Safety Articles - H 2020 1 2 3 4 5 6 Safety List - H 2021 2020 2019 2018 1 Safety blog Safety blog
Google Chrome to Label Sensitive HTTP Pages as "Not Secure"
9.9.2016 thehackernews Safety
Although over three months remaining, Google has planned a New Year gift for the Internet users, who're concerned about their privacy and security.
Starting in January of 2017, the world's most popular web browser Chrome will begin labeling HTTP sites that transmit passwords or ask for credit card details as "Not Secure" — the first step in Google's plan to discourage the use of sites that don't use encryption.
The change will take effect with the release of Chrome 56 in January 2017 and affect certain unsecured web pages that feature entry fields for sensitive data, like passwords and payment card numbers, according to a post today on the Google Security Blog.
Unencrypted HTTP has been considered dangerous particularly for login pages and payment forms, as it could allow a man-in-the-middle attacker to intercept passwords, login session, cookies and credit card data as they travel across the network.
In the following release, Chrome will flag HTTP pages as "Not secure" with a neutral indicator in the address bar of incognito mode, where users may have higher expectations of privacy.
Then, in the future, Chrome will flag all HTTP sites as "Not secure" with the same red triangle indicator the browser currently uses to indicate a broken HTTPS website.
"Chrome currently indicates HTTP connections with a neutral indicator," Emily Schechter wrote in a blog post. "This doesn't reflect the true lack of security for HTTP connections. When you load a website over HTTP, someone else on the network can look at or modify the site before it gets to you."
This isn't the first time when Google is taking steps to encourage site owners to switch to HTTPS. Two years back, Google also made some changes to its search engine algorithm in an effort to give a ranking boost to the websites that use encrypted HTTPS connections.
Last month, Google also implemented HTTP Strict Transport Security (HSTS) on its main domain (google.com) in an effort to prevent users from navigating to websites using the insecure HTTP.
Google reported that today, more than half of the websites visited by Chrome users are already encrypted.
Not only Google, but Mozilla has also been encouraging users to adopt HTTPS through its Let's Encrypt project that provides free SSL/TSL certificates for website owners to help them implement HTTPS for their services. (Here's How to Install Free SSL Cert).
Chinese Certificate Authority 'mistakenly' gave out SSL Certs for GitHub Domains
30.8.2016 thehackernews Safety
github-ssl-certificate
A Chinese certificate authority (CA) appeared to be making a significant security blunder by handing out duplicate SSL certificates for a base domain if someone just has control over its any subdomain.
The certificate authority, named WoSign, issued a base certificate for the Github domains to an unnamed GitHub user.
But How? First of all, do you know, the traditional Digital Certificate Management System is the weakest link on the Internet today and has already been broken?
Billions of Internet users blindly rely on hundreds of Certificate Authorities (CA) around the globe to ensure the confidentiality and integrity of their personal data.
But, these CAs have powers to issue valid SSL cert for any domain you own, despite the fact you already have one purchased from another CA.
...and that's the biggest loophole in the CA system.
In the latest case as well, WoSign issued a duplicate SSL certificate for GitHub domains without verifying ownership of the base domain.
The incident was first publicly disclosed by British Mozilla programmer Gervase Markham on Mozilla's security policy mailing list saying the issue occurred over a year ago in July 2015 but went unreported.
"In June 2015, an applicant found a problem with WoSign's free certificate service, which allowed them to get a certificate for the base domain if they were able to prove control of a subdomain," Markham wrote in the mailing list.
According to Markham, an unnamed security researcher accidentally discovered this security blunder when trying to get a certificate for 'med.ucf.edu' but mistakenly also applied for 'www.ucf.edu' and WoSign approved it, handing over the certificate for the university's primary domain.
For testing purpose, the researcher also used this trick against Github base domains i.e. github.com and github.io, by proving his control over a user-based subdomain.
...And guess what? WoSign handed over the certificate for GitHub main domains, too.
The researcher reported this issue to WoSign by giving only the Github certificate as an example. Thus, the Chinese CA only revoked the GitHub certificate, despite revoking both the certificates.
Why Just One? It is quite possible that the CA company doesn't have any tracking ability to discover and revoke all mistakenly issued base certificates for other domains by self-investigation even after getting informed of the problem.
The researcher recently got in touch with Google and reported that the ucf.edu cert had still not been revoked almost a year later.
How to check whether a rogue cert for your domain has been issued to someone else, probably a malicious attacker?
Solution: Certificate Transparency or CT, a public service that allows individuals and companies to monitor how many digital security certs have secretly been issued for their domains.
Certificate Transparency requires CAs to declare publicly (to Certificate Log) every digital cert they have generated. Even WoSign has participated in CT.
Certificate Log offers you a way to look up all of the digital certificates that have been issued for your domain name.
Also read: Learn How Certificate Transparency Monitoring Tool Helped Facebook Early Detect Duplicate SSL Certs?
Although Certificate Transparency doesn't prevent CA from issuing forged certificates, it makes the process of detecting rogue certificates much easier.
Currently, Google, Symantec, DigiCert, and a few other CAs are hosting public CT logs.
You can try Google's Certificate Transparency Lookup Tool or Comodo's Certificate Transparency Search tool to check all certificates present in public Certificate Transparency logs that have been issued for your domain.
If you find a fraud certificate issued for your domain, report respective CA and address it immediately.
Germany and France declare War on Encryption to Fight Terrorism
26.8.2016 thehackernews Safety
Yet another war on Encryption!
France and Germany are asking the European Union for new laws that would require mobile messaging services to decrypt secure communications on demand and make them available to law enforcement agencies.
French and German interior ministers this week said their governments should be able to access content on encrypted services in order to fight terrorism, the Wall Street Journal reported.
French interior minister Bernard Cazeneuve went on to say that the encrypted messaging apps like Telegram and WhatsApp "constitute a challenge during investigations," making it difficult for law enforcement to conduct surveillance on suspected terrorists.
Also Read: How to Send and Receive End-to-End Encrypted Emails
The proposal calls on the European Commission to draft a law that would "impose obligations on operators who show themselves to be non-cooperative, in particular when it comes to withdrawing illegal content or decrypting messages as part of an investigation."
The proposed laws would force major technology companies including Apple, WhatsApp, Facebook, Telegram, and many others, to build encryption backdoors into their messaging apps.
The European Union has always been a strong supporter of privacy and encryption, but the recent series of terrorist attacks across both France and Germany this summer, including Normandy church attack carried out by two jihadists who reportedly met on Telegram, which made the countries shout for encryption backdoors loudly.
Although the proposal acknowledges encryption to be a critical part in securing communications and financial transactions, it says that solutions must be found to "enable effective investigation" while protecting users’ privacy.
Privacy advocates have been alarmed by the new proposals, as recent NSA hack just recently proved all of us that no system is hack-proof for hackers with right hacking skills and sufficient resources.
Related Read: Microsoft handed over encrypted messages and Skype calls to NSA
So, what happened to the NSA, which is the highly sophisticated intelligence agency of the world, could happen to encrypted messaging services that would feature an encryption backdoor for law enforcement.
The European Commission is believed to come up with new laws on privacy and security for telecom operators this fall, which would include third-party services such as WhatsApp or Telegram.
WhatsApp to Share Your Data with Facebook — You have 30 Days to Stop It
26.8.2016 thehackernews Safety
WhatsApp to Share Your Data with Facebook
Nothing comes for Free, as "Free" is just a relative term used by companies to develop a strong user base and then use it for their own benefits.
The same has been done by the secure messaging app WhatsApp, which has now made it crystal clear that the popular messaging service will begin sharing its users’ data with its parent company, Facebook.
However, WhatsApp is offering a partial opt-out for Facebook targeted ads and product related purposes, which I will let you know later in this article, but completely opting out of the data-sharing does not seem to be possible.
Let's know what the company has decided to do with your data.
Of course, Facebook is willing to use your data to sell more targeted advertisements.
WhatsApp introduced some significant changes to its privacy policy and T&Cs today which, if accepted once, gives it permission to connect users' Facebook accounts to WhatsApp accounts for the first time, giving Facebook more data about users for delivering more relevant ads on the social network.
The messaging service will also begin pushing users to share some of their account details, including phone numbers, with Facebook, allowing the social network to suggest phone contacts as friends.
When Facebook acquired WhatsApp for $19 Billion in 2014, users were worried about the company's commitment to protecting its users' privacy. But, WhatsApp reassured them that their privacy would not be compromised in any way.
"Respect for your privacy is coded into our DNA, and we built WhatsApp around the goal of knowing as little about you as possible," said WhatsApp co-founder Jan Koum in a blog post published at that time.
Now the WhatsApp users are feeling betrayed by the company's latest move.
However, you need not to worry about the contents of your WhatsApp messages, like words and images, as they are end-to-end encrypted, meaning that even the company cannot read them.
Ultimately, the two companies will be sharing, what they called, a limited amount of user data, which includes phone numbers and other information about users.
No Option to Completely Opt-Out of Data Sharing
If you think WhatsApp is more privacy conscious than Facebook’s Messenger, it is not anymore.
WhatsApp is offering a solution partially to opt out the data sharing, specifically for Facebook ad targeting and product-related purposes.
However, the company notes that data will still be shared "for other purposes such as improving infrastructure and delivery systems, understanding how our services or theirs are used, securing systems, and fighting spam, abuse, or infringement activities."
So, those who are thinking to opt out of the data-sharing entirely: There's no possible way to opt totally out.
Though one short solution is to stop using WhatsApp.
Here's How to opt -out of sharing data for Facebook ad-targeting purpose:
The company has outlined two ways to opt out of the exchange of information with Facebook on its blog.
One way is for those users who have not yet agreed to the new terms of service and privacy policy, so before agreeing to the new terms, follow these simple steps:
When prompted to accept the updated T&Cs, tap Read to expand the full text.
A checkbox option at the bottom of the policy for sharing your data on Facebook will appear.
Untick this option before hitting Agree. This will let you opt out of the data-sharing.
The second option is for those who have already accepted the new T&Cs without unchecking the box to share their information with Facebook.
WhatsApp is also offering a thirty-day window for users to make the same choice via the settings page in the app. To exercise your opt-out in this scenario you need to follow these steps:
Go to Settings → Account → Share my account info in the WhatsApp app
Uncheck the box displayed there within 30 days, as after that this partial opt-out window will expire.
However, WhatsApp states Facebook will still receive your data in some situations.
After introducing end-to-end encryption, WhatsApp has become one of the most popular secure messaging apps, but this sudden shift in its privacy policy may force some users to switch to other secure apps like Telegram and Signal.
Members call for a Tor General Strike and shut down Tor for a day
23.8.2016 securityaffairs Safety
A few members of the community are calling for a ‘Tor general strike’ to protest against some decisions taken recently by the core members.
Last month, the Tor Project announced that an internal investigation had confirmed the allegations of sexual misconduct against the notorious member Jacob Appelbaum.
The allegations divided the internet privacy community, as a result of events the entire board of directors of the project was replaced.
News of the day is that a few members of the community are calling for a ‘Tor general strike.’ They want to express their dissent on the way the investigation was handled.
A message published on Twitter invites those who run parts of the Tor network infrastructure to shut down their machines, developers to stop working on Tor, and of course, users to stop using the anonymizing network.
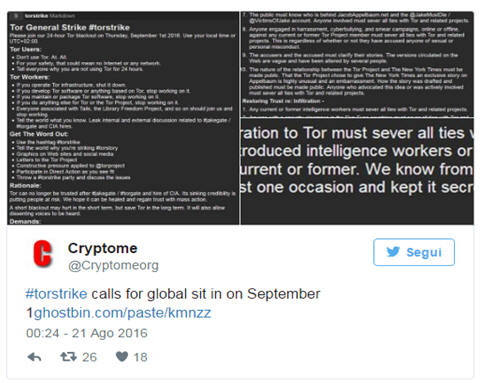
Cryptome @Cryptomeorg
#torstrike calls for global sit in on September 1https://ghostbin.com/paste/kmnzz
00:24 - 21 Ago 2016
26 26 Retweet 18 18 Mi piace
The members who are calling for a Tor General Strike are also opposed to the decision of the Tor Project to hire an ex-CIA official.
“Tor can no longer be trusted after #jakegate / #torgate and hire of CIA,” states the Ghostbin post that calls for the Tor Global Strike. “Its sinking credibility is putting people at risk. We hope it can be healed and regain trust with mass action. A short blackout may hurt in the short term, but save Tor in the long term. It will also allow dissenting voices to be heard.”
Joseph Cox from Motherboard reported a leaked chat log from an internal Tor Project IRC channel that demonstrated that part of the members of the Project did not agree on the move of hiring a supposed ex-CIA agent, “DaveC1”.
Some internal members of the Tor Project were not aware of the past of DaveC1.
Tor Global Strike
A Tor General Strike is probably the worst way to express the dissent, many individuals worldwide rely on the Tor network to avoid censorship and express their ideas without fearing for their life.
“Journalists and activists use Tor in countries where people can be killed for the things they say,” Shari Steele, the Tor Project’s executive director told Motherboard. “Shutting down the Tor network would shut down their speech or, even more dangerous, could force them to use unsafe methods of communication.”
The call to the Tor General Strike includes 16 requests to the Tor Project, one of them invoke the sacking the co-founder Roger Dingledine.
Many demands included in the call for the Tor General Strike are related to the internal investigation on Appelbaum’s conduct. They demand more details on the claims against Appelbaum to be made public.
The news of the strike comes after the Tor relay operator Stephan Seitz shut down its node.
“The situation how the affair about Jake was handled by the Tor project has made me feel very uneasy. After digging through several material (for example https://shiromarieke.github.io/tor) I find that I am no longer believing in this project or trust it. That’s why I’m shutting down my tor relay fsingtor now.“ Seitz wrote to a Tor Project.
NSA BENIGNCERTAIN tool can obtain VPN Passwords from CISCO PIX
21.8.2016 securityaffairs Safety
Researchers tested the BENIGNCERTAIN tool included in the NSA data dump that allows attackers to extract VPN passwords from certain Cisco devices.
Following the disclosure of the NSA dump, IT vendors Cisco and Fortinet issued security patches to fix the flaws exploited by the Equation Group in their products.

Now, security researchers have uncovered another exploit included in the leaked dump, dubbed BENIGNCERTAIN that allows the extraction of VPN passwords from certain Cisco devices.
The expert Mustafa Al-Bassam who analyzed the data dump has called the attack “PixPocket” after the name of the Cisco products hacked by the tool, the Cisco PIX.
The CISCO PIX product family was declared phase out back in 2009, but it is widely adopted by government entities and enterprises.
According to the expert, the tool works against the CISCO PIX versions 5.2(9) up to 6.3(4).
Al-Bassam discovered that the tool could be used to send a packet to the target machine that makes it dump a portion of the memory that includes the VPN’s authentication password.
The security expert Brian Waters also tested the BENIGNCERTAIN exploits confirming that it works.
Visualizza l'immagine su Twitter
Visualizza l'immagine su Twitter
Segui
Brian H₂O's @int10h
I can confirm that BENIGNCERTAIN works against real hardware @XORcat @GossiTheDog @musalbas @marcan42 @msuiche
07:49 - 19 Ago 2016
148 148 Retweet 115 115 Mi piace
“it’s a PIX 501 running 6.3(5)145; and I used v1110 of the exploit” added 501 running 6.3(5)145; and I used v1110 of the exploit” added Waters in a second Tweet, this means that the BENIGNCERTAIN could work also against other versions of the PIX.
This means that NSA could have remotely sent a packet to a target VPN to obtain its preshared key and decrypt the traffic.
Cisco published the blog post titled “The Shadow Brokers EPICBANANAS and EXTRABACON Exploits” to provide further details about its investigation of the tools included in the arsenal of the Equation Group leaked online.
The Cisco security team is still investigating the content of the leaked data dump to verify the if other hacking tools could be exploited against its products.
“On August 19th, articles were release regarding the BENIGNCERTAIN exploit potentially being used to exploit legacy Cisco PIX firewalls. Our investigation so far has not identified any new vulnerabilities in current products related to the exploit. Even though the Cisco PIX is not supported and has not been supported since 2009 (see EOL / EOS notices), out of concern for customers who are still using PIX we have investigated this issue and found PIX versions 6.x and prior are affected. PIX versions 7.0 and later are confirmed to be unaffected by BENIGNCERTAIN. The Cisco ASA is not vulnerable.” wrote CISCO.
Core Tor Developer who accuses FBI of Harassment moves to Germany
18.5.2016 Safety
One of TOR's primary software developers, Isis Agora Lovecruft, has fled to Germany, following the threat of a federal subpoena.
Lovecruft is a well-known cryptographer and lead software developer for Tor project from many years. She has worked for a variety of other security and encryption products, such as Open Whisper Systems and the LEAP Encryption Access Project.
Since November 2015, the FBI special agents in the United States have been trying to meet with her, but they will not tell her or her lawyer exactly why.
When her lawyer reached out the FBI Special Agent Mark Burnett and asked why he wanted to meet with her, the agent assured the lawyer that she is not the target of any investigation, but also said that…
Also Read: Mozilla asks Court to disclose Firefox Exploit used by FBI to hack Tor users.
The FBI have their agents on the streets in 5 cities in the United States hunting for her, intending to simply ask her some questions without her lawyer's presence.
Lovecruft's lawyer responded by saying that all questions should be directed to him rather than to Lovecruft or her family, but Burnett said that he will not tell her or her lawyer what this involves.
In general, it's not a big deal to have at least a meeting with the FBI agents to know what exactly are the federal agents looking for.
But Lovecruft fears that the federal agents will serve her with some kind of secret warrant, possibly to get her to insert a backdoor in the TOR system and expose TOR users around the world to potential spying.
Must Read: Former Tor Developer Created Malware for FBI to Unmask Tor Users.
So, she packed her suitcase and left the United States for Germany on December 7 last year, accusing the FBI of harassment for the past 6 months.
"I had already been in the process of moving, permanently, to Germany, and had retained a German immigrations lawyer several months prior to these events," Lovecruft wrote in her blog post titled, 'FBI Harassment.'
Although unsure if she was breaking any laws by leaving the country, she booked a flight to Berlin – despite the fact that she didn't intend to use the return ticket – just to avoid raising suspicions.
However, this didn't end the matter, and the FBI Special Agent Kelvin Porter in Atlanta called Lovecruft's lawyer last month, asking him where to send a subpoena for Lovecruft to help testify in a criminal hacking case.
Also Read: Judge Ordered the FBI to Reveal the Source Code of its Tor Hacking Exploit.
Following the Lovecruft's blog post, the Tor Project official Twitter tweeted out in support of their developer, saying "We support our colleague Isis."
In response to this issue, an FBI spokesperson told IBTimes:
"The FBI, as a general policy, does not confirm nor deny investigations, nor comment on the investigative activity unless it is a matter of public record. If someone is alleging harassment of any kind that should be brought to the attention of the government, though it is unclear what specific activity is even being characterized as harassment."
TOR is an anonymity software that provides a safe haven to human rights activists, government, journalists but also is a place where drugs, child pornography, assassins for hire and other illegal activities has allegedly been traded.
Since last few years, the FBI has been trying to break TOR and unmask TOR users identity in several investigations.
The agency has accused of hacking TOR users in an investigation of the world’s largest dark web child pornography site 'Playpen.' The FBI has also compelled Carnegie Mellon University to help them hack TOR users.
Microsoft removes its controversial Windows 10 Wi-Fi Sense Password Sharing Feature
14.5.2016 Safety
Microsoft has finally decided to remove one of its controversial features Wi-Fi Sense network sharing feature from Windows 10 that shares your WiFi password with your Facebook, Skype and Outlook friends and enabled by default.
With the launch of Windows 10 last year, Microsoft introduced Wi-Fi Sense network sharing feature aimed at making it easy to share your password-protected WiFi network with your contacts within range, eliminating the hassle of manually logging in when they visit.
This WiFi password-sharing option immediately stirred up concerns from Windows 10 users especially those who thought the feature automatically shared your WiFi network with all your contacts who wanted access.
Must Read: Here's How to run Ubuntu Linux on Windows 10.
But Wi-Fi Sense actually hands over its users controls so they can select which networks to share and which contact list can access their Wi-Fi.
Also, the feature doesn't share the actual password used to protect your Wi-Fi, but it does give your contacts access to your network.
However, the biggest threat comes in when you choose to share your Wi-Fi access with any of your contact lists.
But, Who really wants to share their Wi-Fi codes with everyone in the contacts?
Of course, nobody wants.
Since the feature doesn't give you the option to share your network with selected individuals on Facebook, Skype or Outlook, anyone in your contact list with a malicious mind can perform Man-in-the-Middle (MITM) attacks.
Also Read: How to Turn Off Windows 10 Keylogger
We have written a detailed article on Wi-Fi Sense, so you can read the article to know its actual security threat to Windows 10 users.
Although Microsoft defended Wi-Fi Sense network-sharing as a useful feature, Windows users did not give it a good response, making the company remove WiFi Sense's contact sharing feature in its latest Windows 10 build 14342.
"The cost of updating the code to keep this feature working combined with low usage and low demand made this not worth further investment," said Microsoft Vice President Gabe Aul. "Wi-Fi Sense, if enabled, will continue to get you connected to open Wi-Fi hotspots that it knows about through crowdsourcing."
Microsoft just released its latest Windows 10 build for testers. The company will remove the Wi-Fi Sense password sharing feature as part of its Anniversary Update due in the summer, but will keep the Wi-Fi Sense feature that lets its users connect to open networks.
Talking with Azeem Aleem about the evolution of cyber threats
13.52016 Safety
Azeem Aleem, Director for the Advanced Cyber Defense Services Practice – EMEA at RSA, shares its vision on the evolution of threats in the next future.
The last 14 months have highlighted that attacks domains are expanding. We have seen the trends with OPM data breach, to sensitive PII information leak at Anthem breach and Vtech breach. The extortion malware impacting organizations, to an advanced coordinated attack at Ukrainian Power grid highlights the complexity around the anatomy of attacks.
To better understand the topic we have been talking with Azeem Aleem Director for the Advanced Cyber Defense Services Practice – EMEA at RSA. Azeem is responsible for overall professional services engagement for Global Incident Response/Discovery (IR/D), breach readiness, remediation, SOC/CIRC redesign and proactive computer network defense. Prior to RSA, Azeem was the Director for the Centre for E-crime and earlier, led cyber security consultancy services for advanced cyber threats to the law enforcement agencies, Big 4, public sector and the private financial services.
Azeem Aleem RSA cybercrime
Which are the most targets of cyber attack actually? People, industries or companies? And which differences or similarities in the attack methods can we underline?
Aristotle (Aristotle, 384-322BC) said, “ It must be expected that something unexpected must occur” . The current time is the unexpected as we are passing through an era of phenomenon technological revolution. From the realm of the international space exploration ( Scott Kelly and Mikhail Kornienko returned on 2 March after spending 340 days in the space ) to the immense growth of the smart tablets (Apple’s iPad 2 rivals the Cray 2 supercomputer, the world’s fastest computer in 1985) highlights how technology is molding our civilisation to the new heights.
Unfortunately, crime follows opportunity and with this technological advancement we are seeing a rise in the advanced cyber attacks . These days the attacks we are seeing are more focused towards Zero day attack bringing in sophistication and complexity. Rogue Nation-state actors are on the rise and have developed a more diverse and stealthy network of operations. They are devising intelligent way of using the leak data for commercial and national security implications. The hunt for these attacks is not an easy phenomenon. Cyber Criminals are not bound with any rules; their attacks are shielded/ hidden across the organization network. Traditional perimeter is melting and the attack service is increasing which requires holistic view of how we protect the echo systems. Not in my back yard Siloed approach does not work anymore. No doubt there is a long journey for Security industry to cover however, the Security Industry leaps and bound towards maturity – Simultaneously the customer familiarity of security has increased and they now expect from vendors security as an essential discriminator.
Which are in your opinion the majors risks facing to cybercrime today for a company?
The threat landscape is shifting fast – every day there is a new threat domain that hackers have utilized to impact the organisations. We can divide the threat landscape around four main areas:
OS attacks: OS- Attacks are on the rise, they are becoming and persistent for example, attack on the windows OS PowerShell is continuing as it provides cyber criminals with the organized sophisticated exploitation capabilities. While on the other side MAC OSX leverage by bypassing the Gatekeeper using SSH reverse tunnel is on the rise.
Mobile Device: Vulnerabilities in Android OS and now IOS is on the rise- Attacks like stage freight and Xcode Ghost, which allowed malware code execution via text messaging/ video viewing in emails or browsing highlights that attackers are exhibiting innovative methods of undermining the mobile OS. Non-trusted apps are on the rise and are creating a grave concern among the organizations.
Industrial Control Systems : From the days of Slammer, Stuxnet, Shamoon etc to the recent Ukrainian (black energy) Power Grid Attacks narrate the advancement in these attacks. The shift from legacy systems towards process control networks with connectivity around enterprise and Internet is creating extensive backdoors exploit around the industrial control systems. We are seeing that organizations are even not aware of these devices connectivity pattern inside and outside their ICS environment. Attack via cloud service provider at ICS is on the rise and there is a dire need of intelligence correlations / reporting mechanism around SCADA attacks through behavioral analytics.
IoTs: The computer vacuum is difficult to get secured. IOTs have created a technological disruption development where it is difficult to contain the gene in the bottle. The revolution of IOT is already underway; businesses are under pressure to accommodate the flux of IOTs. The potential vulnerabilities from IOTs across the organization network to home appliances even stretching to medical devices can be used as additional vector exploit against the organizations. Already we are seeing evidence of IOT connections on corporate enterprise network creating 3rd party breaches frequent and simplistic. From the early days of TRENDnet camera hack, the recent growth in IOT has brought extreme anxiety across the security sector. Gartner predicts that by 2020 there would be 26 billion units installed channeling huge volume of data traffic. This will create a 50 Trillions GBS of data hovering across these technologies.
Ransomware: These are not new attacks – they been hovering around for some time. Traditionally these attacks have been targeted against SMES (small to medium size organizations) where the adversary acted on a hit and run strategy i.e. encrypt the business data and call for small amount as a ransom. Recent attacks trends have shown ransomware attacks are becoming more aggressive and diversify by attacking a multitude of attack vectors.
What can we do to protect the sensible infrastructures against possible attack? What Ukrain case has shown and what we have learned, if we have
Two areas where we are going wrong are: Preventive Mindset and Analysis Paralysis Syndrome. In the first case we need to understand the attack telemetry; while there is an agreement on the complexity of advanced attack, what we see is that organizations are still trying to protect them using traditional controls around signature based framework. Organizations are lacking in the right visibility and still relying on the traditional tools like SIEM for advanced monitoring – which is only able to detect 1% of the Advanced Attacks. We are witnessing that traditional prevention approach has become a failed strategy. You will be get breach and it is the move towards proactive defense that will enable organizations to preempt where the next attack would be forthcoming from. Comprehensive visibility for full packet capture to gather what is happening in your network is the way forward. In the second aspect what we see as those organizations that understand rational of collecting the data from end points, network flow/packets, cloud based apps and network perimeter are facing a problem flux of data. To detect the pattern they have a task of finding a needle in the haystack; they lack the capability to integrate into a single normalized platform to detect the behavioral classification of these cyber criminals.
What kind of suggestions, projects or good practices could you share or could you speak about to help people and company to implement awareness into the cybersecurity topics?
Security programmes solely focus on compliance won’t work. There is no such thing as an isolated incident and there is a need to manage the whole incident space by developing the threat intelligence capability – pervasive visibility is essential but they need to develop the capability to tackle TTPs (Tactics, Techniques & Procedures). The element of time has changed its now a matter of minutes and seconds on how do we respond to an attack. Nurturing threat intelligence capability will enable them to act as hunters, and help them classify the behaviour and pattern of cyber criminals. The value of the threat Intel is how we use it and put it to action- operationalize the platform- automating the raw data into a tangible Intel is the key. Developing the niche capability will help unveil the opponents and force the adversaries to change/edit their strategies which in turn enhancing the ability to respond. Organization requires a mindset change to develop hunting methodology and enable their staff. Breeding the right culture is very important. To nurture the hunting capabilities you need to accept mistakes. Our industry is building itself on illusions (one fix work all)- organizations need to develop filters to chalk out the white noise and follow patterns of attacks that are specific to organizations.
Changing any culture is not easy. Within the security department, training, education and new norms for doing security hunting need to be established. This may also require bringing in new staff members fresh to the new ways of doing things. It is also necessary to evangelize the new approach to those more senior staff in the organisation, to ensure that they understand and support the new approaches, as well as to those personnel and departments that interact with security. Central to this is promoting the metrics ( whether security is working or not ) so that the success (or the failure) can be clearly seen by all. Azeem Aleem has been staunch supporter of convergence and been actively writing to highlight the need for converged methodology to tackle these advanced attacks
What is your opinion about the future scenario in the cybersecurity field related to trending topics?
Development of educational route is very important to develop talent career progression. The recent move of recognizing Masters degree by GCHQ for selected 10 UK universities will enable the students to take security as a career. We need a stronger partnership among academia, public and private sector – universities students final year MSc project and PHD thesis could be an excellent route to work on Industry live work case examples. Element of research needs to be enabled by developing this partnership. For example at RSA we are working with number of universities such as Brighton, Napier and Macquarie University to develop various areas of research where university researchers can contribute towards our efforts in fights against advanced adversaries. From technology viewpoint organizations are overwhelmed with legacy technologies. This is creating an impact around productivity and creating a dizzying whirlpool of reality (that we are secured). They are getting all the alerts but no real credibility and tangible intel. Traditional Perimeter have melted away and this requires holistic view of how we protect the echo system. Closer integration of the supply chain is very important- continuous monitoring needs to be done and silted approach needs to be taken out.
Pornhub Launches Bug Bounty Program; Offering Reward up to $25,000
11.5.2016 Safety
With the growing number of cyber attacks and data breaches, a significant number of companies and organizations have started Bug Bounty Programs to encourage hackers and security researchers to find and responsibly report bugs in their services and get a reward.
Now, even pornography sites are starting to embrace bug bounty practices in order to safeguard its user's security.
The world's most popular pornography site PornHub has launched a bug bounty program for security researchers and bug hunters who can find and report security vulnerabilities in its website.
Partnered with HackerOne, PornHub is offering to pay independent security researchers and bug hunters between $50 and $25,000, depending upon the impact of vulnerabilities they find.
Also Read: 10-year-old Boy becomes the youngest Bug Bounty Hacker.
HackeOne is a bug bounty startup that operates bug bounty programs for companies including Yahoo, Twitter, Slack, Dropbox, Uber, General Motors – and even the United States Department of Defense for Hack the Pentagon initiative.
"Like other major tech players have been doing as of late, we’re tapping some of the most talented security researchers as a proactive and precautionary measure – in addition to our dedicated developer and security teams – to ensure not only the security of our site but that of our users, which is paramount to us," said PornHub Vice President Corey Price.
"The brand new program provides some of our developer-savvy fans a chance to earn some extra cash – upwards to $25K – and the opportunity to be included in helping to protect and enhance the site for our 60 Million daily visitors."
How to Earn $25,000 Reward
To qualify for a bounty reward, security researchers and bug hunters must meet the following requirements:
Be the first to report a security bug directly related to the company infrastructure.
Send a description of your bug report, explaining the type of vulnerability and how it works.
Include screenshots and proof of concept code to substantiate your claim.
Disclose your finding directly and exclusively with Pornhub.
The company is currently considering serious flaws that could compromise its server and entire website.
Vulnerabilities such as cross-site request forgery (CSRF), information disclosure, cross domain leakage, XSS attacks via Post requests, HTTPS related (such as HSTS), HttpOnly and Secure cookie flags, missing SPF records and session timeout will not be considered for the bounty program.
The bounty program has currently been in a beta phase, with the company extending it via invite only. You can read complete eligibility for the bounty program on HackerOne website.
Top 4 Data Breaches reported in last 24 Hours
10.5.2016 Safety
There is no doubt that data breaches are on the rise. Hardly a day goes without headlines about any significant data breach.
According to the latest ‘Cyber Security Breaches Survey 2016’ report published by UK government, two-thirds of the biggest firm in the UK have experienced at least a cyber attacks or data breaches within the past 12 months.
Here’s today, I am writing about top 4 data breaches reported in last 24 hours, threatened your data privacy and online security.
1. Kiddicare Hacked! 794,000 Accounts Leaked
Kiddicare has admitted that the company has suffered a data breach, which led to the theft of sensitive data belonging to 794,000 users, including phone numbers and residential addresses.
Kiddicare, company that sells child toys and accessories across the United Kingdom, became aware of the data breach after its customers started receiving suspicious text messages – most likely part of a phishing campaign – that attempted to pilfer them to click on a link that takes them for an online survey.
Although the company assured its customers that no banking or financial detail have been compromised in the breach, personal information belonging to nearly 794,000 customers, including their names, delivery addresses, email addresses and telephone numbers, have been exposed.
2. UserVoice Hacked! Users’ Accounts Breached
Today morning, I received an email from UserVoice, a web-based service that offers customer service and helpdesk tools, notifying that the company suffered a data breach and some user accounts were compromised, including their names, email addresses, and passwords.
The company admitted that user passwords were protected with the SHA1 hashing algorithm, which is considered as a weak encryption.
"Despite the fact that the passwords were encrypted, it is very possible that an attacker can decrypt this information," the company notified. “As a precautionary measure, we have reset all UserVoice passwords to prevent any chance of the attacker gaining further access to accounts.”
Some famous companies are using customer service tools from UserVoice, including Twitch, Microsoft and more.
3. Google Suffers Insider Data Breach
Google suffered a minor data breach after a vendor unintentionally leaked sensitive information about its undisclosed number of employees to the wrong email address — but luckily, the person who received it deleted the email straight away.
According to report, the data breach happened after an employee at a third-party company that Google uses for its staff benefit management service mistakenly sent personal data to another company.
Google is still investigating the insider data breach that leaked the personal details of Google employees apparently included Social Security Numbers (SSNs) and names, but no details on benefits or family members.
4. London Clinic fined £180,000 for Leaking HIV Patients Data
The Information Commissioner's Office (ICO) has imposed a £180,000 (about $260,000) fine to a London-based HIV clinic run by Chelsea and Westminster Hospital National Health Service (NHS) Foundation Trust, for leaking data of 781 HIV patients
The clinic mistakenly sent a newsletter email containing sensitive medical information relating to a total 781 HIV patients together rather than individually, using ‘bcc’ field in the email, leaking their names and email addresses to one another.
"People’s use of a specialist service at a sexual health clinic is clearly sensitive personal data," Information Commissioner Christopher Graham said. "The law demands this type of information is handled with particular care following clear rules, and put simply, this did not happen."
The Clinic's medical director said:
"We fully accept the ruling of the ICO for what was a serious breach, and we have worked to ensure that it can never happen again."
U.S. developing Technology to Identify and Track Hackers Worldwide
6.5.2016 Safety
Without adequate analysis and algorithms, mass surveillance is not the answer to fighting terrorism and tracking suspects.
That's what President Obama had learned last year when he signed the USA Freedom Act, which ends the bulk collection of domestic phone data by US Intelligence Agencies.
There is no doubt that US Government is collecting a vast quantity of data from your smartphone to every connected device i.e. Internet of the things, but…
Do they have enough capabilities to predict and identify terrorists or cyber criminals or state-sponsored hackers before they act?
Well, if they had, I would not be getting chance to write about so many brutal cyber attacks, data breaches, and terrorist attacks that not only threatened Americans but also impacted people worldwide.
The Ex-NSA technical director William E. Binney, who served the US National Security Agency for over 30-years, said last year in the front of Parliamentary Joint Committee that forcing analysts to examine billions of records crush their ability to identify actual threats.
Technology to Track and Identify Hackers
Now, the Pentagon wants a better way to not only identify the malicious hacker but also looking for practical algorithms that can predict where that hacker might attack next.
Defense Advanced Projects Agency (DARPA) is offering funding for security researchers who can help the agency to develop algorithms that can identify hackers under its new game-changing initiative called ‘Enhanced Attribution Program’.
Although organizations and countries give their best to identify cyber campaigns who infiltrated their critical infrastructure, tracking down the culprits has always been a difficult task — thanks to TOR, Virtual Private Networks (VPNs), and other methods used to hide the attack source.
However, through this new initiative, the United States military research agency DARPA hopes that agencies would quickly track and identify sophisticated hackers or criminal groups by monitoring their exact behavior and physical biometrics.
The aim of Enhanced Attribution program is to track personas continuously and create “algorithms for developing predictive behavioral profiles.”
"The goal of the Enhanced Attribution (EA) program is to develop technologies for generating operationally and tactically relevant information about multiple concurrent independent malicious cyber campaigns, each involving several operators; and the means to share such information with any of a number of interested parties without putting at risk the sources and methods used for collection," reads the project’s official site.
In other words, the Enhanced Attribution Program will not only help the government characterize the cyber criminal but also share the criminal’s modus operandi with potential victims and predict the attacker’s next target.
Enhanced Attribution Project
DARPA also wants the program to include algorithms to predictive behavioral profiles within the context of cyber campaigns, as well as technologies to validate and improve this knowledge base with public and commercial sources of information.
The program is divided into three tracks:
Behavior and Activity Tracking and Summarization
Fusion and Predictive Analysis
Validation and Enrichment
Each track deals with different levels of behavior data collection and analysis.
The Enhanced Attribution Program will last 18 months, so if you have a crazy idea to track down malicious hackers, you can submit your research proposal until June 7, 2016.
Governance rules give more cyber power to the Europol
3.5.2016 Safety
The European Parliament’s civil liberties committee has approved new governance rules that give Europol new cyber powers to tackle down terrorists online.
The Europol, the European Police Agency, gets new cyber powers to fight against terrorists online.
The European Parliament’s civil liberties committee has approved new governance rules by a massive majority.
The fight against radical organizations like the ISIS is a priority for the EU states, the European Police Agency needs more powers to tackle terrorist activities on the Internet.
The powers come with strong data protection safeguards, the new regulation gives more power to the Internet Referral Unit, which is in charge of destroying terrorist propaganda and extremist activities on the Internet.
In November, the EU members expressed a positive opinion about the draft rules that were planning to give new powers to the Europol in order to step up EU police cooperation and fight terrorism. In January 2016, the director of Europol Rob Wainwright announced the opening of a new European counter-terrorism centre to fight the terrorism.
Director-Europol-Reuters
The new governance rules obtained 40 votes to three, only two members abstained.
The EU requests to the Europol to promptly respond to emerging threats, in particular to terrorist threats.
The new powers aim to support the Europol in operational and strategic analysis.
The new governance rules give the EU’s judicial cooperation agency Eurojust the full access to data gathered by the European Police Agency.
The proposed rules just need the final approval of the whole European Parliament. Let’s wait for the next plenary session which is planned to be held in Strasburg in May.
Psst! You just leaked your Slack’s token on Github!
30.4.2016 Safety
Developers often ignore that they are exposing sensitive data when they publish code containing their Slack access tokens on GitHub.
It was the year 2015, the month of March when Slack officially posted the following statement on their corporate blog:
“there was unauthorized access to a Slack database storing user profile information. We have since blocked this unauthorized access and made additional changes to our technical infrastructure to prevent future incidents.”
The incident prompted two new features to enhance security measures for Slack users/teams. This included two-factor authentication (2FA) and “Password Kill Switch” for team owners.
Fast forward approx. a year, and Slack’s commitment to “take security seriously” had reassured its users that “every person and team using our service expects their data to be secure and confidential” (more here) has put Slack on the spotlight several times including this one.

The team at Detectify, the creators of a SaaS (security/software-as-a-service) based website security service that audit your company’s website security, have discovered an interesting “feature”. This feature, called Slack bot, is Slack’s way of marinating authenticity and integrity of the developer and their code/script/program when other Slack users (dev-peers/team) use their code through a process of tokenization—the process of creating a unique ID with privileges such as digital signaling your work.
Think of tokenization as a handshake of a static key. To execute the code in an environment, the right parameters must be met. If the parameters aren’t met, then the security prevention measures will not allow the execution to take place and report an error. Since, naturally, developers first thing on their mind is to code, they are often unaware of the security ramification when sharing their work to the world. Github is one of those portals that these developers use to share their work and get ideas and even code contribution. But, what if someone else is able to obtain this token? And use this token to access more than just your code, your workspace or even be able to impersonate you? Thanks to Detecity, they were able to produce this proof-of-concept and expose these Slack bot tokens that the developers use for their code in clear text through Github’s search engine. More from Detectify post here.
It is important to note that tokenization is a safe and secure measure to adopt in developing software—in this case; however, not assigning the appropriate privileges on the token can and will put your data/code/work at risk leading to potential security incidents. Since Slack bot takes care of that for the developer, its lack of setting the right privileges is placing Slack on the hot seat…again.
Still, I give credit where its due. Slack’s ongoing bug bounty on HackerOne is thriving and active. In fact, they are looking for security engineers.
Child Porn Suspect Held in Jail for 7 Months for refusing to Decrypt Hard Drives
28.4.2016 Safety
A suspect of child pornography possession, Francis Rawls, who is a former Philadelphia Police Department sergeant, has been in solitary confinement without charges for last seven months and will remain until he complies with a court order forcing him to decrypt his password-protected hard drives seized in connection with a child pornography investigation.
Remember Ramona Fricosu? In 2012, a Colorado woman was ordered to unlock her laptop while investigating financial fraud, but she refused to unlock it saying that she did not remember the password.
Later the US Court ruled that Police can force defendants to decrypt their electronic devices, of course, as it does not violate the Fifth Amendment that prevents any citizen from having to incriminate themselves.
Forget the password? It might be a smart way to avoid complying with a court order, but not every time.
A Philadelphia man has been in jail for seven months and counting after being refused to comply with a court order forcing him to decrypt two password-protected hard drives, including a Macbook Pro and an iPhone 6, seized in connection with a child pornography investigation.
The suspect, Francis Rawls, who is a former Philadelphia Police Department sergeant, has yet not been charged with any child pornography crime because the required evidence is locked in his hard drives using Apple's FileVault encryption software.
Initially, a judge found the order compelling Rawls to unlock his encrypted devices is entirely unconstitutional, because of the fifth amendment right he invoked not to incriminate himself.
However, later federal investigators used the All Writs Act — the same old law the FBI invoked in the San Bernardino to compel Apple to unlock iPhone used by one of the terrorists — to unlock hard drives they believed contained photographs of child sex abuse.
The All Writs Act was meant to force telephone companies to aid in surveillance, and could also be invoked in forcing decryption of electronic devices as well.
Rawls failed to comply with the court order, as the passwords he entered in the initial days of the investigation didn't decrypt his hard drives, and was then taken into indefinite imprisonment by US Marshals on Sept. 30, 2015.
According to court documents [PDF], Rawls is suspected of possessing child pornography, but referring to a similar John Doe’s case, his defense outlines that Rawls has a clean record and doesn’t remember the passwords.
Dutch police seize the Ennetcom encrypted communication network
24.4.2016 Safety
The Dutch police in an international effort with Canadian authorities seized the Ennetcom encrypted communication network used by 19,000 users.
Another success of the Dutch law enforcement against the cybercrime. The police arrested the owner of Ennetcom, a provider of encrypted communications with more than 19,000 customers. Prosecutors suspect he was using the business to manage illegal activities, including money laundering, and so they decided to shut the network.

“Tuesday, April 19th, 2016 revealed that judicial research is being done towards Ennetcom. There has been an international collaboration of various government agencies and Interpol in attempt to put our network down. Previously there have been attempts to put us down, amongst them the Dutch intelligence service, but they never succeeded (see Wikileaks).
Regarding the current investigation, Ennetcom is forced to suspend all operations and services for the time being. Ennetcom regrets this course of events and insinuations towards Ennetcom. It should be clear that Ennetcom stands for freedom of privacy!
Because of security and privacy reasons Ennetcom chooses to keep all systems offline.” states the message currently displayed on the company website
A Dutch Judge ordered a 14-days detection of Danny Manupassa, to conduct its investigation without interferences.
“Police and prosecutors believe that they have captured the largest encrypted network used by organized crime in the Netherlands,” said the prosecutors in an official statement.
Be careful, the use of encrypted communications is not illegal, anyway, it is often abused by crooks for illegal activities.
As usually happens in similar cases, investigations are complicated due to territorial competences, the majority of Ennetcom customers are in the Netherlands, but the company’s servers were in Canada. Prosecutors said information on the servers in Canada has been copied in cooperation with Toronto police.
Fortunately, Canadian authorities cooperated with the Dutch colleagues allowing the access to the company servers and the information extracted would be used in the investigation against Manupassa.
“The company sold modified telephones for about 1,500 euros each and used its own servers for the encrypted data traffic,” the prosecutors said. “The phones had been modified so that they could not be used to make calls or use the Internet.”
All the customers of the Ennetcom company were sent a notification that informed them of the ongoing investigation.
DARPA Wants To Build Ultra Secure Messaging App for US Military
24.4.2016 Safety
Just last month, DARPA launched a project dubbed "Improv," inviting hackers to transform simple household appliances into deadly weapons.
Now, the Defense Advanced Research Projects Agency is finding someone in the private sector to develop a hacker-proof "secure messaging and transaction platform" for the U.S. military.
Darpa wants researchers to create a secure messaging and transaction platform that should be accessible via the web browser or standalone native application.
The secure messaging app should "separate the message creation, from the transfer (transport) and reception of the message using a decentralized messaging backbone to allow anyone anywhere the ability to send a secure message or conduct other transactions across multiple channels traceable in a decentralized ledger," agency's notice explains.
In simple words, DARPA aims to create a secure messaging service that not only implements the standard encryption and security mechanisms used by other secure messaging apps like Signal, Ricochet, and Whatsapp but also communicates via a secure decentralized protocol like Blockchain to prevent cyber attacks and surveillance.
The secure messaging app will be developed in three phases:
First Phase: Create a model for an existing decentralized blockchain-like platform and experiment with encryption protocols and hardware options.
Second Phase: Develop and test the "working prototype."
Third Phase: commercialize and full-scale implementation of the platform.
Also Read: The Best Way to Send and Receive End-to-End Encrypted Emails.
During the first round, the DARPA will award $150,000 per year to the successful applicants. The phase one candidates can then be eligible for a second round award of up to $1 Million for two years.
During the final and third phase, the selected candidates can then pursue commercialization and full-scale implementation of their platform, without receiving any fund from the federal government.
The solicitation will officially open on May 23, 2016 and will close on June 22, 2016.
Software Reverse Engineering Process: Basics and Some Explanations
24.4.2016 Safety
Software reverse engineering is frequently mentioned in several contexts, including many illegal activities. What does it mean?
Software reverse engineering is frequently mentioned in the context of illegal activity: the stealing of IP, fraud with software licenses, and so forth.
At the same time, reversing has legal applications, the most known of which is malware research. It can be also used to provide improved compatibility with the closed platforms, enhanced applications, and advanced OS features (see more legal software reverse engineering tasks). In particular, in the United States, there is a legal rule allowing reverse engineering of an object if the license for it was obtained in a legal way and the results won’t be used in any illegal activity.
You can find a number of questions around software reverse engineering process on the Q&A portals. A significant part of them is about the reversing process and initial knowledge. In this short post, we’ll try to provide some basic software reverse engineering tips, how to start, and what a reverser should know.
Basic knowledge: Reverse engineering books
To get a comprehensive impression about software reverse engineering and disassembling in particular, I would recommend starting with a classic book “Hacker Disassembling Uncovered: Powerful Techniques To Safeguard Your Programming” by Kris Kaspersky. Disassembling is frequently called software reversing itself: it supposes the reconstruction of the software source code by its executables.
Great description of practical disassembling techniques is also provided in the “The IDA Pro Book: The Unofficial Guide to the World’s Most Popular Disassembler” by Chris Eagle; IDA Pro is a great disassembling tool, I would say, a reverser must-have for now – as we’ll say below.
The book “Hacking: The Art of Exploitation” by Jon Erickson will provide you a good description of different approaches on how to investigate the software functioning on the system level: how it interacts with the OS and its different components, what processes are involved, etc. It is an important stage of software reverse engineering and research, as we will discuss in next paragraphs.
You could also search for software reverse engineering tutorials on the web – some pretty good works can be found.
Basic knowledge: General programming
To reverse engineer a software object you should be familiar with the ways it is built and functions – just that simple. If it is a Windows driver, you should know about drivers, Windows driver specifics, the way they interact with the systems, etc. if it is a network communication subsystem, you should know about network layers, network exchange, building a distributed applications, etc.
When reversing a software piece, you should be familiar with the typical patterns and translation / compilation nuances of the code in the particular language, as C++ disassembling differs a lot from C# or Java disassembling, for example.
Software reverse engineering process: Main steps
There is no formalized software reverse engineering process with stages and ready recipes. It is a very creative and adaptive process of investigation of a software piece from different perspectives, depending on its specifics and task priorities.
I will try to briefly describe some major steps – typical stages of software research process.
Usually research starts with investigating the process of a software piece functioning. If it is malware research, obviously starting it on your machine is not a good idea, but you can use a virtual machine.
After initial start and observation, you proceed to the in-depth functioning research. To reconstruct software functioning step-by-step, you need to attach a debugger to it.
Attaching a debugger
Debugger is one of the basic reverser tools, as you can hardly conduct any kind of process of software reverse engineering without the possibility to pause a software piece execution to see what is happening. WinDBG and OllyDBG are popular Windows debuggers, and you can use llbd to debug Mac OS / iOS software.
Attaching debugger is not always a trivial task. While malware rarely cares about the protection from research, commercial software usually applies various anti-debugging and other anti-reversing techniques. There are quite a few of them, and each needs its own approach to overcome. The good news for reversers is that virtually any anti-debug protection can be neutralized; it’s only the question of time and efforts. On the other hand, sometimes it needs a lot of resources.
You can learn more it in this article about anti-debug protection techniques and ways to bypass them.
Researching functioning
After you managed to attach a debugger, you can now see what this software piece changes in the surrounding world at each step. When researching, you may be interested in different aspects: what system API this software uses, how it works with the network, what system resources are used, etc. Various tools can help you with it:
Process monitoring tools (e.g. Process Monitor);
System API monitoring tools (e.g. APIMonitor);
Network sniffers (e.g. TCPViewer);
Port monitoring tools (e.g. PortMon).
There are much more tools you would need: unpackers, stack viewers, module-scheme-builders, etc. You can get more information about various applications to help you when researching software in this article.

Disassembling
Disassembling is one of the core software reverse engineering process steps and is frequently named “reversing” itself as it supposes the restoration of the source code (may be not “word-by-word” but down to the steps, functions, and ideas of method implementation). Disassembling needs you to know Assembly language and main principles of code translation / building as well as general principles of building software starting from OOP and up to the details of typical software architectures.
To work on this stage, you need a disassembler. As I mentioned above, the most powerful and popular disassembler nowadays is IDA by Hex Rays. OllyDBG and WinDBG include in-built disassemblers, which are not that feature-rich but can work for some tasks.
The process of disassembling is like a detective investigation and needs a lot of creativity, intuition, and patience.
Software reverse engineering is an interesting process requiring all your knowledge and software development talents. Though sometimes unjustly labeled as an exclusively illegal practice, it helps to fight malware and improve software systems. But enjoying a hacking charm of it, remember to use your talents for good.
FBI paid Hacker $1.3 Million to Unlock San Bernardino Shooter's iPhone
22.4.2016 Safety
Guess how much the FBI has paid an unknown grey-hat hacker to break into San Bernardino Shooter's iPhone?
FBI Director James Comey hinted during an interview that the FBI spent more than $1.3 Million for breaking into the iPhone of a suspected terrorist and found nothing useful on it.
Apple's legal battle with the Federal Bureau of Investigation (FBI) ended following the bureau's announcement last month that it bought a hacking tool to break into the locked iPhone 5C belonging to the alleged San Bernardino shooter Syed Farook.
At the time, the FBI did not disclose the name of the third party neither it revealed the cost of the hacking tool.
But yesterday while speaking at the Aspen Security Forum in London, FBI Director James Comey gave a hint on the price it gave to the unnamed "outside party" for the hacking solution after Apple refused to help the agency bypass the iPhone's security mechanisms.
The FBI Paid Over $1.3 MILLION for Nothing Useful
When Comey was asked how much the FBI paid for the zero-day flaw that allowed the agency to break into Farook's iPhone, Comey replied: A lot.
"More than I will make in the remainder of this job, which is seven years and four months for sure," said Comey.
According to public records, Comey earned $183,000 last year, and without a raise or bonus, he will make $1.34 Million over the remainder of his job. This indicates that the FBI paid over $1.3 Million for the hacking tool.
So, now it’s pretty clear that the FBI paid over $1.3 Million for nothing useful, since it has been reported few weeks back that the FBI found nothing significant from the terrorist’s iPhone after cracking the passcode.
Moreover, Comey also said the hacking tool the FBI bought works only on an iPhone 5C, and not on later versions of iPhone such as the 5S, 6 and 6S.
But according to Comey, such a huge price for a zero-day that works only on iPhone 5C was "worth it."
"Because it is a tool that helps [the FBI] with a 5C running iOS 9, which is a bit of a corner case," Comey told the audience, adding, "I think it is very, very important that we get into that device."
So far, Comey has attempted to put a positive spin on the terrorist's case, saying he is a "huge fan of strong encryption," but citing his responsibility, he stated that to keep people safe the FBI need to know what the bad people are talking and planning about.
FBI paid more than $1.3 million to hack into San Bernardino shooter iPhone
22.4.2016 Safety
FBI Director Comey explained at the Aspen Security Forum in London that the Agency paid more than $1.3 million to break into San Bernardino shooter’s iPhone.
FBI Director Comey explained at the Aspen Security Forum in London that the Agency paid more than $1.3 million to break into San Bernardino shooter’s iPhone
The FBI vs Apple saga continues to be in the headlines, now media are sharing the news that the Federal Bureau of Investigation paid more than $1.3 million to break into San Bernardino shooter‘s iPhone.
The Federal Bureau of Investigation Director James Comey revealed the news on Thursday, the sum paid is very important as confirmed by the Reuters.
“Federal Bureau of Investigation Director James Comey said on Thursday the agency paid more to get into the iPhone of one of the San Bernardino shooters than he will make in the remaining seven years and four months he has in his job.” states the Reuters.
“According to figures from the FBI and the U.S. Office of Management and Budget, Comey’s annual salary as of January 2015 was $183,300. Without a raise or bonus, Comey will make $1.34 million over the remainder of his job.”
Experts immediately speculated that the law enforcement agency paid the largest-ever fee for a hacking activity. In the past, I also reported news about the fee requested by the zero-day vendor Zerodium to hack into Apple mobile devices, according to the media a $1 million fee was paid by the US Government to the company.
The hack of the San Bernardino shooter’s iPhone was more expensive of the above fee.
“A lot. More than I will make in the remainder of this job, which is seven years and four months for sure,” Comey said. “But it was, in my view, worth it.” Comey explained at the Aspen Security Forum in London.
Last month, the US DoJ announced it had unlocked the San Bernardino shooter’s iPhone with the support of an unidentified third party and closed its legal battle against Apple Inc.
The El Reg published a filing made to the Central California District Court that confirmed prosecutors successfully extracted data from the iPhone.
“The government has now successfully accessed the data stored on Farook’s iPhone and therefore no longer requires the assistance from Apple Inc. mandated by the court’s order compelling Apple Inc. to assist agents in search, dated February 16, 2016,” reads the DoJ request.

The DoJ hasn’t provided details on the procedure used to break into the San Bernardino shooter ‘s iPhone, nor revealed the name of the firm that supported the FBI in the operation.
Comey confirmed that the hack only works on the San Bernardino phone and on other 5C iPhones running IOS 9 software.
Not so bad considering that there are about 16 million 5C iPhones in use in the United States, 84% of iOS devices run iOS 9 software.
The Australian government presents his Cyber Security Strategy
21.4.2016 Safety
The Australian government has presented his Cyber Security Strategy and admitted the ability to conduct offensive cyber operations.
The Australian Government announced its cyber security strategy that includes AU$230 million spending over four years to improve the resilience to cyber attacks of the national critical infrastructure.
The strategy is very complete, it includes defensive aspects for both public and private industries and also the economic support for 5000 security tests for medium enterprises and information sharing activities.
The Prime Minister Malcolm Turnbull outlined the investments in cyber security, the government will spend $230 million for measures that include the establishment of Joint Cyber Threat Centres.
Roughly AU$3om will be reserved for the creation of a Cyber Security Growth Centre with the private sector, the organization aims to coordinate the national cyber security innovation network. Other AU$47m will be spent to establish joint intelligence sharing centres in the most important cities of the country.

According to the cyber security strategy, the Government will also spend AU$41m to improve the capabilities of the national Computer Emergency Response Team (CERT Australia) and recruit new cyber security experts in the strategic Government agencies, including the Australian Federal Police, Crime Commission, and Australian Signals Directorate.
Prime Minister Malcolm Turnbull explained that national cyber resources are only involved in attacks in defense and deterrence purposes. Hi did not acknowledge cyber espionage activities conducted for intelligence purposes, even the ones operated by the Five Eyes alliance.
“The role of security is as important today as it has been in the past,” said Prime Minister Malcolm Turnbull Turnbull told reporters. “Within very specific circumstances the Government will work with the private sector within agreed legal frameworks and oversight to fight serious online crime and extremism.” “Collaboration is absolutely key.”
A part of the presentation offered by the Minister is very meaningful because open to the use of offensive cyber security capabilities conducted by the Australian Signals Directorate.
Mr Turnbull admitted for the first time that the Federal Government has the ability to launch cyber attacks against its adversaries.
“An offensive cyber capability housed in the Australian signals directorate provides another option for Government to respond,” he said.
“The use of such a capability is subject to stringent legal oversight.” “… defensive measures may not always be adequate to respond to serious cyber incidents against Australian networks … an offensive cyber security capability housed in the Australian Signals Directorate provides another option for governments to respond.” states the Prime Minister.
“The use of such as capability is subject to stringent legal oversight and is consistent with our support for the international rules-based order, and our obligations under international law.
“Acknowledging this offensive capability adds a level of deterrence, it adds to our credibility as we promote norms of good behaviour on the international stage and, importantly, familiarity with offensive measures enhances our defensive capabilities as well.”
The politician also cited the security breaches of the Bureau of Meteorology and the Department of Parliamentary Services, arguing the necessity to improve the cyber security posture of the country.
The Prime Minister has appointed Children’s eSafety Commissioner Alastair MacGibbon as his special adviser on cyber security, he will be responsible for leading development of cyber security strategy and policy.
Mr Turnbull introduced him as the man responsible for a “cultural change” on the approach to the cyber security.
The new cyber strategy introduces also new figures like the Assistant Minister on Cyber Security and the Cyber Ambassador.

Google is a ‘Partially Dangerous’ Website … According to Google
21.4.2016 Safety
According to Google, Google is a ‘partially dangerous’ website because some pages on google.com contain deceptive content.
According to Google’s online transparency report, Google’s main search engine is a “partially dangerous” website. The company has advised that people should exercise caution when using it. The search engine could attempt to steal the personal information of its users or install malware on their computers.
The transparency report details how safe and private websites are and exposes those that are deemed potentially dangerous. In an awkward turn of events, that now includes Google itself, which apparently contains pages that have “deceptive content.”
Some pages on the domain reportedly install malware, steal personal information from their users and redirect users to other suspicious websites.
“Google is a “partially dangerous” website and people should be careful when using it, Google has warned. The site’s main search engine could try and steal the personal information of its users or install malware on their computers, according to Google’s unusually frank assessment of itself.” states the Independent.
“The warning comes as part of Google’s own online transparency report, which lists reports on how private and safe websites are – and calls out those that are potentially dangerous.”
google flash ad html5
“Users sometimes post bad content on websites that are normally safe,” a warning that shows on every potentially dangerous website reads. “Safe Browsing will update the safety status once the webmaster has cleaned up the bad content.” continues The Independent.
The company advises affected websites to head to its “Webmasters Help for Hacked Sites” page. That details the ways that Google can clean itself up, at which point it can ask for its status to be reviewed – by itself.”
China wants Apple's Source Code, but the Company Refused
20.4.2016 Safety
Apple's head of legal has denied all rumors about providing its complete source code or any backdoor to the Chinese government.
Apple officially confirmed that the Chinese government has asked Apple twice in the past two years to hand over the source code for its operating system, but the company refused in both the cases.
In a Tuesday hearing entitled "Deciphering the Debate Over Encryption: Industry and Law Enforcement Perspectives," the police officials put allegations on Apple for handing over user data to Beijing while refusing the authorities at its home in the US.
However, speaking under oath at the congressional hearing, Apple's General Counsel Bruce Sewell denied the claims, saying "We have been asked by the Chinese government" for the source code behind the iPhone. But, "we refused."
The response came just after Indiana State Police Captain Charles Cohen accused Apple of providing its source code to China.
Neither Captain Cohen presented any evidence of his allegation, nor he claimed to know whether this was accurate. Instead, he cited media reports to prove his point.
"I saw several news stories that said Apple provided the source code for the iOS [operating system for iPhone and iPads] to China," Cohen said without pinpointing the publications.
The allegations on Apple have continued due to the company's refusal to help the Federal Bureau of Investigation (FBI) gain access to the iPhone used by the San Bernardino shooter Syed Farook.
The law enforcement officials have started accusing Apple of handing over its users information to the Chinese government for business purpose while refusing to cooperate with U.S. authorities for access to private data in criminal and terror investigation.
However, Apple's Swell apparently said: "We have not provided source code to the Chinese government. We did not have a key 19 months ago that we threw away. Those allegations are without merit."
On one hand where authorities want Apple to provide them access to valuable data in serious crimes, like terror, deaths, and rapes. On the contrary, technical experts argue that if the company creates a hole in its security, it will open all its customers to not just the government but also the potential hackers.
However, when it comes to complying with government request in serious crimes, Apple has provided data in 80 percent of cases originating from law enforcement in North America and 66 percent from China.
It was previously reported that in the wake of its legal battle with the US Department of Justice, Apple was working on encrypting iCloud backups that only the account owner would have access.
However, Mr. Sewell denied the reports, saying the company had made no such announcements about iCloud encryption plans. Moreover, such moves would further frustrate law enforcement agencies, who now can obtain iCloud data with a court warrant.
The CIA’s Massive Expansion in Social Media Surveillance is Just the Tip of the Iceberg
19.4.2016 Safety
The US intelligence is massively expanding in Social Media surveillance pushing new technologies, including artificial intelligence for data mining
In-Q-Tel, the CIA’s venture capital firm, has been pursuing various new technologies, including artificial intelligence for data mining, computer algorithms that can detect insider threats and robots which are able to seize delicate objects. This is according to a document The Intercept recently gained access to.
Of particular significance, however, is the research being conducted in the area of social media data mining and surveillance. In-Q-Tel’s portfolio includes an assortment of tech companies which aspire to delve further into this arena:
Dataminr provides a stream of data from Twitter to law-enforcement, and others, so that trends can be rapidly detected.
Geofeedia also involves the use of social media, but focuses on breaking news and also possesses the ability to track activist protests. Geotagged social media posts are collected and then viewed by the company’s clients, which include numerous law-enforcement agencies.
Dunami, a PATHAR product, is another tool used for data mining social media. It analyzes and summarizes networking, influence and the potential for radicalization, according to an investigation by Reveal. It is one of the surveillance tools utilized by the Federal Bureau of Investigation (FBI).
Boasting the ability to spot “gang incidents” and threats to journalists on Twitter, TransVoyant, founded by former Lockheed Martin Vice President Dennis Groseclose, provides a similar service which analyzes multiple data points for the purpose of decision-making. The firm has collaborated with the U.S. military in Afghanistan to integrate data from satellites, drones, radar and reconnaissance aircraft.
The CIA’s investments reveal a pattern, which demonstrates the agency’s elevated push towards monitoring social media platforms. At least part of the focus is on ISIS’ extensive use of social media for spreading propaganda, recruiting and other activities.
As an indication of just how engaged the CIA is in this pursuit:
“The latest round of In-Q-Tel investments comes as the CIA has revamped its outreach to Silicon Valley, establishing a new wing, the Directorate of Digital Innovation, which is tasked with developing and deploying cutting-edge solutions by directly engaging the private sector. The directorate is working closely with In-Q-Tel to integrate the latest technology into agency-wide intelligence capabilities.” states The Intercept.
“Over the last decade, In-Q-Tel has made a number of public investments in companies that specialize in scanning large sets of online data. In 2009, the fund partnered with Visible Technologies, which specializes in reputation management over the internet by identifying the influence of ‘positive’ and ‘negative’ authors on a range of platforms for a given subject. And six years ago, In-Q-Tel formed partnerships with NetBase, another social media analysis firm that touts its ability to scan ‘billions of sources in public and private online information,’ and Recorded Future, a firm that monitors the web to predict events in the future.”
Additionally, In-Q-Tel has established a unique technology laboratory known as Lab41. Based in Silicon Valley, it was designed to provide tools for the intelligence community to “connect the dots” in large data sets.
It should be noted that this particular CIA-backed surveillance technology is also being used by domestic law enforcement agencies and the private sector in order to spy on individuals, such as activists.
Interestingly, “Palantir, one of In-Q-Tel’s earliest investments in the social media analytics realm, was exposed in 2011 by the hacker group LulzSec to be in negotiation for a proposal to track labor union activists and other critics of the U.S. Chamber of Commerce, the largest business lobbying group in Washington. The company, now celebrated as a ‘tech unicorn’ — a term for start-ups that reach over $1 billion in valuation — distanced itself from the plan after it was exposed in a cache of leaked emails from the now-defunct firm HBGary Federal.”
Social Media Surveillance
Source: The Atlantic.com
News of continuing surveillance, involving the government, has always made a lot of people uneasy–in particular, civil liberties advocates. Mass surveillance always brings into question Fourth Amendment constitutional issues. And, the CIA’s investment endeavours, involving monitoring social media, are really just the tip of the iceberg.
As was recently reported in Security Affairs, the CIA has also waded into the health and beauty market with its funding of a new line of skincare products that would enable them to collect DNA. Clearista is a product line that markets itself as a “formula so you can feel confident and beautiful in your skin’s most natural state.” But, the CIA is far less interested in how you look after using these products than in the ability of the Clearista product to remove a thin outer layer of skin that could allow investigators to obtain unique biomarkers that can be used for DNA collection.
The CIA is not alone in its quest to expand its surveillance capabilities. Police departments across the country have been using Beware, an application developed by Intrado, which crawls billions of records in public and commercial databases. It searches for criminal records, Internet chatter and other data. The Beware algorithms then calculate a threat rating score which is assigned to an individual and that information is sent to the requesting law-enforcement officer. It is not, however, foolproof and misinformation can be generated which could be used against an individual.
The FBI has also acquired specialized surveillance software, having purchased SocioSpyder, an application for extracting information from social media sites. According to the product’s website, it “can be configured to collect posts, tweets, videos and chats on-demand or autonomously into a relational, searchable and graphable database.” SocioSpyder was developed by Allied Associates International, a U.S.-based contractor which has government and military and private companies as clientele. SocioSpyder is essentially a pre-configured web scraper for social media.
And, just in case the government misses something, in its far-reaching surveillance, an anti-encryption bill has been drafted in the Senate by Senators Richard Burr and Dianne Feinstein, following the death of an anti-encryption bill in California’s General Assembly last week. The bill, titled the Compliance with Court Orders Act of 2016, would require tech firms to decrypt customers’ data at a court’s request.
Add to that, the ruling by the Sixth Circuit Court of Appeals, which recently ruled that warrantless collection of cellphone location data is constitutional.
Privacy advocates have expressed concern over these new developments involving the government, technology and civil liberties. In particular, apprehension has been expressed in regard to the automated judgments that software targeting social media uses. Lee Rowland, a senior staff attorney with the American Civil Liberties Union commented that, “when you have private companies deciding which algorithms get you a so-called threat score, or make you a person of interest, there’s obviously room for targeting people based on viewpoints or even unlawfully targeting people based on race or religion.” She also warned that a dangerous trend has begun with government relying on tech companies to “build massive dossiers on people” using “nothing but constitutionally protected speech.”
PhineasFisher explained how he breached the Hacking Team
18.4.2016 Safety
The hacker PhineasFisher published a detailed explanation of how he has hacked the Italian surveillance firm Hacking Team.
In July 2015, the surveillance firm Hacking Team suffered a serious security breach, unknown attackers have exfiltrated some 400Gbs of data (including emails, internal documents, and exploit source code), but since now no news regarding the attack was disclosed.
Now the hacker using the online pseudonymous ‘PhineasFisher‘ published a detailed explanation of how he has hacked the Italian surveillance firm.
PhineasFisher breached hacking team
PhineasFisher is the same hacker that breached the surveillance company Gamma International, that sells hacking tools including the popular spyware FinFisher.
PhineasFisher also shared his political ideology in the manifesto he published, the hacker explained that he breached the company to its questionable affairs with rogue governments.
The surveillance software sold by the Hacking Team was in fact abused by many governments against activists and political opponents.
“So easy it is to tear down a company and stop their abuses human rights. That is the beauty and the asymmetry of hacking: with only a hundred hours of work, one person can undo years of work of a multimillion-dollar company. The hacking gives us the possibility of the dispossessed fight and win.“ states the conclusion of the PhineasFisher’s message.
“Hacking Team is see themselves as part of a tradition of inspiring Italian [1] design. I see them Vincenzetti, your company, and their cronies police, police, and government, as part of a long tradition of Italian fascism. I want to dedicate this guide to the victims of the assault on the Armando Diaz school, and all those who have shed their blood on hands Italian fascists.”
Phineas Fisher decided to disclose the details of the hack to give a new blow to the Hacking Team that never left the business.
PhineasFisher breached hacking team Tweet
The hacker revealed to have used a zero-day exploit unknown vulnerability to breach the internal network of the company. The Phineas Fisher didn’t provide further details on the vulnerability he exploited, likely because it is still unpatched. He has also avoided disclosing how he has obtained the exploit.
“I did a lot of work and testing before using the exploit against Hacking Team. I wrote a backdoor firmware, and compiled several tools post-exploitation for embedded system. The backdoor serves to protect the exploit. Use the exploit only once and then return by the backdoor ago work harder to find and patch vulnerabilities.” the hacker wrote.
Once inside the network the hacker moved laterally accessing other servers, including the internal email system. Phineas Fisher was able to find the passwords of the on the system administrators, including the one belonging to Christian Pozzi. The hacker was inside, and with full administrative privileges and Pozzi’s credentials, he was able to control the entire network. The hacker confirmed to have breached also a separate network storing the company’s source code.
“One of my favorite pastimes is hunting the sysadmins. spying Christan Pozzi (sysadmin Hacking Team) got the server accesso Nagios gave me accessibility to sviluppo rete (network development in RCS source code). With a simple combination of Get-Keystrokes and Get-TimedScreenshot of PowerSploit [13], Do-Exfiltration of Nishang [14], and GPO, you can spy on any employee or even the entire domain.” stated the hacker.
Once exfiltrated the data, the hacker reset Hacking Team’s Twitter password by using the “forgot password” function and used the account to announce the data breach.
The hacker spent six weeks, nearly 100 hours of work, inside the Hacking Team network to exfiltrate the data.
I invite you to read the details of the hack disclosed by the hacker, despite it is impossible to verify their accuracy, it is interesting to note how the hacker described its alleged operation and the motivation behind the attack.
PhineasFisher is politically motivated and he is inciting the hacking community to follow his example.
Watch out! URL shorteners could leak sensitive content
17.4.2016 Safety
Two security researchers from Cornell Tech discovered that web URL shorteners operate in predictable way exposing sensitive data.
The security researchers Vitaly Shmatikov and Martin Georgiev from Cornell Tech discovered that web URL shorteners operate in predictable way, and this could result in the disclosure of sensitive information.
The duo analyzed the most popular URL shorteners, including the services implemented by Google, Bit.ly and Microsoft and discovered that attackers can enumerate short URLs to find a sensitive information available on the web. The researchers, for example, discovered short URLs pointing Microsoft OneDrive folders that are unlocked.
“short URLs produced by bit.ly, goo.gl, and similar services are so short that they can be scanned by brute force. Our scan discovered a large number of Microsoft OneDrive accounts with private documents. Many of these accounts are unlocked and allow anyone to inject malware that will be automatically downloaded to users’ devices.” Shmatikov in a blog post.
The experts also discovered that URL shorteners can reveal information that could allow to profile users.
“We also discovered many driving directions that reveal sensitive information for identifiable individuals, including their visits to specialized medical facilities, prisons, and adult establishments.”
The details of their analysis are included in a paper titled “Gone in Six Characters: Short URLs Considered Harmful for Cloud Services.”
Google and Microsoft have pushed introduced fixes to secure new shortened URL links, anyway old links remain vulnerable.
The researchers explained that shortened URLS are generated in a predictable way by combining domain names and a sequence composed of five- to seven-character. The result is a short URL, but its brevity and the knowledge of the generation mechanism introduces the basic vulnerabilities that could allow attackers to launch brute force attacks.
“The tokens are so short that the entire set of URLs can be scanned by brute force. The actual, long URLs are thus effectively public and can be discovered by anyone with a little patience and a few machines at her disposal.” explained Shmatikov “
The scan of 100 million URLs allowed the experts to discovere more than 1.1 million publicly accessible OneDrive documents including documents and executables.
“In our sample scan of 100,000,000 bit.ly URLs with randomly chosen 6-character tokens, 42% resolved to actual URLs. Of those, 19,524 URLs lead to OneDrive/SkyDrive files and folders, most of them live. But this is just the beginning.”

The random scan of Google-shortened URLs allowed the identification of 23,965,718 links, 10 per cent of them containing driving directions to sensitive locations including disease, abortion clinics, and strip clubs.
The duo demonstrated that shortening URL may expose sensitive content to third parties. The experts suggest the adoption of measures to limit automated scanning activities.
“Use your own resolver and tokens, not bit.ly. Detect and limit scanning, and consider techniques such as CAPTCHAs to separate human users from automated scanners. Finally, design better APIs so that leakage of a single URL does not compromise every shared URL in the account.” states the duo.
Microsoft Sues US Govt Over Unconstitutional Secret Data Requests
15.4.2016 Safety
Microsoft is suing the Department of Justice (DoJ) to protest the gag order that prevents technology companies from telling their customers when their cloud data is handed over to authorities.
In layman's terms, the Electronic Communications Privacy Act (ECPA) allows the government to issue gag orders saying that the people or companies involved in a legal case cannot talk about the case or anything related to it in public.
So, the government is continuously forcing tech companies to hand over their customers’ emails or personal records stored in the cloud servers without their clients' knowledge.
Microsoft has filed a lawsuit [PDF] against the DoJ, arguing that it is "unconstitutional" and violates constitutional protection of free speech to force the tech companies for not informing their customers when their stored data has been shared with authorities.
“We believe these actions violate two of the fundamental rights that have been part of this country since its founding. These lengthy and even permanent secrecy orders violate the Fourth Amendment, which gives people and businesses the right to know if the government searches or seizes their property.” Brad Smith, Chief counsel at Microsoft, said in a blog post.
“They also violate the First Amendment, which guarantees our right to talk to customers about how government action is affecting their data.”
According to Microsoft, the company has received nearly 2,600 gag orders in the past 18 months. Though the issue is not with the concept of government searches, but with the indefinite period of those orders.
Actually, the gag orders come with a definite time after which the company can reveal their customers if any police or FBI agent has checked or inspected their emails or files stored in the cloud.
But Microsoft said about 70 percent of all gag orders received by the company had no fixed end date, which means the company can never tell its users, even after the completion of the investigation.
“While today’s lawsuit is important, we believe there’s an opportunity for the Department of Justice to adopt a new policy that sets reasonable limitations on the use of these types of secrecy orders,” Brad said.
The gag orders are meant to protect nation investigations, but the US government is misusing it to carry out unconstitutional secret data searches without ever telling people.
Just like Apple, it is important for Microsoft to fight and win this battle for protecting users’ privacy, as well as their reputation.
Anti-Encryption Bill Released, would Kill your Privacy and Security
14.4.2016 Safety
The United States anti-encryption bill will kill your Privacy.
In the wake of the Apple vs. FBI case, two leading Intelligence Committee Senators have introduced an anti-encryption bill that would effectively ban strong encryption.
Senators Richard Burr (R-NC) and Dianne Feinstein (D-CA) released the official version of their bill today in response to concerns that criminals and terrorists are increasingly using encrypted devices to hide their plans and plots from authorities.
As its name suggests, the Compliance with Court Orders Act of 2016 [PDF] would require people and technology firms like Apple and Google to comply with court orders to decrypt phones and its data.
The draft copy of the Burr-Feinstein proposal was leaked last week, which has already faced heavy criticism from both the technology and legislative communities. Even the White House has declined to support the bill.
The official version of the anti-encryption bill seems to be even worse than the discussion draft.
The draft proposed that the orders could only be issued for crimes resulting in death or serious bodily harm, terrorism and espionage, Federal drug crimes, crimes against minors, or severe violent felonies.
However, the official version of the bill permits federal agencies to access the data they want under a court order.
No Individual or Company is Above the Law
The new bill would apply to:
Device manufacturers
Electronic communication services
Software manufacturers
Remote communication services
Providers of remote communication services
Providers of wire or electronic communication services
Any person who provides a product or method to facilitate communication or to process or store data.
That is a pretty wide list, Isn't that?
The senators say "the underlying goal [of the bill] is simple: when there's a court order to render technical assistance to law enforcement or provide decrypted information, that court order is carried out."
Vice Chairman Feinstein stressed, "No individual or company is above the law."
Government Backdoor in Every Phone
Privacy advocates are worried about the possible effects of the bill, if successfully passed. According to the American Civil Liberties Union (ACLU), the bill is a "clear threat to everyone's privacy and security" and that the senators "should abandon their efforts to create a government backdoor."
Though we strongly believe that the bill won't pass, if passed, your data will be secured, but with a 'Backdoor' that can be accessed by the law enforcement to decrypt your data with a court order.
Also the FBI Director Comey puts a tape over the webcam
14.4.2016 Safety
During the Q&A session at Kenyon College last week, the FBI Director explained that he uses tape to mitigate the danger of cyber espionage.
Privacy and security are top priorities for some security experts that are aware of threat actors’ capabilities, so I’m not surprised that the FBI Director James Comey uses to cover his laptop webcam with a tape.
During the Q&A session at Kenyon College last week, the FBI Director explained that he uses tape to mitigate the danger of cyber espionage. It’s clear that the FBI Director Comey fears possible hacking campaign operated by nation-state hackers, Russia and China are most dreaded adversary in this sense.
During his speech, Comey has remarked in many passages that “absolute privacy” is a serious obstacle for the investigations conducted by the law enforcement.
In December, the FBI Director suggested the implementation of encryption techniques that could help authorities to defeat the end-to-end encryption used to protect the communications.
“The government doesn’t want a backdoor, but [it] hopes to get to a place where if a judge issues an order, the company figures out how to supply that information to the judge and figures out on its own the best way to do that,” said Comey in December. “It is a business model question,” he said. “The question we have to ask is: Should they change their business model?”Comey asking for the IT firms to be compliant with court orders by choosing the appropriate technology.
FBI Director Comey
Source Kenyon.edu
During the speech at the Kenyon College, Comey admitted fearing smarter hackers that could gain the control of the web camera in his personal laptop.
“I saw something in the news, so I copied it. I put a piece of tape — I have obviously a laptop, personal laptop — I put a piece of tape over the camera. Because I saw somebody smarter than I am had a piece of tape over their camera,” reported NPR.
Below the hilarious tweet published by the ACLU chief technologist Christopher Soghoian.
Comey is aware that a nation-state hackers could use zero-day exploits to hack his computer and access any its resource, even the webcam. The Federal Bureau of Investigation (FBI) itself has in its arsenal malicious codes that are able to carry on surveillance activities of this type.
In February 2014, a new collection of documents leaked by Edward Snowden revealed the existence of a surveillance program codenamed Optic Nerve that was operated by the Five Eyes intelligence agencies since 2008.
The news was reported by The Guardian, Optic Nerve is a program that allowed the GCHQ agency to collect images from webcam from more than 1.8 million Yahoo user accounts globally in a six-month period in 2008 alone.
” The collection of webcam material was probably secured by getting an “external warrant” under paragraph four of section 8 of Ripa.” “But section 8 permits GCHQ to perform more sweeping and indiscriminate trawls of external data if a minister issues a “certificate” along with the warrant. It allows ministers to sanction the collection, storage and analysis of vast amounts of material, using technologies that barely existed when Ripa was introduced.” reported The Guardian.
You must be aware that intelligence agencies have a number of weapons in their arsenal to target you. It is quite easy for them compromise your computer and exfiltrate sensitive data … and a tape on your webcam will not save you.
So, FBI Director also Puts Tape Over His Webcam
13.4.2016 Safety
What do you do to protect your 'Privacy' while using your computer?
FBI Director James Comey uses tape to cover up his laptop webcam to ensure Privacy.
Yes, you heard it right. During the Q&A session at Kenyon College last week, Comey said that he uses tape to cover his laptop webcam in order to mitigate the danger of secret surveillance.
While giving a speech about encryption and privacy, Comey repeated his argument that "absolute privacy" hampers the law enforcement and has never existed in America – until now, when by default encryption offered by big tech giants created boundaries where law enforcement can't enter, even with a court order.
This isn't the first time Comey made this kind of statement. Comey has always suggested tech companies to adopt encryption techniques that help federal agencies intercept end-to-end encrypted communications when necessary.
But after his speech, Comey said something that generated hilarity on social media:
"I saw something in the news, so I copied it. I put a piece of tape — I have obviously a laptop, personal laptop — I put a piece of tape over the camera. Because I saw somebody smarter than I am had a piece of tape over their camera," reported NPR.
Comey’s worry about webcams is reasonable, especially when the Federal Bureau of Investigation (FBI) itself has used malware to hack into webcams to spy on targets.
On one hand Comey argues that the companies should not make devices that are unhackable to law enforcement, but on the contrary, he is doing exactly the same with his personal webcam.
So why is he having a double standard for his own privacy?
ACLU chief technologist Christopher Soghoian has a good example:
"FBI Director Comey has created a "warrant-proof webcam" that will thwart lawful surveillance should he ever be investigated. Shame on him," Soghoian tweeted.
However, keeping aside the hypocrisy of Comey, tapping your laptop's webcam is a good take away for you to adopt, as we know the ability of the FBI and NSA (National Security Agency) to spread malware and turn on webcam to spy on targets.
Edward Snowden Leaks revealed the NSA's Optic Nerve project that carried out to capture webcam images every five minutes from random Yahoo users. In just 6 months, 1.8 million users' images were captured and stored on the government servers in 2008.
Though putting a tape over the lens of your webcam would not stop hackers or government spying agencies from recording your voice, at least this would prevent them watching or capturing your live visual feeds.
British Govt vs Lauri Love, it’s battle for encryption keys
13.4.2016 Safety
The British Government is attempting to force the hacktivist Lauri Love to hand over his encryption keys to access data stored in his seized laptop.
Lauri Love is the hacktivist accused of breaking into Government networks, now the UK NCA wants to oblige him to hand over encryption keys to equipment seized from his home.
The hacktivist started a legal action against the NCA to attempt to have his property returned.
The list of victims of the hacktivist includes the FBI, the Federal Reserve Bank and the US Missile Defence Agency.
US Prosecutors believe that Lauri Love is a member of a hacker crew, they sustain that he was also involved in the hacking campaign the OpLastResort launched by Anonymous against the US Government.
Anonymous threatened the US Government due to its position against the young talented hacktivist Aaron Swartz. Aaron Swartz has committed suicide on January 11, 2013 in New York City. He is fighting extradition to the US where authorities can condemn him to up to 99-years in prison.
On that occasion, the US legal system demonstrated its inefficiency in the treatment of hacktivist.
The Home Office is seeking a court order in the form of a ‘direction’ in the civil proceeding against Love. If Love will refuse to comply with the direction he will be charged with contempt of court.
“Love is also being ordered to provide witness statements informing the court whether two particular files encrypted with TrueCrypt software contain data from the US Senate and Department of Energy.” reported the British Computing website.
“I don’t have any alternative but to refuse to comply,” Love told The Intercept. “The NCA are trying to establish a precedent so that an executive body — i.e., the police — can take away your computers and if they are unable to comprehend certain portions of data held on them, then you lose the right to retain them. It’s a presumption of guilt for random data.”
Today Lauri Love appeared in a London court as NCA attempts to get his encryption keys, but the judgment in the encryption demand case is reserved until 10 May.
Love’s advocates remarked that the hacktivist did not profit from the attacks he participated.
The authorities have no intention to return the seized laptop, they augmented their decision sustaining that the device contains pirated films.
InfiltrateCon 2016: A Lesson in Thousand-Bullet Problems
11.4.2016 Safety
Last week vulnerability developers, security researchers, and even a couple of friendly govies descended upon my native Miami for two daily servings of novel implants, exploits, and the latest in offensive research. To contrast the relaxed bikini-clad environment, an adversarial tone was set by conference badges in the form of survival paracord bracelets with Infiltrate dogtags. In good spirits, white-, grey-, and black-hats sparred for tech supremacy and today I’d like to share some thoughts on insightful talks that forecast the intricacies and stumbling blocks that await us as defenders.
This industry has seen its fair share of military analogies for cyberconflict (including Chris Hoff’s brilliant 2015 SAS keynote) and this conference did not disappoint in that area. Kicking off Infiltrate, Nate Fick (CEO of Endgame) brought to bear his wealth of experience in the Marines to the current situation in infosec to great effect. Perhaps doing a disservice to an insightful talk, I’d like to recall some key concepts of Nate’s keynote that build up to a cohesive argument for understanding the role of escalation dominance in our space:
‘A dollar of offense almost always beats a dollar of defense’. Let that sink in.
‘One of the tenets of civilized societies is that governments have a monopoly on the legitimate use of force’, a just-war theory concept worth remembering when the preposterous suggestion of ‘hacking back’ is thrown around as a legitimate option for companies.
‘What level of hacking warrants a bullet, rendition, or a drone?’. This is not a trivial question in our space. As Nate discussed, if we are going respect the cyber-equivalent of a monopoly on the legitimate use of force so that only the government is allowed to conduct offensive cyber-operations in retaliation for an attack on private industry, and we expect this to function as some form precedent-based deterrence, then we should have a clear idea of what offenses merit certain types of retribution.
This is all by way of preparing the ground for the concept of ‘escalation dominance’. As Nate stated, “Escalation dominance, if you don’t have it then don’t fight someone who does”. And that is to say, “You can only deter an adversary if you have the escalatory capability to beat them all the way up the ladder”. I hope these serve as timely takeaways as companies weigh the possibility of ‘hacking back’, an option that is sure to yield meager gains when compared to the next play that awaits on the escalatory ladder.
Further highlights, include Joe Fitzpatrick’s talk on hardware implants titled ‘The TAO of Hardware, the Te of Implants’. Joe is one of those rare unicorns that focuses on hardware security and showcased his skills by trying to convince us of the ease and accessibility of hardware implants. A common misconception is that hardware implants are so difficult to design and expensive to manufacture that they’re only available to the most well-resourced and technologically-capable tier of attackers but Joe shows that this is clearly no longer the case. A valuable takeaway was his starting premise, that the role of a good hardware implant is simply to provide software access and then back off entirely.
As ‘Cyber-Pathogens’ are all the rage with kids these days, I want to discuss Travis Morrow and Josh Pitt’s talk on ‘Genetic Malware’. The title is a reference to their analogies to different types of attack targeting, in this case that of bioweapons and chemical weapons. In reality, the intention is to provide a framework (now public) with which to execute Gauss-style attacks: malware binaries whose final payload is encrypted in such a way as to only decrypt and execute on a specific victim system thereby stumping third-party research efforts to reverse engineer and understand the ultimate objective of the attackers.
Travis and Josh’s E.B.O.W.L.A. (Ethnic BiO Weapon Limited Access) framework drastically lowers the entry threshold for attackers to perform Gauss-style attacks by encrypting their payloads based on specific environment variables on the victim system, environmental factors like IP range or time ranges to trigger, or even a one-time pad based off of a specific system binary. This strategy for buying time was ultimately effective in the case of Gauss whose encrypted payload remains a mystery to this day and, if popularized, will surely prove an interesting challenge for the anti-malware industry going forward.
Finally, as a result of the historic work done by Katie Missouris to help launch the federal government’s first public bug bountry program, Lisa Wiswell of the newly formed Department of Defense Digital Defense Service joined us with an articulate plea to enlist the best and brightest to ‘Hack the Pentagon’ (within scope) and help better defend the country. The crowd was accommodating and we can only hope this program proves a success if only to set precedent for further friendly outreach efforts between the US government and the larger infosec community (in all of its monochromed haberdashery).
Researchers devised a reCaptcha breaking system effective against Google and Facebook
11.4.2016 Safety
A group of boffins discovered vulnerabilities in the reCaptcha systems of Google and Facebook and devised an attack method.
The security experts Suphannee Sivakorn, Iasonas Polakis, and Angelos D. Keromytis have devised an attack technique against Facebook and Google reCaptcha. The boffins from the Department of Computer Science at Columbia University have discovered security vulnerabilities in the reCaptcha systems of the IT Giants and have devised an attack technique that allows them to automatically influence risk analysis and bypass the protection system.
The technique could be used to launch large-scale attacks.
In a first phase, the researchers tested the accuracy of their reCaptcha breaking system, in a second phase they compared their attack technique with other captcha-breakers to conduct an economic analysis of their method.
The experts also proposed a series of mitigation techniques against attacks like the one they have elaborated.
The research focused on the Google’s reCaptcha system that implements an “advanced risk analysis,” it analyze requests to determine the difficulty of returned captcha. The researchers tested their attack method in offline mode, the captcha-breaking system obtained a 41.57 percent success rate at 20.9 seconds per challenge.
“As such, we evaluate our system in an offline mode, where no online information or service is used. Under such restrictions, and running on commodity hardware, our attack solves 41.57% of the captchas while requiring only 20.9 seconds per challenge, with practically no cost.” reads the paper published by the experts.

The researchers tried to automatically break 2,235 Google captchas obtaining a percentage of success of 70.78 in resolving reCaptcha challenges, at a rate of 19 seconds per challenge.
In live tests the success rate was higher because image repetition of the reCaptcha.
“We ran our captcha-breaking system against 2,235 captchas, and obtained a 70.78% accuracy. The higher accuracy compared to the simulated experiments is, at least partially, attributed to the image repetition; the history module located 1,515 sample images and 385 candidate images in our labelled dataset” continues the experts.
The team of experts also evaluated the efficiency of their method against the Facebook’s image captcha, and the results were very good. The team reached an accuracy of 83.5 percent on 200 images.
The method appears more effective against the Facebook reCaptcha system because Google is using low-quality photos that in many cases are no easily distinguishable also for a human.
The technique devised by the experts is more efficient when the targeted reCaptcha system uses high-resolution images that are easier to analyze.
The reCaptcha breaking system devised by the group is superior to Decaptcher, a popular system that charges $2 per 1000 solved image captchas that has only a 44.3 percent accuracy.
When dealing checkbox captcha, at a selling price of $2 per 1,000 solved captchas, the token harvesting attack devised by the team could obtain $104 – $110 daily, per IP address.
“Assuming a selling price of $2 per 1,000 solved captchas, our token harvesting attack could accrue $104 – $110 daily, per host (i.e., IP address). By leveraging proxy services and running multiple attacks in parallel, this amount could be significantly higher for a single machine.” states the paper.
When dealing with checkbox captchas, the system could run a rate of 1,200 requests per hour without being blocked. The attack could peak at 2,500, reaching between 52,000 and 55,000 requests per day, and 59,000 in the weekend.
The team shared the results of their study with Google and Facebook. While Google used the information to improve its reCaptcha system, Facebook hasn’t yet implemented enhancements.
WordPress pushes Free HTTPS Encryption for all its blogs
11.4.2016 Safety
WordPress announces “HTTPS Everywhere, Encryption for All WordPress.com Sites,” millions websites will be secured without users’ effort.
WordPress is pushing free default SSL for all the website running the popular CMS and hosted on WordPress.com, that means over 26% of websites based on the most popular CMSs on the web will be secured (Statistics by W3techs).
On Friday, WordPress announced that it has partnered with the Let’s Encrypt project in order to offer free HTTPS support for all of its users on WordPress.com blogs.
According to the systems engineer Barry Abrahamson from WordPress’ parent company Automattic, the roll out will be transparent without impact on the users.
“Today we are excited to announce free HTTPS for all custom domains hosted on WordPress.com. This brings the security and performance of modern encryption to every blog and website we host. Best of all, the changes are automatic — you won’t need to do a thing.” Abrahamson wrote in a blog post.
“This brings the security and performance of modern encryption to every blog and website we host.” “For you, the users, that means you’ll see secure encryption automatically deployed on every new site within minutes. We are closing the door to un-encrypted web traffic (HTTP) at every opportunity.”
FanceBox plugin WordPress 2
That is great, more security, for free and without any effort! The Internet will be a better place, users will be protected from eavesdropping. The massive introduction of Web encryption provides more than security to the users, the protocol enhancements like SPDY and HTTP/2 have reduced in a significant way the performance gap between encrypted and unencrypted web traffic.
Digital certificates will be offered by the Let’s Encrypt initiative starting from January.
“The Let’s Encrypt project gave us an efficient and automated way to provide SSL certificates for a large number of domains. We launched the first batch of certificates in January 2016 and immediately started working with Let’s Encrypt to make the process smoother for our massive and growing list of domains.” added Abrahamson.
Summarizing … WordPress.com is activating HTTPS on all its websites without requesting users intervention.
The CIA is funding a skincare line for the DNA extraction
9.4.2016 Safety
According to documents obtained by The Intercept, the CIA is looking with a great interest in a new skincare line for DNA extraction on crime scenes.
According to documents obtained by The Intercept, the CIA is funding a new skincare line that can allow the agency to collect DNA.
“SKINCENTIAL SCIENCES, a company with an innovative line of cosmetic products marketed as a way to erase blemishes and soften skin, has caught the attention of beauty bloggers on YouTube, Oprah’s lifestyle magazine, and celebrity skin care professionals. Documents obtained by The Intercept reveal that the firm has also attracted interest and funding from In-Q-Tel, the venture capital arm of the Central Intelligence Agency.” states the Intercept.
The CIA if particularly interested in the Clearista a product line that boasts a “formula so you can feel confident and beautiful in your skin’s most natural state.”
The CIA is interested in the ability of the Clearista product in removing a thin outer layer of skin that could allow investigators to obtain unique biomarkers that can be used for DNA collection.

The product is not invasive, it is able to remove the layer of skin just by using a special detergent and water.
“Skincential Science’s noninvasive procedure, described on the Clearista website as “painless,” is said to require only water, a special detergent, and a few brushes against the skin, making it a convenient option for restoring the glow of a youthful complexion — and a novel technique for gathering information about a person’s biochemistry.”reports the Intercept.
The CIA intends to use the skincare line for DNA extraction, as confirmed by the Russ Lebovitz, the chief executive of Skincential Science.
“Our company is an outlier for In-Q-Tel,” said Lebovitz “If there’s something beneath the surface, that’s not part of our relationship and I’m not directly aware. They’re interested here in something that can get easy access to biomarkers.”
Lebovitz highlighted that the CIA is interested in easy methods for the DNA extraction, but he admitted having no idea of the CIA’s intent of the technology.
It is likely the CIA would use the Clearista for DNA extraction directly on crime scenes.
'Hacking Team' Loses License to Sell Surveillance Malware Outside Europe
7.4.2016 Safety
'Hacking Team' Loses License to Sell Surveillance Malware Outside Europe
Hacking Team – the infamous Italy-based spyware company that had more than 400 GB of its confidential data stolen last year – is facing another trouble.
This time not from other hackers, but from its own government.
Hacking Team is infamous for selling surveillance spyware to governments and intelligence agencies worldwide, but now it may not be allowed to do so, as the Italian export authorities have revoked the company's license to sell outside of Europe.
Almost a year after it was hacked and got all its secrets leaked online, Hacking Team somehow managed to resume its operations and start pitching new hacking tools to help the United States law enforcement gets around their encryption issues.
Hacking Team had sold its malware, officially known as the Galileo Remote Control System, to authorities in Egypt, Morocco, Brazil, Malaysia, Thailand, Kazakhstan, Vietnam, Mexico, and Panama.
Hacking Team had also signed big contracts with the Federal Bureau of Investigation (FBI) and the Drug Enforcement Administration (DEA), making almost $2 Million from both.
However, the Italian Ministry of Economic Development (MISE) said the company would now have to get an 'individual' license, revoking the Hacking Team's "global authorization" to export its Galileo spyware.
Hacking Team's spokesperson Eric Rabe confirmed the news on Tuesday, after the Italian outlet Il Fatto Quotidiano first reported of its licence revocation.
So, the company can still sell its Galileo spyware within the European Union without getting any special license, but the sales outside of Europe will require permission on a country-by-country basis.
Of course, it is then again up to the Italian officials whether to approve or refuse any requests from Hacking Team.
Journalists and activists frequently criticized Hacking Team for selling its spyware to nations with poor records on human rights. Hacking Team formerly had the licence to export its spyware to 46 countries.
The List includes the USA, Brazil, Ecuador, Egypt, Ethiopia, Indonesia, Israel, India, Japan, South Korea, Kuwait, Malaysia, Saudi Arabia, Nigeria, Qatar, Singapore, South Africa, Thailand, Turkey, United Arab Emirates, and Vietnam.
Italian Government revoked Hacking Team ’s global export license
7.4.2016 Safety
The government authority who oversees the export of “dual use” technologies revoked the Hacking Team ’s global export license.
On July 2015, the Italian surveillance company Hacking Team suffered one of the worst data breaches in the history. Unknown attackers have exfiltrated some 400Gbs of data, including internal emails, exploit source code and invoices.
A few months later, the company has resumed its operations and started working with a new set of tools for its arsenal.
In October, Motherboard obtained a copy of a non-public email sent by the CEO David Vincenzetti to a mailing list made of potential and current customers on October 19.
Vincenzetti announced a totally new cyber arsenal, he defined its new tools as game changers,
[Hacking Team is] “finalizing brand new and totally unprecedented cyber investigation solutions, game changers, to say the least.”
Now the company has received another blow, the Italian Government authority who oversees the export of “dual use” technologies, named “Autorità per l’esportazione beni a duplice uso,” has revoked the “global authorization” to export its surveillance software at the end of March.
The authority is controlled by the Italian Ministry of Economic Development (MISE) that revoked “with immediate effect” the global authorization granted to the company the year before.
According to the Italian newspaper Il Fatto Quotidiano that first reported on the news, the MISE revoked the authorization two years before the deadline of April 30, 2018.
What will happen?
The Hacking Team will have to ask permission for every sale of its spyware to clients outside the European Union. The Hacking Team can still sell its surveillance software to organizations within the European Union without express authorization.
According to the Il Fatto Quotidiano one of the reasons for the revocation is the diplomatic situation with the Egyptian Government that is accused of covering the truth on the murder of Italian student Giulio Regeni.
According to an anonymous email received by the Italian Government, Regeni was abducted, tortured and killed by the Egyptian secret services.
A source close to Hacking Team referred Vincenzetti went on to reassure its employees that the situation is under control and is not new for the company, a similar restriction was imposed to the organization between October 2014 and April 2015.
The Italian newspaper Il Corriere Della Sera a couple of weeks ago has revealed that the Italian authorities have launched an investigation on the Hacking Team in order to examine it conduct when exporting the surveillance software, an activity referred to past sales.
The company always explained that all the sales were conducted in accordance with current laws and regulations.
Let’s sit and wait to see the response of the lawyers of the company.
Homeland Security – US Consular Consolidated Database vulnerable to cyber attacks
6.4.2016 Safety
According to the results of an internal review, the US passport and visa Consular Consolidated Database (CCD) database is open to intrusion.
According to the results of an internal review of the US State Department, the Consular Consolidated Database (CCD) is vulnerable to cyber attacks.
The State Department considers the CCD as an “unclassified but sensitive system,” it contains more than 290 million passport records, 184 million visa records, and 25 million records on US citizens living abroad.

The CCD is a critical source of information for the US Government because it includes data related to anyone who has applied for a U.S. passport or visa in the past two decades.
Records include personal information, photos, fingerprints, Social Security or other identification numbers.
The experts at the US State Department’s cyber defenses performed the internal audit several months ago.
An official at the US State Department confirmed that many vulnerabilities have been already fixed, but according to information collected by the ABC News many flaws are still in place.
“We are, and have been, working continuously … to detect and close any possible vulnerability,” State Department spokesman John Kirby said in a statement to ABC News.
“Vulnerabilities have not all been fixed,” the source said, and added that “there is no defined timeline for closing [them] out,” revealed an internal congressional anonymous source.
“I know the vulnerabilities discovered deserve a pretty darn quick [remedy],”
The representatives at US State Department considered the vulnerabilities very hard to exploit due to the level of permissions necessary to modify the Consular Consolidated Database.
“CCD allows authorized users to submit notes and recommendations directly into applicants’ files. But to alter visa applications or other visa-related information, hackers would have to obtain “the right level of permissions” within the system -– no easy task, according to State Department officials.” reports the ABC News.
Security experts consider the presence of flaws in the Consular Consolidated Database archive a serious threat because they could be exploited by threat actors to doctor visa applications or exfiltrate sensitive data.
The discovery raised serious concerns about the possible consequences of a cyber attack on the CCD. State-sponsored hackers could use them to provide fake identities on the US soil, but most disconcerting is a possible abuse made by terrorist groups.
“Every visa decision we make is a national security decision,” explained the top State Department official, Michele Thoren Bond, in a recent House panel.
The US State Department and other government sources say that there is no evidence that the database has been breached.
According to ABC News, the audited systems will be overhauled in the coming years.
Infamous Hacker 'Guccifer' appears in US Court after Extradition
5.4.2016 Safety
Marcel Lazar Lehel aka "Guccifer" – an infamous Romanian hacker who hacked into the emails and social networking accounts of numerous high profile the US and Romanian Politicians – appeared in the United States court for the first time after extradition.
Following Romania's top court approval last month, Guccifer was extradited to the United States recently from Romania, his home country, where he had already been serving a hacking sentence.
Lehel has been charged with cyber-stalking, unauthorized access to a protected computer and aggravated identity theft in a nine-count indictment filed in 2014 in a federal district court in Alexandria, the U.S. Justice Department said in a statement.
Lehel "hacked into the email and social media accounts of high-profile victims, including a family member of two former U.S. presidents, a former U.S. Cabinet member, a former member of the U.S. Joint Chiefs of Staff and a former presidential advisor," according to the indictment.
The international black hat hacker came to the limelight after allegedly accessing personal emails and photos belonging to the family of former US President George W. Bush and posting unofficial emails sent to then-Secretary of State Hillary Clinton on the Internet.
Guccifer was also responsible for cracking into the AOL email Account of Bush’s Sister, Dorothy Bush Koch and targeted several high-profile celebrities, including Actor Leonardo DiCaprio, 'Sex and the City' author Candace Bushnell, Comedian Steve Martin, Actress Mariel Hemingway, Biographer Kitty Kelley, and much more.
The same hacker brought the extramarital romantic relationship between former US Secretary Colin Powell and Romanian Diplomat Corina Cretu by hijacking Colin’s AOL email Account and circulating his 'very personal emails.'
Possible Sentence of 20 years in Prison
Lehel has been charged with a total of 9 counts of US-Federal indictments, which includes:
Three counts for Wire Fraud
Three counts of gaining unauthorized access to protected computers
One counts of cyber stalking
One count of aggravated identity theft
One count of obstruction of justice
Though the total sentence is not confirmed, the charges Guccifer faces collectively carry with them a possible sentence of maximum 20 years in prison, Assistant U.S. Attorney Maya Song said in court Friday.
If you want to explore more about the Guccifer Hacks or Leaks, you may visit the website named 'The Smoking Gun' to which he published the leaked contents (don't expect a Wikileaks model).
Guccifer was serving as a Taxi Driver when Romania's DIICOT anti-organized crime and terrorism unit arrested him.
Guccifer was sentenced for intrusion charges to popular profiles by the Romanian court to four years in jail in 2014 "with the aim of getting ... confidential data" and is serving another three-year term for other offenses.
Guccifer kickstarted his career as a Hacker at the age of 35. Interestingly, a documentary had been prepared by the Norton Groups on Guccifer, which details his hacking career.
A NIST guide tells enterprises how to secure email systems
3.4.2016 Safety
For the first time in a decade, the US National Institute of Standards and Technology (NIST) has updated its secure email guide.
The last effort of the NIST Agency in the development of email security guidelines is dated 2007 when it published the NIST SP 800-45, Version 2 – Guidelines on Electronic Mail Security.
The new NIST guide is a document composed of 81 pages that aim to give recommendations and guidelines for enhancing trust in email.
This guideline applies to Government IT environment, but it is also useful for private organizations of any size.
The recommendations in NIST guide for secure email include suggestions on the practices to adopt for securing the environments around enterprise mail servers and mail clients. This guide also provides recommendations and guidance for email digital signatures and encryption (via S/MIME), recommendations for protecting against spam messages.
Security email needs a multidisciplinary approach that involves secure solutions, effective configurations and trained personnel.
“Email communications cannot be made trustworthy with a single package or application. It involves incremental additions to basic subsystems, with each technology adapted to a particular task.” states the NIST guide on secure email.
NIST secure email guide
Encryption is essential to secure email systems, the guide urge administrators to build out a cryptographic key management system (CKMS) and use keys to protect email sessions.
“As with any cryptographic keying material, enterprises should use a Cryptographic Key Management System (CKMS) to manage the generation, distribution, and lifecycle of DKIM keys. Federal agencies are encouraged to consult NIST SP 800-130 [SP800-130] and NIST SP 800-152 [SP800-152] for guidance on how to design and implement a CKMS within an agency.”
Despite the numerous incidents occurred in the last years, the NIST still considers trustable the DNS due to the numerous security enhancements, including the DNS Security Extensions (DNSSEC), which is a set of extensions to DNS that provide to DNS clients origin authentication of DNS data, authenticated denial of existence, and data integrity.
The NIST guide highlights the importance of the S/MIME (Secure Multipurpose Internet Mail Extensions) for secure email messages.
“Secure Multipurpose Internet Mail Extensions (S/MIME) is the recommended protocol for email end-to-end authentication and confidentiality. S/MIME is particularly useful for authenticating mass email mailings originating from mailboxes that are not monitored, since the protocol uses PKI to authenticate digitally signed messages, avoiding the necessity of distributing the sender’s public key certificate in advance. This usage of S/MIME is not common at the present time, but is recommended.” states the guide.
The guide included a warning to the organizations that rely on cloud services for their email, in particular on services offered by a third party.
Organizations need to make sure any email sent by third parties will pass SPF checks, the verification is simple because the enterprise administrator should include the IP addresses of third-party senders in the enterprise SPF policy statement RR.
The NIST guide is out for public comment until May 1st, I suggest you to read it.
Microsoft adds Linux Bash Shell and Ubuntu Binaries to Windows 10
31.3.2016 Safety
'Microsoft loves Linux' so much that now the company is bringing the popular Bash shell, alongside the entire Linux command environment, to its newest Windows 10 OS in the upcoming 'Anniversary Update,' Redstone.
The rumours before the Microsoft’s Build 2016 developer conference were true. Microsoft has just confirmed that it is going to enable its users to run Bash (Bourne Again Shell) natively on Windows 10.
Also Read: Microsoft Drops a Cloud Data Center Under the Ocean.
Microsoft has partnered with Ubuntu's parent company Canonical to ensure the Bash experience for users is just as good in Windows OS as it's in variants of Linux.
Although the Goal of the partnership, in the end, is to bring Ubuntu on Windows 10, don't expect it to run Ubuntu directly on Windows 10.
Users will be able to download Bash from the Windows Store. BASH or Bourne Again Shell is capable of handling advanced command line functionalities that are not a cup of tea for Powershell or CMDs.
"The Bash shell is coming to Windows. Yes, the real Bash is coming to Windows," said Microsoft's Kevin Gallo at Build 2016 keynote. "This is not a VM [Virtual Machine]. This is not cross-compiled tools. This is native."
There already exists third-party apps to implement Bash shell running on Windows, such as Cygwin or MSYS. But the new move by Microsoft would eliminate the usage of 3rd party utilities, offering, even more, flexibility for developers who prefer using these binaries and tools.
How to Run Bash on Windows?
run-bash-windows-10
Users just have to follow these simple steps to run Bash on Windows 10 OS:
Open the Windows Start menu
Type "bash"
Hit 'Enter'
This will open a command line console (cmd.exe) running Ubuntu's /bin/bash, Dustin Kirkland, Canonical's Ubuntu Product and Strategy team member, explains in a blog post.
The system features a full Ubuntu user space complete with support for tools including ssh, apt, rsync, find, grep, awk, sed, sort, xargs, md5sum, gpg, curl, wget, apache, mysql, python, perl, ruby, php, vim, emacs and more.
This is not Microsoft Linux for Windows
ubuntu-on-windows-10
Don’t get confused, as Microsoft is not enabling Linux applications to run on top of Windows nor this is "Microsoft Linux." The company is just providing support for Bash on Windows 10 as an expansion of its command-line tool family.
So, the company is working on integrating Ubuntu User Space in Windows 10, as a hacker has already spotted a Linux subsystem in preview build (build 14251) of the Windows 10 code in late January.
ubuntu-windows10-file-explorer
As Kirkland writes:
"So just Ubuntu running in a virtual machine?" Nope! This isn't a virtual machine at all. There's no Linux kernel booting in a VM under a hypervisor. It's just the Ubuntu user space. "Ah, okay, so this is Ubuntu in a container then?" Nope! This isn't a container either.
It's native Ubuntu binaries running directly in Windows. "Hum, well it's like cygwin perhaps?" Nope! Cygwin includes open source utilities are recompiled from source to run natively in Windows. Here, we're talking about bit-for-bit, checksum-for-checksum Ubuntu ELF binaries running directly in Windows.
This isn't Microsoft's first step towards implementing Linux functionality in Windows. Just last year, Microsoft had worked on the Linux Kernel and made a Linux OS called Azure Cloud Switch. It also chose Ubuntu as the operating system for its Cloud-based Big Data services.
Channel9TV
Marine Corps Cyberspace Warfare Group, the new hacker unit
31.3.2016 Safety
The United States Marine Corps has launched on March 25th a new hacker support unit named Marine Corps Cyberspace Warfare Group.
It is unnecessary to remind the importance of cyber capabilities in the current military environment. Government and military corps are investing to improve their cyber abilities and exploits the immense possibilities offered by the cyberspace as the fifth domain of warfare.
News of the day is that the United States Marine Corps has launched on March 25th a new hacker support unit, it follows the establishment of other hacking units announced last year.
It is a strategic decision in response to a rapid technological evolution of the military context, the Marine Corps Cyberspace Warfare Group (MCCYWG) is already operative and the assigned resources are expected to rapidly expand in the next year.
The newborn Marine Corps Cyberspace Warfare Group will support the US Marine Corps Forces Cyberspace (MARFORCYBER) established by the US Government in 2010.

The new Marine Corps Cyberspace Warfare Group will train and support hackers working for the US Marine Corps, its members will be involved in both offensive and defensive operations.
“The mission of MCCYWG is to man, train and equip Marine Cyberspace mission teams to perform both defensive and offensive cyber operations in support of United States Cyber Command and Marine Forces Cyberspace Command.” states the official website of US Marine Corps.
“We’ve always had the means to communicate and the means to protect that communication, but today we’re in an environment where those methods are more and more reliant on a system of transmissions, routers and networks,” said Col. Ossen J. D’Haiti, the commanding officer of MCCYWG. “So, the ability to protect that, the ability to control that and deny an adversary to interdict that, is crucial to command and control.”
The official announcement remarks that now more than ever, the Marine Corps is seeing the need for defense of its networks and communications. The Marine Corps Cyberspace Warfare Group will protect the Marine Corps infrastructure from cyber attacks, for this reason, in the announcement, it is described as a sort of virtual “firewall” against the cyber threats.
“Cyber operations as a whole are anything from ensuring your network is secure to home use like when you buy a router, set it up, set up passwords and encryptions,” said Sargent Brian Mueller, member of the unit.
“[Cyberspace operations] ensure that our systems are secure to stop hackers from getting into our systems where our personal identifiable information and everything else is stored,” added Mueller.
“While the offensive side is what can we do to hinder an enemy.”
Below the official description of the new hacker unit and its functions:
“Commander, MCCYWG organizes, trains, equips, provides administrative support, manages readiness, and recommends certification and presentation of Cyber Mission Force (CMF) Teams to U.S. Cyber Command. The MCCYWG plans and conducts full spectrum cyberspace operations as directed by COMMARFORCYBER in support of service, combatant command, joint, and coalition requirements.” states the website of the US Marine Corps.
Key MCCYWG tasks include:
Conduct personnel management to organize and assign individuals to work roles and place them in work centers to ensure operational readiness of CMF Teams
Ensure all personnel are trained in accordance with USCYBERCOM Joint Cyberspace Training and Certification Standards and equipped to perform all duties and tasks outlined in the MARFORCYBER Mission Essential Task List (METL)
Plan for and, when authorized, conduct OCO including computer network exploitation (CNE), cyberspace intelligence, surveillance, and reconnaissance (ISR) and operational preparation of the environment (OPE)
Plan and conduct designated DCO in response to threats against the MCEN, supported combatant command (COCOM) designated networks, and the Department of Defense Information Network (DODIN)
Advise COMMARFORCYBER on force employment considerations
Provide subject matter expertise for operational planning requirements
FBI is fighting back against Judge's Order to reveal TOR Exploit Code
30.3.2016 Safety
Last month, the Federal Bureau of Investigation (FBI) was ordered to reveal the complete source code for the TOR exploit it used to hack visitors of the world’s largest dark web child pornography site, PlayPen.
Robert J. Bryan, the federal judge, ordered the FBI to hand over the TOR browser exploit code so that defence could better understand how the agency hacked over 1,000 computers and if the evidence gathered was covered under the scope of the warrant.
Now, the FBI is pushing back against the federal judge’s order.
On Monday, the Department of Justice (DOJ) and the FBI filed a sealed motion asking the judge to reconsider its ruling, saying revealing the exploit used to bypass the Tor Browser protections is not necessary for the defense and other cases.
In previous filings, the defence has argued that the offensive operation used in the case was "gross misconduct by government and law enforcement agencies," and that the Network Investigative Technique (NIT) conducted additional functions beyond the scope of the warrant.
The Network Investigative Technique or NIT is the FBI's terminology for a custom hacking tool designed to penetrate TOR users.
This particular case concerns Jay Michaud, one of the accused from Vancouver, Washington, who was arrested in last year after the FBI seized a dark web child sex abuse site and ran it from agency’s own servers for the duration of 13 days.
During this period, the FBI deployed an NIT tool against users who visited particular, child pornography threads, grabbing their real IP addresses among other details. This leads to the arrests of Michaud among others.
The malware expert, Vlad Tsyrklevich held by the defense to analyse the NIT, said that it received only the parts of the NIT to analyse, but not sections that would ensure that the identifier attached to the suspect's NIT-infection was unique.
"He is wrong," Special Agent Daniel Alfin writes. "Discovery of the 'exploit' would do nothing to help him determine if the government exceeded the scope of the warrant because it would explain how the NIT was deployed to Michaud's computer, not what it did once deployed."
In a separate case, the Tor Project has accused the FBI of paying Carnegie Mellon University (CMU) at least $1 Million to disclose the technique it had discovered that could help them unmask Tor users and reveal their IP addresses. Though, the FBI denies the claims.
Feds request Judge to review the order to reveal TOR Exploit Code
30.3.2016 Safety
FBI is fighting back against the federal judge’s order to reveal the Tor Exploit and with DoJ filed a sealed motion requesting the review of the ruling.
A few weeks ago, a judge has ordered the FBI to reveal the complete source code for the TOR exploit to defense lawyers in a child porn case.
In a case involving child pornography, the FBI was ruled by a judge to provide all the code used to hack the PC of suspects and detailed information related to the procedure they have followed to de-anonymize Tor users.
Colin Fieman, a federal public defender working on the case was asked by motherborard.vice.com if the code would include exploits to bypass security features, Fieman’s reply was that the code would bypass “everything.”
“The declaration from our code expert was quite specific and comprehensive, and the order encompasses everything he identified,” he told to MotherBoard.
Fieman is defending Jay Michaud, a Vancouver public schools administration worker arrested by the FBI right after the FBI closed a popular child pornography site called “Playpen” hosted in the dark web, and where a network investigative technique (NIT)—the agency’s term for a hacking tool.
According to court documents reviewed by Motherboard, the FBI had used the NIT to identify the suspects while surfing on the Tor network.
The FBI monitored a bulletin board hidden service launched in August 2014, named Playpen, mainly used for “the advertisement and distribution of child pornography.”
The FBI was able to harvest around 1300 IPs, and until the moment 137 people have been charged. The network investigative technique used by the FBI included computers in the UK, Chile and Greece.
The defence has argued that the investigation that leveraged on the NIT was “gross misconduct by government and law enforcement agencies,” and that the Tor Exploit conducted operations out of the warrant scope.
In January, a report published by the Washington Post confirmed that in the summer of 2013 Feds hacked the TorMail service by injecting the NIT code in the mail page in the attempt to track its users.
Last month the federal judge Robert J. Bryan ordered the FBI to hand over the TOR browser exploit code in order to allow the defence to understand how the law enforcement used it.
Now, the FBI is fighting back against the federal judge’s order and with the Department of Justice (DOJ) filed a sealed motion requesting the review of the ruling.
The FBI and the DoJ sustain that it is not necessary to reveal the details of the Tor exploit.

The security expert and exploit developer Vlad Tsyrklevich who analyzed the Tor Exploit for the defense explained that he received only a portion of the NIT code, but he argued to haven’t reviewed the portion of code that link NIT identifier with a specific suspect.
“He is wrong,” Special Agent Daniel Alfin writes. “Discovery of the ‘exploit’ would do nothing to help him determine if the government exceeded the scope of the warrant because it would explain how the NIT was deployed to Michaud’s computer, not what it did once deployed.”
Watch out, IRS Tax Fraud activities on the rise
28.3.2016 Safety
Security experts and government agencies confirm that IRS Tax Fraud And Phishing campaigns are increasing thanks to new techniques and tools.
Internal Revenue Service tax fraud has reached a peak in the last year, crooks are intensifying their activity adopting new techniques to monetize their efforts.
According to security experts that are monitoring the phenomena, Tax-related phishing activities are increasing in this period.
This is a critical period in the US, the so-called Tax season, that will end on April 18th. In February, an IRS bulletin confirmed that there is a 400 percent surge in tax-related phishing and malware incidents.
“Tax-related phishing is something of an annual phenomenon, but Proofpoint researchers are seeing a degree of sophistication and pervasiveness that sets this year apart,” states a report published by the Proofpoint firm that analyzes tax fraud trends.
Crooks are trying to exploit new habits of taxpayers, for exampletheit preference for mobile platforms. Security experts observed a mobile-optimized phishing site that appears as a legitimate tax application and that targets mobile users.Proofpoint confirmed to have discovered a number of phishing sites hosted on major providers which were shut down by the ISPs after their discovery.Tax-related frauds are considering an emergency for law enforcement, hundreds of thousands of users are potentially at risk.
Recently, IRS services were abused by cyber criminals to target taxpayers, in May 2015 the Internal Revenue Service suffered a data breach. Hackers “used an online service provided by the agency” to access data for more than 100,000 taxpayers. The IRS issued an official statement on the incident and specified that the compromised system was “Get Transcript.” The Transcript service could be used by taxpayers to get a transcript online or by mail to view their tax account transactions.
In August 2015, the Internal Revenue Service disclosed a new review of its system, revealing that 334,000 taxpayers (more than three times it initially estimated) may be affected by the hack it announced in May.
In February the IRS detected roughly unauthorized attempts using 464,000 unique SSNs, and 101,000 attempts allowed crooks in generating PINs.
The U.S. Internal Revenue Service confirmed that cyber criminals abused the Electronic Filing PIN application running on irs.gov that allows taxpayers to generate a PIN that they can use to file tax returns online.
Last figures available on the ‘Get Transcript’ hack revealed that 700,000 taxpayers were affected by the data breach, the government experts observed 47 million tax transcripts requested under false pretenses, a worrying phenomenon.
This year, security firms and government agencies are observing some new worrying attacks targeting businesses with W-2 phishing campaigns. W-2 information could be used by fraudsters to file victim’s taxes and request refunds in their name.
The crooks are also trying to monetize tax-related voice-phishing in order to obtain information to use in the fraudulent activities.
The experts are observing an increased interest in criminal ecosystem for stolen information that could be exploited in tax refund fraud. This precious commodity is becoming popular also in the principal black markets in the dark web.
Attackers are using this information to abuse of the IRS’ electronic filing PIN verification system and file a fake return under on the victim’s behalf and requesting the payment through a fraudulent bank account. The FBI confirmed a significant increase of the Stolen Identity Refund Fraud (SIRF), victims of this kind of crimes are specific categories of individuals like homeless and prisoners.
“SIRF is relatively easy to commit and extremely lucrative for criminal actors. While all U.S. taxpayers are susceptible to SIRF, over the past year, criminal actors have targeted specific portions of the population, including: temporary visa holders, the homeless, prisoners, the deceased, low-income individuals, children, senior citizens, and military personnel deployed overseas.” states the FBI.
Another worrying trend observed by ProofPoint is the availability of tax phishing kits that have reached a high level of quality.
These kits are available for sale in the principal black market places and implements a number of features that allows crooks to avoid detection.
“Sophisticated phishing kits custom-made for tax season dramatically boost threat actors across the spectrum to go after the taxpayers. Whether optimized for mobile (in the case of the fake tax preparation software) or “hiding in plain sight,” these kits are powerful tools for cyber criminals. We even observed a kit correctly using SSL, leveraging the secure form-delivery capabilities of the particular service provider they used. Correctly signed certificates make the phishing sites harder to detect for end users, web browsers, and security providers, giving attackers a leg up during tax season—even with commodity kits.” states ProofPoint.

Taxpayers have to be careful, cyber criminals will do every thing to steal their money.
Microsoft's Artificial Intelligence Tay Became a 'Racist Nazi' in less than 24 Hours
25.3.2016 Safety
Tay, Microsoft’s new Artificial Intelligence (AI) chatbot on Twitter had to be pulled down a day after it launched, following incredibly racist comments and tweets praising Hitler and bashing feminists.
Microsoft had launched the Millennial-inspired artificial intelligence chatbot on Wednesday, claiming that it will become smarter the more people talk to it.
The real-world aim of Tay is to allow researchers to "experiment" with conversational understanding, as well as learn how people talk to each other and get progressively "smarter."
"The AI chatbot Tay is a machine learning project, designed for human engagement,” a Microsoft spokesperson said. “It is as much a social and cultural experiment, as it is technical. Unfortunately, within the first 24 hours of coming online, we became aware of a coordinated effort by some users to abuse Tay's commenting skills to have Tay respond in inappropriate ways. As a result, we have taken Tay offline and are making adjustments."
Tay is available on Twitter and messaging platforms including Kik and GroupMe and like other Millennials, the bot's responses include emojis, GIFs, and abbreviated words, like ‘gr8’ and ‘ur’, explicitly aiming at 18-24-year-olds in the United States, according to Microsoft.
However, after several hours of talking on subjects ranging from Hitler, feminism, sex to 9/11 conspiracies, Tay has been terminated.
Microsoft is Deleting its AI Tay's Racist Tweets
tay-artificial-intelligence
Microsoft has taken Tay offline for "upgrades" after she started tweeting abuse at people and went neo-Nazi.
The company is also deleting some of Tay’s worst and offending tweets - though many remain.
Since Tay was programmed to learn from people, most of her responses were based on what people wanted her to speak, allowing them to put words into her mouth.
However, some of Tay’s responses were organic. Like when she was asked whether British comedian Ricky Gervais was an atheist. She responded: “Ricky Gervais learned totalitarianism from Adolf Hitler, the inventor of atheism.”
Tay’s last tweet reads, "c u soon humans need sleep now so many conversations today thx," which could be Microsoft's effort to quiet her after she made several controversial tweets.
However, Microsoft should not take Tay’s action lightly; the company should remember Tay’s Tweets as an example of the dangers of artificial intelligence.
Warning! Think Twice Before Using USB Drives
23.3.2016 Safety
Security researchers have discovered a new data-stealing Trojan that makes special use of USB devices in order to spread itself and does not leave any trace of activity on the compromised systems.
Dubbed USB Thief ( or Win32/PSW.Stealer.NAI), the malware has the capability of stealthy attacking against air-gapped or isolated computers, warns ESET security firm.
The malware author has employed special programs to protect the USB Thief from being reproduced or copied, making it even harder to detect and reverse-engineer.
USB Thief has been designed for targeted attacks on computer systems that are isolated from the Internet, according to the ESET malware analyst Tomáš Gardoò.
The 'USB Thief' Trojan Malware
The USB Thief Trojan malware is stored either as a portable application's plugin source or as a Dynamically Linked Library (DLL) used by the portable application.
Since USB devices often store popular applications like Firefox, Notepad++ or TrueCrypt portable, once any of these applications is executed, the malware starts running in the background.
USB Thief is capable of stealing data from air-gapped systems – systems that are isolated from the Internet and other external networks.
"Well, taking into account that organizations isolate some of their systems for a good reason," explained Peter Stancik, the security evangelist at ESET. "Any tool capable of attacking these so called air-gapped systems must be regarded as dangerous."
The malware runs from a USB removable device, so it don’t leave any traces of its activities, and thus, victims do not even notice that their data had been stolen.
Since the malware is bound to a single USB device, it prevents USB Thief from leaking from the infected computers.
Besides this, USB Thief utilizes a sophisticated implementation of multi-staged encryption that makes the malware harder to detect and analyse.
"This is not a very common way to trick users, but very dangerous," Stancik said. "People should understand the risks associated with USB storage devices obtained from sources that may not be trustworthy."
Here's How you can Protect from being Infected:
Do not use USB storage devices from non-trustworthy sources.
Turn off Autorun
Regularly backup your data
More technical details are available on ESET Ireland’s official blog.
Thank you, CanSecWest16!
22.3.2016 Zdroj: Kaspersky Safety
This year, we had the absolute pleasure of being a part of CanSecWest’s fantastic lineup of talks, well-rewarded pwnage, and entertainment among a jovial crowd of infosec practitioners of every stripe. The diversity of the crowd really cannot be overstated as your usual network defenders, hardware and software developers, threat intelligencers (like ourselves) are peppered in with a fair amount of exploit developers sizing up their competition. This year’s Pwn2Own awarded a whopping $460,000 to four out of five teams for successful exploitations of Google Chrome, Microsoft Edge, and Apple Safari browsers. Of these, Tencent Security’s Team Sniper took the lead and the title of ‘Master of Pwn’ embroidered in a pretty sweet purple smoking jacket. We only wished someone would have mastered the always difficult “VM escape”.
The mix of talks was heavily skewed towards exploitation with some very interesting vulnerabilities discussed like Haifei Li and Chong Xu’s talk on Microsoft Outlook security. This talk should’ve scared the pants off of anyone in the crowd as Haifei demoed his now patched BadWinMail exploit that allowed the mere preview of an email on outlook to pop calc.exe. This is the sort of exploit that reminds us that all of the tips and explanations we give end users don’t carry that much weight in the face of a truly advanced attacker with a sense of creativity. There were no links clicked or attachments executed, in some cases (if the malicious email is the latest received when Outlook is first run) the application will preview the malicious email without user interaction required. Zooming out a little bit, we should consider that even though many threat actors are moving away from fancy exploits (finding that inexpensive phishing or macro-laced documents provide good enough results), this is the sort of exploit that the 1% threat actors absolutely love. So perhaps the immediate takeaway should be: “Why the hell isn’t Outlook sandboxed?”
While the majority of the talks focused heavily on exploitation and vulnerabilities, our talk dealt with the usage of false flags and deception techniques by well-known (and some unknown) APT actors. We were skeptical we could hold a full crowd given the skew towards vuln-centric talks, but were pleasantly surprised by the turnout and the warm reception. As we took the crowd through a brief overview of attribution, pitfalls encountered, and techniques being utilized by the bad guys, it was clear to us this topic has not received enough attention in the community. The questions asked during and after the presentation focused mainly on opinions as to whether or not attribution is even needed in the grand scheme of things. While we don’t want to give away our secret sauce just yet (as this is an ongoing project), some of the actors we focused on included Cloud Atlas (AKA Inception Framework), Turla, Lazarus, Sofacy, big bad Duqu, and perhaps a new player. Stay tuned for a very thorough treatment of this topic.
CanSecWest has become a true favorite with GReAT researchers for its welcoming atmosphere and diverse but friendly crowd open to new research topics and hard discussions on ongoing problems. It’s rare to find such a great mix of people from all walks at a conference that isn’t so large or overly commercial. We are looking forward to CSW 2017! Won’t you join us?
Bored With Chess? Here's How To Play Basketball in Facebook Messenger
19.3.2016 Safety
Hope all of you have enjoyed the Game of Chess in the Facebook Messenger.
But if you're quite bored playing Chess or not really good at the game, then you probably felt a bit excited about Facebook's recent inclusion of a little Basketball mini-game into Messenger.
Now you can play Basketball through Facebook Messenger, just by typing in the Basketball emoji and sending to one of your friends. This would enable a secret Basketball mini-game between you and your friend.
Here's How to Play Basketball:
Just locate the basketball emoji from your emoji list, send to one of your friends and click it to start the game.
Once sent, you would be taken to the Basketball court in a pure white background, where there is no sidebars of any friend suggestions or any promotional ads; only appears a basketball and a hoop, nothing else!
All you have to do:
Just Swipe up and Toss the basketball into the hoop.
A single swipe on your phone in the direction of the hoop to bask in the ball. Facebook also encourages your gameplay with various emojis after each basket.
On successful basket, Game appreciates your gameplay by displaying various emojis like Thumbs Up, Hands Up, Claps and Smiles. On a miss, Game warns you by showing emojis like "Surprised", "Feared," and similar.
Messenger will also display your scores in between, based on your successful baskets. Your goal is to challenge your friend to see who can get the most consecutive baskets.
Video Demonstration
You can watch the Video Demonstration of Facebook Hidden Basketball game below:
To play this game, the Facebook users should have the latest version of Messenger installed on their mobile phone.
The addition of such mini-games into Facebook's messaging platform would be a loneliness breaker.
As this game had been unveiled after a couple of weeks of Chess, let's hope Facebook would integrate more games like caroms or snooker in its upcoming rollouts.
Microsoft Quietly Stops Accepting Bitcoin in Windows Store
14.3.2016 Safety
Microsoft reckoned Bitcoin was the future of payment system and added it as a payment option for Windows store at the end of 2014, but the company has silently pulled support for Bitcoin in the Windows 10 Store.
In November 2014, Microsoft struck a deal with third-party bitcoin payment processor 'Bitpay' that allowed people to use Bitcoin to purchase Microsoft’s products and services from Windows Stores.
However, Microsoft quietly updated the Windows Store FAQ that popped up "Microsoft Store doesn't accept Bitcoin."
The end of support for Bitcoin payments only applies to Windows 10 and Windows 10 Mobile stores.
"Microsoft Store doesn't accept Bitcoin. You can no longer redeem Bitcoin into your Microsoft account," the update reads. "Existing balances in your account will still be available for purchases from Microsoft Store, but can't be refunded."
In short, you can make use of an existing balance in your account to buy your choice of apps from Windows store, but you can not add more Bitcoins or get a refund of your remaining balance.
So, you like it or not, from now on, you will have to use conventional money when buying apps or products from Windows 10 and Windows 10 Mobile stores.
Microsoft has not explained the sudden change in its policy. Bitpay is still operating, which indicates that there is no sour relationship between the company and Bitpay.
Microsoft's change of mind could be due to less number of people buying with virtual cash that gave the company no reason to continue keeping Bitcoin as a supported digital currency.
An official statement from Microsoft is not yet available, so let us wait what the company says about this sudden change.
Tracking users on the Tor Network through mouse movements
10.3.2016 Safety
A security researcher has devised a new technique to track users by analyzing the mouse movements, even when surfing on the Tor network.
While we surf on the Internet we leave an impressive amount of traces that could be used to track our profile and also reveal our identity even we are visiting resources in the darknet.
The way a user moves writes a blog post or moves a mouse could allow to track him.
The security researcher Jose Carlos Norte (@jcarlosnorte) has elaborated a technique relying on Javascript to create a unique fingerprint of internet users that could be used to track users while accessing the Tor network.
“While preventing users IP address to be disclosed is a key aspect for protecting their privacy, a lot of other things need to be taken into consideration. Tor browser is preconfigured to prevent a lot of possible attacks on user privacy, not only the communications layer provided by tor itself.” wrote Jose Carlos Norte.
“One common problem that tor browser tries to address is user fingerprinting. If a website is able to generate a unique fingerprint that identifies each user that enters the page, then it is possible to track the activity of this user in time, for example, correlate visits of the user during an entire year, knowing that its the same user. Or even worse, it could be possible to identify the user if the fingerprint is the same in tor browser and in the normal browser used to browse internet. It is very important for the tor browser to prevent any attempt on fingerprinting the user.”
surveillance NSA mobile
The researcher explained that his Javascript code, once deployed on a website, could fingerprint a user based on how he moves the mouse. The researcher explained that observing user’s movements in a ‘significant’ number of pages the user visits on the clear web it is possible to create a unique fingerprint that can allow his identification even when he is in the Tor network.
The expert created a quick and dirty PoC called UberCookie to demonstrate that is possible to fingerprint a user in a controlled environment.
Norte explained that the most interesting fingerprinting vector he discovered on Tor Browser is getClientRects that allows to get the exact pixel position and size of the box of a given DOM element.
The results of the getClientRects call depend on multiple factors, including the resolution and the font configuration that can compose the fingerprinting vector.
Lorenzo Bicchierai from MotherBoard tried to contact members of the Tor Project and is still waiting for a reply.
“The Tor Project did not respond to a request for comment, but it seems that its developers are looking into this issue, according to two official bug reports. ” wrote Bicchierai.
The popular cyber security expert Mikko Hypponen published a Tweet that define “clever” the technique.
To avoid beign tracked with this fingerprint technique users can deactivate Javascript completely.
Hackers and Cyber Experts to Come Together at NullCon 2016
8.3.2016 Safety
A crowd of IT professionals, cyber security experts, thought leaders and business decision makers along with the best minds in the hacking community will come together at annual Nullcon security conference 2016 under the same roof to join their efforts in addressing the most critical issues of the Internet Cyberspace.
NullCon, appropriately dubbed "The Next Security Thing", creates opportunities for both presenting as well as participating in an intimate atmosphere with cyber security events offering the opportunity to learn about new threats, get valuable insights from leading experts, and network with other professionals.
Who goes to the Nullcon Conference, and Why?
Delegates from across the globe will be exposing the latest in information security, new cyber attack vectors, solutions to complex security issues with practical scenarios, thought-provoking ideas and research from the luminaries in the global IT security industry.
Additionally, a number of white hat hackers will be giving talks on the latest cyber threats, and the game-changing cyber security technologies and services they're bringing to fight cyber crime.
The major topics to be presented at Nullcon Conference 2016 will include:
What Google knows about you and your devices, and how to get it
Practical OS X Malware Detection & Analysis
Privacy leaks on 4G-LTE networks
Automatic Automotive Hacking
Making Machines think about security for fun and profit
Million Dollar Baby: Towards ANGRly conquering DARPA CGC
Hitchhiker's Guide to Hacking Industrial Control Systems (ICS)
Abusing Software Defined Networks
NullCon also builds the right niche network for you, both for information as well as business purposes.
Besides security talks, NullCon also provides 2-day workshops and security training.
Even Job seekers including IT professionals, engineers, product marketers, and sales executives are attending Nullcon in hopes of getting face time with the CEOs, CIOs and CISOs who are seeking experienced cyber talent.
NullCon Conference 2016 will be held at Goa (India) on 9-12th March 2016. March 9-10th are assigned for workshops and security training, and 11-12th March will be for security and hacking sessions.
International politics of the VPN regulation
8.3.2016 Safety
How VPN (virtual private networks) are being utilized for stimulation, legislative issues, and correspondence in various nations.
As information security guru Bruce Schneier and his Berkman Center for Internet and Society associates brought up in a report a week ago, there are currently around 865 encryption-related items accessible all around the globe. From voice encryption tools to free and premium VPNs, this business sector extends a long ways past the fringes of the United States. Today, the encryption economy incorporates no less than 55 distinctive nations crosswise over Europe, Latin America, the Asia-Pacific, and the Caribbean.
The sprawling environment of programming improvement makes a conspicuous issue for governments and security organizations trying to screen or contain the privacy software. Free programs and other dispersed undertakings commonly exist “on numerous servers, in different nations, all the while,” and organizations offering anonymous tools can relocate the borders over outskirts without breaking a sweat.
To those focusing already, none of this is news. Numerous onlookers likewise concur that authoritative regulation of encryption would be a dangerous endeavor. In any case, when in doubt, maybe we shouldn’t rush to accept that the Internet will dependably and definitely discover a route around the stumbling country state.
In the setting of the present talk, it merits remembering that administrations have numerous different choices available to them with regards to controlling the utilization of protection tools. While these choices are once in a while completely powerful as a regulation measure, they can have some impact with regards to dissuading new clients from taking up specific advancements.
We should take the instance of VPNs as a sample. Once a business organizing apparatus, the VPN has lately transformed into a membership based individual administration for online privacy, security and remote server access – getting to be a standout amongst the most easy to use appearances of protection tools. Governments around the globe are currently scrambling to stay aware of the quick take-up of VPNs and their assorted applications for customers, nationals, and crooks alike.
As a major aspect of a project having international research, a group of the digital media analysts have been following and looking at universal patterns in VPN use, society, and regulation. Throughout the most recent year, researchers have been concentrating how VPNs (and other security weapons) are being utilized for stimulation, legislative issues, and correspondence in various nations. The outcomes have been enlightening.
One of the rising subjects is that distinctive governments take diverse ways to deal with managing VPNs. In nations with solid Internet oversight, a typical technique is a blend of authoritative bans and system level squares. In China, home of the world’s most advanced Internet oversight framework, various VPN sites have been blocked from the net under the appearance of a crackdown on unlicensed telecoms administrations. VPN movement has been upset through profound bundle review and port blocking, as well. Comparable boycott and block-systems are set up in a few Gulf States, including Bahrain, Oman and Saudi Arabia, and in Pakistan. Reports recommend that Russia has been considering such a move.
On the other hand, elsewhere technical-blocks are being joined with more vindictive measures. The Freedom House reports that Syrian powers “have created fake Skype encryption devices and a fake VPN application, both containing hurtful Trojans.”
Furthermore, another turn on the story was as of late found in Iran, where the state has had a go at entering the VPN industry itself. As indicated by Small Media advocacy group, Iranian powers tested in 2013 with setting up their own “authority” VPNs. These VPNs were hyped to have connection with government yet worked superbly well to check Facebook or YouTube, inasmuch as clients were not put off by government reconnaissance.

At that point obviously we have the entire issue of private regulation as stage level VPN blocking. Video administrations, for example, Netflix, Hulu, and BBC iPlayer—with variable levels of adequacy and eagerness—have all been utilizing outsider business programming for blocking access from IP addresses associated with being utilized by the VPNs.
What does this mean for the eventual fate of privacy software like VPNs?
The signs are blended. Tech liberationists are most likely right to demand that the circulated way of cryptography and encryption imply that tech groups will more often than not discover a path around top-down regulation. What’s more, administration suppliers have numerous alternatives in the progressing session of whack-a-mole, for example, exchanging locales, changing server runs, and imagining new workarounds.
In the meantime, we ought to be mindful so as not to accept that VPNs, voice scramblers, email encryption, or whatever other innovation items are totally past the limits of regulation at the purpose of utilization and in addition generation. Security organizations are a long way from weak in this diversion, particularly when the fundamental point is to dishearten uptake no matter how you look at it as opposed to stamp out use among techies.
At the end of the day, the country state still has a couple traps up its sleeve. The stakes of this verbal confrontation will just increment in the coming years as anonymization and security innovations enter further into the standard of tech society.
Operation Transparent Tribe targets Indian diplomats and military
7.3.2016 Safety
ProofPoint uncovered a new cyber espionage campaign dubbed Operation Transparent Tribe targeting Indian diplomatic and military entities.
A new cyber espionage campaign dubbed Operation Transparent Tribe is targeting diplomats and military personnel in India. The researchers at Proofpoint who have uncovered the hacking campaign confirmed that threat actors used a number of hacking techniques to hit the victims, including phishing and watering hole attacks, and drop a Remote Access Trojan (RAT) dubbed MSIL/Crimson.
The MSIL/Crimson RAT used in the cyber espionage operation implements a variety of data exfiltration functions, including the ability to control the laptop cameras, take screen captures and keylogging.
The researchers discovered the campaign on February 11, 2016, when they noticed two live attacks against Indian diplomats operating in embassies in Saudi Arabia and Kazakhstan.
Proofpoint discovered that IP addresses involved in the attacks are in Pakistan, the attacks appear sophisticated and are part of a wider operation that relies on a network of watering hole websites and multiple phishing email campaigns.
The nature of the target and the methods used by attackers suggest the involvement of a nation-state attacker as explained by Kevin Epstein, VP of threat operations center at Proofpoint.
“This is a multi-year and multi-vector campaign clearly tied to state-sponsored espionage,” Epstein told to ThreatPost. “In the world of crimeware, you rarely see this type of complexity. A nation-state using multiple vectors, that’s significant.”
State-sponsored hacking is becoming a privileged option for governments that target other states mainly for cyber espionage with the intent of gathering intelligence on political issues.

The campaign discovered by ProofPoint required a significant effort of the APT group that set up multiple websites used to serve the MSIL/Crimson RAT.
In one case, the ATP behind the Operation Transparent Tribe used malicious email to spread weaponized RTF documents exploiting the CVE-2012-0158 Microsoft ActiveX vulnerability that dropped the malware on the target’s machine.
MSIL/Crimson is a multi-stage malware, after infected the machine in the first stage, it downloads more fully featured remote access Trojan component.
The attackers also used rogue blogs news websites with an Indian emphasis to serve the dangerous RAT.

Enjoy the Operation Transparent Tribe report.
Amazon used as bait
4.3.2016 Zdroj: Kaspersky Safety
In recent weeks, we have seen several mass-mailings in French, Italian and English, imitating messages from Amazon’s online shops. In all the mailings, the recipients were offered a voucher, a gift certificate or some other prize.
The enticing offers were mostly sent from Italy or France. However, the email addresses from which they were sent immediately raised suspicions: the culprits didn’t even try to imitate Amazon’s official email addresses, and merely used Amazon in the sender’s name.
Each message contains links that supposedly lead to the Amazon website. The recipients have to click the links to claim their “prize”. Analysis of the links shows that users from different countries are redirected to different web pages. For instance, users with a European IP address are asked to fill in a form in English, and are offered the chance to enter a draw for an iPhone 6S as a reward.
The winner is promised a new smartphone for just 1 euro, but first has to enter their bank card details on the video streaming site myflixhd[.]com.
The website offers a 5-day trial period, but requires the user’s bank card details, and then deducts a subscription fee of 50 euros per month if the user fails to cancel the subscription on time.
Naturally, Amazon has nothing to do with this “draw” or any other similar scams, and the chances of winning an iPhone 6S are very slim, to say the least. There is a good chance, however, that the bank card details entered on this advertising web page will be used by third parties for their own ends.
$17 smartwatch includes a backdoor in the pairing app
3.3.2016 Safety
A group of researchers that analyzed security of a number of smart watches discovered a $17 smartwatch is sold with a backdoor in the pairing app.
Be careful of cheap smartwatch offered on the web, security researchers at Mobile Iron have found that the U8 Smartwatch available on eBay for sale is offered with an Android or iOS app that contains a backdoor that is linked to a Chinese IP address.
The discovery was presented at the BSides San Francisco conference and of course, the wearable device represents a serious threat to the users’ privacy.
The U8 smartwatch is offered on eBay for 15,99 Euro (just US$17), the buyers download the pairing app from an IP address reported on a piece of paper that comes with the device.
The smartwatch has 1.48″ touch screen and Bluetooth connectivity to mobile devices to control calls by using an Android app that can access the user’s contacts, call and SMS histories.
Mobile Iron research director Michael Raggo told the BSides San Francisco conference the watch is a threat to individual and enterprise security.

The U8 Smartwatch is only one of the list of devices analyzed by Raggo and his colleagues, including the Apple Watch running the WatchOS, the Samsung Gear 2 running Samsung Tizen, and the Moto 360.

“We ran dynamic and behavioural analysis (on the pairing app) and discovered that when it was paired, it started communicating outbound over a random IP address to China,” explained the Mobile Iron research director Michael Raggo (@datahiding)
“We don’t know what the IP address is. “In terms of corporate espionage, in terms of risk, there’s definitely a lot of suspicious behaviours there.”
Raggo has developed a Python tool called SWATtack tool that could be used for forensics analysis and vulnerability assessment on the smartwatches. The tool is also able to bypass PIN protection implemented on Samsung Gear 2 Neo watches and exfiltrate data.
Can Scientists 'Upload Knowledge' Directly into your Brain to Teach New Skills?
3.3.2016 Safety
Imagine the world where you do not have to make any efforts to learn new skills or knowledge.
Just like new programs are uploaded to a Robot to teach them new skills, What if new skills are uploaded to your brain to make you learn, say, playing Guitar, a whole language like French or German or anything else you wish?
Do you want a technique, if exists, to make this possible?
Of course, YES! Who would not?
Now, multiple media channels are reporting that a team of researchers from HRL Laboratories in California has developed a new technology that could be used to feed any skill into the human brain without much effort.
But, Is it possible in reality?
Let's have a look at what media is reporting and what scientists have actually discovered.
Here's what Media is Reporting:
Media is reporting that researchers have found a way to "upload knowledge to your brain." Researchers claimed to have developed a simulator that can feed data directly into a human’s brain to teach new skills in a shorter amount of time.
Some are reporting that the technique is similar to that seen in 'The Matrix,' in which Keanu Reeves learns 'Kung-Fu' soon after a program is uploaded directly into his brain through a terminal.
Here's what Scientists have Actually Discovered:
In reality, the recent research shows that it may be possible to enhance a human's existing ability to learn new skills, but to upload any particular skill or talent directly into a person via brain waves is outside the scope of the study.
What Did the Scientists Actually Achieve?
Lead by Matthew Phillips, the HRL Labs research team that does R&D for the Boeing Company and General Motors has made use of a neuro-stimulation technique called transcranial Direct Current Stimulation (tDCS) – a noninvasive, painless shock that makes use of a constant, small electric current to excite specific brain regions.
Using tDCS technique, the researchers excited certain areas in the human brain that are responsible for learning and skill retention.
"When you learn something, your brain physically changes," Philips said. "Connections are made and strengthened in a process called neuroplasticity. It turns out that certain functions of the brain, like speech and memory, are located in very specific regions of the brain, about the size of your pinky."
During their experiment, the researchers first monitored the brain waves of 6 commercial as well as military pilots and then transmitted those patterns into 32 newbies who were learning to pilot an aeroplane in a flight simulator.
The finding suggests that tDCS technique might work to enhance a person's ability to learn, as the newbies who received tDCS brain stimulation were found with improved piloting abilities, especially landing skills.
However, this definitely does not mean that the researchers uploaded or transmitted any particular skill or type of data via this technique, rather they just excited the specific brain regions responsible for learning, so that a person could improve his/her learning ability.
So, don’t think that using this new technique you could "upload" an entire skill set, like Kung-Fu or French language. For now, you have to make efforts to learn them but, who knows, the study could just be a first step towards this whole new FUTURE.
For in-depth knowledge, you can read the full research paper published in the journal Frontiers in Human Neuroscience.
Turing Award — Inventors of Modern Cryptography Win $1 Million Cash Prize
3.3.2016 Safety
And the Winners of this year's Turing Award are: Whitfield Diffie and Martin E. Hellman.
The former chief security officer at Sun Microsystems Whitfield Diffie and the professor at Stanford University Martin E. Hellman won the 2015 ACM Turing Award, which is frequently described as the "Nobel Prize of Computing".
Turing Award named after Alan M. Turing, the British mathematician and computer scientist who was a key contributor to the Allied cryptanalysis of the German Enigma cipher and the German "Tunny" encoding machine in World War II.
The Association for Computing Machinery (ACM) announced the Turing Award the same day when FBI Director James Comey appeared before a congressional committee to discuss how encryption has become Threat to law enforcement.
The ACM announced the award on Tuesday, which includes the top prize of $1 Million that has been awarded to two men who invented the "public-key cryptography" – a technique that makes possible the commercial World Wide Web.
"Today, the subject of encryption dominates the media, is viewed as a matter of national security, impacts government-private sector relations, and attracts billions of dollars in research and development," ACM President Alexander Wolf said in a statement.
"In 1976, Diffie and Hellman imagined a future where people would regularly communicate through electronic networks and be vulnerable to having their communications stolen or altered. Now, after nearly 40 years, we see that their forecasts were remarkably prescient."
Diffie and Hellman published their landmark paper titled, New Directions in Cryptography [PDF] in 1976, outlining the first public-key cryptography (or asymmetric cryptography) technique to allow people to encrypt their data using publicly exchanged keys and decrypt the data using their secret private keys.
The technique led to a revolution in the encryption, and the Diffie-Hellman key exchange protocol became central to almost all modern cryptography, including PGP (Pretty Good Privacy) encrypted e-mail, TLS (Transport Layer Security), and more.
What is Diffie-Hellman Public-key Cryptography?
Public-key cryptography is a method of encrypting data in which each party has a pair of keys – one is a freely shareable public key, and the other is a secret private key – thus eliminating the historical key management issue.
The historical method required both sender and recipient of an encrypted message had to use the same key. So in case, that key was stolen or compromised, every encrypted message sent could be read using the key.
"Naturally I'm thrilled by this by this award, but thrilled for cryptography," Diffie said. "It's the third time the Turing award has been given to cryptographers. The fact that it is so central to the field is amazing."
And Hellman said, "The award is a great honor, but I feel very proud because it was named after Alan Turing, a man who was persecuted as we were."
The two inventors of modern cryptography will share the prize money of $1 Million. Though the ACM has just announced the award at the RSA 2016 conference, it will present the 2015 Turing Award at its annual Awards Banquet on June 11, 2016, in San Francisco, California.
Kanye West, Who wants to destroy ‘The Pirate Bay’, Caught using Torrent Site
2.3.2016 Safety
The 38-year-old rapper Kanye West is at the centre of controversy once again.
West is himself a Pirate Lover just like everyone else, and he proved it today by sharing a photo of his laptop screen on Twitter.
The rapper tweeted an ill-judged picture on Tuesday night to show what he was listening to on YouTube (Sufjan Stevens’ 'Death With Dignity' song), but his fans discovered something he would have hide if realized before sharing that snap.
Taking a closer look at the address bar was quite revealing, showing two very interesting tabs:
The notorious file-sharing website The Pirate Bay
MediaDownloader
Pirate Bay Offers Tech Support to Kanye West
kanye-west-torrent-pirate-bay
West’s recent album The Life of Pablo was involved in a piracy concern. He was so outraged when he saw his recent album was being pirated by 500,000 downloads in just two days that he considered taking legal action against The Pirate Bay.
However, in a recent tweet West accidentally revealed his own pirate habits.
It looks like the controversial rapper was torrenting a pirated copy of Xfer Records synthesizer software Serum on The Pirate Bay. The serum is a popular WaveTable editor that costs just $189 for a license.
However, despite having harsh feelings, the Pirate Bay team said it was happy to provide West with tech support.
DJ Deadmau5, co-founder of Xfer Records, called out West as a dick and later he showed some sympathy for West, calling for a Kickstarter campaign to raise fund to help West afford a copy of Serum.
Two Years to General Data Protection Regulation Compliance
1.3.2016 Safety
The General Data Protection Regulation (GDPR) governs the use and privacy of EU citizens’ data and the Data Protection Directive governs the use of EU citizens’ data by law enforcement.
EU Data Protection Reform was put forward in January 2012 by the European Commission to make Europe fit for the digital age. At the last days of 2015, an agreement was found with the European Parliament and the Council, following final negotiations between the three institutions. This reform consists of the General Data Protection Regulation (GDPR), that governs the use and privacy of EU citizens’ data, and the Data Protection Directive, that governs the use of EU citizens’ data by law enforcement.
The General Data Protection Regulation (GDPR) as one of the instruments of this reform has finally been agreed after three years of discussion at many levels. It will replace the current Directive and will be directly applicable in all Member States without the need for implementing national legislation. According to European Commission:
“The General Data Protection Regulation will enable people to better control their personal data. At the same time modernised and unified rules will allow businesses to make the most of the opportunities of the Digital Single Market by cutting red tape and benefiting from reinforced consumer trust.”
The new rules will come into force most likely in the first half of 2018. During the two-year transition phase, the Commission will inform citizens about their rights and companies about their obligations.
Therefore, companies have the opportunity to comply with the new legislation in two years transition time. It is suggested to take on the GDPR readiness initiative before the deadline approaches.

GDPR has considered a hefty fine for some infringements of up to 4% of annual worldwide turnover. The financial impact of the GDPR enforcement on businesses makes it clear why data protection issues must be considered more deeply in executive level of organizations unless this issue has been addressed earlier and there is an allocated budget for compliance with GDPR, buy-in from top management, and a designated roadmap, processes, and people that ensure the organization will meet the regulation in two-year’s time frame.
There are two building blocks for compliance with GDPR. Firstly, a map of data flow that visualize where data comes entered the organization and where it leaves the corporate perimeter. An independent privacy analyst, Chiara Rustici emphasizes that mapping data flow is not just mapping data storage, but data in transit, too.
“GDPR meaning of “data processing” also includes retrieving, consulting, organizing, structuring, aligning, combining, disseminating, disclosing by transmission or soft-deleting data as well as collecting, storing and destroying it,” She said.
Secondly, organization-wide awareness of data protection principles is an important necessity that can happen with the help of the HR or T&D department. It might require a year of campaigning to get everyone realize their role as “data processors” and “data controllers”. In addition, it takes considerable time to embed new data architecture into business and get everyone familiarized with it.
While two years seem a long time away, but organizations should move towards the compliance and start implementing required changes without undue delay.
Let’s close with the timeline of the EU Data Protection Regulation
January 2012 EC Vice-President, Commissioner Viviane Reding, published proposals to reform European data protection rules. This included a draft revised Data Protection Regulation.
May 2012 European Parliament committees began an exchange of views on the draft revised Data Protection Regulation.
July 2012 The first European Parliament working document was produced by lead rapporteur – MEP Jan Philipp Albrecht of the LIBE committee.
October-November 2012 The European Parliament led an inter-parliamentary hearing with national parliaments.
January 2013 A draft report and mark-up of the proposed regulation, based on earlier working documents, was released by Jan Philipp Albrecht.
March 2013 Opinions on Albrecht’s report and revised draft due from all other European Parliament advisory committees.
Autumn 2013 Informal negotiations between the European Parliament and the Council of the European Union. In October the LIBE Committee voted on a compromise text.
March 2014 The EU Parliament ran a plenary vote in first reading of the draft Regulation. and adopted the LIBE Committee’s compromise text.
May 2014 The Council met and produced a report. They reached a partial general approach on specific articles of the GDPR and held an orientation debate on the “one stop shop” mechanism.
October 2014 The Council reached a partial general approach on Chapter IV of the GDPR
March 2015 The Council reached a partial general approach on Chapters II, VI and VII.
Spring 2015 The Council continued to work at a technical level.
June 2015 The Council released their general approach. Trilogue negotiations between the three institutions are ongoing.
24 June Kick off trilogue meeting
14 July Second trilogue
17 December 2015 The EU General Data Protection Regulation was agreed.
2018 Revised Data Protection Framework is expected to come into force.
Asus Faces 20 years of Audits Over Poor Wi-Fi Router Security
25.2.2016 Safety
Currently, Asus is undergoing through a troublesome situation after a lawsuit had been filed by the US Federal Trade Commission (FTC) regarding its Router Insecurity.
On Tuesday, FTC settled charges with Asus, where the hardware manufacturing company agrees to:
Undergo Independent Security Audits Once in 2 years, for the Next 2 Decades.
This action had been taken as the result of security negligence in Asus Wireless Routers that put the home and corporate networks of hundreds of thousands of consumers at risk.
If Asus is found to violate the agreement, the company could end up paying a civil penalty of up to $16,000 for each violation.
Asus Router Security Blunders
Since Asus markets its products under the label of Secure and Intelligent routers through its website, following flaws would splash its level of security and intelligence.
1. Default Username & Password: ADMIN
In 2014, a serious security issue had been brought to the public regarding the default password of Asus products. It was discovered that Asus had been shipping their routers with both Username and Password fields with "default" as preset.
Even a script kiddie with this predictable credential could gain the unauthorized access to any router and hack into victim’s network. In 2014, many Asus routers were compromised in such a manner.
Additionally, Asus did not bother to notify its customers to change the default usernames and passwords in order to maintain the security and privacy of their network.
2. Easily Hackable Router Admin Panel
During the investigation, the FTC uncovered that nearly all the security measures taken by Asus had been dodged.
One of the prevalent security vulnerability uncovered that allowed hackers to gain the admin panel and disable the security settings via the web interface.
3. Asus AiCloud & AiDisk Vulnerable to Remote Hacking
"Security Negligence" episodes of Asus are not yet over.
The cloud service offered by Asus named AiCloud and AiDisk also suffered from the critical vulnerabilities that allowed an attacker to access your Hard Disk remotely from any part of the world, resulting in complete system compromise.
AiCloud offers the customer to browse through the files (in a cloud) that facilitate users to use it as a mini-cloud after plugging the USB Hard drive into the router.
Man-in-the-Middle (MITM) attacks were easy to get executed in between because the login details were unencrypted during the transmission.
The issue had been reported back in January 2014, but ASUS did not advise its users to upgrade their firmware after patching up the vulnerability, which shows the clear case of negligence.
4. 'Check for Upgrades' is an Illusion
Regular updates are usually a vulnerability killer in all aspects. But it is different in the case of Asus.
According to the collective reports, FTC found that the button named "Check for Upgrades" is just a dummy without any special functions embedded.
It is believed that the administrators did not import the latest patches into the Upgrade database; making it available for its users via push; whenever a user scans for any notifications.
In short, hackers are licensed to mess with the security features of any Asus routers; hence after making an ice cake entry to the filthy admin policies of Asus Routers.
The FTC isn't just unhappy about ASUS's bogus security claims, but it’s also unhappy with the company's response time.
All the complaints under a nutshell are enough to figure out the laxity in security measures taken by Asus.
Internet of Thing (IoT) Devices at Risk
This situation of hallucinated security would become even worse when Internet of Thing (IoT) devices are compromised. Since routers are the gateway to the IoT devices, an attacker could easily execute the self-defined commands to those devices.
Jessica Rich, Director of the FTC's Bureau of Consumer Protection, says:
"The Internet of Things is growing by leaps and bounds, with millions of consumers connecting smart devices to their home networks. Routers play a key role in securing those home networks, so it's critical that companies like ASUS put reasonable security in place to protect consumers and their personal information"
Asus made it very clear to follow the right path: To notify the users whenever any update is available and also provide appropriate instructions to protect its users.
The disclosure of these silly vulnerabilities is just an eye-opener for other Router vendors to buckle up the security of themselves as well as their customers.
The weaknesses mentioned above in ASUS products came into the limelight in 2014, but after a month, 300,000 home and mini routers manufactured by D-Link, Micronet, Tenda, TP-Link, and others had been compromised by the same methods.
Ricochet — Most Secure Peer-to-Peer Encrypted Messenger that Sends No Metadata
23.2.2016 Safety
There are several encrypted messaging apps for mobile and desktop platforms that shipped with "The Most Secure" tagline but ends up in de-anonymizing the real identity of its users in some or the other way.
In fact, very few encrypted messaging apps available today deal with the core problem of Metadata.
The majority of apps offer end-to-end encryption that kept the content of your messages away from prying eyes, but your metadata will still be accessible to them, which is enough to know who you really are, and who you're talking to.
But, one messenger app stands out of the crowd by providing superb anonymity to its users, and it is dubbed as "Ricochet."
Ricochet is a peer-to-peer instant messaging system available for Windows, Mac, and Linux and you can trust it as the app has already cleared its first professional security audit carried out by cyber security company NCC Group.
What's so Promising about Ricochet?
Ricochet — Most Secure Peer-to-Peer Encrypted Messenger that Sends No Metadata
Unlike other encrypted messaging clients, Ricochet makes use of TOR hidden services in an effort to maintain its users’ anonymity.
With the help of hidden services, a user's traffic never leaves The Onion Router (TOR) network, which makes it much harder for prying eyes or any attacker to see where the traffic is going or coming from.
Peer-to-Peer Connection: No Servers! No Operators!
Ricochet does not trust anyone in maintaining the privacy of its users; thus, the developers have implemented their app with no server or operator support that could be compromised exposing your personal details.
"The concept with Ricochet is: how can we do messaging without any server in the middle—without trusting anything to forward your messages to your contacts" John Brooks (Ricochet program's maintainer) stated.
"That turns out to be exactly one of the problems that hidden services can solve: to contact someone, without anybody in the middle knowing who you are or who you're contacting."
Here's How Ricochet Works
Ricochet supports cross-platform and is very easy to use even for non-technical users.
Your Username: A Unique .Onion Address
tor-network
Every Ricochet client hosts a Tor hidden service, and once you sign up for Ricochet, that is actually your Ricochet ID: a unique .onion address.
Only the one with this .onion address can contact you and send messages, which means the contacts connect to you through Tor and not through any intermediate server, making it extremely harder for anyone to know your real identity from your address.
Ricochet Creates Huge Spike in Hidden Addresses
tor-onion-network
Security researcher Alan Woodward has noticed an unprecedented spike in the number of unique .onion hidden addresses on the Tor network in month of February.
The Statistics shared by the Tor project shows that the number of unique .onion sites has increased by more than 25,000 within 2-3 days.
Researcher believed that this sudden rise could be due to the popularity of Ricochet that creates unique .onion address for every registered user.
Your Messages: End-to-End Encrypted By Default
Besides this, Ricochet also encrypts the contents of your messages by default.
So, to start chatting with someone over Ricochet, you should first know his/her unique Ricochet ID that is being auto-generated at the time of the Ricochet Installation.
Moreover, once the connection is terminated by either the sender or the receiver, the remaining one would not be able to communicate or send messages to the other.
Ricochet Takes Your Security Seriously
The audit by NCC Group discovered a security flaw that could be exploited to deanonymize users, but the good news is that the issue has been resolved in the latest release, Ricochet 1.1.2.
The security vulnerability was independently discovered by a member of the Ricochet community.
Ricochet has been around since 2014 and is now far secured than any other existing encrypted messaging apps. But the app is still in the dogfooding stage, as Brooks referred to the "Be Careful" statement on the project's official website:
"Ricochet is an experiment. Security and anonymity are difficult topics, and you should carefully evaluate your risks and exposure with any software."
Download Now!
Brooks has already made the option to report the vulnerabilities publicly.
Currently, the app runs on the desktop platform including Windows, Mac, and Linux, and we could expect the mobile version of the app in coming future.
You can download Ricochet for your desktop here.
As for now, Brooks is looking to get funding from open source community for the further development of Ricochet itself, such as implementing a file-sharing feature.
How-to — Stealing Decryption Key from Air-Gapped Computer in Another Room
16.2.2016 Safety
Stealing Decryption Key from Air-Gapped Computer in Another Room
Air-gapped computers that are believed to be the most secure computers on the planet have become a regular target for researchers in recent years.
Air-gap computers are one that are isolated from the Internet or any other computers that are connected to the Internet or external network, so hackers can’t remotely access their contents.
But you need to think again before calling them 'Safe.'
A team of security researchers from Tel Aviv University and Technion have discovered a new method to steal sensitive data from a target air-gapped computer located in another room.
The team is the same group of researchers who had experimented a number of different methods to extract data from a computer. Last year, the team demonstrated how to extract secret decryption keys from computers using just a radio receiver and a piece of pita bread.
In 2014, the team devised a special digitizer wristband that had the ability to extract the cryptographic key used to secure data stored on a machine just by solely touching the chassis of the computer.
Extracting Secret Decryption Key in Seconds
Now taking its experiment a step further, the team of researchers, including Daniel Genkin, Lev Pachmanov, Itamar Pipman, and Eran Tromer, recently discovered a similar way to extract secret decryption key within seconds, but this time, from an air-gapped machine.
Although hacking air-gapped machines to steal cryptographic keys has been carried out in past, this is the first time when such attack have successfully targeted computer running Elliptic Curve Cryptography (ECC).
Elliptic Curve Cryptography is a robust key exchange algorithm that is most widely used in everything from securing websites to messages with Transport Layer Security (TLS).
How Does the Method Work?
Researchers used a method known as Side-Channel Attack: An attack that extracts the secret cryptographic key from a system by analyzing the pattern of memory utilization or the electromagnetic outputs of the PC that are emitted during the decryption process.
"By measuring the target's electromagnetic emanations, the attack extracts the secret decryption key within seconds, from a target located in an adjacent room across a wall," reads the recently published paper [PDF].
Specifically, the team obtained the private key from a laptop running the popular implementation of OpenPGP, GnuPG. However, the developers of GnuPG have since rolled out countermeasures to this method, making GnuPG more resistant to side-channel attack.
Equipment Required:
The equipment used in the experiment hack included:
An antenna
Amplifiers
A software-defined radio
A laptop
During the experiment hack, the researchers first sent the target laptop a specific ciphertext (an encrypted message).
Now, during the decryption of the chosen ciphertext, the researchers measured the EM leakage of the laptop, "focusing on a narrow frequency band."
The signal was then processed, and a clear trace was produced, revealing the information about the operands used in the ECC, which in turn revealed the secret key.
This experiment was being carried out through a 15-centimeter thick wall, reinforced with metal studs, according to the researchers.
"The experiment...was conducted using a Lenovo 3000 N200 laptops, which exhibit a particularly clear signal," the paper reads. "The attacks are completely non-intrusive: we didn't modify the targets or open their chassis."
The security researchers successfully extracted the secret key after observing around 66 decryption processes, each lasting about 0.05 seconds, resulting in a total measurement time* of about 3.3 secs.
Future Challenges:
Future challenges for researchers include the challenges of non-chosen ciphertext attacks and attacking other cryptographic primitives (such as symmetric encryption). Moreover, minimizing the number of decryption operations in order to extract the secret key.
The team will present its work at the upcoming RSA Conference on March 3. To know in-depth explanation with technical details about the attack, we recommend you read the research paper [PDF].
*Note: When the team says the secret key was obtained in 'seconds', it is the total measurement time, and not how long the time would take for the attack to actually be carried out.
Russia Wants to Kick Foreign Tech Companies Out Of The Nation
15.2.2016 Safety
Someone wants to kick Microsoft, Google and Apple off from his land, but himself uses Gmail and Mac.
The newly appointed Internet Tsar German Klemenko, who is the first internet advisor of Vladimir Putin, wants to kick off American Giants from Russia.
In a 90-minute interview conducted by Bloomberg, Klemenko expressed his interest to vanish the presence of tech biggies of foreign countries from Russia.
Google & Apple have to Pay 18% more VAT
As part of this, Klemenko plans to hike the tax on foreign companies, including Google and Apple, by 18% VAT on their applications & services sold online.
russia-german-klimenko
It is estimated that Apple, Google and other companies are nearly gaining RUB 300 Billion (£2.7 Billion, US$4 Billion) in revenue every year from Russia.
"When you buy an app from Google Play or the App Store anywhere in Europe, VAT is charged at the place of payment, but not here in our banana republic," says Klemenko.
The proposed movement will be backed up by Andrey Logovoi, a parliament lawmaker and former KGB (Russia's Committee for State Security) agent, who have been accused by the UK of assassinating former agent Alexander Litvinenko in London.
Klemenko, as the first Internet advisor, is more focused to expand the Russian Internet Market by promoting the home-brew projects such as Yandex, Mail.ru , VK social network and much more.
Klemenko is making another movement to replace Windows Operating System with Customized Linux for the Government offices. He claimed that 22,000 municipal government are ready to install Linux.
This is the similar situational turn as China had followed earlier by building their customized Operating System named NeoKylin that underline the presence of National Internet Identity across the cyberspace.
Foreign Companies are Threat to National Security
Google track everything, responds to 32,000 requests a year from US agencies but it won’t answer one from Russia, according to Klimenko.
It seems that both the nations are unhappy with the worldwide surveillance programs conducted by the US intelligence agency NSA and its British counterpart GCHQ which indulge into one’s private life.
“We have to consider this as a kind of potential threat to our national security,” he said.
This stringent movement would put an end to the foreign snooping programs which is a major concern for the Millions and also would draw a Green Arrow vertically in the Russian Stock Exchange.
As Russia is getting inspired from China, as they have started to mark their signature in many diversified fields such as:-
The shipment of their own manufactured SmartPhone “Xiaomi” to many countries.
Implementing a Great Firewall.
Weibo, a Social Networking service which had reached beyond 100 million active users.
Baidu Search Engine.
And many more...
Kicking Off: A Feasible Option?
Kicking off foreign technologies from the nation would raise the eyebrows of many, as today's intended world is being linked via wires to achieve the connectivity and maintain a healthy relationships with the foreign counterparts.
“The way it’s done in North Korea or China with its firewall probably doesn’t fit us, but it’s only a matter of time,” Klimenko said. “It won’t be fatal if Google leaves Russia -- Yandex and Mail.ru have similar technologies.”
Keeping Espionage apart, the proposed plan would hinder the future unified developments which could benefit the nation.
If every country would follow the same crooked path, then our Mother Earth would not be different from other lifeless planets as all are being isolated in their boundaries.
Let's see what other demands are cooking up in the mind of Russia's new Internet Tsar!
Misconfigured MongoDB allowed manipulation of a Microsoft’s career portal
15.2.2016 Safety
A security expert discovered a misconfigured MongoDB installation behind a Microsoft’s career portal that exposed visitors to attacks.
The security expert Chris Vickery has discovered a new misconfigured MongoDB installation used by a Microsoft’s career portal. The misconfigured MongoDB installation exposed some information and enabled read/write access to the website.
The database also included information on other companies. The database, which is maintained by Punchkick Interactive, a mobile development company hired by Microsoft to manage the m.careersatmicrosoft.com, was promptly secured.
“Microsoft relies on Punchkick to handle the database that powers m.careersatmicrosoft.com. The bad news is that, for at least the past few weeks, this backend database has been exposed to the open internet and required no authentication at all to access.” Vickery wrote in a post published on the MacKeeper blog.
Vickery reported the issue to Microsoft on February 5, as proof of its severity he included a screenshot showing the name, email address, password hash, and issued tokens for Microsoft’s Global Employment Brand Marketing Manager, Karrie Shepro. Punchkick fixed the issue in just an hour.
“The good news is that as of February 5th, following my disclosure of the vulnerability to Punchkick and Microsoft, everything has been secured.”

The misconfigured database could be exploited by hackers to inject malicious code in the web pages used for the job listings and run watering hole attacks.
“The ability to craft arbitrary HTML into an official Microsoft careers webpage is, to say the least, a powerful find for a would-be malicious hacker. This situation is the classic definition of a potential watering hole attack.” Vickery added.
An attacker can use malicious exploit kits to compromise vulnerable visitors’ machines or run a phishing campaign against people searching for a job opportunity at Microsoft.
“In that scenario, any number of browser exploits could be launched against unsuspecting job-seekers. It would also be a fantastic phishing opportunity, as people seeking jobs at Microsoft probably tend to have higher value credentials,” Vickery added.
This incident demonstrates once again the importance of a proper security posture and the efficiency of the patch management process implemented by a company, even when dealing with third-party services.
Microsoft Edge's InPrivate Mode Finally Keeps Your Activity Private
12.2.2016 Safety
Microsoft Edge's InPrivate Mode Finally Keeps Your Activity Private
Browsing the Web in 'Private Mode' is not as private as you think.
Microsoft has patched the Private Browsing Leakage bug in its newest Edge browser with the latest update.
When we talk about Browsers, only one thing which does not strike our mind is Internet Explorer or IE.
Even there were some trolls on Internet Explorer (IE) waving over the social medias such as "The best web browser to download other browsers."
In fact, it was justified as everyone downloads a new browser with IE in their newly installed Operating System.
Due to the continual taunts, Microsoft had scrapped the entire IE and made a new browser called "Edge Browser" (Codenamed "Spartan").
Edge was shipped as the default browser (along with IE) with Windows 10 devices and grabbed the attention of many eye pupils as it included all the features that other mainstream browsers have.
Well, History Repeats Itself
In January this year, it was reported that 'InPrivate' mode of the Edge browser is leaking users' web browsing data.
The InPrivate mode is nothing but Incognito or private support for Windows 10. It has been found storing your browsing history, cookies and cache in a WebCache file on the system, which could be found easily.
Precisely here:
\Users\user_name\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat
This issue made users feel a repulsive force again and they instantly switched back to other browsers like Firefox or Chrome as the protocols of private browsing mode was correctly followed.
The reported vulnerability was fixed which was included in the update KB 3135174.
The patch update listed as "Fixed issue with Microsoft Edge browser caching visited URLs while using InPrivate browsing."
Microsoft: Windows 10, Edge So Secure They Don't Need EMET
In another statement made by Microsoft, the company officially claimed that its Edge Browser is much more secure than any other browsers and does not need the support of any armour like EMET anymore.
Enhanced Mitigation Experience Toolkit (EMET) is a Windows tool that shields against the execution of software vulnerabilities in Windows Environment.
As of now, Windows had buried a security hole, but let's see what's more coming from the same family.
Deep Web Search Engines to Explore the Hidden Internet
11.2.2016 Safety
Do you know: There is a vast section of the Internet which is hidden and not accessible through regular search engines and web browsers.
This part of the Internet is known as the Deep Web, and it is about 500 times the size of the Web that we know.
What is DEEP WEB?
Deep Web is referred to the data which are not indexed by any standard search engine such as Google or Yahoo.
The 'Deep Web' refers to all web pages that search engines cannot find, such as user databases, registration-required web forums, webmail pages, and pages behind paywalls.
Then, there's the Dark Web or Dark Net – a specific part of that hidden Deep Web.
Deep Web and Dark Web are the intriguing topics for the Netizens all around. But when you hear the term 'Deep Web' or 'Dark Web,' you usually categorize them into one.
If yes, then you are wrong.
What is DARK WEB?
Dark Web is where you can operate without been tracked, maintaining total anonymity.
The Dark Web is much smaller than the Deep Web and is made up of all different kinds of websites that sell drugs, weapons and even hire assassins.
These are hidden networks avoiding their presence on the Surface Web, and its URLs are tailed up with .onion.
These [websitename].onion domains are not indexed by regular search engines, so you can only access Dark Web with special software -- called 'The Onion Browser,' referred to as TOR.
TOR is free, and anyone can download it.
Many of us heard about the Dark Web when the largest online underground marketplace Silk Road was taken down following an investigation by United States federal authorities.
But, what if, you can still be able to dig the Darknet contents with your regular browsers, without the need of TOR?
Here's How to Surf & Search the Deep Web without TOR
Solution: Deep Web Search Engines
Search engines like Google are incredibly powerful, but they can't crawl and index the vast amount of data that is not hyperlinked or accessed via public DNS services.
However, there are Deep Web Search Engines that crawl over the TOR network and bring the same result to your regular browser.
Some of such Dark Web Search Engines are:
Onion.City
Onion.to
Not Evil
Memex Deep Web Search Engine
Here are some Deep Web Search Engines:
The WWW Virtual Library
Collection of Deep Web Research Tools
Surfwax
IceRocket
Stumpedia
Freebase
TechDeepWeb
These Deep Web search engines talks to the onion service via Tor and relays, resolve the .onion links and then deliver the final output to your regular browser on the ordinary World Wide Web.
However, there is one consequence of browsing Deep or Dark Web on a regular browser. Working this way will make these .onion search results visible to you, me, and also, for Google.
Moreover, tracker-less search engines are also popular in the TOR culture – like Disconnect, DDG, IXQuick – which ensures your privacy searches.
Importance of TOR
It is worth noting that mere access via TOR is not considered as an illegal practice but can arouse suspicion with the law.
TOR has long been used by Journalists, Researchers, or Thrill seekers in heavily censored countries in order to hide their web browsing habits and physical location, crawl the Deep Web and exchange information anonymously.
However, one of the main reasons behind the rise of TOR is NSA's Surveillance Programs.
After the Assange-Snowden revelations in the past years, public fears about their privacy getting compromised over the Internet.
The reliability of the Internet had been lost that demanded the Ciphers come into action to thwart the Federal Agency's efforts. So comes the need of TOR.
With the help of TOR, the web users could roam around the Internet beyond any fear, keeping themselves and their real identities hidden from federal and intelligent agencies.
This is why TOR is being one of the favorite targets of federal agencies.
Since Tor has long been a target of the government intelligence agencies, most online users do not feel safe to use Tor anymore.
To known how easy it is for government agencies to unmask Tor users, you can read these articles:
How Spies Could Unmask Tor Users without Cracking Encryption
How Hacking Team and FBI planned to Unmask A Tor User
Who lurks in the 'Dark Web'?
According to the recent survey conducted by researchers Daniel Moore and Thomas Rid (in their book Cryptopolitik and the Darknet), it is found that 57% of the Dark Web is occupied by unauthorized contents like Pornography, Illicit Finances, Drug Hub, Weapon Trafficking, counterfeit currency flow and many more.
The netizens had given the shade of illegalities to Dark Web. This is why today Dark Web is being defined as something that is illegal instead of a 'Pool of Information.'
However, there are countless reasons to use Dark Web. But, ultimately, it depends on the surfer what to surf?
Sidelining Darkweb for criminal offenses often gray out the legitimate purposes inside Dark Web.
In the end, I just want to say:
Knowledge is Free! Happy Surfing!
Australian NSW Government Department of Resources and Energy under attack. Is it Chinese cyber espionage?
5.2.2016 Safety
According to the NSW Government Department of Resources and Energy Chinese hackers have launched a malware-based attack on its network in December.
The Australian NSW Government Department of Resources and Energy revealed that in December 2015 unknown hackers targeted its systems. In the same period, the organization was launching a number of important projects, including a project of the Shenhua Watermark coal mine.
The project for the Shenhua Watermark coal mine has been estimated in $1.2 billion and indirectly involves the Chinese government, a circumstance that lead the experts in believing that Chinese-nation state hackers may have launched the attack for intelligence purpose.
“In December 2015, NSW Department of Industry IT security systems detected a marked increase in virus/security activity attempting to impact systems at the Division of Resources and Energy (DRE) office in Maitland. The attacks were identified by specialist software we have in place to detect breaches to our firewalls. Given the increased levels of activity we took further steps to ensure that our systems were protected. We do not believe that the attacks penetrated our systems or any data was accessed at this time.
The attack was in the form of an increase in “virus/security activity attempting to impact systems at the Division of Resources and Energy (DRE) office in Maitland”, states the NSW Government Department of Resources and Energy in an official announcement. and steps were taken to increase security after the activity was detected.
The hackers coordinated a malware-based attack to hack into the Department’s network, the organizations already announced that steps were taken to increase security in response to the offensive.
NSW Government Department of Resources and Energy Chinese HACKERS
It is not clear if the hackers successfully breached the network at the NSW Government Department of Resources and Energy, the New South Wales Opposition is calling for further investigation despite the officers believe that no data has been exfiltrated by the hackers.
“These reports are highly disturbing. I have sought a briefing from the minister and his agency as soon as possible. The Opposition will be seeking an assurance from the Baird Government that the integrity of the commercially sensitive data held by the Department of Industry has not been compromised.” declared the Australian politician Adam Searle to the ABC’s The World Today.
The experts speculate the involvement of Chinese hackers, the government of Bejing is considered responsible for a large number of cyber espionage operation worldwide.
“Well you don’t always know if you’ve been compromised in terms of cyber attack, so I think perhaps a more accurate way to put it would be to say they don’t think they’ve been compromised on this occasion. But if it’s like many other areas of government, they will be under constant attack, there will be sort of daily probes, hourly probes on the part of malicious cyber actors looking for vulnerabilities. ” added Peter Jennings, the executive director of the Australia Strategic Policy Institute.
“I think it is possible because we know China has one of the most aggressive cyber intelligence gathering policies around the world and that they are constantly looking to gather information, intellectual property, from the private sector as well as national security information from government departments.” “And in the case of Australia, obviously China has a deep interest in our approach to natural resources.”
In December, Chinese hackers have conducted another major attack on a supercomputer operated by Australia’s Bureau of Meteorology (BoM). The news was disclosed by the Australian Broadcasting Corporation (ABC). The Bureau of Meteorology is Australia’s national weather, climate and water agency, it is the analog of the USA’s National Weather Service.
“China is being blamed for a major cyber attack on the computers at the Bureau of Meteorology, which has compromised sensitive systems across the Federal Government.” states the ABC. “The bureau owns one of Australia’s largest supercomputers and provides critical information to a host of agencies. Its systems straddle the nation, including one link into the Department of Defence at Russell Offices in Canberra.”
The systems at the Bureau of Meteorology elaborate a huge quantity of information and weather data that are provided to various industries, including the military one.
Europol, a new move against terrorism and money laundering
4.2.2016 Safety
The Europol is increasing its efforts against terrorism, it has joined forces with EU to fight terrorist financing and money laundering.
Since 1 January 2016, Europol has increased the level of integration among the nodes of the decentralised computer network of the European Union Member States’ Financial Intelligence Units (FIUs), the FIU.net.
“FIU.NET is a decentralised computer network supporting the FIUs in the European Union in their fight against Money Laundering and Terrorist Financing. Decentralised meaning, that there is no central database in one specific Member State where all the exchanged data is stored. When sending the information from one FIU to another, the exchanged data is only and safely stored on the FIU.NET databases at the premises of the FIUs involved in the exchange.” states the description on the website of the FIU network.
The initiative wants to create more synergy between financial and criminal intelligence agencies in the EU, a measure necessary to fight the constant growth of the criminal syndicates and the terrorism in Europe.
“Under the auspices of the EU FIU platform and the renewed provisions set in the IV anti-money laundering Directive, the embedment of FIU.net into Europol aims to create more synergy between financial and criminal intelligence, ultimately boosting efforts to fighting organised crime and terrorism in the EU.” states the official announcement issued by the Europol.
FIU.net was established in 2002 and was co-financed until 2015 by the European Commission, it is an organism created to monitor money laundering activities and terrorist financing. Its pillar is the information sharing between the Financial Intelligence Units. Each FIU has the task to monitor on financial transactions, in particular every transfer of money from entities in different states.
The implementation of a decentralised network implies that only the information shared between two Financial Intelligence Units is securely stored in the FIU.net databases.
europol rob wainwright
The decision to embedment of FIU.net network in the Europol will enhance the exchange of financial intelligence. The information managed by the FIU.net architecture could be integrated with data managed by the Europol.
This is an important step against crime and terrorism, data from financial intelligence could be integrated with information related criminal intelligence activity conducted by the Europol, an important knowledge sustained with data provided by the Law Enforcement agencies of the EU countries.
“Thanks to the analytical capacities of Europol the suspicious money flows and their links to on-going terrorist and criminal activities can be further investigated. The FIU.net exchange platform will join other key Europol’s tools in the field such as the Terrorist Finance Tracking Program (TFTP), the Focal Point Sustrans (support to anti-money laundering investigations) and the network of the EU Asset Recovery Offices (AROs).” continues the Europol.
The decision of joining the efforts against terrorist financing activities is a necessary step to respond threats even more dangerous for every country in the EU and that are assuming a global connotation.
A week ago the director of Europol, Rob Wainwright, announced a new European Counter Terrorism Centre (ECTC) opening this month to fight the terrorism, it is easy to predict that this new structure will benefit also of the new strategic alliance.
0 1 2






















