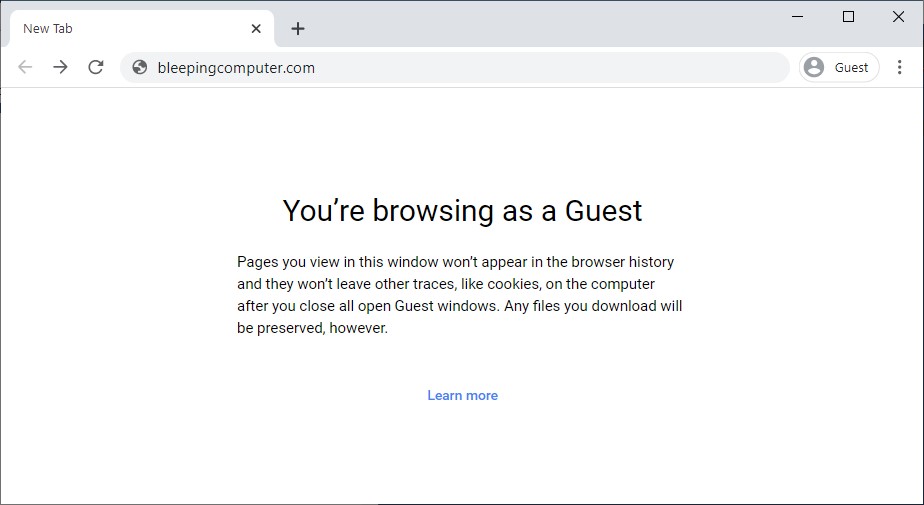
Google Chrome Guest mode
'Default to Guest' mode for Chrome
The Guest mode can be used to allow others to use your computer for browsing or for surfing the web on someone else's device without access to any Chrome profiles.
Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
Google Chrome Gets 'Default to Guest' Mode for Stateless Browsing
15.3.2020 Bleepingcomputer Security
Google announced today that a new 'Default to Guest mode' feature is now available for Windows, Linux, and macOS power users of the Chrome web browser.
The new Google Chrome feature can be enabled using a command-line switch or an enterprise policy, and it allows users to configure the web browser to always launch into Guest Mode.
In this browsing mode, Chrome will delete all browsing activity from the computer after exiting the browser, providing its users with "a stateless browsing experience from session to session."

Google Chrome Guest mode
'Default to Guest' mode for Chrome
The Guest mode can be used to allow others to use your computer for browsing or for surfing the web on someone else's device without access to any Chrome profiles.
The difference between Guest mode and Incognito mode is that you will still be able to access all the info in your profile while using the latter.
"Pages you view in this window won’t appear in the browser history and they won’t leave other traces, like cookies, on the computer after you close all open Guest windows," Google explains. "Any files you download will be preserved, however."
While browsing the web in Guest mode, Chrome will not save any info on:
Websites you visit, including the ads and resources used on those sites
Websites you sign in to
Your employer, school, or whoever runs the network you’re using
Your internet service provider
Search engines (search engines may show search suggestions based on your location or activity in your current Incognito browsing session.)
Toggling on Chrome's Default to Guest mode
Windows users can enable the new feature by following these steps:
Exit all running instances of Chrome.
Right-click on your "Chrome" shortcut.
Choose properties.
At the end of your "Target:" line add the following: chrome.exe --guest
Once complete, use the shortcut to launch Chrome.
Windows users can also open the Command Prompt or PowerShell app (or any other Terminal program), browse to Google Chrome's folder, and launch the browser with the --guest parameter.
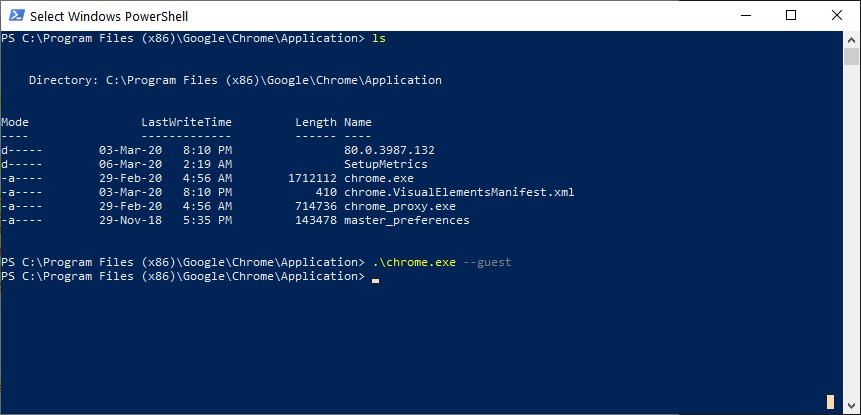
Launching Chrome in Guest Mode from Windows PowerShell
For macOS and Linux users, Google provides this procedure:
Quit all running instances of Chrome.
Run your favorite Terminal application.
In the terminal, find your Chrome application and append --guest as a command-line parameter and hit ENTER to launch Chrome.
To get back to your Chrome profile, users will have to exit all Chrome instances and relaunch the web browser without the --guest command-line switch — Windows users who edited the shortcut will have to change the "Target:" line to its previous contents.
Google Stops Issuing Security Warnings About Microsoft Edge
14.3.2020 Bleepingcomputer Security
Google has toned down its rhetoric by no longer displaying a security warning on its extension store to Microsoft Edge users that tells them to switch to Chrome to be more secure.
As the new Microsoft Edge is based on Chromium, browser extensions designed for Google Chrome are also compatible with Microsoft's new Edge browser.
Starting last month, Microsoft Edge users visiting the Chrome Web Store were greeted with a yellow alert stating that they should switch to Chrome to "use extensions securely".
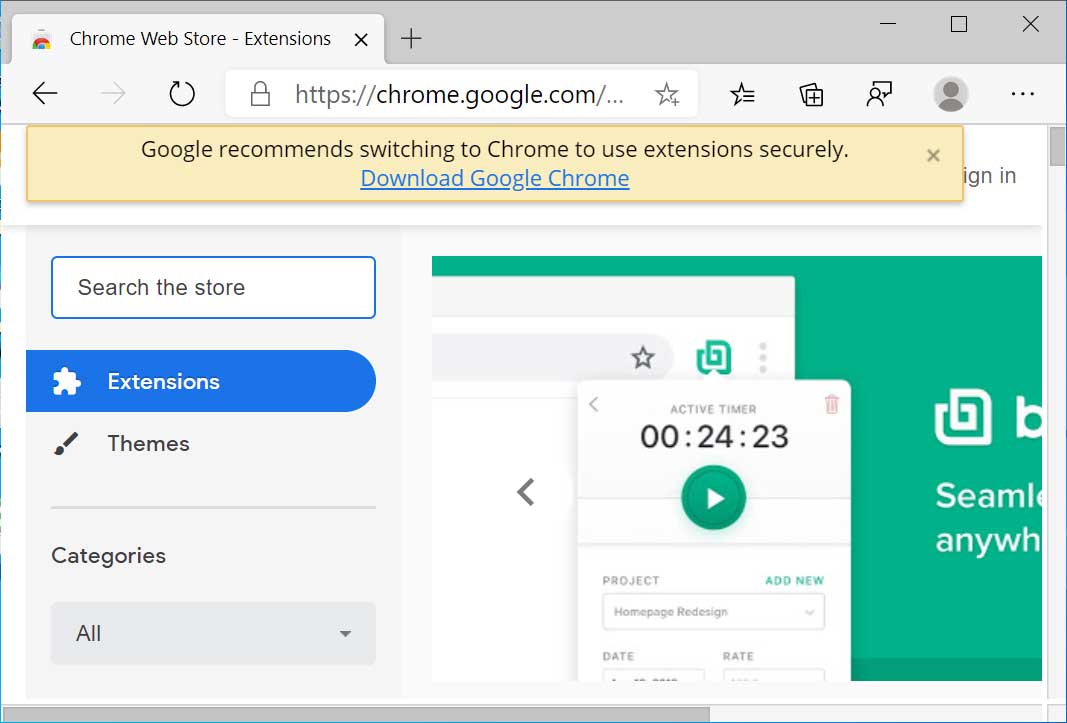
Google warning to Microsoft Edge Users
As Microsoft Edge and Google Chrome run extensions in the same manner, this looked to many like Google was just taking shots at Microsoft's new browser out of fear of losing market share.
Google, though, told BleepingComputer that they are displaying this alert because Microsoft Edge does not support Google's Safe Browsing Feature.
As this feature is used by the Chrome team to pull malicious extensions, Microsoft Edge users would not have the benefit of this security feature and would continue to use the malicious extension.
While true, their alert could have been worded better to indicate the lack of this protection rather than implying that Microsoft Edge is less secure.
Google must have realized that their alert was not making them look so good and is no longer displaying it to Microsoft Edge users.
How to Use Google Chrome Extensions and Themes in Microsoft Edge
7.3.2020 Bleepingcomputer Security
Microsoft's new Edge browser is now available and it comes with an add-on store where you can find Microsoft-approved extensions. As Edge is built on the same Chromium code base, it can also access the Chrome Web Store.
In addition to Microsoft's selection of extensions, you can also download the large selection of Chrome extensions in Edge. Like extension, Edge is also getting support for Chrome themes and you can try it in the Canary builds of the browser.
In this article, we're going to walk you through steps to download and install Chrome extensions and themes in Edge.
Add Chrome extensions to Microsoft Edge
To install Chrome extensions in Edge, follow these steps:
Open Edge (Stable, Beta, Dev or Canary) and click on three dots icon to open its menu.
Once you’ve opened Edge menu, select “Extensions”
In Edge's extension tab, turn on the option “Allow extensions from other stores”.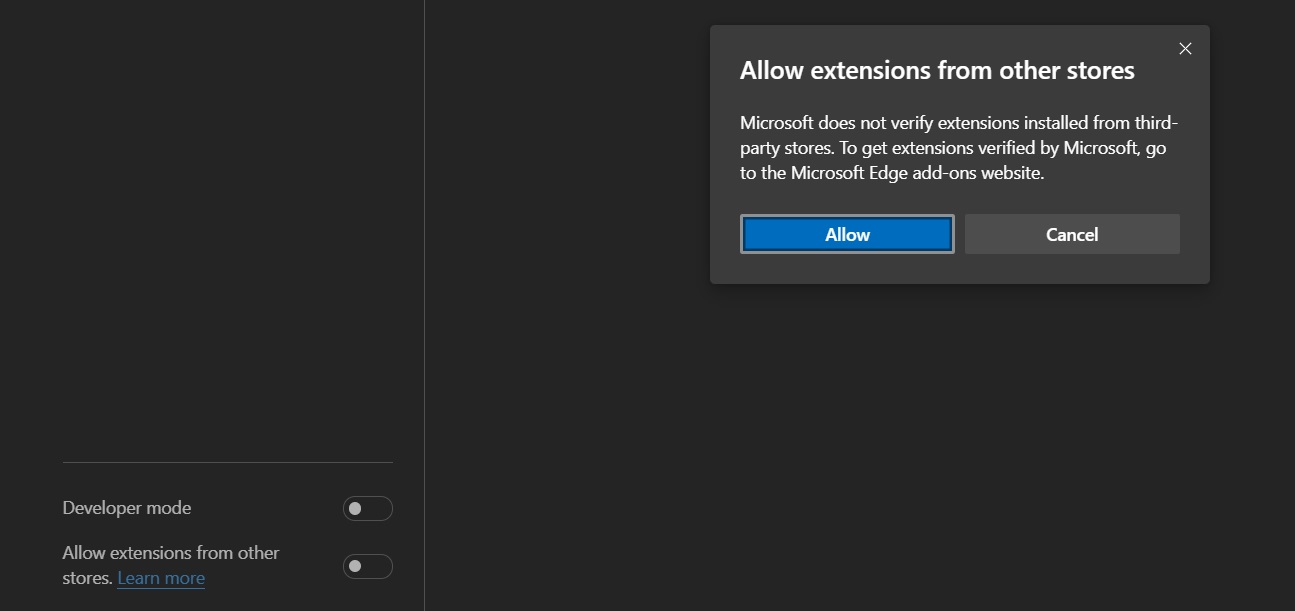
You'll need to click Allow in a pop-up window to confirm that you want to install Chrome extensions in your Edge browser.
Now you can visit the Chrome store and install any extension that you want.
Add Chrome themes to Microsoft Edge
In Edge Canary, you can also install Chrome themes after enabling an experimental flag feature:
In Edge's address bar, type Edge://flags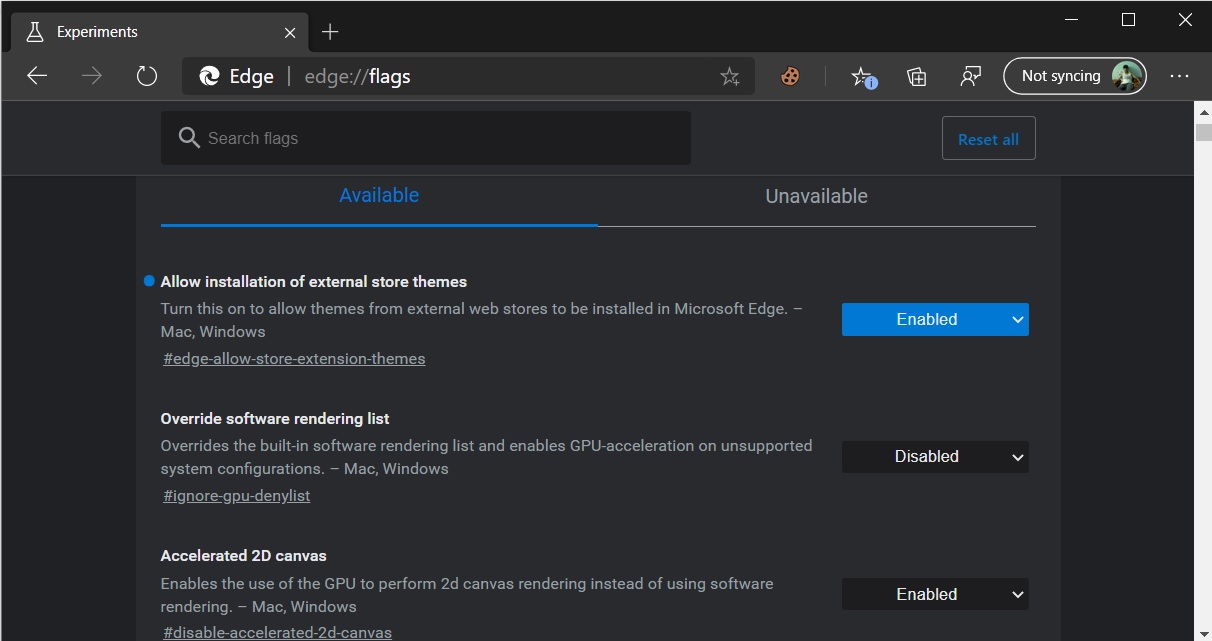
Now search for 'Allow installation of external store themes' and locate the flag with this name.
Enable the flag and relaunch the browser.
You can now head to the Chrome store and install themes.
Any installed theme can be removed by going to Edge settings > Appearance > Custom theme.
Microsoft, Google Offer Free Remote Work Tools Due to Coronavirus
7.3.2020 Bleepingcomputer Security
With employees either being quarantined after international travel or encouraged to work remotely due to the Coronavirus (COVID–19), Microsoft, Google, LogMeIn, and Cisco are offering free licenses to their meeting, collaboration, and remote work tools.
Using these products, remote workers will be able to perform virtual meetings and chat with other employees while working remotely from their homes.
Microsoft Teams free for six months
A tweet by JP Courtois, Microsoft EVP and President, Microsoft Global Sales, Marketing & Operations, stated that Microsoft Teams is now available for free for six months to "support public health and safety by making remote work even easier."
Google offers free access to Hangouts Meet for G Suite users
Google announced this week that they are offering G Suite and G Suite for Education customers free access to their Hangouts Meet video-conferencing features.
This includes the following features:
Larger meetings, for up to 250 participants per call
Live streaming for up to 100,000 viewers within a domain
The ability to record meetings and save them to Google Drive
"These features are typically available in the Enterprise edition of G Suite and in G Suite Enterprise for Education, and will be available at no additional cost to all customers until July 1, 2020," Google stated in their announcement.
LogMeIn offers free Emergency Remote Work Kits
LogMeIn is offering a free Emergency Remote Work Kit that includes free 3-month site-wide licenses to GoToMeeting so that remote workers can join virtual meetings with other employees.
"Starting immediately, we will be offering our critical front-line service providers with free, organization-wide use of many LogMeIn products for 3 months through the availability of Emergency Remote Work Kits. These kits will include solutions for meetings and video conferencing, webinars and virtual events, IT support and management of remote employee devices and apps, as well as remote access to devices in multiple locations. For example, the “Meet” Emergency Remote Work Kit will provide eligible organizations with a free site-wide license of GoToMeeting for 3 months," LogMeIn CEO Bill Wagnar said in a blog post.
Cisco offers free enhanced Webex licenses
As we previously reported, Cisco has enhanced its free Webex license to now support meetings with an unlimited amount of time and up to 100 participants.
Cisco is also offering free 90-day licenses to businesses that are not currently Webex customers.
"Additionally, through our partners and the Cisco sales team, we are providing free 90-day licenses to businesses who are not Webex customers in this time of need. We’re also helping existing customers meet their rapidly changing needs as they enable a much larger number of remote workers by expanding their usage at no additional cost," Cisco announced.
Microsoft MVP Summit Now A Virtual Conf Over Coronavirus Fears
7.3.2020 Bleepingcomputer Security
Microsoft has decided to change its annual in-person MVP Summit held in Seattle, Washington into a virtual online conference over concerns about the continuing spread of the Coronavirus outbreak.
Every year Microsoft invites the members of their Microsoft MVP program to an MVP Summit in Seattle where members can meet their peers, interact with employees, and take part in sessions about Microsoft products.
For those who are active members of the Microsoft MVP community, the Summit is something to be looked forward to and a lot of fun for the attendees.
Scheduled for March 16th through the 20th, this year's in-person MVP Summit has been canceled over concerns about the Coronavirus and being turned into a virtual online conference.
"In light of recent developments globally and the growing concerns around the spread of the COVID-19 virus, Microsoft has decided that this year’s MVP/ Regional Director Summit will be an online-only / virtual event. It will be scheduled for the same week (Mar 16-20)," an email sent to Microsoft MVPs stated.
For those who have registered, Microsoft will be providing further updates soon.
Chrome and Firefox Extension Lets You View Deleted Web Pages
24.2.2020 Bleepingcomputer Security
If you ever browsed the web and were disappointed when a page you were looking for no longer existed, you can use a Google Chrome and Mozilla Firefox browser extension to automatically retrieve the deleted pages from Archive.org.
Archive.org is a non-profit library that archives books, music, software, movies, and websites so that they can be later viewed if ever deleted.
As part of this service, the organization runs a service called the Wayback Machine that has created an archive of over 400 billion web pages that were saved over time.
Archive.org offers a browser extension to show deleted web pages
To help use their service, Archive.org has created a Google Chrome extension and a Mozilla Firefox extension called 'Wayback Machine' that will prompt you to load an archived web page when it is no longer exists on the original web site.
When visiting a site, if the page no longer exists and has been saved to archive.org, the extension will prompt you to view it via the Wayback Machine as shown below.
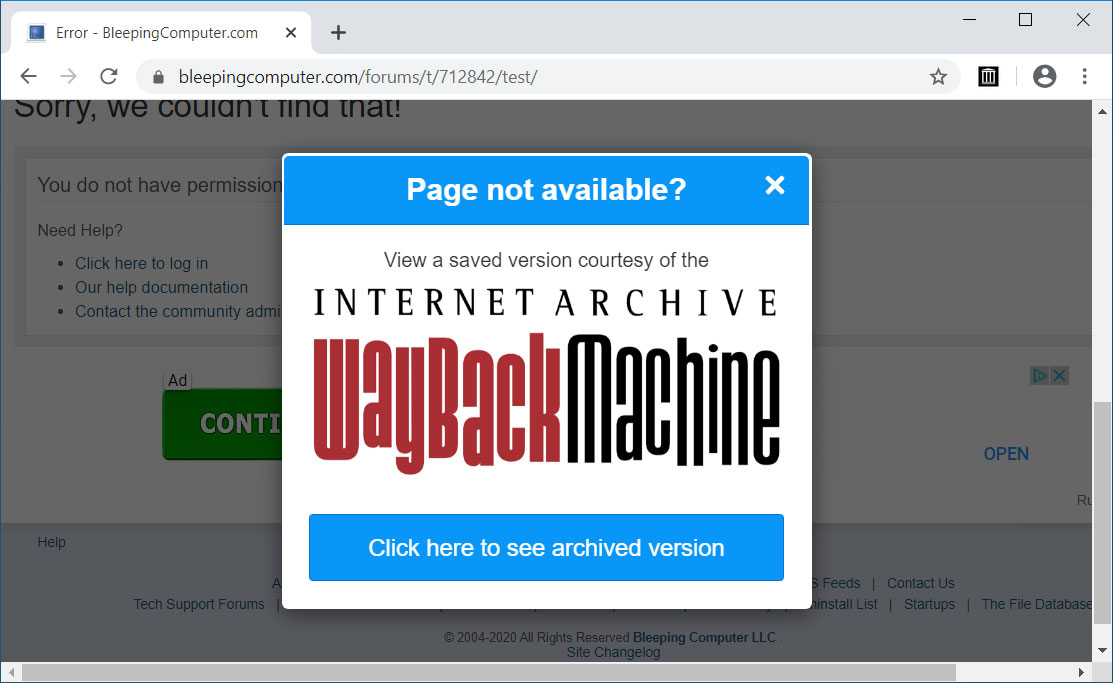
Wayback Machine Extension
Just recently, users welcomed this same ability as a built-in feature to the Brave Browser.
The Wayback Machine, though, offers some additional features than found in Brave.
On any website that you visit, if you right-click the browser page and select 'Wayback Machine' you will be able to retrieve the first version of the page ever saved to Archive.org, the most recent saved version, a list of all saved snapshots of the page, and the ability to save a snapshot of the current page to Archive.org.
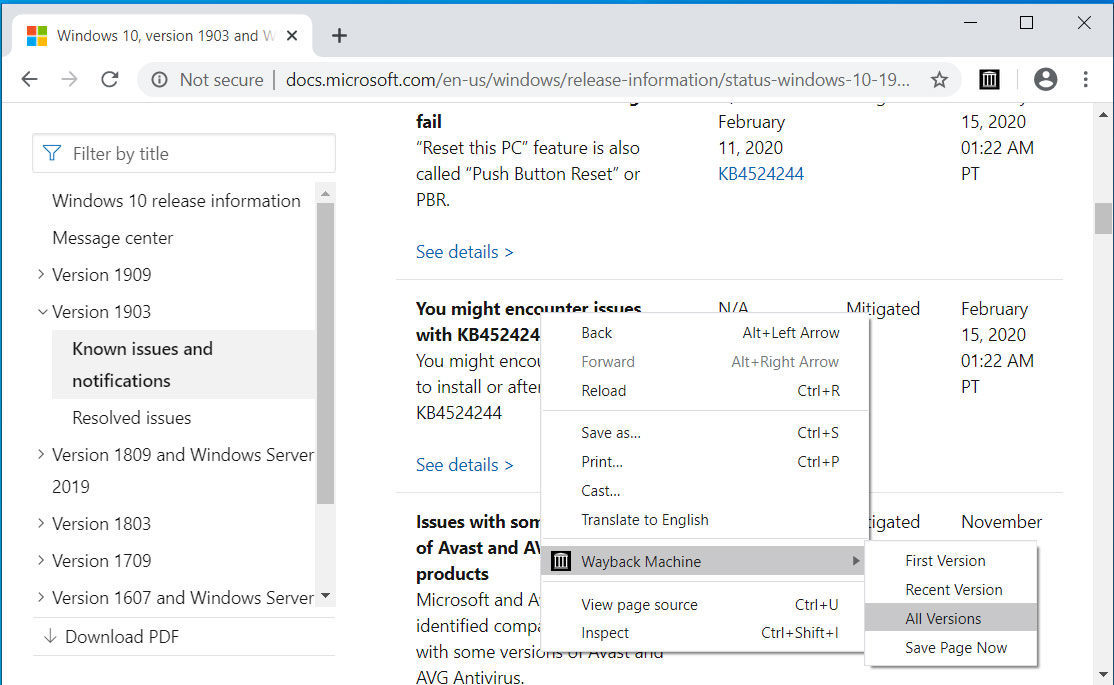
Wayback Machine extension options
If you use the web to research various subjects and want to see how a page has changed over time, this extension will make your life much easier.
Hiding Windows File Extensions is a Security Risk, Enable Now
24.2.2020 Bleepingcomputer Security
Microsoft hides file extensions in Windows by default even though it's a security risk that is commonly abused by phishing emails and malware distributors to trick people into opening malicious files.
A file extension is the letters immediately shown after the last period in a file name and is used by the operating system to determine what program is used to open, view, and utilize the file.
For example, the file report.txt has an extension of .txt, which is associated with the Windows Notepad program to open and view its contents.
By default, Microsoft decides to hide file extensions in Windows so that a file named 'report.txt' is simply shown in File Explorer as 'report'.
The original reason for this was probably to make it less confusing to users, but regardless of the reason, it is a security risk that attackers abuse.
Windows default settings abused by attackers
To illustrate how the hiding of file extensions is a security risk, let's take a look at the following folder containing two files.
With file extensions disabled, they look like the same PDF file as they both have the same name and the same icon.
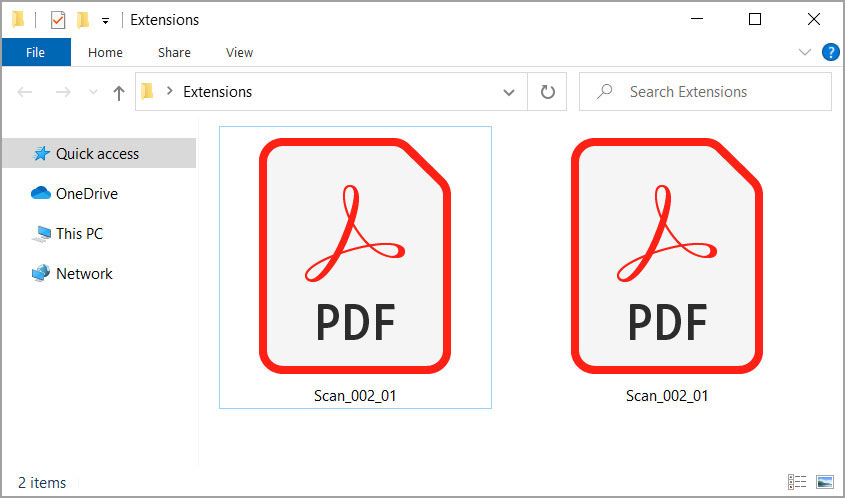
File extensions are hidden in Windows
If we enable extensions, though, we quickly see that these are two different files with one being a PDF as expected, but the other being an executable file that uses a PDF icon.
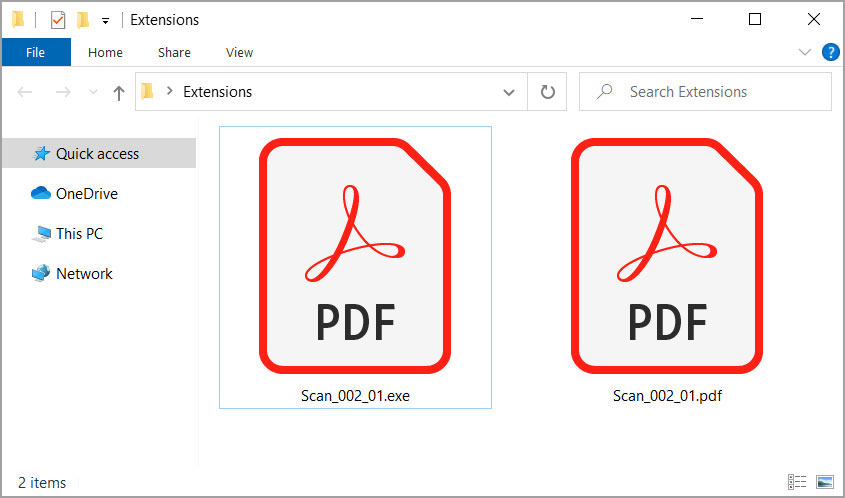
File extensions are now enabled
In this case, the malware executable purposely used the PDF icon normally shown by Adobe Reader to trick users who have file extensions disable that it is a PDF file.
This is not to say strange PDFs you receive via email cannot be a risk, but receiving executables disguised as PDFs should definitely raise more alarms.
Real phishing example abusing file extensions
As an example of how attackers are abusing file extensions, let's take a look at a real phishing email that was sent last year.
This email pretends to be a requested scan of an agreement with an attached ZIP file named Scan_002_01.zip.
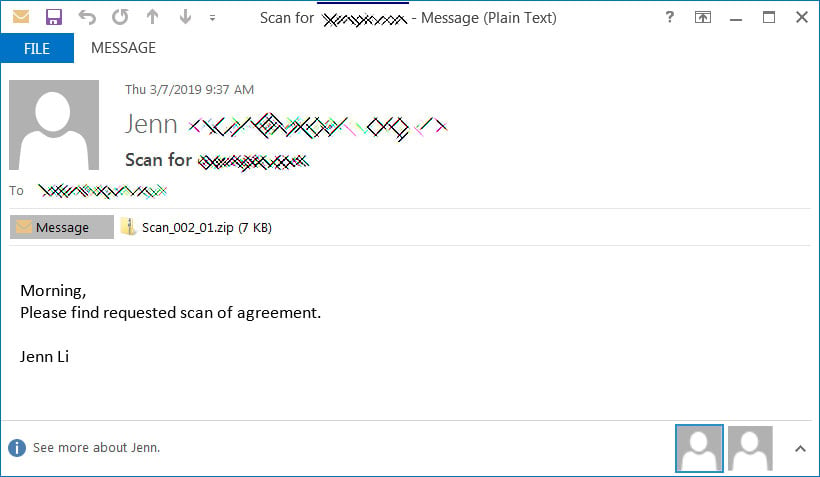
Real phishing email with zip file attachment
When we extract the attachment, we see what appears to be a harmless PDF file.
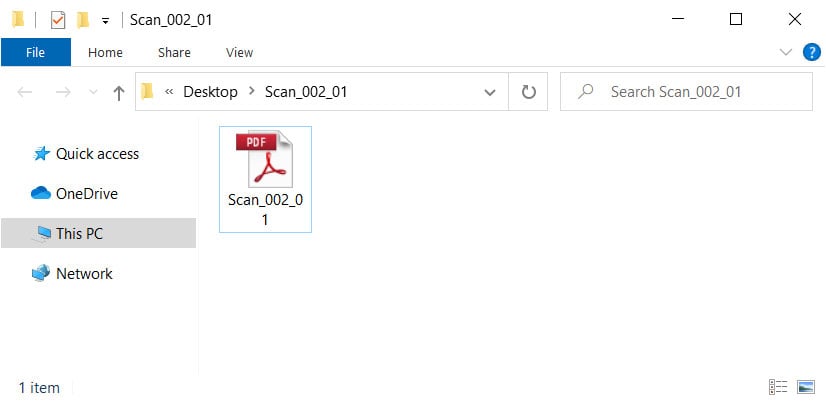
Extracted folder with extensions disabled
When we enable the displaying of file extensions, though, we see that this is not a PDF file, but an executable instead.
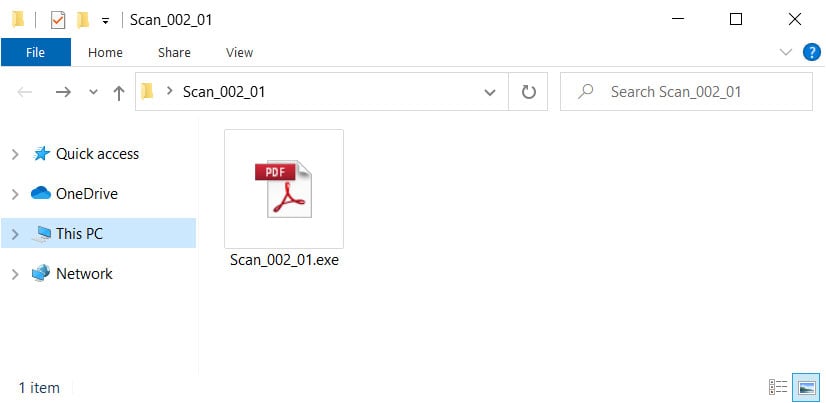
Extracted folder with extensions enabled
Just by unhiding file extensions in Windows, we were able to see that this is not a safe file to execute and potentially saved our computer from being infected with ransomware or installing backdoors that could have compromised the entire network.
How to enable file extensions in Windows 10
I strongly suggest that users enable the showing of all file extensions in Windows 10 so that they know exactly what type of file they are interacting with.
To enable file extensions in Windows 10, please follow these steps:
Search for 'Folder Options' in the Windows 10 Start Menu and when 'File Explorer Options' appears, click on it.
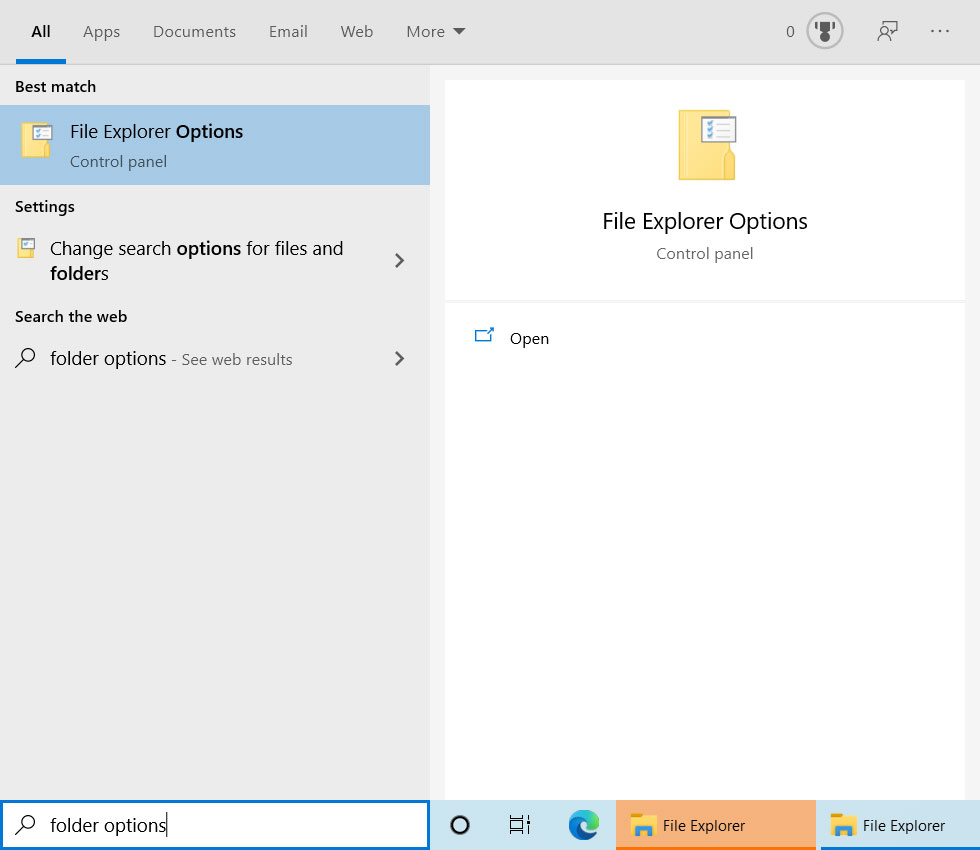
Search for Folder Options
When the File Explorer Options screen appears, click on the View tab and scroll through the Advanced settings until you see an option labeled "Hide extensions for known file types".
Now uncheck the option as shown below.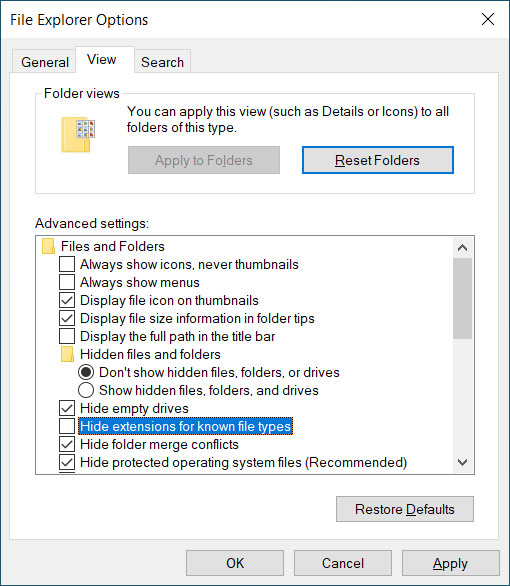
Search for Folder Options
Now press the Apply button followed by the OK button and the File Explorer Options screen will close.
Now all files displayed on the desktop, in folders, or in File Explorer will display a file extension.
Brave Browser Integrates Wayback Machine to View Deleted Web Pages
24.2.2020 Bleepingcomputer Security
Brave Browser has now integrated the Wayback Machine to display web pages that have been removed from a web site or not available due to a web site issue.
The Wayback Machine is a digital archive of the web that is operated by the nonprofit organization Archive.org. Using the Wayback Machine you can save snapshots of existing web pages for archival or retrieve archived versions to see changes over time or deleted pages.
With today's release of Brave Browser 1.4, when you visit a web page and it returns a '404 Not Found' HTTP error code indicating that a page is missing, the browser will prompt you to load the page on the Archive.org's Wayback Machine instead.
As an example, Brave's announcement uses the Whitehouse.gov's Climate Change page that was deleted soon after Trump became president. When visiting the page in Brave, the web server will respond with a '404 Not Found' error code, which will cause Brave to prompt you to check if a saved version is available on the Wayback Machine.
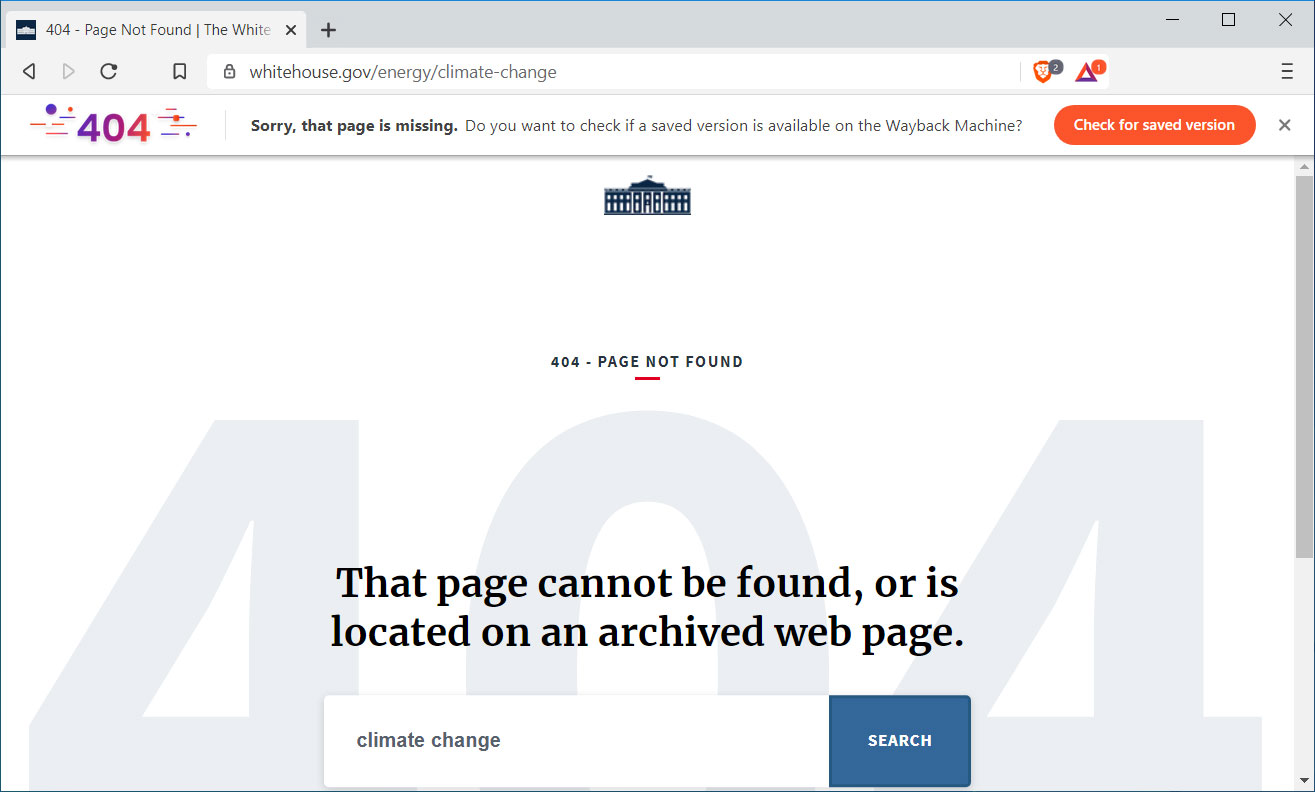
A Missing page prompts to check Wayback Machine
Clicking the 'Check for saved version' button will automatically load the latest saved page from the Wayback Machine as shown below.
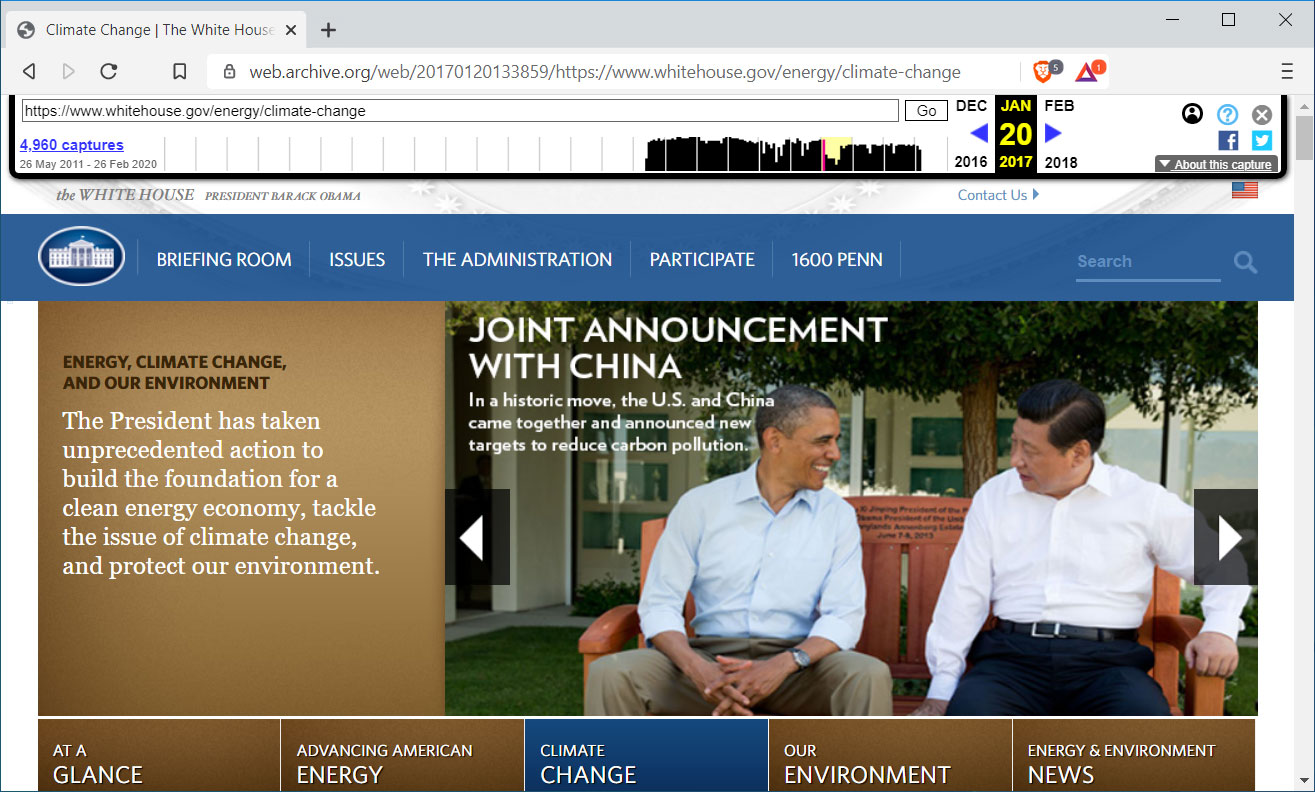
Page loaded from the Wayback Machine
In addition to '404 Not Found' error messages, Brave states it will also utilize the Wayback Machine integration for 14 other HTTP error codes that are displayed when a web server is under maintenance or having an issue. These other error codes are This , 410, 451, 500, 502, 503, 504, 509, 520, 521, 523, 524, 525, and 526.
To take advantage of this new feature, you need to be using Brave Browser 1.4, which can be downloaded here.
uBlock Origin 1.25 Now Blocks Cloaked First-Party Scripts, Firefox Only
24.2.2020 Bleepingcomputer Security
uBlock Origin 1.2.5 has been released with a new feature that blocks first-party tracking scripts that use DNS CNAME records to load tracking scripts from a third-party domain and bypass filters.
A first-party tracking script is when the script loads directly from a subdomain of the web site the script is loaded. For example, if 'www.example.com' was loading a tracking script from 'tracking.example.com', it would be considered a first-party script as they share the same domain.
As uBlock Origin blocks third-party tracking scripts, or scripts loaded from another domain, sneaky tracking companies came up with a method to use CNAME records to load tracking scripts from what appears to be first-party domains.
In a sneaky, or cloaked, first-party tracking script example, 'tracking.example.com' uses a CNAME record to load a script from 'www.badtracker.com'. Even though the script is loading from a remote site, uBlock Origin still sees it as a first-party tracker because the page's HTML loads it from the same domain as the web site.
DNS lookups foil cloaked first-party trackers
On February 19th, 2020, uBlock Origin 1.2.5 was released and allows the ad blocker to block these cloaked tracking scripts by performing a DNS lookup before loading them.
If the subdomain is a CNAME to a third-party host, then uBlock Origin will block the script from loading.
When cloaked first-party trackers are blocked, they will appear in the log as blue entries with the uncloaked domain shown underneath in a smaller font.
![]()
Uncloaked first-party trackers
Unfortunately, the DNS API that allows DNS lookups is only available for Firefox, so Chrome users are out of luck and cannot take advantage of this feature.
When loaded, uBlock Origin will now display a new permission titled 'Access IP address and hosting information' that allows uBlock to use the DNS API.
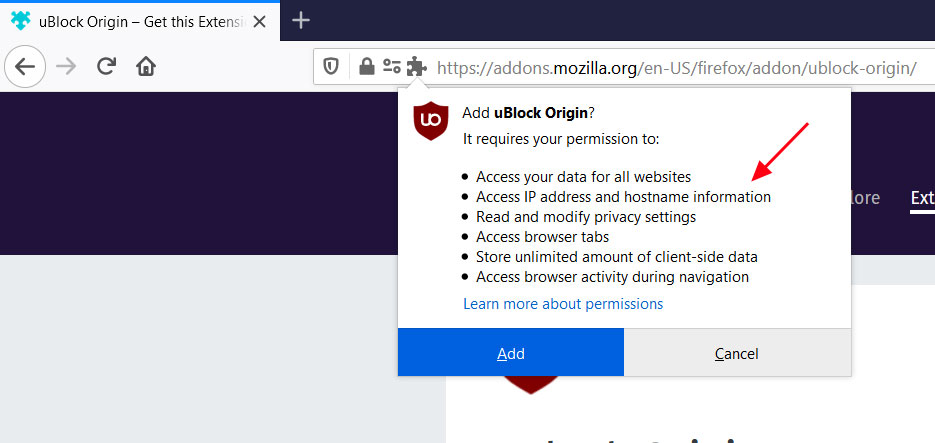
DNS Permission
uBlock Origin can be downloaded from the Mozilla Add-Ons site, or if you have it installed already, you can check for the new update by going into Firefox's extensions page and clicking on 'Check for Updates' as shown below.
Check for Updates
The full changelog for uBlock Origin 1.25 can be found here.
Mozilla Enables DNS-over-HTTPS by Default for All USA Users
24.2.2020 Bleepingcomputer Security
Starting today, Mozilla has begun to enable DNS-over-HTTPS (DoH) by default for users in the USA to provide encrypted DNS resolution and increased privacy.
DNS-over-HTTPS is a new standard that allows web browsers to perform DNS resolution over encrypted HTTPS connections rather than through normal plain text DNS lookups.
As some countries and ISPs block sites or censor content by monitoring DNS traffic, DoH will allow users to bypass these blocks and increase the privacy of their DNS requests.
Mozilla has stated that this will be a gradual rollout of the DoH feature, which means that it will be done slowly over the next few weeks to make sure there are no issues with the implementation as more people begin to use it.
"Today, Firefox began the rollout of encrypted DNS over HTTPS (DoH) by default for US-based users. The rollout will continue over the next few weeks to confirm no major issues are discovered as this new protocol is enabled for Firefox’s US-based users," Mozilla stated in an announcement.
When enabled, Firefox will use the Cloudflare DNS provider by default, but users can switch to NextDNS or a custom provider by going into the Firefox network options.
Mozilla's DoH plans have been met with criticism
When Mozilla's plans were first announced, it was met with criticism as Cloudflare was the only DoH provider being used by Firefox.
This caused security researchers, privacy advocates, and admins to become concerned that so much user data would now be in the hands of a single DNS provider.
Admins were also concerned that Firefox would overrule DNS policies and security precautions put in place by system administrators by forcing DNS through Cloudflare.
To address these concerns, users can use a custom DoH provider or disable it entirely.
In Firefox 73, Mozilla also added NextDNS as an additional DoH provider to give users more choice.
Checking if DoH is enabled in Firefox
With this rollout, it can be confusing to determine if DoH is enabled as it is done through a system addon that manually changes about:config preferences.
To see if the DoH Roll-Out system addon is installed, you can enter about:support in the Firefox address bar and scroll down to the list of 'Firefox Features'.
If you see 'DoH Roll-Out' listed, then DNS-over-HTTPS has been rolled out to your browser and enabled by default.
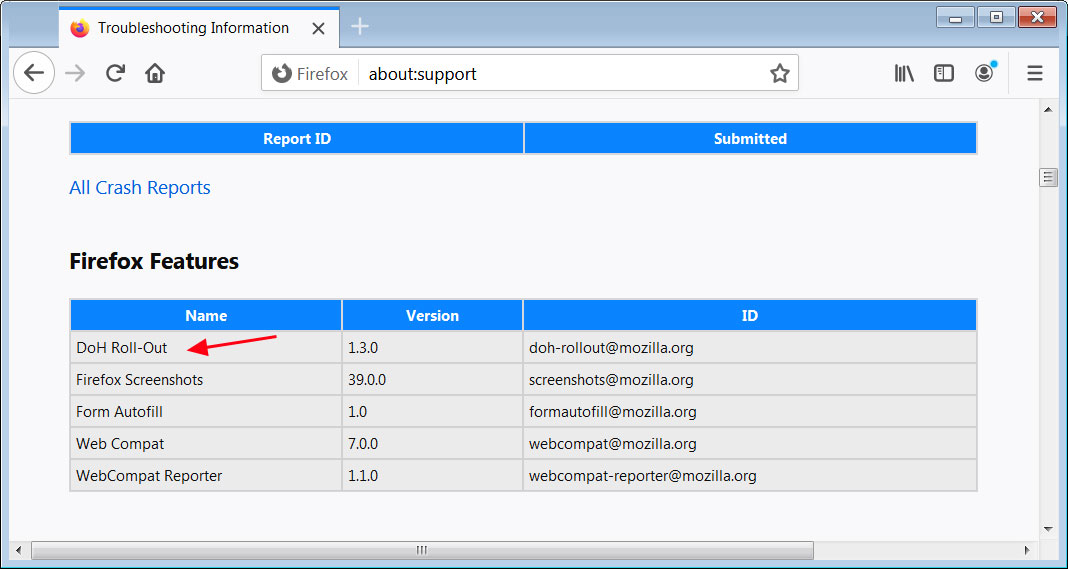
About:support extensions list
Alternatively, you can check if DoH is enabled by going into about:config, accepting the risks, and searching for 'network.trr.mode'.
If DNS-over-HTTPS is enabled by this rollout, you will see the network.trr.mode set to '2'.
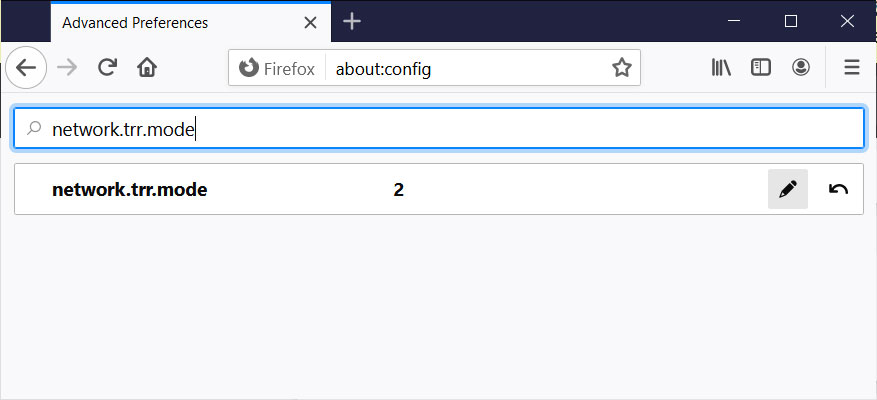
Firefox network.trr.mode setting
Due to the confusion caused by rolling out this feature via a system addon, Mozilla plans to eventually integrate it directly into Firefox.
Google Brings Its Lighthouse Pagespeed Extension to Firefox
24.2.2020 Bleepingcomputer Security
Google has brought its popular Lighthouse extension used by over 400,000 users to Mozilla Firefox so that web developers can test the browser's performance against submitted web pages.
Lighthouse is an open-source tool for testing the performance of web pages through Google's PageSpeed Insights API and was released as an extension for Google Chrome in 2016.
Now that the Mozilla Firefox Lighthouse Extension has been released, Firefox users can perform pages peed tests in their preferred browser.
For those not familiar with Lighthouse, it is a browser extension that allows you to generate a report about a web page's performance using the Google PageSpeed API. This API includes real-time data from Google's Chrome User Experience Report and lab data from Lighthouse.
The report will display information on how fast the page loads, what issues are affecting its performance and will offer suggestions on how to increase the page's performance, accessibility, and SEO.
For example, below is a Lighthouse report for a Google search results page. As you can see, it provides a score ranging from 0-100 for performance, accessibility, best practices, and SEO categories.
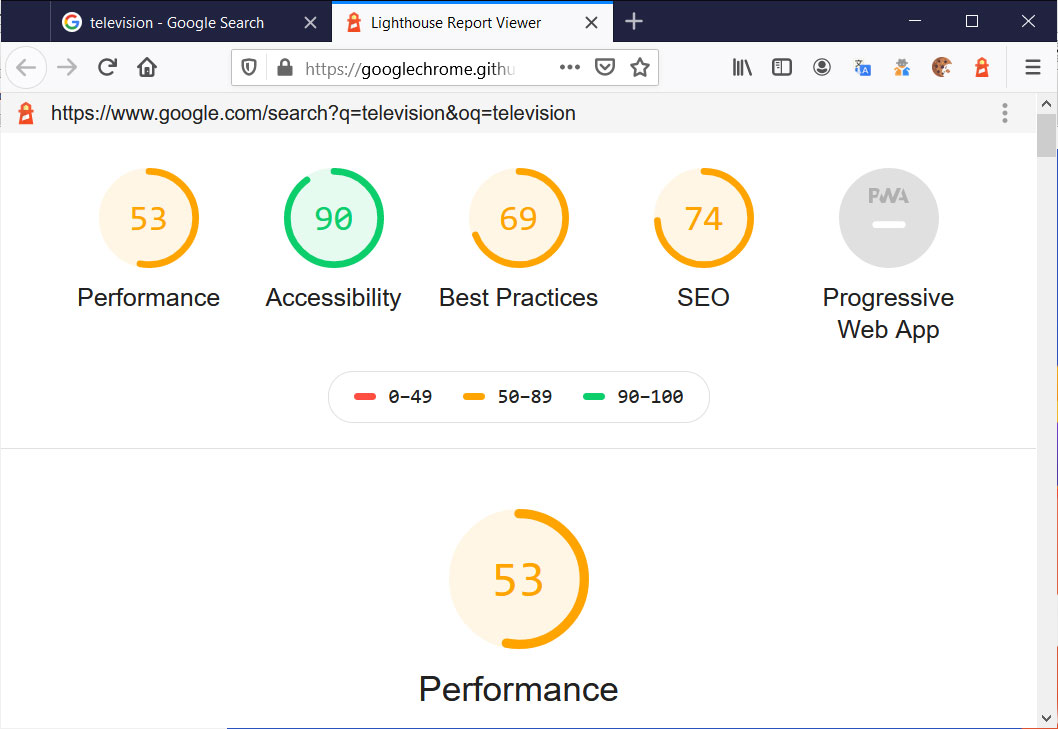
Lighthouse report for Google Search results page
The reports real value comes in the form of suggestions and optimization tips to increase each category's score and thus the speed of the web page.
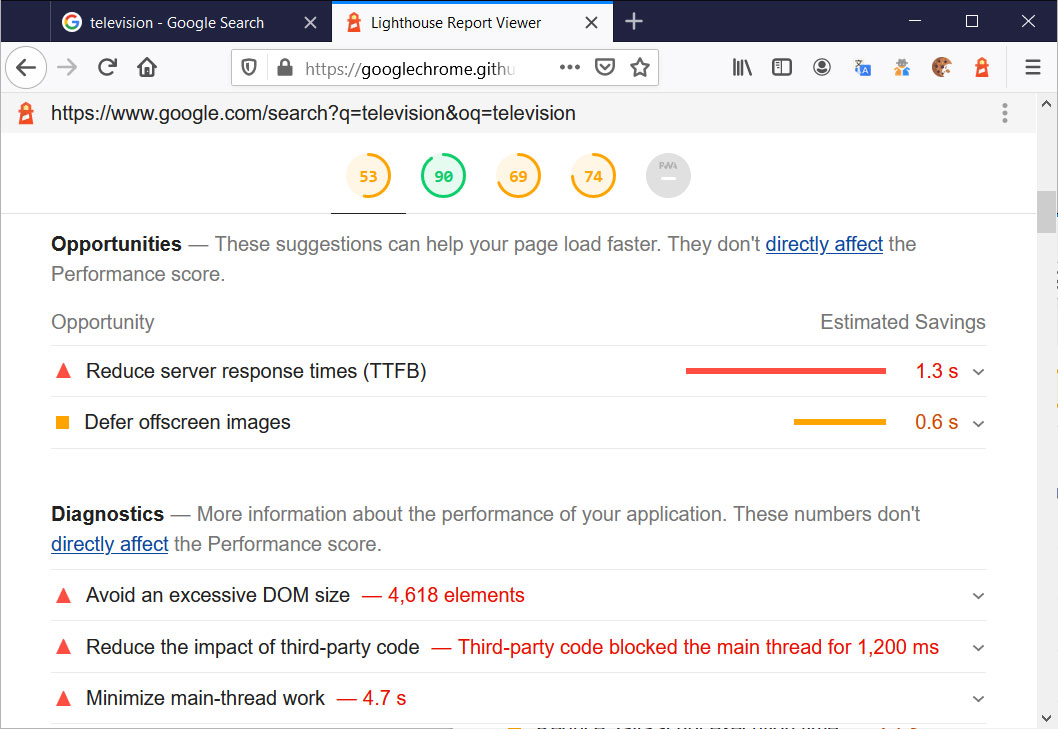
Lighthouse suggestions to improve performance
For web developers, this is a very useful tool and while it is very difficult to achieve a high score, especially if the page display ads, it does provide numerous useful suggestions on how to optimize a web site to increase performance for its visitors.
If you manage a web site and have not used Lighthouse before, you should give it a try as I am sure you will find suggestions that you can use to increase your site's performance.
Mozilla Firefox to Support Chrome's Image Lazy Loading Feature
16.2.2020 Bleepingcomputer Security
Mozilla is adding support for Google Chrome's native image lazy loading feature and it is now available for testing in the Firefox Nightly builds.
Image lazy loading is a web site performance optimization technique that causes the browser to only load images that are currently visible, or about to be visible, on the screen.
This increases performance as the browser will only download and display images as they are needed rather than downloading them all at once.
Traditionally, developers would add lazy loading to a web site through third-party JavaScript libraries, but with the release of Chrome 76, Google has added it as a native feature to the browser.
To use this feature, developers simply need to add the loading="lazy" attribute to their HTML IMG tags as shown below.
Added to Firefox Nightly
In the current Firefox 75 Nightly build, Mozilla has added a new about:config preference named 'dom.image-lazy-loading.enabled' that allows you to enable the native lazy loading in the browser.
To test this feature, simply open the Firefox dev tools, click on the 'Network' tab and then visit the lazy loading demo site.
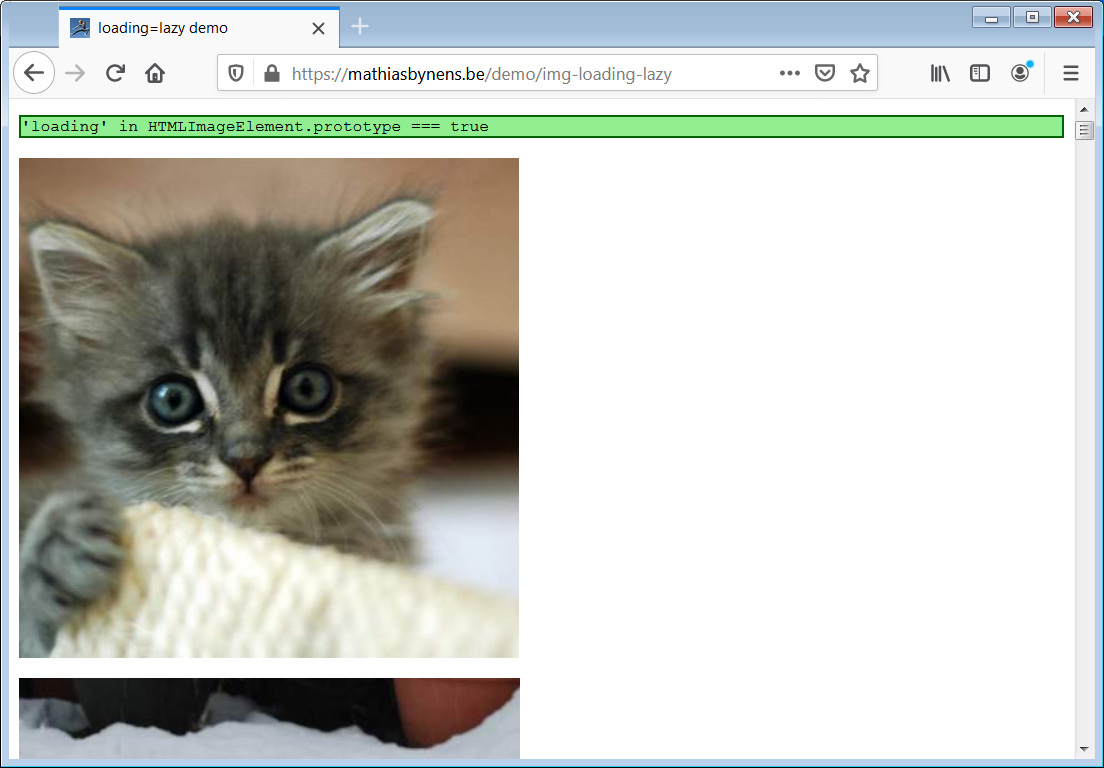
Lazy loading demo page in Firefox Nightly
When you first load the page, you will see that Firefox only downloads the resources and images necessary to display the viewable images in the browser.
As you scroll down, the developer console will show that Firefox downloads more images as they are almost visible in the browser.
With the two largest browser developers supporting native lazy loading, it eliminates one more JavaScript library that needs to be maintained and downloaded from web sites.
Google Removes Dashlane Password Manager from Chrome Web Store
15.2.2020 Bleepingcomputer Security
Google has removed the Dashlane password manager extension used by over 3 million users from the Chrome Web Store due to issues with 'User Data Privacy/ Use of Permissions'.
On Saturday, February 8th, Dashlane posted to the service's status page that their Chrome extension was removed from the Chrome Web Store and can not be downloaded.
"[Investigating] Currently, our Extension cannot be downloaded from the Chrome Web Store. This issue have no impact on users that already have our Chrome extension installed and running. Only users needing to download our Chrome extension for a first time install or a reinstall will encounter the issue. We are working actively with Google to have it back as soon as possible. Thank you for your patience and understanding," Dashlane's status page states.
In a post to Google's Chromium Extensions support group on Monday, Dashlane Senior Engineering Manager Thomas Guillory stated that they received a warning email on Friday about the extension's use of permissions and was told they had 7 days to resolve the issue.
After replying with the reasons for the use of permissions, the extension was removed within 24 hours without an explanation.
Our extension (Dashlane Password Manager, 3M+ users, ID: fdjamakpfbbddfjaooikfcpapjohcfmg) has been removed from the store on Saturday morning.
The reason invoked is User Data Privacy / Use of Permissions. Indeed we are using a very powerful set permissions, but they are needed for Dashlane to work on everywhere. However we are in the dark for the next steps:
- We don't know exactly what permission is causing the problem. Can you be more specific and provide assistance to resolve the issue?
- The extension has been taken down very quickly. We received a first email on Friday (stating that we have 7 days to fix the issue). We reacted instantly by filling the permission justification form and pushing a new version. This apparently had no effect, the extension has been removed 24h hours after. Can you reinstate the extension while we are discussing the issue?
While it is not clear what permissions Google has an issue with, the extension uses a very broad permission set that allows the extension to read and change data on websites, control private settings, apps, extensions, and themes, and communicate with native apps running on the computer.
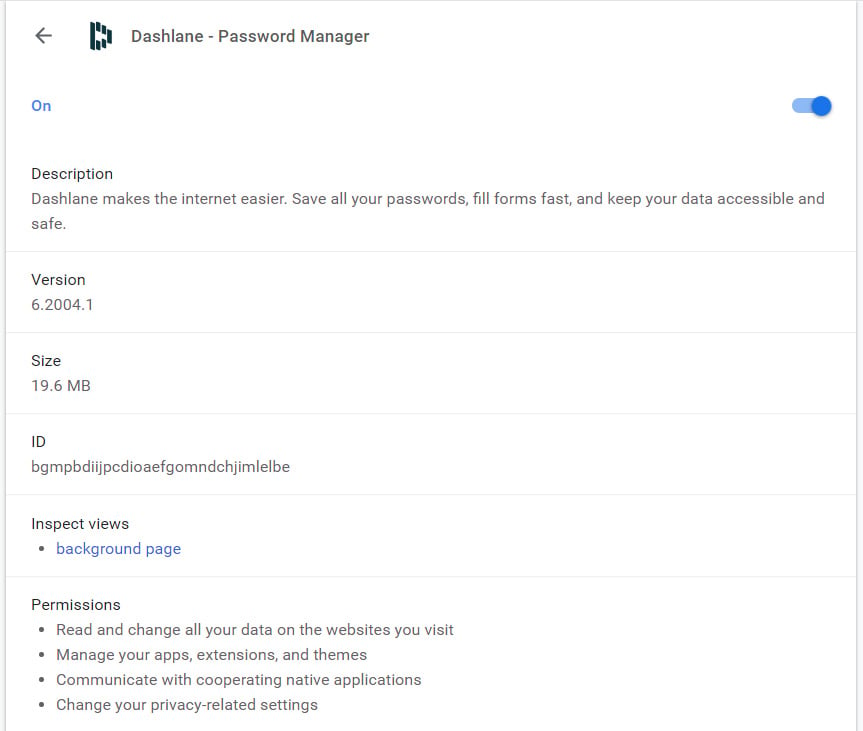
Dashlane extension permissions
The permissions used by Dashlane are:
Read and change all your data on the websites you visit
Manage your apps, extensions, and themes
Communicate with cooperating native applications
Change your privacy-related settings
In comparison, the LastPass password manager extension has far fewer and less intrusive permissions:
Read your browsing history
Display notifications
Google has stated in the past that to remove intrusive and malicious extensions they introduced stricter policies and are requiring extension developers to use permissions as "narrowly-scoped as possible".
"Your extension’s permissions should be as narrowly-scoped as possible, and all your code should be included directly in the extension package, to minimize review time."
It is not known what permission Google has an issue with, but a recent update to Dashlane's status page stated that they are working with Google to get their extension available again.
"Our extension will soon be back in the Chrome Web Store. We are working with Google to give the green light. We apologize for the delay and we thank you again for your patience and for your understanding!"
Update 2/11/20: Both Google and Dashlane have told BleepingComputer that the extension is back in the Chrome Web Store.
Dashlane stated that they "fell afoul of an automated bot, but we’re back up after we were able to speak to a human at Google."
Microsoft Launches Xbox Bounty Program With $20K Maximum Payout
2.2.2020 Bleepingcomputer Security
Microsoft just announced the launch of an Xbox bug bounty program to allow gamers and security researchers to report security vulnerabilities found in the Xbox Live network and services.
Qualified Xbox Bounty Program submissions are eligible for bounty payouts ranging from $500 to $20,000 for a remote code execution submitted via a high-quality report with clear and concise proof of concepts (POCs).
The bounties will be awarded "at Microsoft’s discretion" based on the severity and impact of the security issue disclosed, as well as the quality of the submission.
"Higher awards are possible, at Microsoft’s sole discretion, based on report quality and vulnerability impact," Redmond says.
"Researchers who provide submissions that do not qualify for bounty awards may still be eligible for public acknowledgment if their submission leads to a vulnerability fix."
Security Response
✔
@msftsecresponse
We’re excited to announce the Xbox Bounty Program, which awards up to $20,000 for vulnerabilities in the Xbox network space. Find out more information: https://msrc-blog.microsoft.com/2020/01/30/announcing-the-xbox-bounty-program/ …
224
7:11 PM - Jan 30, 2020
Twitter Ads info and privacy
124 people are talking about this
Vulnerabilities submitted through the Xbox Bounty Program are required to meet the following criteria to be eligible for a bounty award:
• Identify a previously unreported vulnerability that reproduces in our latest, fully patched version of Xbox Live network and services at the time of submission.
• Include clear, concise, and reproducible steps, either in writing or in video format (This allows submissions to be reviewed as quickly as possible and supports the highest bounty awards.)
These are some examples of Xbox Bounty Program in-scope vulnerabilities:
• Cross-site scripting (XSS)
• Cross-site request forgery (CSRF)
• Insecure direct object references
• Insecure deserialization
• Injection vulnerabilities
• Server-side code execution
• Significant security misconfiguration (when not caused by user)
• Using a component with known vulnerabilities (when demonstrated with a working proof of concept)
To send a submission to the Xbox team you have to use the MSRC Submission portal, with the mention that you'll have to abide by the recommended format in Microsoft's bounty submission guidelines.
Additional details on what activities are prohibited under the Xbox Bounty Program and the out of scope vulnerabilities are available on the Xbox bounty page and to follow Coordinated Vulnerability Disclosure throughout the vulnerability reporting process.
For vulnerability submissions that are out of the scope of the Xbox Bounty Program, Microsoft may still offer the security researchers public recognition by adding them to the Online Service Acknowledgements page.
The bounty amounts for in-scope vulnerabilities based on their severity levels are available in the table below.
Security Impact Report Quality Severity
Critical Important Moderate Low
Remote Code Execution High
Medium
Low $20,000
$15,000
$10,000 $15,000
$10,000
$5,000 N/A N/A
Elevation of Privilege High
Medium
Low $ 8,000
$ 4,000
$ 3,000 $5,000
$2,000
$1,000 $0.00 N/A
Security Feature Bypass High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 N/A
Information Disclosure High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Spoofing High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Tampering High
Medium
Low N/A $5,000
$2,000
$1,000 $0.00 $0.00
Denial of Service High/Low Out of Scope
You can find additional information on Microsoft bounty program requirements as well as legal guidelines in the Bounty Terms, the Safe Harbor policy, and the Bounty FAQ.
"Since launching in 2002, the Xbox network has enabled millions of users to share their common love of gaming on a safe and secure service," MSRC Program Manager Chloé Brown said.
"The bounty program supplements our existing investments in security development and testing to uncover and remediate vulnerabilities that have a direct and demonstrable impact on the security of Xbox customers.
Public bounty programs are a valuable approach which combine with ongoing internal testing, private programs and knowledge shared by partners to produce a secure ecosystem to play in."