
Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
According to TrendMicro Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018
24.1.2018 securityaffairs Spam
According to a report published by the security firm TrendMicro, Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018.
The report highlights the growth of damage caused by hackers who adopts new attack vectors techniques like the ones used recently by Lebanese intelligence agency Dark Caracal
According to a report published by TrendMicro, Business Email Compromise (BEC) attacks had surpassed the value of damage to enterprises in the past years and it is estimated that it could reach $ 9 billion dollars in 2018. This rising value of loss for business takes into account new attack vectors like the one from Lebanese Intelligence Agency Dark Caracal malware who utilizes malware in android application.
The report states that the FBI released a public announcement revealing that BEC attacks had become a $ 5.3 billion industry in the past years. In that regard, the report emphasizes that hackers are employing Social Engineering to lure and deceive employees in a myriad of scams to bypass security measures. By using a deep understanding of Human Psychology hackers are circumventing the defenses, as the report states ” it requires little in the way of special tools or technical knowledge to pull off, instead of requiring an understanding of human psychology and knowledge of how specific organizations work.”
The report lists how BEC attacks are usually conducted. The techniques are: Bogus invoice scheme, CEO fraud, Account compromise, Attorney impersonation and Data Theft. The report highlight that these attacks can be classified into two major groups: Credential grabbing and email only.

The credential grabbing technique as detailed by the report has shown an increase in phishing HTML pages that are sent as spam attachments. Also, by employing malware campaign hackers target organizations. One recent example of malware is Zyklon that exploits flaws in Microsoft Office. The charts in the report shown that the attacks have doubled in the period from January to September 2017.
As discovered by researchers in the report, the two main types of malware techniques employed are keyloggers and Remote Access Tools (RAT). Since these tools are low cost and effective they can harvest all credentials on any infected machines. Malware techniques are very hard to detect by anti-virus since they are widely shared in forums or placed in applications commonly used on a daily basis. The report lists the most common malware used in Business Email Compromise attacks: AgentTesla, CyborgLogger, DarkComet, DiamondFox, Dracula Logger, iSpy Keylooger, Knight Logger and Luminosity Link.
The report also suggests how to defend and avoid against BEC attacks: Employee awareness and education, verifying emails received, verification of the legitimacy of executive requests, verification of requests from vendors and suppliers, verification of any requests and the adoption of a security culture within the organization.
Sources:
https://www.ic3.gov/media/2017/170504.aspx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/business-email-compromise-bec-schemes
https://www.trendmicro.com/vinfo/us/security/research-and-analysis/predictions/2018
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://irishinfosecnews.wordpress.com/2018/01/18/bec-attacks-to-exceed-9b-in-2018-trend-micro/
https://www.infosecurity-magazine.com/news/new-attack-group-fires-rats-and/
https://threatpost.com/new-dridex-variant-emerges-with-an-ftp-twist/129546/
http://mashable.com/2018/01/19/dark-caracal-hackers-phish-whatsapp-and-facebook-accounts/#1p4UuGZVVSqx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://www.darkreading.com/vulnerabilities—threats/bec-attacks-to-exceed-$9b-in-2018-trend-micro/d/d-id/1330853
https://www.csoonline.com/article/3247670/email/email-security-in-2018.html
http://www.informationsecuritybuzz.com/expert-comments/business-email-compromise-attacks-exceed-9b-2018-ironscales/
https://in.reuters.com/article/us-lebanon-cyber/lebanese-security-agency-turns-smartphone-into-selfie-spycam-researchers-idINKBN1F726S
https://www.forbes.com/sites/thomasbrewster/2018/01/18/lebanon-surveillance-hits-google-android-lookout-eff/#19ad8aef7971
http://www.computerweekly.com/news/252433527/Powerful-Zyklon-malware-exploiting-MS-Office-flaws
SEC Files Charges in Digital Currency Investment Scam
5.12.2017 securityweek Spam
The US Securities and Exchange Commission said Monday its newly-created Cyber Unit shut down a digital currency investment scam, charging a company that took millions from investors, "falsely promising" a speedy, 13-fold profit.
The SEC's Cyber Unit filed charges against and froze the assets of Dominic Lacroix, a Canadian with a history of securities law violations, and his company PlexCorps in an initial coin offering fraud.
Using Facebook, the company sold securities called PlexCoin -- that its website billed as "the next cryptocurrency" -- to investors in the US and elsewhere, raising $15 million since August, and promising a return of 1,354 percent within 29 days, the SEC said in a statement.
These were the first charges filed by the unit the SEC created in September to focus on fraudulent initial coin offerings of digital currency and other crimes.
"This first Cyber Unit case hits all of the characteristics of a full-fledged cyber scam and is exactly the kind of misconduct the unit will be pursuing," the unit's chief Robert Cohen said in a statement. "We acted quickly to protect retail investors from this initial coin offering's false promises."
The SEC won an emergency court order to freeze the assets of PlexCorps, Lacroix, 35, and his partner Sabrina Paradis-Royer, 26, accusing them of trading in unregistered securities.
PlexCorps promotional materials claimed the company's executives could not be identified for security and privacy reasons when in reality this was because Lacroix had already been pursued by Canadian authorities for securities law violations, the agency said.
The SEC's move comes amid mounting interest in digital currencies, with the most well-established, bitcoin, seeing its value soar this year to dizzying heights, attracting both investor interest and skepticism.
The US Commodities Futures Trading Commission, which regulates trade in derivatives, last week cleared the way for mainstream exchanges, including the CME Group and Cboe Futures Exchange, to offer contracts for futures of the virtual currency.
Cboe was the first out of the gate Monday, announcing it would launch bitcoin futures trading beginning Sunday. CME plans to allow trading in bitcoin futures later this month.
Spam and phishing in Q3 2017
4.11.2017 Kaspersky Spam Analysis
Blockchain and spam
Cryptocurrencies have been a regular theme in the media for several years now. Financial analysts predict a great future for them, various governments are thinking about launching their own currencies, and graphics cards are swept off the shelves as soon as they go on sale. Of course, spammers could not resist the topics of cryptocurrency, mining and blockchain technology.
Last quarter we wrote that many Trojans were downloading ‘miners’ as a payload on victims’ computers, and in third quarter of 2017 this practice became even more widespread.
Fraud, cryptocurrencies and binary options
Financial fraud makes very active use of the cryptocurrency topic: users receive messages that vividly describe the use of special software for trading on the cryptocurrency market and how it can secure their financial future.
Examples of emails with offers “to secure your financial future”
After clicking on a link, users end up on a site where they are once again persuaded to join the ranks of the rich who only have one problem in life – how to spend their money. In reality, such sites are partners for shady brokerage houses, and purveyors of new, inexperienced customers. It is there that new users are redirected.
The plan is to get the victim to deposit a certain amount to their account, usually several hundred dollars, for the opportunity to start trading. We should note here that we’re no longer talking about cryptocurrencies – in most cases, trading involves binary options.
The problem is not even in the questionable legality of the actual trading, but that no one guarantees the honesty of the brokerage offices and, consequently, there are no guarantees that the invested funds will be returned. The fraudsters start by motivating people to invest more and more money, and then simply disappear, leaving the victim to read angry reviews on the Internet from other cheated depositors.
There are also more primitive types of fraud, where the email directly asks the recipient to transfer bitcoins to a specific wallet, with a promise to return the investment with interest five days later. But only the most naïve recipients are likely to fall for such an offer.
Naive users are invited to “invest” bitcoins for a short time at a high high rate of interest
Webcasts
Another example of the cryptocurrency theme being used in spam is that of webcasts. In most cases, scammers suggest taking a study course that will help the user understand more about cryptocurrencies and how to invest in them. Of course, the sums invested in “training” will result in huge profits in the near future, according to the organizers.
Natural disasters and the ‘White House administration’
In August and September, the world’s attention was focused on hurricanes Irma and Harvey, and the earthquake in Mexico. There were dozens of victims of these disasters, and the damage caused was estimated to be billions of dollars. These tragic events inevitably attracted the attention of so-called Nigerian scammers trying to cash in on people’s grief. They sent messages on behalf of family members whose relatives died during the hurricanes and asked for help obtaining an inheritance left by them. Natural disasters were also mentioned in emails promoting job offers and loans.
In the third quarter, ‘Nigerian’ letters also mentioned the name of Donald Trump, the current US president. The authors pretended to be representatives of state or banking organizations, and to make their message sound more important they claimed they were appointed by the US president or were acting on his behalf. The spammers spun the standard tales in their fraudulent letters, promising millions of dollars to users, with the scammers asking for personal information so that they could supposedly track the money transfer. The letters contained identical text but with different layouts and contact details.
Letters ‘from the US president’s office’
B2B fakes in malicious emails
There is still a tendency to create emails with malicious attachments for fake commercial offers. At times their quality is so good that you suspect they could be a man-in-the-middle attack.
The file in the attachment is detected as HEUR: Trojan.Java.Agent.gen. This malware is written to startup and tries to close programs such as Process Hacker, system explorer and security software processes. It then communicates with the remote server and waits for the command to install other malicious programs
The attachment is detected as HEUR: Exploit.MSOffice.Generic, exploiting the vulnerability CVE-2017-0199 in MS Word. As a result, other malicious programs are downloaded to the victim’s computer
Both archives contain the same malicious object, detected as Trojan.Win32.VBKrypt.xtgt. It collects information from the victim’s computer and transfers it to the remote server
Release of new iPhone
In September, Apple unveiled the new models of its smartphone – iPhone 8 and iPhone X. This event was widely covered in the media, and spammers, weren’t going to miss out.
Even before the official presentation, we began to record spam mailings with offers to test the updated phone for free and participate in a prize draw to win one. Some mailings even reported the recipient had won a device before it was publicly unveiled. In most cases, the links in these emails could end up downloading Reimage Repair ‘advertising software’. Immediately after the release of the smartphone, Chinese factories got in on the act, sending out emails advertising various accessories for the new model. Our traps also recorded a large volume of phishing associated with the purchase and delivery of the popular gadget.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q2 and Q3 2017
In the third quarter of 2017, the largest share of spam was recorded in September – 59.56%. The average share of spam in global email traffic was 58.02%, which was almost 1.05 p.p. more than the average for the previous quarter.
Sources of spam by country
Sources of spam by country, Q3 2017
According to the results for the third quarter of 2017, China (12.24%) became the biggest source of spam, after finishing third the previous quarter. Last quarter’s leader Vietnam (11.17%) was second after a decrease of 1.2 p.p. The US fell one place to third (9.62%), while India (8.49%) remained fourth in this rating. Iran rounded off the top 10, accounting for 2.07% of all spam.
Spam email size
Breakdown of spam emails by size, Q2 and Q3 2017
The share of very small emails (up to 2 KB) in spam increased by 9.46 p.p. to 46.87% in the third quarter. The proportion of emails between 5 and 10 KB in size also increased by 6.66 p.p. compared with the previous quarter and amounted to 12.6%.
The number of emails between 10 and 20 KB decreased, however, with their share falling by 7 p.p. There was also a decrease in emails sized 20 to 50 KB. Their share this quarter amounted to 19%, which was a fall of 8.16 p.p. compared to the previous reporting period.
Overall, the number of very small emails continues to grow.
Malicious attachments in email
Top 10 malware families
TOP 10 malware families in Q3 2017
Backdoor.Java.QRat (3.11%) became the most widespread malicious program family in email traffic. Next came the Trojan-Downloader.VBS.Agent family (2.95%), followed by Trojan-Downloader.JS.SLoad (2.94%). The newcomers in this rating – Trojan.Win32.VBKrypt and Trojan-Downloader.VBS.SLoad (a VBS script that downloads and launches other malicious programs on the victim machine, usually cryptographers) occupy fifth and eighth places with 2.64% and 2.02% respectively. The Trojan.PDF.Badur family (1.79%) rounds off the top 10.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q3 2017
Germany remained the country targeted most by malicious mailshots in the third quarter of 2017. Its share increased by 6.67 p.p. and amounted to 19.38%.
China came second, with 10.62% of mail antivirus verdicts recorded there – a drop of 1.47 p.p. compared to Q2. Russia, which came fifth the previous quarter, completed the top three (9.97%) after its share increased by 4.3 p.p. Fourth and fifth were occupied by Japan (5.44%) and Italy (3.90%) respectively.
Phishing
In the third quarter of 2017, the anti-phishing system prevented 59,569,508 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 9.49% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q3 2017.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks was once again Brazil (19.95%, +1.86p.p.).
Geography of phishing attacks*, Q3 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
Australia (16.51%) came second after its share increased by 3.81 p.p. In third place was New Zealand (15.61%, + 3.55pp). China (12.66%) fell from second place to fourth, with its share losing 0.19 p.p. Next came France (12.42%), Peru (11.73%), Argentina (11.43%), Canada (11.14%), Qatar (10.51%,) and Georgia (10.34%).
Brazil 19.95%
Australia 16.51%
New Zealand 15.61%
China 12.66%
France 12.42%
Peru 11.73%
Argentina 11.43%
Canada 11.14%
Qatar 10.51%
Georgia 10.34%
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In the third quarter of 2017, almost half (47.54%) of the heuristic components of the anti-phishing system were recorded on pages with references to brands from financial categories such as Banks (24.1%, + 0.61 p.p.), Payment systems (13.94%, -4.46 p.p.) and Online stores (9.49%, -0.08 p.p.).
Distribution of organizations affected by phishing attacks by category, Q3 2017
Hot topics this quarter
Airline tickets
Last quarter we described a scam involving a free giveaway of airline tickets supposedly by popular airlines, with information being spread via reposts from victims on a social network. In the third quarter, scammers continued to spread the ‘giveaway’ using WhatsApp instead. Judging by the decrease in the number of anti-phishing verdicts in the Airlines category, however, we can assume that this approach wasn’t as effective.
The downturn may also be due to the fact that scammers switched to ‘prize draws’ not only for air tickets but also other prizes, for example, sports shoes, cinema tickets, gift cards for Starbucks, etc.
Before you could claim your prize you had to share information about the prize draw with eight contacts on WhatsApp.
After clicking the button, users are redirected to WhatsApp.
The redirect function in the instant messenger and the message that has to be sent to contacts
This is what the message looks like in the app
The message needs to be sent a minimum of eight times
After sending the message to their contacts the victim, instead of winning a prize, is redirected to some dubious resource, for example, a page where malicious extensions are installed, a new survey, etc.
WhatsApp
WhatsApp users are also subjected to phishing attacks that hide behind the app brand.
More often than not the scammers try to steal money on the pretext of updating the application or paying for a subscription. At one time WhatsApp really did request a subscription payment, although now it’s free.
Scammers offer a choice of subscription – for one year, three years or five. However, victims will lose much more than the stated amount if they enter their bank card details on such a site.
Netflix
Netflix users are another popular target of phishers. The number of attacks on them increased in the third quarter. The criminals usually coax bank card details from users on the pretext of a failed payment or other problems linked to subscription renewal.
Green Card
On the eve of the Green Card lottery conducted by the US government in October-November of each year, we are seeing a surge in activity by scammers offering help to apply.
After completing the form on the fraudulent site, the user is asked to pay for their application. If the victim enters their bank card details, much more money than the amount indicated on the site can end up being withdrawn from their account.
Rap battle
Even niche events can be good cover for phishing activity. On 15 October, a rap battle was held between Russian artist Oxxxymiron and Dizaster, one of the best battle MCs in the US. This followed another battle that took place just a few months earlier between Oxxxymiron and Slava KPSS. Less than 12 hours later a video of the event had gained around 5 million views – and it wasn’t just thematic sites writing about the battle but also a lot of the mainstream Russian media.
Shortly before the publication of the official video, phishing web pages dedicated to the event began to appear online:
If a user tried to view the video, they were prompted to first sign in to the popular Russian social network VKontakte.
After entering the login and password, the victim was redirected to the official page of the Versus site on the social network, and their personal data went to the scammers.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections by Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies. At the same time, the composition of the top three has remained unchanged for several quarters:
Organization % of detected phishing links
Facebook 7.96
Microsoft Corporation 7.79
Yahoo! 4.79
Conclusion
In terms of the average share of spam in global email traffic (58.02%), the third quarter of 2017 was almost identical to the previous reporting period: once again growth was slightly more than one percentage point – 1.05 (and 1.07 p.p. in Q2 2017). As in previous quarters, spammers were quick to react to high-profile events and adapted their fraudulent emails to the news agenda. This quarter they were quickly to use the theme of natural disasters following hurricanes Irma and Harvey, and the earthquake in Mexico. The popular theme of cryptocurrency was also used: trusting victims were offered seminars and ‘help’ with trading that came with profits guaranteed.
Scammers continued to use all available communication channels to spread phishing content, including social networks and instant messengers: in the current quarter, the anti-phishing component prevented more than 59 million attempts to redirect to phishing pages, which is 13 million more than in Q2.
The most common malware family in the third quarter of 2017 was Backdoor.Java.QRat (3.11%), followed by Trojan-Downloader.VBS.Agent (2.95%), and Trojan-Downloader.JS.SLoad (2.94%).
Thirty Percent of CEO Email Accounts Exposed in Breaches: Study
25.10.2017 securityweek Spam
Thirty percent of CEOs from the world's largest organizations have had their company email address and password stolen from a breached service. Given the continuing tendency for users to employ simple passwords and reuse the same passwords across multiple accounts, the implication is that at least some of these CEOs are at risk of losing their email accounts to cyber criminals or foreign nation state hacking groups.
The statistic comes from a report (PDF) published today by F-Secure, whose researchers checked the email addresses of 200 CEOs from the world's largest organizations against a database of leaked credentials. It notes that the 30% figure increases to 63% for tech companies.
Email accounts are highly valuable to cybercriminals, often containing sensitive information. A case in point is the hack and breach of Colin Powell's Gmail account in 2016 and the public exposure of his candid thoughts during the presidential campaign. In one email, for example, he comments, “and [Hillary Clinton] once again looks shifty if not a liar.” Researchers have suggested that Powell's account was breached because he may have used the same email password as he had for his Dropbox account -- details of which were leaked just a few weeks previously.
Business email compromise (BEC) attacks also become very compelling if the finance director receives a transfer instruction that originates from the CEO's genuine email account.
F-Secure found, unsurprisingly, that the top breached services to which CEOs linked their company email addresses were the professional networking site, LinkedIn, and Dropbox. Together they account for 71% of the CEOs.

But it's not just email addresses and password hashes that are exposed in leaked breaches. Eighty-one percent of the CEOs, say the researchers, “have their emails and other details such as physical addresses, birthdates and phone numbers exposed in the form of spam lists and leaked marketing databases.” A mere 18% of CEO email addresses are not associated with any leak or hack.
The reality is that the CEO's email account is a prized target for attackers, and CEOs need to take particular care over protecting them. One approach is to use a private account and personal phone number to disguise the company association -- but F-Secure warns that there are drawbacks in terms of defense in the later stages of the kill chain.
“When using a private email, a personal phone number or a home address to register for a service that the CEO uses to conduct official business, the CEO effectively denies the company's IT, communications, IPR, legal, and security teams a chance to protect the credentials, monitor their misuse or attempts to compromise them and makes it nearly impossible to recover them later,” comments F-Secure CISO, Erka Koivunen. “To an attacker, a CEO who uses private email to register for a service they use in an official capacity, spells a loner - someone who goes it alone and doesn't bother to rely on his/her staff to provide protection.”
The bottom line is that CEOs and their companies need to take particular care in protecting their email account passwords. F-Secure's advice is well-known good password practice. Use unique, long, illogical passwords that do not comprise words that could be found in hackers' word lists. Use a password manager to generate them (but, “Be wary of cloud-based password managers that don’t require access to the device in order to log into them”). Avoid social logins (if you lose the social media account, all of the associated accounts are also lost). Always use multi-factor authentication where it is available (avoiding SMS passcodes if possible: “Offline authenticators or hardware-based tokens are always preferred”).
Key is the password itself. “Use fully random password strings that are as long as a particular service allows, typically 32 characters,” F-Secure Labs lead researcher Jarno Niemela told SecurityWeek. “Passwords like these are secure as long as the service provider is not storing passwords in plain text;” absent, he adds, the possibility of an intelligence agency with a really big budget which could, theoretically, find an MD5 collision.
Even this remote possibility could be limited, he says, if the service provider makes strong efforts to protect the passwords. “Password cracking,” that is, obtaining the plaintext password from a stolen hash, “can be pretty much eliminated by using forced computation, also known as key stretching. This means that the service uses PBKDF2, scrypt, bcrypt or some other scheme that iterates the password hash verification up to millions of times. It effectively makes password cracking millions of times slower -- and even relatively simple passwords will become rather unfeasible, provided that they are not directly in some word list.”
URSNIF spam campaign expose new macro evasion tactics
20.10.2017 securityaffairs Spam
Trend Micro recently observed a new campaign leveraging the Ursnif banking Trojan using new malicious macro tactics payload delivery and evade detection.
Researchers at Trend Micro have recently spotted a new campaign leveraging the Ursnif banking Trojan featuring new malicious macro tactics for payload delivery.
Malicious macros are widely adopted by crooks for malware distribution, usually, they are embedded in documents and attackers trick victims into enabling them. Then the malicious code (i.e. PowerShell) is executed to drop and run the final malware.

Unfortunately, cybercriminals continue to improve the effectiveness of macros tactics in the attempt to evade detection.
Recently, in spam email distributing URSNIF, the researchers observed the malware was using simple checks to evade sandbox detections.
One the tactic used by threat actors is the use of AutoClose, which can run the PowerShell script after the document was closed, evading sandbox detections focused on the analysis of the macro itself.
“This method is becoming a common feature in many malicious macros because it is easy to implement.” reads the analysis from Trend Micro.
“After coercing the victim to enable macros, the macro waits for the would-be victim to close the document and only then will PowerShell execute. Sandbox detections might miss the malicious behavior since the malicious routines will only run after the document is closed.”
Another tactic relies on enumeration variables which allow attackers to determine the Office version by comparing them to certain values.
Microsoft Office provides users several enumeration variables for its macros containing predefined values, but some enumerations are only present in later versions making possible the check of the office version.
The tactic allows the attacker to avoid using the macro for certain Office versions, like Office 2007.
Another sandbox evasion tactic is based on the filename check in the macro. When automating the analysis of a file in a sandbox, the file is sometimes renamed to its MD5, SHA-1 or SHA-256 equivalent. The attackers check the filename length in the VBScript before triggering the malicious action. In presence of long filename that could reveal the use of a sandbox, the macro will not execute the malicious routines to evade detection.
All the techniques observed by the experts use PowerShell scripts to download and execute the final payload. In all cases analyzed by the researchers, the final payload was a variant of the Ursnif Trojan.
“Most of the samples analyzed have one thing in common—they run PowerShell script that downloads and executes another malware. For the samples we analyzed, the malware downloaded is a variant of the URSNIF malware (detected by Trend Micro as TSPY_URSNIF).” concluded Trend Micro
“However, these are not unique to one malware; it is possible that others may be downloaded. As malware and their delivery methods continue to evolve, security must be updated as well.”
Even With The Best Email Spoofing Defences in The World, HMRC is Spoofed
17.10.2017 securityaffairs Spam
Even with the most advanced email protections in place and an entire government organization to support them, the bad actors were able to spoof Her Majesty’s Revenue and Customs (HMRC) emails to spread a Java-based remote administration tool to unsuspecting UK recipients.
In September 2017, Trustwave identified a scam campaign that pretended to come from HMRC. The bad actors registered the cousin domain ‘hmirc-gov.co.uk‘ and sent emails to unsuspecting UK citizens with the subject “VAT Return Query.” The message body warns the recipient that there was an error with their online VAT return as detailed in the attachment. The extra tricky part is that there was no attachment included with the message. What appeared to be an attachment was actually an embedded HTML image with a link to a Microsoft OneDrive location. A user clicking on the “attachment” would download a file named “VAT RETURN QUERY.ZIP” from OneDrive which in turn contains a file called “VAT Return Query.pdf.jar” This Jar file contains the Java RAT malware jRAT which is a popular remote administration tool widely used by bad actors. But HMRC claims to have the most advanced email spoofing protection. How did this happen?
The best email defenses are the ones that prevent the malicious emails from ever reaching the intended recipients. Big data algorithms are successful at limiting traditional attacks where the same email is sent to millions of people. This type of SPAM is pretty obvious when viewed in aggregate and it is rare to find it in your inbox these days. But there are a lot of phishers out there spending a lot of time finding ways around these big data driven defences. Sending emails to smaller groups of people is one way that might work since it starts to look like legitimate email traffic between trusted sender and recipient. The automated tools will likely catch the email if it comes from a suspicious domain (e.g. @J8eZY5FzPJ.net) so the bad actors want to impersonate a legitimate domain. They are able to make the email look however they want, it is simple to make it appear to come from a legitimate domain like your bank, or the tax office. If you can’t trust the email what can you do?
HRMC famously implemented Domain-based Message Authentication, Reporting and Conformance (DMARC) in 2016 after several years of preparation and experimentation. In the first year, they reduced the number of spoofed emails by 300 million! At this point, it is almost impossible for the criminals to send an email from the official HRMC domain. And yet in 2017, the bad actors were distributing jRAT malware under the guise of VAT refund issues at the HRMC. How did they accomplish this? DMARC is very effective at validating emails from legitimate domains, but it cannot defend against cousin domains which look similar enough to the legitimate domain to fool people. To understand this limitation, one must first understand how DMARC works. And to understand DMARC, one must understand SPF and DKIM.
Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) were implemented to provide a way for email recipients to distinguish between legitimate and spoofed emails. The SPF record is defined by the authorized owner of a domain and identifies email servers that are authorized to send email on behalf of that domain. Phishers shouldn’t have access to these authorized email servers so if the recipient’s email system checks the SPF record and compares it against the IP address noted in the message it can identify spoofed messages. Unfortunately, there are situations where SPF might also block legitimate emails messages. For example, if you forward an email message, the IP address of the email server is changed and it would fail the SPF record check — although it is not a malicious message. Similarly, if the authorized sender hasn’t implemented SPF protection, the recipient has no SPF record to validate against. For this reason, few recipients will automatically block ALL messages that fail the SPF validation. So it is an incomplete solution.
In addition to SPF, authorized senders can leverage DomainKeys Identified Mail (DKIM) to mark their email as legitimate. With DKIM, the sender digitally signs the message which allows the recipient to verify that the message came from an authorized sender — slightly different than SPF which is validating the specific, authorized email server. As with SPF, DKIM implementations are not complete, so recipients cannot rely solely on DKIM certificates to distinguish legitimate from unwanted email. They become one more piece of information for the automated tools to make decisions with but not a comprehensive tool.
Due to inconsistent implementations of SPF and DKIM, authorized senders and recipients have been slow to completely rely on these tools. Authorized senders do not know how well the configurations are working to protect their brand from spoofing, and recipients don’t know how many legitimate emails are being dropped by their filtering tools. Domain-based Message Authentication, Reporting and Conformance (DMARC) is intended to address these shortcomings. With DMARC enabled, the authorized sender is able to provide direction to recipients on how to deal with the message when it is received. For example, if the sender has implemented SPF, the DMARC record can instruct recipients’ email filters to drop any message that doesn’t pass SPF validation. In addition, the DMARC framework provides feedback to authorized senders identifying attempts to spoof their email domain.
From the HMRC example, we see that DMARC is very effective for protecting legitimate email domains, but it still doesn’t address the threat of cousin domains that can fool unsuspecting recipients.
“People will never leave HMRC alone because we have 50 million customers. But, we can make those criminals’ jobs as difficult as possible, and force them into using more spurious domains for this purpose, giving our customers a better chance to spot the phish. Sadly you’ll never end phishing as it’s too lucrative a business for the criminals. We just have to make things difficult and affect their ROI.”, says Ed Tucker, head of cyber-security at HMRC and recipient of the 2016 UK Security Professional of the Year award.
Even with the latest DMARC protections in place to validate emails from HMRC’s legitimate domain, the criminals were able to fool people with emails from a domain that looks very similar to the legitimate one — to a human. It is impractical to pre-authorize all email senders since email is the most common way of introduction for new companies so we need to receive an initial email to determine we wish to trust the recipient. We expect our automated tools to allow the trustworthy emails to get through and block the unwanted emails — but we don’t always know the difference ourselves until we receive the message. As good as the tools are, they will never be 100% so we will always have to rely on the human recipient for that last line of defence.
Data Sample in Equifax Hack Scam Possibly From Third-Party Servers
15.10.2017 securityweek Spam
A data sample provided last month by scammers trying to make a profit by claiming to have breached U.S. credit reporting agency Equifax may have been obtained from unprotected Amazon Web Services (AWS) instances owned by a different company.
Hackers exploited a known Apache Struts vulnerability to breach the systems of Equifax. They had access between mid-May and late July and they may have stolen the details of over 145 million consumers in the United States, Canada and the United Kingdom. The compromised information included names, social security numbers (SSNs), dates of birth, addresses and, in some cases, driver’s license numbers, credit card numbers and dispute documents.
Scammers have been trying to make a profit by claiming to sell the stolen Equifax data for several hundred bitcoins, worth millions of dollars. One scam was run by a group calling itself Equihax, which leaked the records of Donald Trump, Kim Kardashian and Bill Gates to prove that they had the Equifax data. They also provided the records of a non-famous individual in an effort to convince people that they were the real Equifax hackers.
While they likely haven’t breached the credit reporting agency, they still may have obtained some Equifax customer data, but not from Equifax itself.
Researchers Aditya K Sood and Rehan Jalil had been looking for potentially new cloud threats when they identified several unprotected AWS instances that referenced Equifax.
“Upon accessing the HTTP service hosted on TCP port 9000/9001, we found that the web server returned a list of APIs,” Sood and Jalil explained in a blog post. “We then queried one of the APIs and found that it was possible to retrieve data.”
While the misconfigured databases reference Equifax, the researchers determined that they actually belong to an unnamed securities lending company based in Chicago. More precisely, they are part of the firm’s QA systems. Some of the data stored in cleartext in the unprotected AWS cloud storage instances was valid, but some of it appeared to be test data, the experts said.
A data sample provided by Sood to SecurityWeek after querying the unprotected servers was in the exact same format as the data shared by scammers, which could mean they and possibly others also discovered these servers.
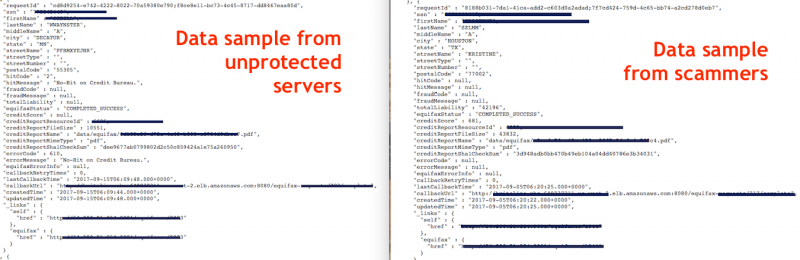
“It could be possible that scammers utilized this security flaw as well. The data dump is the same,” Sood told SecurityWeek.
Sood and Jalil have not named Equifax in their blog post – they only reference a “credit bureau” – but there are various strings referencing “equifax” in the data they found. The credit bureau (i.e. Equifax) has confirmed to the researchers that it does not control the servers exposing data.
The securities lending firm was contacted by the researchers, but it had not taken any action to protect the servers as of October 8. However, some of the sensitive data stored in the databases was encrypted between September 15, when the experts first found the servers, and October 8, when they conducted additional tests.
The relationship between Equifax and the securities lending company is unclear. Equifax has not responded to SecurityWeek’s inquiry regarding these unprotected systems.
Spam Rate Hit 55% in September: Symantec
6.10.2017 securityweek Spam
The spam rate of overall email dropped slightly over the past couple of months to 55% in September, but remains above the year average, a new Symantec report reveals.
Spam rate last month remained above the 54.3% average registered last year, but went as high as 59.4% and 56.4% for the Mining and Manufacturing sectors, respectively, Symantec points out in the Latest intelligence report for September 2017.
Driving spam rate up were massive malicious campaigns dropping variants of the Locky ransomware. During mid-September, six massive Locky distribution runs were observed.
At 55% in September, the spam rate was also higher than the 54% rate that Symantec previously reported for the first half of the year.
Email remains a favorite distribution method for cybercriminals, with users being twice as likely to encounter malware via email, compared to other infection vectors, Symantec says. In their Email Threats 2017 report (PDF), the company also revealed that one in nine users had at least one malicious email sent to them during the first six months of 2017.
Phishing rate came in at one in 2,644 emails for September, slightly down for the second month in a row, but still well above the rates seen earlier in the year, the security company says. In July, phishing rate reached a 12-month peak at one in 1,968 emails.
According to Symantec, spambots remain the primary culprits in the distribution of spam emails, with Necurs (the largest amount of malicious email activity in 2017), Gamut (focuses almost exclusively on advertising spam), Tofsee, BlankSlate, and Waledac being some of the most popular of them.
For malicious payload distribution via email, attackers either use URLs or attachments, with the latter method being the most popular, accounting for 74% of the malicious emails in the first half of 2017.
Email malware increased in September as well, with one in every 312 emails carrying malicious code, the security company says. Thus, September was the sixth month to register growth in email malware. At one in 120 emails, the Agriculture, Forestry, & Fishing sector was impacted the most, followed by the Mining industry at one in 196 emails.
Another noteworthy event in September was the discovery of new links between attacks against the energy sector and the Dragonfly group. Dubbed Dragonfly 2.0, the campaign that Symantec has been monitoring since late 2015 has known victims in the United States, Switzerland and Turkey.