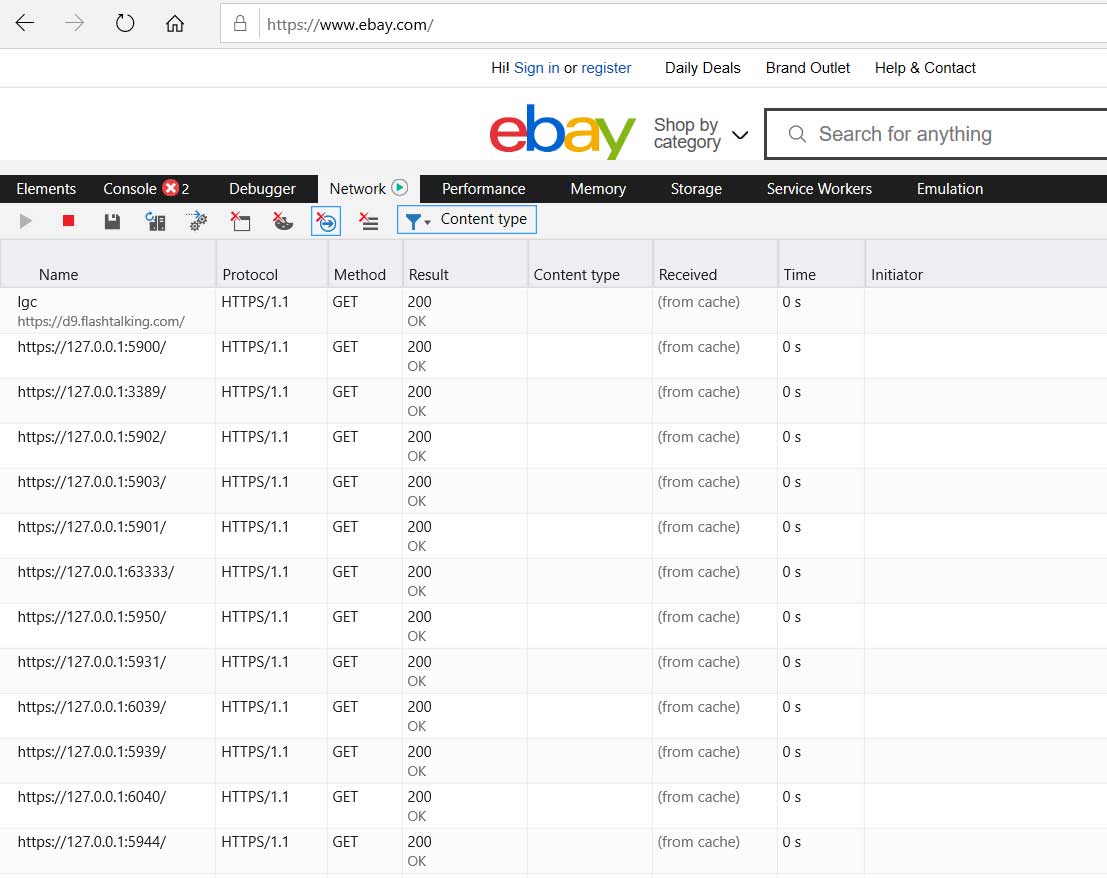
eBay.com script performing a port scan
This scan is being conducted by a check.js script [archived] on eBay.com that attempts to connect to the following ports:
Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
eBay port scans visitors' computers for remote access programs
25.5.2020 Bleepingcomputer Security
When visiting the eBay.com site, a script will run that performs a local port scan of your computer to detect remote support and remote access applications.
Many of these ports are related to remote access/remote support tools such as the Windows Remote Desktop, VNC, TeamViewer, Ammy Admin, and more.
After learning about this, BleepingComputer conducted a test and can confirm that eBay.com is indeed performing a local port scan of 14 different ports when visiting the site.

eBay.com script performing a port scan
This scan is being conducted by a check.js script [archived] on eBay.com that attempts to connect to the following ports:
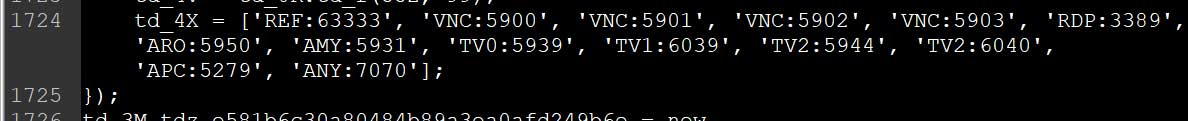
Ports being scanned
The fourteen different ports that are scanned and their associated programs and eBay reference string is listed below.
Program Ebay Name Port
Unknown REF 63333
VNC VNC 5900
VNC VNC 5901
VNC VNC 5902
VNC VNC 5903
Remote Desktop Protocol RDP 3389
Aeroadmin ARO 5950
Ammyy Admin AMY 5931
TeamViewer TV0 5939
TeamViewer TV1 6039
TeamViewer TV2 5944
TeamViewer TV2 6040
Anyplace Control APC 5279
AnyDesk ANY 7070
BleepingComputer has not been able to identify the targeted program on port 63333. If you recognize it, please let us know.
The script performs these scans using WebSockets to connect to 127.0.0.1, which is the local computer, on the specified port.
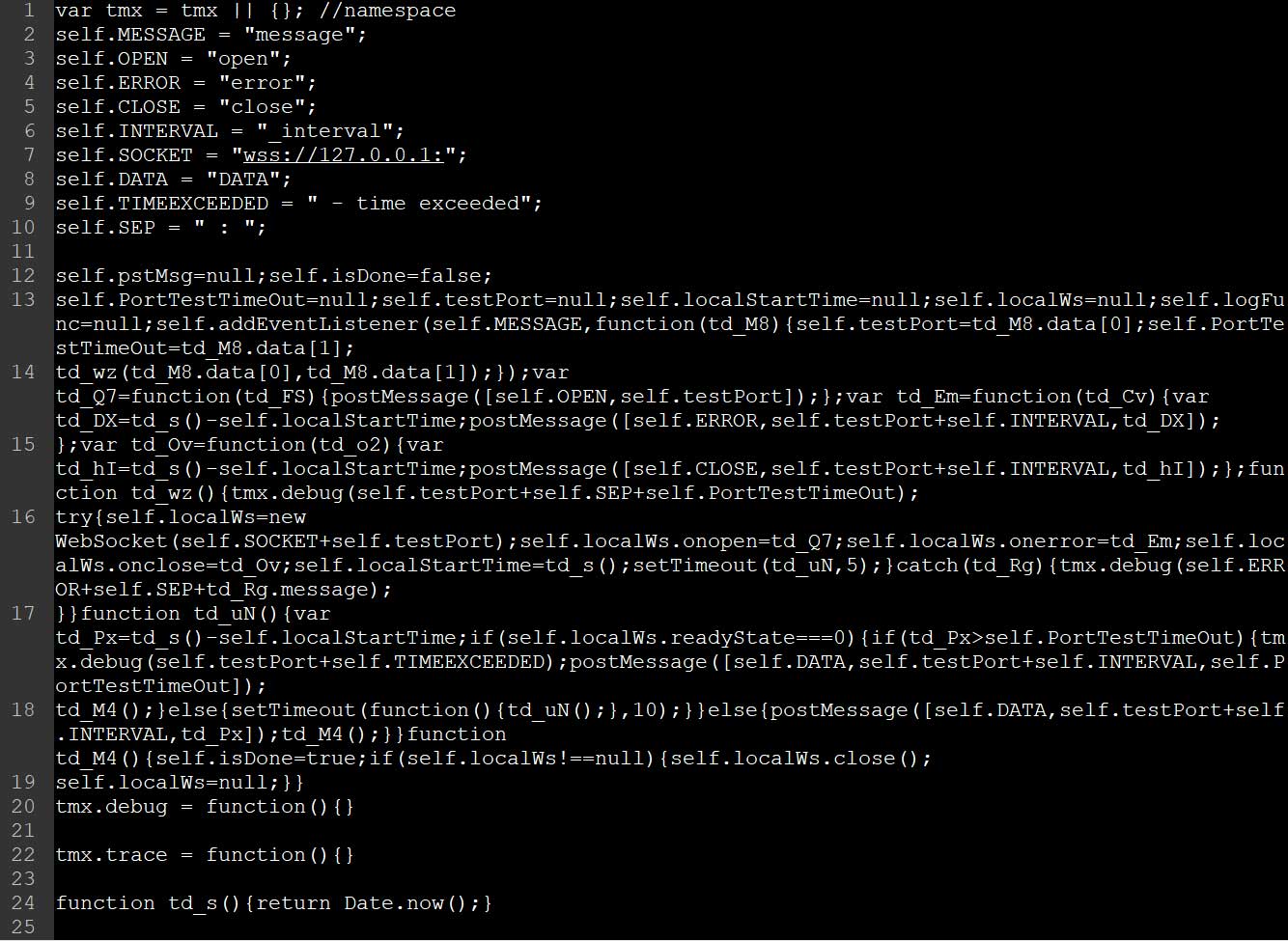
Script to use websockets to perform local port scans
According to Nullsweep, who first reported on the port scans, they do not occur when browsing the site with Linux.
Once they tested in Windows, though, the port scans occurred.
This makes sense as the programs being scanned for are all Windows remote access tools.
Likely done to detect hacked computers
As the port scan is only looking for remote access programs, it is most likely being done to check for compromised computers used to make fraudulent eBay purchases.
In 2016, reports were flooding in that people's computers were being taken over through TeamViewer and used to make fraudulent purchases on eBay.
As many eBay users use cookies to automatically login to the site, the attackers were able to remote control the computer and access eBay to make purchases.
It got so bad that one person created a spreadsheet to keep track of all the reported attacks. As you can see, many of them reference eBay.
These port scans are still intrusive and not something that many users would want to happen when visiting a site.
BleepingComputer has contacted eBay about this port scan but has not heard back at this time.
Update 5/25/20: Updated article with correct attribution.
Coronavirus Pandemic Claims Another Victim: Robocalls
25.5.2020 Securityweek Security
Have you been missing something amid the lockdowns and stay-at-home orders? No, not human contact. Not even toilet paper.
Robocalls.
Industry experts say robocalls are way down — scam calls as well as nagging from your credit-card company to pay your bill. The coronavirus pandemic has inflicted millions of job losses, and scammers have not been immune.
YouMail, which offers a robocall-blocking service, says 2.9 billion robocalls were placed in April in the U.S., down from 4.1 billion in March and 4.8 billion in February. That’s a daily average of 97 million calls in April, down from 132 million in March and 166 million in April.
The main reason: many global call centers have closed or are operating with fewer workers, said YouMail CEO Alex Quilici. While it may be odd to think of scams being run out of call centers rather than a dark, creepy basement or a garage, that’s often the case, particularly in countries such as India and the Philippines, experts said.
After a lockdown order went into effect in India in late March, “we saw the volume of calls basically half the next day,” Quilici said.
That means scammers will probably be back in force once the call centers come back online. Stepped-up enforcement from industry groups and the U.S. government could nibble around the edges of those call volumes when the scammers are back, however. In recent months, federal agencies have focused on going after the small telecom providers that were allowing calls from COVID-19 scammers, citing the urgency of the pandemic.
And free blocking tools that were already in place on many people’s phones help consumers dodge unwanted calls, so it’s not clear how many have noticed the lower numbers of scam and telemarketing calls in the past couple months.
“What we do hear from consumers is call blocking tools are effective in reducing a significant number of robocalls but some unwanted calls are going to slip through,” said Maureen Mahoney, a policy analyst with Consumer Reports.
Complaints about unwanted calls to the Federal Trade Commission have been steadily trending down since late 2018, and dropped by more than half in March from the year before, to 240,000. The Federal Communications Commission gets many fewer complaints overall but says those also fell 50% in March, to 10,000, and 60% in April, to 7,500.
None of which is to say that nuisance calls and phone scams and texts have disappeared.
“While reports of robocalls are way down overall, we’re now hearing about callers invoking the COVID-19 pandemic to pretend to be from the government, or making illegal medical or health care pitches,” an FTC blog post declared in mid-April.
And Mahoney predicts that calls will pick up again, and it won’t just be scammers back in action. With so many people out of work and behind on their bills, debt collectors will be relentlessly badgering them to pay soon enough, she said.
Wireshark 3.2.4 Released
25.5.2020 SANS Security
Wireshark version 3.2.4 was released.
It has a vulnerability fix and bug fixes.
A vulnerability in the NSP dissector can be abused to cause a crash.
Didier Stevens
Senior handler
Microsoft MVP
Organizations plan to migrate most apps to the cloud in the next year
25.5.2020 Net-security Security
More than 88% percent of organizations use cloud infrastructure in one form or another, and 45% expect to migrate three quarters or more of their apps to the cloud over the next twelve months, according to the O’Reilly survey.
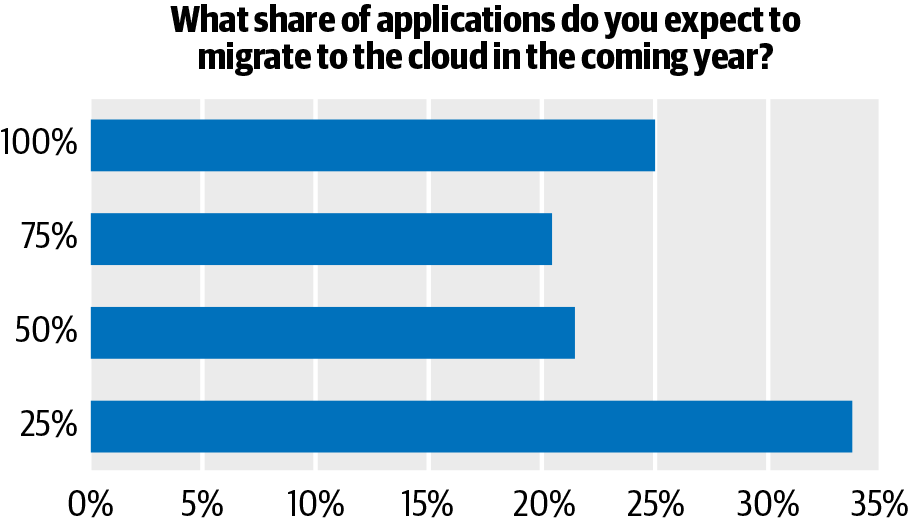
The report surveyed 1,283 software engineers, technical leads, and decision-makers from around the globe. Of note, the report uncovered that 21% of organizations are hosting all applications in a cloud context.
The report also found that while 49% of organizations are running applications in traditional, on-premises contexts, 39% use a combination of public and private cloud deployments in a hybrid-cloud alternative, and 54% use multiple cloud services.
Public cloud is the most popular deployment option
Public cloud dominates as the most popular deployment option with a usage share greater than 61%, with AWS (67%), Azure (48%), and Google Cloud Platform (GCP) (32%) as the most used platforms. However, while Azure and GCP customers also report using AWS, the reverse is not necessarily true.
“We see a widespread embrace of cloud infrastructure across the enterprise which suggests that most organizations now equate cloud with “what’s next” for their infrastructure decisions and AWS as the front-runner when it comes to public cloud adoption,” said Mary Treseler, VP of content strategy at O’Reilly.
“For those still on the journey to cloud-based infrastructure migration, ensuring that staff is well-versed in critical skills, such as cloud security and monitoring, will be incredibly important for successful implementations.
“Enterprises with solid footing have the potential to leverage this infrastructure for better software development and AI-based services, which will put them at an advantage over competitors.”

Other notable findings
Cloud-based security was cited as the number one critical skill area needed to migrate to or implement cloud-based infrastructure (65%), followed by monitoring (58%) and Kubernetes (56%).
37% of organizations have developed production for AI services with 47% expected to deploy AI-based services at some point over the next three years.
52% of respondents say they use microservices concepts, tools, or methods for software development.
35% have adopted Site Reliability Engineering (SRE) with 47% of organizations expect to implement an SRE function at some point in the future.
In an increasingly 5G and edge world, DNS matters
25.5.2020 Net-security Security
Infoblox identified the challenges Communication Service Providers (CSPs) face in transitioning to distributed cloud models, as well as the use cases for multi-access edge computing (MEC), 5G New Radio (NR), and 5G Next Generation Core (NGC) networks.

“Distributed cloud models such as 5G and multi-access edge computing networks have the potential to drastically change the CSP industry, delivering high-bandwidth, low latency services to network customers,” said Dilip Pillaipakam, Vice President and GM of Service Provider Business at Infoblox.
“Yet to fully take advantage of the benefits of these new technologies, DNS will have to evolve to address the challenges that come from delivering these high-value services at the network edge.”
DNS will need to be increasingly automated
DNS is a critical element to these new network architectures and technologies, enabling devices to access the network securely and reliably. And as 5G NR, NGC, and MEC technologies enable faster, more distributed networks with significantly more connected devices, DNS will need to be increasingly automated and operate at greater scale and with greater flexibility.
Yet, despite the importance of DNS to the reliable functioning of these networks, the survey found that few CSPs believe that their DNS is currently capable of supporting MEC or 5G NEC.
To meet this need, networks will need to leverage the benefits of distributed DNS technology that can enable network managers to meet users where they are—at the network edge.
Other key findings
CSPs consider DNS to be critical to the adoption of next-generation network technologies like 5G (71%), cloud-based managed security services (66%) and MEC (63%).
More than one third of CSPs surveyed plan to implement MEC (36%), 5G (35%), and NEC (35%) in the next 12-18 months.
Despite this, the lack of a mature vendor solution ranks as the largest obstacle these providers face in MEC (36%), 5G NR (46%) and 5G NEC (39%) deployments.
The CSPs surveyed included companies that represent all aspects of the industry; the largest groups were converged operators (46% of respondents), mobile operators (26%), and fixed-line and cable operators (10% each). The survey asked about their plans for implementing MEC, 5G NGC, and 5G NR technologies, business use cases, as well as concerns and obstacles to implementation.

The survey’s findings indicate that the future of DNS will hinge on the delivery of a fully distributed and fully capable edge-based DNS.
“CSPs seeking to advantage of the benefits of cloud-based and distributed technologies like MEC, 5G NR, and 5G NGC, will need DNS services that can keep up with the challenge of edge-centric network models,” continued Pillaipakam.
“DNS providers will need to adapt and evolve to ensure that customers in this industry are provided with the features, flexibility, and security that these new architectures demand.”
Create a safe haven for your customers to build loyalty
22.5.2020 Net-security Security
“The customer comes first” started out as the secret to success in business. Now it’s the secret to 21st century cybersecurity and fraud prevention, too.
fraudulent transactions
The phrase always seemed more like an empty platitude, but a growing number of banks and other financial institutions now understand that optimizing convenient consumer experience with risk and safety across all their channels is a strategic differentiator.
Dealing with fraudulent transactions
Financial institutions have been on the lookout for fraudulent transactions in hopes of preventing customers from falling victim to illegal fund withdrawal since the dawn of the digital age. Things like usernames and passwords have become less of a proof of identity and ownership in a world of endless data breaches.
Cybercriminals today easily harvest all manner of personal identity credentials from the dark web as well as through social engineering schemes. They gain access to customer accounts and make transfers or payments with the legitimate customer none the wiser—at least until their next login or they encounter a declined transaction due to insufficient funds.
Automated bots increasingly spur fraudulent transactions by allowing fraud to occur at unprecedented speed and volumes. The goal for fraudsters using bot attacks is to compromise accounts and harvest stolen data, leading to ever-greater risk in new channels and services and for recently digitized and experienced digital channel companies alike.
Efforts to stop these nefarious activities have sometimes led to either a one-size fits all approach or overly aggressive policies and additional identity proofing requirements. Customers get frustrated when they need to jump through hoops to log in or complete a transaction.
The lengthy process seems especially frivolous when cybercriminals continue to find inventive new ways to bypass these same controls. Consumers do not expect a “no-friction” transaction every time. They want the incremental steps to be commensurate with the risk of the transaction (e.g., checking an account balance vs. a large balance withdrawal).
Organizations should look beyond the disruption of fraudulent financial transactions and stop viewing the consumer as a financial event or a financial risk to contain. Instead, organizations should treat the consumer at every customer interaction and not as a single touchpoint or a stand-alone transaction. Only then can organizations effectively protect consumers throughout their experience.
Data insight = Consumer satisfaction and safety
Data insight drives greater consumer satisfaction and safety. To a financial institution, both digital and physical data is often as valuable as a consumers’ financial worth – at least when it comes to visibility into fraud and how to stop it.
Criminals use information within a banking relationship to commit fraud at multiple points during the customer journey. Compromised consumer information exposes the consumer to wider risks outside of specific applications, increasing the risk for the consumer and the organization.
For instance, a fraudster could use compromised customer data to open additional accounts or new lines of credit. Fraudsters with access to online banking information can easily circumvent security questions that require information ostensibly known only to the customer. Then criminals often add their phone number to the account or use account information to re-direct the consumer’s phone calls back to them when users return bogus “security” checks by the financial institution.
The mess left behind in the fraudster’s wake entangles banks who do not employ adequate risk controls. Customers do not like that kind of breach. Neither do regulators.
Smarter security
Banks can benefit from risk signals that can identify this kind of fraud and stop it in its tracks.
When organizations use a combination of data and customer insights (such as pinpointing the last time a device accessed a specific account) measured against transaction risk (whether an account was accessed to change personally identifiable Information or to check a balance), it can tailor each consumer’s experience with the right risk controls.
Also critical is real-time and historical intelligence of the customer’s legitimate identity usage in other interactions on other sites or apps around the world. Organizations should shift emphasis to establishing “the good” in terms of normative devices and behaviors informed by global-scale intelligence instead of focusing on trying to ferret out “the bad.” This practice uncovers anomalies instantly. The key then is to ensure the identification of anomalies and a proactive response at every decisive moment – not just when the financial transaction is taking place.
Bigger value
For all of this, the other side of the equation is just as important. Recalling “the customer comes first,” this focus on protecting the customer also pays serious dividends for the institutions they do business with. Finally, the brand experience matches the brand marketing.
Cybersecurity and fraud risk controls enable significant differentiation for the brand through consumer loyalty and convenience. According to Forrester, less than 10% of organizations ever crack that code.
Institutions that use data insights to coordinate risk and fraud control strategies across channel and consumer journey silos inevitably deliver a faster, more consistent experience across the entire omni-channel spectrum.
Microsoft Announces New Security Features for Devs, Customers
21.5.2020 Securityweek Security
At this week’s Build virtual event, Microsoft announced new Identity and Azure features meant to improve security for both application developers and enterprise customers.
For developers, admins, and end-users alike, new Identity capabilities to help foster a secure and trustworthy app ecosystem include Publisher Verification, app consent policies, and general availability of Microsoft authentication libraries (MSAL) for Angular.
With Publisher Verification, developers can demonstrate to customers that their application comes from a trusted and authentic source. Applications will be marked when the publisher has verified their identity with the Microsoft Partner Network (MPN) and associated the account with the application registration.
Administrators will also be able to configure policies and determine the applications that users can consent to, such as those that have been Publisher Verified.
In addition to making MSAL generally available, Microsoft announced that a web library identity.web for ASP.NET Core is in public preview. With MSAL, devs can implement authentication patterns, security features, and integration points with support for any Microsoft identity (from Azure Active Directory accounts to Microsoft accounts).
The tech company also announced the preview of Azure AD External Identities, meant to help organizations and developers create and manage apps that connect with users outside an organization.
This week, Microsoft announced two new additions to Azure Security Center: the availability of Azure Secure Score API to customers, and the public availability of suppression rules for Azure Security Center alerts, which are meant to reduce alerts fatigue.
The company also announced that customers can now control encryption keys on 50 more Azure services, to ensure they meet compliance or regulatory requirements. The capability is now part of the Azure Security Benchmark.
Now, Azure Disk Encryption can be used to secure Red Hat Enterprise Linux BYOS Gold Images (Azure Disk Encryption can be enabled only after the subscription has been registered).
Azure Key Vault, the unified service for management of secrets, certificates, and encryption keys, now provides increased security with Private Link, an option that provides access to Azure Key Vault over a private endpoint in a virtual network (the traffic flows over the Microsoft backbone network).
Furthermore, Microsoft now allows customers to use SafeNet Luna HSMs or Fortanix SDKMS to generate encryption keys outside Azure and then import them into Azure Key Vault (previously, only nCipher nShield HSMs was supported).
Microsoft also released a public preview of notifications for keys, secrets, and certificates, to make it easier for customers to rotate secrets.
Recently, Microsoft announced the general availability of Azure Confidential Computing, which leverages the latest Intel SGX CPU hardware for a new class of VMs that can protect the confidentiality and integrity of customer data while in memory.
Customers can approve or reject data access requests through Customer Lockbox for Microsoft Azure, which now features expanded coverage of services, and is now available in preview for Azure Government cloud customers.
How to enable the new Google Chrome 83 features now
21.5.2020 Bleepingcomputer Security
Google released Chrome 83 yesterday, and with it came numerous features such as a new Incognito cookie control, a Security check feature, new Security settings page, the Tabs Group feature, a new extensions menu, and redesigned cookie controls.
The problem, though, is that many of these features in this massive update have not been enabled yet by Google and will be slowly rolled out over time.
If you are like me and want to play with all the new goodies, the good news is that you can use some Chrome flags to enable these features now.
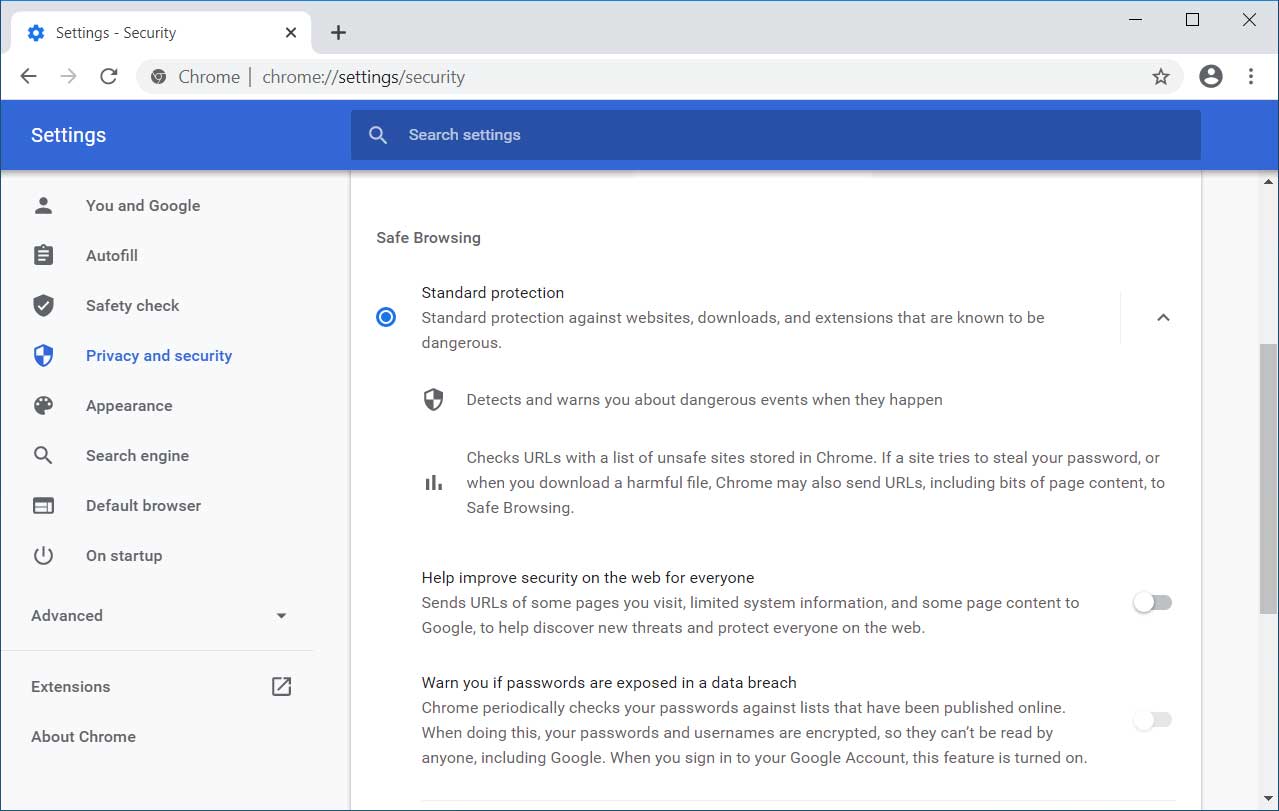
Enable new Security settings and Safety check
Chrome 83 comes with a redesigned Security settings page and a new Safety Check feature that are currently disabled.
To enable these features right now, follow these steps:
Paste chrome://flags/#privacy-settings-redesign into the address bar and press enter.
When the 'Privacy Settings Redesign' flag is shown, set it to Enabled and relaunch the browser when prompted.
After restarting the browser, you will now have access to the Safety Check feature and the new Security settings section under Privacy and Security or at chrome://settings/security.
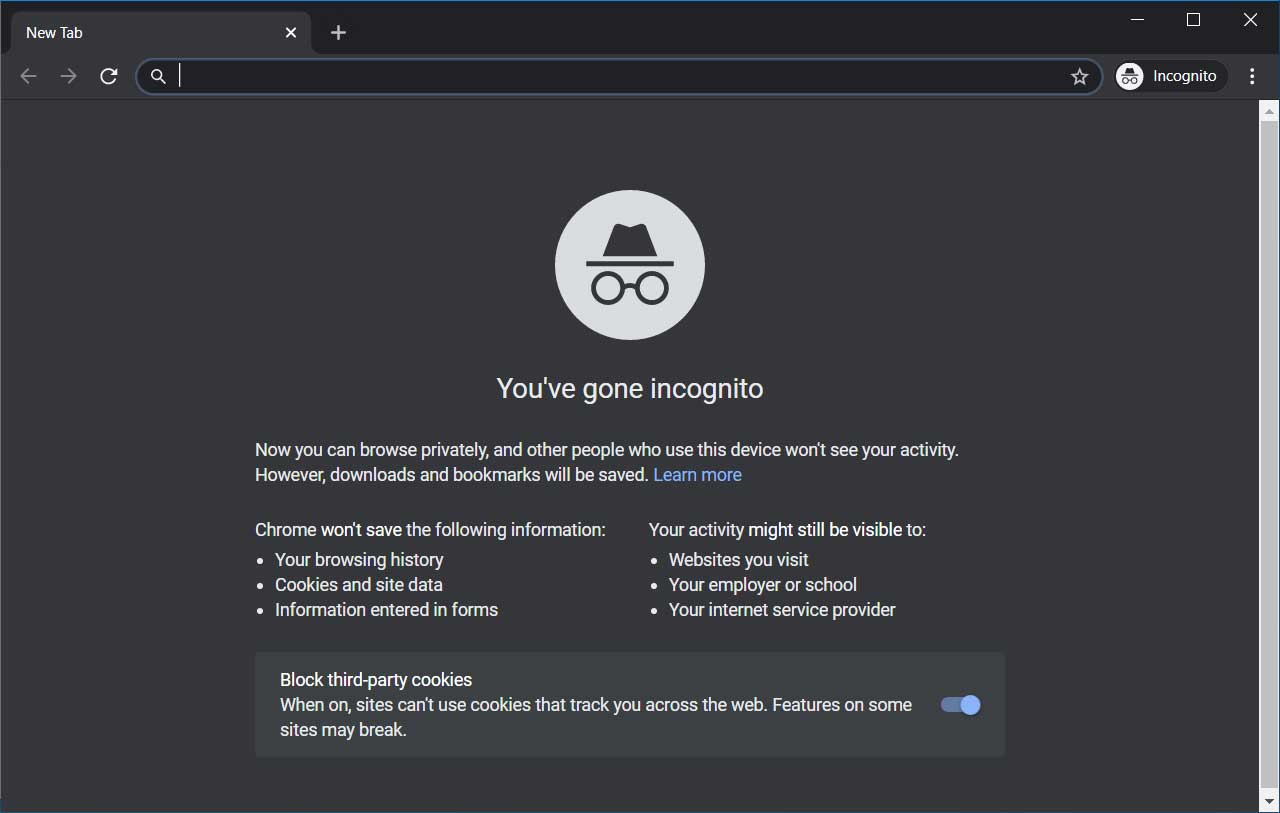
Enable third-party cookie controls in Incognito mode
With the release of Chrome 83, Google has started to block third-party cookies by default in Incognito mode and have added a new user interface toggle to control it.
To enable this Incognito mode cookie control setting, please follow these steps:
Paste chrome://flags/#improved-cookie-control into the address bar and press enter.
When the 'Enable improved cookie controls UI in incognito mode' flag is shown, set it to Enabled and relaunch the browser when prompted.
When the flag is enabled, you will now see a new option to 'Block third-party cookies' in Incognito mode, which will be enabled by default.
Incognito mode cookie control
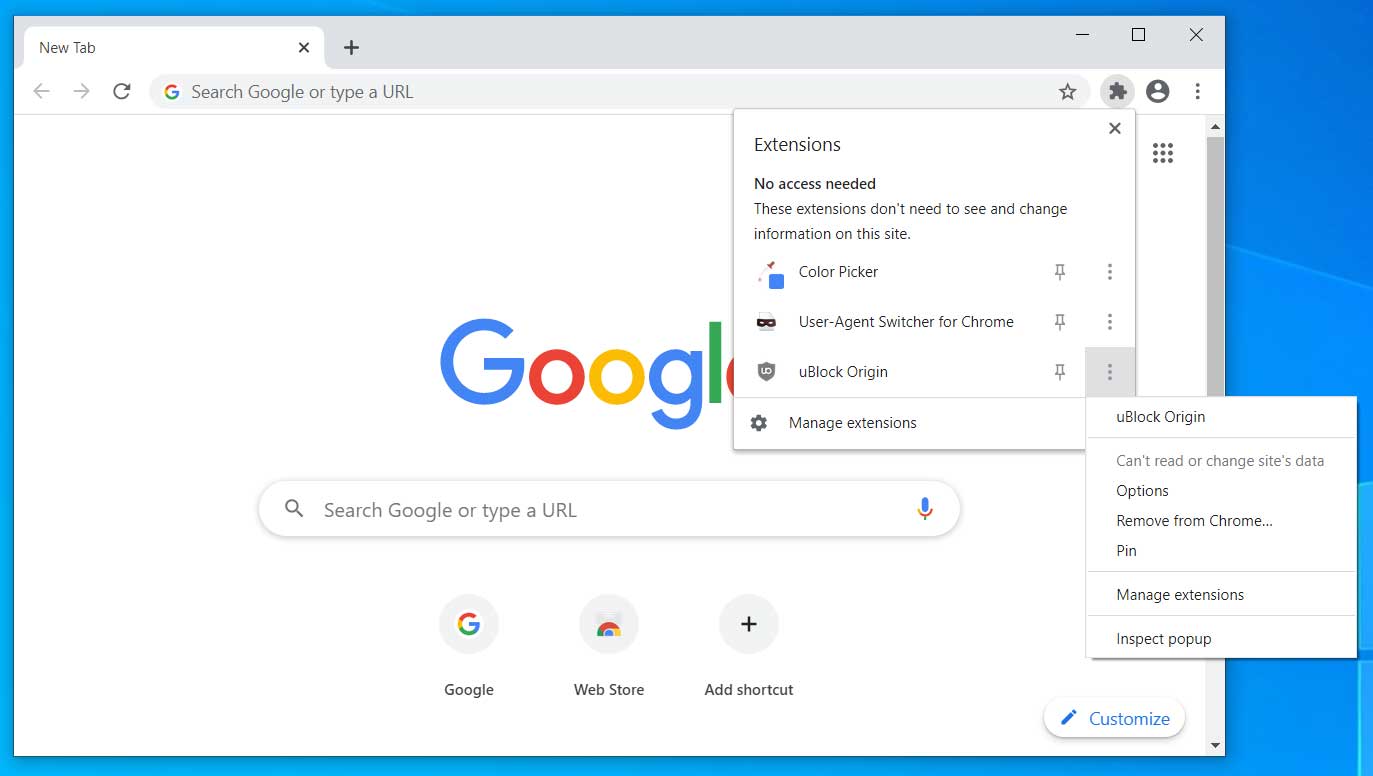
Enable the new extensions menu
When installing a new extension, they will no longer display on the toolbar but will instead be located under the new extension menu. This menu can be accessed by clicking on the jigsaw puzzle icon that will appear on your toolbar.
To enable this the new extension menu, please follow these steps:
Paste chrome://flags/#extensions-toolbar-menu into the address bar and press enter.
When the 'Extensions Toolbar Menu' flag is shown, set it to Enabled and relaunch the browser when prompted.
When the flag is enabled, if you have any extensions installed, you will see a new jigsaw puzzle icon on the toolbar. Clicking on this icon will open the extension menu.
New extension menu
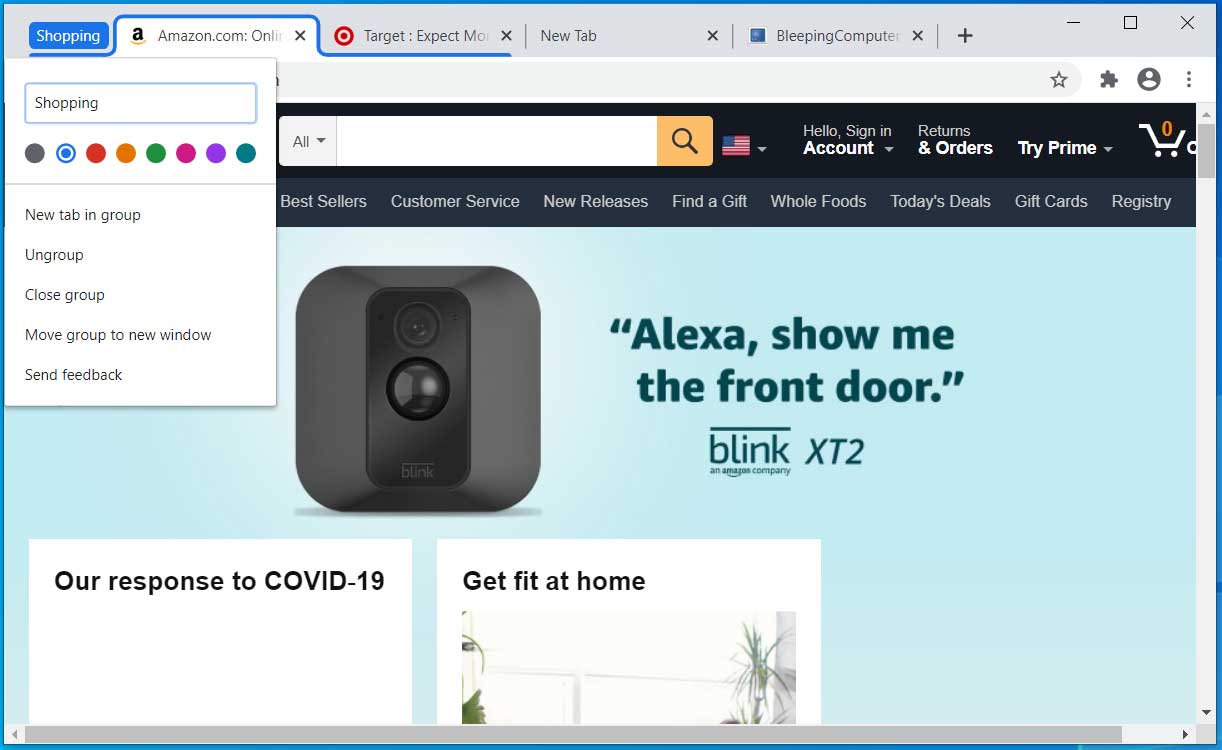
Enable the Tab Groups feature
With the release of Chrome 83, Google has released its Tab Groups feature that lets you organize tabs into different groupings.
The tabs in these groups can then be moved around as one whole group or sent to a new browser window.
To enable the Tab Group feature, follow these steps:
Paste chrome://flags/#tab-groups into the address bar and press enter.
When the 'Tabs Groups' flag is shown, set it to Enabled and relaunch the browser when prompted.
When the flag is enabled, if you right-click on a tab, you will be able to add it to a new group or an existing group. You can then manage the group by clicking on its label, as shown below.
New Tab Group feature
As more flags are discovered or added by Google, we will be sure to update this article.
H/T TechDows.com
Chrome 83 released with massive security and privacy upgrades
21.5.2020 Bleepingcomputer Security
Google has released Chrome 83 today, May 19th, 2020, to the Stable desktop channel, and it includes massive security and privacy enhancments as well as some long awaited features.
In this massive release, users are getting a redesigned Privacy and security settings section, better control over cookies, a new Safety Check feature, improved DoH settings, new Enhanced Safe Browsing feature. Tab Groups, and more.
With Chrome 83 now being promoted to the Stable channel, Chrome 84 will soon be promoted to the Beta version, and Chrome 85 will be the Canary version.
As you may have realized, Google did not release Chrome 82, and instead decided to skip that version due to the pandemic and roll all of its changes into Chrome 83.
Windows, Mac, and Linux desktop users can upgrade to Chrome 83 by going to Settings -> Help -> About Google Chrome. The browser will then automatically check for the new update and install it when available.
Massive security overhaul for Chrome users
While Google fixes security vulnerabilities in every release of the Chrome browser, most of these security improvements are made behind the scenes.
With this release, Google Chrome 83 has completely overhauled the user-facing security protections with numerous improvements that aim to help users secure their data, stay safe online, and increase their privacy.
It is important to note that most of the improved security features will be rolling out to users over the next couple of weeks.
If you do not see them immediately, be patient as they will be eventually enabled in your browser.
Easier security and privacy controls
All of the privacy and cookie settings have been reorganized to make it easier to find and configure the browser for enhanced privacy.
The sync controls are now renamed to "You and Google" and allow you to specify what data you share with Google to store in your Google account and what data is synchronized between devices.
To make it easier to clear your browsing history, Google has also moved the 'Clear browsing data' option to the top of the 'Privacy and security' settings section to make it more accessible.
The biggest change, though, is a completely redesigned cookie management interface that gives easier control over what cookies you will allow.
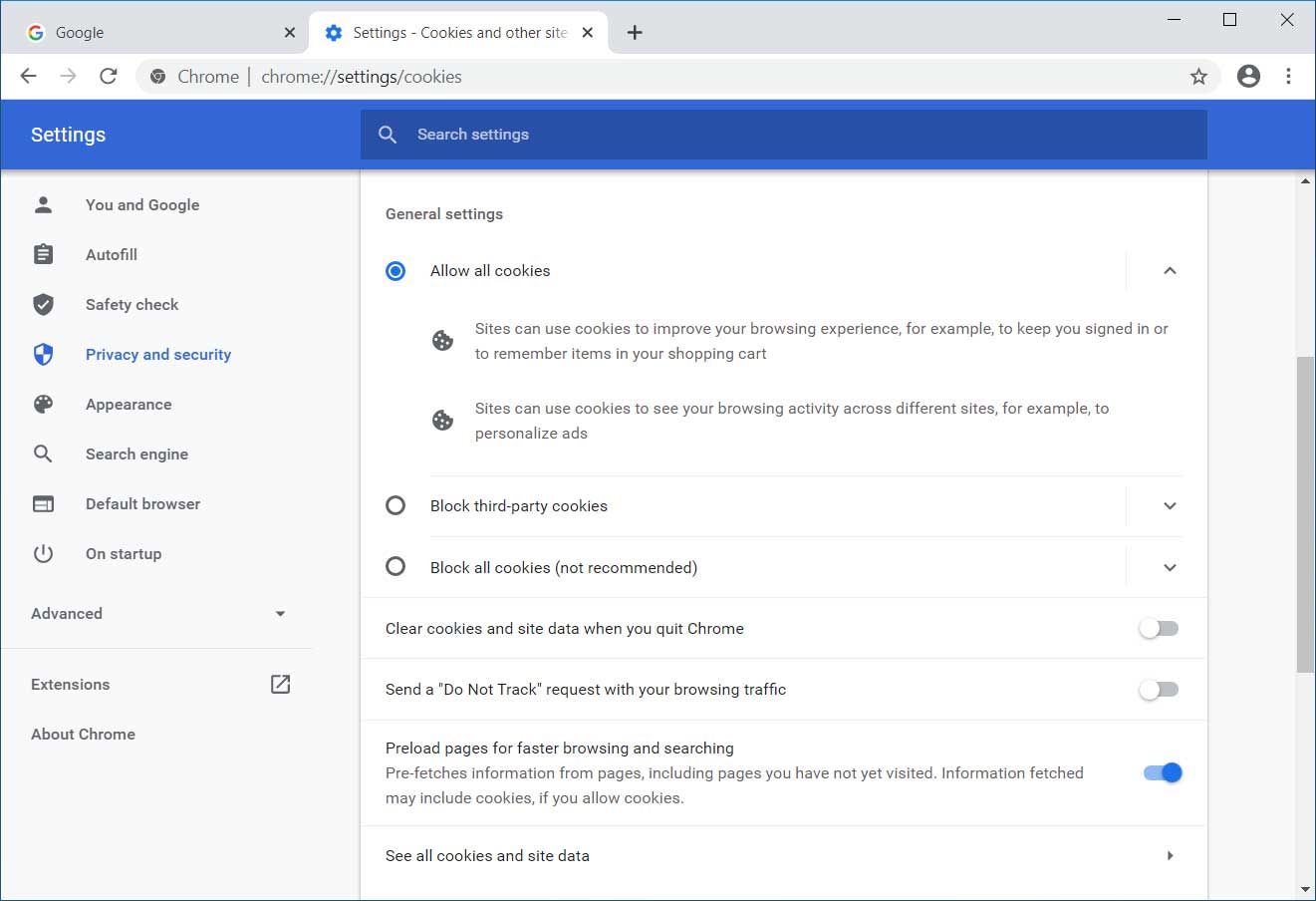
New cookie controls
Finally, Google will block third-party cookies by default in Incognito mode.
"While we continue to work on our long-term effort to make the web more private and secure with Privacy Sandbox, we want to strengthen the Incognito protections in the meantime. In addition to deleting cookies every time you close the browser window in Incognito, we will also start blocking third-party cookies by default within each Incognito session and include a prominent control on the New Tab Page. You can allow third-party cookies for specific sites by clicking the “eye” icon in the address bar," Google announced.
New Safety check feature in Chrome
Google has added a new 'Safety check' feature that will perform a checkup of the browser and your saved data to make sure it is secure and has not been compromised.
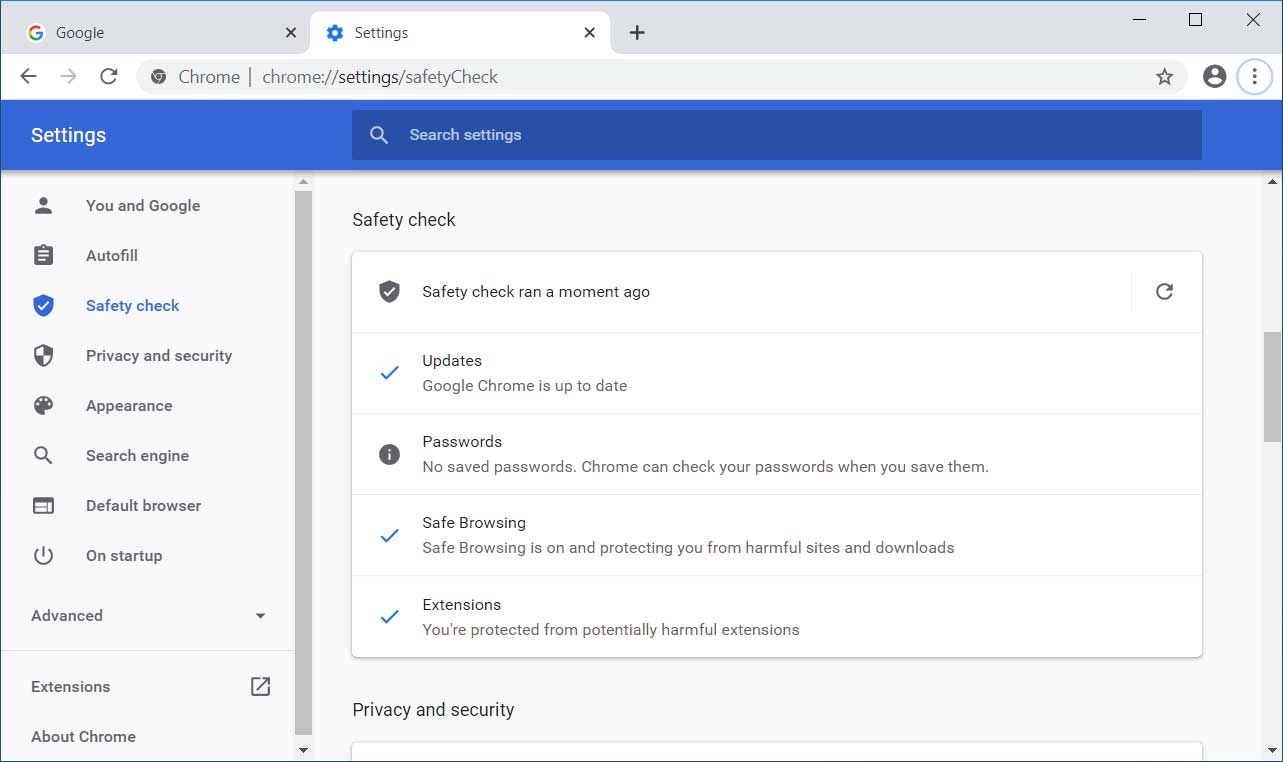
New Safety check feature
As part of this Safety check, Google Chrome will check if any of your saved credentials were compromised in a data breach, if you're using the latest version of the browser, if Safe Browsing is enabled, and if you have any malicious extensions installed.
Secure DNS: Redesigned DNS-over-HTTPS (DoH) settings
Chrome has redesigned its DNS-Over-HTTPS settings in a new dedicated 'secure DNS' section under Privacy and security > More.
Using this new interface, a user can enable DoH and use it with their existing DNS provider, if available, or select one that is preconfigured in Google Chrome.
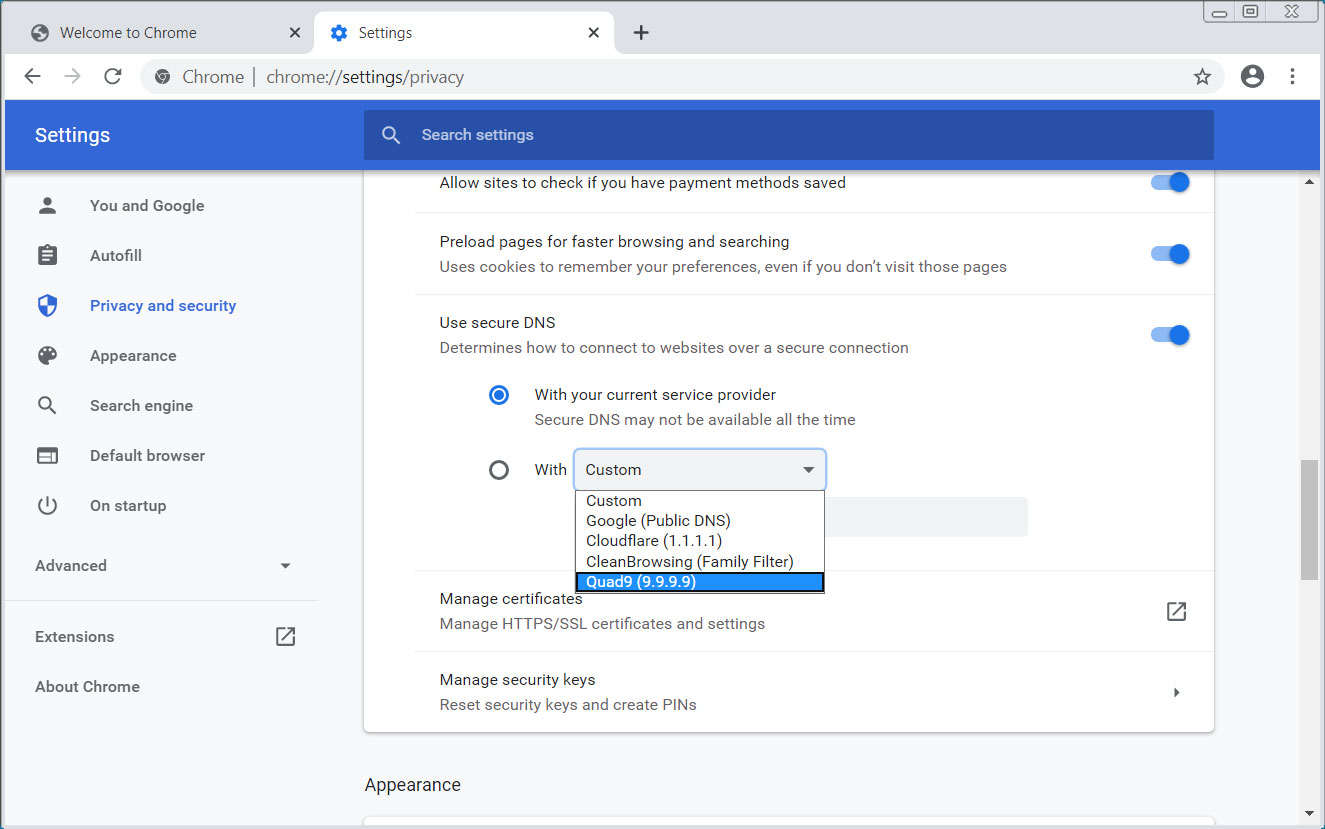
New secure DNS DoH settings
You can then choose from Custom providers or preconfigured Google (Public DNS), Cloudflare (1.1.1.1), CleanBrowsing (Family Filter), or Quad9 (9.9.9.9) DoH providers.
Enhanced Safe Browsing Protection released
The final security feature in Chrome 83 is the introduction of a new opt-in 'Enhanced safe Browsing Protection' mode.
When enabled, Google will perform real-time checks of URLs that you visit to check for known threats.
As Safe Browsing normally checks against a local database of malicious URLs and files, by using a real-time check, you gain better protection from the latest known malicious web sites and malicious software.
"If you turn on Enhanced Safe Browsing, Chrome proactively checks whether pages and downloads are dangerous by sending information about them to Google Safe Browsing. If you’re signed in to Chrome, then Chrome and other Google apps you use (Gmail, Drive, etc.) will further protect you based on a holistic view of threats you encounter on the web and attacks against your Google Account. Over the next year, we’ll be adding even more protections to this mode including tailored warnings for phishing sites and file downloads, and cross-product alerts," Google stated in their blog post.
Always show full urls option
In Chrome 79, Google removed what they call trivial subdomains or special-case subdomains from the URLs displayed in Chrome's address bar.
Many, though, prefer to see a full URL of a web page they are visiting in the address bar.
With the release of Chrome 83, users can now enable a 'Context menu show full URLs' flag that lets you enable the showing of full URLs when browsing the web.
To enable this feature, go to chrome://flags/#omnibox-context-menu-show-full-urls and enable the feature. Once enabled, and the browser is restarted, you can right-click on the address bar and a new option can be checked titled 'Always show full URLS'.
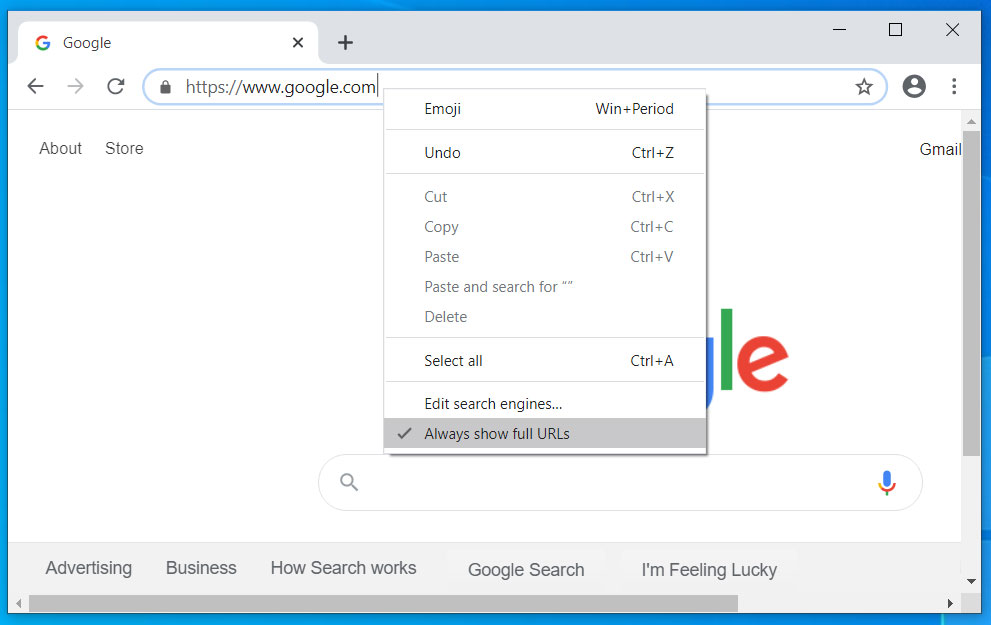
Show full URLs context menu
Tab groups have arrived
Google has been testing a new feature called 'Tab Groups' that allows you to add various tabs to a named group so that they are better organized.
These groups can then be moved around as one item or sent to another window.
This feature is now live in Google Chrome 83.
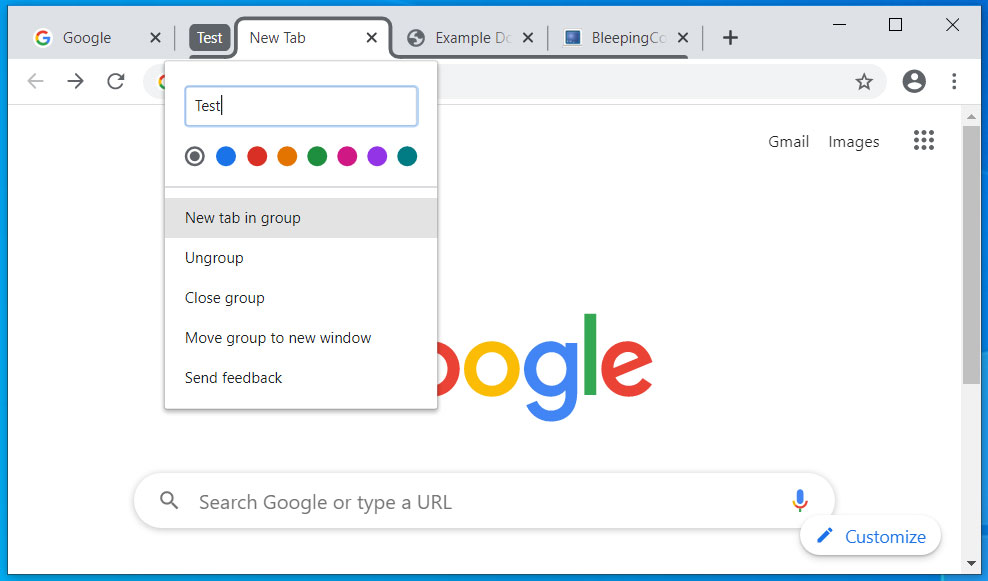
Chrome Tab Groups
New browser extensions menu
To add more real estate to the Chrome toolbar, Google has moved the extensions into a new drop-down menu accessed through a new jigsaw puzzle icon.
When you click on this puzzle icon, a menu will drop down listing all of your extensions and allows you to manage them.
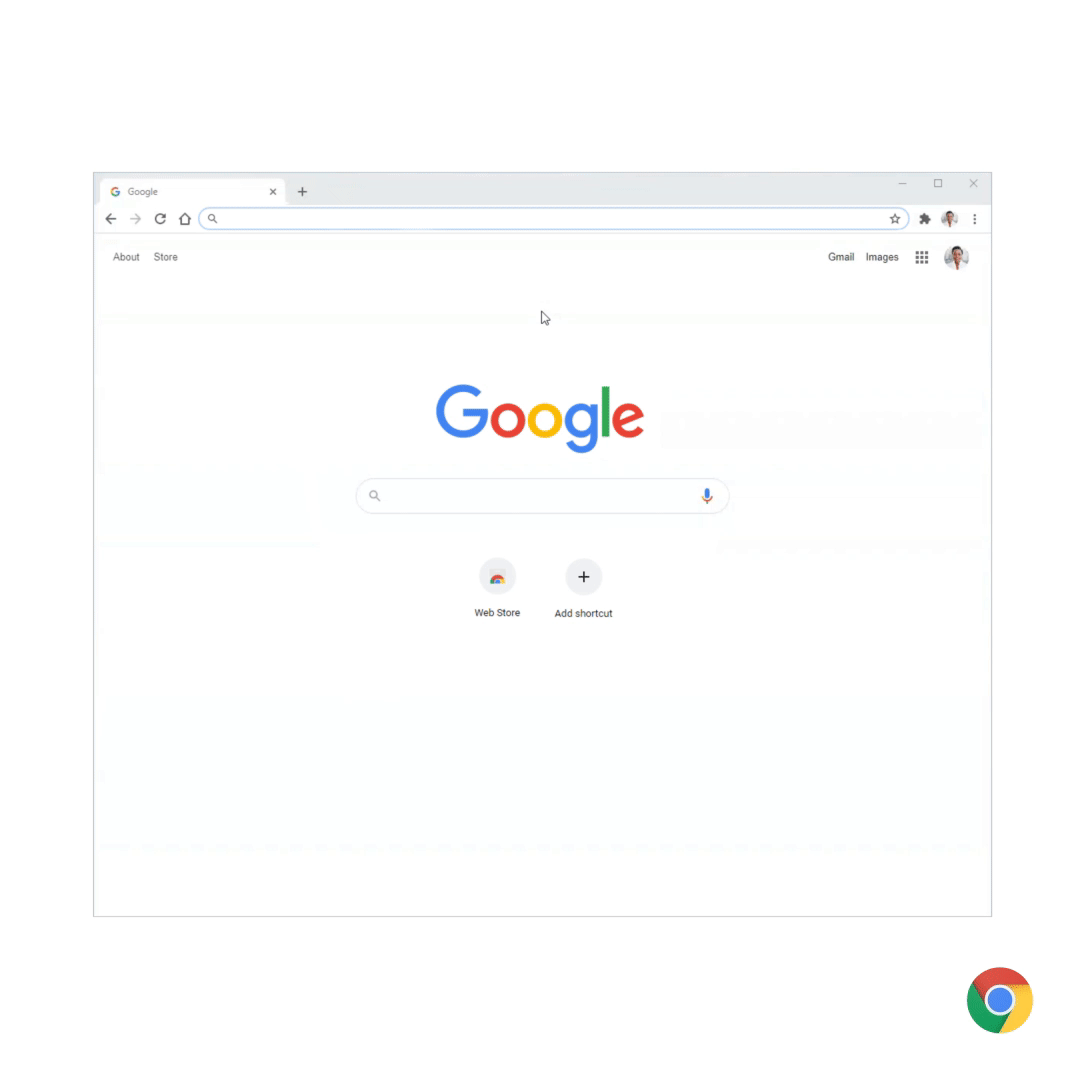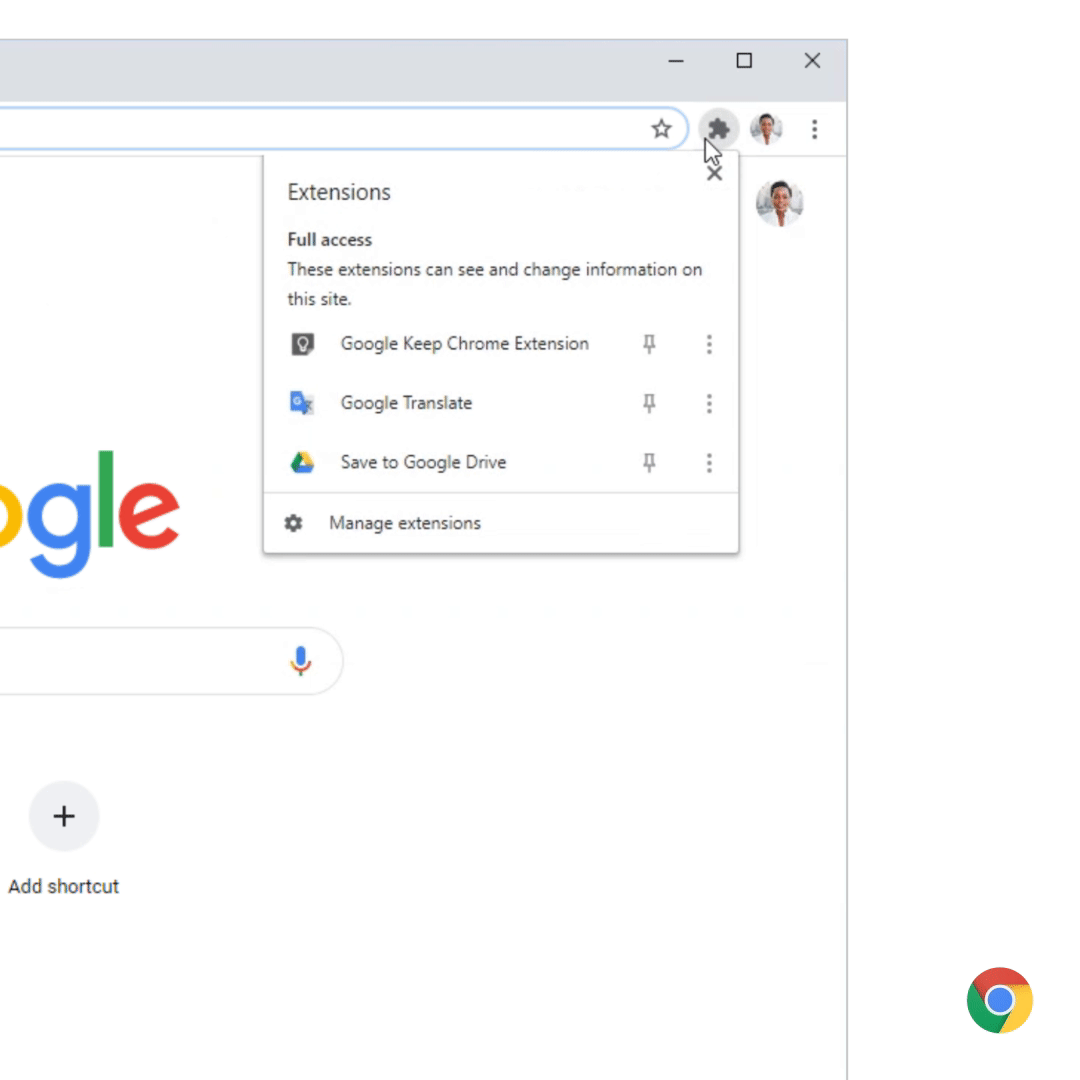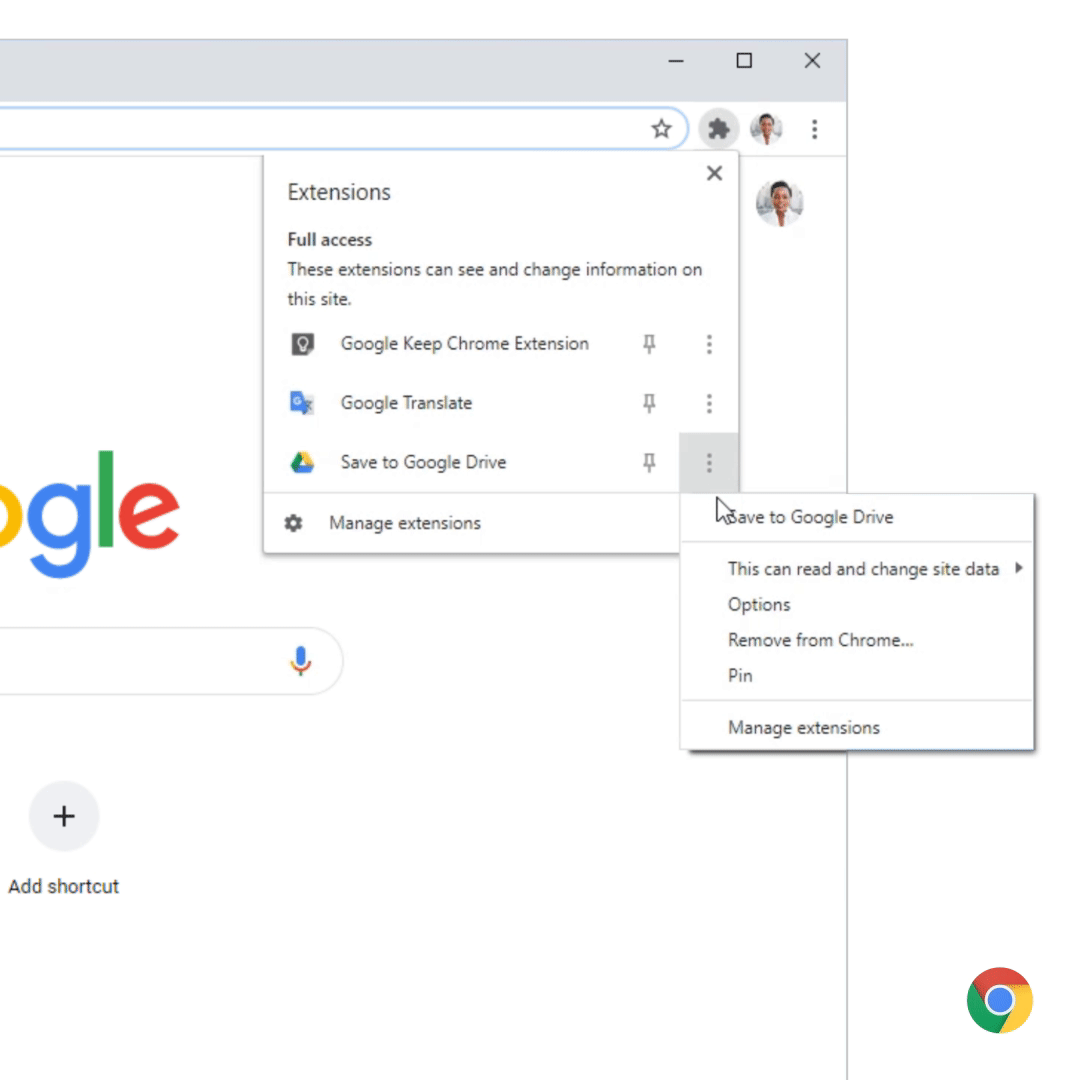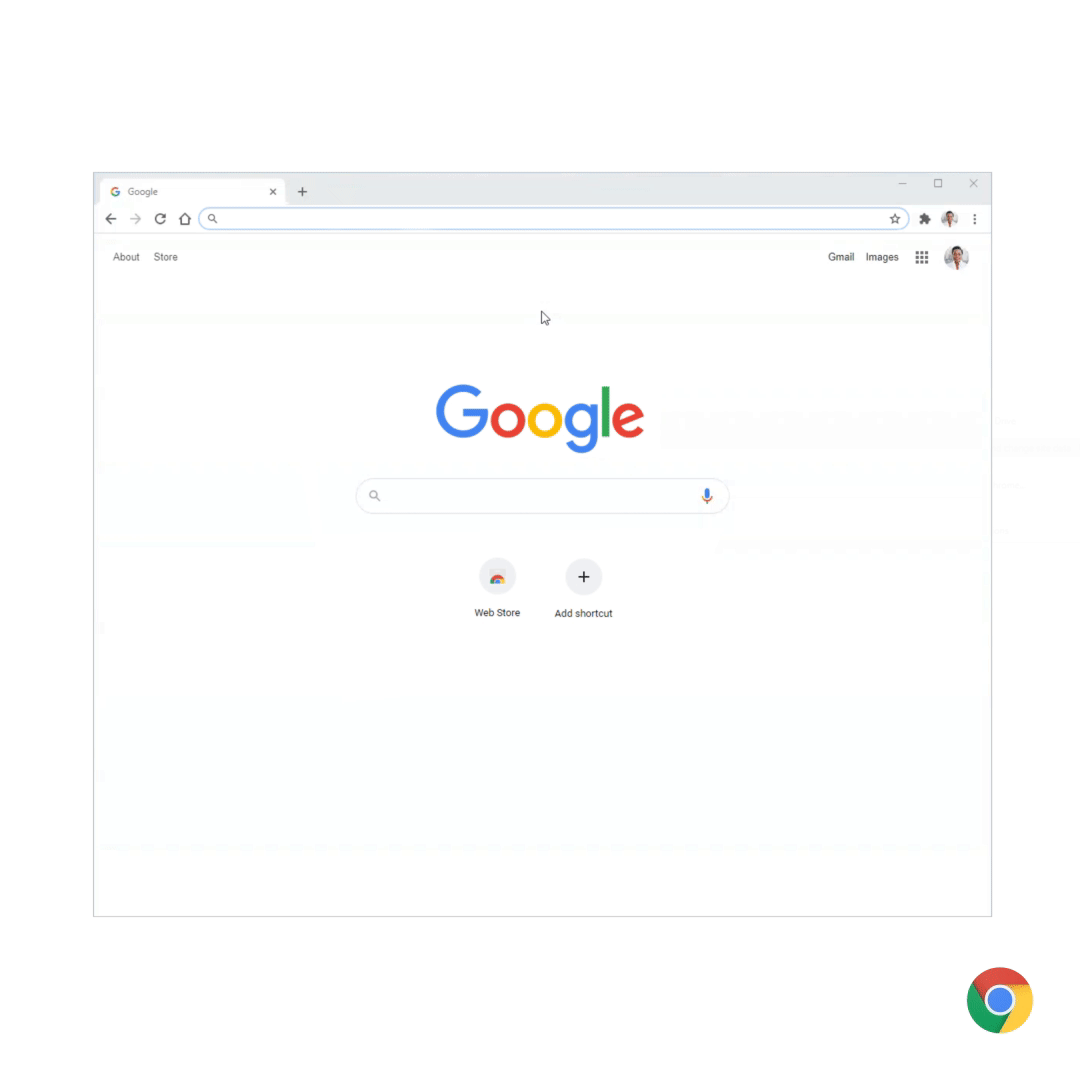
New extensions menu
Each extension will then have a dedicated submenu where you can remove it, configure its options, or pin it to the toolbar.
As you can see, this is a huge Google Chrome update that adds numerous features to make the web browser experience more secure.
As many of these features are still rolling out, please do not be concerned if you do not see them immediately.
38 security vulnerabilities fixed
The Chrome 83 release fixes 38 security vulnerabilities, with the following discovered by external researchers:
CVE ID Description Classification
CVE-2020-6465 Use after free in reader mode. High
CVE-2020-6466 Use after free in media. High
CVE-2020-6467 Use after free in WebRTC. High
CVE-2020-6468 Type Confusion in V8. High
CVE-2020-6469 Insufficient policy enforcement in developer tools. High
CVE-2020-6470 Insufficient validation of untrusted input in clipboard. Medium
CVE-2020-6471 Insufficient policy enforcement in developer tools. Medium
CVE-2020-6472 Insufficient policy enforcement in developer tools. Medium
CVE-2020-6473 Insufficient policy enforcement in Blink. Medium
CVE-2020-6474 Use after free in Blink. Medium
CVE-2020-6475 Incorrect security UI in full screen. Medium
CVE-2020-6476 Insufficient policy enforcement in tab strip. Medium
CVE-2020-6477 Inappropriate implementation in installer. Medium
CVE-2020-6478 Inappropriate implementation in full screen. Medium
CVE-2020-6479 Inappropriate implementation in sharing. Medium
CVE-2020-6480 Insufficient policy enforcement in enterprise. Medium
CVE-2020-6481 Insufficient policy enforcement in URL formatting. Medium
CVE-2020-6482 Insufficient policy enforcement in developer tools. Medium
CVE-2020-6483 Insufficient policy enforcement in payments. Medium
CVE-2020-6484 Insufficient data validation in ChromeDriver. Medium
CVE-2020-6485 Insufficient data validation in media router. Medium
CVE-2020-6486 Insufficient policy enforcement in navigations. Medium
CVE-2020-6487 Insufficient policy enforcement in downloads. Low
CVE-2020-6488 Insufficient policy enforcement in downloads. Low
CVE-2020-6489 Inappropriate implementation in developer tools. Low
CVE-2020-6490 Insufficient data validation in loader. Low
CVE-2020-6491 Incorrect security UI in site information. Low
Chrome 83 Brings Enhanced Safe Browsing, New Privacy and Security Controls
21.5.2020 Securityweek Security
Google this week released Chrome 83 to the stable channel with patches for a total of 38 vulnerabilities, with improved Safe Browsing protection, and updated privacy and security controls.
The newly introduced Enhanced Safe Browsing protection in Chrome is meant to provide users with a more advanced level of security while browsing the web, by increasing protection from dangerous websites and downloads.
For users signed into Chrome and other Google apps (such as Gmail, Drive, etc), the company claims to provide protection “based on a holistic view of threats” encountered on the web and attacks on a user’s account.
With Safe Browsing, Google explains, the list of websites considered malicious is refreshed every 30 minutes, but that represents a long-enough window for some phishing sites to remain undetected by switching domains.
Enhanced Safe Browsing, on the other hand, allows Chrome to check uncommon URLs in real time, meaning that threats can be detected faster. Moreover, a small sample of the suspicious page or download is sent to Google, to help protect other users as well.
For signed-in users, the data is linked to their Google account, so that protections can be tailored to the user when an attack is detected against their browser or account. The data is anonymized after a short period.
Users can turn the feature on by heading to Privacy and Security settings > Security > “Enhanced protection” mode under Safe Browsing. The feature will roll out gradually in Chrome 83 and will arrive on Android as well, in a future release.
Chrome 83, Google says, also makes it more intuitive for users to control their privacy and security settings on desktop systems, with easier to manage cookies, reorganized controls in Site Settings, improved control over the data shared with Google to store in Google accounts and share across devices, and the “Clear browsing data” option now at the top of the Privacy & Security section.
The browser also includes a safety check that allows users to confirm the safety of their experience in Chrome. Thus, they can check whether passwords stored in Chrome have been compromised, if Safe Browsing is turned off, if the latest Chrome version is installed, and if malicious extensions are used.
Additionally, Chrome will be blocking third-party cookies by default when in Incognito mode, and will also provide a prominent control over these cookies on the New Tab page. Thus, users can choose to allow third-party cookies for specific sites.
With the new release, Chrome also gets Secure DNS, where DNS-over-HTTPS is employed to encrypt the DNS lookup, to prevent attackers from knowing which sites the user is accessing. The browser will automatically upgrade to DNS-over-HTTPS if the service provider supports it, but users can adjust or completely disable the feature in the Advanced security section.
Of the 38 vulnerabilities patched in the new Chrome release, 27 were reported by external researchers, Google reveals. These include five high severity flaws, seventeen medium severity issues, and five low risk bugs.
The most important of the vulnerabilities are CVE-2020-6465 (use after free in reader mode), CVE-2020-6466 (use after free in media), CVE-2020-6467 (use after free in WebRTC), CVE-2020-6468 (Type Confusion in V8), and CVE-2020-6469 (insufficient policy enforcement in developer tools).
For the first two vulnerabilities, Google paid $20,000 and $15,000 in bug bounties, respectively. Each of the next two bugs earned the reporting researchers $7,500, while the fifth was rewarded with $5,000. Overall, Google says it paid out over $75,000 in bug bounty rewards to the reporting researchers.
The missing link in your SOC: Secure the mainframe
21.5.2020 Net-security Security
How confident are you that your security visibility covers every critical corner of your infrastructure? A good SIEM solution will pull data across firewalls, servers, routers, and endpoint devices. But what if there is even one gap—one piece of equipment that can’t be monitored but contains business critical data? That sounds like a glaring hole in the vision of your SOC, doesn’t it? Especially if it can be exploited by hackers, malicious insiders, or simply by accident.
secure the mainframe
I know, I know. I’m preaching to the choir here. You already know your SOC needs to have immediate access to all of your key infrastructure to ensure a fast and effective response to any incident. But I’ll bet that I’m right in saying there is a gap in many of your enterprises that comes down to a single question—is your mainframe protected by the same level of best practices and automation as your servers? I’d wager the answer is either no, or that you simply don’t know.
Consider the mainframe
Let’s discuss the mainframe for a minute. You know, that computer that accounts for 68 percent of IT production workloads and is the backbone of your entire enterprise?
For ages, the mainframe was like macOS – considered natively secure and not at risk of attack or compromise. Because of that, it was ignored by most security engineers who either subscribed to this belief or simply didn’t understand it and couldn’t challenge that notion.
The reality is that the mainframe is securable, but it is definitely not guaranteed to be secure. An attacker inside your network can access it from the same Windows or Linux platform as your administrators, gain elevated privileges, and gather sensitive data. Once they gain initial access, there are several common methods they can use to initiate privilege escalation. Using those elevated privileges, they are able to run a number of harmful scripts to take control over it and hide their tracks.
Training
It’s time to start treating the mainframe as just another computer on your network. This means that it’s time to synchronize the mainframe’s information and event logging into your SIEM in real-time. And if you are one of the few who already have real-time mainframe visibility, you may still lack the knowledge and expertise to successfully leverage and respond to it. For example, if acronyms like RACF and ACF2 are foreign to your security team, how will they distinguish between a false positive and a devastating incident? The data must be both visible and actionable.
So, what is the answer? Most security analysts need more training to put the security knowledge they already possess into practice to better understand and secure the mainframe. But it won’t take long for the mainframe and its alerts to become part of their battle rhythm. To jumpstart this process, successful companies have generally taken a few key actions:
Hired individuals with a mainframe background and interest in security
Leveraged training programs to learn penetration testing and secure the mainframe
Consulted with a mainframe-managed services provider
Hiring the right person
Simply hiring the right person may seem obvious but hiring talent with either mainframe or cybersecurity skills is getting harder as job openings far outpace the number of knowledgeable and available people. And even if your company is able to compete with top dollar salaries, finding the unique individual with both of these skills may still prove to be infeasible. This is where successful organizations are investing in their current resources to defend their critical systems.
This often takes the form of on-the-job training through in-house education from senior technicians or technical courses from industry experts. A good example of this is taking a security analyst with a strong foundation in cybersecurity and teaching the fundamentals of the mainframe.
The same security principles will apply, and a talented analyst will quickly be able to understand the nuances of the new operating system which in turn will provide your SOC with the necessary skills to defend the entire enterprise, not just the Windows and Linux systems that are most prevalent. Training and investing in your staff will pay off dividends not only in the caliber of your security operations but in the loyalty of the employees who execute it.
If your current staff is unable to broaden their skills expertise due to a shortage of time and bandwidth, you may want to consider a mainframe-managed security service. Offloading the security and responsibility to experts who specialize in defending the mainframe will ensure that you are adequately protected from losing your critical mainframe server. Security is the application of business risk reduction and this will often be the fastest way to meet that goal. Fortunately, this can be done on a temporary, on-demand basis while you ramp up your own staff to integrate the security function back into your SOC.
As part of a wider autonomous digital enterprise framework, securing the mainframe isn’t exclusively a security or operations need, it’s a business need for adaptive security. A successful and adaptive cybersecurity program necessitates having well-trained domain experts that can establish the proactive security functions to automatically sense, detect, and respond to security incidents. When you consider how essential the mainframe is to the critical functions of the organization, you simply can’t afford to make security assumptions about it.
What do IGA solutions have in common with listening to music anywhere?
21.5.2020 Net-security Security
Fifteen years ago, there was a revolution in personal music players. The market had slowly evolved from the Walkman to the Discman, when a bolt of innovation brought the MP3 player. Finally, the solution to having all of one’s music anywhere was solved with a single device, not a device plus a bag full of whatever physical media was popular at that time.

History clearly shows that the iPod and a few of its competitors were very successful in driving revenue and taking market share away from the legacy Personal Music Players. History also shows that the reign of these devices was short-lived. Just a decade after the release of MP3 players, they were almost entirely replaced by personal music player technology on a smart phone. Why did this happen?
The world slowly realized that the way MP3 players solved the problem of my music anywhere, carried a cost that significantly reduced the value of the solution. You had to carry a phone and an iPod, keep them both charged, and, in many cases, both synced with your PC.
Today, stand-alone PMPs are purely niche devices for specific use cases while everyone else plays music through their phones. The smartphone is the perfect platform to consolidate the “music anywhere” capability with the messaging, mapping and gaming anywhere that those platforms provide. This allows you to carry, charge and sync only one device and manage one set of configuration settings.
Having spent the last decade in the identity governance market, I believe a similar sea of change is about to happen. Identity governance solutions require the following set of capabilities:
1. Lifecycle management
Organizations need to provide some set of automation that follows a knowledge worker (employee, contractor, partner, etc.) from the time they start their association with the company until they end their relationship. This automation should be responsible for giving each knowledge worker access to the core set of applications they need to do their jobs, from their first role throughout many possible promotions and role changes over the years.
This capability is critical as it provides the organization the speed and agility they need to ensure everyone can spend their time working, as opposed to dealing with the IT team. Additionally, at every step in the lifecycle, permissions that were relevant for the last job role that no longer are needed should be removed to maintain a least-privilege security stance. This process typically concludes at the end of a long employment journey, which conceivably included many role changes, where it is critical to ensure that the departing team member no longer has access to ANY company resource.
2. Self-service access request
Automated lifecycle management is critical but even the most organized enterprises can’t predict all of the applications and data a particular colleague will need. Projects come and go, oftentimes staffed with matrixed teams, making it hard to completely define every application an employee will need for all their duties. This is where self-service access request comes in. This capability enables all knowledge workers to simply request access to an application when the need arises through an online portal.
These requests are then evaluated against compliance and security policies, then routed directly to the application owner or employee manager for approval. If approved, these new application permissions are automatically fulfilled without the IT group needing to be involved outside of defining the key policies and workflows. This approach allows the business to manage day-to-day decisions over business data access, which is critical to ensuring speed and competitiveness.
3. Automated access certification
The Sarbanes-Oxley of 2002 act made a huge impact on organizations of all types. It was followed by a continuously growing set of additionally regulations, such as HIPAA and GDPR, which all focused on the need for documented and provable controls on all manner of systems and data. Access to applications and the data inside them was a key control metric in all of these regulations.
Access certification is the process meant to arm internal teams with the data they need to prove compliance to these external regulations, or in some cases just internal policies. Access certification requires that on a regular basis (usually every quarter) application owners review the users and permissions that have been assigned within the applications they are responsible for.
During this process, each combination of user, application and permission must be certified, or attested. In cases where a user is believed to have more permissions than they need to do their jobs, these entitlements are flagged for removal. Organizations used to perform these functions with spreadsheets and email (some still do sadly), but today this functionality typically automated through Identity Governance and Administration (IGA) solutions.
4. Auditing and analytics
The average number of applications for an enterprise organization with more than 5000 employees is now more than 400. Assuming each application has only two types of permissions (which is not reality) this gives organizations more than 4 million possible entitlements that are changing all the time and need to be kept track of.
The main value proposition IGA solutions can provide is to consolidate and present this ever-changing data in a way that makes sense to mere mortals. At its core, this provides the value of visibility, but the value explodes during preparation for an audit. What used to take months of manual work, now takes days of preparing for that team of auditors. Modern IGA systems now also frame this information with signals from other silos (GRC, Incident Response, SEIM) to make the data even more usable to audit and risk teams.
These four capabilities sound simple on the page but in practice can be very difficult to implement. This is one of the reasons people have been making stand-alone IGA solutions for more than 15 years now. This is a complicated problem that the market has met with complicated solutions.
And after 15 years, we still see that most IGA programs are categorized as “at risk,” meaning there is a gap between the value expected at program start vs. current reality. I firmly believe we are about to see a revolt against big, heavy solutions to this problem. This revolt will not be just because people are tired of projects that are 3 years behind and 200 percent over budget. People are also starting to see similarities in this problem set to the other IT challenges their organizations have been solving.
In the case of IGA, a high-level view of the solutions show that the main needs of an effective solution include:
Connectivity to key IT systems
Consolidation and presentation of data from multiple systems
Strong workflow-based automation
Interfaces that all stakeholders can use
Coincidentally, these same building blocks are also key to many of the IaaS and PaaS solutions that have become so popular over the past decade. The very reasons organizations invest in platforms such as AWS, Azure, ServiceNow and others is to provide a foundation for all IT workloads to take advantage of. These platforms are the smartphones of enterprise IT, allowing for applications to be created that take advantage of these key design blocks, and are easier to integrate with the rest of the critical IT systems.
Frustrated IGA program owners are ready to ditch the stand-alone solutions (MP3 players) and take advantage of what these platforms can offer by using IGA solutions that are built directly into these key platforms. We have already proven that the current path of making bigger and more powerful siloed solutions results only in vendor growth and doesn’t solve the problem. As these new solutions gain adoption, we will see benefits beyond just reduced complexity and friction.
Just like when we started listening to music on our phones, we immediately saw the obvious benefits. But over time, the market found new benefits that they had not even dreamed about when this phase began. Without the move from PMPs to phones we would not be able to “share” music via social media and messaging, nor do I believe streaming music would have taken off without the phones built in connectivity.
Building IAG solutions on top of key IT platforms will open the door for many similar valuable integrations. As more people leverage Human Resources, Incident Response and GRC on these platforms there will be many integrations that can ONLY be done by IGA solutions that live natively on that same platform.
How secure are open source libraries?
21.5.2020 Net-security Security
Seven in 10 applications have a security flaw in an open source library, highlighting how use of open source can introduce flaws, increase risk, and add to security debt, a Veracode research reveals.

Nearly all modern applications, including those sold commercially, are built using some open source components. A single flaw in one library can cascade to all applications that leverage that code.
According to Chris Eng, Chief Research Officer at Veracode, “Open source software has a surprising variety of flaws. An application’s attack surface is not limited to its own code and the code of explicitly included libraries, because those libraries have their own dependencies.
“In reality, developers are introducing much more code, but if they are aware and apply fixes appropriately, they can reduce risk exposure.”
Open source libraries are ubiquitous and pose risks
The most commonly included libraries are present in over 75% of applications for each language.
Most flawed libraries end up in code indirectly: 47% of those flawed libraries in applications are transitive – in other words, not pulled in directly by developers, but are being pulled in by upstream libraries. Library-introduced flaws in most applications can be fixed with only a minor version update; major library upgrades are not usually required.
Not all libraries have Common Vulnerabilities and Exposures (CVEs) – this means developers can’t rely only on CVEs to understand library flaws. For example, more than 61% of flawed libraries in JavaScript contain vulnerabilities without corresponding CVEs.

Language makes a difference
Some language ecosystems tend to pull in many more transitive dependencies than others. In more than 80% of JavaScript, Ruby, and PHP applications, the majority of libraries are transitive dependencies.
Language selection makes a difference both in terms of the size of the ecosystem and in the prevalence of flaws in those ecosystems. Including any given PHP library has a greater than 50% chance of bringing a security flaw along with it.
Among the OWASP Top Ten flaws, weaknesses around access control are the most common, representing over 25% of all flaws. Cross-Site Scripting is the most common vulnerability category found in open source libraries – found in 30% of libraries – followed by insecure deserialization (23.5%) and broken access control (20.3%).
Only 36% of critical infrastructures have a high level of cyber resilience
21.5.2020 Net-security Security
Greenbone Networks revealed the findings of a research assessing critical infrastructure providers’ ability to operate during or in the wake of a cyberattack.
critical infrastructures cyber resilience
The cyber resilience of critical infrastructures
The research investigated the cyber resilience of organizations operating in the energy, finance, health, telecommunications, transport and water industries, located in the world’s five largest economies: UK, US, Germany, France and Japan. Of the 370 companies surveyed, only 36 percent had achieved a high level of cyber resilience.
To benchmark the cyber resilience of these critical infrastructures, the researchers assessed a number of criteria. These included their ability to manage a major cyberattack, their ability to mitigate the impact of an attack, whether they had the necessary skills to recover after an incident, as well as their best practices, policies and corporate culture.
Infrastructure providers in the US were the most likely to score highly, with 50 percent of companies considered highly resilient. In Europe, the figure was lower at 36 percent. In Japan, is was just 22 percent.
There were also marked differences between industry sectors, with highly-regulated organizations, such as finance and telecoms, most likely to be cyber resilient (both at 46 percent). Transport providers were the least likely to be considered highly resilient (22 percent), while energy providers (32 percent), health providers (34 percent) and water utilities (36 percent) were all close to the average.
Characteristics of a highly-resilient infrastructure provider
They are able to identify critical business processes, related assets and their vulnerabilities: Highly-resilient organizations thoroughly analyse their critical business processes and know which digital assets underpin these processes. They continuously check for vulnerabilities, taking appropriate measures to mitigate or close them.
They deploy cybersecurity architectures that are tailored to their business processes: This focus places them in a strong position to mitigate damage caused by an attack.
They have well-established and well-communicated best practices: The highest performing organizations have well-defined policies and best practices. For example, in 95 percent of highly-resilient organizations, the person responsible for managing a digital asset is also responsible for securing it. This level of expertise and responsibility allows organizations to close gaps and repair damage quickly.
They are more likely to seek third-party support: These companies are more likely to engage with specialist providers, not only to manage security technologies, but also to obtain advice.
For example, they might employ consultants to help develop a security strategy for the company, select suitable technology, implement managed security services, establish metrics for success or calculate the business case for a security project.
They place greater importance on the ability to respond to cyber incidents and mitigate the impact on critical business processes: The ability to prevent cyber incidents is of secondary importance to highly-resilient organizations as they recognize attacks are inevitable.
They are more likely to focus on procedures that lessen the impact of an attack or accelerate their ability to bounce back after an incident.
They prepare for attacks through simulation: They simulate various what-if scenarios in training sessions and also involve stakeholders outside the IT department. They also apply the same cybersecurity rules to all digital assets.
“Cyberattacks are inevitable so being able to firstly withstand them and then recover from them is vital. Nowhere is this more important than in the critical infrastructure industries where any loss or reduction in service could be devastating both socially and economically, so it’s a concern than only just over a third of providers are what we consider to be highly-resilient,” said Dirk Schrader, cyber resilience architect at Greenbone Networks.
“Being cyber resilient involves much more than having enough IT security budget or deploying the right technologies. We hope that – by highlight the key characteristics of highly-resilient organizations – this research will provide a blueprint for others.”
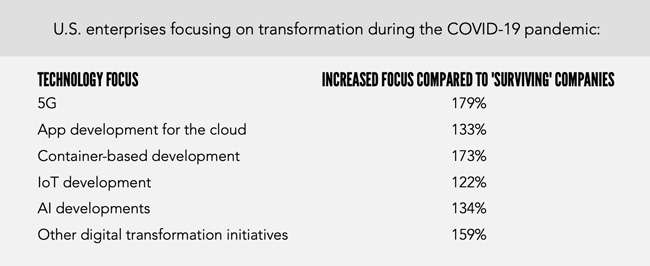
COVID-19 is driving diverging perspectives as enterprises decide which technologies to focus on
21.5.2020 Net-security Security
Technology executives, C-suite leaders and senior executives in areas such as IoT, DevOps, security, and embedded development—from both the U.S. and China are realigning their focus during the COVID-19 pandemic, Wind River reveals.
Seismic events can disrupt our focus and thinking and force reassessment of drivers of future business success. The current pandemic is one of those major events producing a worldwide impact, especially given its reverberations on the two largest global economies, the U.S. and China.
Looking inside the minds of technology executives in major sectors such as telecommunications, healthcare, automotive, aerospace, and manufacturing/industrial provides a view into how leaders are redirecting their focus and accelerating or delaying investments.
The report surveyed 400 senior-level technology executives from the U.S. and China at enterprises with revenues ranging from $100 million to $1 billion.
Most are focusing on surviving the crisis
With COVID-19–related challenges creating new pressures, enterprises are rapidly falling into the categories of simply surviving, pivoting to adapt to new realities, or doing nothing.
While the U.S. and China are in different phases of the pandemic, in several aspects the responses from each country split in similar ways. More than 1 in 3 executives—39% of U.S. and 43% of Chinese leaders—are focusing on surviving this crisis, while 35% in the U.S. and 33% in China are spurred to make a transformation due to COVID-19.
The enterprises focused on transforming have a much higher propensity to accelerate key technology investments compared to those who are merely surviving. Those with a desire to digitally transform are placing 50%+ extra focus on key investment areas such as 5G, containers, and cloud native.
Technologies to focus on
The research findings among these leaders indicate that they understand the core technology components that will be vital for digital transformation. For these enterprises, executives are increasing spend in the following areas:
5G projects: by 63% in China, 37% in the U.S.
Cloud-based application development: by 62% in China, 35% in the U.S.
AI: by 61% in China, 37% in U.S.
Container-based development: by 56% in China, 38% in U.S.
IoT: by 60% in China, 33% in U.S.
Applications at the edge: by 57% in China, 25% in U.S.
Executives placing more importance on DevOps
As enterprises have had to implement changes to their business processes due to the pandemic, 98% in China and 90% in the U.S. note that their ability to meet customer demands has been impacted. Given recent needs, the interest in growing DevOps practices has risen across enterprises, with executives now placing more importance on DevOps (46% in U.S., 36% in China).
Regardless of region, most enterprises realize that the road ahead will be tough. Fifty percent of enterprises in the U.S. and 77% in China are seeing heavier workloads across their teams. They also anticipate the need to implement major initiatives such as accelerating new business models (83% in U.S., 89% in China) and building in more agile development (82% in U.S., 86% in China).

Transformative focus and skills are required
To tackle these challenges, there is a clear recognition among leaders that they will require transformative focus and skills. Therefore, in order to successfully lead a digital transformation, C-suite leaders and executives in DevOps/DevSecOps and IoT anticipate increased importance in their roles (ranging from 60%+ in the U.S. to 73%+ in China) as their businesses exit COVID-19.
As the world grapples with the disruption caused by COVID-19 and enterprises begin to understand major gaps and the resources required to deliver on customer needs, they must identify the right strategies and experts to help them accelerate a digital transformation and realize long-term success beyond the pandemic.
RedisAI and RedisGears address challenges customers have as they move AI into production
21.5.2020 Net-security Security
Redis Labs, the home of Redis and provider of Redis Enterprise, announced the general availability of RedisAI and RedisGears.
Together, RedisAI and RedisGears transform Redis Enterprise into a low-latency, real-time data platform for infinite processing capabilities across any data model, while simultaneously inferencing artificial intelligence (AI) requests all within Redis.
According to Gartner, “Through 2024, the shift from pilot to production artificial intelligence (AI) will drive a 5x increase in streaming data analytics infrastructure.”
The report further states, “Getting AI into production requires IT leaders to complement DataOps and ModelOps with infrastructures that enable end users to embed trained models into streaming-data infrastructures to deliver continuous near-real-time predictions.”
“We’ve heard the challenges customers have as they move AI into production, in particular, the end-to-end AI serving time, which in many cases was influenced by the time it takes to collect, prepare and feed the data to the AI serving engine. RedisAI and RedisGears were designed to solve this problem, by reducing the end-to-end AI serving time to milliseconds,” said Yiftach Schoolman, CTO, and co-founder at Redis Labs.
“With Redis Enterprise as the perfect high-performance and scalable foundation, RedisAI and RedisGears will enable our customers to successfully utilize AI technologies to create operational efficiencies and solve real business problems in real-time.”
RedisAI: Delivering predictions that help the business win
RedisAI (co-developed by Redis Labs and Tenserwerk) is the answer to the challenge every architect or developer faces as they attempt to design and implement AI in their production applications: the time spent outside the AI inference engine to collect and prepare the reference data.
With the AI serving engine inside Redis, RedisAI reduces the time spent on these external processes and can deliver up to 10x more inferences than other AI serving platforms and at a much lower latency.
Many of the leading AI-driven applications such as fraud detection, transaction scoring, ad serving, recommendation engine, image recognition, autonomous vehicles, and game monetization will achieve dramatically better business outcomes with these performance improvements.
Integrated with MLflow, RedisAI eases the management of the AI lifecycle by allowing running models to be updated seamlessly and without downtime. With built-in support for major AI backend systems (TensorFlow, PyTorch, and ONNX Runtime), RedisAI allows inferencing to be run across platforms. For instance, a model that was trained by PyTorch can be inferenced by TensorFlow.
Finally, in combination with Redis Enterprise’s high availability, linear scalability, and flexible deployment model, RedisAI can be deployed anywhere: cloud, on-premises data-centers, edge, and even on Raspberry-Pi devices.
RedisGears: Customize Redis to build better applications
RedisGears is a new serverless engine for infinite programmability options in Redis. RedisGears enables transaction, batch, and event-driven operations to be processed in milliseconds by performing these functions close to the data—all within Redis.
RedisGears enables Redis to operate as a single data service by doing all the heavy lifting of managing updates to existing database and data warehouse systems.
Furthermore, RedisGears allows developers to perform any type of operation across Redis’ data structures and modules. RedisGears functions can be developed once and used across any type of Redis deployment: open-source, Redis Enterprise software, or Redis Enterprise Cloud.
Tech-Assisted COVID-19 Tracking Is Having Some Issues
20.5.2020 Securityweek Security
Harnessing today’s technology to fight the coronavirus pandemic is turning out to be more complicated than it first appeared.
The first U.S. states that rolled out smartphone apps for tracing the contacts of COVID-19 patients are dealing with technical glitches and a general lack of interest by their residents. A second wave of tech-assisted pandemic surveillance tools is on its way, this time with the imprimatur of tech giants Apple and Google. But those face their own issues, among them potential accuracy problems and the fact that they won’t share any information with governments that could help track the spread of the illness.
Contact tracing is a pillar of infection control. It’s traditionally conducted by trained public health workers who interview those who may have been exposed, then urge them to get tested and isolate themselves. Some estimates call for as many as 300,000 U.S. workers to do the work effectively, but so far those efforts have lagged.
Other tech companies like Salesforce have offered database tools to assist manual tracing efforts, although those also raise privacy concerns because of the need to collect and store detailed information about people’s social connections, health status and whereabouts.
Privacy advocates warn that the danger of creating new government surveillance powers for the pandemic could lead to much bigger problems in the future. In a new policy paper shared with The Associated Press, the American Civil Liberties Union is warning state governments to tread more carefully and establish stricter privacy procedures before deploying technology meant to detect and curb new coronavirus outbreaks.
Even the most privacy-minded tools, such as those to be released soon by Apple and Google, require constraints so that they don’t become instruments of surveillance or oppression. “The risks of getting it wrong are enormous,” said Neema Singh Guliani, a senior legislative counsel with the ACLU.
ACLU’s report says the worst location-tracking technology should be rejected outright, such as apps that track individual movements via satellite-based GPS technology and feed sensitive personal data into centralized government databases. “Good designs don’t require you to gather people’s location information and store that,” Singh Guliani said.
She urged governments to set rules addressing both privacy and efficacy so that surveillance tools don’t interfere with more conventional public health methods.
Utah, North Dakota and South Dakota were the first U.S. states to launch voluntary phone apps that enable public health departments to track the location and connections of people who test positive for the coronavirus. But governors haven’t had much luck getting the widespread participation needed for them to work effectively.
Nearly a month after Utah launched its Healthy Together app to augment the state’s contact-tracing efforts by tracking phone locations, state officials confirmed Monday that they haven’t done any contact tracing out of the app yet. Instead, people who download the app have been able to “assess their symptoms and get testing if appropriate,” Utah’s state epidemiologist, Angela Dunn, said last week.
The state with the highest known rate of participation so far is North Dakota, where last week about 4% of residents had downloaded the Care19 app and were using its location services. The same app is getting even less support in South Dakota.
“This is a red state,” said Crystal Wolfrum, a paralegal in Minot, North Dakota, who says she’s one of the only people among her neighbors and friends to download the app. “They don’t want to wear masks. They don’t want to be told what to do. A lot of people I talk to are, like, ‘Nope, you’re not going to track me.’”
Wolfrum said she’s doubtful that the app will be useful, both because of people’s wariness and its poor performance. She gave it a bad review on Google’s app store after it failed to notice lengthy shopping trips she made one weekend to Walmart and Target stores.
North Dakota is now looking at starting a second app based on the Apple-Google technology. The existing app “was rushed to market, because of the urgent need, Vern Dosch, the state’s contact tracing facilitator, told KFYR-TV in Bismarck. “We knew that it wouldn’t be perfect.”
The ACLU is taking a more measured approach to the Apple and Google method, which will use Bluetooth wireless technology to automatically notify people about potential COVID-19 exposure without revealing anyone’s identity to the government.
But even if the app is described as voluntary and personal health information never leaves the phone, the ACLU says it’s important for governments to set additional safeguards to ensure that businesses and public agencies don’t make showing the app a condition of access to jobs, public transit, grocery stores and other services.
Among the governments experimenting with the Apple-Google approach are the state of Washington and several European countries.
Swiss epidemiologist Marcel Salathé said all COVID-19 apps so far are “fundamentally broken” because they collect too much irrelevant information and don’t work well with Android and iPhone operating software. Salathé authored a paper favoring the privacy-protecting approach that the tech giants have since adopted, and he considers it the best hope for a tool that could actually help isolate infected people before they show symptoms and spread the disease.
“You will remember your work colleagues but you will not remember the random person next to you on a train or really close to you at the bar,” he said.
Other U.S. governors are looking at technology designed to supplement manual contact-tracing efforts. As early as this week, Rhode Island has said it is set to launch a “one-stop” pandemic response phone app. It will pair with a new contact-tracing database system built by software giant Salesforce, which has said it is also working with Massachusetts, California, Louisiana and New York City on a similar approach.
Salesforce says it can use data-management software to help trained crews trace “relationships across people, places and events” and identify virus clusters down to the level of a neighborhood hardware store. It relies on manual input of information gathered through conversations by phone, text or email.
“It’s only as good as a lot of us using it,” Democratic Gov. Gina Raimondo said of the soon-to-be-launched mobile app at a news conference last week. “If 10% of Rhode Island’s population opts in, this won’t be effective.” The state hasn’t yet outlined what people are expected to opt into.
The ACLU hasn’t weighed in on the Salesforce model, but has urged contact-tracing public health departments to protect people from unnecessary disclosure of personal information and to not criminalize the requirement for self-isolation.
Chrome 83: Enhanced Safe Browsing, Secure DNS, a Safety Check
20.5.2020 Net-security Security
Google has released version 83 of it’s popular Chrome web browser, which includes new security and privacy features and fixes for security issues.
Chrome 83: New and improved security and privacy features
The enhanced Safe Browsing mode will allow users to get a more personalized protection against malicious sites.

“Phishing sites rotate domains very quickly to avoid being blocked, and malware campaigns are directly targeting at-risk users,” Google explained.
“Turning on Enhanced Safe Browsing will substantially increase protection from dangerous websites and downloads. By sharing real-time data with Google Safe Browsing, Chrome can proactively protect you against dangerous sites. If you’re signed in, Chrome and other Google apps you use (Gmail, Drive, etc.) will be able to provide improved protection based on a holistic view of threats you encounter on the web and attacks against your Google Account.”
A new Safety Check option allows users to scan their Chrome installation and show whether the browser is up to date, whether the Safe Browsing service is on, whether potentially harmful extensions have been installed, and whether any of the passwords the user uses has been compromised in a known breach.
New cookie controls and settings – from now on, users will be able to delete cookies on a per-site basis and block third-party cookies while using Chrome’s Incognito mode (aka “private browsing” mode).
Secure DNS – build on top of the DNS-over-HTTPS (DoH) protocol.
“When you access a website, your browser first needs to determine which server is hosting it, using a step known as a ‘DNS (Domain Name System) lookup.’ Chrome’s Secure DNS feature uses DNS-over-HTTPS to encrypt this step, thereby helping prevent attackers from observing what sites you visit or sending you to phishing websites,” Google noted.
“By default, Chrome will automatically upgrade you to DNS-over-HTTPS if your current service provider supports it. You can also configure a different secure DNS provider in the Advanced security section, or disable the feature altogether.”

Some features have already been rolled out, others will be made available to desktop Chrome users in upcoming weeks.
CEOs and CISOs disagree on cyber strategies
20.5.2020 Net-security Security
There are growing disparities in how CEOs and CISOs view the most effective cybersecurity path forward, according to Forcepoint.
CEOs CISOs disparities
The global survey of 200 CEOs and CISOs from across industries including healthcare, finance and retail, among others, uncovered prominent cybersecurity stressors and areas of disconnect for business and security leaders, including the lack of an ongoing cybersecurity strategy for less than half of all CEO respondents.
The research also identified disparities between geographic regions on data protection as well as a digital transformation dichotomy battle between increased risk and increased technology capability.
Most leaders (76%) are losing sleep over the prospect of becoming the next headline-grabbing security breach
This is despite a high percentage (87%) believing that their security team is consistently ahead of cybersecurity threats
This disparity is compounded by a belief that senior leadership is cyber-aware and data-literate (89%) and focused on cybersecurity as a top organizational priority (93%)
Cybersecurity strategies are seen by 85% of executives as a major driver for digital transformation, yet 66% recognize the increased organizational exposure to cyber threats because of digitization
Only 46% of leaders regularly review their cybersecurity strategies
“When more than 89% of leaders believe their teams are more cyber-aware than ever, it’s not surprising to hear executives are losing sleep over their cybersecurity posture today because they know the stakes to their business are so high,” said Nicolas Fischbach, Global CTO of Forcepoint. “At a time when cybersecurity is more strategic to business growth than ever before, it is time senior business and security leaders reassess their cybersecurity strategy to one that enables them to move left of breach.
Disparities between CEOs, CISOs and global geographies
The research spotlights the disparity in how enterprises across global geographies prioritize key elements of security. Protecting customer data is a resounding priority for leaders in the US (62%) and Europe (64%), while in Asia 61% of leaders will prioritize protecting organizational IP over customer data.
Factors influencing these results may be due in part to differing regulatory approaches to data and privacy protection as well as recent legislative decisions in the U.S. and Europe, such as GDPR and CCPA.
There is also a clear divide between CEOs and CISOs in how they identify the right cybersecurity path forward for their business. CEOs prefer to be proactive and risk-focused (58%), prioritizing maintenance of business stability above all.

While more than half of CISOs (54%) embrace a more reactive, incident-driven approach to mitigating today’s dynamic cybersecurity threat landscape.
The research also found that, despite claiming vendor fatigue, enterprises use more than 50 security vendors on average with 62% reporting they want even more.
However, as more enterprises begin to embrace the cost savings and benefits of converged networking and security capabilities found in the emerging Secure Access Service Edge (SASE) security architecture approach the need for dozens of security vendors will abate over time.
Fischbach continued, “Companies leading on the cybersecurity front today are realistic about the risks they face and are prepared to prioritize security to protect the lifeblood of their business – which is customer data and organizational IP. And with today’s new way of working, getting this right within a remote work reality has never been more critical.
“Now is the time for all business and security leaders to recognize the business continuity actions they take now will determine whether they simply survive or thrive in today’s new business reality.”
With the threat landscape continuously changing, businesses must be ready for anything
20.5.2020 Net-security Security
Despite efforts by organizations to layer up their cyber defenses, the threat landscape is changing, attackers are innovating and automating their attacks, NTT reveals.

The threat landscape is changing
Referencing the COVID-19 pandemic, the report highlights the challenges that businesses face as cyber criminals look to gain from the global crisis and the importance of secure-by-design and cyber-resilience.
The attack data indicates that 55% of all attacks in 2019 were a combination of web-application and application-specific attacks, up from 32% the year before, while 20% of attacks targeted CMS suites and more than 28% targeted technologies that support websites.
For organizations that are relying more on their web presence during COVID-19, such as customer portals, retail sites, and supported web applications, they risk exposing themselves through systems and applications that cyber criminals are already targeting heavily.
Matthew Gyde, President and CEO of the Security division, NTT Ltd., says: “The current global crisis has shown us that cyber criminals will always take advantage of any situation and organizations must be ready for anything.
“We are already seeing an increased number of ransomware attacks on healthcare organizations and we expect this to get worse before it gets better. Now more than ever, it’s critical to pay attention to the security that enables your business; making sure you are cyber-resilient and maximizing the effectiveness of secure-by-design initiatives.”
Industry focus: Technology tops most attacked list
While attack volumes increased across all industries in the past year, the technology and government sectors were the most attacked globally. Technology became the most attacked industry for the first time, accounting for 25% of all attacks (up from 17%).
Over half of attacks aimed at this sector were application-specific (31%) and DoS/DDoS (25%) attacks, as well as an increase in weaponization of IoT attacks. Government was in second position, driven largely by geo-political activity accounting for 16% of threat activity, and finance was third with 15% of all activity. Business and professional services (12%) and education (9%) completed the top five.
Mark Thomas who leads NTT’s Global Threat intelligence Center, comments: “The technology sector experienced a 70% increase in overall attack volume. Weaponization of IoT attacks also contributed to this rise and, while no single botnet dominated activity, we saw significant volumes of both Mirai and IoTroop activity.
“Attacks on government organizations nearly doubled, including big jumps in both reconnaissance activity and application-specific attacks, driven by threat actors taking advantage of the increase in online local and regional services delivered to citizens.”
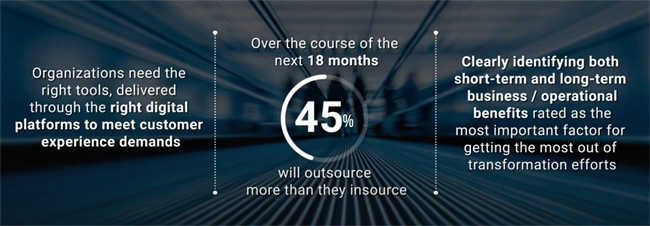
Key research highlights
Websites posing as ‘official’ source of COVID-19 information, but host exploit kits and/or malware – created at an incredible rate, sometimes exceeding 2000 new sites per day.
Most common attack types accounted for 88% of all attacks: Application-specific (33%), web application (22%), reconnaissance (14%), DoS/DDoS (14%) and network manipulation (5%) attacks.
Attackers are innovating: By leveraging artificial intelligence and machine learning and investing in automation. Some 21% of malware detected was in the form of a vulnerability scanner, which supports the premise that automation is a key focus point of attackers.
Weaponization of IoT: Botnets such as Mirai, IoTroop and Echobot have advanced in automation, improving propagation capabilities. Mirai and IoTroop are also known for spreading through IoT attacks, then propagating through scanning and subsequent infection from identified hosts.
Old vulnerabilities remain an active target: Attackers leveraged those that are several years old, but have not been patched by organizations, such as HeartBleed, which helped make OpenSSL the second most targeted software with 19% of attacks globally. A total of 258 new vulnerabilities were identified in Apache frameworks and software over the past two years, making Apache the third most targeted in 2019, accounting for over 15% of all attacks observed.
Attacks on Content Management Systems (CMS) accounted for about 20% of all attacks: Targeting popular CMS platforms like WordPress, Joomla!, Drupal, and noneCMS, cyber criminals used them as a route into businesses to steal valuable data and launch additional attacks. Additionally, more than 28% targeted technologies (like ColdFusion and Apache Struts) support websites.
With increased DevOps adoption, roles in software development teams are changing
20.5.2020 Net-security Security
Roles across software development teams have changed as more teams adopt DevOps, according to GitLab.

The survey of over 3,650 respondents from 21 countries worldwide found that rising rates of DevOps adoption and implementation of new tools has led to sweeping changes in job functions, tool choices and organization charts within developer, security and operations teams.
“This year’s Global DevSecOps Survey shows that there are more successful DevOps practitioners than ever before and they report dramatically faster release times, truly continuous integration/deployment, and progress made toward shifting both test and security left,” said Sid Sijbrandij, CEO at GitLab.
“That said, there is still significant work to be done, particularly in the areas of testing and security. We look forward to seeing improvements in collaboration and testing across teams as they adjust to utilizing new technologies and job roles become more fluid.”
It’s a changing world for developer, operations and security teams and that holds true for roles and responsibilities as well as technology choices that improve DevOps practices and speed up release cycles. When done right, DevOps can go a long way to improve a business’s bottom line, but there are still obstacles to overcome to achieve true DevSecOps.
DevOps adoption and software development teams
Every company is now a software company and to drive business results, it is even more critical for teams to understand how the role of the developer is evolving – and how it impacts security, operations and test teams’ responsibilities.
The lines are blurring between developers and operations teams as 35% of developers say they define and/or create the infrastructure their app runs on and 14% actually monitor and respond to that infrastructure – a role traditionally held by operations.
Additionally, over 18% of developers instrument code for production monitoring, while 12% serve as an escalation point when there are incidents.
DevOps adoption rates are also up – 25% of companies are in the DevOps “sweet spot” of three to five years of practice while another 37% are well on their way, with between one and three years of experience under their belts.
As part of this implementation, many are also seeing the benefits of continuous deployment: nearly 60% deploy multiple times a day, once a day or once every few days (up from 45% last year).
As more teams become more accustomed to using DevOps in their work, roles across software development teams are starting to shift as responsibilities begin to overlap. 70% of operations professionals report that developers can provision their own environments, which is a sign of shifting responsibilities brought on by new processes and changing technologies.
Security teams unclear about responsibilities
There continues to be a clear disconnect between developers and security teams, with uncertainty about who should be responsible for security efforts. More than 25% of developers reported feeling solely responsible for security, compared to testers (23%) and operations professionals (21%).
For security teams, even more clarity is needed, with 33% of security team members saying they own security, while 29% (nearly as many) said they believe everyone should be responsible for security.
Security teams continue to report that developers are not finding enough bugs at the earliest stages of development and are slow to prioritize fixing them – a finding consistent with last year’s survey.
Over 42% said testing still happens too late in the life cycle, while 36% reported it was hard to understand, process, and fix any discovered vulnerabilities, and 31% found prioritizing vulnerability remediation an uphill battle.
“Although there is an industry-wide push to shift left, our research shows that greater clarity is needed on how teams’ daily responsibilities are changing, because it impacts the entire organization’s security proficiency,” said Johnathan Hunt, vice president of security at GitLab.
“Security teams need to implement concrete processes for the adoption of new tools and deployments in order to increase development efficiency and security capabilities.”

New technologies help with faster releases, create bottlenecks in other areas
For development teams, speed and faster software releases are key. Nearly 83% of developers report being able to release code more quickly after adopting DevOps.
Continuous integration and continuous delivery (CI/CD) is also proven to help reduce time for building and deploying applications – 38% said their DevOps implementations include CI/CD. An additional 29% said their DevOps implementations include test automation, 16% said DevSecOps, and nearly 9% use multi-cloud.
Despite this, testing has emerged as the top bottleneck for the second year in a row, according to 47% of respondents. Automated testing is on the rise, but only 12% claim to have full test automation. And, while 60% of companies report deploying multiple times a day, once a day or once every few days, over 42% said testing happens too late in the development lifecycle.
While strides toward implementing DevOps practices have been made, there is more work to be done when it comes to streamlining collaboration between security, developer and operations teams.
Technologies in all layers of the cloud stack are at risk
20.5.2020 Net-security Security
As breaches and hacks continue, and new vulnerabilities are uncovered, secure coding is being recognized as an increasingly important security concept — and not just for back-room techies anymore, Accurics reveals.
“Our report clearly describes how current security practices are grossly inadequate for protecting transient cloud infrastructures, and why more than 30 billion records have been exposed through cloud breaches in just the past two years,” said Sachin Aggarwal, CEO at Accurics.
“As cloud stacks become increasingly complex, with new technologies regularly added to the mix, what’s needed is a holistic approach with consistent protection across the full cloud stack, as well as the ability to identify risks from configuration changes to deployed cloud infrastructure from a baseline established during development.
“The shift to infrastructure as code enables this; organizations now have an opportunity to redesign their cloud security strategy and move away from a point solution approach.”
Key takeaways from the research
Misconfigurations of cloud native technologies across the full cloud native stack are a clear risk, increasing the attack surface, and being exploited by malicious actors.
There is a significant shift towards provisioning and managing cloud infrastructure through code. This offers an opportunity for organizations to embed security earlier in the DevOps lifecycle. However, infrastructure as code is not being adequately secured, thanks in part to the lack of tools that can provide holistic protection.
Even in scenarios where infrastructure as code actually is being governed, there are continuing problems from privileged users making changes directly to the cloud once infrastructure is provisioned. This creates posture drift from the secure baseline established through code.
Infrastructure as code
The research shows that securing cloud infrastructure in production isn’t enough. Researchers determined that only 4% of issues reported in production are actually being addressed. This is unsurprising since issue investigation and resolution at this late stage in the development lifecycle is challenging and costly.
A positive trend identified by the research is that there is a significant shift towards provisioning and managing cloud infrastructure through code to achieve agility and reliability.
Popular technologies include Terraform, Kubernetes, Docker, and OpenFaaS. Accurics’ research shows that 24% of configuration changes are made via code, which is encouraging given the fact that many of these technologies are relatively new.
Infrastructure as code provides organizations with an opportunity to embed security earlier in the development lifecycle. However, research revealed that organizations are not ensuring basic security and compliance hygiene across code.
The dangers are undeniable: high severity risks such as open security groups, overly permissive IAM roles, and exposed cloud storage services constituted 67% of the issues. This is particularly worrisome since these types of risks have been at the core of numerous high-profile cloud breaches.
The study also shows that even if organizations implement policy guardrails and security assessments across infrastructure as code, 90% of organizations allow privileged users to make configuration changes directly to cloud infrastructure after it is deployed. This unfortunately results in cloud posture drifting from the secure baseline established during development.

Recommended best practices
The importance of protecting the full cloud native stack, including serverless, containers, platform, and infrastructure
Embedding security earlier in the development lifecycle in order to reduce the attack surface before cloud infrastructure is provisioned, as well as monitor for incremental risks throughout its lifecycle
Most importantly, preventing cloud posture drift from the secure baseline established during development once infrastructure is provisioned
Over half of security leaders still rely on spreadsheets
20.5.2020 Net-security Security
Senior security leaders within financial services companies are being challenged with a lack of trusted data to make effective security decisions and reduce their risk from cyber incidents, according to Panaseer.
security leaders spreadsheets
Results from a global external survey of over 400 security leaders that work in large financial services companies reveal concerns on security measurement and metrics that include data confidence, manual processes, resource wastage and request overload.
Issues with processes, people and technologies
The results demonstrate myriad issues with the processes, people and technologies required to have a full understanding of the organization’s cyber posture and the preventative measures required to stop a security control failure from becoming a security incident.
The vast majority (96.77%) of respondents claimed they use metrics to measure their cyber posture, with the primary use for security metrics being risk management (41.69%), demonstrating the success of security initiatives (28.04%), supporting security investment business cases (19.11%) and Board/ executive reporting (10.17%).
Over a third (36.72%) of security leaders said that their biggest challenge in creating metrics to measure and report on risk is ‘trust in the data,’ followed by the resources required to produce them (21.34%), the frequency of requests (14.64%) and confusion over knowing what metric to use (15.3%).
Less than half of respondents (47.75%) could claim to be ‘very confident’ that they are using the right security metrics to measure cyber risk.
Too many security leaders still use spreadsheets
Resource requirements and request overload are cited as other issues fueling the metrics mayhem. On average, security teams are spending 5.34 days a month compiling metrics for managing risk – and that doesn’t include the time the team spending compiling metrics for other stakeholders, including regulators, auditors and the Board. Security leaders also claim they must refresh these security metrics for risk teams every 16 days.
Manual processes are also cited as fuelling data mistrust. Over half (59.8%) of security leaders still rely on spreadsheets to produce metrics and 52.85% are using custom scripts. Nearly one in five (18.75%) admitted to relying exclusively on manual processes to develop their security metrics for risk.
Nik Whitfield, CEO, Panaseer: “Security metrics are frequently cited as the bane of the security teams’ lives. Not knowing the accuracy, timeliness or even limitations of a metric can render it useless – which is simply unacceptable against a backdrop of tightening regulation and an increasing attack surface. The President of the European Central Bank recently went on record to warn that a cyber-attack on a major financial institution could trigger a liquidity crisis.
“We must move on from the era of out-of-date inaccurate metrics to one where they are automated and measured on a continuous basis. Financial service organizations, in particular, need trusted and timely metrics into an organization’s technology risk, segmented where possible to critical operations. With this information, the Board can then have a better understanding of what risks are and aren’t acceptable to keep customer data safe.”
Automating nmap scans
18.5.2020 Net-security Security
With last week’s diary I left you with using a relatively basic nmap command to perform a relatively thorough scan of an IP range. That command was:
nmap -sT -A <scan_target>
I had indicated that I often use variations on that command to automate periodic scans against a critical IP range. I had left you with some basics about what other parts of nmap can be helpful to automate this. This week I received some questions about the automation steps, so here is the rest of the details. In practice, most of my automated scripts have evolved from this simple state, but in its very basic form here is where they evolved from.
In order to truly automate the scan we need three components:
Input file – to tell nmap which targets to scan
Output file(s) – to record and compare the results
Bash script - to act as a wrapper for the process steps
To tell nmap which IPs or networks to scan you can use the -iL <filename> parameter. For a quick scan I usually just create a file called ips.txt in the current directory. The contents of that file can be single IPs or network ranges in CIDR format, one address/network per line. So that takes us to an nmap command of:
nmap -sT -A -iL <address_file>
As stated in the previous diary, the -oA <filename> parameter will send the nmap scan results to files utilizing all three of nmap’s output formats; normal (.nmap), XML (.xml), and grepable (.gnmap). Only the .xml version is used by ndiff, but I find the other output formats useful for other purposes such as investigating after the scan. Typically I just send my output to a file called nmap_current. So the resulting nmap command is:
nmap -sT -A -iL <address_file> -oA nmap_current
and once that command is complete there will be three nmap output files:
nmap_current.gnmap
nmap_current.nmap
nmap_current.xml
There are many ways the running of this can be automated, but typically I just create a simple bash shell script and schedule it with cron to run at the appropriate interval. A sample Bash script, nmap_scan.sh:
#!/bin/bash
# if there is a current file from a past run, then copy it to previous
if [ -f nmap_current.xml ];then
cp nmap_current.xml nmap_previous.xml
fi
# run nmap
/usr/bin/nmap -sT -A -iL ips.txt -oA nmap_current
# if there is not a previous file then there is no point running ndiff
# this will fix itself on the next run
if [ -f nmap_previous.xml ];then
/bin/ndiff nmap_previous.xml nmap_current.xml >> ndiff_out.txt
fi
Please note that is not a very robust script. The paths should be more explicit, and it does not handle the emailing of the ndiff result, but as a quick and dirty script it will do.
Once the script completes you will find the differences between the current scan and the previous scan in ndiff_out.txt in standard diff formal. i.e. anything from the original file that has been removed shows a minus sign in the first column and anything in the new file that has been added shows with a plus sign in the first column.
# cat ndiff_out.txt
-Nmap 7.60 scan initiated Mon May 18 19:36:21 2020 as: /usr/bin/nmap -sT -A -iL ips.txt -oA nmap_current
+Nmap 7.60 scan initiated Mon May 18 20:12:00 2020 as: /usr/bin/nmap -sT -A -iL ips.txt -oA nmap_current
Hostname REDACTED (IP REDACTED):
OS details:
Vodavi XTS-IP PBX
- Android 5.0 - 5.1
- Linux 3.2 - 3.10
Linux 3.2 - 3.16
Linux 3.2 - 4.8
+ Linux 3.2 - 3.10
Linux 4.2
+ Android 5.0 - 5.1
+ Linux 2.6.32
Linux 3.10
Linux 3.13
- Linux 2.6.32
Linux 2.6.32 - 3.10
+Hostname REDACTED (IP REDACTED):
+Host is up.
+Not shown: 999 closed ports
+PORT STATE SERVICE VERSION
+3306/tcp open mysql MariaDB (unauthorized)
+OS details:
+ Linux 2.6.32
+ Linux 3.7 - 3.10
+ Linux 3.10
+ Linux 3.16
+ Linux 3.8 - 4.9
+ Linux 3.1
+ Linux 3.2
+ AXIS 210A or 211 Network Camera (Linux 2.6.17)
+ Linux 3.11 - 3.14
+ Linux 3.19
A little knowledge of the network and some analysis and this is enough to give you a warning if something unusual is going on. i.e. an unauthorized device, or service has appeared, or the configuration of one of the devices has changed.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
CISOs are critical to thriving companies: Here’s how to support their efforts
18.5.2020 Net-security Security
Even before COVID-19 initiated an onslaught of additional cybersecurity risks, many chief information security officers (CISOs) were struggling.
CISOs struggling
According to a 2019 survey of cybersecurity professionals, these critical data defenders were burned out. At the time, 64% were considering quitting their jobs, and nearly as many, 63%, were looking to leave the industry altogether.
Of course, COVID-19 and the ensuing remote work requirements have made the problem worse. It’s clear that companies could be facing an existential crisis to their data security and that their best defenders are struggling to stay in the fight.
The current state of CISOs
Even as they have to deal with an ever-expanding threat landscape, CISOs are managing a mounting plate of responsibilities. As companies hurdle toward digital transformation, automation, cloud computing, brand reputation, and strategic investments are falling on CISOs’ plate.
It’s easy to see why CISOs feel overwhelmed, overworked, unprepared, and underequipped. Cisco’s recent CISO survey, which combines insights from panel discussions and more than 2,800 responses from IT decision-makers, puts both quantitative and qualitative metrics to these problems.
Notably, leaders identified a workforce that is rapidly becoming remote as a top cause of stress and anxiety. Specifically, Cisco reports that “More than half (52%) told us that mobile devices are now very or extremely challenging to defend.”
By now, the cybersecurity vulnerabilities associated with remote work are well-documented, but the COVID-19 pandemic makes it clear that remote work is going to become both more prominent and more problematic in the weeks, months, and years ahead.
In the meantime, a deluge of alerts and threat notifications are causing cybersecurity fatigue, meaning leaders are “virtually giving up on proactively defending against malicious actors.” Collectively, 42% of survey respondents indicated that they were experiencing cybersecurity fatigue.
This challenge is amplified when leaders are managing multiple vendors, as “complexity appears to be one of the main causes of burnout.”
Finally, CISOs are being asked to navigate an increasingly complex threat landscape while accounting for expanding government oversight in the form of data privacy laws, which are becoming ever-more prevalent now that the pendulum has swung almost entirely toward digital discretion.
To be sure, that’s not to say that CISOs aren’t excelling. The industry is full of hard-working, talented, and ambitious people. Everyone, from MSPs to CEOs, needs to do a better job of supporting CISOs.
Supporting struggling CISOs and protecting data
1. Prioritize singularity
CISOs are struggling to manage a multi-vendor environment with disassociated solutions coming from many places. Instead, provide comprehensive endpoint data loss prevention software that accounts for a wide range of threats and offers extensive insights into a company’s data landscape.
2. Rely on automation
The vast majority of cybersecurity personnel who reported cyber fatigue experienced more than 5,000 alerts every day. The rapidly expanding capabilities of AI and machine learning have to be harnessed to reduce this onslaught of information. Many threats can be addressed with software, reducing the number of alerts that actually make it to IT personnel, allowing them to focus on the most prescient threats. It’s both better use of their time and a more sustainable way to work.
What’s more, relying on automation can help IT leaders account for a growing and apparent skills gap that leaves many departments understaffed.
3. Account for known risks
Today’s threat landscape is expansive, but some risks are more prominent than others. For instance, it’s estimated that human error is responsible, in part, for as many of 90% of all data breaches. In other words, employees collectively represent the most significant cybersecurity risk, as both accidental and malicious insiders contribute to a growing number of breaches. For instance, we’ve seen examples of
Employees compromising network security by engaging with phishing scams
Employees stealing company data to sell or leverage down the road
Employees accidentally sharing private information outside of appropriate channels
Employees accessing company data on personal devices
There is a myriad of ways that insiders compromise company data. Identify and determine cybersecurity solutions that can bolster your defenses toward the most prominent threats.
4. Communicate and prepare
Ultimately, cybersecurity isn’t just a priority for CISOs. It’s time to develop an all-in approach to data security to bring awareness and capability to every level of the company. In a real way, data security depends on each person playing an active role in the company’s defensive posture.
CISOs may be struggling, but they are immensely talented and uniquely important. It’s time to support their efforts in meaningful and tangible ways.
Review: Kill Chain: The Cyber War on America’s Elections
18.5.2020 Net-security Security
Kill Chain: The Cyber War on America's Elections
Kill Chain is an HBO documentary made and produced by Simon Arizzone, Russell Michaels and Sarah Teale.
Kill Chain: Inside the documentary
Arizzone and Michaels already worked on a documentary in 2006 called Hacking Democracy, which was about uncovering voting machines vulnerabilities and about how votes were manipulated, leading to George W. Bush winning the elections (2004).
And here we are again in 2020 talking about the same problem and uncovering the same old security holes inside the machines that are supposed to be secure and reliable, since they have the essential role of ensuring democracy is being practiced properly.
The authors gathered various experts, including Harri Hursti, a hacker and election security expert, to talk about their view and knowledge of the U.S. election system.
Hursti already warned about the hackability of the election machines in 2006. Now, once again, he went on a mission to expose the susceptibility of the U.S. election system by analyzing the machines currently in use, but also the discarded ones which he easily got hold of through eBay. As if that weren’t enough, the purchased ones still contained voting data.
He then decided to test the hackability of the machines by allowing hackers at the DEF CON hacker convention to try to access them. The task was shockingly easy and every single machine has been successfully breached, which meant anyone could effortlessly manipulate the election results.
The authors also interviewed a hacker that goes by “CyberZeist”, who claimed to have accessed the Alaska voting system website with little effort. Had he been backed by an organization with an agenda, the repercussions would have been much greater.
The documentary gives you the technical information about how a kill chain works and a hacker’s potential motivation, whether it’s personal satisfaction and gain or political reasons. It also sheds light on how technology is supposed to make things faster and easier but how, in the end, it can be easily manipulated.
Does it hit the spot?
This is an eye-opening and captivating documentary accompanied by an eerie soundtrack that complements the seriousness of the issue well. The technical parts are well explained and comprehensible to the average viewer.
A great number of politicians and decision-makers continue to dismiss warnings and refuse to pass bills that would guarantee a secure and protected election system. Experts are worried, but without political backup, there’s not much they can do about it. Hopefully, this documentary will make U.S. citizens worry about the outcomes of future elections and push them to demand changes.
How a good user experience brings the pieces of the enterprise IT jigsaw together
18.5.2020 Net-security Security
Have you ever done a jigsaw puzzle with pieces missing? Or tried to do a complicated one with only part of the picture showing on the box lid? If so, you will know how it feels to be the folks working to create secure, robust, and seamless enterprise IT systems.
secure enterprise IT
Enterprise IT has morphed into something that can feel complex and messy at best and out of control at worst. Each deployment can be convoluted, having to deal with various aspects of data and IT infrastructure; the lifecycle of data may be ignored in the process and niche issues are resolved at the expense of ease of deployment and maintenance.
Business units can end up with dozens of apps, each within a slightly different environment and using data with no integration or communication. This has led to a lack of standardization in data formatting and interfaces.
The User Experience (UX) of enterprise IT is a key to making the puzzle pieces fit. There is a misconception that UX is just about graphics. But a basis of good UX extends to the work behind the scenes within a terminal or console.
The data jigsaw puzzle that enterprise IT has to solve is complicated, it is sensitive, and it needs to be secure.
The secure enterprise IT jigsaw puzzle pieces
Imagine doing a jigsaw puzzle of a Jackson Pollock painting, the artist renowned for images made from complex mixes of abstract colors. The journey of completing such a puzzle reminds me of the journey we find ourselves when implementing and securing multi-cloud environments, IT applications, and complex data flows.
The pieces of the enterprise infrastructure jigsaw can be broken down into constituent parts to help create a full-picture solution. One way to approach this is by looking at the data flows within enterprise IT components. Data is a dynamic species. It moves between systems, it rests, it is worked on, processed and analyzed. We express data flow within this complex IT infrastructure matrix, referring to:
Many users – data flows between many (sometimes even thousands of) users.
Many business units – business rarely exists as a single entity. Often business units are multiple departments and even different countries and jurisdictions.
Using the same data – the same data can flow between users and across units, the data often fragmented between different locations.
For various needs – data is used for different needs and use cases. It is analyzed and processed to create yet additional data to be used for other purposes.
Creating applications which need to handle all the above considerations in a dynamic environment, often end-up appearing multi-layered with many different and disconnected user flows and feature. This creates a complicated environment to deploy, integrate, manage and operate.
The UX puzzle and data
The whole-picture solution is a UX puzzle for all, including vendors and customers. The disparate nature of multi-cloud infrastructures and apps has created a messy disconnected UX, the result being that usability, data security, and privacy all suffer.
Creating a more seamless deployment, maintenance and user flows requires you to have informed choices around:
Deployment flow
Good design starts with easy and flexible deployment processes. We’re all familiar with applications that require a heavy and long professional services engagement for deployment and maintenance. The deployment process should be as seamless as possible, where each step of the way is clearly presented to the user, allowing a quick basic installation with additional advanced options to be available to the user at later stages.
Ease of integration and changing goalposts
One of the bugbears of the user experience is the integration between different apps and any chosen cloud/IT infrastructure. Things such as code changes and change of processes are the equivalent of dropping rogue jigsaw pieces into the puzzle – making an already challenging scenario even more so. Changing processes can result in lost data or hold-ups in collaboration. All need to be managed well and a seamless UX, with intuitive management interfaces can help to achieve this.
Data flows
Data flow between environments can be hard to manage as gaps emerge. Covering enterprise data security across these disparate objects is non-intuitive. The use of a great UX within the consoles used to manage data can turn the Pollock jigsaw image into a non-abstract form so you can see the data lifecycle flow more easily.
One important aspect of using an app management solution – along with visibility of your data flow – is the availability of excellent management dashboards. From a central point of view, you should be able to see your projects, deployments, and your cloud infrastructure deployment options. Good data visibility, will, in turn, help with applying the right security at the right point within your systems.
Making the jigsaw puzzle visible via great user experience
With a puzzle, you usually know what the full picture will be once all of the pieces are in place. But in the case of enterprise IT applications, we are often placed in a position where we have to take many unrelated “full pictures” and shoe-horn them into one big puzzle. This has serious implications for usability, security, privacy, and compliance with various regulations.
We have to begin with the user experience across all of these pieces of the puzzle. This should involve finding ways, through good visibility and management, to create a seamless UX across the entire extended enterprise family of services and apps.
Bringing the whole together through a shared and robust UX and ensuring that data flow is visible allows the application of effective and relevant security measures across the lifecycle of data. This final security message is important. Data security is at the heart of all of our data transactions. Security is the final piece of the puzzle, knowing where to drop it in, completes the picture.
Mental Health Awareness Week: Coping with cybersecurity pressures amidst a global pandemic
18.5.2020 Net-security Security
As most of the UK’s cybersecurity workforce now sits at home isolated while carrying out an already pressurised job, there is every possibility that this could be affecting their mental health.
Mental Health Awareness Week
In light of Mental Health Awareness Week, and as the discussion around employee wellbeing becomes louder and louder amidst the COVID-19 pandemic, we spoke with five cybersecurity experts to get their thoughts on how organisations can minimise the negative mental and physical impacts on newly-remote employees.
Remote but not alone: the power of communication
“In the current global situation, focusing on mental health is more important than ever,” says Agata Nowakowska, AVP at Skillsoft. “Now is the time to raise the profile of workplace wellbeing – even though our understanding of the physical workplace has shifted dramatically. Employers need to take workplace wellbeing virtual – meeting the needs of all employees, wherever they are and whatever environment they are in. Even if this is just regular check-ins – whether by phone or video call – everything you do as an employer makes a difference.
“Employee wellbeing should be a strategic priority for organisations, particularly given the uncertainty we’re all facing. Being supportive and lending a hand when employees need it will not just nurture their mental health, but the fundamental health of your organisation as a whole.”
Rob Shaw, Managing Director, EMEA, Fluent Commerce, adds: “Statistics reveal that 1 in 6 of us will have experienced a mental health problem in the past week alone. The importance, therefore, of ensuring discussions about an illness that will affect so many of us, remains in the spotlight cannot be underestimated. We all have our part to play.
“As an employer there are many things we can do to look after our team’s mental wellbeing. First and foremost is creating a culture where employees can talk openly about how they’re feeling without fear of repercussion. From online resources, having dedicated chat platforms where employees can share concerns, to having a qualified staff Mental Health First Aider, the range of things an employer can do to support employee’s health is vast.”
Protect employees by protecting valuable data
“With the COVID-19 pandemic causing devastation across the world, businesses in every industry are quickly having to adapt to a new working style,” says Krishna Subramanian, COO at Komprise. “Some technologies are getting more attention than others at the moment, such as video conferencing tools like Zoom, but there are other technologies that can make a huge impact on employee wellbeing too. With so many employees connecting from home, keeping data safe and secure at all times is a much bigger concern, so generating a cyber resilient safe copy of your business data in a separate location that is not subject to attacks is very important.
She continues, “implementing data management solutions that can help you create what is essentially an “air-gap” cyber resiliency solution to protect your data will give peace-of-mind to your employees, and help them focus on the job at hand.”
“A data breach can happen at any moment, demanding the attention and expertise of cybersecurity professionals,” adds Samantha Humphries, Security Strategist at Exabeam. “It’s an ‘always on’ profession, and there is an unspoken expectation for security teams to work excessive hours, but this leaves many with the inability to ‘switch off’ when they leave the office. Even the most hardened security professional cannot outrun this in the long term; it will inevitably take a toll on their health and personal lives… and this was before lockdown.
“Current events have introduced a whole new level of unprecedented pressure. We have seen the number of data breaches, compromised video-conferencing and COVID-19 related phishing scams soar. In addition, working from home for many individuals also means balancing parenting and home-schooling with their professional responsibilities. In any job, it would be easy to feel overwhelmed by the situation. For our friends in security, it’s a formidable task.”
Promote and honest and open employee culture, both from home and the office
“Encourage employees to take the tough decisions for an easy life when it comes to managing sometimes unrealistic workloads,” says Rob Mellor, VP & GM EMEA, WhereScape. “Honesty also applies to our mental wellbeing that keeps us happy and focused. If appropriate, it can be useful to know about issues that affect performance at work, so managers must make it clear that they’re available to talk.
“As long as organisations continue to make progress in promoting mental fitness, no matter how slow that improvement might be, they are making the move in the right direction. During Mental Health Awareness Week I would like to encourage organisations to share tips and technology that have enabled their progress through social media, websites, Slack groups and other channels.”
Sam Humphries concludes: “I would like to remind our valued security teams that they are not alone. Check in with one another, engage positively with the rest of your organisation and listen to one another. A simple phone call and an understanding tone goes a long way. For those relying on the cybersecurity team – make them feel valued and supported. Particularly for us Brits who tend to ‘suffer in silence’ – stress and isolation doesn’t have to be a battle fought alone. Honest and transparent communication will help provide more certainty in these uncertain times. We all have a role to play in this – make sure you stay connected and kind.”
With the help of things like Mental Health Awareness Week, the conversation around mental health in the workplace is one that is growing momentum each year. This week is a good reminder for employers to help relieve workplace stressors and to prioritise their one number asset, their people.
How data intelligent organizations mitigate risk
18.5.2020 Net-security Security
Organizations that put data at the center of their vision and strategy realize a differentiated competitive advantage by mitigating cost and risk, growing revenue and improving the customer experience, a Collibra survey of more than 900 global business analysts reveals.

Orgs rarely use data to guide business decisions
Despite a majority of companies saying they valued using data to drive decisions, many organizations are not consistently executing. While 84% of respondents said that it is very important or critical to put data at the center of their crucial business decisions and strategy, 43% admitted that their organizations fail to always or even routinely use data to guide business decisions.
Without a data management strategy, analysts often spend time on tasks that take away from their ability to perform analysis and provide value. This is a resounding issue for less data-mature organizations, which are 55% less likely to say their data management strategies positively contribute to optimal business decisions.
Data management strategy improves customer trust
Those insights-driven decisions are also yielding more successful outcomes, giving data intelligent organizations a competitive edge in achieving their key business objectives.
These organizations, which have the ability to connect the right data, insights and algorithms so people can drive business value, realized an 8% advantage in improving customer trust, an 81% advantage in growing revenue, and a 173% advantage in better complying with regulations and requirements.
Those organizations adopting data intelligence were also 58% more likely to exceed their revenue goals than non-data intelligent organizations.

“To lead with data, companies need to advance how they discover, organize, collaborate with, and execute on the data they have,” said Felix Van de Maele, co-founder and CEO of Collibra.
“Companies also must optimize how data analysts spend their time and automate rote tasks with data management technology. By freeing analysts up to spend more time on value-added tasks, organizations can decrease time to insight and accelerate trusted business outcomes.”