
Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
Backdoored Display Widgets Plugin potentially affects 200,000 WordPress installs abusing them to spam content
15.9.2017 securityaffairs Spam
Around 200,000 WordPress websites using the Display Widgets Plugin were impacted after it was updated to include malicious code.
According to security firm Wordfence, roughly 200,000 WordPress websites were impacted after a plugin they were using was updated to include a backdoor.
“If you have a plugin called “Display Widgets” on your WordPress website, remove it immediately. The last three releases of the plugin have contained code that allows the author to publish any content on your site. It is a backdoor.” reported Wordfence.
“The authors of this plugin have been using the backdoor to publish spam content to sites running their plugin. During the past three months the plugin has been removed and readmitted to the WordPress.org plugin repository a total of four times. The plugin is used by approximately 200,000 WordPress websites, according to WordPress repository.”

The plugin is Display Widgets, the author sold it to a third-party developer on May 19, 2017, for $15,000.
A month after the sale, the plugin was updated by its new owner for the first time showing strange behavior. The plugin had been updated several times since September when it was already removed from the plugin repository multiple times.
The Display Widgets plugin version 2.6.0, released on June 21 was removed from the repository just two days later after experts noticed it was downloading 38 megabytes of code (a Maxmind IP geolocation database) from an external server.
A few days later, on June 30, it was released the version 2.6.1 that was discovered containing a malicious file called geolocation.php and allowed to post new content to websites running the plugin. The code in the page also allowed the author to update and remove content without giving any indication to the site admins.Display Widgets was removed from the WordPress repository on July 1.
Finally, the Display Widgets plugin was removed from the WordPress repository on July 1, anyway, the author continued to issue further releases.
The Version 2.6.2 of Display Widgets was released a week later, the malicious code included was updated, but the plugin was then removed from the plugin repository on July 24. The plugin owner published version 2.6.3 on September 2, also in this case the malicious code was updated to fix a bug. Display Widgets was removed from the WordPress plugin repository on September 8.
Plugin owners speculated that the malicious code was a vulnerability that could be exploited in combination with other plugins to display spam content to users.
According to the experts, WordPress installs using version 2.6.1 to version 2.6.3 of Display Widgets are possibly impacted by the malicious code and might be displaying spam content.
Wordfence highlighted that the new plugin owners may have intentionally acted to compromise the websites using the plugin, because they included a fix for the back door in the latest release, meaning they were aware of its flaw and were exploiting it for malicious purposes.
Further investigation allowed the experts to discover that the man behind plugin spam was the Briton Mason Soiza (23) who bought the plugin in late May. The original author, who goes online with the moniker Strategy11, confirmed that Soiza approached his development team claiming his firm is trying to “build one of the largest WordPress plugin companies” and that they were already distributing over 34 plugins.
One of these plugins dubbed 404 to 301 was found delivering spam for a website owned by Soiza last year. The server used to serve spam to the plugin hosts a website owned. by Soiza. While Soiza claims to have purchased the Display Widgets plugin only earlier this year, experts with Wordfence believe it could be involved in suspicious activities. Wordfence discovered that he used also the Kevin Danna alias and that he has interests in online business such as payday loans, gambling, and escort services, among others.
“He has interests in a wide range of online business that include payday loans, gambling and ‘escort’ services, among others.” reported Wordfence.
Soiza claims to have sold Display Widgets for profit shortly after buying it and denied being involved in any illegal activity.
700 Million Records Found on Server Powering Onliner Spambot
31.8.2017 securityweek Spam
A Paris-based malware researcher known as Benkow has discovered more than 700 million records used by the Onliner spambot on a misconfigured server. The records comprise a large number of email addresses, passwords and SMTP configurations. Researcher Troy Hunt has subsequently added the lists to his Have I Been Pwned (HIBP) website and service.
The IP address of the misconfigured server has been traced to the Netherlands. "Benkow and I," wrote Hunt in a blog post yesterday, "have been in touch with a trusted source there who's communicating with law enforcement in an attempt to get it shut down ASAP." However, since the database was exposed on the internet, it has possibly been accessed and downloaded by other actors.
"It is naive to think that this was not also accessed by other criminal or spammer groups, as this information is of paramount value to those kinds of groups," comments John Bambenek, threat intelligence manager at Fidelis Cybersecurity. He added, "Sometimes humans make mistakes which is why it is essential to build datasets and monitoring to track their activity over the long term. These kind of mistakes are what help us get these hackers arrested so they can become guests of the local Western government’s prison system."
Although the spambot contains a huge number of potential targets, in his own blog post, Benkow describes it being used in a targeted manner. "This spambot is used since at least 2016 to spread a banking trojan called Ursnif. I have seen this spambot targeting specific countries like Italy, or specific business like Hotels."
He suggests that one reason for the targeted approach lies in the improving spam detection and prevention technologies developed and deployed over the last few years: open relays for spam distribution are largely blacklisted. Instead, spammers first compromise a large number of websites (Benkow suggests ten to twenty thousand) which are used to host a PHP script that sends out the emails. Given the "almost infinite number of out-of-date websites on the Internet," says, "it's difficult to blacklist every websites and it's really easy to use them for the spammer."
The email target lists used for malware campaigns are not random, but methodically built. The spammer uses the spambot to send out apparently harmless emails. Benkow gives this example:
"Hello, Champ {friend|champion\enthusiast}! How {are you|is your day}?
{My name is|I'm} Natalia. Do you believe in {fate|destiny}?
Love is inseparable fellow of hope. {Sorry for|Pardon} my English, but I hope you'll {understand|get} that..."
However, the email contains a single pixel, invisible gif used to fingerprint the recipient device. Benkow explains, "When you open this random spam, a request with your IP and your User-Agent will be sent to the server that hosts the gif. With these information, the spammer is able to know when you have opened the email, from where and on which device (iPhone ? Outlook?...). At the same time, the request also allows the attacker to know that the email is valid and people actually open spams :)."
Using this information, the spammer is able to classify targets. In this way, the actual malware-delivering spam can be limited and targeted to prevent the campaign attracting the attention of law enforcement. For example, wasted spam trying to deliver Windows malware to iPhone devices can be avoided.
Benkow believes that researchers should spend more time analyzing spammers and spambots. "In a successful cybercrime campaign there are different parts, the final payload is important but the spam process is very critical too," he writes. "Some malware campaigns like Locky are successful also because the spamming process works well."
Meanwhile, Troy Hunt has performed some analysis on the spambot data. To put the size in perspective, he notes that the database contains almost as many records as the entire population of Europe -- a total of 711 records. It comprises "masses and masses of email addresses" (for spam targets); and email/password combinations (used in the attempt to abuse the owners' SMTP servers to deliver the spam).
Not all the data is immediately usable: "There's also some pretty poorly parsed data in there which I suspect may have been scraped off the web," writes Hunt. "For example, Employees-bringing-in-their-own-electrical-appliances.htmlmark.cornish@bowelcanceruk.org.uk appears twice."
One of the files contains 1.2 million rows that seem to be emails and passwords from a LinkedIn breach. The passwords are in plaintext. "All those passwords [in the LinkedIn breach] were exposed as SHA1 hashes (no salt)," he notes, "so it's quite possible these are just a small sample of the 164m addresses that were in there and had readily crackable passwords."
He also notes that a similar file contains 4.2 million email address and password pairs that almost certainly comes from the massive Exploit.In combo list. "This should give you an appreciation of how our data is redistributed over and over again once it's out there in the public domain," he comments.
Another file contains 3,000 records with email, password, SMTP server and port. "This immediately illustrates the value of the data," he adds: "thousands of valid SMTP accounts give the spammer a nice range of mail servers to send their messages from. There are many files like this too; another one contained 142k email addresses, passwords, SMTP servers and ports."
The unfortunate reality for all of us, he says, is that "email addresses are a simple commodity that's shared and traded with reckless abandon, used by unscrupulous parties to bombard us with everything from Viagra offers to promises of Nigerian prince wealth. That, unfortunately, is life on the web today."
That's just the traditional spam side. Benkow has been tracking Onliner delivery of malware, and particularly Ursnif. It is thought that some 100,000 computers have been infected across the world.
Over 711 Million Email Addresses Exposed From SpamBot Server
30.8.2017 thehackernews Spam

A massive database of 630 million email addresses used by a spambot to send large amounts of spam to has been published online in what appears to be one of the biggest data dumps of its kind.
A French security researcher, who uses online handle Benkow, has spotted the database on an "open and accessible" server containing a vast amount of email addresses, along with millions of SMTP credentials from around the world.
The database is hosted on the spambot server in Netherlands and is stored without any access controls, making the data publicly available for anyone to access without requiring any password.
According to a blog post published by Benkow, the spambot server, dubbed "Onliner Spambot," has been used to send out spams and spread a banking trojan called Ursnif to users since at least 2016.
Ursnif Banking Trojan is capable of stealing banking information from target computers including credit card data, and other personal information like login details and passwords from browsers and software.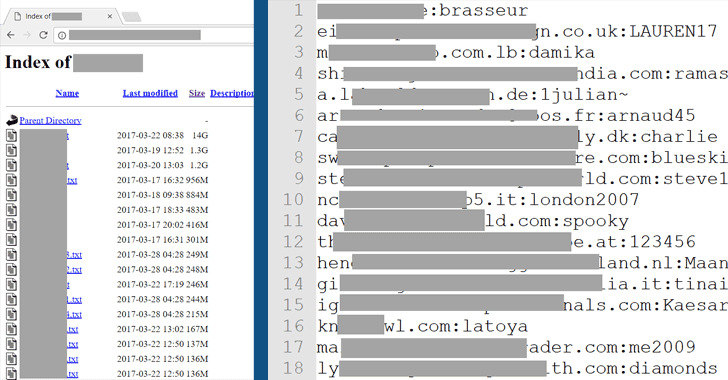
"Indeed, to send spam, the attacker needs a huge list of SMTP credentials. To do so, there are only two options: create it or buy it," Benkow said. "And it's the same as for the IPs: the more SMTP servers he can find, the more he can distribute the campaign."
As the researcher explained, he found "a huge list of valid SMTP credentials"—around 80 millions—which is then used to send out spam emails to the remaining 630 million accounts via internet provider's mail servers, making them look legitimate that bypass anti-spam measures.
The list also contains many email addresses that appear to have been scraped and collected from other data breaches, such as LinkedIn, MySpace and Dropbox.
The researcher was able to identify a list of nearly 2 million email addresses to be originated from a Facebook phishing campaign.
The exposed database has been verified by Troy Hunt, added the leaked email addresses to his breach notification site.
At the time of writing, it is unclear who is behind the Onliner Spambot.
Users can check for their email addresses on the site and those affected are obviously advised to change their passwords (and keep a longer and stronger one this time) for your email accounts and enable two-factor authentication if you haven't yet.
Also, do the same for other online accounts if you are using same passwords on multiple sites.
Onliner Spambot – More than 711 Million email addresses open and accessible online
30.8.2017 securityaffairs Spam
An archive containing more than 630 million email addresses used by the spambot server dubbed ‘Onliner Spambot’ has been published online.
The Onliner Spambot dump is the biggest one of its kind, it was discovered by the security researcher who goes online with the handle Benkow.
The database was hosted on an “open and accessible” server in Netherlands containing a vast amount of email addresses, along with millions of SMTP credentials from around the world.

The popular researcher Troy Hunt has verified the archive and added the leaked email addresses to his breach notification site Haveibeenpwned.com.
Follow
Troy Hunt ✔@troyhunt
Processing the largest list of data ever seen in @haveibeenpwned courtesy of a nasty spambot. I'm in there, you probably are too.
10:22 AM - Aug 28, 2017 · Gold Coast, Queensland
23 23 Replies 176 176 Retweets 196 196 likes
Twitter Ads info and privacy
Follow
Troy Hunt ✔@troyhunt
Interesting feedback: someone found fabricated addresses in the 711m I loaded today AND were getting spam to them https://www.troyhunt.com/inside-the-massive-711-million-record-onliner-spambot-dump/#comment-3493584892 …
7:42 AM - Aug 30, 2017
Photo published for Inside the Massive 711 Million Record Onliner Spambot Dump
Inside the Massive 711 Million Record Onliner Spambot Dump
Last week I was contacted by someone alerting me to the presence of a spam list. A big one. That's a bit of a relative term though because whilst I've loaded "big" spam lists into Have I been pwned...
troyhunt.com
14 14 Replies 13 13 Retweets 43 43 likes
Twitter Ads info and privacy
The Onliner Spambot served has been used by crooks to send out spam messages and spread the Ursnif banking trojan since at least 2016.
The Ursnif Trojan was spread via spam emails that contain malicious attachments that are used to download and execute the malware.
“Indeed, to send spam, the attacker needs a huge list of SMTP credentials. To do so, there are only two options: create it or buy it. And it’s the same as for the IPs: the more SMTP servers he can find, the more he can distribute the campaign.” wrote Benkow.
“I will take as an example the Onliner spambot. This spambot is used since at least 2016 to spread a banking trojan called Ursnif. I have seen this spambot targeting specific countries like Italy, or specific business like Hotels.”
The expert discovered a list of roughly 80 million valid SMTP credentials, that were used to send out the spam messages via internet provider’s mail servers. In this way crooks made their email appear as legitimate and bypass anti-spam systems.
It is impossible to be sure about the source of the data, data may have been collected from major data breaches (i.e. LinkedIn, MySpace and Dropbox) or collected by credentials stealer malware like Pony.
According to Benkow, at least 2 million email addresses were collected through a Facebook phishing campaign.
“It’s difficult to know where those lists of credentials came from. I have obviously seen a lot of public leaks (like Linkedin, Baidu or with every passwords in clear text) but credentials can also came from phishing campaigns, credentials stealer malwares like Pony, or they can also be found in a shop.” continues the expert. “Somebody even show me a spambot with a SQL injection scanner which scan Internet, looks for SQLi, retrieves SQL tables with names like “user” or “admin”.”
At the time of writing, there is no official data on the threat actor behin the Onliner Spambot.
Spam and phishing in Q2 2017
26.8.2017 Kaspersky Spam Analysis
Spam: quarterly highlights
Delivery service Trojans
At the start of Q2 2017, we registered a wave of malicious mailings imitating notifications from well-known delivery services. Trojan downloaders were sent out in ZIP archives, and after being launched they downloaded other malware – Backdoor.Win32.Androm and Trojan.Win32.Kovter. The usual trick of presenting dangerous content as important delivery information was employed by the fraudsters to make recipients open the attachment. The malicious mailings targeted people from different countries and came in a variety of languages.
These fake notifications from delivery services also included malicious links to infect the victim’s computer and steal personal information. The fraudulent link was tied to the tracking number of a non-existent shipment and used the following format:
Http: // domain / name of delivery service __com__WebTracking__tracknum__4MH38630431475701
The domain and the sequence of letters and numbers at the end of the link varied within the same mass mailing.
After a user clicked on the link, the Js.Downloader family Trojan was downloaded, which in turn downloaded the banking Trojan Emotet. This malware was first detected in June 2014, and is still used to steal personal financial information, logins and passwords from other services, as well as to send spam, etc.
WannaCry in spam
In May 2017, hundreds of thousands of computers worldwide were infected by the WannaCry ransomware. While the majority of similar ransomware samples require some sort of user input before a computer is infected, WannaCry could do so without any user actions. It attacks the target using a Windows exploit and then infects all computers within the local network. Like other ransomware of this type, WannaCry encrypts files on the victim’s computer and demands a ransom for decryption. In these attacks, files are encrypted with the extension .wcry and become unreadable.
The media frenzy surrounding the WannaCry ransomware played into spammers’ hands, as all high-profile events usually do. For example, they distributed numerous offers of services to counter the new malware, to prevent infection, training for users, etc. Scammers who earn money via fraudulent mailings also took advantage.
They sent out fake notifications on behalf of well-known software vendors informing recipients that their computers had been infected with ransomware and had to be updated. The link to the supposed update, of course, led to a phishing page. We came across emails that showed the attackers hadn’t taken much care when compiling their mailings, obviously hoping their victims would be in too much of a panic to notice some obvious mistakes (sender’s address, URLs, etc.).
Malware in password-protected archives and the corporate sector
In the second quarter of 2017, we came across new mailings containing malicious attachments in a password-protected archive. They were obviously targeting the corporate sector.
As a rule, the distribution of password-protected archives serves two purposes. First, it is a form of social engineering, with the attackers emphasizing that all confidential data (such as business accounts) is additionally protected by a password. Second, until the files are extracted from the archive, they cannot be fully checked by antivirus software.
These archives contained a malicious program belonging to the Pony/FareIT family. This malware is designed to steal logins and passwords to web services stored in browsers, the URLs on which they were entered, authentication data to FTP servers, file managers, mail clients, synchronization applications, as well as crypto-currency wallets.
This archive contains a malicious program called Trojan-Downloader.MSWord.Agent.bkt, which is a password-protected Microsoft Word file. The document contains a malicious script that downloads other malicious software designed to steal bank data to the user’s computer.
It is worth noting that the tendency to mask malicious mailings as business correspondence has increased. Spammers are now not only copying the style of business emails – they often use the actual details of real companies, copy auto-signatures and logos, and even the subject of the messages can correspond to the company profile. Judging by the domain addresses in the ‘To’ field and by the content of the emails, these mailings also target the B2B sector.
This archive contained a malicious program belonging to the Loki Bot family designed to steal passwords from FTP, mail clients and passwords stored in browsers, as well as crypto-currency wallets.
This archive contains the Exploit.Win32.BypassUAC.bwc malicious program, designed to steal passwords for network resources and email clients. To elevate privilege, the malware uses an exploit that bypasses the protection of the Microsoft Windows UAC component. During the operation it uses legitimate utilities to restore passwords.
This archive contains an XLS-file with a macro that was used to download HawkEye Keylogger to the victim’s computer. This malicious program written in .NET intercepts keystrokes and collects information about the system where it operates: internal and external IP addresses, the OS version as well as the name of the security product and the firewall.
This archive contains two malicious files: EXE, disguised as PDF (detected as Trojan.Win32.VBKrypt.xdps) and an MSWord document with an exploit that uses the CVE-2017-0199 vulnerability. Both malicious programs download a modification of Zeus to the victim’s computer.
Such targeted attacks can have different aims. In the case of ransomware, it is obvious that a company’s intellectual property can be viewed as being much more valuable than the information on a private computer, so a potential victim is more likely to pay the necessary bitcoins to get it back. In the case of spyware designed to steal financial information, fraudsters can potentially hit the jackpot once they get access to a company’s accounts.
Spyware in the B2B sector can also be used in more sophisticated schemes of financial fraud, including MITM attacks during financial transactions. One such scheme disclosed by our colleagues is described here.
Interestingly, although the payload downloaded on the victim’s computer is very different, its main function is the theft of authentication data, which means that most attacks on the corporate sector have financial goals.
We shouldn’t forget about the potentially dangerous situation where an attacker gains access to a corporate network and gets control of industrial equipment.
Overall in the second quarter of 2017, the percentage of spam in email traffic grew slightly from the previous quarter. The number of email antivirus detections increased by 17% in Q2 vs. Q1.
The number of email antivirus detections on the computers of Kaspersky Lab users, Q1 and Q2 2017.
Necurs botnet continues to distribute spam
The Necurs botnet continues to distribute spam, although the volumes are much smaller than in 2016. This botnet operation is characterized by alternating periods of low and high activity, when we register up to 2 million emails a day sent to Kaspersky Lab customers. In addition to malicious mailings from the botnet, Necurs actively spreads pump-and-dump as well as dating spam:
Malicious emails from the Necurs botnet are usually concise, contain files with DOC, PDF or other extensions. Sometimes, instead of attachments, emails include links to cloud storages such as Dropbox from where malicious files are downloaded.
Spam via legal services
Last quarter we wrote that in order to bypass filters, spammers often spread advertising and fraudulent offers via legitimate means. They include, for example, the ‘Invite friends’ field on social networking sites, notifications about comments that are usually sent to the recipient’s email address, or any other method available on the various sites that allow the sending of emails to a user’s list of trusted addresses. In addition, this type of spam is more difficult to detect because the source is legitimate. Spammers also like it because this type of resource makes for easy targeting. For example, they exploit job search sites to publicize easy earnings or for financial fraud:
Domain fraud
Last quarter we discovered several different mass mailings related to the domain fraud.
One of the mailings was sent in the name of a major company involved in the registration of domain names and addressed the administrators of registered domains. They were informed that it was necessary to activate a domain to confirm their administrator status and ability to manage the domain. These measures were allegedly taken in accordance with the amendments made to regulations by ICANN (Internet Corporation for Assigned Names and Numbers).
To do this, the administrator was told they had a limited time to create a PHP file with specific content in the root directory of the site. The email also stated that failure to observe these conditions would mean the confirmation procedure had not been completed and support for the domain would be suspended.
If the script is launched on the victim’s site, the attackers would be able to gain control of the site and to run any code. In addition, the script makes it possible to collect all user data entered on the site where it is registered and run. The fact that many of these fake emails were sent to addresses belonging to banks, means we can assume that the scammers wanted to collect data entered on the website of those banks, including the logins and passwords used for Internet banking.
Administrators also found themselves the target of yet another type of domain fraud. It involved the administrator of an organization receiving an email prompting them to register their domain with search engines to help potential customers find the company on the Internet. These messages came from addresses generated on free hosting.
This service was provided on a fee basis. In order to see the list of tariffs, the recipient was asked to click a link in the email that was “hosted” on a legitimate website. After choosing a tariff, the user had to fill in and send a form that asked for detailed personal information, including credit card information.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q1 2017 and Q2 2017
In Q2 2017, the largest percentage of spam – 57.99% – was registered in April. The average share of spam in global email traffic for the second quarter amounted to 56.97%, which was 1.07 p.p. more than in the previous quarter.
Sources of spam by country
Sources of spam by country, Q2 2017
The second quarter of 2017 saw a change in the top three sources of spam. Vietnam came first, accounting for 12.37% of world spam. It was followed by the previous quarter’s leader the US, whose share dropped by 8.65 p.p. and accounted for 10.1%. China (8.96%, +1.19 p.p.) completed the top three.
India was the fourth biggest source, responsible for 8.77% (+3.61 p.p.) of total spam, followed by Germany (5.06%, -0.31 p.p.).
Russia, in sixth place, accounted for 4.99%, which is only 0.06 p.p. less than in the previous quarter.
The top 10 biggest sources also included Brazil (4.47%), France (4.35%), Iran (2.49%), and the Netherlands with a share of 1.96%.
Spam email size
Breakdown of spam emails by size, Q1 2017 and Q2 2017
In Q2 2017, the share of small emails (up to 2 KB) in spam traffic changed only slightly and averaged 37.41%, which is 1.9 p.p. more than in the first quarter. The proportion of emails sized 2–5 KB remained at the same level: 4.54%; and those of 5–10 KB (7.83%) declined by 1.36 p.p. and accounted for 5.94%.
The proportion of emails sized 10-20 KB reached 18.31% and emails of 20-50 KB — 27.16%. The proportion of more emails sized 100 KB+ was slightly more than 2%.
Malicious attachments in email
Top 10 malware families
TOP 10 malware families in Q2 2017
Trojan-Downloader.JS.SLoad (8.73%) topped the rating of the most popular malware families. Trojan-Downloader.JS.Agent (3.31%) came second, while Trojan-PSW.Win32.Fareit (3.29%) rounded off the top three.
Trojan-Downloader.JS.Agent (3.05%) came fourth followed by Worm.Win32.WBVB (2.59%).
Newcomers to the top 10, Backdoor.Java.QRat (1.91%) and Trojan.PDF.Phish (1.66%), occupied seventh and ninth places respectively.
The Backdoor.Java.QRat family is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is typically distributed via email as a JAR attachment.
Trojan.PDF.Phish is a PDF document containing a link to a phishing site where users are prompted to enter their login and password for a specific service.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q2 2017
Germany (12.71%) was the country targeted most by malicious mailshots in Q2 2017. China, last quarter’s leader, came second (12.09%), followed by the UK (9.11%).
Japan (5.87%) was fourth, with Russia occupying fifth with a share of 5.67%. Next came Brazil (4.99%), Italy (3.96%), Vietnam (3.06%) and France (2.81%).
The US (2.31%) completed the top 10.
Phishing
In the second quarter of 2017, the Anti-Phishing system prevented 46,557,343 attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017.
Geography of attacks
In Q2 2017, Brazil (18.09%) was the country where the largest percentage of users was affected by phishing attacks, although its share decreased by 1.07 p.p. compared to the previous quarter.
Geography of phishing attacks*, Q2 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in that country
The percentage of users attacked in China decreased by 7.24 p.p. and amounted to 12.85%, placing the country second in this ranking. Australia added 1.96 p.p. to the previous quarter’s figure and came third with 12.69%. The percentage of attacked users in New Zealand increased to 12.06% (+ 0.12p.p.), with Azerbaijan (11.48%) in fifth. The Republic of South Africa (9.38%), Argentina (9.35%) and the UK (9.29%) rounded off this top 10.
In the second quarter, Russia (8.74%) exited this top 10 of countries with the largest percentage of users affected by phishing attacks, falling to 18th place.
Brazil 18.09%
China 12.85%
Australia 12.69%
New Zealand 12.06%
Azerbaijan 11.48%
Canada 11.28%
Qatar 10. 68%
Venezuela 10.56%
South Africa 9.38%
Argentina 9.35%
UK 9.29%
TOP 10 countries by percentage of users attacked
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q2 2017, the Banks (23.49%, -2.33 p.p.), Payment systems (18.40%, +4.8 p.p.) and Online stores (9.58%, -1.31 p.p.) categories accounted for more than half (51.47%) of all registered attacks.
Distribution of organizations affected by phishing attacks by category, Q2 2017
Hot topics this quarter
Airline tickets
In the second quarter of 2017, Facebook was hit with a wave of posts that falsely claimed that major airlines were giving away tickets for free. Naturally, there were no promotions giving away airline tickets: fraudsters had created a number of sites on which users were congratulated on winning an air ticket and were asked to perform a series of actions to receive their prize. First, the victims were asked to post the promotional information on their Facebook page. Secondly, the victims had to click the “Like” button. After performing all the necessary actions, the website redirected the user to a resource promoted by the fraudsters. The content of these pages varied – from harmless ads to malicious software.
False browser blocking
Almost all the popular browsers have built-in protection against web threats. When entering a malicious or phishing page, they often warn the user of the potential dangers and recommend not visiting it.
Fraudsters also make use this protection measure for their own purposes and distract the victim with warnings. For example, they simulate the Chrome blocking page. A user who has ever seen this warning from the browser is more likely to trust the page and follow the criminals’ prompts.
The main danger of these pages is that careful examination of the address bar doesn’t help – a browser warning usually “pops up” on untrusted web resources.
However, they may also appear when trying to enter a domain belonging to companies that act as a hosting service. And it is precisely such warnings that cause the victims to have greater trust in them:
As a rule, when a user calls the numbers specified, the fraudsters pretend to be a support service, tricking victims into paying for services they allegedly need.
Punycode encoding
Close examination of the address bar may not help if the phishers use non-Latin characters that are similar to Latin letters to create domain names that are almost identical to the names of popular web resources. Web browsers use Punycode to represent Unicode characters in a URL. However, if all the characters in the domain name belong to the character set of one language, the browser will display them in the language specified rather than in Punycode.
The screenshot of the phishing page below demonstrates this technique.
Sometimes on closer examination, you can see inconsistencies, for example, like the dot under the letter ‘e’.
Have a look at the banner of the blocking site: it displays a URL in Punycode. However, it differs from what we see in the browser. This address is definitely not a domain owned by a well-known company.
Technically, the address is completely different from the original one. Moreover, phishers have used different encodings in the names of pages before. However, for ordinary users, recognizing this type of phishing can be a problem.
Attacks on Uber users
One of Q2’s high-profile news stories was an attack on Uber users. Phishing pages were distributed via spam mailings; recipients were offered a large discount if they completed a “registration” form, where in addition to personal data they had to enter their bank card information. After completing the questionnaire, the user was redirected to the legitimate site of the company.
Because Uber often holds promotions and offers discounts, users are less inclined to doubt the authenticity of the offer.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages hiding behind the names of fewer than 15 companies.
Organization % of detected phishing links
Facebook 8.33
Microsoft Corporation 8.22
Yahoo! 8.01
For the third quarter in a row the top three organizations attacked most often by phishers remained unchanged. In Q1, Yahoo! was the organization whose brand was mentioned most often on phishing pages. However, in the second quarter it dropped to third, giving way to Facebook (8.33%) and Microsoft (8.22%).
One of the phishers’ tricks is to place pages of popular organizations on domains belonging to other popular organizations. In the example below, a link to a free hosting service is shown, and while not all users will know what this is, mentioning Google is more likely to make them think it’s genuine.
The actual data form is usually located on another domain, where a user ends up after clicking on the button.
Conclusion
In Q2 2017, the average share of spam in global email traffic amounted to 56.97%, which was only 1.07 p.p. more than in the previous quarter. One of the most notable events of this quarter – the WannaCry epidemic – did not go unnoticed by spammers: numerous mass mailings contained offers of assistance in combating the ransomware, as well as various workshops and training for users.
In the second quarter, the most popular malware family was the JS.SLoad (8.73%), with another downloader, MSWord.Agent, in second (3.31%). The Fareit Trojan family (3.29%) rounded off the top three.
The Anti-Phishing system prevented over 46.5 million attempted visits to phishing pages on the computers of Kaspersky Lab users. Overall, 8.26% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q2 2017. Noticeably, in their earlier attacks, fraudsters counted on user carelessness and low levels of Internet literacy. However, as users are becoming more cyber savvy, phishers have had to come up with new tricks, such as placing phishing pages on domains owned by well-known organizations.
Spam Rate Hits Two-Year High
7.8.2017 securityweek Spam
In July 2017, global spam rate reached the highest level registered since March 2015, fueled by the emergence of malware families attempting to self-spread via email, according to Symantec.
The global spam rate last month was 54.9%, registering a 0.6 percentage point increase compared to the previous month. Driving the rate upwards was, among other factors, the appearance of malware variants that could spread via spam emails.
The surge was also mirrored in an increase in email malware rate, which reached one in 359 emails in July, up from one in 451 during the previous month. This is the highest rate registered this year, but still lower than the levels registered at the end of last year (the rate reached one in 111 emails in November 2016).
The number of new malware variants, however, went down in July 2017, dropping from 66.3 million to 58.7 million variants, Symantec’s Latest Intelligence report shows.
“This trend in malware being distributed through email seems to be catching on, with several infamous malware families recently adding functionality that allows them to spread via spam email,” Symantec said.
Earlier this year, threats such as WannaCry and NotPetya proved how effective worm-like spreading capabilities could be, and various malware families out there adopted similar tactics. The Emotet banking Trojan added the ability to steal email credentials from infected computers and use them to send spam and spread itself.
The TrickBot banking malware added a module to leverage SMB and spread to computers on the same network (but the functionality isn’t yet active) and also started targeting Outlook data. A ransomware family called Reyptson was observed last month packing the ability to steal Thunderbird email client credentials to send spam messages containing a link to its executable.
“Attackers are increasingly making use of tools already installed on targeted computers or are running simple scripts and shellcode directly in memory. This allows them to minimize the risk of their attacks being discovered and blocked by traditional security tools,” Symantec notes.
The rate of phishing attacks went up as well, reaching one in 1,968 emails, the highest level observed during the past 12 months. The number of web attacks blocked by Symantec decreased slightly, from 1,159,398 per day to 1,158,985 per day. Despite that, July was the fourth consecutive month with elevated web attack activity.
The Mining sector had the highest spam rate (59.1%), followed by Manufacturing (56.9%). The Mining sector had the highest phishing rate at one in 1,263 emails, while the Agriculture, Forestry, & Fishing sector had the highest email malware rate at one in 152 emails.
During July, security researchers also discovered a new type of attack targeting fresh installations of WordPress. As part of the attack, cybercriminals are scanning for a specific setup URL used in new installations of the content management system, and then take over the installation as it hasn’t been yet configured, replacing legitimate resources with their own, and even compromising hosting accounts and all other sites on that account.
Indonesia to Deport 153 Chinese for $450 Million Scam
1.8.2017 securityweek Spam
Indonesia will deport 153 Chinese nationals arrested for alleged involvement in a multimillion-dollar cyber fraud ring targeting wealthy businessmen and politicians in China, police said Tuesday.
The syndicate, who ran their operation from abroad to avoid detection by Chinese officials but did not target any victims in their host country, made around six trillion rupiah ($450 million) since beginning operations at the end of 2016, Indonesia police said.
They were arrested following a tip-off from Chinese authorities.
"We are conducting an intensive investigation and currently coordinating with the Chinese police to deport them," said national police spokesman Rikwanto, who goes by one name.
The group, based in several locations across Indonesia, contacted victims pretending to be Chinese police or law officials, promising to help resolve their legal cases in return for immediate cash transfers, Jakarta police said.
The criminal network included IT specialists who would retrieve information on victims and develop communications systems for contacting them, he said.
Chinese nationals were arrested in Jakarta, the city of Surabaya and on the resort island of Bali in separate raids over the weekend.
"The perpetrators and the victims are Chinese. It just happens that they operate from Indonesia," said Jakarta police spokesman Argo Yuwono.
Police are investigating how several of the Chinese suspects were able to enter the archipelago without a valid passport.
Cyber criminals targeting victims in China have increasingly exploited technological advances to operate from abroad, spreading across Southeast Asia and beyond in recent years.
China has become increasingly assertive in extraditing suspects.
In July, a gang of 44 people from China and Taiwan were arrested in Thailand for allegedly running an elaborate phone scam that conned $3 million from scores of victims, mainly based in China.
Cambodia deported 74 people to China for their role in an alleged telecom fraud, also in July, according to Xinhua.
Last year, 67 alleged criminals were deported from Kenya to China to face investigation for fraud.