Malwarebytes Privacy VPN
During our tests yesterday, you could select from 10 states in the USA and 30 countries around the world.
Safety Articles - H 2020 1 2 3 4 5 6 Safety List - H 2021 2020 2019 2018 1 Safety blog Safety blog
SAP announces security issues in cloud-based products
10.5.2020 Bleepingcomputer Safety
German software maker SAP announced on Monday that it started to fix security issues identified in several of its cloud-based products.
The company discovered the problems following an internal review and has already started working on eliminating the vulnerabilities.
Fixes are coming
Details about the security flaws have not been disclosed. In an advisory this week, the company says that fixing the bugs “will largely be completed in the second quarter 2020.”
The list of affected products includes SAP Success Factors, SAP Concur, SAP/CallidusCloud Commissions, SAP/Callidus Cloud CPQ; as well as SAP C4C/Sales Cloud, SAP Cloud Platform, and SAP Analytics Cloud.
Some of these platforms, along with their infrastructure, were acquired over the years and the company paid billions of U.S. dollars for them.
With this, SAP inherited all the potential gaps and had to align them to the company’s present contractually agreed or statutory IT security standards.
Clients to be contacted
It is estimated that around 9% of SAP's 440,000 customers are impacted by the vulnerabilities. They will be notified of the risk and will receive assistance to remedy the problems.
SAP’s investigation is not complete but the company does not believe that customer data has been compromised as a result of these issues.
“In an effort to ensure that the affected products meet relevant terms and conditions and in addition to technical remediation, SAP has decided to update its security-related terms and conditions. These remain in line with market peers” - SAP
These security updates are not expected to have an impact on the company’s financial outlook for 2020.
Malwarebytes releases new VPN service for Windows
25.4.2020 Bleepingcomputer Safety
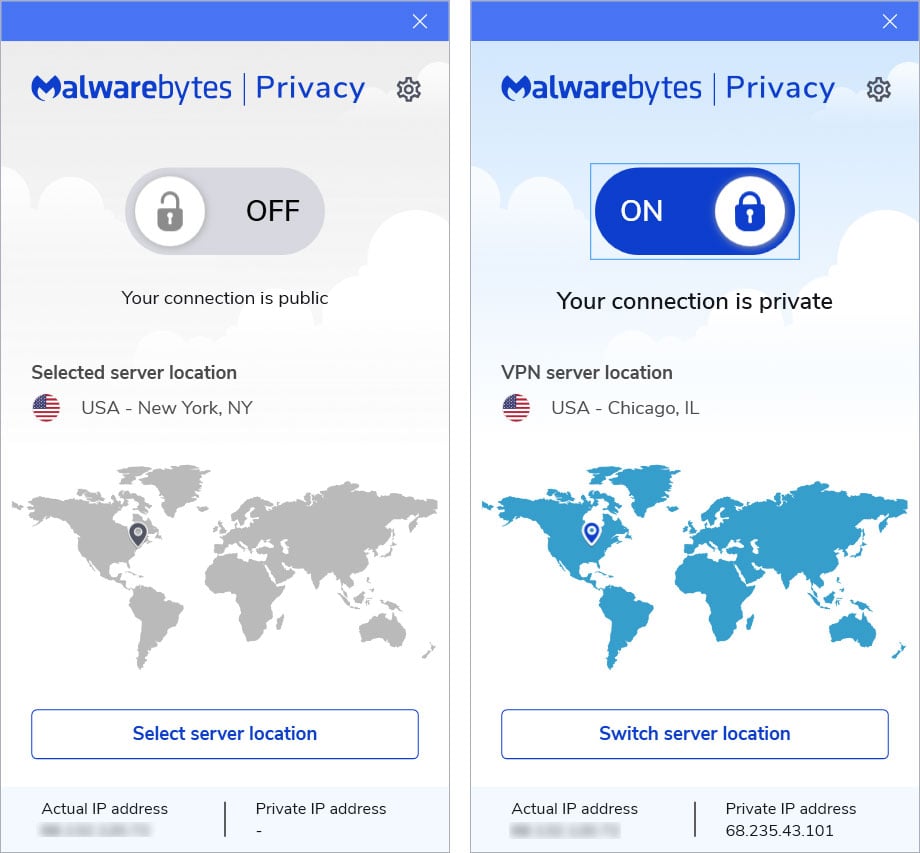
Malwarebytes is expanding into privacy with the release of a new Windows VPN service called Malwarebytes Privacy. Malwarebytes plans on offering Mac, iOS, Android, and ChromeOS versions in the future.
Malwarebytes Privacy is available today for $59.99 as a stand-alone product for supporting five devices or can be bundled with a 1-year license of Malwarebytes Premium for $89.99. When combined, users save $49.99.
Once installed, you can turn the VPN service on and then select the server location of the VPN server you wish to use.

Malwarebytes Privacy VPN
During our tests yesterday, you could select from 10 states in the USA and 30 countries around the world.
The states that Malwarebytes has servers at launch are Georgia, Illinois, Texas, Colorado, California, Florida, New York, New Jersey, Utah, and Washington.
The server locations outside of the USA are Australia, Austria, Belgium, Brazil, Bulgaria, Canada, Czech Republic, Denmark, Finland, France, Germany, Hong Kong, Hungary, Ireland, Italy, Japan, Latvia, Luxembourg, Moldova, Netherlands, New Zealand, Norway, Poland, Romania, Serbia, Singapore, Span, Sweden, Switzerland, and the UK.
Malwarebytes told BleepingComputer that this is not a white-label service, but rather one they developed themselves.
A trusted-third party built the network infrastructure, and Malwarebytes developers created the app and other components.
Malwarebytes Privacy using the modern WireGuard VPN implementation that was recently integrated into the Linux kernel.
Data and log retention policies
Unfortunately, not much is known about Malwarebytes Privacy's logging and data retention policies.
For the best privacy, you want your VPN server to keep no logs at all, and if any are required, to wipe them hourly, or at least daily.
According to Malwarebytes' product page, "Malwarebytes Privacy does not log your online activities, whether it's browsing or accessing any websites."
This is what most people want, but it would be good to get more specific language in a dedicated data retention policy or language in their privacy policy.
Malwarebytes has told BleepingComputer that they will be updating their privacy policy to explicitly call out how data is logged and retained.
"Malwarebytes Privacy does not retain or log any data related to web traffic, DNS requests, IP addresses, user bandwidth or connections once connected to the VPN server. We are in the process of updating our Privacy Policy to explicitly call this out.
While a static IP address is assigned when connecting to the VPN server, Malwarebytes Privacy regularly rotates the client keys for added security and to alleviate any privacy concerns regarding the IP address assignment. Also, the VPN servers enforce a client handshake timeout and do not persist any IP address information after a connection."
Update 4/23/20: Updated to include Malwarebytes' statement.
Cloudflare Launches a DNS-Based Parental Control Service
4.4.2020 Bleepingcomputer Safety
Cloudflare introduced today '1.1.1.1 for Families,' a privacy-focused DNS resolver designed to help parents in their efforts to safeguard their children's online security and privacy by automatically filtering out bad sites.
This new tool makes it simple for parents to add protection from malware and adult content to the entire home network, allowing them to focus on working from home instead of worrying about their kids' online safety.
"1.1.1.1 for Families leverages Cloudflare's global network to ensure that it is fast and secure around the world," Cloudflare's CEO Matthew Prince said in an announcement published today.
"And it includes the same strong privacy guarantees that we committed to when we launched 1.1.1.1 two years ago. And, just like 1.1.1.1, we're providing it for free and it’s for any home anywhere in the world."
Two default options
Cloudflare's new DNS-based parental control service can easily be set up by changing your router's or your computers' primary DNS and your secondary DNS servers to the ones Cloudflare provides.
1.1.1.1 for Families comes with two options: the first one will automatically block malware content only, while the second is designed to block both malware and adult content from reaching your children while they browse the web.
The DNS servers you need to use to activate the parental control service are as follows:
For malware blocking only:
• Primary DNS: 1.1.1.2
• Secondary DNS: 1.0.0.2
For malware and adult content blocking:
• Primary DNS: 1.1.1.3
• Secondary DNS: 1.0.0.3
During the coming months, Cloudflare is also working on developing and providing users with additional configuration settings for the 1.1.1.1 for Families service.
"This year, while many of us are sheltering in place, protecting our communities from COVID-19, and relying on our home networks more than ever it seemed especially important to launch 1.1.1.1 for Families," Prince added.
"We hope during these troubled times it will help provide a bit of peace of mind for households everywhere."
Introducing 1.1.1.1 for Families — the easiest way to add a layer of protection to your home network and protect it from malware and adult content. https://t.co/Fz5vMEqNwv
— Cloudflare | #BuiltForThis (@Cloudflare) April 1, 2020
Cloudflare's DNS just passed a privacy audit
Yesterday, Cloudflare released the results of a privacy audit of their a 1.1.1.1 DNS service by independent auditing firm KPMG, with the results largely backing up the company's statement on how it collects and stores DNS query data on its servers.
Cloudflare when they launched the 1.1.1.1 DNS service two years ago, that logs were automatically wiped within 24 hours and the full IP address of users were never written to logs.
KPMG's audit results released yesterday show that Cloudflare is keeping its word regarding its efforts to protect their user privacy, even though some minor issues were discovered.
Among them, KPMG says that Cloudflare Netflow/Sflow network-wide monitoring implementation retains ".05% of all packets" moving through their network, including IP addresses of DNS queries.
Their audit also revealed that the logs are wiped within 25 hours, while some of the anonymized data is kept indefinitely on Cloudflare's servers.
In all, Cloudflare was found to be configured in a way that supports their public commitments to privacy.
TrickBot Bypasses Online Banking 2FA Protection via Mobile App
29.3.2020 Bleepingcomputer Safety
The TrickBot gang is using a malicious Android application they developed to bypass two-factor authentication (2FA) protection used by various banks after stealing transaction authentication numbers.
The Android app dubbed TrickMo by IBM X-Force researchers is actively being updated and it is currently being pushed via the infected desktops of German victims with the help of web injects in online banking sessions.
TrickBot's operators have designed TrickMo to intercept a wide range of transaction authentication numbers (TANs) including one-time password (OTP), mobile TAN (mTAN), and pushTAN authentication codes after victims install it on their Android devices.
Spotted for the first time in September 2019
TrickMo was initially spotted by CERT-Bund security researchers who said at the time that TrickBot-infected Windows computers will ask for the victims' online banking mobile phone numbers and device types to prompt them to install a bogus security app.
At the moment, the malicious app is only being pushed by the TrickBot operators only to German targets and it will "camouflage" itself as an 'Avast Security Control' app or as 'Deutsche Bank Security Control' utility.
Once installed on their phones, the app will forward text messages containing mTANs sent by the victims' banks to TrickBot's operators who can later use them to make fraudulent transactions.
Avast Security Control installation screen (Lukas Stefanko)
In a report analyzing TrickMo's capabilities published today, IBM X-Force researchers say that the malware is capable of preventing users of infected devices from uninstalling it, sets itself as the default SMS app, monitors running apps, and scrapes on-screen text.
"From our analysis of the TrickMo mobile malware, it is apparent that TrickMo is designed to break the newest methods of OTP and, specifically, TAN codes often used in Germany," IBM's researchers explain.
"Android operating systems include many dialog screens that require the denial, or approval, of app permissions and actions that have to receive input from the user by tapping a button on the screen.
"TrickMo uses accessibility services to identify and control some of these screens and make its own choices before giving the user a chance to react."
This allows the Android Trojan to delete SMS messages it forwards to its masters so that the victims are never aware that their devices received a text message with a 2FA code from their banks.
Wide range of 'features'
The malware is also capable of gaining persistence on infected Android devices by registering a receiver that will listen for android.intent.action.SCREEN_ON and android.provider.Telephony.SMS_DELIVER broadcasts to restart itself after a reboot when the screen turns on or an SMS is received.
TrickMo is heavily obfuscated to hinder analysis and it was recently updated, in January 2020, with code that checks if the malware is running on a rooted device or an emulator.
From its large array of capabilities, the IBM X-Force researchers highlighted TrickMo's main ones designed for:
• Stealing personal device information
• Intercepting SMS messages
• Recording targeted applications for one-time password (OTP)/mobile TAN (mTAN)/pushTAN theft
• Lockdown of the phone
• Stealing pictures from the device
• Self-destruction and removal
TrickBot — a continuously updated banking malware
TrickBot is a modular banking malware continuously upgraded by its authors with new capabilities and modules since October 2016 when it was first spotted in the wild.
Although the first detected variants only came with banking Trojan capabilities used for harvesting and exfiltrating sensitive data, TrickBot has now evolved into a popular malware dropper that will infect compromised systems with other, some times more dangerous, malware strains.
TrickBot can deliver other malware as part of multi-stage attacks, Ryuk ransomware being one of the most notable ones, most likely after all useful information has been already collected and stolen.
The malware is also especially dangerous as it can propagate throughout enterprise networks and, if it gains admin access to a domain controller, it can steal the Active Directory database to obtain other network credentials.
Firefox Reenables Insecure TLS to Improve Access to COVID19 Info
22.3.2020 Bleepingcomputer Safety
Mozilla says that the support for the insecure TLS 1.0 and TLS 1.1 will be reenabled in the latest version of Firefox to maintain access to government sites with COVID19 information that haven't yet upgraded to TLS 1.2 or TLS 1.3.
"We reverted the change for an undetermined amount of time to better enable access to critical government sites sharing COVID19 information," Mozilla said today in an update to the Firefox 74.0 release notes.
Plans to remove TLS
TLS 1.0 and TLS 1.1 support was dropped with the release of Firefox 74.0 on March 10 to improve the security of website connections, with sites that don't support TLS 1.2 or TLS 1.3 to show a "Secure connection failed" error page instead of their contents and an override 'Enable TLS 1.0 and 1.1' button for that web site connection.
In October 2018, all major browser makers including Microsoft, Google, Apple, and Mozilla announced the retirement of the TLS 1.0 and TLS 1.1 protocols released over a decade ago.
With more than 97% of the sites surveyed by Qualys SSL Labs supporting TLS 1.2 and TLS 1.3, the decision to retire the two protocols in favor of newer and better supported TLS 1.3 and TLS 1.3 is logical as they can provide a more secure path moving forward.
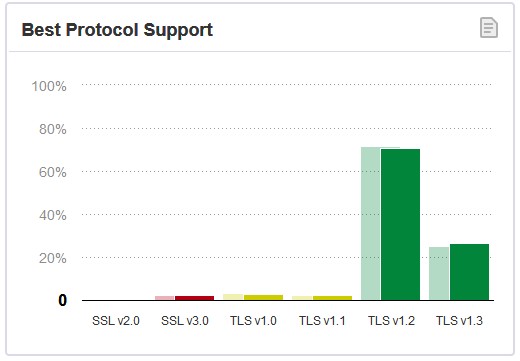
97% of surveyed sites support TLS 1.2 and 1.3 (Qualys SSL Labs)
According to TLS 1.0 and TLS 1.1 usage statistics at the time, the vast majority of users are no longer even using these protocols:
Google reported that only 0.5% of HTTPS connections made by Chrome are using TLS 1.0 or TLS 1.1
Apple reported that on their platforms less than 0.36% of HTTPS connections made by Safari are using TLS 1.0 or TLS 1.1.
Microsoft said that only 0.72% of secure connections made by Edge use TLS 1.0 or 1.1.
Firefox had the largest amount of connections, with 1.2% of all connections using TLS 1.0 or 1.1.
Hundreds of thousands of sites still rely on TLS 1.0 and TLS 1.1
Despite this, as Netcraft reported at the beginning of March 2020, over 850,000 websites are still using the outdated and insecure TLS 1.0 and TLS 1.1 protocols that expose users to a wide range of cryptographic attacks (1, 2) leading to their web traffic being decrypted by attackers.
"The use of TLS 1.0 on e-commerce websites as a measure for protecting user data has been forbidden by the Payment Card Industry Data Security Standard since June 2018, and many websites have already migrated," as Netcraft said.
However, seeing that Mozilla decided to bring back support for the two previously retired TLS protocols, there are enough government sites sharing information on the current coronavirus pandemic to a reversal of the removal decision.
Firefox Password Manager To Be Secured With Windows 10 Credentials
22.3.2020 Bleepingcomputer Safety
Mozilla is making changes to the Firefox Lockwise password manager so that users will need to enter their Windows 10 credentials before being allowed to edit or view saved logins.
One of the biggest problems with browser password managers is that they offer no protection from a person who gains local access to a PC.
Once a person has access to a PC and thus their browser, they can easily access the saved login credentials without being prompted to enter a password or other credentials.
Windows 10 credentials used to secure Lockwise
To resolve this, in the latest Mozilla Firefox Nightly build 76.0a1, when a Windows user attempts to view, copy, or edit saved login credentials in the Lockwise password manager, they will first be prompted to enter their Windows 10 login credentials.
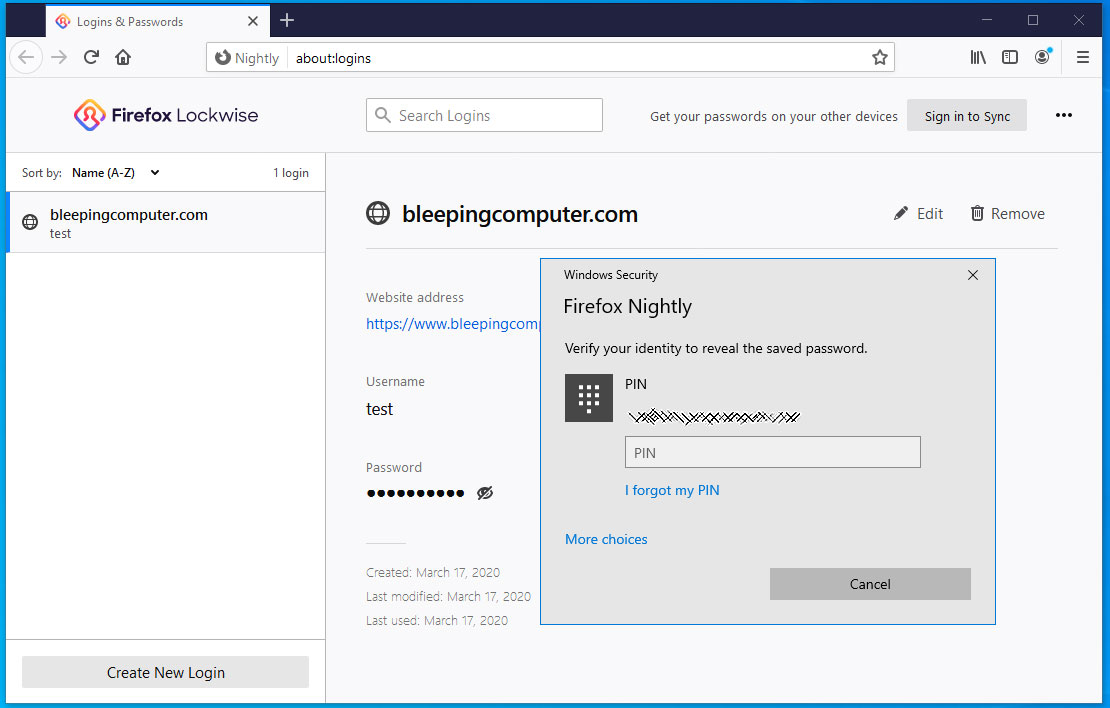
Lockwise prompt for Windows 10 credentials
If a user does not know the password, PIN, or other configured authentication credentials, Firefox will not allow the user to view the credentials.
This method effectively secures the Lockwise password manager so that a local user can not read through the machine owner's saved credentials.
The only caveat is if a user plans on looking up their credentials for numerous accounts in a row, they will currently need to enter their Windows 10 credentials each time.
Office 365 ATP To Block Email Domains That Fail Authentication
15.3.2020 Bleepingcomputer Safety
Microsoft is working on including a new Office 365 Advanced Threat Protection (ATP) feature that would block email sender domains automatically if they fail DMARC authentication as part of an effort to make Office 365 ATP secure by default.
This change was prompted by the fact that, for some custom Office 365 ATP configurations, the default email threat-protection filters might be bypassed and malicious content could inadvertently reach customers' inboxes.
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an email authentication, policy, and reporting protocol that uses the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) email authentication methods to validate mail senders.
As Microsoft explains, "DMARC helps receiving mail systems determine what to do with messages sent from your domain that fail SPF or DKIM checks."
Reject emails if sender domain validation fails
"We see lots of cases where configuration of our protection stack has enabled malicious content to be inadvertently delivered to end users," Microsoft explains on the new feature's Microsoft 365 Roadmap entry. "We’re working on a few features that will help address this problem."
As mentioned in the beginning, the newest Office 365 feature planned is the addition of an automated block for email domains that fail authentication.
"The Antispam policy allows administrators to 'Allow' domains regardless of the reputation of the domain," Microsoft adds. "We’re changing our policies to not honor Allow rules when the domain fails authentication."
Admins who will want to get around it can address the auth issue with the domains they want to whitelist or to add new Exchange mail flow rules (also known as transport rules) to allow messages from sender on specific domains despite the newly imposed block designed to boost email security.
At the moment, until this new Office 365 ATP feature will be rolled out sometime around April 2020, inbound email that fails DMARC are marked by Office 365 as spam instead of automatically being rejected.
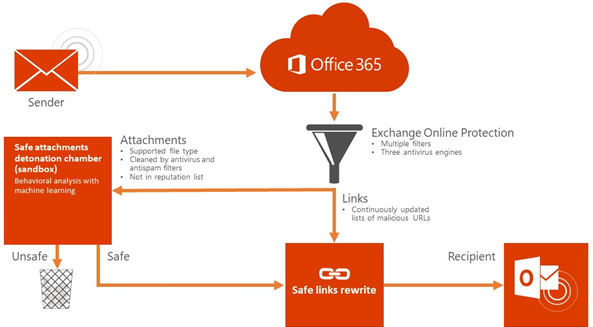
Office 365 fighting attacks (Microsoft)
Part of a larger effort to secure Office 365
This feature is planned to roll out to all environments together with another one designed to also boost the default security of email inboxes protected by Office 365 ATP.
Microsoft is also planning to block malicious content in Office 365 regardless of the custom configurations unless manually overridden by admins or users. Once the new features will be enabled, Office 365 will honor EOP/ATP malware analysis (detonation) verdicts to block known malicious files and URLs automatically.
In October 2019, Microsoft enabled Authenticated Received Chain (ARC) for all for hosted mailboxes to improve anti-spoofing detection and to check authentication results within Office 365. The ARC protocol supplements the DMARC and DKIM email authentication protocols as part of Internet Mail Handlers' effort to combat email spoofing especially when dealing with forwarded messages.
Microsoft also warned Office 365 admins and users against bypassing the built-in spam filters in June 2019, in a support document that also shares guidelines for cases when this can't be avoided.
"If you have to set bypassing, you should do this carefully because Microsoft will honor your configuration request and potentially let harmful messages pass through," the support document says. "Additionally, bypassing should be done only on a temporary basis. This is because spam filters can evolve, and verdicts could improve over time."