Social Articles - H 2020 1 2 3 4 5 6 7 Social List - H 2021 2020 2019 2018 1 Social blog Social blog
Facebook: Cambridge Analytica scandal affected 87 Million users
5.4.2018 securityaffairs Social
Facebook revealed on Wednesday that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
The social network giant recently unveiled clearer terms of service to ensure transparency to its users about data sharing.
Facebook’s chief technology officer Mike Schroepfer provided further details on the case, including new estimations for the number of affected users.
“In total, we believe the Facebook information of up to 87 million people — mostly in the US — may have been improperly shared with Cambridge Analytica,” Schroepfer said.
The CTO also explained how Facebook is implementing new privacy tools for its users that would be available by next week.
“People will also be able to remove apps that they no longer want. As part of this process we will also tell people if their information may have been improperly shared with Cambridge Analytica,” he added.
“Overall, we believe these changes will better protect people’s information while still enabling developers to create useful experiences.”
Facebook- Cambridge Analytica
Next week, on April 11, Facebook founder Mark Zuckerberg would appear at the Congress to address privacy issues.
The hearing will “be an important opportunity to shed light on critical consumer data privacy issues and help all Americans better understand what happens to their personal information online,” said the committee’s Republican chairman Greg Walden and ranking Democrat Frank Pallone in a statement.
“We appreciate Mr. Zuckerberg’s willingness to testify before the committee, and we look forward to him answering our questions.”
The situation for Facebook could get worse after these last revelations, a few days ago Zuckerberg said it would take “a few years” to fix the problems uncovered by the revelations on data misuse.
Zuckerberg tried to reinforce the positive image of its firms, sustaining that one of the biggest error he made is that Facebook is “idealistic,” the
“Well, I don’t think it’s going to take 20 years. I think the basic point that you’re getting at is that we’re really idealistic. When we started, we thought about how good it would be if people could connect, if everyone had a voice. Frankly, we didn’t spend enough time investing in, or thinking through, some of the downside uses of the tools. So for the first 10 years of the company, everyone was just focused on the positive.” Zuckerberg told Vox.com
“I think now people are appropriately focused on some of the risks and downsides as well. And I think we were too slow in investing enough in that. It’s not like we did nothing. I mean, at the beginning of last year, I think we had 10,000 people working on security. But by the end of this year, we’re going to have 20,000 people working on security.”
In response to the Cambridge Analytica case, Facebook deleted dozens of accounts linked to Russia that were used to spread propaganda.
Facebook announced to have revoked the accounts of 70 Facebook and 65 Instagram accounts and removed 138 Facebook pages controlled by the Russia-based Internet Research Agency (IRA), also known as the Russian troll farm due to its misinformation campaigns.
The unit “has repeatedly used complex networks of inauthentic accounts to deceive and manipulate people who use Facebook, including before, during and after the 2016 US presidential elections,” explained Facebook chief security officer Alex Stamos.
Zuckerberg added that the Russian agency“has been using complex networks of fake accounts to deceive people.”
“While we respect people and governments sharing political views on Facebook, we do not allow them to set up fake accounts to do this. When an organization does this repeatedly, we take down all of their pages, including ones that may not be fake themselves.”
Companies Have Little Control Over User Accounts and Sensitive Files: Study
5.4.2018 securityweek Social
Lack of Control Over Sensitive Files Leaves Companies Open to GDPR Failure
Security teams are urged to assume intruders are already on their networks. The quantity and frequency of data loss breaches lends credence to that assumption. The implication is that perimeter defenses are insufficient, and that sensitive data needs to be locked down as far as possible within the networks. A new study shows, however, that 41% of companies have more than 1.000 sensitive files open to everyone with access to the network.
Each year, New York, NY-based data protection and governance firm Varonis analyzes the results of its risk assessments on new and potential customers. Its 2018 Global Data Risk Report (PDF) contains the findings of 130 corporate risk analyses conducted during 2017. It looks for free-form data at risk from existing intruders and potential malicious insiders; and the process examined more than 6 billion individual files from 30 different industries across more than 50 countries.
The results clearly show that companies are struggling to control sensitive data contained in free-form text documents. A common problem is leaving files open to global access groups. For example, 58% of companies have more than 100,000 folders open to everyone -- and the bigger the company, the worse the problem. Eighty-eight percent of companies with more than 1 million folders have more than 100,000 open folders.
The problem becomes more pressing when those files contain sensitive data -- defined here as information subject to regulations such as GDPR, PCI, and HIPAA. The Varonis platform works by looking at both the structure of the network, and the content of the files. In this study it found that 41% of companies have more than 1,000 sensitive files open to everyone.
For these companies any malicious insider or low-privileged intruder can simply access and potentially steal sensitive data, bringing the company into immediate compliance failure. Most regulations either require the principle of least privilege or imply its requirement.
The basis of protecting sensitive files requires two things in particular: the principle of least privilege to restrict access to sensitive documents to authorized persons only; and privileged account management to prevent attackers' access to and unauthorized use of privileged accounts to access restricted documents. However, the Varonis study shows that companies have as little control over their user accounts as they do over their sensitive files.
A common issue with account management is the failure to remove old accounts. This usually happens when the account is no longer necessary, or its owner leaves the organization's employment. These are variously known as 'stale' or 'ghost user' accounts. Varonis found that 65% of companies have more than 1000 stale user accounts. The study does not indicate how many of these stale accounts are also privileged accounts, but with so many sensitive documents open to everyone, an attacker's access to a privileged account isn't necessary.
"User and service accounts that are inactive and enabled (aka 'ghost users') are targets for penetration and lateral movement," warns the Varonis report. "If these accounts are left unmonitored, attackers can steal data or cause disruption without being detected."
The combination of open sensitive files and ghost accounts increases the likelihood of a data breach and compliance failure. The regulation top-of-mind with most security teams right now is the EU's General Data Protection Regulation (GDPR), with the potential for heavy fines, and due to come into force next month.
A common perception is that if a firm can demonstrate strong attempts to protect personal data, it will not be prosecuted to the full by European data regulators. Certainly, regulators will take account of any breached firm's attempts to conform -- but overexposed documents and ghost accounts are a de-facto failure.
Last month, the Irish data protection commissioner discussed how she intends to handle her GDPR remit. Ireland is particularly important because it is the European home of many large U.S. firms (such as Facebook, Google, Twitter, Pfizer, Boston Scientific and Johnson & Johnson) that have extensive offices and/or their European headquarters in what is sometimes known as Dublin's Silicon Docks.
Discussing whether 'state of the art security' would be a mitigating factor over any GDPR-relevant data breach, Ireland's Data Protection Commissioner Helen Dixon told Independent.ie, "it's a theoretical possibility that if they have applied objectively demonstrable state-of-the-art security and there really appears to have been nothing further they could have done, that would certainly be a mitigation criteria [sic]. But, we haven't come across it."
Regardless of all other security controls, if any firm investigated under GDPR has failed to operate least privilege for all documents containing personal data, it will likely be subject to the full sanction of the General Data Protection Regulation -- that is, 4% of global turnover.
Facebook Says 87 Million May be Affected by Data Breach
5.4.2018 securityweek Social
Facebook said Wednesday personal data on as many as 87 million users was improperly shared with British political consultancy Cambridge Analytica.
The new figure eclipses a previous estimate of 50 million in a further embarrassment to the social network roiled by a privacy scandal.
The announcement came as Facebook unveiled clearer terms of service to enable users to better understand data sharing, and as a congressional panel said chief executive Mark Zuckerberg would appear next week to address privacy issues.
Facebook's chief technology officer Mike Schroepfer released the new figures on affected users as he discussed implementation of new privacy tools for users of the huge social network.
"In total, we believe the Facebook information of up to 87 million people -- mostly in the US -- may have been improperly shared with Cambridge Analytica," he said.
The new estimate could deepen the crisis for Facebook, which has been pressured by the disclosures on hijacking of private data by the consulting group working for Donald Trump's 2016 campaign.
Schroepfer said new privacy tools, which had been announced last month, would be in place by next Monday.
"People will also be able to remove apps that they no longer want. As part of this process we will also tell people if their information may have been improperly shared with Cambridge Analytica," he said.
"Overall, we believe these changes will better protect people's information while still enabling developers to create useful experiences."
Zuckerberg on the Hill
Earlier Wednesday, the House of Representatives' Energy and Commerce Committee announced what appeared to be the first congressional appearance by Zuckerberg since the scandal broke on the hijacking of data on tens of millions of users.
The April 11 hearing will "be an important opportunity to shed light on critical consumer data privacy issues and help all Americans better understand what happens to their personal information online," said the committee's Republican chairman Greg Walden and ranking Democrat Frank Pallone in a statement.
"We appreciate Mr. Zuckerberg's willingness to testify before the committee, and we look forward to him answering our questions."
Zuckerberg will likely face multiple congressional hearings as his social media giant battles a firestorm following revelations that the British consulting firm Cambridge Analytica obtained the data of 50 million Facebook users to try and manipulate US voters in the 2016 presidential election.
The Facebook co-founder has also been invited to appear before the Senate's Judiciary Committee on April 10, alongside Google chief Sundar Pichai and Twitter head Jack Dorsey.
His participation is yet unconfirmed but Senator Dianne Feinstein told the San Francisco Chronicle that Zuckerberg had agreed to attend that hearing.
Zuckerberg, who has been making a series of media appearances after staying silent for several days on the breach, said earlier this week it would take "a few years" to fix the problems uncovered by the revelations on data misuse.
He told Vox.com that one of Facebook's problems was that it was "idealistic," focusing on the positive aspects of connecting people and that "we didn’t spend enough time investing in, or thinking through, some of the downside uses of the tools."
The world's biggest social network faces probes on both sides of the Atlantic over the misuse of data, which Facebook attributed to a breach of terms of service by an academic researcher linked to the consulting firm working for Donald Trump's campaign.
Deleting Russian 'trolls'
Late Tuesday, Facebook said it deleted dozens of accounts linked to a Russian-sponsored internet unit which has been accused of spreading propaganda and other divisive content in the United States and elsewhere.
The social networking giant said it revoked the accounts of 70 Facebook and 65 Instagram accounts, and removed 138 Facebook pages controlled by the Russia-based Internet Research Agency (IRA).
The agency has been called a "troll farm" due to its deceptive post aimed at sowing discord and propagating misinformation.
The unit "has repeatedly used complex networks of inauthentic accounts to deceive and manipulate people who use Facebook, including before, during and after the 2016 US presidential elections," said a statement Facebook chief security officer Alex Stamos.
Zuckerberg said in a separate statement on his Facebook page that the Russian group "has been using complex networks of fake accounts to deceive people."
He added: "While we respect people and governments sharing political views on Facebook, we do not allow them to set up fake accounts to do this. When an organization does this repeatedly, we take down all of their pages, including ones that may not be fake themselves."
Facebook to Offer 'Clearer' Terms on Privacy, Data Use
5.4.2018 securityweek Social
Facebook said Wednesday it is updating its terms on privacy and data sharing to give users a clearer picture of how the social network handles personal information.
The move by Facebook follows a firestorm over the hijacking of personal information on tens of millions of users by a political consulting firm which sparked a raft of investigations worldwide.
"We're not asking for new rights to collect, use or share your data on Facebook," said a statement by Facebook chief privacy officer Erin Egan and deputy general counsel Ashlie Beringer.
"We're also not changing any of the privacy choices you've made in the past."
Facebook is under intense pressure to fix the problems which led to the harvesting of some 87 million user profiles by Cambridge Analytica, a consulting firm working on Donald Trump's 2016 campaign.
The company has already unveiled several measures aimed at improving privacy and transparency, but chief executive Mark Zuckerberg has said it may take several years to address all the issues raised in the scandal.
Egan and Beringer said that with the new terms of service, "we explain how we use data and why it's needed to customize the posts and ads you see, as well as the groups, friends and pages we suggest."
They wrote that "we will never sell your information to anyone" and impose "strict restrictions on how our partners can use and disclose data."
The statement said the new terms will offer better information on how Facebook advertising operates as well.
"You have control over the ads you see, and we don't share your information with advertisers," the statement said.
"Our data policy explains more about how we decide which ads to show you."
Egan and Beringer said Facebook will go further in explaining how it gathers information from phones and other devices.
"People have asked to see all the information we collect from the devices they use and whether we respect the settings on your mobile device (the short answer: we do)," they wrote.
Users may offer feedback on the new policy for seven days before Facebook finalizes the new rules and asks its members to accept them.
After Cambridge Analytica scandal Facebook announces Election security Improvements
2.4.2018 securityaffairs Social
After Cambridge Analytica case, Facebook announced security improvements to prevent future interference with elections.
Facebook is under the fire after the revelation of the Cambridge Analytica case and its role in the alleged interference to the 2016 US presidential election.
While the analysts are questioning about the interference with other events, including the Brexit vote, Facebook is now looking to prevent such kind of operations against any kind of election.
Guy Rosen, Facebook VP of Product Management declared that everyone is responsible for preventing the same kind of attack to the democracy and announced the significant effort Facebook will spend to do it.
“By now, everyone knows the story: during the 2016 US election, foreign actors tried to undermine the integrity of the electoral process. Their attack included taking advantage of open online platforms — such as Facebook — to divide Americans, and to spread fear, uncertainty and doubt,” said Guy Rosen.
“Today, we’re going to outline how we’re thinking about elections, and give you an update on a number of initiatives designed to protect and promote civic engagement on Facebook.”
Facebook plans to improve the security of elections in four main areas: combating foreign interference, removing fake accounts, increasing ads transparency, and reducing the spread of false news.
Alex Stamos, Facebook’s Chief Security Officer, added that the company always fight “fake news,” explaining that the term is used to describe many malicious activities including:
Fake identities– this is when an actor conceals their identity or takes on the identity of another group or individual;
Fake audiences– so this is using tricks to artificially expand the audience or the perception of support for a particular message;
False facts – the assertion of false information; and
False narratives– which are intentionally divisive headlines and language that exploit disagreements and sow conflict. This is the most difficult area for us, as different news outlets and consumers can have completely different on what an appropriate narrative is even if they agree on the facts.
“When you tease apart the overall digital misinformation problem, you find multiple types of bad content and many bad actors with different motivations.” said Alex Stamos.
“Once we have an understanding of the various kinds of “fake” we need to deal with, we then need to distinguish between motivations for spreading misinformation. Because our ability to combat different actors is based upon preventing their ability to reach these goals.” said Stamos.
“Each country we operate in and election we are working to support will have a different range of actors with techniques are customized for that specific audience. We are looking ahead, by studying each upcoming election and working with external experts to understand the actors involved and the specific risks in each country.”
Stamos highlighted the importance to profile the attackers, he distinguished profit-motivated organized group, ideologically motivated groups, state-sponsored actors, people that enjoy causing chaos and disruption, and groups having multiple motivations such as ideologically driven groups.
Facebook is working to distinguish between motivations for spreading misinformation and implement the necessary countermeasures.
Facebook
Currently, Facebook already spends a significant effort in combatting fake news and any interference with elections.
Samidh Chakrabarti, Product Manager, Facebook, explained that the social media giant is currently blocking millions of fake accounts each day with a specific focus on those pages that are created to spread inauthentic civic content.
Chakrabarti explained that pages and domains that are used to share fake news is increasing, in response, Facebook doubles the number of people working on safety issues from 10,000 to 20,000. This hard job is mainly possible due to the involvement of sophisticated machine learning systems.
“Over the past year, we’ve gotten increasingly better at finding and disabling fake accounts. We’re now at the point that we block millions of fake accounts each day at the point of creation before they can do any harm.” said Chakrabarti.
“Rather than wait for reports from our community, we now proactively look for potentially harmful types of election-related activity, such as Pages of foreign origin that are distributing inauthentic civic content. If we find any, we then send these suspicious accounts to be manually reviewed by our security team to see if they violate our Community Standards or our Terms of Service. And if they do, we can quickly remove them from Facebook. “
But we all know that Facebook is a business that needs to increase profits, for this reason ads are very important for it.
Facebook is building a new transparency feature for the ads on the platform, dubbed View Ads, that is currently in testing in Canada. View Ads allows anyone to view all the ads that a Facebook Page is running on the platform.
“you can click on any Facebook Page, and select About, and scroll to View Ads.” explained Rob Leathern, Product Management Director.
“Next we’ll build on our ads review process and begin authorizing US advertisers placing political ads. This spring, in the run up to the US midterm elections, advertisers will have to verify and confirm who they are and where they are located in the US,”
This summer, Facebook will launch a public archive with all the ads that ran with a political label.
Russian Hacker Who Allegedly Hacked LinkedIn and Dropbox Extradited to US
1.4.2018 thehackernews Social

A Russian man accused of hacking LinkedIn, Dropbox, and Formspring in 2012 and possibly compromising personal details of over 100 million users, has pleaded not guilty in a U.S. federal court after being extradited from the Czech Republic.
Yevgeniy Aleksandrovich Nikulin, 30, of Moscow was arrested in Prague on October 5, 2016, by Interpol agents working in collaboration with the FBI, but he was recently extradited to the United States from the Czech Republic on Thursday for his first appearance in federal court.
Nikulin's arrest started an extradition battle between the United States and Russia, where he faces significantly lesser criminal charges of stealing $3,450 via Webmoney in 2009. But the Czech Republic ruled in favor of the United States.
In the U.S., Nikulin is facing:
3 counts of computer intrusion
2 counts of intentional transmission of information, code, or command causing damage to a protected computer
2 counts of aggravated identity theft
1 count of trafficking in unauthorized access devices
1 count of conspiracy
According to the maximum penalties for each count, Nikulin faces a maximum of 32 years in prison and a massive fine of more than $1 Million.
The U.S. Justice Department accused Nikulin of allegedly hacking into computers belonging to three American social media firms, including LinkedIn, the online cloud storage platform Dropbox and now-defunct social-networking firm Formspring.
Nikulin reportedly gained access to LinkedIn's network between March 3 and March 4, 2012, Dropbox between May 14 and July 25, 2012, and Formspring between June 13 and June 29, 2012.
The hacker allegedly stole accounts of more than 117 Million LinkedIn users and more than 68 Million Dropbox users. Authorities also say that after stealing data from the three companies, Nikulin worked with unnamed co-conspirators to sell the stolen data.
Besides hacking into the three social media firms, the Justice Department also accused Nikulin of allegedly gaining access to credentials belonging to LinkedIn and Formspring employees, which helped him carry out the computer hacks.
Nikulin appeared in Federal District Court in San Francisco on Friday and pleaded not guilty to the charges against him, the New York times reported.
"This is deeply troubling behavior once again emanating from Russia," said Attorney General Jeff Sessions in a statement. "We will not tolerate criminal cyber-attacks and will make it a priority to investigate and prosecute these crimes, regardless of the country where they originate."
Judge Jacqueline Scott Corley scheduled Nikulin's next court appearance for status on April 2, 2018, and scheduled a detention hearing for April 4, 2018.
Facebook Limits App Access to Users Data
30.3.2018 securityweek Social
Facebook has announced a series of changes to its developer platform to implement tighter user privacy controls and limit how apps can access to user data.
The changes were initially mentioned last week, when the social platform came under fire after reports emerged that millions of Facebook users' personal data was harvested by British firm Cambridge Analytica.
Facebook CEO Mark Zuckerberg apologized for the incident last week and said tighter controls would be coming. Also last week, Facebook paused app review in preparation for the upcoming changes to its developer platform.
The first of the announced privacy improvements have been already implemented, but more are planned for the near future.
“These are critical steps that involve reviewing developers' actions for evidence of misuse, implementing additional measures to protect data, and giving people more control of their information,” Facebook now says.
The first major change Facebook made toward improved user privacy was to prevent applications from “seeing” a person in one’s friends list unless both users have decided to share their list of friends with the app.
“In order for a person to show up in one person's friend list, both people must have decided to share their list of friends with your app and not disabled that permission during login. Also both friends must have been asked for user_friends during the login process,” Facebook explains.
Moving forth, the social platform plans investigating all apps that had access to large amounts of user data before that access was restricted in 2014. Facebook will ban developers from its platform if they are found to have misused personally identifiable information and will notify everyone who used the application.
The company will also require for developers who build applications for other businesses to comply with rigorous policies and terms that will be revealed within the following weeks.
Facebook also plans on encouraging people to manage the apps they use, making it easier for them to revoke apps’ ability to use their data. Users will find it easier to learn what apps are connected to their accounts and to control the data these apps have access to.
On top of that, Facebook also plans on expanding its bug bounty program to allow users file reports when data is misused by app developers, a move that many security experts approve of.
Craig Young, computer security researcher for Tripwire’s Vulnerability and Exposure Research Team, told SecurityWeek in an emailed comment that this move could “start a trend toward more policy-oriented bug bounties from social media platforms.”
“This move by Facebook really makes a lot of sense to me. By expanding their bounty program to include data misuse by app developers, Facebook may have found a way to mobilize their community to self-police. It will be interesting to see if this if spurs new bug bounty participation including people less technical than the typical bug hunter,” he said.
Ilia Kolochenko, CEO of web security company High-Tech Bridge, also believes that this step could determine other companies to start similar moves that would allow them to avoid severe sanctions for privacy violations.
“This is an exciting shift in the bug bounty industry, which untill now has focused on security vulnerabilities. Facebook is the first major company that is asking for researchers to identify data privacy issues. With the GDPR coming into force in a couple of months, data privacy is now high on many organizations’ agendas,” Kolochenko said.
Last week, Facebook said it would make its privacy tools more visible to its users, and today the company announced that it has already implemented the necessary changes.
The settings menu on mobile devices was redesigned, with all the necessary tools now available in a single place and cleared outdated settings to make it obvious what information can and can’t be shared with apps.
Facebook also implemented a new Privacy Shortcuts menu, where users can control their data with just a few taps, in addition to finding clearer explanations of how the controls work.
Now, users can add more layers of protection, such as two-factor authentication, can review the data they’ve shared and delete it, can manage the information the platform uses to show ads, and can also manage who sees their posts and the information included on their profiles.
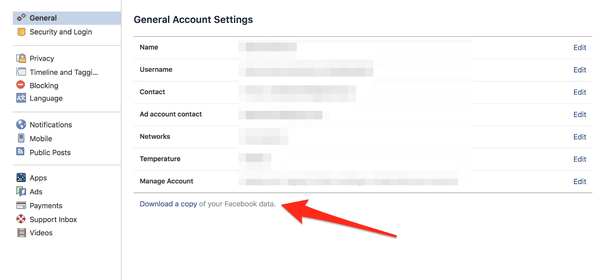
Users can also find, download, and delete their Facebook data, via the Access Your Information option, where management of posts, reactions, comments, and things searched for is possible. Users can delete any information they no longer want on Facebook and can also download a copy of the data shared with Facebook.
Facebook also plans on updating its terms of service and data policy to make it clearer what data is collected and how it is used.
“These updates are about transparency – not about gaining new rights to collect, use, or share data,” Erin Egan, VP and Chief Privacy Officer, Policy and Ashlie Beringer, VP and Deputy General Counsel, Facebook, said.
Facebook Collected Your Android Call History and SMS Data For Years
29.3.2018 thehackernews Social
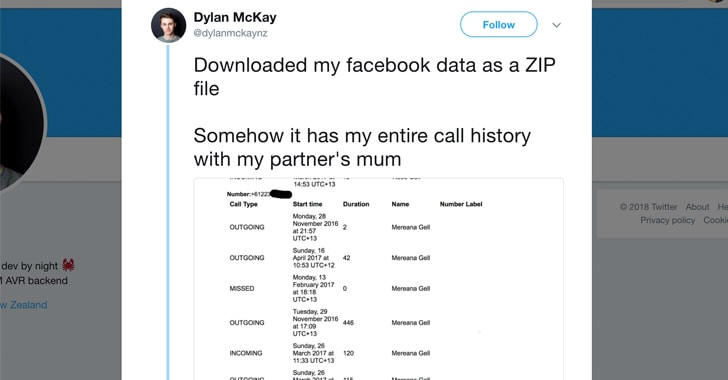
Facebook knows a lot about you, your likes and dislikes—it's no surprise.
But do you know, if you have installed Facebook Messenger app on your Android device, there are chances that the company had been collecting your contacts, SMS, and call history data at least until late last year.
A tweet from Dylan McKay, a New Zealand-based programmer, which received more than 38,000 retweets (at the time of writing), showed how he found his year-old data—including complete logs of incoming and outgoing calls and SMS messages—in an archive he downloaded (as a ZIP file) from Facebook.
Facebook was collecting this data on its users from last few years, which was even reported earlier in media, but the story did not get much attention at that time.
Since Facebook had been embroiled into controversies over its data sharing practices after the Cambridge Analytica scandal last week, tweets from McKay went viral and has now fueled the never-ending privacy debate.
A Facebook spokesperson explained, since almost all social networking sites have been designed to make it easier for users to connect with their friends and family members, Facebook also uploads its users’ contacts to offer same.
As Ars reported, in older versions of Android when permissions were a lot less strict, the Facebook app took away contact permission at the time of installation that allowed the company access to call and message data automatically.
Eventually, Google changed the way Android permissions worked in version 16 of its API, making them more clear and granular by informing users whenever any app tries to execute permissions.
However, developers were able to bypass this change, and Facebook continued accessing call and SMS data until Google deprecated version 4.0 of the Android API in October last year.
Even you can check what data the social network has collected on you so far by going to your Facebook's Settings→Download a copy of your Facebook data→Start My Archive.
If you don't want Facebook to store or continuously upload your contacts to its server, you can turn off the continuous uploading setting in the Messenger app. This change will also delete all your previously uploaded contacts.
Facebook users on Apple devices are on the safer side, as iOS has never allowed silent access to call data.
Facebook Announces New Steps to Protect Users' Privacy
28.3.2018 securityweek Social
Facebook Revamps Privacy Settings Amid Data Breach Outcry
Facebook on Wednesday unveiled new privacy settings aiming to give its users more control over how their data is shared, following an outcry over hijacking of personal information at the giant social network.
The updates include easier access to Facebook's user settings and tools to easily search for, download and delete personal data stored by Facebook.
Facebook said a new privacy shortcuts menu will allow users to quickly increase account security, manage who can see their information and activity on the site and control advertisements they see.
"We've heard loud and clear that privacy settings and other important tools are too hard to find and that we must do more to keep people informed," chief privacy officer Erin Egan and deputy general counsel Ashlie Beringer said in a blog post.
"We're taking additional steps in the coming weeks to put people more in control of their privacy."
The new features follow fierce criticism after it was revealed millions of Facebook users' personal data was harvested by a British firm linked to Donald Trump's 2016 presidential campaign -- although Facebook said the changes have been "in the works for some time."
Earlier this month, whistleblower Christopher Wylie revealed political consulting company Cambridge Analytica obtained profiles on 50 million Facebook users via an academic researcher's personality prediction app.
The app was downloaded by 270,000 people, but also scooped up their friends' data without consent -- as was possible under Facebook's rules at the time.
Egan and Beringer also announced updates to Facebook's terms of service and data policy to improve transparency about how the site collects and uses data.
Deepening tech crisis
Facebook's move comes as authorities around the globe investigate how Facebook handles and shares private data, and with its shares having tumbled more than 15 percent, wiping out tens of billions in market value.
The crisis also threatens the Silicon Valley tech industry whose business model revolves around data collected on internet users.
On Tuesday, tech shares led a broad slump on Wall Street, with an index of key tech stocks losing nearly six percent.
The US Federal Trade Commission this week said it had launched a probe into whether the social network violated consumer protection laws or a 2011 court-approved agreement on protecting private user data.
US lawmakers were seeking to haul Facebook CEO Mark Zuckerberg to Washington to testify on the matter.
Authorities in Britain have seized data from Cambridge Analytica in their investigation, and EU officials have warned of consequences for Facebook.
Facebook has apologized for the misappropriation of data and vowed to fix the problem. Facebook took out full-page ads in nine major British and US newspapers on Sunday to apologize to users.
"We have a responsibility to protect your information. If we can't we don't deserve it," Zuckerberg said in the ads.
Pink-haired Whistleblower at Heart of Facebook Scandal
28.3.2018 securityweek Social
Instantly recognizable with his pink hair and nose ring, Christopher Wylie claims to have helped create data analysis company Cambridge Analytica before turning whistleblower and becoming "the face" of the crisis engulfing Facebook.
Carole Cadwalladr, the Guardian journalist who worked with Wylie for a year on the story, described him as "clever, funny, bitchy, profound, intellectually ravenous, compelling. A master storyteller. A politicker. A data science nerd."
The bespectacled 28-year-old describes himself as "the gay Canadian vegan who somehow ended up creating Steve Bannon's psychological warfare tool," referring to Trump's former adviser, whom the report said had deep links with Cambridge Analytica (CA).
With Wylie's help, Cadwalladr revealed how CA scooped up data from millions of Facebook users in the US.
They then used the information to build political and psychological profiles, in order to create targeted messages for voters.
Facebook insists it did not know the data taken from its site were being used, but the revelations have raised urgent questions over how data of 50 million users ended up in CA's hands.
Shares of the tech giant have since tumbled, with $70 billion (56 billion euros) wiped off in 10 days.
- 'Walter Mitty' -
Wylie studied law and then fashion, before entering the British political sphere when he landed a job working for the Liberal Democrats.
Former Lib Dem colleague Ben Rathe had a less complementary description of Wylie, tweeting that he "thinks he's Edward Snowden, when he's actually Walter Mitty" -- a reference to a fictional character with a vivid fantasy life.
Wylie became a research director for Strategic Communication Laboratories (SCL), the parent company of CA, in 2014.
"I helped create that company," he said of CA in an interview with several European newspapers.
"I got caught up in my own curiosity, in the work I was doing. It's not an excuse, but I found myself doing the research work I wanted to do, with a budget of several million, it was really very tempting," he told French daily Liberation.
Initially, he enjoyed the globetrotting lifestyle, meeting with ministers from around the world.
But the job took a dark turn when he discovered that his predecessor had died in a Kenyan hotel. He believes the victim paid the price when a "deal went sour".
"People suspected poisoning," he told a British parliamentary committee investigating "fake news" on Tuesday.
- 'Repair Facebook!' -
His appearance before MPs saw him swap his usual loud T-shirts for a sober suit and tie, producing hours of testimony against the firm that he left in 2014.
He said he eventually decided to speak out after US President Donald Trump's shock election victory, which he partly attributed to the misuse of personal data for political purposes.
Cambridge Analytica vigorously denies the charges levelled against it, saying that Wylie was merely "a part-time employee who left his position in July 2014" and had no direct knowledge of how the firm had operated since.
Wylie urged British MPs to dig deeper into the story, insisting that his concern was not political and was focussed on abuses in the democratic process -- including during the Brexit referendum campaign.
"I supported Leave, despite having pink hair and my nose ring," he said.
He claimed that various pro-Brexit organisations worked together to get around campaign finance rules, using the services of Aggregate IQ, a Canadian company linked to the SCL group.
Wylie believes that it is "very reasonable" to say that CA's activities may have swung the Brexit vote, although he stressed he was not anti-Facebook, anti-social media or anti-data.
"I don't say 'delete Facebook', but 'repair Facebook'," he told the European newspapers.
However, he admitted to MPs that he had "become the face" of the scandal.
Mozilla Isolates Facebook with New Firefox Extension
28.3.2018 securityweek Social
Mozilla today unveiled the "Facebook Container Extension", a new browser extension designed to help Firefox users reduce the ability of Facebook to track their activity across other web sites.
The new extension, Mozilla says, will help users gain more control over their data on the social platform by isolating their identity into a separate container. Because of that, Facebook would find it more difficult to track users’ activity on other websites via third-party cookies.
The Facebook Container Add-On was launched in the light of news that Facebook at one point allowed applications to harvest large amounts of data on users and their friends and follows Mozilla’s announcement that it has paused Facebook advertising until the social network improves the privacy of its users.
The privacy scandal started with reports that Cambridge Analytica, the data analysis firm hired by Donald Trump's 2016 presidential campaign, harvested 50 million Facebook users’ profiles without their permission.
The social network has been under heavy fire since last week, when the news broke, despite suspending the firm’s account. Many are losing trust in the platform and the use of Facebook data to target voters triggered global outrage.
This is what determined Mozilla last week to pause Facebook advertising, despite Mark Zuckerberg’s assurance that steps will be taken to ensure a situation like the Cambridge Analytica one won’t happen again.
“Facebook knows a great deal about their two billion users — perhaps more intimate information than any other company does. They know everything we click and like on their site, and know who our closest friends and relationships are,” Mozilla said last week.
Now, the browser maker says that users can enjoy both their time on Facebook and navigating on other websites they like. For that to happen, users should have tools that limit the data that others can collect on them, Mozilla included. Because of that, the browser won’t collect data from the use of the Facebook Container extension, except for information on how many times the extension is installed or removed.
The new extension, Mozilla claims, should provide users with the means to protect themselves from any side effects of usage.
“The type of data in the recent Cambridge Analytica incident would not have been prevented by Facebook Container. But troves of data are being collected on your behavior on the internet, and so giving users a choice to limit what they share in a way that is under their control is important,” the browser maker notes.
When installed, the extension deletes the user’s Facebook cookies and logs them out of the social platform. The next time they visit Facebook, the website will open in a new blue-colored browser tab (a container tab).
Users will be able to log into Facebook and use it like they would normally do. When clicking on a non-Facebook link or navigating to a non-Facebook website in the URL bar, those pages load outside of the container.
When clicking on Facebook Share buttons on other browser tabs, the extension loads them within the Facebook container. However, when the buttons are clicked, Facebook receives information on the website that the user shared from.
“If you use your Facebook credentials to create an account or log in using your Facebook credentials, it may not work properly and you may not be able to login. Also, because you’re logged into Facebook in the container tab, embedded Facebook comments and Like buttons in tabs outside the Facebook container tab will not work,” Mozilla explains.
Because of that, Facebook can’t associate information about the activity of the user on websites outside of the platform to their Facebook identity. Thus, the social network won’t be able to use the activity collected off Facebook to send ads and other targeted messages.
“There’s a lot of value in your social data. It’s important to regularly review your privacy settings on all sites and applications that use it. The EFF has useful advice on how to keep your data where you want it to be, under more of your control,” Mozilla notes.
Facebook isn’t the only firm to collect data from user’s activity outside of the core service, but this is a problem that can be solved quickly. Thus, users are advised to review their privacy settings for each app they use regularly.
Canadian Firm Linked to Cambridge Analytica Exposed Source Code
27.3.2018 securityweek Social
Source code belonging to Canada-based digital advertising and software development company AggregateIQ has been found by researchers on an unprotected domain. The exposed files appear to confirm reports of a connection between AggregateIQ and Cambridge Analytica, the controversial firm caught in the recent Facebook data scandal.
On March 20, Chris Vickery of cyber risk company UpGuard stumbled upon an AggregateIQ subdomain hosting source code for the company’s tools. The files, stored using a custom version of the code repository GitLab, were accessible simply by providing an email address.
The exposed information included the source code of tools designed for organizing information on a large number of individuals, including how they are influenced by ads, and tracking their online activities. The files also contained credentials that may have allowed malicious actors to launch damaging attacks, UpGuard said.
The nature of the exposed code is not surprising considering that the firm is said to have developed tools used in political campaigns around the world, including in the United States and United Kingdom.
AggregateIQ has been linked by the press and a whistleblower to Cambridge Analytica, a British political consulting and communications firm said to be involved in the presidential campaigns of Donald Trump and Ted Cruz, and the Brexit “Vote Leave” campaign.
Cambridge Analytica recently came under fire after it was discovered that it had collected information from 50 million Facebook users' profiles and used it to create software designed to predict and influence voters. Facebook has suspended the company’s account after news broke, but the social media giant has drawn a lot of criticism, both from customers and authorities.
According to some reports, AggregateIQ was originally launched with the goal of helping Cambridge Analytica and its parent company SCL Group. In a statement published on its website over the weekend, AggregateIQ denied reports that it’s part of Cambridge Analytica or SCL. It has also denied signing any contracts with the British firm and being involved in any illegal activity.
However, there appears to be some evidence that Cambridge Analytica owns AggregateIQ’s intellectual property, and the files discovered by UpGuard also seem to show a connection.
For example, two of the AggregateIQ projects whose source code was exposed contained the string “Ripon,” which is the name of Cambridge Analytica’s platform. The code also included a piece of text that may have been used in phone calls made by Ted Cruz supporters during his presidential campaign.
Researchers also noticed that one of the user accounts mentioned in the exposed files was named “SCL,” which could be a reference to Cambridge Analytica’s parent company.
“Taken in full, it remains unclear why what resembles a version of the app Cambridge Analytica promised would be ‘revolutionary’ for the Cruz campaign would be found in the development repository of AggregateIQ,” said UpGuard, which plans on publishing follow-up reports on this story.
FTC to Probe Facebook Over Privacy Practices
27.3.2018 securityweek Social
A US consumer protection agency said Monday it has opened an investigation into Facebook's privacy practices, another blow to the social network, which is struggling to deal with a growing crisis on misuse of private data.
The Federal Trade Commission (FTC) confirmed news reports from last week that it had opened an inquiry over the harvesting of data on tens of millions of Facebook users by the British consulting group Cambridge Analytica.
While the FTC normally refuses to comment on its probes, it took the unusual step of confirming a "non-public investigation" into Facebook over whether it mishandled private data or violated a 2011 agreement which settled an earlier probe.
Acting FTC consumer protection chief Tom Pahl said the agency will look into whether Facebook violated its privacy promises or failed to comply with the US-EU agreement on data protection known as the Privacy Shield.
The agency also will also determine if Facebook engaged "in unfair acts that cause substantial injury to consumers in violation of the FTC Act."
The FTC suggested that Facebook could face new legal problems if it violated the consent decree with the consumer agency in 2011 settling charges that it deceived consumers on how it handled private data.
"Companies who have settled previous FTC actions must also comply with FTC order provisions imposing privacy and data security requirements," Pahl said in the statement.
"Accordingly, the FTC takes very seriously recent press reports raising substantial concerns about the privacy practices of Facebook."
Facebook shares reversed early losses and closed up 0.42 percent on Monday, after having lost some 14 percent last week.
Separately, Senate Judiciary Committee chairman Charles Grassley said he had asked Facebook CEO Mark Zuckerberg to appear at a hearing on April 10 "to discuss Facebook's past and future policies regarding the protection and monitoring of consumer data."
Grassley said he also invited Google CEO Sundar Pichai and Twitter CEO Jack Dorsey "to discuss the future of data privacy in the social media industry."
- Germany to boost oversight -
Germany's justice minister meanwhile said Monday that Facebook should face "stricter" oversight and be more transparent with its users.
Speaking after a meeting with European Facebook executives in Berlin, Justice Minister Katarina Barley said the firm's assurances that it had already cracked down on the misuse of personal data were "not enough."
"In future we will clearly have to monitor companies like Facebook more strictly and punish data protection violations severely and quickly," she told reporters.
The world's biggest social network is facing calls on both sides of the Atlantic for more information on how its user data was leaked. Several US states have opened investigations.
A public apology by Zuckerberg has failed to quell outrage over the hijacking of personal data.
Separately, Facebook disputed reports that it had been logging call and text data surreptitiously from its users.
A Facebook statement said call and text history logging "is part of an opt-in feature" for those using Messenger or Facebook Lite on Android.
"This helps you find and stay connected with the people you care about, and provides you with a better experience across Facebook," the statement said, while pointing to ways users can turn off the feature.
In London, authorities said they were assessing data seized in a raid on the offices of Cambridge Analytica as part of their investigation.
About 18 enforcement agents from the Information Commissioner's Office participated in the raid late Friday after getting a court order.
"This is one part of a larger investigation by the ICO into the use of personal data and analytics by political campaigns, parties, social media companies and other commercial actors," the UK agency said.
Cambridge Analytica, which worked on US President Donald Trump's election campaign, has been accused of illegally mining tens of millions of users' Facebook data and using it to target potential voters.
Facebook took out full-page ads in nine major British and US newspapers on Sunday to apologize to users.
"We have a responsibility to protect your information. If we can't we don't deserve it," Zuckerberg said in the ads.
Facebook collected call and SMS data from Android users if not explicitly forbidden
26.3.2018 securityaffairs Social
After the Cambridge Analytica scandal, Facebook made the headlines again, the company collected users’ Android call and SMS metadata for years.
The Cambridge Analytica case it raised the discussion about the power of social networks and the possibility of their abuse for the conditioning of political activities.
The non-professionals have discovered how important their digital experience is and how companies specialized in data analysis operate without their knowledge.
Social network platforms have an impressive quantity of information about and are able not only to profile us but also to influence our choice.
Six years ago I was banned by the “democratic” Wikipedia because I coined a term that described how it is possible to manipulate social network, the voice “Social network poisoning,” was deleted by Wikipedia English but it is still present in Wikipedia Italian version.
Give a look at the translated version … and if you have friends at Wikipedia tell them that was an error to ban me
https://translate.google.it/translate?sl=it&tl=en&js=y&prev=_t&hl=it&ie=UTF-8&u=https%3A%2F%2Fit.wikipedia.org%2Fwiki%2FSocial_Network_Poisoning&edit-text=
Back to the present, many of you probably still don’t know that if you have installed Facebook Messenger app on your Android device, there are chances that the social network giant had been collecting your data (the start time for each call, the duration, and the contact’s name), including contacts, SMS data but not the text, and call history data at least until late last year.
The Facebook Messenger app logged phone call data only related to numbers saved in the phone’s address book. Facebook was collecting such kind of data, this is not a surprise for tech-savvy people because we have discussed it in the past.
In January, the popular Italian expert Simone Margaritelli wrote a blog post (Italian) on Medium inviting users to uninstall Facebook and Whatsapp.
The programmer Dylan McKay was able to find data, including logs of calls and SMS messages, in an archive he downloaded (as a ZIP file) from Facebook.
Mat Johnson, a Professor at the University of Houston Creative Writing Program, also made the same disturbing discovery.
Mat Johnson
✔
@mat_johnson
Oh wow my deleted Facebook Zip file contains info on every single phone cellphone call and text I made for about a year- cool totally not creepy.
12:54 AM - Mar 24, 2018
3,066
2,072 people are talking about this
Twitter Ads info and privacy
The Cambridge Analytica case has is giving users another point of view regarding the collection of such kind of data made by Facebook and the real way they are using for.
A Facebook spokesperson explained that the platform collects this data to improve the users’ experience.

“This [above] screen in the Messenger application offers to conveniently track all your calls and messages. But Facebook was already doing this surreptitiously on some Android devices until October 2017, exploiting the way an older Android API handled permissions.” wrote Sean Gallagher, Ars Technica’s IT and National Security Editor.
“Facebook began explicitly asking permission from users of Messenger and Facebook Lite to access SMS and call data to “help friends find each other” after being publicly shamed in 2016 over the way it handled the “opt-in” for SMS services. That message mentioned nothing about retaining SMS and call data, but instead it offered an “OK” button to approve “keeping all of your SMS messages in one place.””
Facebook denied to collect call data surreptitiously with an official blog post, the social network giant highlighted that it never commercialized the data and that users are in total control of the data uploaded to the platform.
“When you sign up for Messenger or Facebook Lite on Android, or log into Messenger on an Android device, you are given the option to continuously upload your contacts as well as your call and text history.” reads the blog post published by Facebook. “For Messenger, you can either turn it on, choose ‘learn more’ or ‘not now’. On Facebook Lite, the options are to turn it on or ‘skip’. If you chose to turn this feature on, we will begin to continuously log this information, which can be downloaded at any time using the Download Your Information tool.”
Users can check data collected by Facebook going to your Facebook Settings→Download a copy of your Facebook data→Start My Archive.
“Call and text history logging is part of an opt-in feature for people using Messenger or Facebook Lite on Android. This helps you find and stay connected with the people you care about, and provide you with a better experience across Facebook. People have to expressly agree to use this feature. If, at any time, they no longer wish to use this feature they can turn it off in settings, or here for Facebook Lite users, and all previously shared call and text history shared via that app is deleted. While we receive certain permissions from Android, uploading this information has always been opt-in only.” continues Facebook.
If you want to stop Facebook from continuously upload your contacts to its server, you can turn off the uploading feature in the Messenger app. In this way, all previously uploaded contacts will be deleted.
iOS users are not affected by this issue.
Lesson leaned … every time we use an app it is essential to carefully read the documentation that details its work.
Facebook and Cambridge Analytica – What's Happened So Far
25.3.2018 securityweek Social

Top Story— Facebook has just lost over $60 billion in market value over the past two days—that's more than Tesla's entire market capitalisation and almost three times that of Snapchat.
Facebook shares plunge over revelations that personal data of 50 million users was obtained and misused by British data analytics firm 'Cambridge Analytica,' who reportedly helped Donald Trump win the US presidency in 2016.
The privacy scandal that rocked the social media giant was revealed earlier this week when Chris Wylie, the 28-year-old data scientist who worked with a Cambridge University academic, turned into a whistleblower and leaked to the newspapers how poorly Facebook handles people's private information.
Wylie claims Cambridge Analytica created "Steve Bannon's psychological warfare mindf**k tool" that profiles citizens to predict their voting patterns based on the personal information gathered from a variety of sources and then helps political parties target voters with tailored advertisements and messages.
Since lots of things have happened since last week, we have compiled this brief article to explain what has happened so far in "Facebook and Cambridge Analytica" saga and how it keeps growing.
How Cambridge Analytica Collected 50 Million Facebook Users' Data
The story started four years ago when Cambridge psychologist Aleksandr Kogan approached researcher Michal Kosinski to get Facebook users data, which he had collected using a simple ‘online personality quiz’ app that requires users to log in using Facebook to participate.
While Kosinski refused to provide any data his app was used to collect, Cambridge paid Kogan over $800,000 to create a similar quiz app for him with an aim to collect Facebook users’ profile data, including the list of pages they have "liked."
Kogan's personality quiz app, dubbed “thisisyourdigitallife,” was a hit. Although it attracted 270,000 Facebook users to take part, Facebook's APIs at the time let the app also collect a wide range of information about each authorized user's friends.
Since an average Facebook user has hundreds of friends in his/her friend-list, Kogan was able to leverage his user base of 270,000 people to collect data for about 50 million Facebook users for use in its ad-targeting work.
Stop Third-Party Apps From Using Your Facebook Data
Not only Cambridge Analytica's quiz app, there are other thousands of other apps that you might have encountered on your Facebook timeline—such as "how you’ll look in your 80s," "which celebrity you look like," "who’ll be your Valentine this year"—that work on the same model.
All Facebook apps offer access using their Facebook account and ask you to grant the app’s developer a range of information from your Facebook profile, like your name, location, email, and friends list.
Besides this, ‘Login with Facebook’ option that you might have seen on hundreds of thousands of websites works similarly by allowing site admins to offer one-click login/signup for easy to verify your identity.
It would be a good time now to revisit those third-party apps you have granted permission to access your Facebook data and completely revoke them if you don't want them to use your data and limit an app's permissions without entirely revoking it.
To disable such apps from accessing your data, you can follow these steps:
On the desktop computer, click the downward arrow in the top-right corner and select Settings and Apps from the menu. Here you’ll see all the apps where you have logged into Facebook.
On mobile devices, open the menu(bottom-right for iOS, top-right for Android), and then select Settings → Account Settings → Apps → Logged in with Facebook.
For entirely revoking any app, just tap on the remove button (cross icon) next to that app. You can also limit any app's permission by clicking the edit button (pencil icon), next to the cross icon, to view each app’s settings.
From here, you can revoke specific permissions by de-selecting the checkmark next to each data point.
Facebook Founder Mark Zuckerberg Apologizes For the Cambridge Analytica Scandal
Today in an interview with CNN’s Laurie Segall, Facebook founder Mark Zuckerberg apologized for the social media giant’s failure to prevent privacy of its users.
"This was a major breach of trust, and I’m really sorry this happened," Zuckerberg told Laurie.
While addressing the Cambridge Analytica scandal, Zuckerberg acknowledged that it was a huge mistake to allow third-party developers to access users’ data and blindly trust that Cambridge Analytica and other companies involved in data harvesting would actually delete that data just because Facebook has asked them to.
"That ... is probably the biggest mistake that we made here,"
Zuckerberg pledged to solve all the problems and safeguard users’ privacy, explaining how the company has already changed its policies after 2014 to prevent abuse of Facebook's APIs.
"Our responsibility now is to make sure this doesn’t happen again," Zuck assured its customers and shareholders across the world who are furious after knowing about the Cambridge Analytica scandal.
During the interview, Zuckerberg promised to conduct a "full forensic audit" of the platform very soon to find which 3rd-party apps may have gained access to user data without their full consent and would notify everyone whose data was improperly used.
Mark Zuckerberg Says It's Time to Regulate Tech Firms
Some analysts believe that stricter government regulations are required to protect consumers’ privacy over social media companies.
Since social media is playing an essential role in the world, Zuckerberg says he believes it's time to impose more regulations on technology companies, but he also recommends Artificial Intelligence as a better tool to regulate such a rapidly growing community of 2 billion people all over the world
Besides this, Facebook has also planned to have more than 20,000 employees to closely monitor security and privacy operations by the end of this year.
Facebook Faces International Investigation Over Personal Data Use
Facebook is in trouble with governments across the world after this whole Cambridge Analytica mess.
Following reports of the transfer of personal information of over 50 million users from Facebook to data-mining firm Cambridge Analytica, Facebook is facing probes by some countries including the United States, European Union, UK, Israel, India, and Canada.
The United States’ Federal Trade Commission (FTC) has started investigating whether or not the use of personal data from over 50 million users by Cambridge Analytica violated a consent decree Facebook signed with the agency in 2011.
The European Commission has also asked data protection authorities to investigate Facebook's data leak to Cambridge Analytica, and if the commission finds Facebook in breach of data protection laws, it could levy fines on the company.
The social networking site is also facing a separate probe by the U.K. government, who is pursuing a warrant to conduct its on-site investigation to determine whether Cambridge Analytica still has the information, which the company said has been deleted.
Israeli Justice Ministry has also informed Facebook that it is opening an "administrative investigation" into Facebook "and the possibility of additional violations of Israelis’ personal information," the ministry said Thursday.
Cambridge Analytica CEO Suspended After Undercover Recordings Released
Cambridge Analytica has suspended its CEO from the research firm’s board of directors on Tuesday following an undercover video was aired which showed him discussing the use of bribes and prostitutes to sway political elections.
The board said that Alexander Nix would be suspended pending a "full, independent investigation," adding that "In the view of the Board, Mr. Nix’s recent comments secretly recorded by Channel 4 and other allegations do not represent the values or operations of the firm and his suspension reflects the seriousness with which we view this violation."
In an uncover video published by Channel 4 News in London on Monday, Nix found discussing how his firm is engaged in dirty tricks for political clients, like recording videos of operatives offering their opponents bribes.
Nix also told a journalist, who posed as a potential Sri Lankan client, that his firm could also send "some girls around to the candidate’s house" to put the candidate in a compromising position.
However, Cambridge has denied engaging in any of such tactics Nix described in the video.
Cambridge Analytica mess has become one of the biggest scandals in tech right now, and it is becoming messier with each passing day, which could have enormous implications not only for Facebook but for every other online company out there that sells user data for a living.
Facebook shares continued falling and dropped today by 2.66% to $164.89 as of the time of this writing.
UK Regulators Search Cambridge Analytica Offices
24.3.2018 securityweek Social
British regulators on Friday began searching the London offices of Cambridge Analytica (CA), the scandal-hit communications firm at the heart of the Facebook data scandal, shortly after a judge approved a search warrant.
Around 18 enforcement agents from the office of Information Commissioner Elizabeth Denham entered the company's London headquarters at around 8:00pm (2000 GMT) to execute the warrant.
The High Court granted the raid request less than an hour earlier, as Denham investigates claims that Cambridge Analytica may have illegally harvested Facebook data for political ends.
A full explanation of the legal ruling by Judge Anthony James Leonard will be issued on Tuesday, according to the court.
"We're pleased with the decision of the judge," Denham's office said on Twitter.
"This is just one part of a larger investigation into the use of personal data and analytics for political purposes," it added in a statement.
"As you will expect, we will now need to collect, assess and consider the evidence before coming to any conclusions."
The data watchdog's probe comes amid whistleblower accusations that CA, hired by Donald Trump during his primary campaign, illegally mined tens of millions of users' Facebook data and then used it to target potential voters.
Fresh allegations also emerged Friday night about the firm's involvement in the 2016 Brexit referendum campaign.
Brittany Kaiser, CA's business development director until two weeks ago, revealed it conducted data research for Leave.EU, one of the leading campaign groups, via the UK Independence Party (UKIP), according to The Guardian.
'I was lying'
Kaiser, 30, told the newspaper she felt the company's repeated public denials it ever worked on the poll misled British lawmakers and the public.
"In my opinion, I was lying," she said. "In my opinion I felt like we should say, 'this is exactly what we did.'"
CA's suspended chief executive Alexander Nix told MPs last month: "We did not work for Leave.EU. We have not undertaken any paid or unpaid work for them, OK?"
Nix was suspended this week following the Facebook revelations and a further media sting in which he boasts about entrapping politicians and secretly operating in elections around the world through shadowy front companies.
He has already been called to reappear before British lawmakers to explain "inconsistencies" in past testimony about the firm's use of the data.
Meanwhile Facebook founder Mark Zuckerberg has been forced to issue a statement outlining his firm's role in the scandal and apologised Wednesday to its billions of users for the breach.
The company has seen its stock market value plunge by around $75 million amid the crisis, as shares closed the week down 13 percent -- their worst seven days since July 2012.
Cambridge Analytica denies any wrongdoing, and said Friday it was undertaking an independent third-party audit to verify that it no longer holds any of the mined data.
"As anyone who is familiar with our staff and work can testify, we in no way resemble the politically-motivated and unethical company that some have sought to portray," acting CEO Alexander Tayler said in a statement.
He apologised for the firm's involvement, but said it had licensed the data from a research company, led by an academic, that "had not received consent from most respondents".
"The company (CA) believed that the data had been obtained in line with Facebook's terms of service and data protection laws," Tayler said.
New review
Aleksandr Kogan, a University of Cambridge psychologist, created a personality prediction app that harvested the data of 270,000 people who downloaded it -- as well as scooping up the information of their friends.
That was possible under Facebook's rules at the time, and Kogan this week claimed he was being unfairly blamed.
"I'm being basically used as a scapegoat by both Facebook and Cambridge Analytica," he said in interviews Wednesday.
"We were assured by Cambridge Analytica that everything was perfectly legal and within the terms of service" of Facebook, he added.
However, Cambridge University announced Friday it was "undertaking a wide-ranging review" of the episode and had written to Facebook "to request all relevant evidence in their possession".
"Should anything emerge from this review, or from our request to Facebook, the University will take any action necessary in accordance with our policies and procedures," it said in a statement.
Facebook as an Election Weapon, From Obama to Trump
23.3.2018 securityweek Social
The use of Facebook data to target voters has triggered global outrage with the Cambridge Analytica scandal. But the concept is nothing new: Barack Obama made extensive use of the social network in 2008 and stepped up "micro-targeting" in his 2012 re-election effort.
The unauthorized gathering of data on 50 million Facebook users by a British consulting firm that worked for Donald Trump has sparked intense debate on how politicians and marketers -- appropriately or not -- use such personal information.
But Cambridge Analytica, the firm at the center of the firestorm, has stressed it is far from alone in using data gleaned online to precisely target voters.
"Obama's 2008 campaign was famously data-driven, pioneered micro-targeting in 2012, talking to people specifically based on the issues they care about," the British firm said on Twitter.
Former members of the Obama team fiercely dispute any comparison to the Cambridge Analytica case, in which an academic researcher is accused of scooping up a massive trove of data without consent using a Facebook personality quiz, and transferring it improperly to the firm.
"How dare you!" tweeted Michael Simon, who headed Obama's micro-targeting team in 2008, in response to the firm.
"We didn't steal private Facebook profile data from voters under false pretenses. OFA (Obama's campaign) voluntarily solicited opinions of hundreds of thousands of voters. We didn't commit theft to do our groundbreaking work."
Jeremy Bird, a member of the 2012 Obama team, echoed those sentiments, warning: "Do not use the Obama campaign to justify your shady business."
But while Cambridge Analytica's methods for acquiring data are in dispute, the underlying goal -- using social media to take the pulse of voters and find those who are persuadable -- was common to both campaigns.
So-called micro-targeting, which borrows techniques from the marketing world, is as much about mobilizing voters and getting them to the polls as about changing minds.
And micro-targeting long pre-dates the internet, with campaigns as early as 1976 using this method, according to Victoria Farrar-Myers, a political scientist and researcher at Southern Methodist University.
Everyone who uses social media makes a decision to share some personal information, she says, although they "may not be fully aware of how people can utilize that."
"Being able to micro-target a voter down to what magazine they read and what issues might make them turn out does have an advantage for a candidate when they're running for an election."
"The Trump campaign did quite a good job at micro-targeting," she said, noting that it put a heavy focus on seemingly marginal localities that were identified as potentially winnable thanks to socal media, and ended up tipping Republican.
According to documents released by the Federal Election Commission (FEC), Trump's new choice of national security advisor John Bolton also hired Cambridge Analytica to conduct profiling work for his Super PAC fundraising group in support of Republican congressional candidates.
Waking up to problem
What remains unclear is whether the techniques made a difference in the 2016 US election.
Chirag Shah, a Rutgers University professor of information and computer science, said the data gleaned could have been instrumental to Trump's campaign.
"We know from other applications, not just in the political domain, but also all kinds of marketing commercialization domains that these things are very, very instrumental," Shah said.
"It is however speculative to say this really change the outcome of the election. All we can say is that, yes there were people who were influenced or targeted using this data."
Experts also stress that neither the Obama nor the Trump campaign broke any laws on the protection of private data -- or even Facebook's internal rules -- which were tightened in 2015 to prevent developers from collecting people's data without explicit consent.
Shah noted the concerns about improper use of personal data are not new.
"The problem is once people access the data from Facebook, for which they often pay, that data is out of Facebook's hands and out of Facebook's users hands.
"And there's no way that Facebook will be able to track all of the data being shared by third parties, fourth parties."
Rayid Ghani, a University of Chicago researcher who was chief scientist for the 2012 Obama campaign, defended his team's use of Facebook data while arguing for a need for better information that would allow users to know when and how their personal information is collected.
"The public needs to be aware of what data is being collected about them, what it is being used for, who it is shared/sold to, and what they're doing with it," Ghani said in a Medium blog post.
"We need to push corporations to make their privacy policies and terms of use more human-friendly, and less fine-print. "
Worried About Being on Facebook? Some Options Explained
22.3.2018 securityweek Social
Managing Your Privacy with Facebook
A snowballing Facebook scandal over the hijacking of personal data from millions of its users has many wondering whether it's time to restrict access to their Facebook information or even leave the social network altogether, with the #deletefacebook movement gaining traction.
Here are some options open to the worried Facebook user.
Put it to sleep
Putting a Facebook account on hold used to be difficult but has become a lot easier.
To deactivate their account, users need to go on their "settings" page, then on to "manage account", where they can "deactivate" their account. Facebook defines this action as putting activity "on hold".
The move disables a user's profile and removes their name and pictures from most things they have shared.
Some information may still remain visible, like a user's name in a friend's list, or messages exchanged with friends.
If they have second thoughts, users can easily restore a de-activated profile.
Kill the account
Deleting an account is a more radical step, as users will not be able to access it again once they've gone for that option.
Facebook warns users that it can take up to 90 days to purge the network of a user's posts.
Even so, some information is likely to stay online, for example messages sent to friends.
According to French data expert Nathalie Devillier there is also a chance that Facebook holds on to information about some users if asked to by US authorities in the name of national security.
Be more alert
Facebook users can check with the network how much of their personal information is accessible on the network.
In "settings", the option "download a copy of your Facebook data" allows a user to do just that.
Once Facebook has double-checked a user's password, the site compiles and then e-mails a compressed file.
The file gives an overview of the pictures and videos a user has posted, their downloaded apps, message traffic with friends, their "likes", unfriended friends and ads clicked.
The information can be difficult to decrypt, as are some passages in Facebook's privacy rules.
It is possible to exercise some control over some ad preferences. This includes, for example, users deciding whether their relationship status can be used as a criterion for targeted ads.
- Go after Facebook -
Some experts and consumer rights organizations argue that rather than withdraw from Facebook, users should help shift the balance of power between the social network giant and individuals by legal means.
"We must be able to use the service without being under Facebook's surveillance," said Arthur Messaud at Quadrature du Net, a French organization that defends the rights of internet users.
The group is planning a class action suit against Facebook in France, based on a new set of EU data protection rules that come into force in May, Messaud said.
He said one aim of the lawsuit is to force Facebook to seek explicit user consent for the use of data by, for example, ticking a box.
Google, Twitter Security Chiefs Leaving Companies
22.3.2018 securityweek Social
Michael Coates, the chief information security officer (CISO) of Twitter, announced on Wednesday that he has decided to leave the social media giant. Google security chief Gerhard Eschelbeck has also announced his departure.
Coates, who joined Twitter in January 2015, says he will co-found a cybersecurity startup, but has not shared any details.
According to his LinkedIn profile, Coates has been working in cybersecurity since 2004, including at Motorola, Aspect Security and Shape Security. Between March 2010 and October 2013, he led Mozilla's Security Assurance program.
Until recently he was on the global board of directors of the OWASP Foundation, and is presently on the board of several organizations, including Comprehend Systems, Synack, and Vendor Security Alliance.
The Verge reported that Joseph Camilleri, a senior manager for information security and risk, will act as interim CISO at Twitter following Coates’ departure.
Eschelbeck, vice president of security and privacy engineering at Google, also announced his departure on Wednesday, but has not shared his plans for the future.
Eschelbeck, known online as lcamtuf, previously held leadership positions at McAfee, Qualys, Webroot and Sophos. He joined Google in October 2014.
The announcements made by Eschelbeck and Coates come just days after reports that Facebook CISO Alex Stamos is leaving the social media giant in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
“Despite the rumors, I'm still fully engaged with my work at Facebook,” Stamos said in response to a New York Times article on his alleged departure from Facebook. “It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security.”
Growing Mistrust Threatens Facebook After Data Mining Scandal
22.3.2018 securityweek Social
As Facebook reels from the scandal over hijacked personal data, a movement to quit the social network gathered momentum Wednesday, portending threats to one of the most powerful internet firms.
In a sign of the mood, one of those calling it quits was a high-profile co-founder of the WhatsApp messaging service acquired by Facebook in 2014 for $19 billion.
"It is time. #deletefacebook," Brian Acton said in a tweet, using the hashtag protesting the handling of the crisis by the world's biggest social network.
The WhatsApp co-founder, who now works at the rival messaging application Signal, posted the comment amid a growing uproar over revelations that Facebook data was harvested by a British political consulting firm linked to Donald Trump's presidential campaign.
"Delete and forget. It's time to care about privacy," he said.
The huge social network also faces investigations on both sides of the Atlantic over its data practices, and a handful of lawsuits which could turn into class actions that may prove a costly distraction for Facebook.
It remains to be seen whether the uproar would lead to any significant departures, but the topic was active on social media, including on Facebook itself.
Donella Cohen, a Weather Channel product manager, posted on her Facebook page that she would be off the network by midnight.
"The latest revelations are showing just how corrupt and detrimental to society this particular platform is," she wrote.
"I hope that a new social network emerges. One that isn't so greedy as to corrupt the political process in the name of the almighty dollar."
- Fabric of internet -
Yet analysts noted Facebook is unlikely to fade quickly because of how it is woven into the fabric of the internet, with "like" buttons on websites, comments sections for news articles and an ad network that delivers messages to those who are not Facebook members.
The #deleteFacebook movement "is a social media feedback loop from the public -- we saw the same thing with #deleteUber," said Jennifer Grygiel, a communications professor at Syracuse University.
"Sure, some people will delete Facebook, but to truly delete Facebook would mean that users would need to delete Facebook, Instagram, WhatsApp, and Messenger. This is not realistic for most people given how social media has been integrated into everyday life."
Sandra Proske, head of communications for the Finland-based security firm F-Secure, said it's not easy to break up with Facebook.
"If this (scandal) makes you uncomfortable you can choose to not use the site, of course," Proske wrote in a blog post.
"But given how intertwined in our lives Facebook and the sites it has acquired, including Instagram and WhatsApp, have become, you may not consider this an option. And for some people and even some countries, Facebook is the internet."
Proske and others offer suggestions on how Facebook users can improve privacy by limiting what is shared and which apps have access to their data.
Several websites offered tips on how to quit Facebook, while noting that the process is more complicated than it appears.
Facebook offers users the option to "deactivate" an account for users who want to take a break and return later, or to "delete" the account and its data entirely.
But Facebook noted that some data such as posts on friends' timelines might remain in the system even after an account is deleted.
And longtime Facebook users could face complications on dealing with log-ins and authorizations to other websites and apps through the social network.
The tech website The Verge published a guide to deletion, advising users to download a copy of all personal data including photos and posts before quitting.
The website noted that it could take up to 90 days to fully delete an account, and that data may be inaccessible during that period.
It was unclear how many users were following through on plans to quit Facebook, which has more than two billion users worldwide.
But Roger McNamee, an early investor in Facebook, said the social network was losing the trust of its users.
"The issue is a callous disregard for the privacy rights of users and a lack of care with respect to data that had been entrusted to Facebook," McNamee told National Public Radio.
"I'm not sure exactly what's going on here, but I'm afraid there is a systemic problem with the algorithms and the business model of Facebook that allow bad actors to cause harm to innocent users of Facebook."
Zuckerberg on Cambridge Analytica case: we made mistakes
22.3.2018 securityaffairs Social
Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted the company made mistakes.
Finally, Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted that his company has failed in protecting its users, but he pointed out that the company has already adopted necessary measures to prevent future abuses.
“we made mistakes” he said. “We have a responsibility to protect your data, and if we can’t then we don’t deserve to serve you,” reads a statement published by Zuckerberg on Facebook.
“I’ve been working to understand exactly what happened and how to make sure this doesn’t happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years ago. But we also made mistakes, there’s more to do, and we need to step up and do it.”
A team of academics had collected a huge amount of user data and shared the information with Cambridge Analytica which is a commercial data analytics company that allegedly used it to target US voters in the 2016 Presidential election.
The news was confirmed by Facebook over the weekend, the researchers used an app developed by the University of Cambridge psychology lecturer Dr. Aleksandr Kogan to collect user data.
The app named “thisisyourdigitallife” is available to users since 2014, it was provided by Global Science Research (GSR) and asked users to take an online survey for $1 or $2. The app requested access to the user’s profile information, and over 270,000 users gave the app permission to use their personal details for academic research.
The app is a powerful tool to profile users by harvesting information on their network of contacts, its code allowed to collect data from over 50 million users.
Facebook confirmed to have “suspended” any business with Cambridge Analytica (CA) and its holding company.
Facebook discovered the activity in 2015 thanks to claims from its users and adopted the necessary measures to force the involved parties in deleting the data from their servers.
Zuckerberg highlighted that he was not aware of the activities conducted by Cambridge Analytica and that his company prompted interrupted business activities with the firm once discovered it has not deleted collected data.
“Last week, we learned from The Guardian, The New York Times and Channel 4 that Cambridge Analytica may not have deleted the data as they had certified. We immediately banned them from using any of our services.”

Mark Zuckerberg said he would take several measures to prevent threat actors from abusing Facebook users’ data.
The company will assess all apps that had access to large amounts of information before 2014, when the social network giant took the most important steps to prevent bad actors from accessing people’s data.
Facebook will restrict developers’ data access even further to prevent such kind of situation and it will show users a tool at the top of their News Feed to show the apps they used and revoke them permissions to access their data.
The company will ban any developer that does not agree to a thorough audit.
“We’ll require developers to not only get approval but also sign a contract in order to ask anyone for access to their posts or other private data. And we’ll have more changes to share in the next few days.” continues Zuckerberg while announcing more changes.
Below the complete statement published by Zuckerberg.
Mark Zuckerberg
pøed 12 h
I want to share an update on the Cambridge Analytica situation -- including the steps we've already taken and our next steps to address this important issue.
We have a responsibility to protect your data, and if we can't then we don't deserve to serve you. I've been working to understand exactly what happened and how to make sure this doesn't happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years a...
Facebook Rocked by Data breach Scandal as Investigations Loom
21.3.2018 securityweek Social
[UPDATE] Facebook shares plunged Monday as the social media giant was pounded by criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Democratic Senator Amy Klobuchar and Republican John Kennedy called for Facebook chief Mark Zuckerberg to appear before Congress, along with Google and Twitter's CEOs.
The lawmakers said the companies "have amassed unprecedented amounts of personal data" and that the lack of oversight "raises concerns about the integrity of American elections as well as privacy rights."
Facebook's chief of security Alex Stamos said his role has shifted to focusing on emerging risks and election security at the global social network.
Stamos revealed the change after The New York Times reported that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted on his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of other top executives, the Times reported, citing unnamed current and former employees.
- Profiles weaponized? -
Senator Ron Wyden asked Facebook to provide more information on what he called a "troubling" misuse of private data that could have been used to sway voters.
Wyden said he wants to know how Cambridge Analytica used Facebook tools "to weaponize detailed psychological profiles against tens of millions of Americans."
In Europe, officials voiced similar outrage.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
According to a joint investigation by The New York Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through the use of a personality prediction app that was downloaded by 270,000 people, but also scooped up data from friends.
Cambridge Analytica denied misusing Facebook data for the Trump campaign.
Elizabeth Denham, Britain's Information Commissioner who regulates the sector in the country, announced her office would seek a court warrant on Tuesday to search Cambridge Analytica's computer servers.
She said the company had been "uncooperative" to requests for access to its records and missed a Monday deadline stipulated.
Meanwhile, Facebook said it has hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
Facebook shares skidded 6.8 percent by the close of the Nasdaq on concerns about pressure for new regulations that could hurt its business model.
Shares slipped another percent or so to $170 in after-market trades.
The sell-off spread to other technology giants on Wall Street including Apple, Google-parent Alphabet and Netflix. Asian markets extended the losses, with Tokyo-listed Sony down, Samsung falling in Seoul and Tencent retreating in Hong Kong.
'Self-regulation not working'
Jennifer Grygiel, a Syracuse University professor who studies social media, said the disclosures will increase pressure to regulate Facebook and other social media firms, already under scrutiny for allowing disinformation from Russian-directed sources to propagate.
"Self-regulation is not working," Grygiel said.
Daniel Kreiss, a professor of media and communications at the University of North Carolina, said Facebook failed to live up to its responsibilities on election ads.
"The fact that Facebook seems to make no distinction between selling sneakers and selling a presidential platform is a deep problem," Kreiss said.
Brian Wieser at Pivotal Research maintained that the revelations highlight "systemic problems at Facebook," but that they won't immediately impact the social network's revenues.
David Carroll, a media professor at the Parsons School of Design, said Facebook and others will soon be forced to live with new privacy rules such as those set to take effect in the European Union.
"Facebook and Google will have to ask users a lot more permission to track them," Carroll said. "Most people are going to say no, so I think it's going to have a huge impact on these companies."
Carroll has filed a legal action in Britain calling on Cambridge Analytica to disclose what data was gathered and used on him.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 said executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria.
The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
"Facebook data was not used by Cambridge Analytica as part of the services it provided to the Donald Trump presidential campaign," a statement read.
Facebook Security Chief Changes Role to Focus on Election Fraud
21.3.2018 securityweek Social
Facebook's chief of security late Monday said his role has shifted to focusing on emerging risks and election security at the global social network, which is under fire for letting its platform be used to spread bogus news and manipulate voters.
Alex Stamos revealed the change in his role at work after a New York Times report that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted at his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of chief operating officer Sheryl Sandberg and other top executives, the Times reported, citing unnamed current and former employees.
Stamos reportedly decided in December he was done with Facebook, but remained at the social network as part of a plan to smoothly hand his job off to a successor. Neither Facebook nor Stamos directly commented on how long he intended to remain at the company, referring to his tweet in response to queries.
Word from Stamos came as the California-based social media giant faced an onslaught of criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to the explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
In Britain, parliamentary committee chair Damian Collins said both Cambridge Analytica and Facebook had questions to answer.
According to a joint investigation by the Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through a personality prediction app downloaded by 270,000 people, but also scooped up data from friends.
A Cambridge Analytica statement denied misusing Facebook data for the Trump campaign.
Facebook said it had hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 found executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria. The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
Facebook Suspends Trump Campaign Data Firm Cambridge Analytica
19.3.2018 securityweek Social
Facebook says it has suspended the account of Cambridge Analytica, the data analysis firm hired by Donald Trump's 2016 presidential campaign, amid reports it harvested the profile information of millions of US voters without their permission.
According to the New York Times and Britain's Observer, the company stole information from 50 million Facebook users' profiles in the tech giant's biggest-ever data breach, to help them design software to predict and influence voters' choices at the ballot box.
Also suspended were the accounts of its parent organization, Strategic Communication Laboratories, as well as those of University of Cambridge psychologist Aleksandr Kogan and Christopher Wylie, a Canadian data analytics expert who worked with Kogan.
Cambridge Analytica was bankrolled to the tune of $15 million by US hedge fund billionaire Robert Mercer, a major Republican donor. The Observer said it was headed at the time by Steve Bannon, a top Trump adviser until he was fired last summer.
"In 2015, we learned that ... Kogan lied to us and violated our Platform Policies by passing data from an app that was using Facebook Login to SCL/Cambridge Analytica, a firm that does political, government and military work around the globe," Facebook said in a posting late Friday by its vice president and deputy general counsel Paul Grewal.
Kogan also improperly shared the data with Wylie, it said.
Kogan's app, thisisyourdigitallife, offered a personality prediction test, describing itself on Facebook as "a research app used by psychologists."
Some 270,000 people downloaded the app, allowing Kogan to access information such as the city listed on their profile, or content they had "liked."
"However, the app also collected the information of the test-takers' Facebook friends, leading to the accumulation of a data pool tens of millions-strong," the Observer reported.
Facebook later pushed back against the claim of a data breach, issuing a fresh statement on Saturday that suggested the misused data was limited to those who voluntarily took the test.
"People knowingly provided their information, no systems were infiltrated, and no passwords or sensitive pieces of information were stolen or hacked," Grewal said.
Cambridge Analytica meanwhile said it was in touch with Facebook "in order to resolve this matter as quickly as possible."
It blamed the misuse of data on Kogan and said it has since deleted all the data it received from a company he founded, Global Science Research (GSR).
"No data from GSR was used by Cambridge Analytica as part of the services it provided to the Donald Trump 2016 presidential campaign," it said.
- 'Targeting their inner demons' -
But Wylie, who later became a whistleblower, told the Observer: "We exploited Facebook to harvest millions of people's profiles. And built models to exploit what we knew about them and target their inner demons. That was the basis that the entire company was built on."
Kogan legitimately obtained the information but "violated platform policies" by passing information to SCL/Cambridge Analytica and Wylie, according to Facebook.
Facebook said it removed the app in 2015 when it learned of the violation, and was told by Kogan and everyone who received the data that it had since been destroyed.
"Several days ago, we received reports that, contrary to the certifications we were given, not all data was deleted," Grewal wrote.
"We are moving aggressively to determine the accuracy of these claims. If true, this is another unacceptable violation of trust and the commitments they made.
"We are suspending SCL/Cambridge Analytica, Wylie and Kogan from Facebook, pending further information."
- British investigation -
Cambridge Analytica, the US unit of British behavioral marketing firm SCL, rose to prominence as the firm that the pro-Brexit group Leave.EU hired for data-gathering and audience-targeting.
The company is facing an investigation by Britain's parliament and regulators over its handling of information.
On Saturday, Britain's information commissioner Elizabeth Denham said: "We are investigating the circumstances in which Facebook data may have been illegally acquired and used.
"It's part of our ongoing investigation into the use of data analytics for political purposes which was launched to consider how political parties and campaigns, data analytics companies and social media platforms in the UK are using and analyzing people's personal information to micro-target voters."
The New York Times meanwhile reported that copies of the data harvested for Cambridge Analytica were still online and that its team had viewed some of the raw data.
Cambridge Analytica: Firm at the Heart of Facebook Scandal
19.3.2018 securityweek Social
At the center of a scandal over alleged misuse of Facebook users' personal data, Cambridge Analytica is a communications firm hired by those behind Donald Trump's successful US presidential bid.
An affiliate of British firm Strategic Communication Laboratories (SCL), Cambridge Analytica has offices in London, New York, Washington, as well as Brazil and Malaysia.

Here's the story behind the company using data to fuel political campaigns:
What does Cambridge Analytica do?
The company boasts it can "find your voters and move them to action" through data-driven campaigns and a team including data scientists and behavioural psychologists.
Cambridge Analytica"Within the United States alone, we have played a pivotal role in winning presidential races as well as congressional and state elections," with data on more than 230 million American voters, Cambridge Analytica claims on its website.
Speaking to TechCrunch in 2017, CEO Alexander Nix said the firm was "always acquiring more" data. "Every day we have teams looking for new data sets," he told the site.
Who are the company's clients?
As well as working on the election which saw Trump reach the White House, Cambridge Analytica has been involved in political campaigns around the world.
In the US, analysts harnessed data to generate thousands of messages targeting voters through their profiles on social media such as Facebook, Snapchat, or the Pandora Radio streaming service.
British press have credited Cambridge Analytica with providing services to pro-Brexit campaign Leave.EU, but Nix has denied working for the group.
Globally, Cambridge Analytica said it has worked in Italy, Kenya, South Africa, Colombia and Indonesia.
What has the company been accused of?
According to the New York Times and Britain's Observer newspapers, Cambridge Analytica stole information from 50 million Facebook users' profiles in the tech giant's biggest-ever data breach, to help them design software to predict and influence voters' choices at the ballot box.
University of Cambridge psychologist Aleksandr Kogan created a personality prediction test app, thisisyourdigitallife, which was downloaded by 270,000 people.
The tool allowed Kogan to access information such as content Facebook users had "liked" and the city they listed on their profile, which was then passed to SCL and Cambridge Analytica.
The Observer reported the app also collected information from the Facebook friends of people who had taken the test.
Christopher Wylie, a former Cambridge Analytica employee, worked with Kogan and told Canadian television channel CBC the company used "private data they acquired without consent".
Who else is involved?
US hedge fund billionaire Robert Mercer -- and major Republican party donor -- bankrolled Cambridge Analytica to the tune of $15 million (12 million euros).
The Observer said it was headed at the time by Steve Bannon, a top Trump adviser until he was fired last summer.
How has Facebook responded?
Facebook suspended SCL and Cambridge Analytica, as well as Kogan and Wylie. In explaining its decision on Friday, the social media giant said the thisisyourdigitallife app was legitimate, but accused Kogan of subsequently violating Facebook's terms by passing the data on to SCL/Cambridge Analytica.
Facebook said it found out what had happened in 2015 and was told all parties involved had deleted the data.
"The claim that this is a data breach is completely false," Facebook said in a new statement on Saturday, saying app users knowingly provided their information.
Facebook confirms Cambridge Analytica stole its data and used it to influence US voters
19.3.2018 securityaffairs Social
The commercial data analytics company Cambridge Analytica allegedly used data harvested by Facebook to target US voters in the 2016 Presidential election.
A team of academics had collected a huge amount of user data and shared the information with Cambridge Analytica which is a commercial data analytics company that allegedly used it to target US voters in the 2016 Presidential election.
The news was confirmed by Facebook over the weekend, the researchers used an app developed by the University of Cambridge psychology lecturer Dr. Aleksandr Kogan to collect user data.
The app named “thisisyourdigitallife” is available to users since 2014, it was provided by Global Science Research (GSR) and asked users to take an online survey for $1 or $2. The app requested access to the user’s profile information, and over 270,000 users gave the app permission to use their personal details for academic research.
Facebook confirmed to have “suspended” any business with Cambridge Analytica (CA) and its holding company.
“Aleksandr Kogan requested and gained access to information from users who chose to sign up to his app, and everyone involved gave their consent.” states the official statement released by Facebook.
“Like all app developers, Kogan requested and gained access to information from people after they chose to download his app. His app, “thisisyourdigitallife,” offered a personality prediction, and billed itself on Facebook as “a research app used by psychologists.” Approximately 270,000 people downloaded the app. In so doing, they gave their consent for Kogan to access information such as the city they set on their profile, or content they had liked, as well as more limited information about friends who had their privacy settings set to allow it.”
The app is a powerful tool to profile users by harvesting information on their network of contacts, its code allowed to collect data from over 50 million users.

Cambridge Analytica tried to clarify its position declaring that it has deleted all data received from GSR when discovered the way they were obtained.
“When it subsequently became clear that the data had not been obtained by GSR in line with Facebook’s terms of service, Cambridge Analytica deleted all data received from GSR,” CA said in a statement.
“No data from GSR was used by Cambridge Analytica as part of the services it provided to the Donald Trump 2016 presidential campaign.”
We refute these mischaracterizations and false allegations, and we are responding — watch our Twitter feed for more.
— Cambridge Analytica (@CamAnalytica) March 17, 2018
According to a report published by The Intercept exactly one year ago, the situation is quite different. The Intercept sustained that Kogan operated on behalf of Strategic Communication Laboratories (SCL), a military contractor that owns the Cambridge Analytics.
Facebook discovered the activity in 2015 thanks to claims from its users and adopted the necessary measures to force the involved parties in deleting the data from their servers.
“Although Kogan gained access to this information in a legitimate way and through the proper channels that governed all developers on Facebook at that time, he did not subsequently abide by our rules. By passing information on to a third party, including SCL/Cambridge Analytica and Christopher Wylie of Eunoia Technologies, he violated our platform policies.” continues the Facebook statement. “When we learned of this violation in 2015, we removed his app from Facebook and demanded certifications from Kogan and all parties he had given data to that the information had been destroyed. Cambridge Analytica, Kogan and Wylie all certified to us that they destroyed the data.”
Christopher Wylie, a Kogan’s collaborator, confirmed that data has been used in the US presidential election to profile individuals and influence the final vote. Wylie provided evidence to the New York Times and The Guardian that harvested data had not been destroyed.
Facebook also suspended Wylie’s account as confirmed by the whistleblower via Twitter on Sunday.
Suspended by @facebook. For blowing the whistle. On something they have known privately for 2 years. pic.twitter.com/iSu6VwqUdG
— Christopher Wylie (@chrisinsilico) March 18, 2018
Facebook Flaws Exposed Friend Lists, Payment Card Data
13.3.2018 securityweek Social
A researcher last year discovered some information disclosure vulnerabilities in Facebook that exposed users’ friend lists and partial payment card information. The social media giant patched one of the flaws within hours.
Web security consultant Josip Franjkoviæ had been analyzing the Facebook application for Android when he identified a flaw that allowed him to obtain any user’s list of friends via a specially crafted request.
Facebook users can prevent others from seeing their friends, but the vulnerability discovered by Franjkoviæ could have been exploited to obtain this information regardless of the targeted user’s privacy settings.
GraphQL is an open source data query language designed by Facebook for its mobile applications. GraphQL queries can only be used for Facebook’s own applications—only whitelisted query IDs are allowed—and they require an access token.
Franjkoviæ discovered that he could use the client token from the Facebook app for Android, and he could bypass the whitelist by sending a request containing a “doc_id” parameter instead of “query_id.”
Once he bypassed the whitelisting mechanism, the researcher started sending GraphQL queries. While most returned data that had already been public, a query named CSPlaygroundGraphQLFriendsQuery leaked the friend list of the user whose ID was included in the request.
The second issue identified by the expert was also related to GraphQL and it, too, was found during the analysis of the Facebook app for Android. An attacker could have exploited the flaw to obtain partial payment card information by sending a query containing the targeted user’s ID and an access token that could have been taken from a Facebook app.
The security hole was described as an insecure direct object reference (IDOR) bug and it provided access to the first 6 and last 4 digits of a payment card, expiry date, type of card, first name of the cardholder, and zip code and country. Users typically enter credit card details on Facebook to pay for ads.
The friend list leak and whitelist bypass vulnerabilities were reported by Franjkovic to Facebook on October 6, 2017 and they were patched in mid-October. The payment card leak issue was reported in February 2017 and it was patched in 4 hours and 13 minutes. The details of the security holes were only disclosed by Franjkoviæ on Monday and Facebook posted a link to the researcher’s blog post on its Bug Bounty page. The researcher has not disclosed the bug bounty amounts he received for his findings.
This is the third round of Facebook vulnerabilities disclosed by Franjkoviæ this year. He previously shared the details of two account takeover flaws via Oculus integration and Facebook’s partners portal.
BlackBerry Sues Facebook Over Messaging Apps
6.3.2018 securityweek Social
Canadian telecommunications firm BlackBerry sued Facebook on Tuesday, accusing the American social media company of infringing on its patents for messaging apps.
BlackBerry is claiming infringement on patents it holds for message encryption and notifications, and is seeking an injunction as well as damages for lost profits, although no figure was given.
Facebook and its wholly-owned services Instagram and WhatsApp are named as defendants in the lawsuit.
"We have a lot of respect for Facebook and the value they've placed on messaging capabilities, some of which were invented by BlackBerry," BlackBerry spokeswoman Sarah McKinney said in a statement.
She said BlackBerry would like to partner with Facebrook "in our drive toward a securely connected future, and we continue to hold this door open to them."
"However, we have a strong claim that Facebook has infringed on our intellectual property, and after several years of dialogue, we also have an obligation to our shareholders to pursue appropriate legal remedies," McKinney added.
BlackBerry, after abandoning the manufacture of its once-popular smartphones, has refocused its core business on cybersecurity software and services.
Facebook improves link security infrastructure by implementing HSTS Preloading
6.3.2018 securityaffairs Social
Facebook has implemented HSTS preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook has upgraded its link security infrastructure to include HTTP Strict Transport Security (HSTS) preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook and Instagram links will automatically update from HTTP to HTTPS for eligible websites.
“We have recently upgraded our link security infrastructure to include HSTS preloading, which automatically upgrades HTTP links to HTTPS for eligible websites. This will improve people’s security and will also often improve the speed of navigation to sites from Facebook.” reads the announcement published by Facebook.
According to Facebook, the modification aims to improve security and navigation speed for Facebook and Instagram links.
HSTS Preloading Facebook
Facebook determines the links that are eligible for HTTPS based on two sources:
The Chromium preload list, that is currently used in most major browsers;
Recording HSTS headers from sites shared on Facebook, in this case, the browser preload list is updated with any sites that serve HSTS with the preload directive.
Facebook invites websites to support HTTPs and sponsors Let’s Encrypt initiative which provides free TLS certificates and instructions on how to enable HTTPS for most common server software.
Facebook improves link security infrastructure by implementing HSTS Preloading
6.3.2018 securityaffairs Social
Facebook has implemented HSTS preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook has upgraded its link security infrastructure to include HTTP Strict Transport Security (HSTS) preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook and Instagram links will automatically update from HTTP to HTTPS for eligible websites.
“We have recently upgraded our link security infrastructure to include HSTS preloading, which automatically upgrades HTTP links to HTTPS for eligible websites. This will improve people’s security and will also often improve the speed of navigation to sites from Facebook.” reads the announcement published by Facebook.
According to Facebook, the modification aims to improve security and navigation speed for Facebook and Instagram links.
HSTS Preloading Facebook
Facebook determines the links that are eligible for HTTPS based on two sources:
The Chromium preload list, that is currently used in most major browsers;
Recording HSTS headers from sites shared on Facebook, in this case, the browser preload list is updated with any sites that serve HSTS with the preload directive.
Facebook invites websites to support HTTPs and sponsors Let’s Encrypt initiative which provides free TLS certificates and instructions on how to enable HTTPS for most common server software.
A Simple Bug Revealed Admins of Facebook Pages — Find Out How
2.3.2018 thehackernews Social

Facebook Page admins are publicly displayed only if admins have chosen to feature their profiles.
However, there are some situations where you might want to contact a Facebook page admin or want to find out who is the owner of a Facebook page.
Egyptian security researcher Mohamed A. Baset has discovered a severe information disclosure vulnerability in Facebook that could have allowed anyone to expose Facebook page administrator profiles, which is otherwise not supposed to be public information.
Baset claimed to have discovered the vulnerability in less than 3 minutes without any kind of testing or proof of concepts, or any other type of time-consuming processes.
In a blog post, Baset said he found the vulnerability, which he described as a "logical error," after receiving an invitation to like a particular Facebook page on which he had previously liked a post.
Facebook has introduced a feature for page admins wherein they can send Facebook invitations to users asking them if they wished to like their page after liking a post, and a few days later, these interacted users may receive an email reminding them of the invitation.
After Baset received one such email invite, he simply opened "show original" drop-down menu option in email. Looking at the email's source code, he noticed that it included the page administrator's name, admin ID and other details.
The researcher then immediately reported the issue to the Facebook Security Team through its Bugcrowd bug bounty program. The company acknowledged the bug and awarded Baset $2,500 for his findings.
Though Facebook has now patched this information disclosure issue, people who have already received one such page invitation can still find out admin details from the invitation emails.
"We were able to verify that under some circumstances page invitations sent to non-friends would inadvertently reveal the name of the page admin which sent them," Facebook said. "We've address the root cause here, and future emails will not contain that information."
Facebook has now patched this information disclosure issue.
A vulnerability in Facebook exposed email and details of page administrator
28.7.2018 securityaffairs Social
The security researcher Mohamed Baset discovered a vulnerability in Facebook that exposed email and other details of a page administrator.
Facebook has recently addressed an information disclosure vulnerability discovered by the security researcher Mohamed Baset that exposed page administrator.
According to Baset, the flaw is a “logical error” that he discovered after receiving an invitation to like a Facebook page on which he had liked a post.

“One day i liked one of the posts of a specific page but i didn’t liked or followed the page itself after a few days i got an email notification from facebook regarding an invitation to like the page that i did already liked one of its posts, I was amazed by the feature but i realized that this is a feature to target non-fans and i was wondering what could go wrong since this is a new feature ?” state the blog post published by the expert.
“From the investigations that i’m doing sometimes in the office of the fraud and phishing emails i’m always and blindly showing the “Original” of the message (that can be achieved by clicking on the little drop-down menu arrow beside the message reply button)”
The researchers analyzed the source code of the email sent by the social network and discovered it includes the name of the administrator of the page and other info.

The researcher reported the issue to Facebook that acknowledged it and decided to award the expert $2,500 as part of its bug bounty program.
Facebook announced to have paid out more than $880,000 for 400 vulnerability reports submitted by hackers.
Many of you may consider that the issue is not so serious, but this isn’t true because under certain circumstance the data exposure could represent a threat to the users’ privacy
In the case of business or community pages, revealing the identities of the administrators could get them targeted by messages and comments.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much. But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.” reads the blog post published by Sophos. “If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself.”
Facebook Flaw Exposed Page Administrators
27.7.2018 securityweek Social
Facebook recently patched an information disclosure vulnerability that exposed page administrators, researcher Mohamed Baset reported this week.
Baset claimed he discovered the issue, which he described as a “logical error,” within a few minutes of receiving an invitation to like a Facebook page on which he had liked a post.
Looking at the email’s source code, the researcher noticed that it included the name of the page’s administrator and other details.
After being notified through its bug bounty program, Facebook acknowledged the vulnerability and decided to award the expert $2,500 for his findings.
Sophos’ Paul Ducklin has provided an explanation on why such an information disclosure flaw can pose a problem to Facebook page administrators.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much,” Ducklin said. “But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.”
“If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself,” the expert added.
Baset, founder and lead penetration tester at Seekurity, said this was the second time he reported a vulnerability to Facebook without having to write any code to demonstrate his findings.
Facebook reported recently that last year it paid out more than $880,000 for 400 valid vulnerability reports submitted by white hat hackers.
WhatsApp Co-founder Invests $50 Million in Signal
22.2.2018 securityweek Social
Open Whisper Systems, the organization behind the privacy-focused messaging app Signal, announced on Wednesday the launch of the Signal Foundation, with an initial investment of $50 million from WhatsApp co-founder Brian Acton.
The Signal service is used by millions of people and the Signal protocol is used by billions through its integration into popular applications such as WhatsApp, Facebook Messenger and Google Allo.
Despite the success of its product, the Signal team has never had more than seven members and there have only been an average of 2.3 full-time developers.Signal Foundation launches with $50 million investment
With the launch of the Signal Foundation and the $50 million from Acton, Signal will have the resources necessary to expand and accelerate its mission to make private communications accessible to everyone.
“Starting with an initial $50,000,000 in funding, we can now increase the size of our team, our capacity, and our ambitions. This means reduced uncertainty on the path to sustainability, and the strengthening of our long-term goals and values,” said Moxie Marlinspike, founder of Open Whisper Systems and CEO of the Signal Foundation. “Perhaps most significantly, the addition of Brian brings an incredibly talented engineer and visionary with decades of experience building successful products to our team.”
The Signal Foundation is a 501(c)(3) nonprofit organization. Up until now, the Freedom of the Press Foundation acted as a fiscal sponsor for Signal.
Acton, who left WhatsApp and Facebook last year, will serve as executive chairman of the Signal Foundation and will be actively involved in operations and product development.
“After over 20 years of working for some of the largest technology companies in the world, I couldn’t be more excited for this opportunity to build an organization at the intersection of technology and the nonprofit world,” said Acton.
“In the immediate future we are focused on adding to our talented-but-small team and improving Signal Messenger. Our long-term vision is for the Signal Foundation to provide multiple offerings that align with our core mission,” he added.
Facebook Increases Bug Bounty Payout After Audit
10.2.2018 securityweek Social
Facebook decided to increase a researcher’s bug bounty payout after discovering that that a bug he reported could lead to account takeover.
In September 2017, security researcher Josip Franjkoviæ discovered an issue with Facebook’s partners portal, which leaked users’ email addresses. The bug was discovered after one of the researcher’s sites was approved to participate in the Free Basics project by Facebook.
What the researcher discovered was a medium-high impact privacy bug where adding a new admin user would leak their email address in subsequent notification emails.
Basically, for a newly added admin, the notifications emails would contain the admin's primary Facebook email through a parameter in one of the links, the security researcher discovered.
To reproduce the bug, one would simply head to the Settings section at https://partners.facebook.com/fbs/settings/, add a name, and enter an email they control in the email field.
Next, they should simply hit the “Add” button, intercept the POST request to /mobile/settings/requirements/save/, and modify the values [settings.users.userstablecontainer.user_id] GET parameter to the ID of the victim whose email they would like to reveal, then forward the request.
Thus, the email Facebook sends to the user’s controlled address contains the victim's primary mail as part of <a href link >, the security researcher found.
Franjkoviæ reported the discovery on September 30, 2017, and Facebook informed him a couple of days later that they fixed an account takeover vulnerability in their platform. The original privacy leak bug, however, was resolved only in late October, after the researcher informed the company the exploit would still work.
After requesting more information from Facebook, the researcher found that the bug he discovered could result in the leaking of login codes. One other parameter in the email link could “potentially be used to login to the user's account (with some restrictions),” the researcher explains.
The feature, however, wasn’t enabled for the researcher’s account, so he could not notice it in the first place.
“Thank you Facebook's security team for being (more than) fair - they could have awarded only the email leak bug, and I would never know this was an account takeover,” the researcher notes.
Facebook too has confirmed that, after analyzing the bug reported by Franjkoviæ internally, the security team discovered that it could potentially allow an attacker to gain access to another account.
“We did a complete review and we determined that there is no evidence that these tactics were used or that personal information was exposed,” a post by the Facebook Bug Bounty team reads.
Franjkoviæ confirmed in an email discussion with SecurityWeek that Facebook increased the paid bounty to reward him for the more important vulnerability. While he wouldn’t reveal the exact amount he received, he did say it was his biggest bounty to date.
Facebook Acquires ID Verification Startup Confirm
24.1.2018 securityweek Social
Facebook has acquired Confirm, a Boston-based startup that specializes in identity verification solutions. Financial terms of the deal have not been disclosed.
Confirm has developed APIs and SDKs that can be integrated into applications that require easy and secure authentication of driver’s licenses and other government IDs. The company’s product leverages advanced pattern analysis and forensic checks to determine if an ID is legitimate.
Before being acquired by Facebook, the company’s website said its products had been used by more than 750 organizations around the world to authenticate customer identity documents.
“When we launched Confirm, our mission was to become the market's trusted identity origination platform for which other multifactor verification services can build upon,” reads a message posted on the Confirm.io website following the acquisition. “Now, we're ready to take the next step on our journey with Facebook.”
Confirm has informed customers that it will wind down its existing ID authentication products. The company’s employees will join Facebook in Boston.
“We are excited to welcome the Confirm team to Facebook,” a Facebook spokesperson told SecurityWeek. “Their technology and expertise will support our ongoing efforts to keep our community safe.”
Facebook asks users to send a scan or photo of their ID to show account ownership or confirm their name. It is possible that the technology obtained as a result of the Confirm acquisition will be used to improve this system.
Confirm was founded by Walter Doyle, whose consumer mobile company WHERE.com was acquired by PayPal in 2011; mobile entrepreneur and venture capitalist Bob Geiman; and Ralph Rodriguez, founder of Delfigo Security, a multifactor authentication company acquired by IBM.
In January 2016, the company announced that it had raised $4 million in a seed funding round.
Are you a Tinder user? Watch out, someone could spy on you
24.1.2018 securityaffairs Social
Experts at security firm Checkmarx discovered two security vulnerabilities in the Tinder mobile apps that could be exploited to spy on users.
Security experts at Checkmarx discovered two security vulnerabilities in the Tinder Android and iOS dating applications that could be exploited by an attacker on the same wi-fi network as a target to spy on users and modify their content.
Attackers can view a target user’s Tinder profile, see the profile images they view and determine the actions they take.
“The vulnerabilities, found in both the app’s Android and iOS versions, allow an attacker using the same network as the user to monitor the user’s every move on the app. It is also possible for an attacker to take control over the profile pictures the user sees, swapping them for inappropriate content, rogue advertising or other type of malicious content (as demonstrated in the research).” reads the analysis published by Checkmarx.
“While no credential theft and no immediate financial impact are involved in this process, an attacker targeting a vulnerable user can blackmail the victim, threatening to expose highly private information from the user’s Tinder profile and actions in the app.”
An attacker can conduct many other malicious activities, including intercepting traffic and launching DNS poisoning attacks.
The first issue is related to the fact that both the iOS and Android Tinder apps download profile pictures via insecure HTTP connections, this means that an attacker can access the traffic to determine which profiles are viewed by a Tinder user.
SOCIAL NETWORKS / TINDER
An attacker could also modify traffic for example to swap images.
“Attackers can easily discover what device is viewing which profiles,” continues the analysis. “Furthermore, if the user stays online long enough, or if the app initializes while on the vulnerable network, the attacker can identify and explore the user’s profile.” “Profile images that the victim sees can be swapped, rogue advertising can be placed and malicious content can be injected,”
Obviously, such kind of issue could be mitigated with the adoption of HTTPS.
Checkmarx also discovered another issue related to the use of HTTPS, the flaw was called “Predictable HTTPS Response Size”.
“By carefully analyzing the traffic coming from the client to the API server and correlating with the HTTP image requests traffic, it is possible for an attacker to determine not only which image the user is seeing on Tinder, but also which action did the user take.” states Checkmarx. “This is done by checking the API server’s encrypted response payload size to determine the action,”
An attacker that is in the position of analyzing the traffic can discover the user’s interest in a specific profile by detecting a 278-byte encrypted response that is delivered by the API server when he swipes left on a profile picture. Swiping right, the Tinder user likes a particular profile, in this case, the response generated is composed of 374 bytes.
The researchers also noticed that Tinder member pictures are downloaded to the app via HTTP connection, this makes possible for an attacker to view the profile images of those users being swiped left and right.
In order to mitigate this issue, researchers suggest padding requests, if the responses were padded to a fixed size, it would be impossible to discriminate the user’s action.
Checkmarx disclosed both vulnerabilities to Tinder.
Facebook Offers $100,000 Grants for Improving Internet Security
23.1.2018 securityweek Social
Facebook announced on Monday that it’s prepared to award $100,000 grants for research proposals focusing on improving online security, privacy and safety.
The new project, called “Secure the Internet Grants,” is part of the initiative announced last summer by Facebook CSO Alex Stamos. Stamos revealed at the Black Hat conference that the social media giant had prepared $1 million in funding to encourage original defensive research.
For Secure the Internet Grants, university researchers and faculty, NGOs, and non-profit organizations have been invited to submit proposals for innovative and practical technology. A wide range of topics are accepted, including anti-phishing, user safety, post-password authentication, abuse detection and reporting, privacy-preserving technologies, and user security in emerging markets.Facebook launches Secure the Internet Grants
Applicants are required to submit a 2-page proposal detailing their ideas and how the grant funding will be used to put them into practice. Facebook is prepared to award up to $100,000 per proposal, depending on the specific requirements.
The deadline for submitting proposals is March 30. Selected award recipients will be notified in May and winners will be announced at Black Hat USA 2018.
“Good defense comes from understanding offense,” Stamos said last year at Black Hat. “The research presented at Black Hat and elsewhere is critical in understanding the kinds of flaws we face now and in the future, and it helps us build a base of knowledge that can be used to design more trustworthy systems. That being said, the balance of incentives is a bit off, and we need to figure out ways to encourage and celebrate risk-taking defensive research alongside spectacular vulnerability demonstrations.”
Facebook has made significant investments in securing its own platform and the Internet in general.
Last year, Facebook awarded $100,000 to a team of researchers as part of the 2017 Internet Defense Prize for designing a novel technique of detecting spear-phishing attacks in enterprise environments.
As for its own platform, the social media company paid out nearly $900,000 last year for vulnerabilities reported by external researchers, bringing the total paid since the launch of its bug bounty program in 2011 to more than $6.3 million.
Facebook’s founder and CEO, Mark Zuckerberg, recently stated that protecting the community is more important than maximizing profits.
Skype Finally Adds End-to-End Encryption for Private Conversations
17.1.2018 thehackernews Social

Good news for Skype users who are concerned about their privacy.
Microsoft is collaborating with popular encrypted communication company Signal to bring end-to-end encryption support to Skype messenger.
End-to-end encryption assured its users that no one, not even the company or server that transmits the data, can decrypt their messages.
Signal Protocol is an open source cryptographic protocol that has become an industry-wide standard—which is used in Facebook Messenger, Whatsapp, and Google Allo for secure messaging.
Dubbed Private Conversations, the new feature which is about to be introduced in Skype will offer end-to-end encryption for audio calls, text, and multimedia messages like videos and audio files.
"Skype Private Conversations give you enhanced security through end-to-end encryption with an additional layer of security for conversations between you and your friends and family," the company announced.
"Private Conversations can only be between you and one other contact. This is not supported in groups."
How to Start Skype End-to-End Encrypted Calls and Chats
Private Conversations is already available to the Skype Insider program—a platform that allows Skype users to test new features before they rolled out to the rest of its over 300 million of users worldwide.
To initiate a new secure communication with your Skype contact, you need to tap or click on the (+) icon, select 'New Private Conversation' and then select the contact you would like to start the secure communication with.
A Private Conversation will have a lock icon next to your Skype contact's name. Preview messages from Private Conversations will not appear in the chat list or notifications.
Unlike WhatsApp, end-to-end encryption feature is not enabled by default in Skype and users need to select 'New Private Conversation' from the app's "Compose" menu, or from another user's profile to initiate a secure communication—it's like Facebook Messenger's Secret Conversations, which is also based on of Signal.
Unfortunately, Private Conversations also doesn't currently support video calling, but this is secured by the standard encryption that Microsoft already provides with its Skype service.
Also, even with Private Conversations enabled, Skype will still be able to access some information (metadata) about your secure communications, like when you initiate them, and how long the conversation last.
Skype Insider users can test Private Conversations using Skype build version 8.13.76.8 for iOS, Android, Linux, Mac, and Windows Desktop.
How to hack Facebook accounts exploiting CSRF in Oculus app
17.1.2018 securityaffairs Social
Facebook has fixed a couple of vulnerabilities that could have been exploited by attackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
In March 2014, Facebook founder Mark Zuckerberg announced the acquisition of Oculus VR and included the handsets produced by the company to its bug bounty program.
White hat hackers discovered several vulnerabilities in Oculus platform since, including the ones addressed now by Facebook.
The flaws were reported in October by the security consultant Josip Franjkoviæ who analyzed the Oculus application for Windows.
“Oculus enables users to connect their Facebook accounts for a more “social” experience. This can be done using both the native Windows Oculus application and using browsers.” wrote Franjkoviæ. “I took a deeper look at the native Windows flow, and found a CSRF vulnerability which allowed me to connect a victim’s Facebook account to attacker’s Oculus account. Once connected, the attacker could extract the victim’s access token, and use Facebook’s GraphQL queries to take over the account.”

One of the features implemented by the Oculus application is the authentication to a Facebook account, Franjkovic discovered that attackers could have exploited specially crafted GraphQL queries to connect any user’s Facebook account to their Oculus account.
GraphQL is a query language created by Facebook in 2012 for describing the capabilities and requirements of data models for client‐server applications, a GraphQL query is a string that is sent to a server to be interpreted and fulfilled, which then returns JSON back to the client.
Franjkovic discovered that a specially crafted query allowed an attacker to obtain the victim’s access token and use it to impersonate the victim by accessing his account.
In a proof of concept attack, Franjkovic shows how to use a specially crafted query to add a new mobile phone number to the targeted account and use it to reset the victim’s password.
The vulnerability was reported to Facebook on October 24, the social network giant temporary solved the issue by disabling the facebook_login_sso endpoint.
On October 30, Facebook rolled out a patch to address definitively the problem, but a few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
The experts informed Facebook on November 18 that disabled again the facebook_login_sso endpoint to mitigate the problem. A complete patch was rolled out after a few weeks.
Facebook paid the expert for his discoveries and classified the vulnerabilities as critical.
Step by step procedure exploited by the researcher is described on its blog, below the timeline of the hack:
24th of October, 2017, 03:20 – Report sent to Facebook
24th of October, 2017, 10:50 – First reply from Facebook
24th of October, 2017, 11:30 – Temporary fix for the bug (disabled /facebook_login_sso/ endpoint)
30th of October, 2017 – Bug is now fixed.
Flaws Allowed Facebook Account Hacking via Oculus App
17.1.2018 securityweek Social
Facebook recently patched a couple of vulnerabilities that could have been exploited by malicious hackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
Facebook announced the acquisition of Oculus VR back in July 2014 and added Oculus assets to its bug bounty program a few weeks later. Several vulnerabilities have been found in Oculus services since, including a series of flaws that earned a researcher $25,000.
In October, web security consultant Josip Franjkoviæ decided to analyze the Oculus application for Windows, which includes social features that allow users to connect their Facebook account.
Franjkovic discovered that a malicious actor could have used specially crafted GraphQL queries to connect a targeted user’s Facebook account to the attacker’s Oculus account. GraphQL is a query language created by Facebook in 2012 and later released to the public.
According to the researcher, a specially crafted query allowed an attacker to obtain the victim’s access token, which under normal circumstances should not be accessible to third-party apps, and use it to take control of their Facebook account.
Franjkovic demonstrated an account takeover method by using a specially crafted query to add a new mobile phone number to the targeted account and then leveraging that number to reset the victim’s password.
The vulnerability was reported to Facebook on October 24 and a temporary fix, which involved disabling the facebook_login_sso endpoint, was implemented on the same day. A permanent patch was rolled out on October 30.
A few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
This second flaw was reported to Facebook on November 18 and again the facebook_login_sso endpoint was disabled on the same day as a temporary fix. A complete patch was implemented roughly three weeks later.
The researcher has not disclosed the amount of money he earned from Facebook for finding the vulnerabilities, but he told SecurityWeek that the social media giant classified the issues as critical and he was happy with the reward he received.
Facebook revealed last week that it had paid a total of $880,000 in bug bounties in 2017, with an average of roughly $1,900 per submission.
Technical details for the vulnerabilities can be found on Franjkovic’s blog. In the past years, the expert reported several vulnerabilities to Facebook, including ones that could be exploited to hijack accounts.
Microsoft Brings End-to-End Encryption to Skype
17.1.2018 securityweek Social
Microsoft this week announced that end-to-end encrypted communications are now available for preview to Skype insiders.
Called Private Conversations, the newly introduced feature secures both text chat messages and audio calls, Microsoft Program Manager Ellen Kilbourne revealed.
Furthermore, end-to-end encryption is also applied to any files users send to their conversational partners, including images, audio files, and videos. Not only will the contents of these conversations be hidden in the chat list, but they won’t appear in notifications either, to keep user’s information private.
Private Conversations, Kilbourne explains in a post, is using the industry standard Signal Protocol by Open Whisper Systems. The protocol is already providing end-to-end encryption to users of popular messaging applications such as Signal, WhatsApp, and Facebook Messenger.
Users enrolled in Microsoft’s Skype Insider program can already test the new feature by selecting “New Private Conversation” from the compose menu or from the recipient’s profile. As soon as the recipient has accepted the invitation to a private chat, all calls and messages in that conversation will be encrypted end-to-end, until they choose to end it.
Participation in a private conversation will be available from a single device at a time. Skype users will have the possibility to switch the conversation to any of their devices, but exchanged messages are tied to the device being used at the time.
During the preview period, private conversations will be available only to Skype Insiders running the latest version of the application. The chats are also limited to one-to-one conversations, Kilbourne explains.
The Private Conversations feature is currently available to Skype Insiders using Skype version 8.13.76.8 for iOS, Android, Linux, Mac, and Windows Desktop.
Facebook Paid $880,000 in Bug Bounties in 2017
17.1.2018 securityweek Social
Facebook received over 12,000 vulnerability submissions in 2017 and ended up paying $880,000 in bug bounties to security researchers.
Of the large number of received submissions, however, just over 400 reports were found valid during the bug bounty program’s sixth year. Last year, Facebook also paid larger bounties to the submitting researchers, as the average reward per submission increased to almost $1,900, up from $1,675 in 2016.
The number of security researchers participating in the company’s bug bounty program also increased, Jack Whitton, Security Engineer with Facebook's Product Security team, explains in a blog post. 32% of the researchers who received a reward last year submitted for the first time in 2017.
The largest bounty the company has paid to date is a $40,000 reward for ImageTragick, a remote code execution vulnerability introduced by the ImageMagick image processing suite. Last year, the company also paid a $10,000 bounty for a critical vulnerability that could result in deleting any photo from the social media network.
The largest number of valid submissions in 2017, Facebook says, came out of India. The United States ended up on the second position, followed by Trinidad & Tobago in the third place.
Facebook acknowledged more than 100 researchers as part of the bug bounty program in 2017.
“Going forward, we are going to take a number of things into consideration: dollar amount, submission validity, and more. We’re doing this to continue to encourage high-quality submissions, and we will be offering new perks to our top participants such as swag and prizes, access to exclusive events and new features,” Whitton explains.
He also reveals that Facebook is planning on investing more resources into getting more timely responses and payments to researchers in 2018.
Researchers interested in submitting reports as part of Facebook’s bug bounty program are encouraged to follow the best practices the company is listing at facebook.com/whitehat/resources.
“After celebrating our 6th anniversary, we paid out over $880,000 to researchers last year, bringing our total paid out to over $6,300,000,” Whitton says.
Facebook launched its bug bounty program in 2011 and paid over $5 million to researchers by October 2016.
Tool Detects Squatted Accounts on Social Networks, Code Repos
17.1.2018 securityweek Social
Web security company High-Tech Bridge has improved its Trademark Monitoring Radar service with a feature designed to help organizations identify squatted or fraudulent accounts created on social networks and code repositories.
Trademark Monitoring Radar is a free service that hunts for malicious domain names. The service initially allowed organizations to detect potential cybersquatting and typosquatting of their domain or brand. A feature designed to detect phishing websites was later added.
The latest feature allows organizations to find typosquatting or cybersquatting attempts on social networks and code repositories. Users simply enter the name of their own domain and the service displays a list of potentially squatted accounts found on websites such as Facebook, Twitter, YouTube, Google Plus, GitHub and Bitbucket.
High-Tech Bridge told SecurityWeek that new social networks will be added in the upcoming period. The detection algorithms and the database storing information on malicious domains are continuously improved – the company says there is an improvement of roughly 10 percent every month. The results displayed for each tested domain are updated every 24 hours.
The Trademark Monitoring Radar service is fully automated, which can result in false positives. However, the security firm pointed out that it’s virtually impossible to automatically assess the impact of each account. On the other hand, each of the potential problematic accounts is displayed as a link, making it easier for users to manually verify them.
“We prefer to give more than less,” explained Ilia Kolochenko, CEO and founder of High-Tech Bridge. “For some companies, even the same user name can pose a potential problem. We saw when relatively innocent accounts were used in sophisticated credit card fraud.”
It can be useful for organizations to identify squatted or fraudulent accounts on social media websites as they can be abused by malicious hackers in combination with social engineering for spear phishing attacks. As for code repositories, fake accounts can be leveraged for delivering malware, Kolochenko said.
Once the fraudulent domains have been identified, the targeted organization can ask the service provider to take them down. While the process is often simple for major brands, it can be more difficult for smaller companies. “It can take longer or even require an intervention from a law firm,” Kolochenko explained.
Never too late, Skype supports end-to-end encryption for new Private Conversations feature
12.1.2018 securityaffairs Social
It’s official, Microsoft’s Skype is rolling out a new feature called Private Conversations, which uses end-to-end encryption.
The latest version of Skype implements end-to-end encryption and introduces the support for the Signal protocol. which is the protocol used by WhatsApp, Facebook Messenger, Google Allo, and Signal.
Attackers will not able to snoop on Skype Private Conversations will support text, audio calls, and file transfers, thanks to the introduction of the end-to-end encryption.
“We know extra protection is important as you share sensitive information over Skype so we’re excited to announce the preview of end-to-end encrypted Private Conversations, available now for Skype Insiders.” states the announcement published by Microsoft.
“With Private Conversations, you can have end-to-end encrypted Skype audio calls and send text messages or files like images, audio, or videos, using the industry standard Signal Protocol by Open Whisper Systems. The content of these conversations will be hidden in the chat list as well as in notifications to keep the information you share private.”
Currently, Presently, Private Conversations are only available in the Insider builds of Skype that is already included in the desktop version of the app, along with the iOS, Android, Linux, and macOS clients.
Unfortunately, Private Conversations still don’t support video calling, and this is a very big limitation.
Experts criticized Skype in the past because it always failed in implementing end-to-end encryption, this limitation advantaged many other instant messaging services like WhatsApp and Facebook Messenger.
The adoption of the Signal protocol is very important, this is the first time Microsoft doesn’t use a proprietary encryption Skype protocol.
If you want to test the new feature, select “New Private Conversation” from the compose menu or from the recipient’s profile.
“After the recipient accepts your invite, all calls and messages in that conversation will be encrypted end-to-end until you choose to end it.” continues Microsoft. “You can only participate in a private conversation from a single device at a time. You can switch the conversation to any of your devices, but the messages you send and receive will be tied to the device you’re using at the time.”

WhatsApp Flaw Could Allow 'Potential Attackers' to Spy On Encrypted Group Chats
11.1.2017 thehackernews Social

A more dramatic revelation of 2018—an outsider can secretly eavesdrop on your private end-to-end encrypted group chats on WhatsApp and Signal messaging apps.
Considering protection against three types of attackers—malicious user, network attacker, and malicious server—an end-to-end encryption protocol plays a vital role in securing instant messaging services.
The primary purpose of having end-to-end encryption is to stop trusting the intermediate servers in such a way that no one, not even the company or the server that transmits the data, can decrypt your messages or abuse its centralized position to manipulate the service.
In order words—assuming the worst-case scenario—a corrupt company employee should not be able to eavesdrop on the end-to-end encrypted communication by any mean.
However, so far even the popular end-to-end encrypted messaging services, like WhatsApp, Threema and Signal, have not entirely achieved zero-knowledge system.
Researchers from Ruhr-Universität Bochum (RUB) in Germany found that anyone who controls WhatsApp/Signal servers can covertly add new members to any private group, allowing them to spy on group conversations, even without the permission of the administrator.
As described by the researchers, in the pairwise communication (when only two users communicate with each other) server plays a limited role, but in case of multi-user chats (group chat where encrypted messages are broadcasted to many users), the role of servers increases to manage the entire process.
That's where the issue resides, i.e. trusting the company's servers to manage group members (who eventually have full access to the group conversation) and their actions.
As explained in the newly published RUB paper, titled "More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema," since both Signal and WhatsApp fail to properly authenticate that who is adding a new member to the group, it is possible for an unauthorized person—not a group administrator or even a member of the group—to add someone to the group chat.
What's more? If you are wondering that adding a new member to the group will show a visual notification to other members, it is not the case.
According to the researchers, a compromised admin or rogue employee with access to the server could manipulate (or block) the group management messages that are supposed to alert group members of a new member.
"The described weaknesses enable attacker A, who controls the WhatsApp server or can break the transport layer security, to take full control over a group. Entering the group, however, leaves traces since this operation is listed in the graphical user interface. The WhatsApp server can therefore use the fact that it can stealthily reorder and drop messages in the group," the paper reads.
"Thereby it can cache sent messages to the group, read their content first and decide in which order they are delivered to the members. Additionally, the WhatsApp server can forward these messages to the members individually such that a subtly chosen combination of messages can help it to cover the traces."
WhatsApp has acknowledged the issue, but argued that if any new member is added to a group, let's say by anyone, other group members will get notified for sure.
"We've looked at this issue carefully. Existing members are notified when new people are added to a WhatsApp group. We built WhatsApp so group messages cannot be sent to a hidden user," a WhatsApp spokesperson told Wired.
"The privacy and security of our users is incredibly important to WhatsApp. It's why we collect very little information and all messages sent on WhatsApp are end-to-end encrypted."
But if you are not part of a group with very selected members, I'm sure many of you would relatively ignore such notifications easily.
Researchers also advised companies to fix the issue just by adding an authentication mechanism to make sure that the "signed" group management messages come from the group administrator only.
However, this attack is not easy (exception—services under legal pressure) to execute, so users should not be worried about it.
A new Facebook security feature reveals fraudulent Facebook-like mails
1.1.2018 securityaffairs Social
A new Facebook security feature protects users from identity theft, the tech giant is taking note of every email it has “recently” sent to its users.
Facebook has rolled out a new security feature to protect users from identity theft, the tech giant is taking note of every email it has “recently” sent to its users.
The full list of email sent by Facebook is available under the Settings menu on the social network platform.
Facebook users that will receive a message allegedly sent by the social network giant can check its authenticity by viewing the new “See recent emails from Facebook” section at the bottom of the Security and Login page.

If the message is not included in the list it is fraudulent and must be discarded.
“Facebookmail.com is a common domain that Facebook uses to send notifications when we detect an attempt to log in to your account or change a password. If you’re unsure if an email you received was from Facebook, you can check its legitimacy by visiting facebook.com/settings to view a list of security-related emails that have been recently sent.” states the announcement published by Facebook.
Even if threat actors are able to disguise emails, to make them look like official messages sent by Facebook, the new Facebook security feature will help users to identify phishing attacks.
Crooks use phishing attacks to obtain victim’s credentials, access their profile, and perform a wide range of fraudulent activities.
Compromised accounts could be used to send out phishing messages or to spread malware.
Users that will discover email scam pretending to be sent from the Facebook platform can report it to phish@facebook.com.
If your account has been compromised due to a phishing attempt, visit facebook.com/hacked.
“If you’ve checked this tool and determined that an email you received is fake, we encourage you to report it to phish@facebook.com, and if you believe your account has been compromised due to a phishing attempt, you may attempt to regain access to your account at: facebook.com/hacked. ” concludes Facebook.
The Twitter account of the popular security expert John McAfee was hacked
30.12.2017 securityaffairs Social
The official Twitter account of popular cyber security expert John McAfee was hacked today, hackers used it to promote alternative cryptocurrencies.
The official Twitter account of legendary security expert John McAfee was hacked today, attackers used it to send several tweets promoting alternative cryptocurrencies like Siacoin, NXT, XRP, PTOY, and BAT.
At the time of writing, there aren’t further info related to the attack, John McAfee explained that its account was protected with a two-factor authentication process.
This suggests that the attackers have found a way to obtain the authentication code sent by Twitter, this is possible by compromising the mobile device or via an SS7 attack.
In this latter scenario, hackers can exploit a flaw in the SS7 protocol to steal the victim’s identity on the messaging services with just basic skills.
The principal instant messaging services, including WhatsApp and Telegram, rely on the SMS authentication as the primary security verification mechanism, which is routed through SS7 signalling. This means that hackers exploit the SS7 to compromise the verification mechanism and take over the victim’s account and impersonate him.
According to McAfee, someone has compromised his smartphone.
28 Dec
Adam Eivy \[._.]/
@antic
Replying to @officialmcafee
So how did it happen? Was this a breach of twitter, of your 2-factor service (e.g. phone provider). Did you not have 2-factor on for some reason? Curious if this is something that could affect others.
John McAfee
✔
@officialmcafee
If it can affect me it can affect anyone. Most likely my phone was compromised
4:40 AM - Dec 28, 2017
24 24 Replies 2 2 Retweets 28 28 likes
Twitter Ads info and privacy

John McAfee
✔
@officialmcafee
Urgent: My account was hacked. Twitter has been notified. The coin of the day tweet was not me. As you all know... I am not doing a coin of the day anymore!!!!
12:04 AM - Dec 28, 2017
3,922 3,922 Replies 2,726 2,726 Retweets 7,997 7,997 likes
Twitter Ads info and privacy
“The first indication that I had been hacked was turning on my cell phone and seeing the attached image,” he told BBC.

McAfee added that he was on a boat when his account was hacked and for this reason, he was not able to contact the AT&T.
“I knew at that point that my phone had been compromised.” he added
“I was on a boat at the time and could not go to my carrier (AT&T) to have the issue corrected.
“All that the hacker did was compromise my Twitter account. It could have been worse.”
John knows very well that he is a privileged target of several types of attackers, including haters.
John McAfee
✔
@officialmcafee
Though I am a security expert, I have no control over Twitter's security. I have haters. I am a target. People make fake accounts, fake screenshots, fake claims. I am a target for hackers who lost money and blame me. Please take responsibility for yourselves. Adults only please.
4:32 AM - Dec 28, 2017
1,368 1,368 Replies 798 798 Retweets 6,453 6,453 likes
Twitter Ads info and privacy
McAfee’s account was fully restored, Twitter hasn’t commented the incident.
The reality is that is not complex for a persistent attacker to compromise your social media account.
Facebook’s photo tagging system now looks for users in photos they’re not tagged in
24.12.2017 securityaffairs Social
Facebook’s is rolling out a new feature for its photo tagging mechanism, it now looks for users in photos they’re not tagged in.
Facebook is rolling out a new feature for its photo tagging mechanism that will now scan newly uploaded photos and alert all the users it recognizes in that photo. The feature aims to detect if others might be attempting to abuse your image.
“Powered by the same technology we’ve used to suggest friends you may want to tag in photos or videos, these new features help you find photos that you’re not tagged in and help you detect when others might be attempting to use your image as their profile picture,” explained Joaquin Quiñonero Candela, Director, Applied Machine Learning at Facebook.
The photo tagging system analyzes every image Facebook users upload scanning for human faces, then it associates each face with a template composed of a string of numbers computed by the platform.
The photo tagging system compares this template to the face templates of other Facebook users included in any newly uploaded image, then it will send them a notification.

“Now, if you’re in a photo and are part of the audience for that post, we’ll notify you, even if you haven’t been tagged. You’re in control of your image on Facebook and can make choices such as whether to tag yourself, leave yourself untagged, or reach out to the person who posted the photo if you have concerns about it.” added Candela.
The new feature aims to curb any abuse of the social media platform.
Facebook announced new Tools for people with visual impairments, the social network platform will detect people not tagged in an image and inform the user who’s in the photo.
The updates to the photo tagging mechanism will not roll out in Canada and the EU due to local user privacy laws.
Users can disable photo tagging notifications if he won’t receive notifications when others upload photos of the user.























