Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
Google Offers Bonus Bounties for Flaws in Popular Android Apps
20.10.2017 securityweek Security
Google announced on Thursday that it’s prepared to offer a bonus of $1,000 to researchers who find serious vulnerabilities in some of the popular applications present on Google Play.
The new Google Play Security Reward Program was launched by Google in partnership with HackerOne. For the time being, the project only covers a handful of applications whose developers have opted in to the program.
The list includes Alibaba’s AliExpress, Dropbox, Mail.ru, Snapchat, Tinder, the Duolingo language learning app, meditation app Headspace, and the Line messenger app. All of the Android apps developed by Google itself are also eligible for a bonus reward. Other applications may be added in the future.
Researchers who discover a serious vulnerability in one of these Android apps need to report their findings to the respective developer via their HackerOne page or their self-managed bug bounty program. Once the flaw has been fixed, the bounty hunter can request a bonus reward from Google via its Play Security Reward Program.
For the time being, only remote code execution vulnerabilities are eligible for the $1,000 bonus, but other types of security holes may be added in the future. The report must include a proof-of-concept (PoC) and it must work on Android 4.4 and later, but it’s not required to achieve a sandbox escape.
Google noted that the bonus bounty needs to be requested within 90 days of a patch being made available by the developer.
“The program is limited to a select number of developers at this time to get initial feedback. Developers can contact their Google Play partner manager to show interest,” Google employees said in a blog post. “All developers will benefit when bugs are discovered because we will scan all apps for them and deliver security recommendations to the developers of any affected apps.”
Flaws found in Google’s own Android apps can be reported via the Google Vulnerability Reward Program and there is no need to separately request the bonus bounty once the issue has been addressed.
Google Prompt Now Primary Choice for 2-Step Verification
20.10.2017 securityweek Security
Google has taken yet another step toward improving the security of its users by making Google prompt the primary choice for 2-Step Verification (2SV), instead of SMS.
Launched in June last year, Google prompt was designed to improve the security of the login process by informing users of any login attempts on accounts with 2SV enabled. Instead of receiving an SMS message, the user is greeted with a pop-up on the smartphone, and they can log in by simply clicking the “Yes” button.
Considering that it is a more secure 2SV method compared to SMS, Google started inviting users to enable Google prompt this July. The functionality is available for both Android and iOS users, and has been designed to deliver 2SV over an encrypted connection, in addition to providing options such as the blocking of unauthorized access attempts.
“Google prompt is an easier and more secure method of authenticating an account, and it respects mobile policies enforced on employee devices,” the Internet giant claims.
Now, the company has decided to push Google prompt to all users, and is making it the first 2SV choice for them, instead of SMS. Once they enable 2SV, however, users will still be able to use options such as SMS, the Google Authenticator app, backup codes, and Security Keys as their alternative second step.
The change, Google says, will only impact users who haven’t set up two-step verification yet, while those who have won’t be affected. Furthermore, users who attempt to set up 2SV but don’t have a compatible mobile device will be prompted to use SMS instead. To enable 2SV, users should head to their My Account page.
The use of Google prompt, the Internet company points out, requires a data connection. On iOS devices, the feature requires the Google app. For more advanced security requirements, Suite Enterprise domains can enforce Security Keys.
Google prompt is currently rolling out to all users, but it might take up to two weeks before it becomes available everywhere.
Enable Google's New "Advanced Protection" If You Don't Want to Get Hacked
20.10.2017 thehackernews Security
It is good to be paranoid when it comes to cybersecurity.
Google already provides various advanced features such as login alerts and two-factor authentication to keep your Google account secure.
However, if you are extra paranoid, Google has just introduced its strongest ever security feature, called "Advanced Protection," which makes it easier for users, who are usually at high risk of targeted online attacks, to lock down their Google accounts like never before.
"We took this unusual step because there is an overlooked minority of our users that are at particularly high risk of targeted online attacks," the company said in a blog post announcing the program on Tuesday.
"For example, these might be campaign staffers preparing for an upcoming election, journalists who need to protect the confidentiality of their sources, or people in abusive relationships seeking safety."
Even if a hacker somehow gets your password—using advanced phishing attacks, zero-day exploits or spyware—and tries to access your Google account, they will not be able to get in.
To enable Google's Advanced Protection feature, you will need two physical security keys that work with FIDO Universal 2nd Factor (U2F)—which offers a hardware-based two-factor authentication that does not require secret codes via SMS or emails.
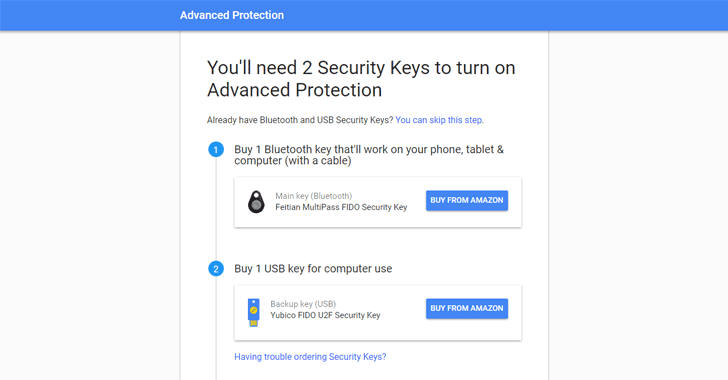
To log into your Google account from a computer or laptop will require a special USB stick while accessing from a smartphone or tablet will similarly require a Bluetooth-enabled dongle, paired with your phone.
"They [security devices] use public-key cryptography and digital signatures to prove to Google that it's really you," the post reads. "An attacker who does not have your Security Key is automatically blocked, even if they have your password."
Google's Advanced Protection offer three features to keep your account safe:
Physical Security Key: Signing into your account requires a U2F security key, preventing other people (even with access to your password) from logging into your account.
Limit data access and sharing: Enabling this feature allows only Google apps to get access to your account for now, though other trusted apps will be added over time.
Blocking fraudulent account access: If you lose your U2F security key, the account recovery process will involve additional steps, "including additional reviews and requests for more details about why you've lost access to your account" to prevent fraudulent account access.
Advanced Protection feature is not designed for everyone, but only for people, like journalists, government officials and activists, who are at a higher risk of being targeted by government or sophisticated hackers and ready to sacrifice some convenience for substantially increased e-mail protection.
Currently, if you want to enrol in the Advanced Protection Program, you will need Google Chrome, since only Chrome supports the U2F standard for Security Keys. However, the technology expects other browsers to incorporate this feature soon.
Google Adds ESET Malware Detection to Chrome
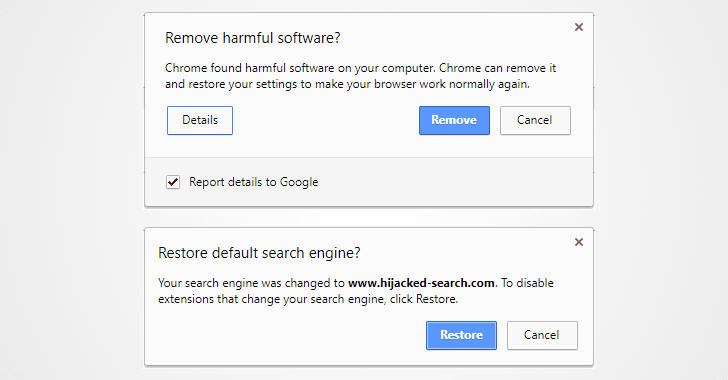
Google has also made a notable change by partnering with anti-virus software firm ESET to expand the scope of malware detection and protection in its browser through the Chrome Cleanup feature.
Chrome Cleanup now has a malware detection engine from ESET, which works in tandem with Chrome's sandbox technology.
"We can now detect and remove more unwanted software than ever before, meaning more people can benefit from Chrome Cleanup," Google said in a blog post published Monday.
"Note this new sandboxed engine is not a general-purpose antivirus—it only removes software that doesn’t comply with our unwanted software policy."
You can sign-up for Google's Advanced Protection here.
BoundHook Hooking Is Invisible to Windows 10's PatchGuard
20.10.2017 securityweek Security
A newly discovered hooking technique can go completely undetected by the current implementation of PatchGuard, CyberArk security researchers warn.
Called BoundHook, the method relies on causing an exception in a very specific location in a user-mode context, as well as on catching that exception to gain control over the thread execution. It can bypass PatchGuard, or Kernel Patch Protection, which was designed by Microsoft to prevent malicious code from running at kernel level on 64-bit versions of Windows.
Hooking is known to provide control over the operating system or applications, and both legitimate and malicious programs can leverage it. The newly discovered method can be used in post-exploitation scenarios where the attacker has already established control over the system.
BoundHook uses the BOUND instruction, which is part of Intel MPX (Memory Protection Extensions) and which was designed to increase software security by checking pointer references susceptible to malicious exploitation at runtime due to memory corruption vulnerabilities.
Because Intel designed it to generate a fault to allow examination of the bound check failure, the BOUND instruction “checks an array index against bounds and raises software interrupt 5 if the test fails,” CyberArk explains. When a bound fault occurs, registered bounds-exception callback routines are executed.
Kernel-mode drivers and shellcode payloads running in kernel-mode are able to register callback routines for bound faults. With no parameters, such a callback routine should return a BOUND_CALLBACK_STATUS.
The researchers also explain that, after the bound fault registration, the kernel-mode code gets a pointer to the user-mode DLL base address. Then it obtains the address of the function to hook, after which it attempts to start writing to that address.
To perform this operation as stealthily as possible and avoid triggering the COW (copy-on-write) protection, one could either manipulate the CR0 register or allocate their “own memory descriptor list (MDL) to describe the memory pages and adjust permissions on the MDL”. The latter method, CyberArk says, is stealthier and “completely invisible by design to the current PatchGuard implementation.”
The security researchers also explain that, writing directly to a DLL’s COW page allows them to hook every process on the system that uses the specific DLL. By setting the kernel-mode code performing the hooking to write the code to a function’s prologue, the researchers’ kernel-mode callback function could take control of the thread when user-mode thread called that function.
Because the hooked page will still be COW, the performed modifications won’t be visible to anti-malware solutions, especially with most anti-virus makers unaware of the new method. Furthermore, user-mode debuggers can’t catch the hook, because “BoundHook’s method traps the execution flow by the kernel bound faults handler.”
“This method is invisible to most PatchGuard (PG) protection mechanisms. The MDL approach to bypass the COW mechanism is not detectable by PG today by design. As for the CR0 modification approach, although the CR0 is protected by PG, since it is modified for a very short period of time, the chance of being caught by PG is minimal,” the security researchers argue.
CyberArk says that BoundHook does not meet Microsoft’s requirements to be considered a security vulnerability, given that machine administrator rights need to be obtained for this method to work.
The researchers were in a similar situation earlier this year, when they disclosed GhostHook, an attack targeting Windows 10’s PatchGuard and able to bypass it and hook a malicious kernel code (rootkit). At the time, Microsoft revealed that the issue, although not a security vulnerability, may be addressed in a future version of Windows.
DMARC Not Implemented by Most Federal Agencies: Report
19.10.2017 securityweek Security
The U.S. Department of Homeland Security (DHS) recently ordered all federal agencies to start using DMARC, but currently only a small percentage have fully implemented the system, according to a report from security firm Agari.
The DHS’s Binding Operational Directive (BOD) 18-01 orders all federal agencies to implement web and email security technologies such as HTTPS, DMARC, SPF/DKIM and STARTTLS in the coming months.
DMARC, which stands for “Domain-based Message Authentication, Reporting and Conformance”, is an authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations using DMARC can specify what happens to unauthenticated messages: they can be monitored but still delivered to the recipient’s inbox (“none” setting), they can be moved to the spam folder (“quarantine” setting), or their delivery can be blocked completely (“reject” setting).DMARC
Federal agencies have been given 90 days to roll out DMARC with at least a “none” setting. Within one year, they will have to fully implement the protocol to ensure that malicious emails are blocked.
Agari has used its DMARC Lookup Tool to check 1,300 domains owned by federal agencies and determined that nearly 82 percent lack DMARC entirely. Roughly nine percent have fully implemented the system (i.e. quarantine or reject), while the other nine percent only monitor emails (i.e. none).
Agari monitors 400 government domains and noticed that nearly 90 percent of them were targeted with fraudulent or unauthorized emails between April and October 2017. Of the more than 336 million emails apparently sent from these domains during that timeframe, more than 85 million, representing roughly a quarter of the total, failed authentication due to being fraudulent or for some other reason.
“DMARC has proven incredibly effective at combating phishing across billions of emails daily,” said Patrick Peterson, founder and executive chairman of Agari. “This DHS directive is an important step to protect our government, businesses and citizenry from cybercrime.”
“We would like to recognize Agari’s customers that pioneered DMARC in the federal government including the U.S. Senate, Health and Human Services, Customs and Border Protection, U.S. Census Bureau, Veterans Affairs and the U.S. Postal Service. We hope their leadership and experience serves as a resource for best practices among their government peers who are beginning this journey,” Peterson added.
Agari also recently analyzed the use of DMARC in Fortune 500, FTSE 100 and ASX 100 companies and found that many had failed to fully implement the standard.
Europol Looks to Solve IP-Based Attribution Challenges
19.10.2017 securityweek Security
Europol Calls for a Solution to the IP Address Attribution Problems Caused by CGNs
Europol has called for the end of carrier grade NAT (CGN) to increase accountability online. This is not a new campaign from Europol, but it now seeks to gain public support: "Are you sharing the same IP address as a criminal?" it asks.
"Law enforcement is using the 'distinguish yourself from a criminal' tactic in order to provoke the 'nothing to hide' scare tactic," Tom Van de Wiele, principal security consultant at F-Secure told SecurityWeek, "which is unfortunate, because as far as our privacy is concerned it's about protection. Privacy is the right to select which people to share what information with. But when it comes to the push of Europol in this case, there is more to it than that."
Van de Wiele sees the call as symptomatic of law enforcement's desire to remove anonymity from the internet, which is effectively an attack against privacy.
Everybody with home computers uses network address translation (NAT) within their routers. The ISP allocates an IP address for the router (usually on a temporary basis), and the NAT ensures incoming traffic to that IP goes to the right computer. It allows one IP address to be used for multiple home computers.
NATs are not a problem for law enforcement -- the problem comes with the carrier grade NATs (CGNs) used by the ISPs. These allow dozens, hundreds and perhaps even thousands of routers or computers or mobile devices to share a single IP address simultaneously. The problem for law enforcement is that the ISP is currently unable to say which computer is being used by a particular IP address at a particular time.
For law enforcement, it means that it is virtually impossible to trace the physical location of an IP address under investigation. "This is relevant as in criminal investigations an IP address is often the only information that can link a crime to an individual," said Europol in an announcement https://www.europol.europa.eu/newsroom/news/are-you-sharing-same-ip-addr... yesterday. "It might mean that individuals cannot be distinguished by their IP addresses anymore, which may lead to innocent individuals being wrongly investigated by law enforcement because they share their IP address with several thousand others – potentially including criminals."
There is some irony in this since in October 2016, the Court of Justice of the European Union (CJEU) ruled that IP addresses can in some circumstances qualify as personal data under European law. Europol is now implying, however, that an innocent user could be investigated by law enforcement solely by the accident of sharing the same IP address as a criminal.
Van de Wiele sees something verging on sinister from this latest push by Europol. "This is another attempt by law enforcement to try and single out individuals and to reduce the possibilities of anonymity to get closer to their active targets while increasing their success of traffic analysis for all traffic they are vacuuming up." He points out that it was law enforcement that forced Facebook into the policy of all users using their own identity, and getting 'friends' to confirm whether profiles are accurate. "These are cold war tactics and they are troubling," he says.
Europol's concern over the growing use of CGNs is not new. It raised the issues in its Internet Organised Crime Threat Assessment (IOCTA) in both 2014 http://www.securityweek.com/europol-analyzes-cybercrime-services-industry and 2016. A study it conducted in summer 2016 showed that 80% of surveyed European cybercrime investigators had encountered problems in their investigations relating to the use of CGN, causing them to be either delayed or stopped. These cases concerned investigations of offenses including online child sexual exploitation, arms trafficking and terrorist propaganda.
Europol's Executive Director Rob Wainwright said yesterday, "CGN technology has created a serious online capability gap in law enforcement efforts to investigate and attribute crime. It is particularly alarming that individuals who are using mobile phones to connect to the internet to facilitate criminal activities cannot be identified because 90% of mobile internet access providers have adopted a technology which prevents them from complying with their legal obligations to identify individual subscribers."
Steven Wilson, Head of Europol's European Cybercrime Center, added: "The issues relating to CGN, specifically the non-attribution of malicious groups and individuals, should be resolved."
This will be difficult. ISPs introduced CGNs, ostensibly as a temporary technical measure, to bridge the gap between the depletion of IPv4 addresses and the uptake of effectively limitless IPv6 addresses. But IPv6 uptake has been far slower than expected. "This was supposed to be a temporary solution until the transition to IPv6 was completed," says Europol, "but for some operators it has become a substitute for the IPv6 transition. Despite IPv6 being available for more than 5 years the internet access industry increasingly uses CGN technologies (90% for mobile internet and 50% for fixed line) instead of adopting the new standard."
Indeed, it could be said that the use of CGNs is actually delaying the transition to IPv6. The 2016 study, 'A Multi-perspective Analysis of Carrier-Grade NAT Deployment', concluded, "CGNs actively extend the lifetime of IPv4 and hence also fuel the demand of the growing market for IPv4 address space, which in turn affects market prices and possibly hampers the adoption IPv6."
"Most peering companies and ISPs are nowhere near being ready when it comes to IPv6," says Van de Wiele; "and with it, we will also see a whole slew of security issues when the SOHO and home users get IPv6 in the process. Having a unique IP address for every user or device without NAT offers tremendous possibilities technically, but that also means you can be tracked more easily by ad companies and other entities such as law enforcement."
In the meantime, what was introduced as a temporary fix has become entrenched. In most cases the use of CGNs is unnoticed and unknown by the user -- and hence, perhaps, this new appeal to public opinion by Europol. However, even if Europol solves the CGN issue, it is not at all clear that it will solve the problem of attribution.
"Unfortunately, CGN is not the only challenge when enforcing enacted laws and prosecuting cybercrime," commented Ilia Kolochenko, CEO of High-Tech Bridge. "A great wealth of currently available VPN service providers that you can purchase for bitcoins open up new opportunities to all kinds of digital offenders and predators." Without backdoor access to the VPN concerned, law enforcement will not have access to the IP address at all.
Furthermore, Kolochenko points out that the ability to tie a particular IP address to a particular physical computer will still not solve the problem. "The new trend in cybercrime," he said, "is to compromise a third-party with a motive to commit crime (e.g. a competitor) and conduct the attack from its infrastructure. On the Dark Web, you can buy compromised machines of law enforcement and judicial officers to be used as proxies for attacks. Most cybercrimes become technically uninvestigable or the price of their investigation outweighs any public interest."
Security Concerns Hamper Migration to Office 365: Report
15.10.2017 securityweek Security
An increasing number of organizations have started using Microsoft’s Office 365 platform, but many haven’t migrated due to security concerns, according to a report published on Thursday by Barracuda Networks.
The study is based on a survey of more than 1,100 organizations of all sizes from North America, Europe, Africa and the Middle East. Nearly two-thirds of respondents said they are using Office 365 and 49% of the remaining organizations plan on migrating. While the number of organizations that started using Office 365 has increased, the adoption rate has declined compared to 2015-2016, when the number of subscriptions doubled.
Nearly 44% of organizations that haven’t moved to Office 365 decided against migrating due to security concerns. Of the companies that plan on migrating, more than 73% said they were concerned about advanced threats in their future Office 365 environment. Nearly 70% of those that have already started using Office 365 are also concerned about sophisticated threats.
More than 86% of respondents are concerned about phishing, impersonation and social engineering attacks, while 92% are concerned about ransomware.
“The very high rates of concern about security—including worries about latent threats, advanced malware, phishing and spear phishing, and especially ransomware—may be the single most important contributing factor to the overall decline in the rate of adoption that the survey revealed,” Barracuda said in its report.
How well are these organizations prepared to handle potential attacks? Only one-third of respondents said they have a third-party security solution designed to protect them against phishing and other social engineering attacks, and 69% said they provide training for their employees.
Despite the fact that email has been one of the main ransomware delivery vectors, more than half of respondents don’t use DMARC or DKIM/SPF, protocols designed to detect and prevent email spoofing.
Microsoft offers its own security service for Office 365, Advanced Threat Protection (ATP), but only 15% of respondents said they use it. On the other hand, many are either using or are planning on using third-party solutions for Office 365 security, archiving and backup.
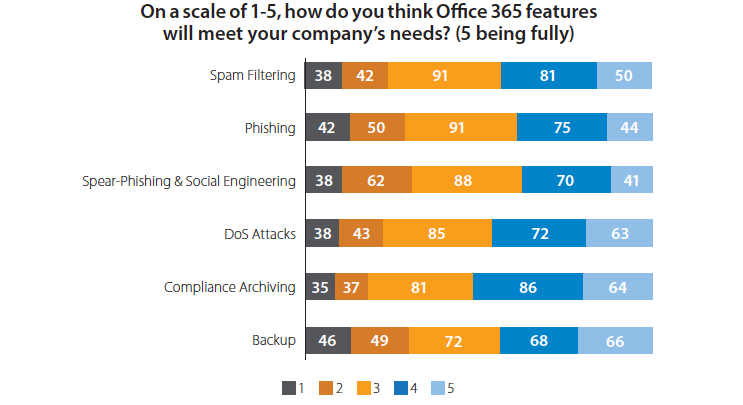
“Overall, respondents reported significant doubts about the effectiveness of native security and other features of Office 365. In particular, they had concerns about these features’ ability to protect them effectively against ransomware, phishing, and spear-phishing or social-engineering attacks,” Barracuda said.
In the past months, there have been several reports of serious vulnerabilities affecting Office 365 and even sophisticated attacks targeting users of the platform.
Akamai to Acquire DNS Security Firm Nominum
15.10.2017 securityweek Security
Akamai Technologies announced on Wednesday that it has agreed to acquire Nominum, a privately-held provider of DNS security solutions for carriers and enterprises.
Terms of the deal were not disclosed, but the all-cash transaction is scheduled to close in Q4 2017, Akamai said.
“By combining Nominum’s carrier-grade cybersecurity solutions with Akamai’s enterprise security offerings and threat intelligence, Akamai intends to serve a larger base of carrier and enterprise customers with more comprehensive security products,” Akamai explained. “These products will be designed to more effectively identify, block, and mitigate cybersecurity threats such as malware, ransomware, phishing, and data exfiltration.”
In early 2017, Akamai lauched a new offering designed to protect enterprises against malware, phishing and data exfiltration attempts through the analysis of DNS requests.
According to a recent report, many companies are not prepared to deal with DNS attacks, and a quarter of the ones that have already been hit reported significant losses. The study from Dimensional Research and Infoblox, based on a survey of over 1,000 IT and security professionals worldwide, revealed that 3 out of 10 companies have already experienced DNS attacks and in most cases it resulted in downtime.
Redwood City, Calif.-based Nominum says more than 100 service providers use its DNS technology in over 40 countries, which processes 1.6 trillion queries daily.
SecureWorks shed light on BRONZE BUTLER group that targets Japanese Enterprises
15.10.2017 Securityaffairs Security
Researchers with Counter Threat Unit at SecureWorks continues to monitor the Bronze Butler cyberespionage group (aka Tick).
Researchers with Counter Threat Unit at SecureWorks are monitoring the Bronze Butler cyberespionage group (aka Tick). The hacker group has been targeting Japanese heavy industry, manufacturing and international relations at least since 2012,
According to the experts, the group is linked to the People’s Republic of China and is focused on exfiltrating confidential data.
“BRONZE BUTLER’s operations suggest a long-standing intent to exfiltrate intellectual property and other confidential data from Japanese organizations. Intrusions observed by CTU™ researchers indicate a focus on networks involved in critical infrastructure, heavy industry, manufacturing, and international relations.” states the analysis published by SecureWorks.
SecureWorks detailed TTPs of the Bronze Butler group, the hackers used spearphishing, strategic web compromises (SWCs) in their targeted attacks and leveraged zero-day exploit to compromise targeted systems.
The threat actor used to maintain access to compromised environments and periodically revisiting them to exfiltrate further data.
“BRONZE BUTLER uses spearphishing emails and SWCs to compromise target networks, often leveraging Flash. The group has used phishing emails with Flash animation attachments to download and execute Daserf malware, and has also leveraged Flash exploits for SWC attacks.” continues the analysis.
Experts observed Bronze Butler leveraging an Adobe Flash zero-day vulnerability (CVE-2016-7836) in a popular Japanese corporate desktop management tool called SKYSEA Client View.
Experts highlighted the ability of the group in discovering a zero-day flaw in a software used in a certain region.
The researchers documented one of the malware in the arsenal of the group, the Daserf backdoor that allows gaining full control over the compromised system.
Bronze Butler developed two versions of the tool over time, in 2016, the hackers shifted from using Daserf to two remote access trojans (RATS) called xxmm and Datper.
The following image shows some of the proprietary tools used by the group between 2012 and 2017.

Analyzing the intent of the group, the researchers concluded the group may be tasked by multiple teams or organizations.
“The focus on intellectual property, product details, and corporate information suggests that the group seeks information that they believe might be of value to competing organizations. The diverse targeting suggests that BRONZE BUTLER may be tasked by multiple teams or organizations with varying priorities.” concluded the report.
Bronze Butler is still active and must be considered a very capable gang.
Credit agency Experian is using scare tactics to sell a service for tracking traded user data on the dark web
9.10.2017 securityaffairs Security
Credit agency Experian is using scare tactics to sell a service for tracking traded user data on the dark web, let’s give a close look at the user agreement
In the dark web, it is quite easy to find a lot of identities of unaware individuals and any other data that could expose companies to frauds.
One of the world’s biggest consumer credit reporting agencies, Experian, is trying to sell an identity theft protection product leveraging the consumers fear of the darknet.
Experian launched at the beginning of September the IdentityWorks Premium program saying it can protect customers from the exposure of personal information on the dark Web. “Is your personal information already being traded on the dark web,” states the of Experian’s advertisements.
“Because of its hidden nature and the use of special applications to maintain anonymity, it’s not surprising that the dark Web can be a haven for all kinds of illicit activity,” Experian says on its own website. “This means if you’ve ever been a victim of a data breach, it’s a place where your sensitive information might live.” states the scaring message from the company.
The company is offering for free a first “Dark Web Email Scan” to allow customers searching for their email on the darknets.
By providing an e-mail address into the scanning service a user grants Experian to, “track and collect certain consumer information specific to,” the user.

By using the “Free Dark Web Email Scan” a user will receive advertisements for Experian products at the e-mail address that is being scanned. The user agreement includes a clause which states that not only will Experian send you advertisements, but “offers for available credit cards, loan options, financial products or services, or credit-related products or services and other offers to customers.”
Experian collects and tracks various data for the users, including credit scores, loan and credit card payments, interest rates.
“I clicked on Experian’s terms of service and found a densely written, nearly 17,600-word document — a contract the length of a novella.
Not surprisingly, this is where you’ll find an arbitration clause preventing you from suing the company — an increasingly common aspect of consumer contracts nowadays. That’s the least of your worries, though.” reported a post published by the Los Angeles Times.
“The terms reveal that Experian “receives compensation for the marketing of credit opportunities or other products or services available through third parties,” which is exactly what it sounds like. You’re giving permission for the company to sell you out.
And if you make it to the very bottom of the contract — no small feat, I assure you — you’ll find this little cow chip: Even if you cancel any Experian service, your acceptance of the arbitration clause “shall survive.”
Disturbing! What do you think about?
Without going into the details of the implementation of the Experian scanning service, it is indisputable the company is using scare tactics to get new customers for its service.
Firefox 57 to Get New XSS Protections
6.10.2017 securityweek Security
Mozilla this week announced plans to boost the Cross-Site-Scripting (XSS) protections in Firefox by treating data URLs as unique origin.
The use of a data URL scheme allows web developers to inline small files directly into HTML or CSS documents, which also results in faster page load times. Because of this mechanism, the browser doesn’t have to perform a large number of HTTP requests to load external resources, as they are already in the page.
However, the same technique allows cybercriminals to craft attack pages and steal usernames, passwords, and other confidential information from unsuspecting users.
By embedding the entire attack code within the data URL, miscreants can launch attacks without having to actually host a full website. The data URL inherits the security context of the embedding element, and this inheritance model opens the door for Cross-Site-Scripting (XSS) attacks.
To prevent such attacks, Firefox 57 will treat data URLs as unique origins and will no longer inherit the origin of the settings object responsible for the navigation. Thus, data URLs loaded inside an iframe will no longer be same-origin with their parent document.
“Starting with Firefox 57, data URLs loaded inside an iframe will be considered cross-origin. Not only will that behavior mitigate the risk of XSS, it will also make Firefox standards compliant and consistent with the behavior of other browsers,” Mozilla notes in a blog post.
However, the company also explains that data URLs that do not end up creating a scripting environment will continue to be considered same-origin. Data URLs in img elements will be treated as such, Mozilla says.
Because of the new security setting, Firefox 57 will block attempts to reach content from a different origin, such as when a script within a data URL iframe attempts to access objects from the embedding context. In Firefox version 56 and older, this was possible because the data URLs inherited the security context.
The security enhancement was announced the same week Mozilla revealed plans to completely remove support for Windows XP and Vista from Firefox starting June 2018. A couple of months ago, the company made the Adobe Flash plugin click-to-activate by default, thus further improving the security of its users.
Firefox Support for Windows XP and Vista Ends June 2018
5.10.2017 securityweek Security
After annoucing in December 2016 that it plans to move Windows XP and Vista users to Firefox Extended Support Release (ESR), Mozilla this week announced that support for the two operating systems will be completely removed in June 2018.
Firefox is the last major browser to offer support for the two outdated and obsolete operating systems, but Mozilla has finally decided to change that.
Google cut the cord on Windows XP and Vista a while back, with Chrome 49 being the last release to work on the old platforms (the browser is currently at version 61). In early 2017, Google dropped support for the platforms in Gmail as well, by removing support for Chrome version 53 and below from the email service.
Despite releasing security updates for Windows XP to tackle Shadow Brokers exploits following the WannaCry outbreak, Microsoft isn’t supporting the platform either. The company ended support for the platform on April 8, 2014, when it released the last security updates for it.
Internet Explorer 8, which is used by as many as 88% of Windows XP users as their standard browser, hasn’t received security updates for almost two years.
“Today we are announcing June 2018 as the final end of life date for Firefox support on Windows XP and Vista. As one of the few browsers that continues to support Windows XP and Vista, Firefox users on these platforms can expect security updates until that date. Users do not need to take additional action to receive those updates,” Mozilla announced in a blog post.
The Internet organization is also encouraging users to upgrade to a versions of Windows that is supported by Microsoft. With no security updates available for unsupported platforms, known vulnerabilities and exploits put their users at risk.
Despite warnings, however, Windows XP and Vista continue to be widely used in enterprise environments. A June 2017 report revealed that the Metropolitan Police Service (MPS, or the Met) was still using over 10,000 XP machines on their network.
The Festive Complexities of SIGINT-Capable Threat Actors
5.10.2017 Kaspersky Security
Attribution is complicated under the best of circumstances. Sparse attributory indicators and the possibility of overt manipulation have proven enough for many researchers to shy away from the attribution space. And yet, we haven’t even discussed the worst-case scenarios. What happens to our research methods when threat actors start hacking each other? What happens when threat actors leverage another’s seemingly closed-source toolkit? Or better yet, what if they open-source an entire suite to generate so much noise that they’ll never be heard?
Thankfully, the 2017 VirusBulletin conference is upon us and, as in previous years, we’re taking the opportunity to dive into an exciting subject, guided by our experience from doing hands-on APT research.
During the past years, we discussed the evolution of anti-malware research into intelligence brokerage, the inherent problems with doing attribution based solely on fifth-domain indicators, and an attempt to have a balanced discussion between defensive cats and the sly mice that elude them. Continuing in this direction, this year we decided to put our heads together to understand the implications that the esoteric SIGINT practice of fourth-party collection could have on threat intelligence research.
A few types of SIGINT Collection
The means by which information is generated and collected is the most important part of an analyst’s work. One must be well aware of the means and source of the information analyzed in order to either compensate or exploit its provenance. For that reason, collection can be categorized by its means of generation in relation to the position of the parties involved, as discussed below. These definitions will serve as functional categories for our understanding as outsiders looking into the more complex spheres of collection dynamics.
To showcase the types of data collection, let’s imagine a competent entity named ‘Agency-A’ as a stand-in for a ‘God on the wire‘-style SIGINT agency interested in fourth-party collection.
There are multiple types of collection categories available to this entity. The more obvious being information collected by Agency-A directly (first-party) or shared with Agency-A by partner services (second-party). Third-party collection, or information collected via access to strategic organizations, whether they realize it or not, has gotten a lot of attention over the past few years. This would include ISPs, ad networks, or social media platforms that aggregate great troves of valuable data.
Similarly, we will use further entities Agency-B as a second semi-competent SIGINT agency upon which Agency-A can be recurringly predatory for the sake of explanation. When necessary an even less competent Agency-C will serve as prey.
Yet, things get most interesting when we start talking about:
“Fourth-party collection – …involves interception of a foreign intelligence service’s ‘computer network exploitation’ (CNE) activity in a variety of possible configurations. Given the nature of Agency-A as a cyber-capable SIGINT entity, two modes of fourth-party collection are available to it: passive and active. The former will take advantage of its existing visibility into data in transit either between hop points in the adversary’s infrastructure or perhaps in transit from the victim to the command-and-control servers themselves (whichever opportunity permits). On the other hand, active means involve the leveraging of diverse CNE capabilities to collect, replace, or disrupt the adversary’s campaign. Both present challenges we will explore in extensive detail further below.”
In less technical terms, fourth-party collection is the practice of spying on a spy spying on someone else. Or with age-old cryptographic interlocutors: Bob is obsessed with Alice. Alice is being spied on by her overzealous neighbour Eve. In order for Bob to be a creeper without arousing suspicion, he decides to spy on Eve with the purpose of getting to know Alice through Eve’s original privacy violation.
As you might expect there are different ways to do this and many of them enjoy the benefit of being near impossible to detect. Where possible, we have added examples of what to us looks like possible active attempts to collect on another’s collection. Otherwise, we have added thought experiments to help us wrap our heads around this shadowy practice. Two examples worth bringing to your attention (reproduced faithfully from our paper):
‘We heard you like popping boxes, so we popped your box so we can watch while you watch’
Attempting to highlight examples of fourth-party collection is a difficult exercise in the interpretation of shadows and vague remnants. While passive collection is beyond our ability to observe, active collection involves the risk of leaving a footprint in the form of artefacts. In the course of APT investigations, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has encountered strange artefacts that defy immediate understanding in the context of the investigation itself. While we cannot be certain of the intent or provenance of these artefacts, they nonetheless fit a conceptual framework of active fourth-party collection. Here’s a few examples:
Crouching Yeti’s Pixelated Servers
In July 2014, we published our research on Crouching Yeti, also known as ‘Energetic Bear’, an APT actor active since at least 2010. Between 2010 and 2014, Crouching Yeti was involved in intrusions against a variety of sectors, including:
Industrial/machinery
Manufacturing
Pharmaceutical
Construction
Education
Information technology
Most of the victims we identified fell into the industrial and machine manufacturing sector, indicating vertical of special interest for this attacker.
To manage their victims, Crouching Yeti relied on a network of hacked websites which acted as command-and-control servers. For this, the attackers would install a PHP-based backend that could be used to collect data from or deliver commands to the victims. To manage the backend, the attackers used a control panel (also written in PHP) that, upon checking login credentials, would allow them to manage the information stolen from the victims.
In March 2014, while investigating one of the hacked sites used by Energetic Bear, we observed that for a brief period of time, the page for the control panel was modified to include an <img src> tag that pointed to a remote IP address in China. This remote 1×1 pixels wide image was likely intended to fingerprint the attackers as they logged into their control panel. The fingerprinting could have been used to collect attributory indicators. The usage of an IP address in China, which appeared to point to yet another hacked server, was most likely an attempt at a rudimentary false flag should this injection be discovered.
NetTraveler’s Most Leet Backdoor
While investigating the Nettraveler attacks, we obtained a disk image of a mothership server used by the threat actor. The mothership, a combination staging and relay server, contained a large number of scripts used by the attackers to interact with their malware, as well as VPN software and other IP masking solutions used to tunnel into their own hacking infrastructure.
Beyond the fortuitous boon of seizing such a content-rich server, GReAT researchers made a further unexpected discovery: the presence of a backdoor apparently placed by another entity.
We believe the backdoor was installed by an entity intent on maintaining prolonged access to the Nettraveler infrastructure or their stolen data. Considering that the NetTraveler operators had direct access to their mothership server and didn’t need a backdoor to operate it, we consider other possible interpretations less likely.
The artefact encountered is the following:
Name svchost.exe
MD5 58a4d93d386736cb9843a267c7c3c10b
Size 37,888
Interestingly, the backdoor is written in assembly and was injected into an empty Visual C executable that served as a template. This unusual implementation was likely chosen in order to confuse analysis or prevent detection by simple antivirus programs.
The backdoor is primitive and does nothing but listen to port 31337 (The most ‘LEET!’ port) and wait for a payload to be sent. The acceptable payload format is depicted here:
The assembly code is then executed and can perform any action chosen by the predatory attackers. The backdoor requires no authentication. Combining this sort of backdoor with Metasploit or other similar frameworks could have easily been used to control the system.
During the last years, we have seen a number of other peculiar incidents and cases which could constitute fourth party collection.”
To read the full paper and learn more about this, refer to “Walking in Your Enemy’s Shadow: When Fourth-Party Collection Becomes Attribution Hell”
Oracle Announces New Cloud Security Services
5.10.2017 securityweek Security
Oracle announced this week at the company’s OpenWorld convention the launch of new cloud security services and improvements to existing products.
One of the new offerings is the Oracle Identity Security Operations Center (SOC), a context-aware intelligence and automation solution designed to help organizations detect and respond to sophisticated threats targeting users, applications, data and cloud workloads.
The Identity SOC leverages the newly released Oracle Security Monitoring and Analytics Cloud Service, which provides security incident and event management (SIEM) and user and entity behavioral analytics (UEBA) capabilities.
Two other major components of the Identity SOC are the Oracle CASB (Cloud Access Security Broker) Cloud Service, which enables organizations to protect business-critical cloud infrastructure and data, and the Oracle Identity Cloud Service, described by the company as a “next-generation comprehensive security and identity platform.”

Oracle also announced that the threat detection and data protection capabilities of the CASB Cloud Service have been expanded. The company says the service now offers enhanced security for both structured and unstructured data with new built-in data loss prevention (DLP) features, and new anti-malware and anti-ransomware capabilities.
The Identity SOC suite integrates with the new Oracle Management Cloud suite, a complete IT security and management solution that combines Management Cloud, Application Performance Monitoring Service, and Infrastructure Monitoring Cloud Service. The company said the security-related enhancements to Management Cloud are powered by machine learning.Oracle OpenWorld keynote
“Our vision for security and management is very simple. We need all of the data in one place. We need purpose-built machine learning that can be used by security and operations professionals, not data scientists. We need automated remediation that does not require human effort. And that’s what we’ve built with Oracle Management Cloud,” Oracle Executive Chairman and CTO Larry Ellison said in his keynote at OpenWorld.
Ellison compared the Management Cloud service to products offered by Splunk and attempted to convince the audience that Oracle’s solutions are far better. He also poked Amazon Web Services (AWS) when introducing his company’s new autonomous database.
Another new service announced by Oracle is the Configuration and Compliance Cloud Service, which helps organizations ensure continuous compliance.
CBS Showtime website was spotted mining cryptocurrency in viewers’ web browsers
26.9.2017 securityaffairs Security
The websites of the CBS’s Showtime was found containing a JavaScript code that allowed someone to secretly mine cryptocurrency in viewers’ web browsers.
Over the weekend, the websites of the CBS’s Showtime were found containing a JavaScript code that allowed someone to secretly mine cryptocurrency in viewers’ web browsers.
The websites Showtime.com and iShowtimeAnytime.com silently injected in the visitors’ browser the code to abuse processor capabilities to mine Monero coins. The hidden code typically consumed as much as 60 percent of the overall CPU capacity on computers while visiting the sites.
The scripts were written by Code Hive, an outfit that develops legitim JavaScript codes that could be added by webmasters to their sites in order to generate revenue as an alternative to serving advertising.
The money mined by the scripts are managed by Code Hive and paid to the website owners.
The CBS case appears very strange, it is unlikely that the entertainment corporation has placed the mining code onto its websites because it already charges subscribers to watch the TV shows online.
It is possible that hackers compromised the website to deploy the mining JavaScript code and remove it before it was discovered, the script, in fact, worked during the weekend and disappeared on Monday.
I sincerely found also this hypothesis very strange, in my humble opinion an attacker that succeed in compromising a site like the CBS one could be more interested in delivering malware to its visitors and cash out its effort in another way.
The code was found between HTML comment tags used by the analytics firm New Relic, but it is unlikely the company would deliberately insert it.
Below the scripts on showtime.com and Showtime Anytime observed by El Reg.

and

New Relic told El Reg that the code was not deployed by its experts.
“We take the security of our browser agent extremely seriously and have multiple controls in place to detect malicious or unauthorized modification of its script at various points along its development and deployment pipeline,” states the company.
“Upon reviewing our products and code, the HTML comments shown in the screenshot that are referencing newrelic were not injected by New Relic’s agents. It appears they were added to the website by its developers.”
Of course, Code Hive knows who is behind the account linked to the mining code, but it doesn’t want to reveal it according to its privacy policy.
“We can’t give out any specific information about the account owner as per our privacy terms,” the outfit informed us. “We don’t know much about these keys or the user they belong to anyway.”
Recently a similar case occurred at the Pirate Bay website.
SecureAuth Acquired for $225 Million, to Merge With Core Security
23.9.2017 securityweek Security
Access control company SecureAuth announced this week that it will merge with Core Security, a firm focused on vulnerability discovery, identity governance, and threat management.
Through the merger, the two are aiming to bring together security operations and identity and access management (IAM).
SecureAuth and Core Security aim to become an independent security vendor that will bring together network, endpoint, vulnerability, and identity security.
Jeff Kukowski, currently the Chief Executive Officer at SecureAuth, will serve as CEO of the combined company. The merger is pending regulatory approval from the U.S. Federal government.
"The security industry must deliver an integrated and relevant approach to our customers. Despite the incredible amount of money spent on security technology, front-line security professionals in the most sophisticated Security Operations Centers (SOC) are challenged in managing and visualizing the full attack surface. Including identity information into the threat landscape alongside traditional network, endpoint, and vulnerability information substantially reduces threat discovery and response time,” Kukowski said.
“We can now deliver an entirely new approach to integrating security operations and deploying advanced machine learning to achieve real automation in the SOC,” Kukowski added.
Backed by K1 Investment Management and Toba Capital, the merged company also announced raising over $200 million.
Responding to a SecurityWeek inquiry on additional details on the funding, Jeff Nolan, CMO of SecureAuth, revealed in an emailed statement that SecureAuth was in fact acquired by K1.
“K1 Investment Management acquired SecureAuth for $225 million, existing investor Toba Capital rolled a portion of their proceeds forward and K1 allocating additional capital for the company. The merger with Core Security, pending regulatory approval, occurred after the acquisition of SecureAuth,” Nolan revealed.
The newly merged company says it will serve 1,500 customers across all industry verticals and monitors over 750 million devices daily. It has 360 employees, over 75 patents issued and pending, and a network of global locations.
In July 2016, Atlanta-based Damballa was bought for what amounts to a pittance by neighboring Roswell-based Core Security.
Google, Spotify Release Open Source Cloud Security Tools
19.9.2017 securityweek Security
Google and music service Spotify announced last week the launch of Forseti Security, a community-driven collection of open source tools designed to improve security in Google Cloud Platform (GCP) environments.
The Forseti toolkit currently includes an inventor tool that provides visibility into GCP resources, a scanner that validates access control policies, an enforcement tool that removes unwanted access to resources, and an add-on that helps users understand, test and develop Identity and Access Management (IAM) policies.Forseti Security
“Forseti gives us visibility into the GCP infrastructure that we didn’t have before, and we use it to help make sure we have the right controls in place and stay ahead of the game,” Spotify said.
“It helps keep us informed about what’s going on in our environment so that we can quickly find out about any risky misconfigurations so they can be fixed right away. These tools allow us to create a workflow that puts the security team in a proactive stance rather than a reactive one. We can inform everyone involved on time rather than waiting for an incident to happen,” the company added.
The Inventory tool continually generates snapshots of GCP resources and provides an audit trail. The Scanner helps detect misconfigurations and security bugs, and informs the team in charge when an issue has been discovered.
Spotify started developing security tools for GCP after moving its operations from in-house data centers to the cloud. The tools are designed to help the company automate its security processes in order to enable its engineering team to develop freely and securely.
Google had been developing its own security tools and since both companies wanted to release them as open source, they decided to collaborate, which led to the creation of the Forseti Security project.
Security experts can submit feature requests and bug reports, or they can contribute to Forseti development efforts.
Was Torrent Site The Pirate Bay Being Sneaky or Creative By Tricking Visitors Into Monero Mining
19.9.2017 securityaffairs Security
Users noticed a cryptocurrency miner surfaced on The Pirate Bay, the world’s largest torrenting for a day over the weekend.
Pop quiz: would you rather A) see ad banners displayed at the top of the website, or B) mine Monero cryptocurrency when you visit a website? Judging by the number of downloads for ad blocking browser extensions, no one likes banner ads. But if you ask The Pirate Bay this week, they will probably say the same thing about secretive Monero mining.
In August, security researchers at Netskope identified a malvertising campaign that downloaded the Zminer coin-miner and then used victims’ computers to mine Monero and Zcash cryptocurrencies for the benefit of the bad actors.
According to Threat Post, “Netskope provided details on two separate operations that have netted 101 Monero, or $8,300 USD, and 44 Zcash, or $10,100 USD so far. Zminer uses Monero on 32-bit Windows systems, and Zcash on 64-bit.”
The Pirate Bay
The challenge with most cryptocurrency mining is that the cost of operating the mining machines (e.g. electricity) eat away at much of the profit potential. But for the bad actors, victims pay the operating costs while the profits are reaped by the ones poisoning the banner ad system. When there are no costs, mining cryptocurrencies can be lucrative.
Last week a very observant Redditor Intertubes_Unclogger noticed that his CPU threads spiked to 80-85% visiting some pages on the very popular Torrent search site, The Pirate Bay (TPB). It is very unlikely that simple web browsing would cause such a spike so it was apparent something unexpected was going on. After some trial and error the Redditor determined that the ScriptSafe Chrome extension was preventing the process that caused the CPU spike. The Reddit community participating in solving the mystery guessed that TPB may have been unknowingly involved in a “shady bitcoin mining operation.” It turns out they were very close to the truth.
TPB was serving up shady Monero mining malware on some of its pages, but it wasn’t unexpected. From the official TPB blog,
“This is only a test. We really want to get rid of all the ads. But we also need enough money to keep the site running,” a site admin posted on The Pirate Bay’s blog, “Let us know what you think in the comments. Do you want ads or do you want to give away a few of your CPU cycles every time you visit the site?”
It turns out that TPB was experimenting with Coin Hive which is described as “a JavaScript miner for the Monero Blockchain that you can embed in your website. Your users run the miner directly in their Browser and mine XMR for you in turn for an ad-free experience, in-game currency or whatever incentives you can come up with.” Coin Hive themselves recommend that websites notify their users rather than sneakily stealing CPU cycles as TPB did. An admin at TPB suggested that there was a mistake made with the initial install as the miner was only expected to use 20-30% of the visitors’ CPU. This sounds a lot like “we didn’t think anyone would notice.”
At the end of the day, the general consensus in the /r/thepiratebay subreddit seems to be supportive of TPB’s attempts to fund their activities through means other than banner ads. And for users that would prefer to choose whether they are mining for someone else’s benefit, there are JavaScript and ad blocker extensions for the web browsers. This is evidence of one more reason why you need to control what is running in your browser.
Mocana Integrates Embedded Security Software With Industrial Cloud Platforms
15.9.2017 securityweek Security
Mocana Integrates Embedded Security Software with AWS IoT, Microsoft Azure IoT, and VMware Liota to Protect Devices
Two constants in current cybersecurity are the growing threat from insecure IoT botnets (Mirai, WireX, etcetera), and the continuing security provided by strong encryption. It is part of the mission of one venture capital funded firm to solve the former by use of the latter.
Mocana was formed in 2002 as an embedded security software company for military applications. With the help of venture capital ($11 million in May 2017 brought the total to $93.6 million), it has expanded into ICS and both the industrial internet of things (IIoT) and consumer IoT.
Mocana Logo
"We're a crypto company," Mocano's CTO Dean Weber told SecurityWeek. "While traditional security has been to provide barriers and layers of network controls -- even for IoT devices -- we offer a different approach. We use cryptography to build a trust platform for IoT, mobile and industrial devices."
The trust platform is provided as source code to device developers, who compile it into different target devices. "We're building in trustworthiness from the ground up," explains Weber. At a simple level, it can be viewed as a replacement for the widely used and hugely abused OpenSSL. Mocana comes in at about one-sixth the size of OpenSSL, and says Weber, "is an order of magnitude faster." It has, since 2002, never had a Common Vulnerabilities and Exposures (CVE) vulnerability cataloged, while OpenSSL has received around 250.
"OpenSSL provides a cryptographic library that gets calls from applications to provide services as necessary. We replace that," explains Weber, "but we do a lot more than OSSL because we start from a root of trust on the platform, and we build an X509 trust chain. The device ends up with a trust value. That trust value represents the cryptographic trustworthiness of the platform. We're building the foundation on a device, which could be an edge device, a sensor, an activator, a switch, a gravitometer, or a flow meter, or accelerometer or whatever."
In effect, a cryptographically trusted edge or IIoT device can communicate securely with its device controller. "Traditionally, that device is going to talk to a gateway service, which may be a PLC or RTU, which would then be connected to a back-end service," says Weber, who is set to speak at SecurityWeek's upcoming ICS Cyber Security Conference. "In the industrial space that would be the ICS SCADA; in the IoT space that might be a cloud service where you bring everything together for analytics or management, or both. At each one of those layers we can provide a trust platform that guarantees through the strength of the cryptography chosen (and we support many different types of crypto) that this communication/device is secure because the crypto is intact."
In the world of consumer IoT devices, any successful infection of the device with a bot will break the chain of trust and outbound traffic can be blocked. In ICS, the integrity of both the IIoT device and its communication with the SCADA device can be guaranteed. In the commercial world, Mocana this week announced that it has verified the integration of its IoT Security Platform with the IoT cloud platforms of Amazon Web Services, Microsoft Azure IoT, and VMware.
"Digital transformation is driving the adoption of IoT technologies that can measure the performance and status of billions of connected devices, says Vikrant Ghandhi, industry director, digital transformation at Frost & Sullivan. "Mocana's IoT Security Platform ensures that IoT devices can be trusted and communicate securely to the public and industrial cloud platforms. Their verification of the interoperability and integration of their cloud to AWS, Microsoft Azure IoT, VMWare-based clouds, and GE Predix is a significant benefit for companies working with Mocana."
Mocana works in the greenfield space -- it helps developers produce new secure devices. This is problematic for many devices already in the field -- especially in the ICS world where IT teams do not like to disturb production devices. Nevertheless, explains Weber, "Customers can get an upgrade if the existing device has either an OpenSSL cryptographic library in place, or sufficient processing power to accommodate Mocana's one. In some of the older brownfield sites there may not be the computer power to run a cryptographic stack. In that case there's not a lot we can do for them other than start to apply our security in the next hop up in the industrial or commercial network. We can develop unique identities for each one of those devices -- at least most of the devices can handle a certificate as a function of identity -- not all, but most."
Mocana makes it as easy as possible for developers to replace OpenSSL in existing devices. It has mapped OpenSSL APIs onto its own cryptographic library, so that the OpenSSL library can simply be replaced by the Mocana library. The device will continue to function without further changes, but using Mocana's secure software without running the risks associated with OpenSSL's known vulnerabilities.
Mocana describes its IoT platform as providing 'military grade' protection. This is a term often used without any justification by companies claiming to provide strong security. In Mocana's case, it is perfectly accurate. Mocana technology is already used inside fighter jets, helicopters, commercial aircraft, oil refineries, water systems, electric smart grids, smart buildings and smart cities.
Zerodium Offers $1 Million for Tor Browser Exploits
14.9.2017 securityweek Security
Exploit acquisition firm Zerodium announced on Wednesday that it’s prepared to offer a total of $1 million for zero-day vulnerabilities in the Tor Browser, the application that allows users to access the Tor anonymity network and protect their privacy.
The controversial company plans on selling the obtained exploits to its government customers to allegedly help them identify people that use Tor for drug trafficking and child abuse, and “make the world a better and safer place for all.”
Zerodium is looking for Tor Browser exploits that work on Windows and Tails, a security and privacy-focused Linux distribution. While the highest rewards can be earned for exploits that work on “high” security settings with JavaScript blocked, the company is also prepared to pay out significant amounts of money for exploits that work only with JavaScript allowed, which is the “low” security setting in Tor Browser.
An exploit that allows both remote code execution and local privilege escalation can earn up to $250,000 if it works on both Windows 10 and Tails 3.x with JavaScript blocked. If the exploit works on only one of the operating systems, it can still be worth up to $200,000.
A remote code execution exploit that does not include privilege escalation capabilities is worth up to $185,000 with JavaScript blocked. Exploits that require JavaScript to be enabled can earn up to $125,000 if they include both code execution and privilege escalation, and $85,000 if it’s only for code execution. The minimum bounty is $75,000 for an RCE-only exploit that works on either Windows or Rails.
Zerodium explained that the exploit must work silently and the only allowed user interaction is visiting a specially crafted web page. Exploits that require controlling or manipulating Tor nodes, or ones that can disrupt the Tor network will not be accepted.
“With the increased number (and effectiveness) of exploit mitigations on modern systems, exploiting browser vulnerabilities is becoming harder every day, but still, motivated researchers are always able to develop new browser exploits despite the complexity of the task, thanks to their skills and a bit of scripting languages such as JavaScript,” Zerodium said.
The Tor Browser bounty will run until November 30, but it may be closed earlier if the $1 million reward pool is paid out.
This is not the first time the company is offering $1 million. Back in 2015, it reportedly paid this amount to a single hacker team who discovered a remote browser-based untethered jailbreak for iOS 9.1.
Zerodium announced last month that it’s prepared to pay up to $500,000 for remote code execution and privilege escalation vulnerabilities affecting popular instant messaging and email applications.
Samsung Launches Bug Bounty Program — Offering up to $200,000 in Rewards
12.9.2017 thehackernews Security
With the growing number of cyber attacks and data breaches, a number of tech companies and organisations have started Bug Bounty programs for encouraging hackers, bug hunters and researchers to find and responsibly report bugs in their services and get rewarded.
Samsung is the latest in the list of tech companies to launch a bug bounty program, announcing that the South Korean electronics giant will offer rewards of up to $200,000 to anyone who discovers vulnerabilities in its mobile devices and associated software.
Dubbed Mobile Security Rewards Program, the newly-launched bug bounty program will cover 38 Samsung mobile devices released from 2016 onwards which currently receive monthly or quarterly security updates from the company.
So, if you want to take part in the Samsung Mobile Security Rewards Program, you have these devices as your target—the Galaxy S, Galaxy Note, Galaxy A, Galaxy J, and the Galaxy Tab series, as well as Samsung's flagship devices, the S8, S8+, and Note 8.
"We take security and privacy issues very seriously; and as an appreciation for helping Samsung Mobile improve the security of our products and minimizing risk to our end-consumers, we are offering a rewards program for eligible security vulnerability reports," the company explains on its bug bounty website.
"We look forward to your continued interests and participations in our Samsung Mobile Security Rewards Program. Through this rewards program, we hope to build and maintain valuable relationships with researchers who coordinate disclosure of security issues with Samsung Mobile."
Not just mobile devices, the tech giant's Mobile Services suite is also part of its bug bounty program, which will also cover apps and services such as Bixby, Samsung Account, Samsung Pay, Samsung Pass, among others.
For the eligibility of a reward, researchers and bug hunters need to provide a valid proof-of-concept (PoC) exploit that can compromise a Samsung handset without requiring any physical connection or third-party application.
The company will evaluate the reward depending on the severity level of the vulnerability (Critical, High, Moderate, and Low) and its impact on devices. The least reward is $200, which is for low-severity flaws, while the highest reward is $200,000, which is for critical bugs.
The Higher reward will be offered for bugs that lead to trusted execution environment (TEE) or Bootloader compromise. The level of severity will be determined by Samsung.
Samsung’s bounty of $200,000 is equal to the bounty reward offered under Apple's bug bounty program but is slightly lower than Microsoft's newly launched bounty program that offers $250,000 for Windows 10 security bugs.
Following the path of major tech companies, the non-profit group behind Tor Project recently joined hands with HackerOne to launch its own bug bounty program, with the highest payout for the flaws has been kept $4,000.
So, what you are waiting for? Hunt for bugs in Samsung products and submit your findings to the company via the Security Reporting page.
Crooks leverage Facebook CDN servers to bypass security solutions
11.9.2017 securityaffairs Security
Crooks are abusing Facebook CDN servers to deliver malware and evading detection exploiting the trust in the CDN network of the social networking giant.
Crooks are abusing Facebook CDN (Content Delivery Network) servers to store malware and to deliver it evading detection exploiting the trust in the CDN network of the social network giant.
Researchers from MalwareHunter team uncovered several campaigns leveraging Facebook CDN servers in the last two weeks, in the past, the same malware group used Dropbox and Google’s cloud storage services to store the same payloads.
In July researchers at Palo Alto Networks published a detailed report on an ongoing malspam campaign targeting Brazil, in that circumstance the crooks used legitimate services like Google and Dropbox to deliver the malware.
Back to the present, the use of Facebook CDN allows the cyber criminals to bypass security solutions because the domain is trusted by them and the related traffic is not blocked. The
Cybercriminals use to send spoofed emails that pose as official communications from local authorities. The messages include a link that leads to Facebook CDN. The link point to URL related to files uploaded by the gang in Facebook groups or other public section.
Below one of the links used by the gang.
https://cdn.fbsbx.com/v/t59.2708-21/20952350_119595195431306_4546532236425428992_n.rar/NF-DANFE_FICAL-N-5639000.rar?oh=9bb40a7aaf566c6d72fff781d027e11c&oe=59AABE4D&dl=1
and the related spam message

Once the victim clicks on the link he will download an RAR or ZIP file containing a link file. The shortcut invokes a legitimate application installed on most windows PC (i.e. Command Prompt or PowerShell) to run an encoded PowerShell script. This technique is known as Squiblydoo, experts observed APT32 using it while targeting Vietnamese interests around the globe.
The encoded PowerShell script downloads and runs another PowerShell script that execute a large number of operations.
“The second PowerShell script downloads a loader DLL file, which in turn downloads a legitimate EXE file and a second DLL.” wrote Catalin Cimpanu from BleepingComputer.
“The twisted maze of operations continues with the creation of another link (shortcut) file that points to a VBS script. The PowerShell script then invokes the shortcut file, which in turn invokes the VBS script, which in turn executes the legitimate EXE file, which in turn side-loads the second DLL file.”
Crooks are targeting only users in Brazil, the attack chain is interrupted by downloading an empty last-stage DLL file when the victim is from another country.
The campaign is delivering the Banload malware downloader which is used to serve the Win32/Spy.Banker.ADYV banking trojan that targets Brazilian users only.
Experts believe the threat actor is the same behind the Banload campaign that targeted Brazil in 2016 and spread the Escelar banking Trojan in 2015.
Experts from MalwareHunter believe the malware group is very sophisticated and well-resourced.
“a campaign MalwareHunter spotted on September 2 pushed out emails that were viewed by at least 200,000 Brazilian users. Two other campaigns also garnered between 70,000-80,000 views each.” continues Bleepingcomputers.
Samsung Offers Up to $200,000 in Bug Bounty Program
8.9.2017 securityweek Security
Samsung on Thursday announced the official launch of the Samsung Mobile Security Rewards Program, which promises bug bounties of up to $200,000 for Critical vulnerabilities in Samsung mobile devices and associated software.
The new vulnerability rewards program is open to members of the security community interested in assessing the integrity of Samsung’s mobile devices and associated software, the company says.
Depending on the severity level of the disclosed vulnerabilities, bug bounties will range between $200 and $200,000. Should vulnerability reports be submitted without a valid Proof-of-Concept, Samsung will decide the qualification for a reward according to reproducibility and severity of the issue, and might significantly reduce the reward amount.
“Higher rewards amount will be offered for vulnerabilities with greater security risk and impact, and even higher rewards amount will be offered for vulnerabilities that lead to TEE or Bootloader compromise. On the other hand, rewards amount may be significantly reduced if the security vulnerability requires running as a privileged process,” the company says.
To qualify for rewards, security researchers need to submit security vulnerability reports that are applicable to eligible Samsung Mobile devices, services, and applications developed and signed by Samsung Mobile. Vulnerabilities in eligible third party applications developed for Samsung are also accepted.
Should two reports be received for the same vulnerability, only the first report is considered. Only reports for vulnerabilities that haven’t been publicly disclosed are accepted.
Researchers can submit findings via the Security Reporting page.
Researchers are encouraged to find vulnerabilities in currently active Samsung Mobile services, as well as in applications developed and signed by Samsung Mobile that are up-to-date with the latest update. As for the vulnerabilities on 3rd party applications, Samsung demands that they are specific to Samsung Mobile devices, applications or services.
Samsung also notes that it accepts vulnerability reports impacting Galaxy S series, Galaxy Note series, Galaxy A series, Galaxy J series, and Galaxy Tab series devices. Interested security researchers are encouraged to read the requirements and guidelines Samsung has published for the program.
“We take security and privacy issues very seriously; and as an appreciation for helping Samsung Mobile improve the security of our products and minimizing risk to our end-consumers, we are offering a rewards program for eligible security vulnerability reports. Through this rewards program, we hope to build and maintain valuable relationships with researchers who coordinate disclosure of security issues with Samsung Mobile,” Samsung says.
Bitdefender Offers Up to $1,500 in Public Bug Bounty Program
7.9.2017 securityweek Security
Bitdefender announced on Wednesday the launch of a Bugcrowd-based public bug bounty program with rewards of up to $1,500.
The Romania-based security firm has been running a bug bounty initiative since late 2015, and it has now decided to launch a public program on Bugcrowd in an effort to take advantage of the skills of the 60,000 hackers registered on the platform.
The program covers the bitdefender.net and bitdefender.com websites and their subdomains, and the Bitdefender GravityZone Business Security and Bitdefender Total Security 2017 products.
The highest payout, between $900 and $1,500, can be earned for serious vulnerabilities, such as default credentials on a production server, local file inclusion, remote code execution, error-based and blind SQL injection, XML external entity (XXE) injection, authentication bypass, command injection, and exposure of sensitive data such as passwords or private API keys. The minimum reward offered by the security firm is $100.
Bitdefender’s bug bounty page on Bugcrowd lists a series of issues that are not in scope, and informs researchers of more than a dozen potential security problems that are considered “accepted risk” and ones that will only earn them kudos points.
“Being proactive rather than re-active to emerging security issues is a fundamental belief at Bitdefender,” said Alexandru Balan, chief security researcher at Bitdefender. “Bugcrowd enables access to a crowd of researchers with a variety of backgrounds and skills for continuous monitoring of security issues. Above that, their team is an extension of ours, working with us to ensure program success from scoping the program, to triaging submissions and ultimately helping us build more secure products.”
A majority of antivirus companies run a vulnerability disclosure program that encourages white hat hackers to responsibly report security holes. Some companies, such as Sophos and ESET, don’t offer any monetary rewards. Others promise significant payouts -- Avast up to $10,000, Kaspersky up to $5,000, and F-Secure up to $15,000. Malwarebytes offers between $100 and $1,000 per bug.
Another unsecured AWS S3 bucket exposed 4 million Time Warner Cable subscriber records
6.9.2017 securityaffairs Security
Experts reported that the AWS S3 storage containing subscriber data was left open by freelancers who handled web applications for the Time Warner Cable.
A few days ago, researchers discovered of thousands of resumes of US Military and intel contractors left unsecured on an Amazon server, now roughly four million Time Warner Cable customers in the US were exposed by a contractor that left them openly accessible on an Amazon AWS S3 bucket.
The unsecured Amazon storage was discovered by researchers at security firm Kromtech, it was left open on the Internet by BroadSoft, one of the top companies that provides cloud-based unified communications.
“One of the top companies that provides cloud-based unified communications has just leaked more than 600GB of sensitive files online. The Kromtech Security Center has discovered not just one but two cloud-based file repositories (AWS S3 buckets with public access) that appear to be connected to the global communication software and service provider BroadSoft, Inc.” states the blog post published by Kromtech.
“They have created an infrastructure for cloud unified communications tools that can be service provider hosted or cloud hosted by BroadSoft. The publically traded company has over 600 service providers across 80 countries and supports millions of subscribers according to their website. Their partners are some of the biggest names in the communication business, telecom, media, and beyond, including Time Warner Cable, AT&T, Sprint, Vodafone among many other well known companies. When 25 of the world’s top 30 service providers by revenue all use BroadSoft’s infrastructure and with so many subscribers it is easy to see that this data leak could have a massive reach.”

Kromtech reported that the AWS S3 storage containing subscriber data was left open by freelancers who handled web applications for the Time Warner Cable (TWC) and other companies.
That exposed customer records include addresses and contact numbers, account settings, phone numbers, usernames, MAC addresses, modem hardware serial numbers, account numbers, and other billing info.
Kromtech discovered the repository in late August, administrators forgot to limit access to authorized users only.
“The problem is that the repository was configured to allow public access and exposed extremely sensitive data in the process. They used Amazon’s cloud but misconfigured it by leaving it accessible. Amazon AWS buckets are protected by default but somehow were left publically available.” continues the blog post.
“It is most likely that they were forgotten by engineers and never closed the public configuration. This would allow anyone with an internet connection to access extremely sensitive documents,”
The experts discovered in the AWS S3 bucked data belonging to four million Time Warner Cable customers collected between November 26, 2010 and July 7, 2017.
TWC is notifying the data leak to the customers who were exposed, BroadSoft did not return a request for comment.
Mozilla to Completely Ban WoSign, StartCom Certificates in Firefox 58
1.9.2017 securityweek Security
Mozilla this week announced plans to completely remove trust in the digital certificates issued by Chinese certificate authority WoSign and its subsidiary StartCom starting with Firefox 58.
The move follows the company’s previously laid out plans to distrust these certificates after over a dozen incidents and issues were brought to the attention of the web browser community since January 2015.
Some of the reported problems include the issuance of certificates without authorization and the backdating of certificates to bypass restrictions. Additionally, the two companies weren’t completely honest to browser vendors about WoSign's acquisition of StartCom and their relationship.
As a result, leading browser vendors and tech companies, including Apple, Google, Microsoft, and Mozilla, decided to distrust certificates issued by the two companies. Microsoft and Google have already announced plans to completely ban WoSign and StartCom certificates in their products.
After initially distrusting these certificates for only one year, Mozilla has finally decided to follow Microsoft and Google and revealed this week that Firefox 58 will completely remove trust in them.
Starting with Firefox 51, Mozilla no longer validates new certificates chaining to the root certificates owned WoSign and StartCom. The company now plans to completely remove these root certificates from Mozilla’s Root Store.
“We plan to release the relevant changes to Network Security Services (NSS) in November, and then the changes will be picked up in Firefox 58, due for release in January 2018,” the company announced.
Mozilla also warns that some website owners would need to migrate to different root certificates. Affected are websites that use certificates chaining up root certificates such as CA 沃通根证书, Certification Authority of WoSign, Certification Authority of WoSign G2, CA WoSign ECC Root, StartCom Certification Authority, and StartCom Certification Authority G2.
In October last year, after Mozilla and Apple revealed plans to take action against its certificates, WoSign decided to make some changes in leadership, operational processes and technology. Qihoo 360, WoSign's largest shareholder, said it was looking to completely separate WoSign and StartCom and asked browser vendors to judge each company separately.
Google mistake is the root cause of Internet Outage in Japan
28.8.2017 securityaffairs Security
A widespread internet disruption occurred in Japan on Friday, Google error it the main cause of the Internet outage that caused the panic in the country.
Google error it the root cause of a widespread Internet outage in Japan that lasted for about an hour on Friday, August 25. The incident was caused by a BGM route hijack that began at 12:22 PM local Japan time and was fixed by 1:01 PM.
Border Gateway Protocol (BGP) is a standardized exterior gateway protocol designed to exchange routing and reachability information among autonomous systems (AS) on the Internet. It interconnects the networks of major Internet service providers that announce which IP addresses are available on their networks.
If an ISP provides wrong information on the availability of IP address blocks we are in presence of a BGM route hijack ISPs.
This is what has happened on Friday when Google wrongly advertised that IP blocks belonging to a Japanese ISPs were found on its network.
BGPMon who analyzed the event confirmed that Google hijacked the traffic NTT Communications Corp., a major ISP who also supports two smaller ISPs named OCN and KDDI Corp. NTT has more than 8 million customers, 7.67 million home users, and 480,000 companies.
“Beginning at 2017-08-25 03:23:34, we detected a possible BGP hijack.
Prefix 210.171.224.0/20, Normally announced by AS7527 Japan Internet Exchange Co., Ltd.
Starting at 2017-08-25 03:23:34, a more specific route (210.171.224.0/24) was announced by ASN 15169 (Google Inc.).
This was detected by 17 BGPMon peers.” reported BGPMon.“
Other ISPs started routing traffic that was destined for Japan to Google’s systems, many services online in Japan went down, including the Nintendo networks.
“A widespread internet disruption hit Japan on Friday, blocking access to banking and train reservation services as well as gaming sites.
The disruption was limited to the networks of NTT Communications Corp. and KDDI Corp.
NTT Communications, which runs the OCN internet service, said the problem occurred because an overseas network service provider that OCN uses suddenly switched internet routes.” reported the Japan Times.
It was chaos in the country, the Internal Affairs and Communications Ministry promptly started an investigation into the incident.
“Nintendo Co. said on its website that some Switch, Wii U and 3DS clients started complaining about poor connectivity at about 12:25 p.m.” continnues the media outlet.
Clients of Resona Bank, Saitama Resona Bank and Kinki Osaka Bank said they had trouble logging in to their accounts, as did customers of online banker Jibun Bank Corp. and Rakuten Securities Inc.
East Japan Railway Co. (JR East) said some users of its Suica mobile payment system complained they weren’t able to use the service, which lets them board trains and buy products using their smartphones.”
Google confirmed the incident and provided further details on it.
“We set wrong information for the network and, as a result, problems occurred. We modified the information to the correct one within eight minutes. We apologize for causing inconvenience and anxieties,” the Google spokesperson told The Asahi Shimbun.

BGPMon published a detailed analysis of the incident, it confirmed that Google hijacked over 135,000 network prefixes, from all over the world, of which over NTT 24,000 prefixes.
“In total we saw over 135,000 prefixes visible via the Google – Verizon path. Widespread outages, particularly in Japan (OCN) were because of the more specifics, causing many networks to reroute traffic toward verizon and Google which likely would have congested that path or perhaps hit some kind of acl, resulting in the outages. Many BGPmon users would have seen an alert similar like the one below, informing them new prefixes were being originated and visible global.” concluded BGPMon.
According to the BGPMon engineer Andree Toonk it’s easy to make configuration mistakes that can lead incidents like this.
“In this case it appears a configuration error or software problem in Google’s network led to inadvertently announcing thousands of prefixes to Verizon, who in turn propagated the leak to many of its peers,” said Toonk.
“Since it is easy to make configurations errors, it clearly is a necessity to have filters on both sides of an EBGP session. In this case it appears Verizon had little or no filters, and accepted most if not all BGP announcements from Google which lead to widespread service disruptions,” Toonk added. “At the minimum Verizon should probably have a maximum-prefix limit on their side and perhaps some as-path filters which would have prevented the wide spread impact.”
Organizations Reminded of DNSSEC Key Signing Key Rollover
22.8.2017 securityweek Security
Organizations are being reminded that the Internet Corporation for Assigned Names and Numbers (ICANN) will soon change the root zone key signing key for the Domain Name System Security Extensions (DNSSEC) protocol. Failure to take action could result in users being unable to access the Internet.
DNS, the system that translates domain names to IP addresses, was not designed with security in mind. In an effort to prevent users from being directed to malicious websites via DNS spoofing attacks, the DNSSEC protocol was introduced in 2010.
DNSSEC aims to prevent attacks by cryptographically signing DNS information, including the root zone, which is the highest level of the DNS structure. If DNSSEC is used, the root zone vouches for the public key of the .com zone (or other TLD zone), which in turn vouches for all .com domains. Since the root zone is at the top of the DNS hierarchy, there is no higher level to vouch for it so its zone key is configured as a so-called “trust anchor,” a key that is declared trustworthy.DNSSEC KSK rollover
The trust anchor key is called a key signing key (KSK), and all recursive name servers performing DNSSEC validation need to have the root zone’s KSK set as a trust anchor. These name server are typically operated by Internet service providers (ISPs) and enterprises, and if the KSK is not configured properly, DNS resolution will no longer work for their users.
Since keeping a cryptographic key alive for a long period of time is considered a bad security practice given the fact that it could get compromised, ICANN plans to periodically change, or roll, the KSK.
A new KSK was generated in October 2016 and it will be used to sign the root zone key set on October 11, 2017. Until this date, all DNSSEC-validating resolvers need to be configured with the new root KSK.
On January 11, 2018, the old KSK will be revoked and March 22, 2018 is the last day on which the old KSK will appear in the root zone. In August 2018, the old key will be deleted from equipment in ICANN’s two key management facilities.
ICANN estimates that roughly 750 million people worldwide use DNSSEC validation and are affected by the KSK rollover so it’s important that stakeholders take action to prevent service disruptions.
In the case of software that supports automated updates of DNSSEC trust anchors, the root zone KSK will be updated automatically at the appropriate time and no action needs to be taken. However, in the case of software that does not support automated updates, DNSSEC trust anchors need to be manually updated. The developers of BIND, the most widely deployed DNS software, have provided instructions for users.
Organizations not using DNSSEC are not impacted, but use of the protocol is recommended for security reasons.
US-CERT has reminded organizations about the October 11 root zone KSK change and advised them to update their key before this date, particularly federal agencies, which, unlike private sector companies, are required to use DNSSEC.
Doctor Implanted 6 MicroChips Under His Skin to Unlock Doors and Secure Data
21.8.2017 thehackernews Security

Biohacking could be a next big thing in this smart world.
At the beginning of this month, several dozen employees of Three Square Market (32M) received microchip implants in their hands during a "chip party," allowing them to log into their office computers, open doors, and pay for food and drinks, by simply waving their hands, AP reported.
But, biohacking is already becoming common in Russia.
It has been reported that a Siberian doctor has already implanted not one, but at least six microchips underneath his skin and turned his body into a multi-functional gadget for doing a number of jobs by just a wave of his hands.
Alexander Volchek, who is an obstetrician/gynaecologist in a hospital in the Novosibirsk region in Russia's north, got his first microchip implant in 2014 and since then he acquired a few more and now has a total of six chips under his skin.
However, Volchek does not want to stop here and hopes to implant a cryptosystem and a glucometer microchip in his body in the near future.
These chips help him perform day-to-day activities just by moving his hand over a bar code scanner, such as opening doors at work and home, paying bills with a wave of his hand—everything works like magic.
Two chip to enter his office
One transport chip
Two memory cards for storing almost a kilobyte of information
One control card for a Siberian ski resort
A syringe with a thick needle is required to inject a microchip, whose standard size is 2x12mm, and minimum size is no more than 1.5x8mm with storage capacity ranges from 800 bytes to 1 kilobyte of information.
One of the microchips serves as Volchek's business card, while another one stores his password, allowing him to unlock his computer.
"My dream as a crypto anarchist is to have an identification tool for encrypting an electronic signature, and of course for medical application," Volchek told RT's video agency Ruptly. "I also want an implanted glucometer that will resolve a ton of problems many are currently facing, but research is still underway."
However, the microchips are not permanently implanted into the skin. They can be easily extracted from the body whenever the user wants to get rid of it.
While the Biometric technology is experiencing an increase in popularity, it also raises widespread concerns about the safety and privacy of people adopting it.
Hackers could misuse this technology against the public itself, and one should not forget that with the advance in technology, the techniques leveraged by hackers and cyber criminals also improves.
Over two years ago, a hacker implanted a small NFC chip in his hand to hack Android smartphones and bypass almost all security measures, demonstrating the risks of Biohacking.
At the end of the same year, another hacker managed to implant a small NFC chip with the private key to his Bitcoin wallet underneath his skin, allowing him to buy groceries or transfer money between bank accounts just by waving his hand.
Information Security Spending to Reach $93 Billion in 2018: Gartner
16.8.2017 securityweek Security
Gartner has predicted that worldwide information security spending will reach $86.4 billion in 2017; a seven percent growth over the year. Spending is expected to increase to $93 billion in 2018.
The fastest growing sector is security services; especially in IT outsourcing, consulting and implementation services. The only area where growth is likely to slow down is hardware support services, which are becoming less necessary with the continuing adoption of virtual appliances, public cloud and Security as a Service (SaaS) solutions.
Much of the growth is thus expected to come from upgrading the IT infrastructure to a perceived more secure posture than by simply buying additional security products.
"Improving security is not just about spending on new technologies," said Sid Deshpande, principal research analyst at Gartner. "As seen in the recent spate of global security incidents, doing the basics right has never been more important. Organizations can improve their security posture significantly just by addressing basic security and risk related hygiene elements like threat centric vulnerability management, centralized log management, internal network segmentation, backups and system hardening," he said.
Faster growth is likely to come from the security testing market, particularly in relation to application security testing as part of DevOps. This is no surprise to RJ Gazarek, Product Manager at Thycotic. "Thycotic research on DevOps security practices," he told SecurityWeek, "has shown that more than 60% of DevOps organizations are not managing credentials in scripts in any way. This is a major security problem that needs to be addressed immediately, especially as more breaches are making the news, and people realize that the way into an organization is to find the department with the weakest security practice and get to work infiltrating."
Neither the growth nor the areas of growth surprise Nathan Wenzler, chief security strategist at AsTech. "If we watch how the trend of attacks has gone over the past several years, we see more and more criminals moving away from targeting servers and workstations, and toward applications and people," he explained.
"As an industry, we've gotten better and better about protecting devices; but now the focus has to turn to other assets, and thus, the increase in spending Gartner is forecasting in DevOps and services. Essentially, wherever the criminals go, corporate spending is soon to follow," Wenzler said.
There is, however, one area in which Gartner sees actual product growth: data leak prevention (DLP). The belief is that fears over the far-reaching and severe implications of the EU General Data Protection Regulation (GDPR) is spurring, and will continue to spur, DLP purchasing through 2018.
GDPR will come into force in May 2018. From that date onward, any company anywhere in the world that handles the personal information of European citizens could be liable for a fine of up to 4% of global turnover if they do not adequately protect that data. "The EU General Data Protection Regulation (GDPR) has created renewed interest, and will drive 65 percent of data loss prevention buying decisions today through 2018," says Gartner.
Where companies already have some form of DLP already in place, Gartner believes that interest is now focused on enhancing the DLP control: "specifically, integrated DLP such as data classification, data masking and data discovery." These will all be required for GDPR compliance, both in protecting the data and being able to retrieve it for removal if required by the user concerned.
Just this week, Amazon Web Services launched a new machine learning security service that helps its customers discover, classify and protect sensitive data.
However, some security experts believe that Gartner is being too conservative in its spending growth estimates. "Gartner has taken a very conservative evaluation on information security spending that it will grow by only 7%," Joseph Carson, chief security scientist at Thycotic, told SecurityWeek. I believe that the actual number will be much higher given that many aggressive regulations will come into enforcement in 2018, including the EU General Data Protection Regulation (GDPR).
"This," he continued, "will force many companies to increase spending on information security and response to avoid becoming either victims or receiving massive financial fines for failure to protect and secure. As we have seen, Maersk reports the cost of the June cyber-attack to be in excess of $300 million. With many other companies counting the losses of both WannaCry and NotPetya, they will likely prefer to prevent these from occurring rather than clean up the mess, resulting in huge financial losses."
But it's not all good news for North American and European vendors. Gartner also points out that China's recently approved cybersecurity law means that by 2020, 80% of large Chinese business security expenditure will be on locally produced products. This will be at the expense of U.S.-manufactured network security products.
In recent years, Asia/Pacific has been a dynamic market, growing by 24% in 2016. Gartner now predicts that, because of the more competitive pricing of Chinese solutions, end-user spending growth in Asia/Pacific will return to single-digit yearly growth from 2018 onward.
Respond Software Automates SOC Analyst Decisions
16.8.2017 securityweek Security
Mountain View, Calif.-based Respond Software has emerged from stealth mode with a new product designed to automate the role of security analysts and $12 million in funding.
Founded by Mike Armistead, Robert Hipps and Chris Calvert, Respond Software develops solutions that aim to make security operations centers (SOCs) more efficient. The company’s goal is to create software that powers what it calls the “self-driving SOC.”
Respond Software
Respond Software’s first product, Respond Analyst, is designed to emulate the decision-making process of an experienced security analyst in an effort to address the problem of overwhelmed SOC staff and shortage of skilled personnel.
According to the company, when put to work in a large enterprise, its product managed to do the work of 26 full-time SOC analysts that process 75 events per hour (based on industry-average productivity data).
The product currently has two modules for network intrusion and compromised system incidents. Respond Analyst consumes data from a company’s existing security products and uses patent-pending Probabilistic Graphical Optimization (PGO) technology to conduct analytical checks and probabilistic scenario simulations to determine whether a potential incident should be escalated to incident response based on likelihood, extent and severity.
The system leverages human feedback from all Respond customers to continually improve its decision-making capabilities.
Respond Software has obtained $12 million in a series A funding round led by CRV and Foundation Capital, which brings the total since the company was founded last year to $15 million. Respond says market demand for the types of solutions it provides is high and expected to grow over the next few years.
“There could not be a more expert team to tackle transforming today’s reactive SOCs to the next generation – a true Security Response Center – much like autonomous vehicles are generating an entirely new ecosystem of capability in transportation,” said Max Gazor, general partner at CRV.
“It’s like having a million more trained analysts instantly at the ready. These days, every organization needs more security resources. With the Respond Software solution, they now have it in spades,” added Paul Holland, general partner at Foundation Capital.
The company’s advisors include Gerhard Eschelbeck, VP of security and privacy engineering at Google, Richard Seiersen, CISO and VP of trust at Twilio, and Izak Mutlu, former CISO of Salesforce.com.
Amazon Launches AWS Data Protection Service
16.8.2017 securityweek Security
Amazon announced this week the launch of Macie, a new security service that helps Amazon Web Services (AWS) users discover, classify and protect sensitive data.
Amazon Macie uses machine learning to automatically identify and protect personally identifiable information (PII), intellectual property and other sensitive data, and informs users of how their data is being accessed or moved via dashboards and alerts.
When deployed, Amazon Macie creates a baseline and then uses a behavior analytics engine to detect risky or suspicious activity. Customers can define automated remediation actions, including for resetting passwords and access control lists (ACLs), and create custom alert management via CloudWatch Events for integration with existing security ticketing systems.
Security and compliance events that could pose a risk are classified into 20 categories, including API keys and credentials stored in source code, high-risk data events, credentials within unencrypted backups, and various activities that could represent the early stages of an attack.
The product can be integrated with security information and event management (SIEM) and managed security service provider (MSSP) services.
Pricing for Amazon Macie is based on the amount of data that is classified, captured and analyzed. Additional fees are charged for the optional Extended Data Retention feature, which increases the metadata retention period.
The Macie console can be found in the AWS Management Console. However, the service is currently supported only in Northern Virginia and Oregon, and it can only protect data stored in Amazon Simple Storage Service (S3) buckets. Next year, Amazon plans on adding support for EC2 environments, DynamoDB, RDS, EFS and AWS Glue.
Amazon Macie has already been used by companies such as Edmunds, Netflix and Autodesk.
The launch of Amazon Macie comes after many high-profile organizations have been caught leaking sensitive data via misconfigured S3 buckets. The list of affected entities includes the United States National Geospatial-Intelligence Agency (NGA), Verizon, Dow Jones & Company, and hundreds of millions of U.S. voters.
Public Cloud Is Most Secure: Report
15.8.2017 securityweek Security
Public cloud environments are more secure than private and hybrid clouds and on-premises networks, according to data collected by cloud security solutions provider Alert Logic over a period of 18 months.
Alert Logic’s 2017 Cloud Security Report is based on the analysis of more than 2.2 million security incidents captured by the company’s products from more than 3,800 customers between August 2015 and January 2017.
The data shows that organizations using public cloud environments have encountered, on average, 405 security incidents, while hybrid networks have experienced nearly 1,000 incidents. Hosted private cloud environments and on-premises networks experienced 684 and 612 incidents, respectively.
In all cases, the most common type of security incident was SQL injection reconnaissance, followed by Joomla web application attacks and SQL injection. Web application attacks are by far the most common, followed by brute force, reconnaissance, and advanced malware attacks.
In the case of web attacks, the most common, accounting for 80 percent of incidents, are SQL injection and remote code execution. The most targeted are content management systems (CMSs) and e-commerce platforms such as Joomla, WordPress, Apache Struts and Magento.
Alert Logic observed more than 630,000 SQL injection attempts, including a few hundred attacks that were complex and likely launched by skilled and determined threat actors.
As for brute-force attacks, WordPress was the most targeted, followed by MS SQL and SSH. While malware attacks represented only 2 percent of the incidents observed by Alert Logic, the company said it had seen an increase in server-side ransomware infections.
“To be fair, our data set does not conclusively prove that public clouds are ‘more secure,’ if such a question can even be framed effectively or answered definitively,” explained Misha Govshteyn, founder of Alert Logic. “But we do know that within our customer base, we less frequently see malicious activity in public-cloud environments, even though web applications are one of the most dominant workloads there. And we know that web apps account for the highest share of attacks leading to breaches.”
“For the moment, even the public cloud is not so secure that there is nothing to worry about; far from it,” Govshteyn added. “While we saw close to 37% more incidents in on-premises data centers, this still leaves each public cloud deployment to withstand just over (on average) around 400 incidents in the 18-month period covered by this report. And even lower incident rates do not necessarily translate to lower risk – especially when, as is increasingly more common, businesses rely on the public cloud to handle their highest value assets.”
Webroot Acquires Security Awareness Training Firm Securecast
15.8.2017 securityweek Security
Endpoint and network security solutions provider Webroot announced on Tuesday that it has acquired Securecast, an Oregon-based company that specializes in security awareness training. Financial terms of the deal have not been disclosed.
Webroot has built on Securecast’s platform to offer managed service providers (MSPs) security awareness programs that their business customers can use to reduce the risks and costs associated with phishing, ransomware and other threats.
Webroot's Security Awareness Training offering is already available in beta and is expected to become generally available sometime this fall. Once it becomes generally available, it will be part of the company’s SecureAnywhere portfolio.
This fully hosted awareness-as-a-service platform includes a sophisticated phishing simulator that allows organizations to test their employees, and an end-user training program designed for educating employees on cybersecurity best practices.
The phishing simulator includes a template library that enables MSPs to test users with real-world attack scenarios. Companies can also design custom phishing attacks that are relevant to their line of business.
The platform is easy to use, it has reporting capabilities, and it includes all the tools needed for an organization to manage its own security awareness training campaign, Webroot said.
“The human factor is a consistent weakness in overall cyber defenses, and security awareness training is the only solution. As cyberattacks, such as phishing, become increasingly sophisticated, users are exposed to a variety of hidden threats that will compromise their own data along with their employer’s data,” said Chad Bacher, SVP of Product Strategy and Technology Alliances at Webroot. “Building on Securecast, Webroot will offer our MSP partners the security awareness training they need to address this evolving threat landscape, and build a profitable new line of business.”
Webroot said the decision to launch a security awareness training service comes in response to requests from MSPs for high-quality, cost-effective and ongoing training.
In its announcement of the acquisition, the security firm cites data from Verizon’s 2017 Data Breach Investigations Report, which revealed that 43 percent of breaches involved social engineering — in most cases phishing. The same Verizon report showed that in a company with 30 or more employees, roughly 15 percent of users who fell victim to phishing once took the bait a second time as well.
Overall Security of Password Managers Debatable, Cracking Firm Says
15.8.2017 securityweek Security
A password recovery firm has claimed that the overall security of password managers is debatable. "Are password managers more secure than keeping a list of passwords in a single Excel spreadsheet?" it asks. "Not necessarily," it concludes.
Announcing the latest version of the Elcomsoft Distributed Password Recovery (EDPR) tool, Oleg Afonin blogged that it can now recover the master passwords for the 1Password, KeePass, LastPass and Dashlane password managers. This can be a legitimate requirement for users who lose or forget their master password -- or in some cases for law enforcement looking for suspects' online account passwords for legal purposes.
"Obviously, if the master password is compromised, all other passwords stored in the vault are compromised as well," writes Afonin. For this reason, password managers go to great lengths to make that password irrecoverable. For example, he writes, "LastPass generates the encryption key by hashing the username and master password with 5,000 rounds of PBKDF2-SHA256, while 1Password employs even more rounds of hashing."
Despite this, Elcomsoft claims to be able to brute force the master keys. In its published benchmarks, it shows that of the four password managers, it takes longest to recover the keys for LastPass; followed by 1Password, Keepass and then Dashlane. It justifies its Excel spreadsheet comment by showing that it takes much longer to brute force encrypted Office 2016 documents than any of the tested four password managers.
In theory, anything can be brute forced if the 'attacker' has sufficient time and computing power available -- Elcomsoft is simply saying it can do so in a timely fashion. SecurityWeek spoke to Dashlane senior manager, Ryan Merchant, about the report; and it is noticeable, if understandable, that he did not address the cracking capabilities of EDPR. Instead, Merchant focused on the overall advantages of using a password manager.
"A web-based password manager keeps your passwords encrypted in secure databases in the cloud," said Merchant. "In order for anyone to access your account, they'll need to possess your strong master password in order to decrypt the password manager's database." This is, of course, exactly what Elcomsoft claims to be able to do.
However, the strength of the password manager, said the Merchant, really lies in its ease of use. "Instead of writing your passwords on sticky notes or reusing the same password for all of your accounts, password managers provide a safe place for you to store, manage, and protect your passwords and other private information," he said.
"Dashlane users in particular do not need to invent, know, type or remember any of their passwords. Dashlane does it for them. In a sense, a Dashlane user has digital accounts, not passwords," he continued. "We have already started to kill the password by making the actual passwords irrelevant to our users."
Password managers aid the user in creating strong, unique passwords for different accounts. This is both more secure and easier to manage than could be done manually by the vast majority of users. Its one theoretical weakness is that if the master password can be cracked, then all the users' different passwords are accessible. For this reason, the developers make it difficult for them to be brute-forced.
What Elcomsoft has done has make it possible, in extremis, for the user to recover them regardless. As a forensic tool, this becomes very valuable -- so long as it cannot also be used by adversaries. SecurityWeek raised this question with Olga Koksharova, marketing director at Elcomsoft.
"As for adversaries," she told SecurityWeek, "speaking about Elcomsoft Distributed Password Recovery it's always a question of being able to log into a system and having administrative rights that would allow them to install the tool and run it. However, adversaries might only need extract just some information from the computer in order to use it afterwards on another workstation with all necessary tools running. In case with password managers, we need to feed a particular file to EDPR in order to brute-force it."
It would not be easy, but it would -- under certain conditions -- be possible for an attacker to make use of EDPR. This, of course, would be much simpler if a user lost or had a mobile device stolen. Koksharova advises, "Never leave your computers with valuable information unattended (lending it to someone is out of question) and always protect the computer itself with strong passwords."
The moral from this story is simple: password managers will almost always be more secure than manually generated and managed passwords -- but they do not relieve the user from all responsibility. The password manager itself still needs to be protected.
Last week, Dashlane published the results of its 2017 Password Power Rankings study, which examined the password practices that different companies encourage or force onto their users.
Dubious Report Highlights Known Risks of Cloud-Based Multiscanners
14.8.2017 securityweek Security
Over the past week, a debate has spurred over a report from security services firm DirectDefense, claiming that Carbon Black’s endpoint detection and response (EDR) solution, Cb Response, is a prolific data leaker and exposes client data.
DirectDefense claims that the issues is related to the product’s ability to automatically upload binaries to a cloud-based multiscanner (namely, Google-owned VirusTotal) to better assess whether they are malicious or not. Specifically, the company says that it was able to pinpoint files uploaded to the multiscanner using the API key associated with Cb Response.
DirectDefense claimed that this setup creates, “the world’s largest pay-for-play data exfiltration botnet,” because clients of the multiscanner can access any of the uploaded files, regardless of where they came from. Further, because Cb Response associates its API key to the uploaded files, one would be able to learn information on Carbon Black enterprise customers based on these files alone.
“When a new file appears on a protected endpoint, a cryptographic hash is calculated. This hash is then used to look the file up in Carbon Black’s cloud. If Carbon Black has a score for this file, it gives the existing score, but if no entry exists, it requests an upload of the file. Since Carbon Black doesn’t know if this previously unseen file is good or bad, it then sends the file to a secondary cloud-based multiscanner for scoring. This means that all new files are uploaded to Carbon Black at least once,” DirectDefense explains.
The explanation is accurate, but only up to a specific point: it doesn’t mention that customers have control over the option to upload binaries to VirusTotal, and that the feature is turned off by default. The report also fails to point out that Carbon Black actually warns customers of the risks involved in enabling the option to share files with VirusTotal, which is an external source.
“By electing to enable the ‘Scan unknown binaries with VirusTotal’ feature, your server will send unknown binaries to Carbon Black with your consent. By electing to enable the ‘Share binary hashes with VirusTotal’ feature, your server will send binary hashes and other metadata to Carbon Black with your consent. Each binary and/or hash and file metadata, as the case may be, will be submitted to VirusTotal and governed solely by the Terms of Service and Privacy Policy of VirusTotal. Carbon Black shall not be responsible for this submission or for any act or omission by VirusTotal,” the warning reads.
Carbon Black, which has already issued a response to the report, points out that the so-called “data leak” vulnerability – which DirectDefense says “is nearly impossible to stop […] with the architecture [Carbon Black] devised – is in fact a feature that only Cb Response customers benefit from. The company also notes that, not only is the option off by default, but it also includes “many options to ensure privacy, and a detailed warning before enabling.”
DirectDefense also claims to have downloaded some of the files supposedly uploaded by Cb Response, and that their analysis led to identifying data pertaining to specific companies, including a streaming company (AWS IAM credentials, Slack API keys, Google Play keys, Apple Store ID), a social media company (hardcoded AWS and Azure keys, along with internal proprietary information, such as usernames and passwords), and a financial services company (shared AWS keys that granted access to customer financial data, trade secrets).
While the report alleges that Carbon Black’s product is the data leaker, the actual issue resides with VirusTotal, which provides access to the analyzed files to those willing to pay. There are numerous other security products that upload files to VirusTotal, and DirectDefense also notes that this might be the case, and even points out that the cloud-based multiscanner is spreading these files further.
“Cloud-based multiscanners operate as for-profit businesses. They survive by charging for access to advanced tools sold to malware analysts, governments, corporate security teams, security companies, and basically whomever is willing to pay. Access to these tools includes access to the files submitted to the multiscanner corpus,” DirectDefense notes.
Some experts following the story have taken a similar route, denouncing the report for inaccurately presenting Carbon Black’s product as being at fault. Some even called the report down right biased, based on DirectDefense’s association with Cylance, a competitor of Carbon Black. Recently named Solutions Partner of the Year by Cylance and using hyperbole-based comments in their report, DirectDefense can be easily accused of intentional smearing.
Security expert Adrian Sanabria, co-founder of Savage Security, calls the report “bullshit” and DirectDefense “opens itself up to criticism and closer scrutiny” by picking on Carbon Black. The reason, he says, is that “dozens of other security vendors either have an option to automatically submit binaries (yes, whole binaries, not just the hash) to VirusTotal or do it without the customers’ knowledge altogether.”
Martin Zinaich, information security officer for the City of Tampa, also points out that the report is biased and that DirectDefense had a hidden agenda when writing it: “DirectDefense poorly executed their discovery disclosure and no doubt did so purposefully. Thereby continuing the role of valued solutions partner.”
However, he also notes that many security professionals would turn to sharing information with VirusTotal without a second thought: “Neither the use of VirusTotal nor the [Carbon Black] disclaimer would make even the most hypersensitive InfoSec professional contemplate data leaking to other users of said service. Moreover, it would hardly cross the mind of a typical endpoint administrator.”
“How many other vendors are leveraging a multiscanner with API access? DirectDefense’s clumsy disclosure should not take away from what they did in fact discover,” Zinaich points out.
In a post denouncing the manner in which some news outlets were quick to report on DirectDefense’s story without waiting for Carbon Black’s response, investigative journalist Brian Krebs too points out that the real issue is the use of VirusTotal within corporate networks without fully understanding what it involves.
“If DirectDefense’s report helped some security people better grasp the risks of oversharing with multiscanners like VirusTotal, that’s a plus,” Krebs notes. However, he also says that “overblown research reports” such as this one should not be taken for granted, especially if the company that discovered the so-called issue didn’t even bother to contact the affected vendor before going public.
So, is the automatic (or manual) upload of files to VirusTotal bad practice? Yes and no. It is both a feature and a risk, depending on how it is used and on how well security teams and admins understand what it involves. On the one hand, sending a file to a multiscanner clearly brings a great deal of benefits by increasing the chances of discovering malicious intent. On the other hand, however, if used irresponsibly, this option could result in data leaks, potentially doing more harm than good. Thus, fully understanding the risks associated with the practice should help companies improve their security stance.
Variety reports a failed attempt of HBO to Offer a ‘Bug Bounty’ to hackers
12.8.2017 securityaffairs Security
According to a report from a leaked memo by Variety, in response to the incident, HBO offered a reward of $250,000, a figure far from the HBO annual budget.
Cyber criminals claiming to have hacked television group HBO networks were demanding millions of dollars in ransom payments from the company while threatening to release more material.
The alleged hackers published a five-minute video letter to HBO chief Richard Plepler claiming to have “obtained valuable information” in a cyber attack. Cyber criminals said they had stolen 1.5 terabytes of data.
The author of the message dubbed himself “Mr. Smith,” confirmed his group obtained “highly confidential” documents and data, including scripts, contracts, and personnel files.
The crooks pretend to receive half of the group’s annual budget of $12 million to $15 million to stop leasing the files.
The hackers claim a long work to compromise the company network, it took six months to break into the company systems, they also added to have purchased $500,000 a year zero-day exploits that let them hack the firm exploiting flaws in Microsoft and other software used by HBO.
According to a report from a leaked memo by Variety, in response to the incident, HBO offered a reward of $250,000. The payment was offered as a “bug bounty,” to discover vulnerabilities in their its computer networks.
Unfortunately, “Mr. Smith” and his crew weren’t satisfied by the offer that doesn’t match their millionaire demands to stop leaking sensitive data, the crooks’ request would be more than $6 million.
HBO did not comment the report by Variety.
Last week, along with the video letter, the hackers released 3.4GB of files. The dump contained technical data related to the HBO’s internal network and administrator passwords, and of course the draft scripts from five Game of Thrones episodes. The huge trove of files also includes a month’s worth of emails from HBO’s vice president for film programming, Leslie Cohen.
HBO is working with forensic experts and law enforcement to identify the hackers and fix the flaws they have exploited to steal the precious content.
Hackers Say Humans Most Responsible for Security Breaches
11.8.2017 securityweek Security
Hackers Say Humans Are the Weakpoint and That Traditional Defenses Cannot Protect Them
Under the principle of set a thief to catch a thief, 250 hackers at Black Hat 2017 were asked about their hacking methods and practices. By understanding how they work and what they look for, defenders can better understand how to safeguard their own systems.
Thycotic surveyed (PDF) a cross section of hackers attending Black Hat. Fifty-one percent described themselves as white hats; 34% described themselves as grey hats using their skills for both good and bad causes; and 15% self-identified as out-and-out black hats.
The hackers' number one choice for fast and easy access to sensitive data is gaining access to privileged accounts (31%). Second is access to an email account (27%), and third is access to a user's endpoint (21%). All other routes combined totaled just 21%.
The hackers also confirmed that perimeter security, in the form of firewalls and anti-virus, is irrelevant and obsolete. Forty-three percent are least troubled by anti-virus and anti-malware defenses, while 29% are untroubled by firewalls. "Hackers today are able to bypass both firewalls and AV using well known applications and protocols or even VPN that hide within expected communications," explains Joseph Carson, Thycotic's chief security scientist. "For example, VOIP, streaming services etc. Because of the ability to hide within normal business applications or the use of authenticated stolen credentials, they are stating that these technologies are no longer sufficient to prevent cyber-attacks on their own."
Overall, the hackers find MFA and encryption their biggest obstacles. "As hackers increasingly target privileged accounts and user passwords," explains Thycotic, "it’s perhaps not surprising that the technologies they considered the toughest to beat include Multi-Factor Authentication (38%) and Encryption (32%), with endpoint protection and intrusion prevention far behind at 8% and 5 % respectively."
Ultimately, however, the hackers believe that humans are most responsible for security breaches. Only 5% consider that insufficient security software is the problem, while 85% named humans as most responsible for security breaches. The problem is 'cyber fatigue'.
Cyber fatigue is blamed on the constant pressure to obey policy and good practice. "'Remembering
and changing passwords' was the top source of cybersecurity fatigue (35%), a major vulnerability that hackers are all too willing to exploit," notes Thycotic. "Other contributing factors included 'Information overload' (30%), 'Never ending software updates' (20%) and 'Living under constant cyber security threats' (15%)."
Perhaps surprisingly, hackers do not consider threat intelligence solutions to be an obstacle. "Because Threat Intelligence solutions are also accessible to hackers, they may be able to easily identify how they work and therefore avoid detection them," suggests Thycotic.
The survey suggests that humans are a weakpoint, traditional perimeter defenses are ineffective, and user credentials are the target. "With traditional perimeter security technologies considered largely irrelevant, hackers are focusing more on gaining access to privileged accounts and email passwords by exploiting human vulnerabilities allowing the hacker to gain access abusing trusted identities," comments Carson. "More than ever, it is critical for businesses to mitigate these risks by implementing the right technologies and process to ward off unsuspecting attacks and access to sensitive data."
His conclusion is that "The new cybersecurity perimeter must incorporate an identity firewall built around employee and data using identity and access management technology controls which emphasizes the protection of privileged account credentials and enhances user passwords across the enterprise with multi-factor authentication."
HBO Offered 'Bounty' to Hackers: Report
11.8.2017 securityweek Security
HBO offered a reward of $250,000 in response to a data breach at the television group that produces "Game of Thrones," according to a report from a leaked memo.
The report by Variety on Thursday said HBO offered the payment as a "bug bounty," which is offered by companies to discover vulnerabilities in their computer networks.
The offer apparently failed to satisfy the attackers who have demanded a ransom of millions of dollars and are threatening to release more files from what is claimed to be a massive data breach.
HBO, a unit of the media group Time Warner, did not respond to a query about the Variety report.
Earlier this week, a video circulating online authored by someone identified only as "Mr. Smith" said the hackers had videos, scripts, personnel files and other sensitive data from the breach.
The hackers demanded "six month salary," which, according to the video, would be more than $6 million.
Last week the hacker group leaked one script of "Games of Thrones" and content from other HBO productions. HBO has said it was working with forensic experts and law enforcement in response to the attack.
Mysterious company is offering up to $250,000 for VM Hacks through a bug bounty
11.8.2017 securityaffairs Security
A mysterious company is offering up to $250,000 for virtual machine (VM) hacks. The “secret” bug bounty program was announced by Bugcrowd.
A mysterious company makes the headlines for offering up to $250,000 for virtual machine (VM) hacks. The “secret” bug bounty program was announced by the crowdsourced security testing platform Bugcrowd.
At the time I was writing the unique information available on the target is that it is an unreleased product.
The program is invitation-only, but anyone can apply for an invite, the organization will contact the final participants.
“Bugcrowd has an exciting opportunity to participate in a private, invite-only program with an undisclosed client, against an unreleased product – with rewards up to $250,000!” reads the announcement published on Bugcrowd.
Candidates must have specific skills on virtual environments, kernel and device driver security, firmware security, and advanced application security.

The hackers must focus their activities in:
Guest VM breakout/isolation failures
Code execution beyond the confines of your guest VM
Privilege escalation within the guest VM made possible by the underlying platform
Any vulnerabilities which could lead to compromise or leakage of data and directly affect the confidentiality or integrity of user data of which affects user privacy (including memory corruption, cross guest VM issues, persistent issues).
Denial/degrading service to other customers, or of the underlying platform itself (excluding DDoS)
Participants can earn between $5,000 and $250,000 for each vulnerability they will report, the duration of the bug bounty program is roughly of 8 weeks, it will start in September.
Bug bounty programs are becoming even more common in the IT security industry, VM hacks are among the issues considered more interesting by the experts. Last year, security experts earned $150,000 for or the hack of the VMware Workstation 12.5.1. reported at the hacking contest 2016 PwnFest held in South Korea at the 2016 Power Of Community (POC) security conference.
This year, during the Pwn2Own contest, the researchers at the Tencent Security’s Team Sniper earned $100,000 for a VMware Workstation exploit that could be exploited by attackers used to escape VMs.
Unnamed Firm Offers $250,000 for VM Hacks
11.8.2017 securityweek Security
An unnamed company is prepared to offer up to $250,000 for virtual machine (VM) hacks as part of a “secret” bug bounty program, crowdsourced security testing platform Bugcrowd announced this week.
The program, which Bugcrowd has described as a hybrid approach, is invitation-only, but anyone can apply for an invite. White hat hackers who believe they have the necessary skills can send a submission and they will be contacted if they have been selected.
While the name of the company running this initiative has not been disclosed, Bugcrowd has revealed that the target is an unreleased product.
The ideal applicant for this program is someone skilled in the areas of virtualization, kernel and device driver security, firmware security, and advanced application security.
Focus areas include guest VM breakout, code execution outside the guest VM, privilege escalation within the guest via the underlying platform, flaws that could result in data leakage (e.g. memory corruption, cross-guest VM issues), and disruption of service to other customers (excluding DoS attacks).
Finding these types of security issues can earn participants between $5,000 and $250,000. The hackers who submit one of the best five reports describing their efforts, attempts, ideas for potential compromise, and other relevant information will be rewarded $10,000.
The bug bounty program will run for a period of roughly 8 weeks, between early September and late October.
It’s not uncommon for companies to pay out significant rewards for VM hacks. Last year, researchers earned $150,000 at a hacking competition in South Korea for finding serious vulnerabilities in VMware Workstation and Fusion.
At ZDI’s Pwn2Own contest, Tencent Security’s Team Sniper earned $100,000 for a VMware Workstation exploit that could be used to escape VMs.
Microsoft also announced recently that it’s prepared to pay up to $250,000 for critical vulnerabilities found in its Hyper-V hypervisor on Windows 10.
Google Pays $10,000 Bug Bounty to High School Student
11.8.2017 securityweek Security
Uruguayan high school student Ezequiel Pereira, who has aspirations of becoming a security researcher one day, has been awarded $10,000 for discovering and reporting a vulnerability in Google’s App Engine server.
While poking around App Engine by changing the Host header in requests sent to the server (*.appspot.com) – in an attempt to get access to internal App Engine apps (*.googleplex.com), Pereira stumbled upon a website that had no security measure in place.
Users accessing apps on googleplex.com are usually required to go through the MOMA login page, which acts as a proxy called “ÜberProxy.”
According to the student, who was using Burp for this endeavor because it allows to easily change the Host header and see the result, most of his attempts to access App Engine apps failed. The server was either returning a 404 Not Found error or was checking whether the request was coming from a Googler account ("username@google.com") instead of a normal Google account.
Eventually, however, he stumbled upon yaqs.googleplex.com, where no username check was performed and where other security measures also appeared to be lacking.
“The website's homepage redirected me to ‘/eng’, and that page was pretty interesting, it had many links to different sections about Google services and infrastructure, but before I visited any section, I read something in the footer: ‘Google Confidential’,” Pereira explains.
Immediately after discovering the issue, the student retraced the steps to make sure it could be reproduced, and then reported the vulnerability to Google, without further poking at the website.
To reproduce the bug using Burp, one would have to go to the Repeater tab, set the target host to "www.appspot.com" and the target port to "443," then check the "Use HTTPS" option, write a raw HTTP request: GET /eng HTTP/1.1
Host: yaqs.googleplex.com
(the request also includes two empty lines at the end), and hit Go.
By exploiting the vulnerability, an attacker could access “an internal Google website,” the student alleges.
The report was immediately confirmed by Google as valid, and the company informed Pereira several weeks later that he was awarded $10,000 for the discovery. Apparently, Google discovered a “few variants [of the exploit] that would have allowed an attacker access sensitive data,” which explains the high reward amount.
Disjointed Tools Challenge Security Operations: Survey
11.8.2017 securityweek Security
Insufficient staffing levels and quality, together with poor orchestration between too many security point products mean that complete breach intolerance is an aspiration not currently achieved by today's security operations centers (SOCs).
This is the conclusion of a new study by Forrester Consulting, commissioned by Endgame, a provider of enterprise threat protection solutions. Forrester surveyed a small number (156) of senior security decision makers (directors, C-Suite and VPs) in US companies with more than 1000 employees (84% have more than 5000 employees). The survey was conducted in May 2017.
'Complete breach intolerance' is defined as stopping all attacks before there is damage to systems or data loss. Breach statistics, however, show how difficult this will be. Of the companies surveyed, 92% have suffered at least one successful breach in the last year. One-third have suffered more than 20 breaches; and one-in-eight have suffered more than 50 successful breaches.
Currently unable to prevent all breaches, 64% of the organizations fear that the next breach could be the big one; or at least, it could be 'somewhat to significantly severe'. The two biggest fears are that it could lead to a loss of revenue, and brand damage. "We have a large presence in our community," said the CISO of a US banking company; "if we had a major breach, it would really be detrimental to our brand. Our reputation would be ruined for the most part."
SOCs are considered an important route to preventing this and improving breach intolerance. Seventy-six percent of the organizations already operate a SOC, with another 17% planning to deploy one in the next 12 months. However, adequately staffing a SOC remains a challenge. Looking at current staffing, only one position (malware engineer) is filled in more than 50% of the organizations. Only 44% of organizations have a Tier 1 analyst; 35% have a SIEM engineer; and only 24% have a forensics specialist. Perceived staff proficiency levels are even worse: 26% for the analyst; and 29% for the SIEM engineer and the forensics specialist.
Given the staffing issues, greater reliance has to be placed on the technology itself. However, inadequate and disjointed tools are a problem. Seventy-one percent of the respondents are using five or more technologies in their SOC, and one-third are using eight or more technologies. "What I'd like to do is reduce the overall risk footprint," said the CISO of a global energy company, "thus being able to reduce the number of tools. There's a lot of work that we're doing to try to reduce overlap of tools."
The primary purpose in reducing the number of tools is to streamline detection and lower false positives. "Lowering our false positives lowers our head count because we don't need as many people watching. That saves us money," said one of the respondents.
"Alert fatigue is a challenge," said another. "If my staff had time to take a look at our architecture, we would be able to reduce the number of tools that we had, or number of providers we had, and really look at things from a holistic approach and not a point solution-type approach. We would reduce the number of vendors we're using, which then in turn would reduce the alerts or reduce that fatigue."
Organizations are looking to reduce their vulnerabilities as well as build more automation between endpoint prevention, detection, and response capabilities, and they are using continuous monitoring to stop advanced threats, says Forrester. Other ways they are improving their strategy is by integrating endpoint security with network security for reduced operational friction.
Despite the challenges, Forrester believes that complete breach intolerance should still be sought. To achieve this, it says, "It is necessary to equip the SOC team with the right tools and skills." To achieve this, it offers four primary recommendations.
The first is the reverse of much current thinking. Since breaches will happen, recent advice has been to concentrate on detection (incident response) over prevention. However, SOCs are currently stretched by the detection alerts they need to triage. "The best way to efficiently achieve complete breach intolerance," suggests Forrester, "is to build a strong layer of prevention-focused controls to lower your organization's attack surface in the first place. This will lower the number of incidents that your SOC staff need to deal with and reduce the 'noise' seen by detection-focused tools."
The second is to reduce internal friction through integrated endpoint prevention, detection and remediation. "If you don't establish a solid foundation of automation and orchestration," it warns, "blind investments in prevention and detection likely won't have the intended effect and will leave you more vulnerable."
The third is to extend detection capabilities beyond static indicators of compromise, such as malware signatures. "Given the prevalence of fileless attacks and novel attack methods utilizing legitimate software, your detection capabilities must go beyond malicious file and process detection... Prioritize tools that include behavior-based detection from a process and user perspective."
The final recommendation is to advance staff skillsets. "While technology is not a substitute for people, you can only maximize it when you have staffed your team appropriately with skilled and trained resources. Remember," it says, "attackers learn new techniques and methodologies for compromising your environment; your defenders should be learning as well."
Most Web Services Don't Care How Weak Your Password Is
10.8.2017 securityweek Security
Password Strength Not Enforced by Popular Websites
GoDaddy has the best password policy among consumer websites; Netflix, Pandora, Spotify and Uber have the worst. This is the finding of a new study into the password practices that different companies encourage or force onto their users.
Dashlane, developer of the Dashlane password manager app that can synchronize passwords across all platforms, has published the findings of its 2017 Password Power Rankings study. It used five researchers to examine the password security criteria of 37 popular consumer sites, and 11 popular enterprise sites. Each site was given one point for each of five good practice criteria.
The criteria tested were password length (that is, at least 8 characters); a required mix of alpha and numeric characters; a password strength assessment tool (such as a color-coded or measurement bar); brute-force challenge or account locking (after ten false logins); and an MFA option. Three points out of the maximum five are considerate to be 'adequate' for the minimum threshold for good password security.
Dashlane accepts that password choice is the responsibility of end users, but believes that the service websites also have a responsibility to help the user. "It's our job as users to be especially vigilant about our cybersecurity, and that starts with having strong and unique passwords for every account," said Dashlane CEO Emmanuel Schalit. "However, companies are responsible for their users, and should guide them toward better password practices."
Of the 37 consumer sites examined, only GoDaddy received a 5/5 score. A further 19 sites are deemed adequate, with either 3 or 4 out of 5. At the top end, this includes many of the sites that could be expected to do well: Apple, Microsoft, PayPal and Skype. Only just adequate includes Facebook, Google, Reddit, Slack, Snapchat, WordPress and Yahoo.
More worrying, however, are those that failed. Amazon, eBay, and Twitter were among those scoring just two points. Dropbox, Evernote and Pinterest scored only one point; and of course, Netflix scored zero.
There is a similar divergence of scores among the enterprise websites. Only Stripe and QuickBooks got top marks, with Basecamp and Salesforce gaining a credible four points. GitHub, MailChimp and SendGrid are 'adequate' with three points. DocuSign and MongoDB (mLab) scored a disappointing two points; while, worryingly, Amazon Web Services and Freshbooks scored only one point.
It should be stressed that this survey relates only to the way in which the service provider helps the user in password choice and use -- it says nothing about the overall security posture of the website itself (for example, whether behavioral access controls are implemented internally and operated passively). Nevertheless, user credentials are frequently involved in data breaches, and service providers should do everything possible to strengthen their defense.
Dashlane noted a few very worrying specifics. Its researchers were able to create passwords using nothing but the lower-case letter 'a' on sites that include Amazon, Dropbox, Google, Instagram, LinkedIn, Netflix, Spotify, Uber, and Venmo. Netflix and Spotify actually accepted 'aaaa' passwords. The concern here is that if such simple passwords are acceptable, many users will choose a similarly simple -- and common -- password.
Earlier this year, an analysis of 10 million passwords revealed that the 25 most popular passwords are used to secure over 50% of accounts. Dashlane's recommendation to online service providers in such cases is basically fourfold. Firstly, passwords should have a minimum length of eight characters. Secondly, they should be required to be a case-sensitive mix of upper and lowercase alpha and numeric characters. Thirdly, the service provider should ban the most popular passwords. And finally, in case an attacker is working through a list of common passwords, an automatic account lock should be applied after a pre-defined number of failed accounts.
While such practices from the service providers will help the user, every web user must remember that that it is his or her responsibility to choose a strong and unique password for each different account.
Hotspot Shield VPN Accused of Spying On Its Users' Web Traffic
8.8.2017 thehackernews Security
"Privacy" is a bit of an Internet buzzword nowadays as the business model of the Internet has now shifted towards data collection.
Although Virtual Private Network (VPN) is one of the best solutions to protect your privacy and data on the Internet, you should be more vigilant while choosing a VPN service which actually respects your privacy.
If you are using popular free virtual private networking service Hotspot Shield, your data could be at a significant risk.
A privacy advocacy group has filed a complaint with the Federal Trade Commission (FTC) against virtual private networking provider Hotspot Shield for reportedly violating its own privacy policy of "complete anonymity" promised to its users.
The 14-page-long complaint filed Monday morning by the Centre for Democracy and Technology (CDT), a US non-profit advocacy group for digital rights, accused Hotspot Shield of allegedly tracking, intercepting and collecting its customers' data.
Developed by Anchorfree GmbH, Hotspot Shield is a VPN service available for free on Google Play Store and Apple Mac App Store with an estimated 500 million users around the world.
Also Read: Secure VPNs (Get Lifetime Subscription) To Prevent ISPs From Spying On You
VPN is a set of networks conjugated together to establish secure connections over the Internet and encrypts your data, thereby securing your identity on the Internet and improving your online security and privacy.
The VPN services are mostly used by privacy advocates, journalists, digital activists and protesters to bypass censorship and geo-blocking of content.
Hotspot Shield does just Opposite of What All it Promises
The Hotspot Shield VPN app promises to "secure all online activities," hide users' IP addresses and their identities, protect them from tracking, and keep no connections logs while protecting its user’s internet traffic using an encrypted channel.
However, according to research conducted by the CDT along with Carnegie Mellon University, the Hotspot Shield app fails to live up to all promises and instead logs connections, monitors users' browsing habits, and redirects online traffic and sells customer data to advertisers.
"It is thusly unfair for Hotspot Shield to present itself as a 48 mechanism for protecting the privacy and security of consumer information while profiting off of that information by collecting and sharing access to it with undisclosed third parties," the CDT complaint reads.
"Consumers who employ Hotspot Shield VPN do so to protect their privacy, and Hotspot Shield’s use of aggressive logging practices and third-party partnerships harm its consumers' declared privacy interests."
Hotspot Shield also found injecting Javascript code using iframes for advertising and tracking purposes.
Reverse engineering of the apps source code also revealed that the VPN uses more than five different third-party tracking libraries.
Researchers also found that the VPN app discloses sensitive data, including names of wireless networks (via SSID/BSSID info), along with unique identifiers such as Media Access Control addresses, and device IMEI numbers.
Also Read: Secure VPN Services — Get Up to 91% Discount On Lifetime Subscriptions
The CDT also claims that the VPN service sometimes "redirects e-commerce traffic to partnering domains."
If users try to visit any commercial website, the VPN app redirects that traffic to partner sites, including ad companies, to generate revenue.
"For example, when a user connects through the VPN to access specific commercial web domains, including major online retailers like www.target.com and www.macys.com,the application can intercept and redirect HTTP requests to partner websites that include online advertising companies," the complaint reads.
The CDT wants the FTC to start an investigation into what the Hotspot Shield's "unfair and deceptive trade practices" and to order the company to stop mispresenting privacy and security promises while marketing its app.
Microsoft to Ban WoSign, StartCom Certificates
8.8.2017 securityweek Security
Windows Will Not Trust New Certificates Issued by WoSign and StartCom After September 2017
Microsoft has finally announced its decision in the case of Chinese certificate authority (CA) WoSign and its subsidiary StartCom. The company has informed customers that its products will soon stop trusting new certificates issued by these CAs.
Following a series of incidents and problems brought to the attention of the web browser community since January 2015, Mozilla, Apple and Google have decided to revoke trust in certificates from WoSign and StartCom.
The list of problems includes backdating certificates to bypass restrictions, issuing certificates without authorization, and misleading browser vendors about WoSign's acquisition of StartCom and their relationship.
Microsoft has now also announced its decision regarding WoSign and StartCom certificates. Windows will continue to trust certificates issued before September 26, 2017, until they expire. However, new certificates issued by the firms after September 2017 will no longer work.
“Microsoft has concluded that the Chinese Certificate Authorities (CAs) WoSign and StartCom have failed to maintain the standards required by our Trusted Root Program,” the company said on Tuesday. “Observed unacceptable security practices include back-dating SHA-1 certificates, mis-issuances of certificates, accidental certificate revocation, duplicate certificate serial numbers, and multiple CAB Forum Baseline Requirements (BR) violations.”
Google also plans on taking drastic action against the two CAs next month. The tech giant has set up a whitelist for some Alexa Top 1M websites using certificates from WoSign and StartCom, but the whitelist will be removed starting with Chrome 61, currently scheduled for release in mid-September.
StartCom and WoSign are not the only CAs that got into trouble with web browser vendors as a result of misissued certificates. Symantec recently announced its decision to sell its certificate business to DigiCert for $950 million after Google announced that all certificates issued by the company will have to be replaced by October 2018, and new certificates would have to be issued through the infrastructure of a subordinate CA.
SMBs Eye Managed Security Solutions: Survey
4.8.2017 securityweek Security
Webroot commissioned Wakefield Research to query 600 SMB IT decision makers in the US, UK and Australia to discover current attitudes towards IT security among companies with less than 500 employees. Such companies are often thought to be more at risk of successful cyber-attacks because of smaller budgets, fewer IT staff, and fewer infosecurity products designed for the smaller company.
The results of the survey (PDF) show the curious mixture of reality and wishful-thinking that often affects perception of infosecurity. For example, only 31% of US SMBs consider ransomware to be a major threat in 2017 -- despite 49% being concerned about 'new forms of malware'. In the UK, ransomware is considerd a bigger threat at 50%, with 59% worrying about new forms of malware. This is despite previous Webroot research (PDF) showing that over 60% of companies have already been affected by ransomware; while most analysts believe the threat is still increasing.
Self-confidence is high. First, 72% of SMBs globally believe that they are at least "almost completely ready to manage IT security and protect against threats"; second, 89% of SMBs around the world believe they have staff who could successfully address and/or eliminate a cyber-attack; and thirdly, 87% are confident in their staff cyber security education.
"The lack of concern about ransomware is leaving a gaping hole in the security of global businesses, as witnessed by the recent outbreaks of WannaCry and not-Petya," comments Adam Nash, Webroot's EMEA regional manager. "This combined with the false sense of security when it comes to businesses' ability to manage external threats is worrying."
Nash believes that SMBs "can no longer afford to put security on the back burner and need to start engaging with the issues and trends affecting the industry." It's not as if they do not understand the costs. Asked about the estimated total cost of a cyberattack "where customer records or critical business data were lost", US respondents replied with an average cost of $579,099.
This was the lowest figure. In the UK, it rises to $974,250; and to a colossal $1,509,938 in Australia.
Outsourcing security is often seen as a solution to the budgetary and staffing problems of SMBs. "Enlisting the help and expertise of a Managed Security Services Provider," comments Nash, "is one way to implement a secure, layered approach to combat external threats.” But it is not yet the norm, with only 13% of SMBs currently outsourcing. The rest use a mix of in-house and outsourced IT security support (37%), or fully in-house security (50%).
This is likely to change. Eighty percent of the respondents expect to use a third-party cyber security provider to manage security in 2017.
Despite an overt appearance of confidence in their own abilities, there seems to be an increasing acceptance of the value of outsourcing. Ninety percent of the respondents believe that outsourcing their IT solutions in the future would improve their security and enable them to address other areas of the business.
The net result highlighted by this survey is that there is a huge opportunity for MSSPs to tap into an awakening but yet unfulfilled demand in the SMB market.
G Suite Admins Can Now Manage SAML Certificates
3.8.2017 securityweek Security
Google on Wednesday announced that G Suite administrators are now able to directly manage X.509 certificates associated with their Security Assertion Markup Language (SAML) applications.
SAML allows users to use G Suite credentials to sign into enterprise cloud apps via Single Sign-On (SSO). Admins are provided with an identity and access management (IAM) service to manage all users and cloud applications, but don’t have to manage individual user IDs and passwords for each cloud application, for each user, as IAM features a unified sign-on across all enterprise cloud software.
With the help of X.509 certificates, SAML can ensure the authenticity and integrity of messages shared between an Identity Provider (IdP) and Service Provider (SP), Google explains. These certificates are automatically associated with a SAML application when it is first installed via the Amin console.
The certificates come with a five-year lifetime. Previously, admins had to contact Google Support to change or rotate an application’s existing certificate, regardless of whether it was about to expire or was compromised.
As soon as a certificate expires, however, users can no longer sign into the associated application using SAML-based SSO.
With the new change, admins can manage X.509 certificates on their own, without having to ask for additional support from Google.
“Today, we’re giving you the ability to do so on your own in the Admin console, where you can easily view certificates in use, identify those about to expire, create new ones, and assign them to applications,” Google notes.
However, only super admins are provided with visibility into the expiration status of SAML certificates and only they can take action on these certificates, the Internet giant also explains.
The new feature is launching to both Rapid Release and Scheduled Release and impacts all G Suite editions. Because it will see a gradual rollout, the feature could take up to 15 days to become visible in some cases.
Admins interested in learning more on how to set up custom SAML applications should head to this support article. Information on SAML certificate rotation and how admins can manage certificates is available here.
Google Wants Symantec Certificates Replaced Until Chrome 70
31.7.2017 securityweek Security
After several months of debate, Google has released its final proposal in the case of Symantec’s certificate authority (CA) business. All Symantec-issued certificates must be replaced by the time Google releases Chrome 70 next year.
Google announced its intention to take action against Symantec for improperly issued digital certificates in March. The announcement came after the company, particularly some of its subsidiaries and WebTrust audited partners, were caught wrongly issuing certificates.
After several proposals on both sides, Google has come up with a final decision. According to the company, between now and March 15, 2018, websites using TLS certificates issued by Symantec before June 1, 2016, should obtain replacements from a trusted CA, including Symantec.
While Symantec will be allowed to release certificates, it will have to find a subordinate certificate authority (SubCA) whose infrastructure it can use. The company expects to have new infrastructure set up by December 1.
Starting with Chrome 66, currently scheduled for release on March 15, 2018, certificates issued on or after June 1, 2016, will no longer be trusted.
Certificates issued through Symantec’s old infrastructure after June 1, 2016, will continue to be trusted, but only until the release of Chrome 70. With the release of Chrome 70, scheduled for release on October 23, 2018, all certificates issued via the company’s old infrastructure will stop being trusted by the web browser.
Mozilla advised Symantec in May to accept Google’s proposal and described the alternative action it had been prepared to take in case an agreement was not reached. Microsoft and Apple have not made any comments on the matter, but based on the outcome of the case involving WoSign and StartCom, at least Apple is likely to follow in Google’s footsteps.
Symantec has promised to step up its game, but recent incidents have shown that the company, and particularly its subsidiaries, still have a long way to go. A researcher managed to trick Symantec’s RapidSSL into revoking TLS certificates by falsely claiming that their associated private keys had been compromised.
Man-Machine Teamwork Needed for Effective Threat Hunting: Report
29.7.2017 securityweek Security
Seven hundred IT and security professionals were surveyed by McAfee to understand the current state and future development of threat hunting -- the active search for existing network breaches.
For this purpose, a threat hunter is defined as an analyst who focuses on clues and hypotheses (rather than waiting for binary alerts from rule-based detections); is human-centric (rather than tool-centric); and works from the assumption of an existing breach. The hunting process is defined as the military OODA concept: observe, orient, decide, act.
To allow comparison of threat-hunting capabilities, the respondents rated the perception of their own maturity from level 1 to level 4. This ranges from hunters who primarily rely on automated alerting with some routine data collection (level 1) to hunters who automate the majority of successful data analysis (level 4).
One of the first insights from the survey and report (PDF) is that successful threat-hunting is a combination of art and science. Level 1 hunters operate largely on an ad hoc basis; for level 2 hunters it is an organized process; but for the most successful hunters at level 4, it is a mix of both.
Looking to improve their maturity, the top four strategies overall are better automation of threat hunting processes, increased use of data analytics, hiring of more experienced employees, and more precise diagnostic tools. Noticeably, and perhaps naturally, the lower level SOCs place hiring staff as the priority, followed by improved use of data analytics. Level 3, which is probably better staffed by definition, seeks first better automation and second increased analytics.
McAfee postulates that lower level SOCs seek to staff-up and chase "shiny new toys... trying to emulate leading
SOCs too soon", while more advanced SOCs "shift their focus from building strong hunting and incident response teams to making them more effective."
One clear differentiation between level 4 hunters and the lower levels is the degree of automation. "Respondents in levels 1 through 3 SOCs," notes the report, "reported deploying automation extensively at an average of 23% compared with 75% of level 4 SOCs."
This carries over into the next stage of cybersecurity -- incident response. Extensive automation quite naturally supplies the greater context needed by incident responders to more accurately scope and triage incidents for rapid incident resolution. This is confirmed in the survey results: "71% of SOCs with a level 4 maturity closed investigations in an average of less than one week -- the majority of which closed in less than 24 hours." The average time for the lower levels is 25 days.
Similarly, says McAfee, "The more mature SOCs also determine the root cause of an attack 70% percent of the time, versus 43% percent of the time for the developing organizations."
Another difference in the operational procedures between the different levels of maturity is the amount of time spent on researching and customizing threat hunting tools. Level 1 hunters spend, on average 10 hours per month. This rises consistently to 17 hours for level 4 hunters. "This," suggests McAfee, "is a good example of both the power of human+machine teaming, and the importance of locally produced intelligence and personalization."
Sandboxes are the most used hunting tool. Noticeably, the more advanced hunters have been using them for longer than the lower levels: four years, on average, for level 4; compared to 2 years for level 1. However, the use made of sandboxes also changes with the level of hunter maturity. Twice as many level 4 hunters use sandboxing for investigation and threat validation rather than just detection and alerting.
All data analysis relies on data. Sixty percent of all four maturity levels use public threat intelligence feeds; but as the maturity level increases, so the hunters begin to rely more on the TTPs they gather internally from their own research. Automated processes to feed threat intelligence into a correlation engine are used by 45% of level 1 hunters, but 77% of level 4 hunters. The nature of the feeds also changes with the levels: 80% of level 4s use ISACs and other private or paid-for feeds compared to 41% of level 1s.
"Threat hunting is here to stay, and is no longer an esoteric practice limited to a few of the edgier practitioners," says McAfee. "Over the next few years, expect to see threat hunting as part of most organizations' analytics driven security operations, backed by extensive automation and machine analytics."
What is clear from this survey, however, is that threat hunting is not simply a case of buying systems to do it. Effective threat hunting leading to efficient incident response is a combination of man and machine, of art and science, with the man tailoring and automating the science to suit his own environment.
Microsoft Is Paying Up To $250,000 With Its New Bug Bounty Program
27.7.2017 thehackernews Security
Microsoft has finally launched a new dedicated bug bounty program to encourage security researchers and bug hunters for finding and responsibly reporting vulnerabilities in its latest Windows versions of operating systems and software.
Being the favourite target of hackers and cyber criminals, every single zero-day vulnerability in Windows OS—from critical remote code execution, mitigation bypass and elevation of privilege to design flaws—could cause a crisis like recent WannaCry and Petya Ransomware attacks.
In past five years the tech giant has launched multiple time-limited bug bounty programs focused on various Windows features, and after seeing quite a bit of success, Microsoft has decided to continue.
"Security is always changing, and we prioritise different types of vulnerabilities at different points in time. Microsoft strongly believes in the value of the bug bounties, and we trust that it serves to enhance our security capabilities."
With its latest bug bounty program, Microsoft is offering up to $250,000 in rewards to cybersecurity researchers and bug hunters who find vulnerabilities in the company's software, which mainly focuses on:
Windows 10, Windows Server 2012 and Insider Previews
Microsoft Hyper-V
Mitigation Bypass Techniques
Windows Defender Application Guard
Microsoft Edge Browser
Below is the chart showing details of the targets, main focus areas and the respective payouts:
"In the spirit of maintaining a high-security bar in Windows, we’re launching the Windows Bounty Program on July 26, 2017," Microsoft says in a blog post. "The bounty program is sustained and will continue indefinitely at Microsoft’s discretion."
Recently, the non-profit group behind Tor Project joined hands with HackerOne and launched a bug bounty program with the payout of up to $4,000 to researchers and bug hunters for finding and reporting flaws that could compromise the anonymity network.
For more granular details about Microsoft's Bug Bounty Program, you can check out the program on the TechNet site.
Microsoft Launches Windows Bug Bounty Program
27.7.2017 securityweek Security
Microsoft announced on Wednesday the launch of a Windows bug bounty program with payouts ranging between $500 and $250,000.
Microsoft has been running several bug bounty programs, but none of them have covered all features of Windows. As part of the new program, the company is prepared to pay out a reward for security holes in any feature of Windows Insider Preview and various focus areas that include the Hyper-V hypervisor, exploit mitigation bypasses, the Windows Defender Application Guard, and the Edge web browser.
“Any critical or important class remote code execution, elevation of privilege, or design flaws that compromises a customer’s privacy and security will receive a bounty,” Microsoft said.
Bounty hunters can earn up to $15,000 for remote code execution, up to $10,000 for privilege escalation, and up to $5,000 for information disclosure, remote denial-of-service (DoS), and tampering or spoofing vulnerabilities found in Windows Insider Preview, the slow ring.
As for the focus areas, the newly added Windows Defender Application Guard (WDAG) category can earn researchers up to $30,000 for a high quality report and functioning exploit demonstrating a vulnerability that can be leveraged to escape the WDAG container to the host.
The highest payout is for vulnerabilities in Hyper-V running on Windows 10, Windows Server 2012 or Windows Insider Preview. Hackers can receive up to $250,000 from Microsoft for a high quality report and exploit demonstrating a remote code execution flaw that allows a guest VM to compromise the hypervisor, a guest to host escape, or a guest to guest escape.
In the other focus areas, hackers can earn up to $200,000 if they find a way to bypass exploit mitigations, and a maximum of $15,000 for remote code execution flaws in Edge.
Researchers who discover vulnerabilities already found internally by Microsoft employees will still get a reward if they are the first to submit a report. They are eligible to receive up to 10 percent of the maximum bounty amount.
Misconfigured Google Groups Expose Sensitive Data
25.7.207 securityweek Security
Researchers at cloud security firm RedLock believe hundreds of organizations may be exposing highly sensitive information by failing to properly configure Google Groups.
Google Groups is a service that allows users to create and take part in online forums and email-based groups. When a group is configured, its creator has to set sharing options for “Outside this domain - access to groups” to either “Private” or “Public on the Internet.”
RedLock’s Cloud Security Intelligence (CSI) team noticed that many Google Groups for Business users have allowed access to their groups from the Internet, and in some cases the configuration error has resulted in the exposure of sensitive information.
Researchers have found names, email and home addresses, employee salary data, sales pipeline data, and customer passwords in the exposed groups.
“We only looked for a sample of such cases and found dozens,” RedLock told SecurityWeek. “Extending that, there are likely hundreds of companies affected by this misconfiguration.”
According to RedLock, the list of affected firms includes IBM’s The Weather Company, which operates weather.com, intellicast.com and Weather Underground; Fusion Media Group, which owns Gizmodo, The Onion, Jezebel and Lifehacker; video ad platform SpotX, which delivers ads to 600 million people worldwide every month; and cloud-based helpdesk support provider Freshworks, whose software is used by more than 100,000 companies.
Organizations using Google Groups have been advised to immediately check their settings to ensure that access is set to private in order to avoid leaking sensitive data.
“Simple misconfiguration errors – whether in SaaS applications or cloud infrastructure – can have potentially devastating effects,” said Varun Badhwar, CEO and co-founder of RedLock.
Badhwar pointed to the recent incidents involving Deep Root Analytics, WWE and Booz Allen Hamilton as examples of the impact such simple errors can have.
“This new issue that the RedLock CSI team discovered has led to the exposure of sensitive information from hundreds of companies simply through the click of a button,” Badhwar explained. “In today’s environment, it’s imperative that every organization take steps to educate employees on security best practices and leverage tools that can automate the process of securing applications, workloads and other systems. In the cloud, for example, a resource only exists for 127 minutes on average – there’s no way for IT teams alone to keep up with this rapid rate of change.”
Internet Bug Bounty Project Receives $300,000 Donation
24.7.2017 securityweek Security
The Internet Bug Bounty (IBB), a project whose goal is to make the Web safer by rewarding white hat hackers who find vulnerabilities in core Internet infrastructure and open source software, announced on Friday that it has secured a $300,000 donation.
Facebook, GitHub and the Ford Foundation, one of the world’s largest charitable organizations, have each donated $100,000 to the IBB. With their donation, GitHub and the Ford Foundation have joined existing sponsors, Facebook, Microsoft and HackerOne.
The IBB rewards researchers who find vulnerabilities in OpenSSL, Nginx, Apache httpd, Perl, PHP, Python, Ruby, Flash, Ruby on Rails, Phabricator, Django, RubyGems and other widely used Internet technologies.
Since its launch in November 2013, the IBB has awarded more than $600,000 for over 600 vulnerabilities found by bounty hunters. This includes over $150,000 awarded last year and $45,000 that hackers decided to donate to charities and nonprofit organizations, such as the Electronic Frontier Foundation (EFF), Hackers for Charity, and the Freedom of the Press Foundation.
Critical security holes such as ImageTragick, Heartbleed and Shellshock earned researchers $7,500, $15,000 and $20,000, respectively.
With the newly raised funds, the IBB plans on expanding the scope of the bug bounty program by adding a new category for flaws in popular data parsing libraries, which are considered increasingly risky. The expansion will also cover technologies that “serve as the technical foundation of a free and open Internet, such as OpenSSL.”
“At Ford Foundation we believe that a secure, free and open internet is critical in the fight against inequality,” said Michael Brennan, Ford Foundation’s technology program officer on the Internet Freedom team. “The open source infrastructure of the internet is part of a public commons that we are committed to help maintain and draw attention to. A necessary part of this maintenance is recognizing and rewarding those who uncover critical vulnerabilities in freely available code that we all rely upon.”
Symantec Tricked Into Revoking Certificates Using Fake Keys
22.7.2017 securityweek Security
Researcher Hanno Böck has tricked Symantec into revoking TLS certificates by falsely claiming that their private keys had been compromised. Comodo was also targeted, but the company did not fall for the same ruse.
Certificate authorities (CAs) are required to revoke certificates whose private keys have been compromised within 24 hours. Keys are often inadvertently exposed by certificate owners and previous research by Böck showed that while it often takes companies more than 24 hours, ultimately they do revoke compromised certificates.
Böck then decided to check if CAs ensure that an allegedly compromised private key actually belongs to a certificate before revoking it.
The researcher set up a couple of test domains and ordered free, short-term certificates for them from Comodo and Symantec’s RapidSSL. He then created fake private keys for the certificates and attempted to trick Symantec and Comodo into revoking them by providing the forged keys.
In order to increase his chances of success, Böck searched the web for private keys that were actually compromised and added them to a Pastebin post along with his forged keys. He then informed Comodo and Symantec about the “compromised” keys and asked them to revoke the certificates.
While Comodo did notice the fake keys among the ones that were actually compromised, Symantec informed him that all the certificates whose private keys were in the Pastebin post, including the fake ones apparently associated with the researcher’s test domains, had been revoked.
“No harm was done here, because the certificate was only issued for my own test domain. But I could’ve also fake private keys of other people's' certificates. Very likely Symantec would have revoked them as well, causing downtimes for those sites” Böck explained.
The researcher was also displeased with the fact that Symantec did not provide a reason for revoking the certificates, which makes it difficult for domain owners to learn from mistakes and improve their processes. Symantec insisted that the keys associated with Böck’s certificates had been compromised, even after he pointed out that the certificates had actually been revoked based on forged keys.
“Symantec did a major blunder by revoking a certificate based on completely forged evidence. There’s hardly any excuse for this and it indicates that they operate a certificate authority without a proper understanding of the cryptographic background,” Böck said.
After the researcher made his findings public, Symantec published a blog post promising to improve its processing of third-party revocation requests.
“First, a gap was identified in the public and private key matching process where keys are verified during the revocation request procedure,” Symantec said. “We performed a modulus comparison, a necessary part of this verification process, but it was incomplete as other parameters in the keys were not checked. Once we became aware of this, we immediately corrected the procedure. We are not aware of any instances where there was customer impact as a result of this process gap other than the test scenario run by the reporting researcher.”
“Secondly, we are reviewing how we communicate with customers during the 3rd party revocation request process to be more consistent and transparent with certificate owners,” it added.
Google and Mozilla are both displeased with Symantec, its subsidiaries and its partners regarding the improper issuance of certificates. There has been a lot of debate over the past few months about how Symantec should be penalized, with the security firm making another counterproposal this week.
Tor Launches Bug Bounty Program — Get Paid for Hacking!
21.7.2017 thehackernews Security
With the growing number of cyber attacks and breaches, a significant number of companies and organisations have started Bug Bounty programs for encouraging hackers, bug hunters and researchers to find and responsibly report bugs in their services and get rewarded.
Following major companies and organisations, the non-profit group behind Tor Project – the largest online anonymity network that allows people to hide their real identity online – has finally launched a "Bug Bounty Program."
The Tor Project announced on Thursday that it joined hands with HackerOne to start a public bug bounty program to encourage hackers and security researchers to find and privately report vulnerabilities that could compromise the anonymity network.
HackerOne is a bug bounty startup that operates bug bounty programs for companies including Yahoo, Twitter, Slack, Dropbox, Uber, General Motors – and even the United States Department of Defense for Hack the Pentagon initiative.
Bug bounty programs are cash rewards gave by companies or organisations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose them.
The Tor Project announced its intention to launch a public bug bounty program in late December 2015 during a talk by the Tor Project at Chaos Communication Congress (CCC) held in Hamburg, Germany. However, it launched the invite-only bounty program last year.
The highest payout for the flaws has been kept $4,000 — bug hunters can earn between $2,000 and $4,000 for High severity vulnerabilities, between $500 and $2,000 for Medium severity vulnerabilities, and a minimum of $100 for Low severity bugs.
Moreover, less severe issues will be rewarded with a t-shirt, stickers and a mention in Tor's hall of fame.
"Tor users around the globe, including human rights defenders, activists, lawyers, and researchers, rely on the safety and security of our software to be anonymous online," Tor browser developer Georg Koppen said in a blog post. "Help us protect them and keep them safe from surveillance, tracking, and attacks."
The Tor Project is a non-profit organisation behind the Tor anonymizing network that allows any online user to browse the Internet without the fear of being tracked.
The Project first announced its plan to launch the bug bounty program weeks after it accused the FBI of paying the researchers of Carnegie Mellon University (CMU) at least $1 Million to help them Unmask Tor users and reveal their IP addresses, though FBI denies the claims.
Tor Offers $4,000 Per Flaw in Public Bug Bounty Program
20.7.2017 securityweek Security
Tor launches bug bounty program
The Tor Project announced on Thursday the launch of a public bug bounty program. Researchers can earn thousands of dollars if they find serious vulnerabilities in the anonymity network.
The Tor Project first announced its intention to launch a bug bounty program in late December 2015. A private program was launched in January 2016 and bounty hunters managed to find three denial-of-service (DoS) flaws, including two out-of-bounds (OOB) read and one infinite loop issues, and four memory corruption vulnerabilities that have been described as “edge-case.”
Now, with support from the Open Technology Fund, Tor has launched a public bug bounty program on the HackerOne platform.
The organization is looking for vulnerabilities in the Tor network daemon and Tor Browser, including local privilege escalation, remote code execution, unauthorized access of user data, and attack methods that can be used to obtain crypto data on relays or clients.
Researchers can earn between $2,000 and $4,000 for high severity bugs. Medium severity vulnerabilities are worth between $500 and $2,000, while low severity issues will be rewarded with a minimum of $100. Even less severe problems will be rewarded with a t-shirt, stickers and a mention in Tor’s hall of fame. On its bug bounty page, the Tor Project provides examples for each category of vulnerabilities, including with CVE references.
Vulnerabilities affecting third-party libraries used by Tor can also earn between $500 and $2,000, but libraries covered by other bug bounty programs, such as OpenSSL, have been excluded.
“Tor users around the globe, including human rights defenders, activists, lawyers, and researchers, rely on the safety and security of our software to be anonymous online. Help us protect them and keep them safe from surveillance, tracking, and attacks,” said Georg Koppen, a longtime Tor browser developer.
Tor first announced its intention to launch a bug bounty program after a team of researchers from Carnegie Mellon University helped the FBI unmask users of the anonymity network by creating more than a hundred new relays on the network. The Tor Project claimed at the time that the U.S. government had paid the university at least $1 million to carry out the attack.
Firms Unite to Hunt Threats From Network to Endpoint
20.7.2017 securityweek Security
Network and Endpoint Threat Hunters Corvil and Endgame Combine to Provide Pan-Infrastructure Detection and Response
Two threat hunting and detection companies have integrated their products to give greater visibility and protection across the entire infrastructure. Corvil, with expertise in real-time traffic analysis, and Endgame, with expertise in endpoint protection, can now share threat intelligence between the two platforms with a single click.
"The challenge today between endpoint security and network security," explains David Murray, Corvil chief business development officer, "is that they often tend to exist each in their own domain, when one of infosecurity's multipliers is the ability to integrate and be able to track a threat across the network and into the endpoint."
Organizations may have dozens of different security tools and technologies that do not adequately talk to each other. "The result," says Murray, "is that security analysts remain horribly overburdened." Training existing staff to a higher skill-set, or buying in new experts is often not an option. "It is important," he continued, to take the intelligence and analytics that we provide and seamlessly integrate it with other security technologies. We've already done this with Cisco's Tetration. Today we're announcing two further integrations, one with Endgame and the other with Palo Alto Networks, that enable comprehensive protection from the perimeter through the network and inclusive of the endpoint."
Endgame's endpoint threat detection platform can see endpoint threats at the kernel level and in memory, but can lose visibility into the path of anomalous communication that leaves the endpoint. "Similarly," adds Murray, "anything that tries to compromise an individual host or server endpoint of any kind has to travel over the network in order to get there. By sharing intelligence back and forth between our two platforms, we're able to provide a stronger fabric for protection."
Both Corvil and Endgame share similar philosophies and have a history of protecting some of the most sensitive and attacked infrastructures: Corvil in fintech, and Endgame in defense and military. Both believe organizations cannot wait to be breached but need to take an aggressive threat-hunting approach to network defense.
"The techniques attackers use today are increasingly aggressive, complex, and difficult to detect," comments Nate Fick, Endgame's CEO. "Security solutions that only identify customer breaches after damage and loss are no longer acceptable. Corvil shares our philosophy of direct, aggressive protection. Extending the visibility, we can offer customers across the network and endpoint represents the most comprehensive solution available on the market."
Both also share the view that their role is to make hunting and protection as easy as possible for the analyst, reducing the customer's reliance on expensive expert analysts. Each has their own virtual assistant. Corvil's Cara automatically generates daily risk reports, while Endgame's Artemis is a natural-language Siri-like assistant that will answer questions like, "What is suspicious on my network today?"
"One of the things we're planning to release in the second phase of integration," Murray told SecurityWeek, "is to extend the capabilities of our respective virtual experts to give both platforms the ability to stretch much further across an attack lifecycle, and be able to triangulate information to make a more active and more precise response."
Speed in detecting a threat loses its value if there is a subsequent delay in responding to that threat. Both platforms have their own built-in response capabilities. Corvil also integrates with Palo Alto Networks (PAN) firewalls. Where PAN micro-segmentation is employed, Corvil can initiate a firewall road block to PAN to isolate the risky host. Similarly, Endgame, has its own more surgical disruptions it can introduce within the host or endpoint.
"Let's say Corvil detects a risky host," explains Murray. "With one click the analyst can see the result in Endgame, and they can trigger an action right there. Similarly, if someone is working in Endgame and has questions about the downstream communication of a suspicious host, the analyst can bring up information about the communication in Endgame and then click to Corvil to further investigate it. Corvil could initiate a firewall road block in PAN directly from Corvil. Corvil can determine the source of the bad behavior and block it so that it can no longer communicate through the firewall. Alternatively, there could be a more surgical disruption within the source through Endgame."
"By combining Endgame's heritage in protecting against nation-state adversaries with Corvil's longstanding leadership in safeguarding algorithmic businesses," says Murray, "we, uniquely, provide critical capabilities that our customers across industries require. Today's partnership with Endgame enables us to cover a wider spectrum of an organization's infrastructure and empower today's overburdened security teams."
The Corvil/Endgame integration is available from today to early adopter customers
Google Warns Users of Potentially Risky Web Apps
19.7.2017 securityweek Security
Google is taking another step to better protect users from malicious third-party web applications: it is now warning users of newly created web apps and Apps Scripts that are pending verification.
The move follows a series of similar protective measures the Internet giant announced earlier this year, after many of its users were hit by a phishing attack where a rogue app was found impersonating Google Docs. To prevent similar incidents, the company tightened OAuth rules and also started scrutinizing new web apps that request user data.
The new warning screen will be accompanied by changes expected to improve the developer experience, the company says, adding that the verification process and the new warnings will expand to existing apps in the coming months.
The new “unverified app” screen that users will see when accessing newly created web applications and Apps Scripts that require verification will replace the “error” page that has been served to developers and users over the past several months. The screen will appear before users are taken to the permissions consent screen, thus only informing users of the app not being yet verified.
Through these new notices, users will be automatically informed if they may be at risk, thus helping them make more informed decisions to keep their information safe. The testing and developing of applications should also be simplified.
“This will help reduce the risk of user data being phished by bad actors. This new notice will also help developers test their apps more easily,” Naveen Agarwal, Identity team, and Wesley Chun, Developer Advocate, G Suite, note in a blog post.
Users have the option to dismiss the alert, which allows developers to test applications without going through the OAuth client verification process first. Google has published a series of steps in a help center article to provide information on how to begin the verification process to remove the interstitial and prepare their app for launch.
The same protections are being applied to Apps Script beginning this week, meaning that all new Apps Scripts requesting OAuth access to data from users in other domains may also get the "unverified app" alert. Additional information was published in a verification documentation page.
“Apps Script is proactively protecting users from abusive apps in other ways as well. Users will see new cautionary language reminding them to ‘consider whether you trust’ an application before granting OAuth access, as well as a banner identifying web pages and forms created by other users,” Agarwal and Chun say.
Next, Google is planning an expansion of the verification process to existing apps as well, meaning that developers of some current apps may have to go through the verification flow. To ensure no issue will hinder the transition, developers should make sure their contact information is up-to-date.
“In the Google Cloud Console, developers should ensure that the appropriate and monitored accounts are granted either the project owner or billing account admin IAM role. In the API manager, developers should ensure that their OAuth consent screen configuration is accurate and up-to-date,” Google says.
The company has published help center articles to provide detailed information on granting IAM roles and on configuring the consent screen.
Court Upholds Gag Orders in National Security Letters
19.7.2017 securityweek Security
The Ninth U.S. Circuit Court of Appeals in San Francisco confirmed a lower court decision Monday that gag orders included in FBI National Security Letters (NSLs) do not violate the First Amendment of the U.S. Constitution's free speech protections.
It has been a long journey to this decision (PDF) centered around five NSLs; three received by CREDO in 2011 and 2013, and two received by Cloudflare in 2012. The two organizations petitioned the district court to have both the information requests and the non-disclosure requirements of the NSLs set aside.
The district court decided that the 2006 NSL Law was unconstitutional and enjoined the government from issuing new requests and enforcing the gag (but stayed the decision pending a government appeal). It did not set aside the existing five NSLs. CREDO and Cloudflare, and the government, appealed the decision.
With the appeals pending, the government enacted the USA FREEDOM Act, which became effective June 2, 2015. Given the new law, the appeals court sent the matter back to the district court. This time, the lower court decided that the NSL law, as amended, is constitutional, and that the FBI had shown sufficient cause. It allowed the government's cross-petition to enforce the NSLs and gags, barring the two 2013 CREDO NSLs.
CREDO and Cloudflare appealed the decision to uphold three of the NSLs, and the government appealed the decision to set aside the two 2013 CREDO NSLs. Meanwhile, the FBI closed its investigations pertaining to the three remaining NSLs, and voluntarily and partly lifted the gagging orders.
But CREDO and Cloudflare persisted, arguing that the whole concept of gagging NSLs contravenes the constitutional right to free speech.
It is this final petition that was rejected by the appeals court on Monday. Ironically, it is the FREEDOM Act that upholds the decision. The FREEDOM Act enforces greater administrative care over the delivery of NSLs and gag orders -- but if that care is taken, the requests become legal. That, at least, is the decision of the Ninth.
"We conclude," announced the three judges, "that § 2709(c)'s nondisclosure requirement imposes a content-based restriction that is subject to, and withstands, strict scrutiny. We further hold that, assuming the nondisclosure requirement is the type of prior restraint for which the Freedman procedural safeguards are required, the NSL law provides those safeguards. The nondisclosure requirement in the NSL law therefore does not run afoul of the First Amendment.
"It is not yet known whether CREDO and Cloudflare will continue the fight and appeal to the Supreme Court. Electronic Frontier Foundation (EFF) staff attorney Andrew Crocker tweeted, "Disappointing 9th Cir ruling in EFF's national security letter case on behalf of @CREDOMobile @Cloudflare. More soon." He added, "Especially disappointing is the court's failure to address permanent NSL gags, which always violate the First Amendment."
In a statement emailed to SecurityWeek, CREDO CEO Ray Morris said, "We are disappointed in the Ninth Circuit's decision and are considering our options for next steps. At CREDO, we know what an uphill battle challenging these gag orders can be and feel that the court missed an opportunity to protect the First Amendment rights of companies that want to speak out in the future."
Last week, EFF published its 2017 report, Who Has Your Back? It explains the issues behind NSLs. "NSLs are akin to subpoenas requiring service providers -- including technology companies, phone companies, and ISPs -- to hand over data to the FBI about users' private communications and Internet activity. These orders are almost always accompanied by gag orders preventing the recipients from ever revealing the letter's existence and which have contributed to widespread abuse of this investigatory tool."
Although Cloudflare was not included in the EFF study, CREDO is one of just 9 companies out of 26 awarded five stars for its attitudes and attempts to protect user privacy.
"Cloudflare's approach to law enforcement requests is that we are supportive of their work but believe that any requests we receive must adhere to the due process of law and be subject to judicial oversight," Doug Kramer, General Counsel at Cloudflare told SecurityWeek. "It is not Cloudflare's intent to make their job any harder, or easier. In 2013, we challenged an FBI request for customer information on a confidential basis through an NSL, which was not an easy decision, because we felt it violated that principle. Although decisions by a federal court and a new statute since that time have improved the NSL process, we think there is additional work to be done and are disappointed the Ninth Circuit ruled the current practice sufficient."
*Updated with comment from Cloudflare
Rapid7 Acquires Security Orchestration and Automation Firm Komand
19.7.2017 securityweek Security
Boston-based IT security and operations software maker Rapid7 (NASDAQ: RPD) on Tuesday announced that it has acquired security orchestration and automation firm Komand.
Founded in late 2015 by Jen Andre, who previously co-founded Threat Stack, Komand’s platform was designed to help security and IT teams automate repetitive tasks, which Rapid7 says will “help its customers reduce time to resolution, maximize resources, and overcome ecosystem complexity.”
Specifically, Rapid7 explained that Komand’s technology will expand Rapid7’s Insight platform’s ability to “empower lean security and IT teams to meaningfully increase productivity across their entire operation and reduce the time it takes to respond to an incident.”
Customers will now have the ability to automatically identify risks, respond to incidents, and address issues significantly faster and with less human intervention, Rapid7 says.
“The need for well-designed security and IT automation solutions is acute; resources are scarce, environments are becoming more complex, all while threats are increasing,” said Corey Thomas, president and CEO of Rapid7. “Security and IT solutions must evolve through context-driven automation, allowing cybersecurity and IT professionals to focus on more strategic activities.”
“We’ve been impressed by the technology developed by the Komand team and believe that together, we’ll be able to build solutions that make security and IT teams significantly more productive,” said Lee Weiner, chief product officer at Rapid7. “The complexity of today’s security and IT ecosystems have put security and IT operations teams at a significant disadvantage when they need to respond quickly. By developing contextualized automation technology, we’ll be able to cut back the time it takes to respond to an incident—when minutes can mean the difference between a minor issue and significant compromise or loss.”
Rapid7 cites use cases including automated risk remediation and patching, malware investigation and containment, and chat ops for responding to routine inquiries.
The terms of the acquisition were not disclosed, though Rapid7 said the purchase is not expected to have a material financial impact to its calculated billings, revenue, and non-GAAP earnings (loss) per share for calendar year 2017, as guided on May 9, 2017.
Both Rapid7 and Komand were Boston-based companies with offices just down the street from each other.
Komand announced in Jan. 2017 that it had closed a $1.25 million seed round of funding.
As part of the acquisition, 12 Komand employees have become employees of Rapid7.
Mozilla Conducts Security Audit of Firefox Accounts
19.7.2017 securityweek Security
Mozilla has asked Germany-based security firm Cure53 to conduct an audit of the Firefox Accounts system and researchers identified a total of 15 issues, including vulnerabilities rated critical and high severity.
Firefox Accounts, also known as FxA, is the system that allows Firefox users to access hosted services provided by Mozilla. Since the component represents Firefox’s central authentication service and it’s likely to be targeted by malicious actors, Mozilla has decided to have it tested.
Tests conducted by Cure53 researchers over a 30-day period in September and October 2016 led to the discovery of 15 issues, which includes six vulnerabilities and nine general weaknesses.
The most serious of the flaws, rated critical, could have allowed hackers to launch cross-site scripting (XSS) and scriptless attacks in an effort to phish users or to steal sensitive information. However, Mozilla pointed out that exploitation of the flaw required registering a relier, a process that is not open to the public.
One of the high severity vulnerabilities found by Cure53 could have allowed arbitrary command execution if the attacker could determine the location for the execution of an application.
The list of high severity flaws also includes another XSS bug and an encryption weakness that may be exploited to increase the efficiency of brute-force attacks. The other problems identified by researchers have been classified as having low or medium severity.
Most of the vulnerabilities have been patched and Mozilla claimed that none of them had been exploited for malicious purposes and none of them put user data at risk.
“Given the amount of the audited code and the complexity of the project, this number of findings classifies as low and translates to an overall positive result of the investigation,” Cure53 said in its report. “Despite the fact that the tests were as thorough as possible on the codebase placed in scope, only a single ‘Critical’ finding was ultimately spotted. Even though this issue was discovered early on in the test, no major design issues were identified. Ultimately, the platform was perceived as rather robust and secured against a wide range of different attacks.”
In the past months, Mozilla commissioned audits for several pieces of software through its Secure Open Source (SOS) program, including for cURL, Dovecot and the Network Time Protocol (NTP).
Risk Intelligence Firm Flashpoint Raises $28 Million
15.7.2017 securityweek Security
Flashpoint, a New York, NY-based threat intelligence and research company that focuses on what it calls “Business Risk Intelligence” (BRI) gleaned from combing the Deep & Dark Web, has raised $28 million in Series C funding.
The company goes beyond what many traditional cyber threat intelligence providers collect, which typically includes technical indicators such as IP addresses, domains, and signatures. Flashpoint collects information and monitors conversations in the underground, including cybercriminal groups and terrorist organizations such as the Islamic State (Daesh) and its supporters.
According to the company, the additional funding will help support adoption of its BRI offerings and support the recruitment of additional threat intelligence analysts.
As Flashpoint explains, the company provides customers with “visibility into real threats with the potential to harm them and the context to help them understand how these threats could impact their business.”
"Traditional cyber threat intelligence, which has been largely focused on indicators of compromise, is insufficient in supporting the risk decision-making process, as it too often limits its focus on events in cyberspace," warned Flashpoint in its Business Risk Intelligence - Decision Report, published in January 2017. "Not all actors constrain their operations solely to the cyber realm; top tier nation-states like the U.S. and Russia use the full-spectrum of their capabilities to achieve their objectives. A threat assessment of Chinese or Russian cyber operations without the context of the national objectives they are supporting fails to provide risk decision-makers with an accurate portrayal of the threat landscape upon which to make business decisions."
Flashpoint says its customer base includes industries such as finance, retail, insurance, healthcare, law, media, energy, technology, telecommunications, defense, aviation, entertainment, hospitality, consumer goods, and manufacturing. The company counts several Fortune 500 and government organizations as customers.
Led by new investor Georgian Partners, the Series C round also included investors Greycroft Partners, TechOperators, Leaders Fund, Jump Capital, Bloomberg Beta, and Cisco Investments also participated in the round. Robert Herjavec, founder and CEO of security firm Herjavec Group and investor on ABC's hit show, Shark Tank, was an early investor in the company, SecurityWeek has confirmed.
The company previously raised $10 million in Series B funding in July 2016 and announced its expansion from cyber threat intelligence into business risk intelligence.
Josh Lefkowitz, CEO and co-founder of Flashpoint, is a SecurityWeek columnist.
Atlassian Launches Public Bug Bounty Program
15.7.2017 securityweek Security
Team collaboration and productivity software provider Atlassian announced this week the launch of a Bugcrowd-based public bug bounty program with rewards of up to $3,000 per vulnerability.
Atlassian has been running a private bug bounty program and the company has now decided to take advantage of all the 60,000 researchers who have signed up on the Bugcrowd platform to help find security holes in its products.
The initiative covers Confluence and JIRA products, including Android and iOS mobile apps, and *.atlassian.io domains hosting services that interact with the company’s products. Bug bounty hunters will have to create their own Atlassian cloud instances using their Bugcrowd email address.Atlassian launches bug bounty program
Other products, the Atlassian websites, customer cloud instances, billing systems, internal or development services, and third-party add-ons are out of scope.
The company is interested in cross-instance data leakage and access, remote code execution, server-side request forgery (SSRF), reflected and stored cross-site scripting (XSS), cross-site request forgery (CSRF), SQL injection, XML external entity (XXE), access control, and directory traversal flaws.
As for rewards, most of the targeted products qualify for “tier 1” rewards. Critical vulnerabilities in these products can earn researchers up to $3,000, while the least serious flaws are worth $100. Confluence Team Calendars is the only “tier 2” product and the maximum reward is $1,500 per flaw.
Since the launch of its bug bounty program, Atlassian has paid out rewards for 39 vulnerabilities, with the average payout at roughly $500.
“The economics of bug bounties are too overwhelming to ignore,” said Daniel Grzelak, head of security at Atlassian. “Our traditional application security practice produces great results early in the lifecycle and deep in our services, but the breadth and depth of post-implementation assurance provided by the crowd really completes the secure development lifecycle. Multiplying the specialization of a single bounty hunter by the size of the crowd creates a capability that just can’t be replicated by individual organizations.”
Edgewise Networks Emerges From Stealth to Bring Zero Trust Networking to the Data Center
12.7.2017 securityweek Security
Burlington, MA-based Edgewise Networks has emerged from stealth mode with a product designed to implement a zero-trust approach to network security.
Founded by Peter Smith and Harry Sverdlove in Spring 2016; backed by venture capital firms .406 Ventures, Accomplice, and Pillar; and supported by Patrick Morley (CEO of Carbon Black), Omar Hussain (CEO of Imprivata), Brian Ahern (CEO of Threat Stack), and Bob Brennan (CEO of Veracode), Edgewise seeks to augment perimeter firewalls and improve on microsegmentation.
Edgewise believes that there is a fundamental flaw in defense-by-firewall. While firewalls can detect and block known bad addresses, they cannot detect bad use of good addresses. This means that any compromise of a 'good' address can allow an attacker straight through the firewall, by policy, and into an attack position.
"There are two commonalities in almost all publicized attacks," comments co-founder Peter Smith. "Firstly, attackers rarely, if ever, enter a network directly on their ultimate target: they gain a foothold, surveil the attack surface and then move laterally to where they can conduct the final attack. Secondly, they invariably accomplish this by introducing malicious code at some stage -- for C&C, for the next stage of the attack, and so on."
Preventing the lateral movement is where firewalls fail. They can see where traffic is coming from, and they can see where it is going; but they cannot see who is in control of the software being used, or the server from which it comes. Consider NotPetya, he said. "The worm spread more or less unabated because the firewalls could not detect any maliciousness in the traffic."
Microsegmentation is an improvement on perimeter firewalls alone; but is still not adequate. "Essentially, it forces all traffic through the firewall. Beside the complexity of installation and management, the firewalls still cannot prevent the attacks because they can still only protect what they can see; and despite the fact that they can see all of the network traffic, they can only look at the traffic to identify malicious behavior -- they cannot look outside of the traffic, cannot look at the hosts to see what software is actually making those communications."
Edgewise sees its product as being more effective than complex microsegmentation, and even easier to use than relatively simple next-gen firewalls.
Firewalls, he continued, can only attribute traffic to the address that sent it and the address that receives it. "They cannot see the actual software that created the connection; or the user controlling the application; or the host on which it is running. There is consequently no guarantee that the application you trust is controlled by the user you think should be controlling it. Most new technology just looks more closely at network packets -- but however much you stare at the packet, it will not tell you the identity of the software producing the communication or the user controlling it on either side of the connection."
Two primary aspects of Edgewise illustrate how it operates. Firstly, it ensures that only trusted applications communicate by mutually validating the identity of the underlying software, users and hosts before allowing the connection. "This approach," says the company, "extends the zero-trust networking model that calls for validating application communications and not trusting addresses to secure internal networks."
Secondly, it uses machine-learning to model application communication patterns and generate optimal protection policies automatically. This serves several purposes. It can be used to generate maximum protection from minimum policies, and to produce a policy map that can be used as a 'what-if' model even by non-experts. New policies can be tested on the map to see exactly what effect they will have on the overall network attack surface.
The result, said Smith, "is that we get rid of all of the unnecessary network attack surface that firewalls cannot see. We stop anything that is not trusted and we build the policies for the customer automatically. We have a machine-learning system that analyzes the communication patterns of the software we protect, and then creates the policies to protect the systems. No user intervention is necessary to build the policies -- only to apply them." Which, he added, can be a single click.
"The user sees a map of how the software communicates," he continued. "He can select the software he particularly wishes to protect, and one click will protect it. Only trustworthy software will be allowed to communicate. We also measure the risk associated with the environment -- the attack surface. We measure how much it is, and how much it would shrink if the customer applies our protection."
Edgewise calls this 'Trusted Application Networking'. "It's what Forrester calls zero-trust networking, and what Gartner calls CARTA," said Smith. "Essentially they boil down to the same thing: assert the identity of communicating software and the entities communicating; do not just blindly trust addresses."
PSD2 and Open Banking Bring Problems and Opportunities for Global Banks
12.7.2017 securityweek Security
Global Banks Should Not Ignore Europe's Payment Services Directive 2 (PSD2)
Payment Services Directive 2 (PSD2) is a new EU banking/finance regulation coming into force in January 2018. It is designed to shake up the finance sector -- perhaps even designed to weaken the overall strength of the banks following the 2008 crash. While being European in origin, American and other global banks should not -- and perhaps cannot -- ignore it.
The banks are considered to be too powerful and monolithic with sole and complete ownership of their customers financial data. The European bureaucrats want to introduce some competition. Their chosen route is to force the banks to provide APIs that will allow third-party apps to access customer data and provide new services not currently offered by the banks. The bureaucrats then believe third-parties will re-invigorate the payments and finance markets for end users.
There are enormous difficulties for the banks -- for while they are required to give third-party access to customer data, they will remain liable for the security of that data under the General Data Protection Regulation (GDPR).
Consider if this is done via a social media organization. That organization will build an app that provides access to, and uses, its customers' financial data. The banks can authenticate the social media organization; but the social media app authenticates the user. It is possible, then, that access to customer financial data will be controlled only by social media logon; and that will almost certainly be less secure than the multi-factor and behavioral security measures that many banks currently use.
But where there are problems, there are also opportunities. The banks that provide effective and efficient APIs could attract new customers from banks that provide poor APIs, all coming from the quality of the third-party apps that use those APIs. As Steve Kirsch, CEO at Token, told SecurityWeek, "In general, when you see a new unstoppable trend, the biggest winners are generally the earliest adopters."
There are two reasons for American banks (and other global banks) to conform to this new European regulation. Firstly, American banks with a European operation will be required to do so. Secondly, European banks with an American operation will bring their APIs with them. Since the customer will be the biggest winner in this new world of open banking, American banks not offering a similar service will be at a disadvantage. "American banks should be rushing to implement open banking on their own," says Kirsch. "It is a major step forward for banking."
The GSM Association (GSMA: the trade body that represents mobile operators with more than 1000 full and associate members) agrees that US banks should get involved. "It should not take a law for American banks to take up PSD2 principles," Marta Ienco, head of government and regulatory affairs at GSMA Personal Data, told SecurityWeek. "Instilling consumer confidence that money is safe, with fewer clunky security measures, will mean more customers want to use their service and trust the company."
GSMA believes that mobile banking is inherently secure. "Operators can leverage user data such as location, account and usage history, which in turn can be used to help verify transactions. Moreover," added Ienco, "this rich data can also help minimize instances of account takeover fraud. So, if someone tries to change the mobile number associated with a bank account, the operator can determine if the original mobile number is still in use, and use it to alert the customer to any suspicious changes to their personal details."
Like many regulations, PSD2 describes what must be done, but not how it can be achieved. This leads to difficulties for both the third-party app developers, and for the banks themselves.
For the developers, it does mandate 2FA; but that is about all. While there are some de facto API standards, such as REST and OAUTH, there are is no standard for the PSD2 banking APIs. "The APIs for different banks could all be completely different in how they work, how their authentication is achieved, and so on," explains Andrew Whaley, VP of engineering at Arxan Technologies. "The practical problems for an organization trying to consume these APIs (such as a social media organization, or whatever) means that the third-party potentially has to build a different adapter for every different bank."
For the banks, one difficulty will be in maintaining their own strict authentication requirements. "PSD2 is clear that the banks are still responsible for the customer data ownership, and the safety of the data," explains Whaley. "So, if the third party gets hold of the data, and its access controls are not particularly strong and someone else gets hold of the data, accidentally or deliberately, the bank is still liable for the third party's failure. The only way the banks can counter this is to bring the technology and countermeasures they already have in their own apps to bear in this space and force their own authentication standards through the API so that they have direct communication with the customer before the third-party can get access to the data."
GSMA agrees that the banks are caught between PSD2 and GDPR. "If banks aren't completely certain of the provenance of a request, and decline a request from a service provider, they could be in violation of PSD2. But if a data breach then takes place, they could also become liable under the rules of GDPR, also coming into effect next year."
PSD2 is a done deal and will come into effect in January 2018. European banks cannot avoid it, and American banks with a European presence (that is, European customers) will need to comply for those European customers. However, the global nature of big bank operations means that PSD2 APIs will inevitably come into play in the US. When that happens, US banks unable to take part in the new world of open banking will be at a distinct disadvantage to those that can.
Google will ban WoSign and StartCom certificates from Chrome 61
11.7.2017 securityaffairs Security
Google is going to completely ban digital certificates issued by the Chinese CA WoSign, and its subsidiary StartCom starting with Chrome 61.
Recently Google warned website owners that it will completely ban digital certificates issued by the Chinese certificate authority WoSign and its subsidiary StartCom. The Tech giant will no longer trust the WoSign certificates starting with Chrome 61.
In September 2016, Mozilla announced that it was planning to ban the Chinese certificate authority WoSign due to a number of violations, including backdating SHA -1 certificates in order to subvert deprecating certs from being trusted.
According to a report published by Mozilla, WoSign failed to report its acquisition of SmartCom and it was also accused of mis-issuing digital certificates for GitHub, allowing arbitrary domain names to be securely signed without ever performing any type of validation.
Mozilla, Apple and Google took the final decision of revoking trust in certificates from WoSign and StartCom due to more than a dozen incidents and issues since January 2015.
In January 2017 Google released Chrome 56 which no longer accepted certificates issued by WoSign or StartCom after October 21, 2016.
Initially, Google has been restricting trust to popular hostnames based on the Alexa Top 1 Million list in order to avoid problems to website owners.

Starting with Chrome 61 it will no longer trust the certificates issued by the Chinese CA, even for the above Alexa Top 1 Million websites.
“As previously announced, Chrome has been in the process of removing trust from certificates issued by the CA WoSign and its subsidiary StartCom, as a result of several incidents not in keeping with the high standards expected of CAs.” states Devon O’Brien of the Chrome Security Team.
“We started the phase out in Chrome 56 by only trusting certificates issued prior to October 21st 2016, and subsequently restricted trust to a set of whitelisted hostnames based on the Alexa Top 1M. We have been reducing the size of the whitelist over the course of several Chrome releases.”
Chrome 61 will reach the Beta channel in late July 20, and the Stable channel in mid-September.
“Beginning with Chrome 61, the whitelist will be removed, resulting in full distrust of the existing WoSign and StartCom root certificates and all certificates they have issued.” continues Devon O’Brien.
Google has not specified if its decision to ban WoSign and StartCom certificates is temporary or permanent. Apple and Mozilla adopted a different approach, both decided to ban the companies for at least one year.
The Chinese CA certificate authority took serious action in hopes of obtaining forgiveness from web browser vendors, it changed leadership and announced the complete separation of WoSign from StartCom.
Google to Completely Ban WoSign, StartCom Certificates in Chrome 61
10.7.2017 securityweek Security
Google last week warned website owners that digital certificates from Chinese certificate authority WoSign and its subsidiary StartCom will no longer be trusted starting with Chrome 61.
Mozilla, Apple and Google last year decided to revoke trust in certificates from WoSign and StartCom as a result of more than a dozen incidents and issues brought to the attention of the web browser community since January 2015.
Problems include backdating certificates to bypass restrictions, issuing certificates without authorization, and misleading browser vendors about WoSign's acquisition of StartCom and their relationship.
Google started taking action against the firms in late January 2017, with the release of Chrome 56, which no longer accepted certificates issued by WoSign or StartCom after October 21, 2016.
In order to minimize impact on website owners, Google has been restricting trust to popular hostnames based on the Alexa Top 1 Million list. This whitelist has been gradually reduced and starting with Chrome 61 it will be removed completely. Chrome 61 will reach the Developer channel in the coming weeks, the Beta channel in late July 20, and the Stable channel in mid-September.
“Sites still using StartCom or WoSign-issued certificates should consider replacing these certificates as a matter of urgency to minimize disruption for Chrome users,” warned Devon O’Brien of the Chrome Security Team.
Apple and Mozilla have decided to ban WoSign and StartCom for at least one year, but Google has not specified for how long it plans on distrusting certificates from these companies.
The certificate authorities had several meetings with browser vendors, changed leadership and promised to completely separate WoSign from StartCom, but they did not convince Apple, Google and Mozilla. Apple was the first to announce plans to revoke trust in their certificates, followed by Mozilla, which justified its decision by arguing that the firms were deceptive.


















