
Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
Redefining business for a digital world with smart security decisions
18.5.2020 Net-security Security
Kurt John is Chief Cybersecurity Officer of Siemens USA, where he is responsible for the information security strategy, governance and implementation for the company’s largest market with ~$23B in annual revenues. In this interview with Help Net Security, he explores a variety of smart security decisions.
smart security decisions
Kurt discusses the challenges modern CISO have to deal with, the importance of IT security certification, he provides his opinion on what an ideal cybersecurity candidate looks like, and much more.
What advice would you give to a newly appointed CISO that was tasked with hiring more security professionals in order to strengthen overall enterprise security?
I would say that we can’t solely depend on data and machine learning tools to guard against hackers trying to break into networks. We need people making sense of the information. Analytics might detect things, but it’s the human who can understand the full story. And that information undoubtedly transcends multiple functions and departments – all using it to keep the business future facing and effective.
The technical skills are sometimes hard to find, but finding someone who has the soft skills and mindset to be collaborative and a strategic partner often can be even harder. Find someone who understands the business’ mission and is invested in achieving that mission as part of a broader team.
What makes a perfect cybersecurity candidate? What are the dos and don’ts for those looking to land a dream information security job?
In my experience, one quality I have seen in most great cybersecurity professionals is that they all enjoy solving problems. Cybersecurity skills are not only the gateway to a good-paying job and career; they also offer people the chance to work on the frontlines of a major challenge that’s affecting millions of people and spanning industries, geographies and backgrounds. It’s crucial they recognize how interconnected this shared challenge is across companies, industries and countries.
Candidates should also be comfortable with ambiguity in a sense. As a technical field, a lot of things are grounded in hard data. However, overall as a field, cybersecurity is still relatively immature and evolving. Add to that the speed of innovation in technology and we have a recipe for an ever-changing environment that requires comfort with ambiguity as well as speed and flexibility to remain relevant.
How can we expect the cybersecurity skills shortage to play out in the near future?
Cybersecurity positions are growing three times faster than other IT positions. When compared to other jobs, they are growing 12 times faster. It’s estimated the amount of additional trained staff needed to close the skills gap is more than 4 million professionals. So, cybersecurity needs to be central to every business strategy today. What we need to do is pivot on what it means to be qualified as well as how we identify and train talent.
That aside, it’s difficult to tell right now, but I see positive events unfolding, including government support and funding for Career and Technical Education (CTE), greater collaboration between private sector and educational institutions in the form of apprenticeship programs; and openness in the private sector to invest in upskilling and reskilling to support workers who traditionally don’t have education or expertise in the cybersecurity field. I’m optimistic that we will be able to move the needle on the skills shortage.
One more thing to consider is that we may need to have a feedback loop that helps us rethink what it means to be a qualified cybersecurity professional in the future. With technology advancing so quickly, I believe that the lower and middle tiers of cybersecurity will be managed by AI and machine learning.
This means that instead of learning how to execute on the technical aspects of patch management, our experts of the future will be able to focus on the implication of output of an automated patch management process such as what is the primary value chain(s) of the business impacted by this vulnerability? What’s the impact to the company if this patch goes wrong? Are there secondary controls we can implement to enhance security until we can install the patch, given that we’re in the middle of supporting this critical infrastructure upgrade?
These questions move the cybersecurity expert from execution to a strategic business partner that front loads and processes more of the business context prior to making recommendations on a path to protect the business.
Can security certifications help with the cybersecurity skills shortage?
Yes, I believe certifications can be helpful in filling specific roles within the cybersecurity field. For example, companies like Siemens continue to hire cybersecurity experts with a focus on securing operational technology in manufacturing plants and at general utility companies to protect critical infrastructure.
However, I believe certifications work best when paired with a holistic cybersecurity education approach that ensures experts not only know their field, but know how their roles fit into the larger cybersecurity landscape.
Security teams are overworked, and many are considering leaving the industry due to burnout. What’s the best way to address the cybersecurity skills shortage while making sure current security professionals have all the resources they need?
First off, mental health and an appropriate work-life balance is crucial in any field to prevent burnout, even cybersecurity. Especially now, as cybersecurity has come into the spotlight due to the remote nature of the pandemic, we must remember that overworking employees will only hurt companies in the long run. Alongside our investment in technology, we need to invest in the people who will use it.
I think that too often companies may be trying to do it all when it comes to cybersecurity. There simply are not enough resources to get it perfect, and even then, vulnerabilities cannot be completely prevented. I have two bits of advice: First, business leaders should integrate cybersecurity much more deeply into their executive priorities. Think of cybersecurity experts as strategic advisors on most parts of business activities.
If there’s an IT system enabling a business process, then cybersecurity should go hand in glove. The second part is that cybersecurity experts need to stop thinking like technical experts and start thinking like CEOs – a very tall order, but it’s critical for success here. This is because cybersecurity is the foundation that will protect business processes and innovation.
Cybersecurity experts need to understand business processes and be able to draw insights and correlations across multiple business functions or processes. This will not happen overnight, but it needs to be one of the core factors upon which cybersecurity experts pivot, in order to be business relevant and future facing. These two bits of advice should help drastically reduce the urgency and hyperactivity around cybersecurity, which often leads to overwork and stress.
Security threats associated with shadow IT
18.5.2020 Net-security Security
As cyber threats and remote working challenges linked to COVID-19 continue to rise, IT teams are increasingly pressured to keep organizations’ security posture intact. When it comes to remote working, one of the major issues facing enterprises is shadow IT.
End users eager to adopt the newest cloud applications to support their remote work are bypassing IT administrators and in doing so, unknowingly opening both themselves and their organization up to new threats.
You’ve probably heard the saying, “What you don’t know can’t hurt you.” In the case of shadow IT, it’s the exact opposite – what your organization doesn’t know truly can and will hurt it.
Shadow IT might sound great at surface level if you think of it as tech-savvy employees and departments deploying collaborative cloud apps to increase productivity and meet business goals. However, there’s a lot more going on below the surface, including increased risk of data breaches, regulation violations and compliance issues, as well as the potential for missed financial goals due to unforeseen costs.
One solution to risks associated with shadow IT is to have workers only use cloud apps that have been vetted and approved by your IT department. However, that approach is oftentimes not possible when shadow apps are acquired by non-IT professionals who have little to no knowledge of software standardization. Additionally, when shadow SaaS apps are used by employees or departments the attack area is hugely increased because many are not secure or patched. If IT departments are unaware of an app’s existence, they can’t take measures to protect companies’ data or its users.
Another solution that organizations use is attempting to block access to cloud services that don’t meet security and compliance standards. Unfortunately, there is a vast discrepancy in the intended block rate and the actual block rate, which Skyhigh Networks calls the “cloud enforcement gap” and represents shadow IT acquisition and usage.
Let’s take a closer look at repercussions of shadow IT usage. Below are some potential ramifications.
Increased risk of data breaches
While some companies such as Microsoft have a disciplined approach to updating and patching on-premises products, not all software providers have the same rigorous approach to security. This and the fact that IT/security departments are unaware of some apps being used by employees creates a perfect storm. Not only is IT unable to run updates for unpatched or out-of-date SaaS software, but there is also a significant lack of control over enterprise data.
Once an IT team loses control over the software being deployed on its network and enterprise data is exposed by shadow IT, they are no longer able to control who has access to that data. In this scenario, confidential enterprise information is completely unprotected and susceptible to all kinds of breaches whether by former employees, insiders or sophisticated attackers.
Compliance issues and regulation violations
Due to users acquiring shadow IT applications, common risk assessments and preventative measures are typically not performed prior to running unauthorized apps. This often leads to users violating existing compliance guidelines established by their company and runs the risk of severe fines.
Shadow IT also exposes companies to the possibility of violating regulations, including SOX, GLBA, HIPAA and GDPR (among others), due to the fact that a majority of these regulations (if not all) touch on data flows and/or storage. When employees employ shadow IT, they are often storing data in unknown and unvetted locations. This lack of security often leads to compliance violations, data breaches and, ultimately, fines.
Missed financial goals due to unforeseen costs
According to Gartner, shadow IT represents as much as 30% to 40% of total IT spend, which can be attributed to several factors. Oftentimes, users and departments buy shadow solutions within a similar product category already covered by company-wide enterprise agreements, doubling up on capabilities and spending budget without the IT department’s knowledge. And, depending on who pays the bill, shadow IT tends to skew reporting, decreasing efficiency due to time consuming audits and redundant tasks.
Solutions to help manage shadow IT
At the end of the day, you want to make sure you are providing IT teams with a SaaS management solution that brings visibility into the usage, renewal schedules, costs, policy enforcement and security to avoid the consequences of shadow IT.
One option is to introduce broad SaaS management and discovery capabilities to track apps using a number of discovery methods. This would provide IT departments with a full picture of their SaaS environment including all applications and users through a single dashboard. SaaS management solutions also have the potential to educate users on the apps available through the business, choose the best solutions and utilize those platforms to their full potential.
While companies work to increase employees’ knowledge of software apps and security risks, generally speaking we still have a lot to learn when it comes to enterprise security and shadow IT. Companies should embrace new technology and apps in a way that keeps their enterprise data protected, network secure and helps employees reach peak performance levels.
Shifting responsibility is causing uncertainty and more security breaches
18.5.2020 Net-security Security
Data security is creating fear and trust issues for IT professionals, according to a new Oracle and KPMG report.

The study of 750 cybersecurity and IT professionals across the globe found that a patchwork approach to data security, misconfigured services and confusion around new cloud security models has created a crisis of confidence that will only be fixed by organizations making security part of the culture of their business.
Data security is keeping IT professionals awake at night
Demonstrating the fear and trust issues experienced by IT professionals, the study found that IT professionals are more concerned about the security of their company’s data than the security of their own home.
IT professionals are 3X more concerned about the security of company financials and intellectual property than their home security.
IT professionals have concerns about cloud service providers. 80 percent are concerned that cloud service providers they do business with will become competitors in their core markets.
75 percent of IT professionals view the public cloud as more secure than their own data centers, yet 92 percent of IT professionals do not trust their organization is well prepared to secure public cloud services.
Nearly 80 percent of IT professionals say that recent data breaches experienced by other businesses have increased their organization’s focus on securing data moving forward.
Legacy data security approaches leave IT professionals playing whac-a-mole
IT professionals are using a patchwork of different cybersecurity products to try and address data security concerns, but face an uphill battle as these systems are seldom configured correctly.
78 percent of organizations use more than 50 discrete cybersecurity products to address security issues; 37 percent use more than 100 cybersecurity products.
Organizations who discovered misconfigured cloud services experienced 10 or more data loss incidents in the last year.
59 percent of organizations shared that employees with privileged cloud accounts have had those credentials compromised by a spear phishing attack.
The most common types of misconfigurations are:
Over-privileged accounts (37 percent)
Exposed web servers and other types of server workloads (35 percent)
Lack of multi-factor authentication for access to key services (33 percent)
Shifting responsibility and security
Organizations are moving more business-critical workloads to the cloud than ever before, but growing cloud consumption has created new blind spots as IT teams and cloud service providers work to understand their individual responsibilities in securing data. Shifting responsibility is clearly a huge issue, and confusion has left IT security teams scrambling to address a growing threat landscape.
Nearly 90 percent of companies are using SaaS and 76 percent are using IaaS. 50 percent expect to move all their data to the cloud in the next two years.
Shared responsibility security models are causing confusion. Only 8 percent of IT security executives state that they fully understand the shared responsibility security model.
70 percent of IT professionals think too many specialized tools are required to secure their public cloud footprint.
75 percent of IT professionals have experienced data loss from a cloud service more than once.
It’s time to build a security-first model
To address increasing data security concerns and trust issues, cloud service providers and IT teams need to work together to build a security-first culture. This includes hiring, training, and retaining skilled IT security professionals, and constantly improving processes and technologies to help mitigate threats in an increasingly expanding digital world.
69 percent of organizations report their CISO reactively responds and gets involved in public cloud projects only after a cybersecurity incident has occurred.
73 percent of organizations have or plan to hire a CISO with more cloud security skills; over half of organizations (53 percent) have added a brand new role called the Business Information Security Officer (BISO) to collaborate with the CISO and help integrate security culture into the business.
88 percent of IT professionals feel that within the next three years, the majority of their cloud will use intelligent and automated patching and updating to improve security.
87 percent of IT professionals see AI/ML capabilities as a “must-have” for new security purchases in order to better protect against things like fraud, malware and misconfigurations.

“The lift-and-shift of critical information to the cloud over the last couple of years has shown great promise, but the patchwork of security tools and processes has led to a steady cadence of costly misconfigurations and data leaks. Positive progress is being made, though,” said Steve Daheb, Senior Vice President, Oracle Cloud.
“Adopting tools that leverage intelligent automation to help close the skills gap are on the IT spend roadmap for the immediate future and the C-level is methodically unifying the different lines of business with a security-first culture in mind.”
“In response to the current challenging environment, companies have accelerated the movement of workloads, and associated sensitive data, to the cloud to support a new way of working, and to help optimize cost models. This is exposing existing vulnerabilities and creating new risks,” said Tony Buffomante, Global Co-Leader and U.S. Leader of KPMG’s Cyber Security Services.
“To be able to manage that increased threat level in this new reality, it is essential that CISOs build security into the design of cloud migration and implementation strategies, staying in regular communication with the business.”
Identity-related breaches on the rise, prevention still a work in progress
18.5.2020 Net-security Security
The number of workforce identities in the enterprise is growing dramatically, largely driven by DevOps, automation, and an increase in enterprise connected devices, which will only continue to accelerate identity growth, an IDSA survey of 502 IT security and identity decision makers reveals.
identity-related breaches
At the same time, compromised identities remain one of the leading causes of a data breach. According to the study, the vast majority of IT security and identity professionals have experienced an identity-related breach at their company within the past two years, with nearly all of them reporting that they believe these breaches were preventable.
“When approaching identity security, professionals must first consider a range of desired outcomes, or results they want to achieve, and then chart their paths accordingly,” said Julie Smith, executive director of the IDSA.
“According to security and identity professionals, these outcomes are still a work in progress, with less than half reporting that they have fully implemented any of the identity-related security outcomes that the IDSA has initially identified as critical to reducing the risk of a breach. In fact, the research shows a clear correlation between a focus on identity-centric security outcomes and lower breach levels.”
Identity-related breaches are ubiquitous
94% have had an identity-related breach at some point
79% have had an identity-related breach within the past two years
66% say phishing is the most common cause of identity-related breaches
99% believe their identity-related breaches were preventable
Identity security is a work in progress
Most identity-related security outcomes are still in progress or planning stages
Less than half have fully implemented key identity-related security outcomes
71% have made organizational changes to the ownership of identity management
Forward-thinking companies are showing results
Forward-thinking companies are much more likely to have fully implemented key identity-related security outcomes
Only 34% of companies with a “forward-thinking” security culture have had an identity-related breach in the past year — far fewer than the 59% of companies with a “reactive” security culture
Less than a quarter of Americans use a password manager
18.5.2020 Net-security Security
A large percentage of Americans currently do not take the necessary steps to protect their passwords and logins online, FICO reveals.
use password manager
As consumers reliance on online services grows in response to COVID-19, the study examined the steps Americans are taking to protect their financial information online, as well as attitudes towards increased digital services and alternative security options such as behavioral biometrics.
Do you use a password manager?
The study found that a large percentage of Americans are not taking the necessary precautions to secure their information online. For example, only 42 percent are using separate passwords to access multiple accounts; 17 percent of respondents have between two to five passwords they reuse across accounts; and 4 percent use a single password across all accounts.
Additionally, less than a quarter (23 percent) of respondents use an encrypted password manager which many consider best practice; 30 percent are using high risk strategies such as writing their passwords down in a notebook. If you’re a security leader and your organization is still not using a password manager, find out how to evaluate a password management solution for business purposes.
“We’re seeing more cyber criminals targeting consumers with COVID-19 related phishing and social engineering,” said Liz Lasher, vice president of fraud portfolio marketing at FICO.
“Because of the current situation, many consumers are only able to access their finances digitally, so it’s vital to remain vigilant against such scams and take the right precautions to protect themselves digitally.”
A forgotten password can affect online purchases
The study shows that consumers struggle with maintaining their current passwords as 28 percent reported abandoning an online purchase because they forgot login information, and 26 percent reported being unable to check an account balance.
Forgotten usernames and passwords even affect new account openings, 13 percent said that it has stopped them from opening a new account with an existing provider.
This is a notable trend as consumers are more willing than ever to do business digitally. The study found that the majority of respondents would open a checking (52 percent) or mobile phone (64 percent) account online, while an overwhelming majority of respondents (82 percent) said they would open a credit card account online.
Consumers trusting physical and behavioral biometrics
However, while there is significant room to improve how consumers protect their login credentials, the survey also found that Americans are becoming more trusting of using physical and behavioral biometrics to secure their financial accounts.
The survey found that 78 percent of respondents said they would be happy for their bank to analyze behavioral biometrics – such as how you type – for security and 65 percent are happy to provide biometrics to their bank; while 60 percent are open to using fingerprint scans to secure their accounts.
Security alternatives
Additionally, when logging into their mobile banking apps, respondents are now considering alternative security measures beyond the traditional username and password. The five most widely used security alternatives are:
One-time passcode via SMS (53 percent)
One-time passcode via email (43 percent)
Fingerprint scan (39 percent)
Facial Scan (24 percent)
One-time passcode delivered and spoken to mobile phone (23 percent)
“Digital services are currently playing a critical role in daily life. It is a good time to evaluate how we protect ourselves and our information online,” said Lasher.
“Customers have been happy to adopt security such as one-time passcodes, and are now showing that they are willing to adopt additional options, such as biometrics, to protect their accounts.
“There are no magic bullets and the ability to layer and deploy multiple authentication methods appropriate to each occasion is key. Financial services organizations and consumers need to continue to keep security best practices top of mind to help combat fraudsters now and in the future.”
Google Chrome will block resource-heavy ads starting August
17.5.2020 Bleepingcomputer Security
The Google Chrome web browser will start unloading ad iframes using too many system resources without the user's knowledge starting with the stable release coming near the end of August.
Chrome will target ads that drain device resources like battery, network data, and CPU processing power, such as those designed to mine for cryptocurrency known as being resource hogs that will drain battery life and network bandwidth.
"In order to save our users’ batteries and data plans, and provide them with a good experience on the web, Chrome will limit the resources a display ad can use before the user interacts with the ad," Chrome Product Manager Marshall Vale said.
'When an ad reaches its limit, the ad's frame will navigate to an error page, informing the user that the ad has used too many resources."
Example of unloaded ad
Example of unloaded ad (Google)
If users click the Details link, they will see a short message explaining why the ad was unloaded and saying that "This ad uses too many resources for your device, so Chrome removed it."
Development on this new feature started during mid-2019 and it is part of a larger effort trying to steer ads into becoming friendlier with Chrome blocking a whole range of abusive or misleading advertisements since version 71 was released in December 2018.
Ads previously included in Chrome's blacklist are the ones that promote and distribute malware, feature hidden click areas, display fake mouse pointers, abuse non-interactive redirects, show fake messages and alerts, and generally display misleading behavior.
To filter these harmful ads, Chrome follows the Better Ads Standards to determine if a site is displaying abusive ads.
Finding the heavy ads
To spot resource-heavy ads, Google is using a thresholds-based system that will automatically mark them as heavy ads if users do not interact with them and they meet these criteria:
Uses the main thread for more than 60 seconds in total
Uses the main thread for more than 15 seconds in any 30-second window
Uses more than 4 megabytes of network bandwidth
As Vale explained, even though only 0.3% of all ads displayed on the web will exceed these thresholds, they are behind 26% of all the network data and 28% of all CPU resources used by ads.
Among the ad behaviors this new feature will discourage, Google mentions ads mining cryptocurrency, ads loading large, poorly compressed images, and ads loading large video files before a user gesture.
Ads that perform expensive operations in JavaScript, including CPU timing attacks and video decoding will also be unloaded automatically if they are marked as resource-heavy ads.
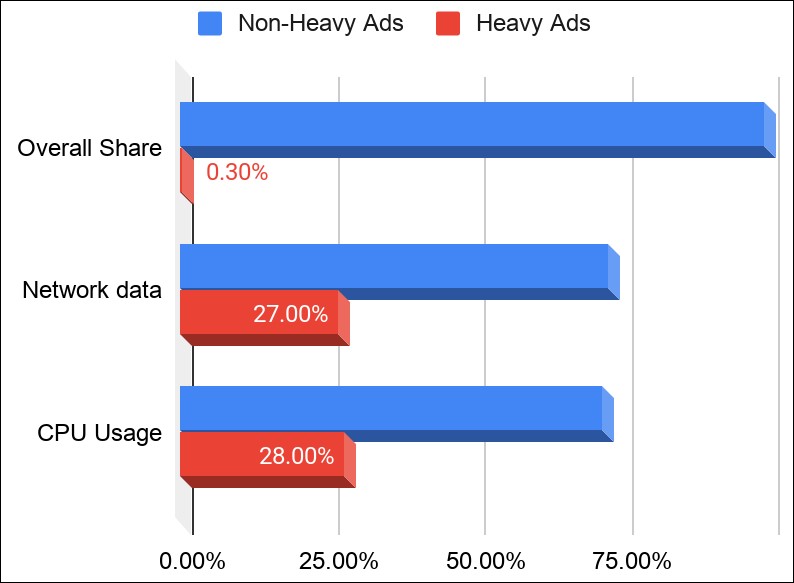
Heavy ads stats (Google)
How to test heavy ad intervention
While the feature is not yet enabled for users of the Chrome stable branch until the end of August 2020, users of Chrome Canary (now at version 84) can easily test it using the following flags:
Enable chrome://flags/#enable-heavy-ad-intervention
Disable chrome://flags/#heavy-ad-privacy-mitigations
As Google explains it, the new behavior is activated when you enable the chrome://flags/#enable-heavy-ad-intervention flag "but by default, there is some noise and variability added to the thresholds to protect user privacy."
When disabling chrome://flags/#heavy-ad-privacy-mitigations, the heavy ad restrictions are applied purely according to the limits.
You can test the intervention on some sample content available on heavy-ads.glitch.me, and can also use it to load arbitrary URLs to test your own sites.
Hashes in PowerShell
As a follow up to yesterday's how-to, I thought hashing might a thing to cover. We use hashes all the time, but it's annoying that md5sum, sha1sum and sha256sum aren't part of the windows command set - or are they? Yup, it turns out that they most definitely are part of PowerShell:
Get-FileHash -path $filename -Algorithm $algo
Where the Algorithm is a string, any one of:
"SHA1","SHA256","SHA384","SHA512","MACTripleDES","MD5","RIPEMD160"
$a = get-filehash -Path .\somefile.txt -Algorithm SHA256
$a
Algorithm Hash Path
--------- ---- ----
SHA256 0ACDA2996D999257BD8E4EE7AD43065626A14105A06DC00973959F9B032DE0E9 somefile.txt
$a.Hash
0ACDA2996D999257BD8E4EE7AD43065626A14105A06DC00973959F9B032DE0E9
But what about string values? If you want to hash a string, there doesn't seem to be a function for that. It turns out that while it's not part of PowerShell as a separate thing, it's pretty easy to access it using the string as an "inputstring" variable:
$stringAsStream = [System.IO.MemoryStream]::new()
$writer = [System.IO.StreamWriter]::new($stringAsStream)
$writer.write("RADIO CHECK")
$writer.Flush()
$stringAsStream.Position = 0
Get-FileHash -Algorithm "SHA256" -InputStream $stringAsStream | Select-Object Hash
Hash
----
A450215BE7B1BC6006D41FF62A9324FEB4CD6D194462CB119391CE21555658BB
So, this gets the job done but it's a bit cludgy, let's drop it into a function, then call the function:
function Get-StringHash ( [String] $InputString, $HashAlgo)
{
$stringAsStream = [System.IO.MemoryStream]::new()
$writer = [System.IO.StreamWriter]::new($stringAsStream)
$writer.write($InputString)
$writer.Flush()
$stringAsStream.Position = 0
Get-FileHash -Algorithm $HashAlgo -InputStream $stringAsStream | Select-Object Hash
}
$a = get-stringhash "LOUD AND CLEAR" "SHA256"
$a
Hash
----
7FE22308D7B971EDCADB8963188E46220E9D5778671C256216AEA712A33D4A3E
$a.Hash
7FE22308D7B971EDCADB8963188E46220E9D5778671C256216AEA712A33D4A3E
This "common infosec functions in PowerShell" thing kinda got started by accident, and got extended when Jim Clausing asked me if I was going to re-write CyberChef in PowerShell?. Of course my answer was "If you're going to put down a dare like that, challenge accepted" - so look for more stories of this type in future. As I introduce more functions, I'll roll them into the same GUI as I presented yesterday, code will get updated in my github ( https://github.com/robvandenbrink ).
Palo Alto Networks addresses tens of serious issues in PAN-OS
15.5.20 Securityaffairs Security
Palo Alto Networks addressed tens of vulnerabilities in PAN-OS, the software that runs on the company’s next-generation firewalls.
Palo Alto Networks has issued security updates to address tens of vulnerabilities in PAN-OS, the software that runs on the company’s next-generation firewalls.
One of the most severe vulnerabilities, tracked as CVE-2020-2018, is an authentication bypass vulnerability in the Panorama context switching feature. The flaw could be exploited by an attacker with network access to a Panorama’s management interface to gain privileged access to managed firewalls.
“An authentication bypass vulnerability in the Panorama context switching feature allows an attacker with network access to a Panorama’s management interface to gain privileged access to managed firewalls. An attacker requires some knowledge of managed firewalls to exploit this issue.” reads the advisory published by the vendor.
This vulnerability does not impact Panorama configured with custom certificates authentication for communication between Panorama and managed devices.
The issue received a CVSSv3.1 Base Score of 9, it affects PAN-OS 7.1 versions earlier than 7.1.26, PAN-OS 8.1 versions earlier than 8.1.12, PAN-OS 9.0 versions earlier than 9.0.6, and all versions of PAN-OS 8.0.
Palo Alto Networks also addressed an XML external entity reference (‘XXE’) vulnerability, tracked as CVE-2020-2012, that could lead to information leak.
The flaw could be exploited by unauthenticated attackers with network access to the Panorama management interface to read arbitrary files on the system.
The vendor also fixed a high-severity vulnerability, tracked as CVE-2020-2011, that could be exploited by a remote, unauthenticated attacker to trigger a denial-of-service (DoS) condition to all Panorama services by sending specially crafted registration requests.
Other high severity issues affect the previous Nginx version used in PAN-OS software, some of them could be exploited without authentication.
Palo Alto Networks also addressed serious cross-site scripting (XSS) vulnerability in the GlobalProtect Clientless VPN can be exploited to compromise a user’s session by tricking the victims into visiting a malicious website.
The full list of vulnerabilities addressed by Palo Alto Networks is available here.
Venafi Acquires Kubernetes Services Provider Jetstack
15.5.20 Securityweek Security
Identity protection provider Venafi this week announced that it has entered a definitive agreement to acquire Jetstack, a company specializing in open source machine identity protection software for Kubernetes.
Founded in 2000, Utah-based Venafi provides solutions for securing and protecting cryptographic keys and digital certificates. The company helps both private organizations and government agencies around the world protect TLS, SSH and code signing machine identities.
Jetstack, a Kubernetes professional services company and a contributor to the open-source community, was founded in 2015 in London. The company builds cloud-native infrastructure using Kubernetes and educates and supports organizations embracing the cloud.
Jetstack is well known for Cert-manager, an open-source piece of software with millions of downloads and a community of hundreds of contributors. The solution provides developers with an easy way to create, connect and consume certificates with Kubernetes and cloud native tools.
With this acquisition, Venafi aims to “transform the way modern applications required by digital transformation are secured.”
According to the company, a flurry of new machines are being created using Kubernetes clusters, cloud instances, service mesh, and microservice APIs, each of them requiring a unique identity to operate securely.
Venafi and Jetstack claim they are uniquely positioned to take advantage of this opportunity, as they can protect machine identities and support enterprises using Kubernetes in mission-critical infrastructure.
The acquisition was announced following a two-year collaboration on accelerating machine identity protection in Kubernetes, multi-cloud, service mesh and microservices ecosystems.
According to Venafi, Jetstack will operate as a separate division. Furthermore, the company says it is committed to keeping existing open source projects open and strengthen the open-source community with further investment.
“Together, we have the chance to do something really special as our joint resources and expertise give us the opportunity to help developers to build fast and securely,” Matt Barker, CEO and co-founder of Jetstack, said.
Patch Tuesday Revisited - CVE-2020-1048 isn't as "Medium" as MS Would Have You Believe
Looking at our patch Tuesday list, I looked a bit closer at CE-2020-1048 (Print Spooler Privilege Escalation) and Microsoft's ratings for that one. Microsoft rated this as:
Disclosed: NO
Exploited: NO
Exploitability (old and new versions)
Unfortunately, this vulnerabiltiy was actually disclosed to Microsoft by the research community (see below), so the code to exploit it absolutely does exist and was disclosed, and a full write-up was posted as soon as the patch came out:
https://windows-internals.com/printdemon-cve-2020-1048/
Long story short, on an unpatched system, you can plant a persistent backdoor on a target host with this one-liner in PowerShell:
Add-PrinterPort -Name c:\windows\system32\ualapi.dll
Then "print" an MZ file (DOS excecutable) to that printer to light it up.
As noted, this backdoor is persistent, and will remain in place even after you apply the patch!
Moral of the story? For me, there are a couple of them:
Don't put too much stock in risk ratings assigned to patches. "Lows" and "Mediums" can bite you just as badly as vulnerabilities rated as "High". This goes for patches as well as scan results or pentest results. If your policy is to patch only Severe and High rated issues, you'll pay for that eventually.
Also, it's a good thing that more vendors are going to monolithic patching. If you apply the current patch set from Microsoft, you get them all - there's no more "cherry picking" allowed!
Anymore, if you see resistence to resolving any security issues in your organization (even lows and mediums), my take would be to tackle this in your Corporate Policies. To help to ensure that any security issues are resolved - whether via patching or correcting a config issue, have your policy call for a formal sign-off for the decision to NOT fix each of those issues. You'll find that management will be reluctant to put in writing "we're choosing to not fix this problem".
Kudos to @peleghd (Peleg Hadar) and Tomer Bar of @safebreach for the initial research and disclosure to Microsoft (acknowledgements here: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1048 ).
Also Yarden Shafir and Alex Ionescu of Winsider for related research and the detailed post referenced in this article.
COVID-19 online fraud trends: Industries, schemes and targets
15.5.20 Net-security Security
The telecommunications, retail and financial services industries have been increasingly impacted by COVID-19 online fraud, according to TransUnion.
COVID-19 online fraud
From a consumer perspective, Millennials have been most targeted by fraudsters using COVID-19 scams.
Overall, the percent of suspected fraudulent digital transactions rose 5% from March 11 to April 28 when compared to Jan. 1 to March 10, 2020. More than 100 million risky transactions from March 11 to April 28 have been identified.
“Given the billions of people globally that have been forced to stay at home, industries have been disrupted in a way not seen on this massive of a scale for generations,” said Shai Cohen, Senior VP of Global Fraud & Identity Solutions at TransUnion.
“Now that many transactions have shifted online, fraudsters have tried to take advantage and companies must adapt. Businesses that come out on top will be those leveraging fraud prevention tools that provide great detection rates and friction-right experiences for consumers.”
Examining fraud types and their impact on industries
“Our data shows that as social distancing changes shopping patterns, fraudsters have taken notice and targeted the more digital forward industries while following the money,” said Melissa Gaddis, senior director of customer success for TransUnion Global Fraud & Identity Solutions.
“For instance, although we found online gaming increased 64% as people stay home, it isn’t immediately lucrative to target those companies since financial information isn’t generally shared there.
“However, telecommunications, e-commerce and financial services all have large digital adoption, financial information and payments at the center of their online experience, and fared relatively well compared to other industries during the pandemic.”
Globally across industries, TransUnion found the countries with the highest percent of suspected fraudulent transactions were: 1) Yemen, 2) Syria and 3) Kazakhstan. In the U.S. overall, TransUnion found the cities with the highest percent of suspected fraudulent transactions were: 1) Springfield, Mass., 2) Akron, Ohio, and 3) Louisville, Ky.
Consumers targeted by COVID-19 schemes
To better understand the impacts of COVID-19 on consumers, 9,215 adults in the U.S., Canada, Colombia, Hong Kong, India, South Africa and the U.K. have been surveyed during the week of April 13.
Nearly three out of 10 respondents (29%) said they had been targeted by digital fraud related to COVID-19, with Millennials (those persons between the ages 26-40) being the most targeted at 34%.
Furthermore, consumers who said their household income is being negatively impacted by the COVID-19 pandemic are more likely to experience digital fraud with 32% reporting being targeted by online COVID-19 scams compared to 22% of people not financially impacted.
“A common assumption is that fraudsters target older generations who are perceived to be less digitally capable,” said Gaddis.
“Our data showed the opposite with younger generations, Millennials and Gen Z (those born in or after 1995), being the most targeted. Adding insult to injury, our survey found Millennials are being financially challenged the most during the pandemic.”
Businesses vulnerable to emerging risks have a gap in their insurance coverage
15.5.20 Net-security Security
The majority of business decision makers are insured against traditional cyber risks, such as breaches of personal information, but most were vulnerable to emerging risks, such as malware and ransomware, revealing a potential insurance coverage gap, according to the Hanover Insurance Group.

The report surveyed business decision makers about cyber vulnerabilities and risk mitigation efforts.
Insurance purchasing decisions influenced by media coverage
Most businesses surveyed indicated they had purchased cyber insurance, and more than 70% reported purchasing a policy on the recommendation of an independent insurance agent.
Purchasing decisions also were heavily influenced by media coverage and prior attack experience. Nearly 90% of study respondents reported experiencing a cyberattack during the past year, and recognized a cyberattack could have a disastrous impact on their businesses.
Other key findings: The insurance coverage gap
The top cybersecurity fear for businesses was breach of personally identifiable information, however, malware-related attacks were the most commonly experienced attack. One in two businesses experienced a malware-related attack in the last year while fewer than one in five businesses experienced a breach of personal information
60% of businesses reported they would be unprofitable in less than two days if they lost access to critical systems or data. And, 92% reported they would experience a negative financial impact
Over 40% of businesses had no cyber insurance or limits of $1 million or less, which may not adequately cover the cost of the average cyberattack
Only 11% of businesses were concerned about cyberattacks threatening their supply chains, yet, 88% reported being dependent on third parties

The role of independent insurance agents
The study also affirmed the important role independent insurance agents can play as experienced advisers, offering risk management counsel and services to help small to mid-sized business owners protect their operations and maximize the benefits of their cyber insurance programs.
“Having the appropriate cyber protection will only become more important as new technologies emerge, businesses become more connected and cyber criminals develop more sophisticated methods,” said Bryan J. Salvatore, president of specialty insurance at The Hanover.
“As businesses grow in complexity, the advice of an independent agent becomes increasingly important in helping business owners understand the many risks they may face and mitigate those evolving threats.”
Educational organizations use cloud apps to share sensitive data outside of IT control
15.5.20 Net-security Security
Many educational organizations are at risk of data security incidents during the current period of working from home and virtual learning, a Netwrix report reveals.

Weak data security controls
According to the survey, even before the COVID-19 pandemic, the majority of educational organizations had weak data security controls.
In particular, 54% of IT professionals in the educational sector confessed that employees put data at risk by sharing it via cloud apps outside of IT knowledge. This is the highest percentage among all verticals surveyed. The move to distance learning increases this risk even more.
Other notable findings
82% of educational organizations don’t track data sharing at all or do it manually, and 50% of them suffered a data breach due to unauthorized data sharing last year.
63% of educational organizations don’t review permissions regularly, and 24% of system administrators admitted to granting direct access rights upon user request.
28% of respondents discovered data outside of secure locations, which is the highest number of all industries surveyed. This data was left exposed for days (40%) or months (33%).
Only 8% of respondents have developed cybersecurity and risk KPIs to evaluate their security posture and track success.
“Distance learning creates many challenges for educational organizations, and cybersecurity is often taking a back seat to operational resilience. The Netwrix survey shows that security processes were not ideal before the pandemic, leaving these institutions even more vulnerable to the growing number of cyber threats today.

“To ensure these institutions can secure their student and employee data, IT professionals need to get back to basics. First, they need to understand what sensitive data they have, and classify it by its level of sensitivity and value to the organization.
“Second, they need to ensure that the data is stored securely, prioritizing the most important data. And last, they need to adopt healthy security practices for granting permissions in order to avoid data overexposure,” said Steve Dickson, CEO at Netwrix.
This Group of CISOs Is Pumping Their Own Money and Advice Into Security Startups
14.5.2020 Securityweek Security
Group of CISO Angel Investors Supports Promising Cybersecurity Startups With Funding and Valuable Expertise
Silicon Valley CISO Investments (SVCI) is a new and so far unique approach to angel investment in security startups. A syndicate of practicing CISOs invests its own money and personal expertise into the success of the syndicate's portfolio companies.
SVCI was formed in September 2019 by seven CISOs and Oren Yunger (currently with GGV Capital, but formerly CISO at Clicktale), and has already invested in three security startups.
The syndicate grew out of an earlier year-long project called Security for Startups, where the CISOs sought to instill security concepts into the foundation of new companies. What they realized, however, was that just eight working practitioners could provide huge insight into the needs of new security products.
SVCI Logo"That idea," Yunger told SecurityWeek, "was that we have very smart people within the group -- but putting the group together would create a force with a collective value greater than the individual parts."
SecurityWeek talked to four SVCI CISOs for a deeper understanding of the purpose and process of CISO-focused security investments
After Security for Startups, it was natural for the participating CISOs to expand their ambition from helping innovative startups be secure, to helping startup vendors produce innovative and effective security products -- and to do that by investing themselves into the startups. What started late last year as a group of eight CISOs has now grown into an Angel syndicate of 46 CISOs, focused in the Bay Area but with members across the country, drawn from all the major industry verticals. The investment from the CISOs is both financial and a supply of unparalleled experience and expertise.
This is a win-win situation. The CISOs financially support promising vendors while simultaneously helping to shape solutions to the very security problems they grapple with every day. The vendors get financial support for their company (perhaps not to the level that can be provided by mainstream venture capital companies), but more importantly, they get an implied endorsement by 46 practicing CISOs -- and most importantly, they get practical feedback on what is needed in their products, supplied by the nation's top experts.
The motivation for the financial support is less to do with making a monetary profit when the portfolio company succeeds, and more to do with making a commitment to help shape effective, innovative security solutions for the most pressing and illusive security problems of today. "We feel that the equity or the capital that SCVI brings to the table is not financial per se," said Yunger. "We're motivated, and we decided to put financial capital behind companies because that ties us into the mission -- we have more on the line when we have a stake in the game -- but the greater value of SVCI is mostly our expertise and experience and knowledge of the subject."
Harshil Parikh, CISO at Medallia, added, "It is surprising how many security products and vendors there are in the community, but they don't listen to us. As security practitioners we come across so many companies and products where we just wish they would listen to the practitioner feedback and build a solution that solves our very legitimate problems. From my perspective I think we are all participants in SVCI to make our voices heard, and drive change within the innovation that startups are delivering."
Avi Shua, CEO and founder of the first investment -- Orca Security -- supports this view. "There is no shortage of money in the market," he told SecurityWeek. "A company like Orca would have no difficulty raising finance. But this unique feedback opportunity from SVCI is something I have not seen elsewhere. So, we jumped at the opportunity."
He explained the nature of the feedback. "We have a Slack channel between Orca and SVCI," he said. "Just three months ago we used the Slack channel to discuss a feature we had in the product and whether it works for the more regulated industries. We learned that it might be problematic for larger organizations. The feedback from SVCI comprised dozens, maybe a hundred messages, providing advice on alternatives, how to implement the feature, the pros and cons. We took the advice and re-implemented the feature and it was immediately sold to a bank and is currently being evaluated by a large Fortune 100 company. This wouldn't have happened without the SVCI advice, because if we had presented it as was, we would have just been told, 'it doesn't work for financial institutions': they wouldn't or couldn't take the time to work with us on how to make it work."
There are two obvious side-effects to such an effective concept. The first is that the major VC companies might be tempted to use SVCI as a sounding-board to augment their own due diligence. If SVCI isn't interested in investing, then maybe they shouldn't either? "It's true that we get a lot of 'inbound' from VC companies that want to introduce companies into the mix," Yunger said. But the bad news is that the syndicate has its own process for finding and evaluating potential investment opportunities.
CISOs tend to know what's going on around them. "They get emails with introductions to new products all the time. Every now and then, they'll raise a hand to the syndicate and say, 'listen, this is a really interesting problem that I'm trying to solve, and I met this team that is dedicated and I can see how this company is going to evolve and become meaningful. We should take a look at it together.' This is how all our new opportunities come to life."
Each opportunity is discussed by all members. A small sub-set of the companies is invited to present to the syndicate, and this is again discussed internally by the entire membership, which may be followed by a request for proof of concept demonstrations. "For each of these steps," continued Yunger, "we have dedicated teams and individuals to enable us to make good decisions. At the end of this, there is an allocation process where people decide whether and how much they may individually wish to invest in the company."
Orca may be a little different. The initial introduction came from a meeting at Black Hat -- but from then on, the opportunity due diligence process was followed.
The second side-effect is the potential for the SVCI syndicate to be overwhelmed by applications for membership from other CISOs. But while there is no set maximum membership figure, the process of joining is difficult. "We're an invite-only group," explained Harshil Parikh. "Potential new members have to be referred by an existing member, and seconded by five other members; and of course, must be an accredited investor."
From then on, material qualification is not difficult. Ian Amit, CISO at Cimpress, demands commitment to participation. "It's less about the size of your bank account," he told SecurityWeek, "and more about your commitment to be part of the process from start to finish.-- to participate in sourcing, in due diligence, in working with the portfolio companies... really being part of that fabric that makes SVCI so unique, and to be able to contribute to the entire process."
Craig Rosen, CISO at ASAPP, added, "For me, engagement is key. There's nothing worse than asking for feedback on a specific technology or platform and having it fall on deaf ears, so it's important that the engagement level stays high. It's our objective to make these new products work well. We're trying to solve really hard problems, many of which have not been solved. We're looking for the level of acceleration that this group provides, and I think given it's focus, given its membership, given the background and experience of its members, we really have an opportunity to accelerate and help solve the problems we're trying to solve faster."
However, it is also worth mentioning that the syndicate has a commitment to diversity. An applicant from within an under-represented vertical, or with a new set of skills, would likely be viewed more favorably.
As it stands, it is difficult to imagine a more compelling endorsement for a new product or technology than the financial backing of almost fifty CISOs, nor a better methodology for product improvement than continuous and active engagement with the top security experts in the country.
Effective Business Continuity Plans Require CISOs to Rethink WAN Connectivity
14.5.2020 Thehackernews Security
As more businesses leverage remote, mobile, and temporary workforces, the elements of business continuity planning are evolving and requiring that IT professionals look deep into the nuts and bolts of connectivity.
CISOs and their team members are facing new challenges each and every day, many of which have been driven by digital transformation, as well as the adoption of other productivity-enhancing technologies.
A case in point is the rapidly evolving need to support remote and mobile users as businesses change how they interact with staffers.
For example, the recent COVID-19 crisis has forced the majority of businesses worldwide to support employees that work from home or other remote locations.
Many businesses are encountering numerous problems with connection reliability, as well as the challenges presented by rapidly scaling connectivity to meet a growing number of remote workers.
Add to that security and privacy issues, and it becomes evident that CISOs may very well face what may become insurmountable challenges to keep things working and secure.
It is the potential for disruption that is bringing Business Continuity Planning (BCP) to the forefront of many IT conversations. What's more, many IT professionals are quickly coming to the conclusion that persistent WAN and Internet connectivity prove to be the foundation of an effective business continuity plan.
VPNs are Failing to Deliver
Virtual Private Networks (VPNs) are often the first choice for creating secure connections into a corporate network from the outside world.
However, VPNs have initially been designed to allow a remote endpoint to attach to an internal local area network and grant that system access to data and applications stored on the network.
For occasional connectivity, with a focus on ease of use.
Yet, VPNs are quickly beginning to show their limitations when placed under the demand for supporting a rapidly deployed remote workforce.
One of the most significant issues around VPNs comes in the context of scalability; in other words, VPNs can be complicated to scale quickly.
For the most part, VPNs are licensed by connection and are supported by an appliance on the network side to encrypt and decrypt traffic. The more VPN users that are added, the more licenses and processing power that is needed, which ultimately adds unforeseen costs, as well as introducing additional latency into the network.
Eventually, VPNs can break under strain, and that creates an issue around business continuity. Simply put, if VPNs become overwhelmed by increased traffic, connectivity may fail, and the ability for employees to access the network may be impacted, the concept of business continuity suffers as a result.
VPNs are also used for site to site connections, where the bandwidth may be shared not only from a branch office to a headquarters office but also with remote users. A situation such as that can completely derail an organization's ability to do business if those VPNs fail.
Perhaps an even bigger concern with VPNs comes in the form of cybersecurity. VPNs that are used to give remote users access to a network are only as reliable as the credentials that are given to those remote users.
In some cases, users may share password and login information with others, or carelessly expose their systems to intrusion or theft. Ultimately, VPNs may pave the way for attacks on the corporate network by allowing bad actors to access systems.
ZTNA Moves Beyond VPNs
With VPN technology becoming suspect in the rapid expansion of remote workforces, CISOs and IT pros are looking for alternatives to ensure reliable and secure connections into the network from remote workers.
The desire to bridge security and reliability is driven by continuity, as well as operational issues. CISOs are looking to keep costs down, provide a level of security, without compromising performance, and still meet projected growth.
Many enterprises thought that the answer to the VPN dilemma could be found in SDP (Software Defined Perimeters) or ZTNA (Zero Trust Network Access), two acronyms that have become interchangeable in the arena of cybersecurity.
ZTNA has been built for the cloud as a solution that shifted security from the network to the applications. In other words, ZTNA is application-centric, meaning that users are granted access to applications and not the complete network.
Of course, ZTNA does much more than that. ZTNA can "hide" applications, while still granting access to authorized users. Unlike VPNs, ZTNA technology does not broadcast any information outside of the network for authentication, whereas VPN concentrators sit at the edge of the network for all to see, making them a target for malicious attackers.
What's more, ZTNA uses inside-out connections, which means IP addresses are never exposed to the internet. Instead of granting access to the network like a VPN, ZTNA technology uses a micro-segmentation approach, where a secure segment is created between the end-user and the named application.
ZTNA creates an access environment that provides private access to an application for an individual user, and only grants the lowest level of privileges to that user.
ZTNA technology decouples access to applications from access to the network, creating a new paradigm of connectivity. ZTNA based solutions also capture much more information than a VPN, which helps with analytics and security planning.
While a VPN may only track a device's IP address, port data, and protocols, ZTNA solutions capture data around the user identity, named application, latency, locations, and much more. It creates an environment that allows administrators to be more proactive and more easily consume and analyze the information.
While ZTNA may be a monumental step forward from legacy VPN systems, ZTNA solutions are not without their own concerns. ZTNA solutions do not address performance and scalability issues and may lack the core components of continuity, such as failover and automated rerouting of traffic.
In other words, ZTNA may require those additional third-party solutions to be added to the mix to support BCP.
Resolving ZTNA and VPN issues with SASE
A newer technology, which goes by the moniker of SASE (Secure Access Service Edge), may very well have the answer to the dilemmas of security, continuity, and scale that both ZTNA and VPNs introduce into the networking equation.
The Secure Access Service Edge (SASE) model was proposed by Gartner's leading security analysts, Neil MacDonald, Lawrence Orans, and Joe Skorupa. Gartner presents SASE as a way to collapse the networking and security stacks of SD-WANs into a fully integrated offering that is both easy to deploy and manage.
Gartner sees SASE as a game-changer in the world of wide-area networking and cloud connectivity. The research house expects 40% of enterprises to adopt SASE by 2024. However, a significant challenge remains, networking and cybersecurity vendors are still building their SASE offerings, and very few are actually available at this time.
One such vendor is Cato Networks, which offers a fully baked SASE solution and has been identified as one of the leaders in the SASE game by Gartner.
SASE differs significantly from the VPN and ZTNA models by leveraging a native cloud architecture that is built on the concepts of SD-WAN (Software-Defined Wide Area Network). According to Gartner, SASE is an identity-driven connectivity platform that uses a native cloud architecture to support secure connectivity at the network edge that is globally distributed.
SASE gives organizations access to what is essentially a private networking backbone that runs within the global internet. What's more, SASE incorporates automated failover, AI-driven performance tuning, and multiple secure paths into the private backbone.
SASE is deployed at the edge of the network, where the LAN connects to the public internet to access cloud or other services. And as with other SD-WAN offerings, the edge has to connect to something beyond the four walls of the private network.
In Cato's case, the company has created a global private backbone, which is connected via multiple network providers. Cato has built a private cloud that can be reached over the public internet.
SASE also offers the ability to combine the benefits of SDP with the resiliency of an SD-WAN, without introducing any of the shortcomings of a VPN.
Case in point is Cato's Instant Access, a clientless connectivity model that uses a Software-Defined Perimeter (SDP) solution to grant secure access to cloud-delivered applications for authorized remote users.
Instant access offers multi-factor authentication, single sign-on, least privileged access, and is incorporated into the combined networking and security stacks. Since it is built on SASE, full administrator visibility is a reality, as well as simplified deployment, instant scalability, integrated performance management, and automated failover.
Cato Networks' Remote Access Product Demo
In Cato's case, continuous threat protection keeps remote workers, as well as the network, safe from network-based threats. Cato's security stack includes NGFW, SWG, IPS, advanced anti-malware, and Managed Threat Detection and Response (MDR) service. Of course, Cato isn't the only player in the SASE game; other vendors pushing into SASE territory include Cisco, Akamai, Palo Alto Networks, Symantec, VMWare, and Netskope.
SASE Address the Problems of VPNs, ZTNA -- and More
With VPNs coming up short and ZTNA lacking critical functionality, such as ease of scale and performance management, it is quickly becoming evident that CISOs may need to take a long hard look at SASE.
SASE addresses the all too common problems that VPNs are introducing into a rapidly evolving remote work paradigm, while still offering the application-centric security that ZTNA brings to the table.
What's more, SASE brings with it advanced security, enhanced visibility, and reliability that will go a long way to improving continuity, while also potentially lowering costs.
Eye-opening statistics about open source security, license compliance, and code quality risk
14.5.2020 Net-security Security
99% of commercial codebases contain at least one open source component, with open source comprising 70% of the code overall, according to Synopsys.

Open source components and security
More notable is the continued widespread use of aging or abandoned open source components, with 91% of the codebases containing components that either were more than four years out of date or had seen no development activity in the last two years.
The most concerning trend in this year’s analysis is the mounting security risk posed by unmanaged open source, with 75% of audited codebases containing open source components with known security vulnerabilities, up from 60% the previous year. Similarly, nearly half (49%) of the codebases contained high-risk vulnerabilities, compared to 40% just 12 months prior.
“It’s difficult to dismiss the vital role that open source plays in modern software development and deployment, but it’s easy to overlook how it impacts your application risk posture from a security and license compliance perspective,” said Tim Mackey, principal security strategist of the Synopsys Cybersecurity Research Center.
Open source adoption continues to soar
Ninety-nine percent of codebases contain at least some open source, with an average of 445 open source components per codebase—a significant increase from 298 in 2018.
Seventy percent of the audited code was identified as open source, a figure that increased from 60% in 2018 and has nearly doubled since 2015 (36%).
Outdated and “abandoned” components are pervasive
Ninety-one percent of codebases contained components that either were more than four years out of date or had no development activity in the past two years.
Beyond the increased likelihood that security vulnerabilities exist, the risk of using outdated open source components is that updating them can also introduce unwanted functionality or compatibility issues.

Use of vulnerable open source components trending upward again
In 2019, the percentage of codebases containing vulnerable open source components rose to 75% after dropping from 78% to 60% between 2017 and 2018. Similarly, the percentage of codebases containing high-risk vulnerabilities jumped up to 49% in 2019 from 40% in 2018.
Fortunately, none of codebases audited in 2019 were impacted by the infamous Heartbleed bug or the Apache Struts vulnerability that haunted Equifax in 2017.
Open source license conflicts continue to put intellectual property at risk
Despite its reputation for being “free,” open source software is no different from any other software in that its use is governed by a license. Sixty-eight percent of codebases contained some form of open source license conflict, and 33% contained open source components with no identifiable license.
The prevalence of license conflicts varied significantly by industry, ranging from a high of 93% (Internet & Mobile Apps) to a relatively low of 59% (Virtual Reality, Gaming, Entertainment, Media).
Unexpected downtime is crippling businesses, causing revenue losses
14.5.2020 Net-security Security
Unexpected downtime is a major challenge for SMBs today. The IT systems of nearly a quarter of SMBs have gone offline in the past year, according to a research from Infrascale.
unexpected downtime
SMBs said the downtime creates business disruption and decreases employee productivity. 37% of SMBs in the survey group said they have lost customers and 17% have lost revenue due to downtime.
“Customer retention is essential for business success,” said Russell P. Reeder, CEO of Infrascale. “It can cost up to five times more to attract a new customer than to retain an existing one, and when customers leave, businesses lose out on vital profit and operational efficiencies. Especially in today’s competitive environment, it’s challenging enough to retain customers. With all the cost-effective solutions available, downtime shouldn’t be a reason for concern.”
19% of SMBs admit that they do not feel their businesses are adequately prepared to address and prevent unexpected downtime. Of those SMBs that said they feel unprepared for unexpected downtime, 13% said they do not feel their business is prepared for unexpected downtime because they have limited time to research solutions to prevent downtime.
28% attributed not feeling prepared for unexpected downtime due to IT teams at their organization being stretched. The same share (28%) said they don’t think their business is at risk from unexpected downtime. Yet 38% of SMBs said they don’t know what the cost of one hour of downtime is for their businesses.
The research is based on a survey of more than 500 C-level executives at SMBs. CEOs represented 87% of the group. Most of the remainder was split between CIOs and CTOs.
Downtime can prompt valuable customers to head for the exit
“Customers today are extremely demanding,” said Reeder. “They are intolerant of delays and downtime.”
Thirty-seven percent of the SMB survey group admitted to having lost customers due to downtime issues. This problem was especially pronounced among business-to-business entities; 46% of B2B businesses have experienced such a loss. As for business-to-consumer SMBs, 25% said they have lost customers due to downtime problems.
Downtime also leads to business disruption and loss of productivity and reputation
Loss of customers and revenue are just two of the downsides of IT system-related downtime. Downtime also can hurt employee productivity and adversely impact a company’s reputation.
SMBs said the biggest downtime risks are business disruption (29%) and decreased employee productivity (21%). As noted above, 17% have lost revenue. Reputation impact (16%) and cost (13%) came in next.
Software failure (53%) and cybersecurity issues (52%) are the most common causes of the downtime that creates these business challenges. A significant but far smaller share of the SMB survey group blamed downtime on hardware failure (38%), human error (36%), natural disaster (30%), and/or hardware theft (24%).
SMB downtime may not last long, but it is still costly
10% of SMBs said their per-hour downtime cost was more than $50,000. Thirteen percent said their per-hour downtime cost was between $40,001 and $50,000.
25% of SMBs said the per-hour cost of downtime for their business was between $20,001 and $40,000. A slightly larger share (26%) said they incur a loss of $10,000 to $20,000 for each hour of downtime, while 27% said their cost of downtime per hour was under $10,000.
The good news is that the survey group indicated downtime typically lasts for minutes instead of hours. 22% of the survey group said their downtime events typically last anywhere from five to 15 minutes.
Just 17% of the group said their downtime commonly stretches on for 15 to 30 minutes, and another 17% said an hour. Just 6% said over an hour.
“The downtime duration results may seem reassuring, but in today’s challenging and fast-moving business environment, every second counts,” said Reeder. “Even if your company was down for minutes, just think of the reputational damage it can cause as well as real costs when data cannot be recovered. There is really no excuse these days for not backing up your data.”
Despite the many downsides of downtime, some SMBs remain unprepared
19% of the B2B survey group said they do not feel their business is prepared for unexpected downtime, and B2C organizations feel even less prepared. 27% of B2C survey participants said they believe their business is unprepared for unexpected downtime.
“These survey results illustrate that there’s plenty of room for improvement when it comes to business uptime,” Reeder added.
“Organizations can benefit from application and server backup, ransomware mitigation, disaster recovery as a service (DRaaS), encryption, and state-of-the-art endpoint protection. Investments in such solutions enable them to avoid downtime and enjoy business continuity, which are essential for a growing and thriving business.”
New features in Nutanix’s HCI platform simplify disaster recovery to protect business critical apps
14.5.2020 Net-security Security
Nutanix, a leader in enterprise cloud computing, announced several new capabilities in its hyperconverged infrastructure (HCI) software and AHV hypervisor to protect business-critical applications and maintain continuous business operations in the face of a possible disaster.
New capabilities include advanced automation for recovering applications and data, support for seamless multi-site disaster recovery (DR), synchronous replication for workloads running on AHV, and a near-zero data loss with “near sync” replication for recovery point objective (RPO) times of approximately 20 seconds.
At a time when business continuity is more important than ever, ensuring businesses have strong recovery policies and procedures is no longer a “nice to have.”
However, customers looking to implement strong DR plans for critical applications, such as those supporting emergency services, had little choice but to deploy complex, often disparate technologies that demand specialized, on-going administration.
The new capabilities in Nutanix HCI and AHV help enable customers to confidently deliver mission-critical applications with significantly less complexity and lower management overhead.
“Maintaining continuous business operations is a high priority for all types of companies and organizations,” said Greg Smith, VP of Product Marketing at Nutanix.
“However, most businesses rely on custom, handcrafted DR implementations to guard against system-wide IT failures. Nutanix now natively delivers automated, easy-to-deploy disaster recovery solutions built to deliver applications that must always be available.”
Multi-site disaster recovery
Nutanix now supports multi-site DR designs, helping enable enterprises to quickly recover from the simultaneous failure of two or more data centers while keeping applications and data available to users.
Particularly valuable in regulated industries like financial services, healthcare, and emergency services where organizations need to deliver uninterrupted service, Nutanix DR leverages advanced automation technology to eliminate the complexity of DR installation and ongoing orchestration.
Application teams can quickly recover from unplanned outages or data corruption and set configurations to adhere to many stringent compliance requirements.
Unmatched near sync disaster recovery
Nutanix now supports near sync replication with an RPO of only about 20 seconds, a 3x improvement from its already industry-leading technology. Nutanix is the only leading HCI vendor to offer a 20-second RPO.
Synchronous data replication for Nutanix AHV
Synchronous replication, or the nearly instantaneous replication of data between multiple locations, is now natively supported on the Nutanix AHV hypervisor. AHV can be used by customers to deliver a highly available service for their most important workloads, such as virtual desktop infrastructure, databases, and general server virtualization.
DR orchestration with runbooks
The latest release gives customers more flexibility and control over the end-to-end recovery process, with more granular control to focus DR resources toward targeted applications.
“Our business users expect a zero recovery point objective, which guarantees no data loss when a failover occurs following a datacenter outage,” said Delfim Da Costa, System and Infrastructure Manager at Infomil, an IT spin-off of a large European retailer and a Nutanix customer since 2015.
“We are delighted to now use Nutanix’s AHV virtualization and to maintain the highest possible SLA for our production workloads.”
These new DR capabilities are included in the Nutanix HCI software and are generally available.
How to implement least privilege in the cloud
12.5.2020 Net-security Security
According to a recent survey of 241 industry experts conducted by the Cloud Security Alliance (CSA), misconfiguration of cloud resources is a leading cause of data breaches.
least privilege cloud
The primary reason for this risk? Managing identities and their privileges in the cloud is extremely challenging because the scale is so large. It extends beyond just human user identities to devices, applications and services. Due to this complexity, many organizations get it wrong.
The problem becomes increasingly acute over time, as organizations expand their cloud footprint without establishing the capability to effectively assign and manage permissions. As a result, users and applications tend to accumulate permissions that far exceed technical and business requirements, creating a large permissions gap.
Consider the example of the U.S. Defense Department, which exposed access to military databases containing at least 1.8 billion internet posts scraped from social media, news sites, forums and other publicly available websites by CENTCOM and PACOM, two Pentagon unified combatant commands charged with US military operations across the Middle East, Asia, and the South Pacific. It configured three Amazon Web Services S3 cloud storage buckets to allow any AWS global authenticated user to browse and download the contents; AWS accounts of this type can be acquired with a free sign-up.
Focus on permissions
To mitigate risks associated with the abuse of identities in the cloud, organizations are trying to enforce the principle of least privilege. Ideally, every user or application should be limited to the exact permissions required.
In theory, this process should be straightforward. The first step is to understand which permissions a given user or application has been assigned. Next, an inventory of those permissions actually being used should be conducted. Comparing the two reveals the permission gap, namely which permissions should be retained and which should be modified or removed.
This can be accomplished in several ways. The permissions deemed excessive can be removed or monitored and alerted on. By continually re-examining the environment and removing unused permissions, an organization can achieve least privilege in the cloud over time.
However, the effort required to determine the precise permissions necessary for each application in a complex cloud environment can be both labor intensive and prohibitively expensive.
Understand native IAM controls
Let’s look at AWS, since it is the most popular cloud platform and offers one of the most granular Identity and Access Management (IAM) systems available. AWS IAM is a powerful tool that allows administrators to securely configure access to AWS cloud resources. With over 2,500 permissions (and counting), IAM gives users fine-grained control over which actions can be performed on a given resource in AWS.
Not surprisingly, this degree of control introduces an equal (some might say greater) level of complexity for developers and DevOps teams.
In AWS, roles are used as machine identities. To grant an application-specific permission requires attaching access policies to the relevant role. These can be managed policies, created by the cloud service provider (CSP), or inline policies, created by the AWS customer.
Reign in roles
Roles, which can be assigned more than one access policy or serve more than one application, make the journey to least-privilege more challenging.
Here are several scenarios that illustrate this point.
1. Single application – single role: where an application uses a role with different managed and inline policies, granting privileges to access Amazon ElastiCache, RDS, DynamoDB, and S3 services. How do we know which permissions are actually being used? And once we do, how do we right-size the role? Do we replace managed policies with inline ones? Do we edit existing inline policies? Do we create new policies of our own?
2. Two applications – single role: where two different applications share the same role. Let’s assume that this role has access permissions to Amazon ElastiCache, RDS, DynamoDB and S3 services. But while the first application is using RDS and ElastiCache services, the second is using ElastiCache, DynamoDB, and S3. Therefore, to achieve least-privilege the correct action would be role splitting, and not simply role right-sizing. In this case, role-splitting would be followed by role right-sizing, as a second step.
3. Role chaining occurs when an application uses a role that does not have any sensitive permissions, but this role has the permission to assume a different, more privileged role. If the more privileged role has permission to access a variety of services like Amazon ElastiCache, RDS, DynamoDB, and S3, how do we know which services are actually being used by the original application? And how do we restrict the application’s permissions without disrupting other applications that might also be using the second, more privileged role?
One native AWS tool called Access Advisor allows administrators to investigate the list of services accessed by a given role and verify how it is being used. However, relying solely on Access Advisor does not connect the dots between access permissions and individual resources required to address many policy decisions. To do that, it’s necessary to dig deep into the CloudTrail logs, as well as the compute management infrastructure.
Least privilege in the cloud
Finally, keep in mind that we have only touched on native AWS IAM access controls. There are several additional issues to be considered when mapping access permissions to resources, including indirect access (via secrets stored in Key Management Systems and Secret Stores), or application-level access. That is a discussion for another day.
As we’ve seen, enforcing least privilege in the cloud to minimize access risks that lead to data breaches or service interruption can be manually unfeasible for many organizations. New technologies are emerging to bridge this governance gap by using software to automate the monitoring, assessment and right sizing of access permissions across all identities – users, devices, applications, etc. – in order to eliminate risk.
Cybersecurity and compliance: Vital priorities for MSPs and their clients
12.5.2020 Net-security Security
Cybersecurity and, to a lesser but growing extent, compliance are the most pressing priorities for MSPs and their customers this year, according to a Kaseya survey of 1,300 owners and technicians of MSP firms in more than 50 countries.

“Respondents to this year’s survey overwhelmingly agreed that their clients need more cybersecurity support from them. This is especially true in today’s uncertain environment,” said Jim Lippie, senior vice president and GM of partner development at Kaseya.
“As more small and midsize businesses look to maintain vital security operations and decrease IT costs internally ahead of an economic downturn, they will lean on the expertise and services provided by MSPs to keep their companies operating.”
While responses to the 2020 survey were collected in December 2019 prior to the coronavirus crisis, the pandemic has only increased the focus on a need for expanded IT security measures.
Companies of all sizes have recently seen an increase in cyberattacks with an influx of personal devices connecting to the corporate network and as malicious actors hope to take advantage of the uncertain times.
“More than half, or 60 percent, of our respondents said their clients experienced downtime from an outage in the past year,” Lippie continued.
“In our current, unprecedented climate, an outage can mean the end for a small business. So for MSPs, who are the IT backbone of these small businesses, there’s a significant opportunity to diversify their clients’ cybersecurity solutions and strategy in order to respond agilely to any threat that comes their way and maintain their livelihood.”
MSPs and priorities: Security dominates
Both MSPs and their customers have faced increased security threats year over year. Because MSPs have access to their clients’ IT environments through remote monitoring and management (RMM) tools, they are an ideal target for malicious actors who see opportunity in the ability to extend the impact of their attacks. In fact, a little more than 1 in 3 respondents (37 percent) said they felt their MSP business was more prone to cybercrime now than it was in 2019.
On top of the concern for their own organization’s security, MSPs must contend with increased cyber risks to their clients. Almost all respondents (95 percent) have had either some or most of their clients turn to them for counsel on cybersecurity plans and best practices.
Additionally, nearly three in four respondents said that 10 to 20 percent of their clients experienced at least one cyberattack in the past year.
Companies need more cybersecurity support from their MSP partners. Among a ranking of several top IT needs, such as “supporting mobile devices,” “legacy system replacement” and “public cloud adoption, migration and support,” 29 percent of respondents listed “meeting security risks” as their clients’ top IT need.
“Cybersecurity services,” like antivirus, anti malware and ransomware protection, followed closely at 14 percent. Together, these two options make up more than 40 percent of responses to the question. With ransomware and malware attacks making headlines every day, MSPs have an opportunity to protect existing and future customers by providing multi-layered security and backup services.
The need for compliance services is growing
With the increasing number of regulations, including the CCPA and the New York Stop Hacks and Improve Electronic Data (SHIELD) Security Act, data privacy has become a necessity for small and large organizations alike. In fact, two-thirds of respondents reported that their clients struggle to meet compliance requirements, and nearly one-third reported an increased need for compliance services in the past two years.
As our dependence on software and other technologies grow, regulators will continue to enact data privacy laws. This presents an opportunity for MSPs to develop and leverage a niche expertise in this space to help clients maintain compliance with an increasingly complex set of regulations.
RMM remains MSPs’ core application of choice
For more than half of respondents (61 percent), RMM remains the most important application, followed by PSA (21 percent) and IT documentation (11 percent).
More important than the applications themselves, however, is integration between these core applications. In fact, nearly 70 percent of respondents said that integration between their core IT applications is very important, and 81 percent responded that this integration could help their organization drive better bottom-line profits.

MSPs show growth through new offerings and value-based pricing
In the past decade, MSPs have evolved greatly from simply providing break-fix services to implementing full-fledged suites of solutions. Driving this evolution is the ability of MSPs to agilely respond to emerging needs in the market.
Nearly 90 percent of respondents consider the expansion of their service offerings important, which makes sense: The most successful, high-growth MSPs — those with an average monthly recurring revenue growth greater than 20 percent — have added about four to five new services to their offerings in the past two years.
Underlying all of this growth is a continued shift toward value-based pricing models. Respondents this year opted for a value-based pricing strategy rather than cost-based or price-match strategies. Value-based pricing strategies develop prices based on the end result and the value delivered to the customer.
Among all respondents, 38 percent reported that more than half of their revenue comes from a value-based pricing strategy. Contrastingly, only 17 percent of respondents reported that the majority of their revenue came from a cost-based pricing strategy.
Cloud support decreases but remains an opportunity for MSP growth
Public and private cloud adoption are among the top IT needs in 2020. However, respondents who manage client cloud environments dropped from 70 percent in the 2019 survey to 56 percent this year for public cloud, and from 59 percent in the 2019 survey to 49 percent for private cloud.
Despite this, there still remains an opportunity for MSPs to grow their cloud management offerings, as nearly a quarter (21 percent) of successful, high-growth MSPs manage their clients’ public cloud environments.
Global remote work transitions fail to consider security gaps
12.5.2020 Net-security Security
Security measures and password best practices have not taken priority in many regions during the shift to remote work due to the COVID-19 pandemic, according to a survey by OneLogin.

Nearly 1 in 5 (17.4%) global respondents have shared their work device password with either their spouse or child, potentially exposing corporate data.
External threats were also a factor with 36% of global respondents admitting they have not changed their home Wi-Fi password in more than a year, leaving corporate devices exposed to a potential security breach.
Remote work implementation speed left companies vulnerable
The speed required to institute remote work in the early part of 2020 has left many companies dealing with security gaps, particularly as it relates to using work devices for personal purposes.
The majority of global remote workers agree (63%) that organizations will align in favor of continued remote work post-pandemic. If this trend continues, many businesses are unknowingly putting company data at risk.
“Organizations everywhere are facing unprecedented challenges as millions of people are working from home,” said Brad Brooks, CEO and president of OneLogin. “Passwords pose an even greater risk in this WFH environment and – as our study supports – are the weakest link in exposing businesses’ customers and data to bad actors.”
Remote work security gaps around the world
A closer look at how individual countries practice security highlights differences in password sharing, willingness to access high-risk websites and more. The study found the following:
Risky sites: US remote workers are 3X as likely to use work devices to access adult entertainment as the French
Home networks: US workers are more likely than any other country to have changed their Wi-Fi password within the last month
Device security: 14% of US remote workers never changed their passwords on their device
Shadow IT: A third of US respondents have downloaded an app on their work device without approval
Password sharing: 1 in 5 (21%) US workers have shared a work-related password electronically – more than twice as many as the UK (7.8%)
(ISC)2 Professional Development Institute: Timely and continuing education opportunities
12.5.2020 Net-security Security
In this Help Net Security podcast, Mirtha Collin, Director of Education for (ISC)², talks about the Professional Development Institute (PDI), a valuable resource for continuing education opportunities to help keep your skills sharp and curiosity piqued.
Each course is designed with input from leading industry experts and based on proven learning techniques. And best of all, these courses are free to members and count for CPEs.
Professional Development Institute
Here’s a transcript of the podcast for your convenience.
Hi, my name is Mirtha Collin and I’m the Director of Education for (ISC)². I’m happy to have the opportunity to join this Help Net Security podcast today to talk to you a little bit about the Professional Development Institute, a major initiative for continuing cybersecurity education that we’re really excited about.
Just to quickly set the table for those listening who may not be aware, (ISC)² is an international nonprofit membership association focused on inspiring a safe and secure cyber world. Best known for the – or CISSP for short – (ISC)² offers a portfolio of credentials that are part of a holistic, programmatic approach to security. Our membership, over 150,000 strong, is made up of certified cyber, information, software and infrastructure security professionals who are making a difference and helping to advance the industry.
The Education Department at (ISC)² develops and delivers training materials and courses that help the cybersecurity community achieve certification and also provides learning opportunities to keep their skills sharp and maintain their certifications. We celebrated our 30th anniversary last year as advocates for the cybersecurity profession, and what I’d like to talk to you about today – PDI – has been a huge step forward for our association.
The Professional Development Institute (which we’ve shortened to “PDI” for obvious reasons) was launched by (ISC)² in February 2019 in an effort to deliver increased member value and keep our members and associates, as well as other industry participants, up to speed on the latest emerging trends in cybersecurity.
A state-of-the-art video production studio was also built in our headquarters to produce engaging high-production content for courses authored by leading cybersecurity professionals.
Let’s back up a minute though. It’s important to understand the lay of the land in cybersecurity education, and why we thought making a major investment in continuing education was something worth doing.
When it comes to certification, (ISC)² exams – as well as the exams of various accrediting bodies in the industry – probe our members on a wide array of knowledge domains to prove that they have the practical skills it takes to manage security systems. The exams focus on real-world examples that only experienced professionals will be familiar with. So, it’s a great system for separating the really knowledgeable pros from those who still need more time in the trenches.
However, cybersecurity is one of the more dynamic fields in the world, and the landscape and technological changes come frequently. What may have been applicable two years ago may no longer be of critical importance, and new challenges and solutions spring up on an annual and sometimes monthly basis.
While (ISC)² routinely updates its exams to make sure the most relevant topics are being covered, certification updates take time to build and process, and don’t happen each and every year. And then there are the “soft skills” aspects of the job that aren’t conducive to testing but are useful to develop, such as how to present to your executive leadership or how to build a high-performing team.
This can create certain gaps in curriculum when rapidly emerging trends develop in a short window of time. And those who became certified several years ago need to keep their skills sharp too, even if they don’t have an exam coming up anytime soon.
This is where PDI comes in and why we think it’s such a revolutionary step in education. This program has resulted in the development of a robust catalogue of continuing professional education courses and the ability to continuously refresh that catalogue based upon clearly articulated member need. So, in other words, as new topics and trends bubble to the surface, we have the ability to quickly design courses to address them and give cybersecurity professionals the ammo they need to be able to understand the basic concepts, at a minimum.
Subject matter experts guide the development of the course material and are supported by a team of highly qualified adult education experts and creative professionals.
We also recognized that cybersecurity professionals have very busy jobs, and don’t normally have a lot of free time to attend classes, which is why we knew that we had to build an on-demand library of courses that they could access whenever they want, at the push of a button from wherever they are in the world.
Given the nature of the different trends in cybersecurity, this is not a one-size-fits-all approach to education either. Some topics understandably require more of a time investment than others to fully grasp. This is why the PDI portfolio includes three formats of courses: Immersive courses are designed to provide an in-depth course on a single topic; Labs are hands-on courses designed to allow students to practice specific technical skills; and Express Learning courses are typically 1-2 hours in length – some are even doable during a lunch break – and they’re designed especially to quickly address emerging industry topics or trends or introduce the learner to a topic.
I think what we’re most proud of so far, in addition to the quality, is the broad range of topic areas we’ve addressed through PDI, which include working with the Internet of Things, industrial control systems, containers, privacy regulations, cyber insurance, mobile security, AI, and the NIST Cybersecurity Framework, as well as building skills such as penetration testing, malware analysis, interpersonal skills, cloud basics, communication with the C-suite, responding to a breach, and many more.
We tailor these courses for those learners with a basic to intermediate knowledge of security concepts, so they can be informative and challenging to almost any learner. And the topics are also designed to be universal so that they apply to what anyone around the world is facing.
In addition to helping learners stay updated on the latest trends, PDI also offers an opportunity for members and associates of (ISC)² to obtain continuing professional education – or CPE – credits to keep their certifications in good standing at no additional cost. More than 100 CPEs can be earned by completing all the courses in the PDI portfolio.
Because of this, all courses include a final assessment. Other learning activities vary by course type and may include instructional videos, video interviews, interactive presentations, knowledge checks, independent readings, webinar excerpts and real-world scenarios.
This was a major undertaking that the entire association got behind, and the program now contains 35 courses, with a total educational value of more than $10,000 per person available.
It’s been so popular that more than 20,000 unique members had enrolled in a PDI course by the end of December last year, which means we delivered more than $7.9 million in equivalent course value within the first 10 months of the program being available.
I should mention that as far as we know, this is the only program of its kind in the industry, where members can get all of this value at no additional cost. Additionally, we are making our courses available to non-members at as a way to encourage continuous learning during the COVID-19 crisis. For more information about this, please go to isc2.org/development.
The feedback we’ve received from our members so far has been outstanding and they’re really engaging with the materials and recommending courses to their friends and colleagues, as well as submitting ideas for future courses to pdi@isc2.org.
Thanks for listening today and thanks to RSA Conference and Help Net Security for giving us an opportunity to spread the message about PDI. You’re all welcome to come check out the content.
If you’d like to explore the PDI portfolio, you can either access My Courses if you’re a member or associate of (ISC)² or simply visit isc2.org/development if you’re not yet a member.
Is remote work here to stay?
12.5.2020 Net-security Security
There’s no doubt COVID-19 set the remote work revolution on a fast track. And on that fast track, VPN usage soared to new heights with no signs of it slowing down. Companies had no choice but to close up shop and send their workers home, and just as quickly had to figure out how to secure that workforce.

But just how big is the spike? In a study conducted by OpenVPN, 30% of employees polled say their company recently implemented remote work capabilities for the first time. 61% already had remote work rules in place.
The accelerated need for virtualization also meant a massive uptick in VPN usage — but not just any VPNs. Business VPNs are booming, according to the study.
“VPNs are critical to our remote minset and provides us with flexibility of being remote.” – a survey participant.
68% of employees say their company expanded VPN usage as a direct result of COVID-19, and 29% say their organization started using a VPN for the first time.
But remote work is not completely new — in fact, it’s been on the rise for some time. Consider these stats:
From 2005 – 2017 there was a 159% jump in remote work. In 2015: 3.9 million U.S. workers were already remote. Today? Over 5 million. And there’s no sign of the surge slowing down now, or ever — especially in the current climate.
The study surveyed workers from 300 different companies across sectors such as technology, energy, education, healthcare, engineering, and construction, and explored how companies are handling the new remote era, during the pandemic.
The study explored how organizations are handling the new COVID-19 remote era — and how they are securing their teams. The study seeks to answer the question: “Is remote work really the future?” If the numbers are any indication, the answer is a resounding YES.
Business VPNs are essential
Businesses are recognizing a layered approach is always the best approach for combating cyberattacks — and a necessary component of this approach is to invest in a reputable business VPN.
Even if every cell phone and laptop comes equipped with a personal VPN in the future, businesses will still need a secure way for workers to access a private network, and they will need an enterprise VPN to do so.
A personal VPN provides you with secure, private access to the internet, which is valuable in its own right — but a business VPN gives you the ability to remotely access private network resources, often essential for completing work, and to securely connect your company’s branches and locations worldwide.
Nearly 70% of employees polled say their companies expanded business VPN usage, and 29% say their organization started using it for the first time. That’s a big boom, mostly due to COVID-19… but is it here to stay?
Surprisingly, not all companies are on board.
Of the 21% of polled employees whose companies have never used a VPN, 71% went on to say their companies are still neglecting to utilize this essential security tool, despite switching to remote work. This suggests many companies still do not have a network security plan in place for remote work, despite the current crisis.
The good news is the companies that have started with secure remote access are almost unanimously in favor of maintaining that protocol: 99% of surveyed employees whose companies use a VPN believe those companies will continue usage after the emergency phase of COVID-19 is over. This encouraging percentage suggests that business VPNs will continue to be an essential part of secure remote access for years to come.
“We have always used VPN for remote work, with 2FA. It would be absolute lunacy to not do so, and there is not a chance on earth that we would discontinue use of our VPN.” – a survey participant.
Is the pandemic pushing organizations to finally go remote?
Employers that have the ability, but have still chosen not to offer their employees remote work capabilities during this time, are falling behind. Those polled describe their employers as uncaring and reckless — willing to risk their health and safety rather than make necessary adjustments.
“My company informed us remote work would be implemented soon. But that doesn’t make up for the fact that so many were furloughed due to lack of preparedness.” – a survey participant.
This illustrates an important point: companies must be prepared, or people will suffer.
Organizations that take the time to establish a secure remote strategy will be far ahead of competitors who choose not to. Offering flexibility can have an enormous impact on companies and the future of their business.
Remote employee: “I have worked from home for five years. Working remotely has given my company and me an edge over other companies that had to suddenly pivot and learn to work remotely. While they still struggle to learn, we have become the leaders and teachers for those who have never done this.”
Office-bound employee: “I think when the economy stabilizes a bit, I may consider finding a different job with a company that provides a safer work environment.”
People have mixed feelings about remote work during this stressful era
According to the study, only 5% of employees claim their company willfully chooses to prevent remote work, despite having the capability to provide it. Of that 5% still working at the office, 53% were worried about increased exposure, 29% claimed more stress and anxiety, and 18% had difficulty procuring childcare, suggesting that working in the office during a pandemic can have immediate and serious consequences for employees’ well-being.
Increased stress and anxiety have been found to have a direct effect on performance at work, which means those few employees still forced to go into the office are likely unable to perform at the level their employers would hope for.
In contrast, 30% of employees report that their company recently implemented remote work capabilities for the first time, while 61% already had remote work capabilities in place.
Of those 91% currently working from home, many report positive impacts on their work: 65% enjoy the flexibility, 40% claim fewer distractions, 36% say working from home lowers their stress and anxiety, and 33% have noticed an increase in their productivity.
Companies that have made this change have happier, less stressed employees — and, of course, the ability to continue operating during these unprecedented times.
Remote work should include secure access
“VPNs/remote access is key to allowing people to work when they can. This is the cornerstone of our business continuity plan.” – a survey participant.
Remote work and business VPNs go hand-in-hand; for your team to have secure access to the resources they need, a business VPN is critical to creating an infrastructure safe from breaches.
Will remote work become the norm? Only time will tell— but COVID-19 has certainly revealed that remote work capabilities often make-or-break a company’s success. Those without the ability to pivot often fall behind — and quickly.
Home workplaces introduce new risks, poor password hygiene
12.5.2020 Net-security Security
Entrust Datacard released the findings of its survey which highlights the critical need to address data security challenges for employees working from home as a result of the pandemic based on responses from 1,000 US full-time professionals.
home workplaces password hygiene
As social distancing mandates took effect in March 2020, employers found themselves in a massive remote work experiment, testing their cybersecurity readiness. Home workplaces introduce new risks as many employees find themselves distracted and are using personal devices to connect to corporate resources.
Bad actors have taken advantage – there was a 350 percent increase in phishing attacks in March, according to Google data.
Home workplaces and password hygiene
When it comes to home workplaces, password hygiene is of the utmost importance. Despite this, the survey found that an astounding 42 percent of employees surveyed still physically write passwords down, 34 percent digitally capture them on their smartphones and 27 percent digitally capture them on their computers.
Additionally, nearly 20 percent of the employees are using the same password across multiple work systems, multiplying the risk of sensitive data if a password is compromised or stolen.
“While many employees are set up to work securely by their employers, they continue to seek simplicity, even if that means insecure password practices and higher risk. As organizations continue to support employees working from home, it’s clear that they need to ramp up cybersecurity training and technology,” said James LaPalme, Vice President & General Manager of Authentication Solutions at Entrust Datacard.
“Encryption combined with advanced authentication, including passwordless solutions that leverage smartphone biometrics, can deliver the frictionless experience employees seek and the confidence organizations require. These solutions will one day make World Password Day obsolete and I don’t think employees or employers will miss it.”
In addition to password practices, the survey revealed several insights into employee sentiment toward remote work and cybersecurity.
Nearly half of workers are receiving COVID-related phishing emails
Employees surveyed are well aware both of phishing scams in general (82 percent) and of phishing scams specifically related to COVID-19 (81 percent) – in fact, 45 percent say they have received a COVID-19-related email from an unknown sender.
Despite this high awareness, roughly one-quarter (24 percent) of employees say they’ve clicked on a link from an unknown sender before determining their legitimacy, while just 36 percent deleted the email and only 12 percent reported the email.
Workers not set up properly for good cyber-hygiene while remote
The majority of employees surveyed (63 percent) are connecting to their company’s VPN during this time, yet they are using unique passwords to access different company resources (64 percent), rather than a more secure solution like single sign on with multifactor authentication.
Anxiety and inadequate technology as key remote work challenges
Most employees (59 percent) surveyed find it more difficult to get their work done while working remotely during the pandemic. Of those who said it’s more difficult, 26 percent are finding it much more difficult.
External distractions, COVID-19 related anxiety and inadequate amenities (i.e. slow internet) are the top three-cited reasons for this heightened difficulty. Additionally, remote workers in education, government, healthcare and manufacturing cite the challenge of work duties that do not always translate to remote work.
Remote workers are sharing devices with family members
While working from home under stay-at-home orders, 36 percent of employees surveyed are using one or more personal devices to access company files — these create opportunities for employees to make use of shadow IT, creating risks (i.e., phishing, malware, DDoS).
Moreover, 29 percent of those using one or more personal devices to work share that device with other members of their household, creating further risk.
Consumers are skeptical their personal data is safe
Survey respondents feel less confident about their security when handling personal business. Sixty-eight percent of respondents are doing more personal business online during the pandemic, including shopping, banking and social media, and more than half (58 percent) are skeptical of the level of security provided by these online vendors and service providers.
Employees — particularly Gen Z — don’t expect a return to the office as usual
Social distancing mandates have forced employers to embrace remote work, and employees to rethink their expectations. Forty-four percent of all respondents expect to work from home either more frequently (33 percent) or permanently (11 percent).
These percentages are markedly higher among Gen Z (ages 18-23) employees, fully half of whom (50 percent) do not anticipate a return to work as usual.
Gain free access to Utilizing Big Data course, a $200 value
12.5.2020 Net-security Security
With in-person education events and conferences cancelled or postponed indefinitely, online courses are becoming the new normal for earning CPEs.
(ISC)² has an online library of more than 30 Professional Development Institute (PDI) courses for continuing education. And, for a limited time, we’re offering non-members – a $200 value!
This (ISC)² course provides an overview of Big Data components, architectures and applications, and shows you how to apply the concept of data flows to gain insights for defending your organization by successfully managing and analyzing large amounts of data.
PDI courses are always free to (ISC)² members, but we know how important it is to all cybersecurity professionals to keep their continuing education on track. During these current challenges, we’re proud to offer free and discounted courses for non-members. The is a great way to become familiar with our trainings.
Leveraging automation to maximize security budgets
10.5.2020 Net-security Security
With the economic impact of COVID-19 increasingly looking like an imminent recession and the way we do work altered perhaps forever, CIOs and CISOs will most likely be managing reduced budgets and a vastly different threat landscape. With the average cost of a breach continuing to skyrocket, the already slim margin for error will shrink even further.
maximize security budgets
Automation can both mitigate inherent risks incurred from rapid ecosystem shifts as well as help IT teams re-evaluate long term spending once operations return to normalcy. By leveraging automated security tools, organizations can develop a dynamic understanding of the assets in their network, the risks most likely to be exploited, and the potential impact to the enterprise. The result is an always up-to-date, prioritized view of the most impactful moves an infosec team can make at any given time to minimize the likelihood of a breach.
The race to meet new threats
The rapid transition to remote work pushed a greater share of digital infrastructure onto new applications, as yet unproven in the enterprise, and distributed risk across potentially insecure employee home networks. 60% of IT teams say that COVID-19 has already impacted their role, a number almost certain to grow as the crisis evolves. Already stretched and under resourced, infosec teams must scramble to secure now widely used cloud, remote access software and collaboration tools.
That impact is just the beginning as organizations need to balance flexible infrastructure with security. Cloud security continues to be a major concern for the enterprise, with 4 in 5 users say they have encountered major security concerns. Some threats, like insecure devices on employee home networks, the same networks managed devices are now connected to, are largely outside the control of infosec teams.
Since malware is 3.75 times more likely to be found on corporate-associated home networks than corporate networks, employees connecting corporate devices to these networks introduces thousands of new endpoints to the threat landscape. With tens to hundreds of millions of security relevant signals to monitor on an ongoing basis, security is no longer a human scale problem. Without automation, infosec teams must prioritize based on guesswork and gut instinct.
Automation to the rescue
Malicious actors ranging from lone wolves to state-affiliated groups have been found to be taking advantage of the COVID-19 crisis at all levels, from phishing emails targeted at stressed employees to credential stuffing attacks aimed at popular enterprise applications.
With risk growing at such an exponential rate, automated management tools can help security teams streamline operations and better manage vulnerabilities. Successful infosec strategies start with asset inventory, an accurate, up-to-date inventory of the hardware and software assets connected to the enterprise network.
The focus needs to be on leveraging tools that keep a continuous, real-time inventory, not only categorizing each asset, but calculating business criticality as well. Since risk is a factor of the likelihood and impact of a breach, understanding business criticality is necessary when calculating impact.
Automated tools can track and inventory vulnerabilities across the entire enterprise attack surface, ranging from a user sharing the same password between work and personal applications to an outdated software version that is missing a critical patch.
The next step is prioritization: a security team lacking human capital is unlikely to have the time or resources to evaluate all vulnerabilities for potential impact and ability to be exploited. Automated risk management tools can streamline the process by analyzing both the immediacy of the vulnerability as well as the impact it would have. For example, if the password re-using employee has a high level of access across the corporate network, an automated security visibility tool could flag that as a higher priority need than the software missing a patch.
Automated prioritization ensures that infosec teams can maximize their resources and focus on vulnerabilities that pose the highest risk at any particular time, a key feature when the risk landscape is rapidly evolving.
Maximize security budgets: Ready for the long haul
Security teams are at the forefront of managing the impact of the current macroeconomic and societal reality. Combining smaller budgets with the need to deploy new devices and on-board new software tools means it is harder than ever to deal with escalating threats from hackers seeking to exploit the expanding digital enterprise. With automation, IT teams can effectively triage existing vulnerabilities and build a solid foundation for long-term security.
Open source algorithms for network graph analysis help discover patterns in data
10.5.2020 Net-security Security
StellarGraph has launched a series of new algorithms for network graph analysis to help discover patterns in data, work with larger data sets and speed up performance while reducing memory usage.

Problems like fraud and cybercrime are highly complex and involve densely connected data from many sources.
One of the challenges data scientists face when dealing with connected data is how to understand relationships between entities, as opposed to looking at data in silos, to provide a much deeper understanding of the problem.
Tim Pitman, Team Leader StellarGraph Library said solving great challenges required broader context than often allowed by simpler algorithms.
“Capturing data as a network graph enables organizations to understand the full context of problems they’re trying to solve – whether that be law enforcement, understanding genetic diseases or fraud detection. We’ve developed a powerful, intuitive graph machine learning library for data scientists—one that makes the latest research accessible to solve data-driven problems across many industry sectors.”
Lower memory usage and better performance
The version 1.0 release by the team at CSIRO’s Data61 delivers three new algorithms into the library, supporting graph classification and spatio-temporal data, in addition to a new graph data structure that results in significantly lower memory usage and better performance.
The discovery of patterns and knowledge from spatio-temporal data is increasingly important and has far-reaching implications for many real-world phenomena like traffic forecasting, air quality and potentially even movement and contact tracing of infectious disease—problems suited to deep learning frameworks that can learn from data collected across both space and time.
Testing of the new graph classification algorithms included experimenting with training graph neural networks to predict the chemical properties of molecules, advances which could show promise in enabling data scientists and researchers to locate antiviral molecules to fight infections, like COVID-19.
The broad capability and enhanced performance of the library is the culmination of three years’ work to deliver accessible, leading-edge algorithms.
Mr Pitman said, “The new algorithms in this release open up the library to new classes of problems to solve, including fraud detection and road traffic prediction.”We’ve also made the library easier to use and worked to optimize performance allowing our users to work with larger data.”
Network graph analysis implementation
StellarGraph has been used to successfully predict Alzheimer’s genes, deliver advanced human resources analytics, and detect Bitcoin ransomware, and as part of a Data61 study, the technology is currently being used to predict wheat population traits based on genomic markers which could result in improved genomic selection strategies to increase grain yield.
The technology can be applied to network datasets found across industry, government and research fields, and exploration has begun in applying StellarGraph to complex fraud, medical imagery and transport datasets.
Alex Collins, Group Leader Investigative Analytics, CSIRO’s Data61 said, “The challenge for organizations is to get the most value from their data. Using network graph analytics can open new ways to inform high-risk, high-impact decisions.”
Biometric device shipments revenue to drop by $2 billion
10.5.2020 Net-security Security
The pandemic is expected to cause a significant pushback on biometric device shipments, creating a major revenue drop of $2 billion over the course of 2020, according to ABI Research.
biometric device shipments revenue
New identification and surveillance needs
At the same, the pandemic has given rise to new identification and surveillance needs, spurring further investments in biometric AI algorithm design, which will give a boost to the face recognition technologies market going forward.
“Contact biometric technologies like fingerprint and vein have been dealt a substantial blow due to new governmental regulations targeting contact and close-proximity interactions. Fingerprint biometrics vendors are struggling to uphold the new stringent hygiene and infectious control protocols.
“These regulations have been correctly introduced for the safety of users and personnel, but they have also affected sales in certain verticals,” explains Dimitrios Pavlakis, Digital Security Analyst at ABI Research.
“On-premises physical access control, user registration, identification, and workforce management systems have been greatly affected in the enterprise and commercial space, but these applications also spread into healthcare, law enforcement, border control, government, civil, and welfare,” Pavlakis adds.
Contact-less fingerprint sensing technologies
While contact-only companies will have additional hurdles to overcome in most markets, innovative companies like Gemalto and IDEMIA have already adapted their solutions offering contact-less fingerprint sensing technologies.
Additionally, fingerprint sensor vendors operating in consumer markets like FPC and Goodix will be mostly affected by smartphone sales, rather than hygiene concerns, due to the personal nature of user authentication.
The total biometric device market is expected to reach $28.2 billion in 2020, with the government and security market taking a significant hit of $1.1 billion. Fingerprint device sales are also expected to decrease in 2020 by $1.2 billion. Not all is bleak, however.
“AI biometric firms are adapting to the biological threat. Biometric technologies are currently undergoing a forced evolution rather than an organic one, with artificial intelligence biometric firms spearheading the charge,” says Pavlakis.
“New IoT and smart city-focused applications will enable new data streams and analytics, monitoring infection rates in real-time, forcing new data-sharing initiatives, and even applying behavioral AI models to predict future outbreaks.”
Face and iris recognition, temperature and fever detection
Face and iris recognition have been brought into the spotlight as key technologies allowing authentication, identification, and surveillance operations for users and citizens wearing protective headgear, face masks, or, with partially covered faces.
These elements that were the bane of face recognition algorithms in the past have now been integrated into algorithm developers’ value proposition followed by further investment boost targeted at surveillance, video analytics and smart city applications.
Temperature and fever detection technologies making use of infrared technologies have also been retrofitted in access and border control while biometric telemedicine applications are providing healthcare support to consumers and patients remotely. AI investments have been primarily instigated by leading Chinese firms like SenseTime, Megvii, Alibaba, and Baidu.
Firefox 76.0.1 released to fix broken Amazon extension, crashes
10.5.2020 Bleepingcomputer Security
Mozilla has released Firefox 76.0.1 to resolve bugs that caused the Amazon Assistant browser extension to no longer function properly and to fix a browser crashes on Windows 7 32-bit systems with Nvidia graphics cards.
Mozilla released Firefox 76 this past Tuesday, and after running into two critical bugs, decided to pause its rollout until fixes could be added to Firefox 76.0.1, which was released today.
Users can trigger an upgrade to the Firefox 76.0.1 by opening the Firefox menu, selecting Help, and then About Firefox. Firefox will then perform a check for new updates and install them.

Firefox 76.0.1
The issues fixed in this release include:
Fixed a bug causing some add-ons such as Amazon Assistant to see multiple onConnect events, impairing functionality (bug 1635637)
Fixed a crash on 32-bit Windows systems with some nVidia drivers installed (bug 1635823)
Firefox 76 broke the Amazon Assistant extension
After Firefox 76 was released, Amazon software engineer Sally Gao created a bug report stating that their Amazon Assistant extension was no longer working properly.
According to Gao, this new release was preventing the Amazon Home feed from appearing, which contains the latest deals, customer recommendations, and a search bar.
"The loading icon continues for a couple of seconds, followed by the message "Sorry about this, I'm having trouble loading". The issue was 100% reproducible on a variety of machines.
We have gotten multiple customer complaints so far after the release today, and given the reproducibility, it seems like it may become a widespread issue as more customers get the latest update.
Our extension makes heavy use of IFrames and IFrame post-messaging for feature components. Nothing in particular looked especially related from the release note summary for version 76, but the issue may be related to some change that can affect IFrame communication. Another possibility is anything that specifically affects browser action APIs, which is how this feature is generated."
Due to the widespread use of the extension, Mozilla decided to pause the rollout of Firefox 76 while the bug was investigated.
Firefox 76 rollout paused
Ultimately, Firefox engineer Rob Wu stated that this was caused by a bug in the runtime.onConnect API and that it would be fixed in a future version of Firefox.
"This bug is caused by runtime.onConnect unexpectedly triggering in the browser action popup panel. (EDIT: not just browser action popups but any other extension page, such as extension tabs and background pages).
This should not happen, the runtime.onConnect event should not be triggered when the event is registered in the same location as runtime.connect."
Mozilla Firefox release manager Ryan VanderMeulen later posted that the fix would be rolled out in Firefox 76.0.1, which was released this morning.
Fix for Windows 7 32-bit browser crashes
In addition to the Amazon extension issue, Windows 7 users running Firefox 76 32-bit were experiencing tab crashes when using the new browser release.
In a bug report posted two days ago, Mozilla says that a bug was discovered that was accounting for 7% of all tab crashes in Windows 7 32-bit users.
"This content crash signature is reappearing in firefox 76 for 32bit users on windows 7 (we had fixed it before in bug 1607574). it's currently accounting for 7% of all tab crashes in the early phase of the 76.0 release."
This issue was ultimately attributed to a similar bug fixed in the past related to Nvidia nvd3d9wrapx.dll that was causing crashes on 64-bit versions of Firefox.
This same bug, though, appeared in the 32-bit version of the same DLL called nvd3d9wrap.dll, which had not been previously fixed.
With the release of Firefox 76.0.1, Mozilla has fixed the issue with Nvidia drivers for 32-bit users as well.
Firefox 76 released with integrated data breach alerts
9.5.2020 Bleepingcomputer Security
Mozilla has released Firefox 76 today, May 5th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with today's release are data breach notifications in the integrated Firefox Lockwise password manager, Picture-in-Picture, and new Audio Worklets for better audio processing.
Windows, Mac, and Linux desktop users can upgrade to Firefox 76 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 76, all other Firefox development branches have also moved up a version bringing Firefox Beta to version 77 and the Nightly builds to version 78.
You can download Firefox 76 from the following links:
Firefox 76 for Windows 64-bit
Firefox 76 for Windows 32-bit
Firefox 76 for macOS
Firefox 76 for Linux 64-bit
Firefox 76 for Linux 32-bit
If the above links haven't yet been updated for Firefox 76, you can also manually download it from Mozilla's FTP release directory.
Below you can find the major changes in Firefox 76, but for those who wish to read the full release notes, you can do so here.
Lockwise now warns of logins leaked in data breaches
With the release of Firefox 76, Firefox's integrated Lockwise password manager will now issue warnings when a web site has had a data breach that you have saved account credentials.
These alerts will be displayed in the Lockwise password manager and display as a red "Website Breach" alert shown below.
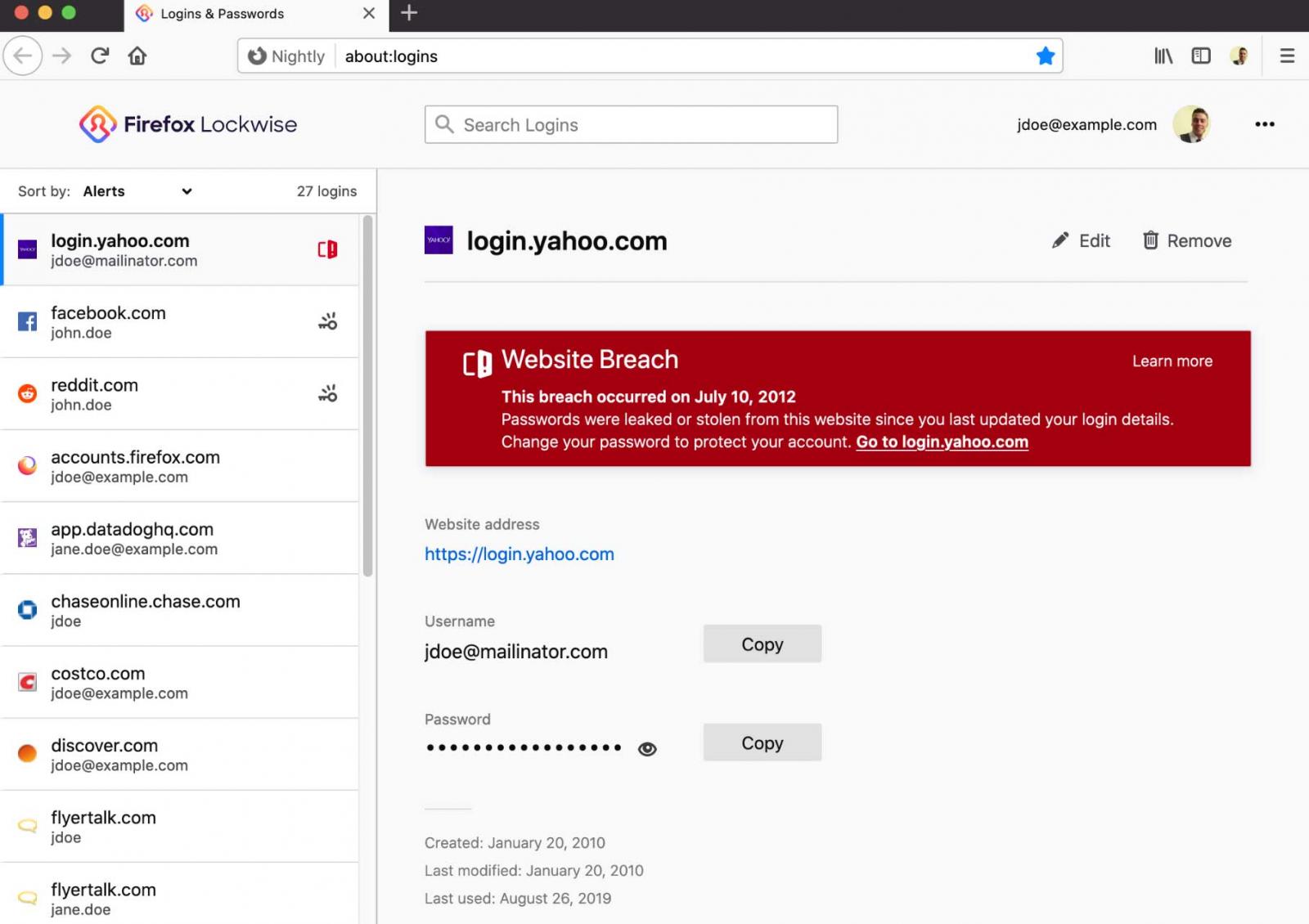
Lockwise warning of data breach
Lockwise will also warn users if your account was found in a data breach and the same password was found to be used for other sites.
This will allow users to change their password at these other sites so that hackers can't use the information found in data breach dumps to breach those accounts as well.
Lockwise now requires OS password to see saved logins
If you do not have a master password setup in Firefox Lockwise, the password manager will now require you to enter your Windows or macOS password before you can view saved login credentials.
Enter operating system password
This extra security will protect your saved login credentials from being viewed by others who may have access to your computer.
Picture-in-Picture
Firefox 76 now supports picture-in-picture to detach a video you are watching into a floating stay-on-top player that allows you to continue watching as you move between different applications.
When watching a video, if you hover over the video you may be shown a 'Picture-in-Picture' dialog that allows you to detach the video.

Picture-in-Picture prompt
In BleepingComputer's tests, this feature is not very reliable and will work with one video on a site and then not work on later videos.
For example. we were able to get the Picture-in-Picture dialog to show on one YouTube video, but on no other videos after that. On Vimeo, we couldn't get it to work at all.
Other bug fixes, improvements, and developer changes
Other changes:
Firefox now supports Audio Worklets that will allow more complex audio processing like VR and gaming on the web; and is being adopted by some of your favorite software programs. With this change, you can now join Zoom calls on Firefox without the need for any additional downloads.
The shadow around the address bar field is reduced in width when a new tab is opened;
The bookmarks toolbar has expanded slightly in size to improve its surface area for touchscreens.
Developer:
Testing mobile interactions using DevTools’ Responsive Design Mode now mimics the device behavior for handling double-tap to zoom. This builds on previous improvements to correctly rendering meta-viewport tags, allowing developers to optimize their sites for Firefox for Android without a device.
Double-clicking table headers in DevTools’ network request table now resizes the column width to fit the content, making it easier to expand the important data.
WebSocket inspection now supports ActionCable message preview, adding to the list of automatically formatted protocols like socket.io, SignalR, WAMP, etc.
Security vulnerabilities fixed
With this release, Mozilla has fixed eleven security vulnerabilities, with four of them rated as 'Critical', three as 'High', four as 'Moderate', and one as 'Low'.
The full list of security issues patched by Mozilla in Firefox 76.0:
CVE-2020-12387: Use-after-free during worker shutdown\
CVE-2020-12388: Sandbox escape with improperly guarded Access Tokens
CVE-2020-12389: Sandbox escape with improperly separated process types
CVE-2020-6831: Buffer overflow in SCTP chunk input validation
CVE-2020-12390: Incorrect serialization of nsIPrincipal.origin for IPv6 addresses
CVE-2020-12391: Content-Security-Policy bypass using object elements
CVE-2020-12392: Arbitrary local file access with 'Copy as cURL'
CVE-2020-12393: Devtools' 'Copy as cURL' feature did not fully escape website-controlled data, potentially leading to command injection
CVE-2020-12394: URL spoofing in location bar when unfocussed
CVE-2020-12395: Memory safety bugs fixed in Firefox 76 and Firefox ESR 68.8
CVE-2020-12396: Memory safety bugs fixed in Firefox 76
GitHub shuts down Popcorn Time repositories due to MPA DMCA notice
9.5.2020 Bleepingcomputer Security
GitHub has shut down two repositories belonging to the video streaming BitTorrent client Popcorn Time after receiving a Digital Millennium Copyright Act (DMCA) infringement notice from the Motion Picture Association.
Popcorn Time is a BitTorrent client with an integrated media player and the ability to browse through a list of copyrighted television shows and movies that can be streamed and watched directly in the client.
Yesterday, GitHub took down two repositories used by the Popcorn Time developers for their Desktop client and API after receiving a DMCA infringement notice from the Motion Picture Association.
We are writing to notify you of, and request your assistance in addressing, the extensive copyright infringement of motion pictures and television programs that is occurring by virtue of the operation and further development of the Popcorn Time repositories (the “Project”) found at:
https://github.com/popcorn-official/popcorn-desktop
https://github.com/popcorn-official/popcorn-api
Our request is specifically aimed at the aforementioned repositories and does not concern any other related repositories.
When visiting these repositories, GitHub now shows a message stating, "This repository is currently disabled due to a DMCA takedown notice. We have disabled public access to the repository. The notice has been publicly posted."
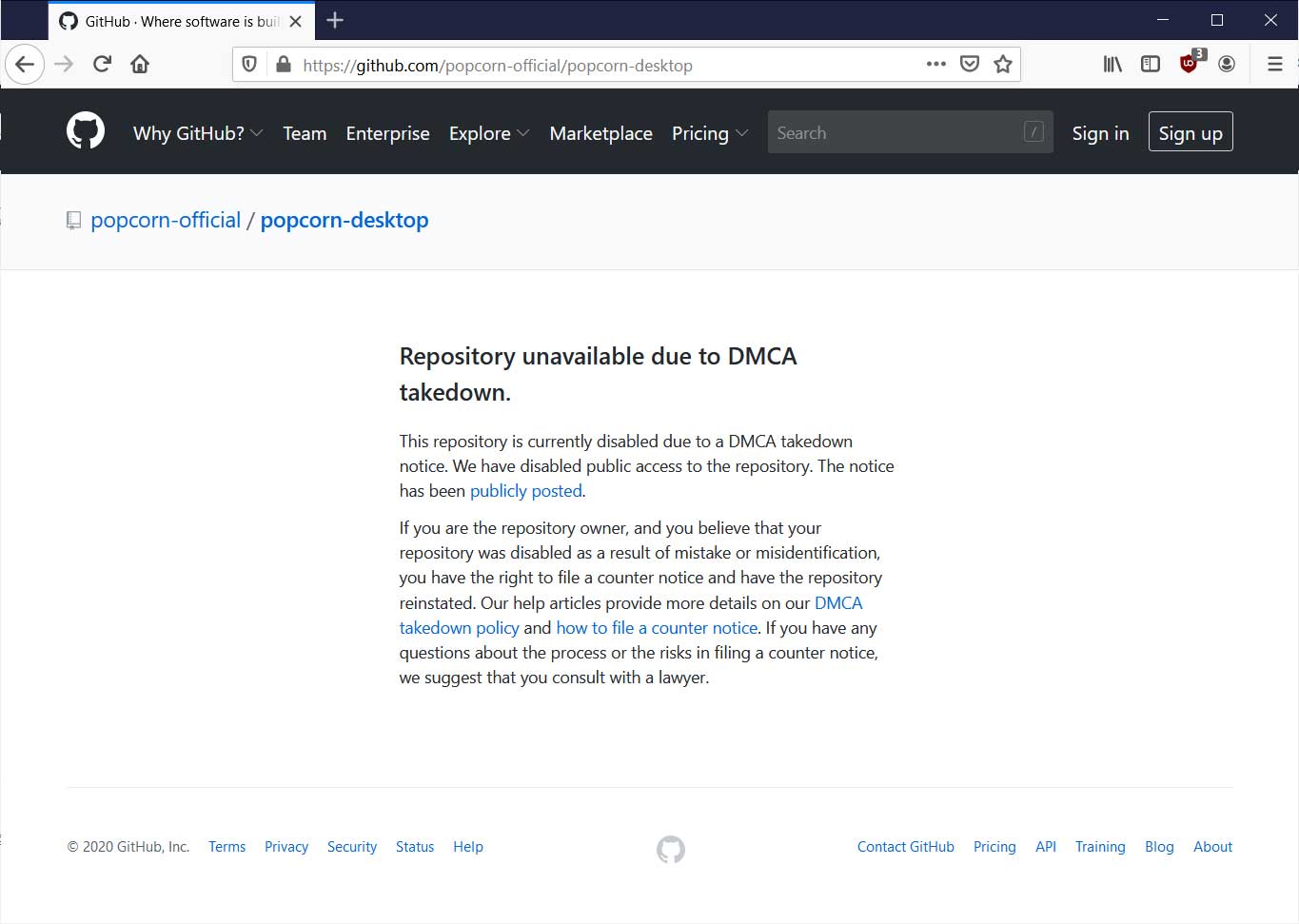
Popcorn Time repository disabled due to DCMA notice
DMCA notifications are a legitimate tool that can be used by copyright owners to force sites, ISPs, hosting companies, and search providers to remove copyrighted content that is being hosted without permission.
These notifications, though, are meant to be issued directly to companies actually hosting copyrighted content from the issuer.
As these GitHub repositories do not contain content that is actually copyrighted to the MPA, movie studios or other clients, some see these DMCA infringement notifications as overreaching and not legitimate.
In a DMCA counter-notification found by TorrentFreak, the Popcorn Time developers agree and have stated that the code in these disabled repositories is "is 100 % ours and do not contain any copyright material please check again."
DMCA counter-notification from Popcorn Time
While the Popcorn Time developers appear willing to push back against these DMCA notifications, GitHub likely will stay neutral and let courts decide if the infringement notifications should be enforced.
BleepingComputer has contacted GitHub with questions but has not heard back at this time.
Firefox 75 released with Windows 10 performance improvements
12.4.2020 Bleepingcomputer Security
Mozilla has released Firefox 75 today, April 7th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with today's release are performance improvements for Windows 10 users, improved search from the address bar, and improved HTTPS compatibility by local caching some trusted certificates.
Windows, Mac, and Linux desktop users can upgrade to Firefox 75 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 75, all other Firefox development branches have also moved up a version bringing Firefox Beta to version 76 and the Nightly builds to version 77.
You can download Firefox 75 from the following links:
Firefox 75 for Windows 64-bit
Firefox 75 for Windows 32-bit
Firefox 75 for macOS
Firefox 75 for Linux 64-bit
Firefox 75 for Linux 32-bit
If the above links haven't yet been updated for Firefox 75, you can also manually download it from Mozilla's FTP release directory.
Below you can find the major changes in Firefox 75, but for those who wish to read the full release notes, you can do so here.
Improved Windows 10 performance, flatpaks, more
Firefox 75 promises better performance on devices running Windows 10 due to the integration of DirectComposition that further improves rendering on laptops with built-in Intel graphics cards with the help of the WebRender GPU-based 2D rendering engine.
"Direct Composition is being integrated for our users on Windows to help improve performance and enable our ongoing work to ship WebRender on Windows 10 laptops with Intel graphics cards," Mozilla says.
Starting with this release, Firefox is also available in the Flatpak application distribution format that makes it a lot easier and more secure to install the web browser on Linux-powered systems.
Firefox 75 will also locally cache all trusted Web PKI Certificate Authority certificates that Mozilla knows, improving security and HTTPS compatibility with misconfigured web servers as a direct result.
Faster search via a revamped address bar
Mozilla has also refreshed the look of the address bar in Firefox 75 by enlarging it every time you start a search, as well as "simplified it in a single view with larger font, shorter URLs, adjusts to multiple sizes and a shortcut to the most popular sites to search."
The built-in search engine is also smarter now as it will provide you with bolded search suggestions and autocomplete based on websites you have in your bookmarks, history, or popular websites.
Firefox 75's address bar will also display your top sites — most recently and frequently visited sites, or sites that you’ve pinned — right under the address bar for quick and easy access.
Revamped Firefox search bar (Mozilla)
This is the full list of changes related to the improved search and address bar:
Focused, clean search experience that's optimized for smaller laptop screens
Top sites now appear when you select the address
Improved readability of search suggestions with a focus on new search terms
Suggestions include solutions to common Firefox issues
On Linux, the behavior when clicking on the Address Bar and the Search Bar now matches other desktop platforms: a single click selects all without primary selection, a double click selects a word, and a triple click selects all with primary selection
Security vulnerabilities fixed
Mozilla has also fixed six security vulnerabilities in Firefox 75, three of them rated as high severity and the other three as having a moderate security impact.
The full list of security issues patched by Mozilla in Firefox 75.0:
• CVE-2020-6821: Uninitialized memory could be read when using the WebGL copyTexSubImage method
• CVE-2020-6825: Memory safety bugs fixed in Firefox 75 and Firefox ESR 68.7
• CVE-2020-6826: Memory safety bugs fixed in Firefox 75
• CVE-2020-6822: Out of bounds write in GMPDecodeData when processing large images
• CVE-2020-6823: Malicious Extension could obtain auth codes from OAuth login flows
• CVE-2020-6824: Generated passwords may be identical on the same site between separate private browsing sessions
Last week, Mozilla also released Firefox 74.0.1 to address two critical zero-day vulnerabilities that were actively exploited by threat actors in the wild that could lead to remote code execution on machines running unpatched Firefox versions.
Other bug fixes, improvements, and developer changes
Enterprise:
Experimental support for using client certificates from the OS certificate store can be enabled on macOS by setting the preference security.osclientcerts.autoload to true.
Enterprise policies may be used to exclude domains from being resolved via TRR (Trusted Recursive Resolver) using DNS over HTTPS.
Developer:
Save bandwidth and reduce browser memory by using the loading attribute on the element. The default "eager" value loads images immediately, and the "lazy" value delays loading until the image is within range of the viewport.
Instant evaluation for Console expressions lets developers identify and fix errors more rapidly than before. As long as expressions typed into the Web Console are side-effect free, their results will be previewed while you type.
Google Advises Against Disabling Sites During the Pandemic
29.3.2020 Bleepingcomputer Security
Google warns businesses against disabling their websites during the COVID-19 and, instead, recommends limiting their functionality to avoid being penalized in Google Search results.
The guidance published by Google Webmaster Trends Analyst John Mueller answers questions from businesses who might want to pause their online business and reduce the impact in Google Search.
"These recommendations are applicable to any business with an online presence, but particularly for those who have paused the selling of their products or services online," Mueller explained.
Limit your site's functionality
Google's recommendation is to avoid if possible to completely shut down a website even when employees work from home schedules during coronavirus lockdowns don't allow them to keep them updated.
This approach should be followed especially in cases where a company's online business is expected to pick up again according to Mueller.
Limiting a site's functionality will allow webmasters to cut down any potential Google Search negative effects stemming from the website's reduce presence for a given period of time.
Website owners and admins are advised to take one or more of the following measures rather than shutting down their sites:
• Disable the cart functionality: This is the simplest approach, which won't change anything for a site's Search visibility.
• Tell customers what's going on: Use a banner to let your customers know of the changes the business and the site are going through.
• Update the site's structured data: Keep product availability information up to date.
• Check the Merchant Center feed: Follow best practices for availability attributes listed in the Merchant Center.
• Tell Google you changed things: Ask Google to recrawl your website using sitemaps or the Search Console.
"This is the recommended approach since it minimizes any negative effects on your site's presence in Search," Mueller added.
"People can still find your products, read reviews, or add wishlists so they can purchase at a later time."
Disable sites for a very limited time only
If you can't follow the recommended approach of limiting your site's functionality to cope with the lull in orders or the decrease in update capability, there are options to reduce the impact of a full site takedown.
"This is an extreme measure that should only be taken for a very short period of time (a few days at most), as it will otherwise have significant effects on the website in Search, even when implemented properly," Mueller explained.
"Keep in mind that your customers may also want to find information about your products, your services, and your company, even if you're not selling anything right now."
Here are the options you have in this situation:
• To urgently disable the site for 1-2 days: return an informational error page with a 503 HTTP result code instead of all content. Make sure to follow the best practices for disabling a site.
• To disable the site for a longer time: provide an indexable homepage as a placeholder for users to find in Search by using the 200 HTTP status code.
• To quickly need to hide your site in Search (while considering the options): temporarily remove it from Search.
Side effects after disabling sites
Among the side effects resulting from disabling your site, webmasters will notice Knowledge Panels losing information, Search Console verification fails, and loss of business info in Search results.
Customers will also have trouble finding first-hand accurate information in Google Search and will need to rely on info from third-party web resources.
To top it all off, once a website goes down without notification customers will not know the reason why it happened without prior warning.
Google Webmasters
✔
@googlewmc
⚡️⚡️⚡️ Do you need to hit pause on your online business for some time? We just published some do's and don't's to help you with maintaining your site's presence in search. Check it out! ⚡️⚡️⚡️https://webmasters.googleblog.com/2020/03/how-to-pause-your-business-online-in.html …
327
7:47 PM - Mar 26, 2020
Twitter Ads info and privacy
220 people are talking about this
Webmasters can also tell Google to crawl their sites less frequently via Search Console during limited functionality but shouldn't block any specific region from accessing their online businesses temporarily or otherwise.
"We hope that with this information, you're able to have your online business up & running quickly when that time comes," Mueller concluded.
"Should you run into any problems or questions along the way, please don't hesitate to use our public channels to get help."
Mozilla Firefox Gets a HTTPS Only Mode For More Secure Browsing
29.3.2020 Bleepingcomputer Security
Mozilla Firefox 76 is getting a new 'HTTPS Only' mode that automatically upgrades all HTTP requests to HTTPS when browsing the web and blocks all connections that can't be upgraded.
When connecting to an HTTP site, your connection is not encrypted and your ISP and programs running on the computer can monitor the data being sent over it. This includes your passwords, credit card info, and other sensitive information.
Due to this, it is always recommended that you only use HTTPS sites, which encrypt the connection between the browser and the web site.
While most web sites are now using HTTPS, some continue to only use the HTTP protocol and Mozilla is adding a new feature that will automatically upgrade your connection to HTTPS or block you from visiting the site.
Mozilla's 'HTTPS Only' mode
Similar to the HTTPS Everywhere addon, when Firefox's HTTPS Only feature is enabled the browser will automatically change any HTTP requests to HTTPS and if unable to connect will display an alert asking if you wish to continue connecting via HTTP.
Being developed for Firefox 76, this feature will not be enabled by default and will also attempt to upgrade subresources like CSS files, scripts, and images to HTTPS and if unable to do so, quietly block them from loading.
Currently, if a Firefox user types foo.com in the address bar then our internal machinery establishes an HTTP connection to foo.com. Within this project we will expose a preference which allows end users to opt into an 'HTTPS Only' mode which tries to establish an HTTPS connection rather than an HTTP connection for foo.com. Further, we will upgrade all subresources within the page to load using https instead of http.
Implementation considerations:
For top-level loads which encounter a time-out we could provide some kind of error page with a button which would allow the end user to load the requested page using http.
For subsource loads we could fail silently and just log some info to the console.
This feature is currently available in the Firefox 76 Nightly builds and can be enabled by toggling the 'dom.security.https_only_mode' setting to 'True' in about:config.
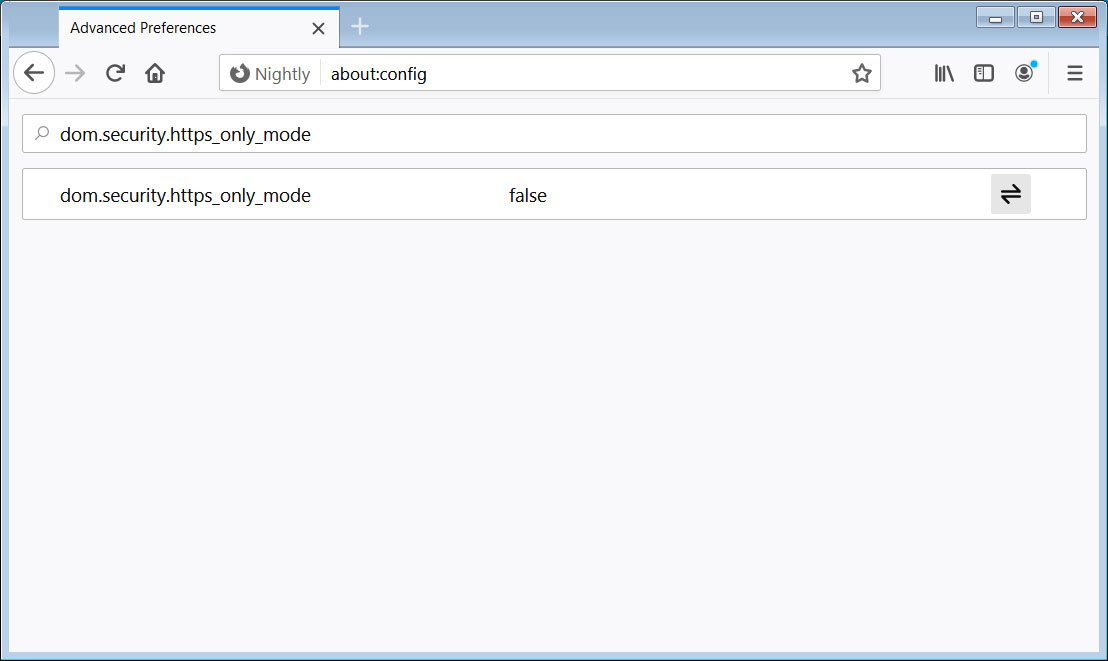
dom.security.https_only_mode flag
Once enabled, if you go to an HTTP site, Firefox will automatically change it to an HTTPS connection. If unable to connect via HTTPS, it will display an alert as shown below.
Warning about an HTTP connection
This alert warns that continuing to the HTTP site is a "Potential Security Risk" and recommends that you do not continue. If you choose to continue, the 'HTTPS Only' mode will be disabled for the site.
Warning: Potential Security Risk Ahead
Nightly detected a potential security threat and did not continue to neverssl.com. If you visit this site, attackers could try to steal information like your passwords, emails, or credit card details.
What can you do about it?
The issue is most likely with the website, and there is nothing you can do to resolve it. You can notify the website’s administrator about the problem.
This is an interesting feature and one that many would enable by default as it only increases the security of the websites you visit with the minor inconvenience of an alert here and there as you browse to insecure web sites.
Google to Abandon Chrome 82 Development Due to Release Delays
28.3.2020 Bleepingcomputer Security
Due to the change in Google Chrome's release schedule because of the Coronavirus pandemic, Google has announced that they are no longer developing Chrome 82 and will skip to Chrome 83 instead.
Last week, Google announced that it was pausing releases of new milestone versions of the Chrome browser due to the adjusted employee work schedules during the Coronavirus outbreak.
This caused the Chrome 81 version that was scheduled for release on March 17th to not be released and stay in the Google Chrome Beta channel.
In a new post to the "Chromium Schedule Update" topic in the Chromium-dev discussion group, Jason Kersey, the Director of Technical Program Management at Google, announced that due to the schedule changes, they are going to abandon Chrome 82 altogether.
With this change, Google Chrome 81 (M81) will remain in the Beta until it is released on the Stable branch, Chrome 82 (M82) will be abandoned, and Chrome 83 (M83) will be moved to the development branch.
This is an update on our earlier decision to pause our branch and release schedule. As we adapt our future milestone schedules to the current change in schedule, we have decided to skip the M82 release to ensure we keep users safe and focus all efforts on maintaining stability.
Here are some of the immediate actions based on the above decision:
We will abandon current M82 branches, remove infra support, and stop testing/merges to the branches
We will not push any new M82 releases to Dev, and we will stop stabilization for Beta
We will move Dev channel to M83 asap
We will keep Beta channel on M81 until M83 is ready to be promoted
While it has not been specifically mentioned, it is assumed that Google Chrome 84 will move to Canary development branch over the next coming weeks.
These changes have not made as of yet and Chrome 82 is still in the Dev channel and Chrome 83 is still in the Canary channel.
Kersey states that there will be another update this week with more information about the upcoming changes.
At this time, Google has not officially announced when they will start releasing new versions of the browser, but if the schedule change lasts long enough, we could see further skipping of versions.
Netflix Party Lets You Watch Shows With Friends to Fight Isolation
22.3.2020 Bleepingcomputer Security
Feeling lonely during the period of social isolation or self-quarantine? A Chrome browser extension lets you binge-watch your favorite Netflix shows with friends and family while text chatting with them.
With social interaction at a minimum during the COVID-19 outbreak, people rightfully feel cooped up and lonely due to not being able to do anything with their friends.
A free Chrome browser extension called Netflix Party may help bring a little social interaction back into your life.
Netflix Party lets you watch shows together
Netflix Party allows friends and family to watch the same show together while providing a text chat room experience.
To use this browser extension, each user must be logged into Netflix and have the Netflix Party extension installed.
A user can then start a Netflix video, pause it, and click on the NP button in the Chrome Omnibar to create a group link that can be shared with others.
When creating this group, I suggest you make it so only the group creator can control the video playback so that other people do not pause the video whenever they want.
Create a Netflix Party
When another user with Netflix Party clicks on the shared link, they will automatically be brought to the selected video and a chat room will be shown on the right side of the screen.
This chat room lets you set your name, use one of a few available avatars, and chat with each other while you are watching the show or movie.
Netflix Party
The group creator can then start the show and pause it as needed and the show will start and pause on the other party member's computers.
In BleepingComputer's tests, the process works very well, but there will be a slight delay between the person controlling the video and others who are part of the party. In our tests, this only caused about a one to two-second delay.
It should also be noted, that this extension does track your activity and what Netflix shows you watch but will tie this data to your anonymous Netflix Party ID.
If this does not bother you, then Netflix Party may be a great way to watch a show or movie with some friends to ease your social isolation.
Google Prioritizes Security Updates After Halting Chrome Releases
22.3.2020 Bleepingcomputer Security
Google has announced today that the release of future Chrome and Chrome OS versions is temporarily paused because of adjusted work schedules caused by employees having to work from home due to the novel coronavirus pandemic.
"Due to adjusted work schedules at this time, we are pausing upcoming Chrome and Chrome OS releases," the announcement published on the Chrome Releases blog says.
"Our primary objectives are to ensure they continue to be stable, secure, and work reliably for anyone who depends on them."
Chrome Developers
✔
@ChromiumDev
Due to adjusted work schedules, we’re pausing upcoming Chrome & Chrome OS releases. Our goal is to ensure they continue to be stable, secure, & reliable for anyone who depends on them. We’ll prioritize updates related to security, which will be included in Chrome 80. Stay tuned.
568
6:01 PM - Mar 18, 2020
Twitter Ads info and privacy
273 people are talking about this
Focus on security updates for Chrome v80
The Google Chrome development team will continue to work remotely throughout the current novel coronavirus outbreak and will prioritize security updates that will be released as Chrome v80 updates.
"We’ll continue to prioritize any updates related to security, which will be included in Chrome 80," Google added.
As proof, Google Chrome 80.0.3987.149 was released right after the company announced that Chrome v81 was delayed, with security fixes patching 13 high severity vulnerabilities.
In a tweet from earlier today on the Chrome Developers Twitter account, users are encouraged to monitor the Chrome Releases Blog for new developments and any new info regarding upcoming Chrome and Chrome OS releases.
Chrome Developers
✔
@ChromiumDev
Please keep an eye on the Chrome Release Blog - https://chromereleases.googleblog.com/ - for updates and additional info.
42
6:26 PM - Mar 18, 2020
Twitter Ads info and privacy
20 people are talking about this
Chrome v81 announcement posts removed
Google Chrome v81 was supposed to start rolling out on March 17th according to a post initially published on the Google Developers blog yesterday.
The new Chrome version should have included support for form elements featuring a modernized look, hit testing for augmented reality, app icon badge support, and initial support for Web NFC.
A full list of Chrome 81 feature deprecations and removals is also available on the Chrome Platform Status page.
Google Play Console warning (AndroidPolice)
On Monday, Google also informed Android developers that they will be experiencing longer than normal app review times due to adjusted work schedules.
As the developers were warned, some of their apps will go through the review process in seven days or more starting this week as reported by AndroidPolice.
"Due to adjusted work schedules at this time, we are currently experiencing longer than usual review times," said A Google spokesperson. "While the situation is currently evolving, app review times may fluctuate, and may take 7 days or longer."
Verily Coronavirus Screening Site Launches, Quickly Runs Out of Slots
21.3.2020 Bleepingcomputer Security
Verily has launched its Project Baseline Coronavirus screening site for people living in the San Francisco Bay Area that lets people check if they need a test and where to get one.
This new site is being launched by Verily, an Alphabet company and sister company to Google, and allows only those people living in the Bay Area to enter their symptoms, recent travel, and other information to determine if a Coronavirus test is necessary.
COVID-19 Screening site
This site is only available for residents living in Santa Clara County and San Mateo County with the hopes of eventually expanding to other locations in the future.
Using this site, though, does have some requirements such as being 18 or older, a U.S. Resident, living in one of the two counties, able to speak and read English, and willing to sign a COVID-19 Public Health authorization form.
Screening requirements
Initially announced as a Google nationwide testing site by President Trump during a Friday press conference, it was quickly clarified as being only available to Bay Area residents.
Since then, Google has announced that they will be working with the U.S. government to release a nationwide site for Coronavirus information.
There is no timeline yet as to when this nationwide site will become available.
Testing appointments quickly run out
Since launching late last night, the screening site's available appointment slots quickly ran out.
When users start the screening process and specify they live in the required regions, the site will immediately state "Unfortunately, we are unable to schedule more appointments at this time. Appointments will continue to expand through this program as we scale capacity in the near future."
BleepingComputer has contacted Verily for more information about how many people scheduled appointments and when more slots would be available but have not heard back as of yet.