
Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
Travel Tech Giant Sabre suffered a Data Breach, traveler data potentially at risk
4.5.2017 securityaffairs Incindent
Travel giant Sabre investigating a data breach that could have exposed payment and customer data tied to bookings processed through its reservations system.
Another day, another data breach, this time the victim is the Travel Tech Giant Sabre that in a SEC filing confirmed it is “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
In its SEC filing, Sabre confirmed that the attackers had been locked out of its systems, anyway we cannot exclude that crooks had accessed personally identifiable information (PII), payment card data, and other information managed by the firm.
“The unauthorized access has been shut off and there is no evidence of continued unauthorized activity,” reads a statement that Sabre sent to affected properties today. “There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected.”
The impact of the incident could be severe, the SynXis Central Reservation product is a rate and inventory management SaaS application that is currently used by more than 32,000 hotels worldwide.
According to the popular expert Brian Krebs, the company Sabre notified the incident to law enforcement and hired the firm Mandiant to investigate the case.
“Today, travel industry giant Sabre Corp. disclosed what could be a significant breach of payment and customer data tied to bookings processed through a reservations system that serves more than 32,000 hotels and other lodging establishments.” wrote Krebs.

This isn’t the first time Sabre suffered a cyber attack, in August 2015, the travel tech giant notified a cyber attack allegedly powered by a Chinese threat actor.
In December 2016, the notorious hackers Karsten Nohl and Nemanja Nikodijevic have demonstrated that the current travel booking systems are deeply insecure, they lack cyber security by design.
The experts explained that it is quite easy to modify any passenger’s reservation, cancel their flight bookings, and even use the refunds to book tickets for themselves.
Information Security Practices of Aadhaar – 135 Million Indian government payment card details leaked
3.5.2017 securityaffairs Incindent
A CIS study estimated number of Aadhaar numbers leaked through 4 gov portals could be around 135 million and 100M bank account numbers.
The Aadhaar is the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017.
The role of the system is crucial for both authenticating and authorizing transactions and is a pillar of the Indian UID (unique identification database).
Every problem with a similar system represents a disaster as explained in a report recently published by the Indian Centre for Internet and Society (CIS) titled “Information Security Practices of Aadhaar (or lack thereof): A documentation of public availability of Aadhaar Numbers with sensitive personal financial information“
The report highlighted the high security implemented by the Aahdaar itself, rather warn of possible data leaks caused by other government agencies accessing the system.
The research paper focus on four government-operated projects: Andhra Pradesh’s Mahatma Gandhi National Rural Employment Scheme; Chandranna Bima; the National Social Assistance Program; and an Andhra Pradesh portal of Daily “Online Payment Reports under NREGA” maintained by the National Informatics Centre.
Aadhaar system
The CIS examined numerous databases used by government offices, many of which included “numerous instances” of Aadhaar Numbers, associated with personal information.
“Actually, Aadhaar has a very strong privacy regulation built into it… But the area we are working on is enforcement,” Aruna Sundararajan, Secretary, Union Electronics and Information Technology Ministry, told The Hindu.
“People are not aware that so a large number of government agencies are making available all this sensitive data. So now, the process is to educate them so that they become aware that Aadhaar data is not meant to be published like this freely,”
According to the report, 135 million Aadhaar numbers and 100 million bank account numbers could have leaked from official portals dealing with government programs of pensions and rural employment.
The leaks represent a significant and “potentially irreversible privacy harm”, they potentially expose citizens to numerous illegal purposes.
Sundararajan confirmed that security and privacy issued will be addressed in the legislative amendments to the country’s IT legislation.
“Other major schemes, who have also used Aadhaar for direct benefit transfer [DBT] could have leaked PII similarly due to lack of information security practices. Over 23 crore beneficiaries have been brought under Aadhaar programme for DBT and if a significant number of schemes have mishandled data in a similar way, we could be looking at a data leak closer to that number,” concluded the report.
State-Affiliated Hackers Responsible for Nearly 1 in 5 External Data Breaches: Verizon DBIR
27.4.2017 securityweek Incindent
The Verizon Data Breach Investigations Report (DBIR) is industry's go-to analysis of security incidents and successful breaches over the previous year. The latest report was published Thursday.
The 2017 DBIR (PDF) marks the report's 10-year anniversary. Over the last decade, it has grown from an analysis of Verizon's own breach data knowledgebase to now include breach data from 65 different organizations. The latest report includes analyses of 42,068 incidents and 1,935 breaches from 84 countries.
Highlights show that the insider threat remains fairly constant as the cause of 25% of breaches, but with 75% being perpetrated by outsiders. The externally-caused breaches, according to Verizon, comprise 51% involving organized crime groups, 18% from state-affiliated actors, 3% comprising multiple parties, and 2% involving partners.
DBIR 2017 from VerizonSixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.
Verizon's figures show that the finance sector is the most frequently breached vertical. Twenty-four percent of breaches affected financial organizations. This was followed by healthcare at 15%; retail and accommodation combined at 15%; and public entities at 12%.
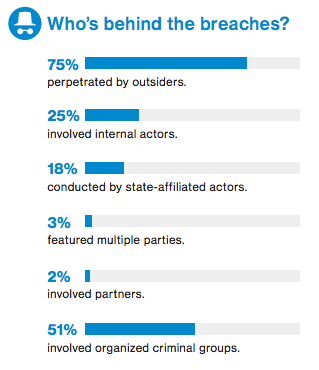
Other key statistics highlighted by Verizon include most of malware is installed via malicious email (66%); an even higher percentage (73%) of breaches are financially motivated; and that 21% were related to cyberespionage.
Verizon hopes that these statistics on recent breaches can help practitioners better protect their organizations today.
"Insights provided in the DBIR are leveling the cybersecurity playing field," said George Fischer, president of Verizon Enterprise Solutions. "Our data is giving governments and organizations the information they need to anticipate cyberattacks and more effectively mitigate cyber-risk. By analyzing data from our own security team and that of other leading security practitioners from around the world, we're able to offer valuable intelligence that can be used to transform an organization's risk profile."
This intent is further aided by a breakdown of methods used to attack the different vertical sectors. For example, the report notes that the accommodation and food services sector "was dominated by POS breaches. Most of them are opportunistic and financially motivated and involve primarily malware and hacking threat actions. Time-to-compromise is quick but time-to-discovery and containment remains in the months category."
One frequently highlighted attack vector is the web application attack, noted particularly in the financial and insurance; information; and retail sectors. "Attackers are always looking for the weakest link in your IT infrastructure, before leveraging expensive 0-days and complicated APT attacks," explains Ilia Kolochenko, CEO of High-Tech Bridge. "Today, the majority of large organizations and governments can be easily breached via their web and mobile (backend) applications."
He adds that this attack vector is still growing with the increasing use of third-party cloud services and applications, "which are exploited by hackers to compromise your trusted third-party and get access to your data afterwards... The report confirms Google's research, which found a 32% increase in website hacking in 2016. Application security becomes a major problem for organizations and should be addressed as a high priority," he suggests.
If there is any weakness in the DBIR as a guide for what to do today, it is that DBIR is an historical analysis of what has already happened in the recent past. For example, the report states that 51% of breaches included malware. On its own, this could persuade organizations to beef up their anti-malware defenses. However, because the analysis looks at past breaches rather than current threats, there is no clear indication of the current growth in non-malware attacks. Anti-malware defenses will not detect such attacks (which typically might use OS apps such as PowerShell) because there is no malware to detect.
Another example could be ransomware. Ransomware is difficult to place in the analysis because it is not a breach within Verizon's definition of breach (actual exfiltration of data), but clearly more than an incident. Furthermore, it is not unusual for infected organizations to decline to disclose the incident -- both of which factors could affect Verizon's statistics. To solve this issue, Verizon used telemetry data from McAFee for its information source.
McAfee's figures confirmed Verizon's own statistics -- that is, that the incidence of ransomware continues to rise -- but McAfee can provide greater detail. The difference is that McAfee's telemetry provides threat statistics, while the DBIR provides breach statistics. To get a complete view of the current situation, organizations need to consider both recent breaches and currently evolving threats.
Nevertheless, DBIR remains an invaluable resource for security practitioners. "From the beginning, it concludes, "our primary goal was, and still remains, to help organizations understand the threats they are facing, and enable them to make sound evidence-based risk management decisions."
Chipotle Investigating Payment Card Breach
26.4.2017 securityweek Incindent
Fast-casual restaurant chain Chipotle Mexican Grill, which has more than 2,000 locations in the United States and other countries, informed customers on Tuesday that its payment processing systems have been breached.
Chipotle said it recently detected unauthorized activity on the network that supports payment processing for its restaurants. The company’s investigation into the incident is ongoing and only limited information has been made public for now.
An initial investigation showed that attackers may have accessed data from cards used at restaurants between March 24 and April 18, 2017, but it’s unclear how many locations are affected.
Chipotle has notified law enforcement and it’s working with cybersecurity firms and its payment processor to investigate the incident. The company believes the breach has been contained, and pointed out that it has implemented some security enhancements.
“Consistent with good practices, consumers should closely monitor their payment card statements,” the company stated. “If anyone sees an unauthorized charge, they should immediately notify the bank that issued the card. Payment card network rules generally state that cardholders are not responsible for such charges.”
Chipotle’s disclosure of the data breach coincided with the company’s financial report for the first quarter of 2017. The restaurant said its revenue increased by 28.1% to $1.07 billion compared to the first quarter of 2016.
Several other major restaurant chains reported suffering data breaches in the past months, including Shoney’s, CiCi’s, Arby’s, Wendy’s and Noodles & Company.
Technical issue at the Jharkhand govt website caused the exposure of more than 1.4 million Aadhaar numbers
24.4.2017 securityaffairs Incindent
Personal information associated with more than a million Aadhaar numbers published on Jharkhand govt website due to a technical problem.
Digital identities of more than a million citizens have been exposed due to a coding error on a website maintained by the Jharkhand Directorate of Social Security.
“We got to know about it this week itself. Our programmers are working on it, and the matter should be addressed very soon,” said MS Bhatia, secretary of the state’s social welfare department.
The Jharkhand Directorate contains personal information of more than 1.6 million pensioners, the technical issue compromised citizen records containing names, addresses, Aadhaar numbers and bank account details of the beneficiaries of Jharkhand’s old age pension scheme.
“Their personal details are now freely available to anyone who logs onto the website, a major privacy breach at a time when the Supreme Court, cyber-security experts and opposition politicians have questioned a government policy to make Aadhaar mandatory to get benefits of a variety of government schemes and services.” reported the Hindustantimes.com.
The glitch exposed transaction-level data on pension paid to the citizens.
Aadhaar system
The Hindustantimes.com highlighted that the publishing of Aadhaar numbers is in contravention of Section 29 (4) of the Aadhaar Act.
Earlier this year, the Unique Identification Authority of India (UIDAI) blacklisted an Aadhaar service provider for 10 years due to a data leak that exposed the Aadhaar number of MS Dhoni, former captain of the Indian cricket team.
Incidents and abuses involving the Indian biometric ID system are not a rarity.
According to the Congress leader Jairam Ramesh the incident “makes a complete mockery of all that Jaitley and Ravi Shankar Prasad have said in Parliament.”
“Will the CEO of UIDAI take any action against the government of Jharkhand for making this dataset public? And if they don’t, does that mean they condone this act?” said Pranesh Prakash, policy director at the Centre for Internet and Society.
The Aadhaar is the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017, it is mandatory to provide an Aadhaar number when filing income tax returns.
Unfortunately, according to Ramesh, the system caused several problems to people, in some cases citizens had been denied their legally mandated welfare entitlements.
InterContinental Hotels Group, the international hotel chain confirmed a second credit card breach
19.4.2017 securityaffairs Incindent
The InterContinental Hotels Group announced that last week payment card systems at more than 1,000 of its hotels had been compromised by crooks.
The multinational hotel chain owns prestigious brands like Holiday Inn and Crowne Plaza.
This is the second time that the InterContinental Hotels Group suffers a credit card breach, early this year the hotel chain informed its customers that payment cards used between August and December 2016, at restaurants and bars of the 12 US hotels were affected by the data breach. The affected properties include the InterContinental San Francisco and Holiday Inn Resort – Aruba, the InterContinental Chicago Magnificent Mile.
On Friday the company published on its website a credit card breach notification informing it customers that a second breach occurred at select hotels between Sept. 29 and Dec. 29 last year.
“Many IHG-branded locations are independently owned and operated franchises, and certain of these franchisee operated locations in the Americas were made aware by payment card networks of patterns of unauthorized charges occurring on payment cards after they were legitimately used at their locations. To ensure an efficient and effective response, IHG hired a leading cyber security firm on behalf of franchisees to coordinate an examination of the payment card processing systems of franchise hotel locations in the Americas region.” reads the announcement published by the InterContinental Hotels Group.
“The investigation identified signs of the operation of malware designed to access payment card data from cards used onsite at front desks at certain IHG-branded franchise hotel locations between September 29, 2016 and December 29, 2016. Although there is no evidence of unauthorized access to payment card data after December 29, 2016, confirmation that the malware was eradicated did not occur until the properties were investigated in February and March 2017. “
The company highlighted that there’s no evidence payment card data was accessed after that some payment systems have been compromised with a malware.
The malware that infected the systems at the InterContinental Hotels Group was able to siphon credit card data from track in the magnetic strip (i.e. customers’ card number, expiration date, and internal verification code).
“The malware searched for track data (which sometimes has cardholder name in addition to card number, expiration date, and internal verification code) read from the magnetic stripe of a payment card as it was being routed through the affected hotel server. There is no indication that other guest information was affected. ” continues the credit card breach notification.
It is still unclear the number of properties affected by the second breach, customers can use a free web tool published by the company to search for potentially affected hotels in select states (US and Puerto Rico) and cities.
Data managed by the online tools suggests that more than a thousand hotels were affected by the incident.
The company confirmed that the investigation is still and it will update periodically data provided by the tool according to its findings.
The bad news is that several properties don’t participate in the investigation.
In response to the incidents, the company is improving security of its payment systems in order to repel malware-based attacks.
The hotels affected by this second breach had not yet implemented the announced improvement.
“Before this incident began, many IHG-branded franchise hotel locations had implemented IHG’s Secure Payment Solution (SPS), a point-to-point encryption payment acceptance solution. Properties that had implemented SPS before September 29, 2016 were not affected. Many more properties implemented SPS after September 29, 2016, and the implementation of SPS ended the ability of the malware to find payment card data and, therefore, cards used at these locations after SPS implementation were not affected. ” reads the announcement.
Cybercriminals Steal Card Data From Shoney's Restaurants
18.4.2017 securityweek Incindent
Cybercriminals managed to steal payment card data from nearly 40 Shoney’s restaurants after planting malware on their point-of-sale (PoS) systems.
Security blogger Brian Krebs learned from his sources in the financial industry that a fraud pattern had been spotted on cards used at locations of the Nashville, Tennessee-based restaurant chain. Shortly after Krebs published a blog post on Friday, Best American Hospitality Corp. confirmed that some of the Shoney's corporate affiliated restaurants it manages and operates had been hit by a data breach.
The company hired Kroll Cyber Security to investigate the incident. The security firm determined that hackers had remotely installed malware on payment processing systems at tens of Shoney’s restaurants.
The malware was designed to steal data such as cardholder name, card number, expiration date and internal verification code as it was being routed through the infected device. Investigators determined that in some cases the malware may not have obtained cardholder names.
Kroll’s investigation showed that some of the impacted locations were breached on December 27, 2016, while others were first compromised on January 11. Best American Hospitality is confident that the breach was contained by March 6.
As of last year, there were roughly 150 company-owned and franchised Shoney's restaurants across 17 U.S. states. Best American Hospitality said the breach affected 37 locations in South Carolina, Tennessee, Louisiana, Alabama, Georgia, Mississippi, Virginia, Missouri, Florida and Arkansas.
Several other major restaurant chains reported suffering data breaches in the past months, including CiCi’s, Arby’s, Wendy’s and Noodles & Company.
IHG warns of card-stealing malware at front desks
In addition to restaurants, several major hotel chains also reported being hit by card-stealing malware. One of them is InterContinental Hotels Group (IHG), which in early February confirmed that systems processing payments for bars and restaurants at 12 of the properties it manages had been compromised.
Now, IHG has informed customers that it has identified malware which may have stolen data from cards used at hotel front desks. The malware is believed to have stolen data between September 29 and December 29, 2016, but the company only received confirmation that the threat had been neutralized in February and March, when the affected properties were investigated.
Here's How Hacker Activated All Dallas Emergency Sirens On Friday Night
14.4.2017 thehackernews Incindent
Last weekend when outdoor emergency sirens in Dallas cried loudly for over 90 minutes, many researchers concluded that some hackers hijacked the alarm system by exploiting an issue in a vulnerable computer network.
But it turns out that the hackers did not breach Dallas' emergency services computer systems to trigger the city's outdoor sirens for tornado warnings and other emergencies, rather they did it entirely on radio.
According to a statement issued on Monday, Dallas City Manager T.C. Broadnax clarified the cause of the last Friday's chaos, saying the "hack" used a radio signal that spoofed the system used to control the siren network centrally.
"I don't want someone to understand how it was done so that they could try to do it again," Broadnax said without going much into details. "It was not a system software issue; it was a radio issue."
First installed in 2007, the Dallas outdoor emergency warning system powers 156 sirens made by a company called Federal Signal.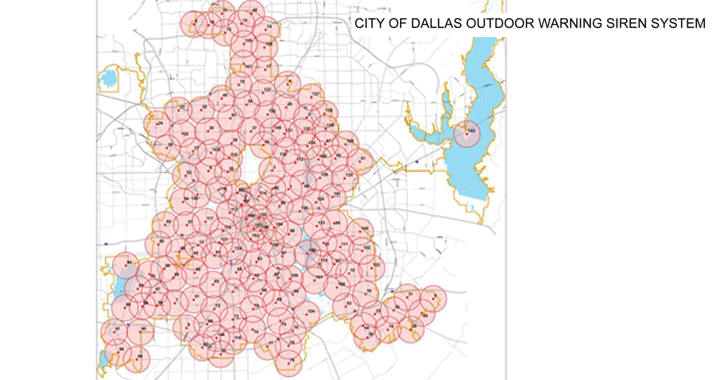
The city officials did not provide details on how the Emergency Alert System (EAS) works, but noted that "it's a tonal-type system" that's usually controlled by tone combinations used by the EAS broadcast over the National Weather Service's weather radio, and by Dual-Tone Multi-Frequency (DTMF) or Audio Frequency Shift Keying (AFSK) encoded commands from a command center terminal sent over an emergency radio frequency.
The Federal Communications Commission (FCC) currently has the 700MHz range of radio frequency reserved for US public safety.
This suggests that the emergency system could be compromised by outside radio equipment replicating the tonal code required to trigger the alarms — which, in other words, is known as a "radio replay" attack.
It is believed that the hacker who managed to trigger alarm last Friday somehow managed to gain access to the siren system documentation to know the exact tonal commands that trigger an alarm, and then just played that command signal repeatedly.
According to the city officials, the decade-old radio-based system was disabled hours after the breach and went live over the weekend with encryption to protect the language of tones as a measure to prevent such attacks.
The Dallas City Council has also voted to pay $100,000 more to its emergency siren system contractor to increase the security of the city's current system.
Once again Three mobile customers in UK experienced data breach
22.3.2017 securityaffairs Incindent
UK Three mobile customers experienced a new data breach, this time a technical issue caused the exposure of their personal details.
It has happened again, customers of the company Three UK experienced a new data breach.
Some customers logging into their accounts were able to view personal data (names, addresses, phone numbers) and call histories of other users.
The company promptly started an internal investigation and urged those affected to contact the customer service, it also confirmed that no financial data was exposed.
The Guardian confirmed that several customers were affected, it reported the case of several users presented with the data usage and call and text history of others when they logged in on Sunday night.
One customer cited by The Guardian, Mark Thompson, said it was a “shocking breach of data privacy”. He wrote on Three UK’s Facebook page: “Care to explain just how my details have been shared, how many people have had access to my personal information, for how long, and how many of your other customers have had their details leaked by yourselves to other members of the public as well?”

Three UK has 9 million customers in the UK, but according to the company only a small portion of customers has been affected by the issue.
“We are aware of a small number of customers who may have been able to view the mobile account details of other Three users using My3,” a spokesman said. “No financial details were viewable during this time and we are investigating the matter.”
The Information Commissioner’s Office announced it “will be looking into this potential incident involving Three”.
“Data protection law requires organisations to keep any personal information they hold secure. It’s our job to act on behalf of consumers to see whether that’s happened and take appropriate action if it has not.” said a spokeswoman from the ICO.
It isn’t the first time Three UK makes the headlines, in November 2016 the mobile carrier confirmed a major cyber security breach which exposed personal data of a portion of its customers, roughly 133,000 users.
Authorities arrested three men for this crime.
McDonald's App Leaks Details of 2.2 Million Customers
20.3.2017 securityweek Incindent
A vulnerable application used by millions of McDonald’s customers in India was recently found to leak personal information on its users.
Dubbed McDelivery, the web application was found to be leaking the personal information of over 2.2 million users. According to Fallible, the software security startup that discovered the bug, user data such as names, email addresses, phone numbers, home addresses, home co-ordinates, and social profile links were leaked by the application.
The issue, they reveal, resides in an unprotected publicly accessible API endpoint that was designed to deliver user details, which is coupled with serially enumerable integers as customer IDs. The pair can be used to pull the personal information pertaining to all of the application’s users.
“The mistake in this case was trivial and ought to have been fixed in a day at max. The app/website provides a facility to retrieve the current user details but does not check if the user ID being asked is the same user who has logged in. The user ID in this case is a plain number that starts from 1 and can be enumerated easily,” Abhishek Anand, Fallible co-founder, told SecurityWeek.
The vulnerability was discovered and disclosed on Feb. 7, and the company received acknowledgement from a Senior IT Manager at McDonald’s on Feb. 13, but the issue was addressed only last week, it seems. According to Fallible, however, McDonald’s fix wasn’t released in a timely manner and was also incomplete.
“We have always respected a company's request if they wanted more time to fix any issue but sadly they stopped responding after 4 weeks which led to us warning users that their data is out in the open. In fact, the 'fix' applied right now is incomplete and the vulnerability exists even now and we have intimated the same to the concerned company,” Anand told us.
Over the weekend, McDonald's published a statement on Facebook, saying that it has released an updated iteration of the McDelivery application and that it is prompting all users to update as soon as possible, as a precautionary measure.
“We would like to inform our users that our website and app does not store any sensitive financial data of the users like credit card details, wallets passwords or bank account information. The website and app has always been safe to use, and we update security measure on regular basis. As a precautionary measure, we would also urge our users to update the McDelivery app on their devices,” the statement reads.
According to Fallible, many companies in India ignore user data protection, mainly because there are no strong data protection and privacy laws or penalties. Furthermore, “there is a similar lack of push from non-government organizations to improve this scenario,” the company says. In the past, the security firm has discovered over 50 instances of data leaks in several Indian organizations.
In January, Fallible revealed that many third-party applications unnecessarily store keys or secrets that could allow attackers to access and leak data related to some of the most popular online services, including Twitter, Flickr, Dropbox, Slack, and Uber, as well as Amazon AWS (Amazon Web Services).
Travel Agent Association Breach Highlights Supply Chain Threat
16.3.2017 securityweek Incindent
The Association of British Travel Agents (ABTA) today informed users of a breach that may have affected up to 43,000 customers.
In a statement, CEO Mark Tanzer explained that he "recently became aware of unauthorized access to the web server supporting abta.com by an external infiltrator exploiting a vulnerability." That would seem to rule out insider action -- the web server was hacked.
The incident apparently occurred on Feb. 27 on a web server "managed for ABTA through a third-party web developer and hosting company." This phrase is repeated three times throughout the statement as if trying to reassure customers that it was not ABTA's 'fault'. Legally, that doesn't work. ABTA is clearly the data controller in this instance, and the data controller retains responsibility regardless of any third-party data processor (that is, the web-hosting company). If any subsequent investigation finds lack of regulatory compliance contributing to this breach, it is ABTA that will be held liable.
This highlights a major problem for all businesses: how to adequately security audit the supply chain.
"As this breach highlights," comments Ross Brewer, VP and EMEA MD of LogRhythm, "companies need to be conscious of third parties they work with as they can end up being a chink in their armor that they aren't aware of. Unfortunately, it's not uncommon for suppliers or partners to fall short in terms of security, jeopardizing the security of large organizations like ABTA."
Tony Pepper, co-founder and CEO of Egress, makes the same point. "It's one thing to be confident that you're ticking all the right boxes, but it's another to assume that other businesses are being just as thorough." It is, adds Dave Hartley, Associate Director at MWR InfoSecurity, "a powerful example of the dangers of divesting security responsibilities to third party developers and hosting providers." You can divest responsibility, but you cannot easily divest liability.
ABTA has reported the incident to the UK's data protection regulator, the Information Commissioners Officer (and the police). It will be some time before any compliance decision is made by the ICO.
In the meantime, ABTA is playing down the severity of the incident.
"The majority of the data," says the statement, "related to email addresses and passwords for any ABTA Member or customer of an ABTA Member that had registered on abta.com. These passwords were encrypted – which means to the human eye it will look like a jumble of characters -- and so there is a very low exposure risk of identity theft or online fraud."
The key phrase here is 'these passwords were encrypted'. But it doesn't specify whether they were encrypted or hashed, nor what hash algorithm was used, nor whether the hashes were salted. All of these details play into how easily the passwords can be decrypted -- which may simply be too easily.
"Encryption will hardly make a difference to the incident," warns Ilia Kolochenko, CEO of High-Tech Bridge. "Hashed passwords can be quite easily bruteforced, and taking into consideration modern computing capacities, including elastic cloud infrastructure, attackers will probably get the majority of passwords in plaintext without much effort."
The statement also says, "We are not aware of any information being shared beyond the infiltrator." This is another phrase designed to be reassuring but is ultimately meaningless unless the infiltrator is already known and apprehended (which of course is entirely possible). If this was a remote hack, then there is simply no way of knowing what the hacker may have done with the information.
This is particularly relevant to a part of the stolen data. Potentially accessed data includes a "smaller volume of data uploaded via the website by ABTA Members using the 'self-service' facility on abta.com, where ABTA Members have uploaded documentation in support of their membership." We don't know what members may have included in the uploaded supporting documentation, but it is likely to include names, addresses, phone numbers and so on in free text.
While ABTA says the passwords were encrypted, it does not say the documents were encrypted. This data is valuable to identity thieves, and victim members of ABTA will need to monitor their bank accounts and credit scores for years to come. Cyber criminals are well-known to be patient in their use of personal information for criminal purposes. As the ABTA statement says, victims "should remain vigilant regarding online and identity fraud: actively monitor your bank accounts and any social media and email accounts you may have."
In the meantime, victims should immediately change their ABTA password, and change any identical or even similar password used on any other account, to something strong and unique. Organizations, however, need urgently find some way to security audit their supply chain; a necessity that will only become more important as the EU's General Data Protection Regulation comes into force.
Roughly a year ago, Google decided to open source its Vendor Security Assessment Questionnaire (VSAQ) framework to help companies improve their security programs. While not an official product of the search giant, the interactive questionnaire application was developed to support security reviews by facilitating the collection of information and allowing users to display it in a template form.
It's Fappening Again! Private Photos of Emma Watson and Others Leaked Online
16.3.2017 thehackernews Incindent

Are you clicking nude selfies? That is fine and not any criminal act, but this act can land you in trouble — here's how!
Almost three years after a wave of private photographs of celebrities leaked online, "The Fappening 2.0" appears to be underway with the circulation of alleged naked pictures of female celebrities, including Emma Watson and Amanda Seyfried on Reddit and 4chan.
Back in 2014, anonymous hackers flooded the Internet with private photographs of major celebrities, including Jennifer Lawrence, Kim Kardashian, Kate Upton and Kirsten Dunst by hacking thousands of Apple's iCloud accounts.
The Fappening hackers have since been sent to prison.
The Fappening 2.0: It's Happening Again!
However, in the latest leak, which has been heralded online as "The Fappening 2.0," the personal photographs of Amanda Seyfried and Emma Watson — ranging from regular selfies to explicitly sexual photos — have been leaking online since Tuesday night.
According to a screenshot from an original 4chan thread, unknown hackers will be posting more intimate photos of female celebrities, including Kylie Jenner, Marisa Tomei, Jennifer Lawrence and several others, over the next few days, which indicates it's just the beginning of The Fappening 2.0.
The affected celebrities did not immediately comment on the invasion of any privacy on their side, but the photographs appear to be authentic.
A representative for Watson has also confirmed that she is taking legal action against the latest leak and that some of the images circulating online are legitimate, saying:
"Photos from a clothes fitting Emma had with a stylist a couple of years ago have been stolen. They are not nude photographs. Lawyers have been instructed and we are not commenting further."
While, leaked images of Watson show the actor posing in various swimsuits and outfits in front of a mirror, the alleged photos of actors Amanda Seyfried and Jillian Murray are much more explicit, appearing to show the stars nude and, in some images, engaging in sexual activity.
There are also pictures and videos that the leaker claims to be of Watson filming herself naked in the bathtub, while another showing her masturbating. But since the face of the woman in the shots can not be seen, this can't be confirmed.
There is yet no information on the source of the leaks or how the personal photos of celebrities were obtained, but the anonymous hackers are claiming that these leaks are just the tip of an iceberg and they're about to release the next batch of celebrities to get their photos leaked.
The most famous celebrities in the list of next wave of private photographs of celebrities appear to be Marisa Tomei, Kylie Jenner, and Jennifer Lawrence.
How To Keep Your Private Photos Private
The Fappening 2.0: Best way to keep your nude selfies off the Internet — Just don't click them!
CLICK TO TWEET
If you are looking for the best way to keep your photos off the Internet, the simplest solution to this is — Don't click them. But if you do so, there are a few steps that you can follow to minimize the risk:
Do not click on any suspicious links or attachments in the email you received.
When in doubt, contact the sender to confirm that he or she actually sent the email to you or not.
Never provide your personal or financial information through an email to anyone.
No service, be it Google, Apple, or Microsoft, ever asks for your password or any other sensitive personal information over an email.
It's always a good idea to regularly update your passwords and security questions.
Enable two-factor authentication on your accounts and always choose a strong and different password for all your accounts. If you are unable to create and remember different passwords for each site, you can use a good password manager.
Cybercriminals Hijack Magento Extension to Steal Card Data
14.3.2017 securityweek Incindent
Cybercriminals have been abusing a payment module to steal credit card data from online shops powered by the Magento ecommerce platform, web security firm Sucuri reported on Friday.
The targeted module is the Realex Payments Magento extension (SF9), which integrates with the Realex Realauth Remote payment gateway. The Realex Payments extension allows Magento store owners to process mail and telephone orders by entering the payment details themselves.
The extension itself is not vulnerable, but attackers can abuse it after they compromise the targeted Magento shop. In the attacks observed by Sucuri, hackers added a malicious function called sendCcNumber() to an SF9 file named Remote.php.
The function collects personal and financial data entered by users on the compromised website and sends it back to an email address controlled by the attacker.
The malicious function also leverages the online service binlist.net, which allows users to identify the issuer of a card based on the first six digits of the card number.
Sucuri said it had tracked “massive attacks” where hackers had injected malicious scripts into Magento websites in an effort to steal card data.
“Magento credit card stealers are indeed on the rise. While the information here is specific to Magento, realize that this can affect any platform that is used for ecommerce,” said Bruno Zanelato, malware analyst and team lead at Sucuri. “As the industry grows, so will the specific attacks targeting it. That’s why it is so important to keep your Magento website up to date and apply all the latest security patches!”
These types of attacks are not uncommon, and cybercriminals have used various tricks to evade detection and ensure that their malware is persistent.
In a campaign documented a few months ago, attackers hid stolen card data in harmless-looking image files related to products sold on the compromised website. More recently, researchers identified a piece of malware that restored itself on Magento websites after it had been removed.
640,000 stolen PlayStation accounts being sold on the Dark Web
10.3.2017 securityaffairs Incindent
The seller that goes online with moniker SunTzu583 is offering 640,000 PlayStation accounts for USD 35.71 (0.0292 BTC), it source is still a mystery.
The dark web is the right place where to buy stolen login credentials to major web services, last week the colleagues at HackRead reported the sale of more than 1 million Gmail and Yahoo accounts by a seller that goes online with the “SunTzu583” moniker
A few days later, the same vendor that was offering Gmail and Yahoo accounts for sale started selling PlayStation accounts.

SunTzu583 is offering for sale 640,000 PlayStation accounts for USD 35.71 (0.0292 BTC). The source of the stolen accounts is not clear, the dump includes emails and clear-text passwords.
SunTzu583 confirmed that the archive was not directly stolen from PlayStation network, but it does contain unique accounts of PlayStation users. The seller added that even if the accounts may work for other web services they are first of all PlayStation accounts.
A few months ago, several Playstation users reported their accounts have been hacked and that crooks have stolen the funds. Sony denied its server were hacked by crooks and added that the PlayStation accounts were accessed by using credentials from third-party data breaches.
At the time I was writing there is no confirmation about the authenticity of the 640,000 PlayStation accounts.
It is any way suggested to change the passwords for PS accounts, as usual, it is important to share the passwords for all the websites for which use the same login credentials.
Recently other gaming platforms were hacked, including the Clash of Clans forum, ESEA, and Epic Games.
Cloudflare tries to downplay the impact of the Cloudbleed incident
3.3.2017 securityaffairs Incindent
According to Cloudflare, an initial analysis conducted its experts reveals that no personal data was leaked due to the CloudBleed issue.
On February 17 the Google Project Zero researcher Tavis Ormandy disclosed a serious bug in Cloudflare infrastructure, so-called Cloudbleed.
Ormandy discovered that Cloudflare was leaking a wide range of sensitive information, including authentication cookies and login credentials.
“On February 17th 2017, I was working on a corpus distillation project, when I encountered some data that didn’t match what I had been expecting. It’s not unusual to find garbage, corrupt data, mislabeled data or just crazy non-conforming data…but the format of the data this time was confusing enough that I spent some time trying to debug what had gone wrong, wondering if it was a bug in my code. In fact, the data was bizarre enough that some colleagues around the Project Zero office even got intrigued.” Ormandy wrote in a security advisory. “We fetched a few live samples, and we observed encryption keys, cookies, passwords, chunks of POST data and even HTTPS requests for other major cloudflare-hosted sites from other users. Once we understood what we were seeing and the implications, we immediately stopped and contacted cloudflare security.”
Follow
Tavis Ormandy @taviso
Cloudflare have been leaking customer HTTPS sessions for months. Uber, 1Password, FitBit, OKCupid, etc. https://bugs.chromium.org/p/project-zero/issues/detail?id=1139 …
12:00 AM - 24 Feb 2017
5,204 5,204 Retweets 3,252 3,252 likes
The flaw was introduced in September 2016, but it had the greatest impact between February 13 and February 18, when one in every 3.3 million requests going through Cloudflare’s systems may have resulted in memory leakage. The bug itself was addressed within hours, but it took several days to contain the incident due to the fact that leaked data had been cached by search engines.
Cloudflare co-founder and CEO Matthew Prince published a detailed blog post to analyze this “extremely serious bug” with a potentially massive impact.
The experts at Cloudflare analyzed the logs of the servers and confirmed that no evidence of malicious exploitation and that the vast majority of customers were not impacted.
“Given that the data that leaked was random on a per request basis, most requests would return nothing interesting. But, every once in awhile, the data that leaked may return something of interest to a hacker.” reads the analysis published by Cloudflare.

“If a hacker were aware of the bug before it was patched and trying to exploit it then the best way for them to do so would be to send as many requests as possible to a page that contained the set of conditions that would trigger the bug. They could then record the results. Most of what they would get would be useless, but some would contain very sensitive information,”.
“The nightmare scenario we have been worried about is if a hacker had been aware of the bug and had been quietly mining data before we were notified by Google’s Project Zero team and were able to patch it,”.
The Cloudbleed flaw was exploited more than 1.2 million times from 6,500 sites potentially exposed to the issue.
According to the experts, every time customer data is present, the company reaches out to the customer to share the data that it has discovered and provides the necessary support to mitigate any impact of the accidental exposure.
“Generally, if customer data was exposed, invalidating session cookies and rolling any internal authorization tokens is the best advice to mitigate the largest potential risk based on our investigation so far.” reads CloudFlare.
Users who are concerned that their data may have been exposed by Cloudbleed are invited to give a look at the list of potentially affected websites, meantime the experts at Cloudflare are still investigating the incident. Ormandy believes the company downplayed the risk.
“It is not correct to conclude that no passwords, credit cards, health records, social security numbers, or customer encryption keys were ever exposed,” Prince added. “However, if there was any exposure, based on the data we’ve reviewed, it does not appear to have been widespread. We have also not had any confirmed reports of third parties discovering any of these sensitive data types on any cached pages.”
Researchers at CloudFlare have seen approximately 150 customers’ data on the more than 80,000 cached pages they have purged from search engine caches
Yahoo Reveals 32 Million Accounts Were Hacked Using 'Cookie Forging Attack'
2.3.2017 thehackernews Incindent
Yahoo has just revealed that around 32 million user accounts were accessed by hackers in the last two years using a sophisticated cookie forging attack without any password.
These compromised accounts are in addition to the Yahoo accounts affected by the two massive data breaches that the company disclosed in last few months.
The former tech giant said that in a regulatory filing Wednesday that the cookie caper is likely linked to the "same state-sponsored actor" thought to be behind a separate, 2014 data breach that resulted in the theft of 500 Million user accounts.
"Based on the investigation, we believe an unauthorized third party accessed the company's proprietary code to learn how to forge certain cookies," Yahoo said in its annual report filed with the US Securities and Exchange Commission (SEC).
"The outside forensic experts have identified approximately 32 million user accounts for which they believe forged cookies were used or taken in 2015 and 2016. We believe that some of this activity is connected to the same state-sponsored actor believed to be responsible for the 2014 security incident."
"Forged cookies" are digital keys that allow access to accounts without re-entering passwords.
Instead of stealing passwords, hackers trick a web browser into telling Yahoo that the victim had already logged in by forging little web browser tokens called cookies.
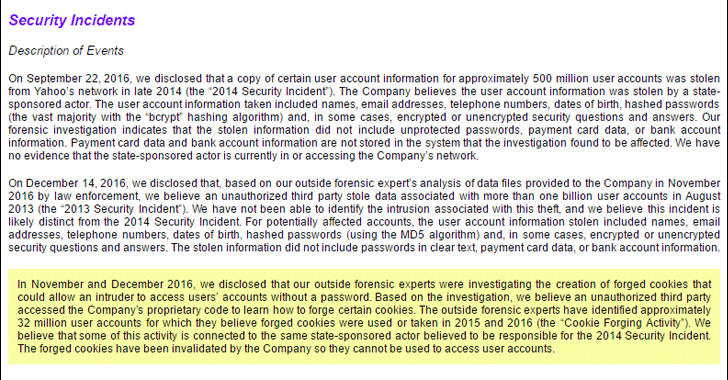
Yahoo revealed the cookie caper in December last year, but the news was largely overlooked, as the statement from Yahoo provided information on a separate data breach that occurred in August 2013 involving more than 1 Billion Yahoo accounts.
In a statement, the company said the hackers might have stolen names, email addresses, hashed passwords, telephone numbers, dates of birth, and, in some cases, encrypted or unencrypted security questions and answers.
Yahoo began warning its customers just last month that some state-sponsored actors had accessed their Yahoo accounts by using the sophisticated cookie forging attack.
However, the good news is that the forged cookies have since been "invalidated" by Yahoo so they cannot be used to access user accounts.
Yahoo's CEO Marissa Mayer Loses Bonus
In the meantime when Yahoo revealed about the scope of the cookie caper, Yahoo CEO Marissa Mayer said she would forgo her annual bonus, which is US$2 Million, and any 2017 equity award, which is usually about $12 Million of stock, in response to the security incidents occurred during her tenure.
"When I learned in September 2016 that a large number of our user database files had been stolen, I worked with the team to disclose the incident to users, regulators, and government agencies," Mayer wrote in a note published Monday on Tumblr.
"However, I am the CEO of the company and since this incident happened during my tenure, I have agreed to forgo my annual bonus and my annual equity grant this year and have expressed my desire that my bonus be redistributed to our company’s hardworking employees, who contributed so much to Yahoo’s success in 2016."
Besides this, Yahoo's general counsel and secretary Ronald Bell also resigned as of Wednesday after the company revealed that "senior executives and relevant legal staff were aware that a state-sponsored actor had accessed certain user accounts by exploiting the Company’s account management tool."
The ongoing revelation of security incidents in the company has hit Yahoo's credibility badly. Just last month, Yahoo and Verizon Communications Inc. agreed to reduce the price of the upcoming acquisition deal by $350 Million in the wake of the two data breaches.
The deal, which was previously finalized at $4.8 Billion, now valued at about $4.48 Billion in cash and is expected to close in the second quarter.
Boeing notified 36,000 employees following an accidental data leak
28.2.2017 securityaffairs Incindent
A Boeing employee inadvertently leaked the personal information of 36,000 co-workers late last year, the aerospace giant is notifying them the incident.
The aerospace giant Boeing notifies 36,000 employees following an accidental data leak. A company employee inadvertently leaked the personal information of his co-workers late last year, the man sent by email a company spreadsheet to his spouse who didn’t work at the company.
The file shared by the man contained sensitive, personally identifiable information of 36,000 Boeing employees, including names, places of birth, BEMSID, or employee ID numbers, and accounting department codes.
The data leak was publicly disclosed earlier February after the Boeing’s Deputy Chief Privacy Officer Marie Olson notified the security breach to the Attorney General for the state of Washington Bob Ferguson.
Boeing
According to Olson, the spreadsheet also included “hidden columns” containing social security numbers and dates of birth.
According to the breach notification, the incident occurred on Nov. 21, 2016, it was discovered on Jan. 9, but Boeing notified the security breach starting from Feb. 8.
In response to the breach, Boeing has destroyed copies of the spreadsheet from both the Boeing employee’s computer and his spouse’s PC.
“Both the employee and his spouse have confirmed to us that they have not distributed or used any of the information,” reads the Boeing breach notification.
Boeing experts don’t believe the data have been used inappropriately, anyway, it is offering employees two years access to a free identity theft protection service.
In order to avoid similar incidents in the near future, the company plans to require additional training to its employees on how to manage sensitive data and it to implement additional controls to sensitive information.
Unfortunately, this isn’t the first time that the company suffered similar incidents, in several cases, laptops containing sensitive data were stolen. In December 2006, thieves have stolen a laptop containing data related to 382,000 employees.
Hundreds of Arby's Restaurants Hit by Card Breach
10.2.2017 securityweek Incindent
Arby’s Restaurant Group, one of the largest fast food sandwich restaurant chains in the United States, admitted this week that its payment processing systems had been breached by cybercriminals.
Arby’s told journalist Brian Krebs, who learned about the incident from sources in the financial industry, that it was alerted to the breach in mid-January by industry partners. The company said it had not disclosed the incident to the public at the FBI’s request.
The fast food chain said it immediately brought in Mandiant and other security experts to remove the malware from its systems and investigate the incident. The company is confident that the compromised systems have been cleaned up.
The investigation is ongoing, but the breach appears to have affected Arby’s corporate-owned restaurants and not franchised locations. Of Arby’s more than 3,300 stores in the U.S., over 1,000 are corporate restaurants, but not all of them are impacted.
It is unclear how many payment cards may have been stolen, but Krebs is aware of an alert from PSCU, a credit union service organization with over 800 members, which warned that more than 355,000 credit and debit cards issued by its members were compromised in a breach at a major fast food restaurant chain.
The PSCU alert estimated that the breach occurred between October 25, 2016 and January 19, 2017.
Arby’s is not the only major fast food restaurant chain targeted by cybercriminals. Wendy’s launched an investigation in January 2016 and initially determined that roughly 300 of its restaurants had been hit by a hacker attack that started in 2015.
Wendy’s later determined that the actual number of affected locations exceeded 1,000 and experts believe the incident affected hundreds of thousands of cards.
Arby’s Restaurant Group confirmed a massive card breach hit its stores
10.2.2017 securityaffairs Incindent
Arby’s Restaurant Group, one of the largest fast food sandwich restaurant chains in the US, confirmed that its PoS systems had been breached by crooks.
Hundreds of Arby’s Restaurants suffered a card breach, the Arby’s Restaurant Group is the second-largest quick-service fast-food sandwich restaurant chain in the US. Arby’s has more than 3,330 stores in the United States, one-third of those is directly owned by the company.
Brian Krebs first learned about the card breach from its sources in the financial industry, later representatives from the group confirmed him the incident. Arby’s Restaurants discovered the security breach in the mid-January when it was alerted by industry partners.
“Sources at nearly a half-dozen banks and credit unions independently reached out over the past 48 hours to inquire if I’d heard anything about a data breach at Arby’s fast-food restaurants. Asked about the rumors, Arby’s told KrebsOnSecurity that it recently remediated a breach involving malicious software installed on payment card systems at hundreds of its restaurant locations nationwide.” wrote Brian Krebs
Why was the incident disclosed only now?
According to the company, the card breach was publicly disclosed only now due to an explicit request made by the FBI.
“A spokesperson for Atlanta, Ga.-based Arby’s said the company was first notified by industry partners in mid-January about a breach at some stores, but that it had not gone public about the incident at the request of the FBI.” continues Krebs.
“Arby’s Restaurant Group, Inc. (ARG) was recently provided with information that prompted it to launch an investigation of its payment card systems,” the company said in a written statement provided to KrebsOnSecurity.
“Upon learning of the incident, ARG immediately notified law enforcement and enlisted the expertise of leading security experts, including Mandiant,” their statement continued. “While the investigation is ongoing, ARG quickly took measures to contain this incident and eradicate the malware from systems at restaurants that were impacted.”
The company hired Mandiant and other security experts to remove sanitize its systems and investigate the card breach. At the time I was writing, the company confirmed that systems have been cleaned up.
“Although there are over 1,000 corporate Arby’s restaurants, not all of the corporate restaurants were affected,” said Christopher Fuller, Arby’s senior vice president of communications. “But this is the most important point: That we have fully contained and eradicated the malware that was on our point-of-sale systems.”
Crooks used a malware to compromise PoS systems at the Arby’s Restaurant Group, it is not clear how many payment cards may have been affected.
According to Krebs, who is aware of an alert from PSCU, more than 355,000 credit and debit cards issued by its members were compromised in a card breach at a major fast food restaurant chain.
The PSCU dated the card breach in the period between October 25, 2016 and January 19, 2017.
On July 2016, another major fast food restaurant chain suffered a card breach, the Wendy’s fast-food chain determined that roughly 1,000 of its restaurants had been breached by cyber criminals.
SCADA Honeywell XL Web II Controller exposed password in clear text
6.2.2017 securityaffairs Incindent
The web-based SCADA system Honeywell XL Web II Controller is affected by multiple flaws that can be remotely exploited to expose passwords in clear text.
A popular web-based SCADA system designed by Honeywell is affected by multiple vulnerabilities that can be remotely exploited to expose passwords in clear text.
In order to access the password in clear text, the attacker just has to access a particular URL to trigger one of the flaws.
The vulnerabilities affect some versions of Honeywell XL Web II controllers, a system that is widely adopted in critical infrastructure across various industries, including energy, wastewater, and manufacturing.
According to the ICS-CERT security advisory, the majority of the affected products is located in Europe and the Middle East.
The Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued a security advisory to warn of the flaws.
“Independent researcher Maxim Rupp has identified vulnerabilities in Honeywell’s XL Web II controller application.” reads the security advisory. “An attacker may use these vulnerabilities to expose a password by accessing a specific URL. The XL Web II controller application effectively becomes an entry point into the network where it is located.”
Follow
ICS-CERT @ICSCERT
ICS-CERT issued advisory ICSA-17-033-01 Honeywell XL Web II Controller Vulnerabilities to ICS-CERT web site http://go.usa.gov/x9Hqg
6:13 PM - 2 Feb 2017
19 19 Retweets 5 5 likes
Follow
Maxim Rupp @mmrupp
#Honeywell XL1000C500 XLWebExe-2-01-00 and prior + XLWeb 500 XLWebExe-1-02-08 and prior.
Coming soon. #ICS #Advisory
8:24 PM - 6 Jan 2017
1 1 Retweet 2 2 likes
The affected products are the Honeywell XL1000C500 XLWebExe-2-01-00 and prior, and XLWeb 500 XLWebExe-1-02-08 and prior.
Honeywell has produced a new version (version 3.04.05.05) to address the vulnerabilities, in order to receive the security updates customers have to contact their local Honeywell Building Solutions branch.
The attacker can also exploit other flaws in the Honeywell XL Web II controllers, he can carry out a path traversal attack by accessing a specific URL, open and change some parameters by accessing a particular URL, or establish a new user session.
The researcher Maxim Rupp that discovered the flaws has detailed them in a blog post recently published.
12 InterContinental Hotels Group properties suffered a massive data breach
5.2.2017 securityaffairs Incindent
Hackers compromised payment systems at 12 US properties of the InterContinental Hotels Group and stolen card data with a malware.
The hospitality giant InterContinental Hotels Group (IHG) has confirmed that payment systems of 12 US hotels were victims of a massive data breach. Just a month ago the company InterContinental Hotels Group (IHG) confirmed an ongoing investigation of alleged card breach at some of its properties.
The InterContinental Hotels Group (IHG) informed its customers that payment cards used between August and December 2016, at restaurants and bars of the 12 US hotels were affected by the data breach. The affected properties include the InterContinental San Francisco and Holiday Inn Resort – Aruba, the InterContinental Chicago Magnificent Mile.
The hackers used a malware to infect payment systems and steal card data, including cardholders’ name, card number, expiration date, and internal verification code.
“IHG hired leading cyber security firms to examine the payment card processing systems for the hotels that it manages in the Americas region. Based on the investigation, IHG is providing notification to guests who used their payment card at restaurants and bars of 12 company managed properties during the time periods from August 2016 – December 2016. An investigation of other properties in the Americas region is ongoing.” reads the official announcement published by the company.
The hospitality giant confirmed that the malicious code used by crooks did not affect payment cards used at the front desk.
“Findings show that malware was installed on servers that processed payment cards used at restaurants and bars of 12 IHG managed properties. Cards used at the front desk of these properties were not affected.” continued the statement from the company.
The InterContinental Hotels Group reported the security breach to the law enforcement and is collaborating with the payment card networks to allow banks monitoring for fraudulent transactions.
At the time I was writing there is no news regarding the number of affected customers.
IHG established a dedicated call center to answer any questions of the guests, for additional information about the security breach it is possible to visit the following website:
www.ihg.com/protectingourguests.
Law Enforcement Raid Blamed For LeakedSource Shutdown
27.1.2017 SecurityWeek Incindent
The controversial data breach notification service LeakedSource has been down for nearly 24 hours and it is rumored that the website has gone offline following a law enforcement raid.
LeakedSource is the service that disclosed many of the mega breaches that came to light in 2016, including the ones affecting FriendFinder Networks, VerticalScope, Last.fm, LinkedIn, DailyMotion and Rambler. These leaks have led to 2016 being a record year for data breaches, with a total of more than 4.2 billion records exposed.
The operators of LeakedSource have not been active on Twitter since January 10 and users have complained on several occasions about the website being down. The service is now once again offline, but this time some people believe it will not be returning.
A message (cached) posted on Thursday by a user on a hacking forum claimed “LeakedSource is down forever and won’t be coming back.”
“Owner raided early this morning. Wasn't arrested, but all SSD's got taken, and Leakedsource servers got subpoena'd and placed under federal investigation. If somehow he recovers from this and launches LS again, then I'll be wrong. But I am not wrong,” the user said.
While this statement has led some to believe that the owner of LeakedSource has been targeted by law enforcement in the United States, the company claimed in the past that it was based outside the U.S.
Users have complained on several hacker forums that they had just purchased a subscription on LeakedSource. Others have already started advertising alternative services.
SecurityWeek has reached out to LeakedSource representatives and will update this article if they respond.
Some members of the industry said they would not be surprised if the reports of a raid turn out to be true. Troy Hunt, the Australian security expert who runs the breach notification service Have I Been Pwned, pointed out that, unlike the website he operates, LeakedSource has often been used for malicious purposes.
LeakedSource stored a lot of sensitive information – its databases allegedly held 3.1 billion accounts – and users who paid for a subscription were given access to data such as usernames, passwords (hashed and clear text), email addresses, and IP addresses.
Hunt noted that while LeakedSource had been operating from behind CloudFlare, its real IP address could have been easily obtained by law enforcement using freely available services such as CrimeFlare.
“By late 2016, it was becoming apparent that their actions were erring very much on the black side of grey. There was a constant flow of data that wasn't appearing anywhere else in the usual trading circles before first coming to air via their service,” Hunt said in a blog post.
“Speculation was rife that there was incentivisation occurring not just to provide data that had already been obtained, but to actively seek out new targets that could subsequently be added to the feed of data then monetised by selling the personal information of the victims to whomever was willing to pay for it. This was always rumoured amongst those ‘in the scene’, but it's not yet clear whether this contributed to the take down or if it was solely due to the services directly provided on the site,” he added.
4.2 Billion Records Exposed in Data Breaches in 2016: Report
27.1.2017 Securityweek Incindent
2016 was a record year for data breaches, as the number of exposed records exceeded 4.2 billion, nearly four times than the previously set record.
The latest release of Risk Based Security’s annual Data Breach QuickView report shows that there were 4,149 data breaches reported during 2016, down from the 4,326 data breaches reported in 2015. The number of exposed records, however, reached an all-time high that might not be easily equaled: 4.281 billion. The previous record was established in 2013 at 1.106 billion.
Over half of the compromised records came from Myspace and Yahoo last year. The former confirmed in May that over 400 million accounts were compromised in a data breach that took place in 2013, while the latter revealed two different hacking incidents, a 2014 one, which resulted in 500 million compromised accounts, and a 2013 one, with over 1 billion compromised accounts.
However, these weren’t the only popular services to have suffered massive data breaches that were reported last year: Mail.Ru (25 million compromised records), LinkedIn (167 million), Tumblr (65 million), VK (170 million), VerticalScope (45 million), and Last.fm (43 million) are also on the list. In fact, the top 10 breaches in 2016 exposed a total of more than 3 billion records.
According to Risk Based Security’s report (PDF), no less than 94 breaches in 2016 had exposed one million or more records. However, 50.4% of the data breaches reported last year exposed only between one and 10,000 records, while 37.2% of them exposed less than 1,000 records.
Business (80.9% of the number of records exposed) and Government (5.6%) sectors were hit the most in last year’s incidents, with the Medical industry (0.3%) and Education (less than 0.1%) next on the list. A great amount of breaches hit “Unknown” industries (13.1% of the exposed records).
The report also notes that 53.3% of the breaches were the result of hacking operations, and that they accounted for 91.9% of the exposed records. Malware accounted for 4.5% of the data breaches, but only 0.4% of the compromised records were affected. Misconfigured databases and other inadvertent web based disclosures exposed over 253 million records in 2016, the report reveals.
Breaches involving U.S. entities accounted for 47.5% of the breaches last year, and for 68.2% of the exposed records, the firm notes. A report from CyberScout (formerly IDT911) and the Identity Theft Resource Center (ITRC) this week revealed that 1,093 breaches were disclosed by organizations in the United States last year, up 40% compared to 2015.
Only 18.3% of the incidents reported last year were the result of insider activity, including accidental, malicious and unknown intent. “56.3% of incidents originating from malicious insiders had no confirmed record count, while 39.3% of incidents originating from insider accidents had no confirmed count,” the report reads.
Email addresses were exposed in 42.6% of the data breaches, with emails and passwords considered the prize targets of these incidents. In fact, the number of impacted passwords skyrocketed last year, reaching 3.2 billion, although it was of only 151 million in 2015.
“With 102 countries reporting at least one data breach in 2016, Risk Based Security’s research suggests that no industry, organization size or geographic location, is immune to a data breach. The total number of reported breaches tracked by Risk Based Security has exceeded 23,700, exposing over 9.2 billion records,” the security firm notes.
180,000 members of an underground ‘Upskirt’ porn website have been leaked online
26.1.2017 securityaffairs Incindent
The personal details of 180,000 members of the underground ‘Upskirt’ porn website The Candid Board have been leaked online.
Some data breaches are more uncomfortable the others due to the nature of the affected services, porn and dating websites belong to these categories.
The personal details of roughly 180,000 members of the underground ‘Upskirt’ porn website The Candid Board have been leaked online due to a misconfigured database. The Candid Board is an ‘Upskirt’ porn website focused on the sharing of images, videos, and discussions about girls and women who appear to be unaware they are being spied.
The leaked data includes 178,201 unique email addresses, usernames, hashed passwords, dates of birth, IP addresses and other information such as ‘join date’, ‘last post date’ and ‘reputation’ point statistics.
The subscription fee is at $19.99 a month, but it seems that there were no financial data included in the data leak.
The IBTimes UK obtained the leaked data from a source who wished to remain anonymous and analyzed it.
“The details from the leaked database, which has now been secured, were reportedly obtained from September 2015. They were being managed by a US-based cloud hosting provider called Webair.”
“Rather than try to track down a forum administrator, who probably doesn’t want to be tracked down, I decided to contact the hosting company Webair,” our source said. “I made my way through an automated system and pushed the buttons for tech support.
“When I described the issue to the support on the other side, he immediately understood what the problem was. It was almost as if they were aware of the problems in their system. We didn’t talk for long. He said he would contact the client and then we hung up.”
Among the leaked details there were 70 military records and 19 government email addresses.
If you want to verify if your email has been exposed you can visit the data breach notification website HaveIBeenPwned that has uploaded the data to its service. In this specific case, the service will allow only verified owners to check for their email.
“It’s amazing how much personal data people will entrust sites of this nature with,” said the popular expert Troy Hunt. “Members provided accurate email addresses and birthdates which combined with their IP address now very clearly ties them back to a site of very questionable legal status.”
IBTimes UK tested a number of the IP numbers in the leaked data and verified that they match their corresponding email address.
“In one example, an IP search for the person using the email “wales.gsi.gov.uk” brought up the result: http://host246.welsh-ofce.gov.uk.”
The source also confirmed to be in possession of another large chunk of data from multiple boards operated by the same company, it seems he had access to another leaked database containing tens of thousands of records from a website called NonNudeGirls.
The recent incident is not an isolated case, in September records belonging to 800,000 users of Brazzers porn website were leaked online.
While the stolen data relates to login details for the Brazzers forum rather than the main site, it is thought that many users have duplicated their passwords across both.
Western Union agreed to pay $586 Million to settle fraud charges
23.1.2017 securityaffairs Incindent
The money transfer leader company Western Union has agreed to forfeit $586 million to settle fraud charges and admitted it facilitated scammers.
Money transfer leader company Western Union has admitted to facilitating wire fraud and it has agreed to pay $586 million to settle fraud charges from the U.S. Federal Trade Commission (FTC) and the Department of Justice.
The services offered by the Western Union’s have often exploited by crooks and fraudsters because the company has failed to maintain a proper anti-fraud program.
The U.S. Federal Trade Commission (FTC) and the Department of Justice accused the company of not taking immediate action against cyber criminals that used its service to transfer money that is the result of illicit activities.
Since 2001, the US authorities have convicted 29 owners and employees of Western Union agents for their active participation in fraud schemes.
“As this case shows, wiring money can be the fastest way to send it – directly into the pockets of criminals and scam artists,” said Acting Assistant Attorney General David Bitkower. “Western Union is now paying the price for placing profits ahead of its own customers. Together with our colleagues, the Criminal Division will both hold to account those who facilitate fraud and abuse of vulnerable populations, and also work to recoup losses and compensate victims.”
“Our investigation uncovered hundreds of millions of dollars being sent to China in structured transactions designed to avoid the reporting requirements of the Bank Secrecy Act, and much of the money was sent to China by illegal immigrants to pay their human smugglers,” said U.S. Attorney Eileen M. Decker. “In a case being prosecuted by my office, a Western Union agent has pleaded guilty to federal charges of structuring transactions – illegal conduct the company knew about for at least five years. Western Union documents indicate that its employees fought to keep this agent – as well as several other high-volume independent agents in New York City – working for the Western Union because of the high volume of their activity. This action today will ensure that Western Union effectively controls its agents and prevents the use of its money transfer system for illegal purposes.”
Western Union has been charged with violating several laws, including the Bank Secrecy Act (BSA) and the FTC Act.
The FTC said Western Union had received, between January 1, 2004 and August 29, 2015, 550,928 complaints regarding fraudulent transfers.
Fraudulent money transfers are related to online dating, lottery, family emergency scams and other illegal activities. The total of the transfers totaled more than $632 million, but prosecutors believe it is just the tip of the iceberg. Many victims don’t file a complaint and fraud-reporting mechanisms are not available everywhere.
“Western Union maintains a database of complaints it receives about fraud-induced money transfers. Based on information in that database, between January 1, 2004 and August 29, 2015, Western Union received at least 550,928 complaints about fraud-induced money transfers, totaling at least $632,721,044. Over 80% of the complaints in the database were from U.S. consumers” reads the complaint.

Western Union has agreed to forfeit $586 million, the money will be used to compensate the victims of the frauds.
“The Western Union Company (Western Union), a global money services business headquartered in Englewood, Colorado, has agreed to forfeit $586 million and enter into agreements with the Federal Trade Commission, the Justice Department, and the U.S. Attorneys’ Offices of the Middle District of Pennsylvania, the Central District of California, the Eastern District of Pennsylvania and the Southern District of Florida. In its agreement with the Justice Department, Western Union admits to criminal violations including willfully failing to maintain an effective anti-money laundering program and aiding and abetting wire fraud.” states the settlement.
The FTC has ordered Western Union to implement and maintain a comprehensive anti-fraud program, it prohibits the company from transmitting a money transfer that it knows or reasonably should know is fraud-induced, and requires it to:
block money transfers sent to any person who is the subject of a fraud report;
provide clear and conspicuous consumer fraud warnings on its paper and electronic money transfer forms;
increase the availability of websites and telephone numbers that enable consumers to file fraud complaints; and
refund a fraudulently induced money transfer if the company failed to comply with its anti-fraud procedures in connection with that transaction.
Western Union isn’t the unique money transfer company targeted by the FTC, MoneyGram agreed to pay $18 million in 2009 to settle charges.
Western Union Pays $586 Million to Settle Fraud Charges
20.1.2017 Securityweek Incindent
Global financial services company Western Union has admitted to facilitating wire fraud and it has agreed to forfeit $586 million as part of a settlement with the U.S. Federal Trade Commission (FTC) and the Department of Justice.
Western Union’s services have often been used by fraudsters and cybercriminals, and authorities in the United States have been displeased with the fact that the company has failed to maintain a proper anti-fraud program.
Furthermore, the company has been accused of not taking immediate action against agents that knowingly processed fraud payments in return for a cut of the illegal profits. Since 2001, the Department of Justice has convicted 29 owners and employees of Western Union agents for their role in fraud schemes.
According to authorities, Western Union has violated several laws, including the Bank Secrecy Act (BSA) and the FTC Act.
The FTC said Western Union had received, between January 2004 and August 2015, more than 550,000 complaints regarding fraudulent transfers involving advance-fee, online dating, lottery, and family emergency scams. These transfers totaled more than $632 million, but they are believed to represent only a fraction as not all complaints have been logged, not all victims filed a complaint, and fraud-reporting mechanisms are not available everywhere.
As part of its settlement with the FTC and the Justice Department, Western Union has agreed to forfeit $586 million, a sum that will be used to compensate fraud victims. The process through which the money will be distributed will be established at a later date.
The company will also implement and maintain a comprehensive anti-fraud program, thoroughly vet new and renewing agents, and suspend or terminate agents that don’t comply with its policies.
The FTC has ordered Western Union to stop processing fraud-induced and telemarketing-related money transfers, provide more fraud warnings, create additional channels for fraud complaints, and refund fraudulent transfers.
MoneyGram, Western Union’s main competitor, was also targeted by the FTC. The company agreed to pay $18 million in 2009 to settle charges.
Hello Kitty database leaked online, 3.3 million fans affected
10.1.2017 securityaffairs Incindent
The Hello Kitty MongoDB database leaked online one year ago recently surface on the web, it includes 3.3 million records belonging to Hello Kitty fans.
The security researcher Chris Vickery discovered a Sanrio database that was misconfigured and exposed to the public in 2015.
On December 2015, Vickery reported the discovery to Databreaches.net and Salted Hash.
According to Vickery not only the primary database sanriotown.com was affected, the fan portals of the following websites were also impacted by the leak:
hellokitty.com;
hellokitty.com.sg;
hellokitty.com.my;
hellokitty.in.th;
mymelody.com.
The expert noticed that 186,261 of the records belonged to Sanrio users under the age of 18.
At the time of its discovery, Sanrio explained that it doesn’t believe the data was stolen. Now the same MongoDB database has surfaced online and the 3.3 million records put Hello Kitty fans at risk.
During the weekend, the data breach notification service LeakedSource confirmed that a Sanrio database containing 3,345,168 million users has surfaced online.
The records contained in the leaked database include first and last names, gender, encoded birthday (easily reversible), country, email addresses, SHA-1 hash passwords, password hint questions with corresponding answers, and other information.

Vickery confirmed that data available via LeakedSource is identical to what he discovered more than a year ago.
The unique difference between the two databases is a field, dubbed ‘incomeRange,’ in the LeakedSource records that was not present in the original archive. The “incomeRange” attribute comes with values running from 0 to 150, but it is still unclear its meaning.
Chris Vickery discovered many other clamorous cases of open MongoDB exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
A few hours ago I published another post related to cyber attacks against misconfigured MongoDB databases.
MongoDB ransom attacks soar, according to the Australian Communications and Media Authority Antipodes the number of hacked systems more than double to 27,000 in just a day. According to the experts, the hackers are implementing an extortion mechanism copying and deleting data from vulnerable databases.
ESEA data breach, 1.5 million gamers’ records leaked
9.1.2017 securityaffairs Incindent
The E-Sports Entertainment Association (ESEA), one of the largest competitive video gaming communities was hacked, 1.5 million players have been affected.
Bad news for gamers, the E-Sports Entertainment Association (ESEA), one of the largest competitive video gaming communities was hacked in December. The data breach exposed the profiles of more than 1.5 million players.
The incident was also confirmed on Saturday by the breach notification service LeakedSource that reported 1,503,707 ESEA records were compromised.
The records include username, first and last name, password bcrypt hash, email address, registration date, city, state (or province), last login, date of birth, zip code, phone number, website URL, Steam ID, Xbox ID, and PSN ID.
As you can see the profiles are very detailed, the use of the bcrypt hash protect users’ passwords, anyway gamers are exposed to a wide range of malicious activities such as social engineering attacks and spear phishing attacks.
ESEA shared the link to the following “Outage and Security Update” via Twitter.
“Recently news has been made that ESEA’s user data has been leaked online. We expected something like this could happen but have not confirmed this is ESEA’s data. We notified the community on December 30th, 2016 about the possibility this could happen. The type of data and storage standards was disclosed. We have been working around the clock to further fortify security and will bring our website online shortly when that next round is complete. This possible user data leak is not connected to the current service outage.”
Segui
ESEA ✔ @ESEA
ESEA Outage and Security Update
Read: http://tl.gd/n_1spgt4i
04:29 - 8 Gen 2017
47 47 Retweet 100 100 Mi piace
The company was informed of the data breach on December 27 and issued a security warning on December 30, 2016. At the time I was writing, ESEA only confirmed the data leak, but still hasn’t admitted that profiles were accessed from its systems.
The news of the ESEA data breach is circulating on the Internet, many players confirmed it on Reddit.
Segui
Jimmy Whisenhunt ✔ @jimmywhis
.@BigSecurityNews confirmed my ESEA account info after they asked a couple 'larger' followed users to help verify
05:10 - 8 Gen 2017
8 8 Retweet 16 16 Mi piace
Segui
Jimmy Whisenhunt ✔ @jimmywhis
.@BigSecurityNews confirmed my ESEA account info after they asked a couple 'larger' followed users to help verify
05:10 - 8 Gen 2017
8 8 Retweet 16 16 Mi piace
Salted HASH, quoting a LeakedSource spokesperson, reported that the ESEA data breach was part of a ransom scheme. Crooks demanded $50,000 in payment to avoid disclosing the hack.
In response to the incident, the company reset passwords, multi-factor authentication tokens, and security questions.