
Dozens of cases were reported through the and on , the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website suggests it was compromised by attackers.
Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
Japan-based digital exchange Coincheck to refund to customers after cyberheist
29.1.2018 securityaffairs Incindent
Coincheck announced it will refund about $400 million to 260,000 customers after the hack, the company will use its own funds.
On Friday the news of the hack of the Japan-based digital exchange Coincheck caused the drop in the value of the major cryptocurrencies, the incident had a significant impact on the NEM value that dropped more than 16 percent in 24 hours.
The company suspended the operations of deposits and withdrawals for all the virtual currencies except Bitcoin, the exchange announced it was investigating an “unauthorised access” to the exchange.
According to the company, the hackers stole worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalization.
The hackers stole 58 billion yen ($530 million), an amount of money that is greater than the value of bitcoins which disappeared from MtGox in 2014.
Coincheck was founded in 2012, it is one of the most important cryptocurrency exchange in Asia.
The company announced it will refund about $400 million to customers after the hack.
Coincheck will use its own funds to reimburse about 46.3 billion yen to its 260,000 customers who were impacted by the cyberheist.
“At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It’s worth 58 billion yen based on the calculation at the rate when detected,” said Coincheck COO Yusuke Otsuka.
“We’re still examining how many of our customers are affected,”
Experts believe that the Financial Services Agency will to take disciplinary measures against Coincheck.
It has been estimated that as many as 10,000 businesses in Japan accept bitcoin and bitFlyer, nearly one-third of global Bitcoin transactions in December were denominated in yen.The Cryptocurrencies, and in particular Bitcoin, are very popular in Japan, in April, the Bitcoin was proclaimed by the local authorities as legal tender.
According to Japanese bitcoin monitoring site Jpbitcoin.com, in November, yen-denominated bitcoin trades reached a record 4.51 million bitcoins, or nearly half of the world’s major exchanges of 9.29 million bitcoin.
Japanese media criticized the company blaming the management to have underestimated the importance of security of its investor, they said Coincheck “expanded business by putting safety second”.
Politicians and experts that participated in the World Economic Forum in Davos issued warnings about the dangers of cryptocurrencies, it is expected that government will adopt further measures to avoid abuse and illegal uses of cryptocrurrencies.
Japan's Crypto Exchange to Refund to Customers After Theft
28.1.2018 securityweek Incindent
Japan-based virtual currency exchange Coincheck said Sunday it will refund about $400 million to customers after hackers stole hundreds of millions of dollars' worth of digital assets.
The company said it will use its own funds to reimburse about 46.3 billion yen to all 260,000 customers who lost their holdings of NEM, the 10th biggest cryptocurrency by market capitalization.
On Friday, the company detected an "unauthorised access" of the exchange, and later suspended trading for all cryptocurrencies apart from bitcoin.
The resulting 58 billion yen ($530 million) loss exceeded the value of bitcoins which disappeared from MtGox in 2014.
The major Tokyo-based bitcoin exchange collapsed after admitting that 850,000 coins -- worth around $480 million at the time -- had disappeared from its vaults.
The high-profile demise of MtGox failed to douse the enthusiasm for virtual currencies in Japan, which in April became the first country in the world to proclaim it as legal tender.
Nearly one third of global bitcoin transactions in December were denominated in yen, according to specialist website jpbitcoin.com.
As many as 10,000 businesses in Japan are thought to accept bitcoin and bitFlyer, the country's main bitcoin exchange, saw its user base pass the one-million mark in November.
Many Japanese, especially younger investors, have been seduced by the idea of strong profits as the economy has seen years of ultra-low interest rates offering little in the way of traditional returns.
Major Japanese newspapers on Sunday labelled the management of virtual currencies at Coincheck as "sloppy" and said the company had "expanded business by putting safety second".
Local media added the Financial Services Agency was expected to take disciplinary measures against Coincheck, which proclaims itself "the leading bitcoin and cryptocurrency exchange in Asia", following the theft.
Bell Canada Hit by Data Breach
24.1.2018 securityweek Incindent
Bell Canada has started informing customers that their personal data has been compromised in a breach that reportedly affects up to 100,000 individuals.
Bell told customers that their names and email addresses were aaccessed by hackers, but the company said in an emailed statement that the attackers also obtained phone numbers, usernames and/or account numbers for a limited number of people. The telecoms company, however, says there is no evidence that credit card or banking information has been compromised.
In response to the incident, Bell has implemented additional authentication and identification requirements for accessing accounts. The company has also advised users to frequently change their password and security questions, and regularly review their financial and online accounts for unauthorized activity.
“The protection of consumer and corporate information is of primary importance to Bell,” John Watson, Executive Vice-President of Customer Experience at Bell Canada, told customers. “We work closely with the RCMP and other law enforcement agencies, government bodies and the broader technology industry to combat the growth of cyber crimes.”
Lisa Baergen, marketing director with Vancouver-based NuData Security, a Mastercard company, pointed out that even limited information such as names and email addresses can be useful to malicious actors.
“We all know bad actors are very talented at preparing fraud schemes with that information, such as phishing scams or dictionary attacks – where fraudsters try certain common passwords based on the user’s personal information,” Baergen said.
“Bell is doing the right thing by evaluating the extent of the damage and keeping customers updated,” she added. “However, to avoid damage after a breach, companies that share clients with Bell can consider applying multi-layered security solutions based on passive biometrics to protect their business and their customers from account takeover of another type of fraud. Online security technologies that evaluate a user or a transaction based on their behavior and not only on their – potentially stolen – static information, thwart all fraudulent attempts that inevitably come after a data breach.”
This is the second time Bell Canada has informed customers of a data breach. In May last year, the company admitted that approximately 1.9 million active email addresses and roughly 1,700 names and active phone numbers were accessed by a hacker.
Bell told SecurityWeek that the latest incident is unrelated to the cyberattack disclosed in May.
Bell Canada suffers a data breach for the second time in less than a year
24.1.2018 securityaffairs Incindent
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, this is the second security breach in a few months.
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, including names, phone numbers, email addresses, usernames and account numbers.
“The protection of consumer and corporate information is of primary importance to Bell,” John Watson, Executive Vice-President of Customer Experience at Bell Canada, told customers. “We work closely with the RCMP and other law enforcement agencies, government bodies and the broader technology industry to combat the growth of cyber crimes.”
The Royal Canadian Mounted Police has launched an investigation into the security breach at Bell Canada.
“We are following up with Bell to obtain information regarding what took place and what they are doing to mitigate the situation, and to determine follow up actions,” said the federal privacy watchdog’s spokeswoman Tobi Cohen.
Bell company added that there is no evidence that financial data (i.e. credit card data) has been compromised.
Bell Canada
This the second time that Bell Canada has been a victim of a data breach, in May 2017 an anonymous hacker obtained access to about 1.9 million active email addresses and about 1,700 customer names and active phone numbers.
As part of the incident response procedure, Bell confirmed to have implemented additional security measures, for accounts’ authentication.
Bell Canada advised users to monitor their financial and online accounts for unauthorized activity and recommends customers to use strong passwords and frequently change them.
The Canadian Government plans to review the Personal Information Protection and Electronic Documents Act that would require companies to notify data breaches.
Unfortunately, until now only the province Alberta has mandatory reporting requirements for private-sector companies that suffer a data breach.
40,000 Potentially Impacted in OnePlus Payment System Hack
22.1.2018 securityweek Incindent
Up to 40,000 OnePlus customers may have been impacted after attackers managed to compromise the company’s payment page.
In a Friday post on the OnePlus forums, the Chinese smartphone company confirmed the attack and also revealed that the attackers managed to inject rogue code into its payment page, allowing them to steali credit card information enteredin by users.
The company launched an investigation last week, after some of its users started complaining about fraudulent transactions occurring on their credit cards following purchases made on oneplus.net.
“We are deeply sorry to announce that we have indeed been attacked, and up to 40k users at oneplus.net may be affected by the incident. We have sent out an email to all possibly affected users,” a company’s employee said in a forum post.
The malicious script, the employee revealed, was designed to capture and send data directly from the user's browser. The script has been removed, the compromised server quarantined, and relevant system structures have been reinforced, the company says.
All OnePlus users who entered credit card information on the oneplus.net website between mid-November 2017 and January 11, 2018, may be impacted by the breach. The hack happened around the same time OnePlus 5T, the latest flagship smartphone from the Chinese maker, was launched.
Immediately after being alerted on the incident, the company also suspended credit card payments on its website, but continued to support PayPal payments.
The malicious code injected in the payment page was designed to steal credit card information such as card numbers, expiry dates, and security codes that the users would enter on the website during the compromise period.
According to OnePlus, the incident didn’t impact users who paid via a saved credit card. Users who paid via the "Credit Card via PayPal" method and those who used PayPal to pay should not be affected either.
“We cannot apologize enough for letting something like this happen. We are working with our providers and local authorities to better address the incident. We are also working with our current payment providers to implement a more secure credit card payment method, as well as conducting an in-depth security audit,” the OnePlus employee said.
Not only should enterprises assume they have been or will be breached, but also should savvy consumers assume their financial data is bound to be compromised, Tyler Moffitt, Senior Threat Research Analyst, Webroot, pointed out in an emailed statement to SecurityWeek. Thus, Moffitt encourages users to take steps to be warned when unauthorized transactions occur on their accounts.
“Additionally, when online shopping, it is inherently more secure for consumers to use their PayPal accounts than enter their credit card data upon checkout – it is best practice to enter credit card information as rarely as possible. Most merchants have PayPal, Masterpass or Visa Checkout options available, which are more secure payment protocol alternatives,” Moffitt concluded.
OnePlus admitted hackers stole credit card information belonging to up to 40,000 customers
21.1.2018 securityaffairs Incindent
OnePlus confirmed that a security breach affected its online payment system, hackers stole credit card information belonging to up to 40,000 customers.
OnePlus confirmed that a security breach affected its online payment system, a few days ago many customers of the Chinese smartphone manufacturer claimed to have been the victim of fraudulent credit card transactions after making purchases on the company web store.
OnePlus has finally confirmed that its online payment system was breached, following several complaints of from its customers who made purchases on the company’s official website.
Dozens of cases were reported through the and on , the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website suggests it was compromised by attackers.
On January 19, the company released a statement to admit the theft of credit card information belonging to up to 40,000 customers. The hacker stole the credit card information between mid-November 2017 and January 11, 2018 by injecting a malicious script into the payment page code.
The script was used by attackers to sniff out credit card information while it was being entered by the users purchasing on the web store.
“We are deeply sorry to announce that we have indeed been attacked, and up to 40k users at oneplus.net may be affected by the incident. We have sent out an email to all possibly affected users.” reads the statement.
“One of our systems was attacked, and a malicious script was injected into the payment page code to sniff out credit card info while it was being entered. The malicious script operated intermittently, capturing and sending data directly from the user’s browser. It has since been eliminated.”
OnePlus is still investigating the breach to determine how the hackers have injected the malicious script into its servers.
The script was used to sniff out full credit card information, including card numbers, expiry dates, and security codes, directly from a customer’s browser window.
OnePlus said that it has quarantined the infected server and enhanced the security of its systems.
Clients that used their saved credit card, PayPal account or the “Credit Card via PayPal” method are not affected by the security breach.
As a precaution, the company is temporarily disabling credit card payments at , clients can still pay using PayPal. The company said it is currently exploring alternative secure payment options with our service providers.
OnePlus is notifying all possibly affected OnePlus customers via an email.
“We are eternally grateful to have such a vigilant and informed the community, and it pains us to let you down. We are in contact with potentially affected customers. We are working with our providers and local authorities to address the incident better,” continues the statement.
OnePlus confirms up to 40,000 customers affected by Credit Card Breach
20.1.2018 thehackernews Incindent
OnePlus has finally confirmed that its online payment system was breached, following several complaints of fraudulent credit card transactions from its customers who made purchases on the company's official website.
In a statement released today, Chinese smartphone manufacturer admitted that credit card information belonging to up to 40,000 customers was stolen by an unknown hacker between mid-November 2017 and January 11, 2018.
According to the company, the attacker targeted one of its systems and injected a malicious script into the payment page code in an effort to sniff out credit card information while it was being entered by the users on the site for making payments.
The malicious script was able to capture full credit card information, including their card numbers, expiry dates, and security codes, directly from a customer’s browser window.
"The malicious script operated intermittently, capturing and sending data directly from the user's browser. It has since been eliminated," OnePlus said on its official forum. "We have quarantined the infected server and reinforced all relevant system structures."
However, the company believes users who shopped on its website using their saved credit card, PayPal account or the "Credit Card via PayPal" method are not affected by the breach.
OnePlus is still investigating the incident and committed to conducting an in-depth security audit to identify how hackers successfully managed to inject the malicious script into its servers.
Meanwhile, credit card payments will remain disabled on the OnePlus.net store until the investigation is complete as a precaution, though users can make purchases through PayPal.
"We are eternally grateful to have such a vigilant and informed the community, and it pains us to let you down. We are in contact with potentially affected customers. We are working with our providers and local authorities to address the incident better," OnePlus says.
OnePlus is notifying all possibly affected OnePlus customers via an email and advises them to keep a close eye on their bank account statements for any fraudulent charges or look into cancelling their payment card.
The company is also looking into offering a one-year subscription of credit monitoring service for free to all affected customers.
Customers reporting OnePlus payment website was hacked and reported credit card fraud
17.1.2018 securityaffairs Incindent
Several customers of the Chinese smartphone manufacturer. OnePlus claim to have been the victim of fraudulent credit card transactions after making purchases on the company webstore.
A large number of OnePlus users claim to have been the victim of fraudulent credit card transactions after making purchases on the official website of the Chinese smartphone manufacturer.
Dozens of cases were reported through the support forum and on Reddit, the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website indicating suggest it was compromised by attackers.
“I purchased two phones with two different credit cards, first on 11-26-17 and second on 11-28-17. Yesterday I was notified on one of the credit cards of suspected fraudulent activity, I logged onto credit card site and verified that there were several transactions that I did not make” claims one of the victims. “The only place that both of those credit cards had been used in the last 6 months was on the Oneplus website.”
Security researchers at Fidus analyzed the payment page after reading the claims on the official forum and discovered that card details are hosted ON-SITE exposing data to attacks.
“We stepped through the payment process on the OnePlus website to have a look what was going on. Interestingly enough, the payment page which requests the customer’s card details is hosted ON-SITE.” reads a blog post published by Fidus. “This means all payment details entered, albeit briefly, flow through the OnePlus website and can be intercepted by an attacker. Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted.”

The experts speculate the servers of the company website might have been compromised, likely the attackers exploited some flaws in the Magento eCommerce platform used by OnePlus.
There are two methods used by crooks to steal credit cards from Magento-based stores:
Using Javascript on client-side. The malicious JavaScript is hosted on the web page which causes the customer’s machine to silently send a crafted request containing the payment data to a server controlled by attackers. The researchers who analyzed the payment page on the OnePlus site did not find any malicious JavaScript being used.
The second method relies on the modification of the app/code/core/Mage/Payment/Model/Method/Cc.php file through a shell access to the server. The Cc.php file handles the saving of card details on the eCommerce website. Regardless if card details are actually saved or not, the file is called regardless. Attackers inject code into this file to siphon data.
OnePlus declared that it does not store any credit card data on its website and all payment transactions are carried out through a payment processing partner.
“At OnePlus, we take information privacy extremely seriously. Over the weekend, members of the OnePlus community reported cases of unknown credit card transactions occurring on their credit cards post purchase from oneplus.net. We immediately began to investigate as a matter of urgency, and will keep you updated. ” reads the statement published by the company.
“No. Your card info is never processed or saved on our website – it is sent directly to our PCI-DSS-compliant payment processing partner over an encrypted connection, and processed on their secure servers. “
“The Chinese smartphone maker also confirms that purchases involving third-party services like PayPal are not affected.”
OnePlus excluded that its website is affected by any Magento vulnerability, since 2014, it has entirely been re-built using custom code.
Data breach of the Aadhaar biometric system poses a serious risk for 1 Billion Indian residents
6.1.2018 securityaffairs Incindent
The Tribune announced to have “purchased” a service that provided it an unrestricted access to the residents’ records in the Aadhaar system.
According to The Tribune, hackers have breached the Unique Identification Authority of India’s Aadhaar biometric system and gained access to personally identifiable information (i.e. names, addresses, phone numbers) of more than 1 billion Indian residents.
The Tribune announced to have “purchased” a service being offered by anonymous sellers over WhatsApp that provided it an unrestricted access to details for any individual whose data are stored in the Aadhaar system.
Attackers offered a portal to access Indian citizen data by knowing the Aadhaar user’s ID number. The service allowed the journalist to retrieve the resident’s name, address, postal code, photo, phone number, and email address, by providing the Aadhaar ID.
The hackers are offering the access to the portal for 500 rupees and are charging an additional 300 rupees for an application that allows printing a Aadhaar card.
“Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far.” states The Tribune.
“It took just Rs 500, paid through Paytm, and 10 minutes in which an “agent” of the group running the racket created a “gateway” for this correspondent and gave a login ID and password. Lo and behold, you could enter any Aadhaar number in the portal, and instantly get all particulars that an individual may have submitted to the UIDAI (Unique Identification Authority of India), including name, address, postal code (PIN), photo, phone number and email.”
The Unique Identification Authority of India denies that Aadhaar system has been breached, but The Tribune revealed that when contacted, UIDAI officials in Chandigarh expressed shock over the full data being accessed, and admitted it seemed to be a major national security breach.
“Except the Director-General and I, no third person in Punjab should have a login access to our official portal. Anyone else having access is illegal, and is a major national security breach.” Sanjay Jindal, Additional Director-General, UIDAI Regional Centre, Chandigarh told The Tribune.

According to the investigation conducted by The Tribune, the breach could have involved lakh village-level enterprise (VLE) operators hired by the Ministry of Electronics and Information Technology (ME&IT) under the Common Service Centres Scheme (CSCS) across India, offering them access to UIDAI data.
CSCS operators were initially tasked with making Aadhaar cards across India, but later this function was restricted to post offices and designated banks.
More than one lakh VLEs are now suspected to have gained this illegal access to UIDAI data to provide “Aadhaar services” to common people for a charge, including the printing of Aadhaar cards.
247,000 DHS current and former federal employees affected by a privacy incident
4.1.2017 securityaffairs Incindent
A privacy incident suffered by the Department of Homeland Security (DHS) exposed data related to 247,167 current and former federal employees.
A data breach suffered by the Department of Homeland Security exposed data related to 247,167 current and former federal employees that were employed by the Agency in 2014.
The data breach affected a database used by the DHS Office of the Inspector General (OIG) that was stored in the Department of Homeland Security OIG Case Management System.
“On January 3, 2018, select DHS employees received notification letters that they may have been impacted by a privacy incident related to the DHS Office of Inspector General (OIG) Case Management System. The privacy incident did not stem from a cyber-attack by external actors, and the evidence indicates that affected individual’s personal information was not the primary target of the unauthorized transfer of data.” reads the announcement published by the DHS.
Exposed data includes employee names, Social Security numbers, birth dates, positions, grades, and duty stations.
The incident also affected a second group of individuals (i.e., subjects, witnesses, and complainants) associated with Department of Homeland Security OIG investigations from 2002 through 2014 (the “Investigative Data”).
The data leak was the result of an unauthorized copy of the DHS OIG investigative case management system that was in the possession of a former DHS OIG employee.
The copy was discovered as part of an ongoing criminal investigation being conducted by Department of Homeland Security OIG and the U.S. Attorney’s Office
The data breach was discovered on May 10, 2017, as part of an ongoing criminal investigation conducted by OIG and the U.S. Attorney’s Office.
The Department of Homeland Security sent notification letters to affected individuals, it is also implementing additional security measured to limit access to such kind of information.
All individuals potentially affected by the incident are being offered 18 months of free credit monitoring and identity protection services.
“Department of Homeland Security is implementing additional security precautions to limit which individuals have access to this information and will better identify unusual access patterns. ” continues the Department of Homeland Security.
“We will continue to review our systems and practices in order to better secure data. DHS OIG has also implemented a number of security precautions to further secure the DHS OIG network,”
247,000 DHS Employees Affected by Data Breach
4.1.2018 securityweek Incindent
Information on nearly a quarter million Department of Homeland Security (DHS) employees was exposed as part of an "unauthorized transfer of data", the DHS announced.
The privacy incident involved a database used by the DHS Office of the Inspector General (OIG) which was stored in the DHS OIG Case Management System.
The incident impacted approximately 247,167 current and former federal employees that were employed by DHS in 2014. The exposed Personally identifiable information (PII) of these individuals includes names, Social Security numbers, birth dates, positions, grades, and duty stations.
Individuals (both DHS employees and non-DHS employees) associated with DHS OIG investigations from 2002 through 2014 (including subjects, witnesses, and complainants) were also affected by the incident, the DHS said.
The PII associated with these individuals varies depending on the documentation and evidence collected for a given case and could include names, social security numbers, alien registration numbers, dates of birth, email addresses, phone numbers, addresses, and personal information provided in interviews with DHS OIG investigative agents.
The data breach wasn’t the result of an external attack, the DHS claims. The leaked data was found in an unauthorized copy of the DHS OIG investigative case management system that was in the possession of a former DHS OIG employee.
The data breach was discovered on May 10, 2017, as part of an ongoing criminal investigation conducted by DHS OIG and the U.S. Attorney’s Office.
“The privacy incident did not stem from a cyber-attack by external actors, and the evidence indicates that affected individual’s personal information was not the primary target of the unauthorized exfiltration,” DHS explained.
The Department said that notification letters were sent to select DHS employees to inform them that they might have been impacted. DHS also says that it conducted a thorough privacy investigation, a forensic analysis of the compromised data, and assessed the risk to affected individuals before making the incident public.
Following the incident, the DHS says it is implementing additional security precautions to limit access to the type of information that was released in this incident and to better identify unusual access patterns.
“We will continue to review our systems and practices in order to better secure data. DHS OIG has also implemented a number of security precautions to further secure the DHS OIG network,” DHS notes.
Additional information for the affected individuals is available in an announcement and FAQ published on Jan 3.
Forever 21 confirms Payment Card Breach and provides further info on the incident
1.1.2018 securityaffairs Incindent
FOREVER 21 confirmed the presence of a malware at some point of sale (POS) systems in stores across the US.
On November 2017, the US clothes retailer FOREVER 21 announced it has suffered a security breach, the company now confirmed that hackers stole payment card data from its locations throughout the country for several months during 2017.
Even if the investigation is still ongoing, FOREVER 21 confirmed the presence of a malware at some point of sale (POS) systems in stores across the US, the malicious code was used at least between April 3, 2017, and November 18, 2017.
The payment made on the company website, forever21.com, were not affected by the incident.
The company explained that it has been using encryption technology since 2015 to protect its payment processes, but the investigation revealed that the encryption was switched off for some POS terminals at certain stores, a circumstance that allowed crooks to install the malware.
“The investigation determined that the encryption technology on some point-of-sale (POS) devices at some stores was not always on. The investigation also found signs of unauthorized network access and installation of malware on some POS devices designed to search for payment card data. The malware searched only for track data read from a payment card as it was being routed through the POS device. In most instances, the malware only found track data that did not have cardholder name – only card number, expiration date, and internal verification code – but occasionally the cardholder name was found.” reads the advisory published by the company.
“The investigation found that encryption was off and malware was installed on some devices in some U.S. stores at varying times during the period from April 3, 2017 to November 18, 2017. In some stores, this scenario occurred for only a few days or several weeks, and in some stores this scenario occurred for most or all of the timeframe.”
FOREVER 21
The company pointed out that not every POS terminal in affected stores was infected with the malware
“Each Forever 21 store has multiple POS devices, and in most instances, only one or a few of the POS devices were involved. Additionally, Forever 21 stores have a device that keeps a log of completed payment card transaction authorizations,” the company said while explaining the incident.
“When encryption was off, payment card data was being stored in this log. In a group of stores that were involved in this incident, malware was installed on the log devices that was capable of finding payment card data from the logs, so if encryption was off on a POS device prior to April 3, 2017, and that data was still present in the log file at one of these stores, the malware could have found that data.”
The company advised customers who shopped at its locations to monitor their credit transactions for any suspicious activity.
Ancestry.com Responds Well To RootsWeb Data Breach
30.12.2017 securityaffairs Incindent
The popular expert Troy Hunt notified the Ancestry.com security team of an unsecured file on a RootsWeb server containing “email addresses/username and password combinations as well as usernames from a RootsWeb.com server”.
When you think of personal security questions, you might think of your mother’s surname or other family information that normally isn’t shared — unless you are building your family tree with an online genealogy search. When Ancestry.com notifies its users of a potential security breach it sounds worse than most.
Ancestry.com is a company with millions of customers that use their online tools to research their family tree. The company also hosts servers for RootsWeb, a free, community-driven collection of genealogy tools and discussion forums. On December 20th, 2017, Troy Hunt, of HaveIBeenPwned.com, notified the Ancestry.com security team of an unsecured file on a RootsWeb server containing “email addresses/username and password combinations as well as usernames from a RootsWeb.com server”, and a quick and detailed investigation ensued.

According to Ancestry.com’s blog post detailing the incident, the security team reviewed the file identified by Hunt, and determined that it does contain login details for 300,000 accounts although they describe, “the majority of the information was old.” They continued their investigation and determined that of the 300,000 accounts, 55,000 had been reused by users on both the RootsWeb and Ancestry websites. Most of the 55,000 were “from free trial, or currently unused accounts,” but 7,000 login credentials were in use by active Ancestry.com users. Ancestry.com supports millions of users so this breach represents less than 1% of their users, however, they still took the potential impacts seriously and acted accordingly.
The internal investigation points to the RootsWeb surname list information service which Ancestry.com retired earlier this year. “We believe the intrusion was limited to the RootsWeb surname list, where someone was able to create the file of older RootsWeb usernames and passwords as a direct result of how part of this open community was set up, an issue we are working to rectify”, according to the blog post by Ancestry.com CISO, Tony Blackman.
He continued with, “We have no reason to believe that any Ancestry systems were compromised. Further, we have not seen any activity indicating the compromise of any individual Ancestry accounts.” According to Ancestry, the RootsWeb servers do not host any credit card or social insurance numbers so the potential impact of this breach appears to be minimized.
The RootsWeb website is currently offline while the Ancestry teams complete their investigation, make the appropriate configuration changes and “ensure all data is saved and preserved to the best of [their] ability.”
In addition, the Ancestry has locked the 55,000 accounts found in the exposed file, requiring users to change their passwords the next time they attempt to log on. They sent emails to all 55,000 email addresses advising them of the incident and recommended actions, and commit to “working with regulators and law enforcement where appropriate.”
To summarize, the Ancestry.com security team responded quickly when notified of a potential breach, determined the potential scope and impact, took swift action to minimize damages, notified impacted users, clearly and publicly described the event. Troy Hunt’s tweet describes it best, “Another data breach from years ago, this time from @Ancestry’s services. Really impressed with the way they handled this: I got in touch with them bang on 72 hours ago and they’ve handled it in an exemplary fashion.”
Troy Hunt
✔
@troyhunt
Another data breach from years ago, this time from one of @Ancestry's services. Really impressed with the way they handled this: I got in touch with them bang on 72 hours ago and they've handled it in an exemplary fashion https://blogs.ancestry.com/ancestry/2017/12/23/rootsweb-security-update/ …
Nissan Finance Canada Suffers Data Breach — Notifies 1.13 Million Customers
22.12.2017 thehackernews Incindent
It's the last month of this year, but possibly not the last data breach report.
Nissan warns of a possible data breach of personal information on its customers who financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.
Although the company says it does not know precisely how many customers were affected by the data breach, Nissan is contacting all of its roughly 1.13 million current and previous customers.
In a statement released Thursday, Nissan Canada said the company became aware of an "unauthorized access to personal information" of some customers on December 11.
"Nissan Canada Finance recently became aware it was the victim of a data breach that may have involved an unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada," the company said.
It's believed that the unknown hacker(s) may have had access to the following information:
Customers' names
Home addresses
Vehicle makes and models
Vehicle identification numbers (VIN)
Credit scores
Loan amounts
Monthly payments
The company says there no indication, at least at this moment, that if the data breach also includes payment information and contactable information like email addresses or phone numbers.
The company offers 12 months of free credit monitoring services through TransUnion to all of its financed customers.
Since the investigation into the data breach incident is still ongoing, it is not clear if the hack also impacts customers outside of Canada and customers who did not obtain financing through NCF.
"We sincerely apologize to the customers whose personal information may have been illegally accessed and for any frustration or inconvenience that this may cause," Nissan Canada president Alain Ballu said. "We are focused on supporting our customers and ensuring the security of our systems."
Nissan Canada has contacted Canadian privacy regulators, law enforcement, and data security experts to help rapidly investigate the matter.
Nissan Canada Informs 1.1 Million Customers of Data Breach
22.12.2017 securityweek Incindent
Nissan Canada revealed on Thursday that the personal information of some customers may have been compromised as a result of a data breach discovered by the company on December 11.
The incident affects individuals who have financed their vehicles through Nissan Canada Finance (NCF) and INFINITI Financial Services Canada. The exact number of impacted customers has yet to be determined, but Nissan is notifying all 1.13 million current and past customers.
While the company believes not all customers are affected, it has decided to offer all of them free credit monitoring services through TransUnion for a period of 12 months. NCF is in the process of sending out emails and letters to individuals whose information may have been compromised.
The attacker could have stolen names, addresses, vehicle details, vehicle identification numbers (VINs), credit scores, loan amounts, and information on monthly payments. Nissan Canada says the incident does not appear to involve payment card information.
There is no indication that Nissan or Infiniti customers in Canada who did not obtain financing through NCF or customers outside of Canada are impacted.
The company is working with law enforcement and data security experts to investigate the incident and has not made any comments on who might be behind the attack. Canadian privacy regulators have also been informed of the breach.
This is not the first time Nissan has been targeted by hackers. Back in 2012, the company reported finding malware on its global information systems network. Last year, the company was forced to shut down its global websites due to a cyberattack apparently motivated by anger over Japan's controversial whale and dolphin hunts.
Nissan Finance Canada hacked, 1.13 million customers may have been exposed
22.12.2017 securityaffairs Incindent
Nissan Finance Canada announced on Thursday that the personal information of 1.13 million customers may have been exposed as a result of a data breach.
Nissan Finance Canada has been hacked, personal information of 1.13 million customers may have been exposed as a result of a data breach discovered by the company on December 11 (The biz took 10 days to disclose the incident).
The company notified customers via email the incident, it confirmed that its systems were compromised, with “unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance or Infiniti Financial Services Canada.”
“We apologize for any frustration and anxiety this may cause our customers, and we thank you for your patience and support as we work through this issue.”
Nissan published a quite similar message on its website too, it added that at this time, there is no indication that customers who financed vehicles outside of Canada are affected. According to Nissan Canada, compromised data includes customer names, addresses, vehicle makes and models, vehicle identification numbers (VINs), credit scores, loan amounts and monthly payment figures.
Financial information belonging to the customers, such as payment card data was not affected.
“Nissan Canada Finance (NCF) is notifying its customers in Canada that it is a victim of a data breach that may have involved unauthorized person(s) gaining access to the personal information of some customers that have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.” states the message published on the company website.
“On December 11, 2017, NCF became aware of unauthorized access to personal information.” “While the precise number of customers affected by the data breach is not yet known, NCF is contacting all of our current and past customers – approximately 1.13 million customers – who have financed their vehicles through Nissan Canada Finance and INFINITI Financial Services Canada.”

The company is investigating the attack with the help of law enforcement trying to figure out the extension of the incident and potential impact on its customers.
“We are still investigating precisely what personal information has been impacted,” the company added.
Nissan is offering 12 months of credit monitoring services through TransUnion at no cost.
California Voter Data Stolen from Insecure MongoDB Database
18.12.2017 securityweek Incindent
An improperly secured MongoDB database has provided cybercriminals with the possibility to steal information on the entire voting population of California, Kromtech security researchers reported.
The information was taken from an unprotected instance of a MongoDB database that was exposed to the Internet, meaning that anyone connected to the web could have accessed, viewed, or edited the database’s content.
Named 'cool_db', the database contained two collections, one being a manually crafted set of voter registration data for a local district, while the other apparently including data on the voting population from the entire state of California: a total of 19,264,123 records.
Bob Diachenko, head of communications, Kromtech Security Center, explains that the security firm was “unable to identify the owner of the database or conduct a detailed analysis.” It appears that the database has been erased by cybercriminals who dropped a ransom note demanding 0.2 Bitcoin for the data.
Given the presence of said ransom note, the incident is believed to be related to the MongoDB ransack campaign that resulted in tens of thousands of databases being erased in January 2017. Similar attacks were observed in September as well, when MongoDB decided to implement new data security measures.
“We were able to analyze the stats data we saw in our report (metadata on total number of records, uptime, names of the collection etc.), as well as 20-records sample extracted from the database shortly before it has been wiped out and ransom note appeared,” Diachenko says.
Kromtech's security researchers haven’t determined who compiled the voter database but believe that a political action committee might have been behind it, given the unofficial name the repository had.
The miscreants behind the attack used ransomware to wipe out the voter data, but are believed to have copied the database to their server first. “Once in the hands of cyber criminals this voter data could end up for sale on the Dark Web. If this were an official database, deleting parts of that data could affect someone’s voting process,” the security researchers note.
The first, smaller collection (4GB) contained data structured with rows containing many fields that included home address, phone number, date of birth, and many more.
Based on EstractDate information, the database appears to have been created on May 31, 2017.
The second, much larger collection (22GB) in the database, which appears to be the complete California voter registration records, contains a total of 409,449,416 records.
The data in the larger collection includes: District, RegistrantId, CountyCode, DistrictName and ObjectId.
“This is a massive amount of data and a wakeup call for millions citizens of California who have done nothing more than fulfil the civic duty to vote. This discovery highlights how a simple human error of failing to enact the basic security measures can result in a serious risk to stored data. The MongoDB was left publically available and was later discovered by cyber criminals who seemed to steal the data, which origin is still unknown,” Diachenko concludes.
The researchers note that the database has been taken down after being initially discovered in early December. The Secretary of State of California was aware of the leak and “looking into it,” Diachenko said.
Collection of 1.4 Billion Plain-Text Leaked Passwords Found Circulating Online
12.12.2017 thehackernews Incindent
Hackers always first go for the weakest link to quickly gain access to your online accounts.
Online users habit of reusing the same password across multiple services gives hackers opportunity to use the credentials gathered from a data breach to break into their other online accounts.
Researchers from security firm 4iQ have now discovered a new collective database on the dark web (released on Torrent as well) that contains a whopping 1.4 billion usernames and passwords in clear text.
The aggregate database, found on 5 December in an underground community forum, has been said to be the largest ever aggregation of various leaks found in the dark web to date, 4iQ founder and chief technology officer Julio Casal noted in a blog post.
Though links to download the collection were already circulating online over dark-web sites from last few weeks, it took more exposure when someone posted it on Reddit a few days ago, from where we also downloaded a copy and can now verify its authenticity.
Researchers said the 41GB massive archive, as shown below, contains 1.4 billion usernames, email, and password combinations—properly fragmented and sorted into two and three level directories.
The archive had been last updated at the end of November and didn't come from a new breach—but from a collection of 252 previous data breaches and credential lists.
The collective database contains plain text credentials leaked from Bitcoin, Pastebin, LinkedIn, MySpace, Netflix, YouPorn, Last.FM, Zoosk, Badoo, RedBox, games like Minecraft and Runescape, and credential lists like Anti Public, Exploit.in.
"None of the passwords are encrypted, and what's scary is that we've tested a subset of these passwords and most of the have been verified to be true," Casal said. "The breach is almost two times larger than the previous largest credential exposure, the Exploit.in combo list that exposed 797 million records."
"This new breach adds 385 million new credential pairs, 318 million unique users, and 147 million passwords pertaining to those previous dumps."
The database has been neatly organized and indexed alphabetically, too, so that would-be hackers with basic knowledge can quickly search for passwords.
For example, a simple search for "admin," "administrator" and "root," returned 226,631 passwords used by administrators in a few seconds.
Although some of the breach incidents are quite old with stolen credentials circulating online for some time, the success ratio is still high for criminals, due to users lousy habit of re-using their passwords across different platforms and choosing easy-to-use passwords.
The most common yet worst passwords found in the database are "123456", "123456789", "qwerty," "password" and "111111."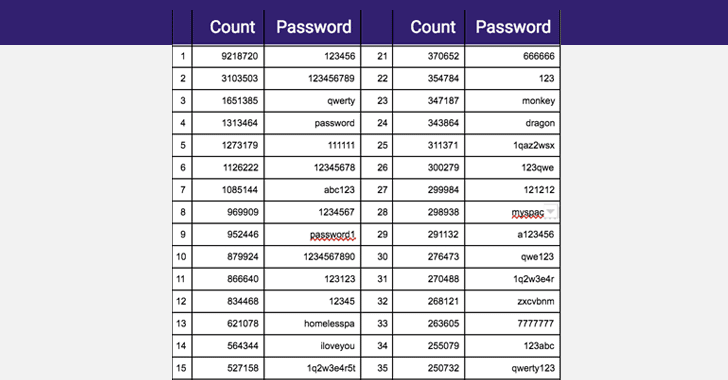
It is still unclear who is responsible for uploading the database on the dark web, but whoever it is has included Bitcoin and Dogecoin wallets for any user who wants to donate.
To protect yourself, you are strongly advised to stop reusing passwords across multiple sites and always keep strong and complex passwords for your various online accounts.
If it's difficult for you to remember and create complex passwords for different services, you can make use of the best password manager. We have listed some good password managers that could help you understand the importance of such tool and choose one according to your requirement.
Cybersecurity Incidents Hit 83% of U.S. Physicians: Survey
12.12.2017 securityweek Incindent
A majority of physicians in the United States have experienced a cybersecurity incident, and many are very concerned about the potential impact of a cyberattack, according to a study conducted by professional services company Accenture and the American Medical Association (AMA).
A survey of 1,300 doctors revealed that 83% of clinical practices experienced some type of cybersecurity incident. The most common is phishing (55%), followed by malware infections (48%), improper access to electronic protected health information, or ePHI (37%), network breaches (12%), and ransomware and other attacks involving ransom demands (9%).
More than half of respondents said they were either very concerned or extremely concerned about future cyberattacks, particularly that they may result in interruption to their business or electronic health records (EHR) getting compromised. Physicians are also worried about patient safety (53%), civil or criminal liability (36%), damage to reputation (34%), costs associated with incident response (32%), impact on revenue (30%), fines (25%), and medical device security (19%).
When asked about the impact of past cybersecurity incidents on their business, 64% of respondents said it had caused downtime of four hours or less, but in 12% of cases normal operations were suspended for 1-2 days, and in 4% of cases for more than two days.
In response to incidents, the most common actions were notification of the internal IT team (65%), notification or education of employees (61%), implementation of new policies and procedures (59%), and notification of the EHR or health IT vendor (56%).
While doctors are concerned about the security risks associated with the use of electronic systems, they also noted that the ability to share data with outside entities is in most cases very important.
The study also shows that physicians often trust third parties to keep their ePHI data secure. In many cases, they either get assurance from the vendor or simply trust that their data is being protected. Many also sign contracts or rely on their privacy officer to ensure that sensitive information is stored securely.
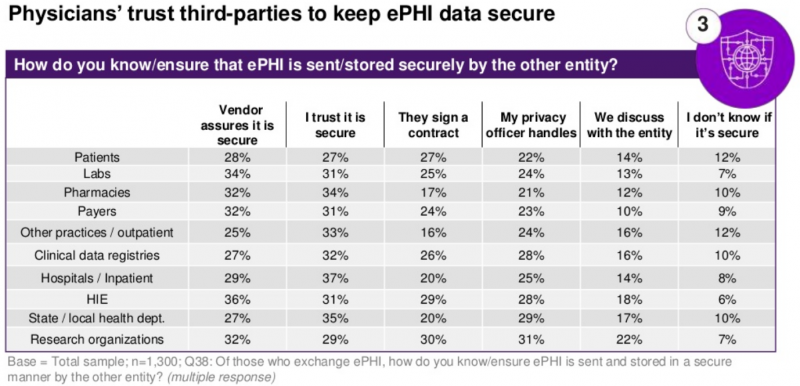
Nearly half of organizations have an in-house person responsible for cybersecurity and 17% said they are interested in appointing someone to such a position. Others either outsource security management (26%), or share security management with another practice (23%). Some physicians said they received donated cybersecurity software or hardware.
When it comes to security training, half of respondents named tips for good cyber hygiene as the factor that would boost their confidence in their security posture. Others named simplifying the legal language of HIPAA (47%), easily digestible summary of HIPAA (44%), explaining the more complex rules described by HIPAA (40%), and guidance on conducting risk assessments (38%).
A collection of 1.4 Billion Plain-Text leaked credentials is available online
12.12.2017 securityaffairs Incindent
A 41-gigabyte archive containing 1.4 Billion credentials in clear text was found in dark web, it had been updated at the end of November.
Another monster data dump was found online, the huge archive contains over 1.4 billion email addresses, passwords, and other credentials in clear text.
The huge trove of data, a 41-gigabyte archive, has been found online on December 5 by security shop @4iQ.
According to 4iQ founder and chief technology officer Julio Casal, the archive is the largest ever aggregation of various leaks found in the dark web to date.
“While scanning the deep and dark web for stolen, leaked or lost data, 4iQdiscovered a single file with a database of 1.4 billion clear text credentials — the largest aggregate database found in the dark web to date.” reads a post published by 4iQ on Medium.
“None of the passwords are encrypted, and what’s scary is the we’ve tested a subset of these passwords and most of the have been verified to be true.”

The 41-gigabyte file had been updated at the end of November, it aggregates data from a collection of 252 previous data breaches and credential lists.
It is still unclear who collected this data, the unique information we have at this time is the Bitcoin and Dogecoin wallet details left for donations.
Collector organized and indexed data alphabetically, the total amount of credentials is 1,400,553,869.
“The breach is almost two times larger than the previous largest credential exposure, the Exploit.in combo list that exposed 797 million records.” continues Julio Casal.
“This new breach adds 385 million new credential pairs, 318 million unique users, and 147 million passwords pertaining to those previous dumps.”
Digging the archive, it is possible to verify that users continue to use weak passwords, the top password is still 123456, followed by 123456789, qwerty, password and 111111.
Not only … the expert observed that users tend to reuse the same passwords for multiple online services.
“Since the data is alphabetically organized, the massive problem of password reuse — — same or very similar passwords for different accounts — — appears constantly and is easily detectable.” states the post.
The researchers highlighted that 14% of exposed credentials are new and in clear text.
“We compared the data with the combination of two larger clear text exposures, aggregating the data from Exploit.in and Anti Public. This new breach adds 385 million new credential pairs, 318 million unique users, and 147 million passwords pertaining to those previous dumps.” continues the expert.
As usual, let me suggest avoiding password reuse on multiple sites and of course use strong passwords.
Database of 1.4 Billion Credentials Found on Dark Web
11.12.2017 securityweek Incindent
Researchers have found a database of 1.4 billion clear text credentials in what appears to be the single largest aggregate database yet found on the dark web. These are not from a new breach, but a compilation of 252 previous breaches, including the previous largest combo list, Exploit.in.
The database was found by 4iQ on 5 December 2017. Announcing the discovery, the firm's founder and CTO Julio Casal, said, "This is not just a list. It is an aggregated, interactive database that allows for fast (one second response) searches and new breach imports... The database was recently updated with the last set of data inserted on 11/29/2017. The total amount of credentials (usernames/clear text password pairs) is 1,400,553,869."
It is a database designed to be used. It includes search tools and insert scripts explained in a README file. Another file called 'imported.log' lists the breach sources; for example '/inputbreach/linkedin110M_1 865M'. There are four such LinkedIn input files, in a total of 256 inputs.
The data is structured in an alphabetic directory tree fragmented in 1,981 pieces to allow fast searches. In a test, 4iQ notes, "searching for 'admin,' 'administrator' and 'root' returned 226,631 passwords of admin users in a few seconds." The combination of database structure and clear text credentials makes it an easy tool for bad actors to use for bad purposes. "Now even unsophisticated and newbie hackers can access the largest trove ever of sensitive credentials in an underground community forum," comments Casal. "Is the cyber crime epidemic about become exponentially worse?"
The raw data has probably been available to criminals on the dark web from soon after many of the breaches -- but this new database takes out much of the labor needed to use the stolen credentials.
"Large databases of passwords containing both hashed and clear text have been available for years, that are easy to download to use with password cracking software," Joe Carson, chief security scientist at password protection firm Thycotic, told SecurityWeek. "These password databases are available to both skilled hackers and script kiddies with basic knowledge that can be easily used with software that is easily downloadable from the internet. Today all you need is a computer and an internet connection to be a hacker."
But use of these databases still required effort. "In the past hackers would have accessed each breached database containing passwords, and correlated them on their own," he added; "but why do that when someone will do it for you and make it easy downloadable?"
Freelance security consultant and researcher Robin Wood (aka DigiNinja, author of the widely used Pipal password analyzer), explains how the database could be used by bad actors. "The most obvious," he says, "is to take large chunks of the files and spray them against popular sites to see which still work." This is basic 'credential stuffing'.
Carson notes that "previous research has found that at least 25 percent of leaked google passwords are still active and still work, which means that many people still fail to change their passwords even after a major data breach has occurred." The implication is that credential stuffing from this new database could prove very effective for the hackers.
Wood adds, "[The announcement] doesn't say whether the [discovery] lists which individual dump the creds came from, although it does say which sources were used to create the list; so that is a good list of targets to start with."
However, he also warns that the searchable nature of this database gives additional concerns. "It can also be used for more targeted attacks. Pick your target company and search for references to it in the list to find staff, contractors or suppliers. This could give both an initial foothold into the company, or -- if someone is already in -- to help move around if credentials have been reused internally."
What isn't clear is where this database has come from, nor why it has suddenly appeared on the dark web. Clearly, considerable time and effort has gone into its design and creation to make it large scale and easy to use; but it doesn't appear to have a direct monetization methodology for now. "There is not [sic] indication of the author of the database and tools," writes Casal, "although Bitcoin and Dogecoin wallets are included for donation." Of course, the author could be intending to 'charge' for future maintenance of the database with new additions as they become available.
"My first thought," comments Wood, "was whether this is the database that was behind the recently shut down LeakedBase site." LeakedBase was an online service that provided paid access to leaked credentials. It was shut down just days before 4iQ made its discovery. "Their database," continued Wood, "gave out clear text passwords, so it could be the same. Maybe the owners decided it was too risky running a site giving access to the creds but wanted to drop it out there and try to make some money off donations instead."
Whatever the reasons behind this database, its availability on the dark web provides an additional threat to users who don't change their passwords. "It is clear that people do not even change passwords after a major data breach," says Carson. "It is also poor hygiene that the companies impacted by these data breaches still do not force a password reset leaving many of their customers' accounts exposed and vulnerable to abuse by cybercriminals."
NiceHash: security breach leads to 60 million lost – Iceman is behind?
8.12.2017 securityaffairs Incindent
NiceHash has been hacked, roughly to 60$ million (4,736.42 BTC) have been stolen while the bitcoin is crossing the 14k$ mark for the first time.
A dark day for cryptocurrency miners, NiceHash has been hacked. Closely to 60$ millions (4,736.42 BTC) have been stolen while the bitcoin is crossing the 14k$ mark for the first time.
The hacker’s bitcoin address cleary shows the steal of 4,736.42 BTC in a window of 48 hours:https://bitinfocharts.com/bitcoin/address/1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq
NiceHash users are furious by the time of reaction of the team. It took about 24 hours to realize that big amounts have been stolen.
I’ve contacted a member of Iceman and knowing this security breach for some reason he explained that NiceHash actually owned their users’ bitcoin wallets in order to save transactions fees and collect unclaimed BTC. This issue leads to a massive security breach which allows access to all NiceHash wallets. He claimed that by reverse engineering of their miner client, Iceman group was able to access their API.
Is Iceman really behind this attack?
About the Author: Marc Miller
Marc Miller is a web journalist, focused on cybercrime.
He started a blog called: THE PURPLE HAT – Cyber Gangs NAKED, dedicated to exposing the methods and works of cybercrime gangs such as “CARBANAK” or similar sophisticated syndicated Cybercrime organizations.
In the past. he worked as a web front-end programmer. Also, he is passionate about hardware, hacking, security and marketing.
NiceHash Hacked – Crooks have allegedly stolen $60m worth of Bitcoin
7.12.2017 securityweek Incindent
The cryptocurrency mining market NiceHash confirmed it has fallen victim to a hacking attack that may have resulted in the loss of $60m worth of Bitcoin
Cryptocurrency companies continue to be a privileged target of hackers, the last victim in order of time is the cryptocurrency mining market NiceHash. The NiceHash marketplace allows users to buy and sell their computing cycles to mine cryptocurrency, the company confirmed it was hacked, attackers stole its entire Bitcoin wallet.
“Unfortunately, there has been a security breach involving NiceHash website. We are currently investigating the nature of the incident and, as a result, we are stopping all operations for the next 24 hours.” reads the statement issued by NiceHash.
“Importantly, our payment system was compromised and the contents of the NiceHash Bitcoin wallet have been stolen. We are working to verify the precise number of BTC taken.”

The security breach has been reported to law enforcement, the company is also investigating the attack.
Even if NiceHash did not provide financial data on the security breach, it has been estimated hackers have stolen around $60m.
NiceHash declared that it is fully committed to restoring the service with the highest security measures, it doesn’t want to exit from the market due to the incident.
The company doesn’t provide further details on the hack, as a precaution it recommends users to change their online passwords.
“While the full scope of what happened is not yet known, we recommend, as a precaution, that you change your online passwords.” concludes the statement.“We are truly sorry for any inconvenience that this may have caused and are committing every resource towards solving this issue as soon as possible.”
The security breach was disclosed just hours after NiceHash confirmed its website was down for maintenance.
NiceHash
@NiceHashMining
Dear NiceHash user, our service is currently under maintenance.
We are sorry for the inconvenience and please stay tuned for updates.
Thank you for your understanding.
8:52 AM - Dec 6, 2017
201 201 Replies 64 64 Retweets 179 179 likes
Twitter Ads info and privacy
At the time of writing, The NiceHash website still shows a maintenance page.
PayPal Subsidiary Data Breach Hits Up to 1.6 Million Customers
5.12.2017 thehackernews Incindent
Global e-commerce business PayPal has disclosed a data breach that may have compromised personally identifiable information for roughly 1.6 million customers at a payment processing company PayPal acquired earlier this year.
PayPal Holdings Inc. said Friday that a review of its recently acquired company TIO Networks showed evidence of unauthorized access to the company's network, including some confidential parts where the personal information of TIO's customers and customers of TIO billers stored.
Acquired by PayPal for US$233 Million in July 2017, TIO Network is a cloud-based multi-channel bill payment processor and receivables management provider that serves the largest telecom, wireless, cable and utility bill issuers in North America.
PayPal did not clear when or how the data breach incident took place, neither it revealed details about the types of information being stolen by the hackers, but the company did confirm that its platform and systems were not affected by the incident.
"The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal's customers' data remains secure," The data breach in TIO Networks was discovered as part of an ongoing investigation for identifying security vulnerabilities in the payment processing platform.
As soon as PayPal identified an unauthorized access to the TIO's network, PayPal took action by "initiating an internal investigation of TIO and bringing in additional third-party cybersecurity expertise to review TIO's bill payment platform," PayPal press release [PDF] reads.
The company has begun working with companies it services to notify potentially affected customers.
Besides notifying, the company is also working with a consumer credit reporting agency, Experian, to provide free credit monitoring memberships for fraud and identity theft to those who are affected by the breach.
To protect its customers, TIO has also suspended its services until a full-scale investigation into the incident is completed.
"At this point, TIO cannot provide a timeline for restoring bill pay services, and continues to recommend that you contact your biller to identify alternative ways to pay your bills," TIO's Consumer FAQ reads.
"We sincerely apologize for any inconvenience caused to you by the disruption of TIO's service."
Since the investigation is ongoing, PayPal will communicate with TIO customers and merchant partners directly as soon as the company has more details on the incident. Also, the affected customers will be directly contacted by the company.
PayPal-owned company TIO Networks data breach affects 1.6 million customers
4.12.2017 securityaffairs Incindent
PayPal confirmed that one of the companies it owns, TIO Networks, suffered a security breach, that affected 1.6 million customers.
PayPal confirmed that one of the companies it owns, TIO Networks, suffered a security breach, hackers have accessed servers that stored information for 1.6 million customers.
The company TIO Networks was recently acquired by PayPal for $238 million, it is a Canadian firm that runs a network of over 60,000 utility and bills payment kiosks across North America.
On November 10, PayPal suspended the operations of TIO’s network due to the discovery of “security vulnerabilities” affecting the TIO platform and issues with TIO’s data security programme that does not follow PayPal’s security standards.
“While we apologise for any inconvenience this suspension of services may cause, the security of TIO’s systems and the protection of TIO’s customers are our highest priorities.” said TIO Networks.
“We are working with the appropriate authorities to safeguard TIO customers.”
“The PayPal platform is not impacted by this situation in any way and PayPal’s customers’ data remains secure.
“Our investigation is ongoing. We will communicate with TIO customers and merchant partners directly as soon as we have more details. Customer updates will also be posted at www.tio.com.”
The Canadian firm disclosed the data breach, but did not provide any other details.

On Friday, December 1, PayPal published a press release that includes more details on the hack.
“PayPal Holdings, Inc. (Nasdaq: PYPL) today announced an update on the suspension of operations of TIO Networks (TIO), a publicly traded payment processor PayPal acquired in July 2017. A review of TIO’s network has identified a potential compromise of personally identifiable information for approximately 1.6 million customers.” reads the press release.
“The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal’s customers’ data remains secure.”
TIO systems are completely separate from the PayPal network, this means that PayPal’s customers’ data were not affected by the incident.
PayPal confirmed that the attackers stole the personal information of both TIO customers and customers of TIO billers, but it avoided to disclose what type of information the hackers compromised.
Likely attackers accessed personally-identifiable information (PII) and financial details.
PayPal is notifying affected customers of the data breach and is offering free credit monitoring memberships.
The customers of TIO Networks can visit the TIO Networks website for more information on the data breach.
“TIO has also begun working with the companies it services to notify potentially affected individuals, and PayPal is working with a consumer credit reporting agency to provide free credit monitoring memberships. Individuals who are affected will be contacted directly and receive instructions to sign up for monitoring.” continue the Press Release.
Breach at PayPal Subsidiary Affects 1.6 Million Customers
4.12.2017 securityweek Incindent
PayPal informed customers on Friday that personal information for 1.6 million individuals may have been obtained by hackers who breached the systems of its subsidiary TIO Networks.
TIO is a publicly traded bill payment processor that PayPal acquired in July 2017 for roughly $230 million. The company is based in Canada and it serves some of the largest telecom and utility network operators in North America. TIO has more than 10,000 supported billers and it serves 16 million consumer bill pay accounts.
On November 10, PayPal announced that TIO had suspended operations in an effort to protect customers following the discovery of security vulnerabilities on the subsidiary's platform. PayPal said it had found issues with TIO’s data security program that did not adhere to its own standards.
An investigation conducted in collaboration with third-party cybersecurity experts revealed that TIO’s network had been breached, including servers that stored the information of TIO clients and customers of TIO billers. PayPal said the attackers may have obtained personally identifiable information (PII) for roughly 1.6 million customers.
Affected companies and individuals will be contacted via mail and email, and offered free credit monitoring services via Experian.
While it’s unclear exactly what type of data the hackers have gained access to, the information shared by PayPal and TIO suggests that payment card data and in some cases even social security numbers (SSNs) may have been compromised.
PayPal has highlighted that TIO’s systems have not been integrated into its own platform. “The PayPal platform is not impacted in any way, as the TIO systems are completely separate from the PayPal network, and PayPal’s customers’ data remains secure,” the company said.
The New York State Department of Financial Services (DFS), an agency responsible for regulating financial services and products, has also issued a statement on the incident.
“DFS is working with our regulated entity, PayPal, to investigate and address issues related to cybersecurity vulnerabilities identified at PayPal’s subsidiary, TIO Networks,” the DFS said. “We applaud PayPal’s rapid response to the matter, which put consumers and business clients first, and we appreciate their efforts to inform DFS, as required, in a timely manner. Events like these illustrate the necessity of DFS’s landmark cybersecurity regulation and underscore the strength and effectiveness of our strong state-based financial services regulatory framework, including for the fintech industry.”
TIO said services will not be fully restored until it’s confident that its systems and network are secure.
The Shipping Giant Clarkson has suffered a security breach
30.11.2017 securityaffairs Incindent
Clarkson, one of the world’s largest providers of shipping services publicly disclosed a security breach.
Clarkson confirmed the hackers may release some of the stolen data, it hasn’t provided further details due to the ongoing law enforcement investigation.
The information disclosed by the company suggests cyber criminals blackmailed the company requesting the payment of a ransom in order to avoid having its data leaked online.
According to Clarkson, the hackers compromised a single user account to access the systems of the shipping giant.
“Clarkson PLC confirms that it was subject to a cybersecurity incident which involved unauthorised access to the Company’s computer systems.” Clarkson said in a statement.
“Our initial investigations have shown the unauthorised access was gained via a single and isolated user account which has now been disabled.”
The company has disabled the account after the incident and has started notifying affected customers and individuals.
The company had been expecting the cyber criminals to publish part of the stolen data on Tuesday, but nothing is still happening.

The company said it has been conducting a review of the security of its architecture and announced new IT security measures.
“As you would rightly expect, we’re working closely with specialist police teams and data security experts to do all we can to best understand the incident and what we can do to protect our clients now and in the future,” said Andi Case, CEO of Clarkson. “We hope that, in time, we can share the lessons learned with our clients to help stop them from becoming victims themselves. In the meantime, I hope our clients understand that we would not be held to ransom by criminals, and I would like to sincerely apologise for any concern this incident may have understandably raised.”
Bitcoin Gold (BTG) dev team warns its users about a security breach
29.11.2017 securityaffairs Incindent
The development team of the Bitcoin Gold (BTG) cryptocurrency is warning all users users about a security breach involving its Windows version of wallet app
The development team of the Bitcoin Gold (BTG) cryptocurrency is warning all users users about a security breach involving the official Windows wallet application offered for download via its official website. Bitcoin Gold is the fork of the official Bitcoin cryptocurrency that was created on October 25.
The Bitcoin Gold website does not include links to the installers for the official wallet apps, but links to files hosted in a GitHub repository used by the development team
The development team of the Bitcoin Gold (BTG) explained that attackers gained access to this GitHub account and replaced the legitimate Windows installer with a “suspicious” file that were created to steal funds from the victims and other information.
Developers confirmed the Linux version of the official wallet app was not changed during the incident.
The development team discovered the security breach over the weekend when the experts noticed that the SHA-256 checksum for the Windows installer did not match the original SHA-256 checksum for the file present on the GitHub repository.
“Please be aware that for approximately 4.5 days, a link on our Download page and the file downloads on our Github release page have been serving two suspicious files of unknown origin.” reads the security advisory.
Below are the correct SHA-256 checksums for BTG’s Windows wallet app.
Windows file SHA-256:
53e01dd7366e87fb920645b29541f8487f6f9eec233cbb43032c60c0398fc9fa
bitcoingold-0.15.0-win64-setup.exe
Further investigation allowed the development team to discover that the “malicious” file was available in the GitHub repository between November 21, 2017, 09:39 UTC, and November 25, 2017, 22:30 UTC.
The bad news for end-users is that the malware was not detected by antivirus software.
“Until we know otherwise, all users should presume these files were created with malicious intent – to steal cryptocurrencies and/or user information. The file does not trigger antivirus / anti-malware software, but do not presume the file is safe.” continues the advisory.
“Any user who verified the SHA-256 checksum of the download against the checksum listed on our Download pages is already aware the file is not authentic and should not have used the file, but nobody should assume that all users take this important step.”

Affected users urge to transfer funds to new wallet addresses and reinstall affected computers.
“If the file was used, the computer on which it was used should be addressed with extreme caution; the file should be deleted, the machine should be thoroughly checked for malware and viruses (or wiped clean), and any cryptocurrencies with wallets accessible on that machine should be moved to new wallet addresses immediately,” suggested the Bitcoin Gold development team that meantime has restored the original files and has secured its GitHub account.
BTG is currently the fifth most popular cryptocurrency on the market, ranked behind Bitcoin (BTC), Ethereum (ETH), Bitcoin Cash (BCH), and Ripple (XRP).
Imgur Discloses 2014 Breach Affecting 1.7 Million Users
27.11.2017 securityweek Incindent
Popular image hosting website Imgur notified users on Friday that hackers had stolen data associated with 1.7 million accounts as a result of a breach that occurred back in 2014.
The company learned about the hack from Australian security expert Troy Hunt, operator of the Have I Been Pwned breach notification service, and immediately began taking steps to address the situation.
“I want to recognise Imgur’s exemplary handling of this: that's 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure,” Hunt said.
Others also praised the company for the way it handled the incident, with many comparing it to Uber, which attempted to cover up a massive 2016 breach that hit more than 57 million users.
Only email addresses and passwords were apparently compromised in the Imgur breach and the company says it does not ask users to provide any other data, such as real names, addresses or phone numbers.
At the time of the hack, the passwords had been stored as hashes generated using the SHA-256 algorithm, which can be cracked. The MD5Decrypt service, for example, can reveal the plaintext password from an SHA-256 hash if it’s one of the 3.7 billion strings stored in its database. Imgur said it switched to the more secure bcrypt algorithm sometime last year.
Imgur is among the world’s largest 50 websites, with more than 150 million active users every month. In 2014, when the breach occurred, the site had roughly 130 million active monthly users. Some news articles describe these figures as “unique visitors,” which suggests that not all of these users have registered an account, especially since an account is not needed to view images posted on the website.
Nevertheless, it’s possible that the actual number of compromised accounts is much higher than 1.7 million. Hunt pointed out that the data he came across only appears to include passwords that were cracked. “I don’t know how much more data may have been originally obtained,” the expert said.
Hunt also noted that 60% of the compromised accounts had already been exposed in previous breaches tracked by Have I Been Pwned.
Imgur has notified affected users and is requiring them to change their passwords. The company’s investigation into this incident is ongoing.
“We take protection of your information very seriously and will be conducting an internal security review of our system and processes,” said Roy Sehgal, Chief Operating Officer of Imgur.
Imgur was hacked in 2014, 1.7 million user accounts were compromised
25.11.2017 securityaffairs Incindent
Imgur, the popular image sharing service, confirms email addresses and passwords were stolen in a security breach occurred in 2014.
Are you an Imgur user?
News of the day it that the popular image sharing service Imgur was hacked in 2014, the incident was confirmed by the company a few days after Uber admitted to have concealed a data breach that exposed 57 Million records in 2016 and paid hackers to delete stolen records.
Imgur admitted that it had suffered a data breach back in 2014 that, email addresses and passwords of 1.7 million user accounts were accessed by hackers, a small portion of the 150 million user base.
The company said the breach didn’t include personal information because its service has “never asked” for real names, addresses, or phone numbers.
“On November 23, Imgur was notified of a potential security breach that occurred in 2014 that affected the email addresses and passwords of 1.7 million user accounts. While we are still actively investigating the intrusion, we wanted to inform you as quickly as possible as to what we know and what we are doing in response.” reads a data breach notification published by Imgur on its website.
The company had been notified on Thanksgiving of a data breach on November 23 by a the popular expert Troy Hunt, who runs the data breach notification service Have I Been Pwned.
Have I been pwned?
✔
@haveibeenpwned
New breach: imgur was hacked in 2013. 4 years later, 1.7M records with email addresses and cracked passwords surfaced. 60% were already in @haveibeenpwned. Read more: http://www.zdnet.com/article/imgur-reveals-hackers-stole-login-data/ …
1:02 AM - Nov 25, 2017
Imgur confirms it was hacked
The hackers stole email addresses and passwords.
zdnet.com
4 4 Replies 232 232 Retweets 188 188 likes
Twitter Ads info and privacy
Hunt informed the company on Thursday, a US national holiday observing Thanksgiving, when most businesses are closed.
One day later, the company started resetting the passwords of affected accounts and published a data breach notice.
The company said that the stolen passwords were protected with the SHA-256 hashing algorithm that can be easily cracked using brute force attacks.
“We have always encrypted your password in our database, but it may have been cracked with brute force due to an older hashing algorithm (SHA-256) that was used at the time. We updated our algorithm to the new bcrypt algorithm last year.” continues the data breach notice.
Imgur is investigating the incident, but it is still unclear how it is possible that the incident was revealed only three years later.
Below the Troy Hunt’s comment about the incident handling procedure implemented by the company.
“I want to recognise @imgur’s exemplary handling of this: that’s 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure. Kudos!” Hunt tweeted.
“This is really where we’re at now: people recognise that data breaches are the new normal and they’re judging organizations not on the fact that they’ve had one, but on how they’ve handled it when it happened.”
Troy Hunt
✔
@troyhunt
I want to recognise @imgur's exemplary handling of this: that's 25 hours and 10 mins from my initial email to a press address to them mobilising people over Thanksgiving, assessing the data, beginning password resets and making a public disclosure. Kudos! https://twitter.com/haveibeenpwned/status/934210666335891456 …
1:03 AM - Nov 25, 2017
8 8 Replies 145 145 Retweets 360 360 likes
Twitter Ads info and privacy
According to Hunt, 60 percent of email addresses were already in Have I Been Pwned‘s database of more than 4.8 billion records.
Imgur users that want to check if their accounts have been exposed in the security breach can do it on the data breach notification service Have I Been Pwned that according to Hunt already includes 60 percent of email exposed in the hack.
Imgur is just the last notorious victim of a data breach, other companies revealed major security breaches they had suffered many years ago, including Uber, Yahoo, LinkedIn, and MySpace.
After Getting Hacked, Uber Paid Hackers $100,000 to Keep Data Breach Secret
22.11.2017 thehackernews Incindent
Uber is in headlines once again—this time for concealing last year's data breach that exposed personal data of 57 million customers and drivers.
On Tuesday, Uber announced that the company suffered a massive data breach in October 2016 that exposed names, e-mail addresses and phone numbers of 57 million Uber riders and drivers along with driver license numbers of around 600,000 drivers.
However, instead of disclosing the breach, the company paid $100,000 in ransom to the two hackers who had access to the data in exchange for keeping the incident secret and deleting the information, according to a report published by Bloomberg.
Uber said none of its own systems were breached, rather two individuals outside the company inappropriately accessed and downloaded 57 million Uber riders' and drivers' data that was stored on a third-party cloud-based service.
The cyberattack exposed the names and driver license numbers of some 600,000 drivers in the United States, and the names, emails, and mobile phone numbers of around 57 million Uber users worldwide, which included drivers as well.
However, the company said other personal details, such as trip location history, credit card numbers, bank account numbers, Social Security numbers or dates of birth, were not accessed in the attack.
Uber Hid 57 Million User Data Breach For Over a Year
According to Bloomberg report, former Uber CEO Travis Kalanick learned of the cyber attack in November 2016, when the company was negotiating with the Federal Trade Commission (FTC) on a privacy settlement.
So, the company chose to pay the two hackers $100,000 to delete the stolen information and keep quiet about the incident and finally agreed to the FTC settlement three months ago, without admitting any wrongdoing.
Uber Technologies Inc. only told the FTC about the October 2016 data incident on Tuesday, when the breach was made public by Bloomberg.
However, this secret payment eventually cost Uber security executives their jobs for handling the incident.
Now Uber CEO Dara Khosrowshahi has reportedly asked for the resignation of Uber Chief Security Officer Joe Sullivan, and one of his deputies, Craig Clark, who worked to keep the attack quiet.
"None of this should have happened, and I will not make excuses for it. While I cannot erase the past, I can commit on behalf of every Uber employee that we will learn from our mistakes," Khosrowshahi said.
"We are changing the way we do business, putting integrity at the core of every decision we make and working hard to earn the trust of our customers."
Uber is notifying regulatory authorities and offering affected drivers free credit monitoring and identity theft protection.
The company also says that it is monitoring the affected accounts for fraudulent activity and that riders do not need to take any action against this incident. It's likely that Uber will be forcing its customers to reset their passwords for its app.
Unbelievable: Uber concealed data breach that exposed 57 Million records in 2016
22.11.2017 securityaffairs Incindent
Unbelievable: Uber concealed data breach that exposed 57 Million records in 2016 and paid hackers to delete stolen records.
Uber CEO Dara Khosrowshahi announced on Tuesday that hackers broke into the company database and accessed the personal data of 57 million of its users, the bad news is that the company covered up the hack for more than a year.
The attackers accessed also the names and driver’s license numbers of roughly 600,000 of its drivers in the United States.
The hack happened in 2016, it was easy for hackers that according to a report published by Bloomberg, obtained credentials from a private GitHub site used by the Uber development team. The hackers tried to blackmail Uber and demanded $100,000 from the company in exchange for avoiding publish the stolen data.
“Two attackers accessed a private GitHub coding site used by Uber software engineers and then used login credentials they obtained there to access data stored on an Amazon Web Services account that handled computing tasks for the company. From there, the hackers discovered an archive of rider and driver information. Later, they emailed Uber asking for money, according to the company.” states Bloomberg.
In a statement on Tuesday, Khosrowshahi said the intruders accessed cloud-hosted data stores:
“I recently learned that in late 2016 we became aware that two individuals outside the company had inappropriately accessed user data stored on a third-party cloud-based service that we use. The incident did not breach our corporate systems or infrastructure.
At the time of the incident, we took immediate steps to secure the data and shut down further unauthorized access by the individuals. We subsequently identified the individuals and obtained assurances that the downloaded data had been destroyed. We also implemented security measures to restrict access to and strengthen controls on our cloud-based storage accounts.” reads a CEO’s statement.
“You may be asking why we are just talking about this now, a year later. I had the same question, so I immediately asked for a thorough investigation of what happened and how we handled it.”

The situation is more unbelievable, rather than to notify the data breach to customers and law enforcement as is required by the California’s data security breach notification law, the Uber’s chief of information security Joe Sullivan ordered to pay the ransom and to cover the story destroying any evidence. The payout was disguised as a bug bounty prize complete with non-disclosure agreements signed. It is a good way to hide the payment, Uber is running a bug bounty program to encourage white hat hackers to responsibly disclose vulnerabilities affecting its services.
“Uber acquiesced to the demands, and then went further. The company tracked down the hackers and pushed them to sign nondisclosure agreements, according to the people familiar with the matter. To further conceal the damage, Uber executives also made it appear as if the payout had been part of a “bug bounty” — a common practice among technology companies in which they pay hackers to attack their software to test for soft spots.” reported The New York Times“
“The details of the attack remained hidden until Tuesday. The ride-hailing company said it had discovered the breach as part of a board investigation into Uber’s business practices.”
As a result of the new board investigation Sullivan and one of his lieutenants were ousted.
The CEO explained that such kind of thing will not happen again in the future because Uber put the customers’ security and trust as the pillar of its business.
“While I can’t erase the past, I can commit on behalf of every Uber employee that we will learn from our mistakes. We are changing the way we do business, putting integrity at the core of every decision we make and working hard to earn the trust of our customers.” added Khosrowshahi.
The CEO added that forensics experts haven’t found evidence that data were downloaded, anyway the company is monitoring the affected account for fraudulent activities.
Below the list of actions the company has taken in response to the incident:
I’ve asked Matt Olsen, a co-founder of a cybersecurity consulting firm and former general counsel of the National Security Agency and director of the National Counterterrorism Center, to help me think through how best to guide and structure our security teams and processes going forward. Effective today, two of the individuals who led the response to this incident are no longer with the company.
We are individually notifying the drivers whose driver’s license numbers were downloaded.
We are providing these drivers with free credit monitoring and identity theft protection.
We are notifying regulatory authorities.
While we have not seen evidence of fraud or misuse tied to the incident, we are monitoring the affected accounts and have flagged them for additional fraud protection.
The New York Attorney General Eric Schneiderman has also launched an investigation into Uber data breach.
This isn’t the first time the company has experienced security breaches, it suffered the first data breach in May 2014, but the event was discovered on February 2015.
In the attack, the names and driver’s licenses of more than 50,000 of the company’s drivers were compromised.
At the time, the giant announced a data breach that resulted in unauthorized access to the driver partner license numbers of roughly 50,000 of its drivers.
In June 2016, security experts from the Integrity firm have found more than a dozen flaws in the Uber website that could be exploited by hackers to access driver and passenger data. The researchers discovered a total of security 14 issues, four of which cannot be disclosed.
Equifax earnings release: Security breach related expenses cost $87.5 Million in Q3
12.11.2017 securityaffairs Incindent
Equifax announced during the third quarter of 2017, it incurred $87.5 million in expenses related to the cyber attack that was reported in September.
It is very difficult to estimate the overall losses caused by a cyber attack because victims incur in direct and indirect costs that aren’t easy to calculate.
This week the credit reporting agency Equifax announced during the third quarter of 2017, it incurred $87.5 million in expenses related to the cyber attack that was reported on September 7, 2017.
The expenses associated with the massive attack include “costs to investigate and remediate the cybersecurity incident and legal and other professional services related thereto, all of which were expensed as incurred.”
The expenses are divided in $55.5 million in product costs, $17.1 million in firms hired as part of the incident investigation and response (i.e. security firm Mandiant, attorney’s), and $14.9 million in activities to support customers.
“During the third quarter of 2017, we recorded $87.5 million ($59.3 million, net of tax) for expenses related to the cybersecurity incident announced September 7, 2017. The components of the costs are as follows:
(In millions)
Three Months Ended
September 30, 2017
Product cost
$ 55.5
Professional fees
17.1
Consumer support
14.9
Total
$ 87.5
Expenses Incurred. In the third quarter of fiscal 2017, the Company recorded $27.3 million of pretax expenses related to the cybersecurity incident.” reported Equifax. “These expenses are included in Selling, General and Administrative expenses in the accompanying Consolidated Statements of Income for the three and nine months ended September 30, 2017. Expenses include costs to investigate and remediate the cybersecurity incident and legal and other professional services related thereto, all of which were expensed as incurred. “Equifax data breach
Unfortunately, the expenses could increase in the incoming months because the agency would be liable for additional costs stemming from the free credit file monitoring and identity theft protection that it is already offering all U.S. consumers.
“Additionally, as a result of the cybersecurity incident, we are offering free credit file monitoring and identity theft protection to all U.S. consumers. We have concluded that the costs associated with providing this service are a contingent liability that is probable and estimable.” Equifax added in the earnings release.
“We have therefore recorded an estimate of the expenses necessary to provide this service to those who have signed up or will sign up by the January 31, 2018 deadline. We have incurred $4.7 million through September 30, 2017 and have estimated a range of additional costs between $56 million and $110 million.”
Equifax also reported other costs associated with the breach, such as billions in market cap due to a falling share price after the security breach was disclosed.
Equifax: Hack Related Expenses Cost Company $87.5 Million in Q3
10.11.2017 securityweek Incindent
Equifax on Thursday said that during the third quarter of 2017, it incurred $87.5 million in expenses related to the massive hack that was disclosed on September 7, 2017.
The credit reporting agency provided a breakdown of expenses as follows: $55.5 million in product costs, $17.1 million professional fees—a good portion which likely was paid to FireEye's Mandiant division, attorney's, and any other firms hired as part of the incident investigation and response. Customer support costs was marked at $14.9 million.
The expenses related to the cybersecurity incident, the company says, include “costs to investigate and remediate the cybersecurity incident and legal and other professional services related thereto, all of which were expensed as incurred.”
The company also said that it would be liable for additional costs stemming from the free credit file monitoring and identity theft protection that it is offering all U.S. consumers.
“We have therefore recorded an estimate of the expenses necessary to provide this service to those who have signed up or will sign up by the January 31, 2018 deadline. We have incurred $4.7 million through September 30, 2017 and have estimated a range of additional costs between $56 million and $110 million,” Equifax said in an earnings release.
Soon after the breach was disclosed, Chief Security Officer Susan Mauldin and Chief Information Officer David Webb announced their immediate departure from the company.
Equifax says that it maintains data on more than 820 million consumers and more than 91 million businesses worldwide.
In addition to the direct costs associated with the breach, Equifax has lost billions in market cap due to a falling share price after the breach was disclosed. Immediately prior to the breach being disclosed, shares of Equifax traded at roughly $142. Shares of the company (NYSE: EFX) are currently trading at $106.20 in after hours trading.
Hack of Global Law Firm Appleby Exposes Rich and Famous
7.11.2017 securityweek Incindent
'Paradise Papers' Expose Financial Moves by Global Elite
Following the huge 2016 leak of documents stolen from Panamanian firm Mossack Fonseca (aka, the Panama Papers), the expected analyses of documents stolen more recently from the Appleby law firm (aka, the Paradise Papers) has begun. The route is the same in both cases -- the German newspaper Suddeutsche Zeitung obtained the stolen documents from an anonymous source (possibly the hacker, or via a third party), and passed them to the International Consortium of Investigative Journalists (ICIJ).
The ICIJ then worked with 95 media partners to explore a total of 13.4 million documents comprising those stolen from Appleby together with other documents from the smaller family-owned trust company, Asiaciti, and from company registries in 19 secrecy jurisdictions.
Very little is known about the actual hack of Appleby. The firm released a statement over the weekend in response to a BBC Panorama program broadcast on Sunday, and other media coverage beginning to appear via ICIJ's media partners. The ICIJ says it "and its media partners will be publishing multiple stories in the coming days and weeks." These stories will disclose the efforts taken by the rich and famous to use offshore tax regulations to their best advantage -- ranging from the Queen of England and Apple (BBC report) to the rock star Bono and many, many more.
Appleby says, "We wish to reiterate that our firm was not the subject of a leak but of a serious criminal act. This was an illegal computer hack. Our systems were accessed by an intruder who deployed the tactics of a professional hacker and covered his/her tracks to the extent that a forensic investigation by a leading international Cyber & Threats team concluded that there was no definitive evidence that any data had left our systems."
The greater part of the Appleby statement is an attempt at brand damage limitation. "The journalists do not allege, nor could they, that Appleby has done anything unlawful. There is no wrongdoing. It is a patchwork quilt of unrelated allegations with a clear political agenda and movement against offshore."
That the hack and leak of documents is politically motivated is clear and obvious. This is pure hacktivism with a motivation similar to that of the Occupy Movement -- and the reality is that hacktivism is difficult to defend against.
"While the mechanics of the breach itself have yet to be revealed, this was clearly a targeted attack," comments Mark Sangster, VP and industry security strategist at eSentire. "Appleby took appropriate response steps in notifying their clients; but you can't insure [against] this. This class of events demonstrates why law firms must protect their clients' confidential information. No amount of cyber insurance, data back strategies, nor business continuity planning can ever put this genie back in the bottle."
Incident response is relatively meaningless if no incident is detected -- or not, as in this case, detected until too late.
"Financial information, particularly tax arrangements," says Andy Waterhouse, EMEA director at RSA Security, "can be as sensitive as medical information and if exposed can be the source of embarrassment and reputational damage for Appleby's clients. Even if they are not breaking any laws, it's the public perception that can be damaging. When selecting partners, these individuals expect that their data will be highly guarded to prevent such exposure. The fact that they have been exposed in this way creates a huge break in trust with Appleby and could have serious ramifications in the long term on its own reputation as a vault of secrecy."
The whole incident demonstrates why data protection regulators are increasingly specifying the need to use encryption to protect sensitive information. Since no organization can guarantee that it will never be breached, and since business continuity and cyber insurance are meaningless against the loss of this type of data, encryption is the most effective defense.
The ICIJ tells us, "The Paradise Papers documents include nearly 7 million loan agreements, financial statements, emails, trust deeds and other paperwork over nearly 50 years from inside Appleby, a prestigious offshore law firm with offices in Bermuda and beyond." There are clearly many documents that are now historical documents. These, at the very least, should have been encrypted.
Hilton Reaches $700,000 Settlement Over Data Breaches
2.11.2017 securityweek Incindent
U.S. hotel chain Hilton has reached a settlement with the states of New York and Vermont over the payment card breaches suffered by the company in 2014 and 2015.
Hilton has agreed to pay $700,000 – $400,000 to New York and $300,000 to Vermont – and promised to take steps to improve its data security and breach disclosure practices.
The Attorneys General of New York and Vermont launched an investigation into two separate security incidents reported by Hilton back in 2015. The hotel chain determined at the time that attackers had accessed information on at least 363,000 credit cards.
The first intrusion was discovered on February 10, 2015, when a computer services provider informed Hilton of suspicious traffic from one of its systems. An investigation revealed that malware designed to steal payment card data had been active on the company’s systems between November 18 and December 5, 2014.
In the second intrusion, discovered in July 2015, attackers used a piece of malware to collect more than 363,000 payment card numbers between April 21 and July 27, 2015. Investigators discovered the data in a file that had been prepared for exfiltration.
However, Hilton only informed customers about the breaches in November 2015, more than 9 months after the first intrusion was discovered. Hilton argued that there had been no evidence that the payment card data was actually exfiltrated by the attackers, but investigators were unable to review all logs due to steps taken by the cybercriminals to cover their tracks.
Authorities were displeased with the fact that it took the company so long to alert customers. In accordance with New York’s General Business Law, organizations must disclose data breaches in the “most expedient time possible and without unreasonable delay,” which Hilton did not do.
The investigation conducted by the Vermont and New York Attorneys General also revealed that Hilton had not been in compliance with certain requirements of the Payment Card Industry Data Security Standard (PCI DSS).
Authorities also determined that Hilton broke laws prohibiting deceptive acts and practices by telling customers that their personal information was protected using reasonable data security mechanisms.
As part of the settlement, in addition to paying $700,000, Hilton has agreed to notify consumers faster in case of future incidents, create and maintain a comprehensive data security program, and perform annual assessments for PCI DSS compliance.
Hilton is just one of the many hotel chains that suffered payment card breaches in the past few years. The list also includes Hyatt, Trump, Millennium, InterContinental, Omni, Mandarin Oriental, and Kimpton hotels.
IBM Helps Banks Prevent New Account Fraud
31.10.2017 securityweek Incindent
IBM Security announced on Tuesday the launch of a product designed to help banks and other service providers protect their customers against new account fraud (NAF).
As an increasing number of financial institutions allow consumers to open new accounts via the Internet – without the need to physically visit a branch and verify their identity – it has become easier for fraudsters to make a profit using the vast amounts of personal information available for sale on the dark web.
Social security numbers, dates of birth, security questions and other personally identifiable information (PII) is often available for sale for just a few dollars, allowing fraudsters to open new bank accounts that they can use for various types of illegal activities.
IBM’s Trusteer New Account Fraud aims to help financial institutions and other organizations identify fraudulent accounts. The product leverages machine learning to assess risks by checking device and network information associated with the user creating the new account in order to verify their identity.
The solution compares the IP address, geolocation and time zone data, and behavioral biometrics against IBM’s global fraud network. If the data does not match the legitimate user, the activity is likely fraudulent.
IBM pointed out that an individual does not need to be a customer of the bank where the fraudster attempts to open a new account. Organizations that deploy the product will be warned of fraudulent activity even if the targeted consumer is not their customer.
“To address NAF, it is most critical to detect it at its earliest stage: the enrollment process. This way, the provider can stop the process before any damage is done to the rightful owner of the stolen data or to the provider itself,” explained Limor Kessem, executive security advisor at IBM.
“To shorten the time to detection, service providers need a proven way to assess the risk of a new digital identity, predict potential fraud during the enrollment process and detect issues without impacting the legitimate users that frequent the site,” she added. “There are some challenges here, especially since fraudsters use valid or partially valid information to open new accounts, which can sometimes enable their scams to go unnoticed.”
A Javelin Strategy & Research study published earlier this year showed that 15.4 million U.S. consumers fell victim to identity fraud in 2016, and losses resulting from NAF are expected to reach $8 billion by next year.
Police Probe Hack of London Plastic Surgery Clinic
30.10.2017 securityweek Incindent
British police said Tuesday they were investigating the theft of data from a London plastic surgery clinic, with reports that sensitive images of celebrities have been stolen.
London Bridge Plastic Surgery said it was still establishing the extent of the hack, adding that it believed those responsible have previously targeted US medical providers.
"On Tuesday, 17 October the Metropolitan Police Service was informed of a data theft from a cosmetic surgery clinic in London," the police force said in a statement.
"Detectives from the Met's Organised Crime Command are investigating," it said, adding that no arrests have been made.
The clinic, which is located in the upmarket Marylebone district, said it was "horrified" that its patients had been targeted.
"Regrettably, following investigations by our IT experts and the police, we believe that our security was breached and that data has been stolen," it said in a statement.
"The group behind the attack are highly sophisticated and well known to international law enforcement agencies, having targeted large US medical providers and corporations over the past year."
Clients include British former glamour model Katie Price, who has previously praised the clinic for an "amazing result" after a facelift.
The Daily Beast, a US news site, said a hacking group calling itself The Dark Overlord had sent their reporter stolen photos of genitalia during surgery, using a surgery email address.
"There are some royal families in here," the hackers were quoted as saying, claiming to have stolen a database including patients' names.
"We're going to pitch it all up for everyone to nab. The entire patient list with corresponding photos. The world has never seen a medical dump of a plastic surgeon to such degree," they said.
APNIC Whois-related problem led to accidental exposure of authentication data
24.10.2017 securityaffairs Incindent
APNIC Deputy Director General Sanjaya confirmed that Whois data were accidentally exposed online included authentication details.
The Asia-Pacific Network Information Centre (APNIC) is a non-profit organization that provides Internet addressing services in the Asia-Pacific region. The APNIC made the headlines because it was informed about a Whois-related security incident that led to the exposure of authentication data.
According to the APNIC Deputy Director General Sanjaya, Whois data exposed online included authentication details for Maintainer and IRT objects. The incident was discovered on October when a member of the eBay Red Team reported that a third-party website had been republishing downloadable Whois data.
The incident affected Maintainer and Incident Response Team (IRT) objects in the APNIC Whois database.
Both Maintainer and IRT objects include an “auth” attribute that specifies a hashing format and stores an access password in the specified format. The “auth” hashes were accidentally included in downloadable data.
“A Maintainer (mntner) is an object in the APNIC Whois Database. Every object in the APNIC Whois Database is protected by a Maintainer via the ‘mnt-by’ attribute. This ensures that only authorized people that have access to this Maintainer can make changes to other objects that are protected by this Maintainer.” reported the APNIC in a blog post.
“An Incident Response Team (IRT) object is an object in the APNIC Whois Database that contains contact information for an organization’s administrators responsible for receiving reports of network abuse activities.
The ‘auth’ attribute in a Maintainer or IRT object specifies the hashing format used and stores the password in its hashed format.
The error that occurred saw the ‘auth’ hashes included in the downloadable whois data feed (not published on APNIC’s whois itself).”

The problem was promptly fixed, the exposed data included hashed passwords that could be cracked by threat actors to modify Whois data.
The good news is that according to the APNIC there is any evidence of abuse.
The organization warned of the potential risks related to any unauthorized changes of the data.
“Although password details are hashed, there is a possibility that passwords could have been derived from the hash if a malicious actor had the right tools.
If that occurred, whois data could potentially be corrupted or falsified for misuse. Our investigations to date have found no evidence of this occurring.” continues the security organization.
“It is important to note, however, that any public misrepresentation of registry contents on whois would not result in a permanent transfer of IP resources, as the authoritative registry data is held internally by APNIC.”
The non-profit organization has been working with affected users urging them to change passwords, the process was completed on Monday.
“All Maintainer and IRT passwords have now been reset, so there is no need to change them again if you are an APNIC resource holder,” Sanjaya added. “However, if you wish to change the new passwords to something more memorable, you should not choose the previous password (and if the old password was being used elsewhere on other systems, you should change those passwords).”
APNIC is currently working to determine the root cause of the incident.
APNIC Whois Error Led to Exposure of Passwords
24.10.2017 securityweek Incindent
The Asia-Pacific Network Information Centre (APNIC), the non-profit organization that provides Internet addressing services in the Asia-Pacific region, informed the community on Monday of a Whois-related security incident that led to the exposure of authentication data.
According to APNIC Deputy Director General Sanjaya, downloadable Whois data included authentication details for Maintainer and IRT objects. APNIC discovered the incident on October 12 after a member of eBay’s Red Team reported that a third-party site had been republishing downloadable Whois data. The issue was resolved the next day.
The exposed data included password hashes that attackers may have been able to crack and use to falsify or corrupt Whois data.
APNIC says it has not found any evidence of abuse, but it’s still analyzing logs. The organization pointed out that any unauthorized changes would only result in public misrepresentation of Whois data and not actually cause the transfer of IP resources.
Sanjaya said the incident was related to Maintainer and Incident Response Team (IRT) objects in the APNIC Whois database. The role of the Maintainer is to protect objects in the database against unauthorized access, while the IRT contains contact information for reporting abuse to an organization.
Both Maintainer and IRT have an “auth” attribute that specifies a hashing format and stores an access password in the specified format. An error during the upgrade of the APNIC Whois database caused the “auth” hashes to be included in downloadable data.
Since learning of the leak, APNIC has been working with affected users to have the exposed passwords changed. The process was completed on Monday.
“All Maintainer and IRT passwords have now been reset, so there is no need to change them again if you are an APNIC resource holder,” Sanjaya said. “However, if you wish to change the new passwords to something more memorable, you should not choose the previous password (and if the old password was being used elsewhere on other systems, you should change those passwords).”
APNIC is now trying to determine what led to the error and what can be done to prevent such incidents when upgrades are performed in the future.
Nearly 100 Whole Foods Locations Affected by Card Breach
24.10.2017 securityweek Incindent
Amazon-owned Whole Foods Market informed customers last week that a recent hacker attack aimed at its payment systems affected nearly 100 locations across the United States.
Whole Foods has set up a webpage where customers are being provided some details about the breach. The page allows users to check if the store they made purchases in has been hit.
According to the company, cybercriminals may have stolen payment cards used at taprooms and full table-service restaurants in various cities in Alabama, Arizona, Arkansas, California, Colorado, District of Columbia, Florida, Georgia, Hawaii, Idaho, Illinois, Indiana, Kansas, Maine, Michigan, Minnesota, Missouri, Nevada, New Hampshire, New Jersey, New Mexico, New York, North Carolina, Ohio, Oregon, Pennsylvania, Tennessee, Texas, Virginia, Washington and Wisconsin. The largest number of affected locations is in California.Whole Foods hacked
Whole Foods said it had learned of unauthorized access to some payment systems on September 23 and replaced affected point-of-sale (PoS) devices by September 28. However, the investigation conducted by the firm in collaboration with cybersecurity forensics experts revealed that hackers had gained access to some stores in as early as March 10.
The malware planted on PoS systems was designed to collect cardholder names, account numbers, card expiration dates, and internal verification codes.
The supermarket chain pointed out that the incident only impacted payment systems at taprooms and restaurants within stores. Payments made at primary store checkout systems were not affected. The company has also highlighted that the breach does not impact Amazon.com, which uses separate systems.
The web page set up by the company to provide information about the breach includes recommendations on how customers can protect themselves and how to avoid being liable for any fraudulent charges on their credit and debit cards.
Fast food restaurant chain Sonic Drive-In also confirmed this month that it had suffered a payment card breach. It’s unclear how many locations are affected, but some experts reported that millions of cards may have been stolen in the attack.
Whole Foods Market confirms that nearly 100 locations were affected by card breach
24.10.2017 securityaffairs Incindent
According to the Whole Foods Market, crooks may have stolen payment cards at taprooms and full table-service restaurants at nearly 100 locations.
At the end of September, the Amazon-owned grocery chain Whole Foods Market notified customers a security breach. According to the security breach notification issued by the company, cybercriminals were able to gain unauthorized access to credit card information for customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
The Amazon-owned company notified customers last week that the payment systems security breach affected nearly 100 locations across the United States. The company published a page to provide users details about the allow them to check if the store they made was compromised by the hackers.
“Whole Foods Market has resolved the incident previously announced on September 28, 2017, involving unauthorized access of payment card information used at certain venues such as tap rooms and full table-service restaurants located within some stores.” states the company.
“These venues use a different point of sale system than the company’s primary store checkout systems, and payment cards used at the primary store checkout systems were not affected.”
According to the company, crooks may have stolen payment cards at taprooms and full table-service restaurants using a malware.
Whole Foods hired a cybersecurity forensics firm to conducted the investigation that discovered the intrusion occurred as early as March 10.
Crooks used a PoS malware designed to siphon card data, including cardholder names, account numbers, card expiration dates, and internal verification codes.
The affected locations are in various cities in Alabama, Arizona, Arkansas, California, Colorado, District of Columbia, Florida, Georgia, Hawaii, Idaho, Illinois, Indiana, Kansas, Maine, Michigan, Minnesota, Missouri, Nevada, New Hampshire, New Jersey, New Mexico, New York, North Carolina, Ohio, Oregon, Pennsylvania, Tennessee, Texas, Virginia, Washington and Wisconsin. The largest number of affected locations is in California.
“The investigation determined that unauthorized software was present on the point of sale system at certain venues. The software copied payment card information—which could have included payment card account number, card expiration date, internal verification code, and cardholder name—of customers who used a payment card at these venues at dates that vary by venue but are no earlier than March 10, 2017 and no later than September 28, 2017.” continues the firm.
The supermarket chain pointed out that payments made at primary store checkout systems were not affected, the breach does not impact Amazon.com.

The page set up by the company also provides suggestions to the customers on how to protect themselves from fraudulent activities involving their payment cards.
South Africa – About 30-million identity numbers and other personal and financial information leaked online
19.10.2017 securityaffairs Incindent
South Africa – About 30-million identity numbers and other personal and financial information leaked online, it is the largest data leak in the country.
About 30-million identity numbers and other personal and financial information had been hacked and leaked online, it could be the biggest data breach suffered by the South Africa.
The data breach was discovered by the popular cyber security expert Troy Hunt, he discovered an about 27 gigabytes dump that contained a wide range of sensitive information belonging to South Africans, including citizens ID numbers, personal income, age, employment history, company directorships, race group, marital status, occupation, employer and previous addresses.
Follow
Troy Hunt ✔@troyhunt
South African followers: I have a very large breach titled "masterdeeds". Names, genders, ethnicities, home ownership; looks gov, ideas?
8:40 AM - Oct 17, 2017 · Melbourne, Victoria
45 45 Replies 128 128 Retweets 69 69 likes
Twitter Ads info and privacy
Fortunately, the huge trove of data wasn’t offered for sale yet, but it is a matter of time.
The dump includes information from at least as far back as the early 1990s, the analysis of date of file suggest the security breach took place in April 2015.
The source of the database is still unknown, Hunt shared some information on it to speed up its identification.
Data headers suggest the source may be Government, but we cannot exclude in this phase that data could be related to a financial organization or credit bureau.
South Africa data leak
According to the editorial staff at the iafrikan.com website, the source of data is the GoVault platform of the Dracore Data Sciences.which counts among its customers TransUnion, one the largest credit bureaux in South Africa.
“I first checked their GoVault platform as it is advertised as “the goldmine of information offers easy access to the contact details of South African consumers and homeowners.” states the website iafrikan.com.
“They’ve [Dracore] fucked up in a seriously large scale here. They’ve collected an enormous volume of data and I’m not sure the owners of that data ever gave their consent. That may still be legal, but the backlash will be severe. They then published that data to a web server with absolutely zero protection and, of course, unauthorized parties found it. You yourself [iAfrikan] found it very quickly just by searching for it. There is now going to be a very serious spotlight shone on them for the sheer incompetence of their actions and they’re in no position the threaten those who’ve reported this to them responsibly,” said Hunt when speaking to iAfrikan.
At this stage we can conclusively stop calling it a data hack or data breach, it is more like a leak, and I’m being kind calling it a leak as the DATA IS STILL UP ON THE WEBSITE AS I TYPE THESE WORDS!!!” concluded iAfrikan.”
Pizza Hut notifies card breach while users have already reported fraudulent transactions
16.10.2017 securityaffairs Incindent
Pizza Hut U.S. notified customers over the weekend a “temporary security intrusion” on PizzaHut.com that exposed payment card and contact information.
Pizza Hut U.S. notified customers over the weekend a “temporary security intrusion” on PizzaHut.com, the security breach might have exposed payment card and contact information.
The popular restaurant chain notified users via email, according to Pizza Hut, the hackers had access to the website for a total of roughly 28 hours, between the morning of October 1, 2017 through midday on October 2, 2017.
“Pizza Hut has recently identified a temporary security intrusion that occurred on our website,” reads the email sent by Pizza Hut.
“We have learned that the information of some customers who visited our website or mobile application during an approximately 28-hour period (from the morning of October 1, 2017, through midday on October 2, 2017) and subsequently placed an order may have been compromised.”
“Pizza Hut identified the security intrusion quickly and took immediate action to halt it,” the company added. “The security intrusion at issue impacted a small percentage of our customers and we estimate that less than one percent of the visits to our website over the course of the relevant week were affected.”

All those users that placed an order in this time window could be affected, the company estimates that less than one percent of website visits during that week were impacted.
Some of those customers are angry because of the delay in the notification, some of them also faced problems with their payment cards.
Follow
Peter Yoachim @PeterYoachim
Hey @pizzahut, thanks for telling me you got hacked 2 weeks after you lost my cc number. And a week after someone started using it.#timely
7:03 PM - Oct 14, 2017 · Seattle, WA
4 4 Replies 2 2 Retweets 3 3 likes
Twitter Ads info and privacy
Follow
Michael Richardson @marichardsonjr
@pizzahut great security there & thanks for the delay in notifying us after thieves already charged our accts. Keep up the excellent work
9:47 PM - Oct 14, 2017
1 1 Reply 2 2 Retweets 3 3 likes
Twitter Ads info and privacy
Follow
Dustin Falgout @dustinfalgout
@pizzahut, 2 wks after you lost my cc # and a week after someone started using it, I hear about the breach online. Ty 4 the heads up. #fail
10:54 PM - Oct 15, 2017
1 1 Reply Retweets likes
Twitter Ads info and privacy
External cybersecurity consultants hired by the company determined that the attackers may have obtained information such as name, billing ZIP code, delivery address, email address, and payment card data, including card number, expiration date and CVV.
Pizza Hut estimates that less than one percent of website visits during that week were impacted.
“The security intrusion at issue impacted a small percentage of our customers and we estimate that less than one percent of the visits to our website over the course of the relevant week were affected,” read a message sent only to those affected. “That said, we regret to say that we believe your information is among that impacted group.”
A call center operator told McClatchy that about 60,000 people across the U.S. were affected.
The restaurant chain was already a victim of a security breach, in 2012 two hackers that went by the names of Oday and Pyknic defaced the company’s Australia website and claimed to have obtained roughly 260,000 Australian payment cards.
Many other restaurant chains reported suffering a security breach in the past months, including Arby’s, Chipotle. Wendy’s, and Sonic Drive-In.
Hyatt Hotels Hit by Another Card Breach
15.10.2017 securityweek Incindent
Chicago-based hotel operator Hyatt Hotels Corporation informed customers this week that their credit card information may have been stolen by cybercriminals. This is the second data breach discovered by the company within a period of two years.
The incident affects three hotels in the United States (all in Hawaii), three in Puerto Rico, 18 in China, four in Mexico, three in Saudi Arabia, three in South Korea, and one each in Brazil, Colombia, Guam, India, Indonesia, Japan and Malaysia.
According to Hyatt, malware planted by cybercriminals on certain hotel IT systems harvested information from payment cards manually entered or swiped at some hotel front desks between March 18, 2017 and July 2, 2017.
The malware was designed to steal data such as cardholder name, card number, expiration date, and internal verification code. No other information appears to have been compromised.Hyatt Hotels hacked again
“While we estimate that the incident affected a small percentage of payment cards used by guests who visited the group of affected Hyatt hotels during the at-risk time period, the available information and data does not allow Hyatt to identify each specific payment card that may have been affected,” said Chuck Floyd, global president of operations at Hyatt Hotels Corporation.
Back in 2015, Hyatt suffered a payment card breach that affected 250 of its hotels worldwide. The company claimed at the time that it had strengthened the security of its systems.
“Our enhanced cybersecurity measures and additional layers of defense implemented over time helped to identify and resolve the issue,” Floyd said this week.
However, the company’s enhanced security measures were obviously not enough, given that hackers had access to its systems for well over three months.
“The harvested customer payment card data – including expiration dates and verification codes - is extremely valuable data that will be sold on the Dark Web or used in credit card cycling scams. It’s also easily combined with other stolen data to build entirely new synthetic personas for all manner of fraud,” explained Lisa Baergen, marketing director at NuData Security.
“The travel and leisure industry – like so many consumer-facing sectors - has time and again shown itself extremely vulnerable to breaches,” Baergen added. “This latest concerning breach is just one more reason why companies such as Hyatt must adopt more advanced security and authentication measures based on trusted identity, and consumers must diligently, routinely check their credit files for suspicious credit applications and consider freezing their credit profiles.”
Equifax Website Redirects Users to Adware, Scams
15.10.2017 securityweek Incindent
A security researcher noticed recently that an Equifax service designed for obtaining free and discounted credit reports had been redirecting users to websites set up to serve adware and scams.
Independent security analyst Randy Abrams wanted to find his credit report on Equifax’s website when he was redirected to a website offering a fake Flash Player installer. The browsing session was taken through multiple domains before the final page was reached.
It’s not uncommon for cybercriminals to deliver malware using fake Flash Player installers, but in this case the website pushed adware.
Equifax website redirects to fake Flash installer
The Equifax webpage, hosted at aa.econsumer.equifax.com, did not redirect the connection when accessed by SecurityWeek on Thursday morning. Abrams believes Equifax removed the malicious code from its website sometime on Wednesday.
An analysis of the domains involved in the redirection chain shows that they can lead not only to adware. The final destination depends on the type of device and the geographical location of the user.
SecurityWeek has seen redirects to fake Android and iOS updates, premium SMS services, and other scammy sites. Various online security services detect the domains involved in the attack as malicious, and while there is no evidence of actual malware being served, the possibility cannot be ruled out.
After visiting the compromised site several times from the same device, the user is taken to a website belonging to a legitimate business that is likely trying to promote its site via ad networks or SEO (search engine optimization) services.
Contacted by SecurityWeek, an Equifax spokesperson stated, “We are aware of the situation identified on the equifax.com website in the credit report assistance link. Our IT and Security teams are looking into this matter, and out of an abundance of caution have temporarily taken this page offline. When it becomes available or we have more information to share, we will.”
Equifax recently informed customers that hackers breached its systems after exploiting an Apache Struts 2 vulnerability that had been patched and exploited in the wild since March. The attackers gained access to the personal information of more than 140 million individuals, including hundreds of thousands of Canadian and British citizens.
“I'm really not trying to kick Equifax while they are down. There are already 150 million other people doing that. I just sort of tripped over them,” Abrams said in a blog post.
“I know that nobody is surprised at my find, but watching Equifax is getting to be like watching a video of United Airlines ‘deplaning’ a passenger... It hurts,” he added.
Many of Equifax’s cybersecurity failings came to light following the breach, including the fact that the company directed customers to the wrong website and website vulnerabilities.
UPDATE. After an investigation, Equifax determined that the problem was caused by a third-party vendor's code. The company has provided the following statement to SecurityWeek:
“Despite early media reports, Equifax can confirm that its systems were not compromised and that the reported issue did not affect our consumer online dispute portal.
The issue involves a third-party vendor that Equifax uses to collect website performance data, and that vendor’s code running on an Equifax website was serving malicious content. Since we learned of the issue, the vendor’s code was removed from the webpage and we have taken the webpage offline to conduct further analysis.”
UPDATE 2. The same script also caused problems for another Big Three credit reporting agency, TransUnion.
Cloud App Security Firm ShiftLeft Exits Stealth With $9 Million in Funding
15.10.2017 securityweek Incindent
ShiftLeft emerged from stealth mode on Wednesday with a new solution designed to protect cloud applications and microservices, and with more than $9 million in funding.
The company’s fully automated security-as-a-service (SECaaS) solution is designed to help organizations secure their applications by providing threat detection capabilities in the continuous integration (CI) and continuous development (CD) processes.
ShiftLeft’s product extracts all security-relevant information from the codebase of each software build and uses it to create a custom Microagent that provides runtime protection. The product can identify potential risks and point developers to the line of code that causes the issue.ShiftLeft emerges from stealth
According to ShiftLeft, the solution can help identify known and unknown vulnerabilities, including issues introduced by the usage of open source software, and data leakage without false positives.
Developers can prioritize bug fixes, DevOps teams can obtain deep visibility into data flows, while security teams can protect applications without disrupting the pace of the CI/CD process.
“The adoption of Cloud increases the pace of innovation by allowing us to deliver features even faster,” said Chetan Conikee, CTO and co-founder of ShiftLeft. “But this pace of change defeats traditional security.ShiftLeft embraces this change to enhance security for cloud-native applications by creating a custom Microagent for each version of each application. This application-specific security is both automated and accurate. We no longer have to buy off-the-shelf security products, write policies, and tune them manually as we sift through hundreds of false positives.”
The announcement of ShiftLeft’s formal launch was accompanied by news that the company raised $9.3 million in a Series A funding round led by Bain Capital Ventures and Mayfield, with participation from individual investors such as Sanjay Poonen, COO of VMware; Tobias Knaup, CTO of Mesosphere; and Prabhu Goel, creator of Verilog.
Accenture Exposed Data via Unprotected Cloud Storage Bucket
15.10.2017 securityweek Incindent
Consulting and technology services giant Accenture inadvertently exposed potentially sensitive information by leaving it unprotected in four Amazon Web Services (AWS) S3 buckets.
The cloud storage containers were discovered on September 17 by Chris Vickery of cyber resilience company UpGuard and they were secured a couple of days later after Vickery notified Accenture of his findings.
The largest of the buckets stored 137 GB of data, including 40,000 plaintext passwords, hashed passwords, access keys for the Enstratus cloud infrastructure management platform, email data, and information on the consulting firm’s ASGARD database. The same container also stored credentials for Accenture’s Google and Azure accounts, and data dumps from an event tracker, including IP addresses and other Accenture client data.
Another bucket stored internal access keys and credentials for an API apparently used by Accenture to authenticate credentials, configuration files for the same API, a master access key for the company’s AWS Key Management Service account, and private signing keys.
The unprotected containers also stored information on Accenture’s cloud stores, including VPN keys and other data that UpGuard believes could have been used by malicious actors to obtain insight into the company’s operations.
Some of the private keys and certificates found in one of the buckets may have allowed attackers to decrypt traffic between Accenture and its clients, UpGuard said.
“Taken together, the significance of these exposed buckets is hard to overstate. In the hands of competent threat actors, these cloud servers, accessible to anyone stumbling across their URLs, could have exposed both Accenture and its thousands of top-flight corporate customers to malicious attacks that could have done an untold amount of financial damage,” explained UpGuard’s Dan O’Sullivan.
“It is possible a malicious actor could have used the exposed keys to impersonate Accenture, dwelling silently within the company’s IT environment to gather more information,” O’Sullivan added.
However, Accenture, whose customers include 94 of the Fortune Global 100 companies, has downplayed the potential impact of the leak, claiming that there was no risk to any of its clients and that no active credentials or other information had been compromised. The company said none of the exposed files stored production data and the credentials could not have been used to access customer systems. Accenture is also confident that its security systems would have caught any intrusion attempts.
This is not the first time UpGuard has found an unprotected AWS S3 bucket exposing sensitive information. In the past months, the company discovered that a Republican Party contractor exposing the details of 198 million American voters, recruiting firm TalentPen exposing information on job applicants at security firm TigerSwan, a call center services provider exposing the details of Verizon customers, and Booz Allen Hamilton exposing U.S. military files. In all cases, data was leaked online due to unprotected Amazon Web Services (AWS) S3 buckets.
In order to help organizations prevent leaks caused by third-party vendors, UpGuard announced on Tuesday the launch of CyberRisk, a new product that automates risk assessment for third-party vendors.
Nearly 700,000 UK Nationals Affected by Equifax Breach: Company
15.10.2017 securityweek Incindent
Nearly 700,000 British consumers may have had personal data compromised in the massive breach at Equifax, the US credit reporting agency said Tuesday.
"Although our UK business was not breached, the attack regrettably compromised the personal information of a range of UK consumers," the company said in an emailed statement.
The company, which last month announced one of the most potentially damaging data breaches affecting some 145 million Americans, said the attackers also accessed a file containing 15.2 million records on 693,665 British nationals.
"Equifax takes this illegal and unprecedented breach of consumers' data extremely seriously and has begun writing to the groups of consumers outlined below to notify them of the nature of the breach and offer them appropriate advice," the statement said.
The company said it waited for a forensic analysis of the cyber attack before determining its course of action for Britons.
"Once again, I would like to extend my most sincere apologies to anyone who has been concerned about or impacted by this criminal act," said Patricio Remon, president for Europe at Equifax Ltd.
"It has been regrettable that we have not been able to contact consumers who may have been impacted until now, but it would not have been appropriate for us to do so until the full facts of this complex attack were known, and the full forensics investigation was completed."
Last week, former Equifax chief Richard Smith blamed a combination of human and technical error for the breach, which is not the largest on record but which could have leaked sensitive financial information on consumers.
An internal investigation determined the unauthorized access occurred from mid-May through July 2017, according to the company.
Equifax collects information about people and businesses around the world and provides credit ratings used for decisions regarding loans and other financial matters.
Hyatt Hotels suffered a new payment card breach, the second in two years
14.10.2017 securityaffairs Incindent
The Hyatt Hotels Corporation notified customers that their credit card information may have been stolen by crooks, the second time in 2 years.
The Hyatt Hotels Corporation made the headlines once again, the company notified customers that their credit card information may have been stolen by crooks.
The data breach affects three hotels in the United States, 18 in China, four in Mexico, three in Puerto Rico, three in Saudi Arabia, three in South Korea, and facilities in Brazil, Colombia, Guam, India, Indonesia, Japan, and Malaysia.
“We understand the importance of protecting customer information and securing our systems, and we regret to inform you that we discovered signs of and then resolved unauthorized access to payment card information from cards manually entered or swiped at the front desk of certain Hyatt-managed locations between March 18, 2017 and July 2, 2017. A list of affected hotels and respective at-risk dates is available here.” states the breach notification.

According to Hyatt, crooks planted a malware on payment systems at certain hotels to harvest credit card data from guests that physically entered or swiped at some hotel front desks between March 18, 2017 and July 2, 2017.
The malicious code allowed crooks to siphon cardholder name, card number, expiration date, and internal verification code.
“Based on our investigation, we understand that such unauthorized access to card data was caused by an insertion of malicious software code from a third party onto certain hotel IT systems. Our enhanced cybersecurity measures and additional layers of defense implemented over time helped to identify and resolve the issue.” continues the notification.
At the time, Hyatt is not able to identify each specific payment card that may have been affected by the data breach.
“While we estimate that the incident affected a small percentage of payment cards used by guests who visited the group of affected Hyatt hotels during the at-risk time period, the available information and data does not allow Hyatt to identify each specific payment card that may have been affected,” said Chuck Floyd, global president of operations at Hyatt Hotels Corporation.
Unfortunately, this isn’t the first time the company discovered a data breach, this is the second incident in the last two years.
In January 2016, the Hyatt Hotels Corporation announced a total of 250 of its resorts were compromised in a malware-based attack in 2015, hackers stole customer payment card information.
At the time of the incident, the company announced a significant enhancement of cybersecurity measures to protect its payment systems, but the actions were obviously not enough.
Accenture – Embarrassing data leak business data in a public Amazon S3 bucket
14.10.2017 securityaffairs Incindent
The leading global professional services company Accenture exposed its business data in a public Amazon S3 bucket. Disconcerting!
Another Tech giant has fallen victim of an embarrassing data leak, this time the leading global professional services company Accenture exposed its business data in a public Amazon S3 bucket.
The incident exposed internal Accenture private keys, secret API data, and other information, a gift for attackers that want to target the firm or its clients
The unsecured Amazon S3 bucket was discovered by researchers at UpGuard that privately reported to Accenture on Sept. 17. The company solved the problem in one day.
“The UpGuard Cyber Risk Team can now reveal that Accenture, one of the world’s largest corporate consulting and management firms, left at least four cloud-based storage servers unsecured and publicly downloadable, exposing secret API data, authentication credentials, certificates, decryption keys, customer information, and more data that could have been used to attack both Accenture and its clients.” states the report published by UpGuard.
“Taken together, the significance of these exposed buckets is hard to overstate. In the hands of competent threat actors, these cloud servers, accessible to anyone stumbling across their URLs, could have exposed both Accenture and its thousands of top-flight corporate customers to malicious attacks that could have done an untold amount of financial damage.”

The popular researcher Chris Vickery found four servers left open online containing a huge trove of company secrets such as authentication credentials, certificates, decryption key, logs of customer data, decryption keys, customer information, and more data that could have been used to target both Accenture and its clients.
Vickery also found software used by Accenture’s Cloud Platform enterprise-level management service.
Accenture is trying to downplay the data leak.
“There was no risk to any of our clients – no active credentials, PII and other sensitive information was compromised,” Accenture noted in a statement. “The information involved could not have provided access to client systems and was not production data or applications.”
“There was no risk to any of our clients – no active credentials, PII or other sensitive information was compromised,” “We have a multi-layered security model, and the data in question would not have allowed anyone that found it to penetrate any of those layers. The information involved could not have provided access to client systems and was not production data or applications.”
The four buckets discovered by Vickery are:
acp-deployment that contained internal access keys, credentials used by Accenture’s identity API, plaintext documents containing a master access key for Accenture’s account with Amazon Web Services’ Key Management Service, and also private signing keys.
acpcollector that contained data related to the maintenance of Accenture’s cloud stores, including VPN keys for the company’s private network and a master view of its cloud ecosystem.
acp-software is a 137 GB-bucket, the largest one, that contained database dumps of Accenture client credentials, hashed passwords and 40,000 plaintext passwords. It also included access keys for Accenture’s Enstratus cloud management platform and data from its Zenoss event tracker system, including JSession IDs that if not expired could be plugged into cookies in order to bypass authentication.
acp-ssl, contained encryption key stores that provide access to a number of Accenture environments. more key stores in a folder called “acp.aws.accenture.com,” as well as certificates that, in theory, could be used to decrypt traffic between Accenture and clients.
This is absurd … One of the core services in the Accenture’s portfolio is the security of its customers. Who accessed the data of the company and its customers while it was unsecured only. The impact could be disastrous, probably many customers will choose partners that could ensure them a higher level of security.
In September Viacom Vickery discovered Viacom left the keys of its digital kingdom on a publicly exposed AWS S3 bucket.
Earlier September, researchers from cybersecurity company UpGuard have discovered thousands of files containing personal data on former US military, intelligence, and government workers have allegedly been exposed online for months.
On August, Vickery discovered more than 1.8 million voter records belonging to Americans have been accidentally leaked online by a US voting machine supplier for dozens of US states.
In June, Vickery discovered that a top defense contractor left tens of thousands sensitive Pentagon documents on Amazon Server Without any protection in places.
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In July, he discovered data belonging to 14 million U.S.-based Verizon customers that have been exposed on an unprotected AWS Server by a partner of the telecommunications company. In December 2015, the security expert discovered U.S.-based Verizon customers that have been exposed on an unprotected AWS Server by a partner of the telecommunications company. In December 2015 the security expert discovered 191 million records belonging to US voters online, on April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak, in June 2017 Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
Recently also the giant Deloitte suffered an embarrassing incident that exposed clients’ secret emails.
Disqus Discloses 2012 Breach Impacting 17 Million Users
9.10.2017 securityweek Incindent
Commenting service Disqus informed customers on Friday of a data breach that apparently occurred back in 2012 and which affected roughly 17.5 million user accounts.
Disqus learned of the breach from Troy Hunt, the Australian security expert who created the Have I Been Pwned breach notification service. Hunt said it took the company just under 24 hours after being notified to take action to protect impacted accounts and disclose the breach to the public.
According to Disqus, whose service is used to post roughly 50 million comments every month, the information stored in the database obtained by Hunt had been dated between 2007 and July 2012, which is likely around the time when the breach occurred.
The exposed data includes usernames, email addresses, sign-up dates, last login dates and, for roughly one-third of the 17.5 million accounts, password hashes (SHA-1 with salt). While Disqus said no plaintext passwords were exposed and the hashes are unlikely to be cracked, Hunt pointed out that it’s not difficult to crack SHA-1 hashes, even with a salt.
While Disqus’ investigation is still in progress, the company says there is no evidence of unauthorized logins as a result of this incident. Nevertheless, affected users are being notified and their passwords have been reset. The firm does not believe the data has been widely distributed or readily available.
“We’ve taken action to protect the accounts that were included in the data snapshot. Right now, we don’t believe there is any threat to a user accounts,” said Jason Yan, co-founder and CTO of Disqus. “Since 2012, as part of normal security enhancements, we’ve made significant upgrades to our database and encryption in order to prevent breaches and increase password security. Specifically, at the end of 2012 we changed our password hashing algorithm from SHA1 to bcrypt.”
Data from the Have I Been Pwned service showed that 71% of the 17.5 million Disqus accounts were also compromised in other data breaches.
In addition to the Disqus database, Hunt also obtained information stolen from URL shortening service Bitly (9 million accounts) and Kickstarter (5.2 million accounts) back in 2014.
Unlike the Disqus incident, which does not appear to have been detected back in 2012, the Bitly and Kickstarter breaches were detected at the time of the attacks and users were notified. Both Bitly and Kickstarter informed users that there is no new information and no action needs to be taken.
U.S. Banking Regulator Hit by 54 Breaches in 2015, 2016
9.10.2017 securityweek Incindent
The U.S. Federal Deposit Insurance Corporation (FDIC) in the last two years may have suffered as many as 54 data breaches involving personally identifiable information (PII), revealed a report from the FDIC Office of Inspector General (OIG).
Created in response to the thousands of bank failures in the 1920s and 1930s, the FDIC is an independent agency that provides insurance to depositors. The standard insurance amount is $250,000 per depositor, per insured bank.
The report, made public last week, focuses on the FDIC’s processes for responding to data breaches, and it’s based on an audit conducted in response to concerns raised by the chairman of the Senate Committee on Banking, Housing, and Urban Affairs.
The OIG’s audit focused on 18 of 54 suspected or confirmed breaches discovered by FDIC between January 1, 2015 and December 1, 2016. The 18 incidents reviewed by auditors affected more than 113,000 individuals.
The audit found that in 13 of the 18 cases the FDIC did not complete some key breach investigation activities, such as assessing impact and convening the data breach management team, within the timeframe established in the agency’s Data Breach Handling Guide (DBHG).
It took the organization, on average, more than 9 months to notify affected individuals after discovering a breach. It took between 145 days and 215 days to send out notifications to impacted people after the decision was made to notify victims. In one incident that affected nearly 34,000 people, the FDIC sent out the notifications exactly one year after the breach was discovered.
The failure to notify affected individuals and investigate the breaches in a timely manner was due to the lack of an incident response coordinator, the failure to provide adequate training to information security managers, and insufficient privacy staff for managing incident response activities, the OIG said in its report.
The audit also found that the FDIC failed to adequately document key assessments and decisions; failed to clearly define the purpose, scope, governance structure and key operating procedures of its data breach management team; and it did not track and report key breach response metrics.
A report published last year by the House of Representatives Science, Space and Technology Committee revealed that threat actors believed to be from China breached the systems of the FDIC in 2010, 2011 and 2013, and planted malware on a significant number of servers and workstations. The committee concluded that the agency’s CIO had attempted to cover up the incident.
Disqus Discloses 2012 Breach Impacting 17 Million Users
9.10.2017 securityweek Incindent
Commenting service Disqus informed customers on Friday of a data breach that apparently occurred back in 2012 and which affected roughly 17.5 million user accounts.
Disqus learned of the breach from Troy Hunt, the Australian security expert who created the Have I Been Pwned breach notification service. Hunt said it took the company just under 24 hours after being notified to take action to protect impacted accounts and disclose the breach to the public.
According to Disqus, whose service is used to post roughly 50 million comments every month, the information stored in the database obtained by Hunt had been dated between 2007 and July 2012, which is likely around the time when the breach occurred.
The exposed data includes usernames, email addresses, sign-up dates, last login dates and, for roughly one-third of the 17.5 million accounts, password hashes (SHA-1 with salt). While Disqus said no plaintext passwords were exposed and the hashes are unlikely to be cracked, Hunt pointed out that it’s not difficult to crack SHA-1 hashes, even with a salt.
While Disqus’ investigation is still in progress, the company says there is no evidence of unauthorized logins as a result of this incident. Nevertheless, affected users are being notified and their passwords have been reset. The firm does not believe the data has been widely distributed or readily available.
“We’ve taken action to protect the accounts that were included in the data snapshot. Right now, we don’t believe there is any threat to a user accounts,” said Jason Yan, co-founder and CTO of Disqus. “Since 2012, as part of normal security enhancements, we’ve made significant upgrades to our database and encryption in order to prevent breaches and increase password security. Specifically, at the end of 2012 we changed our password hashing algorithm from SHA1 to bcrypt.”
Data from the Have I Been Pwned service showed that 71% of the 17.5 million Disqus accounts were also compromised in other data breaches.
In addition to the Disqus database, Hunt also obtained information stolen from URL shortening service Bitly (9 million accounts) and Kickstarter (5.2 million accounts) back in 2014.
Unlike the Disqus incident, which does not appear to have been detected back in 2012, the Bitly and Kickstarter breaches were detected at the time of the attacks and users were notified. Both Bitly and Kickstarter informed users that there is no new information and no action needs to be taken.
Forrester, one of the most influential research and advisory firms was hacked
9.10.2017 securityaffairs Incindent
Forrester Research announced today that Forrester.com experienced a security breach this week, attackers were ultimately detected and shut out of the system
Forrester, one of the most influential research and advisory firms in the world, revealed on Friday to have suffered a security breach the past week.
The attackers broke into the infrastructure hosting the Forrester.com website, that is also used to allow customers download market research documents according to their contracts.
The advisory firm supports decision makers of its customers by providing trends, statistics, and other market research.
According to company’s Chief Business Technology Officer, Steven Peltzman, crooks stole valid Forrester.com login credentials that allowed them to take over the website.
“The hacker used that access to steal research reports made available to our clients,” Peltzman said.
“There is no evidence that confidential client data, financial information, or confidential employee data was accessed or exposed as part of the incident,”

Hackers did not access confidential client data, financial information, or confidential employee.
Stolen data are anyway a precious commodity in the hands of cyber spies that can access sensitive information related to the customers’and projects.
“We recognize that hackers will attack attractive targets — in this case, our research IP. We also understand there is a tradeoff between making it easy for our clients to access our research and security measures,” said George F. Colony, Chairman and Chief Executive Officer of Forrester. “We feel that we have taken a common-sense approach to those two priorities; however, we will continuously look at that balance to respond to changing cybersecurity risk.”
Forrester is the major financial and business organization that suffered a data breach in the past month, recent victims in order of time are Equifax, Deloitte, and the US Securities and Exchange Commission (SEC).
Research Reports Stolen in Forrester Website Hack
9.10.2017 securityweek Incindent
Forrester, one of the world’s most influential market research and advisory firms, informed customers late on Friday that its main website had been breached.
According to Forrester Chief Business Technology Officer Steven Peltzman, a hacker accessed information provided to customers through the company’s website, Forrester.com, using stolen credentials.
The organization said the attacker managed to steal research reports made available to customers, but believes no confidential client data, financial information, or employee data has been compromised.
Forrester said the attack was detected while it was being carried out and the company took immediate action to limit its impact. The investigation is ongoing, but there is no evidence to date that the hacker stole anything other than research intellectual property.
Law enforcement has been notified and the firm is further strengthening its internal security processes and systems in response to the incident.
“We recognize that hackers will attack attractive targets — in this case, our research IP. We also understand there is a tradeoff between making it easy for our clients to access our research and security measures,” said George F. Colony, chairman and CEO of Forrester. “We feel that we have taken a common-sense approach to those two priorities; however, we will continuously look at that balance to respond to changing cybersecurity risk.”
Forrester disclosed the breach on Friday after the market closed so the potential impact of the incident on the company’s shares has yet to be seen.
A major cybersecurity incident can have a significant impact on a company’s stock. The breach suffered recently by consumer credit reporting agency Equifax, which affected more than 140 million individuals, led to the company losing roughly $10 billion in market value within a few days of the hacker attack coming to light.
Fast Food Chain Sonic Confirms Card Breach
5.10.2017 securityweek Incindent
Sonic Drive-In, a fast food restaurant chain with more than 3,500 locations across the United States, confirmed on Wednesday that cybercriminals may have stolen customers’ credit and debit card information using a piece of malware.
The company has provided only little information about the incident, but says it’s working with law enforcement and third-party forensics firms to investigate the breach. Sonic said it delayed notifying customers of the intrusion at the request of law enforcement.
“Sonic Drive-In has discovered that credit and debit card numbers may have been acquired without authorization as part of a malware attack experienced at certain Sonic Drive-In locations,” the company stated.
Customers who used their cards at Sonic Drive-In locations this year are being offered 24 months of free fraud detection and identity theft protection services via Experian. Consumers can enroll until December 31.
While it’s unclear which locations were hit by the malware attack and how many customers are impacted, security blogger Brian Krebs last week learned of a cybercrime marketplace selling a batch of 5 million cards, at least some of which appear to come from Sonic’s systems.
The cards were put up for sale on September 18, but IBM researchers said the first batch appeared on a different cybercrime service that checks card validity for fraudsters on September 15, which suggested that the attackers had been collecting card data on an ongoing basis.
The data offered on the cybercrime website had been offered for $25-$50 per card. Interested parties could purchase information from cards owned by individuals in a certain state or city — fraudulent transactions made in the area of the victim are less likely to trigger any alarms.
Sonic’s shares dropped 2 percent to $24.74 on Wednesday.
“Will customer loyalty be shaken? If the past as with the Wendy’s breach is prologue, then the answer is a qualified maybe, and if so, then only slightly,” Robert W. Capps, VP of Business Development at NuData Security, told SecurityWeek after the breach came to light.
“However, this - coupled with the tsunami of recent breaches - might just be the game changers that lead US Federal authorities to better protect the data collection, processing and storage of customer data,” Capps added.
The list of major restaurant chains that informed customers of a payment card breach in the past year includes Wendy’s, Cicis, Arby’s, Chipotle, Shoney’s, and Noodles & Company.
It's 3 Billion! Yes, Every Single Yahoo Account Was Hacked In 2013 Data Breach
4.10.2017 thehackernews Incindent
The largest known hack of user data in the history just got tripled in size.
Yahoo, the internet company that's acquired by Verizon this year, now believes the total number of accounts compromised in the August 2013 data breach, which was disclosed in December last year, was not 1 billion—it's 3 Billion.
Yes, the record-breaking Yahoo data breach affected every user on its service at the time.
Late last year, Yahoo revealed the company had suffered a massive data breach in August 2013, which affected 1 billion user accounts.
The 2013 hack exposed user account information, including names, email addresses, telephone numbers, dates of births, hashed passwords (using MD5), and, in some cases, "encrypted or unencrypted security questions and answers," Yahoo said in 2016.
At that time, Yahoo did confirm that hackers did not obtain bank account details or credit card information tied to the Yahoo accounts.
The data breach was attributed to state-sponsored hackers. Since the disclosure of the breach last year, there have been many developments in the incident.
However, the recent announcement by Yahoo makes it clear that if you had an email account on Yahoo, you were part of the infamous data breach.
Oath, the Verizon subsidiary into which Yahoo was merged, made the announcement in a filing with the SEC on Tuesday, which reads:
"Subsequent to Yahoo's acquisition by Verizon, and during integration, the company recently obtained new intelligence and now believes, following an investigation with the assistance of outside forensic experts, that all Yahoo user accounts were affected by the August 2013 theft."
The statement clearly suggests that if you had an account on Yahoo in 2013, you were affected by the data breach.
So for whatever reason you did not change your password last year after the disclosure of this massive breach, you should now change your passwords immediately and enable two-factor authentication (2FA).
Also, if you are using the same password and answers to security questions somewhere else, change them too.
Deleting Yahoo account may not be a good option to opt for, as Yahoo recycles deleted accounts after 30 days, which would allow anyone to hijack it. So, even if you don't want to use your Yahoo account, just enable 2FA and leave it.
Yahoo has also started notifying the affected account holders, requiring them to change their passwords immediately, and assuring them that the stolen data "did not include passwords in clear text, payment card data, or bank account information."
One should note that this breach is separate from the 2014 breach disclosed by Yahoo in September last year, affecting as many as 500 Million user accounts.
Yahoo attributed the 2014 breach to a state-sponsored hacking group. In March 2016, US federal prosecutors charged two Russian intelligence officers and two criminal hackers in connection with the breach.
Recently, credit reporting service Equifax also announced that an additional 2.5 million American consumers were also impacted by the massive breach the company disclosed last month, bringing the total possible victims to 145.5 million from 143 million.
Yahoo hack – All 3 Billion Yahoo accounts were hacked in 2013 attack
4.10.2017 securityaffairs Incindent
The Yahoo hack occurred in 2013 is bigger than originally stated, Verizon confirmed that all 3 Billion Yahoo accounts were hacked in the attack.
The Yahoo hack occurred in 2013, the biggest known data breach suffered by a tech company, is bigger than originally stated.
Verizon Communications, which acquired Yahoo for $4.48 billion in June, announced on Tuesday that the 2013 Yahoo hack affected all three billion of company user accounts.
Last year, Yahoo declared that the incident affected one billion accounts, and it wasn’t the unique incident suffered by the company. In 2014, hackers accessed 500 million accounts in a separate security breach.
Attackers accessed names, birth dates, phone numbers, security questions, backup email addresses and passwords of Yahoo, a gift for hackers that could use the same data to access any other account owned by Yahoo users that share same credentials. Unfortunately, the hashed passwords were protected with a weak algorithm that was very easy to crack.
The 2013 Yahoo hack influenced the deal to acquire Yahoo in June and had a significant impact on the price of the acquisition., it’s very strange that the real extent of the incident was disclosed only now.
“That investigators did not discover the full extent of the 2013 incident before Verizon closed the deal to acquire Yahoo in June was surprising to outside cybersecurity analysts.” reported The New York Time.
According to Verizon, the support of outside forensic experts allowed it to discover that every single account was exposed in the 2013 Yahoo hack.
“Subsequent to Yahoo’s acquisition by Verizon, and during integration, the company recently obtained new intelligence and now believes, following an investigation with the assistance of outside forensic experts, that all Yahoo user accounts were affected by the August 2013 theft. While this is not a new security issue, Yahoo is sending email notifications to the additional affected user accounts. The investigation indicates that the user account information that was stolen did not include passwords in clear text, payment card data, or bank account information. The company is continuing to work closely with law enforcement.” Verizon said in a statement issued on Tuesday.
“Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon’s experience and resources,”
On August, a hacking collective based in Eastern Europe began offering Yahoo’s data for sale on the Dark Web. According to security firm InfoArmor, the Yahoo database was sold for $300,000 on the dark web.
Unfortunately, at least three different buyers, including two “prominent spammers” paid the hacker to gain the entire database and likely use it in espionage activities.
“But last August, a geographically dispersed hacking collective based in Eastern Europe quietly began offering the whole database for sale, according to Andrew Komarov, chief intelligence officer at InfoArmor, an Arizona cybersecurity firm, who monitors the dark corners of the internet inhabited by criminals, spies and spammers.” reported the New York Times. “Three buyers — two known spammers and an entity that appeared more interested in espionage — paid about $300,000 each for a complete copy of the database, he said.”
According to InfoArmor, the hackers who broke into the Yahoo database are likely based in Eastern Europe.
2013 Yahoo hack
Yahoo still considers the breaches in 2014 and 2013 as unrelated events.
It is still unclear who is behind the attack, security experts attributed the 2013 Yahoo hack to a Russian APT group.
“In March, the Department of Justice charged four men, including two Russian intelligence officers, with the 2014 breach. Investigators said the Russian government used stolen Yahoo data to spy on a range of targets in the United States, including White House and military officials, bank executives and even a gambling regulator in Nevada, according to anindictment.” added The New York Time.
“The stolen data was also used to spy on Russian government officials and business executives, federal prosecutors said. What made that theft particularly egregious, Justice Department officials said, was that the two intelligence officers who were indicted had worked for an arm of Russia’s Federal Security Service, or F.S.B., that is charged with helping foreign intelligence agencies track cybercriminals.”
Once again let me suggest Yahoo users reset their passwords and change security questions as soon as possible on every website, including ones for which they used the same Yahoo credentials.
Amazon's Whole Foods Market Suffers Credit Card Breach In Some Stores
29.9.2017 thehackernews Incindent
Another day, another data breach. This time Amazon-owned grocery chain has fallen victim to a credit card security breach.
Whole Foods Market—acquired by Amazon for $13.7 billion in late August—disclosed Thursday that hackers were able to gain unauthorized access to credit card information for its customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
Whole Foods Market has around 500 stores in the United States, United Kingdom, and Canada.
The company did not disclose details about the targeted locations or the total number of customers affected by the breach, but it did mention that hackers targeted some of its point-of-sale (POS) terminals in an attempt to steal customer data, including credit details.
The company also said people who only shopped for groceries at Whole Foods were not affected, neither the hackers were able to access Amazon transactions in the security breach.
Instead, only certain venues such as taprooms and table-service restaurants located within its stores—which use a separate POS system—were impacted.
Whole Foods Market has hired a cybersecurity firm to help it investigate the credit card breach and contacted law enforcement authorities of this incident.
"When Whole Foods Market learned of this, the company launched an investigation, obtained the help of a leading cybersecurity forensics firm, contacted law enforcement, and is taking appropriate measures to address the issue," Whole Foods said in a statement on its website.
The company is also encouraging its customers to closely monitor their credit card statements and "report any unauthorized charges to the issuing bank."
According to Whole Foods Market, none of the affected systems being investigated are, in any way, connected to Amazon.com systems.
Whole Foods Market has become the latest of the victim of the high-profile cyber attack. Earlier this month, Global tax and auditing firm Deloitte suffered a cyber attack that resulted in the theft of private emails and documents of some of its clients.
Also last week, the U.S. Securities and Exchange Commission (SEC) also disclosed that unknown hackers managed to hack its financial document filing system and illegally profited from the stolen information.
Last month, credit rating agency Equifax publicly disclosed a breach of its systems that exposed personal details, including names, addresses, birthdays and Social Security numbers, of potentially 143 million US customers.
Amazon-owned grocery chain Whole Foods Market suffered payment card breach
29.9.2017 securityaffairs Incindent
News of the day is that another big company suffered a security breach, the victim is the Amazon-owned grocery chain Whole Foods Market.
has fallen victim to a credit card security breach.
Whole Foods Market has around 500 stores in the United States, United Kingdom, and Canada, the company acquired by Amazon for $13.7 billion in late August, it now notified customers a credit card security breach.
According to the security breach notification, crooks were able to gain unauthorized access to credit card information for customers who made purchases at certain venues like taprooms and full table-service restaurants located within some stores.
“Whole Foods Market recently received information regarding unauthorized access of payment card information used at certain venues such as taprooms and full table-service restaurants located within some stores.” read the data breach notification announcement. “These venues use a different point of sale system than the company’s primary store checkout systems, and payment cards used at the primary store checkout systems were not affected.”
At the time there the firm hasn’t provided details about the attack, it is still unclear which locations were affected and the total number of customers impacted.

The attackers targeted point-of-sale (POS) systems to siphon customer financial data.
The company pointed out that customers that used their payment cards only for groceries at Whole Foods were not affected, hackers targeted only certain venues which use a separate POS system.
Whole Foods Market clarified that hackers were not able to access Amazon transactions in the security breach.
The company is already investigating the incident and has hired a cybersecurity firm to help it, of course the firm promptly reported the incident to law enforcement.
“When Whole Foods Market learned of this, the company launched an investigation, obtained the help of a leading cybersecurity forensics firm, contacted law enforcement, and is taking appropriate measures to address the issue,” states Whole Foods.
The firm encourages its customers to monitor their credit card statements and bank accounts and report any unauthorized charges.
This is the last data breach suffered by major organizations, last week it Deloitte confirmed a security breach that exposed private emails and documents of some of its clients.
Recently credit rating agency Equifax publicly disclosed a major breach that affected 143 million Americans, meanwhile the U.S. Securities and Exchange Commission (SEC) also admitted that hackers compromised its financial document filing system.
Amazon's Whole Foods Investigating Payment Card Breach
29.9.2017 securityweek Incindent
Whole Foods Market, the supermarket chain acquired recently by Amazon for $13.7 billion, informed customers this week that it has launched an investigation after learning that some of its point-of-sale (PoS) systems may have been hacked.
The company has provided only few details as the investigation is ongoing. However, it said the incident appears to impact taprooms and full table-service restaurants located within some of its stores.

Whole Foods pointed out that these venues rely on different PoS systems than the store that houses them. The affected payment systems are also not connected to Amazon.com, the company said.Whole Foods hacked
Law enforcement has been notified and a cyber security firm has been called in to assist Whole Foods’ investigation. The supermarket chain has promised to provide additional information as it learns more about the incident.
“While most Whole Foods Market stores do not have these taprooms and restaurants, Whole Foods Market encourages its customers to closely monitor their payment card statements and report any unauthorized charges to the issuing bank,” the company told customers.
The company’s statement suggests that it learned of the data breach from an external source – it’s likely that payment card issuers noticed a pattern of fraudulent transactions involving cards used at Whole Foods Market locations.
“Companies face threats every day and breaches will occur. In a contested environment like this, segmenting the networks, like Whole Foods did with its unique restaurant and taproom environment, saves other parts of the business from also being breached,” said Michael Daly, CTO of Raytheon's cybersecurity businesses.
“Financial systems within the larger Whole Foods system were not affected. The climate and operations controls were not compromised protecting massive amounts of food and inventory. Whether the segmented approach was happenstance or not, there is a lesson to be taken from today’s breach,” Daly added.
Fast food restaurant chain Sonic Drive-In is also investigating a possible data breach. Millions of payment cards that may have come from the company’s systems were recently put up for sale on a cybercrime marketplace.
Breach at Fast Food Chain Sonic Could Impact Millions: Report
27.9.2017 securityweek Incindent
Sonic Drive-In, a fast food restaurant chain with more than 3,500 locations across the United States, has apparently suffered a data breach that may have resulted in the theft of millions of payment cards.
Security blogger Brian Krebs reported on Tuesday that his sources in the financial industry had noticed a pattern of fraudulent transactions involving cards used at Sonic.
The company confirmed that it has launched an investigation, but it has not provided any information on the possible number of affected restaurants and customers.
“Our credit card processor informed us last week of unusual activity regarding credit cards used at SONIC,” Sonic said in an emailed statement. “The security of our guests’ information is very important to SONIC. We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor. While law enforcement limits the information we can share, we will communicate additional information as we are able.”
According to Krebs, a cybercrime marketplace specializing in payment cards, called “Joker’s Stash,” is selling a batch of 5 million cards, at least some of which appear to come from Sonic. The investigative journalist pointed out that the 5 million records could be originating from multiple companies whose systems have been breached by the same cybercrime group.
Cybercriminals typically rely on point-of-sale (PoS) malware to steal payment card data from merchants. The stolen data can be used to physically clone the cards, which can then be used to purchase high-value items that can be turned into a profit.
The credit and debit card data offered on Joker’s Stash is sold for $25-$50 and is advertised as “100% fresh.” This suggests that the cards were obtained recently and issuers did not get a chance to cancel them.
The cards are indexed based on city, state and ZIP code, allowing fraudsters to acquire only ones from their area, making it less likely to trigger any alarms when the cards are used to make fraudulent purchases.
“Will customer loyalty be shaken? If the past as with the Wendy’s breach is prologue, then the answer is a qualified maybe, and if so, then only slightly. However, this - coupled with the tsunami of recent breaches - might just be the game changers that lead US Federal authorities to better protect the data collection, processing and storage of customer data,” said Robert W. Capps, VP of Business Development at NuData Security.
“Like Wendy’s, Target and an alarming number of other major data breaches, the Sonic breach is bound to be a painful reminder that personal data is an irresistible target, no matter how diligent any company’s efforts are in data protection,” Capps added. “Until PII data is rendered worthless by advanced authentication such as passive biometrics, consumers will continue to suffer the consequences of industry and legislative inaction.”
The list of major restaurant chains that informed customers of a payment card breach in the past year includes Wendy’s, Cicis, Arby’s, Chipotle, Shoney’s, and Noodles & Company.
Adobe Accidentally Posts Private PGP Key
25.9.2017 securityweek Incindent
Adobe’s product security incident response team (PSIRT) accidentally published a private PGP key on its blog. The compromised key was quickly revoked and a new key was generated after the incident came to light.
Adobe PSIRT updated its PGP key on Friday and published the new public key, which should have been valid until September 2018, on its blog. However, Finland-based security researcher Juho Nurminen noticed that scrolling down in the blog post also revealed the private PGP key, which Adobe, obviously, should have kept private.
Pretty Good Privacy (PGP), which relies on the OpenPGP standard, allows users to protect information sent over the Internet, typically via email. Confidential data is encrypted using a public key, which users share with anyone who wants to communicate with them, and decrypted using a private key, which should be kept secret.
In Adobe’s case, the accidental disclosure of the private key could have allowed anyone to decrypt encrypted emails that normally only the company would be able to read.
The key accidentally published on Adobe’s blog was generated using Mailvelope, an open source browser extension for OpenPGP. Some security experts pointed out that the mistake made by Adobe was likely due to the way the Mailvelope interface is designed.
When users want to export a key, they can export either the public key, the private key, or both by selecting the “All” option. The Adobe employee responsible for the leak likely selected the “All” option and copied the generated data without realizing that it contained the private key as well.
However, it’s worth noting that the Mailvelope interface does display a warning when private keys are exported.
Adobe has removed the blog post and revoked the compromised private key, but users captured screenshots and a copy of the post still exists on websites such as Archive.is. The company has generated a new key pair, this time using GPGTools.
SecurityWeek has reached out to Adobe for comment and will update this article if the company responds.
“If you let your your PGP/GPG private key slip, your leak cuts both ways, potentially affecting both you and the other person in the communication, for messages in either direction,” said Sophos’ Paul Ducklin.
“Don’t make this mistake yourself if you use public-key cryptography tools,” the expert added. “It’s an easy mistake to make when you’re copying text – so, to borrow a saying from carpentry, measure twice, cut once.”
Adobe accidentally leaked online its Private PGP Key
25.9.2017 securityaffairs Incindent
The Adobe product security incident response team (PSIRT) accidentally published a private PGP key on its blog, once discovered the issue it quickly revoked it.
On Friday, the Adobe PSIRT updated its Pretty Good Privacy (PGP) key and published the new public key on the blog post. The new key should have been valid until September 2018, but something strange has happened. The security expert Juho Nurminen first noted that scrolling down in the blog post containing there were present both public and private PGP keys.


Follow
Juho Nurminen @jupenur
Oh shit Adobe
7:49 PM - Sep 22, 2017
154 154 Replies 3,877 3,877 Retweets 5,440 5,440 likes
Twitter Ads info and privacy
In a PKI infrastructure, messages to be sent to the recipient are encrypted with the public key it has shared (in the Adobe case it was published in the blog post), and only the legitimate recipient can read it by using the associated private PGP key.

The accidental disclosure of the private key could have allowed anyone to decrypt encrypted email messages sent by the users to the company.
The Adobe PGP key was generated using Mailvelope, a popular open source browser extension for OpenPGP.
Mailvelope allows users to export either the public key, the private key, or both by selecting the “All” option. The Adobe employee who was exported the public PGP key likely selected the “All” option and copied the generated data without noticing it was sharing the private PGP key as well.
Adobe has promptly removed the blog post and revoked the compromised private key, but it was too late because it is still possible to find copy of the post online. Adobe has generated a new key pair, and this time avoiding using Mailvelope, but using GPGTools.
U.S. Watchdog Confirms Probe of Huge Equifax Data Breach
14.9.2017 securityweek Incindent
A U.S. consumer protection watchdog agency said Thursday it has begun an investigation into a massive data breach at credit bureau Equifax that may have leaked sensitive information on 143 million people.
The Federal Trade Commission joins US congressional committees promising to probe the causes and implications of what could be the worst breach of personal information in the United States.
"The FTC typically does not comment on ongoing investigations," said Peter Kaplan, the agency's acting director of public affairs.
"However, in light of the intense public interest and the potential impact of this matter, I can confirm that FTC staff is investigating the Equifax data breach."
The hack disclosed last week at Equifax, one of the three major credit bureaus which collect consumer financial data, potentially affects more than half the adult population.
While not the largest breach -- Yahoo attacks leaked data on as many as one billion accounts -- the Equifax incident could be the most damaging because of the nature of data collected: bank and social security numbers and personal information of value to hackers and others.
US lawmakers have expressed concern over the implications of the hack and have called for hearings.
The House Energy and Commerce Committee announced it would hold an October 3 hearing with Equifax chief executive Richard Smith.
"We know members on both sides of the aisle appreciate Mr Smith's willingness to come before the committee and explain how our constituents might be impacted and what steps are being taken to rectify this situation," said a statement from Senators Greg Walden and Bob Latta.
Smith earlier this week offered an expanded apology to consumers in a column in USA Today.
"Consumers and media have raised legitimate concerns about the services we offered and the operations of our call center and website. We accept the criticism and are working to address a range of issues," Smith wrote.
"We are devoting extraordinary resources to make sure this kind of incident doesn't happen again."
Equifax said in a "progress report" on its website that criminals exploited a vulnerability in a website application called Apache Struts.
Security researcher Kevin Beaumont said in a blog post that he warned of the vulnerability in March and urged companies to fix it. "I kept reissuing warnings," Beaumont said in a blog this week. "And then I gave up. Many Fortune 500 companies are still running these systems."
Equifax Hack Exposes Personal Info of 143 Million US Consumers
10.9.2017 thehackernews Incindent
It's ironic—the company that offers credit monitoring and ID theft protection solutions has itself been compromised, exposing personal information of as many as 143 million Americans—that's almost half the country.
Equifax, one of the three largest credit reporting firm in the United States, admitted today that it had suffered a massive data breach somewhere between mid-May and July this year, which it actually discovered on July 29—that means the data of 143 million people were exposed for over 3 months.
However, it's unknown why Equifax waited 6 weeks before informing their millions of affected customers about the massive security breach.
Based on Equifax's investigation, unknown hackers exploited a security vulnerability on its website to gain unauthorized access to certain files.
Stolen data includes consumers' names, Social Security numbers, and birth dates for 143 million Americans, and in some instances, driving licence numbers and credit card numbers for about 209,000 citizens.
Also Read: How you can Protect Yourself from possibly the WORST Leak of Personal Data Ever.
The company said that some personal information for Canadian and British residents was also compromised.
Moreover, reportedly, three senior executives at Equifax, namely John Gamble (CFO), Joseph Loughran and Rodolfo Ploder, sold almost $2 million worth of their shares just days after the company learned of this massive hack.
Equifax is currently investigating the security incident and has reportedly hired FireEye's security firm Mandiant to help the company in hack aftermath.
Meanwhile, all Equifax customers are advised to visit http://www.equifaxsecurity2017.com website to check if their information has also been stolen. Users just need to enter the last 6 digits of their SSN and last name.
However, it is not that simple. The website is not giving a clear answer about whether or not your data may have been affected in the hack, but making it clear to those who were not exposed. Yes, it's confusing.
Equifax is asking affected customers to sign up for credit-monitoring and identity theft protection services—isn't this funny?
Don't worry; it's free for affected users.
The company has not yet confirmed whether the hackers have contacted it for any extortion demand, but since the breach is major, Americans quickly need to take necessary actions to protect themselves and their loved ones.
For this, you can head on to our article on How to Protect Yourself after this Security Mishap.
Stay tuned for more information, stay safe online.
Equifax Data Breach: Steps You should Take to Protect Yourself
10.9.2017 thehackernews Incindent
Equifax has suffered one of the largest data breaches in history that has left highly sensitive data of as many as 143 million people—that's nearly half of the US population—in the hands of hackers.
Based on the company's investigation, some unknown hackers managed to exploit a security flaw on the Equifax website and gained unauthorized access to certain files between mid-May and July 2017.
The information accessed primarily include full names, birth dates, Social Security numbers, addresses and, in some cases, driver's license numbers—most of the information that's banks, insurance companies, and other businesses use to confirm a consumer identity.
The company added that 209,000 credit card numbers were also obtained by the attackers, along with "certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers."
Equifax is one of the three major organizations in the United States that calculates credit scores, which means the company has access to an extraordinary amount of personal and financial information for virtually all American adults.
Here's How Roughly Equifax Handled the Massive Data Breach
For a second, keep aside the scope and severity of the data breach, and let's talk about the how Equifax handled the breach after discovering it and what all it did for its customers.
First of all, the third largest U.S. credit reporting firm took over five weeks to publically disclose the data breach, which began in mid-May that means the data of 143 million people were exposed for over 3 months.
What's more? Reportedly, three senior Equifax executives, namely John Gamble (CFO), Joseph Loughran and Rodolfo Ploder, were permitted to sell almost $2 million worth of their shares just days after the company learned of this massive hack.
However, the company officials told Bloomberg that the employees were unaware of the data breach at the time of the sale.
Wait there's even more: After revealing the data breach on Thursday, Equifax did not contact everyone who was affected, rather it asked customers to go to its special website to figure out whether they were affected by entering the last 6 digits of their SSN and last name.
But it's not that simple. The website is not giving a clear answer about whether or not your data may have been affected, but making it clear to those who were not exposed. It's confusing.
What Would Be Hackers Next Move?
With this data in hand, it's most likely that hackers are already selling your personal information on the dark web or attempting to extort the company, like cyber criminals do in most massive data breach cases.
The Game of Thrones hackers did the same by leaking upcoming episodes of the widely watched show after HBO refused to their $6 Million ransom demand for the 1.5 terabytes of data they claimed to have stolen from the company.
Same happened to Netflix in April this year when the company refused to meet 50 Bitcoins ransom demand of a hacking group calling itself The Dark Overlord, which then leaked 10 back-to-back episodes of the Season 5 premiere of Netflix's "Orange Is the New Black."
Although Equifax has not yet confirmed whether the hackers have contacted the company for any demand or not, the breach is major, and all 143 Million Americans quickly need to take action to protect themselves and their loved ones.
Here's what all you can do to Protect Yourself:
1. Enroll in TrustedID Premier
Equifax is offering a year of free credit monitoring and identity theft protection program for free for one year through TrustedID Premier that you should sign up if you are a US resident—the service is free whether or not you have been affected by the breach.
The program offers services such as Equifax credit report, 3 bureau credit file monitoring, Equifax credit report lock, Social Security number monitoring and up to $1M identity theft insurance.
However, Equifax's own identity protection service is not enough, you must follow below steps to help ensure you're doing everything to protect your identity.
2. Monitor your accounts
In upcoming days, the personal and payment cards details are likely to be sold in underground black markets, resulting in financial loss and identity theft to millions of customers.
So, users are advised to be vigilant in reviewing their bank account statements, checking for any changes in their personal information and reporting any unauthorized transactions to the respective bank.
3. Freeze Your Credit Report
Since your stolen Social Security number can be misused by hackers to open new accounts in your name or ruin your credit score, you should consider placing a credit freeze request.
Freezing your credit will make it difficult for anyone to open a new account in your name, as you (or anyone masquerading as you) will need the PIN that you got when you froze your credit to unfreeze your account.
To freeze your credit, contact these credit bureaus: Equifax: 1-800-349-9960, Experian: 1‑888‑397‑3742, and TransUnion: 1-888-909-8872.
4. Change your Passwords and Logins
Meanwhile, all customers are advised to reset their account passwords and login information on the website.
5. Watch out for tax season
It's important for you to know that identity thieves can use your stolen social security number to file fraudulent tax returns and get refunds.
So, you should consider filing your taxes early.
6. Watch Out for Scams
Users are strongly advised to be cautious if they receive any suspicious or unrecognised phone call, text message, or email from anyone saying you must pay taxes or a debt immediately—even if they provide your personal information.
7. Already Experienced Identity Theft? Here's what to do now:
If you have already a victim to the identity theft, visit the FTC Identity Theft Recovery website and fill in the form. The Federal Trade Commission will provide you with a specific identity theft report and "to-do" recovery plans.
Massive Credit Bureau Hack Raises Troubling Questions
9.9.2017 securityweek Incindent
It could be the worst-ever data breach for American consumers, exposing some of the most sensitive data for a vast number of US households.
The hack disclosed this week at Equifax, one of the three major credit bureaus which collect consumer financial data, potentially affects 143 million US customers, or more than half the adult population.
While not the largest breach -- Yahoo attacks leaked data on as many as one billion accounts -- the Equifax incident could be the most damaging because of the nature of data collected: bank and social security numbers and personal information of value to hackers and others.
"This is the data that every hacker wants to steal your identity and compromise your accounts," said Darren Hayes, a Pace University professor specializing in digital forensics and cybersecurity.
"It's not like the Yahoo breach where you could reset your password. Your information is gone. There's nothing to reset."
Some reports suggested Equifax data was being sold on "dark web" marketplaces, but analysts said it was too soon to know who was behind the attack and the motivation.
"This could be a mercenary group or it could be a nation-state compiling it with other data" for espionage purposes, said James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, a Washington think tank.
"This is the kind of information I would go after if I were a nation-state, to set up psychographic targeting for information and political warfare."
- National security risks -
Peter Levin, chief executive at the data security firm Amida Technology Solutions and a former federal cybersecurity official, said he is concerned over the national security impact of the breach, which follows a leak of data on millions of US government employees disclosed in 2015.
"The implications with regard to national security are very large," he said. Because most federal employees also have credit reports, "those people have now been hacked twice," Levin said, offering potential adversaries fresh data to be used against them.
"We've just given the bad guys a lot more information," he said. "Even if they didn't perpetrate the attack, they can buy the data."
An FBI statement said the US law enforcement agency "is aware of the reporting and tracking the situation as appropriate."
The breach raised numerous questions among experts, such as why the company waited more than a month to notify consumers after learning of the attacks July 29.
Some analysts expressed concern that a company with a mission to safeguard sensitive data allowed a breach of this scope to take place.
"Equifax knew it was a prime target for cyberattacks," said Annie Anton, who chairs the Georgia Tech School of Interactive Computing and specializes in computer security research.
"It's amazing that one flaw could lead to a breach involving 140 million people. They should have safeguards in place. Even if a breach happens, it shouldn't grow to that scale."
Even more surprising, Anton said, is that Equifax still used social security numbers for verification despite the known risks from storing these key identifiers.
Anton noted that she testified before Congress in 2007 recommending that credit bureaus be required to use alternatives to social security numbers "and it still hasn't been fixed."
Some details of the attack remain unclear, including whether the data stolen was encrypted -- which would make it harder for the hackers to monetize.
At least two class-action lawsuits on behalf of consumers were filed following the disclosure claiming Equifax failed to adequately protect important data.
Equifax "should have been better prepared for any attempt to penetrate its systems," said attorney John Yanchunis, who filed one of the lawsuits.
Separate lawsuits announced Friday meanwhile said Equifax may have violated securities laws by allowing three high-ranking Equifax executives to sell shares worth almost $1.8 million in the days after the hack was discovered.
An Equifax spokesperson told AFP the executives "had no knowledge that an intrusion had occurred at the time they sold their shares."
Equifax stock fell 13.6 percent in New York trades on Friday following the disclosure.
- How to respond-
The potential impact of the Equifax breach prompted some experts to suggest the government revisit the idea of social security numbers issued for life.
"The government should consider changing social security numbers since there have been so many breaches," Hayes said.
Levin added that he "would be in favor of issuing new social security," even though "it's a fraught political discussion."
Others said the US could follow a European rule set to take effect in 2018 requiring companies to notify consumers within 72 hours of a data breach.
"Companies will put more into cybersecurity if there are tough penalties associated with data breaches," Hayes said.
The House Financial Services Committee will hold hearings on the breach, committee chair Jeb Hensarling said while expressing concern over a "very troubling situation."
New York state attorney general Eric Schneiderman said his office was launching a formal probe to determine if Equifax adequately notified consumers and had appropriate safeguards in place.
*Updated
Equifax data breach could impact 143 million US consumers
8.9.2017 securityaffairs Incindent
Equifax, one of the three major US consumer credit reporting agencies is the last victim of a data breach that may have affected upwards to 143 million Americans.
According to a statement published by the Equifax, crooks exploited an unnamed U.S. website application vulnerability from mid-May to July to access sensitive data in its systems.
“Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. consumers. Criminals exploited a U.S. website application vulnerability to gain access to certain files. Based on the company’s investigation, the unauthorized access occurred from mid-May through July 2017. The company has found no evidence of unauthorized activity on Equifax’s core consumer or commercial credit reporting databases.” reads the statement.
Equifax waited 6 weeks before informing the affected customers about the massive security breach, while it confirmed to have identified unauthorized access to “limited personal information for certain UK and Canadian residents.”
Equifax discovered the intrusion on July 29, this means that attackers had access to the company’s systems for nearly 3 months.
Hackers managed to access sensitive information for 143 million Americans, including Social Security numbers, birth dates, addresses, and some driver’s license numbers.
Attackers also accessed credit card numbers for about 209,000 citizens and some personal information for Canadian and British residents.
“The information accessed primarily includes names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed.” continues the company.

The company has set up the website www.equifaxsecurity2017.com for customers to check if their data was compromised.
Equifax is asking affected customers to sign up for credit-monitoring and identity theft protection services, it is ironic because these are the same services the company offers to its customers.
Equifax announces an investigation on the data breach is ongoing.
143 Million Affected in Hack of U.S. Credit Agency
8.9.2017 securityweek Incindent
A major American credit reporting agency entrusted to safeguard personal financial information said Thursday hackers looted its system in a colossal breach that could affect nearly half the US population as well as people in Britain and Canada.
Equifax said that a hack it learned about on July 29 had the potential to affect 143 million US customers, and involved some data for British and Canadian residents.
The Atlanta-based company disclosed the breach in a release that did not explain why it waited more than a month to warn those affected about a risk of identity theft.
Filings with the US Securities and Exchange Commission showed that three high-ranking Equifax executives sold shares worth almost $1.8 million in the days after the hack was discovered.
An Equifax spokesperson told AFP the executives "had no knowledge that an intrusion had occurred at the time they sold their shares."
Copies of SEC filings regarding the transactions were on an investor relations page at the company's website.
Equifax collects information about people and businesses around the world and provides credit ratings used for decisions regarding loans and other financial matters.
It also touts a service protecting against identity theft.
"The fact that it is a credit company that people pay to be protected from breaches, and now they have been breached... it feels like a betrayal of trust to a point," said Aires Security chief executive Brian Markus, whose firm specializes in computer network defenses.
He considered the breach "gigantic," made worse by the fact that Equifax stores extensive personal information about people and keeps it up to date.
Markus wondered what level of responsibility Equifax is going to take if stolen information is used for fraud or identity theft, and advised people to enlist credit monitoring services to alert them to trouble.
- 'Strikes at the heart' -
Equifax released a statement saying that it learned of the breach on July 29 and "acted immediately" with the assistance of an independent cybersecurity firm to assess the impact.
"Criminals exploited a US website application vulnerability to gain access to certain files," the statement said.
An internal investigation determined the unauthorized access occurred from mid-May through July 2017, according to the company.
Equifax said the hackers obtained names, social security numbers, birth dates, addresses and, in some instances, driver's license numbers from the database, potentially opening up victims to identity theft.
The company said credit card numbers were compromised for some 209,000 US consumers, as were credit dispute documents for 182,000 people.
Equifax vowed to work with British and Canadian regulators to determine appropriate next steps for customers affected in those countries, but added in the release that it "found no evidence that personal information of consumers in any other country has been impacted."
"This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do," said company chairman and chief executive Richard Smith.
"I apologize to consumers and our business customers for the concern and frustration this causes."
He added that Equifax is reviewing its overall security operations.
Equifax said it had established a website to enable consumers to determine if they are affected and would be offering free credit monitoring and identity theft protection to customers.
The company is the latest to announce a major breach. Yahoo last year disclosed two separate cyber attacks which affected as many as one billion accounts.
More than 400 million accounts were affected by a breach disclosed last year at the hookup site Adult Friend Finder, and other firms affected in recent years included Heartland Payment Systems and retail giant Target.
"Every company out there is potentially susceptible in today's cyber landscape," Markus said of hacking attacks, some even by nation states. "These incidents can put companies out of business."
Equifax shares were down more than 13 percent to $124 in after-market trades that followed news of the hack.
Taringa Data Breach, over 28 Million users affected
5.9.2017 securityaffairs Incindent
The data breach notification website LeakBase reported to the colleagues at THN the Taringa data breach, over 28 Million users’ data exposed.
Taringa, also known as ‘The Latin American Reddit’, is a popular social network used by netizens in Latin America to create and share thousands of posts every day on general interest topics.
The data breach notification website LeakBase reported to the colleagues at THN that Taringa suffered a data breach. LeakBase has obtained a copy of the stolen database containing details on 28,722,877 accounts, including usernames, hashed passwords, and hashed passwords. LeakBase has shared a dump of 4.5 million Taringa users with the peers at The Hacker News in order to check the data.
The hashing algorithm used to protect the passwords is the weak MD5 that is considered no more secure because it can be easily cracked, in fact, LeakBase researchers already cracked 93.79 percent (nearly 27 Million) of hashed passwords is a few days.
Experts at THN contacted users whom emails were included in the dump they received, they confirmed the authenticity of their credentials.
It seems that the data breach is dated back August, but the company did not publicly disclose it. The company Taringa only reported the data breach to users who logged in to the website.

In response to the data breach, Taringa is sending a password reset link via an email to its users when they access their account with an old password.
LeakBase researchers successfully cracked 26,939,351 out of 28,722,877 passwords MD5-hashed. The archive contains more than 15 Million unique passwords. Below statistics related to the Taringa data breach:
The bad news is that also, in this case, Taringa users adopted easy to guess passwords such as 123456789, 123456, 1234567890, 000000, 12345, and 12345678. Most passwords were six characters long, the circumstance suggests the Taringa platform did not force users to choose strong passwords.

The most used email services are hotmail.com and gmail.com.
Taringa users are anyway recommended to change the password as soon as possible.
Further details on the LeakBase’s analysis are available at the following link
https://leakbase.pw/analysis/taringa/