Safety Articles - H 2020 1 2 3 4 5 6 Safety List - H 2021 2020 2019 2018 1 Safety blog Safety blog
Microsoft Extends Office Bounty Program
18.9.2017 securityweek Safety
Microsoft has announced an extension to its Microsoft Office Bounty Program, which is now set to run until December 31, 2017.
Launched in mid-March 2017, the bounty program was initially set to run until June 15, 2017, promising payouts between $6,000 to $15,000, depending on the discovered vulnerability’s severity and type. The program was launched for Office Insider Builds on Windows.
Microsoft now says that researchers can submit their bug reports until December 31, 2017, and that the extension is retroactive for any cases submitted during the interim. The company is looking for issues in the Office Insider Builds, which provide users with early access to new Office capabilities and security innovations.
“The engagement we have had with the security community has been great and we are looking to continue that collaboration on the Office Insider Builds on Windows. This program represents a great chance to identify vulnerabilities prior to broad distribution,” Phillip Misner, Principal Security Group Manager, Microsoft Security Response Center, notes in a blog post.
Participating researchers can earn the maximum bug reward of $15,000 for vulnerabilities such as Elevation of privilege via Office Protected View sandbox escape; Macro execution by bypassing security policies to block Office macros in Word, Excel, and PowerPoint; and Code execution by bypassing Outlook’s automatic attachment block policies for a predefined set of extensions.
Only high quality reports on these types of vulnerabilities will be awarded the maximum payout. Low quality reports, the company says, won’t be awarded more than $9,000. Proof of concept is required for reports to be eligible, but a functioning exploit isn’t, Microsoft explains in the bounty program’s terms page.
Eligible submissions should identify “an original and previously unreported vulnerability in the current Office Insider build on a fully patched Windows 10 desktop,” the tech giant says. Submissions that can be reproduced on the previous build but not on the current aren’t considered eligible.
Microsoft also notes that “the first eligible external report received on an internally known issue under active development will receive a maximum of $1,500.”
Participating researchers should send their submissions to secure@microsoft.com.
Chrome to Label FTP Resources as "Not Secure"
15.9.2017 securityweek Safety
Google announced on Thursday that future versions of Chrome will label resources delivered via the File Transfer Protocol (FTP) as “Not secure.”
The change will be implemented starting with Chrome 63, currently scheduled for release in December 2017. The move is part of Google’s long-term plan to flag all non-secure connections in an effort to alert users and encourage website owners and administrators to migrate to HTTPS.
“We didn't include FTP in our original plan, but unfortunately its security properties are actually marginally worse than HTTP (delivered in plaintext without the potential of an HSTS-like upgrade),” Google software engineer Mike West explained.
West pointed out that FTP usage for top-level navigations was 0.0026% in the last month. In the case of downloads, there were roughly 5% that were conducted over something other than HTTP/HTTPS, which could be FTP.
Google has encouraged website developers to migrate the downloads they offer, particularly for executable files, from FTP to HTTPS, and pointed as an example to the Linux Kernel Archives, which plans on terminating all FTP services by the end of the year.
Chrome developers have been discussing the possibility of removing built-in support for FTP since January 2014, but for the time being the use of the protocol will only be marked as “not secure.”

“When a feature gets usage that low, we generally start talking about removing it. Especially if it exposes attack surface or is fundamentally unsafe on the network, as FTP does and is,” said Google’s Chris Palmer.
FTP has been around in its current form since the 1980s. Support for the SSL and TLS protocols can be added via the FTP Secure (FTPS) extension, but FTPS is not supported by web browsers.
“As for FTPS, I'm glad it exists, but if we were going to focus on getting server operators to migrate to a new protocol, we would focus (and are focusing) on HTTPS,” Palmer added.
Incapsula Updated Review — New Security Options, Improved Delivery and Reliability
7.9.2017 thehackernews Safety
It's been close to five years since we last looked at Incapsula, a security-focused CDN service known for its DDoS mitigation and web application security features.
As one would expect, during these five years the company has expanded and improved, introducing lots of new features and even several new products.
Most recently, Incapsula underwent an extensive network expansion that includes new PoPs in Asia including two new data centers in New Delhi and Mumbai.
This seems like an excellent opportunity to revisit the service and see how it has evolved.
Acquisition, Award and Growth
Before we jump into Incapsula's service upgrades, we want to mention the changes in the company itself briefly.
The most notable of those is Incapsula’s 2014 acquisition by Imperva—an authority in web application security and a four-time Gartner Magic Quadrant leader for web application firewalls.
The acquisition boosted Incapsula’s security capabilities, resulting in its own cloud-based WAF also being recognised by Gartner analysts. Similarly, Incapsula’s DDoS mitigation solutions were awarded a leadership position in a Forrester Wave for DDoS Service Providers report.
Even more impressive is the company’s growth.
When we reviewed Incapsula, its services had a few thousand users. It is now the platform of choice for numerous prominent organisations, including some of the largest bitcoin exchanges (BTC China, Bitstamp & Unocoin), online retailers (KickUSA) and popular SaaS companies (Moz).
Today, Incapsula services are being used by over 160,000 organisations worldwide.
Incapsula Service Review
Leveraging its newfound success and resources, Incapsula spent the last five years investing heavily in its technology, both to boost its legacy business and to venture into new directions, such as addressing its customers’ non-security needs.
New DDoS Protection Options
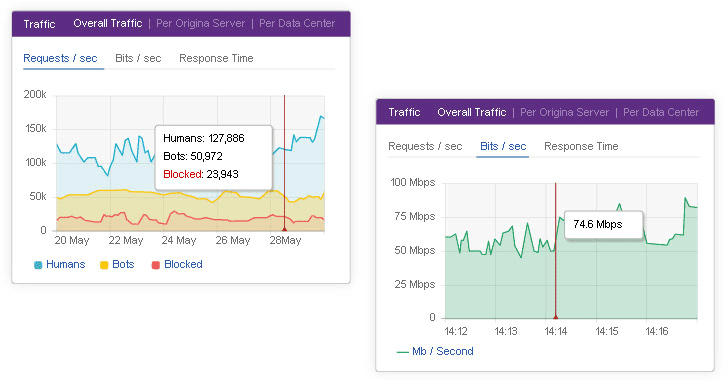
Incapsula was always known for its DDoS mitigation. Playing to its strengths, many of its newest features expand its DDoS mitigation capabilities.
When we first reviewed Incapsula, they were already mitigating layer 3-4 and layer 7 DDoS attacks.
Today, Incapsula has evolved to protect against direct-to-DNS attacks. It now also offers a BGP-enabled DDoS mitigation service to complement its previous CDN-based offering. This BGP-based solution allows Incapsula to protect any type of online service (email servers, FTP, you name it) in addition to websites and web applications.
To address the increase in attack sizes and demand from new customers, Incapsula improved network protection by upgrading its scrubbing capacity to over 3.5 tbps.
One of its most interesting solutions is DDoS protection for individual IPs.
Usually, this kind of protection is only available to companies that have an entire Class C subnet. Incapsula, however, has found a smart way around that requirement, which makes it an excellent choice for small and medium businesses that don’t own a subnet but still find themselves bombarded by DDoS assaults.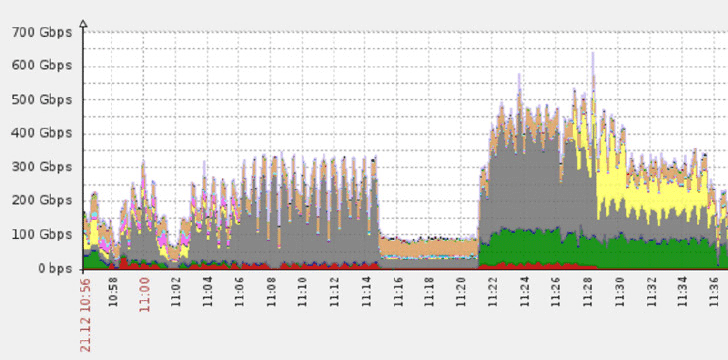
Incapsula recently mitigated a massive 650gbps DDoS flood
Using its array of new technologies, Incapsula has mitigated some of the largest and highest profile attacks in recent memory, including a record-setting 650gbps DDoS flood and a recent 54-hour assault against a prominent US college.
These are just a few prominent examples. To give you some idea of the entire scope of Incapsula activity, in the first quarter of 2017 the company mitigated an average of 266 network layer attacks and 1,099 application layer assaults every week. This adds up to just over 17,500 attacks in a quarter.
Performance and Reliability
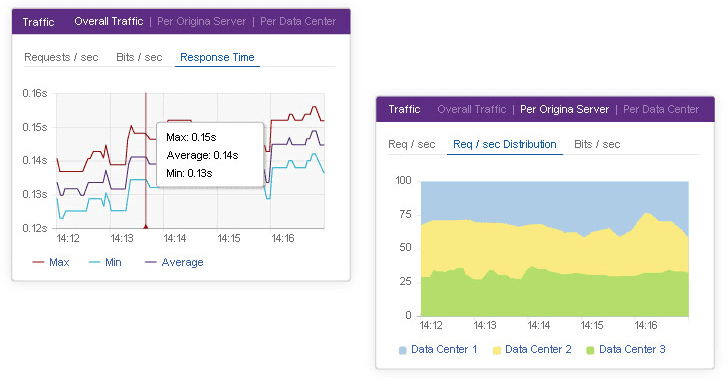
In addition to its new anti-DDoS solutions, and the benefits that Imperva brought to its cloud-based WAF, Incapsula also expanded its offering to include several reliability and performance features.
In our opinion, the most interesting of these is a cloud-based load balancer that offers one centralised option for both in-data center and cross-data center load management.
The service is not TTL reliant, which enables near-instant rerouting. What’s more, the traffic distribution techniques it uses are more accurate than most appliance counterparts. Specifically, it has the ability to distribute the load, based on the actual volume of process requests on each end server and the ability to perform failover in a matter of seconds.
These benefits and the fact that the service is offered in a subscription-based model makes it great value for money; especially for organisations that operate several data centers and need to purchase multiple services and appliances. On the performance front, Incapsula’s CDN offering was boosted by a host of additional control and optimisation features. These offer granular control over caching policies based on resource type and file location, as well as the ability to purge cache in real-time, a standard issue for many CDN platforms.
Other new control features include an Incapsula application rule engine that governs application end delivery through custom policies. These offer a literally limitless amount of custom optimisation options that are most likely to benefit larger and more complex sites.
A Security First Application Delivery Platform
Five years ago we mostly viewed Incapsula as a CDN based WAF with some DDoS mitigation solutions. The service has since outgrown that description.
Incapsula's new availability and application delivery services, as well as many new security features, make Incapsula what it always claimed to be: a full-fledged application delivery platform that marries security, performance and availability in one cost-effective service package.
That said, Incapsula is still a security first enterprise-grade service, so it isn’t a good alternative to free CDNs on the market.
However, for commercial organisations looking for more than an underlying CDN and check box security, we recommend checking out Incapsula. You can start by signing up for a free enterprise plan trial to see if it’s a good fit.
Google Introduces App Engine Firewall
25.8.2017 securityweek Safety
Google on Thursday informed cloud platform customers that the beta release of its App Engine firewall is available for testing.
The Google App Engine firewall allows developers and administrators to easily allow or block traffic from specified IP addresses by defining a set of rules and ordering them based on priority.
Hosting an application in the cloud has many benefits, but unwanted traffic can have a negative impact on workloads and it can result in significant costs.
According to Google, the App Engine firewall addresses this problem by returning an HTTP 403 Forbidden response to requests from denied IP addresses before they hit the application.
“App Engine firewall replaces the need for a code-based solution within your app that still allows requests in, but which can cost you resources and still expose your app,” explained Lorne Kligerman, product manager at Google.
The App Engine firewall can be accessed from the Google Cloud Console or via the App Engine Admin API and the gcloud command-line tool. Users can specify which IPs they want to allow -- for example, allow only IPs from the organization’s private network, or only traffic coming through a third-party web application firewall (WAF) set up to proxy requests to the app.
They can also deny certain types of traffic, including denial-of-service (DoS) and other attacks. Users are also offered a “Test IP” feature that allows them to check if the rules they’ve configured work properly.
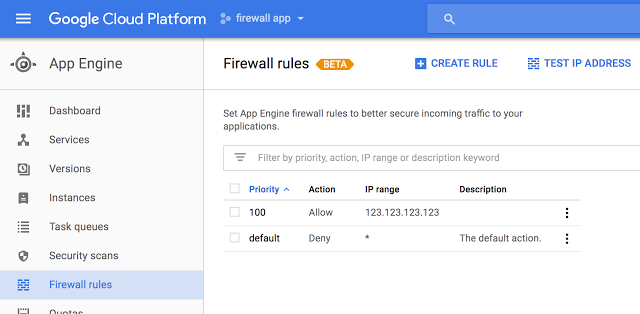
“With App Engine firewall, it’s easy to set up network access to your app and focus on what matters most: your app, without worrying about access control within your code,” Kligerman said.
Since the App Engine firewall is still in beta, Google advises against using it in production environments.
This is not the only security feature available for the Google App Engine. Google’s cloud platform also includes identity and access management (IAM), a security scanner for identifying vulnerabilities, and a DoS protection service.
Uber Settles Complaint Over Data Protection for Riders, Drivers
16.8.2017 securityweek Safety
Uber agreed to implement new data protection measures to settle complaints that it failed to prevent improper snooping on driver and customer information, officials said Tuesday.
The ridesharing giant had faced complaints that it allowed some employees to use the "God view" to monitor customer movements that could allow Uber managers to keep tabs on journalists investigating the ridesharing giant.
A separate complaint said that Uber had also failed to prevent a data breach that allowed hackers to gain access to personal information on some 100,000 drivers.
The Federal Trade Commission announced a settlement on an investigation into allegations that Uber failed to live up to data protection claims.
"Uber failed consumers in two key ways: First by misrepresenting the extent to which it monitored its employees' access to personal information about users and drivers, and second by misrepresenting that it took reasonable steps to secure that data," said FTC acting chairman Maureen Ohlhausen in a statement.
"This case shows that, even if you're a fast growing company, you can't leave consumers behind: you must honor your privacy and security promises."
The settlement contains no financial penalty, but Uber agreed to implement "a comprehensive privacy program" that will include independent audits, the FTC said. If it fails to live up to the agreement it could face fines.
The agency which enforces consumer and privacy protection said Uber had announced in November 2014 -- but failed to enforce -- a "strict policy" prohibiting employees from accessing rider and driver data except for legitimate business purposes.
The FTC added in a statement that Uber "did not take reasonable, low-cost measures" that could have prevented a breach by using better practices to protect data in the internet cloud.
Uber, which has become the world's most valuable venture-backed startup despite complaints from regulators and others, has been roiled by a series of revelations about a toxic work culture and questionable business practices.
Its chief executive Travis Kalanick resigned in June, but investors and board members are battling over his successor and a lawsuit by one investor alleges Kalanick has been working behind the scenes to manipulate the board.
Cylance Launches Next-Gen Endpoint Security for Consumers
3.8.2017 securityweek Safety
CylancePROTECT Home Edition Will Allow Businesses to Offer Protection to Employee-Owned Devices at Home
The BYOD threat is a known security weakness for most companies that operate an 'own device' policy. While there are endpoint management products that provide a degree of safety, the mere fact that the device is owned outside of the network and used both inside and outside of the corporate environment means that it must be treated as insecure and a potential threat.
“The virtual borders of corporate networks are no longer defined by the corporate firewall," explains Christopher Bray, SVP/GM Consumer at Cylance Inc. "Because of the proliferation of work and personal devices at home, the distinction between the corporate network and employee's home networks has become blurred. CISOs and their security teams have a difficult time controlling their security risk and exposure from cybersecurity threats originating from employees' homes."
CylancePROTECT Home Edition
While corporate security has received a fillip from the introduction of next-gen AI and machine-learning malware detection, no such solution is available to home users. Home users usually ignore anti-malware, or use one of the free home versions of traditional AV -- which is not the perfect solution for modern malware.
"CylancePROTECT Home Edition," Bray told SecurityWeek, "is the first next-generation antivirus available to consumers and provides families with the only enterprise-class, next generation security software built for home use. We do this by using artificial intelligence to eliminate the need for updates and popups, and with an easy-to-use and elegant interface. We're excited to roll out the Home Edition to customers as the next step in Cylance's mission to protect all devices and people.”
This move is likely to be well-received by corporate CISOs. "I think this is a great idea," said Steven Lentz, CSO and Director of information security at Samsung Research America. "It's good that companies are offering home users protection since I bet a good amount of them are infected, or don't know they have embedded malware/ransomware on their systems.
"Cylance," he told SecurityWeek, "has a good reputation, so I would believe and hope that their offering should be pretty good. Home users are such a large target area -- and vendors need to be more proactive and protect against all the various malware." Lentz does not believe that 'traditional AV' does a good enough job against modern malware. "I am glad Cylance is doing this for the home user. I hope they offer it for free, like RansomFree [next-gen from Cybereason; but limited to ransomware]. It would also be great if Cylance offered the product for Mac as well as Windows."

Lentz gets half his wishes. It is not free. It "will be sold on an annual basis, paid for by the employer for employees to use on their home systems," Bray told SecurityWeek. "Companies recognize the risk of today's threats combined with the new working environment where employees telecommute and can use personal devices to access company assets." Although used at home, it provides additional security for the business.
It also represents pretty good value. It is priced per household, allowing the employee to protect up to 10 family members' devices no matter where they are in the country. Further, it can be viewed as an employment benefit -- protecting the corporate network while providing a free service to employees and their families.
But Lentz gets his second wish: it is available for both Windows and Mac. "With our company mission to protect every device under the sun," said Bray, "this is the first step in our future plans (which will include iOS and Android)."
One of the traditional problems for any company installing security on employee devices is the privacy pushback; many employees are wary about having company software on their personal device reporting back to the company security team. Users like the freedom of allowing other family members to use their devices, and not having to worry about corporate security policies. There is no issue with CylancePROTECT Home Edition -- it is completely stand-alone and designed to protect the user without reference to the company.
"Home Edition does not send any metrics or reports to the company," explained Bray. "We architected the product very deliberately to ensure complete privacy for the employees. Their deployments are physically separate so it is impossible for the company to have any view into their personal systems. This data, however, is easily accessed by the employee themselves through their own cloud console through which they can manage, configure and view their personal deployments. This also gives the employee the additional benefit of deploying and managing protection across their family's systems irrespective of physical location; kids at college, parents in another city..."
In summary, Home Edition is a complete next-gen anti-malware product, free to the end user (paid for by his employer) and coming with no privacy encumbrances. If Lentz is a good example, it will be welcomed by CISOs -- but they may well wish it were free.
Cylance Inc closed a $100 million Series D funding round in June 2016.
Researchers Demo Physical Attack via Car Wash Hack
29.7.2017 securityweek Safety
LAS VEGAS - BLACK HAT USA - Researchers have created proof-of-concept (PoC) exploits to demonstrate how hackers can cause physical damage to vehicles and injure their occupants by remotely hijacking a connected car wash.
The attack was detailed in a presentation at the Black Hat security conference this week by WhiteScope founder Billy Rios, a researcher best known for finding vulnerabilities in medical devices and industrial control systems (ICS), and Dr. Jonathan Butts, founder of QED Secure Solutions and committee chair for the IFIP Working Group on Critical Infrastructure Protection.
The experts pointed out that automated car wash systems are essentially ICS and, just like industrial systems, they can be hacked and manipulated.
Their research has focused on LaserWash, an automated car wash which, according to its creator, PDQ Manufacturing, can “think for itself.”LaserWash car wash can be hacked remotely
Rios and Butts discovered that the web-based administration panel for the product, which is in many cases accessible directly from the Internet, has many features, including for sending email alerts and a widget for social media.
However, the more problematic issue is that both the owner and engineer accounts for the web interface are protected by weak default passwords. They also discovered that the authentication mechanism can be bypassed by a hacker.
Once they gain access to the web interface, a hacker can take control of the car wash system. The PoCs developed by the researchers show how an attacker can disable safety signals and take control of the bay doors, which can be used to either lock the vehicle in or unexpectedly strike it and its occupants. Hackers can also take control of the robotic washing arm and continuously discharge water or hit the vehicle and its occupants, the researchers said.
Rios first informed PDQ of the LaserWash vulnerabilities back in February 2015, just before disclosing his findings at Kaspersky’s Security Analyst Summit. However, the vendor ignored Rios for more than a year.
Now that Rios and Butts developed PoC exploits that demonstrate the risks in a real world scenario, PDQ has confirmed the existence of the flaws and claims it’s working on developing fixes.
According to an advisory published by ICS-CERT on Thursday, the vulnerabilities affect several models of PDQ’s LaserWash, Laser Jet and ProTouch automatic car wash systems.
ICS-CERT warned that the flaws can be exploited remotely even by an attacker with a low skill level, and provided a series of measures recommended by the manufacturer for mitigating the threat. The steps include changing the default password and ensuring that the equipment is behind a firewall.
VMware API Allows Limited vSphere Users to Access Guest OS
29.7.2017 securityweek Safety
LAS VEGAS - BLACK HAT USA - Researchers discovered that a VMware API can be abused by vSphere users with limited privileges to access the guest operating system without authentication. VMware has provided workarounds for preventing potential attacks exploiting the vulnerability.
VMware vSphere is a virtualization product that includes ESXi hypervisors, vCenter Server for managing vSphere environments, and the vSphere Client, which is used to manage virtual machines (VMs).
The security issue was discovered by employees of data center and cloud security firm GuardiCore while analyzing VMware’s Virtual Infrastructure eXtension (VIX) API, which helps users write scripts to automate VM operations and manipulate files within the guest OS.
The VIX API includes functionality that allows direct access to the guest OS. While this functionality is primarily designed for use by VMware Site Recovery Manager, VMware Update Manager and VMware Infrastructure Navigator, GuardiCore researchers discovered that it can also be abused by vSphere users with limited privileges to access the guest OS.
GuardiCore at Black Hat
In a presentation at the Black Hat security conference in Las Vegas, Ofri Ziv, VP of research at GuardiCore, revealed that an attacker can exploit the vulnerability to gain full control of the guest OS, including for arbitrary code execution with elevated privileges, lateral movement across the targeted data center (including to isolated networks), and data theft.
Ziv pointed out that such an attack is unlikely to be detected by many security products as it doesn’t leave any trace. The flaw impacts guest machines running ESXi 5.5 and VMware tools prior to version 10.1.0.
In order to exploit this flaw, the attacker requires basic knowledge of how the VIX API works and a limited vSphere account. This account needs to have the “Virtual Machine -> Configuration -> Advanced,” “Virtual Machine -> Interaction -> Guest Operating System Management by VIX API” and the “Host -> Configuration -> Advanced Settings” privileges for the attack to work.
This means that the attacker would most likely be a malicious insider. The vulnerability can be highly useful for breaking segmentation, which is a critical requirement for virtual environments. Even VMware tells customers that guest VMs should be isolated from the host and other guests running on the same host.
Ziv told SecurityWeek in an interview that isolation between VMs and their host is particularly important in financial institutions and other organizations where IT teams should not be allowed to access the sensitive data stored inside the VMs they manage.
VMware, which assigned this vulnerability the identifier CVE-2017-4919 and an “important” severity rating, published an advisory on Thursday. The company informed customers that vCenter Server versions 5.5, 6.0 and 6.5 are affected, and provided workarounds for VMs running on ESXi 6.0. The problematic functionality in the VIX API can be disabled manually in the case of VMware Tools 9.10.0 through 10.0.x. Starting with VMware Tools 10.1.0, the function has been disabled.
GuardiCore has released an open source risk assessment tool, PoC exploits, and a fork of open-vm-tools to address the vulnerability in ESXi 5.5. The company has also published a blog post containing technical details.
Google Inviting 2-Step Verification SMS Users to Google Prompt
18.7.2017 securityweek Safety
Google this week will start inviting 2-Step Verification (2-SV) SMS users to try Google Prompt, its year-old method of approving sign-in requests on smartphones.
Launched in June 2016, Google prompt allows users to approve sign-in requests via 2-SV by simply tapping “Yes” on a prompt. Available for both Android and iOS users, Google prompt received an improvement in February 2017, when Google added real-time security information about the login attempt, such as when and where it was made.
Google Prompt offers 2-SV over an encrypted connection and provides users with additional security features as well, including the option to block unauthorized access to their account.
While 2-SV users can also login by tapping a Security Key or by entering a verification code sent to their phone, in addition to using prompts, Google is now inviting those who receive a SMS on their phones to try Google prompts when they sign in.
“The invitation will give users a way to preview the new Google Prompts sign in flow instead of SMS, and, afterward, choose whether to keep it enabled or opt-out,” the Internet giant explains in a blog post.
In July last year, the National Institute of Standards and Technology (NIST) started deprecating SMS 2-step verification, just months after security researchers published a paper revealing that vulnerabilities in the mechanism expose it to simple bypass attacks.
“Overall, this is being done because SMS text message verifications and one-time codes are more susceptible to phishing attempts by attackers. By relying on account authentication instead of SMS, administrators can be sure that their mobile policies will be enforced on the device and authentication is happening through an encrypted connection,” Google notes.
According to the company, only 2-SV SMS users will receive the notification to test Google prompts, meaning that those using Security Key aren’t affected. The use of Google prompt requires a data connection. On iOS devices, it also requires the Google Search app to be installed. Enterprise edition domains can enforce security keys for more advanced security requirements.
“While users may opt out of using phone prompts when shown the promotion, users will receive follow-up notifications to switch after 6 months,” the company concludes.
New IBM Z Mainframe Designed to "Pervasively Encrypt" Enterprise Data
17.7.2017 securityweek Safety
New IBM Z14 Mainframe Introduces Encryption Engine Capable of Running More Than 12 Billion Encrypted Transactions Per Day
The combination of an explosion in data breaches and increasingly severe regulatory requirements requires a new approach to security: the mainframe is back. IBM has announced its latest mainframe, the IBM z14, in what it calls "the most significant re-positioning of mainframe technology in more than a decade."

Encryption is seen as the best solution for both data loss and regulatory compliance. But encryption is hard, requiring more time and processing power than most companies have at their disposal. At the same time, it is becoming an increasingly attractive solution. More than nine billion data records have been lost or stolen since 2013; and only 4% were encrypted. Next year, the General Data Protection Regulation (GDPR) could, in theory, impose fines of up to 4% of global turnover for the loss of unencrypted personal data.
Photo of IBM Z14 MainframeA second regulation requiring widespread encryption is the NYSDFS cyber security regulation. This states, "As part of its cybersecurity program, based on its Risk Assessment, each Covered Entity shall implement controls, including encryption, to protect Nonpublic Information held or transmitted by the Covered Entity both in transit over external networks and at rest." 'Nonpublic Information' could almost be interpreted as 'everything'. The automatic facility to encrypt everything in transit and at rest -- as does the IBM Z -- will make its capabilities particularly attractive to banks and financial institutions that are governed by the New York State Department of Financial Services.
Encryption, where possible, is the one single solution that can solve both data loss (if it's encrypted, it's not lost) and compliance. IBM discussed the problem with 150 of its clients over three years and came up with its solution: a new mainframe with sufficient power and versatility to provide pervasive encryption.
IBM Z, says the firm, makes it possible, for the first time, for organizations to pervasively encrypt data associated with an entire application, cloud service or database in flight or at rest with one click. "The standard practice today," it says, "is to encrypt small chunks of data at a time, and invest significant labor to select and manage individual fields." But this approach doesn't scale, so encryption is often incomplete and/or inaccurate.
Encryption is only a solution, of course, if the decryption keys are kept safe. IBM Z offers what the company calls 'tamper-responding encryption keys'. Keys are invalidated at any sign of intrusion, and can be restored in safety. This key management system is designed to meet Federal Information Processing Standards (FIPS) Level 4 standards, and can be extended beyond the mainframe to other devices such as storage systems and servers in the cloud.
IBM's solution has been to introduce more power into a new mainframe: a massive 7x increase in cryptographic performance over the previous generation z13 -- driven by a 4x increase in silicon dedicated to cryptographic algorithms. "This is 18x faster than compared x86 systems (that today only focus on limited slices of data)," it claims, "and at just five percent of the cost of compared x86-based solutions."
These aren't the only large numbers associated with the new mainframe -- IBM claims it features the world's fastest microprocessor running at 5.2GHz. A single system can support more than 12 billion encrypted transactions per day; supports the world's largest MongoDB instance with 2.5x faster NodeJS performance than compared x86-based platforms; two million Docker Containers; and 1000 concurrent NoSQL databases.
Few companies will want to pay mainframe prices for compliance alone. However, IBM is also previewing new Z/OS software that aids with private cloud service delivery, enabling owners to transition from an IT cost center to a value-generating service provider.
It is also being incorporated into the IBM Cloud, where it will initially be used as an encryption engine for cloud services, and to run IBM blockchain services in six new centers in Dallas, London, Frankfurt, Sao Paulo, Tokyo and Toronto.
"The powerful combination of IBM Z encryption and secure containers differentiates IBM Blockchain services on the cloud by supporting the trust models new blockchain networks require,” said Marie Wieck, general manager, IBM Blockchain. "Enterprise clients also benefit from the ease of use making management transparent to the application and the user."
Windows 10 Will Now Let You Reset Forgotten Password Directly From the Lock Screen
17.7.2017 thehackernews Safety
Microsoft is making every effort to make its Windows 10 Fall Creators Update bigger than ever before by beefing up its security practices and hardening it against hackers and cyber attacks in its next release.
Microsoft is finally adding one of the much-requested features to Windows 10: Pin and Password recovery option directly from the lock screen.
Yes, the next big update of Windows 10, among other features, will allow you to recover your forgotten pin and password, allowing you to reset your Windows password directly from the lock screen.
In Windows 10 Fall Creators Update, you will see "Reset password" or "I forgot my PIN" options on the login screen along with the sign-in box, mspoweruser confirmed.
Once you click on the option, Windows 10 will take you to the OOBE where Cortana will help you reset your password, after you successfully verify your identity using either your secondary email, your phone number, or Microsoft Authenticator.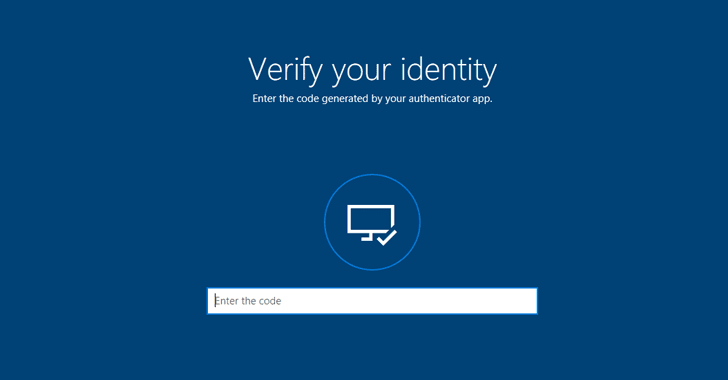
A verification code will be sent to the option you chose, and once you entered and verified your identity, you will be able to reset the password and regain access to your computer directly from the login screen.
The tech giant is currently testing this new feature in its Windows 10 Insiders build 16237, making it much easier for them to recover their Microsoft Accounts.
You can use this option if you have either activated the Windows Hello authentication system or have a PIN to secure your account.
With the launch of Windows 10 Creator Update (also known as RedStone 3), which is expected to release sometime between September and October 2017, the company has already planned to:
Remove the 30-year-old SMB v1 file sharing protocol.
Build AI-powered antivirus software.
Build its EMET anti-exploit tool into the kernel of the operating system.
Support three different flavours of the Linux OS – Ubuntu, Fedora, and SUSE – directly through their Windows Store.
Add new anti-ransomware feature, called Controlled Folder Access, as part of its Windows Defender.
Besides this new upgrade, Windows 10 Fall Update also includes improvements to Acrylic Material translucency effects, Task Manager, Mixed Reality headset and much more.
You can check out the complete list here.
How encryption can help startups in protecting their data
16.7.2017 securityaffairs Safety
The deployment of encryption in modern businesses does not only guarantee hundred percent security but it also reduces the surface of attack.
Data protection has become the top objective for many businesses in the world today. Especially after the ransomware incident, hacked credit card databases and the Apple leak. Businesses are scratching their heads in anticipation of what could hit them next?
It is a brilliant idea from the executives to prioritize data protection over everything. Nonetheless, it is equally difficult to harmonize security processes across several systems and devices. Even the most cautious and watchful business owners can leave out data unprotected.
Encryption is highly regarded as one of the best-sought solutions for this problem. The deployment of encryption in computers, cloud systems, mobile phones and other business avenues does not only guarantee hundred percent security but it also substantially eliminates the potential of being attacked and incurring financial loss.
encryption
How does encryption work?
Creating a synergy with other security measures, encryption secures the data and its trafficking to other parties. After being encrypted, a file becomes impossible to crack or decipher, and it becomes difficult to break into sensitive or valuable business information.
How can business owners encrypt their company’s data?
As a responsible and clever business owner, you must place a high emphasis on data breaches and financial losses, and this can only be achieved by employing complete encryption of devices and network. Encryption can be implemented and help in the following areas for protection of your valuable data:
Wi-Fi Hotspots
A laptop acts as a blessing when traveling and you require access to company files, but using an unsecured Wi-Fi public hotspot can backfire pretty badly and make you vulnerable to attacks.
Emails
With email becoming the standard medium for the exchange of sensitive information, it is equally important to keep the process encrypted to avoid losing information to data thieves. All businesses should engage in premium level encryption to protect their data, irrespective of whether probable hackers possess physical access to computers or not.
Passwords
Your password is an essential element of encryption. To make the password hack-proof, make it long; 10 or more characters is advisable. The code should consist both upper and lower case letters, numbers, and special characters. It is recommended to keep separate passwords for each system and device, and document them in a safe place if remembering them is a hard job to do.
Cloud
Despite its attractiveness such as affordability, convenience, and sharing, Cloud Storage solutions are quite vulnerable to external attacks. Dropbox and other big names in the Cloud storage scene offer built-in data encryption of your data stored on their servers. But, the point to be highlighted here is that they also hold the decryption keys, which, in certain situations might be used to access your stored information. There are many products which give an extra protection layer to cloud storage locations.
Search Engines
Like it or not, Google, Yahoo, and other search engines will catalog every search you perform on the internet. Your online web search choices are then attached to your computer’s IP address and are subsequently used to customize the advertising and searches for your machine. This cataloging might seem unobtrusive and perhaps even useful, but it is also a risk for future public embarrassment and social faux pas. Don’t let these search engines store your searches for ‘anti-depressants,’ ‘love advice,’ ‘divorce lawyers,’ and ‘anger management’. To avoid it, a VPN browser can help you cloak your IP address so you can keep your private searches private. If you are connected to a VPN, your online traffic is redirected to a 3rd party server, which encrypts the information.
USB and External Drives
Portable data storage and plug and play devices sure are useful, but attached with it are the theft/loss strings. Gladly, products such as BitLocker To Go, helps keep portable storage drives encrypted when fallen into the wrong hands.
A password to open a company PC would be useless if one can get away with the hard disk. All it would require is, to connect the hard drive to another system and alas, access to all the data right in front. To avoid this mishap, Microsoft BitLocker software for Ultimate Windows 7 or Vista (or the Enterprise or Pro Windows 8), that offers complete hard drives encryption. To turn on the feature, just go to Control Panel > System and Security > BitLocker Drive Encryption.
In a Nutshell…
Guarding your sensitive information against theft and vulnerability isn’t a tough task in today’s digital world, particularly with the progressive adoption of cloud computing. The fact of the matter is, despite all the security measures, sometimes, hackers and cyber criminals still can find their way through a company’s or individual’s system, making it vulnerable to date theft or data leakage.
For that reason, it is said to consider prudently what (and when) you want to save on the cloud, and consult with a professional cloud services provider to find out what encryption level suits you best.
In the modern business environment, which is increasingly depending upon on computers and cloud-based storage, nothing is or at least should be, dearer to you than a rock-solid encryption strategy which can ensure your long-term safety and success.
Eternal Blues scanner allowed to find 50,000 EternalBlue-vulnerable host
1.7.2017 securityaffairs Safety
The Eternal Blues scanner allowed administrators worldwide to discover more than 50,000 computers vulnerable to the NSA-linked EternalBlue exploit.
Recently the security researcher Elad Erez developed Eternal Blues, a free EternalBlue vulnerability scanner that could be used by administrators to assess networks.

Now Elad Erez published data collected by the Eternal Blues over the two weeks, the results are disconcerting, more than 50,000 scanned hosts are still vulnerable to the exploit. The data is even more worrisome if you consider that a single vulnerable machine could expose the entire network to the attackers.
The administrator of a network composed of 10,000 hosts discovered the only two machines were still vulnerable, in information that was crucial to protect the entire network.
As of July 12, the Eternal Blues tool was used to scan more than 8 million IPs, 1.5 million are located in France.

Erez revealed that vulnerable machines were found in around 130 countries, top 3 countries had more than 30,000 vulnerable machines.
53.82% of the vulnerable hosts still have SMBv1 enabled, 1 out of 9 hosts in a network is vulnerable to EternalBlue.
Although Eternal Blues found only around 50,000 vulnerable systems,
Erez explained that the number of vulnerable machines is much higher than 50,000, he explained that issues with the tool prevented it from correctly counting the number of vulnerable hosts.
Erez issued a new release of the tool on July 2 that fixes the above problems.
Below the results of the scan:
More than 8 million IPs were scanned. France taking the lead with 1.5 million
The top 3 vulnerable countries (out of ~130), had more than 30,000 vulnerable hosts altogether
The majority (53.82%) of hosts nowadays still have SMBv1 enabled
1 out of 9 hosts in a network is vulnerable to EternalBlue
One network, with almost 10,000 hosts (not IPs), had 2 vulnerable hosts. How could anyone find that without Eternal Blues?
Erez is satisfied by the scanner that has increased in a significant way the level of awareness on EternalBlue exploit allowing administrators to secure their networks.
“Unfortunately, exploitation of EternalBlue is still a very good method of invoking remote code execution. It is available in more than 50,000 hosts scanned by Eternal Blues (as for July 12, 2017). Yes, even after all the latest attacks by WannaCry and NotPetya. I’m here to remind you, sometimes it takes just 1 vulnerable machine to take you down.” concluded the expert.
“Although numbers are quite high (remember, these are IPs scanned with my tool only), I feel like awareness did increase somewhat. Running Eternal Blues is, by definition, being aware of the problem. So good for you for taking responsibility and checking your network status. Now it’s patching time!”
Administrators are recommended to periodically scan their networks for Eternal Blue flaw, to apply the latest patches and disable the SMBv1 protocol.
Dell Launches Endpoint Security Product for Air-Gapped Systems
13.7.2017 securityweek Safety
Dell announced on Thursday the availability of a new version of its Endpoint Security Suite Enterprise product designed specifically for air-gapped systems.
The solution is designed to protect isolated computers from malware, insiders and other threats using artificial intelligence and predictive mathematical models provided by endpoint security firm Cylance.
Researchers demonstrated in the past years that malware can leverage several methods to exfiltrate sensitive data from air-gapped systems, including through noise, LEDs, heat and radio frequencies.Dell Launches Endpoint Security Product for Air-Gapped Systems
Since isolated systems are not connected to the Internet, the security products installed on them cannot automatically receive regular malware definitions and other updates. By teaming up with Cylance, whose mathematical models only require a few updates per year, Dell has developed a solution that can protect a device without requiring an Internet connection.
In addition to threat protection features, Endpoint Security Suite Enterprise provides data encryption capabilities designed for securing files on any device against both external attacks and insiders (e.g. malicious USB drives). IT teams can enforce encryption policies on multiple endpoints and operating systems without disrupting productivity, Dell said. The product also includes web protection filtering capabilities.
Three versions of Dell Endpoint Security Suite Enterprise are currently available: one for systems with an Internet connection, one for devices that connect to an on-premises server for updates, and one for systems that are completely isolated.
"Highly-regulated organizations and government agencies need to deploy air gap solutions to protect their highly sensitive data, but have been unable to take advantage of the latest security technology that requires cloud connections," said Brett Hansen, vice president of Endpoint Data Security and Management at Dell.
"Dell is responding to their heightened needs by adapting our flagship Endpoint Security Suite Enterprise solution for on-premises, air gap environments – giving these organizations an advanced threat protection solution that has been inaccessible to them before now," Hansen added.
The air gap version of Dell Endpoint Security Suite Enterprise is available now in the United States and other select countries around the world.
Free Scanner Finds 50,000 EternalBlue-Vulnerable Systems
13.7.2017 securityweek Safety
More than 50,000 computers vulnerable to the NSA-linked EternalBlue exploit were found by a free vulnerability scanner in recent weeks.
Dubbed Eternal Blues, the tool was designed to provide network administrators with visibility into the EternalBlue-vulnerable machines in their networks, but without actually exploiting the flaw. In the wake of WannaCry, NotPetya, and other global infections leveraging the NSA-linked exploit, knowing whether a network is vulnerable or not is certainly a good idea.
According to Elad Erez, the security researcher who built the scanner, data collected through Eternal Blues over the past couple of weeks reveals that more than 50,000 scanned hosts are vulnerable to the exploit.
Erez also warns that sometimes all it takes is a single vulnerable machine to compromise an entire network. Using Eternal Blues, the administrator(s) of a network with around 10,000 hosts found the only two machines that were still vulnerable, thus securing the entire environment.
As of July 12, over 8 million IPs were scanned using Eternal Blues, most of which (1.5 million) are located in France. Vulnerable machines were found in around 130 countries and the top 3 countries “had more than 30,000 vulnerable hosts altogether,” the security researcher says.
Over half (53.82%) of the vulnerable hosts still have SMBv1 enabled, the researcher also discovered. Moreover, he notes that 1 out of 9 hosts in a network is vulnerable to EternalBlue.
Although Eternal Blues found only around 50,000 vulnerable systems, Erez warns that the number is much higher. Issues with the scanner prevented it from correctly reporting the number of vulnerable host. The researcher addressed those in a version released on July 2, but didn’t take previous findings into account when presenting the above numbers.
According to Erez, however, awareness on EternalBlue appears to have increased. The mere fact that admins are using the scanner is proof of that, he says.
To keep systems and networks secure, admins should apply the latest patches, perform periodic assessments of risks in their networks, and disable SMBv1, the researcher says. He also advises enabling automatic updates on Windows systems.
“Please, don’t be mistaken – recent ransomware attacks are the ones that made all the buzz, since they actually tell you when they hit you. I believe there are many more EternalBlue-based attacks which remain off the radar and are still unknown to,” the researcher points out.
Let's Encrypt Wildcard Certificates a 'Boon' for Cybercriminals, Expert Says
12.7.2017 securityweek Safety
To speed up the adoption of HTTPS, free and open Certificate Authority (CA) Let’s Encrypt will start issuing wildcard certificates as of January 2018.
Created by Mozilla, the University of Michigan, and the Electronic Frontier Foundation (EFF), with Cisco and Akamai as founding sponsors, Let’s Encrypt is pushing for a fully encrypted World Wide Web. The move should help better protect user data from eavesdroppers, but some concerns have been raised about the new offering.
Let’s Encrypt came out of private beta in December 2015 and issued its millionth certificate in March 2016. Last week, the organization announced it had already issued over 100 million security certificates, thus becoming one of the largest CAs by number of issued certificates.
Now, the organization is moving to accelerate HTTPS deployment by starting to issue wildcard certificates, “a commonly requested feature.”
“A wildcard certificate can secure any number of subdomains of a base domain (e.g. *.example.com). This allows administrators to use a single certificate and key pair for a domain and all of its subdomains, which can make HTTPS deployment significantly easier,” Josh Aas, ISRG Executive Director, notes.
Let’s Encrypt’s over 100 million digital certificates are used to secure around 47 million domains, which also benefit from the CA’s fully automated DV certificate issuance and management API. According to Aas, Let’s Encrypt’s service already helped the percentage of encrypted page loads to rise from 40% to 58%.
The organization will be offering wildcard certificates free of charge via an upcoming ACME v2 API endpoint. Only base domain validation via DNS will be supported in the beginning, but the CA may explore additional validation options over time.
“We decided to announce this exciting development during our summer fundraising campaign because we are a nonprofit that exists thanks to the generous support of the community that uses our services. If you’d like to support a more secure and privacy-respecting Web, donate today,” Aas concludes.
Let’s Encrypt’s goal might be improved security and privacy for all users, but it doesn’t mean that its certificates can’t be misused. In March 2017, encryption expert Vincent Lynch revealed that, over a 12-month period, Let’s Encrypt issued over around 15,000 security certificates containing the term PayPal for phishing sites.
According to Kevin Bocek, chief security strategist for Venafi, Let’s Encrypt’s introduction of free wildcard certificates is great for privacy, but a boon for cybercriminals.
“Cybercriminals can create thousands of fake websites using Let’s Encrypt’s wildcard certificates, all with a seemingly trustworthy glowing green padlock in the web browser address field,” Bocek told SecurityWeek. “We have seen bad actors abuse Let’s Encrypt certificates before: more than 14,000 certificates were issued for PayPal phishing websites by Let’s Encrypt, a powerful example of how bad guys exploit Certificate Authority business processes.”
“There’s no putting the Let’s Encrypt genie back in the bottle, but this means every organization could be a victimized by malicious websites designed to spoof their customers and partners,” Bocek added. “This means every organization must monitor the internet for malicious certificates. Google’s Certificate Transparency initiative and other similar technologies allow organizations to spot fake or malicious certificates regardless of the CA.”
Katyusha Scanner — Telegram-based Fully Automated SQL Injection Tool
12.7.2017 thehackernews Safety
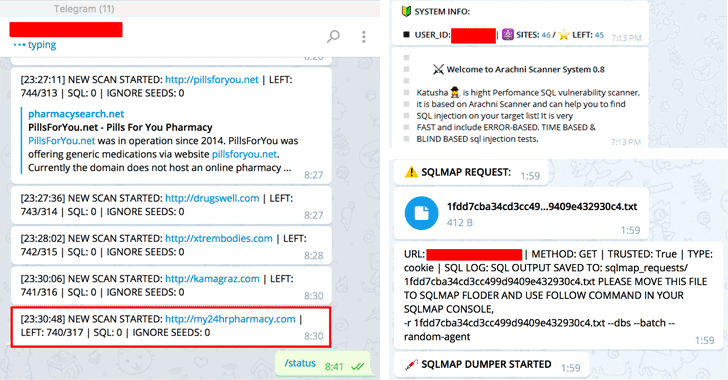
A new powerful hacking tool recently introduced in an underground forum is making rounds these days, allowing anyone to rapidly conduct website scans for SQL injection flaws on a massive scale — all controlled from a smartphone using the Telegram messaging application.
Dubbed Katyusha Scanner, the fully automated powerful SQLi vulnerability scanner was first surfaced in April this year when a Russian-speaking individual published it on a popular hacking forum.
Researchers at Recorded Future's Insikt Group threat intelligence division found this tool for sale on an underground hacking forum for just $500. Users can even rent the Katyusha Scanner tool for $200.
According to the researchers, Katyusha Scanner is a web-based tool that's a combination of Arachni Scanner and a basic SQL Injection exploitation tool that allows users to automatically identify SQLi vulnerable sites and then exploits it to take over its databases.
Arachni is an open source vulnerability scanning tool aimed towards helping users evaluate the security of their web applications.
What makes this tool stand out of line is its 'Infrastructure-as-a-Service' model.
Remotely Control Hacking Tool Via Telegram
Katyusha Scanner is abusing the Telegram messaging application to control its operations, such as sending and receiving commands.
The Katyusha Scanner tool is quite easy to setup and use, allowing anyone to conduct large-scale penetration attacks against a large number of targeted websites simultaneously with the mere use of their smartphones.
The Pro version of the tool not just identifies vulnerable websites, but also allows hackers to establish a "strong foothold within vulnerable web servers" and automatically extract "privileged information such as login credentials."
Once the scan is complete, Katyusha Scanner sends a text message to the criminals with the vulnerable site name, its Alexa web ratings, helping criminals identify popular websites that would likely be more profitable for them to attack, and the number of databases.
The criminals, even with no technical knowledge, can download any exfiltrated data available by just clicking on their smartphones to issue commands.
Katyusha Scanner also allows for the automatic dumping of databases and can be used on both Linux as well as Windows machines.
"The availability of a highly robust and inexpensive tool...Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits," researchers at Recorded Future wrote.
Many buyers praised the quality of the tool on the black market site, one of the satisfied customers who got immediate success in obtaining access to eight web servers wrote:
"Excellent support! The seller has configured the software for my server, which was failing before, however, right now it flies divinely! I highly recommend the software, and it has found eight SQL vulnerabilities in half a day, great automation of the routine. Very grateful to the seller."
Another wrote: "The author has helped with the product setup after the purchase, and (Katyusha) has immediately found SQL vulnerability. Thank you for the great product."
Initially, Katyusha Scanner was sold for $500, but due to unexpectedly high demand, a light version of the tool with slightly limited functionality was released on May 10, 2017, at just $250.
With the release of the most recent Katyusha 0.8 Pro update at the end of June, the author also made the scanner available for rent at $200 per month for the first time.
SQLi Vulnerability Scanner Available on Hacking Forum at $500
11.7.2017 securityweek Safety
A fully automated SQLi vulnerability scanner is available for purchase on a hacking forum for just $500, Recorded Future security researchers have discovered.
Dubbed Katyusha Scanner, the powerful tool was posted on a popular hacking forum by a Russian-speaking individual, on April 8, 2017. The scanner takes advantage of the functionality of Telegram messenger, as well as of Anarchi Scanner, an open-source penetration testing tool, the security researchers reveal.
The application has already received numerous updates, the last of them introduced on June 26, 2017, as Katyusha 0.8 Pro. Because of “outstanding support” from its author, the scanner immediately gained popularity among users, and started being praised for its intuitive and straightforward interface, and for performance capabilities.
Not only does the scanner allow miscreants to control the hacking process using a standard web interface, but it also provides users with the possibility to “upload a list of websites of interest and launch the concurrent attack against several targets simultaneously,” the researchers say. The operation can be seamlessly controlled via Telegram messenger.
Apparently, the scanner’s name specifically reflects this capability, making reference to the multiple-rocket launcher developed by the Soviet Union during World War II.
“Similar to the very lethal weapon conceived 70 years ago, Katyusha Scanner allows criminals to initiate large-scale penetration attacks against a massive number of targeted websites with several clicks using their smartphones,” Recorded Future explains.
Katyusha Scanner was made available at $500, with a light version released on May 10, 2017 at $250. The latter variant has slightly limited functionality, but was introduced due to the high demand the original scanner registered. Along with the Katyusha 0.8 Pro update at the end of June, the author also made the tool available for rent at $200 per month.
Recorded Future researchers warn that “the Pro version offers significantly more robust functionality, not only capable of identification but also establishing a strong foothold within vulnerable web servers and an automatic extraction of privileged information such as login credentials.”
Once the scan has been completed, the tool can display the Alexa web rating for each identified target, providing cybercriminals with “immediate visibility into the popularity of the resource and possible profit level in the future.”
The scanner can search and export email/password credentials, is multi-threaded (with support for concurrent sessions), and offers a module framework, Telegram messenger interface, and web interface. Furthermore, it allows for automatic dumping of databases, supports SQLMAP reports and file upload (the list of targeted websites), and can be used on both Linux and Windows.
The web shell module features CMS family identification (Bitrix, WordPress, OpenCart, etc.), login credentials brute-forcing (concurrent with SQLi scan), and automatic web shell upload.
Available scanning options include SQL injection (sql_injection) — Error-based detection (Oracle, InterBase, PostgreSQL, MySQL, MSSQL, EMC, SQLite, DB2, Informix, Firebird, SaP Max DB, Sybase, Frontbase, Ingres, HSQLDB, MS Access), Blind SQL injection using differential analysis (sql_injection_differential), and Blind SQL injection using timing attacks (sql_injection_timing – MySQL, PostgreSQL, and MSSQL).
“Despite the fact that SQLi attacks have been around for over 20 years, we are still seeing them successfully being used as common attack vectors by online criminals The availability of a highly robust and inexpensive tool such as Katyusha Scanner to online criminals with limited technical skills will only intensify the compromised data problem experienced by various businesses, highlighting the importance of regular infrastructure security audits,” Recorded Future concludes.
What is the hype around Firewall as a Service?
10.7.2017 thehackernews Safety
Admit it. Who would not want their firewall maintenance grunt work to go away?
For more than 20 years, companies either managed their edge firewall appliances or had service providers rack-and-stack appliances in their data centers and did it for them.
This was called a managed firewall — an appliance wrapped with a managed service, often from a carrier or managed security service provider (MSSP).
The provider assumed the management of the firewall box, its software, and even its policy and management from the over-burdened IT team. But customers ended up paying for the inefficiency of dealing with appliances (i.e. “grunt work”) because the problem just shifted to the provider. A new architecture was needed - a transformation from an appliance form factor to a true cloud service.
In a 2016 Hype Cycle for Infrastructure Protection report, Gartner analyst Jeremy D'Hoinne initiated the emerging category of Firewall as a Service (FWaaS).
He defined FWaaS as “...a firewall delivered as a cloud-based service or hybrid solution (that is, cloud plus on-premises appliances). The promise of FWaaS is to provide simpler and more flexible architecture by leveraging centralized policy management, multiple enterprise firewall features and traffic tunneling to partially or fully move security inspections to a cloud infrastructure”
Recently, in the 2017 Magic Quadrant for Unified Threat Management (SMB Multifunction Firewalls), the analysts reference a Gartner client survey indicating 14% of respondents were likely (8%) or very likely (6%) to consider moving all the firewall security functions to FWaaS.
FWaaS isn't merely packaging of legacy appliances into a managed service. It is challenging the decades-old concept of the appliance as the primary form factor to deliver network security capabilities.
What is an FWaaS?
FWaaS offers a single logical firewall that is available anywhere, seamlessly scales to address any traffic workload, enforces unified policy, and self-maintained by a cloud provider.
Let’s look at these elements in more detail.
• Single, global firewall instance — One firewall instance for the entire global organization is radically different than the current architecture that places a network security stack at each location, a regional hub or a datacenter.
With FWaaS every organizational resource (data center, branch, cloud infrastructure or a mobile user) plugs into the FWaaS global service and leverages all of its security capabilities (application control, URL filtering, IPS, etc).
• Seamlessly scales to address inspection workload — FWaaS provides the necessary compute resources to perform all security processing on all traffic regardless of source or destination.
IT teams no longer need complex sizing processes to determine the appliance capacity needed to plan for today’s business requirements and future growth.
For example, the increase in SSL traffic volume pressures appliance processing capacity and can force unplanned. FWaaS can scale to accommodate these needs without disrupting the customer’s business operations.
• Enforcing a unified policy — A single firewall, by design, has a single security policy. While legacy appliance vendors created centralized management consoles to ease managing distributed appliances, IT must still consider the individual firewalls instances per location and often customize policies to the locations’ unique attributes.
In heterogenous firewall environments (often created due to M&A) security policy is hard to configure and enforce increasing exposure to hackers and web-borne threats. Contrast that with a single cloud-based firewall that uniformly applies the security policy on all traffic, for all locations and users.
• Self-maintained — One of the most painful aspects of firewall management is maintaining the software through patches and upgrades. It is a risky process that could impact business connectivity and security.
Many IT teams tend to skip or completely avoid software upgrades, leaving enterprise exposed. Because the cloud-based firewall software is maintained by the FWaaS provider and is shared by all customers, the firewall is kept up to date by quickly fixing vulnerabilities and bugs, and rapidly evolving with new features and capabilities that the customers can immediately access.
FWaaS is bringing genuine relief to overburdened IT teams within enterprises and service providers. Instead of wasting cycles on sizing, deploying, patching, upgrading and configuring numerous edge devices, work can now shift to delivering true security value to the business through early detection and fast mitigation of true risk.
FWaaS Providers
FWaaS is not a mere concept. It has been deployed in production deployments and by several vendors.
Cato Networks is a provider of the Cato Cloud, built from the ground up to deliver Firewall as a Service.
Cato provides an optimized, global SD-WAN, ensuring resilient connectivity to its FWaaS in from all regions of the world. Cato can completely eliminate edge firewalls by inspecting both WAN and Internet-bound traffic. The Cato Cloud FWaaS further extends to mobile users and cloud datacenters.
Zscaler provides FWaaS for Internet-bound traffic from remote branches and mobile users. To secure WAN traffic, customers must rely on other means.
Palo Alto Networks recently announced a similar service. It uses its next generation firewall within a cloud service to protect users, whether in remote locations or mobile, accessing the Internet.
FWaaS is a viable alternative for IT teams that waste time and money to sustain their distributed edge firewall environments — the so-called appliance sprawl.
With FWaaS, they can now reduce the operational and capital expense of upgrading and refreshing appliances as well as the attack surface resulting from delayed patches and unmitigated vulnerabilities.
By simplifying the network security architecture, FWaaS makes IT more productive and the business secure.
Researcher released Eternal Blues, a free EternalBlue vulnerability scanner
1.7.2017 securityaffairs Safety
The security researcher Elad Erez developed Eternal Blues, a free EternalBlue vulnerability scanner that could be used to assess networks.
Now systems administrators and hackers have a new free tool, dubbed Eternal Blues, to scan networks looking at computers vulnerable to the NSA EternalBlue exploit.
EternalBlue is one of the hacking tools that the ShadowBrokers hacker group stolen to the NSA-linked Equation Group. The ShadowBrokers group leaked online the EternalBlue tool in April this year, a few weeks later Microsoft released security updates to fix the flaw exploited by the NSA exploit.
In May, the security expert Miroslav Stampar, a member of the Croatian Government CERT, discovered a new worm, dubbed EternalRocks, that exploits the EternalBlue flaw in the SMB protocol to spread itself like the popular WannaCry ransomware.
Security experts discovered later another hacking tool dubbed EternalRocks, a malware that uses 7 NSA exploits and that leverages the EternalBlue flaw to spread itself like WannaCry ransomware.
The Eternal Blues tool was developed by the researcher Elad Erez, of course, it designed for testing purposes and not to identify networks to hack.
“Eternal Blues is a free EternalBlue vulnerability scanner. It helps finding the blind spots in your network, these endpoints that are still vulnerable to EternalBlue.” explained Elad Erez.
“Just hit the SCAN button and you will immediately start to get which of your computers are vulnerable and which aren’t. That’s it.”

Companies and organizations can scan their networks for computers vulnerable to the EternalBlue exploit.
The tool was developed spread awareness and allow not technical organizations to assess their networks.
“The majority of latest WannaCry, NoPetya (Petya, GoldenEye or whatever) victims, are not technical organizations and sometimes just small business who don’t have a security team, or even just an IT team to help them mitigate this. Running NMap, Metasploit (not to mention more commercial products) is something they will never do. I aimed to create a simple ‘one-button’ tool that tells you one thing and one thing only – which systems are vulnerable in your network.” added Erez.
Erez also published the following tips to the admins who will use the tool.
If you’re about to run it in your working environment, please update the IT/Security team in advance. You don’t want to cause (IDS/IPS/AV) false alarms
If vulnerable systems were found – please take a Windows update asap
For god sake, please disable SMBv1 already. Whether your systems are patched or not. This protocol was written over 3 decades ago…!
If you would like to enjoy the tool but disallow sending anonymous statistics (which is so uncool), disable access to my website
The developer informed users that his tool sends back to him anonymous usage statistics through Google Analytics.
Free EternalBlue Vulnerability Scanner Released
30.6.2017 securityweek Safety
A free tool that can scan networks to discover computers that are vulnerable to the NSA-linked EternalBlue exploit is now available.
EternalBlue is a tool that hacker group ShadowBrokers allegedly stolen from the National Security Agency (NSA)-linked Equation Group. It was made public in April this year, one month after Microsoft released patches for it and for various other exploits. -
In addition to being fully ported to Metasploit, EternalBlue was one of the seven NSA exploits to have been included in a network worm dubbed EternalRocks. What made the exploit famous, however, was its use in the global WannaCry outbreak.
Weeks before WannaCry, however, a stealth Remote Access Trojan (RAT) was using the exploit to compromise systems. The cryptocurrency miner Adylkuzz was also abusing EternalBlue before WannaCry. Additionally, the UIWIX ransomware was using the exploit around the same time as WannaCry.
Over the past week, EternalBlue came into focus once again, as it started being used in yet another worldwide outbreak by the destructive NotPetya wiper.
Microsoft president and chief legal officer Brad Smith has already warned of the risks that stockpiling exploits brings along, and a bi-partisan group of lawmakers already announced the introduction of the 'Protecting Our Ability to Counter Hacking Act of 2017' -- the PATCH Act.
This, however, does little to protect companies from attacks leveraging EternalBlue, especially if they are unaware of the existence of vulnerable machines within their networks. Dubbed Eternal Blues, the newly released free tool is meant to provide a helpful hand by scanning their network for computers that can be compromised via this exploit.
According to the tool’s developer Elad Erez, Eternal Blues has been already tested on real world networks. The utility wasn’t meant to exploit the vulnerability, but only to find it and notify of its existence.
“The majority of latest WannaCry, NotPetya victims are not technical organizations and sometimes just small business who don’t have a security team, or even just an IT team to help them mitigate this. I aimed to create a simple ‘one-button’ tool that tells you one thing and one thing only – which systems are vulnerable in your network,” Erez explains.
The developer also advises admins who find vulnerable computers using his tool to apply the necessary patches as soon as possible, and also to disable SMBv1, even on patched systems, considering that the protocol was written over three decades ago. The tool, he reveals, sends anonymous usage statistics through Google Analytics, including number of scanned computers and found vulnerabilities.
Microsoft to Make EMET Native to Windows 10
29.6.2017 securityweek Safety
Microsoft is no longer interested in retiring its Enhanced Mitigation Experience Toolkit (EMET) but will instead make it native to Windows 10, the tech giant announced this week.
Initially released in 2009, EMET was designed to protect against certain zero-day software vulnerabilities at a time when there was a 3-4 years gap between Windows releases. The tool helped Microsoft disrupt common exploit kits and even features Windows 10 compatibility.
Seven years later, after it had already accelerated the release of new Windows iterations, Microsoft said EMET was no longer needed. The company initially announced plans to retire EMET on Jan. 27, 2017, but then pushed the end-of-life date back 18 months, to July 31, 2018, based on customer feedback.
In November 2016, as a reply to Microsoft’s claim that Windows 10 doesn’t need EMET to deliver great protection, CERT vulnerability analyst Will Dormann said in a blog that EMET includes additional protections that Windows 10 doesn’t.
Now, Rob Lefferts, Director of PM, Windows Enterprise and Security at Microsoft, says that feedback from customers who “are clearly fans of threat protections offered through EMET the Enhanced Mitigation Experience Toolkit (EMET)” determined the company to make the tool native to Windows 10 in the form of Windows Defender Exploit Guard.
The Exploit Guard is meant to pack both EMET capabilities and new vulnerability mitigations, in an attempt to deliver new prevention capabilities and make exploitation of vulnerabilities dramatically more difficult. The tool would also include a new class of intrusion prevention capabilities.
“Using intelligence from the Microsoft Intelligent Security Graph (ISG), Exploit Guard comes with a rich set of intrusion rules and policies to protect organziations from advanced threats, including zero day exploits. The inclusion of these built-in rules and policies addresses one of the key challenges with host intrusion prevention solutions which often takes significant expertise and development efforts to make effective,” Lefferts says.
Windows 10 Fall Creators Update will bring EMET back, alongside a variety of additional security improvements, Lefferts also announced. These include Windows Defender Application Guard (WDAG) and “substantial updates” to Windows Defender Device Guard and Windows Defender Antivirus.
“Windows Defender Advanced Threat Protection (ATP) will include seamless integration across the entire Windows threat protection stack to protect, detect and respond with rich, centralized management. In addition, we’re extending the reach of Windows Defender ATP to include Windows Server OS to protect customers across platforms,” Lefferts notes.
WDAG should prevent attackers from compromising local machines or moving laterally into the network by isolating malware downloaded via the browser or zero-day exploits. “With more than 90% of attacks using a hyperlink to initiate stealing credentials, installing malware, or exploiting vulnerabilities,” the browser emerges as the most common target for attackers, and Microsoft will focus on securing it.
Microsoft also plans on integrating Windows Defender Device Guard into Windows Defender ATP response capabilities, to ensure customers have better control over applications. Further, Windows 10 should deliver “a new level of security” to enterprises, along with new analytic capabilities, Microsoft says.
Microsoft Adding Artificial-Intelligence Based Advanced Antivirus to Windows 10
28.6.2017 thehackernews Safety
Microsoft is making every effort to make its Windows operating system more secure and advanced than ever before by beefing up its security practices and hardening it against hackers and cyber attacks in its next release.
With the launch of its Windows 10 Creator Update (also known as RedStone 3), which is expected to release sometime between September and October 2017, Microsoft is planning to release lots of security features in an effort to prevent major global malware crisis.
Just a few days ago, we reported about Microsoft's plan to build its EMET or Enhanced Mitigation Experience Toolkit into the kernel of the upcoming Windows 10 to boost the security of your computer against complex threats such as zero-day vulnerabilities.
Also, the tech giant has planned to remove the SMBv1 (Server Message Block version 1) — a 30-year-old file sharing protocol which came to light last month after the devastating WannaCry outbreak — from the upcoming Windows 10 (1709) Redstone 3 Update.
Now, Microsoft is turning to artificial intelligence (AI) to create next generation of antivirus software.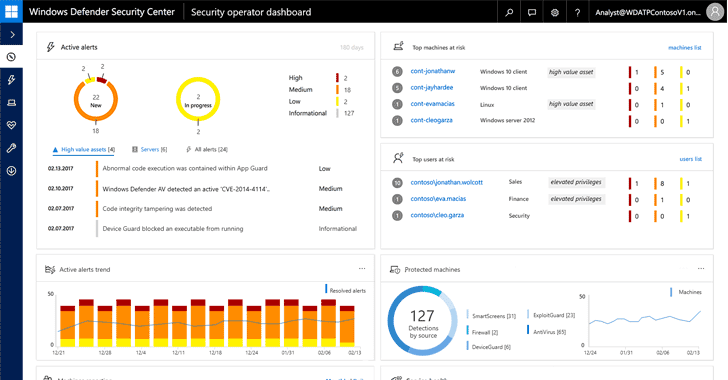
Microsoft has revealed that its Windows Defender Advanced Threat Protection (ATP), a Windows 10 enterprise service that flags early signs of infection, will soon be augmented with AI-driven malware analysis.
"The stack will be powered by our cloud-based security intelligence, which moves us from a world of isolated defenses to a smart, interconnected, and coordinated defense grid that is more intelligent, simple to manage, and ever-evolving," Microsoft explains in a blog post.
In the Fall Creators Update for Windows 10, Microsoft will use a broad range of data from Redmond's cloud services, including Azure, Endpoint, and Office, to create an AI-driven antivirus that can pick up on malware behavior and protect other PCs running the operating system.
So, when a new file is discovered by Microsoft's anti-malware cloud service and determined to be malware, its signature will be created, and the AI system will then look for similar malware on other Windows PCs that have network connectivity.
It means this new AI-driven anti-malware system will eliminate the need for users and sysadmins to configure clients and servers to install local patches of antivirus signatures, stopping attacks as they happen and before they have an impact.
Microsoft told CNET that its upcoming update would rely on machine learning from more than 400 Million PCs running Windows 10 to prevent the next global malware crisis like WannaCry and Petya Ransomware attacks.
According to Rob Lefferts, Windows Enterprise, and Security Director, 96 percent of cyber-attacks involve new and zero-day malware, which takes the company hours to create signatures.
But the new AI system will significantly speed up that process by looking for instances of odd behavior within apps to detect an attack.
"If Word were to start allocating memory in big chunks when it never does, we would be able to detect that," Lefferts said. "We built the machine learning models around common applications like Word."
Besides this new upgrade, Windows Defender Advanced Threat Protection also includes some new features like browser-focused Application Guard and cloud-related Device Guard and Exploit Guard.
Akamai Launches New DNS Security Product
28.6.2017 securityweek Safety
Content delivery network and cloud services provider Akamai announced on Tuesday the launch of a new product designed to protect enterprises against malware, phishing and data exfiltration attempts through the analysis of DNS requests.
The new solution, Enterprise Threat Protector, aims to address the risks associated with DNS communications. According to Akamai, the product leverages threat data from the company’s Cloud Security Intelligence system to determine the “intent” of DNS requests and detect potentially targeted attacks.
Enterprise Threat Protector analyzes an organization’s recursive DNS requests and blocks connections to domains associated with suspicious or malicious activity, including malware drop sites, ransomware, and phishing pages.Akamai logo
Akamai says the product can also disrupt communications between infected hosts and command and control (C&C) servers. It’s not uncommon for malware to rely on DNS for data exfiltration and Enterprise Threat Protector should prevent attempts to send data outside the protected organization.
Security teams can also utilize the new product to improve compliance and enforce acceptable use policies.
Since Enterprise Threat Protector is a cloud-based solution, it’s highly scalable and it can be configured and deployed within minutes without the need for new hardware or complex changes to the network.
"Our customers' security teams are facing adversaries that consistently shift attack tactics and vectors, specifically seek out gaps in defenses and can be incredibly persistent in attempts to find weaknesses in a company's security posture. Enterprises need quick-to-deploy and easy-to-manage cloud-based solutions that can address these unique issues as part of their overall security strategy," said John Summers, vice president and general manager of Enterprise Products at Akamai. "With Enterprise Threat Protector, we're providing our customers with a powerful, intelligent solution that can help detect and stop targeted attacks in their tracks."
Cloudflare Launches New App Store for Websites, $100 Million Development Fund
27.6.2017 securityweek Safety
Cloudflare Launches New Website App Store and Partners With Venture Firms to Launch $100 Million Development Fund
In December 2016 Cloudflare acquired Eager, a firm with a system for developing apps and integrating them into websites. The outcome of that acquisition is launched today with Cloudflare Apps, a free platform that enables developers to build apps and make them available to the 6 million websites that use the Cloudflare network.
In effect, Cloudflare is relaunching its own app store; but in a format that it now intends to grow. It has partnered with its first three venture capital investors to support app developers from a new $100 million Cloudflare Development Fund. Qualified developers will now have the opportunity to receive a cash investment, marketing support, and technical advice from the participating venture capital partners.
That financing is in the same tradition as that used by Sun when it launched Java, by Apple when it launched the Apple Apps Platform, and by Salesforce when it launched force.com. "When we discussed our plans with our investors," Matthew Prince, co-founder and CEO of Cloudflare, told SecurityWeek, "it was their idea to establish financing to help developers produce the next big idea in value-added apps. Now, if a developer is interested in building some new app only made possible by the Cloudflare network, it can apply for financing to help make it possible."
The investors concerned are New Enterprise Associates (NEA), Venrock, and Pelion Venture Partners. Cloudflare's app platform is an exciting opportunity for developers and investors," commented Bryan Roberts, Partner, Venrock. "Building on the success of other app platforms like Java and the iPhone App Store, Cloudflare is giving entrepreneurs the opportunity to rethink and shape how the next generation of Internet companies get built."
Cloudflare has long offered a few apps, but nothing that could be called a serious app store. This new venture is intended to change that with a completely new platform. "The Apps Platform is a collection of APIs that allow developers to easily produce apps that can run across the network," Prince told SecurityWeek. "It's similar to the platform built by Apple. We make it easy for the developers to produce apps, and easy for them to get paid for those apps. The existing apps will continue to work; but we believe this will enable a whole new class of website apps that couldn't exist without a network like Cloudflare that can efficiently deploy the code globally. The platform allows developers to take advantage of Cloudflare resources around the world, and then be able to make it much easier for anyone, whether a small niche WordPress site or a large organization, to use those apps."
"When you build a startup, you need three things: a way to efficiently reach customers, a way to get paid, and capital to finance your development," explained Prince. Together the Cloudflare Apps Platform and Development Fund solve these three challenges."
The Cloudflare network comprises some 6 million website customers that use Cloudflare's approximately 115 worldwide data centers for security -- such as DDoS mitigation-- and performance optimization. The basic service is free, but more advanced options can be paid for.
The new app service will add app code to delivered customer web pages as the page passes through Cloudflare's data centers. This provides both flexibility and control. Developed apps can be added to websites by customers simply by specifying which sites or pages on which they should run. For the customer, everything is automatic and requires zero coding.
Traditionally, of course, apps provide vulnerabilities. Android itself, for example, is quite secure -- it is that Android apps that can introduce problems to the Android ecosphere. SecurityWeek asked Prince if the new app platform could introduce vulnerabilities either to the Cloudflare network, or its customers.
Potentially, yes, he admitted; but then explained Cloudflare's approach -- which is closer to Apple than it is to Android. "We've taken an approach similar to Apple. We review all apps before deployment, and each one is individually sandboxed and cannot affect any other app," he explained. The control element comes because no code is ever installed on the customer's website, merely added to the page between the website and the viewer's browser. This makes it even stronger than the walled garden, because without hacking Cloudflare itself, there is no possible equivalent to the iOS weak point, sideloading.
"If a vulnerability is ever discovered, much like Apple we can withdraw that application from any customer that is using it and prevent any other customer from using it in the future. So, while there is a potential that an app vulnerability may slip through the vetting and the static analysis that we do before it is delivered, it is never deployed software. The app is code that is running on our hardware and injected into web pages as they pass through our systems; and we can simply turn it off without any effect on the customer's website."
"VigLink [one of the three VC investors] has always focused on empowering publishers, and the launch of Cloudflare Apps is a watershed moment," enthuses Oliver Roup, CEO and founder. Incremental publisher revenue is delivered without compromising user experience, now a single click away from more than 4 million of the web's savviest publishers. A better Internet isn't just faster and safer, it's more lucrative too."
Human error is the root cause of password reset email sent to AA customers
27.6.2017 securityaffairs Safety
UK car insurance company AA accidentally sent out a ‘password update’ email to its customers, the incident was caused by a human error.
UK car insurance company AA accidentally sent out a “password update” email to its customers, the messages led the motorists to log into the motoring organization’s website to change their passwords. The concurrent access of a so large number of customers crashed the AA servers, then its customers couldn’t access their profiles, believing their accounts were compromised by hackers.
In reality, the incident was caused by a human error, according to AA no passwords had been changed and people couldn’t access their account because the server was flooded with access requests.

The AA company reassured its customers by confirming that the change password messages were sent out for error.
Follow
The AA ✔ @TheAA_UK
The email was sent by us, but in error. Your password hasn't been changed, and your data remains secure. Sorry for any confusion.
2:08 PM - 26 Jun 2017
9 9 Retweets 8 8 likes
Twitter Ads info and privacy
In a first time, the company confirmed that something of strange was happening to its customers, the message it posted on Twitter led use into believing that its customers were targeted by a phishing campaign.
Follow
The AA ✔ @TheAA_UK
We’re aware an email has been sent to members re password change Please don’t ring the number in the email. We’re looking into this urgently
10:05 AM - 26 Jun 2017
77 77 Retweets 19 19 likes
Twitter Ads info and privacy
Further investigation revealed the password reset messages were triggered by an error made by an internal,
Summarizing, if you are an AA customers ignore the password reset message sent by the company.
Microsoft Extends Edge Bounty Program Indefinitely
22.6.2017 securityweek Safety
Microsoft this week announced that the Edge Web Platform bounty program launched for Windows Insider Preview (WIP) last year has been extended indefinitely.
The program was launched on August 4, 2016, and Microsoft says that it has already paid over $200,000 in bounties over the ten-month period.
Because the program helped it make significant improvements to Edge’s security, the technology giant decided to extend the program indefinitely.
“Keeping in line with our philosophy of protecting customers and proactively partnering with researchers, today we are changing the Edge on Windows Insider Preview (WIP) bounty program from a time bound to a sustained bounty program,” Akila Srinivasan, Microsoft Security Response Center, announced.
The Edge Web Platform bounty on WIP was launched to determine researchers to report remote code execution (RCE), same origin policy bypass vulnerabilities (such as UXSS), and referrer spoofing bugs in the browser.
Moving forth, the company will continue to accept critical remote code execution and important design issues that could result in a customer’s privacy and security being compromised.
The program will continue indefinitely on Microsoft’s discretion, and reporting researchers can earn bounty payouts ranging from $500 to $15,000, depending on the severity of the reported vulnerability.
According to Microsoft, researchers who report qualifying vulnerabilities already found internally by Microsoft are eligible for a bounty of maximum $1,500 (only the first reporter receives the payout).
To qualify for the bounty program, vulnerabilities must be reproducible on the latest Windows Insider Preview (slow track), Srinivasan says.
Interested researchers are required to report Microsoft Edge browser security bugs to secure@microsoft.com via Coordinated Vulnerability Disclosure (CVD) policy.
For information on the Microsoft Bounty Programs, researchers should refer to this page on the company’s Security TechCenter website, and to the associated terms and FAQs.
Three years ago ProtonMail was launched. Today, it is launching ProtonVPN
21.6.2017 securityaffairs Safety
ProtonMail announced ProtonVPN is now available to the general public. ProtonVPN is officially out of beta.
You can now directly get ProtonVPN by visiting https://protonvpn.com
After more than 1 year of development, and four months of beta testing by over 10’000 members of the ProtonMail community, we’re finally making ProtonVPN available to everyone. And we really mean everyone, because consistent with our mission to make privacy and security accessible to every single person in the world, we’re also releasing ProtonVPN as a free VPN service.
It has been a long and exciting journey to get here since our team first met at CERN in 2013. Back then, we had an ambitious vision to build an Internet that was free and could continue to reach its full potential as a tool for social progress. Indeed, that was the vision that inspired Tim Berners-Lee to create the World Wide Web at CERN in 1989.
Since then, the Internet has met or even exceeded its promise in certain areas, but this has not come without a cost to society. While the Internet has done a great deal of good, over the course of this digital revolution, we have also lost control over our data, our most intimate secrets, and ultimately our privacy. In certain countries, the Internet has even become a tool for oppression and control, instead of the beacon of hope and freedom it once was.
Back in 2013, we embarked on a journey to change this, by building the tools that could make privacy and security the default online. In 2014, on the 25th anniversary of the web, our efforts culminated with the release of ProtonMail, the world’s first end-to-end encrypted email service. Since then millions of people around the world have embraced our vision, and thanks to your support (and the numerous donations along the way), email is much safer today than it was several years ago.
However, when considering the scope of all that we do online, email is just a small piece of the online world. That’s why we have decided to build ProtonVPN, to better protect the activists, journalists, and individuals who are currently using ProtonMail to secure their online lives. A VPN (Virtual Private Network) allows users to browse the web without being tracked, bypass online censorship blocks, and also increases security by passing all internet traffic through a strongly encrypted tunnel.
The importance of VPNs for online security and privacy is increasing day by day. Back in April of this year, Obama-era FTC rules designed to protect the privacy of internet browsing history were rolled back. Fast forward to today, and attempts are being made to dismantle net neutrality in the US, and several European governments are now calling for increased online surveillance. Last but not least, for over 1.5 billion people around the world, the Internet does not live up to its promise of freedom of information. Instead, the Internet is a highly restricted and censored place, constantly under surveillance, where making a wrong move could lead to imprisonment or worse.
We are also aware that as ProtonMail becomes a stronger force for digital freedom, the censorship of ProtonMail in certain countries is not a matter of if, but a matter of when. Earlier this year, we took the first steps to improve ProtonMail’s availability under censorship by launching an Onion site. With ProtonVPN, we can ensure the accessibility of not only ProtonMail, but all of the world’s digital knowledge and information. This is why we are committed to providing a free version of ProtonVPN.
However, we have done more than make ProtonVPN free. We have also worked to make it the best VPN service ever created, by addressing many of the common pitfalls with VPNs. For example, ProtonVPN features a Secure Core architecture which routes traffic through multiple encrypted tunnels in multiple countries to better defend against network based attacks, and also features seamless integration with the Tor anonymity network. You can learn about all the steps we took to build a secure VPN here.
Lastly, we’re building a VPN service that can be worthy of your trust. We understand that when it comes to VPNs, trust is paramount. Whether it is our transparent VPN threat model, our Swiss jurisdiction, our reputation, our relationship with the community, or the fact that you actually know who we are, we’re committed to building and operating ProtonVPN with the same level of transparency that has come to characterize ProtonMail.
ProtonVPN
To all of you who have supported us over the years, thank you for your support. Unlike companies like Google and Facebook who abuse user privacy to sell advertisements, ProtonMail and ProtonVPN are entirely dependent on users upgrading to paid accounts to cover operating expenses. Without your support, these projects would not be able to thrive and grow. If you appreciate the security and privacy that ProtonVPN provides, and have the means to do so, please consider upgrading to a paid account. This allows us to support the millions around the world without these means.
With your help, the revolution we have started with ProtonMail will continue, and we will reach the day where the Internet serves all of us equally, and reaches its full potential as a tool for freedom.
Best Regards,
The Proton Technologies Team
You can find our launch press release here: https://protonvpn.com/blog/launch-press-release
Next Windows 10 Version May Have Built-in EMET Anti-Exploit Program
21.6.2017 thehackernews Safety
It seems Microsoft is planning to build its EMET anti-exploit tool into the kernel of Windows 10 Creator Update (also known as RedStone 3), which is expected to release in September/October 2017.
So you may not have to separately download and install EMET in the upcoming version of the Windows 10.
If true, this would be the second big change Microsoft is making in its Windows 10 Fall update after planning to remove SMBv1 to enhance its users security.
EMET or Enhanced Mitigation Experience Toolkit, currently optional, is a free anti-exploit toolkit for Microsoft's Windows operating systems designed to boost the security of your computer against complex threats such as zero-day vulnerabilities.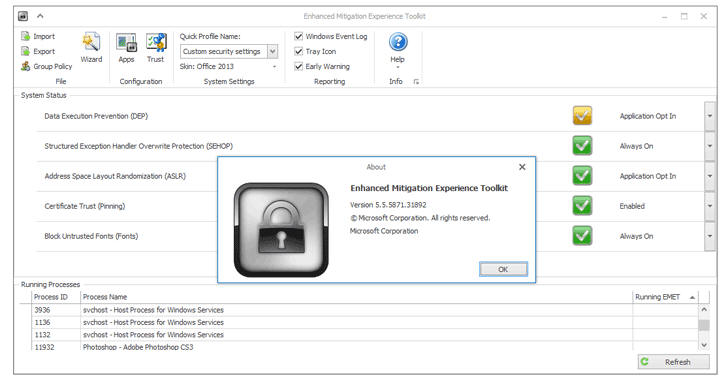
"EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and antimalware software," Microsoft site reads.
Basically EMET detects and prevents buffer overflows and memory corruption vulnerabilities, often used in zero-day attacks.
A few EMET features are already built into Windows 10 including DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization), but the current version of Windows 10 doesn't offer the same level of protection as Windows 10 with EMET installed.
The following chart, created by researchers from Carnegie Mellon University's Software Engineering Institute, clearly indicates that Windows 10 with EMET offers better protection than alone Windows 10 does.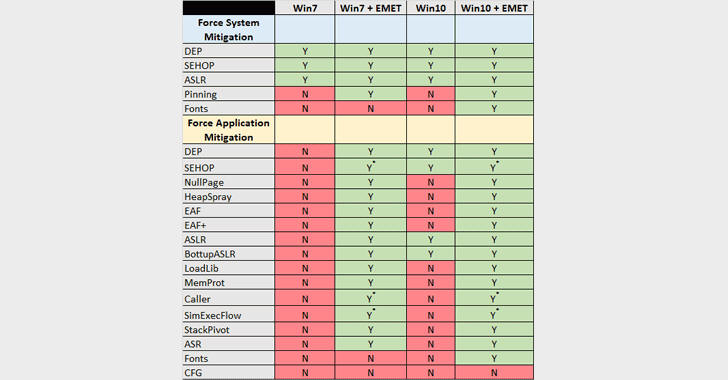
Since Microsoft has already announced that the company will discontinue the support of EMET in July 2018, we believe the company has planned to built-in support for all remaining EMET features in the next version of Windows 10.
"There are no plans to offer support or security patching for EMET after July 31, 2018. For improved security, our recommendation is for customers to migrate to Windows 10," Microsoft said last year.
A tweet from Alex Ionescu, Windows security expert, with a screenshot hints that Microsoft may release its next stable version of Windows 10 with "built-in EMET into the kernel."
Also, we noticed that Alex's tweet was later retweeted by at least two security researchers from Microsoft team, which indirectly confirms the news.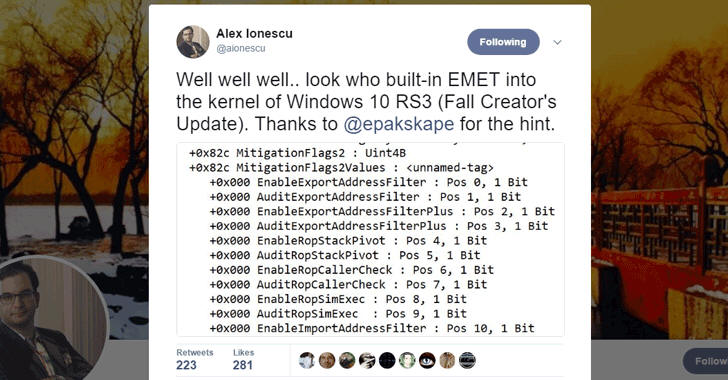
However, we tried to reach out to two of the Microsoft researchers, one of them hasn't responded yet, while other denied commenting at this moment.
EMET provides both system-wide as well as application-specific protection, which works by watching internal operating system operations for known security exploits and holes, and blocking attacks both on the OS and third-party applications.
The tool also mitigates the system against the well-known "untrusted fonts" attack, which is often leveraged in Web-based cyber attacks to compromise PCs and install malware.
Besides this, EMET also offers buffer overflow protection to applications that may be vulnerable to stack and buffer overflow attacks that malware uses to interact with the operating system.
So, let's just wait for the big news to be confirmed by Microsoft.
Microsoft to Remove SMBv1 Protocol in Next Windows 10 Version (RedStone 3)
20.6.2017 thehackernews Safety
The Server Message Block version 1 (SMBv1) — a 30-year-old file sharing protocol which came to light last month after the devastating WannaCry outbreak — will be removed from the upcoming Windows 10 (1709) Redstone 3 Update.
The SMBv1 is one of the internet's most ancient networking protocols that allows the operating systems and applications to read and write data to a system and a system to request services from a server.
The WannaCry ransomware, which wreaked havoc last month, was also leveraging an NSA's Windows SMB exploit, dubbed EternalBlue, leaked by the Shadow Brokers in its April data dump.
The WannaCry ransomware menace shut down hospitals, telecommunication providers, and many businesses worldwide, infecting hundreds of thousands of unpatched Windows servers running SMBv1 in more than 150 countries within just 72 hours on 12th of May.
Although Microsoft patched the vulnerability in SMBv1 in March in MS17-010, the company meanwhile strongly advised users to disable the three decades old protocol completely.
And you should disable it completely.
I mean come on, since Windows Vista you have SMBv2 and later SMBv3, and you are continuing to allow the old and horribly insecure SMBv1 protocol to run on your network.
Strange! Because there's no excuse to continue.
Ned Pyle, the principal program manager for Microsoft's Windows Server High Availability and Storage division, has also published a blog post this month, enlisting products from other vendors that are still using SMBv1 and begged them to stop using it now.
Pyle also hinted that the company has been planning to remove SMBv1 from Windows 10 Fall Creators Update (Version 1709), which is expected to release in September/October 2017.
"SMB1 is being removed (fully or partially, depending on SKU) by default in the RS3 release of Windows and Windows Server. This is coming, folks," Pyle wrote.
Microsoft has recently announced the beta release of Windows 10 "Creators Update," also known as "Redstone 2" (Version 1703), which disables the SMB1 protocol by default, and after testing and getting feedback from the community, the company has decided to completely remove the protocol in the next stable version of the operating system.
A Microsoft representative has just confirmed this to Threatpost, saying "We can confirm that SMBv1 is being removed for Redstone 3 [codename for the Windows 10 Fall Creators Update]."
Meanwhile, the company has published a document, which describes registry settings, PowerShell commands as well as group policy settings to disable SMBv1 in your Windows environment manually.
Nmap 7.50 released with many significant improvements
17.6.2017 securityweek Safety
The Nmap project announced the release of Nmap 7.50, the first big release since last December that has hundreds of improvements.
Nmap 7.50 is the new release of the popular the Network Mapper, the previous release dates back December 2016 and the new one brings hundreds of improvements.
Nmap 7.50
Nmap 7.50 includes the Npcap packet capturing driver and library for Window, instead WinPcap that is no longer maintained. The Npcap a new set of APIs to improve performance and ensure software compatibility with most popular OSs, including Windows 10.
The new version includes loopback packet capture and injection and raw wireless sniffing.
“It is a replacement for WinPcap, which served us well for many years, but is no longer maintained. Npcap uses newer APIs for better performance and compatibility, including Windows 10 support. We also added loopback packet capture and injection, raw wireless sniffing for beacon frames and such, and extra security features such as requiring Administrator access.” states the Seclists.org.Nmap 7.50 also improved the Nmap Scripting Engine, maintainers released a detection script for the MS17-010 vulnerability exploited by the Wannacry ransomware and for the Sambacry flaw tracked as CVE 2017-7494.
The new release also includes more than 300 new service detection fingerprints and many other improvements.
You can download the Nmap 7.50 source code and binary packages for Linux, Windows, and Mac are available here.
Millions of Devices Remain Exposed via SMB, Telnet Ports: Rapid7
16.6.2017 securityweek Safety
Despite being exploited in wide-spread malicious attacks, SMB, telnet, RDP, and other types of improperly exposed ports continue to put both enterprises and consumers at risk, a new Rapid7 report reveals.
Focused on providing an overview of the regional exposure to help Internet service providers (ISPs) worldwide address existing issues, Rapid7’s second National Exposure Index report (PDF) provides information on improperly exposed services and ports rendering systems and user data vulnerable to attacks. It includes data gathered through scanning the web for exposed services, including encrypted and unencrypted protocols, or those meant for public use.
Two of the improperly secured services that continue to make computers vulnerable to attacks are Server Message Block (SMB) and telnet. The former was recently associated with the massive WannaCry outbreak that hit over 160 countries, while the latter has been exploited by Internet of Things botnets such as Mirai, Persirai, or Hajime.
Apparently, there are 5.5 million machines with SMB port exposed, up from 4.7 million prior to May 2017, when WannaCry emerged. The ransomware managed to spread fast via a worm component leveraging the SMB-targeting EternalBlue exploit. Of the total endpoints exposing Microsoft file-sharing services (SMB, TCP port 445), 800,000 of them are confirmed Windows systems, Rapid7 says.
According to Shodan founder John Matherly, over 2 million machines with SMB appear in the device search engine, and most of them (90%) run SMB version 1. He also notes that, while Windows devices running SMB should have been already patched, given that Microsoft released security updates even for unsupported platform iterations, tens of thousands continue to be vulnerable.
Things aren’t better when it comes to devices with exposed telnet (port 23), as there are just under 10 million such devices out there at the moment. Granted, this is a great improvement when compared to the 14.8 million exposed devices discovered last year, but it also means that millions of devices can still fall victim to malware such as distributed denial of service (DDoS) botnets.
The 33% drop seen in the number of exposed telnet nodes is the result of two developments, Rapid7 says. On the one hand, ISPs might have taken stance and started closing port 23 following botnet attacks, while on the other hand the botnets themselves are taking nodes offline to protect themselves from rivals (except BrickerBot, which is only focused on rendering devices unusable).
However, there are other inappropriate services exposed to the Internet as well, including FTP (port 21), RDP (port 3389), PPTP (port 1723), rpcbind (port 111), MySQL (port 3306), and others more. Overall, Rapid7’s scan for these inappropriate services revealed over 90 million nodes.
The company’s report also reveals that Zimbabwe, Hong Kong SAR, Samoa, Republic of the Congo, Tajikistan, Romania, Ireland, Lithuania, Australia, and Estonia are the most exposed countries. When it comes to major cyber superpowers, China and the Russian Federation are among the top 50 most exposed nations, while the United States has “a relatively low exposure in relation to its enormous IPv4 address space.”
Rapid7 chose 30 service ports to scan for their report, but also had a look at two “canary” TCP ports, port 5 and port 61439, which have no well-known service associated with them, thus being unlikely to ever respond to port scanning. However, the company picked up responses from 3.2 million devices from these two ports, and discovered that over 2.3 million IPs (located in 133 countries) responded to both probes.
The report also points out that there are a series of services that have been specifically designed for public use, thus are expected to be exposed to the Internet, although some of them aren’t encrypted, such as HTTP. Many of these, however, are encrypted-by-default, including HTTPS, SSH, IMAPS, POP3S, SMTPS, and FTPS.
The good news, Rapid7 says, is that 3% more nodes are running fewer services compared to last year, partly because of a decrease in telnet exposure. However, the company also believes that “individuals and organizations are beginning to be more careful about what they expose to the world.”
“Server ransomware, ransomworm propagation, insecure Internet of Things, and dozens more headlines reminded us, almost monthly, that the internet is, indeed, a fragile ecosystem that needs deliberate care and attention. Being mindful of both what your organization deploys and how those services are deployed and maintained can have a significant impact on the health of the entire internet,” the company concludes.
Centrify Launches Bug Bounty Program
15.6.2017 securityweek Safety
Centrify, a Santa Clara, Calif.-based provider of identity and access management (IAM) solutions, has teamed up with Bugcrowd for a public bug bounty program that offers researchers up to $3,000 per vulnerability.
Centrify has been running a private bug bounty program for the past two years, but it has now decided to allow all the 50,000 hackers on the Bugcrowd platform to find and report vulnerabilities.
The program covers the company’s main website, centrify.com, and its Identity Service and Privilege Service products.
The products are built on a cloud platform for which bug bounty hunters will have to register their own tenants for testing. The focus areas include web applications and the underlying REST API, and clients and installable agents.
Centrify said only its centrify.com website is in scope and bounty hunters have been instructed to focus on vulnerabilities exploitable in current web browsers and user authentication flaws. Subdomains or related hosts are not covered, but centrify.force.com/partners, centrify.force.com/support and partners.centrify.com can be tested for privilege escalation.
Researchers can earn the top rewards – $3,000 for flaws in the Identity and Privilege products and $1,500 for flaws in the corporate website – if they find vulnerabilities that have a P1 priority rating. This includes critical server misconfigurations, server-side injections, broken authentication and session management, sensitive data exposure, and cryptographic issues.
The least serious vulnerabilities affecting Centrify products can earn researchers $200, or $100 if they affect the company’s website.
“As a leader in identity services, it is incumbent upon us to fully vet the security on our platform to ensure that each user’s access to apps and infrastructure is secure and that we continue to deliver the best solutions,” said Raun Nohavitza, Senior Director of IT at Centrify. “Bugcrowd’s platform, organization, experience with triage and relationship with the security community make their bounty program very attractive. With Bugcrowd we’re not only doing the right thing for our security offerings in the best way possible, but we’re also getting consistent administration and management for our ongoing program.”
New Tor Browser 7.0 implements multiprocess mode, content sandbox, and Unix domain sockets
9.6.2017 securityaffairs Safety
The Tor Project Team has announced the release of Tor Browser 7.0, it comes with multiprocess mode, content sandbox, and Unix domain sockets.
The Tor Project has released the stable release of Tor Browser 7.0 that includes many security features and according to the development team, it also improved performance.
The Tor network implements an anonymous communication system that leverages on more than 7,000 relays set up by volunteers worldwide. The project aims to protect user’s anonymity online by concealing the users’ location and implementing algorithms to avoid dragnet surveillance or traffic eavesdropping.
“The Tor Browser Team is proud to announce the first stable release in the 7.0 series. This release is available from the Tor Browser Project page and also from our distribution directory.” reads the official announcement.
Tor Browser 7.0
The Tor Browser is built on top of Mozilla’s Firefox Extended Support Release (ESR), a version designed for groups who deploy and maintain the desktop environment in large organizations such as universities and other schools, county or city governments, and businesses.
The Tor Browser 7.0 is based on Firefox 52 ESR and implements two major features:
multiprocess mode;
content sandbox;
The Development team enabled both features by default on macOS and Linux, unfortunately, it is still working on the sandboxing for Windows systems.
Mac and Linux users can improve the security of their Tor Browser by using only Unix domain sockets for communication through the Tor network.
“Most notably we hope having Mozilla’s multiprocess mode (e10s) and content sandbox enabled will be one of the major new features in the Tor Browser 7.0 series, both security- and performance-wise.” states the announcement.
“While we are still working on the sandboxing part for Windows (the e10s part is ready), both Linux and macOS have e10s and content sandboxing enabled by default in Tor Browser 7.0. In addition to that, Linux and macOS users have the option to further harden their Tor Browser setup by using only Unix Domain sockets for communication with tor.”
The switch to ESR 52 introduces new system requirements for Windows and macOS users: On Windows Tor Browser 7.0 won’t run on non-SSE2 capable machines anymore. On Apple systems, the minimum system requirement is OS X 10.9.
The Tor Browser 7.0 also improves the resilience to tracking and fingerprinting attacks.
“cookies, view-source requests and the Permissions API are isolated to the first party URL bar domain now to enhance our tracking related defenses. On the fingerprinting side we disabled and/or patched several new features, among them WebGL2, the WebAudio, Social, SpeechSynthesis, and Touch APIs, and the MediaError.message property.” states the announcement.
4 Possible Ways to Make Your Browser Hacker-Proof
7.6.2017 securityaffairs Safety
Browsers are constantly targeted by hackers. Here are 4 ways you can make your browser hacker-proof. Use them to stay secure on the web.
Browsers have long been a hot target of numerous hacking-related incidents. They are the primary source of hacking incidents as we search, share, watch and download files from browsers. Moreover, various vulnerabilities exists in browsers, emphasizing the fact of using necessary tools to make your browser hacker-proof.
Ensuring that browsers are secured with the essential protocols is important. After all, hackers are becoming exceedingly experienced, penetrating into numerous prominent companies and government agencies this year alone as witnessed from the WannaCry ransomware cyberattack.
Although web browsers do a good job at ensuring security loopholes are rectified as early as possible, but more often than not, some updates arrive late and you can’t rely on them alone. It could be that your browser isn’t updating or you’ve got extensions and plugins installed that have potential security loopholes.
To ensure your online safety, we’ve come up with four online security tips that will help keep your browser safe hackers.
Keep Your Browser Up-to-Date
Keeping your browser updated is the easiest way to ensure the safety of your browser. Browser updates carry necessary patches which secure you against hacking incidents and make your browser hack-proof on the web.
Google Chrome, Firefox and Opera come packed with default settings for automatic updates. You need to click the ‘install updates automatically’ option for uninterrupted and smooth connectivity.
browser hacker-proof
Fortunately, most browsers these days are automatically updated. For instance, if you installed Microsoft’s new Windows 10 operating system, its default setting is to automatically update your software and issue patches, including for its Edge browser.
Uninstall Unnecessary Plug-ins
No matter how secure your browser might get, third-party plug-ins can never be completely trusted as plug-ins can read, make changes and access the websites you visit.
There are some plug-ins that come with the browser and might never be used. So, one way to give yourself an extra layer of protection is to delete unneeded plug-ins.
Disable Unnecessary Browser Extensions
There is a misconception regarding plug-ins and extensions. While plug-ins handle video or other content that the browser does not support, extensions are small programs that add new features to your browser and personalize your browsing experience.
You can find numerous extensions on Google Chrome and Firefox which enhance your online browsing functionality. Having said that, extensions have their disadvantages. Some extensions need passwords so they can work to their full potential. That leaves an open door to hackers and other cyber criminals who install malware.
While installing an extension, be mindful of the source – trustworthiness of the maker. You can read reviews for authenticity.
Use VPN Extension
When it comes to making your browser hack-proof, no other tool does it better than a VPN extension. This extension promises fast speed internet capability and does not maintain any logs of its users. In addition, you can evade censorship laws in any country by connecting to a server maintained in another country – all while being anonymous on the web.
There are numerous extensions that provide strong features needed to make the browser hacker-proof such as blocking ads, dodging online trackers, safeguarding against malware & providing WebRTC leak protection. With a Chrome VPN extension, you get an encrypted connection which masks your physical IP with a virtual IP – maintaining your online secrecy.
Government Contractors Required to Provide Insider Threat Awareness Training
5.6.2017 securityweek Safety
Change Two to the National Industrial Security Program Operating Manual (NISPOM 2) came into force at the end of May 2017. One of the biggest changes involves a new requirement for contractors to implement extensive insider threat training for all staff with access to government classified information. These new requirements are specified in section 3-103.
NISPOM 2 (PDF) defines the insider threat as "The likelihood, risk, or potential that an insider will use his or her authorized access, wittingly or unwittingly, to do harm to the national security of the United States." Section 3-103 places new burdens on contractors to mitigate this threat.
There are three sub-sections. Section 3-103 (a) concerns the contractor's insider threat program personnel. These must be trained in counterintelligence; response procedures; applicable laws and regulations; and applicable civil liberties and privacy issues.
Section 3-103 (b) specifies the training that all cleared personnel must receive prior to gaining access to classified information. This includes training in the detection and reporting of suspicious activity; methodologies used by adversaries to recruit insiders; indicators of insider threat behavior; and counterintelligence.
Section 3-103 (c) specifies the maintenance of "a record of all cleared employees who have completed the initial and annual insider threat training."
The effect of the new requirements has been summarized by Bay Dynamics federal systems engineer Thomas Jones as threefold: to ensure contractors understand the consequences of breaking the rules; to teach contractors how to spot indications of insider threat behavior in others; and to make it clear who should be contacted if anything is spotted. In other words, a key aspect of NISPOM 2 is to cultivate contractors monitoring contractors. "It's letting people know that they are being watched, and that changes behavior," he said.
While there is universal acknowledgement of the serious nature of the insider threat, there is also some concern that NISPOM 2 may not have its desired effect. Failure to abide by the conditions will mean that untrained contract personnel will not be able to access classified information, while the contractor itself could lose the contract. Fully conforming to NISPOM 2, however, places a substantial financial burden on the contractor with no clear way to recover costs.
Those costs are likely to affect smaller contractors to a greater extent than larger firms who will be better positioned to absorb at least some of them. As such, some of the smaller firms may be squeezed out of bidding; and a dynamic and agile part of the market may be lost to government contracts.
But there is also another concern -- NISPOM 2 may have the opposite effect to its purpose; it could reduce rather than enhance security. Government agencies, including the DoD, are required to operate their own insider threat mitigations. Members of Bryan Cave LLP's national security practice have pointed out (Bloomberg) that these requirements are not being met 'uniformly or quickly'.
The danger, they suggest, is that if confidential data is withdrawn from non-compliant contractors, it "may simply place sensitive information where it may be no more secure from outsider access than it was in the hands of the contractor, and it may be less secure." Furthermore, removing data from contractors and centralizing it on improperly secured government systems "may provide cyber threat actors with a much more lucrative target for attack by focusing on the data from numerous, threatened contractors stored in a single government site, making it unnecessary to attack numerous contractors' individual systems."
The bottom-line, however, is that NISPOM 2 is here and in effect. Any contractor wishing to bid for government contracts that involve handling sensitive data must now have the insider threat mitigation requirements of NISPOM 2 in place and operational.
Nexpose appliances were shipped with a week default SSH configuration
4.6.2017 securityaffairs Safety
Security experts at Rapid7 have discovered a security issue in the SSH configuration for its Nexpose appliances tracked as CVE-2017-5243.
Owners of Nexpose appliances have to apply an update to their systems to fix the issue in the default SSH configuration.
The devices were shipped with an SSH configuration that allowed obsolete algorithms to be used for key exchange and other functions.

The Nexpose appliances were allowing to used weak and out of date encryption algorithms such as AES192-CBC, Blowfish-CBC, and 3DES-CBC, and KEX algorithms such as diffie-hellman-group-exchange-sha1.
“Because these algorithms are enabled, attacks involving authentication to the hardware appliances are more likely to succeed. ” states the advisory published by Rapid7.
“This vulnerability is classified as CWE-327 (Use of a Broken or Risky Cryptographic Algorithm). Given that the SSH connection to the physical appliances uses the ‘administrator’ account, which does have sudo access on the appliance, the CVSS base score for this issue is 8.5.”
Nexpose devices designed to help users analyze vulnerabilities and reduce the surface of attack. The issue affects all the Nexpose appliances, owners with root access can fix the problem by editing /etc/ssh/sshd_config file in the appliance to ensure only modern ciphers, key exchange, and MAC algorithms are accepted.
Follow
Rapid7 ✔ @rapid7
Disclosure on CVE-2017-5243: Nexpose hardware appliance SSH enabled obsolete algorithms http://r-7.co/2rBFsE9 (Thanks to @LiamMSomerville)
5:58 PM - 31 May 2017
5 5 Retweets 7 7 likes
Twitter Ads info and privacy
After updating the configuration file, users need to verify that the changes have been correctly applied. Any missing part of the configuration may trigger a syntax error on service restart with consequent loss of connectivity.
“You can run this command and compare the three output lines with the configuration block above:
egrep “KexAlgorithms|Ciphers|MACs” /etc/ssh/sshd_config
“After verifying the configuration change, restart the SSH service by running “service ssh restart”. Once that completes, verify you can still connect via ssh client to the appliance in a separate terminal. Do not close the original terminal until you’ve successfully connected with a second terminal.” states the advisory.
“This change should not impact connections from Nexpose instances to the physical appliance. The main impact is shoring up access by SSH clients such that they cannot connect to the appliance using obsolete algorithms,” Huckins wrote.
The vulnerability could have let an attacker in a privileges position on the network to force an algorithm downgrade between an SSH client and the Nexpose appliance during the authentication phase.
In order to mitigate the issue, it is possible to remove server-side support for the out of date encryption algorithms.
Terra Privacy Product Uses Dynamic Whitelisting to Block Attacks
26.5.2017 securityweek Safety
Terra Privacy announced on Wednesday a new product that uses dynamic whitelisting to block malware and phishing attacks. A free beta version of the endpoint security product is available for testing.
Terra Privacy was founded by Michael Wood, the cryptographer who designed the REDOC II encryption system. The company’s latest product, Hacker Deterrent Pro, uses dynamically-generated whitelists to ensure that web browsers and other applications only communicate with the servers they are supposed to.
Hacker Deterrent Pro has three main features: Two-Factor Browsing, App Firewall, and DNS Shield.
Two-Factor Browsing ensures that the browser only communicates with trusted domains. To achieve this, the product creates a real-time transient whitelist that contains only the names of webpages opened by the user and the names of other sites from which content is pulled, while any other connection attempt is blocked.
This prevents browser-based threats from communicating with their command and control (C&C) servers, and it can also be used to block commercial trackers.
Traditional whitelisting can be impractical as users have to manually add each website. Hacker Deterrent aims to address this problem by creating transient whitelists that are empty when the web browser is first opened. Each time the user visits a website, that site is automatically added to the whitelist and removed from the whitelist when the page is closed.
This method can also be efficient against sophisticated phishing attacks as Hacker Deterrent Pro will block unauthorized domains even if they look legitimate. The vendor demonstrated its product’s capabilities by showing how it could block phishing sites that use a recently disclosed Unicode-based technique.
According to the company, the solution can also block non-browser Trojans that inject themselves into running processes by preventing them from communicating with domains other than ones belonging to the hijacked app’s developer. For example, the explorer.exe process, which is often targeted by malware, should only be allowed to communicate with Microsoft servers.
The app firewall initially blocks all applications from accessing the Web, and provides information about the app and the host it wants to connect to, allowing users to determine if the connection should be allowed.
The product’s DNS Shield allows users to select DNS servers based on their personal preferences, blocking ISPs from adding their own list of DNS servers. For instance, users can choose DNS servers that reject connections to IPs that are known to host malware.
The beta version of Hacker Deterrent Pro can be tested for free. The commercial version of the product, expected to become available in mid-July, will cost $39.99 per year per endpoint. The solution works on Windows PCs using the Chrome and Firefox web browser.
Vera Enables Multi-Factor Authentication for Specific Data
25.5.2017 securityweek Safety
Multi-factor authentication (MFA) is the security industry's response to failings in the simple and traditional userID/password authentication approach. MFA is considered to be a primary solution to help defeat phishing and to demonstrate compliance. But it suffers from one major drawback: user friction.
Put simply, MFA delays business. Users don't like it, and business managers see it as a delay in business processes. The industry is responding with attempts to reduce that friction. Earlier this week, Preempt launched a product that applies behavioral-based MFA to specified applications. Now Vera has announced an add-on to its data-centric solution that allows MFA to be limited to specified data.
Vera's methodology is to attach the additional authentication requirement to an existing data classification. Assuming particularly sensitive data is already classified within the Vera product as 'secret' (or perhaps, given the imminence of the European General Data Protection Regulation (GDPR), as 'PII'), then the additional MFA will be automatically applied to all such labeled data.
The result is that any attempted access to that data -- wherever the data is located or whomever the applicant is -- will result in an MFA challenge. This process defends the data against successful phishing (an attacker may steal log-in credentials, but won't get by the MFA challenge) and simultaneously helps ensure compliance with PII-protecting regulations.
"Providing the right level of protection to enterprise data is," explains Prakash Linga, CTO and co-founder of Vera, "key to complying with regulations like the NY DFS and the EU GDPR. Furthermore, the ability to layer context-driven authentication to specific files and emails lets companies appropriately protect their information wherever it travels."
The process does not require that all recipients of Vera MFA-protected data be Vera customers. If a protected document is sent to a trusted but external recipient, Vera will first validate the email address and then challenge the recipient with Vera's native two-factor Twilio-based authentication challenge.
"Alongside our own native capabilities, we're also launching integrations with Duo Security and RSA SecureID to let businesses simplify their multi-factor authentication strategy," announced Chuck Holland, Vera's director of product management, in an associated blog post. The Duo and SecureID are 'out-of-the-box' plug and play integrations.
Earlier this month, Vera announced a strategic investment of $15 million led by Hasso Plattner Ventures. Yair Re'em, general partner of Hasso Plattner Ventures, said at the time his firm's first venture into cybersecurity is prompted by "the crumbling state of enterprise security [which] has clearly demonstrated the need for a fundamental paradigm shift in cybersecurity."
Talking about Vera's adoption of data-centric security over perimeter-based security, new board member Chris Rust said, "The enterprise network perimeter has collapsed and those clinging to solutions trying to save or resurrect it are fighting a battle long since lost. Vera is the driving force behind a positive and profound shift away from perimeter-based security and towards a more flexible and reliable data-centric model."
Vera's new MFA offering adds strong authentication to corporate data wherever it travels.
New Product Allows Easy Addition of Multi-Factor Authentication to Any Application
24.5.2017 securityweek Safety
New Multi-factor Authentication Offering Seeks Balance Between Strong Security and Ease of Use
The correct balance between strong security and excessive control is difficult. Without strong security, such as multi-factor authentication (MFA), organizations will be breached. With excessive control (such as MFA always and everywhere), business will be impeded, employees will be disgruntled, and controls will be bypassed. A new behavioral authentication product announced today by security firm Preempt allows optional MFA, based on user behavior, on any application.
Preempt's new "Any App" offering seeks to solve the growing concern over the insider threat by allowing policy to dictate whether user access to any application should be challenged by multi-factor authentication requirements, or simply allowed. This increases security without increasing unnecessary impediment to business.
The insider threat is insidious. It can come from innocent users, 'malicious' users motivated by curiosity or worse, or hackers inside the network with stolen credentials. While modern network analytics can detect 'unusual' behavior, they cannot automatically distinguish between simple unusual and malicious unusual. The result is a large number of alerts that need to be investigated but are often false positives.
Preempt's Any App takes a different approach by imposing strong security in the form of multi-factor authentication requirements on any specified application whenever -- but only if -- 'unusual' user behavior is detected. This is an advance on the more usual and common approach of applying MFA to web applications only.
"Security teams want to better protect their organization and application from threats and breaches by adding policies that require users to validate their identity via authentication techniques before accessing corporate applications," explains Ajit Sancheti, co-founder and CEO of Preempt. But while adding MFA to web applications is relatively simple, protecting on-premises applications is more complex. Integrating secure authentication into each application requires significant resources, which typically leads to the majority of internal applications not being protected by MFA.
Any App, he continues, "removes the need for application customization, and turns the task of adding MFA support to applications into a simple matter of defining policy, which saves both time and money, while also protecting the organization from security breaches."
Any App works at the network layer for both Windows and Linux environments, and acts as an LDAP or Kerberos proxy. When a user first seeks access to an application, the application will attempt to verify the user. Any App proxies this request, and based on security policy can either allow access or require MFA.
If policy requires additional authentication, the organization's MFA solution is automatically triggered. Since Any App is vendor neutral, the MFA can come from the existing deployment of a range of vendors such as Duo, OKTA, and SecureAuth.
The behavioral policy engine within Any App allows the security team to define the conditions necessary to invoke MFA. For example, if the access request comes from an unmanaged device, or if the user is connecting to a new asset or from a new location or new device. This allows the security team to automatically apply more stringent controls without requiring individual alert analysis.
Any App attempts to allow the security team to define and control the balance between strong security and ease of use. It reduces the cost of strong security while activating it only where policy decides it is necessary.
WordPress Launches Public Bug Bounty Program
18.5.2017 securityweek Safety
The WordPress security team announced this week the launch of a public bug bounty program that covers the WordPress content management system (CMS) and several related assets.
WordPress has been running a private bug bounty program for roughly seven months and it has now decided to make it public.
The program is hosted on the HackerOne platform and it covers the WordPress CMS and other open-source projects, including BuddyPress, bbPress and GlotPress. Researchers can also report flaws discovered in the WordPress.org (including subdomains), WordCamp.org, BuddyPress.org, WordPress.tv, bbPress.org and Jobs.WordPress.net websites.
White hat hackers have been advised to submit vulnerability reports that include detailed information on the flaw and proof-of-concept (PoC) code. Participants have also been asked to avoid privacy violations and causing damage to live WordPress sites, and give developers a reasonable amount of time to address security holes before their details are made public.
The list of vulnerabilities that experts can report includes cross-site scripting (XSS), cross-site request forgery (CSRF), server-side request forgery (SSRF), remote code execution and SQL injection.
The bug bounty program does not cover vulnerabilities affecting plugins – these should be reported to the app’s developer, but the WordPress plugins team should be alerted as well.
While exceptions may exist, the WordPress security team says it’s typically not interested in basic information disclosure issues, mixed content warnings, lack of HTTP security headers, brute force attacks, XSS flaws that can only be exploited by users with elevated privileges, and reports generated by automated scans.
The WordPress security team has not provided any information on rewards, but it did say that seven researchers have so far earned more than $3,700, which indicates an average of roughly $500 per vulnerability report. The bounties will be paid out by Automattic, the company behind WordPress.com, which runs its own bug bounty program on HackerOne.
According to WordPress developers, the CMS currently powers more than a quarter of the top ten million websites on the Internet. Given the platform’s popularity, it’s no surprise that researchers often find security holes, including serious vulnerabilities that end up being exploited to hack thousands of websites.
Hopefully, the launch of a public bug bounty program will streamline vulnerability reporting to avoid the disclosure of unpatched flaws by researchers who are frustrated with the lack of communication.
Mozilla Tells Symantec to Accept Google's CA Proposal
3.5.2017 securityweek Safety
Mozilla has shared details about its own position in the debate between Symantec and Google regarding improper issuance of digital certificates. The organization advised Symantec to accept Google’s offer, but it has also described alternative action it may take if an agreement is not reached.
Google announced in March its intent to stop trusting all Symantec-issued digital certificates due to the certificate authority’s failure to play by the rules. Symantec, its subsidiaries and its partners had been accused of making too many exceptions from Baseline Requirements (BR) in favor of their customers.
The developer of the Chrome web browser initially proposed the reduction of the validity period for newly issued Symantec certificates to nine months or less, gradual distrust and replacement of all existent certificates, and the removal of extended validation (EV) status for Symantec certificates.
Symantec called Google’s statements “exaggerated and misleading,” and pointed out that the changes could have a serious impact for its customers.
After some debate, Google made a second proposal that involves Symantec partnering with one or more existing CAs and using their infrastructure and validation process. Symantec would still handle business relations with customers and all CAs would be cross-signed by the company.
“It's worth noting that this proposal minimizes any impact to Symantec customers, existing or new,” said Ryan Sleevi, a software engineer on the Google Chrome team. “It provides a graceful transition path that does not negatively impact existing customers who have special needs - such as those of pinning or certain roots. It does not prohibit Symantec from continuing to use and operate its existing infrastructure for non-Web cases, but eliminates the security risk from doing so.”
Last week, Symantec came forward with its own proposal for restoring trust. The cybersecurity giant’s proposal includes auditing of all active certificates by a third-party auditor, more transparency, shorter validity for certificates, and several operational improvements.
Google is still not satisfied with the steps Symantec has offered to take, and it plans on continuing public discussions on the matter.
Mozilla, which has been conducting its own investigation into Symantec’s CA business, also has some concerns regarding Symantec’s proposal. The browser vendor says some of the proposed actions either don’t make any difference or they are simply not enough for regaining trust.
Mozilla has advised Symantec to accept Google’s second proposal and said it’s open to discussing its implementation. However, if Symantec refuses, Mozilla may take alternative action to “reduce the risk from potential past and future mis-issuances by Symantec, and to ensure future compliance with the BRs and with other root program requirements.”
Mozilla’s proposal requires Symantec to clean up its public key infrastructure (PKI) and cut off parts that are not compliant with BR. The organization could also limit the validity of newly-issued certificates to 13 months, and progressively reduce the lifetime of existing certificates to the same period.
Kali Linux 2017.1 is arrived, more power for password-cracking with cloud GPUs
28.4.2017 securityaffairs Safety
Kali Linux 2017.1 rolling release was announced, the popular distro comes with a set of significant updates and features.
The popular Kali Linux distribution has a new weapon in its hacking arsenal, it can use cloud GPUs for password cracking.
Kali Linux is the most popular distribution in the hacking community, it is a Debian-based distro that includes numerous hacking and forensics tools.
Kali linux
This week, the Kali development team has included new images optimized for GPU-using instances in Azure and Amazon Web Services. The images will improve the password cracking abilities of the Kali Linux distro giving it more power for brute-force attacks exploiting the GPUs computational power.
“Due to the increasing popularity of using cloud-based instances for password cracking, we decided to focus our efforts into streamlining Kali’s approach. We noticed that Amazon’s AWS P2-Series and Microsoft’s Azure NC-Series allow pass-through GPU support so we made corresponding AWS and Azure images of Kali that support CUDA GPU cracking out of the box. You can check out our Cracking in the Cloud with CUDA GPUs post we released a few weeks back for more information.” states the official announcement.
Now is you want to test your password against brute-force attacks you can download the GPU-enhanced images and run in cloud services, the bad news is that this means that also black hats have a new powerful weapon in their hands.
The new Kali Linux, version 2017.1, also adds support for Realtek’s RTL8812AU wireless chipsets, it is a very useful feature because these chipsets are used by major modem-makers like Belkin, D-Link, and TP-Link.
“A while back, we received a feature request asking for the inclusion of drivers for RTL8812AU wireless chipsets. These drivers are not part of the standard Linux kernel, and have been modified to allow for injection. Why is this a big deal? This chipset supports 802.11 AC, making this one of the first drivers to bring injection-related wireless attacks to this standard, and with companies such as ALFA making the AWUS036ACH wireless cards, we expect this card to be an arsenal favorite.” continues the announcement.
The driver can be installed using the following commands:
apt-get update
apt install realtek-rtl88xxau-dkms
Reading the Kali Linux Bug Tracker List we can notice the new support for the OpenVAS 9 vulnerability scanner.
Enjoy it!
Cryptology for Business and Organizations on the 21st century
27.4.2017 securityaffairs Safety
Cryptology is the mathematical foundation of penetration testing and can be adopted as a resource for securing assets and communications.
An overview of the science of the occult, that brings forth a new level of security in the age of digital privacy. Cryptology is the mathematical foundation of penetration testing and can be adopted as a resource for securing assets and communications. Join us in this quest into the science of occult.
Cryptology is the branch of mathematics that encompasses cryptography, cryptanalysis, Steganography and Lock picking. The etymology of the word is “kryptós +logos”, which means the study of the occult. Cryptography is a process in which an insecure message suffers a mathematical process generating a secure message from its process. The insecure message is called plaintext, and the encoded message is called ciphertext.

The reverse process of cryptography to obtain the plaintext from ciphertext is called cryptanalysis. Steganography is a mathematical function where a secret message is hidden in other secret messages. Lock picking is an attack in physical device of codification, where a key opens a lock.
Cryptology can give businesses and organizations a new degree of security when implemented by laying out an in-depth defense of data. A cryptograph algorithm, also called a cypher, is a mathematical function that is used for encryption and decryption of a message. Restricted algorithms maintain a secret how the algorithm works and can be compromised if the key is revealed to anyone. The range of all possible values of the key is called keyspace.
There are two types of symmetric algorithms: Symmetric and Public Key. Symmetric algorithms have the property of calculating the encryption key from the decryption key and vice versa. Symmetric algorithms can be divided into Block Ciphers and Stream Ciphers.
Public key algorithms, also called asymmetric algorithms, have the property of having a different encryption key for encryption and decryption. The decryption key cannot be calculated from the encryption key and the encryption key can be made public. The encryption key is called public key and the decryption key is called private key.
The main goal of cryptography is to provide confidentiality, authentication, integrity and nonrepudiation to the sender and the receiver of a communication. Cryptology is the mathematical foundation of modern day penetration testing. Penetration Testing uses some tools of cryptanalysis like THC Hydra in an attack, which is defined as a cryptanalysis attempt. The loss of a key through other means is called a compromise. Brute force, also called dictionary attack, is one case of cryptanalysis.
Cryptology is also related with penetration testing also in the security of the algorithm. Lars Knudsen classifies four types of breaking an algorithm: Total Break, Global Deduction, Instance Deduction and Information Deduction.
Cryptanalysis is used in Side Channel Attacks, where physical elements are analyzed and can give authorities and law enforcement agencies means of monitoring a suspect by generating a thermal image through the walls.
The Implications of the development of Cryptology and side channel attacks can permit law enforcement agencies a new degree of chain of custody with risking the lives of personnel while investigating suspects.
In Global Deduction Attack, cryptanalysis can find the key without knowing it but instead having an equivalent function that is accepted as the key. The study of discrete logarithms takes place in elliptic curves cryptanalysis, in which Pollard Rho attack is used to break into public key algorithms.
It is important to organizations and governments to develop and use Cryptology as a resource of protection aligned with other good practices adopted in the information security strategy. As of today, Cryptology can adapt to every business being incorporated in its best practices of security with a very low expenditure using open sources models like PGP.
The development in information security and cryptology together can help fill the gap in new talent sourcing and development of a national network of a labor force, and difficult attackers from gaining access to sensitive data.
Sources:
www.blackhat.com/presentations/bh-usa-07/De_Haas/Presentation/bh-usa-07-de_haas.pdf
Schneier, Bruce – Applied Cryptography – 2nd Edition.
http://2we26u4fam7n16rz3a44uhbe1bq2.wpengine.netdna-cdn.com/wp-content/uploads/061112_1445_Chapter7The11.jpg
https://wongmichael.files.wordpress.com/2013/04/model-of-conventional-cryptosystem.png?w=300&h=252
http://openpgp.org/
http://truecrypt.sourceforge.net/
https://www.scmagazineuk.com/tel-aviv-team-first-to-steal-high-level-pc-crypto–through-a-wall/article/531456/
MasterCard launches Credit Card with Built-In Fingerprint Scanner
21.4.2017 thehackernews Safety
MasterCard has unveiled its brand new payment card that has a built-in biometric fingerprint scanner, allowing customers to authorize payments with their fingerprint, without requiring a PIN code or a signature.
The company is already testing the new biometric payment cards, combined with the on-board chips, in South Africa and says it hopes to roll out the new cards to the rest of the world by the end of 2017.
Don't Worry, It Still Supports PIN-based Transactions as Fallback
Wait — If you think that this feature would not allow you to share your card with your child and spouse, don’t worry — Mastercard has a solution for this issue as well.
The company has confirmed that even if the card is configured to expect the fingerprint for authenticating a purchase, but it does still have a PIN as a fallback, in case, for some reason EMV readers fail to read fingerprint or you have yourself handed it to your child for shopping.
Stores & Retailers Don't Need New Hardware
According to Mastercard, the new biometric payment card will not require store owners and businesses to buy any new hardware, like fingerprint scanners, because the sensor in the card reads your fingerprint.
Since both the data and the scanner exist on the same card, the new payment cards work with existing EMV card terminal infrastructure — the standard chip/swipe readers you can find at many stores these days, though old magnetic stripe-only terminals won't be compatible.
But, Banks Need to Adopt New Technology
Before this new cards can be adopted worldwide, your banks or financial institution will have to get on board with the new tech.
If you want the new biometric card, you are currently required to go to your bank branch in order to have your fingers scanned and registered for the new tech. Your fingerprints will then be converted into an encrypted digital template that is stored on the card's EMV chip.
You can save up to two fingerprints, but both would have to be yours — you can not authorise someone else, even from your family, to use your card with their fingers.
Once your templates are saved, your card is ready to be used at compatible terminals across the world.
Merchants don't have to purchase new equipment to accept your fingerprint-enabled payment card but will have to update their machinery in an effort to use the new tech.
Now, while shopping at any store, just place your biometric payment card into a retailer's EMV terminal and then put your finger on the embedded sensor to pay. Your fingerprints will be verified against a template stored on your card to approve your transaction.
Can Fingerprints be Forged? And Other Concerns...
This new card is made in an attempt to make face-to-face payments more convenient and more secure, but this type of biometric verification is useless when it comes to online shopping, and so, does not provide any security over credit card frauds.
"Whether unlocking a smartphone or shopping online, the fingerprint is helping to deliver additional convenience and security," MasterCard security chief Ajay Bhalla said. "[A fingerprint is] not something that can be taken or replicated and will help our cardholders get on with their lives knowing their payments are protected."
But that isn't true.
Fingerprints can be faked, unfortunately, and we have seen previous research in which high-resolution images were used to make fake fingerprints for malicious purpose. So, criminals could put a fake fingerprint on top of their finger to shop from stolen cards.
In addition to biometric cards, MasterCard is also planning to bring contactless payments, which should function similar to mobile payments like Apple Pay where users authenticate themselves via fingerprint while holding their smartphones against the terminal.
This is How Google Secures Devices for Its 61,000 Employees
20.4.2017 securityweek Safety
Google Details Its Implemenation of Tiered Access to Secure Devices for More Than 61,000 Employees
The easiest solution to access control is binary: network access is either granted or denied. It's a blunt tool that doesn't suit the modern business culture of maximizing user productivity and creativity. Granularity in access control, allowing users to access what is needed when it is needed, is a more suitable model for the modern business.
Google chose the Tiered Access model for its own workforce of some 61,000 employees. In a new whitepaper (PDF) and blog published today, it explains that it has "a culture of innovation that requires the freedom and flexibility to connect many different devices to many different assets and services."
This is an attitude that will resonate with many modern businesses.
"Tiered access was implemented in order to provide an access model appropriate for [Google's] very heterogeneous environment. It helps ensure the security of corporate resources while allowing users to make informed trade-offs around access and security controls." Many organizations offer their staff flexibility in the devices they use -- especially where a BYOD policy is in place.
Tiered access is achieved by first analyzing the client base devices and data sources; analyzing the services that are to be accessed; and choosing a gateway/access technology that can evaluate policies and make access decisions between the client base and service.
Google uses its own internally developed tools to collect the device data; but suggests other companies could use security reporting systems (logs), patch management systems, asset management systems and centralized management dashboards. The purpose is to gather device attributes and device state into a central repository.
The device attributes allow the definition of device baselines, based on things like vendor and operating system, and built-in security features. The device state, continuously monitored, highlights deviations from the device baseline. These two attributes can be used to associate devices to the different tiers.
"For example," explains Google, "an Android device at Google may access more sensitive data in higher trust tiers if it is a 'Fully Managed' device, meaning it provides full device control and access to detailed system and network logs." A lower trust tier is made accessible to BYOD devices with a work profile.
Between the device and the service sits an Access Control Engine that provides a service-level authorization to enterprise applications on a per-request basis. It queries the central repository in order to make policy decisions on what access is allowable -- it is where policy is defined and managed by security.
The 'tiers' in tiered access are levels of sensitivity applied to the organization's different services. Google uses just four tiers: untrusted; basic access; privileged access; and highly privileged access. It chose four tiers as a compromise between too many (making the system over-complex), and too few (which effectively recreates the binary access that the tiered approach seeks to improve).
While this is the current state of Google's tiered access solution to its on-site and mobile workforces, development is ongoing. It has four areas currently under consideration. The first is to increase the granularity of the system by improving "the precision of access decisions while balancing the need for users to understand security requirements."
The second is to add user attributes to the device attributes by considering "the user’s observed behavior and how that compares to normal activity as analyzed with machine learning." This will allow access based on both the device and current user behavior.
The third is to drive self-selection of trust tiers by encouraging people to voluntarily move across trust tiers in real-time; for example, to be at 'fully trusted' for the next two hours only.
Finally, Google hopes to improve the service on-boarding process. Since services are added or updated all the time, they all need to be classified in terms of risk and sensitivity. "To scale," suggests Google, "service owners must be empowered to make the right tier assignments themselves, which is a process that is constantly improving."
Google hopes that by sharing its own experiences in developing and deploying tiered access, IT and security admins will feel empowered to develop a flexible and powerful access control system that better suits today's business. Its Tiered Access project goes hand-in-hand with the larger BeyondCorp project that challenges traditional security assumptions that private or 'internal' IP addresses represented a 'more trusted' device than those coming from the internet. Part of BeyondCorp is discussed in the Google Infrastructure Security Design Overview.
The security is still secure
16.4.2017 Kaspersky Safety
The WikiLeaks report and Kaspersky Lab's products
Recently WikiLeaks published a report that, among other things, claims to disclose tools and tactics employed by a state-sponsored organization to break into users’ computers and circumvent installed security solutions.
The list of compromised security products includes dozens of vendors and relates to the whole cybersecurity industry. The published report includes a description of vulnerabilities in software products that can be used to bypass protection and jeopardize users’ security.
Customers’ security is a top priority for Kaspersky Lab, and as such we take any information that could undermine users’ protection very seriously. We thoroughly investigate all reported vulnerabilities.
The published report contains descriptions of two vulnerabilities in Kaspersky Lab’s products that have already been fixed. It also includes a number of mentions related to the company’s technologies and past Advanced Persistent Threat (APT) research. I’d like to take this opportunity to address possible concerns regarding the report and provide reliable first-hand information to demonstrate that no current Kaspersky Lab products and technologies are vulnerable.
Vulnerabilities in security solutions
First of all, I’d like to emphasize that the vulnerabilities in Kaspersky Lab’s products listed in the report are related to older versions of the products, and they were publicly disclosed and fixed some time ago. The current versions of our products are not vulnerable to the tools and tactics listed.
The “heapgrd” DLL inject vulnerability was discovered and fixed in Kaspersky Lab products back in 2009. The vulnerability allowed a malefactor to load a third-party DLL instead of the WHEAPGRD.dll file and thus bypass protection. It was patched starting with Kaspersky Internet Security 9 and Kaspersky Antivirus for Workstations MP4. The products that were mentioned in relation to these vulnerabilities (Kaspersky Internet Security 7 and 8 and Kaspersky Antivirus for Workstations MP3) are outdated and no longer supported. All current Kaspersky Lab solutions are subject to mandatory testing against these vulnerabilities prior to release.
The TDSS Killer’s DLL inject vulnerability mentioned in the WikiLeaks report was fixed in 2015.
Product behavior specifics
The report also says Kaspersky Lab’s security solutions do not block DLL injections into user processes and svchost.exe. In fact, we do protect against this sort of attack — in a smarter way that elegantly combines protection and a better user experience.
Nowadays, it’s common practice for legitimate applications to inject their code into user processes. To effectively distinguish legitimate from malicious actions, track changes, and restore unwanted amendments an application may make to the system, Kaspersky Lab’s products have included the System Watcher component since 2011. System Watcher monitors all processes on a device, including svchost.exe, and is capable of detecting malicious behavior, blocking it, and rolling back malicious changes.
The report also describes several tools and malicious programs that were used to collect data and infiltrate the users’ computers. However, all of them can be neutralized with Kaspersky Lab’s products. Let’s take a closer look at them.
First, the RickyBobby fileless Trojan is allegedly not detected by Kaspersky Lab’s products, which is not the case. All personal and enterprise level products can detect this Trojan, prevent the infection, and disinfect a system that was protected by a third-party or outdated security solution.
Second, the report mentions two other malware samples (Fine Dining and Grasshopper) that allegedly are not detected by Kaspersky Lab’s products. However, the report doesn’t provide further details of the malware. We will keep investigating the issue and report the findings as soon as details are available.
That said, we are skeptical: It’s said Fine Dining relies on the aforementioned DLL inject vulnerability in TDSS Killer, which is already fixed. Also it’s worth mentioning that Kaspersky products provide multiple layers of protection — such as emulation, heuristics, System Watcher, and Automatic Exploit Prevention — including those powered by industry-leading machine learning. These technologies are capable of detecting cyberthreats proactively based on their behavior and are constantly improved to address new techniques employed by malicious actors. The analysis of the report makes us optimistic that our customers are already protected against both Fine Dining and Grasshopper.
Third, the report mentions HammerDrill, API Memcry, and Trojan Upclicker, which use a variety of techniques to try to avoid detection by the emulator technology.
Kaspersky Lab’s emulator’s history dates back to the early 90s. It’s rated one of the best in the cybersecurity industry, and it’s continuously improved. The functionality to address the described Trojan Upclicker cloaking method was included in the emulator more than a year ago, for example. The other two tools are effectively managed by the multilayer protection available in Kaspersky Lab’s products both for home users and enterprise customers.
Fourth, the report mentions an MBR File Handle component that is able to circumvent security solutions’ drivers and thus upload malware into the Master Boot Record of the operating system.
In fact, this trick is foiled by the antirootkit technology included in Kaspersky Lab products, which enables them to reliably detect and remove infections — even the most advanced bootkits.
Fifth, another tool mentioned in the report is the Bartender program, which collects data on installed software. This functionality is not malicious and is used by many legitimate applications. However, Kaspersky Lab’s products do provide protection against such activity should a user select the high security level setting.
Fun facts
The other two mentions of Kaspersky Lab in the context of malware creation are actually fun facts.
First, the tool called DriftingShadows checks if Kaspersky Lab’s products are installed on the device, and if it finds them, it does … nothing. This means that the malware creators failed to sneak past our products. They now avoid protected devices so that their malware doesn’t get caught.
Second, the documents also describe a game called “Bonus: Capture the Flag” played among malware creators. It involves attempts to create a malware sample that bypasses Kaspersky Lab’s protection. In other words, malefactors consider our products a gold standard of cybersecurity.
Wrap-up
Investigating the existing report thoroughly, we found two vulnerabilities and several other mentions of Kaspersky Lab, including discussions regarding our reports on the Duqu 2.0 and Equation cyberespionage campaigns. Both vulnerabilities were fixed quite some time ago and pose no threat to our customers. The same goes for the other malicious tools and techniques mentioned.
However, we are staying vigilant and continuously monitoring the situation. WikiLeaks may yet publish more details. In any case, we’d like to reassure customers that addressing any possible vulnerabilities will be our top priority.
No development process guarantees immediate, perfect, permanent invincibility. We are committed to constantly improving the development process, and we also make significant efforts to perfect the process of fixing newly discovered vulnerabilities.
Psycho-Analytics Could Aid Insider Threat Detection
12.4.2017 securityweek Safety
Psycho-Analytics Could Help Detect Future Malicious Behavior
The insider threat is perhaps the most difficult security risk to detect and contain -- and concern is escalating to such an extent that a new bill, H.R.666 - Department of Homeland Security Insider Threat and Mitigation Act of 2017, passed through Congress unamended in January 2017.
The bill text requires the Department of Homeland Security (DHS) to establish an Insider Threat Program, including training and education, and to "conduct risk mitigation activities for insider threats." What it does not do, however, is explain what those 'mitigation activities' should comprise.
One difficulty is that the insider is not a uniform threat. It includes the remote attacker who becomes an insider through using legitimate but stolen credentials, the naive employee, the opportunistic employee, and the malicious insider. Of these, the malicious insider is the most intransigent concern.
Psycho-analytics Used for Insider Threat Detection
Traditional security controls, such as access control and DLP, have some but little effect. In recent years, these have been supplemented by user behavior analytics (UBA), using machine learning to detect anomalous user behavior within the network.
"Behavioral analytics is the only way to... get real insight into insider threat," explains Nir Polak, CEO of Exabeam. "UBA tells you when someone is doing something that is unusual and risky, on an individual basis and compared to peers. UBA cuts through the noise to give real insight – any agencies looking to get a handle on insider threat should be looking closely at UBA."
Humphrey Christian, VP of Product Management, at Bay Dynamics, advocates a combination of UBA and risk management. "A threat is not a threat if it's targeting an asset that carries minimal value to the organization. An unusual behavior is also not a threat if it was business justified, such as it was approved by the employee's manager," he told SecurityWeek. "Once an unusual behavior is identified, the application owner who governs the application at risk, must qualify if he indeed gave the employee access to the asset. If the answer is 'no', then that alert should be sent to the top of the investigation pile."
Learn to Detect Insider ThreatsThis week a new paper published by the Intelligence and National Security Alliance (INSA) proposes that physical user behavioral analytics should go a step further and incorporate psycho-analytics set against accepted behavior models. These are not just the baseline of acceptable behavior on the network, but incorporate the psychological effect of life events both inside and outside of the workplace. The intent is not merely to respond to anomalous behavior that has already happened, but to get ahead of the curve and be able to predict malicious behavior before it happens.
The INSA paper starts from the observation that employees don't just wake up one morning and decide to be malicious. Malicious behavior is invariably the culmination of progressive dissatisfaction. That dissatisfaction can be with events both within and outside the workplace. INSA's thesis is that clues to this progressive dissatisfaction could and should be detected by technology; machine learning (ML) and artificial intelligence (AI).
This early detection would allow managers to intervene and perhaps help a struggling employee and prevent a serious security event.
Early signs of unhappiness within the workplace can be relatively easy to detect when they manifest as 'counterproductive work behaviors' (CWBs). INSA suggests that there are three key insights "that are key to detecting and mitigating employees at risk for committing damaging insider acts." CWBs do not occur in isolation; they usually escalate; and they are seldom spontaneous.
Successful insider threat mitigation can occur when early non-harmful CWBs can be detected before they escalate.
Using existing studies, such as the Diagnostic and Statistical Manual of Mental Disorders Vol. 5 (DSM-5), INSA provides a table of stressors and potentially linked CWBs. For example, emotional stress at the minor level could lead to repeated tardiness; at a more serious level it could lead to bullying co-workers and unsafe (dangerous) behavior. INSA's argument is that while individual CWBs might be missed by managers and HR, patterns -- and any escalation of stress indicators -- could be detected by ML algorithms. This type of user behavior analytics goes beyond anomalous network activity and seeks to recognize stressed user behavior that could lead to anomalous network activity before it happens.
But it still suffers from one weakness -- that is, where the stressors that affect the user's work occur entirely outside of the workplace; such as divorce, financial losses, or family illness. Here INSA proposes a more radical approach, but one that would work both inside and outside the workplace.
"In particular," it suggests, "sophisticated psycholinguistic tools and text analytics can monitor an employee's communications to identify life stressors and emotions and help detect potential issues early in the transformation process."
The idea is to monitor and analyze users' communications, which could include tweets and blogs. The analytics would look for both positive and negative words. An example is given. "I love food ... with ... together we ... in ... very ... happy." This sequence could easily appear in a single tweet; but the use of 'with', 'together', and 'in' would suggest an inclusive and agreeable temperament.
In fairness to doubters, INSA has done itself no favors with the misuse of a second example. Here Chelsea (formerly Bradley) Manning is quoted. "A second blog post," says INSA, "substantiates that Life Event and identifies an additional one, 'Relationship End/Divorce' with two mentions for each Life Event." The implication is that psycholinguistic analysis of this post would have highlighted the stressors in Manning's life and warned employers of the potential for malicious activity. The problem, however, is that the quoted section comes not from a Manning blog post before the event, but from the chat logs of his conversation with Lamo in May 2010 (see Wired) after WikiLeaks had started publishing the documents. The linguistic analysis in this case might have helped explain Manning's actions, but could do nothing to forewarn the authorities.
The point, however, is that psycholinguistic analysis has the potential to highlight emotional status, and over time, highlight individuals on an escalating likelihood of developing first minor CWBs and ultimately major CWBs. The difficulty is that it really is kind of creepy. That creepiness is acknowledged by INSA. "Use of these tools entails extreme care to assure individuals' civil or privacy rights are not violated," it says. "Only authorized information should be gathered in accordance with predefined policies and legal oversight and only used for clearly defined objectives. At no point should random queries or 'What If' scenarios be employed to examine specific individuals without predicate and then seek to identify anomalous bad behavior."
Users' decreasing expectation of privacy would suggest that sooner or later psycholinguistic analysis for the purpose of identifying potential malicious insiders before they actually become malicious insiders will become acceptable. In the meantime, however, it should be used with extreme caution and with the clear, unambiguous informed consent of users. What INSA is advocating, however, is an example of what law enforcement agencies have been seeking for many years: the ability to predict rather than just respond to bad behavior.
DARPA Wants Hardware With Built-in Security
12.4.2017 securityweek Safety
DARPA seeking solutions for more secure hardware
The U.S. Defense Advanced Research Projects Agency (DARPA) announced this week a new program that aims to develop a framework for building hack protections directly into hardware.
The agency pointed out that the integrated circuits found in many devices often have vulnerabilities that can be exploited with software exploits, and software patches represent only a temporary solution.
As part of a new 39-month program named System Security Integrated Through Hardware and Firmware (SSITH), DARPA hopes to receive proposals for new chip architectures which would disarm software attacks that leverage hardware flaws.
The SSITH project focuses on two main technical areas: developing a secure hardware architecture and tools to help manufacturers take advantage of security innovations, and identifying a methodology and metrics for determining the security status of new systems.
Some chip makers, such as Intel, have already been integrating various protections into their products, but DARPA wants design tools that would be widely available, leading to built-in security becoming a standard for integrated circuits used in U.S. Department of Defense and commercial systems.
DARPA said proposals should address one or more of the seven hardware vulnerability classes in the Common Weaknesses Enumeration (CWE) list. These include code injections, permissions and privileges, buffer errors, information leakage, resource management, numeric errors, and cryptographic issues.
The agency pointed out that more than 2,800 incidents have involved one of these vulnerabilities, and SSITH program manager Linton Salmon, of DARPA’s Microsystems Technology Office, believes more than 40 percent of software weaknesses can be addressed by removing these types of flaws.
“Security for electronic systems has been left up to software until now, but the overall confidence in this approach is summed up in the sardonic description of this standard practice as ‘patch and pray,’” said Salmon “This race against ever more clever cyberintruders is never going to end if we keep designing our systems around gullible hardware that can be fooled in countless ways by software.”
Experts interested in submitting a proposal can learn more about the project and have the opportunity to team up with others on Friday, April 21, 2017, at the Booz Allen Hamilton Conference Center.
Mandatory Certificate Authority Authorization Checks Will Boost Domain Security
12.4.2017 securityweek Safety
The issuance of SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates is expected to become a more secure process this September, after the implementation of mandatory Certificate Authority Authorization (CAA) checks.
After Certificate Authorities (CAs) and browser makers voted last month to make CAA checking mandatory, the new standard will be implemented starting September 8, 2017, according to Ballot 187 on the CA/Browser Forum site. Starting then, all CAs will have to check CAA records at issuance time for all certificates, which should prevent them from issuing certificates if not permitted to.
CAA is a DNS Resource Record that “allows a DNS domain name holder to specify one or more Certification Authorities (CAs) authorized to issue certificates for that domain and, by implication, that no other CAs are authorized.”
Domain owners will be able to set an issuance policy that all publicly-trusted CAs should comply with, thus preventing CAs from wrongfully issuing HTTPS certificates. This new standard should also mitigate the issue that “the public CA trust system is only as strong as its weakest CA,” Ballot 187 also reveals.
CAs will have to check “for a CAA record for each dNSName in the subjectAltName extension of the certificate to be issued.” This standard, however, doesn’t prevent CAs to check CAA records at any other time.
Apparently, CAA checking isn’t required in specific scenarios, such as for “certificates for which a Certificate Transparency pre-certificate was created and logged in at least two public logs, and for which CAA was checked.”
If the CA or an Affiliate of the CA is the DNS Operator of the domain’s DNS, CAA checking becomes optional, the same as “for certificates issued by a Technically Constrained Subordinate CA Certificate as set out in Baseline Requirements section 7.1.5, where the lack of CAA checking is an explicit contractual provision in the contract with the Applicant.”
CAs are also required to document potential issuances that were prevented by the CAA, and should also send reports of the requests to the contact(s) stipulated in the CAA iodef record(s), if present.
17 out of 19 voting CAs (94%) voted in favor of the new CAA standard. All three participating browser makers (Mozilla, Google, and Apple) voted in favor.