There are no details about the number of victims that fell for the trick, but it is likely a large one since the scammers create a believable message using carefully selected extracts from real news releases and television broadcasts.
Social Articles - H 2020 1 2 3 4 5 6 7 Social List - H 2021 2020 2019 2018 1 Social blog Social blog
Phishing on Instagram Baits Russians With Free Money Promise
22.2.2020 Bleepingcomputer Phishing Social
A large-scale phishing campaign is running on Instagram to bait Russians with a fake presidential decree that promises a lump-sum payment for a citizen to start their own business.
The crooks have invested notable effort to promote the announcement and make it look credible. Since the start of the campaign, more than 200,000 people viewed the messages.
Elaborate scheme to gain trust
There are no details about the number of victims that fell for the trick, but it is likely a large one since the scammers create a believable message using carefully selected extracts from real news releases and television broadcasts.
This appears to be a more elaborate advance payment scam, where victims are duped into paying a fee to get a promised larger amount, which is upwards of 100,000 rubles (~$1,600). In the process, the payment card info is also collected.
In one video from a TV program distributed part of the campaign, the fraudsters used a segment that informs about the results of a "social contracts program" from several Russian regions.
"The first results of the so-called «social contracts program» are being summed up in several Russian regions. These are one-off payments that allow one to start their own business. Many people were able to solve their harsh situation thanks to that program."
Security researchers from Russian antivirus company Doctor Web found that the fraudsters rely on advertisements delivered on Instagram to promote the lure. Along with the presidential decree detail, which the crooks gave the number 1122B and dated it February 11, 2020, makes for a convincing tale.
"A pre-created Facebook profile is used as the advertiser for the campaign," say the experts in a brief report on Monday.
The posts are delivered through targeted advertising from accounts that impersonate Russian federal TV channels like Channel One Russia, Russia-1, and Russia-24.
These are accompanied by posts from users saying that they benefited from the advertised payment. The comments are fake, though, their role being to increase trust in the information presented.
Doctor Web found two phishing websites part of this campaign, both with valid digital certificates and purporting to be "official resources of the Russian Ministry of Economic Development:"
https://news-post.*****.net/
https://minekonovrazv.*****.net/
Once landed on one of these websites, users have to check if they are entitled to get the money by providing their full name and date of birth. A random sum is generated next, and a fee of 300 rubles (~$5) is requested for the electronic application to get it.
The checkout page asks for more details, including the phone number and information on the payment card (name, number, CVV code). Needless to say that the crooks get both the registration fee and all the data provided.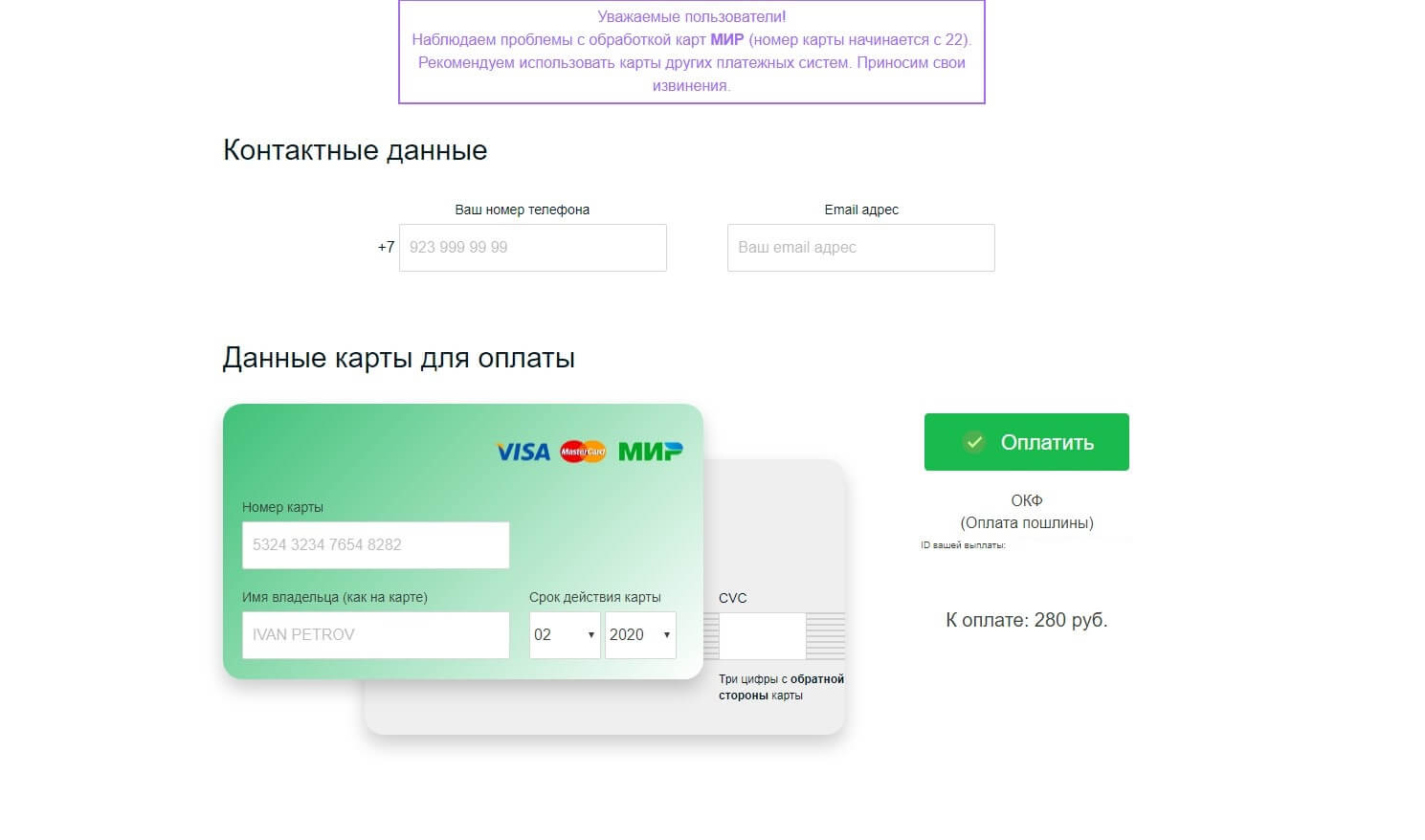
Twitter Outage Prevents Users From Sending New Tweets
9.2.2020 Bleepingcomputer Social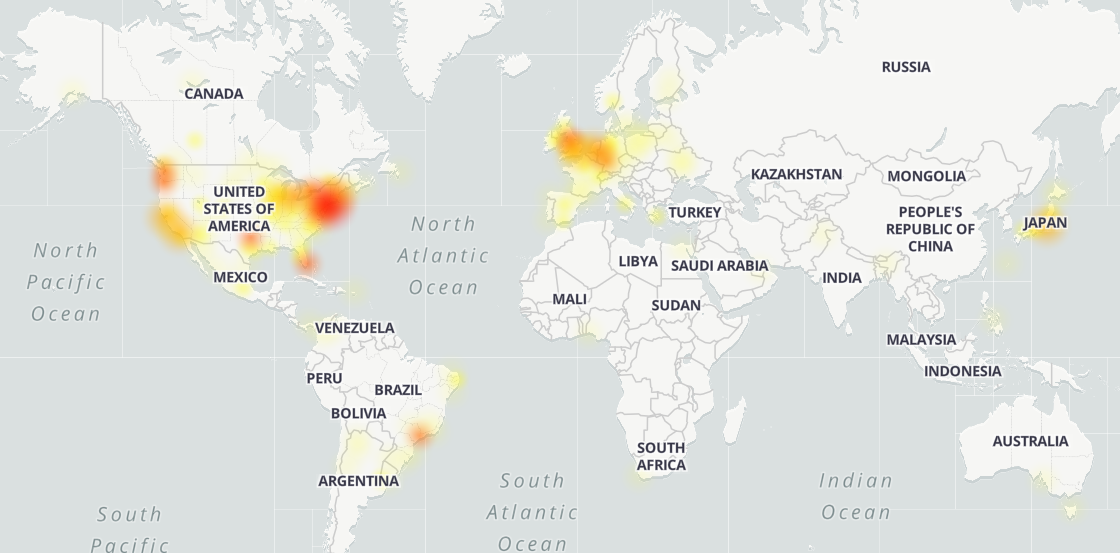
Twitter outage map (downdetector)
Twitter is experiencing a worldwide service disruption preventing users from sending tweets from the social networking platform's app, website, or TweetDeck.
There is a workaround for this issue: if you are using TweetDeck you can still send new tweets by scheduling a tweet.
"You might be experiencing trouble sending new Tweets, but we’re working on fixing this now. Sorry for the interruption and we’ll let you know when things are back to normal," Twitter says on its status page.
Twitter Support
✔
@TwitterSupport
You might be experiencing trouble sending new Tweets, but we’re working on fixing this now. Sorry for the interruption and we’ll let you know when things are back to normal.
12.6K
10:48 PM - Feb 7, 2020
Twitter Ads info and privacy
4,849 people are talking about this
"The Twitter data team is investigating a possible system irregularity currently affecting all data products and real time APIs," the company's API status page details.
"The presence and scope of any customer impact has not been determined at this time, but we will provide an update as soon as we know more."
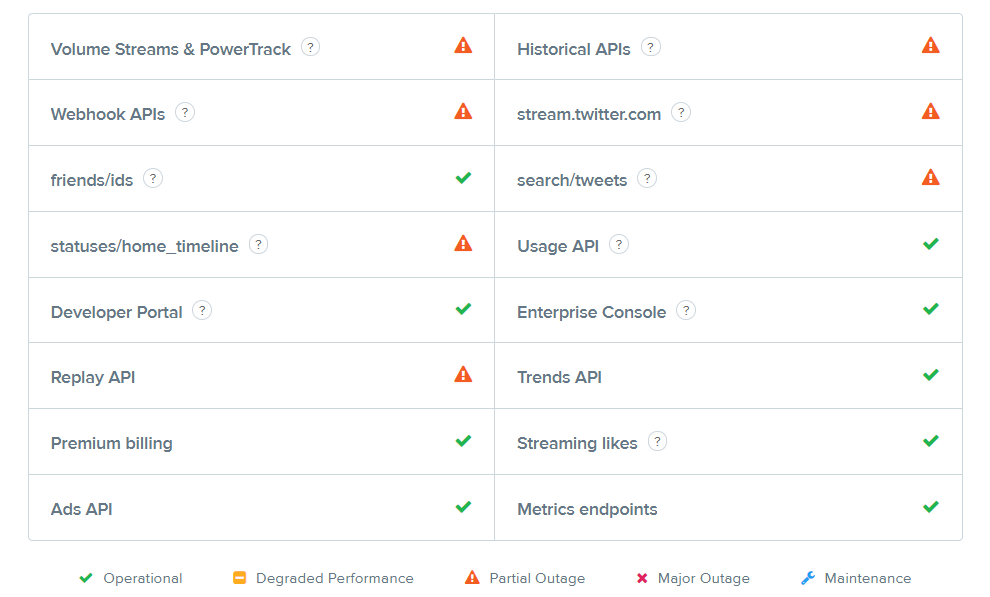
Currently affected Twitter services
Update: Twitter is back: "You can get back to Tweeting –– this problem has been fixed! Thanks for sticking with us through that."
Twitter Support
✔
@TwitterSupport
Replying to @TwitterSupport
You can get back to Tweeting –– this problem has been fixed! Thanks for sticking with us through that. 💙
2,926
11:07 PM - Feb 7, 2020
Twitter Ads info and privacy
1,332 people are talking about this
WhatsApp Bug Allowed Attackers to Access the Local File System
9.2.2020 Bleepingcomputer Social
Facebook patched a critical WhatsApp vulnerability that would have allowed potential attackers to read files from a user's local file system, on both macOS and Windows platforms.
"A vulnerability in WhatsApp Desktop when paired with WhatsApp for iPhone allows cross-site scripting and local file reading," Facebook's security advisory explains. "Exploiting the vulnerability requires the victim to click a link preview from a specially crafted text message."
All WhatsApp Desktop versions before v0.3.9309 are affected by this issue when paired with WhatsApp for iPhone versions prior to 2.20.10.
Local system read permissions
The vulnerability tracked as CVE-2019-18426 received an 8.2 high severity CVSS 3.x base score, but, although it could be exploited remotely, it also required user interaction for exploit attempts to be successful.
The flaw was discovered by PerimeterX researcher Gal Weizman when he found a gap in WhatsApp's Content Security Policy (CSP) that allowed for cross-site scripting (XSS) on the desktop app.
While investigating his discovery, Weizman was able to gain read permissions on the local file system on both Windows and macOS WhatsApp desktop apps.
The researcher says that "the theoretical concept is as follows: if you run an old version of a vulnerable app, one can exploit that vulnerability and do bad things to you."
"I did however demonstrated how I use fetch() API, for example, to read files from the local OS like the content of C:\Windows\System32\drivers\etc\hosts file in this case," Weizman added.
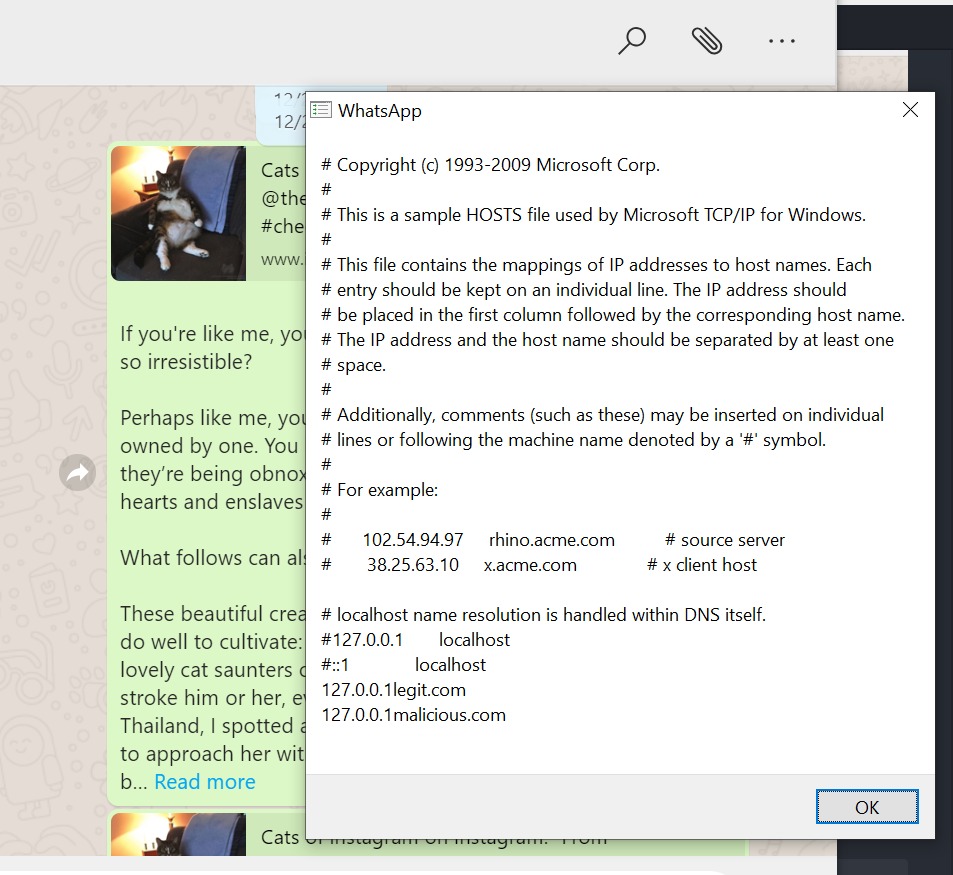
Reading the local Windows hosts file (Gal Weizman)
Before being patched by Facebook, the flaw could have enabled attackers to inject malicious code and links within messages sent to unsuspecting users, with the end goal of
"These message modifications would be completely invisible to the untrained eye," PerimeterX CTO Ido Safruti explains. "Such attacks would be possible by simply modifying the JavaScript code of a single message prior to delivery to its recipient."
"For reference, WhatsApp has over 1.5 billion monthly active users, so attacks could be executed on a large scale resulting in grave implications," Safruti added.
A technical deep dive on how the vulnerability works and a detailed explanation of the process behind its discovery are available here.
PerimeterX
@perimeterx
PerimeterX researcher @WeizmanGal has discovered a security vulnerability in WhatsApp that can be used to aid #phishing campaigns, spread #malware and put millions of users at risk. Learn more in the new blog from CTO @safruti: http://bit.ly/2UA2bhV #cybersecurity
7
5:35 PM - Feb 4, 2020
Twitter Ads info and privacy
See PerimeterX's other Tweets
Facebook previously fixed a WhatsApp bug that could be used to crash the app in a loop on the phones of a group's members and another one that allowed attackers to modify or replace media files from a device's external storage before the recipient could see them.
Yet another critical vulnerability in WhatsApp for Android and iOS that could crash the app when the user answered a call was patched in October 2018, while a flaw discovered by CheckPoint and used by Weizman as inspiration for his research that would allow message alteration in chats was fixed in August 2018.
Twitter Fixed Issue Exploited to Match Phone Numbers to Accounts
8.2.2020 Bleepingcomputer Social
Twitter says that it discovered and fixed an issue exploited by attackers to match specific phone numbers to their corresponding Twitter accounts.
"On December 24, 2019 we became aware that someone was using a large network of fake accounts to exploit our API and match usernames to phone numbers," Twitter explains.
"We immediately suspended these accounts and are disclosing the details of our investigation to you today because we believe it’s important that you are aware of what happened, and how we fixed it."
During the following investigation, the company's security team found additional accounts that might have exploited the same vulnerable API endpoint to get access to accounts' phone numbers.
It is possible that some of these IP addresses may have ties to state-sponsored actors. We are disclosing this out of an abundance of caution and as a matter of principle. - Twitter
Although the malicious accounts were located in countries from all around the globe, a large number of requests to the affected API were coming from IP addresses within Iran, Israel, and Malaysia.
According to Twitter, the API endpoint that was abused in this attack would normally allow people who have created new accounts to find their friends on Twitter.
This works by querying which users have a phone number associated with their accounts and also have enabled the 'Let people who have your phone number find you on Twitter' option in their Settings.
Those who did not have this setting enabled in their accounts or did not have a phone number associated were not exposed to attacks exploiting this Twitter API vulnerability.
After our investigation, we immediately made a number of changes to this endpoint so that it could no longer return specific account names in response to queries. Additionally, we suspended any account we believe to have been exploiting this endpoint. - Twitter
After discovering the issue and the attacks that abused it, Twitter suspended all the involved accounts and fixed the security flaw affecting the API endpoint.
"Protecting the privacy and safety of the people who use Twitter is our number one priority and we remain focused on stopping abuse of Twitter’s API as quickly as possible," Twitter said.
"We’re very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day."
In 2018, Twitter fixed a bug affecting the permissions dialog when authorizing certain apps that left direct messages exposed to third parties without the user knowing it.
Twitter also announced in June 2019 that an issue the Android app exposed some users’ protected tweets for over 4 years if some changes were made to their accounts' settings.
In more related news, a week ago, the OurMine crew resurfaced and started taking control of high-profile social media accounts in a hacking spree that still continues, with eBay losing control of their Twitter account today.
Russia Threatens Facebook, Twitter With Fines, Demands User Data
2.2.2020 Bleepingcomputer Social
Roskomnadzor, Russia's telecommunications watchdog, announced today that it has instituted administrative proceedings against Facebook and Twitter because of their refusal to move the data of Russian users on servers located inside the country's borders.
"These companies did not provide information on meeting the requirements for localizing the databases of Russian users of the corresponding social networks on servers located in the Russian Federation, as provided for in part 5 of Article 18 of the Law on Personal Data No. 152-ФЗ," the Roskomnadzor stated today.
"Administrative proceedings were instituted on the grounds of an administrative offense in accordance with part 8 of article 13.11 of Administrative Code of the Russian Federation, which provides for an administrative fine in the amount of 1 million to 6 million rubles." [$16,000 to $94,000]
The administrative proceedings protocol was signed by a Twitter representative according to the Russian telecom watchdog. While Facebook did not send a representative to the meeting, the company will receive a copy of the protocol within three days according to Russian law.
Bans might also come after Facebook and Twitter get fined
Even though the fines Facebook and Twitter were threatened with might seem laughable on face value, the consequences they might come with are quite serious.
LinkedIn was banned in Russia in November 2015 after it failed to adhere to the law mandating it to store Russians' data on Russian servers.
"Based on a court decision that has entered into legal force, the LinkedIn social network has been entered into the register of violators of the rights of personal data subjects and sent to block telecom operators," the Roskomnadzor said at the time.
The block came two months after the Roskomnadzor filed a complaint against the company in response to an earlier LinkedIn data breach, asking it to move the data of Russian users within Russia according to privacy law enacted in September 2015.
Facebook previously warned of an incoming ban
Facebook was previously threatened to be banned in the country during September 2017 for the same reason. Twitter agreed to the demands of Russian officials at the time and proceeded to inform the Roskomnadzor that it was planning to move Russian users' data by mid-2018.
Roskomnadzor said Friday that a complaint will also be filed in Russian courts next week as reported by The Moscow Times.
A new law signed by Russian President Vladimir Putin last month imposes higher fines for repeat offenders of up to 18 million rubles ($280,500).
ProtonMail
✔
@ProtonMail
(1/2) The Russian government has blocked ProtonMail and ProtonVPN within Russia. We are reaching out to the appropriate authorities to get the block lifted as soon as possible. https://www.reuters.com/article/us-russia-protonmail/russia-blocks-encrypted-email-service-protonmail-idUSKBN1ZS1K8 …
552
4:16 PM - Jan 29, 2020
Twitter Ads info and privacy
342 people are talking about this
In related news, Proton Technologies' security-focused ProtonMail and ProtonVPN services were blocked by the Russian government on January 29.
This ban was prompted by Proton's refusal to register their services with Russian authorities — which was asked from all VPN providers operating in Russia as we reported last year — to provide info on the owners of email inboxes used to send the bombing threats.
ProtonMail and ProtonVPN users are advised by the company to access the two services with the help of the Tor service, specifically created to help circumvent censorship.