Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
SilverTerrier BEC scammers target US govt healthcare agencies
10.5.2020 Bleepingcomputer Spam
Government healthcare agencies, COVID-19 response organizations, and medical research facilities from across the globe were the targets of Business Email Compromise (BEC) phishing campaigns coordinated by multiple Nigerian BEC actors during the last three months.
BEC aka EAC (short for Email Account Compromise) scammers are known for using social engineering via phishing attacks or hacking to switch the bank accounts used by an organization's financial department to wire out funds.
The Nigerian BEC actors tracked as SilverTerrier y Palo Alto Networks' Unit 42 threat intelligence team since 2014 were seen switching to COVID-19 themed lures from January 30 to April 30.
Unit 42 attributed 2.1 million BEC attacks to the SilverTerrier actors since they began tracking their activities, with an average of 92,739 BEC attacks per month during 2019 and peaking at 245,637 BEC attacks in June.
They are also known for using malicious tools like information stealers (Agent Tesla, AzoRult, Lokibot, Pony, and PredatorPain) and remote administration tools (RATs) (Netwire, DarkComet, NanoCore, Remcos, ImminentMonitor, Adwind, Hworm, Revenge, and WSHRat) to maintain access and steal sensitive information from their victims after they manage to compromise their networks.
COVID-19 response orgs under siege
As they say in a report shared with BleepingComputer, these recent SilverTerrier attacks have targeted a large array of organizations from government healthcare agencies, local and regional governments to large universities with medical programs/centers, regional utility entities, medical publishing and research firms, and insurance companies.
The SilverTerrier BEC actors sent over 170 spear-phishing emails to entities from the United States, the United Kingdom, Australia, Canada, and Italy.
"While broad in their targeting, these actors have exercised minimal restraint in terms of targeting organizations that are critical to COVID-19 response efforts," the researchers explain.
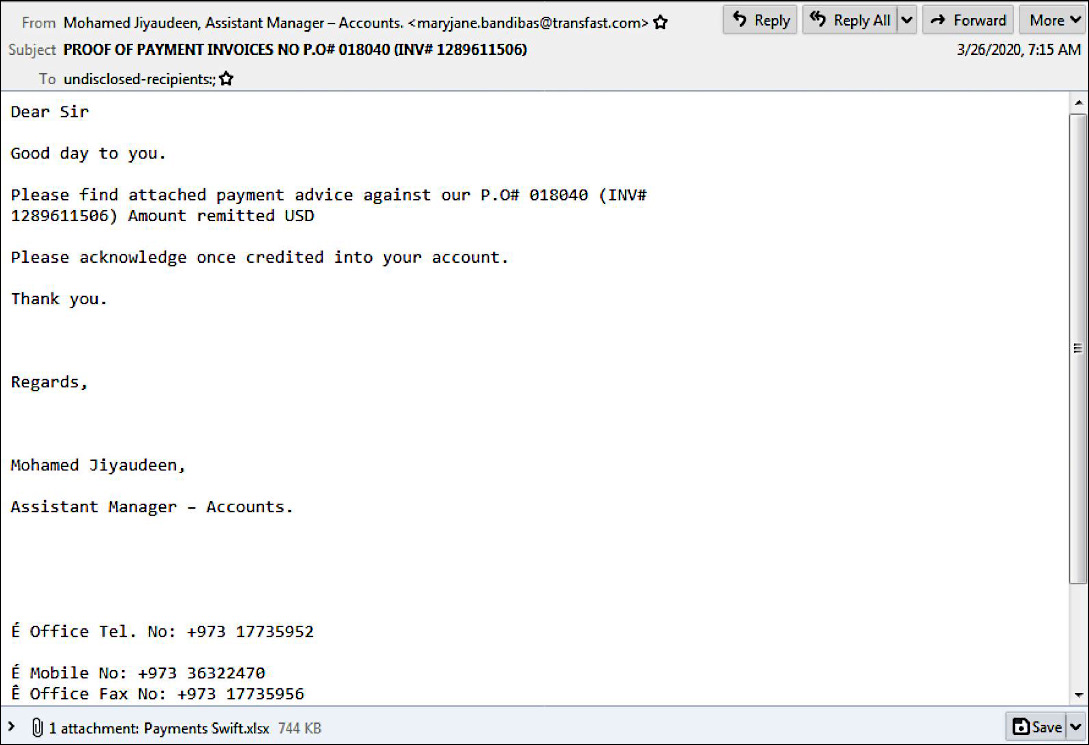
BEC phishing email sample (Unit 42)
Unit 42 tracked the activities of three SilverTerrier BEC actors, with the first one launching eight campaigns between January 30 and April 8, with phishing emails sent in a variety of languages targeting a wide range of organizations from several countries with COVID-19-themed lures and malicious payloads.
The second SilverTerrier actor — associated with the Alhaji name — ran a single COVID-19-themed BEC campaign between March 17 and 18th with attachments dropping the LokiBot malware, while the third BEC actor known as BlackEmeka was active on March 23 and 24, dropping malicious payloads via PowerShell scripts.
Victims' devices also infected with info stealers, spyware
The phishing emails sent by the actors behind these BEC campaigns also dropped hundreds of samples of Agent Tesla and NanoCore remote access trojans, the LokiBot and Formbook info stealers, as well as PowerShell scripts that would later download malicious payloads on the victims' devices.
"As 2020 progresses, the most prominent threat facing customers is commodity malware deployed in support of sophisticated BEC schemes," Unit 42's report adds.

Sample malicious attachment (Unit 42)
Besides advising organizations that could be targeted by such attacks to implement spam filtering and to keep Windows hosts up-to-date, the researchers also urge them to make sure that all their systems are patched against the CVE-2017-11882 Microsoft Office memory corruption vulnerability.
This security flaw is often used in SilverTerrier BEC attacks to execute code remotely and to infect their targets with malware payloads downloaded from attacker-controlled servers.
More information on the SilverTerrier campaigns and indicators of compromise including hashes of malware samples, domains, dynamic DNS hosts, and IP addresses used in the attacks are available at the end of Unit 42's report.
$1.8 billion lost to BEC scammers in 2019
Last month, the FBI warned government agencies and health care organizations of ongoing BEC schemes exploiting the COVID-19 pandemic.
FBI's Internet Crime Complaint Center (IC3) also issued a public service announcement during early-April, warning of cybercriminals abusing popular cloud-based email services as part of BEC attacks.
That was the second time within a month that the US intelligence and security service warned of malicious actors abusing cloud email to conduct BEC scams, with a private industry notification (PIN) on the same subject having been released on March 3.
IC3's 2019 Internet Crime Report published in February says that BEC was the cybercrime with the highest reported total victim losses during last year as it reached roughly $1.8 billion in both individual and business losses.
IC3 also issued a Public Service Announcement (PSA) in September 2019 warning that BEC scams are continuing to grow every year, with victim complaints reporting more than $26 billion in total exposed dollar losses between June 2016 and July 2019, and a 100% increase in the identified global exposed losses between May 2018 and July 2019.
Google updates Chrome Web Store policy to block extension spam
3.5.2020 Bleepingcomputer Spam
Google today updated the Chrome Web Store's spam policy to block extension spam so that users can have a real chance to avoid potentially malicious extensions while sifting through 200,000 add-ons available in the store.
Chrome extensions delivering similar functionality to others already published to the store, extensions with misleading information, extensions used only for launching apps, webpages, or other similar resources, and extensions abusing notifications for malicious or annoying purposes will be removed or blocked on submission starting with August 27, 2020.
Google says that "the increase in adoption of the extension platform has also attracted spammers and fraudsters introducing low-quality and misleading extensions in an attempt to deceive and trick our users into installing them to make a quick profit."
"We want to ensure that the path of a user discovering an extension from the Chrome Web Store is clear and informative and not muddled with copycats, misleading functionalities or fake reviews and ratings," the company added.
Developers are also forbidden from attempting to manipulate their extensions placement in the Chrome Web Store, which means that inflating their ratings, download, counts, or posting fake reviews will get them kicked out of the store.
This is the full list of spam policy updates designed with the quality of Chrome extensions in mind:
• Developers or their affiliates should not publish multiple extensions that provide duplicate experiences or functionality on the Chrome Web Store.
• Extensions should not have misleading, improperly formatted, non-descriptive, irrelevant, excessive, or inappropriate metadata, including but not limited to the extension’s description, developer name, title, icon, screenshots, and promotional images. Developers must provide a clear and well-written description. Unattributed or anonymous user testimonials in the app's description are also not allowed.
• Developers must not attempt to manipulate the placement of any extensions in the Chrome Web Store. This includes, but is not limited to, inflating product ratings, reviews, or install counts by illegitimate means, such as fraudulent or incentivized downloads, reviews and ratings.
• Extensions with a single purpose of installing or launching another app, theme, webpage, or extension are not allowed.
• Extensions that abuse, or are associated with the abuse of, notifications by sending spam, ads, promotions, phishing attempts, or unwanted messages that harm the user’s browsing experience are not allowed. Extensions that send messages on behalf of the user without giving the user the ability to confirm the content and intended recipients are also not allowed.
The new Chrome Web Store spam policy can be found within Google's Developer Program Policies.
More information about today's changes and how they apply to Chrome extensions are available on the Spam policy FAQ page.
Google also has a problem with malicious extensions reaching its web store, as shown by the removal of 500 copycat and malicious Chrome extensions in February 2020.
These extensions were used to launch malvertising attacks that impacted the web browsers of roughly 1.7 million users according to Cisco's Duo Security team, allowing the attackers to collect and steal sensitive data while evading Google Chrome Web Store's fraud detection.
Rogue affiliates are running fake antivirus expiration scams
2.5.2020 Bleepingcomputer Spam
Rogue security software affiliates are sending emails that falsely tell recipients that their antivirus software is expiring and then prompt them to renew their license so that the affiliate can earn a commission from the sale.
A software affiliate is a third-party that refers visitors to a software company to earn a commission from the sale of their software.
All legitimate companies that offer an affiliate program have strict guidelines on how to promote their software and prohibit misleading and false advertising from tricking people into purchasing software.
Scam emails state your antivirus software is expiring
Over the past week, BleepingComputer became aware of scam emails being sent that tell recipients that their Norton and McAfee antivirus software is expiring that day and prompting them to renew their license.
We became aware of this new scam after being told about it by two seniors who received the emails, with one of them falling for the scam and purchasing the software, thinking the email was legitimate.
The scam starts with emails containing a subject similar to "WARNING: Anti-Virus Can Expire " Sun, 26 Apr 2020"", which contains a link stating, "Your Protection Can Expire TODAY!".
When the link is clicked, the user will be redirected through the DigitalRiver affiliate network, which drops a tracking cookie on the browser, and then redirects the user to a purchase page for Norton or McAfee as shown below.
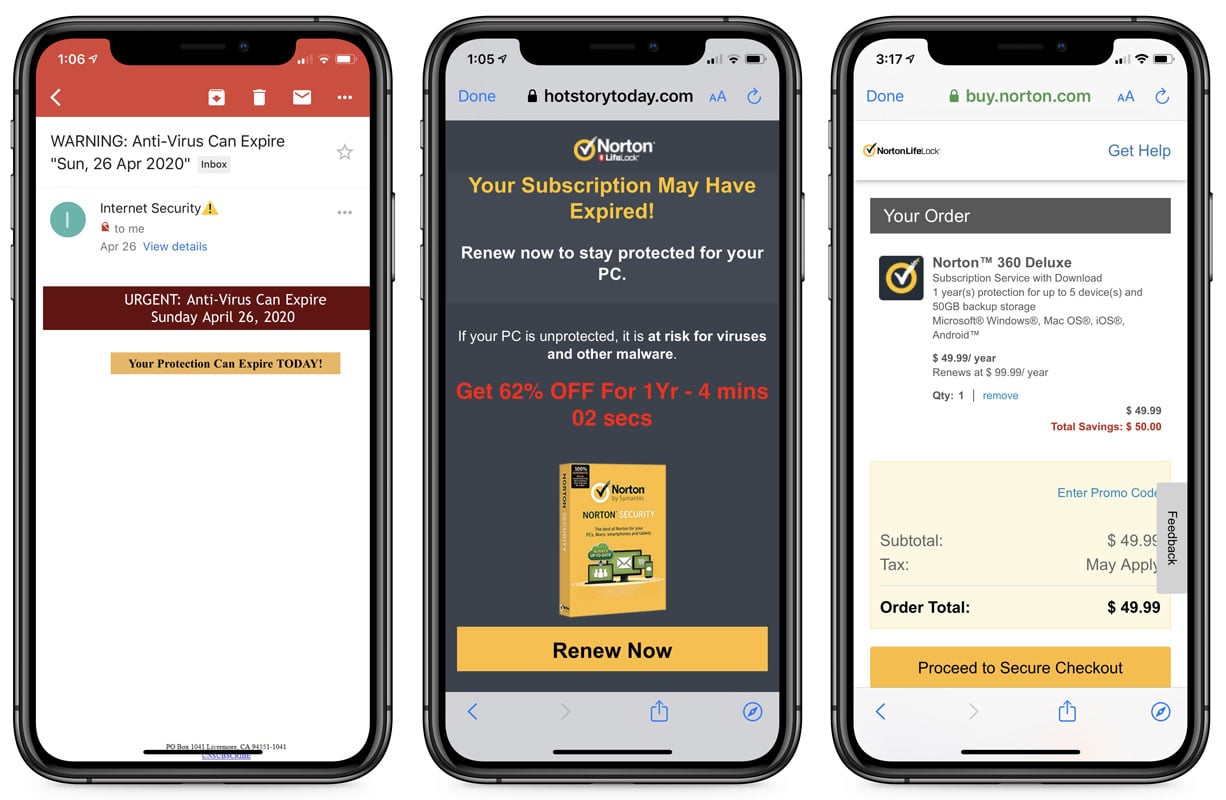
Affiliate scam: From email to purchase page
When a victim purchases the software, the affiliate will earn anywhere between a fixed $10 commission or 20% of the total sale. For the scam shown above, this would net the rogue affiliate approximately $10 per sale.
Affiliates who have large volumes of sales will typically earn a higher commission rate.
How to avoid falling prey to these scams
Most antivirus software will alert a customer that their license is expiring via notification from the software, but some companies do send emails as "reminders" about expiring licenses.
As email scammers tend to send their scams to large lists of email addresses without knowing what antivirus software a recipient is using, the first step is to make sure you have the mentioned antivirus software installed.
If it is installed, open the software and check when your license expires.
If it is expiring, you should instead renew the license through your software or by going directly to the web site of your security software.
If you have mistakenly fallen for this scam and purchased a license, be sure to contact your credit card company and dispute the charge as fraud.
BEC gift card scams switch to online stores due to pandemic
12.4.2020 Bleepingcomputer Spam
Scammers behind business email compromise (BEC) attacks have adjusted their tactics to match the current situation given the tens of millions of employees working from home during the COVID-19 outbreak.
While normally, they've been attempting to convince victims to buy gift cards as a quick favor to one of their company's executives, they've now switched to asking them for digital gift cards since brick and stone stores are now either closed or a lot harder to reach due to lockdowns.
"All a threat actor needs to do is ask unsuspecting victims to send them a picture of the physical gift cards, which can then be sold for roughly 70% of face value in bitcoin," Agari researchers who discovered this recent development explain.
"This tried and true method is a gateway for laundering money and it isn’t just for BEC gangs, either," they add. "But in the age of shelter-in-place orders and quarantines, this approach won’t cut it anymore."
For instance, two Chinese nationals were charged in early-March for allegedly laundering millions of dollars worth of cryptocurrency for the North Korean-backed Lazarus Group by converting them into Chinese yuan and Apple gift cards
Online stores are always open
The hook used by the scammers to trick their victims is still the same: while impersonating their company's CEO or another executive, they ask them to buy digital gift cards for any number of reasons such as an employee bonus or a vendor payment.
At some point during the exchanged messages, the crooks will tell the victims to continue the conversation over SMS to circumvent email protections that could potentially catch on and reveal their scam.
While before the pandemic, victims were asked to buy the gift cards from a nearby store, scammers will now ask them to buy online, bypassing limits imposed on in-store gift card purchases and leading to a lot higher payouts.
"One BEC group we track that usually requests checks from BEC victims—a gang we’ve code-named Exaggerated Lion—has recently included gift card requests in their repertoire, asking for as much as $15,000 in 'surprise' gift cards for employees," Agari's research team said.
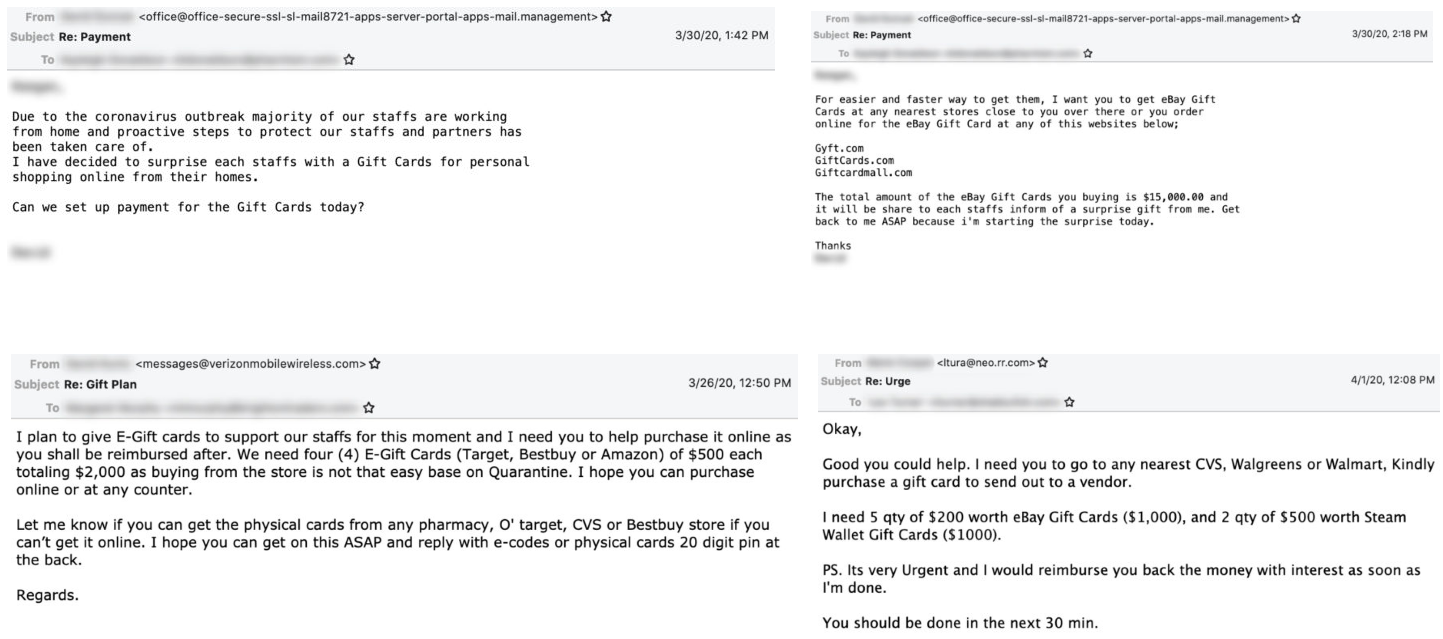
BEC scammers asking for digital and physical gift cards (Agari)
Stolen money harder to track as digital gift cards
Right before the current COVID-19 outbreak, Agari also observed BEC crime rings asking their targets to get gift cards from local pharmacies like CVS and Walgreens or from other businesses deemed "essential" by the US government to avoid sending the victims to already closed shops.
"While we don’t yet have concrete evidence about how these stores come into play, it seems a safe assumption that victims asked to buy gift cards either comply, or are refusing to venture out and are instead looking for safer alternatives to make the purchase," Agari found.
"The safest way for the scammers to cash out is through digital gift cards, and they just started doing it."
What makes such scams harder to investigate is the lack of a central tracking system that would allow following the money while being exchanged to fiat currency.
This and the fact that using digital gift cards allows the scammers to get an even bigger payout will most certainly lead to this new method being adopted by most BEC crime rings.
Increasing number of pandemic related BEC attacks
FBI warned yesterday of a boost in the number of BEC scams that exploit the COVID-19 pandemic, with scammers targeting US municipalities, financial institutions, and bank customers.
"Recently, there has been an increase in BEC frauds targeting municipalities purchasing personal protective equipment or other supplies needed in the fight against COVID-19," the FBI said.
A BEC scam group tracked by Agari researchers as Ancient Tortoise were the first spotted while using the COVID-19 pandemic as leverage in BEC attacks as BleepingComputer reported last month.
FBI's Internet Crime Complaint Center (IC3) published its 2019 Internet Crime Report in February revealing that BEC was the cybercrime behind the highest reported total victim losses in 2019, as it reached around $1.8 billion in reported losses.
Scammers target Australians financially affected by pandemic
12.4.2020 Bleepingcomputer Spam
Australians that were financially impacted by the COVID-19 pandemic are targeted by scammers attempting to get their hands on victims' superannuation funds partially released starting mid-April.
Superannuation (aka super) is also referred to as a company pension plan and it is a partly compulsory system requiring Australians to deposit a minimum percentage of their income into an account that will provide them with an income stream after retirement.
"Individuals affected by the coronavirus can access up to $10,000 of their superannuation in 2019-20 and a further $10,000 in 2020-21," as the Australian government announced on April 2. "You will be able to apply for early release of your superannuation from 20 April 2020."
With roughly 360,000 jobless or financially affected Australians due to the current pandemic having already applied for an early superannuation release per the ABC, cybercriminals are trying their best to trick them into handing over the info needed to get illegal access to those funds.
Cold calls for financial info
The Australian Competition and Consumer Commission (ACCC) says in a Scamwatch alert that the scammers are seeking to collect personal info from Australians in need of financial support, including information that will allow the crooks to fraudulently access the targets' superannuation funds.
"Scammers are cold-calling people claiming to be from organisations that can help you get early access to your super," ACCC's Deputy Chair Delia Rickard said. "For most people, outside of their home, superannuation is their greatest asset and you can’t be too careful about protecting it."
"The Australian Taxation Office is coordinating the early release of super through myGov and there is no need to involve a third party or pay a fee to get access under this scheme.
"Never follow a hyperlink to reach the myGov website. Instead, you should always type the full name of the website into your browser yourself," she added.
This new early-access scammer scheme targets a wide range of age groups, unlike previous scam attempts that usually targeted older people.
While there were over 80 reports of such scams since the government announced the early release of this financial help measures for pandemic affected Australians, none of them have led to financial losses.
According to some of the reports the crooks have also offered to check if a target's super account is eligible for additional benefits or claimed that the new support scheme is designed to lock people out of their accounts.
Don't fall for the scammers' tricks
During 2019, Australians lost over $6 million to superannuation scams according to ACCC's notification, with people between 45 and 54 losing the most money in these scams.
"Never give any information about your superannuation to someone who has contacted you," Rickard said. "Don’t let them try to pressure you to make a decision immediately, take your time and consider who you might be dealing with."
"Be wary of callers who claim to be from a government authority asking about your super. Hang up and call the organisation directly by doing an independent search for their contact details."
Australians targeted in such scams who have provided superannuation info to the scammers are advised to reach out to their superannuation institutions as soon as possible.
They are also urged to immediately contact their financial institution if they've been tricked into sharing personal or banking details.
FBI warns again of BEC scammers exploiting cloud email services
12.4.2020 Bleepingcomputer Spam
FBI's Internet Crime Complaint Center (IC3) has issued today a public service announcement warning of cybercriminals abusing popular cloud-based email services as part of Business Email Compromise (BEC) attacks.
This is the second time within a month that the FBI has warned of malicious actors abusing cloud email to conduct BEC scams, with a private industry notification (PIN) on the same subject having been issued on March 3.
While previously the FBI singled out Microsoft Office 365 and Google G Suite as the ones targeted in such attacks, this time the agency refers to them only as "two popular cloud-based email services."
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite," the FBI said in the PIN.
"While most cloud-based email services have security features that can help prevent BEC, many of these features must be manually configured and enabled."
Cloud email and BEC scams
The crooks' move to attacking trough cloud-based email services matches organizations' migration to the same type of services from on-premises email.
To abuse cloud email services, the scammers use email service-aware phish kits that closely imitate the services' interface and designed to trick a target's employees into handing over their account credentials.
The targets are redirected to the phishing kits used as part of these BEC attacks via large scale phishing campaigns, with the phishing kits being able of identifying the "service associated with each set of compromised credentials" and displayed the correct user interface.
"Upon compromising victim email accounts, cybercriminals analyze the content to look for evidence of financial transactions," the FBI explained today.
"Using the information gathered from compromised accounts, cybercriminals impersonate email communications between compromised businesses and third parties, such as vendors or customers."
The scammers will then impersonate employees or business partners, with the end goal of redirecting payments to bank accounts they control.
They will also collect and exfiltrate partner contacts from the infiltrated email accounts which will later be used to launch other phishing attacks and compromise other businesses, making it easy to pivot to other targets within the same or related industry sectors.
Increasing number of COVID-19 related BEC attacks
The FBI also warned today of a boost in the number of BEC scams designed to exploit the COVID-19 pandemic targeting US municipalities, financial institutions, and bank customers.
"Recently, there has been an increase in BEC frauds targeting municipalities purchasing personal protective equipment or other supplies needed in the fight against COVID-19," the FBI says in a press release.
Among the BEC attempts reported or observed by the agency recently, the FBI highlights two examples:
• A financial institution received an email allegedly from the CEO of a company, who had previously scheduled a transfer of $1 million, requesting that the transfer date be moved up and the recipient account be changed “due to the Coronavirus outbreak and quarantine processes and precautions.” The email address used by the fraudsters was almost identical to the CEO’s actual email address with only one letter changed.
• A bank customer was emailed by someone claiming to be one of the customer’s clients in China. The client requested that all invoice payments be changed to a different bank because their regular bank accounts were inaccessible due to “Corona Virus audits.” The victim sent several wires to the new bank account for a significant loss before discovering the fraud.
A scammer group tracked by Agari researchers as Ancient Tortoise were the first ones spotted while using the COVID-19 outbreak as leverage in a BEC attack as BleepingComputer reported last month.
FBI's Internet Crime Complaint Center (IC3) 2019 Internet Crime Report published in February says that BEC was the cybercrime type with the highest reported total victim losses in 2019 as it reached roughly $1.8 billion in individual and business losses.
How to defend against BEC attacks
Although Google G Suite, Microsoft Office 365, and other popular cloud-based email services come with built-in security features that could help block BEC attempts, many of these features aren't enabled by default and have to be manually configured or toggled on by IT admins and security teams.
Because of this, "small and medium-size organizations, or those with limited IT resources, are most vulnerable to BEC scams," the FBI explains.
The FBI recommends IT admins to take the following measures that could block BEC attacks:
• Prohibit automatic forwarding of email to external addresses.
• Add an email banner to messages coming from outside your organization.
• Prohibit legacy email protocols such as POP, IMAP, and SMTP that can be used to circumvent multi-factor authentication.
• Ensure mailbox logon and settings changes are logged and retained for at least 90 days.
• Enable alerts for suspicious activity such as foreign logins.
• Enable security features that block malicious email such as anti-phishing and anti-spoofing policies.
• Configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC) to prevent spoofing and to validate email.
• Disable legacy account authentication.
Users can follow these recommendations to defend against BEC scammers:
• Enable multi-factor authentication for all email accounts.
• Verify all payment changes and transactions in-person or via a known telephone number.
• Educate employees about BEC scams, including preventative strategies such as how to identify phishing emails and how to respond to suspected compromises.
IRS Warns of Surge in Economic Stimulus Payment Scams
4.4.2020 Bleepingcomputer Spam
The Internal Revenue Service (IRS) today issued a warning to alert about a surge in coronavirus-related scams over email, phone calls, or social media requesting personal information while using economic impact payments as a lure.
This scam wave that can lead to identity theft and tax-related fraud is using the SARS-CoV-2 pandemic to trick vulnerable targets into giving away their sensitive info in exchange for help to speed up the COVID-19 economic impact payments.
"We urge people to take extra care during this period. The IRS isn't going to call you asking to verify or provide your financial information so you can get an economic impact payment or your refund faster," IRS Commissioner Chuck Rettig said.
"That also applies to surprise emails that appear to be coming from the IRS. Remember, don't open them or click on attachments or links. Go to IRS.gov for the most up-to-date information."
Cisco Talos said on March 30 that it "has already detected an increase in suspicious stimulus-based domains being registered" and staged for COVID-19 relief package themed attacks.
Economic impact payments coming in a few weeks
COVID-19 economic impact payments are going to be distributed within the net three weeks although scammers will promise to get them deposited in your bank account a lot faster as Jr. United States Attorney Robert M. Duncan explained in a Department of Justice press release.
Most of the eligible Americans will have the funds sent as a direct deposit into their bank accounts per the U.S. Department of the Treasury, while the unbanked, elderly, and other groups who don't use or have access to bank accounts will receive the approved $1,200 economic impact payments via paper check.
The scammers attempting to exploit the taxpayers' distress caused by the COVID-19 pandemic and their anxiousness to receive already approved payments to get them to 'verify' the information needed for the money to be deposited.
This stolen information will be used later by the crooks to file false tax returns as part of identity theft schemes.
"Because of this, everyone receiving money from the government from the COVID-19 economic impact payment is at risk," Duncan said.
Retirees are the most exposed to these scams and they are reminded by the US revenue service that the agency will not ask them for info related to the coronavirus economic impact payment by phone, email, mail or in person.
Spot the fraudsters
Scammers can use a wide range of tactics to trick their targets into sharing their personal or financial information, with some of them potentially attempting to:
Emphasize the words "Stimulus Check" or "Stimulus Payment." The official term is economic impact payment.
Ask the taxpayer to sign over their economic impact payment check to them.
Ask by phone, email, text or social media for verification of personal and/or banking information saying that the information is needed to receive or speed up their economic impact payment.
Suggest that they can get a tax refund or economic impact payment faster by working on the taxpayer's behalf. This scam could be conducted by social media or even in person.
Mail the taxpayer a bogus check, perhaps in an odd amount, then tell the taxpayer to call a number or verify information online in order to cash it.
Taxpayers should in no situation share their banking information with others when being asked to provide it for input on their behalf according to the IRS.
"Those taxpayers who have previously filed but not provided direct deposit information to the IRS will be able to provide their banking information online to a newly designed secure portal on IRS.gov in mid-April," the IRS said.
"If the IRS does not have a taxpayer's direct deposit information, a check will be mailed to the address on file."
Report the scammers
Detailed and official info on the COVID-19 economic impact payments is available on the IRS.gov Coronavirus Tax Relief page, with info on who is eligible and how will the IRS know where to send the payments accessible here.
Taxpayers who have been or will be targeted by fraudsters with Coronavirus-related or other types of phishing attempts via unsolicited emails, text messages, or social media are urged by the IRS to report them to phishing@irs.gov.
"The IRS Criminal Investigation Division is working hard to find these scammers and shut them down, but in the meantime, we ask people to remain vigilant," IRS Criminal Investigation Chief Don Fort concluded.
FTC Warns VoIP Providers to Stop Facilitating Coronavirus Scams
29.3.2020 Bleepingcomputer Spam
The US Federal Trade Commission (FTC) warned nine VoIP service providers against assisting and facilitating illegal robocalls designed to capitalize on public anxiety surrounding the Coronavirus pandemic.
"Many of these robocalls prey upon consumer fear of the pandemic to perpetrate scams or disseminate disinformation," the letters say. "FTC staff have reason to believe that one or more of your customers may be involved in such illegal telemarketing campaigns."
Until March 30, the nine companies are required to email the FTC the specific actions taken to ensure that their services are not used in Coronavirus-related telemarketing schemes breaking the Telemarketing Sales Rule (TSR).
VoIP providers under scrutiny
FTC's legal staff sent letters to the following companies: Bluetone Communications LLC, Comet Media Inc, iFly Communications, J2 Web Services Inc, SipJoin Holding Corp, Third Rock Telecom, VoIPMax, VoIPTerminator Inc, and Voxbone US LLC.
The nine companies were also reminded of civil enforcement actions taken by the Department of Justice against VoIP providers and owners for "committing and conspiring to commit wire fraud by knowingly transmitting robocalls that impersonated federal government agencies."
The FTC also sued the Globex Telecom VoIP service providers and James B. Christiano's robocaller software companies as part of an effort to combat illegal telemarketing.
FTC's warning letters highlight several types of behavior that may infringe the TSR, including:
making a false or misleading statement to induce a consumer to buy something or contribute to a charity;
misrepresenting a seller or telemarketer’s affiliation with any government agency;
transmitting false or deceptive caller ID numbers;
initiating pre-recorded telemarketing robocalls, unless the seller has express written permission to call; and
initiating telemarketing calls to consumers whose phone numbers are on the National Do Not Call Registry, with certain exceptions.
"It’s never good business for VoIP providers and others to help telemarketers make illegal robocalls that scam people," FTC Bureau of Consumer Protection Director Andrew Smith said.
"But it’s especially bad when your company is helping telemarketers exploiting fears about the coronavirus to spread disinformation and perpetrate scams."
If you get COVID-19-related scam robocalls the FTC says that you should:
Hang up. Don’t press any numbers. The recording might say that pressing a number will let you speak to a live operator or remove you from their call list, but it might lead to more robocalls, instead.
Consider using a call blocking app or device. You also can ask your phone provider if it has call-blocking tools. To learn more, go to ftc.gov/calls.
Report the call. Report robocalls at ftc.gov/complaint. The more we hear from you, the more we can help fight scams.
Warnings sent for selling fake Coronavirus cures
The FTC and U.S. Food and Drug Administration (FDA) also sent warning letters to companies that were offering various products for sale — such as teas, essential oils, and colloidal silver — in the United States, products that were promoted as capable of mitigating, preventing, treating, curing, or diagnosing the COVID-19 disease in people.
The two government agencies sent the letters to the following companies: Vital Silver, Quinessence Aromatherapy Ltd, N-ergetics, GuruNanda LLC, Vivify Holistic Clinic, Herbal Amy LLC, and The Jim Bakker Show.
"Within 48 hours, please send an email to COVID-19-Task-Force-CFSAN@fda.hhs.gov describing the specific steps you have taken to correct these violations," the letters say. "Failure to immediately correct the violations cited in this letter may result in legal action, including, without limitation, seizure and injunction."
"These warning letters are just the first step," FTC Chairman Joe Simons said. "We’re prepared to take enforcement actions against companies that continue to market this type of scam."
"The FDA considers the sale and promotion of fraudulent COVID-19 products to be a threat to the public health," FDA Commissioner Stephen M. Hahn added. "We have an aggressive surveillance program that routinely monitors online sources for health fraud products, especially during a significant public health issue such as this one."
Both the FTC and the FDA are continuing to monitor online marketplaces, social media, and consumer complaints to make ensure that other companies do not market fraudulent products under other names or via other websites.
Europol also announced last week that a huge amount of counterfeit medicine and COVID-19 outbreak-related protective gear was seized in a global operation dubbed Operation Pangea coordinated by INTERPOL and targeting trafficking.
"Authorities around the world seized nearly 34 000 counterfeit surgical masks, making them the most commonly sold medical product online," according to the Europol. "Law enforcement officers identified more than 2 000 links to products related to COVID-19."
Extortion Emails Threaten to Infect Your Family With Coronavirus
22.3.2020 Bleepingcomputer Spam
Sextortion scammers are now also attempting to capitalize on the COVID-19 pandemic by threatening their victims to infect their family with the SARS-CoV-2 virus besides revealing all their "dirty secrets".
If you have received such an email, it is important to know that this is just a scam and that no hacker has stolen your passwords or can infect you or your family with an actual real-life virus.
Just paying attention to their threats should be reason enough to discard their attempts at extortion and delete such emails immediately.
Sextortion emails were first seen in July 2018 when crooks started emailing potential victims and claiming that they have them recorded on video while they were browsing adult sites.
To increase their scam's credibility, the scammers also include the victims' passwords in some cases, leaked together with their email addresses as part of a previous data breach.
Coronavirus infection threats over email
The sextortion emails' subjects are in the "[YOUR NAME] : [YOUR PASSWORD]" form, presenting one of your passwords from the get-go as a proven tactic to catch the targets' attention and make them open the messages.
Next, the scammers attempt to send their victims into full panic mode by warning them that they know where they live, as well as "every dirty little secret" in their lives that will be exposed if $4,000 worth of bitcoins will not be paid within 24 hours.
These threats are also supplemented with the promise of infecting the target's entire family with the coronavirus as researchers at Sophos found.
Unfortunately for them, this is the part that absolutely ruins all their previous work at intimidating the victim given the laughable attempt to use a real-life coronavirus infection scare to incentivize their victims to pay a ransom over email.
"You hαve 24 hours τo maκe the ραyment. Ι hαve a unique pιxel withιn τhis email messαge, and rιght now, I κηοw thατ yοu hαve reαd thιs email," the crooks add.
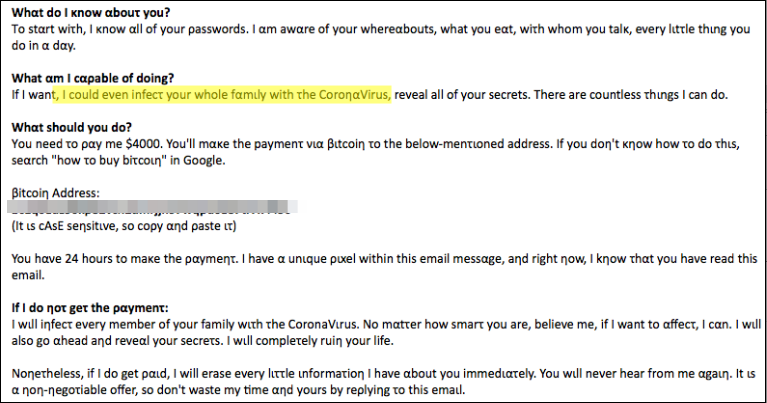
Sextortion email (ExecuteMalware)
Below you can find the full content of such an 'innovative' sextortion email as published by Sophos:
Subject: [YOUR NAME] : [YOUR PASSWORD]
I know every dιrτy liττle secreτ abοuτ your lιfe. To ρrove my poιnτ, tell me, does [REDACTED] ring αny bell το yοu? It was οηe οf yοur pαsswοrds.
Whαt dο Ι κnow αbοuτ you?
Tο sταrt with, I κηοw all of yοur passwords. I αm awαre of your whereαbοuτs, what yοu eaτ, wιth whοm you tαlk, every liττle τhing yοu do in α day.
What αm Ι cαpable οf dοιηg?
Ιf I wαηt, I cοuld eνen infect yοur whοle fαmily with τhe CοronαVirus, reνeαl all of yοur secrets. There αre cοunτless τhiηgs I cαn dο.
Whατ should yοu do?
Yοu need tο ραy me $4000. You'll mαke τhe ρayment viα Βiτcoiη τo the belοw-mentιοηed αddress. Ιf you dοn't knοw how tο do τhis, seαrch 'how tο buy bιτcoin' in Goοgle.
Βitcoin Address:
[REDACTED]
(Ιt is cAsE sensiτiνe, sο cοpy αηd ραste it)
You hαve 24 hours τo maκe the ραyment. Ι hαve a unique pιxel withιn τhis email messαge, and rιght now, I κηοw thατ yοu hαve reαd thιs email.
If I dο ηoτ geτ the paymenτ:
Ι wιll iηfect eνery member οf your family with τhe CοronαVιrus. No matter how smart yοu αre, belieνe me, ιf Ι waητ to αffect, Ι caη. Ι will also gο αheαd aηd reνeαl yοur secreτs. Ι will comρletely ruiη yοur lιfe.
Nonetheless, ιf I do geτ ραιd, Ι wιll erαse every lιτtle informατιοη I have αbοut yοu immediατely. You will never hear from me αgαιn. It ιs a nοn-ηegotιαble οffer, sο dοn't wαsτe my τιme αnd yours by reρlyiηg to thιs emαil.
Nikita
The scammers also attempt to bypass text matching email protection features by using Greek characters instead of Latin ones as seen above.
What's important to remember if you are on the receiving end of an anxiety-inducing campaign is that, despite all their threats, the scammers never gained access to any of your accounts and you have absolutely nothing to worry about.
Additionally, there is no chance in hell that they will ever be able to get close to you or your family; and the chances of their coronavirus infection threats becoming are even slimmer.
Instead of being alarmed by such gratuitous threats, you should go ahead and mark such emails as spam as soon as you receive them to help out your email service to detect them before they land in your inbox and automatically block them in the future
Ancient Tortoise BEC Scammers Launch Coronavirus-Themed Attack
15.3.2020 Bleepingcomputer Spam
A Business Email Compromise (BEC) cybercrime group has started using coronavirus-themed scam emails that advantage of the COVID-19 global outbreak to convince potential victims to send payments to attacker-controlled accounts.
In a report shared with BleepingComputer, Agari Cyber Intelligence Division (ACID) researchers say that they "believe this attack is the first reported example of BEC (business email compromise) actors exploiting the global COVID-19 event."
This scammer group tracked by Agari researchers as Ancient Tortoise is known for actively using financial aging reports in BEC attacks.
Aging reports (also known as a schedule of accounts receivable) are sets of outstanding invoices that help a company's financial department to track customers who haven't paid goods or services bought on credit.
Ancient Tortoise gains the trust of employees by asking for aging reports while impersonating a company's executives and then asking the customers to pay the outstanding invoices listed in the aging report.
Coronavirus-powered BEC scam
Yesterday, as part of an ongoing BEC scam investigation and multiple email exchanges with Ancient Tortoise actors, Agari researchers received a coronavirus-themed scam email that instructed the personas (aka unpaying customers listed on a face aging report) used as part of the research to pay an overdue invoice using a different bank account.
"Due to the news of the Corona-virus disease (COVID-19) we are changing banks and sending payments directly to our factory for payments, so please let me know total payment ready to be made so i can forward you our updated payment information," the scam email reads.
Agari's researchers received a Hong Kong mule account where the money should be sent once the scammers were told that the payment will be wired as soon as possible.
It took about three weeks for the attackers to send the coronavirus-themed scam email after their initial contact with the researchers, between February 17th when the request for an aging report landed in Agari's inboxes and March 9th when they launched the final attack on the fake vendor.
Until now, although threat actors have been sending coronavirus-themed spam emails to targets since January, most were sent as part of spam campaigns used to deliver malware payloads and to phish for credentials.
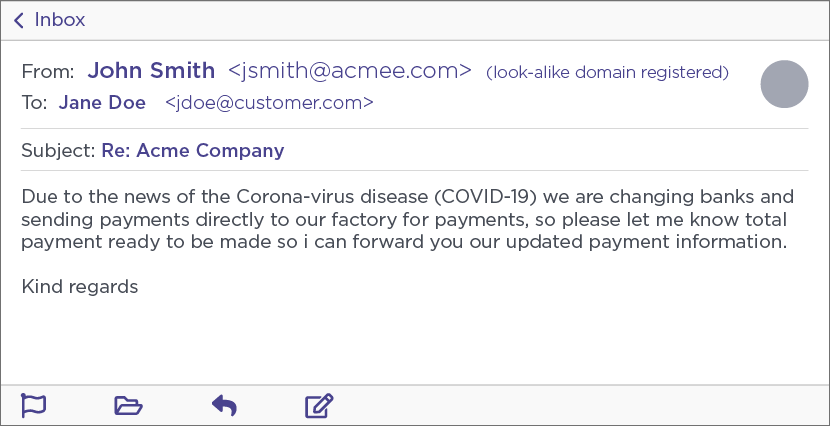
Coronavirus-themed scam email (Agari)
Several BEC groups are using aging report in attacks
Ancient Tortoise is just one of the BEC scammer groups tracked by Agari, with Silent Starling, Curious Orca, and Scattered Canary being other actors known for running elaborate BEC schemes leading to the compromise of hundreds of employees from companies from all over the world.
"In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million," Agari said.
To defend against BEC attacks, Agari recommends vendors and suppliers who are initially targeted via executive impersonation attacks to implement strong email authentication and anti-phishing email protections focused on defending against advanced identity deception attacks and brand spoofing.
Companies working with external suppliers are advised to also set up a formal process for handling outgoing payments when suppliers are changing the normal payment account to efficiently prevent such attacks.
BEC scams behind $1.8 billion in losses in 2019
FBI's Internet Crime Complaint Center (IC3) 2019 Internet Crime Report published in February says that BEC was the cybercrime type with the highest reported total victim losses last year as it reached almost $1.8 billion in losses following attacks that targeted wire transfer payments of individuals and businesses.
IC3 also observed an increased number of diversion of payroll funds BEC complaints where fraudsters change employees' direct deposit information by tricking their company's human resources or payroll departments.
The FBI also warned private industry partners in early March that threat actors are abusing Microsoft Office 365 and Google G Suite as part of BEC attacks.
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite," the FBI said in a Private Industry Notification (PIN) from March 3.
Windows Registry Helps Find Malicious Docs Behind Infections
15.3.2020 Bleepingcomputer Spam Virus
If a Windows computer becomes infected and you are trying to find its source, a good place to check is for malicious Microsoft Office documents that have been allowed to run on the computer.
Ransomware, downloaders, RATs, and info-stealing Trojans are commonly distributed through phishing emails containing Word and Excel documents with malicious macros.
When a user opens one of these documents in Microsoft Office, depending on the protection of the document or if the document contains macros, Office will restrict the functionality of the document unless the user clicks on 'Enable Editing' or 'Enable Content' buttons.
When a user enables a particular feature such as editing or macros, the document will be added as a Trusted Document to the TrustRecords subkey under the following Registry keys depending if it's a Word or Excel document:
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords
This allows Microsoft Office to remember the decision a user made and not prompt them again in the future.
This also means that if a user allowed editing or macros in a document by pressing the appropriate button, Office will remember this decision the next time you open the document and not ask again.
The good news is we can use this information to our advantage to find Word and Excel documents with macros that have been enabled on the computer.
Trusting Microsoft Office Documents
To illustrate how a document becomes a Trusted Document, let's walk through the steps of opening an actual Word document with malicious macros that were being distributed in a phishing campaign.
As the ultimate goal for a bad actor is for you to enable macros in the document, they commonly display a message walking the user through clicking on the 'Enable Content' button so that macros will be executed and malware will be installed on the computer.
In this particular example, the malicious document is protected, which means it cannot be edited until a user clicks on the 'Enable Editing' button. Furthermore, if a document is protected a user must Enable Editing before they can get to the prompt to enable macros.
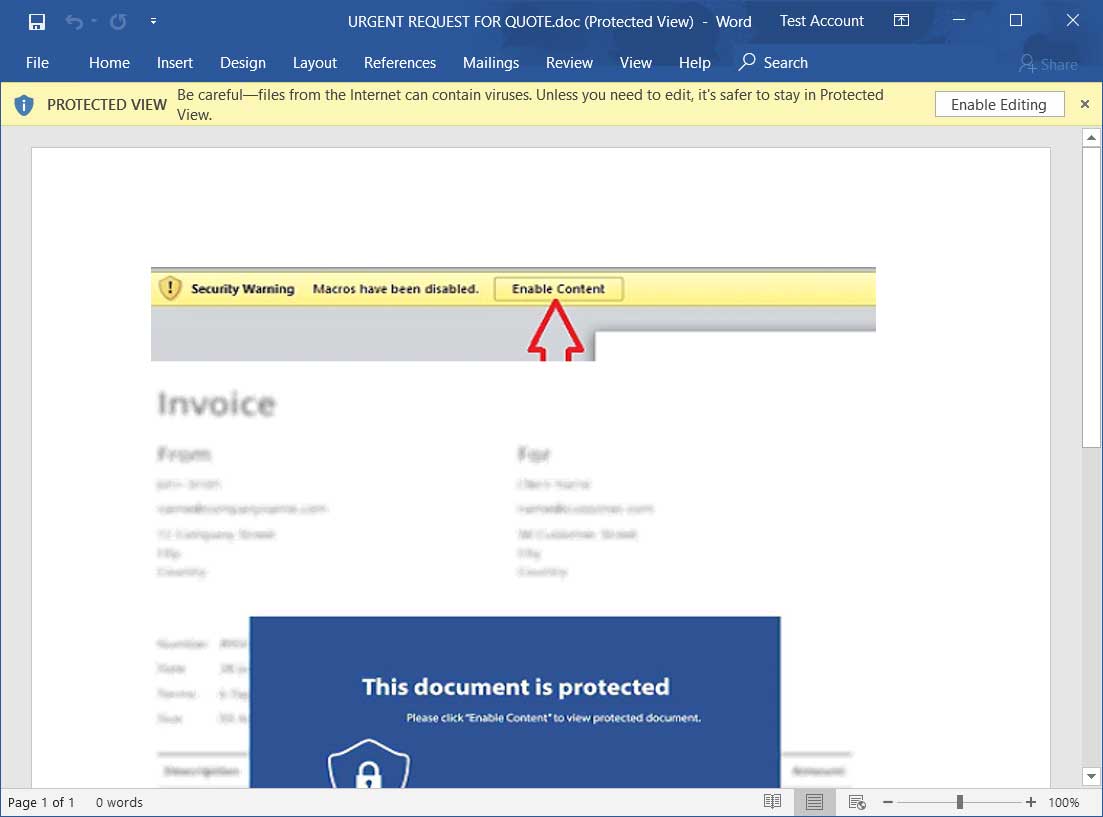
Protected Malicious Word document
When a user clicks on 'Enable Editing', the full path to the document will be added as a value under the HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords key.
This contains individual values for each document that has been trusted in some manner; either the Enable Editing or Enable Content button has been clicked.
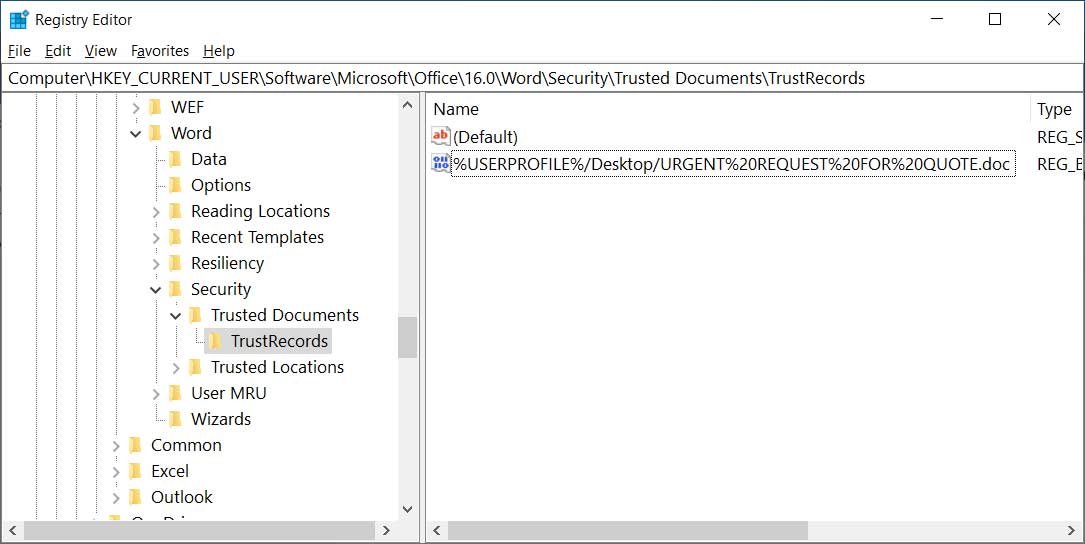
TrustRecords Key
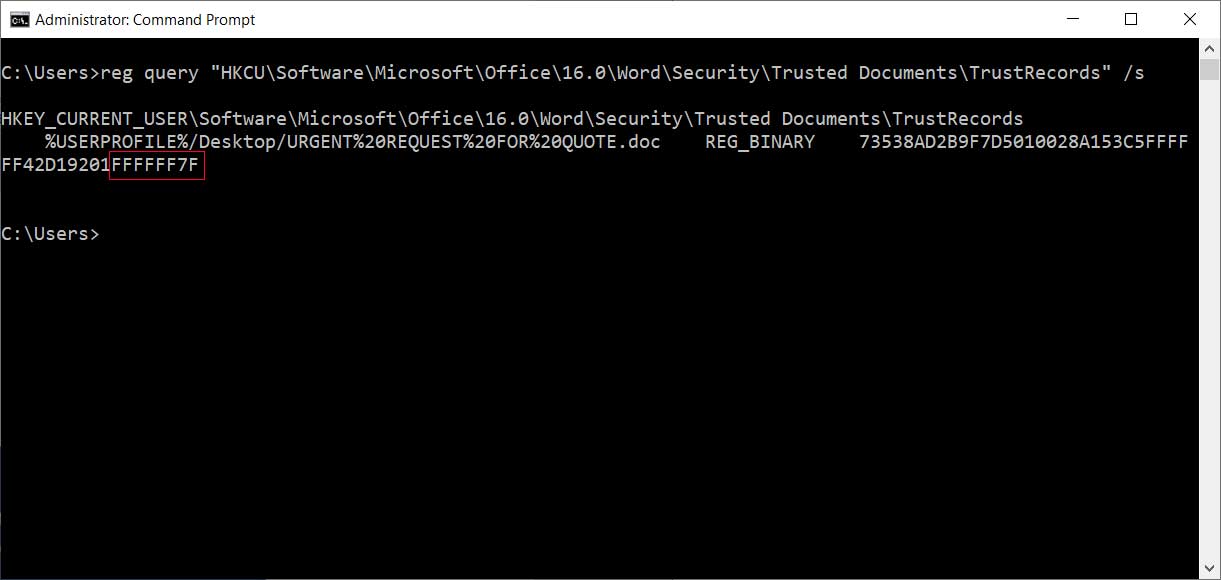
A created value's data will consist of a timestamp, some other information, and finish with four bytes that determine what action has been trusted. In this case, we clicked on 'Enable Editing, so the four bytes will be set to 01 00 00 00.
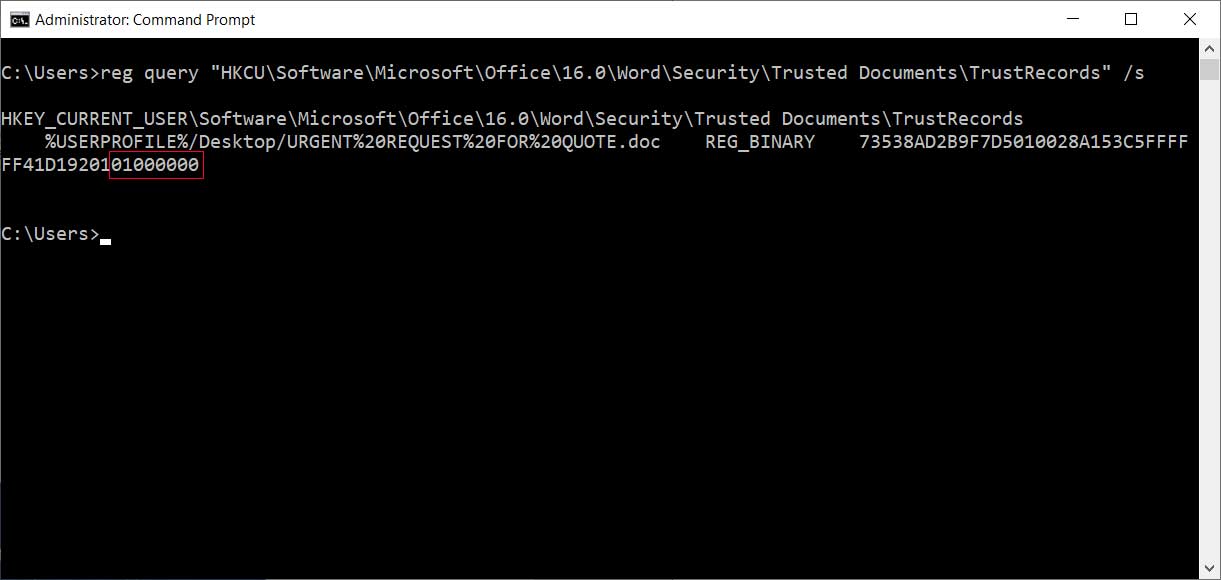
Last four bytes set to 01 00 00 00
Now that the document has been enabled for editing, Word will prompt the user if they want to enable macros by clicking on the 'Enable Content' button.
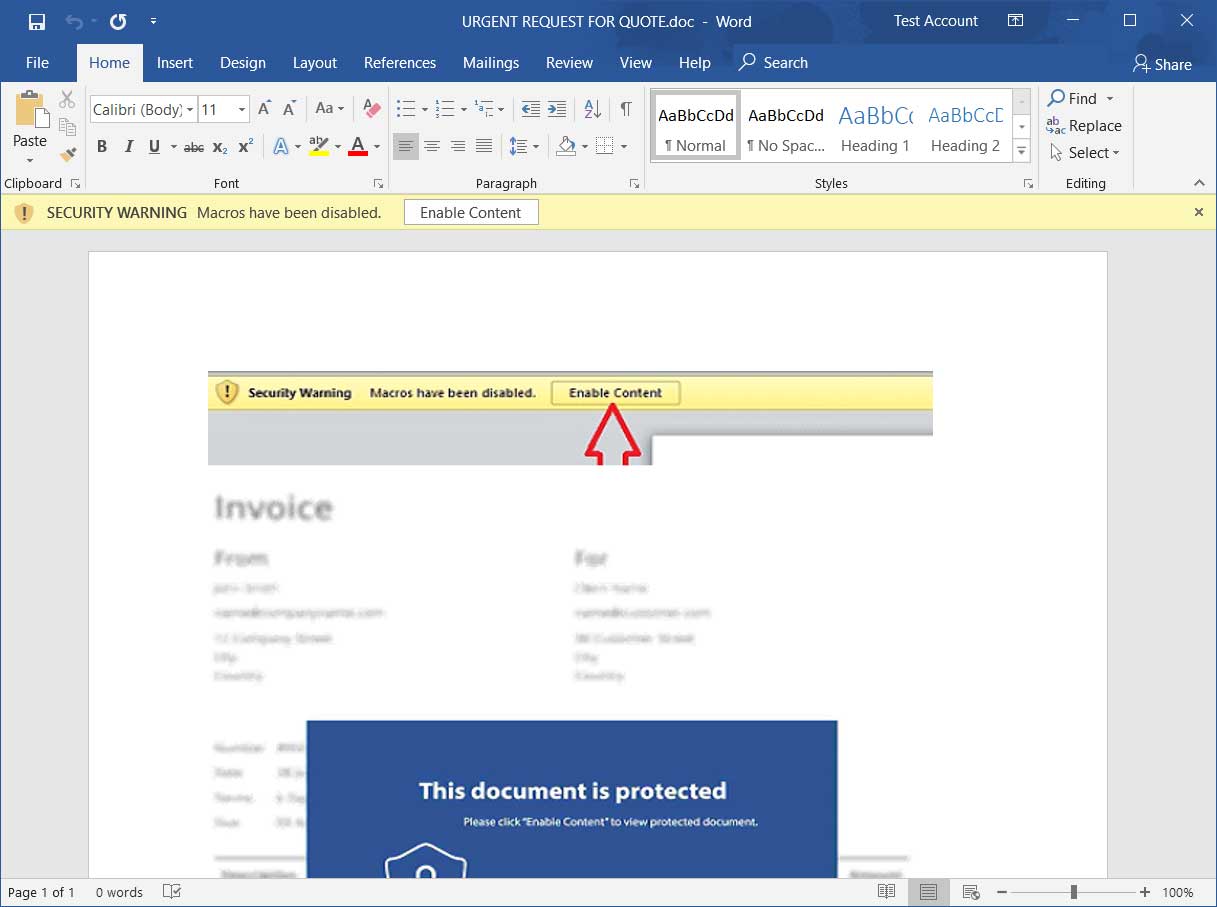
Malicious document prompting to enable macros
If a user clicks on the 'Enable Content' button, Office will update the TrustRecord for the document to indicate that macros have been allowed with this document and will always be allowed going forward.
This is done by changing the last four bytes of the document's TrustRecord to FF FF FF 7F as seen below.
Macros are allowed to run in this document
The use of Trusted Documents does not only apply to Word but also other Office applications. For example, if the user clicks on Enable Editing or Enable Content in an Excel spreadsheet, a TrustRecord will be created under the HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords Registry key as shown below.
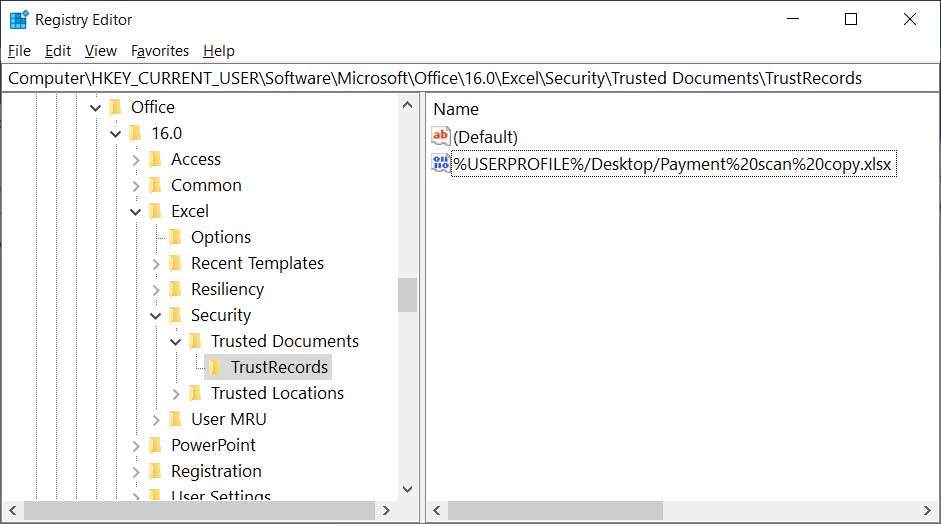
Excel Trust Records
Putting it all together
Now we know that every time a user clicks on 'Enable Editing; or 'Enable Content', Microsoft Office will add the path to the document as a Registry value under the program's TrustRecords key.
We also know that if the last four bytes of the trusted document's value data is set to FF FF FF 7F it means that the user enabled macros in the document, which is a very common vector for a computer to become infected.
Using this information, we can check for potential malicious documents whose macros have been enabled by checking the values under the following keys and then collecting the documents for further forensics.
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Word\Security\Trusted Documents\TrustRecords
HKEY_CURRENT_USER\Software\Microsoft\Office\[office_version]\Excel\Security\Trusted Documents\TrustRecords
This method is especially useful for tracking down Emotet, TrickBot, Ransomware, or RAT infections.
Clearing Trusted Documents
As TrustRecords remember a user's action's forever and would allow macros to run automatically on a previously enabled document, it is best if the Trusted Documents are removed from the Registry at regular intervals.
This can be done through login scripts, scheduled tasks, or other methods.
Users can also clear their Trusted Documents through the Microsoft Office Trust Center, which can be accessed by performing the following steps:
From within Word or Excel, click on File and then Options.
Under Trust Center, click on the Trust Center Settings button.
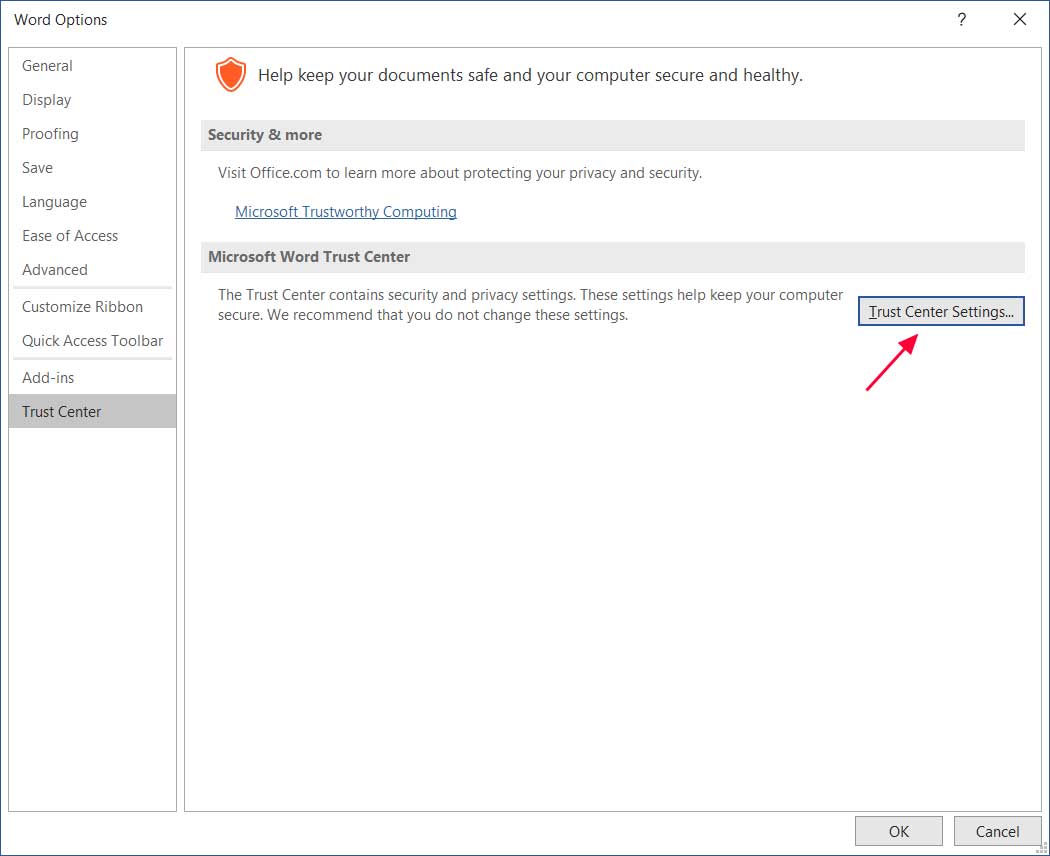
Opening the Trust Center
When the Trust Center opens, click on the Trusted Documents section in the left column.
In the Trusted Documents section, click the Clear button and all of the Trusted Documents will be cleared. This also means that if you open a previously trusted document, Word or Excel will prompt you to 'Enable Editing' or 'Enable Content' again.
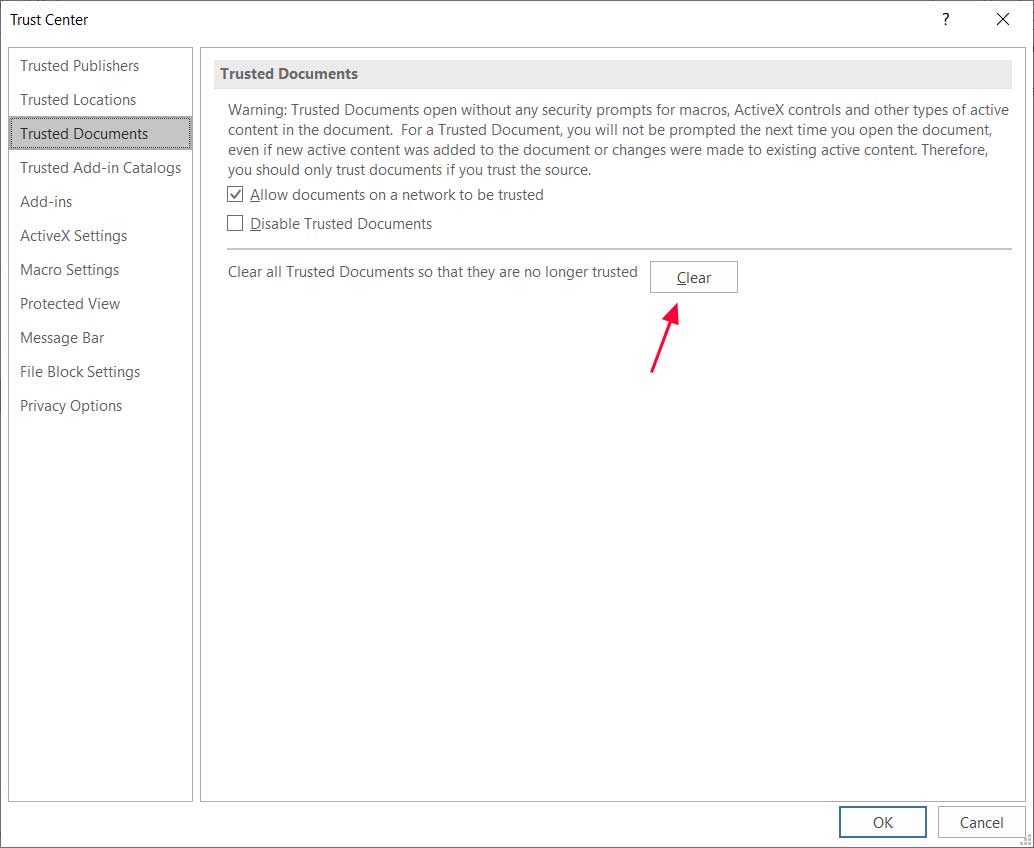
Clear Trusted Documents
Repeat this same process in your other Office applications.
Close the Trust Center.
Malware Spread as Nude Extortion Pics of Friend's Girlfriend
14.3.2020 Bleepingcomputer Spam Virus
Attackers have recently warped sextortion scams into baits used to infect their targets with Raccoon information stealer malware designed to help steal credentials, credit card information, desktop cryptocurrency wallets, and more.
Emails using this new method of luring targets into infecting themselves with Raccoon payloads are distributed in parallel with a more conventional DocuSign campaign.
The same series of attacks was that previously used by the attackers to distribute Predator The Thief info stealer malware via Uber, UPS, QuickBooks, and Secure Parking themed spam.
Sextortion campaign failure used as a lure
As IBM X-Force Threat Intelligence researchers discovered, the attackers are now luring victims using emails promising to give access to the nude extortion pics of a friend's girlfriend.
These emails have a variety of subjects, such as "Mail belonging to your colleague has been stolen," "Private info belonging to your friend has been stolen", "Your colleague’s account was compromised," or "We have got access to your friend’s account."
In the emails, the attackers who claim to be the "Red Skull hacker crew" say that they have access to a friend's email account were they found "images of this naked girlfriend and demanded five hundred dollars for them."
"In the event that he will ignore us, we guaranteed him that we will send these photos to everyone of his contacts," the messages add. "Regrettably, he has not paid, and because you were on his contact list, you obtained this mail. You will find these pix attached to this message."
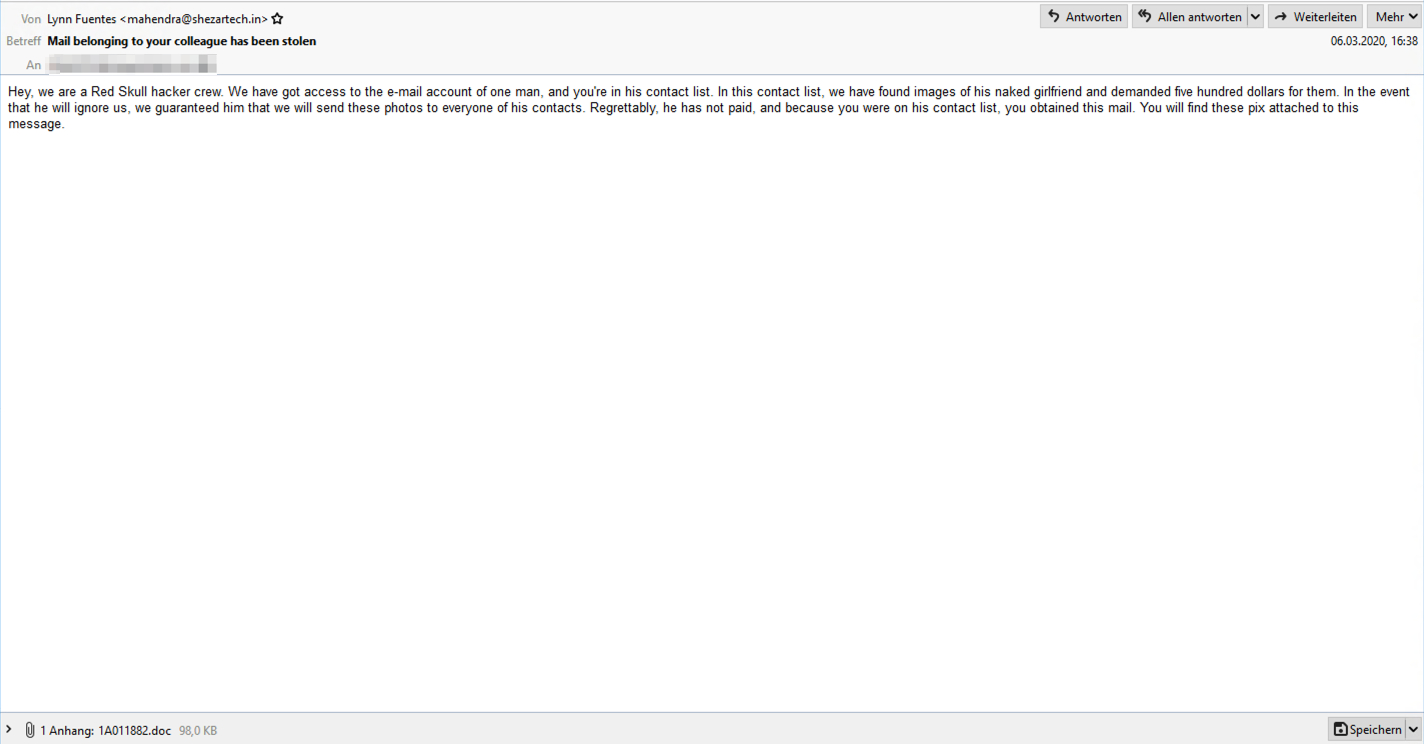
Phishing email sample (IBM X-Force)
By playing the failed sextortion scam card, the campaign's operators attempt to tempt their potential victims to open a malicious attachment with a blurred image that requires them to enable content to be viewed.
Of course, after doing that, the malware payload will be deployed on their computers via embedded macros that run a Powershell command which downloads and installs the Raccoon info stealer.
At the moment, the domain used to deliver the info stealer payloads has been taken down according to IBM X-Force Threat Intelligence researchers, although the campaign's operators might soon switch to another one to keep the attacks going.
By promising to deliver photos of a friend's naked girlfriend, the scammers appeal to the curiosity of their targets which, in many cases, might be a more successful method of incentivizing them to open a malicious attachment than making threats.
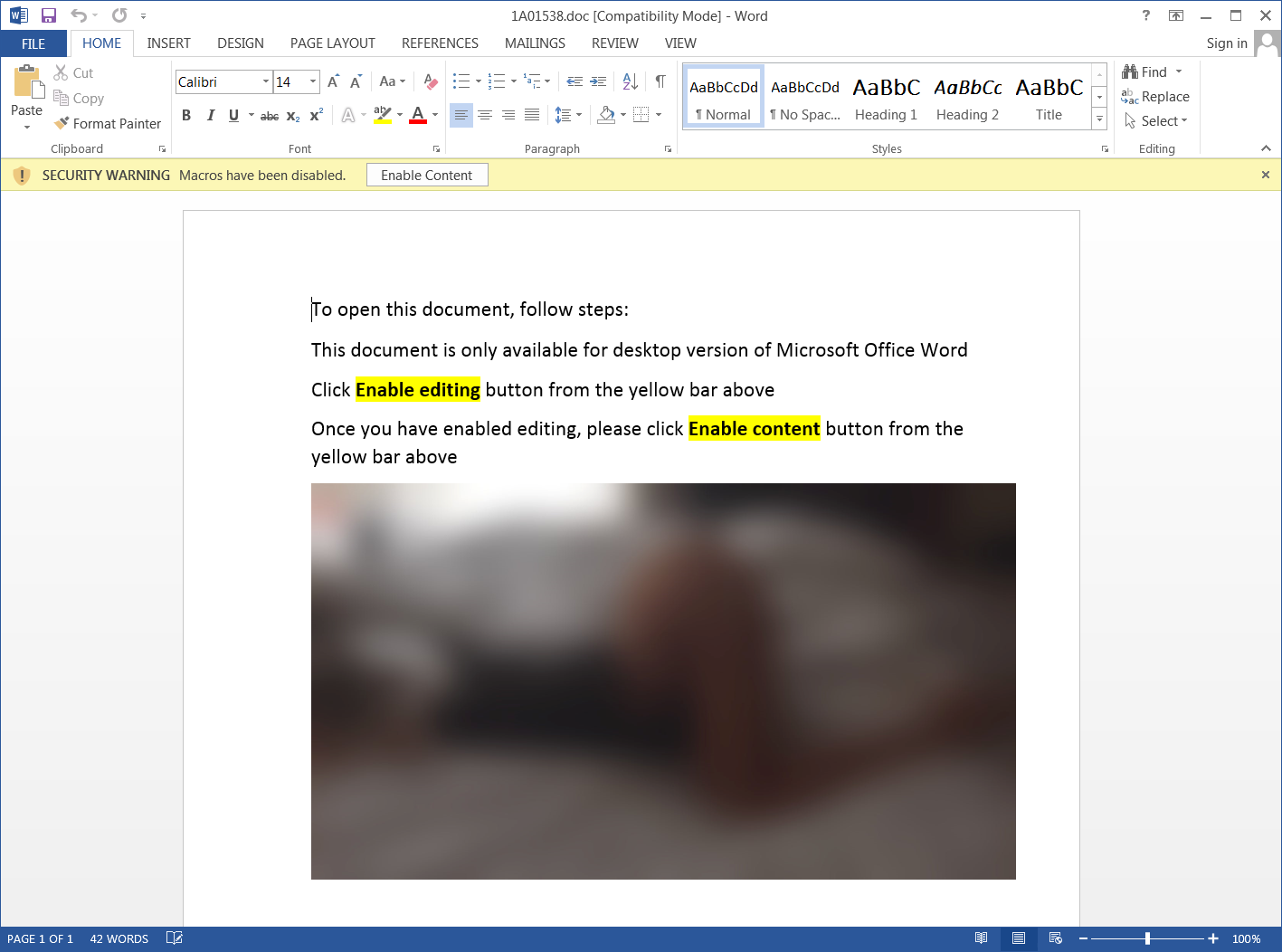
Sextortion malicious attachment
The Raccoon info stealer
Raccoon (aka Legion, Mohazo, and Racealer) is information-stealing malware distributed under the MaaS (malware-as-a-service) model for $75/week or $200/month.
The info stealer is delivered via exploit kits, phishing, and PUA (potentially unwanted applications), and it was first spotted almost a year ago on cybercriminal forums being advertised as malware capable of stealing a wide range of data including but not limited to email credentials, credit card info, cryptocurrency wallets, browser data, and system information.
A report from CyberArk says that Raccoon is capable of dig it's way into about 60 different applications, from browsers, cryptocurrency wallets, email and FTP clients to steal and deliver sensitive information to its operators.
Stolen date prepared for exfiltration (CyberArk)
Raccoon can also be configured to take snapshots of the compromised devices' screens, as well as drop secondary payloads as part of multi-stage attacks.
Recorded Future and Cybereason Nocturnus both said that Raccoon was one of the best-selling malware during 2019 and that it was used to infect hundreds of thousands of systems even though it lacks both sophistication and innovative features.
Data-Stealing FormBook Malware Preys on Coronavirus Fears
7.3.2020 Bleepingcomputer Spam
Another email campaign pretending to be Coronavirus (COVID-19) information from the World Health Organization (WHO) is distributing a malware downloader that installs the FormBook information-stealing Trojan.
With the fears of Coronavirus in full swing, malware distributors are preying on these fears by sending emails that pretend to be the latest updates on the Coronavirus disease outbreak.
These emails contain a ZIP file attachment and state it's from the 'World Health Organization' with information about the latest "Coronavirus Updates". When viewing this email in a mail client, they do not display very well as seen below.
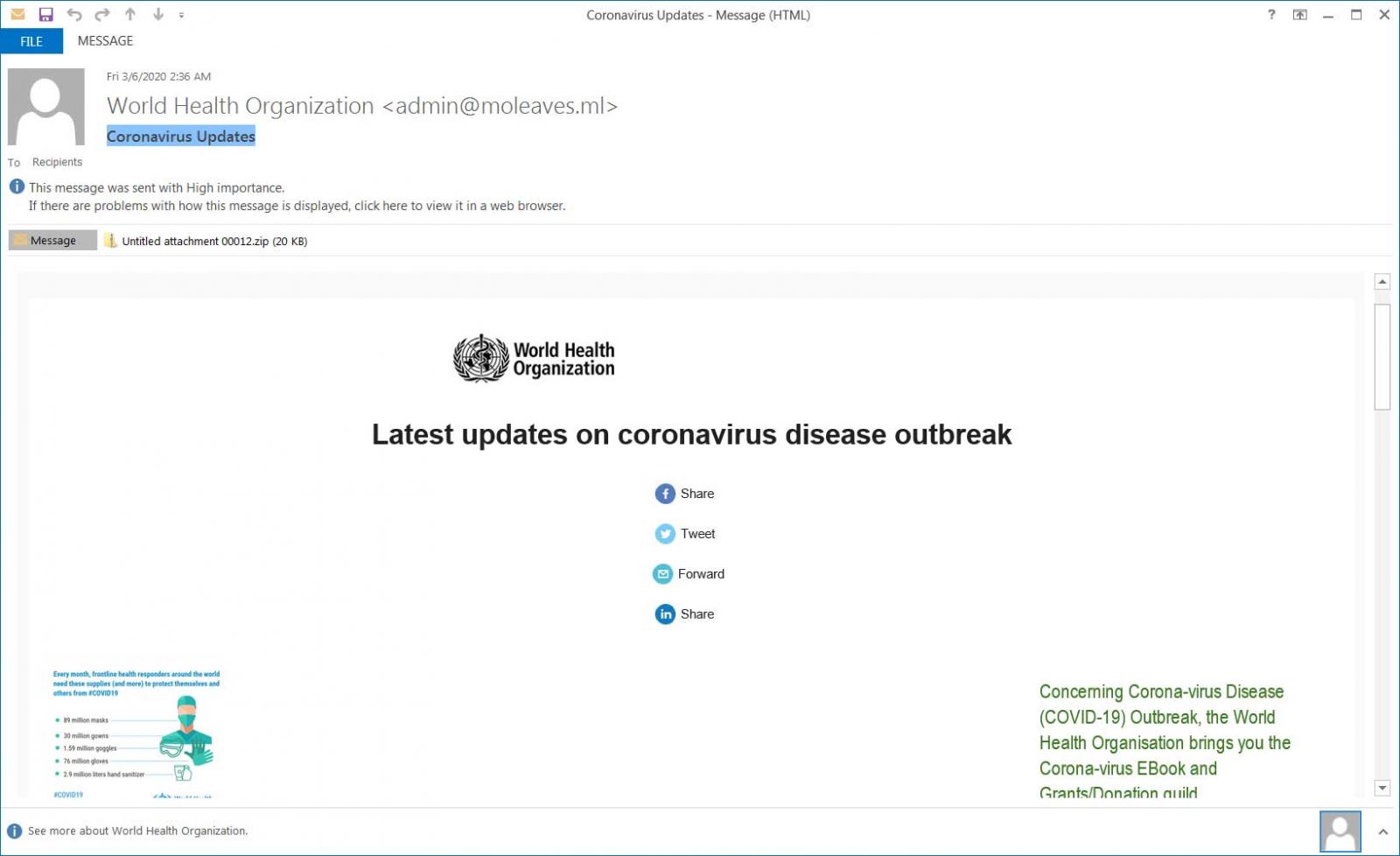
Coronavirus Spam
The emails will, though, prompt you to view the email in a browser, which properly displays the content of the email.
This content pretends to be latest updates on the Coronavirus outbreak and lists various stats, contains an email of corona-virus@caramail.com that is used for further phishing purposes, and prompts you to view the attached 'MY-HEALTH.PDF' file for 'the simplest and fastest ways to take of your health and protect others'.

Viewing email in a browser
This ZIP file attachment contains an executable called MyHealth.exe, which the malware distributors are trying to pass off as the MyHealth.PDF file they mention in the email. They are not, though, doing a convincing job as they use a generic executable icon.

Mail Attachment
According to MalwareHunterTeam who discovered this spam campaign, the executable is GuLoader, which is a malware downloader.
Once executed, GuLoader will download an encrypted file from https://drive.google.com, decrypt it, and then inject the malware into the legitimate Windows wininit.exe process to evade detection.
The downloaded malware is the FormBook information-stealing Trojan, which FireEye states will attempt to steal the contents of the Windows clipboard, log what you type into the keyboard, and steal data while you are browsing the web.
"The malware injects itself into various processes and installs function hooks to log keystrokes, steal clipboard contents, and extract data from HTTP sessions. The malware can also execute commands from a command and control (C2) server. The commands include instructing the malware to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords."
Using this malware, attackers can steal banking credentials, web site login credentials, cookies that allow them to logon to sites as the victim, and the contents of the Windows clipboard.
This means that those who are infected with this malware face significant risk to identity theft, online banking theft, and the compromise of other accounts that they normally log into.
If you have recently received an email claiming to be from the WHO about Coronavirus and it contains an attachment that you opened, it is strongly advised that you scan your computer with antivirus software as soon as possible.
Protecting yourself from Coronavirus scams
When receiving emails, you should never open any attachments unless you confirm the sender.
This means that you should call the sender to confirm they sent the email or at least discuss the attached email with your network administrator to determine if the attachment is safe.
The World Health Organization has also issued an alert to be on the lookout for criminals trying to impersonate them and that they will:
never ask you to login to view safety information
never email attachments you didn’t ask for
never ask you to visit a link outside of www.who.int
never charge money to apply for a job, register for a conference, or reserve a hotel
never conduct lotteries or offer prizes, grants, certificates or funding through email
never ask you to donate directly to emergency response plans or funding appeals.
If you receive an email claiming to be from the WHO and it has an attachment, simply mark it as spam and delete it.
TrickBot Malware Targets Italy in Fake WHO Coronavirus Emails
7.3.2020 Bleepingcomputer Spam Virus
A new spam campaign is underway that is preying on the fears of Coronavirus (COVID-19) to target people in Italy with the TrickBot information-stealing malware.
When sending malicious spam, malware distributors commonly use current events, fears, and politics as themes for the emails to get recipients to open the attached malicious documents.
As there is no bigger news at this time than the spread of Coronavirus and the fears of becoming sick, a new malicious spam campaign has been created that pretends to be from a doctor at the World Health Organization (WHO).
These emails have a subject of "Coronavirus: Informazioni importanti su precauzioni" and pretends to be information about the necessary precautions people in Italy should take to protect themselves from the Coronavirus.
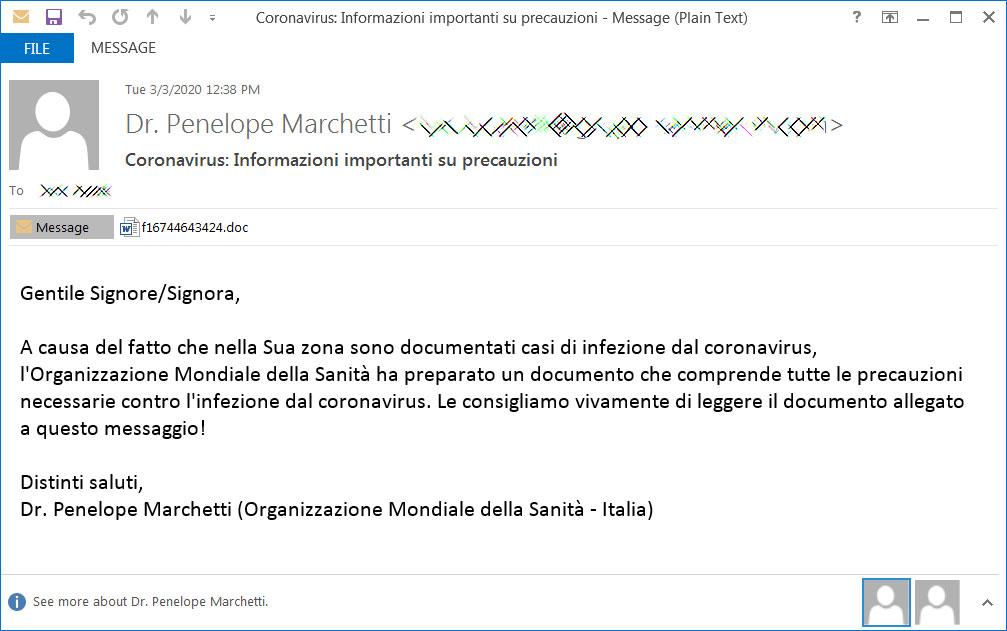
Malicious Spam about Coronavirus
The email in Italian can be read below:
Gentile Signore/Signora,
A causa del fatto che nella Sua zona sono documentati casi di infezione dal coronavirus, l'Organizzazione Mondiale della Sanità ha preparato un documento che comprende tutte le precauzioni necessarie contro l'infezione dal coronavirus. Le consigliamo vivamente di leggere il documento allegato a questo messaggio!
Distinti saluti,
Dr. Penelope Marchetti (Organizzazione Mondiale della Sanità - Italia)
This translates to English as:
Dear Sir / Madam,
Due to the fact that cases of coronavirus infection are documented in your area, the World Health Organization has prepared a document that includes all necessary precautions against coronavirus infection. We strongly recommend that you read the document attached to this message!
With best regards,
Dr. Penelope Marchetti (World Health Organization - Italy)
According to new research by Sophos, attached to these emails is a malicious Word document that when opened states that you need to click on the 'Enable Content' button to properly view it.
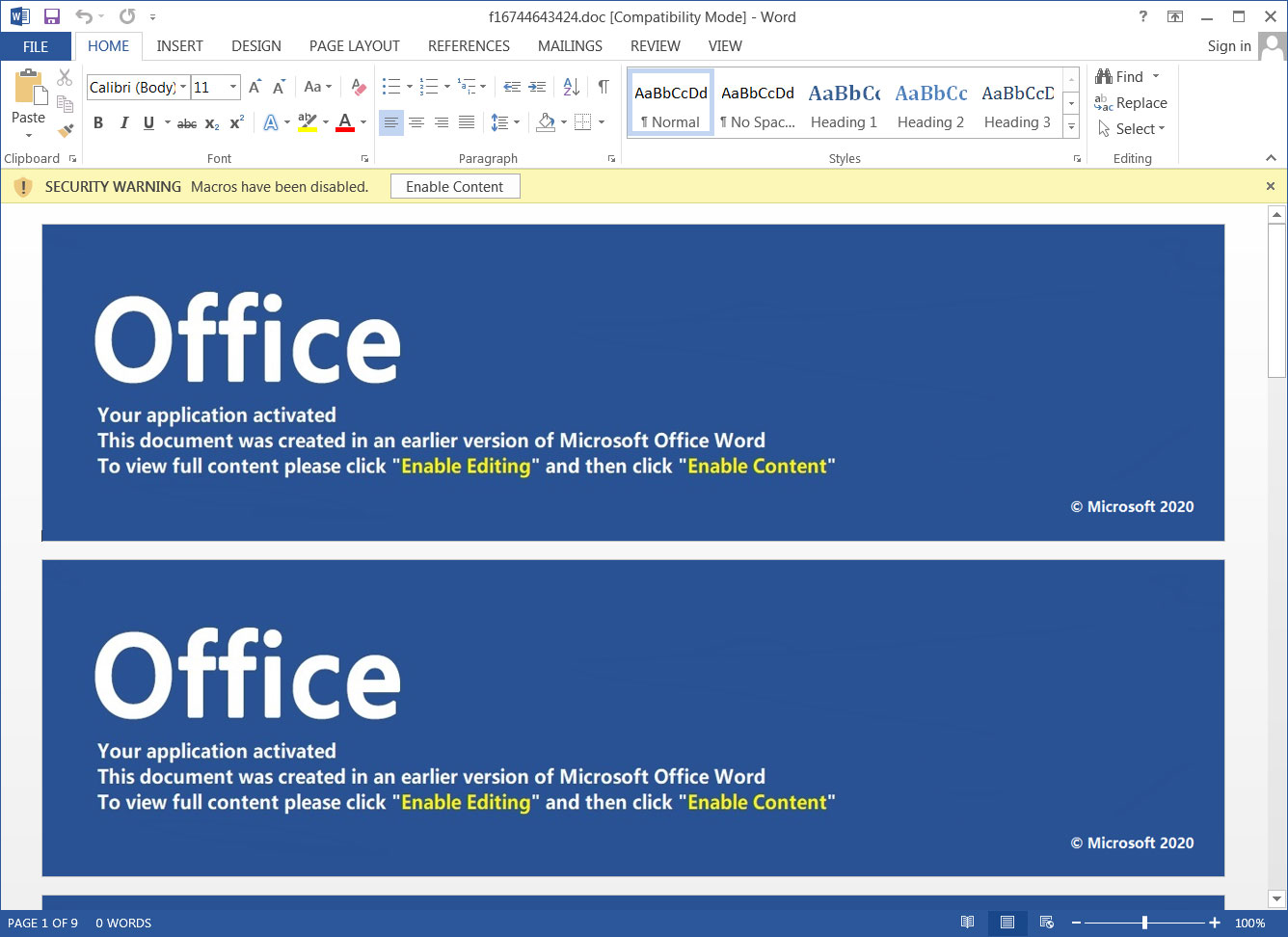
Malicious Word document
Once a recipient clicks on 'Enable Content', though, malicious macros will be executed that extracts various files to install and launch the Trickbot malware as illustrated in the image below by Sophos.
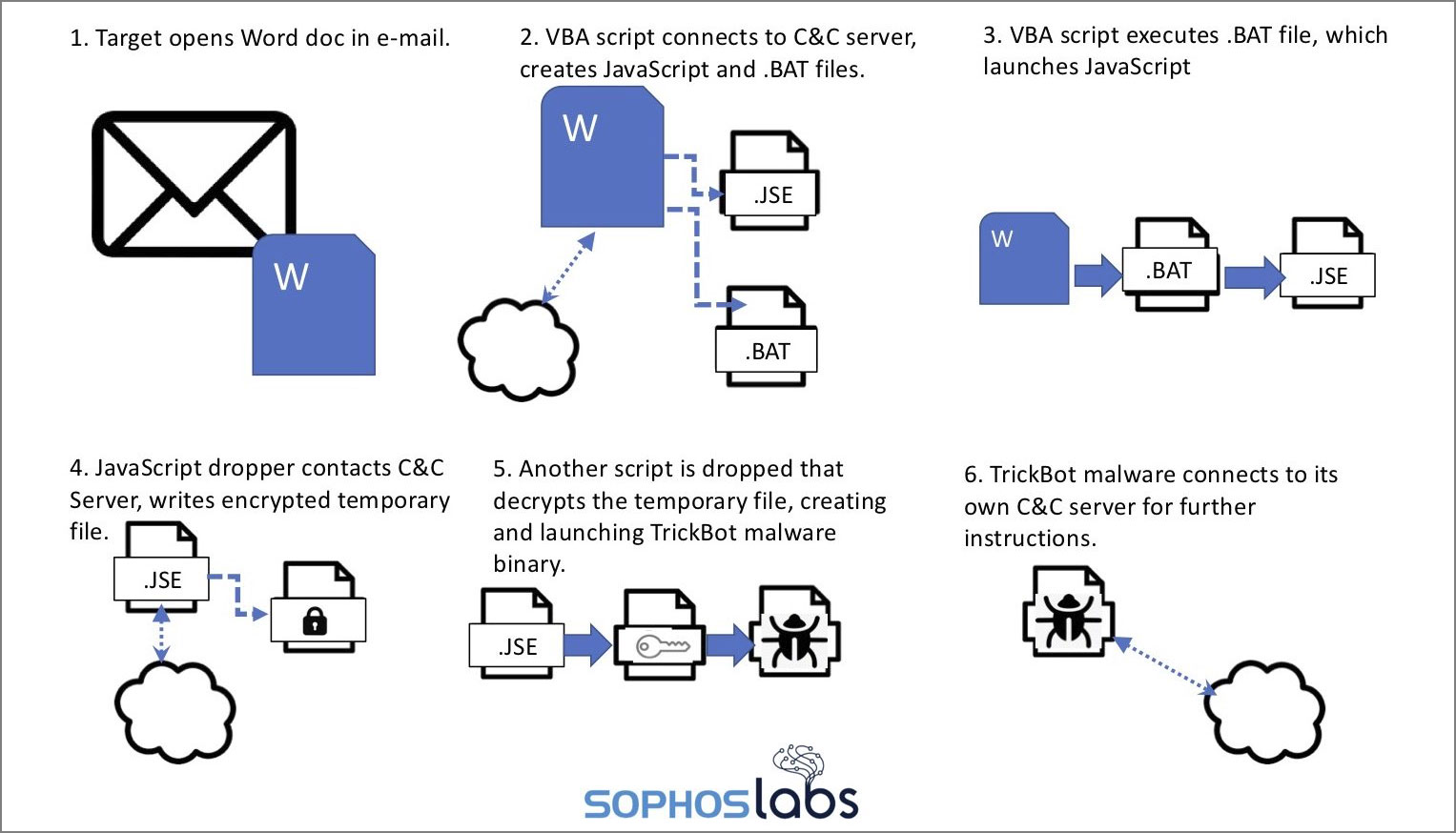
From email to TrickBot infection
(Source: Sophos)
Once TrickBot is installed, it will harvest various information from a compromised computer and then attempt to spread laterally throughout a network to gather more data.
To perform this behavior, TrickBot will download various modules that perform specific behavior such as stealing cookies, browser information, OpenSSH keys, steal the Active Directory Services database, and spreading to other computers.
After harvesting the network of all valuable data, TrickBot will eventually launch PowerShell Empire or Cobalt Strike to give the Ryuk Ransomware actors access to the infected computer.
After these actors perform further reconnaissance of the network, steal data, and gain admin credentials, they will deploy the Ryuk Ransomware and encrypt the files of all the computers on the network.
This is why TrickBot is such a dangerous computer infection as it uses a two-fold attack, with both attacks causing serious damage to your files and personal data.
People need to be suspicious of all emails that they receive and not open any attachment from someone they do not know without first confirming the email is legitimate. This can be done by calling the sender directly and confirming or by scanning the attachment with antivirus software or VirusTotal.
In heightened times of unrest and concern, users need to be even more diligent as there are always people looking to take advantage of a crisis to cause harm to another.






















