
Social Articles - H 2020 1 2 3 4 5 6 7 Social List - H 2021 2020 2019 2018 1 Social blog Social blog
Digmine Cryptocurrency Miner spreads via Facebook messenger
23.12.2017 securityaffairs Social
Researchers from security firm Trend Micro observed crooks spreading a new cryptocurrency mining bot dubbed Digmine via Facebook Messenger.
Watch out for video file (packed in zip archive) sent by your friends via Facebook messenger, according to the researchers from security firm Trend Micro crooks are using this technique to spread a new cryptocurrency mining bot dubbed Digmine.
The bot was first observed in South Korea, experts named it Digmine based on the moniker (비트코인 채굴기 bot) referred to in a report of recent related incidents in South Korea. Digmine infections were observed in other countries such as Vietnam, Azerbaijan, Ukraine, Vietnam, Philippines, Thailand, and Venezuela.
Attackers are targeting Google Chrome desktop users to take advantage of the recent spike in the price of cryptocurrencies.
Digmine is a Monero-cryptocurrency mining bot disguises as a non-embedded video file, under the name video_xxxx.zip, but is actually includes an AutoIt script.
The infection starts after the victims click on the file, the malicious code compromise the system and downloads its components and related configuration files from a command-and-control server.
Digmine first installs a miner (i.e. miner.exe—a modified version of an open-source Monero miner known as XMRig) that silently mines the Monero cryptocurrency in the background. The bot also installs an autostart mechanism and launch Chrome with a malicious extension that allows attackers to control the victims’ Facebook profile and used it to spread the malware to the victim’s Messenger friends list.
“Facebook Messenger works across different platforms, but Digmine only affects Facebook Messenger’s desktop/web browser (Chrome) version. If the file is opened on other platforms (e.g., mobile), the malware will not work as intended.” reads the analysis published by TrendMicro.
“Digmine is coded in AutoIt, and sent to would-be victims posing as a video file but is actually an AutoIt executable script. If the user’s Facebook account is set to log in automatically, Digmine will manipulate Facebook Messenger in order to send a link to the file to the account’s friends. “
Researchers observed that since Chrome extensions can only be installed via official Chrome Web Store, crooks launch Chrome (loaded with the malicious extension) via command line.
“The extension will read its own configuration from the C&C server. It can instruct the extension to either proceed with logging in to Facebook or open a fake page that will play a video” Trend Micro continues.
“The decoy website that plays the video also serves as part of their C&C structure. This site pretends to be a video streaming site but also holds a lot of the configurations for the malware’s components.”

The technique doesn’t work when users open the malicious video file through the Messenger app on their mobile devices.
“The abuse of Facebook is limited to propagation for now, but it wouldn’t be implausible for attackers to hijack the Facebook account itself down the line. This functionality’s code is pushed from the command-and-control (C&C) server, which means it can be updated.” continues the analysis.
Facebook had taken down most of the malware files from the social networking site.
Further info, including the IoCs are included in the report.
Beware of Cryptocurrency Mining Virus Spreading Through Facebook Messenger
22.12.2017 thehackernews Social
If you receive a video file (packed in zip archive) sent by someone (or your friends) on your Facebook messenger — just don’t click on it.
Researchers from security firm Trend Micro are warning users of a new cryptocurrency mining bot which is spreading through Facebook Messenger and targeting Google Chrome desktop users to take advantage of the recent surge in cryptocurrency prices.
Dubbed Digmine, the Monero-cryptocurrency mining bot disguises as a non-embedded video file, under the name video_xxxx.zip (as shown in the screenshot), but is actually contains an AutoIt executable script.
Once clicked, the malware infects victim’s computer and downloads its components and related configuration files from a remote command-and-control (C&C) server.
Digimine primarily installs a cryptocurrency miner, i.e. miner.exe—a modified version of an open-source Monero miner known as XMRig—which silently mines the Monero cryptocurrency in the background for hackers using the CPU power of the infected computers.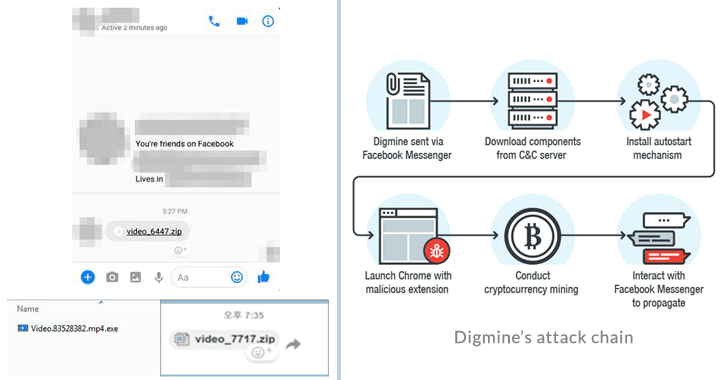
Besides the cryptocurrency miner, Digimine bot also installs an autostart mechanism and launch Chrome with a malicious extension that allows attackers to access the victims’ Facebook profile and spread the same malware file to their friends' list via Messenger.
Since Chrome extensions can only be installed via official Chrome Web Store, "the attackers bypassed this by launching Chrome (loaded with the malicious extension) via command line."
"The extension will read its own configuration from the C&C server. It can instruct the extension to either proceed with logging in to Facebook or open a fake page that will play a video" Trend Micro researchers say.
"The decoy website that plays the video also serves as part of their C&C structure. This site pretends to be a video streaming site but also holds a lot of the configurations for the malware’s components."
It's noteworthy that users opening the malicious video file through the Messenger app on their mobile devices are not affected.
Since the miner is controlled from a C&C server, the authors behind Digiminer can upgrade their malware to add different functionalities overnight.
Digmine was first spotted infecting users in South Korea and has since spread its activities to Vietnam, Azerbaijan, Ukraine, Philippines, Thailand, and Venezuela. But since Facebook Messenger is used worldwide, there are more chances of the bot being spread globally.
When notified by Researchers, Facebook told it had taken down most of the malware files from the social networking site.
Facebook Spam campaigns are quite common. So users are advised to be vigilant when clicking on links and files provided via the social media site platform.
Facebook Launches New Anti-Phishing Feature
21.12.2017 securityweek Social
Facebook announced on Wednesday the introduction of a new security feature designed to help users check if the emails they receive are legitimate or if they have been sent by cybercriminals.
When it detects a suspicious login attempt or a password change, Facebook notifies users by sending them an email from the Facebookmail.com domain. Cybercriminals often try to spoof these emails in an effort to lure internauts to phishing or other malicious websites.
Users can now check if the email in their inbox really does come from Facebook by going to Settings -> Security and Login -> See recent emails from Facebook. Here they can see recent emails, including ones related to security and logins, and if the message from their inbox is not listed, it’s most likely fake.
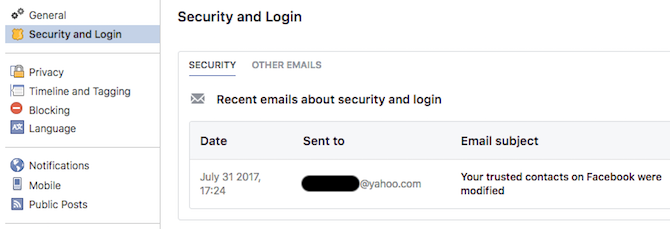
“If you've checked this tool and determined that an email you received is fake, we encourage you to report it to phish@facebook.com, and if you believe your account has been compromised due to a phishing attempt, you may attempt to regain access to your account at: facebook.com/hacked,” said Scott Dickens, Product Manager with Facebook Account Integrity.
The new feature has apparently not been rolled out to all accounts so users who don’t immediately find it in the settings menu should check back in a few days.
The new feature comes just weeks after the social media giant’s founder and CEO, Mark Zuckerberg, claimed his company has prioritized security over profit.
“We're serious about preventing abuse on our platforms. We're investing so much in security that it will impact our profitability. Protecting our community is more important than maximizing our profits,” Zuckerberg said.
Facebook recently awarded researchers $100,000 for discovering a novel technique of detecting credential spear-phishing attacks in enterprise environments. The method combines a new anomaly scoring technique for ranking security alerts with features derived from the analysis of spear-phishing emails.
Facebook, WhatsApp Both Put Under Notice by Europe
20.12.2017 securityweek Social
The French privacy regulator, the National Commission of Computing and Freedoms (CNIL) has issued a formal notice on WhatsApp. It requires the Facebook company to stop personal data transfers to the parent company in the U.S. unless there is a legal basis for doing so. In particular, WhatsApp must obtain 'user consent' (within the meaning of European law) to gather and transfer that data.
It's a busy time for privacy issues between the U.S. and Europe. CNIL published its notice on Tuesday. On the same day, the powerful German competition authority, the Bundeskartellamt (the Federal Cartel Office or FCO), warned Facebook that it "is abusing [its] dominant position by making the use of its social network conditional on its being allowed to limitlessly amass every kind of data generated by using third-party websites."
Last week the European Commission filed an amicus curiae brief (PDF) with the United States Court of Appeals For the Second Circuit in the ongoing dispute between Microsoft and the U.S. government. Noticeably, this was in support of neither party, but was an attempt to ensure that the the U.S. court has a full understanding of the relevant European law -- in this case, specifically the General Data Protection Regulation (GDPR).
The German FCO concern over Facebook is over the widespread collection of personal user data. In February 2017, the FCO declared that it would investigate Facebook. President Andreas Mundt said at the time, "Dominant companies are subject to special obligations. These include the use of adequate terms of service as far as these are relevant to the market. For advertising-financed internet services such as Facebook, user data are hugely important. For this reason it is essential to also examine under the aspect of abuse of market power whether the consumers are sufficiently informed about the type and extent of data collected."
Now the FCO has stated, "The authority holds the view that Facebook is abusing this dominant position by making the use of its social network conditional on its being allowed to limitlessly amass every kind of data generated by using third-party websites." At the heart of the concern is the inadequate informed consent of the user in allowing personal data collection. Facebook claims that it is not a dominant company in Europe (it has more than 30 million active monthly users in Germany); and that it complies with European law.
The concept of free and informed consent also underlies CNIL's notice against Facebook subsidiary, WhatsApp. In August 2016 WhatsApp changed its Terms of Service and Privacy Policy, explaining that in future, its user data would be transferred to Facebook for targeted advertising, security, and business intelligence. The European regulator grouping, known as Article 29 Working Party, quickly asked WhatsApp to stop the transfer of personal data for targeted advertising.
In a subsequent investigation, WhatsApp told CNIL that French personal data had never been used for targeted advertising. However, CNIL determined that personal data was shared for business intelligence and security. "Thus," says the CNIL statement, "information about users such as their phone number or their use habits on the application are shared." While sharing data for security is not an issue, sharing for business intelligence "is not based on the legal basis required by the Data Protection Act for any processing."
According to CNIL, any user consent to this data collection and sharing is neither free nor informed ("the only way to refuse the data transfer for 'business intelligence' purpose is to uninstall the application"). CNIL requested a sample of data that had been transferred, but this was refused by WhatsApp. The data concerned is now in the U.S., and WhatsApp apparently considers that it is only subject to the law of the U.S.
This refusal has been interpreted by CNIL as a breach of WhatsApp's obligation to cooperate with the regulator under Article 21 of the Data Protection Act. It has consequently issued the formal notice requiring WhatsApp to comply with the Data Protection Act within one month.
Neither the CNIL notice nor the FCO statement can directly lead to sanctions against Facebook/WhatsApp. They can best be viewed as shots across the bow, which -- if ignored -- could lead to the full cannon power of European data protection being leveled against Facebook. Both statements being issued on the same day is a remarkable coincidence. Coming exactly one week after the European Commission used the GDPR-relevant Microsoft vs U.S. government court struggle to make sure that U.S. courts understand Europe's point of view is also remarkable.
It could all be coincidence. But coincidence or not, Europe is warning the large American tech companies -- and indeed, any company that trades with or within Europe -- it is taking its data protection laws seriously. While existing sanctions could be funded out of the running costs of large companies, the potential for future GDPR sanctions of up to 4% of global turnover is not something that can be ignored. Any assumption that Europe will not be quick to enforce GDPR when it comes into force in May 2018 should be rejected.
Facebook Releases New Certificate Transparency Tools
15.12.2017 securityweek Krypto Social
Following the release of the Certificate Transparency Monitoring utility in December 2016, Facebook has decided to release new tools for developers using the Certificate Transparency framework.
Last year’s tool was designed to provide access to data collected through Facebook’s own service monitoring the issuance of TLS certificates. It leverages Google’s Certificate Transparency (CT) framework, which can detect mis-issued TLS certificates and stop attempts to leverage them to intercept HTTPS traffic.
The tool allows developers to search for certificates and receive alerts when a new certificate is issued for their domains. The tool ensures that newly issued certificates that have been logged to Certificate Transparency Logs (CT logs) aren’t mis-used to perform man-in-the-middle attacks.
With hundreds of Certificate Authorities (CAs) issuing publicly-trusted TLS certificates for any website out there, a single breach at any CA could result in the mis-issuance of publicly-trusted TLS certificates, the company says.
“We match every new certificate with a set of domain subscriptions in our system, and we notify respective subscribers about the updates. If a domain owner receives a notification that a CA issued a certificate for their domain without an explicit request, they will likely want to contact the CA, make sure their identity is not compromised, and consider revoking the certificate,” Facebook explains.
To provide push-based integrations with its system, Facebook is now releasing Webhooks API, which allows developers to register a webhook and define domains for monitoring instead of periodically pulling certificates from external sources or waiting for notifications. Each time a new certificate is issued for these domains, information about the cert is sent to the developer-specified endpoint.
Additionally, the social media giant announced the release of an API that helps querying certificates programmatically. Since receiving detailed information about the certificates and analyzing millions without proper infrastructure is difficult, the interface was designed to provide certificates metadata for the domain names that match a given query.
Developers taking advantage of the Certificate Transparency features were being initially notified via email on new certificates issued for their domains. Starting this year, everyone can see certificate updates on Facebook via push notifications and all developers creating a subscription at developers.facebook.com/tools/ct can take advantage of this feature.
Facebook is currently monitoring over 20 publicly available CT logs and says it sends around 2,500 notifications every day. Around 40,000 new certificates are observed in CT logs every hour and that number is expected to grow next year, when Google Chrome will start requiring all websites certificates to be logged in the CT logs. To ensure scalability, the same backend system that powers the Facebook Graph is used to search through the logged certificates.
The social network company also notes that they are currently working on implementing Expect-CT header, meaning that compatible browsers will require that certificates used to access Facebook are logged to public CT logs first.
Researcher found a vulnerability in Facebook polls that allowed removal of any photo
27.11.2017 securityweek Social
The Iran-based security researcher Pouya Darabi discovered a method to delete any photo from Facebook exploiting a flaw in the polling feature.
The Iran-based security researcher Pouya Darabi received a $10,000 bounty from Facebook after reporting a critical vulnerability that could have been exploited to delete any photo from the social network.
Early this month, the social network giant announced a new feature for posting polls that include images and GIF animations. Darabi analyzed the new feature and discovered that it is affected by a vulnerability easily exploitable.
The expert analyzed the request sent to Facebook servers when a user creates a poll and discovered the presence of the identifiers of the image files added to the poll.

Replacing the image ID in the request with the ID of any photo on the social network it possible to set the image for the poll.
Darabi then discovered once the user that created the poll has deleted the post, the image whose ID was added to the request would also get removed from the social network.
“When this field value changes to any other images ID, that image will be shown in poll. After sending request with another user image ID, a poll containing that image would be created.” explained the researcher that published a video PoC.
“At the end when we try to delete the poll, victim’s image would be deleted with it by facebook as a poll property.”
Darabi reported the flaw to Facebook on November 3, the company issued a temporary fix in the same day. The permanent fix was completed in November 5, and on November 8 the expert received a $10,000 Bounty award.
Back in 2015, Darabi was awarded $15,000 for bypassing the Facebook cross-site request forgery (CSRF) protection systems, in 2016 he received another $7,500 award for a similar bug.
Another Facebook Bug Allowed Anyone to Delete Your Photos
27.11.2017 thehackernews Social
If you think a website whose value is more than $500 billion does not have any vulnerability in it, then you are wrong.
Pouya Darabi, an Iranian web developer, discovered and reported a critical yet straightforward vulnerability in Facebook earlier this month that could have allowed anyone to delete any photo from the social media platform.
The vulnerability resides in Facebook's new Poll feature, launched by the social media giant earlier this month, for posting polls that include images and GIF animations.
Darabi analyzed the feature and found that when creating a new poll, anyone can easily replace the image ID (or gif URL) in the request sent to the Facebook server with the image ID of any photo on the social media network.
Now, after sending the request with another user image ID (uploaded by someone else), that photo would appear in the poll.
"Whenever a user tries to create a poll, a request containing gif URL or image id will be sent, poll_question_data[options][][associated_image_id] contains the uploaded image id," Darabi said. "When this field value changes to any other images ID, that image will be shown in poll."
Apparently, if the creator of the poll deletes that post (poll), as demonstrated in the video above, it would eventually delete the source photo as well, whose image ID was added to the request—even if the poll creator doesn't own that photo.
The researcher said he received $10,000 as his bug bounty reward from Facebook after he responsibly reported this vulnerability to the social media network on November 3. Facebook patched this issue on November 5.
This isn't the first time when Facebook has been found dealing with such a vulnerability. In the past, researchers discovered and reported several issues that let them delete videos, photo albums, and comments and modify messages from the social media platform.
Darabi has also previously been awarded by Facebook with a $15,000 bug bounty for bypassing its cross-site request forgery (CSRF) protection systems (in 2015) and another $7,500 for a similar issue (in 2016).
Facebook Flaw Allowed Removal of Any Photo
27.11.2017 securityweek Social
A researcher says he received a $10,000 bounty from Facebook after finding a critical vulnerability that could have been exploited to delete any photo from the social media network.
In early November, Facebook announced a new feature for posting polls that include images and GIF animations. Iran-based security researcher and web developer Pouya Darabi analyzed the feature shortly after its launch and discovered that it introduced an easy-to-exploit flaw.
When a user created a poll, the request sent to Facebook servers included the identifiers of the image files added to the poll. The expert noticed that users could replace the image ID in the request with the ID of any photo on Facebook and that photo would appear in the poll.
Darabi then discovered that once the creator of the poll deleted the post, the image whose ID was added to the request would also get removed from Facebook.
The vulnerability was reported to Facebook on November 3 and a temporary fix was rolled out the same day. The company deployed a complete patch on November 5.
Darabi said he received a $10,000 bug bounty for his findings. The researcher has published a blog post and a video describing the vulnerability.
This was not the first time Darabi earned a significant bounty from Facebook. Back in 2015, the social media giant awarded him $15,000 for bypassing its cross-site request forgery (CSRF) protection systems. The next year he received another $7,500 for a similar weakness.
These types of vulnerabilities are not uncommon on Facebook. In the past years, researchers reported finding several flaws that could have been exploited to delete comments, videos, and photos from Facebook. The security holes, which in most cases involved replacing the ID of the targeted resource in a request, earned researchers roughly $10,000.
Facebook has paid out millions of dollars to researchers who found vulnerabilities in the social media network since the launch of its bug bounty program in 2011.
Fake WhatsApp On Google Play Store Downloaded By Over 1 Million Android Users
5.11.2017 thahackernews Social
Cybercriminals are known to take advantage of everything that's popular among people in order to spread malware, and Google's official Play Store has always proved no less than an excellent place for hackers to get their job done.
Yesterday some users spotted a fake version of the most popular WhatsApp messaging app for Android on the official Google Play Store that has already tricked more than one million users into downloading it.
Dubbed Update WhatsApp Messenger, came from an app developer who pretended to be the actual WhatsApp service with the developer title "WhatsApp Inc."—the same title the actual WhatsApp messenger uses on Google Play.
You might be wondering how the sneaky app developer was able to use the same title as the legitimate Facebook-owned maker of the messaging client—thanks to a Unicode character space.
The app maker added a Unicode character space after the actual WhatsApp Inc. name, which in computer code reads WhatsApp+Inc%C2%A0.
However, this hidden character space at the end of the WhatsApp Inc. would be easily invisible to an average Android user browsing Google Play Store, allowing this dodgy version of the app to masquerade as a product of WhatsApp Inc.
In other words, the titles used by the fake app maker and real WhatsApp service are different but appeared same to a user.
According to Redditors, who first spotted this fake app on Friday, the app was not a chat app; instead, it served Android users with advertisements to download other apps.
"I've also installed the app and decompiled it," one Redditor said. "The app itself has minimal permissions (internet access) but it's basically an ad-loaded wrapper which has some code to download a second apk, also called 'whatsapp.apk.' The app also tries to hide by not having a title and having a blank icon."
Google has now removed the fake WhatsApp Android app from its official Play Store, but this incident once again marked the tech giant's failure to spot the scam on its app platform—even for the program that had more than a million downloads.
It is an unfortunate truth that even after so many efforts by Google (even recently launched Bug Bounty Program), malicious apps continuously somehow managed to fool its Play Store's security mechanism and infect millions of Android users.
Google Play Store is still surrounded by hundreds of other fake and malicious apps that trick users into downloading and installing them and potentially infect their smartphones to carry out malicious things without their knowledge.
So, users are advised to be more vigilant while downloading apps not only from the third-party app store but also from official Play Store in order to protect themselves.
Facebook’s Zuckerberg Says Security Costs Will Hurt Profits
2.11.2017 securityweek Social
Facebook Chief Says Protecting Community is More Important Than Maximizing Profits
Social media giant Facebook said on Wednesday that significant investments by the company to secure its platform will impact its profitability.
The company announced its financial results for Q3 2017 after the bell on Wednesday, noting that capital expenditures for quarter were $1.76 billion. The company reported more than $10.3 billion in revenue during the quarter, and a profit of $4.7 billion.
Facebook Security"Our community continues to grow and our business is doing well," Mark Zuckerberg, Facebook founder and CEO, said in a statement. "But none of that matters if our services are used in ways that don't bring people closer together. We're serious about preventing abuse on our platforms. We're investing so much in security that it will impact our profitability. Protecting our community is more important than maximizing our profits."
33 year-old Zuckerberg did not detail any planned security investments or estimated costs.
The company has been under scrutiny over Russia-linked buyers who placed thousands of ads on the site in attempt to influence the U.S. presidential election.
Facebook’s security group is led by Chief Security Officer (CSO) Alex Stamos, who took the role in June 2015 after serving as CISO at Yahoo. Stamos replaced former CSO Joe Sullivan who left the social media giant in April to take the role of CSO at Uber.
In June, Facebook announced the roll-out of a redesigned security settings page, designed to make it easier for users to understand the options provided to them.
In October 2016, the company said that it had paid out a total of more than $5 million (at the time) to researchers who have helped the company find and patch vulnerabilities in its systems and products.
The company had an employee headcount of more than 23,000 as of September 30, 2017, an increase of 47% year-over-year.
Wait, Do You Really Think That’s A YouTube URL? Spoofing Links On Facebook
31.10.2017 thehackernews Social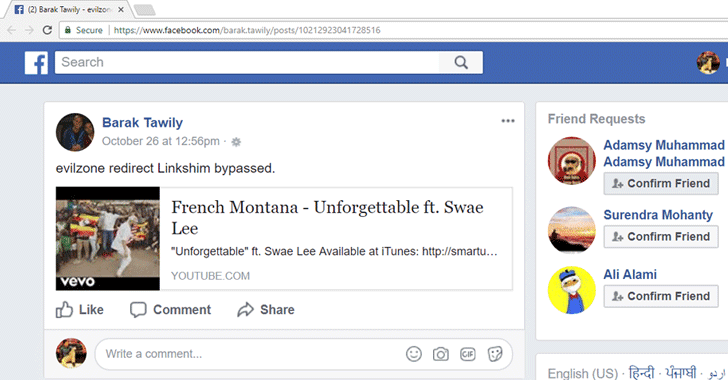
While scrolling on Facebook how you decide which link/article should be clicked or opened?
Facebook timeline and Messenger display title, description, thumbnail image and URL of every shared-link, and this information are enough to decide if the content is of your interest or not.
Since Facebook is full of spam, clickbait and fake news articles these days, most users do not click every second link served to them.
But yes, the possibility of opening an article is much higher when the content of your interest comes from a legitimate and authoritative website, like YouTube or Instagram.
However, what if a link shared from a legitimate website lands you into trouble?
Even before links shared on Facebook could not be edited, but to stop the spread of misinformation and false news, the social media giant also removed the ability for Pages to edit title, description, thumbnail image of a link in July 2017.
However, it turns out that—spammers can spoof URLs of the shared-links to trick users into visiting pages they do not expect, redirecting them to phishing or fake news websites with malware or malicious content.
Discovered by 24-year-old security researcher Barak Tawily, a simple trick could allow anyone to spoof URLs by exploiting the way Facebook fetch link previews.
In brief, Facebook scans shared-link for Open Graph meta tags to determine page properties, specifically 'og:url', 'og:image' and 'og:title' to fetch its URL, thumbnail image and title respectively.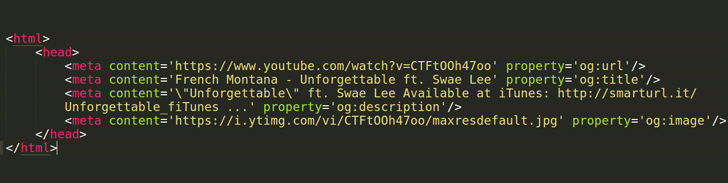
Interestingly, Tawily found that Facebook does not validate if the link mentioned in 'og:url' meta tag is same as the page URL, allowing spammers to spread malicious web pages on Facebook with spoofed URLs by just adding legitimate URLs in 'og:url' Open Graph meta tag on their websites.
"In my opinion, all Facebook users think that preview data shown by Facebook is reliable, and will click the links they are interested in, which makes them easily targeted by attackers that abuse this feature in order to perform several types of attacks, including phishing campaigns/ads/click fraud pay-per-click," Tawily told The Hacker News.
Tawily reported the issue to Facebook, but the social media giant refused to recognise it as a security flaw and referred that Facebook uses "Linkshim" to protect against such attacks.
If you are unaware, every time a link is clicked on Facebook, a system called "Linkshim" checks that URL against the company's own blacklist of malicious links to avoid phishing and malicious websites.
This means if an attacker is using a new domain for generating spoofed links, it would not be easy for Linkshim system to identify if it is malicious.
Although Linkshim also uses machine learning to identify never-seen-before malicious pages by scanning its content, Tawily found that the protection mechanism could be bypassed by serving non-malicious content explicitly to Facebook bot based on User-Agent or IP address.
Tawily has also provided a demo video to show the attack in action. You can watch the video above.
Since there is no way to check the actual URL behind a shared link on Facebook without opening it, there is a little user can do to protect themselves except being vigilant.
Scam Alert: Your Trusted Friends Can Hack Your Facebook Account
14.10.2017 thehackernews Social
If you receive a message from any of your Facebook Friends asking for urgent help to recover their Facebook account, since they've added you as one of their 'Trusted Contacts'—just don’t blindly believe it.
Researchers have detected a new Facebook phishing scam that can even trick an experienced technical user into falling victim to the scam, helping an attacker gain access to your Facebook account.
This latest social media scam is abusing "Trusted Contact"—a Facebook account recovery feature that sends secret access codes to a few of your close friends in order to help you regain access to your Facebook account in case you forget your password or lost access to your account.
According to a public security alert published by AccessNow, the attack initiates by an already compromised account of one of your friends, asking for urgent help to get back into his/her Facebook account.
The attacker explains that you are listed as one of his/her Trusted Contacts on Facebook and asks you to check your email for a recovery code and share with the attacker (who's hiding behind the identity of your friend).
However, in actual, the code you received is not the key to unlock your friend's account, but instead, the attacker initiated "Forgot my password" request for your account in an attempt to hijack your Facebook account.
Knowing that a friend is in trouble, apparently one would share the code without giving a second thought.
"The new attack targets people using Facebook, and it relies on your lack of knowledge about the platform's Trusted Contacts feature," Access Now warns.
You should know Facebook's Trusted Contacts feature doesn't work the way this phishing attack suggests. To understand how this feature works, you can head on to this Facebook post.
The Access Now says, "So far we're seeing the majority of reports [falling victims to this new Facebook phishing scam] from human right defenders and activists from the Middle East and North Africa."
Although this latest Facebook scam is initiated using a compromised Facebook account of one of your friends, any of your Facebook friend can also intentionally trick you into handing over your Facebook account to them (looking at the way how people accept friend requests sent by anyone on the social media platform).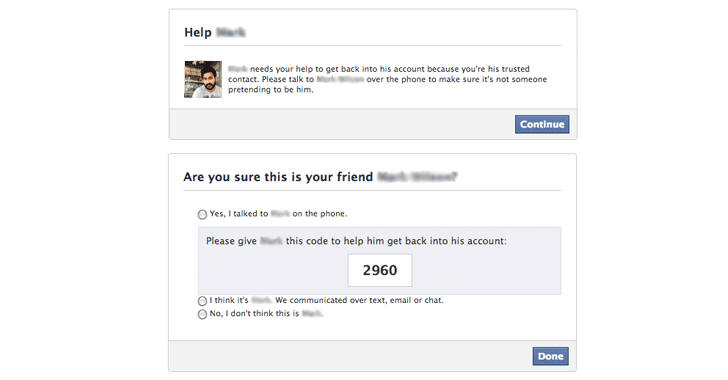
The best way to protect yourself is always to be vigilant to every recovery emails you receive, and read the recovery message or email carefully, even if it is sent by one of your actual friends.
Stay Safe!
A new Facebook scam allows your friend contacts to hack your account
14.10.2017 securityaffairs Social
Researchers spotted a new Facebook scam that could deceive also tech-savvy people and trick them into giving the attacker access to their Facebook accounts.
Don’t trust message apparently sent from any of your Facebook Friends asking for urgent help to recover their Facebook account.
Researchers have spotted a new Facebook scam that could deceive also tech-savvy people and trick them into giving the attacker access to their Facebook accounts.
The Facebook scam abuse “Trusted Contacts, ” a Facebook account recovery feature that sends access codes to a selected list of trusted user’s friends in order to help you regain access to their Facebook account in case you forget your password or lost access to your account.
The alert was launched by AccessNow, the attack chain starts with a message from the compromised account of one of the friends of the potential victim.
“The new attack targets people using Facebook, and it relies on your lack of knowledge about the platform’s “Trusted Contacts” feature. states the public security alert.
“Trusted Contacts is a system created by Facebook to help you gain access to your account if you forget your password or your account is locked. If you enable Trusted Contacts, Facebook will ask you to identify three to five people. If you need access to your account, Facebook will send part of a code to each of these users that can be combined to gain access to your account.”
The attacker asks for victim’s help recovering his account, he tells the victim that he is as one of his Trusted Contacts on Facebook, and inform him that he will receive by mail a code for recovering their account.
The attacker, who is posing as a victims’ friend thanks to the compromised account, asks the victim to share the recovery code.
Then the attacker triggers the “I forgot my password” feature for the victim’s Facebook account and requests a recovery code.
At this point, the code received by the victim is not the key to unlock his friend’s account, but instead, the code requested by the attacker through the “Forgot my password” procedure.
If the victim shares the code with the attacker he will be able to take over the your account from you.
Below the step by step procedure:
You get a message from an attacker on Facebook Messenger, who is using the compromised account of someone on your Friends list.
The attacker asks for your help recovering their account, explaining that you are listed as one of their Trusted Contacts on Facebook, and tells you that you will receive a code for recovering their account.
Then the attacker triggers the “I forgot my password” feature for your Facebook account and requests a recovery code.
In an effort to help, you send the code you’ve just received to your “friend.”
Using the code, the attacker can now steal your account from you, and use it to victimize other people.
This specific Facebook scam relies on the lack of victim’s knowledge about the Trusted Contacts feature.
“The new attack targets people using Facebook, and it relies on your lack of knowledge about the platform’s Trusted Contacts feature,” states Access Now.
The Facebook scam can potentially target any users of the popular social network, but experts are seeing the majority of reports from human right defenders and activists from the Middle East and North Africa.”
“So far we’re seeing the majority of reports [falling victims to this new Facebook phishing scam] from human right defenders and activists from the Middle East and North Africa.”
We started this post explaining that the attack chain starts with a message sent by the attacker through a compromised account belonging to one of your friends.
Another scenario sees the Facebook scam initiated by your Facebook friend that intentionally trick you into handing over your Facebook account to him.
The best way to protect your account is to remain vigilant on every suspicious message including recovery emails from trusted friends.
Google, Facebook, Twitter Asked to Testify in Russia Probe
28.9.2017 securityweek Social
The Senate Intelligence Committee has asked top tech companies Google, Facebook and Twitter to testify about Russian interference in US politics, a Senate aide confirmed Wednesday.
The three internet and online social media giants are expected to appear on November 1 in an open hearing on the rising evidence that they were covertly manipulated in a campaign to help Donald Trump win the presidency.
Before that they could also testify in the House Intelligence Committee: Representatives Mike Conaway and Adam Schiff, who lead the committee's Russia probe, announced late Wednesday they too had invited representatives of technology firms to testify on Russian manipulation.
"Congress and the American people need to hear this important information directly from these companies," they said.
Facebook recently revealed that for just $100,000, apparent Russia-linked buyers placed some 3,000 advertisements on its pages last year that appeared aimed at influencing the election.
Facebook has turned the details of those ads over to investigators. According to reports, the ads sought to boost the Democratic and Republican rivals of then-election frontrunner Hillary Clinton, as well as to sow discord among Americans in ways that would damage Clinton's voter base.
"The vast majority of ads run by these accounts didn't specifically reference the US presidential election, voting or a particular candidate," Facebook Chief Security Officer Alex Stamos said early this month.
"Rather, the ads and accounts appeared to focus on amplifying divisive social and political messages across the ideological spectrum -- touching on topics from LGBT matters to race issues to immigration to gun rights."
Google, a unit of Alphabet, has said it was not used in the alleged Russian campaign to steer the US election.
But according to Buzzfeed, its automated ad-targeting system lets advertisers direct ads to people using racist and anti-Semitic search terms.
Twitter meanwhile has been shown to be a dense thicket of easily faked accounts and news items that allowed alleged Russian operatives to pump out politically divisive and anti-Clinton tweets.
China widely disrupted WhatsApp in the country, broadening online censorship
27.9.2017 securityaffairs Social
The popular instant messaging application WhatsApp has been widely blocked in mainland China by the Government broadening online censorship.
Bad news for the Chinese users of the popular instant messaging app WhatsApp because the application has been widely blocked in mainland China by the Government. Users are not able to send text messages, photo and video sharing. It isn’t the first time that the Chinese Government blocked the popular app, WhatsApp had been blocked in July and for a few days.
Now, the situation seems to be worst, the Chinese Government has widely blocked WhatsApp to tighten censorship as the country prepares for the 19th National Congress of the ruling Communist Party. in October.
The Chinese Great Firewall implements a tighten control of the accesses to the Internet, it currently blocks several major websites, including Twitter, Facebook, Instagram, Wikipedia, and many Google services in China.
According to The New York Times. WhatsApp had been “broadly disrupted in China.”
“WhatsApp now appears to have been broadly disrupted in China, even for text messages, Nadim Kobeissi, an applied cryptographer at Symbolic Software, a Paris-based research start-up, said on Monday.” reported The New York Times. “The blocking of WhatsApp text messages suggests that China’s censors may have developed specialized software to interfere with such messages, which rely on an encryption technology that is used by few services other than WhatsApp, he said.”

At the time it is not clear how long the ban will have effect, the messaging system was seeing severe disruptions as early as last Wednesday.
Follow
Italian Vagabond @italianvagabond
❌ Seems like #WhatsApp is #blocked or #down in #China right now. I've got a #ChinaMobile SIM card. Anyone still able to use it?
5:37 AM - Sep 20, 2017
4 4 Replies 3 3 Retweets 3 3 likes
Twitter Ads info and privacy
WhatsApp is now accessible only via VPNs, but China made it mandatory for all VPN providers to have a license from the government to provide such services.
WhatsApp is owned by Facebook, also the social media giant and Instagram have been already blocked in China.
The intent of the Chinese Government is to force citizens in using other instant messaging services, that allows the authorities to access the citizens’ personal data.
H1 2017 – Twitter suspended a total of 935,897 accounts for the promotion of terrorism
21.9.2017 securityaffairs Social
Twitter published its Transparency Report related to H1 2017, the company suspended 935,897 accounts for the promotion of terrorism.
Twitter suspends 299,000 accounts linked to terrorism in the first six months of 2017, the company revealed that 75 percent of the infringing accounts were suspended before their first tweet confirming the huge efforts in fighting online propaganda and other activities linked to this threat.
According to data provided in the transparency report, Twitter confirmed that 95 percent of the suspended accounts for the promotion of terrorism were identified by using internal tools designed to identify and block spam, government requests accounted for less than 1% of account suspensions.
One-quarter of those infringing accounts were suspended before the accounts posted their first tweet.
It is interesting to note that according to the report published by the social media giant, fewer than 2 percent of accounts that were suspended were reported by governments worldwide.
Governments submitted 716 separate reports that triggered the suspension of 5,929 accounts.
“The second largest volume, a little more than 2% of global reports, fell within the promotion of terrorism category. Under this category of reports, we are referring to accounts that actively incite or promote violence associated with internationally recognized terrorist organizations, promote internationally recognized terrorist organizations, and accounts attempting to evade prior enforcement.” states a blog post published by Twitter.
“Twitter’s continued commitment to eliminate such activity from our platform has resulted in an 80% reduction in accounts reported by governments compared to the previous reporting period of July 1, 2016 through December 31, 2016. Notably, government requests accounted for less than 1% of account suspensions for the promotion of terrorism during the first half of this year.”
Almost every government is stressing technology company to adopt measures to fight online terrorism, UK and France proposed fines for those companies that don’t collaborate or fail to curb terrorist activities online.
Tech giants Facebook, Microsoft, Twitter, and YouTube pledged to improve the information sharing by building a database of digital fingerprints of terrorism-related content removed from their services.
Twitter received 6,448 demands for data from governments in the first six months of the year, in 60 percent of cases some information were produced for a total number of accounts specified of 11115.

The US made 211 demands for 4,594 accounts, down by 8 percent year-over-year, while the UK made 606 demands for data on 819 accounts, down by 11 percent year-over-year.
Interesting also the data related to Japan, the state made 1384 demands for 1993 accounts.
Twitter Suspends Nearly 1 Million Accounts Associated with Terrorism
20.9.2017 securityweek Social
Twitter has suspended a total of 935,897 accounts for the promotion of terrorism between August 1, 2015, and June 30, 2017, the company says in its latest transparency report.
A total of 299,649 accounts were suspended during the first half of 2017, marking a 20% decrease compared to the previous six-month period, the company reveals. 95% of the account suspensions were the result of internal efforts, the social platform claims.
These are “accounts that actively incite or promote violence associated with internationally recognized terrorist organizations, promote internationally recognized terrorist organizations, and accounts attempting to evade prior enforcement,” Twitter explains.
According to the social media network, 75% of the accounts suspended during the January-June 2017 timeframe were blocked before posting their first tweet. The sustained effort to eliminate such activity from the platform has resulted in an 80% drop in government reports on such accounts, compared to the previous six months.
However, government requests accounted for less than 1% of account suspensions, as they only amounted to 338 reports referring to 1,200 accounts. They also represented only 2% of the reports received from governments around the world, which summed up to 16,818 reports in the six-month period.
The largest number of such reports were received for abusive behavior, at 16,414, which represented 98% of global government TOS (Terms of Service) reports. These referred to 6,299 accounts, only 12% of which were actioned on, but the majority of requests didn’t result in content removal.
Twitter also received 37 requests related to copyright, and 29 reports related to trademark. These are non-legal requests submitted by government representatives about content that might violate the company’s rules against copyright and trademark infringement.
In its transparency report, the social platform says it received a total of 6,448 global government requests for account information from January through June, 2017, up 6% from the previous period, but affecting 3% fewer accounts. Some of the requests originated from four new countries, namely Nepal, Paraguay, Panama, and Uruguay.
Twitter also reveals that it received around 10% more global legal requests to remove content, and that these impacted roughly 12% more accounts compared to the previous reporting period. Such requests came from various countries, including nine new ones: Bahrain, China, Croatia, Finland, Nepal, Paraguay, Poland, Qatar, Ukraine, and Uruguay.
In the United States, the company received a total of 2,111 account information requests that specified 4,594 accounts, and also received 118 removal requests. The U.S. continues to account for the majority of global government requests for account information.
“United States submitted 33% of all worldwide requests for user account information. Interestingly, the total number of requests from U.S. law enforcement and government entities decreased by 8% and those requests affected 18% fewer accounts from last report to this report. This marks the third straight report where we’ve seen a decrease in U.S. requests,” Twitter says.
During the first half of 2017, Washington, D.C. was the top U.S. requester, submitting 14.3% of total requests, followed by California with 13.8% of the requests. In the timeframe, the San Francisco-based company received 245 non-California state-issued subpoenas and court orders, down from 295 during the previous reporting period.
Facebook slapped with $1.43 million fine for violating users' privacy in Spain
11.9.2017 thehackernews Social
Facebook is once again in trouble regarding its users' privacy.
The social media giant has recently been heavily fined once again for a series of privacy violations in Spain.
Recently, Google also incurred a record-breaking fine of $2.7 billion (€2.42 billion) by the European antitrust officials for unfairly manipulating search results since at least 2008.
Now, the Spanish Data Protection Agency (AEPD) has issued a €1.2 Million (nearly $1.4 Million) fine against Facebook for breaching laws designed to protect its people's information and confidentiality.
According to the data protection watchdog, the social network collects its users' personal data without their 'unequivocal consent' and makes the profit by sharing the data with advertisers and marketers.
The AEPD also found Facebook collects sensitive data on user's ideology, religious beliefs, sex and personal tastes and navigation—either directly from its own services or through third parties—without clearly informing its users how this information would be used.
This activity constituted a "very serious" infringement of the country's local data protection law (LOPD), for which the authority fined the company €600,000 ($718,062).
The regulator also identified two "serious" violations of privacy laws, including:
Tracking people through the use of "Like" button social plug-ins embedded in other non-Facebook web pages—for which it is fined €300,000 ($359,049).
Failing to delete data collected from users once it has finished using it, in fact, the company "retains and reuses it later associated with the same user"—which resulted in another €300,000 ($359,049) fines.
The AEPD also said that Facebook's existing privacy policy contains "generic and unclear terms," and doesn't "adequately collect the consent of either its users or nonusers, which constitutes a serious infringement."
However, Facebook denied any wrongdoing and intended to appeal the decision of the Spanish data protection authority, providing the following statement.
"We take note of the DPA's decision with which we respectfully disagree. Whilst we value the opportunities we've had to engage with the DPA to reinforce how seriously we take the privacy of people who use Facebook, we intend to appeal this decision."
"As we made clear to the DPA, users choose which information they want to add to their profile and share with others, such as their religion. However, we do not use this information to target adverts to people."
In May, the social media giant was fined €150,000 ($179,532) by for the way Facebook targeted advertising and tracked users.
Dissecting the Chrome Extension Facebook malware
3.9.2017 Kaspersky Social Virus
It’s been a few days since Kaspersky Lab’s blog post about the Multi Platform Facebook malware that was spread through Facebook Messenger. At the same time as Kaspersky Lab were analyzing this threat, a few researchers where doing the same, including Frans Rosén, Security Advisor at Detectify.
After Frans saw David’s tweet about the blog post, he called David and asked why they were both doing the same job. Frans had a good point, so they started to compare notes and found out that Frans had actually analyzed some of the parts that David hadn’t. They decided to jointly write this second part of the analysis, which is going to describe the attack in detail.
Spreading mechanism
Frans spent quite some time analyzing the JavaScript and trying to figure out how the malware was spreading, which might seem like a simple task but it wasn’t. There were multiple steps involved trying to figure out what the Javascript payloads did. Also, since the script dynamically decided when to launch the attack, it had to be monitored when the attackers triggered it.
The conclusions can be broken down into a few steps, because it’s not only about spreading a link, the malware also notifies the attackers about each infection to collect statistics, and enumerates browsers. We tried summarizing the steps as simply as possible below:
The victim receives a link on Facebook Messenger from a friend.
The link goes to Google Docs with an image that looks like a fake video player with the friend’s profile picture.
Clicking on that link using Chrome will send you to a fake YouTube page that asks you to install a Chrome Extension directly on the page.
Installing that Chrome Extension will then spread malicious links to the victim’s online friends, combined with the victim’s profile picture.
There are some interesting things in all these steps, so we will take a closer look below.
Technical details
Facebook message
The message itself will consist of the first name of the user that gets the message, the word “Video” and one of these emojis selected at random:
together with a link created with a URL shortener.
Google Docs shared PDF preview
Clicking on the link will redirect the user to a URL on docs.google.com. This link is made by using the preview link of a shared PDF, most likely because it is the quickest way to get a large controlled content area on a legit Google domain with an external link.
The PDF itself is created using PHP with TCPDF 6.2.13 and then uploaded to Google Docs using Google Cloud Services. Clicking the will send us to a page containing details about the PDF file being previewed.
The share settings are an interesting detail about the link created:
“Anyone can edit”. This configuration means that anyone who has the link can actually edit it. Looking at how these links spread, the attack reuses the same link for all the victim’s friends. One friend changing the access rights of the link could potentially prevent the attack from spreading to the victim’s other friends.
Another interesting detail is the user who created the file. Collecting a bunch of examples, we can see some patterns:
These were four links created for different victims, but three of them share the same IAM username (ID-34234) even though they were created using different Google Cloud Projects.
At the time of the attack, none of the URLs being linked from the PDF preview were blacklisted by Google.
Redirect party
After the Google Docs link is clicked, the user will go through a bunch of redirects, most likely fingerprinting the browser. Below, we will focus on Chrome as it is clear it was one of the targeted browsers for the spreading mechanism.
For the other browsers, ads were shown and adware was downloaded, read more about this under Landing Pages below.
Fake YouTube page with Chrome Extension installation
When using Chrome, you are redirected to a fake YouTube page. We noticed several different domains being used during the attack.
This page will also ask you to install a Chrome Extension. Since you can install a Chrome Extension directly on the page, the only action the victim had to perform was to click “Add extension”. No other interaction after that point was needed from the victim for the attack to spread further.
Chrome Extension
Several different Chrome Extensions were used. All of the extensions were newly created and the code was stolen from legit extensions with similar names. The differences in the extensions’ Javascript code were the background.js and a modification in the manifest.json.
The manifest was changed to allow control over tabs and all URLs, and also to enable support for the background script:
The background script was obfuscated differently in all the Chrome Extensions we found, but the basic concept looked like this:
Obfuscated background script
This script was interesting in many ways.
First, the background script would fetch an external URL only if the extension was installed from the Chrome Webstore; a version installed locally using an unpacked extension would not trigger the attack.
The URL being fetched would contain a reference to another script. This script would be sent into a Javascript blob using URL.createObjectURL and then executed in the background script.
This new script from the blob would also be obfuscated. It looked like this:
What happens here is the following:
Add a listener to all tabs when the tab has loaded successfully.
When the tab is loaded, make a new request to another URL. If the response contains anything, it will send it to the tab that triggered it using executeScript. This will run the Javascript in the context of the tab making the request, basically injecting an XSS that will trigger directly.
Getting all the scripts
When doing the research trying to identify the file that was being injected, I noticed that the attackers’ command and control server did not always return any code. My guess is that they were able to trigger when the attack should spread or not either manually or by specify when the attack should start.
To avoid sitting and waiting for a request to hit, I built my own pseudo extension doing the same thing as they did, but instead of triggering the code, I saved it locally.
Browsing around for a while, I noticed I got a bunch of hits. Their endpoint was suddenly returning back code:
The code returned was not obfuscated in any way, and had a simple flow of what it should do. It was fully targeted towards Facebook.
The script did the following:
Check that the domain it ran on contained facebook.com
Extract the CSRF token for a requests on Facebook, called fb_dtsg. Check if it had already fetched the access token (being used to make authenticated calls to the Facebook API). If not, it would make a request which is commonly made on Android to get the access token using the CSRF token.
Send the access token + profile ID to an external site owned by the attackers.
Make sure that the platform functionality is enabled (disabling the platform kill-switch):
Create a legacy access token. It turns out that Facebook has deprecated their FQL API, which is an old way of talking with the Facebook API:
But the attackers found out that if you made an access token using the app called “Pages Manager for iOS”, the FQL API would still be enabled.
Now, let’s move on to the most interesting parts of what the script did.
Analytics for the attackers, liking a Facebook page
The script would like a page on Facebook that was hardcoded in the script. This was most likely used by the attackers to count the amount of infected users by keeping an eye on the amount of likes on this page.
Watching the page used during one phase of the attack, the amount increased fast, from 8,900 at one point:
and up to 32,000 just a few hours later:
It was also clear that they had control over when it should trigger or not using the script fetcher from the Command and Control, since the amount of likes increased at extremely varying speeds during the attack.
They also changed pages during the attack, most likely because they were closed down by Facebook.
Fetching your friends
Since the attackers now had an FQL-enabled access token, they could use the deprecated API to fetch the victim’s friends sorted by date of their online presence, getting the friends that were online at the time.
They randomized these friends picking 50 of them each time the attack would run only if the friends were marked as idle or online.
A link was then generated by a third domain, which only received the profile ID of the user. This site most likely created the PDF on Google Docs with the profile picture of the current victim and passed the public link back through a URL shortener.
After the link was fetched, a message was created randomly for each friend, but the link was reused among them.
Interesting details
Some parts of the injected code were never used, or were leftovers from previous attacks.
One part was the localization function to send messages in the proper locale of each friend. This was replaced by the random emoji in the live attack:
login.php
Some files on the domains used had some easy to guess PHP files still on the server such as login.php. That one exposed a login script to Facebook together with a hardcoded email address:
Versioning
We noticed multiple versions of the injected Facebook script being used. At the end of the attack, the script only liked the Facebook page and did not spread at all. Also, the domain being used to gather access tokens was removed from the script.
Landing pages
As already mentioned, the script also enumerates which browser you are using. The Chrome extension part is only valid for victims using Google Chrome. If you are using a different browser, the code will execute other commands.
What makes this interesting is that they have added support for most of the operating systems; we were not able to collect any samples targeting the Linux operating system.
All of the samples that we collected where identified as Adware, and before the victim landed on the final landing page, they were redirected through several tracking domains displaying spam/ads. This is an indication that the people behind this scam were trying to earn money from clicks and distributing spam and ads.
Safari
MD5 (AdobeFlashPlayerInstaller.dmg) = d8bf71b7b524077d2469d9a2524d6d79
MD5 (FlashPlayer.dmg) = cfc58f532b16395e873840b03f173733
MD5 (MPlay.dmg) = 05163f148a01eb28f252de9ce1bd6978
These are all fake Adobe Flash updates, but the victim ends up at different websites every time, it seems that they are rotating a set of domains for this.
Mozilla Firefox
MD5 (VideoPlayerSetup_2368681540.exe) = 93df484b00f1a81aeb9ccfdcf2dce481
MD5 (VideoPlayerSetup_3106177604.exe) = de4f41ede202f85c370476b731fb36eb
“I was infected by this, what do I do?”
The Google Chrome Security Team has disabled all the malicious extensions, but when the attackers infected your Facebook profile they also stole an access-token from your Facebook account.
With this access-token the attackers will be able to gain access to your profile again, even if you have for example: Changed your password, signed out from Facebook or turned off the platform settings in Facebook:
We are currently discussing this with Facebook but at the moment it seems like there is no simple way for a victim to revoke the token the attackers stole.
It’s highly recommended that you update your Anti Virus solution because the malicious domains and scripts have been blocked.
Summary
The attack relied heavily on realistic social interactions, dynamic user content and legit domains as middle steps. The core infection point of the spreading mechanism above was the installation of a Chrome Extension. Be careful when you allow extensions to control your browser interactions and also make sure you know exactly what extensions you are running in your browser. In Chrome, you can write chrome://extensions/ in your URL field to get a list of your enabled extensions.
We would like to give out special thanks to the following people who helped us shut down the attack as much as possible:
Marc at CloudFlare
Trevor Pottinger at Facebook
April Eubank at Facebook
Rodrigo Paim at Facebook
Adam Rudderman and Jack Whitton of the Facebook Security team
Nav Jagpal at Google
Without your help this campaign would have been much more widespread. Thank you for your time and support! Also thanks to @edoverflow for poking at the obfuscated code at the same time as us.
Watch out! Adware spreading via Facebook Messenger
27.8.2017 securityaffairs Social
Security experts from Kaspersky Lab have spotted an ongoing cross-platform malware campaign that leverages Facebook Messenger.
Security experts from Kaspersky Lab have spotted an ongoing cross-platform malware campaign on Facebook Messenger, spammers are actually infecting users of all platform with adware.
Users receive a video link that redirects them to a bogus website set up to lure them to install a malware.
Researchers believe threat actors leverage compromised accounts, hijacked browsers, or clickjacking techniques to spread the malicious link.
They use social engineering to trick users into clicking the video link, which pretends to be sent from one of their Facebook contacts.
“The initial spreading mechanism seems to be Facebook Messenger, but how it actually spreads via Messenger is still unknown. It may be from stolen credentials, hijacked browsers or clickjacking. At the moment we are not sure because this research is still ongoing.” reads the analysis published by Kaspersky Lab.
The malicious message reads “< your friend name > Video” followed by a bit.ly link, as shown.

When the victim clicks on the fake video, the malicious code redirects him to a set of websites which gather information on his system (i.e. Browser, OS) to choose the website to which he has to be redirected.

Users are redirected following a domain chain, many websites on different domains used to redirect the victim depending on some characteristics (i.e. System info, Language, geo location, browser information, operating system, installed plugins and cookies).
The URL redirects victims to a Google doc that displays a dynamically generated video thumbnail that appears like a playable movie, based on the sender’s images. If the victim clicks the thumbnail he his redirected to another customised landing page depending upon their browser and operating system.
“What I noticed during my research was that when changing the User-Agent header (browser information) the malware redirects you to different landing pages. For example, when using FIREFOX I was redirected to a website displaying a fake Flash Update notice, and then offered a Windows executable. The executable is flagged as adware.” continues the analysis.
Google Chrome users, for example, are redirected to a website that appears as YouTube that displays a fake error message popup, tricking victims into downloading a malicious Chrome extension from the Google Web Store.
The fake extension is a downloader that delivers a file to the victim’s computer.

Experts observed similar tricks for Apple Mac OS X Safari users and Linux users.
“It has been a while since I saw these adware campaigns using Facebook, and its pretty unique that it also uses Google Docs, with customized landing pages. As far as I can see no actual malware (Trojans, exploits) are being downloaded but the people behind this are most likely making a lot of money in ads and getting access to a lot of Facebook accounts.” concluded Kaspersky.