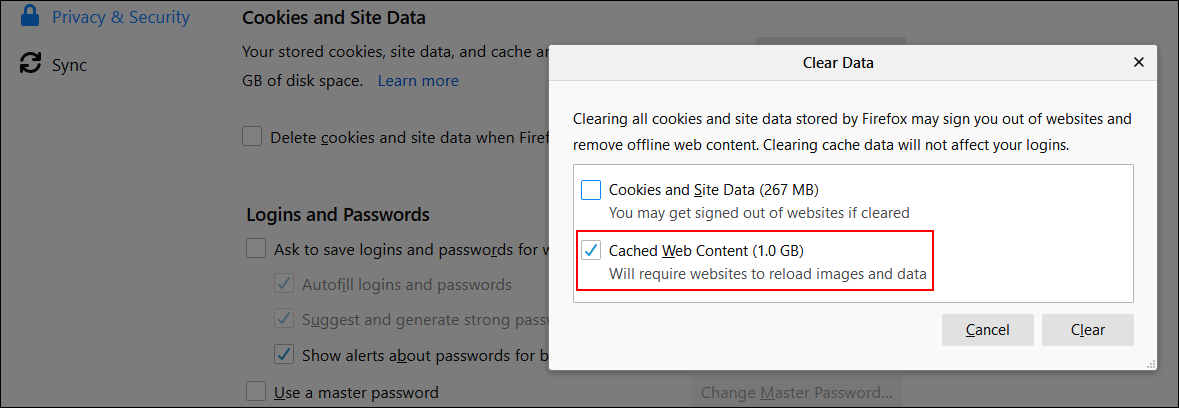
Clear the Firefox cache
To clear Mozilla Firefox's cache, you have to click the menu button and go to Options > Privacy & Security > Cookies and Site Data > Clear Data.
Social Articles - H 2020 1 2 3 4 5 6 7 Social List - H 2021 2020 2019 2018 1 Social blog Social blog
Twitter Reveals That Firefox Cached Private Data For Up to 7 Days
4.4.2020 Bleepingcomputer Social
Twitter disclosed an issue in the way the Mozilla Firefox web browser cached data that may have lead to private media shared in DMs and data downloads being inadvertently stored in the browser's cache.
If you use Firefox for browsing Twitter's platform, media files you privately shared within direct messages or Twitter data archive downloads could have been stored within the browser's cache.
This means that threat actors could have stolen your private data using malicious tools designed to go through Firefox's cache, while anyone could have got their hands on your personal information if you ever logged in on Twitter from a public computer.
"We recently learned that the way Mozilla Firefox stores cached data may have resulted in non-public information being inadvertently stored in the browser's cache," Twitter said.
"This means that if you accessed Twitter from a shared or public computer via Mozilla Firefox and took actions like downloading your Twitter data archive or sending or receiving media via Direct Message, this information may have been stored in the browser’s cache even after you logged out of Twitter."
Twitter notification
Twitter notification
Luckily, the private data stored by Firefox within its cache is automatically being removed after the browser’s default cache retention period of 7 days is reached, with all the accidentally stored private info also being deleted in the process.
Users of other web browsers such as Google Chrome and Safari were not affected by this issue according to the social networking giant.
Twitter says that it has made a change to its platform that will prevent Firefox from caching users' personal information going forward.
"If you use, or have used, a public or shared computer to access Twitter, we encourage you to clear the browser cache before logging out, and to be cautious about the personal information you download on a computer that other people use," Twitter adds.

Clear the Firefox cache
To clear Mozilla Firefox's cache, you have to click the menu button and go to Options > Privacy & Security > Cookies and Site Data > Clear Data.
There you have to uncheck the Cookies and Site Data option and only check Cached Web Content (as shown above) and then click the Clear button.
"We’re very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day," Twitter concluded.
"If you have any questions or concerns regarding this incident, you can contact Twitter’s Data Protection Officer by completing the online form located here."
Twitter kills SMS-based tweeting in most countries
2.5.2020 Bleepingcomputer Social
Twitter announced today that it has turned off the Twitter via SMS service because of security concerns, a service which allowed the social network's users to tweet using text messages since its early beginnings.
"We want to continue to help keep your account safe," the company's support account tweeted earlier today.
"We’ve seen vulnerabilities with SMS, so we’ve turned off our Twitter via SMS service, except for a few countries."
However, as the company added, Twitter users will still be able to use "important SMS messages" to log in onto the platform and to manage their accounts.
If you were using Twitter via SMS, you can log in at https://t.co/fuPJa3nVky or download our mobile app to enjoy the full Twitter experience. To set up notifications
Web and browser: https://t.co/jya0PvArPZ
Mobile push: https://t.co/d5fUuF1ANU
— Twitter Support (@TwitterSupport) April 27, 2020
Users who were using Twitter over SMS are advised to transition to the social network's web platform or to the Twitter mobile app "to enjoy the full Twitter experience."
For the time being, Twitter has also decided not to kill SMS-based two-factor authentication (2FA) and password verification.
Twitter previously temporarily turned off the users' ability to tweet via text messages between September 4 and September 5, 2019, to protect their accounts after Jack Dorsey's Twitter account, the company's CEO, got hacked.
"We’ve now turned this feature back on for a few locations that depend on SMS to Tweet," Twitter said. "It remains turned off for the rest of the world."
As Twitter's Communications team tweeted and Brandon Borrman, Vice President Global Communications at Twitter said at the time, "the phone number associated with the account was compromised due to a security oversight by the mobile provider" which allowed the attackers to compose and send tweets via SMS using Dorsey's phone number.
An update: The phone number associated with the account was compromised due to a security oversight by the mobile provider. This allowed an unauthorized person to compose and send tweets via text message from the phone number. That issue is now resolved.
— Brandon Borrman (@bborrman) August 31, 2019
In February, Twitter discovered and fixed an issue actively exploited by attackers to match specific phone numbers to their corresponding Twitter accounts using a large network of fake accounts.
During October 2019, Twitter also revealed that some users' phone numbers and email addresses provided for account security like 2FA may have been used accidentally for ad targeting.
"No personal data was ever shared externally with our partners or any other third parties," Twitter said at the time. "As of September 17, we have addressed the issue that allowed this to occur and are no longer using phone numbers or email addresses collected for safety or security purposes for advertising."
Twitter First: Trump Video Retweet Tagged as 'Manipulated Media'
14.3.2020 Bleepingcomputer Social
For the first time, Twitter has labeled a video as 'Manipulated Media' that attempts to portray Joe Biden as stating that Donald Trump should be re-elected.
In a video tweeted by White House social media director Dan Scavino, it looks as if Joe Biden is saying that "We can only re-elect Donald Trump."
In reality, though, this video has been deceptively cut short to fit this message when in fact Biden stated "We can only re-elect Donald Trump if in fact we get engaged in this circular firing squad here. It's got to be a positive campaign, so join us."
Dan Scavino
✔
@DanScavino
· Mar 8, 2020
Sleepy Joe💤in St. Louis, Missouri today:
“We can only re-elect @realDonaldTrump.”#KAG2020LandslideVictory🇺🇸
Embedded video
Josh Jordan
✔
@NumbersMuncher
The full video is just a little different.
You'd think snowflakes who whine about fake news would be more careful before spreading... fake news. 
628
6:03 PM - Mar 8, 2020
Twitter Ads info and privacy
214 people are talking about this
After this video started heavily circulating on social networks and amassing over 6 million views on Twitter, Washington Post's Cat Zakrzewski noticed that for the first time Twitter applied its 'Manipulated Media' label to the video.
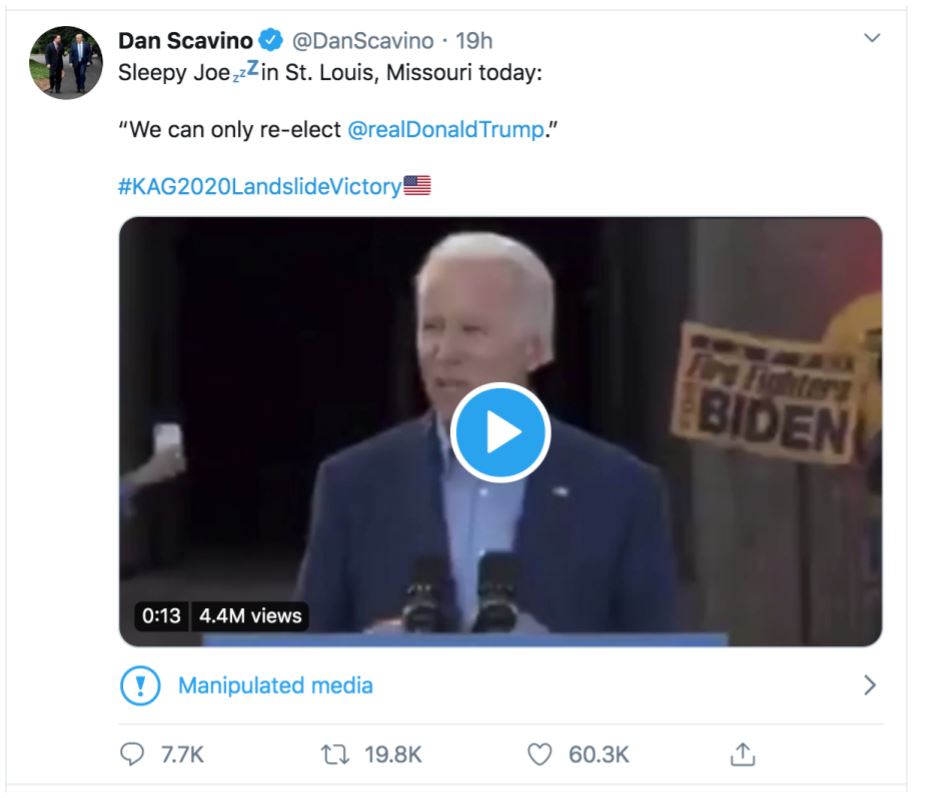
Twitter Manipulated Media
This 'Manipulated Media' label is part of Twitter's new guidelines and approach to synthetic and manipulated media being shared on the social network. Twitter has told BleepingComputer that these guidelines went into effect on March 5th, 2020.
Tweets that share synthetic and manipulated media are subject to removal under this policy if they are likely to cause harm. Some specific harms we consider include:
Threats to the physical safety of a person or group
Risk of mass violence or widespread civil unrest
Threats to the privacy or ability of a person or group to freely express themselves or participate in civic events, such as: stalking or unwanted and obsessive attention;targeted content that includes tropes, epithets, or material that aims to silence someone; voter suppression or intimidation
Under these guidelines, if a shared media is significantly and deceptively altered or fabricated, they will use the following checklist to determine if it should be labeled as 'Manipulated Media' or removed outright.
Handling deceptive media on Twitter
Handling deceptive media on Twitter
Twitter is not the only one labeling this video as deceptive, as Zakrzewski later found that Facebook has now also labeled the video on their platform as "Partly False Information".
Facebook marking video as 'Partly False Information'
Facebook marking video as 'Partly False Information'
According to Twitter, due to a technical issue, the 'Manipulated Media' label is only being displayed when the tweet is shown in a timeline and are working on a for this issue.
WhatsApp, Telegram Group Invite Links Leaked in Public Searches
24.2.2020 Bleepingcomputer Social
Invite links for WhatsApp and Telegram groups that may not be intended for public access are available through simple lookups on popular web search engines.
Both companies took some steps to protect the privacy of their users but more effort is necessary to make the links completely non-discoverable via public searches, thus allowing anyone to find them and join the group.
The issue was signaled on Friday by Jordan Wildon, multimedia journalist at Deutsche Welle, who warned that the lapse allowed the discovery of some unexpected, even groups for illegal activities.
source: Jordan Wildon
Wilson tweeted that he found invite links to groups for illegal porn, far-right, and anti-government movements.
Jane Wong, a mobile app reverse said that her Google search revealed around 470,000 results for WhatsApp invite links, allowing anyone to join the groups and access to members' phone numbers.
In all fairness, the privacy of these links is the responsibility of the admins generating them. By sharing them on the surface web - the internet that is indexed by conventional search engines - is a sure way to have them indexed by public search services.
Google's public search liaison Danny Sullivan explained that this is normal behavior, the same as when "a site allows URLs to be publicly listed."
Using special search parameters, several users discovered that Telegram channels were in the same situation. It is unclear whether the admins made the invite links discoverable knowingly or in error. Regardless, some very unsavory results are not difficult to find.
In November 2019, the same issue was reported privately to Facebook through its bug bounty program as groups were discoverable in public searches.
The company responded that the behavior was intentional, yet, for some reason, expressed surprise at Google indexing them.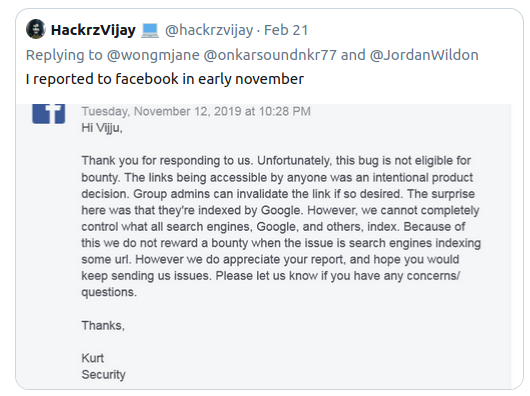
source: HackrzVijay
Over the weekend, Wong discovered that WhatsApp made a first step towards keeping private the invite links by removing the listings from Google.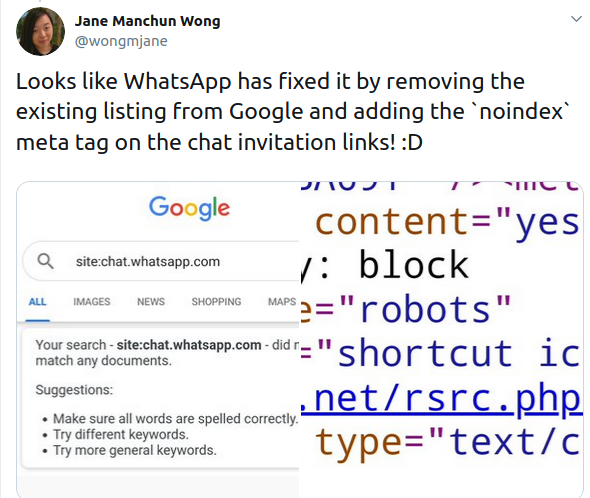
Source: Jane Wong
It also followed with appending the 'noindex' meta tag that prevents web crawlers from indexing the page with the link and thus keep it away from search results. Telegram has not yet taken action, it would seem.
However, the correction is present only when using Google. Other search engines (e.g. Bing, Yandex, Yahoo) still list the links in public results.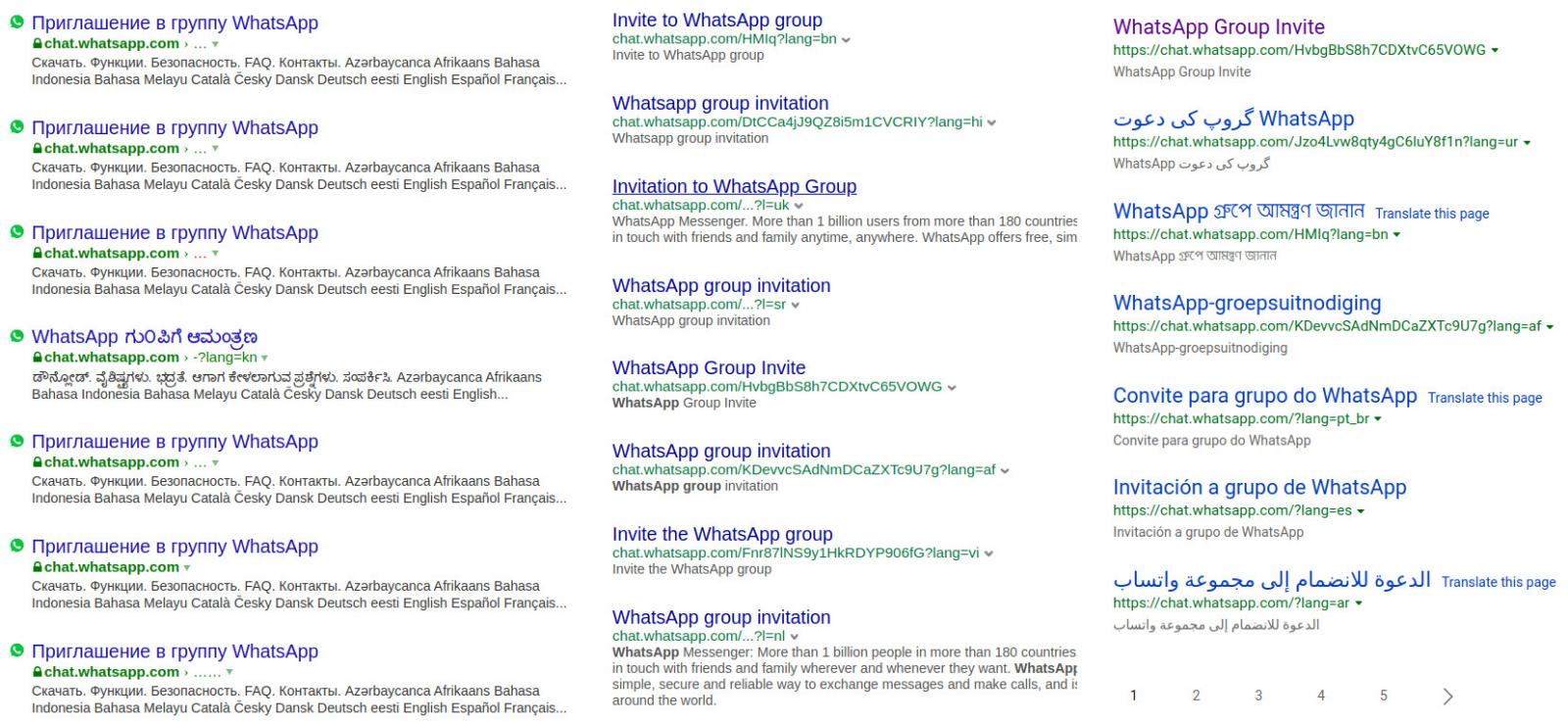
Group and channel admins should be aware that an invite link available on a public page is automatically indexed by search engines and present in search results. If the link is meant to be private, administrators should provide it directly to members.
WhatsApp Phishing URLs Skyrocket With Over 13,000% Surge
23.2.2020 Bleepingcomputer Social
The number of WhatsApp phishing URLs has skyrocketed in Q4 2019 after a 13,467.6% huge QoQ surge in the number of unique phishing URLs targeting its users being discovered by email security company Vade Secure since Q3 2019.
Vade Secure's Phishers' Favorites report for Q4 2019 highlights the 25 most impersonated brands in phishing attacks with the list being compiled after examining phishing URLs detected by Vade Secure's technology.
"Leveraging data from more than 600 million protected mailboxes worldwide, Vade's machine learning algorithms identify the brands being impersonated as part of its real-time analysis of the URL and page content," Vade Secure says.
WhatsApp's 5,020 unique phishing URLs detected by Vade Secure and its ascent as the 5th most impersonated brand in phishing attacks (up 63 spots) was the driving force behind social media brands' increase in the share of URLs used in phishing attacks from 13.1% in Q3 to 24.1% in Q4 2019.
Vade Secure explains that "the staggering growth in phishing URLs stems primarily from a campaign inviting recipients to the so-called Berbagi WhatsApp group, which advertises pornographic content.
"Moreover, it appears web hosting provider 000webhost was hacked and used to host the phishing pages."
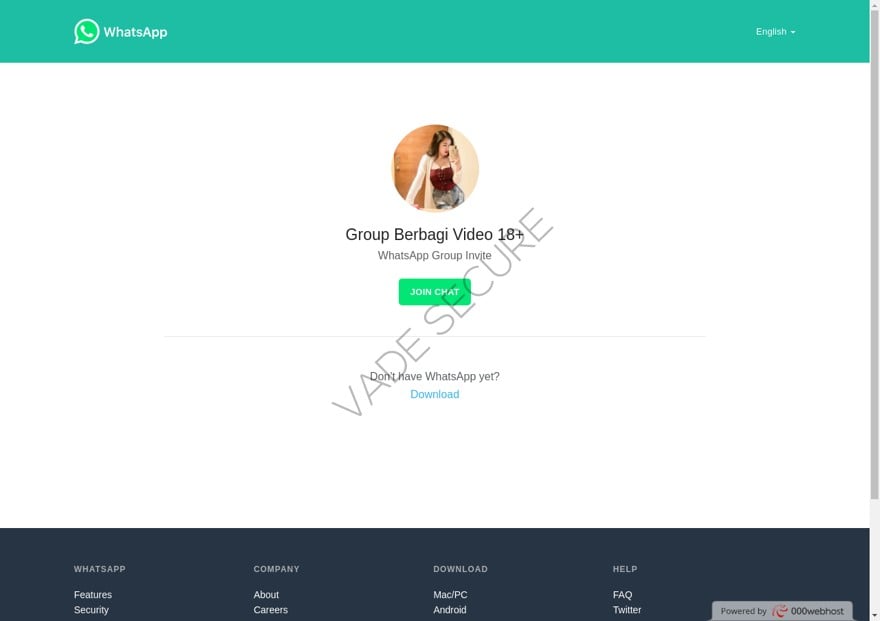
Berbagi WhatsApp group invite (Vade Secure)
The other two social media brands in the top 25 brands used as bait in phishing attacks are Facebook which took the second spot at the top and Instagram which rose 16 spots in the top, up to #13.
The former was by phishers as a lure in 9,795 phishing URLs while the latter made an appearance in 1,401, almost doubling its previous quarter's numbers with a 187,1% QoQ growth.
Even though Facebook saw an 18.7% decrease in the number of URLs observed in phishing attacks, it was actually up 358.8% on a year-over-year basis.
"Regarding Facebook, one plausible explanation for its consistent popularity could be the rise of social sign-on using Facebook Login," Vade Secure senior director Ed Hadley explains.
"With a set of Facebook credentials, phishers can see what other apps the user has authorized via social sign-on—and then compromise those accounts."
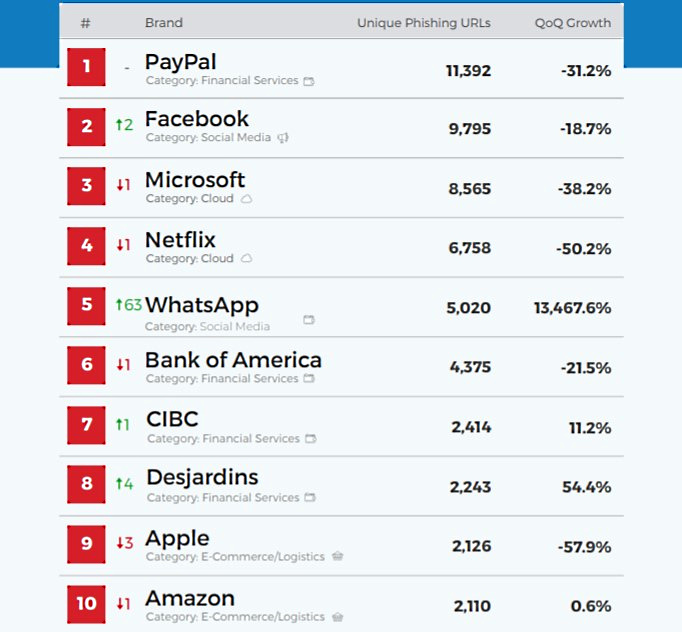
Top 10 most impersonated brands in phishing attacks (Vade Secure)
In related news, Facebook-owned WhatsApp announced a week ago that it now has over two billion users around the world.
"Today we remain as committed as when we started, to help connect the world privately and to protect the personal communication of two billion users all over the world," the company said.
Earlier this month, Facebook patched a critical WhatsApp bug that could have allowed attackers to read files from users' local file systems, on the macOS and Windows platforms.
In December 2019, security researchers discovered another WhatsApp vulnerability that could be used to crash the app in a loop on the phones of all members of a group.
During late October 2018, Google Project Zero researcher Natalie Silvanovich also found a critical WhatsApp vulnerability activated by Android or iOS users answering a call and that could have lead to fully compromise the app.