
Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
Drupal Patches Flaw Exploited in Spam Campaigns
22.6.2017 securityweek Exploit Spam
Drupal security updates released on Wednesday address several vulnerabilities, including one that has been exploited in spam campaigns.
The flaw exploited in the wild, patched with the release of Drupal versions 7.56 and 8.3.4, is a moderately critical access bypass vulnerability tracked as CVE-2017-6922.
The problem is that files uploaded by anonymous users to a private file system can be accessed by all anonymous users, not just the user who uploaded them, as it should be. The security hole only affects websites that allow anonymous users to upload files to a private file system.
Drupal has known about attacks exploiting this flaw since October 2016. At the time, it warned that misconfigured websites had been abused by malicious actors to host files and point users and search engines to them. The latest updates for Drupal 7 and 8 introduce a protection that should prevent exploitation.
“For example, if a webform configured to allow anonymous visitors to upload an image into the public file system, that image would then be accessible by anyone on the internet. The site could be used by an attacker to host images and other files that the legitimate site maintainers would not want made publicly available through their site,” the Drupal Security Team said in its October 2016 advisory.
Drupal 8.3.4 also patches a critical issue related to how the PECL YAML parser handles unsafe objects. An attacker can exploit the flaw, tracked as CVE-2017-6920, for remote code execution.
Another vulnerability fixed in Drupal 8 is a less critical improper field validation bug (CVE-2017-6921).
“A site is only affected by this if the site has the RESTful Web Services (rest) module enabled, the file REST resource is enabled and allows PATCH requests, and an attacker can get or register a user account on the site with permissions to upload files and to modify the file resource,” Drupal said in its advisory.
The Drupal Security Team warned users in mid-April that a serious vulnerability affected a third-party module named References, which had been used by more than 121,000 websites. The module had no longer been supported and Drupal initially advised users to migrate to a different product. However, a new maintainer took over the project shortly after and the flaw was addressed.
Creators of Bitcoin Miners Face $12 Million Fine for 'Ponzi Scheme' Scam
7.6.2017 thehackernews Spam
Creators of Bitcoin Miners Face $12 Million Fine for 'Ponzi Scheme' Scam
Every time a new topic trends on the Internet, scammers take advantage of it.
You must have heard of Bitcoin and how in recent days it has made some early investors millionaire overnight.
Yes, the Bitcoin boom is back, and it's real — a digital currency that has just crossed a new milestone today. The current price of 1 BTC or 1 Bitcoin = US$2,850.
An American con man took advantage of this boom in Bitcoin market to run bogus bitcoin mining schemes and earn millions of dollars.
But the bogus schemes ended as the United States Securities and Exchange Commission (SEC) has won a legal battle against two bogus, but now defunct, Bitcoin companies operated by Homero Joshua Garza — GAW Miners and ZenMiner.
Garza is now facing a $12 Million (£9.2 Million) penalty for running the bogus schemes – what lawmakers have certified was a "Ponzi scheme."
According to the SEC, Garza used the "lure of quick riches" in order to get people to invest in the bitcoin mining schemes, which means those who add their computing power to help verify transactions, a practice known as mining, are rewarded with Bitcoins.
Garza's GAW Miners and ZenMiner purported to provide shares in cloud-based Bitcoin mining machinery, but nothing like that was ever built by the operator.
Garza told investors that he had enough computing power to mine a lot of bitcoins on their behalf and share the proceeds, but in reality, he just used cash from new investors to reward earlier joiners, which is nothing but a fraudulent "ponzi" scheme, according to the SEC.
The SEC said: "Most investors paid for a share of computing power that never existed." It also said that about 10,000 investors joined the bogus schemes and handed over $20 Million to Garza.
Few got back their money they invested, but many left without a single penny.
The complaint against the Bitcoin mining schemes was filed on 1 December 2015, and on June 2, the US District of Connecticut federal court sided with the SEC, ordering both GAW Miners and ZenMiner to pay a combined of $10,384,099 in disgorgement and prejudgment interest, along with $1,000,000 in damages.
Both GAW Miners and ZenMiner companies have now been shut down.
However, a ruling is yet to be made on the Bitcoin funds collected by Garza. In 2014, when Garza was running the bogus schemes from his home in Connecticut, 1 BTC was equal to $450, and today it is around $2,800.
So, the $20 Million funds Garza took from the investors today worth around $150 million.
Business email compromise (BEC), the 5 billion dollar scam
7.5.2017 securityaffairs Spam
The Federal Bureau of Investigation report reveals that Business email compromise scams caused losses to businesses for 5 billion dollars over four years.
Business email compromise (BEC) continues to be a profitable attack technique for crooks and a serious threat to businesses.
The FBI has published data related to this specific criminal practice, and financial figures are astonishing.
The fraud scheme is very simple, busy employees receive a request to transfer funds by representatives of high management of their company.
The request could be sent by an attacker that either compromises a company’s email accounts or sets up a phishing message that submits a fake invoice to the victim from someone posing as a contractor or business partner.
It is clear that businesses and personnel using open source e-mail are most targeted by Business Email Compromise, in many cases the criminals spoofed e-mails of individuals within enterprises who are entitled to submit such payment requests.
Individuals responsible for handling wire transfers within specific companies are privileged targets of criminals which compose well-worded e-mail requests for a wire transfer.
The attacker behind Business Email Compromise scams shows a deep knowledge of their victims, their requests are proportional to the economic capabilities of the target and of the specific individual used as the sender of the request. The criminals sent e-mails concurrently with business travel dates for executives whose e-mails were spoofed.
The statement issued by the FBI in 2015 reported three different versions of the Business Email Compromise based on complaints received since 2009:
Version 1
A business, which often has a long standing relationship with a supplier, is asked to wire funds for invoice payment to an alternate, fraudulent account. This particular version has also been referred to as “The Bogus Invoice Scheme,” “The Supplier Swindle,” and “Invoice Modification Scheme.”
Version 2
The e-mail accounts of high-level business executives (CFO, CTO, etc) are compromised. The account may be spoofed or hacked. A request for a wire transfer from the compromised account is made to a second employee within the company who is normally responsible for processing these requests. This particular version has also been referred to as “CEO Fraud,” “Business Executive Scam,” “Masquerading,” and “Financial Industry Wire Frauds.”
Version 3
An employee of a business has his/her personal e-mail hacked. Requests for invoice payments to fraudster-controlled bank accounts are sent from this employee’s personal e-mail to multiple vendors identified from this employee’s contact list. The business may not become aware of the fraudulent requests until they are contacted by their vendors to follow up on the status of their invoice payment.
Data provided by the FBI is related to BEC crimes occurred between 2013 and December 2016, cyber criminals have earned $5,302,890,448 from 40,203 cases involving US and international businesses.
The FBI also confirmed that BEC scams continue to increase, 2,370 percent over the past year.
The FBI set up a reporting site for BEC scams and observed that between June and December of last year, US businesses reported losses of $346,160,957 in 3,044 attacks.
In the same period, non-US businesses reported losses of $448,464,415, but the overall number of BEC scams was much lower: 774. These data confirm that BEC scams are an emergency for US firms.
“The BEC/EAC scam continues to grow, evolve, and target small, medium, and large businesses. Between January 2015 and December 2016, there was a 2,370% increase in identified exposed losses. The scam has been reported in all 50 states and in 131 countries. Victim complaints filed with the IC3 and financial sources indicate fraudulent transfers have been sent to 103 countries.” states the Alert published by the FBI.
Based on the financial data, Asian banks located in China and Hong Kong remain the primary destinations of fraudulent funds; however, financial institutions in the United Kingdom have also been identified as prominent destinations.”

Stolen funds were mostly diverted to Asian banks located in China and Hong Kong, but Feds also confirmed that the use of British banks is on the rise.
The FBI report highlights that many recent attacks were preceded by a malware-based attack, mainly ransomware, likely because the crooks evaluate the ability of the firm to pay.
The FBI confirmed an increase of Real estate scams (+480 percent respect 2016).
The report also suggests company further security measures to prevent Business Email Compromise attacks, including the implementation of a two-step verification process. For example:
Out-of-Band Communication: Establish other communication channels, such as telephone calls, to verify significant transactions. Arrange this two-factor authentication early in the relationship and outside the e-mail environment to avoid interception by a hacker.
Digital Signatures: Both entities on EACh side of a transaction should utilize digital signatures. This will not work with web-based e-mail accounts. Additionally, some countries ban or limit the use of encryption.
Give a look at the report, it is full of interesting data.
Spam and phishing in Q1 2017
6.5.2017 Kaspersky Spam
We wrote earlier about a sharp increase in the amount of spam with malicious attachments, mainly Trojan encryptors. Most of that spam was coming from the Necurs botnet, which is currently considered the world’s largest spam botnet. However, in late December 2016, the network’s activity almost ceased completely and, as time showed, it wasn’t just a break for the festive season. The volume of spam sent from this botnet remained at an extremely low level for almost the entire first quarter of 2017.
In Q1 2017, the percentage of spam in email traffic amounted to 55.9%.
Tweet
Why has Necurs stopped distributing spam? We know that the botnet is active and the bots are waiting for commands. Perhaps the criminals behind the botnet got scared by all the fuss made about encryptors and decided to temporarily suspend their mass mailings.
We still continue to register malicious mass mailings from what is presumably the Necurs botnet, though their volume is a fraction of the amount recorded in December:
The number of malicious messages caught by our traps that were presumably sent by the Necurs botnet
As before, the emails usually imitate various types of bills and other official documents:
The email above contained an attached MSWord document with macros that downloaded the Rack family encryptor (detected as Trojan.NSIS.Sod.jov) to the victim machine.
In addition to malicious mailings from the botnet, we came across a mass mailing about pump-and-dump stock schemes:
As a rule, mass mailings exploiting this subject are distributed in huge volumes over a very short period of time. This is because the fraudsters have to pump and dump shares quickly, before their scams are discovered on the stock exchange. This type of stock fraud is against the law, so cybercriminals try to wind up the affair within a couple of days. The Necurs botnet is ideal for this sort of scam due to its size – according to estimates, it currently exceeds 200,000 bots.
The average share of spam in Russia’s email traffic in Q1 2017 was 61.6%.
Tweet
Does this sharp drop mean we have reached peak crypto-spam mass mailing and it’s about to disappear? Unfortunately, no.
The total volume of malware detected in email decreased, but not that dramatically – 2.4 times less than the previous quarter.
The number of email antivirus detections, Q4 2016 vs Q1 2017
Malicious mass mailings are still being sent out and, although their volume has decreased, cybercriminals are using a variety of techniques to deceive both security solutions and users.
Malicious emails with password-protected archives
In the first quarter we observed a trend towards packing malware into password-protected archives to complicate detection of malicious emails.
All the classic tricks were used to make potential victims open the archives: fake notifications about orders from large stores, various bills, money transfers, resumes, or the promise of lots of money.
The attached archives usually contained office documents with macros or JavaScript scripts. When launched, the files downloaded other malicious programs on the user’s computer. Interestingly, after the decline in Necurs botnet activity, the harmful “payload” that spread via spam became much more diverse. The cybercriminals sent out ransomware and spyware, backdoors and a new modification of the infamous Zeus Trojan.
The attachments above contain Microsoft Word documents with macros that download several different modifications of a Trojan encryptor belonging to the Cerber family from onion domains in different zones. This malicious program selectively encrypts data on the user’s computer and demands a ransom for decrypting it via a site on the Tor network.
The archive in the message above contains the Richard-CV.doc file with macros that downloads representatives of the Fareit spyware family from the onion.nu domain. These malicious programs collect confidential information about the user and send it to the remote server.
There was yet another case involving downloadable spyware, this time from the Pinch family. The Trojan collects passwords, email addresses, information about the system configuration and registry settings. Among other things, it harvests information from instant messaging services and mail clients. The obtained data is encrypted and sent to the criminals by email. According to our information received from KSN, the program is most widespread in Russia, India and Iran.
Most email antivirus detections occurred in China – 18% of all spam.
Tweet
It’s worth pointing out that this spyware was spread using fake business correspondence. Emails were sent out using the names of real small and medium businesses with all the relevant signatures and contacts, rather than using the name of some made-up organization.
Unlike other emails, the example above does not contain a password-protected archive. The request to enter a password is just a trick: the fraudsters want the user to enable Microsoft Word macros to run the malicious script.
The contents of the email above include a password-protected document with a script in Visual Basic that downloads the Andromeda bot on the victim machine. The latter establishes a connection with the command center and waits for commands from the owners. It has broad functionality and can download other malicious programs on the user’s computer.
This fake notification from an e-store contains a malicious script. On entering the password and launching the malicious content, the Receipt_320124.lnk file is created in the %TEMP% catalogue. It, in turn, downloads a Trojan-banker of the Sphinx family, which is a modification of the older and infamous Zeus, on the victim computer.
As we can see, very different mass mailings with malicious attachments now contain files packed in a password-protected archive. Most likely, this trend will continue: a password-protected document is likely to appear more trustworthy to the user, while causing problems for security solutions.
Spam via legal services
Modern virtual platforms for communication (messengers, social networks) are also actively used by spammers to spread advertising and fraudulent offers. Cybercriminals register special accounts for spamming in social networks and to make their messages look more authentic they use techniques similar to those used in traditional mass mailings (for example, the personal data from the account and that sent in the email are the same). The same type of spam, for example, ‘Nigerian letters’, offering earnings, etc. can be distributed via email traffic and social networks. A notification about a message is usually sent to the recipient’s email address; in this case, the technical header of the email is legitimate, and it is only possible to detect the spam by the contents of the message. Spam distributed directly via email, can be easily detected by technical headers. The same cannot be said for messages sent via legitimate services, especially if the address of the service is added to the user’s list of trusted addresses.
Today’s email spam filters can cope effectively with the task of detecting spam that is sent in the traditional way, so spammers are forced to look for new methods to bypass filters.
Holidays and spam
The first quarter of 2017 saw festive spam dedicated to New Year, St. Patrick’s Day, Easter and Valentine’s Day. Small and medium-sized businesses advertised their services and products and offered holiday discounts. Offers from Chinese factories were timed to coincide with the Chinese New Year, which was celebrated in mid-February.
Spammers also sent out numerous offers to participate in a survey and get coupons or gift cards from major online stores, hoping to collect the recipients’ personal information and contact details.
Burst of B2B spam
In the first three months of 2017, we also recorded a large number of mass mailings containing offers to buy company databases from specific industries. This type of spam remains popular with spammers and primarily targets companies or individual representatives of large businesses rather than ordinary users. Therefore, these messages are sent mainly to people or companies from a list of contacts or addresses for a particular business segment that is obtained, as a rule, in the same way – via spam.
The offers are sent on behalf of firms or their representatives, but they are often completely impersonal.
Spammers have databases of companies for any business segment, as well as the contact details of participants at major exhibitions, seminars, forums and other events. To make recipients interested in their offers, spammers often send several free contacts from their collections.
Statistics
Proportion of spam in email traffic
Percentage of spam in global email traffic, Q4 2016 and Q1 2017
Compared to Q4 2016, there was a decline in the overall proportion of spam in global email traffic in the first three months of 2017. In January, the proportion fell to 55.05%, while in February the share was even lower – 53.4%. However, in March the level of spam showed an upward trend, rising to 56.9%. As a result, the average share of spam in global email traffic for the first quarter of 2017 was 55.9%.
Percentage of spam in Russia’s email traffic, Q4 2016 and Q1 2017
The spam situation in the Russian segment of the Internet was somewhat different from the global one. In January 2017, the proportion of junk email increased to almost 63% and stayed in the 60-63% range until the end of the quarter. In February, as was the case with overall global traffic, there was a decline – to 60.35% – followed by an increase to 61.65% in March. The average share of spam in Russian email traffic in the first quarter of 2017 was 61.66%.
Sources of spam by country
Sources of spam by country, Q1 2017
In the first quarter of 2017, the US remained the leading source of spam – its share accounted for 18.75%. Representatives from the Asia-Pacific region – Vietnam (7.86%) and China (7.77%) – came second and third.
Trojan-Downloader.JS.Agent remained the most popular malware family spread via email.
Tweet
Germany was the fourth biggest source, responsible for 5.37% of world spam, followed by India (5.16%). Russia, in sixth place, accounted for 4.93% of total spam.
The top 10 biggest sources also included France (4.41%), Brazil (3.44%), Poland (1.90%) and the Netherlands (1.85%).
Spam email size
Breakdown of spam emails by size, Q4 2016 and Q1 2017
In Q1 2017, the share of small emails (up to 2 KB) in spam traffic decreased considerably and averaged 29.17%, which is 12.93 p.p. less than in the fourth quarter of 2016. The proportion of emails sized 2–5 KB (3.74%) and 5–10 KB (7.83%) also continued to decline.
Meanwhile, the proportion of emails sized 10-20 KB (25.61%) and 20-50 KB (28.04%) increased. Last year’s trend of fewer super-short spam emails and more average-sized emails has continued into 2017.
Malicious attachments in email
Top 10 malware families
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
TOP 10 malware families in Q1 2017
The Backdoor.Java.Adwind family (2.36%) in fifth place is a cross-platform multifunctional backdoor written in Java and sold on DarkNet as malware-as-a-service (MaaS). It is also known under the names of AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRat. It is typically distributed via email as a JAR attachment.
A newcomer – Trojan-Downloader.MSWord.Cryptoload (1.27%) – occupied ninth place. It’s a JS script containing malware, which it installs and runs on the computer.
Trojan-Downloader.VBS.Agent (1.26%) rounded off the Top 10.
Countries targeted by malicious mailshots
Distribution of email antivirus verdicts by country, Q1 2017
In Q1 2017, China (18.23%) was the country targeted most by malicious mailshots. Germany, last year’s leader, came second (11.86%), followed by the UK (8.16%) in third.
Italy (7.87%), Brazil (6.04%) and Japan (4.04%) came next, with Russia occupying seventh place with a share of 3.93%. The US was in ninth place with (2.46%), while Vietnam (1.94%) completed the Top 10.
Phishing
In the first quarter of 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. Overall, 9.31% of unique users of Kaspersky Lab products worldwide were attacked by phishers in Q1 2017.
Geography of attacks
China (20.88%) remained the country where the largest percentage of users is affected by phishing attacks, although its share decreased by 1.67 p.p.
Geography of phishing attacks*, Q1 2017
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Brazil decreased by 0.8 p.p. and amounted to 19.16%, placing the country second in this ranking. Macao added 0.91 p.p. to the previous quarter’s figure and came third with 11.94%. Russia came fourth with 11.29% (+0.73 p.p.), followed by and Australia on 10.73% (-0.37p.p).
TOP 10 countries by percentage of users attacked
Country %
China 20.87%
Brazil 19.16%
Macao 11.94%
Russia 11.29%
Australia 10.73%
Argentina 10.42%
New Zealand 10.18%
Qatar 9.87%
Kazakhstan 9.61%
Taiwan 9.27%
Argentina (10.42%, +1.78 p.p.), New Zealand (10.18%), Qatar (9.87%), Kazakhstan (9.61%) and Taiwan (9.27%) completed the top 10.
Organizations under attack
Rating the categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections of Kaspersky Lab’s heuristic anti-phishing component. It is activated every time a user attempts to open a phishing page while information about it has not yet been included in Kaspersky Lab’s databases. It does not matter how the user attempts to open the page – by clicking a link in a phishing email or in a message on a social network or, for example, as a result of malware activity. After the security system is activated, a banner is displayed in the browser warning the user about a potential threat.
In Q1 2017, the ‘Banks’ (25.82%, -0.53 p.p.), ‘Payment systems’ (13.6%, +2.23 p.p.) and ‘Online stores’ (10.89%, +0.48 p.p.) categories accounted for more than half of all registered attacks. The total share of ‘Financial organizations’ was a little over 50% of all phishing attack
Distribution of organizations affected by phishing attacks by category, Q1 2017
In addition to financial organizations, phishers most often targeted ‘Global Internet portals’ (19.1%), although their share decreased by 5.25 p.p. from the previous quarter. ‘Social networking sites’ (9.56%) and ‘Telecommunication companies’ (5.93%) also saw their shares fall by 0.32 p.p. and 0.83 p.p. respectively. The percentage of the ‘Online games’ category accounted for 1.65% while the figure for ‘Instant messaging’ was 1.53%.
TOP 3 attacked organizations
Fraudsters continue to focus most of their attention on the most popular brands, enhancing their chances of a successful phishing attack. More than half of all detections of Kaspersky Lab’s heuristic anti-phishing component are for phishing pages using the names of fewer than 15 companies.
In Q1 2017, Kaspersky Lab products blocked 51 million attempts to open a phishing page.
Tweet
The TOP 3 organizations attacked most frequently by phishers remained unchanged for the second quarter in a row. Yahoo! was once again the organization whose brand was mentioned most often on phishing pages (7.57%, – 1.16 p.p.). Facebook (7.24%), whose share fell by 0.13 p.p., was second, while Microsoft (5.39%, -0.83 p.p.) came third.
Organization % of detected phishing links
Yahoo! 7.57
Facebook 7.24
Microsoft Corporation 5.39
In order to reach the widest possible audience with one attack, scammers often mention a variety of brands expecting the victims to react to at least one of them. This is facilitated by authentication with existing accounts, which many Internet services use trying to make life easier for their users. Therefore, a page offering to use different accounts to enter a site does not arouse suspicions. This allows fraudsters to steal user data from several different resources using just one phishing page.
Phishing page prompting the user to login via the accounts of other web resources to access a file
This phishing page uses a similar trick under the pretext of accessing the Google Drive service
Hot topics this quarter
Payment systems
In the first quarter Q1 2017, 13.6% of detections of Kaspersky Lab’s heuristic anti-phishing component fell under the ‘Payment Systems’ category. It means that every eighth attack targeted this category, which has been popular with phishers for several quarters now.
PayPal (28.25%) came first on the list of attacked payment systems, followed by Visa (25.78%) and American Express (24.38%).
Organization %*
PayPal 28.25
Visa Inc. 25.78
American Express 24.38
MasterCard International 16.66
Others 4.94
* The percentage of attacks on an organization as a total of all attacks on organizations from the ‘Payment Systems’ category
The goal of phishers attacking customers of popular payment systems is to get personal and payment data, login details for accounts, etc. Criminals often place fraudulent content on reputable resources in order to gain the trust of the user and bypass blacklisting. For example, we came across a fake PayPal support page located on the Google Sites service (the primary domain is google.com). After clicking on the banner, the user is redirected to a phishing page, where they are asked to enter their account data for the payment system.
Phishing page using the PayPal brand located on the Google domain
Another trick used by phishers is to place phishing content on the servers of government agencies. This is possible because a significant number of government agencies do not pay much attention to the security of their web resources.
Phishing page using the PayPal brand located on a server belonging to Sri Lankan government
Phishing page using the PayPal brand located on a server belonging to the Bangladesh government
Emails threatening to block an account or asking to update data in a payment system were used as bait.
Online stores
Every tenth phishing attack targeted users of online stores. In Q1 2017, Amazon (39.13%) was the most popular brand with phishers.
Organization %
Amazon.com: Online Shopping 39.13
Apple 15.43
Steam 6.5
eBay 5.15
Alibaba Group 2.87
Taobao 2.54
Other targets 28.38
By using the Amazon brand, cybercriminals are trying not only to steal login data but also all the personal information of the user, including their bank card details. Also, they often place fake pages on domains that have a good reputation (for example, on a domain owned by Vodafone).
Phishing page using the Amazon brand located on the Vodafone domain
Earning money with anti-phishing
In addition to standard phishing emails and pages, we often come across other methods of tricking users. Scammers often exploit people’s desire to make easy money by offering cash to view advertising, automatic stock trading programs and much more.
Spam emails offering quick money on the Internet
In the first quarter of 2017, we saw a rather interesting fraudulent resource which claimed to be combating phishing sites. All you had to do if you wanted to make some quick cash was to register and perform several tasks, the essence of which was to evaluate web pages using the following options: malicious, safe, does not load. Only the content of the page was evaluated, while its address was not displayed.
After checking 31 sites, it turned out that $7 needed to be paid to withdraw the money that was earned
For each ‘checked’ site, the user earned about $3. To withdraw that money, they had to transfer $7 to the owners of the resource as confirmation that they were an adult and financially solvent. Of course, no ‘earnings’ were ever received after that.
Conclusion
Although the beginning of Q1 2017 was marked by a decline in the amount of spam in overall global email traffic, in March the situation became more stable, and the average share of spam for the quarter amounted to 55.9%. The US (18.75%) remained the biggest source of spam, followed by Vietnam (7.86%) and China (7.77%).
The first quarter of 2017 was also notable for the decrease in the volume of malicious spam sent from the Necurs botnet: the number of such mass mailings decreased significantly compared to the previous reporting period. However, the lull may be temporary: the attackers may have decided to suspend mass mailings until all the hype about encryptors subsides.
Trojan-Downloader.JS.Agent (6.14%) once again topped the rating of the most popular malware families detected in email. Trojan-Downloader.JS.SLoad (3.79%) came second, while Trojan-PSW.Win32.Fareit (3.10%) completed the top three.
In Q1 2017, the Anti-Phishing system was triggered 51,321,809 times on the computers of Kaspersky Lab users. China (20.88%) topped the rating of countries most often attacked by phishers. Financial organizations remained the main target for phishers, and we expect this trend to continue in the future.
Researchers Expose Huge Ad Scam Operation
1.5.2017 securityweek Spam
Researchers from security frim RiskIQ recently discovered a large ad scam operation where cybercriminals employed advanced automation techniques to deliver scam ads from millions of different domain names.
Dubbed NoTrove, the threat actor managed to stay ahead of detection and takedown efforts, while also building a network that generated huge amounts of traffic. The group was first observed a year ago, but the security researchers believe that it has been operating since at least 2010.
NoTrove was mainly focused on getting as much web traffic as possible, for monetary gain, and RiskIQ associated the group to 78 campaigns, including scam survey rewards, fake software downloads, and redirections to PUPs (Potentially Unwanted Programs). Although the used domains were short-lived, the generated traffic from scam ad deliveries was so large that it even pushed one of them to a 517 ranking on the Alexa top 10,000 web sites.
The actor was observed switching between 2,000 randomly generated domains and more than 3,000 IP addresses, operating across millions of Fully Qualified Domain Names (FQDNs). An FQDN is a complete web address, typically including subdomains for ad scammers, RiskIQ security researchers explain in their report (PDF).
The NoTrove FQDNs show high-entropy (they are highly random hosts), which shows that automation was used when creating them. Next to the high-entropy hosts, the researchers identified campaign-specific middle hosts, which appear to label the type of scam employed in the campaign, along with high-entropy or randomly worded domains, also generated using automation.
“With high-entropy domains and always-shifting hosting, we’ve seen NoTrove burn through just under 2,000 domains and over 3,000 IPs. Combined with the 78 variations of campaign-specific middle word variants and randomized hostnames, we’ve seen NoTrove operate across millions of FQDNs. Typically, one IP used by NoTrove will house a set of domains, but each campaign-specific *.domain.tld campaign variant will be hosted on its own IP, usually a Choopa or Linode droplet,” the researchers say.
“NoTrove harms not only visiting users, but also legitimate advertisers, adversely affecting those reliant on the credibility of the digital advertising ecosystem such as online retailers, service providers and media outlets. Constantly shifting infrastructure means simply blocking domains and IPs isn't enough. We must now begin utilizing machine learning to leverage human security teams who increasingly depend on accurate, automated scam detection,” RiskIQ threat researcher William MacArthur said.
Personalized Spam and Phishing
20.4.2017 Kaspersky Spam
Most spam, especially the sort that is mass-mailed on behalf of businesses, has quite an impersonal format: spammers create a message template for a specific mailing purpose and often drastically diversify the contents of that template. Generally, these kinds of messages do not personally address the recipient and are limited to common phrases such as “Dear Client”. The most that personal data is ever involved is when the name of the mailbox (or part of it) is substituted with the electronic address that the spammer has. Any specifics that may help the recipient ascertain whether the message is addressed personally to him or not, for example, an existing account number, a contract number, or the date of its conclusion, is missing in the message. This impersonality, as a rule, attests toa phishing attempt.
Lately, however, we have been noticing an opposite tendency occurring quite often, wherein fraud becomes personalized and spammers invent new methods to persuade the recipient that the message is addressed personally to him. Thus, in the malicious mailing that we discovered last month, spammers used the actual postal addresses of the recipients in messages to make them seem as credible as possible. This information is sold to evildoers as ready-to-use databases with physical addresses (they are frequently offered for sale in spam messages), collected by evildoers from open sources, or obtained by evildoers when hacking email accounts, for example. Of course, cybercriminals will not have very many of these addresses at their disposal (compared to generated addresses), but they are much more valuable.
The way spammers organize their personalized attacks plays an important role as well. In general, messages are mass mailed on behalf of an existing company, while the technical headers of fake messages use the company’s actual details.
There are several ways to use valid details. The most unsophisticated method is spoofing, which is substitution of technical headers in messages. The headers can be easily placed with any mass mailing program. In particular, during the spoofing process, the “From” field contains the real address of the sender that the fraudsters have. In this case, spam will be mass-mailed on behalf of the spoofed company, which can stain the company’s reputation quite seriously. Yet, not all technical headers can be substituted when spoofing, and good anti-spam filters will not let these messages through.
Another method entails sending spam from so-called hijacked infrastructure, which is much harder to do technically, as the mail server of the target company has to be hacked. After gaining control over it, an evildoer can start sending messages with legitimate technical headers from any email address owned by the company and on behalf of any employee who works there. At the same time, the fake message looks quite credible for anti-spam filters and freely travels from server to server, as all of the necessary certificates and digital signatures in the header correspond to genuine counterparts. This would result in losses by both the recipient, who takes the bait of the evildoers (network infection and theft of personal data or business information), and the company, whose infrastructure is abused by the evildoers.
Usually, cybercriminals select small businesses (with up to several dozen employees) as victims for hacking. Owners of so-called parked domains are of particular interest, as parked domains are used by a company without creating a website on these domains.
In the samples detected by us, personalized malicious spam was mass-mailed on behalf of an existing business that was a small company specialized in staff recruitment. The messages contained order delivery notifications that are typical of malicious spam, but also indicated the real postal addresses of the recipients. The messages also contained URLs that were located on legitimate domains and were constantly changing throughout the mailings. If a user navigates to the URL, then malicious software will be downloaded to the user’s computer.
In this way, we may affirm that spam is becoming more personalized and mailing is becoming targeted. With the rising digital literacy of users, this is exactly what evildoers rely upon; It is not so easy to remember all your subscriptions, all your online orders, or where you’ve left your personal data, including addresses. Such an information load calls for the use of smart security solutions and the employment of security measures to protect your “information-driven personality”.
Lithuanian Man Arrested Over $100 Million Email Scam
23.3.2017 securityweek Spam
A Lithuanian man has been indicted in the United States for convincing two U.S.-based Internet companies into wiring over $100 million to bank accounts he controlled as part of an email fraud scheme.
Evaldas Rimasauskas, 48, was arrested late last week in Lithuania on the basis of a provisional arrest warrant, the New York Office of the FBI said.
The indictment (PDF) claims that Rimasauskas has orchestrated a fraudulent scheme in or around 2013 through in or about 2015, to deceive targeted companies, including a multinational technology company and a multinational online social media company, into wiring funds to bank accounts he controlled.
Rimasauskas registered a company in Latvia with the same name as an Asian-based computer hardware manufacturer, and also opened, maintained, and controlled accounts at banks in Latvia and Cyprus in the name of this company. Then, he started sending fraudulent phishing emails to victim companies – which regularly conducted multimillion-dollar transactions with the legitimate manufacturer – to direct money these companies owed for legitimate goods and services to the accounts he controlled.
As soon as the victim companies wired money to his accounts, Rimasauskas quickly transferred the funds to different bank accounts in various locations throughout the world, including Latvia, Cyprus, Slovakia, Lithuania, Hungary, and Hong Kong.
Further, the individual “caused forged invoices, contracts, and letters that falsely appeared to have been executed and signed by executives and agents of the Victim Companies, and which bore false corporate stamps embossed with the Victim Companies’ names, to be submitted to banks in support of the large volume of funds that were fraudulently transmitted via wire transfer,” U.S. Attorney’s Office, Southern District of New York, says.
Over the course of the scheme, these false and deceptive representations resulted in Rimasauskas causing victim companies to transfer a total of over $100,000,000 in U.S. currency to the accounts he controlled.
Rimasauskas is charged with one count of wire fraud, three counts of money laundering (each carries a maximum sentence of 20 years in prison), and one count of aggravated identity theft. The maximum potential sentences will be determined by the judge.
“From half a world away, Evaldas Rimasauskas allegedly targeted multinational internet companies and tricked their agents and employees into wiring over $100 million to overseas bank accounts under his control. This case should serve as a wake-up call to all companies – even the most sophisticated – that they too can be victims of phishing attacks by cyber criminals. And this arrest should serve as a warning to all cyber criminals that we will work to track them down, wherever they are, to hold them accountable,” acting U.S. Attorney Joon H. Kim said.
The 1.4 Billion records recently leaked come from the DB of the World’s Biggest Spam Networks
7.3.2017 securityaffairs Spam
A few days ago the experts Chris Vickery announced that he will reveal the source of a massive data leak. Now he said it is from world’s biggest spam networks.
A few days ago the popular cyber security expert Chris Vickery from security firm MacKeeper announced that he will shortly reveal the source of a huge data breach impacting individuals.
The huge archive contains 1.4 billion email addresses, names, physical addresses and IP addresses. For sure it will be one the largest data breach of 2017.
Vickery also offered a teaser of the leak, also reducing the number of identities by 30,000.

Follow
Chris Vickery @VickerySec
Teaser screenshot of that DB's summary data:
3:22 AM - 4 Mar 2017
59 59 Retweets 44 44 likes
Security experts made several hypotheses about the name of the alleged victim of the data breach, one of them was the Aadhaar, the world’s largest biometric ID system, with over 1.123 billion enrolled members as of 28 February 2017.
The Unique Identification Authority of India (UIDAI) promtly denies their archive was the source of the leak.
The reality is quite different.
Vickery shared the data with the expert Steve Ragan from Salted Hash and discovered an unsecured repository of backup files linked to a notorious spamming organization called River City Media (RCM).
“This is the story of how River City Media (RCM), Alvin Slocombe, and Matt Ferris, accidentally exposed their entire operation to the public after failing to properly configure their Rsync backups.” reported Salted Hash.
“The data from this well-known, but slippery spamming operation, was discovered by Chris Vickery, a security researcher for MacKeeper and shared with Salted Hash, Spamhaus, as well as relevant law enforcement agencies.”

The huge archive includes sensitive information about the operations of the River City Media, a company that claims to be a legitimate marketing firm, but that is the source of billion spam messages per day.
Vickery didn’t reach out to RCM directly, he was not able to fully verify the huge data leak but he explained that the archive includes addresses he knew very well and that were accurate
“The situation presents a tangible threat to online privacy and security as it involves a database of 1.4bn email accounts combined with real names, user IP addresses, and often physical address,” Vickery said. “Chances are that you, or at least someone you know, is affected.”
What about the spamming business?
No doubts, spamming operations are very profitable.?
The leaked data shows that the RCM sent 18 million emails to Gmail users and 15 million to AOL users in a single day, and the company earned around $36,000. Not so

River City Media spam operation 2
The River City Media company used many illegal hacking techniques to target send spam messages to as many users as possible.
One of these techniques is the Slowloris attack, a method that is used to paralyze a web server rather than subvert it in this manner.
“Purposely throttling your own machinery to amass open connections on someone else’s server is a type of Slowloris attack [https://en.wikipedia.org/wiki/Slowloris_(computer_security)]. The twist here is that the spammer is not trying to completely disable the receiving server, he is only temporarily stressing the resources in order to overwhelm and force the processing of bulk email.” Vickery explained in a blog post.
Vickery defined illegal the hacking activity of the RCM due to the presence of scripts and logs enumerating the groups’ many missions to probe and exploit vulnerable mail servers. The leaked backusp include chat log in which personnel at the company admit and describe the adoption of hacking methods.

“In that screenshot, a RCM co-conspirator describes a technique in which the spammer seeks to open as many connections as possible between themselves and a Gmail server. This is done by purposefully configuring your own machine to send response packets extremely slowly, and in a fragmented manner, while constantly requesting more connections.”
The expert has shared details of RSM’s operations with other parties, including Microsoft, Apple, Salted Hash, Spamhaus and of course law enforcement.
To block the activity of the group, Spamhaus announced the blacklisting of the entire infrastructure used by the RCM from its Register of Known Spam Operations (ROKSO) database. The service tracks professional spam campaigns.
Chris Vickery discovered many other clamorous cases of open database exposed on the Internet. In December 2015 the security expert discovered 191 million records belonging to US voters online, in April 2016 he also discovered a 132 GB MongoDB database open online and containing 93.4 million Mexican voter records.
In March 2016, Chris Vickery has discovered online the database of the Kinoptic iOS app, which was abandoned by developers, with details of over 198,000 users.
In January 2017, the expert discovered online an open Rsync server hosting the personal details for at least 200,000 IndyCar racing fans.
Database of 1.4 Billion Records leaked from World’s Biggest Spam Networks
6.3.2017 thehackernews Spam
A database of 1.4 billion email addresses combined with real names, IP addresses, and often physical address has been exposed in what appears to be one the largest data breach of this year.
What's worrisome? There are high chances that you, or at least someone you know, is affected by this latest data breach.
Security researcher Chris Vickery of MacKeeper and Steve Ragan of CSOOnline discovered an unsecured and publicly exposed repository of network-available backup files linked to a notorious spamming organization called River City Media (RCM), led by notorious spammers Matt Ferrisi and Alvin Slocombe.
Spammer’s Entire Operation Exposed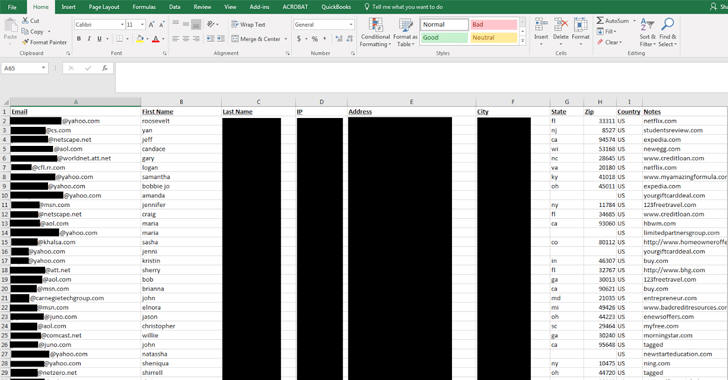
The database contains sensitive information about the company's operations, including nearly 1.4 Billion user records, which was left completely exposed to anyone – even without any username or password.
According to MacKeeper security researcher Vickery, RCM, which claims to be a legitimate marketing firm, is responsible for sending around a billion unwanted messages per day.
Besides exposing more than a billion email addresses, real names, IP addresses and, in some cases, physical addresses, the leak exposed many documents that revealed the inner workings of RCM's spam operation.
"The situation presents a tangible threat to online privacy and security as it involves a database of 1.4bn email accounts combined with real names, user IP addresses, and often physical address," Vickery said. "Chances are that you, or at least someone you know, is affected."
Vickery wasn't able to fully verify the leak but said he discovered addresses he knew were accurate in the database.
Wondering how spamming operations can be profitable? One leaked text shows a single day of activity of RCM that sent 18 million emails to Gmail users and 15 million to AOL users, and the total take of the spamming company was around $36,000.
Illegal Hacking Techniques Used by RCM
The company employed many illegal hacking techniques to target as many users as possible. One of the primary hacking methods described by the researchers is the Slowloris attacks, a method designed to cripple a web server rather than subvert it in this manner.
"[Slowloris is] a technique in which the spammer seeks to open as many connections as possible between themselves and a Gmail server," Vickery writes in a blog post published today.
"This is done by purposefully configuring your own machine to send response packets extremely slowly, and in a fragmented manner, while constantly requesting more connections."
The researchers have reported that details of RSM’s operations and its abusive scripts and techniques have been sent to Microsoft, Apple, Salted Hash, Spamhaus, and others affected parties.
Meanwhile, the researchers have also notified law enforcement agencies, which they says, have expressed keen interest in the matter.
In response to the latest discovery, Spamhaus will be blacklisting RCM’s entire infrastructure from its Register of Known Spam Operations (ROKSO) database that tracks professional spam operations and lists them using a three-strike rule.
Spammers Leak 1.4 Billion User Records
6.3.2017 securityweek Spam
A company run by a couple of known spammers has unknowingly leaked a series of files containing sensitive information about its operations, including nearly 1.4 billion user records.
River City Media (RCM), which claims to be a legitimate marketing firm, is run by Matt Ferris and Alvin Slocombe, both listed in Spamhaus’ Register of Known Spam Operations (ROKSO).
Slocombe is said to be involved with the bulletproof spam host Cyber World Internet Services, which is believed to have launched spam campaigns using aliases such as Ad Media Plus, RCM Delivery, eBox, Brand 4 Marketing and Site Traffic Network.
MacKeeper researcher Chris Vickery, who has made a name for himself after finding misconfigured databases exposing large amounts of potentially sensitive data, discovered a freely accessible Rsync backup belonging to River City Media.
The leaked data has been analyzed by Vickery, Spamhaus, and IDG’s CSO Online. Law enforcement has also been alerted as some of the exposed files appear to contain evidence of illegal activities. Tech giants such as Microsoft and Apple have also been notified.
According to Vickery, the leaked data includes documents (e.g. financial data), backups and chat logs. One of the most interesting files is a database containing 1.37 billion user records, including names, email addresses, physical addresses and IPs.
The expert, whose investigation showed that much of the data appears to be valid, believes the vast amount of information was collected by the spammers through credit checks, sweepstakes, education opportunities and other similar activities.
“Well-informed individuals did not choose to sign up for bulk advertisements over a billion times. The most likely scenario is a combination of techniques,” Vickery said in a blog post. “One is called co-registration. That’s when you click on the ‘Submit’ or ‘I agree’ box next to all the small text on a website. Without knowing it, you have potentially agreed your personal details can be shared with affiliates of the site.”
The exposed data, which Vickery believes will lead to the downfall of this “spam empire,” also includes information on the illegal tools and techniques used by RCM. For example, one of the leaked files describes a technique leveraged by the spammers to target Gmail servers by opening as many connections as possible between them and the targeted server.
“This is done by purposefully configuring your own machine to send response packets extremely slowly, and in a fragmented manner, while constantly requesting more connections,” the researcher explained. “Then, when the Gmail server is almost ready to give up and drop all connections, the spammer suddenly sends as many emails as possible through the pile of connection tunnels. The receiving side is then overwhelmed with data and will quickly block the sender, but not before processing a large load of emails.”
Spammers Leak 1.4 Billion User Records
6.3.2017 securityweek Spam
A company run by a couple of known spammers has unknowingly leaked a series of files containing sensitive information about its operations, including nearly 1.4 billion user records.
River City Media (RCM), which claims to be a legitimate marketing firm, is run by Matt Ferris and Alvin Slocombe, both listed in Spamhaus’ Register of Known Spam Operations (ROKSO).
Slocombe is said to be involved with the bulletproof spam host Cyber World Internet Services, which is believed to have launched spam campaigns using aliases such as Ad Media Plus, RCM Delivery, eBox, Brand 4 Marketing and Site Traffic Network.
MacKeeper researcher Chris Vickery, who has made a name for himself after finding misconfigured databases exposing large amounts of potentially sensitive data, discovered a freely accessible Rsync backup belonging to River City Media.
The leaked data has been analyzed by Vickery, Spamhaus, and IDG’s CSO Online. Law enforcement has also been alerted as some of the exposed files appear to contain evidence of illegal activities. Tech giants such as Microsoft and Apple have also been notified.
According to Vickery, the leaked data includes documents (e.g. financial data), backups and chat logs. One of the most interesting files is a database containing 1.37 billion user records, including names, email addresses, physical addresses and IPs.
The expert, whose investigation showed that much of the data appears to be valid, believes the vast amount of information was collected by the spammers through credit checks, sweepstakes, education opportunities and other similar activities.
“Well-informed individuals did not choose to sign up for bulk advertisements over a billion times. The most likely scenario is a combination of techniques,” Vickery said in a blog post. “One is called co-registration. That’s when you click on the ‘Submit’ or ‘I agree’ box next to all the small text on a website. Without knowing it, you have potentially agreed your personal details can be shared with affiliates of the site.”
The exposed data, which Vickery believes will lead to the downfall of this “spam empire,” also includes information on the illegal tools and techniques used by RCM. For example, one of the leaked files describes a technique leveraged by the spammers to target Gmail servers by opening as many connections as possible between them and the targeted server.
“This is done by purposefully configuring your own machine to send response packets extremely slowly, and in a fragmented manner, while constantly requesting more connections,” the researcher explained. “Then, when the Gmail server is almost ready to give up and drop all connections, the spammer suddenly sends as many emails as possible through the pile of connection tunnels. The receiving side is then overwhelmed with data and will quickly block the sender, but not before processing a large load of emails.”