Security Articles - H 2020 1 2 3 4 5 6 7 8 9 10 Security List - H 2021 2020 2019 2018 1 Security blog Security blog
Tips to Stay Secure on Summer Vacations
7.7.2017 securityaffairs Security
In the excitement of summer vacations, most of us forget to equip ourselves with the privacy tools and needed security measures. Yet, such flawed data security could ruin your vacations as the cyber goons always remain on work.
Therefore, here we have listed some essential steps that are must to secure your sensitive information you carry with yourself while traveling.
Don’t Divulge the plans for your summer vacations
In the era of the globally connected smart world, internet users often share their personal experiences on their social accounts. Yet, these people who are connected with us through our social accounts are not the one to whom we are closely familiar with.
There are some common concerns and security tips while using your social account and sharing personal details on it. You may wait until you return from the vacations to upload the pictures or your location updates instead of confessing at the spot. However, the ones who are making such divulgence are providing cyber thefts a real-time opportunity to exploit your sensitive data.
Graham Cluley, Chief Technology Officer at UK tech security firm Sophos says;
“Social networks are great fun, and can be advantageous but people really need to understand that it’s a complicated world and you need to step wisely.”
“People should just exercise common sense online, but the problem with common sense is that it’s not very common. If you wouldn’t invite these people into your house to see your cat, you certainly wouldn’t let them see pictures from holiday.”
To remain secure, there are few tips you should follow while traveling;
Make your post visible to the people you know and not let them on public display.
Disable the GPS feature from your phone and social media accounts.
Don’t provide check-ins to your places such as Hotels, Airport, and others.
Keep Your Devices and Web Browsers Updated
Updating your devices and web browsers is a consistent advice from security experts as a precaution to avoid security flaws and cyber attacks. Unpatched devices are at a risk of vulnerability exploitations which could be averted through updating your systems and devices.
Carrying devices such as Smartphones, laptops, and tablets make your vacation more happening, joyous and memorable. Yet, they could cause trouble when their systems are outdated.
summer vacations
Infosec Analyst Yasin Soliman says;
“Don’t forget to check the browser software installed on your devices. The ever-increasing uptick of web-based services for work and play means it’s vital that your web browser remains safe and secure when traveling.”
A recommended privacy measure also includes secure browsers that you should have on your devices.
Turn off the Wi-Fi devices Not in Use
You should turn off all the Wi-Fi connections at home when going to the vacations. Keeping that Wi-Fi on could provide an opportunity to cyber criminals who could easily exploit vulnerabilities in an open Wi-Fi.
Communications director of the Internet Education Foundation, Danielle Yates says,
“An open and unsecured network can be accessed by anyone within range and, further, if communications are not secure, it’s possible someone with malicious intent could intercept emails or even view private files and records.”
However, you must make sure that all the IoT devices in your house are disconnected from the internet. Also while traveling you should avoid public Wi-Fi connections that could be harmful to your device’s security.
Disable GPS When Not Necessary
While on vacations most of the people are new to the places they want to visit. Therefore, they often enable GPS for directional help and leave it on. Yet, such excitement could expose you to the vulnerability and security threats.
Kim Crawley, Information security writer says;
“While on holiday, only turn GPS on your phone or tablet when you need to use it. Not only will you save your battery; you’ll also be more difficult for an attacker to geolocate. This advice also applies to when you’re not on holiday. There are a lot of websites, apps, and online services these days that’ll ask for your geolocation to be enabled. Never enable it unless you absolutely must.”
Government Accountability Office said,
“Specifically, they are concerned that location data can be used for purposes other than to provide services to the consumer, such as selling the data to others for marketing. They also have concerns that location data can be used to track where consumers are, which can, in turn, be used to steal their identity, stalk them, or monitor them without their knowledge. In addition, location data can be used to infer other sensitive information about individuals such as their religious affiliation or political activities.”
USB Outlets Should be Avoided
To attract the travelers and visitors most of the hospitality industry organizations such as Hotels provide the facility of USB outlets to charge their devices. However, if you are one of the travelers it’s never a great idea to charge your device from such outlets.
The owner of Sherpa Intelligence LLC, Tracy Z. Maleeff elaborates the reason of this as;
“These ubiquitous ports could possibly do harm to your devices rather than just charge them. Unlike a regular outlet plug, charging via a USB plug could result in a transfer of data from the port to your device. Why risk having malware loaded onto your device when you only wanted a charge?”
To overcome these problems you could use alternatives such as phone charger or a regular wall outlet.
Follow Basic Security Precautions
The previously discussed privacy measures are necessary to follow while being on vacations. Also, they are especially applicable while traveling but there are some basic online security precautions you must follow as a primary layer of defense. Without these, you could be in trouble.
David Jamieson, a Cyber Security individual described some of these measures;
“If ever there is a time to encrypt your laptop, ensure your files are backed up or stored in the cloud, turn on your firewall, confirm your anti-virus and anti-malware applications are up-to-date, and use complex passwords for your web accounts, THIS IS THE TIME. Criminals do NOT let down their guard; rather, they constantly work hard to steal from us.”
So, keeping yourself vigilant could save you from data thefts. Basic privacy measures such as avoiding public Wi-Fi, using secure browsers and software updates should be among your highest concerns while exploring the world.
Have a Pleasant Journey
Being data security literate just require some simple techniques to remember. Yet, such minute incentives could exempt you from the unease of being prone to vulnerabilities. With your data being secure, you could have a much joyous experience of swimming, camping, and the sunbath.
Websites Increasingly Using Security Technologies: Mozilla
30.6.2017 securityweek Security
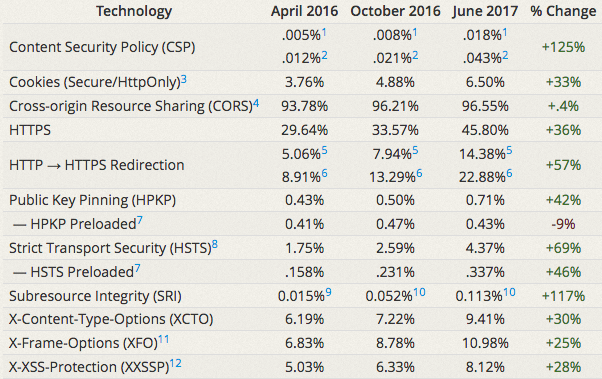
An analysis conducted using Mozilla’s Observatory tool has showed that modern security technologies are increasingly used by Alexa top 1 million websites.
Observatory, a free and open source tool developed by Mozilla Information Security Engineer April King, was announced in August 2016. The tool is designed to allow website developers and administrators to determine if they are using available security technologies at their full potential.
Observatory grades websites based on their use of security technologies such as Content Security Policy (CSP), Contribute.json, cookies, cross-origin resource sharing (CORS), HTTP Public Key Pinning (HPKP), HTTP Strict Transport Security (HSTS), redirections, subresource integrity, and X-Content-Type-Options, X-Frame-Options and X-XSS-Protection headers.
When the tool was first launched, King pointed out that usage rates of modern defensive security technologies were very low. A few months later, Observatory showed some improvements and the most recent data also shows an upward trend in the adoption of these technologies.
For example, the number of Alexa top 1 million websites using CSP has increased by 125 percent since April 2016. The number of sites using HTTPS has also increased by 36 percent, or roughly 119,000 websites, over the same period.

King pointed out that the increasing use of CSP is surprising, especially since the technology is not easy to implement on both new and existing websites.
According to King, more than 50,000 websites used the Mozilla Observatory to assess their level of security and over 2,500 of them have improved from a failing grade to an A or A+. Over 27,000 sites previously rated F got better grades in the past 8 months.
However, while there have been significant improvements, more than 93 percent of sites scanned using Observatory still received an F as of June 2017. Only less than one percent of the world’s most popular websites received an A+, A or B grade.
UK's Metropolitan Police Still Using 10,000 Windows XP Computers
29.6.2017 securityaffairs Security
Legacy Windows XP systems used by public authorities in the UK remains a concern. The WannaCry outbreak last month followed by the current 'NotPetya' outbreak -- both using a vulnerability patched in newer versions of Windows, but initially unpatched in XP -- highlights the problem.
Information obtained by Steve O'Connell, a member of the London Assembly and a Conservative Party spokesperson for policing and crime, shows that the Metropolitan Police Service (MPS, or the Met) was still using 18,293 XP machines on their network at the time of providing the information. Since XP is no longer supported by Microsoft, it is left vulnerable to any new exploits such as EternalBlue and DoublePulsar -- and it appears that only the tendency for WannaCry to crash XP rather than infect it prevented the worldwide outbreak from being far worse than it was.
The Met's position is more precarious than implied by O'Connell's figures. Last month, the UK's data protection regulator, the ICO, published findings (PDF) from a consensual audit of the Met. While finding some areas of 'good practice', it also noted other areas in need of improvement.
In particular, one area for improvement includes the continued use of XP on some desktops and laptops leading to "a residual risk to personal data." But in relation to WannaCry and NotPetya, this risk is magnified by weaknesses in both the Met's backup and business continuity procedures. "Backup arrangements for file systems are not tested to ensure that they are recoverable in the event of a disaster."
Furthermore, "The database used to store BC information is unsupported and not backed up."
The ICO's conclusion was that "The audit has identified considerable scope for improvement in existing arrangements to reduce the risk of non-compliance [with the Data Protection Act]."
The combination of a vulnerable system and untested recovery capabilities is particularly susceptible to ransomware -- and even more so where the ransomware attacks are more intent on mischief than collecting ransoms, as seems to be the case with both WannaCry and NotPetya. The threat to, or potential loss of, personal data stored by the Metropolitan Police is particularly concerning.
"It is vital the Met is given the resources to step up its upgrade timeline before we see another cyber-attack with nationwide security implications," warns O'Connell. But, of course, things are never so simple. SecurityWeek reached out to the Met to confirm O'Connell's figures, and received the following statement:
"The MPS is undergoing a complete refresh of its information technology processes, infrastructure, and equipment - including its desktop computers.
"However, the upgrade programme is not as simple as it would be for many other organizations due to the amount of specialist legacy software upon which parts of the MPS still rely.
"Replacements or remediation for this software that are compatible with a more modern operating system have to be ready before the roll-out is completed to ensure continued operational effectiveness.
"We have completed the upgrade of just over 17,000 devices to Windows 8.1, and this reduces the number of desktops running Previous XP to around 10,000."
The spokesperson did not know, and was unable to find out in time for this article, whether the Met has patched all its Windows systems (not just the XP ones) against MS17-010 vulnerabilities (also known as the EternalBlue vulnerabilities) after the WannaCry outbreak. However, he did add, "The entire Met ICT estate has a number of layers of industry-leading security, which we have been monitoring closely over the past 24 hours. The MPS estate currently remains un-impacted by the cyber-attack and our security checks continue."
The complicating factor of legacy software on legacy systems is a problem, and not just for the Met. "I'm sympathetic to the fact that financially stretched government agencies and public services may not feel that an OS upgrade is the best use of scarce resources," independent security expert David Harley told SecurityWeek.
"Sometimes," he continued, "there are technical reasons for not upgrading a system required to run specific software or peripherals. There may be systems for which an OS upgrade is expected to damage functionality for other reasons, such as underpowered hardware. There are systems that may not require updating because they're fully air-gapped, I suppose. And the risk from running systems that can no longer be updated is sometimes overhyped: there's plenty of malware that doesn't rely on unpatched Windows versions to allow it to execute."
But none of this means that organizations can relax their efforts to upgrade XP systems. "Nonetheless," concluded Harley, "the risk of attack by malware that makes use of vulnerabilities in unpatched machines (such as the new Petya variant that apparently makes use of EternalBlue) is quite significant enough to make it unwise to rely on systems that are no longer normally updated, even if the agencies concerned are taking advantage of rare events like Microsoft's XP patch in May... After all, dangers to their data, systems and internal processes don't only affect their 'business' but all of us."
The bottom line is that 10,000 XP systems still in use by the Metropolitan Police Service is really 10,000 too many.
Corvil Integrates its Security Analytics Into Cisco's Tetration Platform
26.6.2017 securityweek Security
At Cisco Live, Las Vegas Monday, IT analytics firm Corvil announced the integration of its Security Analytics with the Cisco Tetration Analytics platform. The intention is to combine Corvil's realtime packet-level analysis with Tetration's vast big data repository of downstream application-level data flows to provide an early, rich, granular and consistent detection of anomalous communications indicative of compromise.
Tetration was launched by Cisco in June 2016. It was described as "a platform designed to help customers gain complete visibility across everything in the data center in real time -- every packet, every flow, every speed." The aim is to provide CIOs and CISOs complete visibility into today's complex, dynamic and heterogenous data center.
In February 2017, Cisco announced Tetration 2, now automating policy enforcement and providing APIs. "Cisco is continuing its tradition of open ecosystems by working with partner companies to build applications and integrations with their solutions," it announced. It can be used, said the announcement, to "define use cases specific to their environment, and deploy validated application segmentation policies."
It is into this that Corvil has integrated its Security Analytics product.
"Cisco records the communications flows, and puts those flows into this big repository called Tetration," David Murray, chief business development officer at Corvil, told SecurityWeek. "It then uses those flows to be able to map application interdependencies and say here is how applications are communicating -- but it's a lot of data they're aggregating, billions of flows that are communicating on an ongoing basis, across an enterprise."
This is an essential step in the evolution of network surveillance, suggests Murray. "If you think about historical systems surveillance -- especially where regulation and governance requires that surveillance -- the original perimeter and signature surveillance is no longer adequate. Surveillance has now evolved into monitoring what is communicating with what and when -- but even then it is hard to provide sufficient granularity. It is increasingly not just who is communicating with what and when, but also what is actually being communicated."
This is where Corvil's Security Analytics with its realtime packet-level analyses adds value to Tetration. "For example," said Murray, "flow data by its nature is going to see a certain amount of communication between two points. It may even understand that a particular protocol is being used; for example, it might recognize DNS traffic. But by opening up the packet we are able to see what is happening within that flow; that, for example, there is something tunneling within that DNS traffic. Or we're able to see specific filenames, or error types that are being reported back and forth within that communication. Furthermore, we're able to see things like which user is logged on by analyzing packet data for LDAP and Kerberos."
This is where the integration with Tetration 2 becomes particularly valuable. "By taking this information," he continued, "and enriching the flow data (such as administrator level tunneling data with a particular type of fileset) we provide the ability to initiate an automatic response through Tetration that says 'immediately quarantine that host'."
The value of Corvil to Tetration customers is that security policy enforcement can be invoked on an analysis of the flow content rather than just the flows themselves. The value of Tetration to Corvil is that it provides a massive big data repository of downstream data that can be analyzed to provide more accurate responses and reduce false positives.
"Improvements in security operations, network optimization, and business process optimization hinge on applying advanced analytics techniques to network data,” said Shamus McGillicuddy, senior analyst for Enterprise Management Associates. "The depth and insight from Corvil Analytics combined with Cisco's Tetration Analytics will provide richer understanding of workload characteristics, improved detection of evasive security threats, and more effective transaction insight. This type of integration is needed to drive tighter alignment between network, application, security, and business teams."
"It takes an ecosystem to address today's complex challenges of data center visibility, service assurance, and security," said Murray. "The combination of Cisco Tetration's data and our packet-level data helps provide very granular and enforceable security policies."
Further information on the integration of Corvil Security Analytics with Cisco Tetration Analytics will be available at Cisco Live this week.
Elastic Beam Emerges From Stealth With API Security Solution
21.6.2017 securityweek Security
Redwood City, Calif.-based Elastic Beam emerged from stealth mode on Wednesday with the launch of a security solution designed to detect and block cyberattacks targeting application programming interfaces (APIs).
The company’s flagship product, API Behavioral Security (ABS), is an engine that uses artificial intelligence (AI) to detect threats in real time. Data from ABS is sent to the API Security Enforcer (ASE) to block the attack and prevent the attacker from reconnecting.
According to Elastic Beam, its solution can detect data exfiltration, unauthorized changes or removal of data, distributed denial-of-service (DDoS) attacks, code injections, brute force attempts and authentication via stolen credentials, API memory attacks, WebSocket attacks and other types of external and insider threats.
The product, designed for API gateways, API management platforms and app servers, works in both public and hybrid cloud environments and on premises. The vendor says it also has the ability to scale automatically using elastic clustering.
“We look at the whole traffic pattern between the end-point/client and the system being accessed,” Bernard Harguindeguy, founder and CEO of Elastic Beam, told SecurityWeek. “We implemented AI algorithms that combine advanced AI techniques with our strong API behavior and security expertise to automatically sort out sessions that are not normal.”
“The system does not use predefined policies or security rules, it is self-learning, and uses the AI engine to continuously update knowledge of the environment and traffic. It uses much more than a traditional baseline to identify an attack. Also the attacks are identified as such – not just anomalies. So we will flag anomalies if something is ‘off’ but not really an attack – and we will identify an attack when we believe that it is truly an attack,” Harguindeguy explained.
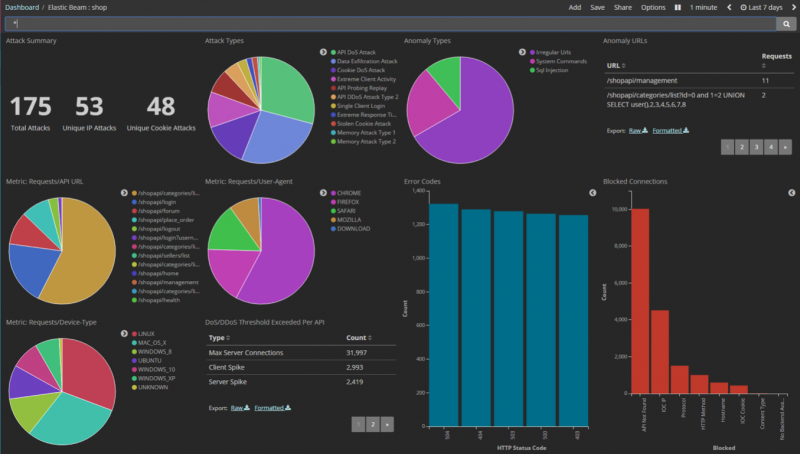
For forensic analysis and reporting purposes, Elastic Beam says its product provides tracking and reporting capabilities for all API activity. The solution also includes a decoy API feature that relies on a deception mechanism to lure hackers and capture attack information for analysis.
The product is available through a subscription pricing model based primarily on API transaction volumes. Elastic Beam, which has so far been funded by its founders and angel investors, says ABS has already been tested in banks, government agencies, cloud services and IoT environments.
WebSites Found Collecting Data from Online Forms Even Before You Click Submit
21.6.2017 thehackernews Security
'Do I really need to give this website so much about me?'
That's exactly what I usually think after filling but before submitting a web form online asking for my personal details to continue.
I am sure most of you would either close the whole tab or would edit already typed details (or filled up by browser's auto-fill feature) before clicking 'Submit' — Isn't it?
But closing the tab or editing your information hardly makes any difference because as soon as you have typed or auto-filled anything into the online form, the website captures it automatically in the background using JavaScript, even if you haven't clicked the Submit button.
During an investigation, Gizmodo has discovered that code from NaviStone used by hundreds of websites, invisibly grabs each piece of information as you fill it out in a web form before you could hit 'Send' or 'Submit.'
NaviStone is an Ohio-based startup that advertises itself as a service to unmask anonymous website visitors and find out their home addresses.
There are at least 100 websites that are using NaviStone's code, according to BuiltWith, a service that tells you what tech sites employ.
Gizmodo tested dozens of those websites and found that majority of sites captured visitors' email addresses only, but some websites also captured their personal information, like home addresses and other typed or auto-filled information.
How Websites Collect 'Data' Before Submitting Web Forms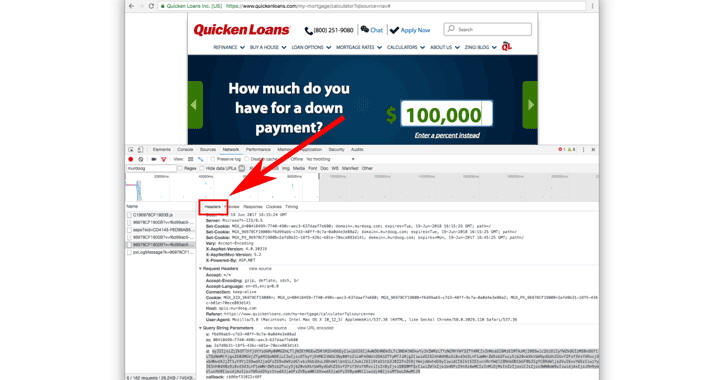
Using JavaScript, the websites in question were sending user's typed or auto-filled information of an online form to a server at "murdoog.com," which is owned by NaviStone, leaving no option for people who immediately change their minds and close the page.
When the publication asked NaviStone that how it unmasks anonymous website visitors, the company denied revealing anything, saying that "its technology is proprietary and awaiting a patent."
However, when asked whether email addresses are gathered in order to identify the person and their home addresses, the company's chief operating officer Allen Abbott said NaviStone does not "use email addresses in any way to link with postal addresses or any other form of PII [Personal Identifiable Information]."
"Rather than use email addresses to generate advertising communications, we actually use the presence of an email address as a suppression factor, since it indicates that email, and not direct mail, is their preferred method of receiving advertising messages," Abbott said.
Some websites using NaviStone's code are collecting information on visitors who are not even their customers and do not share any relationship with the companies.
"Three sites—hardware site Rockler.com, gift site CollectionsEtc.com, and clothing site BostonProper.com—sent us emails about items we'd left in our shopping carts using the email addresses we'd typed onto the site but had not formally submitted," Gizmodo writes.
After the story had gone live, NaviStone agreed to no longer collect email addresses from visitors this way, as Abbott said, "While we believe our technology has been appropriately used, we have decided to change the system operation such that email addresses are not captured until the visitor hits the 'submit' button."
Disable Auto-Fill; It’s Leaking Your Information!
In order to protect yourself from such websites collecting your data without your consent, you should consider disabling auto-fill form feature, which is turned on by default, in your browser, password manager or extension settings.
At the beginning this year, we also warned you about the Auto-fill feature, which automatically fills out web form based on data you have previously entered in similar fields but can be misused by attackers hiding fields (out of sight) in the web form and stealing your personal information without your knowledge.
Here's how to turn this feature off in Chrome:
Go to Settings → Show Advanced Settings at the bottom, and under the Passwords and Forms section uncheck Enable Autofill box to fill out web forms with a single click.
In Opera, go to Settings → Autofill and turn it off.
In Safari, go to Preferences and click on AutoFill to turn it off.
Also, think twice before filling your details into any web form, before it gets too late.
Cisco Talos releases the BASS open source malware signature generator
21.6.2017 securityaffairs Security
Cisco Talos intelligence group released an open source framework named BASS that is designed for automatically generating antivirus signatures from malware.
BASS is an automated signature synthesizer, it is able to automatically create signatures from the analysis of a malicious code that belongs to previously generated clusters.
The BASS tool aims to simplify malware analysis and its main goals are to improve resource usage and make malware analysis easier.
BASS is designed to reduce the resource usage of Cisco ClamAV open source antivirus engine, it aims to generate more pattern-based signatures instead of hash-based signatures.
Every day the ClamAV database is integrated with thousands of new signatures and many of them are hash-based. Unfortunately, using hashes to detect a malware allows the identification of single malicious file and not an entire malware cluster.

“BASS (pronounced “bæs”) is a framework designed to automatically generate antivirus signatures from samples belonging to previously generated malware clusters. It is meant to reduce resource usage of ClamAV by producing more pattern-based signatures as opposed to hash-based signatures, and to alleviate the workload of analysts who write pattern-based signatures. The framework is easily scalable thanks to Docker.” reads the description for the Framework published on GitHub.
“Please note that this framework is still considered in the Alpha stage and as a result, it will have some rough edges. As this tool is open source and actively maintained by us, we gladly welcome any feedback from the community on improving the functionality of BASS.”
BASS is written in Python framework implemented as a cluster of Docker containers. It is scalable and implements web services that allow it interacting other tools.
Experts at Cisco Talos explained the BASS framework is able to import malware clusters from various sources. Once the malware cluster is filtered to check that the files correspond to the input expected by BASS framework, the binaries are disassembled using IDA Pro or other disassemblers, then BASS searches the samples for common code that can be used to generate the signature.
Time to Detect Compromise Improves, While Detection to Containment Worsens: Report
21.6.2017 securityweek Security
Cost of Malvertising is Minimal; Price of Zero-days is Rising, Researchers Say
Throughout 2016, Trustwave investigated hundreds of data breaches in 21 different countries, and conducted thousands of penetration tests across databases, networks and applications. An analysis of key findings from this activity is presented in the 2017 Trustwave Global Security Report published Tuesday (PDF).
The result is a mixed bag. Overall, security defenses have slightly improved, but attacks continue to evolve. Detection is improving. Trustwave says the median time to detect a compromise has decreased from 80.5 days in 2015 to 49 days in 2016. The difference between self-detected and third-party detections is, however, dramatic: just 16 days for self-detected and 65 days for externally detected.
It should surprise no-one that a company that has invested in security technology able to detect intrusions would detect intrusions faster than a company that relies on external detections. Nevertheless, this demonstrates the effectiveness of those controls in reducing the dwell time and reducing the attackers' window for exfiltration.
Containment, however, has not improved to any similar degree. The duration from intrusion to containment has dropped from 63 days in 2015 to 62 days in 2016; but the time taken from detection to containment has worsened slightly from 2 days to 2.5 days.
According to Trustwave's figures, North America geographically, and retail vertically, are the most breached sectors. POS breaches rose sharply -- particularly in North America, which has been slow to adopt EMV cards -- from 22% of breaches in 2015 to 31% in 2016.
Malvertising remained the number one source of traffic to exploit kit landing pages; and the cost of malvertising is remarkably low. Trustwave ran its own experiment running online ads testing for vulnerable versions of Flash. "Researchers," notes the report, "estimate an attacker could reach approximately 1,000 computers with exploitable vulnerabilities for about $5 -- less than $.01 per vulnerable machine — far less than the $80 to $400 per 1,000 computers attackers pay for access to infected machines, depending on geolocation."
SecurityWeek asked Lawrence Munro, worldwide VP of SpiderLabs at Trustwave, for his two biggest takeaways from this year's report. What concerns him most is the continuing instance of common vulnerabilities in the majority of applications. "These are not esoteric vulnerabilities," he said, "but ones that map closely to the OWASP Top 10." During 2016, Trustwave's application scanning services found that 99.7% of applications had at least one vulnerability, while the mean number of vulnerabilities was 11 per application.
"Trustwave's on-demand penetration testing service, uncovered almost 30,000 vulnerabilities in web applications in 2016. Analysts classified 79 percent of them as informational or low-risk vulnerabilities, 11 percent as medium-risk, 7 percent as high-risk and 3 percent as critical, the most severe category."
Among the critical vulnerabilities, 13.8% involved authentication bypass. 5.7% involved Heartbleed leakage, 5.1% involved vertical privilege escalation, 4.8% was unencrypted sensitive data and 4.2% were SQLi vulnerabilities.
It is worth stressing that Trustwave's vulnerability scanning was undertaken for customers on commercial applications -- and the clear implication is that developers are still not building in security during development before release.
Munro's second takeaway is the cost of vulnerabilities for sale on the underground market. Trustwave's researchers discovered an alleged zero-day Windows vulnerability being offered for sale at $95,000. Although not following through with an actual purchase, Trustwave researchers on the underground forums believe this was a genuine zero-day being genuinely sold.
"The offer first appeared on a website," explains the report, "that serves as an underground marketplace for Russian-speaking cybercriminals to buy and sell coding services, access to exploit kits and botnet resources, and other illegitimate products and services. A user going by the name 'BuggiCorp' posted a message on May 11 offering to sell a local privilege escalation (LPE) exploit for the Windows kernel for $95,000."
In part, the sale offer reads (translated): "[the vulnerability] exists in all OS [versions], starting from Windows 2000. [The] exploit is implemented for all OS architectures (x86 and x64), starting from Windows XP, including Windows Server versions, and up to current variants of Windows 10."
Trustwave concludes that this was a genuine zero-day being offered for sale, partly because the seller insisted on using the forum's administrator as an escrow party. "The escrow requirement," notes the report, "suggests the offer was real: If BuggiCorp could not deliver the exploit as promised, it would not get paid."
What most intrigued Munro, however, was not the sale of zero-days on the dark web; but the price being demanded. "If zero-days can trade at these figures on the dark web," he asked, "what does that say about the effectiveness of current bug bounty schemes, which rarely pay out anything like this amount?"
Cisco Releases Open Source Malware Signature Generator
20.6.2017 securityweek Security
Cisco’s Talos intelligence and research group announced on Monday the availability of a new open source framework designed for automatically generating antivirus signatures from malware.
The tool, named BASS, has been described as an automated signature synthesizer. The framework creates signatures from malware belonging to previously generated clusters and its main goals are to improve resource usage and make malware analysis easier.
Talos says BASS is designed to reduce the resource usage of Cisco’s ClamAV open source antivirus engine by generating more pattern-based signatures instead of hash-based signatures. The tool can also help reduce the workload of analysts who write pattern-based signatures.
The Python-based framework is implemented as a cluster of Docker containers, which makes it easily scalable, and it leverages web services to interact with other tools.
According to Talos, thousands of signatures are added to the ClamAV database every day and many of them are hash-based. The problem with hash-based signatures, compared to bytecode- and pattern-based signatures, is that a signature is used to identify a single file instead of an entire malware cluster. This has several disadvantages, including a bigger memory footprint.
Pattern-based signatures are easier to maintain compared to bytecode signatures, which is why Cisco prefers this type of signature.
The BASS framework takes malware clusters from various sources and each file is unpacked using ClamAV unpackers. Once the malware cluster is filtered to ensure that the files correspond to the input expected by BASS (i.e. Portable Executable files), the binaries are disassembled using IDA Pro or other disassembler, and the tool searches the samples for common code that can be used to generate the signature.
The source code for the Alpha version of BASS is available on GitHub. Cisco Talos will maintain the tool, but the company welcomes any feedback for improving its functionality.
Cloud Security Firm ShieldX Emerges From Stealth
20.6.2017 securityweek Security
ShieldX Networks Emerges From Stealth Mode With New Product to Protect Cloud Infrastructure
San Jose, CA-based cloud security start-up ShieldX Networks has today emerged from stealth with a new product, Apeiro. Apeiro takes microsegmentation as its baseline, and then layers additional security on top. In November 2015, the company completed a $9 million Series A financing round led by Bain Capital Ventures with participation from Aspect Ventures.
ShieldX delivers its security through microsegmentation that "provides full security controls, as well as visibility, automation and coordination across multiple cloud environments. As a result, a breach in one area of the network will not compromise other areas," claims the company.
ESG Labs has certified that Apeiro "supports VMware vSphere, OpenStack/KVM, and AWS environments, with additional cloud support on the horizon. Highly available and multi-tenant, Apeiro REST APIs support integration with DevOps-oriented processes." It also verifies that Apeiro "is fast and easy to deploy over an existing infrastructure (ShieldX boasts 15 minutes), and enables organizations to natively, automatically segment and secure cloud workloads at scale, across both physical and multi-cloud infrastructures."
But, claims ShieldX, microsegmentation alone is not enough. "Note that microsegmentation only restricts who can communicate to who and not what they say to each other," Dr. Ratinder Paul Singh Ahuja, CEO and founder of ShieldX told SecurityWeek. "This then creates the situation where a compromised system can still propagate malware because microsegmentation by itself doesn't inspect that level of detail in the communications between systems."
In a Friday blog post he gave an example. "The recent WannaCry malware propagated laterally within businesses using the Server Message Block (SMB) protocol. As a matter of policy, you are not going to use micro-segmentation to block the SMB port, or for example, the SQL port, in communications between applications and users in your network as those are used to carry legitimate traffic to conduct business. Yet these are common techniques used for exploits. So, if you now depend on microsegmentation alone to secure your data center or public cloud traffic, you could easily fall prey to WannaCry or the next generation of attack."
Apeiro provides deep packet inspection (DPI), visibility, policy management, and enforcement at cloud scale. Organizations can implement security policies on-demand, based on microsegmentation application-aware access control; threat detection from a combination of 10,000+ threat definitions; malware detection through integration with third-party products such as FireEye; TLS decryption/termination; and URL filtering. DLP is expected in a future release.
Although both the ShieldX announcement and the ESG Labs review specify 'FireEye', Ahuja told SecurityWeek that it is singled out only because many of ShieldX customers already use FireEye. "Apeiro can integrate with other advanced malware detection technologies as well as offer that capability from the ShieldX cloud if customers don't have such systems in place," he said.
The 10,000+ threat definitions, he added, "are sourced commercially as well as from our own research. These are dynamically updated and pushed out to Apeiro installations from the ShieldX cloud."
"We chose ShieldX as our cloud security partner," says Joe Jozen, VP of Tokyo Electron Device Limited (TED), "because our customers want to leverage the power and cost saving benefits of cloud innovation without compromising security. The Tokyo 2020 Olympics are a perfect example of how the partnership between TED and ShieldX will be critical to enabling the secure storage and transfer of information while protecting against cyber threats to provide a safe, enjoyable and connected experience for attendees."
In May 2017, ShieldX was featured in Gartner's 'Cool Vendors in Cloud Security, 2017'. "ShieldX is a pure-play security vendor with a cross-cloud microsegmentation product branded Apeiro that functions as network security middleware to support hosts and containers," writes Gartner. It "will appeal to I&O and security and risk management leaders in enterprises that have a virtualized infrastructure requiring segmentation, especially where those clouds are or will be heterogeneous, or if the enterprise is more a Mode 2 (i.e., DevOps) style and needs Mode 2 security for it."
BAE Systems accused of selling mass surveillance software Evident across the Middle East
18.6.2017 securityaffairs Security
BC Arabic and the Danish newspaper Dagbladet accuse British BAE Systems of selling mass surveillance software called Evident across the Middle East.
The British company BAE Systems has been selling mass surveillance software called Evident across the Middle East, the findings are the result of a year-long investigation by BBC Arabic and the Danish newspaper Dagbladet. The surveillance software was acquired after the purchase of Danish company ETI in 2011, and experts believe it was used by totalitarian governments to persecute opponents and activists.
“You’d be able to intercept any internet traffic,” a former employee told the BBC. “If you wanted to do a whole country, you could. You could pin-point people’s locations based on cellular data. You could follow people around. They were quite far ahead with voice recognition. They were capable of decrypting stuff as well.”
Journalists reported that one of the customers for the Evident software before the ETI acquisition was the Tunisian government, and according to a former Tunisian intelligence official, the surveillance software was used to track down President’s opponents.
“ETI installed it and engineers came for training sessions,” he explained. “[It] works with keywords. You put in an opponent’s name and you will see all the sites, blogs, social networks related to that user.”
Fearing a new Arab Spring, several Middle Eastern governments started internet surveillance to identify and persecute dissents, it was a great business opportunity for Western companies like BAE.
BAE Systems and other firms sustain they are committed to operating ethically and responsibly, respecting laws on international exports to overseas governments.
Freedom of information requests from the BBC and the Denmark newspaper Dagbladet Information demonstrate BAE sold systems to Saudi Arabia, the United Arab Emirates, Qatar, Oman, Morocco, and Algeria.
According to dissidents, the mass surveillance systems made their dirty job.
“I wouldn’t be exaggerating if I said more than 90 per cent of the most active campaigners in 2011 have now vanished,” Yahya Assiri, a former Saudi air force officer now in exile, told El Reg.
Evident was installed by numerous government organizations and the company improved it by adding new decryption add-ons.
The British government expressed concern that the software misuse, it cannot be excluded that Evident could be also used against the Western target.
“We would refuse a licence to export this cryptanalysis software from the UK because of Criteria 5 (national security) concerns,” the British export authority told its Danish counterparts in an email over the sale of Evident to the UAE. The Danes approved the sale anyway.
BAE sells surveillance software in Middle East
The consequences of such sales could come back to haunt the West, according to Dutch MEP Marietje Schaake. She warns that the costs could be very heavy indeed.
“Each and every case where someone is silenced or ends up in prison with the help of EU-made technologies I think is unacceptable,” said Dutch MEP Marietje Schaake.
“I think the fact that these companies are commercial players, developing these highly sophisticated technologies that could have a deep impact on our national security, on people’s lives, requires us to look again at what kind of restrictions may be needed, what kind of transparency and accountability is needed in this market before it turns against our own interest and our own principles.”
Threat Hunting Sqrrl Raises $12.3 Million for Global Expansion
15.6.2017 securityweek Security
Cambridge, Mass-based Sqrrl -- one of the new breed of threat hunters -- has raised $12.3 million in Series C funding. This follows $7 million Series B funding in February 2015, and raises the total investment in the firm to $28.5 million.
Announced this week, the latest investment is led by Boston-based Spring Lake Equity Partners, which will now take a seat on Sqrrl's board. Existing investors Matrix Partners, Rally Ventures and Accomplice also took part. It follows Sqrrl's impressive growth rate of doubling revenue every year for the last four years. The new money will be used to expand Sqrrl's marketing reach, and this is expected to include expansion into Europe.
Sqrrl LogoThe company currently employs about 50 people, mostly in Cambridge. It hopes to expand to about 75 worldwide employees before the end of the year.
"Spring Lake invests in companies with technology platforms that have both a proven track record of customer success and high growth potential," said Jeff Williams, Spring Lake Partner. "Sqrrl's Threat Hunting Platform is enabling Fortune 2000 companies and government agencies to detect and investigate threats that have evaded detection. We are very impressed with their pioneering technology and their leading position in the rapidly growing threat hunting market space."
Threat hunting is considered de rigueur for today's SOCs. Traditional defenses are failing to stop advanced attackers -- who, by definition, are difficult to detect. Threat hunting systems don't wait for the inevitable breach but actively seek out the hidden and subtle indications of an attacker's presence. Threat hunting brings advanced analytics and queries to network data, and is part of the rapidly-evolving machine-learning security revolution.
"Threat hunting has become a top-level initiative in organizations with modern security operations, and those organizations have realized the significant advantages that threat hunting offers to reduce their overall security risk." explains Sqrrl CEO Mark Terenzoni. "Sqrrl makes it feasible for any organization to start threat hunting, and we are excited to use this funding to enable even more organizations to move their security operations from a reactive to proactive security posture."
Sqrrl was formed in 2012, evolving from an NSA database project known as Accumulo. Accumulo was open-sourced in 2011 and became Apache Accumulo. Six of the seven original members of the Sqrrl had worked for the NSA. Sqrrl's platform is built on top of Accumulo.
IBM Adds New Service to Cloud Identity Offering
13.6.2017 securityweek Security
IBM Security announced on Tuesday that a new product designed to help organizations manage how their employees access business applications has been added to the company’s Cloud Identity offering.
IBM Cloud Identity Connect is a new Identity-as-a-Service (IDaaS) that provides quick and secure access to popular cloud applications using single sign-on (SSO) from any device, both from the cloud and on-premises.
According to IBM, the new product aims to address the challenges of managing and securing multiple identities in hybrid cloud environments, which Gartner believes will be the most popular type of cloud.
The new service, expected to become available in the IBM Cloud Marketplace on June 15, can be tested for 30 days for free. Customers of IBM Cloud applications such as Verse and Connections Cloud can use Cloud Identity Connect as a free one-year subscription for up to five apps.
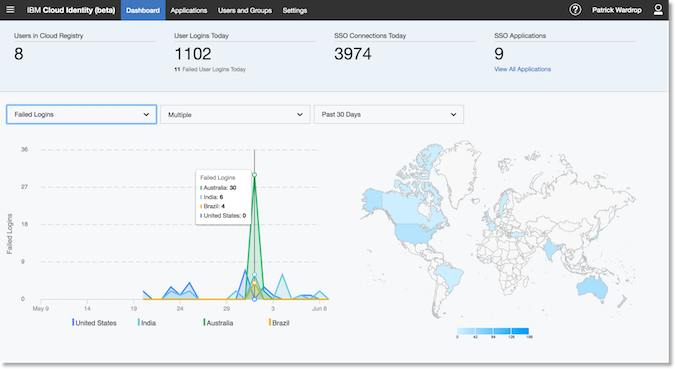
“Businesses need to infuse identity everywhere. Cloud Identity Connect makes it easier than ever before for customers to inspire productivity and efficiency – while ensuring their enterprise is securely managed and can effectively transition to the cloud,” said Jason Keenaghan, Director of Strategy and Offering Management, IAM and Fraud, IBM Security. “Regardless of where an organization is in that transition process, IBM is now positioned to scale on-premise and cloud offerings to meet the unique needs of nearly any business at any time.”
IBM’s Cloud Identity offering also includes Cloud Identity Service, a comprehensive suite of identity and access management (IAM) capabilities designed to make it easier for organizations to move their IAM program to the cloud, and MaaS360 UEM, which is advertised as ideal for organizations that need unified endpoint management (UEM) for mobile devices.
Qualys Launches Container Security Product
13.6.2017 securityweek Security
Cloud-based security and compliance solutions provider Qualys on Monday announced a new product designed for securing containers across cloud and on-premises deployments.
Qualys Container Security, which the company expects to become available in beta starting in July 2017, aims to help organizations proactively integrate security into container deployments and DevOps processes by extending visibility, vulnerability detection and policy compliance checks.
One of the main features of the initial release will allow users to discover containers and track changes in real time. Organizations can visualize assets and relationships, enabling them to identify and isolate exposed elements.Qualys
The product also provides vulnerability analysis capabilities for images, registries and containers. These capabilities can be integrated via the Qualys API into an organization’s Continuous Integration (CI) and Continuous Development (CD) tool chains, allowing DevOps and security teams to scan container images for known flaws before they are widely distributed.
“Containers are core to the IT fabric powering digital transformation,” said Philippe Courtot, chairman and CEO of Qualys. “Our new solution for containers enables customers on that journey to incorporate 2-second visibility and continuous security as a critical part of their agile development.”
In addition to Container Security, Qualys has announced a new add-on for the company’s Vulnerability Management product. The add-on, named Security Configuration Assessment (SCA), provides cloud-based tools for automating configuration assessment of IT assets using Center for Internet Security (CIS) benchmarks.
The SCA add-on allows companies to scan their systems and assess, monitor and remediate security-related issues introduced by improper configurations. The product is already available for an annual subscription whose price depends on number of IPs.
“Recent global cyber-attacks have served as a reminder that companies must take a proactive stance in securing the infrastructure and operations underpinning their digital transformation,” Courtot said. “Qualys SCA helps customers automate the security best practices behind leading benchmarks, and integrate them with DevSecOps for a more proactive approach towards securing today’s digital business.”
Illumio Raises $125 Million to Expand Adaptive Segmentation Business
7.6.2017 securityweek Security
Data center and cloud segmentation firm Illumio announced today that it has raised a further $125 million in a Series D funding round. This adds to the $100 million Series C financing raised in April 2015, and brings the firm's total funding to $267 million.
New and existing investors, including Andreessen Horowitz, General Catalyst, 8VC, Accel and Data Collective (DCVC) all participated -- buoyed by the firm's annualized bookings growth of 400 percent from the first to second year in market. Illumio's customers now include nine of the largest 15 financial companies in the U.S., and four of the top seven SaaS providers.
Illumio LogoThe new capital will be used to expand Illumio's global reach in field sales, marketing and customer support; and continuing R&D. The purpose, said Illumio in a statement today, is to "enable the company to accelerate its vision of making adaptive segmentation the foundation for cybersecurity in every enterprise data center and public cloud."
Segmentation is not a new security concept. In its most basic form, company computers are segmented from the public internet, and OT is segmented from IT, with firewalls. But as cyber attackers have become more sophisticated, and data center infrastructures more complex, the need for internal segmentation has grown. It is the most effective method for containing the insider threat, and for preventing the lateral movement of attackers who breach the firewall perimeter defense.
Indeed, segmentation is increasingly required for compliance and regulations. For example, PCI DSS v3.2 (1.3.6) states, "Place system components that store cardholder data (such as a database) in an internal network zone, segregated from the DMZ and other untrusted networks." Such requirements are only likely to increase both as part of compliance and as a means of demonstrating best security practices to regulators.
"Given the exponential growth of cybersecurity risks, it's clear that segmentation is now one of the largest market opportunities in enterprise software," said Larry Unrein, Global Head of J.P. Morgan Asset Management's Private Equity Group.
But the traditional methods for segmentation -- firewalls and router-enforced zoning -- are difficult, complex and expensive in modern dynamic data centers and public clouds. This is the market and approach that Illumio seeks to disrupt. Rather than imposing rules on separate routers and firewalls around the infrastructure, Illumio provides a platform that invokes the inherent security already available within individual devices.
The segmentation is controlled and enforced from a central policy compute engine (PCE) that activates and manages the enforcement capabilities in existing assets. It doesn't require additional hardware or software that add complexity, become performance chokepoints, and increase costs. Illumio's approach is to allow the right degree of segmentation to precisely where it is needed: a granular and adaptive method.
Using this approach, Morgan Stanley reduced its firewall rules by 90 percent with Illumio, while another customer has reduced 15,000 firewall rules to 40 security policies -- all defined in, contained in, and controlled by the PCE.
"The security segmentation market is already a multi-billion-dollar opportunity," said Andrew Rubin, CEO and co-founder of Illumio; "and Illumio's traction with customers such as Salesforce, Morgan Stanley and Workday demonstrates that the Illumio Adaptive Security Platform can solve these challenges at scale. Illumio is uniquely suited to address the needs of large and small organizations as they shift focus away from the perimeter and towards having complete visibility and control inside the data center and cloud compute environments."
Oracle Improves Cloud Security Offering
5.6.2017 securityweek Security
Oracle enhances cloud security offering
Oracle on Monday announced enhancements to its Identity-based Security Operations Center (SOC) cloud services, including improvements to machine learning, artificial intelligence and contextual awareness.
The Oracle Identity SOC offering includes several cloud services, including the Cloud Access Security Broker (CASB), Identity, Security and Monitoring Analytics, and Configuration and Compliance.
An improvement to the Oracle Identity Cloud Service is the addition of adaptive access capabilities, which aim to address the risks posed by compromised credentials by evaluating each login attempt and providing real-time risk analysis based on factors such as location, device and time of day.
The Oracle CASB Cloud Service can now detect abnormal and risky behavior using supervised and unsupervised machine learning techniques. The product’s user behavior analytics engine establishes a historical baseline for each user and cloud service, and compares all activity with these baselines in order to identify potential threats.
In addition to native automated remediation capabilities, data from the CASB service can be fed to third-party ticketing and incident management systems.
Oracle also announced that its CASB Cloud Service now provides security monitoring and threat detection capabilities for the company’s other SaaS applications, including Human Capital Management (HCM), Enterprise Resource Planning (ERP), and Customer Experience (CX) solutions.
The list of CASB-supported applications now also includes the Slack team communication and collaboration platform. Other supported apps are Salesforce.com, Microsoft Office 365, Box, Google G-Suite, GitHub, Rackspace, AWS and ServiceNow.
The list of supported third-party security solutions, which until now included solutions from Fortinet, Sophos, Palo Alto Networks and Check Point, has also been expanded with the addition of a Blue Coat web gateway that provides visibility into cloud activity.
“We are making a large investment in providing comprehensive security solutions that can help enterprises adapt, manage and strengthen their security posture against external and internal risks,” said Oracle’s Peter Barker. “Our expertise in data science and machine learning enable Oracle to bring unique, scalable and dependable security services to customers transitioning workloads to the Oracle Cloud or third party clouds.”
Google Rolls Out Business-Focused Security Enhancements for Gmail
1.6.2017 securityweek Security
Google today announced a series of improvements to Gmail’s security aimed at making the service better at protecting business data.
As part of the newly rolled out update, Gmail will provide customers with early phishing detection capabilities and "click-time warnings" for malicious links that might have been included in messages coming from outside sources. External reply warnings were also rolled out to help prevent data loss, Andy Wen, Senior Product Manager, Counter Abuse Technology at Google, says.
Gmail’s updated phishing detection mechanism takes advantage of machine learning, and Wen claims the service can keep sneaky spam and phishing messages out of customers’ inboxes with an over 99.9% accuracy. He also points out that 50%-70% of all messages received in Gmail are spam.
To improve their spam detection accuracy, Google launched early phishing detection, a dedicated machine learning model designed to selectively delay messages to perform rigorous phishing analysis. Only potentially suspicious messages will be flagged and delayed to perform additional checks on their content.
According to Wen, this should impact less than 0.05% of messages on average but should result in improved user data protection. In some cases, the additional checks could result in some messages arriving in the user’s inboxes with a delay of up to 4 minutes.
The feature, however, isn’t meant to replace anti-malware/phishing software, and admins can control it from the Admin console. The feature is launched On by default, Google says.
Paired with Google Safe Browsing machine learning, the detection models also aim at finding phishy and suspicious URLs and flagging them to the user.
These models leverage techniques such as reputation and similarity analysis on URLs, thus resulting in Gmail generating new URL click-time warnings for phishing and malware links. The feature was rolled out for Gmail on Android in the beginning of the month.
Aiming at preventing data loss, Gmail now displays unintended external reply warnings to users when they try to respond to someone outside the company domain. The service should know if the recipient is an existing contact or someone the user interacts with regularly, thus avoiding unnecessary warnings being displayed.
“This feature can give enterprises protection against forged email messages, impersonation, as well as common user-error when sending mail to the wrong contacts,” Google explains.
In addition to these enhancements, Google’s email service also received new built-in defenses against ransomware and polymorphic malware, meant to help it block millions of other messages that could potentially harm users.
The feature is meant to correlate spam signals with attachment and sender heuristics, and should result in successfully predicting messages containing new and unseen malware variants, Sri Somanchi, Product Manager, Gmail anti-spam, says.
“We classify new threats by combining thousands of spam, malware and ransomware signals with attachment heuristics (emails that could be threats based on signals) and sender signatures (already marked malware),” Wen notes.
US Says No Laptop Ban on Board Flights From Europe for Now
1.6.2017 securityweek Security
US aviation security officials stepped back Tuesday from imposing a ban on carry-on computers on flights coming from Europe, which had been proposed to guard against possible bomb-laden electronics from the Islamic State group.
But the Department of Homeland Security said a ban, already in place for US-bound flights from the Middle East, could still be implemented for Europe if the threat level worsens.
In a phone discussion with European Home Affairs Commissioner Dimitris Avramopoulos and Transport Commissioner Violeta Bulc Tuesday, DHS Secretary John Kelly "made it clear" a ban on passengers carrying tablet and computer-sized electronics on board flights to the United States "is still on the table," DHS said in a statement.
"Secretary Kelly affirmed he will implement any and all measures necessary to secure commercial aircraft flying to the United States –- including prohibiting large electronic devices from the passenger cabin -– if the intelligence and threat level warrant it."
A European Commission spokesperson confirmed the discussion, saying that no decision had been made on the laptop ban, but that the two sides "agreed to intensify talks" on tightening aviation security.
On March 21, Washington announced a ban on carry-on laptops and other electronics larger than cellphone on direct flights to the United States from 10 airports in Turkey, the Middle East and North Africa.
The move came after intelligence officials learned of efforts by the Islamic State group to fashion a bomb into consumer electronics.
From any of those airports, US-bound passengers were forced to keep their electronics in checked baggage.
One day later Britain announced a similar ban for flights originating from six countries, and by early May DHS was threatening to impose a similar restriction for flights from Europe to the United States.
That would have a huge effect on the coming high travel season, with more than 3,250 flights a week scheduled to leave EU airports for the US this summer.
But after weeks of discussions, no decision was made. EU officials acknowledge that the decision is in the hands of US authorities.
DHS spokesman David Lapan said that Europan officials would be given ample warning ahead of any ban.
Ohio Companies Unite to Share Threat Intelligence
1.6.2017 securityweek Security
Cybersecurity is a form of asymmetric warfare. The attackers need to only succeed once; the defenders must succeed constantly. The attackers share weapons and methods continuously; the defenders are often isolated silos of private knowledge that comes only from the attacks against themselves. Threat intelligence sharing between the defenders is a primary method of reducing the attackers' inherent asymmetric advantage.
But intelligence sharing is difficult, comprising both human and technology problems. The human element is largely around 'trust' -- with whom can you share potentially sensitive commercial information. The technology problem involves constraining the shared data to intended recipients and ensuring there is no breach of data protection regulations.
These problems have been successfully tackled by seven Fortune 500 companies in Columbus Ohio. They came together in 2014 to form and capitalize the Columbus Collaboratory -- an Information Sharing and Analysis Organization (ISAO). As a private and voluntary ISAO, they solved the 'human' problem. Last week they adopted the TruStar intelligence sharing platform to solve the technology problem.
The Collaboratory comprises seven major non-competitive firms in several separate sectors: Nationwide Insurance, Cardinal Health, LBrands (which includes Victoria's Secret, and Bath & Body Works), Huntington Bank, OhioHealth, American Electric Power, and Batelle. It was formed with $28 million commitment from the members, and a $5 million Ohio Third Frontier Grant.
The non-competitive nature is important. "Columbus lends itself to such an approach," Jeff Schmidt, VP and chief cyber security innovator, told SecurityWeek. "It's an important commercial center, but is not dominated by any one vertical." This allows the members to come together with no fear of disclosing sensitive data to competitors. While Schmidt sees the group potentially growing with new members, he doesn't believe the non-competitive element will ever change.
One of the first things Schmidt did when he joined the organization in October 2016 was to bring the liaison officers from the different companies together. "Nothing encourages trust more than face-to-face meetings," he said -- drawing perhaps from his earlier experience as Director at the InfraGard National Members Alliance.
The Collaboratory offers its members three primary services: cybersecurity, advanced analytics and talent solutions. "By sharing threat intelligence," he said, "we can break out of the silo model, pool ideas and resources, and better protect against cybersecurity threats." But, he added, "One of the nice features is that being completely private, there is no mandatory reporting from the Collaboratory to any outside agency, such as the FBI. In that way, it is different than other government-sponsored information sharing platforms."
These other platforms include ISACs (created by the DHS) and InfraGard (created by the FBI). "We've seen what works and what doesn't work," he said. "A lot of the inhibitors to effective information sharing are legal and philosophical -- if I share this information is the FBI or the NSA going to get it. Removing that variable is a net help." The individual members, many designated as part of the national critical infrastructure, may have their own vertical reporting responsibilities -- but the Collaboratory itself has none.
The final piece of the puzzle came into place last week with the adoption of the TruSTAR information exchange platform. "There is a common desire in business to share intelligence," commented Paul Kurtz, former cybersecurity advisor to the White House and now co-founder and CEO of TruSTAR, "but those legal and philosophical inhibitors have made it difficult."
The TruSTAR platform provides a walled enclave where data can be shared with just the Collaboratory members. Data can be redacted before sharing -- indeed, TruSTAR will automatically detect any likely PII with a point, click and redact facility to prevent its sharing -- and anonymized to prevent attribution. Only data specifically allowed for wider sharing can leave the enclave to be shared among the wider TruSTAR community. In this way, it maximizes sharing both between the members and with the wider community, while protecting any data that should not be shared. This is further enhanced with TruSTAR's selective version capability.
"If members wish to share a redacted document within the Collaboratory, and a more redacted version with the Wider TruSTAR community," added Schmidt, "then TruSTAR can accommodate selective version sharing."
For the most part, the shared information will be indicators of compromise, behaviors, patterns, attackers' infrastructures and not PII. If any PII slips in it can be redacted. In this way, Schmidt believes that the members can stay the right side of data protection regulations, including GDPR when it arrives next year. If anything, the structure imposed upon shared data is likely to make breach notification simpler and more efficient; making it easier for members to comply with GDPR's 72-hour notification requirement.
It's early days for the Columbus Collaboratory; but does the theory work in practice? "Yes," said Kurtz. "One example was a firm that thought it had a staff problem only to find that other companies were having the same problem. It wasn't staff, it was subtle indications of an intruder that only became apparent through intelligence sharing."
The Columbus Collaboratory, aided in this instance by the TruSTAR sharing platform, is unique. But it is an example to other regions where different companies can come together and share their threat intelligence, safely, securely, compliant with data protection regulations, and with no three-letter agency inhibitions.
Endpoint Security Firm Tanium Raises $100 Million
26.5.2017 securityweek Security
Emeryville, CA-based endpoint security and systems management firm Tanium announced on Thursday that it has raised $100 million through the sale of common stock.
The latest funding round was led by TPG Growth and it brought in a new investor. The $100 million raised through the issuance of common stock – previous funding rounds offered only preferred stock – brings the company’s value to $3.75 billion.
Part of the proceeds have been used to repurchase shares from David Hindawi, co-founder and executive chairman of Tanium, to allow him to fund his charity projects. The rest will be used to provide liquidity to early employees and investors, and for general corporate purposes.
Tanium raises $100 million
With this funding round, Tanium has raised a total of $407 million. The company reported a revenue growth of more than 100% last year, and it claims to have brought on board nearly 100 new enterprise customers. Clients include U.S. government agencies, 12 of the top 15 banks, and six of the top 10 retailers.
The company’s plans for the future include expansion in the EMEA and APAC regions, establishing a strong presence in the media and manufacturing sectors, further investment into IT operations products and modules, and growth in existing industries.
“Tanium is unique in our industry. In contrast to the cybersecurity-only companies, we provide an endpoint platform that allows communication for massive numbers of assets in a way enterprises have never had before, which is useful across not only security but also operations issues in IT,” said Tanium CEO Orion Hindawi.
“Because of that breadth of offering, our investors see Tanium having longevity and potential that exceeds the typical cybersecurity landscape, and we will work hard to continue proving them right by driving our platform further into both security and operations with each passing quarter,” he added.
Last month, Hindawi published an open letter addressing accusations that the company exposed a California hospital’s network during sales demos, and reports of a toxic staff relations culture.
Endpoint Security Firm Tanium Raises $100 Million
26.5.2017 securityweek Security
Emeryville, CA-based endpoint security and systems management firm Tanium announced on Thursday that it has raised $100 million through the sale of common stock.
The latest funding round was led by TPG Growth and it brought in a new investor. The $100 million raised through the issuance of common stock – previous funding rounds offered only preferred stock – brings the company’s value to $3.75 billion.
Part of the proceeds have been used to repurchase shares from David Hindawi, co-founder and executive chairman of Tanium, to allow him to fund his charity projects. The rest will be used to provide liquidity to early employees and investors, and for general corporate purposes.
Tanium raises $100 million
With this funding round, Tanium has raised a total of $407 million. The company reported a revenue growth of more than 100% last year, and it claims to have brought on board nearly 100 new enterprise customers. Clients include U.S. government agencies, 12 of the top 15 banks, and six of the top 10 retailers.
The company’s plans for the future include expansion in the EMEA and APAC regions, establishing a strong presence in the media and manufacturing sectors, further investment into IT operations products and modules, and growth in existing industries.
“Tanium is unique in our industry. In contrast to the cybersecurity-only companies, we provide an endpoint platform that allows communication for massive numbers of assets in a way enterprises have never had before, which is useful across not only security but also operations issues in IT,” said Tanium CEO Orion Hindawi.
“Because of that breadth of offering, our investors see Tanium having longevity and potential that exceeds the typical cybersecurity landscape, and we will work hard to continue proving them right by driving our platform further into both security and operations with each passing quarter,” he added.
Last month, Hindawi published an open letter addressing accusations that the company exposed a California hospital’s network during sales demos, and reports of a toxic staff relations culture.
Apps Essential to Modern Living But Treated Carelessly: Report
25.5.2017 securityweek Security
A new research report takes an unusual angle. Rather than analyzing a threat or an attacker, it looks at the psychology of the user -- or more specifically, the user of smartphones and apps. What it found is that the modern use of apps is so interwoven with daily life, they have almost become part of their users' DNA.
The Application Intelligence Report (AIR: PDF) is a new intelligence survey produced by A10 Networks. A10 surveyed 2,000 business and IT professionals in more than 20 different countries -- and it is important to note that these were professionals rather than unemployed teenagers glued to their phones.
The purpose, says Andrew Hickey in an associated blog, a director at A10 Networks, is to "better understand how the global workforce's experiences and behaviors with apps impact personal and corporate security... Why they use them. Their perception of personal and business security when using them. And potential behavioral risks to businesses and IT teams."
The result is sobering, and could fuel a raft of psychology and sociology theses. It first demonstrates how apps and their use is deeply interwoven into everyday life. For example, 42% of respondents globally say they 'cannot live without their apps' while another 44% said 'it would be a struggle' to live without them.
The detail varies by both age demographic and geolocation. Newly emerged and emerging economies seem particularly attached or reliant on their apps: China (99%), India (97%), Brazil (96%) and South Korea (90%). It is the older economies that seem less reliant. Germany ranks highest of participants who say, 'I can easily live without apps' (30%), followed by France (23%), and Great Britain and Japan (21%). Similarly, respondents under the age of 40 are much more likely to say they cannot live without apps than those over 40.
This basic pattern largely repeated itself throughout the survey. For example, in an emergency that would allow people to take only one item, 45% of respondents elected to grab their phone. It was 74% in China, but only 29% in France.
While details such as these are interesting and possibly surprising (perhaps depending on the reader's geolocation and age demographic), it is the attitude towards security that becomes sobering. "At least four out of five (83%) respondents either agree or strongly agree that they think about security risks when first downloading an app," says the report, "but after that, security becomes much less of a thought or priority in dictating behavior."
One reason seems to be a belief that it is the developer, or the company IT department, that is responsible for app security. Forty-seven percent of respondents "expect to be protected from cyber-attacks by either their company or third-party app developers."
This lax personal attitude to security best shows itself in the use of passwords. One in 10 (11%) of all respondents said they never change their passwords for their apps, while another three out of 10 (29%) use the same password for the majority of their apps. Fewer than one in five (17%) use a different password for every app. The usual demographics apply: 50% of the 21-30 demographic either never change passwords or use the same password the majority of the time, compared with only 26% of those aged over 50.
Surprisingly, the US (49%) is second only to South Korea (52%) in using the same password for the majority of apps -- but less surprisingly, Germany leads in best practices for those who use different passwords (34%).
The effect of poor personal security is born out in practice. Globally, 13% of all respondents have been the victim of identity theft. This grows to 39% in China (a figure that, pro rata, suggests more people than the entire population of the US). Thirty-one percent of respondents have had their phone hacked; and 24% of respondents under the age of 30 have had their phone stolen.
A10 Network draws few conclusions from this report, instead inviting its study and promising to 'dig deeper' in the future. "From a cultural perspective," blogs Hickey, "IT can study the app-blended life, consider user behavior as a factor in security planning, build enterprise-wide security awareness and influence a security-minded culture.
"And from a technology perspective, IT pros can use this data to make the case for improved per-app visibility, per-app analytics, performance, removal of security blind spots and implementation of tighter controls across all application environments." But one thing is immediately obvious: companies with a BYOD policy cannot afford to leave the security of mobile devices to the user.
Flashpoint Enhances Risk Intelligence Platform
24.5.2017 securityweek Security
Just as global intelligence firm Stratfor extracts and presents geopolitical intelligence from the noise of available information, so now does Flashpoint extract cyber business risk intelligence (BRI) from the noise of deep and dark web conversations.
Flashpoint is not new to BRI. It raised $10 million in Series B funding in July 2016 and announced its expansion from cyber threat intelligence into business risk intelligence. "Looking beyond cyber threat Intelligence, BRI ultimately informs decision-making, improves preparation, and mitigates risk throughout an entire organization," said Flashpoint at the time.
That process has now come to fruition with today's launch of the Flashpoint Intelligence Platform 3.0. It aims to convert and present the raw intelligence gleaned from the deep and dark web as actionable business risk intelligence that will help customers take a more strategic role in security planning.
Most threat intelligence ultimately comes from the deep and dark web. This is where cyber criminals share information, trade malware and boast about exploits. But access is difficult. The deepest and darkest areas are well-protected, and only accessible to 'approved' people. Flashpoint has a team of expert analysts, often with 3-letter agency backgrounds, who spend the time and effort necessary to get into the darkest corners.
This is where Flashpoint gleans its threat intelligence. It comes from actual dialogue between threat actors; from black market products and services; from where malicious tactics, techniques and procedures (TTPs) are discussed; and where weapons and training manuals are shared.
But threat intelligence falls short of business risk intelligence. "Some threat intelligence solutions can be no different than URL filtering, merely contributing to the greater noise," warns Gartner Research VP, Greg Young. "Instead, good threat intelligence solutions are customized and able to deliver a high-confidence alert to initiate an actionable response. Peering out at what often looks like a world of shadows and hostility, security teams can see specificity as a key to the achievement of their best success with limited resources."
For most organizations, access to any threat intelligence comes from surface web reports produced by different security vendors. These often discuss individual threats discovered by individual vendors, often focusing on their own product sphere. While these are valuable, they present a piecemeal view of the overall threat landscape.
In this sense, Flashpoint is vendor-neutral: it provides intelligence rather than product. Its new development is to generate and present actual risk intelligence from the raw threat intelligence. But its team of analysts don't just gather intelligence from the dark web, it converts it through analysis reports into business actionable information -- in short, it adds context that goes beyond cyber.
"Traditional cyber threat intelligence, which has been largely focused on indicators of compromise, is insufficient in supporting the risk decision-making process, as it too often limits its focus on events in cyberspace," warned Flashpoint in its Business Risk Intelligence - Decision Report, published in January 2017. "Not all actors constrain their operations solely to the cyber realm; top tier nation-states like the U.S. and Russia use the full-spectrum of their capabilities to achieve their objectives. A threat assessment of Chinese or Russian cyber operations without the context of the national objectives they are supporting fails to provide risk decision-makers with an accurate portrayal of the threat landscape upon which to make business decisions."
The Intelligence Platform 3.0 provides access to Flashpoint's analyses with a finished intelligence experience. Users can use it to search Flashpoint's reports, focusing on specific areas of interest and including both cybercrime intelligence and physical threat intelligence -- or they can pivot directly into a sanitized sandbox of the original threat actor data. The result helps the security team understand the overall threat landscape, and provides the materials necessary to translate threats into business risks consumable by senior management.
Yahoo Ditching ImageMagick Highlights Issues in Bug Responsibility Ecosystem
23.5.2017 securityweek Security
ImageMagick, an open source command line graphics file editor, has been retired by one of its major consumers: Yahoo. The product has been beset by flaws and bugs for several years, but this appears to have been one too many for Yahoo. Following discovery of a bleed vulnerability, Yahoo fixed it by retiring the product.
The flaw itself, discovered by researcher Chris Evans, was fixed by ImageMagick two months ago. Last week, however, he blogged about his discovery of its persistence at Yahoo. For Evans, it is symptomatic of a wider issue: vendor (ImageMagick) and consumer (in this case Yahoo) responsibility for upstream fixes.
ImageMagick (using his own fix) fixed the problem. Could or should it have done more to ensure that its consumers also applied that fix? Yahoo is (or was) a consumer. Could it or should it have done more to apply upstream fixes?
A solution, suggests Evans, is, "Probably less trivial than it sounds; both Box and Yahoo! appear to have been running old versions of ImageMagick with known vulnerabilities."
The vulnerability, exploited by Evans on Yahoo, provided "a way to slurp other users' private Yahoo! Mail image attachments from Yahoo servers." It was present in the RLE (Utah Raster Toolkit Run Length Encoded) image format. An attacker, writes Evans, "could simply create an RLE image that has header flags that do not request canvas initialization, followed by an empty list of RLE protocol commands. This will result in an uninitialized canvas being used as the result of the image decode."
In his own POC he attached an 18-byte exploit file as a Yahoo! Mail attachment, sent it to himself and clicked on the image in the received mail to launch the image preview pane. "The resulting JPEG image served to my browser," he writes, "is based on uninitialized, or previously freed, memory content."
He reported the problem to Yahoo, and was pleased with Yahoo's response. It was fixed well within Yahoo's self-imposed 90-day deadline, and, he says, the communication was excellent. Compare this to his comments on communication with Box: "communications were painful, as if they were filtered through a gaggle of PR representatives and an encumbrance of lawyers."
The fix itself was simple and complete: Yahoo retired ImageMagick.
Despite its problems over the last few years, Yahoo has come a long way with improving its vulnerability response approach. In 2013, High-Tech Bridge (HTB) found numerous XSS flaws in Yahoo servers. "Each of the discovered vulnerabilities," it said at the time, "allowed any @yahoo.com email account to be compromised simply by sending a specially crafted link to a logged-in Yahoo user and making him/her click on it."
The HTB researcher was offered a $12-50 Yahoo store voucher for each of the flaws. This time, however, Evans as offered a total of $14,000 for this and a separate issue yet to be documented. When Evans suggested donating it to charity, Yahoo doubled the charitable award to $28,000.
SecurityWeek has asked Yahoo for a comment on the issue, but has not yet received a reply.
Financial Firms Struggle on Compliance for non-Email Communications
20.5.2017 securityweek Security
Financial services is perhaps the most regulated sector in industry. SEC, FINRA and Gramm-Leach-Bliley are merely the better known of a raft of regulations. Key to all of them is the requirement to manage and retain communications. But just as regulations tend to increase and become more complex, so too have the different methods of communication that need to be monitored ballooned. What was once just email now includes SMS, public IM, a variety of social media and more. At the same time, regulators are becoming more active.
The 2017 Electronic Communications Compliance Survey (PDF) from Smarsh demonstrates continuing industry concern over its ability to capture and retain relevant staff communications, especially from mobile devices. Interestingly, Europe's GDPR will add to the regulation mix, but will expand the industry coverage from finserv to any organization doing business with Europe. While finserv regulations are concerned with financial data in communications, GDPR is concerned with personal data in communications. Different detail, but same basic problem: the control of regulated data getting dispersed in uncontrolled communications.
The problem is the same. So it follows that the difficulties and concerns voiced by finserv organizations over communications compliance will apply to all industry sectors by the end of May 2018.
Smarsh surveyed 119 finserv individuals in compliance supervisory roles ranging from c-level to operations. It found that the top three concerns for regulatory compliance are non-email communications, mobile devices, and simply understanding new and challenging regulations. In each case, the level of concern has increased dramatically over 2016 levels.
Non-email and mobile device communications overlap. Employees are increasingly using personal devices for non-email quick communication with customers, potential customers, colleagues and friends. Text/SMS messaging is considered to pose the greatest compliance risk (52% of respondents). Noticeably, in December 2016 FINRA fined a Georgia firm $1.5 million partly for failure to retain approximately one million text messages sent using firm-issued devices.
All of this is against a backdrop of more frequent, deeper and broader regulatory examinations. In 2015, 27% of firms were examined in a 12-month period; in 2016 it was 42%; and in 2017 it rose to 47%. The biggest single change in the examinations has been the regulators' increasing requests for social media communications. In 2015, 19% of examiners requested social media comms -- but by 2017, this had increased to 44% for LinkedIn, 27% for Facebook, 21% for Twitter, and 6% for Instagram.
The examiners are also looking at firms' mobile communication policies. In the last year, 21% of the examined respondents had to provide their mobile device communications policy. Policy, however, has its own issues. Of those firms that allow text/SMS messaging, 36% do not have a written policy governing its use. Smarsh suggests, however, that any firm not supervising mobile use should now expect to be fined.
The problem for business is that mobile communications is not a risk that can be avoided. "Firms need to leverage new and emerging channels to communicate with their customers and stay competitive, but they're failing to manage the risk," explains Stephen Marsh, CEO and founder of Smarsh.
Simple prohibition is not a solution. Where it is used, survey respondents' confidence in its effectiveness is low. Asked if they would be able to prove that prohibition is working, the confidence gap over text/SMS, and also LinkedIn, stands at 67%. For Twitter it is 57%, and for public IM it is 55%.
"This year's survey," comments CEO Stephen Smarsh, "reinforces that policies of prohibition are a barrier to growing business and workforce productivity. They do not deliver compliance confidence, and they simply don't work. Early 2017 examples of text-related firm penalties all have one thing in common: all prohibited its use for business communication. More than two thirds (67 percent) of respondents have no or minimal confidence that they could prove their prohibition of text messaging is actually working."
There is a bonus. While compliance is the primary driver for communications archiving and supervision, 88% of the respondents recognize that communications data can also help identify more general security risks to the organization. "More than half of respondents (59%)," notes the report, "confirm that their organization uses this data to identify fraudulent activity, among other purposes, such as supporting e-discovery and HR issues, and detecting market abuse."
It is worth stressing that the 2017 Smarsh survey relates directly to compliance in the financial services industry. The arrival of the General Data Protection Regulation in May 2018 will create the same basic communications content compliance requirements across all industries. In preparing for GDPR, all industry sectors can learn from the non-email communications compliance problems already being experienced by Finserv.
What's Driving Stress Levels of Security Operations Teams?
18.5.2017 securityweek Security
Security Operations Teams Are Overwhelmed by Vulnerabilities and Volume of Threat Alerts, Study Finds
One of the reasons the WannaCrypt ransomware spread so far and so fast is because it leveraged what was for some Windows users a 0-day exploit, and for others an n-day exploit. For users of unsupported Windows version, it was 0-day -- there had been no patch. But for many users of supported versions of Windows, it was an n-day exploit; that is, the exploit was used during the variable-n number of days between a patch being issued by Microsoft, and the patch being implemented by the user.
N-day exploits are an increasing problem because, if anything, the time between issue and implementation of patches is increasing.
A new study, prepared for Bay Dynamics by EMA and published today, helps to explain why this is happening. Bay Dynamics, a maker of cyber risk analytics software, completed a $23 million Series B financing round in July 2016.
Four hundred security professionals ranging from management to operational staff in mid-market, enterprise and very large enterprise organizations and representing a wide range of industry sectors were questioned about stress in their daily lives.
What emerged, in a nutshell, is that operations staff are overwhelmed by the sheer volume of vulnerabilities; they are falling behind in efforts to remediate them; and tend to under-report the problem to their seniors.
To put this into context, on average, a mid market firm might have 10 full time staff servicing ten new vulnerabilities per month across just under 2,000 assets (almost 20,000 vulnerabilities to service every month). For a very large enterprise those figures translate to 100 staff servicing more than 1.3 million vulnerabilities every month. Seventy-four per cent of security teams admit they are overwhelmed by the volume of maintenance work required.
Since full and timely patching is an impossibility, security teams are required to prioritize their efforts -- but this is also a problem. Nearly 80% of the respondents admitted that their patching approval process is significantly manual. "This," notes the report, "included emails, spreadsheets, and other electronic documents for tracking and approval. With the volumes of patching that have to be reviewed, these labor intensive manual steps drive high inefficiencies and stress."
To be fair, 'too many vulnerabilities' is not considered to be the primary stress driver for security teams. It ties in second place (at 21%) with stress caused by management, one point behind the primary cause of stress, 'not enough manpower'. The report postulates that security teams "are creating a security facade around their security program maturity. This could be a natural extension of what they are conveying to their upper management."
If this is true, it would go a long way to explain the often-discussed disparity between operations staff and senior management over the maturity of an organization's security posture: senior management invariably claims a more mature posture than that reported by security operations.
The survey also makes clear that the prioritization of vulnerabilities and threats is also problematic. Sixty-eight percent of respondents prioritize vulnerabilities based on their severity. This severity is relatively easy to gauge from the vendor's alert and the IT infrastructure. Threats, however, are a little different.
Fifty-eight respondents prioritize vulnerabilities based on the severity of identified threats -- but 52% of threat alerts are improperly prioritized by systems and must be manually reprioritized.
"While severity of alerts should be a key indicator of how both vulnerabilities and threats should be prioritized for action by operations," suggests the report, "it is not the only factor and should not be considered the primary indicator unless the prioritization algorithm has sufficient context within its framework."
The problem here is that the majority of current alerting systems, such as SIEMs, do not usually provide sufficient context for automatic priority decision-making. Newer machine-learning anomaly detection systems have the potential, eventually, to provide better and more complete context; but for now, they are known to create a high level of false positives.
The difficulty in being able to automatically and correctly prioritize vulnerabilities is delaying their solution. Analysts are spending between 24 and 30 minutes investigating each alert; and are falling behind. Sixty-four percent of alert tickets are not worked per day, and analysts are continuously falling further behind in their workload -- explaining why 'dwell time' for breaches is over six months.
There are two possible solutions. The first is more manpower -- but given the sparsity of suitable security analysts, this would be difficult. The second is automation through better security tools.
"To succeed," suggests the report, "tools must be made smarter by providing more useful context around the technical, financial, and behavioral aspects of the incidents. This will reduce the number of false positives and misclassified alerts so that only the real, most critical threats are at the top of the investigation pile." If this can be achieved, "a day in the life of a security pro will become significantly less stressful." And the next WannaCrypt perhaps a little less successful.
Corvil Launches Automated Security Tool for Financial Exchanges
17.5.2017 securityweek Security
Financial services (finserv) is one of America's defined critical infrastructure sectors. The DHS summarizes, "The Financial Services Sector represents a vital component of our nation's critical infrastructure. Large-scale power outages, recent natural disasters, and an increase in the number and sophistication of cyberattacks demonstrate the wide range of potential risks facing the sector."
One specialized sub-section of finserv is the trading floor, which is increasingly automated. Traders deal in many billions of dollars every day, with buy or sell decisions often based on algorithms monitoring market conditions. The integrity of the trading floor -- its systems and its algorithms -- needs to be protected and validated. The consequences could be dire.
In October 2016, the value of sterling fell by 8% overnight. In this instance it was thought to be caused by an algorithm triggered by a negative comment from the French president following the UK's Brexit vote -- but it should not have happened.
This crash was caused by false logic in an algorithm -- but it could equally be caused by malicious manipulation. Guarding against such occurrences in many of the world's leading trading floors is Corvil, a Dublin-based security firm that uses algorithms to monitor and protect trading activity.
But while trading networks have Corvil security analyzing trading patterns, they have very little traditional security software. Their problem is similar to that affecting OT networks and ICS -- the priority is maintaining operation rather than adding new security overheads. For trading floors, the absolute priority is performance and minimal trading latency -- speed is the trader's primary advantage over competitors.
Nevertheless, financial exchanges are becoming increasingly concerned about their cyber security. Last month, a sys admin with KCG, a global American securities trading firm, was arrested and accused of creating malware to steal valuable source code and encryption keys that gave him direct access to the data files that are the core of the company’s business. He was detected because he attempted to log into an analyst's desktop at the same time as the analyst also attempted to do so -- on a Saturday. His discovery was serendipitous; but he had already been exfiltrating data undetected for four months.
It is this known difficulty for the IT-centric CISO to see into the workings of the OT-centric trading network that is causing increasing concern in financial exchange organizations. A survey among members of the International Organization of Securities Commissions (IOSCO), Corvil's director of product management Graham Ahearne told SecurityWeek, highlighted particular concern over "over financial and reputational impact; halting trading activity; ongoing disruption of the market and integrity compromise that might lower confidence in and the reputation of financial actors; the infiltration of multiple exchanges using a range of different types of cyber-attack techniques in tandem; data manipulation and compromise of data integrity; and the leaking of insider information on an ongoing basis…" In other words, all the security concerns of IT networks without any of their security controls.
Corvil already provides a streaming analytics platform to most of the world's trading floors. It captures, decodes, and learns from network data on the fly. It detects anomalous trading behavior as it happens -- but what it doesn't do is detect the anomalous network behavior that might indicate the presence of a cyber intruder.
Today, Corvil has announced the new Corvil Virtual Security Expert, called Cara -- a new tool that "acts as a virtual security expert that autonomously identifies vulnerabilities and possible attacks within the trading environments that often process trillions of dollars' worth of transactions daily," says Corvil. It operates on the existing Corvil platform and adds zero overhead to existing network speeds. It is largely just a different set of algorithms interpreting the existing data streams in a different way.
"Cara," explains Ahearne, "is a software module that sits dormant on the existing network while the market is open. It can sit on any Corvil appliance, which is already installed on the majority of financial exchange trading networks throughout the globe. Because it is dormant, it adds zero overhead to the operation of the trading network. But as soon as the market closes it activates automatically and replays the whole day's traffic captured during the day. It runs multi-dimensional security analytics that detect patterns of compromise, and pinpoints the most important issues for investigation."
Cara uses machine learning algorithms to look for known attack techniques, exploit patterns, unusual data movements etc; and presents a summary report of its findings in an email delivered to security stakeholders overnight. The reports are designed to be accessible to non-technical senior management, yet provide enough information for the security team to know exactly where to look for potential problems. "The purpose," explained Ahearne, "is to both automate anomaly analysis and reduce the customer's need for highly technical staff." It would, in fact, have detected the exfiltration of KCG data automatically.
Cara, comments Dan Cummins, a senior analyst at 451 Research, "gives security teams a relatively quick way to extend automated risk assessments, which combine machine-learning anomaly detection and threat detection analytics, to electronic trading networks."
The approach Corvil has taken provides zero overhead security to what is in effect an OT network. This is a perennial problem for many companies with OT; and provides a long-term expansion path for Corvil. "We have seen the parallels," Ahearne told SecurityWeek, "and it is a possible future expansion. But for now, we are focused on solving the cyber security problems of trading floors with our Virtual Security Expert."
Google to Scrutinize Web Applications Requesting User Data
15.5.2017 securityweek Security
In the light of a recent phishing attack targeting Gmail users, Google is updating its app identity guidelines and is implementing a more thorough review process for new web applications that request user data.
The attack unfolded a couple of weeks back, when Gmail users started receiving phishing emails pretending to come from a known recipient looking to share content with them on Google Docs. A link in these emails didn’t take users to the expected content but instead opened a login page, where a certain Google Docs app requested permissions to access the recipient’s contacts and emails.
Google managed to stop the attack within hours and said that less than 0.1% of Gmail users were impacted by the incident. To prevent similar situations from happening again, the company decided to tighten OAuth rules, updated its anti-spam systems, and announced augmented monitoring of suspicious third-party apps that request information from users.
The company now says that new web applications that request access to user data will face more scrutiny. Google’s enhanced risk assessment will also result in some web applications requiring a manual review.
“Until the review is complete, users will not be able to approve the data permissions, and we will display an error message instead of the permissions consent page. You can request a review during the testing phase in order to open the app to the public. We will try to process those reviews in 3-7 business days. In the future, we will enable review requests during the registration phase as well,” Google announced.
Web app developers will continue to use their applications for testing purposes before they are approved. For that, they need to log in with an account registered as an owner/editor of that project in the Google API Console, where they will also be able to add more testers and to initiate the review process.
Additionally, the company announced updated app identity guidelines to further enforce the Google API user data policy which states that apps must not mislead users (meaning that they should have unique names and should not copy other apps).
In line with this policy, the company decided to update the app publishing process, risk assessment systems, and user-facing consent page “to better detect spoofed or misleading application identities.” As a result, web app developers may see an error message when registering new applications or modifying existing app attributes in the Google API Console, Firebase Console, or Apps Script editor.
“These changes may add some friction and require more time before you are able to publish your web application, so we recommend that you plan your work accordingly,” Google says. The company also encourages developers to review previous posts on their responsibilities when requesting access to user data from their applications.
Mozilla Revamps Bug Bounty Program
12.5.2017 securityweek Security
Mozilla announced on Thursday that it has relaunched its web security bug bounty program. White hat hackers are now provided clear information on how much money each type of vulnerability can earn them.
Mozilla has been running a bug bounty program since 2004. The organization initially rewarded only vulnerabilities found in its software, but in 2010 it expanded the program to include web properties.
The organization says it has paid out more than $1.6 million since 2010, but it has experienced some issues in communicating what types of flaws and which online properties are considered the most problematic.
“A hypothetical SQL injection on Bugzilla presents a different level of risk to Mozilla than a cross-site scripting attack on the Observatory or an open redirect on a community blog,” explained Mozilla security engineer April King. “To a bounty hunter, the level of risk is often irrelevant — they simply want to know if a class of bug on a specific site will pay out a bounty and how much it will pay out.”
Mozilla has decided to expand the list of websites and bug classes covered by its bug bounty program, and it now aims for greater transparency by providing more detailed information on payouts.
For instance, a remote code execution vulnerability in a critical website can earn bounty hunters $5,000, while an authentication bypass or a SQL injection can be worth up to $3,000. Cross-site request forgery (CSRF), cross-site scripting (XSS), XML external entity (XXE) and domain takeover flaws affecting critical sites can receive a payout of up to $2,500.
Critical properties include the main Firefox and Mozilla websites, and domains related to services such as ABSearch, add-ons, Bugzilla, crash reports, downloads, Firefox-related services, Push, Shield, Test Pilot, tracking protection and source control.
“Having a clear and straightforward table of payouts allows bounty hunters to devote their time and effort to discovering bugs that they know will receive a payout. The hunters will also know the exact amount of the payouts,” King said.
In addition to expanding the list of properties eligible for monetary rewards, Mozilla informed users that there are some new bug classes that can qualify for its bug bounty Hall of Fame.
Beware! Built-in Keylogger Discovered In Several HP Laptop Models
12.5.2017 thehackernews Security
Beware! A Built-in Keylogger Discovered In Several HP Laptops
Do you own a Hewlett-Packard (HP) laptop?
Yes? Just stop whatever you are doing and listen carefully:
Your HP laptop may be silently recording everything you are typing on your keyboard.
While examining Windows Active Domain infrastructures, security researchers from the Switzerland-based security firm Modzero have discovered a built-in keylogger in an HP audio driver that spy on your all keystrokes.
In general, Keylogger is a program that records every keystroke by monitoring every key you have pressed on your keyboard. Usually, malware and trojans use this ability to steal your account information, credit card numbers, passwords, and other private data.
HP computers come with Audio Chips developed by Conexant, a manufacturer of integrated circuits, who also develops drivers for its audio chips. Dubbed Conexant High-Definition (HD) Audio Driver, the driver helps the software to communicate with the hardware.
Depending upon the computer model, HP also embeds some code inside the audio drivers delivered by Conexant that controls the special keys, such as Media keys offers on the keypad.
Keylogger Found Pre-Installed in HP Audio Driver
According to researchers, the flawed code (CVE-2017-8360) written by HP was poorly implemented, that not just captures the special keys but also records every single key-press and store them in a human-readable file.
This log file, which is located at the public folder C:\Users\Public\MicTray.log, contains a lot of sensitive information like users' login data and passwords, which is accessible to any user or 3rd party applications installed on the computer.
Therefore, a malware installed on or even a person with physical access to a PC can copy the log file and have access to all your keystrokes, extracting your sensitive data such as bank details, passwords, chat logs, and source code.
"So what's the point of a keylogger in an audio driver? Does HP deliver pre-installed spyware? Is HP itself a victim of a backdoored software that third-party vendors have developed on behalf of HP?" Modzero researchers question HP.
In 2015, this keylogging feature was introduced as a new diagnostic feature with an update version 1.0.0.46 for HP audio drivers and existed on nearly 30 different HP Windows PC models shipped since then.
Affected models include PCs from the HP Elitebook 800 series, the EliteBook Folio G1, HP ProBook 600 and 400 series, and many others. You can find a full list of affected HP PC models in the Modzero's security advisory.
Researchers also warned that "probably other hardware vendors, shipping Conexant hardware and drivers" may also be affected.
How to Check if You are Affected and Prevent Yourself
If any of these two following files exist in your system, then this keylogger is present on your PC:
C:\Windows\System32\MicTray64.exe
C:\Windows\System32\MicTray.exe
If any of the above files exist, Modzero advises that you should either delete or rename the above-mentioned executable file in order to prevent the audio driver from collecting your keystrokes.
"Although the file is overwritten after each login, the content is likely to be easily monitored by running processes or forensic tools," researchers warned. "If you regularly make incremental backups of your hard-drive - whether in the cloud or on an external hard-drive – a history of all keystrokes of the last few years could probably be found in your backups."
Also, if you make regular backups of your hard drive that include the Public folder, the keylogging file in question may also exist there with your sensitive data in plain text for anyone to see. So, wipe that as well.
SOP Bypass in Microsoft Edge Leads to Credential Theft
12.5.2017 securityweek Security
A bug in Microsoft Edge could allow for bypassing the Same Origin Policy (SOP) and for stealing user passwords in plain text, stealing cookies, spoofing content, and other vulnerabilities, independent security researcher Manuel Caballero says.
The bug is created because a window can be forced “to change its location as if the initiator were the window itself,” the security researcher says. Applying this to iframes in the target page and adding data-uri with code can lead to a full SOP bypass.
Basically, a tab hosting a malicious site could change the location of a PayPal tab to a bank website, and the site would receive PayPal as its referrer instead of the malicious domain. This happens because Microsoft Edge confuses the real initiator of the request.
By leveraging the bug and an injection, an attacker could immediately retrieve user passwords, Caballero says (previously, he suggested that passwords could be stolen by logging out the user and expecting Edge to autocomplete). The bug isn’t new, but Microsoft failed to resolve it to date, he suggests.
The issue, he explains, is that both Edge and Internet Explorer confuse the initiator of a request when the location of the tag is changed in the middle of a server-redirect. This technique can be used to spoof the referrer. As an example, whatsmyreferrer can be tricked into considering that the user is coming from microsoft.com.
For that, one would need to open a new window with a server-redirect to microsoft.com, block the thread until Microsoft starts loading, and then set the location to whatsmyreferrer.com. However, the final location needs to be set from the target window itself using a self-reference, the researcher underlines.
In a recent blog post, Caballero details the steps and code required to make the bypass work. He explains that, in addition to spoofing the referrer, one can also set the location of an iframe to a data-uri, and also provides the code necessary to do so. This also results in a full SOP bypass, the notes.
The security researcher also notes that Edge autocompletes any input-password box without ids/names, provided that it is on the proper domain and has the required format. As a result, one can inject code in domains with saved passwords and have Edge immediately autocomplete them.
“Faking the originator leads to a referrer spoof, but thanks to the existence of data-uris and the fact that most sites render iframes, we can end up turning this vulnerability into a full SOP bypass. Then, because the password manager tries to be smart and complete everything without checking too much, we can simply render a universal snipped of code that will work everywhere,” Caballero concludes.
Microsoft Kills SHA-1 Support in Edge, Internet Explorer 11
11.5.2017 securityweek Security
As of May 9, 2017, Microsoft Edge and Internet Explorer 11 browsers no longer offer support for websites that are protected with a SHA-1 certificate.
Introduced in 1995, the SHA-1 cryptographic hash function has been proven insecure several times, with the first attacks against it demonstrated over a decade ago. After an attack method that lowered the cost of an SHA-1 collision in 2015, Google demonstrated earlier this year that this type of attacks is becoming increasingly practical.
Over the past few years, the industry has been moving away from SHA-1, yet numerous sites still use it. As of January 2017, most Certificate Authorities have stopped issuing new certificates that use the cryptographic hash function, and only one fifth of websites were still using such certs in March, which is looking much better compared to last fall, when 35% of websites were still using SHA-1.
Other web browsers makers revealed plans to deprecate SHA-1 a couple of years ago, and Microsoft confirmed a year ago plans to make a similar move. Initially, Edge and Internet Explorer 11 would display a warning when encountering sites using SHA-1, but starting this week, they are no longer loading these sites, the tech giant says.
“Beginning May 9, 2017, Microsoft released updates to Microsoft Edge and Internet Explorer 11 to block sites that are protected with a SHA-1 certificate from loading and to display an invalid certificate warning,” the company announced.
The change, however, impacts only SHA-1 certificates that chain to a root in the Microsoft Trusted Root Program where the end-entity certificate or the issuing intermediate uses SHA-1. This means that enterprises or self-signed SHA-1 certificates won’t be affected by this. They are, however, encouraged to migrate to SHA-2 based certificates as fast as possible.
“Microsoft recommends that all customers migrate to SHA-2, and the use of SHA-1 as a hashing algorithm for signing purposes is discouraged and is no longer a best practice. The root cause of the problem is a known weakness of the SHA-1 hashing algorithm that exposes it to collision attacks. Such attacks could allow an attacker to generate additional certificates that have the same digital signature as an original,” the company notes.
Mozilla and Google also moved forth with the removal of support for SHA-1 certificates in Firefox and Chrome earlier this year. The ultimate purpose is to completely disable the algorithm in all these browsers.
RedLock Emerges from Stealth With Cloud Security Platform
9.5.2017 securityweek Security
Cloud security startup RedLock emerged from stealth mode on Tuesday with a cloud infrastructure security offering and $12 million in funding from several high profile investors.
According to the company, its RedLock Cloud 360 platform is designed to help organizations manage security and compliance risks in their public cloud infrastructure without having a negative impact on DevOps.
The company says its product can help security teams identify risks in their cloud infrastructure by providing comprehensive visibility into workloads and the connections between user activity, network traffic, configurations, and threat intelligence data. The solution works across multiple public cloud services, such as Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform.
RedLock emerges from stealth mode
RedLock Cloud 360 uses machine learning and correlation with third-party data sources to establish a baseline for user and network behavior, which allows it to quickly identify anomalies. The product monitors new and existing cloud workloads for policy violations, including policies set by security teams and security best practices defined by NIST, CIS and PCI.
The solution continuously assigns a score to every workload based on risky attributes and behavior, which helps security personnel assess the risks and prioritize their response. Data provided by the product can also be integrated with third-party tools to speed up response.
RedLock Cloud 360 also includes forensics capabilities that allow organizations to go back to any point in time and identify threats. Users can also review a history of changes for each workload and determine the root cause of a security incident.
The platform also provides reporting features that allow organizations to compile reports for auditors, management and the board of directors.
RedLock has come out of stealth mode with $12 million in funding from Sierra Ventures, Storm Ventures, Dell Technologies Capital, and other investors.
While the company has only now announced the general availability of its cloud security platform, the product has already been used by several companies, including security firm Proofpoint. Pricing for RedLock Cloud 360 is subscription-based and it depends on the number of workloads deployed in the customer’s cloud environment.
Yahoo Paid Out $2 Million in Bug Bounty Program
9.5.2017 securityweek Security
Yahoo reported on Monday that between the launch of its bug bounty program in 2013 and December 2016 it had paid out a total of more than $2 million.
A comparison to the previous report shows that the Internet giant awarded bounty hunters roughly $400,000 in 2016.
Since the launch of its program three years ago, Yahoo has worked with more than 2,000 researchers from 80 countries, and its HackerOne page lists a total of 3,500 resolved vulnerability reports. The company said it rewarded nearly 200 researchers last year.
“Yes, this all comes with a degree of vulnerability. After all, we’re asking some of the world’s best hackers to seek out soft spots in our defenses,” said Andrew Rios, security engineer at Yahoo. “But it’s acceptable risk. The right incentives combined with some hackers who actually want to do some good has resulted in a diverse and growing global community of contributors to our security.”
Yahoo did not want to share any information on its largest single payout, but pointed to a post that explains how the company evaluates each vulnerability report. The blog post published by the company on Monday references a recent Flickr account hijacking exploit that earned a researcher $7,000.
“Most bounties accounted for less impactful vulnerabilities, but some were more substantial,” Rios said.
In comparison, Facebook has paid out more than $5 million since the launch of its program in 2011, while Google has awarded experts $9 million since 2010.
Google’s biggest single reward last year was $100,000 (of a total of $3 million). Facebook is also known to award significant bounties – the largest payout to date was $40,000 for a remote code execution vulnerability introduced by the ImageMagick image processing suite.
Travel Tech Giant Sabre Investigating Data Breach
3.5.2017 securityweek Security
Travel technology giant Sabre revealed that it has launched an investigation after detecting unauthorized access to sensitive information processed through one of its systems.
Southlake, Texas-based Sabre said in an SEC filing this week that it’s “investigating an incident involving unauthorized access to payment information contained in a subset of hotel reservations processed through the Sabre Hospitality Solutions SynXis Central Reservation system.”
The SynXis Central Reservation product is a rate and inventory management SaaS application used by more than 32,000 hotels worldwide.
The company has notified law enforcement and hired third-party experts to help investigate the incident. Security blogger Brian Krebs reported that Sabre hired Mandiant to assist its investigation.
In its SEC filing, Sabre said the attackers had been locked out of its systems. However, the company believes the investigation may reveal that the hackers had accessed personally identifiable information (PII), payment card data, and other information.
“While we don’t know the specifics of who had unauthorized access to the information and what tactics were used, we’ve seen from similar attacks that hackers gain access with co-opted credentials of someone with too much access,” Ken Spinner, VP of Field Engineering at Varonis Systems, told SecurityWeek.
“A breach of this magnitude underscores the need for SaaS services, especially those hosted on cloud providers, to increase their security posture capabilities at a faster rate,” said John Martinez, VP of Solutions at Evident.io. “Not all cloud-borne vulnerabilities are covered by traditional security tools; These threats require security tooling and services that are born in, and optimized for the cloud.”
This is not the first time Sabre has publicly admitted being targeted by hackers. Back in August 2015, the company confirmed investigating a cybersecurity incident following reports that it had been targeted by a China-linked threat actor.
Late last year, researchers warned that global distribution systems (GDS) from some of the world’s top service providers, including Sabre, were affected by vulnerabilities that could have been exploited by fraudsters to steal travel tickets.
Graph theory applied to a portion of the Dark Web shows it a set of largely isolated dark silos
1.5.2017 securityaffairs Security
A group of researchers conducted a study on the Dark Web leveraging the Graph theory. This hidden space appears as composed by sparse and isolated silos.
A group of experts from the Massachusetts Institute of Technology’s SMART lab in Singapore has recently published an interesting research paper on the Dark Web.
The researchers collected and analyzed the dark web (a.k.a. the “onionweb”) hyperlink graph, they discovered highly dissimilar to the well-studied world wide web hyperlink graph.
The team led by Carlo Ratti, director of MIT’s Senseable City Lab, used the Graph theory as a tool for analyzing social relationships for the dark web.
The experts analyzed the Tor network, one of the most popular darknet, they used crawler leveraging the tor2web proxy onion.link.
It is important to highlight that the team focused its analysis on the Tor Network, that anyway represents just a portion of the dark web.
The team crawled onion.link using the commercial service scrapinghub.com, they used two popular lists of dark web sites trying to visit them and accessing all linked pages using a breadth-first search.
The team just included in their analysis websites which responded to avoid including in their results services that no longer exist.
“I.e., if we discover a link to a page on domain v, but domain v could not be reached after >10 attempts across November 2016–February 2017, we delete node v and all edges to node v.
In our analysis, before pruning nonresponding domains we found a graph of 13,117 nodes and 39,283 edges. After pruning, we have a graph of 7, 178 nodes and 25, 104 edges (55% and 64% respectively)” states the researchers.
The first discrepancy emerged from the research is related to the number of the active .onion domain. The maintainers at the Tor Project Inc. states that the Tor network currently hosts ∼60, 000 distinct, active .onion addresses, meanwhile the team of experts has found only 7, 178 active .onion domains.
The researchers attribute this high-discrepancy to various messaging services— particularly TorChat, Tor Messenger, and Ricochet in which each user is identified by a unique .onion domain.
The Graph-theoretic results show that ∼30% of domains have exactly one incoming link—of which 62% come from one of the five largest out-degree hubs. 78% of all nodes received a connection from at least one of them.

The most intriguing aspect of the research is that 87% of sites do not link to any other site, this discovery has a significant impact on all graph-theoretic measures (see darkweb out-degree in the following image).
“We conclude that in the term “darkweb”, the word “web” is a connectivity misnomer. Instead, it is more accurate to view the darkweb as a set of largely isolated dark silos” wrote the experts. reads the paper. “In our darkweb graph, each vertex is a domain and every directed edge from u → v means there exists a page within domain u linking to a page within domain v. The weight of the edge from u → v is the number of pages on domain u linking to pages on domain v.”
I believe this research could be a starting point for further works, Ratti and his team, along with other researchers could conduct further investigations on the Dark Web, not limiting their analysis to the Tor Network.
Ratti announced that his team is working on the definition of new models to use in further researches.
“As next step,” Ratti said, “we are planning to develop a model to explain how a network develops when nodes do not trust each other.”
Four Essential Security & Privacy Extensions for Chrome
26.4.2017 securityaffairs Security
Here are the top four extensions for the Chrome browser to keep your online activity safe, secure and private.
The recent global wave of cybercrimes, particularly via exploiting loopholes in many leading browsers, has put internet privacy and online security directly in the line of fire. Internet users, in general, are worried about securing their data against the threats posed by hackers and the vulnerabilities in their favorite browsers.
Talking about browsers, Chrome is one of the most used browsers in the world. There are many extensions developed for the Chrome browser that provides an added layer of security and privacy. Following is our review of the essential extensions for Chrome that can protect your online privacy.
Privacy Chrome Extensions
PureVPN Chrome Extension
What sets PureVPN extension apart from all other privacy extensions is its completeness. While users need a different extension for each category of privacy they may be looking for, PureVPN is an all-in-one package. It blocks ads, provides malware protection, protection against hackers and viruses, and encrypts any data sent over the internet. Of course, it allows users to change their location as well, enabling them to access geo-restricted content too. This easy-to-use Chrome extension contains quick access features that make it one of the most trending extensions currently being used by thousands of users around the world.
HTTPS Everywhere
While this extension only provides partial security, it is a great tool for users who are looking for better and more secure ways of encrypting their communication. HTTPS Everywhere works with many popular websites, communication platforms, as well as social media platforms, making instant communications secure around the world. It has been developed as a joint venture between The Tor Project and the Electronic Frontier Foundation.
Disconnect Search
This free chrome extension has a specialized built-in feature that allows users to make private searches and browse anonymously on Chrome. The developers claim that they do not collect any private information, IP addresses or search logs, which makes it secure. Along with the free Chrome extension, the developers have also created it as a web service, which makes it simpler to use and configure according to users’ desired preferences.
Ghostery
This extension is known for its mysterious capabilities of revealing the “invisible” web. It can display a list of all trackers, web bugs, pixels on the page, and beacons. The invisible web is used by hundreds of websites to gather behavioral data of different users and then target them with related ads. Advanced options in the extension also allow users to specifically identify whether someone is tracking their browsing activities. Despite the detailed insight that this extension can provide, it doesn’t feature any tool to address the loopholes that compromise user data.
Organizations Fail to Maintain Principle of Least Privilege
26.4.2017 securityweek Security
Security requires that confidential commercial data is protected; compliance requires the same for personal information. The difficulty for business is the sheer volume of data generated makes it difficult to know where all the data resides, and who has access to it. A new report shows that 47% of analyzed organizations in 2016 had at least 1,000 sensitive files open to every employee; and 22% had 12,000 or more.
These figures come from the Varonis 2016 Data Risk Assessments report. Each year Varonis conducts more than 1,000 risk assessments for both existing and potential customers. For its latest analysis of data risk, it has selected, at random, 80 of these assessments. They cover 33 industries in 12 different countries. Forty-two of the organizations have fewer than 1000 employees, and 38 have 1001 or more employees.
One of the problems highlighted by Varonis is that organizations fail to maintain the principle of least privilege in their access control. It found a total of 48 million folders, or an average of 20% of all folders, accessible to global groups. "Many data breaches are opportunistic or rudimentary in nature, and many originate from an insider, or an insider whose credentials or system has been hijacked," warns Varonis. "Excessive user access through global groups is a key failure point for many security and compliance audits."
That's not to say that all organizations fail. At one end of the scale, a government entity had only 29 of 290,000 folders open to everyone (with none containing sensitive files); while at the other end, an insurance firm had 35% of 86.4 million folders open to all employees.
Focusing more specifically on 'sensitive' files (potentially containing PII, PHI, card details, SSNs and intellectual property), Varonis found a similar range of access. One company in the construction trade had only 0.01% of almost 1000 sensitive files open to the everyone group. Conversely, a banking institution had 80% of more than 245,000 sensitive files accessible to every employee.
Apart from audit and compliance issues, Varonis points to the Panama Papers as an illustration of the dangers. In April 2016, 11.5 million confidential files belonging to the Panama law firm Mossack Fonseca were leaked to a German newspaper, revealing how its clients hid billions of dollars in tax havens.
Stale data is another risk highlighted in the report. Varonis defines stale data as any data that hasn't been touched in six months or more. "Stale data represents little value to the business while it's not being used, but still carries with it risk and potential financial liability if used inappropriately." It also adds a management and cost burden, especially if it is maintained on high-performance storage.
The amount of stale data found by Varonis ranged from just 0.03% (still 21 gigabytes of data) in an investment management firm, to 527 terabytes in more than 35,000 folders at an environment firm.
Varonis also found numerous problems with both permissions and passwords. Issues with permissions include protected folders found in deeper levels of the file system, which "may contain users and permissions which are not visible at the higher levels, leading an administrator to mistakenly assume that permissions to a folder are configured correctly."
Unresolved security identifiers are also a problem. These occur when a user on an ACL is deleted from Active Directory. "They can potentially give unauthorized users (like hackers) access to data," warns Varonis.
One of the problems with passwords is the tendency to allow non-expiring passwords, which, warns Varonis, "allow unlimited time to brute force crack them and indefinite access to data via the account." An insurance firm had 58% of its 246,865 using non-expiring passwords. But an education organization had 100% of 257,000 using such passwords -- and 90% of these were stale enabled users.
Varonis believes that organizations spend too much time and money in defending specific threats to keep attackers off the network; rather than protecting the data itself from both opportunistic insiders and hackers that breach the 'perimeter'. In January of this year, a separate report (PDF) from Forrester (commissioned by Varonis) concluded that "an overwhelming majority of companies face technical and organizational challenges with data security, are focused on threats rather than their data, and do not have a good handle on understanding and controlling sensitive data."
"Many point products are designed to mitigate specific threats," said David Gibson, VP of strategy and market development with Varonis. "If they're used tactically, instead of supporting a strategy that improves the overall security of data, they can not only cost a lot of money, but also provide a false sense of security. Ransomware, for example, exploits the same internal deficiencies that a rogue or compromised insider might -- insufficient detective capabilities and over-subscribed access. Too many organizations look for tools that specifically address ransomware, but neglect to buttress core defenses that would mitigate more than just this specific threat."
What Is Metadata Retention, And How Do You Maintain Your Privacy?
24.4.2017 securityaffairs Security
As Australia’s newly approved Data Retention law comes into effect, how does the law actually affect the average coutry internet user?
As Australia’s newly approved Data Retention law comes into effect, internet users across the country are frantically searching for a way to dodge government surveillance and ISP tracking. But how does the law actually affect the average Australian internet user? What is metadata anyway? And what can you do to protect your metadata?
Read on to get the answers to some of the most frequently asked questions following Australia’s Data Retention Law.
What Metadata Is?
In layman terms, Metadata is data about data. To put it more eloquently, Metadata describes a set of data, explaining how and when it was collected and by whom. It summarizes basic information about data, making it easier to find and work with particular instances of data.
What’s Included In The Metadata?
Metadata isn’t as much related to what you type on a handheld device or utter on the phone. Rather it is the trail of footprints you leave behind when you visit sites, download files, are online. Understandably, it can give ISPs, telecom companies, snoopers and government agencies everything about your internet activity.
What People Says About Metadata Retention?
It is safe to say that when it comes to online privacy, the average internet user in Australian still doesn’t grasp the implications of the new Data Retention law. In an interview with News.com.au, Dr Jake Goldenfein from Swinburne University of Technology explained,
“When it comes to your online data and the privacy protections afforded to it, there’s a lot we don’t know. Unfortunately we just don’t really know what ISPs are doing with data really. We don’t know if it’s being anonymised and sold, or the degree to which the data they collect is being regulated by privacy law because evidently it depends on the structure of the data bases through which it’s retained.”
While the average internet user in Australia would identify freedom as a constitutional right, many are unable to relate the concept with online freedom and privacy.
However, Digital Rights advocacy groups across Australia have proactively rallied against the law. They recently called for a “National Get A VPN Day” to emphasize upon internet users the importance of protecting their personal data, and online privacy and freedom.

How To Protect Your Data From Metadata Retention Law?
Now that you know the importance of Metadata in tracking your trail digital footprints, you should have also realized how easy it is for your ISP, Telecom Company or the Government to keep a tab on your online activity.
However, there are many ways you can actually wipe out this digital trail and avoid any awkward encounters with the authorities. To completely avoid metadata retention, VPN is the most effective and the cheapest way to prevent your data from ISPs, telecom companies and Govt. Agencies. You can protect your data by getting the most secure VPN service such as IVACY VPN, which is considered the best VPN for Australia to stop Metadata Retention.
How VPN Helps You In Protecting Your Personal Information?
Since all your data is encrypted during the data transfer process, there is no way it can be tracked or cracked by ISPs, telecom companies, government agencies or any other third-party for that matter.
Once you’re connected to a VPN, the only information about you that your ISP will be able to see is that you’re connected to a VPN server. All other personal information is encrypted with advanced security protocols of the VPN, making it impossible for your ISP to crack it.
It is understandable, therefore, why digital right groups in Australia promptly called for National Get A VPN Day right after the Data Retention law was passed.
Tanium Blasted for Using California Hospital Network for Sales Demos
22.4.2017 securityweek Security
Tanium Accused of Exposing California Hospital’s Network in Sales Demos Without Client Permission
Earlier this week, Orion Hindawi, CEO of systems and security management company Tanium, published an open letter covering two issues of current 'bad press'. The first is that Tanium has a toxic staff relations culture. Hindawi denies this: "Mission-oriented, hard-charging, disciplined, even intense, but not toxic."
The second issue is less easy to dismiss. It stems from an initial report in The Wall Street Journal, subsequently picked up by numerous other media outlets.
"For years, cybersecurity startup Tanium Inc. pitched its software by showing it working in the network of a hospital it said was a client..." wrote the WSJ. The problem here is that the demo was live and uncensored, giving out details of the client's name (the El Camino Hospital in Mountain View, California) and IT infrastructure, apparently without authorization to do so.
'Start-up' is a misleading description: Tanium is neither new (it was founded ten years ago), nor small (it was last valued at $3.5 billion). It has, however, been growing rapidly; and that might be part of the problem. In May 2014 it raised $90 Million in funding from Silicon Valley VC firm Andreessen Horowitz; and added a further $52 million in March 2015.
"When you start to develop a new product," Stuart Okin, SVP of Product at 1E told SecurityWeek, "the very first thing you do is solve the problem of how you are going to demonstrate it." 1E spent three months solving this problem at the start of developing Tachyon, a competing product that bears some similarities to Tanium.
Both products must scale to huge numbers, and need to be able to demonstrate this ability. Okin's solution was to develop an in-house emulator using virtual machines. Tanium doesn't seem to have had such a plan. Exactly what happened isn't clear, beyond that Tanium seems to have had a direct link into the hospital's system and was able to demonstrate the product in action, live.
In doing so, viewers would have been able to discover information about the network's infrastructure and its strengths and weaknesses -- knowledge that would have been invaluable to a potential attacker. In his letter, Hindawi acknowledges mistakes. Without mentioning El Camino, he writes, "We should have done better anonymizing that customer’s data."
But he also makes the point, "Other than the few customers who have signed those documents [allowing Tanium demonstrations] and provided us remote access to their Tanium platforms, we do not -- and in fact cannot -- demonstrate customer environments with Tanium." This implies that someone at El Camino provided the physical connection that allowed the Tanium demonstrations.
But the hospital denies this. In a separate statement, a spokesperson said, "El Camino Hospital was recently made aware that Tanium, a former third-party vendor that provided a desktop management program, had been using hospital desktop and server management information as part of a sales demonstration. El Camino Hospital was not aware of this usage and never authorized Tanium to use hospital material in any sales material or presentation."
Clearly, these two statements do not align. "This is a very embarrassing incident for the cybersecurity industry, as it undermines trust towards the large and reputable players," High-Tech Bridge CEO Ilia Kolochenko told SecurityWeek. "However, anyone can make a mistake, and prior to any conclusions or accusations, a thorough investigation should be duly performed. Many successful companies become victims of their own success -- it’s very challenging to maintain skyrocketing growth and assure that every employee respects all the internal procedures and policies in their integrity. In the cybersecurity industry, this problem is especially important, as startups grow very quickly and handle extremely sensitive data. I hope that all companies, not just Tanium, will learn a lesson and revise their internal policies and their practical enforcement."
Mistakes were certainly made, but the bottom line is that it should never have happened. "Using live customer environments for demos is a rookie move, and certainly not representative of standard practice among security software vendors," commented Okin. "There are established protocols for this -- such as demo rigs in the cloud. The 'wild west' startup approach doesn't fly in the security space, especially as these products and solutions are there to protect information, and you often find yourself engaged in heavily regulated environments."
He added that security companies should never be able to VPN into clients' infrastructures, unless it is an essential part of the service offered. This incident, he said, breaks the essential trust that is necessary between security vendor and client.
Ambient Light Sensors Put Browser Data at Risk: Researchers
20.4.2017 securityweek Security
The ambient light sensors present in phones, tablets and laptops can be abused to obtain potentially sensitive information from a user’s web browser, researchers warned.
Ambient light sensors measure light intensity in the environment, which is useful for adjusting the brightness of the display and for proximity detection. The data collected by the sensor is fairly precise and the frequency of readings is relatively high.
Last year, researcher Lukasz Olejnik analyzed theoretical security and privacy implications of ambient light sensors. The expert recently teamed up with Artur Janc and they demonstrated how the W3C’s ambient light sensor API can be abused to steal data from web browsers.
Some members of the industry have proposed allowing websites to access ambient and other sensors without requiring explicit permission from the user. Recent versions of Firefox and Chrome have already implemented the W3C API – it’s enabled by default in the former and it can be manually activated in the latter.
Proof-of-concept (PoC) exploits created by the researchers show how an attacker can determine a user’s browsing history based on the color of links, and how they can steal cross-origin resources, such as images and frames.
In order to determine which websites have been visited by a user, Olejnik and Janc relied on the fact that a site can apply different styles to links that have been visited and ones that have not been accessed.
An attacker can create a webpage that sets link styles to white for visited links and black for not-visited links. The attacker’s page then starts displaying a list of popular domain names one by one. If a link has been visited, the screen turns white; if it hasn’t been accessed, it turns black. The ambient sensor can log the light level when each link is displayed, and determine if that website had been accessed by the user.
Researchers also demonstrated how an attacker can steal cross-origin resources, such as account recovery QR codes. In this case, the hacker’s website embeds an image of the QR code from the targeted domain into their own site. The image is converted to monochrome using SVG filters, and it’s scaled so that each pixel is expanded one by one to fill up the screen. The exploit goes through each pixel, and the ambient sensor logs a white or black pixel depending on what is on the screen.
In their experiments, researchers determined that this technique can be used for a fully reliable exploit at a rate of one bit per 500 ms. At this rate, an attacker can exfiltrate an 8-character password in 24 seconds, a 20x20 QR code in 3 minutes and 20 seconds, and a 64x64 pixel image in just over half an hour. As for stealing a user’s browsing history, it takes 8 minutes and 20 seconds to go through 1,000 popular URLs and determine if they have been visited.
While it’s unlikely that such an obvious attack can be carried out while the phone is used, Olejnik and Janc pointed out that an attack can be conducted at night via a site that uses the screen.keepAwake API to keep the display on while the exploit is running.
Researchers believe these types of attacks could be prevented by limiting the frequency of sensor readings. An even more efficient mitigation involves limiting the precision of sensor output (i.e. make it difficult for the color of the screen to influence the sensor reading).
Attacks can also be prevented if browser vendors require users to grant permission before giving websites access to the sensor. Both Google and Mozilla have been notified of the potential risks.
Microsoft Kills Support for Windows Vista
13.4.2017 securityweek Security
While expected for some time, Microsoft this week ended support for its Windows Vista operating systems. The change entered into effect on April 11, the very same day Microsoft began rolling out Windows 10 Creators Update to its users.
Windows Vista has been receiving software updates for the past 10 years, but Microsoft has decided that the time has come to move on.
“As of April 11, 2017, Windows Vista customers are no longer receiving new security updates, non-security hotfixes, free or paid assisted support options, or online technical content updates from Microsoft,” the company notes on its support website.
Data coming from netmarketshare shows that the move would impact only 0.72% of all desktop users out there, but that is still a significant figure, considering that many of the Windows Vista computers are used within business environments.
A November report from Duo Security revealed that 65% of the security company’s clients' Windows users were using Vista. The threat this poses to enterprise networks is amplified by the continuous use of an even older operating system within business environments: Windows XP. The platform currently has 7.44% of the desktop operating system market, yet it hasn’t received updates since 2014.
Now that support has ended, Windows Vista will continue to work as before, only that it will become increasingly vulnerable to security risks and malware. What’s more, Internet Explorer 9, which runs on Vista, isn’t supported either, meaning that users are exposed to additional threats when browsing the web using this application.
“Also, as more software and hardware manufacturers continue to optimize for more recent versions of Windows, you can expect to encounter more apps and devices that do not work with Windows Vista,” Microsoft says.
In fact, major browser makers have already announced their end of support for the platform. Mozilla revealed in December 2016 that it would no longer support Vista and XP starting this year, while Google’s Chrome 49 was the last browser iteration released for the two platforms. Gmail isn’t offering support for the operating systems either, after it dropped support for Chrome 53 and older versions in February.
To further determine users to move away from Windows Vista, Microsoft also stopped providing Microsoft Security Essentials for download on this platform. Antimalware signature updates will continue to arrive for installed instances for a limited time, after which users will remain exposed to newer threats.
“Please note that Microsoft Security Essentials (or any other antivirus software) will have limited effectiveness on PCs that do not have the latest security updates. This means that PCs running Windows Vista will not be secure and will still be at risk for virus and malware,” Microsoft notes.
Mozilla Wants 64 Bits of Entropy in Certificate Serial Numbers
6.4.2017 securityweek Security
Mozilla this week announced an update to its CA Certificate Policy, which now requires the use of 64 bits of entropy in certificate serial numbers.
The change was included in Mozilla’s CA Certificate Policy 2.4.1, and arrives nearly one year after the CA/Browser Forum adopted Ballot 164, which required Certificate Authorities to use greater randomization when issuing certificates, to mitigate collision attacks and make preimage attacks more difficult.
The ballot also proposed replacing entropy with cryptographically secure pseudo-random number generator (CSPRNG). Thus, Section 7.1 of the Baseline Requirements was modified to “Effective September 30, 2016, CAs SHALL generate Certificate serial numbers greater than zero (0) containing at least 64 bits of output from a CSPRNG.”
The change was proposed after it was demonstrated that hash collisions can allow attackers to forge a signature on the certificate of their choosing and that random bits made the security level of a hash function twice as powerful. While adding random bits was encouraged before, the ballot made it a requirement.
The updated CA Certificate Policy also states that CP and CPS documents now need to be submitted to Mozilla each year, in addition to audit statements, and that these documents need to be provided in English starting June 1, 2017. The company also updated the applicable versions of some audit criteria.
Mozilla also notes that submitted documentation must be openly licensed and that the Common CCADB Policy and the Mozilla CCADB Policy are incorporated by reference in Mozilla’s CA Certificate Policy version. Further, the new Common CA Database (CCADB) Policy makes official a number of existing expectations regarding the CCADB, and there are additional requirements on OCSP responses, the company says.
The organization has already sent the CA Communication to the Primary Point of Contact (POC) for each CA and asked them to respond to 14 action items. Additionally, there are discussions in the mozilla.dev.security.policy forum about upcoming changes, questions and clarification about policy and expectations, root certificate inclusion/change requests, that CAs are invited to contribute to.
“With this CA Communication, we re-iterate that participation in Mozilla’s CA Certificate Program is at our sole discretion, and we will take whatever steps are necessary to keep our users safe. Nevertheless, we believe that the best approach to safeguard that security is to work with CAs as partners, to foster open and frank communication, and to be diligent in looking for ways to improve,” the company said.
Still problems for Schneider Electric, Schneider Modicon TM221CE16R has a hardcoded password
5.4.2017 securityaffairs Security
The firmware running on the Schneider Modicon TM221CE16R (Firmware 1.3.3.3) has a hardcoded password, and there is no way to change it.
I believe it is very disconcerting to find systems inside critical infrastructure affected by easy-to-exploit vulnerabilities while we are discussing the EU NIS directive.
What about hard-coded passwords inside critical systems?
Unfortunately, it’s happened again, the firmware running on the Schneider Modicon TM221CE16R (Firmware 1.3.3.3) has a hardcoded password. The bad news for users is that they a cannot change the password and there is no firmware update available to fix this issue.
The firmware encrypted the XML file containing user and password with the fixed key “SoMachineBasicSoMachineBasicSoMa”.
It is quite easy for an attacker to open the control environment (SoMachine Basic 1.4 SP1), decrypt the file, and take control over the device.
“The password for the project protection of the Schneider Modicon TM221CE16R is hard-coded and cannot be changed.” reads the security advisory published by Simon Heming, Maik Brüggemann, Hendrik Schwartke, Ralf Spenneberg of Germany’s Open Source Security.”The protection of the application is not existent.”
![]()
The same team of researchers discovered another security issue affecting the Schneider TM221CE16R Firmware 1.3.3.3 hardware. The experts discovered that the password used to protect the applications can be easily retrieved by a remote unauthenticated user. The Application Protection is used to prevent the transfer of the application from a logic controller into a SoMachine Basic project.
“The password for the application protection of the Schneider Modicon TM221CE16R can be retrieved without authentication. Subsequently the application may be arbitrarily downloaded, uploaded and modified. CVSS 10.” reads a separate security advisory published by the team.
The experts discovered that a user just needs to send the following command over Modbus using TCP Port 502:
echo -n -e '\x00\x01\x00\x00\x00\x05\x01\x5a\x00\x03\x00' | nc IP 502
“After that the retrieved password can be entered in SoMachine Basic to download, modify and subsequently upload again any desired application”, continues the advisory.
Brain-Inspired System Aims to Improve Threat Detection
22.3.2017 securityweek Security
Cyber Microscope
A new "brain-inspired" computer system promises improved detection of cyber threats by looking for specific patterns that can more efficiently reveal indicators of compromise in a network.
Dubbed the Neuromorphic Cyber Microscope, the system was designed by Lewis Rhodes Labs in partnership with Sandia National Laboratories and aims to address the limitation current systems have when it comes to the detection of more complex indicators of compromise, which the researchers call “new species of ‘bad apples’.”
The designers of the system explain that many modern cybersecurity systems might be looking for general indicators of compromise or only for specific patterns, and often require interaction from security analysts to correctly sort the real dangers from false alarms.
By using its brain-inspired design, the new system promises not only to address this limitation by looking for complex patterns that indicate specific “bad apples,” but also to offer energy consumption savings, as it requires “less electricity than a standard 60-watt light bulb,” its creators claim.
The Microscope’s processor is based on the neuroscience research of Dr. Pamela Follett, a co-founder of Lewis Rhodes Labs. The research was used by her husband, David Follett, co-founder and CEO of Lewis Rhodes Labs, as the basis for a computational model of how the brain processes information.
A team led by computer systems expert John Naegle considered cybersecurity as the domain where the neuromorphic processor would excel.
“We quickly realized that we could use this architecture to greatly accelerate our ability to look for patterns and even look for complex versions of these patterns,” Naegle said.
While conventional detection systems compare the received data against a library of malicious patterns, the Neuromorphic Cyber Microscope was designed to compare streaming data to suspicious patterns in a time-dependent manner, which should improve its detection efficiency.
According to Sandia, it tested the system in a demonstration environment and discovered that it could perform efficiently even when the “bad apple” patterns got more complex, in comparison with a state-of-the-art conventional system that slowed exponentially. Further, the laboratory claims that the Microscope is “more than 100 times faster and 1,000 times more energy-efficient than racks of conventional cybersecurity systems.”
At the moment, however, the Neuromorphic Cyber Microscope is only in the early stages of deployment.
Sandia and Lewis Rhodes Labs are also exploring alternative uses for the general neuromorphic architecture, including a type of machine learning used for audio and image processing and sorting numbers efficiently.
US Bans Laptops, Tablets From Cabins on Flights From Middle East
21.3.2017 securityweek Security
The United States warned Tuesday that extremists plan to target passenger jets with bombs hidden in electronic devices, and banned carrying them onto flights from 10 Middle East airports.
Senior US officials told reporters that nine airlines from eight countries had been given 96 hours, beginning at 3:00 am (0700 GMT), to ban devices bigger than a cellphone or smartphone from the cabin.
Laptops, tablets and portable game consoles are affected by the ban -- which applies to direct flights to the United States -- but they may still be stowed in the hold in checked baggage.
Passengers on approximately 50 flights per day from some of the busiest hubs in the Middle East, Turkey and North Africa will be obliged to follow the new emergency ruling.
"The restrictions are in place due to evaluated intelligence and we think it's the right thing to do and the right places to do it to secure the safety of the traveling public," one US official said.
The officials, speaking on condition of anonymity, refused to discuss the "intelligence information" that led the Transportation Security Administration to issue the order.
But one said that concerns had been "heightened by several successful events and attacks on passenger lanes and airports over the last years."
No end date
The official would not go into detail about which attacks had raised fears, but did cite an incident from February of last year in which suspected Somali Islamists blew a hole in the side of Daallo Airlines passenger jet with a small device. Only the bomber was killed and the plane landed safely.
CNN quoted a US official as saying the ban was believed to be related to a threat posed by Al-Qaeda in the Arabian Peninsula, known as AQAP.
"Evaluated intelligence indicates that terrorist groups continue to target commercial aviation and are aggressively pursuing innovative methods to undertake their attacks, to include smuggling explosive devices in various consumer items," an official said.
The airports touched by the ban are Queen Alia International in Amman, Jordan; Cairo International in Egypt; Ataturk in Istanbul, Turkey; King Abdulaziz International in Jeddah, Saudi Arabia; King Khalid International in Riyadh, Saudi Arabia; Kuwait International; Mohammed V International in Casablanca, Morocco; Hamad International in Doha, Qatar; and the Dubai and Abu Dhabi airports in the United Arab Emirates.
No US carriers make direct flights from these airports, so they are unaffected by the ban, which will hit Royal Jordanian, EgyptAir, Turkish Airlines, Saudi Airlines, Kuwait Airways, Royal Air Maroc, Qatar Airways, Emirates and Etihad Airways.
The airlines and their host governments have already been informed of the order by US officials, and some of them have begun informing passengers about the restriction.
Airlines will be responsible for policing the cabin ban, and if they fail to do so could lose their rights to operate US routes.
No end date has been put on the order, and officials would not say whether the restriction might spread to other airports.
Microsoft Started Blocking Windows 7/8.1 Updates For PCs Running New Processors
20.3.2017 thehackernews Security
You might have heard the latest news about Microsoft blocking new security patches and updates for Windows 7 and Windows 8.1 users running the latest processors from Intel, AMD, Qualcomm, and others.
Don't panic, this new policy doesn't mean that all Windows 7 and 8.1 users will not be able to receive latest updates in general because Microsoft has promised to support Windows 7 until 2020, and Windows 8.1 until 2023.
But those who have upgraded their machines running older versions of Windows to the latest processors, or manually downgraded their new laptops to run Windows 7/8.1 would be out of luck.
A recently published Microsoft Knowledge Base article suggests that if you are running the older version of operating systems on your computers that feature new processors, including Intel's 7th generation Core i3, i5 and i7 ("Kaby Lake"), AMD Ryzen ("Bristol Ridge") and Qualcomm 8996 chips or later, the security updates will not install.
Instead, you will see error messages when using Windows Update to get patches for Windows 7 and Windows 8.1. The error messages read:
"Unsupported Hardware.
Your PC uses a processor that is not supported on this version of Windows, and you will not receive updates."
"Windows could not search for new updates. An error occurred while checking for new updates for your computer. Error(s) found: Code 80240037 Windows Update encountered an unknown error."
So, What's the Solution ? (According to Microsoft)
Users would require upgrading their systems to the newest version of Windows, i.e. Windows 10, despite Windows 7 being supported to 2020 and Windows 8.1 to 2023.
Microsoft announced this limitation in January 2016, when the company said making Windows 7 and Windows 8.1 OSes run on the latest processors was "challenging."
"For Windows 7 to run on any modern silicon, device drivers and firmware need to emulate Windows 7's expectations for interrupt processing, bus support, and power states- which is challenging for WiFi, graphics, security, and more," Terry Myerson, VP of Microsoft's Windows and Devices Group, said last year.
The initial announcement also included PCs that use 6th-generation Intel processors ("Skylake"), but Microsoft backed off on its plan and released a list of Skylake-based systems that will be fully supported to receive security updates through the official end of support phase for Windows 7 and Windows 8.1, i.e. January 14, 2020, and January 10, 2023, respectively.
Microsoft Indirectly forcing users to adopt Windows 10
This end of updates for new devices doesn't come as a surprise to some PC owners, as Microsoft is making every effort to run its latest Windows on all Windows computers since the launch of Windows 10.
An alarm for those still running Windows Vista on their machines: The operating system will no longer receive security updates, non-security hotfixes, paid assisted supports, or online technical updates from Microsoft beginning April 11, 2017.
So, it's high time for Windows Vista users to upgrade their PCs to the latest version of Windows operating system in order to protect your devices from malware or other security threats.
Ditch Windows for Linux; Try This:
No doubt Windows 10 has been viewed as a welcome successor to Windows 8, both by businesses and individuals, with more enhanced security features. But the OS has also come under scrutiny from those who are concerned about their privacy.
So why not switch to a free Windows 10 alternative? Privacy concerned people can move to Linux operating systems, such as Ubuntu – a Debian-based OS and part of open source Linux family, and Fedora – Red Hat's Linux distro with estimated 1.2 Million users.
How to Browse The Internet Securely And Anonymously
8.3.2017 securityaffairs Security
These are some of the top methods you can use to browse the internet securely and anonymously.
Even as the world becomes more aware of the imminent threat to our online privacy, few people understand the need to hide crucial information, such as IP addresses and private data streams, from entities such as our Internet Service Providers (ISPs), various online advertising companies, and our governments. Thankfully, fortifying your online privacy is not rocket science.
With the array of online encryption tools such as IP Changer software, Virtual Private Networks, and the popular Tor Browser, internet users are not short of options. Herein are some of the best ways to browse the internet securely and anonymously.
Tor
The Onion Router, abbreviated and more commonly known as Tor, is one of the most sought after online anonymity tools. Tor focuses on making your location untraceable by masking your IP address under layers and layers of smokescreen and encryption to cover up the origins of your connection.
Already, a sizeable percentage of the internet is already using the Tor Browser – a modified version of the Mozilla Firefox Browser – to keep their identities hidden while on the internet. Not only does it act as an IP changer, it also keeps trackers at bay. Tor can be described as the most user-friendly option in this list, and also the most all-encompassing encryption tool since it integrates more than one encryption technique in the form of browser extensions to give users comprehensive online security. Being an open-source project, it is also completely free.
However, using the Tor browser will still require you to change your online behavior in order to retain maximum anonymity. It comes with a number of warnings, tips, and tricks that every privacy-conscious individual should follow when browsing the internet. Tor is not without its limitations but has so far proved to be the most viable option for people of all calibers.
Virtual Private Networks
VPNs are considered heavy-duty online anonymity tools for a reason. These services focus on helping users to disguise their traffic in addition to keeping their IP addresses hidden whenever they connect to the internet. They are also considered powerful IP changer software. VPNs are only able to encrypt internet traffic, though, meaning that users’ ISPs will still be able to see how much traffic you generate from website to website, but will not be able to see the actual content. The same applies to snooping governments and any malicious parties who may wish to steal your vital information such as login credentials.
The only catch is that a good VPN service will cost you. However, the expense can often be overlooked because this technique does not have a lot of weaknesses. If you’re living in a country where the government has sanctioned the blocking of all VPN connections, there are stealth VPNs that will allow you to browse the internet undetected. As such, VPNs are the preferred option for people living in countries with extreme internet censorship and heavy government surveillance.
Browser Extensions for Privacy
For much lighter, but just as effective online privacy, users can always choose to install a privacy-centric browser extension. At the top of the list of extensions users can get is Ghostery, which is compatible with Chrome, Firefox, and Internet Explorer, and EFF’s Privacy Badger. Unlike VPNs and Tor, browser extensions will not function as IP changer software since they do not hide your IP address.
The only notable difference between the two extensions is that Ghostery is more hands-on than Privacy Badger is. With Ghostery, you are allowed to tweak your privacy settings, such as which trackers to block. It also allows you to see all the trackers that are being used on you for every website that you visit, allowing you to choose which websites to show your information to and which to block out completely. It is quite handy when it comes to keeping advertisers from logging your information.
Privacy Badger, on the other hand, is a bit more intuitive than the former option. This extension monitors websites that are tracking your browsing habits and either block out the websites in total or keeps their tracking methods from working on you. Despite being based on an ad-blocking codebase, it does a lot more than just keep you safe from annoying ads. Its intuitive design allows it to learn from your browsing habits, meaning that you don’t have to constantly adjust the settings.
Changing Your IP Address
IP bans are the primary reason why people change their IP addresses. Whether a certain online service is not yet available in your country or you have been explicitly banned from a specific website, changing your IP address can be a viable way of gaining access to the website.
Methods range from the fairly complicated manual method, which involves resetting your modem or using different devices, to downloading IP changer software.
The latter option is often preferred over the former. IP changer software can be used to change your IP address multiple times even if you’re using the same device. Unlike other encryption services, however, IP changer software only alters your real IP address. The IP changer software will not mask your traffic or help you block any trackers; it simply displays a different IP address than the one that is actually assigned to you.
You might opt for IP changer software if your privacy needs are basic. It simply throws off your ISP and government on your real location, sometimes helping you circumvent government-imposed censorship and other bans put in place by your ISP. IP changer software is by no means a comprehensive option like Tor or VPNs, but it does work. You can choose from a wide range of IP changer software on the internet, or alternatively, you can go for a VPN service that provides the IP changer option to keep your real location well under wraps.
HTTPS Everywhere
Even as the whole internet is in the process of fully adopting SSL, there is still a notable percentage that does not support the security protocol. It is essential in keeping web traffic free from malicious interceptors. Web sites that still display unencrypted connections by default are significantly less safe.
The HTTPS browser extension allows users to force an HTTPS connection on countless websites. However, since it depends on the website users are connecting to, it is still a viable solution despite not being the best option in this list.
Many of these privacy-centric tools and software rely on IP changing tactics, masking your traffic, or securing your connections via a number of channels. You might not think you’re a target for hackers, but based on the indiscriminate hacking that is going on nowadays, it pays to take precautions.
Secdo Automates End-to-End Incident Response with Preemptive IR
8.3.2017 thehackernews Security

As vast volumes of digital data are created, consumed and shared by companies, customers, employees, patients, financial institutions, governments and so many other bodies, information protection becomes a growing risk for everyone.
Who wants to see personal customer purchasing data flying into the hands of strangers? What company can tolerate the pilfering of its intellectual property by competitors? What government can stand idly by while its military secrets are made public?
To protect their valuable and private information, organizations purchase numerous cyber security systems – like intrusion detection systems, firewalls, and anti-virus software – and deploy them across their networks and on all their computers.
In fact, a typical bank, manufacturer or government department might have dozens of such products operating at all times.
Cyber security systems work non-stop to thwart network infiltration and data-theft. Whenever they notice an activity that seems outside the scope of regular use, they issue an alert to notify cyber security personnel who investigate the reason for the alert and take remedial action if necessary.
For example, if someone tries to access a computer and repeatedly enters the wrong password, an alert will be issued. When an email attachment containing a virus is opened, another alarm will be raised.
Despite all of these security systems and their alerts, strong networks are breached, and the information is stolen. Why does this still happen?
Over-Detection and False Positives
Cyber security systems work by noticing unusual activities and behaviors of people and software. But they often get it wrong. Try as they may, in order to be ultra-careful, cyber security systems flag a lot of activities that they determine to be potentially malicious but, in reality, are not.
Yes, you keyed in your password three times until you got it right, but you aren’t a data pirate. That still causes an alert.
From your office computer, you inadvertently accessed a website that is off-limits to your company. Honest mistake, but another alert.
This happens so frequently that, every day, hundreds or even thousands of alerts turn out to be nothing of note.
Can you believe it? The average enterprise in the US receives more than 10,000 alerts every day. Most of them aren’t incidents that should demand attention. But how do you know until you look into them?
This daily load of false positives distracts cyber security professionals from dealing with legitimate security alerts.
As more and more time is wasted chasing after false positives, security staffs have to resort to triage – that is, they try to figure out which alerts are important and require a response, and which ones are false and should be ignored. They aren't always accurate. Sometimes, an analyst spends weeks tracking down an incident that turns out to be irrelevant.
Conversely, sometimes, the alert that is ignored is the real emergency!
Distracted to Ruin
A good example that shows how false positives can be ruinous to an organization is the Target Data Breach.
Target, the second-largest discount-store retailer in the United States, was forced to admit to more than 70 million shoppers that their personal and financial information had been compromised.
With a large cybersecurity team and a significant budget for tools and technologies that protect data, how could this happen to Target? (Or Ebay? Or JP Morgan Chase? Or Yahoo?)
Target's problem wasn't that some sort of hacker had succeeded in bypassing its robust cyber security systems. In fact, the company's detection systems deployed specifically to monitor such intrusion attempts had generated alerts confirming that malicious software was present. So why wasn't it dealt with?
As these important alerts were buried among thousands of daily false positives, they did not achieve high enough attention to warrant the prompt action that they demanded. They were missed. This simple oversight led to one of the largest and most costly data breaches in history, estimated at more than $300 million!
In short, while detecting cyber threats and alerting security personnel is crucial, it is not nearly enough. Organizations must institute an accurate, real-time alert validation methodology that unfailingly determines which of the thousands of daily alerts deserve attention and which are just "noise."
But the devil is in the details.
Secdo Automates the Incident Response Process End to End
Secdo's Preemptive Incident Response platform automatically validates every single alert, distinguishing between false positives and real threats that deserve serious investigation.
Secdo provides all the context – the "who, what, where, when and how" – to help security analysts determine the severity of a real alert. Then, Secdo empowers security teams to respond quickly and precisely to combat the threat.
The Secdo platform comprises three modules:
Observer
Analyzer
Responder
Observer
According to Secdo, effective cyber security begins with preemptive data collection. Like a battery of digital cameras that see and record everything, Observer records and stores every activity that occurs on every endpoint (computer) and server (we call these "hosts") in the network.
Everything on every host, even when they number in the tens of thousands! Observer enables security and IT teams to see how any host, user, or process behaved now or in the past – just like the ability to view any video from any camera now or in the past at the click of a mouse.
Observer enables quick investigations and threat-hunting. It provides facilities for easy ad-hoc inquiries, enabling analysts to investigate any alert and hunt for threats effectively. Security analysts can use the intuitive investigation interface to ask questions about any event and always get a conclusive answer.
For example:
Who accessed the website www.youshouldnotgothere.ru on January 24th between 13:31 and 15:09?
Which hosts have file iamarealthreat.exe on their hard drive?
Which endpoints sent out companyfinancials.xlsx in emails last night?
Answers to these and other questions are displayed promptly and helpfully to the security analyst.
Results returned from an Observer inquiry
Analyzer
Non-stop, Analyzer correlates the mass of data stored by Observer. If Observer is like thousands of digital cameras recording everything, Analyzer is the intelligence that connects all the individual videos into coherent stories that can be reviewed anytime.
For example, malicious software from my boss’s computer is trying to send data out to a foreign website, an event that triggers an alert. It sounds like a simple case, but the full story might read like this:
"Yesterday, I received an email from a particular address. I clicked on the attachment, looked at it, and thought about it no more. However, unbeknownst to me, the attachment wrote a bit of malware on my hard drive. Two hours later, it started to search my computer until it found a password file that enabled it to jump to my boss’s computer. There, at midnight, the malware woke up, searched my boss’s hard drive until it found a file called secretcompanyplans.docx. It connected to a website in Ukraine and attempted to send the file. This is what triggered the alert."
The security analyst will see the limited information in the alert which says: "The boss’s endpoint attempted to connect to www.ohnodontgothere.ua."
How can the analyst know the entire story of the alert in order to understand that there is an attachment to an email on my computer that started the whole incident?
Merely preventing access to the bad website will not eradicate the danger. Perhaps this piece of malware is so smart that it will wake up again and try some other tricks like sending another file to a different website. That will just trigger another alert and require another security analyst to fix the same problem tomorrow.
The full story is necessary to fix the entire problem once and for all..
Secdo's Analyzer helps analysts get to the root of every problem and understand its full scope so they can remediate it at its root cause.
Analyzer's Causality Engine places all events received from the Observer data into causality chains (the story) in anticipation of alerts, preparing the forensics that will be necessary for any future security investigation.
As alerts are triggered from any source (any of the many cyber security systems that the organization has deployed), Analyzer automatically correlates the alerts with their appropriate causality chains, placing them into their full context. IT and security teams are able to see the chain of events (the entire story) of exactly what happened from this moment backward into the past.
With the full context, Analyzer can accurately distinguish false alerts so that analysts don’t have to endure unnecessary distractions. It accurately priorities and presents each genuine alert, displaying the entire context including the attack chain starting from root cause (how did this incident start?), all entities involved (where has it spread?) and damage assessment (what did the bad guys do to us so far?) – the entire story.
With all this information presented graphically before their very eyes, security analysts can properly analyze real alerts and respond correctly in seconds.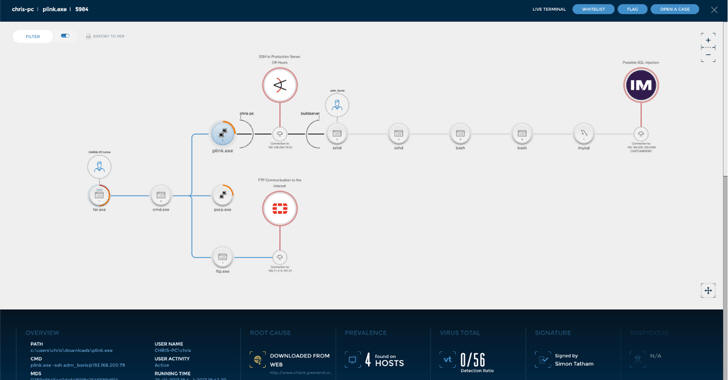
Analyzer presents a graphic representation of the entire causality chain including root cause
In our example, Secdo would enable the analyst to see that the malicious attachment on my computer started the entire chain of events, that it jumped to my boss's computer and that both malicious processes must be cleaned as well as other files or commands they might have written and anything else that is pertinent to this incident.
Responder
So, what do you do once you have found an actual cyber breach that requires a firm and accurate response?
Before Secdo, IT personnel usually had to confiscate your computer, wipe it clean and reinstall Windows and all your applications and data files. Everything. This could take hours or even days. What an interruption to your productivity and what a cost to the company!
With Secdo, the process is a lot faster and smarter, and doesn't interfere with your work. Responder gives security and IT people the ability to remotely access and surgically resolve any threat on any host without impacting productivity.
Responder provides numerous powerful containment and remediation capabilities including patented ICEBlock™ that safely freezes a process in memory while the endpoint remains on the network. You can keep working securely while all this takes place.
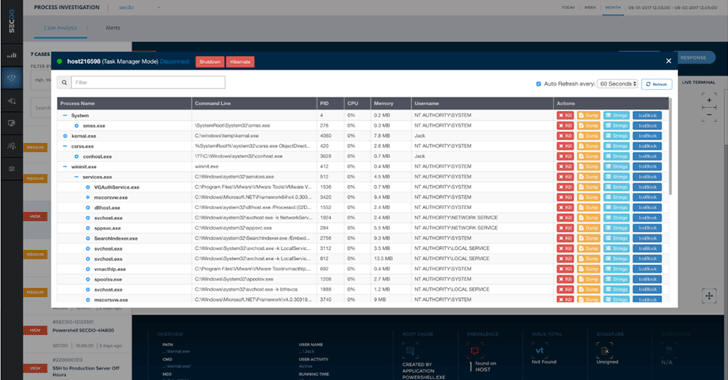
Responder enables IT to deal with specific threats on any host without impacting user productivity
Responder even takes security a step further. Its plentiful and powerful response capabilities can be fully automated adding protection to the organization into the future.
Conclusion
Digital data is an attractive target for cyber attackers who would steal it for nefarious purposes. Organizations employ security analysts and deploy numerous security products to help them defend against cyber attacks.
These products may generate thousands of alerts every day, and most of these are false positives. Due to the overwhelming daily volume, security teams cannot deal with all alerts and must triage them.
Analysts need an automatic, accurate way to separate out the false positives and prioritize the real ones so that they can focus on real threats. They need to see the entire scope of incidents in order to determine the proper course of remediation. They require remote, surgical response tools that enable them to accurately eradicate threats while maintaining business productivity.
Secdo's Preemptive Incident Response (PIR) transforms the traditional IR process from reactive to proactive by continuously collecting and storing all host activity data – BEFORE an incident occurs.
All activity data from all endpoints and servers (hosts) is automatically correlated in causality chains (context) in anticipation of future incidents. As alerts are ingested from detection systems, they are connected with their appropriate causality chains, preparing full forensic evidence even before Incident Response teams get involved.
With full context, false positives can be eliminated accurately, and real alerts can be prioritized correctly. Security analysts can quickly investigate each alert, already observing its root cause, full activity, entities involved and damage assessment.
With this level of visibility and context, accompanied by a suite of advanced surgical remediation tools, analysts can respond remotely, promptly and precisely to threats while maintaining business productivity.
UK's 1E Challenges Tanium With New Endpoint Detection & Response (EDR) Tool
8.3.2017 securityweek Security
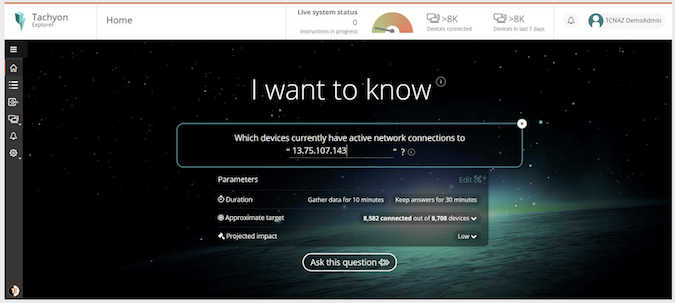
Tachyon Takes on Tanium With Promise to Go From Detection to Remediation Across the Entire IT Estate in Seconds
Time to detect and time to remediate is the difference between an incident and data loss. But while there have been dozens of new products designed to help the security team detect incidents, there has been very little that helps IT Ops remediate rapidly across the entire estate.
One of the problems is that detection and remediation are separate operations often handled by separate teams: security and IT. But security is not IT's only customer -- it must also respond to compliance, audit, and virtually every operational department in the organization with requests for enhancements or completely new apps.
The result is a huge workload made more difficult by the false positives that come from many of today's threat detection systems. According to 1E's own research involving 1000 IT professionals, more than half spend 25% of their time responding to unplanned incidents coming from urgent security updates, configuration changes and software audits.
Today 1E has launched Tachyon, designed to give IT operations instant actionable access into the furthest reaches of the entire IT estate (up to 1.5 million endpoints), regardless of distribution or operating system. Agents on every endpoint, whether server, desktop, mobile or IoT device can be queried from the Tachyon server. Incidents can be isolated and remedial action taken -- within seconds across the entire estate.
Stuart Okin, SVP of product at 1E, told SecurityWeek to think of Tachyon's front end like 'a Google for the IT estate'. Questions can be asked and replies drawn from every endpoint in seconds. Based on those answers, remedital action can be taken -- again within seconds.
Okin gave an example involving abuse of Java. Assume that the security team has learned that a Java vulnerability is being exploited, and has passed this information to IT Ops. A single question to Tachyon asking for device software filtered by Java displays all devices at risk. A second question looks for historical evidence of connection to the attacker's IP address. Within seconds, all (if any) compromised devices have been located.
Further communication with the attacker can be blocked instantly by instructing Tachyon to add a new rule to the local firewall blocking that IP address. Repeating the process will now confirm that no devices can connect to the attacker.
This principle applies across the board. If the security team learns of current a threat or detects indications of compromise through other threat intelligence systems, and can define the threat, the IT team can use Tachyon to locate and remediate within seconds. Of course, it needn't be a security threat -- it could be a threat to regulatory status, or a requirement from audit. It could be used, for example, to locate privileged accounts with access to sensitive data and to remove any that are not strictly necessary. Confirmation with precise details on the remaining privileged accounts can be sent to audit as necessary.
Okin stressed that Tachyon is not designed to replace any existing investments, but to work with them to enhance their performance. Microsoft SCCM is an example. "While other vendors are promoting a rip-and-replace approach, we built Tachyon from the ground up to layer on top of Microsoft SCCM, with a light footprint that enables speed and responsiveness," commented Sumir Karayi, founder and CEO of 1E.
This was confirmed by a Fortune 500 health insurance company, which was one of the first users of Tachyon. "We rely heavily on Microsoft SCCM and other 1E solutions to automate everyday IT tasks such as software updates, but lacked the ability to identify and remediate severe problems instantly," said the organization's infrastructure engineer manager. "1E's Tachyon adds those real-time capabilities - helping us 'save the day' in an emergency. With Tachyon, we can now address big problems in seconds rather than hours, in an organized, controlled way."
Key to Tachyon's workings are agents on each endpoint. These query the device and maintain a secure communication with the Tachyon server. They provide the functionality for remedial steps, and ensure that the system is eminently extensible by allowing additional functionality to be introduced without requiring any upgrade to the core system. It is designed to be endpoint cross platform, supporting Microsoft, Mac, Linux, mobile and IoT -- making it suitable for large corporations and the emerging internet of things.
The strength of the Tachyon approach is that it doesn't replace anything, nor does it attempt to automate decision making. Indeed, where remedial action can be described as an 'impactful change', a second approval can be required before the remediation is actioned. It makes existing systems work more efficiently and very much faster. Organizations will still need threat analysts to recognize possible incidents; and IT Ops to effect remediation where necessary. Tachyon allows the two teams to work together far more effectively, so that a potential incident can go to detection and remediation in seconds rather than hours or days.
FCC gives full powers to US ISPs, they can sell users’ data without consent
7.3.2017 securityaffairs Security
The United States Federal Communications Commission (FCC) announced the suspension of the privacy rules just before they came into effect.
Someone considers the privacy the modern utopia, it is daily threatened by law enforcement and intelligence agencies and authoritarian regimes.
Unfortunately, I have bad news for privacy defenders.
On October 2016, the United States Federal Communications Commission (FCC) passed a set of privacy rules on ISPs that limit them from using user data for marketing or commercial purposes. The rules prohibit ISPs from sharing user data with third parties without the user’s explicit consent. The set of rules also requires ISPs to implement “reasonable measures” to protect data from cyber threats.
Back to the present, the FCC announced the suspension of the privacy rules just before they came into effect.
“”Until that happens, however, we will work together on harmonizing the FCC’s privacy rules for broadband providers with the FTC’s standards for other companies in the digital economy. Accordingly, the FCC today stayed one of its rules before it could take effect on March 2.” reads a joint statement of FCC chairman Ajit Pai And Acting FTC chairman Maureen K. Ohlhausen on protecting Americans’ online privacy.
“This rule is not consistent with the FTC’s privacy framework. The stay will remain in place only until the FCC is able to rule on a petition for reconsideration of its privacy rules.”
This means that Internet Service Providers (ISPs) can use customers’ data for the commercial purposes.
Consider that ISPs are a sort of sentinel of the Internet, from their point of view it is possible to monitor users’ activities and profile them.
Data collected on the users then are shared with advertising firms for commercial purposes.
Ajit Pai is the Chairman of the Federal Communications Commission, he was designated Chairman by President Donald Trump in January 2017.
Ajit Pai is known as an opponent of the net neutrality, he publicly defined it “a mistake.”
Pai is arguing that the privacy rules favored IT tech giants like Google and Facebook, which are regulated by the Federal Trade Commission (FTC), over ISPs like Verizon and Comcast.
FCC
So, he is asking for the equity in the treatment for IT firms by the FTC and the FCC.
“All actors in the online space should be subject to the same rules, enforced by the same agency.” FCC said in a statement.
The FCC will block new privacy rules because it will never go in contrast with IT giants like Google and Facebook on the way they commercialize usersì data, it is likely the FCC would never restore those suspended rules on ISPs.
CrowdStrike Vs NSS Labs, Round 2: NSS Hits Back
6.3.2017 securityweek Security
In February 2017, endpoint protection firm CrowdStrike took the unusual step of suing independent product testing organization NSS Labs, "to hold it accountable for unlawfully accessing our software, breaching our contract, pirating our software, and improper security testing."
The immediate purpose of the suit was to support action for an injunction to prevent NSS Labs from publishing test result details of CrowdStrike's Falcon endpoint security product within its latest public test. The injunction failed, and NSS published the results.
At the time, NSS Labs issued brief statements but published no lengthy response to CrowdStrike's blogged accusations of 'unlawful conduct' and 'deeply flawed methodology'. Now it has done so.
"Given the serious inaccuracies CrowdStrike has been promoting in their blog and elsewhere, we decided that we needed to tell our side of the story," blogged NSS CEO Vikram Phatak. The blog amounts to a step-by-step refutation of CrowdStrike's accusations.
Where CrowdStrike claims the tests are incomplete (it disconnected its cloud-based Falcon before the tests were complete) and the results therefore invalid, NSS claims that CrowdStrike's results were not penalized. "CrowdStrike did not receive a zero (0) for the parts of the test we were unable to complete - because we believed that penalizing CrowdStrike for disabling the product could mislead the public." It also points out that Falcon had missed various attacks before the disconnection, and that those attacks would remain missed whether the full testing had been completed or not.
A primary thrust of CrowdStrike's arguments is that it had "declined to participate in a public test after completing a private test with NSS, based on NSS' flawed and improper testing execution."
The NSS response is that it is not open for individual companies to withdraw from a public test. "NSS Labs informed CrowdStrike that our position, as always, is that if a product is good enough to sell to the public, it is good enough to be tested and that we would purchase their product if necessary." NSS tried to buy the product, was blocked by CrowdStrike, but "found an enterprise who would be willing to work with us to purchase the product."
CrowdStrike Falcon was subsequently part of the NSS public tests, but failed to complete because CrowdStrike disconnected it from its cloud before completion.
It is an unsightly squabble; but one that has been threatening for many months. Next-gen endpoint protection firms have tended to claim that the in situ anti-virus products do not work. Those 'legacy' firms have responded that independent testing would settle the issue. To begin with, next-gens replied that their products could not be tested in the same way as legacy products (and it should be said that they had a point).
The testing laboratories, however, have spent considerable time and effort in improving their testing techniques specifically for next gens -- and many next-gens are now happy to take part. Three other next-gen products included in the same tests did rather well: Cylance at 99.69%, SentinelOne at 99.79%, and Invincea at 99.49%. CrowdStrike did less well at 74.17%.
Anup Ghosh, founder and CEO at Invincea, accepts that there have been difficulties in testing, but believes that cooperation rather than withdrawal is the answer. "We are really excited about how well we did in the NSS Labs AEP test," he told SecurityWeek. "We won't comment on competitors or competitors' behavior. I think you know our stance on third party testing: it should be done early and often and with multiple reputable third party testers. NSS Labs does a good job in 'real world' exploits and evasions techniques, but every test shop has its pros and cons. That's why we try to participate in as many public reputable third party tests as possible."
SecurityWeek approached CrowdStrike for a response to the NSS blog, but has not recieved a reply.
Google Increases Bug Bounty Payouts by 50% and Microsoft Just Doubles It!
4.3.2017 thehackernews Security
Well, there's some good news for hackers and bug bounty hunters!
Both tech giants Google and Microsoft have raised the value of the payouts they offer security researchers, white hat hackers and bug hunters who find high severity flaws in their products.
While Microsoft has just doubled its top reward from $15,000 to $30,000, Google has raised its high reward from $20,000 to $31,337, which is a 50 percent rise plus a bonus $1,337 or 'leet' award.
In past few years, every major company, from Apple to P*rnHub and Netgear, had started Bug Bounty Programs to encourage hackers and security researchers to find and responsibly report bugs in their services and get rewarded.
But since more and more bug hunters participating in bug bounty programs at every big tech company, common and easy-to-spot bugs are hardly left now, and if any, they hardly make any severe impact.
Sophisticated and remotely exploitable vulnerabilities are a thing now, which takes more time and effort than ever to discover.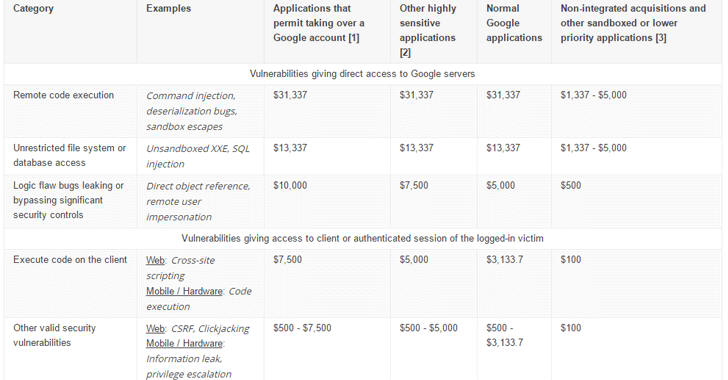
So, it was needed to encourage researchers in helping companies find high-severity vulnerabilities that have become harder to identify.
Until now, Google offered $20,000 for remote code execution (RCE) flaws and $10,000 for an unrestricted file system or database access bugs. But these rewards have now been increased to $31,337 and $13,337, respectively.
For earning the top notch reward of $31,337 from the tech giant, you need to find command injections, sandbox escapes and deserialization flaws in highly sensitive apps, such as Google Search, Chrome Web Store, Accounts, Wallet, Inbox, Code Hosting, Google Play, App Engine, and Chromium Bug Tracker.
Types of vulnerabilities in the unrestricted file system or database access category that can earn you up to $13,337 if they affect highly sensitive services include unsandboxed XML eXternal Entity (XXE) and SQL injection bugs.
Since the launch of its bug bounty program in 2010, Google has paid out over $9 Million, including $3 Million awarded last year.
Microsoft has also increased its bug bounty payouts from $20,000 to $30,000 for vulnerabilities including cross-site scripting (XSS), cross-site request forgery (CSRF), unauthorized cross-tenant data tampering or access (for multi-tenant services), insecure direct object references injection, server-side code execution, and privilege escalation bugs, in its Outlook and Office services.
Both the tech giants are trying their best to eliminate any lucrative vulnerability or backdoor into their software and products to avoid any hacking attempts and make them more secure.
Hackers will get the payout reward after submitting the vulnerabilities along with a valid working proof-of-concept.
So, what are you waiting for? Go and Grab them all!
Microsoft Temporarily Doubles Bounty Payouts for Online Services Bugs
3.3.2017 securityweek Security
For the next two months, developers who report vulnerabilities as part of Microsoft’s Online Services bounty program will receive doubled rewards for their work, the company announced.
Starting on March 1, 2017 until May 1, 2017, eligible vulnerability discoveries submitted for Microsoft Office 365 Portal and Microsoft Exchange Online will be rewarded twice as much as before.
Developers interested in getting the double rewards should be looking for vulnerabilities in six of the company’s domains: portal.office.com, outlook.office365.com, outlook.office.com, *.outlook.com, and outlook.com.
Microsoft launched the Online Services Bug Bounty program in September 2014 , and expanded it in April 2015 and August 2015 to add various Azure and Office 365 properties. Last year, the company added OneDrive to the program.
The company would normally pay between $500 and $15,000 for vulnerabilities in the online services, but bugs submitted during March and April can bring payments between $1,000 and $30,000. All of the vulnerabilities listed in the Online Services Bug Bounty Terms are eligible for the increased bounties.
On its Online Services Bug Bounty portal, Microsoft lists as eligible submissions the following types of vulnerabilities: Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Unauthorized cross-tenant data tampering or access (for multi-tenant services), Insecure direct object references, Injection Vulnerabilities, Authentication Vulnerabilities, Server-side Code Execution, Privilege Escalation, Significant Security Misconfiguration (when not caused by user).
“We realize the desire of researchers and customers to security test our services to ensure they can trust us and our solutions. We also believe that if a researcher informs us of a security flaw in our Office 365 services, they should be awarded for protecting us. These discoveries along with our internal security testing efforts contribute to keeping our users safe,” Akila Srinivasan and Travis Rhodes, Microsoft Security Response Center, note in a blog post.
HackerOne Offers Free Service to Open Source Projects
3.3.2017 securityweek Security
Bug bounty platform provider HackerOne announced on Thursday that open source projects can benefit from its Professional services at no cost if they can meet certain conditions.
HackerOne, which recently raised $40 million in a Series C financing round, already hosts bug bounty programs for 36 open source projects, including GitLab, Ruby, Rails, Phabricator, Sentry, Discourse, Brave and Django. To date, these projects have resolved more than 1,200 vulnerabilities.
The company hopes to have other open source projects sign up for its services now that it has launched its Community Edition program.
Through the new program, open source applications can use HackerOne’s Pro service for free. The service provides the mechanisms necessary for vulnerability submissions, coordination, analytics, detecting duplicates, and paying out bounties.
It’s worth pointing out that while open source projects can benefit from this offer at no cost, HackerOne will still charge the usual 20 percent payment processing fee in the case of programs that pay out cash bounties.
A project is eligible for the offer if it’s covered by an Open Source Initiative (OSI) license, and it has been active for at least 3 months. Accepted projects are required to add a “SECURITY.md” file to their project root to provide details on submitting vulnerabilities, advertise the bug bounty program on their website, and commit to responding to new bug reports within a week.
“Our HackerOne program has been a definite success for us – a new way to get actionable security reports that improve the security of the open source Discourse project for everyone,” said Jeff Atwood, co-founder of Discourse. “A public bounty program is an essential element of the defense in depth philosophy that underpins all security efforts.”
HackerOne and Synack have been awarded a combined $7 million to help the U.S. Department of Justice and its components run bug bounty initiatives. One of these initiatives is Hack the Army, which received over 100 eligible vulnerability reports and paid out roughly $100,000 to participants.
Tor webmail provider Sigaint is unavailable at least since February 11
2.3.2017 securityaffairs Security
Dark net webmail provider For the third consecutive week, the popular Tor web email service SIGAINT is unavailable and the real cause is a mystery.
SIGAINT is one of the largest web email services on the TOR network that is used to send messages preserving the user’s anonymity.
For the third consecutive week, the popular email service is unavailable and the real cause is a mystery.
The service has run for years despite the attempt of law enforcement agencies of deanonymizing its users.
The SIGAINT (sigaintevyh2rzvw.onion) service is constantly under attack of Government agencies, in April 2015 its administrator warned the users of cyber attacks alleged launched by law enforcement agency who tried to hack the service.
In 2015, according to the Administrator, a persistent attacker with access to nearly 70 bad Tor exit nodes (around 6 percent of the total) tried to compromise the email service.
One of the administrators of SIGAINT confirmed that his server was targeted by 58 malicious Tor exit nodes, but a member of the Tor Project, Philipp Winter, discovered other 12 bad exit nodes.
Back to the present, the email provider has been down since at least February 11, and there is no news about what’s happening to the service. Of course, rumors on the Internet are speculating on possible cause of the outage,
“Been happening for a few days actually. Possibly weeks if I didnt notice it. Wanted to check out my email on sigaint, the front abuse page as its named didnt load. So i loaded up wiki and tried out the .onion site and still didnt work.” wrote a Reddit user in a thread titled ‘Cant access sigaint ? ‘. “Tried another day and then another day and still nothing. Im not using bridges or anything, is this happening to more people? Thanks for answers. Wasnt sure where to post this so thought this would be a good place I hope.”

Anyway, even if the Sigaint service is still down, there are many other dark web email providers, below a short list published by freedomhacker.net.
RuggedInbox – s4bysmmsnraf7eut.onion
Torbox –torbox3uiot6wchz.onion
Bitmessage – bitmailendavkbec.onion, clearweb
Mail2Tor – mail2tor2zyjdctd.onion
RiseUp – nzh3fv6jc6jskki3.onion, clearweb
Lelantos – lelantoss7bcnwbv.onion paid accounts only
Autistici – wi7qkxyrdpu5cmvr.onion, clearweb
AnonInbox – ncikv3i4qfzwy2qy.onion paid accounts only
VFEMail – 344c6kbnjnljjzlz.onion, clearweb
Just for curiosity, a Sigaint user is offering 20k to get back it emails.
“Hello friends, back again. Since my original post I have heard from a few others who are on board to put down money in order to get their emails back. I personally would be willing to chip in $10,000 for a download of all my emails from my accounts. Maybe more. There is no question I could get another $10,000 from a few friends who also would want their emails. Maybe more.” reads the user.
“Sigaint if you are reading this and plan to never return, please reach out. Stupidly enough, I pretty much stored my entire life on the Sigaint email. I had thought we would make 3 letter agencies cry forever 🙁
Do you want to stay anonymous as for some reason you cannot show face as Sigaint? Claim to be a hacker who stole the emails from Sigaint and we can use the mods of the hub, tmg, or a market as escrow.”
9 Popular Password Manager Apps Found Leaking Your Secrets
1.3.2017 thehackernews Security
Is anything safe? It's 2017, and the likely answer is NO.
Making sure your passwords are secure is one of the first line of defense – for your computer, email, and information – against hacking attempts, and Password Managers are the one recommended by many security experts to keep all your passwords secure in one place.
Password Managers are software that creates complex passwords, stores them and organizes all your passwords for your computers, websites, applications and networks, as well as remember them on your behalf.
But what if your Password Managers itself are vulnerable?
Well, it's not just an imagination, as a new report has revealed that some of the most popular password managers are affected by critical vulnerabilities that can expose user credentials.
The report, published on Tuesday by a group of security experts from TeamSIK of the Fraunhofer Institute for Secure Information Technology in Germany, revealed that nine of the most popular Android password managers available on Google Play are vulnerable to one or more security vulnerabilities.
Popular Android Password Manager Apps Affected By One Or More Flaws
The team examined LastPass, Keeper, 1Password, My Passwords, Dashlane Password Manager, Informaticore's Password Manager, F-Secure KEY, Keepsafe, and Avast Passwords – each of which has between 100,000 and 50 Million installs.
"The overall results were extremely worrying and revealed that password manager applications, despite their claims, do not provide enough protection mechanisms for the stored passwords and credentials," TeamSIK said.
In each application, the researchers discovered one or more security vulnerabilities – a total of 26 issues – all of which were reported to the application makers and were fixed before the group's report went public.
Encryption Keys for Master Key Hard-Coded in the App's Code
According to the team, some password manager applications were vulnerable to data residue attacks and clipboard sniffing. Some of the apps stored the master password in plain text or even exposed encryption keys in the code.
For example, one high severity flaw affected Informaticore's Password Manager app, which was due to the app storing the master password in an encrypted form with the encryption key hard coded in the app's code itself. A similar bug was also discovered in LastPass.
In fact, in some cases, the user's stored passwords could have easily been accessed and exfiltrated by any malicious application installed on the user's device.
Besides these issues, the researchers also found that auto-fill functions in most password manager applications could be abused to steal stored secrets through "hidden phishing" attacks.
And what's more worrisome? Any attacker could have easily exploited many of the flaws discovered by the researchers without needing root permissions.
List of Vulnerable Password Managers and Flaws Affecting Them
Here's the list of vulnerabilities disclosed in some of the most popular Android password managers by TeamSIK:
MyPasswords
Read Private Data of My Passwords App
Master Password Decryption of My Passwords App
Free Premium Features Unlock for My Passwords
1Password – Password Manager
Subdomain Password Leakage in 1Password Internal Browser
HTTPS downgrade to HTTP URL by default in 1Password Internal Browser
Titles and URLs Not Encrypted in 1Password Database
Read Private Data From App Folder in 1Password Manager
Privacy Issue, Information Leaked to Vendor 1Password Manager
LastPass Password Manager
Hardcoded Master Key in LastPass Password Manager
Privacy, Data leakage in LastPass Browser Search
Read Private Data (Stored Master password) from LastPass Password Manager
Informaticore Password Manager
Insecure Credential Storage in Microsoft Password Manager
Keeper Password Manager
Keeper Password Manager Security Question Bypass
Keeper Password Manager Data Injection without Master Password
Dashlane Password Manager
Read Private Data From App Folder in Dashlane Password Manager
Google Search Information Leakage in Dashlane Password Manager Browser
Residue Attack Extracting Master Password From Dashlane Password Manager
Subdomain Password Leakage in Internal Dashlane Password Manager Browser
F-Secure KEY Password Manager
F-Secure KEY Password Manager Insecure Credential Storage
Hide Pictures Keepsafe Vault
Keepsafe Plaintext Password Storage
Avast Passwords
App Password Stealing from Avast Password Manager
Insecure Default URLs for Popular Sites in Avast Password Manager
Broken Secure Communication Implementation in Avast Password Manager
Researcher also going to present their findings at HITB conference next month. For more technical details about each vulnerability, users can head on to the TeamSIK report.
Since the vendors have addressed all these above-listed issues, users are strongly advised to update their password manager apps as soon as possible, because now hackers have all the information they require to exploit vulnerable versions of the password manager apps.
U.S. Oil and Gas Industry Lagging in Security: Report
24.2.2017 securityweek Security
The oil and gas industry in the United States is largely unprepared to address cybersecurity risks in operational technology (OT) environments, according to a study commissioned by German engineering giant Siemens.
Of the 377 individuals who took part in a survey conducted by the Ponemon Institute, more than two-thirds admitted having to deal with at least one incident in the past year that resulted in OT disruption or loss of confidential information. Furthermore, there are concerns that some attacks may have gone undetected.
Interestingly, one in five of respondents admitted that their organizations had been targeted in attacks involving sophisticated pieces of malware such as Duqu and Flame.Oil and gas industry cybersecurity
Many believe their organization is at a low to medium level when it comes to OT cybersecurity readiness, and only 35 percent believe they are properly prepared, the report shows.
Well over half of respondents believe the risk is greater in OT than in IT environments, and 67 percent believe cyber threats have had a significant impact on the risk to industrial control systems (ICS). When comparing IT to OT, only one-third of respondents said cybersecurity operations covering these areas are fully aligned.
Sixty-nine percent of those who took part in the study are concerned about the risks associated with third-parties in the supply chain, and many said they had difficulties in mitigating risks across the oil and gas value chain.
A majority of the security experts working in the U.S. oil and gas industry are most concerned about negligent and malicious or criminal insiders. The type of information that is considered the most at risk includes exploratory information (72%), production information (60%), potential partners and acquisition targets (56%), financial reports (53%), and operational information (50%).
Only 41 percent said their organization continually monitors the OT infrastructure, but fewer are actually capable of assessing risks, identifying the source of an attack, or remediating an incident. More than half of respondents said they outsource or would consider outsourcing OT security operations.
When asked about the factors that pose a risk to their organization, roughly 60 percent of respondents named either outdated and aging control systems, or IT products that are known to be vulnerable used in production environments.
Netflix releases the Stethoscope tool to improve security
23.2.2017 securityaffairs Security
Netflix has released the Stethoscope open source web application that provides recommendations for securing their devices.
Netflix has released Stethoscope, an open source web application that provides recommendations for securing computers, smartphones, and tablets.
Netflix intends to follow a “user focused security” approach that aims to provide employees information to improve their security posture, rather than relying on the enforcement of mandatory policies.
The vast majority of attacks against business targets corporate users causing security incidents and data breaches. The humans are the weakest link in the security chain, for this reason, Netflix decided to focus its approach on the users considering “the true context of people’s work”.
The company believes that productivity could be improved if employees don’t have to deal with too many rules and processes. That is why the Netflix Stethoscope scans their devices and provides recommendations on security measures that should be taken, but allows them to perform the tasks on their own time.
The tool doesn’t apply any corrective directly but allows employees to perform the necessary action to secure their systems.
“Stethoscope is a web application that collects information for a given user’s devices and gives them clear and specific recommendations for securing their systems.” reads the description of the tool. “By providing personalized, actionable information–and not relying on automatic enforcement–Stethoscope respects people’s time, attention, and autonomy, while improving our company’s security outcomes.”
Stethoscope analyzes several aspects of employee’s device, including the presence of security software (firewall), disk encryption, automatic updates, operating system and software updates, screen lock, and jailbreaking or rooting.
This information is elaborated by the Stethoscope tool that rates them based on the criticality of the tasks to complete.

Netflix Stethoscope is a Python-based tool with a user interface developed with the React framework. The tool does not have its own data store, data sources are implemented as plugins, making the application scalable and allowing users to add new dataset and new security checks.
“The various data sources are implemented as plugins, so it should be relatively straightforward to add new inputs. We currently support LANDESK (for Windows), JAMF (for Macs), and Google MDM (for mobile devices).” continues the description from Netflix.
Netflix Stethoscope will likely include also Facebook’s Osquery is the list of future data sources.
The tool is an open project, everyone can contribute, the Stethoscope source code is available on GitHub.
Netflix Releases Open Source Security Tool "Stethoscope"
23.2.2017 securityweek Security
Netflix this week released Stethoscope, an open source web application that gives users specific recommendations for securing their computers, smartphones and tablets.
Stethoscope was developed by Netflix as part of its “user focused security” approach, which is based on the theory that it is better to provide employees actionable information and low-friction tools, rather than relying on heavy-handed policy enforcement.
Netflix believes employees are more productive when they don’t have to deal with too many rules and processes. That is why Stethoscope scans their devices and provides recommendations on security measures that should be taken, but allows them to perform the tasks on their own time.
Stethoscope analyzes a device’s disk encryption, firewall, automatic updates, operating system and software updates, screen lock, jailbreaking or rooting, and installed security software. Each of these factors is attributed a rating based on its importance.
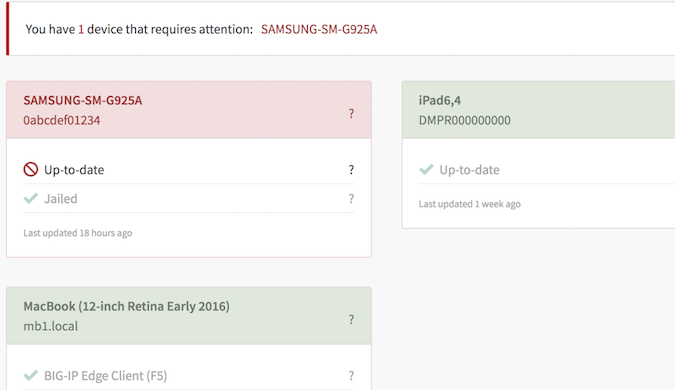
Stethoscope was developed in Python (backend) and React (frontend), and it does not have its own data store. Data sources are implemented as plugins, allowing users to add new inputs.
For the time being, the application supports LANDESK for Windows computers, JAMF for Macs and Google MDM for mobile devices. However, Netflix wants to extend the list of data sources and Facebook’s Osquery is first on the list.
The modular architecture allows users to add new security checks and other functionality by developing plugins.
The Stethoscope source code, along with instructions for installation and configuration, are available on GitHub. Netflix has invited users to contribute to the tool, particularly with new plugins.
Stethoscope is not the only open source security tool released by Netflix. The company has made available the source code for several of the applications it uses, including the XSS discovery framework Sleepy Puppy, and the threat monitoring tools Scumblr and Sketchy.
CompTIA Offers New Security Analyst Certification
21.2.2017 securityweek Security
An ISACA survey released during RSA week sought to illustrate the state of cyber security workforce development and its current trends. The results would surprise no-one in the industry: recruiting security talent is hard.
But the ISACA survey makes two particularly interesting statements: firstly, that 70% of enterprises "require a security certification for open cyber security positions"; and secondly, that for 55% of enterprises, "practical hands-on experience is the most important cyber security candidate qualification." Since a candidate cannot get experience without first getting a position, new candidates for open cyber security jobs need as much help with other 'qualifications' as possible.
Today, CompTIA has announced a new security qualification: CSA+. It sits between Security+ (covering essential principles for network security and risk management), and CASP (the CompTIA Advanced Security Practitioner, which certifies critical thinking and judgment across a broad spectrum of security disciplines).
CSA+ focuses on the skills required for the use of threat detection tools, data analysis and the interpretation of results to identify vulnerabilities, threats and risks. It certifies a proficiency in data driven security.
"By placing greater emphasis on data analytics, we get a real-time, holistic view of the behavior of the network, its users and their devices to identify potential vulnerabilities and strengthen them before an intrusion happens,” explained CompTIA's senior director for products, James Stanger.
This is perhaps the most critical area of the overall cyber security skills gap, and one that is growing faster than most. The Bureau of Labor Statistics states, "Employment of information security analysts is projected to grow 18 percent from 2014 to 2024, much faster than the average for all occupations. Demand for information security analysts is expected to be very high, as these analysts will be needed to create innovative solutions to prevent hackers from stealing critical information or causing problems for computer networks."
"Data analytics is key," says Jim Lucari, senior manager of certification at HP Enterprise. "Everybody in technology should have this CSA+. It should be mandatory if you're going to stay in IT over the coming decade." The CSA+ qualification could help potential employers gauge candidates' aptitude and skill level for this critical area.
CSA+ exams are available globally via Pearson VUE Testing centers. However, it is not an entry-level security qualification. Although private individuals could use it as part of a project to get into cyber security, it might better suit career advancement than career entry. "Because of the advanced nature of CompTIA CSA+," Stanger told SecurityWeek, "we recommend that candidates for the certification have a minimum of three to four years of hands-on information security or related experience; and hold CompTIA Network+ and Security+ certifications."
One of the recommendations from the ISACA survey suggests that employers should "Groom employees with tangential skills -- such as application specialists and network specialists -- to move into cyber security positions."
Putting such staff through the CSA+ certification could provide a cost-effective approach to filling the cyber analyst security gap. "We recommend a minimum of five days of intensive 'boot camp' style training," said Sanger; "or a quarter or semester of academic instruction."
Germany Bans Internet-connected 'Spy' Doll Cayla
18.2.2017 securityweek Security
German regulators have banned an internet-connected doll called "My Friend Cayla" that can chat with children, warning Friday that it was a de facto "spying device".
Parents were urged to disable the interactive toy by the Federal Network Agency which enforces bans on surveillance devices.
"Items that conceal cameras or microphones and that are capable of transmitting a signal, and therefore can transmit data without detection, compromise people's privacy," said the agency's head, Jochen Homann.
"This applies in particular to children's toys. The Cayla doll has been banned in Germany. This is also to protect the most vulnerable in our society."
The doll works by sending a child's audio question wirelessly to an app on a digital device, which translates it into text and searches the internet for an answer, then sends back a response that is voiced by the doll.
The German regulators in a statement warned that anything a child says, or other people's conversations, could be recorded and transmitted without parents' knowledge.
"A company could also use the toy to advertise directly to the child or the parents," it said.
"Moreover, if the manufacturer has not adequately protected the wireless connection, the toy can be used by anyone in the vicinity to listen in on conversations undetected."
Genesis Toys, which manufactures the doll, says on its website that it "is committed to protecting your and your family's personal information.
"Our objective is to ensure that our products and services are safe and enjoyable for our customers".
It also says Cayla "is programmed to not utter, display or say words or images that would be inappropriate for children to see or hear".
The company regularly reviews "encryption and physical security measures" to guard against unauthorized access to customers' personal information.
But it warns on its website that "unfortunately no method of transmission over the Internet, or method of electronic storage, is 100 percent secure".
The regulation agency added that it would "inspect other interactive toys and, if necessary, will take further action".
The European Consumer Organization said it welcomed the decision but criticized the fact consumers would struggle to get compensation.
Its head Monique Goyens said that "if connected toys, such as this speaking doll, can be hacked to spy on or talk to children, they must be banned."
She added that "EU product laws need to catch up with digital developments to deal with threats such as hacking, data fraud or spying".
CrowdStrike Sues NSS Labs to Prevent Publication of Test Results
15.2.2017 securityweek Security
CrowdStrike filed suit against NSS Labs
On February 10, 2017, next-gen endpoint protection firm CrowdStrike filed suit against security product testing firm NSS Labs, and sought a temporary restraining order to prevent publication of CrowdStrike comparative test results. On February 13, the injunction was denied by the District Court of Delaware. On February 14, NSS published the results as part of its Advanced Endpoint Protection Group Test Results.
CrowdStrike explained the background in a blog post yesterday. It filed suit, it said, to hold NSS "accountable for unlawfully accessing our software, breaching our contract, pirating our software, and improper security testing. Regardless of test results (which we have not seen), CrowdStrike is making a stand against what we believe to be unlawful conduct."
CrowdStrike had earlier commissioned NSS to undertake a private test of its products, but was dissatisfied with the test methods, calling them "deeply flawed". Because of this it decided not to participate in the subsequent public test, and prohibited NSS from using its software. But according to CrowdStrike, NSS "colluded with a reseller and engaged in a sham transaction to access our software to conduct the testing. In doing so, NSS breached their contract with CrowdStrike, violated our end user licensing agreement (EULA), misappropriated our intellectual property, and improperly used credentials. Once we became aware that an unauthorized user account associated with a reseller was used for the tests, we suspended access immediately. Any test results that NSS did obtain are incomplete and materially flawed."
Product testing has long been a problem for the newer endpoint protection companies. In June 2016, Sophos blasted Cylance, and added, "when the playing field is leveled, and Cylance's product comes under real scrutiny, the company cries foul, puts the fear of lawsuits into the minds of its partners, and accuses others of 'smoke and mirrors' tactics."
Now the threat of a lawsuit has become a reality between CrowdStrike and NSS Labs. In the meantime, many of the new endpoint protection companies, including Cylance, have modified their attitudes. Cylance was amongst the tested products, as was SentinelOne and Invincea. These last three did rather well in the overall scores: Cylance at 99.69%, SentinelOne at 99.79%, and Invincea at 99.49%. CrowdStrike did less well at 74.17% -- but as CrowdStrike claimed, the results 'are incomplete'; and as NSS Labs admits, "The Falcon Host's final rating may have been different had it completed the test."
There are two primary issues here: is it possible to conduct fair comparative tests for advanced endpoint protection products (aka, machine-learning or next-gen AV); and is the law a valid method of preventing them?
Opinions differ on the first. David Harley blogged in WeLiveSecurity on Monday (although I understand it was written well before this current issue): Next-gen security software: 'Myths and marketing'. Quoting a question I asked him months ago (basically, is there any way to compare 1st- and 2nd-gen AV products), he said, "yes, of course there is."
Vesselin Bontchev, who is possibly the ultimate culprit ("I practically invented independent competent anti-virus testing while I was working at the Virus Test Center at the University of Hamburg in the early '90s") takes the opposite view. He believes that neither products nor testing are anywhere near as competent as they should be. "Whenever there is a major conflict, like this CrowdStrike vs NSS Labs story," he wrote yesterday, "you can usually bet that both sides are in the wrong. CrowdStrike probably have a crappy product they want to sell and didn't like the test results, while NSS Labs probably has a crappy and/or incomplete testing methodology and CrowdStrike found some legitimate flaws in it."
The law, however, is a heavy instrument to prevent public testing. SecurityWeek asked NSS to comment, and was told via email by CEO Vikram Phatak, "While CrowdStrike's request for a Temporary Restraining Order and Preliminary Injunction were denied by the Federal court, they are still suing us at present, and so we are limited in what we can say. Whether or not it is their intent, their suit has the effect of keeping us from debating the facts publicly.
"We obviously disagree and are disappointed with CrowdStrike's characterization of NSS as portrayed in their recent blog post... And as far as Crowdstrike's suit against NSS, we believe the judge's ruling and memorandum speak for themselves."
SecurityWeek also approached CrowdStrike, the Anti-Malware Testing Standards Organization (of which both CrowdStrike and NSS Labs are members), and another independent test lab for comments. We have so far received no response (although an informal reply from CrowdStrike did say, "Things are moving quickly today. Keep an eye on your inbox for an update"). If any comments are received they will be added as an update to this post.
Meanwhile, customers are left with an ongoing problem: can test results be trusted? There is no easy answer to this. The best solution is for customers to insist on an on-site trial periods to see whether a preferred solution is actually up to the job.
Websites Can Now Track You Online Across Multiple Web Browsers
15.2.2017 thehackernews Security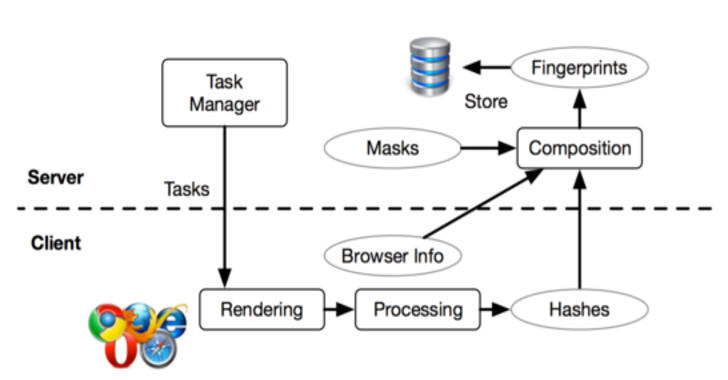
You might be aware of websites, banks, retailers, and advertisers tracking your online activities using different Web "fingerprinting" techniques even in incognito/private mode, but now sites can track you anywhere online — even if you switch browsers.
A team of researchers has recently developed a cross-browser fingerprinting technique — the first reliable technique to accurately track users across multiple browsers based on information like extensions, plugins, time zone and whether or not an ad blocker is installed.
Previous fingerprinting methods usually only work across a single browser, but the new method uses operating system and hardware level features and works across multiple browsers.
This new fingerprinting technique ties digital fingerprint left behind by a Firefox browser to the fingerprint from a Chrome browser or Windows Edge running on the same device.
This makes the method particularly useful to advertisers, enabling them to continue serving targeted advertisements to online users, even if they avoid them by switching browsers.
The new technique can be found in a research paper titled (Cross-)Browser Fingerprinting via OS and Hardware Level Features [PDF] by Lehigh University’s Yinzhi Cao and Song Li, and Washington University in St. Louis’ Erik Wijmans.
The cross-browser fingerprinting technique relies on "many novel OS and hardware features, especially computer graphics ones" that are slightly different for each computer.
For example, the technology can be used to identify the machine by performing 20 unique WebGL tasks while rendering 3D graphics in web browsers with carefully selected computer graphics parameters, such as texture, anti-aliasing, light, and transparency.
In total, 36 new features work independently of a particular browser, although they are not confined to one specific web browser on the machine.
The features tested currently includes time zone, number of CPU cores, GPU, hash values of GPU rendering results, plugins, fonts, audio, screen ratio and depth, WebGL, Ad blocking, canvas, cookies, encoding, and language.
The researchers provided both a practical demonstration as well as open source code online on GitHub. They performed a test which involved 3,615 fingerprints and 1,903 users and found that their method successfully identified 99.2% of users.
On the other hand, a single-browser fingerprinting technique called AmIUnique had a success rate of 90.8%.
"This approach is lightweight, but we need to find all possible fingerprintable places, such as canvas and audio context: If one place is missing, the browser can still be somehow fingerprinted. We leave it as our future work to explore the correct virtualization layer," the paper notes.
The researchers also noted that this new cross-browser fingerprinting technique is not too bad, as in some cases, the method can be used as part of stronger multi-factor user authentications across multiple browsers.
For example, Banks can use this technique to check if a user logging into an online account is using the computer that has been used on every previous visit, making sure the login was legitimate even if the user is using a different machine to usual.
The researchers plan to present their paper at the Network and Distributed System Security Symposium scheduled for February 26 through March 1 in San Diego, California.
IBM's Watson Aims its Power at Security Operations Centers
14.2.2017 securityweek Security
Insider IBM's Cyber Range in Cambridge MA
Watson for Cyber Security Integrates With IBM's New Cognitive Security Operations Center
The power of IBM's cognitive computing Watson has been directed at cyber security. For the last year, Watson has been absorbing the collective knowledge of a million cyber security studies, scientific reports and analyses. Now Watson is ready to stand behind the shoulders of the analysts that sift through the network alerts thrown up by the QRadar security intelligence platform in what IBM calls its Cognitive SOC.
Watson's purpose is to advise the analysts. It gains its knowledge through parsing the free text documents that hold the greater part of the world's security knowledge. Human analysts could never read the volume of data that is available -- but it is light work for a machine. Watson takes free text documents and parses them; absorbing key knowledge and relationships. Some of the data it absorbs could be wrong; but Watson relies on the power of collective crowd knowledge to sift the wheat from the chaff. The result is a huge and accessible corpus of security expertise.
IBM LogoThe human analysts are also struggling with the sheer volume of events coming from their security intelligence platform. According to IBM, security teams must sift through up to 200,000 security events every day. Most of these are false positives that still need to be checked; but the result is up to 20,000 hours wasted every year. This is expected to double over the next five years.
Given the dearth of analysts, and especially the sparsity of expert analysts, this is a problem that will only get worse. Security intelligence platforms, such as QRadar, can generate huge volumes of warnings -- they create their own subset of Big Data. But the bloom of Big Data is wearing thin: the haystack is getting bigger, but mostly it just makes finding the needle harder.
Watson hides its own big data of knowledge within the machine, and then uses the power of the machine to direct the analyst to more targeted threat hunting in the QRadar alerts. The new app, IBM QRadar Advisor with Watson, is the first tool to tap Watson's security insights; and is already being used by 40 IBM customers including Avnet, University of New Brunswick, Sogeti.
"Today's sophisticated cybersecurity threats attack on multiple fronts to conceal their activities, and our security analysts face the difficult task of pinpointing these attacks amongst a massive sea of security-related data," explains Sean Valcamp, Chief Information Security Officer at Avnet.
"Watson makes concealment efforts more difficult by quickly analyzing multiple streams of data and comparing it with the latest security attack intelligence to provide a more complete picture of the threat. Watson also generates reports on these threats in a matter of minutes, which greatly speeds the time between detecting a potential event and my security team's ability to respond accordingly."
While Watson and QRadar are the key elements of the Cognitive SOC, IBM is extending it to the endpoint with the announcement of BigFix Detect. This is an endpoint detection and response (EDR) solution designed to detect and respond to malicious behavior in endpoints.
"The Cognitive SOC is now a reality for clients looking to find an advantage against the growing legions of cybercriminals and next generation threats," said Denis Kennelly, Vice President of Development and Technology, IBM Security. "Our investments in Watson for Cybersecurity have given birth to several innovations in just under a year. Combining the unique abilities of man and machine intelligence will be critical to the next stage in the fight against advanced cybercrime."
IBM is planning to improve the analyst (man) Watson (machine) interface with a new research project code-named Havyn -- a voice-powered security assistant that will make Watson respond to the analysts' verbal commands and natural language. IBM is not the only vendor seeking to use natural language as the interface between man and machine. Earlier this month Dynatrace announced Davis focused on monitoring the IT ecosystem. "It gives," announced the firm, "non-technical teams the ability to monitor and understand network health and performance issues via familiar communication tools. 'davis' has effectively 'consumerized' IT – this is an industry first."
Similarly, Endgame announced Artemis in late January. Artemis is a natural language chat interface between analysts and the Endgame Detect and Respond platform. The purpose behind Havyn, Davis and Artemis is to reduce the time spent by analysts in hunting out threats.
The IBM Cognitive SOC can be built on premise or built in the cloud through IBM Managed Security Services.
In November 2016, IBM Security unveiled a new global headquarters in Cambridge, Massachusetts, which features a physical Cyber Range designed to allow organizations in the private sector to prepare for and respond to cyber threats.
Qualys Expands Detection, Web App Security, and Data Sharing Portfolio
14.2.2017 securityweek Security
SAN FRANCISCO - RSA CONFERENCE 2017 - Cloud-based security and compliance solutions provider Qualys this week announced new tools and features to provide customers with improved detection capabilities, expanded web application security features, and improved vulnerability data sharing.
Qualys added two new detection solutions to its Cloud Platform, in the form of Qualys File Integrity Monitoring (FIM) and Indicators of Compromise (IOC), both meant to deliver more critical security and compliance functions in a single cloud-based dashboard. FIM and IOC bring to the Qualys Cloud Agent a combination of prevention and detection by adding continuous visibility of breaches and system changes to the single-pane view of security and compliance posture that the Agent already offers.
Qualys FIM was designed to log and centrally track file change events across global IT systems, while offering a single-view dashboard for identifying critical changes, incidents, and audit risks caused by various factors, including normal patching and administrative tasks, change control exceptions or violations, and malicious activity.
A cloud-based solution, FIM doesn’t require the deployment and maintenance of complex security infrastructure, which also results in improved compliance, reduced downtime, and limited damage from compromise. With FIM, customers get features such as out-of-the-box profiles based on industry best practices and vendor-recommended guidelines, real-time change engine to monitor files and directories specified in the monitoring profile, and automated change reviews of workflows.
Qualys IOC, on the other hand, continuously monitors endpoint activity for suspicious activity that could signal the presence of known malware, unknown variants, and threat actor activity on devices both on and off the network. The solution brings together endpoint detection, behavioral malware analysis, and threat hunting techniques, the company says.
Qualys IOC provides customers with continuous event collection through Cloud Agent's data collection and delta processing techniques, as well as with highly scalable detection processing (as analysis, hunting, and threat indicator processing are performed in the cloud). Moreover, the solution offers actionable intelligence for security analysts, to help them prioritize responses for critical business systems.
According to Qualys, security administrators will benefit from multiple enhancements that FIM and IOC bring to the Cloud Agent and cloud-based processing platform, including easy setup and no maintenance needs (modules can be instantly activated), minimal impact on performance (the Cloud Agent monitors file changes and system activity locally but sends all data to the Cloud Platform), unified security posture (FIM and IOC alert data is presented in a single, integrated view), and integration with AssetView (providing dynamic dashboards, interactive and saved searches, and visual widgets to analysts).
“Breaches continue to rise despite the investments in traditional mechanisms that organizations have deployed to support their businesses in the new era of digital transformation. Our new disruptive services for FIM and IOC extend the capabilities of our Cloud Agent platform, allowing companies to get the visibility and prevention they need against cyber threats from one single platform, drastically reducing their security costs,” Philippe Courtot, chairman and CEO, Qualys, said.
Expanded web application security offerings
With the release of Qualys Web Application Scanning (WAS) 5.0 and Web Application Firewall (WAF) 2.0 this week, the company added new functionality to its web application security offerings, in an attempt to provide customers with scalable fast scanning, detection and patching of websites, mobile applications and Application Programming Interfaces (APIs), in one unified platform.
The newly released WAS 5.0 offers not only programmatic scanning of Simple Object Access Protocol (SOAP) APIs, but also the testing of REpresentational State Transfer (REST) API services, Qualys announced. Moreover, it delivers scanning of IoT (Internet of Things) services and mobile apps, as well as API-based business-to-business connectors, and can automatically load-balance scanning of multiple applications across a pool of scanner appliances for efficiency. Moreover, improvements made to Progressive Scanning allow customers to scan very large sites, one slice at a time, to cover large applications that are problematic to scan in a short window.
WAF 2.0, on the other hand, offers one-click virtual patching feature to address both false-positives and the inability to quickly patch vulnerabilities; out-of-the-box security templates for popular platforms such as Wordpress, Joomla, Drupal and Outlook Web Application; and support for VMWare, Hyper-V, and Amazon Web Services, along with features such as load-balancing of web servers, health checks for business-critical web applications, custom security rules based on HTTP request attributes, reusable Secure Socket Layer profiles, detailed event log information, and centralized management.
Both Qualys WAS 5.0 and WAF 2.0 are available now as annual subscriptions. Pricng for Qualys WAS starts at $1,695 for small businesses and $2,495 for larger enterprises, while pricing for the WAF soluton starts at $1,995 for small businesses and $9,995 for larger enterprises.
Vulnerability data sharing
In addition to the expanded portfolio, Qualys also announced a partnership with crowdsourced security testing company Bugcrowd to allow joint customers to share vulnerability data across automated web application scanning and crowdsourced bug bounty programs.
The joint integration between Bugcrowd Crowdcontrol and Qualys Cloud Platform brings together automated web application scanning (WAS) and penetration-testing crowd in a single solution. Thus, joint customers should be able to eliminate vulnerabilities discovered by Qualys WAS from their list of offered bug bounties, while focusing on Bugcrowd programs and critical vulnerabilities that require manual testing.
The initial stage in this collaboration allows Bugcrowd customers who also have Qualys WAS to import vulnerability data into the Bugcrowd Crowdcontrol platform and use it to optimize their bug bounty program scope and incentives. In the future, joint customers running a bug bounty platform on Bugcrowd will be able to import unique vulnerabilities from Crowdcontrol into Qualys WAS and apply one-click patches through the fully integrated Qualys Web Application Firewall.
“With the move of IT to the cloud and all the digital transformation efforts underway, web apps are exploding and securing these apps is now front and center. By combining the automation of Qualys Web Application Scanning (WAS) and Bugcrowd's crowd sourcing platform, organizations can now cover a much larger number of applications and secure them more effectively at a lower cost,” Sumedh Thakar, Chief Product Officer, Qualys, said.
HPE Launches Threat Investigation, IoT Data Security Products
14.2.2017 securityweek Security
Hewlett Packard Enterprise (HPE) announced on Tuesday the launch of a new threat investigation solution, ArcSight Investigate, and a new SecureData product for IoT and big data.
HPE Security ArcSight Investigate is a product designed to provide security operations center (SOC) teams fast and intuitive search functionality to help them identify and respond to significant threats.
ArcSight Investigate can be integrated with Hadoop and other ArcSight products, including Data Platform (ADP) and Enterprise Security Manager (ESM).HPE
The product is expected to become generally available in the second quarter. In the meantime, organizations interested in ArcSight Investigate can sign up for the early access program.
HPE has also unveiled SecureData for Hadoop and IoT. The product enables organizations to secure IoT data at rest, in transit and in use through integration with the Apache NiFi data processing and distribution platform.
As for protecting big data, HPE SecureData for Hadoop and IoT integrates with Hortonworks DataFlow (HDF) in order to secure information throughout the dataflow management and streaming analytics process. HPE says the original format of the encrypted data is preserved for processing and enabling secure big data analytics.
“While IoT and big data analytics are driving new ways for organizations to improve efficiencies, identify new revenue streams, and innovate, they are also creating new attack vectors for leaking sensitive information to adversaries,” said HPE’s Albert Biketi. “HPE SecureData enables business users to easily build data security in, delivering persistent protection in IoT and big data ecosystems, and allowing organizations to securely innovate.”
HPE SecureData for Hadoop and IoT is generally available worldwide as part of the company’s SecureData offering.
ThreatConnect Launches New Threat Intelligence Products
14.2.2017 securityweek Security
Threat intelligence firm ThreatConnect announced this week the launch of a new suite of products designed to help organizations understand adversaries, automate their security operations, and accelerate threat mitigation.
The new products, built on the ThreatConnect Platform, have been named TC Complete, TC Analyze, TC Manage and TC Identify.
TC Complete, the company’s flagship product, is a security operations and analytics platform that aims to enable companies to efficiently run their security operation center (SOC) by giving them the ability to orchestrate security processes, analyze data, respond to threats, and report progress from a single location. TC Complete incorporates the features and benefits of all the other ThreatConnect products.
Another new product is TC Identity, which provides vetted threat intelligence collected from over 100 open source feeds, ThreatConnect communities, the company’s research team and, optionally, intelligence from members of the TC Exchange program.
TC Manage is an intelligence-driven orchestration tool that enables organizations to automate threat data management processes, including notifying team members when manual tasks need to be performed, or sending indicators to defensive tools for blocking or alerting.
The last new product is the TC Analyze threat intelligence platform, which provides a central location for analyzing data and integrating with existing security tools. The platform allows analysts to better understand which threats are relevant, gain visibility into attack patterns, and share threat intelligence with executives and other stakeholders.
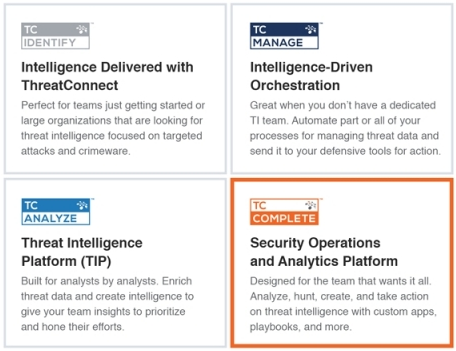
“By introducing our new innovative suite of products, we are able to address all levels of need in the marketplace. With these four specific products, ThreatConnect allows any organization with any size security team the option to extend its capabilities,” said ThreatConnect VP of Product Andy Pendergast. “We conducted substantial research into organizations’ current and potential intelligence needs to protect their environment and came up with these specific products to reach them where they are now and where they need to be in the future.”
RSA Unveils Business-Driven Security Offering
13.2.2017 securityweek Security
RSA, which since September is part of Dell Technologies, on Monday unveiled a new approach and product improvements designed to help organizations manage cyber risk.
With its new Business-Driven Security architecture, RSA aims to provide organizations the tools needed to link security information to business context and protect the most sensitive assets.
The RSA Business-Driven Security solutions focus on threat detection and response, consumer fraud protection, identity and access assurance, and business risk management.
This includes the RSA NetWitness Suite, which provides visibility and actionable insight for detecting advanced threats and understanding the full scope of an incident. The new capabilities added to the product enable organizations to monitor any infrastructure by collecting data from public clouds (e.g. AWS, Microsoft Azure), virtual environments, and physical infrastructure.RSA launches new solution
The launch of Business-Driven Security also brings improvements to RSA SecurID Access. RSA says the multi-factor authentication and access management product now offers a better way for delivering strong security to users, devices and applications.
The latest release of the RSA Fraud & Risk Intelligence Suite brings a centralized platform designed to improve fraud detection and investigation. The new platform should enable organizations to better protect their customers against cyberattacks by allowing them to obtain additional insights, including from internal and external sources, and other anti-fraud tools.
The offering also includes the RSA Archer Ignition Program, which helps organizations manage business risk through a combination of Governance Risk and Compliance (GRC) use cases, quick launch services and education offerings.
Finally, the Business-Driven Security architecture is operationalized via the new RSA Risk & Cybersecurity Practice. The practice aims to reduce business risk through risk management, identity assurance, incident response, and advanced cyber defense.
“Despite best efforts, today’s security approaches are in dire need of transformation because they fall short when they are put into action. This forces organizations into a downward cycle of investment and re-investment,” said Rohit Ghai, President, RSA. “RSA is proud to provide a new architecture and array of Business-Driven Security solutions that are engineered to enable the most critical elements of a sound security strategy: linking business context with security incidents to more strategically address and manage business risk to protect what matters most.”
Microsoft Unveils New Security and Risk Capabilities in Office 365
13.2.2017 securityweek Security
Microsoft has unveiled several new capabilities in Office 365 to help customers better manage risks and protect against threats, including Office 365 Secure Score, Threat Intelligence Private Preview, and Advanced Data Governance Preview.
Office 365 Secure Score was designed as a security analytics tool that applies a score to the customers’ Office 365 security configuration. Secure Score, says Alym Rayani, director for Microsoft's Office Security and Compliance team, was created to provide customers with improved visibility into their Office 365 security configuration and into the security features available to them.
With the help of this new tool, customers will not only be able to understand their current Office 365 security configuration, but also to learn how implementing additional controls can improve their security and reduce risk, Rayani says.
Secure Score provides access to Score Analyzer via the Secure Score Summary. The Secure Score (or the numerator) is the sum of the points associated with the security configurations that a customer has adopted. The total score (or the denominator) is the sum of the points associated with all of the security controls available on the customer’s Office 365 plan.
The Score Analyzer allows customers to track and report their score over time. Customers are provided with access to a graph that shows their score on any date in the past, while also offering info on the specific actions they completed and which were available to them. The tool also offers support for exporting the score results to a CSV file for further use within an organization.
Secure Score also offers suggestions on possible actions that could improve one’s security position. These suggestions, Microsoft says, are prioritized depending on their effectiveness and impact to end users, meaning that those that are highly effective but have low impact on user experience are placed at the top.
The Office 365 Threat Intelligence, now in private preview, leverages the Microsoft Intelligent Security Graph to deliver actionable insights to global attack trends. The cost of data breaches is increasing, but even organizations that are properly prepared for a breach can diminish long-term costs.
The new Office 365 feature, Microsoft says, was designed to analyze data from global datacenters, Office clients, email, user authentications and other incidents and to deliver information about malware families inside and outside organizations, including breach information. Furthermore, it integrates with other Office 365 security features, including Exchange Online Protection and Advanced Threat Protection.
“Office 365 Threat Intelligence provides this visibility, along with rich insights and recommendations on mitigating cyber-threats, ultimately supporting a proactive defense posture, leading to long-term reduced organizational costs,” Rayani notes.
With the help of Office 365 Advanced Data Governance, customers can find and retain important data while eliminating redundant, obsolete and trivial data. By leveraging machine learning, it can deliver proactive policy recommendations; can classify data based by analyzing numerous factors, including data type, age, and user interaction; and can take action such as preservation or deletion.
According to Microsoft, this means that organizations have a better grasp of their data and no longer expose themselves to unnecessary risks because they retain data they no longer need, but which could be exposed in the event of a data breach.
While Office 365 Secure Score is now available to organizations with an Office 365 commercial subscription and which are in the multi-tenant and Office 365 U.S. Government Community clouds, Office 365 Threat Intelligence and Advanced Data Governance should become available by the end of March 2017 as part of the Office 365 Enterprise E5 plan and the Secure Productive Enterprise E5 offering.
Gmail Delivers Spoofed Messages Without Warning, Researchers Find
11.2.2017 securityweek Security
Spoofed emails could easily land in user’s Gmail inboxes without even warning them of suspicious activity, security researchers have discovered.
While spam is normally used to deliver malicious documents or links to unsuspecting users, spoofed emails have a bigger chance of luring potential victims, because they are likely to click on a link or open a document coming from what they believe is a trusted contact. When it comes to spoofed messages, the sender is impersonated or changed to another, thus making messages appear legitimate.
Which users may expect Gmail to warn them of such suspicious activity, researchers at the Morphus Segurança da Informação recently discovered that this doesn’t always happen. According to them, users should revise the trust they have on Gmail blocking messages with spoofed senders, even when no alert is displayed regarding the legitimacy of that message.
“We realized that a message that appears in your Gmail inbox folder even with an important sign, coming from one of your Gmail contacts with no spoof or security alert, may have been forged and impersonated by a fraudster or cybercriminal,” Renato Marinho, Director at Morphus Segurança da Informação, explains.
Marinho explains that the Simple Mail Transfer Protocol (SMTP) defines the “mail envelop and its parameters, such as the message sender and recipient,” and not the message content and headers. Thus, a SMTP transaction includes Mail From (establishes the return address in case of failure), Rcpt to (the recipient address), and Data (a command for the SMTP server to receive the content of the message).
The value “From” displayed in the email is usually equivalent to the value used in the SMTP command “mail from” but, because it is part of the message content, “can be freely specified by the system or person issuing commands to the SMTP server.” Basically, an attacker simply needs to change the “From” to a desired value to spoof the sender, but that is almost certainly going to trigger anti-spam or anti-phishing mechanisms, Marinho explains.
However, attackers could also attempt to send spoofed messages on behalf of a certain domain by changing the “Mail from:” SMTP command as well, a practice that can be combated by applying spoofing protection mechanisms. Among them, SPF (Sender Policy Framework) allows admins to specify the IP addresses of the mail servers that are allowed to send e-mail messages on behalf of their domain.
To verify if these protections are effective, the security researchers decided to test the spoofing of Gmail and Yahoo addresses. They discovered that, if the SMTP server’s IP address wasn’t allowed in the SPF policy of their generic domain, the message wouldn’t be delivered. When a SPF policy was in place, however, the message was delivered in Gmail, albeit Yahoo continued to block it.
Even more surprising, the researcher says, was that the message landed in the Inbox folder, and not in Spam. Further, there was almost no indication that the message wasn’t legitimate, except for a “via [the generic domain]” mention near the sender’s address. This mention, however, appears only in the web interface, but isn’t displayed in the Android or iOS applications.
After successfully spoofing messages between @gmail.com accounts, the researchers attempted to apply the strategy to corporative domains hosted by Google. They discovered not only that the messages were delivered without a warning, but that the spoofed account profile picture was also delivered (which could easily add a sense of legitimacy to the message).
“During our experiments, we’ve found a curious scenario in which Gmail detects the spoofed message. It happened when we tried to spoof an address that apparently does not exists on Gmail user base. In this situation, unlike the successful scenarios, Gmail forwarded the message to Spam folder and adds a special security alert informing that they could not verify if the message was really sent by gmail.com,” the researcher explains.
To stay protected, users are advised to pay attention to messages in their inbox coming from “@gmail.com” via another server, because they should normally be delivered by Gmail. They should also have a look at the message details, which ware available in the web application, by clicking on the “down-arrow” near “to me”. However, a spoofed message is more likely to be noticed if the full header is examined.
The researchers contacted Google Security team to report the findings, but the bug won’t be tracked as a security issue, it seems. “Although it has not been considered a security bug, in our opinion, it would be better if Gmail could at least adopt the same behavior we saw when trying to spoof a non-existing Gmail account,” Marinho says.
Demisto Raises $20 Million to Help Enterprises Fight Alert Fatigue
11.2.2017 securityweek Security
Demisto, a Cupertino, Calif.-based maker of software that helps Security Operations teams fight “alert fatigue” and reduce the time to respond to a breach, announced on Thursday that it has closed a $20 million Series B round of funding.
In addition to announcing the new funding, the company introduced the latest version of its security operations platform. The company’s new “Demisto Enterprise 2.0 Security Operations Platform” is an incident management platform designed to help customers integrate threat feeds and manage indicators to automate threat hunting operations.
The platform is available now with annual pricing starting at $100,000 for up to two analysts.
“Demisto was built to make security analysts’ lives easier with its combined incident response case management and security orchestration platform,” said Slavik Markovich, CEO of Demisto.
“Demisto simplifies the way enterprises manage incident response with its automated and collaborative incident response platform that delivers unprecedented insight and resolution into complex threats,” explains Jay Leek, managing director at ClearSky and former CISO of Blackstone.
According to the company, the new funds will be used to expand operations and accelerate new product development and customer rollouts, and support sales and marketing efforts.
With offices in Silicon Valley and Tel Aviv, the new funding brings Demisto’s total funding to $26 million.
Research Unearths 5 Secrets for Higher Performing CISOs
11.2.2017 securityweek Security
IANS Research has developed a model designed to help chief information security officers to maintain their inherent promise: that is, "to safeguard critical assets across space and time."
This model, which it calls CISO Impact, rests on two fundamental capabilities: technical excellence and organizational engagement. The former involves eight domains from access control to incident response; while the later includes seven factors from running infosec like a business to getting Business to own the risk.
From this model, combined with insights from more than 1,200 high-performing CISOs and information security teams, IANS has developed what it terms 'The 5 Secrets of High-Performing CISOs'.
"The connected world is a dangerous place," says Stan Dolberg, chief research officer at IANS Research, "and because of this, CISOs and their teams must lead their organizations to adopt safe business practices. However, the challenge remains that many CISOs are leading from a position of little authority or influence. The CISO Impact diagnostic provides specific ways for CISOs to assert information security leadership skills that are commonly found in organizations one step ahead on the maturity curve. Our goal is to inform, contextualize and prioritize where to invest skills, practices, and technologies. Armed with this strong guidance, CISOs can chart their own paths to leadership."
Related: Learn More at SecurityWeek's 2017 CISO Forum
Put bluntly, the purpose of this report is to help lower performing CISOs to perform better through using the methods already used by high performing CISOs. The five secrets to achieving career success are:
Lead without authority
Embrace the change agent role
Don't wait to be invited to the party
Build a cohesive cyber cadre
It's a 5 to 7-year journey to high impact
Each of these 'secrets' is discussed in the report and supported by statistical research evidence. For example, 100% of high performers lead despite having no authority, using "persuasion, negotiation, conflict management, communication, education." Only 3% of low performers succeed in this.
For the second 'secret', the report states, "High-performing CISOs know the value of engaging to drive change," says the report. "In the CISO Impact data, 3 out of 4 of high performers embrace this approach, compared to 1 in 20 of the low performers. To embrace this role, know the business, know yourself, and get ready to 'make lemonade'."
The third secret is not so widely adopted by the high performers. "More than half of high performers in the CISO Impact data set didn't wait for executives to have an epiphany that security matters," states the report. "They leveraged the power of simulation to generate the emotional experience of loss or compromise that is fundamental to an engaged executive team." Less than 1% of low performers did similar.
In secret 4, "High performers patiently assemble and train more than a team -- they culture a cyber cadre." This approach is adopted by 85% of high performers; but by only 1.4% of low performers.
The fifth secret warns that there is no quick fix. "Five to seven years is a realistic time frame for building the trust, the program, the team, and the value of information security to the point where information security is baked in."
These five secrets provide excellent advice for improving company security and enhancing CISO careers. As stand-alone research, however, the report has several problems. The first is the distinction between a high performer and a low performer. The second is that it is easier to be a high performer in some companies than it is in others.
Martin Zinaich (CSSLP, CRISC, CISSP, CISA, CISM and more) is information security officer for the City of Tampa, comments: "'You must lead without authority' -- that is so very true! You have to do that both technically and from an organic business integration standpoint. Yet," he told SecurityWeek, "the study shows that 60% of high performing security leaders report into risk and business roles (that have authority) -- and 95% of lower performing CISOs report to the CIO (where they don't). Those two stats show the simple reality that it is very difficult to lead without authority. Almost every non-technical safe corporate wide business practice I have seen where the CISO is lacking authority has come via post breach, regulations or working with the Audit department."
The danger for research statistics is that some of the low performers could be high performers in a different company with more resources and/or a more receptive C-Suite.
A similar issue occurs in the fifth secret; that is, 'it's a 5 to 7-year journey to high impact'. The reality is that few CISOs will remain in one position for that long -- in fact, it is probably only the high performing CISOs already occupying a high-flying position with a security-aware company that will do so.
Such concerns, however, only impact the statistical difference between high and low performing security officers. The basic arguments contained within the five secrets remains quality advice for any CISO who wants to better secure his organization and improve his career potential.
The IANS Research report, "The 5 Secrets of High-Performing CISOs" will be presented at the RSA Conference next week.
HackerOne Penetrates VC Pockets for $40 Million
9.2.2017 securityweek Security
Bug bounty platform provider HackerOne announced on Wednesday that it has raised $40 million in a Series C financing round led by Dragoneer Investment Group.
The San Francisco-based startup offers a software-as-a-service platform that provides the technology and automation to help organizations run their own vulnerability management and bug bounty programs.
The company says the new funds will be used to invest in technology development, expand market reach, and strengthen its hacker community of more than 100,000 white hat hackers.
HackerOne Logo
The company was co-founded by Alex Rice, the company’s CTO and the man behind Facebook’s bug bounty program, Merijn Terheggen, who serves as CEO, Jobert Abma (tech lead) and Michiel Prins (product lead). HackerOne gained publicity in November 2013 when it announced hosting the Internet Bug Bounty project funded by Microsoft and Facebook.
According to the security startup, more than 38,000 security vulnerabilities have been resolved across more than 700 HackerOne customers, with more than $14 million in bug bounties awarded to date, $7 million of which was awarded in 2016.
In 2016, the U.S. Department of Defense (DoD) selected HackerOne to run the U.S. federal government's first bug bounty challenge, Hack the Pentagon, which HackerOne says resolved more than 138 vulnerabilities discovered by 1,400 hackers.
In October 2016 the DoD announced that it awarded a combined $7 million to HackerOne and Synack for helping the organization’s components launch their own bug bounty initiatives. With $3 million awarded to HackerOne, the company will help the DoD run challenges similar to Hack the Pentagon, while Synack will provide assistance for a private program open only to highly vetted researchers, the DoD said, adding that the private program will focus on the Pentagon’s sensitive IT assets.
Other HackerOne customers include Airbnb, CloudFlare, General Motors, GitHub, New Relic, Nintendo, Qualcomm, Starbucks, Uber and Lufthansa.
“Our customers typically receive their first valid security vulnerability report the same day they challenge our diverse community of hackers to examine their code,” said Marten Mickos, CEO of HackerOne. “There’s no such thing as perfect software and bug bounty programs are the most efficient and cost-effective solution for finding security vulnerabilities in live software.”
NEA, Benchmark and Strategic Investors also participated in the Series C round.
Rockwell Automation Teams With Claroty on Industrial Network Security
9.2.2017 securityweek Security
Rockwell Automation this week announced that it teaming up with industrial cybersecurity startup Claroty to combine their security products and services into future, combined security offerings.
Rockwell, an industrial automation giant with more than 22,000 employees, said that after a competitive review process it selected Claroty for its anomaly-detection software purpose built for industrial network security.
Armed with $32 million in funding through Series A and a Series B rounds, Claroty exited stealth mode in September 2016 to announce a security platform designed to provide “extreme visibility” into Operational Technology (OT) environments and protect critical infrastructure from cyber threats.
Claroty has built a platform that provides broad support for control system manufacturers and employs “high-fidelity models and advanced algorithms” to monitor industrial control systems (ICS) communications and provide security and process integrity alerts. The platform can inspect a large number of industrial control protocols; with support for both open and proprietary protocols from vendors including Siemens, Rockwell Automation/Allen Bradley, Yokogawa, Emerson, GE, Schneider Electric, Mitsubishi, Honeywell, ABB and more.
“More connected control systems combined with the potential for more attacks on those systems have made cybersecurity a top concern in the industrial world,” said Scott Lapcewich, vice president and general manager, Customer Support and Maintenance, Rockwell Automation. “Claroty’s deep-visibility software platform and expertise in industrial security made the company a natural fit for substantial collaboration as we grow our existing portfolio of security service and support offerings.”
“The Claroty platform can detect a bad actor’s activities at any stage, whether they’re trying to gain a foothold on a network, conduct reconnaissance or inflict damage,” said Amir Zilberstein, co-founder and CEO, Claroty. “It also can detect human errors and other process integrity issues, which are often more common than threats from bad-actors. For example, the software monitors for critical asset changes that, if done incorrectly, could result in unexpected downtime. The system also identifies network-configuration issues that could expose a system to outside threats.”
Absolute Extends Self-Healing Capabilities to Third-Party Software
8.2.2017 securityweek Security
Vancouver, Canada-based endpoint security company Absolute announced this week the launch of a new product that provides self-healing capabilities to third-party security and management applications.
Absolute’s Persistence technology is embedded in the firmware of over one billion PCs and mobile devices from manufacturers such as Dell, ASUS, HP, Microsoft, Lenovo, Acer, Samsung, Toshiba, Panasonic and Fujitsu. This approach aims to ensure that IT teams are provided uncompromised visibility and real-time remediation capabilities for devices, data and applications.
The company’s Absolute Device & Data Security (DDS) product is designed to allow organizations to monitor endpoints and data stored on computers and cloud storage devices, and quickly address incidents.
Absolute has now announced the availability of Application Persistence, a product that provides self-healing capabilities to third-party endpoint controls, including antiviruses, VPNs, encryption, and management tools.
A recent study has shown that more than half of enterprises have at least six agents installed on their endpoints, and when one of these agents is removed or compromised, the organization can remain exposed to further attacks.
Absolute’s technology aims to address the risk by allowing endpoint agents to repair themselves when removed or compromised by external actors or insider threats, giving enterprises more control over their endpoints, including improved visibility and real-time remediation. Furthermore, it provides IT teams the capabilities needed to ensure that compliance requirements are met.
The company says the self-healing capabilities work even if the machine is not on the corporate network, its firmware is flashed, the hard drive is replaced, or the operating system is reinstalled.
Absolute said its Application Persistence product has already been tested by organizations in the healthcare, financial services and manufacturing industries. The product is available worldwide to enterprises, OEMs, security firms, and independent software vendors (ISVs).
Google Challenges Search Warrant Ruling
8.2.2017 securityweek Security
Google is planning to appeal a ruling made Friday that it must comply with search warrants involving customer data stored on servers outside of the United States. The case is similar to an earlier case involving Microsoft. In July 2016, the 2nd U.S. Circuit Court of Appeals in New York said Microsoft could not be forced to turn over emails stored on a server outside of the US. Now, however, Magistrate Judge Thomas Rueter in Philadelphia has taken the opposite view with Google.
Both cases involve search warrants issued under the 1986 Stored Communications Act (SCA). Microsoft was also initially ordered to comply. It appealed, and eventually Judge Susan Carney of the appeals court said that the SCA does not give US courts authority to force internet companies in the United States to seize customer email contents stored on foreign servers. At the time, Microsoft chief legal officer Brad Smith said, "It makes clear that the US Congress did not give the US Government the authority to use search warrants unilaterally to reach beyond US borders."
Google expected this precedent to be upheld in its own refusal to comply with a similar search warrant. The government's key argument is that no search is undertaken on foreign soil -- the data is lawfully brought back to the US, and the search is lawfully conducted within the US. For Microsoft, this argument was rejected; but for Google it has been accepted.
"Though the retrieval of the electronic data by Google from its multiple data centers abroad has the potential for an invasion of privacy, the actual infringement of privacy occurs at the time of disclosure in the United States," Rueter wrote.
Google has said it will appeal the ruling. "The magistrate in this case departed from precedent, and we plan to appeal the decision. We will continue to push back on overbroad warrants," it said in a statement.
If the appeal process fails, the case could have serious implications for US/EU business relations. EU data protection laws prevent the export of European personal information to any country that does not have adequate (that is, equivalent) data protection laws. That exclusion would include the US were it not for the special agreement known as Privacy Shield. It is the Privacy Shield that allows US tech giants such as Google and Facebook to operate in Europe; but it also allows any US commercial business to trade with the European Union.
Many commentators believe that Privacy Shield will fail European constitutional examination. It currently exists largely because of the political will on both sides to make it exist; but that will is already being eroded by new President Trump's apparent isolationism and support for US law enforcement.
Speaking to SecurityWeek about the effect of President Trump's executive order titled 'Enhancing Public Safety in the Interior of the United States' might have on Privacy Shield, David Flint (a senior partner at the MacRoberts law firm) commented, "It is unclear at this stage..." But he also added, "The more concerning issue for Privacy Shield is that there is a possible carve out for national security and similar issues and it remains unclear as to the extent that the new Administration will seek to define all foreigners' PII as 'a security issue'."
Privacy Shield, he explained, "is a complex interconnected matrix of law, policy and 'comfort letters'; absent any of these three legs, it is likely that some national data protection authorities may consider that there is no longer confidence in the implementation of that matrix (of which many were skeptical) and declare the US as having inadequate protection - now, and certainly after GDPR implementation."
Poland-based privacy consultant Alexander Hanff was more forthright. "Trump's Executive Order has accelerated the demise of a transatlantic lie - a lie which would have been exposed eventually by the CJEU [the Court of Justice, Europe's ultimate constitutional court] anyway; a lie which circumvents the constitutional rights of EU Citizens."
With such concern over an executive order that does not directly deal with European PII, it is difficult to see how US government access to European data directly from US companies -- especially when the data may be physically stored in Europe -- can withstand a legal challenge to the European courts. It is fair to say that in the current climate, if Google is forced to hand over foreign data on the basis of a search warrant, it could prove the end of Privacy Shield. Search warrants and the FBI could be as toxic to Privacy Shield as Prism and the NSA were to its predecessor Safe Harbor.
Rocket AI and the next generation of AV software
7.2.2017 Kaspersky Security
The annual Conference on Artificial Intelligence and Neural Information Processing Systems (NIPS) was held in Barcelona on 5–10 December 2016. This is, most likely, one of the two most important conferences in the AI field. This year, 5,680 AI experts attended the conference (the second of these large conferences is known as ICML).
This is not the first year that Kaspersky Lab is taking part in the conference – it is paramount for our experts to be well informed on the most up-to-date approaches to machine learning. This time, there were five Kaspersky Lab employees at NIPS, each from a different department and each working with machine learning implementation in order to protect users from cyberthreats.
However, my intent is to tell you not about the benefit of attending the conference but about an amusing incident that was devised and put into action by AI luminaries.
Rocket AI is the Next Generation of Applied AI
This story was covered in detail by Medium, and I shall only briefly relate the essence of the matter.
Right as the conference was happening, the www.rocketai.org website was created with this bubble on the main page (see picture below):
Rocket AI and the next generation of AV software
Please note that this is not just AI, but the next generation of AI. The idea of the product is described below.
Rocket AI and the next generation of AV software
The Temporally Recurrent Optimal Learning™ approach (abbreviated as “TROL(L)”), which was not yet known to science, was actively promoted on Twitter by conference participants. Within several hours, this resulted in five large companies contacting the project’s authors with investment offers. The value of the “project” was estimated at tens of millions of dollars.
Rocket AI and the next generation of AV software
Now, it’s time to lay the cards on the table: the Rocket AI project was created by experts in machine learning as a prank whose goal was to draw attention to the issue that was put perfectly into words by an author at Medium.com: “Artificial Intelligence has become the most hyped sector of technology. With national press reporting on its dramatic potential, large corporations and investors are desperately trying to break into this field. Many start-ups go to great lengths to emphasize their use of “machine learning” in their pitches, however trivial it may seem. The tech press celebrates companies with no products, that contribute no new technology, and at overly-inflated cost.”
In reality, the field of machine learning features nothing new; popular approaches to artificial intelligence are actually decades-old ideas.
“Clever teams are exploiting the obscurity and cachet of this field to raise more money, knowing that investors and the press have little understanding of how machine learning works in practice,” the author added.
An Anti-Virus of the Very Next Generation
It may seem that the outcome of the prank brought out nothing new: investors feel weakness for everything they hear about. Investment bubbles have existed and will continue to exist. Just our generation saw the advent of dotcoms, biometrics, and bitcoins. We have AI now, and I am sure that 2017 will give us something new as well.
Yet, after I had taken a peek at data-security start-ups, which are springing up like mushrooms after a rain and which claim that they employ the “very real” AI (of the very next generation), an amusing idea crossed my mind.
What would happen if we did the same thing that the respected AI experts did? We could come to agreements with other representatives in the cybersecurity area (I would like to point out the principle of “coopetition”, which combines market competition and cooperation in the areas of inspection and user protection) and create a joint project. Meet Rocket AV.
Rocket AI and the next generation of AV software
If respected IT experts were to advertise it all over their Twitter accounts, then — who knows? — maybe we could attract tens of millions of dollars’ worth of investments.
But no, it’d probably be better for us to continue doing what we are best at: protecting users from cyberthreats. This is the essence of True CyberSecurity.