
Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
Gaming hardware manufacturer Razer suffered a data leak
14.9.20 Incindent Securityaffairs
Gaming hardware manufacturer Razer suffered a data leak, an unsecured database managed by the company containing gamers’ info was exposed online.
Gaming hardware manufacturer Razer has suffered a data leak, this is the discovery made by the security researcher Bob Diachenko. The expert discovered an unsecured database that exposed the information of approximately 100,000 individuals who purchased items from Razer’s online store
Razer is the world leader in high-performance gaming hardware, software and systems.
The unsecured database was discovered on August 19, it contained customers’ info, including a name, email address, phone number, order numbers, order details, and billing and shipping addresses.
“The exact number of affected customers is yet to be assessed, as originally it was part of a large log chunk stored on a company’s Elasticsearch cluster misconfigured for public access since August 18th, 2020 and indexed by public search engines,” he wrote in a post on LinkedIn. “Based on the number of the emails exposed, I would estimate the total number of affected customers to be around 100K.”
Diachenko attempted to report his discovery to Razer, but it took time before the database was secured on September 9th. The company thanked the researcher for his support.
“I have immediately notified the company via their support channel on the exposure, however my message never reached right people inside the company and was processed by non-technical support managers for more than 3 weeks until the instance was secured from public access.” continues the post.
“We were made aware by Mr. Volodymyr of a server misconfiguration that potentially exposed order details, customer and shipping information. No other sensitive data such as credit card numbers or passwords was exposed. The server misconfiguration has been fixed on 9 Sept, prior to the lapse being made public.” reads a statement from the vendor.
“We would like to thank you, sincerely apologize for the lapse and have taken all necessary steps to fix the issue as well as conduct a thorough review of our IT security and systems. We remain committed to ensure the digital safety and security of all our customers.”
Exposed data could be abused by threat actors to carry out spear-phishing attacks against the gamer and obtain other info, including financial data.
People that have ever purchased products from Razer’s online store must be vigilant about any unsolicited message from the gaming firm.
For any update on the incident always refer the Razer official website.
350 million decrypted email addresses left exposed on an unsecured server
28.8.20 Incindent Securityaffairs
Experts found an unsecured data bucket containing seven gigabytes worth of unencrypted files that include 350,000,000 strings of unique email addresses.
Original post at: https://cybernews.com/security/350-million-email-addresses-left-exposed-on-an-unsecured-server/
The CyberNews research team uncovered an unsecured data bucket owned by an unidentified party, containing seven gigabytes worth of unencrypted files that include 350,000,000 strings of unique email addresses.
The massive trove of emails was left on a publicly accessible Amazon AWS server, allowing anyone to download and access the data. This is a huge leak even by today’s standards, with an average of 7 million records being exposed daily in 2020.
As cyberattacks become ever more frequent and sophisticated across the board, both organizations and individuals are still struggling to catch up with cybercriminals when it comes to data security. The 350 million email leak discovered by CyberNews is only the latest example of this cybersecurity gap that continues to grow despite increasing investment in the security industry.
On June 10, the exposed S3 bucket was closed by Amazon and is no longer accessible.
To see if your email address has been exposed in this or other security breaches, use our personal data leak checker.
What data is in the bucket?
The publicly available Amazon S3 bucket contained 67 files.
21 files in the bucket were CSV files containing email addresses
Seven CSV files contained email addresses that were hashed
Seven CSV files contained emails that were hashed and salted for an additional layer of encryption using the unreliable MD5 algorithm
The remaining seven CSV files were unencrypted, each of which included 50,000,000 strings of unique email addresses of (presumably) US users
Example of leaked email addresses:

Besides the CSV files, the bucket also contained voice recordings of several sales pitches to digital marketers about RepWatch, which appears to be a long-defunct domain reputation management tool and may or – considering when the files were uploaded – may not be related to the CSV files stored in the bucket.
Screenshot from the latest forum discussion about RepWatch in 2013:

The CSV files appear to have included the same set of 350 million unique emails, separated into three groups: hashed, hashed and salted, and unencrypted files. The dates and times when the files were created suggest that the unidentified owner uploaded the files to the bucket in stages: hashed and salted emails were uploaded first, while the unencrypted files were uploaded last.
The timeline of uploads might indicate that these emails have been either stolen or acquired on the black market back in October 2018, and then gradually decrypted by the owner of the bucket.
Who had access?
The unsecured bucket was located in the US and hosted on an Amazon S3 server that has been exposed for what seems to be at least an 18-month period.
While it is unclear if any malicious actors have accessed the S3 bucket, anyone who knew where to look could have downloaded and accessed the CSV files, without needing any kind of permission.https://googleads.g.doubleclick.net/pagead/ads?client=ca-pub-5928161074779380&output=html&h=280&adk=3371048370&adf=3264790055&w=616&fwrn=4&fwrnh=100&lmt=1598550333&num_ads=1&rafmt=1&armr=3&sem=mc&pwprc=8526721217&tp=site_kit&psa=1&guci=1.2.0.0.2.2.0.0&ad_type=text_image&format=616×280&url=https%3A%2F%2Fcybernews.com%2Fsecurity%2F350-million-email-addresses-left-exposed-on-an-unsecured-server%2F&flash=0&fwr=0&pra=3&rh=154&rw=616&rpe=1&resp_fmts=3&wgl=1&fa=27&adsid=ChAI8LOd-gUQhY3UkNq_2aIvEkUAdIfKkOHmGMbt2swUA2nn0_5aF7_g8ORQhkUoQq9d0WsLRqhi8unJ-RyGTgtyOLUXx-Ef0J1azFcJqxKKpOSAKfBBJxI&dt=1598550333271&bpp=1&bdt=2329&idt=1&shv=r20200820&cbv=r20190131&ptt=9&saldr=aa&abxe=1&prev_fmts=0x0%2C616x280&nras=3&correlator=184525495110&frm=20&pv=1&ga_vid=310975659.1590091446&ga_sid=1598550333&ga_hid=1040183046&ga_fc=0&iag=0&icsg=171799229091&dssz=42&mdo=0&mso=0&u_tz=120&u_his=1&u_java=0&u_h=720&u_w=1280&u_ah=680&u_aw=1280&u_cd=24&u_nplug=3&u_nmime=4&adx=104&ady=3630&biw=1148&bih=481&scr_x=0&scr_y=0&eid=21066922%2C21066944&oid=3&pvsid=935534131577982&pem=827&rx=0&eae=0&fc=1408&brdim=0%2C0%2C0%2C0%2C1280%2C0%2C1280%2C680%2C1163%2C481&vis=1&rsz=%7C%7Cs%7C&abl=NS&cms=2&fu=8320&bc=31&jar=2020-08-27-17&ifi=2&uci=a!2&btvi=2&fsb=1&xpc=yhl9t2wzen&p=https%3A//cybernews.com&dtd=54
If the emails were stolen to begin with, however, their owners should assume that their email addresses have already been sold on the black market 18 months ago.
What can threat actors do with this data?
Although most people think that having their email exposed will not result in any serious damage, there are many reasons why email addresses are bought and sold on the dark web. In many cases, an email address is merely the first avenue of attack against an unsuspecting target and can conceivably cause the victim significant harm down the line.
Here are some examples of how potential attackers can use the data found in the unsecured Amazon S3 bucket against the owners of the exposed email addresses:
Spamming 350 million email IDs
Carrying out phishing attacks
Brute-forcing the passwords of the email accounts
Attackers can also combine the leaked email addresses with data from other breaches and build more detailed pictures of their potential targets. They can then conduct elaborate phishing and social engineering attacks to gain access to the victims’ accounts on other digital services such as entertainment and shopping platforms or even online banking.
In the worst-case scenario, an exceptionally successful phishing or social engineering attack can even lead to identity theft, whereby attackers accrue so much personal data from their target that they are then able to take out loans in their victim’s name.This is why large email lists can fetch relatively good prices on the black market, where emails can go for $5-$50 per 100,000 addresses depending on their quality. With 350 million unique email addresses stored in this bucket, the value of this leak could fall anywhere between $17,500 and $175,000.
What happened to the data?
Due to the fact that we were unable to identify the owner of the exposed data bucket, we reached out to Amazon to help them secure it on June 10. They were able to close the bucket on the same day.
What to do if you have been affected?
Since the number of emails exposed by the unidentified owner of the data bucket is so massive, there is a chance that your email address might be among those leaked.
To make sure your account is safe when it comes to this email breach, we recommend doing the following:
Use our personal data leak checker to see if your email has been leaked.
If your email happens to be among those leaked, we strongly recommend that you immediately change your email password.
Watch out for potential spam messages and phishing emails. Clicking on suspicious messages or any links therein is a risk that may result in your computer being infected with malware.
Even if your email address has not been exposed in this or other breaches, securing your email account is key if you want to keep it from joining the 7 million daily leaked records statistics cited above.
Here’s how:
Create long, strong, and unique passwords that are difficult to guess, or use a password manager to generate strong passwords for you.
Change your passwords approximately every 30 days.
Enable two-factor authentication (2FA) for as many of your online accounts as possible.
Freepik Discloses Data Breach Impacting 8.3 Million Users
24.8.20 Incindent Securityweek
Freepik Company, the organization behind the Freepik and Flaticon websites, has disclosed a data breach that impacted approximately 8.3 million of their users.
Freepik is a search engine that provides users with access to high-quality graphics resources, including images, vectors, illustrations, and the like. On Flaticon, users can find over 3 million vector icons in various file formats.
The attackers, Freepik Company explains, exploited an SQL injection vulnerability in Flaticon, which allowed them to access user information.
“[I]n our forensic analysis, we determined that an attacker extracted the email and, when available, the hash of the password of the oldest 8.3M users. To clarify, the hash of the password is not the password, and cannot be used to log into your account,” the company announced.
The company reveals that for 4.5 million of the affected users no hashed password was leaked, because federated logins (with Google, Facebook and/or Twitter) were used, exclusively. For these users, only the email address was leaked.
For 3.77 million users, both the email address and a hash of the password were leaked. 3.55 million of these passwords were hashed using bcrypt, while for the remaining 229,000 salted MD5 was used.
Freepik says that it has since updated the hash for all user passwords to bcrypt, and that those who had a password hashed with salted MD5 have been prompted to reset it.
“Users who got their password hashed with bcrypt received an email suggesting them to change their password, especially if it was an easy to guess password. Users who only had their email leaked were notified, but no special action is required from them,” the company announced.
Freepik also added that it is regularly scanning the passwords and emails that have been leaked on the Internet to identify those that match credentials of Freepik and Flaticon users, and that it disables any passwords found to have been leaked, while also notifying the affected users.
“Due to this incident, we have greatly extended our engagement with external security consultants and did a full review with a first-class agency of our external and internal security measures. We took some important short term measures to increase our security and have planned medium and long term extra security measures,” the company revealed.
Popular Freepik site discloses data breach impacting 8.3M users
22.8.20 Incindent Securityaffairs
Freepik, one of the most popular online graphic resources sites online has disclosed a security breach that impacted 8.3 Million users.
Freepik, the popular website that provides high-quality free photos and design graphics, has disclosed a major security breach that impacted 8.3 Million users.
Freepik says that hackers were able to steal emails and password hashes for 8.3M Freepik and Flaticon users in an SQL injection attack against the company’s Flaticon website.
Freepik is one of today’s most popular sites online, it is currently ranked #97 on the Alexa Top 100 sites list, while Flaticon is ranked #668.
The company is notifying the impacted registered users via email.
“We have recently notified all affected users of a security breach in Freepik Company, affecting Freepik and Flaticon. The security breach was due to a SQL injection in Flaticon that allowed an attacker to get some user’s information from our database.” reads the statement published by Freepik.
“We immediately notified the competent authorities of the breach, and in our forensic analysis, we determined that an attacker extracted the email and, when available, the hash of the password of the oldest 8.3M users.”
Freepik said the hacker obtained usernames and passwords for the oldest 8.3 million users registered on its Freepik and Flaticon websites.
According to the company, 4.5M out of these 8.3M user records had no hashed password because they used exclusively federated logins, this means that attackers only accessed their email address.
“For the remaining 3.77M users the attacker got their email address and a hash of their password,” continues the statement. “For 3.55M of these users, the method to hash the password is bcrypt, and for the remaining 229K users the method was salted MD5. Since then we have updated the hash of all users to bcrypt.”
The company did not disclose technical details of the incident, such as when the intrusion took place.
The company is currently investigating the incident.
In response to the incident the company canceled passwords for the accounts that had a password hashed with salted MD5 and urge them via email to reset the password.
“Users who got their password hashed with bcrypt received an email suggesting them to change their password, especially if it was an easy to guess password. Users who only had their email leaked were notified, but no special action is required from them.” reads the statement.
Experian South Africa Suffers Data Breach Affecting Millions; Attacker Identified
20.8.20 Incindent Thehackernews
The South African arm of one of the world's largest credit check companies Experian yesterday announced a data breach incident that exposed personal information of millions of its customers.
While Experian itself didn't mention the number of affect customers, in a report, the South African Banking Risk Information Centre—an anti-fraud and banking non-profit organization who worked with Experian to investigate the breach—disclosed that the attacker had reportedly stolen data of 24 million South Africans and 793,749 business entities.
Notably, according to the company, the suspected attacker behind this breach had already been identified, and the stolen data of its customers had successfully been deleted from his/her computing devices.
"We have identified the suspect and confirm that Experian South Africa was successful in obtaining and executing an Anton Piller order which resulted in the individual's hardware being impounded and the misappropriated data being secured and deleted."
Experian South Africa has already reported the breach to law enforcement and the appropriate regulatory authorities.
The company claims there is no evidence indicating whether the stolen data includes consumers' credit or financial information or used for fraudulent purposes before authorities had it deleted.
"Our investigations also show that the suspect had intended to use the data to create marketing leads to offer insurance and credit-related services."
"The compromise of personal information can create opportunities for criminals to impersonate you but does not guarantee access to your banking profile or accounts. However, criminals can use this information to trick you into disclosing your confidential banking details," says SABRIC CEO, Nischal Mewalall.
Besides releasing this information, SAFPS also recommended that credit reporting agency customers should immediately apply for a free Protective Registration listing with Southern Africa Fraud Prevention Service that has been designed to alert users when their identity is compromised.
You can also regularly check your credit report for free here.
Former Uber Security Chief Charged Over Covering Up 2016 Data Breach
20.8.20 Incindent Thehackernews
The federal prosecutors in the United States have charged Uber's former chief security officer, Joe Sullivan, for covering up a massive data breach that the ride-hailing company suffered in 2016.
According to the press release published by the U.S. Department of Justice, Sullivan "took deliberate steps to conceal, deflect, and mislead the Federal Trade Commission about the breach" that also involved paying hackers $100,000 ransom to keep the incident secret.
"A criminal complaint was filed today in federal court charging Joseph Sullivan with obstruction of justice and misprision of a felony in connection with the attempted cover-up of the 2016 hack of Uber Technologies," it says.
The 2016 Uber's data breach exposed names, email addresses, phone numbers of 57 million Uber riders and drivers, and driver license numbers of around 600,000 drivers.
The company revealed this information to the public almost a year later in 2017, immediately after Sullivan left his job at Uber in November.
Later it was reported that two hackers, Brandon Charles Glover of Florida and Vasile Mereacre of Toronto, were behind the incident to whom Sullivan approved paying money in exchange for promises to delete data of customers they had stolen.
All this started when Sullivan, as a representative for Uber, in 2016 was responding to FTC inquiries regarding a previous data breach incident in 2014, and during the same time, Brandon and Vasile contacted him regarding the new data breach.
"On November 14, 2016, approximately 10 days after providing his testimony to the FTC, Sullivan received an email from a hacker informing him that Uber had been breached again."
"Sullivan's team was able to confirm the breach within 24 hours of his receipt of the email. Rather than report the 2016 breach, Sullivan allegedly took deliberate steps to prevent knowledge of the breach from reaching the FTC."
According to court documents, the ransom amount was paid through a bug bounty program in an attempt to document the blackmailing payment as bounty for white-hat hackers who point out security issues but have not compromised data.
"Uber paid the hackers $100,000 in BitCoin in December 2016, despite the fact that the hackers refused to provide their true names (at that time)," federal prosecutors said. "In addition, Sullivan sought to have the hackers sign non-disclosure agreements. The agreements contained a false representation that the hackers did not take or store any data."
"Moreover, after Uber personnel were able to identify two of the individuals responsible for the breach, Sullivan arranged for the hackers to sign fresh copies of the non-disclosure agreements in their true names. The new agreements retained the false condition that no data had been obtained. Uber's new management ultimately discovered the truth and disclosed the breach publicly, and to the FTC, in November 2017."
Just last year, both hackers were pleaded guilty to several counts of charges for hacking and blackmailing Uber, LinkedIn, and other U.S. corporations.
In 2018, British and Dutch data protection regulators also fined Uber with $1.1 million for failing to protect its customers' personal information during a 2016 cyber attack.
Now, if Sullivan found guilty of cover-up charges, he could face up to eight years in prison, as well as potential fines of up to $500,000.
Experian South Africa discloses data breach, 24 million customers impacted
20.8.20 Incindent Securityaffairs
The South African branch of consumer credit reporting agency Experian disclosed a data breach that impacted 24 million customers.
The South African branch of consumer credit reporting agency Experian disclosed this week a data breach that impacted 24 million customers.
The company revealed that only personal information was exposed in the data breach, no financial or credit-related information was compromised.
The company declared that it has identified the origin of the attack and has already wiped stolen data from the devices used by the attackers.
The credit agency did not disclose the exact number of impacted users, but according to a report published by the South African Banking Risk Centre (SABRIC) the security incident may have impacted 24 million South African citizens and 793,749 local businesses.
“Experian – a consumer, business and credit information services agency – has experienced a breach of data which has exposed some personal information of as many as 24 million South Africans and 793 749 business entities to a suspected fraudster.” reads the report.
The company already reported the incident to law enforcement and the appropriate regulatory authorities and is going to notify the impacted customers.
The local authorities were able to identify the crooks behind the attack. A court order obtained by Experian allowed to seize the fraudsters’ equipment and stolen data was secured and deleted.
At the time the company is not aware of fraudulent use of the stolen data, it also pointed out that the attackers did not compromise its infrastructure.
“Our investigations indicate that an individual in South Africa, purporting to represent a legitimate client, fraudulently requested services from Experian. The services involved the release of information which is provided in the ordinary course of business or which is publicly available.” reads a statement released by the agency.
“We can confirm that no consumer credit or consumer financial information was obtained. Our investigations do not indicate that any misappropriated data has been used for fraudulent purposes. Our investigations also show that the suspect had intended to use the data to create marketing leads to offer insurance and credit-related services.”
“I would like to apologise for the inconvenience caused to any affected parties. Our first priority is to help and support consumers and businesses in South Africa.” said Experian Africa CEO Ferdie Pieterse.
Experian advises anyone who may have concerns to regularly check their credit report.
Google Chrome Browser Bug Exposes Billions of Users to Data Theft
11.8.20 Incindent Threatpost
The vulnerability allows attackers to bypass Content Security Policy (CSP) protections and steal data from website visitors.
A vulnerability in Google’s Chromium-based browsers would allow attackers to bypass the Content Security Policy (CSP) on websites, in order to steal data and execute rogue code.
The bug (CVE-2020-6519) is found in Chrome, Opera and Edge, on Windows, Mac and Android – potentially affecting billions of web users, according to PerimeterX cybersecurity researcher Gal Weizman. Chrome versions 73 (March 2019) through 83 are affected (84 was released in July and fixes the issue).
CSP is a web standard that’s meant to thwart certain types of attacks, including cross-site scripting (XSS) and data-injection attacks. CSP allows web admins to specify the domains that a browser should consider to be valid sources of executable scripts. A CSP-compatible browser will then only execute scripts loaded in source files received from those domains.
“CSP is the primary method used by website owners to enforce data-security policies to prevent malicious shadow-code executions on their website, so when browser enforcement can be bypassed, personal user data is at risk,” Weizman explained, in research released on Monday.
Most websites use CSP, the researcher noted, including internet giants like ESPN, Facebook, Gmail, Instagram, TikTok, WhatsApp, Wells Fargo and Zoom. Some notable names were not affected, including GitHub, Google Play Store, LinkedIn, PayPal, Twitter, Yahoo’s Login Page and Yandex.
To exploit the vulnerability, an attacker first needs to gain access to the web server (through brute-forcing passwords or another method), in order to be able to modify the JavaScript code it uses. Then, the attacker could add a frame-src or child-src directive in the JavaScript to allow the injected code to load and execute it, bypassing the CSP enforcement and thus bypassing the site’s policy, explained Weizman.
Because of the post-authentication aspect of the bug, it ranks as a medium-severity issue (6.5 out of 10 on the CvSS scale). However, because it affects CSP enforcement, this has vast implications,” Weizman said, comparing it to having an issue with seatbelts, airbags and collision sensors.
“[Because of the] increased perception of safety, the damage caused in an accident when this equipment is faulty is much more severe,” the researcher said. “In a similar way, website developers may allow third-party scripts to add functionality to their payment page, for example, knowing that CSP will restrict access to sensitive information. So, when CSP is broken, the risk for sites that relied on it is potentially higher than it would have been if the site never had CSP to begin with.”
The vulnerability was present in Chrome browsers for more than a year before being fixed, so Weizman warned that the full implications of the bug are not yet known: “It is highly likely that we will learn of data breaches in the coming months that exploited it and resulted in the exfiltration of personally identifiable information (PII) for nefarious purposes.”
Users should update their browsers to the latest versions to avoid falling victim to an exploit.
Intel investigates security breach after the leak of 20GB of internal documents
8.8.20 Incindent Securityaffairs
Intel is investigating reports of an alleged hack that resulted in the theft and leak of 20GB of data coming from the chip giant.
Intel is investigating reports that an alleged hacker has leaked 20GB of exfiltrated from its systems. The stolen data includes source code and developer documents and tools, some documents are labeled as “confidential” or “restricted secret.”
The hackers shared the documents on the file-sharing site MEGA.
The leak was first published by Till Kottmann, a Swiss software engineer, who manage a very popular Telegram channel on data leak. In the past, he shared data on several leaks from major companies including Microsoft, Adobe, GE, Disney, AMD, Lenovo, Motorola, Qualcomm, Mediatek, and Nintendo.
The engineering received the files from an anonymous hacker who claimed to have hacked the company earlier this year, the experts believe that this leak is just a first lot on a larger collection.
Several media outlets independently analyzed the data leak and verified the authenticity of the data.
“Per our analysis, the leaked files contained Intel intellectual property respective to the internal design of various chipsets. The files contained technical specs, product guides, and manuals for CPUs dating back to 2016.” reported ZDNet.
A company spokesperson told SecurityWeek that the data appears to come from the Intel Resource and Design Center. The Center manages information for use by our customers, partners and other external parties.
Below a list of the content included in the leak:
Intel ME Bringup guides + (flash) tooling + samples for various platforms
Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
Silicon / FSP source code packages for various platforms
Various Development and Debugging Tools
Simics Simulation for Rocket Lake S and potentially other platforms
Various roadmaps and other documents
Binaries for Camera drivers Intel made for SpaceX
Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
Kabylake FDK training videos
Intel Trace Hub + decoder files for various Intel ME versions
Elkhart Lake Silicon Reference and Platform Sample Code
Debug BIOS/TXE builds for various Platforms
Bootguard SDK (encrypted zip)
Intel Snowridge / Snowfish Process Simulator ADK
Various schematics
Intel Marketing Material Templates (InDesign)
The good news is that the leaked files doesn’t contain sensitive data about customers or employees of the chip maker.
Intel investigates security breach after the leak of 20GB of internal documents
7.8.2020 Incindent Securityweek
Intel is investigating reports of an alleged hack that resulted in the theft and leak of 20GB of data coming from the chip giant.
Intel is investigating reports that an alleged hacker has leaked 20GB of exfiltrated from its systems. The stolen data includes source code and developer documents and tools, some documents are labeled as “confidential” or “restricted secret.”
The hackers shared the documents on the file-sharing site MEGA.
The leak was first published by Till Kottmann, a Swiss software engineer, who manage a very popular Telegram channel on data leak. In the past, he shared data on several leaks from major companies including Microsoft, Adobe, GE, Disney, AMD, Lenovo, Motorola, Qualcomm, Mediatek, and Nintendo.
The engineering received the files from an anonymous hacker who claimed to have hacked the company earlier this year, the experts believe that this leak is just a first lot on a larger collection.
Several media outlets independently analyzed the data leak and verified the authenticity of the data.
“Per our analysis, the leaked files contained Intel intellectual property respective to the internal design of various chipsets. The files contained technical specs, product guides, and manuals for CPUs dating back to 2016.” reported ZDNet.
A company spokesperson told SecurityWeek that the data appears to come from the Intel Resource and Design Center. The Center manages information for use by our customers, partners and other external parties.
Below a list of the content included in the leak:
Intel ME Bringup guides + (flash) tooling + samples for various platforms
Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
Silicon / FSP source code packages for various platforms
Various Development and Debugging Tools
Simics Simulation for Rocket Lake S and potentially other platforms
Various roadmaps and other documents
Binaries for Camera drivers Intel made for SpaceX
Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
Kabylake FDK training videos
Intel Trace Hub + decoder files for various Intel ME versions
Elkhart Lake Silicon Reference and Platform Sample Code
Debug BIOS/TXE builds for various Platforms
Bootguard SDK (encrypted zip)
Intel Snowridge / Snowfish Process Simulator ADK
Various schematics
Intel Marketing Material Templates (InDesign)
The good news is that the leaked files doesn’t contain sensitive data about customers or employees of the chip maker.
Intel Investigating Data Leak of Technical Documents, Tools
7.8.20 Incindent Securityweek
Intel is investigating reports that a claimed hacker has leaked 20GB of data coming from the chip giant, which appear to be related to source code and developer documents and tools.
“The information appears to come from the Intel Resource and Design Center, which hosts information for use by our customers, partners and other external parties who have registered for access,” an Intel spokesperson told SecurityWeek. “We believe an individual with access downloaded and shared this data.”
According to an individual behind the leak, the files “were given to me by an Anonymous Source who breached them earlier this Year, more details about this will be published soon.”
"Most of the things here have NOT been published ANYWHERE before and are classified as confidential, under NDA or Intel Restricted Secret," the individual claims.
Contents of data claimed to be in the leak include:
• Intel ME Bringup guides + (flash) tooling + samples for various platforms
• Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
• Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
• Silicon / FSP source code packages for various platforms
• Various Intel Development and Debugging Tools
• Simics Simulation for Rocket Lake S and potentially other platforms
• Various roadmaps and other documents
• Binaries for Camera drivers Intel made for SpaceX
• Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
• Kabylake FDK training videos
• Intel Trace Hub + decoder files for various Intel ME versions
• Elkhart Lake Silicon Reference and Platform Sample Code
• Debug BIOS/TXE builds for various Platforms
• Bootguard SDK (encrypted zip)
• Intel Snowridge / Snowfish Process Simulator ADK
• Various schematics
• Intel Marketing Material Templates (InDesign)
The same individual previously leaked proprietary source code from tens of companies, including Microsoft, Adobe, Johnson Controls, GE, AMD, Lenovo, Motorola, Qualcomm, Mediatek, Disney, Daimler, Roblox, and Nintendo. They said at the time that most of the information comes from improperly configured or exposed DevOps infrastructure.
Incident Response Analyst Report 2019
6.8.20 Incindent Securelist
As an incident response service provider, Kaspersky delivers a global service that results in global visibility of adversaries’ cyber-incident tactics and techniques used in the wild. In this report, we share our teams’ conclusions and analysis based on incident responses and statistics from 2019. As well as a range of highlights, this report will cover the affected industries, the most widespread attack tactics and techniques, how long it took to detect and stop adversaries after initial entry and the most exploited vulnerabilities. The report also provides some high-level recommendations on how to increase resilience to attacks.
The insights used in this report come from incident investigations by Kaspersky teams from around the world. The main digital forensic and incident response operations unit is called the Global Emergency Response Team (GERT) and includes experts in Europe, Latin America, North America, Russia and the Middle East. The work of the Computer Incidents Investigation Unit (CIIU) and the Global Research and Analysis Team (GReAT) are also included in this report.
Executive summary
In 2019, we noticed greater commitment among victims to understand the root causes of cyberattacks and improve the level of cybersecurity within their environments to reduce the probability of similar attacks taking place again in the future.
Analysis showed that less than a quarter of received requests turned out to be false positives, mostly after security tools issued alerts about suspicious files or activity. The majority of true positive incidents were triggered by the discovery of suspicious files, followed by encrypted files, suspicious activity and alerts from security tools.
Most of the incident handling requests were received from the Middle East, Europe, the CIS and Latin America, from a wide spectrum of business sectors, including industrial, financial, government, telecoms, transportation and healthcare. Industrial businesses were the most affected by cyberattacks, with oil and gas companies leading the way. They were followed by financial institutions, dominated by banks, which bore the brunt of all money theft incidents in 2019. Ransomware’s presence continued in 2019 and was felt most by government bodies, telecoms and IT companies in various regions.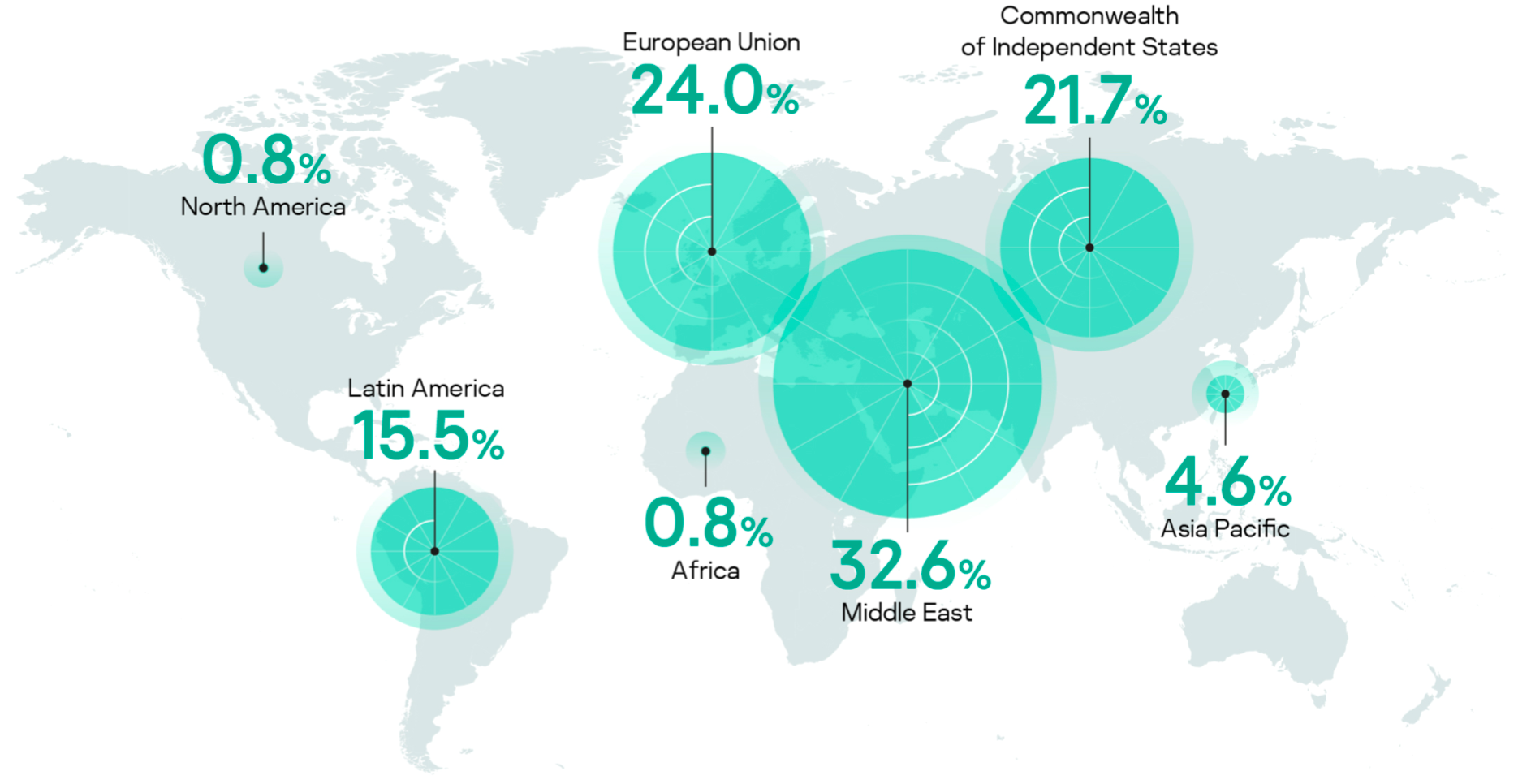
Verticals and industries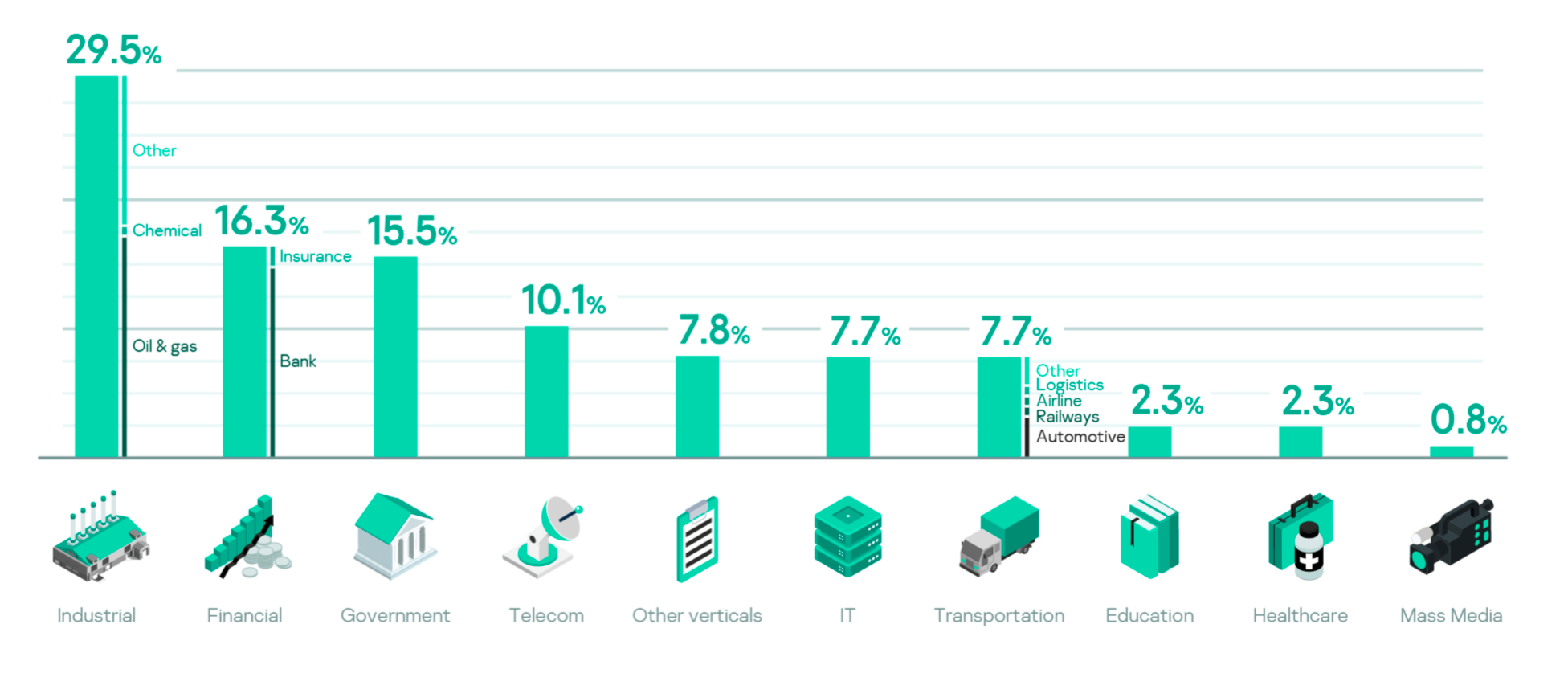
Adversaries used a variety of initial vectors to compromise victims’ environments. Initial vectors included exploitation, misconfiguration, insiders, leaked credentials and malicious removable media. But the most common were exploitation of unpatched vulnerabilities, malicious emails, followed by brute-force attacks.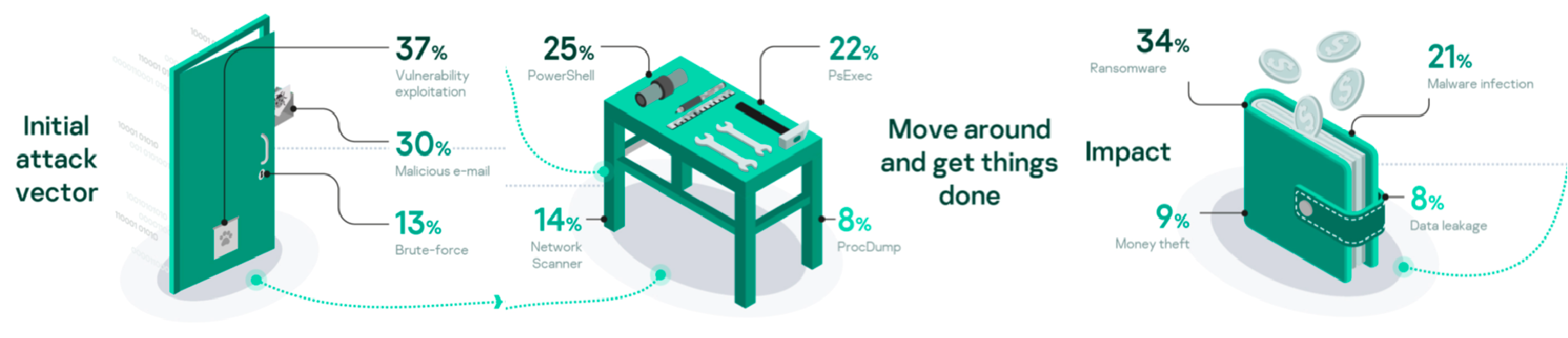
In addition to exploiting vulnerabilities, adversaries used several legitimate tools in different attack phases. This made attacks harder to discover and allowed the adversaries to keep a low profile until their goals were achieved. Most of the legitimate tools were used for credential harvesting from live systems, evading security, network discovery and unloading security solutions.
Although we started working on incidents the first day of a request in 70% of cases, analysis revealed that the time between attack success and its discovery varies between an average of one day in ransomware incidents to 10 days in cases of financial theft, up to 122 days in cyber-espionage and data-theft operations.
Recommendations
Based on 2019 incident response insights, applying the following recommendations can help protect businesses from falling victim to similar attacks:
Apply complex password policies
Avoid management interfaces exposed to the internet
Only allow remote access for necessary external services with multi-factor authentication – with necessary privileges only
Regular system audits to identify vulnerable services and misconfigurations
Continually tune security tools to avoid false positives
Apply powerful audit policy with log retention period of at least six months
Monitor and investigate all alerts generated by security tools
Patch your publicly available services immediately
Enhance your email protection and employee awareness
Forbid use of PsExec to simplify security operations
Threat hunting with rich telemetry, specifically deep tracing of PowerShell to detect attacks
Quickly engage security operations after discovering incidents to reduce potential damage and/or data loss
Back up your data frequently and on separated infrastructure
Reasons for incident response
Significant effects on infrastructure, such as encrypted assets, money loss, data leakage or suspicious emails, led to 30% of requests for investigations. More than 50% of requests came as a result of alerts in security toolstacks: endpoint (EPP, EDR), network (NTA) and others (FW, IDS/IPS, etc.).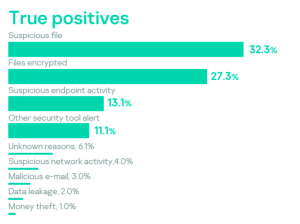
Organizations often only become aware of an incident after a noticeable impact, even when standard security toolstacks have already produced alerts identifying some aspects of the attack. Lack of security operations staff is the most common reason for missing these indicators. Suspicious files identified by security operations and suspicious endpoint activity led to the discovery of an incident in 75% of cases, while suspicious network activities in 60% of cases were false positives.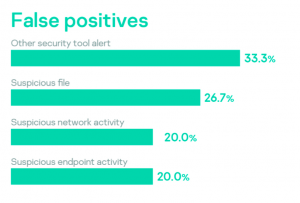
One of the most common reasons for an incident response service request is a ransomware attack: a challenge even for mature security operations. For more details on types of ransomware and how to combat it, view our story “Cities under ransomware siege“.
Distribution of reasons for top regions
A suspicious file is the most prevalent reason to engage incident response services. This shows that file-oriented detection is the most popular approach in many organizations. The distribution also shows that 100% of cases involving financial cybercrime and data leakage that we investigated occurred in CIS countries.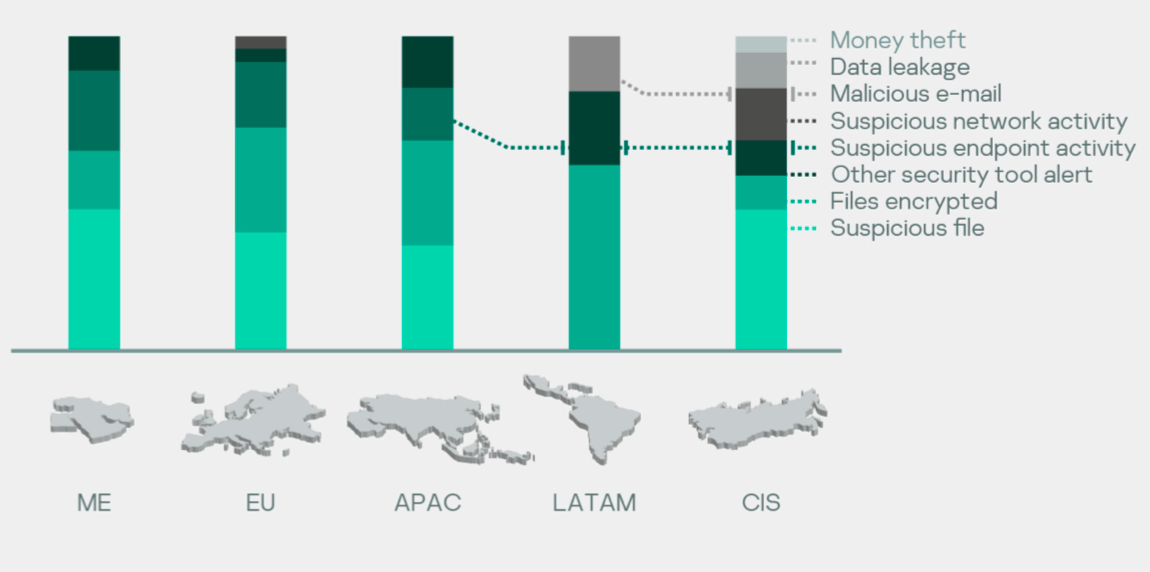
Distribution of reasons for industries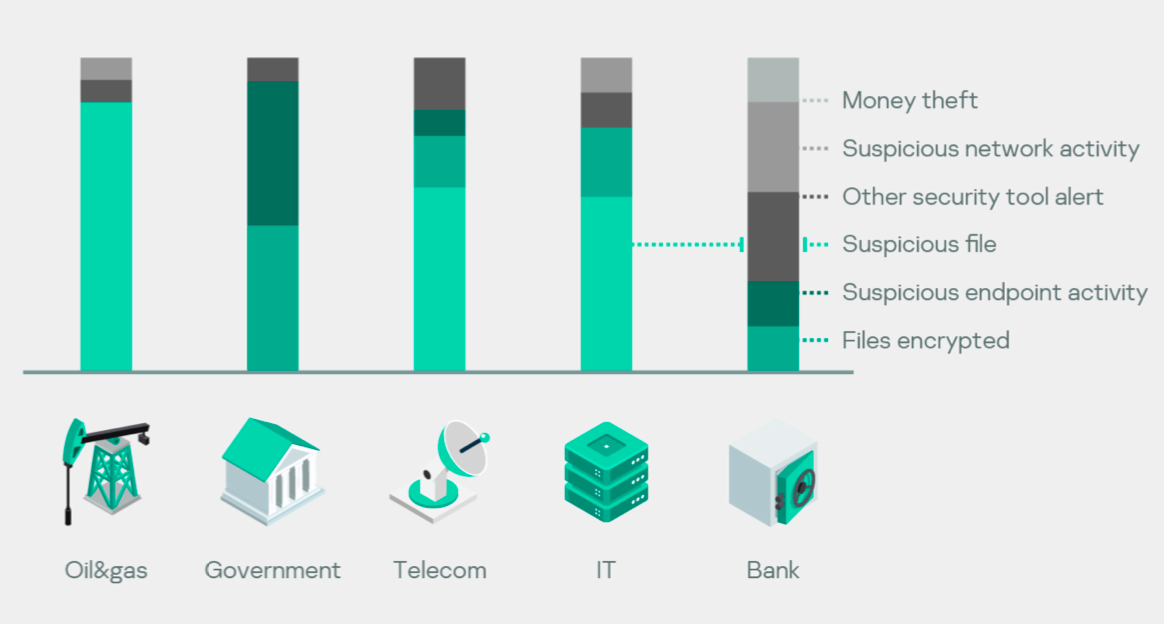
Although, different industries suffered from different incidents, 100% of money theft incidents occurred inside the financial industry (banks).
Detection of ransomware once the repercussions had been felt occurred primarily within the government, telecom and IT sectors.
Initial vectors or how adversaries get in
Common initial vectors include the exploitation of vulnerabilities (0- and 1-day), malicious emails and brute-force attacks. Patch management for 1-day vulnerabilities and applying password policies (or not using management interfaces on the internet) are well suited to address most cases. 0-day vulnerabilities and social engineering attacks via email are much harder to address and require a decent level of maturity from internal security operations.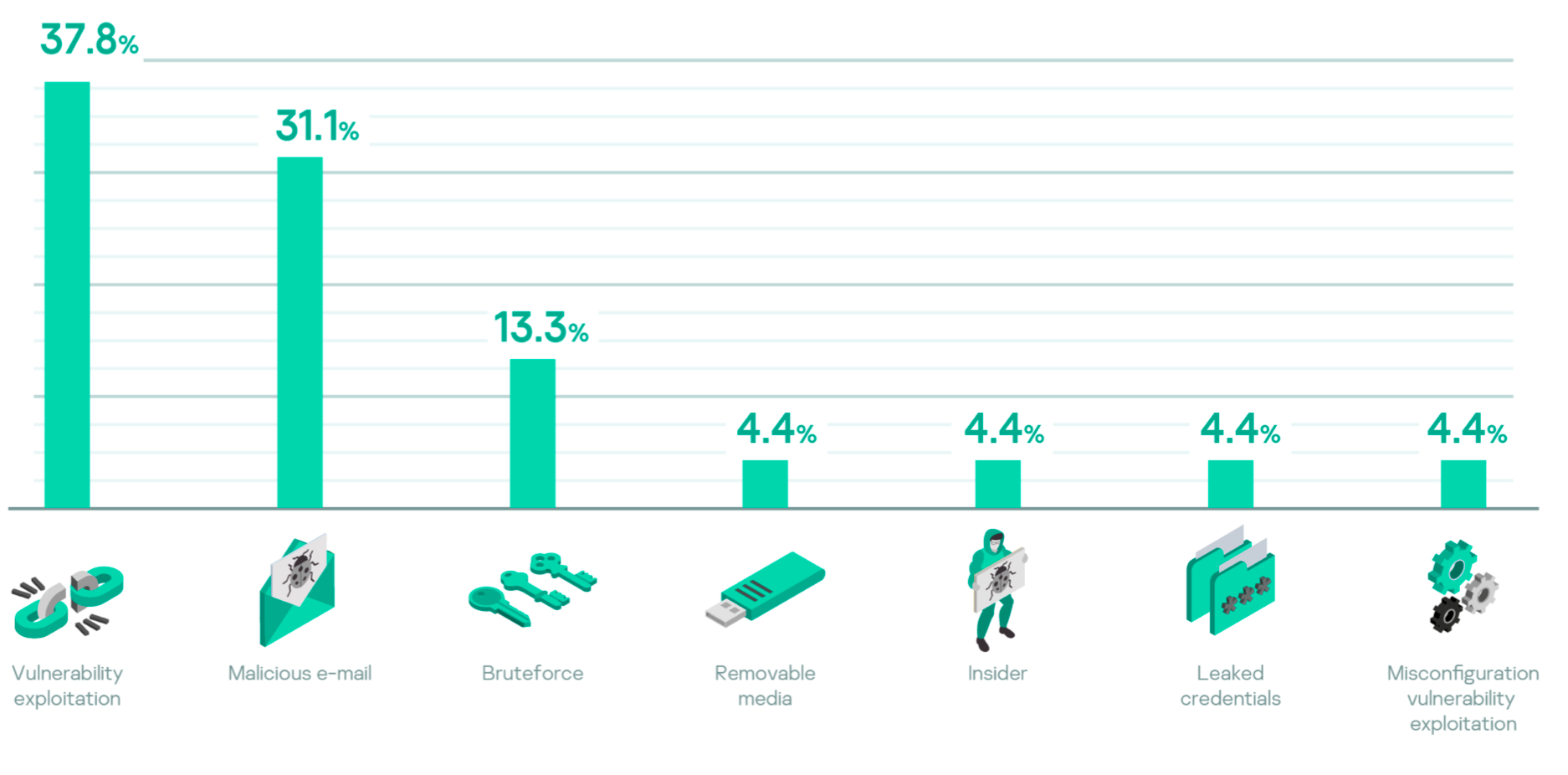
By linking the popular initial compromise vectors with how an incident was detected, we can see detected suspicious files were detected from malicious emails. And cases detected after file encryption mostly took place after brute-force or vulnerability exploitation attacks.
Sometimes we act as complimentary experts for a primary incident response team from the victim’s organization and we have no information on all of their findings – hence the ‘Unknown reasons’ on the charts. Malicious emails are most likely to be detected by a variety of security toolstack, but that’s not showing distrubution of 0- to 1-day vulnerabilities.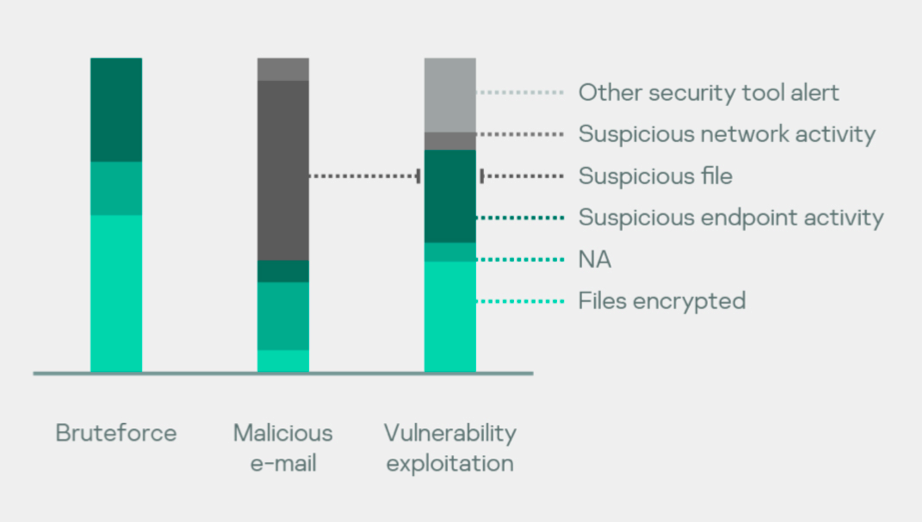
The distribution of how long an attack went unnoticed and how an organization was compromised shows that cases that begin with vulnerability exploitation on an organization’s network perimeter went unnoticed for longest. Social enginnering attacks via email were the most short-lived.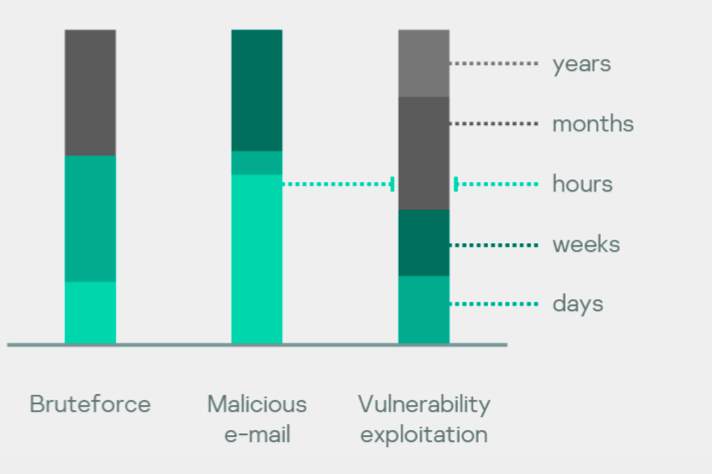
Tools and exploits
30% of all incidents were tied to legitimate tools
In cyberattacks, adversaries use legitimate tools which can’t be detected as malicious utilities as they are often used in everyday activities. Suspicious events that blend with normal activity can be identified after deep analysis of a malicious attack and connecting the use of such tools to the incident. The top used tools are PowerShell, PsExec, SoftPerfect Network Scanner and ProcDump.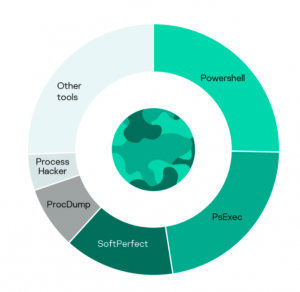
Most legitimate tools are used for harvesting credentials from memory, evading security mechanisms by unloading security solutions and for discovering services in the network. PowerShell can be used virtually for any task.
Let’s weight those tools based on occurrence in incidents – we will also see tactics (MITRE ATT&CK) where they are usually applied.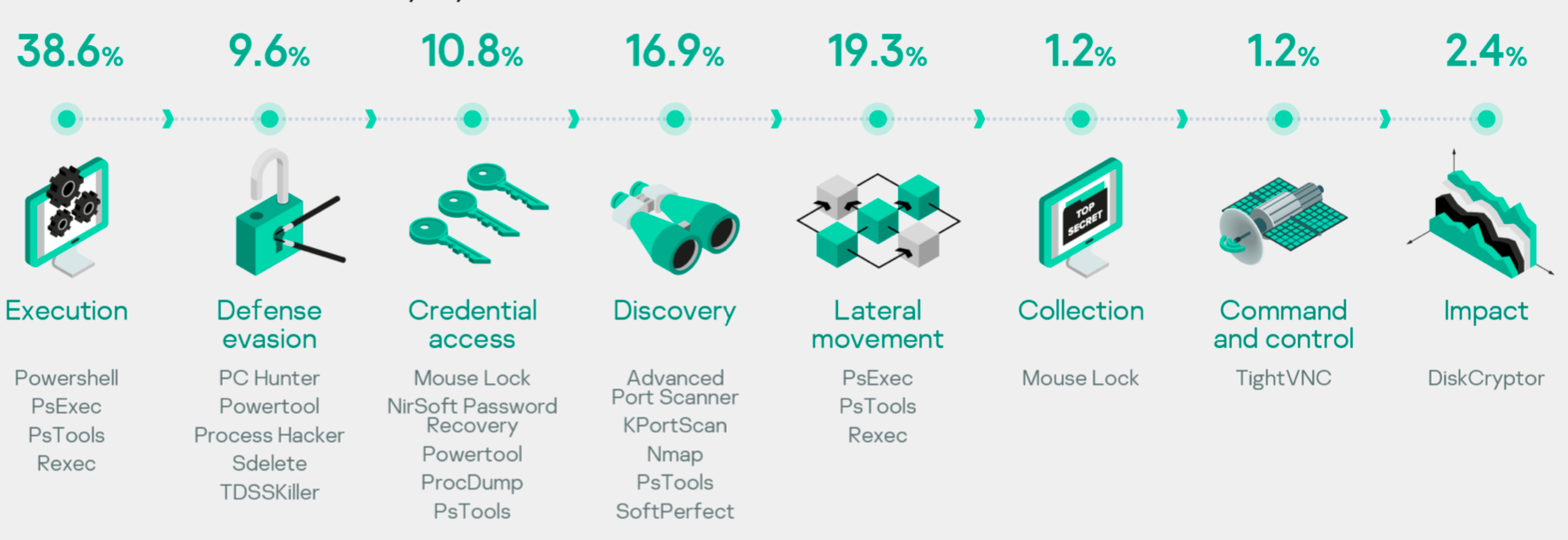
Exploits
Most of the identified exploits in incident cases appeared in 2019 along with a well-known remote code execution vulnerability in Windows SMB service (MS17-010) being actively exploited by a large number of adversaries.
MS17-010 SMB service in Microsoft Windows
Remote code execution vulnerability that was used in several large attacks such as WannaCry, NotPetya, WannaMine, etc. CVE-2019-0604 Microsoft Sharepoint
Remote code execution vulnerability allows adversaries to execute arbitrary code without authentication in Microsoft Sharepoint. CVE-2019-19781 Citrix Application Delivery Controller & Citrix Gateway
This vulnerability allows unauthenticated remote code execution on all hosts connected to Citrix infrastructure.
CVE-2019-0708 RDP service in Microsoft Windows
Remote code execution vulnerability (codename: BlueKeep) for a very widespread and, unfortunately, frequently publicly available RDP service. CVE-2018-7600 Drupal
Remote code execution vulnerability also known as Drupalgeddon2. Widely used in installation of backdoors, web miners and other malware on compromised web servers. CVE-2019-11510 Pulse Secure SSL VPN
Unauthenticated retrieval of VPN server user credentials. Instant access to victim organization through legitimate channel.
Attack duration
For a number of incidents, Kaspersky specialists have established the time period between the beginning of an adversary’s activity and the end of the attack. As a result of the subsequent analysis, all incidents were divided into three categories of attack duration.
Rush hours or days Average weeks Long-lasting months or longer
This category includes attacks lasting up to a week. These are mainly incidents involving ransomware attacks. Due to the high speed of development, effective counteraction to these attacks is possible only by preventive methods.
In some cases, a delay of up to a week has been observed between the initial compromise and the beginning of the adversary’s activity. This group includes attacks that have been developing for a week or several weeks. In most cases, this activity was aimed at the direct theft of money. Typically, the adversaries achieved their goals within a week. Incidents that lasted more than a month were included in this group. This activity is almost always aimed at stealing sensitive data.
Such attacks are characterized by interchanging active and passive phases. The total duration of active phases is on average close to the duration of attacks from the previous group.
Common threat:
Ransomware infection Common threat:
Financial theft Common threat:
Cyber-espionage and theft of confidential data
Common attack vector:
Downloading of a malicious file by link in email
Downloading of a malicious file from infected site
Exploitation of vulnerabilities on network perimeter
Credentials brute-force attack
Common attack vector:
Downloading a malicious file by link in email
Exploitation of vulnerabilities on network perimeter
Common attack vector:
Exploitation of vulnerabilities on network perimeter
Attack duration (median):
1 day Attack duration (median):
10 days Attack duration (median):
122 days
Incident response duration:
Hours to days Incident response duration:
Weeks Incident response duration:
Weeks
Operational metrics
False positives rate
False positives in incident responses are a very expensive exercise. A false positive means that triage of a security event led to the involvement of incident response experts who later ascertained that there was no incident. Usually this is a sign that an organization doesn’t have a specialist in threat hunting or they are managed by an external SOC that doesn’t have the full context for an event.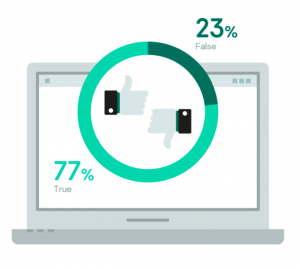
Age of attack
This is the time taken to detect an incident by an organization after an attack starts. Usually detecting the attack in the first few hours or even days is good; with more low-profile attacks it can take weeks, which is still OK, but taking months or years is definitely bad.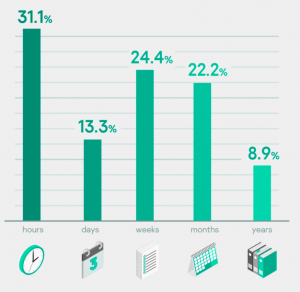
How fast we responded
How long it took us to respond after an organization contacted us. 70% of the time we start work from day one, but in some cases a variety of factors can influence the timeframe.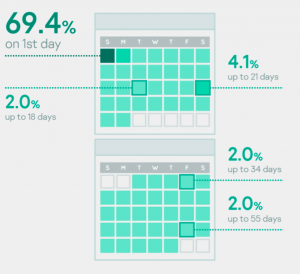
How long response took
Distribution of the time required for incident response activities can vary from a few hours to months based on how deep the adversaries were able to dig into the compromised network and how old the first compromise is.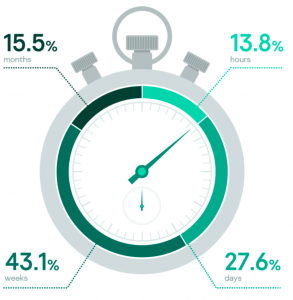
MITRE ATT&CK tactics and techniques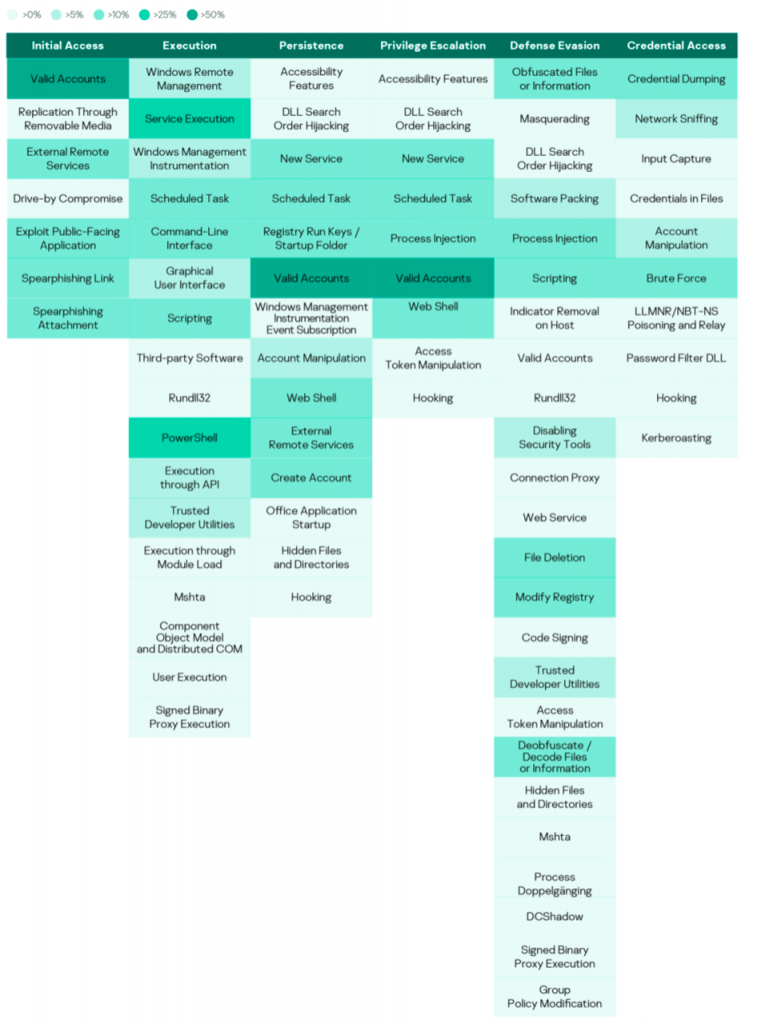
Conclusion
In 2019, the cyberattack curve was not flattened. There was an increase in the number of incidents accompanied by greater commitment among victims to understand the full attack picture. Victims from all regions suffered from a variety of attacks and all business types were targeted.
Improved security and audit planning with continuous maintenance of procedures along with rapid patch management could have minimized damages and losses in many of the analyzed incidents. In addition, having security monitoring and an investigation plan either on-premises or performed by a third party could have helped in stopping adversaries in the early phases of the attack chain, or start detections immediately after compromise.
Various tactics and techniques were used by adversaries to achieve their targets, trying multiple times till they succeeded. This indicates the importance of security being an organized process with continuous improvements instead of separate, independent actions.
Adversaries made greater use of legitimate tools in different phases of their cyberattacks, especially in the early phases. This highlights the need to monitor and justify the use of legitimate administration tools and scanning utilities within internal networks, limiting their use to administrators and necessary actions only.
Applying a powerful auditing policy with a log retention period of at least six months can help reduce analysis times during incident investigation and help limit the types of damage caused. Having insufficient logs on endpoints and network levels means it takes longer to collect and analyze evidence from different data sources in order to gain a complete picture of an attack.
Hacker leaks passwords for 900+ Pulse Secure VPN enterprise servers
5.8.20 Incindent Securityweek
ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum.
ZDNet has reported in exclusive that a list of plaintext usernames and passwords for 900 Pulse Secure VPN enterprise servers, along with IP addresses, has been shared on a Russian-speaking hacker forum.
ZDNet has obtained a copy of the list with the help of threat intelligence firm KELA and verified confirmed the authenticity of the data.
The list includes:
IP addresses of Pulse Secure VPN servers
Pulse Secure VPN server firmware version
SSH keys for each server
A list of all local users and their password hashes
Admin account details
Last VPN logins (including usernames and cleartext passwords)
VPN session cookies
According to Bank Security, all the Pulse Secure VPN servers included in the list were vulnerable to the CVE-2019-11510 flaw.
The CVE-2019-11510 flaw in Pulse Connect Secure is a critical arbitrary file read vulnerability.
“Unauthenticated remote attacker with network access via HTTPS can send a specially crafted URI to perform an arbitrary file reading vulnerability.” reads the advisory.
The vulnerability could be easily exploitable by using publicly available proof-of-concept code.
In august 2019, researchers from BadPackets analyzed the number of Pulse Secure VPN endpoints vulnerable to the CVE-2019-11510. Using the online scanning service BinaryEdge the researchers found 41,850 Pulse Secure VPN endpoints exposed online, 14,528 of them vulnerable to CVE-2019-11510.
Most of the vulnerable hosts were in the U.S. (5,010), followed by Japan (1,511), the U.K. (830) and Germany (789).

The researchers also analyzed the distribution of the vulnerable hosts by industry and discovered that the flaw affects hosts in:
According to BadPacket, 677 out of the 913 unique IP addresses found in the list were detected by Bad Packets CTI scans to be vulnerable to CVE-2019-11510 immediately after the exploit was made public in 2019.
U.S. military, federal, state, and local government agencies
Public universities and schools
Hospitals and health care providers
Electric utilities
Major financial institutions
Numerous Fortune 500 companies
Likely the threat actors who compiled this list scanned the internet for Pulse Secure VPN servers between June 24 and July 8, 2020, and exploited the CVE-2019-11510 vulnerability to gather server details.
Companies on the list have to update their Pulse Secure servers and of course, change their passwords.
ZDNet researchers pointed out that ransomware operators could use the leaked credentials to target large enterprise.
“Making matters worse, the list has been shared on a hacker forum that is frequented by multiple ransomware gangs. For example, the REvil (Sodinokibi), NetWalker, Lockbit, Avaddon, Makop, and Exorcist ransomware gangs have threads on the same forum, and use it to recruit members (developers) and affiliates (customers).” reported ZDNet.
Reading the 2020 Cost of a Data Breach Report
4.8.20 Incindent Securityaffairs
2020 Cost of a Data Breach Report: the global total cost of a data breach averaged $3.86 million in 2020, down about 1.5% from the 2019 study.
Every year, I write about the annual report published by the Ponemon Institute on the cost of a data breach, it is a very interesting study that explores the economic impact of a “data breach.”
This year the researchers analyzed 524 breaches that occurred between August 2019 and April 2020, in organizations of all sizes, across 17 geographies and 17 industries.
According to the 2020 Cost of a Data Breach Report, the global total cost of a data breach averaged $3.86 million in 2020, down about 1.5% from the 2019 study. Victim organizations The average time to identify and contain a data breach was 280 days in the 2020 study, quite identical to 2019 (279).
This year, the experts analyzed the impact of vulnerability testing and red team testing on the cost of a data breach and discovered that conducting red team testing could allow reducing average costs of about $243,000, while conducting vulnerability testing could allow reducing costs of about $173,000.
The report for the first time explores the cost impact of remote work and the security skills shortage.
“Organizations with remote work arrangements cited costs that were nearly $137,000 higher than the global average of $3.86 million, while organizations estimated that the security skill shortage increased costs by an average of $257,000 compared to the global average.” reads the post published by IBM that introduces the report.
For the first time, the report goes deep into analyzing the per-record cost of a data breach based on the type of records involved. The experts pointed out that the customer personally identifiable information (PII) was the most expensive type of record. The customer PII records have a cost of an average $150 per lost or stolen record, followed by intellectual property records ($147), anonymized customer records ($143) or employee PII ($141). Unfortunately, customer PII was present in 80% of the incident analyzed.
52% of data breaches observed in 2020 were caused by malicious attacks.
The analysis of the attack vectors revealed that most prominent ones were compromised credentials (19% of malicious breaches), cloud misconfiguration (19%) and vulnerabilities in third-party software (16%).
For the first time, the report analyzed the cost of breaches involving destructive malware, experts estimated that the average destructive malware breach cost $4.52 million and the average ransomware breach cost $4.44 million. The overall average cost of a malicious breach was $4.27 million.
You can explore the impacts of these cost factors and more – some that amplify costs and others that mitigate costs – using the interactive cost calculator that is a companion to this year’s report. You can register to access the full calculator to see the estimated impact of 25 cost factors on the average cost of a data breach in 17 geographies and 14 industries.See the 2020 Cost of a Data Breach report and calculator.
Another novelty for the 2020 Cost of a Data Breach Report is represented in the analysis of data breach based on the type of attacker.
Most of the malicious breach was caused by financially motivated threat actors (53%), followed by nation-state actors (13%) and hacktivist threat actors (13%). According to the experts, the average cost of a breach was higher for state-sponsored breaches ($4.43 million) and hacktivist breaches ($4.28 million) than financially motivated breaches ($4.23 million).
Let me suggest reading the full Cost of a Data Breach Report, which contains a lot of interesting data. IBM Security also implements an interactive calculator, a global map and other tools for exploring the data for insights and recommendations.
Havenly discloses data breach, 1.3M accounts available online
4.8.20 Incindent Securityaffairs
Havenly, a Denver-Based company, that realized an interior designer marketplace has disclosed a data breach that impacted 1.3 million users.
The US-based interior design web site Havenly has disclosed a data breach after the known threat actor ShinyHunters has leaked for free the databases of multiple companies on a hacker forum.
Last week, BleepingComputer reported that ShinyHunterswas offering on a hacker forum the databases stolen from eighteen companies, over 386 million user records available online.
The threat actors released nine new databases belonging to several companies, including Havenly, Indaba Music, Ivoy, Proctoru, Rewards1, Scentbird, and Vakinha. The remaining nine databases were already released by ShinyHunters in the past.
The ShinyHunters hacker posted the Havenly database containing 1.3 million user records for free.
The leaked records included a login name, full name, MD5 hashed password, email address, phone number, zip, and other data related.
The company has notified impacted users via email, it admitted to having recently discovered the data breach, in response to the incident it has forced a password reset.
“We take the security of our community very seriously. As a precaution, we wanted to let you know that we recently became aware of a potential incident that may have affected the security of certain customer accounts. We are working with external security experts to investigate this matter.” reads the data breach notification.
“However, in the meantime, out of an abundance of caution, we are logging all existing customers out of their Havenly accounts and asking our customers to reset their password when they next log in to the Havenly website. As a best practice, we also encourage all of our customers to use different passwords across all online services and applications, and to update those passwords now and on a regular basis,”
The company revealed that financial data was not exposed because it does store only the last four digits of users’ credit cards.
“We suspect that many of you will be concerned about the credit card numbers that you’ve used with Havenly in the past. Please note: we do NOT store credit card information, apart from the last 4 digits of the card in some cases, which is not enough to engage in credit card fraud,” Havenly disclosed.
Havenly users could check if their data was exposed by querying the popular data breach notification service Have I Been Pwned.
Users are invited to change passwords for any other service where they share the same Havenly’ login credentials to avoid being victims of credential stuffing attacks.
NTT Communications Data Breach Affects Customers, Threatens Supply Chain
30.5.2020 threatpost Incindent
Attackers managed to compromise NTT Communication’s Active Directory server and a construction information management server.
Japan-based systems integrator NTT Communications has disclosed a recent data breach that it said impacted hundreds of customers.
The total affected comes to as many as 621 customers, the company said, but security experts worry about the impacts of the data breach due to the company’s positioning as a systems integrator, which could create widespread ramifications for its supply-chain partners. NTT Communications is a subsidiary of Fortune 500 company Nippon Telegraph and Telephone Corp., the largest telecommunications company in Japan (and one of the largest worldwide).
“At this point, we have completed initial actions such as stopping the server that served as a stepping stone [for the breach], but we will contact customers who may have been affected in order. At the same time, we are implementing measures to prevent recurrence,” according to the company’s translated data-breach disclosure.
The company said on Thursday that the data breach occurred on May 7. The hack was detected by the company on May 11 and has since been remediated. NTT Communications did not clarify what kind of data may have been accessed, nor did it mention how attackers were able to move laterally on the network. Threatpost has reached out for further clarification.
However, local media reports say that information leaked may have involved the Japan Self-Defense Forces (i.e., Japan’s military forces).
NTT Communications first discovered the intrusion after detecting suspicious activity on its Active Directory server. According to its data-breach notice, attackers initially targeted a cloud server within its Singapore operations (it is unclear the method that hackers used for the initial infection). This was then used as a stepping stone to reach several other servers within the company’s service-management segment, including NTT Communications’ Active Directory server and a construction-information management server. NTT Communications believes that attackers used the latter server to reach its Japanese hosting and cloud services, and ultimately steal files.
“BHE [short for Biz Hosting Enterprise, NTT’s cloud hosting service] has transitioned the environment of its customers to new services,” according to its data-breach notice. “We believe that Server B [the cloud server], which was being removed due to the migration, the overseas operation server, and some communication routes were used as the intrusion route for the attackers.”
The company said it has also discovered and blocked external websites that were being used by the attackers to communicate with the malware. Moving forward, NTT Communications said it will continue to investigate the internal server group and will take steps to further improve security measures.
However, Joseph Carson, chief security scientist and Advisory CISO at Thycotic, told Threatpost that the NTT Communications data breach could have “serious cascading impacts,” particularly given the compromise of the Active Directory server, which is a popular directory service developed by Microsoft for Windows domain networks.
“Once an Active Directory Server is compromised, or an attacker has gained Domain Admin access (keys to the kingdom), it is game over,” said Carson. “That is when you start to unplug from the internet and begin a deep digital forensics, and ultimately, a massive clean-up. If your AD is completely compromised, then a true eradication of the incident likely means rebuilding your Active Directory, which for any large organization is not an easy feat.”
Other security experts worry about the ripple-effect impacts of the data breach on NTT Communications’ supply-chain partners.
“Major IT and security providers often have deep access to customer environments and sensitive information, and this makes service providers and software companies prime targets for attack,” Jack Mannino, CEO at nVisium, told Threatpost. “These types of attacks often go unnoticed for extended periods and pose a risk across the IT supply chain.”
ICT solutions provider NTT Com discloses security breach
30.5.2020 Securityaffairs Incindent
NTT Communications (NTT Com), a subsidiary of tech giant NTT Corp, disclosed a data breach that impacted hundreds of customers.
NTT Communications (NTT Com), a subsidiary of the tech giant NTT Corp, disclosed a data breach that impacted hundreds of customers.
NTT Com provides network management, security and solution services[3] to consumers, corporations and governments.
NTT Com Group has more than 30 companies in the Asia-Pacific region, Europe and the Americas.
The company launched an investigation after discovering unauthorized access to some systems on May 7, then this week it confirmed that threat actors may have been stolen.
“NTT Communications (hereafter NTT Com) detected an unauthorized access to our equipment that has been made by an attacker on May 7, and the possibility that some information may have leaked to the outside was confirmed on May 11.” reads the data breach notification.
Experts at NTT Com initially noticed suspicious activity on an Active Directory server, then they discovered that threat actors have breached an operational server and an information management server that stored customer information.
The internal investigation revealed that attackers initially targeted a server in Singapore, then used it for lateral movements and reach the infrastructure in Japan.
In response to the incident, the company shut down impacted servers to avoid the malware from spreading and communicating with external servers.
According to NTT, the security breach could impact 621 companies whose information was stored on the information management server.
The company announced that it has taken additional measures to prevent similar attacks in the future.
Other major Japanese companies recently disclosed security breaches, some of them took place years ago, including NEC, Mitsubishi Electric, Pasco and Kobe Steel.
26 million LiveJournal accounts being shared on hacker forums
29.5.2020 Bleepingcomputer Incindent
A database containing over 26 million unique LiveJournal user accounts, including plain text passwords, is being shared for free on multiple hacker forums.
For some time, rumors have been circulating that LiveJournal was breached in 2014 and account credentials for 33 million users were stolen.
Since approximately May 8th, 2020, links to a data dump allegedly containing 33,717,787 unique accounts have been circulating on various hacker forums.
According to posts sharing the links, the database dump contains email addresses, usernames, profile URLs, and passwords. The passwords were converted to plain text after initially being stored as MD5 hashes.
Hacking forum post
Today, numerous people have shared the alleged LiveJournal database with Troy Hunt of Have I Been Pwned, who added it to their data breach notification service.
Hunt has told BleepingComputer that it appears to be the same data breach that was discussed last year.
Instead of classifying the data breach as being from 2014, though, Hunt is stating it is from 2017 based on the data dump's file name of 'LiveJournal_com_2017_33.7M.txt.'
"There's contradictory info: the Forum post says 2014 but then the file I sent you a screen cap of says 2017. There's no time stamps in the file to make it any clearer but the earliest evidence I have (based on community feedback) is 2018."
"I generally err on the side of the later date otherwise you end up with people saying "I didn't create an account until 2016 and I'm in there so you have the date wrong"," Hunt told BleepingComputer.
BleepingComputer was able to find links to the circulating database within five minutes of talking to Hunt.
Sample of alleged LiveJournal database
BleepingComputer has since been able to independently confirm with a few people that information for old accounts was accurately included in the database.
LiveJournal has denied being compromised
Denise Paolucci replied to Hunt's tweet today, stating that her company Dreamwidth Studios has been dealing with credential stuffing attacks that overlap with the credentials in the LiveJournal database.
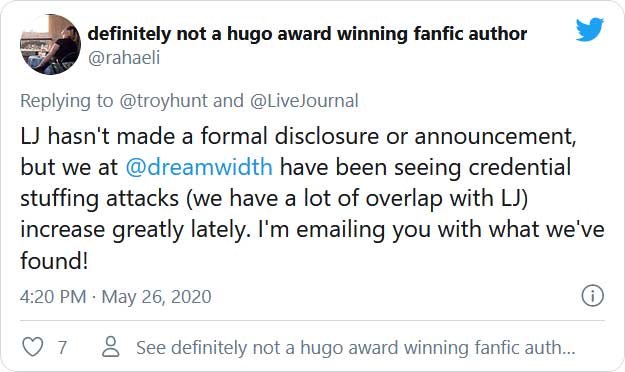
Paolucci shared links to Dreamwidth maintenance bulletins with BleepingComputer from 2017 and 2018 that indicate that credentials from this LiveJournal database were used in credential stuffing attacks.
In the 2017 maintenance bulletin, two customers referenced that their accounts at LiveJournal had been compromised.
"LiveJournal refugees should be especially careful not to reuse their passwords from there. A large number of people I know, including myself, got "Caught you on camera watching porn" spam, giving our old LiveJournal passwords as "evidence." In its earlier days, LJ must have been very sloppy about protecting user passwords," a customer posted.
"Let me be scrupulously careful here in how I phrase this: There are files ("dumps") on the black market that claim to be from a LiveJournal breach in 2014, and I've never seen anyone who was listed in the dumps say that their information was incorrect (and have seen many who have said it was)," Paolucci responded.
To this day, LiveJournal has never confirmed that a data breach has occurred or that the database is legitimate.
BleepingComputer has emailed LiveJournal about the circulating database but has not heard back at this time.
What should LiveJournal users do?
Hunt has added the database to the Have I Been Pwned data breach notification service, and users can use it to confirm if their email address is part of the database.
If the service shows that your email address was included, you should immediately change your passwords on LiveJournal to be safe.
This database is potentially six years old, so it hoped that users would have changed their password over the years, but to be safe, do so again.
If you use the same password at other sites, be sure to switch to a unique and complex password at these other sites.
Arbonne MLM data breach exposes user passwords, personal info
29.5.2020 Bleepingcomputer Incindent
International multi-level marketing (MLM) firm Arbonne International exposed the personal information and credentials of thousands after its internal systems were breached by an unauthorized party last month.
Arbonne is a privately held California-based company acquired by Groupe Rocher in 2018, with annual revenues of over $500 million and a network of more than 200,000 independent consultants from the United States, the United Kingdom, Canada, Australia, Poland, and New Zealand.
Data breach impacts thousands of Californians
"On the evening of April 20, 2020, Arbonne became aware of unusual activity within a limited number of its internal systems," Arbonne says in a data breach notification letter filed with the Office of the Attorney General of California.
"On April 23, 2020, the investigation identified a data table containing limited personal information that may have been accessible to unauthorized actor."
According to Arbonne's breach notification, 3,527 California residents were impacted in the incident, with the following types of personal information being exposed to unauthorized access: names, email and mailing addresses, order purchase histories, phone numbers, and Arbonne account passwords.
While the company shared the number of affected Californians, the total number of impacted individuals is currently unknown although Maryland, New York, New Mexico, North Carolina, and Rhode Island residents are advised to contact their Attorney General for more info.
BleepingComputer has reached out to Arbonne for more details but had not heard back at the time of this publication. This article will be updated when a response is received.
Arbonne says that the affected users' payment card or government ID information, such as Social Security numbers, was not exposed in the breach based on the ongoing investigation's results
Passwords reset for all affected user accounts
"While our investigation is ongoing, in an abundance of caution, we forced a password reset for all users whose passwords may have been subject to unauthorized access and we notified these users to ensure they were aware of this incident," Arbonne added.
The data breach experienced by the MLM company was also reported to the FBI and relevant regulators.
Following the incident, Arbonne provides all impacted individuals with twelve months of free credit monitoring, fraud consultation, and identity theft restoration services from Kroll.
The company also provides a customer service support hotline at 800-ARBONNE, open "Monday through Friday, 7 am – 8 pm Pacificexcluding national holidays."
Last month, the U.S. Federal Trade Commission warned Arbonne to direct its independent consultants to stop making claims on social media that some of its products "treat or prevent Coronavirus Disease 2019 ('COVID-19')."
The company answered by stating that all representatives who failed to adhere to FTC guidelines will have their accounts de-registered.
An archive with 20 Million Taiwanese’ citizens leaked in the dark web
29.5.2020 Securityaffairs Incindent
Security experts from Cyble discovered in the dark web a database containing details of over 20 Million Taiwanese citizens.
A few weeks ago, threat intelligence firm Cyble discovered in the dark web a database containing details of over 20 Million Taiwanese citizens.
According to the experts, the leak includes government data of an entire country, it was leaked online by a reputable actor that goes online with moniker ‘Toogod.”
“A few weeks ago, our researchers came across a leaked database on the darkweb where a known and reputable actor ‘Toogod” dropped the database of “Taiwan Whole Country Home Registry DB” comprising of 20 Million+ records.” reads a post published by Cyble.
The database size is 3.5 GB, exposed data includes full name, full address, ID, gender, date of birth, and other info.
The seller claims the database dates back as 2019, but Cyble researchers noted the last DOB record was from 2008. The database contains certain records with ‘NULL/empty’ DoB records, making it impossible to determine how recent the dump is.
Experts are still investigating the leak and will provide an update as soon as possible.
Cyble researchers have acquired the leak and will add soon its data to its AmIBreached data breach lookup service.
Design Marketplace Minted Confirms Recent Data Breach
29.5.2020 Securityweek Incindent
Minted, an online marketplace of crowdsourced art and graphic designs, this week confirmed that it was the victim of a data breach earlier this month.
Founded in 2007 and headquartered in San Francisco, the online marketplace holds regular design challenges in which thousands of independent artists and designers participate. Thousands of designs are submitted each week and marketplace visitors vote to help choose the winners, which end up being sold on the site.
Information on a security incident affecting Minted became public several weeks ago, when a hacking group referred to as Shiny Hunters started advertising user records stolen in multiple fresh data breaches, including information exfiltrated from Minted.
At the time, the hackers said they were in possession of 5 million user accounts, and were asking for $2,500 for the data.
Minted, which appears to have been alerted on the data breach only after the first reports emerged in online media, launched an investigation into the incident, and discovered that hackers were indeed able to breach its user account database on May 6, 2020.
The investigation revealed that the cybercriminals managed to compromise customer names, along with the login credentials to their Minted accounts, which include email addresses and passwords (hashed and salted).
Additionally, the hackers accessed the telephone numbers and billing and shipping addresses of users. For some of them, the date of birth was also exposed (for less than 1% of the impacted users).
“Based on our investigation to date, we have no reason to believe that the following information was affected: payment or credit card information, customer address book information, or photos or personalized information that customers added to Minted designs,” the company said.
Although the affected passwords were not stored in plain text, Minted is requesting customers to change passwords for their Minted accounts, as well as for any other online accounts for which the same email address and password combination was used.
“As always, customers should be cautious of any unsolicited communications that ask for personal information and avoid clicking on links or downloading attachments from suspicious emails,” Minted also says.
“End users will want to continue vigilance when it comes to spear phishing or targeted emails about their accounts. By sharing their password or some other sensitive information from the breach, a criminal's email will entice them to open attachments or click on links related to these attacks and thus compromise their systems further. People need to make sure they are using different passwords for various sites and accounts. In the unfortunate event of a data breach, they only need to change the one password versus now being susceptible to attacks on their accounts on different sites because they used the same password,” James McQuiggan, security awareness advocate at KnowBe4, said in an emailed comment.
Security breach impacted Cisco VIRL-PE infrastructure
29.5.2020 Securityaffairs Incindent
Cisco discloses security breach that impacted VIRL-PE infrastructure, threat actors exploited SaltStack vulnerabilities to hack six company servers.
Cisco has disclosed a security incident that impacted part of its VIRL-PE infrastructure, threat actors exploited vulnerabilities in the SaltStack software package to breach six company servers.
These issues affect the following Cisco products running a vulnerable software release:
Cisco Modeling Labs Corporate Edition (CML)
Cisco Virtual Internet Routing Lab Personal Edition (VIRL-PE)
Cisco’s advisory states that the SaltStack software package is bundled with some Cisco products, hackers exploited SaltStack issues to compromise six company servers:
us-1.virl.info
us-2.virl.info
us-3.virl.info
us-4.virl.info
vsm-us-1.virl.info
vsm-us-2.virl.info
“Cisco infrastructure maintains the salt-master servers that are used with Cisco VIRL-PE. Those servers were upgraded on May 7, 2020. Cisco identified that the Cisco maintained salt-master servers that are servicing Cisco VIRL-PE releases 1.2 and 1.3 were compromised. The servers were remediated on May 7, 2020.” reads the advisory.
The six servers are part of the backend infrastructure for VIRL-PE (Internet Routing Lab Personal Edition), a service that allows Cisco users to model and simulate their virtual network environment.
Cisco has it fixed and remediated all breached VIRL-PE servers on May 7, when it upgraded them by applying the patches for the SaltStack software.
Cisco also confirmed that the Cisco Modeling Labs Corporate Edition (CML), a network modeling tool, is affected by the issues.
At the end of April, researchers from F-Secure disclosed a number of vulnerabilities in the “Salt” framework, including two issues that could be exploited by attackers to take over Salt installations.
The two flaws, tracked as CVE-2020-11651 and CVE-2020-11652, are a directory traversal issue and an authentication bypass vulnerability respectively. Chaining the issue, an attacker could bypass authentication and run arbitrary code on Salt master servers exposed online.
Immediately after the public disclosure of the issues. administrators of Salt servers started reporting attacks exploiting the above vulnerabilities last week, threat actors used them to deliver backdoors and miners.
Shortly after the disclosure of the flaws, threat actors exploited them in several attacks against organizations, including mobile operating system vendor LineageOS, Digicert CA, blogging platform Ghost, cloud software provider Xen Orchestra, and search provider Algolia.
Japanese ICT Solutions Provider NTT Com Discloses Data Breach
29.5.2020 Securityweek Incindent
NTT Communications (NTT Com), a subsidiary of Japanese tech giant NTT Corp, on Thursday disclosed a data breach impacting hundreds of customers.
In a post on its Japanese-language website, NTT Com, a provider of information and communications technology (ICT) solutions, said it detected unauthorized access to some systems on May 7 and over the following week it determined that some files may have been stolen.
The company first noticed suspicious activity on an Active Directory server, but later determined that the intrusion also impacted an operational server and an information management server that stored customer information. The attack is believed to have initially targeted a server in Singapore, from where the attackers moved to systems located in Japan.
Impacted servers were shut down and the company took steps to prevent a piece of malware found on its systems from communicating with external servers.
NTT says the incident could impact 621 companies whose information was stored on the information management server.
NTT has promised to share additional information, but says it will not name any of the impacted customers. The company says it has taken measures to prevent these types of attacks in the future.
NTT is not the first major Japanese company to disclose a data breach this year. Mitsubishi Electric, NEC, Pasco and Kobe Steel also admitted getting hacked, but they said the breaches occurred in the past several years.
It was recently revealed that the attack on Mitsubishi, which is said to have involved exploitation of a vulnerability in Trend Micro’s OfficeScan product, may have resulted in the theft of information on a prototype missile.
Hackers Sell Data from 26 Million LiveJournal Users on Dark Web
28.5.2020 Theatpost Incindent
Passwords and other credentials have been listed on Have I Been Pwned as attack rumors circulate.
A database containing credentials from more than 26 million LiveJournal accounts has been leaked online and is being sold on the Dark Web and hacker forums.
The data contained in the files appears to be from a 2014 incident in which 33 million accounts were hacked, according to a published report. Though rumors of that breach have been in circulation for a couple of years – and there is some debate over when it actually occurred – the incident was never officially confirmed by LiveJournal, sources said.
Hackers, however, seem to have been busy using and selling data from the breach to mount attacks, ultimately sharing it with Troy Hunt from Have I Been Pwned. The data-breach notification service added a listing about the LiveJournal leak on Tuesday, citing mid-2019 as the time news of the breach surfaced.
The listing categorizes the breach as having occurred in January 2017, compromising 26,372,781 user accounts; the hackers stole email addresses, passwords and user names for members of the blogging service. A source who requested that the info be attributed to nano@databases[dot]pw turned the info over to Hunt, according to the listing.
“An archive of the data was subsequently shared on a popular hacking forum in May 2020 and redistributed broadly,” according to the listing.
Still, other evidence points to the breach happening sooner, according to another report. A now-defunct data-leak tracking service, We Leak Info, tweeted in July 2019 about a 2014 leak of 33 million LiveJournal accounts.
No matter the timeline, it does seem that LiveJournal was compromised and user information has been in the hands of bad actors for some time, who already have acted on that information with various types of attacks, ranging from the credential stuffing to email-based extortion, according to various sources.
The Have I Been Pawned listing cites “multiple reports of credential abuse” against a company called Dreamwidth, a spinoff of LiveJournal based on its original code base with a significant number of crossover users.
While Dreamwidth never confirmed the attacks, a Twitter user called “definitely not a huge award-winning fanfic author” who claims to be a co-founder of the site tweeted in response to Hunt on Tuesday that the site has definitely seen an uptick in credential-stuffing attacks.
The tweet seems to be backed up by a blog post from Dreamwidth co-founder and former LiveJournal staffer Mark Smith from April, which informs users of an update to the site’s authentication mechanism from outdated and insecure LiveJournal protocols to more secure web infrastructure.
“We are making some changes to how we do authentication (how you log in) that will unfortunately break a number of older clients that you might be using to talk to Dreamwidth,” he wrote, “This is very unfortunate, but we think that the tradeoffs in improved security are very much worth it.”
The post stops short, however, at acknowledging that any attacks were occurring based on data leaked from a LiveJournal breach.
“We do not believe, and have no evidence of, our database ever being leaked or accessed other than by the three staff members who maintain Dreamwidth’s infrastructure,” Smith wrote. “We are making these changes not because of some extrinsic motivation but because we believe that they’re the right thing to do.”
Meanwhile, there is earlier evidence from a couple of years ago that shows threat attackers using LiveJournal data for other scams.
A Twitter user who responded to a tweet by Hunt in 2018 – when rumors were circulating about a potential unconfirmed LiveJournal breach–said that hackers tried to extort money from him based on acquiring data from the breach. Freelance software engineer Alexander Mikhailian said his LiveJournal password was leaked and he received an extortion letter “asking to transfer $800 [in] bitcoins or else.”
Real estate app leaking thousands of user records and sensitive private messages
28.5.2020 Securityaffairs Incindent
The CyberNews research team uncovered an unsecured Amazon Simple Storage Service bucket of confidential user chat logs belonging to Real estate app Tellus, a US-based software company.
Tellus is a software company based in Palo Alto, California, backed by “well-known investors” that aims to “reimagine Real Estate for the modern era.” The company’s app portfolio includes the Tellus App, a real estate loan, management and investing program. Its target users are American landlords and tenants who can receive and pay rent money, as well as keep all of their ownership and rent related data like rental listings, personal information, and correspondence between tenants and landlords in one place.
The data bucket in question contains a folder with 6,729 CSV files related to the Tellus app that include the app’s user records, chat logs, and transaction records left on a publicly accessible Amazon storage server.
How we found the Tellus app bucket
We discovered the exposed data by scanning through open Amazon Simple Storage Service (S3) buckets, which are online servers that can be used to store data for websites, apps, archives, IoT devices, and more.
Amazon S3 buckets are also known for being challenging to secure, leaving many servers unprotected – and often in the news.
We identified Tellus as the owner of the database and notified the company about the leak. As of May 15, the data bucket security issue has been fixed by the Tellus security team and the data is no longer accessible.
What’s in the data bucket?
The unsecured and unencrypted Amazon S3 bucket contains, among other things:
16,861 user records, including 3,194 verified property owner records and 1,294 verified tenant records stored in separate files
Chat logs of private messages between thousands of Tellus platform users, including landlords, tenants, building managers, investors, and Tellus support staff between early 2018 and January 2020
Tens of thousands of timestamped property owner transaction records
Detailed tenant lead and payment records, including transaction metadata
All of this data is conveniently stored in spreadsheet format that can be easily opened, read, and downloaded by anyone who knows what to look for.
The exposed user records contain:
Full names of users, including verified tenants and property owners
Traceable user IDs used in transaction records and other logs
Email addresses
Phone numbers
Example of leaked user records:
The private messages in the chat logs and tenant lead files contain not only the texts of the conversations themselves, but also deeply sensitive content attached therein, including:
Full names of the parties involved in the conversation
Rent amounts and dates when they are due
Tenants’ rented home addresses
Case charges and court dates
Tenant document scans
Screenshots of sensitive images, including other conversations on social media
Example of leaked private messages:
Example of leaked tenant lead messages:

Example of leaked transaction records:

This means that, in the worst-case scenario, leaving the Tellus S3 bucket unsecured and unencrypted might have led to the continued exposure of data belonging to the entire Tellus user base over a period of up to two years, from 2018 to 2020.
Who had access?
The exposed data was hosted on an Amazon Simple Storage Service (S3) server and located in the US. It is currently unknown for how long the data was left unprotected, and we assume that anyone who knew what to look for could have accessed the data bucket without needing any kind of authentication during the unspecified exposure period.
With that said, it is unclear if any malicious actors have accessed the unsecured data bucket until it was closed by Tellus.
What’s the impact?
While numbers-wise this might not appear like a major leak, the impact on the nearly 17,000 Americans whose records were exposed could be significant if certain data was made publicly available.
Here’s how attackers might use the information found in the Tellus S3 bucket against the exposed users:
Blackmailing both tenants and landlords by threatening to publicize the sensitive content found in their private messages and transaction logs
Using the information found in private messages to mount targeted phishing attacks, hack online bank accounts, and engage in identity theft
Spamming emails and phones
Brute-forcing the passwords of the email addresses
Brute-forcing the passwords of the Tellus accounts and stealing the funds therein
Account credentials of 26+ million LiveJournal users leaked online
27.5.2020 Net-Security Incindent
A data dump containing account information of over 26 million LiveJournal users has been offered for sale on dark web marketplaces and is now being shared for free on underground hacker forums.
livejournal data dump
The data dump, supposedly originating from a 2014 LiveJournal breach, contains email addresses, usernames, profile URLs and plain text passwords of 33+ million users.
After removing duplicates, Troy Hunt has added the dump to the Have I Been Pwned? service, which potentially affected users can use to check whether they’ve been affected. He also dated the data dump to 2017 because the year was included in the data dump’s file name.
When did the breach happen?
The story of this data breach and leak is an interesting one.
There have been rumors about a supposed LiveJournal breach for years, though the blogging platform, which is owned by Russian media company Rambler Media Group, never confirmed them.
Back in 2018, Hunt received reports about a sextortion campaign targeting LiveJournal users and using their passwords:
Denise Paolucci, one of the owners of Dreamwidth, an online journal service based on the LiveJournal codebase (and with a significant crossover in user base), said on Tuesday that the data dump has been available on the black market since at least October of 2018, when they first reported people getting spam extortion emails with passwords in them.
“Beginning in March of 2020, and again in May of 2020, we saw several instances of Dreamwidth accounts being broken into and used for spam. We believed at the time, and continue to believe, that the source of the password information being used to break into these accounts is the same black-market file that claims to be LiveJournal password data. Every user we asked whether they had used the compromised password on LiveJournal before confirmed that they had,” she explained.
“We have no way to tell for sure whether LiveJournal has actually had a data breach, or whether the file that’s circulating is real or fake. All we can say for certain is that none of the evidence we’ve seen has disproven the claim made by the people offering the file that the file contains usernames and passwords taken from LiveJournal. We’ve contacted LiveJournal about our findings several times, and they’ve told us each time that they don’t believe the situation warrants disclosure to their users. However, at this point we must advise that you treat the file as legitimate and behave as though any password you used on LiveJournal in the past may be compromised.”
Past and current LiveJournal users are advised to change their passwords to a new, long and unique one and to do the same on any other account where they used the same one.
Qatar Tracing App Flaw Exposed 1 Mn Users' Data: Amnesty
27.5.2020 Securityweek BigBrothers Incindent
A security flaw in Qatar's controversial mandatory coronavirus contact tracing app exposed sensitive information of more than one million users, rights group Amnesty International warned Tuesday.
The glitch, which was fixed on Friday after being flagged by Amnesty a day earlier, made users' ID numbers, location and infection status vulnerable to hackers.
Privacy concerns over the app, which became mandatory for residents and citizens on pain of prison from Friday, had already prompted a rare backlash and forced officials to offer reassurance and concessions.
Users and experts had criticised the array of permissions required to install the app including access to files on Android devices, as well as allowing the software to make unprompted phone calls.
Despite insisting the unprecedented access was necessary for the system to work, officials said they would address privacy concerns and issued reworked software over the weekend.
"Amnesty International's Security Lab was able to access sensitive information, including people's name, health status and the GPS coordinates of a user's designated confinement location, as the central server did not have security measures in place to protect this data," the rights group said in a statement.
"While Amnesty International recognises the efforts and actions taken by the government of Qatar to contain the spread of the COVID-19 pandemic and the measures introduced to date, such as access to free healthcare, all measures must be in line with human rights standards."
More than 47,000 of Qatar's 2.75 million people have tested positive for the respiratory disease -- 1.7 percent of the population -- and 28 people have died.
Like other countries, Qatar has turned to mobiles to trace people's movements and track who they come into contact with, allowing officials to monitor coronavirus infections and flag possible contagion.
"The Ehteraz app's user privacy and platform security are of the utmost importance," Qatar's health ministry said in a statement on Tuesday.
"A comprehensive update of the app was rolled out on Sunday May 24 with expanded security and privacy features for all users."
But Etheraz, which means "Precaution", continues to allow real-time location tracking of users by authorities at any time, Amnesty said.
"It was a huge security weakness and a fundamental flaw in Qatar's contact tracing app that malicious attackers could have easily exploited," said Claudio Guarnieri, head of the group's security lab.
"The Qatari authorities must reverse the decision to make use of the app mandatory," he said.
23% of leading banks had an exposed database with potential data leakage
27.5.2020 Net-Security Incindent
Reposify unveiled research findings of critical asset exposures and vulnerabilities in attack surfaces of the world’s leading multinational banks.
Researchers measured the prevalence of exposed sensitive assets including exposed databases, remote login services, development tools and additional assets for 25 multinational banks and their 350+ subsidiaries.
Banks deal with exposed database threat
23% of banks had at least one misconfigured database exposed to the internet resulting in potential data leakage issues
54% of the banks had at least one RDP exposed to the internet
31% of banks had at least one vulnerability to Remote Code Execution
Multiple unsecured FTP servers with anonymous authentication were discovered
The myriad of exposures such as RDP, unsecured FTP and misconfigured development tools can be leveraged by attackers to gain unauthorized access to banks’ internal networks and result in data breach attacks. The exposed databases which were discovered place customer and other sensitive data at direct and imminent risk of exposure.
Banking industry DX challenges
In recent years, the banking industry has gone through a massive digital transformation. Alongside the many benefits, the increase in digitization and connectivity have created great security challenges and made the banking industry even more susceptible to cyber-attacks.
“The interconnectedness of IT systems and growth in third-party partners have expanded the external attack surface and potential weak points.” said Yaron Tal, CEO, Reposify.
“Banks’ IT ecosystems are in a constant state of flux and network perimeters are extending well beyond firewalls and control systems. Banks’ actual attack surfaces are simply much bigger than most realize.”
Visibility of internet facing assets inventory
Banks typically have well-established security programs which are heavily regulated by various institutions yet 84% of the exposed assets are likely to be under IT and security teams’ radars and out of the scope of traditional asset management and security tools.
Gaining visibility of the complete internet facing assets inventory is critical. External and continuous view allows teams to know at any given moment which of their known or unknown devices and services are exposed to the internet and to take steps to proactively manage and mitigate the risks.
3 hacking forums have been hacked and database have been leaked online
25.5.2020 securityaffairs Incindent
Three hacking forums Nulled.ch, Sinfulsite.com, and suxx.to have been hacked and their databases have been leaked online
Researchers from intelligence firm Cyble made the headlines again, this time they have discovered online the databases of three hacking forums. The three forums are Sinful Site, SUXX.TO and Nulled, they were all hacked.
These cybercrime forums are places of aggregations for hackers and cybercriminals, that could use them to participate in general discussion and sharing related resources.

Members of the forums share and sell data leaks, hacking tools, malware, tutorials, and much more. The databases appear to have been leaking in May 2020.
“Recently, the Cyble Research Team obtained the database leaks of these hacking forums which appear to have been leaking in May 2020. The Cyble’s researchers obtained-:
The databases of SUXX.TO and Nulled contains detailed information of their users, which appears to be dumped on 20 May 2020.
The full database of Sinful Site including the private messages, which appear to be dumped on 15 May 2020.
” reads the post published by security firm Cyble.
Cyble experts said that all the above databases have been indexed at AmIBreached data breach lookup service.
Hackers leak credit card info from Costa Rica's state bank
25.5.2020 Bleepingcomputer Incindent
Maze ransomware operators have published credit card data stolen from the Bank of Costa Rica (BCR). They threaten to leak similar files every week.
The hackers are doing this in support of their claim to have breached BCR in the past and the bank’s denial of these intrusions.
Valid numbers inside
In a post on their “leak” site this week, Maze operators shared a 2GB spreadsheet with payment card numbers from customers of Banco de Costa Rica.
The attackers say that they released the data because they are not looking to make any profit off it. Instead, they want to draw attention to the bank’s security lapses when it comes to protecting sensitive information.
Several screenshots from the database accompany the announcement, showing unencrypted credit card numbers. Together, the images contain data for at least 50 cards (some are listed multiple times). Previously, they published over 100 partial numbers (last four digits removed) with expiration date and verification codes.
BleepingComputer checked several numbers with two online validation services and most of them passed the check. Bank identification number (BIN) details showed that they were Visa or MasterCard debit cards issued by BCR.
It should be noted that one of the card validation sites states that the validity of a number does not guarantee that it is also in use. However, the details were confirmed when verified on a second online checker.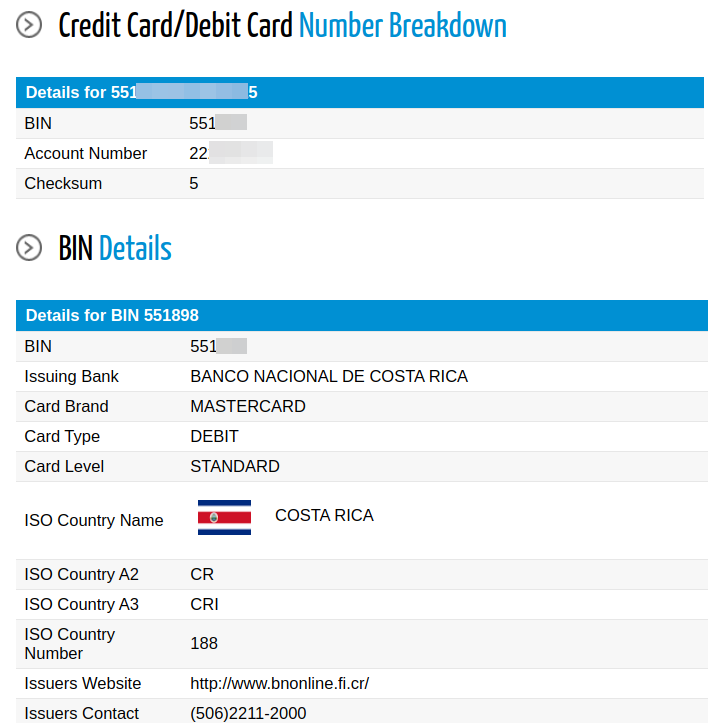
On April 30, Maze ransomware operators claimed to have more than 11 million cards from BCR, with 4 million being unique and 140,000 belonging to “US citizens.”
Maze said that they first gained access to the bank’s network in August 2019 and again in February 2020, to check if security had improved.
They chose to exit without encrypting the systems the second time because it “was at least incorrect during the world pandemic” and “the possible damage was too high.” But they did not leave empty-handed.
Battle of statements
BleepingComputer contacted BCR on May 1 to confirm either of the two incidents but received no reply. However, the bank issued a public statement that day saying that following an “exhaustive verification” they can “firmly confirm that the institution’s systems have not been violated.”
In response, Maze released four days later a spreadsheet with details about systems they claim to be from BCR’s network. On May 21 they dumped the payment card data.
The bank issued another statement on May 22 reiterating that multiple analyses from internal and external specialists confirmed that the systems were not accessed without authorization and that clients’ transactions were not impacted.
At the beginning of the month, Maze told BleepingComputer that they reached out to the bank multiple times with a ransom demand and that they may sell the card data on the dark web.
Even if they spared BCR's systems from encryption, the ransom was for showing the institution the vulnerable spots on its network.