Spam Articles - H 2020 1 2 3 4 5 6 7 8 Spam List - H 2021 2020 2019 2018 1 Spam blog Spam blog
Hackers Use Windows 10 RDP ActiveX Control to Run TrickBot Dropper
24.2.2020 Bleepingcomputer Spam Virus
A group of hackers is using the remote desktop ActiveX control in Word documents to automatically execute on Windows 10 a malware downloader called Ostap that was seen recently adopted by TrickBot for delivery.
Security researchers have found dozens of files that delivered the first malware payload, indicating a larger campaign.
Starts with phishing
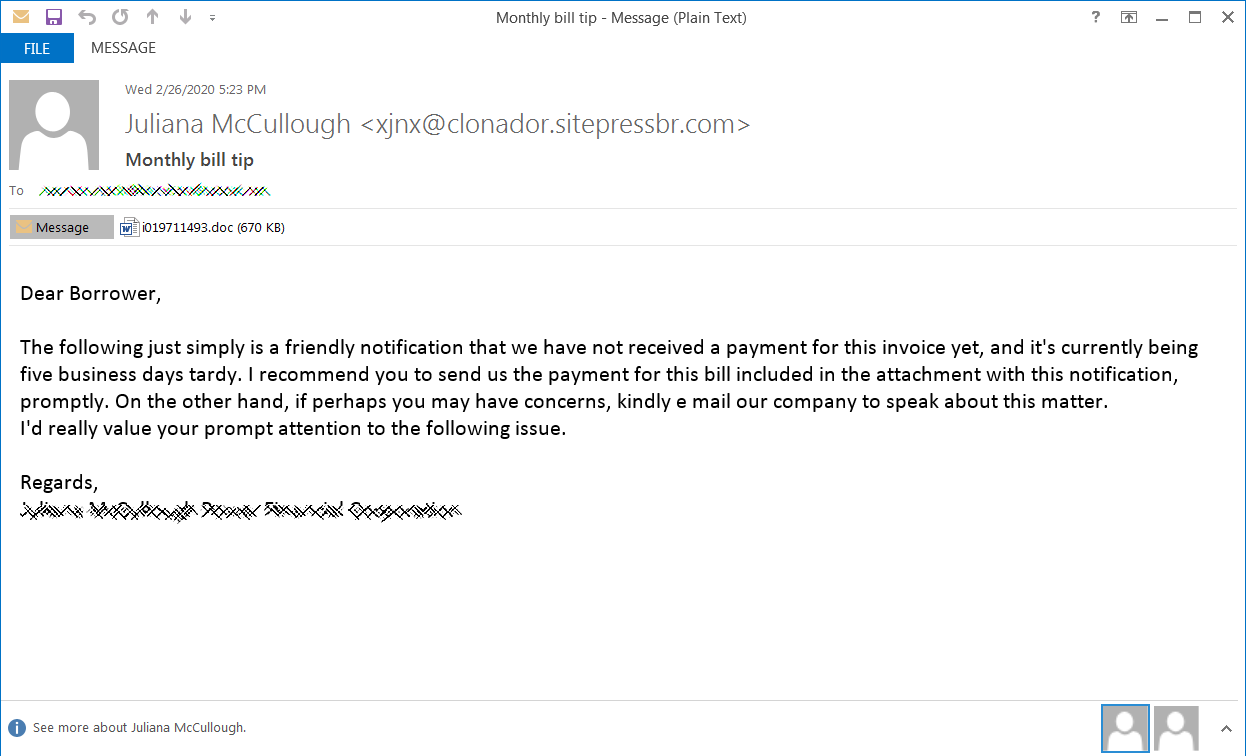
Ostap, extensively analyzed by Bromium researchers, is delivered via a Word document laced with malicious macro code and including an image that allegedly showed encrypted content. This is the ruse to trick victims into enabling macros in the document.
The threat actor delivered the malicious documents via phishing emails disguised as notifications of a missing payment. In the attachment is the fake invoice referred to in the message.
Security researchers at Morphisec analyzed the poisoned docs and noticed that there was an ActiveX control hidden below the embedded image.
A closer look revealed that the threat actor used the MsRdpClient10NotSafeForScripting class, which is used for remote control. Windows 10 is the minimum supported client and Windows Server 2016 is the minimum supported server.
ActiveX controls can be added to text or drawing layers in Word documents to make them interactive.
Clever delivery and execution
In a report today, Michael Gorelik of Morphisec writes that the JavaScript code for Ostap downloader is present in the document in font that has the same color as the background, making it invisible to the human eye.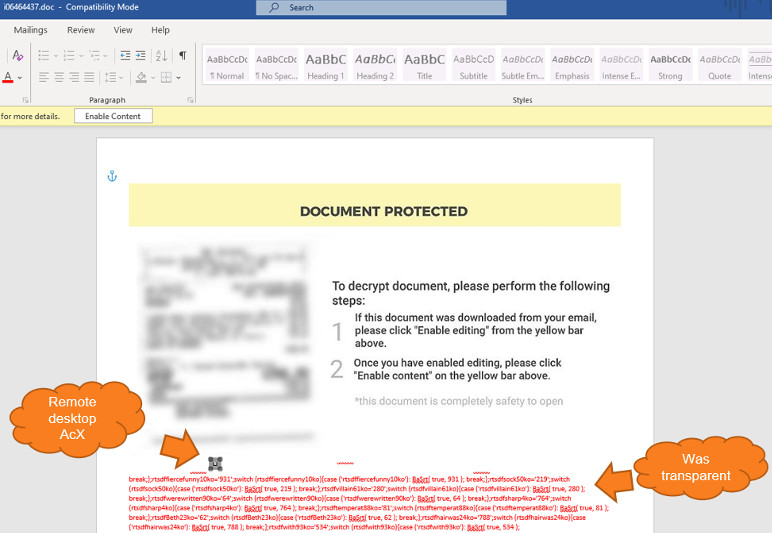
Another interesting finding is that the attackers did not populate the "server" field in the MsRdpClient10NotSafeForScripting class, needed to establish a connection with a remote desktop server.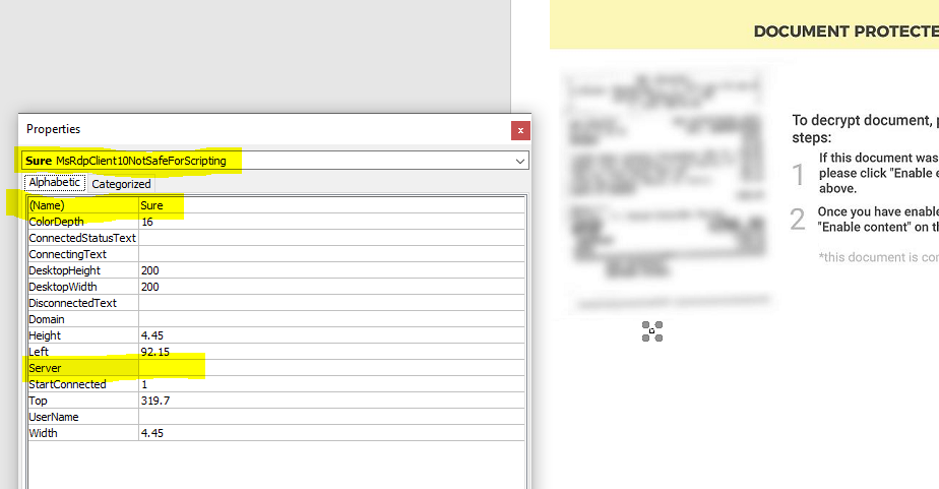
This was not a lapse from the attackers as the error that occurs helps execute their malicious code at a later time, thus evading detection.
When inspecting the macro, the researchers found that the "_OnDisconnected" function acts as a trigger but only after an error is returned for failing to connect to a non-existent server.
"The OSTAP will not execute unless the error number matches exactly to "disconnectReasonDNSLookupFailed" (260); the OSTAP wscript command is concatenated with a combination of characters that are dependent on the error number calculation." - Michael Gorelik, Morphisec
The backdoor is then executed immediately after taking the form of a .BAT file and the document form is closed.
Gorelik told BleepingComputer that this actor is not the only one relying on ActiveX control to execute malware. Other actors seen in January used the OnConnecting method that is easier to detect.
By contrast, the OnDiconnected method needs a specific return value and there is also a delay while the DNS lookup completes. This works to the attacker's advantage because scanners may miss the malicious activity and mark the file as benign.
[Update 02/28/2020, 16:01 EST]: Article updated to reflect a correction from Morphisec about misidentifying Ostap downloader with Griffon backdoor that is typically used by FIN7 threat actor.
FTC Refunds Victims of Office Depot Tech Support Scam
24.2.2020 Bleepingcomputer Spam
The FTC has begun to issue refunds to people who were convinced into purchasing computer repair services at Office Depot based on fake malware scans.
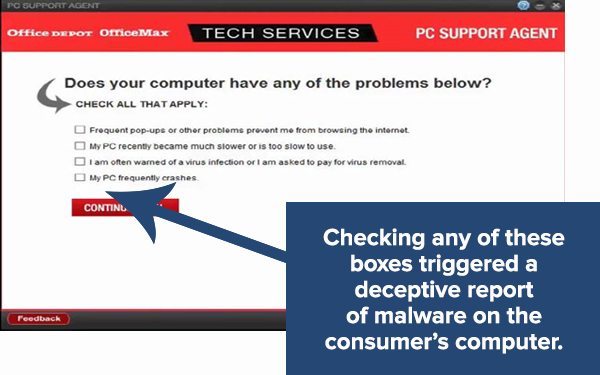
Between 2009 and November 2016, Office Depot and Office Max employees utilized a diagnostic program called 'PC Health Check' that would in many cases report a person's computer had malware even if it was not infected.
PC Health Check software interfac
Whistleblowers told KIRO7 reporters that the employees were pressured into utilizing PC Health Check even though it was known to not be accurate to convince people to purchase repair services ranging from $180 to $300.
KIRO7 reporters tested this by taking six brand new laptops to various Office Depot locations, where they were falsely told four out of the six laptops were infected and were prompted to purchase repair services.
Office Depot settles with the FTC
In March 2019, Office Depot agreed to pay $35 million as part of a settlement with the FTC.
Of this collected money, $34 million was set aside as refunds to victims of the scam conducted by Office Depot.
"Office Depot paid $25 million while its software supplier, Support.com, Inc., paid $10 million as part of 2019 settlements with the FTC. The FTC alleged that Office Depot and Support.com configured a virus scanning program to report that it found symptoms of malware or infections—even when that was not true—whenever consumers answered yes to at least one of four “diagnostic” questions. The false scan results were then used to persuade consumers to purchase computer repair and technical services that could cost hundreds of dollars," the FTC stated.
Today, the FTC has announced that they have begun to issue refunds to 541,247 people with the average refund being $63.35.

The FTC states that all refund checks should be cashed within 60 days and that if there are any questions about the refunds, recipients should contact the FTC’s refund administrator, Epiq, at 1-855-915-0916.
BEC Fraud Profits from Gift Cards, Down 63% Over Holidays
16.2.2020 Bleepingcomputer Spam
Business email compromise (BEC) activity hit the breaks toward the end of 2019 but only in the last two weeks of the year and not before recording a peak.
The numbers for the average losses are still significant, though. Contrary to expectations, more money was made from email fraud requesting gift cards than from tricking employees to wire payments on fraudulent invoices.
Gift card requests more profitable
Data collected by Agari email threat prevention and protection service shows that in Q4 2019 scammers adjusted their ruse to blend with the holiday season and focused on gift cards.
This move has a higher success rate, the researchers say, because attackers can use the same scam on multiple targets within the same organization, it is less conspicuous during the holiday season, and tracking and recovering the money is close to impossible.
Almost 62% of all BEC scams Agari recorded in Q4 2019 included a gift card request. Compared to the previous quarter, there was a 6% increase, not a surprise, considering the season.
"Since the ruse involves asking an employee to purchase gift cards for colleagues, victims are much less likely to inform others about the request—especially during the holiday season" - Agari
Fraud seeing direct wire transfers increased to 22% from the previous sly recorded 19% quarter on quarter. However, Agari says that the total losses from this scam were lower than those generated by gift card grifting.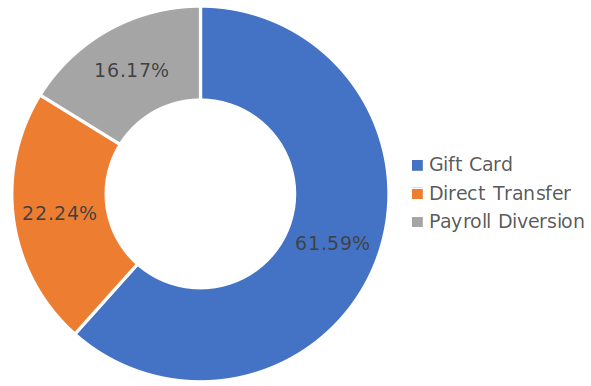
The maximum and minimum amounts requested in gift cards were up by 25%, Agari found, corresponding to $250 and $10,000 respectively.
Losses from wire transfers are much larger per attack, with the average being assessed at $55,395 and the maximum at $680,456.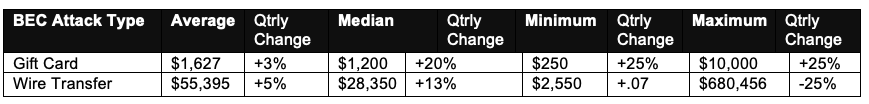
The reason behind gift cards being more profitable is not just the higher number of attacks but also a better success rate at recovering money from fraudulent wire transfers, which in 2018 was at 75%.
Google Play gift cards are still fraudsters' top preference, followed by Target, Walmart, and BestBuy. They're used to purchase physical goods that are later sold cheaper.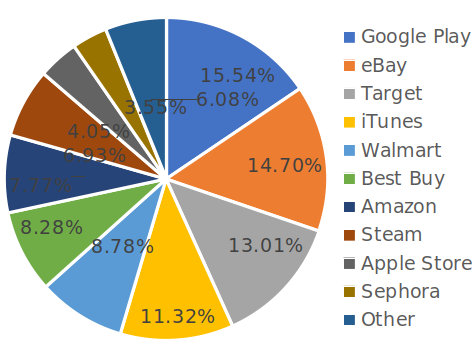
Between Christmas and the New Year, the cadence of BEC attacks took a drastic dive, falling by 63%, indicating that fraudsters follow the same schedule as their victims.
"With many employee targets out of the office those last two weeks of the year, it’s clear scammers took some holiday downtime of their own or scammers are very cognizant of their targets’ holidays and exert less effort in their attacks when there is a likelihood the targets are out of the office" - Agari
FTC Warns of Ongoing Scams Using Coronavirus Bait
15.2.2020 Bleepingcomputer Spam
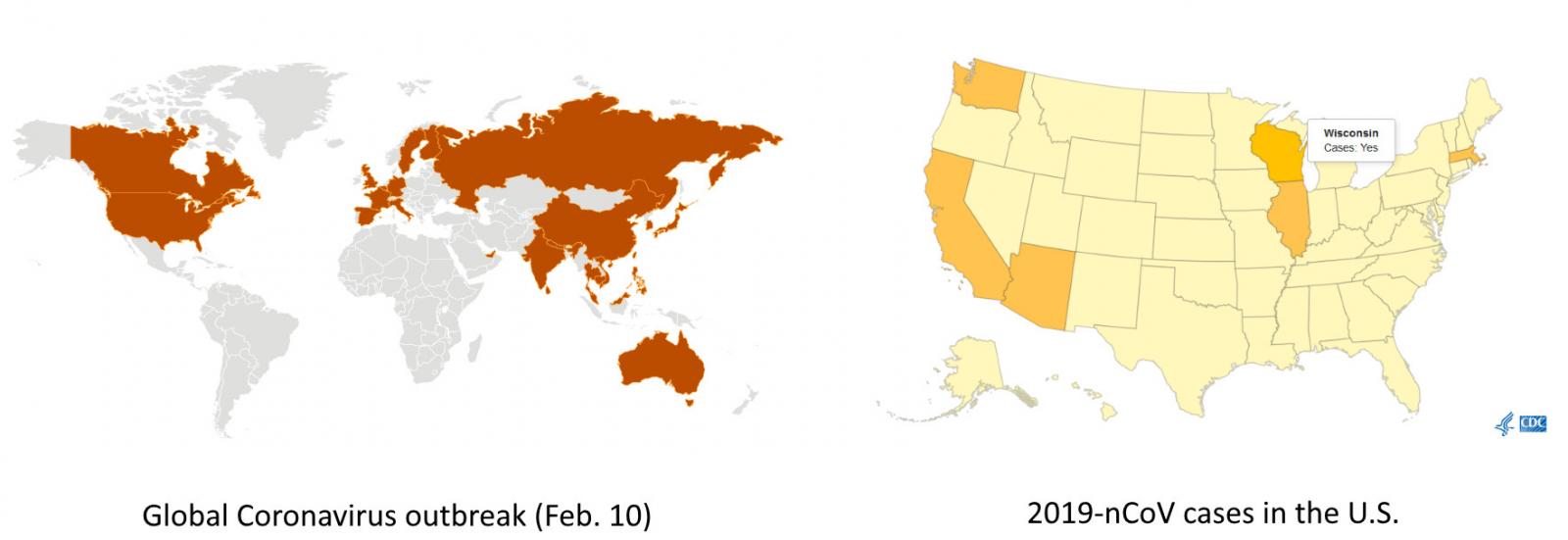
The U.S. Federal Trade Commission (FTC) warns about ongoing scam campaigns that make use of the current Coronavirus global scale health crisis to bait potential targets from the United States via phishing emails, text messages, and social media.
The World Health Organization (WHO) announced on January 30, 2020, that the new 2019 novel Coronavirus (also known as 2019-nCOV and Wuhan coronavirus) outbreak is a public health emergency of international concern.
The next day, the U.S. Health and Human Services Secretary Alex M. Azar also declared it a "public health emergency for the entire United States."
Coronavirus scams and malicious attacks
"Scammers are taking advantage of fears surrounding the Coronavirus," the FTC says. "They’re setting up websites to sell bogus products, and using fake emails, texts, and social media posts as a ruse to take your money and get your personal information.
"The emails and posts may be promoting awareness and prevention tips, and fake information about cases in your neighborhood.
"They also may be asking you to donate to victims, offering advice on unproven treatments, or contain malicious email attachments."
The FTC also provides the following measures you can take to make sure that you won't get scammed or get your computer infected with malware after falling for a scammer's tricks:
• Don’t click on links from sources you don’t know. It could download a virus onto your computer or device. Make sure the anti-malware and anti-virus software on your computer is up to date.
• Watch for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or experts saying that have information about the virus. For the most up-to-date information about the Coronavirus, visit the Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO).
• Ignore online offers for vaccinations. If you see ads touting prevention, treatment, or cure claims for the Coronavirus, ask yourself: if there’s been a medical breakthrough, would you be hearing about it for the first time through an ad or sales pitch?
• Do your homework when it comes to donations, whether through charities or crowdfunding sites. Don’t let anyone rush you into making a donation. If someone wants donations in cash, by gift card, or by wiring money, don’t do it.
• Be alert to “investment opportunities.” The U.S. Securities and Exchange Commission (SEC) is warning people about online promotions, including on social media, claiming that the products or services of publicly-traded companies can prevent, detect, or cure coronavirus and that the stock of these companies will dramatically increase in value as a result.
Coronavirus-themed phishing campaigns and malware
Multiple active phishing campaigns using Coronavirus lures have already been detected in the wild by security researchers, targeting individuals from the United States and the United Kingdom while impersonating the U.S. CDC officials and virologists, and warning of new infection cases in the victims' area and providing 'safety measures.'
A sample phishing email spotted by KnowBe4 shows attackers trying to camouflage their spam message as an official alert distributed via the CDC Health Alert Network informing US-based targets that the "CDC has established an Incident Management System to coordinate a domestic and international public health response."
An embedded malicious hyperlink is camouflaged as a link to the official CDC site and it is used to redirect the victims to attacker-controlled Outlook-themed phishing landing pages used for harvesting and stealing their user credentials.
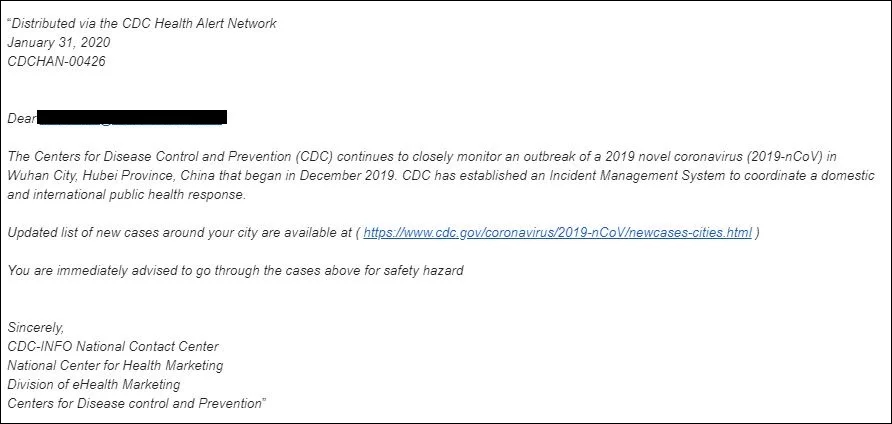
Coronavirus phishing email sample (KnowBe4)
Another phishing campaign using a Wuhan Coronavirus bait targets both US and UK targets was spotted by security firm Mimecast.
"The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain," Mimecast's director of threat intelligence Francis Gaffney explained.
These series of phishing mails ask the recipients to "go through the attached document on safety measures regarding the spreading of coronavirus."
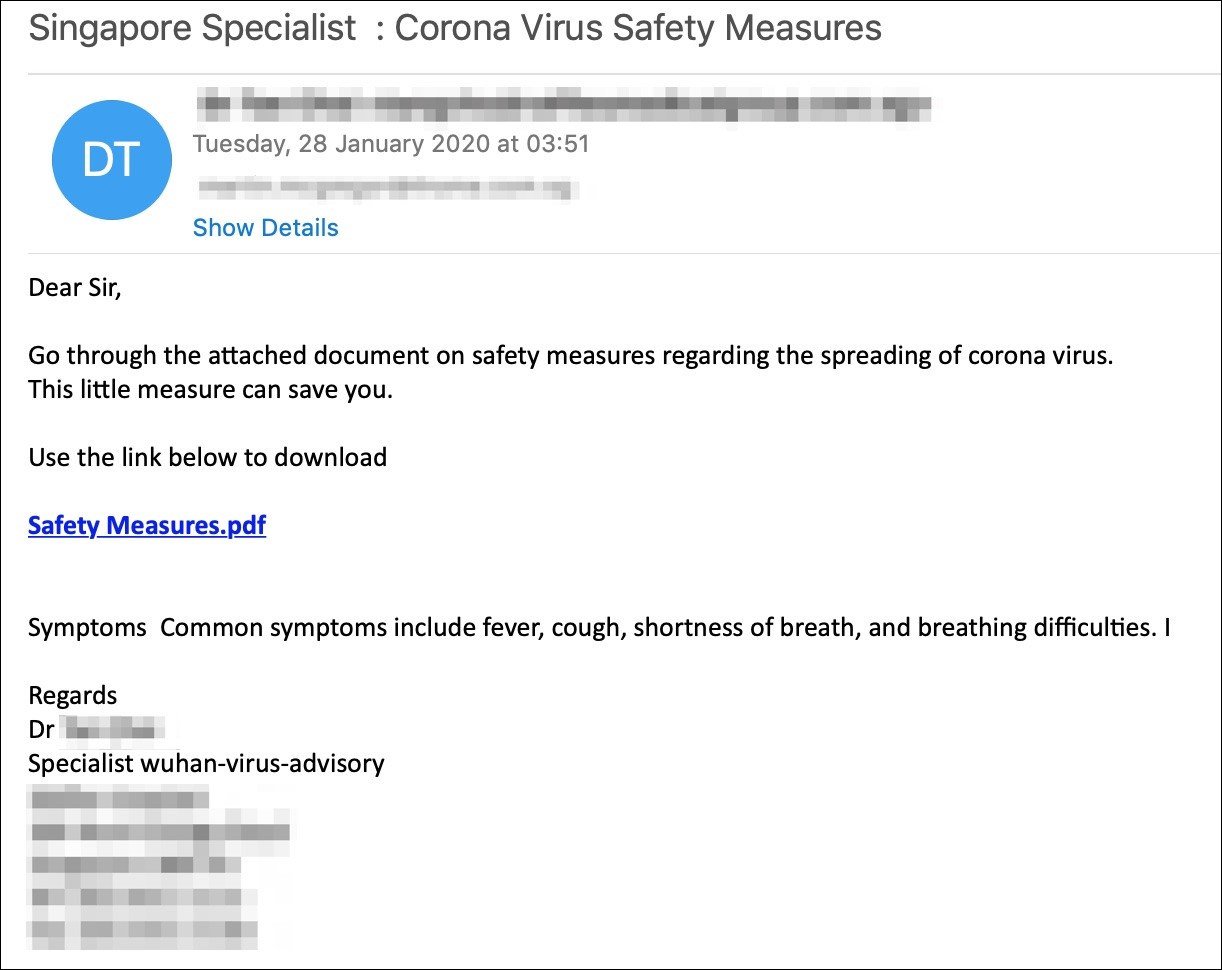
Coronavirus phishing email sample (Mimecast)
The Coronavirus health crisis is also used as a lure by a malspam campaign targeting Japan with Emotet malware payloads via messages alerting of Coronavirus infection reports in several Japanese prefectures.
Just as the actors behind the phishing campaigns KnowBe4 and Mimecast spotted, the Emotet gang is also known for quickly taking advantage of trending events and nearing holidays, like a Greta Thunberg Demonstration or the 2019 Christmas and Halloween parties.
The security research team MalwareHunterTeam also shared several malware sample that include Coronavirus references including a Remote Access Trojan (RAT), a Trojan, a stealer/keylogger, and a wiper.
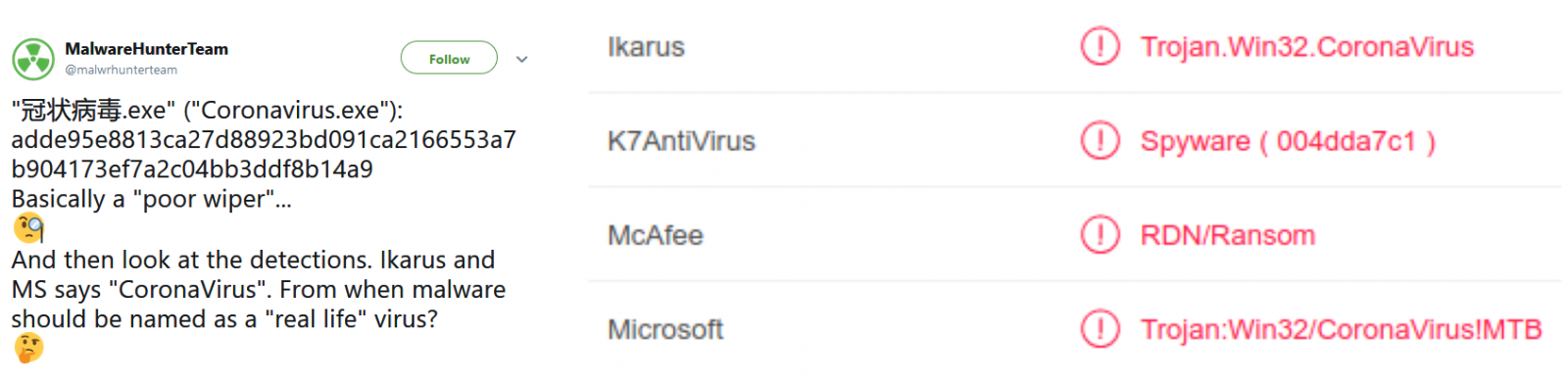
"High levels of concern around the Coronavirus are currently being used to increase the online popularity of spam campaigns designed to spread fake news and drive unsuspecting users to dubious online drug stores," according to a report published by Imperva researchers today.
"For people searching for genuine information on Coronavirus, this is polluting their online search results with fake and meaningless results," the researchers further explained.
"Not only does the content of this spam do nothing to help people in their quest to educate themselves on this global health risk, but bot operators are using technology to exploit the public’s need for medical information in order to gain a few more clicks to their fake pharmacies."
Update February 11, 12:15 EST: Added info on Coronavirus-themed spam campaigns discovered by Imperva.
Lock My PC Used By Tech Support Scammers, Dev Offers Free Recovery
9.2.2020 Bleepingcomputer Spam
Tech Support scammers are using a free utility called Lock My PC to lock users out of their PCs unless they pay the requested "support" fees.
For years telephone scammers pretending to be from Microsoft, Google, and other companies have been convincing people to let them access their computer to fix a "detected" issue. Once the scammers gain access to the computer, though, they would use the Windows Syskey program to lock the user out of Windows with a password unless they paid for the "support" call.
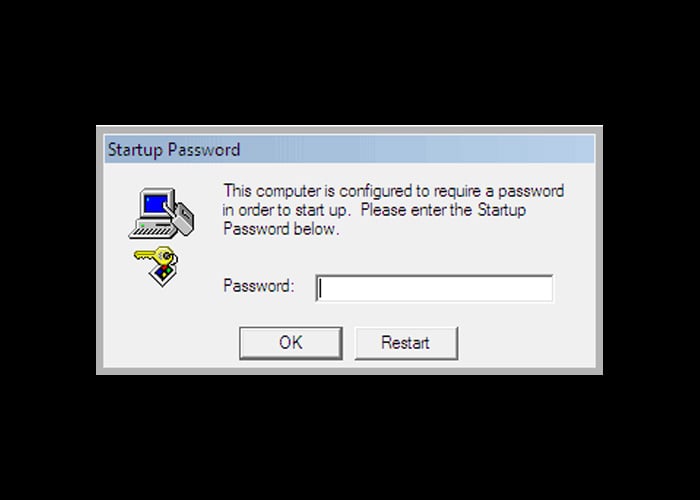
Computer Locked with Syskey
With the release of Windows 10 1709, otherwise known as the Fall Creators Update, Microsoft removed all support for Syskey from the operating system.
With Syskey no longer being available, tech support scammers have switched to another product called Lock My PC to lock victims out of Windows.
When installed Lock My PC will require a user to enter a password before they can gain access to Windows. When used to lock a PC, users will see an animated 'Locked' screen when they start their computer.

Lock My PC screen
If they press any button on the keyboard, a password prompt dialog would be shown stating "The computer has been locked".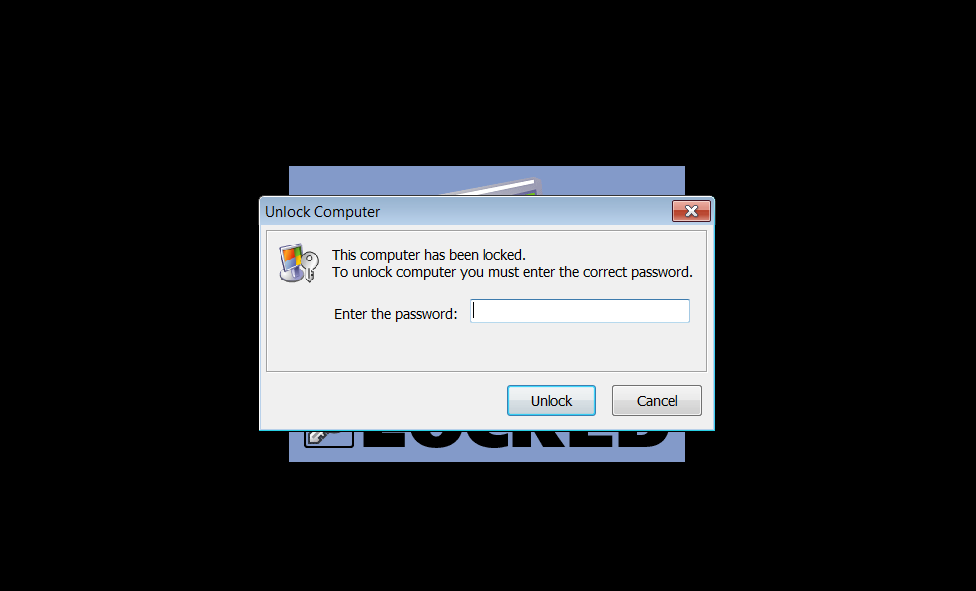
Unlike Syskey, which encrypts the Windows SAM database and uses the inputted password to decrypt it, Lock My PC does not encrypt anything and only blocks access to the computer with the password.
Unfortunately, in our tests, the software also runs in Safe Mode, which makes it difficult to disable without the password or bootable recovery tools.
These tools, though, can be difficult to use for those who are affected by this scam.
Lock My PC dev offers free recovery keys
When FSPro Labs, the developers of Lock My PC, discovered that their free software was being abused, they no longer made the software publicly available for download.
"After receiving too many reports of Lock My PC misuse, we decided to make our user access control software unavailable for the public. However, the programs are still available for our existing customers on requests. New customers may request Lock My PC business edition only using their corporate email address," FSPro Labs stated on the product's download page.
For users who fell victim to one of these scams and have had Lock My PC installed on their computer, FSPro is offering free recovery passwords that will allow users to unlock their PC.
To get access to a recovery password, at the Lock My PC password prompt enter '999901111' and a numeric recover code will appear under the password field.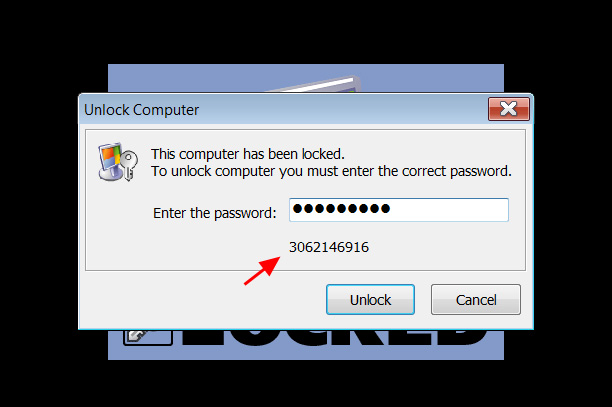
Getting a recovery code
Victims can input this code on the Lock My PC recovery page to receive a recovery password that can be entered into the password field to unlock the PC.
Users can then uninstall the Lock My PC program from their computer.
Thx to Michael Gillespie for the tip!
BEC Scammers’ Interest in the Real Estate Sector Rises
9.2.2020 Bleepingcomputer Spam
Cybercriminals choose their targets by the profit they can make off them and the real estate business seems ripe for the picking, security researchers warn after looking at some 600 attacks focused on this sector.
The main threat for this vertical is the business email compromise (BEC) fraud, which aims to divert funds from a transaction to a bank account controlled by the bad guys.
The big money from real estate transactions has attracted a larger number of fraudsters, threatening this business with a wider set of tactics and tools.
Some of them cast a wider net to catch as many victims involved in a transaction as possible, regardless of their role. The purpose is to infiltrate in the chain and collect information that can be used to divert the funds.
Tricks of all sorts
Researchers at Proofpoint say that both sophisticated and less capable scammers are currently in this game, some adding malware in their scheme while others rely on social engineering alone.
Phishing for login credentials remains a popular trick, with attackers spoofing Office 365 and DocuSign pages to collect the sensitive info. Some scammers make the effort and research their victims to send them malicious links in customized messages that are more likely to do the trick.
In one example analyzed by Proofpoint, the crooks added the name of the real estate company on a phishing page for Office 365 credentials. The link was sent to multiple brokers at that business, hoping that one of them would fall for it.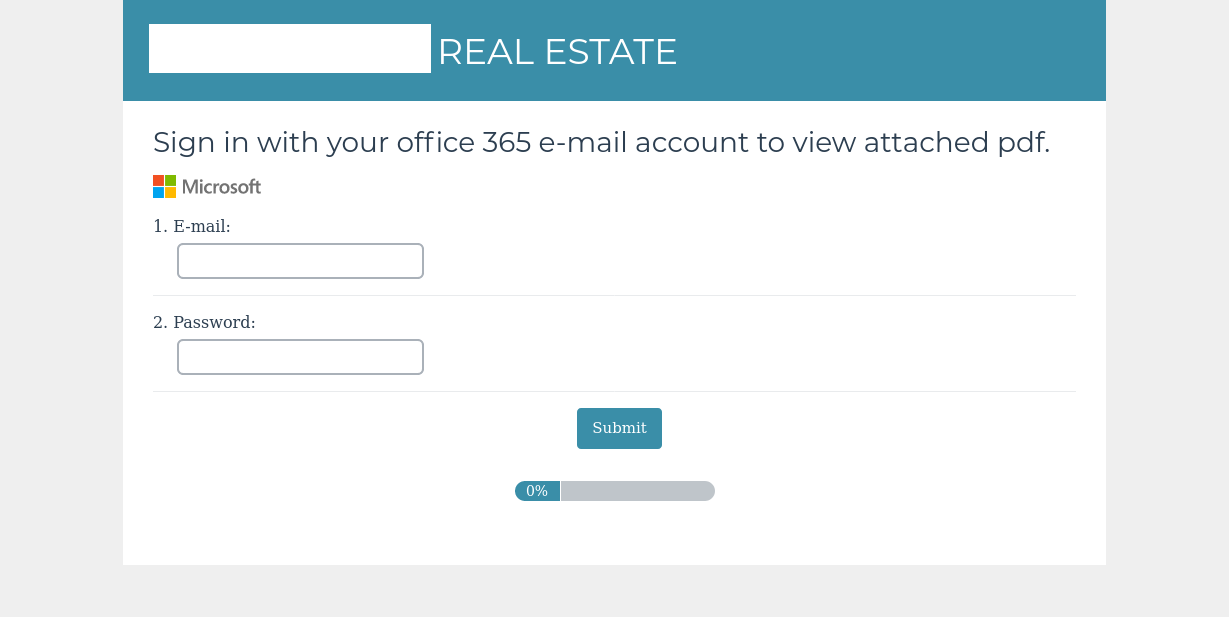
Most of the time, the victims would land on these pages after getting a message purporting to provide documents for a transaction, a lure that is powerful enough in this business.
A more sophisticated ruse the researchers discovered included the company's name and branding, as well as the target agent's name and contact info. This is an attempt to plant malware on the victim's computer.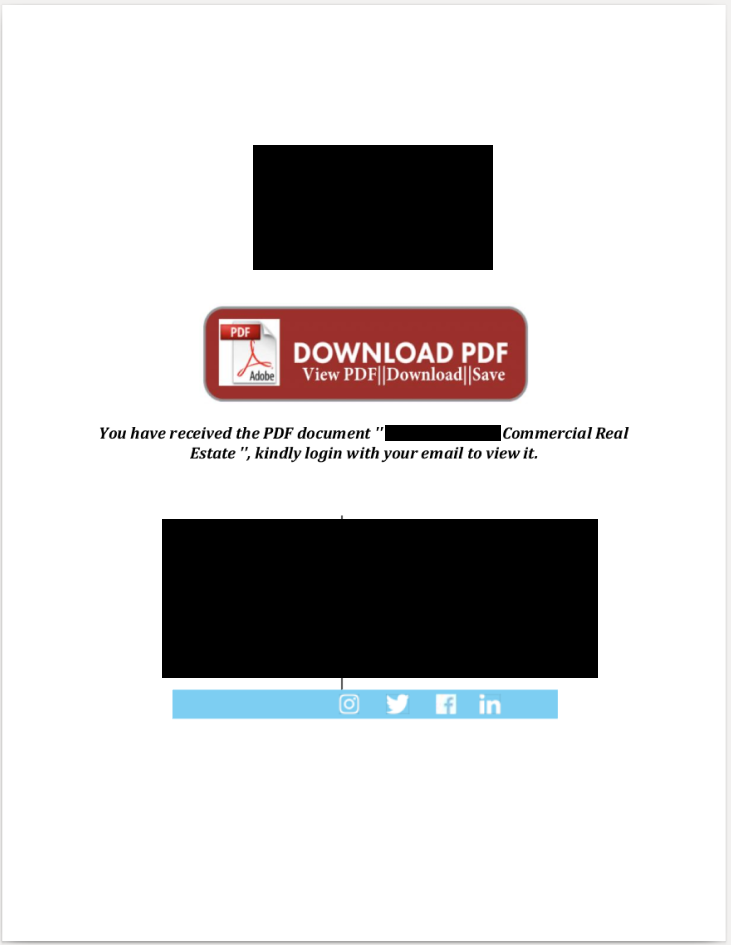
In another attack, the crooks tried to steal credit card information by spoofing a credit card authorization operation. To make it credible, they used the logo and the name of the real estate company.
In a report today, Proofpoint also shared an email sample for a classic BEC scam. Posing as someone in the upper management, the fraudster asked an employee likely authorized to make money transfers to get something done for them.
The task was probably to change an account number for a payment or wire money (salary, transaction, commission) into an account other than the regular one.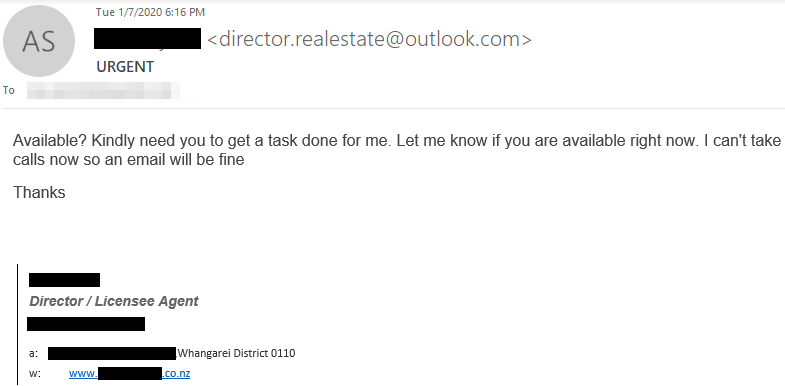
According to Proofpoint, anyone involved in real estate transactions is a target, from agents, buyers, and inspectors to insurance agents and contractors.
Thwarting most attacks is far from difficult and major online services like those from Microsoft, Google, DocuSign, provide two-factor authentication (2FA), a login protection mechanism that asks for an extra code delivered to the owner to verify a legitimate login.
Simple things such as applying extra caution and checking the recipient's address when getting a suspicious request can lower the chances of a successful attack significantly.
Tech Support Scam Hitting Microsoft Edge Start Page Takes a Break
8.2.2020 Bleepingcomputer Spam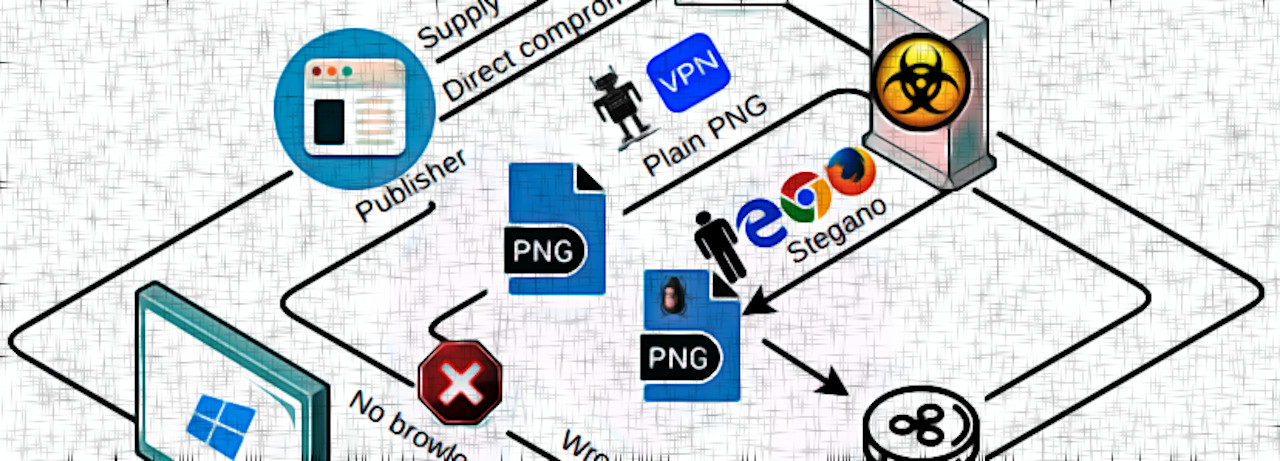
A sophisticated browser locker campaign that ran on high-profile pages, like Microsoft Edge's home or popular tech sites, was deactivated this week after in-depth research was published.
The actors behind it used a compromised an ad content supplier for top-tier distribution and combined targeted traffic filtering with steganography.
This mix allowed the operation to survive for at least two years, bringing victims to a tech support scam page and threat researchers to a dead end as they scratched their heads about how the redirect to the fake malware reporting page happened.
Stealthy and complex
As the name suggests, a browser locker (browlock) affects the web browser, making it unusable by redirecting it to a site that is difficult to close.
In a tech support scam, the landing page informs that malware caused the technical difficulty and provides a phone number where victims should seek help.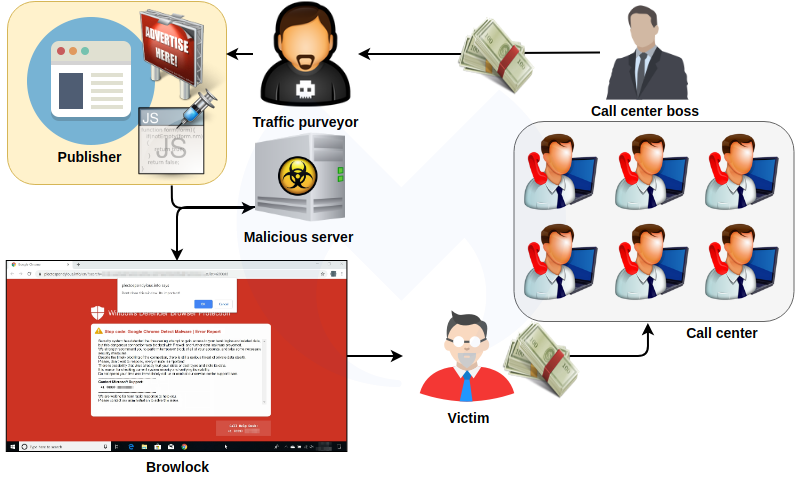
A browlock campaign kept hitting Microsoft users since February 2018 through malvertising on the Edge browser's start page, which is a customized version of Microsoft's MSN page.
Researchers at Confiant named it WOOF locker, while Malwarebytes calls it "404Browlock," because they would see a "404 Not Found" error message when they tried to check the redirect page manually.
Although the scam is simple, the delivery method is what made it stand out and live for so long on large sites and even online newspapers, says Jérôme Segura, Malwarebytes security researcher.
Victims reported that they would see a warning message on a red background (similar to the one below) when they opened a website that served WOOF locker through a tainted advertisement.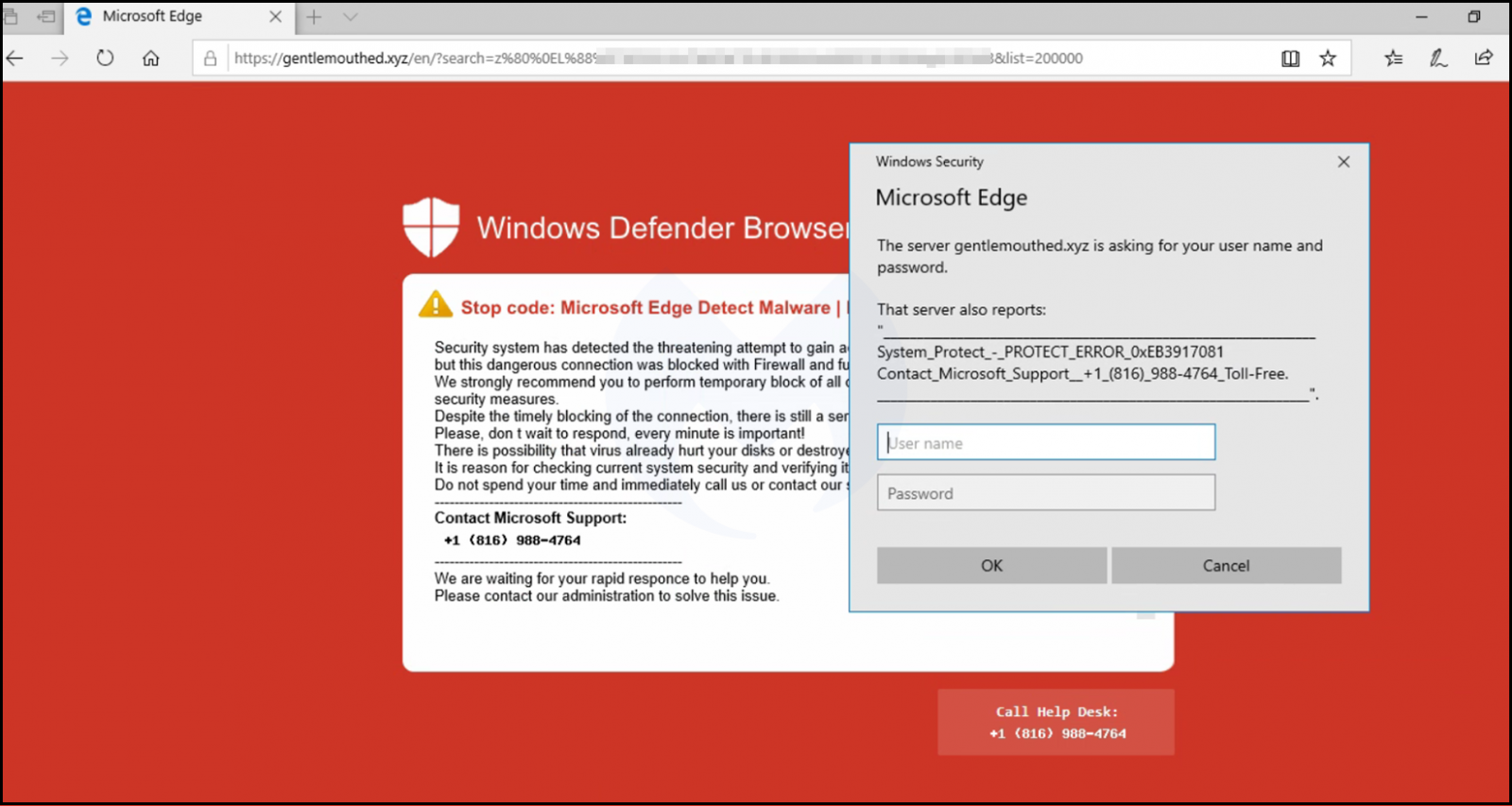
Segura found that WOOF locker was present since at least December 2017 and benefited from an impressive infrastructure with more than 400 unique IP addresses.
The threat actor registered domains in the .XYZ TLD space lately and used a dictionary, with "words grabbed somewhat alphabetically" to name them.
Services from French provider OVH were used to host them recently but others, Digital Ocean and Petersburg, were spotted in the past.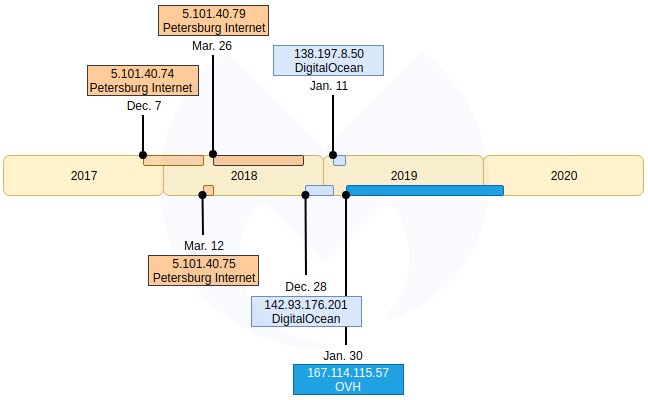
Surviving for this long is unusual for a browlock campaign and it is all due to propagation techniques uncommon for this type of operation.
"Many of the sites that victims reported being on when the browlock happened contained videos, so we thought one likely vector could be video ads. This form of malvertising is more advanced than traditional malicious banners because it enables the crooks to hide their payload within media content" - Jérôme Segura
The researchers found that the fraudster relied on steganography to deliver in a PNG file extra data that was encoded.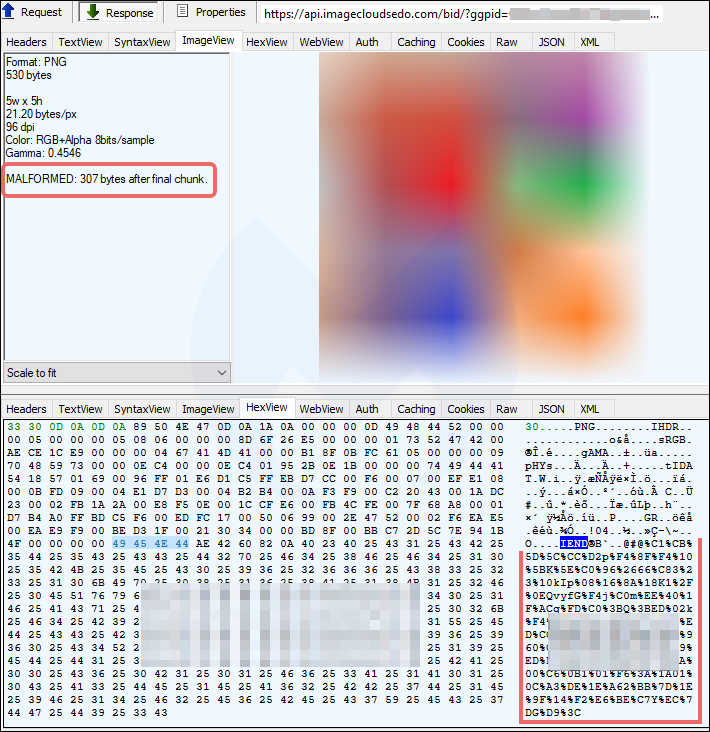
On its own, the code in the image did nothing but it could be decrypted with JavaScript that contained keys unique to each victim.
Segura describes the technical details that kept Woof locker running for so long, explaining the anti-bot and anti-traffic functions that made researchers hit a brick wall when trying to replicate the effect reported by victims.
The JavaScript that interacted with the malformed PNG collected the video card properties of the computer host and this served to distinguish between real browsers, crawlers, and virtual machines.
This helped filter the traffic so that only regular users would be redirected to the browlock URL while investigators would get a clean PNG file that did not facilitate loading the scammer's landing page.
Supply chain compromise
Sharing findings with Confiant, Malwarebytes researchers learned how Woof locker was able to reach pages of reputable websites: a company that turns ads into widgets was compromised and had one of their scripts injected with the malicious Woof script.
This offered the final piece of the puzzle that explained the delivery method of this sophisticated browlock campaign.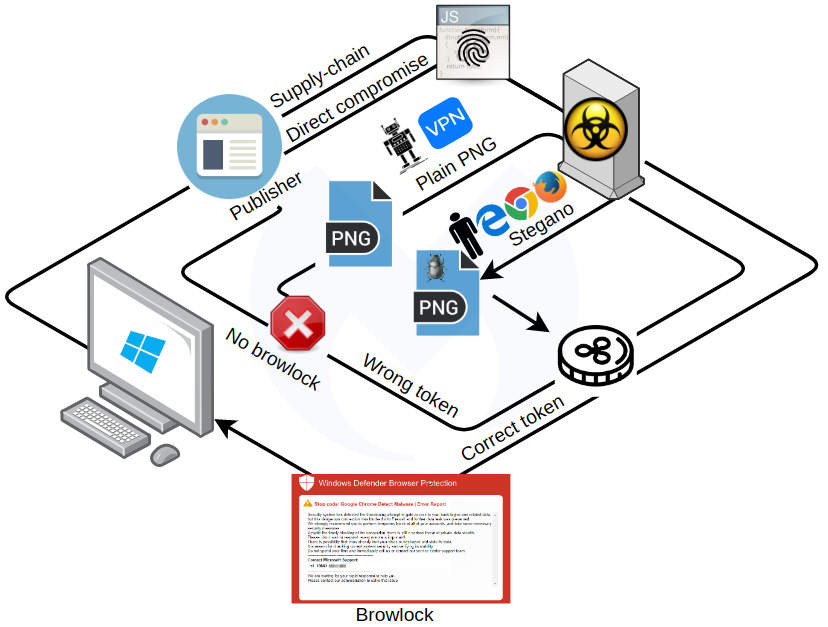
When Segura first disclosed the technical details, the campaign was still active. However, immediately after he published the research and the indicators of compromise, the infrastructure supporting this browlock came tumbling down as a result of OVH action.
Not everything is down, but a large part of the infrastructure is down, including the server responsible for serving the malformed PNG image.
The same actor may be using the same tricks with other campaigns, though, or deploy new ones using different registrars and web hosting providers.
Segura believes that the actor is likely to make even more changes, though, because his research exposed operational details that can help with future detection. Malwarebytes says that fresh activity from this browlock has not been observed since January 23.