
Safety Articles - H 2020 1 2 3 4 5 6 Safety List - H 2021 2020 2019 2018 1 Safety blog Safety blog
F-Secure Looks to Address Cyber Security Risks in Aviation Industry
19.3.2018 securityweek Safety

Aviation, as part of the transportation sector, falls within the critical infrastructure. While it may not have the same security issues as ICS/SCADA-based manufacturing and utilities, it has certain conceptual similarities; including, for example, a vital operational technology infrastructure with increasing internet connectivity, and the associated cyber risks.
It also has one major difference -- the close physical proximity of its own customers. Catastrophic failure in the aviation industry has a more immediate and dramatic effect on customers -- and for this reason alone, a trusted brand image is an essential and fragile part of success in the aviation industry. Without customer trust, customers will not fly with a particular airline.
Historically, aviation security has primarily focused on physical safety, and has become highly efficient in this area. But in recent years, the customization of new aircraft to provide newer and unique passenger experiences -- such as the latest in internet-connected in-flight entertainment systems -- has added a new cyber risk.
Matthieu Gualino, deputy director of the International Civil Aviation Organization Aviation Security Training Center, described the three current areas of cyber risk as flight control (the critical systems needed to fly the aircraft -- high impact, low likelihood); the operational cabin (systems used to operate and maintain aircraft -- medium impact, medium likelihood); and passengers (systems with direct passenger interaction -- low impact, high likelihood).
The problem today is that aviation security is experienced in operational technology, security and safety; but less experienced in the rapidly evolving world of cyber security. To help counter this risk, Finland's F-Secure has launched its new Aviation Cyber Security Services to help secure not just aircraft, but the entire aviation industry: aircraft, infrastructure, data, and -- most importantly to F-Secure -- reputation. Customers are unlikely to fly with companies they do not trust; and successful cyber-attacks rapidly eliminate customer trust and confidence; even, suggests F-Secure, a minor breach of something like an in-flight entertainment system.
"Off-the-shelf communication technologies are finding their way into aircraft, which makes security much more complicated than in the past," said Hugo Teso, head of aviation cybersecurity services at F-Secure and a former pilot. "Because these off-the-shelf technologies weren't necessarily created to meet the rigorous safety requirements of airlines, the aviation industry is making cyber security a top priority. But they need a partner that understands both cyber security and the details of airline operations, because it's an industry where those details make a big difference."
The new service integrates security assessments of avionics, ground systems and data links, vulnerability scanners, security monitoring, incident response services, and specialized cyber security training for staff.
The primary problem is not unknown to the security industry -- the need to protect safety-critical systems from less significant but more exposed and vulnerable systems (such as those with an internet connection). "A key protection measure is separating systems into different 'trust domains'," explains F-Secure's head of Hardware Security Andrea Barisani, "and then controlling how systems in different domains can interact with one another. This prevents security issues in one domain, like a Wi-Fi service accessible to passengers, from affecting safety-critical systems, like aircraft controls or air to ground datalinks."
Data diodes are typically used for this type of system segmentation, because they provide unidirectional data flows where complete bidirectional isolation is not possible. "It is essential for any data diode to be implemented in a manner that allows no attack, parsing errors or ambiguities, failures to affect their correct operation," Barisani told SecurityWeek. "Our team is routinely involved in testing data diode security to provide assurance on their operation, improve their design and fix any issues well before their certification."
Diodes are part of the separation of the vulnerable passenger facilities from the critical flight operations. "In-flight entertainment and connectivity (IFE/IFC) are two of the most exposed systems in modern aircraft," explained Teso. "Facing directly the passengers, those systems are a major cyber security concern to any operator as any incident would have important brand damage for them. Not to safety though. Due to the way aircraft are designed, built and upgraded any incident involving or originating in the cabin of the airplane will be isolated from the most critical, and safety related, systems."
F-Secure is keen not to promote its new service with the 'fear factor'. The aviation industry already does an excellent job at maintaining the safety of its flights. The new cyber risk is currently primarily against aviation's brand reputation, and the threat of a cyber hijack taking over an aircraft in flight, is, suggests Teso, more likely in the movies than in reality.
But that doesn't mean it can be dismissed or forever ignored, or even limited to civil aviation. The aviation industry, including both civil and military aircraft, shares a common core of technologies, although the threat model differs between the two. Nevertheless, commented Teso, "F-Secure aviation cyber security services is not limited to any specific part of the aviation industry. If it's part of Aviation, our services have it covered."
Firefox 63 to Distrust All Symantec Root Certificates
13.3.2018 securityweek Safety
Mozilla this week detailed its plans to completely distrust Symantec root certificates in Firefox 63, set to arrive in October 2018.
Over the past couple of years, numerous problems have emerged regarding the wrongful issuance of certificates issued by the Certification Authority (CA) run by Symantec, one of the oldest and largest CAs.
These issues prompted Internet companies such as Google and Mozilla to gradually remove trust in all Symantec TLS/SSL certificates and also resulted in Symantec selling its CA business to DigiCert.
Mozilla expressed concerns that the deal wouldn’t bring the expected changes, as the same Symantec team would be in charge of certificate issuance for DigiCert. The CA, however, said it would validate all certificates requested through Symantec and issue them through its own infrastructure.
The Symantec certificates snafu resulted in browser vendors gradually removing trust in TLS/SSL certificates issued by the company, even after the announced DigiCert acquisition. Trust in older certificates will be removed first.
For Mozilla, this will happen in May 2018, when Firefox 60 will display an untrusted connection warning for websites using certificate issued before 2016-06-01 that chain up to a Symantec root certificate.
Starting in January 2018, Firefox 58 has been displaying notices in the Browser Console to warn about the Symantec certificates issued before 2016-06-01, to encourage site owners to replace their TLS certificates. In October 2018, Firefox 63 will distrust all Symantec root certificates for website server TLS authentication.
“Firefox 60 is expected to enter Beta on March 13th carrying with it the removal of trust for Symantec certificates issued prior to June 1st, 2016, with the exception of certificates issued by a few subordinate CAs that are controlled by Apple and Google,” Mozilla now says.
All Symantec brands will be affected by this move, including GeoTrust, RapidSSL, Thawte, and VeriSign. Mozilla has already made the change in Firefox Nightly.
The browser vendor also points out that numerous websites (roughly 1% of the top one million) continue to use TLS certificates no longer trusted in Firefox 60, although their number has been declining steadily. Thus, website operators are encouraged to replace the untrusted certificates as soon as possible, to avoid any disruptions.
“In Firefox 63, trust will be removed for all Symantec TLS certificates regardless of the date issued (with the exception of certificates issued by Apple and Google subordinate CAs as described above),” Mozilla concluded.
Funny? Useful? Cool? Kali Linux natively on Windows 10
7.3.2018 securityaffairs Safety
It’s funny, but it is true, the popular Kali Linux hacking distro is available for download on the official Microsoft App Store on Windows 10.
Kali Linux is now natively available on Windows 10, without requiring dual boot or virtualization.
Kali Linux isn’t the unique Linux distribution available on the Windows App Store, Windows users can download other popular distros, including as Ubuntu, Fedora, and OpenSUSE.
The Linux distribution can be used directly on Windows by exploiting the feature called Windows Subsystem for Linux (WSL)
“For the past few weeks, we’ve been working with the Microsoft WSL team to get Kali Linux introduced into the Microsoft App Store as an official WSL distribution, and today we’re happy to announce the availability of the ‘Kali Linux’ Windows application,” reads the announcement published on the Kali Linux website.
“For Windows 10 users, this means you can simply enable WSL, search for Kali in the Windows store, and install it with a single click. This is especially exciting news for penetration testers and security professionals who have limited toolsets due to enterprise compliance standards.”
To enable the WSL follow these steps:
Access the “Apps and features” menù item under the Control Panel
Select “Programs and Features” from the right panel
Click the “Turn Windows features on or off” from the left menu
Check the “Windows Subsystem for Linux”
Save the operation and Reboot the system
Alternatively, users can open PowerShell as Administrator and run the following command before restarting the machine.
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux
At this point, you can search for Kali Linux on Windows Store and download it.
Offensive Security has published a video to show how to use the distribution on Windows 10.
It is important to remind that the Kali Linux on Windows does not come with any hacking testing tools pre-installed, this means that you need to download them when needed.
Experts noticed that Antivirus software, including Windows Defender, can flag the distro’s packages as a malware.
Paypal issue allows disclosure of account balance and recent transactions
24.2.2018 securityaffairs Safety
Paypal issue allows for enumeration of the last four digits of payment method and for the disclosure of account balance and recent transactions of any given PayPal account.
Introduction
This post details an issue which allows for enumeration of the last four digits of payment method (such as a credit or debit card) and for the disclosure of account balance and recent transactions of any given PayPal account.
This attack was submitted to PayPal’s bug bounty program where it was classified as being out of scope, which is something that would admittedly be unavailing to refute since their program scope does not mention anything about attacks on their interactive voice response system.

Prerequisites and Reconnaissance
In order to get started, the attacker would require knowledge of two pieces of information pertaining to an account, which would be the e-mail address and phone number linked to it.
Armed with knowledge of the e-mail address and phone number linked to an account, the attacker would visit the Forgot Password page on PayPal’s website, and enter the e-mail address associated with the targeted account.
The attacker would then be presented with the type of card linked to the account, as well as the last two digits of the same.

Attacking the Interactive Voice Response System
On first glance, the interactive voice response system on PayPal’s phone-based customer support seemingly allows for a maximum of three attempts at submitting the correct last four digits per phone call.
However, if the first attempt at submission is incorrect, the caller will not be notified of a successful submission in subsequent attempts made during the same phone call. This makes any additional attempts given to a caller during the same phone call completely cosmetic.
To get around this presumed limitation, the attacker would have to make only one attempt at submitting a possible combination of the last four digits per phone call.

Additionally, limiting the number of attempts to one submission per phone call makes the task of enumerating the correct combination much more time-efficient, and not to mention, it allows for easily distinguishing between a correct attempt and an incorrect one.
Furthermore, upon have tested this theory with my own account, I have been able to conclude that there is no limit on the number of submission attempts which can be made in this manner, meaning that hypothetically, an attacker could call 100,000 times to enumerate the last four digits entirely on their own.
That would, however, be disregarding the last two digits retrieved from the Forgot Password page, the knowledge of which effectively makes the attack much more feasible–by reducing the number of possible combinations from 100,000 to just 100.
Once the correct combination of the last four digits has been found, the attacker would simply have to use the interactive voice response system to retrieve information about the account.
After having entered the correct last four digits, the account’s current balance will automatically read off by the machine.
Additionally, to retrieve information about recent transactions, an attacker would simply have to say “recent transactions”, and the same would then be read off.
Attack Efficacy and Efficiency
If the aforementioned prerequisites have been met, an attacker would without fail have the ability to enumerate the correct last four digits of the payment method linked to an account. This information could then further be used to retrieve the account’s current balance and recent transactions as well.
Moreover, after having timed various attempts at submission of the last four digits, it was found that an attempt at submission would on average take around 30 seconds. The fastest possible time would be 27 seconds per phone call.
If we take the fastest possible time as our average, enumerating all possible combinations from 00XX to 99XX would take at most around 45 minutes. This time could then be halved by adding another phone in the mix to consecutively make calls with.
Possible Fixes
Users should be allowed to opt for privacy settings which keep the amount of data revealed on the Forgot Password page to a minimum. This would be similar to how Twitter allows its users to hide information about the email address and/or phone number linked to their account when attempting to reset its password.
It would also be similar to how Facebook allows users to choose whether their full names show up or not when their e-mail address is entered on the password reset page.
Perhaps some measures could be deployed where the last two digits of credit or debit card, if they need to be shown at all, are only shown when the request matches a certain criteria, such as if/when the request has been made from a recognizable device or location.
Conclusion
This issue allows for enumeration of the last four digits of the payment method on an account, which then allows for the disclosure of the account’s current balance and recent transactions.
An attacker with knowledge of the targeted account’s email address and phone number would first use PayPal’s Forgot Password page to retrieve the last two digits of the payment method linked to the account.
The attacker would then be able to accurately enumerate the last four–or rather the first two of the last four digits–of the payment method on the account by making phone calls to PayPal’s phone-based customer support and interacting with the interactive voice response system.
Once the attacker has successfully enumerated the last four digits of credit/debit card or bank account linked to the account, they would then be able to query the current account balance and recent transaction information at will.
Lastly, I would like to note that since there is no human interaction required or involved in the attack, it would essentially be a backdoor into PayPal accounts–allowing attackers to query current account balance and recent transaction information of any given account, at any time.
GitHub Enforces Stronger Encryption
23.2.2018 securityweek Safety
GitHub this week permanently disabled a series of weak cryptographic standards across its software development platform in an attempt to better protect users.
As of Feb. 22, 2018, the TLSv1/TLSv1.1 standard is no longer used on HTTPS connections to GitHub. The change affects all web, API, and git connections to https://github.com and https://api.github.com, Patrick Toomey, Application Security Engineer, GitHub, says.
The platform also retired the diffie-hellman-group1-sha1 and diffie-hellman-group14-sha1 encryption standards, a move that affects all SSH connections to github.com. This change follows the enabling of the diffie-hellman-group-exchange-sha256 standard on GitHub in September 2017.
The removal of these weak cryptographic standards was initially announced last year, and GitHub has since focused on ensuring that the change won’t have a major impact on its users. At the moment, only a small fraction of traffic uses the deprecated algorithms and clients are expected to automatically transition to the new ones, but some clients are expected to be impacted.
These include older systems that, although no longer maintained, continue to access Git/the GitHub API using the deprecated algorithms. To help mitigate this, the platform disabled support for the old algorithms for one hour on February 8, 2018. This provided a two week grace period for impacted systems to be upgraded.
“As noted above, the vast majority of traffic should be unaffected by this change. However, there are a few remaining clients that we anticipate will be affected. Fortunately, the majority of clients can be updated to work with TLSv1.2,” Toomey notes.
Impacted clients include Git Credential Manager for Windows prior to version 1.14.0, Git clients that shipped with Red Hat 5, 6, and 7 (updating to versions 6.8 and 7.2 or greater should resolve this), JDK releases prior to JDK 8, and Visual Studio (which ships with specific versions of Git for Windows and the Git Credential Manager for Windows).
Newer versions of these programs, however, include support for TLSv1.2 and updating ensures that clients continue to work properly with GitHub even after the deprecation.
Palo Alto Networks Releases New Rugged Firewall
21.2.2018 securityweek Safety
Palo Alto Networks on Tuesday announced that it has updated its PAN-OS operating system and released a new next-generation firewall designed for use in industrial and other harsh environments.
The new PA-220R is a ruggedized NGFW that can be used by various types of organizations, including power plants, utility substations, oil and gas facilities, manufacturing plants, and healthcare organizations. During beta testing, the product was also used for railway systems, defense infrastructure, and even amusement parks.
Palo Alto Networks PA-220R rugged firewall
The PA-220R is designed to withstand extreme temperatures, vibration, humidity, dust, and electromagnetic interference.
Palo Alto Networks said the product works with various industrial applications and protocols, including OSIsoft PI, Siemens S7, Modbus, DNP3, and IEC 60870-5-104.
“For early-engagement customers and many of our expected users of the PA-220R, the situation is that they have industrial assets in harsh environments that have been modernized or are being modernized as part of their OT digital transformation initiatives,” explained Del Rodillas, director of industrial cybersecurity product marketing at Palo Alto Networks. “In many of these initiatives, the automation piece is cutting-edge, but the provisions for cybersecurity are lagging, leaving these organizations exposed.”
“As additional motivation for the security upgrade, some harsh-environment remote sites have grown in complexity and require local segmentation to improve visibility and control over local traffic. There are also use cases which require direct site-to-site connectivity instead of requiring users to go up through SCADA first in order to get to other sites,” Rodillas added.
The PA-220R firewall runs Palo Alto Networks’ PAN-OS operating system, which the company updated to version 8.1 this week.
According to Palo Alto Networks, PAN-OS 8.1 brings many improvements, including simplified implementation of application-based security policies, streamlined decryption of SSL traffic, better performance thanks to new hardware, new management features, and enhanced threat detection and prevention.
Effective Tips for Internet Safety for Kids You Must Read
19.2.2018 securityaffairs Safety
Online safety for your kids is very important. However, that doesn’t necessarily mean that it needs to be hard work.
The key thing is to learn how to get parental controls set up properly so that you won’t have to worry as much about online safety when your kids start to use the internet for both school projects and entertainment.
There are many ways that the version of the internet that your kids see can be fine-tuned. One option is to use a free content filter that is offered by all of the major providers.
There are also sophisticated software that is available for sale that you can invest in if you feel the need for a more advanced solution.
In order to determine which is best for you, we will be covering some of the major parental control options that are available to you.
In this article, we will be discussing various parent control options that are available to you. However, keep in mind, that although there are some very useful parental control tools that are available – it is still important for you to watch what your children are doing when they are online as much as you can. There is no substitute when it comes to parental supervision of children.
Content filters
All of the major UK broadband providers, including EE, Virgin Media, TalkTalk, Sky, and BT offer content filters as a standard feature.
They block off sites that contain material that is inappropriate for children, like self-harming, pornography, and other nasty material. Access to sites that are known to contain malware and viruses are also restricted. The best internet packages will have this as standard nowadays.
Which broadband providers offer the best security?
You will need to decide whether or not you want to use the filters when you are getting your broadband first set up. The settings can be changed at any time by simply logging into your account. So you can always change your mind on whether you want to use the filters or not.
Software
Some broadband providers offer parental control software as part of their broadband packages. This type of software is widely available. Content filters are network-level filters and are applied to anyone who uses the connection.
By contrast, parental control software affects only the device that it is installed on. So for example, if you install parent control software on your desktop computer, it will not affect what your children are doing when they are using their tablets and phones.
In addition to filtering inappropriate content out, like gambling-related, violent and pornographic sites, some of this software also lets you monitor the online activity of your children and even restrict what times of days certain websites can be used.
This can definitely come in handy. You will finally have a way of keeping them off of sites like Facebook and YouTube when they are supposed to be doing their homework.
In general, any device that is able to access the internet has its own onboard parental control sets that can be tinkered with before allowing your children to use it.
That is particularly helpful if the broadband company provides you with the software that is the kind that applies to just one device at a time.
For example, Apple’s iPad and iPhone, have a broad range of restrictions, and you cause the settings menu to easily access them. You can lock them in place and protect them using a password.
Those devices, in addition to many others, also allow you to disable paid transactions inside of games and apps. That way your kids can run up any bills without you knowing about it!
There is no such thing as a flawless system. That is why it is a very good idea to make use of all of the different tools that are available to you.
When you place restrictions on the way devices can be used and also install software, it makes it double unlikely that your children will be exposed to any unsuitable or harmful material while they are online.
This will help to put your mind at ease, which is so important these days with all of the dangers lurking online.
Web browsers
At times your web browser, which is the program that is used for browsing the internet, allows you to block out certain kinds of websites.
Those settings may be used in conjunction with whatever software you have installed on your computer already which provides you with an added layer of protection.
For example, when the Google Chrome browser is used – which is a free download that is available to use – it includes a feature that allows you to set up different account profiles for managers and supervised users, which gives you full control of how your children can use the internet when they are online.
Once again it is best to use these features of the browser in combination with other parental controls, especially since the settings apply only to the Chrome browser. More tech-savvy, older children can quickly discover a workaround, such as downloading another web browser other than Google Chrome.
Websites
On certain internet platforms and websites, like iTunes, YouTube, and Google, there is a family-friendly filter that can be switched on that should block out any content that isn’t suited for children to see.
Once again, keep in mind that there is no such thing as a flawless system so that is why it makes sense to use these features in combination with other kinds of parental controls.
This is only really effective to use with very young children since older kids can figure out how the filter can be turned off if they get curious enough and want to look at things that they know they aren’t allowed to.
General advice on how to get safe online
Get Safe Online, an internet safety initiative has provided the advice below. We hope you find it helpful to manage your children’s experiences online.
Set some boundaries even before your child gets their first internet connected device – whether it is a console, laptop, tablet, or mobile device. After they have their device, it might be harder to change the settings or how they use it.
Network-level parental controls are offered by all major providers. When you switch to a different broadband package, you will have an option for turning content filtering on, so that adult material is blocked.
Keep in mind that doesn’t mean all bad stuff will be blocked – there is no such thing as a fully effective filter. You will need to stay vigilant and supervise your children.
Have a discussion with your children about what is appropriate and safe to share and post online.
All videos, photos, and comments are part of a person’s ‘digital footprint’ and may be seen by anybody and be available forever on the internet.
Speak with your children about the type of content they view online, along with the precautions they need to take when they are communicating with others online – for example, to never share personal information with strangers.
Keep in mind that services such as YouTube and Facebook have a reason for having minimum age limits of 13 years old. Don’t cave in to pressure – speak with your child’s school and other parents to be sure everyone is on the same page.
Explain to your children that being online doesn’t provide them with protection or anonymity. Make sure that you clearly tell them that they shouldn’t do anything over the internet that they wouldn’t feel completely comfortable doing in real life.
Microsoft Brings Windows Defender ATP to Windows 7, 8.1
13.2.2018 securityweek Safety
Microsoft on Monday announced plans to make Windows Defender Advanced Threat Protection (ATP) available for Windows 7 SP1 and Windows 8.1 devices.
First announced in early 2016, Windows Defender ATP was packed in Windows 10 in an attempt to harden the platform and provide users with a unified endpoint security tool.
Improvements made to Windows Defender ATP since include protection against code injection attacks, detection of suspicious PowerShell activities, and the ability to fend off emerging threats via Windows Defender Exploit Guard.
While these enhancements make Windows 10 a more secure platform, organizations that use a mixture of Windows 7 and Windows 10 devices remain exposed to attacks, and Microsoft aims at tackling the issue with the addition of support for older platform iterations in Windows Defender ATP.
“Starting this summer, customers moving to Windows 10 can add Windows Defender ATP Endpoint Detection & Response (EDR) functionality to their Windows 7, and Windows 8.1 devices, and get a holistic view across their endpoints,” Rob Lefferts, Partner Director, Windows & Devices Group, Security & Enterprise, Microsoft, notes in a blog post.
Windows 7 and Windows 8.1 will get a behavioral based EDR solution to provide insight into threats on an organization’s endpoints. All events are logged in the Windows Defender Security Center, which is the cloud-based console for Windows Defender ATP.
“Security teams benefit from correlated alerts for known and unknown adversaries, additional threat intelligence, and a detailed machine timeline for further investigations and manual response options,” Lefferts notes.
He also notes that the solution will allow organizations to run third-party antivirus solutions on the endpoints, although pairing it with Windows Defender Antivirus (also known as System Center Endpoint Protection (SCEP) for down-level) would be the best option. The advantage when using it with Windows Defender Antivirus would be that both malware detections and response actions would be available in the same console.
Microsoft plans on providing its customers with access to a public preview of the down-level EDR solution in spring, so that security teams would learn more on what the solution has to offer in terms of detecting suspicious behavior on Windows 7 and Windows 8.1 devices.
Making Windows Defender ATP available for older Windows releases is only one more step Microsoft makes in its attempt to broaden the availability of its security product. In November, the company announced partnerships to bring the tool to macOS, Linux, iOS, and Android devices as well.
On Monday, SentinelOne revealed plans to bring Windows Defender ATP to its Mac and Linux users too, courtesy of integration with the SentinelOne Endpoint Protection Platform (EPP). The company is already providing customers with beta access to the solution.
Once the planned integration is complete, new events from onboarded MacOS and Linux devices will start natively surfacing into the Windows Defender ATP console, without the need for additional infrastructure, the company says.
“With Windows Defender ATP for Windows 10, Windows Server 2012R2 and 2016, now for Windows 7 and Windows 8.1 and our partner integration for non-Windows devices, we give security teams a single solution to detect and respond to advanced attacks across the majority of their endpoints,” Lefferts concludes.
Meltdown/Specter-based Malware Coming Soon to Devices Near You, Are You Ready?
2.2.2018 thehackernews Safety
It has been few weeks since the details of the Spectre, and Meltdown processor vulnerabilities came out in public and researchers have discovered more than 130 malware samples trying to exploit these chip flaws.
Spectre and Meltdown are security vulnerabilities disclosed by security researchers earlier this month in many processors from Intel, ARM and AMD used in modern PCs, servers and smartphones, among other devices.
These CPU vulnerabilities could enable attackers to bypass memory isolation mechanisms and access everything, including memory allocated for the kernel containing sensitive data like passwords, encryption keys and other private information.
Researchers from independent antivirus testing firm AV-TEST detected at least 139 malware samples, as of today, which are related to these CPU vulnerabilities, as shown in the growth graph.
You can find SHA256 hashes for all malware samples here. 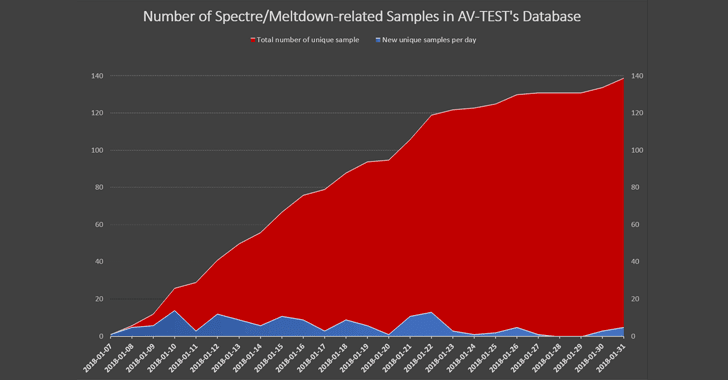
Meanwhile, cybersecurity firm Fortinet also tracked and analyzed many malware samples 'trying to exploit' recently disclosed CPU vulnerabilities, most of which includes re-compiled or extended version of the JavaScript-based proof-of-concept (PoC) exploit released last month.
"The rate at which the cybercriminal community is targeting known vulnerabilities is clearly accelerating, with the WannaCry and NotPetya exploits serving as perfect examples of the need to patch vulnerable systems as soon as possible," Fortinet said.
"Which is why our concerns were raised when we recently learned about some of the largest vulnerabilities ever reported—ones that affect virtually every processor developed since 1995 by chip manufacturers Intel, AMD, and ARM."
Another news makes this situation, even more, worse—Intel halted all its CPU firmware patches for the Meltdown and Spectre flaws last week after it caused issues like spontaneous reboots and other 'unpredictable' system behaviour on affected PCs.
So, until Intel and other vendors do not come up with stable security patches for the Meltdown and Spectre attacks that don’t cause systems to break, users are recommended to keep their operating system, web browsers, antivirus and other software up-to-date.
Kaspersky Launches New Security Product for Exchange Online
2.2.2018 securityweek Safety
Kaspersky Lab has expanded its small and medium-sized business (SMB) offering with a new cloud-based product designed to provide an extra layer of security for the Exchange Online email service in Microsoft Office 365.
The new product, Kaspersky Security for Microsoft Office 365, is designed to protect users against malware, phishing, spam, and other email-borne threats.
Exchange Online includes built-in anti-malware and anti-spam features, but Kaspersky says its own product – part of the company’s Business Hub offering – works in conjunction with Microsoft’s protections and offers native integration.
Kaspersky says its product relies on various security technologies, including machine learning-based detection, an anti-phishing engine that uses neural networks, sandboxing, attachment filtering mechanisms, and data from the company’s threat intelligence network.
The new product analyzes incoming emails and places suspicious messages in quarantine. Administrators are informed of the potential threats via a central console shared with the Kaspersky Endpoint Security Cloud product. The console allows customers to view each potentially malicious email and restore them in case of false positives.
According to the security firm, Kaspersky Security for Microsoft Office 365 is capable of recognizing if a file attached to an email is the type it claims to be, and it can detect malicious macros hidden in harmless-looking Office documents.
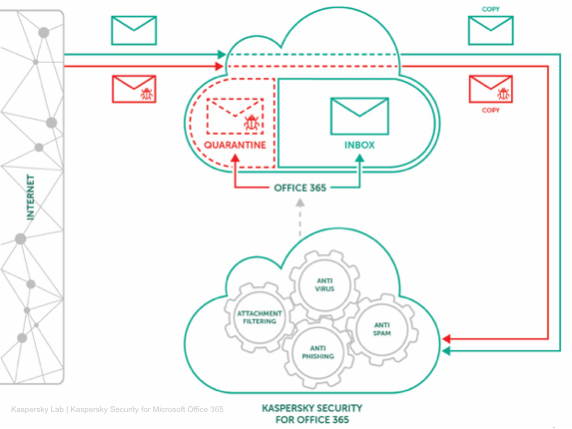
Since there has been a lot of debate recently on the implications of the physical location of data stored in the cloud, Kaspersky allows users to specify which data center they want to use for processing emails.
Furthermore, given the recent controversy regarding the company uploading sensitive files from an NSA contractor’s computer to its own servers, Kaspersky has highlighted that the new product does not upload any files to its systems. Instead, quarantined emails are stored in the customer’s Exchange Online account.
Security Explorations Launches New Research Program
30.1.2018 securityweek Safety
After 10 years of conducting complex research often without expecting any monetary rewards, Poland-based Security Explorations has now decided to launch a commercial offering that gives organizations the chance to gain exclusive or non-exclusive access to the company’s most interesting and unique projects.
Security Explorations is known for conducting in-depth research into digital satellite platforms, Nokia phones, and Java, including Java SE, Oracle Java Cloud Service and the Java VM in Oracle Database, Apple Quicktime for Java, and Google App Engine for Java. The firm’s findings - a total of more than 200 vulnerabilities - were reported to the respective vendors and in many cases made public.
Google did award the company $100,000 following the discovery of more than 30 vulnerabilities in the search giant’s App Engine product. However, Security Explorations said most of its research so far was done pro bono in an effort to raise awareness of flaws that put both users and vendors at risk.
In addition to its on-demand security analysis service, Security Explorations has now decided to launch a Security Research Program (SRP) that allows organizations to obtain access to the results of complex and unique research conducted by the company.Security Explorations launches Security Research Program
The first research offered through the SRP targets digital video broadcasting (DVB) devices from STMicroelectronics. The vendor’s products were analyzed several years ago as part of Security Explorations’ analysis of digital satellite TV platforms. Security Explorations believes STMicroelectronics, which exited the set-top box business two years ago, and other vendors have done little to address vulnerabilities, leaving devices at risk of attacks and failing to prevent premium TV piracy.
According to Security Explorations, its research into STMicroelectronics chipsets can be useful to other companies in this industry as it can help them identify the presence of vulnerabilities, develop patches, and conduct further security research.
Companies interested in Security Explorations research offered via the SRP can opt for an exclusive purchase (EP) and become the owner of the research material - the information will not be provided to anyone else from that point on - or they can choose the access only (AO) option and obtain a copy of the materials. Both options provide access to research reports, proof-of-concept (PoC) code, and tools, and Security Explorations is prepared to provide clarifications if needed, but the offer does not include ongoing support.
In the case of the STMicroelectronics research, pricing for the AO option is 50,000 EUR (roughly 62,000 USD). Information on pricing for exclusive purchases is only provided under a non-disclosure agreement (NDA).
“Each material released as part of our SRP program is separately priced,” Adam Gowdiak, CEO and founder of Security Explorations, told SecurityWeek. “The final price depends on the complexity of the research process and the amount of hours dedicated by Security Explorations to complete it. The impact of discovered vulnerabilities is also taken into account.”
“For our first material, the SRP AO price is less than the offers we have received for reverse engineering work of some PayTV solutions. The SRP EP price is set to be a fraction of the costs of replacing vulnerable ST chipsets / STB devices still deployed to the market,” Gowdiak added. “In general, SRP AO will be below the costs of conducting a given research (it should be always more attractive to purchase access to SRP material than to engage its own resources / achieve given research results on its own).”
Gowdiak says his company is currently working on two undisclosed projects, one of which will be released to the public for free, while the other one will be offered through the new program. He says the goal of the new offering is to help fund the firm’s non-commercial research.
Security Explorations will typically pick its research targets and once the analysis has been completed the company will announce it on its website and reach out to potentially interested parties. The vendor whose products have been analyzed can acquire exclusive rights to the materials to ensure that it cannot fall into the wrong hands, it can acquire access to the research, or ignore the report and instead work on improving the security of its products on its own.
“While the latter does not warrant that vulnerabilities or exploitation techniques targeted by SRP get found or remediated, the net effect should be always positive: a vendor putting additional resources into security, new weaknesses being discovered and fixed, flawed products being recalled/replaced from the market,” Security Explorations said.
Gowdiak has described the new offering as an alternative to bug bounty programs and security evaluations - with some significant differences.
“For Bug Bounties, a researcher decides about a target, a vendor decides about a reward (if any). For a consulting work, a customer decides about a target, a provider decides about a price for security evaluation services. For SRP, we decide both about a target and a price for our work,” Gowdiak explained.
The advantages of this approach for the company conducting the research include not being “the vendor’s hostage for consulting gigs and bug bounties,” which results in unbiased and independent research, and eliminating the issues that can arise during the disclosure process, Gowdiak said.
Security Explorations has reserved the right to deny access to any organization to its research, but the company has admitted that it has no way of enforcing its license terms and ensuring that its findings are not abused.
Hard-coded Password Lets Attackers Bypass Lenovo's Fingerprint Scanner
30.1.2018 thehackernews Safety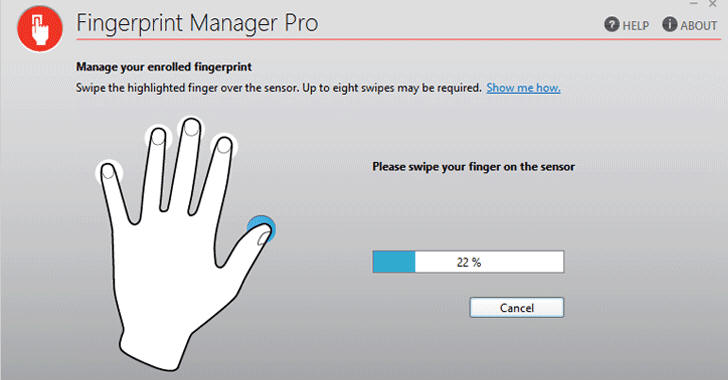
Lenovo has recently rolled out security patches for a severe vulnerability in its Fingerprint Manager Pro software that could allow leak sensitive data stored by the users.
Fingerprint Manager Pro is a utility for Microsoft Windows 7, 8 and 8.1 operating systems that allows users to log into their fingerprint-enabled Lenovo PCs using their fingers. The software could also be configured to store website credentials and authenticate site via fingerprint.
In addition to fingerprint data, the software also stores users sensitive information like their Windows login credentials—all of which are encrypted using a weak cryptography algorithm.
According to the company, Fingerprint Manager Pro version 8.01.86 and earlier contains a hard-coded password vulnerability, identified as CVE-2017-3762, that made the software accessible to all users with local non-administrative access.
"Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in," the company said in its advisory, giving brief about the vulnerability.
The vulnerability impacts Lenovo ThinkPad, ThinkCentre and ThinkStation laptops, and affects more than two dozen Lenovo ThinkPad models, five ThinkStation Models and eight ThinkCentre models that run Windows 7, 8 and the 8.1 operating systems.
Here's the full list of Lenovo devices compatible with Fingerprint Manager Pro and impacted by the vulnerability:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
Lenovo has credited security researcher Jackson Thuraisamy with Security Compass for discovering and responsibly reporting the vulnerability.
The popular Chinese computer manufacturer strongly recommends its ThinkPad customers to update their devices to Fingerprint Manager Pro version 8.01.87 or later to address the issue. You can also head on to the company's official website to do so.
Since Microsoft added native fingerprint reader support with Windows 10 operating system, thus eliminating the need for the Fingerprint Manager Pro software, Lenovo laptops running Windows 10 are not impacted by the vulnerability.
Intel Working on CPUs With Meltdown, Spectre Protections
27.1.2018 securityweek Safety
Intel is working on CPUs that will include built-in protections against the notorious Meltdown and Spectre attacks, CEO Brian Krzanich revealed on Thursday during a conference call discussing the company’s latest earnings report.
Intel has released some microcode updates to address the vulnerabilities, but the patches have caused serious problems for many users, which has led to Intel and other vendors halting updates.
“Our near term focus is on delivering high quality mitigations to protect our customers’ infrastructure from these exploits. We're working to incorporate silicon-based changes to future products that will directly address the Spectre and Meltdown threats in hardware. And those products will begin appearing later this year,” Krzanich said.Intel to release CPUs with Meltdown and Spectre protections
“However, these circumstances are highly dynamic and we updated our risk factors to reflect both the evolving nature of these specific threats and litigation, as well as the security challenge, more broadly,” he added.
The latest financial report shows that the company had a great 2017, with a record fourth-quarter revenue of $17.1 billion and a record full-year revenue of $62.8 billion. Despite its reputation taking a hit due to the Meltdown and Spectre vulnerabilities, the company expects 2018 to also be a record year.
It’s worth noting, however, that one of the factors that could cause results to differ from the company’s expectations are vulnerabilities in Intel processors and other products. In addition to the security flaws themselves, Intel is concerned about the adverse performance and system instability introduced by mitigations, associated lawsuits, the negative publicity they generate, and the impact they may have on customer relationships and reputation, the company said.
Several class action lawsuits have already been filed against Intel, accusing the company of violating state consumer laws by misleading customers about its product and breaching warranties.
Krzanich sold all the stock he was legally allowed to, worth roughly $24 million, just weeks before the existence of Spectre and Meltdown came to light, which has raised insider trading concerns.
Intel has denied the allegations, but French publication LeMagIT reported this week that Intel started informing its partners of the flaws on the same day the company’s CEO sold his shares, specifically November 29.
Less than 10% of Gmail users enabled two-factor authentication
24.1.2018 securityaffairs Safety
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
The availability of billions of credentials in the criminal underground due to the numerous massive data breaches occurred in the last years makes it easy for crooks to take over users’ accounts.
We always suggest enabling two-factor authentication to improve the security of our accounts, unfortunately, the suggestion is often ignored.
“Even if someone else gets your password, it won’t be enough to sign in to your account,” states Google’s page on 2FA.
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
Considering that Google has more than 2 billion monthly active devices, the number of exposed accounts is very huge.
Milka made the disconcerting revelation at the Usenix’s Enigma 2018, two-factor authentication (2FA) implemented by Google allows its users to access the account by providing login credentials along with an authentication code sent to the user via SMS or voice call or generated through the Google mobile app.

Source: The Register
This data demonstrates the lack of awareness of cyber threats and the way to mitigate them.
Many users believe that configure and use 2FA for their accounts can make their experience worse.
The Register asked Milka why Google didn’t just make two-factor mandatory across all accounts and received the following answer:
“The answer is usability,” he replied. “It’s about how many people would we drive out if we force them to use additional security.”
Contrary to what you can think, it is very easy to enable 2FA for your account, Google published a step-by-step guide.
The risk of identity theft increases when users share the same credentials among many web services.
Milka also cited a 2016 Pew study saying that only 12 percent of Americans use a password manager.
On the other side, Google is working to improve both the users’experience and security for example to employing machine learning systems that are able to spot suspicious activities related to the accounts under accounts.
For example, usually, when an attacker gets access to an account, he shuts down notification to the legitimate owner and starts exploring the content of the email by searching for passwords, license, and activation codes, cryptocurrency wallet addresses and credentials, intimate photos, and other sensitive documents, including copies of ID cards.
When Google detects one of the above actions immediately triggers mitigation countermeasures.
Can Biometrics Solve the Authentication Problem?
22.1.2018 securityweek Safety
Are Biometrics as a Form of Authentication Over-hyped and Unreliable?
When Apple introduced the Touch ID fingerprint access button, commentators believed it would kick-start the ever-promising, never-quite-delivering biometric market. But Touch ID was defeated by hackers within days. When Apple introduced the FaceID biometric, the same happened – it was defeated within weeks. In November 2017, F-Secure demonstrated that Android’s Trusted Face Smart Lock can be defeated by a selfie. Also in November, researchers at the University of Eastern Finland concluded that voice impersonators can fool speaker/voice recognition systems.
There is probably no physical biometric factor that has not been defeated by hackers or researchers. Which begs the question: are biometrics as a form of authentication over-hyped and unreliable? Can they possibly provide an alternative to the much denigrated password?
Biometrics in use
Large-scale use of biometric authentication is primarily tied to smartphones. The wide-range of sensors built into these handheld and ubiquitous devices make them an ideal tool for face and iris recognition (camera), voice (microphone), and touch (fingerprint). This authenticates the user to the device, allowing further authorized access to other devices via the phone (although this does not, in itself, confirm that it is the authenticated user still operating the phone).
Banks are increasingly using voice and face recognition via smartphones for mobile banking purposes. Barclays introduced phone-based voice authentication, and HSBC allowed selfie-based face authentication in 2016.
Biometrics are also used in stand-alone situations, where they can be used to access restricted buildings or rooms. For example, in December 2017, Los Angeles Airport started trialing facial biometrics to speed out-bound passenger flow. The passenger’s facial image is compared to the facial image captured during the immigration process to prove identity.
In such circumstances, biometrics are very popular; but we need to differentiate between consumer smartphone-based biometrics and corporate usage. Biometrics are not currently used widely within industry. The main reasons are cost, possible privacy issues, and because it cannot be guaranteed that every member of the workforce has a smartphone.
Biometric strengths
Biometric authentication has several distinct advantages over passwords. These include:
Ease of use – “Biometrics are incredibly popular with users,” explains Shane Young, president & CEO of inBay Technologies. “Inherent biological... features are convenient: they are part of who we are, always with us and in most cases, we don’t have to think too much to use them (unlike remembering a password).”
Numerous surveys have confirmed this. A July 2016 survey conducted by Visa said two-thirds of Europeans would welcome the use of biometrics in payments. An August 2017 survey by Unisys suggests that 68% of users would trust organizations more if they were to use biometric authentication; 63% believe it is more secure than PIN and password; and 57% believe fingerprints to be the most secure form of authentication.
Can’t be lost – Associated with ‘ease of use’ is the idea that, unlike passwords, biometrics can be neither lost nor forgotten because the user is the biometric. This is true, but needs two qualifications. Firstly, if the biometric device is a smartphone, then the phone itself can – and often is – lost or stolen. Secondly, like a password, it is the device that is authenticated at a point in time. Subsequent use of an authenticated device could be by anyone. In reality, the ‘cannot-be-lost’ argument offers little advantage for smartphone biometrics over passwords other than it is easier to forget a complex password than to lose a personal device, and it is easier to use than inputting a complex password.
Automatically unique – Biometrics are automatically unique to each user. This argument might not hold up against detailed scientific analysis – even fingerprints cannot be guaranteed to be 100% unique. Voices can be imitated and twins can have identical faces – but in general, the risk of such ‘collisions’ occurring naturally is very small.
Biometric Weaknesses
Biometric authentication also has several weaknesses. These include:
Additional cost – A biometric solution cannot be implemented without incurring additional cost. “Anytime you require hardware, you incur additional cost – both monetary costs and costs in convenience (and therefore, cost to user adoption),” explains Ian Paterson, CEO of Plurilock. “Fingerprints require fingerprint readers, facial recognition requires special infrared cameras to work well, and retinal scans are even more cumbersome.”
Susceptibility to cloning or coercion – No biometric has yet proven itself to be proof against cloning. “Mainstream biometrics really means mobile devices, where – for the most part – they have only proven reliable enough at scale to be a convenience feature, used in parallel with the passcode as backup,” says security researcher and consultant, Stewart Twynham. “Even Tim Cook’s keynote announcement of Face ID came with the caveat that you should protect your data with a passcode if you have an ‘evil twin’.”
The implication is that biometrics are only as strong as the built-in biometrics found in the majority of contemporary smartphones – and these biometrics are routinely spoofed by researchers and hackers within days or weeks of their release.
“Whether a particular biometric method is useful or not depends on the sensor quality and ease of duplicating a particular biometric,” comments Jarno Niemela, lead researcher at F-Secure Labs. “For example fingerprints are a field where the attacker has significant advantage, since they are easy to copy and can be obtained from about anything that a person has been handling, or even from a photo.”
A related weakness in smartphone-based biometrics comes with the nature of smartphones – their mobility. This could allow a physical attacker to coerce the user into authenticating the device remotely. Since it is the device rather than the user of the device that is authenticated for mobile apps (whether they are banking apps or corporate access), a physical attacker such as a burglar could employ user-coercion (in crypto terms, aka ‘rubber-hose decryption’) to defeat biometric authentication.
Difficult to change – Despite the apparent strength of their apparent immutability, it is possible that biometric templates may need to be changed – but this is considerably more complex and costly than simply changing a password. There are two primary scenarios: theft of the biometric templates, and the aging of the user.
“Biometric data,” comments Carl Leonard, principal security analyst with Forcepoint, “is arguably more valuable than passwords since biometrics are, on the whole, immutable. The breach of the US Office of Personnel Management in 2015,” he adds, “included personal data of individuals including fingerprints.”
“The big problem with biometrics,” says Joseph Carson, chief security scientist at Thycotic, “is when they are compromised you cannot change them; it is like a hard-coded password which is a bad idea to use in today’s security world.”
The second scenario is an unknown quantity. Biometric characteristics actually do change over time. For example, fingerprints get worn through incessant use and/or injury, and voices change with age and illness. Where biometrics are already in use, their use is too recent to know whether this will prove a problem over time. Machine learning techniques could be used to adapt the template slowly with minute changes as they occur, but this simply adds more complexity and cost to the solution.
Privacy push-back – Despite consumer acceptance of smartphone-based biometrics, there is less overwhelming acceptance from corporate users. Many such users are unhappy about handing permanent personal data to what might prove to be a temporary employer. Such personal and perhaps conflicting attitudes to the private nature of biometrics are reflected in some contemporary legal concerns.
For example, comments Darren Abernethy, senior global privacy manager at TrustArc, “Some laws, such as the EU’s rapidly approaching General Data Protection Regulation (GDPR, which takes effect May 25, 2018), treat newly defined ‘biometric data’ as in essence sensitive personal information (SPI). The mandatory use of biometric data for authentication purposes creates the ironic situation where an individual must offer sensitive information – and likely separately provide explicit consent for its processing – in order to access a particular piece of hardware/software that itself may not otherwise contain SPI.”
This even tips over into constitutional issues. “There is a relevant Constitutional Fifth Amendment consideration with biometric data as well,” adds Abernethy; “namely, that whereas the government forcing an individual to reveal a traditional text-based password would amount to impermissible compelled testimonial self-incrimination, the same is not true with respect to a fingerprint.” In law enforcement scenarios, biometric authentication of smartphones is less secure than ‘forgettable’ passwords, since the user can be compelled to unlock the phone with biometrics; but not with a password.
Biometric Viewpoints
For at least a decade, each new year has started with predictions that this will be the year in which biometrics takes over authentication. It hasn’t happened yet. Nevertheless, the obvious advantages of biometrics remain compelling. The predictions continue; but have become more tempered.
“In 2018,” TrustArc’s Abernethy told SecurityWeek, “we’ll see less emphasis on traditional passwords and more on ways to achieve security via 2-factor authentication techniques involving biometric solutions like voice recognition, facial scans and fingerprints. For security vendors, the storage and record-keeping stakes are higher to protect biometric data because contrary to a credit card number that can be discontinued, you can’t replace a person’s facial structure with a new one once a facial scan is compromised.”
The biggest advantage is that biometrics reduce user ‘friction’; that is, the amount of effort required to properly authenticate yourself before using a system. The greater the friction, the greater the likelihood that the user will try to circumvent the controls that inhibit easy working. Biometrics do not eliminate friction, but they drastically reduce it.
The biggest disadvantages include cost, complexity, and a lack of clear proof that biometrics cannot be circumvented or defeated. More sophisticated biometric sensor devices can improve their reliability, but that will always come with a cost. “Next improvement in fingerprint scanning,” comments F-Secure’s Niemela, “will be sensors that are capable of also identifying the blood vessels in fingers, in which case just duplicating a visible print will not be enough.”
A 3D facial recognition system with infrared scanning would also improve facial scans. “With infrared cameras,” he adds, “cold objects (such as a photo image) will not show at all, or at least not correctly; and even a mask will very likely present a distorted thermal image.”
The improving technology of biometric scanners can be seen in Microsoft’s Windows Hello facial recognition system. In December 2017, researchers demonstrated that specially printed face images could defeat Microsoft’s ‘near infrared’ imaging in Windows 10 versions 1511 and 1607 – but not in the latest 1703 and 1709 versions.
Nevertheless, the continuing discussion over whether biometrics provide an adequate alternative, or addition, to passwords to solve the authentication problem ignores one underlying issue. Regardless of whether authentication is by either or both methods, it is a point-in-time authentication. Neither can ensure that the current user is the originally authenticated user. Current thinking is that this can be best solved by continuous and passive biometric behavioral user monitoring – which, notes Plurilock’s Paterson – has the additional advantage of not requiring any extra hardware.
Behavioral biometrics aggregates a potentially wide-range of features that can be gathered passively from each individual user. Some of these have been used by security officers for many years. For example, if the IP address of a local employee suddenly switches to Russia or China, the system can be fairly certain that it is not the legitimate user, and can block further access.
New behavioral biometric applications are adding additional options, such as the user’s keyboard cadence and mouse gestures. How many different ‘biometrics’ are included in such authentication can be tailored to the system being accessed: particularly sensitive areas of the environment can require additional continuous authentication.
It is a new approach that is yet to be proven over time or at scale – but it promises much. If the user is continuously monitored, it reduces the reliance on the initial authentication. This cannot be eliminated, but could be designed to reduce user friction on access. Less strong passwords or more basic fingerprint or face scanners could be used, with the knowledge that any intruder will be immediately recognized by the behavioral biometrics.
It is possible that we are entering a new debate before the old one is settled. It could be that the debate will become one of whether passwords or static biometrics should be paired with continuous behavioral biometrics.
The argument is similar to whether perimeter defenses should be replaced by incident response defenses. In this analogy, static passwords or biometrics are akin to perimeter defenses (anti-virus and firewalls); while behavioral monitoring is akin to network anomaly detection. The answer is the same in each case: you need both defenses, and you need both methods of authentication to remain secure.
“The premise of [static] biometric authentication is a powerful and effective security measure,” summarizes James Romer, EMEA chief security architect at SecureAuth. “But It is important to remember that authentication via facial recognition is not new and that no security measure is a silver bullet. No single authentication technique is beyond the reach of cyber criminals. Devices will be hacked and sensors will be tricked. It is important to layer such technology with adaptive authentication methods, such as IP reputation, phone number fraud prevention capabilities or behavioral biometrics. Effective security depends on layers.”
The bottom-line is that authentication is a risk valuation. Individual security officers need to balance the increased friction and cost of multiple layers of authentication, including passwords and/or biometrics and ongoing behavioral biometrics, to the risk involved to their own data in their own environment. What might be the right solution for one organization or environment might be the wrong solution for another.
WPA3 to Bring Improved Wireless Security in 2018
9.1.2018 secrityweek Safety
Wi-Fi Alliance Announces WPA3, the Successor to Wi-Fi's WPA2 Security Protocol
The Wi-Fi Alliance -- comprising 15 major sponsor members (including Apple, Cisco, Dell, Intel, Microsoft, Qualcomm and more) and hundreds of contributing members -- has announced that WPA3 will be introduced during 2018.
WPA3 is not an immediate replacement for WPA2, which will continue to be maintained and enhanced. In particular, the Alliance will introduce new testing enhancements for WPA2 to reduce the potential for vulnerabilities caused by network misconfigurations; and will further safeguard managed networks with centralized authentication services.
New Wi-Fi Alliance WPA3 certified devices will take some time to filter into widespread use. Use of the new specification will require WPA3 devices and WPA3 routers -- and since the vast majority of home wi-fi users never buy a router but use the one supplied by their ISP, many users won't become WPA3 compatible before they change ISPs. That could take several years.
WPA3 Security ProtocolNevertheless, there are some welcome enhancements over the WP2 specification that has kept users largely, but not entirely, protected for around two decades.
Four new capabilities for both personal and enterprise networks have been announced. There are no technical details in the Wi-Fi announcement, leading to some conjecture over exactly how they will be introduced.
The first will be to provide "robust protections" even when the user fails to use a strong password. Mathy Vanhoef, the researcher who discovered the KRACK WPA2 vulnerability, has suggested on Twitter, "That means dictionary attacks no longer work. The handshake they're referring to is likely Simultaneous Authentication of Equals (SAE). Which is also called Dragonfly;" adding, "The standards behind WPA3 already existed for a while. But now devices are *required* to support them, otherwise they're won't receive the "WPA3-certified" label."
The second will simplify the process of configuring security on wi-fi devices that have limited or no display interface. The obvious use will be for small personal devices, like wearables such as smart watches -- but it could also play some role in improving the future security of the industrial internet of things.
The third will improve the security of open wi-fi hotspots -- such as cafes, hotels and airport lounges -- by giving each user individualized data encryption. On this, Vanhoef commented, "This might refer to Opportunistic Wireless Encryption: encryption without authentication." It won't make the use of wi-fi hotspots completely secure, but should go some way to reassuring security officers who know that corporate employees work from hotspots while traveling.
The fourth will be a 192-bit security suite aligned with the Commercial National Security Algorithm (CNSA) Suite, that will further protect wi-fi networks with higher security requirements; such as government, defense, and industrial.
We can expect that new WPA3 devices will start to appear over the next few months -- particularly since many of the manufacturers will be members of the Alliance. However, the devices will need wait for the launch of the Wi-Fi Alliance's formal certification process before they can be truly called such. The Wi-Fi Certified designation will be important to reassure buyers.
"Security is a foundation of Wi-Fi Alliance certification programs, and we are excited to introduce new features to the Wi-Fi CERTIFIED family of security solutions," commented Edgar Figueroa, president and CEO of Wi-Fi Alliance. "The Wi-Fi CERTIFIED designation means Wi-Fi devices meet the highest standards for interoperability and security protections."
Wi-Fi Alliance launches WPA2 enhancements and announced WPA3
9.1.2018 secrityaffairs Safety
The Wi-Fi Alliance introduced several key improvements to the Wi-Fi Protected Access II (WPA2) security protocol and announced its successor WPA3.Wi-Fi security will be dramatically improved with the introduction of the WPA3 protocol.
The arrival of WPA3 protocol was announced on Monday by the Wi-Fi Alliance, it is the successor of WPA2 protocol for the security of Wi-Fi communication.
WPA3 will build on the core components of WPA2, anyway, the alliance plans to roll out three enhancements for WPA2 in the first part of the year.
“Wi-Fi Alliance is launching configuration, authentication, and encryption enhancements across its portfolio to ensure Wi-Fi CERTIFIED devices continue to implement state of the art security protections.” reads the announcement published by the Wi-Fi Alliance.
“Four new capabilities for personal and enterprise Wi-Fi networks will emerge in 2018 as part of Wi-Fi CERTIFIED WPA3”
The WPA2 is known to be vulnerable to KRACK attacks and DEAUTH attacks. The three key enhancements to the WPA2 protocol will address authentication, encryption, and configuration issues.
The Wi-Fi Alliance includes tech giants like Apple, Cisco, Intel, Qualcomm, and Microsoft it announced WPA3-certified devices for later 2018. They will include two features to improve protection when users choose weak passwords and simplify the choice of proper security settings on devices with limited or no interface screens.

Another feature will strengthen user privacy in open networks by using individualized data encryption. The last feature is a 192-bit security suite, aligned with the Commercial National Security Algorithm (CNSA) Suite from the Committee on National Security Systems, that will ensure the protection of Wi-Fi networks with higher security requirements such as government and defense.
“Security is a foundation of Wi-Fi Alliance certification programs, and we are excited to introduce new features to the Wi-Fi CERTIFIED family of security solutions,” concluded Edgar Figueroa, president and CEO of Wi-Fi Alliance. “The Wi-Fi CERTIFIED designation means Wi-Fi devices meet the highest standards for interoperability and security protections.”
Further information will be made available once the WPA3 program will be launched.
DMARC Implemented on Half of U.S. Government Domains
4.1.2018 securityweek Safety
Government agencies in the United States have made progress in the implementation of the DMARC standard in response to a Department of Homeland Security (DHS) directive, but the first deadline is less than two weeks away.
The Binding Operational Directive (BOD) 18-01 issued by the DHS in mid-October instructs all federal agencies to start using web and email security technologies such as HTTPS, STARTTLS and DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations can set the DMARC policy to “none” in order to only monitor unauthenticated emails, “quarantine” to send them to the spam or junk folder, or “reject” to completely block their delivery.
The DHS has ordered government agencies to implement DMARC with at least a “none” policy by January 15. Organizations will then need to set their DMARC policy to “reject” within one year.
A few days after the DHS made the announcement, security firm Agari checked over 1,000 domains owned by federal agencies and found that only 18% had implemented DMARC. By mid-November it increased to 34% and in December it reached 47%.
However, only 16% of them had deployed “quarantine” or “reject” policies by December, an increase of two percentage points compared to the previous month.
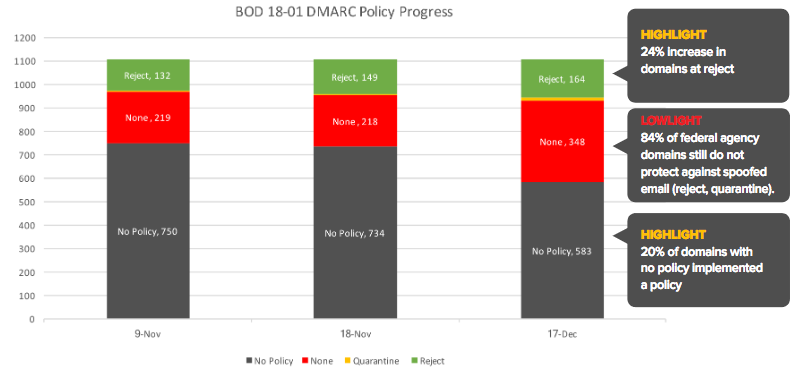
More than 20 agencies have fully implemented DMARC, including the Federal Communications Commission (FCC), the Federal Trade Commission (FTC), the Senate, the Postal Service, the Department of Health and Human Services (HHS), and Department of Veterans Affairs.
The HHS has deployed DMARC across more than 100 of its domains, including ones used by Healthcare.gov, the National Institutes of Health (NIH), and the Centers for Disease Control and Prevention (CDC).
Agari said the overall email attack rate for government customers that had implemented DMARC dropped to less than one percent.
“Deploying a DMARC policy where p=none is simple, but it is only the first step,” Agari said in a report published on Tuesday. “To fully protect against phishing threats against both the federal government and the public at large (and maintain strong email governance), federal agencies must ultimately move to Quarantine and Reject policies.”
Windows Hello Face Recognition Tricked by Photo
21.12.2017 securityweek Safety
The facial recognition-based authentication system in Windows Hello has been bypassed by researchers using a printed photo, but the method does not work in the latest versions of Windows 10.
Windows Hello, a feature available in Windows 10, allows users to quickly and easily log into their devices using their face or fingerprints. The face authentication system uses near-infrared (IR) imaging and it’s advertised by Microsoft as “an enterprise-grade identity verification mechanism.”
Researchers have demonstrated on several occasions that face authentication can be bypassed, but some systems, such as Apple’s Face ID, are more difficult to bypass than others. In the case of Windows Hello, experts managed to bypass facial authentication using only a photograph of the legitimate user printed in a certain way.
Matthias Deeg and Philipp Buchegger of Germany-based penetration testing firm SySS managed to conduct successful attacks using low-resolution near-IR photos even with the “enhanced anti-spoofing” feature enabled, which should make it more difficult to trick the system.
“By using a modified printed photo of an authorized user, an unauthorized attacker is able to log in to or unlock a locked Windows 10 system as this spoofed authorized user,” the researchers said in an advisory. “Thus, by having access to a suitable photo of an authorized person (frontal face photo), Windows Hello face authentication can easily be bypassed with little effort, enabling unauthorized access to the Windows system.”
The attack was successfully replicated on Windows 10 versions 1511 and 1607 even with the “enhanced anti-spoofing” feature enabled. In newer versions of the operating system, such as 1703 and 1709, the method no longer works if the anti-spoofing mechanism is turned on.
However, the researchers highlighted that updating to newer versions of Windows 10 and enabling the anti-spoofing feature is not enough to block attacks. Users must also reconfigure Hello Face Authentication.
Windows 10 Hello facial recognition feature can be spoofed with photos
20.12.2017 securityaffairs Safety
Experts discovered that the Windows 10 facial recognition security feature Hello can be spoofed using a photo of an authorized user.
Security experts at pen-test firm Syss have discovered that the Windows 10 facial recognition security feature dubbed Hello can be spoofed in the simplest way, using a photo of an authorized user.
“Microsoft face authentication in Windows 10 is an enterprise-grade identity verification mechanism that’s integrated into the Windows Biometric Framework (WBF) as a core Microsoft Windows component called Windows Hello. Windows Hello face authentication utilizes a camera specially configured for near infrared (IR) imaging to authenticate and unlock Windows devices as well as unlock your Microsoft Passport.”
The bad news for the users is that even if they have installed the fixed versions shipped in October (builds 1703 or 1709) the technique is effective. In this scenario, users need to set up the facial recognition from scratch to make it resistant to the attack.
“Due to an insecure implementation of the biometric face recognition in some Windows 10 versions, it is possible to bypass the Windows Hello face authentication via a simple spoofing attack using a modified printed photo of an authorized person.” states the security advisory published on Full Disclosure.
The attack devised by the researchers works on both the default config, and Windows Hello with its “enhanced anti-spoofing” feature enabled.
“Thus, by having access to a suitable photo of an authorized person (frontal face photo), Windows Hello face authentication can easily be bypassed with little effort, enabling unauthorized access to the Windows system.” reads the
“Both, the default Windows Hello configuration and Windows Hello with the enabled “enhanced anti-spoofing” feature on different Windows 10 versions are vulnerable to the described spoofing attack and can be bypassed. If “enhanced anti-spoofing” is enabled, depending on the targeted Windows 10 version, a slightly different modified photo with other attributes has to be used, but the additional effort for an attacker is negligible. In general, the simple spoofing attack is less reliable when the “enhanced anti-spoofing” feature is enabled.”

The Proof of Concept (PoC) detailed by the researchers worked against a Dell Latitude running Windows 10 Pro, build 1703; and a Microsoft Surface Pro running 4 build 1607.
The experts tried to use the “enhanced anti-spoofing” feature on Surface Pro’s , but claimed its “LilBit USB IR camera only supported the default configuration and could not be used with the more secure face recognition settings.”
They successfully bypassed the default Windows Hello configuration on both test devices running all tested Windows 10 versions.
Firewall Bursting: A New Approach to Better Branch Security
18.12.2017 thehackernews Safety
One of the most common network security solutions is the branch firewall. Branch firewall appliances can pack into a single device a wide range of security capabilities including a stateful or next-generation firewall, anti-virus, URL filtering, and IDS/IPS.
But the reality is that most of these edge devices lack the processing power to apply the full scope of capabilities on all of the necessary traffic.
If the firewall deployed in the branch cannot scale to address critical security needs, an alternative strategy must be used. Wholesale appliance upgrades are easy but expensive. Regional security hubs are complex and also costly.
A new approach, called firewall bursting, leverages cloud scalability to offer an easier, more cost-effective alternative to branch office security. (You can find a great table comparing the different Firewall approaches here.)
Costly Appliance Upgrades and Secure Hub Architectures
The existing methods of evolving branch security force IT into a tough trade-off: the cost and complexity of managing appliance sprawl or the complexities of a two-tier network security architecture.
Upgrading all branch firewalls to high-performance, next-generation branch firewalls improve network security, no doubt. Branch offices gain more in-depth packet inspection and more protections to be applied on more traffic. This is a relatively straightforward, but very costly, solution to achieving stronger security.
Aside from the obvious, the firewall upgrade cost, there are also the costs of operating and maintaining the appliance, which includes forced upgrades. Sizing branch firewall appliances correctly can be tricky.
The appliance needs enough power to support the mix of security services across all traffic—encrypted and unencrypted—for the next three to five years.
Alone that would be complex, but the constantly growing traffic volumes only complicate that forecast. And encrypted traffic, which has become the new norm of virtually all Internet traffic, is not only growing but must be first decrypted, exacting a heavy processing toll on the appliance.
All of which means that IT ends up either paying more than necessary to accommodate growth or under provision and risk compromising the company’s security posture.
Regional hubs avoid the problems with upgrading all branch firewalls. Instead, organizations continue with their branch routers and firewalls, but backhaul all traffic to a larger firewall with public Internet access, typically hosted in a regional co-location hub.
The regional hub enables IT to maintain minimal branch security capabilities while benefitting from advanced security.
However, regional hubs bring their own problems. Deployment costs increase as regional hubs must be built out at significant hosting expense and equipment cost. And we’re not just speaking about throwing up an appliance in some low-grade hosting facility.
Hub outages impact not just one small office but the entire region. They need to be highly available, resilient, run the up-to-date software, and maintained by expert staff.
Even then, there are still the same problems of forced upgrades due to increased traffic volume and encrypted traffic share, this time, though, of only the hub firewall appliances.
The network architecture is also made far more complex, particularly for global organizations. Not only must they rollout multiple regional hubs, but multiple hubs must be deployed in geographically dispersed regions or those regions with a high concentration of branches.
In short, while the number of firewall instances can be reduced, regional hubs introduce a level of complexity and cost often too excessive for many organizations.
Firewall Bursting: Stretching your Firewalls to the Cloud
Cloud computing offers a new way to solve the edge firewall dilemma. With "cloud bursting," enterprises seamlessly extend physical data center capacity to a cloud datacenter when traffic spikes or they exhaust resources of their physical datacenter.
Firewall bursting does something similar to under-capacity, branch firewalls. Edge security processing is minimized where firewall capacity is constrained, and advanced security is applied in the cloud, where resources are scalable and elastic.
The on-premise firewall handles basic packet forwarding, but anything requiring "heavy lifting," such as decryption, anti-malware or IPS, is sent to the cloud. This avoids forced branch firewall upgrades.
Firewall bursting is similar to the regional hub approach, but with a key difference: the IT team isn't responsible for building and running the hubs. Hubs are created, scaled, and maintained by the cloud service provider.
Who Delivers Firewall Bursting Capabilities?
Secure web gateways (SWGs) delivered as cloud services, can provide firewall bursting for Internet traffic. However, since firewalls need to apply the same inspection to WAN traffic, SWGs only offer a partial solution.
Purpose-built, global Firewall as a Service (FWaaS) is another option. FWaaS providers, such as Cato Networks, create a global network of Points of Presence (PoPs), providing a full network security stack specifically built for cloud scalability.
While the PoPs are distributed, they act "together" as a single logical firewall instance. The PoPs are highly redundant and resilient, and in case of outages, processing capacity seamlessly shifts inside or across PoPs, so firewall services are always available.
The PoPs are capable of processing very large volumes of WAN and Internet traffic. Because adding processing capacity either within PoPs or by adding new PoPs is transparent to customers, you don't have to adjust policies or reconfigure your environment to accommodate changes in load or traffic mix.
Summary
With firewall bursting customers can keep their current edge firewalls and still improve security. If you are running out of gas on your edge firewalls, you have options.
Beyond the obvious approaches of firewall upgrades and hub-and-branches set up, new innovations like FWaaS are now available.
FWaaS leverages cloud elasticity and scalability to globally extend network security with minimal impact on current network design.
Firewall refresh, capacity upgrades, mergers and acquisition, all represent a great opportunity to look at firewall bursting and FWaaS to evolve your network security beyond the edge.
AIG Creates New Model to Score Client Cyber Risk
13.12.2017 securityweek Safety
Insurance giant American International Group said this week that it has developed a new cyber benchmarking model that quantifies and scores the cyber risk of its clients.
The new model, AIG says, evaluates a client’s cyber security maturity against 10 common attack patterns across 11 commonly used technology devices.
While the insurer did not provide details on the attack patterns and technologies used to benchmark cyber risk, it says the model “incorporates critical security data, such as current threat intelligence from multiple sources, effectiveness of an organization’s cyber controls, potential impact of a cyber breach on an organization, and insights gained from the thousands of cyber claims handled by AIG.”
“We developed the model based on historical insights and patterns of how companies experience cyber breaches – the points of entry and the types of attacks and vulnerabilities seen in the vast majority of cyber breach scenarios,” says Tracie Grella, Head of Cyber Risk Insurance at AIG. “Companies have been demanding a way to benchmark their cyber maturity against these known cyber risks to quantify what they are up against and where they stand.”
Clients that provide the required information can receive a report detailing security scores, peer benchmarking, and key risk mitigation controls to help quantify cyber risk.
To support its new model, AIG also announced the launch of CyberMatics, an analytics tool that leverages cyber threat detection firms CrowdStrike and Darktrace. CyberMatics, AIG explains, verifies inputs into AIG’s model from clients’ cyber security tools, which AIG says will provide greater confidence in underwriting information, and ultimately allows for better tailored terms and conditions in cyber insurance policies.
“AIG is partnering with Darktrace to leverage its AI technology to address a cumbersome and outdated process for assessing cyber risk -- manual questionnaires asking for information that most corporations don’t even know the correct answers to, leading to high premiums based on little to no hard evidence,” a Darktrace spokesperson told SecurityWeek.
“As an insurer, we gain a better understanding of the level of risk we are taking on with each client so we can react accordingly,” said Grella. “Our new model combined with CyberMatics can help our clients make informed and quantifiable decisions about their preparedness for cyber security risk events and insurance cover.”
In 2014, AIG expanded its cyber insurance offering to include property damage and bodily injury that could be caused as a result of cyberattacks.
While AIG has developed its own model to rank client cyber risk, third part solutions are also available to help brokers and underwriters. In August 2014, FireEye announced a new line of services designed specifically to help brokers and underwriters gain visibility into enterprises' exposure to cyber threats.
National Institute of Standards and Technology releases a second Draft of the NIST Cybersecurity Framework
10.12.2017 securityaffairs Safety
The National Institute of Standards and Technology (NIST) has published a second draft of a proposed update to the NIST Cybersecurity Framework.
“On December 5, 2017 NIST published the second draft of the proposed update to the Framework for Improving Critical Infrastructure Cybersecurity (a.k.a., draft 2 of Cybersecurity Framework version 1.1).” states the NIST.
“This second draft update aims to clarify, refine, and enhance the Cybersecurity Framework, amplifying its value and making it easier to use. The new draft reflects comments received to date, including those from a public review process launched in January 2017 and a workshop in May 2017.”
The NIST Cybersecurity Framework was first released in 2014, it aims to help organizations, particularly ones in the critical infrastructure sector, in managing cybersecurity risks.

At the time, the NIST published the Framework for Improving Critical Infrastructure Security, a document that proposed cybersecurity standards and practices to build out a security program.
Today the NIST Cybersecurity Framework is considered a best practice guide implemented by numerous organizations and business.
The Cybersecurity Framework was developed based on an executive order issued by former U.S. President Barack Obama and current Trump’s administration also considers the Framework a set of best practices to be implemented by government agencies and critical infrastructure operators.
A cybersecurity executive order issued by the current administration of Donald Trump also requires federal agencies and critical infrastructure operators to use the framework.
After four years since its first release, NIST is now working on an updated version. A first draft of the NIST Cybersecurity Framework was released in January and now the second draft is available since December 5.
Like previous Version 1.0 issued in February 2014, this second draft is the result of extensive consultation with the private and public sectors.
The changes are based on 120 comments submitted in response to the first draft and discussions between 500 individuals who attended a workshop back in May.
According to the summary the update:
Declares applicability of Cybersecurity Framework for “technology,” which is minimally composed of Information Technology, operational technology, cyber-physical systems, and Internet of Things;
Enhances guidance for applying the Cybersecurity Framework to supply chain risk management;
Summarizes the relevance and utility of Cybersecurity Framework measurement for organizational self-assessment;
Better accounts for authorization, authentication, and identity proofing; and
Administratively updates the Informative References.
The second draft was released along with an updated roadmap that details plans for advancing the framework’s development process.
Every comment on the second draft of the NIST Cybersecurity Framework can be sent to cyberframework(at)nist.gov until January 19, 2018.
The NIST plans to release the final V1.1 within this fall, likely in “early calendar year 2018.”
The organization aims to check if the revisions in version 1.1 reflect the changes in the current cybersecurity landscape. It is also important to evaluate the impact of the updated version on organizations currently implementing the version 1.0 of the framework.
NIST Publishes Second Draft of Cybersecurity Framework
8.12.2017 securityweek Safety
Framework for Improving Critical Infrastructure Cybersecurity 2.0
The National Institute of Standards and Technology (NIST) announced this week that it has published a second draft of a proposed update to the “Framework for Improving Critical Infrastructure Cybersecurity,” better known as the NIST Cybersecurity Framework.
Introduced in 2014, the framework is designed to help organizations, particularly ones in the critical infrastructure sector, manage cybersecurity risks. Some security firms and experts advise businesses to use the NIST Cybersecurity Framework as a best practice guide. Others, however, believe such static guidelines cannot keep up with the constantly evolving threat landscape, and malicious actors may even use it to devise their attack strategy.NIST updates Cybersecurity Framework
The Cybersecurity Framework was developed based on an executive order issued by former U.S. president Barack Obama. A cybersecurity executive order issued by the current administration of Donald Trump also requires federal agencies and critical infrastructure operators to use the framework.
Nearly four years have passed since the Cybersecurity Framework was released and NIST is now working on an updated version. A first draft was released in January and a second draft was made available on December 5.
According to NIST, the second draft for version 1.1 of the Cybersecurity Framework “focuses on clarifying, refining, and enhancing the Framework – amplifying its value and making it easier to use.”
The second draft also comes with an updated roadmap that details plans for advancing the framework’s development process.
The modifications are based on 120 comments submitted in response to the first draft and discussions between 500 individuals who attended a workshop back in May.
Comments and feedback on the second Cybersecurity Framework draft can be sent to NIST (cyberframework(at)nist.gov) until January 19, 2018. The organization has fallen behind on the development of the updated framework – it had initially anticipated that the final V1.1 would be published this fall, but it now hopes to have it done in “early calendar year 2018.”
NIST is particularly interested in learning if the revisions in version 1.1 reflect the changes in the current cybersecurity ecosystem, and the impact of the updated version on organizations currently using version 1.0 of the framework.
Google to Block Third-Party Software from Injecting Code into Chrome Browser
3.12.2017 thehackernews Safety
To improve performance and reduce crashes caused by third-party software on Windows, Google Chrome, by mid-2018, will no longer allow outside applications to run code within its web browser.
If you are unaware, many third-party applications, like accessibility or antivirus software, inject code into your web browser for gaining more control over your online activities in order to offer some additional features and function properly.
However, Google notes that over 15 percent of Chrome users running third-party applications on their Windows machines that inject code into their web browsers experience crashes—and trust me it's really annoying.
But don't you worry. Google now has a solution to this issue.
In a blog post published Thursday on Chromium Blog, Google announced its plan to block third-party software from injecting code into Chrome—and these changes will take place in three steps:
April 2018 — With the release of Chrome 66, Google will begin informing users if code injection causes their browsers to crash, alerting them with the name of the responsible application and a guide to update or remove it.
July 2018 — Chrome 68 will start blocking third-party software from injecting code into Chrome processes. But if this blocking prevents Chrome from starting, the browser will restart and allow the injection. But it will also display a warning for guiding users to remove that particular software.
January 2019 — With no exception, starting with Chrome 72, Google will completely block code injection by any third-party software.
However, there will be some exceptions. Google Chrome will continue to allow Microsoft-signed code, accessibility software, and IME software to inject code into your browsers.
Today's blog post is an advance notification for all developers out there, whose applications rely on code injection to function properly, forcing them to use either Native Messaging API calls or Chrome extensions to add functionality to the web browser.
"With Chrome extensions and Native Messaging, there are now modern alternatives to running code inside of Chrome processes," Google said.
According to Google, both methods can be used by developers to retain their app features without having to risk browser crashes.
"Fewer crashes mean more happy users, and we look forward to continuing to make Chrome better for everyone," Google said while summing up its blog post.
So, companies have almost 13 months to remove the code injecting bits from their software. Google is encouraging developers to use Chrome Beta channel and test their code, though these changes will more likely take effect in the Dev or Canary channels even sooner.
Now, what you are waiting for? Get ready to start rewriting your code.
Cryptocurrency Mining Scripts Now Run Even After You Close Your Browser
3.12.2017 thehackernews Safety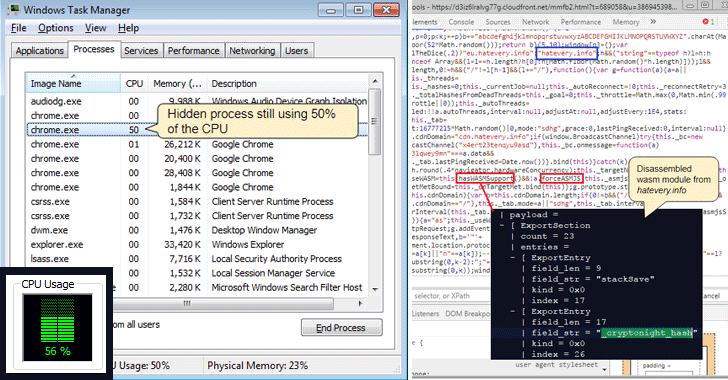
Some websites have found using a simple yet effective technique to keep their cryptocurrency mining javascript secretly running in the background even when you close your web browser.
Due to the recent surge in cryptocurrency prices, hackers and even legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of their visitor's PC to mine Bitcoin or other cryptocurrencies.
After the world's most popular torrent download website, The Pirate Bay, caught secretly using Coinhive, a browser-based cryptocurrency miner service, on its site last month, thousands of other websites also started using the service as an alternative monetization model to banner ads.
However, websites using such crypto-miner services can mine cryptocurrencies as long as you're on their site. Once you close the browser window, they lost access to your processor and associated resources, which eventually stops mining.
Unfortunately, this is not the case anymore.
Security researchers from anti-malware provider Malwarebytes have found that some websites have discovered a clever trick to keep their cryptocurrency mining software running in the background even when you have closed the offending browser window.
How Does This Browser Technique Work?
According to a blog post published Wednesday morning by Malwarebytes, the new technique works by opening a hidden pop-under browser window that fits behind the taskbar and hides behind the clock on your Microsoft's Windows computer.
From there (hidden from your view), the website runs the crypto-miner code that indefinitely generates cryptocurrency for the person controlling the site while eating up CPU cycles and power from your computer until and unless you notice the window and close it.
Researchers say this technique is a lot harder to identify and able to bypass most ad-blockers because of how cleverly it hides itself. The crypto-miner runs from a crypto-mining engine hosted by Amazon Web Servers.
"This type of pop-under is designed to bypass adblockers and is a lot harder to identify because of how cleverly it hides itself," Jérôme Segura, Malwarebytes' Lead Malware Intelligence Analyst, says in the post. "Closing the browser using the "X" is no longer sufficient."
To keep itself unidentified, the code running in the hidden browser always takes care of the maximum CPU usage and maintains threshold to a medium level.
You can also have a look at the animated GIF image that shows how this clever trick works.
This technique works on the latest version of Google's Chrome web browser running on the most recent versions of Microsoft's Windows 7 and Windows 10.
How to Block Hidden Cryptocurrency Miners
If you suspect your computer CPU is running a little harder than usual, just look for any browser windows in the taskbar. If you find any browser icon there, your computer is running a crypto-miner. Now simply, kill it.
More technical users can run Task Manager on their computer to ensure there is no remnant running browser processes and terminate them.
Since web browsers themselves currently are not blocking cryptocurrency miners neither does the integrated Windows Defender antivirus software, you can use antivirus programs that automatically block cryptocurrency miners on web pages you visit.
For this, you can contact your antivirus provider to check if they do.
Alternatively, you can make use of web browser extensions, like No Coin, that automatically block in-browser cryptocurrency miners for you, and regularly update themselves with new mining scripts that come out.
Created by developer Rafael Keramidas, No Coin is an open source extension that blocks Coin Hive and other similar cryptocurrency miners and is available for Google Chrome, Mozilla Firefox, and Opera.
No Coin currently does not support Microsoft Edge, Apple Safari, and Internet Explorer. So, those using one of these browsers can use an antimalware program that blocks cryptocurrency miners.
HP Silently Installs Telemetry Bloatware On Your PC—Here's How to Remove It
3.12.2017 thehackernews Safety
Do you own a Hewlett-Packard (HP) Windows PC or laptop?
Multiple HP customers from around the world are reporting that HP has started deploying a "spyware" onto their laptops—without informing them or asking their permission.
The application being branded as spyware is actually a Windows Telemetry service deployed by HP, called "HP Touchpoint Analytics Client," which was first identified on November 15.
According to reports on several online forums, the telemetry software—which the HP customers said they never opted to have installed and had no idea was continually running in the background—was pushed out in a recent update.
However, it's not yet clear whether the software has come with the latest Microsoft's Windows updates, or via HP's support assistant processes.
An official description of the software says that the program "harvests telemetry information that is used by HP Touchpoint's analytical services."
HP Touchpoint Makes Your Computer Slow
HP customers also complained that the installation slowed down their system significantly.
On HP's customer forum, one user even reported that due to more than 95 percent CPU usage by the analytics service, his system anti-malware software started checking for suspicious activity.
Another user owning an HP laptop head on to Reddit and said:
"So today all of a sudden, I'm experiencing a considerable slowdown in my laptop (Pavilion P3V59PA). Once I look for the problem in Task Manager, I found out that the program called HP Touchpoint Analytics Client (and it's subsequent follow up) constantly jumping the memory usage (~300Mb at a minimum, ~nearly 2Mb at maximum)."
"I don't remember ever installing this program whatsoever, and in control panel, I found that for some reason this program was silently installed today, without my consent."
German blog reader Detlef Krentz contacted borncity this weekend and wrote:
"I noticed that HP secretly installed the program 'HP Touchpoint Analytics Client' on all my HP devices on November 20, 2017. The program connects every day to HP. The files sent can be found under 'Program Data/HP/HP Touchpoint Analytics Client/Transfer Interface.'"
The program seems to send data to the company's server once per day. If you own an HP PC or laptop, you can find this data under ProgramData\HP\HP Touchpoint Analytics Client\Transfer Interface on the Windows drive.
While responding to the allegations, HP said that the company has been shipping the same software on HP laptops since 2014 as part of its Support Assistant software and that it only collects anonymous information about the computer's hardware performance.
However, the only thing that the company has changed is the name.
"HP Touchpoint Analytics is a service we have offered since 2014 as part of HP Support Assistant. It anonymously collects diagnostic information about hardware performance. No data is shared with HP unless access is expressly granted. Customers can opt-out or uninstall the service at any time," HP said in a statement.
"HP Touchpoint Analytics was recently updated, and there were no changes to privacy settings as part of this update. We take customer privacy very seriously and act in accordance with a strict policy, available here."
Here’s How to Remove HP Touchpoint Analytics Client
If you don't want this application to send data from your computer to HP's servers, you can disable the service or uninstall the program completely, which is relatively quickly and easily.
To uninstall this service, go to Control Panel and right-click on the program name, and select Uninstall to remove it.
Alternatively, you can just press Windows+R, type "appwiz.cpl," and press Enter to load the Programs and Features control panel applet. Now, select "HP Touchpoint Analytics Client" from the list and click the "Uninstall/Change" to remove the service from your PC.
A few months ago, HP was caught using a built-in keylogger that silently spied on your all keystrokes, and stored every single key-press in a human-readable file located at the public folder, making it accessible to any user or 3rd party app installed on the PC.
Recently, Lenovo has also settled a massive $3.5 million fine from the Federal Trade Commission (FTC) for preinstalling spyware onto laptops without users' consent.
At least six thousand Lantronix Serial-To-Ethernet devices are leaking Telnet passwords
3.12.2017 securityaffairs Safety
Security researcher discovered thousands of Lantronix Serial-to-Ethernet devices connected online that leak Telnet passwords.
The security researcher Ankit Anubhav, principal researcher at NewSky Security, has discovered thousands of Serial-to-Ethernet devices connected online that leak Telnet passwords.
Hackers can use the leaked passwords to launch cyber attacks against the equipment that is connected to them.
Serial-to-Ethernet “device servers” are used by companies to connect to remote equipment that only exposed a serial interfaces.
The flawed Serial-to-Ethernet “device servers” are manufactured by the US vendor Lantronix.
The products UDS and xDirect easily allow to manage the devices via a LAN or WAN connection, such type of devices allows to easily implement Ethernet connectivity to virtually any device or machine with a serial interface.
Users just need to connect the device RS-XXX serial connector to the product that exposes an RJ-45 Ethernet connector that can be used to control the device.
The “device servers” are widely adopted in to give connectivity to ICS (Industrial Control Systems), most of them are very old equipment that only comes with serial ports.
According to Ankit Anubhav, a half of Lantronix device servers are exposed online leaking their Telnet passwords. An attacker can take over the device via Telnet and use the privileged access to send serial commands to the connected devices.
“6,464 Lantronix device servers that may be connected to critical ICS-grade equipment are proudly exposing their passwords,” Anubhav told Bleeping Computer. “This accounts for 48% of the devices on Shodan.”
Imagine the potential dangers of a cyber attack against an ICS equipment exposed online through the vulnerable Lantronix device.
Anubhav explained that data exposure is an old flaw that could be exploited by attackers to retrieve the setup config of Lantronix devices by sending a malformed request on port 30718.
The Metaploit hacking platform includes a Lantronix “Telnet Password Recovery” module that could be exploited to retrieve the setup record from Lantronix serial-to-ethernet devices via the config port (30718/udp, enabled by default on old versions of Lantronix devices) and extracts the Telnet password in plain text.
Once again patch management is the root cause of the problem, vulnerable devices have not installed security updates to fix the issue.
Google Chrome will block code injection from third-party software within 14 months
2.12.2017 securityaffairs Safety
Google announced the block of code injection from third-party applications into the Chrome browser. Developers have 14 months to update their code.
Google continues to improve security of its product and services, the IT giant announced the for blocking third-party applications from injecting code into the Chrome browser.
The decision of the company will have a significant impact on many applications from third-party, including antivirus and security software that use to inject code into the browser processed to intercept cyber threats.
“Roughly two-thirds of Windows Chrome users have other applications on their machines that interact with Chrome, such as accessibility or antivirus software.” states the blog post published on Google Chromium.
“In the past, this software needed to inject code in Chrome in order to function properly; unfortunately, users with software that injects code into Windows Chrome are 15% more likely to experience crashes”
The tech giant will introduce the security improvements in three main phases over a 14-months plan.
Below the plan
Phase 1:
In April 2018, starting with Chrome 66 will begin showing users a warning after a crash, alerting them that third-party software attempted to inject code into the browser and providing suggestions on possible fixes or instructions to remove that software.

Phase 2:
Starting from July 2018, Chrome 68 will begin blocking third-party software from injecting into Chrome processes.
If this blocking prevents the Chrome browser from starting, it will restart and allow the injection. Google experts decided that in this scenario, the browser will show a warning that guides the user to remove the software.
Phase 3:
In January 2019, Chrome 72 will remove the warning and will block code injection by default.
Google will allow some exceptions for Microsoft-signed code, accessibility software, and IME (Input Method Editor) type-assist software.
“While most software that injects code into Chrome will be affected by these changes, there are some exceptions. Microsoft-signed code, accessibility software, and IME software will not be affected. As with all Chrome changes, developers are encouraged to use Chrome Beta for early testing.” continues Google.
According to the search giant, fewer crashes means more happy users and the company is committed in giving the users a better experience.
Developers of Windows software that works with Chrome are encouraged to switch Chrome channels and test their code through the Beta channel that allow to test it on next versions of the browser.
Developers can start using new modern Chrome features such as browser extensions or the Native Messaging API, instead of the code injection.
Chrome to Block Apps from Injecting into Its Processes
2.12.2017 securityweek Safety
Google’s Chrome web browser will soon prevent third-party software from injecting code into its processes.
The search giant announced that the change is planned for Chrome 68 for Windows, which is currently on track to be released in July 2018. Before the switch, however, Chrome 66 will start warning users when other software is injecting code into one of its processes.
Around two thirds of Chrome users on Windows have other applications that interact with the browser, such as accessibility or antivirus software. While some of the software needed to inject code in Chrome to ensure proper functionality, this could lead to unexpected crashes.
“Users with software that injects code into Windows Chrome are 15% more likely to experience crashes,” Chris Hamilton of the Chrome Stability Team explains.
Hamilton also points out that Chrome extensions and Native Messaging provide new, modern alternatives to running code inside of Chrome processes.
This is why Chrome 68 will start blocking third-party software from injecting code into Chrome on Windows. Before that, however, Chrome 66 will start displaying a warning after a crash, informing users on other software injecting code into the browser.
The browser will also guide users into how to update or remove the third-party software responsible for the crash.
In July 2018, Chrome 68 will start blocking code injections only if the blocking won’t prevent the browser from starting. If it will, Chrome will restart and allow the injection, while also warning the users on the matter and providing guidance into removing the troubling software.
Starting in January 2019, when Chrome 72 is set to be released in the stable channel, the browser will always block code injection.
“While most software that injects code into Chrome will be affected by these changes, there are some exceptions. Microsoft-signed code, accessibility software, and IME software will not be affected,” Hamilton says.
ProtonMail Launches Encrypted Contacts Manager
22.11.2017 securityweek Safety
Swiss-based encrypted email services provider ProtonMail announced on Tuesday the launch of a new tool designed to help users securely manage their contacts.
According to the vendor, the new ProtonMail contacts manager has been in development for more than a year and it adds powerful functionality for managing the address book.
What makes ProtonMail Contacts highly secure is the fact that it uses zero-access encryption. This means contact information is encrypted and it can only be decrypted by the user – not even ProtonMail can access the data.
The company says the new encrypted contacts manager is ideal for journalists and other individuals for whom it’s critical that contact information is protected.
ProtonMail noted that the new feature secures phone numbers, physical addresses and other information added by the user, but it does not use zero-access encryption for email addresses as it would break email filtering functionality and it wouldn’t represent a significant privacy improvement considering that the service needs to know the recipient’s email address in order to deliver messages.
On the other hand, the new ProtonMail Contacts tool does provide some protection for email addresses by using digital signatures to verify their integrity. The digital signatures mechanism, which provides a cryptographic guarantee that contact data hasn’t been tampered with, covers all the information stored in the address book, not only email addresses. If the application detects an invalid signature, it displays an error message to alert the user.
“This is a big security benefit for many reasons,” ProtonMail said in a blog post. “For example, if an attacker wanted to intercept the communications between you and a sensitive contact, one way to do it could be to secretly change the email address or phone number you have saved for that contact, such as changing john.smith(at)protonmail.com to john.snnith(at)protonmail.com, which might escape your notice.”
The new contacts manager relies on new private and public key pairs for each account. The private key is generated based on the user’s password and it’s stored on the client side, preventing ProtonMail from gaining access to the encryption key. The same key pair is used both for encrypting contact information and digital signing.
The new contacts manager is currently only available for the web version of ProtonMail, but it will soon be added to the iOS and Android apps as well. Future versions of the tool will also allow users to store keys created for sending PGP-encrypted messages, ProtonMail said.
The source code for ProtonMail’s web client, including the contacts manager, is available on GitHub.
ProtonMail Contacts – ProtonMail launches world’s first encrypted contacts manager
22.11.2017 securityaffairs Safety
ProtonMail launched ProtonMail Contacts, the world’s first contact manager with both zero-access encryption and digital signature verification.
ProtonMail is announcing today the launch of the world’s first encrypted contacts manager that also features digital signature verification. Starting immediately, the new contacts manager is available to all of ProtonMail’s 5 million users around the world.
The development and launch of this feature was driven by the feedback that the company received from many of its users in the investigative journalism space. “Last year, we had the unique opportunity to meet with many of our users in the field at the Second Asian Investigative Journalism Conference in Kathmandu, Nepal, and one message that we heard over and over again was the need for better ways to protect sources,” says ProtonMail co-founder Dr. Andy Yen, “the new encrypted contacts manager today is the result of over one year of research and development into how we can best meet the needs of the thousands of activists, journalists, and dissidents who rely on ProtonMail to protect their privacy.“
In addition to protecting sensitive contact details with zero-access encryption (meaning that ProtonMail itself cannot decrypt the data, and cannot reveal the private contact details to third parties), ProtonMail’s new contact manager also utilizes digital signatures to verify the integrity of contacts data. This provides a cryptographic guarantee that nobody (not even ProtonMail), has tampered with the contacts data.
“Combining encryption with digital signatures provides powerful protection that guarantees not only the privacy, but also the authenticity of the contacts saved in ProtonMail, and reduces the need to trust ProtonMail, as even we cannot access or change this information without your knowledge,” says Dr. Yen. In line with standard company practice, the software behind ProtonMail’s encrypted contacts manager is fully open source.
-> For more details about ProtonMail’s encrypted contacts manager, please refer to our launch blog post here: https://protonmail.com/blog/encrypted-contacts-manager/
-> The link to this press release can be found here: https://protonmail.com/blog/contacts-press-release/
-> ProtonMail’s media kit can be found here: https://protonmail.com/media-kit/
Windows 8 and newer versions fail to properly implement ASLR
21.11.2017 securityaffairs Safety
CC/CERT is warning the Address Space Layout Randomisation (ASLR) isn’t properly implemented in versions of Microsoft Windows 8 and newer.
The researcher Will Dormann from the Carnegie-Mellon CERT has discovered the Address Space Layout Randomisation (ASLR) isn’t properly implemented in versions of Microsoft Windows 8 and newer.
15 Nov
Matt Miller
@epakskape
Replying to @wdormann and 3 others
It is possible to enable bottom-up ASLR system-wide, but I'm not sure if it can be done via the WDEG UI, @markwo might know. Agree with your feedback here. I passed it on to the team.
Will Dormann
@wdormann
Actually, with Windows 7 and EMET System-wide ASLR, the loaded address for eqnedt32.exe is different on every reboot. But with Windows 10 with either EMET or WDEG, the base for eqnedt32.exe is 0x10000 EVERY TIME.
Conclusion: Win10 cannot be enforce ASLR as well as Win7! pic.twitter.com/Jp10nqk1NQ




The Address Space Layout Randomization (ASLR Protection) is a security mechanism used by operating systems to randomize the memory addresses used by key areas of processes, it makes hard for attackers to find the memory location where to inject their malicious code.
The Address Space Layout Randomisation is particularly effective against stack and heap overflows and is able to prevent arbitrary code execution triggered by any other buffer overflow vulnerability. The security measures are present in almost any modern operating system, including Windows, Linux, macOS, and Android.
Applications running on Windows 8 and newer versions were allocated addresses with zero entropy, this means that it was possible to predict where the code is allocated in memory due to the failure of the randomisation. Windows 10 has the problem, too.
The CERT/CC published a security advisory late last, Dormann found the ASLR issue while he was analyzing a recently fixed bug in Microsoft’s equation editor, tracked as CVE-2017-11882, that could be exploited by remote attackers to install a malware without user interaction.
“Microsoft Windows 8 introduced a change in how system-wide mandatory ASLR is implemented. This change requires system-wide bottom-up ASLR to be enabled for mandatory ASLR to receive entropy. Tools that enable system-wide ASLR without also setting bottom-up ASLR will fail to properly randomise executables that do not opt in to ASLR.” states the security advisory.
According to the CERT, the bug only affects applications using mandatory ASLR, while applications that used opt-in Address Space Layout Randomisation and that never used ASLR aren’t affected.
According to the CERT/CC the problem was introduced with Windows 8 with a change in the mandatory Address Space Layout Randomisation implementation.
“Starting with Windows 8, system-wide mandatory ASLR is implemented differently than with prior versions of Windows. With Windows 8 and newer, system-wide mandatory ASLR is implemented via the
HKLM\System\CurrentControlSet\Control\SessionManager\Kernel\MitigationOptions
binary registry value. The other change introduced with Windows 8 is that system-wide ASLR must have system -wide bottom-up ASLR enabled to supply entropy to mandatory ASLR.” continues the advisory.
The CERT explained that both EMET and Windows Defender Exploit Guard can enable mandatory Address Space Layout Randomisation for code that isn’t linked with the
/DYNAMICBASE
flag.
“Both EMET and Windows Defender Exploit Guard enable system-wide ASLR without also enabling system-wide bottom-up ASLR. Although Windows Defender Exploit guard does have a system-wide option for system-wide bottom-up-ASLR, the default GUI value of “On by default” does not reflect the underlying registry value (unset).” states the advisory.
“This causes programs without
/DYNAMICBASE
to get relocated, but without any entropy. The result of this is that such programs will be relocated, but to the same address every time across reboots and even across different systems.”

16 Nov
Matt Miller
@epakskape
Replying to @wdormann
Set bit 15 (0x10000) in HKLM\System\CurrentControlSet\Control\Session Manager\Kernel\MitigationOptions (REG_QWORD). The WDEG team is looking at how to better support this from the UI.
Will Dormann
@wdormann
Or for those not proficient in setting bits in binary registry values (such as myself), either manually set the values indicated in this picture, or if you don't care about clobbering any existing system-wide mitigations, import this .REG file:https://gist.github.com/wdormann/43cffbf823b5c5da8682985ef31c16a9 … pic.twitter.com/i4YNpET0wq

Replies 3 3 Retweets 7 7 likes
Twitter Ads info and privacy
Dormann explained that sysadmins can set a registry value to force bottom-up Address Space Layout Randomisation.
“The CERT/CC is currently unaware of a practical solution to this problem. Please consider the following workaround:
Enable system-wide bottom-up ASLR on systems that have system-wide mandatory ASLR
To enable both bottom-up ASLR and mandatory ASLR on a system-wide basis on a Windows 8 or newer system, the following registry value should be imported:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel]
"MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00" concludes the CC/CERT
Windows 8 and Later Fail to Properly Apply ASLR
21.11.2017 securityweek Safety
Address Space Layout Randomization (ASLR) isn’t properly applied on versions of Microsoft Windows 8 and newer, an alert from Carnegie Mellon University-run CERT Coordination Center (CERT/CC) warns.
The issue is created by the tools that enable system-wide ASLR on newer Windows systems without also setting bottom-up ASLR, a vulnerability note explains.
Starting with Windows 8, system-wide bottom-up ASLR is required for mandatory ASLR to receive entropy, but executables that do not opt in to ASLR aren’t properly randomized if the tools that enable system-wide ASLR don’t also set bottom-up ASLR.
ASLR was introduced in Windows Vista to prevent code-reuse attacks by loading executable modules at non-predictable addresses. Because of this feature, attack methods relying on code being loaded to a predictable or discoverable location, such as return-oriented programming (ROP), were mitigated.
ASLR, however, requires that the code is linked with the /DYNAMICBASE flag to opt in to ASLR, which represents an implementation weakness, the vulnerability note from DHS-sponsored CERT/CC reveals.
To protect applications that don't opt in to using ASLR (or other exploit mitigation techniques), Microsoft released the Enhanced Mitigation Experience Toolkit (EMET), which allows users to specify both system-wide and application-specific mitigations on the system.
Thus, EMET acts as a front-end GUI for system-wide exploit mitigations built in to the Windows operating system. When it comes to application-specific mitigations, the EMET library is loaded into the process space of the applications to be protected.
Starting with the Windows 10 Fall Creators update, Microsoft made EMET native to the operating system by incorporating its capabilities into the Windows Defender Exploit Guard. Both EMET and Windows Defender Exploit Guard can enable mandatory ASLR on a per-application or system-wide basis.
Starting with Windows 8, system-wide mandatory ASLR is implemented via the HKLM\System\CurrentControlSet\Control\Session Manager\Kernel\MitigationOptions binary registry value and requires system-wide bottom-up ASLR enabled to supply entropy to mandatory ASLR.
“Both EMET and Windows Defender Exploit Guard enable system-wide ASLR without also enabling system-wide bottom-up ASLR. […] This causes programs without /DYNAMICBASE to get relocated, but without any entropy. The result of this is that such programs will be relocated, but to the same address every time across reboots and even across different systems,” CERT/CC explains.
Because of this issue, non-DYNAMICBASE applications are relocated to a predictable location on Windows 8 and newer systems that have system-wide ASLR enabled via either EMET or Windows Defender Exploit Guard. This also makes exploitation of the vulnerability easier in some instances.
The CERT team notes that no practical solution to the problem is known at the moment, but that enabling system-wide bottom-up ASLR on systems that have system-wide mandatory ASLR should mitigate the issue.
Importing the following registry value enables both bottom-up ASLR and mandatory ASLR on a system-wide basis on Windows 8 or newer systems:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\kernel]
"MitigationOptions"=hex:00,01,01,00,00,00,00,00,00,00,00,00,00,00,00,00
“Note that importing this registry value will overwrite any existing system-wide mitigations specified by this registry value. The bottom-up ASLR setting specifically is the second 01 in the binary string, while the mandatory ASLR setting is the first 01,” the CERT team notes.
System-wide mandatory ASLR could cause issues on systems with older AMD/ATI video card drivers in use, but the problem was addressed in the Catalyst 12.6 drivers released in June, 2012.
Microsoft was notified on the vulnerability on November 16, the vulnerability note explains.
Global Cyber Alliance launched the Quad9 DNS service to secure your online experience
20.11.2017 securityaffairs Safety
Global Cyber Alliance launched the Quad9 DNS service, the free DNS service to secure your online experience and protect your privacy.
The Global Cyber Alliance (GCA) has launched the Quad9 DNS service (9.9.9.9), a new free Domain Name Service resolver that will check user’s requests against the IBM X-Force’s threat intelligence database.
The Quad9 DNS service non only offer common resolution services implemented by DNSs but it will also add the security checks to avoid you will visit one of the the 40 billion malicious websites and images X-Force marked as dangerous.
The Global Cyber Alliance (GCA) was co-founded by a partnership of law enforcement and research organizations (City of London Police, the District Attorney of New York County and the Center for Internet Security) focused on combating systemic cyber risk in real, measurable ways.
GCA also coordinated the threat intelligence community to incorporate feeds from 18 other partners, “including Abuse.ch, the Anti-Phishing Working Group, Bambenek Consulting, F-Secure, mnemonic, 360Netlab, Hybrid Analysis GmbH, Proofpoint, RiskIQ, and ThreatSTOP.”
Back in 1988 some large /8 blocks of IPv4 addresses were assigned in whole to single organizations or related groups of organizations, either by the Internet Corporation for Assigned Names and Numbers (ICANN), through the Internet Assigned Numbers Authority (IANA), or a regional Internet registry.
Each /8 block contains 224 = 16,777,216 addresses, and IBM secured the 9.0.0.0/8 block which let the company dedicate 9.9.9.9 to the project.
“IBM Security, Packet Clearing House (PCH) and The Global Cyber Alliance (GCA) today launched a free service that gives consumers and businesses added privacy and security as they access the internet. The new Quad9 Domain Name System (DNS) service protects users from accessing millions of malicious internet sites known to steal personal information, infect users with ransomware and malware, or conduct fraudulent activity.” reads the announcement published by the GCA.
According to the GCA, Quad9 has no impact on the speed of the connections, it is leveraging the Packet Clearing House global assets around the world with 70 points of presence in 40 countries.
The alliance believes that Quad9 points of presence will double over the next 18 months, further improving the speed, performance, privacy and security for users globally.
Quad9 DNS service
The organization is specifically committed to protect the users’ privacy, Quad9 service doesn’t retain request data.
“Information about the websites consumers visit, where they live and what device they use are often captured by some DNS services and used for marketing or other purposes”, it said.
The Quad9 service aims to cover not only traditional PCs and laptops, but can also Internet of Things (IoT) devices such as smart thermostats and connected home appliances. These devices often do not receive important security updates and are also difficult to secure with traditional anti-virus tools, yet remain connected to the internet leaving them vulnerable to hackers.
Full instructions on what a DNS service does and how to switch to Quad9 can be found here.
Group Launches Secure DNS Service Powered by IBM Threat Intelligence
18.11.2017 securityweek Safety
A newly announced free Domain Name System (DNS) service promises automated immunity from known Internet threats by blocking access to websites flagged as malicious.
Called Quad9, because the IP address of the primary DNS server being 9.9.9.9, the new service was launched by IBM Security, Packet Clearing House (PCH) and The Global Cyber Alliance (GCA) and is aimed to provide increased security and privacy online to consumer and businesses alike.
The Quad9 service was designed to keep users safe from millions of malicious Internet sites that have been already flagged for stealing personal information, infecting users with ransomware and other type of malware, or for conducting fraudulent activity.
The service routes users’ DNS queries through a secure network of servers and uses threat intelligence from over a dozen cyber security companies to provide real-time perspective on whether the websites are safe or not. The users’ browsers are automatically blocked from accessing a website that the system has detected as being infected.
Quad9 harvests intelligence from IBM X-Force’s threat database and also taps feeds from 18 additional partners, including Abuse.ch, the Anti-Phishing Working Group, Bambenek Consulting, F-Secure, mnemonic, 360Netlab, Hybrid Analysis GmbH, Proofpoint, RiskIQ, and ThreatSTOP.
The service was designed to protect traditional PCs and laptops, along with Internet connected TVs, DVRs, and Internet of Things (IoT) products such as smart thermostats and connected home appliances. Many of these devices do not receive important security updates and are difficult to secure although they remain connected to the Internet, which leaves them vulnerable to hackers.
Performance should not be affected when using the new DNS service, IBM says. At launch, Quad9 has points of presence in over 70 locations across 40 countries, leveraging PCH’s expertise and global assets. The service’s points of presence should double over the next 18 months, in an attempt to improve speed, performance, privacy, and security.
Quad9 says it does not store, correlate or otherwise leverage personally identifiable information (PII) from its users. To take advantage of the new DNS service’s benefits, users only need to set their devices to use 9.9.9.9 as their DNS server.
“Setting up DNS filtering requires just a simple configuration change. Most organizations or home users can update in minutes by changing the DNS settings in the central DHCP server which will update all clients in a few minutes with no action needed at end devices at all. The service is and will remain freely available to anyone wishing to use it,” Quad9’s website reads.
Quad9 started as the brainchild of GCA, but each of the involved partners is responsible for a different aspect of the service. GCA offers system development capabilities, PCH is responsible for Quad9’s network infrastructure, while IBM provides X-Force threat intelligence and the service’s IP address 9.9.9.9.
Other services providing similar (free) offerings include Cisco-owned OpenDNS, and Google’s Public DNS (which uses 8.8.8.8 and 8.8.4.4 as its DNS server IPs).
“Protecting against attacks by blocking them through DNS has been available for a long time, but has not been used widely. Sophisticated corporations can subscribe to dozens of threat feeds and block them through DNS, or pay a commercial provider for the service. However, small to medium-sized businesses and consumers have been left behind – they lack the resources, are not aware of what can be done with DNS, or are concerned about exposing their privacy and confidential information,” said Philip Reitinger, President and CEO of the Global Cyber Alliance.
While the service looks promising, it remains to be seen how it will perform when compared to already established offerings, Lenny Zeltser, Vice President of Products at Minerva Labs, an Israel-based provider of endpoint security solutions, told SecurityWeek in an emailed comment.
“Based on the iniquitous DNS protocol, Quad9 promises to secure network activities in a non-intrusive manner and in a manner that’s easy to deploy. That’s wonderful. Though I’m encouraged by these aspects of the offering, I am curious how it compares to the well-established Cisco Umbrella (formerly OpenDNS) service, which has been around for a while and earned trust among end-users and IT practitioners. Similarly, Google DNS servers provide some network security benefits to their users,” Zeltser said.
Joseph Carson, chief security scientist at Thycotic, a Washington D.C. based provider of privileged account management (PAM) solutions, told SecurityWeek that the new service’s focus on privacy is more than welcomed. Privacy as we know it is disappearing fast, with everyone being watched and monitored 24/7 when in public places, in an attempt to improve security and deliver tailored experiences, he says.
“The new DNS service from Quad9, with a focus on both privacy and security, is a step in the right direction. It is a must needed level of protection in today’s world of cyber threats and helps put the balance back in the consumers. While many governments and ISP’s are removing the ability for citizens to surf the internet with privacy and confidence in security, Quad9 has stepped in to bring a bit of balance back. It will help bring some peace of mind to many who want to surf the internet without being continuously targeted and limit personal information flowing through the internet without their knowledge,” Carson said.
“It is also important to note that what Quad9 is providing is not 100% security. Therefore, you must continue to be cautious when using the internet and always question any suspicious links or advertisements displayed. This will not stop you from getting phishing emails or social media threats so it is always important to take additional steps. Continue to do best practices when purchasing anything online and manage your credentials and passwords securely,” he concluded.