
face recognition technology concept illustration of big data and security in city with crowd
Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
ACLU Sues Clearview AI Over Faceprint Collection, Sale
30.5.2020 threatpost Security
Watchdog group said company has violated the Illinois BIPA and ‘will end privacy as we know it’ without intervention.
The American Civil Liberties Union (ACLU) has sued a New York-based startup for amassing a database of biometric face-identification data of billions of people and selling it to third parties without their consent or knowledge
The U.S. citizens’-rights watchdog organization has filed suit in the Circuit Court of Cook County in Illinois against Clearview AI, on behalf of a number of organizations comprised of vulnerable communities—such as survivors of sexual assault or domestic violence and undocumented immigrants—for violating the the Illinois Biometric Information Privacy Act (BIPA).
Clearview has been collecting what are called “faceprints,” or unique biometric identifiers similar to someone’s fingerprint or DNA profile, and then selling them to “private companies, police, federal agencies and wealthy individuals, allowing them to secretly track and target whomever they wished using face recognition technology,” ACLU Staff Attorney Nathan Freed Wessler wrote in a blog post published Thursday.“The company has captured these faceprints in secret, without our knowledge, much less our consent, using everything from casual selfies to photos of birthday parties, college graduations, weddings and so much more,” he wrote, adding that Clearview “will end privacy as we know it if it isn’t stopped.”
BIPA is an Illinois law aimed at protecting people “against the surreptitious and nonconsensual capture of their biometric identifiers, including faceprints,” according to the ACLU’s complaint, which also lists its Illinois branch as well as the Chicago Alliance Against Sexual Exploitation, Sex Workers Outreach Project Chicago, Illinois State Public Research Interest Group Inc. and Mujeres Latinas En Accion as plaintiffs.
The complaint demands that the court immediately order Clearview to stop its capture of biometric identifiers of the citizens of Illinois. “Clearview’s actions clearly violate BIPA,” Wessler wrote.

face recognition technology concept illustration of big data and security in city with crowd
Clearview was founded by Australian entrepreneur Hoan Ton-Thatand, who has been under fire and harsh scrutiny for his company’s business practices since late last year. He has defended his company’s practices and intentions as well as welcomed the privacy debate, stating in various published reports that the technology is meant to be used by law enforcement to help solve crimes and not to violate people’s privacy.
Clearview not only sells a database of faceprints to its clients, but it also provides access to a smartphone app that allows them to upload a photo of an unknown person and instantly receive a set of matching photos.
Ton-Thatand told CNN that more than 600 law-enforcement agencies in the United States and Canada are using Clearview’s technology, citing an example of how it was utilized by police in an investigation into a child-predator ring in New Jersey. Another published report outlined how the technology was used to quickly identify and arrest a person causing a disturbance in New York’s Fulton Street subway station.
Still, Clearview’s unauthorized scraping of biometric data from photos across social media platforms like Facebook, Twitter and YouTube has spurred those companies to send Clearview cease-and-desist letters.
Now Clearview is facing this new legal challenge from the ACLU and the individuals represented in the Illinois case, who in their complaint argue that due to the “immutability of our biometric information and the difficulty of completely hiding our faces in public,” unfettered collection of face-recognition data “poses severe risks to our security and privacy.”
“The capture and storage of faceprints leaves people vulnerable to data breaches and identity theft,” according to the complaint.
The plaintiffs also raised concerns that having access to this biometric information also could lead to unwanted or invasive tracking and surveillance of people in places where they should feel safe, such as in houses of worship, domestic-violence shelters or Alcohol Anonymous meetings.
The data also could be used to identify people at protest or political rallies and put them in danger from organizations or people who don’t agree with their political views.
“For our clients — organizations that serve survivors of domestic violence and sexual assault, undocumented immigrants, and people of color — this surveillance system is dangerous and even life-threatening,” Wessler wrote. “It empowers abusive ex-partners and serial harassers, exploitative companies, and ICE agents to track and target domestic violence and sexual assault survivors, undocumented immigrants, and other vulnerable communities.”
The lawsuit is not the first time a company has faced a legal challenge to faceprint-data collection by a technology company based on violation of the Illinois BIPA. Last September, a lawsuit filed against Vimeo used the same law to challenge the ad-free video platform’s collection and storage of users’ facial biometrics in videos and photos without their consent or knowledge.
Why is SDP the most effective architecture for zero trust strategy adoption?
29.5.2020 Net-Security Security
Software Defined Perimeter (SDP) is the most effective architecture for adopting a zero trust strategy, an approach that is being heralded as the breakthrough technology for preventing large-scale breaches, according to the Cloud Security Alliance.
SDP zero trust
“Most of the existing zero trust security measures are applied as authentication and sometimes authorization, based on policy after the termination of Transport Layer Security (TLS) certificates,” said Nya Alison Murray, senior ICT architect and co-lead author of the report.
“Network segmentation and the establishment of micro networks, which are so important for multi-cloud deployments, also benefit from adopting a software-defined perimeter zero trust architecture.”
SDP improves security posture
A zero trust implementation using SDP enables organizations to defend new variations of old attack methods that are constantly surfacing in existing network and infrastructure perimeter-centric networking models.
Implementing SDP improves the security posture of businesses facing the challenge of continuously adapting to expanding attack surfaces that are, in turn, increasingly more complex.
Network security implementation issues
The report notes particular issues that have arisen that require a rapid change in the way network security is implemented, including the:
Changing perimeter, whereby the past paradigm of a fixed network perimeter, with trusted internal network segments protected by network appliances such as load balancers and firewalls has been superseded by virtualized networks, and the ensuing realization that the network protocols of the past are not secure-by-design.
IP address challenge, noting that IP addresses lack any type of user knowledge to validate the trust of the device. With no way for an IP address to have user context, they simply provide connectivity information but do not get involved in validating the trust of the endpoint or the user.
Challenge of implementing integrated controls. Visibility and transparency of network connections is problematic in the way networks and cyber security tools are implemented. Today, integration of controls is performed by gathering data in a SIEM for analysis.
Employees abandoning security when working remotely
29.5.2020 Net-Security Security
48% of employees are less likely to follow safe data practices when working from home, a report from Tessian reveals.

The global shift to remote working poses new security challenges for businesses and traditional security solutions are failing to curb the problem of the insider threat and accidental data loss.
Remote work compounds insider threats
While 91% of IT leaders trust their staff to follow best security practices when working remotely, 52% of employees believe they can get away with riskier behavior when working from home. 48% cite “not being watched by IT” as a reason for not following safe data practices, closely followed by “being distracted” (47%).
Additionally, staff report that security policies are a hindrance — 51% say such policies impede productivity and 54% will find workarounds if security policies stop them from doing their jobs.
Eighty-four percent of IT leaders also say data loss prevention is more challenging when employees are working from home and 58% of employees think information is less secure when working remotely.
Abandoning security when working remotely: Data loss is pervasive
30% of breaches involve internal actors exposing company information, as a result of negligent or malicious acts. Insider threats and data loss over email is particularly challenging for IT leaders to control, due to lack of visibility of the threat. Key findings reveal:
U.S. employees are more than twice as likely as UK workers to send emails to the wrong person (72% vs. 31%).
IT leaders in US organizations with over 1,000 employees estimate that 480 emails are sent to the wrong person every year. Yet, Tessian platform data reveals that employees send at least 800 misdirected emails per year —1.6x more than IT leaders estimate.
U.S. employees are twice as likely to send company data to their personal email accounts than their UK counterparts (82% vs. 35%).
IT leaders in US organizations with over 1,000 employees estimate that just 720 emails are sent to unauthorized accounts a year. The reality, per Tessian platform data, is at least 27,500 unauthorized emails are sent a year — 38x more than IT leaders estimate.
One-third (34%) of employees take company documents with them when they leave a job, with U.S. workers twice as likely as UK workers to do so (45% vs. 23%).
IT leaders rely on security awareness training, policies and legacy technologies to prevent data loss, yet these practices may not be as effective as they think. The report finds that employees who receive security training every 1-3 months are almost twice as likely to send company data to personal accounts as those who receive training once a year (80% vs. 49%).
“Businesses have adapted quickly to the abrupt shift to remote working. The challenge they now face is protecting data from risky employee behaviors as working from home becomes the norm,” said Tim Sadler, CEO at Tessian.
“Human error is the biggest threat to companies’ data security, and IT teams lack true visibility of the threat. Business leaders need to address security cultures and adopt advanced solutions to prevent employees from making the costly mistakes that result in data breaches and non-compliance.
“It’s critical these solutions do not impede employees’ productivity though. We’ve shown that people will find workarounds if security gets in the way of them doing their jobs, so data loss prevention needs to be flexible if it’s going to be effective.”

Differences by age and company size
In addition to differences in safe security practices by region, there are also notable contrasts among age groups and startups vs. large enterprises. For example:
50% of workers from small companies (2-49 employees) agree they’re less likely to follow safe data practices when working from home, compared to only 30% from companies with 1,000 employees or more.
Workers in the 18-30 age demographic are 3x more likely to send emails to the wrong person — 69% vs. 21% of workers who are 51 or older. And while 31-40 year olds are more careful on email, 57% admit to sending misdirected emails.
41% of workers aged 18-30 have taken company documents with them when they’ve left a job, compared to only 13% of workers aged 51 and older.
Global WAN optimization market forecast to reach $1.4 billion by 2025
29.5.2020 Net-Security Security
The WAN optimization market is expected to grow from $1,047.1 million in 2020 to $1,446.2 million by 2025, at a Compound Annual Growth Rate (CAGR) of 6.7% during the forecast period of 2020-2025, according to ResearchAndMarkets.
WAN optimization market
Most cloud-based applications need good bandwidth and low latency for effective utilization. In large-scale WAN deployments, latency, bandwidth constraints, and packet losses are inevitable.
WAN optimization enables enterprises and service providers to save money and reduce costs with reduced bandwidth requirements and increased user efficiency by alleviating the effects of latency and distance between branch offices, data centers, and cloud.
Customer experience is a critical and important factor in this application era. Digital transformation fails to produce the desired business impact, unless application performance is protected and delivered optimally to all users.
The important challenge of IT teams of every organization is to dynamically orchestrate the performance and user experience of every application in real-time, irrespective of the size, location, and complexity of network environments, which can be solved with the help of WAN optimization solutions.
Banking, finance, and insurance to hold highest market share
Based on verticals, the banking, financial services, and insurance (BFSI) segment of the WAN optimization market is projected to hold the highest market share during the forecast period. The BFSI vertical is adopting innovative technologies, primarily due to changes in the centralized and computerized process in this vertical.
The vertical includes commercial banks, non-banking financial organizations, and insurance companies. It is witnessing the rapid growth of new technologies related to financial security and data due to the confidential nature of the data that needs to be always secured.
Online banking, mobile banking, and electronic payments are growing at a rapid pace as banks evolve from a traditional payment processing and enquiry-based business to digital banking. The volume, geographical reach, and accessibility of retail environments are vital.
The quick adoption of WAN optimization is expected in the financial services vertical due to the need to connect all the remote branches of companies to a core banking system, which is not possible without Application Delivery Controller (ADC).
With the introduction of WAN optimization-as-a-service, financial services institutions are able to do cost-savings as the services get billed on the basis of their usage. Financial firms do not have to invest in new hardware and software.
The flexibility of cloud-based operating models also enables financial institutions to experience shorter development cycles for new products.
Large enterprises segment to record a higher market share in 2020
Large enterprises are organizations with the employee strength of more than 1,000 employees and annual revenue higher than one billion. These organizations need the expertise of IT staff to manage specific applications and IT infrastructure due to the large amount of data they generate.
They always focus on the adoption of those industry solutions that can help them in increasing their operational efficiency. WAN optimization solutions help large enterprises motivate and encourage employees by offering enhanced user experience.
They also assist large enterprises in increasing client base with the help of innovative and exciting gamified techniques. Enterprises are expected to continue to adopt on-premises and cloud-based WAN optimization solutions at a faster pace.
Cloud segment to hold a higher market share
The cloud deployment model is gaining traction in the market due to its several advantages, such as cost-savings for additional hardware and software, and scalability, over the on-premises deployment model.
In the cloud deployment method, vendors such as Aryaka Networks offers WAN optimization as a cloud-based service. One of the other important advantages of WAN optimization-as-a-service is that enterprises can customize solutions according to their requirements, whenever new applications are installed.
This cloud-based service provides benefits, such as reduced licensing costs, ability to cut out unnecessary IT staff, focus on maintenance, and flexibility in expansion of businesses. However, for cloud deployment enterprises need to analyze the benefits of their existing set up as well as those that a cloud-based service can give them.
North America to record the highest market share in 2020
The North American region is a receptive market toward the adoption of WAN optimization solutions. The region is witnessing huge demands for SD-WAN solutions due to the rising demand for the next-generation 5G network.
Enterprises in the region are shifting to managed SD-WAN services due to the rapidly changing technological landscape. Telecom providers in North America are providing services for both accelerating and monitoring application performance by integrating different toolsets.
Major North American WAN optimization vendors are developing new technologies, which are making the WAN optimization process much efficient and cost-effective. North America mainly consists of the US and Canada.
In terms of market size, the US is expected to hold a larger market size in the region. The US is witnessing heavy investments in the broadband infrastructure in the country and is contributing to the growth of the WAN optimization market in the region.
CISO Conversations: Mastercard, Ellie Mae Security Chiefs Discuss the People Problem
28.5.2020 Securityweek Security
In SecurityWeek's CISO Conversations series, we talk to top Chief Information Security Officers from major organizations within the critical industries to discuss the role of the CISO, and what it takes to be a successful CISO.
In this feature, SecurityWeek talks to Mastercard CISO Ron Green, and Ellie Mae CISO Selim Aissi from the finance sector, concentrating on the people problem for CISOs.
One of the biggest changes in security within business over the last two decades has been its emergence from a siloed technical office within the IT department into a mainstream function of the business itself. The CISO has followed, from being a technical expert under the CIO to someone who must now understand business processes, be able to talk business with the business leaders, and be thoroughly immersed and integrated into the entire organization. The CISO may remain under the CIO – which is a complex issue itself discussed elsewhere in this series.
The need to be business competent raises one of the primary questions on the role of the modern CISO: should he or she be a businessperson with some understanding of security, or a technical expert with some understanding of business? Green and Aissi believe it must be both in equal measure.
“I think it’s a balance of the two,” says Aissi. “I think If either one of the two aspects is stronger than the other, then the CISO will not be successful. I think if a CISO is a salesman, a great communicator all the time but doesn’t have the technical chops, then that's a problem. And if the CISO is way deep into the technology and does not focus on the people aspects, on processes, on communication, then that CISO will also fail. It really does require a good balance between the two.”
Green agrees. He comes from a technical background, doing device exploitation and forensics for the Secret Service. This technical background insures he understands exactly what his technical security team is saying – but the need to understand the business is equally important. “I do a lot of translating to take the very technical issues and turn them into something that the business leaders who drive the company can understand – so they can make informed assessments on best paths based on the way I express the means and concerns of the security team.”
For Green, the CISO is a bridge between the two worlds, and he must have one foot firmly planted on each side.
GlobeAissi believes there are five attributes that a good CISO needs. The first is to be a master of tactics – to be involved with all the operational challenges that arise from security incidents, to be involved with the deployment of tools, and aware of all the operational events happening all the time. The second is to be comfortable talking to people. The range of people the CISO must interact with Is huge, from business leaders to technicians, from risk people to governance, and people in other countries.
The third is to take a strategic (rather than just tactical) view of things. “Being in the weeds all the time is not a good thing,” he said. “The CISO needs to step up, and say, OK, are we really moving forward as an organization; are we maturing the security program? That's orthogonal to the purely tactical operational aspect -- being strategic at the same time as being operational.”
The fourth is being a good communicator. This is essential to being Green’s bridge between security and business. It goes both ways, being able to translate technical security issues into a language that business leaders understand – that is, in terms of risk – and to translate new business processes into technical solutions for the IT and security teams. But the ability to communicate, and enthuse, goes beyond just talking to business leaders – it requires the ability to communicate effectively with everyone in the company, from the board to employees and one’s own staff, and even customers.
The fifth is being a visionary, which takes the strategic requirement to the next level. The CISO, says Aissi, “must be able to see and predict that in two years from now we're going to see this kind of attack, or this new trending attack pattern, and get ready for that. A CISO can't be just reacting all the time.”
Mastering these five attributes, says Aissi, makes a good CISO – but the good CISO must have control of them all, all the time. Nevertheless, being asked to focus on one, Aissi answered, ‘people.’ “Hire the best talent, trust them, make sure they grow,” he said.
: Communications Sector CISOs at Verizon and AT&T: Mastercard, Ellie Mae CISOs Discuss the People ProblemAissi warns that there must be enough technical understanding throughout the organization to be able to understand the challenges that exist. “The threat landscape is moving extremely fast in terms of malware advances, and evasion techniques, so it’s difficult to track threats. You also need to have the whole company as aware as possible about security. That requires continuous awareness programs. A new CISO can build all kinds of amazing technologies, but if somebody clicks on the wrong attachment, then none of that is going to work if it leads to a brand new zero-day. The people delivering the threats get smarter every day, and so must we.”
The first ‘people’ requirement is probably the most difficult: ‘hire the best talent’. Given the cybersecurity skills gap, there are too many companies looking for too little talent. “There aren’t enough security professionals to fill the jobs that are vacant,” says Green. “There are more than 350,000 roles unfilled right now and within three years we will be looking at over 1 million.”
The problem is, he added, “there's no school conveyor belt producing cybersecurity experts. So, we must go and find the talent, because it’s not being created and sent to us.” Mastercard has a couple of initiatives designed to do just this – the most ambitious perhaps being the Cybersecurity Talent Initiative.
“In this initiative, which currently involves Mastercard, Microsoft and Workday,” he explained, “we have partnered with the U.S. federal government. If a student chooses a cybersecurity degree and enrolls with us, on graduation they go and work for the government for two years. There’s about a dozen agencies involved, such as the CIA, the DoD, the FBI and others. The graduate works for them getting real world experience in handling threat actors, whether they are fraudsters or nation states. And after the two years are complete, they have the option of working for one of the three partner companies – and after working a further two years for us, we will pay off their student debt up to around $75,000.”
That's a benefit to everyone. “The student gets his or her loans paid off, while the federal government gets exposure to talent they would not otherwise get. The government doesn't often pay as much as the private sector,” he added, “but they offer some really cool missions that can be enticing for people to stay. And then the partner companies get people that have real world experience along with the college background to come and work for us and protect our organizations. It's a win/win for all parties,” he said.
There is a philosophical problem here. Do large companies that can afford such initiatives cause problems lower down the talent supply food chain by poaching all the top talent? “It can do,” admits Green, but then points out a common attitude among many leading CISOs. “We’re all part of the same ecosphere, often connected by complex supply chains. It’s to everyone’s advantage if the global level of cybersecurity is raised.” Here, he has partnered with the Global Cyber Alliance “to create a small business cyber security toolkit, which provides best practices explaining why a lot of things are necessary, but we also provide a free tool to do things. There are other things we do, like being part of the Cyber Readiness Institute.”
And then there’s Girls4Tech. This is an ambitious STEM education program developed for middle school girls, and not just in the U.S. The aim is to introduce technology as an interest to 1 million girls by 2025. “This year,” said Green, “we have introduced cybersecurity and artificial intelligence into the scheme.”
Bringing women into cybersecurity serves two purposes. Firstly, it increases the overall pool of available talent, because, as Green says, “There are not a lot of women in this space.” Secondly, diversity adds new ways of thinking about problems. It is also worth mentioning that women are disproportionately successful in cybersecurity – there is a higher ratio of female CISOs than there are women in security teams.
Not many CISOs will have the funds for such initiatives – but the principle is clear: CISOs cannot wait for talent to knock at the door, CISOs must go and find and then nurture that talent.
Keeping talent is almost as difficult as finding it. This is what Aissi meant by “Hire the best talent, trust them, make sure they grow.”
“Once you’ve found the talent,” says Green, “you keep them by providing a good mission that does the right thing.” Remuneration cannot be ignored in this – Green (who has already been CISO at Mastercard for six years despite the average span of just two to four years for the life of a CISO at one place) comments, “I remember my days of being a Secret Service agent, having three kids, having to take out a second mortgage to make the right things happen, planning for getting my kids to college... there were a lot of things I couldn't do for them. Those are not problems for me now.”
This is what the company can do for its staff – but the CISO can also do a lot. “Once we've brought the right people here, they need a good mission that does the right thing -- you got to love what you do,” said Green. “But more than just providing a cool job, it's got to be a place that actually encourages you to do the things you have a passion for.” Green has encouraged his staff to be involved with the local community.
“We've had a really focused effort on allowing people to contribute in their communities,” he said “If they have a passion for a charity, or want to engage in training people in cybersecurity, volunteer work, we actively support it by giving staff five days for voluntary work. If they work there for 40 hours, we'll contribute an hourly rate to the charity or organization as a match. If our staff put in the time, we will contribute a salary equivalent to the time spent. People get a chance to do the things they love.”
An important part of keeping good staff is trust. “The company puts a lot of faith and trust in the people they bring on board. I do that with my employees as well,” said Green. Key to this is the CISO forging a strong relationship with the board, which allows the release of funds for the projects that will keep staff engaged.
“The company really wants to invest to ensure we have the right technologies, the right people, and the right capabilities available to us. So, we've enabled things like the fusion center. We have a cyber range which allows our people to test our technologies before we actually deploy them in our environment and also gives us a place for our employees to engage in real world scenarios where they can feel they are in the middle of a fight and get experience from it without actually being in a real fight. It’s a great opportunity to create an environment where we can go full-out,” he said. “We can put malware that steals information from our network on it, and allow my team to go in and fix the situation—not in theory, but actually do it.”
Most CISOs will look with envy at what the big companies can afford to do. But the principle is clear. CISOs need to surround themselves with strong, talented staff that they trust. Those people will not come knocking at the door, so CISOs need to be proactive and imaginative within their budgets to go and find them.
Having found talent, an equal amount of effort needs to be spent on keeping them. Budgets may not run to Mastercard’s cyber range, but all CISOs can maintain continuous interest, encouragement and trust in their staff. Technology can only go so far in ensuring cybersecurity – people go the extra mile.
A New Free Monitoring Tool to Measure Your Dark Web Exposure
28.5.2020 Thehackernews Security
Last week, application security company ImmuniWeb released a new free tool to monitor and measure an organization's exposure on the Dark Web.
To improve the decision-making process for cybersecurity professionals, the free tool crawls Dark Web marketplaces, hacking forums, and Surface Web resources such as Pastebin or GitHub to provide you with a classified schema of your data being offered for sale or leaked.
All you need to launch a Dark Web search is to enter your domain name.
The volume of stolen credentials on the Dark Web is booming
This week, over 26 million user records, including plaintext passwords, stolen from LiveJournal appeared on a Dark Web marketplace for as low as $35. The present week is likewise sadly marked with a compromise of 31 SQL databases (with 1.6 million rows of client data) from webshop owners.
There were 7,098 breaches reported in 2019, exposing over 15.1 billion records, a new worst year on record according to Risk Based Security report. Over 80% of data breaches within the hacking category involve usage of lost or stolen credentials, says the Data Breach Investigations Report 2020 by Verizon.
While over 21 million of stolen login credentials from Fortune 500 companies were readily available for sale in the Dark Web, according to ImmuniWeb report from 2019.
ImmuniWeb Dark Web monitoring tool in action
ImmuniWeb says that its Deep Learning AI technology is capable of distinguishing and removing duplicates and fake records, providing actionable and risk-scored data to its clients.
Here is an example of findings for a well-known financial institution:
Interestingly, for Gartner, there are over 100,000 mentions of detected login credentials and other data. However only 14% pass the AI-enabled validation, and as low as 466 were assigned a critical risk, potentially exposing apparently valid passwords from business-critical web resources:
In its press release, ImmuniWeb also mentions that on top visibility across 30 billion of stolen credentials, the free online test likewise detects and provides full technical details:
Phishing Campaigns
Domain Squatting
Trademark Infringement
Fake Social Networks Accounts
For example, for Yahoo, 131 ongoing phishing campaigns are targeting its clients, over 1,000 cybersquatted or typosquatted domains, many of which redirect to malware and ransomware doorways.
The hyperlinks to the malicious websites are displayed in a safe manner, with each entry also equipped with a screenshot to enable security professionals to assess the risk without the need to open dangerous web resources in their browser.
The tool is also available via a free API, making it an invaluable instrument for SOC security analysts to timely spot security emerging web security and privacy threats.
Last time we mentioned ImmuniWeb was among Top 10 Most Innovative Cybersecurity Companies after RSA 2020, and it seems that while successfully pursuing its growth track, their team doesn't forget to contribute to the cybersecurity community. Good work!
Solving the security challenges of remote working
28.5.2020 Net-Security Security
Unprecedented times call for unprecedented actions and the ongoing COVID-19 pandemic has caused what is likely to be the biggest shift towards remote working that the world has ever seen. But, while the technology has been around for quite some time, recent events demonstrate just how few businesses are capable of switching from an office-based setup to a remote one in a fast, secure, and non-disruptive manner.
security challenges remote working
There’s a significant number of reasons why it is prudent to have a remote working infrastructure in place. Truth be told, “in the event of a global pandemic” probably wasn’t very high up most people’s list before 2020. In normal circumstances, common occurrences like adverse weather, transportation issues, and power outages can also severely affect the productivity of business if employees can’t access what they need outside the office.
That being said, proper implementation of any remote working program is key. In particular, the right security tools must be in place, otherwise businesses risk exposing themselves to a wide range of cyber threats.
This article examines some of the major considerations for any business looking to tackle the security challenges of remote working and implement a program that will enable employees to work both effectively and securely from anywhere.
Security challenges of remote working: Finding the right approach
Historically, office-based businesses have managed off-site workers through the use of virtual private networks (VPNs) and managed devices with installed software agents – also known as the mobile device management (MDM) approach. While still a relatively popular strategy today, it raises an increasing number of privacy concerns, mainly because it gives businesses the ability to monitor everything employees do on their device. VPN technology is also widely considered to be outdated and its complexity means skilled IT professionals are required to manage/maintain it properly.
For businesses without legacy technology to consider, a bring your own device (BYOD) approach is often preferable. Not only does it significantly reduce IT costs, but employees will always be able to work on their device in the event of unforeseen circumstances that prevent them from traveling to the office.
Unlike a managed device approach, employees using their own personal devices have more freedom over what and where they can view or download sensitive data, making robust security even more critical. Below are three security technologies that can be used to complement the flexibility a BYOD program provides:
1. Data loss prevention technology keeps businesses in control
One of the biggest issues with a BYOD approach is how to prevent sensitive data loss or theft from unmanaged devices. The use of data loss prevention (DLP) technology can significantly mitigate this, giving businesses much more control over their data than they would otherwise have. With DLP in place, any unauthorized attempts to access, copy or share sensitive information – whether intentional or not – will be prevented, keeping it out of the wrong hands and helping to prevent security breaches.
2. Behavioral analytics quickly detects suspicious user activity
Implementation of user and entity behavior analytics (UEBA) is a great way to quickly detect anomalous behavior that might indicate a potential security breach amongst your remote workforce. UEBA works by learning and establishing benchmarks for normal user behavior and then alerting security teams to any activity that deviates from that established norm. For instance, if a remote worker typically logs in from London but is suddenly seen to be logging in from Paris, particularly under the current circumstances, this would raise an immediate alert that something is amiss.
3. Agentless technology delivers robust security without breaching privacy
Employees using personal devices as part of a BYOD program can often be resistant to agent-based security tools being installed on them. Not only are some – like MDM – considered an invasion of privacy, but they can also impact device performance and functionality. Conversely, agentless security tools utilize cloud technology, meaning they require no installation but still give security teams the control they need to monitor, track and even wipe sensitive data if/when necessary.
Furthermore, because agentless security tools only monitor company data on the device, employees can be confident that their personal data and activity remain completely private. Leading agentless security solutions even include cloud based DLP as part of their offering, meaning businesses can cover multiple bases in one go.
Over the last few months, the pandemic has forced many businesses to fundamentally change the way they operate. For some, this switch to remote working has been quick and painless, but for many others, a lack of foresight or advanced planning has made it a significant challenge.
Of course, hindsight is a wonderful thing, but even in the midst of this pandemic, it’s not too late to change tack. By combining BYOD with powerful cloud security and analytics technology, businesses of all shapes and sizes can quickly establish an effective, secure remote working program, keeping the wheels of business turning when even the most unexpected things happen.
HackerOne Says Bug Bounty Hunters Earned $100 Million Through Its Platform
28.5.2020 Securityweek Security
HackerOne announced on Wednesday that its bug bounty platform has helped researchers earn more than $100 million since the company started paying hackers in October 2013.
The San Francisco-based company reported in late February that it had paid out a total of over $82 million in bounties, $40 million of which was awarded in 2019 alone. At the time, it also said that seven white hat hackers exceeded $1 million in lifetime earnings, and 13 others surpassed $500,000. In April 2020, hackers earned nearly $6 million.
HackerOne says it currently has nearly 300 employees and more than 700,000 hackers have signed up on its platform, looking for vulnerabilities in the systems and products of over 1,900 government and private organizations.
The company says an average of 84 new hackers signed up on its platform every hour in the past 7 years, with $6,000 being paid out every hour.
Business seems to be good even during the current coronavirus pandemic — a 17.5% increase was allegedly recorded since February — and HackerOne estimates that the total amount paid to hackers will reach $1 billion within five years.
HackerOne has raised more than $110 million in funding, including $36.4 million in a Series D round last year.
Bugcrowd, one of HackerOne’s main competitors, told SecurityWeek it is not disclosing total payouts at this time.
However, the company, which is also based in San Francisco, reported in November 2019 that it paid out over half a million dollars in bug bounties in one week of October. It awarded 550 hackers a total of $1.6 million that month.
Bugcrowd has raised over $80 million, including $30 million announced last month as part of a Series D funding round.
C-suite execs often pressure IT teams to make security exceptions for them
28.5.2020 Net-Security Security
The C-suite is the most likely group within an organization to ask for relaxed mobile security protocols (74%) – despite also being highly targeted by malicious cyberattacks, according to MobileIron.

The study combined research from 300 enterprise IT decision makers across Benelux, France, Germany, the U.K. and the U.S., as well as 50 C-level executives from both the U.K. and the U.S. The study revealed that C-level executives feel frustrated by mobile security protocols and often request to bypass them.
Make security exceptions for the C-suite
68% of C-level executives said IT security compromises their personal privacy, while 62% said security limits the usability of their device, and 58% claimed IT security is too complex to understand.
76% of C-level executives admitted to requesting to bypass one or more of their organization’s security protocols last year. Of these, 47% requested network access to an unsupported device, 45% requested to bypass multi-factor authentication (MFA) and 37% requested access to business data on an unsupported app.
“These findings are concerning because all of these C-suite exemptions drastically increase the risk of a data breach,” said Brian Foster, SVP Product Management, MobileIron.
“Accessing business data on a personal device or app takes data outside of the protected environment, leaving critical business information exposed for malicious users to take advantage of. Meanwhile, MFA – designed to protect businesses from the leading cause of data breaches, stolen credentials – is being side-stepped by C-Suite execs.”
C-level execs highly vulnerable to cyberattacks
The study also revealed that C-level execs are highly vulnerable to cyberattacks:
78% of IT decision makers stated that the C-suite is the most likely to be targeted by phishing attacks, and 71% claimed the C-suite is the most likely to fall victim to such attacks.
72% of IT decision makers claimed the C-suite is the most likely to forget or need help with resetting their passwords.
“These findings highlight a point of tension between business leaders and IT departments. IT views the C-suite as the weak link when it comes to cybersecurity, while execs often see themselves as above security protocols,” said Foster.
“In today’s modern enterprise, cybersecurity can’t be an optional extra. Businesses need to ensure they have a dynamic security foundation in place that works for everyone within the organization. This means that mobile security must be easy to use, while also ensuring that employees at every level of the business can maintain maximum productivity without interference, and without feeling that their own personal privacy is being compromised.”
Application threats and security trends you need to know about
27.5.2020 Net-Security Security
Applications are a gateway to valuable data, so it’s no wonder they are one of attackers’ preferred targets.
And since modern applications aren’t a monolithic whole but consist of many separate components “glued together” over networks, attackers have at their disposal many “doors” through which they can attempt access to the data.

Easy targets will remain popular
Some of these doors are more popular than others. According to the latest Application Protection Report by F5 Networks, attackers love to:
1. Exploit PHP vulnerabilities such as CVE-2018-12613 and CVE-2018-20062, and poorly secured PHP-enabled admin interfaces.
“PHP is a widespread and powerful server-side language that’s been used in 80% of sites on the web since 2013. It underpins several of the largest web applications in the world, including WordPress and Facebook,” F5 analysts explained the attraction.
2. Engage in injection attacks and formjacking (the latter especially when targeting the retail sector).
In 2019, formjacking payment cards was resposible for 87% of web breaches and 17% of known breaches in total (up from 71% and 12% in 2018). In 2019, the retail sector was the most significant formjacking target. 81% percent of retail breaches were from formjacking attacks, while nearly all other sectors tended to be breached most often through the access tier.
“The lesson is clear: for any organization that accepts payment card via the web, their shopping cart is a target for cyber-criminals,” the analysts pointed out.
3. Getting access to accounts (and especially email accounts) via phishing, brute forcing, credential stuffing or using stolen credentials.
“Access tier attacks are any that seek to circumvent the legitimate processes of authentication and authorization that we use to control who gets to use an application, and how they can use it. The result of this kind of attack is a malicious actor gaining entry to a system while impersonating a legitimate user. They then use the legitimate user’s authorization to accomplish a malicious goal— usually data exfiltration,” the analysts explained.
Attackers use a number of tactics to keep these attacks unnoticed, but organizations also have a lot of defensive options at their disposal to prevent them.
4. Go after unmonitored, vulnerable, poorly secured or misconfigured APIs.
“In the days of monolithic apps, whatever core business logic generated value needed to be supported by a user interface, storage, and other meta-functions. Now it is sufficient to develop a single specialized service, and use APIs to either outsource other functions to bring an app to market, offer the service to other app owners, or both,” the analysts explained.
Their widespread used makes them a big target, and a combination of factors make them rich targets:
They are often configured with overly broad permissions
Lack of visibility and monitoring.
There are solutions to these problems
Attackers go where the data is, and that’s why organizations in each sector/industry should develop risk-based security programs and tailor controls and architecture to reflect the threats they actually face, the analysts advise.

To counter access attacks, organizations should implement multi-factor authentication where fitting and possible, but should also consider:
Checking passwords against a dictionary of default, stolen, and well-known passwords
Making sure the system can detect and prevent brute force attacks by, for example, using CAPTHA, slowing down sessions, setting up alarms, etc.
Creating simple methods for users to report suspected phishing
Encrypting or eliminating confidential data from the organization’s email caches
Enabling logging (to be able to discover what the attackers did when they gained access).
Spotting and foiling injection and formjacking attacks can be done with securing servers, patching injection vulnerabilities,employing change control, using web application firewalls (WAFs), through testing and watching of all third-party components on sites with forms accepting critical information, and so on.
But organizations should be aware that the injection landscape is constantly changing, and they have to follow the trends and adapt.
Finally, organizations can mitigate the risk of API attacks by:
Making (and maintaining) an inventory of their APIs
Deploying authentication for them and storing credentials securely
Limiting their permissions
Monitoring them (by logging connections and reviewing them)
Encrypting the API connections
Testing APIs
Implementing API security tools.
What’s trending on the underground market?
27.5.2020 Net-Security Security
Trust has eroded among criminal interactions, causing a switch to e-commerce platforms and communication using Discord, which both increase user anonymization, Trend Micro reveals.
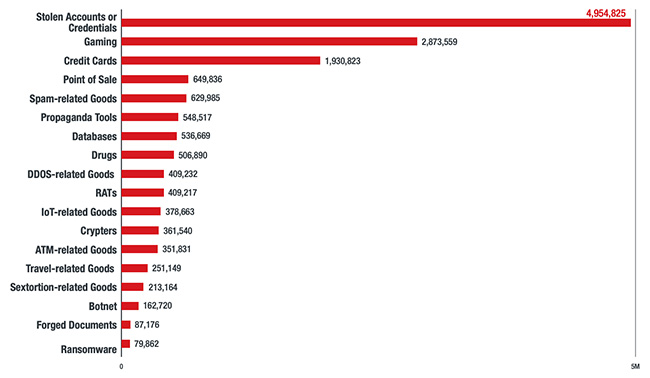
Popular underground goods and services
The report reveals that determined efforts by law enforcement appear to be having an impact on the cybercrime underground. Several forums have been taken down by global police entities, and remaining forums experience persistent DDoS attacks and log-in problems impacting their usefulness.
Loss of trust led to the creation of a new site, called DarkNet Trust, which was created to verify vendors’ and increase user anonymity. Other underground markets have launched new security measures, such as direct buyer-to-vendor payments, multi-signatures for cryptocurrency transactions, encrypted messaging, and a ban on JavaScript.
Trends for cybercrime products and services
The report also illustrates the changing market trends for cybercrime products and services since 2015. Commoditization has driven prices down for many items. For example, crypting services fell from $1,000 to just $20 per month, while the price of generic botnets dropped from $200 to $5 per day.
Pricing for other items, including ransomware, Remote Access Trojans (RATs), online account credentials and spam services, remained stable, which indicates continued demand.
However, there has been a high demand for other services, such as IoT botnets, with new undetected malware variants selling for as much as $5,000. Also popular are fake news and cyber-propaganda services, with voter databases selling for hundreds of dollars, and gaming accounts for games like Fortnite can fetch around $1,000 on average.
Other underground market trends
Other notable findings include the emergence of markets for:
Deepfake services for sextortion or to bypass photo verification requirements on some sites.
AI-based gambling bots designed to predict dice roll patterns and crack complex Roblox CAPTCHA.
Access-as-a-Service to hacked devices and corporate networks. Prices for Fortune 500 companies can reach up to US$10,000 and some services include access with read and write privileges.
Wearable device accounts where access could enable cybercriminals to run warranty scams by requesting replacement devices.
Underground market trends will likely shift further in the months following the global COVID-19 pandemic, as attack opportunities continue to evolve. To protect against the ever-changing threat landscape, it is recommended to implement a multi-layered defense approach to protect against the latest threats and mitigate corporate security risk.
Maintaining the SOC in the age of limited resources
27.5.2020 Net-Security Security
With COVID-19, a variety of new cyber risks have made their way into organizations as a result of remote working and increasingly sophisticated, opportunistic threats. As such, efficiency in the security operations center (SOC) is more critical than ever, as organizations have to deal with limited SOC resources.
Limited SOC resources
The SOC is a centralized team of analysts, engineers, and incident managers who are responsible for detecting, analyzing, and responding to incidents and keeping security operations tight and resilient – even when security strategy fails. During the first 100 days of COVID-19, there was a 33.5 percent rise in malicious activity, putting increased pressure on these teams. Rapidly changing attack methods make keeping up an immense challenge.
With all of this in mind, it’s easy for the SOC to become overwhelmed and overworked. To avoid this and protect the business, it’s important to keep morale high, production efficient and automation reliance balanced on need. Read on to explore the do’s and don’ts of maintaining SOC operations throughout the pandemic.
Do: Prevent burnout before it’s too late
The SOC requires a high level of technical expertise and, because of that, the number of suitable and competent analysts holding positions in the field are scarce.
Beyond the skills shortage, the job of a SOC is made even more difficult and overwhelming by the lack of employee awareness and cybersecurity training. Untrained employees – those who don’t know how to appropriately identify a live threat – can lead to a high noise-to-signal ratio by reporting things that may not be malicious or have high click-through rates. This means organizations are not putting enough emphasis on building what could be the strongest defense for their business – the human firewall. Ninety-five percent of cyberattacks begin with human error, causing more issues than the SOC can handle.
For those that are implementing training, it’s likely they’re not seeing their desired results, meaning an uptick in employee mistakes. For one, cyber hygiene across organizations saw large deterioration by late March, with blocked URL clicks increasing by almost 56 percent. The organizations experiencing this downgrade in employee cyber resiliency should take the time to re-think their methods and find alternatives that keep their staff engaged rather than implementing irregular, intensive training with boring content just to check a box.
Coupling this with rapidly changing threat activity, the SOC is under immense pressure, which could lead to a vicious cycle where analysts leave their roles, creating open vacancies that are difficult to fill.
Don’t: Jump headfirst into automation
With limited SOC resources, one may think automated alerts and post-breach threat intelligence are the answer to ensuring proper attention is kept on an enterprise’s security.
On one hand, automation can help alleviate time spent on administrative action. For example, it can help detect threats more quickly, giving teams more time to focus on threat analysis.
However, post breach threat intelligence and automated alerts can also lead to fatigue and a lot of time spent investigating, which could be at a higher cost than the administration burden. Not to mention, machine learning can also learn bad behaviors and, in itself, be a vulnerability –threat actors can learn machine patterns to target systems at just the right time.
The SOC should therefore adopt automation and intelligence only where it makes the most sense, layering in preventive measures to reduce that fatigue. Organizations should be critical of the technologies they take on, because ultimately, a quick response can create an added burden. Instead, they should focus on improving the metrics that have a positive impact on the SOC and employees, such as a reduction in reported cases and dwell time, as well as the ratio of good-to-bad things reported. With the right training, technology, and policies, the SOC – and the business – can get the most out of its investment.
Do: Improve virtual collaboration practices
A recent (ISC)2 survey found that 90 percent of cybersecurity executives are working remotely. Like every other employee in a digitally-connected company, an organization’s SOC is also likely not in the office right now. This is a challenge, as some have become accustomed to putting their SOC, other IT teams, and the technology that they use in close proximity to one another to create a stronger, more resilient approach. This extends the SOC’s operational knowledge and creates a faster response in time of crisis.
Given the current pandemic, most teams are unable to have this physical proximity, stretching the bounds of how they operate, which could put a strain on larger business operations. This can inhibit communication and ticketing, which is seamless when seated together. For instance, folks may be working on different schedules while remote, making it hard to communicate in real-time. Remote scenarios can also deepen data silos amongst teams who aren’t in communication. These challenges increase the amount of time it takes the SOC to find and address a potential threat, widening the attack surface.
As such, organizations should be mindful and strategic about their new cross-functional operation and create new ways for teams to collaborate in this new virtual frontier. For instance, businesses should:
Ensure access to their enterprise: Start thinking about disaster recovery and business continuity as the tools needed to ensure security or even access to the “castle” that was once considered their enterprise.
Consider their tools: Adjust communication styles and interactions by adopting tools, like Microsoft Teams, Slack, or Skype, to help everyone stay in constant communication or keep the channel open during traditional working hours.
Focus on training: Develop training and documentation that can be used by operations teams in a consistent fashion. This could include a wiki and other tools that help with consistent analysis and response.
Keep operations running globally: Establish formal standups and handovers for global teams.
Maintain visibility through technology: Adopt SaaS technologies that enable the workforce and offer visibility to do their jobs.
Change the hiring approach: When hiring, realize that this is a “new” world where proximity is no longer a challenge. With the right tools and processes, business can take the chains off when hiring smart people.
Recognize and reward success: Morale is the most important thing when it comes to SOC success. Take breaks where needed, reward those that are helping the business succeed and drive success based on goals and metrics.
The cyber threats posed by COVID-19 and impacting the SOC are rapidly evolving. Despite current circumstances, malicious actors are not letting up and organizations continue to be challenged. Due to the limited number of SOC analysts equipped with the skills to keep organizations protected, the risk of burnout risks is high and the industry does not have the staff to fill vacant roles. With all of this in mind, SOC analysts must be supported in their roles as they work to keep businesses safe, by adopting the right technologies, processes and collaboration techniques.
Patented algorithms predict, identify, diagnose and prevent abnormalities in complex systems
27.5.2020 Net-Security Security
The COVID-19 pandemic has forced public health, supply chain, transportation, government, economic and many other entities to interact in real time. One of the challenges in large systems interacting in this way is that even tiny errors in one system can cause devastating effects across the entire system chain.

Now, Purdue University innovators have come up with a possible solution: a set of patented algorithms that predict, identify, diagnose and prevent abnormalities in large and complex systems.
“It has been proven again and again that large and complex systems can and will fail and cause catastrophic impact,” said Shimon Y. Nof, a Purdue professor of industrial engineering and director of Purdue’s PRISM Center.
“Our technology digests the large amount of data within and across systems and determines the sequence of resolving interconnected issues to minimize damage, prevent the maximum number of errors and conflicts from occurring, and achieve system objectives through interaction with decision makers and experts.”
Applying systems science and data science to solve problems
Nof said this technology would be helpful for smart grids, healthcare systems, supply chains, transportation systems and other distributed systems that deal with ubiquitous abnormalities and exceptions, and are vulnerable to cascading or large amount of failures.
This technology integrates constraint modeling, network science, adaptive algorithms and state-of-the-art decision support systems.
“Our algorithms and solution apply systems science and data science to solve problems that encompass time, space and disciplines, which is the core of industrial engineering,” said Xin Chen, a former graduate student in Nof’s lab who helped create the technology.
Nof said the novelty of the technology lies in three main areas. First, analytical and data mining tools extract underlying network structures of a complex system and determine its unique features. A robust set of algorithms then are analyzed based on the objectives for system performance, structures and features of fault networks in the system.
Finally, algorithms with specific characteristics are applied to manage errors and conflicts to achieve desired system performance.
ThreatList: People Know Reusing Passwords Is Dumb, But Still Do It
26.5.2020 Threatpost Security
Even seeing data breaches in the news, more than half of consumers are still reusing passwords.
More than half of people haven’t changed their password in the last year – even after they’ve heard about a data breach in the news.
That’s according to a recent survey, “Psychology of Passwords: The Online Behavior That’s Putting You At Risk,” that examined the online security and password behaviors of 3,250 global respondents – and found that people still employ an alarming number of very common and very risky habits, even though they know better.
Researchers said that password reuse was the biggest security faux pas being committed by respondents. In fact, password reuse has actually gotten worse over the years: When asked how frequently they use the same password or a variation, 66 percent answered “always” or “mostly” – which is up 8 percent from the same survey in 2018.
Worse, 91 percent of respondents said they know using the same (or a variation of the same) password is a risk. They still do so anyways.
“Our survey shows that most people believe they are knowledgeable about the risks of poor password security; however, they are not using that knowledge to protect themselves from cyber threats,” said researchers with LastPass by LogMeIn, in a recent report.
In the wake of the COVID-19 health crisis, in which people find themselves working from home and spending time online more than ever due to global orders to stay at home, protecting personal data when using the internet is more crucial than ever, researchers said. However, people still seem to underestimate how much of that data is stored online and don’t take the necessary precautions to keep it safe from cybercriminals. These bad actors, coincidentally, have ramped up their threat behavior to take advantage of people’s new dependence on conducting business and personal activities online.

With breaches being disclosed daily – affecting large, popular brands like Macy’s and Marriott – why would consumers continue to reuse passwords? One reason is that people underestimate how valuable their information is, researchers explain. In fact, 42 percent of respondents said they think their accounts aren’t valuable enough to be worth a hacker’s time. When asked further about why they reuse passwords, 60 percent of users said they are afraid of forgetting their login information, while 52 percent said they want to “be in control” and know all of their passwords.
“People seem to be numb to the threats that weak passwords pose,” said researchers. “Technology like biometrics is making it easier for them to avoid text passwords all together and many people are simply comfortable using the ‘forgot password’ link whenever they get locked out of their accounts.”

When it does come to security, the majority of respondents are prioritizing their financial accounts over their email, medical records and work-related accounts. For instance, 69 percent of respondents said they would create stronger passwords for their financial accounts, and 62 percent said that they have multi-factor authentication (MFA) enabled for their financial accounts. On the flip side, only 29 percent said they would create a stronger password for work-related accounts, and 22 percent said they have MFA enabled for work-related accounts.

The big “password problem” has plagued the security industry for years. Poor password hygiene, including reusing passwords or picking easy-to-guess passwords, is greatly exacerbating many of the major issues that plague the cybersecurity landscape, security experts like Troy Hunt have said in the past. Making matters worse, passwords are appearing left and right online as part of major data breaches – yet victims aren’t changing their passwords at all across various platforms. The Collection #1 data dump, which included 773 million credentials, and subsequent Collection #2-5 dumps, show exactly how many passwords are available on the Dark Web and underground forums.
“Respondents are protecting their work accounts at a lower rate than their personal,” said researchers. “We can see that security behaviors are flawed for personal data, and these bad habits extend into your business.”
How do I select a backup solution for my business?
26.5.2020 Net-Security Security
42% of companies experienced a data loss event that resulted in downtime last year. That high number is likely caused by the fact that while nearly 90% are backing up the IT components they’re responsible for protecting, only 41% back up daily – leaving many businesses with gaps in the valuable data available for recovery.
In order to select an appropriate backup solution for your business, you need to think about a variety of factors. We’ve talked to several industry professionals to get their insight on the topic.
Oussama El-Hilali, CTO, Arcserve
select backup solutionBefore selecting a backup solution, IT leaders must ask themselves where the majority of data generated by their organization resides. As SaaS-based collaboration and storage systems grow in popularity, it’s essential to choose a backup solution that can protect their IT environment.
Many people assume cloud platforms automatically back up their data, but this largely isn’t the case. They’ll need a solution with SaaS backup capabilities in place to safeguard against cyberattacks and IT outages.
To further prevent downtime, organizations should also consider backup solutions that offer continuous replication of data. That way, in case of unplanned outages, they can seamlessly fail over to a replica of their systems, applications and data to keep the organization up and running. This is also helpful in case of a ransomware attack or other data corruption – organizations can revert to a “known good” state of their data and pick up where they left off before the incident. Generally, all backup tools should provide redundancy by using the rule of three – have at least three copies of your data, store the copies on at least two different media types, and keep at least one of those copies offsite.
Finally, it’s important to weigh the pros and cons of on-prem versus cloud-based backups. Users should keep in mind that, in general, on-prem hardware is more susceptible to data loss in the event of a natural disaster. There’s no “one size fits all” solution for every organization, so it’s best to take a holistic look at your specific needs before you start looking for a solution – and continue to revisit and update the plan as your organization evolves.
Nathan Fouarge, VP Of Strategic Solutions, NovaStor
select backup solutionWhen looking for a backup solution for your business there are a number of questions to ask to narrow down the solutions you want to look at.
Here’s what you should be prepared to answer in order to select a backup solution for your business:
How much downtime can you afford, or how fast do you need to be back up and running? In other words what is your restore time objective (RTO).
How much data am I willing to lose? In other words what is your restore point objective (RPO). Are you willing to just take daily backups so you have the possibility to lose an entire days’ worth of work or do you need a solution that can do hourly or continuous backup?
How long do I need to keep historical data? Do you have some compliancy requirements that makes you keep your data for a long time?
How much data do you have to backup and what type of data/applications do you need to back up?
How many copies of the data and where do you want to store it? Do you want to do the recommended 3-2-1 backup solution so 3 copies of the data. Do you want to keep all the backups locally, offsite(USB drive or replicated NAS), cloud?
Then the ultimate question of how much you are willing to spend for a backup solution.
Once you have all of those questions answered then you can look into what solutions fit your into what you are looking for. More than likely once you start looking for solutions that fit your criteria you will have to reevaluate some of the answers to the questions above.
Konstantin Komarov, CEO, Paragon Software
select backup solutionThe most important part is how you backup your data, not how you organize it. The key aim is to provide the safety regardless of whether you back up a single database or clone the entire system. The best practice and the most cost-effective way would be to implement “incremental backups” and replicate the data both to the local storage and to the cloud.
Incremental backup is an approach when replication is performed only to some updated part of the system or database, not the entire one. This enables to shorten the time of the backup process and amount of storage space used. Replication to both the local storage and to the cloud may guaranty the best safety of your data in case the physical disk you are baking the data up to is damaged or lost.
However, to make the backup effective and non-stop, it needs to be scheduled and managed with an application deployed on some dedicated end-point which should work side-by-side with your IT infrastructure not to slow down or prevent the entire system. So, the best decision would be to build up your own backup, using open cloud backup platforms, which consists of the ready-to-go algorithm and tools to create a solution fully adjusted to the needs of a particular business.
Ahin Thomas, VP, Backblaze
select backup solutionWhen choosing a backup solution for your business, consider three factors: optimize for remote first, sync vs. backup, and recovery.
As businesses grow, implementing a strong backup strategy is challenging, especially when access to employees can change at a moment’s notice. That’s why it’s important to have a backup solution that is easy to deploy and requires little to no interfacing with employees—your COVID-stressed IT team will thank you.
Secondly, Dropbox and Google Drive folders are not backup solutions. They require users to drop files in designated folders, and any changes made to a file are synced across every device. A good backup solution will ensure all data is backed up to the cloud, and will work automatically in the background, backing up all new or changed data.
Data recovery is the final piece of the puzzle, and most often overlooked. Data loss emergencies are stressful, so it is vitally important to understand how recovery works before you choose a solution. Make sure it’s fast, easy, and works whether you’re on or off site. And test it regularly! You never know when your coworker (aka kid) will spill a sippy cup all over your laptop.
Nigel Tozer, Solutions Director EMEA, Commvault
select backup solutionFor many organizations, the realization that their backup products are no longer fit for purpose comes as a very unwelcome discovery. Anyone arriving at this kind of crossroads faces some big decisions: one of the most frequently occurring is whether to add to what you have, or go for something new.
For anyone in that position, there are four simple considerations that can help inform decisions about backup strategy:
Flexibility – Make sure your backup solution supports a wider ecosystem than just what you’re using today. You don’t want it to hinder your agility or cloud adoption down the line.
Automation – Look for solutions where intelligent automation, even AI, can help dispense with the specialist or mundane elements of backup processes and free up busy IT teams’ time.
Budget – Low cost software that needs a dedupe appliance as you grow, or an appliance with a rigid upgrade path can turn out to be more costly long term – so do your research.
Consolidation – Many products typically means silos, wasted space and more complexity. Consolidating to a backup platform instead of multiple products can make a real difference in infrastructure savings, and reduced complexity.
What hinders successful threat hunting?
26.5.2020 Net-Security Security
As more organizations implement successful threat hunting operations, a SANS Institute survey finds that they are facing common challenges with employing skilled staff and collecting quality threat intelligence.
successful threat hunting
“Without a sufficient number of skilled staff, high-quality intelligence, and the right tools to get visibility into the infrastructure, success with threat hunting will remain limited,” says survey author Mathias Fuchs.
“A world where we’ll see a unified, widely accepted golden standard of threat hunting remains in the future, but we are headed in the right direction.”
Key challenges in threat hunting
The survey highlights key challenges, limitations, and successes that organizations self-identify about their approach to threat hunting. Results indicate that threat hunting has arrived in the majority of organizations:
65% of respondent organizations report they are already performing some form of threat hunting
Another 29% are planning to implement threat hunting within the next 12 months
With the concept of threat hunting being relatively new for many organizations, however, only 29% of respondents consider themselves mature or very mature in their threat hunting, with nearly 68% self-identifying their threat hunting as immature or still maturing.
Struggling to attract qualified threat hunters
Many organizations indicate that one of their top challenges is finding and employing the right experts to enable them to maintain an advanced threat hunting operation. A second main challenge respondents face is the quality of threat intelligence upon which their threat hunting is based.
Even though many organizations struggle to attract qualified threat hunters, only 21% of respondents currently outsource their threat hunting activities to external parties. Despite that, the majority of respondents rely on externally produced threat intelligence, yet only one-third of respondents claim they are highly satisfied with their sources. This presents an opportunity for organizations to improve, as well-curated threat intelligence can be leveraged to augment inexperienced threat hunters.
Measuring the benefit of threat hunting
The survey data also showed that organizations are beginning to have methodologies in place that enable them to measure the benefit of threat hunting, which bodes well for broader industry.
“Measuring the benefits of threat hunting is important,” Fuchs says. “Good threat hunting means that you probably never hear from these teams. The only indication for upper management that threat hunting even exists is that they have to foot the bill. That might be a tough sell, so if we have more ways to express the benefit of threat hunting, funding might get better, which ultimately might advance the general maturity level of threat hunting in the industry.”
Global DX spending to grow 10.4% in 2020
26.5.2020 Net-Security Security
Spending on the digital transformation (DX) of business practices, products, and organizations will continue at a solid pace despite the challenges presented by the COVID-19 pandemic, IDC reveals.
dx spending
Global spending on DX technologies and services is forecast to grow 10.4% in 2020 to $1.3 trillion. While this is notably slower than the 17.9% growth in 2019, it remains one of the few bright spots in a year characterized by dramatic reductions in overall technology spending.
“COVID-19 has upended the global economy, with direct negative implications on the way businesses invest in IT,” said Craig Simpson, senior research manager with IDC’s Customer Insights and Analysis Group.
“DX technology investment has not gone unscathed, but so far it has been affected to a lesser extent since many large-scale DX projects underway or planned are instrumental to broader strategic business initiatives. Compared to IDC’s pre-COVID-19 forecast, the five-year growth rate for digital transformation spending has declined by less than two percentage points.”
Spending by industries
The industries that will see the slowest year-over-year growth in DX spending are the ones experiencing the greatest impact from the economic downturn caused by the pandemic. Personal and consumer services, which includes hotels, theme parks, casinos, and movie theaters, will only see an increase of 5.3% in its DX spending this year, down from 18.4% growth in 2019.
Similarly, discrete manufacturing, the industry with the largest digital transformation spending amount, will only grow 6.6% this year, down from 14.5% growth in 2019. The industries expected to see the strongest growth in DX spending in 2020 are construction (16.3%) and healthcare (15.7%), both of which will see spending grow more slowly than last year.
“COVID-19 has wiped off almost $500 billion of worldwide DX technology investment between 2020-2023 from our pre-COVID-19 forecast,” added Eileen Smith, program vice president with IDC‘s Customer Insights and Analysis Group.
“Yet despite these losses, pockets of growth opportunities exist across most industries when diving deep into specific use cases that solve specific business problems. A few examples include RPA-based claims processing in insurance, digital visualization in education, omnichannel commerce platforms in telecommunications, and clinical trial operational excellence in process manufacturing.”
DX use cases
The DX use cases – discretely funded efforts that support a particular program objective – that will receive the most spending this year include autonomic operations ($51 billion), robotics manufacturing ($47 billion), and root cause ($35 billion), all of which will be driven by the manufacturing sector.
The DX use cases that will see the greatest year-over-year growth in spending are virtualized labs and digital visualization in the education sector, robotic process automation-based claims processing in insurance, and augmented design management in the professional services industry. Of the 278 DX use cases identified, only nine will see a decline in spending this year.
The United States will remain the largest geographic market for DX spending, delivering roughly one third of the worldwide total in 2020. Western Europe will be the second largest region for DX spending, following closely by China. These two regions will also deliver the strongest year-over-year growth in DX spending at 13.6% for China and 12.8% for Western Europe.