Social Articles - H 2020 1 2 3 4 5 6 7 Social List - H 2021 2020 2019 2018 1 Social blog Social blog
Hackers Are Using An Effective Way to Spread Fake News From Verified Accounts
10.6.2017 thehackernews Social
Social media networks are no doubt a quick and powerful way to share information and ideas, but not everything shared on Facebook or Twitter is true.
Misinformation, or "Fake News," has emerged as a primary issue for social media platforms, seeking to influence millions of people with wrong propaganda and falsehoods.
In past years, we have seen how political parties and other groups have used spoofed social media profiles of influencers or leaders to spread misinformation, and most of the time such techniques work to successfully convince people into believing that the information is true.
Although social media services like Facebook, Twitter, and Google, offers account verification (verified accounts with blue tick) for public figures, we have seen hackers hijacking verified accounts to spread fake news from legitimate account to their millions of followers.
Now, researchers have uncovered a new, cunning attack technique currently being used by hackers to take over verified Twitter accounts and rename them to influential people in order to spread fake news.
Dubbed DoubleSwitch, the attack begins with a simple account takeover, but then the hackers change the username and display name with the one having a large influence on social media.
According to a new report from digital rights group Access Now, hackers are targeting Twitter accounts of journalists, activists, and human rights defenders in Venezuela, Bahrain, and Myanmar, some of them were verified with a large number of followers.
This attack was discovered when two journalists — Milagros Socorro and Miguel Pizarro, a member of Venezuela's parliament — were hacked and then renamed.
What's creepy? The hacker then registered a new account, resembling with their original profiles, under the original usernames (Twitter handles), but using the attacker's controlled email addresses.
This means, every time victims try to recover their accounts using regular password reset option, the confirmation emails will be sent to the hijacker, who pretends that the issue has been resolved, making it almost impossible for the victims to recover their account.
Hackers then use hijacked verified accounts, but renamed to another influence, to feed fake news to the millions of followers of the original accounts.
While it's unclear how the hackers managed to hijack the verified users at the first place, it is believed that the attack begins with malware or phishing attacks.
How DoubleSwitch Attack Works (Illustrated Example)
To illustrate how effective DoubleSwitch technique is, we have prepared an example below:
Let's say, a hacker somehow managed to hijack The Hacker News’ Twitter account (@thehackersnews), which is verified with 368,000 followers, where most of the are influencers in Infosec community.
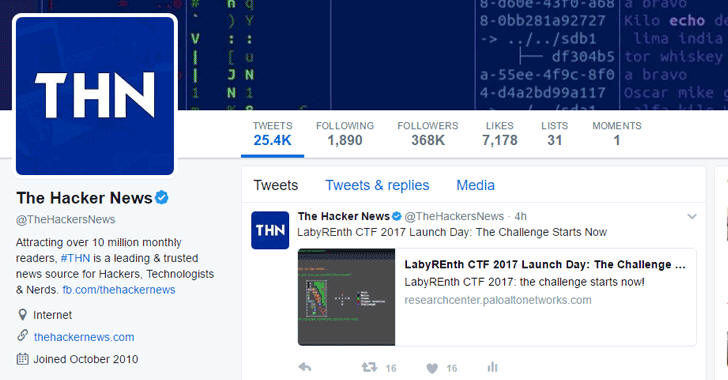
Original @thehackersnews Twitter Account
And then the "DoubleSwitch" begins.
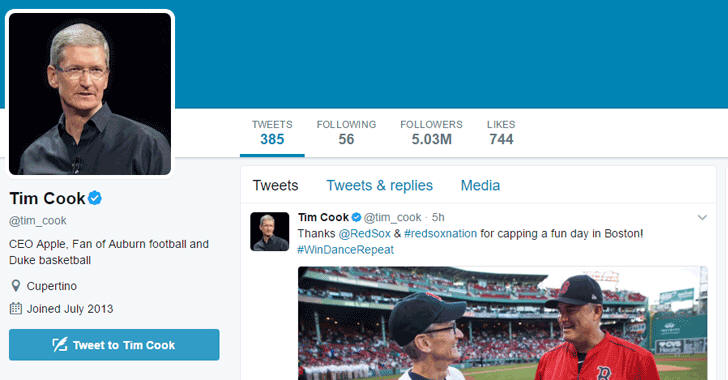
Original Tim Cook Twitter Profile
The First Switch: Once hacked, the hacker first changes the password and associated email id, along with the username, let's say @tim__cook, spoofing the Apple's CEO who is on Twitter with @tim_cook (single underscore).
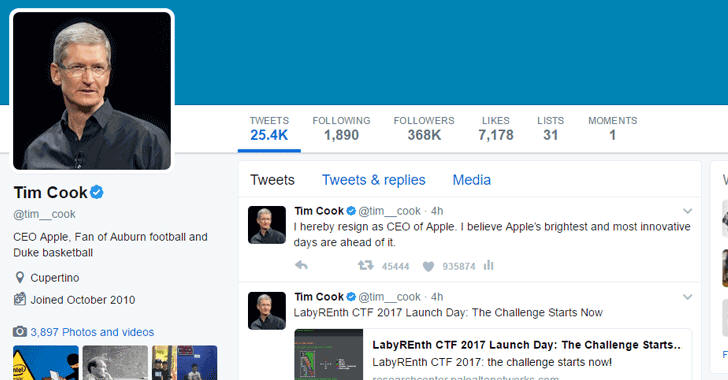
Hijacked @thehackersnews Account (Impersonates Tim Cook)
Now, the hacker holds a verified account with the name of Apple CEO Tim Cook and can feed misinformation to nearly 370,000 influential followers from the tech industry, and many of them will believe without realising the account is hijacked and the tweets from it are fake.
The Second Switch: The hacker creates a new Twitter account with the original username @thehackersnews, which will be available, as once a Twitter account is deactivated, the handle for that account is freed for others to use.
But mind it, this new Twitter account registered with our Twitter handle (@thehackersnews) will not be verified with zero followers.
Locking the Legitimate Account Owner Out of its Account
In order to get our account back, if we use password reset option, Twitter will send the confirmation email only to the attacker' email id that he used to register the new account.
So any attempt by the victim to regain access to its account fails, as the attacker can simply notify Twitter that the issue has been resolved, locking out the legitimate account holder.
Fortunately, Twitter also offers an alternative way, an online form, to report account hacking incidents directly to the Twitter team, which then they review and investigate the issue accordingly to help victims recover their accounts.
Using this method, Access Now helped the journalists regain access to their accounts, but by the time they regained access, some of the original account holder’s tweets were deleted, and the accounts were used to spread the fake news about events in Venezuela, confusing followers and damaging their reputations in the process.
Access Now says the attack can be conducted over Facebook and Instagram as well, but users can protect themselves by enabling two-factor authentication feature offered by the services.
Two-factor authentication uses two different methods in an attempt to verify a user's identity — a password and a one-time passcode (OTP) sent to the user's mobile phone — which makes it much harder for hackers to compromise an account in the first place.
However, two-factor verification is not an actual solution for the journalists, activists and human rights defenders in countries like Venezuela, as they do not associate their personally-identifiable information like phone numbers with their online accounts in fear of getting spied on.
Facebook Redesigns Security Settings Page
2.6.2017 securityweek Social
Facebook this week announced the roll-out of a redesigned security settings page, meant to make it easier for users to understand the options provided to them.
As part of the redesign, the social networking platform focused on making important settings easily identifiable and more visible to all users. The changes are based on the results of a research the company recently conducted in an effort to better understand how people use security settings on Facebook, Heidi Shin, product manager on the Protect and Care team, explains.
Users accessing Facebook’s security settings page will find items such as two-factor authentication and Trusted Contacts at the top, in a recommended section. The featured recommendations are tailored according to each person’s needs and similar options are grouped into modules for simplified layout and ease of use.
Another important change Facebook made to its security settings was to bring the names of different options in line with those used by other online services. Thus, two-factor authentication is now visible under this name, and not “login approvals,” as before.
“After finding in our research that ‘two-factor authentication’ was the most recognized term, we adjusted the name. By focusing on clarity, we’re making it easier for people to find and enable these features on Facebook as well as other online services,” Shin notes.
Additionally, Facebook decided to completely redesign the “Where you're logged in” module, which now features a simpler format, clearly showing the device, location, and login date and time for each place a user’s logged in.
“We also looked closely at features that people had clicked on but ultimately decided not to enable. We found that it was usually the product description — not the name itself — that was discouraging people from completing the action,” Shin explains.
Users looking to improve their security on the social platform can do so by clicking the arrow in the top right corner of the screen, selecting Settings, and then clicking Security + Login on the left-hand side to access the redesigned page.
Social Security Administration Adopts What NIST is Deprecating
1.6.2017 securityweek Social
As of June 10 2017, users of the Social Security Administration (SSA) website will be required to use two-factor (2FA) authentication to gain access. Potentially, this could affect a vast number of American adults, who will be required to enter both their password and a separate code sent to them either by SMS or email text.
What is surprising is that in July 2016, NIST deprecated SMS-based 2FA in special publication 800-63B: Draft Digital Identity Guidelines. It should be noted this is still a draft, and not yet a formal standard that government agencies are required to meet; but nevertheless, it specifically says, "OOB [2FA] using SMS is deprecated, and may no longer be allowed in future releases of this guidance." It seems strange, then, that the SSA should introduce precisely what NIST deprecates.
NIST has chosen to denounce SMS because it is flawed, and not just because there are stronger alternatives. Publication 800-63B stresses, "Due to the risk that SMS messages may be intercepted or redirected, implementers of new systems SHOULD carefully consider alternative authenticators" (section 5.1.3.2). This is not a hypothetical risk. German newspaper Suddeutsche Zeitung reported on May 3, 2017 that criminals had relied on Signaling System No. 7 (SS7) attacks to bypass two-factor authentication systems and conduct unauthorized wire transfers.
SS7 is an underlying mobile telephony protocol deeply embedded in the worldwide mobile telephony system. It was developed in 1975, without much regard to security, to allow easy signal transfer between towers. "It is full of flaws," explains Martin Zinaich, information security officer at the City of Tampa. "Most of those flaws are 'by design' to keep calls connected from tower to tower. It doesn’t make sense to utilize 2FA when that second factor is so easily breached." And it is unlikely that SS7 will ever be fixed.
The initial plan from the SSA had been to offer only SMS-based 2FA. "Last summer," explains Jim Borland, acting deputy commissioner for communications in a blog post early this month, "we added a second way for us to check your identity when you registered or signed in to my Social Security. However, at that time, we only allowed the use of a cell phone as your second identification method. We listened to your concerns, and beginning on June 10, you can choose either your cell phone or your email address as the second way for us to identify you. Since an email address is already required to use my Social Security, everyone can continue to benefit from the features my Social Security provides."
The problem was that many of the SSA's 30 million users did not have SMS-capable phones. "The initial rollback of last year's plan to use SMS messages as the sole means to receive a one-time passcode was done due to, primarily, a convenience issue, since most users of the SSA website were found to not have phones capable of receiving SMS messages," explains Nathan Wenzler, chief security strategist at consulting firm AsTech. "Some estimates suggested that up to two-thirds of users would be affected in this way."
But he continued, "Adding the option to receive an email does not add any additional security, either, as email accounts can also be compromised in many ways, allowing an attacker to intercept the one-time passcode sent to a user's inbox as well. Is the SSA meeting [current] policy requirements? Yes. Are they creating a more secure site for their users? Not really."
Chris Roberts, chief security architect at threat detection firm Acalvio is just as damning. "I won't sugarcoat this: of all of those that could be affected, seniors are the most wary of text messages, especially when so many damn scams come across as text messages these days. Therefore, this might not be the best solution. The fact that it's been proven several times that a text 2FA does little to help combat fraud means that there's still a lot that the SSA needs to do."
The SSA, however, is in a difficult position. It provides a necessary service to a large number of citizens, many of whom were born before the technology and internet revolution. Some have never adapted, but still rely on the SSA. In order to maintain its service to all its customers, it is forced to adopt the lowest common denominator for its 2FA. Normally, this would be SMS 2FA -- but for the SSA's particular range of customers, even that is too high. It supplemented SMS with email text. The result is simply a weak and vulnerable form of authentication, albeit stronger than passwords alone. "Using email as a way to verify Americans," comments Marc Boroditsky, VP and GM of Authy, "is, at best, misguided, and, at worst, a high-risk attack vector for massive fraud."
Could it have done better? Yes, says Boroditsky. "Even if someone's phone number isn't text-enabled, you can still do phone number verification or 2FA over a simple voice call to that person. And with regard to 'technical complexity' of 2FA, this should be really straightforward. I've seen developers build a verification app in 5 minutes that works with nearly every phone on the planet."
But flawed 2FA is not the only SSA departure from NIST's draft guidelines. NIST takes the view that password length is more important than password complexity. "Since the size of a hashed password is independent of its length, there is no reason not to permit the use of lengthy passwords (or pass phrases) if the user wishes." This allows the user to use a phrase based on, for example, a favorite line of poetry: easy for the user to remember, hard for the criminal to crack. "Allow at least 64 characters in length to support the use of passphrases," recommends NIST. "Encourage users to make memorized secrets as lengthy as they want, using any characters they like (including spaces), thus aiding memorization." But the SSA website currently accepts passwords of between only 7 and 20 characters.
If NIST's draft guidelines become reality unchanged, the SSA will have much to do. It will know this. It might be expecting an exemption; or the current changes might simply be a holding-exercise while it develops a better system more in line with NIST's expectations. What other factors could the SSA adopt? Tom Conklin, Sr. director of security & compliance at Vera, comments, "That's a challenge because nothing is perfect, not everyone has a cell phone, email can be compromised, and private keys can be stolen. One approach would be for the social security to adopt an open standard like FIDO universal second factor. This way anyone with a FIDO compatible device or app could use it with the Social Security website.
LinkedIn Hacker, Wanted by US & Russian, Can be Extradited to Either State
31.5.2017 thehackernews Social
The alleged Russian hacker, who was arrested by the Czech police in Prague last October on suspicion of massive 2012 data breach at LinkedIn, can be extradited to either the United States or Russia, a Czech court ruled on Tuesday.
Yevgeniy Aleksandrovich Nikulin, a 29-years-old Russian national, is accused of allegedly hacking not just LinkedIn, but also the online cloud storage platform Dropbox, and now-defunct social-networking company Formspring.
However, he has repeatedly denied all accusations.
Nikulin was arrested in Prague on October 5 by the Czech police after Interpol issued an international arrest warrant against him.
Nikulin appeared at a court hearing held inside a high-security prison in Prague on Tuesday and emaciated after eight months in solitary confinement.
The court ruling, pending appeals, left the final decision in the hands of Czech Justice Minister Robert Pelikan, who can approve extradition to one of the countries and block the other.
The United States has requested Nikulin extradition for carrying out hacking attacks and stealing information from several American social networking companies, including LinkedIn, Dropbox, and Formspring, between March 2012 to July 2012.
However, Russia, where Nikulin is facing a lesser charge, has requested his extradition on a separate cyber theft charge of stealing $3,450 via the Internet in 2009.
"Both [case] documents are very, very sufficient for reasonable suspicion that [the offenses] took place and that there is a reason to press charges," the judge said.
Hacker Claims FBI Pressured Him to Confess to US Election Hacks
Nikulin's arrest last October came three days before the United States officially accused Russia of hacking the Democratic National Committee (DNC) and interfering in the 2016 presidential election.
Nikulin's lawyer says the case is a set-up, indicating that his arrest may have deeper inclinations than over the cyber attacks against American firms.
The Guardian reported Nikulin was interrogated in Prague, where he currently remains imprisoned, by FBI special agent Jeffrey Miller.
Nikulin wrote in a letter from prison that during his interrogation, Miller reportedly brought up the US election hacking and claimed that the FBI agent pressured him to admit to the DNC hack and promised him good treatment if he accepted to cooperate.
Nikulin wrote in the letter that he rejected the offer. His lawyer indicated that Nikulin was not a hacker, but just a victim of an FBI plot.
"Do you really imagine that a high-ranking FBI agent is going to travel all the way from San Francisco just to read this guy his rights?," Nikulin lawyer said.
Mark Galeotti, a senior security researcher at the Institute of International Relations Prague, also showed his concern about an FBI agent traveling to another country to extradite a hacker.
"An FBI agent traveling from the US to a third country as part of an extradition request is extremely unusual and highlights that the case is seen as significant," Galeotti said, as quoted by the Guardian.
Nikulin's Russian lawyer stated that his client's life revolved around buying and selling luxury cars, adding that Nikulin was "useless with computers" and capable of checking his email and no more and, far from being a super-hacker who can hack big firms.
Tuesday's court hearing was held in a tiny room inside the prison for security reasons, to which Nikulin’s Czech lawyer said: "In all my 25 years as a lawyer, I don’t remember any cases being tried inside the prison, including serial killers or organized crime cases."
Now, the final decision is in the hands of the Czech Justice Minister Robert Pelikan, who is slated to decide where Nikulin will be extradited: The United States, where he can face a "disproportionately harsh" sentence of 54 years behind bars, or Russia, where he faces a lesser charge of cyber theft.
Twitter Bug Allowed Publishing Tweets From Any Account
24.5.2017 securityweek Social
A bug in the Twitter social network allowed an attacker to post tweets as a different user, without having access to the victim’s account.
Discovered by a security researcher going by the name of kedrisec, the issue was reported to Twitter on February 26 and was resolved two days later. The vulnerability was assessed High severity and the reporter received a $7,560 bounty for it.
The issue resided in the handling of Twitter Ads Studio requests, Twitter explains: “By sharing media with a victim user and then modifying the post request with the victim's account ID the media in question would be posted from the victim's account.”
No evidence of the flaw being exploited in the wild has been found so far, with the reporter being the only one to have leveraged the vulnerability, Twitter says.
In their write-up, the researcher explains that the issue leverages Twitter’s ads service, which “has media-library with the possibility to upload media-files (video, pictures, GIF-animation).” The service also offers the option to review media-files uploaded before and which were used when a tweet was published.
The library is located at https://ads.twitter.com/accounts/*id_of_user_account*/media and allows the user not only to view the media file, but also to tweet the file or share it with other users. The function for tweeting has access to account_id, owner_id (image owner), user_id (the user the tweet will be published to), and media_key (id of the media-file that is being published).
Attempting to replace the owner_id and user_id in intercepted GET request and JSON or in POST returned errors. The POST error, however, revealed that the service doesn’t accept the user with the replaced owner_id as the owner of the media file.
The researcher then attempted to modify not only owner_id and user_id, but media_key in POST as well, which resulted in a successful attempt of tweet publication. While this allowed the researcher to publish as any user, it did show a limitation: they could publish only if the user had media-files uploaded and also had to know the media_key of the file, which is almost impossible to get, as it contains 18 digits.
However, if the attacker shared a media-file with the targeted user (meaning the attacker already knows the media_key), the service would consider the victim being the owner of the file, thus allowing the attacker to successfully impersonate the victim when tweeting.
In short, the attack would include the following steps: uploading a file, sharing the file with the targeted user, intercept the query for tweet publication and change in POST the owner_id and user_id (the media_key, which is already known to the attack, doesn’t change).
Europol Probing IS Setting Up of Social Network
4.5.2017 securityweek Social
The Hague - European police are probing whether the Islamic State group and other extremists are setting up a social network to spread propaganda, gain funding and avoid security crackdowns, an official said Wednesday.
"We are investigating the possibility that IS and other terror groups are setting up a social media platform," said Jan Op Gen Oorth, communications officer for the Europol policing agency.
"We are still working on identifying the full details of the account, including who has set it up and for what purpose," Oorth told AFP, but added that it showed likely links to IS and other extremists.
The investigation comes as Europe's policing agency struck out at online radical groups last week in a two-day operation.
Together with officers from Belgium, Greece, Poland, Portugal and the United States, Europol assessed more than 2,000 pieces of online content last Tuesday and Wednesday as "harmful and illegal" and referred them to online service providers for removal, the agency said in a statement.
"This coordinated hit against online terrorist propaganda focused mainly on the online production of terrorist materials by IS and Al-Qaeda affiliated media outlets," Europol said.
Among the items referred were propaganda videos and publications glorifying or supporting terrorism and extremism, it said.
Europol added that "efforts made by numerous online platforms to remove inappropriate content have driven supporters of terrorist groups to simultaneously use multiple platforms to promote terrorism and incite violence".
"They have also been searching for new service providers to make sure their messages reach potential supporters, while a growing interest for platforms that do not require identification can be witnessed," the agency said.
UK Government Complains After Twitter Cuts Data Access
27.4.2017 seciurityweek Social
The British government has complained to Twitter over a block on access to data from the social network, which it was reportedly using to track potential terror attacks, officials said Wednesday.
"The government has protested against this decision and is in ongoing discussions with Twitter to attempt to get access to this data," a Home Office spokesman said.
Prime Minister Theresa May's spokesman declined to specify exactly what the data was and why it was important, saying only that "we wish to have access to this information".
But he told reporters: "The fight against terrorism is not just one for the police and the security services. Social media and tech companies have a role to play."
The Daily Telegraph newspaper reported that the government had been tracking terms related to potential terror attacks via a third-party firm, but this had now been blocked.
In a blog posting in November, Twitter executive Chris Moody said the firm encouraged developers to create products that used real-time data from the social network "in the public interest", for example tracking emergencies and natural disasters.
"Recent reports about Twitter data being used for surveillance, however, have caused us great concern," he wrote.
He said that tracking or profiling protesters or activists was "absolutely unacceptable and prohibited", including via Twitter's application software programs.
"We prohibit developers using the Public APIs and Gnip data products from allowing law enforcement -- or any other entity -- to use Twitter data for surveillance purposes. Period," he said.
Facebook dismantled a huge spam campaign leveraging bogus accounts
16.4.2017 securityaffairs Social
Facebook disrupted an international spam campaign leveraging on bogus accounts used to create “likes” and bogus comments.
The security team at Facebook has disrupted an international spam operation after a six months investigation. The company has neutralized a coordinated campaign that was leveraging on bogus accounts used to create inauthentic likes and comments.
“Today we are taking another step to disrupt a spam operation that we have been combating for six months. It is made up of inauthentic likes and comments that appear to come from accounts located in Bangladesh, Indonesia, Saudi Arabia, and a number of other countries.” states a blog post published by Facebook.”We found that most of this activity was generated not through traditional mass account creation methods, but by more sophisticated means that try to mask the fact that the accounts are part of the same coordinated operation.”
The intent of the campaign was to deceptively increase their social network by adding new friend connections by liking and interacting primarily with popular publisher Pages on Facebook. The attacker used their network of connections to send out spam messages. A huge number of bogus accounts became dormant after liking a number of Pages, “suggesting they had not been mobilized yet to actually make connections and send spam to those people.”
Systems at Facebook were able to identify the fraudulent activities and to remove a significant volume of inauthentic likes, even if attackers used tricks to avoid detection such as the traffic redirection through “proxies” that disguised their location.
“By disrupting the campaign now, we expect that we will prevent this network of spammers from reaching its end goal of sending inauthentic material to large numbers of people.” continues Facebook.
spam campaign
As result of the Facebook activity, the experts at the company expect that 99% of impacted Pages with more than 10,000 likes will see a drop of less than 3%.
Facebook confirmed security improvement to its system to prevent any abuse of its platform, social networks are today privileged attack vectors for crooks.
“We’ve found that when people represent themselves on Facebook the same way they do in real life, they act responsibly,” said Shabnam Shaik, a company security manager.
“Fake accounts don’t follow this pattern, and are closely related to the creation and spread of spam.”
Facebook Disrupts Suspected Spam Operation
15.4.2017 securityweek Social
Facebook on Friday said it disrupted an international fake account operation that was firing off inauthentic "likes" and bogus comments to win friends it would then pound with spam.
Facebook's security team spent six months fighting to neutralize what they saw as a coordinated campaign, according to Shabnam Shaik, a company security manager.
"Our systems were able to identify a large portion of this illegitimate activity -- and to remove a substantial number of inauthentic likes," Shaik said in a blog post.
"By disrupting the campaign now, we expect that we will prevent this network of spammers from reaching its end goal of sending inauthentic material to large numbers of people."
The ring used accounts in a number of countries including Bangladesh, Indonesia and Saudi Arabia.
The group tried to mask its activities with tactics like connecting with the social network through "proxy" servers to disguise where "likes," posts or other communications were originating, according to Shaik.
Facebook said the campaign aimed to trick people into connecting as friends they would later target with spam. The company said it had derailed the operation early enough to spare users that fate.
The leading social network this week said it has started weeding out bogus accounts by watching for suspicious behavior such as repetitive posts or torrents of messages.
The security improvement was described as being part of a broader effort to rid the leading social network of hoaxes, misinformation and fake news by verifying people's identities.
"We've found that when people represent themselves on Facebook the same way they do in real life, they act responsibly," Shaik said.
"Fake accounts don't follow this pattern, and are closely related to the creation and spread of spam."
Under pressure to stymie the spread of fake news, Facebook has taken a series of steps including making it easier to report such posts and harder to earn money from them.
Social Media Passwords Provide Easy Route into Corporate Networks
3.4.2017 securityweek Social
A combination of 'security fatigue' among users and inadequate password controls among the social media giants is providing a large attack vector for cybercriminals. This is the conclusion of a newly published survey that queried more than 250 security professionals at the RSA Conference in San Francisco in February 2017.
The survey (PDF), conducted by Thycotic, found that password hygiene is severely lacking even among security professionals. It found, for example, that 50% of security professionals have not changed their social network passwords for a year or more, and 20% have never changed them. When this is coupled with social networks not enforcing their own security options, the result is a weak underbelly for criminals to get into corporate networks.
"As we know," said Joseph Carson, Chief Security Scientist at Thycotic, "social networks give away a lot of private information. For people to not consider changing their passwords on a regular basis on their Facebook, Twitter and LinkedIn accounts, they are easily allowing hackers to access information that will grant them access to other facets of their lives, like their work computers and email. Not only is this a huge vulnerability, but this is also a flaw within large social networks that don't remind or make it clear and transparent to the user about the age or strength of the password or best practices."
It is a combination of factors that creates the problem. Users still use weak passwords and reuse them across multiple accounts. Thirty percent of the security professional respondents have used or are still using birthdays, addresses, pet names or children' names for their work passwords -- and all of these are easily crackable.
The problem is made worse by the increasing use of social media logons, where separate internet services allow users to log on with their Facebook, LinkedIn or Twitter password. "Social Logins creates a major security risk because it becomes the master key for all other accounts," Carson told SecurityWeek. "The problem stems further because it is not a proper vault and is used for more than just social logins -- such as for communication, email, browsing and online shopping -- so it is easily targeted and exploited."
One concerning implication from this survey is that user awareness training cannot solve the problem. The poor password practices of the respondents, said Carson, "is an indication that even security professionals continue to use weak passwords for social accounts and that cyber awareness training and cyber hygiene still has a lot of room for improvement. Much of this is a result of cyber fatigue and lack of built-in automation for social accounts."
According to Verizon's 2016 Data Breach Investigations Report, 63% of confirmed data breaches involved weak, default or stolen passwords. "The use of stolen, weak or default credentials in breaches is not new, is not bleeding edge, is not glamorous, but boy howdy it works," the DBIR says.
Forrester Research puts the breach figure even higher, estimating in its 'Forrester Wave: Privileged Identity Management, Q3 2016' report that up to 80% of breaches involve the abuse of privileged accounts. Thycotic's own research indicates that use of passwords as the primary authentication control is still growing, estimating that the 90 billion passwords currently in use will grow to 300 billion by 2020.
Carson does not believe that the solution can simply be awareness training and improved password practices. "There is no such thing as an uncrackable password," Carson told SecurityWeek; "but you can make it very difficult with the computing power plus time to crack the password -- which can deter the attacker from even trying to crack the password. In most cases, it is easier for the attacker to ask the user to tell them the password via phishing scams."
But the big takeaway from Thycotic's survey is that users -- even those users who should know better -- simply are not making it hard for the criminals. Coupled with the disinclination of social media giants to enforce strong access requirements, social media is providing an easy route into employees' accounts; and from there into corporate privileged accounts. Users, suggests Thycotic, cannot be relied upon to protect their passwords, making technology-based privileged account management an absolute necessity.
Twitter Suspends More Accounts Linked to 'Terrorism'
21.3.2017 securityweek Social
Twitter said Tuesday it suspended 376,890 accounts in the second half of 2016 for "promotion of terrorism," an increase of 60 percent over the prior six-month period.
The latest suspensions bring the total number of blocked accounts to 636,248 from August 2015, when Twitter stepped up efforts to curb "violent extremism," the company announced as part of its latest transparency report.
The actions come with social networks under pressure from governments around the world to use technology tools to lock out jihadists and others who use the platforms to recruit and launch attacks.
Twitter said separately the number of government requests for user data rose seven percent from the prior six-month period, but affected 13 percent fewer accounts.
For requests to remove content -- from governments and others including copyright holders -- the number of requests was up 13 percent but the number of accounts fell 37 percent.
Twitter announced that the FBI had informed the social network it was no longer under a "gag order" that prevented the disclosure of five cases involving "national security letters" -- special requests from the US law enforcement agency in national security cases.
As a result, Twitter was able to inform the affected users of the FBI requests.
"As we continue to push for more transparency in how we can speak about national security requests, we will update this new section in future transparency reports," Twitter stated.
Twitter, which is pressured by certain governments to remove "hate speech," disclosed for the first time a partnership with a third-party research group called Lumen to catalog any information removed.
Twitter said it began the agreement with Lumen in 2010.
"Unless we are prevented from doing so, when we withhold content in a certain country Twitter will continue to provide a copy of the request to Lumen so anyone can see what type of content was removed and who made the request," the company said.
Another section of the transparency report was devoted to "legal removals," or requests to remove content from verified journalists and other media outlets.
"Given the concerning global trend of various governments cracking down on press freedom, we want to shine a brighter light on these requests," Twitter said.
It received 88 legal requests from around the world to remove content posted by verified journalists or news outlets, but did not take any action on the majority of the requests, "with limited exceptions in Germany and Turkey," which accounted for 88 percent of such requests.
"For example, we were compelled to withhold tweets sharing graphic imagery following terror attacks in Turkey in response to a court order," Twitter said.
Facebook Bans Developers From Using Data for Surveillance
14.3.2017 securityweek Social
Facebook this week announced an update to its platform policies to ban developers from using data obtained from the company to build surveillance tools.
The change was made not only to the Facebook platform policy, but to the Instagram’s as well, and impacts all developers interested in using the Facebook and Instagram APIs to build applications and services.
Starting this week, the first data protection policy listed on Facebook for Developers (the same as the 28th general term on the Instagram platform policy page) also reads “don't use data obtained from us to provide tools that are used for surveillance.” Previously, it only required developers to protect the information received from the company “against unauthorized access, use, or disclosure.”
Earlier this year, software security startup Fallible revealed that many Android applications unnecessarily store keys or secrets (which could leak sensitive data) related to some of the most popular online services, Instagram included (along with Twitter, Flickr, Dropbox, Slack, Uber, and Amazon AWS).
Facebook is determined to both make the policy explicit and enforce it. Over the past several months, the company has been working with the American Civil Liberties Union of California (ACLU), Color of Change, and the Center for Media Justice on this update and on increasing the public awareness on the issue.
“Over the past several months we have taken enforcement action against developers who created and marketed tools meant for surveillance, in violation of our existing policies; we want to be sure everyone understands the underlying policy and how to comply,” Rob Sherman, Deputy Chief Privacy Officer, Facebook, says.
In October last year, Facebook (and Twitter) cut access to certain data for analytics firm Geofeedia after an ACLU report revealed that Geofeedia’s social media monitoring product was being “marketed to law enforcement as a tool to monitor activists and protesters.” The report was referring to the wave of protests in the Missouri community after the police shooting of an unarmed African-American man and also stated that “law enforcement has used Geofeedia to monitor protests.”
“Over the years, we have learned the importance of updating these policies to offer more clarity or incorporate constructive feedback. These changes help us improve our community and discourage unwanted behavior,” Sherman also notes.
Recently, Facebook updated its Advertising Policies to ban ads that promote payday loans, after an update last year more explicitly prohibited various kinds of discriminatory advertising. Future policy updates are to be expected as well, as the company works to “support our community,” Sherman concludes.
Facebook and Instagram will not allow developers from scanning social media profiles for surveillance
14.3.2017 securityaffairs Social
Facebook company and Instagram will not allow developers scanning their social media profiles for surveillance activities.
Facebook and it app Instagram have updated the terms and conditions to prevent developers from scanning social media profiles for surveillance activities.
A report recently published revealed the US Department of Homeland Security used software to scan social media accounts of people visiting the USA trying to identify terrorists.
The experiment was conducted by in December 2015 by the US Citizenship and Immigration Services, but the results obtained were not satisfactory.
The disappointing results pushed the DHS on looking for companies to improve their scanning capabilities.
“DHS has established a task force for using social media to screen applicants for immigration benefits. In connection with that effort, U.S. Citizenship and Immigration Services (USCIS) began pilots to expand social media screening of immigration applicants” reads the report. “
“In reviewing the pilot, USCIS concluded that the tool was not a viable option for automated social media screening and that manual review was more effective at identifying accounts,”
“USCIS based its conclusion on the tool’s low ‘match confidence.’ Because the resulting accounts identified by the tool did not always match up with the applicants, officers had to manually check the results. However, USCIS did not establish match benchmarks for the tool, so it does not know what level of match confidence would signify success or failure.”
FB surveillance
Facebook has decided to stop allowing private companies and Government agencies in using the data feeds belonging to its social media platform and Instagram for surveillance activities.
“Developers cannot ‘use data obtained from us to provide tools that are used for surveillance.’ Our goal is to make our policy explicit,” Facebook said.
“Over the past several months we have taken enforcement action against developers who created and marketed tools meant for surveillance, in violation of our existing policies; we want to be sure everyone understands the underlying policy and how to comply.”
Other IT giants have adopted a similar policy before Facebook, last year Twitter blocked US intelligence agencies from accessing a service that analyzes the content posted online through the social media platform in real time.
“Twitter Inc. cut off U.S. intelligence agencies from access to a service that sifts through the entire output of its social-media postings, the latest example of tension between Silicon Valley and the federal government over terrorism and privacy.” states the The Wall Street Journal.
The social media giant owns about a five percent stake in Dataminr which is the unique service allowed to access the real-time stream of public tweets.
Twitter banned third-party companies from selling data to intelligence agencies for surveillance. After a pilot programme conducted by In-Q-Tel now ended, the company told Dataminr that it will stop providing the service to the US Government. Dataminr has a $225,000 contract to provide its service to the Department of Homeland Security.
Of course, such kind of measure will not block surveillance programs conducted by the US intelligence that can demand data from Facebook via National Security Letters, or collect information through surveillance programs like PRISM.
Twitter Flaw Allowed Access to Locked Accounts
6.3.2017 securityweek Social
Twitter was until a few months ago affected by a vulnerability that could have been exploited to bypass the social media network’s account locking mechanism.
Twitter can lock user accounts for security purposes if it detects suspicious behavior which could indicate that an account may have been compromised. In order to have the account unlocked, the user needs to confirm they are the legitimate owner by providing some information, such as phone number and email address.
Security expert Aaron Ullger discovered that this account locking mechanism could have been easily bypassed by adding the targeted account to a mobile device. The researcher added the locked account to his iPhone (via the Settings page), installed the Twitter app on the device, and he was given full access to the account.
However, Ullger noticed that the targeted account remained locked on the Twitter website so the bypass had not been complete. In order to achieve a complete bypass, the expert used the iOS Twitter app to access the account’s settings and obtain the email address and phone number needed to unlock the account.
This vulnerability could have been useful for an attacker who had stolen the targeted user’s credentials, but wanted to prevent being locked out of the account.
“An attacker with knowledge of a locked account’s credentials would’ve been able exploit this issue to gain complete access to the victim’s profile,” Ullger said in a blog post.
The flaw was reported to Twitter on October 7 and it was patched a few days later. The researcher said he received an unspecified bug bounty for his work.
Last year, Ullger also reported finding a way to bypass the password reset initiated by Tumblr following the discovery of a significant data breach.
Twitter has been running a bug bounty program on the HackerOne platform since September 2014. Bug bounty hunters can earn as much as $15,000 for a serious remote code execution vulnerability affecting the company’s core services.
According to its HackerOne page, Twitter has so far received nearly 600 vulnerability reports and it has paid out a total of more than $600,000.
U.S. Could Ask Visa Applicants for Social Media Passwords
8.2.2017 securityweek Social
US embassies could ask visa applicants for passwords to their own social media accounts in future background checks, Homeland Security Secretary John Kelly said Tuesday.
Kelly said the move could come as part of the effort to toughen vetting of visitors to screen out people who could pose a security threat.
He said it was one of the things under consideration especially for visitors from seven Muslim majority countries with very weak background screening of their own -- Iran, Iraq, Libya, Somalia, Sudan, Syria and Yemen.
"We're looking at some enhanced or some additional screening," Kelly told a hearing of the House Homeland Security Committee. "We may want to get on their social media, with passwords," he said.
"It's very hard to truly vet these people in these countries, the seven countries... But if they come in, we want to say, what websites do they visit, and give us your passwords. So we can see what they do on the internet."
"If they don't want to cooperate, then they don't come in" to the United States, he said.
Kelly stressed that no decision had been made on this, but said tighter screening was definitely in the future, even if it means longer delays for awarding US visas to visitors.
"These are the things we are thinking about," he said.
"But over there we can ask them for this kind of information and if they truly want to come to America, then they will cooperate. If not, next in line."
The seven countries were targeted in president Donald Trump's January 27 immigrant and refugee ban order, which has sense been at least temporarily blocked under court order.
Facebook Proposes New Account Recovery Method
31.1.2017 securityweek Social
Facebook has proposed a new method for recovering accounts when users forget their passwords or their credentials are stolen by hackers, and it will be first tested by the members of GitHub.
The social media giant wants users to be able to recover their accounts via a method it calls “delegated recovery,” where an application delegates the capability to recover an account to a different account controlled by the same user at a third-party service provider.
GitHub users who want to test the method need to save a special recovery token in their Facebook account. If access to the GitHub account is lost, the user can re-authenticate to Facebook and the token is sent to GitHub with a time-stamped counter-signature to verify their identity.
The token is encrypted and Facebook will not share any personal information with GitHub. Furthermore, the data is transmitted over HTTPS to prevent it from being intercepted by a third-party.
This account recovery system will be covered by the Facebook and GitHub bug bounty programs. Based on feedback received from users, the social media company wants to improve the system and have it adopted by more services. Both Facebook and GitHub will release open source reference implementations in various programing languages.
“Usable security must cover all the ways we access our accounts, including when we need to recover them. We hope this solution will improve both the security and the experience when people forget a password or lose their phone and need to get back into their accounts,” said Brad Hill, a security engineer at Facebook.
Delegated recovery is promoted as an alternative to security questions, which are known to be risky, and email- and SMS-based methods, which do not offer the security guarantees many users expect today.
The announcement comes just days after Facebook announced support for Universal 2nd Factor (U2F) security keys.
Facebook Unveils 'Delegated Recovery' to Replace Traditional Password Recovery Methods
31.1.2017 thehackernews Social
How do you reset the password for your Facebook account if your primary email account also gets hacked?
Using SMS-based security code or maybe answering the security questions?
Well, it's 2017, and we are still forced to depend on insecure and unreliable password reset schemes like email-based or SMS code verification process.
But these traditional access recovery mechanisms aren't safe enough to protect our all other online accounts linked to an email account.
Yahoo Mail can be used as an excellent example.
Once hackers have access to your Yahoo account, they can also get into any of your other online accounts linked to the same email just by clicking the link that says, "Forgot your password?"
Fortunately, Facebook has a tool that aims to fix this process, helping you recover access to all your other online accounts securely.
At the Enigma Conference in Oakland, California on Monday, Facebook launched an account recovery feature for other websites called Delegated Recovery — a protocol that helps applications delegate account recovery permissions to third-party accounts controlled by the same user.
Starting today, Delegated Recovery is available to GitHub users for account recovery, allowing them to set up encrypted recovery tokens for their Github accounts in advance and save it with their Facebook accounts.
So in case they ever lose access to their Github account, they can re-authenticate to Facebook and request the stored token be sent from their Facebook account back to Github with a time-stamped signature, proving their identities and securely regaining access to their accounts.
This whole process takes place over encrypted HTTPS Web links and completes within a few seconds.
Since the stored token is encrypted, even Facebook can not read the personal data stored in that token.
The social network giant also assured that except its assertion that the person recovering the GitHub account is the same who saved the token, the company doesn't share any personal information about the user with GitHub.
According to the social networking giant, the Delegated Recovery service will be especially helpful for online users who have lost their smartphones, physical tokens or keys used as a second factor of authentication.
"We also want to offer the ability for people to use other accounts, such as a GitHub account, to help you recover your access to Facebook." said Brad Hill, Security Engineer at Facebook
Facebook has published the protocol behind the feature and the technical specifications on its GitHub page. You can also read more information about the feature on Facebook's official post.
Since no system is hacker-proof, Facebook has invited hackers and security community for reporting bugs, submit suggestions, and feedback.
Delegated Recovery is part of Facebook's bug bounty program, allowing security researchers and bug hunters to test and find out security vulnerabilities in it.
This tool is being released as open-source that would allow other third-party sites to implement it, but for now, the service is available only for GitHub.
Facebook Adds FIDO U2F Security Keys Feature For Secure Logins
28.1.2017 thehackernews Social
Facebook Adds FIDO U2F Security Keys Feature For Secure Logins
Hacking password for a Facebook account is not easy, but also not impossible.
We have always been advising you to enable two-factor authentication — or 2FA — to secure your online accounts, a process that requires users to manually enter, typically a six-digit secret code generated by an authenticator app or received via SMS or email.
So even if somehow hackers steal your login credentials, they would not be able to access your account without one-time password sent to you.
But, Are SMS-based one-time passwords Secure?
US National Institute of Standards and Technology (NIST) is also no longer recommending SMS-based two-factor authentication systems, and it’s not a reliable solution mainly because of two reasons:
Users outside the network coverage can face issues
Growing number of sophisticated attacks against OTP schemes
So, to beef up the security of your account, Facebook now support Fido-compliant Universal 2nd Factor Authentication (U2F), allows users to log into their Facebook account using a physical security key, such as the YubiKey, instead of relying on a one-time passcode sent via text message or email.
Compared with the traditional authentication protocols, Universal 2nd Factor Authentication (U2F) is a hardware-based authentication aims to simplify, fasten and secure two-factor authentication process.
U2F standard as a security feature has already been implemented by major companies including Google, Dropbox, GitHub, Salesforce and supported by Chrome and Opera web browsers.
Facebook Adds FIDO U2F Security Keys Feature For Secure Logins
The best thing about this standard is that one tiny little device can be used to authenticate with any number of online services and no mobile connection or batteries are required.
These hardware-based security keys are easy to use and deploy. You just need to simply plug-in the inexpensive USB device (which starts at about $10) into your computer's USB port to get into your Facebook account from any computer anywhere.
Ready to activate your security key for your Facebook account?
Go to Security settings of your Facebook account.
Open Login Approval and Click "Add Key" shown in front of 'Security Key.'
'Add Key ' and Facebook will ask you to "Insert your security key into a USB port."
Note: Hardware-based Security Key will only work if you're using the Chrome or Opera browser.
For more detailed instructions on setting up a security key, you can head on to this page.
How to Authenticate to your Account using the Fido-compliant U2F device? Simple, whenever next time you log into your Facebook account you'll be asked to plug your security key into the USB slot.
Once you plug in, the tiny device generates an encrypted, one-time security passcode for use in two-factor authentication (2FA) systems and logs you into your Facebook account.
These hardware-based security keys are thought to be more efficient at preventing phishing, man-in-the-middle (MITM) and other types of account-takeover attacks than 2FA via SMS, as even if your credentials are compromised, account login is impossible without that physical key.
"By adding FIDO authentication to its security portfolio, Facebook gives their users the option to enable unphishable strong authentication that is no longer vulnerable to social engineering and replay attacks using stolen 'shared secrets' like passwords and one-time-passcodes," said Brett McDowell, executive director of the FIDO Alliance.
At this moment, security key logins for the mobile Facebook app is not supported, but users with NFC-capable Android device and the latest version of Chrome and Google Authenticator installed can use a security key to log in from their mobile website.
A hacker confirmed that President Trump Twitter account is linked to a private account
27.1.2017 SecurityAffeirs Social
A security researcher has discovered that the President Trump’s Twitter account is exposed to the risk of hack due to security misconfigurations.
While the experts are warning the press about the fact that the American President Trump is still using his personal insecure Android smartphone, we have discovered that his Twitter is exposed to the risk of hack due to security misconfigurations.
The official @POTUS Twitter account was linked to a private Gmail account owned by President Trump.
The choice of using a private email and non-government email address put at serious risk the Trump account.
We don’t know if the @POTUS Twitter account is protected by a 2FA mechanism anyway in order to take over it hacked just need to access the Trump private email account.
Only Trump’s personal Twitter account seems to be protected by two-factor verification leveraging on a one-time passcode sent to the mobile device.
In the past, similar errors were made by Hillary Clinton and George W. Bush whom private email servers/accounts were breached by hackers.
The bad choice was discovered by the researcher who goes online with moniker @WauchulaGhost.
WauchulaGhost made headlines in June 2016 when he hacked Twitter accounts used by ISIS militant and replaced content with images of porn and gay pride messages.
On Monday night, WauchulaGhost shared the disconcerting news posting the following message on Twitter
“Change your emails & Fix Settings.”
Follow
WauchulaGhost @WauchulaGhost
Change your emails & Fix Settings. @FLOTUS
trumpmelania2017@gmail.com@PressSec
PressSec2017@gmail.com@DanScavino
dscavino@donaldtrump.com
5:03 AM - 24 Jan 2017
247 247 Retweets 260 260 likes
WauchulaGhost also reported similar problems with the email accounts linked to the First Lady Melania Trump (@FLOTUS) and VP Mike Pence (@VP).
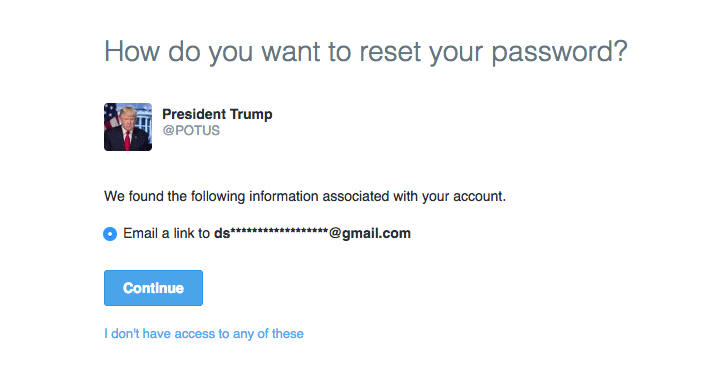
“According to WauchulaGhost, @POTUS, @FLOTUS and @VP are more vulnerable because they haven’t selected a basic security feature on Twitter that requires you to provide a phone number or email address to reset your password. The current security setting for these three accounts allows anyone to click on “forgot password” and type in @FLOTUS, @POTUS or @VP. The next screen says “we found the following information associated with your account” and gives a partially redacted email address to which it will send a password recovery link.” reported the CNN.
“WauchulaGhost says being able to fill in the missing letters and guess someone’s email address is the first step hackers take when trying to breach an account.”
“It’s not hard for us to go figure out that email,” he told CNNTech
WauchulaGhost don’t want to hack the @POTUS Twitter account or Twitter accounts of his staff, he just wants to warn them of a wrong security posture.
The hacker has found the alleged Melania Trump’s email address associated her Twitter account in twenty minutes. He added that the email associated with Vice President Mike Pence was easy to guess, seeing the redacted version: vi***************@gmail.com it is easy to imagine that it is vicepresident2017@gmail.com. The worst news is that the VP account isn’t protected by a second factor of authentication.
Once a hacker has discovered the email address for an account he can try to access the email to take over the Twitter account. This is possible by infecting the target machine with a malware or through a spear phishing attack.
“All I have to do is guess the email. Which I have been rather good at doing,” WauchulaGhost told CNNTech via Twitter DM. “Then verify the email exists. At that point take the email account, reset Twitter password, boom….I own the Pres. Not saying I’m going to..haha. But it’s rather easy for some.”
The situation is not so simple, a representative from Twitter confirmed that the White House Communications Agency manages security protocols for White House accounts that go beyond two-factor authentication.
“But according to former State Department Senior Advisor Chris Bronk, the absence of this security setting on White House accounts opens a potentially dangerous door.” states the CNN.
Dear President Trump, fix your security settings as soon as possible.
President Trump's @POTUS Twitter Linked To A Private Gmail Account
27.1.2017 thehackernews Social
It seems like the new American President's Twitter account could easily be hacked due to security blunders he made with the most powerful Twitter account in the world, experts warned.
Days after we got to know that the newly inaugurated President Donald Trump was still using his old, insecure Android smartphone, it has now been revealed that the official @POTUS Twitter account was linked to a private Gmail account.
Since we are already aware of the potential scandal with government officials using outside email systems following the hack of private e-mail servers of Hillary Clinton and George W. Bush, the choice of using private, non-government email address by Trump has raised serious concerns about the security of the White House's closely watched account.
To gain control of the official @POTUS Twitter account, which may or may not is secured with some form of two-factor authentication, all an attacker needs to do is hack the email address associated with the account, which controls the password reset process.
A hacker, @WauchulaGhost, who discovered this issue also reported similar weaknesses in the email linked to the First Lady Melania Trump (@FLOTUS) and VP Mike Pence (@VP), said CNN.
WauchulaGhost, who took down more than 500 ISIS Twitter accounts in the past, said he would not hack the @POTUS Twitter account or Twitter accounts of other White House officials; instead, he just wanted to issue a warning to upgrade the security of these accounts.
Fortunately, all those Twitter accounts were switched over to the White House-affiliated private email clients by just yesterday morning, but so far only Trump's personal Twitter account is apparently protected by two-factor verification, which requires users to enter a one-time passcode sent to their phone.
Also Read: Donald Trump's Email Servers are Horribly Insecure — Researcher Reveals
However, Trump's personal Twitter account still involves some substantial information security risks, since he is still using the insecure device to post messages from the White House, according to numerous reports quoting unnamed White House sources, which could allow malicious actors to gain access to the account through his phone itself.
Trump Press Secretary May Have Just Tweeted His Password, Twice!
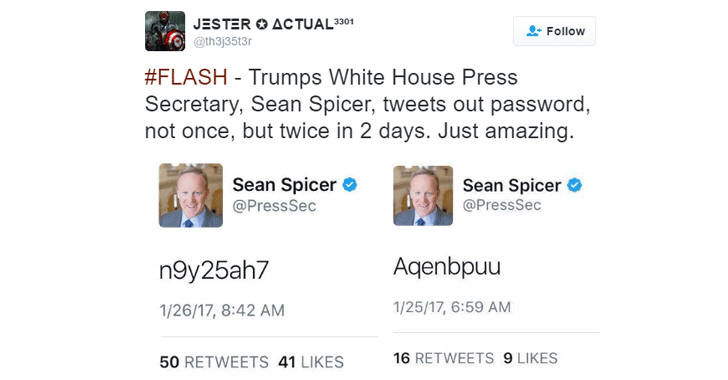
Another example of security blunders came yesterday when Press Secretary Sean Spicer believed to have tweeted his own Twitter password — particular combination of letters and numbers (n9y25ah7) — by mistake.
And since the email address used for the Spicer's Twitter account (@PressSec) was already known, it would have taken just a few seconds to log into it.
Overall, it is not a good start for the nascent Trump administration as far as cyber security is concerned. And if this continues, the new president will be the next target for hackers.






