
Safety Articles - H 2020 1 2 3 4 5 6 Safety List - H 2021 2020 2019 2018 1 Safety blog Safety blog
The Mistakes of Smart Medicine
6.4.2017 Kaspersky Safety
As numerous studies have shown, smart houses, smart cars, and smart cities are undeniably beneficial to people in everyday life, but quite often can become a threat to their safety. It is not only a matter of personal data leakage. Just imagine that, for example, a smart refrigerator, affected by a third party at one point or another, would begin identifying expired products as fresh. There is yet another more dismal scenario: the system of a smart car turns the vehicle to the right at high speed, catching the driver unaware…
However, both existing and predictable threats that emerge from home IoT devices are only part of the problem related to the infrastructure around us becoming “smarter”. A technological boom in medicine both encouraged medical institutions to use exclusively information systems in processing data and led to the emergence of new types of technological equipment and personal devices that can be used to interact with traditional systems and networks. This means that the threats that are relevant for them can also be relevant for medical systems.
Entry Points for Accessing Valuable Data
For the medical industry, the main attack vector is related to personal data and information on the health condition of patients. The first step in evaluating the security level for data is identifying entry points within the infrastructure of medical institutions where healthcare data can be collected, stored, and/or taken advantage of by an evildoer.
Possible entry points can be classified as follows:
information systems on the computer network of a medical institution (servers, workstations, admin panels for medical equipment, etc.) that access the Internet;
medical equipment that is connected to an enterprise network;
medical equipment that is not a network node but connects to a workstation (for example, via USB);
portable devices of patients (advanced fitness trackers, pacemakers and cardiac monitors, insulin pumps, etc.) and mobile devices that can track health indicators (mobile smartphones and smart watches);
other wireless information systems (Wi-Fi, Bluetooth, or RF), which can be mobile ECG devices, pulse oximeters, event monitors for tracking the medical condition of high-risk patients, and so on.
For the last three classes mentioned above, a detailed first-hand analysis of specific models related to these classes is required. It is for exactly this reason that those devices deserve an article of their own. For now, we will focus on devices and their components that do not require physical access and are frequently accessible from the Internet.
Portable Devices May Port Medical Histories
We’ve already written the following about the security of portable devices in March of 2015: “Just imagine, if a fitness tracker with a heart-rate monitor is hacked, then any shop owner will be able to track the heart rate of buyers as they look at discounts in the shop. The influence of advertisements on people can be learned in the same manner. Moreover, a hacked fitness tracker with a heart-rate monitor can be used as a lie detector.”
Owing to the increasing accuracy of sensors, gadgets that collect data on the health condition of their owners can potentially be used in serious ambulatory care to assess a patient’s health. However, the level of security for these gadgets has not been developing as fast as their capabilities.
Tracking vital signs with the help of mobile devices may become an integral part of ambulatory care in the nearest future
Information that is collected by tracking vital signs can be used by both the owner of the device and the vendor of the infrastructure that the tracking app operates on. For users, the heart-rate parameter can signify that a certain activity should be decreased, specific medicines should be taken, etc., while vendors can send collected data to medical companies that can use it to assess the overall health of the client.
Thus, the main advantage of data collected by a gadget is not the depth of its analysis (any medical examination will yield more accurate results than readings from a fitness tracker) but the ability to evaluate changes in a patient’s health condition dynamically. Scenarios for using the information are limited by the imagination and enterprise of the owner, as well as by laws related to personal data.
If we look at the same piece of information from the perspective of a cybercriminal, then an owner of such a device will have not the most favorable outlook – analysis of certain parameters (for example, heart rate, sleep quality, or average ADL score) allows a criminal to gain an overview of a victim’s health. Any additional information may be provided by a gadget that is connected to the mobile device and is capable, for instance, of measuring the blood pressure or blood sugar levels of its user. After making conclusions about the ailments of a victim, an evildoer can provoke their aggravation.
Attacks to obtain health data can be divided into three basic types: those that violate data privacy, those that compromise data integrity, and those that attack data availability. Main vectors can be defined for each of those.
Types of attack that violate the privacy of medical data:
man-in-the-middle attacks on a sensor channel between the sensor and the service that stores the sensor’s data;
unauthorized access to local and remote data storage.
Types of attacks on data integrity:
unauthorized access to data storage with possible data substitution;
man-in-the-middle spoofing attacks on channels in order to substitute transmitted data;
modification (substitution) of data (spoofing attacks) and their transmission to consumers (as a service that stores data or an app).
Attacks on availability:
ransomware attacks (encryption/deletion of user data).
Entry points for malicious code that commits theft or substitutes data on a mobile device depend on a specific combination of device and software.
Online Medical Data
Yet, I would like to review another entry point in detail – information systems on a medical institution’s network that are accessible from the Internet.
Medical institutions utilize automated healthcare data storage solutions, which store miscellaneous information about patients (diagnosis results, information about prescribed drugs, medical histories, etc.). The infrastructure of such a system may include various hardware and software components, which can be merged into data storage networks and can be accessible from the Internet in one form or another.
Regarding solutions for storage of healthcare data, several software packages, which can be exploited as entry points into medical infrastructure, can be given as examples.
Hospital information systems (HISs) are software packages that control medical information coming from various sources, including the systems mentioned below.
Electronic Health Records (EHR) systems are dedicated software that enable storage of structured patient data and documentation of patient medical history.
Network-attached storage (NAS) refers to dedicated network storage devices, which can be both specialized devices for storing healthcare data or enterprise devices employed in the medical-institution
DICOM-complaint (Digital Imaging and Communications in Medicine) devices and PACS (picture archiving and communication system) servers are medical information systems based on the DICOM standard and include the following components:
a DICOM client, which is a medical device that is capable of transmitting data to a DICOM server;
a DICOM server, which is a hardware and software package that provides for the receipt and storage of data from clients (in particular, these devices can be PACS servers);
a DICOM diagnostic workstation and DICOM printers, both of which are hardware and software packages that are responsible for processing, visualizing, and printing medical images.
A key feature of the above-mentioned systems is a web interface (a web app) that is used to control them over the Internet. A web interface may have vulnerabilities that can be exploited by an evildoer, who can gain access to valuable information and processes. It is worth reviewing these systems in detail and verifying whether they are accessible from the Internet, i.e. if they are a potential entry point for evildoers.
Electronic Health Records (EHR)
In order to evaluate the number of apps that are available from the outside (from the Internet) and can work with EHR, a list of software employed in these tasks should be created and then a dork list should be organized. Dorks are special search-engine queries that are aimed at finding web components of required software among all of the resources indexed by a search engine.
Here is an example of a dork query that uses Google to search for the login form of EHR software components:
intitle:”<vendor_name> Login” & inurl:<vendor name>
The example of a discovered web component (a login form) of software that is intended to work with EHR
It should be noted that some of the resources found in the search results turned out to be traps for evildoers (honeypots). This fact alone indicates that analysts are seeking to track threats related to medical infrastructure. To check if an identified resource is a honeypot, an IP address should be submitted to a special service, HoneyScore, which, by scanning a number of the resource’s attributes (for example, the hosting provider), reaches a verdict on whether or not the resource is a honeypot. Nevertheless, a significant part of the discovered resources is represented by actual systems.
126 discovered resources that meet the search criteria
Each of the discovered web resources is a potential entry point that can be exploited by an evildoer to access the infrastructure. For example, many discovered systems lack protection against an exhaustive password search, which means that a criminal can use brute-force attacks. Then, by using a hacked account, the evildoer can gain privileged access to the system through the interface or find or exploit online vulnerabilities in order to access the system in the future.
An example of a discovered web interface for logging into an EHR system
Hospital Information Systems (HISs)
A “hospital information system” is quite a vast notion that includes a set of methods and technologies for processing medical information. In our case, we are interested only in the HIS components that have a web interface for controlling and visualizing medical information.
Let’s consider the software of OpenEMR as an example. This software is used in medical institutions as a medical-data management solution, and it is certified by the Office of the National Coordinator for Health Information Technology (ONC). Some of its components are written in the PHP programming language, which means that a potential entry point for an evildoer can be a web server that maintains these OpenEMR components.
The next Google dork query returned 106 search results that meet the following criterion:
inurl:”/interface/login/login_frame.php” intitle:”Login” intext:”Username:”
After a quick analysis of the search results, it became obvious that components of the majority of the discovered OpenEMR systems have vulnerabilities, including some critical ones. This means that these vulnerabilities open up the OpenEMR database to being compromised. This comes with the fact that exploits for the discovered vulnerabilities are publicly available.
An example of a vulnerable HIS that was openly exposed
For example, analyzing different software versions revealed that information had been published on the vulnerabilities for the vast majority of software installed on the hosts.
OpenEMR version Number of hosts (%) Availability of public exploits
4.2.0 31,4 Yes
4.1.2 14,3 Yes
4.1.0 11,4 Yes
4.2.1 5,7 No
4.0.0 5,7 Yes
4.1.1 2,8 Yes
4.3.1-dev 2,8 No
2.8.3 2,8 Yes
3.2.0 2,8 Yes
Proprietary (modified) version 8,5 –
Unknown version 11,4 –
Network Attached Storage (NAS)
There are at least two types of NAS servers that have been used by medical institutions: dedicated “medical” NAS servers and common ones. While the former have strict security requirements for the data stored on them (for example, compliance with the Health Insurance Portability and Accountability Act), the security of the latter rests on the conscience of their developers and the medical institutions that use this type of NAS in their infrastructure. As a result, non-medical NAS may be left working without any updates for years and thus gather a great number of known vulnerabilities.
A list of dorks should be created to select NAS devices located in medical institutions out of all of the other devices indexed by search engines.
The next query is for the Censys search engine, which specializes in indexing devices with IP addresses and finds all of the devices (workstations, servers, routers, NAS servers, etc.) that belong to companies whose names contain words that directly or indirectly define these companies as medical institutions (“healthcare”, “clinic”, “hospital”, and “medical”):
autonomous_system.organization: (hospital or clinic or medical or healthcare)
The Censys search engine found approximately 21,278 hosts that are related to medical institutions
The Censys report, which is shown below, lists the top 10 countries where these hosts are located.
Country Hosts
United States 18 926
Canada 1113
Iran 441
Saudi Arabia 379
Republic of Korea 135
Australia 81
Thailand 33
United Kingdom 32
Puerto Rico 28
Vietnam 27
Afterward, only those hosts that are FTP servers can be taken out from the search results that contain the hosts. In order to do this, the query in the search engine should be more specific and, for example, only the hosts that contain an open FTP port and whose banners contain the “FTP” line should be searched for (this is the information that a server sends to a client during attempts to connect to its port):
(tags: ftp) and autonomous_system.organization: (health or clinic or medical or healthcare)
The search results displayed 1,094 hosts with operational FTP servers, which presumably belong to medical institutions.
Additionally, a list of vendor-specific NAS devices can be obtained from the narrowed-down search results. For this, the typical characteristics of a device must be known. These may be included in responses from services that are active on the device (for example, an FTP-server response to a connection attempt may contain the name of the device and its firmware version). The next query allows for selection of only those hosts that contain the “NAS” line in their banner (generally, several QNAP Systems models have this property) from all found hosts:
(metadata.description: nas) and autonomous_system.organization: (health or clinic or medical or healthcare)
The discovered QNAP Systems NAS servers that belong to medical organizations
A ProFTPd web-server release that has vulnerabilities was installed on each of the found NAS. For this release, there is also publicly available and easily accessible information about its exploits.
PACS Servers and DICOM Devices
The most common type of devices that utilize the DICOM format are PACS servers that print patient images that have been received from other DICOM devices.
It is possible to enter the following primitive query in the Shodan search engine to start searching for DICOM devices:
DICOM port:104
Accordingly, the search results will display hosts (mostly workstations and servers) that are used in medical institutions for storing and processing patient DICOM images.
The list of hosts that are used to process/store DICOM images
Also, it might be worth searching for diagnostic DICOM workstations, which are dedicated PACS systems used for processing, diagnosing, and visualizing data. As an example, the following query for the Censys search engine can be used:
pacs and autonomous_system.organization: (hospital or clinic or medical or healthcare)
Analysis of the search results may reveal dedicated software for a diagnostic workstation.
The login forms of diagnostic workstations used for visualization of patient data
Aside from that, there are also admin panels used to access DICOM servers in the search results.
A login form for accessing a DICOM server
Non-medical Systems with “Pathologies”
The systems described above handle valuable medical data. Therefore, security requirements for those systems must be high. However, let’s not forget that besides potential entry points, there are dozens of other points an evildoer can use that are not directly related to medical systems but are located in the infrastructure along with valuable data.
Here are several examples of non-medical systems that can be used as a potential entry point into a computer network with the goal of subsequently moving on to resources where medical information is stored:
any servers (web servers, FTP servers, e-mail servers, etc.) that are connected to the network of an institution and are accessible from the Internet;
a medical institution’s public Wi-Fi hotspots;
office printers;
video surveillance systems;
SCADA controllers;
automated systems for controlling mechanical and electrical components of a building (building management systems, BMS).
Each of the mentioned systems may have a vulnerability that can be taken advantage of by an evildoer in order to gain access to medical infrastructure.
For example, the popularity of the Heartbleed vulnerability can be evaluated. This requires entering the following query into the Censys search engine:
autonomous_system.organization: (hospital or clinic or medical or healthcare) and 443.https.heartbleed.heartbleed_vulnerable: 1
The search engine showed 66 hosts that met the criteria and were potentially vulnerable to Heartbleed. Additionally, this was after the existence of the vulnerability, and its dangers had been given wide coverage by the mass media. Generally speaking, when referring to Heartbleed, it should be noted that the problem is global in nature. According to a report by the founder of Shodan, approximately 200,000 websites still remain vulnerable.
Stay Healthy
In order keep evildoers from stealing medical data from institutions, we, along with taking essential security measures typical for enterprise infrastructure, recommend doing the following:
exclude from external access all of the information systems that process medical data or any other patient-related data;
all of the medical equipment that connects to a workstation (or is a network node) should be isolated in a dedicated segment, while the operational parameters of the equipment can be modified by using the workstation (or remotely);
any online information systems should be isolated in a “demilitarized” zone or completely excluded from an enterprise network;
continuously monitor medical-system software for updates and update software regularly;
change default passwords that are set up for the login forms of medical systems and delete unwanted accounts from the database (for example, test accounts);
create strong passwords for all accounts.
Google Announces New Accounts Sign-in Rules
4.4.2017 securityweek Safety
Google on Monday announced the rollout of a new Accounts sign-in page and of a series of updates to the policies that 3rd-party Single Sign-On (SSO) providers should comply with.
Starting on April 5, 2017, users will benefit from an updated experience when securely signing into their accounts, courtesy of a new Google Accounts login page. The new design, Google says, is meant to make the browser login experience consistent across computers, phones and tablets.
This change, Google also announced, is expected to impact organizations that use third-party applications within their networks, as well as those using a third-party SSO provider. “We recommend contacting your developer(s) or SSO provider to see if any updates are necessary,” Google says.
In a separate announcement, the Internet giant revealed that the changes affect Google and 3rd-party applications on iOS, mobile browsers on iOS and Android, and web browsers (Chrome, Firefox and other modern browsers).
Starting April 5, users of 3rd-party SSO providers will be better informed on the account they’re authenticating as well as the permissions they’re granting to applications. Android applications using the standard authentication libraries are already prompting users to select appropriate account information, meaning that these changes won’t impact them as well, the company reveals.
“It’s important that your users are presented with account information and credential consent, and apps should make this process easy and clear. One new change that you may now see is that only non-standard permission requests will be presented in the secondary consent screen in your application,” Google explains.
At the moment, app permissions requested by an application are displayed together, but users should have greater visibility into permissions being requested beyond the standard “email address” and “profile” consent, Google says. If additional permissions are requested by the app, a secondary consent screen is displayed.
Users will also have greater visibility into the 3rd-party application’s name and will also be able to click-through to get the developer’s contact information. Thus, application developers should use public-facing email addresses so that users could easily contact them for support or assistance.
“If your application may also be used by G Suite customers that employ a 3rd-party Single Sign-On (SSO) service, we recommend that you utilize the hd and/or login_hint parameters, if applicable. Even with the changes to the 3rd-party SSO auth flow, these parameters will be respected if provided. You can review the OpenID Connect page in the documentation for more information,” Google also notes.
G Suite users may notice redirection when signing into 3rd-party SSO providers as well. When no accounts are signed in, the user will be prompted to confirm the account after signing in to the 3rd-party SSO provider, which is meant to ensure that they’re signed in with the correct G Suite account. Users automatically opt into “email address” and “profile” consent, but will be redirected back to the application once they consent to any additional non-standard permissions that may be requested.
If the user is already signed in to one or more accounts matching the hd hint, the Account Chooser will display all the accounts and the user will have to select the appropriate G Suite account. Next, the user will be redirected to the 3rd-party SSO provider, then back to the application.
Symantec API Flaws reportedly let attackers steal Private SSL Keys and Certificates
28.3.2017 thehackernews Safety
A security researcher has disclosed critical issues in the processes and third-party API used by Symantec certificate resellers to deliver and manage Symantec SSL certificates.
The flaw, discovered by Chris Byrne, an information security consultant and instructor for Cloud Harmonics, could allow an unauthenticated attacker to retrieve other persons' SSL certificates, including public and private keys, as well as to reissue or revoke those certificates.
Even without revoking and reissuing a certificate, attackers can conduct "man-in-the-middle" attack over the secure connections using stolen SSL certs, tricking users into believing they are on a legitimate site when in fact their SSL traffic is being secretly tampered with and intercepted.
"All you had to do was click a link sent in [an] email, and you could retrieve a cert, revoke a cert, and re-issue a cert," Byrne wrote in a Facebook post published over the weekend.
Symantec knew of API Flaws Since 2015
Byrne said he first discovered the issues surrounding Symantec certificates in 2015 and agreed to "limited non-disclosure," as Symantec said the company would take nearly two years to fix the problems.
"Symantec committed to finding and replacing all of the certificates which MAY have been impacted, and then replace them... that they would do so within six months for every cert they could identify, and within two years for every cert period," Byrne said.
The researcher did not disclose any details to the public until last week when Google disclosed its plan to gradually distrust Symantec-issued certificates inside Google Chrome after discovering several issues with the company and four of its third-party cert resellers.
"Given Google's experience and actions here, it appears that Symantec did not fix these issues as they committed to," Byrne said.
However, Byrne was not able to verify that the vulnerability he found were exactly the same issue Google engineers disclosed last week.
According to Byrne, the certificate request and delivery API Symantec provides to its third-party resellers accept URI-based UIDs "without proper authentication, or in some cases, any authentication at all."
Since the API server didn't authenticate users prior to accessing certificate information, any potential tech-savvy customer could have easily intercepted an email containing the API-generated link or took their own UID and modified one of its parameters.
This would have, eventually, allowed the malicious attacker to access information on other Symantec customers, identifying high-value targets, and perform automated attacks.
Gaining Full Control Over Another User's SSL Certificates
Using the same API vulnerabilities, the attacker could have even gained full control over another customer's certificates, which includes obtaining public and private keys, revoking certs, or reissuing certs with new passphrases.
Currently, neither the researcher nor the company has discovered any evidence to prove such a scenario, but the possibility alone was enough for Byrne when considering disclosure.
"It would then be trivial to compromise DNS for a particular organization or person they wanted to attack. At that point, they could pretend to be that person's bank, their credit card company, their employer, anyone," Byrne added.
"Perhaps the worst compromise would be to spoof a patch and update server, for an entire company. Then every single machine at that company could be compromised simultaneously."
According to the researcher, Symantec has since fixed some of the issues, but not all. We have reached out to Symantec, and will update the story as soon as we hear back from the company.
Symantec has not yet responded to the Byrne's disclosure, though the company has recently published two blog posts accusing Google of "exaggerated and misleading" claims the search engine made last month regarding its CAs.
Google Stops Trusting Symantec-Issued Certificates
24.3.2017 securityweek Safety
Google is displeased with the fact that Symantec has failed to ensure that its partners don’t improperly issue digital certificates, which is why the tech giant has announced its intent to gradually stop trusting all of the company’s existing certificates in Chrome.
Symantec, and particularly some of its subsidiaries and WebTrust audited partners, have been caught by Google and others wrongly issuing certificates. In 2015, Google told Symantec to step up its game after a subsidiary certificate authority (CA) issued unauthorized google.com certificates.
More recently, Symantec’s GeoTrust and Thawte were found to have wrongly issued more than 100 certificates, including for domains such as test.com and example.com.
According to Google software engineer Ryan Sleevi, an investigation revealed that Symantec’s partners misissued at least 30,000 certificates in the past years. These certificates were issued by four organizations: CrossCert (Korea Electronic Certificate Authority), Certisign Certificatadora Digital, Certsuperior S. de R. L. de C.V., and Certisur S.A.
Symantec has authorized these companies to perform validation for certificate information, but failed to properly audit them, and according to the Baseline Requirements, the cybersecurity giant is liable for any issues. Another problem is that there is no way to distinguish certificates validated by Symantec from certificates validated by the company’s partners, Sleevi said.
“Despite having knowledge of these issues, Symantec has repeatedly failed to proactively disclose them. Further, even after issues have become public, Symantec failed to provide the information that the community required to assess the significance of these issues until they had been specifically questioned,” Sleevi explained. “The proposed remediation steps offered by Symantec have involved relying on known-problematic information or using practices insufficient to provide the level of assurance required under the Baseline Requirements and expected by the Chrome Root CA Policy.”
As a result of Symantec’s failings, Google wants to remove the recognition of Extended Validation status for certificates issued by the company, and reduce the accepted validity period for newly issued certificates to nine months or less. Under the current proposal, all existing certificates will gradually become untrusted.
Since Symantec-issued certificates account for a significant percentage of the total, Google wants the certificates to be replaced gradually in order to avoid disruptions for websites and their visitors.
Starting with Chrome 59, the maximum age of Symantec-issued certificates will be decreased to 33 months and by Chrome 64 it will be reduced to 9 months.
Symantec said it strongly objects to Google’s decision, and called the action unexpected and the announcement irresponsible. The company said it hopes Google did not intend to create uncertainty and doubt within the community about its SSL/TLS certificates. Symantec's statement reads:
Google’s statements about our issuance practices and the scope of our past mis-issuances are exaggerated and misleading. For example, Google’s claim that we have mis-issued 30,000 SSL/TLS certificates is not true. In the event Google is referring to, 127 certificates – not 30,000 – were identified as mis-issued, and they resulted in no consumer harm. We have taken extensive remediation measures to correct this situation, immediately terminated the involved partner’s appointment as a registration authority (RA), and in a move to strengthen the trust of Symantec-issued SSL/TLS certificates, announced the discontinuation of our RA program. This control enhancement is an important move that other public certificate authorities (CAs) have not yet followed.
While all major CAs have experienced SSL/TLS certificate mis-issuance events, Google has singled out the Symantec Certificate Authority in its proposal even though the mis-issuance event identified in Google’s blog post involved several CAs.
We operate our CA in accordance with industry standards. We maintain extensive controls over our SSL/TLS certificate issuance processes and we work to continually strengthen our CA practices. We have substantially invested in, and remain committed to, the security of the Internet. Symantec has publicly and strongly committed to Certificate Transparency (CT) logging for Symantec certificates and is one of the few CAs that hosts its own CT servers. Symantec has also been a champion of Certification Authority Authorization (CAA), and has asked the CA/Browser Forum for a rule change to require that all certificate authorities explicitly support CAA. Our most recent contribution to the CA ecosystem includes the creation of Encryption Everywhere, our freemium program, to create widespread adoption of encrypted websites.
We want to reassure our customers and all consumers that they can continue to trust Symantec SSL/TLS certificates. Symantec will vigorously defend the safe and productive use of the Internet, including minimizing any potential disruption caused by the proposal in Google’s blog post.
We are open to discussing the matter with Google in an effort to resolve the situation in the shared interests of our joint customers and partners.
Google Chrome to Distrust Symantec SSLs for Mis-issuing 30,000 EV Certificates
24.3.2017 thehackernews Safety
google-symantec-ssl-certificate
Google announced its plans to punish Symantec by gradually distrusting its SSL certificates after the company was caught improperly issuing 30,000 Extended Validation (EV) certificates over the past few years.
The Extended Validation (EV) status of all certificates issued by Symantec-owned certificate authorities will no longer be recognized by the Chrome browser for at least a year until Symantec fixes its certificate issuance processes so that it can be trusted again.
Extended validation certificates are supposed to provide the highest level of trust and authentication, where before issuing a certificate, Certificate Authority must verify the requesting entity's legal existence and identity.
The move came into effect immediately after Ryan Sleevi, a software engineer on the Google Chrome team, made this announcement on Thursday in an online forum.
"This is also coupled with a series of failures following the previous set of misissued certificates from Symantec, causing us to no longer have confidence in the certificate issuance policies and practices of Symantec over the past several years," says Sleevi.
One of the important parts of the SSL ecosystem is Trust, but if CAs will not properly verifying the legal existence and identity before issuing EV certificates for domains, the credibility of those certificates would be compromised.
Google Chrome Team started its investigation on January 19 and found that the certificate issuance policies and practices of Symantec from past several years are dishonest that could threaten the integrity of the TLS system used to authenticate and secure data and connections over the Internet.
Under this move, the Google Chrome team has proposed following steps as punishment:
1. EV certificates issued by Symantec till today will be downgraded to less-secure domain-validated certs, which means Chrome browser will immediately stop displaying the name of the validated domain name holder in the address bar for a period of at least a year.
2. To limit the risk of any further misissuance, all newly-issued certificates must have validity periods of no greater than nine months (effective from Chrome 61 release) to be trusted in Google Chrome.
3. Google proposes an incremental distrust, by gradually reducing the "maximum age" of Symantec certificates over the course of several Chrome releases, requiring them to be reissued and revalidated.
Chrome 59 (Dev, Beta, Stable): 33 months validity (1023 days)
Chrome 60 (Dev, Beta, Stable): 27 months validity (837 days)
Chrome 61 (Dev, Beta, Stable): 21 months validity (651 days)
Chrome 62 (Dev, Beta, Stable): 15 months validity (465 days)
Chrome 63 (Dev, Beta): 9 months validity (279 days)
Chrome 63 (Stable): 15 months validity (465 days)
Chrome 64 (Dev, Beta, Stable): 9 months validity (279 days)
This means, starting with Chrome 64, which is expected to come out in early 2018, the Chrome browser will only trust Symantec certificates issued for nine months (279 days) or less.
Google believes this move will ensure that web developers are aware of the risk of future distrust of Symantec-issued certs, should additional misissuance events occur, while also giving them "the flexibility to continue using such certificates should it be necessary."
IBM and SecureKey Announce Blockchain-Based Identity Verification
20.3.2017 securityweek Safety
The blockchain promise took a step closer to fruition today with IBM and SecureKey making a joint announcement of a blockchain-based digital identity network.
Built on the Linux Foundation's open source Hyperledger Fabric v1.0 and the IBM Blockchain service, a new digital identity and attribute sharing network will go live in Canada later in 2017.
SecureKey Technologies is a Toronto-based identity and authentication provider. It had already decided that it didn't want to use a central broker-based system to hold identities, because that would be a huge target for hackers. Nor did it want to be in the position of handing out too much personal data to everyone who demanded it.
"Right now, I would argue a driver's license shares too much," explains Greg Wolfond, founder and CEO of SecureKey. "A girl goes to a bar, and she has to share her name, address and weight with the bouncer. That's crazy. All he needs to know is that she's over 21. How to make this work electronically we couldn’t solve well until we saw it on Hyperledger."
The new service, currently consumer-centric, will work with the trust people have in their bank. It will start in Canada, but both IBM and SecureKey intend to take it global. Leading Canadian banks, including BMO, CIBC, Desjardins, RBC, Scotiabank and TD, joined the digital identity ecosystem in October, 2016, and collectively invested $27M in SecureKey.
The result is a bank-verified identity that can be used via a mobile app provided by the bank. Users will be able to control what identifying information they share from the blockchain stored trusted credentials to the organizations of their choice, and for those organizations to quickly validate the user's identity to arrange new services. For example, once the users have proven their identity with their bank and a credit agency, they can grant permission to share only specified data with a utility to create a new account.
"What IBM is building with SecureKey and members of the digital identity ecosystem in Canada, including major banks, telecom companies and government agencies, will help tackle the toughest challenges surrounding identity," said Marie Wieck, general manager, IBM Blockchain. "This method is an entirely different approach to identity verification, and together with SecureKey, we have a head start on putting it on the blockchain. This is a prime example of the type of innovation permissioned blockchain networks can accelerate."
Personal data is one of the most highly regulated areas of computing. European laws, which will apply to European data regardless of the nationality of the data-holding organization, have two particularly difficult concepts: firstly, that only the required amount of personal data is held, and secondly, that users have a right to have that data removed.
The ability to provide only the required data for identification in each different circumstance goes a long way to satisfy the first problem. The second is, under normal circumstances, more difficult. The blockchain was originally designed to be immutable, with the effect that Europe's 'right-to-be-forgotten' could not be applied.
IBM claims to have solved this problem. Jerry Cuomo, IBM's vice-president of blockchain technologies, said that IBM has solved this problem while still adhering to Blockchain immutability. "We do have a patent pending, so I don't want to go into too much detail," he said. "But we solved it without deleting from the blockchain, which is pretty cool."
The system solves some, but not all, of the identity problems described and solved by the Global Identity Foundation's Identity 3 project. The big advantage is that it provides only the necessary elements of personal identity to prove personal identity in each instance. This is similar to Identity 3. Where it differs, however, is that the totality of the personal data is still under the control of a single organization. A basic principle of Identity 3 is 'anonymity at the root of identity'; and this clashes with the concept of bank-based verification.
It also ultimately limits the global potential of the system: individual governments will still be able to access the data. This will be of limited importance to most users where it is their own government able to access their data; but (unless solved) would prevent the expansion of the system across national borders. To expand globally, IBM and SecureKey may be forced to offer localized versions in different countries.
Identity 3's anonymity at the root of identity split across multiple verifiers solves this issue. At a technical level, Chinese Identity 3 identities could be trusted within the US, and American Identity 3 identities could be trusted in China. This is unlikely to happen with a Canada-based blockchain system.
Despite these limitations, the SecureKey IBM Blockchain solution offers huge potential. For the moment it is described as a 'consumer' solution. Over time we can expect it to expand. "You have to solve for individual identity first but then it is very applicable to businesses," Wolfond told SecurityWeek. "We are already engaging in a few projects to bring business use to life."
U.S. Warns of Security Issues With HTTPS Inspection Products
17.3.2017 securityweek Safety
The U.S. Department of Homeland Security's US-CERT has issued a new alert warning about problems with some HTTPS inspection products.
The alert, 'HTTPS Interception Weakens TLS Security (TA17-075A)' warns that "Failure [by the SSL/TLS interception software] to perform proper validation or adequately convey the validation status increases the probability that the client will fall victim to MitM attacks by malicious third parties."
This alert follows the publication earlier this month of a detailed study of the problem. The study concluded that HTTPS interception before the endpoint (such as that done by anti-virus products) can weaken rather than strengthen network security. The CERT Coordination Center (CERT/CC) first raised the issue two years ago in a blog post titled 'The Risks of SSL Inspection' -- but US-CERT has only now issued an alert.
The reason for this long delay between unofficial and official warnings is probably twofold. Firstly, the "blog post for CERT was mostly an observation based on a very small sample set of HTTPS inspection solutions that I was able to test myself," author Will Dormann, a vulnerability analyst at CERT/CC, told SecurityWeek. "It was posed as an issue that needed to be investigated, with the goal that folks with the devices in question could perform their own testing and ideally get back to us with the results."
It was, in short, a valid but not-scientific analysis of the problem. The new scientific paper, he adds, "appears to have used my blog post as motivation. But they were able to take it much further and provide some real-world statistics about the prevalence of HTTPS interception. This presumably took some time to develop and collect results."
Dormann believes that the arrival of this paper and the availability of an easy-to-use test website (badssl.com) have combined to make the time right for a US-CRERET alert.
The second motivation for the alert is the increasing use of encryption by malicious actors to bypass security defenses and to hide data exfiltration. Dell highlighted the problem in its 2016 Threat Report. At least 900 million users were affected by encrypted hacks in 2015, it said.
Industry's response has been to install HTTPS inspection software to unpack the encryption and allow traffic inspection. This interception can be found in a range of products including anti-virus, firewalls, DLP, and secure web gateways. They operate by performing the customer's own 'legal' MitM attack on the traffic -- but in doing so they break the end-to-end encryption from the trusted server to the end client.
The problem comes in how the HTTPS inspection product then attempts to provide its own 'trust' to the client -- and tests have shown that many of the products are lacking. "Many HTTPS inspection products do not properly verify the certificate chain of the server before re-encrypting and forwarding client data," warns US-CERT, "allowing the possibility of a MitM attack. Furthermore, certificate-chain verification errors are infrequently forwarded to the client, leading a client to believe that operations were performed as intended with the correct server." It adds, "Because client systems may connect to the HTTPS inspection product using strong cryptography, the user will be unaware of any weakness on the other side of the HTTPS inspection."
This leaves industry with a difficult choice: to inspect HTTPS traffic for reasons of security and risk increasing the attack surface in the process; or to leave alone and find other ways to protect against encrypted bad intent. "There are compelling business reasons for corporations to be able to 'see into' encrypted traffic flows," comments Erka Koivunen, chief information security officer at F-Secure Corporation. "For instance, financial institutions may want to extend their control into encrypted traffic flows in terms of content inspection and Data Loss Prevention. It is no wonder the vendor community is pressurized to come up with 'innovative' ways to terminate HTTPS encryption by means of MitM."
But he doesn't think using good-intentioned MitM is the answer. "The research by CERT/CC and the US-CERT advisory seem to confirm our point of view," he told SecurityWeek. "MitM'ing HTTPS traffic adds unnecessary complexity and creates a risky tradeoff between content inspection and communications security." F-Secure has chosen not to provide an HTTPS inspection capability.
"Most of the functionality can, however, be enforced at an endpoint level," he added, "and this is where F-Secure has committed to excel. We believe that endpoint security solutions will continue to play a central role in enterprise security. While the 'other endpoint' will increasingly reside in the cloud, the security stack needs to be complemented with security in the cloud."
This won't suit all organizations; particularly those that choose 'security in depth'. US-CERT recommends that whether HTTPS inspection is employed or not, organizations should take additional steps to secure communications -- and points to the earlier alert (TA15-120A): Securing End-to-End Communications. This recommends using the latest version of TLS or SSL; using certificate pinning; the use of DNS-based Authentication of Named Entities (DANE); and using network notary services.
For HTTPS inspection products, suggests US-CERT, organizations could "use badssl.com as a method of determining if their preferred HTTPS inspection product properly validates certificates and prevents connections to sites using weak cryptography."
It is true, High Tech Bridge CEO Ilia Kolochenko, told SecurityWeek, "many organizations wrongly implement HTTPS interception by forcing all their client devices to trust any certificate. In a corporate environment, this can significantly facilitate phishing and drive-by-download attacks." But, he added, "US-CERT's recommendations, as well as HPKP usage, can solve this problem in a quite reliable manner."
Privacy Guard – Let’s evaluate privacy risks caused by the apps installed on our device
16.3.2017 securityaffairs Safety
Privacy Guard is an Android app that evaluates the risks of data privacy relying on the permissions requested by the apps installed on a device.
Mobile devices collect a large volume of personal information that could be used for malicious purposes by adversaries. In order to increase the awareness of user towards the possibility of data leakage and the importance of protecting personal data stored in smartphones, we developed: ‘Privacy Guard‘.
Privacy Guard is an Android app that evaluates the risks of data privacy relying on the permissions requested by the apps installed on a device.
Privacy Guard was developed at Iswatlab (http://www.iswatlab.eu/?page_id=499), the cyber security lab of the Department of Engineering of the University of Sannio (Italy), from an idea of and under the supervision of Corrado Aaron Visaggio, which is the responsible of the lab and: Antonio Altieri, Fabrizio Giorgione, Alfredo Nazzaro, and Assunta Oropallo.
On the basis of our studies on malicious apps that exfiltrate sensitive data (http://www.iswatlab.eu/?p=461), we found out that both trusted apps and malicious apps take a lot of sensitive data. Such data can be then used for different purposes that produce revenue for the adversary who obtained it: to sell user’s profile to a third party for marketing purposes, to feed OSINT platforms, to realize identity thefts or for accomplishing frauds and scams.
The point is that the user grants those permissions which allow the data exfiltration when installs the application on the device. The core problem is that the common user ignores completely the kind of permissions that are granted, and, what is more severe, ignores which risk a certain combination of permissions exposes her privacy too.
If an app requires the permission to send SMS and the permission to read contacts, SMS, and some other personal identifiable information stored in the device, it exposes the user to the possibility that the app sends that sensitive information to a third party by SMS.
Relying on such observations, we created a model that identifies which apps have the most dangerous combination of permssions for data privacy.
It is important to remark that Privacy Guard does not evaluate if a data exfiltration happens on a device, but it just identifies those apps which require a combination of permissions that can be strong indicators of activities that affect data privacy preservation.
Privacy Guard is intended to first monitor the potential risks for a user’s data privacy and, as second aim, to stimulate and increase the awareness of user towards the kind of apps she installs on her device, from a security perspective.
Let’s now look at how Privacy Guard works.
Permissions have been grouped into categories and each permission has been assigned a score, ranging from 1 to 10, to describe its dangerousness.
The permissions have been divided into four categories:
Hardware permissions: every permission which requests a direct access to a hardware device;
Data access permissions: every permission which requests a direct access to data stored on the devices;
Communication permissions: every permission which gives the chance to send information either over a network or to another device.
System permissions: every permission which can be requested only by system applications.
To compute a value representing applications’ data leakage capabilities the followed formula has been developed:
(1) (Hn*Wh +Dn * Wd) * MAX(C)
Hn : the normalized sum of hardware permissions’ score requested by an application;
Dn: the normalized sum of data permissions’ score requested by an application;
MAX(C): the maximum value among the communication permissions requested by an application;
Wh: weight assigned to hardware permissions. After empirical considerations, it has been assigned the value 3;
Wd: weight assigned to data permissions. After empirical considerations, it has been assigned the value 7.
However, (1) to represent data leakage capabilities of applications is not enough: some permissions are far more dangerous if used in combination with other permissions. In order to take this into account, the hardware and data access categories have been divided into sub-categories:
Network access Data Acquisition
Change hardware configuration Personal data access
Non-combinable
The communication permissions have been divided considering range and bandwidth. Every combination of this subcategories was considered, assigning a score, ranging from 1 to 10, to each combination. These values act as a penalty to the base score.range and bandwidth. Every combination of this subcategories was considered, assigning a score, ranging from 1 to 10, to each combination. These values act as a penalty to the base score.range and bandwidth. Every combination of .range and bandwidth. Every combination of this subcategories was considered, assigning a score, ranging from 1 to 10, to each combination. These values act as a penalty to the base score.
First of all the application shows a message to synthesize the results and the list of all the applications with the related data leakage score, while if there are one or more applications that exceed a certain threshold, at the top of screen will be shown a message that indicates the number of applications that exceed this value.

It’s possible to explore the details of each app. Privacy Guard shows the list of all the activated permissions with a brief description. If one application requires a permission particularly suspect, the application shows a warning to explain at the user how that permission can be used for malicious purposes.

It’s possible to explore the details of each app. Privacy Guard shows the list of all the activated permissions with a brief description. If one application requires a permission particularly suspect, the application shows a warning to explain at the user how that permission can be used for malicious purposes.
It’s possible to conduct the analysis only on the user’s application or including all the system’s applications. Privacy Guard is available on the in the Play Store at the following address
https://play.google.com/store/apps/details?id=com.ssr.privacyguard.
1 in 5 Websites Still Use SHA-1: Report
8.3.2017 securityweek Safety
While most certificate authorities (CAs) haven’t been issuing certificates using the SHA-1 cryptographic hash function for more than two months, 1 in 5 websites worldwide still use such certificates, according to analysis by security firm Venafi.
Not only did CAs migrate to the more secure SHA-2 certificates on Jan. 1, 2017, but major browser makers also decided to adopt the change, including Google, Microsoft and Mozilla, and their browsers no longer trust sites that use SHA-1 certificates. Even Facebook announced plans to retire SHA-1.
Despite that, many webmasters are still behind with the transition, as 21% of all websites that use certificates still use the insecure cryptographic hash function, Venafi says, based on the analysis of over 33 million publicly visible IPv4 websites. Granted, things are looking much better compared to last fall, when 35% of websites were still using SHA-1, but recent research has proven that the crypto function is officially broken.
SHA-1 has been long said to be vulnerable to collision attacks, but it wasn’t until this year that the function was proven fundamentally broken. What’s surprising, however, is that webmasters didn’t transition to SHA-2 or SHA-3 sooner. It’s doubtful that they would knowingly leave their sites vulnerable.
“I suspect that many organizations may simply be unware that they still have any SHA-1 certificates on their networks because they are relying on certificate authority (CA) tools to manage their keys and certificates. The problem with this approach, especially now that free and very low cost certificates are widely available, is that anyone in your organization can get and install a certificate that uses weak hashing algorithms and install it on your network,” said Venafi’s Shelley Boose.
In addition to making both websites and their users vulnerable to attacks, the continuous use of SHA-1 can also disrupt the browsing experience, because web browsers display warnings when encountering insecure sites, prompting users to look for alternatives. The green padlock that browsers display to mark HTTPS transactions will no longer be associated with SHA-1 sites, and performance issues might also alter users’ experience, Venafi notes.
Firefox 52 Warns of Login Fields on Insecure Pages
8.3.2017 securityweek Safety
Released this week, the latest version of the Firefox Web browser warns users when they are entering their passwords on pages that are not secure.
The change was initially announced last year, when Mozilla introduced the warning in Firefox DevEdition 46, in an attempt to raise awareness on the risks that requesting sensitive information over non-secure connections pose. Last year, the warning was meant for developers, but the latest browser release brings it to end-users as well.
Starting with Firefox 52.0, users will receive a warning when encountering non-secure HTTP pages with logins. A “This connection is not secure” message will be automatically displayed when the user clicks into the username and password fields on any page that doesn’t use HTTPS.
Starting with the release of Firefox 51 in January, the browser has been displaying a struck-through lock icon for all pages that don’t use HTTPS, to make it clear that those pages are not secure. It even displayed a warning when users were entering a password on an insecure page. Now, the warning message is displayed as soon as the user clicks on the username or password field.
Firefox 52 also implements the Strict Secure Cookies specification, thus forbidding insecure HTTP sites from setting cookies with the “secure” attribute. In the newly published release notes, Mozilla explains that this change will prevent insecure sites from setting cookies with the same name as an existing “secure” cookie from the same base domain.
The browser update brings a variety of bug fixes as well, including patches for Critical issues: asm.js JIT-spray bypass of ASLR and DEP; Memory Corruption when handling ErrorResult; Use-after-free working with events in FontFace objects; Use-after-free using addRange to add range to an incorrect root object; Use-after-free working with ranges in selections; and memory safety bugs.
High risk vulnerabilities were also addressed in Firefox 52, such as: Segmentation fault in Skia with canvas operations; Pixel and history stealing via floating-point timing side channel with SVG filters; Memory corruption during JavaScript garbage collection incremental sweeping; and Use-after-free in Buffer Storage in libGLES (affecting Windows computers only).
Firefox 52.0 was released with support for all major desktop platforms, namely Linux, macOS, and Windows. Furthermore, it is part of the ESR (Extended Support Release) branch, meaning that it should receive support for about a year.
ReBreakCaptcha – How to breaking Google’s ReCaptcha v2 using Google’s APIs
3.3.2017 securityaffairs Safety
The researcher East-Ee Security devised a proof of concept bypass of the Google’s reCaptcha V2 verification system dubbed ReBreakCaptcha.
East-Ee Security proposed a proof of concept bypass of the Google’s reCaptcha V2 verification system dubbed ReBreakCaptcha. The PoC uses the Google web-based tools for its purpose. According to the author, ReBreakCaptcha “lets you easily bypass Google’s reCaptcha v2 anywhere on the web.”
The CAPTCHA (Completely Automated Procedures for Telling Computers and Humans Apart) service was devised to defeat bots and scripts that can be used to register thousands of accounts at a time. ReCaptcha is the CAPTCHA solution proposed by Google that leverages image, audio or text challenges to verify the presence of a human while accessing the online service.

The ReBreakCaptcha is able to byPass reCaptcha V2 via a script that leverages Google APIs to capture audio challenges as sound files.
The ReBreakCaptcha works in three stages:
Audio Challenge – Getting the correct challenge type.
Recognition – Converting the audio challenge audio and sending it to Google’s Speech Recognition API.
Verification – Verifying the Speech Recognition result and bypassing the ReCaptcha.
The ReBreakCaptcha technique uses a way to get an audio challenge as part of the reCaptcha process.
“Some of you may notice that instead of an audio challenge, sometimes you get a text challenge,” reads the blog post published by the East-Ee Security researcher. “To bypass it and get an audio challenge, you simply click the ‘Reload Challenge’ button until you get the correct type.”
Once the ‘get an audio challenge’ option is selectes the reCaptcha allows the users to either play the audio file from the web page or download it.
“Let’s download the audio file and send it to Google Speech Recognition API. Before doing so, we will convert it to a ‘wav’ format, which is requested by Google’s Speech Recognition API. Now we have the audio challenge file and are ready to send it to Google Speech Recognition. How can this be done? Using (Google’s own) API,” continues the post.
Then the author sends the audio to the Speech Recognition that turns back the results in text format.
“We will send the ‘wav’ audio file and the Speech Recognition will send us back the result in a string (e.g. ‘25143’). This result will be the solution to our audio challenge,” East-Ee Security explains.
If you are interested in the ReBreakCaptcha technique, give a look at the Python-based proof of concept script available on GitHub.
Palo Alto Networks Acquires Breach Detection Startup LightCyber
1.3.2017 securityweek Safety
Palo Alto Networks on Tuesday announced that it has acquired breach detection firm LightCyber for $105 million in cash.
The network security company said that LightCyber’s machine learning, behavioral analytics platform will be integrated into Palo Alto’s Next-Generation Security Platform to help customers better detect breaches throughout the entire attack lifecycle.
LightCyber has raised more than $32 million in funding since being founded in 2011.
Palo Alto Networks LogoLightCyber’s platform doesn’t look at a specific packet or field to detect possible malicious activity, but instead detects attacks by identifying suspicious behavior inside the network.
“We look at the behavior. This means that every file access and every protocol could be used as an attack indication - even were it alright under a different context,” Gonen Fink, CEO of LightCyber, explained to SecurityWeek back in March 2013. “What we do is model each computer and user separately, and maintain those models over time. Everything we do is based on history we gather from the network.”
"This technology will complement the existing automated threat prevention capabilities of our platform to help organizations not only improve but also scale their security protections to prevent cyber breaches,” Mark McLaughlin, chairman and CEO of Palo Alto Networks, said in a statement.
The technology integration is expected to be completed by the end of the calendar year, Palo Alto said.
In a 2013 interview with SecurityWeek, LightCyber's Fink told us that his favorite startup (other than his own) was a company called Cyvera. Ironically, Palo Alto Networks also acquired that company in early 2014.
In addition to announcing the acquisition, Palo Alto on Tuesday announced that total revenue for the fiscal second quarter 2017 came in at $422.6 million, compared with total revenue of $334.7 million for the fiscal second quarter 20106—a 26 percent increase year over year. These figures fell short of Wall Street expectations, sparking shares of the company (NYSE:PANW) to plummet more than 20 percent in after-hours trading.
"While fiscal second quarter revenue of $423 million was yet another record for the company, we were disappointed that we came in below top-line expectations due to some execution challenges, which we are moving quickly to address," McLaughlin said.
Windows 10 Option to Block Installation of Win32 Apps
28.2.2017 securityweek Safety
Windows 10 could soon allow users to block the installation of applications coming from other sources than the Microsoft Store, a feature that would likely help prevent the installation of malware.
The feature, which would essentially prevent users from installing Win32 applications, is said to be currently tested as part of the latest build to have been pushed to users in the Insider Preview program (which is Windows 10 build 15042).
Win32 is the core set of application programming interfaces (APIs) available in the Microsoft Windows operating systems and is often referred to as the Windows API. In addition to Win32 apps, however, Windows 10 users can also install software built using Microsoft’s Universal Windows Platform, or UWP.
This new platform is the framework for applications that support not only Windows 10 computers, but also other devices running under the platform, such as Xbox One, HoloLens, and phones. Microsoft Store, the app portal accessible from all these devices, only accepts UWP applications, and the tech company even released a converter to help developers port Win32 apps to UWP.
With millions of Win32 applications available out there, it might take a while before all developers switch to the new framework, especially if users aren’t in a hurry to embrace UWP applications.
What the newly observed change does is to let users block Win32 apps from being installed, by selecting an option to “Allow apps from the Store only” from the Windows 10’s Apps & Features settings screen. According to Vitor Mikaelson, even when this option is selected, already installed Win32 apps will be allowed to run normally.
The option is expected to become available in all Windows 10 editions once the Creators Update arrives in April, which will also allow enterprise users to benefit from it. Basically, admins will be able to install necessary apps and then turn the feature on to keep unwanted applications away. This option will essentially prevent malware from being installed on Windows 10 devices, either with or without user’s consent, unless it is being distributed via Microsoft Store.
The upcoming feature will also offer options such as to allow applications from anywhere without warning, or to prefer those from the Microsoft Store but still allow those from other sources (which will trigger a prompt to inform users that they are installing applications that are not from the Windows Store).
Firefox Users Fingerprinted via Cached Intermediate CA Certificates
22.2.2017 securityweek Safety
An attacker can discover various details about Firefox users due to the manner in which the browser caches intermediate CA certificates, a researcher has discovered.
When the server doesn’t deliver the complete certificate chain, Firefox loads the website if the intermediate CA certificate is cached, security researcher Alexander Klink discovered. By determining which websites use the same intermediate, an attacker could figure out some details about the user, the researcher says.
Normally, root Certificate Authorities (CAs) don’t use the main root certificate to secure connections, but generate intermediate certificates instead. Webservers use these intermediates to generate certificates for each user, and deliver these (server certificates) to the browser along with the intermediate CA certificate when establishing a connection.
When a server is misconfigured, only the server certificate is sent, which should result in the user getting an error instead of the website. However, if the intermediate CA certificate has been already cached, the user will be able to connect. While Chrome and Internet Explorer don’t rely on the entire chain to deliver a website, Firefox does, but uses cached CAs even when in Private Mode, the researcher has discovered.
According to Klink, an attacker could use this knowledge to determine specific details about targeted users, based on the intermediate CA certificates cached by their browsers. However, these details would be limited to geolocation, maybe browsing habits, and whether the victim’s browser runs in a sandbox (which would lack cached certificates). The attacker could sell this information to advertising companies or could leverage it to deliver specific content to the targeted users.
“In addition to the purely »statistical« view of having a fingerprint with a sequence of n bits representing the cache status for each tested CA, the fingerprint also contains additional semantic information. Certain CAs have customers mostly in one country or region, or might have even more specific use-cases which lets you infer even more information − i.e. a user who has the »Deutsche Bundestag CA« cached is most probably located in Germany and probably at least somewhat interested in politics,” the researcher explains.
Klink also notes that he contacted Mozilla on the matter in January, but that there are no details on what course of action the organization will take. The “cleanest solution” would be to avoid connecting to incorrectly configured servers, even if the intermediate CA is cached, but “Mozilla is reluctant to implement that without knowing the impact,” the researcher says.
Users can stay protected by regularly cleaning up their profiles, by creating new ones, by cleaning up existing ones from the Firefox UI, or by using the certutil command line tool. They can also block third-party requests with an addon, mainly because “the attack obviously needs to make (a lot of) third-party requests,” Klink concludes.
Cisco Launches New Firepower Firewalls
22.2.2017 securityweek Safety
Cisco announced on Wednesday the launch of four new threat-focused Firepower next-generation firewalls (NGFWs) designed for banks, retailers and other businesses that conduct a high volume of sensitive transactions.
The new products are part of the Firepower 2100 series NGFWs, which provide throughput ranging between 1.9 and 8.5 Gbps, and support up to two dozen 1 Gigabit Ethernet (GE) ports or sixteen 10 GE ports.
According to Cisco, the new firewalls have a dual CPU, multi-core architecture designed to optimize firewall, cryptographic and threat inspection functionality.
Cisco Firepower firewall appliance
“The design employs Intel multi-core CPUs for Layer 7 threat inspections (app visibility, intrusion detection, URL filtering, malware and file inspection, user identity, etc.) and a combination of merchant and a Network Processing Unit (NPU) for layer 2-4 traffic (stateful firewall, NAT, VPN-SSL encryption/decryption, and more),” explained Cisco’s David Stuart.
The networking giant says firewalls typically slow down throughput performance by up to 50 percent with intrusion prevention functionality fully enabled, but claims its new product can have a less than one percent impact.
Cisco also announced that it has made some improvements to its local, centralized and cloud-based management tools. This includes a web-based interface in the Firepower Device Manager to help users quickly deploy appliances via a setup wizard.
It also includes enhancements to the Firepower Management Center (FMC), which allows users to automate various security tasks, such as assessments, tuning, containment and remediation. The FMC can now also automatically receive third-party and customer-specific intelligence via the Threat Intelligence Director (TID).
Finally, Cisco said its Cloud Defense Orchestrator, designed for cloud-based policy management, now supports the Cisco Web Security Appliance (WSA) v. 11 and is available via a Europe-based cloud.
Yahoo Notifies Users of Sophisticated Breach Methods
16.2.2017 securityweek Safety
Yahoo said Wednesday it was notifying some users that hackers may have been able to use a maneuver to break into their accounts without stealing passwords.
The latest notifications were in response to the record breach disclosed late last year affecting an estimated one billion users -- which involved forging of "cookies" or files used to authenticate users when they log into their accounts.
The notification indicates the investigation into the attacks are in the final stage, according to a source familiar with the matter, noting that messages had been sent to "a reasonably final list" of Yahoo users.
A Yahoo spokesman said the company was notifying all potentially affected users and that it had "invalidated" the forged cookies.
"As we have previously disclosed, our outside forensic experts have been investigating the creation of forged cookies that could have enabled an intruder to access our users' accounts without a password," the company said in a statement.
"The investigation has identified user accounts for which we believe forged cookies were taken or used."
Yahoo announced in September that hackers in 2014 stole personal data from more than 500 million of its user accounts. It admitted another cyber attack in December, this one dating from 2013, affecting more than a billion users.
The data breaches have been a major embarrassment for a former internet leader that is in the process of selling its core operations to telecom giant Verizon for $4.8 billion.
Some reports Wednesday said the two companies had agreed to discount the price by $250 million to $300 million following disclosure of the attacks.
Neither Yahoo nor Verizon commented on the reports.
Yahoo is selling its main operating business as a way to separate that from its more valuable stake in Chinese internet giant Alibaba.
The share-tending entity, to be renamed Altaba, Inc., will act as an investment company.
ExtraHop Introduces Real Time Wire-Level Threat Detection
14.2.2017 securityweek Safety
IT analytics firm ExtraHop Networks today announced ExtraHop Addy, a cloud-based machine-learning wire data analytical tool that is being trained to automatically detect anomalies on the fly as they are happening.
Seattle, Washington-based ExtraHop was born in 2007. It was founded by senior architects Raja Mukerji and Jesse Rothstein, formerly from F5 Networks, with a vision of tapping wire data to provide the most complete and definitive information on the current state of the IT infrastructure. Since then ExtraHop has picked up hundreds of global customers, including Sony, Lockheed Martin, Microsoft, Adobe, and Google.
But the working of the infrastructure is not the only diagnosis that can be drawn from wire data. Wire data has been described by Rothstein as "everything on the network, from the packets to the payload of individual transactions. It is a very deep, very rich source of data... And it's definitive." Inevitably, within that data, are any and all subtle indications of cyber security compromise.
Machine-learning threat detection tools are not new. For the most part, however, they are high-speed forensic tools that rapidly analyze huge volumes of log data -- they can tell you what happened, but not necessarily what is happening.
Addy is a new SaaS offering that takes the data already derived from ExtraHop Network and analyzes it in the cloud. It builds a continuous baseline of normal behavior for every device on the network; it then analyzes what is happening against what it would expect to happen; and it highlights anomalies or issues to the IT team -- or the security team. This takes its potential beyond IT infrastructure monitoring into real time threat detection.
Early access customers have already demonstrated Addy's security value. One large cable company detected a server unexpectedly probing other systems in the datacenter; and were immediately able to shut down the compromised server. A financial services firm was able to detect the Dyn DDoS attack in real time and route DNS traffic through an unaffected region to avoid downtime. And a national medical institution averted two potential security breaches when Addy detected international servers probing their DNS, as well as reverse DNS lookups.
Addy learns from both the customer's own environment and also crowd-sourced domain expertise. This means that the behavioral baseline for every device in the network is continuously improving, the accuracy of alerts is increasing, and false positives are minimized.
For the most part, the wire data sent to the cloud for analysis is kept in customer-specific compartments. Although that data includes nothing personally identifiable, this is an added assurance for customers concerned with any form of network data sharing, or are otherwise concerned about the evolving data protection laws.
"ExtraHop provides a real-time view across the entire IT environment," explains Rothstein. "With Addy, we're taking the next step, applying machine learning techniques to this vast data set while leveraging the scale, elasticity, and compute power of the cloud."
Addy is available through an Early Access Program for select participants now, and will be available generally in April 2017.
Cisco Launches "Umbrella" Secure Internet Gateway
10.2.2017 securityweek Safety
Cisco announced this week the launch of Umbrella, a cloud-based Secure Internet Gateway (SIG) solution designed to provide visibility and protection for devices on and outside the corporate network.
Organizations are increasingly relying on software-as-a-service (SaaS) products, such as WebEx, Office 365, Google Docs, Salesforce and Box. While these applications can significantly improve productivity, they are often used over untrusted Internet connections without being protected by a VPN.
Cisco wants to address this problem with the launch of Umbrella. The new cloud service aims to provide safe and secure access from anywhere, even if a VPN is not used.Cisco Umbrella
The networking giant obtained the Umbrella technology when it acquired OpenDNS in 2015. The company said the new product combines the original technology with machine learning models designed for uncovering threats and blocking malicious connections on the DNS and IP layers, Cisco Talos threat intelligence, and Advanced Malware Protection (AMP) technology for detecting and blocking malicious files in the cloud.
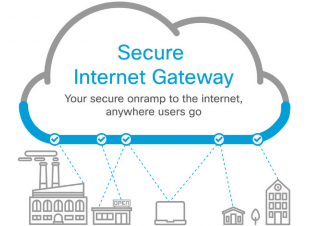
With Umbrella, Cisco promises enhanced visibility and control, including for sensitive data in SaaS applications via Cloudlock technology, and intelligence from the more than 100 billion requests resolved every day.
Cisco said the cloud-based SIG provides reliable and fast connectivity, and it can be easily integrated with existing appliances, intelligence platforms and custom tools.
“Umbrella was built upon the OpenDNS platform, a platform that has been delivered from the cloud since its inception. Then we integrated technology from across the Cisco security portfolio, including capabilities from the Cloud Web Security proxy, and the Advanced Malware Protection (AMP) file inspection,” said Brian Roddy, who oversees Cisco’s Cloud Security Business. “These technologies haven’t just been stitched together, but re-engineered to be delivered within Umbrella, so that they’re easy to use and able to deliver even more effective security.”
5 Anti-Surveillance tools that can help you enhance online security and privacy
9.2.2017 securityaffairs Safety
The current digital era is filled with all sorts of cyber dangers. The following tools will help you remain safe by enhancing your online security and privacy.
There are many software tools that can help you preserve and protect your privacy online. For your benefit, I’ve compiled a list of the top 5 software tools that can help you protect your online privacy and security.
DuckDuckGo: Privacy Search Engine
DuckDuckgo was launched in 2008 as an alternative search engine that respects user privacy and claims to have a “superior search experience with smarter answers.” It is one of the most popular search engines that provide real privacy and smarter search without tracking user activity.
This search engine doesn’t log or share any personally identifiable information. DuckDuckGo doesn’t use any cookie and it immediately discards IP addresses of users, nor does it keep any record of searches performed.
PureVPN: VPN Software
PureVPN is a highly regarded Hong Kong-based VPN service offering an unusually wide range of software clients for different platforms, which include Windows, Mac, Ubuntu Linux, and mobile apps for Android, iOS and manual configuration for Windows Phone.
PureVPN operates a self-managed VPN network that currently stands at 750+ Servers in 141 countries, which include seldom-covered areas such as Oceania, Africa, and Central America. It provides an extra layer of privacy. It doesn’t collect or log your online activities and doesn’t monitor what you do online. It promises the best online privacy.
PureVPN has a wide variety of security protocols like OpenVPN, IPSec/L2TP, PPTP, SSTP, and IKEv2. It encrypts your entire internet with 256-bit encryption to protect data and online activities.
ProtonMail: Email Encryption Software
ProtonMail is a free and encrypted email client which provides and enhances your email security to keep your data safe. It’s also available on smartphone devices with special apps for Android & iOS. It provides complete email security with end-to-end encryption. Your emails as well as your contacts always stay private.

Cryptocat: Secure Chat software
Cryptocat is one of the most secure chat software for your computer which allows you to chat with your friends in complete privacy. Every message you send via this app is secured with end-to-end encryption, which ensures all of your communications with other Cryptocat users remains protected.
This open source desktop application is available for Windows, OS X and Linux. With this software, you can also share encrypted files, pictures and videos to your buddies safely and easily. Cryptocat users can also receive messages even when they’re offline.
HTTPS Everywhere: Privacy Browser Extension
HTTPS Everywhere is a free extension which is available on Chrome, Firefox and Opera. This extension is developed primarily by the Tor project and Electronic Frontier Foundation (EFF). This extension encrypts your communications with many websites and makes websites use the more secure HTTPS connection instead of HTTP, if they support it.
We hope that the above extensions will help you out in increasing your online privacy and security. If you have any suggestions that you think are worth adding to this list, feel free to let us know.
About Author (Anas Baig):
Anas Baig is a Digital Marketer & Security Enthusiast. He loves to read & write about Digital Security. If you are interested to get tweets about Marketing & Security !
Palo Alto Networks Unveils Big Product Updates, New Firewalls
7.2.2017 securityweek Safety
Palo Alto Networks on Tuesday announced the launch of PAN-OS 8.0, which brings major improvements to the company’s Next-Generation Security Platform, and several new hardware and virtual firewall appliances.
According to the company, PAN-OS 8.0 introduces more than 70 new enhancements and capabilities, including for securing cloud deployments and SaaS applications, preventing the theft and abuse of credentials, simplifying security operations, and blocking threats.
The threat prevention features are designed to prevent sandbox evasion, block command and control (C&C) communications, automate intelligence integration, and improve threat detection and alerting mechanisms.
PAN-OS 8.0 is designed to address credentials theft by automatically identifying and blocking phishing websites, preventing users from entering credentials on phishing sites, and providing a policy-based multi-factor authentication framework natively in the firewall to avert the use of stolen credentials.Palo Alto Networks
As for cloud and SaaS, the latest version of the operating system brings optimized workflow automation features for cloud services, and improved visibility, reporting and automation for SaaS applications.
Palo Alto Networks also announced the release of new hardware and virtual firewall appliances that complement PAN-OS 8.0. In addition to the existing 16 hardware appliances, the company now offers six new devices designed to provide improved traffic visibility and control.
The new appliances are PA-5260, PA-5250 and PA-5220 of the PA-5200 series, PA-850 and PA-820 of the PA-800 series, and the PA-220. The PA-5200 series devices are ideal for data centers, the PA-800 series is designed for medium-size networks and branch offices, and the PA-220 is ideal for small branch offices and remote locations.
Some of the new VM-Series virtual firewalls offer performance of up to 16 Gbps and are ideal for service providers and data centers, while the lower-end models are designed for minimal resource consumption and are best suited for virtual branch offices.
ENISA Report Provides ICS-SCADA Protection Recommendations
6.2.2017 securityweek Safety
ENISA Publishes "Communication Network Dependencies for ICS-SCADA Systems" Report for Critical Infrastructure Protection
The clear emergence of cyber weapons used for political interference -- cyber espionage such as the OPM breach probably related to China; political manipulation such as the breach and leaks relating to the DNC by Russia; and physical damage such as the Ukraine power outages by Russia or its supporters -- has focused attention on the security of the critical national infrastructures. Much of that infrastructure is controlled and operated by ICS/SCADA systems.
The European Union Agency for Network and Information Security (ENISA) has published a new analysis and recommendations on 'Communication network dependencies for ICS/SCADA Systems' (PDF). The report concentrates on two of the primary causes of security concern: network segmentation and communication between the segments; and the wider issue of communications with the outside world that often uses the Internet.
The report was compiled from an analysis of stakeholder conversations with members of the ENISA ICS and SCADA groups together with data from official sources and other ICS/SCADA experts in the field. It highlights three primary causes for concern, and makes eight specific security recommendations for its target audience of asset owners and operators of electricity, oil, gas, transport, health, water supply, and the manufacturing industry.
The three worrying attack scenarios are remote compromise allowing an attacker to take control of one or multiple assets within the network; the insider threat from a disgruntled employee, contractor or third-party staff with in-depth knowledge of the infrastructure; and the risk of infection during the maintenance or upgrade process. Associated with the third concern is the website where the update files and firmware are located.
Related: Learn More at SecurityWeek's ICS Cyber Security Conference
The report examines ICS/SCADA communication networks and their interdependencies, and examines the threats, vulnerabilities, incidents and attacks affecting those networks while focusing on those that might result in cascading effects. It also presents a gap analysis to highlight areas that require further work.
A section on security good practices outlines the necessary steps in first understanding and then protecting the network. This includes a list of technology and processes that can "greatly increase the protection of the availability, integrity, confidentiality and non-repudiation" of the network and its communications.
Finally, it presents a list of eight "high-level recommendations for manufacturers, operators and security experts that will help them to improve the security level and resilience of the ICS/SCADA systems and communication network functions." These are:
1. Include security as a main consideration during the design phase of ICS SCADA systems.
2. Identify and establish roles of people operating in ICS/SCADA systems.
3. Define network communication technologies and architecture with interoperability in mind.
4. Establish brainstorming and communication channels for the different participants on the lifecycle of the devices to exchange needs and solutions.
5. Include the periodic ICS/SCADA device update process as part of the main operations of the systems.
6. Establish periodic ICS/SCADA security training and awareness campaign within the organization.
7. Promote increased collaboration amongst policy decision makers, manufacturers and operators at EU Level.
8. Define guidelines for the establishment of reliable and appropriate cybersecurity insurance requirements.
These recommendations, modified where necessary, would make part of good practice for any industry. The ENISA report goes further to focus their particular relevance to operational technology. For example, for the first 'security by design' recommendation, it explains that, "Traditionally, only safety is included as one of the main considerations during the design of an ICS/SCADA system or infrastructure (alongside efficiency, real-time constraints, etc.). However, the concept of security is not, although it is now one of the main risk sources that should be covered to prevent future attacks and incidents."
While users have little control over ICS/SCADA development and manufacturing processes, ENISA recommends that "during the design phase, the security of the devices, and the communications between them, has to be one of the main concepts that will impact on the choice of devices, measures to implement, and overall design of the architecture."
As a result of this process, writes ENISA, "the systems' security is increased as many threats have been mitigated. This can be measured via risk assessment, vulnerability assessment or penetration test."
This basic structure is repeated for each of the recommendations: a description of the issue, action required, and effect of implementation. The result is a thorough examination of the ICS/SCADA security landscape together with practical steps to improve the security posture of the critical national infrastructure.
Exabeam Challenges Traditional SIEMs With New Security Intelligence Platform
1.2.2017 securityweek Safety
Exabeam Leverages UEBA Experience to Launch New Next-Generation Security Intelligence Platform
SIEMs, although still a must-have for most enterprises, are considered to be past their sell-by date; and are being supplanted by the rising star of user and entity behavior analytics (UEBA). Now one UEBA leading light claims that it was just the beginning -- UEBA was part of a route map on the path to a complete next generation security management platform.
"We started," Nir Polak, Exabeam's CEO and founder, told SecurityWeek, "as a SIEM-helper." The intention was always to be more, but the route to a complete platform was designed to be in steps. SIEMs, he suggested are broken, difficult to use and no longer fit for today's needs; and a SIEM-helper was the obvious starting point. "SIEMs were born some 20 years ago, before the age of big data and before the skills gap became as severe as it is today. So, we used machine language and analytics to help find the threats for the SIEMs."
Now, he added, "we're moving to the next phase, ready to take on the incumbents -- Splunk, ArcSight and QRadar -- head on." He announced Tuesday the arrival of the Exabeam Security Intelligence Platform, with the two most important additions being a log manager and an incident responder.
The UEBA side works by building a user fingerprint for all employees. This is compiled automatically from logs. Whenever user behavior deviates from that fingerprint it can be indicative of an intrusion. False positives are minimized, explained Polak, by marrying data science with security experience. In science, a sudden change of logon IP address would be a big anomaly; but it could signify nothing more than a change of home ISP. Security experience will say that it only becomes an issue if combined with other anomalies. "If the user IP address changes and uncommon credentials are used or perhaps access is attempted from a strange location, then it becomes a security concern."
Analytics work best on big data, and the bigger the better. This is the reasoning behind the launch of the new Exabeam Log Manager product. While many products have, or are, log managers, they are priced by the byte collected. "This can rapidly become expensive," explained Polak; "so customers reduce their bills by reducing the number of logs they try to collect."
But threat detection through analyzing big data works better with bigger data -- the analytics improve their accuracy with more data to analyze. "We have built," said Polak, "a log management system based on open source big data technology, and we're changing the market by eliminating cost-per-byte charges. Our system is priced not by byte but by the number of employees in the organization. Customers can put in as much data as they want and the cost will change relatively little."
He illustrated the effect by saying that one beta customer who used the system for a month "has already put 30x the amount of data into the Exabeam log manager as he had previously put into Splunk."
The new Exabeam Incident Responder is designed to improve the efficiency and speed of response. Detecting an anomaly is only the first step -- it needs response. Not all companies have senior analysts to cover all eventualities, and junior staff might have neither the knowledge or experience to respond efficiently. "To address chronic security hiring shortfalls," explains Exabeam, "Incident Responder provides automated playbook creation and execution, so that detected attacks are shut down quickly and completely."
It includes out-of-the-box playbooks for most common attacks, such as phishing attacks, malware, stolen passwords, and data theft. "We've developed playbooks for different events so that the customer knows exactly how to respond to any particular situation," said Polak. He expanded on phishing as an example. "A large organization may get hundreds or thousands of suspected phishing emails per day. The playbook knows how to respond to a suspected phishing email; examine, check links, sandbox and detonate, etc." Done automatically, they can all be examined in a fraction of the time it would take without the automated playbook.
"Threat detection is one side of the picture; effective incident response is the other," said Ryan Makamson, senior infosec analyst for Washington State University. "Exabeam Incident Responder helps even new analysts respond consistently and efficiently to internal and external threats."
Both the new Log Manager and Incident Responder will be on show at the RSA Security Conference, February 13-17, in San Francisco.
Gmail will stop allowing JavaScript (.js) file attachments starting February 13, 2017
26.1.2017 securityaffairs Safety
Google announced Gmail will soon stop allowing users to attach JavaScript (.js) files to emails for obvious security reason.
Google announced Gmail will soon stop allowing users to attach JavaScript (.js) files to emails for obvious security reason. JavaScripts files, like many other file types (i,e, .exe, .jar, .sys, .scr, .bat, .com, .vbs and .cmd) could represent an insidious threat for the recipient, for this reason starting with February 13, 2017, .js files will no more be allowed.
“Gmail currently restricts certain file attachments (e.g. .exe, .msc, and .bat) for security reasons, and starting on February 13, 2017, we will not allow .js file attachments as well. Similar to other restricted file attachments, you will not be able to attach a .js file and an in-product warning will appear, explaining the reason why.” states Google.
It will be not possible to attach such kind of files, if users will try to attach a .js file the Google will display a warning message while blocking the potentially dangerous file.
Google suggests users share such kind of potentially harmful files through Google Drive, Cloud Storage or similar online storage services.
“If you still need to send .js files for legitimate reasons, you can use Google Drive, Google Cloud Storage, or other storage solutions to share or send your files.”

JavaScript files have been exploited in several malicious campaigns recently, crooks leveraged on this kind of file to spread download and install various malware such as the dreaded Locky Locky were embedding the Locky binary in JavaScript files attached to spam emails.
The analysis of the JavaScript revealed the existence of numerous variables that contain chunks of strings that are concatenated at runtime to compose the malicious code.ealed
“Loading the JavaScript into an editor shows the same familiar obfuscation found in the previous Locky downloader script variants.” continues the analysis.
“It also shows the use of numerous variables containing chunks of strings, which are concatenated at runtime to build needed strings like ActiveXObject names and methods.”
The encrypted Locky ransomware binary was stored in a set of large arrays, at runtime it was decrypted and saved to disk. When the ransomware binary is decrypted it is possible to notice a significant surge in CPU usage from wscript.exe.
In previous campaigns, the experts only noticed the use of scripts as a container for the downloader, instead of the malicious code itself.downloader, instead of the malicious code itself.downloader, instead of the malicious code itself.downloader, instead of the malicious code itself.
Recently security experts spotted a new ransomware, Ransom32, that is the first ransomware variant that has been developed in the JavaScript scripting language.
Do you need another proof to consider JavaScript attachments potentially dangerous?
adrotate banner=”9″]
TorWorld helps you to manage a Tor node, promising an upcoming Tor-as-a-Service
25.1.2017 securityaffairs Safety
The TorWorld initiative aims to build a community area for those people that desire to set up either a Tor Relay or a Tor Exit node.
We all recognize the importance of the Tor network, an important instrument to protect users’ anonymity and avoid censorship. Today I desire to present you an interesting initiative launched by Tor passionates, the TorWorld, belonging to the CryptoWorld Foundation.
The CryptoWorld Foundation groups several organizations that provide anonymity services. The TorWorld aims to build a community area for those people that desire to set up either a Tor Relay or a Tor Exit node.
According to Bleepingcomputer.com, the project born out of a real necessity:
“The idea for ‘TorWorld’ came about four months ago,” Beard, one of TorWorld’s founding members told Bleeping Computer.
“We originally ran a few Guard Relays for a little over a year privately,” Beard continued. “After we had an issue with our Guard nodes being removed by our ISP at the time because of a misunderstanding, we thought about possibly setting up a service dedicated to running Tor nodes, and educating people on Tor.”
“Eventually we started that [idea], and at first we looked for automation scripts to make it easier for us to deploy multiple Tor servers in a fast and dynamic way,” Beard said. “To our surprise, we couldn’t find a single script.”
The team at the TorWorld published scripts simplify the set up of a Tor node, including Bash scripts for quickly deploying Tor guard (entry) nodes, Tor relay (middle) servers, Tor bridges (unlisted relays), and Tor exit nodes.
The project is ambitious and we can only wish the team great success, representatives from the TorWorld confirmed that the intention of the team to become a hosting provider for Tor servers and they are thinking to a sort of Tor-as-a-Service (TaaS).
Beard explained that the final goal it to allow users to create a Tor nodes on top of TorWorld’s server infrastructure in a single click thanks to a set of open-sourced Bash scripts.
This is an important step, unfortunately, today the set up of a Tor node is not a simple operation for everyone despite it is very well documented on the official Tor Project website.
“We’ll be adding more dynamic customization options for the FastRelay, and FastExit scripts,” Beard added.
TorWorld will also offer a platform to manage abuse notices for Tor servers operated by its users. It will be a paid service because a TorWorld team will handle their abuse notifications.
We all know that darknets represent a facilitator and aggregator for cyber criminal communities and the Tor network is one of the most popular anonymizing netwotk in the criminal underground.
The TorWorld will not allow criminal uses of its infrastructure.
Currently, there is no certainty about when and how the TorWorld TaaS service will be ready, anyway I’ll monitor its progress with a great interest and admiration.
Researchers Link "de-identified" Browsing History to Social Media Accounts
24.1.2017 Securityweek Safety
Researchers Demonstrate How "de-identified" Web Browsing Histories Can be Linked to Social Media Accounts
While the use of cookies and other tracking mechanisms used to track computers is widespread and well understood, it is often believed that the data collected is effectively de-identified; that is, the cookies track the computer browser, not the person using the computer.
This is the message often promulgated by the advertising industry: tracking cookies allow targeted advertising without compromising personal privacy. Now new research from academics at Stanford and Princeton universities demonstrates that this need not be so.
In the new study 'De-anonymizing Web Browsing Data with Social Networks' (due to be presented at the 2017 World Wide Web Conference Perth, Australia, in April) the researchers show that de-identified web browsing histories can be linked to social media profiles using only publicly available data. Once the social media profile associated with a browsing pattern is known, the person is known.
The basic premise is that social media users are more likely to click on links posted by people they follow. This creates a distinctive pattern that persists in the browsing history. "An adversary can thus de-anonymize a given browsing history," states the report, "by finding the social media profile whose 'feed' shares the history's idiosyncratic characteristics."
The theory was tested against Twitter -- chosen because it is largely public, has an accessible API, and wraps its links in the t.co shortener. Assuming an 'adversary' has access to browsing histories, he can then easily deduce (through timing or referrer information) which links came from Twitter. The pattern of those referrals from Twitter can then be used to identify the user concerned by matching it with users' Twitter profile characteristics. The same approach could also be used against users with Facebook or Reddit accounts.
"Users may assume they are anonymous when they are browsing a news or a health website," comments says Arvind Narayanan, an assistant professor of computer science at Princeton and one of the authors of the research, "but our work adds to the list of ways in which tracking companies may be able to learn their identities."
The approach is not foolproof. Nevertheless, say the researchers, "given a history with 30 links originating from Twitter, we can deduce the corresponding Twitter profile more than 50 percent of the time." In fact, in a test involving 374 volunteers who submitted web browsing histories, the method was able to identify more than 70 percent of those users by comparing their web browsing data to hundreds of millions of public social media feeds.
"All the evidence we have seen piling up over the years showing the strong limits of data anonymization, including this study," comments Yves-Alexandre de Montjoye, an assistant professor at Imperial College London (not associated with the research), "really emphasizes the need to rethink our approach to privacy and data protection in the age of big data."
The problem goes beyond simple user privacy, since it could be used to target persons of interest. "The idea would be to look at something such as my Twitter account (as in who I'm following) and to determine what links I'm seeing," explains F-Secure security advisor Sean Sullivan. "And then, to find the 'User X' with the highest correlation between site visits and links seen. At which point, if I'm User X, I could be targeted by somebody who controls one of the sites visited."
At a purely 'commercial' level, this could be used to target individuals with high value goods. But it could also be used to find and target specific individuals prior to a network attack.
The researchers accept that their current methodology is not 100% accurate, but add an "adversary may fruitfully make use of other fingerprinting information available through URLs, such as UTM codes. Thus, the main lesson of our paper is qualitative: we present multiple lines of evidence that browsing histories may be linked to social media profiles, even at a scale of hundreds of millions of potential users."
Furthermore, it claims, "our attack has no universal mitigation outside of disabling public access to social media sites, an act that would undermine the value of these sites." It calls for "more research into privacy-preserving data mining of browsing histories."
China Cracks Down on Bids to Bypass Online Censorship
24.1.2017 Securityweek Safety
Beijing - China has announced a 14-month campaign to "clean up" internet service providers and crack down on devices such as virtual private networks (VPNs) used to evade strict censorship.
The ruling Communist party oversees a vast apparatus designed to censor online content deemed politically sensitive, while blocking some Western websites and the services of internet giants including Facebook, Twitter and Google.
It passed a controversial cybersecurity bill last November, tightening restrictions on online freedom of speech and imposing new rules on service providers.
But companies and individuals often use VPNs to access the unfettered internet beyond China's "Great Firewall".
Telecom and internet service providers will no longer be allowed to set up or rent special lines such as VPNs without official approval, the ministry of industry and information technology said Sunday.
Its "clean up" campaign would last through March 2018, it said in a statement on its website.
The announcement comes days after President Xi Jinping extolled globalisation and denounced protectionism in a keynote speech at the World Economic Forum in Davos, where he insisted that China was committed to "opening up".
China's internet access services market has grown rapidly, and the "first signs of disorderly development are also appearing, creating an urgent need for regulation", the statement said.
The new rules were needed to "strengthen internet information security management", it added.
IT expert Li Yi told the Global Times newspaper, which often takes a nationalistic tone, the new regulations were "extremely important".
While some multinationals such as Microsoft needed VPNs to communicate with overseas headquarters, other companies and individuals "browse overseas internet pages out of illegal motivations", Li said.
A 2015 report by US think tank Freedom House found that China had the most restrictive Internet policies of 65 countries it studied, ranking below Iran and Syria.
China is home to the world's largest number of internet users, which totaled 731 million as of December, the government-linked China Internet Network Information Center said Sunday.
Lavabit Email Service Returns with New Encryption Platform
24.1.2017 Securityweek Safety
Lavabit, the secure email service that shut down in 2013 after the NSA requested access to Eduard Snowden's email account, is recommencing operations on a new secure end-to-end communications platform, Lavabit owner Ladar Levison announced on Friday.
In August 2013, the service was suspended after the NSA requested its Secure Sockets Layer (SSL) private keys to access the email account of its users. The NSA was reportedly interested in Snowden’s account at the time, but Lavabit suggested that, with the SSL key in its hands, the US government would have been able to access any account.
Lavabit’s closing at the time prompted other online services to take a similar route, including Silent Circle, which shut down its Silent Mail service “to prevent spying,” and Groklaw, a technology news site focused on legal issues. Several months later, Silent Circle and Lavabit formed the Dark Mail Alliance, focused on offering the “next-generation of private and secure email.”
The relaunch of Lavabit’s email service, Levison says, isn’t meant only to continue sustaining online freedom, justice, and liberty, but also to address some of the main issues that email services today face. He also points out that the reopening builds on the Dark Internet Mail Environment (DIME), open source secure end-to-end communications platform for asynchronous messaging across the Internet.
“Today, we start a new freedom journey and inaugurate the next-generation of email privacy and security,” Levison notes on the Lavabit website.
DIME was created with Kickstarter funding, which also helped Levison come up with Magma, an associated DIME-capable free and open source mail server. Released on Friday together with Magma, the end-to-end encrypted global standard was designed to offer multiple modes of security (Trustful, Cautious, and Paranoid), and to address security problems so far have neglected.
The platform was designed as an evolution of OpenPGP and S/MIME, which don’t provide automatic encryption and don’t protect metadata. DIME, on the other hand, encrypts all facets of an email transmission (body, metadata and transport layer), thus aiming to deliver the greatest protection possible without sacrificing functionality.
“DIME is the only automated, federated, encryption standard designed to work with different service providers while minimizing the leakage of metadata without a centralized authority. DIME is end-to-end secure, yet flexible enough to allow users to continue using their email without a Ph.D. in cryptology,” Levison says.
Users can rely on the server to handle all privacy issues, meaning they would have to “trust” the server (Trustful mode), can set it to only store and synchronize encrypted data, including encrypted copies of a user’s private keys and encrypted copies of messages (Cautious mode), or can place a minimum amount of trust in the server, denying it access to private keys (encrypted or decrypted), but losing functionality, as webmail access won’t be available (Paranoid mode).
The service is available for existing users to regain access to their accounts in “Trustful” mode and update their credentials to the new DIME standard, as well as for new users to pre-register for an account.
Lavabit also made the free, open source library, and the associated command line tools for creating and handling the new DIME standard available for everyone, and says that any domain admin can deploy Magma or implement their own encrypted DIME compatible server. Clients for Windows, Mac OS X/iOS, and Linux/Android are also expected to be released.
“Today, the democratic power we transfer to keep identities safe is our own. With your continued patronage, we will restore privacy and make end-to-end encryption an automatic, ubiquitous and open source reality,” Levison concluded.
In 2014, Snowden’s revelations about widespread online surveillance resulted in a push to encrypt email and keep messages free from the government, and the move regained momentum last year, after Apple decided not to provide the FBI with assistance to access San Bernardino’s iPhone, claiming that it was actually asking for a backdoor to all iPhones out there.
Symantec Revokes Wrongly Issued Certificates
23.1.2017 Securityweek Safety
Symantec has revoked numerous wrongly issued certificates, including for domains such as example.com and test.com. This is not the first time the security firm’s certificate issuance practices have come under scrutiny.
The misissued certificates were spotted via the Certificate Transparency (CT) system by Andrew Ayer, founder of SSLMate. The expert discovered several certificates for example.com, which he confirmed were not authorized by the domain’s owner. He also identified certificates for domains such as test.com, test1.com, test2.com, and others containing the string “test.”
Ayer found more than 100 wrongly issued certificates attributed to Symantec and its subsidiaries GeoTrust and Thawte. The problematic certificates have several entries with the value “test,” which suggests they have been issued for testing purposes.
19 Jan
Andrew Ayer @__agwa
This is a HUGE no-no. There are very specific rules certificate authorities must follow to verify that a certificate request is authorized.
Follow
Andrew Ayer @__agwa
Even if the certs were only for testing, if a system allows employees to bypass authorization, it will allow attackers to bypass it too.
10:50 PM - 19 Jan 2017
Retweets likes
Steven Medin, PKI policy manager at Symantec, said the certificates had been issued by one of the company’s WebTrust audited partners. Medin said this partner’s privileges have been reduced to restrict further issuance and the reported certificates have all been revoked.
Ayer has advised domain owners to monitor CT logs to determine if unauthorized certificates have been issued for their websites. Since this is not the first time Symantec has misissued certificates, the expert has also recommended excluding the company via CAA records, which allow users to specify which CA can issue certificates for their domain.
In October 2015, Google asked Symantec to improve its certificate issuance practices after Thawte was caught releasing certificates for google.com domains. The company claimed to have issued the certificates for testing purposes, but it ultimately decided to terminate some employees after completing its investigation.
Symantec’s certificate business also made the news in February 2016, when the company asked browser vendors to allow it to issue nine new SSL certificates signed with SHA-1 for Worldpay after the payment processor failed to upgrade some devices before the December 31, 2015, deadline.
Lavabit — Encrypted Email Service Once Used by Snowden, Is Back
21.1.2017 thehackernews Safety
Texas-based Encrypted Email Service 'Lavabit,' that was forced to shut down in 2013 after not complying with a court order demanding access to SSL keys to snoop on Edward Snowden's emails, is relaunching on Friday.
Lavabit CEO Ladar Levison had custody of the service's SSL encryption key that could have helped the government obtain Snowden's password. Although the FBI insisted it was only after Snowden's account, that was the key to the kingdom that would have helped the FBI agents obtain other users’ credentials as well.
But rather than complying with the federal request that could compromise the communications of all of its customers, Levison preferred to shut down his encrypted email service, leaving its 410,000 users unable to access their email accounts.
Now, Levison has announced that he is reviving Lavabit with a new architecture that fixes the SSL problem — which according to him, was the biggest threat — and includes other privacy-enhancing features that will help its users send emails that he can't eavesdrop, even if ordered to do so.
Levison is releasing the source code for an open-source end-to-end encrypted global email standard that promises surveillance-proof messaging that even hides the metadata on emails to prevent agencies like the NSA or FBI from being able to find out with whom Lavabit users communicate.
Dubbed Dark Internet Mail Environment (DIME), the standard will be available on Github today, along with an associated mail server program called Magma, which is ready for use with the Dark Internet Mail Environment.
"DIME is the only automated, federated, encryption standard designed to work with different service providers while minimizing the leakage of metadata without a centralized authority," Levison said in a blog post.
"By encrypting all facets of an email transmission (body, metadata, and transport layer), DIME guarantees the security of users and the least amount of information leakage possible."
According to Levison, Magma server is designed to offer an easy-to-use application so that even non-technical users with existing email clients can use Lavabit encrypted email service with ease.
DIME standard includes a ‘Trustful’ encryption mode, which requires users to trust the server to manage the encryption and their keys.
"The server performs the encryption on your behalf, and as such, you must trust that the server will not be rewritten in such a way that it captures your password, or peeks at your messages during processing," Levison said.
Also, the DIME also offers Cautious Mode and Paranoid Mode for users who want absolute control over their encryption keys, so that their keys never transmits anywhere. Paranoid means Lavabit will never store a user’s private keys on its server.
Initially, the new Lavabit service will only be accessible to its existing customers and only in Trustful mode.
However, if you were not LAvabit customer in the past before the service shut down, you can pre-register and wait for the eventual rollout.
ZeroNet could be a solution against censorship and much more
4.1.2017 securityaffairs Safety
ZeroNet is a new and revolutionary decentralized P2P internet that promise to avoid censorship and improve user privacy on the open web.
ZeroNet is a decentralized and open source web platform. It’s based on BitTorrent(p2p) technology and BitCoin cryptography. These features ensure a decentralized censorship-resistant network.
The contents published by users can never be deleted because they’re distributed directly to other visitors without any central server. The content remains online so long as at least one user serving it. It’s impossible to shut down websites in the ZeroNet.
“When a site is updated by its owner, all nodes serving that site (previous visitors) will receive only the incremental updates done to the site content.” states the official website of the project.
ZeroNet implements a network whereby users can access and surf websites that are hosted on other user’s machines, it doesn’t include centralized servers.
“It’s nowhere because it’s everywhere!” declares ZeroNet site
You can create a free website using ZeroNet. There are no costs for hosting because the website is stored automatically your website. This could be a challenge to web hosting companies. It is always online with no downtime and can be accessible if your internet is unavailable if you have visited the website previously.
The site owner can accept payment directly to the site address.
Is ZeroNet anonymous?
If you want to hide your IP address, ZeroNet supports Tor network. The level of anonymity implemented is the same of the one implemented for BitTorrent, but a combined use with the Tor network will allow protecting user’s anonymity.
ZeroNet is made to work with anonymity networks: you can easily hide your IP using the Tor network.
Furthermore, you don’t need to remember your password, because your account is protected by same cryptography as a Bitcoin wallet.

In order to ensure integrity files, when you visit a site you download a file named “content.json”, it contains all other file names with relative hashes and cryptographic signature by the site owner. Then you download other files and verify them using hashes included in the “content.json”. This prevents in some way the diffusion of corrupted files or malicious code.

Another feature is multi-user site for example if you want to post on forum or blog. Sending your auth address to the site owner, it creates a new file and set your auth address as the valid signer. The site owner publishes a new “content.json” declaring that you can be signed a file.
Below the list of features implemented by ZeroNet:
Easy, zero configuration setup.
Password-less BIP32 based authorization: Your account is protected by the same cryptography as your Bitcoin wallet.
Real-time updated sites.
Namecoin .bit domains support.
SQL Database support: Allows for easier site development and faster page load times.
Anonymity: Full Tor network support with .onion hidden services instead of ipv4 addresses
TLS encrypted connections.
Automatic, uPnP port opening.
Plugin for multiuser (openproxy) support.
Works with any browser/OS.
ZeroNet users also have access to
ZeroBoard: Simple message board demo for dynamic content distribution
ZeroBlog: Self publishing blog demo
ZeroTalk: Decentralized, P2P forum demo
ZeroMail: End-to-end encrypted, distributed, P2P messaging site. To improve privacy it uses a BitMessage-like solution and will not expose the message recipient.
ZeroChat: The finished site for the tutorial of creating a server-less, SQL backed, real-time updated P2P chat application using ZeroNet in less than 100 lines of code
ZeroMe: Decentralized, Twitter-like P2P social network.
One of the questions in the FAQ session camptured my attention:
What happens when someone hosts malicious content?
The answer is very clear:
The ZeroNet sites are sandboxed, they have the same privileges as any other website you visit over the Internet. You are in full control of what you are hosting. If you find suspicious content you can stop hosting the site at any time.
Firefox 52 more privacy oriented with a Tor protection mechanism
2.1.2017 securityaffairs Safety
Mozilla development team announced a new privacy protection mechanism that will come with Firefox 52, it aims to prevent websites from fingerprinting users.
Mozilla announced the introduction of a new privacy protection mechanism to Firefox 52 that prevents websites from fingerprinting through system fonts.
The technique is widely adopted by advertising companies via hidden scripts delivered with ads that take the list of local fonts and along with other data create a unique fingerprint (ID) for each user.
The companies aim in this was to deliver targeted ads and track users across the web.
The experts at Mozilla have implemented a feature to only expose whitelisted system fonts to avoid fontlist fingerprinting. The new feature will be included in the stable branch of Firefox 52, scheduled for release on March 7, 2017.
The user privacy protection mechanism was already implemented by Mozilla in the Tor Browser, it was developed to block websites from identifying visitors based on the fonts installed on their machines.
The font fingerprinting protection is already available in Firefox 52 Beta.
“Defending against font fingerprinting is complex. We have to worry about distinguishing attacks via differing installed font sets, text rendering engine differences, and font variants. There are a variety of tickets involved.” states the Tor Development Team.
“In #13313, we introduced a Tor Browser pref, “font.system.whitelist”, which accepts a list of fonts and excludes all others from the browser.”
How does the feature work?
The feature leverages a whitelist of system fonts for each operating system, the browser will not block queries for system fonts but it will provide the same answer for every user making impossible to discriminate them.
The practice of font fingerprinting relies on website operators deploying Flash or JS scripts that query the user’s browser for a list of locally installed fonts.
The news confirms the intention of Mozilla to protect users’ privacy, in July the development team launched the Tor Uplift project, a significant effort in improving privacy features implemented in FireFox.
“To uplift all of the Tor Browser patches to mainline Firefox. The general approach is to add preferences for anything that breaks the web and set them to default “off” so that the behavior of default Firefox does not change. All bugs are tagged with [tor]. The Tor Browser design document is here.” states the description of the project.
Tor Project Releases Sandboxed Tor Browser 0.0.2
12.12.2016 thehackernews Safety
The non-profit organization behind TOR – the largest online anonymity network that allows people to hide their real identity online – has launched an early alpha version of Sandboxed Tor Browser 0.0.2.
Yes, the Tor Project is working on a sandboxed version of the Tor Browser that would isolate the Tor Browser from other processes of the operating system and limit its ability to interact or query low-level APIs that can lead to the exposure of real IP addresses, MAC addresses, computer name, and more.
Sandboxing is a security mechanism for separating running programs. When an application is sandboxed, its process runs in a separate environment from the underlying operating system, so that errors or security issues in that application can not be leveraged to affect other parts of the OS.
Sandbox applications are enabled in their own sequestered area and memory, where they can be worked on without posing any threat to other applications or the operating system.
Major modern browsers, including Chrome, Firefox, and Edge, use sandboxed environments to separate themselves from the operating system.
However, the Tor Browser, which itself is based on the open-source Mozilla Firefox browser, did not use the sandboxing environment that left the browser somewhat insecure even after so many privacy protection features.
Just rewind the FBI's 2015 investigation into child pornography site Playpen, in which the agency hacked into some 8,700 computers across 120 different countries.
The FBI used Tor exploits to identify and catch visitors of PlayPen hiding their real identity using Tor. Such exploits targeting the Tor Browser can also be used to unmask the identity of journalists, political dissidents, and others.
Keeping this in mind, the Tor Project started working on a Sandboxed version of the Tor Browser in September this year.
The idea behind the move is that exploits and vulnerabilities targeting Tor Browser are trapped inside the sandbox environment and can not get out and affect the rest of the computer or unmask anyone.
Tor developers have released the first version of its new and improved Tor Browser, though the version is still very much an alpha; so one can expect bugs, some potentially major ones.
One of the developers working on the project describes the browser features as:
A Gtk+3 based UI for downloading/installing/updating Tor Browser, configuring tor, and launching the sandboxed browser. Think `tor-browser-launcher`, that happens to run Tor Browser in a bunch of containers.
Linux seccomp-bpf + namespace based containers for Tor Browser, that attempts to prevent/mitigate exploits and reduce the amount of personally identifiable information to a minimum, centered around bubblewrap (runtime dependency).
This version is yet only available for Linux. Official binaries should be available sometime next week. For now, confident users could compile it themselves from the source code, though I strongly suggest people to wait.
If you are more privacy conscious, you should use a Virtual Private Network (VPN) with Tor.
As I previously recommended, Privatoria VPN provides a number of great features, including VPN, VPN Tor, Proxy, Proxy Tor, and Anonymous Emails, which makes it one of the reliable VPN services available in the market.
You can try Privatoria VPN Free Trial today and secure your web experience.
How much cost a StingRay? Surveillance is a profitable business
12.12.2016 securityaffairs Safety
Motherboard published an interesting blog post which includes further details on the cost of StingRay phone surveillance equipment.
A couple of years ago I published a post on Stingray Technology trying to explain how governments track cellular devices.
A StingRay is an IMSI-catcher (International Mobile Subscriber Identity) designed and commercialized by the Harris Corporation. At the time of the article, the cellular surveillance system was costing as much as $400,000 in the basic configuration, and its price varied with add-ons ordered by the agency.
The IMSI-catcher is a surveillance solution used by military and intelligence agencies for telephone eavesdropping. It allows for intercepting mobile phone traffic and tracking movements of mobile phone users. Essentially, an IMSI catcher operates as a bogus mobile cell tower that sits between the target mobile phone and the service provider’s real towers. The IMSI catcher runs a Man In the Middle (MITM) attack that could not be detected by the users without using specific products that secure communication on mobile devices.
The use of the IMSI-catcher is raising a heated debate in the United States because devices like StingRay and other similar cellphone tracking solutions are being widely adopted by law enforcement agencies across the country.
StingRay allows law enforcement to intercept calls and Internet traffic, send fake texts, inject malware on a mobile device, and to locate the targets.
Now Curtis Waltman from Motherboard published an interesting blog post which provided further details on the cost of the StingRay phone surveillance tool.
Waltman published data provided by the Rochester Police Department in New York that responded to the Cell Site Simulator Census, an initiative that census the cellphone surveillance equipment use and policy.
“A mapping of police departments and agencies nationwide that are using IMSI catcher (Stingray) technology. Included in this mapping is a focus on the policies, procedure and contractual agreements that department’s are formulating as they adopt the controversial surveillance device.” states the description for the census.
Data shared by Motherboard are very interesting and provides useful insights about their surveillance systems, their components, and prices. It a “completely unredacted quote list of Harris Corporation products”.
Documents shared by the Rochester Police Department show clearly how Harris sells the Stingray equipment to law enforcement.
According to the documents, devices are often sold in packages, like the StingRay II Vehicular System that is offered for sale with devices (i.e. Three different kinds of Harris’ Harpoon signal amplifiers) that allow its use for a patrol vehicle.
How much cost a StingRay II Vehicular System?
The package includes a laptop, three kinds of software for accessing different types of cellular networks, and an AmberJack cellphone tracker goes for a grand total of $148,000.
“The Amberjack is an important accessory for the surveillance systems like Stingray, Gossamer, and Kingfish. It is a direction-finding system antenna that is used for cellular device tracking. It costs nearly $35,015″ I wrote in a blog post published early this year.
The prices for the AmberJack is quite similar I published early this year.
According to documents published by Motherboard, The KingFish package, Harris Corporations smaller, mobile version of the StingRay, is sold for $157,000.
The single KingFish device is not so expensive as I have reported early this year.
“Kingfish is a surveillance transceiver that is used by law enforcement and intelligence agencies to track cellular devices and exfiltrate information from mobile devices over a targeted area. It could be concealed in a briefcase and allows gathering of unique identity codes and shows connections between phones and numbers being dialed. Its cost is slightly higher than $25,000.” 
The Rochester PD expressed its interest for the entire KingFish, except the laptop.
The company is including in the surveillance packages also training activities that go for $12,000.
“These packages also come with the option of a training package, costing $12,000, and a one year maintenance package that will cost $169,000 if your department decided to splurge for the whole line of Harris’ products (this was 2011 so the 4G network cell site simulator the HailStorm wasn’t released yet.) Training isn’t included interestingly enough, so police departments are more or less forced to pay for training on these complicated and powerful devices.” states the post published by Motherboard.
The note at the end of the document provides also further details of the surveillance technology, including the specifications required to use the equipment in a real scenario.
“The StingRay and Kingfish can be run out of a car’s cigarette lighter, while the StingRay II requires a 2000W power inverter. That is hungrier for power than almost any household appliance, save a dryer or oven.” continues the post.
If you are interested in StingRay surveillance technology, give a look at the article “StingRay Technology: How Government Tracks Cellular Devices”
Password Manager Pro — Easiest Way to Keep Enterprises Secure
1.12.2016 thehackernews Safety
Recent corporate breaches have taught us something important — the average enterprise user is spectacularly bad at choosing good passwords.
As modern enterprise is becoming a hybrid organization with infrastructure spread across on-premises data centers as well as in the cloud, security of information, applications, and assets has become a paramount concern.
Cyber security is no longer an optional strategy for businesses, where limited visibility into the password practices of employees and ineffective monitoring of privileged credentials could end up an organization with a serious security breach and identity theft.
The first line of defense for any organization or company is passwords, but most organizations grossly underestimate the need to comply with corporate password policies and meet IT regulatory requirements.
Large enterprises have a policy in place that requires end users to choose strong passwords that can withstand dictionary and brute-force attacks, but it comes out to be non-effective, as there are still possibilities that users will go against the policy and pick a simple password.
Even if an organization's IT department forces their employees to choose strong passwords, those strong passwords are stored in text-based files like spreadsheets, or even worse, Word documents.
Not to mention how secure these files are and how able they are to restrict who can access which passwords.
We know that Ignorance is Bliss, but in this case, ignorance can place your enterprise and its data at risk.
In addition to the issues related to creating strong, unique passwords and securely storing them, large enterprises face another important issue - sharing the impersonal administrative accounts among the team members, which can be very challenging. For example, a particular 'administrator' account on Windows will be used by multiple users and all of them will be using the same log in credentials.
The Solution? Password Manager for Enterprise:
Password Manager for Enterprise
Password Manager not only forces one to have strong, unique passwords, but also remembers on your behalf, determines when those passwords have to change, and includes an admin console for controlling all passwords and access to critical services within the enterprise.
I'm impressed with ManageEngine's privileged password management solution — Password Manager Pro that already has VMWare, Walmart, EMC2, and NASA on its customer list.
Password Manager Pro (PMP) is specially designed for enterprise teams and provides a complete solution to control, manage, monitor, and audit the entire lifecycle of privileged access, helping them detect suspicious events in real-time.
Password Manager Pro encrypts and stores all your sensitive data in a centralized vault, including passwords, documents, and digital identities, which are then retrieved through a Web interface.
Administrators can consolidate all the passwords, create an inventory, define password policy, set password expiration, and share passwords among authorized users by granting them exclusive privileges or temporary access.
Deploying Password Manager Pro is easy, as it only takes a few minutes for the web-based management software to install its database and web-server, which is available for Windows and Linux.
However, users can access their portal through mobile apps or browser extensions from any device, including Android, iOS, and Windows.
In a single package, Password Manager Pro offers three solutions:
1. Privileged Account Management
Password Manager Pro
Once deployed, Password Manager Pro automatically discovers all IT assets in your network and lists all the privileged accounts associated with them, which enables administrators to quickly secure all the privileged identities by enforcing password management best practices.
This includes the use of strong passwords, securing sensitive data and passwords with AES 256-bit strong encryption, and securely sharing administrative passwords across your organization based on need, with granular access restrictions.
Most importantly, the Password Manager Pro is also designed to automate the password reset and synchronization process across the entire enterprise for a broad range of target systems.
This centralized and enterprise-wide 'Automated Password Resets' feature helps IT administrators get rid of unchanged passwords and protect all sensitive resources from unauthorized access.
In other words, Password Manager Pro allows IT administrator to reset passwords when required or automatically randomizes through scheduled tasks in order to ensure usage of strong passwords and periodic resets by creating and enforcing strict password policies.
2. Remote Access Management
One of the outstanding features of Password Manager Pro is its ability to help administrators launch a direct connection with all remote devices, including those in remote data centers, with just one click from the product's GUI.
With its secure gateways, Password Manager Pro helps you provide remote access to your IT resources to employees and third-party contractors without even disclosing the passwords in plain-text. In other words, PMP enables remote login to devices without sharing passwords at all!
From its web-interface, authorized users can directly launch RDP, SSH, Telnet, and SQL console sessions, wherein all connections will be tunneled through Password Manager Pro's server and require no direct connectivity between the user device and remote host.
This feature has obvious advantages like saving time that usually used to copy/paste passwords from the document, and increasing accountability as PasswordManager Pro tracks access and usage of passwords.
3. Privileged Session Management
The remote connections to devices launched from Password Manager Pro's GUI can be closely monitored through PMP's Privileged Session Manager. All actions done by the users during the privileged session are video recorded and stored for forensic audits. The video records can be played back anytime, to trace actions to users.
Password Manager Pro also includes a session shadowing feature that offers session recording capabilities to real-time monitoring of sensitive privileged sessions launched by other users.
If any suspicious activity is discovered, administrators can immediately terminate sessions in real time, giving admins complete control over privileged sessions.
One can also enable two-factor authentication (2FA) and mobile access for authorized users or groups.
How to Get Password Manager Pro?
password-manager-pro-enterprise
Password Manager Pro supports several different user access roles including super admin, admin, and regular password users. An online demo of Password Manager Pro is available here, in case you want to have a quick look to the application.
Besides this, ManageEngine Password Manager Pro is now available in MSP edition as well, which is specially designed for the Managed Service Providers who manages the IT and network infrastructure of their customers.
ManageEngine's Password Manager Pro MSP Edition allows businesses to manage administrative passwords of their clients separately from a single management console or offer Password Management Service to them.
So, if ManageEngine Password Manager Pro fits for your organization, you can give it a try. Pricing depends on the level, number of administrators and language.
The cost varies widely, from the annual subscription of $495 for Standard edition, Single-language, and 2-admin (the number of users is unlimited) to $19,995 for an Enterprise edition, Multi-language, 200-admin, perpetual license.
All editions of ManageEngine Password Manager Pro can be downloaded (Windows/Linux) directly from the ManageEngine official website.
To understand how Password Manager Pro helps mitigate security risks related to privileged access, you can simply download the eBook for free.
Research on unsecured Wi-Fi networks across the world
25.11.2016 Kaspersky Safety
The very nature of wireless Wi-Fi networks means that hackers or criminals simply need to be located near an access point in order to eavesdrop and intercept network traffic. Poorly configured access point encryption or services that allow data to be sent without any encryption pose a serious threat to user data.
Confidential data can be protected by encrypting traffic at wireless access points. In fact, this method of protection is now considered essential for all Wi-Fi networks. But what actually happens in practice? Is traffic always encrypted on public Wi-Fi networks? How does the situation differ from country to country? Kaspersky Security Network statistics can answer all these questions. We compared the situation with Wi-Fi traffic encryption in different countries using data from our threat database. We counted the number of reliable and unreliable networks in each country that has more than 10 thousand access points known to us (this obviously excludes Antarctica and other regions where there is not enough data to draw any conclusions).
Security of Wireless Networks
Using statistics from Kaspersky Security Network (KSN), we analyzed data from across the world for almost 32 million Wi-Fi hotspots accessed by the wireless adapters of KSN users.
Encryption type used in public Wi-Fi hotspots across the world
Approximately 24.7% of Wi-Fi hotspots in the world do not use any encryption at all. This basically means that by using an antenna capable of sending and receiving data at 2.4 GHz, any individual located near an access point can easily intercept and store all user traffic and then browse it for data they are interested in. Fortunately, modern online banking systems and messengers do not transfer unencrypted data. But this is the only thing that prevents users of Wi-Fi networks with unencrypted traffic from revealing their passwords and other essential data when using an unsecure access point.
The WEP (Wired Equivalent Privacy) protocol for encryption of data transferred over Wi-Fi is used by approximately 3.1% of all analyzed access points. The protocol was the first to be created, quite a long time ago, and is now completely unreliable – it would take hackers just a few minutes to crack it. From a data security point of view, using WEP is not much different from using open networks. This protocol is being relegated to oblivion everywhere, but as we see from the chart above, it can still be found in use.
Around three-quarters of all access points use encryption based on the Wi-Fi Protected Access (WPA) protocol family. The protocols from this family are currently the most secure. The effort required to hack WPA depends on its settings, including the complexity of the password set by the hotspot owner. It is worth noting that an attempt to decipher traffic from “personal” (WPA-Personal, PSK authentication) wireless networks (with public access points) can be made by intercepting the handshakes between the access point and the device at the beginning of the session. “Corporate” versions are protected from this sort of interception because they use internal company authorization. When it comes to “personal” WPA2 attacks, the situation is similar to that of WPA and mostly depends on the strength of the password set by the hotspot owner.
It is only fair to note that during a standard attack on a Wi-Fi access point, a personal computer can generate from 50 to 300 keys per second on average. If the encryption key is strong, it will take years to hack it. Still, no one can guarantee that the key used at a cafe will be secure and that the attacker will have nothing but a PC at their disposal.
Overall, it can be said that today’s WPA/WPA2 “non-enterprise” versions are reasonably, but not absolutely, secure. In particular, they allow brute-force and dictionary attacks. There are ready-to-use publicly available tools (aircrack-ng and similar software) for performing such attacks, as well as a large number of manuals.
Research on unsecured Wi-Fi networks across the world
Share of Wi-Fi hotspots that use unreliable WEP or do not encrypt data (by country)
We would like to note that the five countries with the highest proportion of unsecured connections include Korea (47.9% of unsecured Wi-Fi access points), while France (40.14%) and the US (39.31%) rate 9th and 12th respectively in the list.
Germany appears to be the most secure among Western European countries, with 84.91% of access points secured by WPA/WPA2 protocol encryption.
Share of Wi-Fi hotspots that use WPA/WPA2 (by country)
However, even when using an encrypted connection, you should not completely rely upon this security measure. There are several scenarios that could compromise even well-encrypted network traffic. These include fake access points with names that duplicate or mimic real ones (for example, TrainStation_Free or TrainStation Free) and compromised routers forwarding traffic without encryption to attackers (malware tools that infect such devices are already “in the wild”). At any rate, taking care of your own security is a good idea.
Recommendations for Users
There are several simple rules that help protect personal data when using open Wi-Fi networks in cafes, hotels, airports, and other public places.
Do not trust networks that are not password-protected.
Even if a network requests a password, you should remain vigilant. Fraudsters can find out the network password at a coffee shop, for example, and then create a fake connection with the same password. This allows them to easily steal personal user data. You should only trust network names and passwords given to you by employees of the establishment.
To maximize your protection, turn off your Wi-Fi connection whenever you are not using it. This will also save your battery life. We recommend disabling automatic connection to existing Wi-Fi networks too.
If you are not 100% sure the wireless network you are using is secure, but you still need to connect to the internet, try to limit yourself to basic user actions such as searching for information. You should refrain from entering your login details for social networks or mail services, and definitely not perform any online banking operations or enter your bank card details anywhere.
To avoid being a target for cybercriminals, you should enable the “Always use a secure connection” (HTTPS) option in your device settings. It is recommended to enable this option when visiting any websites you think may lack the necessary protection.
If possible, connect via a Virtual Private Network (VPN). With a VPN, encrypted traffic is transmitted over a protected tunnel, meaning criminals won’t be able to read your data, even if they gain access to them.
And, of course, you should use dedicated security solutions. They inform users about any potential dangers when connecting to a suspicious Wi-Fi network and prevent any passwords or other confidential data from being compromised if there is a threat.
One example of a dedicated solution is the Secure Connection tool included in the latest versions of Kaspersky Internet Security and Kaspersky Total Security. This module protects users connected to Wi-Fi networks by providing a secure encrypted connection channel. Secure Connection can be launched manually or, depending on the settings, activated automatically when connecting to public Wi-Fi networks, when navigating to online banking and payment systems or online stores, and when communicating online (mail services, social networks, etc.).
Antivirus Firm Kaspersky launches Its Own Secure Operating System
24.11.2016 thehackernews Safety
The popular cyber security and antivirus company Kaspersky has unveiled its new hack-proof operating system: Kaspersky OS.
The new operating system has been in development for last 14 years and has chosen to design from scratch rather than relying on Linux.
Kaspersky OS makes its debut on a Kraftway Layer 3 Switch, CEO Eugene Kaspersky says in his blog post, without revealing many details about its new operating system.
The Layer of 3-switch is the very first tool for running the Kaspersky OS, which is designed for networks with extreme requirements for data security and aimed at critical infrastructure and Internet of Things (IoT) devices.
What's new in Kaspersky OS than others?
Kaspersky OS is based on Microkernel Architecture: The new secure OS is based on microkernel architecture that enables users to customize their own operating system accordingly.
So, depending on a user's specific requirements, Kaspersky OS can be designed by using different modifications blocks of the operating system.
Kaspersky OS is non-Linux: Yes, one of the three major distinctive features of the new OS mentioned by Kaspersky is that the GUI-less operating system has been constructed from scratch and does not contain "even the slightest smell of Linux."
"All the popular operating systems are not designed with security in mind, so it is simpler and safer to start from the ground up and do everything correctly. Which is just what we did," says Kaspersky.
But what makes Kaspersky OS Hack-Proof?
It is the operating system's inbuilt security system. Yes, Kaspersky OS inbuilt security system has the ability to control the behavior of applications and the OS modules.
Kaspersky OS claims itself as practically unhackable OS, because for gaining unauthorized access, any hacker would need to break the digital signature of an account holder, which is possible only with a quantum computer.
"In order to hack this platform a cyber-baddie would need to break the digital signature, which – anytime before the introduction of quantum computers – would be exorbitantly expensive," says Kaspersky.
Kaspersky talked about the recent DDoS attacks that affected numerous websites in past few months. He guaranteed that Kaspersky OS would protect devices, such as industrial control systems, SCADA or ICS, and IoTs, from cyber attacks.
The most severe one was the recent massive DDoS attack on Dyn's DNS servers, which knock down popular sites like Amazon and Twitter. The attack was carried out by Mirai botnets that had infected smart devices like security cameras.
So, Kaspersky says it is mandatory to protect the IoT and other critical infrastructure (like industry, transport, and telecoms) from IT threats.
"I also hope it's clear that it's better – no matter how difficult – to build IoT/infrastructure devices from the very beginning in such a way that hacking them is practically impossible. Indeed, that is a fundamental goal with Kaspersky OS," he says.
More details about Kaspersky's secure operating system is coming soon. Stay Tuned!
NIST Small Business Information Security guide for Small businesses
18.11.2016 securityaffairs Safety
The NIST Small Business Information Security: The Fundamentals guide aims to provide basic cybersecurity recommendations to small businesses.
I have always stressed the necessity to improve cyber security posture for small businesses that are most exposed to threat actors across the world. Now the National Institute of Standards and Technology has released a cybersecurity guide to support small businesses in securing their IT infrastructure.
The NIST “Small Business Information Security: The Fundamentals” guide aims to provide basic cybersecurity recommendations for small businesses through a risk assessment process.
“Businesses of all sizes face potential risks when operating online and therefore need to consider their cybersecurity,” she said. “Small businesses may even be seen as easy targets to get into bigger businesses through the supply chain or payment portals.” reads the NIST announcement.
“Many small businesses think that cybersecurity is too expensive or difficult; Small Business Information Security is designed for them,” Toth said. “In fact, they may have more to lose than a larger organization because cybersecurity events can be costly and threaten their survival.” In fact, the National Cyber Security Alliance found that 60 percent of small companies close down(link is external) within the six months following a cyberattack.

This guide is an important exercise for small-business owners that are not experienced in cybersecurity, it explains to them how to protect their information systems from cyber threats.
The Small Business Information Security: The Fundamentals guide proposes a classic approach that follows the IDENTIFY/PROTECT/DETECT/RESPONSE/RECOVER steps focusing on understanding and managing risks for small businesses. The guide also includes worksheets that could be used by small businesses to identify the information they manage. It is essential to assess the information assets and identify potential risks to it.
Of course, the guide is based on NIST’s Framework for Improving Critical Infrastructure Cybersecurity, which was issued in 2014.
The NIST highlighted that the new guide describes how to:
limit employee access to data and information;
train employees about information security;
create policy and procedures for information security;
encrypt data;
install web and email filters; and
patch, or update, operating systems and applications.
The guide also suggests install surge protectors and uninterruptible power supplies, considering to transfer the risks with cybersecurity insurance; and find reputable cybersecurity contractors.
Bypassing Two-Factor Authentication on Outlook Web Access
7.11.2016 securityaffairs Safety
Enterprises running Exchange Server using two-factor authentication on Outlook Web Access (OWA) could be hacked due to a design flaw.
New troubles for enterprises running Exchange Server, two-factor authentication implementations on Outlook Web Access (OWA) could be easily bypassed due to a design flaw.
An attacker can bypass two-factor authentication to access email inboxes, calendars, contacts and other sensitive data of targeted enterprises.
The weakness is related to the fact that Exchange Server also exposes the Exchange Web Services (EWS) interface alongside OWA, but this is not protected by two-factor authentication.
The attackers can then hack OWA server by targeting EWS that shares the same port as Outlook Web Access.

The design issue disclosed last week by researcher Beau Bullock from Black Hills Information Security who privately reported it to Microsoft on Sept. 28.
Bullock explained that the principal problem is that Outlook Web Access and Exchange Web Services run on the same web server and are both enabled by default, and often enterprises ignore it.
Even enabling 2FA on OWA, EWS is still exposing a single factor authentication for the same infrastructure.
In his test, Bullock set up an OWA server protected by Duo for Outlook 2FA, then he targeted the EWS on the same server using a test account’s credentials.
Bullock used a tool called MailSniper that he developed for searching mailboxes for sensitive data in a Microsoft Exchange environment.
“At DerbyCon 6.0 I released a tool called MailSniper for searching mailboxes for sensitive data in a Microsoft Exchange environment. MailSniper utilizes Exchange Web Services (EWS) when connecting to an Exchange server to retrieve messages from a user’s inbox. EWS is a web-based API enabled on Exchange servers that Microsoft recommends customers use when developing client applications that need to interface with Exchange. ” Bullock wrote a blog post.
Below a video PoC published by the expert:
Summarizing, Bullock demonstrated that the lack of 2FA for Exchange Web Services could be exploited by attackers to hack into Outlook Web Access server.
“In conclusion, it appears that Outlook portals that are being protected by two-factor authentication might not be covering all of the authentication protocols to Microsoft Exchange. In this post it was demonstrated that Exchange Web Services is not being protected by a popular two-factor authentication software, and it was possible to still read emails of a user after only obtaining their login credentials. Exchange has other services that might have a similar problem such as MAPI over HTTP, and Autodiscover. I tested against one third-party 2FA software, and Microsoft’s own Azure Multi-Factor authentication but I’d imagine others likely have the same problem.” concluded Bullock.
Safety1
Simplifying SSH keys and SSL Certs Management across the Enterprise using Key Manager Plus
2.11.2016 thehackernews Safety
Simplifying SSH keys and SSL Certs Management across the Enterprise using Key Manager Plus
With rapidly growing web-based services and widely expanding locations, organizations are using more and more SSL certificates as well as SSH keys than ever.
From authentication, confidentiality, and integrity to preventing the organization from industrial espionage, SSL certificates play an important role.
Managing SSL certificates across networks to ensure protection and prevent unanticipated failures is critical, and it also becomes complicated with multiple locations, divisions as well as the fastest growing use of external cloud-based services.
This not only complicates the process of managing individual SSL certificate and SSH key for an administrator but also costs organizations heavily.
A key solution for this issue is to use an advanced and efficient SSL certificate and SSH Key management system.
An effective solution enables an organization to know what kinds of certificates and keys it has, simplifies certificate discovery and monitor across multiple vendors, and also automates certificate renewal and transfer process.
We recently got an opportunity to test and review Key Manager Plus from ManageEngine, which is a division of Zoho Corporation that develops remote administration software for IT businesses.
And we were quite impressed by this product that simplifies even complex processes of key management, where most organizations fail, leaving themselves vulnerable to cyber attacks.
ManageEngine Key Manager Plus
ManageEngine-Key-Manager-Plus-tool.png
ManageEngine Key Manager Plus is a comprehensive, web-based solution that offers centralized management and visibility over the SSL certificates and SSH keys across any organization and helps administrators accurately monitor and manage them.
This application comes with a web-based interface that works on any modern web browser such as Edge, Firefox, and Chrome and you can easily deploy it on your computer with an automated installer.
The dashboard of this application is designed in such a way that after login, you get a broad and easily understandable graphical presentation of all digital assets (SSL certs and SSH keys) used by your organization.
Its user interface and easy to navigate features offer users to keep track of all important details, like the algorithm's encryption type, key length, the creation date of any issue and control new certificate signing requests, as well as access to wider range of tools.
SSL-SSH-Key-Manager-Plus-ManageEngine
Besides centrally creating and deploying new keys, ManageEngine Key Manager Plus also allows administrators to harden security policies by:
1. Periodically Rotating Key Pairs: Automatically rotating privileged SSH key pairs prevents misuse of keys, reduces security risks, meets compliance requirements and minimizes the operational burden on IT teams.
2. Delete Unwanted Keys: It is always important to monitor the environment in order to determine which keys are no longer in use and removing them. Key Manager Plus does same. It prevents unauthorized access to privileged accounts by removing unwanted SSH keys from vulnerable endpoints.
3. Terminate or Regulate access: Generally, in a large organization, SSH access is neither controlled nor monitored, which is a cause of most cyber threats to an organization. Administrators can easily monitor and terminate access anytime to prevent violations by obsolete accounts.
4. Alerts and Notifications: Besides key management, it is always important for an administrator to keep track of SSL certificates, which are about to expire or invalid in order to prevent downtime. This application allows you to set customizable and recurring notifications that alert you when the validity of your SSL cert is about to expire.
Switching to SHA-2 SSL Certificates [Migration Guide]
Nearly a million websites on the Internet are using an insecure algorithm, and leading web browsers, including Chrome and Firefox, have already declared that they could start rejecting website using potentially vulnerable SHA-1 certificates.
Since SHA-1 certs could result in system downtime, errors, and security threats, all organizations need to migrate to SHA-2 signed certificates before January 1, 2017.
ManageEngine solves this issue as well. Here's a quick step-by-step guide on how to find and replace SHA-1 with secure SHA-2 certificates in your organization using ManageEngine Key Manager Plus.
Conclusion: ManageEngine Key Manager Plus is an efficient and user-friendly solution that not only helps network administrators bypass complicated and time-consuming compliance processes by providing all the necessary tools for monitoring and managing SSL certificates and SSH keys in the first place, but also predict and prevent security breaches at their organizations.
So, if ManageEngine Key Manager Plus fits for your organization, you can give it a try. The company offers three edition of the latest Key Manager Plus version is 4.5, which includes:
Free Edition: This version of Key Manager Plus is free for lifetime and offers you to manage up to 5 keys in an organization.
Evaluation Edition: This version is a 30-day evaluation edition that allows you to manage up to 10 keys in an organization (Number of keys can be increased based on request during the period of evaluation).
Standard Edition: The prices for this edition start at $595 per year for managing 50 keys.
All editions of ManageEngine Key Manager Plus can be downloaded (Windows/Linux) directly from the ManageEngine official website, and an online demo is also available, in case you want to have a quick look to the application.
AV-TEST study sees search engine results even more poisoned with malicious links
31.10.2016 securityaffairs Safety
According to a study published by the independent anti-virus testing outfit AV-TEST, the number of malicious search engine results has been increasing.
The vast majority of the Internet users blindly trust data provided in response to their queries to the search engines. Actually, search engine results are increasingly poisoned with malicious links, the experts noticed a significant increase of the phenomena compared to the past.
It has been estimated that poisoned search engine results are displayed almost six times this year compared to 2013.
The threat is serious, Google and other search engines even more frequent provides malicious links in search results that lead to compromised websites used by crooks to deliver malware.
According to a study published by the independent anti-virus testing outfit AV-TEST, the number of malicious search engine results has been increasing year by year since 2013. The data are worrisome if we consider that across the year the defensive solutions have been more sophisticated.
The study analyzed search engine results in various queries from Google, Bing, Yandex and Faroo. The experts also analyzed over the past two years more than 515 million Twitter updates including malicious links.
“Search engines such as Google and others provide access to roughly more than 1 billion websites and globally handle 4 to 6 billion search queries – daily.” reads the study. “AV-TEST analyzed 80 million websites and discovered an unsettling trend.
“the number of infected results has been increasing year by year since 2013, despite the fact that search engine operators use many tools and technologies to try to filter them out.”
Experts at AV-TEST.org examined 80 million websites, identifying 18,280 infected web pages, while in the year up to August the organization inspected 81 million websites spotting more than 29,632 infected web pages.

It is important to remark that the search engine results were recorded by disabling the Google Safe Browsing feature.
“Both evaluations from AV-TEST through the year 2015 up until August 2016 ultimately yield two important final results (without Google safe browsing)” reads the study.
2015, 80 million websites examined: 18,280 infected web pages
2016 (up to Aug.), 81 million websites examined: 29,632 infected web pages
search engine results study
Both figures are disconcerting is compared with search engine results obtained in a past study dated 2013.
“By comparison: already in 2013, among roughly 40 million web pages examined, 5,060 malware threats were found. You don’t need to be a mathematician to see this clear growth trend.” continues the study.
The researchers performed also a sort of counter-test visiting the pages with malware threats found by AV-TEST, with the Google Safe Browsing tools. They reported the following results:
2015: 18,280 pages with malware threats, 555 Google warnings
2016: 29,632 pages with malware threats, 1,337 Google warnings

Maik Morgenstern, chief technology officer at AV-TEST.org, explained that discrepancy in the number of threats for search engine results due to the dynamic content of the web pages. It means that tools see something different everytime they access the site due to dynamic content such as malicious ads.
“It could be the ads on the website that have been flagged as suspicious by us and that changes every time you access the site,” said Morgenstern. “Or the website is delivering different content randomly or it does so by checking the user agent or location of the user.
“Also I do not know what the interval is that Google/Bing are scanning the sites for malware. There will always be a certain timeframe where malicious content could be on the site without Google/Bing knowing it, even if they were able to detect it. It is also possible that we flagged content as suspicious that is not considered suspicious by Google/Bing.”
Classified U.S. Defense Network Outage Hits Air Force’s Secret Drone Operations
13.10.2016 thehackernews Safety
U.S. drones are again in news for killing innocent people.
The Air Force is investigating the connection between the failure of its classified network, dubbed SIPRNet, at Creech Air Force Base and a series of high-profile airstrikes that went terribly wrong in September this year.
Creech Air Force Base is a secret facility outside Las Vegas, where military and Air Force pilots sitting in dark and air-conditioned rooms, 7100 miles from Syria and Afghanistan, remotely control their "targeted killing" drone campaign in a video-game-style warfare.
From this ground zero, Air Force pilots fire missiles just by triggering a joystick on a targeted areas half a world away, as well as operate drones for surveillance and intelligence gathering.
Drone operation facility at Creech Air Force Base -- a key base for worldwide drone and targeted killing operations -- has been assigned as ‘Special Access Programs’, to access SIPRnet.
What is SIPRnet?
SIPRNet, or Secret Internet Protocol Router Network, is a global United States military Internet system used for transmitting classified information, intelligence, targets, and messages at the secret level.
In other words, SIPRNet is completely parallel Internet, uses the same communications procedures and has been kept separate from the ordinary civilian Internet.
Approximately 3 Million people with secret clearances have access to SIPRNet, which includes Pentagon and military officials, Intelligence agencies, FBI, as well as diplomats in US embassies all around the World.
Classified Network Crashed at Creech Base
The network at Creech Air Force Base was crashed in early September that impacted "critical services," and has not been completely rebuilt, according to US government contracting records.
"On 9 September 2016, the SIPRNet system currently in operation at Creech AFB failed, and critical services were impacted," reads a contracting notice posted by the US government in early October.
"The services were somewhat restored with the use of multiple less powerful devices. This temporary solution stabilized the services, but will not be able to maintain the demand for very long. If this solution fails, there is currently no other backup system."
The officials would not say whether the failure was due to internal technical faults, a cyber attack, or a state-sponsored hacker. They would also not say if JWICS — a separate internet system that handles top-secret information — at Creech was also affected.
US Drones Killed around 100 Innocents within Two Weeks
Within weeks of the computer disaster, a series of airstrikes went terribly wrong, which resulted in scores of deaths in Syria, Afghanistan, and Somalia, according to BuzzFeed News.
On September 17, 62 Syrian soldiers were accidentally killed by US airstrikes in the middle of a ceasefire. On September 28, 15 innocent civilians were reportedly killed in Afghanistan by a US drone, as well as 22 Somali soldiers were reportedly killed in Somalia by US drone strikes.
All the cases are under review and investigation, and there has been no official explanation for targeting innocent people, though the United States expressed its regrets quickly after the incident, according to reports.
On October 7, the Air Force quietly announced that Creech base would be subject to a surprise cyber security inspection and warned personnel to be wary of phishing attacks and to be extra careful in securing their login credentials.
Has U.S. Classified Network Been Hacked?
These classified networks are definitely not connected to the Internet, but this does not mean that malware or well-resourced hackers can never found their ways into these critical networks.
If confirmed, this would not be the first time, when a classified computer network of US military has been compromised.
In the year 2008, The Pentagon acknowledged a significant cyber attack, Operation Buckshot Yankee, where a foreign intelligence agent used a USB drive to infect military computers used by the Central Command in overseeing combat zones in Iraq and Afghanistan with a specially crafted malware.
You might be aware of Chelsea Manning (then known as Bradley Manning), an army soldier who made headlines in 2013 when she was sentenced to 35 years in prison for leaking over 700,000 classified files to WikiLeaks.
Manning allegedly downloaded those secret documents from SIPRNet using a Lady Gaga CD.
Since these classified networks have a significant role in US national security, terrorist groups and state-sponsored hackers belonging to sophisticated nation-states like China, Russia, Iran, and North Korea have always shown large interest in targeting them.
Reverse engineering a Smarter Coffee machine for fun and a security lesson
10.10.2016 securityaffairs Safety
Simone Margaritelli has done a reverse engineering of the Smarter Coffee IoT Machine Protocol to control the machine from his terminal. What is the lesson?
While security industry is stressing the need to adopt a security by design approach for IoT devices, security researchers continue to find flawed and poorly designed smart objects.
Clearly, such kind of devices is a privileged target for crooks that could abuse them to conduct a wide range of illegal activities.
Ok … but it’s time for a coffee break now and surfing the web I found a curious and interesting article of a popular Italian hacker, Simone Margaritelli, aka evilsocket. Simone is a former blackhat hacker now mobile security researcher and senior ASM/C/C++ developer for Zimperium firm, he is the creators of the popular tool bettercap.
Like me, Simone loves coffee so a few days ago he bought a Smarter Coffee machine that can be controlled via a mobile application that allows users to prepare a good coffee with many options.
Simone Margaritelli decided to do a reverse engineering of the Smarter Coffee IoT Machine Protocol with the intent of control the coffee machine even from his terminal.
The expert focused its analysis on classes and methods present in the source code of the app, then he found something of interest in the am.smarter.smarterandroid.models.a class.

The researcher discovered the way the app and the machine communicate and which is the protocol they use.
“Each of these “packets” is sent to tcp port 2081 of the machine, the protocol is very simple.
First byte: the command number.
Second byte to N: optional data ( depending on the command code ).
Last byte: always 0x7e which indicates the end of the packet.
Responses can vary, but for most of the commands they are:
First byte: response size
Second byte: status ( 0 = success otherwise error code )
Last byte: always 0x7e.
An example command and response, the one to keep the coffee warm for 5 minutes for instance, would be:
COMMAND : 0x3e 0x05 0x7e
RESPONSE : 0x03 0x00 0x7e”
At this point, it was a joke for Simone to write a simple console to send commands to the Smarter Coffee machine as you can see in the video PoC published by the hacker.
Simone has published the code on GitHub, below a few sample of the commands available to control the coffee machine.
Make one cup of coffee: coffee make.
Make two cups using the filter instead of the beans in the grinder coffee make –filter.
Keep coffee warm for ten minutes coffee warm –keep-warm=10.
Simone Margaritelli highlighted that anyone on the same network of the machine could send commands to the device due to the absence of authentication.
“Even if the mobile app requires you to register an account, access to port 2081 is completely unauthenticated ( in fact, I’ve found that the user account is only used for statistics using the Firebase API ), anyone on your network could access it and even flash a new firmware with no authentication required ( I reversed the
UPDATE_FIRMWARE
packet as well but you won’t find it on the repo 😛 )” Simone wrote in a blog post.
MITRE will award $50,000 for a solution that detects rogue IoT Devices
11.10.2016 securityaffairs Safety
MITRE has challenged the security community to devise new methods that could help in detecting rogue IoT devices on a network.
The non-profit research and development organization MITRE has challenged security researchers to propose new methods and technologies that could help in detecting rogue Internet of Things (IoT) devices on a network.
The goal of the Unique Identification of IoT Devices Challenge is to prevent abuses of IoT devices devising a solution that can help administrators monitor IoT devices.
Flawed IoT devices and poorly configured smart objects are a privileged target for hackers that compromise them to compose powerful botnet.
Recently IoT botnets were observed launching massive DDoS attacks against the OVH websites and the KrebsonSecurity.com.
Mitre will give a $50,000 reward to the researchers who will propose a non-traditional method for enumerating IoT devices through passive network monitoring.
“The MITRE Challenge, Unique Identification of IoT Devices, seeks to discover possible solutions to this potential threat so our sponsors can reap the benefits of this technological evolution, while minimizing the risks.” states the MITRE.
“We are looking for non-traditional approaches for identifying IoT devices. In the future, manufacturers may embed unique digital signatures into each device. For today, we need to be able to monitor the products already in use.
We’re looking for a game-changing approach to identifying devices that would require no modification to the existing inventory, e.g., no change in protocols or manufacturing.”
MITRE Unique Identification of IoT Devices Challenge offers participants from around the world the recognition and promotion for coming up with a game-changing solution, and the opportunity to connect with government agencies looking for IoT solutions.

The challenge, that will begin in November, is open to research teams, companies and also to individuals.
Participants will have six weeks to propose their solutions for detecting bogus IoT devices.
MITRE has created a testbed network composed of a wide range of devices having different characteristics.
“The MITRE IoT team has built a model home network to serve as a testbed for the Challenge. This robust home system includes a broad array of affordable devices with diverse operating characteristics. We believe that the identification techniques that prove effective in a home system will translate to industrial, healthcare, military, smart city, and other IoT networks.” reads the MITRE.
According to EurActiv, the European Commission is working on a legislation aimed at securing IoT devices. The legislation will force vendors and manufacturers to adopt a security by design approach for their smart objects.
Challenge! WIN $50,000 for Finding Non-traditional Ways to Detect Vulnerable IoT Devices
11.10.2016 thehackernews Safety
Challenge — WIN $50,000 for Discovering Non-traditional Ways to Find Vulnerable IoT Devices
If you are concerned about the insecurity of Internet of Things, have good hands at programming and know how to hack smart devices, then you can grab an opportunity to earn $50,000 in prize money for discovering the non-traditional ways to secure IoT devices.
Internet of Things (IoT) market is going to expand rapidly over the next decade. We already have 6.5 billion to 8 billion IoT devices connected to the Internet worldwide, and the number is expected to reach 50 billion by 2020.
While IoT is going to improve life for many, the number of security risks due to lack of stringent security measures and encryption mechanisms in the devices have increased exponentially.
This rise in the number of security risks would continue to widen the attack surface, giving hackers a large number of entry points to affect you some or the other way.
Recently, we saw a record-breaking DDoS attack (Distributed Denial of Service) against the France-based hosting provider OVH that reached over one Terabit per second (1 Tbps). The attack was carried out via a botnet of infected IoT devices, dubbed Mirai Malware.
So, the threat to and with IoT is Big, and we have to look for a solution right now because tomorrow it will be very late.
We already have some ways to find vulnerable IoT devices, like Shodan and Censys search engine. While Shodan has been designed specifically to locate any devices that have been carelessly plugged into the Internet, Censys employs a more advanced approach to finding vulnerabilities in the devices by daily scanning the whole Internet.
However, other creative ways to discover vulnerable IoT devices include a Flying Drone with a tracking tool capable of sniffing out data from Internet-connected devices.
Challenge — Find Ways to Detect Vulnerable IoT Devices
Now, in an attempt to find a solution that can help network admins monitor IoT devices, non-profit research and development organization MITRE has challenged researchers to come up with new ideas for detecting rogue IoT devices on a network.
The good news: You can earn $50,000 for your idea.
Researchers who will find and report a non-traditional, game-changing approach for identifying IoT devices while passively observing the network, without the requirement of modification to the existing protocols and manufacturing, can earn up to $50,000.
"We are looking for a unique identifier or fingerprint to enable administrators to enumerate the IoT devices while passively observing the network," reads MITRE website.
Along with the prize money, MITRE has also promised:
Recognition and Promotion.
The opportunity to connect with government agencies looking for IoT solutions.
The chance to work with MITRE experts to better understand the government's needs.
The MITRE IoT team has created a model home network that will serve as a testbed for the Challenge. This powerful home network includes a broad range of affordable devices with diverse operating characteristics.
"We believe that the identification techniques that prove effective in a home system will translate to industrial, healthcare, military, smart city, and other IoT networks," the team writes.
This Challenge is open to individual entrepreneurs, college teams looking for showcasing their talents and small companies who want to make their mark in the IoT market.
The registration period has already started so that you can register here. The challenge will begin in early November for approximately six weeks, so all participants will have to demonstrate a unique, simple and affordable solution to identify rogue IoT devices within this short period.
The winner will be announced before the end of December. So, if you think you have the potential to find out a solution to this issue, then what are you waiting for? Register yourself today.