
The discovery confirms that crooks continue to use COVID-19 lures in malspam campaigns. In the campaign monitored by Vipre Labs, attackers used spam email samples containing GuLoader.
Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
Experts observed a spike in COVID-19 related malspam emails containing GuLoader
24.5.2020 Securityaffairs Spam
Security experts observed a spike in the use of the GuLoader since March 2020 while investigating COVID-19-themed malspam campaigns.
Researchers from Vipre Labs observed a spike in the use of GuLoader in COVID-19-themed campaign since March 2020.

The discovery confirms that crooks continue to use COVID-19 lures in malspam campaigns. In the campaign monitored by Vipre Labs, attackers used spam email samples containing GuLoader.
The GuLoader is a popular RAT that appeared in the threat landscape in 2019 and that was involved in other COVID-19 campaigns, it is written in VB5/6 and compressed in a .rar/.iso file.
GuLoader is usually employed in spam campaigns using bill payments, wire transfers or COVID lures.
In the last campaign observed by experts, the downloader utilizes cloud hosting services to keep the payload encrypted.
“This malware downloader utilizes cloud hosting services like Microsoft OneDrive or Google Drive to keep its payload encrypted. Also, GuLoader is used to download Remote Access Trojan (RAT) or files that allow attackers to control, monitor, or steal information on the infected machine.” reads the analysis.
The malware implements anti-analysis techniques, such as an anti-debugger. In order to achieve persistence, GuLoader creates a folder in which to place a copy of itself and modifies a registry key.
Now the loader implements process hollowing and use the child processes to download, decrypt, and map the payload into memory.
Common payloads downloaded by the loader are Formbook, NetWire, Remcos, Lokibot, and others.
The analysis published by Vipre Labs includes technical details about the threats, including Indicators of Compromise (IoCs).
In early March, experts at MalwareHunterTeam uncovered a COVID-19-themed campaign that was distributing the GuLoader malware to deliver the FormBook information-stealing Trojan.
The campaign was using emails that pretend to be sent by members of the World Health Organization (WHO).
Microsoft warns of “massive campaign” using COVID-19 themed emails
22.5.2020 Securityaffairs Spam
Experts from the Microsoft Security Intelligence team provided some details on a new “massive campaign” using COVID-19 themed emails.
Researchers from the Microsoft Security Intelligence team provided some details on a new massive phishing campaign using COVID-19 themed emails.
The messages used weaponized Excel documents, the IT giant observed a spike in the number of malicious documents in malspam campaigns which use Excel 4.0 macros.
“For several months now, we’ve been seeing a steady increase in the use of malicious Excel 4.0 macros in malware campaigns. In April, these Excel 4.0 campaigns jumped on the bandwagon and started using COVID-19 themed lures.” states Microsoft in a Tweet.
The latest COVID-19 campaign began in April, the messages purport to be from the Johns Hopkins Center and use an Excel attachment. Once opened the attachment, it will show a graph of Coronavirus cases in the United States and trick the victims into enabling the macros to start the infection.
The macros drop a remote access tool (RAT) named NetSupport Manager, it is a legitimate application that is abused by attackers to take control over victim systems.
“The hundreds of unique Excel files in this campaign use highly obfuscated formulas, but all of them connect to the same URL to download the payload. NetSupport Manager is known for being abused by attackers to gain remote access to and run commands on compromised machines.” continues Microsoft.
The NetSupport RAT employed in this COVID-19-themed campaign also drops multiple components, including several .dll, .ini, and other .exe files, a VBScript, and an obfuscated PowerSploit-based PowerShell script. Then it connects to a command and control server, allowing threat actors to send further commands.
Below the Indicators of Compromise (IoCs) shared by Microsoft:
Below a list or recommendations to avoid this threat:
Keep your anti-virus software up to date.
Search for existing signs of the threat using IoCs in your environment.
Keep applications and operating systems running and up to date.
Be vigilant with attachments and links in emails.
BEC Scammers target unemployment and CARES Act claims
21.5.2020 Bleepingcomputer Spam
A group of business email compromise (BEC) Nigerian scammers has been targeting U.S. unemployment systems and COVID-19 relief funds provided through the CARES Act.
The threat actor, which researchers call Scattered Canary, used the IRS and state unemployment websites to file hundreds of fraudulent claims on behalf of U.S. citizens, and receive benefit payments.
Exploiting Gmail feature
Scattered Canary used social security numbers and personally identifiable information from identity theft victims to create fake accounts on websites for processing CARES Act payments.
By taking advantage of a feature in Gmail, they were able to use for the fraudulent claims variations of the same email address. Replies to any of those addresses would be delivered to a single Gmail account, though.
This works because Google does not read the dots in usernames and treats addresses that are visually different as belonging to the same user. Using Google’s example, sending messages to the addresses below will reach the same account:
john.smith@gmail.com
jo.hn.sm.ith@gmail.com
j.o.h.n.s.m.i.t.h@gmail.com
The Agari Cyber Intelligence Division (ACID), a company that offers protection against advanced email attacks, identified 259 different variations of a single address that was used by Scattered Canary for this large-scale fraudulent activity.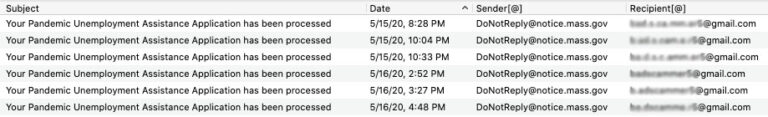
Hundreds of fraudulent claims
The researchers found that the BEC scammers over two weeks (April 15-29) filed through the website set up by the IRS at least 82 fraudulent claims for CARES Act for financial relief caused by the COVID-19 pandemic.
“The only information needed by Scattered Canary to file these claims was an individual’s name, address, date of birth, and social security number” - Agari
Of the 82 claims, at least 30 passed verification and likely paid, the researchers say in a report today.
At least 174 fraudulent claims for unemployment were filed by the threat actor since April 29 in Washington. The scammer received notifications regarding the amount they were eligible to receive based on previous year earnings.
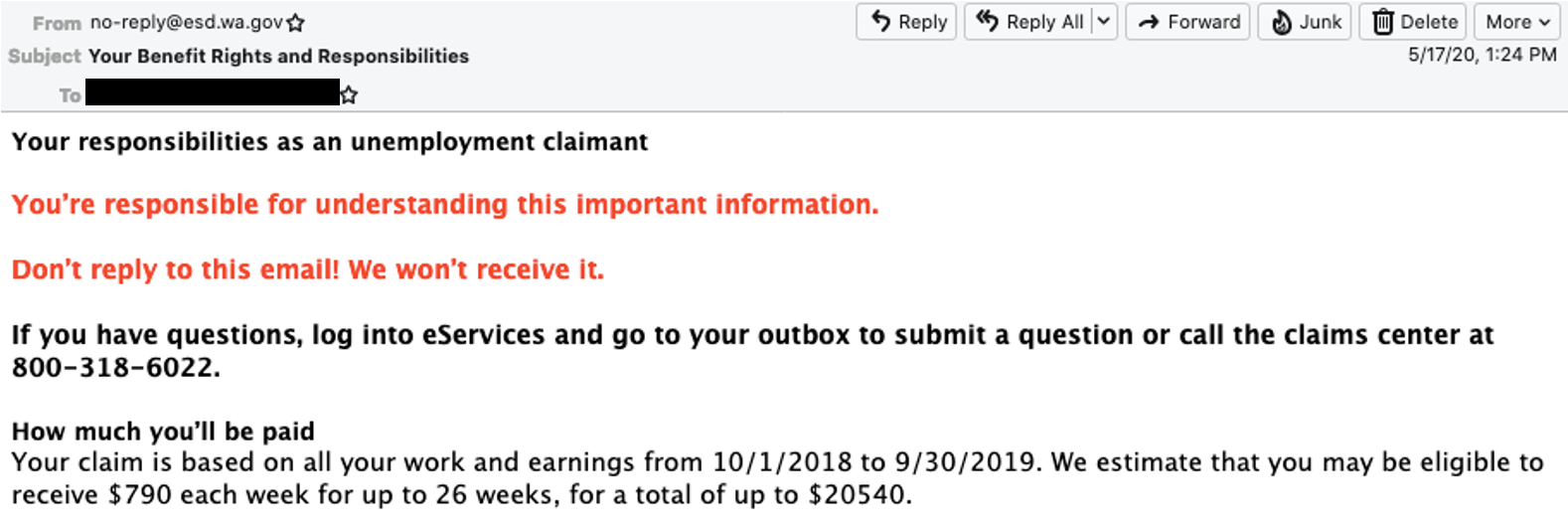
One email from the Washington Employment Security Department (ESD) informed them that they could receive up to $790 each week.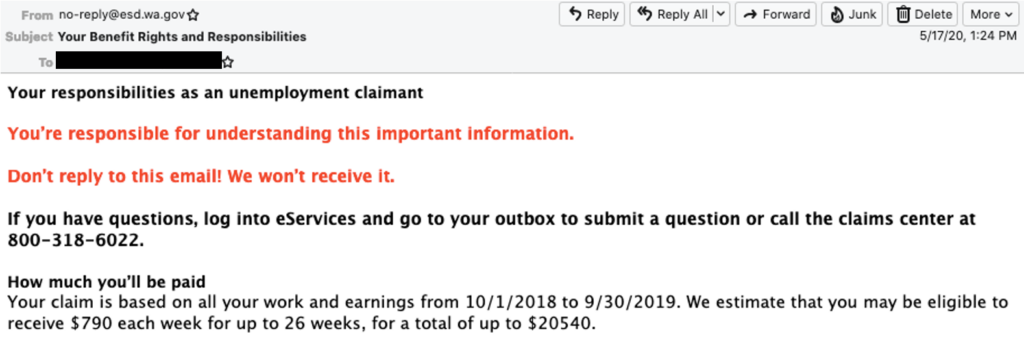
The researchers found that Scattered Canary also filed 17 unemployment claims in Massachusetts on May 15 and 16, and based on their visibility, all were accepted. Each claim is eligible for a different sum, with a maximum weekly benefit of $823.
In Hawaii, where such activity has not been reported previously, the fraudsters filed two unemployment claims on May 17.
Old scammers know how to cash in
The illegal payments are cashed through Green Dot prepaid cards, which can be used to receive government benefits up to four days in advance.
Agari identified 47 such cards, all set up in the name of the same person Scattered Canary defrauded.
Recently, the U.S. Secret Service issued an alert regarding a spate of fraudulent unemployment claims across the country, listing Washington as the most targeted state, followed by North Carolina, Massachusetts, Rhode Island, Oklahoma, Wyoming, and Florida.
Scattered Canary is likely one of the groups involved in these illegal schemes. The group has been in this business for at least 11 years, its activity focusing on various types of fraud (tax, unemployment, disaster relief, student aid, social security), romance scams and fake jobs for money muling.
Agari has been tracking the actor since its early days, as it started as a one-man operation running Craigslist scams. It soon moved to romance scams
Fraudulent Unemployment, COVID-19 Relief Claims Earn BEC Gang Millions
21.5.2020 Threatpost Spam
The business email compromise (BEC) gang Scattered Canary has filed more than 200 fraudulent claims for unemployment benefits and for COVID-19 relief funds.
An infamous business email compromise (BEC) gang has submitted hundreds of fraudulent claims with state-level U.S. unemployment websites and coronavirus relief funds. Researchers who tracked the fraudulent activity said cybercriminals may have made millions so far from the fraudulent activity.
Behind the attacks is Scattered Canary, a highly-organized Nigerian cybergang that employs dozens of threat actors to target U.S. enterprise organizations and government institutions. Since April 29, Scattered Canary has filed more than 200 fraudulent claims on the online unemployment websites of eight U.S. states; including at least 174 fraudulent claims with the state of Washington, for instance, and at least 17 fraudulent claims with the state of Massachusetts.
“In addition to the fraudulent unemployment activity against these states, we have also found evidence that links Scattered Canary to previous attacks targeting CARES Act Economic Impact Payments, which were meant to provide relief caused by the COVID-19 pandemic, as well as new scams targeting Hawaii unemployment benefits,” Patrick Peterson, founder and CEO of Agari, said in a Tuesday analysis. “We have also identified the methods Scattered Canary is using to create numerous accounts on government websites and where the stolen funds are directed.”
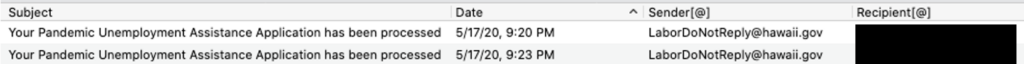
So far, the gang has targeted the unemployment websites of Florida, Massachusetts, North Carolina, Oklahoma, Rhode Island, Washington and Wyoming. And, most recently, on May 17, researchers observed Scattered Canary file its first two unemployment claims on Hawaii’s Department of Labor and Industrial Relations website.
“Based on our observations of Scattered Canary’s activity, the group seems to be setting their sights on Hawaii as their next target of fraudulent unemployment claims, which has not been previously reported,” said researchers.
The cybergang also previously targeted the COVID-19 relief fund provided by the CARES Act, which is meant to provide relief to families as a result of the coronavirus pandemic. The threat group filed at least 82 fraudulent claims for the relief fund between April 15 and April 29, using the Internal Revenue Service (IRS)-backed relief fund website to process claims from individuals who weren’t required to file tax returns. Of these filed claims, at least 30 were accepted and paid out by the IRS, they said.
“The only information needed by Scattered Canary to file these claims was an individual’s name, address, date of birth and Social Security number,” said researchers.
When asked by Threatpost where the group may have accessed this data, an Agari spokesperson said: “For the first time in over a year, we have seen a spike in W2 scams. And what’s interesting about this is that the increase in W2 scams occurred post April 15. Scattered Canary has a history and experience in W2 scams. We think that Scattered Canary is getting the personal identifiable information (PII) from the W2s.”
Based on communications sent to Scattered Canary, researchers said that unemployment claims were eligible to receive up to $790 a week (totaling $20,540 over a maximum of 26 weeks), while the CARES Act includes $600 in Federal Pandemic Unemployment Compensation each week through July 31. This adds up to a maximum potential loss as a result of these fraudulent claims of $4.7 million, said researchers.
Threatpost has reached out to the U.S. Treasury Department for comment.
Fraud Techniques
Researchers noted that Scattered Canary has utilized almost 50 Green Dot prepaid cards, which are prepaid debit cards, to “cash out” its fraudulent claims.
“Prepaid cards have previously been exploited to facilitate payroll-diversion BEC attacks because the cards can be used to receive direct deposit payments,” said researchers. “Green Dot cards are also advertised as being able to receive government benefits, such as unemployment payments, up to four days before they’re due to be paid, making them an attractive vehicle for groups like Scattered Canary to use in scams.”
The cybergang also used a trick that researchers call “Google dot accounts” to scale its operation. This trick abuses a legitimate Google feature – the tech company directs incoming email to the same account, regardless of where the period placement is within the email address. So, if one creates a Gmail account with an email address containing a period (e.g. attack.er01@gmail[.]com), Google strips out the period in its interpretation of the email (attacker01@gmail[.]com). That means that attack.er01@gmail[.]com and a.t.t.a.c.k.e.r.01@gmail[.]com all direct incoming email to the same account, though they may seem different.
Attackers leveraged this to create multiple versions of the same Google address for each target website – ultimately creating a fast and efficient method for carrying out the wide-scale financial crime. In fact, researchers found 259 different variations of a single email address used by Scattered Canary to create accounts on state and federal websites to carry out these fraudulent activities.
Threatpost has reached out to Google for further comment on the “Google dot accounts” tactic leveraged by the cybercriminals.
Moving forward, researchers warn that Scattered Canary will continue to take advantage of the ongoing coronavirus pandemic-relief efforts and unemployment-benefit offerings.
“As we’ve seen across the entire email threat landscape, cybercriminals have been quick to exploit the COVID-19 pandemic,” researchers said. “We have seen a more than 3,000 percent increase in COVID-19-themed phishing attacks since the beginning of February.”
Scammers steal $10 million from Norway's state investment fund
17.5.2020 Bleepingcomputer Spam
Fraudsters running business email compromise scams were able to swindle Norfund, Norway’s state investment fund, out of $10 million.
The attackers took their time before pulling the trigger and took action to ensure that the theft would be discovered long after they got the money.
Professional BEC operation
The scammers got access to the email system, which allows them to monitor communication between Norfund employees and their partners. This also allowed them to figure out who’s responsible for money transfers.
According to Norfund CEO Tellef Thorleifsson, the scammers spent several months in the system, learning the ropes and carefully preparing the robbery.
The scammers created a Norfund email address to impersonate an individual authorized to wire large sums of money through DNB, the bank Norfund uses for these operations.
They falsified the payment information to divert the transfer to their account in a different country than that of the legitimate recipient. It is not uncommon for a parent company to have subsidiaries in other regions of the world.
"The defrauders manipulated and falsified information exchange between Norfund and the borrowing institution over time in a way that was realistic in structure, content and use of language. Documents and payment details were falsified" - Norfund
A microfinance institution in Cambodia was supposed to receive a loan of $10 million but the money was sent to an account in Mexico, controlled by the fraudsters.
Delaying the discovery
A fraudulent wire transfer can be blocked if it is detected in time but Norfund had no chance at this or at recovering at least some of the money because the attackers took steps to delay the discovery of the illegal transfer.
The robbery occurred on March 16 but it came to light more than a month later, on April 30, when the attackers tried their luck once more. However, this attempt was detected internally and stopped.
This much of a delay was caused by the attacker sending an email to the Cambodian beneficiary saying that coronavirus circumstances in Norway would cause a delay in transferring the funds.
In an announcement on Wednesday, Norfund said that the scam was the result of "an advanced data breach."
"It was wonderfully done,“ the CEO said at a press conference on Wednesday, Aftenposten reports.
"This is a grave incident. The fraud clearly shows that we, as an international investor and development organisation, through active use of digital channels are vulnerable. The fact that this has happened shows that our systems and routines are not good enough. We have take immediate and serious action to correct this" - Tellef Thorleifsson
A private equity company, Norfund is owned by the Norwegian Ministry of Foreign affairs. It was established by the Parliament in 1997 to support economic growth in countries struggling with poverty.
Norfund gets its investment capital from the state budget and uses it on companies or through local investment funds in countries in Central America, South-East Asia, or Sub-Saharan Africa.
Malspam with links to zip archives pushes Dridex malware
Introduction
In recent weeks, I continue to run across examples of malicious spam (malspam) pushing Dridex malware. While malspam pushing Dridex can use attachments (usually Excel spreadsheets with malicious macros), I tend to focus on malspam using links to zip archives for Dridex. Today's diary, provides a quick rundown of link-based Dridex activity on Tuesday, 2020-05-12.
Chain of events for these infections:
Link from malspam
Downloaded zip archive
Extracted and execute VBS file
Initial Dridex DLL dropped under C:\ProgramData\ directory
HTTPS/SSL/TLS traffic caused by Dridex
Three different Dridex DLLs loaded through copies of legitimate system files made persistent through a Windows registry entry, a scheduled task, and a shortcut in the Windows startup menu
The malspam
See the following images for 4 examples of the 14 samples I collected on Tuesday 2020-05-12.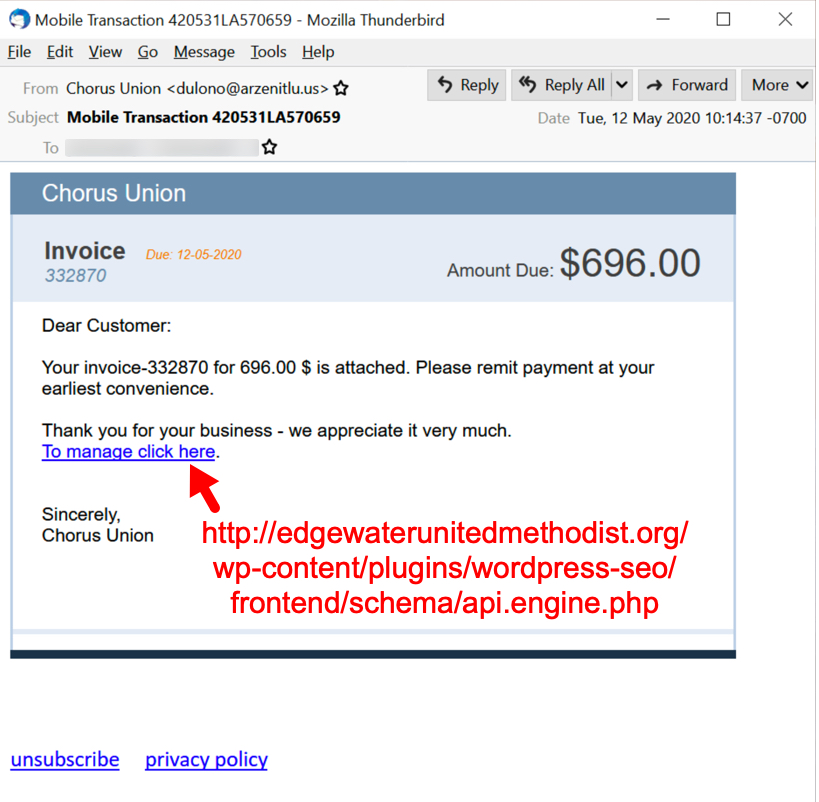
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 1 of 4.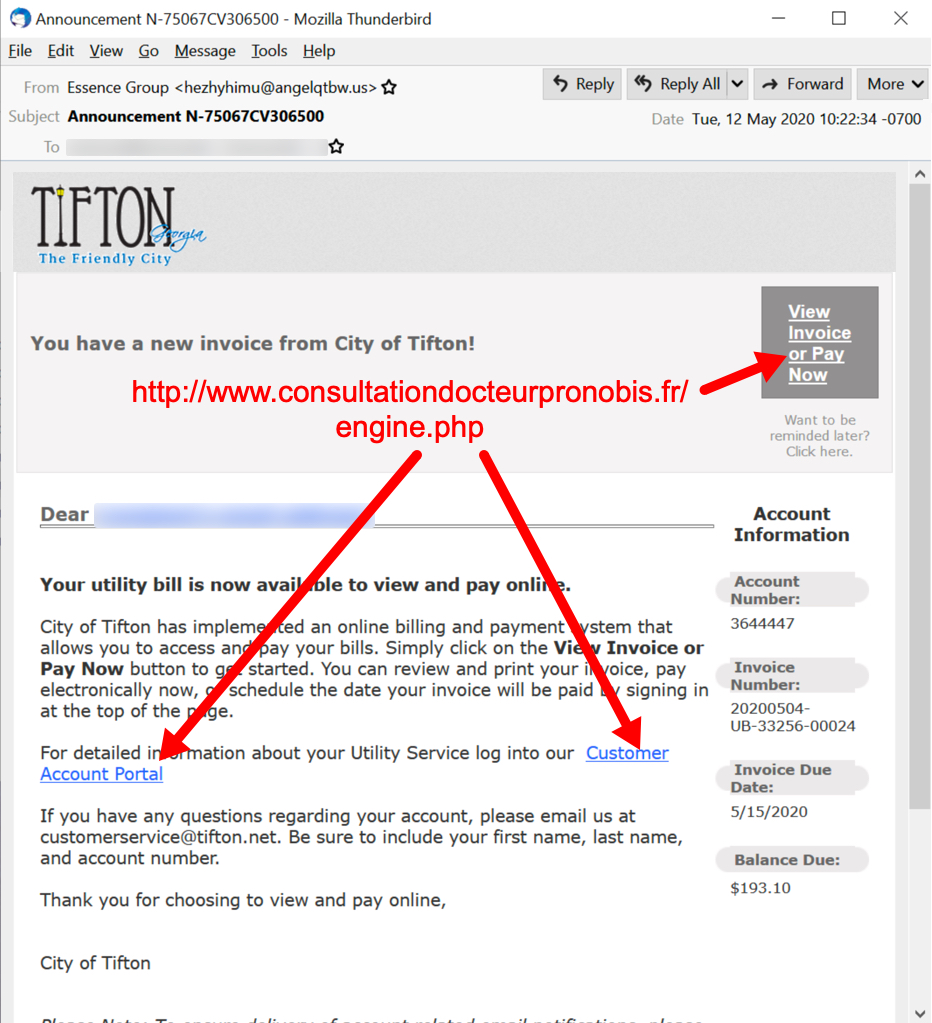
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 2 of 4.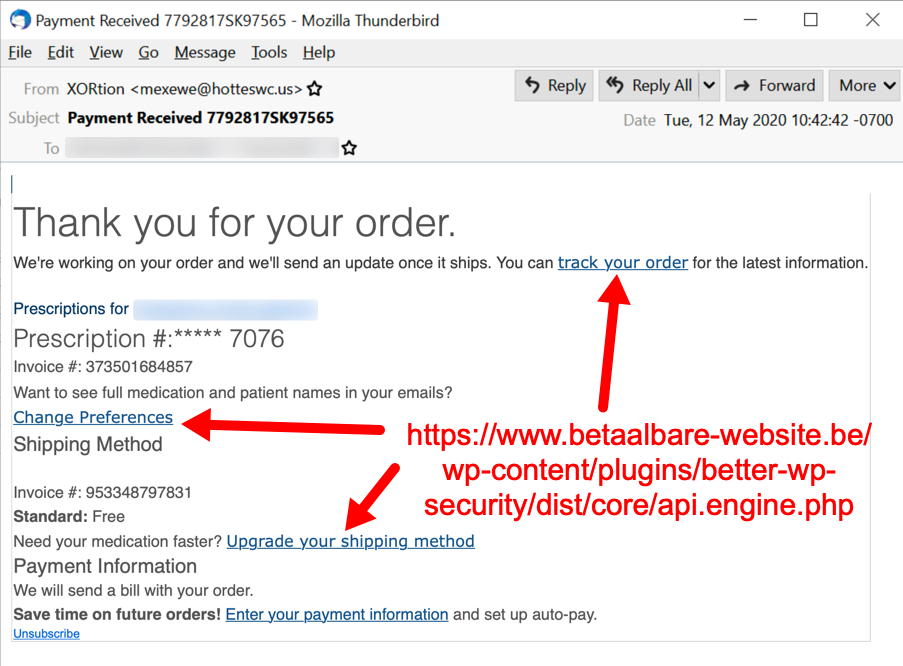
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 3 of 4.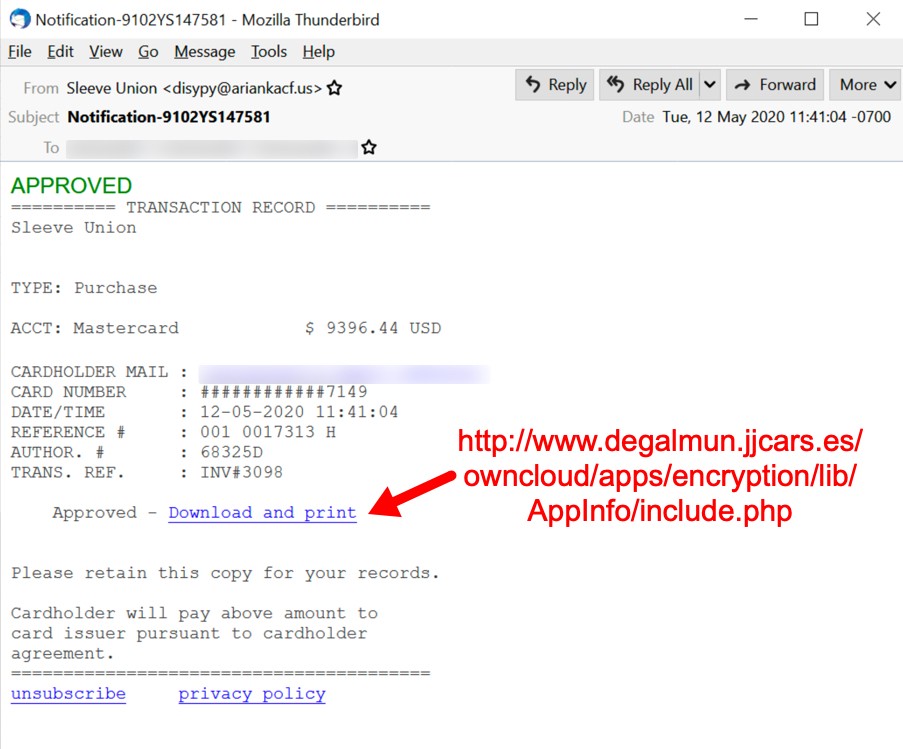
Shown above: Malspam pushing Dridex malware on Tuesday 2020-05-12, example 4 of 4.
Downloading the zip archive
When successfully downloading a zip archive from one of the email links, you get a redirect to another URL that returns the zip. These URLs are aware of the IP address you're coming from, so if you're a researcher coming from a VPN or other address the server doesn't like, it will redirect you to a decoy website. If you try the same email link more than once (and you're from the same IP address), each successive attempt will give you the decoy website. These decoy websites are different for each new wave of Dridex malspam that uses links for zip archives.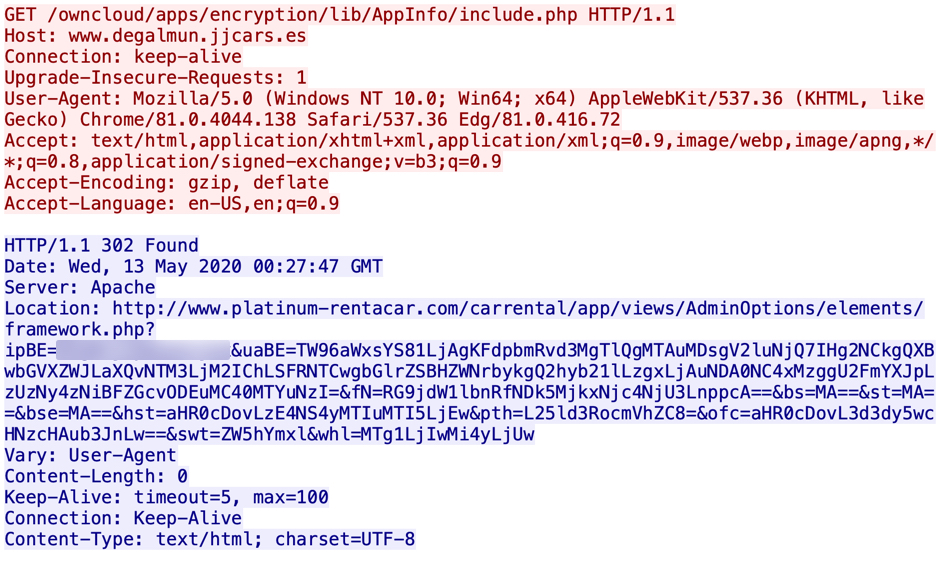
Shown above: Link from an email provides a successful redirect that will return a malicious zip archive.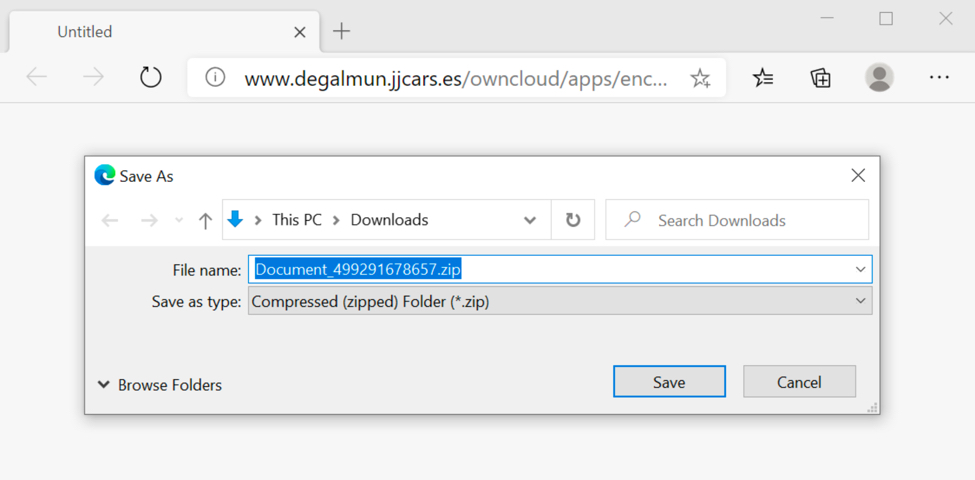
Shown above: Saving the malicious zip archive.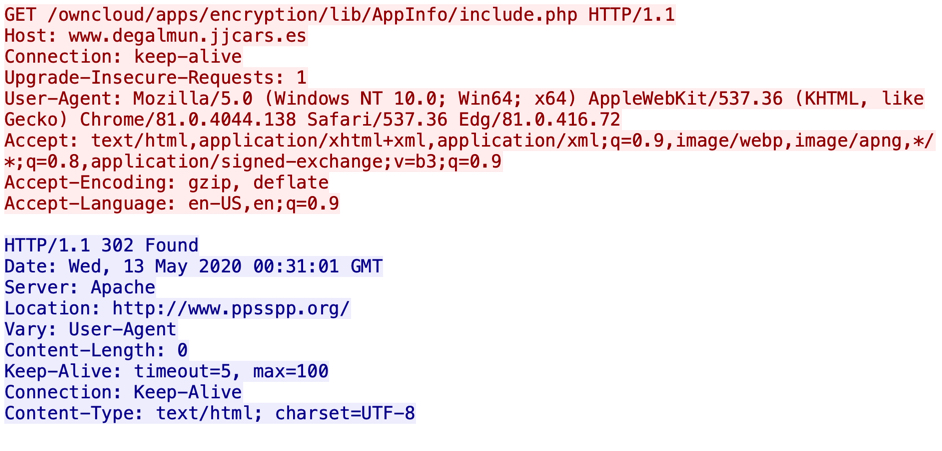
Shown above: Link from an email redirects to a decoy website.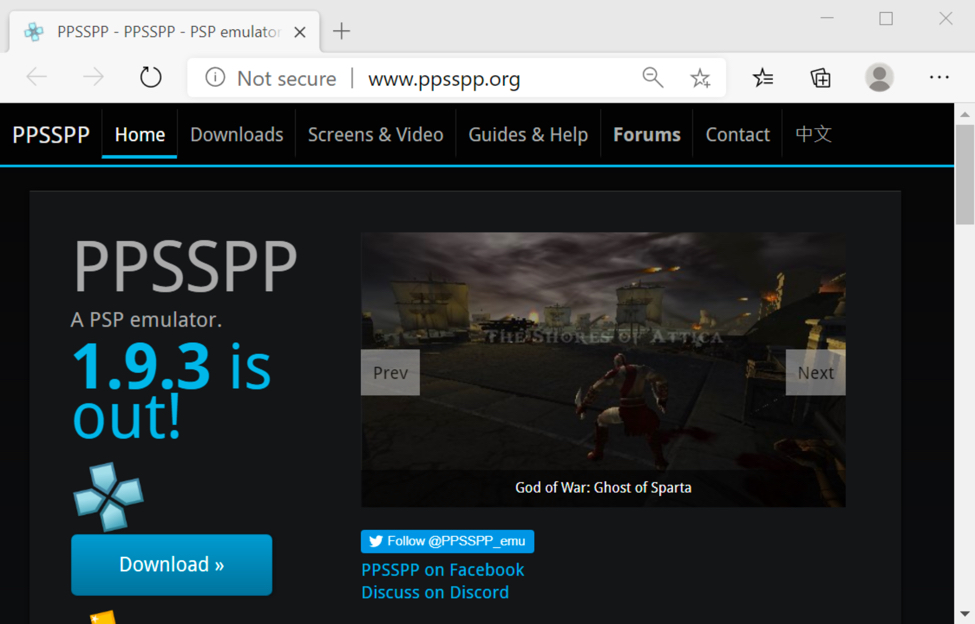
Shown above: Decoy website when the server doesn't like the IP you're coming from. The decoy site from the 2020-05-12 wave was www.ppsspp.com.
The zip archive contains a VBS file, which will use Windows script host to run and install Dridex on a vulnerable Windows host.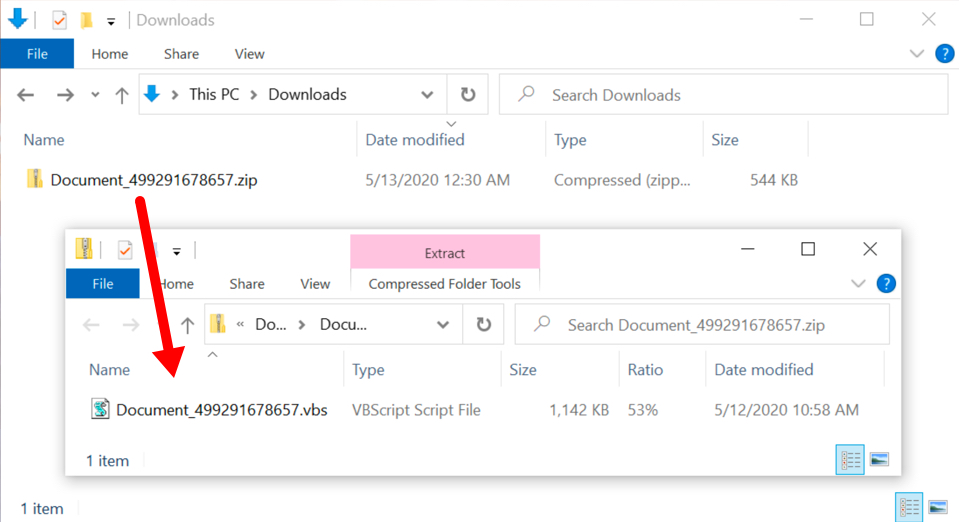
Shown above: The downloaded zip archive contains a VBS file.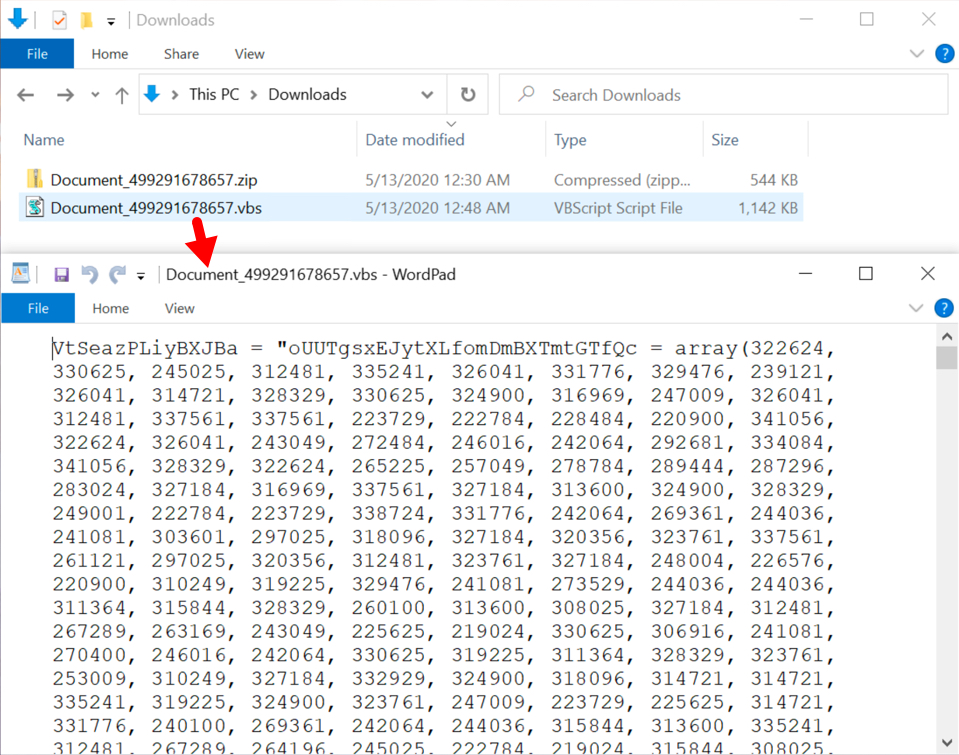
Shown above: Start of the contents on the extracted VBS file.
Infection traffic
Infection traffic was typical for what I normally see with Dridex infections.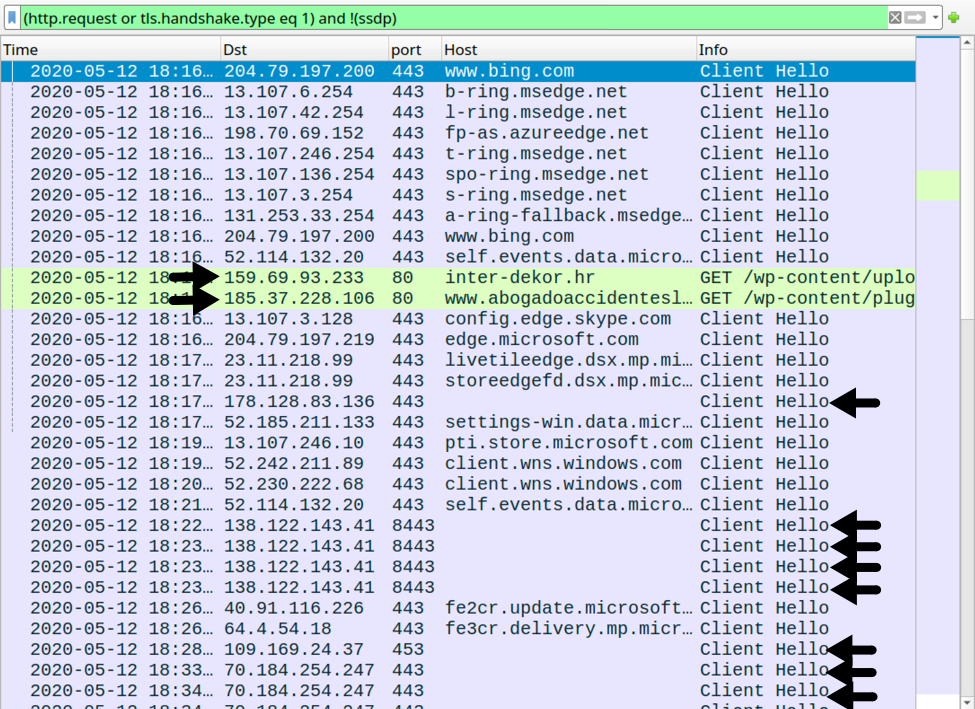
Shown above: Traffic from an infected Windows 10 host filtered in Wireshark. Dridex traffic is noted with the arrows.
Indicators of Compromise (IoCs)
Data from 14 email examples of malspam with links to zip archives pushing Dridex:
Date: Tue, 12 May 2020 10:14:37 -0700
Date: Tue, 12 May 2020 10:22:34 -0700
Date: Tue, 12 May 2020 10:42:42 -0700
Date: Tue, 12 May 2020 10:52:58 -0700
Date: Tue, 12 May 2020 11:17:48 -0700
Date: Tue, 12 May 2020 11:21:09 -0700
Date: Tue, 12 May 2020 11:41:04 -0700
Date: Tue, 12 May 2020 11:51:54 -0700
Date: Tue, 12 May 2020 11:57:37 -0700
Date: Tue, 12 May 2020 12:12:12 -0700
Date: Tue, 12 May 2020 12:24:10 -0700
Date: Tue, 12 May 2020 12:32:41 -0700
Date: Tue, 12 May 2020 12:49:01 -0700
Date: Tue, 12 May 2020 12:56:48 -0700
7 different sending mail servers:
Received: from angelqtbw.us ([147.135.60.145])
Received: from ariankacf.us ([147.135.60.150])
Received: from arzenitlu.us ([51.81.254.89])
Received: from falhiblaqv.us ([147.135.99.6])
Received: from hotteswc.us ([147.135.60.146])
Received: from ppugsasiw.us ([147.135.99.18])
Received: from pufuletzpb.us ([147.135.99.8])
14 different spoofed senders:
From: Abg Deem <qytahae@hotteswc.us>
From: Abg Icarus <fecavu@pufuletzpb.us>
From: Abg Navy <pozhubae@pufuletzpb.us>
From: Amity Save <rymushuki@angelqtbw.us>
From: Arid Save <hygaenuta@angelqtbw.us>
From: Chorus Union <dulono@arzenitlu.us>
From: Continuum Union <betypuso@arzenitlu.us>
From: Cool Union <lefele@ppugsasiw.us>
From: Essence Group <hezhyhimu@angelqtbw.us>
From: Goal Save <havysha@falhiblaqv.us>
From: Laced Save <rukazha@hotteswc.us>
From: Seeds Group <gyzhixe@hotteswc.us>
From: Sleeve Union <disypy@ariankacf.us>
From: XORtion <mexewe@hotteswc.us>
14 different subject lines:
Subject: Announcement N-75067CV306500
Subject: Customer your Booking N-1341KM290237
Subject: Invoice 9497989GM301562
Subject: Invoice-376198HW271105
Subject: Mobile Transaction 420531LA570659
Subject: Notification-9102YS147581
Subject: Payment Received 245906CW349815
Subject: Payment Received 7792817SK97565
Subject: Prevention_216443WF226975
Subject: Prevention_739687SL4713
Subject: Recipient your Inquiry N-0650581WC836637
Subject: Report-03551HJ5068
Subject: Your Bell e-Bill is ready 70605KU2719
Subject: Your Transaction was Approved 8877WA048712
13 different links from the emails:
hxxp://brisbaneair[.]com/class.cache.php
hxxp://carbonne-immobilier[.]com/images/2016/icons/list/api.core.php
hxxp://edgewaterunitedmethodist[.]org/wp-content/plugins/wordpress-seo/frontend/schema/api.engine.php
hxxp://inter-dekor[.]hr/wp-content/uploads/wysija/bookmarks/medium/framework.php
hxxp://iris[.]gov[.]mn/app/framework.php
hxxp://masterstvo[.]org/modules/mod_rokgallery/templates/showcase_responsive/dark/cache.php
hxxp://www[.]consultationdocteurpronobis[.]fr/engine.php
hxxp://www[.]degalmun.jjcars[.]es/owncloud/apps/encryption/lib/AppInfo/include.php
hxxps://azparksfoundation[.]org/wp-content/themes/twentynineteen/sass/blocks/styles.php
hxxps://equineantipoaching[.]com/wp-includes/sodium_compat/namespaced/Core/ChaCha20/lib.php
hxxps://rudhyog[.]in/surat/include/login/api.core.php
hxxps://www[.]betaalbare-website[.]be/wp-content/plugins/better-wp-security/dist/core/api.engine.php
hxxps://www[.]boosh[.]io/class.lib.php
Traffic from an infected Windows host
159.69.93[.]233 port 80 - inter-dekor[.]hr - GET /wp-content/uploads/wysija/bookmarks/medium/framework.php
185.37.228[.]106 port 80 - www[.]abogadoaccidenteslaboralesen-madrid[.]com - GET /wp-content/plugins/drpsassembly/css/inc.php?[string of variables and base64-encoded data]
178.128.83[.]136 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
138.122.143[.]41 port 8443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
109.169.24[.]37 port 453 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
70.184.254[.]247 port 443 - no associated domain - HTTPS/SSL/TLS traffic caused by Dridex
Examples of malware from an infected Windows host:
SHA256 hash: ff8e2e72b1282b72f1a97abb30553d2b8d53366f429083f041c553d2a90878f6
File size: 571,519 bytes
File name: Report_224726231283.zip
File description: File downloaded from link in malspam pushing Dridex
SHA256 hash: a61b462f61f526c4f9d070ba792ecd4a8b842f815ed944b7f38169698bed047e
File size: 1,260,284 bytes
File name: Report~224726231283.vbs
File description: VBS file extracted from downloaded zip archive (designed to infect vulnerable host with Dridex)
SHA256 hash: 223e3e76df847b4e443574e616e56b348213bd0361a7f6789d21754de571cce7
File size: 714,240 bytes
File location: C:\ProgramData\qEWTLCuYyH.dll
File description: Initial Dridex DLL dropped by above VBS file
Run method: regsvr32.exe -s C:\ProgramData\qEWTLCuYyH.dll
SHA256 hash: 9a9e0ab271f8a27f689a350db3cecc84320dd3c708085c75d14adbafdd9da2a1
File size: 700,416 bytes
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\CloudStore\DyGykefYBHT\DUser.dll
File description: Dridex DLL persistent on an infected Windows host (1 of 3)
File note: DLL loaded by bdeunlock.exe in the same directory, persistent through registry update
SHA256 hash: 9197396ed203f804226fb94548b4b899a46feaa7f7ff963fbccff232b5a79277
File size: 696,320 bytes
File location: C:\Users\[username]\AppData\Roaming\Thunderbird\Profiles\mng7115w.default-release\crashes\Niby8ztx\VERSION.dll
File description: Dridex DLL persistent on an infected Windows host (2 of 3)
File note: DLL loaded by iexpress.exe in the same directory, persistent through Startup menu shortcut
SHA256 hash: 28b9c07de53e41e7b430147df0afeab278094f3585de9d78442c298b0f5209e3
File size: 978,944 bytes
File location: C:\Users\[username]\AppData\Roaming\Adobe\Acrobat\DC\JSCache\Y3skYJ7F3B\DUI70.dll
File description: Dridex DLL persistent on an infected Windows host (3 of 3)
File note: DLL loaded by bdeunlock.exe in the same directory, persistent through a scheduled task
Final words
When a Dridex-infected Windows host is rebooted, the locations, names, and file hashes of the persistent Dridex DLL files are changed.
Dridex remains a feature of our threat landscape, and it will likely continue to be. Windows 10 hosts that are fully patched and up-to-date have a very low risk of getting infected from Dridex, so it pays to follow best security practices.
Email examples, malware samples, and a pcap from an infected Windows host used in today's diary can be found here.
Microsoft Edge is getting a new feature to reduce web spam
10.5.2020 Bleepingcomputer Spam
Microsoft Edge is now giving users the ability to hide those pesky browser notification dialog boxes that are commonly used by web sites to push their content, or even spam, on visitors.
For those not familiar with the term "browser notifications", they are a feature that allows web sites to ask visitors if they would like to sign up to receive notifications of new content. The web sites can then push content to subscribers via the browser, even when a visitor is not on the website or when the browser is not being used.
While notification subscription dialogs are annoying from legitimate sites, they are even more annoying from the multitude of scam sites that abuse them.
Lately, a common tactic by scam sites is to show browser notifications dialog boxes and state that you need to "Allow" the notifications before you can play a video, download a file, or visit a site.
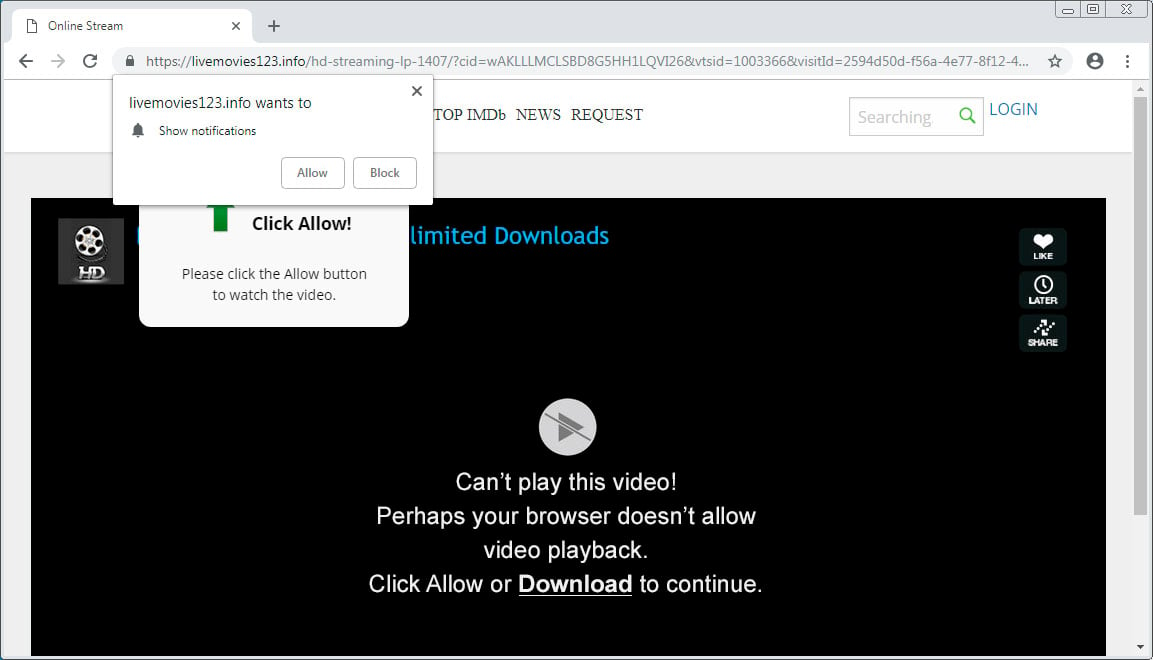
Browser notification spam site
Once you accept the subscription, these scam sites will begin to send a steady stream of unwanted advertisements associated with online dating sites, unwanted browser extensions, adult sites, web games, and even malware.
Microsoft Edge lets you hide browser notification prompts
Microsoft is bringing a new feature called "Quiet notification requests" to the Edge browser that will block all browser notification dialogs from being displayed.
This feature is already available in Microsoft Edge Beta 83, and you can try it out now by following these steps:
Open Edge settings.
Navigate to Site permissions > Notifications Enable “Quiet notification requests”
Enable “Quiet notification requests”
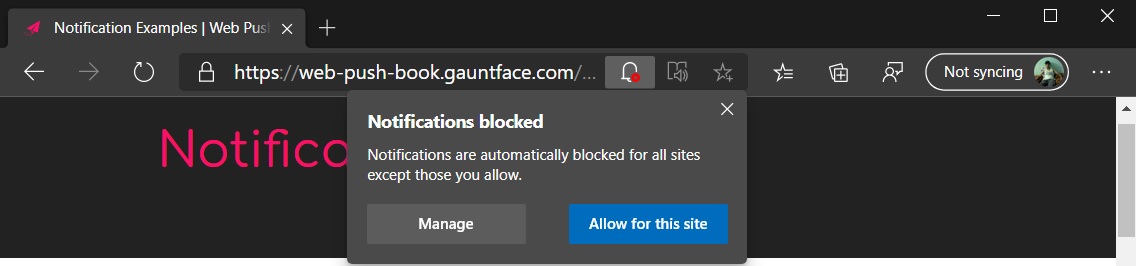
Once this feature is enabled, when visiting a site that would typically show a browser notification subscription dialog, the browser will hide the prompt and display a small bell icon in the address bar instead.
If a user wants to see the notification, they can then click on the bell, and a dialog will open that allows you to decide if you wish to allow notifications or not, as shown below.
This feature is going to be very useful as people are commonly receiving advertisements through web site notifications and have no idea how they are getting them.
By muting the constant stream of browser subscription notification dialogs, this will significantly decrease the amount of webspam that users are receiving.
Unemployed Americans offered ‘remote jobs’ as money mules
10.5.2020 Bleepingcomputer Spam
Cybercriminals are exploiting the increasing number of layoffs during the current pandemic to recruit new money mules which can later be used to help them launder money gained from illicit activities.
Some phishing messages discovered by PhishLabs researchers are trying to convince targets from Canada and the United States who might have lost their jobs due to the COVID-19 outbreak to start working from home, promising them $5,000 per month.
The potential victims are not provided with any other info regarding what the remote jobs require but are instead asked to request more info via email.
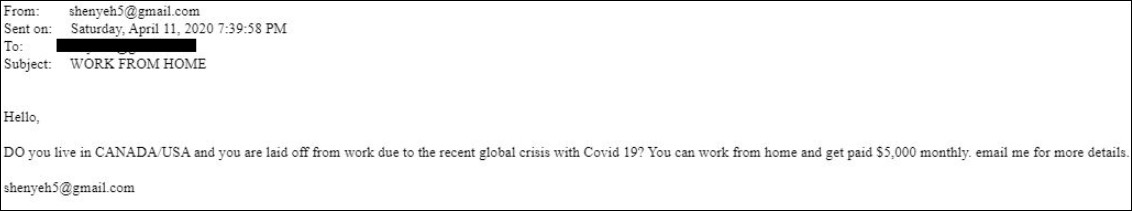
Image: PhishLabs
Personal assistant jobs used as a lure
Others impersonate Wells Fargo Human Resource (HR) representatives who are supposedly recruiting remote workers from across the United States to take up personal assistant positions that require running errands and doing personal chores.
"Our great company is now short of staff because of the current pandemic outbreak in the works which is very sad," the fraudsters say. "This is a part time job if you interested let us know by your response to this message."
If the unemployed victim will accept the crooks' job offer they will be sent to run a series of common errands the PhishLabs report explains.
However, "[a]t some point, after the cybercriminal has ideally established trust and credibility, the victim will be given the task of moving funds that, unbeknownst to them, are stolen."
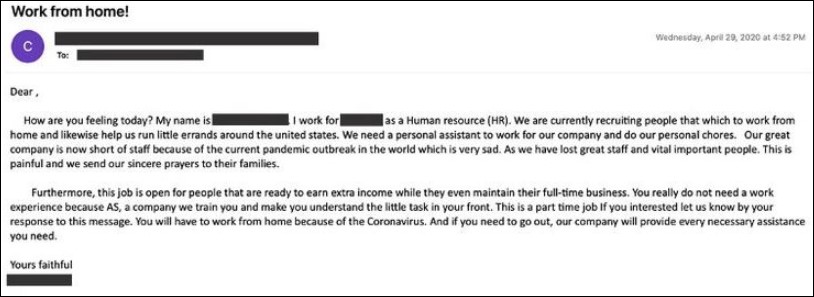
Image: PhishLabs
These scammers indiscriminately prey on any jobless individuals who have lost their positions during the pandemic and are exposing the accidental money mules to very serious legal consequences that could lead to prison time and fines of hundreds of thousands of US dollars.
"Money mules may be witting or unwitting accomplices who receive ill-gotten funds from the victims and then transfer the funds as directed by the fraudsters," according to a US Department of Justice press release.
"The fraudsters enlist and manipulate the money mules through romance scams or 'work-at-home' scams, though some money mules are knowing co-conspirators who launder the ill-gotten gains for profit," by draining the funds into other accounts that are difficult to trace.
FBI: Accidental money mules are also criminals
Money mule operations used by business email compromise (BEC) and other cybercrime schemes to launder their ill-gotten money can, at times, recruit hundreds of money mules.
They are later organized in international money laundering networks that, eventually, get hunted down by law enforcement and prosecuted (1, 2, 3, 4).
Last month, the FBI also warned about cybercriminals behind money mule scheme increasingly exploiting the public fear and uncertainty surrounding the COVID-19 pandemic.
"Acting as a money mule—allowing others to use your bank account, or conducting financial transactions on behalf of others—not only jeopardizes your financial security and compromises your personally identifiable information, but is also a crime," the FBI informed.
"Protect yourself by refusing to send or receive money on behalf of individuals and businesses for which you are not personally and professionally responsible."