on Foreign Relations (CFR)
5.8.2016 securityaffeirs Security
We bring to the attention of the Security Affairs readers the interesting speech and interview dated 29/06/2016 of CIA Director John O. BRENNAN at the Council on Foreign Relations (CFR). The main themes addressed are:
Relations with the European partners in the USA and after BREXIT-axis ENGLAND
Terrorism, DAESH, the situation in Syria and Iraq
CYBERSECURITY
Geoengineering and SAI program
Cia Director BRENNAN email hacked
Brennan interviewed by journalist Judy Woodruff of the PBS “NewsHour” has pointed out that Europe must forge better than the request for a referendum by the Eurosceptics after the UK exit. The Brexit, however, will not affect the collaboration of intelligence between the US and the UK in the months and years to come, rather it will be strengthened. The effects of global instability and conflict scenarios are producing movements of displaced persons of the order of 65 million units.
In the Middle East, the geographic borders and national identities are constantly being redefined. The real threat of the ISIL than Al-Qaeda is that it has gone from a few hundred fighters to tens of thousands also improved their ability to conceal their communications.
As for the environment, Brennan estimates that $ 10 billion a year for the next government intervention limiting SAI programs of global warming or sowing methods with stratospheric particles that can help reflect the sun’s heat more or less in the same way in which volcanic eruptions do.
With respect to this last issue, there are questions with concern if behind these operations do not conceal stratosphere military domain. Global warming and the reduction of CO2 could be addressed without introducing potentially harmful elements as in the example of volcanic eruptions but more simply and at lower cost with the repopulation of the great forests.
Another concern for Brennan is the North Korea and the nuclear threat from Kim Jung with its continuous and frantic search of military capabilities in the nuclear field. We come now to the point that concerns us more closely, or the threat cyber, on this issue there is strong concern as to the public and private companies attacks are still rising and are becoming more sophisticated; here is the thought and words of Brennan:
Regarding the domain of Cyber threat here is the thought and words of Brennan:
“Another strategic challenge is dealing with the tremendous power, potential, opportunities, and risks resident in the digital domain. No matter how many geopolitical crises one sees in the headlines, the reliability, security, vulnerability, and the range of human activity taking place within cyberspace are constantly on my mind.
On the cybersecurity front, organizations of all kinds are under constant attack from a range of actors—foreign governments, criminal gangs, extremist groups, cyber-activists, and many others. In this new and relatively uncharted frontier, speed and agility are king. Malicious actors have shown that they can penetrate a network and withdraw in very short order, plundering systems without anyone knowing they were there until maybe after the damage is already done.
While I served at the White House, cyber was part of my portfolio, and it was always the subject that gave me the biggest headache. Cyber-attackers are determined and adaptive. They often collaborate and share expertise, and they come at you in so many different ways, with an ever-changing array of tools, tactics, and techniques.
Moreover, our laws have not yet adequately adapted to the emergence of this new digital frontier. Most worrisome from my perspective is that there is still no political or national consensus on the appropriate role of the government—law enforcement, homeland security, and intelligence agencies—in safeguarding the security, the reliability, the resiliency, and the prosperity of the digital domain.
The intelligence community is making great strides in countering cyber-threats, but much work needs to be done. As we move forward on this issue, one thing we know is that private industry will have a huge role to play as the vast majority of the Internet is in private hands. Protecting it is not something the government can do on its own.
Right up there with terrorism, global instability, and cybersecurity is nuclear proliferation and the accompanying development of delivery systems, both tactical and strategic, that make all too real the potential for a nuclear event.
Unsurprisingly, top of my list of countries of concern is North Korea, whose authoritarian and brutal leader has wantonly pursued a nuclear-weapons program to threaten regional states and the United States instead of taking care of the impoverished and politically repressed men, women, and children of North Korea.
So what else is there besides terrorism, global instability, cybersecurity, and nuclear proliferation that worries the CIA director and keeps CIA officers busy around the clock and around the globe? Well, as a liberal-arts guy from the baby-boomer generation, the rapid pace of technological change during my lifetime has been simply dizzying. Moreover, as we have seen with just about every scientific leap forward, new technologies often carry substantial risks, to the same degree that they hold tremendous promise…”
This ATM Hack Allows Crooks to Steal Money From Chip-and-Pin Cards
5.8.2016 thehackernews Hacking
Forget about security! It turns out that the Chip-and-PIN cards are just as easy to clone as magnetic stripe cards.
It took researchers just a simple chip and pin hack to withdraw up to $50,000 in cash from an ATM in America in under 15 minutes.
We have been told that EMV (Europay, MasterCard and Visa) chip-equipped cards provides an extra layer of security which makes these cards more secure and harder to clone than the old magnetic stripe cards.
But, it turns out to be just a myth.
A team of security engineers from Rapid7 at Black Hat USA 2016 conference in Las Vegas demonstrated how a small and simple modifications to equipment would be enough for attackers to bypass the Chip-and-PIN protections and enable unauthorized transactions.
The demonstration was part of their presentation titled, "Hacking Next-Gen ATMs: From Capture to Washout," [PDF]. The team of researchers was able to show the audience an ATM spitting out hundreds of dollars in cash.
Here's How the Hack Work
The hack requires two processes to be performed.
First, the criminals need to add a small device known as a Shimmer to a point-of-sale (POS) machine (here, ATM's card reader) in order to pull off a man-in-the-middle (MITM) attack against an ATM.
The shimmer sits between the victim's chip and the card reader in the ATM and can record the data on the chip, including PIN, as the ATM reads it. It then transmits this data to the criminals.
The criminals then use a smartphone to download this stolen data and recreate the victim's card in an ATM, instructing it to eject cash constantly.
Tod Beardsley, a security research manager for Rapid7, told the BBC that shimmer is basically a tiny RaspBerry-Pi-powered device that could be installed quickly to the outside of the ATM without access to the internals of the cash machine.
"It's really just a card that is capable of impersonating a chip," Beardsley said. "It's not cloning."
The perpetrators would only be able to replicate each card for a few minutes and use it to fraudulently withdraw money, enabling them to make between up to $50,000, but Beardsley suggests that a network of hacked chip-and-pin machines could create a constant stream of victims.
Researchers have disclosed full details about the issue in Chip-and-PIN ATMs to banks and major ATM manufacturers and said they hope the institutions (currently unnamed) are examining the issue.
Torrentz.eu Shuts Down Forever! End of Biggest Torrent Search Engine
5.8.2016 thehackernews Security
Over two weeks after the shutdown of Kickass Torrents and arrest of its admin in Poland, the world's biggest BitTorrent meta-search engine Torrentz.eu has apparently shut down its operation.
The surprise shutdown of Torrentz marks the end of an era.
Torrentz.eu was a free, fast and powerful meta-search engine that hosted no torrents of its own, but combined results from dozens of other torrent search engine sites including The Pirate Bay, Kickass Torrents and ExtraTorrent.
The meta-search engine has announced "farewell" to its millions of torrent users without much fanfare, suddenly ceasing its operation and disabling its search functionality.
At the time of writing, the Torrentz.eu Web page is displaying a message that reads in the past tense:
"Torrentz was a free, fast and powerful meta-search engine combining results from dozens of search engines."
When try to run any search or click any link on the site, the search engine refuses to show any search result, instead displays a message that reads:
"Torrentz will always love you. Farewell."
Launched back in 2003, Torrentz has entertained the torrent community for more than 13 years with millions of visitors per day.
However, today, the popular meta-search engine has shut down its operation from all Torrentz domains, including the main .EU domain (both HTTP and HTTPS version) as well as other backups such as .ME, .CH, and .IN.
Although many copyright holders were not happy with the site with both RIAA and MPAA have reported the site to the U.S. Government in recent years, says TorrentFreak, there is no news of any arrest or legal takedown of the site in this case.
Still, it would be fair enough to wait for an official announcement from the site owners.
Hack Apple & Get Paid up to $200,000 Bug Bounty Reward
5.8.2016 thehackernews Apple
So finally, Apple will pay you for your efforts of finding bugs in its products.
While major technology companies, including Microsoft, Facebook and Google, have launched bug bounty programs over last few years to reward researchers and hackers who report vulnerabilities in their products, Apple remained a holdout.
But, not now.
On Thursday, Apple announced at the Black Hat security conference that the company would be launching a bug bounty program starting this fall to pay outside security researchers and white hat hackers privately disclose security flaws in the company's products.
How much is a vulnerability in Apple software worth? Any Guesses?
It's up to $200,000.
Head of Apple security team, Ivan Krstic, said the company plans to offer rewards of up to $200,000 (£152,433) to researchers who report critical security vulnerabilities in certain Apple software.
While that's certainly a sizable bounty reward — one of the highest rewards offered in corporate bug bounty programs.
Apple Bug Bounty Program — Invite Only, For Now
Well, for now, Apple is intentionally keeping the scope of its bug bounty program small by launching the program as invitation-only that will be open only to limited security researchers who have previously made valuable bug disclosures to Apple.
The company will slowly expand the bug bounty program.
Launching in September, the program will offer bounties for a small range of iOS and iCloud flaws.
Here's the full list of risk and reward:
Flaws in secure boot firmware components: Up to $200,000.
Flaws that could allow extraction of confidential data protected by the Secure Enclave: Up to $100,000.
Vulnerabilities that allow executions of malicious or arbitrary code with kernel privileges: Up to $50,000.
Flaws that grant unauthorized access to iCloud account data on Apple servers (remember celebrity photo leak?): Up to $50,000.
Access from a sandboxed process to user data outside of that sandbox: Up to $25,000.
For the eligibility of a reward, researchers will need to provide a proof-of-concept (POC) on the latest iOS and hardware with the clarity of the bug report, the novelty of the bounty problem and the possibility of user exposure, and the degree of user interaction necessary to exploit the flaw.
Decision Comes in the Wake of the FBI Scandal
Earlier this year, Apple fought a much-publicized battle with the FBI over a court order to access the locked San Bernardino shooter's iPhone.
When the FBI forced Apple to unlock the shooter's iPhone, it refused, eventually making the bureau hire professional hackers to break into the iPhone -- supposedly paying out over $1 Million.
Perhaps the company is trying to eliminate these lucrative backdoors into its software to make its iOS devices so secure that even the company can not crack them.
Největší internetové hrozby letošního léta
5.8.2016 Zdroj: Novinky/Bezpečnost Viry
Hned před několika různými škodlivými kódy by se měli mít na pozoru tuzemští uživatelé. Podle analýzy společnosti Eset se nezvaní návštěvníci šíří především prostřednictvím souborů v nevyžádaných e-mailech – to je případ i škodlivého kódu JS/Danger.ScriptAttachment, který je aktuálně nejrozšířenější internetovou hrozbou.
Ještě v červnu stál malware JS/Danger.ScriptAttachment za čtvrtinou všech odhalených útoků. V červenci to však bylo už více než 45 procent. Jde tedy o téměř dvojnásobný meziměsíční nárůst.
„Škodlivý kód JS/Danger.ScriptAttachment je zákeřný především v tom, že nemusí škodit sám o sobě, ale může do napadeného zařízení stáhnout další druhy malwaru. Nejčastěji jde o ransomware, který zařízení zašifruje a za jeho opětovné zpřístupnění požaduje po oběti výkupné,“ vysvětlil Miroslav Dvořák, technický ředitel společnosti Eset.
Ransomware je souhrnný název pro rodinu vyděračských virů, jako jsou například známí záškodníci TeslaCrypt či Locky. Tyto škodlivé kódy začnou šifrovat obsah počítače a uživateli zobrazí oznámení, že za dešifrování počítače musí zaplatit, jinak se ke svým datům údajně již nikdy nedostane.
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat. V některých případech to ale není možné.
Pozor na bankovní účty
Druhým nejrozšířenějším škodlivým kódem se stal Java/Adwind, přestože jeho podíl byl výrazně nižší – 3,23 procenta. V počítači dovede tento škodlivý kód napáchat velkou neplechu. Otevírá totiž útočníkům zadní vrátka do počítače, prostřednictvím kterých se pak kyberzločinci snaží vysát lidem bankovní účet.
Vrásky na čele dělá bezpečnostním expertům také škodlivý kód Nemucod, který ještě v květnu představoval druhou nejrozšířenější hrozbu. Aktuálně mu díky podílu 3,16 % však patří až třetí příčka.
Nemucod útočí prakticky úplně stejně jako JS/Danger.ScriptAttachment. Uhnízdí se tedy v počítači a může potom stahovat další nezvané návštěvníky.
10 nejrozšířenějších počítačových hrozeb – červenec 2016
1. JS/Danger.ScriptAttachment (45,46 %)
2. Java/Adwind (3,23 %)
3. JS/TrojanDownloader.Nemucod (3,16 %)
4. VBA/TrojanDownloader.Agent.BJL (3,06 %)
5. VBA/TrojanDownloader.Agent.BJQ (2,81 %)
6. VBA/TrojanDownloader.Agent.BKP (2,72 %)
7. VBA/TrojanDownloader.Agent.BJG (2,71 %)
8. VBA/TrojanDownloader.Agent.BJC (1,99 %)
9. VBA/TrojanDownloader.Agent.BJU (1,98 %)
10. VBA/TrojanDownloader.Agent.BKW (1,98 %)
Zdroj: Eset