
Then the threat actor leaked 1.8M identity cards belonging to citizens of the Madhya Pradesh state on their forum.
Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
25 million Mathway user records available for sale on the dark web
25.5.2020 Securityaffairs Incindent
A threat actor is offering for sale on a dark web marketplace a database containing 25 million user records belonging to the Mathway.
A data breach broker, known as Shiny Hunters, is offering for sale on a dark web marketplace a database that contains 25 million user records for Mathway.
Early May, Shiny Hunters attempted to sell on a dark web marketplace databases containing more than 73.2 million user records from 11 different companies.
Shiny Hunters started offering the Tokopedia dump, then it began proposing 22 million user records for Unacademy and data allegedly obtained from the hack of the Microsoft’s GitHub account.
Recently the group has begun selling databases for the meal kit and food delivery company HomeChef, the photo print service ChatBooks, and Chronicle.com.
Mathway is a free math problem solver, from basic algebra to complex calculus, it instantly solves users’ math problems simply by typing their problem in (or point their camera and snap a pic!). Users will receive instant free answers through their website or mobile apps (both iOS and Android).
The Mathway app has over 10 million installs on Android Play Store and the Apple Store.
The dump was discovered by cyber intelligence firm Cyble, which confirmed that the archive was being sold in private sales in underground markets.
The Shiny Hunters group is offering for sale the Mathway database for $4,000.
Users’ records in the dump include email addresses and hashed passwords.
“We are aware of reports of a potential data compromise. We are working with cybersecurity experts to investigate further, and will take the appropriate steps to ensure the security of customer information.” reads a statement published by Mathway.
Mathway is currently investigating the security breach, meantime its users should also change their password on the site and on any other site where they used the same credentials.
Mathway users could check if their account was impacted by the data breach by querying the Cyble’s AmIBreached data breach lookup service.
Personal details and documents for millions of Indians available in the deep web
24.5.2020 Securityaffairs Incindent
Researchers have discovered a dump containing 29.1M Indian jobseekers personal details that was offered for free in the hacking underground.
Researchers discovered a dump containing 29.1M Indian jobseekers personal details that was offered for free in the hacking underground.
An anonymous entity told Cyble researchers that the data were stored on an unprotected elastic search instance that is no longer accessible.
While Cyble was investigating the issue, a threat actor published more than 2,000 Indian Identity cards (Aadhaar cards) on one hacking forum, files appears to have originated from 2019.

Then the threat actor leaked 1.8M identity cards belonging to citizens of the Madhya Pradesh state on their forum.
“Cyble has indexed this information on their data breach monitoring and notification platform, Amibreached.com. People who are concerned about their information leakage, can ascertain the risks by registering to the platform.” reads the post published by Cyble.
Cyble researchers also discovered that a threat actor posted 2.3 GB (zipped) file on one of the hacking forums.
This time the leak contains a lot of personal details of millions of Indians Job seekers from different states. At the time of writing this article, the experts are still investigating the source of the leak.
“It appears to have originated from a resume aggregator given the sheer volume and detailed information.” state the experts.
“Cyble researchers have identified a sensitive data breach on the darkweb where an actor has leaked personal details of ~29 Million Indian Job Seekers from the various states. The original leak appears to be from a resume aggregator service collecting data from various known job portals. Cyble’s team is still investigating this further and will be updating their article as they bring more facts to the surface. This breach includes sensitive information such as email, phone, home address, qualification, work experience etc.”
Crooks could use personal information exposed in both data leaks to conduct various malicious activities, including identity thefts, scams, and corporate espionage.
Online education site EduCBA discloses data breach and reset customers’ pwds
24.5.2020 Securityaffairs Incindent
The online education portal EduCBA discloses a data breach and is resetting customers’ passwords in response to the incident.
Online education website EduCBA discloses a data breach, it has started notifying customers that in response to the incident it is resetting their passwords.
EduCBA is a leading global provider of skill based education with 500,000+ members across 40+ Countries. It offers 2500+ courses prepared by top-notch professionals from the Industry to help participants achieve their goals successfully.
The company is notifying by email the incident to its customers confirming that their data have been accessed by an unauthorized party.
“Therefore, as a caution, we have invalidated passwords of all the users. You may retrieve your password here,” the data breach notification.
The data breach notification doesn’t include technical details about the attack, it only states that email, name, password, courses visited, etc may have been compromised.
The online education website states that no financial information was exposed as they use third-party processors such as PayPal and 2Checkout to process payments. 
Source BleepingComputer
As a precaution, EduCBA states that they have reset all user’s passwords.
As usual, customers that have used their EduCBA credentials at other sites have to change their passwords at these sites too.
Customers should remain vigilant of cyber attack, crooks may use their data to carry out spear-phishing attacks.
Voter information for 2 millions of Indonesians leaked online
24.5.2020 Securityaffairs Incindent
A hacker has leaked the 2014 voter information for close to 2 million Indonesians on a well-known hacker forum and threatens to release 200 million.
A threat actor has published the 2014 voter information for close to 2 million Indonesians on a popular hacker forum and threatens to release data for a total of 200 million voters.
The dump includes voter records in individual PDF files that were allegedly stolen from the general election commission of Indonesia KPU.
According to intelligence firm Under the Breach, the PDFs were organized by Indonesia cities, threat actor leaks information on 2,300,000 Indonesian citizens. Leaked details include names, addresses, ID numbers, birth dates, and more, they appear to date back to 2013.
The KPU replied that the data was public information, it was available for anyone during the 2014 election. The KPU highlighted that its systems were not hacked.
Online education site EduCBA discloses data breach after hack
24.5.2020 Bleepingcomputer Incindent
Online education site EduCBA has started notifying customers that they are resetting their passwords after suffering a data breach.
EduCBA is an online education site based out of India that offers over 2,500 online courses and job oriented learning programs focus on finance, technology, and business to their 500,000 learners.
Yesterday, EduCBA began emailing data breach notifications to customers stating that their systems were hacked and user data was exposed.
The notification is a bit strange as it does not go into great detail about what information was stolen and simply states, "email, name, password, courses visited, etc may have been compromised."
BleepingComputer has emailed EduCBA to clarify what other information is referenced by 'etc' but has not heard back as of yet.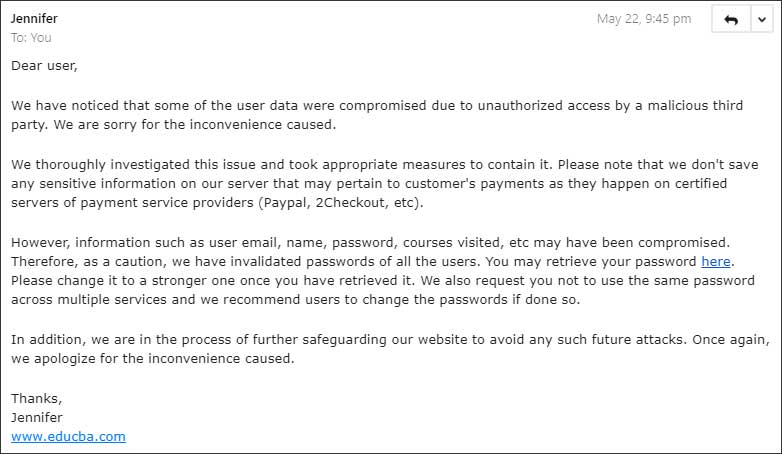
Source: BleepingComputer
They have stated that no financial information was accessed as they use third-party processors such as PayPal and 2Checkout to process payments.
As a precaution, EduCBA states that they have reset all user's passwords.
"Therefore, as a caution, we have invalidated passwords of all the users. You may retrieve your password here," the data breach notification reads.
A comment on twitter, though, states that the password for their account was not reset.
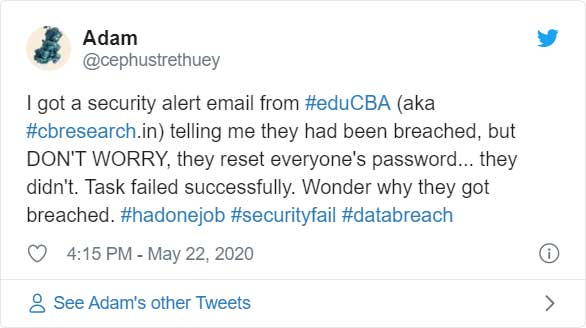
If you have an account at EduCBA, you should immediately change your password to a unique one only used at that site.
If your EduCBA password was used at other sites, it is strongly advised that you change the passwords at these sites to a strong and unique one as well.
Voter info for millions of Indonesians shared on hacker forum
24.5.2020 Bleepingcomputer Incindent
A threat actor has shared the 2014 voter information for close to 2 million Indonesians on a well-known hacker forum and claims they will release a total of 200 million at a later date.
In the forum post, the threat actor states that the voter records are stored in individual PDF files that they took from the KPU, the general election commission of Indonesia.
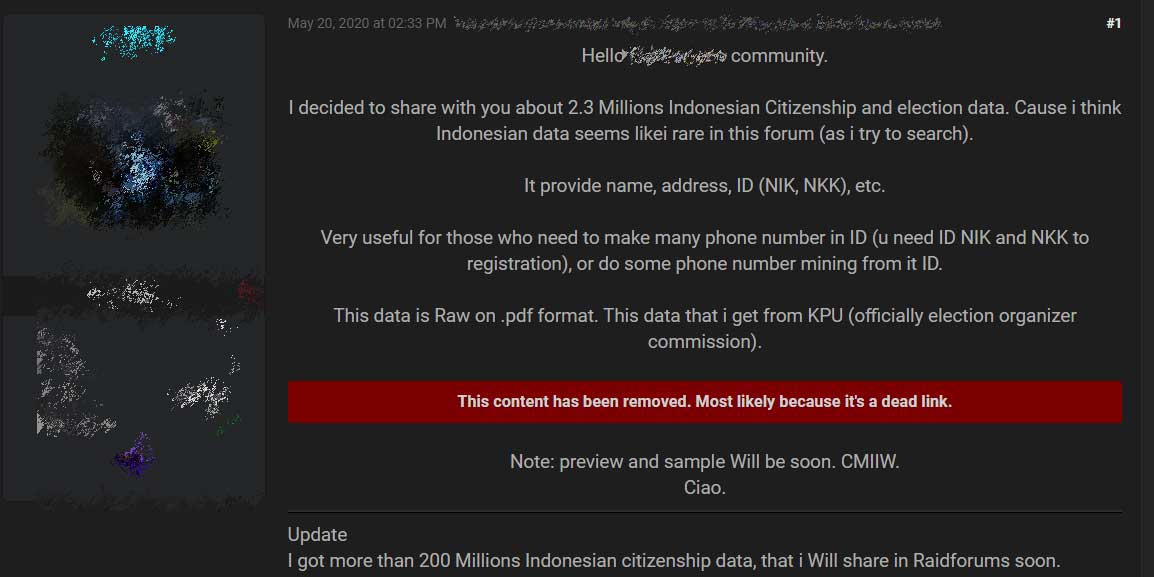
Forum post leaking the voter information
Cyber intelligence firm Under the Breach, who shared a sample with BleepingComputer, stated that these PDFs were organized by Indonesia cities.
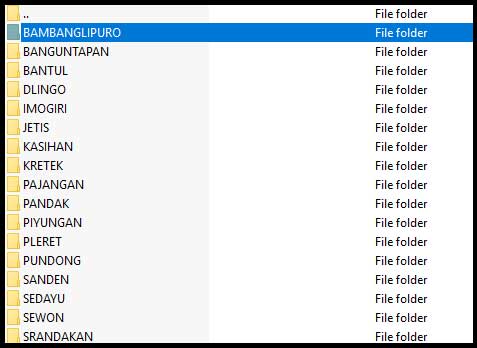
Data organized by city
In each folder are PDF files that contain the ID numbers, names, places of birth, dates of birth, and addresses for Indonesian voters, as can be seen below.
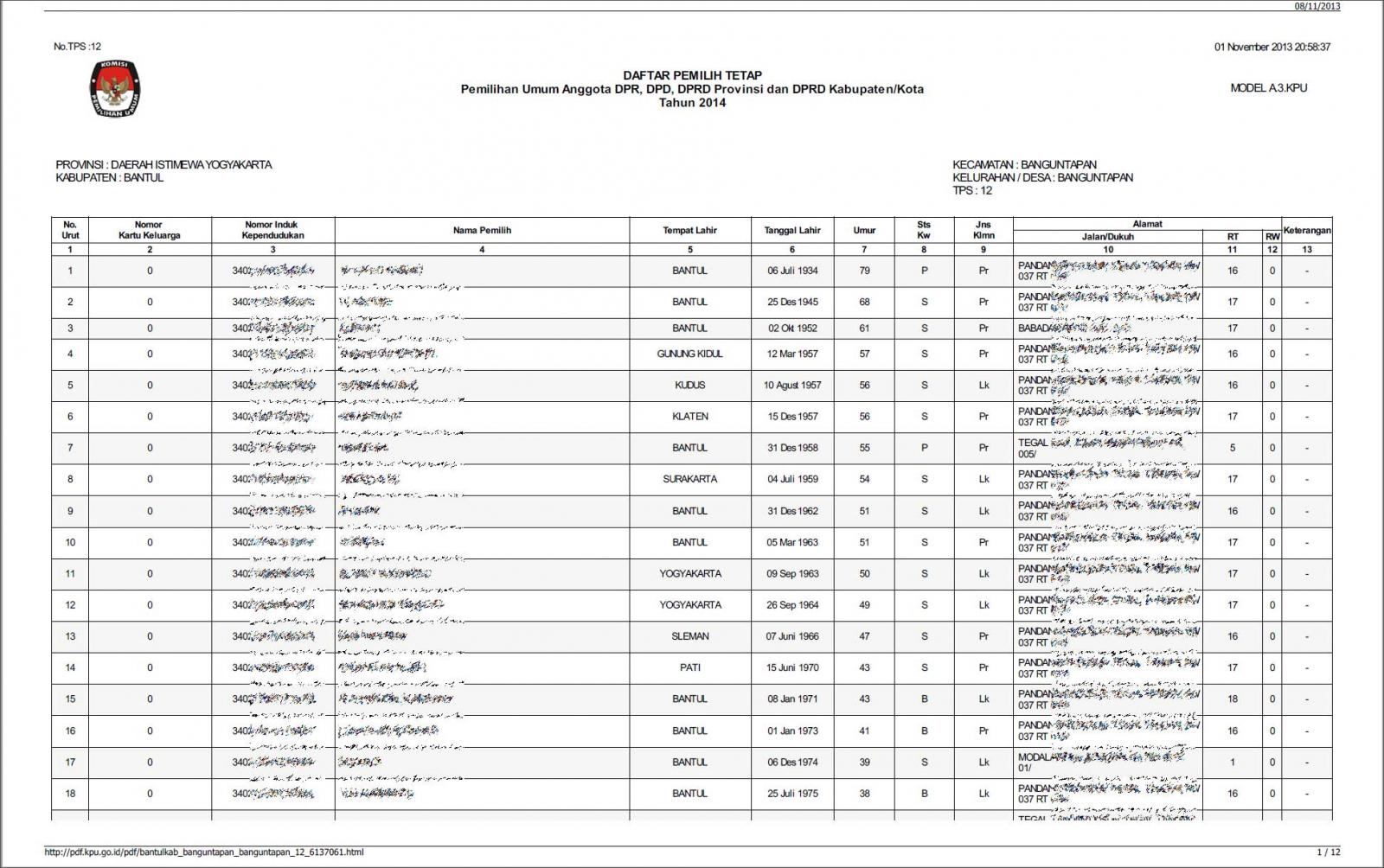
Example of PDF containing voter information
The KPU tweeted a statement that the data was not leaked or hacked, but that it was public information to anyone during the 2014 election.
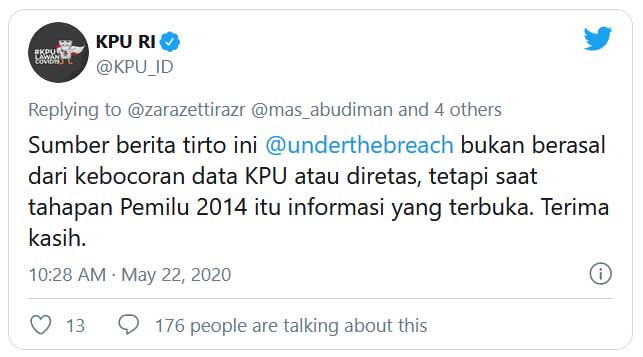
If this data was actually meant to be public, as expressed by Under the Breach, it even more concerning that such sensitive data was released on purpose.
In a comment to the New York Times, the KPU stated they are looking into the breach but continue to deny that they were hacked.
Mathway investigates data breach after 25M records sold on dark web
24.5.2020 Bleepingcomputer Incindent
A data breach broker is selling a database that allegedly contains 25 million Mathway user records on a dark web marketplace.
Mathway is a calculator that allows users to type in math questions and receive an answer for free through their website or via Android and iOS apps.
The Mathway app is top-rated, with over 10 million installs on Android and ranked as #4 under education in the Apple Store.
Earlier this month, cyber intelligence firm Cyble told BleepingComputer that they were tracking a potential data breach of Mathway after a purported database was being sold in private sales.
This week, a data breach seller known as Shiny Hunters began to publicly sell an alleged Mathway database on a dark web marketplace for $4,000.

Mathway database advertisement
In a sample of the database shared with BleepingComputer, the most concerning of the exposed data are the email addresses and hashed passwords. Otherwise, the data is mostly what appears to be system data.
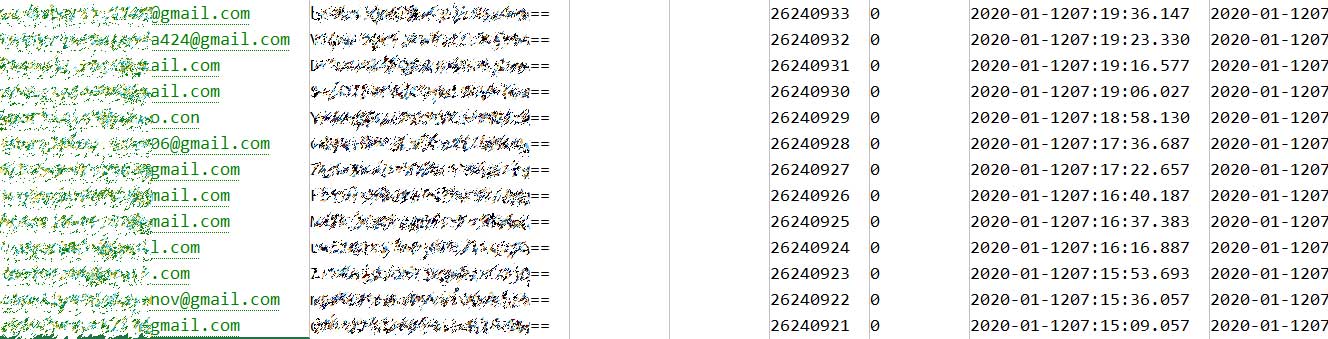
Database sample
Mathway told BleepingComputer that they are currently investigating the reports of a data breach.
"We are aware of reports of a potential data compromise. We are working with cybersecurity experts to investigate further, and will take the appropriate steps to ensure the security of customer information." Mathway said in a statement to BleepingComputer.
In a second email, Mathway told BleepingComputer that they should have more information soon.
If you use Mathway and want to check if your account is part of this breach, you can use Cyble's AmIBreached data breach lookup service.
To be safe, all Mathway users should also change their password on the site.
If you use this same password at any other site, you should change it to a new unique password at that site as well.
It is suggested that you use a password manager to help keep track of unique and complex passwords at every site that you visit.
Hacker shares 40 million Wishbone user records for free
23.5.2020 Bleepingcomputer Incindent
A hacker has leaked 40 million Wishbone user records that contain a treasure trove of information that could be used to perform phishing campaigns, account takeovers, and credential stuffing attacks.
BleepingComputer has been able to independently confirm that the data is legitimate as it contains user records for people we know have used the app and who have confirmed the accuracy of the data.
Wishbone database leaked on hacker forums
Wishbone is a popular app for iOS and Android that allows users to create comparisons between two images that people can then vote on.
For weeks, BleepingComputer has been aware of a data breach broker selling an alleged database containing 40 million user records for the Wishbone app through private deals.
According to cyber intelligence firm Cyble, who shared this information with BleepingComputer, the database was circulating privately since March.
Yesterday, a different data breach seller publicly advertised the sale of the Wishbone database on a popular hacker forum where they were selling it for $8,000.
Wishbone database for sale
This seller told BleepingComputer in previous conversations that he collects, trades, and buys databases from data breaches and then sells them to others.
We were also told that this database was dumped at the end of January 2020.
Today, another data breach seller and competitor known as Shiny Hunters, decided to leak the entire database for free on the same hacker forum.
Wishbone database leaked for free
Shiny Hunters have been responsible for the sale of numerous data breaches, including one for Microsoft's private GitHub repository. Since then, some of these have been confirmed as data breaches by the affected companies.
We can expect to see tensions escalate between the two threat actors as both brokers are known to sell legitimate data.
This could lead to other private databases being leaked for free as each tries to spoil the other's sales.
What's in the database
Samples of the Wishbone database have been shared with BleepingComputer that unfortunately contains a great deal of data that can be useful to threat actors.
This exposed data includes usernames, email addresses, hashed MD5 passwords, mobile numbers, Facebook and Twitter access tokens, gender, date of birth, MD5, profile images, and much more.
A full list of the exposed information can be seen in the leaked table structure below:
uid,username,email,name,mobile_number,country_code,fbid,access_token,auth_token,ip,create_time,twitter_id,twitter_access_token,twitter_access_secret,gender,date_of_birth,password,image,follower_count,device_token,android_device_token,is_admin,timezone,displaying_post_date,is_device_active,shared_for_date,show_second_session_date,apple_idfa,google_advertiser_id,stickers_left,deleted_at,updated_at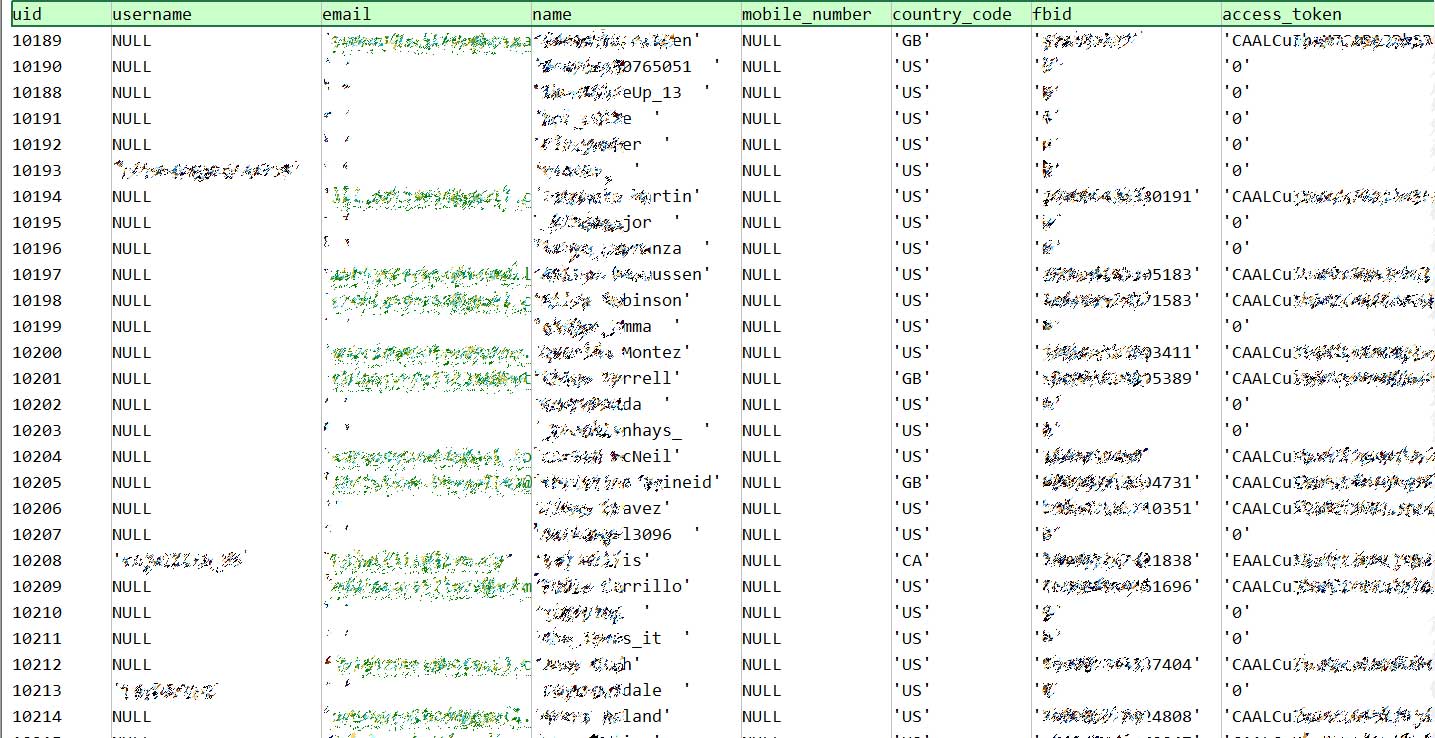
Sample of records in database
BleepingComputer has contacted Wishbone with a sample of the data but has not received a response.
Unfortunately, this is typical for companies that we contact to notify of alleged data breaches.
What should Wishbone users do now?
As some of the exposed data in this database file has been confirmed as accurate, it does appear to be a legitimate breach.
Due to this, out of an abundance of caution, I would suggest that all Wishbone users immediately change their passwords on the app.
If they have logged in via Facebook or Twitter, it is also suggested that you disconnect these apps from your Facebook account and Twitter accounts until it is confirmed if the data breach is real.
Finally, if you use your Wishbone password at other sites, you should change it there.
To check if your information was exposed in this database, you can check using Cyble's AmIBreached data breach lookup service.
Home Chef Serves Up Data Breach for 8 Million Records
22.5.2020 Threatpost Incindent
The meal-kit company’s customer records were leaked as part of the Shiny Hunters breach.
Mail-order meal kits have become even more popular as the coronavirus pandemic has kept people home and cooking on a regular basis. Unfortunately, one of these, the popular Kroger’s Home Chef service, recently served up a side of data breach along with its perfectly measured ingredients.
According to a notice posted on the Home Chef website, the company “recently learned of a data security incident impacting select customer information.” That info includes email addresses, names, phone numbers, encrypted passwords and the last four digits of credit-card numbers.
Perhaps most importantly for any fraudsters planning to use the information, “other account information such as frequency of deliveries and mailing address may also have been compromised,” Home Chef said – data that a cybercriminal could use to cook up a convincing phishing email.
The “encrypted passwords” are no guarantee against account takeover, security researchers warned.
“While the customer passwords in the leaked database were encrypted, there are tools that cybercriminals can leverage to decrypt them and potentially gain access to a number of accounts across multiple services that their victims use,” said Anurag Kahol, CTO at Bitglass, via email, adding that 65 percent of people use the same password for multiple or all of their accounts. “All consumers, not just users impacted by this incident, should improve their password hygiene by diversifying their login credentials across different accounts in order to mitigate the chances of their account being hijacked.”
The service is notifying all impacted customers and is urging password changes; it also said that “we are taking action to investigate this situation and to strengthen our information-security defenses to prevent similar incidents from happening in the future.”
It offered no details as to how the breach occurred – Threatpost has reached out for comment.
Unfortunately, meal-kit companies are a somewhat obvious target for attackers during pandemic time, according to James Carder, chief security officer and vice president of LogRhythm.
“Home Chef is one of the key players in the multi-billion-dollar meal -kit delivery industry and is owned by one of the biggest supermarket retailers, Kroger,” he said, via email. “A company of this size must take responsibility for ensuring that sufficient security measures are in place to protect customer data and rapidly respond to cyberthreats. This is especially true now, as demand for deliver services continues to grow amid the coronavirus crisis. All companies in this sector must not falsely assume that they are immune to attack just because they have become an essential service to help people during a challenging time.”
The company didn’t specify how many customers were affected, but earlier this week Bleeping Computer reported that the company was one of several caught up in the Shiny Hunters credential dump bonanza on an underground forum. In all, 8 million records were put up for sale from Home Chef starting two weeks ago, according to the outlet.
The Shiny Hunters group made a splash earlier this month, allegedly compromising 73.2 million user records from over 11 companies worldwide.
The group claimed that it broke into Microsoft’s GitHub account and stole 500 GB of data from the tech giant’s own private repositories on the developer platform. Researchers earlier this month also observed Shiny Hunters stealing log-in data for 91 million users of Indonesia’s largest e-commerce platform, Tokopedia, and then selling it on the dark web for $5,000.
The Florida Unemployment System suffered a data breach
22.5.2020 Securityaffairs Incindent
Officials revealed that the Florida Unemployment System suffered a data breach that impacted some residents who have made unemployment claims.
The Florida Department of Economic Opportunity revealed that the Florida Unemployment System suffered a data breach that impacted some residents who have made unemployment claims.
It has notified 98 people that have been impacted by the incident, government representatives didn’t disclose when the breach took place either the number of the affected individuals and the type of information compromised.
The agency spokeswoman Paige Landrum announced that the breach was addressed within one hour after the officials became aware of it. The Florida Department of Economic Opportunity is offering tho the impacted citizens identity protection services for free.
Impacted users should be vigilant and report any unauthorized activity on their financial accounts.
“The DEO has received more than 2 million claims seeking unemployment benefits from Floridians since the coronavirus pandemic caused mass business closings around the state, though only 1.6 million claims have been verified.” reported the AP agency. “Just under 1 million jobless workers in Florida have been paid more than $2.6 billion in benefits.”
State Sen. Linda Stewart, D-Orlando, expressed concern about the response of the agency to the security breach and the measures it has adopted to prevent future incidents. Stewart sent a letter to Department of Management Services Secretary Jonathan Satter, whose office oversees information technology for other state agencies.
“Given the agency’s (DEO) track record with processing unemployment applications, I’m sure you will understand the great concern I have that all remedies have been quickly taken and that Floridians can be assured that their personal information is now secured and will be protected from future attacks,” Stewart wrote.
The good is that the Florida Department of Economic Opportunity is not aware of malicious activity abusing exposed data.
Industry Reactions to Verizon 2020 DBIR: Feedback Friday
22.5.2020 Securityweek Incindent
Verizon this week published its 2020 Data Breach Investigation Report (DBIR). The report is based on insights from thousands of incidents and it’s more detailed and more thorough than ever.
The report covers threat actors, including their activities and their tools, an analysis of the targeted industries, and a regional analysis.
According to Verizon, malware incidents are down, external hackers were behind most breaches, and a majority of attacks were financially motivated.
Industry professionals comment on Verizon 2020 Data Breach Investigation Report (DBIR)
Industry professionals have commented on various findings in the latest DBIR.
And the feedback begins...
Tim Erlin, VP, product management and strategy, Tripwire:
“We often think of ransomware as a breach, but the DBIR categorizes most ransomware activity as an incident because while you may have lost access to the data, the attacker hasn’t actually stolen it. While that may give you some comfort, it doesn’t mean that a ransomware incident is materially less impactful to the security folks who have to deal with it.
The fact that “misconfiguration” is in the top five action varieties for breaches is an important acknowledgment that not all incidents are the result of an exploited vulnerability. Misconfigurations actually lead to more breaches than exploited systems, but organizations often don’t put the same effort into assessing them as they do scanning for vulnerabilities.
At a high level, the key things for every organisation to worry about are brute force and stolen credentials, and web applications.
It’s tempting to downplay vulnerability management based on this data, but the details show that, by and large, the organizations that are doing it reasonably well are safer, and the organizations that aren’t are very, very vulnerable. One key lesson, though, is that an organization can do both. The old adage “you can’t protect what you don’t know about” is true for vulnerability management. Asset management is a prerequisite for vulnerability management.”
Chad Anderson, senior security researcher, DomainTools:
“This report further goes to show that attackers do not have to be sophisticated to be effective. We see that only 45% of all breaches in this report involved some kind of traditional hacking and only 4% of the breaches in total had more than four attacker actions. Simple, low-hanging fruit for financial gain continues to dominate this space and shows where so much of our security posture can be improved with user education and basic, industry-standard security practices.
Phishing and trojans are down and ransomware is up as Ransomware-as-a-Service (RaaS) groups like REvil are on the rise. Lots of work has gone into spotting phishing domains early with machine learning algorithms and endpoint detection is improving all the time. This makes sense as most of the breaches featured in this report focus on financially motivated organized crime groups. RaaS pays, especially in this COVID-era where attackers are targeting hospitals and essential businesses that may not have the time to turn around and properly rebuild their infrastructure after key data and parts have been compromised.”
Bob Rudis, chief data scientist, Rapid7:
“First: Attacker dwell time is significantly reduced, but that matters little to ransomware attackers, an attack vector that has only gotten worse over time. We need to keep improving this statistic, but also need to work even harder on preventing phishing attacks and shoring up internal configurations.
Second: It is no real surprise that naked S3 buckets and wide-open databases received a significant mention in the DBIR. The Rapid7 team finds millions of SMB servers, databases, and other inappropriately exposed services each time we run our Project Sonar scans. Organisations must implement stronger controls and have finely honed practices and playbooks for deploying services safely.
Third: Zombie credentials never die, they just get re-used in every gosh darn attack. Attackers have amassed a cadre of billions of credentials and that stash seems to get bigger every week. There is so little risk in reusing them (either because organisations are blind to the login attempts or because regional authorities just don't seem to care) and so much to gain when one set of credentials actually works, that we'll continue to see this mode of attack until organisations finally implement multi-factor authentication across the board.”
Jamie Akhtar, CEO and co-founder, CyberSmart:
“The fact that 28% of cybercrime victims are small businesses comes as no surprise- this is a trend we have seen for a while. It's a real misconception that any business is too small to be targeted. As we continually see, that's just not how a lot of these large-scale attacks work. But small organisations, especially those who have little IT expertise on staff, often aren't sure where to start when it comes to protecting themselves from threats. This is why the UK government's Cyber Essentials scheme is so helpful; it provides proven standards for basic cyber hygiene that any business (or individual for that matter) can follow to safeguard against the vast majority of these kinds of attacks.”
Mark Bower, SVP, comforte AG:
“The report shows the Great Digital Train Robbery is alive and well. External, multi-faceted and industrialized hacking continues to pepper large enterprises at 72% of overall victims. It’s no surprise that web application patters, around 45% of attacks, expose technology services firms, retail, financial and Insurance services and professional services most to compromise. They are the highest aggregators of highly sensitive data with substantial 3rd party data sharing risk.
Personal data theft is trending up, now 49% of retail breaches, overtaking payment data at 47% putting privacy regulation risk high on the compliance agenda. 70% of breaches were from external actors, insiders 30%, and human left doors open in 22% of cases. In a world quickly moving to post-covid cloud IT, now 24% of investigated breaches, enterprises have no choice but to modernise data security strategies to neutralize data from attack or become a victim.
The numbers don’t lie - the barrier between attackers and valuable sensitive data can be broken, enabling rapid data theft and abuse unless the real data has no value in the attacker’s hands. Industries that progressively shielded data with contemporary security measures like data tokenization and encryption showed a strong decline in breach impact (POS attack incidents trended close to zero), but attackers followed the path of least resistance – to online compromise opportunities – now 50% of retail breaches.”
Tim Mackey, principal security strategist, Synopsys CyRC (Cybersecurity Research Center):
“In all cyberattacks, it is the attacker who defines the rules, and often opportunism is the best play in any numbers game. The 2020 DBIR confirms that most successful breaches employed opportunistic tactics ranging from social engineering and credential attacks through to opportunistic hacks and exploits of misconfigurations. This means that we could see a material reduction in breaches if basic principles such as securing S3 buckets, applying password security to databases, having a patch management strategy and applying reasonable malware protections were in place.
If we look beyond the basics and dig into an attack strategy, such as exploiting a vulnerability, we’re really looking at targeting a process and exploiting its weaknesses. In the case of a vulnerability exploit, the success is directly related to both a patch management strategy and how accurate the software asset management list matches what’s currently deployed. The exploit becomes actionable if there is any software that isn’t part of the asset manifest which then means it’s likely missing patches. While such manifests and processes are manageable when describing systems managed by enterprise IT teams, the weakest and most opportunistic link could be the remote worker or an employee’s mobile device which creates a bridge between the processes of enterprise IT and the practices of consumer “IT”. This is why zero-trust network architectures are interesting and also why patch policies must include open source governance – attackers look for blind spots in process as those blind spots enable them to invest in more sophisticated attacks.”
Murali Palanisamy, CEO, appviewX:
"Drilling down into Verizon's 2020 version of the DBIR tells us two things: One, the number of incidents and data breaches is snowballing year-on-year, confirming the trend that digital transformation will result in threat vectors compounding and growing in number. And two, hacking for financial gain has taken precedence over malware and other low-impact techniques as the primary motivator for malicious actors.
The need for heightened security infrastructures for all systems (internal, external, critical, and peripheral) notwithstanding, there are simply too many endpoints today to be protected individually by security teams -- given that hackers are actively gunning to exploit even the tiniest weak link in the system. Automation of security systems is the name of the game here, which will not only reduce the manual effort involved (which eliminates human error), but also allow for enterprises to scale security along with business growth at every level, without having to expend time and effort on implementing it from scratch when it is needed -- scalability is the most important buzzword in high growth ecosystems in this day and age.”
Balaji Parimi, CEO, CloudKnox Security:
“The Verizon DBIR validates something we’ve been seeing for a long time – that cloud storage misconfigurations are on the rise and emerging as one of the top threats to cloud infrastructure. Managing cloud infrastructure is very complex and the unprecedented levels of automation leaves a lot of room for these types of mistakes. Enterprises need to adopt a prevention first approach, by making sure that only properly trained personnel have the permissions to perform such risky operations. AWS and other cloud providers are touting this as one of the top security priorities to address this misconfiguration problem.”
Satnam Narang, Staff Research Engineer, Tenable:
“The findings in the Data Breach Investigations Report (DBIR) 2020 show that while attack vectors may fluctuate over time, cybercriminals often set their sights on low-hanging fruit. Zero-days may garner most of the attention, but foundational cyber hygiene issues enable most breaches. The motivation for cybercriminals is primarily financial. As the Cybersecurity and Infrastructure Security Agency (CISA) recently underscored in a recent report about the top 10 routinely exploited vulnerabilities, cybercriminals focus their efforts on exploiting unpatched vulnerabilities. It’s a cost-effective measure that provides the most bang for the buck, because they don’t have to spend the capital needed to acquire zero-day vulnerabilities when there are so many unpatched systems to take advantage of. As the DBIR notes, even if a newly-discovered vulnerability wasn’t patched in a network, those same systems would likely also be vulnerable to a plethora of other vulnerabilities, which signifies a lack of basic cyber hygiene.
Ransomware increased by 2.6% from last year, landing at number three in the most common Malware breach variety, while also taking the number two spot for most common malware incident variety, according to the DBIR. What’s changed in that time is that ransomware isn’t solely devoted to encrypting files anymore. Cybercriminals have escalated their attacks to another level, siphoning off sensitive information from organizations whose files they’ve encrypted. These cybercriminals threaten to publish this sensitive information publicly, often publicly sharing a teaser of files from organizations they’ve compromised. The belief is that naming and shaming these victims would encourage them to pay the ransom demand, and in many cases, that’s proven to be true.”
Chris Morales, head of security analytics, Vectra:
“The 2020 Verizon DBIR highlights who is targeting what industry and what they are doing. Attribution is interesting in the sense that it demonstrates who is behind a breach and what they do. The motives behind an attack tend to be consistent for each industry, as does the risk and data in those industries.
Nevertheless, what happened last year will only paint a partial picture of the tools, tactics and procedures being implemented now in what is a dramatically shifted threat landscape over the last few months. A threat landscape that might be more permanent than temporary.
For example, an increase in the use of SaaS, such as Office 365 and Zoom, for intrusion and lateral movement techniques. The higher obfuscation of command and control and data exfiltration in companies that previously would never allow remote work from home.”
Shahrokh Shahidzadeh, CEO, Acceptto:
“The Verizon DBIR highlights the top actions for breaches, which continue to be credentials, misconfiguration and phishing. Credentials are still the favorite attack surface, and within the past three years, range fluctuates between 75%-81%. The reduction in malware is aligned with the previous year’s trend and is a function of the risk balloon getting squeezed as alternative attacks reward balance out. Besides, if you think about January 2020 alone, and weigh in the key breaches reported during the first month of 2020, then you will realize the shift is insignificant.
These reports are usually a trailing indicator given a significant number of breaches that occurred in 2019 simply have not been discovered yet. And yes, understanding the threat balloon risk and the associated financial motivation is how we deal with risk management. That said, any <6% reduction is simply noise.”
Rick Holland, Chief Information Security Officer, Vice President Strategy, Digital Shadows:
“The prominence and continued use of stolen credentials indicates that there is still work to be done to prevent breaches.
One thing that strikes me about this year's DBIR report is that the data set is pre-pandemic. The "current state of security" is dramatically different today than it was two months ago. I'm very interested to see how the new remote working paradigm impacts next year's report.
It is essential to understand the data set and limitations for any reporting. The fact that the DBIR's primary analytical data focus is from the 2019 caseload doesn't devalue the report; there are still many year over year trends that are useful for defenders. Also, the DBIR should serve as one of many data points in your risk management strategy, which should be complemented by an organization's own internal incident and breach reporting.”
Olivier Gaudin, CEO and founder, SonarSource:
“The findings from the Verizon report demonstrate that, as an industry, we are spending more time reacting to threats rather than proactively taking steps to ensure assets are secure before they go to market. This is why it’s crucial to think about security as early as when developers are actually coding applications. Technology that provides code security feedback throughout software development workflows does exist, and not only will it help organizations prevent future incidents, it also supports the growth of their development team with regards to bolstering the security of the product. Developers get to learn and leverage secure coding practices, resulting in more secure applications delivered to end-users. This type of technology can also identify and eliminate the most commonly exploited web app vulnerabilities, according to Verizon’s report--SQL injection and PHP injection vulnerabilities.”
Data Breach Hits Florida Unemployment System
22.5.2020 Securityweek Incindent
Some Florida residents who have made unemployment claims may have had personal data stolen, officials said Thursday.
The Florida Department of Economic Opportunity has notified 98 people who were part of a data breach associated with unemployment claims, agency spokeswoman Paige Landrum said in an email. Officials didn’t say when the breach occurred, how many people were affected or what information was taken.
The breach was addressed within one hour of officials learning of it, Landrum said. In an abundance of caution, the department is making available identity protection services at no charge to affected individuals, Landrum said. Victims have been advised to report any unauthorized activity on their financial accounts.
The DEO has received more than 2 million claims seeking unemployment benefits from Floridians since the coronavirus pandemic caused mass business closings around the state, though only 1.6 million claims have been verified. Just under 1 million jobless workers in Florida have been paid more than $2.6 billion in benefits.
State Sen. Linda Stewart, D-Orlando, expressed concern about the breach Thursday in a letter to Department of Management Services Secretary Jonathan Satter. Satter’s department oversees information technology for other state agencies.
“Given the agency’s (DEO) track record with processing unemployment applications, I’m sure you will understand the great concern I have that all remedies have been quickly taken and that Floridians can be assured that their personal information is now secured and will be protected from future attacks,” Stewart wrote.
The DEO has not received any reports of malicious activity, Landrum said.
Santander, one of the biggest European banks, was leaking sensitive data on their website
22.5.2020 Securityaffairs Incindent
Santander Consumer Bank, the Belgian branch of the bank, had a misconfiguration in its blog domain that was allowing its files to be indexed.
Our new research recently discovered a security issue with Santander, the 5th largest bank in Europe and the 16th largest in the world. This Spanish multinational bank controls approximately $1.4 trillion in total assets globally, and has a $69.9 billion total market capitalization on the Euro Stoxx 50 stock market index.
Our analysts found that the Belgian branch, Santander Consumer Bank, has a misconfiguration in its blog domain, allowing its files to be indexed.
When we looked through these files, we were able to see sensitive information, including an SQL dump and JSON file that can be used by hackers to potentially phish Santander’s bank customers.
We contacted Santander immediately when we discovered the misconfiguration on April 15. Representatives from the leading European bank responded to our emails and seem to have fixed the issue, as we are presently unable to access the information.
A Santander Consumer spokesperson said:
“The incident highlighted relates specifically to the Santander Consumer Bank Belgium blog only. The blog contains only public information and articles, and therefore no customer data or critical information from the blog has been compromised. Our security team has already fixed the issue to ensure the blog is secure.”
What exactly is wrong with the Santander website?
When we visited the Santander blog on its Belgian domain, we noticed that the www endpoint of the blog subdomain had a misconfiguration that allowed all of its files to be indexed by search engines
Included in these indexed files was an important info.json file that seemed to contain its Cloudfront API keys.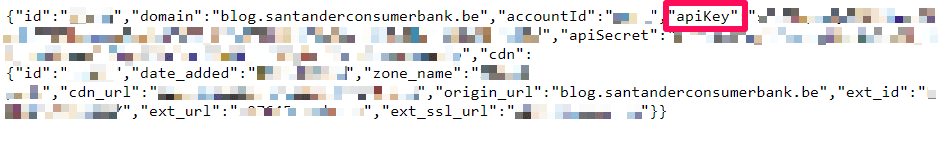
Cloudfront is a Content Display Network (CDN) created by Amazon. Websites use CDNs to host large files, such as videos, PDFs, large images and other static content, that would normally slow down their own websites. Because these large files are hosted on the CDNs instead, websites are faster for users.
If a hacker were to get a hold of Santander’s apparent Cloudfront API keys, they would be able to switch out the content hosted on Cloudfront with any other content.
For example, if a PDF or Word document was hosted on Cloudfront, and this document contained sensitive information – such as what accounts a customer should send money to – then the hacker would be able to switch that document out with their own version. In that way, they’d be able to change the real account number to his own, and thereby steal the customer’s money.
If a static HTML file was hosted, then the hacker would be able to switch that out with an entire webpage, allowing them to create a phishing page to steal the user’s financial information, all while on Santander’s official Belgian domain.
How to protect yourself
On April 15, we notified Santander’s Belgian website of the misconfiguration, and on April 24 they responded and seem to have fixed the issue. Their CyberSecurity Team stated: “We take cyber security seriously and strive to maintain the highest security standards and best practices and welcome responsible disclosure attitudes in security researchers.”
When we checked for the misconfiguration again on April 27, we received the following message:
Forbidden
You don’t have permission to access this resource.
For Santander’s customers, as well as all other banking customers, we’d recommend that you always check the domain and subdomain that a suspicious bank email is sending you to. Make sure that the domain is the bank’s real domain, but also know that important financial information requests would never be hosted on the blog subdomain of a bank.
Editor’s note: this article was updated on May 19 to reflect new information in collaboration with BitSight that the keys may not have been active Cloudfront API keys at the time of our discovery.
Original post:
https://cybernews.com/security/one-of-biggest-european-banks-leaking-sensitive-data-on-website/
Meal delivery service Home Chef discloses data breach
22.5.2020 Securityaffairs Incindent
Meal delivery service Home Chef has confirmed that it recently suffered a security breach that exposed its customer information.
Meal delivery service Home Chef has disclosed a data breach that exposed its customer information. Home Chef also explained that only a portion ot its customers were impacted in the security incident.
In early May, Shiny Hunters hacking group started offering for sale the databases containing tens of millions from user records from over 11 companies.
Below the complete list published by BleepingComputer:
Company User Records Price
Tokopedia 91 million $5,000
Home Chef 8 million $2,500
Bhinneka 1.2 million $1,200
Minted 5 million $2,500
Styleshare 6 million $2,700
Ggumim 2 million $1,300
Mindful 2 million $1,300
StarTribune 1 million $1,100
ChatBooks 15 million $3,500
The Chronicle Of Higher Education 3 million $1,500
Zoosk 30 million $500
At the time, the Shiny Hunters were offering more than 8 million records for $2500.
Now the company confirmed the data breach, saying that the incident has impacted select customer information.
Exposed data includes email addresses, names, phone numbers, hashed passwords, and the last four digits of credit card numbers.
“Was My Credit Card Information Compromised? Home Chef does not store complete credit or debit card information” reads the FAQ published by the company.
“Information such as frequency of deliveries and mailing address may also have been compromised,”.
Home Chef also underlined the fact that it does not store complete credit or debit card information. The company is investigating the incident and announced that it is taking action to strengthen its security defenses and prevent similar incidents in the future.
Although the company stores passwords in encrypted format, it recommends users to change the password in an abundance of caution following these process:
Visit www.homechef.com
Click on “Log in”
Click on “Account Information”, which is located under the “Account” dropdown menu
Complete the “Change Your Password” section and click “Save your settings.” There’s no need to adjust the other sections on the Account page (e.g. “Subscription”)
Home Chef users should remain vigilant against phishing attacks and suspicious activity in their accounts.
The company is notifying the incident to the impacted users.
Hackers Start Leaking Files Stolen From Shipping Giant Toll
22.5.2020 Securityweek Incindent
Hackers claim to have obtained more than 200 GB of archived data from Australian transportation and logistics giant Toll, and they have already started leaking it after the company refused to pay a ransom.
Toll admitted earlier this month that it was hit by ransomware for the second time this year. The company initially said that the attack, which involved Nefilim ransomware, did not result in any data getting stolen, but it later confirmed that the cybercriminals did manage to steal some files after gaining access to a corporate server.
Toll said the compromised server stored information on current and former employees and details on commercial agreements with enterprise customers, but claimed that customer operational data was not exposed.
Nefilim is designed to encrypt files on infected systems, but its operators are also known to steal data from victims and threaten to make it public if a ransom is not paid.
Toll said it would not be paying the ransom and the cybercriminals announced on Wednesday on their website that they are releasing “part 1” of the stolen files.
The website set up by the cybercriminals is named “Corporate Leaks” and it can be accessed via the Tor anonymity network. It currently stores information allegedly stolen from seven companies that refused to pay up.
The cybercriminals claim to have stolen more than 200 GB of archived files from Toll and they have so far made available a 2 GB archive.
SecurityWeek has seen a list of over 18,000 files that the hackers claim to have stolen from Toll, and these only appear to be the files included in the “part 1” archive. They seem to include various types of financial documents, such as financial reports, board reports, payroll documents, and invoices, going as far back as 2003. However, none of the files in the list appears to be more recent than 2018.
In a statement published on Wednesday, Toll informed customers that “the attacker has now published to the dark web some of the information that was stolen from that server.”
“As a result, we are now focused on assessing and verifying the specific nature of the stolen data that has been published. As this assessment progresses, we will notify any impacted parties as a matter of priority and offer appropriate support,” the company said.
According to its website, Toll has more than 40,000 employees and a global logistics network that spans across 1,200 locations in over 50 countries.
Japan suspects HGV missile data leak in Mitsubishi security breach
21.5.2020 Securityaffairs Incindent
Japan continues to investigate a cyberattack that hit this year Mitsubishi Electric Corp., it suspects a possible leak of data including details of a prototype missile.
Japan is still investigating a cyberattack that was disclosed by Mitsubishi Electric Corp. early this year.
In January, the company disclosed a security breach that might have exposed personal and confidential corporate data, at the time, it claimed that attackers did not obtain sensitive information about defense contracts.
Mitsubishi revealed that personal data on some 8,000 people also might have been leaked.
The breach was detected almost eight months ago, on June 28, 2019, with the delay being attributed to the increased complexity of the investigation caused by the attackers deleting activity logs.
The intrusion took place on June 28, 2019, and the company launched an investigation in September 2019. Mitsubishi Electric disclosed the security incident only after two local newspapers, the Asahi Shimbun and Nikkei, reported the security breach.
Mitsubishi Electric had also already notified members of the Japanese government and the Ministry of Defense.
Now, the authorities suspect a data leak that could have exposed details of a prototype missile.
“The suspected leak involves sensitive information about a prototype of a cutting-edge high speed gliding missile intended for deployment for the defense of Japan’s remote islands amid China’s military assertiveness in the region.” states the AP press agency.
“The ministry suspects the information might have been stolen from documents sent from several defense equipment makers as part of a bidding process for the project, Mitsubishi Electric did not win the bid, Japanese media reports said.”
The advanced prototype missile was designed to be deployed in Japan’s remote islands as a deterrence to military activities conducted by China in the area.
Chief Cabinet Secretary Yoshihide Suga announced that the Defense Ministry is investigating “the possible impact of the information leak on national security.”

The Defense Ministry was working on a prototype of supersonic missile known as HGV, a technology also being studied by the U.S., China, and Russia.
In January, the two media outlets attributed the cyber attack to a China-linked cyber espionage group tracked as Tick (aka Bronze Butler).
The hacker group has been targeting Japanese heavy industry, manufacturing and international relations at least since 2012,
According to the experts, the group is linked to the People’s Republic of China and is focused on exfiltrating confidential data.
The ministry suspects the information might have been stolen from documents sent from several defense equipment makers as part of a bidding process for the project, Mitsubishi Electric did not win the bid, Japanese media reports said.
Other Japanese defense contractors were hit by cyber attacks, including NEC Corp. , Pasco Corp. and Kobe Steel Ltd.
Meal Kit Service Home Chef Confirms Data Breach
21.5.2020 Securityweek Incindent
Subscription meal kit service Home Chef has confirmed that it recently suffered a data breach impacting customer information.
Earlier this month, a group of hackers referred to as 'Shiny Hunters' started advertising on the dark web data stolen in several fresh data breaches, including information claimed to have been stolen from Home Chef.
At the time, the hackers were demanding $2,500 for the data stolen from Home Chef, claiming to be in the possession of no less than 8 million such records.
Chicago-based Home Chef this week confirmed the breach, saying that the incident has impacted “select customer information.”
According to the company, the hackers accessed user data such as email addresses, names, phone numbers, hashed passwords, and the last four digits of credit card numbers.
“Information such as frequency of deliveries and mailing address may also have been compromised,” the company says.
Home Chef also underlined the fact that it does not store complete credit or debit card information.
“We are taking action to investigate this situation and to strengthen our information security defenses to prevent similar incidents from happening in the future,” the company notes.
Although the company does not store plaintext passwords, users are advised to change their account passwords. They are also advised to remain vigilant against phishing attacks and to keep an eye out for any suspicious activity in their accounts.
Home Chef also explained that not all of its customers were impacted in the incident, and that those who did not receive a notification of the breach yet were likely not affected, at least not directly.
What the company has yet to confirm is the total number of impacted users.
Home Chef announces data breach after hacker sells 8M user records
21.5.2020 Bleepingcomputer Incindent
Home Chef, a US-based meal kit and food delivery service, announced a data breach today after a hacker sold 8 million user records on a dark web marketplace.
Last week, BleepingComputer reported that a hacking group actor named Shiny Hunters was selling the user records for eleven companies on a dark web marketplace. The threat actor was selling these databases for $500 to $2,500.
The user records for Home Chef was one of the databases being sold and allegedly contained 8 million user records.

Dark web marketplace ad for Home Chef database
The threat actor was selling this database for $2,500 and provided a sample showing the type of information in the database table.
This information includes a user's email, encrypted password, last four digits of their credit card, gender, age, subscription information, and more.
Sample of the sold user database
At the time of our reporting, BleepingComputer emailed Home Chef but never received a response.
Home Chef issues data breach notification
Now, almost two weeks later, Home Chef has officially disclosed the data breach in a "Data security incident" notice posted to their web site.
"Protection of customer data is a top priority for Home Chef, and we work hard to safeguard our customers’ information. We recently learned of a data security incident impacting select customer information," their data security incident FAQ states.
According to this notification, Home Chef states that a customer's email address, name, phone number, encrypted passwords, the last four digits of credit card numbers, and other account information were accessed.
Home Chef states that only the last four digits of a customer's credit card was accessed and that they do not store complete payment information in their databases.
In a statement to BleepingComputer, Home Chef confirmed that this data breach notification is related to the database that was being sold online.
What Home Chef customers should do
While the passwords leaked in this data breach were encrypted, threat actors can use programs to decrypt the password.
Therefore, if you are a Home Chef customer, you should immediately change your password to a strong and unique one.
If that same password was used at another site, you should change it at any other site that also uses it.
When changing your passwords, be sure to use a unique and strong password at every site so that a data breach does not affect your account at other companies.
Update 5/20/20: Updated article to include Home Chef's statement.
EasyJet hacked: data breach affects 9 million customers
21.5.2020 Bleepingcomputer Incindent
EasyJet, the UK's largest airline, has disclosed that they were hacked and that the email addresses and travel information for 9 million customers were exposed. For some of these customers, credit card details were also accessed by the attackers.
In a data breach notification disclosed today, EasyJet states that they have suffered a cyberattack, and an unauthorized third-party was able to gain access to their systems.
During this attack, the threat actors were able to access the email addresses and travel information for nine million customers. For approximately 2,208 customers, credit card details were also exposed.
"Our investigation found that the email address and travel details of approximately 9 million customers were accessed. These affected customers will be contacted in the next few days. If you are not contacted then your information has not been accessed. Other than as referenced in the following paragraph, passport details and credit card details of these customers were not accessed."
"Our forensic investigation found that, for a very small subset of customers (2,208), credit card details were accessed. Action has already been taken to contact all of these customers and they have been offered support," EasyJet stated in a "Notice of cyber security incident."
Once EasyJet learned of the attack, they notified the UK's National Cyber Security Centre and the ICO.
EasyJet states that they are notifying affected customers and that all of those affected will receive the notification by May 26th, 2020.
What should an EasyJet customer do?
If you are an EasyJet customer and are concerned you have been exposed or received a data breach notification, you should take the following steps.
As your travel information and email address have been exposed, you should be on the lookout for targeted phishing emails that utilize this info.
If you receive any emails about upcoming travel, do not reply with any sensitive information and instead go to easyjet.com to interact directly with the company.
Those whose credit card details were exposed should monitor their statements for any fraudulent activity and report anything detected immediately.
It is also suggested that you contact your credit card company, explain the situation, and request a new credit card and number to be safe.
BleepingComputer has contacted EasyJet for more information but has not heard back as of yet.
Japan Suspects Missile Data Leak in Mitsubishi Cyberattack
21.5.2020 Securityweek Incindent
Japan is investigating a possible leak of data including details of a prototype missile in a massive cyberattack earlier this year on Mitsubishi Electric Corp., officials said Wednesday.
The suspected leak involves sensitive information about a prototype of a cutting-edge high speed gliding missile intended for deployment for the defense of Japan’s remote islands amid China’s military assertiveness in the region.
Chief Cabinet Secretary Yoshihide Suga told reporters that the Defense Ministry is investigating “the possible impact of the information leak on national security.”
Suga declined to give further details.
The Defense Ministry has been studying a prototype missile known as HGV, which flies at supersonic speeds and is also being developed by the U.S., China and Russia.
The ministry suspects the information might have been stolen from documents sent from several defense equipment makers as part of a bidding process for the project, Mitsubishi Electric did not win the bid, Japanese media reports said.
Mitsubishi said in a statement Wednesday that it had reported to the Defense Ministry in February a possible leak of sensitive information related to a cyberattack earlier this year. Mitsubishi has acknowledged that its personal data on some 8,000 people also might have been leaked.
The company said it is continuing to cooperate with in the investigation, while pledging to step up its information security.
Several other Japanese defense contractors, including NEC Corp. , Pasco Corp. and Kobe Steel Ltd., were also hit by cyberattacks this year.
EasyJet data breach: 9 million customers affected
20.5.2020 Net-security Incindent
British low-cost airline group EasyJet has revealed on Tuesday that it “has been the target of an attack from a highly sophisticated source” and that it has suffered a data breach.
EasyJet data breach
The result? Email address and travel details of approximately 9 million customers and credit card details (including CVV numbers) of 2,208 customers were accessed.
How did the attackers manage to breach EasyJet?
EasyJet did not share in their official notice about the incident when it happened, but told the BBC that they became aware of it in January and that the customers whose credit card details were stolen were notified in early April.
They also did not say how the attackers got in, only that it seems that they were after “company intellectual property.” Grabbing customer info might have been an afterthought or a secondary goal, then.
Richard Cassidy, senior director security strategy at Exabeam, says that by looking at recent breaches in the aviation industry, the tools, tactics and procedures (TTPs) being used are largely the same ones that have led to significant breaches in other industries.
“Attackers need credentials to access critical data – we can be certain of this – and often it is social engineering techniques that reveal those credentials. They then laterally move through systems and hosts to expand their reach and embed themselves within the infrastructure, providing multiple points of entry and exit. If an attacker can achieve this – as we are seeing here – it is then a case of packaging and exfiltrating critical data,” he added.
“Some airlines are doing it right – implementing state of the art behavioural analytics technologies that learn the normal behaviour of the network and immediately notify the security team when anomalies occur. Many, however, still need to understand that there is a better way to manage security, risk and compliance requirements and it most certainly is not ‘what we’ve always done’. In an industry that has defined ‘automation’ and ‘process efficiencies’, applying the same to Information Security would quite literally revolutionise their ability to detect, respond and mitigate against the largely traditional raft of attack TTP’s we’ve seen targeted at aviation this past decade.”
Professor Alan Woodward of the University of Surrey noted that the stolen credit card information might have been the result of a Magecart attack:
It would not be the first time for an airline to be targeted by Magecart attackers – British Airways was hit in 2018.
Advice for affected customers
“There is no evidence that any personal information of any nature has been misused, however, on the recommendation of the ICO [the UK’s data protection watchdog], we are communicating with the approximately 9 million customers whose travel details were accessed to advise them of protective steps to minimise any risk of potential phishing,” said EasyJet Chief Executive Officer Johan Lundgren.
“We are advising customers to continue to be alert as they would normally be, especially should they receive any unsolicited communications. We also advise customers to be cautious of any communications purporting to come from easyJet or easyJet Holidays.
Unsolicited communications may take the form of fake invoices, refund offers, requests for additional data, and so on.
“Always check the sender name and email address match up and if you’re being asked to carry out an urgent action, verify the legitimacy of the request by contacting EasyJet directly using details on their website,” advised Tim Sadler, CEO, Tessian.
“Cybercriminals have not missed a trick to capitalize on the COVID-19 crisis, and we’ve seen a huge increase in the number of cyber attacks and scams during this time. The travel industry especially has been severely impacted by COVID-19, and there’s no telling how much more damaging this cyber breach will be to EasyJet’s future. Moving forward, organisations should prioritise security protocols, implement sophisticated protection software, and ensure all employees are aware of security best practices, and carrying them out at all times.”
The UK National Cyber Security Centre (NCSC) has advised affected customers to:
Be vigilant against any unusual activity in their bank accounts or suspicious phone calls and emails asking them for further information
Change their password on their EasyJet accounts (and other accounts that have the same password)
Check if their account has appeared in any other public data breaches, and to
Depending on their nature, report any fraud attempts to the police, the NCSC, and their bank’s fraud department.
Verizon Data Breach Report: DoS Skyrockets, Espionage Dips
20.5.2020 Threatpost Incindent
Denial of Service (DoS), ransomware, and financially-motivated data breaches were the winners in this year’s Verizon DBIR.
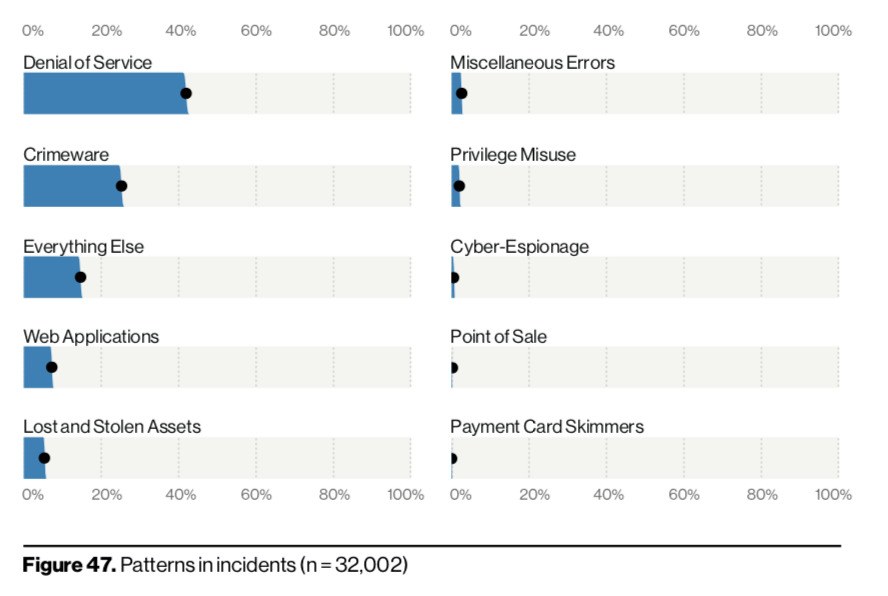
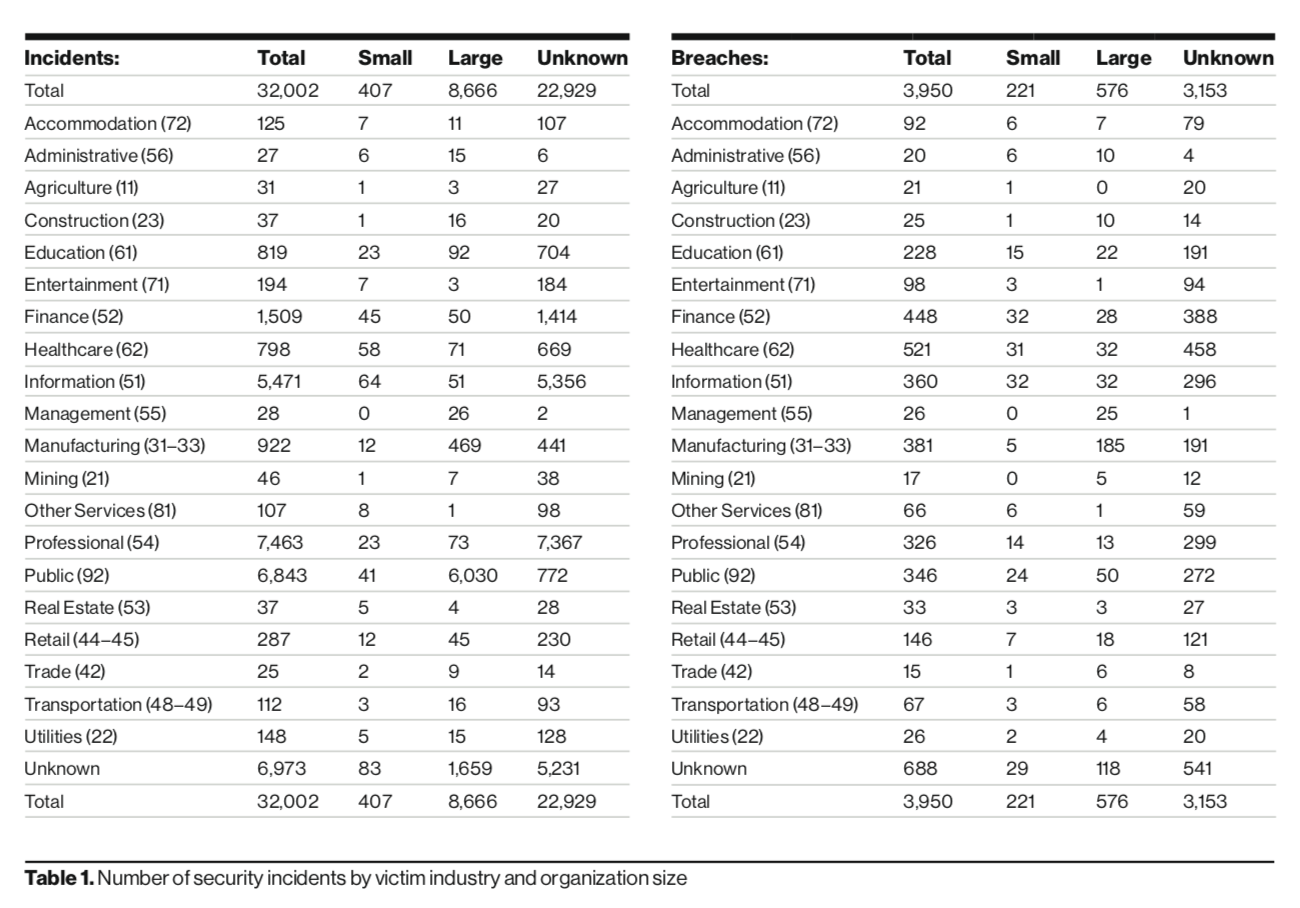
Denial-of-service (DoS) attacks have spiked over the past year, while cyber-espionage campaigns have spiraled downwards. That’s according to Verizon’s 2020 Data Breach Investigations Report (DBIR) released Tuesday, which analyzed 32,002 security incidents and 3,950 data breaches across 16 industry verticals.
Notably, this year DoS attacks increased in number (13,000 incidents) and were also seen as a bigger part of cybercriminals’ toolboxes (DoS attacks made up 40 percent of security incidents reported), beating out crimeware and web applications. While DoS attacks use differing tactics, they most commonly involve sending junk network traffic to overwhelm and crash systems. It doesn’t help that cybercriminals have been creating new and dangerous botnets to launch DoS attacks, like Kaiji or Mirai variants, over the past few years.
“While the amount of this traffic is increasing as mentioned, in DDoS, we don’t just look at the number of attacks that are conducted,” said researchers. “We also look at the bits per second (BPS), which tells us the size of the attack, and the packets per second (PPS), which tells us the throughway of the attack. What we found is that, regardless of the service used to send the attacks, the packet-to-bit ratio stays within a relatively tight band and the PPS hasn’t changed that much over time, sitting at 570 Mbps for the most common mode.”
Cyber espionage attacks meanwhile have seen a downward spiral, dropping from making up 13.5 percent of breaches in 2018 to a mere 3.2 percent of data breaches in 2019. That may come as a surprise given that espionage campaigns were actually on the rise in the 2019 Verizon DBIR. In addition, a slew of cyber espionage campaigns (such as ones targeting the WHO, several governments in the Asia-Pacific region and more) were unearthed over the past year – but researchers say under reporting may be a factor in the dipping statistics.
“The drop in raw numbers could be due to either under-reporting or failure to detect these attacks, but the increase in volume of the other patterns is very much responsible for the reduction in percentage,” said researchers.
In fact, financially motivated breaches continue to not only be more common than espionage campaigns by a wide margin (making up 86 percent of all breaches), but also increasing over the past year, they said.
Breach Origins
When it comes to data breaches, almost half (45 percent) stemmed from actual hacks, while 22 percent used social attacks. Twenty-two percent breaches involved malware and 17 percent were created by errors. And 8 percent of breaches stemmed from misuse by authorized users.
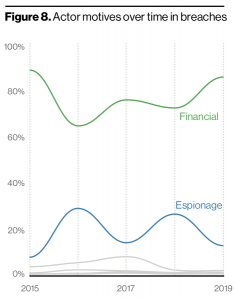
In fact, internal actors were only behind 30 percent of breaches, with the majority (70 percent) actually coming from external actors. While researchers said that incidents stemming from “insider actors” have grown over the past few years, that’s likely due to increased reporting of internal errors rather than evidence of actual malice from these actors.
“External attackers are considerably more common in our data than are internal attackers, and always have been,” said researchers. “This is actually an intuitive finding, as regardless of how many people there may be in a given organization, there are always more people outside it. Nevertheless, it is a widely held opinion that insiders are the biggest threat to an organization’s security, but one that we believe to be erroneous.”
Malware Down
Malware has been on a consistent and steady decline as a percentage of breaches over the last five years, researchers said, due in part to the increasing level of access by cybercriminals to credentials.
“We think that other attack types such as hacking and social breaches benefit from the theft of credentials, which makes it no longer necessary to add malware in order to maintain persistence,” said researchers.
Accordingly, the top malware “varieties” in data breaches was topped by password dumpers (which are used to collect credentials), followed by capture app data and ransomware.
Ransomware attacks continue to grow over the past year and have created high-profile headlines and headaches for companies, such as Norsk Hydro. Ransomware is the third most common “malware breach” variety and the second most common “malware incident” variety. Part of this continued growth can be explained by the ease with which attackers can kick off a ransomware attack, researchers stressed.
“In 7 percent of the ransomware threads found in criminal forums and market places, ‘service’ was mentioned, suggesting that attackers don’t even need to be able to do the work themselves,” said researchers. “They can simply rent the service, kick back, watch cat videos and wait for the loot to roll in.”
Vertical-Specific Findings
The Verizon DBIR also broke down data breaches by vertical to show that cybercriminals are drastically changing how they are targeting industries. For instance, Point of Sale (PoS)-related attacks once dominated breaches in the accommodation and food services industry – however, they have been replaces by malware attacks and web application attacks.
“Instead, responsibility is spread relatively evenly among several different action types such as malware, error and hacking via stolen credentials,” said researchers. “Financially motivated attackers continue to target this industry for the payment card data it holds.”
The educational services industry saw phishing attacks trigger 28 percent of breaches, and 23 percent of breaches stem from hacking via stolen credentials. Ransomware is a top threat for the education space, with ransomware accounting for approximately 80 percent of malware infections in the incident data.
Ransomware attacks, triggered by financial motivations, also plagued the healthcare industry. Other top security issues leading to breaches include lost and stolen assets and basic human error. However, privilege misuse, which has topped data breach causes for healthcare in the past, for the first time this year wasn’t an issue in the “top three”. In the 2019 report, privilege misuse at 23 percent of attacks, while in 2020, it has dropped to just 8.7 percent.
Despite that, “This year, we saw a substantial increase in the number of breaches and incidents reported in our overall dataset, and that rise is reflected within the Healthcare vertical,” said researchers. “In fact, the number of confirmed data breaches in this sector came in at 521 versus the 304 in last year’s report.”
Finally, financial and insurance industries were plagued by phishing attacks and web applications attacks that leverage the use of stolen credentials. The attacks in this sector are perpetrated by external actors who are financially motivated to get easily monetized data (63 percent), internal financially motivated actors (18 percent) and internal actors committing errors (9 percent).
The Positives
Breach timelines continue to show promising results. The number of companies discovering incidents in days or less is up, while containment in that same timeframe surpassed its historic 2017 peak.
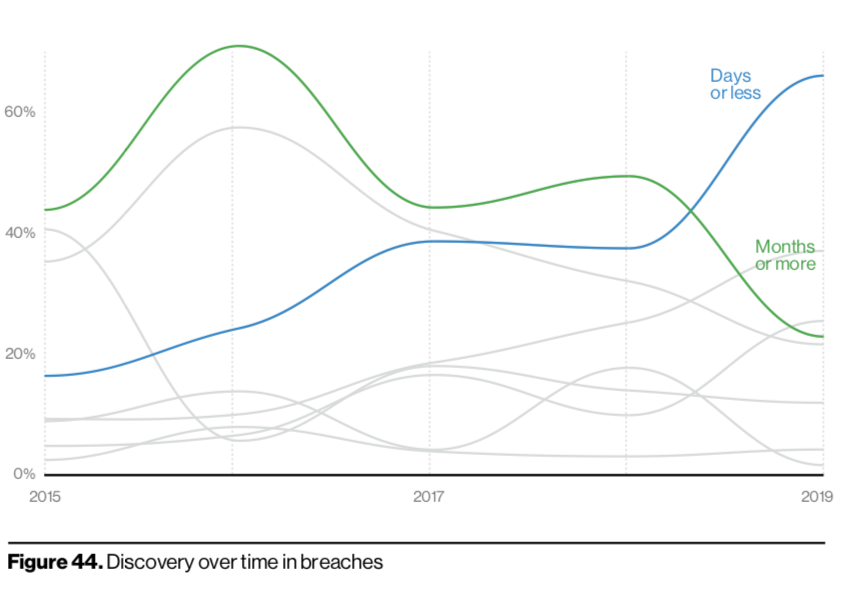
Researchers also warned to keep in mind that the positive incident response numbers are likely due to the inclusion of more breaches detected by managed security service providers (MSSPs) in the report’s sampling. Also, it still took a quarter of companies dealing with data breaches months or more.
“All in all, we do like to think that there has been an improvement in detection and response over the past year,” said researchers.
EasyJet Hackers Take Off with Travel Details for 9M Customers
20.5.2020 Threatpost Incindent
The vacation-centric airline is warning victims about social-engineering attacks.
European budget airline EasyJet has been hacked, with attackers making off with personal details for 9 million customers.
It was, the airline said, a “highly sophisticated attack” that exposed the email addresses and travel itineraries of the victims, along with payment-card information for 2,208 customers.
EasyJet CEO Johan Lundgren said that the effort overwhelmed what he characterized as the airline’s “robust” security profile.
“We take the cybersecurity of our systems very seriously and have robust security measures in place to protect our customers’ personal information,” he said in a media statement. “However, this is an evolving threat as cyberattackers get ever more sophisticated.” He added, “Every business must continue to stay agile to stay ahead of the threat. We will continue to invest in protecting our customers, our systems and our data.”
EasyJet said that it complied with regulations and reported the breach to the UK’s Information Commissioner’s Office (ICO), the watchdog responsible for information security. It’s also informing customers of the breach, it said, and has addressed the issue that allowed the attackers into their systems. There’s no word on the nature of that vulnerability — Threatpost has reached out for comment.
Affected EasyJet customers should be concerned over social-engineering attacks that could make use of the travel information to craft highly convincing emails bent on luring victims into clicking on a malicious link or attachment, or submitting more personal information via a phishing page.
“Since we became aware of the incident, it has become clear that owing to COVID-19 there is heightened concern about personal data being used for online scams,” Lundgren said. “As a result, and on the recommendation of the ICO, we are contacting those customers whose travel information was accessed and we are advising them to be extra vigilant, particularly if they receive unsolicited communications.”
Jeff Sakasegawa, trust and safety architect at Sift, noted that the issue comes at a particularly sensitive time for airlines as people restrict travel due to the coronavirus pandemic.
“Throughout this crisis, we’ve seen highly elevated fraud rates across the travel and transportation industry, as scammers continue to target carriers, hotels and aggregator sites despite lowered transaction volume,” he said via email. “The credit-card info exposed in this incident will very likely end up being sold through Dark Web marketplaces for pennies per card, and likely result in payment fraud attacks across a variety of websites. Travel merchants should be extra vigilant at this time and ensure they review all suspicious transactions in order to avoid costly chargebacks and penalty fees from payment providers.”
Loyalty card fraud is another potential follow-on issue.
“Phishing and credit-card information aside, gaining access to loyalty programs can make airline data breaches especially lucrative for attackers,” said Michael Reitblat, CEO and co-founder at Forter, via email. “Unlike consumer bank accounts and credit cards, loyalty programs typically aren’t well monitored by either the airline or the consumer. This makes air miles – a form of digital currency – an easy target. In fact, fraud attack rates against airlines increased by 72 percent last year. Credit monitoring is an important precaution, but customers should also monitor all airline loyalty accounts carefully to ensure fraudsters aren’t taking advantage of their miles.”
The airline industry is no stranger to data breaches, including high-profile incidents at British Airways and Cathay Pacific. BA for its part is facing a class-action lawsuit after exposing personal and financial details of a half-million customers, and was hit with a hefty $230 million fine last year. Cathay Pacific meanwhile was served an enforcement notice from the Hong Kong government last year, in the wake of “unauthorized personnel” accessing the personal data for up to 9.4 million passengers, including their passport numbers, along with a small amount of card information.
“We know by looking at recent breaches in the aviation industry the tools, tactics and procedures (TTPs) being used are largely the same ones that have led to significant breaches in other industries,” Richard Cassidy, senior director of security strategy at Exabeam, told Threatpost. “Attackers need credentials to access critical data — we can be certain of this — and often it is social-engineering techniques that reveal those credentials. Attackers then laterally move through systems and hosts to expand their reach and embed themselves within the infrastructure, providing multiple points of entry and exit. If an attacker can achieve this — as we are seeing here — it is then a case of packaging and exfiltrating critical data.”
Security Service of Ukraine arrested the popular hacker Sanix who sold billions of stolen credentials
20.5.2020 Securityaffairs Incindent
The Ukrainian Secret Service (SSU) has arrested a hacker known as Sanix, who was selling billions of stolen credentials on hacking forums and Telegram channels.
The popular hacker Sanix has been arrested by the Ukrainian Secret Service (SSU). The man is known in the cybercrime underground for selling billions of stolen credentials. The officials did not disclose the man of the cybercriminals, they only said that the man has been arrested in Ivano-Frankivsk, Ukraine.
“The Security Service of Ukraine has identified and detained a hacker known as Sanix. Early last year, it caught the attention of global cybersecurity experts by posting on one of the forums the sale of a database with 773 million e-mail addresses and 21 million unique passwords.” reads a press release published by the SSU.
“SBU cyber specialists recorded the sale of databases with logins and passwords to e-mail boxes, PIN codes for bank cards, e-wallets of cryptocurrencies, PayPal accounts, information about computers hacked for further use in botnets and for organizing DDoS attacks”
The man was known for aggregating data, including users’ credentials, in lists that were offered for sale via Telegram (where he used the nickname Sanixer) or in hacking forums.
Sanix was identified by the investigator Brian Krebs as the source of Collection 1 in January 2019. Some of the most popular collections sold in the past by the same hacker are known as Collection #1, #2, #3, #4, #5, Antipublic, and others.
Sanix has been active on the cybercrime underground at least since 2018, he focuses in the sale of stolen data from organizations.
It has been estimated that the man amassed billions of unique username-password combinations.
Stolen credentials were bought by fraudsters, hackers, and scammers to carry out a broad range of malicious activities, such as launching malspam campaign or take over users’ accounts.
During searches at his residence, SSU officers seized computer equipment containing two terabytes of stolen information, phones with evidence of illegal activities and cash from illegal transactions in the amount of almost 190,000 Ukrainian hryvnias (roughly $7,000) and more than $3000.