The archive includes also pay scales and residency of psychologists and employees at SOCOM.

Experts at Potomac Healthcare Solutions promptly fixed the issue, even if they initially did not seem to take the claim seriously.
Incindent Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Incindent List - H 2021 2020 2019 2018 1 Incident blog Incident blog
11GB archive of Top Secret US SOCOM data accidentally leaked
5.1.2017 securityaffairs Incindent
The popular security expert Chris Vickery discovered a 11GB archive of Top Secret US SOCOM data that was accidentally leaked.
A subcontractor of the Pentagon has exposed top-secret information of the US Military Special Operations Command (SOCOM) medics.
Exposed records include names, locations, Social Security Numbers, and salaries of the Military SOCOM personnel, the database also included names and locations of at least two analysts of Special Forces. Analysts data have Top Secret government clearance.
The precious archive was accessible on the web and data stored in without encryption, a 11-gigabytes gift to nosy people.
The database was discovered by the popular researcher Chris Vickery, the same expert that discovered several open MongoDB exposed on the Internet.
“A recent data breach discovery of mine contained the names, locations, Social Security Numbers, salaries, and assigned units for scores of psychologists, and other healthcare professionals, deployed within the US Military’s Special Operations Command (SOCOM). Not a single username or password was guarding this intel, which weighed in at over 11 gigs.” reads a blog post published by Vickery.
Vickery discovered the precious archive and reported it to Potomac Healthcare Solutions, the company that provides healthcare workers to the US Government through Booz Allen Hamilton.
The archive includes also pay scales and residency of psychologists and employees at SOCOM.
Experts at Potomac Healthcare Solutions promptly fixed the issue, even if they initially did not seem to take the claim seriously.
“It is not presently known why an unprotected remote synchronization (rsync) service was active at an IP address tied to Potomac,” added Vickery.
“It shouldn’t take over an hour to contact your IT guy and kill an rsync daemon.”
The exposed data in the wrong hand could allow attacks to conduct a wide range of malicious activities, from kidnapping to scams.
“It’s not hard to imagine a Hollywood plotline in which a situation like this results in someone being kidnapped or blackmailed for information,” he says.
“Let’s hope that I was the only outsider to come across this gem.”
In December 2015 the security expert Chris Vickery discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
Yahoo Admits 1 Billion Accounts Compromised in Newly Discovered Data Breach
15.12.2016 thehackernews Incindent
In what believe to be the largest data breach in history, Yahoo is reporting a massive data breach that disclosed personal details associated with more than 1 Billion user accounts in August 2013.
…And it's separate from the one disclosed by Yahoo! in September, in which hackers compromised as many as 500 Million user accounts in late 2014.
What's troubling is that the company has not been able to discovered how "an unauthorized third party" were able to steal the data associated with more than one Billion users.
The data breach officially disclosed on Wednesday actually occurred in 2013 and, just like the one in 2014, allowed the cyber crooks to obtain personal information of its users but not credit card details.
Here's what Yahoo's chief information security officer Bob Lord says the hackers obtained:
"The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5) and, in some cases, encrypted or unencrypted security questions and answers."
The hashed passwords used an aging algorithm called MD5 that can easily be cracked. Moreover, in some incidents, the hack revealed unencrypted security questions and answers that would provide quick access to users accounts.
The public disclosure of this latest data breach came upon "further analysis" of data that law enforcement provided Yahoo in November.
Change your Password and Security Q&A Immediately
Of course, if you are one of those potentially affected users, you are strongly recommended to change your passwords and invalidate affected security questions.
Also, if you are using the same password and answers for security questions somewhere else, change them too.
Yahoo has started notifying the account holders affected by the massive data breach, requiring them to change their passwords immediately.
Both the data breaches at Yahoo! came after the company negotiated a deal to sell its core internet business to Verizon Communication Inc for $4.8 Billion.
The September disclosure of half a billion users' breach prompted Verizon to say in October that it might withdraw from the agreement to buy Yahoo.
Here's the statement from Verizon spokesman Bob Verettoni about the recent largest data breach:
"As we've said all along, we will evaluate the situation as Yahoo continues its investigation. We will review the impact of this new development before reaching any final conclusions."
Previous data breach news had already magnified company's problems, and now when another data breach affecting a Billion users has been disclosed, would Yahoo be able to save its acquisition deal?
Yahoo admits one billion accounts exposed in a newly discovered data breach
15.12.2016 securityaffairs Incindent
The tech giant Yahoo admitted crooks have probably stolen details from more than a billion user accounts, and the incident is not linked to previous ones.
Bad news for Yahoo!, the company admitted crooks have probably stolen details from more than a billion user accounts. In 2013, hackers broke into the systems of Yahoo and accessed one billion user accounts containing names, addresses, phone numbers, and hashed passwords easy to crack. The passwords were protected with MD5 hashing algorithm that is easy to crack, the leaked data also include some encrypted and cleartext security questions and answers have been compromised too.
The company is urging its customers to reset their passwords.
According to the Yahoo CISO, Bob Lord, data is genuine and this discovery is not linked to past data breaches. The company dates the incident back in August 2013 and blames an unauthorised third party that it hasn’t identified.
“We analysed this (stolen) data with the assistance of outside forensic experts and found that it appears to be Yahoo user! data,” Lord says.
“Based on further analysis of this data by the forensic experts, we believe an unauthorised third party, in August 2013, stole data associated with more than one billion user accounts.
“We have not been able to identify the intrusion associated with this theft. “
The incident is alarming if we also consider past breaches alleged suffered by the Tech Giant.
“The number of affected accounts was double the number implicated in a 2014 breach that the internet company disclosed in September and blamed on hackers working on behalf of a government. News of that attack, which affected at least 500 million accounts, prompted Verizon Communication Inc to say in October that it might withdraw from an agreement to buy Yahoo’s core internet business for $4.83 billion.” reported the Reuters.
It seems that no financial data was exposed in the incident, anyway we have to consider that Yahoo users are not exposed to a great potential risk of attacks such as identity theft. Crooks can exploit stolen data to target users with social engineering attacks and launch spear phishing campaigns.
Of course, the news will have a significant impact on the acquisition of the company by Verizon because the hackers have stolen the main asset of the tech giant, the data. Analysts speculate a possible interference with the announced $4.8 billion sale of the company to Verizon.
“we will review the impact of this new development before reaching any final conclusions.” commented Verizon.
A Yahoo spokesman told Reuters that the company has been in communication with Verizon during its investigation, he is confident the data breach will not affect the acquisition.
Ashley Madison Dating Site Agrees to Pay $1.6 Million Fine Over Massive Breach
15.12.2016 thehackernews Incindent
Ashley Madison, an American most prominent dating website that helps married people cheat on their spouses has been hacked, has agreed to pay a hefty fine of $1.6 Million for failing to protect account information of 36 Million users, after a massive data breach last year.
Yes, the parent company of Ashley Madison, Ruby Corp. will pay $1.6 Million to settle charges from both Federal Trade Commission (FTC) and 13 states alleging that it misled its consumers about its privacy practices and did not do enough to protect their information.
Not only the company failed to protect the account information of its 36 Million users, but also it failed to delete account information after regretful users paid a $20 fee for "Full Delete" of their accounts.
Moreover, the Ashley Madison site operators were accused of creating fake accounts of "female" users in an effort to attract new members.
Avid Life Media denied the claim at the time, but a year later when the company rebranded as Ruby Corp., it admitted that tens of thousands of female users on AshleyMadison.com had just been lines of code.
Last year, a group of hackers released tons of gigabytes of critical data belonging to the company's internal operation as well as millions of Ashley Madison users that led to blackmails and even suicides.
Ruby Corp. was intended to pay a total of $17.5 Million fine -- $8.75 million fine to the FTC and another $8.75 million to 13 states that also filed complaints -- but the company can afford to pay just $1.6 Million fine.
"Today's settlement closes an important chapter on the company's past and reinforces our commitment to operating with integrity and to building a new future for our members, our team and our company," Rob Segal, Ruby's newly-appointed CEO, wrote in a blog post.
Besides this, Ruby Corp. has agreed to 20 years' worth of the FTC overseeing its network security to ensure that user data is being protected.
Here's the federal court order [PDF] that requires Ashley Madison to:
Perform a risk assessment to protect customer data
Implement new data security protocols
Upgrade systems based on the assessments
Offer periodic security risk assessment (both internal and third-party)
Require "reasonable safeguards" against any potential cyber attacks from their service providers
Ashley Madison was hacked in July 2015, resulting in the disclosure of personal information belonging to 35 Million users, including their usernames, first and last names, passwords, credit card data info, street names, phone numbers, transactions records, and email addresses.
Employee’s Provident Fund organisation, India website found INSECURE
8.12.2016 securityaffairs Incindent
Security firm’ Eioneus Systems’ claims to have found a serious security flaw in Universal Account Number(UAN) website (India).
In a recent incident an information security firm’ Eioneus Systems’ claims to have found a serious security flaw in Universal Account Number(UAN) website (India) which could have led to the theft of millions of user’s data. Eioneus Systems is an information Security firm based out of Pune. According to the official at Eioneus Systems Snehil Khare, the issue was reported immediately to CERT-IN, NIC, and other government sources which were felt necessary at the time.

As per reports the issue was critical and gave access to country’s entire Provident Fund database. Moreover, it stated that vulnerability could be exploited to gain complete access to the machine leading to full compromise. Well, the tech firm demonstrated an excellent behavior in doing a responsible vulnerability disclosure.
Due to the sensitive nature of the incident, complete details of the vulnerability was not shared but it came to light that the bug gave access to information such as Provident fund balance, Individual’s KYC details, phone numbers, PAN numbers, bank details ;etc of every provident fund user in the country. The tech firm has shared few screenshots to support their claims of accessing the massive database.


In a chat with Security Affairs, Snehil Khare clarified his intentions further stating “Our motive is to do a responsible vulnerability disclosure and not to abuse the information which was accessed. Our intention was to draw the attention of authorities towards major security concern identified, without ignoring it.”
According to Eioneus systems , the issue came to their knowledge on 3rd Dec 2016 while browsing the website for usual UAN related features that website offers. The issue was reported immediately to CERT-IN (Computer emergency response team) and was acknowledged by CERT-IN in no time.


85 Million user accounts stolen from the Video-sharing website Dailymotion
6.12.2016 securityaffairs Incindent
The popular video sharing website Dailymotion has suffered a massive data breach that leads the exposure of 87 million accounts.
According to the data breach notification service LeakedSource, millions of user accounts allegedly stolen from the Video-sharing Website Dailymotion. LeakedSource confirmed to have received a database containing 87.6 million accounts belonging to roughly 85 million users having unique email addresses.
The records include usernames, email addresses and more than 18 million of them includes password hashes.
The passwords were protected with the Bcrypt hashing algorithm, with 10 rounds of rekeying. Fortunately, the website used the Bcrypt hashing algorithm which is considered secure and hard to crack.

Source: Bleepingcomputer.com
According to the data breach notification service LeakedSource, hackers have stolen the Dailymotion archive around October 20.
Risks and countermeasures
Bcrypt hashing algorithm gives a reasonable level of security to the users, anyway, I suggest Dailymotion users change their password after the data breach.
The bad news is that all the email contained in the Dailymotion websites could be used by spammers in their campaign, crooks could also use them to target them with targeted phishing campaigns.
In November the company that owns AdultFriendFinder and other adult websites, FriendFinder Networks, has been hacked, data breach exposes 412 million accounts making this the largest 2016 hack. Also in this case LeakedSource obtained the leaked data.
DailyMotion Hacked — 85 Million User Accounts Stolen
6.12.2016 thehackernews Incindent
This time a popular video sharing platform DailyMotion has allegedly been hacked and tens of millions of users information have been stolen.
Breach notification service LeakedSource announced the data breach on Monday after the company obtained 85.2 Million records from Dailymotion.
According to LeakedSource, the DailyMotion data breach appears to have taken place on October 20, 2016, which means it is possible that hackers have been circulating the data for over a month.
The stolen data consists of 85.2 Million unique email addresses and usernames and around 20 percent of the accounts (more than 18 Million users) had hashed passwords tied to them.
The passwords were protected using the Bcrypt hashing algorithm with ten rounds of rekeying, making it difficult for hackers to obtain user's actual password.
Bcrypt is a cryptographic algorithm that makes the hashing process so slow that it would literally take centuries to actual brute-force password of a user.
ZDNet received a sample of the stolen data and confirmed that the data came from the Dailymotion website, but representatives for Vivendi, the majority owner of Dailymotion did not yet respond to any comments.
If you are one of the 18 million DailyMotion users who had their hashed password leaked, you are advised to change your password on the entertainment website as well as on others where you have reused your password.
LeakedSource has added the DailyMotion stolen data to its search index, so you can check if your account has been affected.
Also use a good password manager to create complex passwords for different sites as well as remember them. We have listed some good password managers that could help you understand the importance of password manager and choose one according to your requirement.
Data breach at the Japanese Shiseido, 420,000 users’ records exposed
5.12.2016 securityaffairs Incindent
The Japanese giant of the cosmetic industry Shiseido Co. announced a data breach. Data leak on 420,000 shoppers, including financial information.
Another week, a new data breach has been announced by the press, this time the victim is the Japanese giant of the cosmetic industry Shiseido Co.
The company Shiseido announced the incident on Friday, the hackers broke into the online store, which sells cosmetics products and that is run by the subsidiary IPSA Co.
The firm IPSA discovered the data leak when it received a report from a payment agency on Nov. 4.
The firm revealed that hackers accessed personal information on about 420,000 customers, and compromised data may have leaked.
“Japanese cosmetics maker Shiseido Co. said Friday that the online store run by subsidiary IPSA Co. has suffered illegal access and that personal information on about 420,000 customers may have leaked as a result.” reported The Mainichi website.
According to the Japanese press agency, the stolen records include customers’ names and addresses. The company confirmed that also financial data of a portion of customers may have been exposed, credit card information on up to around 56,000 of the customers may also have leaked.
The company admitted that credit card data belonging to users who made purchases at the online store between December 14, 2011, and November 4, 2016 may have been exposed.
Shiseido promptly reported the data breach to the Japanese authorities, including the Ministry of Economy, Trade and Industry. The Japanese police started an investigation on the case.
In response to the incident, IPSA company has temporarily suspended the online store.
Personal data of 134,000 United States Navy sailors leaked
24.11.2016 securityaffairs Incindent
Personal Data belonging to 134,386 United States Navy current and former sailors were leaked. NCIS and HPE are investigating the case.
The United States Navy has confirmed that the personal data of 134,386 current and former employees were leaked.
Names and social security numbers of the internal staff were stored in a laptop used by a Hewlett Packard Enterprise Services staffer that was compromised.
The Naval Criminal Investigative Service (NCIS) and HPE who are investigating the incident discovered that “unknown individuals” accessed the personal data of the United States Navy employees.
“Oct. 27, 2016, the Navy was notified by Hewlett Packard Enterprise Services (HPES) that one of the company’s laptops operated by their employee supporting a Navy contract was reported as compromised.” reads the Security Breach Notification of Sailors’ PII.
“After analysis by HPES and a continuing Naval Criminal Investigative Service (NCIS) investigation, it was determined Nov. 22, 2016, that sensitive information, including the names and Social Security Numbers (SSNs) of 134,386 current and former Sailors were accessed by unknown individuals.”

The US Navy did not disclose details of the incident and there is no evidence that exposed data were abused by the unknown attackers.
It is still unclear if the laptop was lost, stolen or if a malware exfiltrated data on its hard disk.
“We are in the early stages of investigating and are working quickly to identify and take care of those affected by this breach,” naval personnel chief Vice Admiral Robert Burke says.
“The Navy takes this incident extremely seriously – this is a matter of trust for our sailors.”
The United States Navy will notify employees affected by the security breach in “coming weeks.”
The Navy is reviewing credit monitoring service options for affected people.
Cisco data leak – Job applications portal leaked personal information
7.11.2016 securityaffairs Incindent
Cisco data leak – Cisco has fixed a security vulnerability in the company Professional Careers portal that exposed personal information of the users.
Cisco data leak – Cisco has fixed a security vulnerability existing in the company Professional Careers portal that may have leaked personal information. Cisco has notified the issue to the affected users via mail in which it clarifies that just a “limited set of job application related information” was leaked from the mobile version of the website.
What happened?
According to the security advisory sent by CISCO to its users, data leakage was the result of an “incorrect security setting” placed after system maintenance on a third party site.
Cisco data leak includes name, username, password, email, address phone number, answers to security questions, education and professional profile, cover letter and resume text, and other personal information.
The incorrect configuration was exposing data from August 2015 to September 2015, and again from July 2016 to August 2016. The issue was discovered by an unnamed researcher that ethically reported it to the company.
“An independent security researcher discovered that a limited set of job application related information from the Cisco Professional Careers mobile website was accessible. Cisco’s investigation found this to be the result of an incorrect security setting following system maintenance.” reads the security note. “The issue was immediately fixed and passwords to the site have been disabled. Because Cisco takes its responsibility to protect information seriously, and since many people use the same passwords on multiple websites, we wanted to alert you to this incident. As a precaution, users of Cisco’s Professional Careers Website will need to reset their passwords at their next login by clicking “forgot my password”. “
Cisco confirmed that at the time it fixed the issue it has not found evidence of unauthorized accesses to its systems, however it discovered an unexplained connection to the server.
“We do not believe that the information was accessed by anyone beyond the researcher who found and reported the issue. However, there was an instance of unexplained, anomalous connection to the server during that time, so we are taking precautionary steps.” states Cisco.
In response to the incident Cisco precautionary reset password of the users of Cisco Professional Careers Website
“Upon learning this, the setting was immediately corrected and user passwords to the site were reset. Because Cisco takes its responsibility to protect information seriously, and since many people use the same passwords on multiple websites, we wanted to alert you. As a precaution, as a user of the Cisco Professional Careers Website, you will need to reset your password at their next login by clicking “forgot my password” reads the NOTICE OF DATA BREACH of the Cisco data leak.

The exposed data could be used for social engineering attacks against the users. Cisco offered free 90-day fraud alerts on their accounts to the affected users.
Office of the Comptroller of the Currency reported a former employee stolen data from office
1.11.2016 securityaffairs Incindent
A former employee of the Office of the Comptroller of the Currency downloaded 10,000 records onto thumb drives before his retirement in November 2015.
On Friday, the US banking regulator told Congress about a potential “major information security incident” after it discovered that a former employee has downloaded a large number of files onto thumb drives before his retirement in November 2015. According to the Office of the Comptroller of the Currency, there was no evidence that suggests that the former employee has publicly disclosed the data neither he has misused it.
The Office of the Comptroller is tasked with protecting consumers and the regular activity on financial markets.

The banking regulator confirmed the former employee downloaded a large number of files onto two removable thumb drives, the stolen information was encrypted. According to the Office of the Comptroller of the Currency, the security breach was only detected last month after a routine security assessment.
The OCC reported that when the former employee was contacted by the Agency, he “was unable to locate or return the thumb drives to the agency.”
“The OCC has deemed the breach a “major incident” because the devices containing the information are not recoverable and more than 10,000 records were removed, the agency said.” reported the Reuters.
“An official familiar with the investigation declined to comment on a possible motive. The official, who was not authorized to discuss the case, noted that a large batch of unclassified personnel records were among the cache.”
Experts have downplayed the risks for the users arguing that the information was not released to unauthorized sources.It is quite frequent that employees or consultants report missing thumb drives containing sensitive data.
It is quite frequent that employees or consultants report missing thumb drives containing sensitive data.
Recently the National Security Agency went in the headlines again after a contractor was accused of having harvested high-confidential information from the Agency systems.
Mass Surveillance of Cell Phone Data by AT&T Service Provider
31.10.2016 securityaffairs Incindent
AT&T has been data-mining and willingly sharing user phone data, through its “Hemisphere” Project, which is essentially a mass surveillance program.
The NSA may be the well-known governmental entity notorious for conducting spy surveillance of its citizens and its massive record retention program, but the private sector is also capitalizing on such opportunities. AT&T, a telecommunications conglomerate with diversified revenues of more than $146 billion reported in 2015, is branching out by selling its “Hemisphere” services to the US Justice Department. AT&T has been data-mining and willingly sharing user phone data, through its “Hemisphere” Project, which is essentially a mass surveillance program. The Hemisphere program, first whispered about as early as 2013, reportedly utilizes data provided by the cell phone company dating back to the 1980s.
AT&T has not commented publically on the program, but reported documents published highlight the fact that the telephone company is providing the service through its already established infrastructure. All at the cost of additional fees to the buyer, of course.
AT&T has collected and retained, in the past, phone call logs and other “Metadata” with of extensive 380 million user database. Research conducted by the NSA revealed that telephone metadata can reveal sensitive personal information of the user. Collected meta-data consists of non-content phone user information, which can pose a threat to user privacy.
att-mass-surveillance-hamisphere-project
Image: The logo of the “Hemisphere Project” (AT&T)
Verizon Communications has also been the subject of a forced compliance order issued by the U.S. Foreign Intelligence Surveillance Court that resulted in handing over electronic data to the NSA. This data included all calling records maintained on a daily basis- without disclosure to the user. The order itself covered location, frequency, and duration of the calls, but not the actual content of the communication. Additionally, the user is not aware of any such privacy invasions nor may be the subject of any criminal investigations.
Previously, the NSA might have been the only entity that had the resources to support such surveillance with the infrastructure to house such extensive data. AT&T’s access to its hundreds of millions of customer, however, gave the telecommunications company ample opportunity and infrastructure to collect data on everything that happens within its network. The communication of two or more users in regards to “who”, “what”, “when”, and “where” are collected and stored. This data, accessed through AT&T’s vast user network, along with the location data provided by cell phones, leaves a distinct digital trail that law enforcement should be able to follow. We’re talking about a massive amount of information, especially considering AT&T’s market share and reach. AT&T’s landline customers alone consist of more than 75% of the entire market share.
Documents revealed confirm a link between the collections of phone data to the formation of an “alliance” with law enforcement agencies, who are eager for such information provided by AT&T’s vast network. The revenue received by AT&T for such a service, although morally or ethically ambiguous in nature, amounts to millions per year.
AT&T’s willingness to data-mine information is one unique characteristic of this alliance. Usually, a private entity provides such information under the enforcement of a legal warrant. AT&T itself seeking an alliance (a sort of public-private partnership) with a governmental agency, is a rather different type of partnership.
Cell phone providers, in the past, have hardly played such a cooperative role, and certainly not such a prosperous one. FBI’s battle with Apple regarding the San Bernardino shooter’s iPhone indicated that Apple publically opposed such an alliance. It refused to cooperate with investigators in order to create software that would unlock the shooter’s iPhone. Apple believed that creating, in essence a backdoor to unlock its software, would set a dangerous precedent. Apple ultimately propagated against the invasion of cell phone privacy by refusing to cooperate with investigators in a terrorism case. AT&T has no such reservations.
Formerly, the US-NSA has had legal authority to access phone user information under the USA Patriot Act of 2001. Some of the same powers granted to the USA Patriot Act are now available under the USA Freedom bill (2016), but with some restrictive guidelines. The NSA is also facing several lawsuits filed by the American Civil Liberties Union (ACLU) over its controversial bulk collection of phone data. Several rulings have vilified the ACLU’s claim on the basis that:
“While others who have brought legal challenges to the bulk collection program, plaintiffs [in this case] lack direct evidence that records involving their calls have actually been collected.”
AT&T’s stand on these published documents is in opposition to Snowden’s views on the matter.
att-mass-surveillance-2
[IMAGE] Edward Snowden’s on the cover of Time in 2013.
Edward Snowden, in an interview with European reporters on Oct. 26th 2016, further fueled the massive public debate on mass surveillance by cell phone service providers. Snowden claimed that the public is not able to stop targeted surveillance from huge government organizational programs. According to him, this was the reason behind the massive data breaches and cyber-attacks that have taken place in recent years:
“In our current state of the art, offense is easier than defense. This is an unfortunate artifact of the fact that governments around the world have prioritized offensive capabilities for the benefit of spying on people so much more strongly than they have defensive capabilities, preventing our countries from being hacked”.
In the continuing saga of Edward Snowden, his comments on the cooperation of AT&T with governmental agencies suggest that governmental agencies are focusing most of their resources on the offensive-end, leaving them vulnerable to defend against massive data breaches and hacks. Because of a lacking in defense, vulnerabilities can be exploited, as evidenced by the cyber-attack at the Office of Personnel Management, the recent Democratic National Committee hacks, and other such infrastructural attacks. These could have been prevented with a focus on bolstering defense:
“[Its] fear of the power grid being attacked—these were preventable problems”- Edward Snowden
If such cyber-attacks can compromise the security of private and governmental agencies, then what is the defense against such a compromise in critical sectors, such as energy or manufacturing? Previous Reports, published in 2015, have in fact stated that the energy sector in the U.S. is not prepared to defend itself against cyber threats.
Snowden’s reasoning isn’t incorrect as he makes a justifiable argument. Moreover, his narrative has consistently warned of mass surveillance activities taking place without the knowledge of the mass public. He has sacrificed his entire career on reporting breaches of user privacy by intelligence agencies. The former NSA contractor is a whistle-blower, he exposed the questionable practices of his employer, a governmental agency, but he is also an advocate of safeguarding user privacy at the hands of surveillance agencies.
You may ask, “If AT&T volunteers user phone information- is it still illegal?” The answer lies somewhere in the middle. In essence, this is capitalism at its finest, an exchange between buyer and seller that constitutes a business transaction. The information at the heart of this debate is legitimized at the source and wrapped around an added financial incentive. However, the threat of user privacy against mass surveillance is a very real one, and not just in the U.S
Red Cross Blood Service incident. The Australian largest ever leak of Personal data
30.10.2016 securityaffairs Incindent
The Australian Red Cross Blood Service confirmed the data leak that exposed a backup database containing the personal details of donors.
This data leak is considered by security experts one of the most severe due to the nature of the target, the Australian Red Cross Blood Service. The sensitive database was discovered on October 24 by a security expert that was scanning the Web for exposed web servers.
One of its third-party service providers inadvertently exposed a backup database containing the personal details of 550,000 individuals.
The database remained accessible online between September 5 and October 25.

The man who discovered the database reported his discovery to the popular security expert Troy Hunt who runs the data breach notification service haveibeenpwned.com.
The 1.74Gb database contains 1.3 million records containing the name of donors, gender, date of birth, country of birth, physical and email addresses, phone number, blood type, type of donation, donation dates, and eligibility answers.
“In the Red Cross’ case, the data that was ultimately leaked was a database backup. That 1.74GB was simply a mysqldump file that had everything in it. Taking a database backup is not unusual (in fact it’s pretty essential for disaster recovery), it’s what happened next that was the problem.” wrote Troy Hunt in a blog post.
“The database backup was published to a publicly facing website. This is really the heart of the problem because no way, no how should that ever happen. There is no good reason to place database backups on a website, let alone a publicly facing one. There are many bad reasons (usually related to convenience), but no good ones.”
Hunt reported the issue to the Red Cross and the ausCERT, meanwhile, the Australian Red Cross Blood Service reported the incident to the Australian Cyber Security Centre, Federal Police and the Office of the Information Commissioner.
According to the Australian Red Cross Blood Service, the database contains registration information for 550,000 individuals who had donated between 2010 and 2016.
“This file contained registration information of 550,000 donors made between 2010 and 2016. The file was part of an online application to give blood and information such as names, addresses, dates of birth and some personal details are included in the questionnaire.” states the announcement published by the organization.
It is still unclear is someone else accessed the database, anyway IDCARE, Australia and New Zealand’s national identity support service have determined that there is low risk for the donors.
TalkTalk Telecom Ordered to Pay Record £400,000 Fine Over 2015 Data Breach
7.10.2016 thehackernews Incindent
TalkTalk, one of the biggest UK-based Telecoms company with 4 million customers, has been issued with a record £400,000 ($510,000) fine for failings to implement the most basic security measures to prevent the hack that made global headlines last year.
The penalty has been imposed by the Information Commissioner's Office (ICO) over the high-profile cyber attack occurred in the company last October, which allowed hackers to steal the personal data of its 156,959 customers "with ease."
The ICO said on Wednesday that TalkTalk, which offers TV, phone and broadband services, could have prevented the cyber attack if the company had implemented even basic security measures to protect its customers’ data.
The hacked data of 156,959 customers included full names, postal addresses, dates of birth, telephone numbers, email addresses and TalkTalk accounts information. The hacker also had even access to bank account details and sort codes in almost 16,000 cases.
"When it came to the basic principles of cyber-security, TalkTalk was found wanting," Information Commissioner Elizabeth Denham said.
"Today's record fine acts as a warning to others that cyber security is not an IT issue, it is a boardroom issue. Companies must be diligent and vigilant. They must do this not only because they have a duty under the law, but because they have a duty to their customers."
The regulator also revealed that the targeted database software, which held details of customers inherited from the 2009 takeover of a rival Tiscali UK operations, was out of date and affected by an easily-patchable vulnerability.
As a result, the hackers attacked three vulnerable web pages using a well-known hacking technique called SQL injection and got hold of the customers' data.
TalkTalk has been attacked several times last year. Before the October cyber attack, the company's system had been breached twice — first in July and then in September 2015. But the telecom did not learn anything from its past mistakes.
"Yes, hacking is wrong, but that is not an excuse for companies to abdicate their security obligations," the watchdog said. "TalkTalk should and could have done more to safeguard its customer information. It did not, and we have taken action."
In response to the ICO's decision, TalkTalk has said that it is disappointed with the fine imposed by the ICO, but it will gladly hang its head in shame.
The company released the following statement:
"During a year in which government data showed nine in ten large UK businesses were successfully breached, the TalkTalk attack was notable for our decision to be open and honest with our customers from the outset. This gave them the best chance of protecting themselves and we remain firm that this was the right approach for them and our business."
"As the case remains the subject of an ongoing criminal prosecution, we cannot comment further at this time."
The investigation of the data theft is still ongoing.
Arrests Over TalkTalk Hack:
Few days after the attack, a 15-year-old boy from County Antrim, Northern Ireland, was arrested in connection with the TalkTalk Data Breach.
A second arrest was made within the week when the Metropolitan Police Cyber Crime Unit (MPCCU) arrested a 16-year-old boy from Feltham in west London.
Another arrest was made on November last year when police arrested a 16-year-old boy from London in connection with the hack.
An investigation by the Metropolitan Police Cyber Crime Unit has been running separately to the ICO’s investigation.
Yahoo Data Breach, the company confirms the incident that exposed 500M accounts
23.9.2016 securityaffairs Incindent
The announcement about the Yahoo data breach is online, the company confirmed that hackers managed to access data from at least 500 million user accounts.
Today I wrote about the imminent announce of the Yahoo data breach related to an incident that resulted in the leakage of 200 million Yahoo account credentials this summer.
The company has finally made the announce, the news related the Yahoo data breach is in the headlines. The IT giant confirmed that hackers have stolen at least 500 million user accounts in a data breach dating back to 2014.
Yahoo also added that its security experts suspect the involvement of nation-state actors.
“We have confirmed that a copy of certain user account information was stolen from the company’s network in late 2014 by what it believes is a state-sponsored actor. The account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (the vast majority with bcrypt) and, in some cases, encrypted or unencrypted security questions and answers.” reads the security notice issued by Yahoo.
“The ongoing investigation suggests that stolen information did not include unprotected passwords, payment card data, or bank account information; payment card data and bank account information are not stored in the system that the investigation has found to be affected. Based on the ongoing investigation, Yahoo believes that information associated with at least 500 million user accounts was stolen and the investigation has found no evidence that the state-sponsored actor is currently in Yahoo’s network. Yahoo is working closely with law enforcement on this matter.”
This summer the notorious hacker Peace advertised 200 Million Yahoo accounts on Dark Web, and the company was aware of the sale.
Peace offered for sale the 200 million of Yahoo account credentials (from “2012 most likely,”) on The Real Deal black marketplace. Yahoo was informed of the events and launched an internal investigation avoiding public comment on the case. The hacker was offering the data leak for 3 bitcoins (roughly $1,800 at the time of the disclosure).

The security notice informs users that the company is taking the necessary action to protect them. Below the list published by Yahoo:
We are notifying potentially affected users. The content of the email Yahoo is sending to those users will be available at https://yahoo.com/security-notice-content beginning at 11:30 am (PDT).
We are asking potentially affected users to promptly change their passwords and adopt alternate means of account verification.
We invalidated unencrypted security questions and answers so they cannot be used to access an account.
We are recommending that all users who haven’t changed their passwords since 2014 do so.
We continue to enhance our systems that detect and prevent unauthorized access to user accounts.
We are working closely with law enforcement on this matter.
We encourage our users to follow these security recommendations:
Change your password and security questions and answers for any other accounts on which you used the same or similar information used for your Yahoo account.
Review your accounts for suspicious activity.
Be cautious of any unsolicited communications that ask for your personal information or refer you to a web page asking for personal information.
Avoid clicking on links or downloading attachments from suspicious emails.
Yahoo is encouraging users to use the Yahoo Account Key in order to definitively eliminates the need to use a password.
Qatar National Bank 1.5 Gb archive leaked online
28.4.2016 Incindent
The Qatar National Bank (QNB) is investigating a possible data leak after that a 1.5 GB archive containing 15,000 files was shared online.
Another incident involved the banking industry, this time the Qatar National Bank (QNB) is investigating a major data leak. Several sources online, including Cryptome, have published a large number of files allegedly stolen from the systems at Qatar National Bank.
Security experts speculate that the precious archive might have been stolen by an insider.
“Referring to social media speculation in regard to an alleged data breach, it is QNB Group policy not to comment on reports circulated via social media. QNB would like to take this opportunity to assure all concerned that there is no financial impact on our clients or the Bank.” reads a statement published on Tuesday by the QNB. “QNB Group places the highest priority on data security and deploying the strongest measures possible to ensure the integrity of our customers’ information. QNB is further investigating this matter in coordination with all concerned parties.”
The 1.5 Gb archive was shared online by several Twitter accounts that published a global-files.net link.
The data leak includes more than 15,000 files containing banking information, QNB user profiles, payment card details, passwords, email addresses, physical addresses, and phone numbers.
Giving a look to the leaked archive we can notice that the user profiles are stored in folders likely linked to government organizations, including intelligence agencies., in Qatar and other countries. One of the folders includes information on people working at Qatar-based media company Al Jazeera.
A folder includes user profiles belonging to Banks/Organizations meanwhile another folder includes data belonging to Al Jazeera staffers.

Source Securityweek
Multiple sources who have reviewed the leaked data dump have confirmed the data appears to be genuine.
“One researcher, speaking on condition of anonymity, also confirmed that he had successfully used leaked customer internet banking credentials from the data dump to begin logging in to the customer’s account, purely for research purposes. But he said the bank’s systems then sent a one-time password to the customer’s registered mobile number, which would serve as a defense against any criminals who might now attempt to use the leaked data to commit fraud.” reported Bankinfosecurity.com.
The incident comes a few weeks after the Bangladesh’s central bank cyber heist, a couple of days ago the security firm BAE Systems published a report that revealed the involvement of a custom malware attack in the data breach.
Hundreds of Spotify credentials leaked online
27.4.2016 Incindent
Security experts reported that hundreds of Spotify credentials appeared online and some users claim their accounts were hacked.
Hundreds of Spotify account credentials appeared online on the website Pastebin, the information includes emails, usernames, passwords, account type and other details.
The popular Swedish streaming service denied any data breach and confirmed that its systems weren’t compromised by hackers. Spotify confirmed that it “has not been hacked” and its “user records are secure.”
“Spotify has not been hacked and our user records are secure. We monitor Pastebin and other sites regularly. When we find Spotify credentials, we first verify that they are authentic, and if they are, we immediately notify affected users to change their passwords.” states Spotify.
According to the Techcrunch media agency, the Spotify security team proactively resets hacked passwords, a number of users are also reporting problems with their accounts.
Techcrunch reached out random users in the list confirming we’ve confirmed that these users’ Spotify accounts were compromised.
It is not clear if the account details were stolen by Spotify or result from other breaches.
The Pastebin post also includes other information on the uses (e.g. account type [family, premium], subscription auto-renews, country).

This isn’t the first time that Spotify suffers a security incident, in May 2014 it investigated unauthorized access to its systems and internal company data.
We cannot exclude that data comes from previous incidents, but victims reached by Techcrunch told it otherwise.
“So far, over a half-dozen have responded, confirming that they did experience a Spotify account breach recently. They became aware of the breach in a number of ways – for example, one said he found songs added to his saved songs list that he hadn’t added. Another also found his account had been used by an unknown third party.” continues Techcrunch.
Some users reported problems while accessing the platform, other have found that their account email had been changed to a new email address not belonging to them.

As usually happens in these cases, it is strongly suggested to change passwords.
Stay tuned.
How Did Hackers Who Stole $81 Million from Bangladesh Bank Go Undetected?
26.4.2016 Incindent
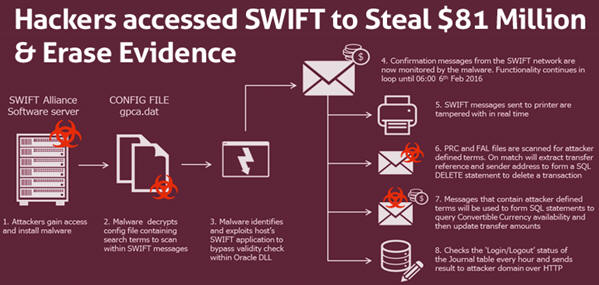
Investigators from British defense contractor BAE Systems discovered that hackers who stole $81 million from the Bangladesh Central Bank actually hacked into software from SWIFT financial platform, a key part of the global financial system.
The hackers used a custom-made malware to hide evidence and go undetected by erasing records of illicit transfers with the help of compromised SWIFT system.
The Bangladesh Bank hackers, who managed to steal $81 Million from the bank last month in one of the largest bank heists in history, actually made their tracks clear after hacking into SWIFT, the heart of the global financial system.
SWIFT, stands for the Society for Worldwide Interbank Financial Telecommunications, is a global messaging network used for most international money and security transfers.
More than 11,000 Global Banks on HIGH ALERT!
Nearly 11,000 Banks and other financial institutions around the World use SWIFT system to send securely and receive payment instructions through a standardized system of codes.
Recently, Bangladesh police investigators uncovered evidence revealing that the Bank was using second-hand $10 network switches without a Firewall to run its network, which offered hackers access to the bank’s entire infrastructure, including the SWIFT servers.
Now, researchers from British defense contractor BAE Systems reported Monday that the Bangladesh Bank hackers used a piece of sophisticated, custom-made malware to manipulate logs and erase the history of the fraudulent transactions, which even prevent printers from printing the fraudulent transactions.
The malware also has the capability to intercept and destroy incoming messages confirming the money transfers. These malware capabilities prevented hackers to remain undetected.
"This malware appears to be just part of a wider attack toolkit and would have been used to cover the attackers' tracks as they sent forged payment instructions to make the transfers," security researcher Sergei Shevchenko wrote in a blog post.
When and How Did They Get Detected?
The hackers had attempted to steal $951 Million in total from Bangladesh central bank account at the Federal Reserve Bank of New York using fraudulent transactions, but a simple typo (spell error) by hackers halted the further transfers of the $850 Million funds.
The BAE researchers believe the malware used to target Alliance Access, a piece of software that allows banks to connect to the SWIFT network.
According to SWIFT's official website, Alliance Access has more than 2,000 installations worldwide. So even though the SWIFT financial system is used by around 11,000 banks and financial institutions, all of them are not affected by the notorious malware.
"By modifying the local instance of SWIFT Alliance Access software, the malware grants itself the ability to execute database transactions within the victim network," Shevchenko said.
SWIFT To Issue Emergency Security Update
Meanwhile, Brussels-based SWIFT confirmed to Reuters that the company was aware of the nasty malware used to target its client software and that it would roll out a security software update on Monday to fix the issue, along with a special warning to financial institutions.
SWIFT Spokeswoman Natasha Deteran said the software update was intended "to assist customers in enhancing their security and to spot inconsistencies in their local database records."
Facebook hacked, someone deployed a malicious webshell on its server
22.4.2016 Incindent
Facebook hacked! The security expert Orange Tsai discovered the presence of a malicious webshell on one of the company servers.
The security expert Orange Tsai from the DevCore firm has found a malicious web shell on Facebook Server. The researcher was analyzing the Facebook’s infrastructure when noticed a domain called files.fb.com. Intrigued, the expert has tried to access the domain discovering that it was hosting an instance of the Accellion File Transfer Appliance that is used by companies or secure file transfers.
Once accessed the domain it displayed a login interface for the File Transfer Appliance then he decided to investigate the presence of security vulnerabilities in the software.
He verified that Facebook already fixed known flaw in the software then he decided to search for new security issues in the appliance. Tsai discovered a total of 7 zero-day flaws, including cross-site scripting, remote code execution, and local privilege escalation vulnerabilities.

He exploited a pre-auth SQL injection flaw to upload a webshell to the Facebook server and gain its control. At this point, he noticed something of really strange, someone had anticipated him by uploading a webshell to the server.
“While collecting vulnerability details and evidences for reporting to Facebook, I found some strange things on web log. First of all I found some strange PHP error messages in “/var/opt/apache/php_error_log” These error messages seemed to be caused by modifying codes online?” wrote Tsai. “I followed the PHP paths in error messages and ended up with discovering suspicious WEBSHELL files left by previous “visitors”.”

At this point, he tried to collect more data related to the alleged intrusion and discovered that the threat actor attempted to collect the login credentials of company employees who used the Accellion File Transfer Appliance.
The expert sustains that hackers used a script that had harvested at least 300 @fb.com and @facebook.com credentials in the period of time between February 1 and February 7.
By analyzing the logs he also discovered that threat actors gained access on two occasions to the system, the first time in July 2015 and later in September 2015.
The unauthorized accessed in July occurred just days before Rapid7 disclosed two vulnerabilities in the Accellion File Transfer Appliance.
Of course, there is no evidence that the intrusions were carried out by the same hacker and how the attackers breached the systems deploying the malicious webshell.
Tsai reported his discoveries to Facebook that admitted the existence of the Webshell and rewarded him with $10,000. He also reported the flaws discovered in the Accellion platform to the company.
American company lost $100 million to BEC fraud
17.4.2016 Incindent
American company lost $100 million to email fraud, U.S. says
The Reuters Agency reported that an unidentified American company was the victim of a clamorous email fraud, scammers have stolen from the firm nearly $100 million.
According to the US authorities, fraudsters used a fake email address in order to pose as one of its legitimate business partners.
Reuters reported the US authorities have filed a civil forfeiture lawsuit in federal court in New York seeking to recover nearly $25 million derived from the fraud which is being held in at least 20 bank accounts around the world.
The authorities confirmed about $74 million has been returned to the US company.
According to Tom Brown, a former Manhattan federal prosecutor the complaint filed on Thursday “appears to be the largest email scam that I’ve seen.”
This is another clamorous case of BEC (business email compromise) scam suffered by a US company. A week ago, a report issued by the FBI revealed that cyber criminals have pilfered more than $2.3bn from 17,642 victims since 2013 with BEC attacks.
It is a critical situation, the number of business email compromise BEC scams continues to increase on a global scale.
“The Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. Formerly known as the Man-in-the-E-mail Scam, the BEC was renamed to focus on the “business angle” of this scam and to avoid confusion with another unrelated scam.” reports the statement issued in 2015 by Internet Crime Complaint Center (IC3) and the FBI.
cybercrime
The BEC scam has been going on from August to September and was discovered when a Cyprus-based bank noticed suspicious transfers.
According to authorities, the scammers created a fake email address that resembled that of one of the company’s vendors in Asia.
“The perpetrators then posed as a vendor while communicating with a professional services company that was hired to handle the details and logistics of vendor payments for the American corporation, the lawsuit said.” states the Reuters.
The lawsuit reported that scammers convinced the American company to send $98.9 million to an account at Eurobank Cyprus Ltd, which is the bank that noticed the suspect transfers.
The Eurobank without any forcing restrained nearly $74 million of the funds in September.
“The remaining $25 million was laundered through other accounts in locations including Cyprus, Latvia, Hungary, Estonia, Lithuania, Slovakia, and Hong Kong, authorities said.” continues the lawsuit.
The prosecutors have followed the money across banks worldwide, they requested foreign governments to restrain the accounts used in the BEC scam and 20 of them have refunded the stolen funds.
FBI reveals BEC attacks pilfered $2.3bn from US companies
9.4.2016 Incindent
According to a report recently issued by the FBI, cyber criminals have pilfered more than $2.3bn from 17,642 victims since 2013 with BEC attacks.
According to the FBI, cyber criminals have stolen more than $2.3bn from 17,642 victims since 2013 in BEC attacks.
The situation is critical, the number of business email compromise BEC scams continues to increase on a global scale.
“The Business Email Compromise (BEC) is a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. Formerly known as the Man-in-the-E-mail Scam, the BEC was renamed to focus on the “business angle” of this scam and to avoid confusion with another unrelated scam.” reports the statement issued in 2015 by Internet Crime Complaint Center (IC3) and the FBI.
Scammers use to pretend to be executives that send emails to employees that tricked into thinking the messages are legit, hand over sensitive information to the attackers.
The attackers use the stolen data to steal money to the victims or resell them in the cyber criminal underground.
“FBI officials are warning potential victims of a dramatic rise in the business e-mail compromise scam or “B.E.C.,” a scheme that targets businesses and has resulted in massive financial losses in Phoenix and other cities.” states the new alert issued by the FBI.
Attackers focus their attack on all the internal staff that in charge to manage bank accounts and can make wire transfers. Businesses that work with foreign suppliers or that regularly perform wire transfer payments are a privileged target for scammers.
“The schemers go to great lengths to spoof company e-mail or use social engineering to assume the identity of the CEO, a company attorney, or trusted vendor. They research employees who manage money and use language specific to the company they are targeting, then they request a wire fraud transfer using dollar amounts that lend legitimacy.”
According to the FBI, since January 2015, there was a 270 per cent rise in BEC attacks against victims in every U.S. state and in at least 79 countries.
Each company has lost between $25,000 and $75,000 per attack.
A number of illustrious victims suffered BEC scams, In January 2015 crooks stole over $50 million from aircraft systems manufacturer FACC, in March 2016 data belonging to all current and past Seagate employees were stolen due to a W-2 phishing campaign.
Recently, security experts at Trend Micro discovered a Business Email Compromise Campaign leveraging on the Olympic Vision keylogger that targets Middle East and Asia Pacific Companies.

The FBI warned companies to improve authentication mechanisms for their services, for example, by adopting multi-factor authentication processes. It is essential to train employees in the BEC attack techniques in order to avoid being victims of scammers.
APT6 compromised the US government networks for years
5.4.2016 Incindent
The federal bureau of investigation issued an alert related the APT6 state-sponsored hacking group that has compromised the US Government networks for years.
The FBI revealed that “a group of malicious cyber actors have compromised and stolen sensitive information from various government and commercial networks” since at least 2011.
The alert was published online by AlenVault on the Open Threat Exchange platform.
“The FBI has obtained and validated information regarding a group of malicious cyber actors who have compromised and stolen sensitive information from various government and commercial networks. This group utilized the domains listed herein in furtherance of computer network exploitation (CNE) activities in the United States and abroad since at least 2011. Research and analysis indicate that these domains were associated with the command and control (C2) of customized malicious software. Furthermore, these domains have also been used to host malicious files – often through embedded links in spear phish emails. Any activity related to these domains detected on a network should be considered an indication of a compromise requiring mitigation and contact with law enforcement.” states the FBI CYWATCH A-000067-DM.

The nature of the attacks, the usage of custom-made hacking tools, and the targets of the threat actors suggests it is a group of state-sponsored hackers.
The alert includes a list of 59 Indicators of Compromise, it is a collection of websites used by hackers as command and control servers to carry spear phishing campaigns on target organizations. The domains used by the hackers were dismissed in late December 2015. The IoCs provided by the Feds could allow private actors to monitor their networks searching for the presence of the threat.
The group, identified as APT6 compromised the US government infrastructure for years exfiltrating sensitive data.
It wasn’t the first time that US Government networks are breached by foreign hackers, last year a group of nation-state attackers, likely Chinese hackers, breached the systems of the Office of Personnel Management.
The problem is there is no certainty that the US Government completely blocked these hackers, in fact some experts speculate they might still be within Government networks.
Lorenzo Bicchierai from Motherboard reached Kurt Baumgartner, a researcher at the Russian security firm Kaspersky Lab, for a comment on the APT6.
“This is one of the earlier APTs, they definitely go back further than 2011 or whatever—more like 2008 I believe,” said Baumgartner.
Baumgartner hasn’t provided information regarding the origin of the threat, anyway experts believe that China and Russia have the necessary cyber capabilities to infiltrate the government networks.
Be Careful, APT6 is in the wild so report any suspicious activity linked to the IoCs included in the alert.
Personal Data of 50 Million Turkish Citizens Leaked Online
5.4.2016 Incindent
Personal details of nearly 50 Million Turkish citizens, including the country's President Recep Tayyip Erdogan, have been compromised and posted online in a massive security breach.
A database, which contains 49,611,709 records, appeared on the website of an Icelandic group on Monday, offering download links to anyone interested.
If confirmed, the data breach would be one of the biggest public breaches of its kind, effectively putting two-thirds of the Nation's population at risk of identity theft and fraud.
However, The Associated Press (AP) reported on Monday that it was able to partially verify the authenticity of 8 out of 10 non-public Turkish ID numbers against the names in the data leak.
50 Million Turkish Citizens' Personal Data leaked Online
The leaked database (about 6.6 GB file) contains the following information:
First and last names
National identifier numbers (TC Kimlik No)
Gender
City of birth
Date of birth
Full address
ID registration city and district
User's mother and Father's first names
To prove the authenticity of the data, the group of hackers published the personal details of Turkish President Recep Tayyip Erdogan, along with his predecessor Abdullah Gul, and Prime Minister Ahmet Davutoglu.
The attack seems to be politically motivated, as the hackers wrote the following message on the database's front page, featuring Erdogan's profile:
"Who would have imagined that backwards ideologies, cronyism and rising religious extremism in Turkey would lead to a crumbling and vulnerable technical infrastructure?"
Lessons Posted by Hackers
Besides the leaked database, the hackers also provided some lessons to learn from this leak. Under the heading Lessons for Turkey, the hackers wrote:
'Bit shifting isn't encryption,' referring to the fact that the data was improperly protected.
'Index your database. We had to fix your sloppy DB work.'
'Putting a hardcoded password on the UI hardly does anything for security,' though the hackers didn't specify in what UI.
'Do something about Erdogan! He is destroying your country beyond recognition.'
Under the heading Lessons for the United States, the hackers addressed US citizens, asking them not to elect Republican front-runner Donald Trump since he 'sounds like he knows even less about running a country than Erdogan does.'
Links to Download the Database
The database is available online on a Finland-based server. Though the source of the leaked data is currently unknown, it is likely from a Turkish public administration office that deals with users' personal information.
If the authenticity of all 50 Million records gets verified, the breach will be the biggest leaks after the one that occurred in U.S. government's Office of Personnel Management (OPM) in April 2015 that…
...compromised the personal information of over 22 Million U.S. federal employees, contractors, retirees and others, and exposed Millions of sensitive and classified documents.
Is the hack of an email server behind the Panama Papers?
5.4.2016 Incindent
Which is the source of Panama Papers? According to Mossack the hackers breached its systems, according to the experts its email server was breached.
The Panama Papers is a huge trove of strictly confidential documents from the Panamanian law firm Mossack Fonseca was leaked online during the weekend, it is largest data leaks ever.
The entire archive of the firm contains more than 11.5 Million files including 2.6 Terabytes of data related the activities of offshore shell companies used by the most powerful people around the world, including 72 current and former heads of state.
It’s important to clarify that many clients of the Mossack Fonseca weren’t breaking any law and that the services offered by the firm are legal. Of course, such kind of services could have been abused to evade taxes.
The Panama Papers case is exposing the offshore activities of hundreds of politicians and public figures around the world, including , Vladimir Putin and the Iceland’s prime minister David Gunnlaugsson. Be careful, despite one of the most illustrious figures of the Panama Papers is Vladimir Putin his name does not appear in the leaked documents.
Panama Papers
According to Bloomberg, the co-founder of the Mossack Fonseca firm, Ramon Fonseca, confirmed to the Panama’s Channel 2 the authenticity of the leaked documents.
The Panama Papers documents were shared with the German newspaper Suddeutsche Zeitung by an anonymous source and the International Consortium of Investigative Journalists (ICIJ).
The journalists of the ICIJ have investigated the documents for an entire year and now are disclosing their disconcerting findings.
The Panama Papers include emails, bank records, and invoices, but how is it possible? Who is the anonymous source and how it has exfiltrated the data from the computers at the Mossack Fonseca?
According to Ramon Fonseca, the confidential documents had been obtained illegally by hackers, likely the data breach affected an e-mail server of the company last year.
The media agency El Espanol confirmed this hypothesis, Mossack Fonseca firm sent an email to its clients confirming that it is investigating the causes of the data breach and that it’s taking “all necessary steps to prevent it happening again”.
“This firm, considered the largest platform figureheads of Latin America and has a large portfolio of Spanish customers, said in a statement that it has opened an investigation after confirming that “unfortunately” has suffered an “attack on your server email”.” reported the El Espanol.
“Mossack Fonseca says it is taking “all necessary steps to prevent it happening again”; which has “reinforced” its security systems; and is working with “expert consultants” to determine the exact information they have accessed “unauthorized persons”. The firm, through its Director of Marketing and Sales, apologizes to its customers and offers an email to clarify any further questions.”
The ICIJ has identified more than 214,000 organizations for a total turnover of several billion dollars.
DB with records of 50 Million Turkish Citizens Leaked Online. Are they recycled data?
4.4.2016 Incindent
A database containing records of 50 Million Turkish Citizens appeared online in the weekend. Is it a new or a recycled archive?
Details of almost 50 Million Turkish citizens have been leaked online, the bulk data was hosted on a server with the IP address 185.100.87.84. The archive was published during the weekend, the publishers claim they it belongs to 49,611,709 Turkish citizens, the complete 1.5GB archive (mernis.sql.tar.gz – 1.5GB compressed – 6.6GB uncompressed) is available for download on both Torrent and Magnet URL.
The archive includes also the personal details of the President Recep Tayyip Erdogan.

The above data is usually included in a standard Turkey ID card, but at the time I was writing it is not known the source of the personal information data is currently unknown.
It is not clear if the archive was populated with older data from other security breached, like the one that suffered the country in 2009.
Experts speculate that data have been stolen from a government agency managing data of Turkish citizens.
Below the message left by the hackers that appear to be politically motivated:
“Who would have imagined that backwards ideologies, cronyism and rising religious extremism in Turkey would lead to a crumbling and vulnerable technical infrastructure?”
Hackers have something against Erdogan, … and Trump
Lesson to learn for Turkey:
Bit shifting isn’t encryption.
Index your database. We had to fix your sloppy DB work.
Putting a hardcoded password on the UI hardly does anything for security.
Do something about Erdogan! He is destroying your country beyond recognition.
Hackers have found a baffling situation, it seems administrators hardcoded the password in one of the user interface they accessed.
“Putting a hardcoded password on the UI hardly does anything for security.”
The Panama Papers — Biggest leak in History Exposes Global Corruption
4.4.2016 Incindent
A huge trove of confidential documents from the Panamanian law firm Mossack Fonseca was made public on Sunday in what's known as One of the World’s Largest Data Leaks ever, called The Panama Papers.
Over 11.5 Million Leaked Files including 2.6 Terabytes of Data
Even larger than the NSA wires leak in 2013, the "Panama Papers" includes 2.6 Terabytes of private data, exposing an enormous web of offshore shell companies frequently used by many of the richest and most powerful members around the globe to evade taxes, hoard money, and skirt economic sanctions.
Shared with German newspaper 'Suddeutsche Zeitung' by an anonymous source, the leaked documents then passed on to the International Consortium of Investigative Journalists (ICIJ) – in which 370 Reporters from 100 News Media organizations looked into the massive leak for a year.
After a year-long investigation, ICIJ and its reporting partners began publishing a series of leaks on Sunday based on the Panama Papers, which involves more than 11.5 Million files including emails, invoices and bank records, and implicates 72 current and former heads of state.
World's Top Leaders and Rich Personalities Exposed
Panama-Papers-Leak
According to ICIJ, the leaked documents range from 1977 to December 2015 and include details on 214,000 offshore shell companies with links to 140 politicians including the President of Argentina, the King of Saudi Arabia and Prime Minister of Iceland.
The Panama Papers has unearthed 12 current and former world leaders, including monarchs, presidents, and prime ministers, who have been using offshore tax havens, including a $2 Billion paper trail that leads to Russian President Vladimir Putin.
Though Putin himself isn't directly implicated in the leak, a number of his family members and close friends are involved.
The documents exposed that Sergey Roldugin, one of Putin's oldest friends, owns 3 offshore companies worth over $100 Million: International Media Overseas, Sonnette Overseas and Raytar Limited.
The leaked documents also include details on at least 33 people and enterprises blacklisted by the United States, including Mexican drug lords and a number of terrorist organizations.
"The files contain new details about major scandals ranging from England's most infamous gold heist, an unfolding political money laundering affair in Brazil and bribery allegations convulsing FIFA, the body that rules international soccer," the ICIJ wrote in its overview of the leak on Sunday.
Besides this, over 500 Indians figure is on the Mossack Fonseca’s list of offshore companies, foundations, and trusts. The list has names of big personalities including film stars Amitabh Bachchan and Aishwarya Rai Bachchan to DLF owner K.P. Singh along with 9 members of his family.
According to the German newspaper, Mossack Fonseca is the world's fourth-biggest offshore law firm that enables their clients to keep their financial affairs secret, no matter how shady, citing some of its clients, which include "criminals and members of various Mafia groups," along with government officials and their relatives and close associates.
The leaks also revealed that some global banks including HSBC, UBS, Deutsche Bank, Credit Suisse, and others have worked with Mossack Fonseca to create offshore accounts.
In response to the ICIJ's report, Mossack Fonseca issued a statement saying that the firm, as a registered agent, is only helping its clients incorporate companies and that it conducts thorough due diligence in every case it meets and quite often exceeds 'all relevant local rules, regulations and standards to which the firm is bound.
vBulletin resets passwords after a targeted attack
30.3.2016 Incindent
vBulletin has suffered a severe attack last week that breached one of the Germany servers, in response it informed users that all passwords had been reset.
vBulletin has suffered a severe attack last week, in response it informed users that all passwords had been reset. According to the vBulletin developer Paul Marsden one of the Germany servers was breached by an unauthorized party.
“Due to the discovery yesterday of unauthorized access to of one of the VBG servers it is possible the hacker may have gained access to other vb systems as well. Therefore we have again taken the precaution of resetting all user password hashes. To be able to login to the site you will need to use the lost password functionality.
http://www.vbulletin.org/forum/login.php?do=lostpw
We apologise for any inconvenience this may cause.” said Marsden.
The attackers have breached the Germany (VBG – “vbulletin-germany.com”) server, a circumstance that could have allowed them to access other systems of the organization, including “vBulletin.com” and “vBulletin.org.”
At the time I was writing there aren’t other details on the data breach, Marsden highlighted that hackers haven’t used any exploits, a claim supported by the fact that the hackers server doesn’t run any instance of the popular CMS.
Mardden believes attackers have carefully planned the attack:
“I can tell you it wasnt via any vB exploit – in fact, the VBG site doesnt run vbulletin. Someone clearly targetted the site, it was obvious they had planned this quite carefully.”said Marsden.
This isn’t the first time that the platform is targeted by hackers, in November 2015, the official forum was shut down after a hacker using the online moniker “Coldzer0” defaced it.
The website has been defaced and the forum was displaying the message “Hacked by Coldzer0.”
According to DataBreaches.net, vBulletin, Foxit Software forums have been hacked by Coldzer0 that stole hundreds of thousands of users’ records.
The hacker published screenshots that show he managed to upload a shell to the forum website and accessed user personal information, including user IDs, names, email addresses, security questions and answers, and password salts).

As usual, I strongly suggest users to change the passwords on any other website where they shared the same login credentials.
1 million Gmail accounts victim of state-sponsored hacking
28.3.2016 Incindent
Google is improving its Gmail warning service to help protect the customers from state-sponsored hacking and surveillance activities.
Google confirmed that one million Gmail accounts might have been targeted by nation-state hackers.
The news is worrying, the company is observing a significant increase in the number of hacking attacks on user email accounts.
Google announced that it is able to identify operations carried out by state-sponsored hackers and it is its intention to notify potentially affected customers.
Google hasn’t provided details on the number of affected customers, anyway , it confirmed that the list of victims “often” includes “activists, journalists, and policy-makers taking bold stands around the world.”
Google confirmed that only a limited number of customers are targeted by state-sponsored hackers, roughly less than 0.1% of users ever receive a notification from the company that anyway consider critic to inform users on ongoing attacks.
In the past, users received a warning through a pink Warning tab present on top of Gmail urging victims to adopt necessary countermeasures.
Google state-sponsored hacking notifications
Now Google has improved the notification messages using a full-page warning related to state-sponsored hacking.
“Today, we’re launching a new, full-page warning with instructions about how these users can stay safe. They may see these new warnings instead of, or in addition to, the existing ones.”

Google is improving its “safe browsing” security notifications, a mechanism to inform users when they are going to open suspicious links included in receiving emails. The users will receive a full-page notice before opening the link, meanwhile, in the past the same notification was provided before a link was clicked.
“Safe Browsing already protects Gmail users by identifying potentially dangerous links in messages. Starting this week, Gmail users will begin to see warnings if they click these links, further extending this protection to different web browsers and email apps. ” States the security advisory published by Google.
Google is continuing to push email encryption to protect its customers from government surveillance. Google is working with IT Giants, including Comcast, Microsoft, and Yahoo, to propose a new secure email mechanism.
In the last weeks, Google implemented a mechanism to warn Gmail users when they send and receive email over unsecured connections.
“This has had an immediate, positive effect on Gmail security. In the 44 days since we introduced it, the amount of inbound mail sent over an encrypted connection increased by 25%. We’re very encouraged by this progress! ” states Google.
“Given the relative ease of implementing encryption and its significant benefits for users, we expect to see this progress continue.”
Hackers stole records of 1.5 million customers of Verizon Enterprise
25.3.2016 Incindent
Hackers reportedly stole the records of 1.5 million customers of Verizon Enterprise which are offered for sale in the criminal underground.
According to KrebsOnSecurity, data leaked after a security reach at Verizon Enterprise Solutions are available in the cyber criminal underground. Records of 1.5 million customers of Verizon Enterprise are available for sale, the entire archive is offered for $100,000, but buyers can pay for a set of 100,000 customer records that goes for $10,000.
“Earlier this week, a prominent member of a closely guarded underground cybercrime forum posted a new thread advertising the sale of a database containing the contact information on some 1.5 million customers of Verizon Enterprise.” wrote the popular investigator Brian Krebs.
The crooks also offered information about Verizon security flaws that likely allowed hacking one of the systems at the company.
“Buyers also were offered the option to purchase information about security vulnerabilities in Verizon’s Web site,”.
The situation in embarrassing because Verizon Enterprise also offers security services to its customers for the protection of their data. 97 percent of Fortune 500 companies are customers of the Verizon Enterprise.
verizon enterprise
The database is available in multiple formats, including MongoDB. There have been many incidents over the past period where misconfigured MongoDB databases exposed a large number of records of sensitive information.
Verizon Enterprise representatives have confirmed the data breach suffered by their website and the presence of the flaw exploited by the attackers, already fixed by its experts. The company noted that the hackers have not gained access to customer proprietary network information or other data.
“Verizon recently discovered and remediated a security vulnerability on our enterprise client portal,” Verizon said in an emailed statement.
“Our investigation to date found an attacker obtained basic contact information on a number of our enterprise customers,” Verizon told to Brian Krebs. “No customer proprietary network information (CPNI) or other data was accessed or accessible.”
Stolen data could be exploited by attackers in spear-phishing attacks as explained by Krebs.
“Even if it is limited to the contact data for technical managers at companies that use Verizon Enterprise Solutions, this is bound to be target-rich list,” he wrote.
Buhtrap group stole tens of millions of dollars from Russian banks
18.3.2016 Incindent
From August 2015 to February 2016 Buhtrap group managed to conduct 13 successful attacks against Russian banks for a total amount of $25.7 mln.
Since August of 2015, the Buhtrap group has conducted 13 successful attacks against financial institutions stealing more than ₽1.86 billion RUB ($27.4M USD). In April 2015, ESET discovered a malware campaign dubbed Operation Buhtrap, a conjunction of the Russian word for accountant “Buhgalter” and the English word “trap”. So far Buhtrap has not been seen anywhere else in the wild, 88 percent of targets have been in Russia and ten percent in Ukraine. Analysts have also likened the campaign to the Anunak/Carbanak campaign, which also targeted Russian and Ukrainian Banks.
The modus operandi of these particular cybercriminals is usually associated with targeted attacks rather than cyber fraud, which make this move to financial crime unusual and effective.
In the last wave of, the attackers hit Russian banks by pretending to be FinCERT, a center established by the Russian Central Bank for dealing with cyber-attacks in Russia’s financial sector.
According to a report released by the security firm Group-IB, Buhtrap has been active since 2014, despite their first attacks against financial institutions were only detected in August 2015. Earlier, the group had only focused on targeting banking clients. At the moment, the group is known to target Russian and Ukrainian banks, below the timeline of the attacks published by Group-IB:

The Buhtrap timeline is a sequence of successful attacks, in August 2015 the hackers stole ₽25.6 million RUB ($375,617 USD), two months later a new campaign resulted in the losses of ₽99 million RUB ($1.4 million USD).
In November 2015, the group raked ₽75 million RUB ($1.1 million USD) with two distinct campaigns against two banks. In December the group reached a peak in its activity targeting 5 banks and taking down ₽571 million RUB ($8.3 million USD). They also conducted two successful attacks in January and two more a month later. In all, the group has stolen ₽1.86 billion RUB ($27.4M USD) from banks in Russia
The activities continued in January and February stealing dozen million dollars from banks in Russia.
In February 2016, a developer for Buhtrap leaked the complete source code for the malware used by the group because he wasn’t paid by the gang. Experts who have analyzed it discovered that the code is related to an earlier revision and not to the one used in the recent attacks.
“Earlier, the group had only focused on targeting banking clients. At the moment, the group is known to target Russian and Ukrainian banks.” states the report.
“In many respects, this group’s activity has led to the current situation where attacks against Russian banks causing direct losses in the hundreds of millions of rubles are no longer taken as something unusual,”
The tactic used by the Buhtrap group is consolidated, the hackers register typo domains or domains that are familiar to the victim, and from there they rent servers where mail servers were set up to send phishing emails on behalf of the legitimate company avoiding being filtered as spam.
The group used a custom malware which is able to detect security software and other defensive solutions. The malware uses to track every banking operation made by the victims, the malicious code notice these operations, it downloads a legitimate remote access tool (LiteManager) which is used to carry on fraudulent transfer orders.
What to expect in the next months?
The experts have no doubt, the group will continue its activity, likely improving its TTPs, researchers at Group-IB fears that the public availability of the gang’s malware may trigger the number of campaigns against banks conducted by other criminal organizations.
“The published source codes are active. Their wide distribution may trigger the increase in the number of attacks using this malware conducted by other groups. The builder interface is presented below.” states the report.
Let me suggest to give a look at the interesting report published by Group-IB, it is full of precious information on the Buhtrap group, including indicators of compromise.
Placing a skimmer on Gas Station Card Scanner in less than 3 seconds
14.3.2016 Incindent
Attack ATM is very simple for criminals, a video released by Miami Beach Police shows two men installing a credit card skimmer in less than 3 seconds.
In October, the CENTRAL MEANS OF PAYMENT ANTIFRAUD OFFICE (UCAMP) of the Italian Ministry of Economy and Finance released the annual report on Payment card frauds.
This year I was one of the experts who worked on the MEF – Annual Report on Payment Card Frauds No. 5/2015, an interesting document full of detailed data on the phenomena of payment card frauds. The document focus on payment card frauds (unrecognized transactions) issued in Italy and used everywhere.
Credit card frauds are a global emergency, ATMs are a privileged target of cyber criminals worldwide, we discussed several times about illegal practices used by crooks to steal credit card data. ATM hacking, ATM malware and also about ATM skimming are the most common type of attack against these machines.
Unfortunately, the attack against an ATM is very simple for criminal organizations, a video recently released by Miami Beach Police shows two men installing a credit card skimmer at a local gas station in less than three seconds.
The video shows how a criminal crew goes into action while the store clerk is serving one customer, which it is actually an accomplice.
The man keeps is face far from the camera, protecting it with a cap while the accomplice tampers with the ATM.
Just three second to completely compromise payment card terminal by attaching a skimmer that allows the crooks to steal credit card data from every customer of the store.
In the specific case, the skimmer was storing the stored card data locally, for this reason, the criminals will return to dismount the device. The most sophisticated gang user skimmers that are able to transfer data via Bluetooth once it has been stolen from the card.
Card data are then offered in the cyber criminal underground or to clone payment cards and use them to purchase items that can be resold quickly, like electronic devices, gift cards and luxury items.

Source – CBS Miami
The theft of credit card data is a particularly worrying phenomenon, especially in the US where the merchants are slightly moving to the EMV standard that is considered more secure because new payment cards will use a built-in chip to authorize the transactions.
Payment card frauds in the U.S. account for nearly 50 percent of global fraud losses, according to the Nilson Report; security experts maintain that the main reason is that the country is the last in the world to implement the EMV (EuroPay, MasterCard, and Visa).
Fortunately, the situation is changing also in the U.S., where the banking consumers are about to benefit from EMV against payment frauds, too.
The deadline for the move to EMV was October 1, 2015, but my merchants are still in delay and in many cases retailers still allow customers to swipe their cards.
Despite the enormous improvement introduced with EMV, we cannot consider it as a complete remediation against card frauds, in particular against “Card-Not-Present” (CNP) frauds.
EMV still doesn’t protect users when dealing with e-commerce or mobile commerce platforms.
“The reality is EMV credit cards cannot prevent PoS RAM Scraper attacks. EMV was developed to prevent credit card counterfeiting and not RAM scraping. If the EMV credit card’s Tracks 1 and 2 data are sent to the PoS system for processing, it will become susceptible to RAM scraper attacks because the decrypted data resides in RAM,” states a blog post published by Trend Micro.
Bangladesh says hackers stole $100 Million from its US Federal Reserve account
10.3.2016 Incindent
Unknown hackers have stolen more than $100 million from the Bangladesh Bank account at the US Federal Reserve Bank.
According to Bloomberg, the Bangladesh’s Finance Minister Abul Maal Abdul Muhith is accusing the U.S. Federal Reserve for the theft of at least $100 million stolen from the Bangladesh’s account. Bangladesh is threatening the US for a legal fight to retrieve the funds, explained Muhith in a press conference held in Dhaka on Tuesday. The central bank of Bangladesh declared the funds had been stolen from an account by hackers, the experts had traced some of the missing funds in the Philippines.
“We kept money with the Federal Reserve Bank and irregularities must be with the people who handle the funds there,” Muhith said. “It can’t be that they don’t have any responsibility.”
While the central bank of Bangladesh is blaming Chinese hackers, the Federal Reserve is denying the security breach of security took place.
On Monday, a spokeswoman for the US Federal Reserve Bank of New York confirmed there was no evidence of a security breach, neither that the Bangladesh Bank account had been hacked.

The Fed spokeswoman clarified that every payment follows standard protocols and is authenticated by the SWIFT message system used by financial institutions
“To date, there is no evidence of any attempt to penetrate Federal Reserve systems in connection with the payments in question, and there is no evidence that any Fed systems were compromised,” said New York Fed spokeswoman Andrea Priest.
Currently, the US Fed and the Bangladesh Government are investigating the incident.
The Bangladesh’s central bank has about $28 billion in foreign currency reserves, according to the country’s Prothom Alo newspaper, at least 30 transfer requests were made on February 5 using the Bangladesh Bank’s SWIFT code. Five transfers were successfully completed.
How is possible?
Difficult to say because there aren’t details on the event. It is likely hackers breached Bangladesh Bank in early February stealing credentials for payment transfers, then they used the credentials to order transfers out of a Federal Reserve Bank of New York account held by Bangladesh Bank.
Anyway it is a complex hack, attackers had a deep knowledge about Bangladesh Bank’s procedures for ordering transfers, likely they spied on Bangladesh Bank staff to gather the information.
Other incidents involved the US Feds in the past, in 2014 a British citizen was accused of hacking its servers and leaking sensitive data.
IRS is warning taxpayers of a new surge in tax-related incidents
23.2.2016 Incindent
It is a nightmare for taxpayers according to an IRS bulletin there is a 400 percent surge in tax-related phishing and malware incidents.
This year the IRS already reported 1,026 malware and phishing incidents, compared to 254 this time last year.
The IRS is warning taxpayers of newer forms of attacks aiming victims into disclosing credentials to third-party tax preparation service accounts.
“The Internal Revenue Service renewed a consumer alert for e-mail schemes after seeing an approximate 400 percent surge in phishing and malware incidents so far this tax season.” states the bulletin. “The emails are designed to trick taxpayers into thinking these are official communications from the IRS or others in the tax industry, including tax software companies. The phishing schemes can ask taxpayers about a wide range of topics. E-mails can seek information related to refunds, filing status, confirming personal information, ordering transcripts and verifying PIN information.”
The IRS Commissioner John Koskinen used the adjective “dramatic” to describe this surge in tax-related incidents inviting taxpayers to watch out for scammers.
“This dramatic jump in these scams comes at the busiest time of tax season,” said Koskinen. “Watch out for fraudsters slipping these official-looking emails into inboxes, trying to confuse people at the very time they work on their taxes. We urge people not to click on these emails.”
IRS building
Threat actors are very interested in using the tax season as a lure, in a common attack scenario victims receive an email containing links to the domain used to serve malware. In other cases, the attackers used emails with attachments that include documents embedding malicious macros. Once the victims open the document, the macro drops a malware on the victim’s machine, including dreaded ransomware like CryptoLocker, TeslaCrypt and Locky.
These are the alarming statistics provided by the IRS:
There were 1,026 incidents reported in January, up from 254 from a year earlier.
The trend continued in February, nearly doubling the reported number of incidents compared to a year ago. In all, 363 incidents were reported from Feb. 1-16, compared to the 201 incidents reported for the entire month of February 2015.
This year’s 1,389 incidents have already topped the 2014 yearly total of 1,361, and they are halfway to matching the 2015 total of 2,748.
Recently IRS services were abused by crooks to target taxpayers, in May 2015 the Internal Revenue Service was breached by hackers that “used an online service provided by the agency” to access data for more than 100,000 taxpayers. The IRS issued an official statement on the incident and specified that the compromised system was “Get Transcript.” The Transcript service could be used by taxpayers to get a transcript online or by mail to view their tax account transactions.
In August 2015, the Internal Revenue Service disclosed a new review of its system, revealing that 334,000 taxpayers (more than three times it initially estimated) may be affected by the hack it announced in May.
A couple of weeks ago the IRS detected roughly unauthorized attempts using 464,000 unique SSNs, and 101,000 attempts allowed crooks in generating PINs.
The U.S. Internal Revenue Service confirmed that cyber criminals abused the Electronic Filing PIN application running on irs.gov that allows taxpayers to generate a PIN that they can use to file tax returns online.
Stolen card data of 100,000 Britons for sale on the clear web
15.2.2016 Incindent
A website on the clear web is offering for sale stolen card data from more than a million people worldwide including more than 100,000 Britons.
According to a report published by The Times, the website Bestvalid.cc is offering for sale stolen credit and debit card details of 100,000 Britons.
Banking details stolen from more than a million people worldwide goes for £1.67, the list of victims includes former senior adviser to the Queen, bankers, doctors and lawyers.
The site is available on the surface web since at least June and journalists are surprised that law enforcement hasn’t yes seized it.
“The National Crime Agency must act immediately to get this site closed. I will be writing to the NCA to bring this issue to their attention,” said Keith Vaz, chairman of the home affairs select committee.
Politicians are urging the intervention of the police, black marketplaces could be used by the organized crime and radical groups to fund terrorism and other illegal activities.
Aligned with the offer in many black markets hosted on dark web, Bestvalid.cc appears like an ordinary e-commerce, it includes a customer service and refund services for faulty products.
Users can buy stolen payment card data, often completed with further information (i.e. common answer to online banking security questions, postal address of the card holder) that could be used for more sophisticated scams.
A journalist at the Times paid for a lot of data including information from one person he is in contact. He paid in Bitcoin of course and received a package including debit card number, security code, expiry date, mobile phone number and postal address.
When the journalist presented the data to the victim, Laia Humbert-Vidan, 30, a radiotherapy physicist from London, said was disconcerted.
“I don’t feel like the police are able to protect anyone from online fraud. If they were, these types of sites would not exist in the first place.” said Laia Humbert-Vidan.
In the last months the underground market was flooded of data from major data breaches, including the TalkTalk and Carphone Warehouse,
Bestvalid is not hidden in the dark web, it is easy to access and it is one of the biggest websites offering stolen card data.

The cybercrime has a significant economic impact on the economy of every Government, it costs the UK £27 billion a year, and the Centre for Economics and Business Research estimated the same cost at £34 billion a year for businesses alone.
A replica of AlphaBay market used to steal login credentials
12.2.2016 Incindent
Fraudsters operating on the AlphaBay darknet market have deployed a replica of the popular marketplace to steal login credentials from peers.
Paul Mutton, security experts at Netcraft, discovered a fake version of the Alphabay Market (pwoah7foa6au2pul.onion), one of the most popular black markets hosted in the dark web.
Paul Mutton speculates that fraudsters have deployed the fake version of the Alphabay Market in an attempt to steal login credentials.
“Fraudsters operating on the AlphaBay darknet market are using phishing attacks to steal login credentials from other criminals. In this particular attack, the phishing site mimics the address of one of AlphaBay’s Tor hidden services.” wrote Mutton.
AlphaBay is today one of the most interesting black markets, it offers any kind of illegal products and services. It emerged in 2014 following the seizure down of Silk Road, it was founded by members of Russian carding forum and today it is the most important black market for payment card frauds.
The fake website mimics the login page of the Alphabay black market, including the CAPTCHA protection mechanism.

When Alphabay users login to the bogus website are redirected to the legitimate AlphaBay Market.
In order to replicate the legitimate website it was necessary to reproduce also the .onion address that is associated to the hidden service. This address is derived from the public key used to authenticate the connection, this means that it is very difficult to convincingly impersonate the site without having access to the owner’s key pair.
Fraudsters have computed a partial match using tools such as scallion and generate a similar address like pwoah7f5ivq74fmp.onion.
“However, in the case of this phishing attack, the fraudster has simply created a lookalike domain on the public internet, using the address pwoah7foa6au2pul.me.pn.” wrote Mutton.
“This phishing attack makes use of a me.pn domain, which was likely chosen because addresses under this domain can be registered for free, and the “.me.pn” string bears a (somewhat tenuous) similarity to the .onion TLD, at least in terms of its length.”
As explained by Mutton, this phishing attack is another example of fraudsters defrauding fraudsters.
It’s obvious that similar attacks represents a threat only for new users who are deceived by the replica, meanwhile AlphaBay veteran members will never fall victim of such kind of attack.