Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
Ashley Madison to Pay $11.2 Million to Data Breach Victims
17.7.2017 thehackernews Incindent
Ashley Madison, an American most prominent dating website that helps people cheat on their spouses has been hacked, has agreed to an $11.2 Million settlement for roughly 37 million users whose personal details were exposed in a massive data breach two years ago.
Though the parent company of Ashley Madison, Ruby Corp., denies any wrongdoing, the company has pledged to pay around $3,500 to each of the hack's victims for the settlement.
The settlement has to be reviewed by a federal judge in St. Louis.
Ashley Madison marketed itself as a means to help people cheat on their spouses, with a tagline "Life is short. Have an affair."
The site was breached in July 2015 and hackers dumped nearly 100 gigabytes' worth of sensitive data belonging to 37 million users of the casual sex and marriage affair website onto the dark web.
The leaked data included victims' usernames, first and last names, email addresses, passwords, credit card data information, street names, phone numbers, and transactions records, which led to blackmails and even suicides.
The 2015 data breach cost Ruby Corp, formerly known as Avid Life, over a quarter of its revenue and forced the Toronto-based company to spend millions of dollars to boost security and user privacy.
Ruby Corp was already forced to pay $1.66 Million to settle charges from Federal Trade Commission (FTC) and 13 states, alleging that the service misled its consumers about its privacy policy and didn't do enough to protect their information.
Besides this, the company also agreed to 20 years' worth of the FTC overseeing its network security to ensure that its user data is being protected. This includes:
Performing a risk assessment to protect customer data.
Implementing new data security protocols.
Upgrading systems based on the assessments.
Offering periodic security risk assessment (both internal and third-party).
Requiring "reasonable safeguards" against any potential cyber attacks from their service providers.
Now, according to Reuters, the company has to pay $11.2 million to users who were affected by the breach – users with valid claims can get up to $3,500 depending on their losses attributable to the breach.
Insider Steals Customer Data From Global Healthcare Group
15.7.2017 securityweek Incindent
Major International Healthcare Organization Bupa Loses Customer Details to Insider Threat
Bupa, a major international healthcare group, announced yesterday, "We recently discovered an employee of our international health insurance division (which is called 'Bupa Global'), had inappropriately copied and removed some customer information from the company.
Sheldon Kenton, Managing Director at Bupa Global, announced, "Around 108,000 international health insurance policies are affected," and added; "The data taken includes: names, dates of birth, nationalities, and some contact and administrative details including Bupa insurance membership numbers."
DataBreaches soon added some detail. "DataBreaches.net first became aware of the Bupa breach on June 23, when a listing appeared on the now-gone Alpha Bay marketplace by a vendor calling himself 'MoZeal'." MoZeal was a new member to AlphaBay, having joined on 2 May 2017; and DataBreaches conjectures "that 'MoZeal' is likely the rogue employee that Kenton referred to."
DataBreaches provided the full list of stolen data as provided by MoZeal, which turns out to be more expansive than that provided by Bupa. It includes separate home and office fax, email address, mobile and landline phone numbers. DataBreaches also questions the Bupa statement. "While Bupa reports that 108,000 were affected, MoZeal's listing and thread indicated that there were over 130,000 in the U.K. alone, and that overall there were about 500,000 – 1 million records for sale."
SecurityWeek asked Bupa to clarify this, and was told, "All of the information and statements we have made public this week remain valid. We are aware of a report that suggests that on 23 June 2017 'a former employee claimed to have 1m records for sale'. Our thorough investigation established that 108,000 policies, covering 547,000 customers, had been copied and removed. The disparity in numbers claimed and those taken relates to duplicate copies of some records."
For now, Bupa is providing little more information. It is contacting those customers who are affected "to apologize and advise them as we believe the information has been made available to other parties." This implies that affected customers should be particularly wary about phishing attempts seeking additional information, either for complete identity theft or just to steal bank account details or card numbers.
Earlier this week, Kaspersky Lab published a study on "The Human Factor in IT Security", showing the extent to which employees are making businesses vulnerable from within. Kaspersky's principal security researcher David Emm believes employees rank at the very top of the list of threats to data and systems. "When insider-assisted attacks do occur," he told SecurityWeek, "the impact of such attacks can be devastating as they provide a direct route to the most valuable information -- in this case, customer data."
David Kennerley, director of threat research at Webroot, adds, "Because of the nature of the information that's been leaked, Bupa Global customers who have been affected need to be extra vigilant, without doubt they are now prime targets for phishing attacks and other targeted activities, as well as possible identify theft."
The potency of identity theft should not be underestimated. On Monday this week Alf Goransson -- the CEO of Securitas, Sweden's largest security firm -- was declared bankrupt by the Stockholm District Court (it is expected to be rescinded). A fraudulent loan had been taken out in his name in April after his identity was stolen at the end of March. The perpetrator also used his name to request bankruptcy. The bankruptcy led to Goransson's automatic deregistration by the Swedish Companies Registration Office as the Securitas CEO.
In the Bupa incident, the perpetrator is known and has been dismissed, and Bupa is taking 'appropriate legal action'. In response to SecurityWeek's request for clarity, Bupa said, "It was an existing employee." It was neither an ex-employee, nor a contractor. "Just to reiterate," continued Bupa, "the employee had access to this information as part of their job and chose to abuse their position. The employee responsible has been dismissed. Bupa has a zero-tolerance attitude towards data theft."
Bupa has not said how it discovered the breach, whether it was via its own internal controls or because a third-party (such as law enforcement) recognized it on the dark web. Nor has it said exactly when it discovered the breach, nor when it dismissed the employee.
The UK data protection regulator, the Information Commissioners Office (ICO), confirmed that it knows about the incident and told SecurityWeek, "Organizations have a duty to protect people's privacy and personal data. We have been made aware of an issue involving Bupa Global and are making enquiries." However, the ICO declined to tell SecurityWeek when it had been informed of the breach.
Since DataBreaches knew about the loss on 23 June, it is likely that Bupa knew about it around the same time. That implies that the AlphaBay takedown occurred after MoZeal's offer to sell Bupa data, and before Bupa disclosed the loss. The timing is most probably coincidental; but nevertheless, the only SecurityWeek question that Bupa completely ignored, was this: "Does the theft of your data and its subsequent offer for sale on AlphaBay have anything whatsoever to do with AlphaBay being taken down?" When companies limit the information they provide in their disclosures, there is a great temptation to fill in the gaps.
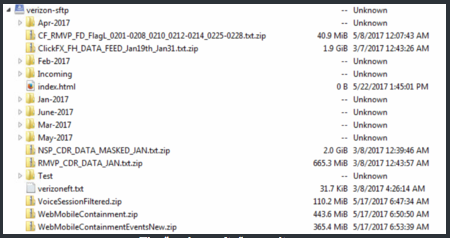
Verizon Downplays Leak of Millions of Customer Records
13.7.2017 securityweek Incindent
The personal details of millions of Verizon customers were exposed online due to a misconfigured Amazon Web Services (AWS) S3 bucket operated by a third-party vendor, but the telecoms giant has downplayed the incident.
Cyber resilience firm UpGuard reported on Wednesday that its researchers discovered an unprotected AWS S3 bucket containing information on as many as 14 million Verizon customers, including names, addresses, phone numbers, PINs used for identity verification purposes, customer satisfaction data, and service purchases.
The data, which appears to represent daily logs collected over the first six months of 2017, was not exposed by Verizon itself, but by NICE Systems, an Israel-based partner that provides call center services. UpGuard reported the leak to Verizon on June 13, but the exposed database was only protected on June 22.
“Beyond the sensitive details of customer names, addresses, and phone numbers—all of use to scammers and direct marketers—the prospect of such information being used in combination with internal Verizon account PINs to takeover customer accounts is hardly implausible. To do so would enable impersonators to tell Verizon call center operators to do whatever was wished of them,” UpGuard said in a blog post.

In a statement published on its corporate website, Verizon downplayed the incident, claiming that the details of only 6 million unique customers were exposed. The company blamed the leak on human error, and pointed out that no one other than UpGuard had accessed the unprotected cloud storage area.
“The overwhelming majority of information in the data set had no external value, although there was a limited amount of personal information included, and in particular, there were no Social Security numbers or Verizon voice recordings in the cloud storage area,” Verizon said.
“To further clarify, the data supports a wireline portal and only includes a limited number of cell phone numbers for customer contact purposes. In addition, to the extent PINs were included in the data set, the PINs are used to authenticate a customer calling our wireline call center, but do not provide online access to customer accounts,” the company added.
Experts believe this is a serious incident, even if no one else downloaded the data from the cloud storage.
“Sure, a mid-air miss is better than an air flight disaster, but neither should ever happen,” John Gunn, chief marketing office for VASCO Data Security, told SecurityWeek. “Data such as this can be used by hackers for all types of attacks, especially phishing attacks, by giving them legitimacy in the mind of the victim. We saw this recently with the DocuSign breach and the subsequent successful attacks against their users.”
Willy Leichter, vice president of marketing at Virsec, believes “this will be a heated board-level issue for a $1 billion company like Nice, and a $125 billion-plus company like Verizon.”
“If the European General Data Protection Regulation (GDPR) was in effect (it is starting in May 2018) there could be a fine as large at $5 billion (4% of annual revenue) for this single incident,” Leichter said.
More than 14 Million Verizon Customers’ records exposed by a third party firm
13.7.2017 securityaffairs Incindent
Data belonging to 14 million U.S.-based Verizon customers have been exposed on an unprotected AWS Server by a partner of the telecommunications company.
The notorious security expert Chris Vickery, UpGuard director of cyber risk research. as made another disconcerting discovery, more than 14 million US customers’ personal details have been exposed after the third-party vendor NICE left the sensitive records open on an unprotected AWS Server.
NICE Systems is an Israeli firm that offers several solutions for intelligence agencies, including telephone voice recording, data security, and surveillance systems.
Exposed data also revealed that NICE Systems has a partnership with Paris-based telecommunication company “Orange,” it seems that the third-party firm collects customer details across Europe and Africa.
“The data repository, an Amazon Web Services S3 bucket administered by a NICE Systems engineer based at their Ra’anana, Israel headquarters, appears to have been created to log customer call data for unknown purposes;” reads a blog post published by Vickery. “Verizon, the nation’s largest wireless carrier, uses NICE Systems technology in its back-office and call center operations. In addition, French-language text files stored in the server show internal data from Paris-based telecommunications corporation Orange S.A.—another NICE Systems partner that services customers across Europe and Africa.”

The exposed data are sensitive information of millions of customers, including names, phone numbers, and account PINs (personal identification numbers).
The huge trove of data is related to the customers’ calls to the Verizon’s customer services in the past 6 months.
“Beyond the risks of exposed names, addresses, and account information being made accessible via the S3 bucket’s URL, the exposure of Verizon account PIN codes used to verify customers, listed alongside their associated phone numbers, is particularly concerning.” continues the expert, “Possession of these account PIN codes could allow scammers to successfully pose as customers in calls to Verizon, enabling them to gain access to accounts—an especially threatening prospect, given the increasing reliance upon mobile communications for purposes of two-factor authentication.”
It is still unclear why Verizon allowed NICE to collect call details, experts speculate the third party vendor was tasked to monitor the efficiency of its call-center operators for Verizon.
The incident demonstrates the risks of third-party vendors handling sensitive data. UpGuard pointed out the long interval of time between the initial notification to Verizon by UpGuard (June 13th) to the closure of the breach (on June 22nd)
“Finally, this exposure is a potent example of the risks of third-party vendors handling sensitive data,” reads the blog post from UpGuard.
“NICE Systems’ history of supplying technology for use in intrusive, state-sponsored surveillance is an unsettling indicator of the severity of this breach of privacy.”
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak, in June 2017 Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
Alarming Percentage of Employees Hide Security Incidents: Report
10.7.2017 securityweek Incindent
Policy and Engagement Are Key to Addressing Insider Threats
The human factor, also often known as the insider threat, has long been known but rarely quantified. Kaspersky Lab has attempted to do just that -- to answer the question, 'What role do employees play in a business's fight against cybercrime?'
Kaspersky used the B2B International market research company to query 5,000 businesses around the globe; and the results are alarming. "Fifty-two percent of businesses admit that employees are their biggest weakness in IT security, with their careless actions putting business IT security strategy at risk," explains the Kaspersky report.
The extent of the issue is illustrated by the top three vulnerability concerns all being related to the human factor or employee behavior: inappropriate sharing (47%); data on lost mobile devices (46%); and inappropriate use of IT resources (44%). The supply chain, increasingly used by advanced hackers as an entry point, figures fourth at 43%.
This concern is verified by actual cybersecurity incidents. "Among the businesses that faced cybersecurity incidents in the past 12 months, one-in-ten (11%) [of] the most serious types of incidents involved careless employees," states the report. This is second only to incidents involving malware, standing at 23%.
Even here, however, the human factor is important. Forty-nine percent of businesses reported being attacked by malware this year (an increase of 11% over last year). The top contributing factors behind the reported incidents are all human factors: careless/uninformed employees (53%); accidental loss of hardware (38%); and phishing/social engineering (36%).
The more dangerous targeted attacks are also increasing, with 27% of businesses reporting incidents (up 6% on the previous year). "Of these attacked businesses, over a quarter (28%) believe phishing/ social engineering contributed to the attack," notes the report.
Here Kaspersky makes an additional point: it isn't enough to simply increase social engineering and phishing awareness, it is also important to create an environment in which employees are willing to own up to errors. Kaspersky calls this the 'hide and seek' problem: employees sometimes hide their mistake leaving the business to seek the source of the problem.
"Employees," the report explains, "don't always take action when their company is hit by a security incident. In fact, in 40% of businesses around the world, employees hide an incident when it happens." This tendency varies by size of company: as low as 29% of very small businesses; at 42% of SMBs; and as high as 45% of enterprises with more than 1,000 employees.
Kaspersky warns against a big stick approach to this problem. "If employees are hiding incidents, there must be a reason why. In some cases, companies introduce strict, but unclear rules and impose extra responsibility on employees, warning them not to do this or that, or they will be held responsible if something goes wrong. Such policies only foster fears, and leave employees with just one option — to avoid punishment whatever it takes."
BYOD is another area where the human factor continues to cause concern. "Almost half (48%) of businesses overall," says Kaspersky, "are worried about employees inappropriately sharing company data via the mobile devices that they bring to work." This is a particular concern for small businesses, where it rises to 57%. The concern is justified in practice: according to the research, more than half (54%) of businesses have had data exposed because employees have lost devices.
Kaspersky warns that policy alone is not enough to defend against the human factor. "A policy, alone, will not protect a business from threats -- partly because IT security policies are not always followed by the staff that they are designed for, and partly because they cannot cover every possible risk." In fact, 44% of respondents admitted that employees simply do not properly follow policy.
Kaspersky's solution is to find the right balance of policy and engagement: policy to define correct behavior; and engagement to make employees want to follow policy. "Staff training is essential in raising awareness among personnel and motivating them to pay attention to cyberthreats and countermeasures -- even if they are not part of their specific job responsibilities. Installing updates, ensuring that anti-malware protection is on, and managing personal passwords properly shouldn't always be at the bottom of an employee's to-do list."
US Food Payment Kiosk Vendor Avanti Markets Hacked, Biometric data stolen
10.7.2017 securityaffairs Incindent
US payment kiosk vendor Avanti Markets that installs its self-service payment devices in corporate breakrooms across America suffered a security breach.
The US payment kiosk vendor Avanti Markets that installs its self-service payment devices in thousands of corporate breakrooms across America suffered a security breach.
According to the popular investigator Brian Krebs who first reported the news, the systems of the company were infected by a malware that stole customer data including names, e-mail addresses, credit card accounts as well as biometric data.
“Avanti Markets, a company whose self-service payment kiosks sit beside shelves of snacks and drinks in thousands of corporate breakrooms across America, has suffered of breach of its internal networks in which hackers were able to push malicious software out to those payment devices, the company has acknowledged.” wrote Brian Krebs.”The breach may have jeopardized customer credit card accounts as well as biometric data, Avanti warned.”
The company admitted the breach and it is informing people that their data were exposed.
“On July 4, 2017, we discovered a sophisticated malware attack which affected kiosks at some Avanti Markets. Based on our investigation thus far, and although we have not yet confirmed the root cause of the intrusion, it appears the attackers utilized the malware to gain unauthorized access to customer personal information from some kiosks.” states the data breach notification issued by the Avanti Markets. “Because not all of our kiosks are configured or used the same way, personal information on some kiosks may have been adversely affected, while other kiosks may not have been affected.”
Biometric data that were allegedly stolen by hackers are fingerprints, used by the company to allow users to make rapid payments.
Avanti Markets already notified law enforcement the security breach and launched an internal investigation. In response to the security breach, the company cleaned the affected machines, changed its passwords, blocked payment processing at affected locations.
Avanti Markets will offer affected individuals free credit monitoring and a call centre helpline.
“Another source told this author that Avanti’s corporate network had been breached, and that Avanti had made the decision to turn off all self-checkouts for now — although the source said customers could still use cash at the machines.” continues Krebs.
According to a Krebs’s source that has spoken under a condition of anonymity, the company did not adopt basic security measures to project data, such as the P2Pe encryption.
“I was told that about half of the self-checkouts do not have P2Pe,” the source said, on condition of anonymity. P2Pe or “point-to-point encryption,” and it’s a technology that encrypts sensitive data such as credit card information at every point in the card transaction.
“In theory, P2Pe should be able to protect card data even if there is malicious software resident on the device or network in question.”
The analysis conducted by Risk Analytics revealed that cyber criminals used the PoSeidon malware, a memory scraper malware that is able to steal data directly from the memory of the PoS systems. According to the experts, the PoS malware was used by Russian cybercriminals to target payment systems worldwide.

Cisco Security Team spotted for the first time the malware in March 2015, the experts defined it as the most sophisticated PoS malware at the time of the discovery.
Experts at Risk Analytics believes the threat actor has been active since 2015, they observed that the traffic they identified matched Cisco’s 2015 analysis of PoSeidon and uses the same SSL certificate spotted by Cisco experts in past investigation.
Why AA didn’t inform customers after a massive data leak
5.7.2017 securityaffairs Incindent
A backup containing sensitive information on more than 100,000 AA customers was exposed online, but the company didn’t disclose the incident.
UK car insurance company AA is being heavily criticized over its handling of a data breach that exposed customer email addresses and partial credit card number in April.
A server misconfiguration is the root cause for the exposure of data from the AA’s online shop. The issue exposed backup files containing orders for maps, motoring accessories and other products.

The incident was publicly disclosed last week when security experts Troy Hunt criticized the way AA has downplayed a massive data breach that exposed about 13GB of DB backups.
Follow
Troy Hunt ✔ @troyhunt
Extremely disappointing to see an organisation cover up and downplay a breach that includes credit card data. Very poor form by @TheAA_UK https://twitter.com/josephfcox/status/881863275029434368 …
3:34 PM - 3 Jul 2017
121 121 Retweets 118 118 likes
Twitter Ads info and privacy
The AA confirmed the incident affected AA shop & retailers orders rather than sensitive info. It was rectified & we take this seriously.”
26 Jun
Sajid Nawaz Khan @snkhan
@TheAA_Help Can you advise whether the breach reported by @troyhunt is genuine? Was customer data downloaded by a unauthorised third party?
Follow
The AA ✔ @TheAA_Help
@snkhan This incident was related to the AA shop & retailers’ orders rather than sensitive info. It was rectified & we take this seriously.
3:37 PM - 26 Jun 2017
Retweets 1 1 like
Twitter Ads info and privacy
According to Troy Hunt, the leak exposed also partial payment details (the last four figures of credit card numbers) of the users and other sensitive information.
Follow
Troy Hunt ✔ @troyhunt
Exposed data included card type, expiry and last 4 digits. Multiple customers who had their data compromised confirmed. Time to come clean. https://twitter.com/theaa_help/status/881889755688030209 …
5:09 PM - 3 Jul 2017 · Amsterdam, The Netherlands
19 19 Retweets 48 48 likes
Twitter Ads info and privacy
According to Motherboard the leaked dump contains 117,000 unique email addresses as well as portions of credit card data.
“The data obtained by Motherboard contains 117,000 unique email addresses, as well as full names, physical addresses, IP addresses, details of purchases, and payment card information. Those card details include the last four digits of the credit card and its expiry date.” states the blog post published by Motherboard.
“The data also appears to include a number of password hashes, and according to security researcher Scott Helme, an expired certificate and private encryption key.”
“This is essentially the username and password that the AA use to login to their Secure Trading account,” Helme wrote in an analysis of the breach shared with Motherboard.”
Even is a small portion of a credit card number has been exposed, this data can be used for identity verification exposing the owners to identity theft.
The ICO confirmed it is aware of the incident and that it is investigating the case.
“Businesses and organisations are obliged by law to keep people’s personal information safe and secure. We are aware of an incident involving the AA and are making enquiries.” an ICO spokesperson told El Reg.
According to the AA, the data was “only accessed several times.”
“Legal letters warning against a dissemination breach under the ‘Computer Misuse Act’ will be issued. The ICO [Information Commissioner’s Office] has been informed and we have commissioned a full independent investigation into the issue. We take any data issues incredibly seriously and would like to reassure our AA Shop customers that their payment details have not been compromised,” reads the statement from AA.
A few days ago, the UK car insurance company accidentally sent out a ‘password update’ email to its customers, at the time the incident declared the problem was caused by a human error.
Google employees affected by the Sabre data breach
3.7.2017 securityaffairs Incindent
Google has notified some employees that they may have been hit by the data breach suffered by travel technology firm Sabre.
In May, the Travel Tech Giant Sabre confirmed in a SEC filing it was “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
The intruders gained access to the system after hijacking an internal account on the SynXis system.
“The unauthorized access has been shut off and there is no evidence of continued unauthorized activity,” reads a statement that Sabre sent to affected properties in May. “There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected.”
The impact of the incident could be severe, the SynXis Central Reservation product is a rate and inventory management SaaS application that is currently used by more than 32,000 hotels worldwide.
Later, the company confirmed the hackers had managed to access personally identifiable data, payment card details, and other information.
Google employees were affected by the Sabre data breach because it was using booking services provided by the Carlson Wagonlit Travel (CWT), a company that uses the SynXis platform.
Google notified affected employees via letter, the IT giant learned of the Sabre breach on June 16 from Carlson Wagonlit Travel (CWT).

Google notified employees that their name, contact information and payment card details may have been accessed by attackers, who breached the reservations system between August 10, 2016 and March 9, 2017.
“We recently learned that certain hotel reservations made for Google business travel were
among the many reservations affected by a security incident impacting a third-party provider’s
electronic reservation system that serves thousands of travel agencies and hotels. This did not
affect Google’s systems. However, this incident impacted one of the travel providers used by
Googlers, Carlson Wagonlit Travel (CWT).” states the letter.
“Sabre’s investigation discovered no evidence that information such as Social Security, passport, and driver’s license numbers were accessed,” Google said. “However, because the SynXis CRS deletes reservation details 60 days after the hotel stay, we are not able to confirm the specific information associated with every affected reservation.”
To protect its employee, Google opted to offer affected ones two years of identity protection and credit monitoring services.
Google is working with CWT and Sabre to address this issue. Sabre hired cybersecurity firm Mandiant to support its investigation. The company also notified law enforcement and the payment card brands about the data breach.
“We are offering you 24 months of complimentary identity protection and credit monitoring
services. These services, described below, will be provided by AllClear ID and are available as
of the date of this notice. You can use them at any time during the next 24 months:” states Google.
Google Employees Hit by Sabre Breach
3.7.2017 securityweek Incindent
Google has notified some employees that their personal information may have been compromised as a result of the data breach suffered by travel technology firm Sabre.
Sabre informed customers in early May that it had launched an investigation after detecting unauthorized access to its SynXis Central Reservation System, a rate and inventory management product used by more than 32,000 hotels worldwide.
The company said the hackers had managed to access personally identifiable data, payment card details and other information. An investigation revealed that the attackers gained access to the system after hijacking an internal account on the SynXis platform.
In a letter sent out to affected employees, Google said it learned of the breach on June 16 from Carlson Wagonlit Travel (CWT), one of the companies used by the tech giant to book business travel and one of the many organizations that uses the SynXis product. Google pointed out that the breach did not impact its own systems.
Google told employees their name, contact information and payment card details may have been stolen by attackers, who had access to the reservations system between August 10, 2016 and March 9, 2017.
“Sabre’s investigation discovered no evidence that information such as Social Security, passport, and driver’s license numbers were accessed,” Google said. “However, because the SynXis CRS deletes reservation details 60 days after the hotel stay, we are not able to confirm the specific information associated with every affected reservation.”
Google has decided to offer affected employees two years of identity protection and credit monitoring services.
Sabre has yet to provide an update on this incident. The company has alerted law enforcement and payment card issuers, and contracted Mandiant to assist its investigation.
Anthem agreed to pay $115m to settle a class-action suit brought on by the 2015 data breach
27.6.2017 securityaffairs Incindent
Anthem, the largest US healthcare insurance company, has agreed to pay $115m to settle a class-action suit brought on by the 2015 data breach.
The attack on Anthem exposed 78.8 million records and according to experts that investigated the case, it was probably not a smash-and-grab raid but instead a sustained, low-key siphoning information over a period of months. The attack was conducted to stay below the radar of the company’s IT and security teams, using a bot infection to exfiltrate data out of the organization.
The records include names, dates of birth, addresses, and medical ID numbers, financial and medical records were not exposed.
Investigators reported that customized malware was used to infiltrate Anthem’s networks and steal data. The exact malware type was not disclosed but is reported to be a variant of a known family of hacking tools. However, an independent security consultancy reports that the attack may have been started up to three months earlier. The consultancy said that it noticed ‘botnet type activity’ at Anthem affiliate companies back in November 2014.
Back to the present, the settlement fund will cover costs incurred by victims of the breach.
According to the settlement’s “Alternative Compensation” section, customers who already received credit monitoring services can elect to receive a small cash compensation that ranges from $36 up to $50 in some instances.
The Judge Lucy Koh at District Court for the Northern District of California will review the proposal, it could be the largest data breach settlement in history if approved by the judge.
In March 2017, the US retail giant Target has entered a settlement with the US Attorneys General and it has agreed to pay $18.5 million over the 2013 data breach.
“After two years of intensive litigation and hard work by the parties, we are pleased that consumers who were affected by this data breach will be protected going forward and compensated for past losses,” lead attorney Eve Cervantez said.

As is usually the case with settlements, Anthem will not have to admit to any wrongdoing.
The settlement was also generous with attorneys, a third of the package for a total amount of $37,950,000 will cover their fees.
Experian, who is handling the credit and identity monitoring services for the victims of the Anthem data breach, will receive an additional $17m.
Average Cost of Data Breach Drops Globally, Rises to $7.35 Million in U.S.
21.6.2017 securityweek Incindent
Cost of Data Breach Drops Globally, But Rises 5% in U.S.
The 2017 IBM Security and Ponemon Institute annual report on the cost of a breach shows that the cost of stolen records and the total cost of a breach continues to rise -- at least in America. The lost- or stolen-record cost rose from $221 to $225 each, while the average total cost of a breach increased from $7.01 million to $7.35 million for organizations in the United States.
In the European countries included in the study -- France, Germany Italy and the United Kingdom -- these costs actually fell. For example, in the UK, the average per capita cost of a data breach decreased from £102 to £98 and the average total organizational cost decreased from £2.53 million in 2016 to £2.48 million in 2017.
The annual Cost of Data Breach Study (PDF) is one of security's yearly benchmark reports. This year, Ponemon Institute, sponsored by IBM, analyzed the cost-effect of data breaches for more than 400 companies in 13 countries. However, it should be noted that not everyone believes it is possible to accurately define and compare different breaches in different companies over time. In recent years both Verizon and ENISA have said it is too difficult.
SecurityWeek asked Diana Kelley, global executive security advisor to IBM Security, whether such criticisms are fair. "It's hard to do these comparisons," she admitted, "but Ponemon goes to great pains over many months using a consistent methodology to ensure they are valid." While the breached companies change, the methodology for data gathering remains consistent, and the bottom line, she added, is that "IBM is confident in their validity, and we are seeing a picture of what can save us money when we have a breach; and also things that result in that cost being higher than perhaps it needs to be."
In America, the key factors in reducing the cost of a breach are incident response, encryption and education. Having an incident response team in place resulted in a $19 reduction in cost per lost or stolen record, followed by extensive use of encryption ($16 reduction per record) and employee training ($12.50 reduction per record). None of this is rocket science, suggested Keeley; "but sometimes it takes science-backed data figures to make us realize just how important they are."
Notable factors increasing the cost of a breach include the involvement of third-parties in a data breach (increasing the cost $17 per record), compliance failures and s 'rush to notify'. The first of these is a well-understood threat vector. "Organizations need to evaluate the security posture of their third-party providers – from payroll to cloud providers to CRM – to ensure the security of employee and customer data," says IBM.
The latter two, however, are worth considering in relation to the difference in breach costs between America and Europe together with the different compliance regulations of the two areas. "In Europe," suggested Keeley, "we've had the EU Data Protection Directive for many years, and now we have the upcoming GDPR. This area has been dealing with very strict data privacy laws for a very long time. We suspect that this is the primary reason for the difference -- because of this ongoing need to be more mature with data protection, it has led to a more efficient and optimized series of response programs in Europe."
IBM does not claim that this is a proven conclusion, but just one worth considering. If it is true, however, it leads to further useful speculation. At one level, it supports the EU's insistence on strict and rigid rules. But it also confirms that security really can work -- breaches may not be preventable, but effective incident response will certainly make them less costly.
There could be other causes, of course. Do Europeans simply spend more on security than their American counterparts, or do they use it more efficiently? This is difficult to answer. The two regions are broadly similar, although the US is considered to be the richer (according to the Federalist Debate, GDP is around 40% higher in the US than in the EU).
Certainly, according to IDC's 2016 Worldwide Revenue for Security Technology Forecast, "the United States will be the largest market for security products throughout the forecast. In 2016, the U.S. is forecast to see $31.5 billion in security-related investments. Western Europe will be the second largest market with revenues of nearly $19.5 billion this year."
It would appear from this that European companies do not spend more on security than America companies -- which leads us back to the idea that strict data privacy laws can spur companies to more efficient data protection. The upcoming GDPR, of course, will affect US companies in ways they were not affected by the existing European laws.
If the hypothesis that conforming to strict compliance requirements can improve security and reduce breach costs, then over the next few years the cost of a breach in the US might start to decrease in line with Europe. "It's going to be interesting," Keeley told SecurityWeek. "Looking at the processes, procedures and technology within GDPR, there's a lot in there that can really help a company mature their overall data program. We can't predict the future -- but we shall see."
There is, of course, a huge amount of data within the Cost of Breach Study. Usually, it takes readers a considerable amount of time to isolate and analyze the particular information of interest. Here we have looked at just one area: the effect of compliance on the cost of a breach. This year, however, the study is accompanied by an online tool that will help companies delve deeper into different areas of the study: such as the effect of customer churn following a breach, the effect of employing a CISO on costs, and so on.
"This interactive tool," IBM told SecurityWeek, "allows you to explore the data from the report on your own, uncover trends and learn more about the cost of a data breach directly related to specific industries and/or security measures."
Database of Over 198 Million U.S. Voters Left Exposed On Unsecured Server
19.6.2017 thehackernews Incindent
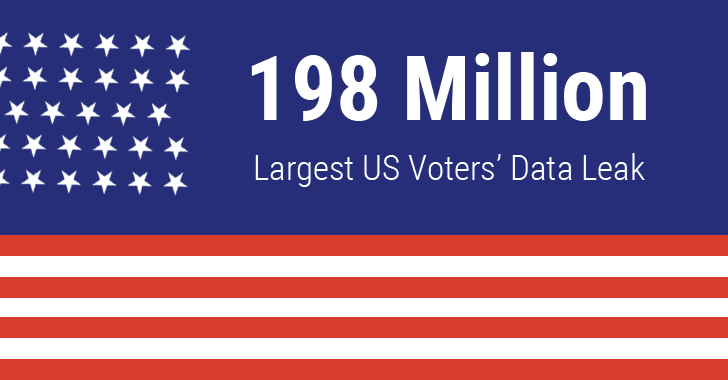
Information on more than 198 Million United States citizens, that's over 60% of the US population, was exposed in what's believed to be the largest ever known exposure of voter-related to date.
This blunder was caused by Deep Root Analytics (DRA), a data analytics firm employed by the US Republican National Committee (RNC), who "mistakenly" left sensitive personal details of more than 198 million US voters exposed on an unsecured Amazon S3 server.
Chris Vickery, a security researcher at UpGuard, who discovered the exposed database said anyone could have downloaded more than a Terabytes of files containing voters data without the need for any password from the Amazon S3 server maintained by DRA.
Vickery is the same security researcher who discovered over 191 million voter records stored in an unsecured database in late 2015. In April, Vickey also reported information on 93 million Mexican voters.
Vickery discovered the exposed databases on June 12, which included uniquely identified data on each voter, including their first and last name, date of birth, phone number, home and mailing address, party affiliation, voter registration data, and ethnicity, along with a flag should the person appear on the federal Do-Not-Call registry.
Deep Root Analytics, which is a big data analytics firm that helps advertisers identify audiences for political ads, confirmed to the Gizmodo in a statement on Monday, saying "We take full responsibility for this situation."
However, the server was secured two days later after Vickery responsibly reported the blunder to the federal regulators.
You would be surprised to know that the Republican National Committee paid Deep Root nearly a Million dollars between January 2015 and November 2016 for their work during the election and another $4.2 Million to TargetPoint.
It is believed that the US voters data was also compiled by at least two other contractors, TargetPoint Consulting Inc. and Data Trust.
According to the report, a smaller folder for the 2016 election included in the database contained files for Ohio and Florida, arguably the two most crucial battleground states.
Another folder named 'data_trust' appears to reference Data Trust, was entirely downloadable by any individual accessing the URL of the database and contained two massive stores of personal information collectively representing 198 million potential voters.
"Consisting primarily of two file repositories, a 256 GB folder for the 2008 presidential election and a 233 GB folder for 2012, each containing fifty-one files - one for every state, as well as the District of Columbia," explained UpGuard's Dan O'Sullivan in a blog post.
Also, one folder called "Post-Elect 2016" contained information on voters’ likely views about topics like whether they voted for former President Barack Obama and US President Donald Trump’s "America First" foreign policy.
Deep Root has contracted a security firm, Stroz Friedberg, to perform a thorough investigation of the data exposure.
DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed
19.6.2017 securityaffairs Incindent
The popular security expert Chris Vickery revealed the DRA firm left 1.1 TB of data unsecured on an Amazon S3, 198 million US voter records exposed.
Researcher Chris Vickery has found nearly 200 million voter records in an unsecured Amazon S3 bucket maintained by Deep Root Analytics (DRA), it is the largest exposure of its kind in history.
The records include the voter’s first and last name, home and mailing address, date of birth, phone number, party affiliation, ethnicity, voter registration data, and a flag should the person appear on the federal Do-Not-Call registry.
The voter files also include other attributes that could have been used for analysis based on ethnicity and religion.
In 2015, Vickery discovered an archive exposed online containing 191 million voter records.
DRA is a Republican big data analytics firm, the popular expert discovered the huge trove of data on June 12, then he reported the issue to the authorities and the company secured it in two days.
The archive contains complete voter files compiled by DRA and at least two other contractors, Target Point Consulting Inc. and Data Trust.
Voter information is considered public, but sometimes it is not easy to access them even if they are freely available. Anyway, it is forbidden the use of such data for commercial purposes.
The archive discovered by Vickery on the DRA S3 bucket (“data_trust”) contains a collection of personal information representing between 150 to 198 million potential voters.
“Salted Hash has seen an example voter record, and many of the profile fields are similar to those from two years ago.” reported Salted Hash.
“Using an internal “RNC ID” – each voter in the database can be uniquely identified and associated with the logged data points.”
The archive discovered by Vickery contains information on 2008, 2012, while data related to 2016 are associated only with details on voters in Ohio and Florida.
Vickery also found another folder in the S3 bucket belonging to Target Point. The records included in the folder used the same “RNC ID” for each voter, but the update timestamps are recent (January 2017).
According to UpGuard’s Dan O’Sullivan, data discovered by the expert “provide a rare glimpse in to a systematic large-scale analytics operation.”
“The result is a database of frightening scope and intrusiveness into the modeled personal and political preferences of most of the country – adding up in total to an unsecured political treasure trove of data which was free to download online.”
Many of the Target Point data were focused on post-election data, they included scores for potential voters on specific topics.
“For example, one 50 GB file contained scores for potential voters, signifying their potential to support a given policy, such as President Trump’s foreign policy stance of “America First”, or how concerned they’ll be with auto manufacturing as an issue.” states Salted Hash.
The discovery highlights the risks for organizations in using cloud storage without implementing necessary security policies.
Amazon offers several tools and the guidance to secure the infrastructure of its customers, but evidently it is not enough.
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
In March, he announced a 1.37 billion records data leak.
Buckle Inc. confirmed credit card breach at its stores
18.6.2017 securityaffairs Incindent
An official statement issued by the Buckle Inc. retail confirmed that a point-of-sale malware was discovered on cash registers at its stores.
A few hours ago, the popular investigator and cyber security expert Brian Krebs contacted the Buckle Inc. company after sources in the financial sector reported him about a possible card breach at the retailer.
“On Friday morning, KrebsOnSecurity contacted The Buckle after receiving multiple tips from sources in the financial industry about a pattern of fraud on customer credit and debit cards which suggested a breach of point-of-sale systems at Buckle stores across the country.” reported KrebsOnSecurity.
An official statement issued by the retail confirmed that a point-of-sale malware was discovered on cash registers at Buckle retail stores.
The Buckle Inc. is a clothier that operates more than 450 stores in 44 US states, on Friday the company disclosed that payment systems at its retail locations were infected by a malware used to steal credit card data.
Store front for The Buckle, a Kearney, Neb., based clothing chain.
According to the company, the PoS malware was stealing customer credit card data between Oct. 28, 2016 and April 14, 2017. According to the company, online sales were not affected by the card breach.
“We became aware that The Buckle, Inc. was a victim of a security incident in which a criminal entity accessed some guest credit card information follow purchases at some of our retail stores. We immediately launched a thorough investigation and engaged leading third party forensic experts to review our systems and secure the affected part of our network.” states the announcement published by the company.
“Through that investigation we learned that our store payment data systems were infected with a form of malicious code, which was quickly removed. Based on the forensic investigation, we believe that no social security numbers, email addresses or physical addresses were obtained by those criminally responsible. There is also no evidence that the buckle.com website or buckle.com guests were impacted.”
Crooks used malware to capture data stored on the magnetic stripe and clone the cards.
The Buckle Inc. confirmed that its stores are equipped with EMV-capable card terminals, this means that customers who shopped at compromised Buckle stores using a chip-based card would not be affected by the card breach.
The company is currently investigating the card breach with card brands and forensic investigation services.
“All Buckle stores had EMV (“chip card”) technology enabled during the time that the incident occurred and we believe the exposure of cardholder data that can be used to create counterfeit cards is limited. However, it is possible that certain credit card numbers may have been compromised.” states the company.
“We take the protection of payment card data very seriously. We are cooperating fully with card brands and forensic investigation services. Any affected individuals either have or will likely receive communications from their issuing banks with additional instructions and/or replacement cards. In line with best practice, we recommend that individuals closely monitor their payment card account statements.”
CashCrate Cash-for-Surveys Site breached, 6 Million accounts stolen
15.6.2017 securityaffairs Incindent
According to the data breach notification site LeakBase hackers have stolen 6 million accounts for the CashCrate Cash-for-Surveys Site.
Another day another data breach, this time hackers have stolen 6 million accounts for CashCrate, a site where users can be paid to complete online surveys. The news was reported by Motherboard who obtained the database and confirmed that records include user email addresses, passwords, names, and physical addresses.
The data breach notification site LeakBase provided Motherboard with a copy of the CashCrate archive.
CashCrate allows companies to pay users that test their products and services, or that participate in daily surveys.
The analysis of the database revealed that the earliest accounts date back to 2006, and the bad news is that accounts registered from 2010 have MD5 hashed passwords.
“Accounts from mid 2010 onwards appear to have passwords hashed with the notoriously weak MD5 algorithm, meaning that hackers may be able to crack the hashes and obtain the real login credentials.” states Motherboard.

Motherboard has verified that the accounts are legitimate, it also noticed it its post that CashCrate does not use basic web encryption on its website.
The company is notifying all its users about the security breach.
“We’re in the process of notifying all our members about the breach. While we’re still investigating the cause, at this point it appears that our third-party forum software was compromised, which led to the breach. We’ve deactivated it until we’re confident it’s secure,” a CashCrate spokesperson told Motherboard in an email.
“We have also confirmed that any users who have logged in since October 2013 have passwords that are fully hashed and salted, and we’re looking into why some inactive accounts have plaintext passwords. Those will be hashed and salted immediately,” the spokesperson added.
If you are a CashCrate user change your password now and in case you shared same login credentials on other websites you must change the passwords also for them.
GameStop Confirms Payment Card Breach
12.6.2017 securityweek Incindent
GameStop Admits Hackers Had Access to Its Website for Six Months
Video game and electronics retailer GameStop has started warning customers that their personal details and payment card data may have been stolen by cybercriminals.
Security blogger Brian Krebs reported on April 7 that the GameStop.com website had apparently been breached. Krebs learned at the time from his sources in the financial industry that hackers had stolen names, addresses and card data entered on the site between mid-September 2016 and early February 2017.
The company confirmed at the time that it had launched an investigation, but it only started notifying each impacted customer last week, specifying which of their payment cards may have been compromised.
“Although the investigation did not identify evidence of unauthorized access to payment card data, we determined on April 18, 2017 that the potential for that to have occurred existed for certain transactions,” the company wrote in a letter mailed to customers.
It turns out that hackers had access to the company’s website between August 10, 2016, and February 9, 2017. During this time, the cybercriminals may have stolen information provided when an order was placed, including names, addresses, card numbers, card expiration dates, and CVV codes. Payments made in stores do not appear to have been impacted.
The company has not shared any information on how many of its customers have been affected by the breach.
GameStop has provided some recommendations on how impacted customers can protect themselves, but it has not offered to pay for any specialized fraud protection services. The company has promised to enhance the security of its network to prevent future incidents.
Insecure Hadoop Clusters Expose Over 5,000 Terabytes of Data
3.6.2017 thehackernews Incindent
Until last year, cyber criminals were only targeting computers of individuals and organisations with ransomware and holding them for ransom, but then they started targeting unprotected online databases and servers around the globe for ransom as well.
Earlier this year, we saw notorious incidents where tens of thousands of unprotected MongoDB and Elasticsearch databases were hacked and held for ransom in exchange of the data the hackers had stolen and deleted from the poorly configured systems.
Now, cyber crooks have started targeting unprotected Hadoop Clusters and CouchDB servers as well, making the ransomware game nastier if your servers are not securely configured.
Nearly 4,500 servers with the Hadoop Distributed File System (HDFS) — the primary distributed storage used by Hadoop applications — were found exposing more than 5,000 Terabytes (5.12 Petabytes) of data, according to an analysis conducted using Shodan search engine.
This exposure is due to the same issue — HDFS-based servers, mostly Hadoop installs, haven't been properly configured.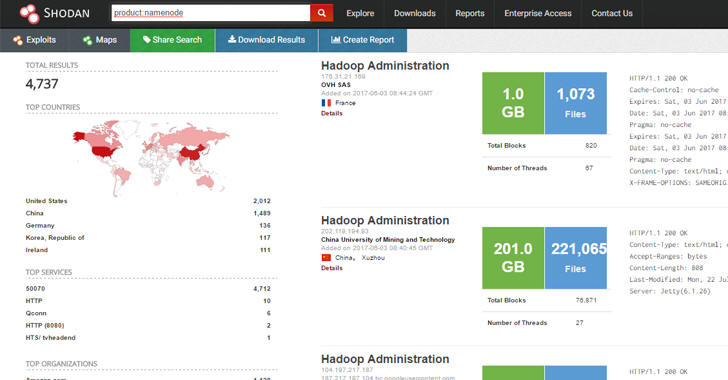
The Hadoop Distributed File System (HDFS) is a distributed file system that is being designed to store vast data sets reliably and to stream those data sets at high bandwidth to user applications.
Like other Hadoop-related techs, HDFS has become a primary tool for managing large clusters of data and supporting big data analytics applications.
In a blog post, Shodan Founder John Matherly revealed that while the focus had been on MongoDB and Elasticsearch databases exposed on the Internet, Hadoop servers turned out to be "the real juggernaut."
Although MongoDB has over 47,800 servers exposed on the Internet that exposes 25TB of data, Hadoop has just 4,487 servers in total but exposes a considerably higher amount of data of more than 5,000TB.
Most of the Hadoop servers that expose data on the Internet are located in the United States (1,900) and China (1,426), followed by Germany (129) and South Korea (115).
A majority of the HDFS instances are hosted in the cloud with Amazon Web Services leading the charge with 1,059 instances and Alibaba with 507.
While we saw ransom attacks aimed at unprotected MongoDB and Elasticsearch databases last year, Matherly said those attacks have not been stopped and are still targeting CouchDB and Hadoop servers.
"The ransomware attacks on databases that were widely publicised earlier in the year are still happening," says Matherly. "And they're impacting both MongoDB and HDFS deployments."
Matherly has also shared all the necessary steps on how to replicate the searches on Shodan search engine that users could follow in order to conduct their own investigations.
Administrators are encouraged to configure their Hadoop servers to run them in secure mode by following the instructions provided by the company.
Unsecure Hadoop Distributed File System installs 5 PB of Data
3.6.2017 securityaffairs Incindent
According to Shodan search, unprotected Hadoop Distributed File System installations expose 5 PB of data.
Hadoop servers that are not securely configured expose vast amounts of data, according to an analysis conducted using the Internet search engine Shodan.
A study conducted by Shodan revealed that nearly 4,500 servers with the Hadoop Distributed File System (HDFS) were found to expose 5,120 TB (5.12 PB) of data.
The overall volume of data exposed by HDFS system is greater than the one related to MongoDB installs.
“However, in terms of data volume it turns out that HDFS is the real juggernaut.” reads the analysis published by Shodan. “To give you a better idea here’s a quick comparison between MongoDB and HDFS:”
MONGODB HDFS
Number of Servers 47,820 4,487
Data Exposed 25 TB 5,120 TB
“Even though there are more MongoDB databases connected to the Internet without authentication in terms of data exposure it is dwarfed by HDFS clusters (25 TB vs 5 PB).”
Most of the servers with the Hadoop Distributed File System are located in the United States (1,900) and China (1,426), followed by Germany and South Korea with 129 and 115 servers, respectively.
The majority of the HDFS install are hosted in the cloud, mainly Amazon (1,059 instances) and Alibaba (507).
In 2016, security experts observed ransom attacks aimed at unsecured MongoDB database installs exposed online.
According to the researchers, the hackers were implementing an extortion mechanism copying and deleting data from vulnerable databases.
Crooks requested the payment of a ransom in order to return data and help the company to fix the flaw they exploited.
Similar ransom attacks later began targeting Elasticsearch, CouchDB and Hadoop servers, such kind of attacks still target Hadoop and MongoDB installations. and a majority of the Internet-exposed MongoDB servers appear to have already been compromised.
According to Shodan founder John Matherly, a majority of the MongoDB servers exposed on the Internet have already been already compromised.
First attacks observed by the experts targeting HDFS installs erased most directories and created a directory named “NODATA4U_SECUREYOURSHIT.” no ransom was asked to the victims.
Querying Shodan for “NODATA4U_SECUREYOURSHIT” string, the popular search engine retrieves more than 200 Hadoop Distributed File System installs.

The blog post published by Shodan includes instructions on how to search Hadoop Distributed File System installs exposed online.
OneLogin Investigating Breach at U.S. Data Center
1.6.2017 securityweek Incindent
Identity and access management solutions provider OneLogin informed customers on Wednesday that it had detected unauthorized access at its U.S. data center.
OneLogin CISO Alvaro Hoyos said the breach was detected on May 31 and blocked the same day. Law enforcement has been notified and an independent security firm has been called in to assess the impact and cause of the intrusion.
While Hoyos’ statement contains few details, the emails sent to affected customers reveal that all users served by the company’s U.S. data center are impacted and may have had their information compromised.
OneLogin said it can’t provide additional information on the incident due to the ongoing law enforcement investigation, but a support page made available to customers mentions that the exposed information can be used to decrypt encrypted data.
The company, whose services are used by more than 2,000 enterprises in 44 countries, is requiring affected customers to force a OneLogin directory password reset for all their users, generate new certificates for apps that use SAML SSO, generate new API credentials and OAuth tokens, and generate new directory tokens for Active Directory and LDAP connectors.
The list of required actions also includes updating credentials for third-party apps such as G Suite and Workday, generating new Desktop SSO tokens, recycling any secrets stored in Secure Notes, updating credentials for third-party app provisioning, updating admin credentials for apps that use form-based authentication, replacing RADIUS shared secrets, and instructing end-users to update their passwords for form-based authentication apps.
The long list of instructions for IT teams suggests that this was a significant breach that could have serious consequences.
The incident comes less than a year after OneLogin admitted that hackers gained access to Secure Notes data after stealing an employee’s password.
Secure Notes are normally protected using multiple levels of AES-256 encryption, but a bug caused the data to be visible in clear text in the company’s log management system, to which attackers had access for several weeks.
Target agreed to pay $18.5 Million over 2013 data breach
25.5.2017 securityaffairs Incindent
Target, the US retail giant, has entered a settlement with the US Attorneys General and it has agreed to pay $18.5 million over the 2013 data breach.
Target, the US retail giant, has entered a settlement with the Attorneys General of 47 states and it has agreed to pay $18.5 million over the data breach suffered in 2013.
Nearly 40 Million credit and debit card accounts belonging to Target customers have been stolen during the traditional holiday shopping season in 2013.
The company intends to compensate the costs incurred by its customers and to compensate for the damage it has caused to the consumers.
Target data breach
The company will pay the overall amount of money to all the Attorneys General involved in the investigations, $1.2 million will be paid to the Illinois Attorneys General and roughly $1 million to the Connecticut that lead the legal action against the company.
According to the settlement, Target accepted to implement an information security program to protect its customer.
“TARGET shall, within one hundred and eighty ( 180) days after the Effective Date of this Assurance, develop, implement, and maintain a comprehensive information security program (” Information Security Program”) that is reasonably designed to protect the security, integrity, and confidentiality of Personal Information it collects or obtains from Consumers.” reads the settlement.
The Information Security Program shall cover administrative, technical, and physical safeguards appropriate to:
The size and complexity of TARGET’ s operations;
The nature and scope of TARGET’ s activities;
The sensitivity of the Personal Information that TARGET maintains.
The company will adopt further measures to protect its customers, including network segmentation, access control, and management, file integrity monitoring, whitelisting, logging, change control, and the adoption of payment card security technologies.
The settlement established that the cyber security of the company’s systems must be assessed by a third-party, at the same time the company has to audit any vendor or subcontractor it works with. Let’s remind that the hackers that broke into the company payment systems used as entry point an HVAC contractor.
Target admitted last year that the data breach had cost it $290 million, the company paid $67 million to Visa card issuers, $19 million to MasterCard card issuers, over $20 million to banks and credit unions, and $10 million to the affected consumers.
Hackers Steal 17 Million Users' Data From Indian Restaurant App Zomato
19.5.2017 securityweek Incindent
India's largest restaurant and food delivery app Zomato announced Thursday that the data of 17 million users had been stolen from its database, including names, email addresses and protected passwords.
The startup said the "hashed" passwords could not be decrypted but recommended users change their login details if they use the same password for other services.
Zomato's chief technology officer Gunjan Patidar said customers' financial information was stored separately from the stolen data and was not compromised by the hack.
"No payment information or credit card data has been stolen/leaked," he said in a statement on Zomato's website, adding they were scanning all possible breaches in their system.
"Your credit card information on Zomato is fully secure, so there's nothing to worry about there."
Those affected had been logged out of the website and app and had their passwords changed "as a precaution", he added.
A report on an online hacker news website carried in local media said the trove of personal data was being auctioned on the dark web for roughly $1,000 by a hacker using an alias.
The hack of the internationally popular e-commerce startup comes on the heels of the "WannaCry" cyberattack, the world's biggest ransomware attack to date.
The culprits demanded payment in virtual currency and threatened to delete files on compromised computers, which numbered in the hundreds of thousands worldwide.
Zomato, which boasts 120 million user visits a month, said it was "plugging any security gaps" and would further enhance its security measures after the database breach.
The company -- a so-called "unicorn" startup because it is valued at more than $1 billion -- was founded in 2008 and it now operates in 23 nations. np/cc/klm
Zomato Data breach – Nearly 17 million usernames and hashed passwords stolen
19.5.2017 securityaffairs Incindent
Nearly 17 million Zomato usernames and hashed passwords have been stolen by hackers., the company suspects it is an insider’s job.
Nearly 17 million Zomato usernames and hashed passwords have been stolen by hackers.
Zomato is the Indian largest online restaurant guide, the company confirmed data breach announcing that hackers have stolen accounts details of millions of its users.
“about 17 million user records from our database were stolen. The stolen information has user email addresses and hashed passwords.” reads the data breach notification issued by the company.
The company tried to downplay the incident explaining that hashed password are hard to decrypt.
“We hash passwords with a one-way hashing algorithm, with multiple hashing iterations and individual salt per password. This means your password cannot be easily converted back to plain text. We however, strongly advise you to change your password for any other services where you are using the same password.” continues the statement
The reality is quite different, hackers could easily obtain computational resources to crack the passwords.
Zomato confirmed that hackers did not access financial information of the users that are stored in a separate database that was not involved in the attack.
“Payment related information on Zomato is stored separately from this (stolen) data in a highly secure PCI Data Security Standard (DSS) compliant vault. No payment information or credit card data has been stolen/leaked,” the company claims.
The company suspects that the hack is an insider’s job.
“Our team is actively scanning all possible breach vectors and closing any gaps in our environment. So far, it looks like an internal (human) security breach – some employee’s development account got compromised,” the company said.
According to the HackRead website, data stolen by the hackers are already offered for sale on a darkweb marketplace, the vendor “nclay” is offering the full dump for BTC 0.5587 (USD 1,001.43).

Zomato Customers should change their password and stay vigilant on suspicious email, crooks could exploit stolen data to launch a phishing campaign.
The Electronic signature technology provider DocuSign suffered a data breach
17.5.2017 securityaffairs Incindent
Hackers broke into the system of the technology provider DocuSign and accessed customers email. The experts warn of possible spear phishing attacks.
The Electronic signature technology provider DocuSign suffered a data breach, hackers have stolen emails from one of its servers.
On Monday the company informed its customers of the data breach and warned them of fake emails set up to deliver weaponized Word documents, it also reported the incident to law enforcement agencies who are currently investigating the case.
DocuSign data breach
The malicious messages appeared to come from addresses such as dse@docus.com and dse@docusgn.com, they have the following subject lines:
“Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature” and “Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.”
Threat actor behind the DocuSign hack launched a phishing campaign against the customers of the firms, anyway, announced hackers have broken into a “non-core system.” designed for sending service-related email announcements to users.
Spear Phishing campaigns following a data breach represent a serious threat for customers of the hacked firm.
The company notified the incident to the customers and advised users to be vigilant and to report any suspicious email to spam@docusign.com.
“[The emails] may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like ‘docusgn.com’ without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than docusign.com or docusign.net,” DocuSign added.
According to DocuSign, hackers only accessed email addresses, there is no evidence that attackers accessed personal and financial information such as names, physical addresses, passwords, social security numbers, and payment card.
Below an excerpt from the data breach notification statement issued by DocuSign:
Last week and again yesterday, DocuSign detected an increase in phishing emails sent to some of our customers and users – and we posted alerts on the DocuSign Trust Center and in social media.
The emails “spoofed” the DocuSign brand in an attempt to trick recipients into opening an attached Word document that, when clicked, installs malicious software.
As part of our process in routine response to phishing incidents, we confirmed that DocuSign’s core eSignature service, envelopes and customer documents remain secure.
However, as part of our ongoing investigation, yesterday we confirmed that a malicious third party had gained temporary access to a separate, non-core system used for service-related announcements.
A complete forensic analysis has confirmed that only a list of email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.
The company said it has blocked the hack and locked out attackers from its systems, it also announced additional security controls.
Data Stolen in DocuSign Breach Used for Email Attacks
16.5.2017 securityweek Incindent
Electronic signature technology provider DocuSign informed customers on Monday that they may receive malicious emails after cybercriminals managed to steal email addresses from one of its servers.
DocuSign recently issued a couple of malicious email campaign alerts to warn users of fake emails set up to deliver malware via macro-enabled Word documents.
The fake messages appeared to come from addresses such as dse@docus.com and dse@docusgn.com, and they carried the subject line “Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature” and “Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.”
On Monday, DocuSign admitted that the spike in malicious emails was the result of a security breach. According to the company, hackers breached a “non-core system” designed for sending service-related email announcements to users.
The firm said the attackers only accessed email addresses; there was no evidence that names, physical addresses, passwords, social security numbers, payment card data or other information had been compromised.
“No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure,” DocuSign stated.
The company said it locked the attackers out of its systems and rolled out additional security controls. Law enforcement agencies have been notified of the incident.
DocuSign-themed spam campaigns are not uncommon, but having a list of email addresses that are known to belong to the company’s customers increases the likelihood of recipients opening the malicious emails.
DocuSign has advised users to be wary of these malicious emails and forward any suspicious messages to spam@docusign.com.
“[The emails] may appear suspicious because you don’t recognize the sender, weren’t expecting a document to sign, contain misspellings (like ‘docusgn.com’ without an ‘i’ or @docus.com), contain an attachment, or direct you to a link that starts with anything other than docusign.com or docusign.net,” DocuSign said.
Hackers Hit Bell Canada, Access Customer Information
16.5.2017 securityweek Incindent
Bell Canada on Monday said that an unknown hacker managed to access customer information on nearly 2 million customers, including email addresses, customer names and/or telephone numbers.
The company said that approximately 1.9 million active email addresses and approximately 1,700 names and active phone numbers were accessed illegally in the attack.
There is no indication that any financial, password or other sensitive personal information was accessed, a statement read.
The telco said the incident is not connected to the recent global WannaCry ransomware attacks, and believes there is “minimal risk involved for those affected” by the situation.
While Bell Canada dismissed the data stolen by hackers as having minimal risk, having access to customer lists opens the opportunity for targeted phishing attacks to customers who expect communications from the company. Being able to send a targeted phishing message to a customer and personally address them by name will certainly result in a much higher success rate than a typical blind spamming campaign would yield.
The company said it has been working with the Royal Canadian Mounted Police cybercrime unit on the investigation and has informed the Office of the Privacy Commissioner.
Clash of Greed
6.5.2017 Kaspersky Incindent
In 2015, the game Clash of Clans was bringing in about 1.5 million dollars per day for its developer, Supercell. Later on, the company launched a new project, Clash Royale, after addressing the flaws of their first game and implementing battles with real players into the new game, which shares the same characters and the same cartoonish design as the first project. Yet, the more popular game is, the higher the probability that fraudsters will be looking to make a fortune on that popularity by, for example, organizing phishing attacks on the player base.
The money-making model for both of the games has been thoroughly thought-out: anyone can play without investing real money. But this would mean putting a lot of effort into the games and losing more often to other players who basically purchase and upgrade either rare and strong cards with extremely low drop rates or battle units and building levels (when talking about Clash of Clans). In this regard, the majority of the game’s players do not have much money but are full of ambition. These players often seek not-so-legal ways to procure and upgrade rare cards to put less effort into winning battles and ranking up to play in the premier leagues.
This has been exploited by fraudsters, who subtly abuse human foibles such as cupidity, love for freebies, and the desire to be the top player. Phishing attacks, though always quite similar in their nature, are very competently planned. Phishing websites are designed with holidays in mind (either New Year’s Eve or Christmas) or are linked to game updates that include additions to the game or changes in the game’s mechanics (new cards, units, balancing, etc.).
Here, for example, is the headline of a phishing website targeted at Clash of Clans players. It was designed specially for New Year’s Eve, and, according to the published description, the developer of the game supposedly gives out New Year’s gifts to players, including game currency, building level upgrades, etc.
The address of the website contains the phrase “eventchristmasandnewyear”, which makes the website look even more credible.
Victims can choose what they want from a list that includes gold, crystals, resources, and building upgrades.
The intention of the fraudsters becomes obvious as early as at the next step, where victims are prompted fill out a form by entering the credentials of their Google and Facebook accounts. After that, these credentials are passed on to the fraudster and the victims are robbed of both of their accounts.
The form created by the fraudsters offers “authorization” with Google and Facebook credentials
Also, fraudsters reacted quickly to the release of the latest updates, which included new battle arenas and legendary cards. On behalf of Supercell, players were offered their choice of one of the “legendaries”, as well as gold and crystals. Of course, in order to obtain these, Google and Facebook credentials were required.
One of their recent releases was “a gift from the developers”, which gives the player the option of selecting their desired hero or resources
Input fields for credentials
After sending the credentials, the victim receives a message to confirm their registration. It can be assumed that the evildoers may need this to ascertain the authenticity of the user-specified credentials.
To avoid falling victim to this fraudulent scheme, it is a good idea to follow these simple rules: do not use any links from social network groups, especially if the groups are not official, or from e-mail messages received from unknown users, even though they may promise you progress in the game or imminent profit. It certainly couldn’t hurt to install good security software that features anti-phishing functionality with database updates on malicious and phishing links that cover every subject. If the “free lunch” being offered proves to be too tempting, then go to the game developer’s official website and verify whether the holiday offer is genuine.